Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
38 results about "Data at Rest" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
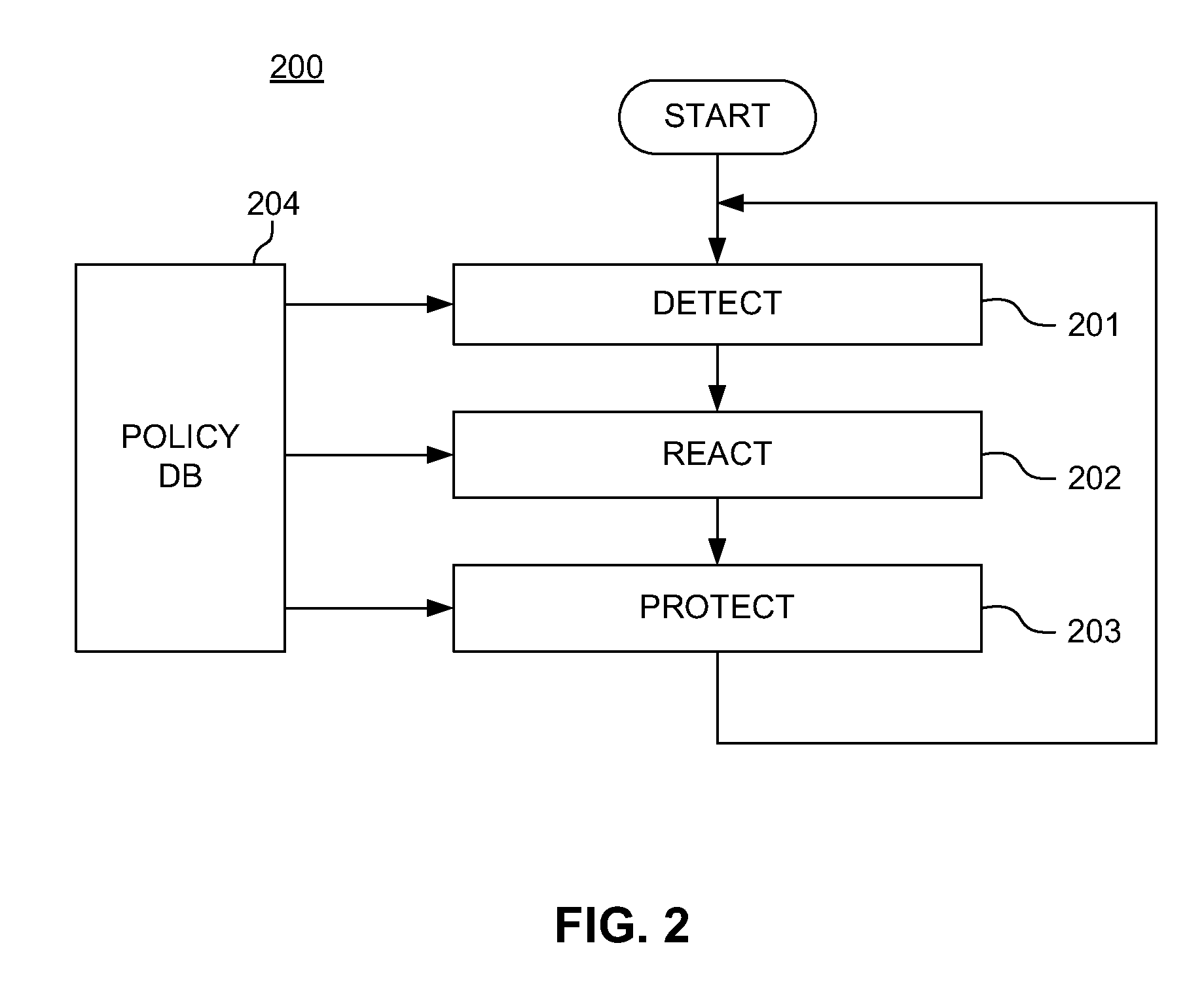
Data at rest in information technology means inactive data that is stored physically in any digital form (e.g. databases, data warehouses, spreadsheets, archives, tapes, off-site backups, mobile devices etc.).
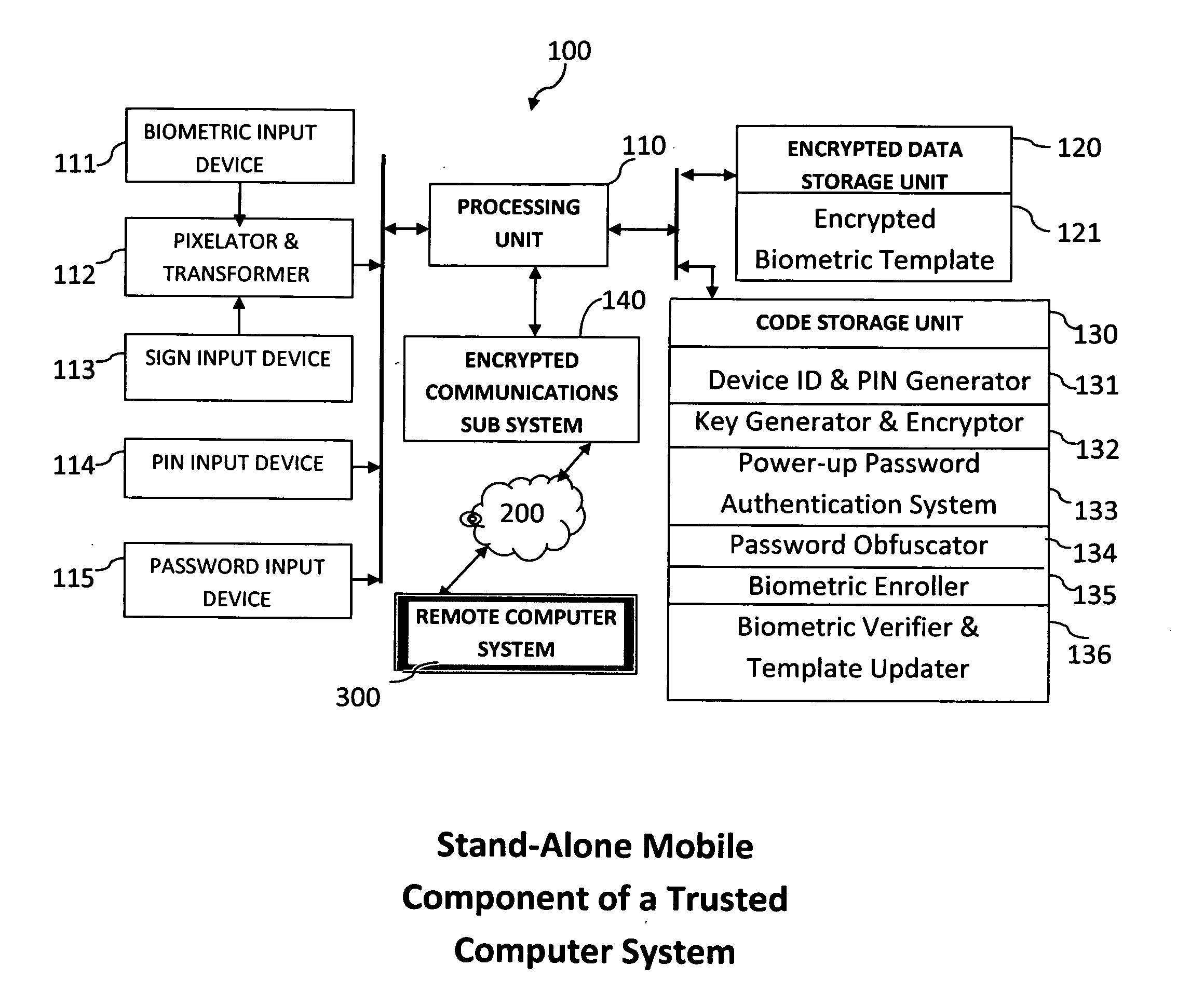
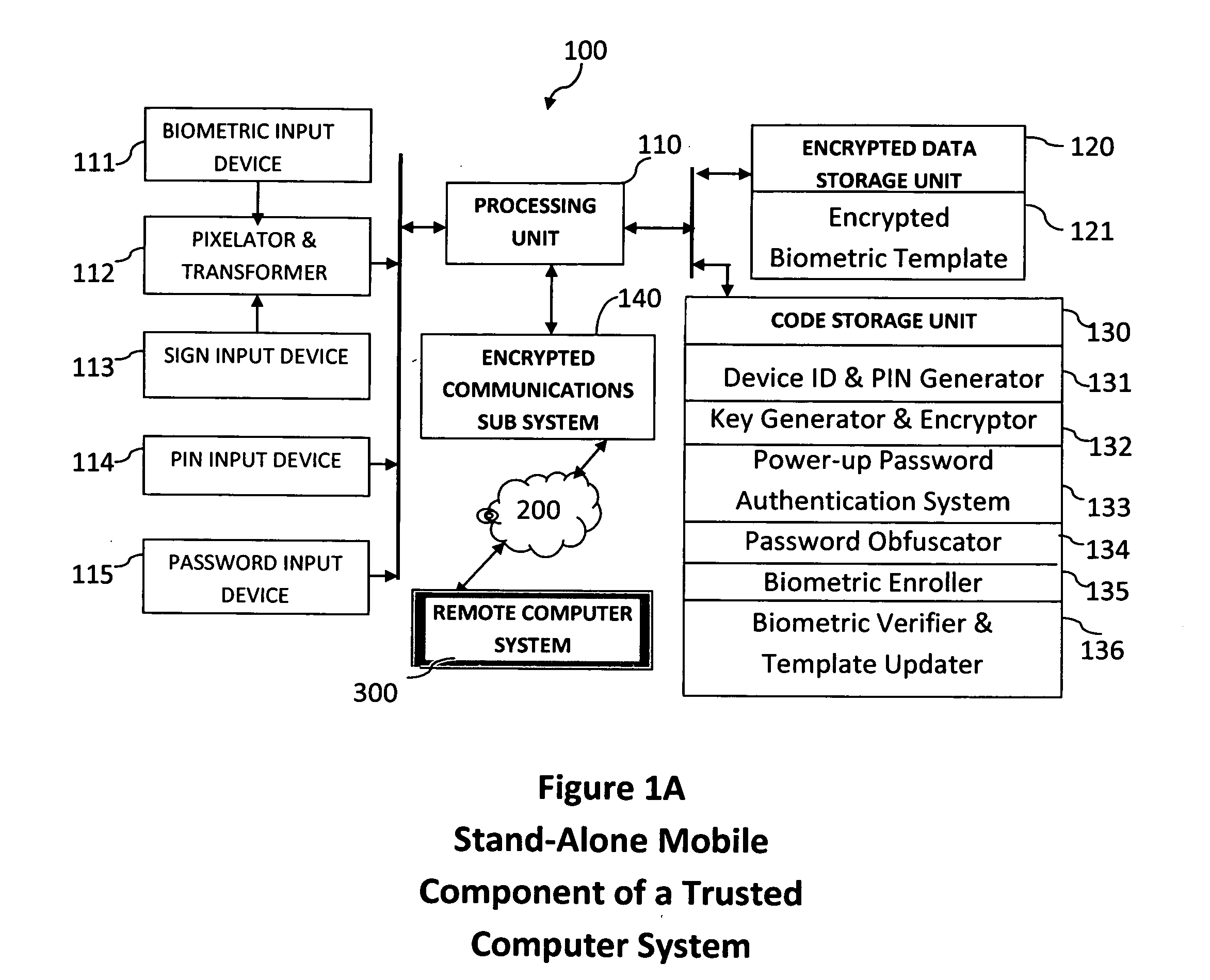
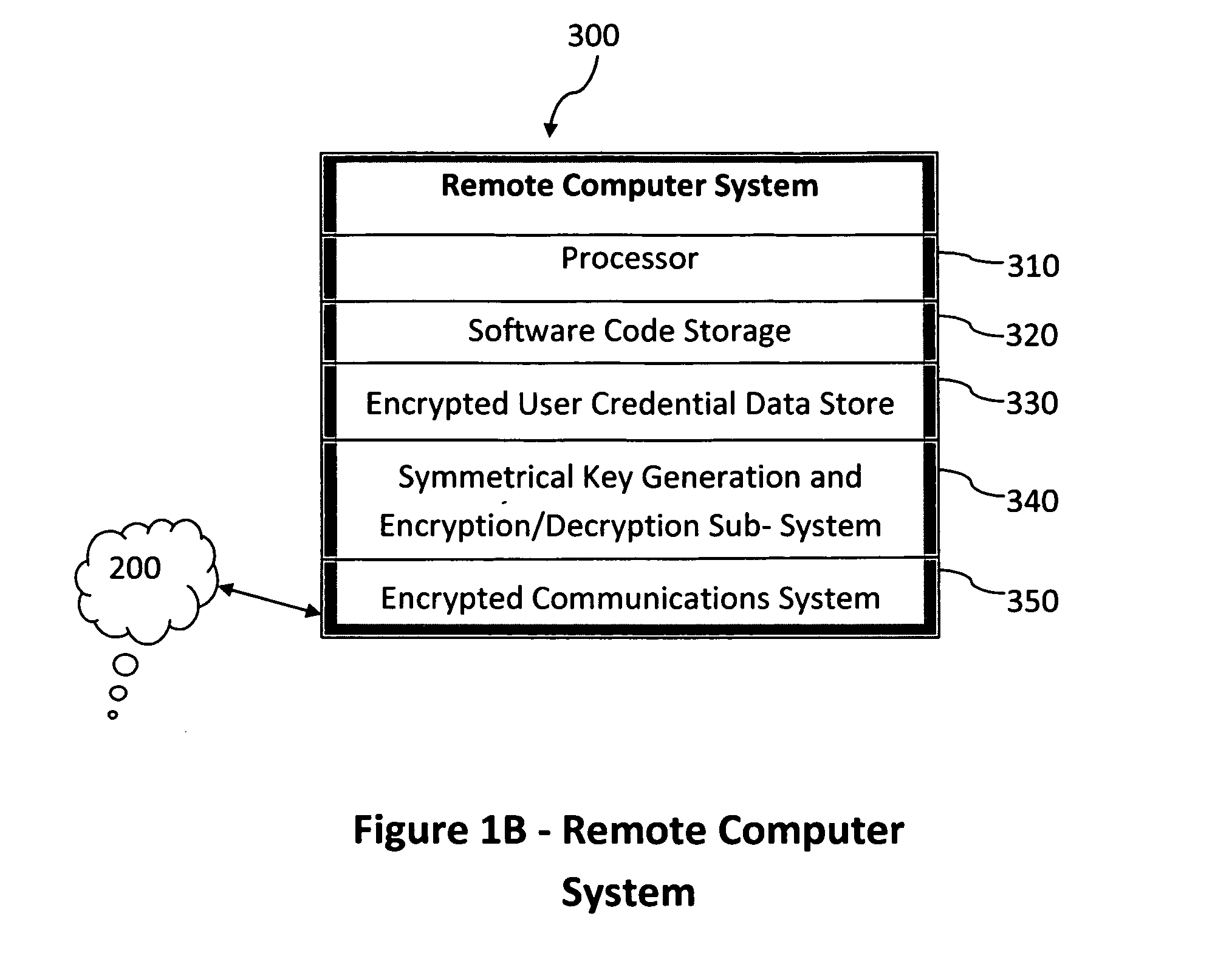
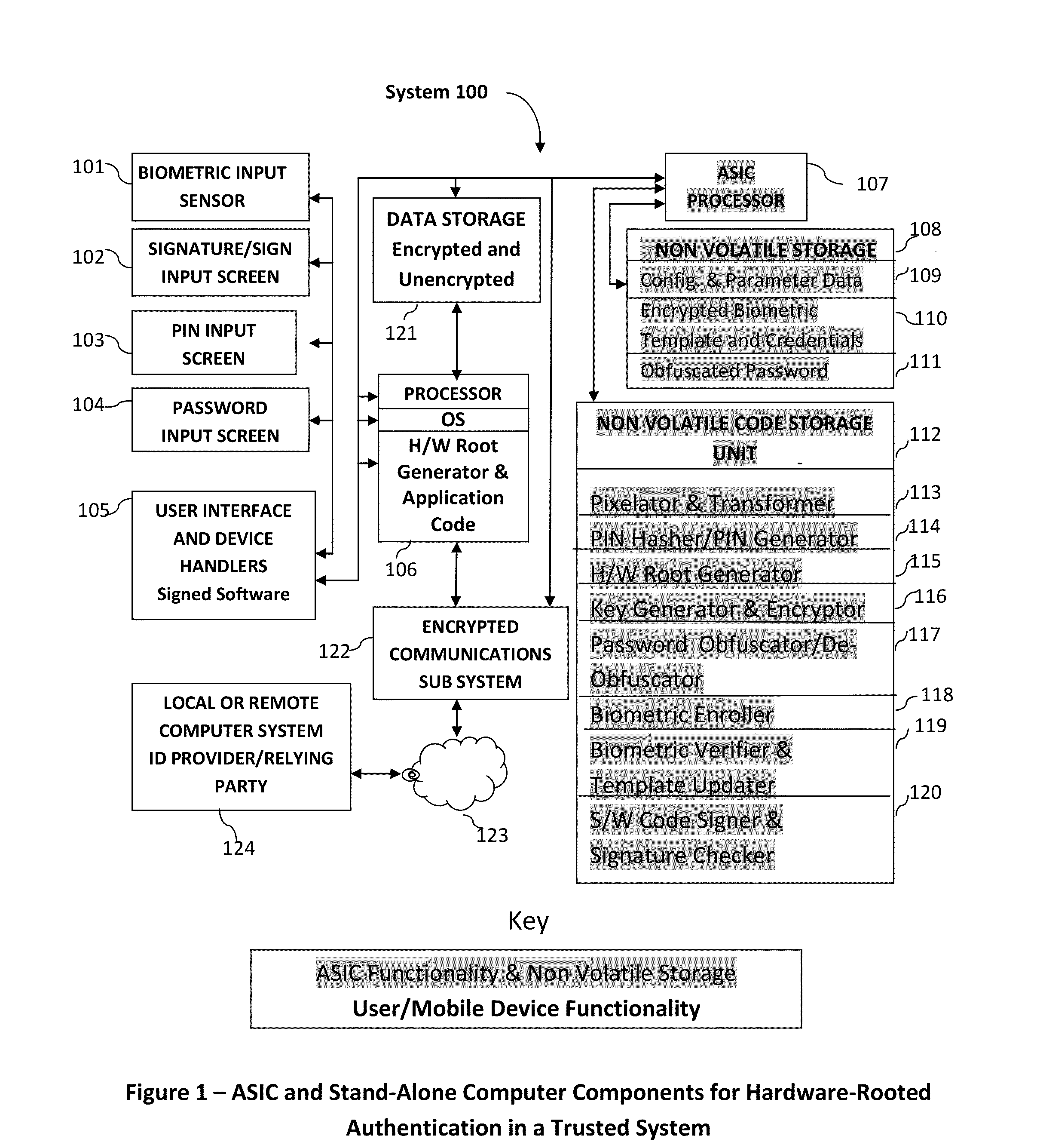
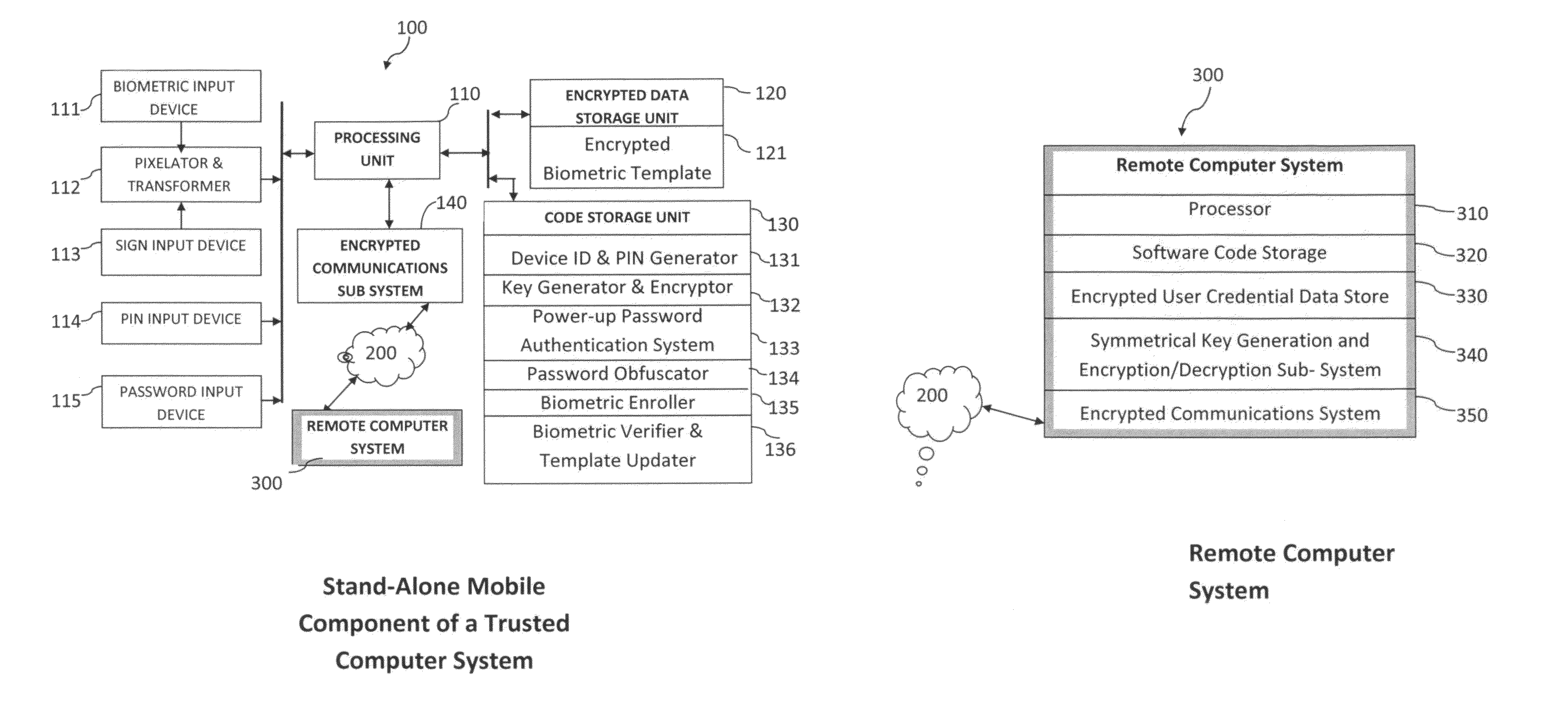
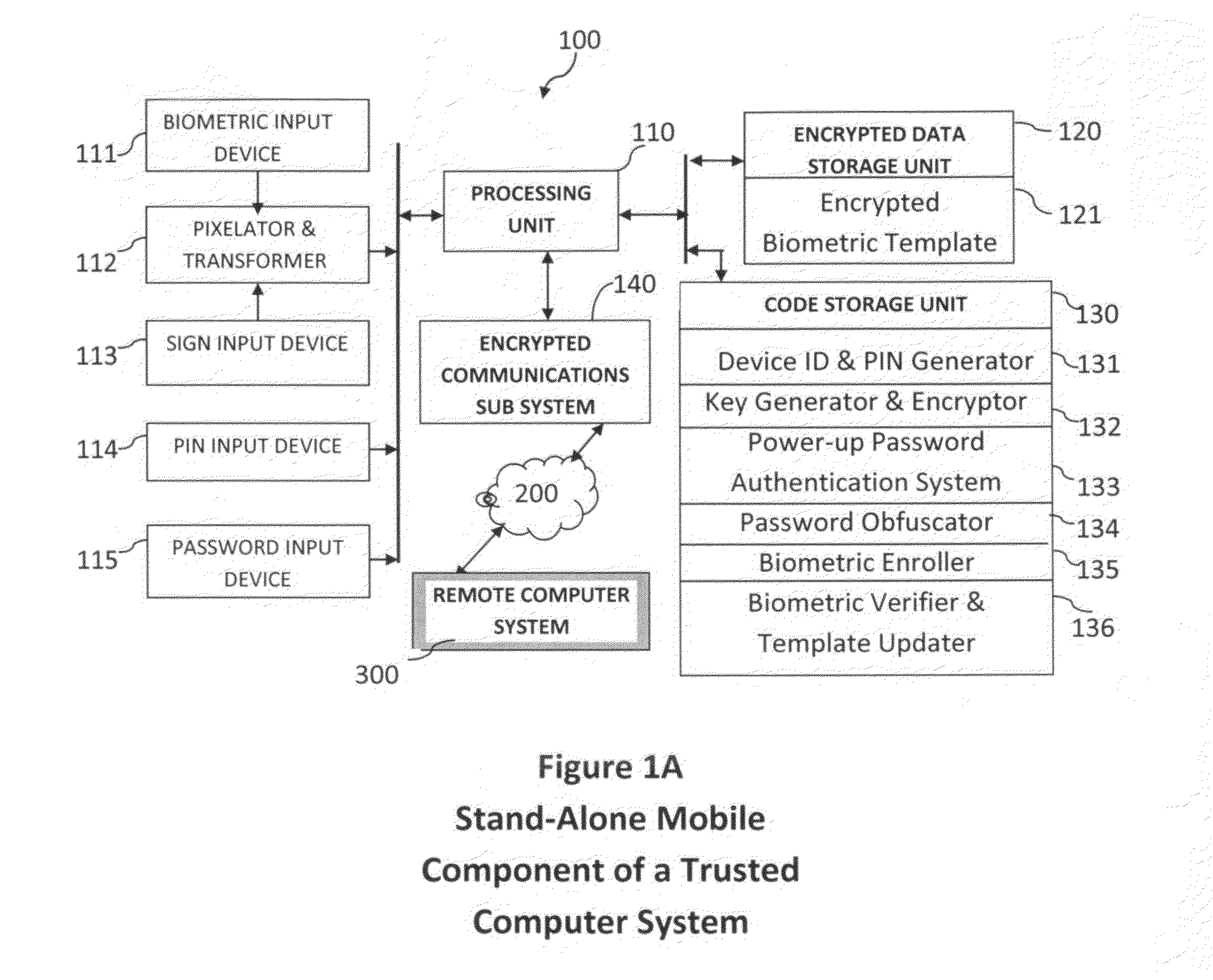
Method and system for combining a PIN and a biometric sample to provide template encryption and a trusted stand-alone computing device
ActiveUS20110126024A1Secure EncryptionEasy to useDigital data processing detailsUser identity/authority verificationBiometric dataTrust relationship
Biometric data, suitably transformed are obtained from a biometric input device contained within a stand-alone computing device and used in conjunction with a PIN to authenticate the user to the device. The biometric template and other data residing on the device are encrypted using hardware elements of the device, the PIN and Password hash. A stored obfuscated password is de-obfuscated and released to the device authentication mechanism in response to a successfully decrypted template and matching biometric sample and PIN. The de-obfuscated password is used to authenticate the user to device, the user to a remote computer, and to encrypt device data at rest on the device and in transit to and from the remote computer. This creates a trusted relationship between the stand-alone device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the device.
Owner:BIOCRYPT ACCESS LLC
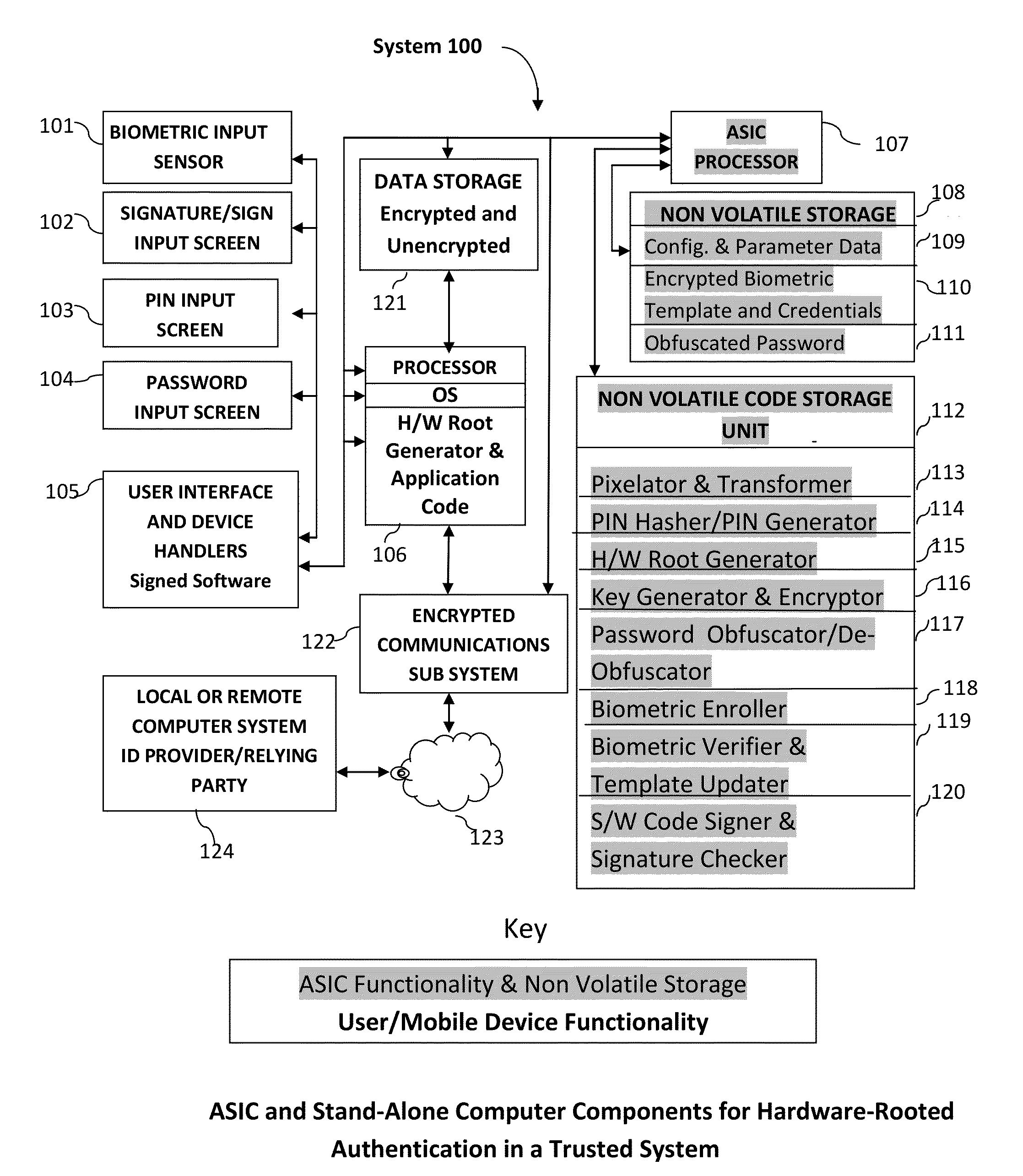
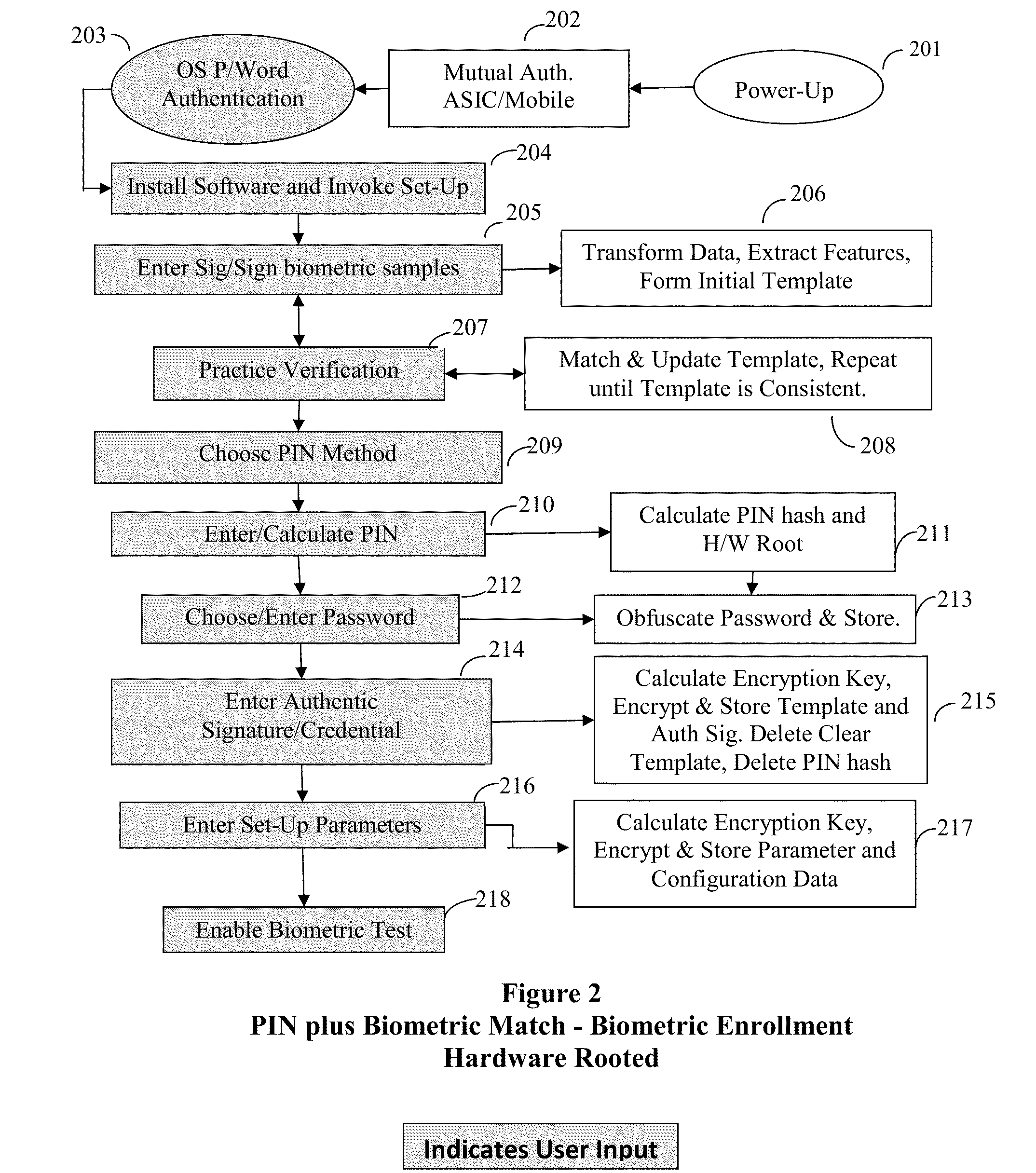
Method and System for Providing Password-free, Hardware-rooted, ASIC-based Authentication of a Human to a Mobile Device using Biometrics with a Protected, Local Template to Release Trusted Credentials to Relying Parties
InactiveUS20140365782A1Significant productivityMaximum safetyUser identity/authority verificationInternal/peripheral component protectionBiometric dataPassword hashing
Biometric data, which may be suitably transformed are obtained from a biometric input device contained within a stand-alone computer or a mobile device, which may contain an ASIC chip connected to or incorporated within the stand-alone computer or mobile device and which includes the capability for capturing one or more biometric samples and for biometric feature extraction, matching and encryption. For extra security, the biometric matching is used in conjunction with a PIN to authenticate the user to the stand-alone computer or mobile device. The biometric template and other sensitive data residing on the mobile device are encrypted using hardware elements of the mobile device (or the ASIC) together with the PIN hash and / or the Password hash. An obfuscated version of the Password, stored on the ASIC or the mobile device is de-obfuscated and released to the mobile device authentication mechanism, including a Trusted Platform Module if present, in response to a successfully decrypted template and matching biometric sample and PIN. A de-obfuscated password is used to authenticate the user to the mobile device and the same or a different de-obfuscated password may be used to authenticate the user to a remote computer using the SSL / TLS or a process based upon a symmetric encryption algorithm. The locally generated password may be used to encrypt data at rest on the mobile device or ASIC and the remote authentication password may be used to encrypt data in transit to and from a remote computer. This creates a trusted relationship between the stand-alone computer or mobile device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the mobile device or for secure transmission of data. A similar method may be used, with the signature / sign biometric modality to determine whether the holder of an IC chip card is, in fact the card owner.
Owner:BIOCRYPT ACCESS LLC
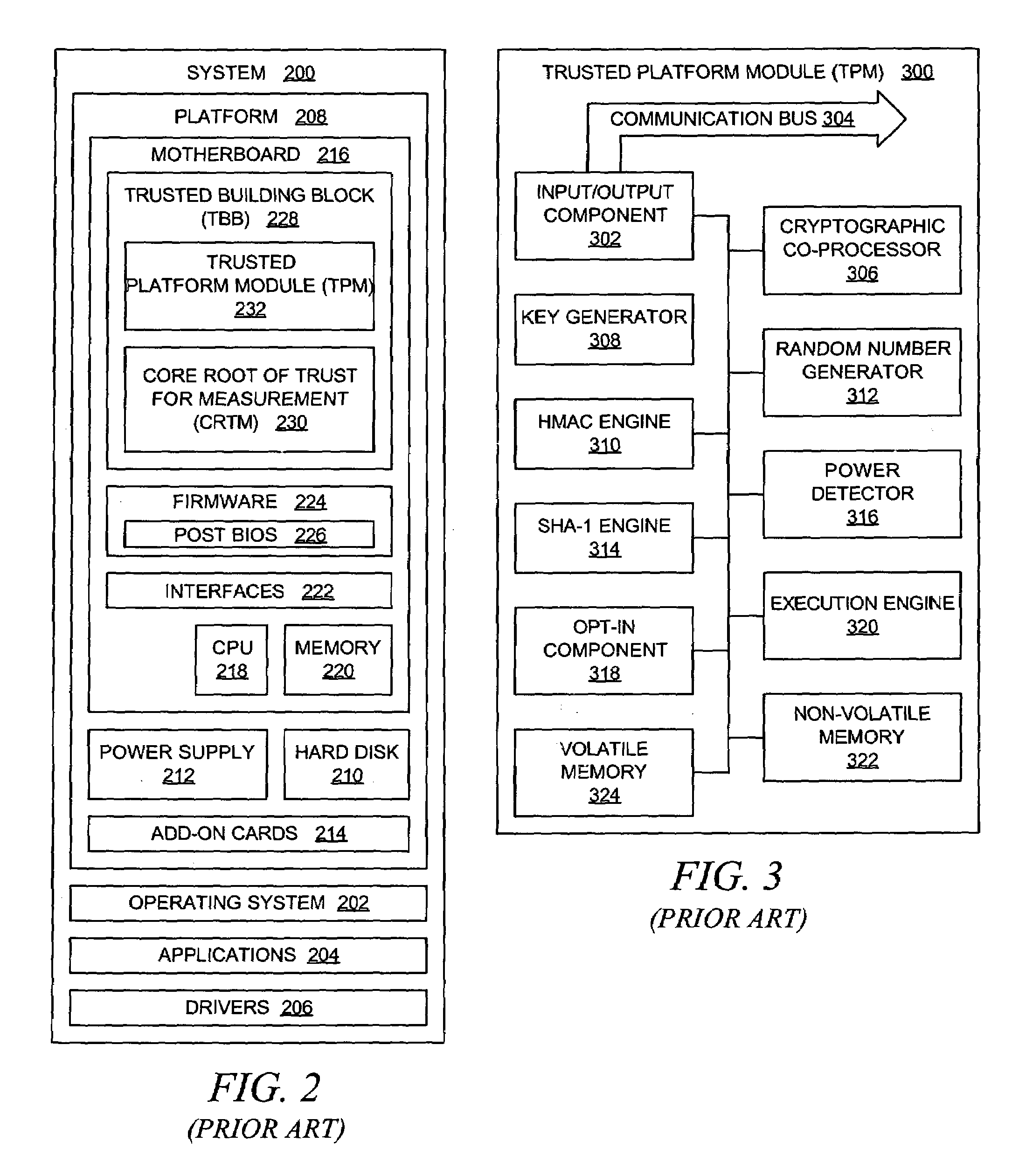
Method and system for bootstrapping a trusted server having redundant trusted platform modules
InactiveUS20050257073A1Safe storageInput/output to record carriersMemory loss protectionData processing systemTrusted Platform Module
Multiple trusted platform modules within a data processing system are used in a redundant manner that provides a reliable mechanism for securely storing secret data at rest that is used to bootstrap a system trusted platform module. A hypervisor requests each trusted platform module to encrypt a copy of the secret data, thereby generating multiple versions of encrypted secret data values, which are then stored within a non-volatile memory within the trusted platform. At some later point in time, the encrypted secret data values are retrieved, decrypted by the trusted platform module that performed the previous encryption, and then compared to each other. If any of the decrypted values do not match a quorum of values from the comparison operation, then a corresponding trusted platform module for a non-matching decrypted value is designated as defective because it has not been able to correctly decrypt a value that it previously encrypted.
Owner:IBM CORP
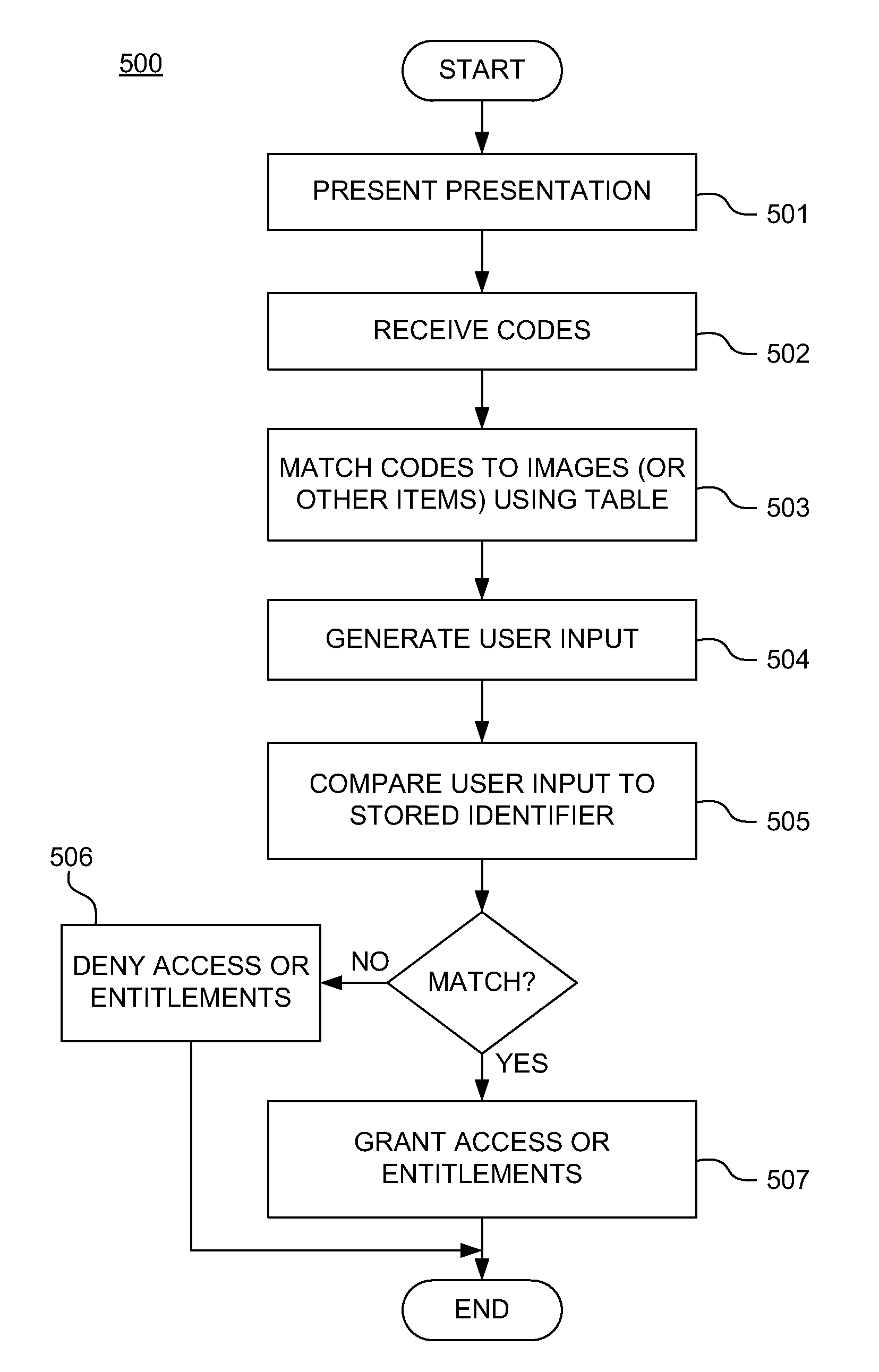
Adaptive policies and protections for securing financial transaction data at rest
ActiveUS20110314529A1Shorten the time to marketAcceptable levelDigital data processing detailsUser identity/authority verificationTransaction dataDisplay device
A system for challenge-response authentication is provided by receiving, from an external terminal over a communication network, a request for access to a service. A plurality of objects is presented to a user via a display. A plurality of codes is received over the communication network, each of the plurality of codes corresponding to one of the plurality of objects. The plurality of codes are matched to a plurality of alphanumeric characters according to a predetermined table. An alphanumeric string is generated from the plurality of alphanumeric characters and the alphanumeric string is compared to a user identifier stored in a database. Based on the comparing, a determination is made as to whether to grant the user access to the service.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
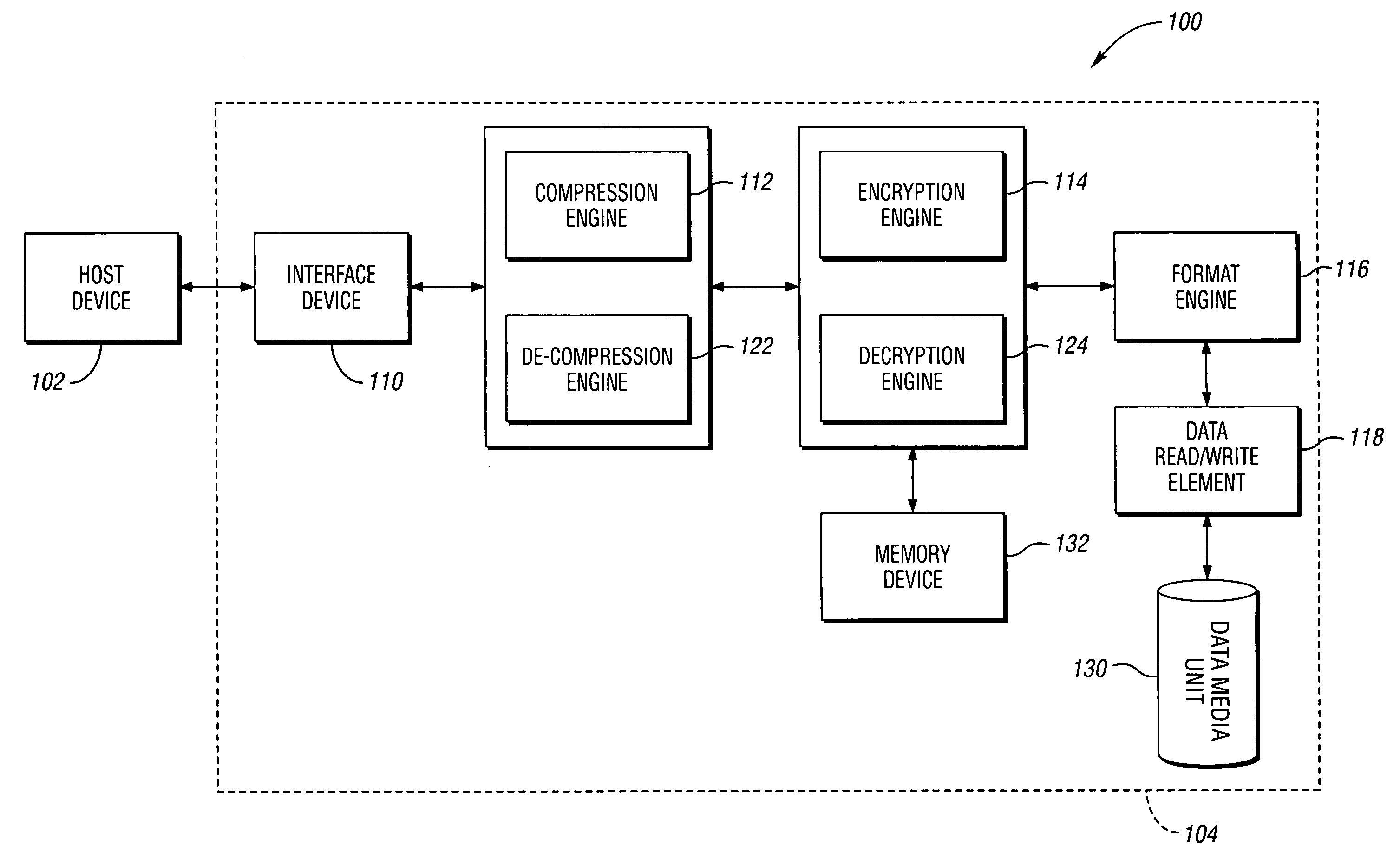
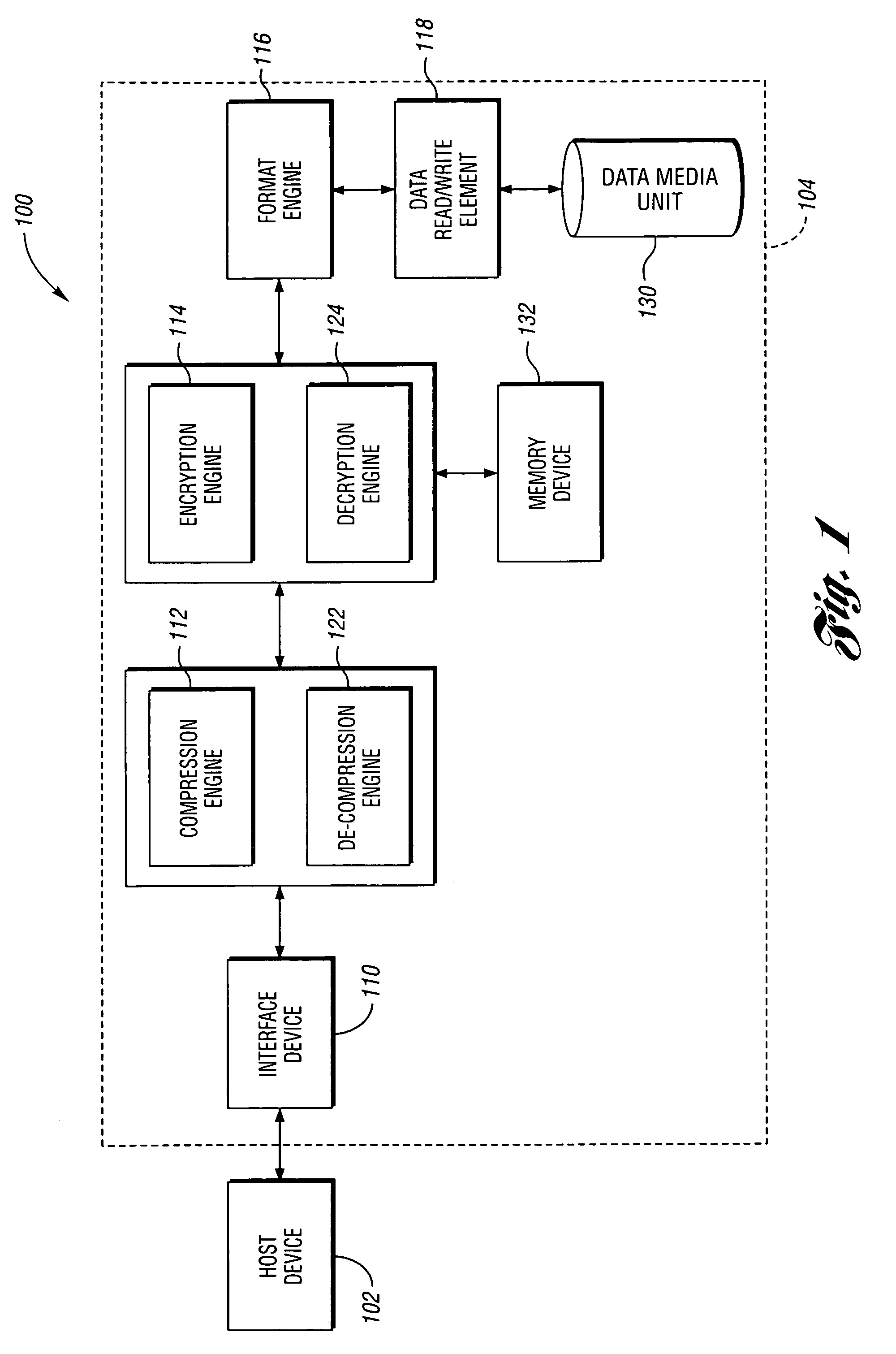
System, method and data storage device for encrypting data
A system, method and data storage device for encrypting data to provide at-rest data encryption of data in the data storage device. The system includes a compression engine for receiving a host data stream packet and selectively generating a compressed data packet, and an encryption engine in electronic communication with the compression engine for receiving an unencrypted data packet from the compression engine. The unencrypted data packet comprises the compressed data packet when the compression engine generates the compressed data packet. The unencrypted data packet comprises the host data packet when the compression engine does not generate the compressed data packet. The encryption engine generates an encrypted data packet having an encrypted component corresponding to the unencrypted data packet and a set of meta data indicative of one or more characteristic of the encrypted data packet.
Owner:ORACLE INT CORP
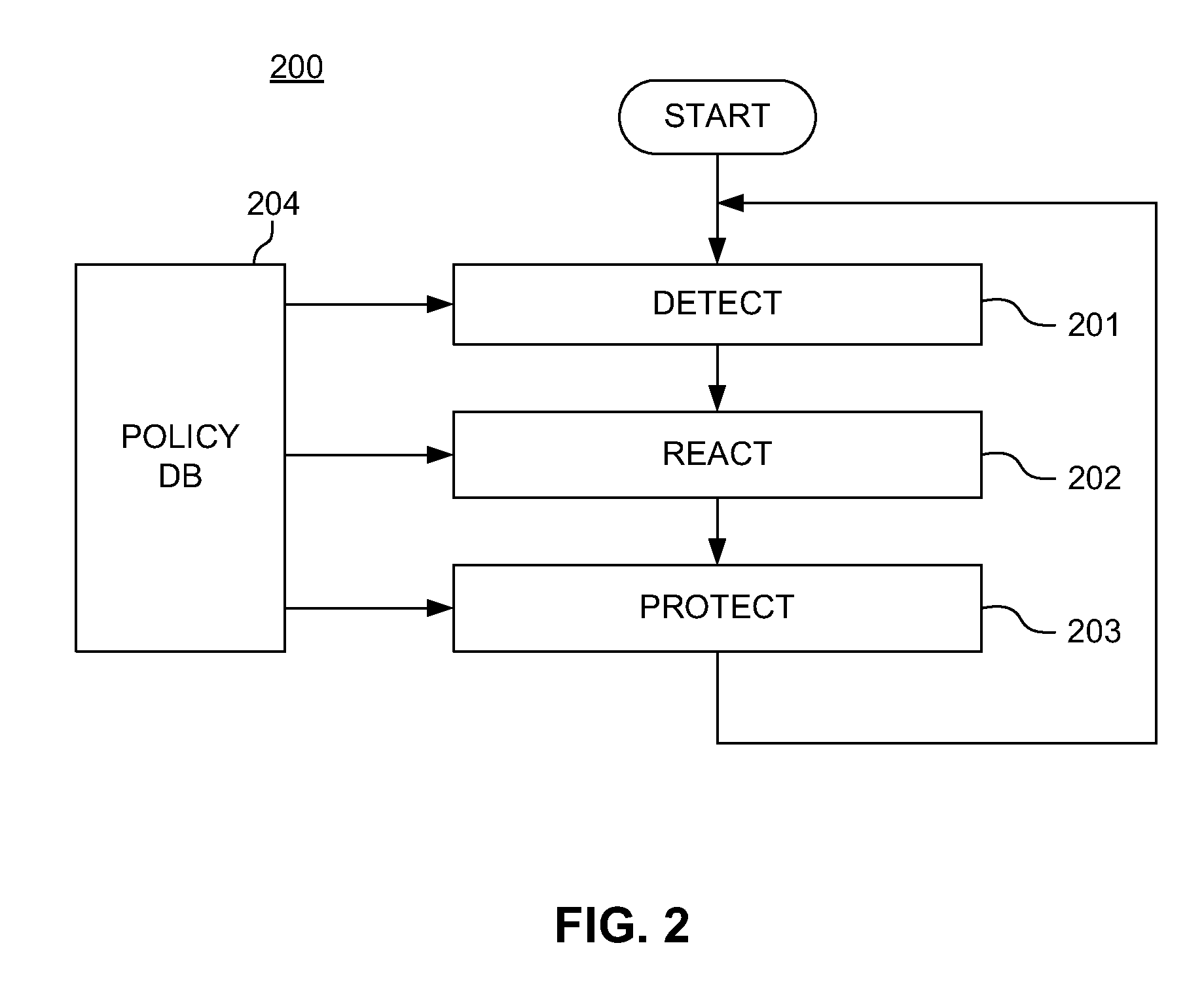
DLP-enforced loss scanning, sequestering, and content indexing
A system and method is disclosed for implementing a data loss prevention (DLP) system configured to protect sensitive data in conjunction with corresponding content indexing (CI) metadata. In response to detecting a data loss risk, such as to data at rest (e.g., stored on a file system) and / or to data in motion (e.g., data being transmitted across a network) the system may perform any number of data loss prevention actions, including sequestering the data. The system may utilize an interface to a content indexing system in order to discover CI metadata associated with the data and sequester the CI metadata associated with the data. One or more common sequestration rules may be applied to the sequestration of the data and of the metadata. For example, the data and metadata may be encrypted using the same key and / or sequestered in the same location.
Owner:VERITAS TECH
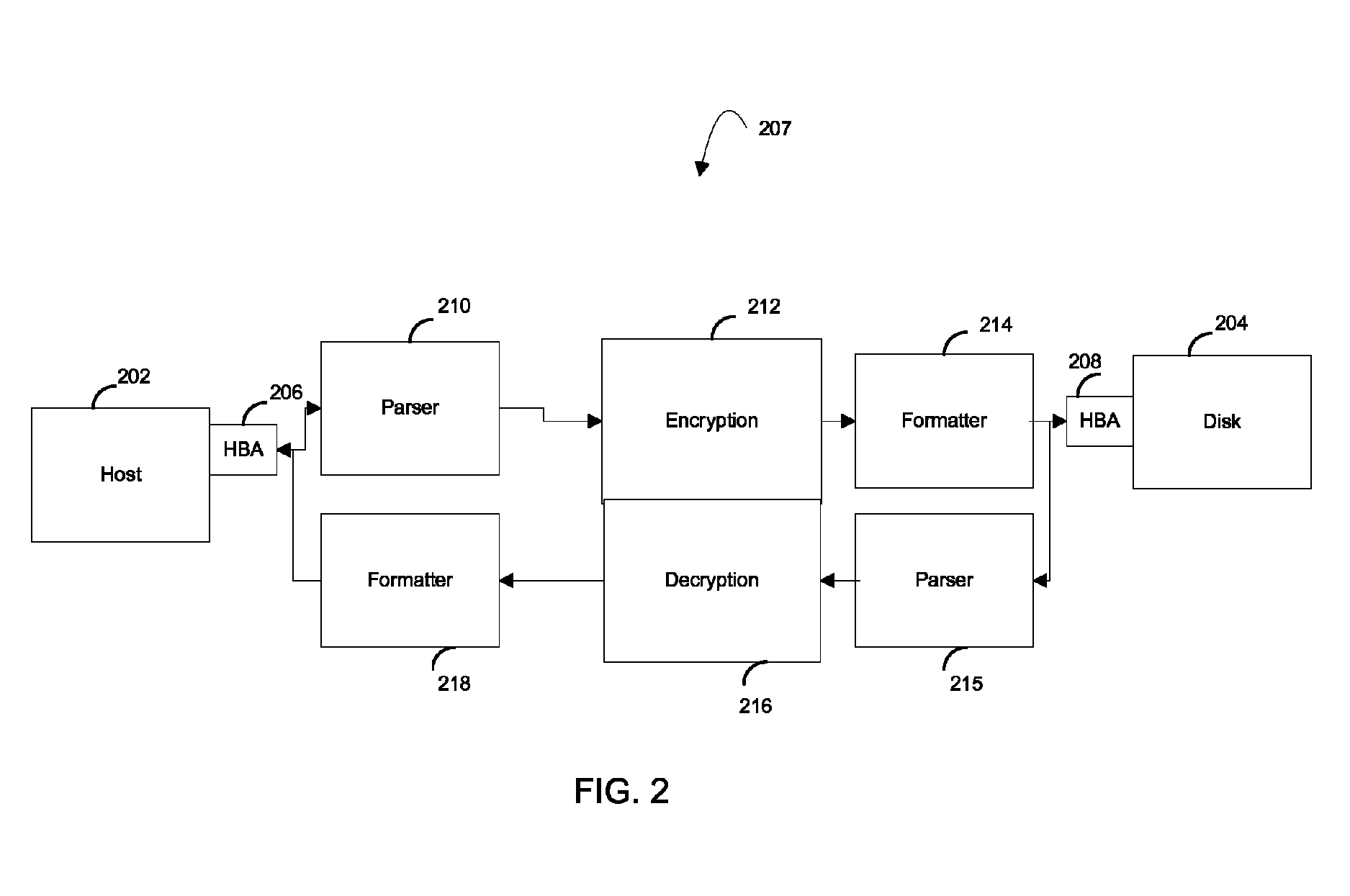
Method and apparatus for performing encryption of data at rest at a port of a network device
Methods and apparatus for performing encryption for data at rest at a port of a network device such as a switch are disclosed. Specifically, when data is received from a host during a write to a storage medium such as a disk, the data is encrypted by the port prior to transmitting the encrypted data to the storage medium. Similarly, when a host attempts to read data from the storage medium, the port of the network device receives the encrypted data from the storage medium, decrypts the data, and transmits the decrypted data to the host. In this manner, encryption and decryption of data at rest are supported by the port of the network device.
Owner:CISCO TECH INC
X-ray ct apparatus, myocardial perfusion information generating system, x-ray diagnostic method and myocardial perfusion information generating method
ActiveUS20080273782A1Reduce injection volumeMaterial analysis using wave/particle radiationRadiation/particle handlingX-rayData at Rest
An X-ray CT apparatus has an image generating unit and a blood flow information acquiring unit. The image generating unit acquires projection data at rest and at non-rest from a myocardial part of an object into which contrast medium is injected continuously in a state in which each concentration of the contrast medium can be considered to be constant and reconstructs contrast CT image data at the rest and at the non-rest using the acquired projection data. The blood flow information acquiring unit obtains third blood flow information based in first blood flow information derived from the contrast CT image data at the rest and second blood flow information derived from the contrast CT image data at the non-rest.
Owner:TOSHIBA MEDICAL SYST CORP
Adaptive policies and protections for securing financial transaction data at rest
ActiveUS8850539B2Shorten the time to marketIncrease propensityDigital data processing detailsUser identity/authority verificationTransaction dataDisplay device
A system for challenge-response authentication is provided by receiving, from an external terminal over a communication network, a request for access to a service. A plurality of objects is presented to a user via a display. A plurality of codes is received over the communication network, each of the plurality of codes corresponding to one of the plurality of objects. The plurality of codes are matched to a plurality of alphanumeric characters according to a predetermined table. An alphanumeric string is generated from the plurality of alphanumeric characters and the alphanumeric string is compared to a user identifier stored in a database. Based on the comparing, a determination is made as to whether to grant the user access to the service.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
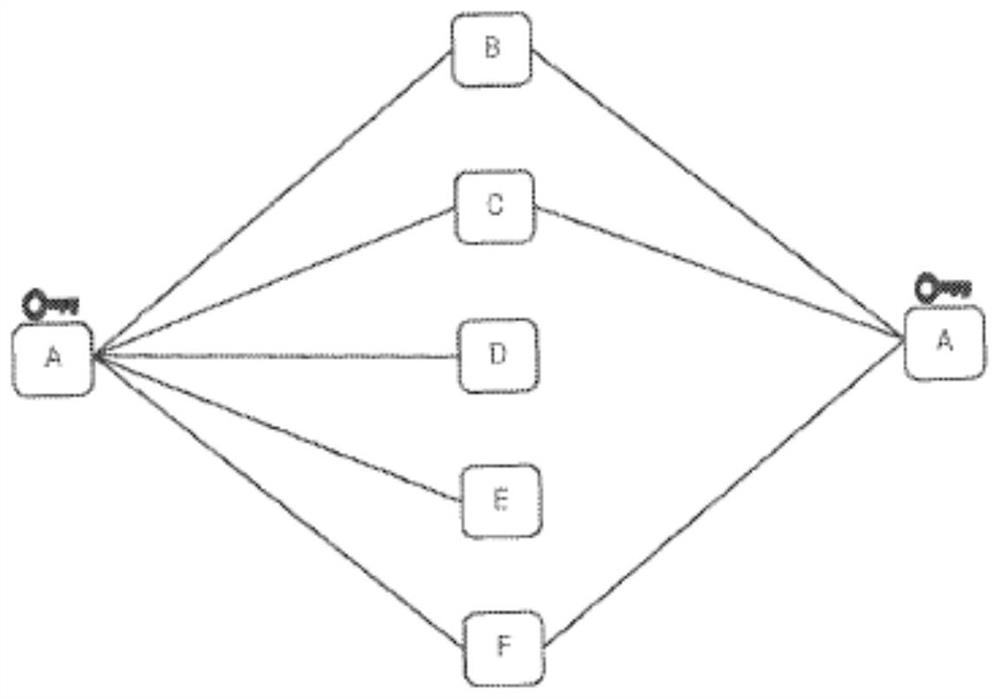
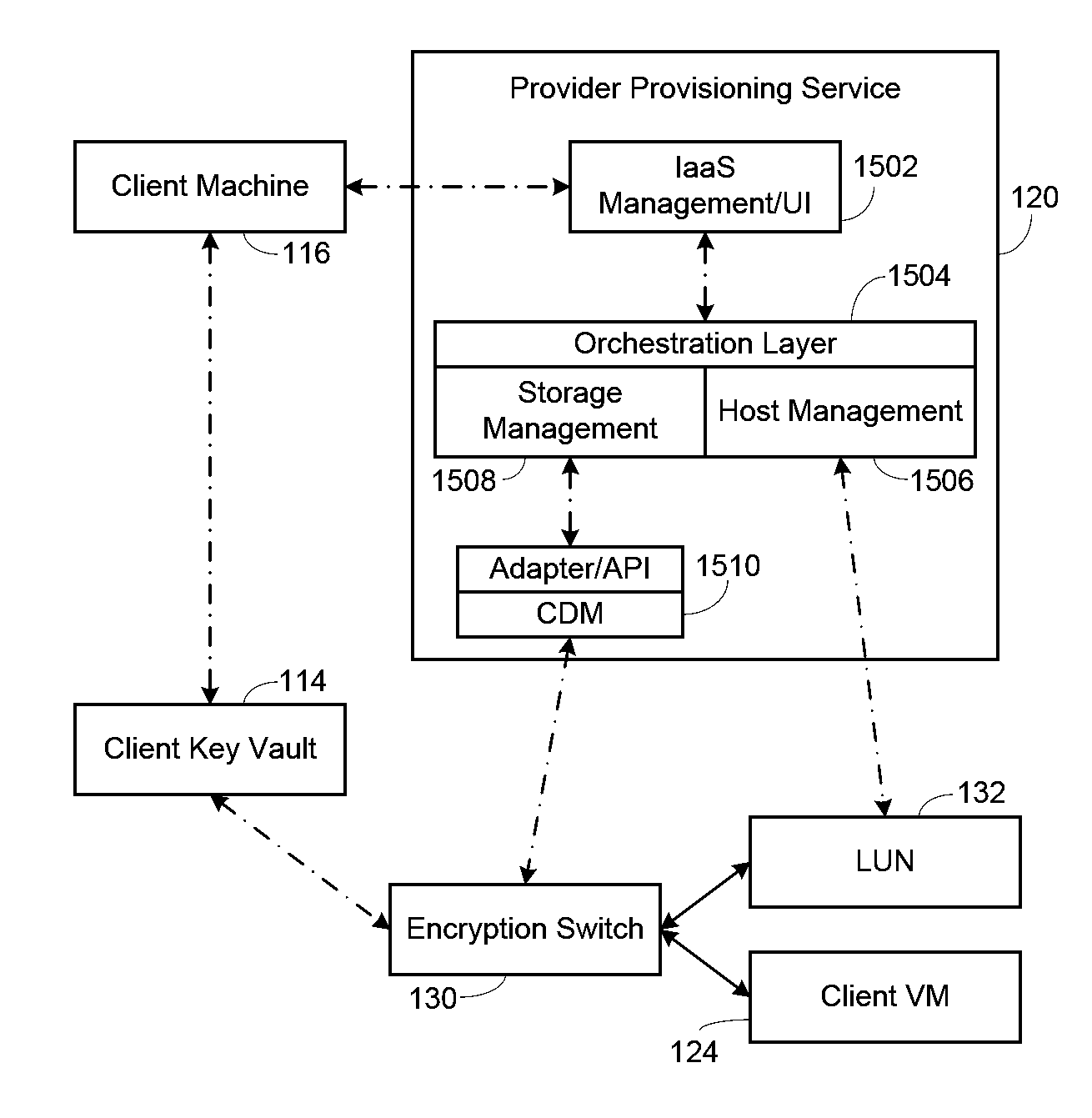
Public Cloud Data at Rest Security
An encryption switch which is used in a cloud environment to secure data on the LUNs used by the clients. A client provides a certificate to the cloud service. The encryption switch develops a cloud crypto domain (CCD) as a secure area, with the data at rest on the LUNs encrypted. The encryption switch develops a master key for client use in the CCD, which is provided to the client encrypted by the client's public key. Data encryption keys (DEKs) are created for each LUN and provided to the client. The DEKs are stored in a key vault by the client for use if needed. The cloud service provisions a client VM to be used with the encrypted LUN and develops a nexus between the LUN and the client VM for the encryption switch to use in data operations. The client communicates through the client VM to access the LUN.
Owner:AVAGO TECH INT SALES PTE LTD
Constructing flexibly-secure systems in a disaggregated environment
ActiveUS20200174949A1Provide securityAdjustable capacityPublic key for secure communicationUnauthorized memory use protectionData centerParallel computing
Server resources in a data center are disaggregated into shared server resource pools, which include a pool of secure processors. Advantageously, servers are constructed dynamically, on-demand and based on a tenant's workload requirements, by allocating from these resource pools. According to this disclosure, secure processor modules for new servers are allocated to provide security for data-in-use (and data-at-rest) in a dynamic fashion so that virtual and non-virtual capacity can be adjusted in the disaggregate compute system without any downtime, e.g., based on workload security requirements and data sensitivity characteristics. The approach herein optimizes an overall utilization of an available secure processors resource pool in the disaggregated environment. The resulting disaggregate compute system that is configured according to the approach cryptographically-protects workload data whenever it is outside the CPU chip.
Owner:IBM CORP
Method and system for combining a PIN and a biometric sample to provide template encryption and a trusted stand-alone computing device
ActiveUS8842887B2Easy to useUser identity/authority verificationCharacter and pattern recognitionBiometric dataTrust relationship
Owner:BIOCRYPT ACCESS LLC
Developing initial and subsequent keyid information from a unique mediaid value
InactiveUS20110038479A1Multiple keys/algorithms usageUser identity/authority verificationAccess networkData at Rest
A technique for using a key repository to store data encryption keys provides a way to access key records in the key repository using a key identifier constructed from a media identifier associated with a data storage medium on which encrypted data is or will be stored. The media identifier is hashed and added to a counter value to produce the key identifier. In some embodiments, the technique is implemented in an encryption switch that provides data-at-rest encryption for a storage access network, but in other embodiments, the technique may be implemented in other devices, including data storage devices and hosts.
Owner:AVAGO TECH INT SALES PTE LTD
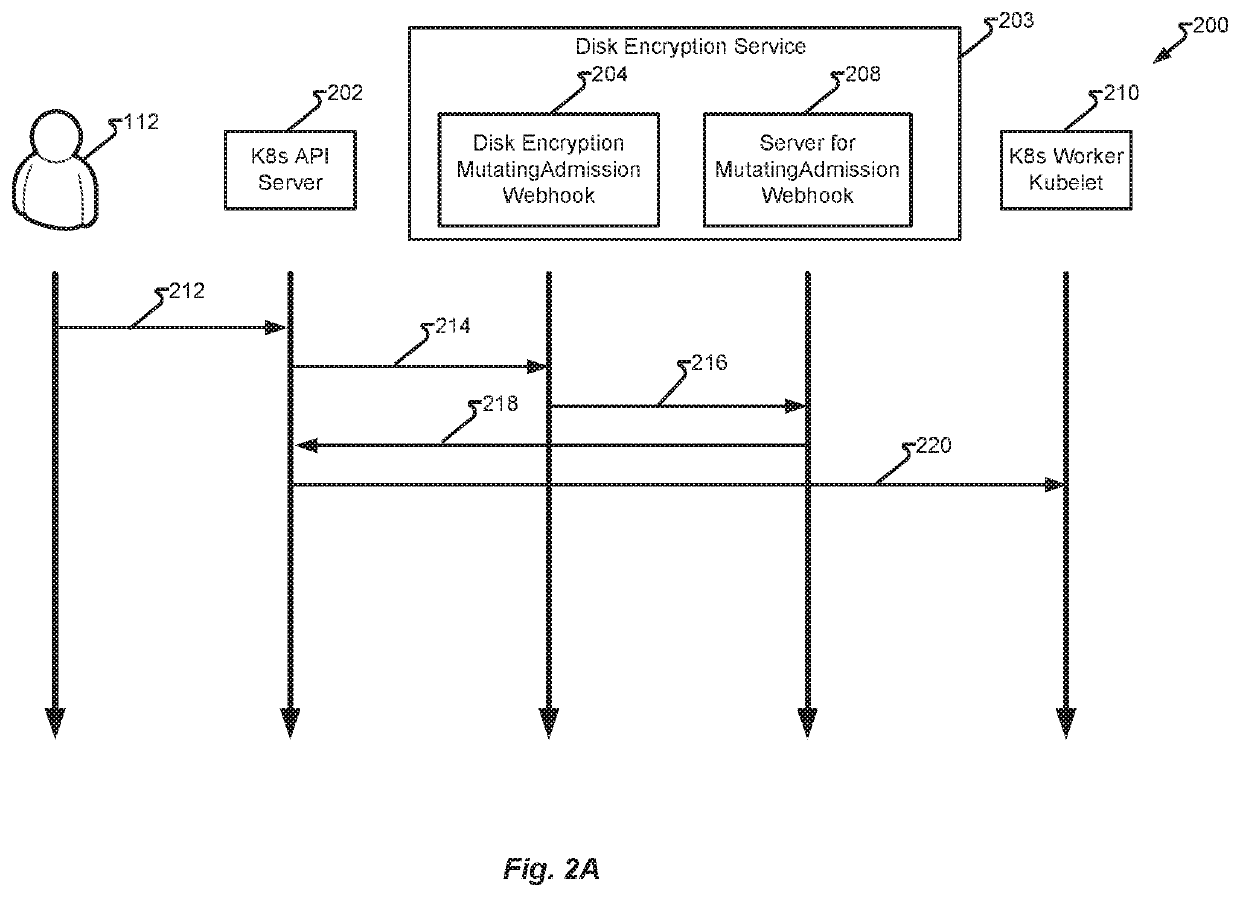
Method to encrypt the data at rest for data residing on kubernetes persistent volumes
ActiveUS20220012373A1Maintain usability and encryptionShort response timeDigital data protectionInternal/peripheral component protectionEncrypted functionData at Rest
When performing data encryption at rest of data residing on Kubernetes persistent volume, existing methods rely on storage provider's encryption capabilities, which instill limitations that hinder deployment. Accordingly, systems and methods are described that receive a Pod specification comprising a disk encryption request and automatically annotate the specification to include specifications for the disk encryption (e.g., secret, key, etc.) to mount a persistent volume having a disk encrypted according to the generated specification.
Owner:AVAYA MANAGEMENT LP
Method and system for bootstrapping a trusted server having redundant trusted platform modules
InactiveUS7664965B2Safe storageInput/output to record carriersMemory loss protectionData processing systemTrusted Platform Module
Multiple trusted platform modules within a data processing system are used in a redundant manner that provides a reliable mechanism for securely storing secret data at rest that is used to bootstrap a system trusted platform module. A hypervisor requests each trusted platform module to encrypt a copy of the secret data, thereby generating multiple versions of encrypted secret data values, which are then stored within a non-volatile memory within the trusted platform. At some later point in time, the encrypted secret data values are retrieved, decrypted by the trusted platform module that performed the previous encryption, and then compared to each other. If any of the decrypted values do not match a quorum of values from the comparison operation, then a corresponding trusted platform module for a non-matching decrypted value is designated as defective because it has not been able to correctly decrypt a value that it previously encrypted.
Owner:INT BUSINESS MASCH CORP
Method and apparatus for performing encryption of data at rest at a port of a network device
ActiveUS8266431B2User identity/authority verificationDigital computer detailsComputer hardwareData at Rest
Methods and apparatus for performing encryption for data at rest at a port of a network device such as a switch are disclosed. Specifically, when data is received from a host during a write to a storage medium such as a disk, the data is encrypted by the port prior to transmitting the encrypted data to the storage medium. Similarly, when a host attempts to read data from the storage medium, the port of the network device receives the encrypted data from the storage medium, decrypts the data, and transmits the decrypted data to the host. In this manner, encryption and decryption of data at rest are supported by the port of the network device.
Owner:CISCO TECH INC
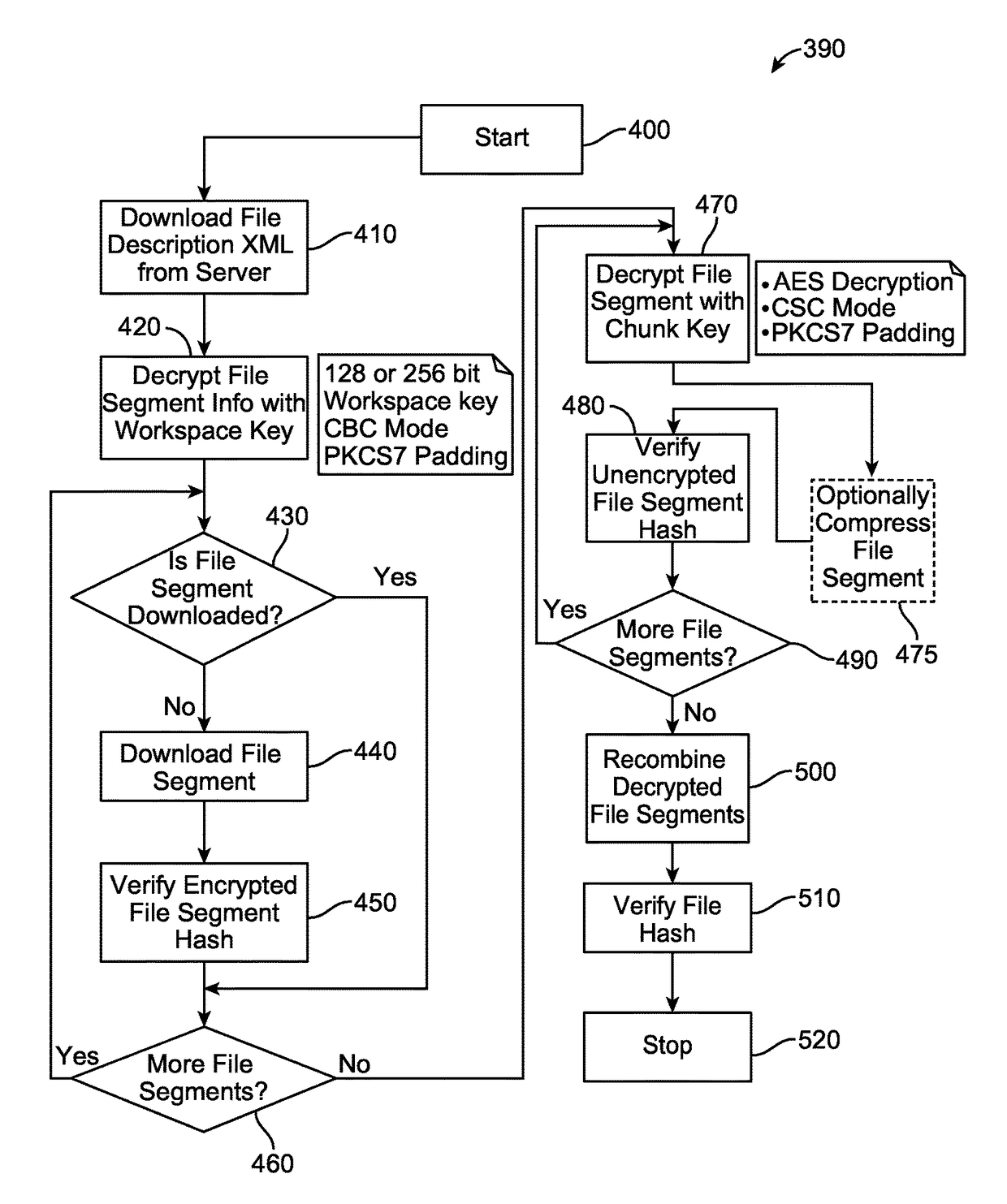
Systems and methods for security hardening of data in transit and at rest via segmentation, shuffling and multi-key encryption
ActiveUS9990502B2Key distribution for secure communicationMultiple keys/algorithms usageContextual integrityComputerized system
Systems and methods for security hardening of a file in transit and at rest via segmentation, shuffling and multi-key encryption are presented. The method including segmenting at a first computer system a file into a plurality of file segments, and encrypting the plurality of file segments using a plurality of encryption keys in order to generate a corresponding plurality of encrypted file segments, wherein each file segment of the plurality of file segments is encrypted using a respective encryption key of the plurality of encryption keys. Additionally included is bidirectional data transformation of a file by obfuscating at a first computer system digital values of the file in order to generate corresponding obfuscated digital values of the file, wherein the obfuscated digital values of the file retain their contextual integrity and referential integrity.
Owner:TOPIA TECH
Developing initial and subsequent keyID information from a unique mediaID value
InactiveUS8189790B2User identity/authority verificationUnauthorized memory use protectionAccess networkData at Rest
A technique for using a key repository to store data encryption keys provides a way to access key records in the key repository using a key identifier constructed from a media identifier associated with a data storage medium on which encrypted data is or will be stored. The media identifier is hashed and added to a counter value to produce the key identifier. In some embodiments, the technique is implemented in an encryption switch that provides data-at-rest encryption for a storage access network, but in other embodiments, the technique may be implemented in other devices, including data storage devices and hosts.
Owner:AVAGO TECH INT SALES PTE LTD
Method for streaming SVD computation field of invention
InactiveUS20130013659A1Fast wayComputationally efficientComplex mathematical operationsStreaming dataData set
The present disclosure is directed to techniques for efficient streaming SVD computation. In an embodiment, streaming SVD can be applied for streamed data and / or for streamed processing of data. In another embodiment, the streamed data can include time series data, data in motion, and data at rest, wherein the data at rest can include data from a database or a file and read in an ordered manner. More particularly, the disclosure is directed to an efficient and faster method of computation of streaming SVD for data sets such that errors including reconstruction error and loss of orthogonality are error bounded. The method avoids SVD re-computation of already computed data sets and ensures updates to the SVD model by incorporating only the changes introduced by the new entrant data sets.
Owner:GUAVUS NETWORK SYST PVT
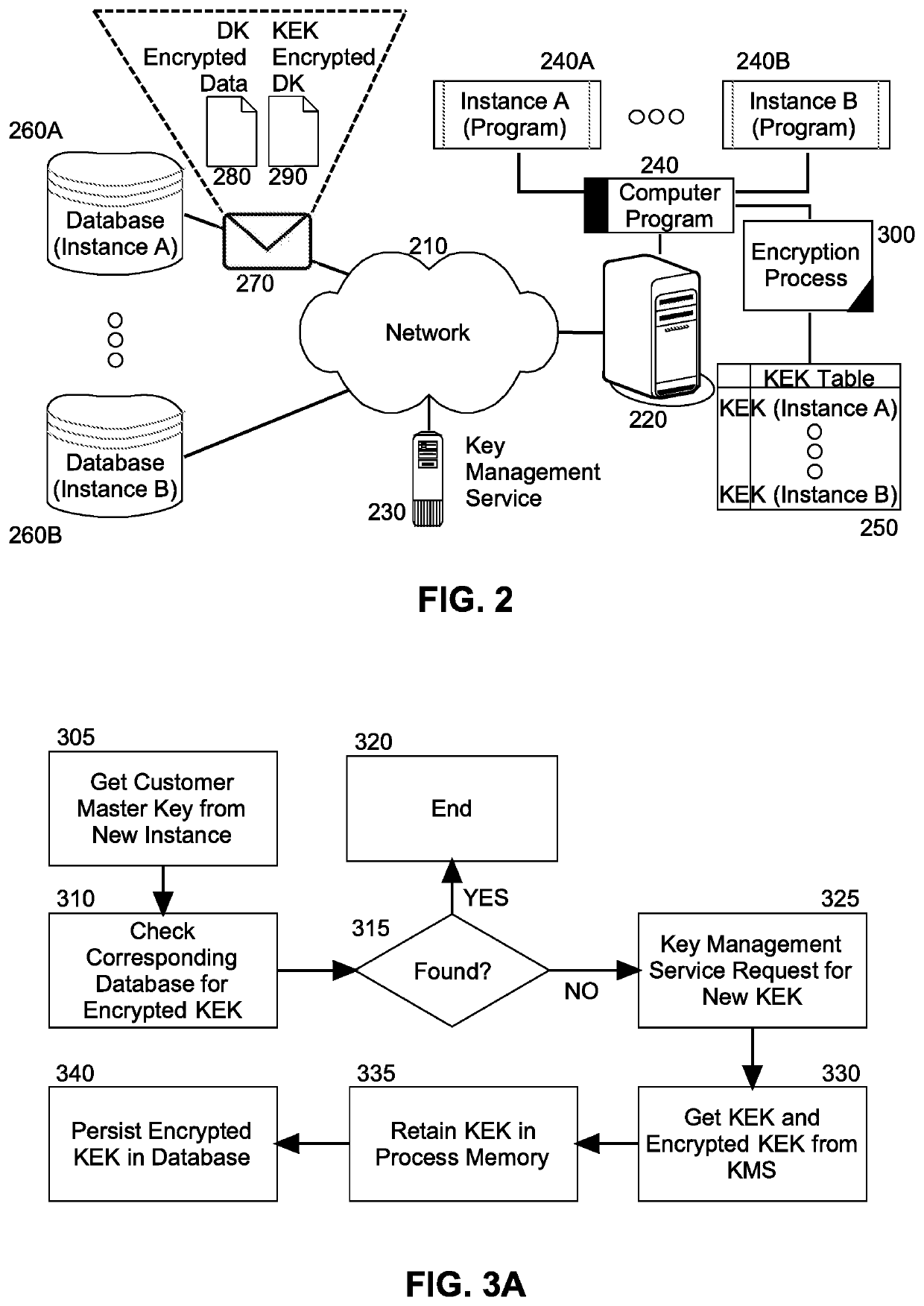
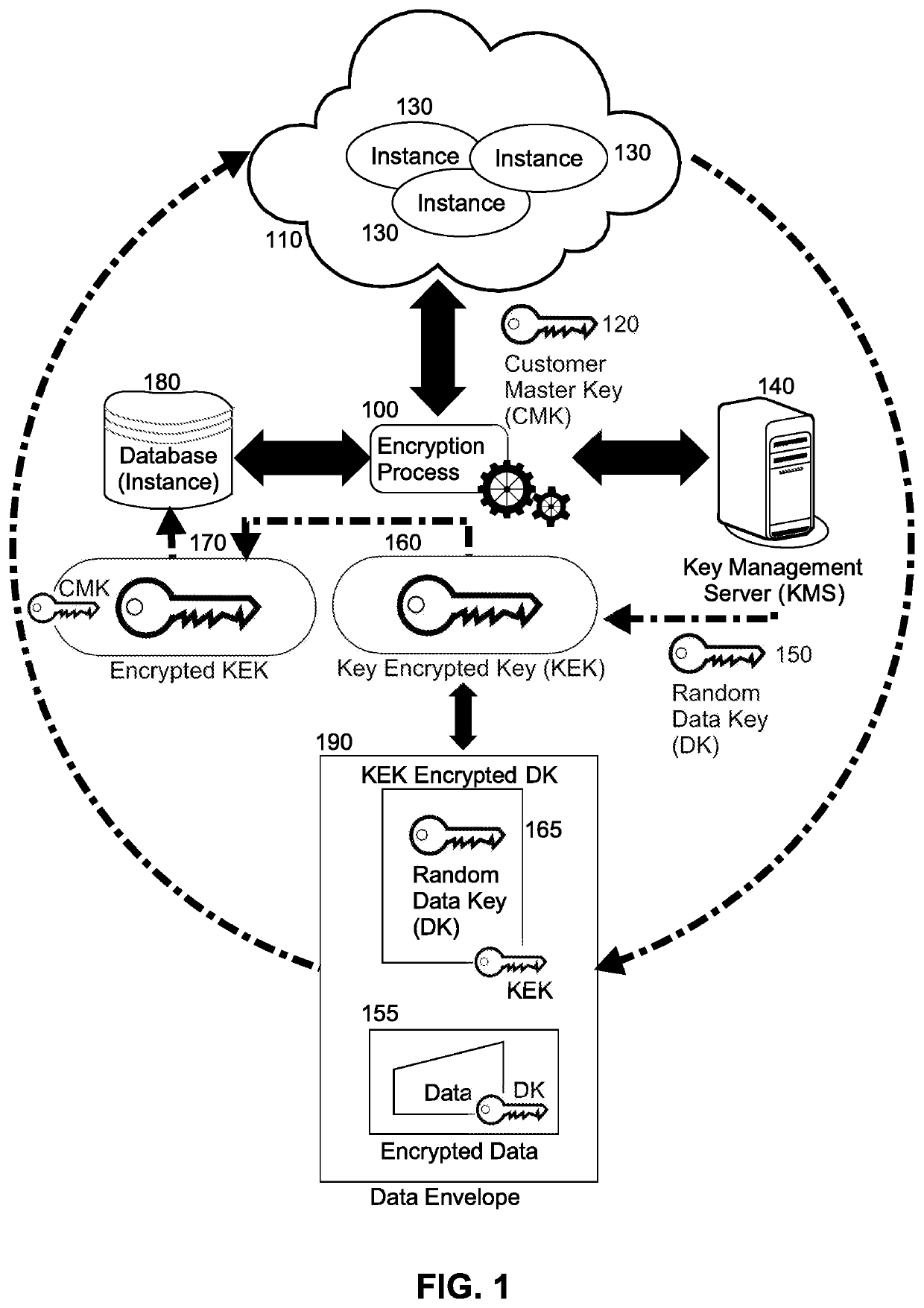
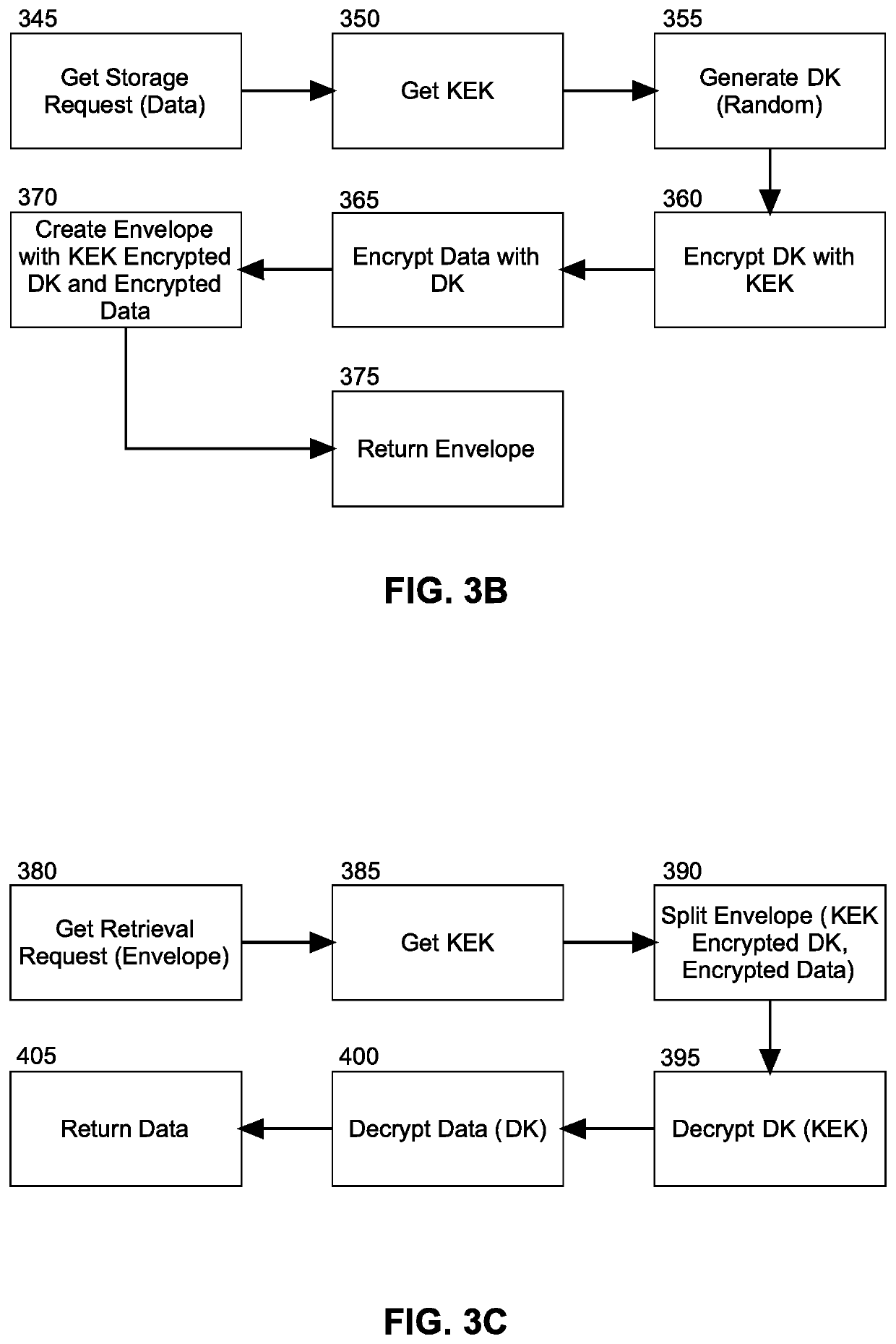
Securing data at rest utilizing cloud provider service agnostic encrypted data transportability
ActiveUS20200195425A1Key distribution for secure communicationMultiple keys/algorithms usageEngineeringTerm memory
Securing at rest data on a cloud hosted server includes, for each cloud hosted instance of a computer program, creating a key encrypted key (KEK) using a unique customer master key (CMK) corresponding to the instance, but only an encrypted form of the KEK is persisted in a database for the corresponding instance whereas the unencrypted KEK is retained in memory of the encryption process only. Thereafter, in response to a request to persist data by a corresponding instance of the computer program, a data key (DK) is randomly generated and encrypted with the KEK in memory for the corresponding instance. The data itself also is encrypted with the DK and an envelope with the encrypted DK and the encrypted data returned to the requestor, thus ensuring that the data and the encryption keys are never moved or persisted in an un-encrypted form.
Owner:GOOGLE LLC
Passwordless security system for data-at-rest
PendingCN111868728AKey distribution for secure communicationPublic key for secure communicationInternet privacyEngineering
The disclosed embodiments relate to a passwordless method for securing data-at-rest. The method includes encrypting and / or decrypting data with a cryptographic key. For example, the encrypted data canbe stored on a non-transitory computer memory of a first device. The method can include generating key shards based on the cryptographic key, which can be reconstituted from the key shards, and distributing the key shards among devices such that the encrypted data is secured at the first device because the first device is incapable of decrypting the encrypted data due to an absence of the cryptographic key.
Owner:阿塔卡玛有限责任公司
Data processing method and device for banking system
The invention discloses a data processing method and device for a banking system, and the method comprises the steps: to-be-processed data is exported in an online subsystem to a batch subsystem afterthe switching of accounting dates; the batch subsystem extracts and obtains T-day data from the to-be-processed data; the batch subsystem performs batch processing on the T-day data to obtain processing result data; and the batch subsystem writes the processing result data back to the online subsystem. .After an accounting day is switched, static data of the day before day cutting is obtained forbatch processing under the uninterrupted online transaction of 7 * 24 hours, and the processing result data is written back to the online subsystem after batch processing, so that the method and thedevice do not bring day cutting time pressure to the system in the data synchronization process, and have good practical application significance.
Owner:BANK OF CHINA
Public cloud data at rest security
ActiveUS8856548B2User identity/authority verificationUnauthorized memory use protectionData operationsService provision
An encryption switch which is used in a cloud environment to secure data on the LUNs used by the clients. A client provides a certificate to the cloud service. The encryption switch develops a cloud crypto domain (CCD) as a secure area, with the data at rest on the LUNs encrypted. The encryption switch develops a master key for client use in the CCD, which is provided to the client encrypted by the client's public key. Data encryption keys (DEKs) are created for each LUN and provided to the client. The DEKs are stored in a key vault by the client for use if needed. The cloud service provisions a client VM to be used with the encrypted LUN and develops a nexus between the LUN and the client VM for the encryption switch to use in data operations. The client communicates through the client VM to access the LUN.
Owner:AVAGO TECH INT SALES PTE LTD
Action posture storage method and device, medium and electronic equipment
PendingCN114331808ASave storage resourcesReduce read resourcesDigital data information retrievalImage memory managementAnimationEngineering
The invention discloses an action posture storage method and device, a medium and electronic equipment. The action posture storage method comprises the following steps: establishing a first basic storage area, a second basic storage area and an association relationship between the first basic storage area and the second storage area; obtaining a current animation video stream in a predetermined format; forming each piece of skeletal animation data matched with the current animation video stream according to the current animation video stream; the basic picture in the preset format is formed according to the animation skeleton data and stored in the second basic storage area, and the animation skeleton data are arranged in a preset range. According to the action posture storage method and device, the medium and the electronic equipment, the preset format basic picture is formed according to each piece of skeleton data and is stored in the second basic storage area, and each preset format basic picture stores animation information of all time points of one skeleton. Dynamic data with changes are reserved, static data are deleted, and storage resources are saved.
Owner:米哈游科技(上海)有限公司
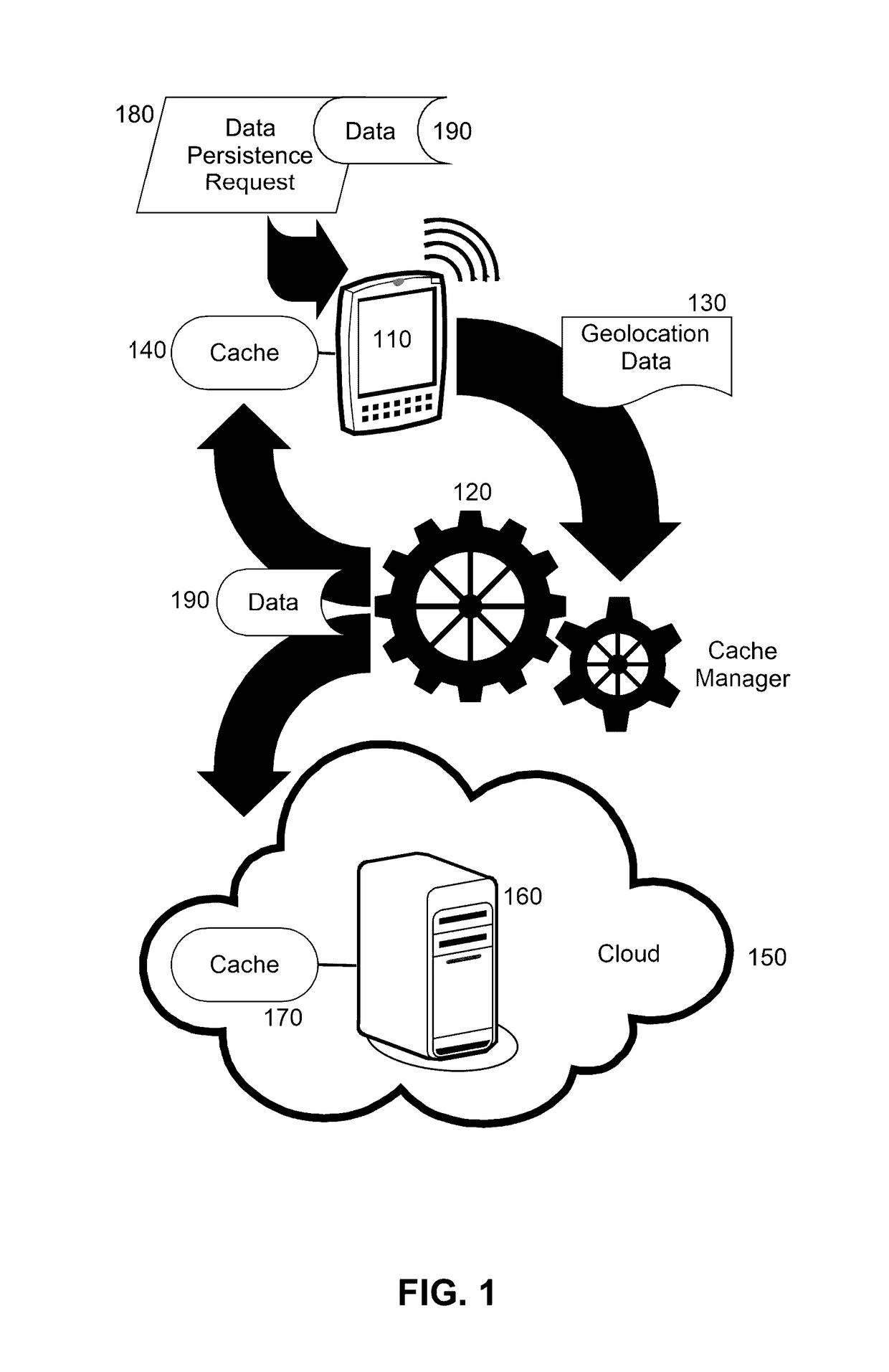
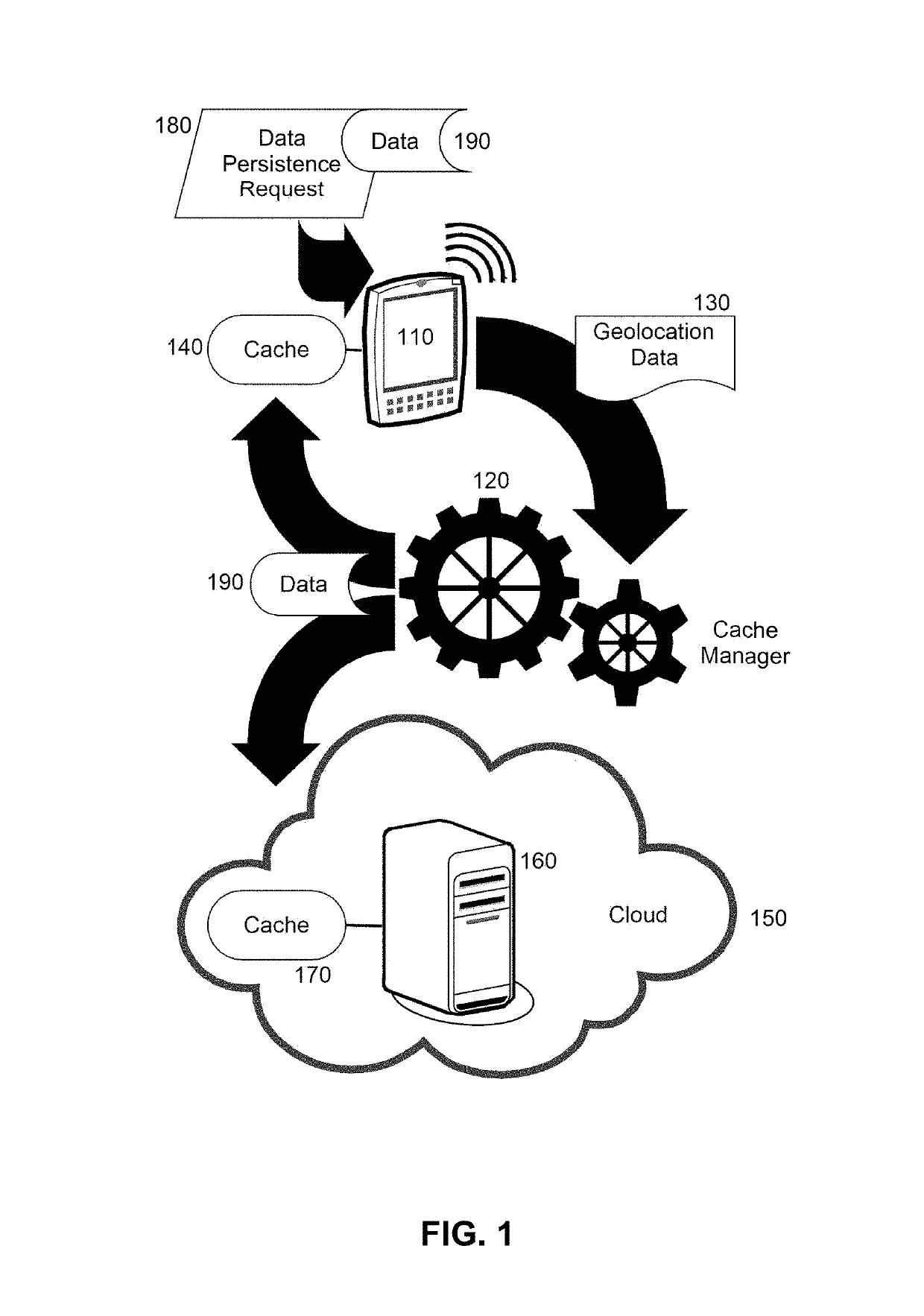
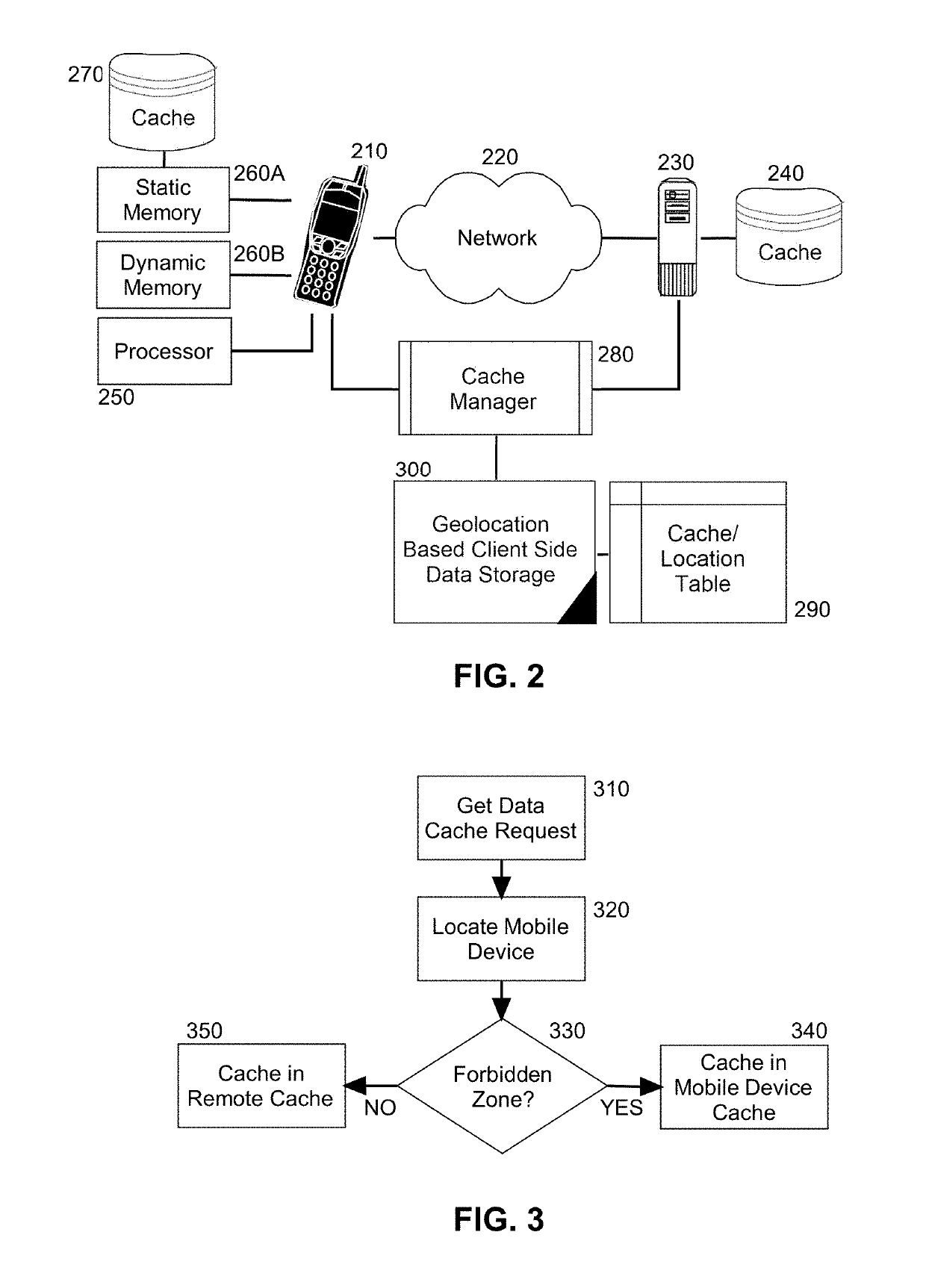
Limiting client side data storage based upon client geo-location
Embodiments of the present invention provide a method, system and computer program product for limiting client side data storage based upon client geolocation. In an embodiment of the invention, a method for the differentiated treatment of data at rest in a mobile device includes receiving in a cache manager a request to cache data in a cache of a mobile device. Also, a geolocation for the mobile device is retrieved contemporaneous with the receipt of the request. Thereafter, it is determined from the geolocation whether or not the mobile device is present within a restricted geographic zone. Finally, in response to determining that the mobile device is present within a restricted geographic zone, the cache manager is directed to cache the data in a cache in the mobile device. But, otherwise the cache manager is directed to cache the data in a cache disposed in the computer communications network.
Owner:IBM CORP
Limiting client side data storage based upon client geo-location
Embodiments of the present invention provide a method, system and computer program product for limiting client side data storage based upon client geolocation. In an embodiment of the invention, a method for the differentiated treatment of data at rest in a mobile device includes receiving in a cache manager a request to cache data in a cache of a mobile device. Also, a geolocation for the mobile device is retrieved contemporaneous with the receipt of the request. Thereafter, it is determined from the geolocation whether or not the mobile device is present within a restricted geographic zone. Finally, in response to determining that the mobile device is present within a restricted geographic zone, the cache manager is directed to cache the data in a cache in the mobile device. But, otherwise the cache manager is directed to cache the data in a cache disposed in the computer communications network.
Owner:IBM CORP
Passenger elevator entering key failure fault identification method
ActiveCN112919278AProcessing speedHigh precisionElevatorsSustainable buildingsKey pressingData at Rest
The invention relates to a passenger elevator entering key failure fault identification method. The method comprises the steps that S1, door state data, person existence data, running static data and elevator video data of an elevator are collected; S2, elevator key fault time periods are obtained according to the door state data, the person existence data and the operation static data; and S3, elevator video data corresponding to the elevator key fault time periods are selected, non-elevator key fault filtering is carried out, and finally whether elevator key faults exist or not is output. According to the passenger elevator entering key failure fault identification method, the failure fault of the elevator key can be effectively identified, the identification speed is high, and the precision is high.
Owner:ZHEJIANG NEW ZAILING TECH CO LTD
Securing data at rest utilizing cloud provider service agnostic encrypted data transportability
ActiveUS11310035B2Key distribution for secure communicationMultiple keys/algorithms usageEngineeringTerm memory
Securing at rest data on a cloud hosted server includes, for each cloud hosted instance of a computer program, creating a key encrypted key (KEK) using a unique customer master key (CMK) corresponding to the instance, but only an encrypted form of the KEK is persisted in a database for the corresponding instance whereas the unencrypted KEK is retained in memory of the encryption process only. Thereafter, in response to a request to persist data by a corresponding instance of the computer program, a data key (DK) is randomly generated and encrypted with the KEK in memory for the corresponding instance. The data itself also is encrypted with the DK and an envelope with the encrypted DK and the encrypted data returned to the requestor, thus ensuring that the data and the encryption keys are never moved or persisted in an un-encrypted form.
Owner:GOOGLE LLC
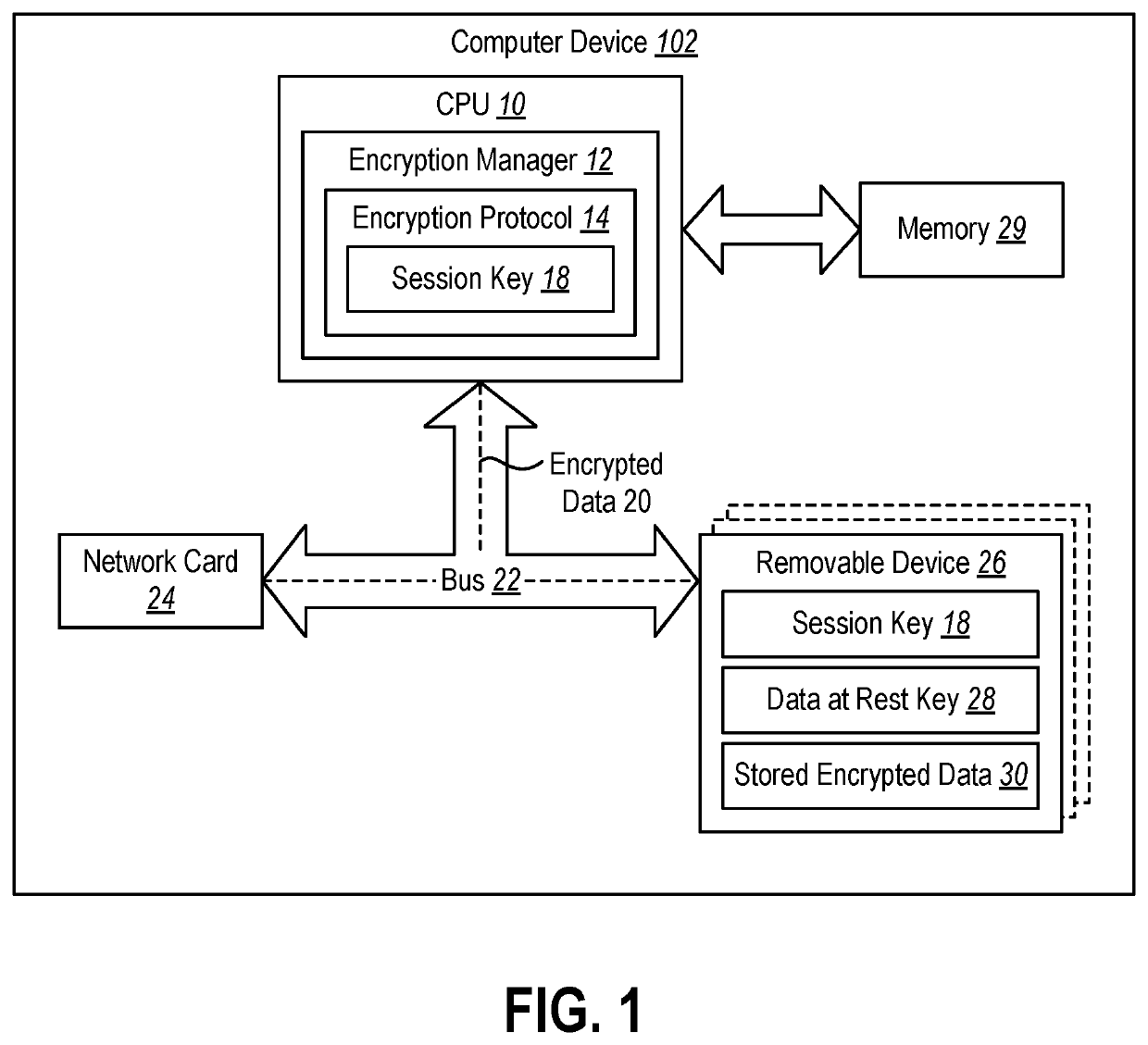
Protecting device detachment with bus encryption
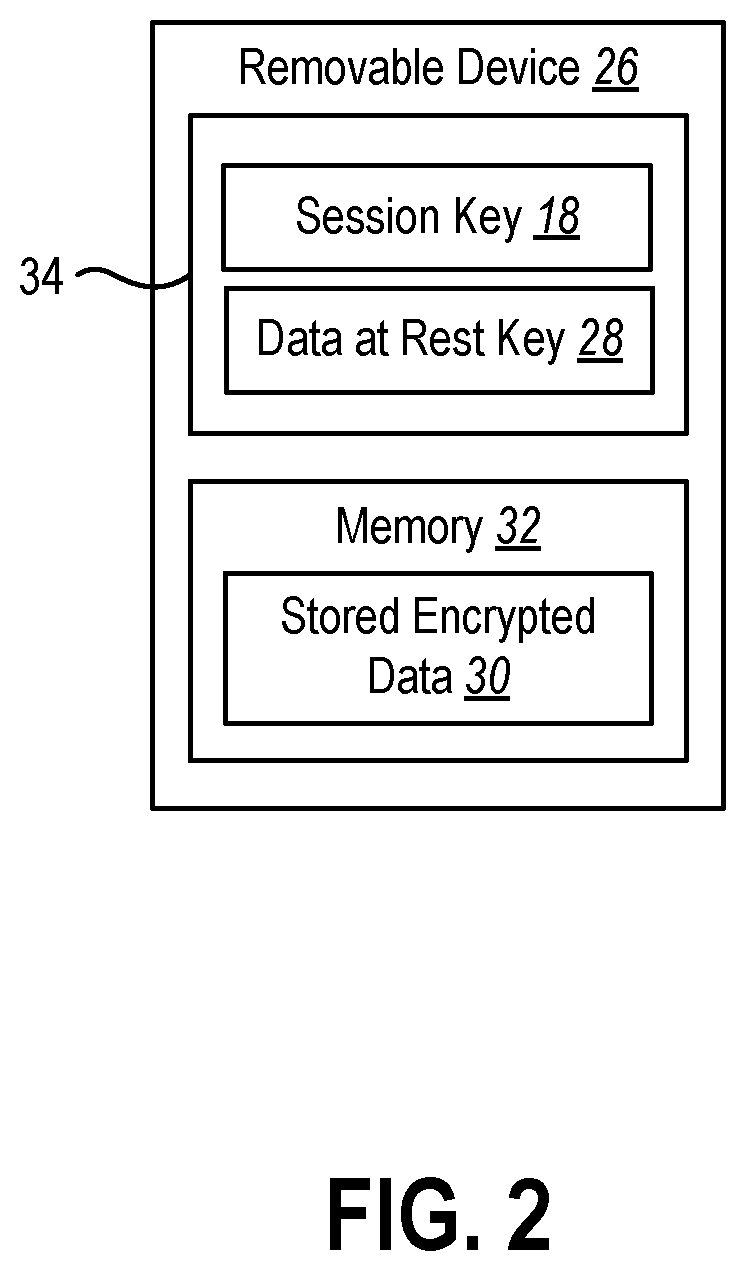
PendingUS20210264064A1Well formedKey distribution for secure communicationMultiple keys/algorithms usageAttackBus encryption
The present disclosure relates to devices and methods for protecting data from physical attacks. The devices and methods may establish an encryption protocol to encrypt data transmitted over a bus to one or more removable devices in communication with a computer device. The devices and methods may use the encryption protocol to communicate with the removal devices and perform storage requests at the removal devices. The devices and methods may also perform another layer of encryption on the data stored at the removal devices using a data at rest key stored on the removal devices.
Owner:MICROSOFT TECH LICENSING LLC
Data-at-rest (DAR) encryption for integrated storage media
ActiveCN107688750AImprove throughputConvenient timeMemory architecture accessing/allocationDigital data protectionHost controller interfaceEngineering
An improved system for providing transparent, in-line encryption of data-at-rest (DAR) stored by a host controller of a host device. An encryption core is instantiated in a hardware device physicallycoupled to a system board within the host device. The encryption core includes a storage device proxy, an encryption engine, and a plurality of host device proxies. Each host proxy among the pluralityof host proxies interfaces the host controller to one persistent storage device among a plurality of persistent storage devices within the host device via the storage device proxy. The storage deviceproxy exposes the plurality of persistent storage devices to the host controller as a single persistent storage device. The encryption core encrypts and decrypts DAR exchanged between the host controller and an encrypted storage device.
Owner:THE BOEING CO
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com