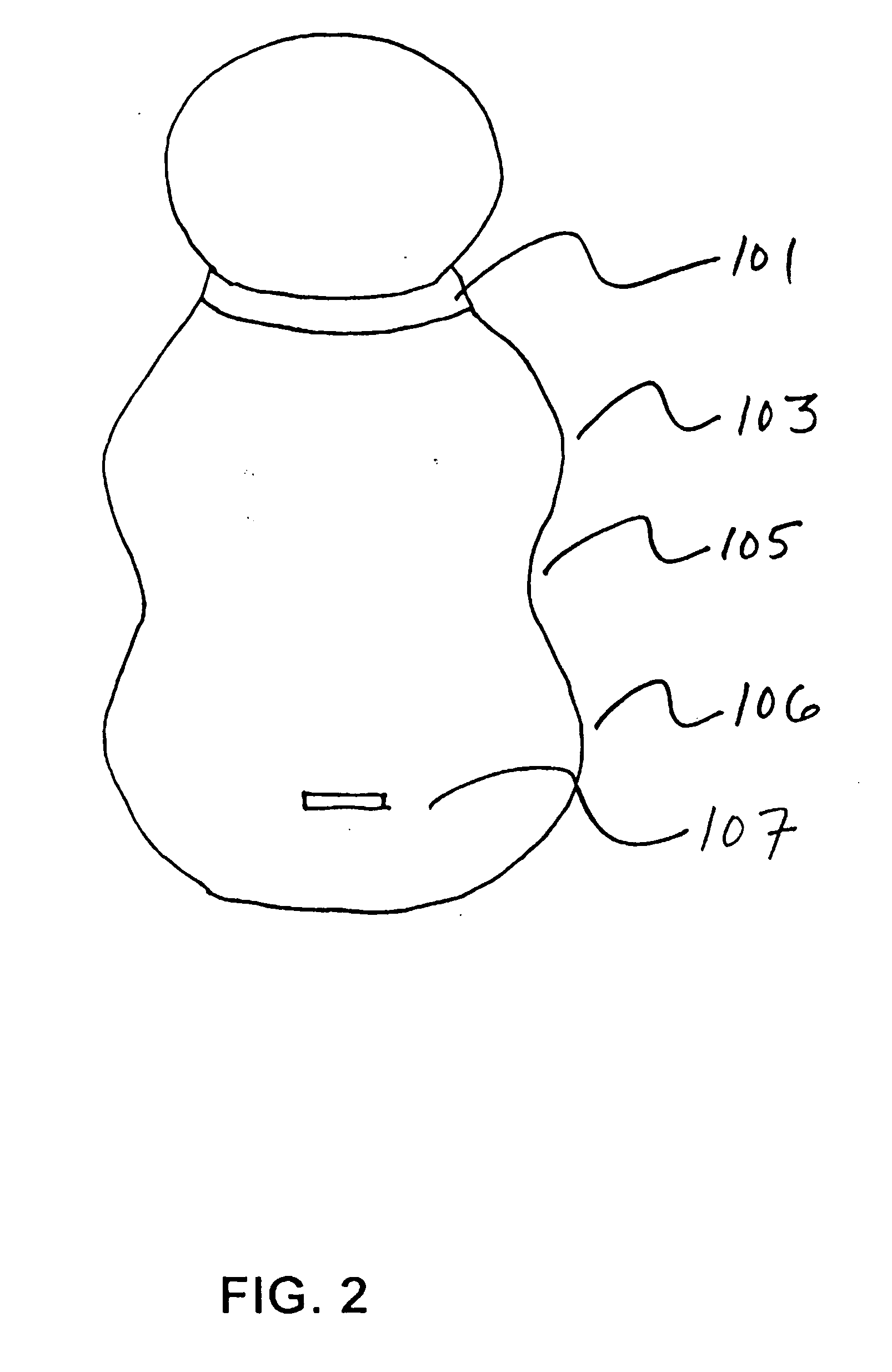Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
219results about How to "Maximum safety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
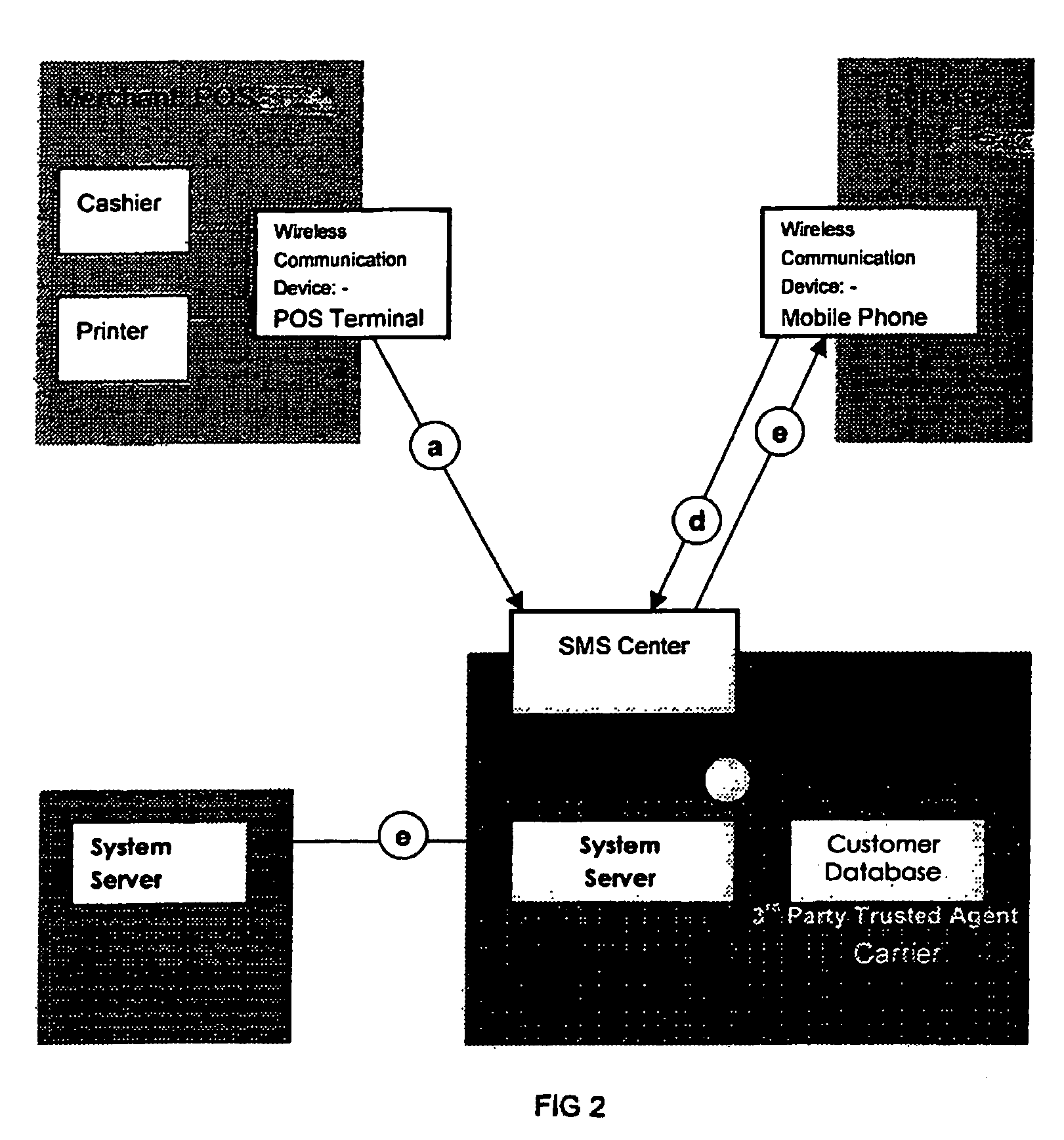
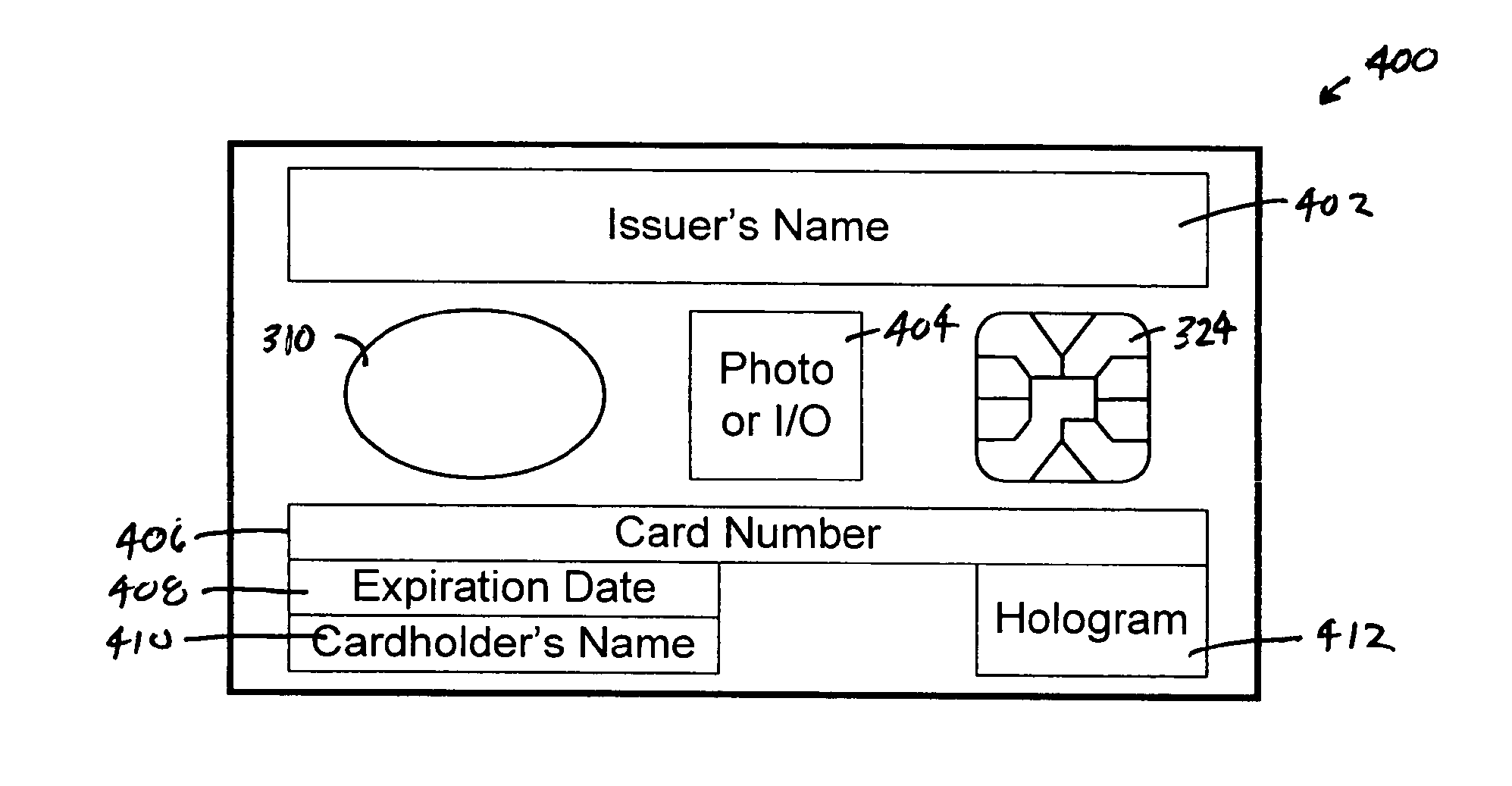
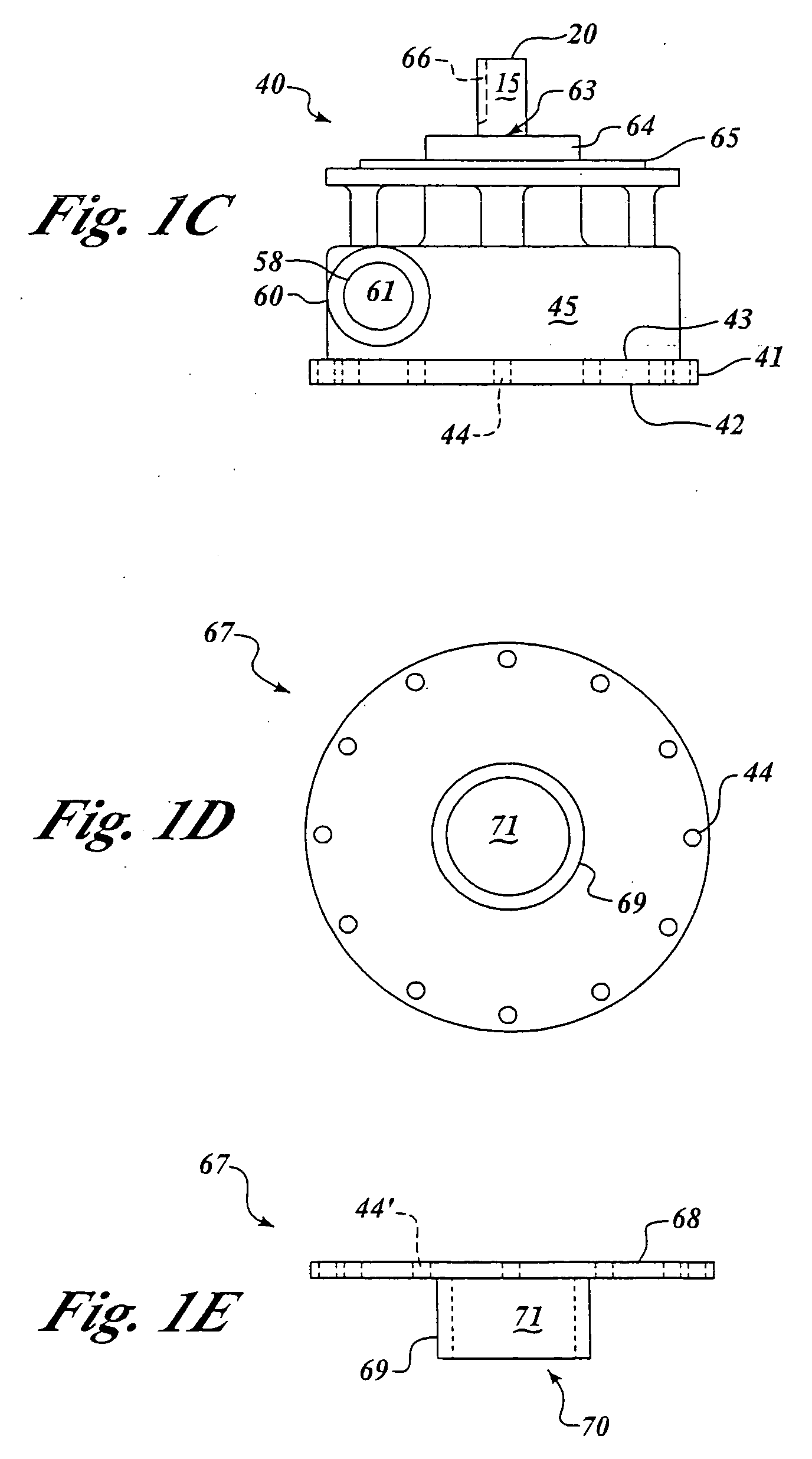
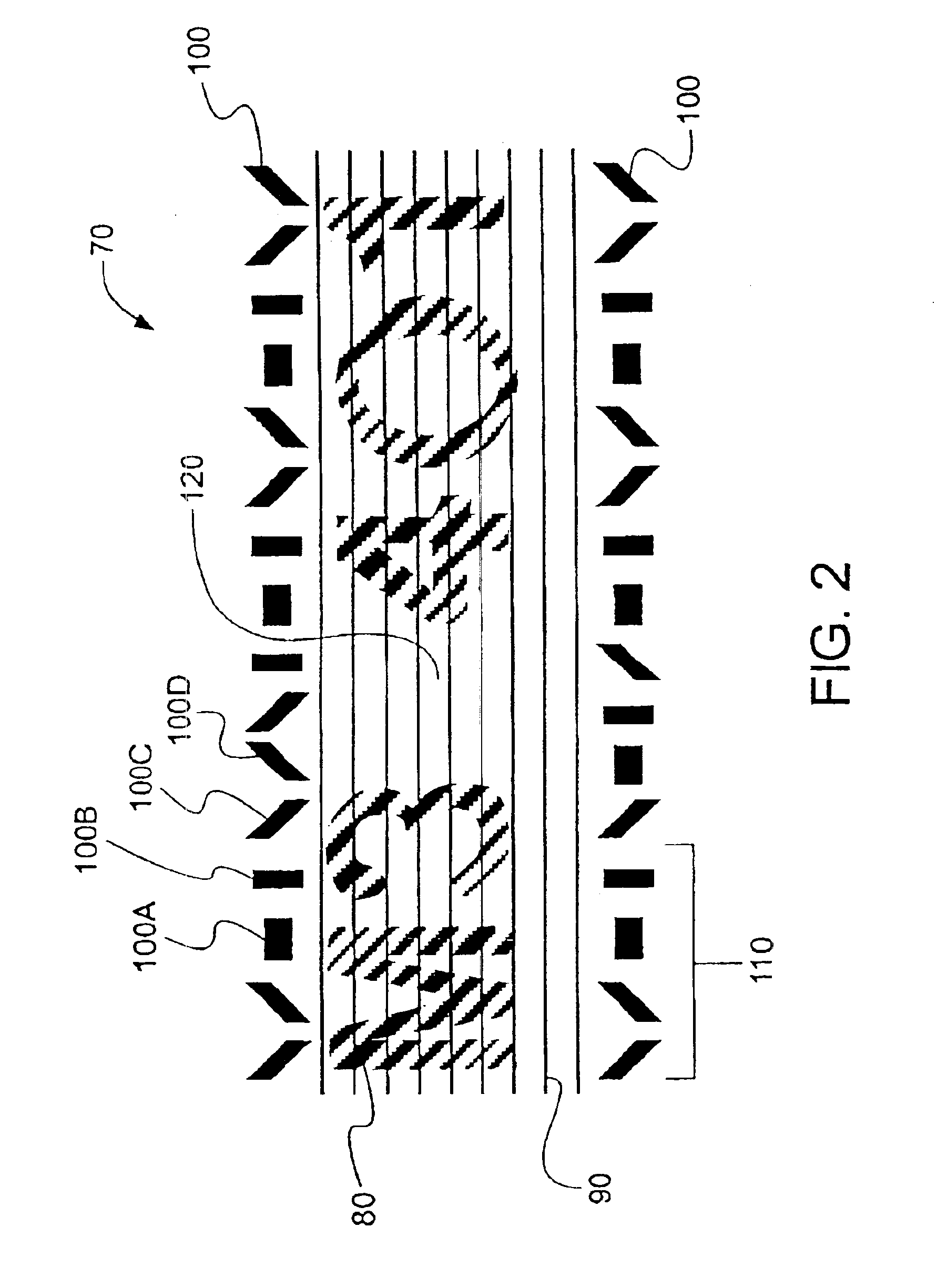
System, method and apparatus for electronic ticketing
InactiveUS20050001711A1Reduce riskMaximum safetyElectric signal transmission systemsDigital data processing detailsInternet privacySystems approaches
The present invention provides a system, method and apparatus for securely granting access to an event. For example, in one embodiment of the present invention, an apparatus, such as an electronic card, ticket or information carrier, contains biometric data about a user. When the “ticket” is purchased or authenticated, event access information is stored on the electronic card or ticket by an entity authorized by the event provider. The user is allowed access to the event when the biometric data stored on the electronic card or ticket matches the user's biometric data and the event access information is validated. The user's biometric data is authenticated via a biometric sensor on the electronic card or ticket. The user's biometric data can also be authenticated by the entity granting access to the event.
Owner:INNOVATION CONNECTION CORP
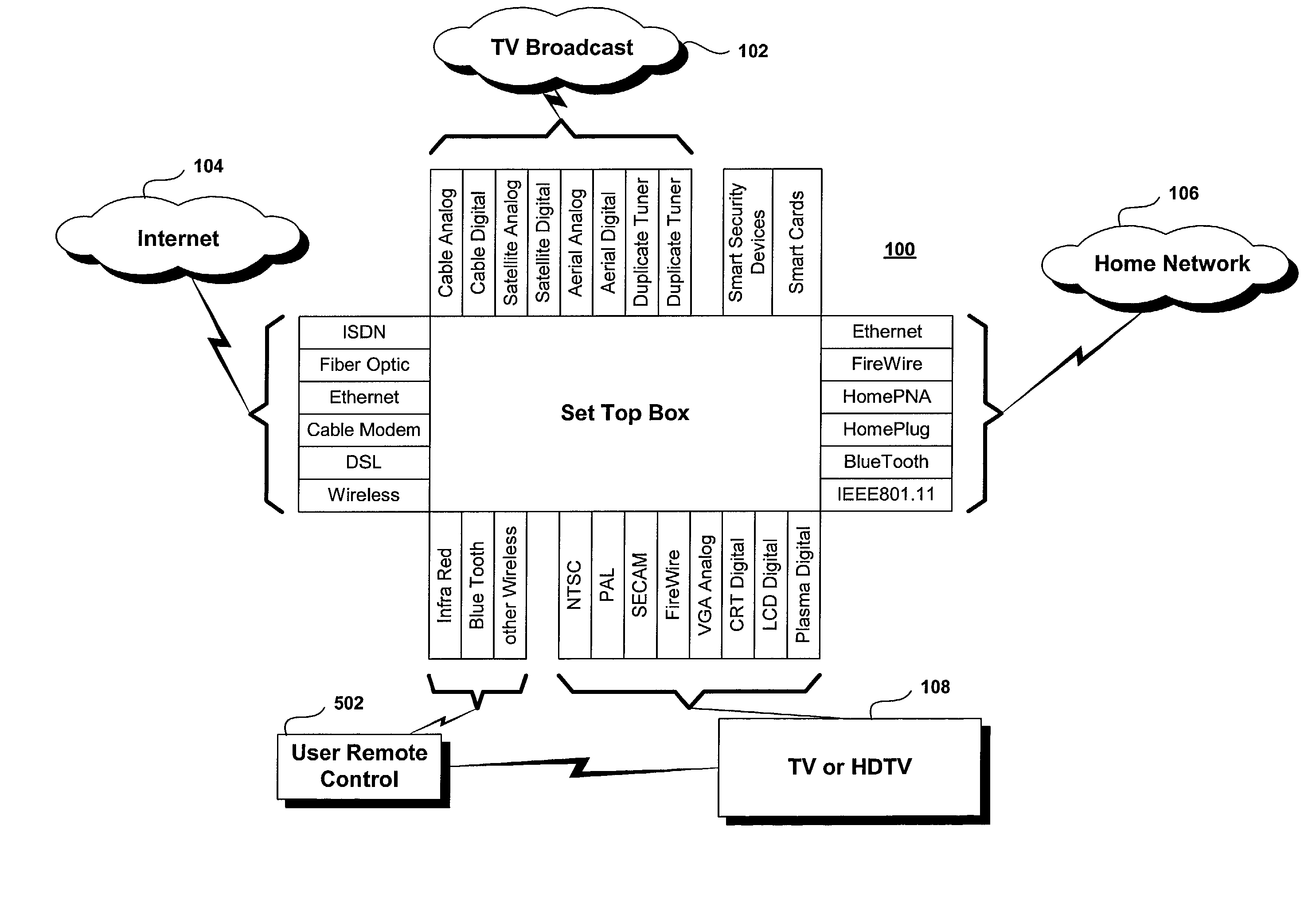
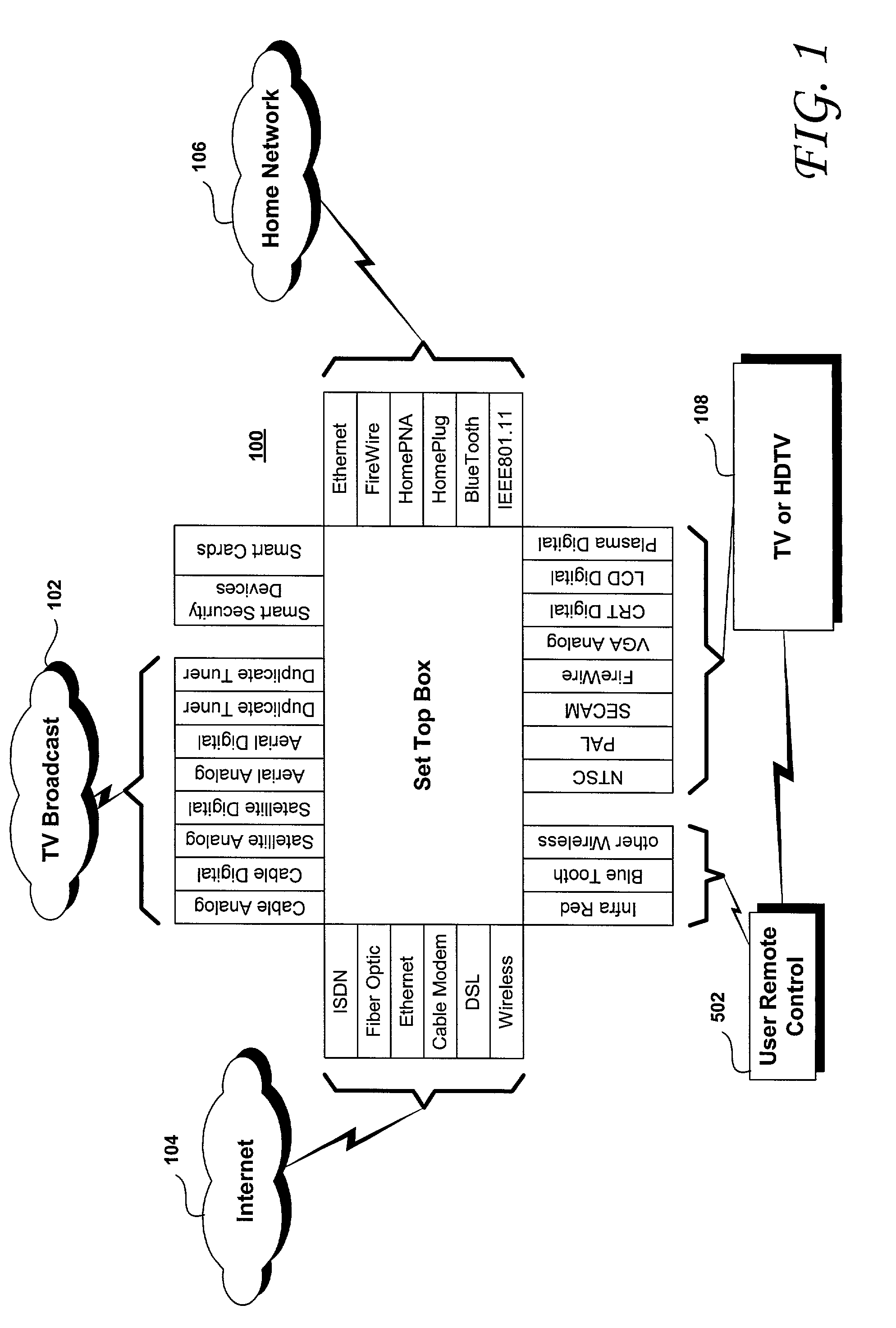
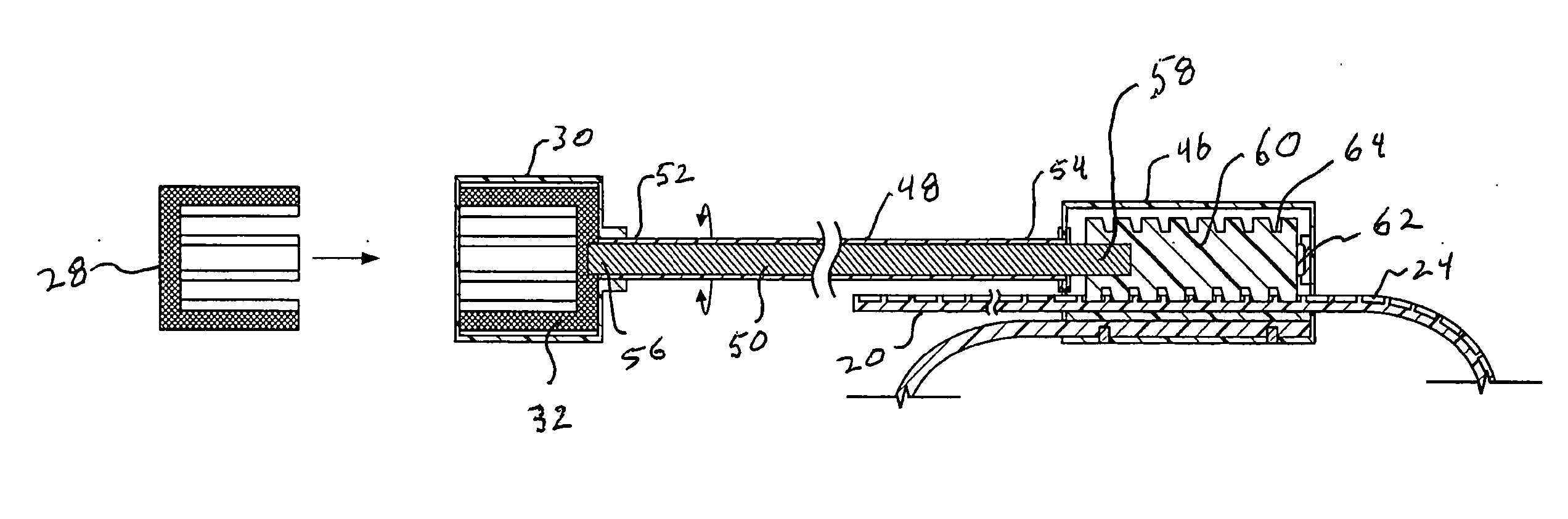
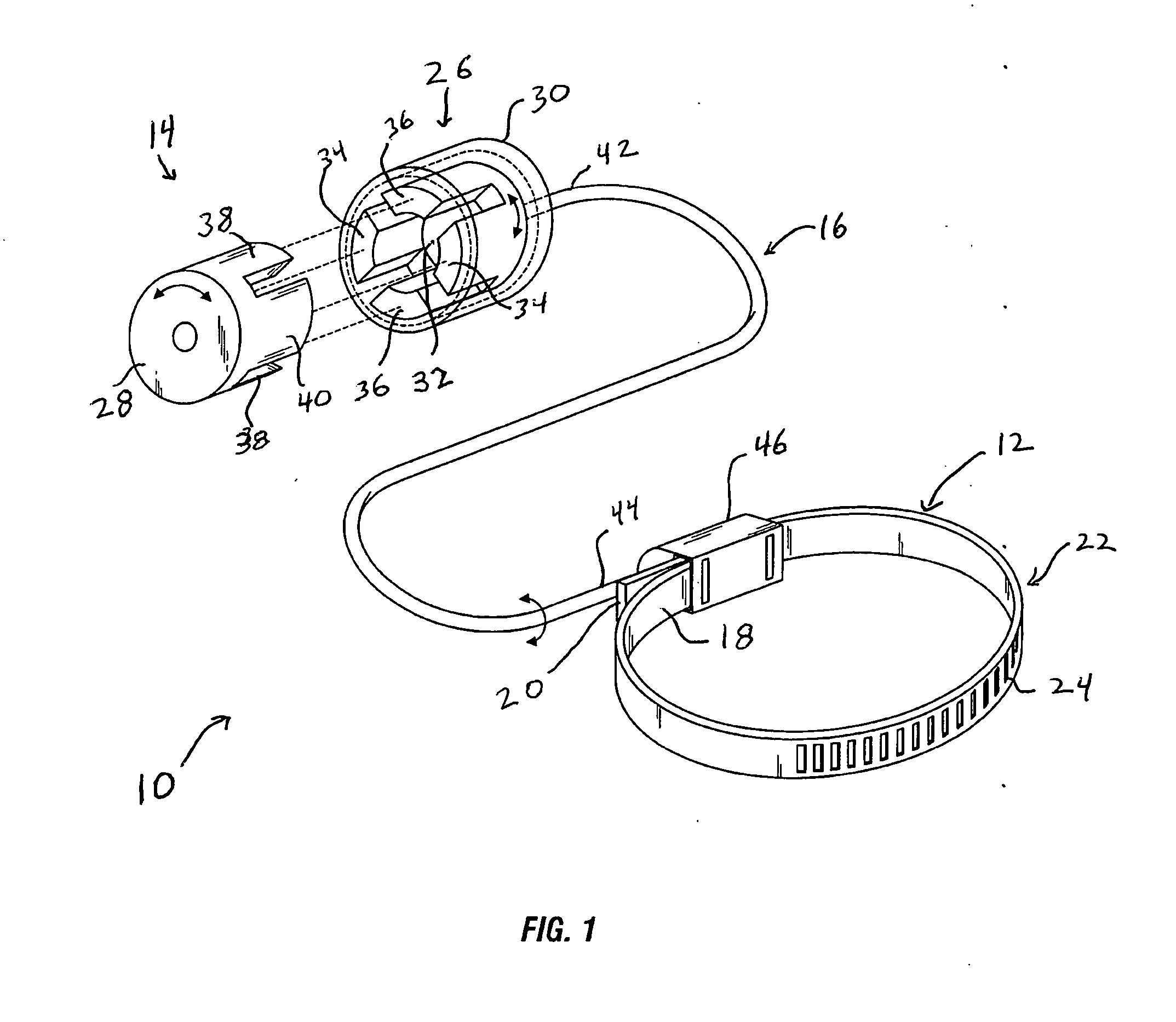
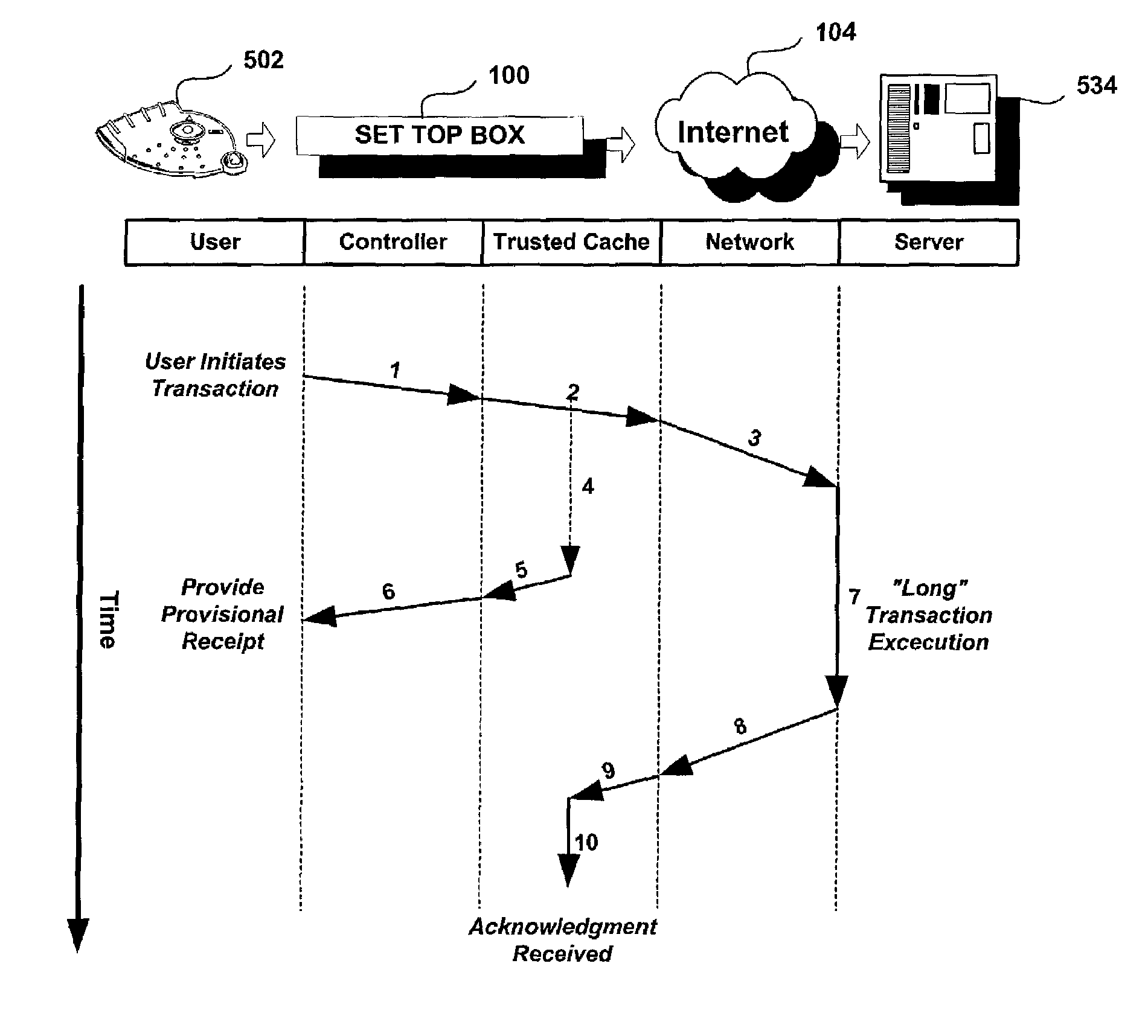
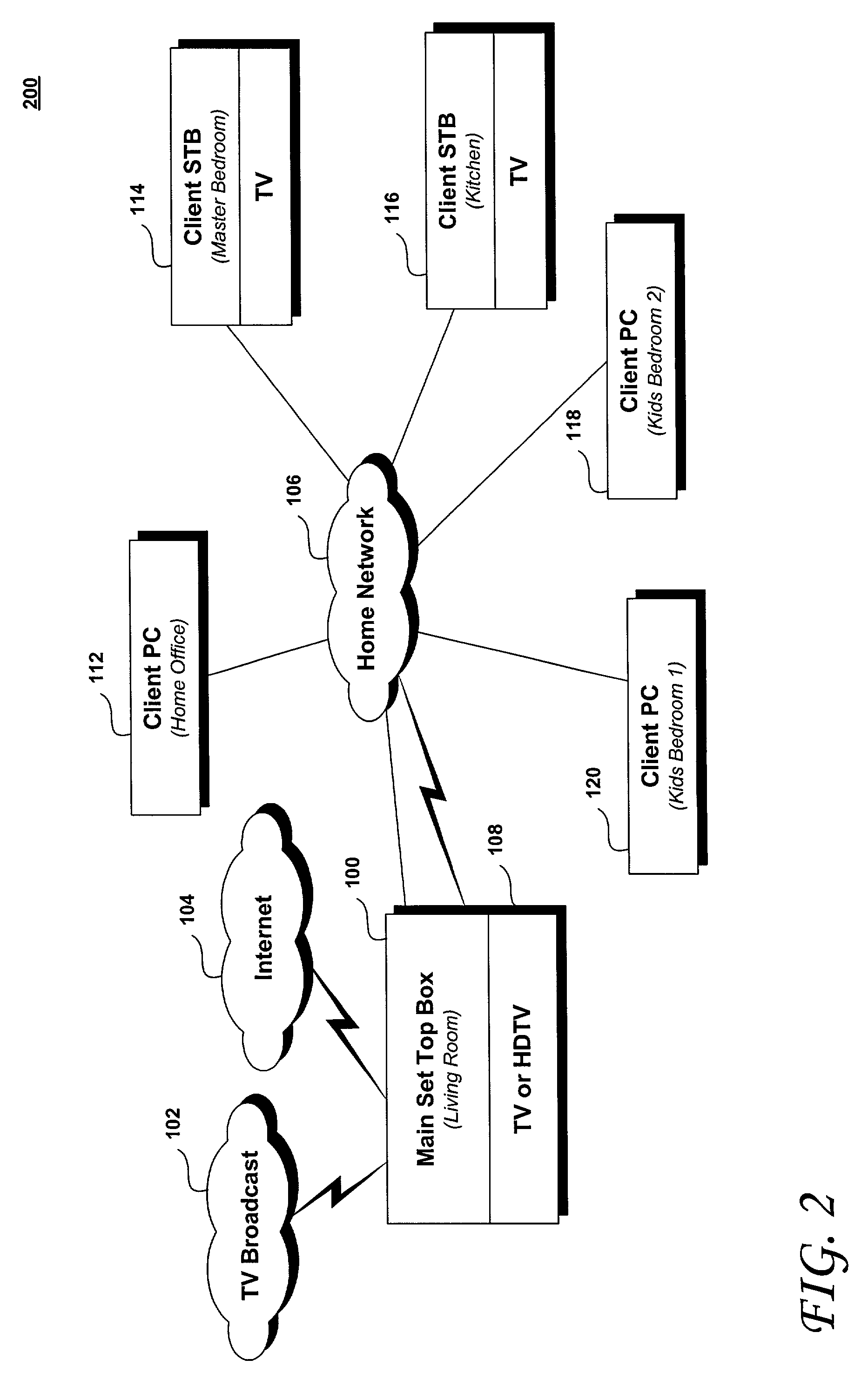
Trusted transactional set-top box
InactiveUS20020174444A1Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsTransactional memorySet top box
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
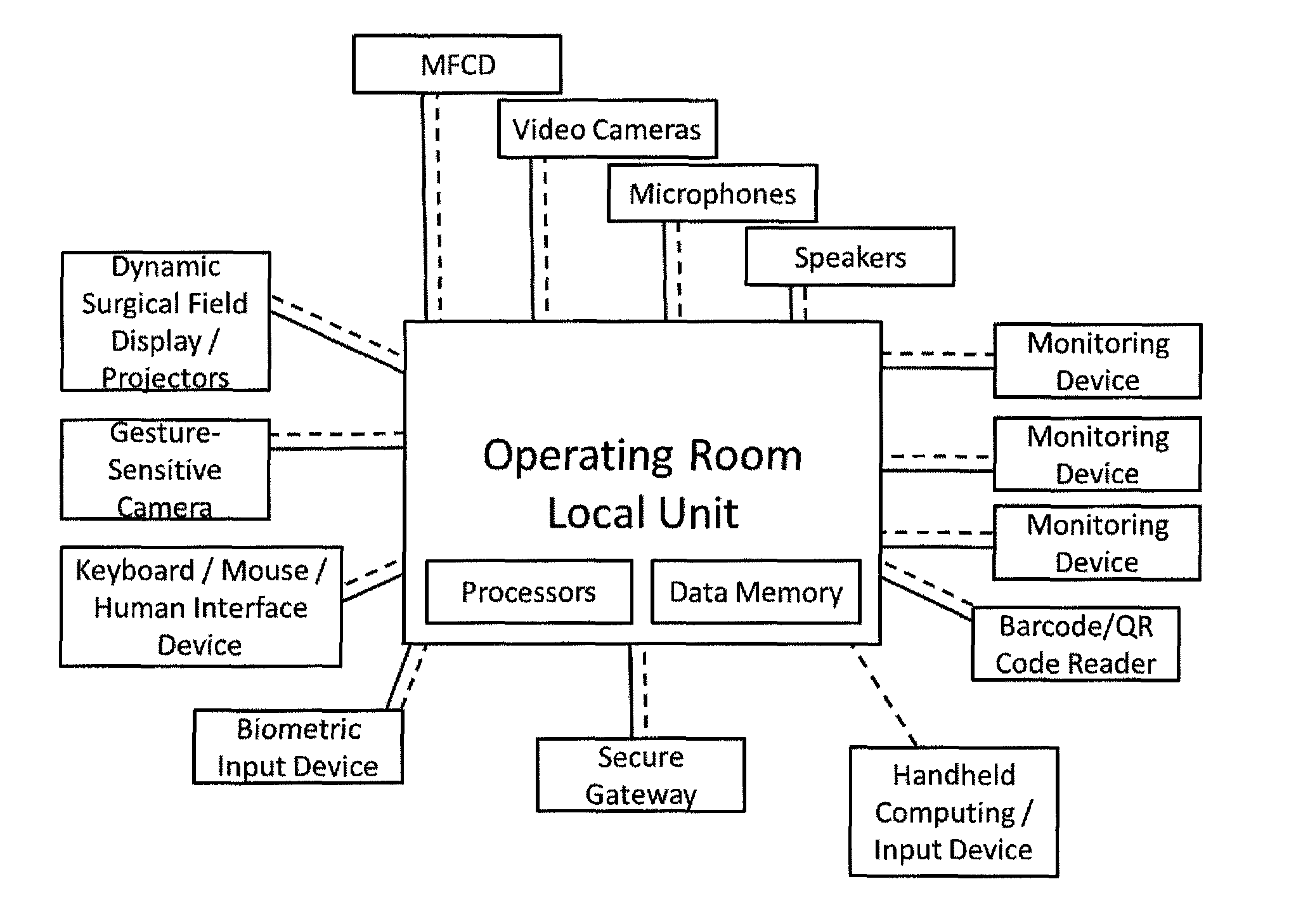
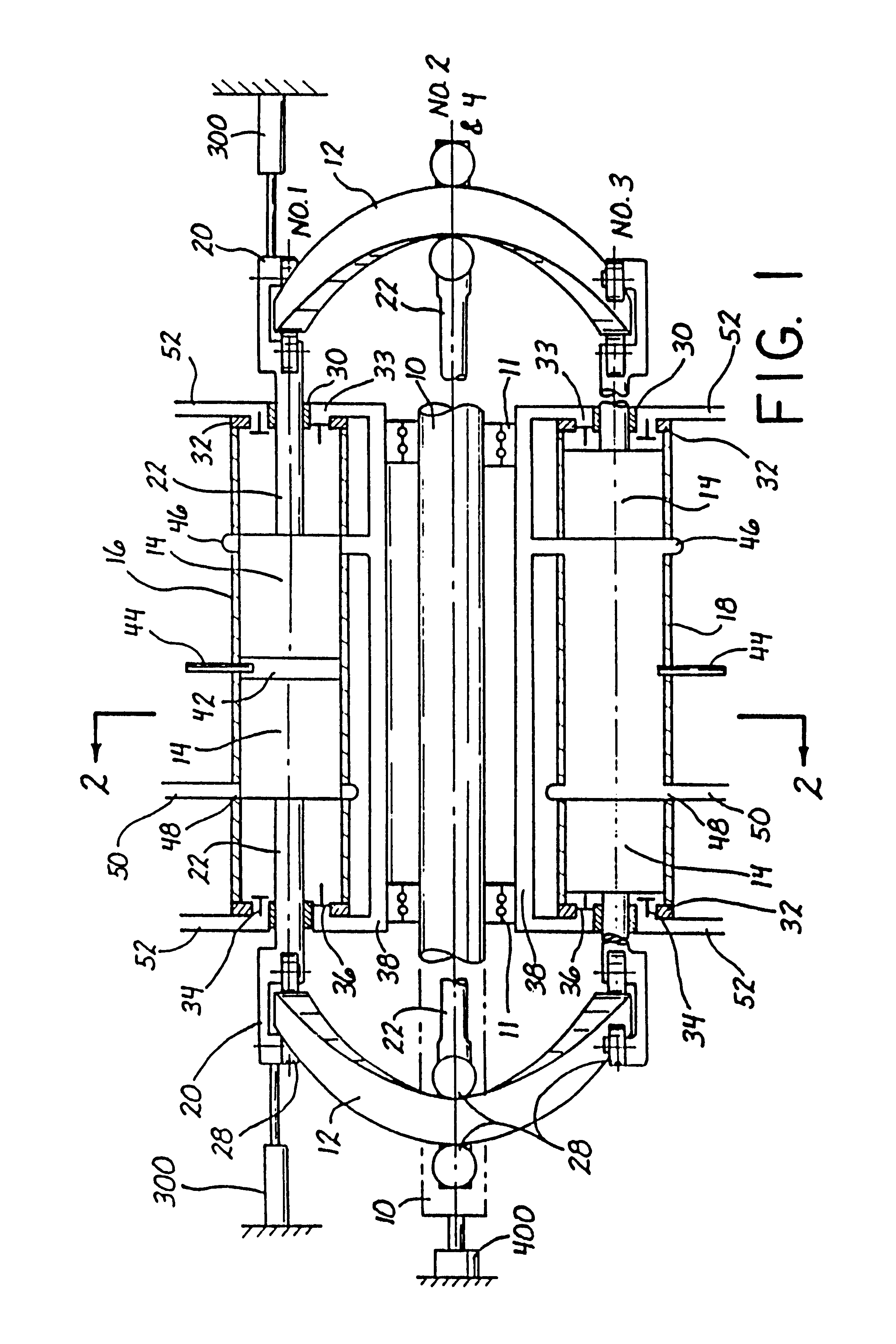
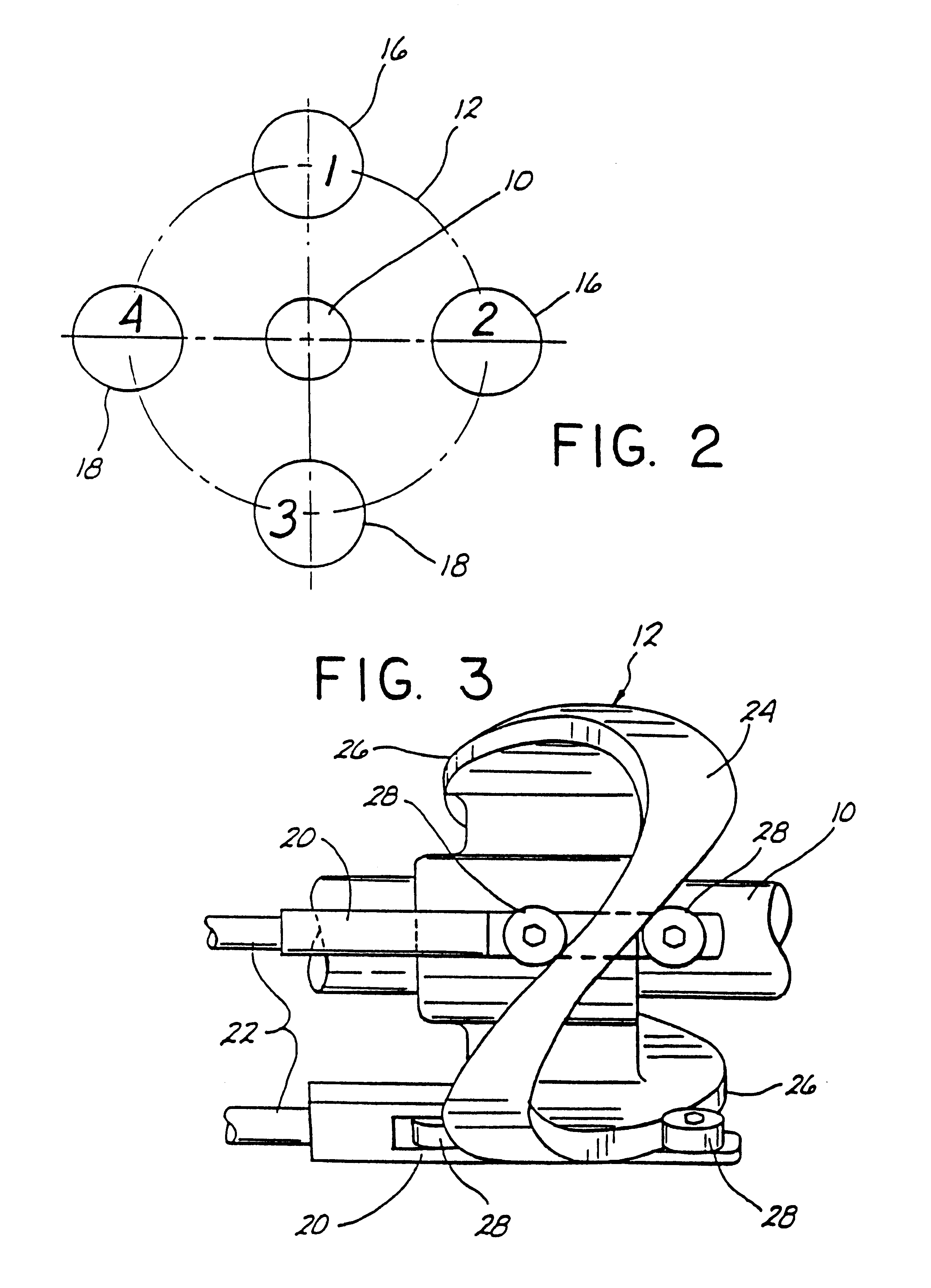
Consolidated healthcare and resource management system
ActiveUS8930214B2Reduce in quantityImprove efficiencySurgical systems user interfaceOffice automationResource Management SystemThe Internet
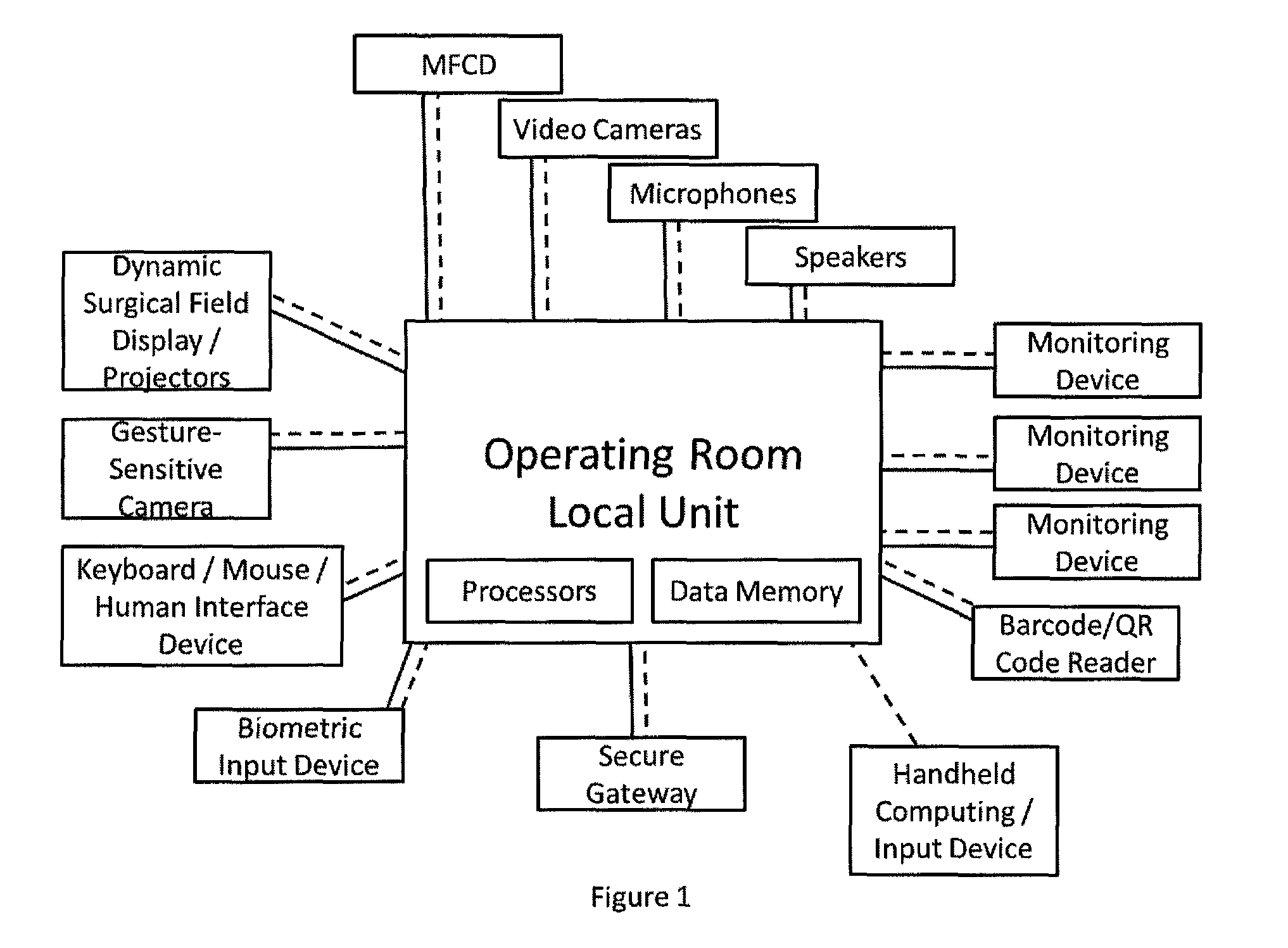
A technical procedure and information enhancement system comprising a multi-function colored display; a computing device having memory and processors; a touch-free gesture-responsive computer input device; computer-readable media containing computer instructions for displaying a plurality of electronic pages selected from the group consisting of a pre-procedural page, a procedure preparation page, an intra-procedural page and a post-procedural page; connection to the internet; a backup memory; a microphone; one or more video cameras situated to record the medical procedure, speakers, and an electronic signature pad.
Owner:PARALLAX ENTERPRISES
Secure File Drawer and Safe
ActiveUS20130198521A1Improve securityReduce riskMultiple keys/algorithms usagePublic key for secure communicationClient-sideOnline document
An online file storage system having secure file drawer and safe is disclosed for securely storing and sharing confidential files. The system comprises a web-based user interface, tools for setting up server-side encryption method and client-side encryption method, tools for synchronizing encryption between different computers, tools for uploading files, tools for tracking files, tools for granting the right of access to files to the owner of other safes, and tools for generating authenticity certificate for proving the upload time and the substance of the files in a future time.
Owner:WU JIANQING
System and method for facilitating electronic financial transactions using a mobile telecommunication device
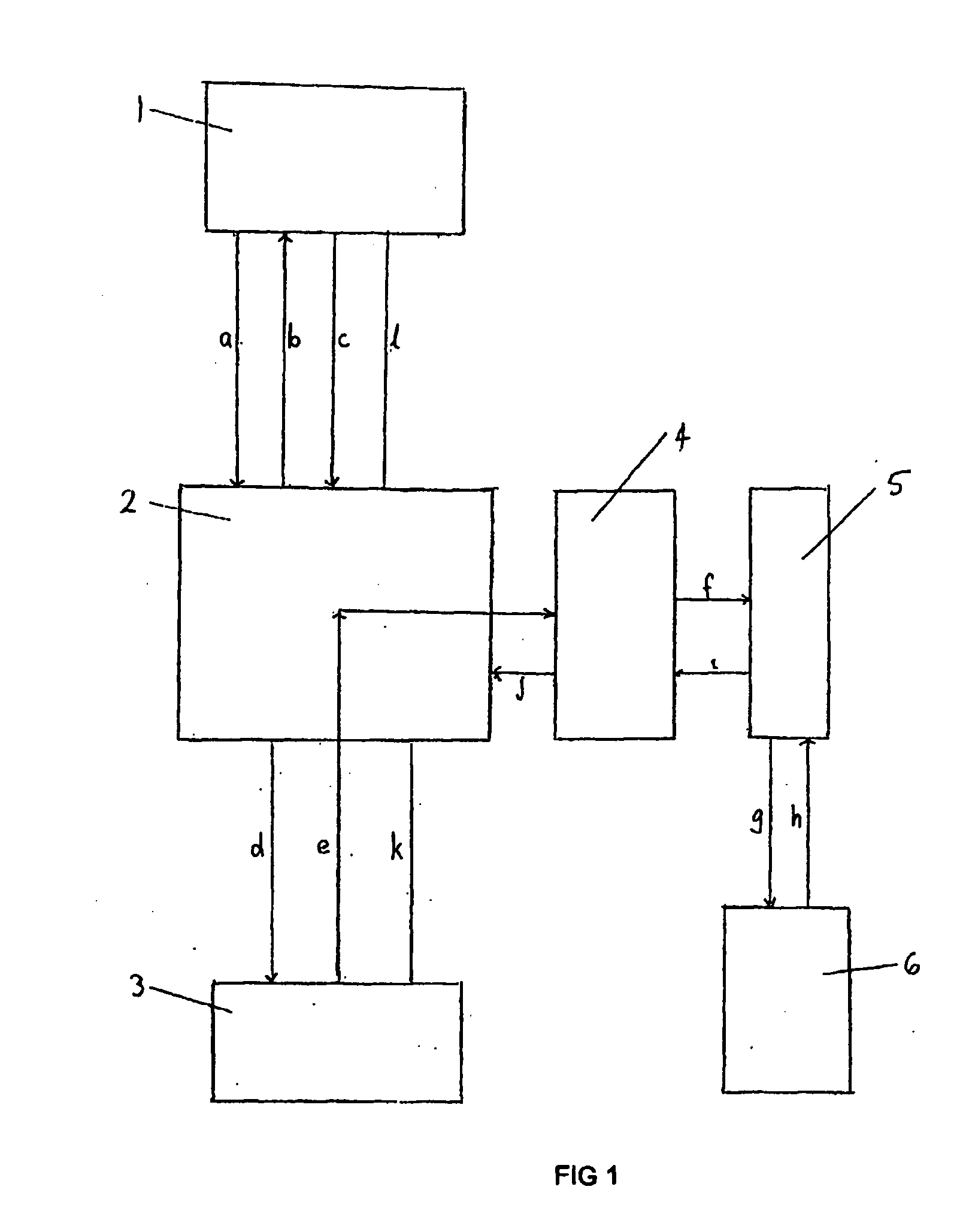
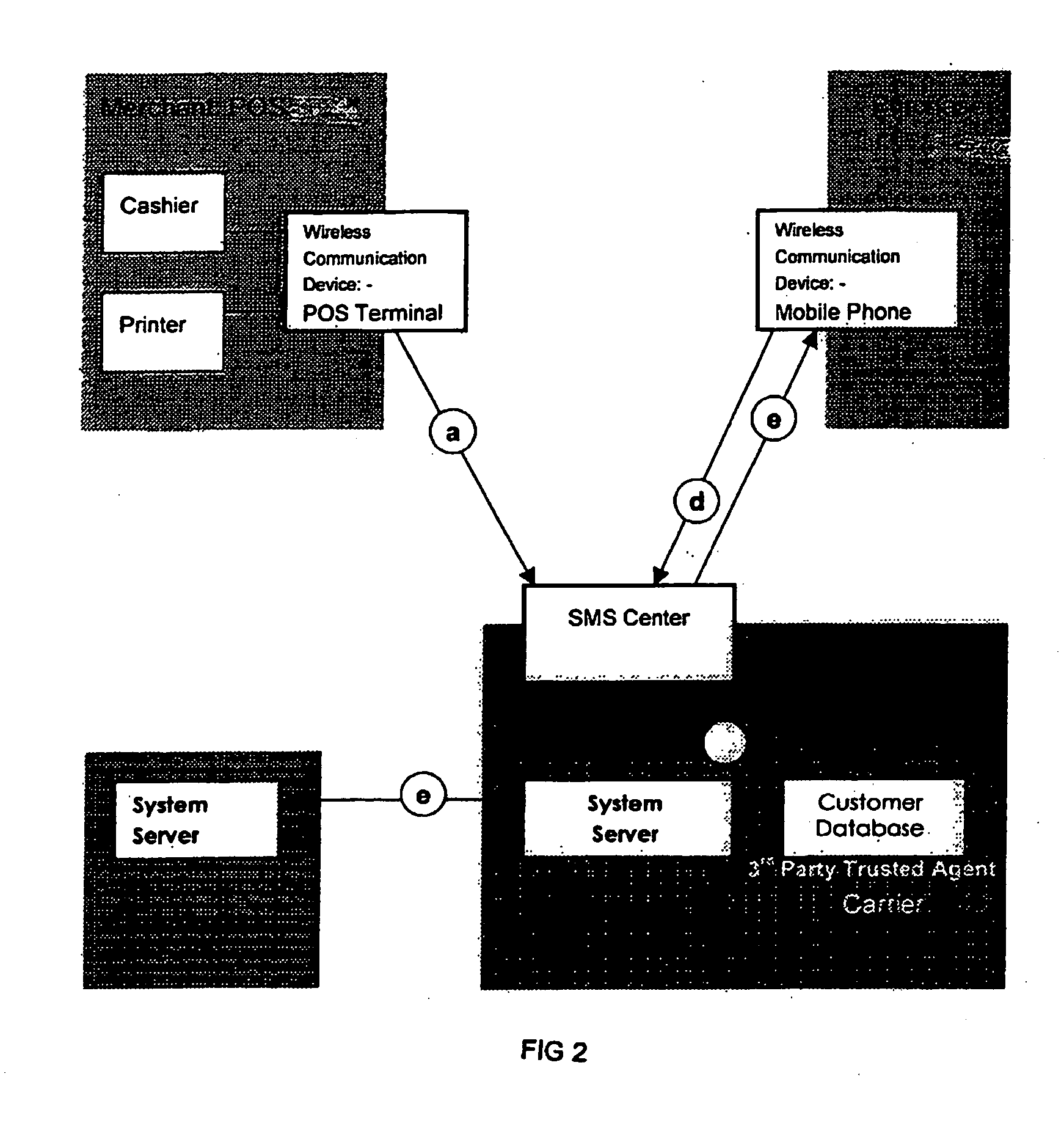
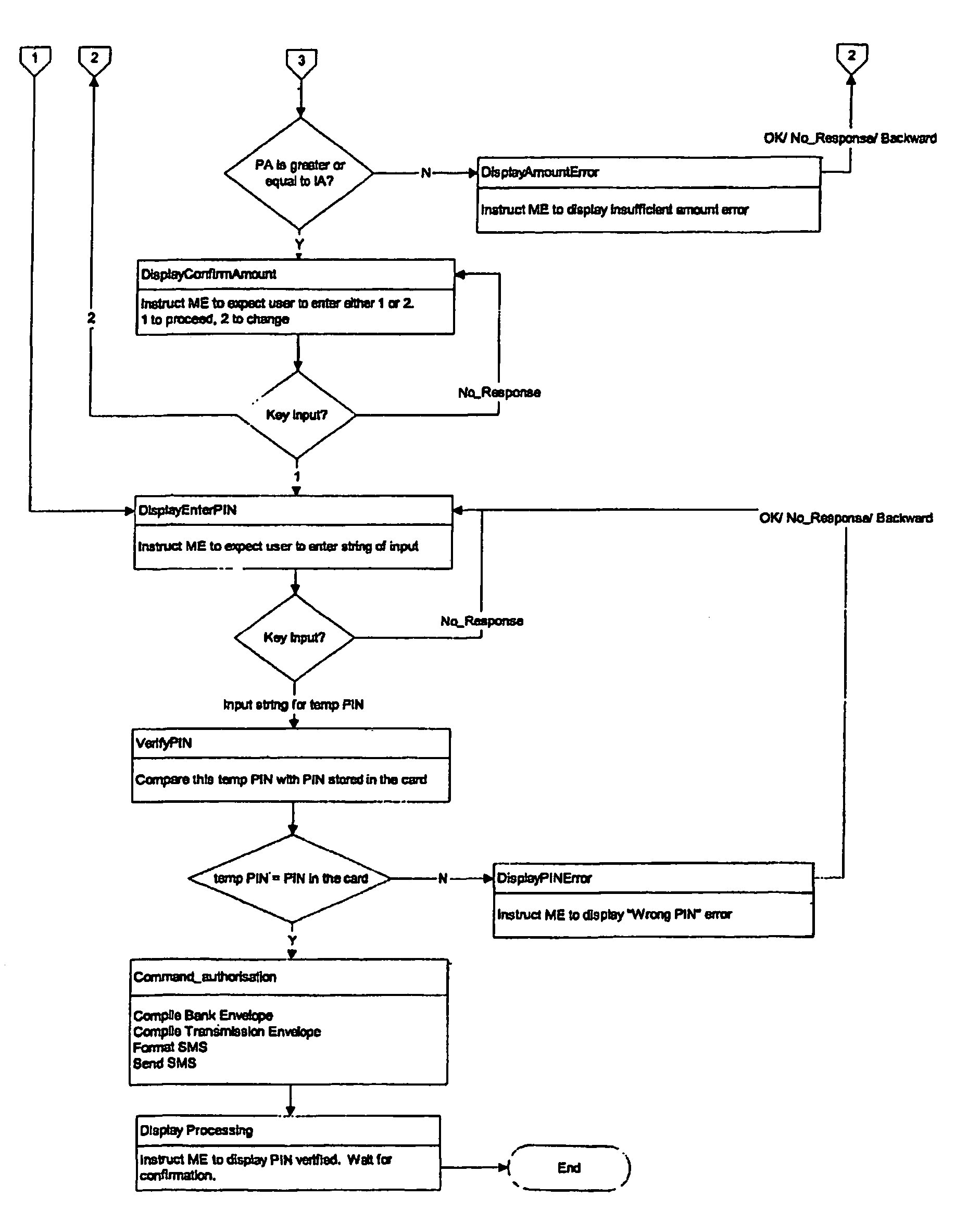
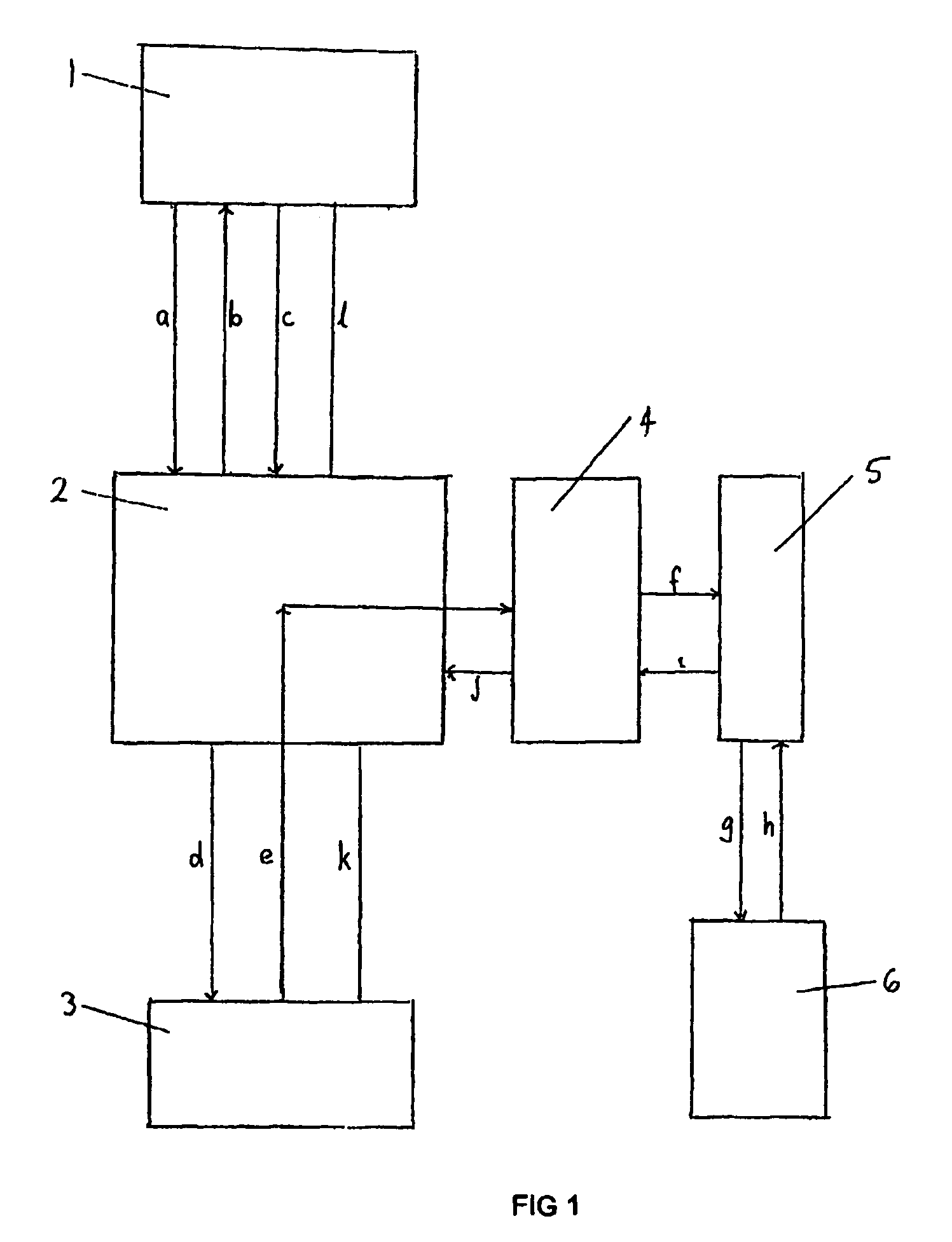
InactiveUS20050177517A1Improve securityFurther level of securityAccounting/billing servicesUser identity/authority verificationPaymentComputer module
A transaction processing system for processing a transaction between a supplier and a customer, said system comprising a supplier device for initiating the transaction, a system server and a mobile communication device, said device containing a message processing program module for enabling local verification of the transaction within the mobile device, wherein a transaction message is sent from the supplier device to the system server, a message requesting payment for the transaction is sent from the system server to the mobile communication device, the transaction is authorised and verified at the mobile telecommunications device from which a verification message is sent back to the system server, and the transaction is then processed.
Owner:LEUNG GARY +7
System and method for facilitating electronic financial transactions using a mobile telecommunication device
InactiveUS7379920B2Improve securityFurther level of securityAccounting/billing servicesUser identity/authority verificationPaymentComputer module
A transaction processing system for processing a transaction between a supplier and a customer, said system comprising a supplier device for initiating the transaction, a system server and a mobile communication device, said device containing a message processing program module for enabling local verification of the transaction within the mobile device, wherein a transaction message is sent from the supplier device to the system server, a message requesting payment for the transaction is sent from the system server to the mobile communication device, the transaction is authorized and verified at the mobile telecommunications device from which a verification message is sent back to the system server, and the transaction is then processed.
Owner:LEUNG GARY +7
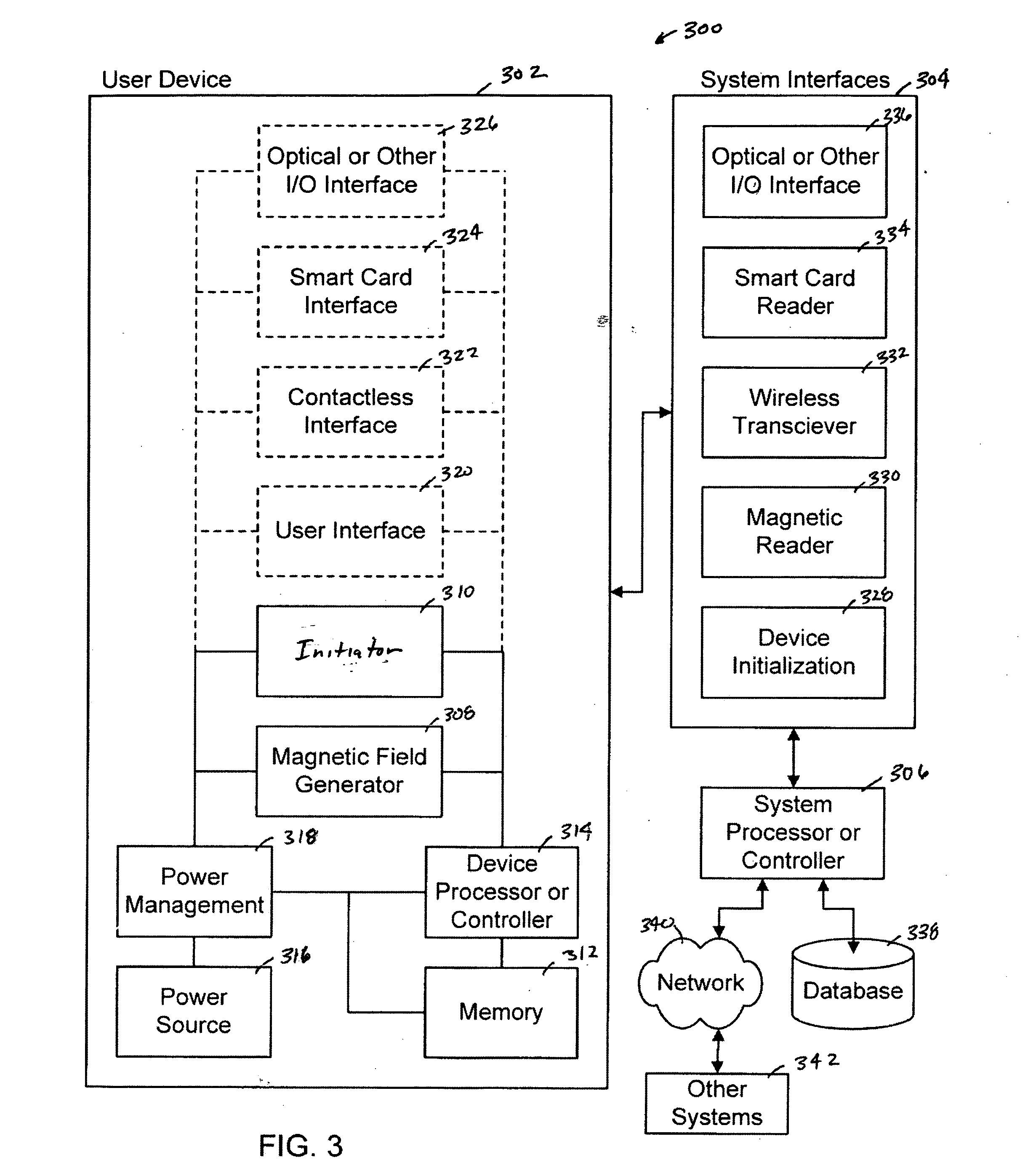
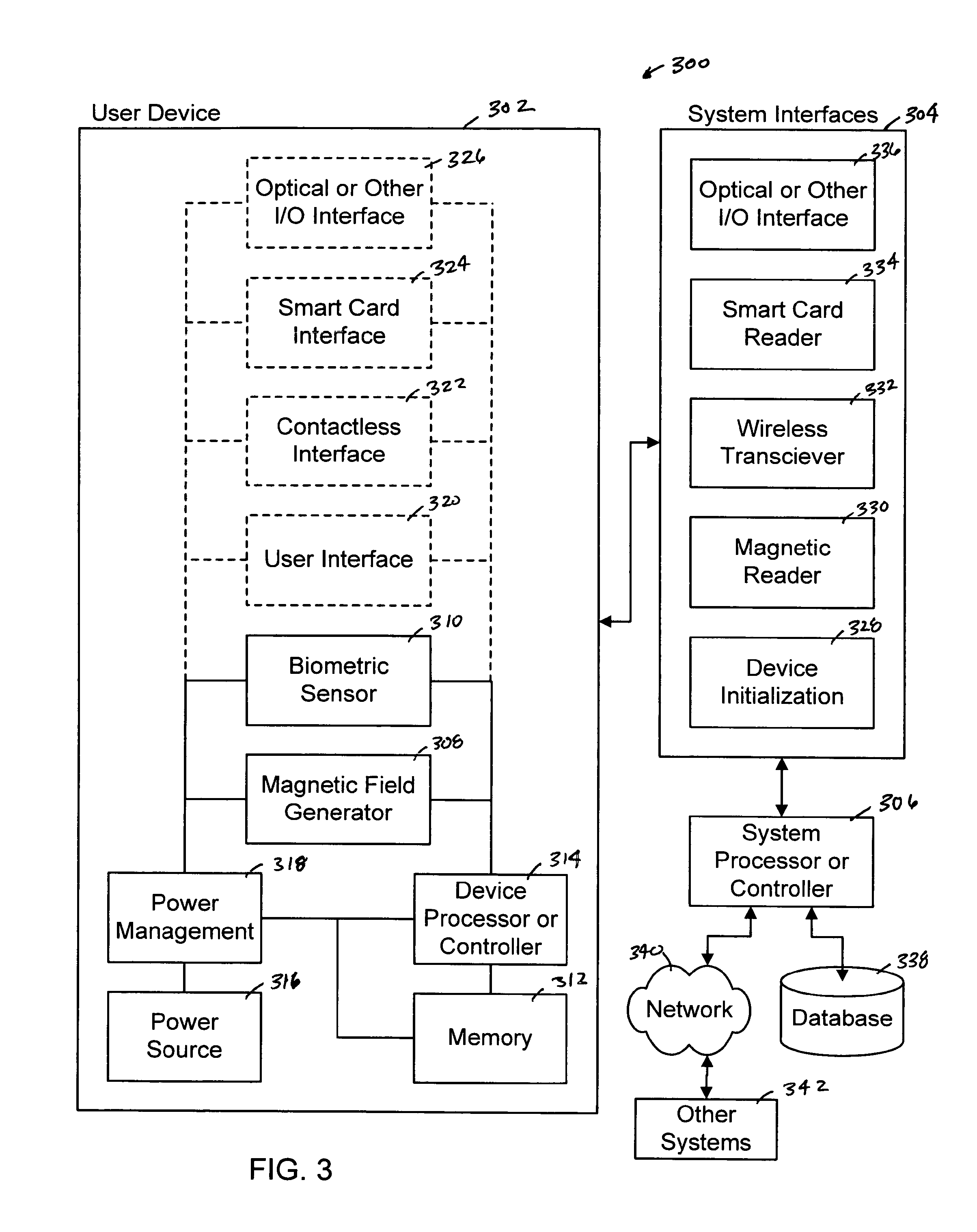
System, method and apparatus for enabling transactions using a user enabled programmable magnetic stripe
ActiveUS20060161789A1Reduce riskMaximum safetyDigital data processing detailsUnauthorized memory use protectionUser deviceSystems approaches
The present invention provides a system, method and apparatus that includes a user device having a magnetic field generator disposed within a substrate that is normally inactive, an initiator mounted on the substrate, a memory disposed within the substrate and a processor disposed within the substrate that is communicably coupled to the magnetic field generator, the initiator and the memory. The processor is operable to process information received from the initiator, generate a time varying code in response to the received information and activate the magnetic field generator. A power source is also disposed within the substrate. The magnetic field generator can create a spatial magnetic signal using a magnetic stripe and one or more induction coils, or create a time-varying magnetic signal for emulating data obtained from swiping a traditional magnetic stripe card through a magnetic card reader.
Owner:RAMPART ID SYST
Methods and devices for continuous sampling of airborne particles using a regenerative surface
InactiveUS20040232052A1Increase volume of materialImprove concentrationFixed microstructural devicesVolume/mass flow measurementEngineeringAtmospheric sciences
Airborne particles are impacted on a collection surface, analyzed, and then the collection surface is regenerated. Thus, the same collection surface can be used in numerous cycles. The analysis can be focused on one or more properties of interest, such as the concentration of airborne biologicals. Sensors based on regenerative collection surfaces may be incorporated in many networks for applications such as building automation.
Owner:FLIR DETECTION
Natural Skin Products Containing Dairy and Processes
InactiveUS20100233128A1Maximum efficiencyMaximum safetyCosmetic preparationsBiocideNatural productAdditive ingredient
A skincare product containing one or more dairy products, and one or more ingredients such as a natural oil, an herb, a fruit, a vegetable, a grain, honey, sea salt, egg yolk and mixtures thereof, for application to human skin in order to improve the well-being of said skin. The skincare product is applied to the skin in order to cleanse, beautify, promote attractiveness, and / or alter the feel or appearance of the skin. Furthermore, the skincare product is applied to the skin by rubbing, pouring, sprinkling, and / or spraying the skincare product onto the skin.
Owner:MCI MEDIA CAPITAL
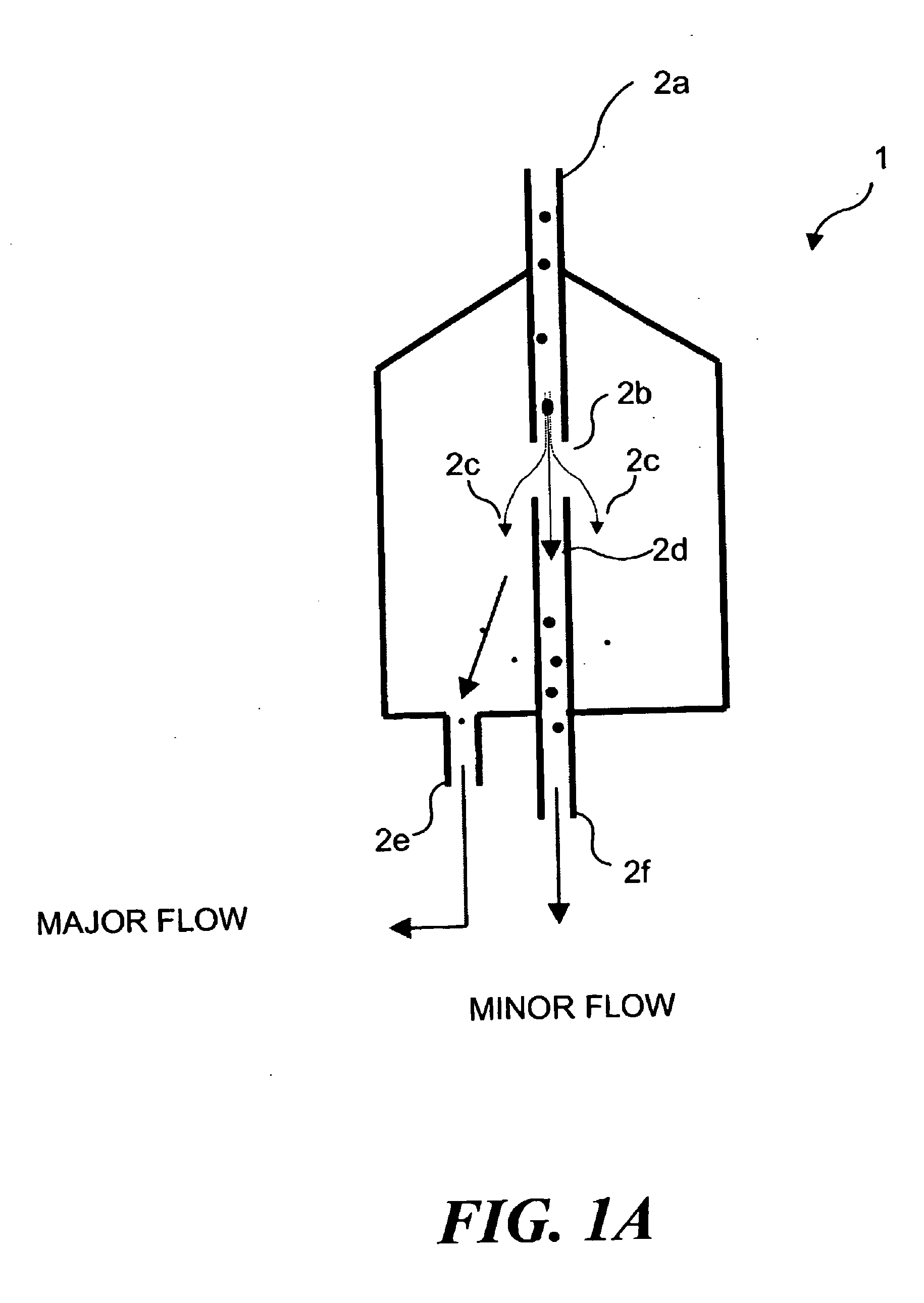
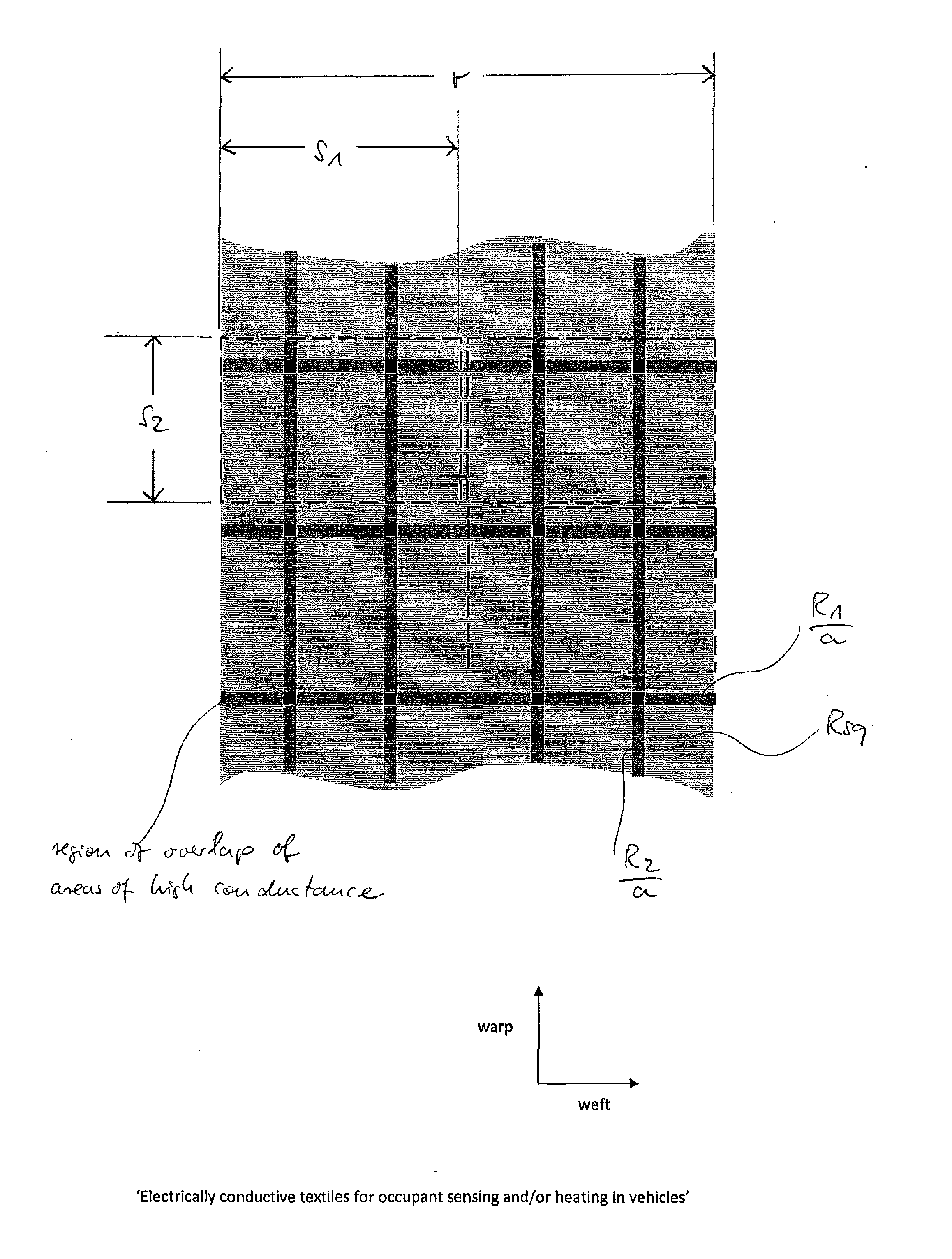
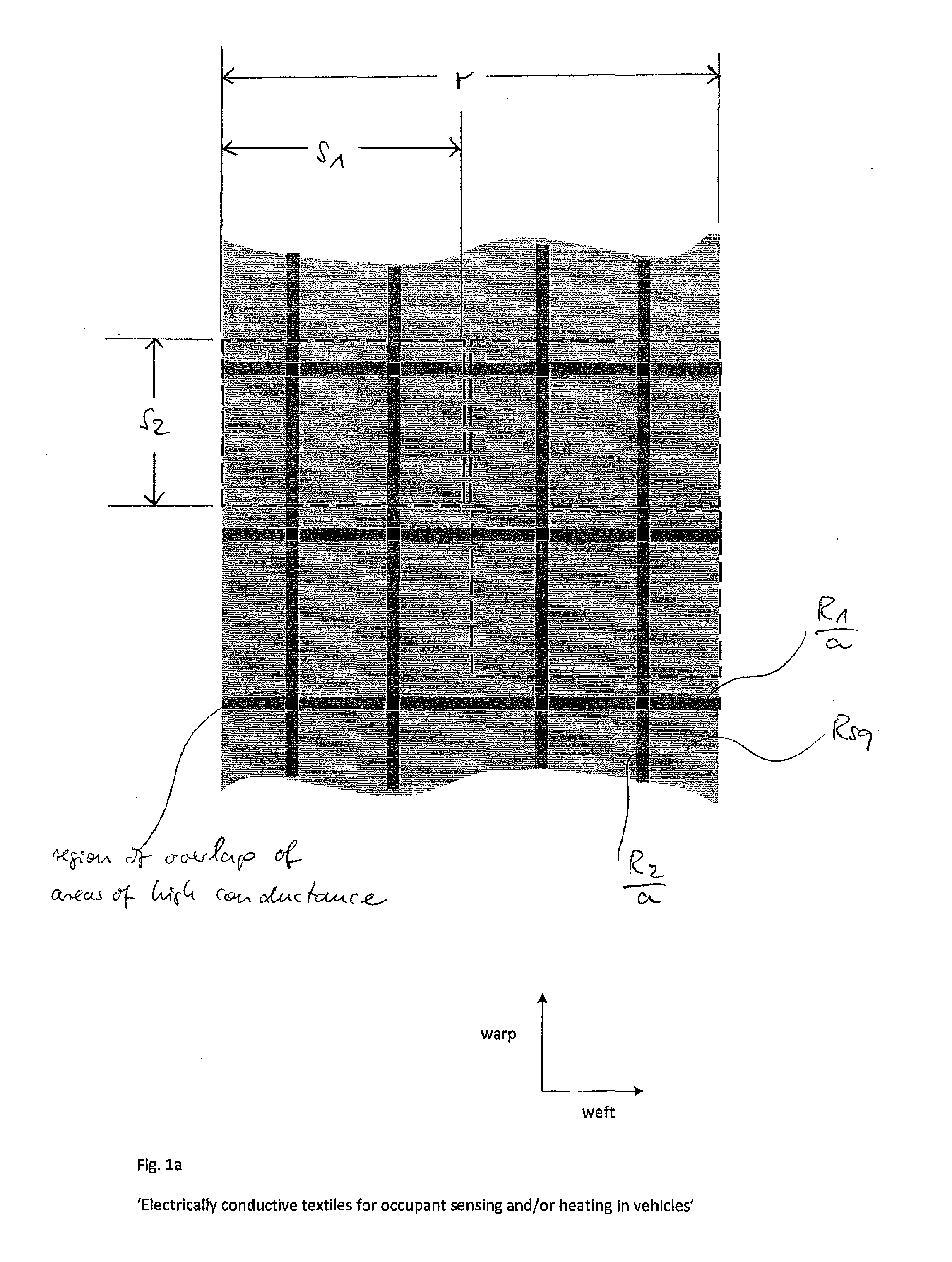
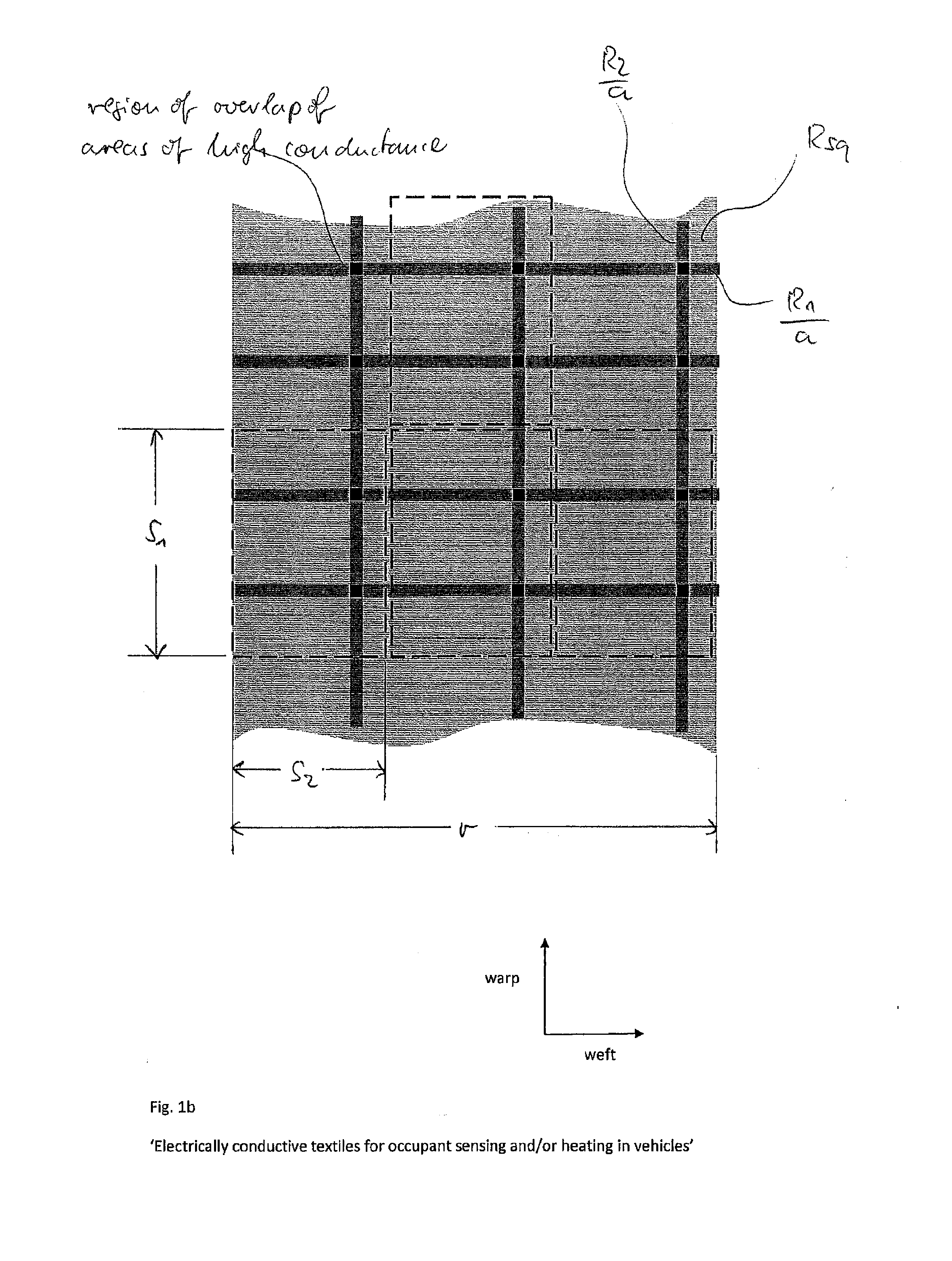
Electrically conductive textiles for occupant sensing and/or heating applications
InactiveUS20140246415A1Maximum of passenger comfortMaximum of operational safetyVehicle seatsOhmic-resistance heating detailsConductive textileElectrical and Electronics engineering
A flexible heater and / or electrode comprises a woven textile material having a warp direction and a weft direction, said textile material comprising at least one region having a low electrical conductance and at least two regions having a high electrical conductance. The at least two regions of high electrical conductance are adjacent to said at least one region of low electrical conductance. At least one of said at least two regions of high electrical conductance is operatively connected to a connection terminal of said heater and / or electrode, said connection terminal for connecting said heater and / or electrode to an electronic control circuit.
Owner:IEE INT ELECTRONICS & ENG SA
Transdermal magnetic coupling gastric banding
InactiveUS20070213751A1Large safety marginAvoid adjustmentTubular organ implantsObesity treatmentEngineeringGastric banding
A transdermally actuated gastric banding assembly is provided which includes an adjustable gastric band, a drive assembly and a transmission assembly positioned between the driver assembly and the adjustable gastric band. The drive assembly includes an internal component configured to be mounted within the body of the patient and an external component configured to operate transdermally so as to affect movement of the internal component. At least one of the internal and external components includes a magnetized member. A proximal end of the transmission assembly is connected to the internal component. A distal end of the transmission assembly is connected to a movable portion of the adjustable gastric band. In one embodiment, the internal component is mounted for rotational movement. In a further embodiment, at least one of the internal component and external component includes a plurality of magnetized members situated asymmetrically about a circumference of the at least one internal and external component.
Owner:TYCO HEALTHCARE GRP LP
Trusted transactional set-top box
InactiveUS7346917B2Poor resolutionMaximum safetyTelevision system detailsAnalogue secracy/subscription systemsPrivate networkThe Internet
A set top box (STB) includes a trusted transactional cache and associated transactional protocol and enables e-commerce transactions to be securely committed to a remote server extremely quickly and with little network overhead. The invention does away with the user concern of whether the transaction was successful. The STB operates equally well on robust private networks as on unpredictable Internet or wireless networks, and avoids upsetting users who would otherwise have to wait in front of a display screen for confirmation of completion of the transaction after a temporary communication failure with the central site. The method may advantageously be used to provide cost-effective micro-payments solutions. The STB may include a dual headed display capability in which data and video maybe be directed to separate displays. The STB may feature an embedded ticket printer, as well as an embedded barcode scanner. This enables non computer literate users to more conveniently track transactions committed via the STB, or to take advantage of promotional coupons. The STB features an embedded hardware true Random Number Generator to produce maximum entropy encryption keys, therefore providing maximum secure and fool-proof means to protect private data using government authorized encryption schemes.
Owner:MUDALLA TECH INC THOITS LOVE HERSHBERGER & MCLEAN
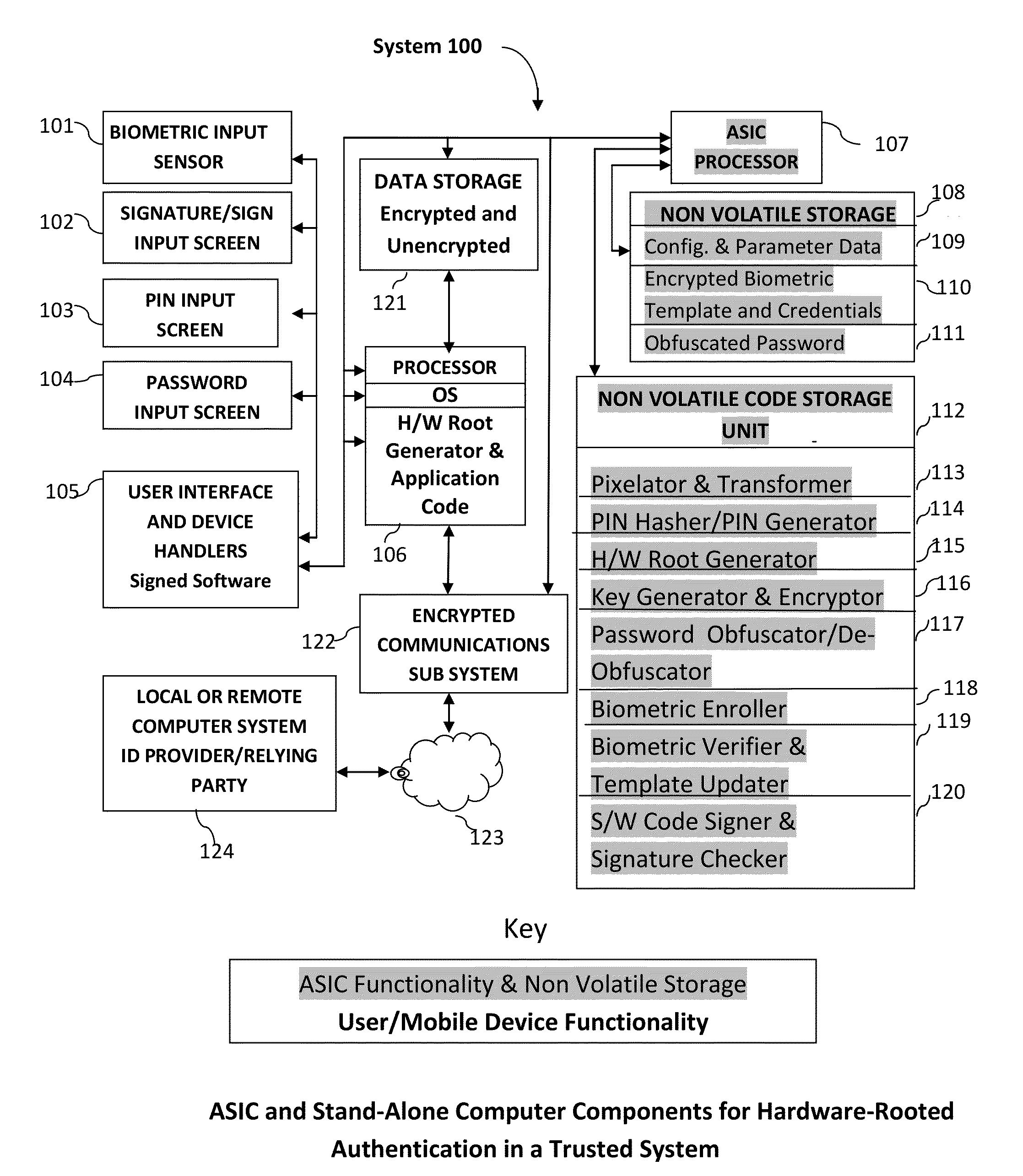
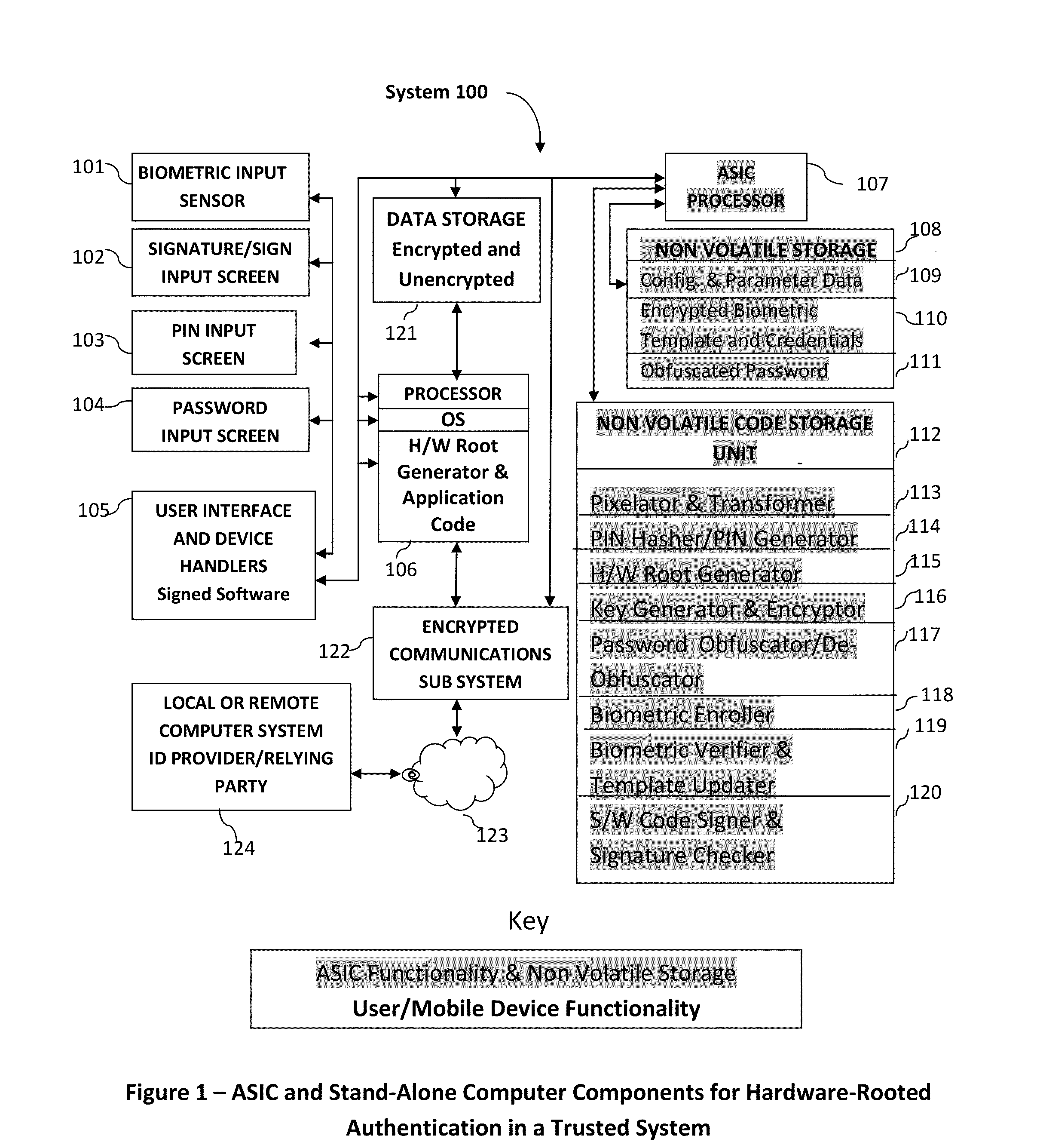
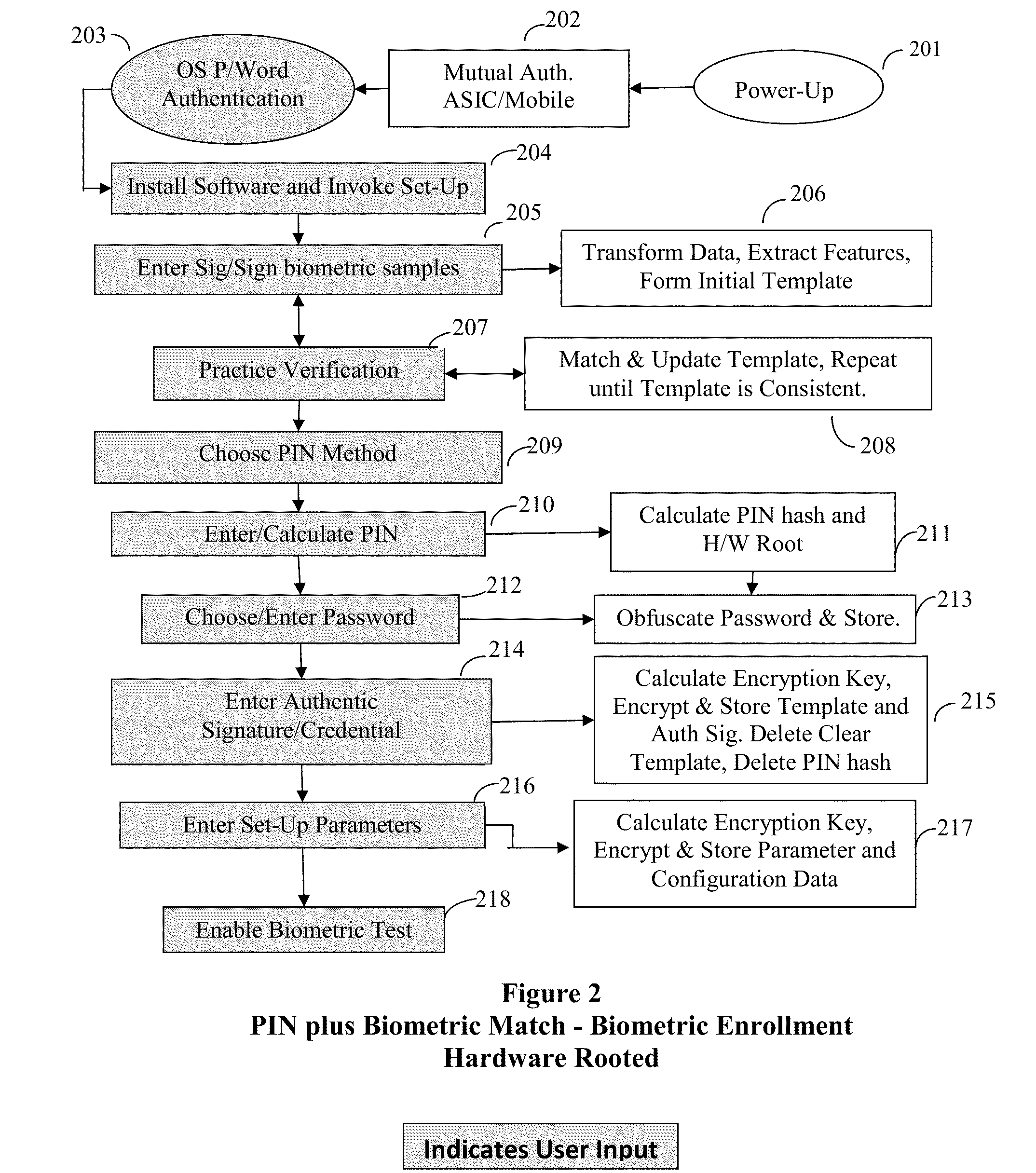
Method and System for Providing Password-free, Hardware-rooted, ASIC-based Authentication of a Human to a Mobile Device using Biometrics with a Protected, Local Template to Release Trusted Credentials to Relying Parties
InactiveUS20140365782A1Significant productivityMaximum safetyUser identity/authority verificationInternal/peripheral component protectionBiometric dataPassword hashing
Biometric data, which may be suitably transformed are obtained from a biometric input device contained within a stand-alone computer or a mobile device, which may contain an ASIC chip connected to or incorporated within the stand-alone computer or mobile device and which includes the capability for capturing one or more biometric samples and for biometric feature extraction, matching and encryption. For extra security, the biometric matching is used in conjunction with a PIN to authenticate the user to the stand-alone computer or mobile device. The biometric template and other sensitive data residing on the mobile device are encrypted using hardware elements of the mobile device (or the ASIC) together with the PIN hash and / or the Password hash. An obfuscated version of the Password, stored on the ASIC or the mobile device is de-obfuscated and released to the mobile device authentication mechanism, including a Trusted Platform Module if present, in response to a successfully decrypted template and matching biometric sample and PIN. A de-obfuscated password is used to authenticate the user to the mobile device and the same or a different de-obfuscated password may be used to authenticate the user to a remote computer using the SSL / TLS or a process based upon a symmetric encryption algorithm. The locally generated password may be used to encrypt data at rest on the mobile device or ASIC and the remote authentication password may be used to encrypt data in transit to and from a remote computer. This creates a trusted relationship between the stand-alone computer or mobile device and the remote computer. The system also eliminates the need for the user to remember and enter complex passwords on the mobile device or for secure transmission of data. A similar method may be used, with the signature / sign biometric modality to determine whether the holder of an IC chip card is, in fact the card owner.
Owner:BIOCRYPT ACCESS LLC
On-type biometrics fingerprint soft keyboard
InactiveUS7486810B1Safety be ensureMaximum safetyCharacter and pattern recognitionDigital data authenticationFingerprintPersonal computer
One embodiment of this invention addresses the use of biometrics for accessing a touch screen keyboard on a tablet personal computer (PC), and ensuring security if the PC is left unattended. The core idea is to assign biometrics to soft keyboards without the use of a physical keyboard. In this example, every key on the keyboard will be assigned a biometric fingerprint associated with the corresponding finger that would type it. When a user types, a portion of its fingerprint touches the keys. By storing the portions and assigning the portions to the soft keyboard, it is ensured that every key typed is associated with the corresponding key fingerprint portion, thus ensuring maximum biometric security. In addition, the keystroke delays and word delays can be recorded and compared with previous data for added security.
Owner:IBM CORP
System, Method and Apparatus for Enabling Transactions Using a Biometrically Enabled Programmable Magnetic Stripe
InactiveUS20110240748A1Reduce riskMaximum safetyPayment architectureIndividual entry/exit registersData streamControl circuit
The present invention provides a system, method and apparatus that includes a magnetic field generator that is normally inactive and includes a magnetic stripe either mounted on the substrate or disposed within a substrate, one or more induction coils disposed within the substrate underneath a length of the magnetic stripe and a control circuit disposed within the substrate that is connected to the one or more induction coils. The control circuit generates a time-varying magnetic signal by pulsing the one or more induction coils underneath the magnetic stripe when activated by a processor. The time-varying magnetic signal is transmitted to a magnetic stripe reader and emulates a data stream generated by swiping a static magnetic stripe card through the magnetic stripe reader but is not created by swiping the magnetic stripe of the apparatus through the magnetic stripe reader or using an adapter to interface with the magnetic stripe reader.
Owner:INNOVATION CONNECTION CORP
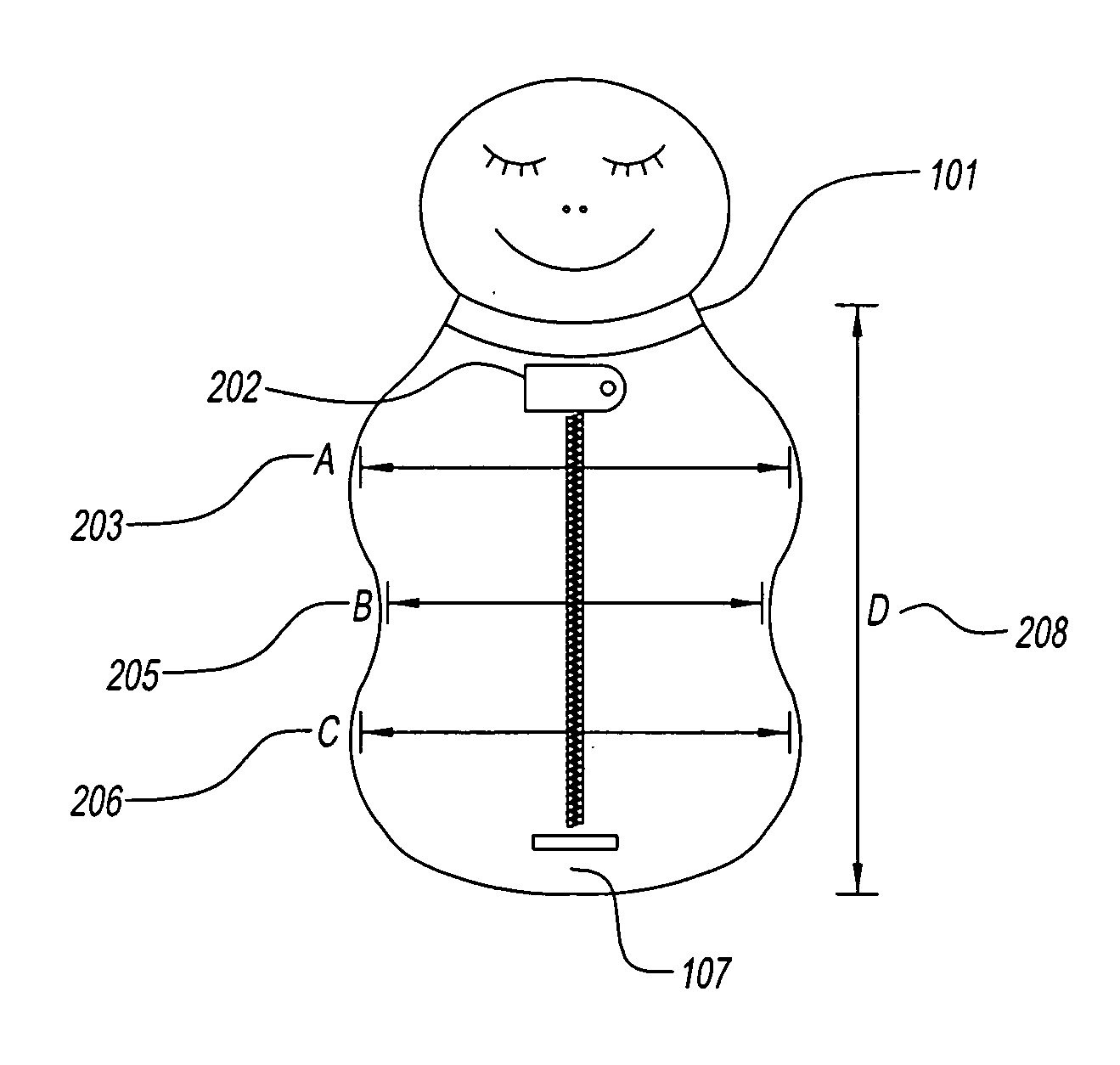
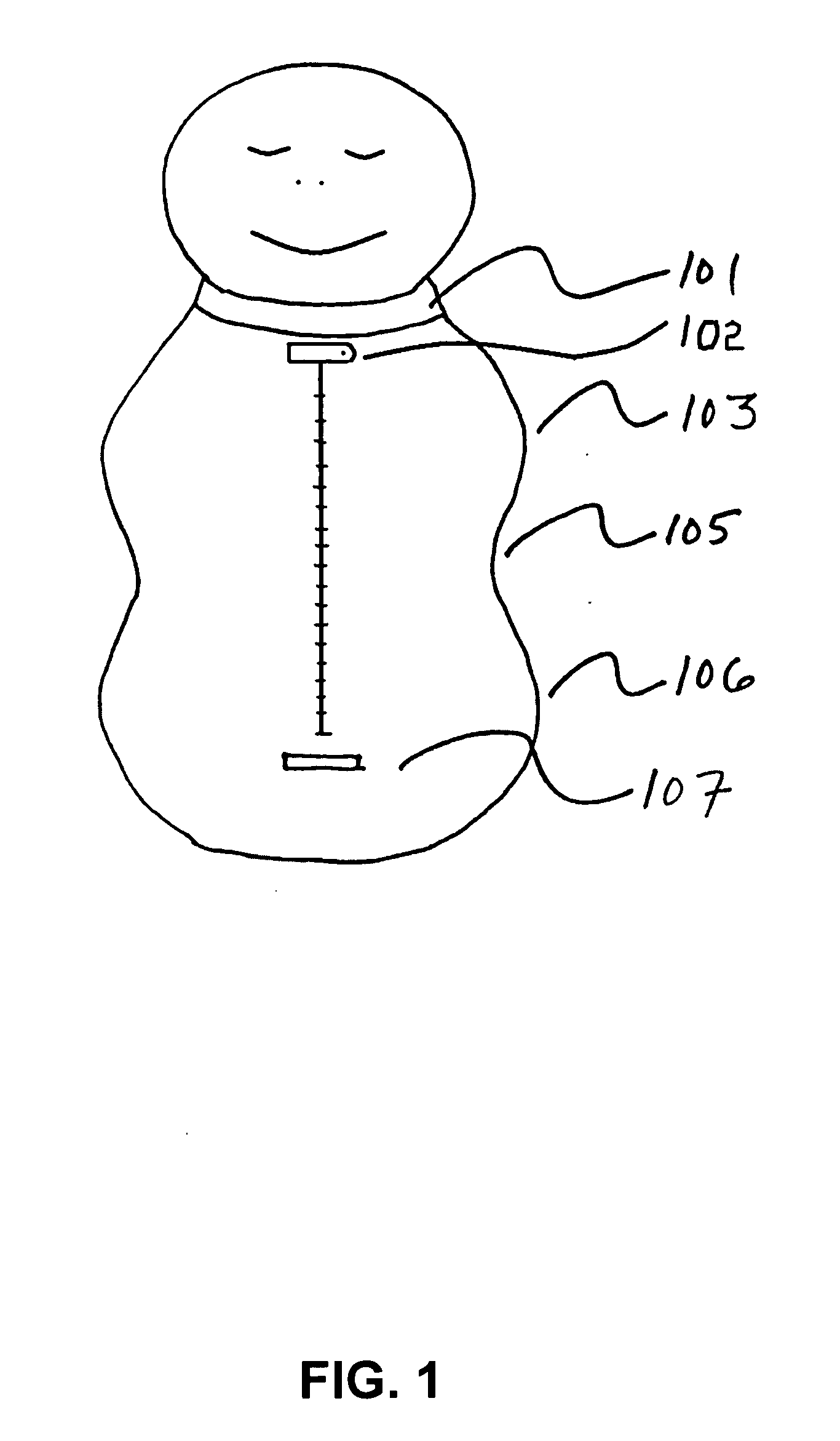
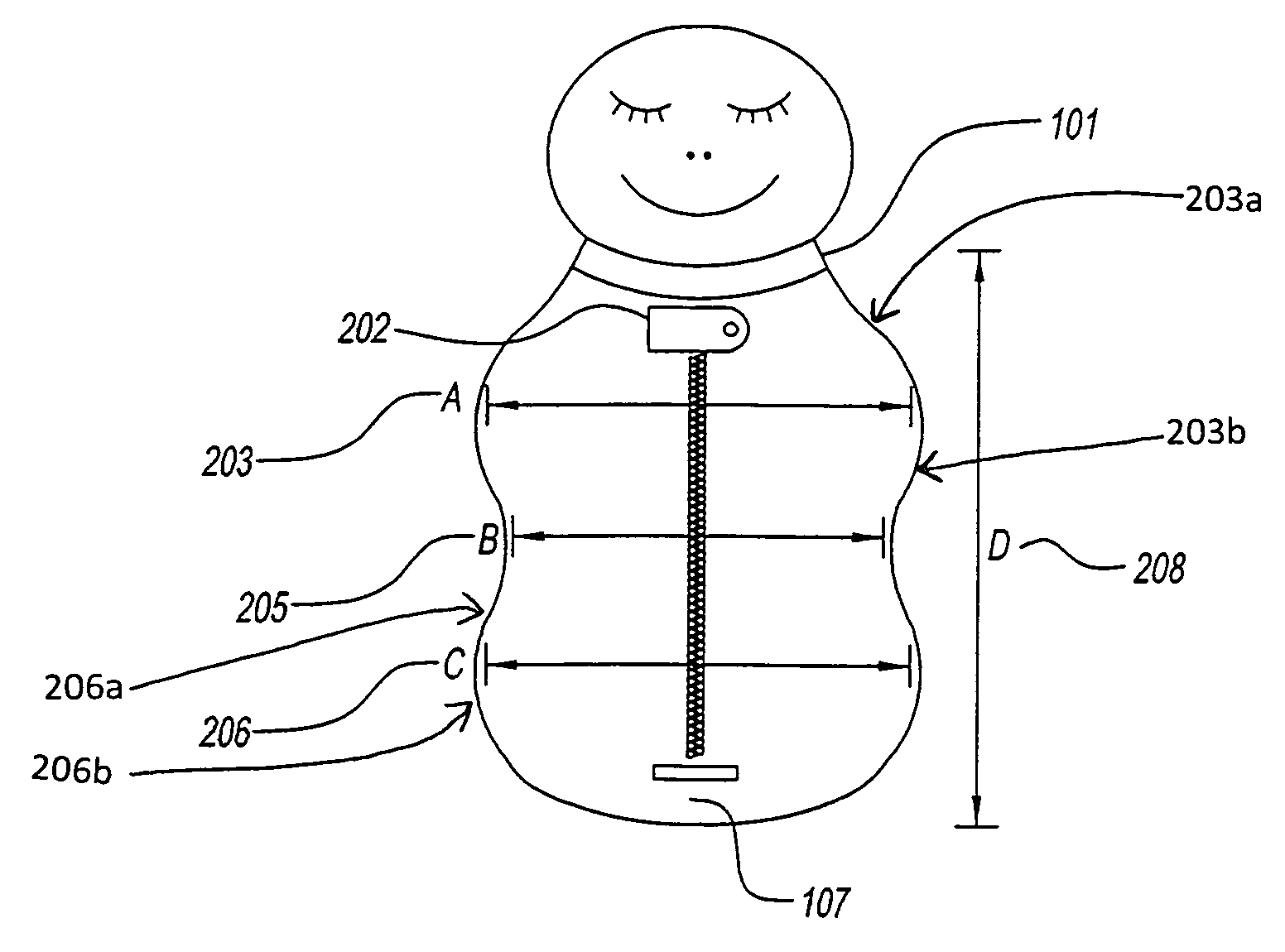
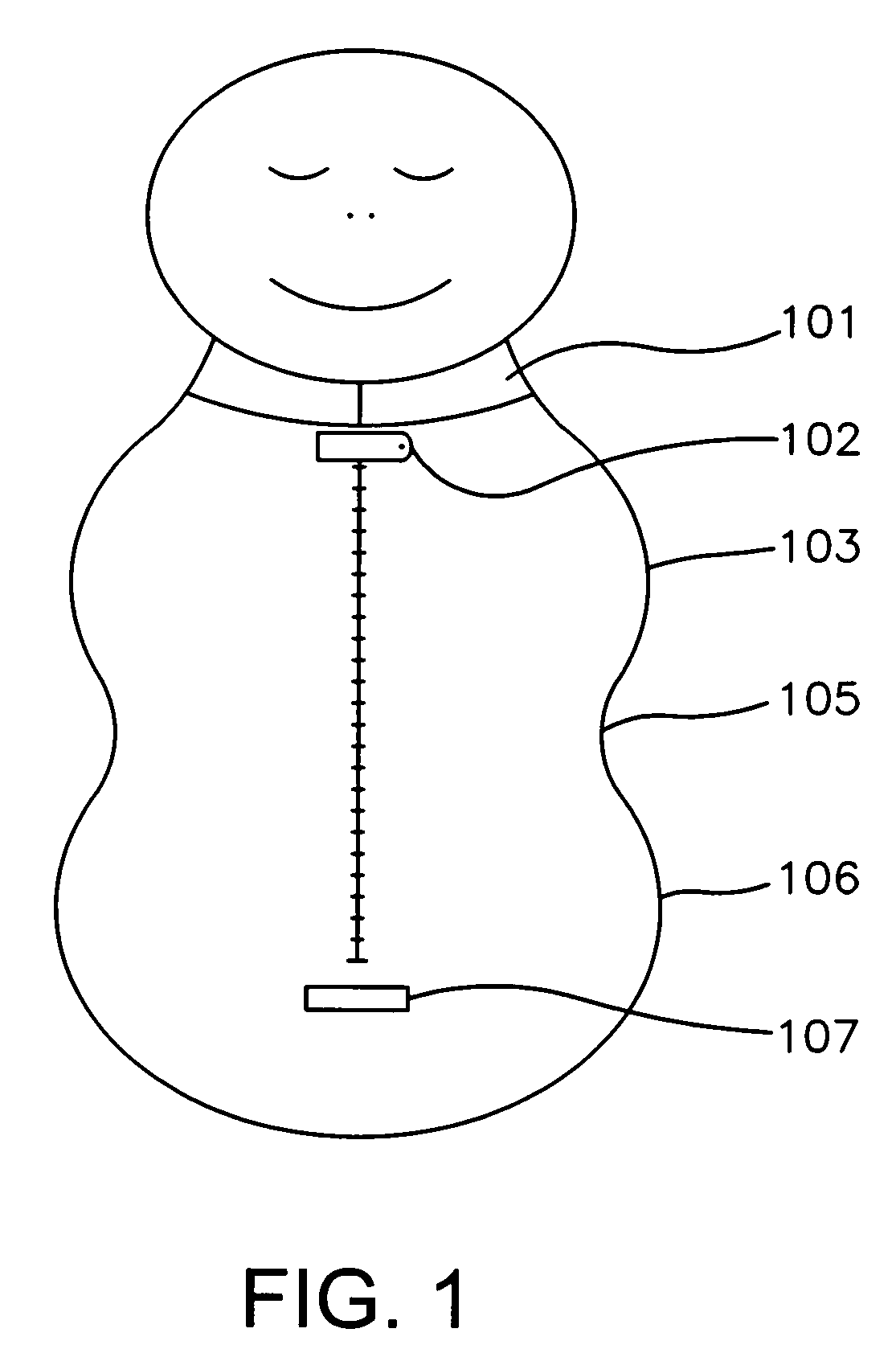
Ergonomic swaddling garment
Ergonomic garment for swaddling an infant garment with an elongate retractable fabric shell having an outer surface and inner surface defining an interior volume for receiving the arms, legs and trunk of an infant therein. Garments have a head end for receiving the arms of said infant, a foot end for receiving the legs of said infant, and a mid section for receiving the trunk of said infant that is narrower than said head end and said foot end, and a neck opening at the head end for receiving a neck of said infant. Garments have an ergonomic peanut-like shape. Garments have a reversible closure means accessing said interior volume of said fabric shell extending longitudinally along the central axis of said fabric shell from said head end to said foot end, a chin protector closure means and optionally a means for accepting an automotive seat belt. Detachable arms and / or leggings and attached retractable arms and / or leggings garments are shown. Porous light-permeable and antimicrobial fabric embodiments are described.
Owner:BARSKI KAREN H
Impeller components and systems
InactiveUS20050019154A1Large capacityReduce fluid turbulenceCircumferential flow pumpsPump componentsImpellerMechanical power transmission
The present invention relates generally to systems and methods for facilitating the movement of fluids, transferring mechanical power to fluid mediums, as well as deriving power from moving fluids. The present invention employs an impeller system in a variety of applications involving the displacement of fluids, including for example, any conventional pumps, fans, compressors, generators, circulators, blowers, generators, turbines, transmissions, various hydraulic and pneumatic systems, and the like.
Owner:DIAL DISCOVERIES
Capillary force vaporizers
ActiveUS20090220222A1Easy to assembleEliminate needSpace heating and ventilationMedical devicesCapillary networkEngineering
The present invention concerns capillary force vaporizers for use in vaporizing liquids and emitting pressurized vapors. In one embodiment, the inventive capillary force vaporizer includes a porous member, a heater component to convey heat to the porous member, and a vapor containment region. The porous member further includes a capillary network, a surface for receiving liquid and a vaporization area in which vapor is produced from the liquid. The vapor is collected and pressurized within the vapor containment region, which includes one or more openings for the release of vapor at a velocity greater than zero. Several different embodiments for capillary force vaporizers and systems comprising capillary force vaporizers are disclosed along with methods for their use.
Owner:VAPORE
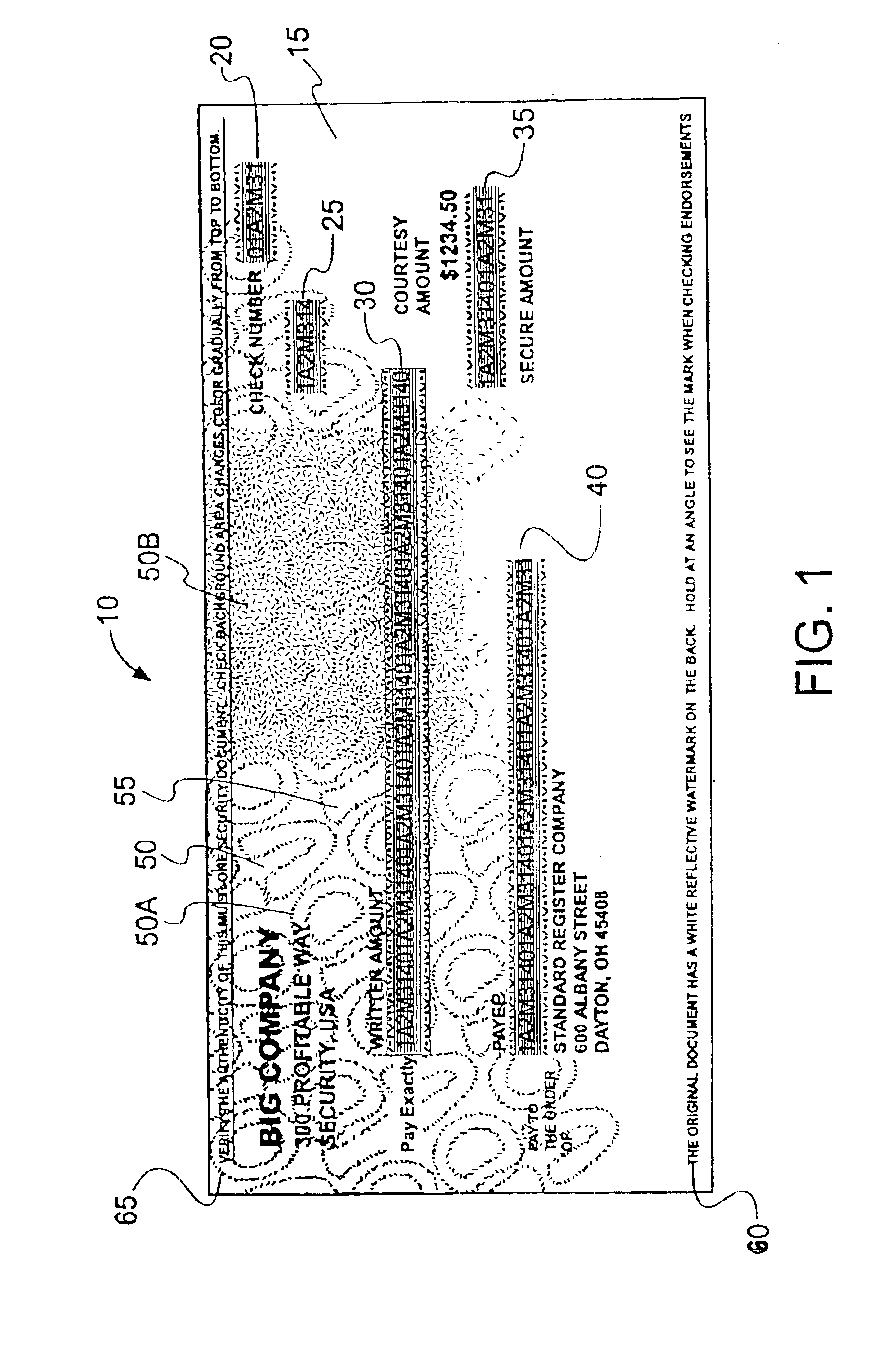
Secure document with self-authenticating, encryptable font
InactiveUS6886863B1Simplistic approachMaximum safetyOther printing matterRecord carriers used with machinesDocument preparationSecurity information
A self-authenticating encryptable font for creating secure documents. The document onto which the font is printed includes a surface containing one or more transaction fields such that transactional data from the font is printed within at least one of these fields. The font includes human-readable characters that are defined by a fill pattern made up of spaced marks and a patterned background. Security characters, made up of one or more encryptable data elements, may also be included. The encryptable data elements may be either fixed or randomly variable with regard to each human-readable character, independent of the human-readable characters, or capable of alteration by an encryption algorithm. The presence of the unique human-readable characters and the encryptable data elements give the impression that the document on which they are printed may be subject to security enhancements, while alterations to the encryptable data elements by an algorithm can be used during the printing process to incorporate additional security information into the document. A user wishing to self-authenticate encrypted information incorporated into the encryptable data elements merely passes the document through an appropriately-configured scanning device, then compares the decrypted information with overt indicia on the document.
Owner:TAYLOR COMM INC
Ergonomic swaddling garment
Ergonomic garment for swaddling an infant garment with an elongate retractable fabric shell having an outer surface and inner surface defining an interior volume for receiving the arms, legs and trunk of an infant therein. Garments have a head end for receiving the arms of said infant, a foot end for receiving the legs of said infant, and a mid section for receiving the trunk of said infant that is narrower than said head end and said foot end, and a neck opening at the head end for receiving a neck of said infant. Garments have an ergonomic peanut-like shape. Garments have a reversible closure means accessing said interior volume of said fabric shell extending longitudinally along the central axis of said fabric shell from said head end to said foot end, a chin protector closure means and optionally a means for accepting an automotive seat belt. Detachable arms and / or leggings and attached retractable arms and / or leggings garments are shown. Porous light-permeable and antimicrobial fabric embodiments are described.
Owner:BARSKI KAREN H
Portable device and method of communicating medical data information
InactiveUS20080177155A1Avoid the needMaximum safetyAmpoule syringesElectrotherapyData informationMedical device
A portable medical device for communication of medical data information has a medical device part that includes a first processor and first storage means, and means for executing one or more medical related functions, a communication device part comprising a second processor, second storage means, and communication means. The medical device part and the communication device part are connected allowing for exchange of data information according to a predetermined protocol. The exchange of communication may be under the control of the medical device part, but the functionalities of each device part otherwise is separated. Also disclosed is a method for communication of medical data information.
Owner:NOVO NORDISK AS
System, method and apparatus for enabling transactions using a biometrically enabled programmable magnetic stripe
ActiveUS8015592B2Reduce riskMaximum safetyDigital data processing detailsUnauthorized memory use protectionUser deviceComputer science
The present invention provides a system, method and apparatus that includes a user device having a magnetic field generator disposed within a substrate that is normally inactive, a biometric sensor mounted on the substrate, a memory disposed within the substrate and a processor disposed within the substrate that is communicably coupled to the magnetic field generator, the biometric sensor and the memory. The processor is operable to process biometric information received from the biometric sensor to verify that a user is authorized to use the apparatus and activate the magnetic field generator when the user is verified. A power source is also disposed within the substrate. The magnetic field generator can create a spatially varying magnetic signal using a magnetic stripe and one or more induction coils, or create a time-varying magnetic signal for emulating data obtained from swiping a magnetic stripe card through a magnetic card reader.
Owner:INNOVATION CONNECTION CORP
Air circulation system
InactiveUS7059536B2Restricts build-upAvoid burnsAir-treating devicesMechanical apparatusAir cycleControl theory
An air circulation system for use with or without ductwork having an outside air stream and a return air stream includes a controller and a return damper apparatus operatively connecting the return air stream to the controlled environment. The air circulation system further includes a heating unit and an air mass sensor disposed adjacent to the return damper apparatus. The air mass sensor selectively and directly detecting a ventilation rate of air moving through the return damper apparatus and communicates the ventilation rate to the controller which selectively modulates operation of the heating unit in dependence upon the ventilation rate.
Owner:MESTEK
Adiabatic, two-stroke cycle engine having novel scavenge compressor arrangement
InactiveUS6279520B1Improve thermal efficiencyReduce heat lossReciprocating piston enginesAir compressionExhaust valve
An engine structure and mechanism that operates on various combustion processes in a two-stroke-cycle without supplemental cooling or lubrication comprises an axial assembly of cylindrical modules and twin, double-harmonic cams that operate with opposed pistons in each cylinder through fully captured rolling contact bearings. The opposed pistons are double-acting, performing a two-stroke engine power cycle on facing ends and induction and scavenge air compression on their outside ends, all within the same cylinder bore. The engine includes a novel compressor arrangement having an intake valve comprising a V-shaped double reed valve with an apex pointing toward the intake port and an exhaust valve having a V-shaped double reed valve with an apex pointing away from the exhaust port. The compressor arrangement may further include rectangular intake and exhaust ports, a rectangular piston rod and rectangular crosshead bearings.
Owner:LOWI JR ALVIN
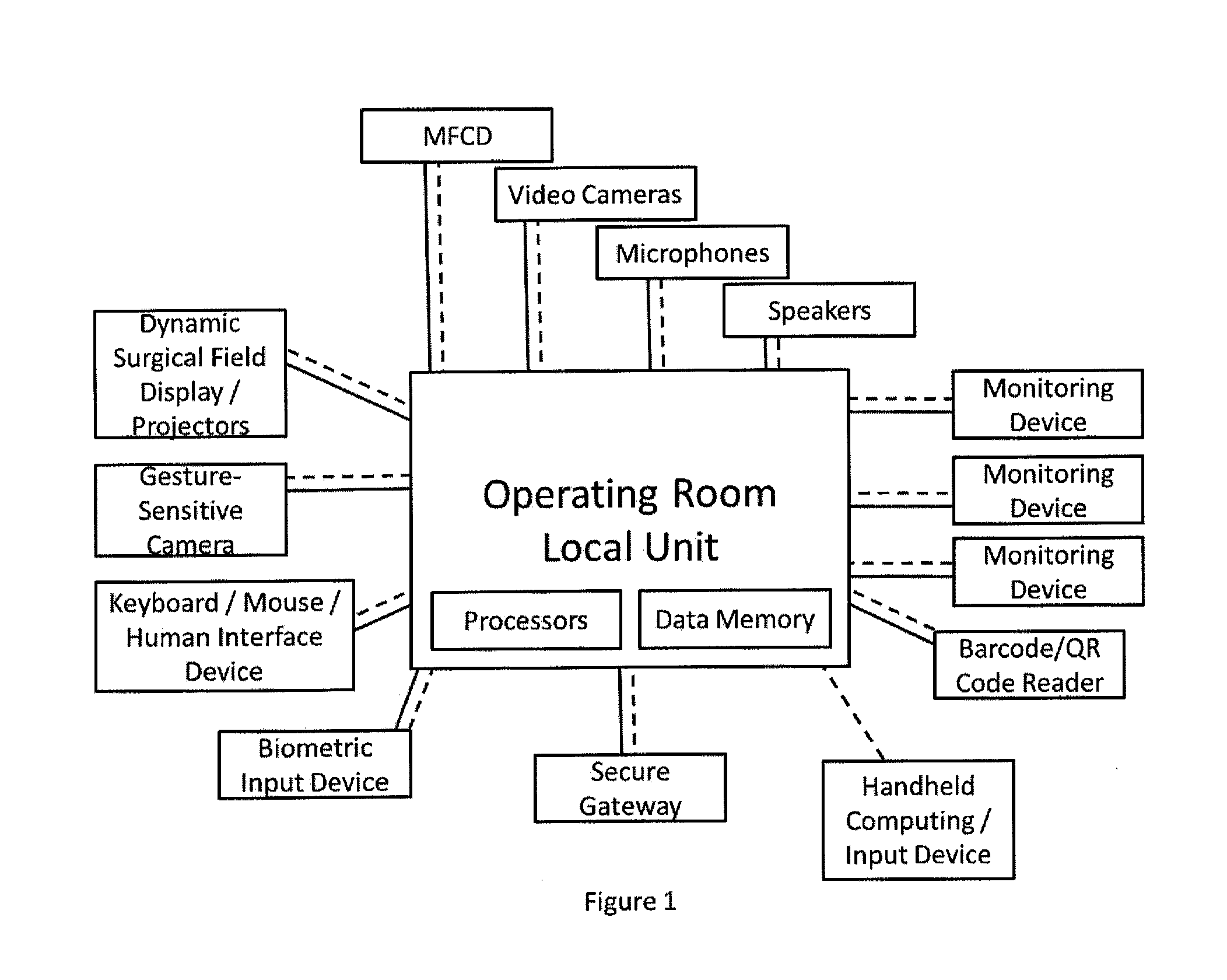
Consolidated Healthcare and Resource Management System
ActiveUS20120323597A1Easy to customizeImprove resource managementSurgical systems user interfaceOffice automationResource Management SystemDisplay device
A technical procedure and information enhancement system comprising a multi-function colored display; a computing device having memory and processors; a touch-free gesture-responsive computer input device; computer-readable media containing computer instructions for displaying a plurality of electronic pages selected from the group consisting of a pre-procedural page, a procedure preparation page, an intra-procedural page and a post-procedural page; connection to the internet; a backup memory; a microphone; one or more video cameras situated to record the medical procedure, speakers, and an electronic signature pad.
Owner:PARALLAX ENTERPRISES
Leg exercise machine
ActiveUS8430800B2Quick start capabilityPrecise positioningResilient force resistorsSpace saving gamesLeg exerciseRange of motion
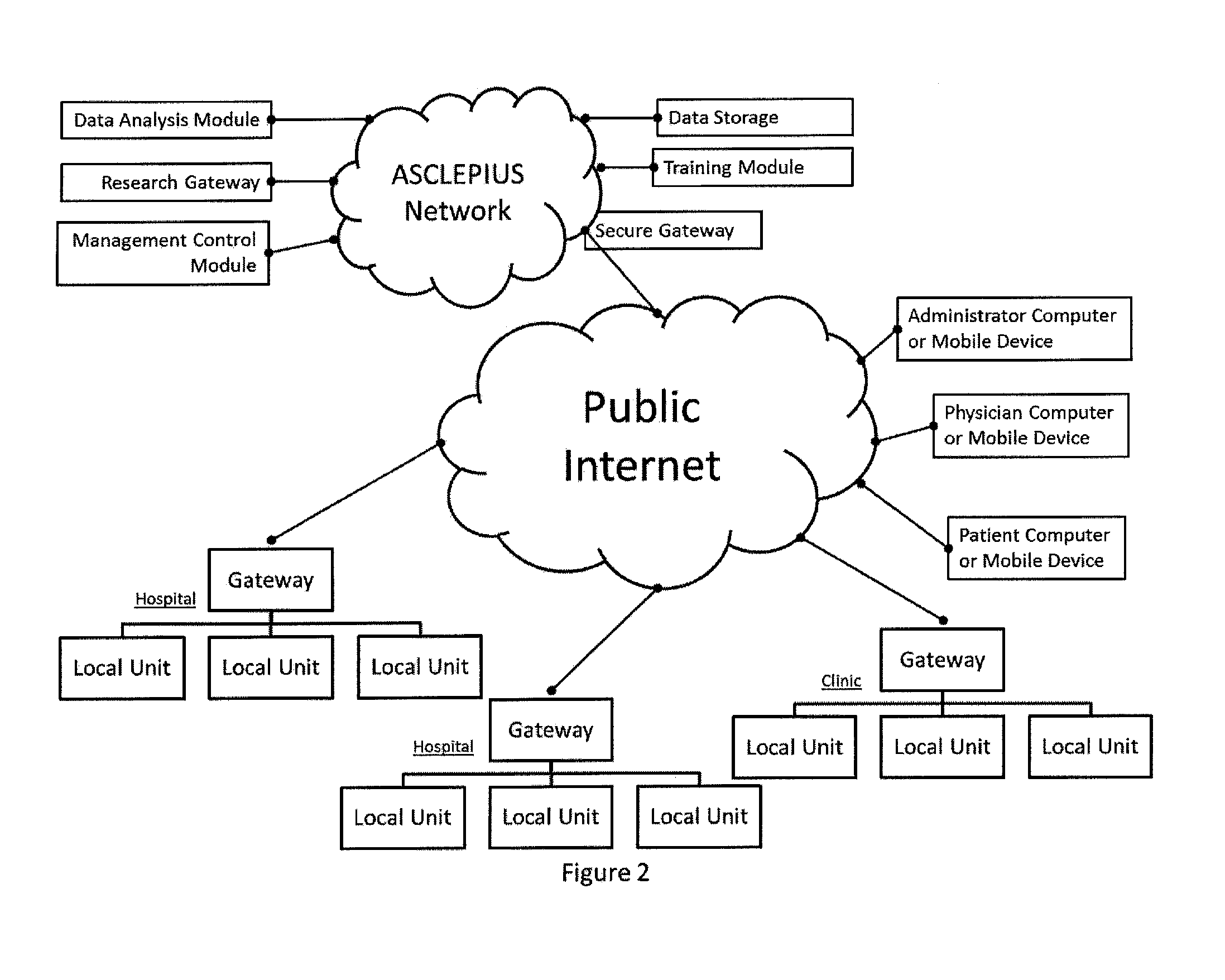
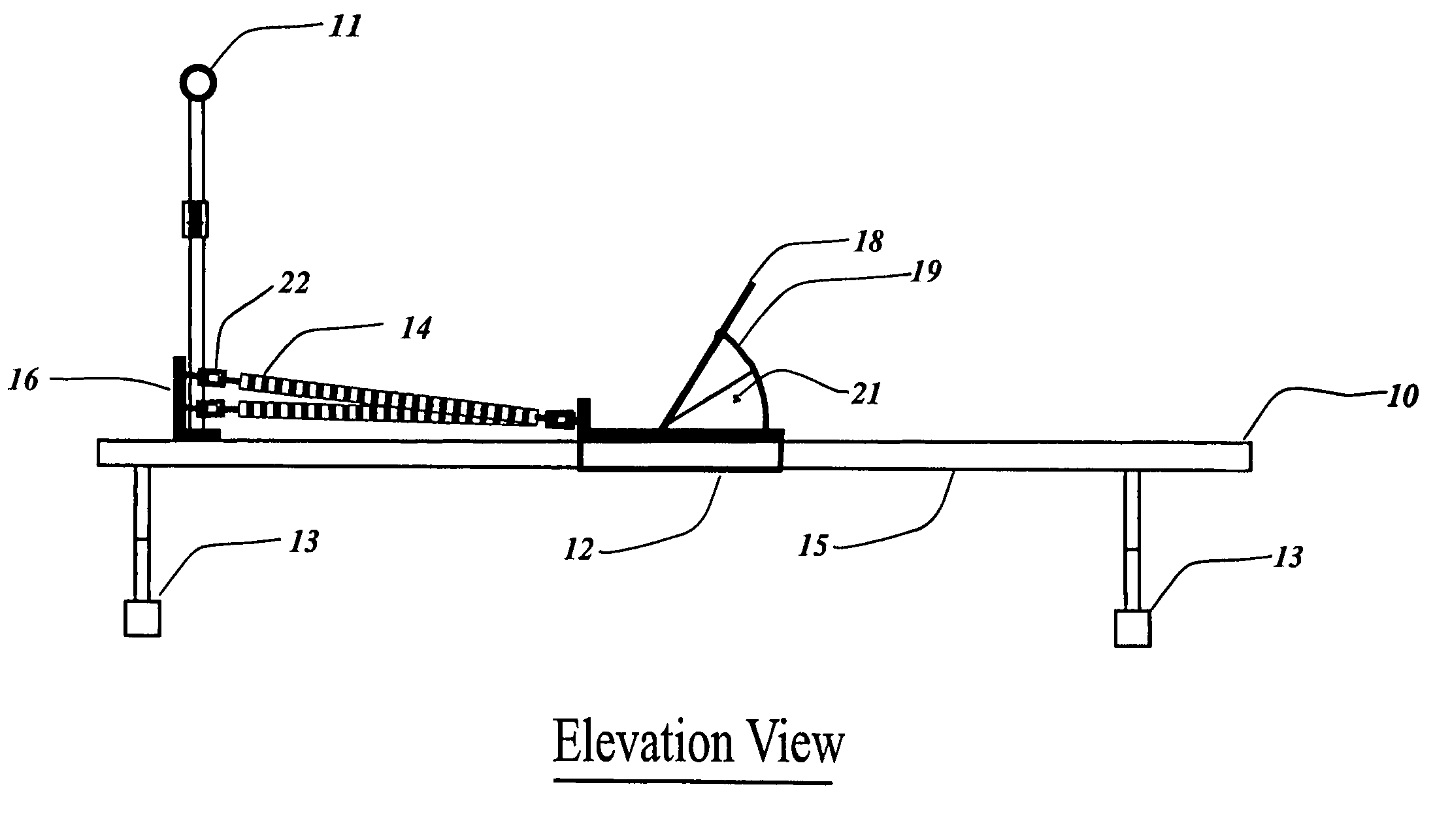
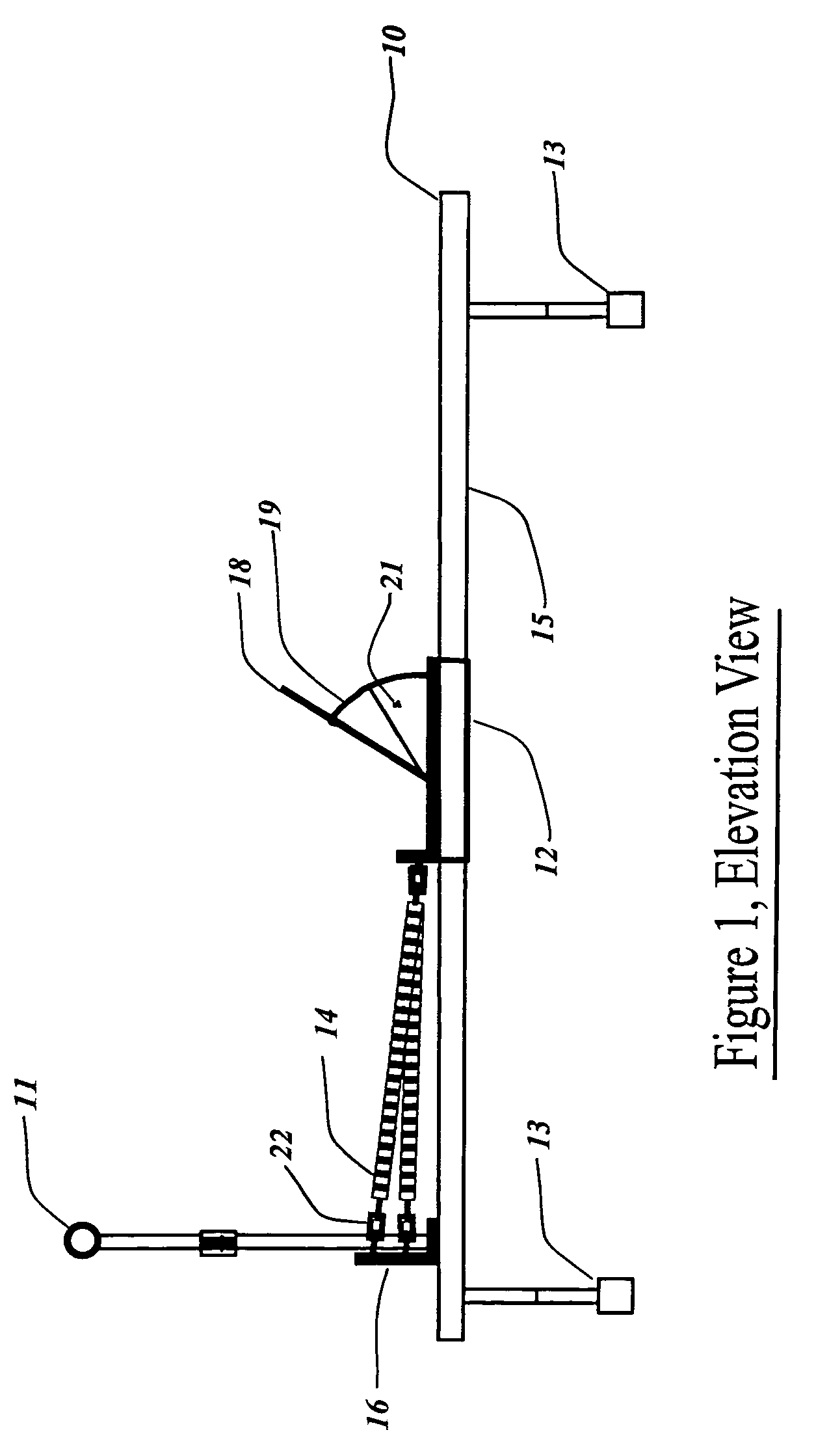
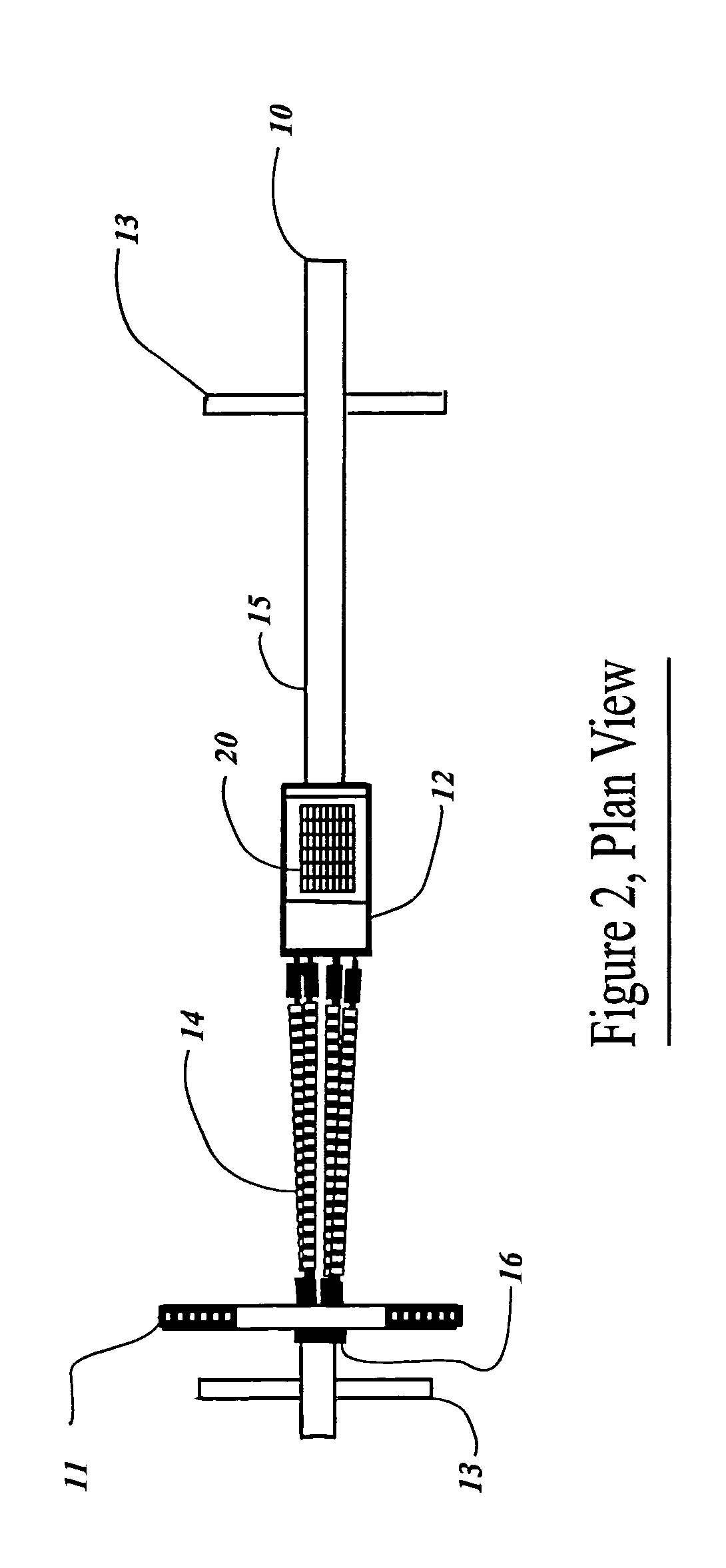
The invention is directed to be a hand portable exercise and training machine to improve the user's initial linear quickness and speed from a stationary or set position. The machine consists of a horizontal beam mounted above the floor with a movable foot sled, a stationary spring retainer bracket and a removable handle bar post and assembly mounted on it. Springs are attached to the front of the foot sled and the opposite end of the springs are attached to the stationary retainer bracket adjacent to the vertical handle bar post. The invention is an exercise device that applies spring resistance to the full range of motion in the user's leg as it pertains to the initial drive phase (first 3-6 steps) of a sprint. The machine can be collapsed for transport and re-assembled without the use of tools.
Owner:NOLAN GREGORY JOSEPH +1
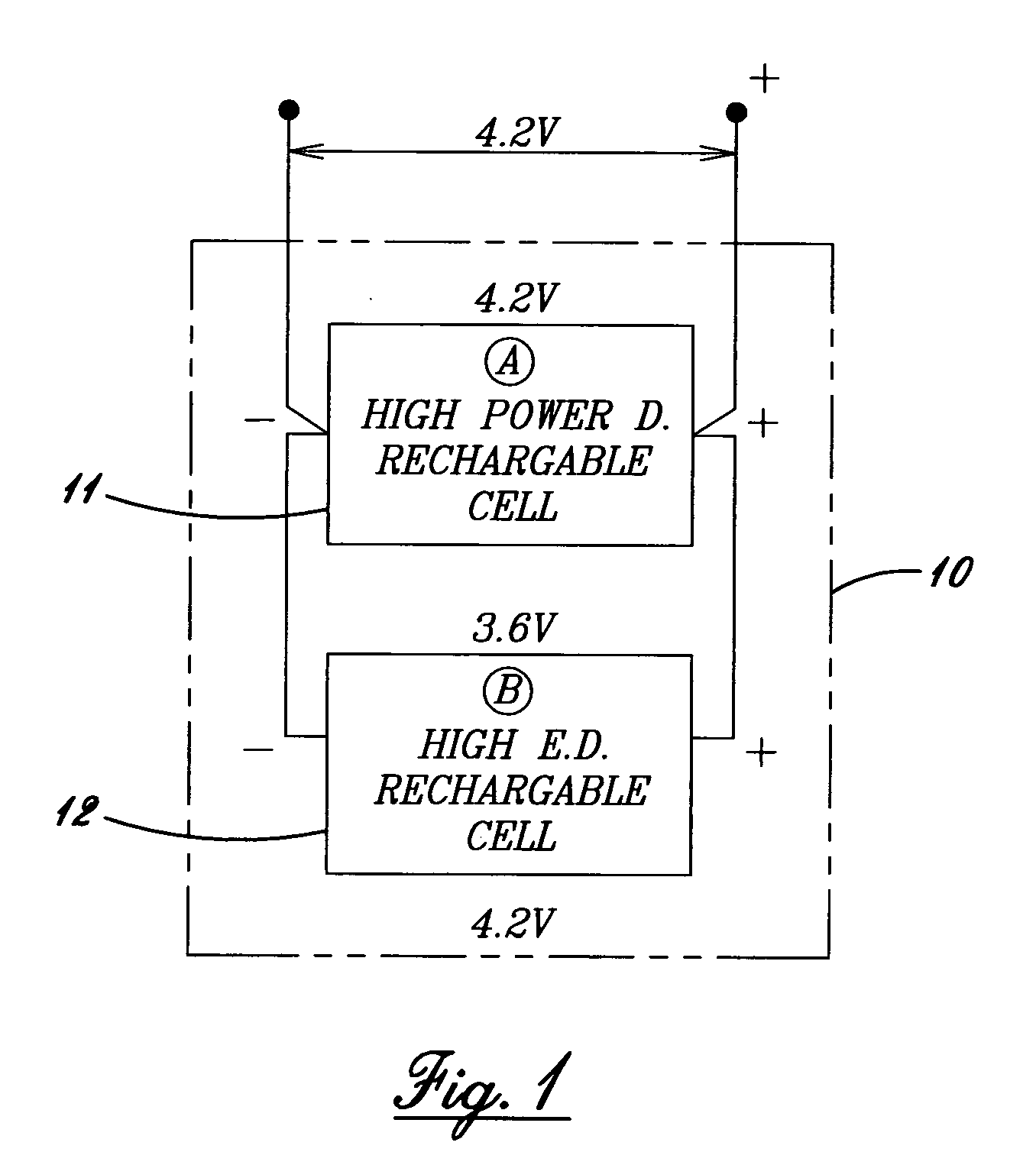
Hybrid rechargeable battery having high power and high energy density lithium cells
InactiveUS20060208692A1Increase powerSafe rechargingBatteries circuit arrangementsOrganic electrolyte cellsNanoparticleHigh energy
A hybrid rechargeable lithium battery, which includes a plurality of high power rechargeable cells, having nano-particles therein, and high energy density rechargeable cells, with the high energy cells recharging the high power cells. The battery preferably includes a low volt parallel charger to simultaneously and individually charge both the high power and high energy cells, through a protective device. All cells are then discharged in series at high voltage, and are individually protected from over discharge. A rechargeable battery having both high power and high energy density cells is thus provided.
Owner:LITHDYNE +1
Membrane syringe
InactiveUS20040116869A1Reduce manufacturing costMaximum safetyClosuresInfusion syringesPrefilled SyringeMembrane configuration
The syringe is a prefillable or prefilled syringe having a syringe cylinder which is delimited to one side by a plunger and which to the other side opens into a syringe connection having a free end closed by a membrane. The syringe cylinder, the syringe connection and the closing membrane are formed as one piece as a plastic injection molded part.
Owner:TRANSCOJECT
Apparatus and method for controllable downhole production of ionizing radiation without the use of radioactive chemical isotopes
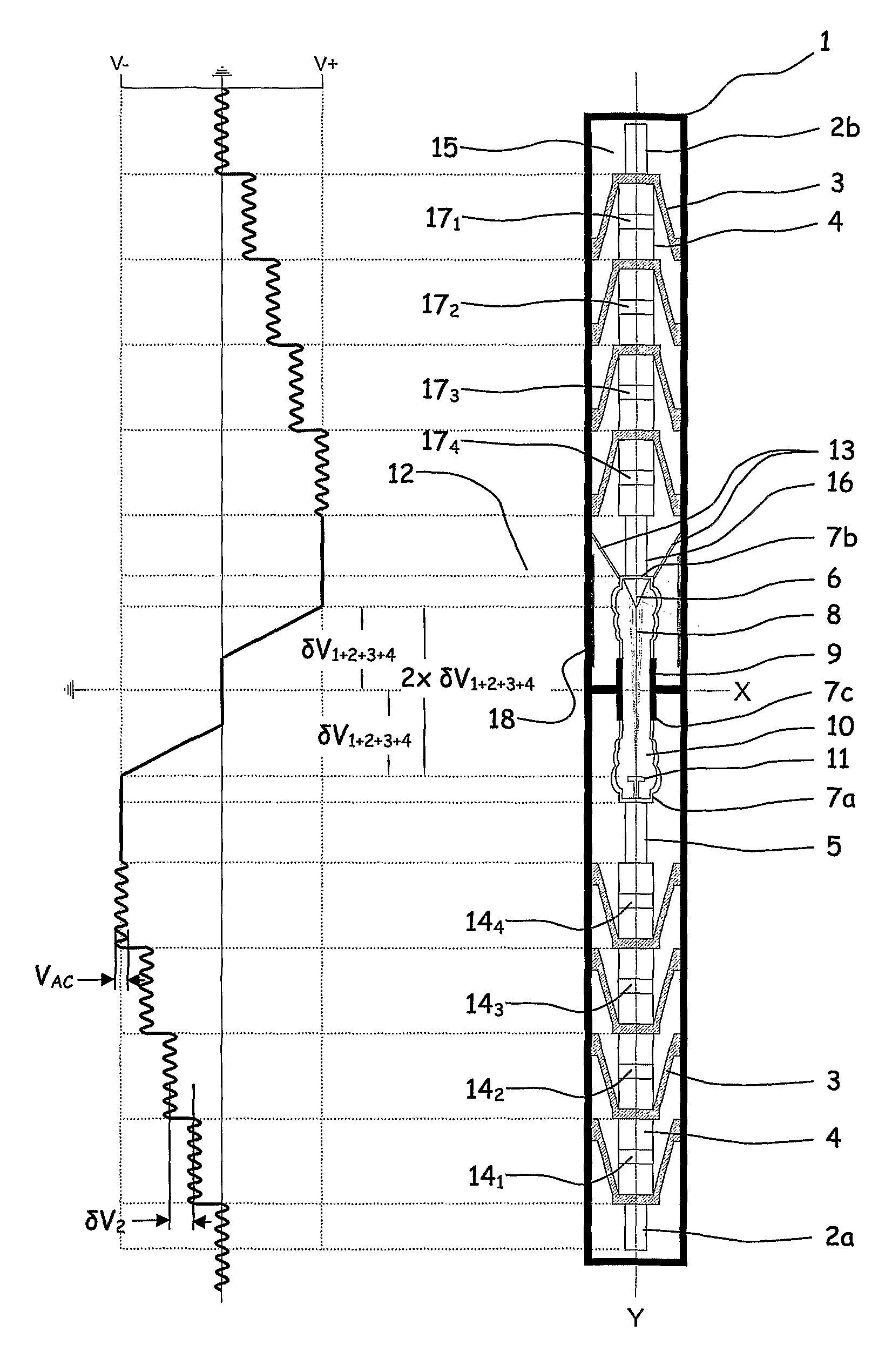
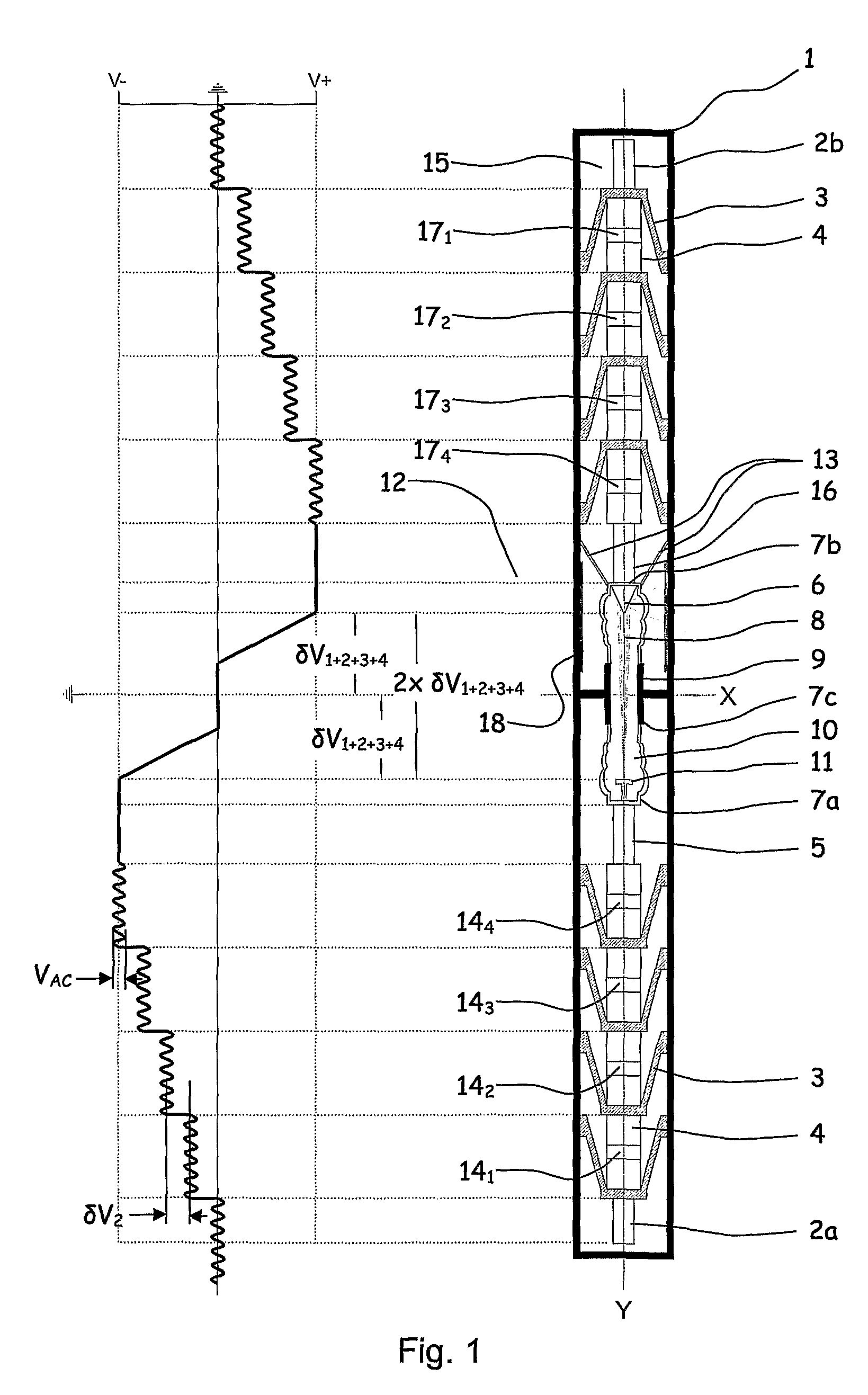
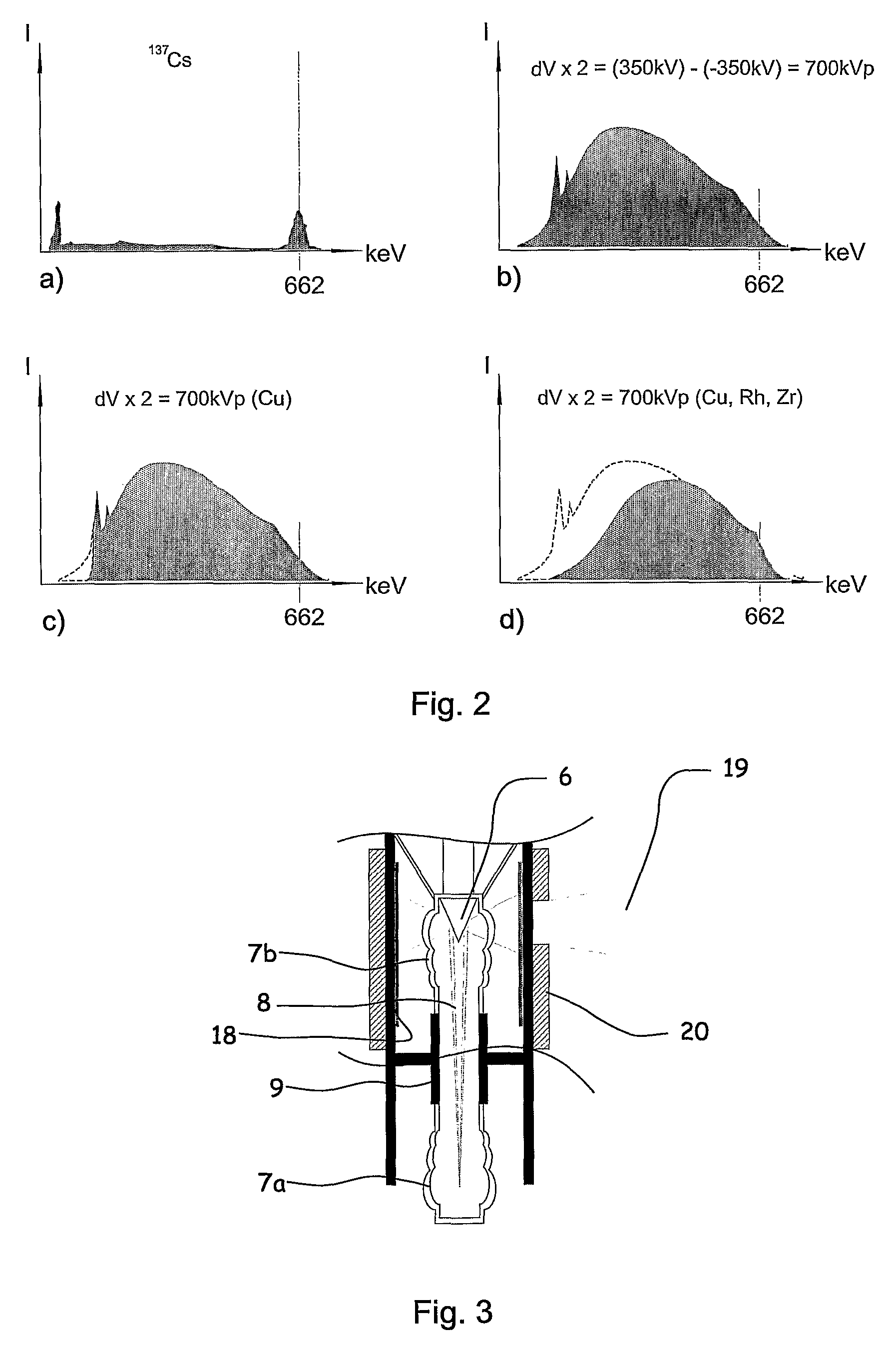
Apparatus for the controllable downhole production of ionizing radiation (12), the apparatus including at least a thermionic emitter (11) which is arranged in a first end portion (7a) of an electrically insulated vacuum container (9), and a lepton target (6) which is arranged in a second end portion (7b) of the electrically insulated vacuum container (9); the thermionic emitter (11) being connected to a series of serially connected negative electrical-potential-increasing elements (141, 142, 143, 144), each of said electrical-potential-increasing elements (141, 142, 143, 144) being arranged to increase an applied direct-current potential (δV0, δV1, δV1+2, . . . , δV1+2+3) by transforming an applied, driving voltage (VAC), and to transmit the increased, negative direct-current potential (δV1, δV1+2, . . . , δV1+2+3+4) and also the driving voltage (VAC) to the next unit in the series of serially connected elements (141, 142, 143, 144,5), and the ionizing radiation (12) exceeding 200 keV with a predominant portion of the spectral distribution within the Compton range.
Owner:VISURAY TECH
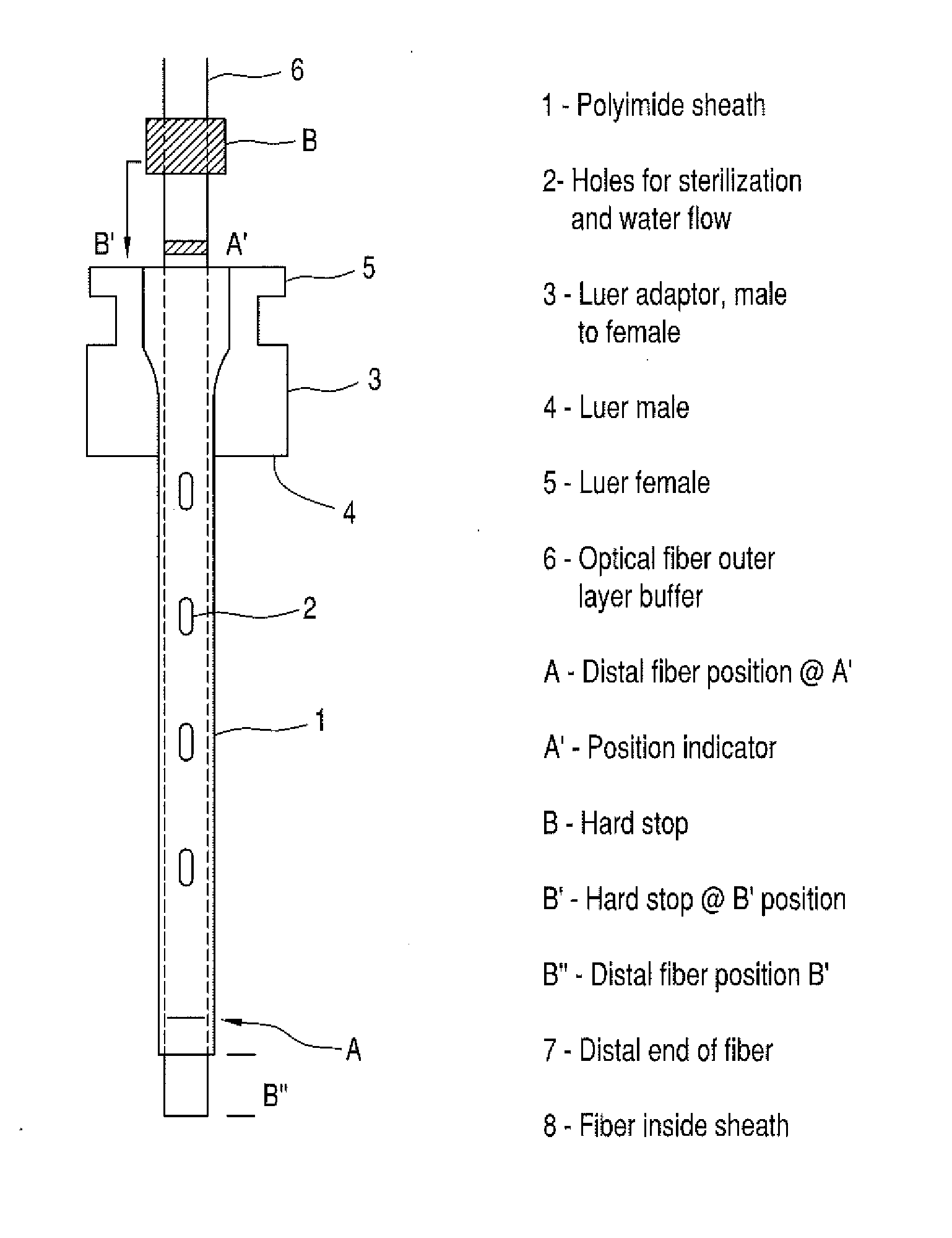
Protective Sheath for Surgical Laser Fiber
A protective sheath of the type used to protect a scope during insertion of a fiber into the scope may include holes for improved fluid flow and for ease of sterilization, reinforcement, a luer connector to position the sheath relative to a scope and to enable use of a seal, pin vise or other device to secure the fiber to sheath during insertion or withdrawal of the sheath from the scope, and / or markings to facilitate positioning of the sheath relative to the scope and / or trimming of the fiber.
Owner:BROWN JOE DENTON
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com