Secure password storage and verification method and device
A technology for password storage and verification methods, which is applied in secure communication devices, encryption devices with shift registers/memory, user identity/authority verification, etc., can solve problems such as inability to resist attacks by conventional password attacks, and achieve increased difficulty, Storage and verification security, the effect of increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
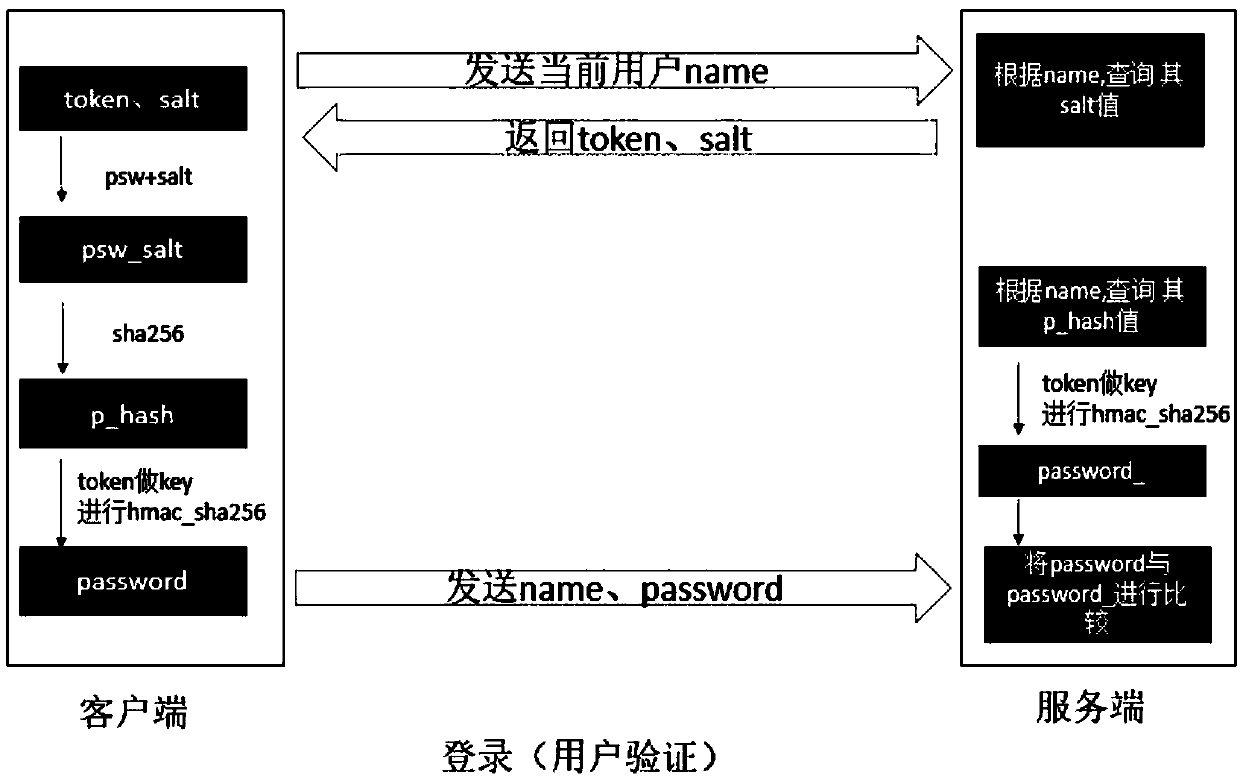
[0111] Preferably, step S20 specifically includes:
[0112] S21), the client obtains the user name and password of the user;
[0113] S22), the client sends the user name of the user to the server;
[0114] S23), the server generates a unique token for this session;
[0115] S24), the server sends the token and the user's Salt corresponding to the user name stored in the server to the client together;
[0116] S25), the client calculates the hash value password after adding Salt to the user's password;
[0117] S26), the client splices the hash value password and the user name;
[0118] S27), the client uses the token as the key, and uses hmac_sha256_hex to calculate the secondary hash value password;
[0119] S28), the client sends the secondary hash value password to the server.
[0120] In this embodiment, the client sends the obtained user name and user password to the server, and the server generates a token and sends it to the client. After the password is concatenat...
Embodiment 2
[0122] Preferably, step S30 specifically includes:
[0123] S31), the server receives the user name and the secondary hash value password sent by the client;
[0124] S32), the server side queries the hash value password corresponding to the user name from the server side through the user name;
[0125] S33), the server side splices the hash value password and the user name;
[0126] S34), the server uses the unique token generated by this session with the client as the key, and uses hmac_sha256_hex to calculate the hash value password stored on the server side to obtain the secondary hash value password;
[0127] S35), the server side compares and verifies the client's secondary hash value password and the server side's secondary hash value password;
[0128] S36), the server sends the verification result to the client;
[0129] If the passwords are consistent, the verification is passed;
[0130] If the passwords do not match, the verification fails.
[0131] In this em...
Embodiment 3
[0133] Preferably, the secure password storage verification method also includes a password modification process, including:
[0134] S41), the client obtains the user name and new password of the user;
[0135] S42), the client acquires a new Salt from the server;
[0136] S43), the client adds Salt to the new password of the user;
[0137] S44), the client obtains a new hash value password through hash algorithm calculation;
[0138] S45), the client stores the user name, the new Salt and the hash value password to the server.
[0139] In this embodiment, when modifying the password, the client will obtain a new Salt. Since the Salt is randomly generated by the server, it is not easy to leak. After adding the Salt to the new password, it will be encrypted by a hash algorithm and then stored on the server to update the user. password, the old password stored on the server will be overwritten and invalidated.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com