Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
604 results about "Electronic content" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic Content Management (ECM), also known as enterprise content management, is the practice of capturing, storing, retrieving, and managing documents, various records, emails, and other electronic documents that organizations create.
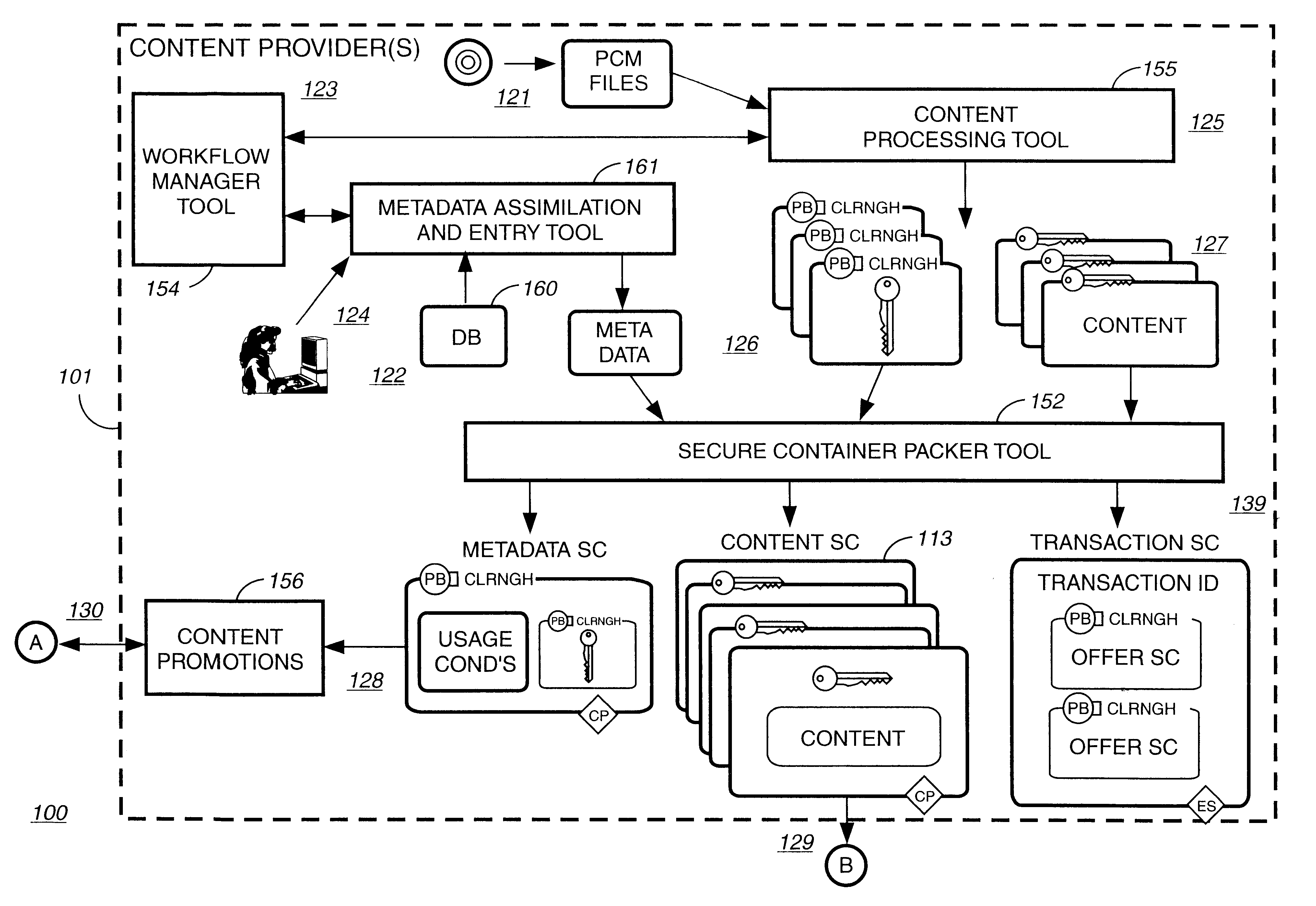
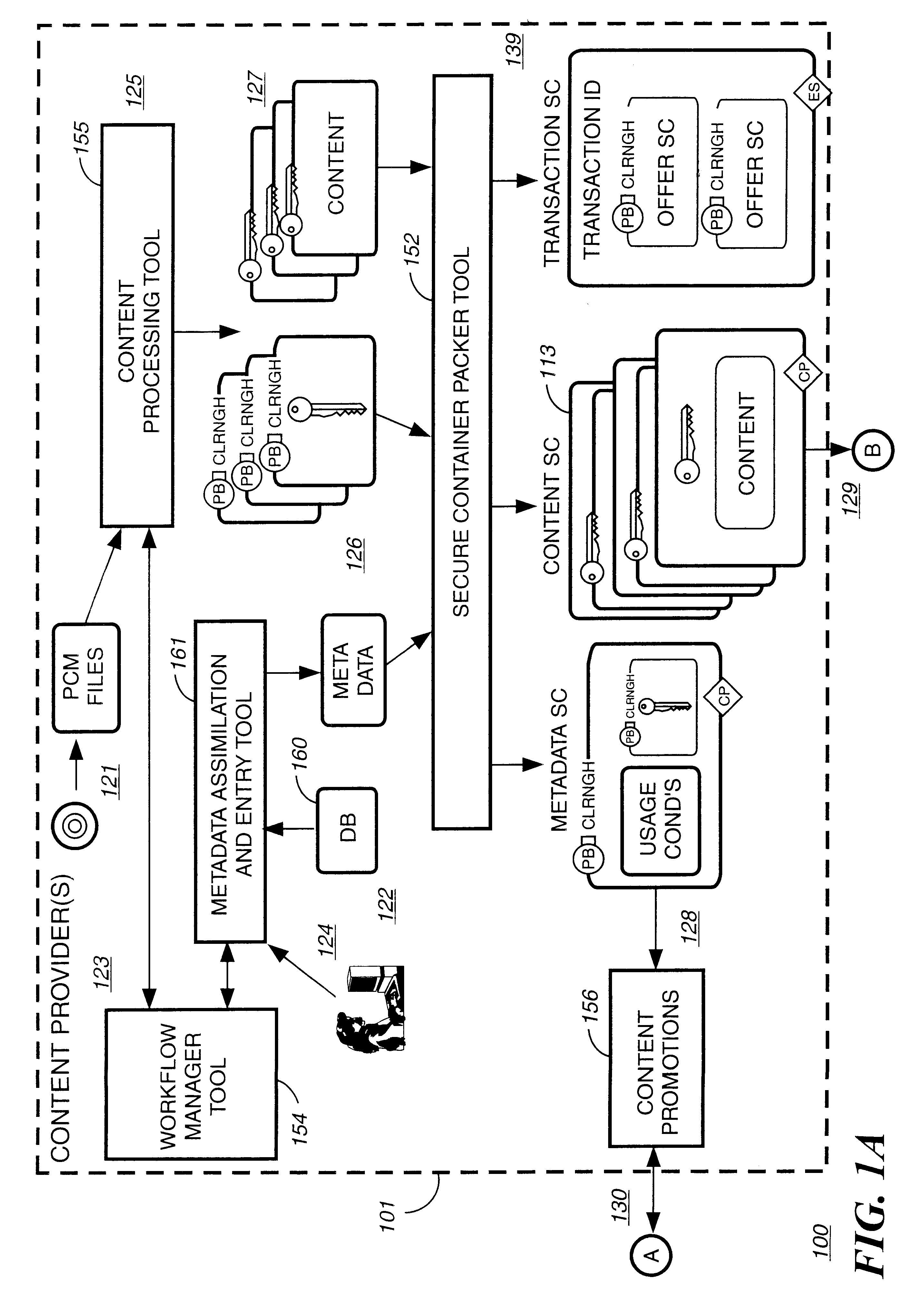
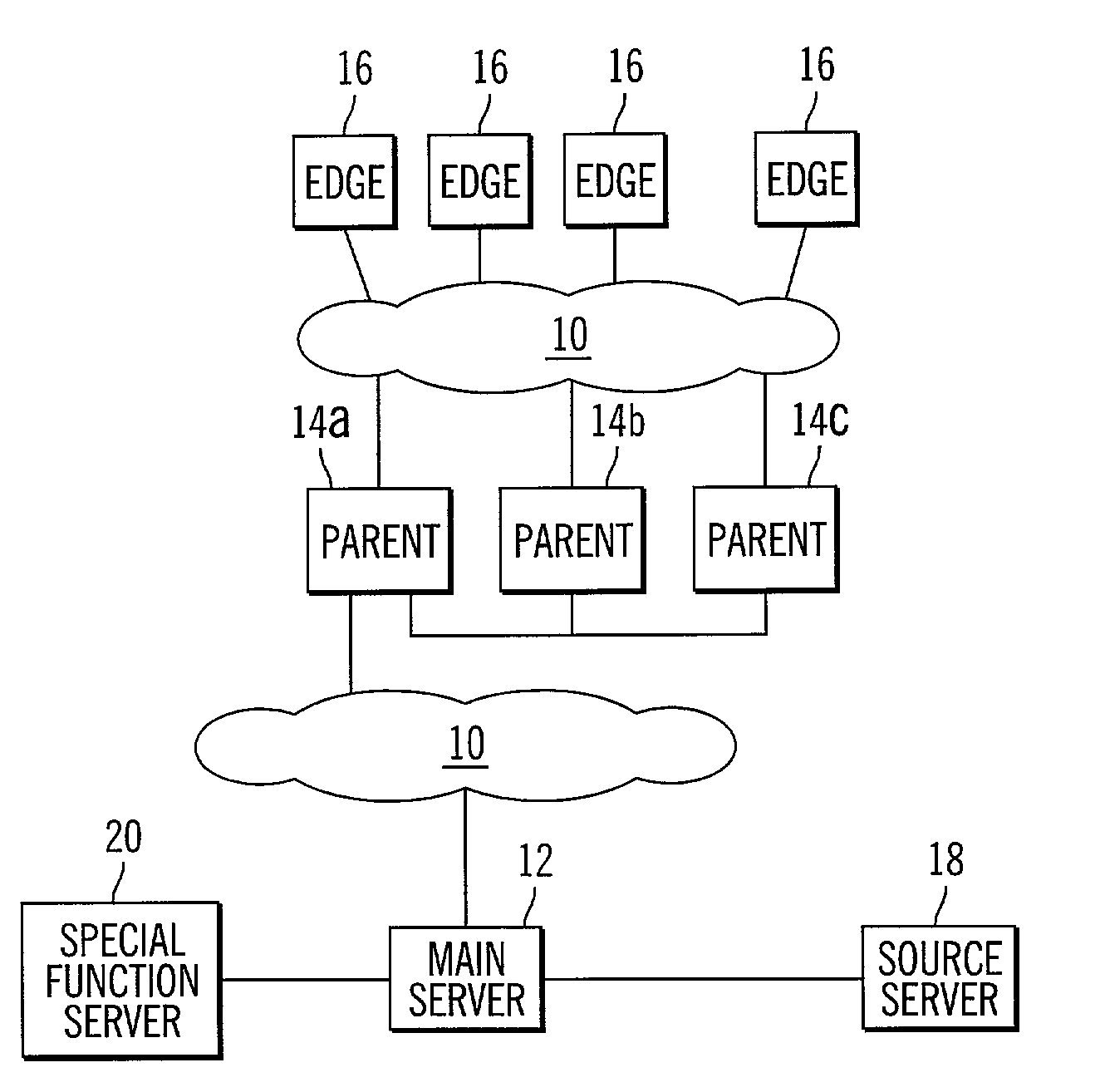
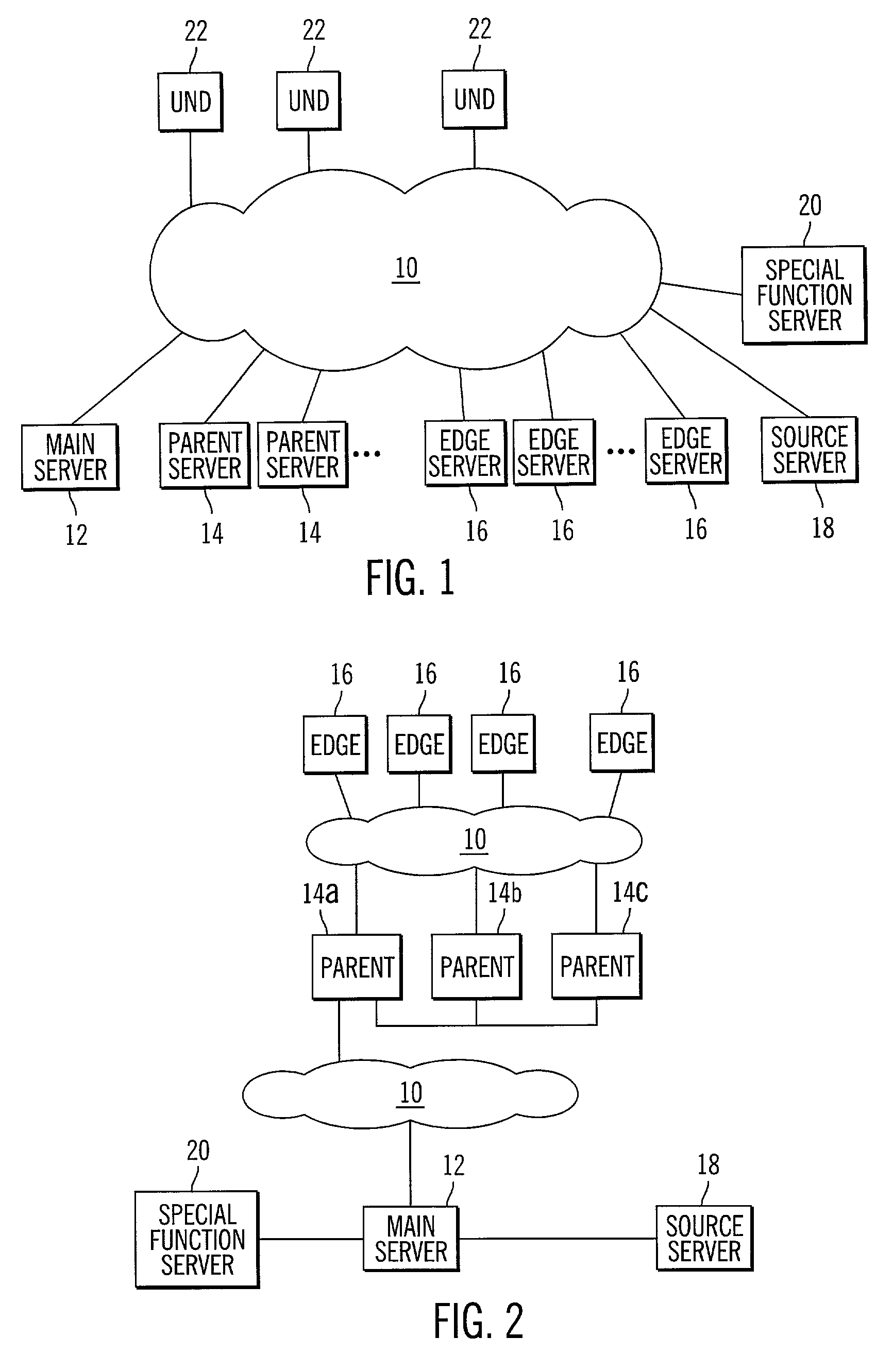
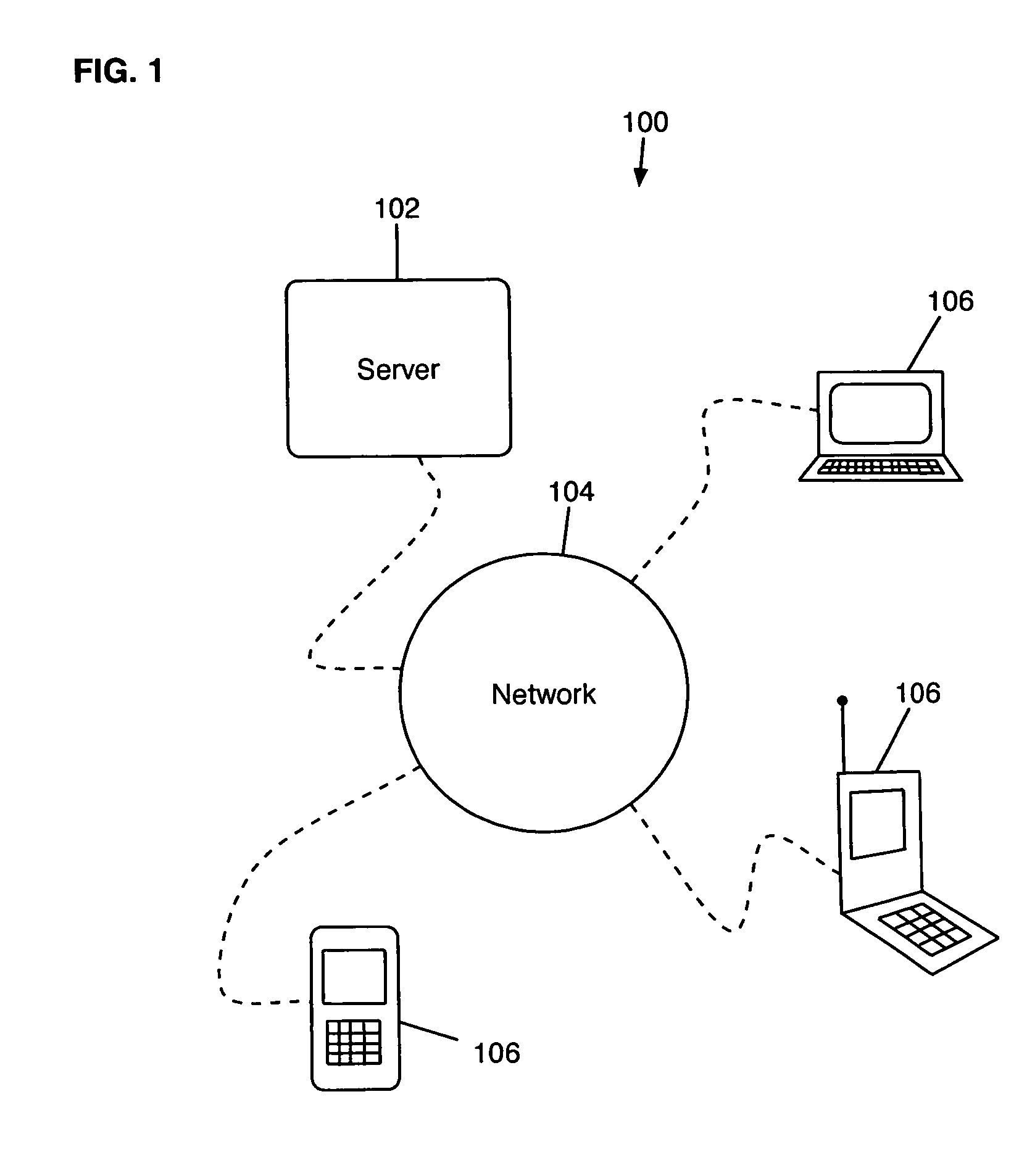
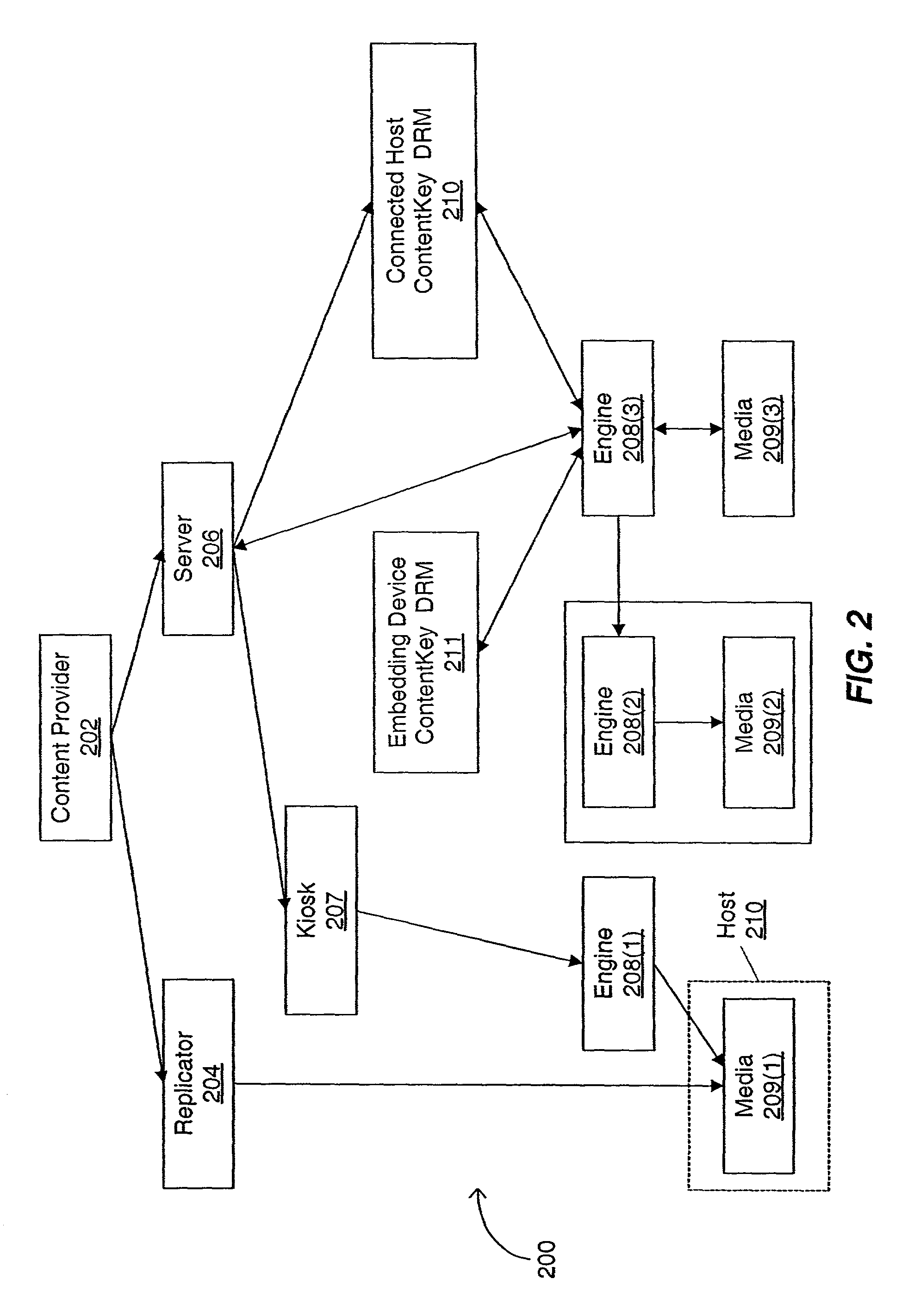
Electronic content delivery system
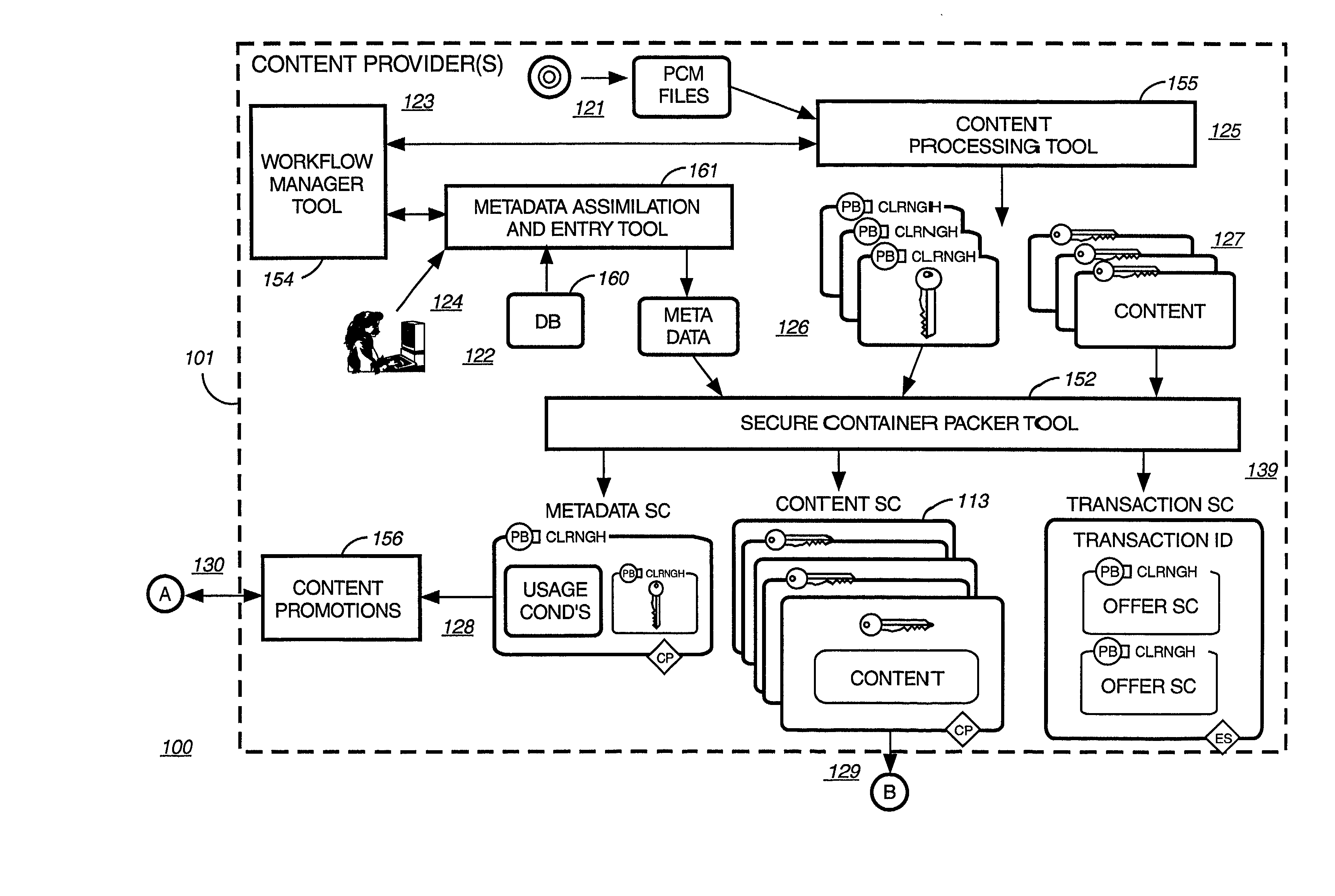
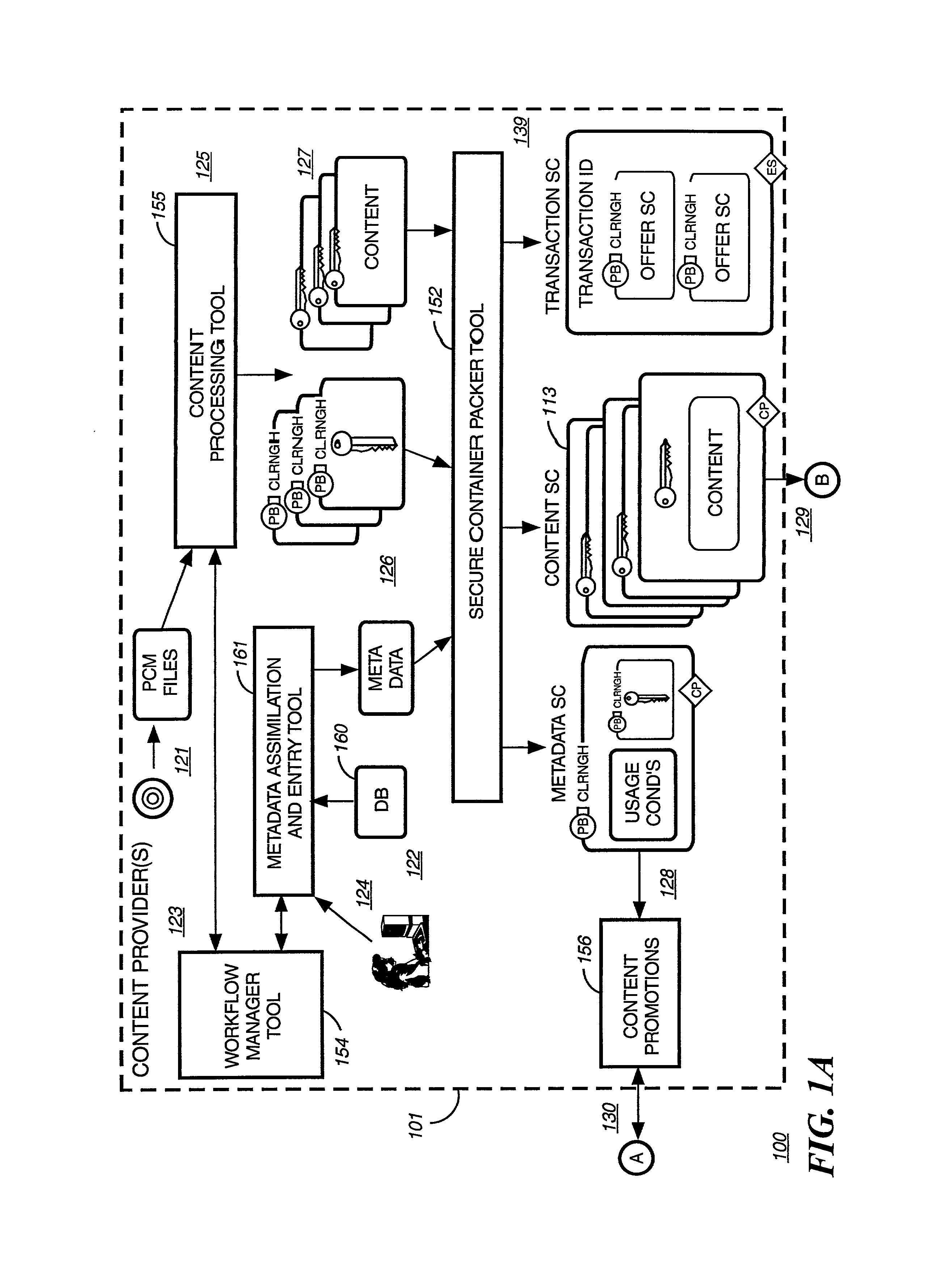
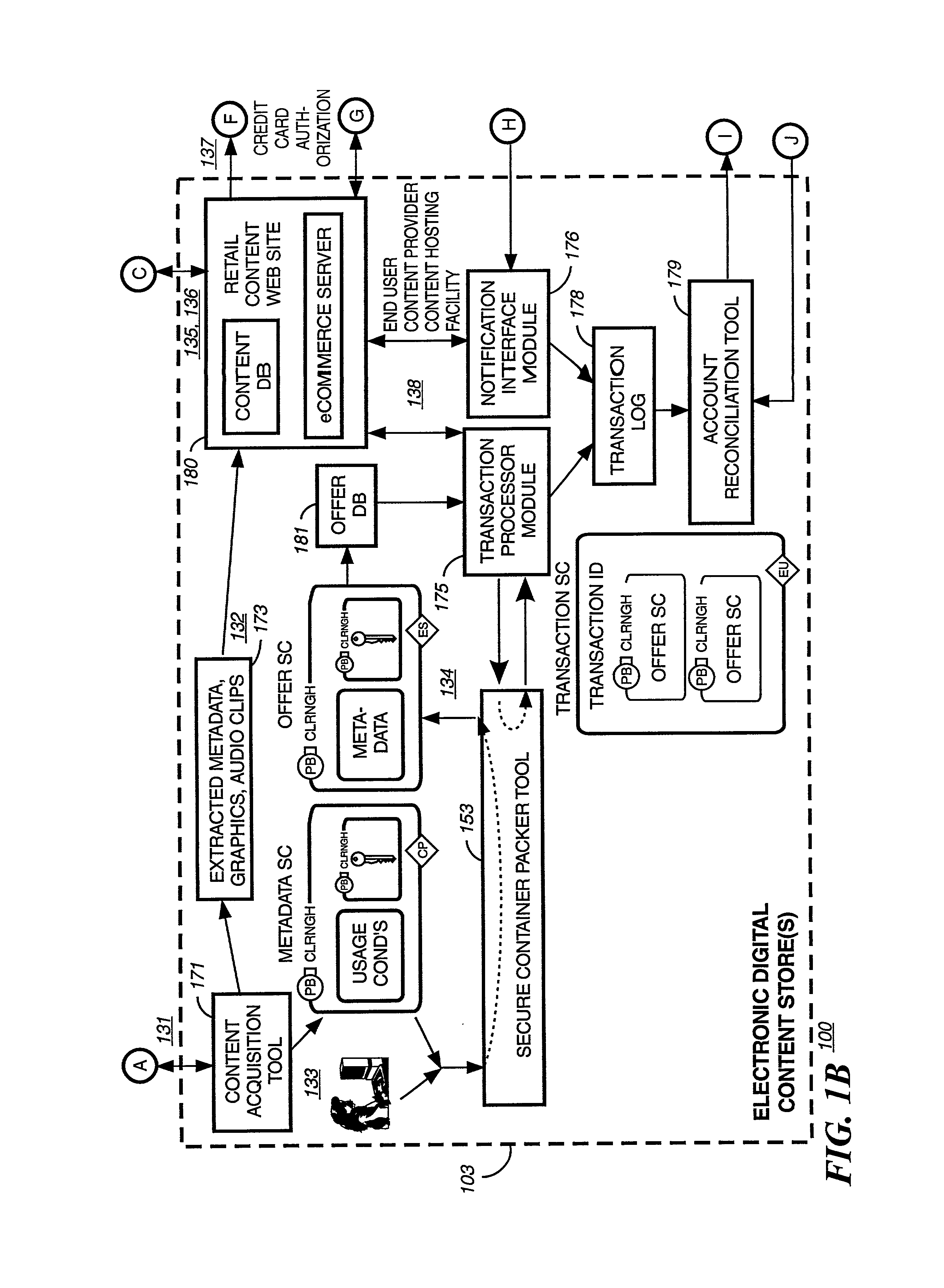
InactiveUS6226618B1Key distribution for secure communicationDigital data processing detailsDelivery systemSystem safety
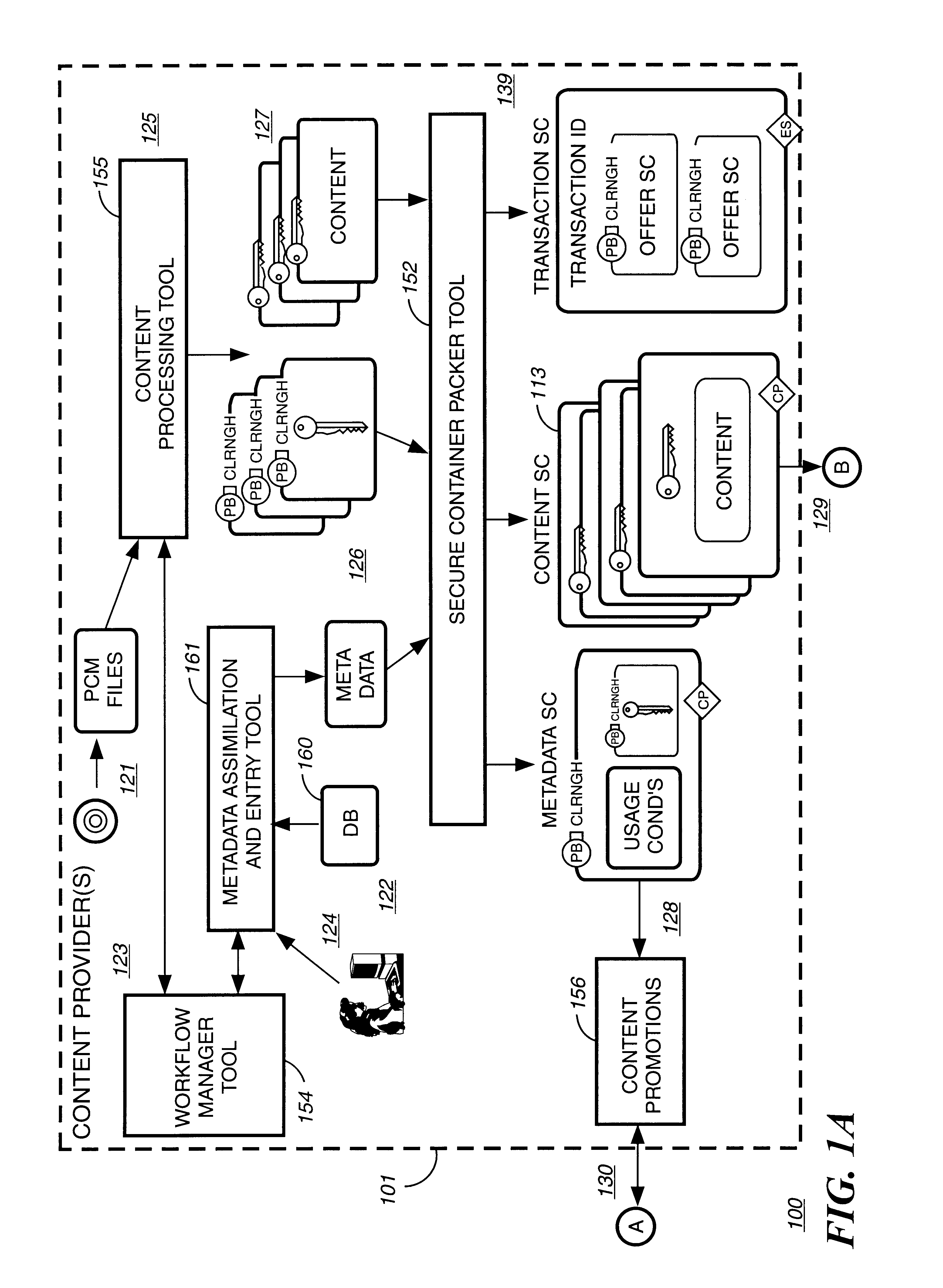
Disclosed is a method and apparatus of securely providing data to a user's system. The data is encrypted so as to only be decryptable by a data decrypting key, the data decrypting key being encrypted using a first public key, and the encrypted data being accessible to the user's system, the method comprising the steps of: transferring the encrypted data decrypting key to a clearing house that possesses a first private key, which corresponds to the first public key; decrypting the data decrypting key using the first private key; re-encrypting the data decrypting key using a second public key; transferring the re-encrypted data decrypting key to the user's system, the user's system possessing a second private key, which corresponds to the second public key; and decrypting the re-encrypted data decrypting key using the second private key.
Owner:LEVEL 3 COMM LLC
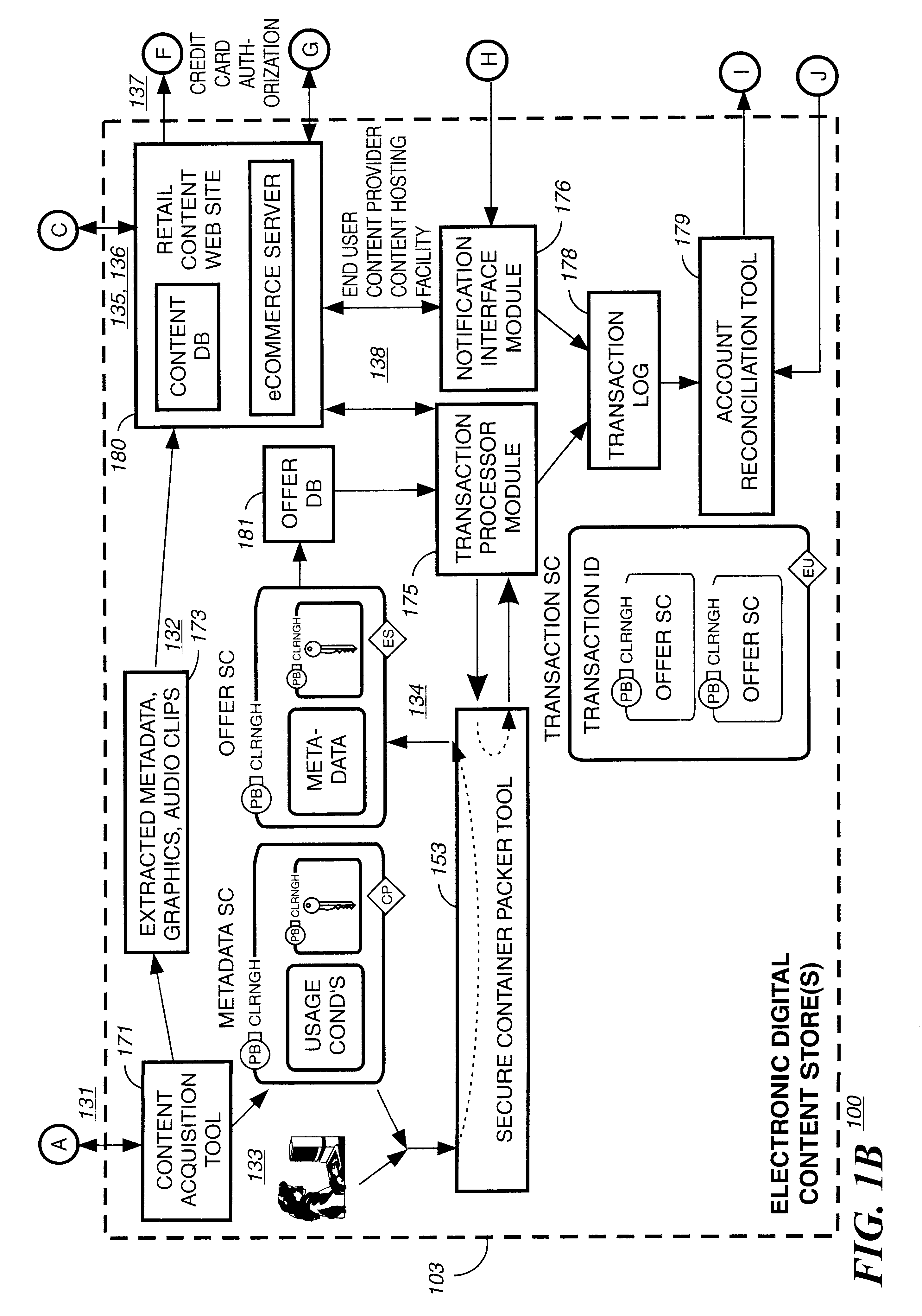
Secure electronic content distribution on CDS and DVDs
InactiveUS6611812B2Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
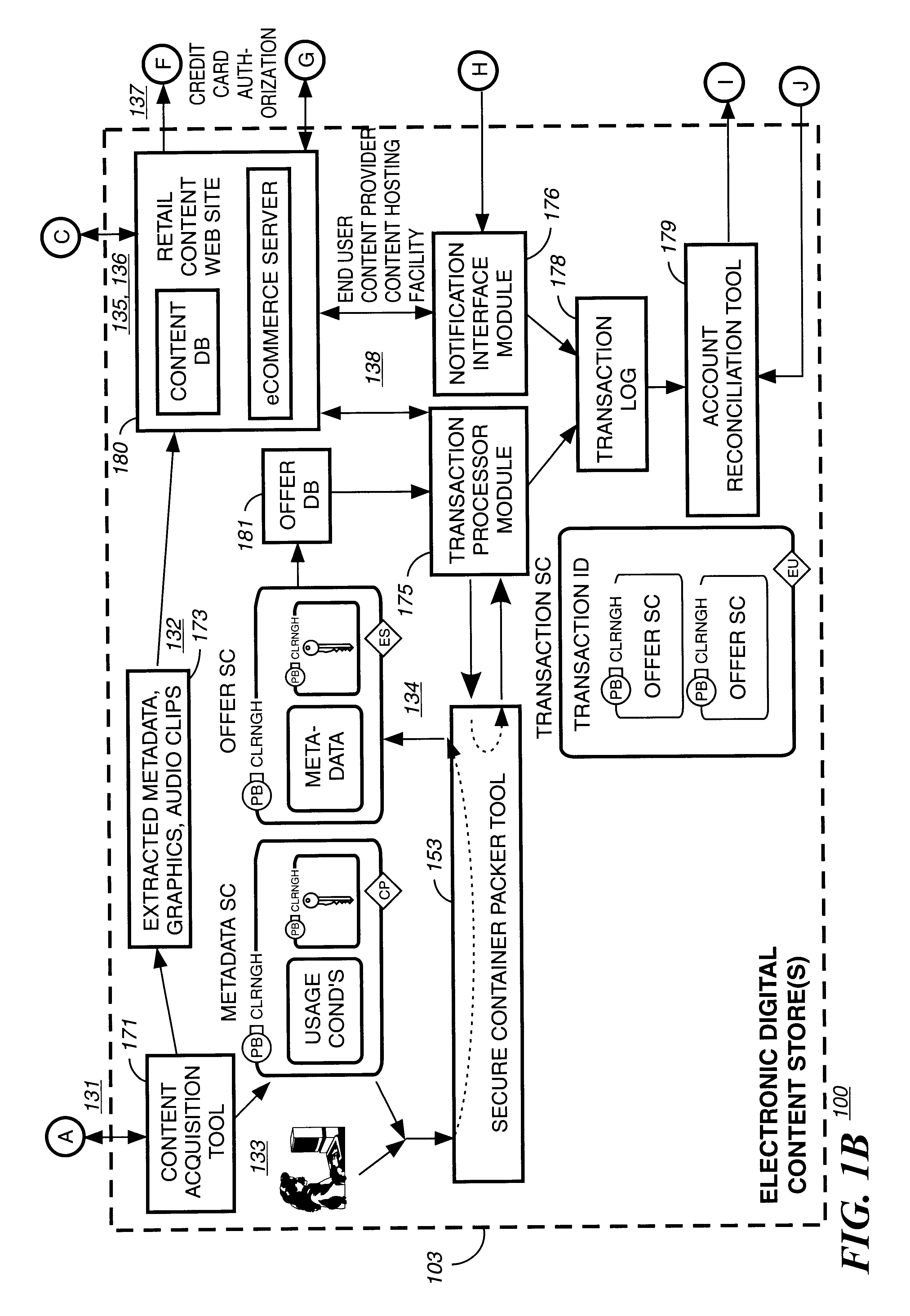
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
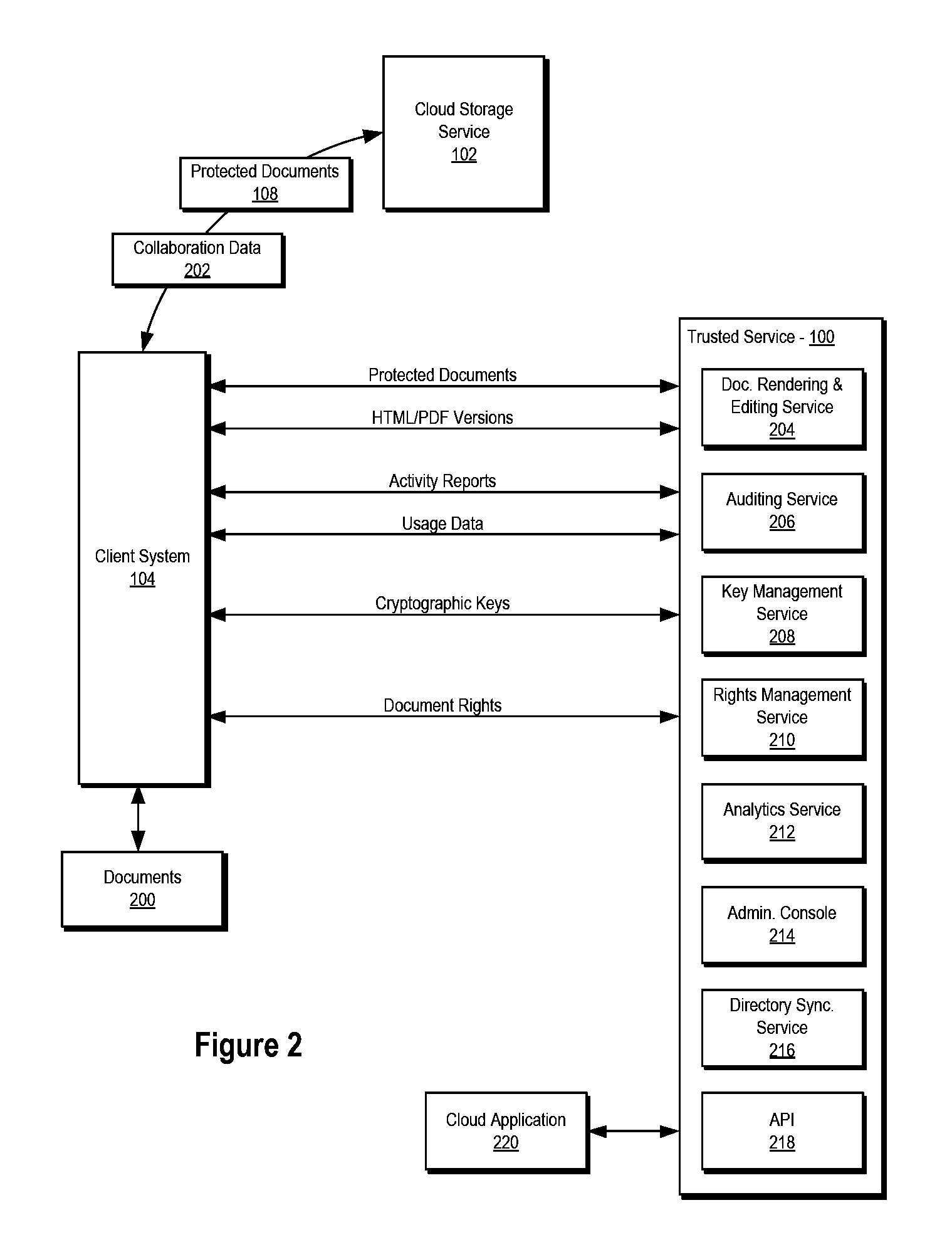
Systems and methods for managing documents and other electronic content
InactiveUS20130254699A1Reduce riskOffice automationSpecial data processing applicationsThird partyInternet privacy
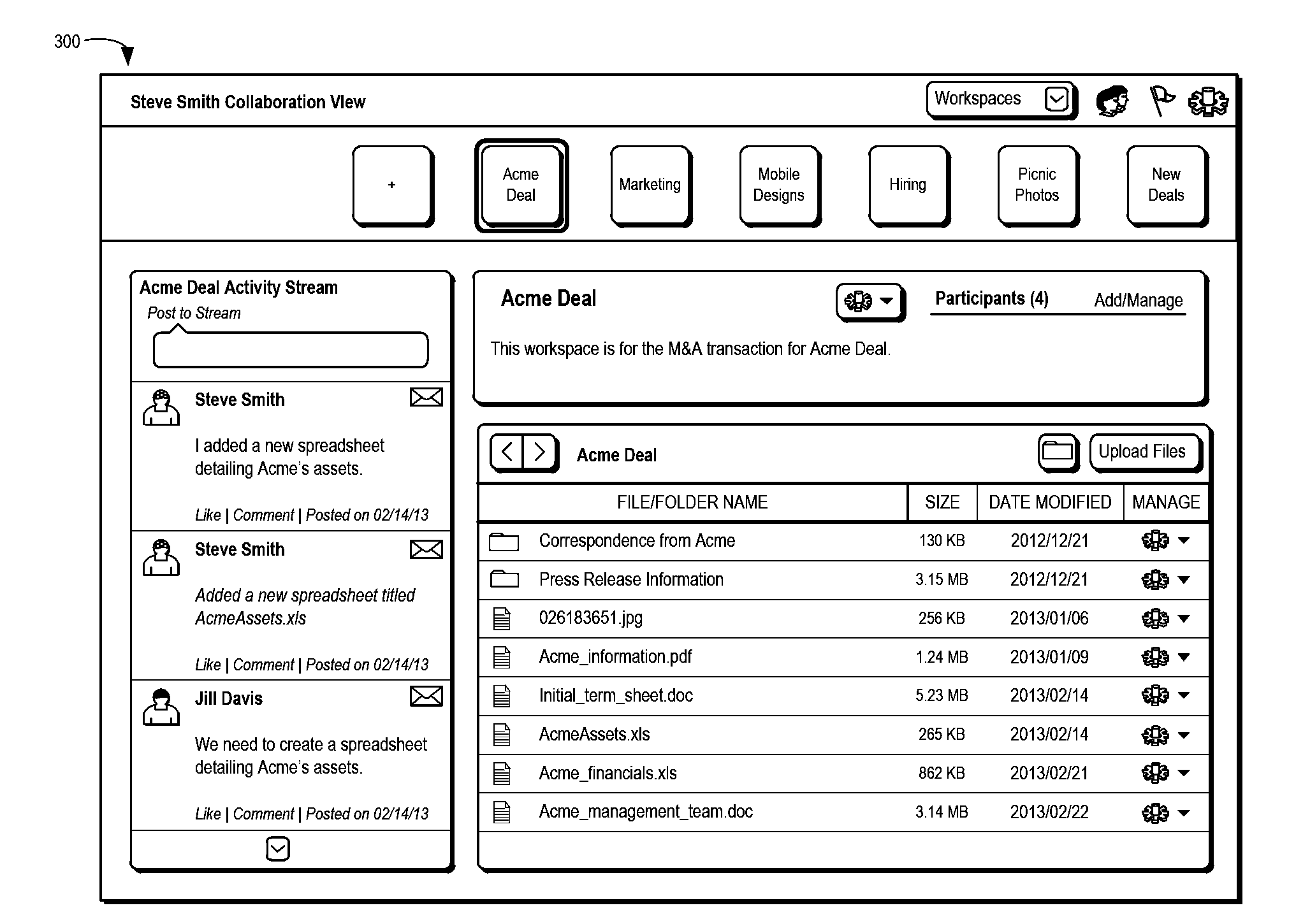
This disclosure relates to systems and methods for managing documents and other electronic works. Certain embodiments relate to enabling secure, governed, and / or audited collaboration and / or document management over cloud storage platforms (e.g., third-party cloud storage platforms). Further embodiments relate to providing key and rights management as well as collaboration services in conjunction with cloud storage services.
Owner:BASHIR TAUSEEF +4
Integrated messaging, contacts, and mail interface, systems and methods
InactiveUS20080261569A1Special service for subscribersSubstation equipmentService provisionMessage passing
Systems and methods for integrating and aggregating content for a mobile device are provided. Electronic content gathered from service providers over a network is presented in an intuitive, efficient and effective manner to easily allow a mobile device user seamless access to a variety of electronic content and functionality. An integrated message system for organizing information for registered accounts on a mobile device is also provided. The system includes an aggregated content interface presenting a number of service provider indicators. The system also includes submenus corresponding to each of the service provider indicators of the aggregated content interface. Each of the submenus includes a plurality of tabbed interfaces that replicate the functionality of a service provider.
Owner:VIRGIN MOBILE USA
Network configured for delivery of content for download to a recipient
InactiveUS7024466B2Increase speed and efficiencyEffective controlMultiprogramming arrangementsMultiple digital computer combinationsEdge serverNetwork architecture
Owner:BLOCKBUSTER LLC
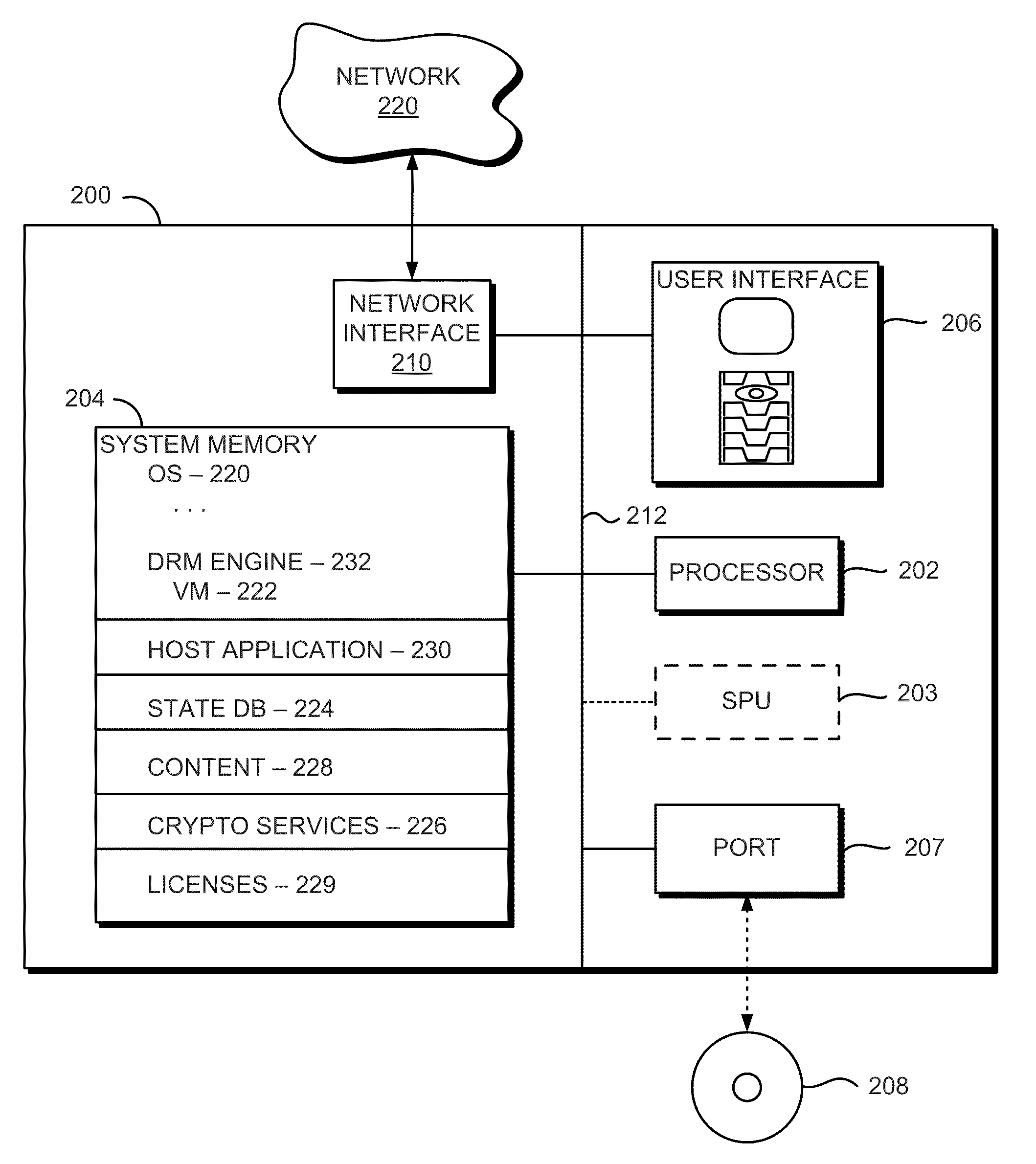
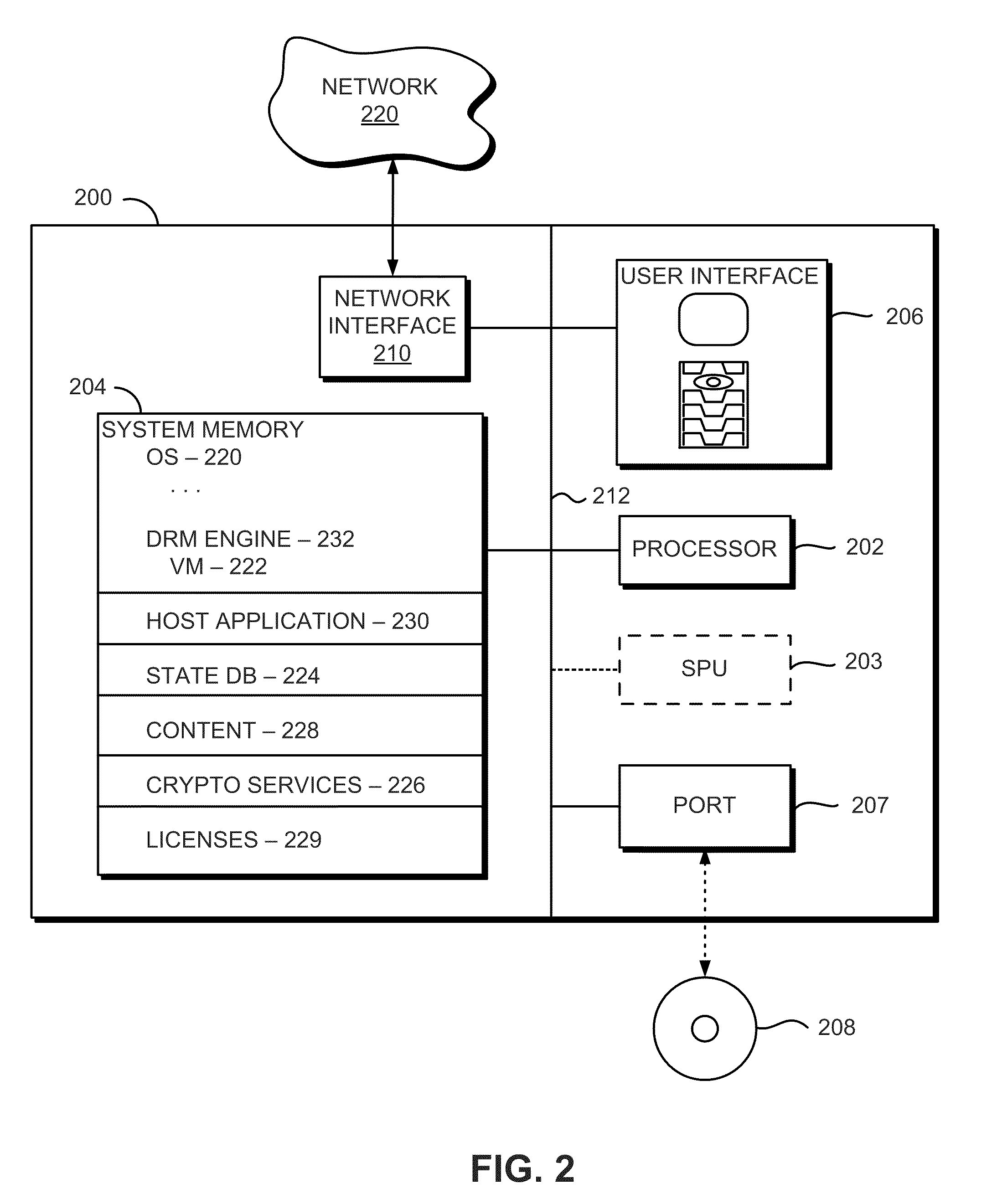
System and method for accessing protected content in a rights-management architecture
InactiveUS6996720B1Digital data processing detailsUnauthorized memory use protectionPersonalizationDigital rights management system
A digital rights management system for the distribution, protection and use of electronic content. The system includes a client architecture which receives content, where the content is preferably protected by encryption and may include a license and individualization features. Content is protected at several levels, including: no protection; source-sealed; individually-sealed (or “inscribed”); source-signed; and fully-individualized (or “owner exclusive”). The client also includes and / or receives components which permit the access and protection of the encrypted content, as well as components that allow content to be provided to the client in a form that is individualized for the client. In some cases, access to the content will be governed by a rights construct defined in the license bound to the content. The client components include an object which accesses encrypted content, an object that parses the license and enforces the rights in the license, an object which obtains protection software and data that is individualized for the client and / or the persona operating the client, and a script of instructions that provides individualization information to a distributor of content so that the content may be individualized for the client and / or its operating persona. Content is generally protected by encrypting it with a key and then sealing the key into the content in a way that binds it to the meta-data associated with the content. In some instances, the key may also be encrypted in such a way as to be accessible only by the use of individualized protection software installed on the client, thereby binding use of the content to a particular client or set of clients.
Owner:MICROSOFT TECH LICENSING LLC
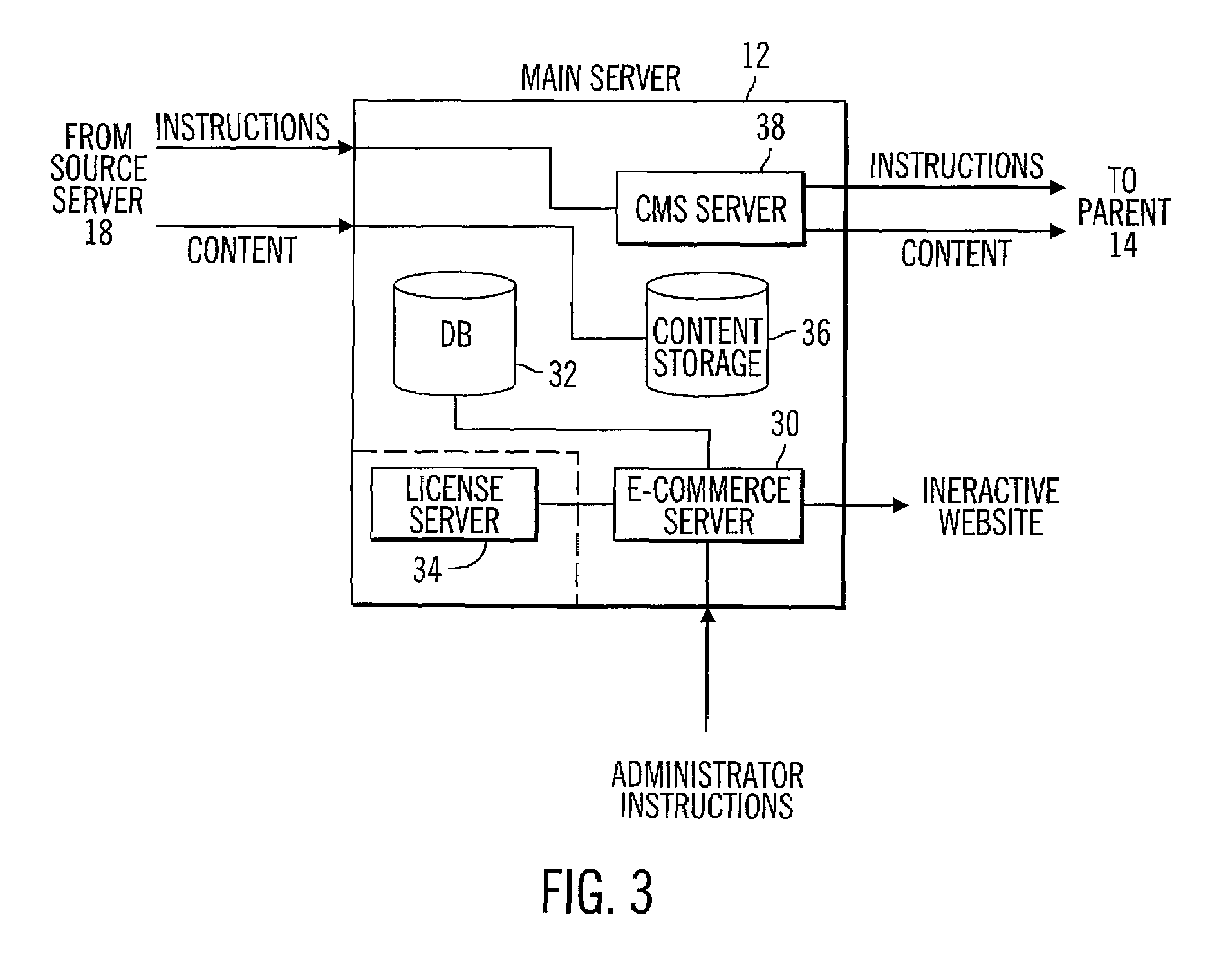
Content management systems and methods
InactiveUS20130219459A1Less timeMany timesTransmissionSpecial data processing applicationsContent managementContent management system
This disclosure relates to systems and methods for managing content. In one embodiment, a method of managing electronic content from a plurality of a user's computing devices is disclosed. Content from the devices is automatically uploaded to a media hub service that securely routes, processes, synchronizes, and / or stores the content in accordance one or more user-specified policies.
Owner:INTERTRUST TECH CORP
Secure electronic content distribution on cds and dvds
InactiveUS20030105718A1Key distribution for secure communicationDigital data processing detailsDigital contentComputer terminal
A method to delivery encrypted digital content to a end user system for playing the content comprising the steps of: reading from a computer readable medium metadata which has previously associated with the content. A user selects from the metadata associated content to decrypt and the end user system establishes a secure connection with an authorization authority for decrypting the content. The end user system receives a secure container containing the decrypting key for decrypting at least part of the previously encrypted content as permitted. The system creates a secure container using the encrypting key from a clearing house, wherein the secure container has an encrypting key therein from the end user system; transferring the secure container to the clearing house for authentication of permission to decrypt the content. The system receives from the clearing house, a secure container encrypted using the encrypting key of the end user system containing the decrypting key for decrypting at least part of the previously encrypted content stored on the computer readable medium as permitted; and playing at least part of the previously encrypted content by decrypting the secure container using the encrypting key of the end user system to access the decrypting key for decrypting at least part of the encrypted content.
Owner:WISTRON CORP
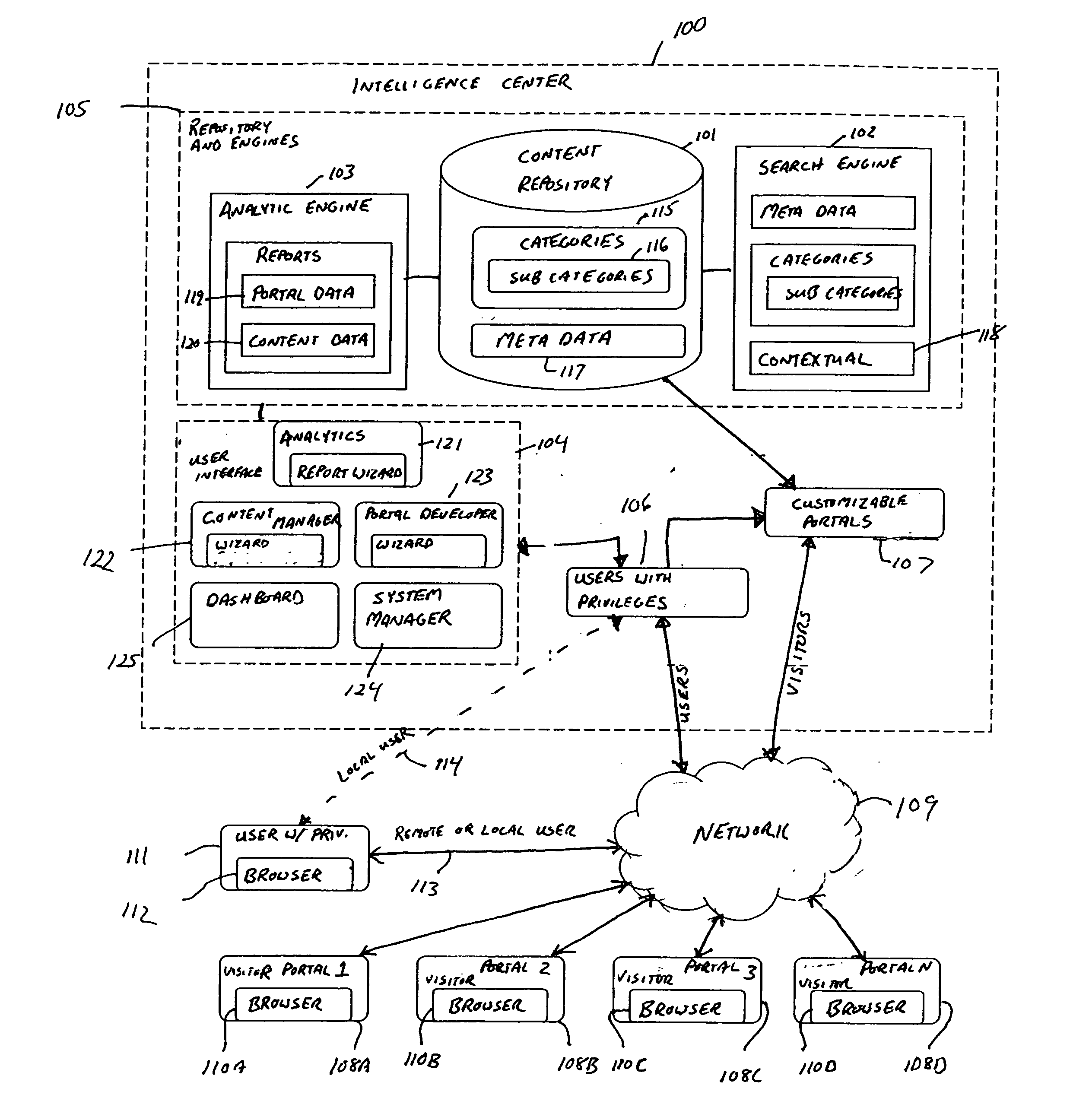
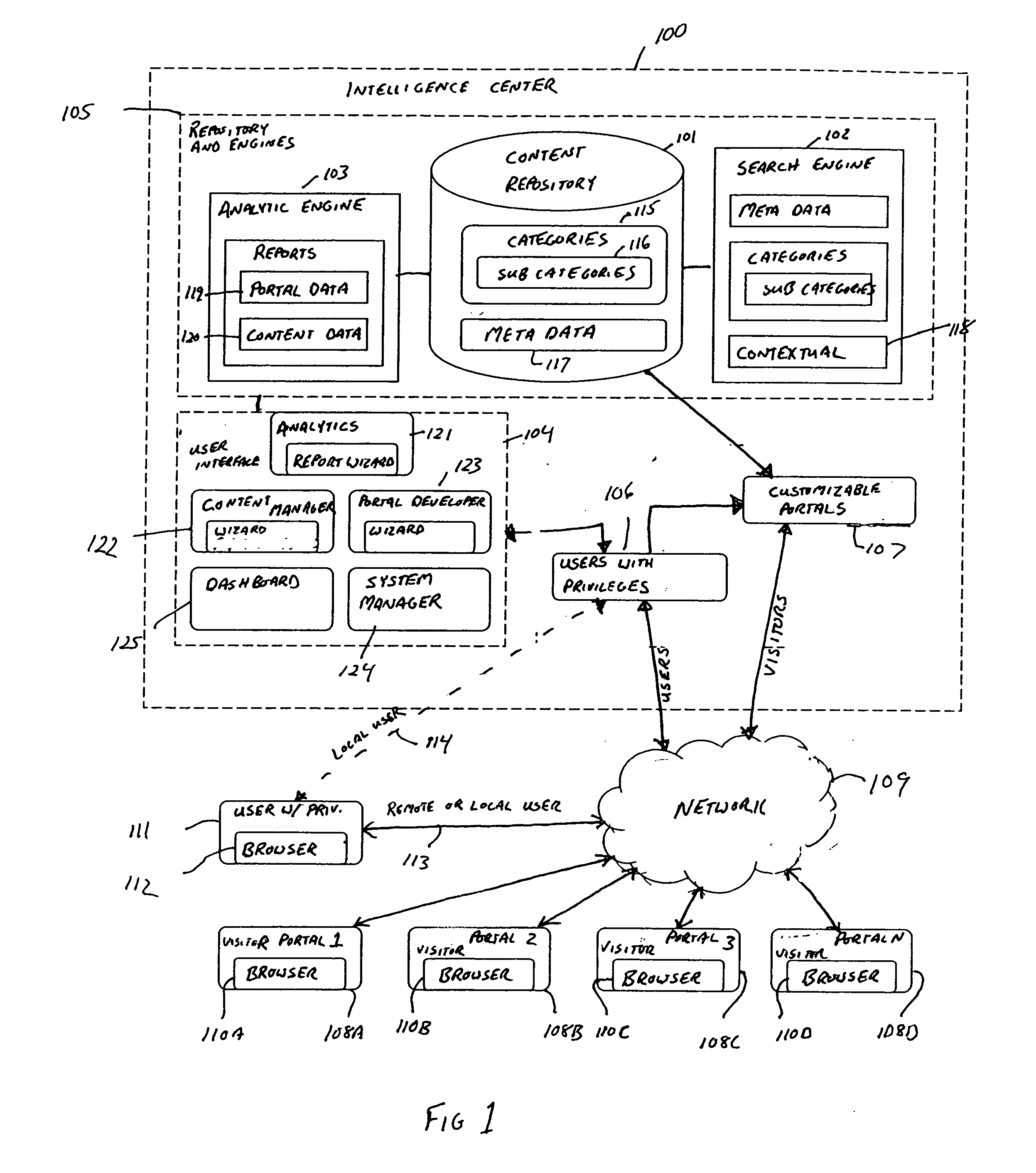
System and method for providing intelligence centers
ActiveUS20050278297A1Customer relationshipDigital data processing detailsWeb browserContent management
Disclosed herein, among other things, is a system comprising a content repository, a communication portal developer, a content manager, and an analytic engine. The content repository is adapted to store electronic content in a computer-readable storage medium. The communication portal developer includes at least one wizard to create a plurality of customizable portals without coding software. Each customizable portal is accessible to one or more selected visitors through a web browser. The content manager is adapted to publish selectable electronic content to selectable portals. The content manager includes at least one wizard to populate and manage the electronic content within the content repository. The analytic engine analyzes electronic content use and visitor behavior while logged into their customizable portal. In various embodiments, the analytics are provided in real time or near real time. Other embodiments are disclosed herein.
Owner:CALLIDUS SOFTWARE
Apparatus and method for creating and using documents in a distributed computing network
Owner:TRINTUITION
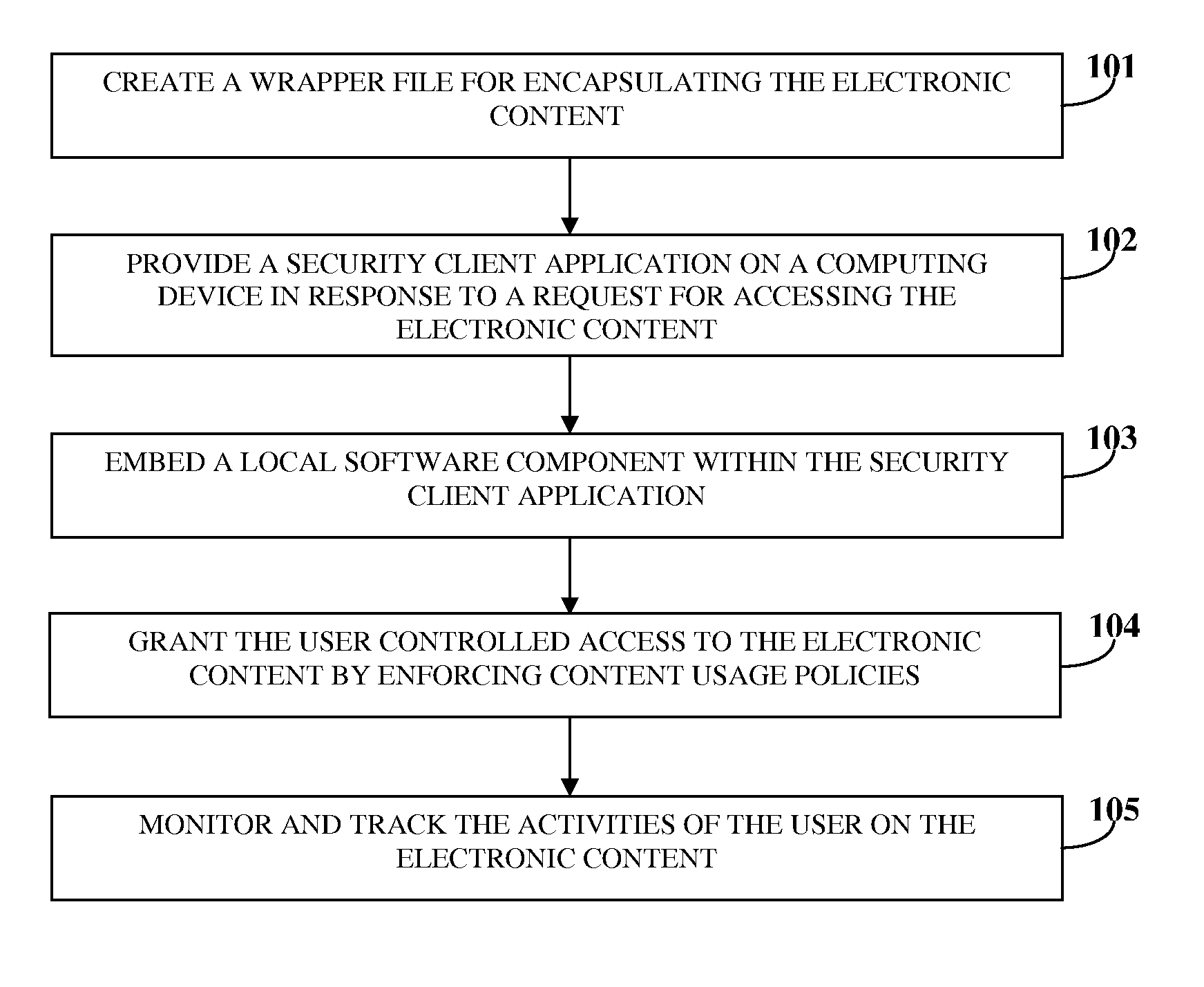
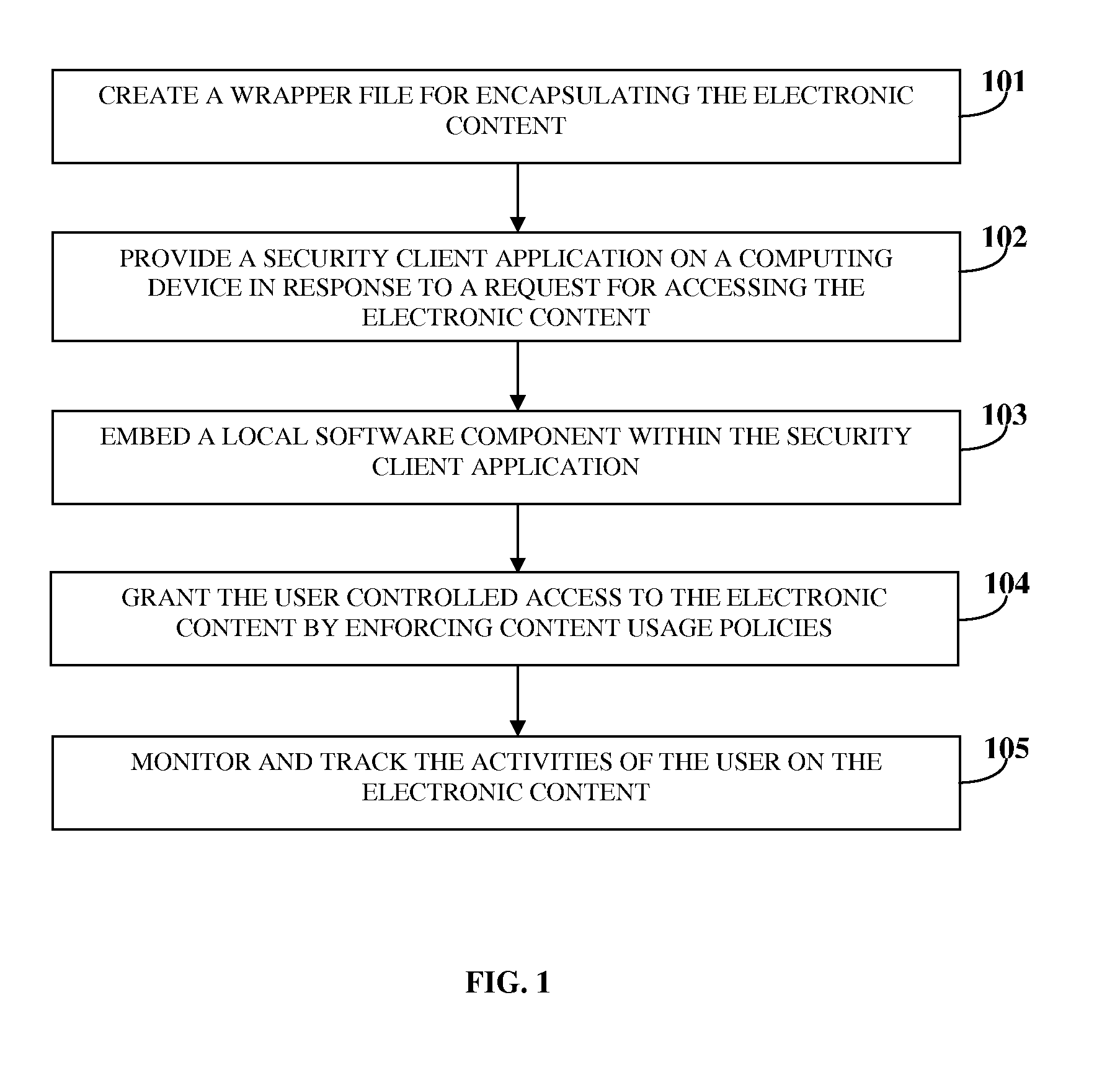
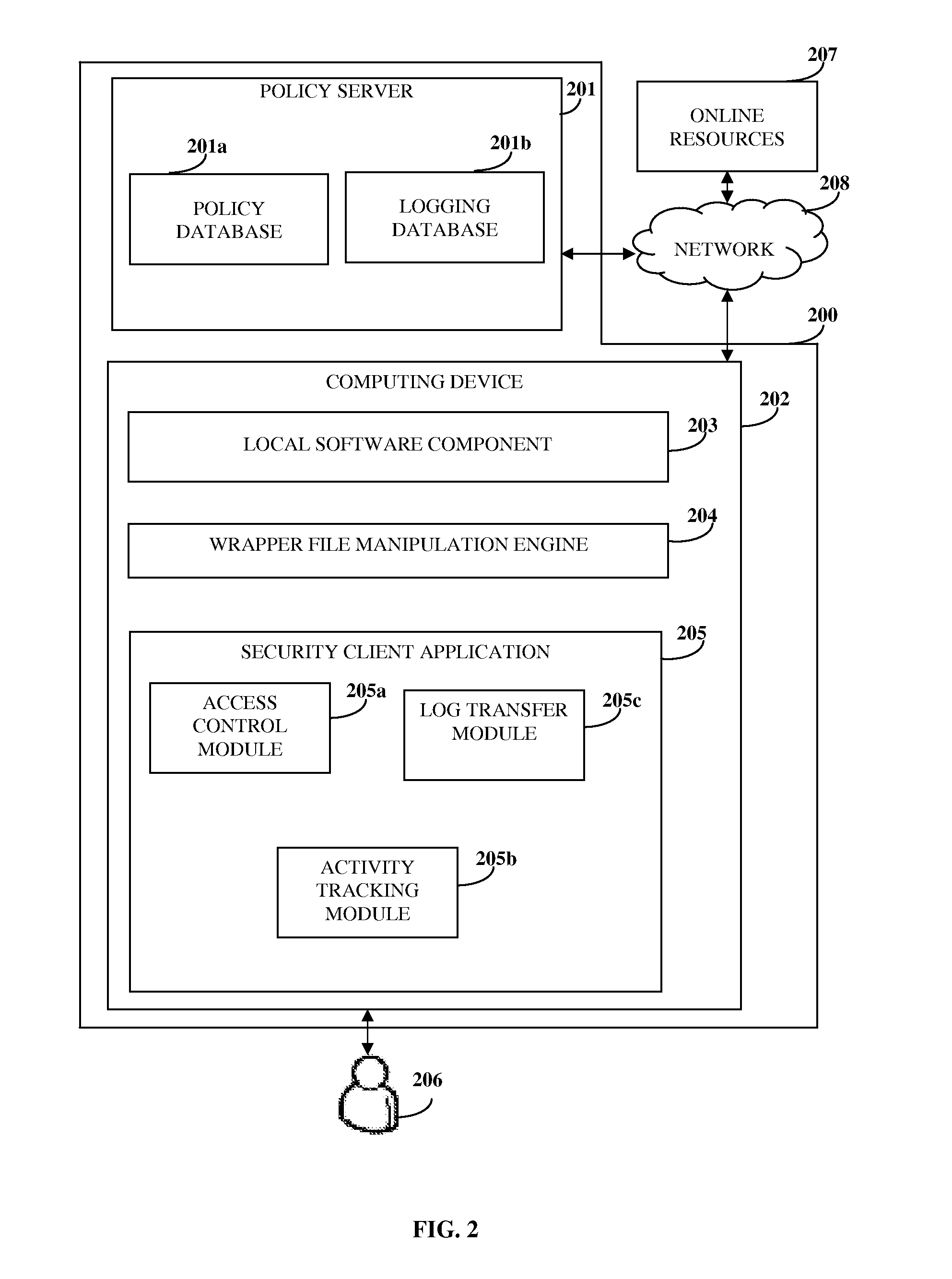
System To Secure Electronic Content, Enforce Usage Policies And Provide Configurable Functionalities
ActiveUS20100146269A1Avoid misuseDigital data processing detailsAnalogue secracy/subscription systemsClient-sideSystem protection
A computer implemented method and system for managing electronic content security and access within a networked environment are provided. A proprietary wrapper file is created for encapsulating the electronic content upon transferring the electronic content to the computing device of a user. The proprietary wrapper file is configured for enforcing content usage policies on the electronic content and for performing configurable functionalities. A security client application is provided on the computing device in response to a request for accessing the electronic content. A local software component employed for accessing the electronic content is embedded within the security client application. The user is granted controlled access to the electronic content by enforcing the content usage policies through the wrapper file. The activities of the user on the electronic content are monitored and tracked by the security client application to ensure compliance of the activities with the enforced content usage policies.
Owner:PAWAA SOFTWARE PVT +1
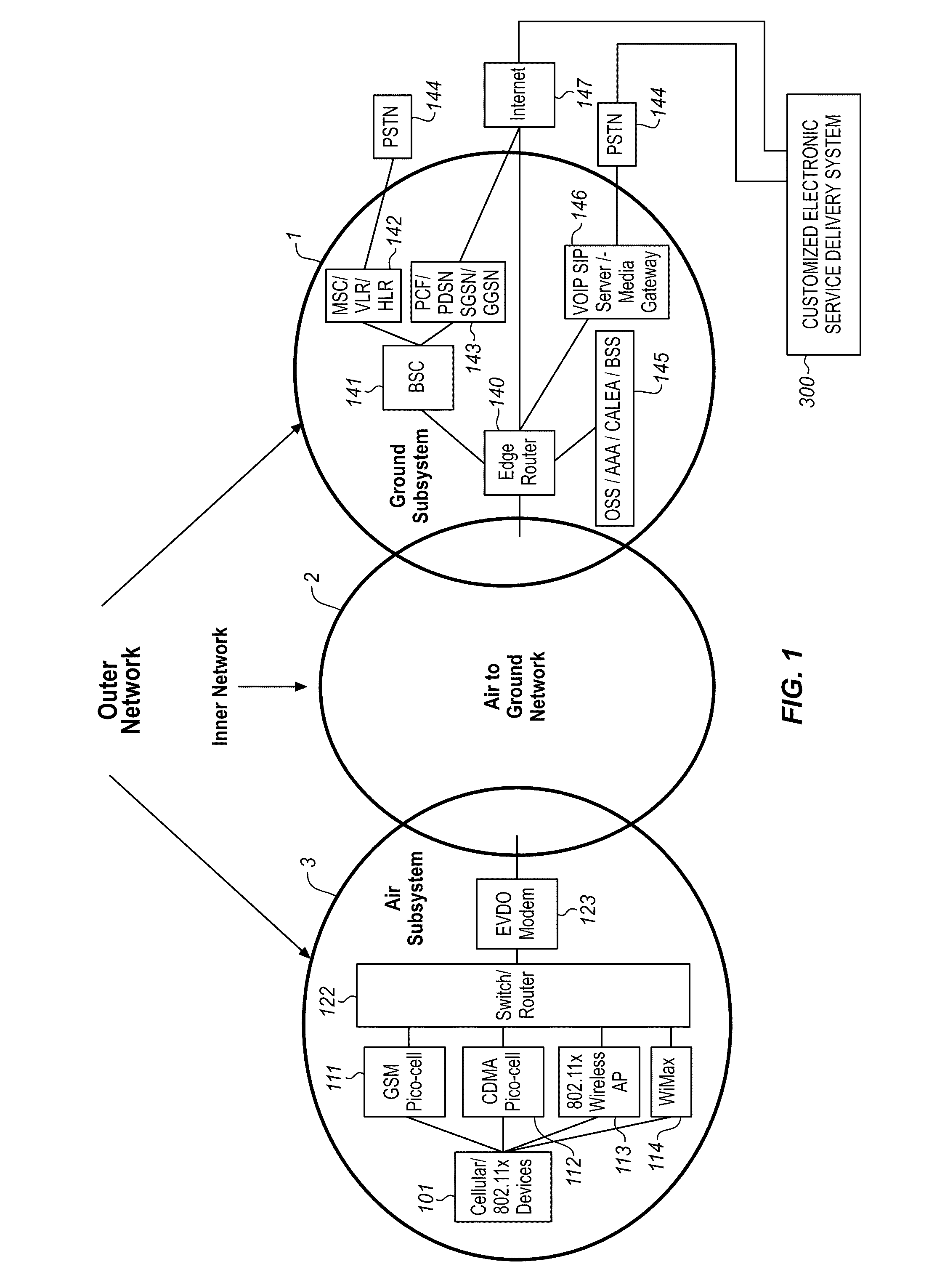
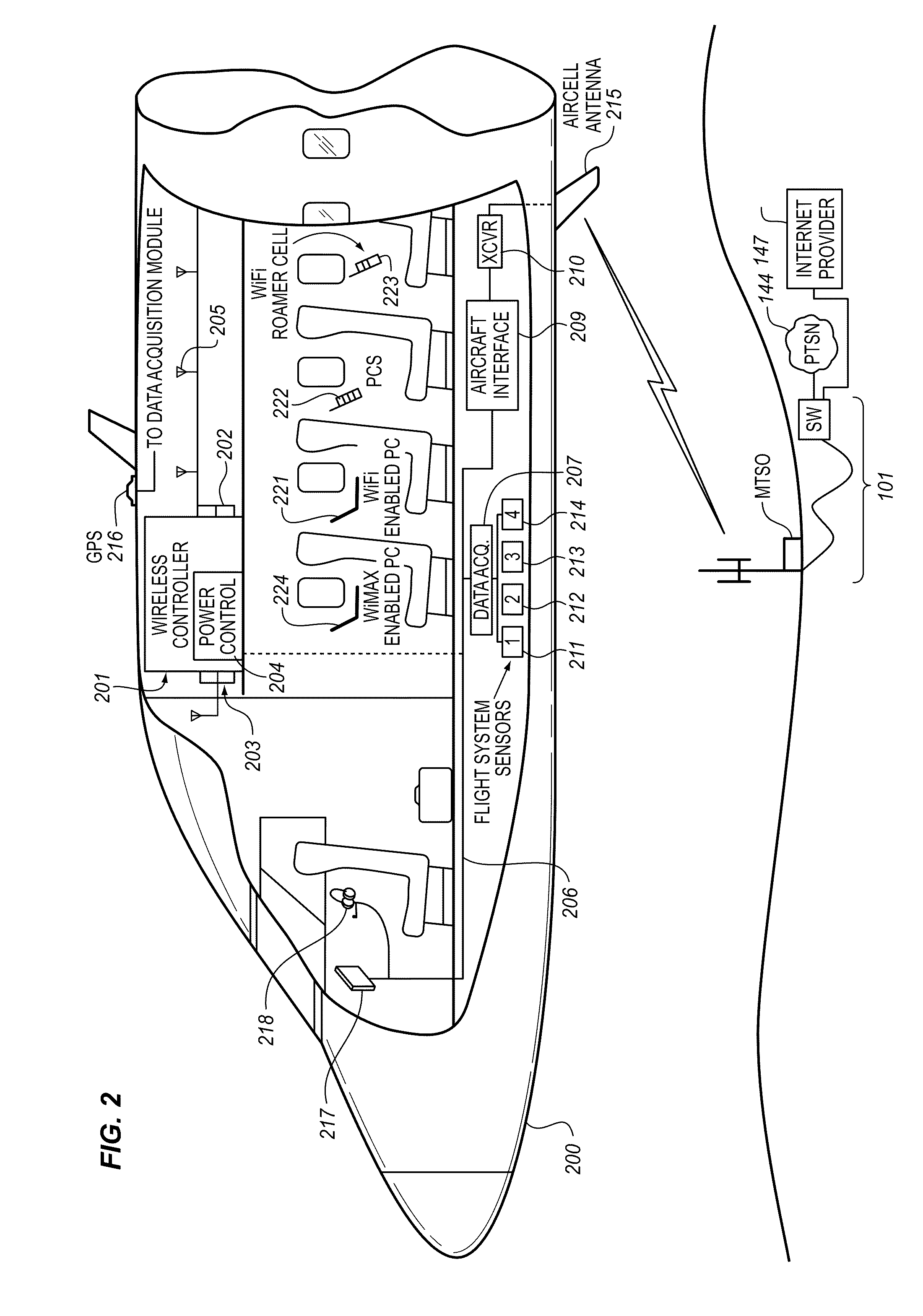
System for customizing electronic content for delivery to a passenger in an airborne wireless cellular network
InactiveUS8078163B2Improve travel experienceComplete banking machinesNetwork topologiesProgram planningWireless cellular networks
Owner:GOGO BUSINESS AVIATION LLC
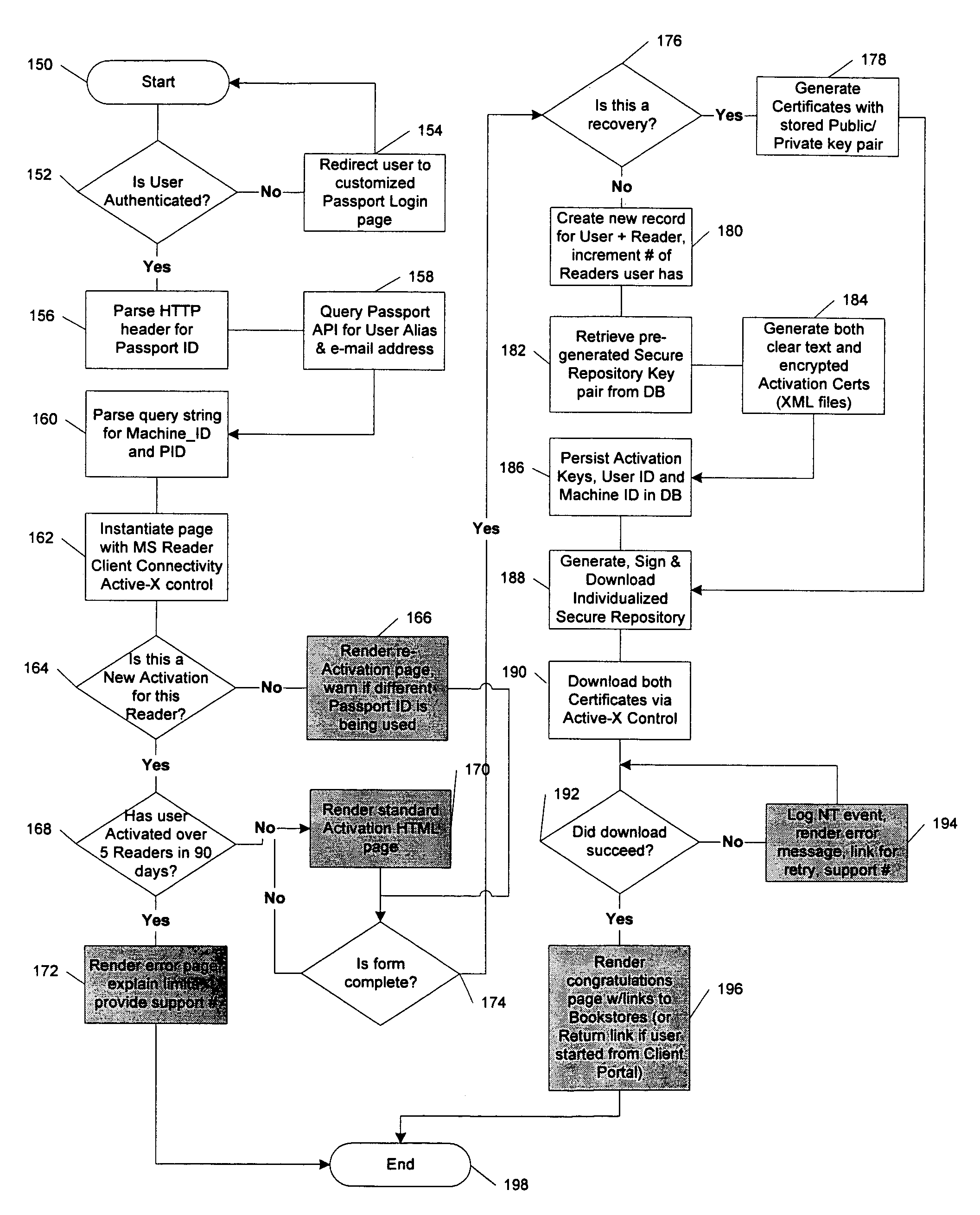
System and method for activating a rendering device in a multi-level rights-management architecture
InactiveUS7017189B1Digital data processing detailsUser identity/authority verificationPersonalizationDigital rights management system
Owner:MICROSOFT TECH LICENSING LLC
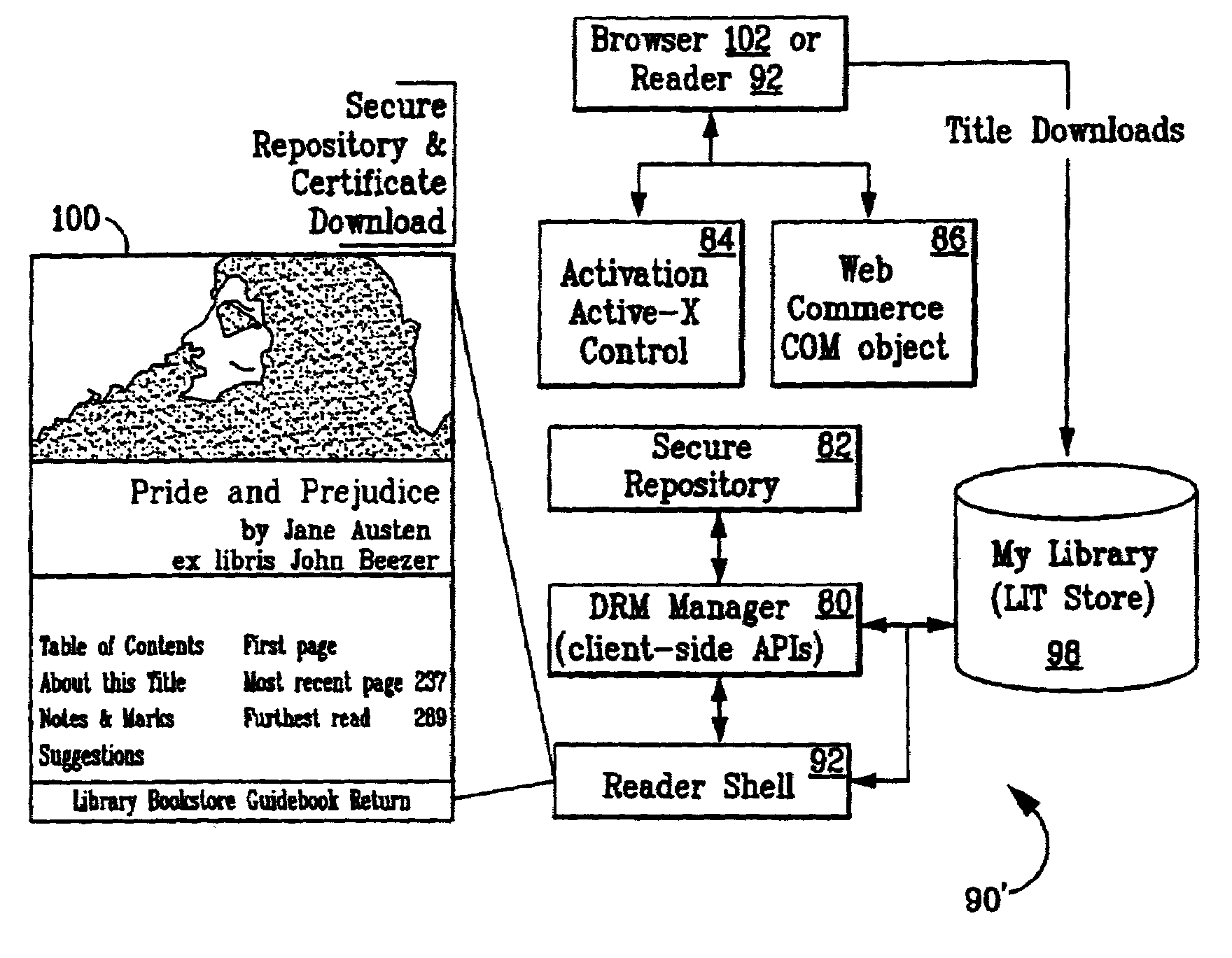
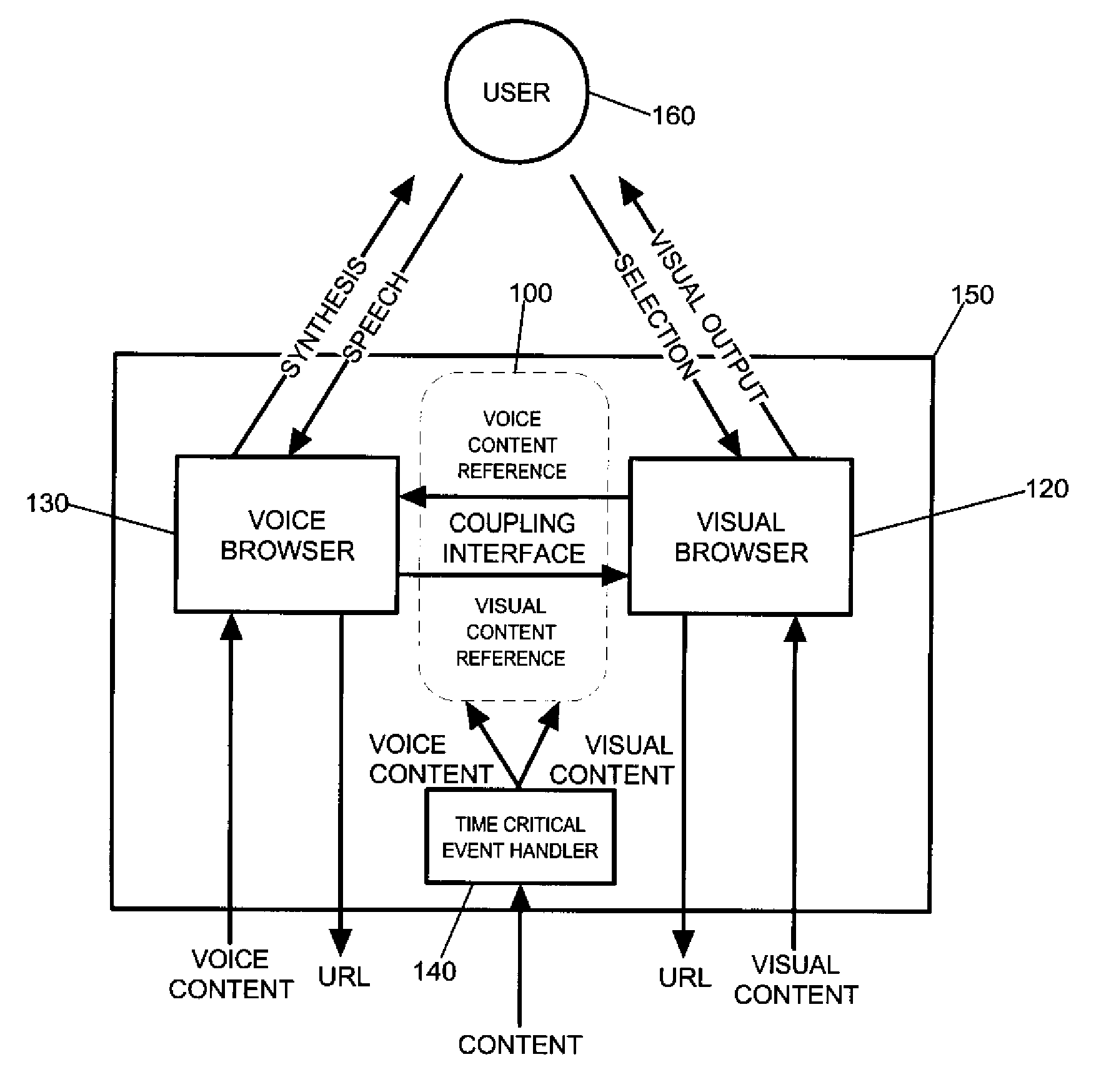
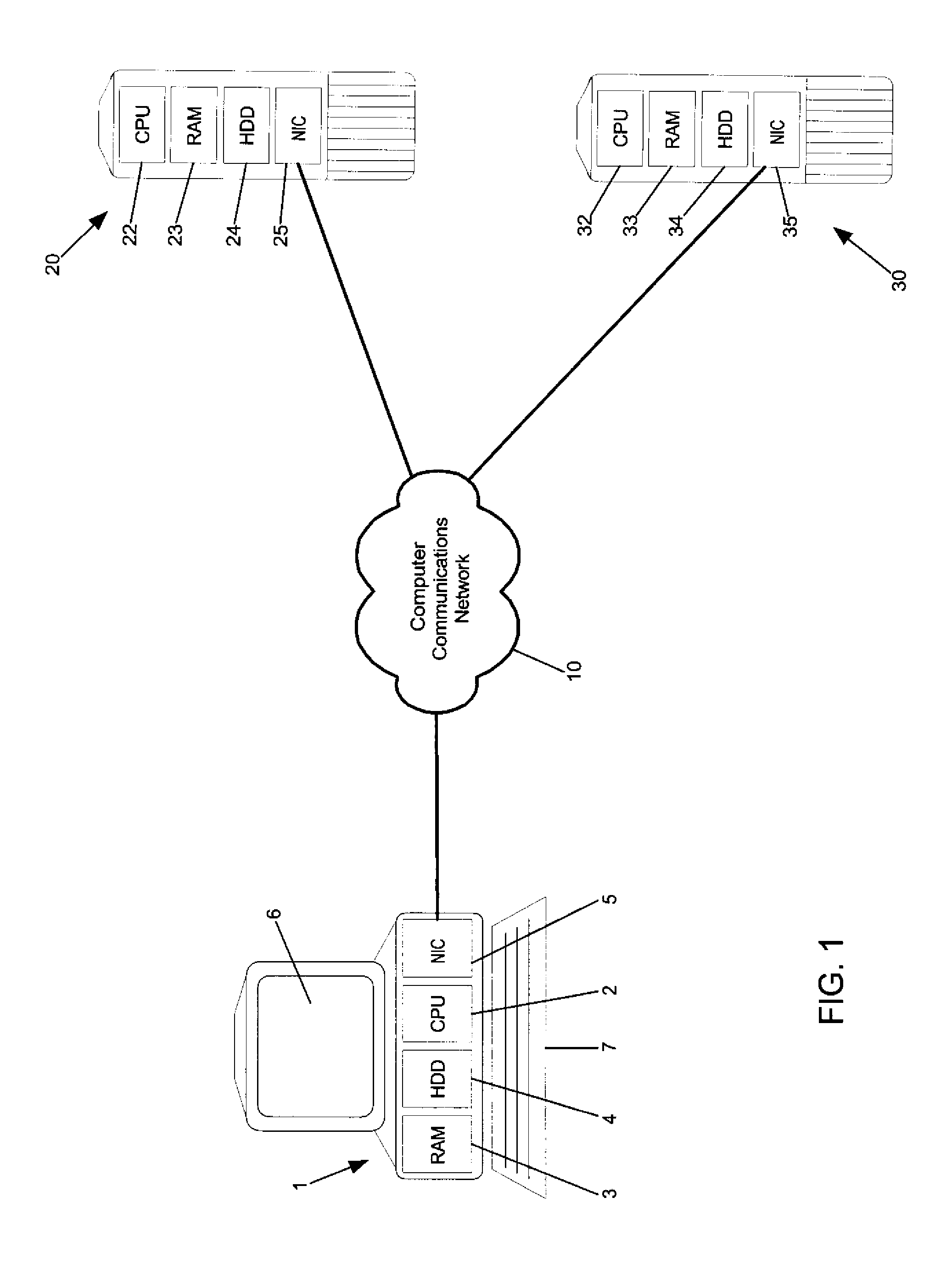
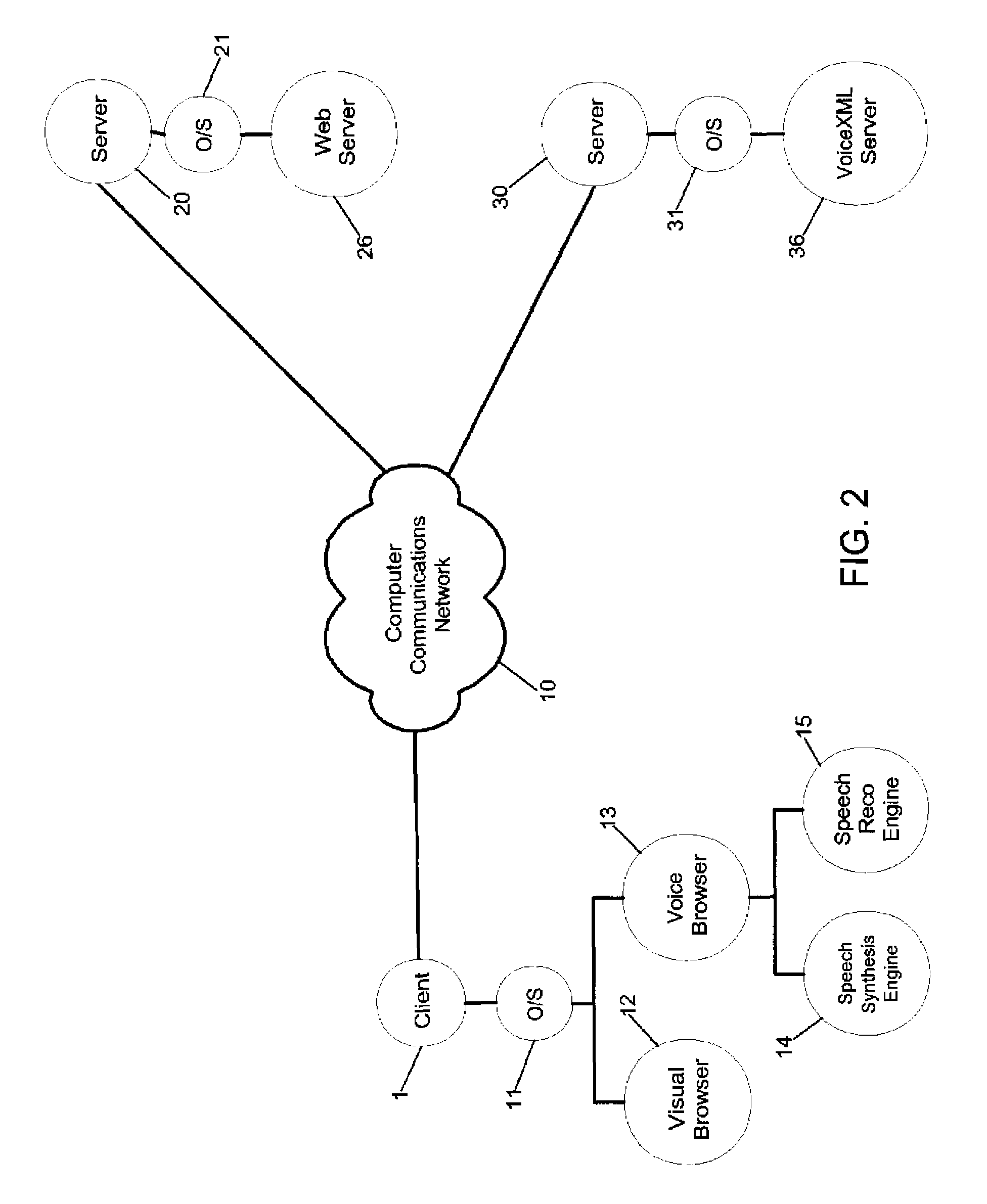
Method and apparatus for coupling a visual browser to a voice browser
InactiveUS7657828B2Web data retrievalNatural language data processingVisual presentationAccess network
A method and apparatus for concurrently accessing network-based electronic content in a Voice Browser and a Visual Browser can include the steps of retrieving a network-based document formatted for display in the Visual Browser; identifying in the retrieved document a reference to the Voice Browser, the reference specifying electronic content formatted for audible presentation in the Voice Browser; and, transmitting the reference to the Voice Browser. The Voice Browser can retrieve the specified electronic content and audibly present the electronic content. Concurrently, the Visual Browser can visually present the network-based document formatted for visual presentation in the Visual Browser. Likewise, the method of the invention can include the steps of retrieving a network-based document formatted for audible presentation in the Voice Browser; identifying in the retrieved document a reference to the Visual Browser, the reference specifying electronic content formatted for visual presentation in the Visual Browser; and, transmitting the reference to the Visual Browser. The Visual Browser can retrieve the specified electronic content and visually present the specified electronic content. Concurrently, the Voice Browser can audibly present the network-based document formatted for audible presentation in the Voice Browser.
Owner:NUANCE COMM INC
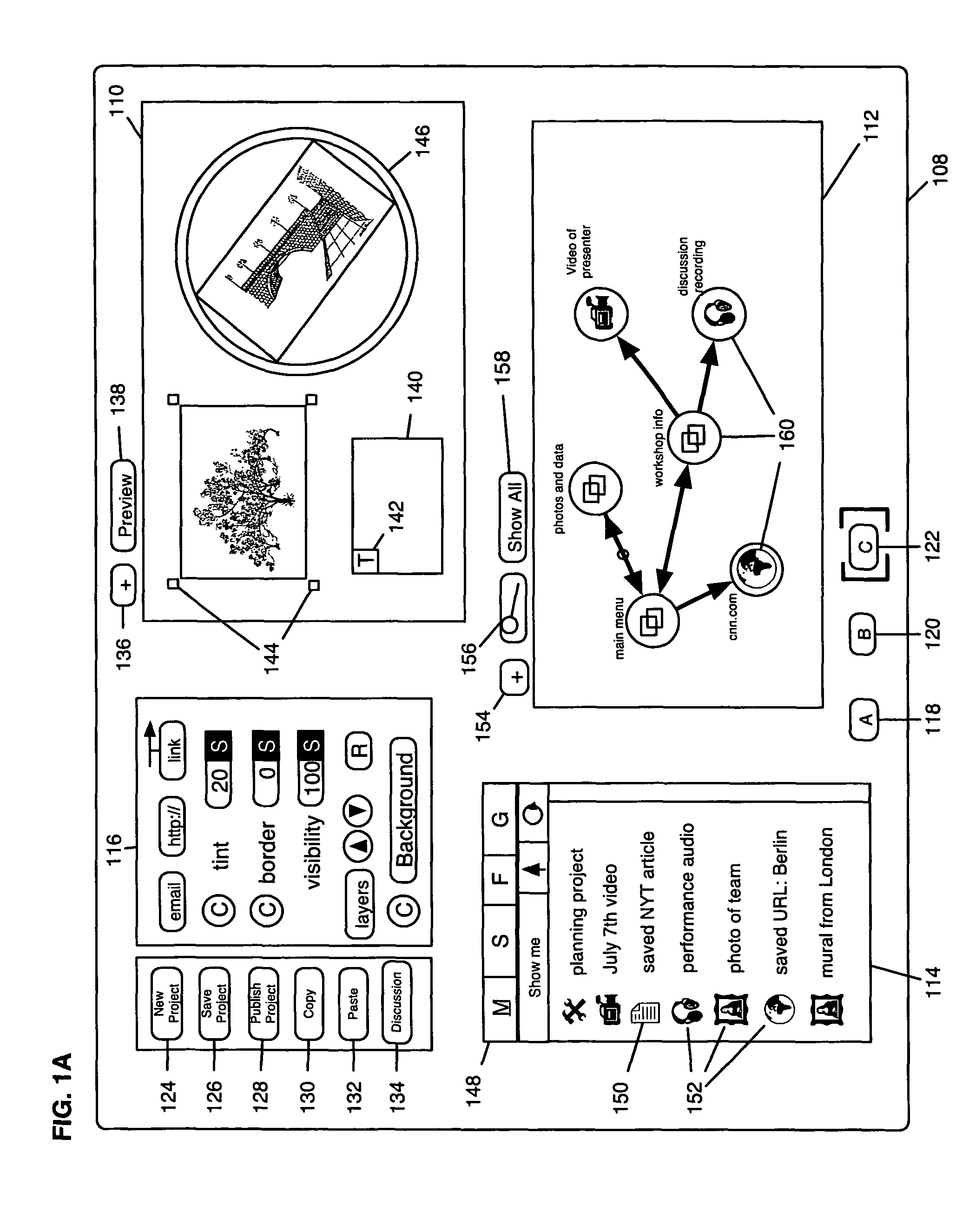
Apparatus and method for creating and using documents in a distributed computing network
InactiveUS20050246283A1Computer security arrangementsOffice automationPaper documentDocument preparation
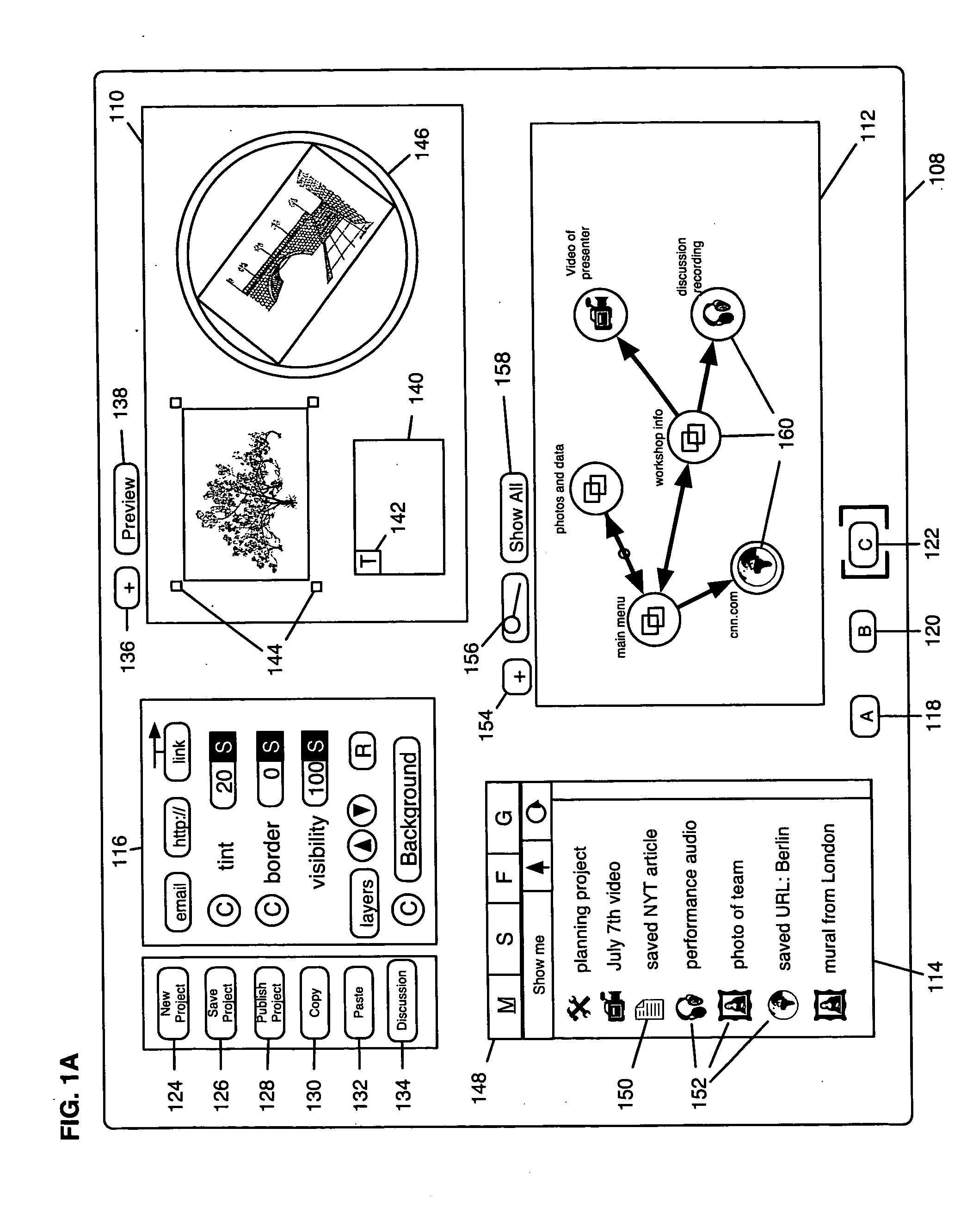
An authoring application for allowing users to create, control and distribute electronic content including a canvas interface for constructing a project of the electronic content from a plurality of resource files, the canvas interface having: a canvas area for constructing screen elements of the selected resource files to create screens; a path area for illustrating a relationship among the screens of the project; and a properties area for adjusting characteristics of the selected screen elements, a reader interface for allowing the users to view the project, the reader interface being accessible from the canvas interface and a resource interface for managing groups, membership in groups, and user accounts, said groups and user accounts having varying levels of control over the project.
Owner:TRINTUITION
Adaptive spam message detector
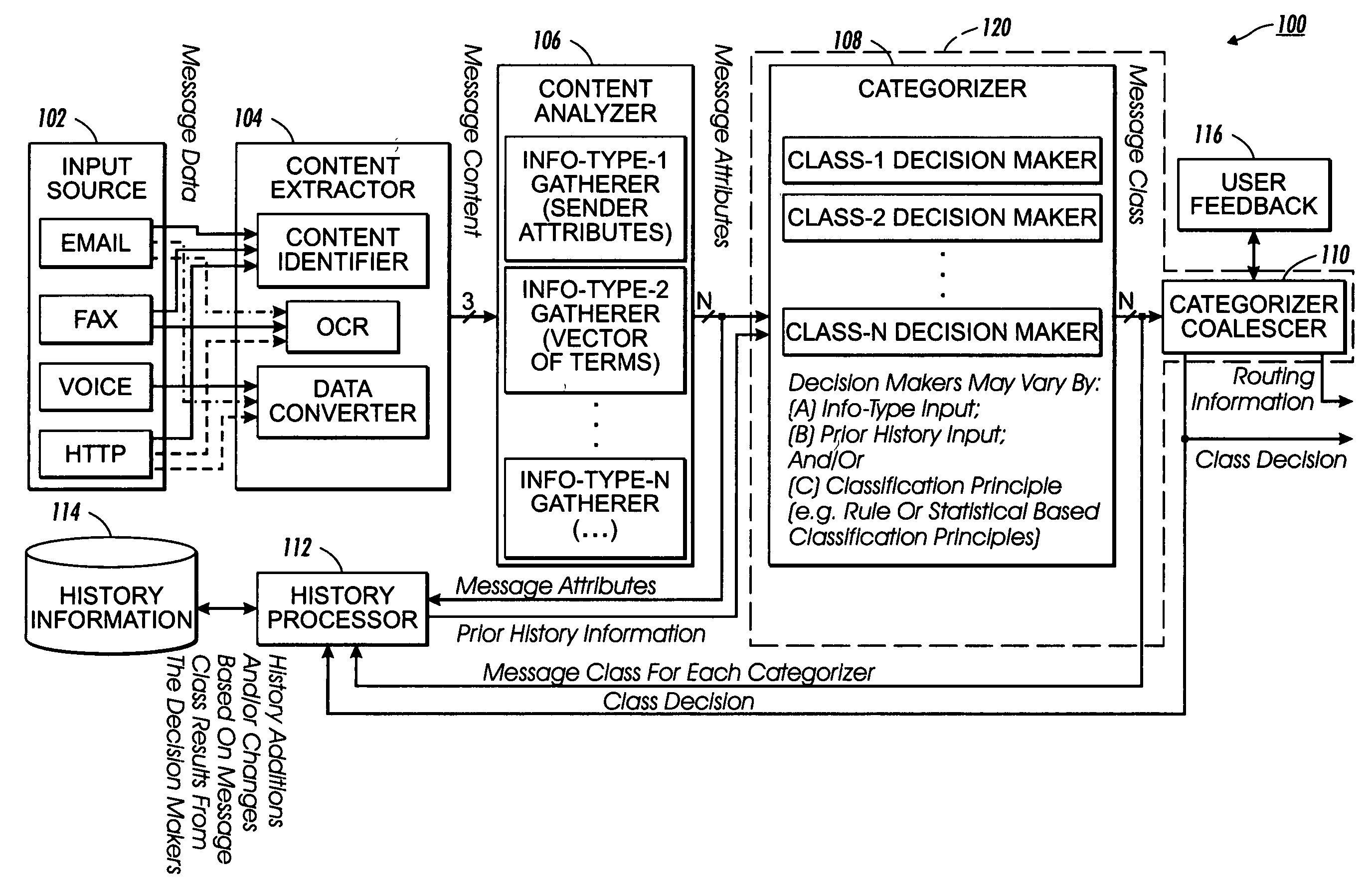
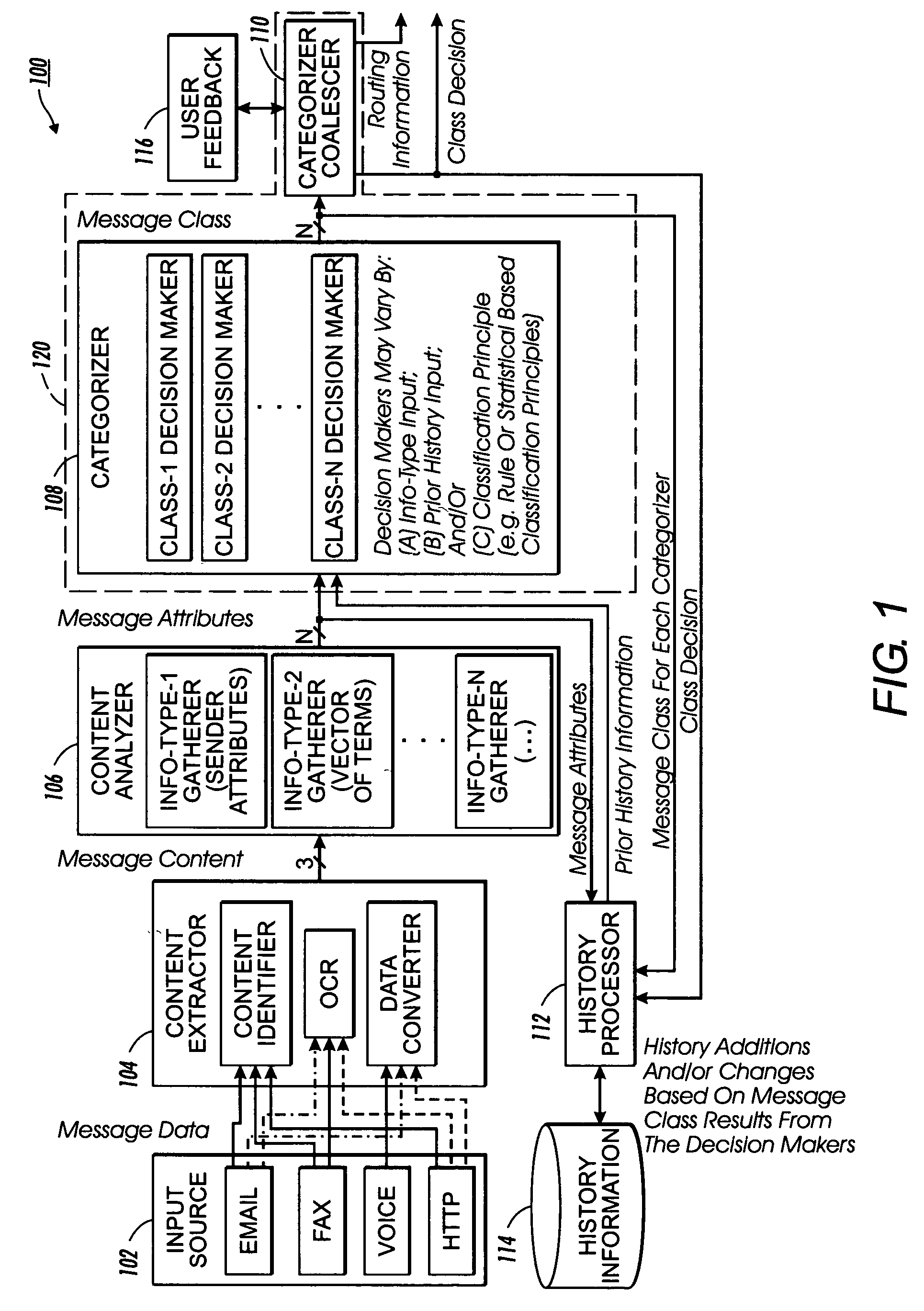
InactiveUS20060123083A1Loss of productivityWasted attentionMultiple digital computer combinationsData switching networksInformation typeDecision maker
Electronic content is filtered to identify spam using image and linguistic processing. A plurality of information type gatherers assimilate and output different message attributes relating to message content associated with an information type. A categorizer may have a plurality of decision makers for providing as output a message class for classifying the message data. A history processor records the message attributes and the class decision as part of the prior history information and / or modifies the prior history information to reflect changes to fixed data and / or probability data. A categorizer coalescer assesses the message class output by the set of decision makers together with optional user input for producing a class decision identifying whether the message data is spam.
Owner:XEROX CORP
Electronic content search and delivery based on cursor location
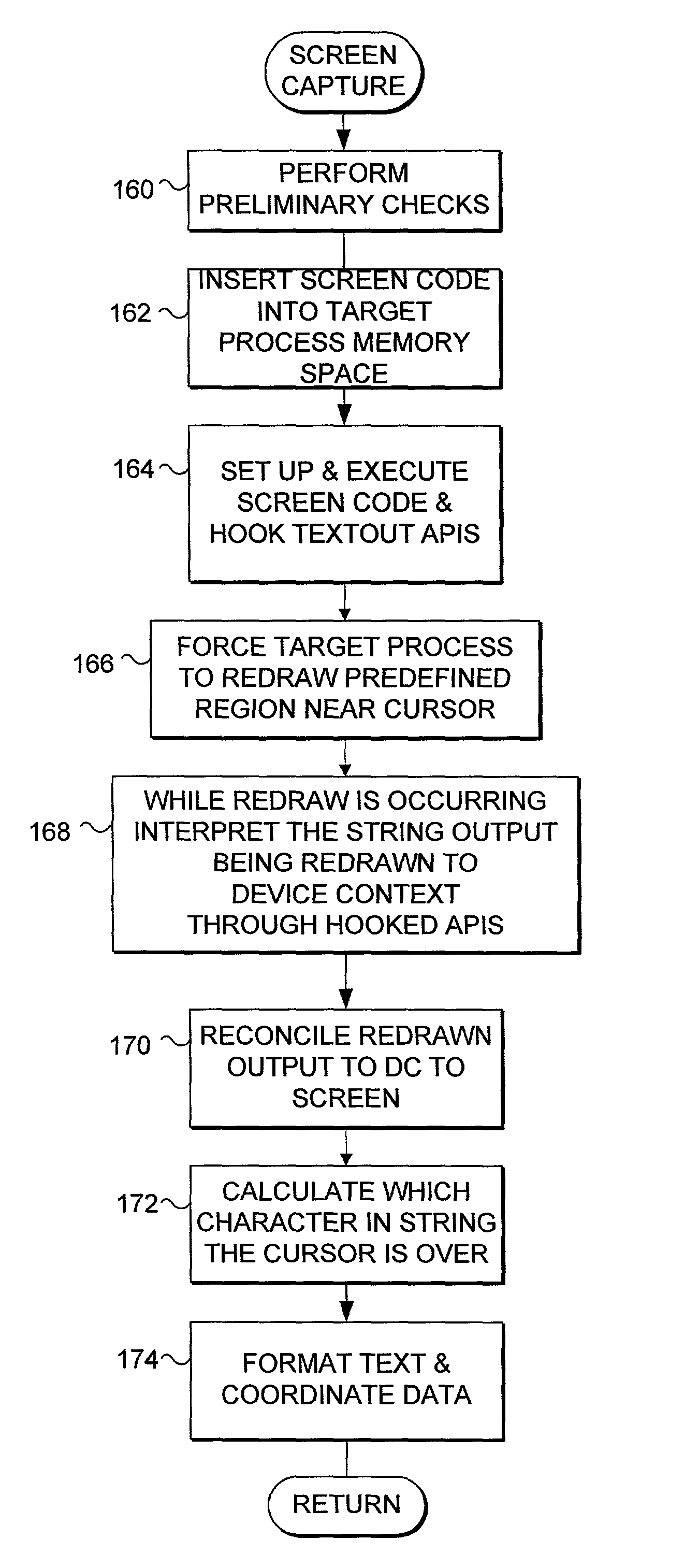
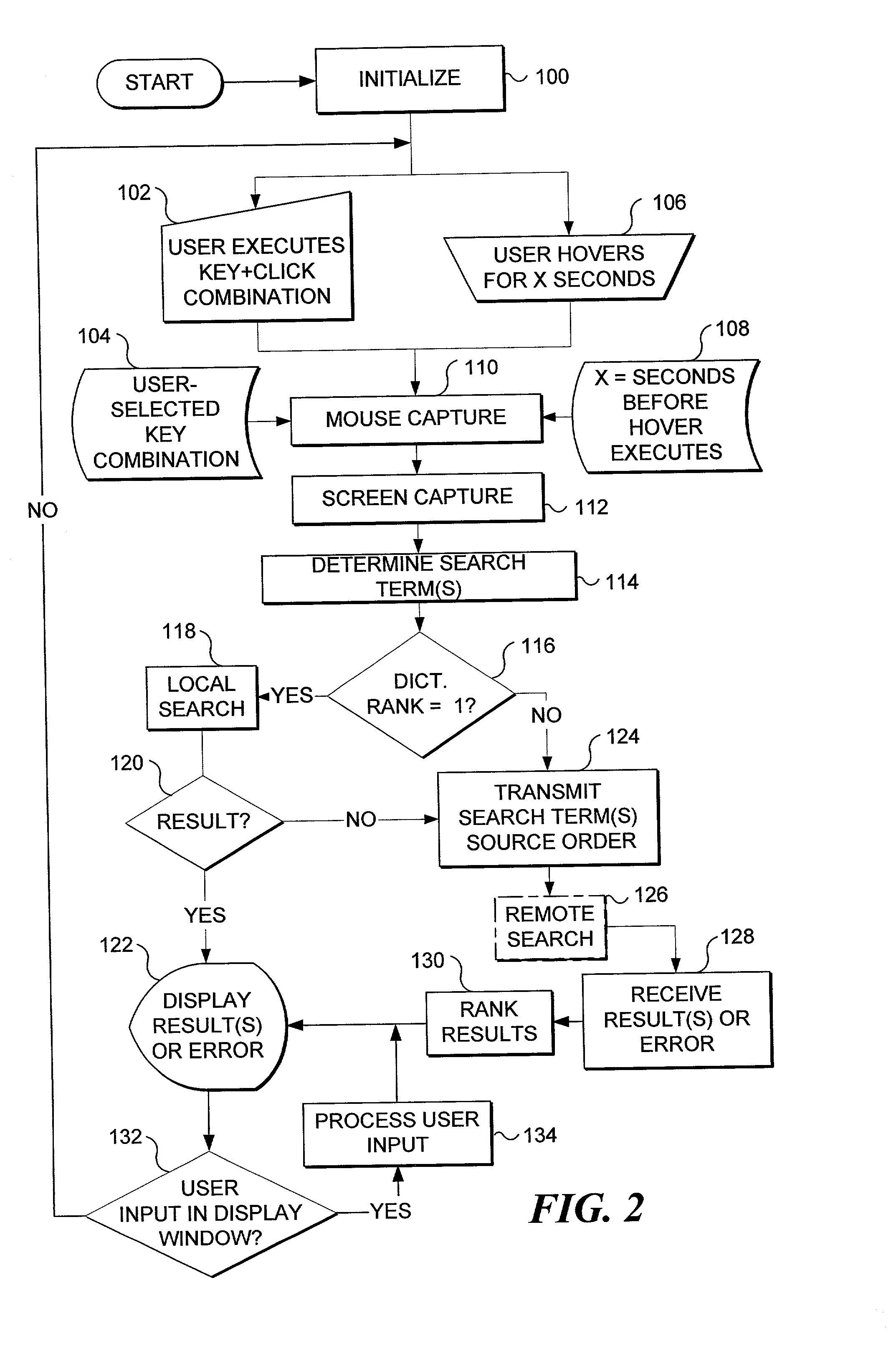
InactiveUS7100123B1Faster and reliable word recognitionFaster and reliable recognitionUnstructured textual data retrievalComparison of digital valuesOperational systemData storing
An electronic search is automatically initiated when a cursor hovers in one location for a predetermined time. A target process associated with a target window is forced to re-render data to the target window in an update region that includes the detected cursor location. From the re-rendered data, a primary word and context words near the cursor location are determined. One or more local or remote electronic data stores are searched for substantive content related to the words. The content is prioritized according to user preference and displayed in a semitransparent window that is persistently visible to a user, yet does not obscure other content in an underlying window and does not shift the focus from an active window. Re-rendering is accomplished by invalidating an update region of the target window, and forcing the operating system to issue a paint message, causing the target process to redraw the update region.
Owner:MICROSOFT TECH LICENSING LLC
Blister package with electronic content monitoring system
InactiveUS7113101B2Universal applicabilityEfficient operabilityContainer decorationsLevel indicationsMonitoring systemBlister pack
A replicate can be secured to a blister package intended to contain articles, such as pills, and is used to record the removal of individual articles from the blisters. To remove an article from a blister one will usually press against the blister to push the article through a frangible closure seal, breaking the seal in the process. The replicate includes a backing sheet which carries a plurality of traces alignable with corresponding blisters so that when the article is removed from the blister it will not only break the seal but it will also break the corresponding trace. All of the traces are connected to an integrated circuit which may also be formed or provided on the backing sheet, as is a power source for the integrated circuit. The breaking of the trace is an event that is recorded in the integrated circuit for later accessability. The replicate may be secured to the blister package after the package has been produced by conventional form-fill-seal equipment. The individual traces can be formed into a grid of closely spaced traces so that alignment of the traces with the individual blisters is less critical. The replicates may be formed by printing or other conventional methods on a roll of lidstock. After forming the individual replicates are severed from the roll of lidstock for securement to a blister package.
Owner:INTELLIGENT DEVICES SEZC
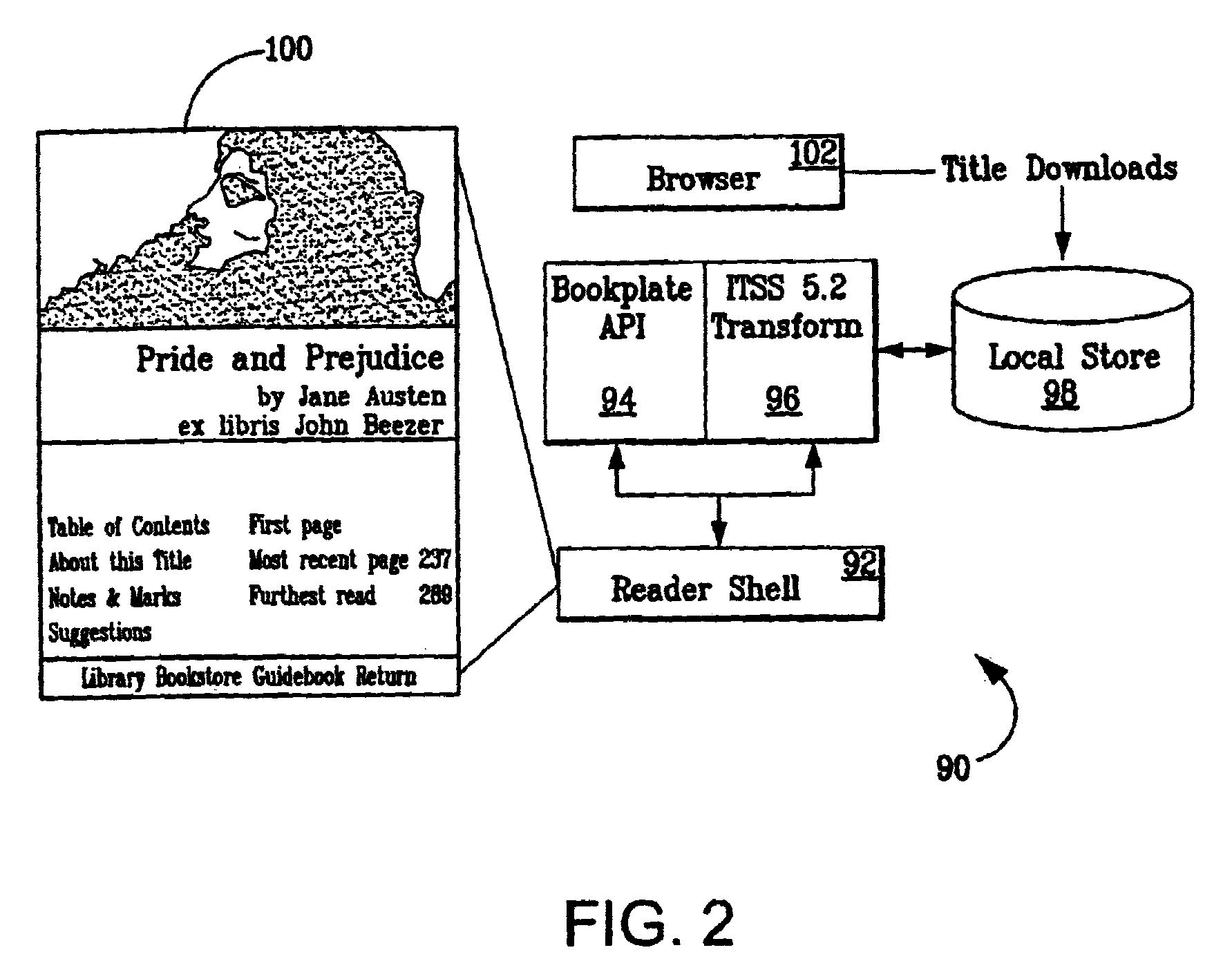
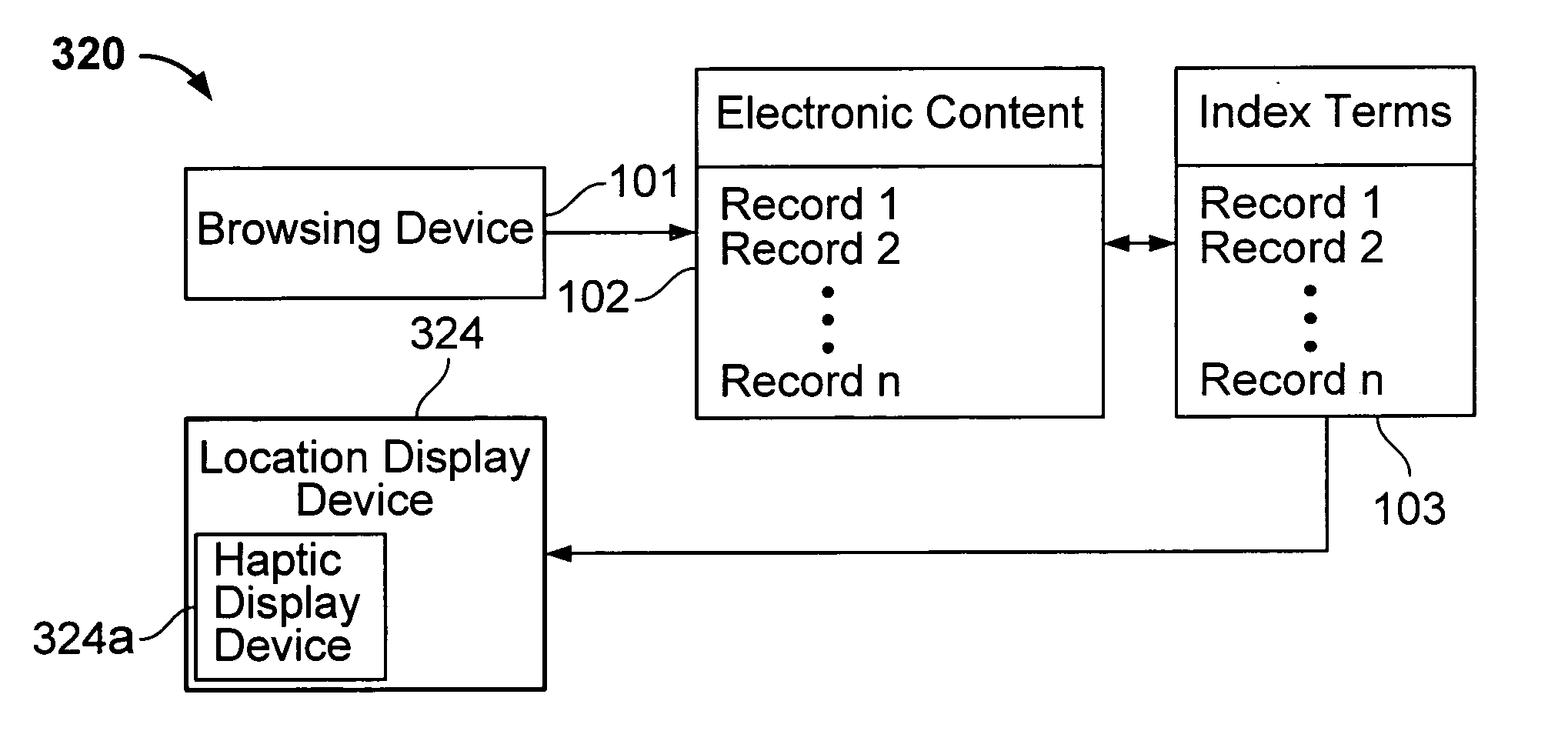
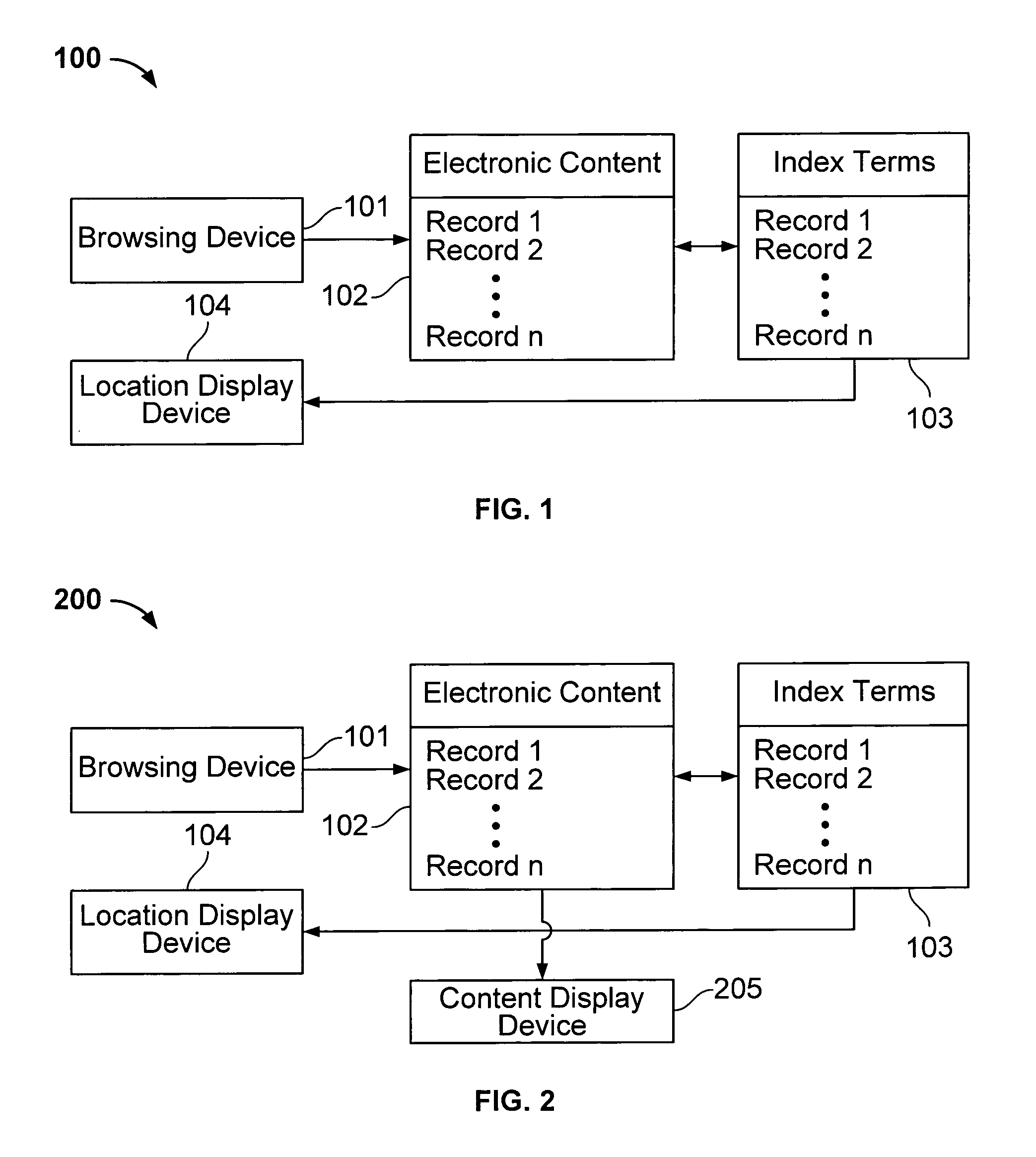
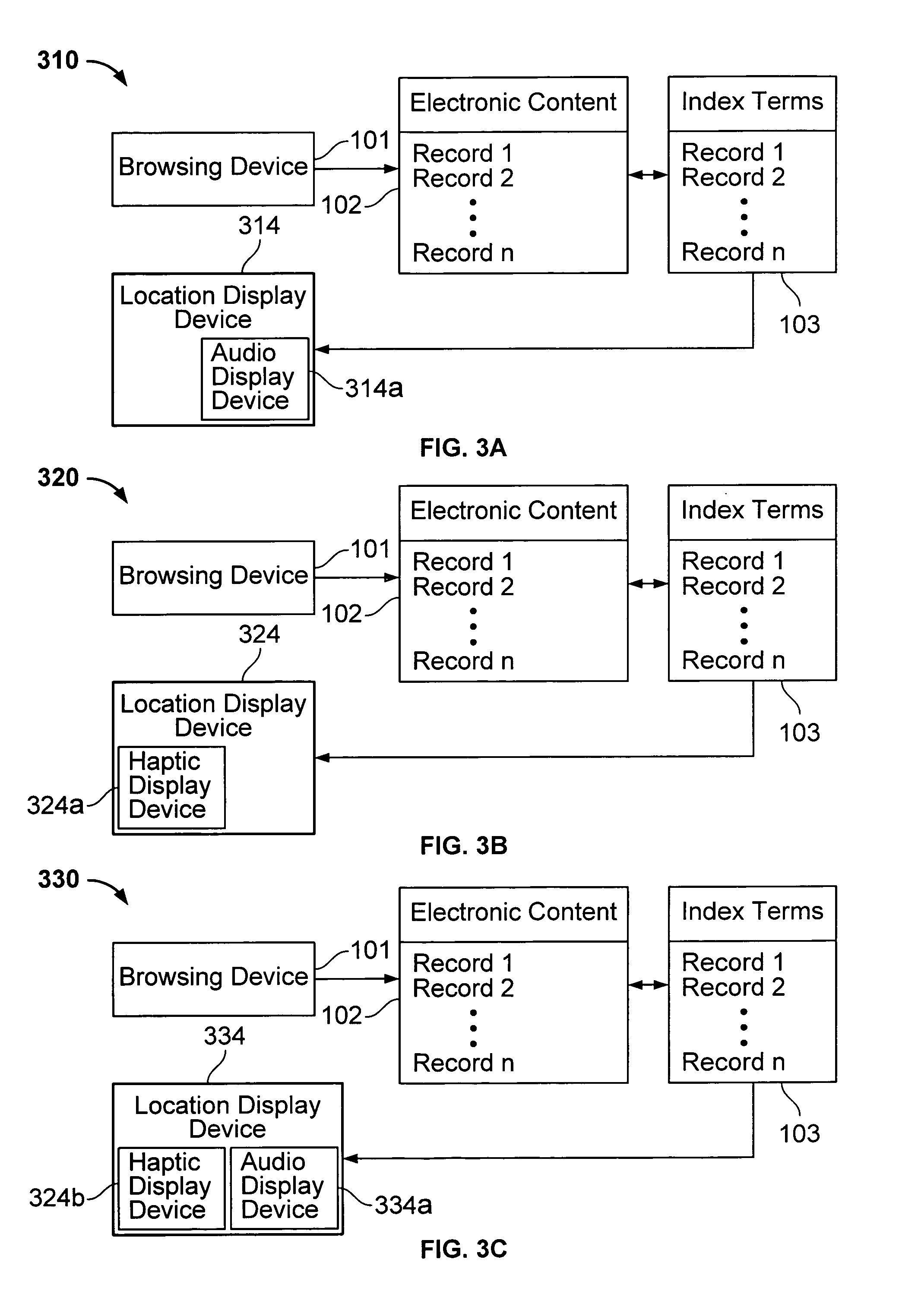
Interface including non-visual display for use in browsing an indexed collection of electronic content
InactiveUS7089292B1Facilitate indexingInput/output for user-computer interactionCathode-ray tube indicatorsImage resolutionVariable resolution
The invention facilitates browsing of an indexed collection of electronic content by displaying information identifying a current location within the collection of electronic content using a non-visual display (e.g., audio display and / or haptic display). The information identifying the current location can be displayed with variable resolution and the content of the display of the information identifying the current location can be dependent on the resolution. The invention can be used to browse any type of electronic content, including, for example, audio content, visual content, text content or some combination of such content. The invention can be used to browse electronic content that is indexed in any way, such as, for example, electronic content that is indexed (partly or entirely) alphabetically, numerically or by date.
Owner:VULCAN PATENTS
Method and system for electronic content storage and retrieval with galois fields on cloud computing networks
InactiveUS20120278622A1Web data indexingDigital data processing detailsCloud storageCloud communications
A method and system for electronic content storage and retrieval with Galois Fields on cloud computing networks. The electronic content is divided into plural portions and stored in plural cloud storage objects. Storage locations for the plural cloud storage objects are selected using a Galois field and the plural cloud storage objects are distributed across the cloud network. When the electronic content is requested, the plural portions are retrieved and transparently combined back into the original electronic content. No server network devices or target network devices can individually determine locations of all portions of the electronic content on the cloud communications network, thereby providing layers of security and privacy for the electronic content on the cloud communications network.
Owner:LESAVICH STEPHEN +1
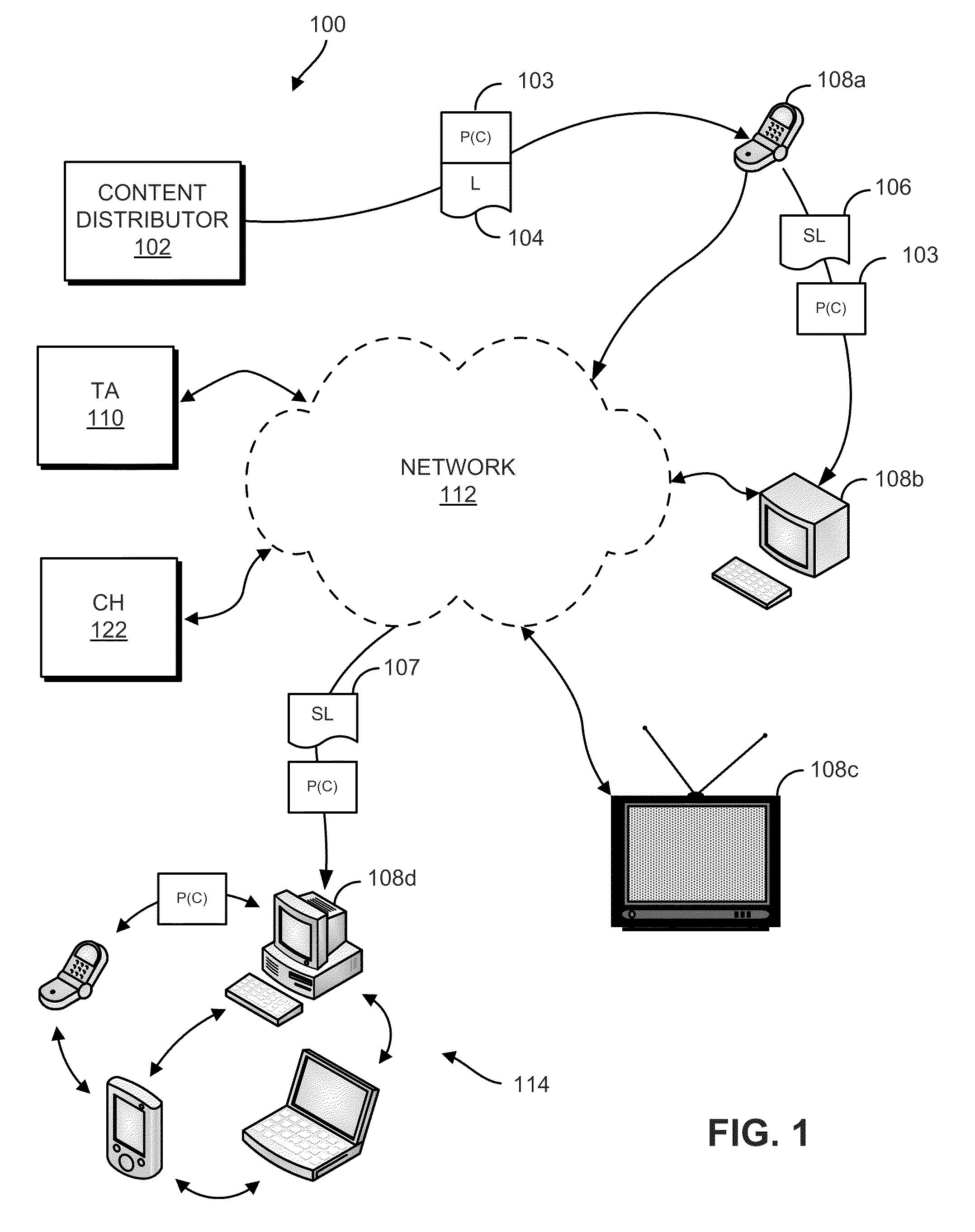
Systems, methods and apparatus for content distribution
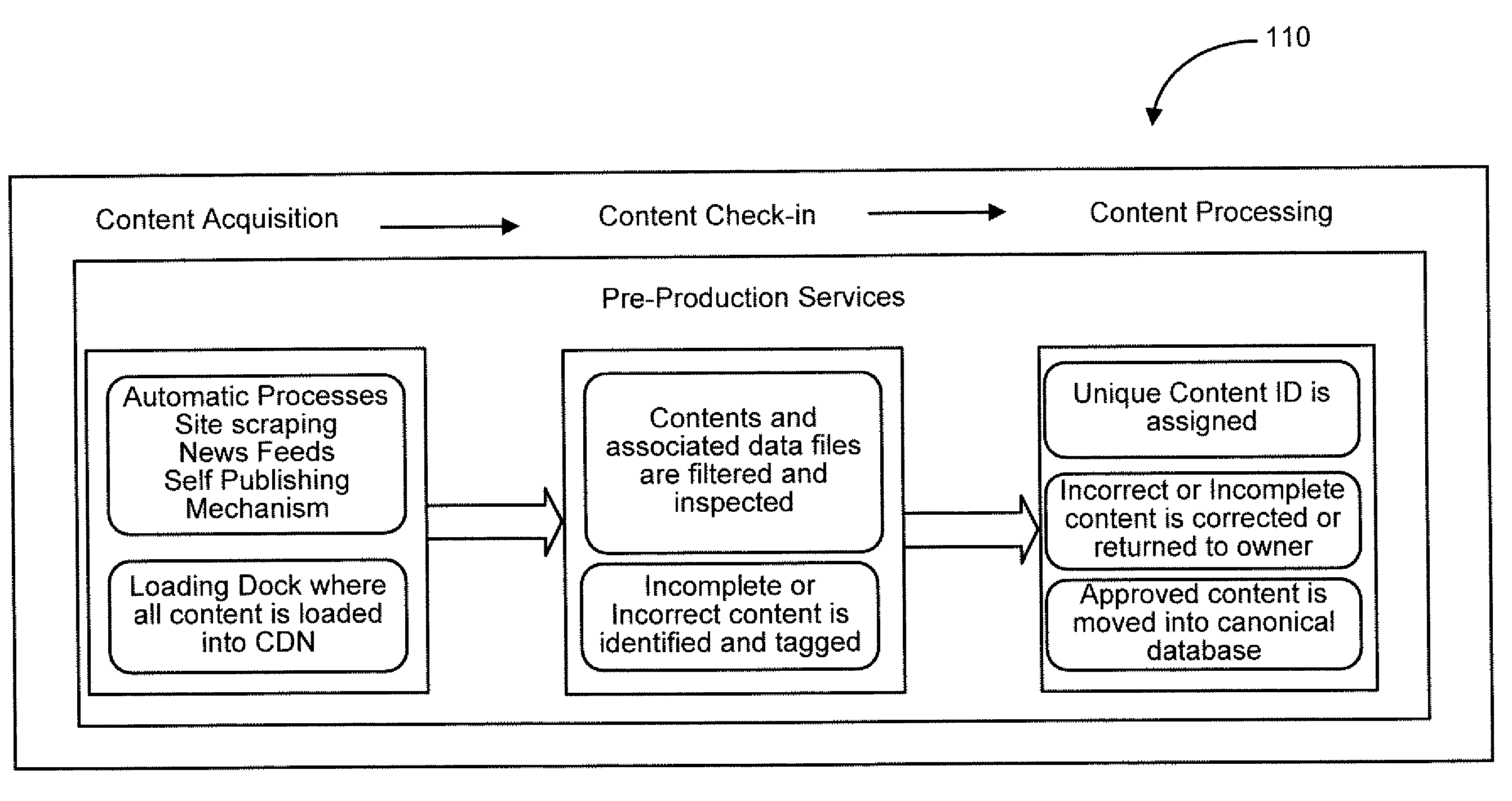
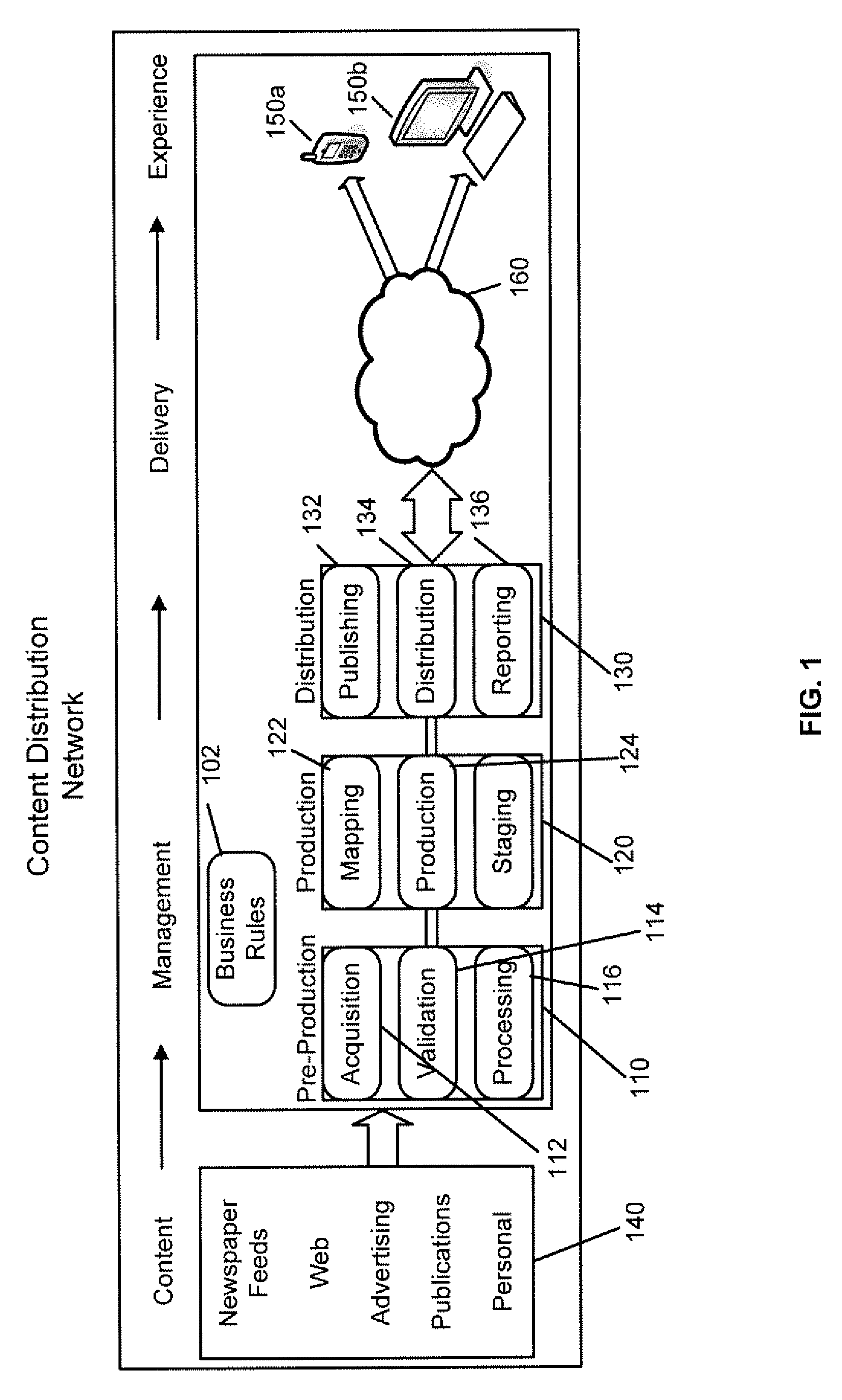
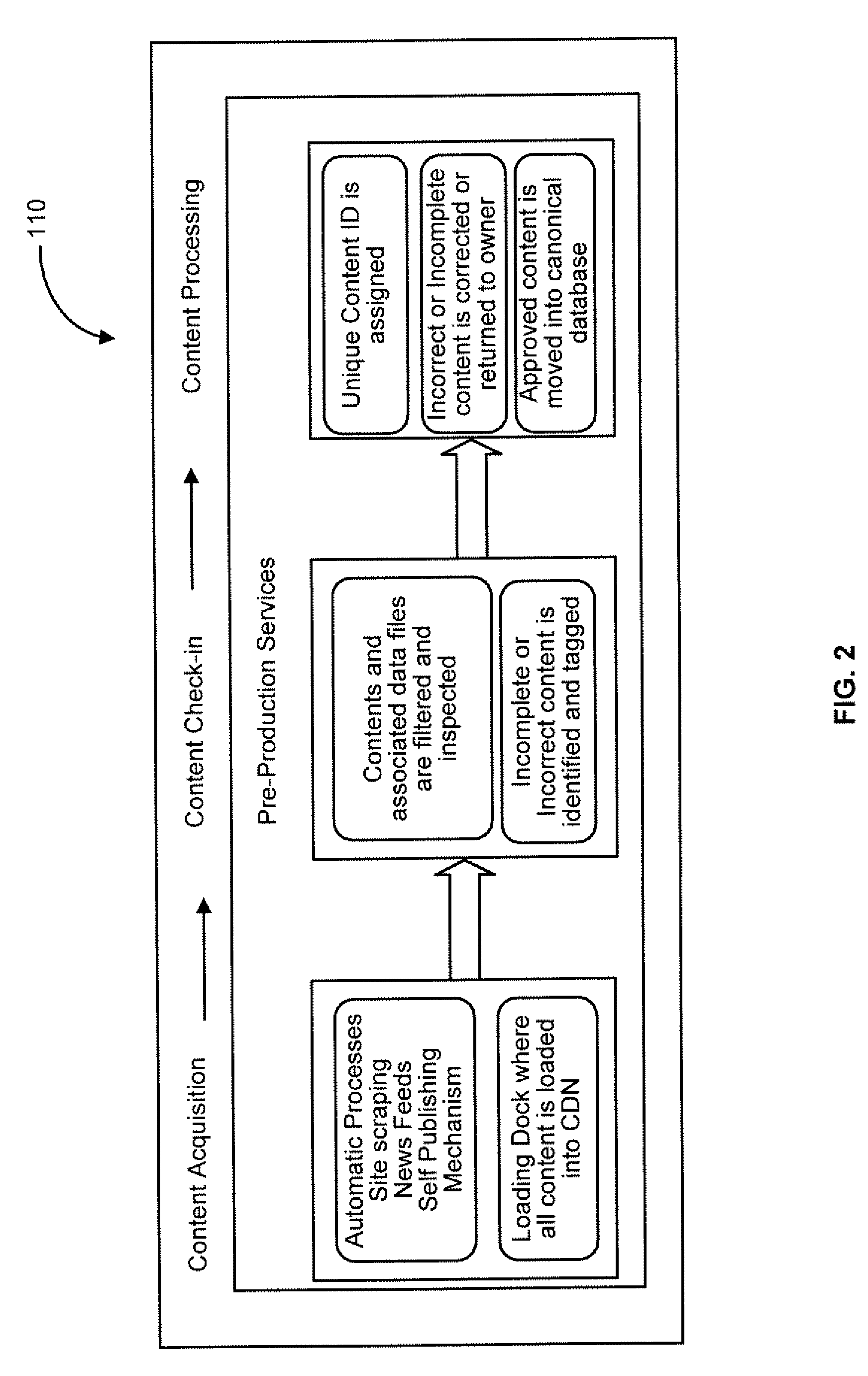
A system for and method of electronic content distribution is disclosed. Such content may be electronic book content, newspaper content, magazine content, and other types of content. The system includes: a processor having logic configured for filtering electronic content to remove incorrect information. The electronic content is automatically gathered from one or more content sources external to the system. The system also includes logic for assembling electronic content in a manner indicative of a predetermined template, and distributing the assembled electronic content for transmission at a scheduled time. The system also includes a communication network having an active channel configured to transmit the assembled electronic content. The system also includes a media device configured to receive and display the assembled electronic content when the media device is communicatively coupled to the active channel.
Owner:SKIFF
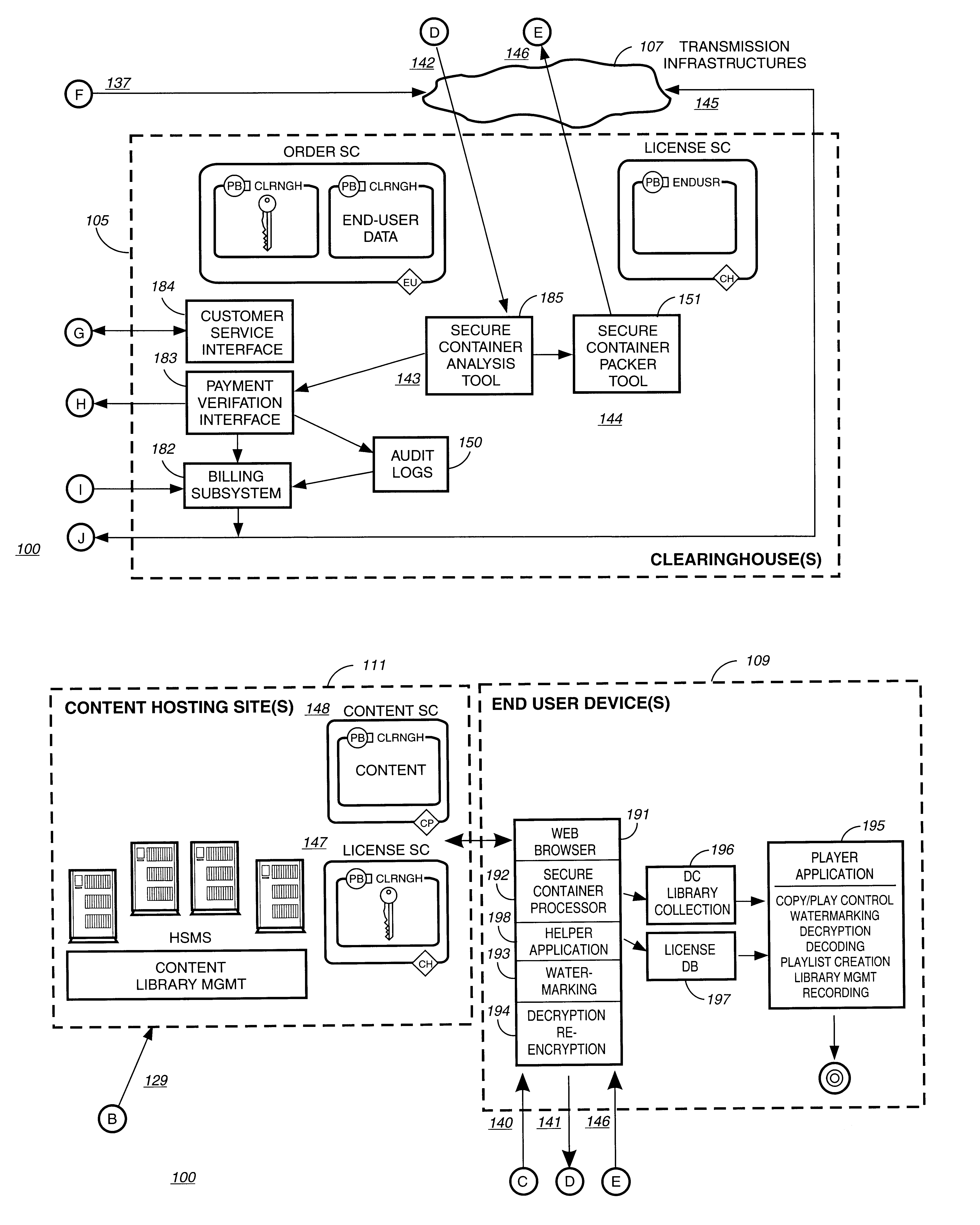
Securing digital content system and method
InactiveUS20070033397A1Key distribution for secure communicationDigital data processing detailsDigital contentContent security
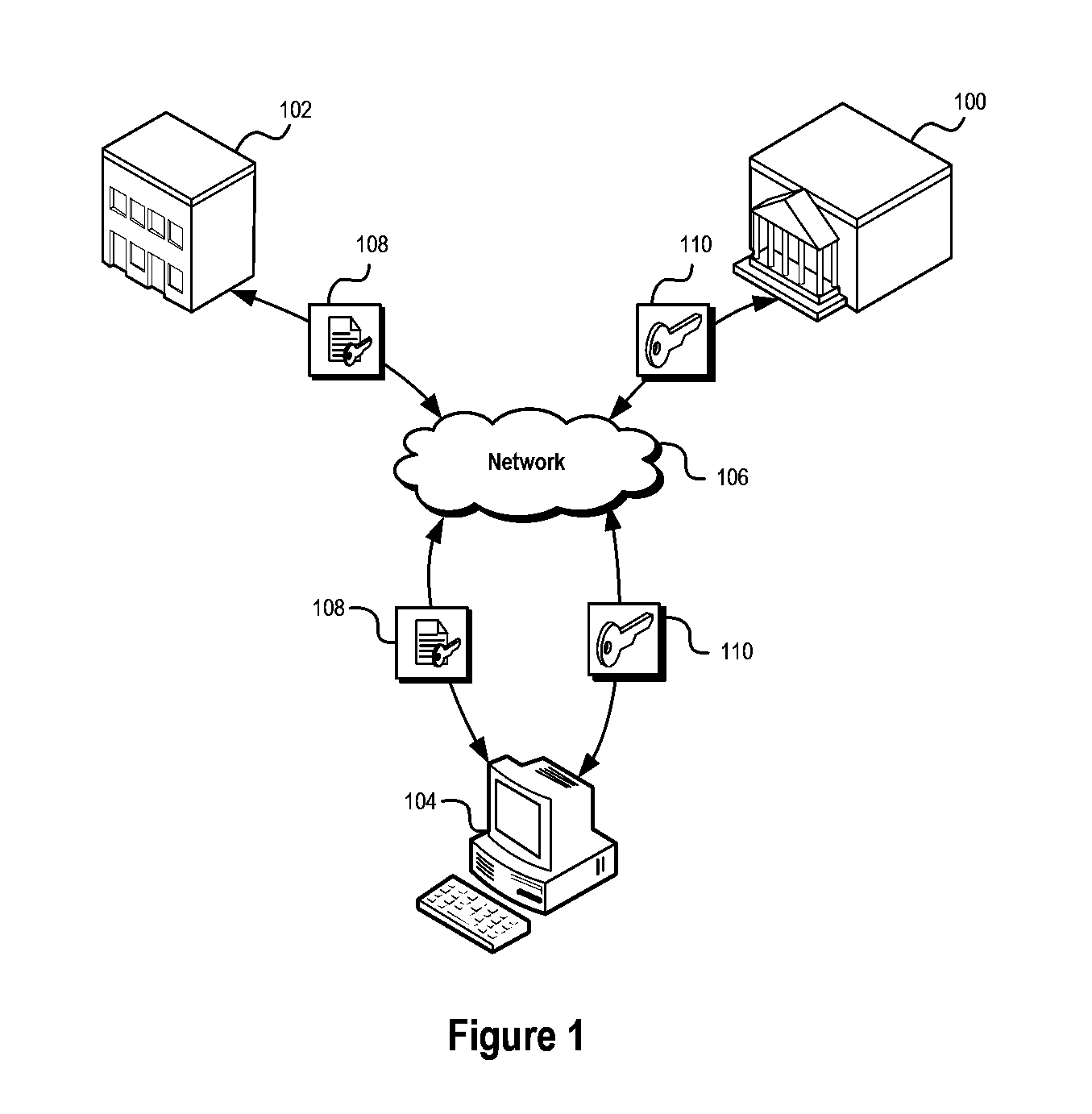
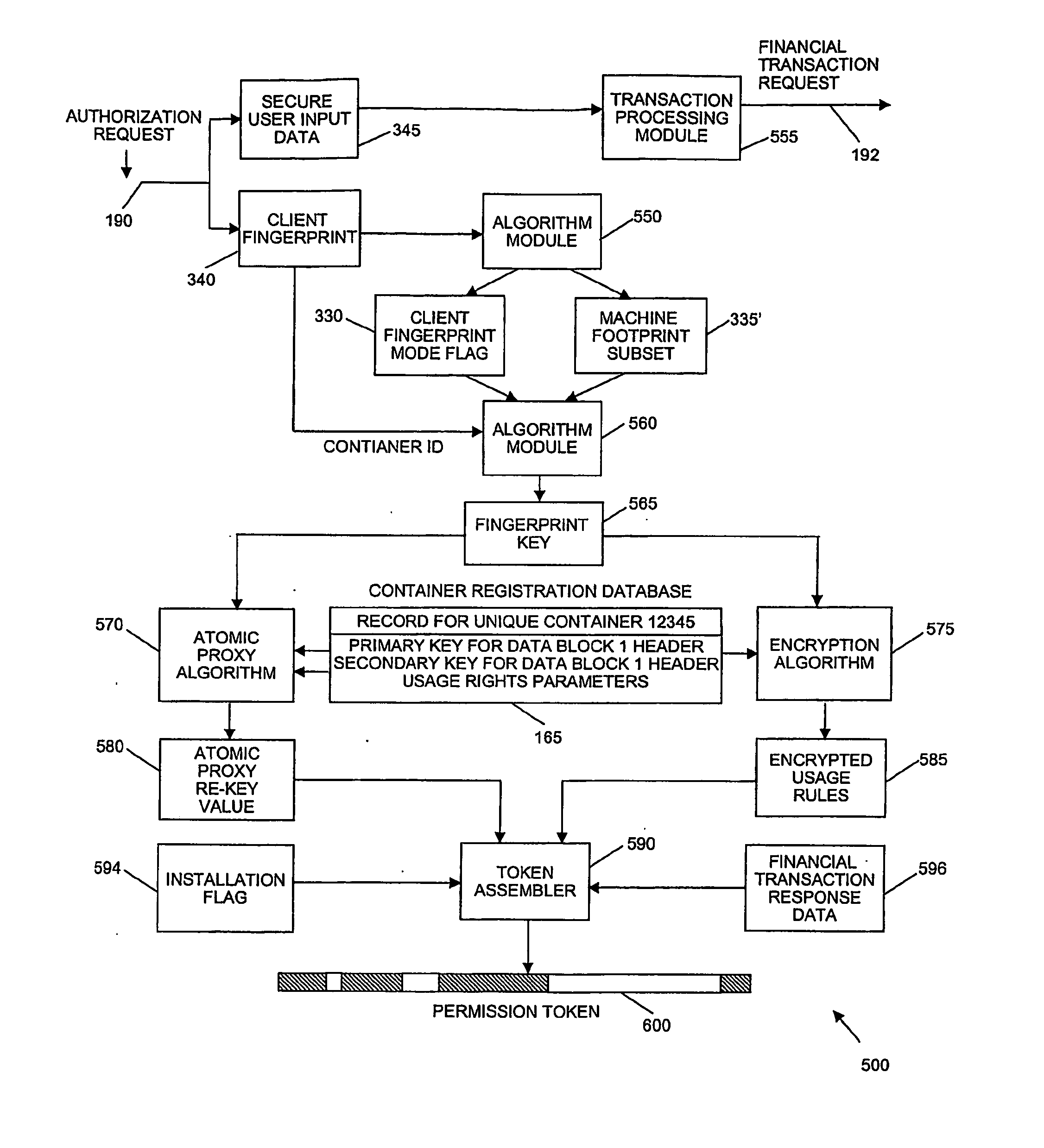
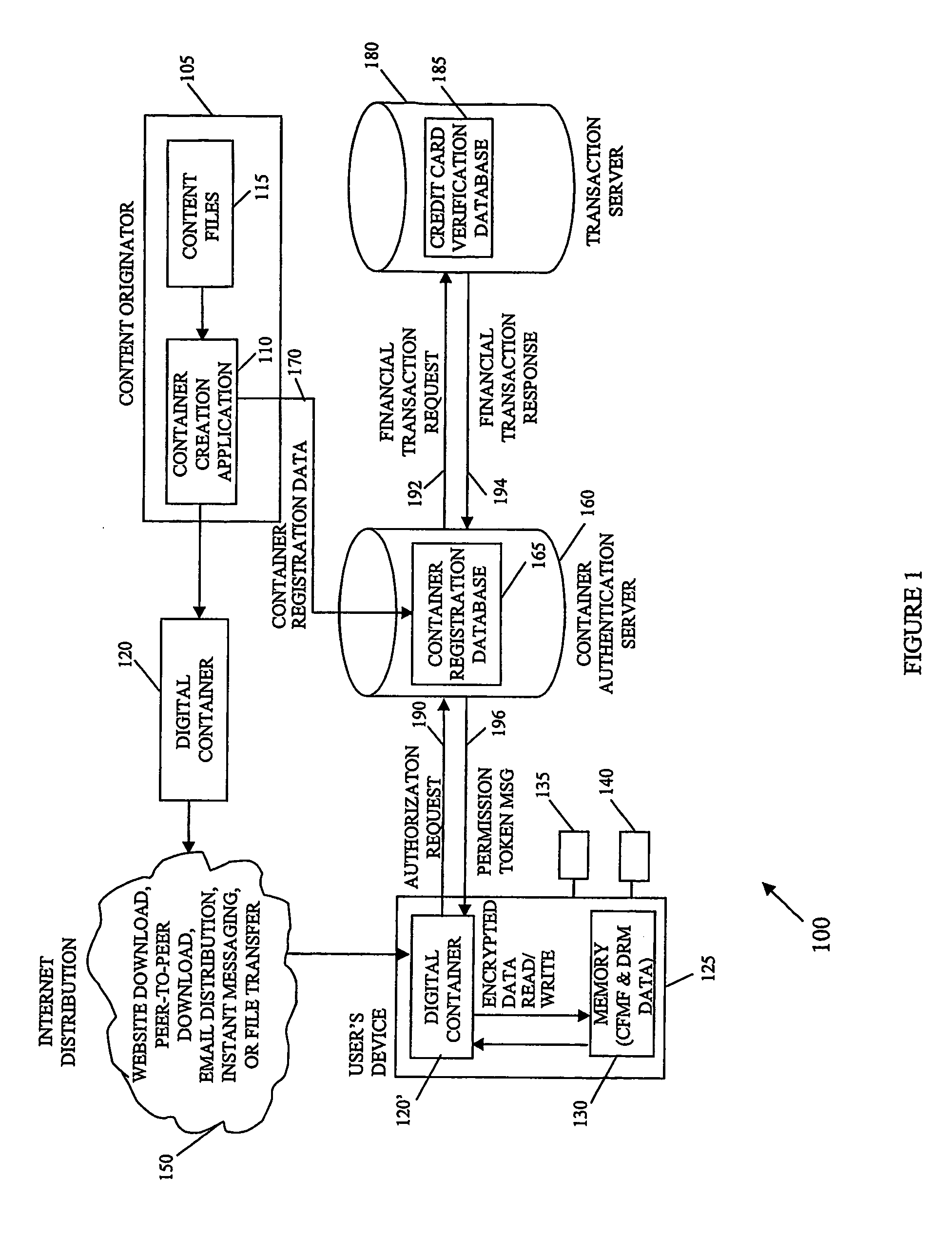
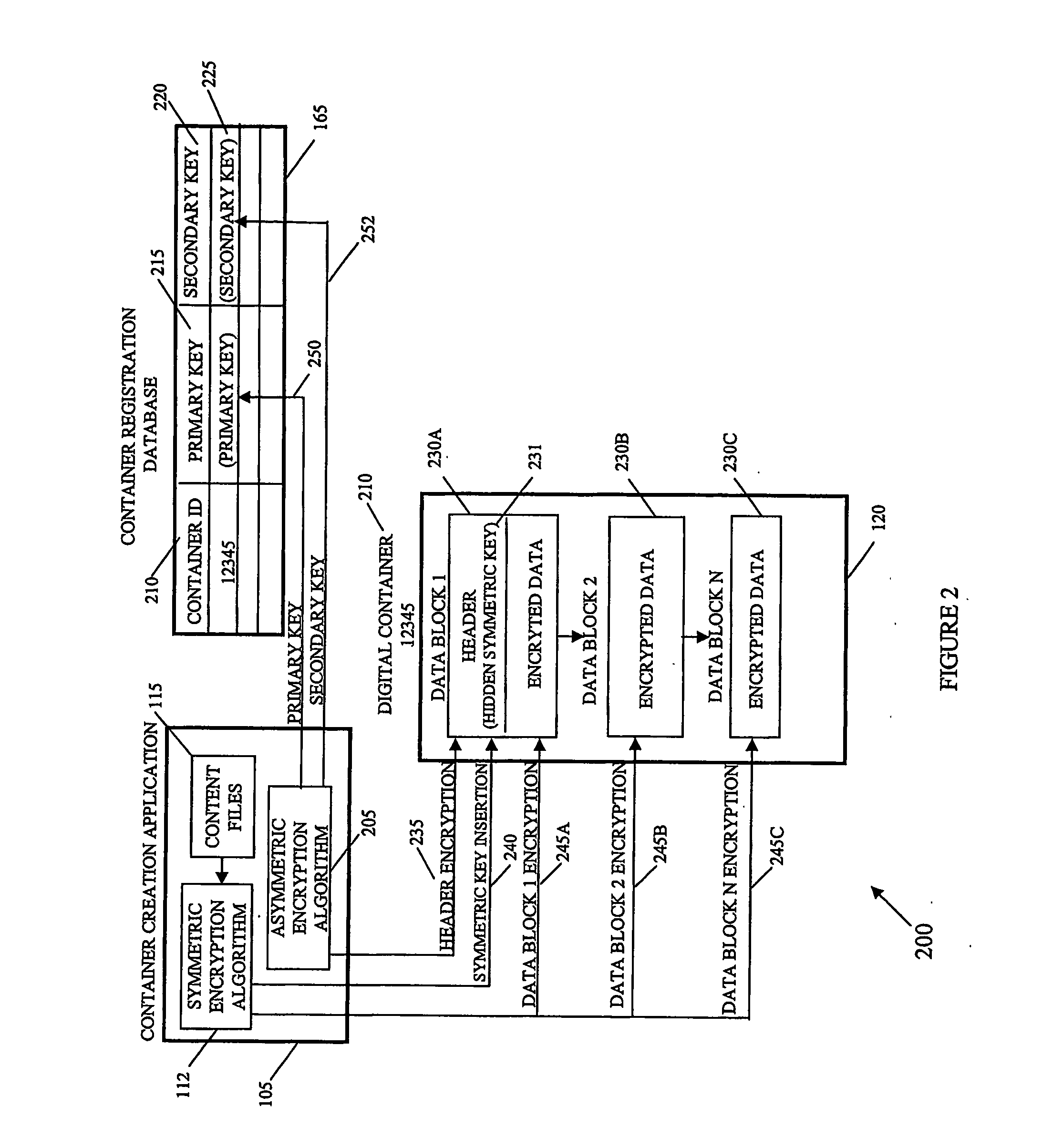
A system and method of encrypting digital content in a digital container and securely locking the encrypted content to a particular user and / or computer or other computing device is provided. The system uses a token-based authentication and authorization procedure and involves the use of an authentication / authorization server. This system provides a high level of encryption security equivalent to that provided by public key / asymmetric cryptography without the complexity and expense of the associated PKI infrastructure. The system enjoys the simplicity and ease of use of single key / symmetric cryptography without the risk inherent in passing unsecured hidden keys. The secured digital container when locked to a user or user's device may not open or permit access to the contents if the digital container is transferred to another user's device. The digital container provides a secure technique of distributing electronic content such as videos, text, data, photos, financial data, sales solicitations, or the like.
Owner:DIGITAL REG OF TEXAS
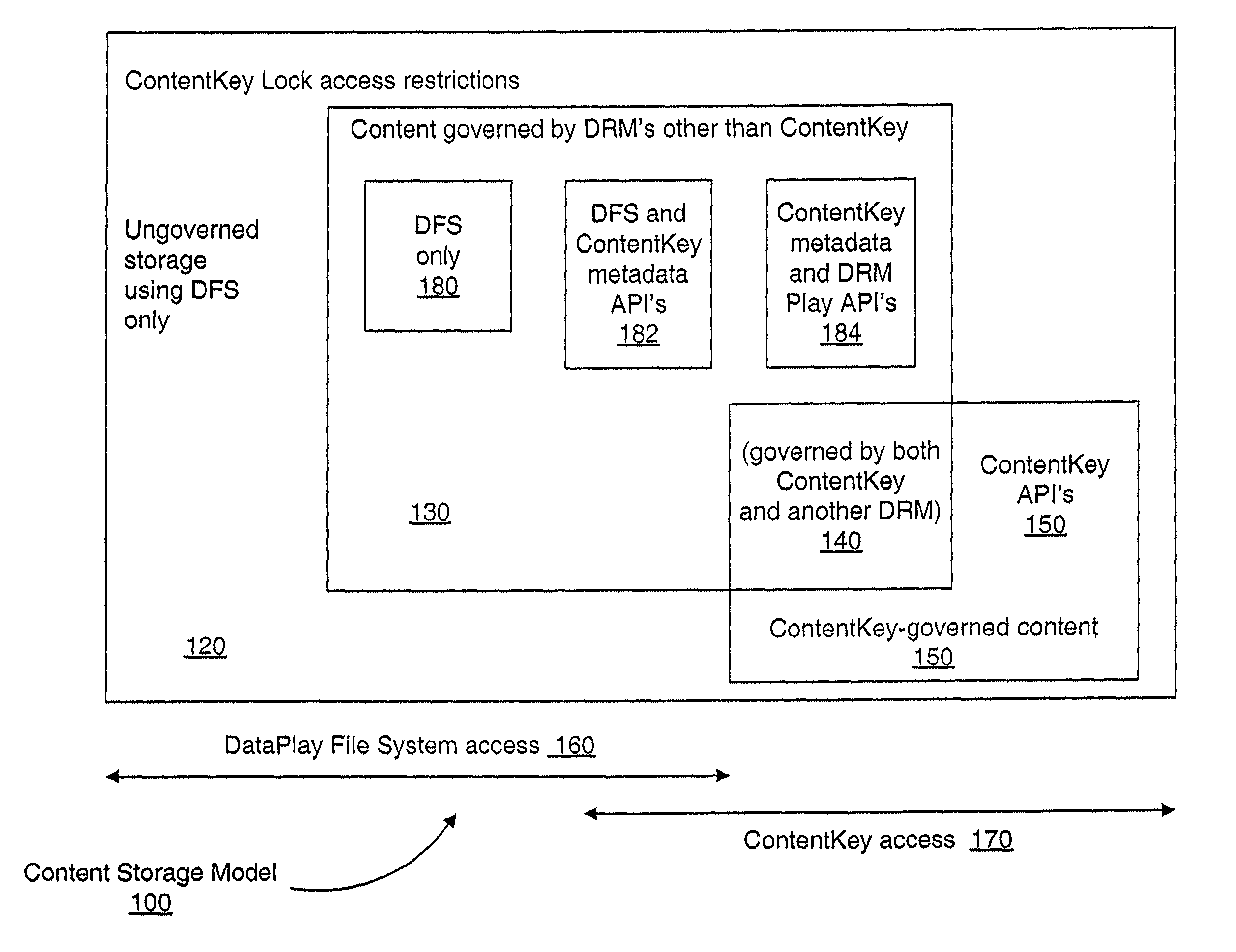
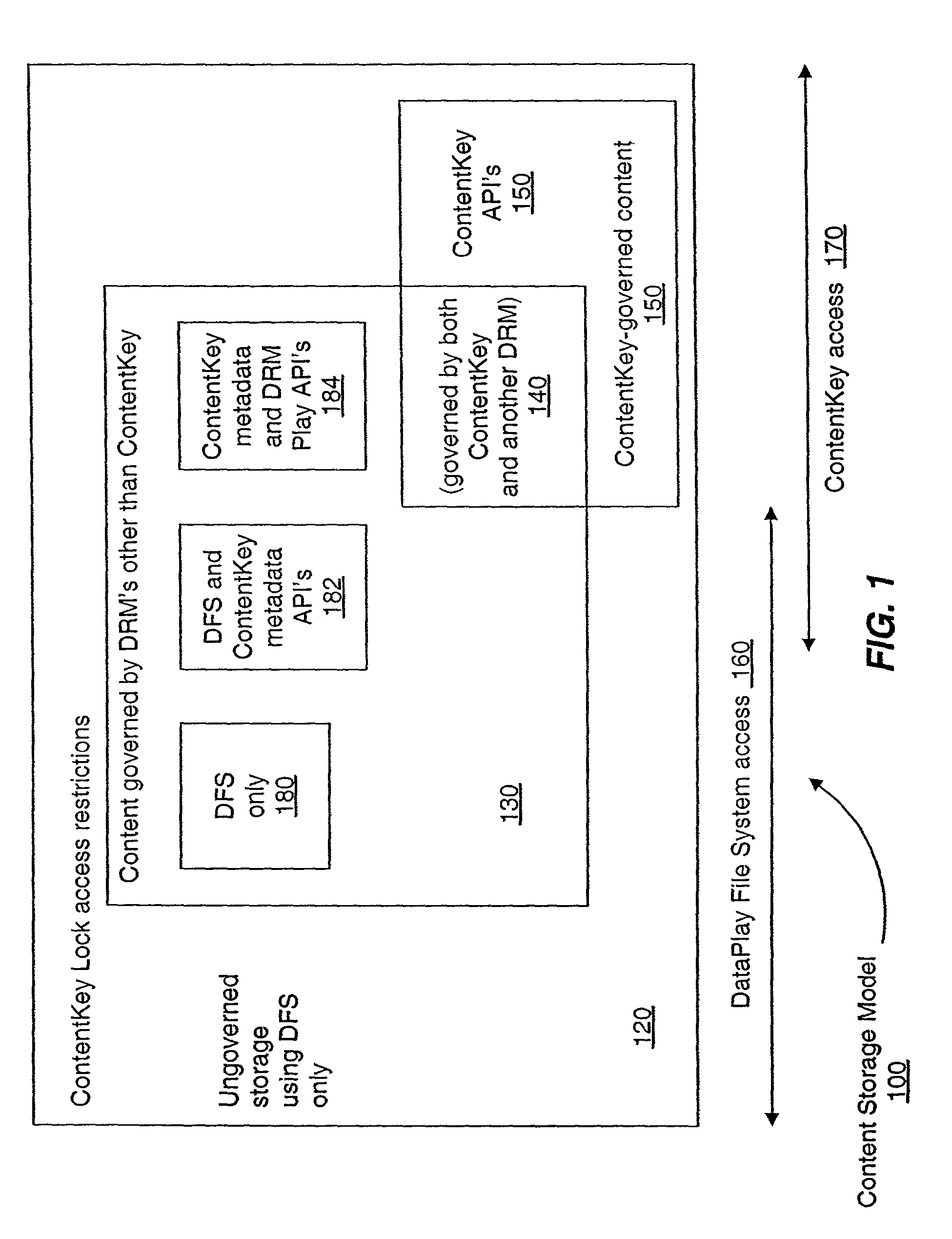
Secure access method and system
A secure electronic content system and method is provided. The system includes a controller including an interface component, a host system coupled to the controller, the host system configured to present content under predetermined conditions, the host system operable with a navigation protocol, the host system further including a system manager operable with an associations component configured to be at least partially run by the host system, a translator configured to provide meanings and generate commands within the host system at least a first digital rights management (DRM) component configured to provide encoding and access rules for the content; and a file system component including a file system application programming interface (API) configured to provide a logical interface between a plurality of components.
Owner:DATAPLAY
Content Sharing Systems and Methods
ActiveUS20100299522A1Increase salesLoss of revenueUser identity/authority verificationSelective content distributionContent sharingPeer-to-peer
Systems and methods are described for peer-to-peer sharing of electronic content. In one embodiment, if a license associated with a content item permits a sharing peer to share the content item with a receiving peer, the sharing peer rebinds a cryptographic key associated with the content item to the receiving peer and generates a sharing license for the content item. The sharing peer sends the sharing license and the content item to the receiving peer for consumption.
Owner:NOKIA TECHNOLOGLES OY
System and method for analyzing, generating suggestions for, and improving websites
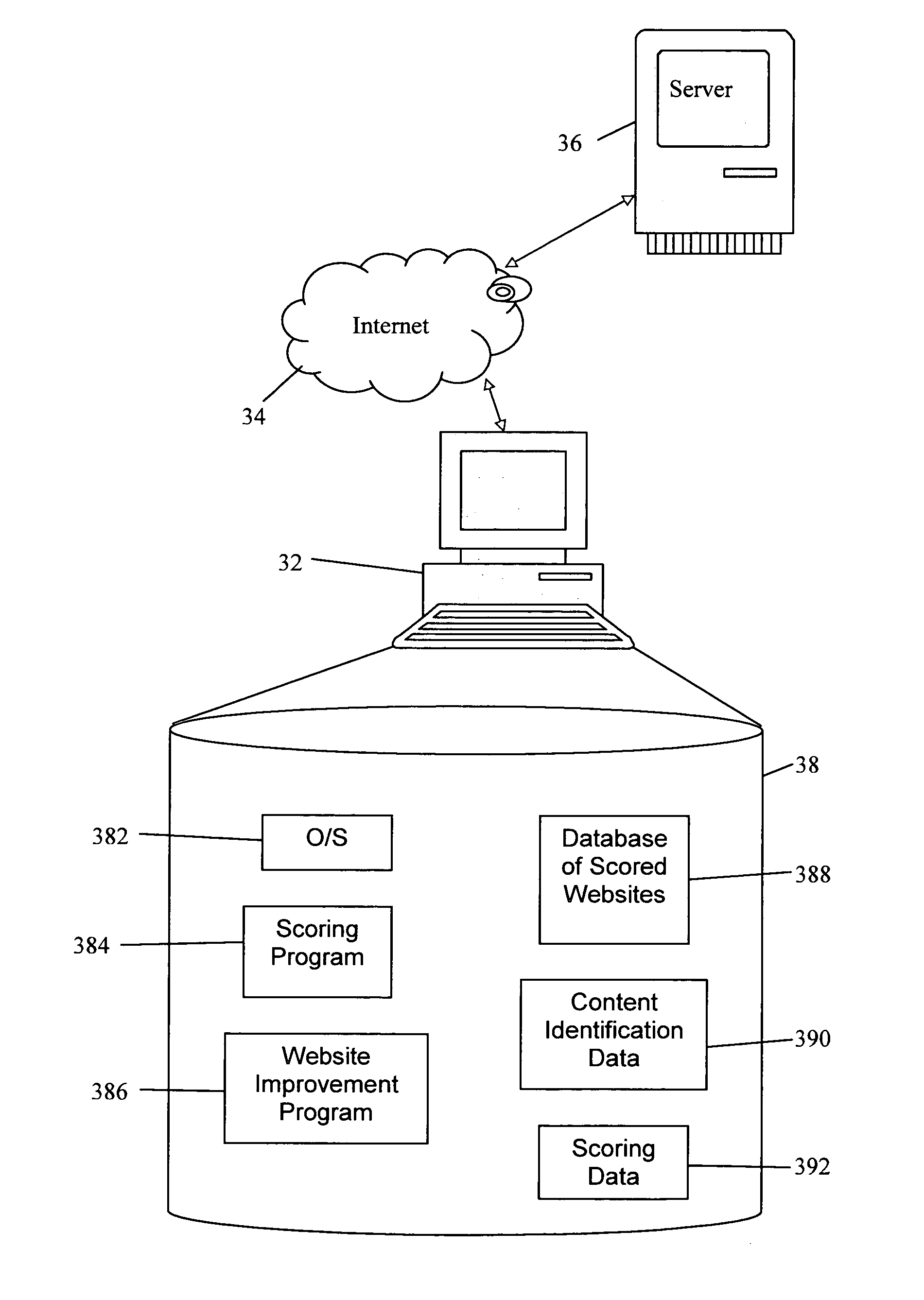
ActiveUS20060253345A1Acutation objectsDigital data processing detailsData analysis systemAnalysis method
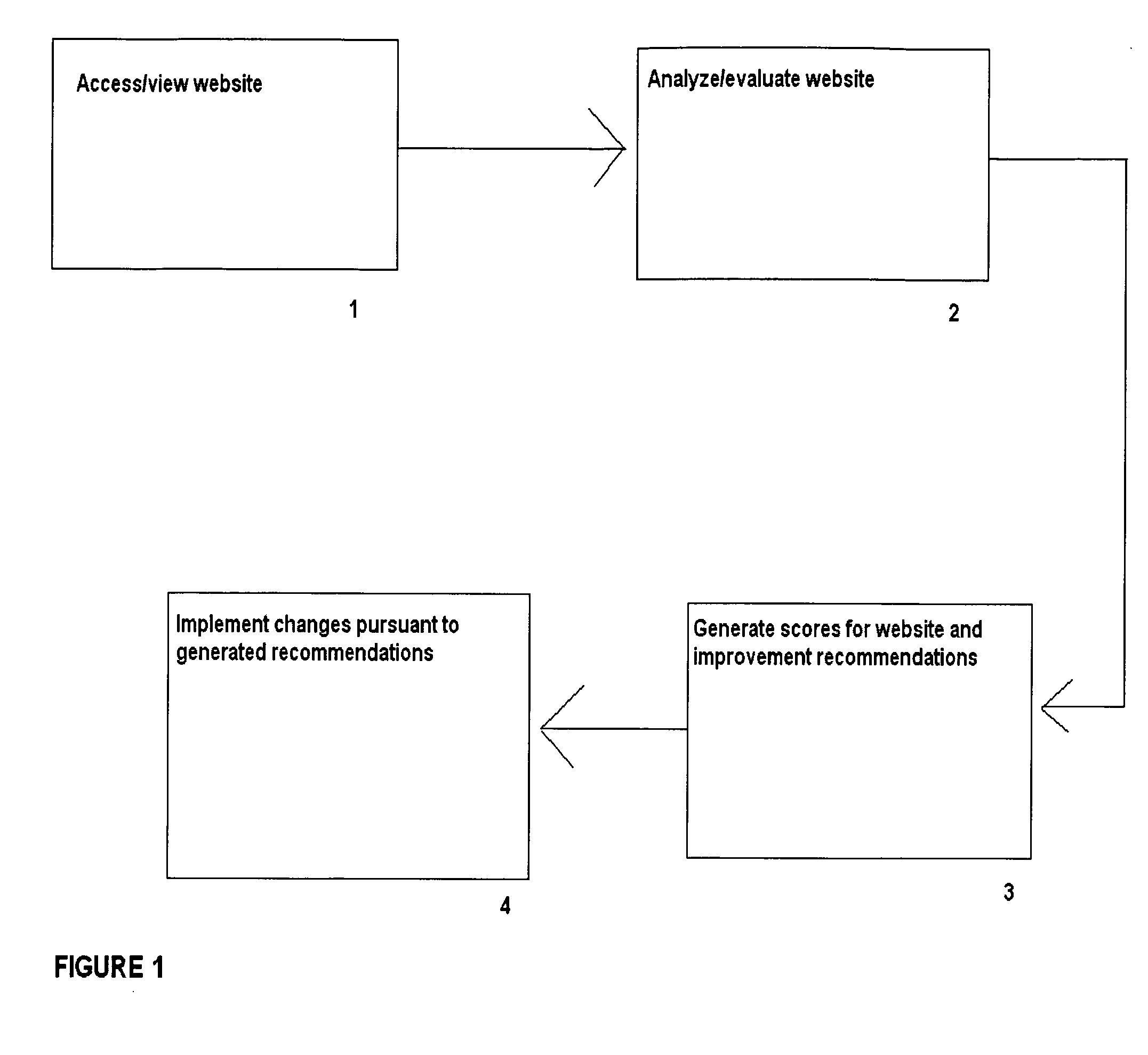
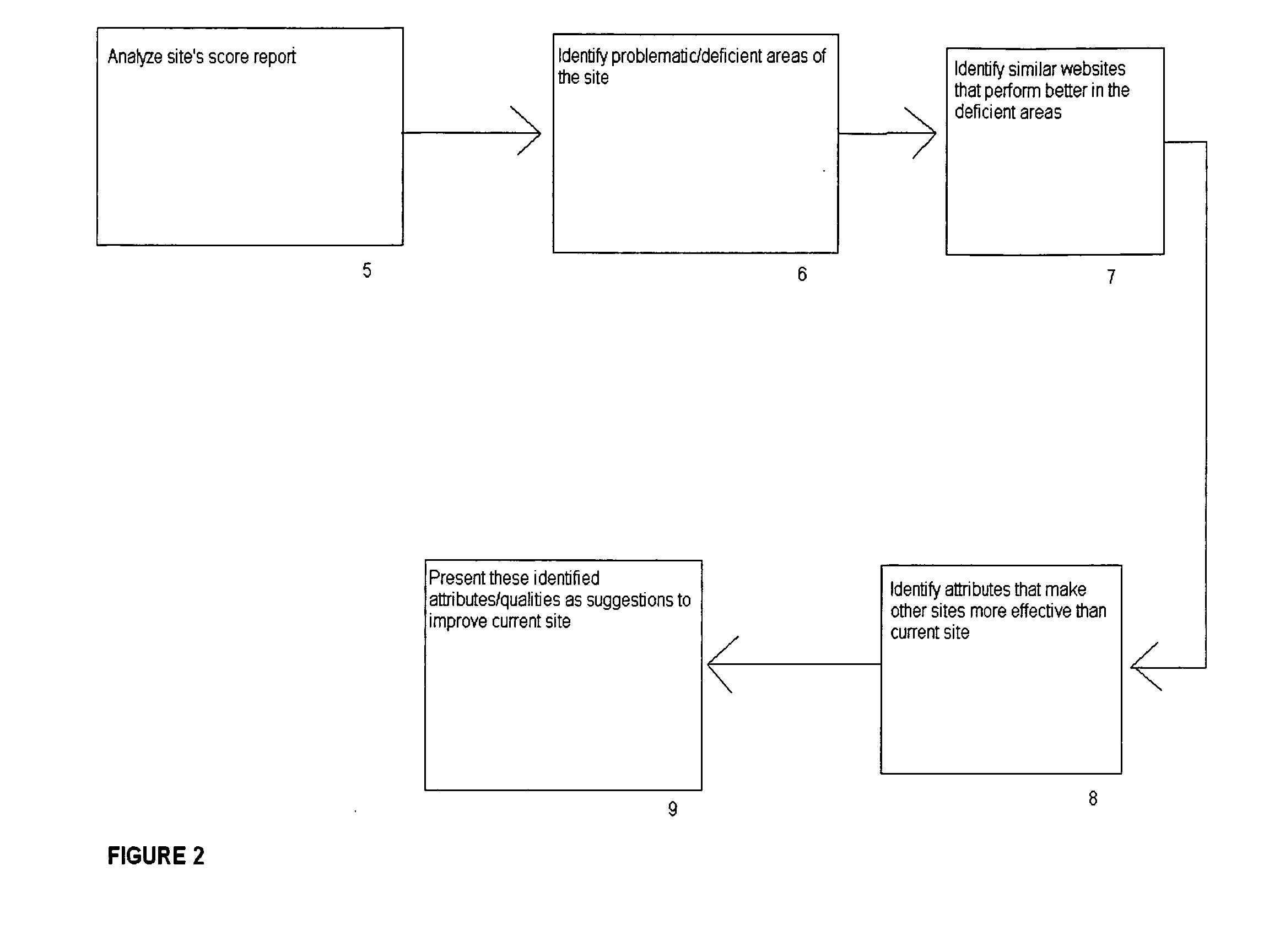
A content and data analysis method for evaluating and improving a website, by accessing the website to be analyzed, analyzing the content and data associated with the website, scoring the website based on a multitude of criteria, generating suggestions for improving the website, and implementing changes and improvements to the website. An electronic content and data analysis system and software program including an accessing mechanism for viewing the website to be analyzed, an analyzing mechanism for reviewing the content and data associated with the website, a scoring mechanism for attributing scores to the website based on a multitude of criteria; a generating mechanism for providing suggestions for improving a website; and an editing mechanism for implementing changes and improvements to a website is disclosed.
Owner:HEBER YOSI
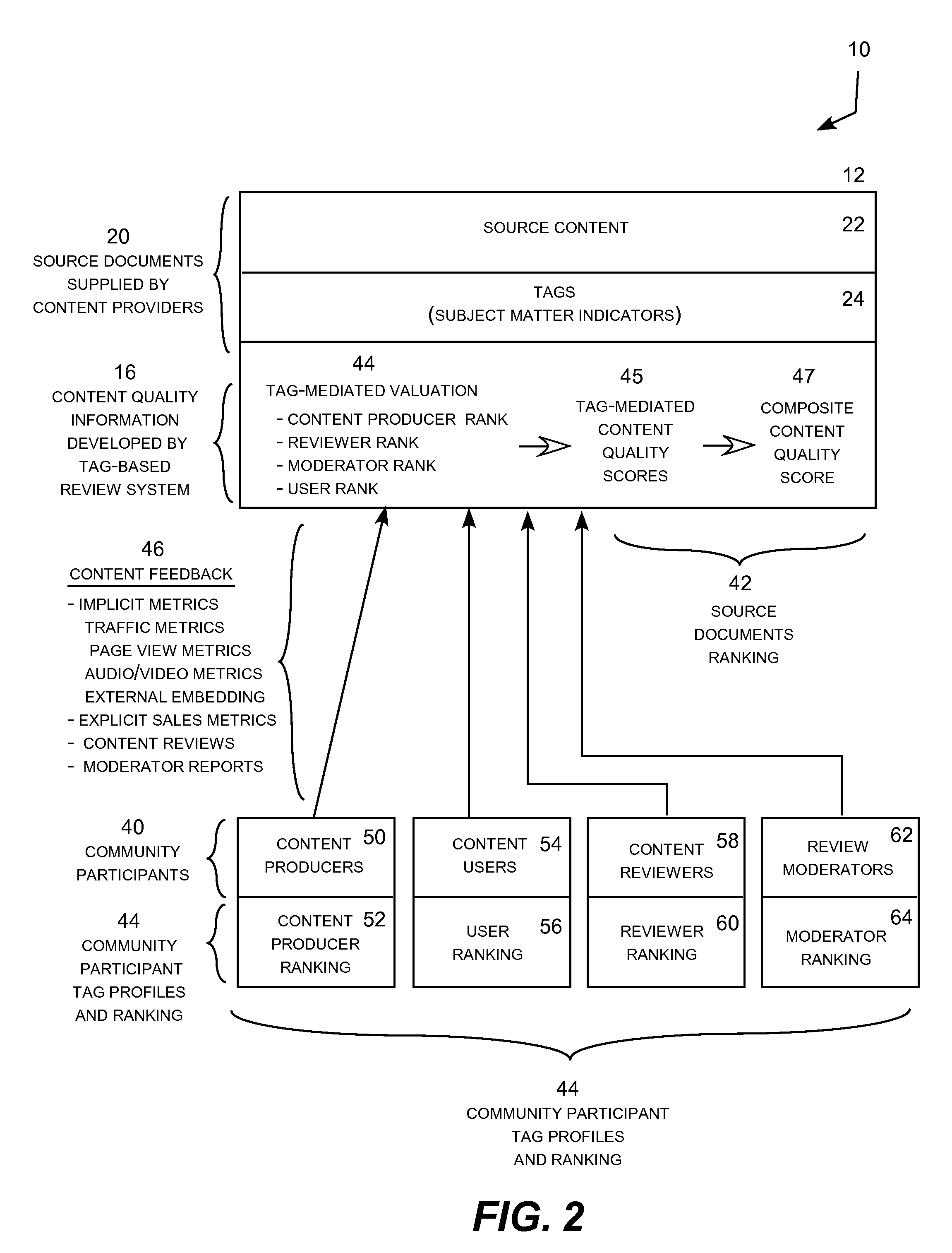
Tag-mediated review system for electronic content
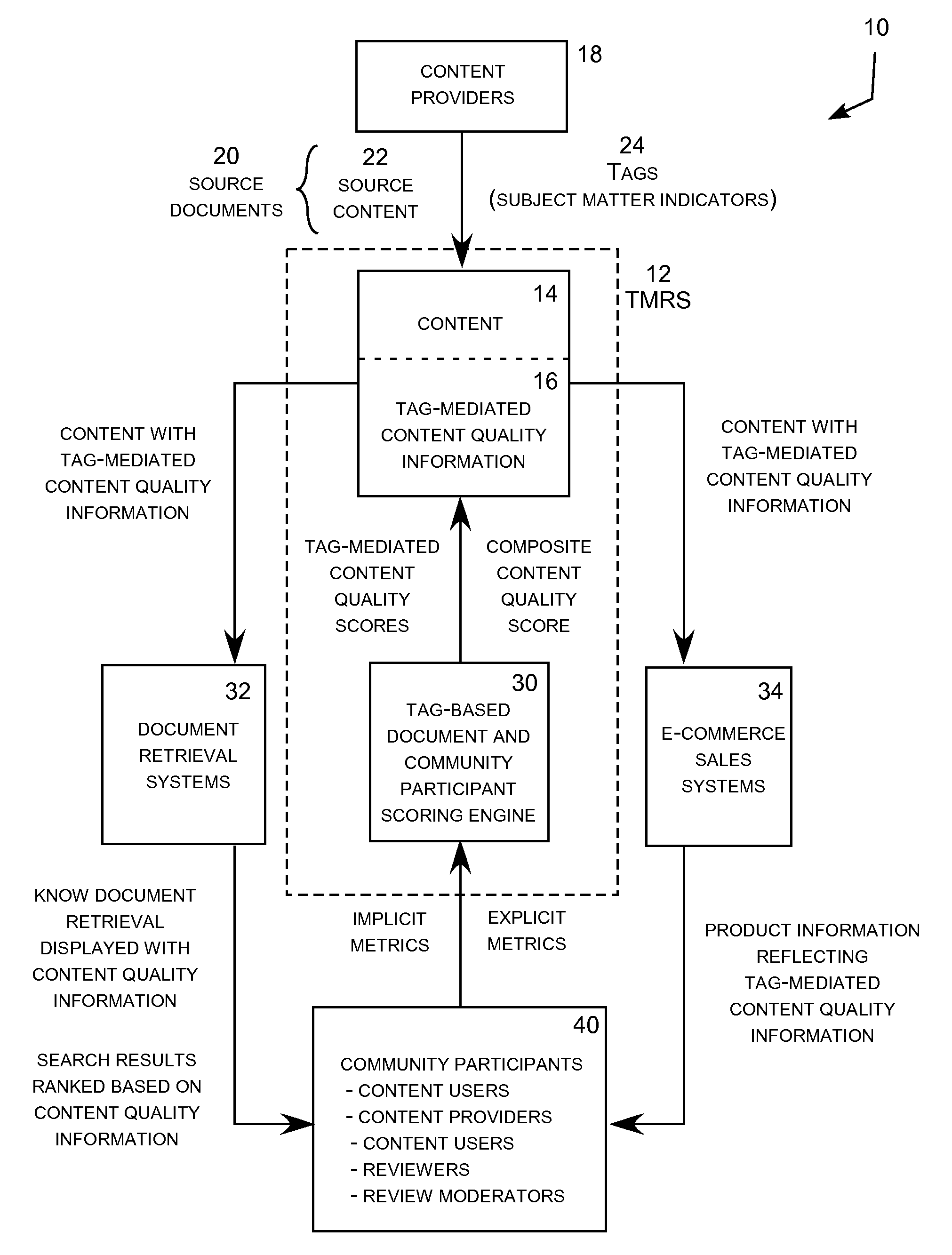
InactiveUS20080201348A1Increase search engine visibilityEase with which metadataDigital data processing detailsSpecial data processing applicationsSubject matterRanking
A tag-mediated review system for electronic content that ranks content based upon several ascertainable factors, including the implicit engagement with the content by users (typically online viewers); the expertise and success in the topical domain by reviewers; and the review activity of users or viewers. The system extends implicit metrics to tracking of user interaction including the receipt of video and audio content over the web. Document ranking is mediated by tags that identify the subject matter addressed by an associated document as the ranking mediators for computing content quality scores values for user and reviewer activity. The tag-mediated content quality scores, which are content quality scores for the subject matter area identified by the associated tags, can be exposed to end-users and used directly or indirectly to complement search engine retrieval algorithms.
Owner:UQAST
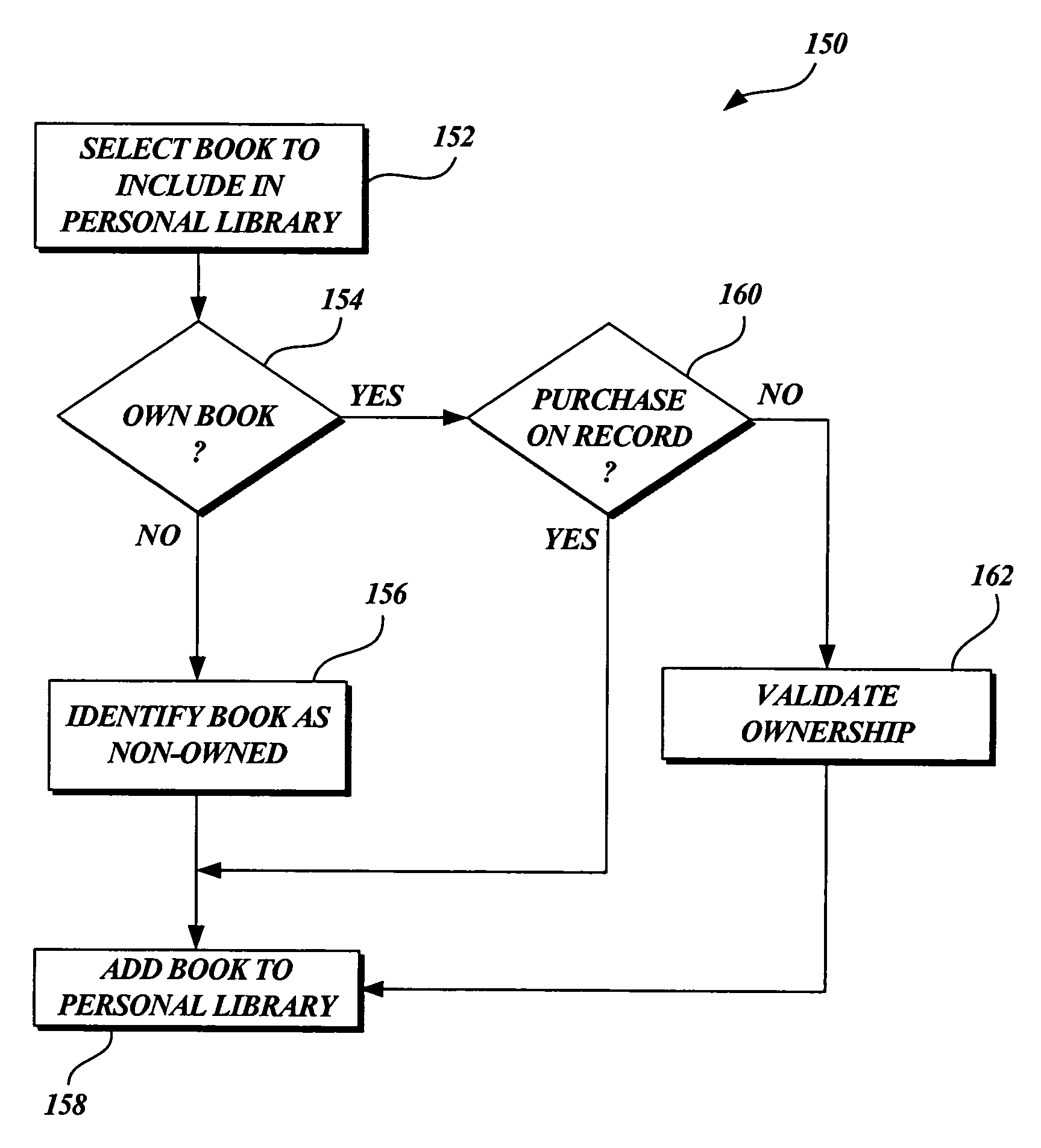
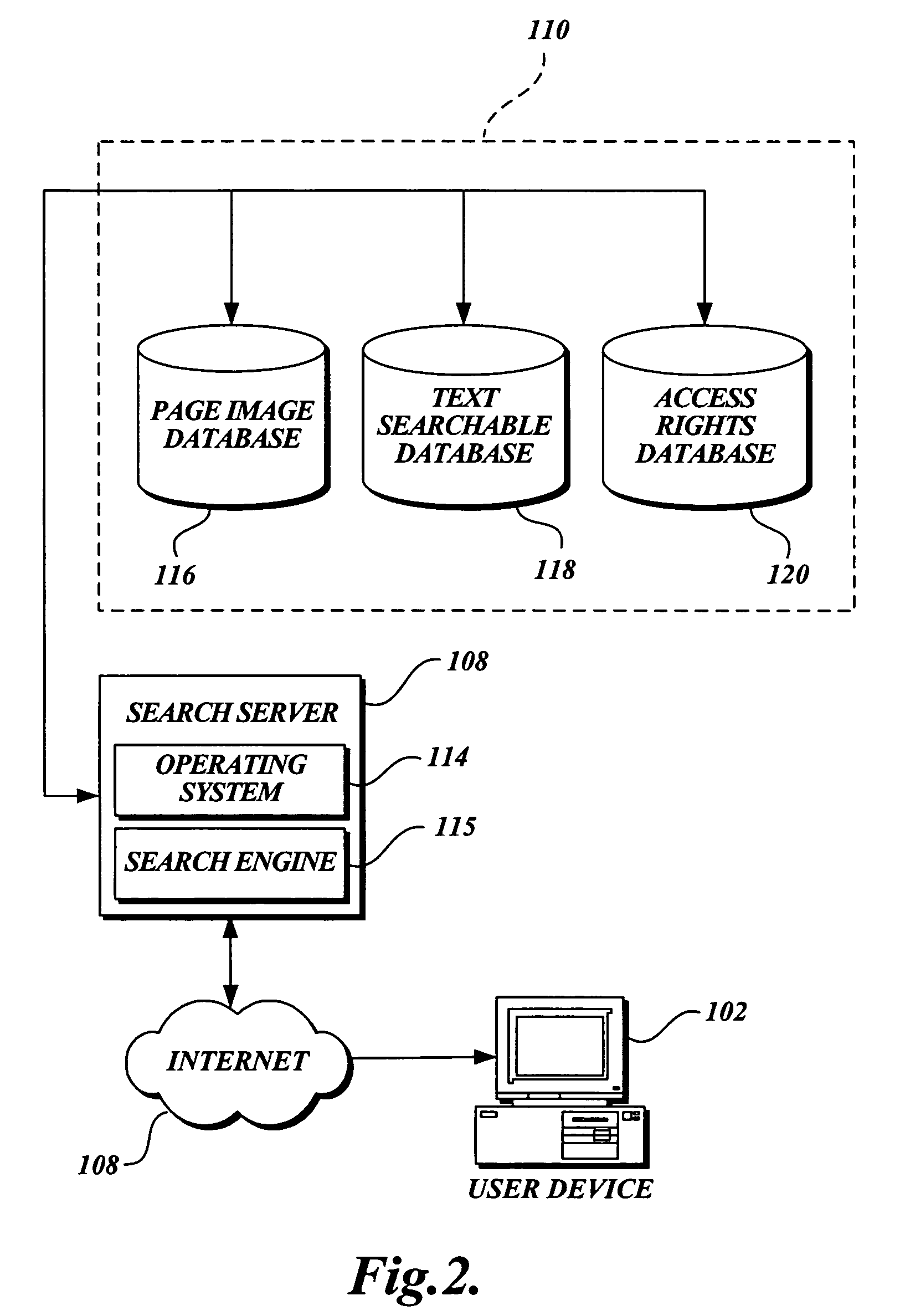
Method and system for access to electronic images of text based on user ownership of corresponding physical text
Methods and apparatus of the invention enable users to request access to one or more electronic images of pages in a physical text. When the user is identified and user ownership of the physical text is confirmed, the user is given access to the requested electronic images in accordance with the one or more access rules. Electronic images of pages may be automatically added to a user-personalized library of electronic content for later access. A flag associated with the user and the pages images may be set to indicate confirmed user ownership of the physical text. A user may purchase a physical text itself or purchase an item that the physical text normally accompanies. Electronic page images may be acquired by scanning printed pages of the text or from a user upload. Access to the electronic images of a physical text is based on user ownership of the physical text.
Owner:AMAZON TECH INC
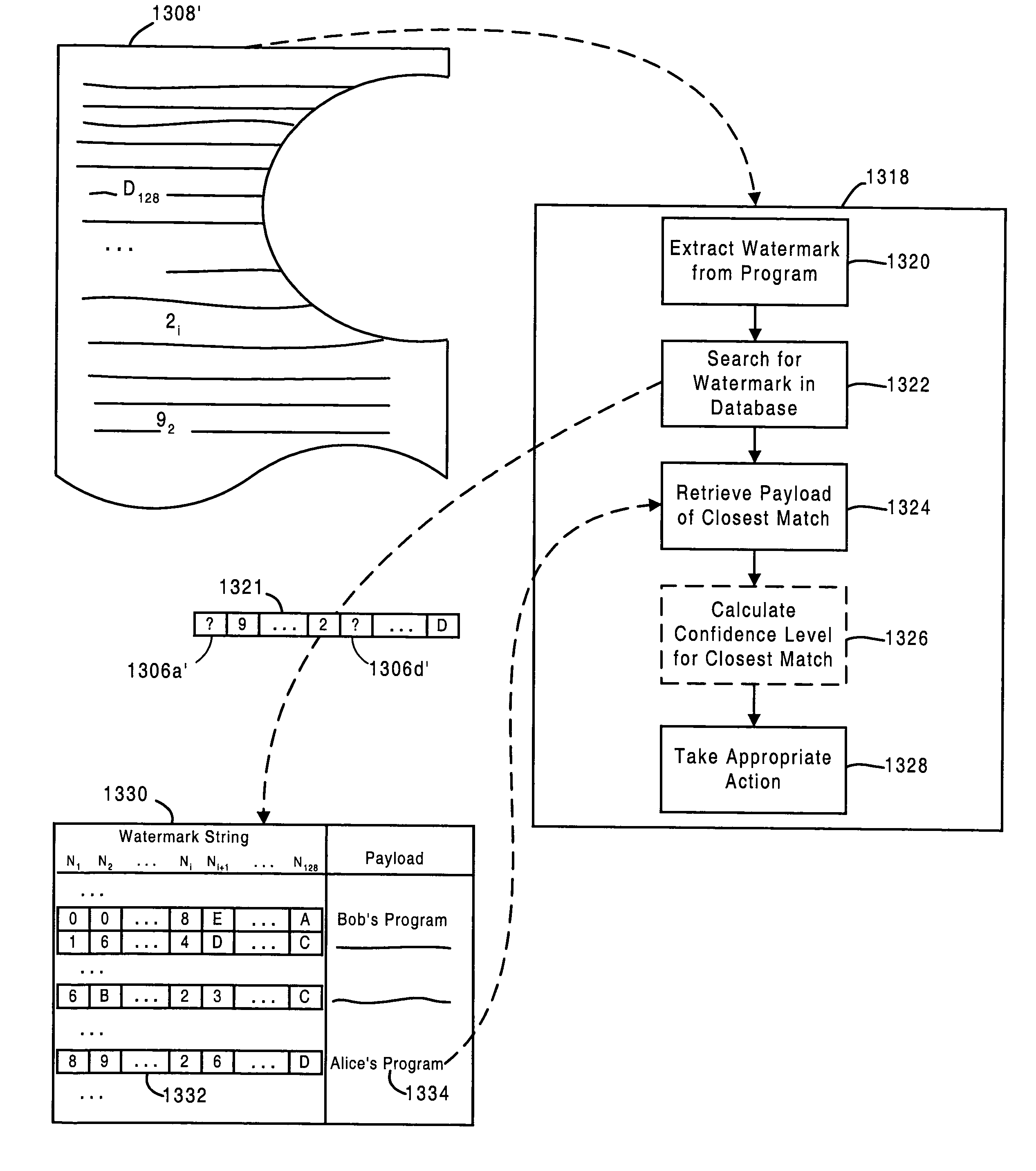
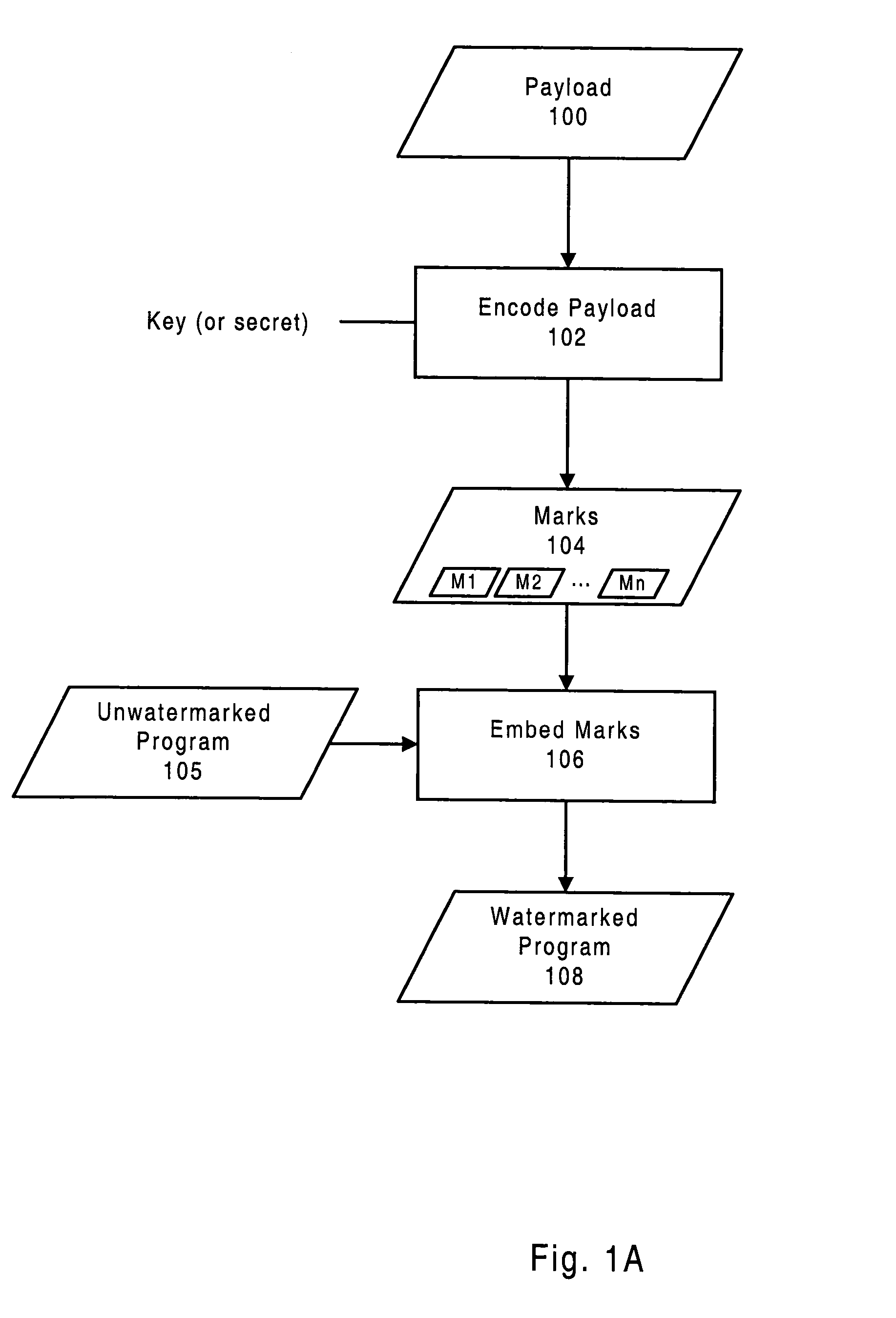
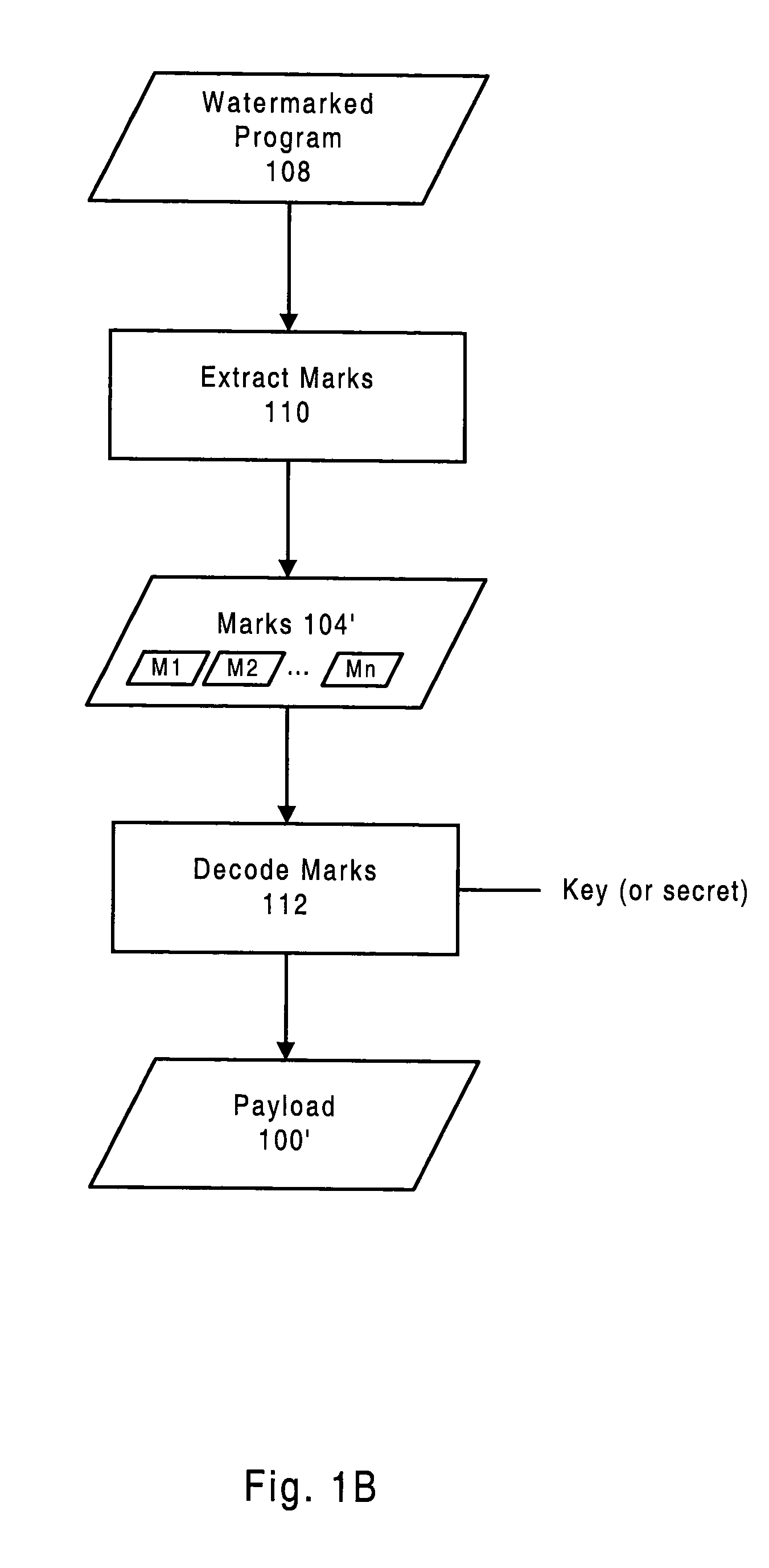
Systems and Methods for Watermarking Software and Other Media
InactiveUS20080028474A1Facilitating effective legal recourseDifficult to imageMathematical modelsDigital data processing detailsSoftwareElectronic content
Systems and methods are disclosed for embedding information in software and / or other electronic content such that the information is difficult for an unauthorized party to detect, remove, insert, forge, and / or corrupt. The embedded information can be used to protect electronic content by identifying the content's source, thus enabling unauthorized copies or derivatives to be reliably traced, and thus facilitating effective legal recourse by the content owner. Systems and methods are also disclosed for protecting, detecting, removing, and decoding information embedded in electronic content, and for using the embedded information to protect software or other media from unauthorized analysis, attack, and / or modification.
Owner:INTERTRUST TECH CORP
Secure personal content server
InactiveUS7475246B1Risk minimizationPrevent access to informationDigital data processing detailsUser identity/authority verificationData setSecure transmission
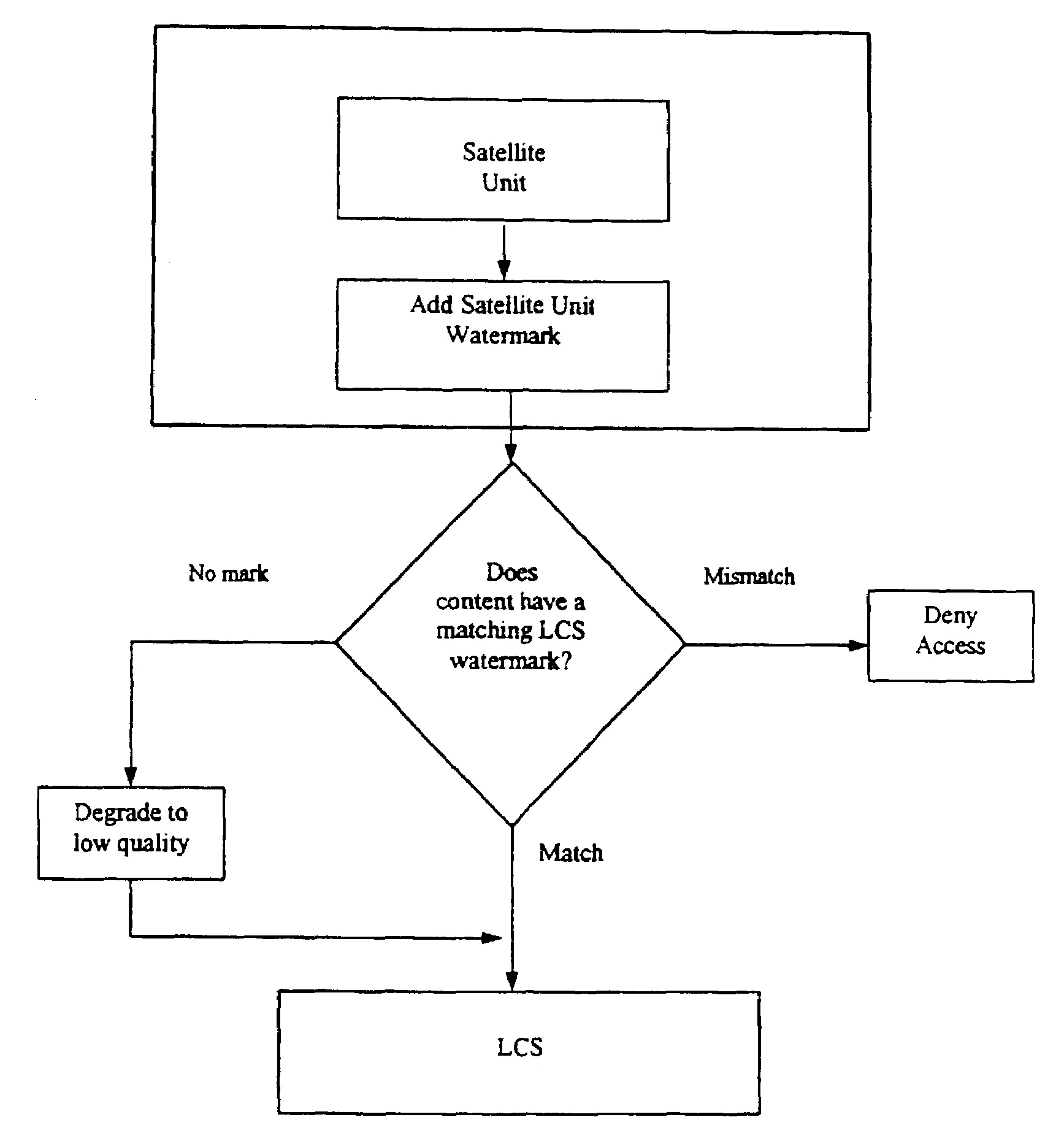
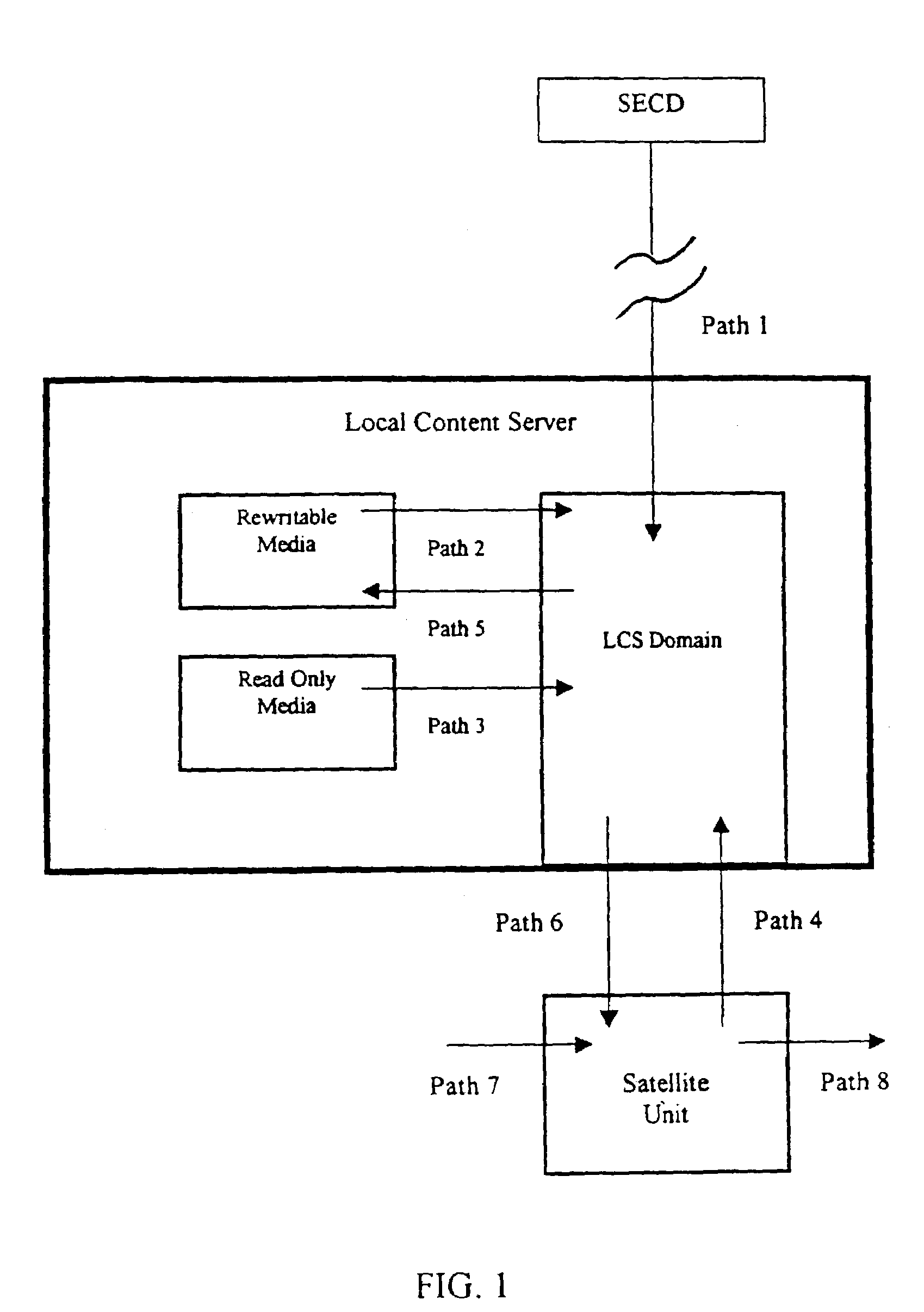
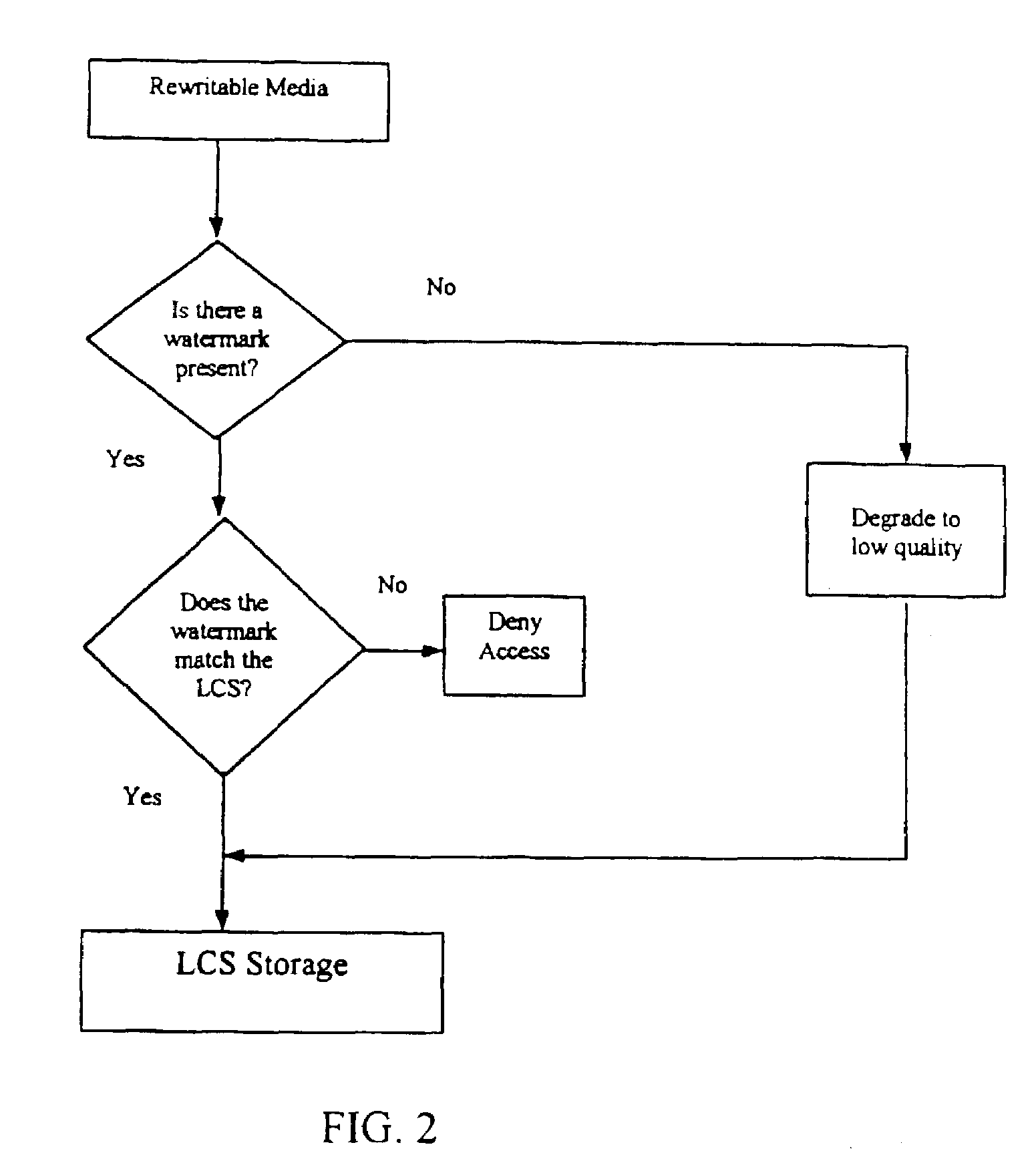
A local content server system (LCS) for creating a secure environment for digital content is disclosed, which system comprises: a communications port in communication for connecting the LCS via a network to at least one Secure Electronic Content Distributor (SECD), which SECD is capable of storing a plurality of data sets, is capable of receiving a request to transfer at least one content data set, and is capable of transmitting the at least one content data set in a secured transmission; a rewritable storage medium whereby content received from outside the LCS may be stored and retrieved; a domain processor that imposes rules and procedures for content being transferred between the LCS and devices outside the LCS, and a programmable address module which can be programmed with an identification code uniquely associated with the LCS. The LCS is provided with rules and procedures for accepting and transmitting content data. Optionally, the system may further comprise: an interface to permit the LCS to communicate with one or more Satellite Units (SU) which may be connected.
Owner:WISTARIA TRADING INC
Programmable virtual book system
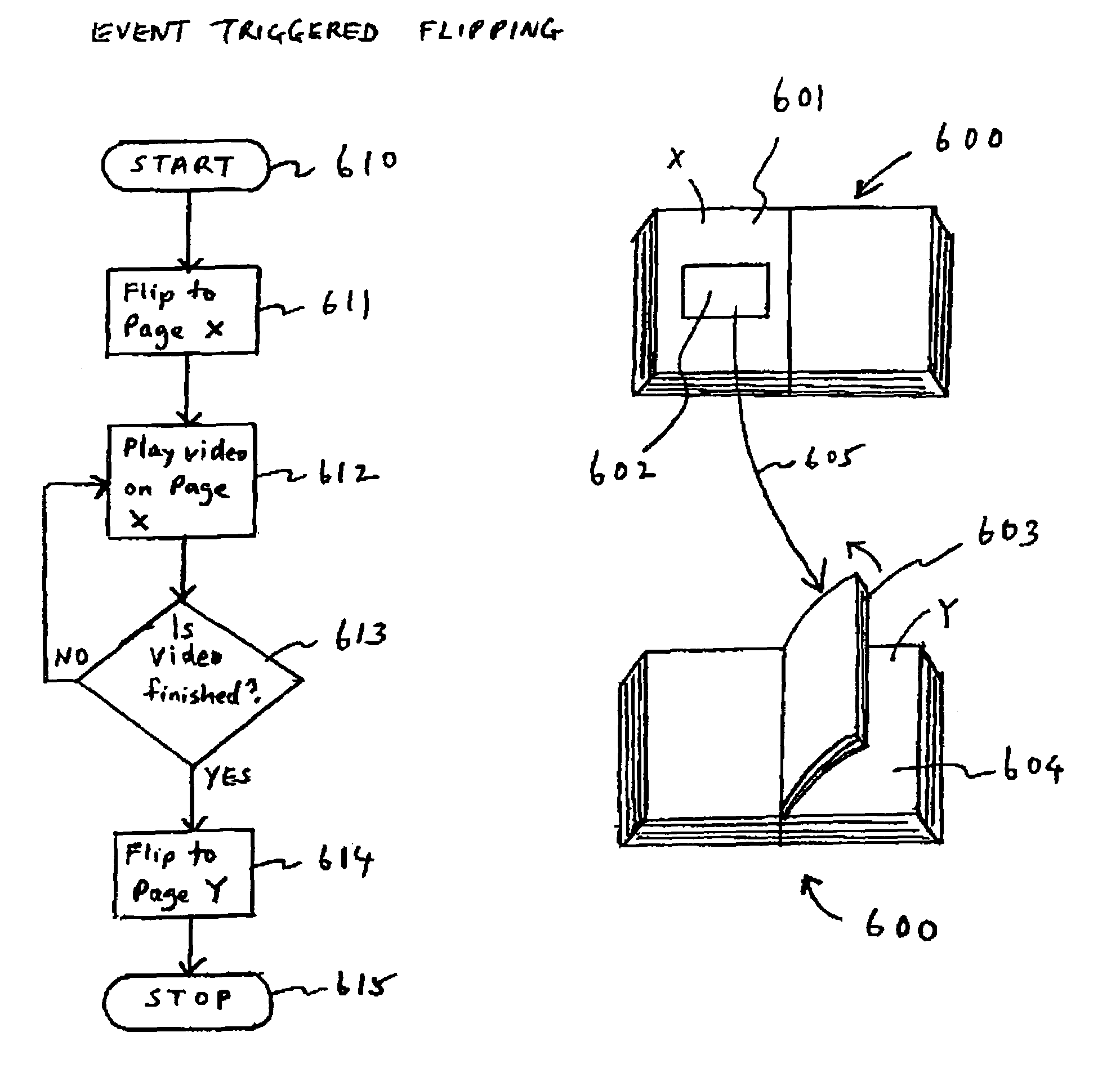
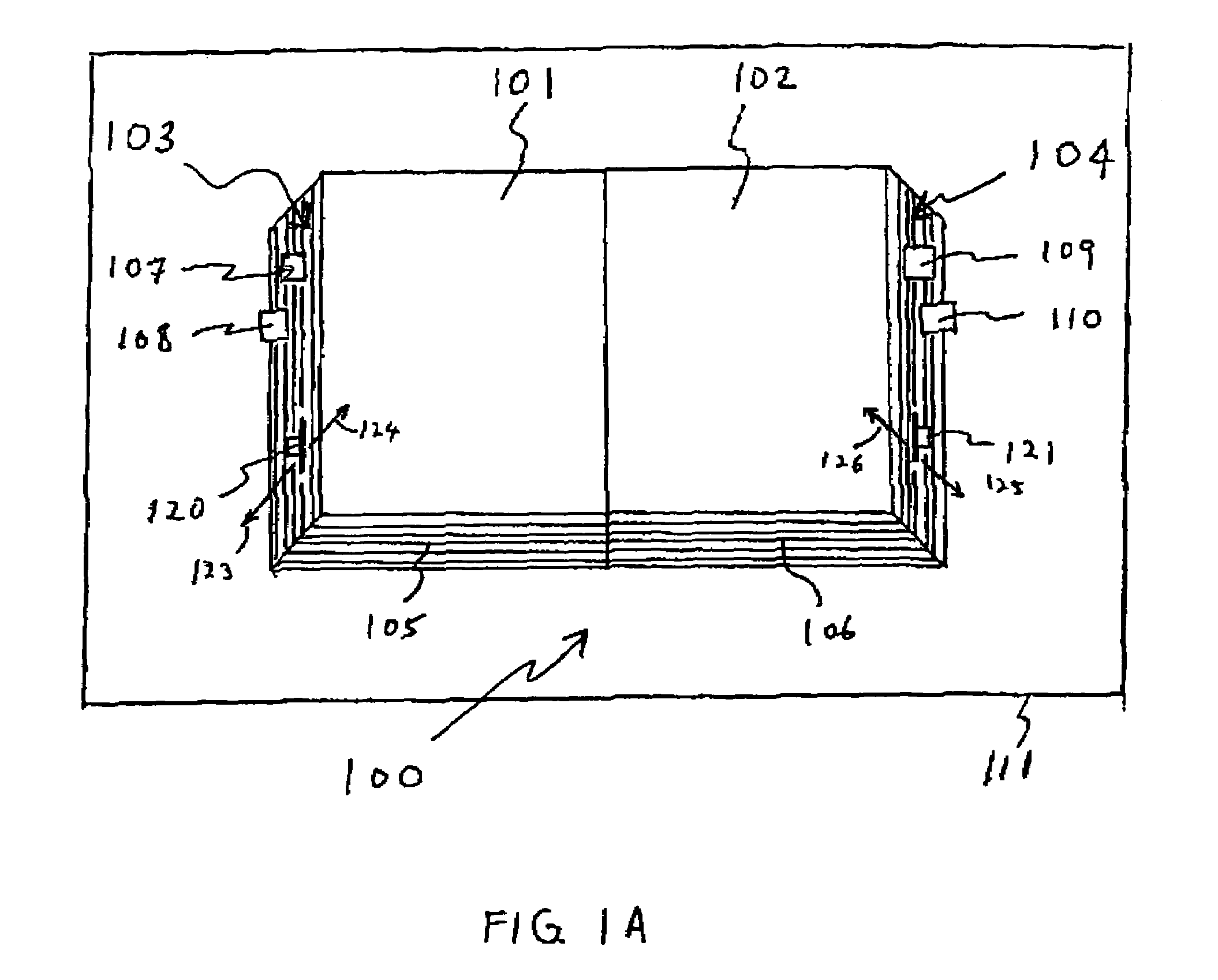
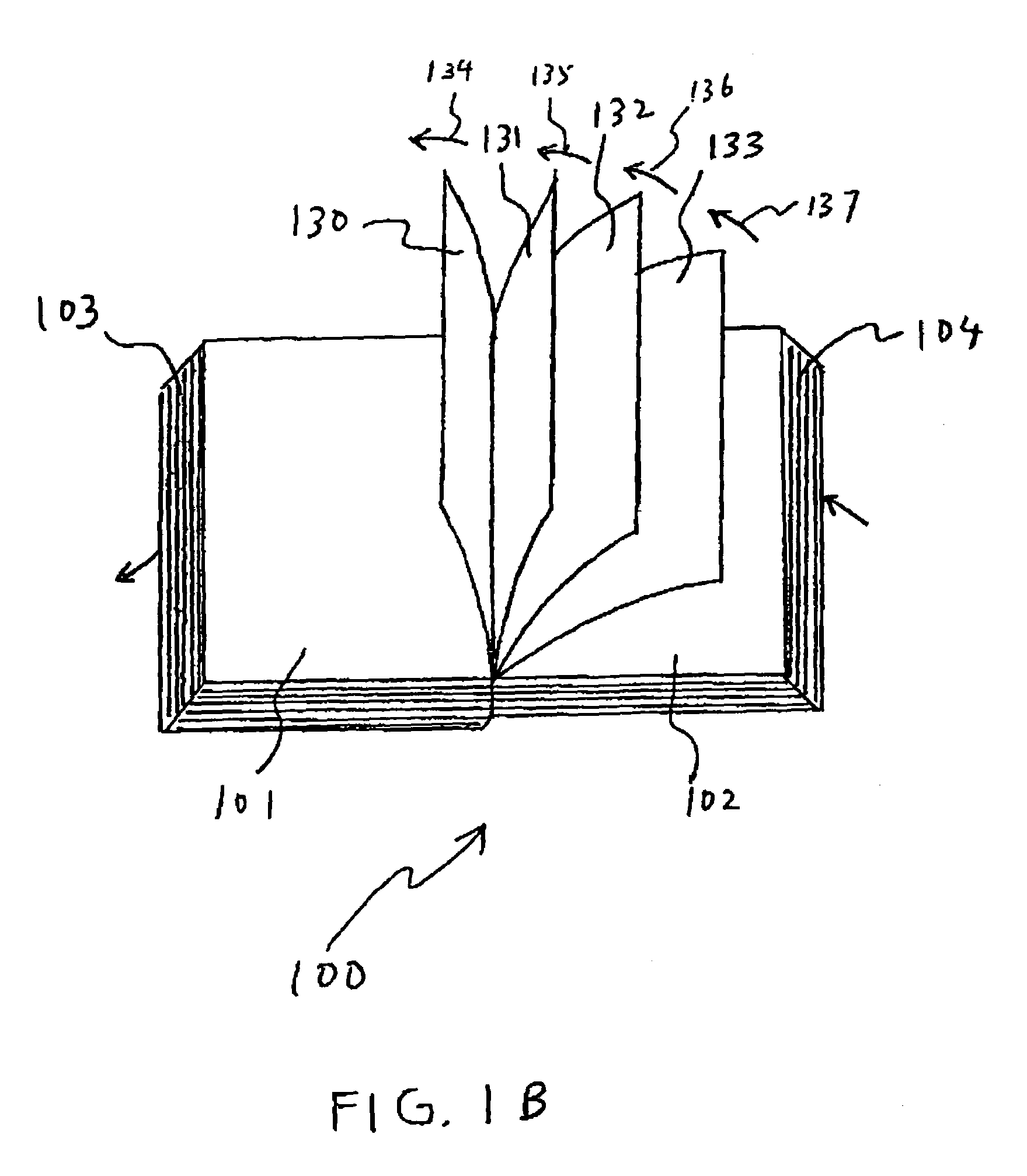
ActiveUS7009596B2Quick configurationDigital computer detailsCathode-ray tube indicatorsElectronic informationProgram specification
An electronic information browsing system that provides a book-like interface—a virtual book—for presenting electronic contents. Specifically, an electronic information browsing system that allows users to configure its behavior via data and program specification encapsulated in a dynamic file format. Configurable behavior includes but not limited to the kind of contents to be displayed in the virtual book, the sources of the contents to be displayed, the static aspects of the virtual book such as the book dimensions and the dynamic aspects of the virtual book such as when a page is to be flipped, how the flipping of pages is contingent upon the execution of certain pre-specified events, etc.
Owner:SINO STAR GLOBAL
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com