Method for Anti-debugging
An anti-debugging and sub-process technology, applied in the field of anti-debugging, can solve the problems of not providing the same or similar API and being unusable
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Exemplary embodiments of the present invention will be described in detail with reference to the accompanying drawings. The technical scope of the present invention is applicable to various systems and is not limited to specific operating systems or hardware.
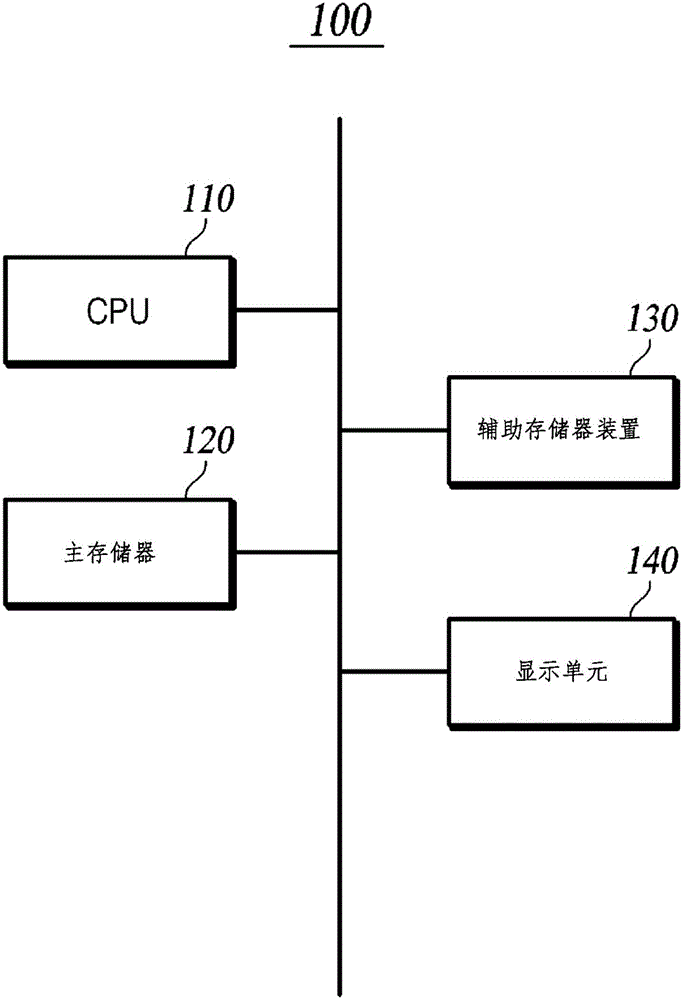
[0025] figure 1 is a block diagram illustrating the configuration of a computer for providing anti-debugging.
[0026] figure 1 An example of a computer for providing anti-debugging to mutually monitor process states of whether a parent process and a child process are debugged is illustrated. When a program stored in the auxiliary memory 130 is executed, the program is loaded into the main memory 120 and processed by a central processing unit (CPU) 110 , and the processing result is displayed on the display unit 140 . When the program is executed, a child process having the same form as that of the program is created (forked), and the program itself becomes the parent process of the child process. The parent ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com