Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
907 results about "Auxiliary memory" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Auxiliary memory, also known as auxiliary storage, secondary storage, secondary memory or external memory, is a non-volatile memory that is not directly accessible by the CPU, because it is not accessed via the input/output channels. In RAM devices data can be deleted or changed. It is used to store a large amount of data at lesser cost per byte than primary memory, it is two orders of magnitude less expensive than primary storage.
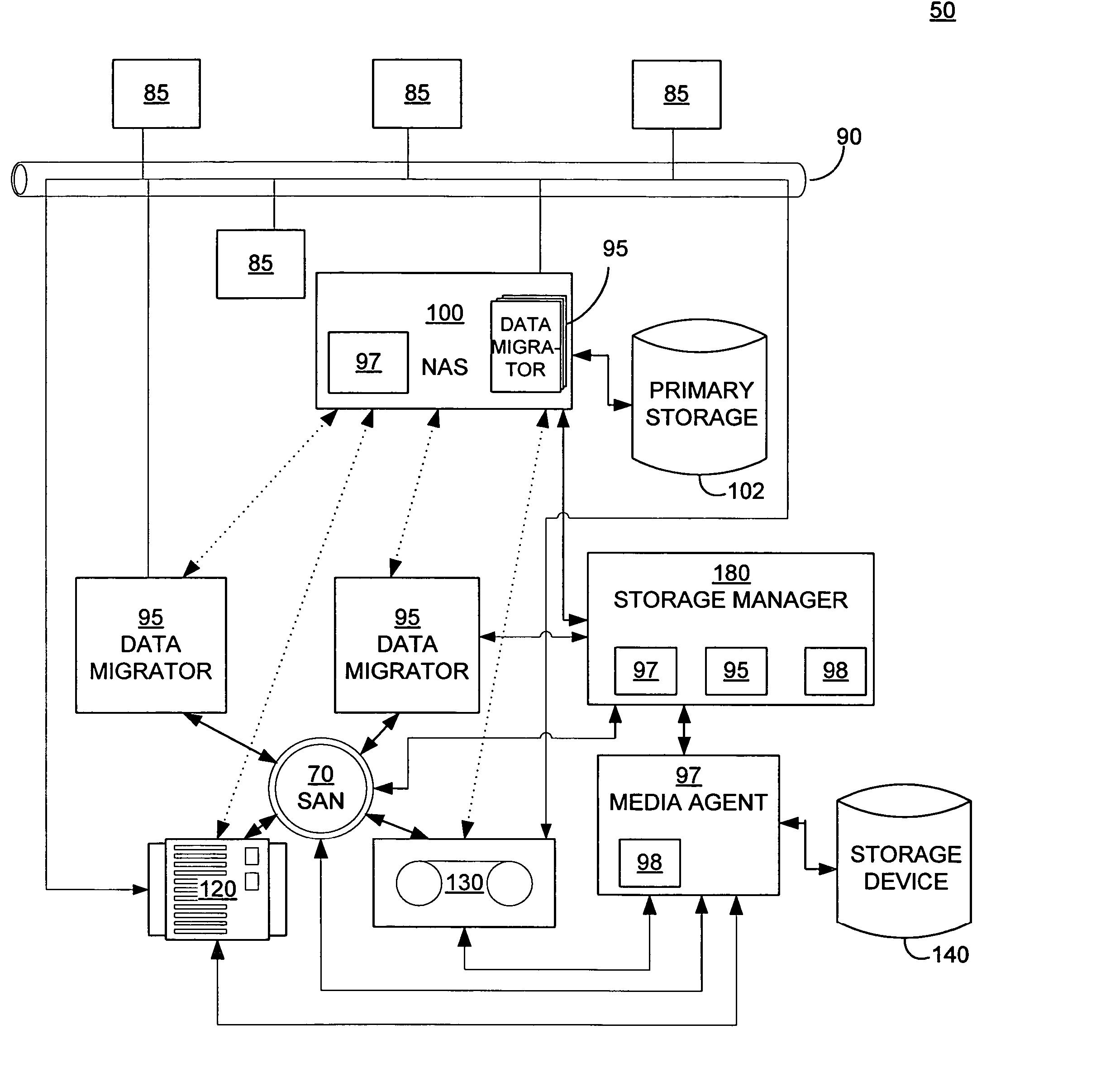
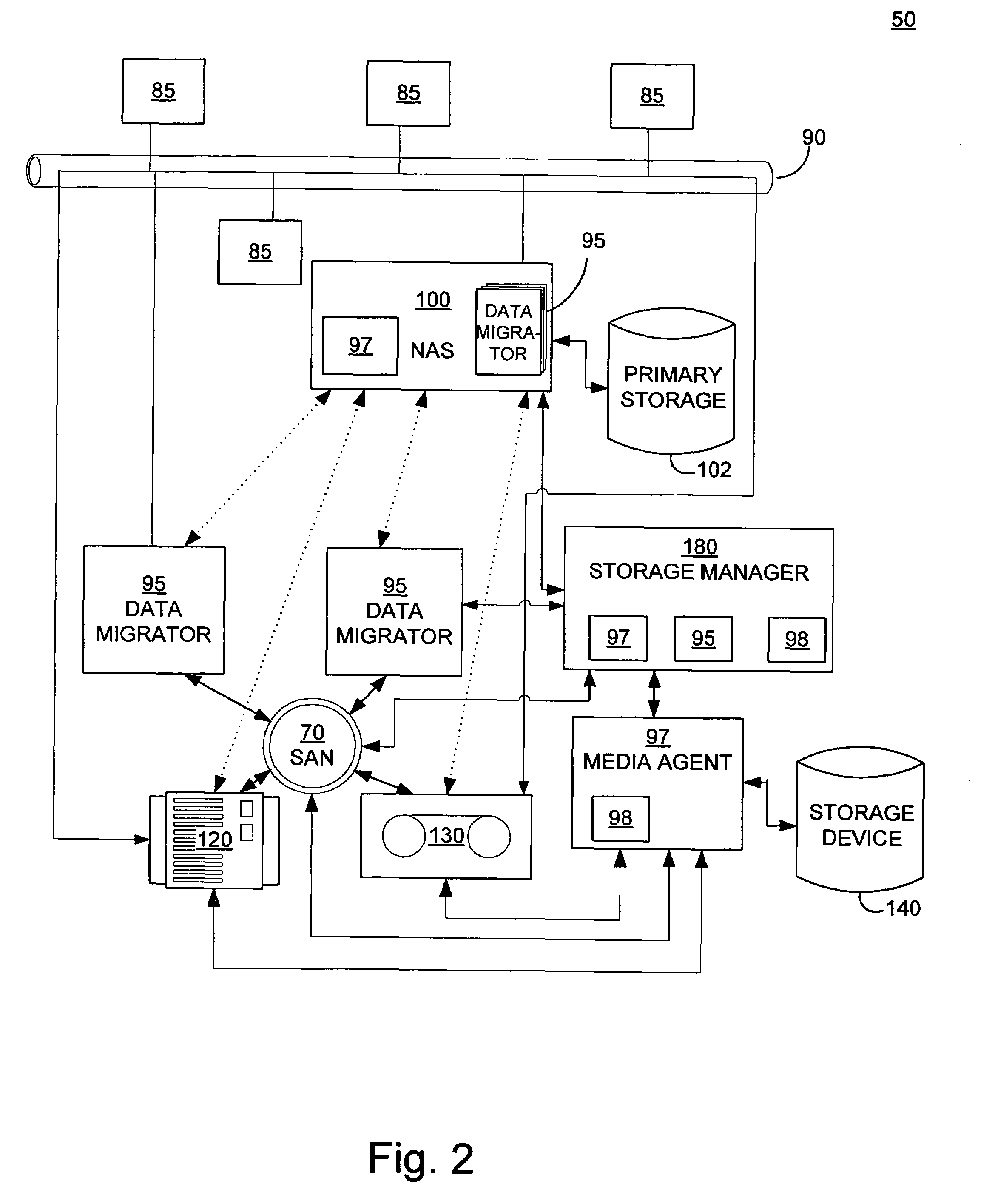
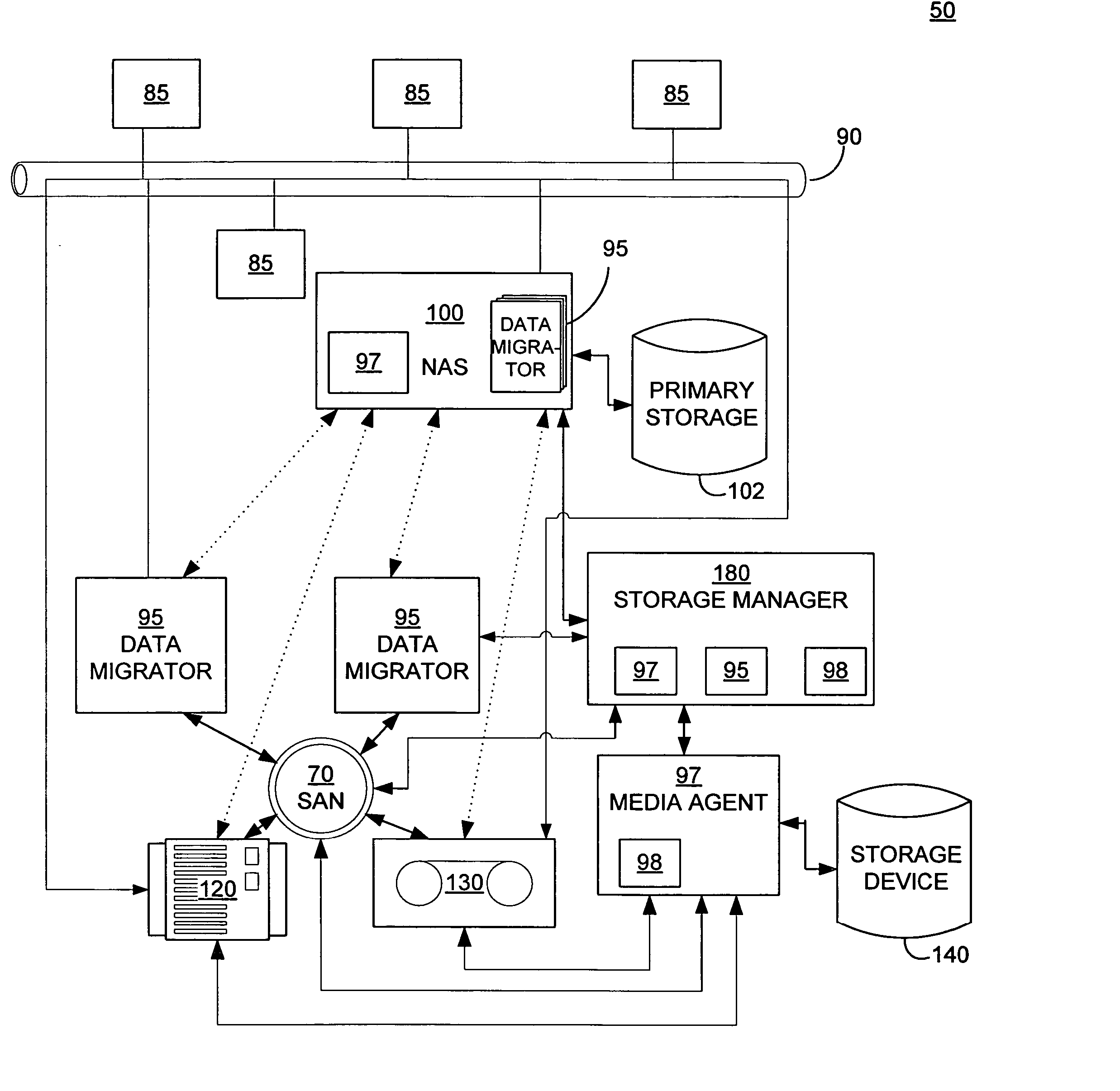
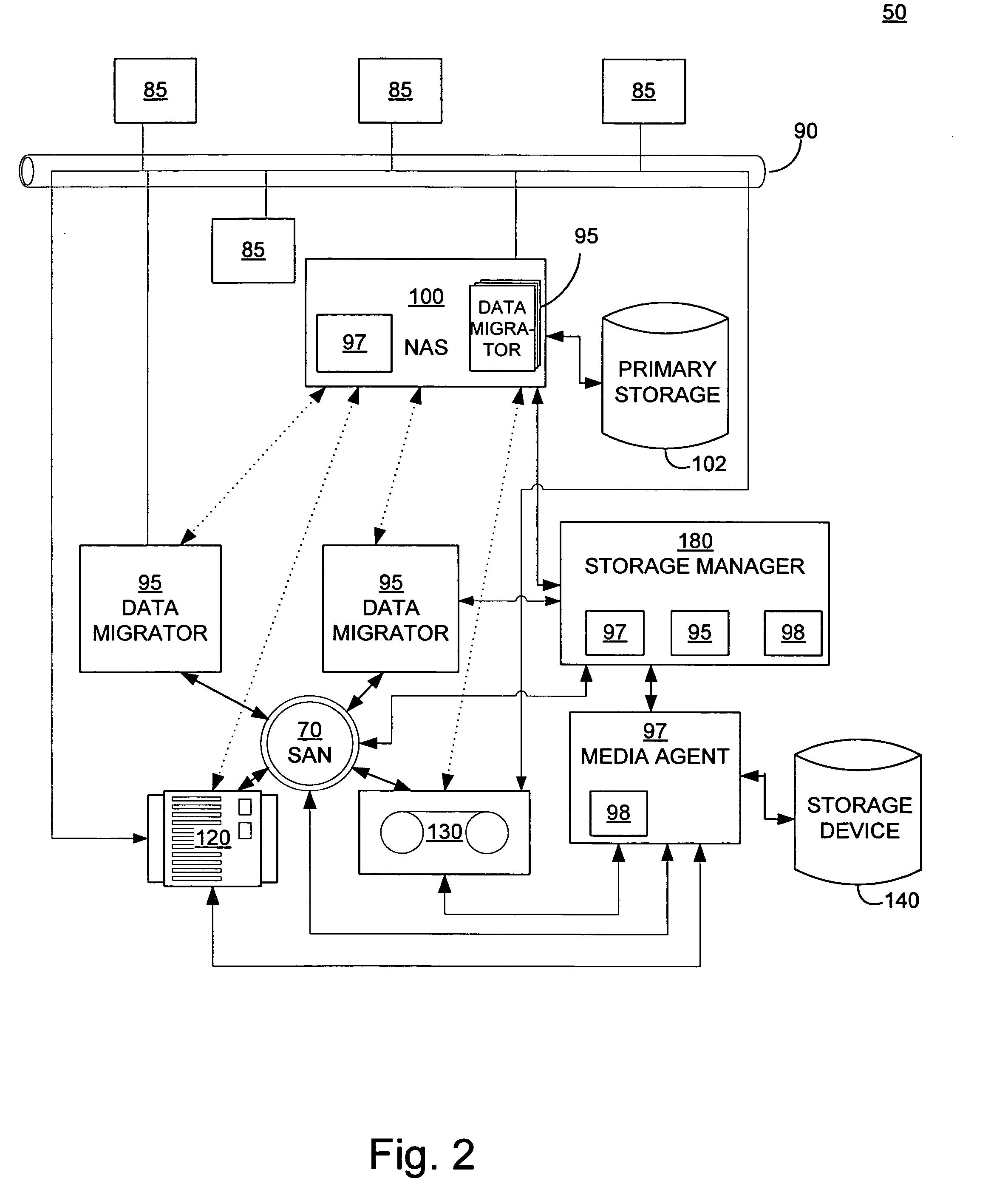
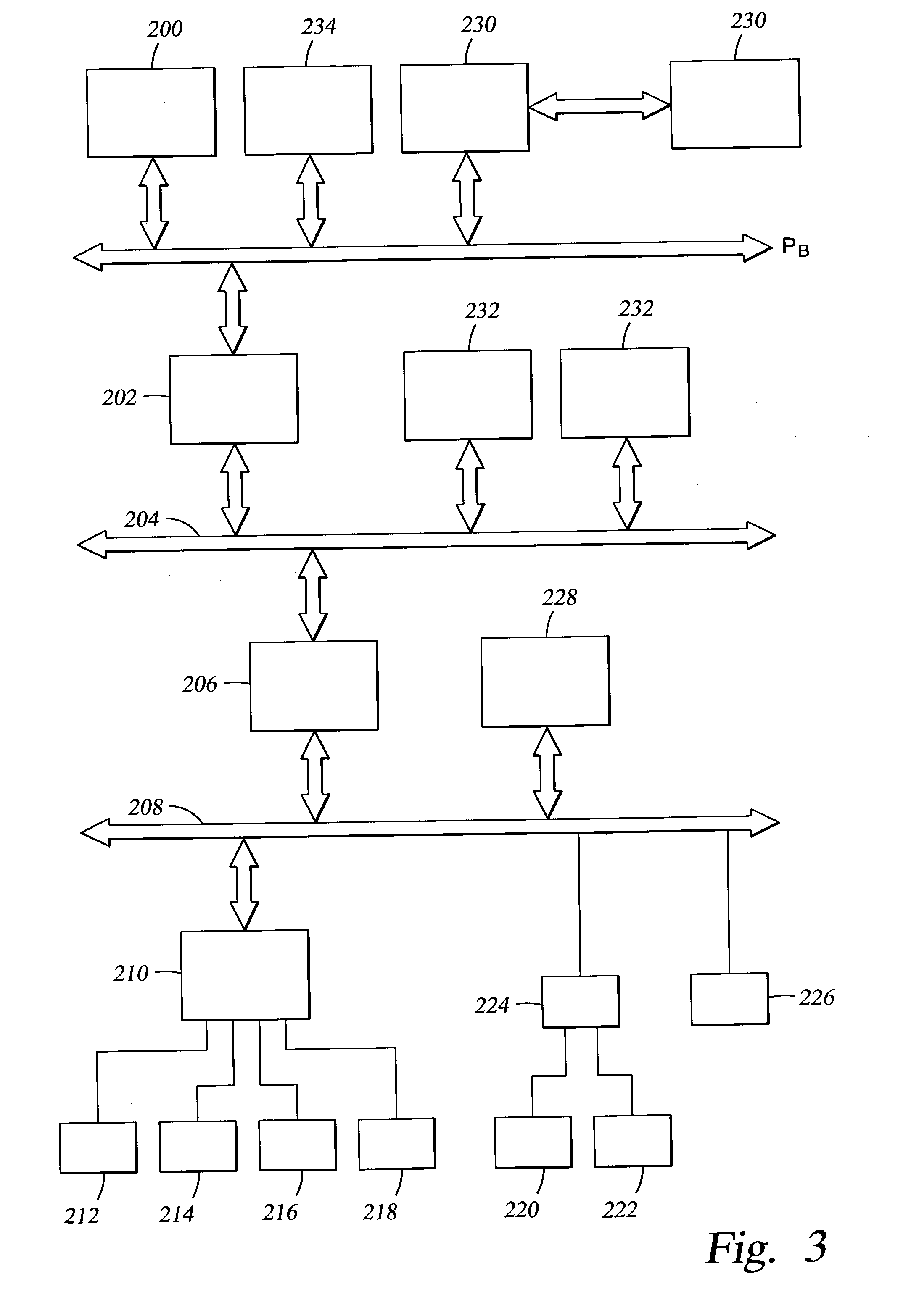
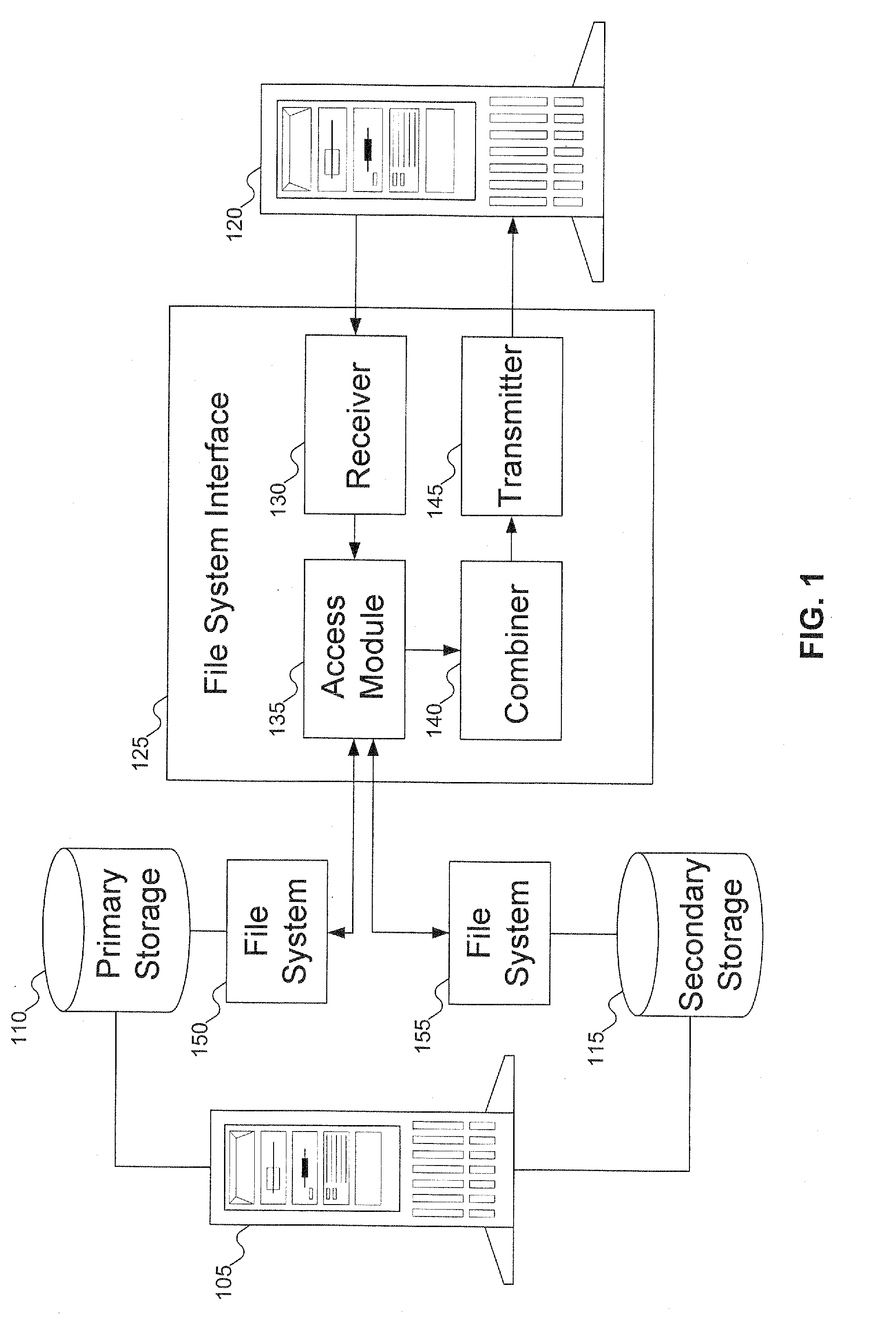
Systems and methods for performing storage operations using network attached storage
ActiveUS7546324B2More processedData processing applicationsDigital data information retrievalAuxiliary memoryData storing
Systems and methods for performing hierarchical storage operations on electronic data in a computer network are provided. In one embodiment, the present invention may store electronic data from a network device to a network attached storage (NAS) device pursuant to certain storage criteria. The data stored on the NAS may be migrated to a secondary storage and a stub file having a pointer pointing to the secondary storage may be put at the location the data was previously stored on the NAS. The stub file may redirect the network device to the secondary storage if a read request for the data is received from the network device.
Owner:COMMVAULT SYST INC
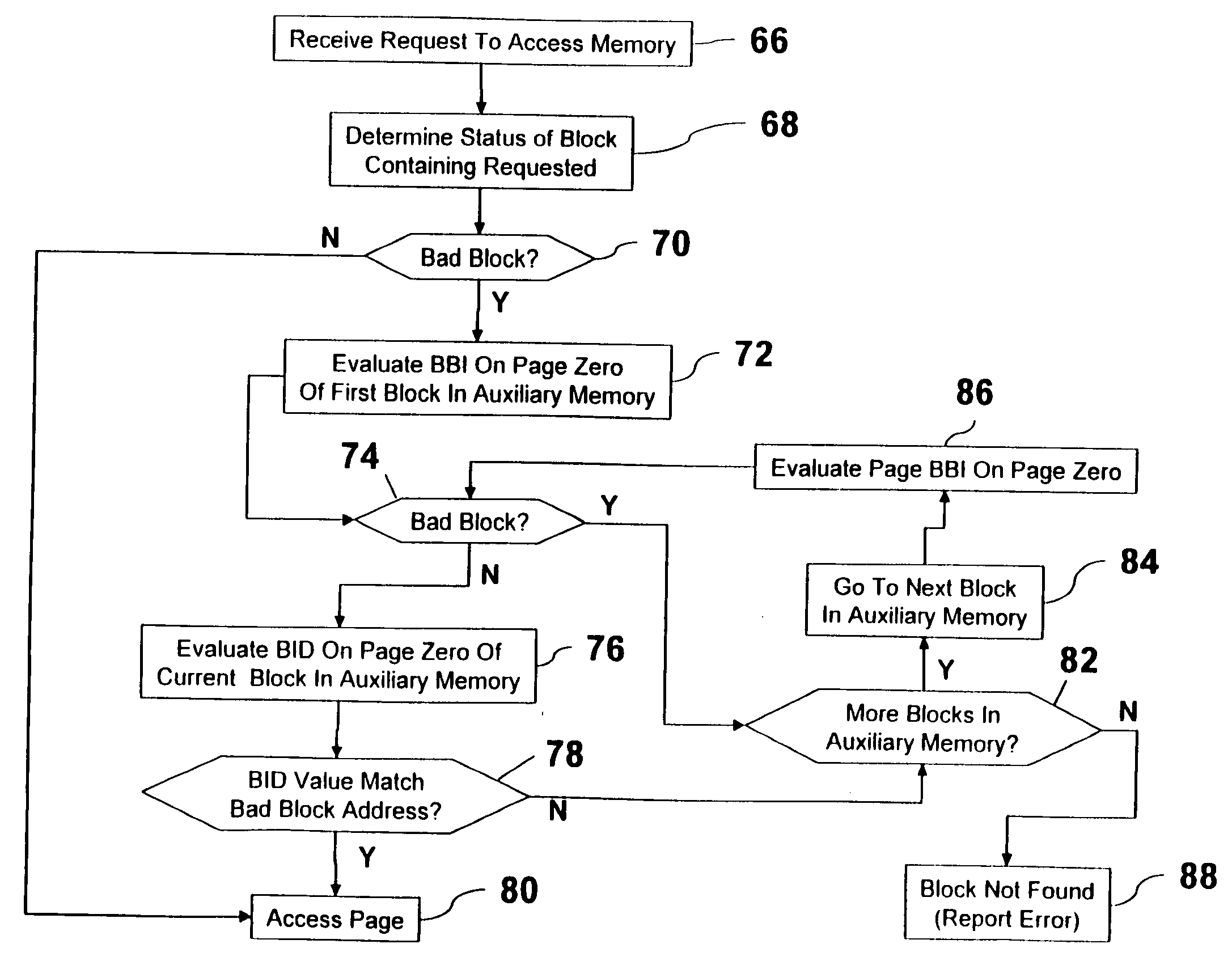
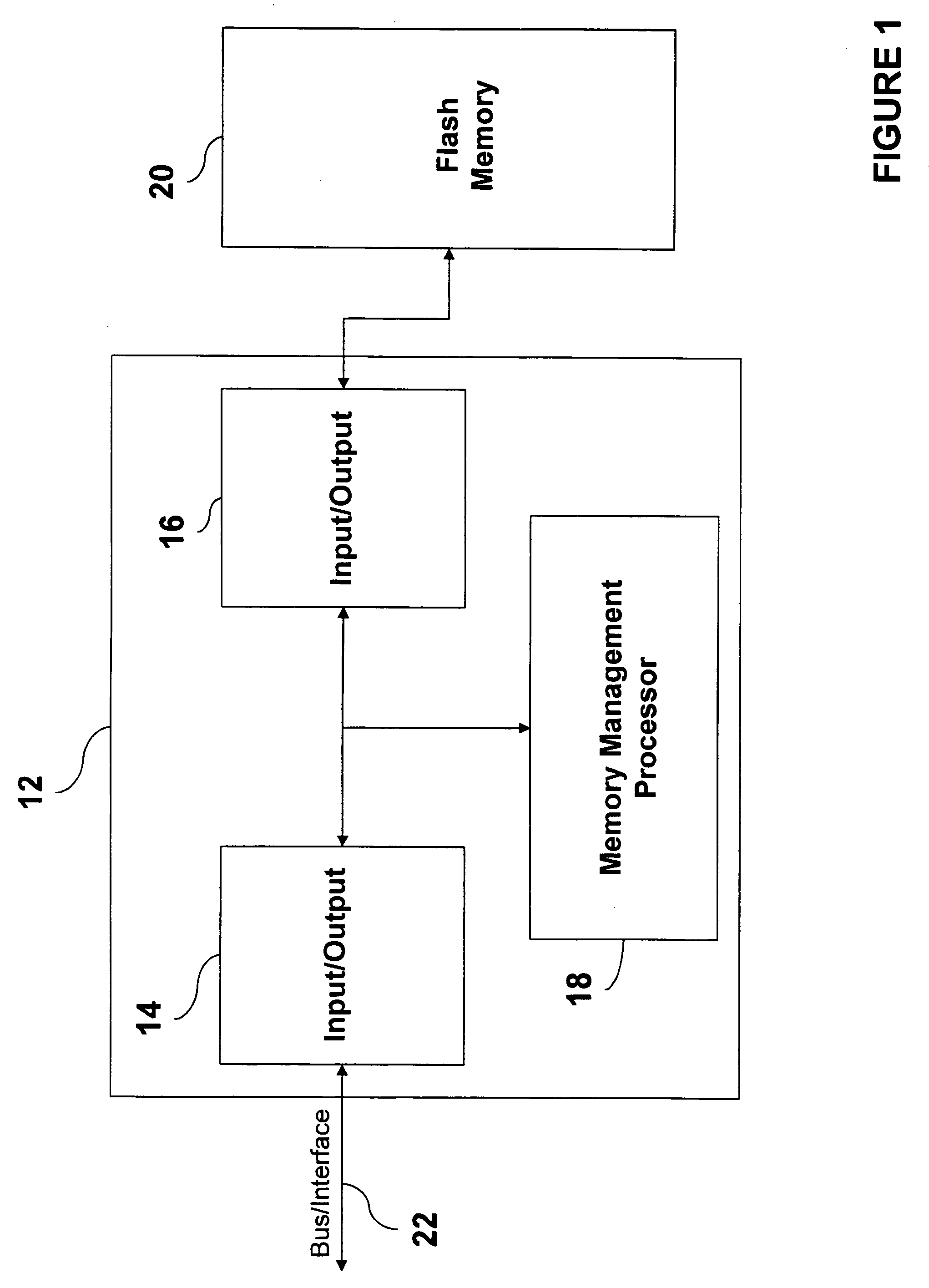
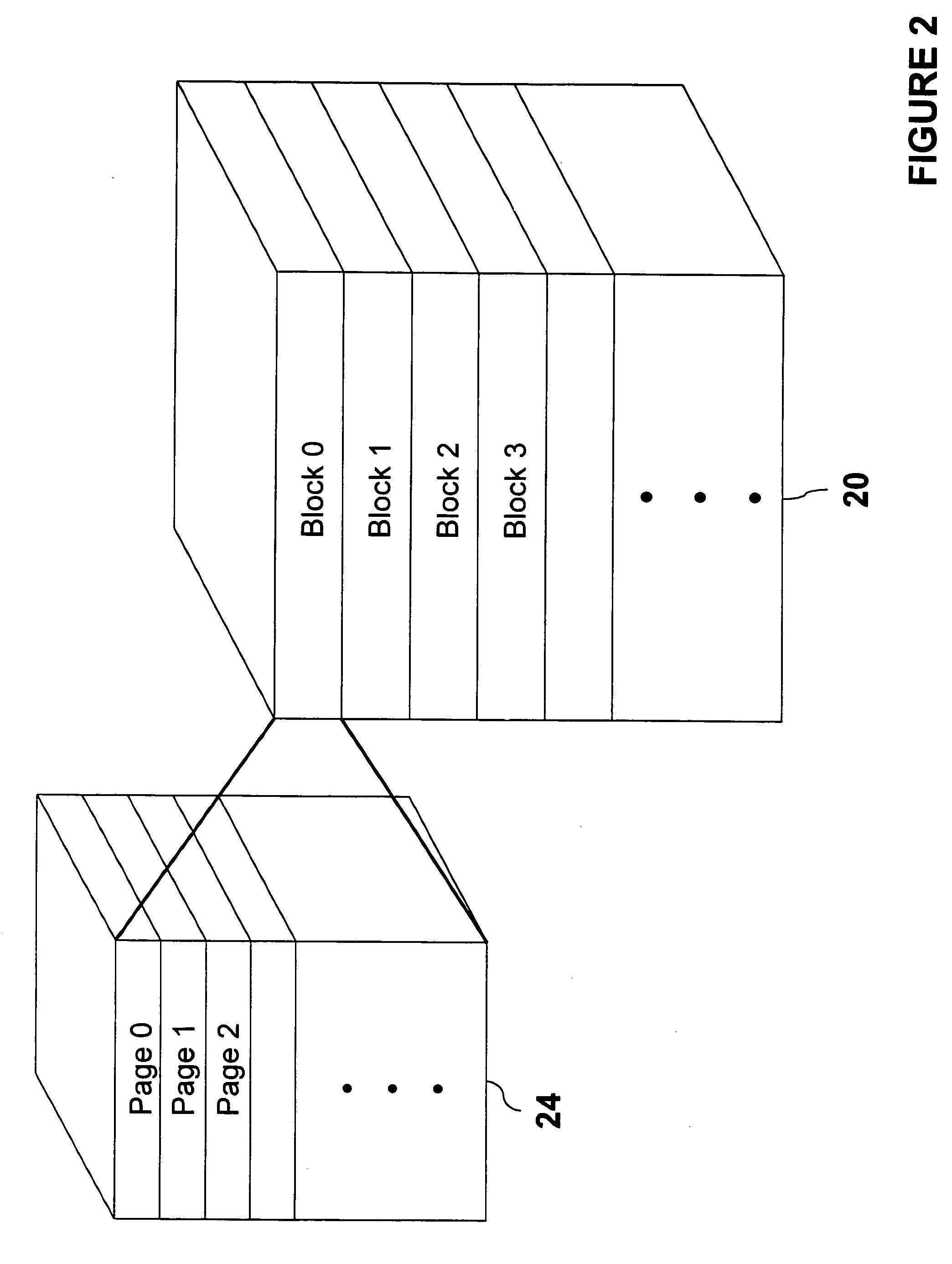
NAND flash memory management
A memory controller is utilized to overcome NAND flash memory's propensity for comprising bad blocks of memory. The memory controller utilizes minimal hardware and is essentially transparent to a device requesting access to the NAND memory. A NAND flash memory device is configured to comprise a set of main blocks of memory and a set of auxiliary blocks of memory. Each block is divided into pages of memory and each page includes metadata. The metadata includes a block status indicator, indicating whether a block is good or bad. When receiving a request to access a page in the NAND flash memory, if the block in which the page resides is good, that block is accessed. If the block is bad, auxiliary memory is searched until a block containing the address of the bad block in its metadata is found. The found block is accessed in lieu of the bad block.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for performing storage operations using network attached storage
ActiveUS20060010154A1More processedData processing applicationsDigital data information retrievalAuxiliary memoryData storing
Systems and methods for performing hierarchical storage operations on electronic data in a computer network are provided. In one embodiment, the present invention may store electronic data from a network device to a network attached storage (NAS) device pursuant to certain storage criteria. The data stored on the NAS may be migrated to a secondary storage and a stub file having a pointer pointing to the secondary storage may be put at the location the data was previously stored on the NAS. The stub file may redirect the network device to the secondary storage if a read request for the data is received from the network device.
Owner:COMMVAULT SYST INC
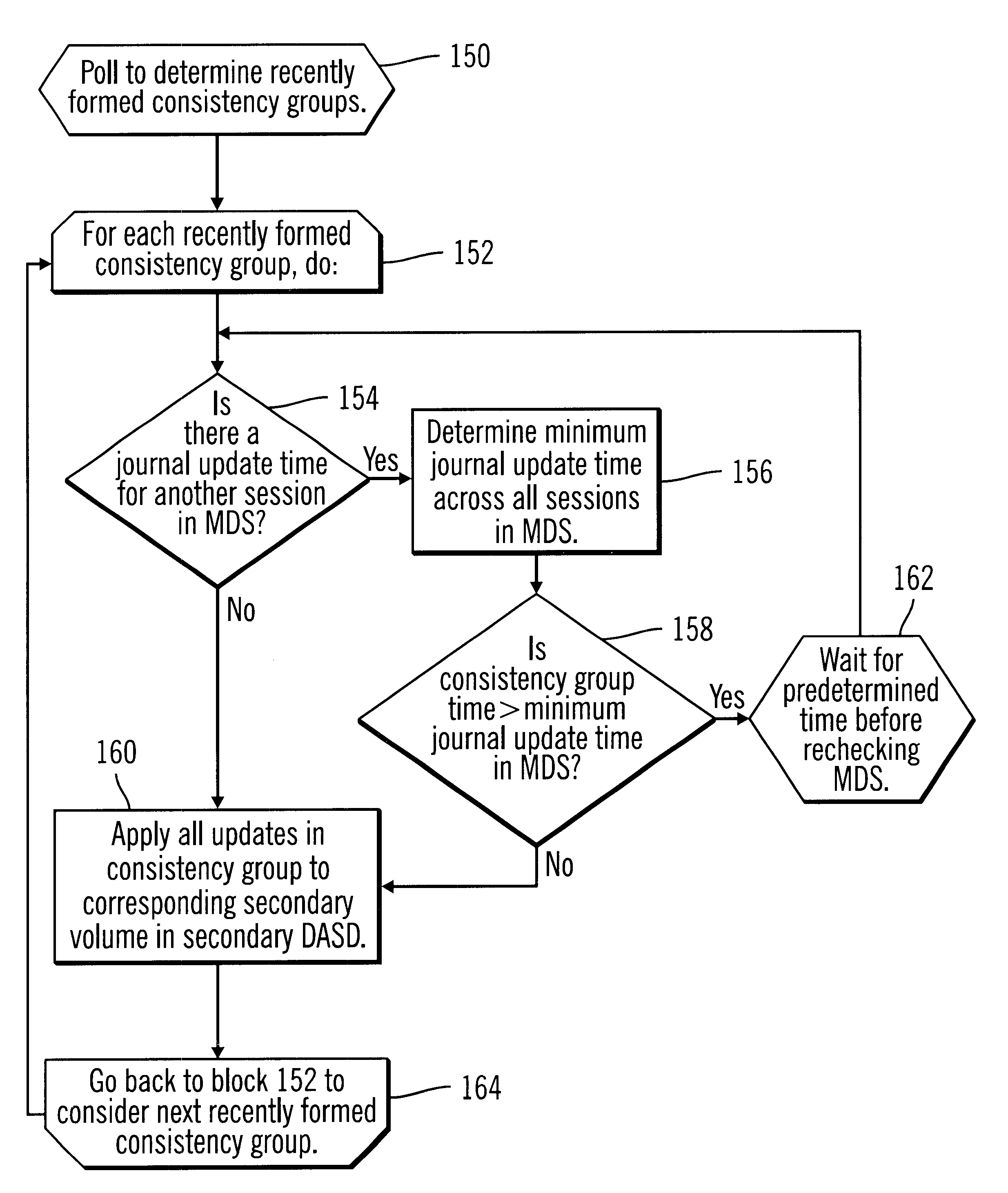
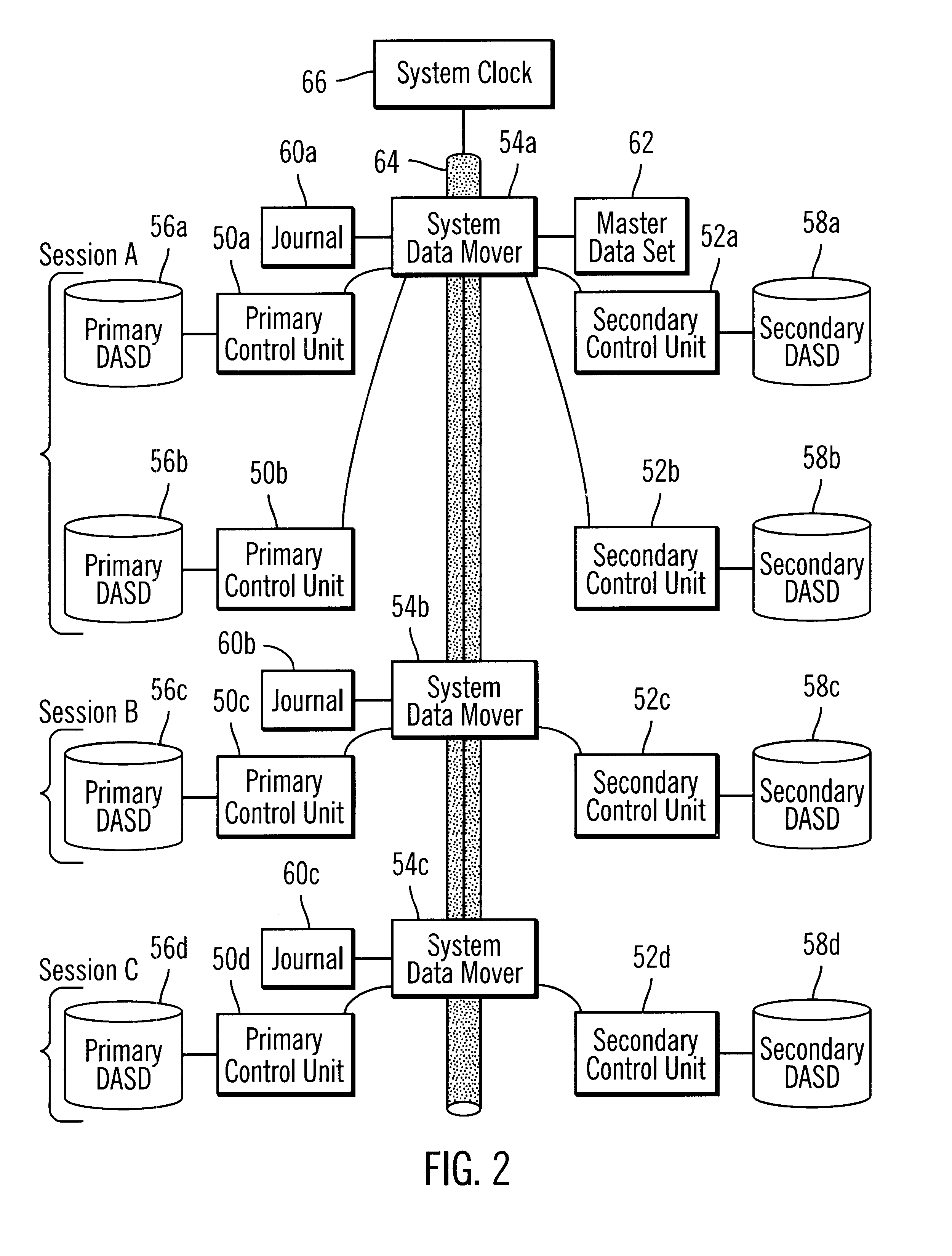
Method, system and program for maintaining data consistency among updates across groups of storage areas using update times
InactiveUS6463501B1Data processing applicationsMemory loss protectionRenewal timeComputerized system
A system, method, and program for maintaining data consistency among updates to data storage areas are provided. Each update has an update time the update was made. There are multiple groups of data storage areas. For each group, updates to the data storage area in the group are stored in a journal for storing updates to the group, wherein there are multiple journals. An indication is made in a memory area for each group of a group update time comprising a most recent update time of the updates in the group. The update time for each update in the group is not greater than the group update time. A determination is made of a minimum group update time across all the groups. At least one update is applied to storage if the update time for the update does not exceed the minimum group update time. The data storage areas may be partitioned among a plurality of computer systems, and may be maintained in at least one primary and secondary storage. The data storage areas may also comprise volumes, with each group including at least one volume. The groups of updates may also be maintained in a journal.
Owner:IBM CORP
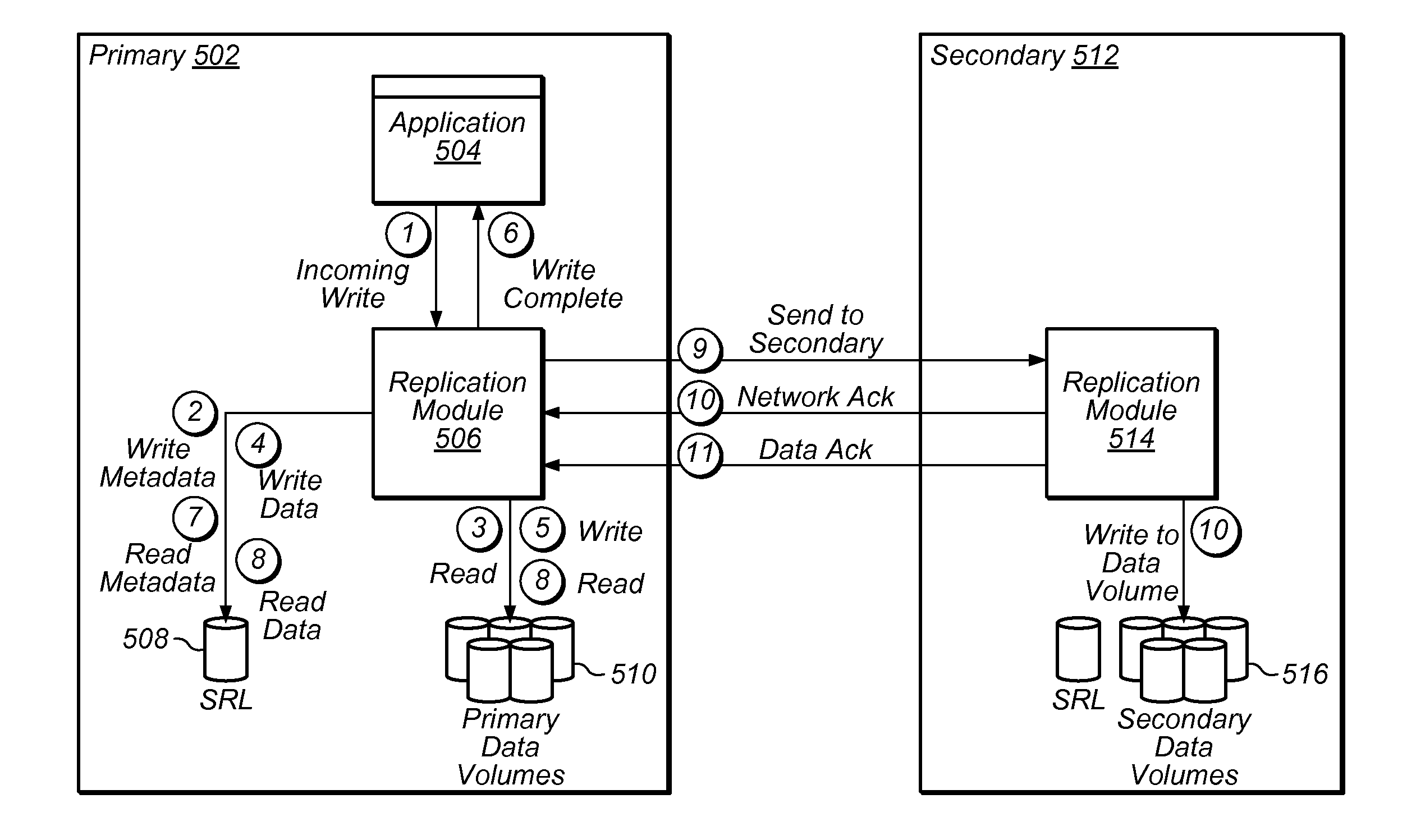
Efficient Logging for Asynchronously Replicating Volume Groups
ActiveUS20110099342A1The process is compact and efficientReduce memoryMemory loss protectionError detection/correctionAuxiliary memoryData store
A system and method for logging for asynchronously replicating volume groups. A write request to write data to a location in a volume may be received. Metadata associated with the write request may be stored. It may be determined if the write request possibly overlaps with one or more earlier write requests to the volume that have not yet been replicated to a secondary storage. The data may be stored in a replication log only if the write request possibly overlaps with one or more earlier write requests to the volume. The data may not be stored in the replication log if the write request does not overlap with one or more earlier write requests to the volume. The data may be written to the location in the volume. Changes to the volume may periodically be replicated to the secondary storage using the replication log.
Owner:VERITAS TECH
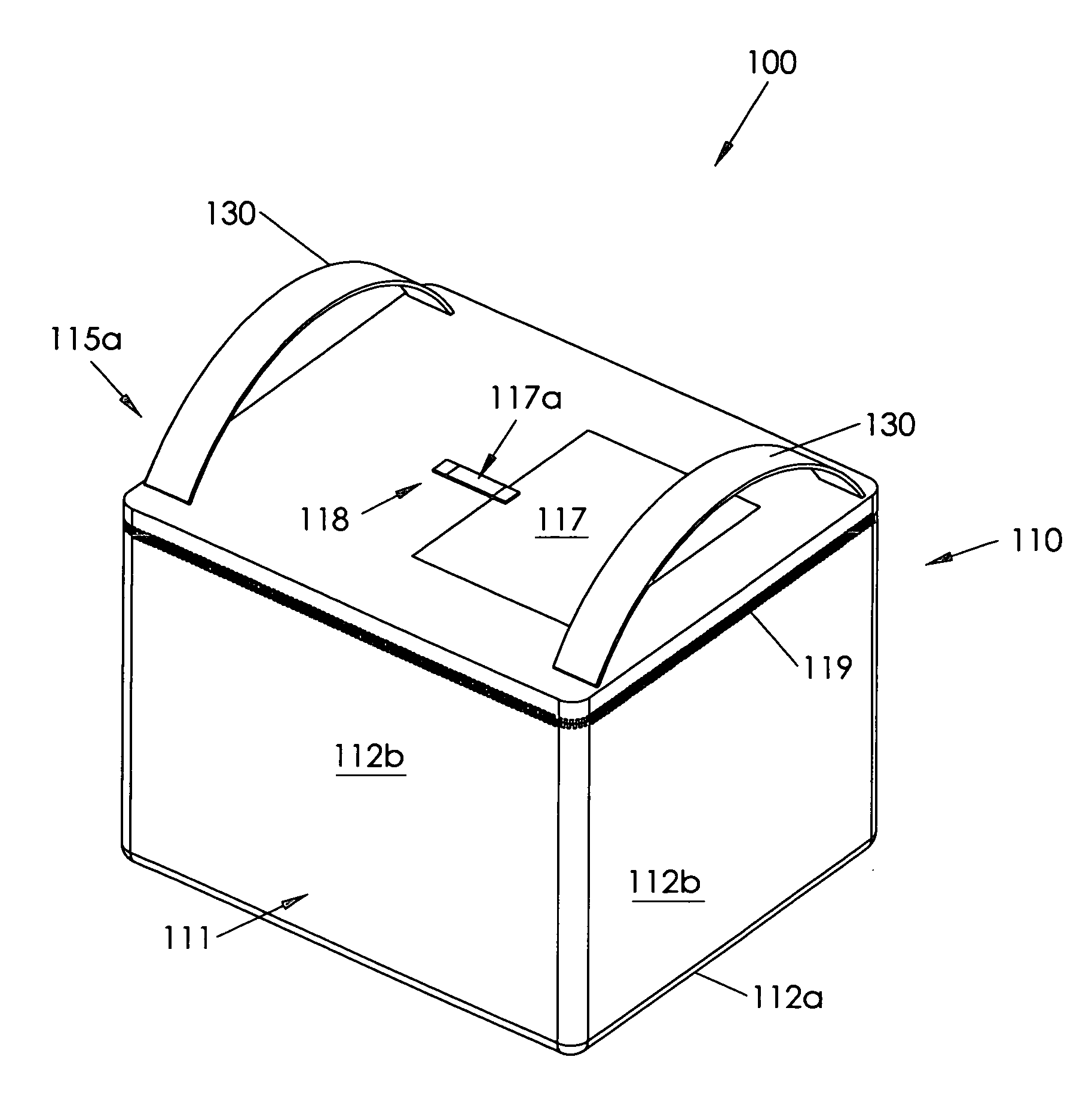
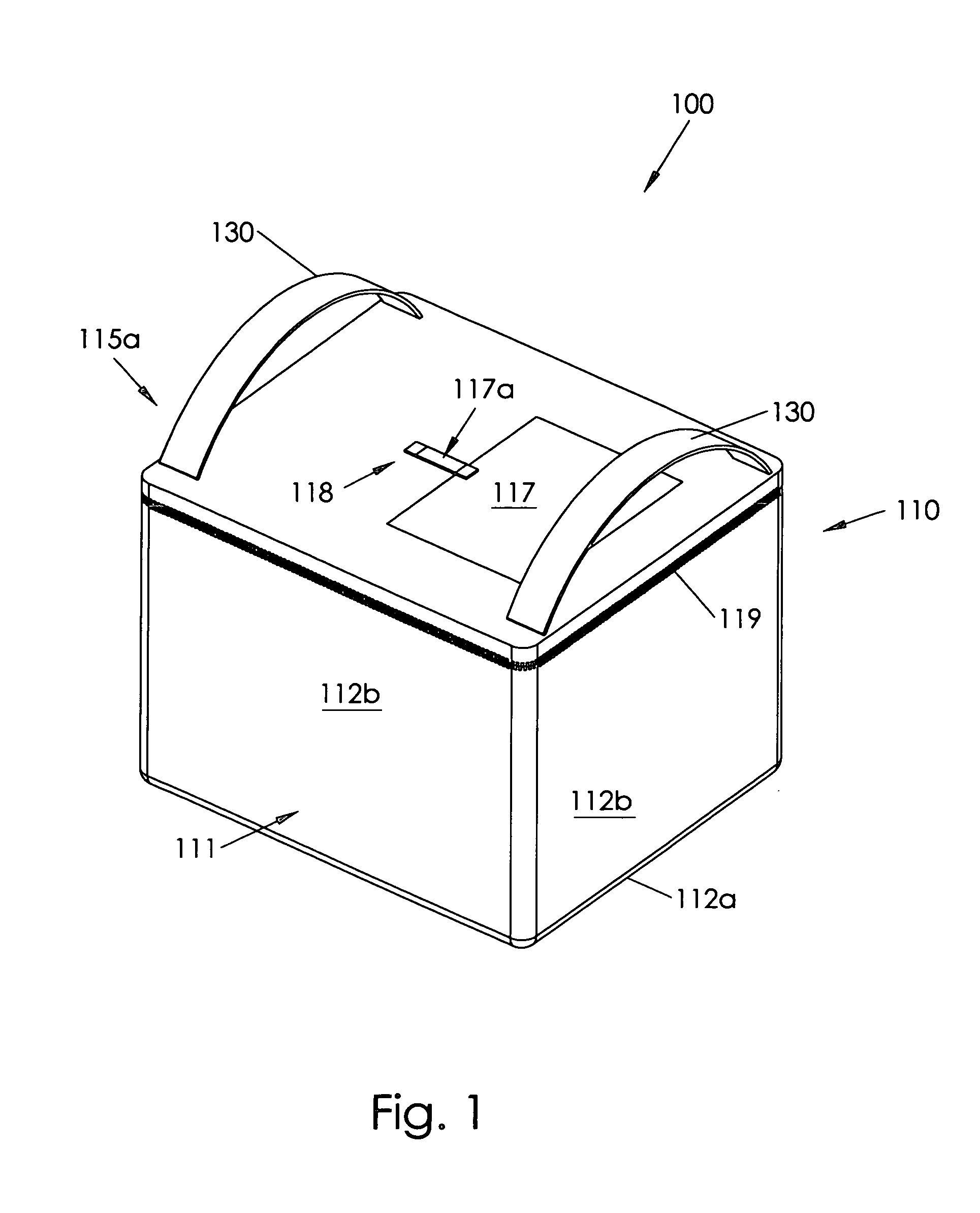
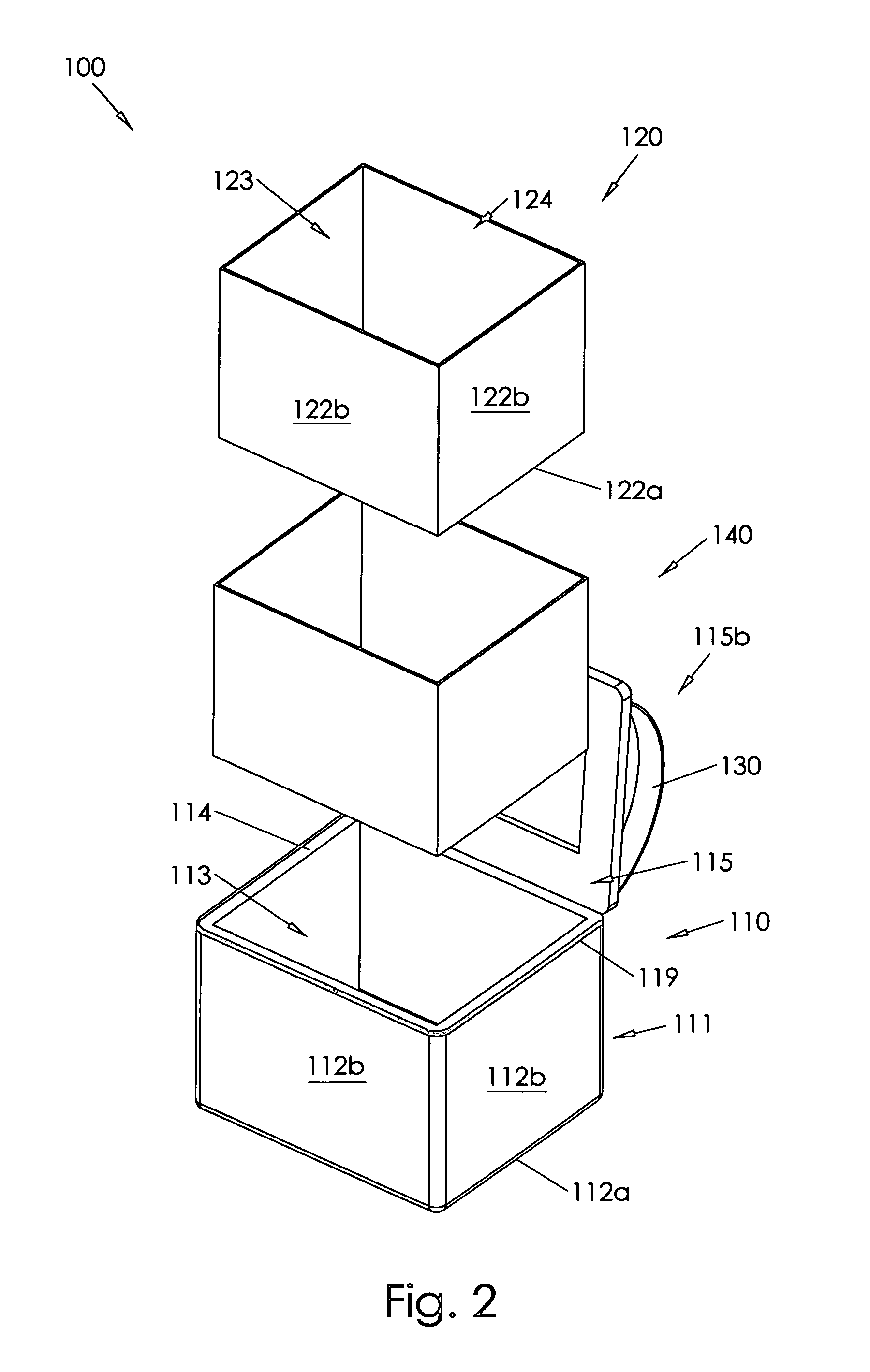
Insulating container
InactiveUS7677406B2Easy constructionEasy accessDomestic cooling apparatusClosuresRubber materialAuxiliary memory
Owner:MAXSON FLOYD S
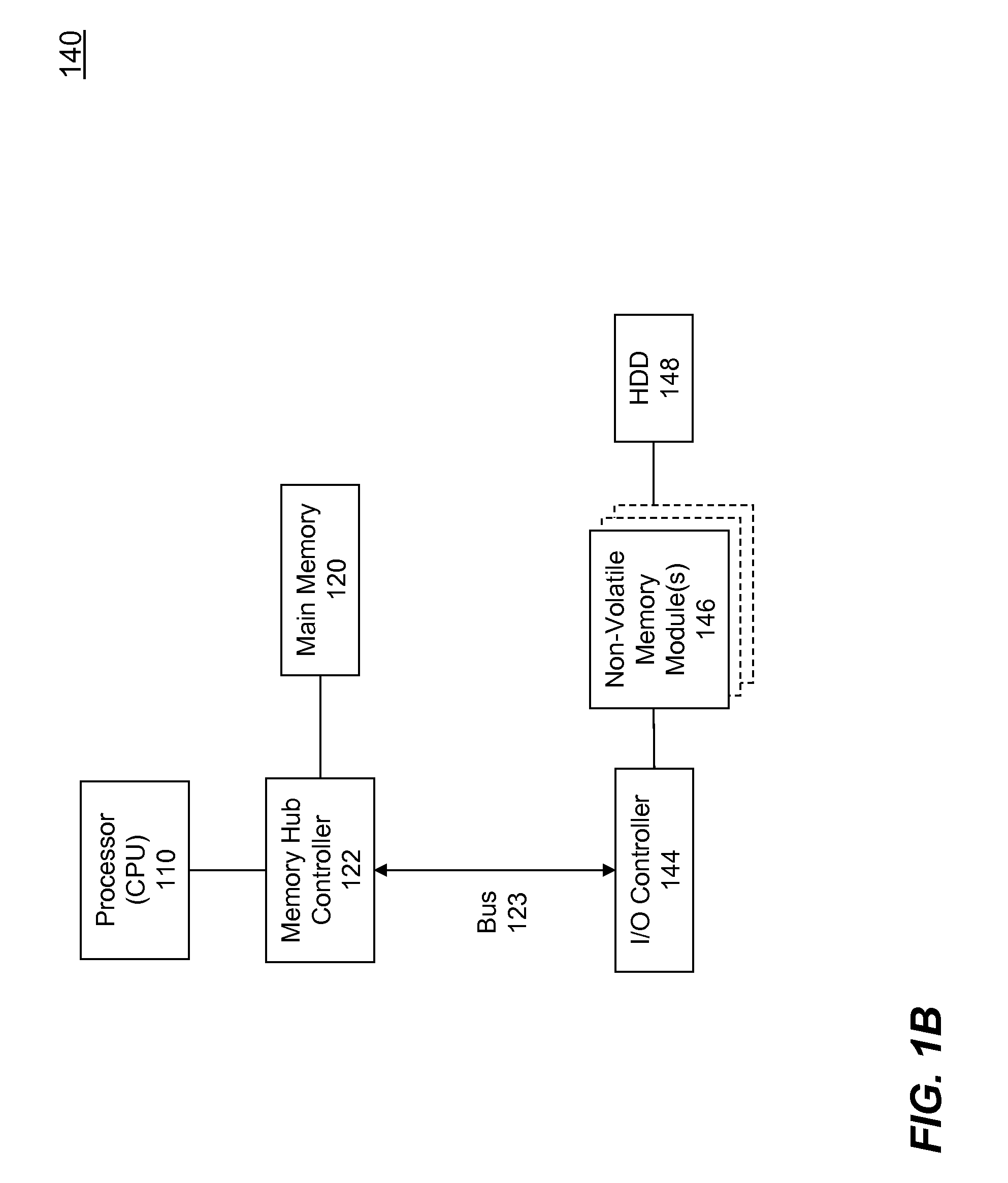
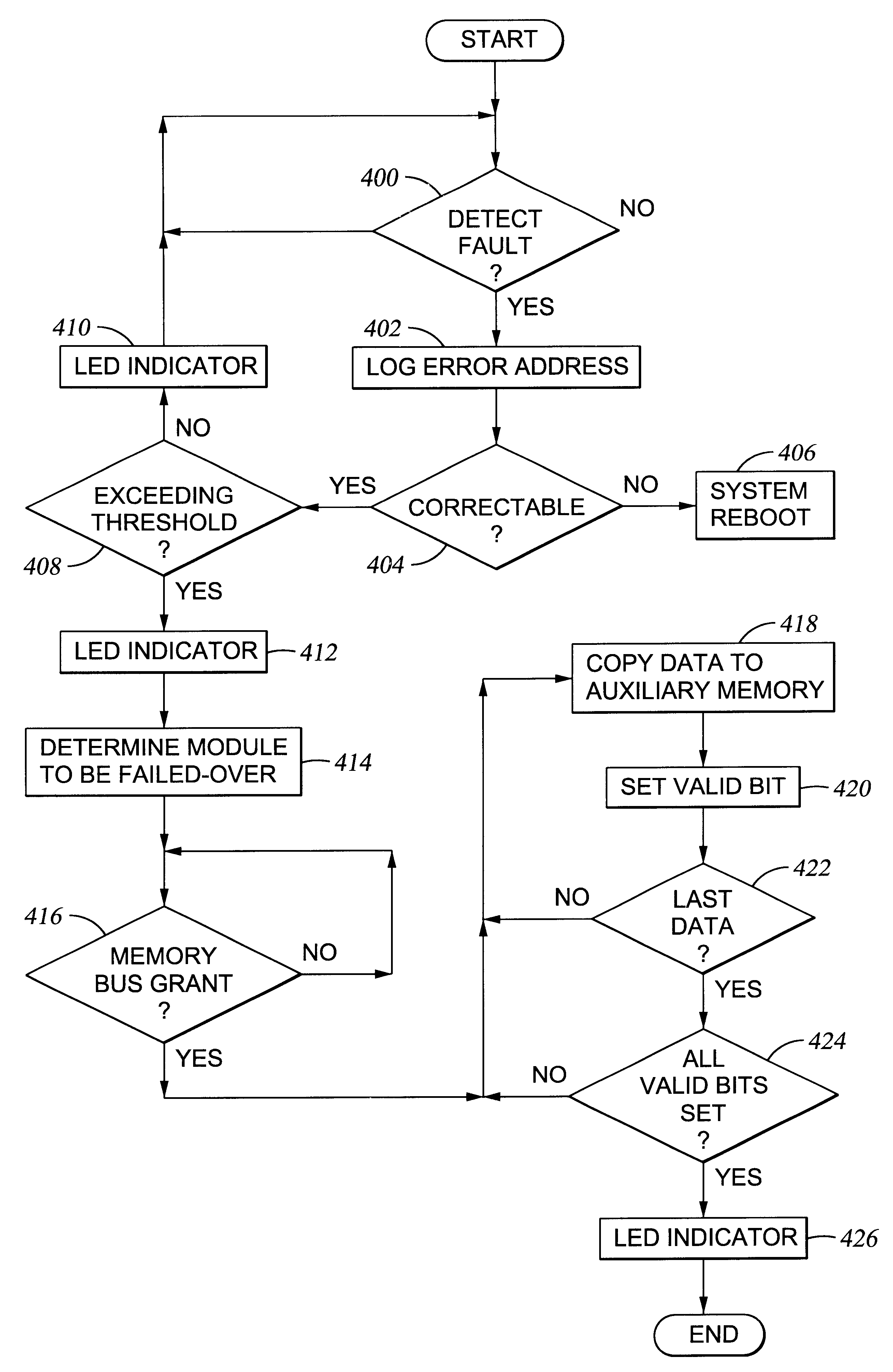
Fail-over of multiple memory blocks in multiple memory modules in computer system
InactiveUS20040073829A1Error detection/correctionEmergency protective arrangements for automatic disconnectionFailoverMemory address
A computer system has a memory controller for controlling accesses to multiple memory modules, each having multiple memory blocks, and a fail-over circuit for failing-over individual memory blocks from multiple memory modules. The digital information stored in an individual memory block that has experienced memory errors in excess of a permissible threshold is copied to an auxiliary memory location. The memory accesses directed to the failed-over memory block are intercepted and redirected to the auxiliary memory location. Tags are stored to identify failed-over memory modules and corresponding auxiliary memory modules, so a tag look-up for an accessed memory address can generate a hit signal when the memory access is to a failed-over memory module and cause the auxiliary memory module to respond to the memory access.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
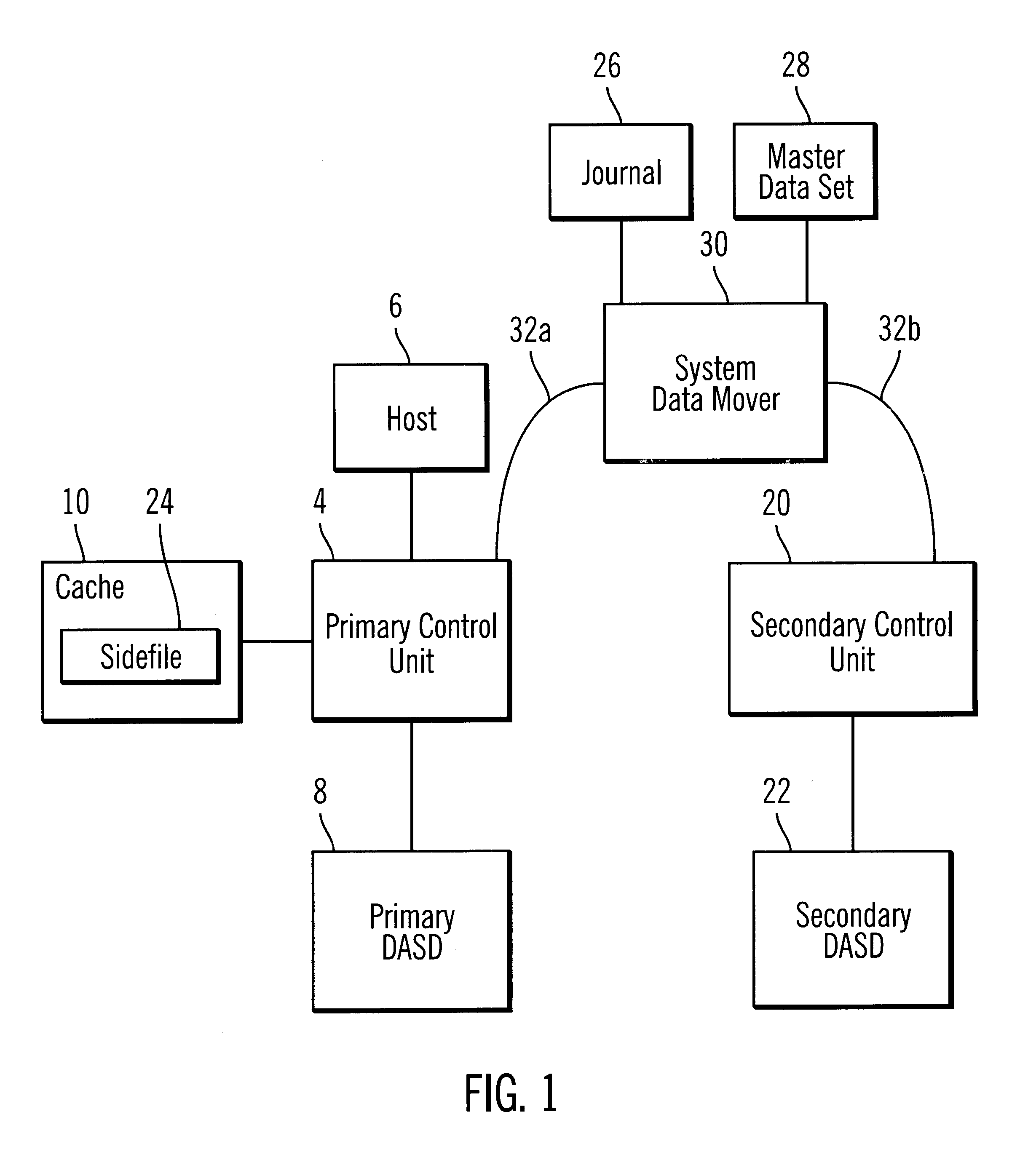
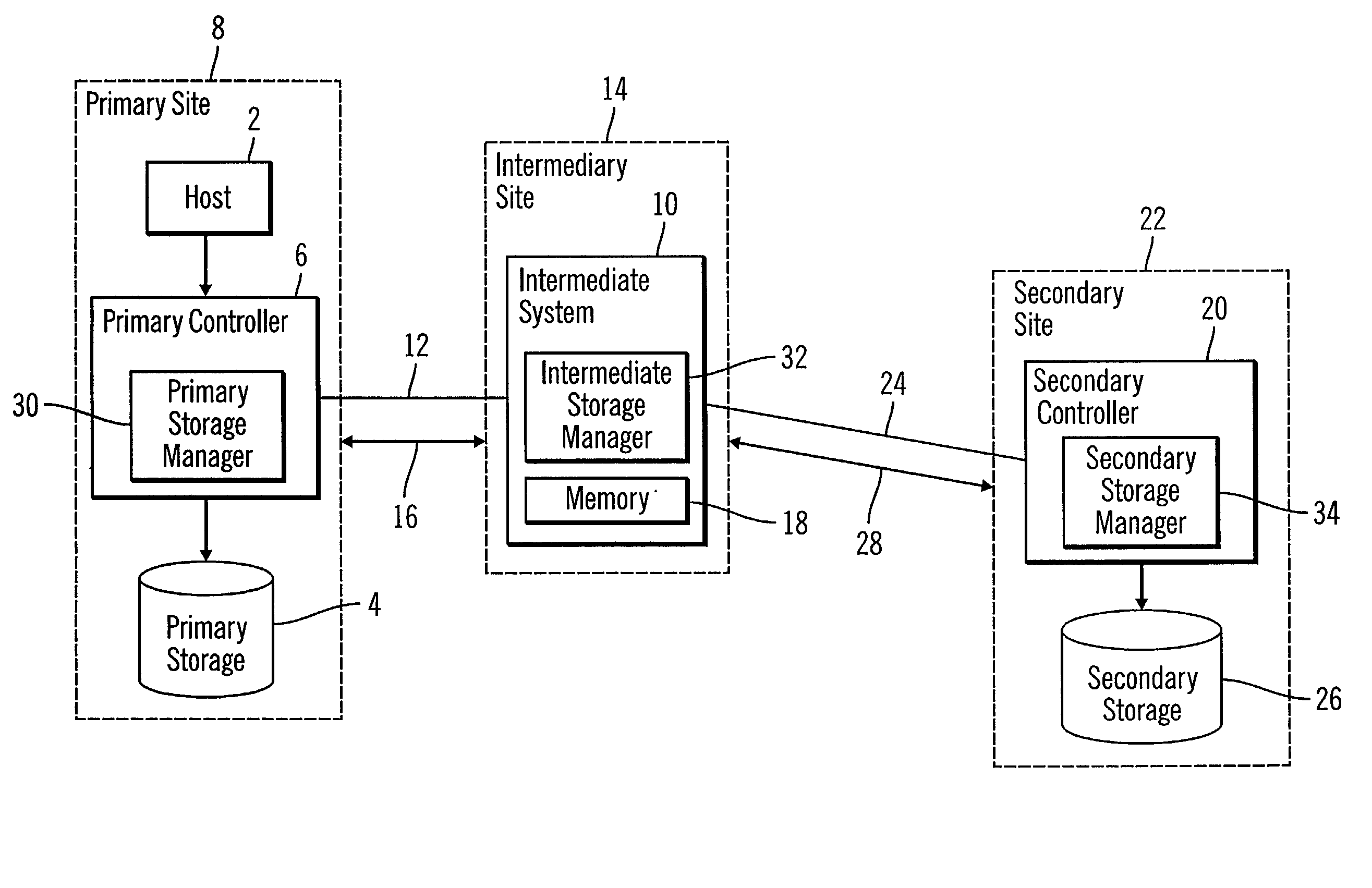
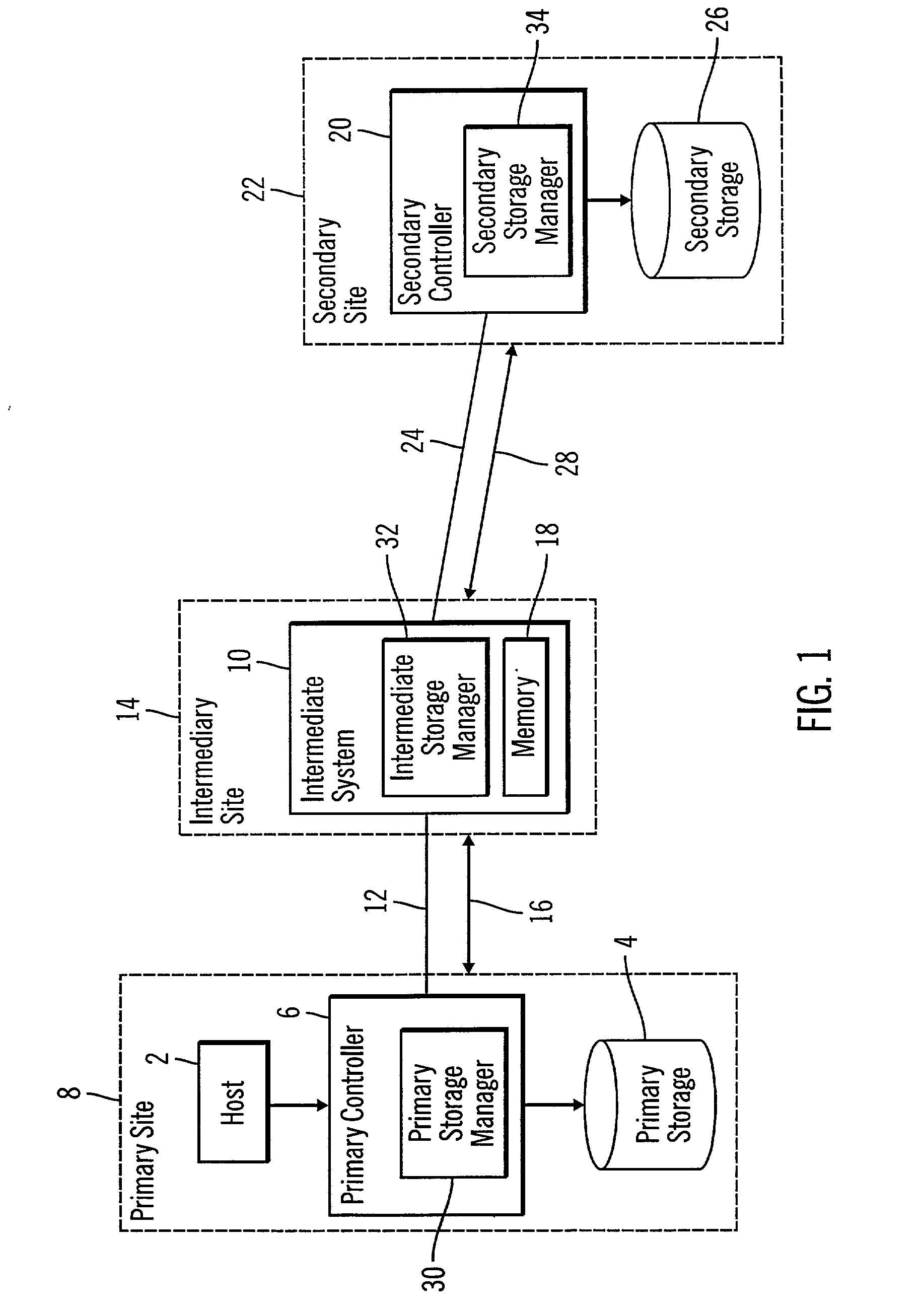
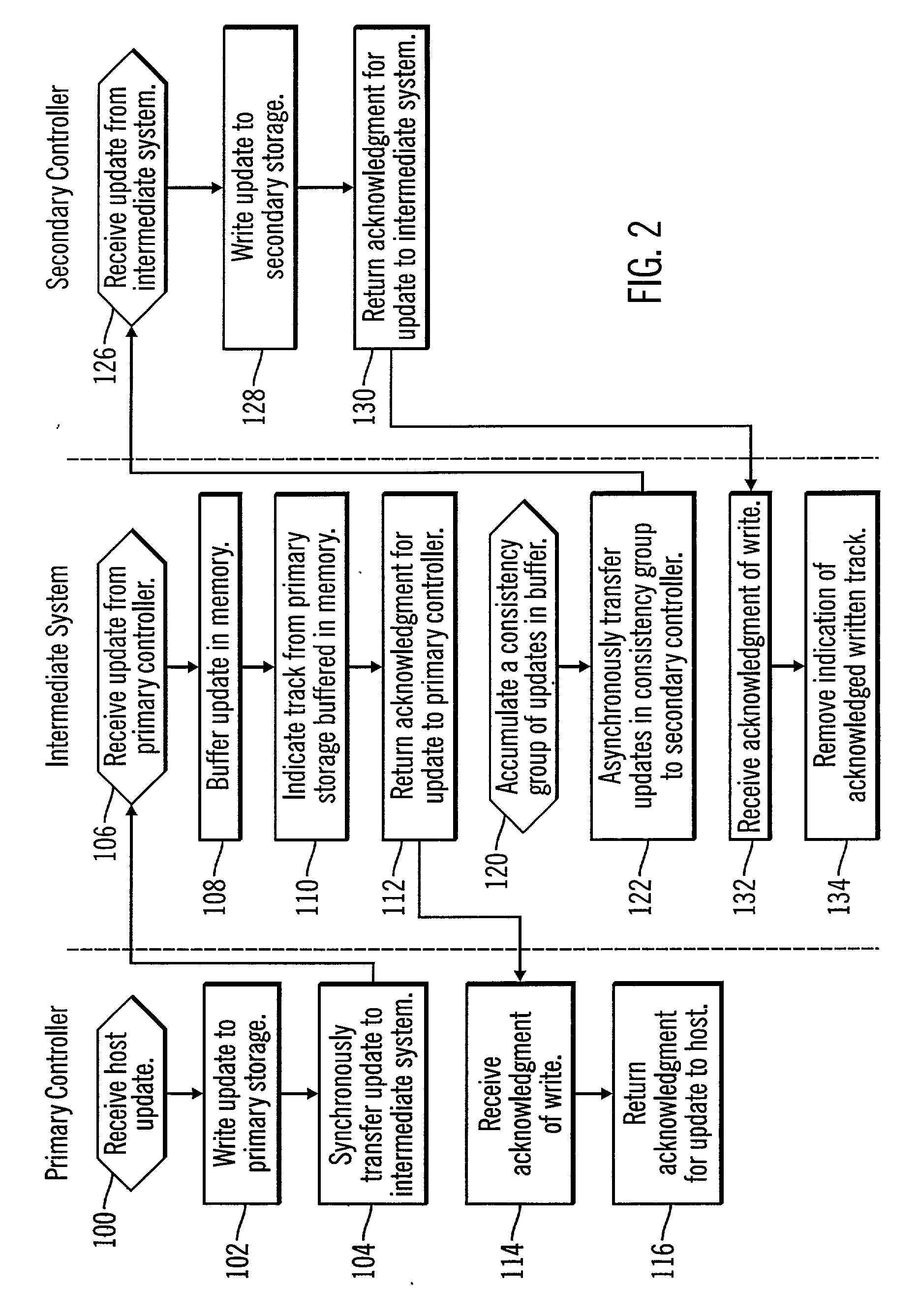
Method, system, and program for providing a mirror copy of data
InactiveUS20040034808A1Error prevention/detection by using return channelInput/output to record carriersTransfer modeAuxiliary memory
Provided are a method, system, and program for providing a mirror copy of data. An update to a primary storage is received and transferred to an intermediate system in a first transfer mode. The update is transferred from the intermediate system to a secondary storage in a second transfer mode, wherein the secondary storage provides a mirror copy of updates to the primary storage.
Owner:IBM CORP
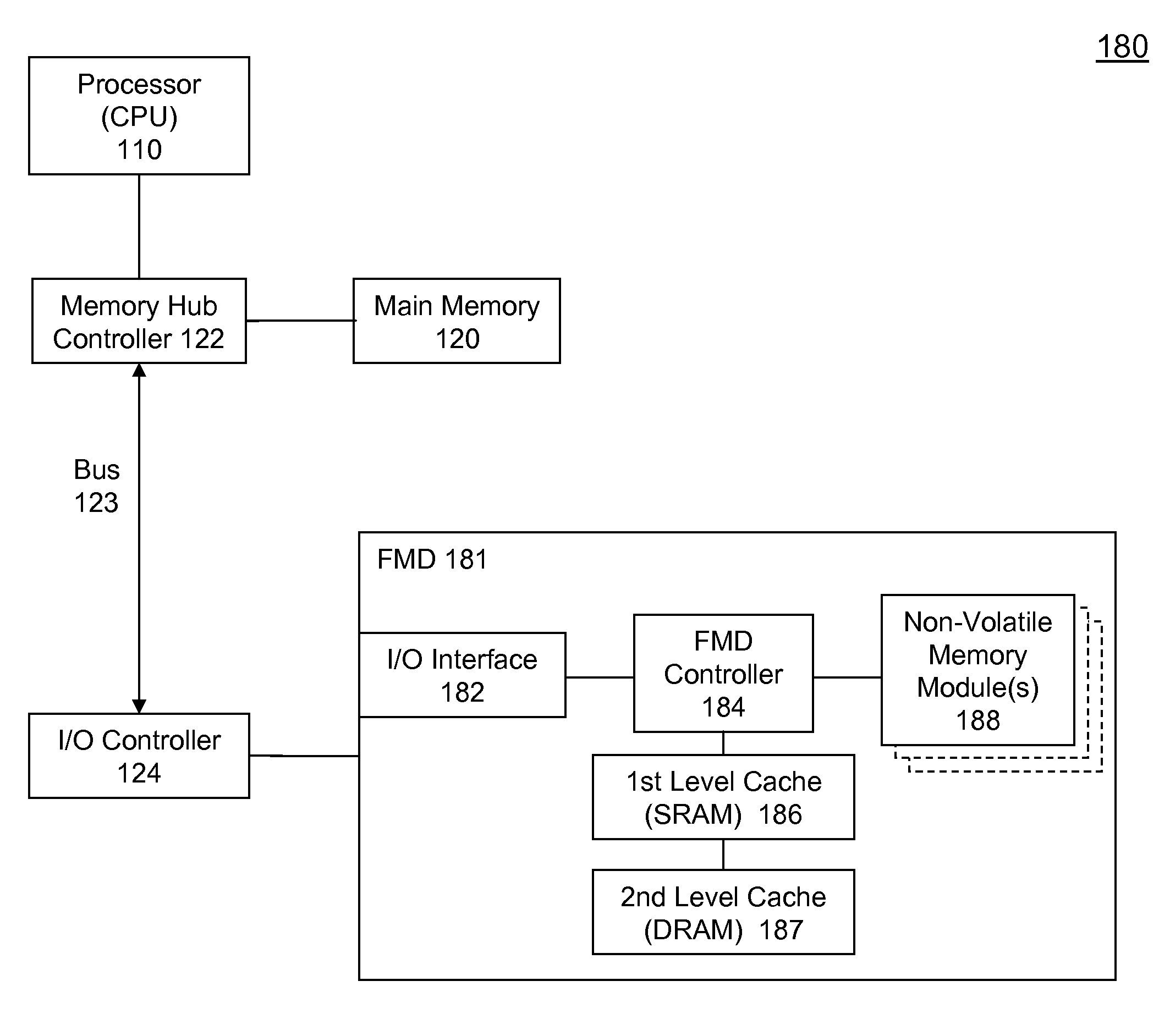
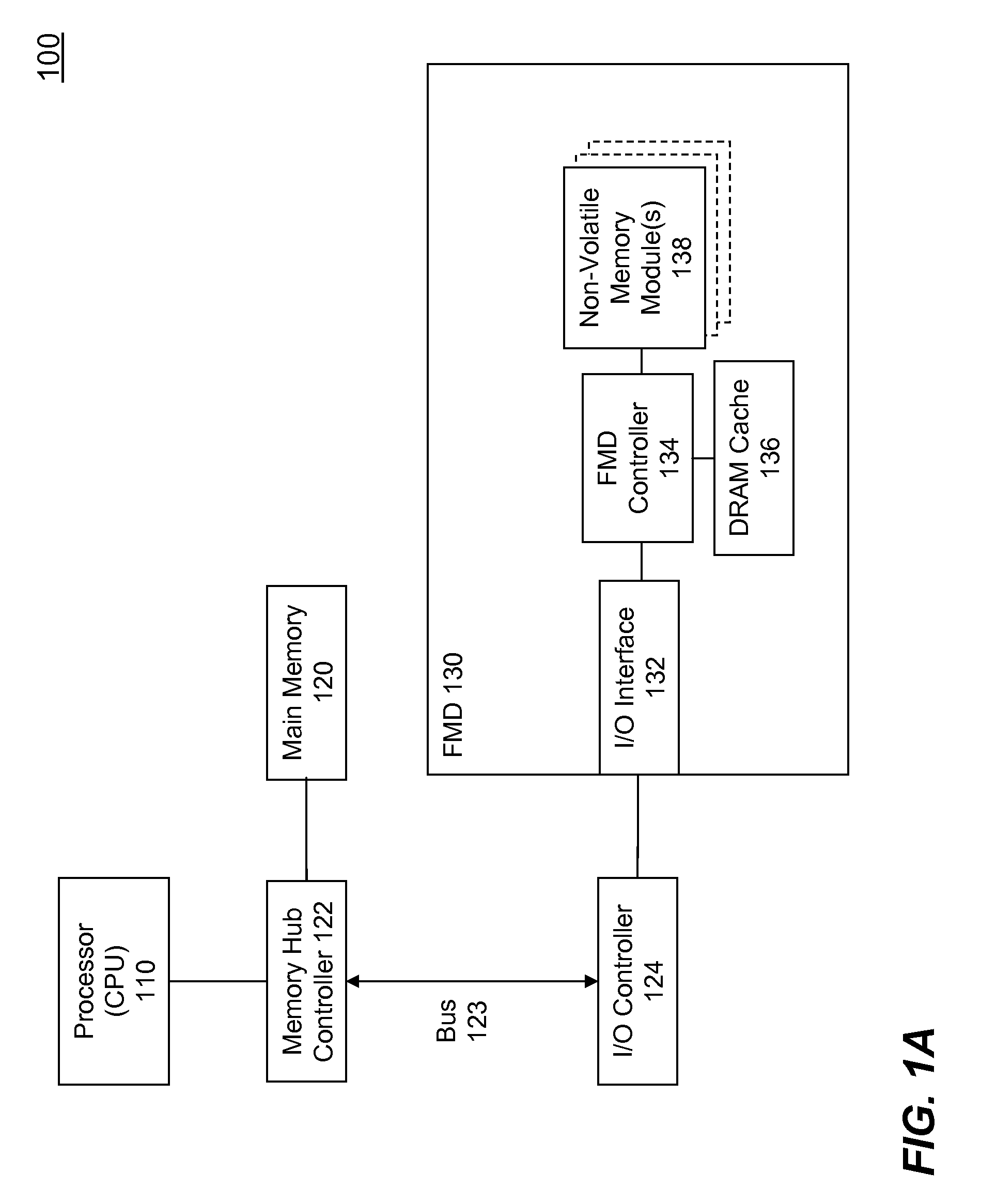
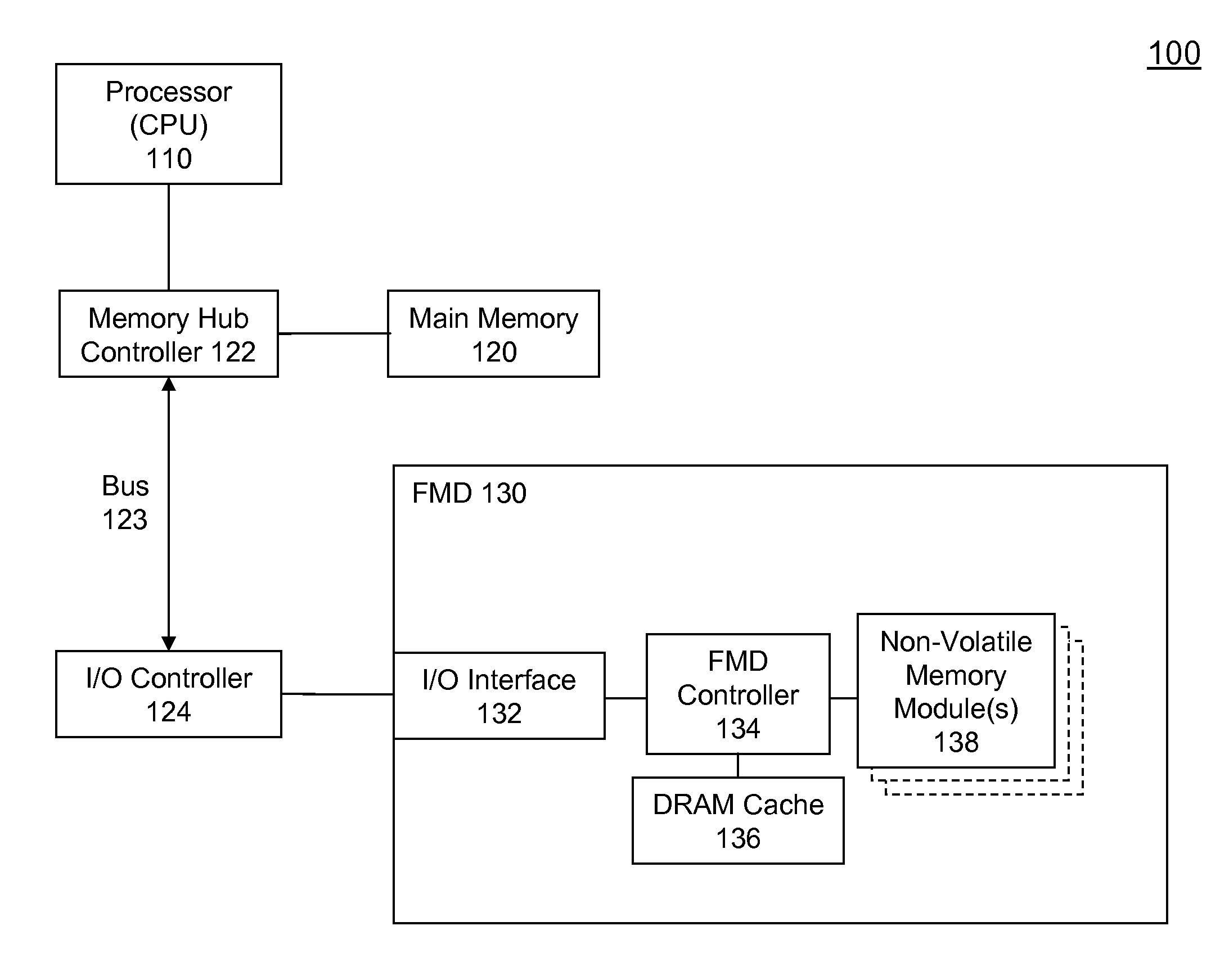
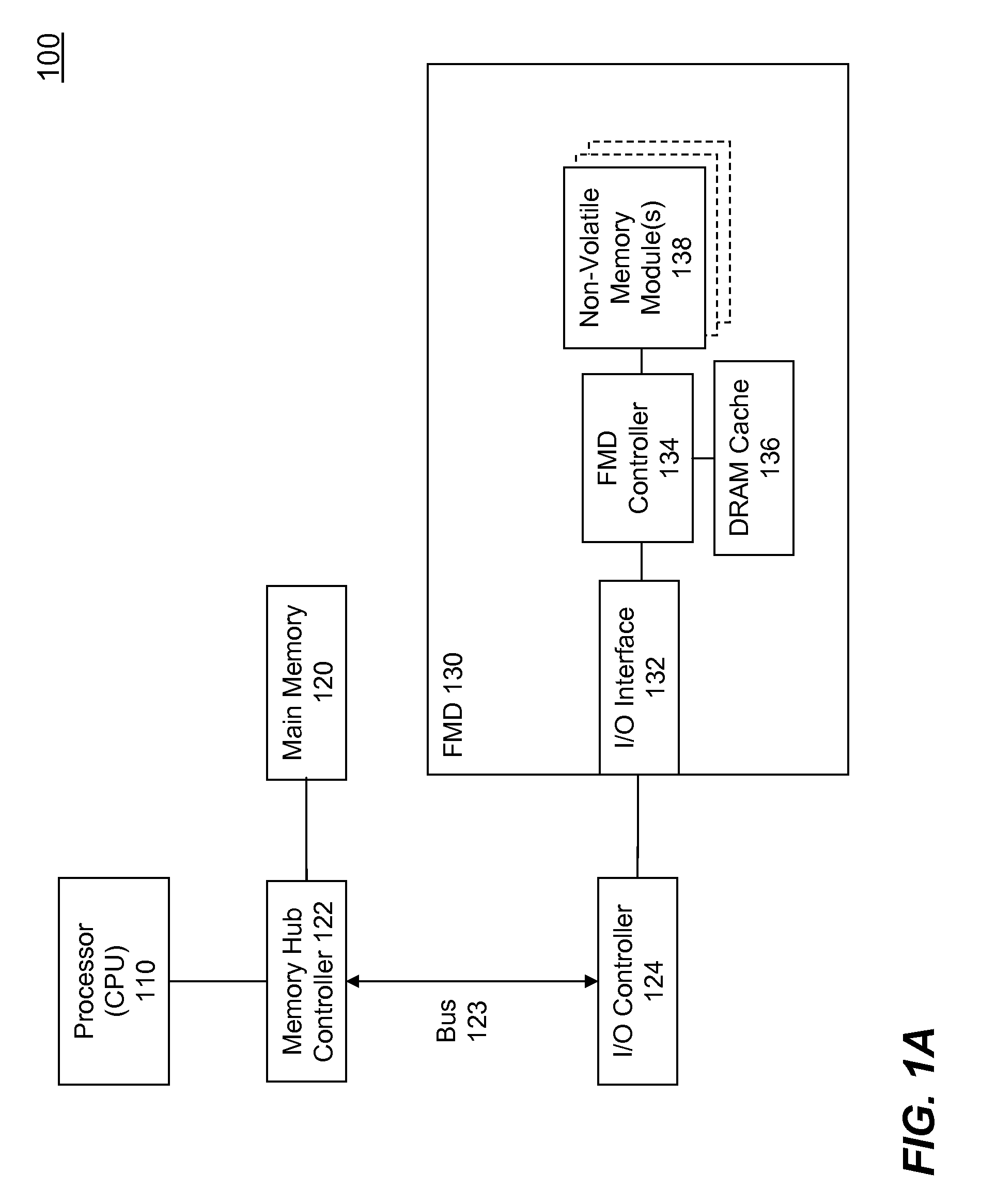
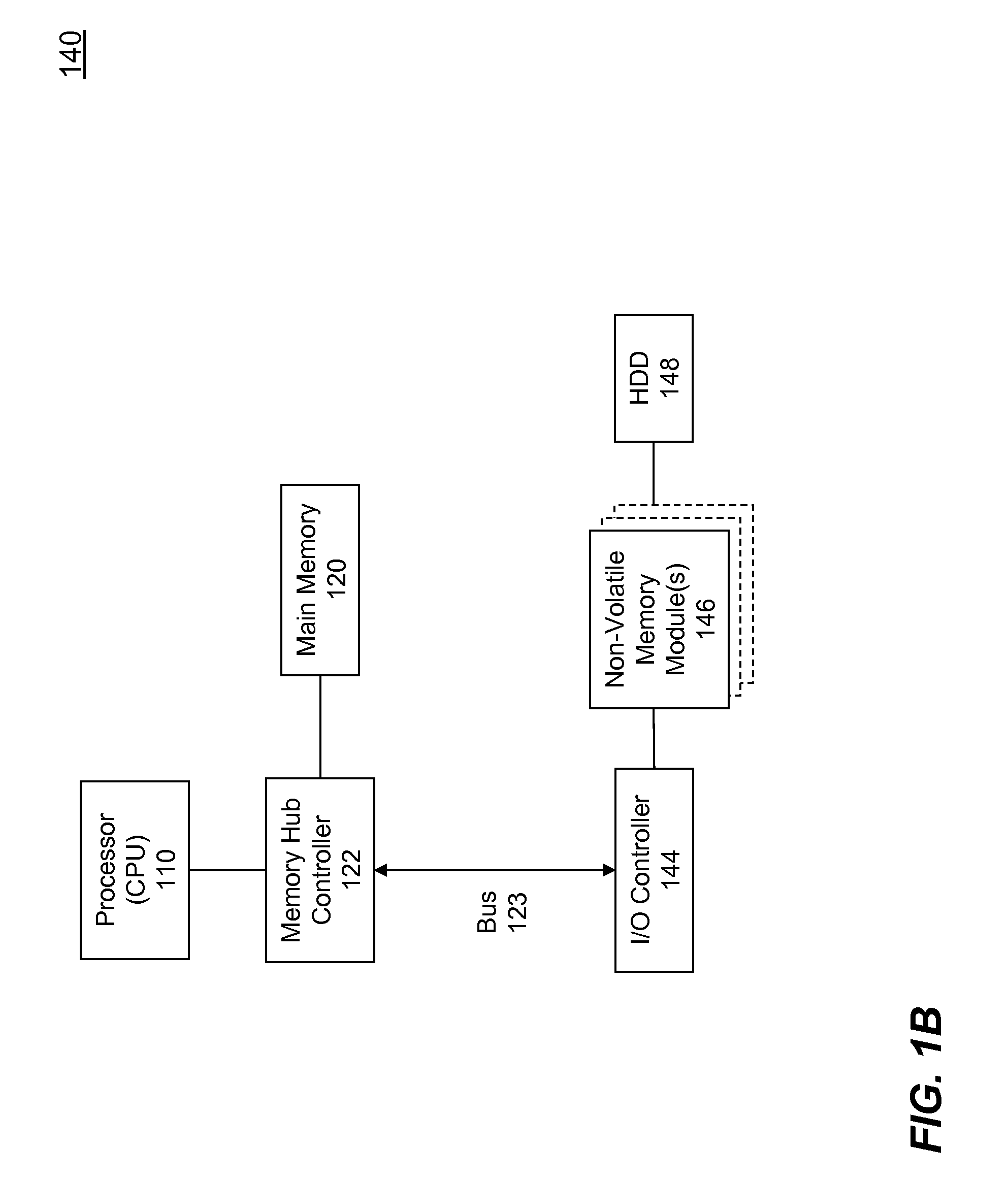
High Performance Flash Memory Devices (FMD)
InactiveUS20080147968A1Improve performanceImprove efficiencyError detection/correctionMemory adressing/allocation/relocationControl dataAuxiliary memory
High performance flash memory devices (FMD) are described. According to one exemplary embodiment of the invention, a high performance FMD includes an I / O interface, a FMD controller, and at least one non-volatile memory module along with corresponding at least one channel controller. The I / O interface is configured to connect the high performance FMD to a host computing device The FMD contoller is configured to control data transfer (e.g., data reading, data writing / programming, and data erasing) operations between the host computing device and the non-volatile memory module. The at least one non-volatile memory module, comprising one or more non-volatile memory chips, is configured as a secondary storage for the host computing device. The at least one channel controller is configured to ensure proper and efficient data transfer between a set of data buffers located in the FMD controller and the at least one non-volatile memory module.
Owner:SUPER TALENT TECH CORP
Fail-over of multiple memory blocks in multiple memory modules in computer system
InactiveUS6505305B1Error detection/correctionEmergency protective arrangements for automatic disconnectionFailoverMemory address
A computer system has a memory controller for controlling accesses to multiple memory modules, each having multiple memory blocks, and a fail-over circuit for failing-over individual memory blocks from multiple memory modules. The digital information stored in an individual memory block that has experienced memory errors in excess of a permissible threshold is copied to an auxiliary memory location. The memory accesses directed to the failed-over memory block are intercepted and redirected to the auxiliary memory location. Tags are stored to identify failed-over memory modules and corresponding auxiliary memory modules, so a tag look-up for an accessed memory address can generate a hit signal when the memory access is to a failed-over memory module and cause the auxiliary memory module to respond to the memory access.
Owner:HEWLETT PACKARD DEV CO LP
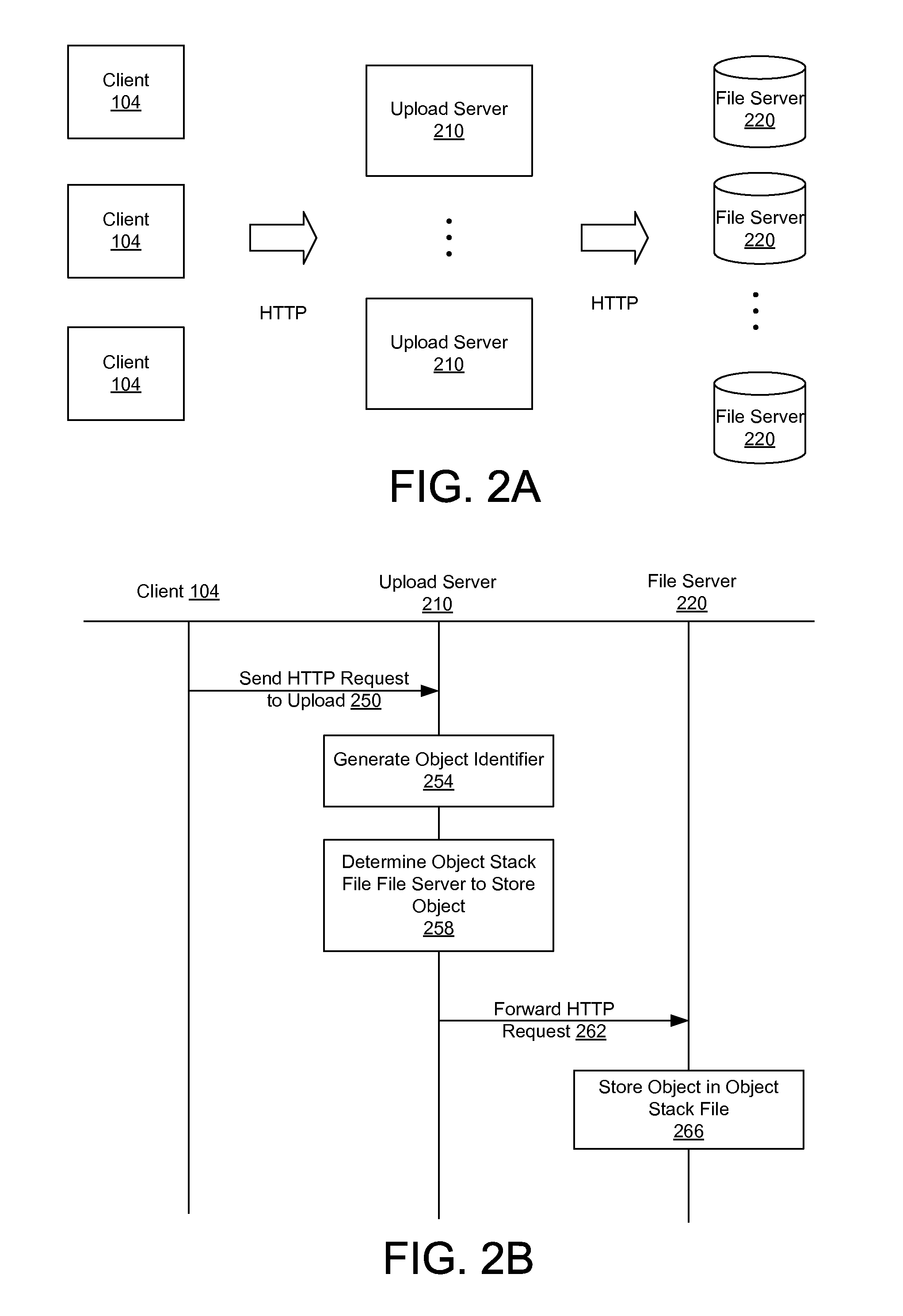
Efficient storage and retrieval for large number of data objects
ActiveUS20120246129A1Efficiently and promptly serveReduce in quantityDigital data processing detailsStill image data indexingAuxiliary memoryFile server
A data object management scheme for storing a large plurality of small data objects (e.g., image files) in small number of large object stack file for storage in secondary storage (e.g., hard disks). By storing many individual data objects in a single object stack file, the number of files stored in the secondary storage is reduced by several orders of magnitude, from the billions or millions to the hundreds or so. Index data for each object stack file is generated and stored in primary storage to allow efficient and prompt access to the data objects. Requests to store or retrieve the data objects are made using HTTP messages including file identifiers that identify the files storing the data objects and keys identifying the data objects. A file server stores or retrieves the data object from secondary storage of a file server without converting the requests to NSF or POSIX commands.
Owner:META PLATFORMS INC
Cache coherent support for flash in a memory hierarchy
ActiveUS20100293420A1Memory architecture accessing/allocationMemory adressing/allocation/relocationMemory hierarchyRandom access memory
System and method for using flash memory in a memory hierarchy. A computer system includes a processor coupled to a memory hierarchy via a memory controller. The memory hierarchy includes a cache memory, a first memory region of random access memory coupled to the memory controller via a first buffer, and an auxiliary memory region of flash memory coupled to the memory controller via a flash controller. The first buffer and the flash controller are coupled to the memory controller via a single interface. The memory controller receives a request to access a particular page in the first memory region. The processor detects a page fault corresponding to the request and in response, invalidates cache lines in the cache memory that correspond to the particular page, flushes the invalid cache lines, and swaps a page from the auxiliary memory region to the first memory region.
Owner:ORACLE INT CORP
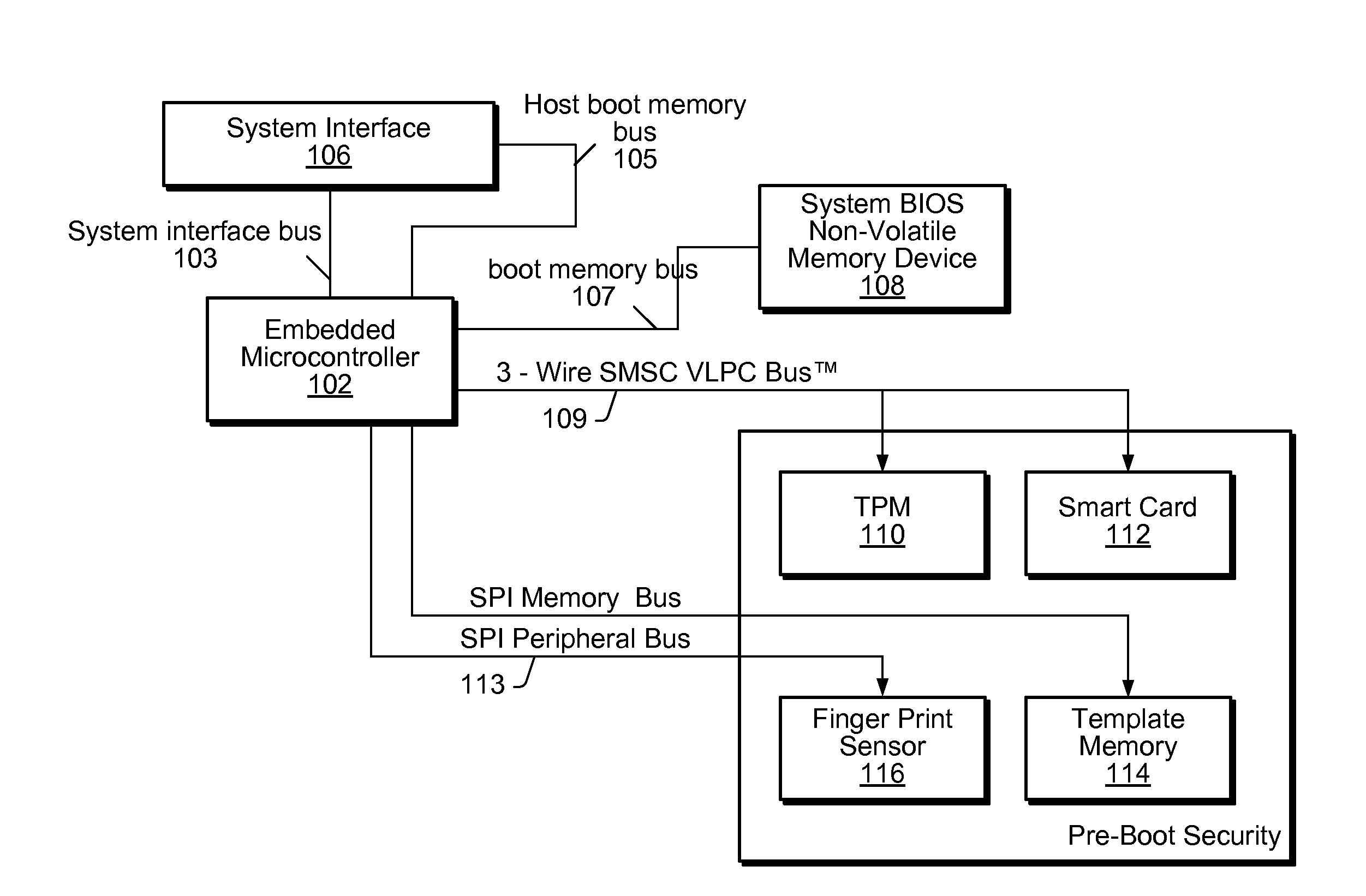
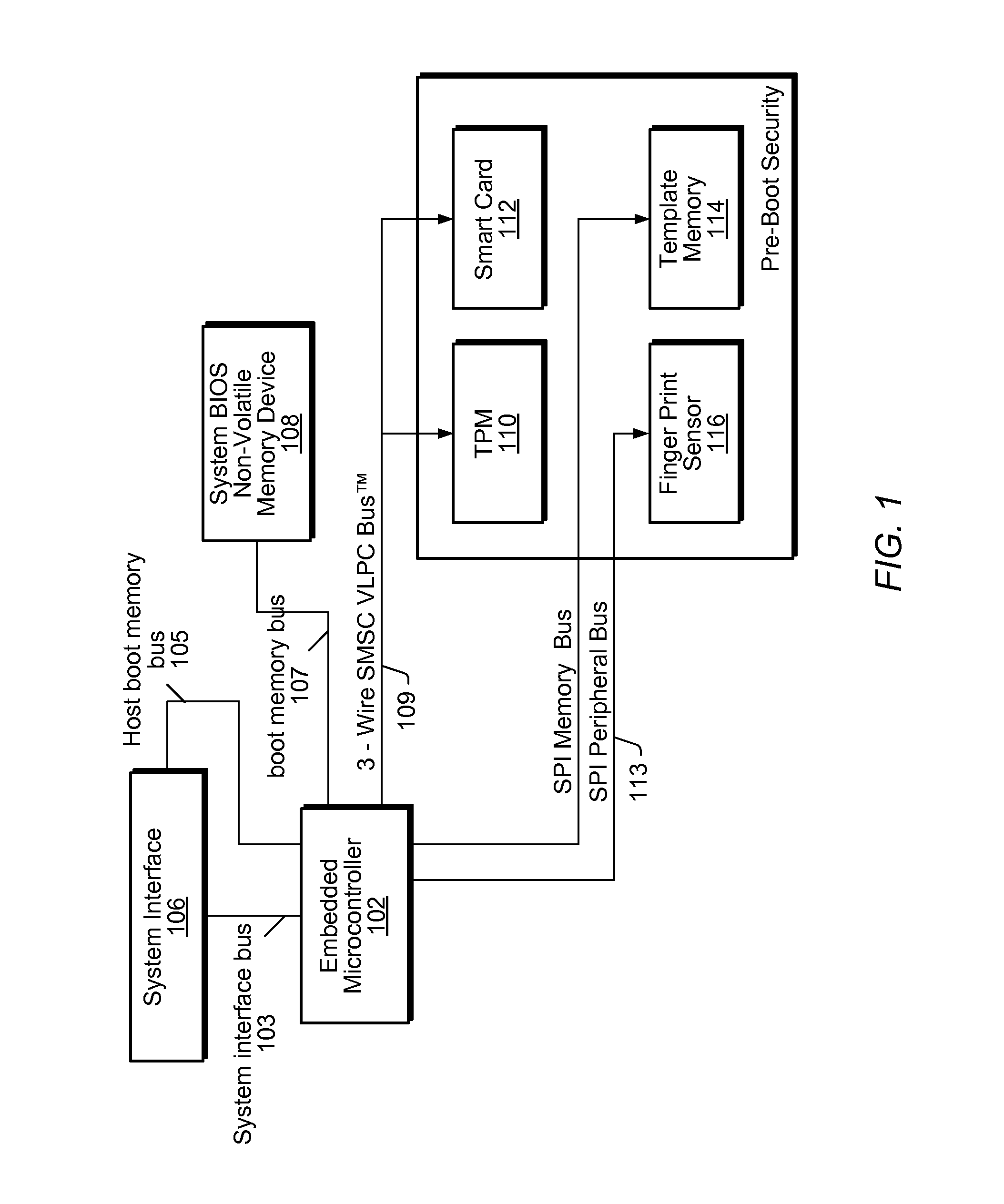
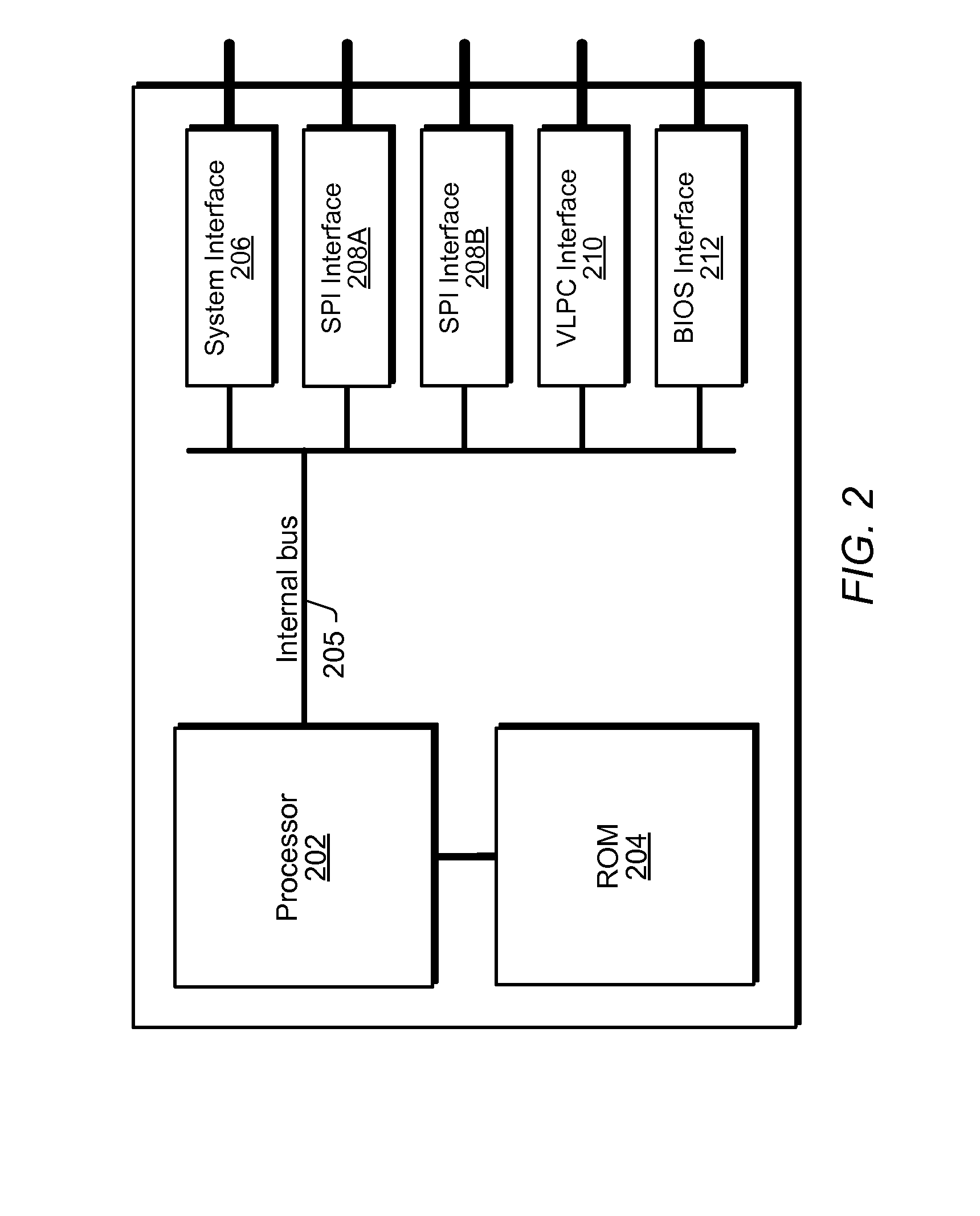
Enhancing Security of a System Via Access by an Embedded Controller to A Secure Storage Device
ActiveUS20090327678A1Improve securityVolume/mass flow measurementAnalogue secracy/subscription systemsMicrocontrollerSystem verification
System and method for performing pre-boot security verification in a system that includes a host processor and memory, an embedded microcontroller with an auxiliary memory, e.g., an on-chip ROM, or memory controlled to prohibit user-tampering with the contents of the memory, and one or more pre-boot security components coupled to the embedded microcontroller. Upon power-up, but before host processor boot-up, the embedded microcontroller accesses the auxiliary memory and executes the program instructions to verify system security using the one or more pre-boot security components. The one or more pre-boot security components includes at least one identity verification component, e.g., a smart card, or a biometric sensor, e.g., a fingerprint sensor, a retinal scanner, and / or a voiceprint sensor, etc., and / or at least one system verification component, e.g., TPM, to query the system for system state information, and verify that the system has not been compromised.
Owner:MICROCHIP TECH INC
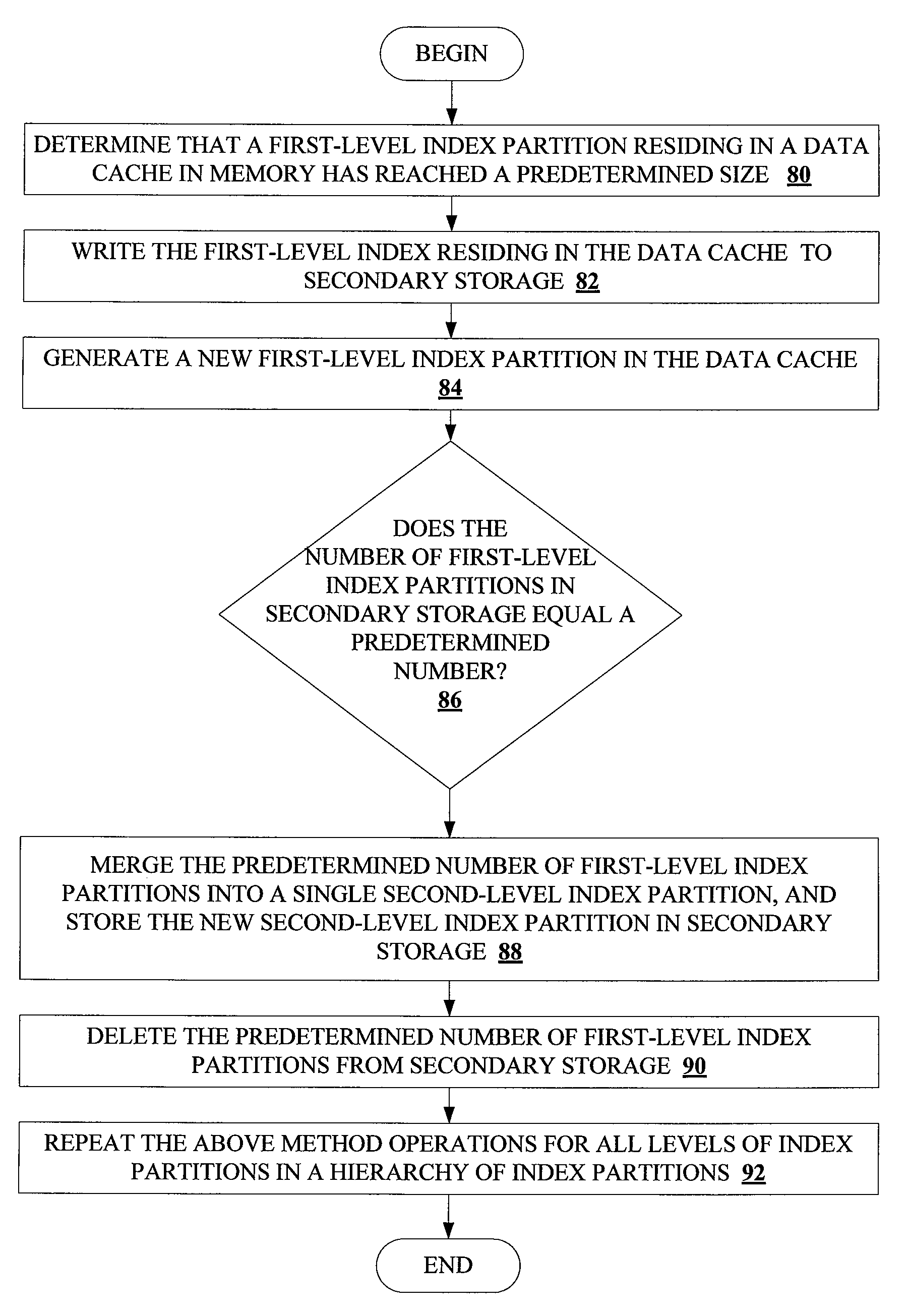
Method and system for dynamically partitioning very large database indices on write-once tables
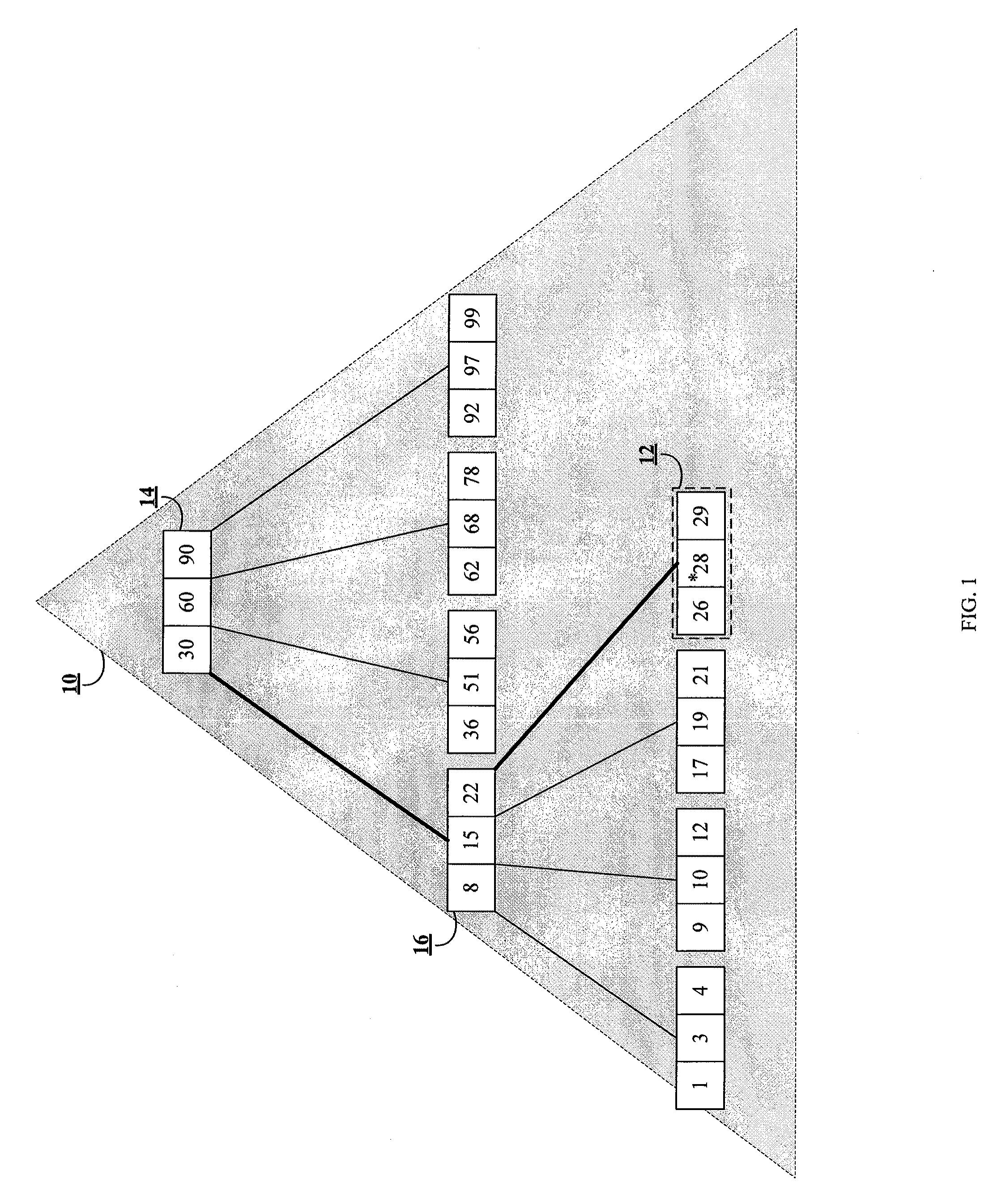
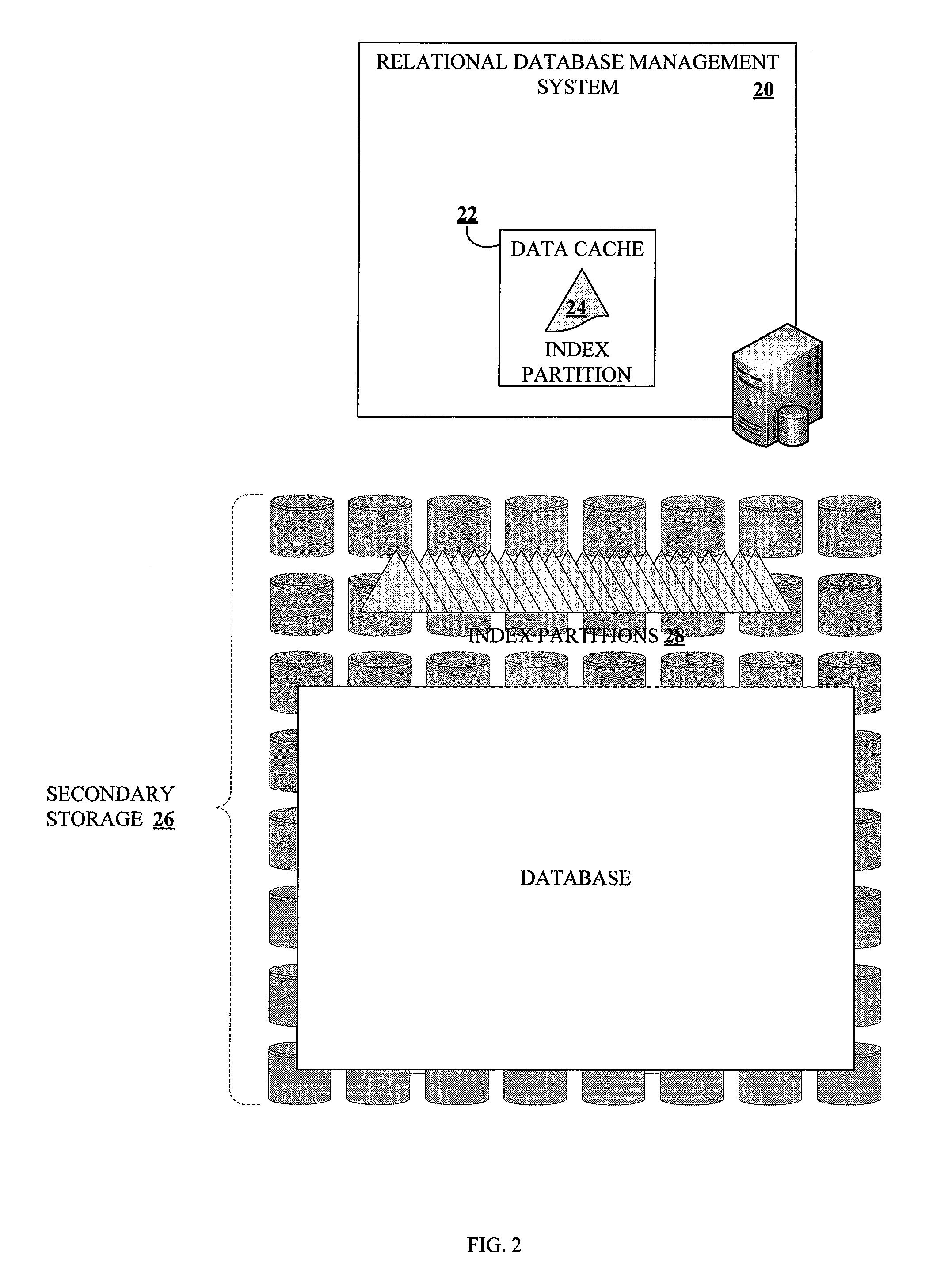
ActiveUS20100161569A1Increase in sizeAvoid performance degradationDigital data processing detailsRelational databasesDatabase indexIncrease size
Methods and systems for partitioning and dynamically merging a database index are described. A database index includes a single first-level index partition stored in a data cache. As the first-level index partition in the data cache reaches a predetermined size, it is copied to secondary storage and a new index partition is generated in the data cache. When the number of index partitions in secondary storage reaches some predetermined number, the index partitions are merged to create a single index partition of a higher level in a hierarchy of index partitions having an exponentially increasing size with each increase in level within the hierarchy.
Owner:SAP AG
Compound automotive rearview mirror
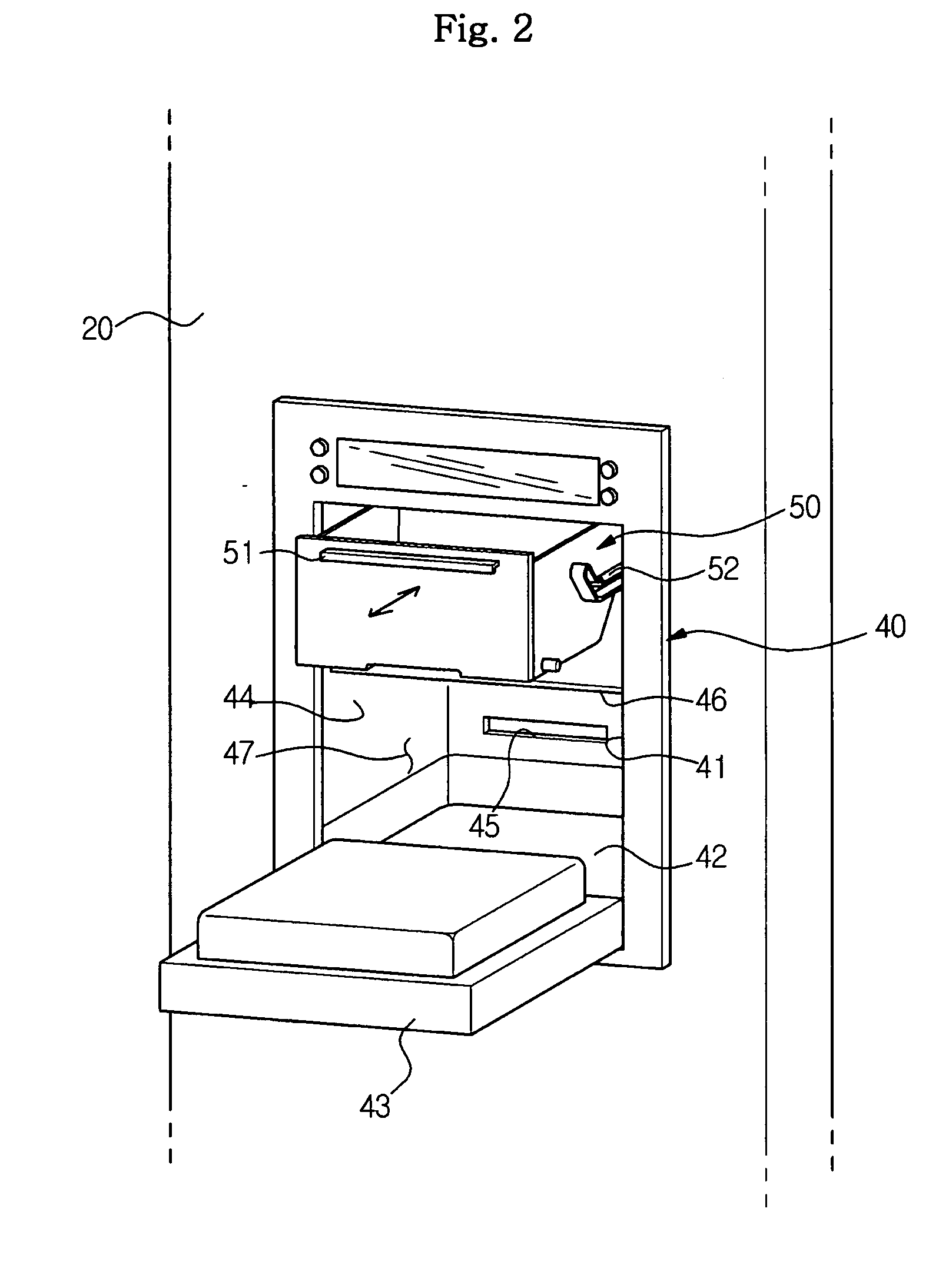
InactiveUS20080225421A1Inexpensive and easy to manufactureMirrorsOptical viewingMobile vehicleAuxiliary memory
A composite mirror adapted for use as an outside rearview mirror of a motor vehicle includes a main or primary viewing mirror and an auxiliary blindzone viewing mirror juxtaposed to expose the vehicle blindzone to the vehicle operator. The main viewing mirror is generally of unit magnification. The auxiliary mirror is composed of a planar array of reflecting facets mimicking a convex mirror. The main and auxiliary mirrors can be combined in constant or variable reflectivity applications.
Owner:PLATZER GEORGE E
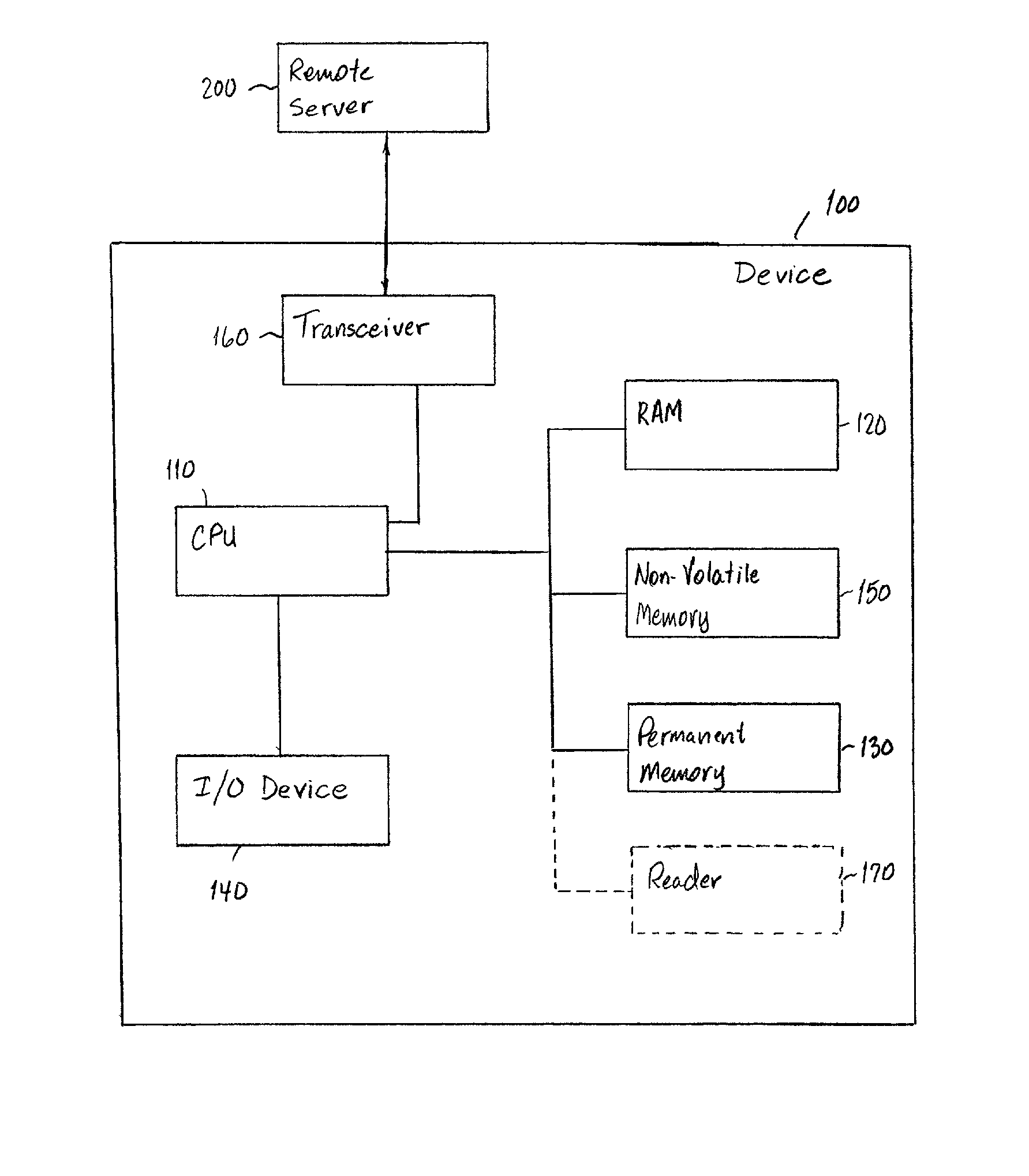
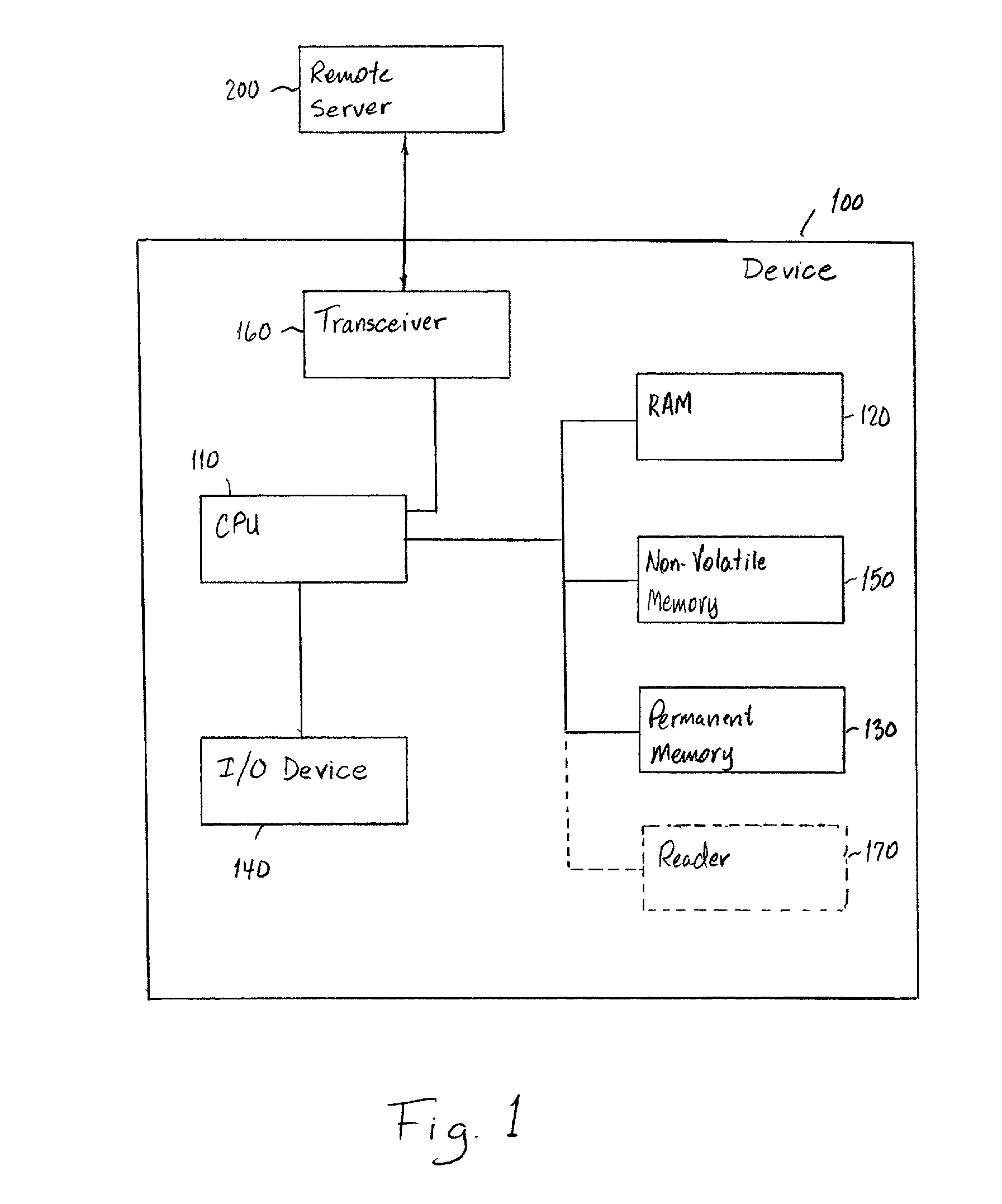
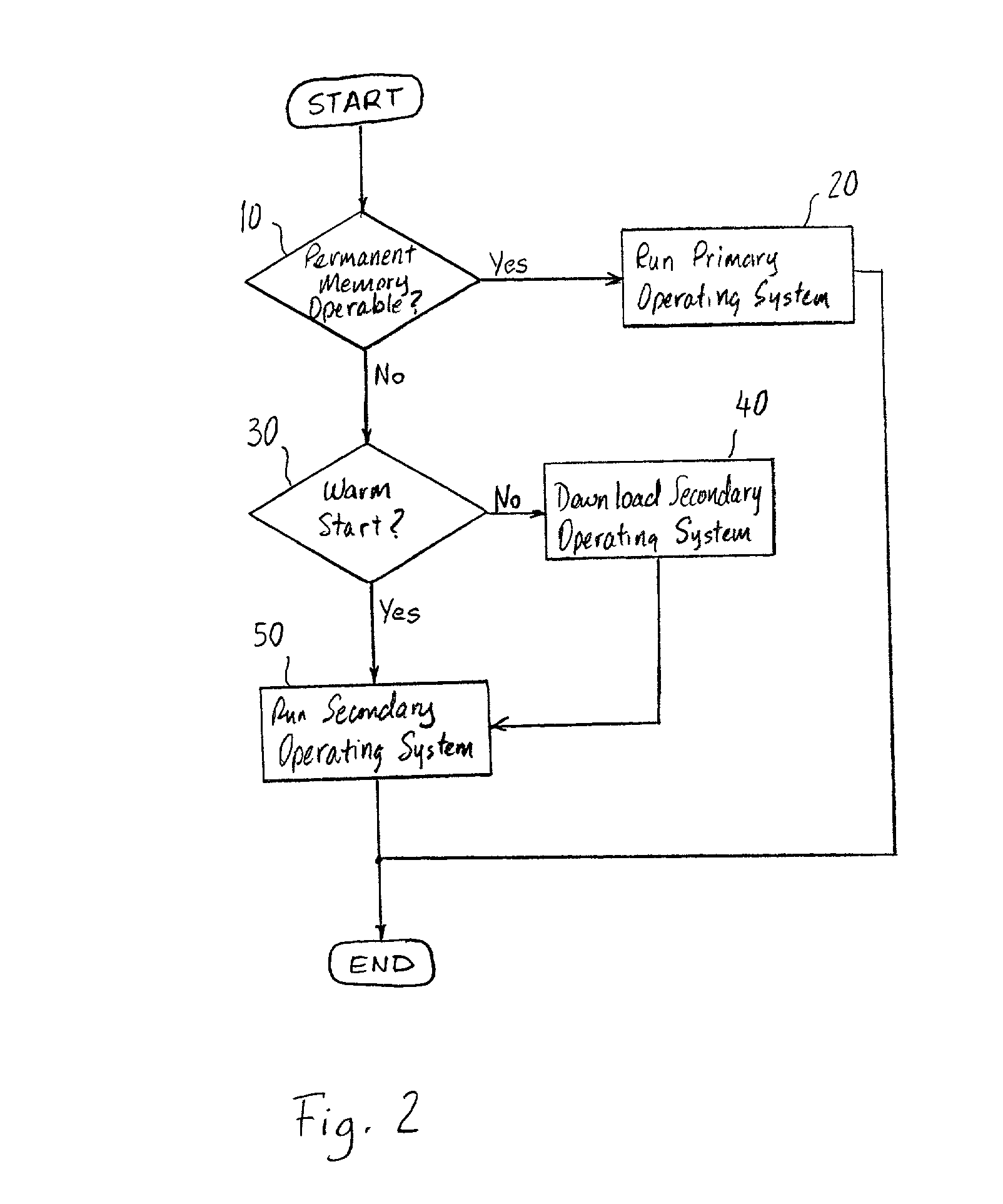
Crash recovery system
A set top box for a television includes a hard drive, a random access memory, and a non-volatile memory. To maintain functionality of the device after a crash of the hard drive, the non-volatile memory includes an executable program for downloading a secondary operating system from a remote server or other secondary storage during a startup when the primary operating system in the hard drive is not accessible. The secondary operating system is stored in the random access memory and is a functional subset of the primary operating system to allow the use of the primary functionality of the set top box until the hard disk drive is repaired or replaced.
Owner:NOKIA TECHNOLOGLES OY
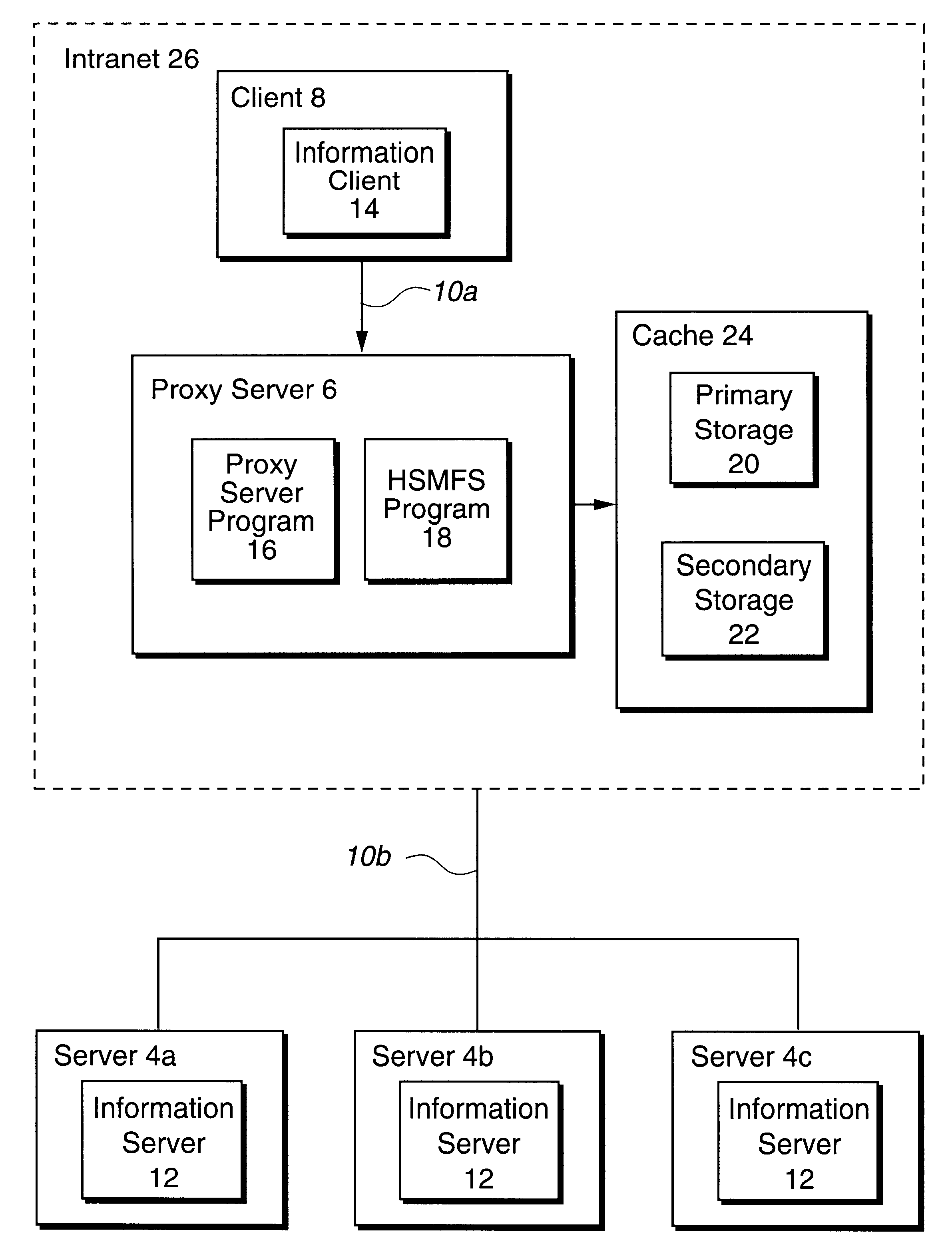
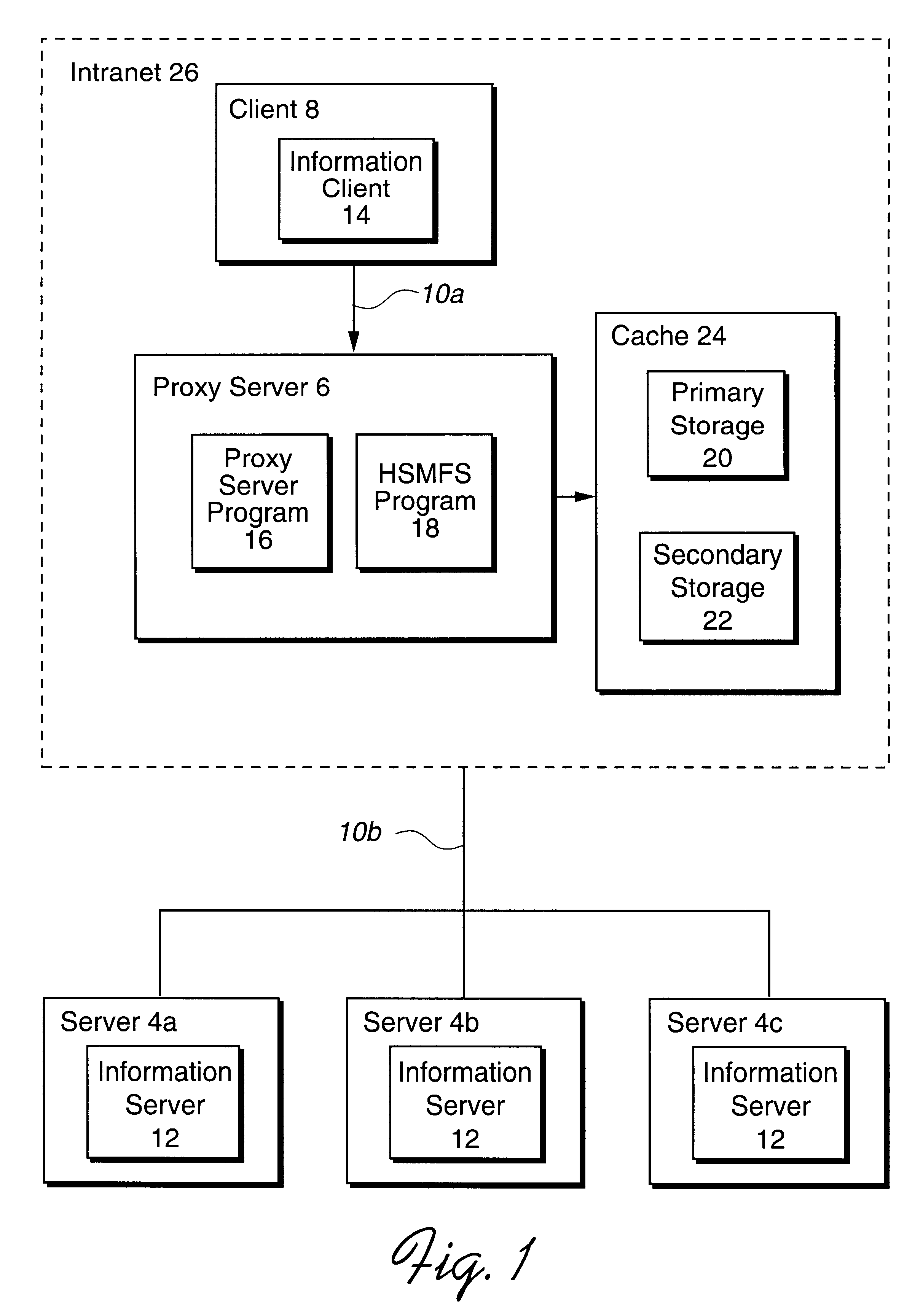
System, method and program for migrating files retrieved from over a network to secondary storage
InactiveUS6442601B1Save bandwidth resourcesIncrease speedMultiple digital computer combinationsSecuring communicationAuxiliary memoryUnit of time
Disclosed is a system, method, and program for caching files retrieved from a server over a network. A computer system receives a request from a requesting computer system for a file maintained on the server. The computer system is capable of communicating with the server via the network. The computer system retrieves the requested file from the server over the network and stores a copy of the requested file in a primary storage. The computer system further returns another copy of the requested file to the requesting computer system. The computer system determines retrieved files to migrate from the primary storage to a secondary storage and migrates the determined retrieved files from the primary storage to the secondary storage. To determine the files to migrate from primary storage to secondary storage, the computer system may determine a distribution of file requests per unit of time according to file size for files maintained in the primary storage and the secondary storage. The computer system then processes the determined distribution and a provided maximum number of file requests per unit of time to determine a minimum file size for migration. Files having a size greater than the minimum file size for migration are migrated from the primary storage device to the secondary storage device.
Owner:COMCAST IP HLDG I
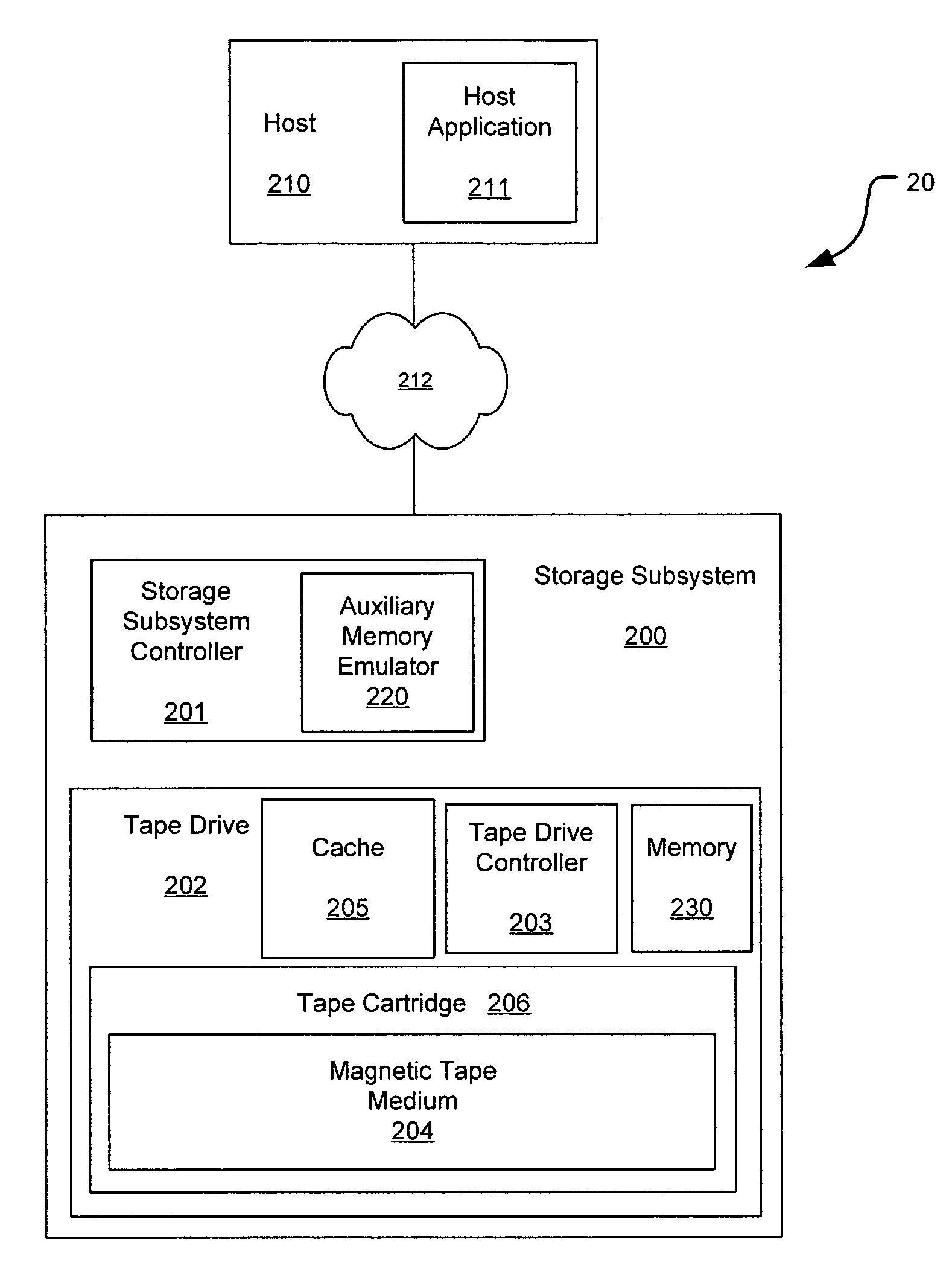
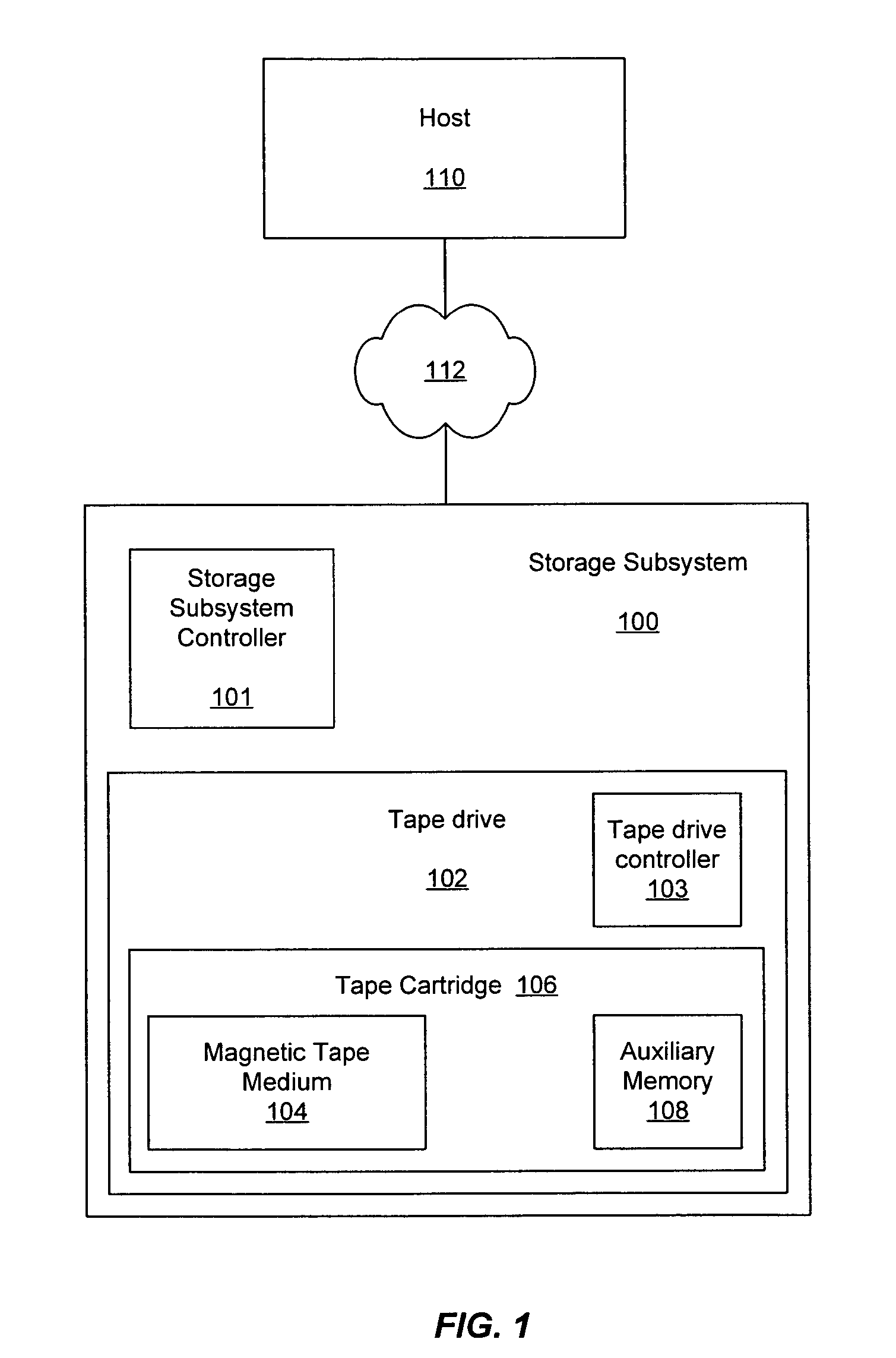
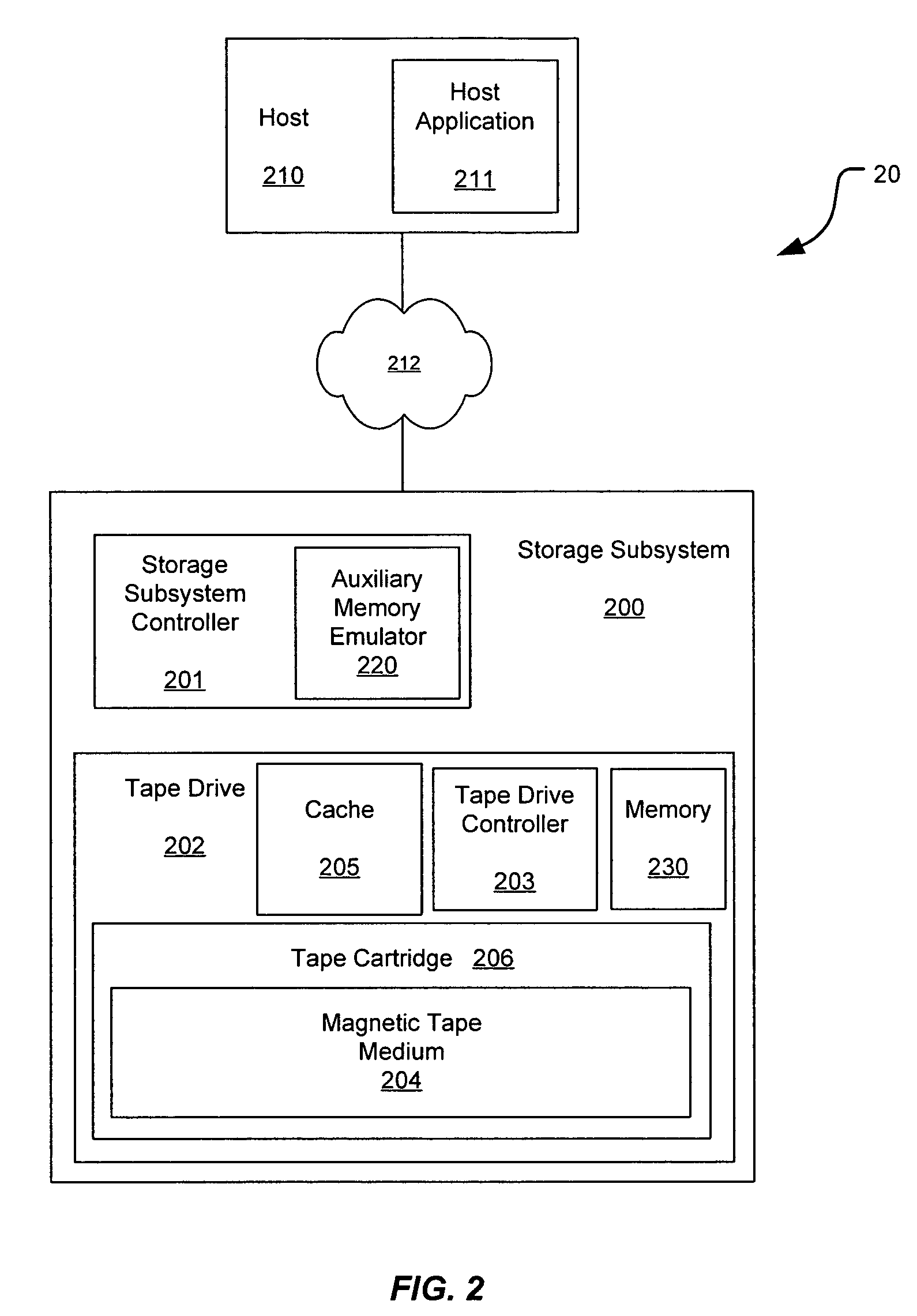
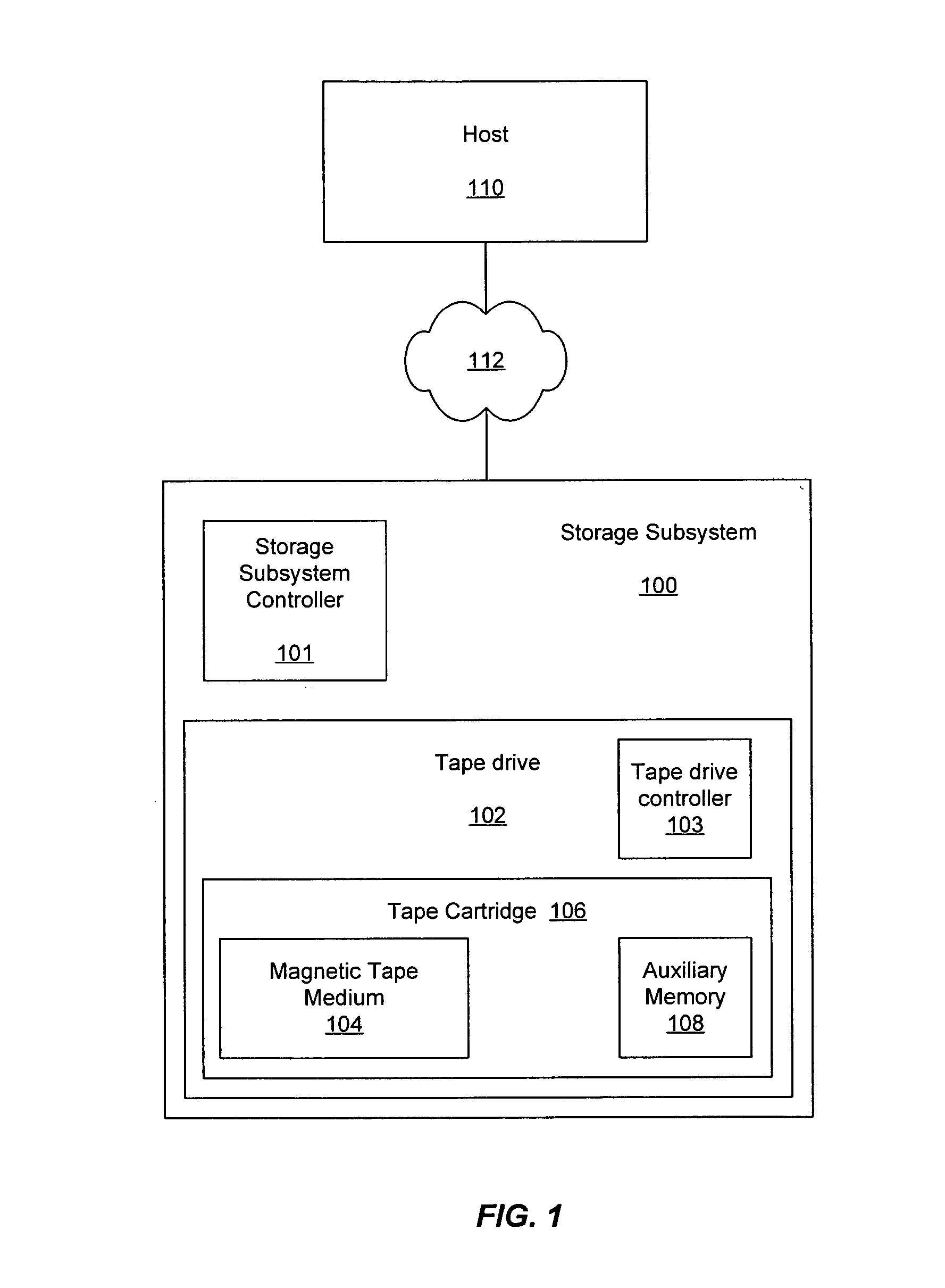
Methods and systems for providing predictive maintenance, preventative maintenance, and/or failure isolation in a tape storage subsystem
ActiveUS7277246B2Input/output to record carriersFilamentary/web record carriersMagnetic tapeAuxiliary memory
A system and method of operating a storage system is provided. The storage system includes a tape cartridge having a magnetic tape medium and a tape drive for reading and writing data to the magnetic tape medium of the tape cartridge. Performance data associated with specific operating loci (e.g., bands, directions, tracks, segments, etc.) of the tape drive and tape medium are collected, analyzed, and stored, allowing for analysis and detection of trends over time. In one example, tape usage events are monitored and when they cross a threshold the system may remove particular tapes in a preventative maintenance approach to reduce system outage. Performance data is collected and analyzed with a portion of the performance data being saved to emulated medium auxiliary memory (EMAM) on the magnetic tape, and a portion of the of the performance data saved in non-volatile storage in the drive.
Owner:QUANTUM CORP
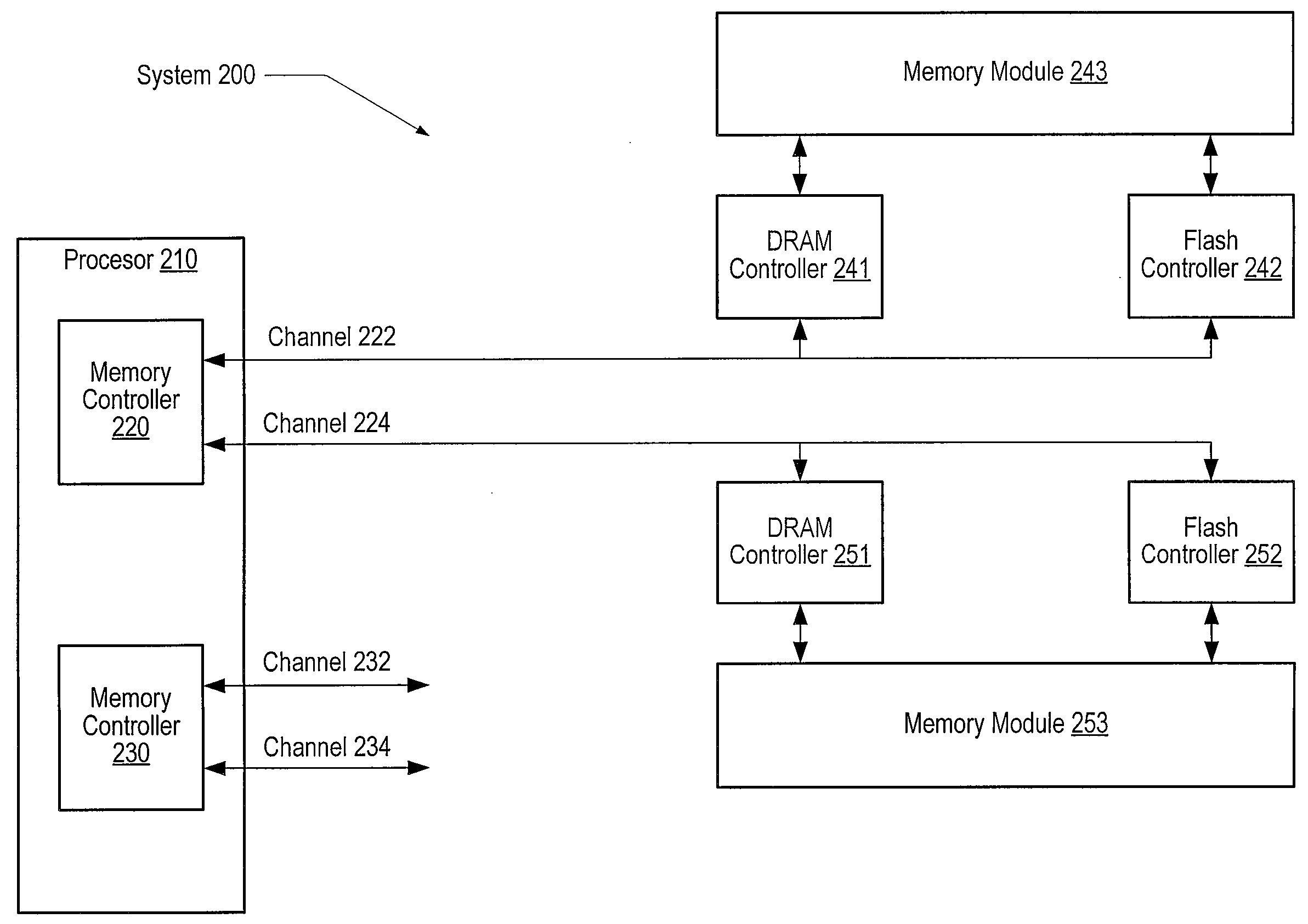
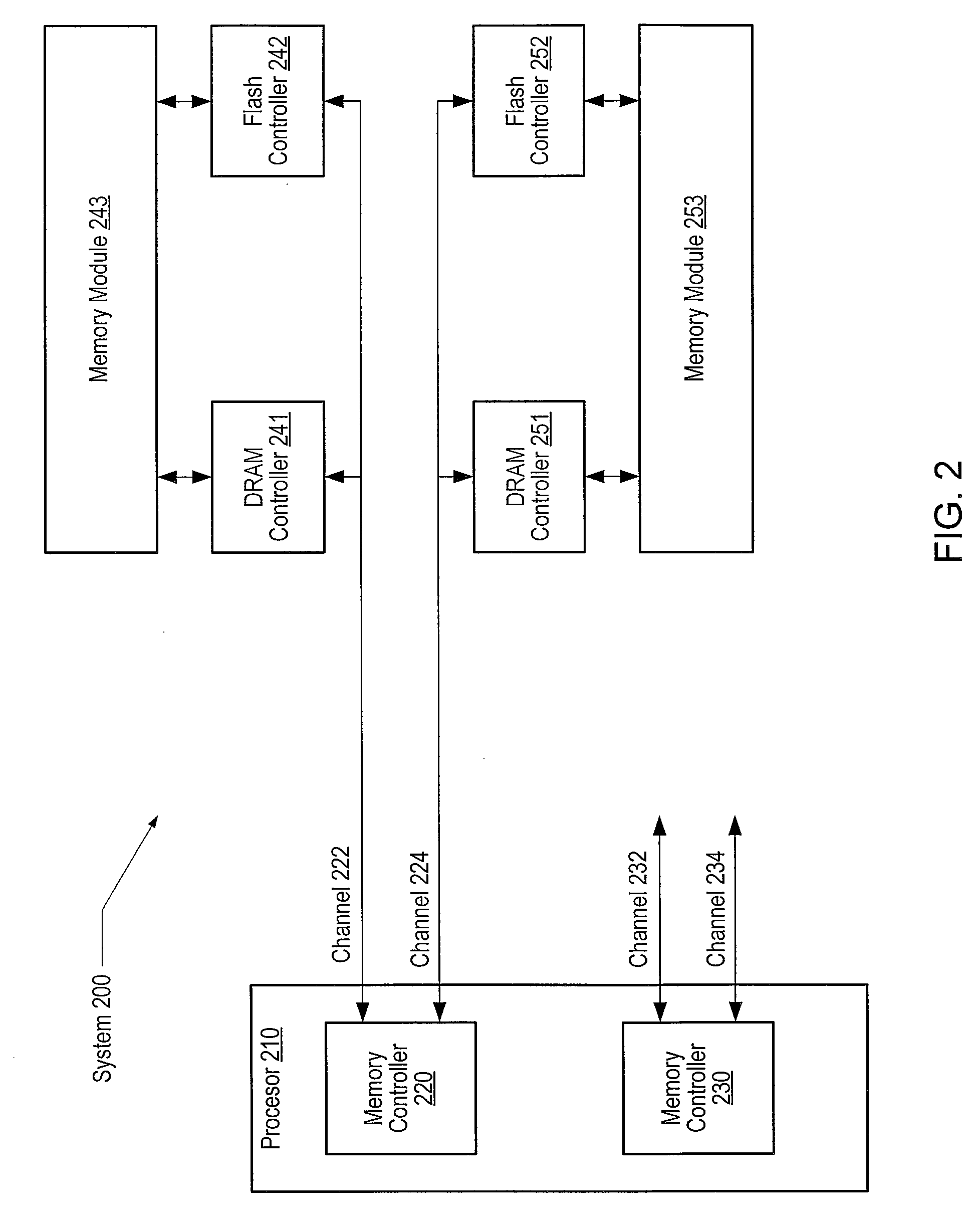
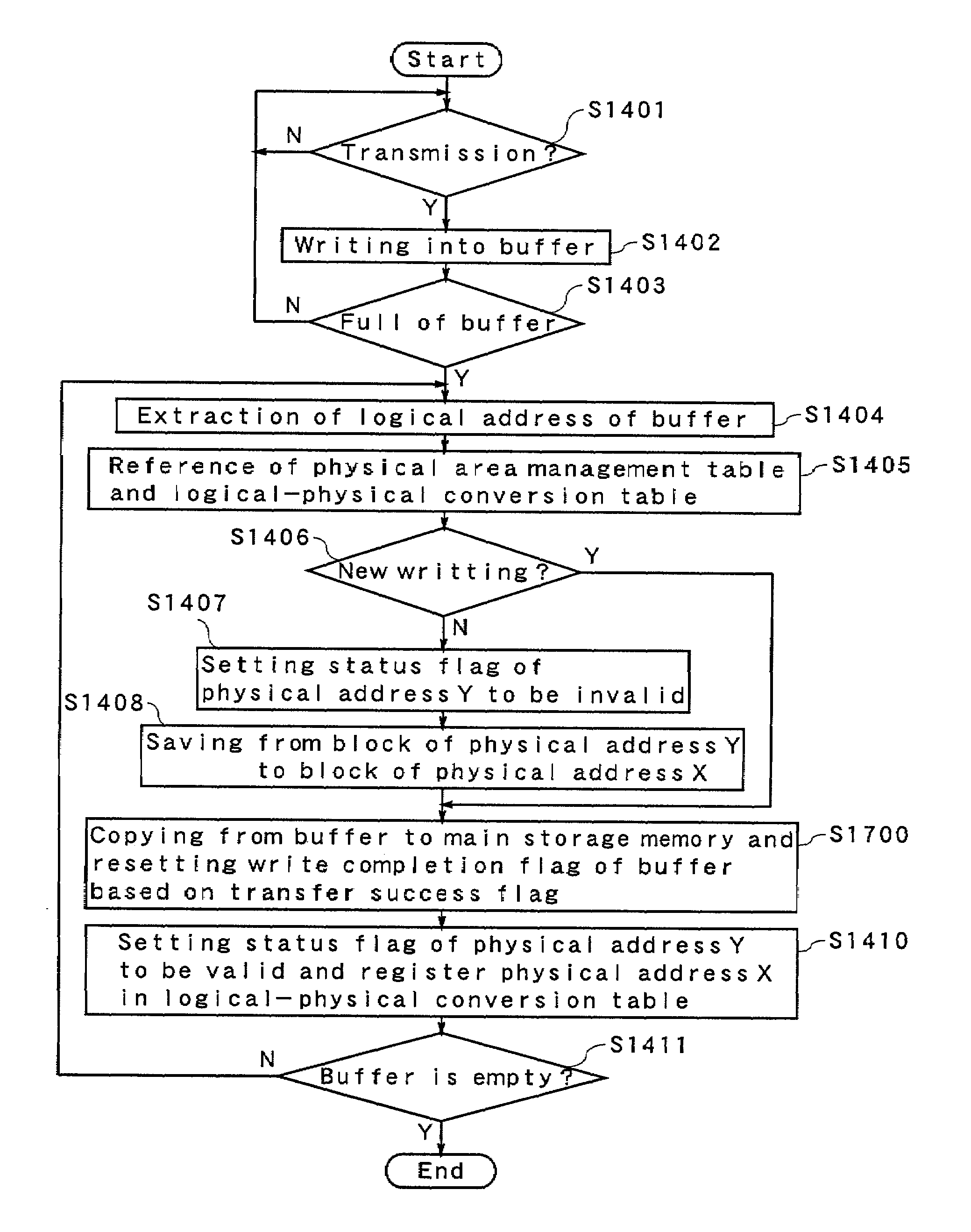
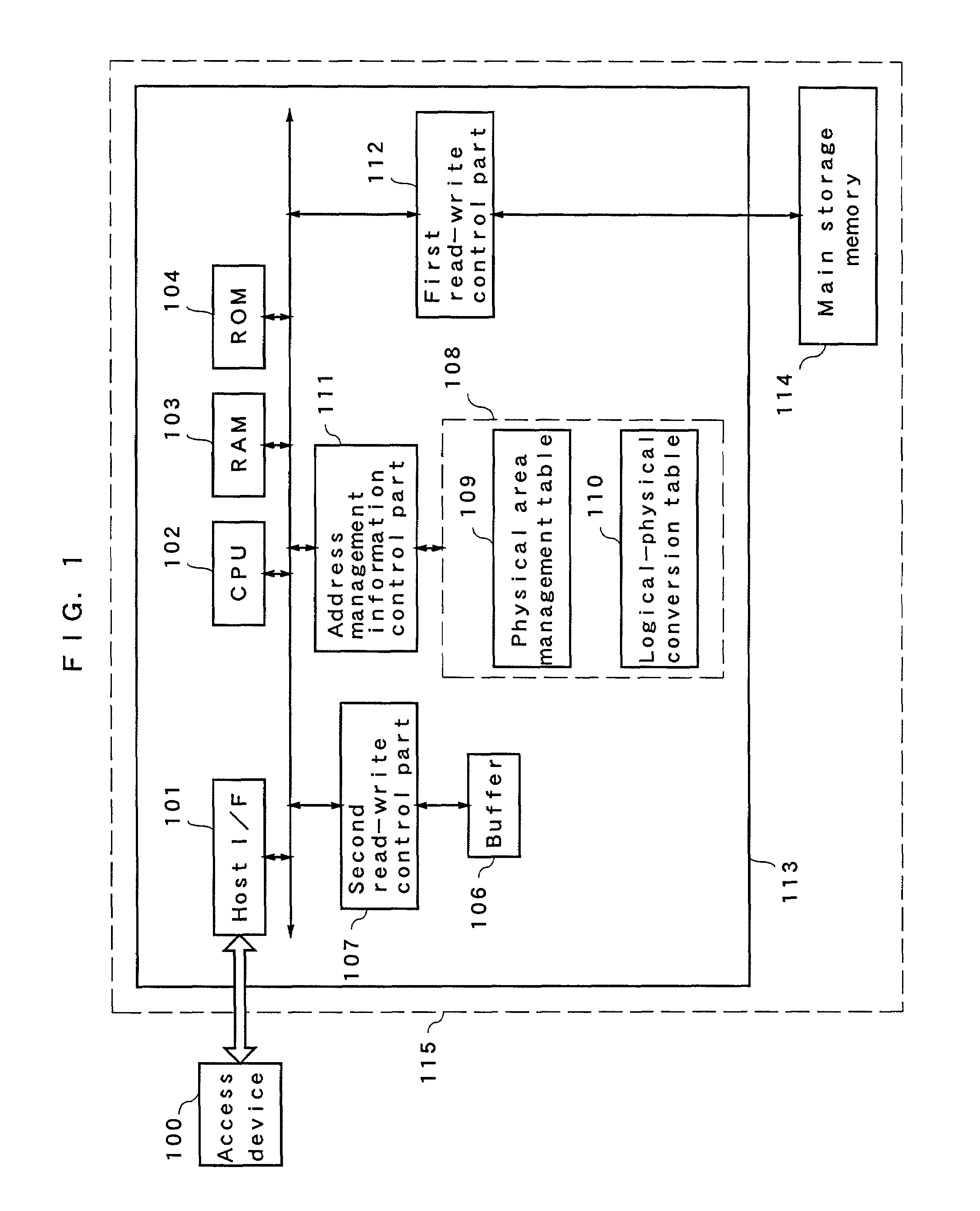
Memory controller, nonvolatile storage device, nonvolatile storage system, and data writing method
InactiveUS7702846B2Increase speedHigh-speed performanceMemory architecture accessing/allocationMemory adressing/allocation/relocationAuxiliary memoryMemory controller
A nonvolatile storage device is provided with a nonvolatile main storage memory whose erase size is larger than a cluster size, and a buffer, i.e. a nonvolatile auxiliary storage memory. At the time of writing data in the memory, the data is temporarily stored in the buffer, then, a plurality of data in the buffer are collectively taken out to be stored in the main storage memory. Data in an original block is saved in a write block in the main storage memory. Thus, the data can be written in the main storage memory at a high speed.
Owner:PANASONIC CORP
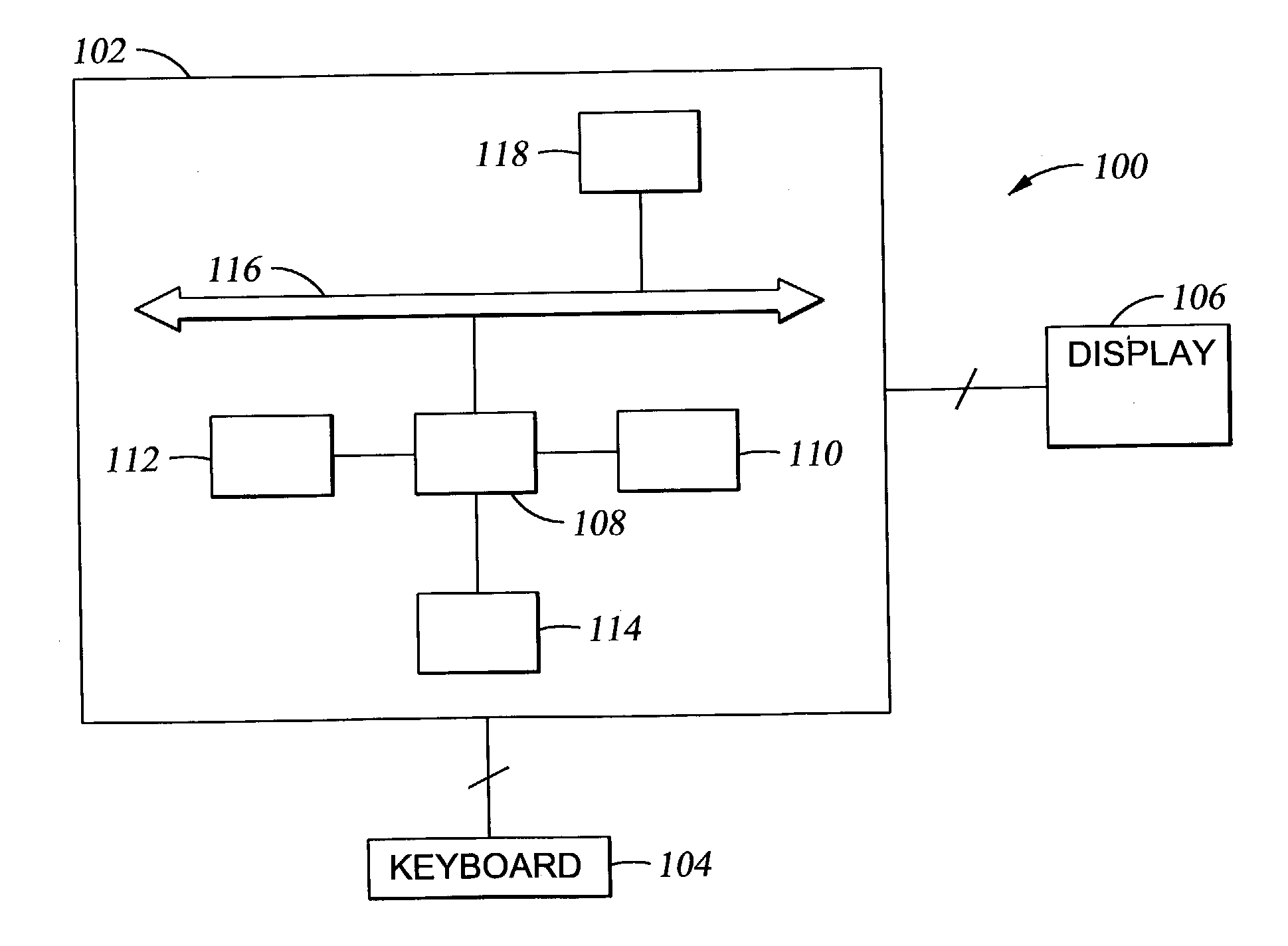
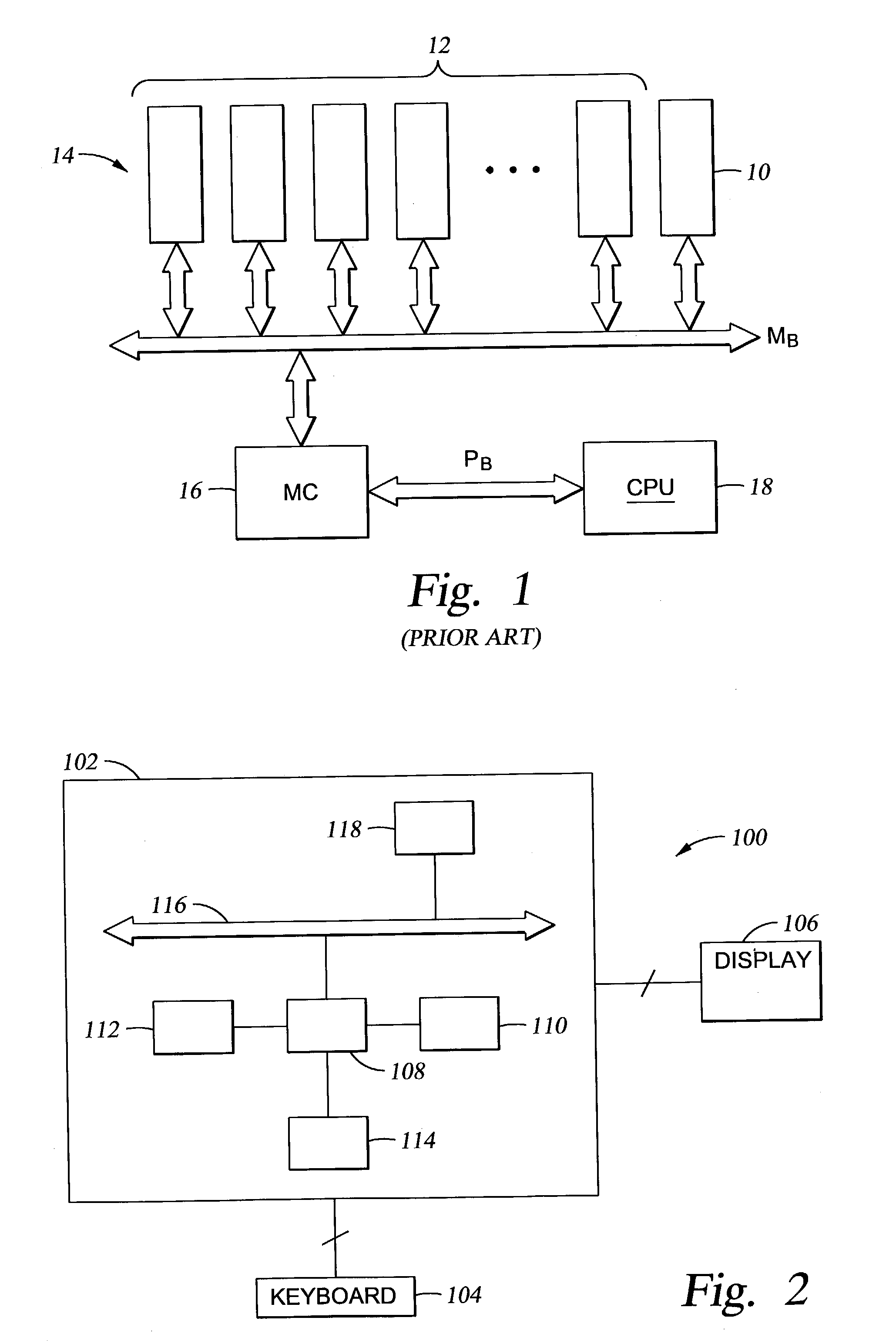
Method and apparatus for memory management in a multi-processor computer system
ActiveUS20050172099A1Avoid accessMemory architecture accessing/allocationMemory adressing/allocation/relocationManagement unitMulti processor
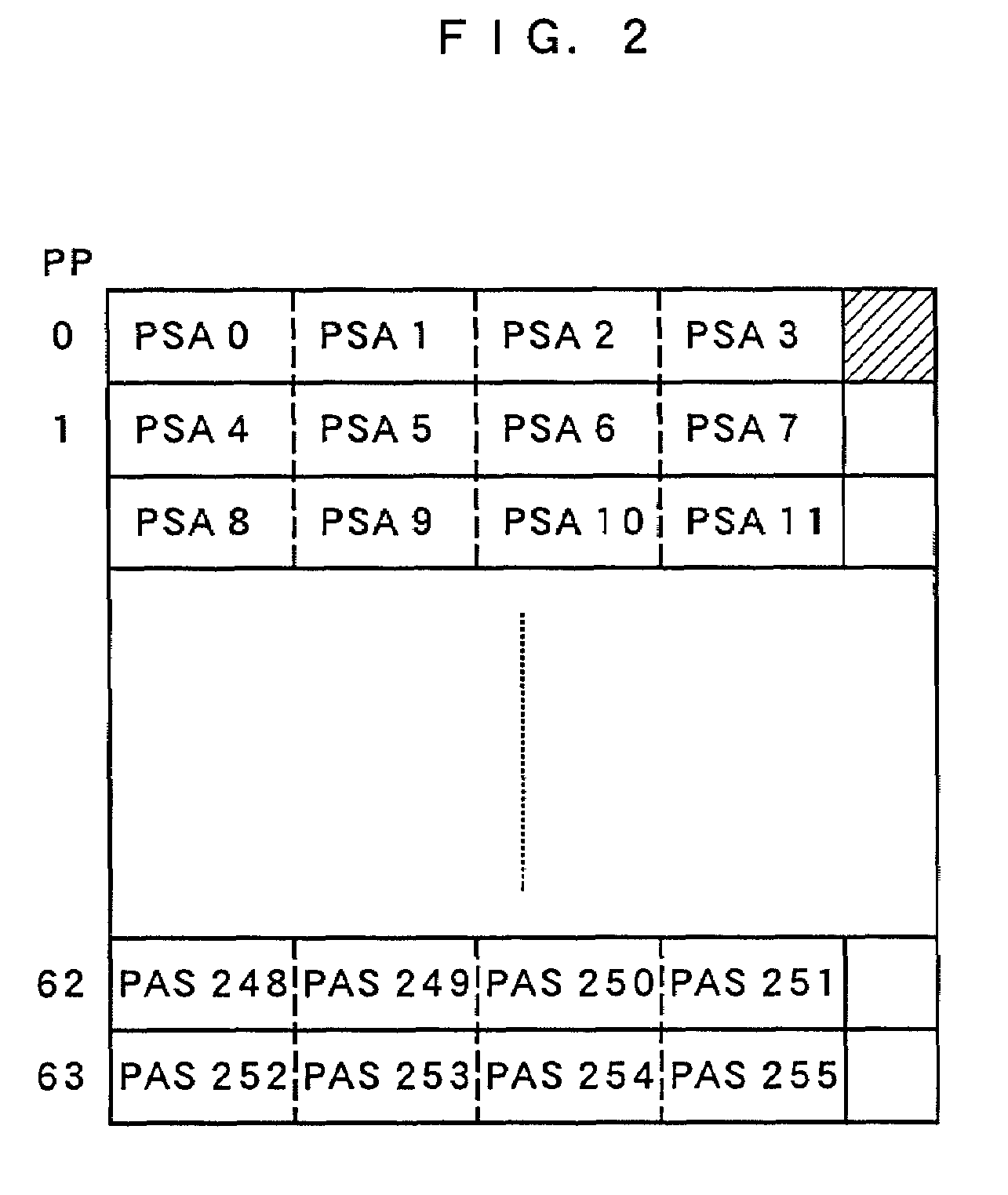
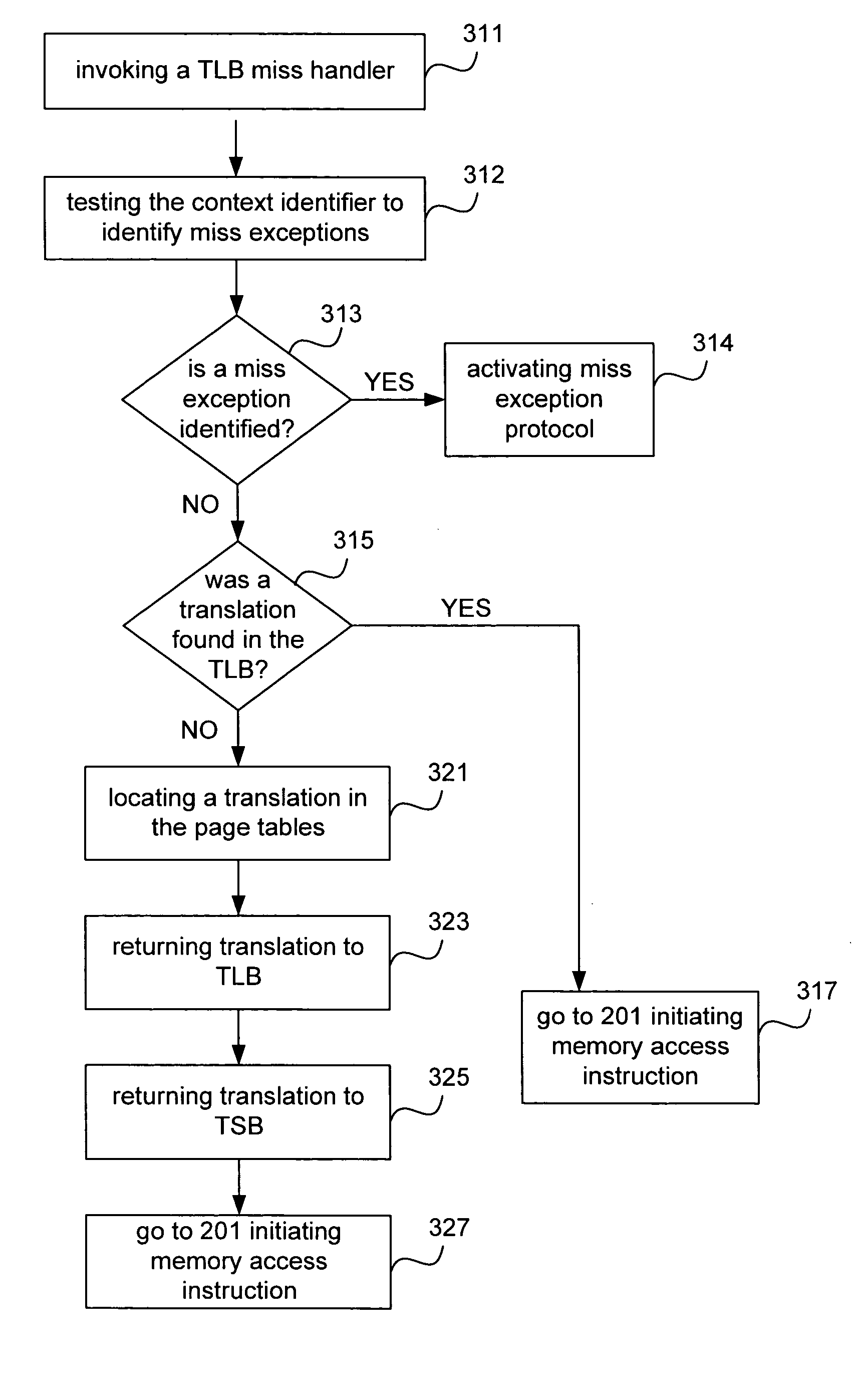
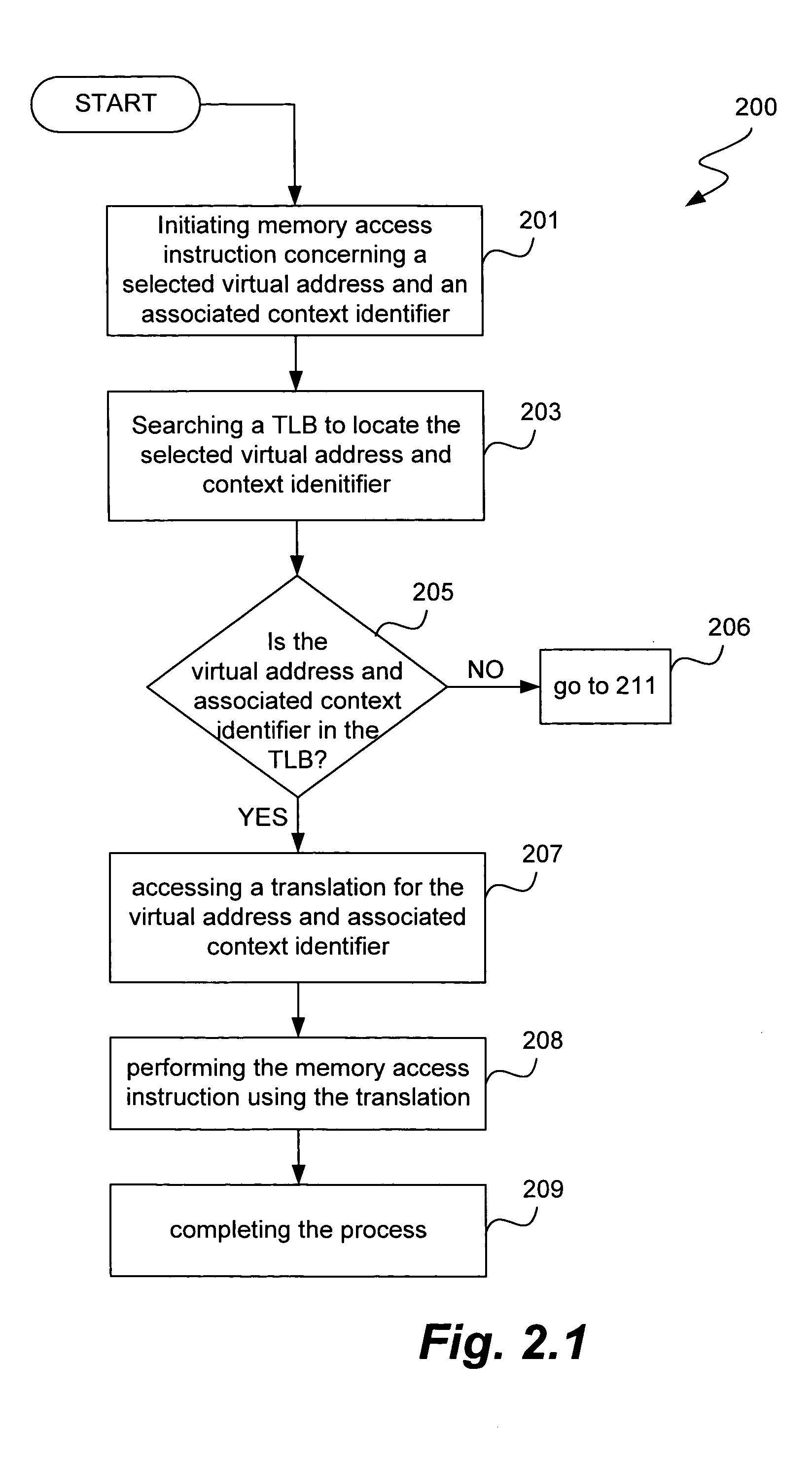
Improved techniques and systems for accommodating TLB shootdown events in multi-processor computer systems are disclosed. A memory management unit (MMU) having a TLB miss handler and miss exception handler is provided. The MMU receives instructions relative to a virtual address. A TLB is searched for the virtual address, if the virtual address is not found in the TLB, secondary memory assets are searched for a TTE that corresponds to the virtual address and its associated context identifier. The context identifier is tested to determine if the TTE is available. Where the TTE is available, the TLB and secondary memory assets are updated as necessary and the method initiates memory access instructions. Where the TTE is unavailable, the method either resolves the unavailability or waits until the unavailability is resolved and then initiates memory access instructions, thereby enabling the desired virtual address information to be accessed.
Owner:ORACLE INT CORP
High performance flash memory devices (FMD)
InactiveUS7827348B2Improve performanceImprove efficiencyError detection/correctionStatic storageControl dataAuxiliary memory
High performance flash memory devices (FMD) are described. According to one exemplary embodiment of the invention, a high performance FMD includes an I / O interface, a FMD controller, and at least one non-volatile memory module along with corresponding at least one channel controller. The I / O interface is configured to connect the high performance FMD to a host computing device The FMD contoller is configured to control data transfer (e.g., data reading, data writing / programming, and data erasing) operations between the host computing device and the non-volatile memory module. The at least one non-volatile memory module, comprising one or more non-volatile memory chips, is configured as a secondary storage for the host computing device. The at least one channel controller is configured to ensure proper and efficient data transfer between a set of data buffers located in the FMD controller and the at least one non-volatile memory module.
Owner:SUPER TALENT TECH CORP
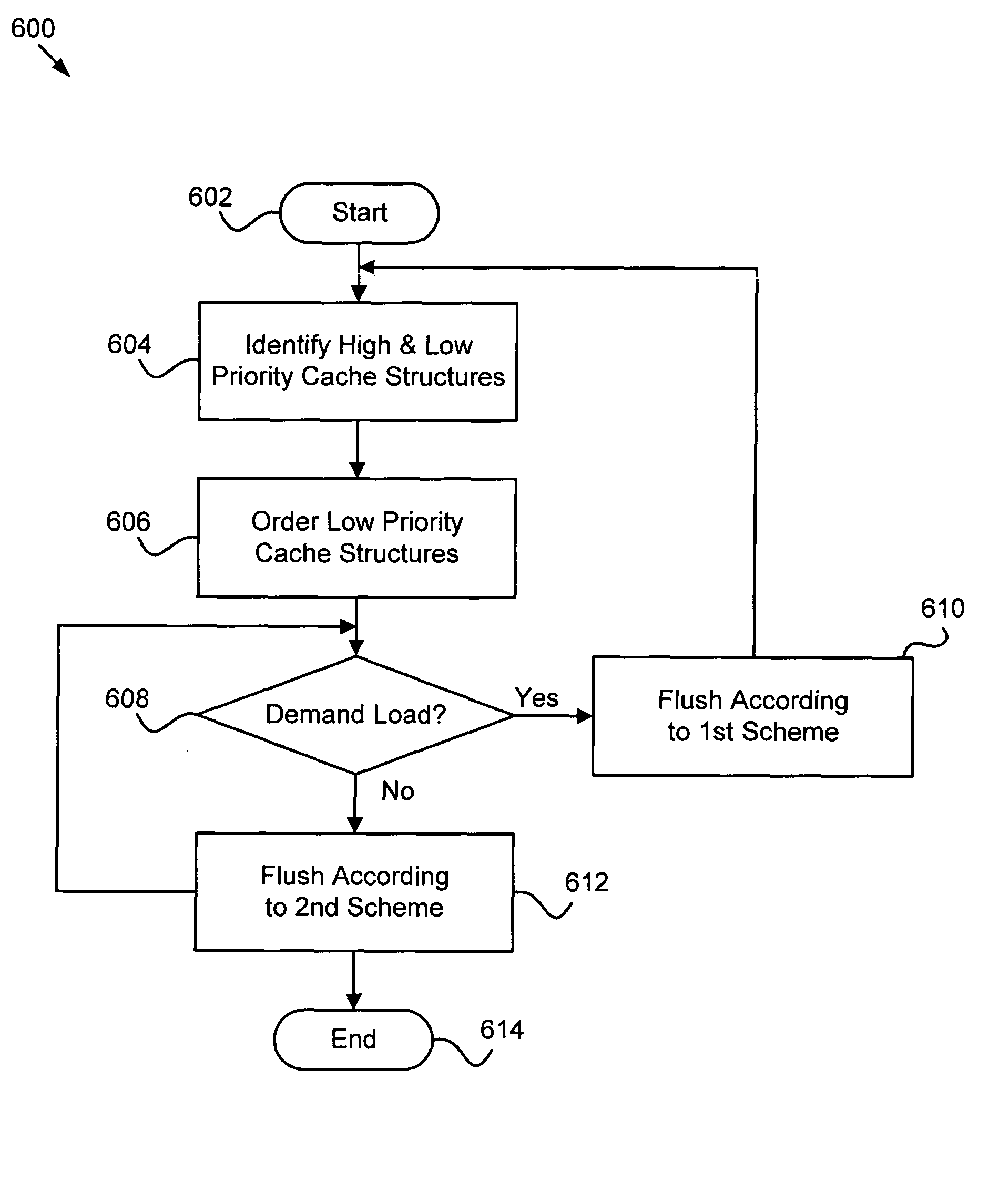
Apparatus, system, and method flushing data from a cache to secondary storage
InactiveUS20050055512A1Good choiceMemory adressing/allocation/relocationInput/output processes for data processingParallel computingAuxiliary memory
An apparatus, system, and method is provided for flushing data from a cache to secondary storage. The apparatus, system, and method identifies predefined high priority cache structures and predefined low priority cache structures. The apparatus, system, and method selectively flushes low priority cache structures according to a first scheme when the cache is under a demand load and according to a second scheme when the cache is under substantially no demand load. The first scheme is defined to flush low priority cache structures as efficiently as possible and the second scheme is defined to flush low priority cache structures in a less efficient manner.
Owner:IBM CORP
Refrigerator
InactiveUS20080168794A1Avoid excessive rotationImprove space efficiencyLighting and heating apparatusDomestic refrigeratorsAuxiliary memoryEngineering
A refrigerator including an auxiliary receiving chamber is disclosed. The refrigerator includes a main body having a storage chamber, and a door which opens or closes the storage chamber and has a receiving space formed at a back side of the door. The door includes an auxiliary storage area having an opening to store goods, an auxiliary receiving chamber disposed in the auxiliary storage area to move back and forth, an auxiliary door to open or close the opening, and an opening / closing member to extract or retract the auxiliary receiving chamber.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for hierarchical storage management using shadow volumes
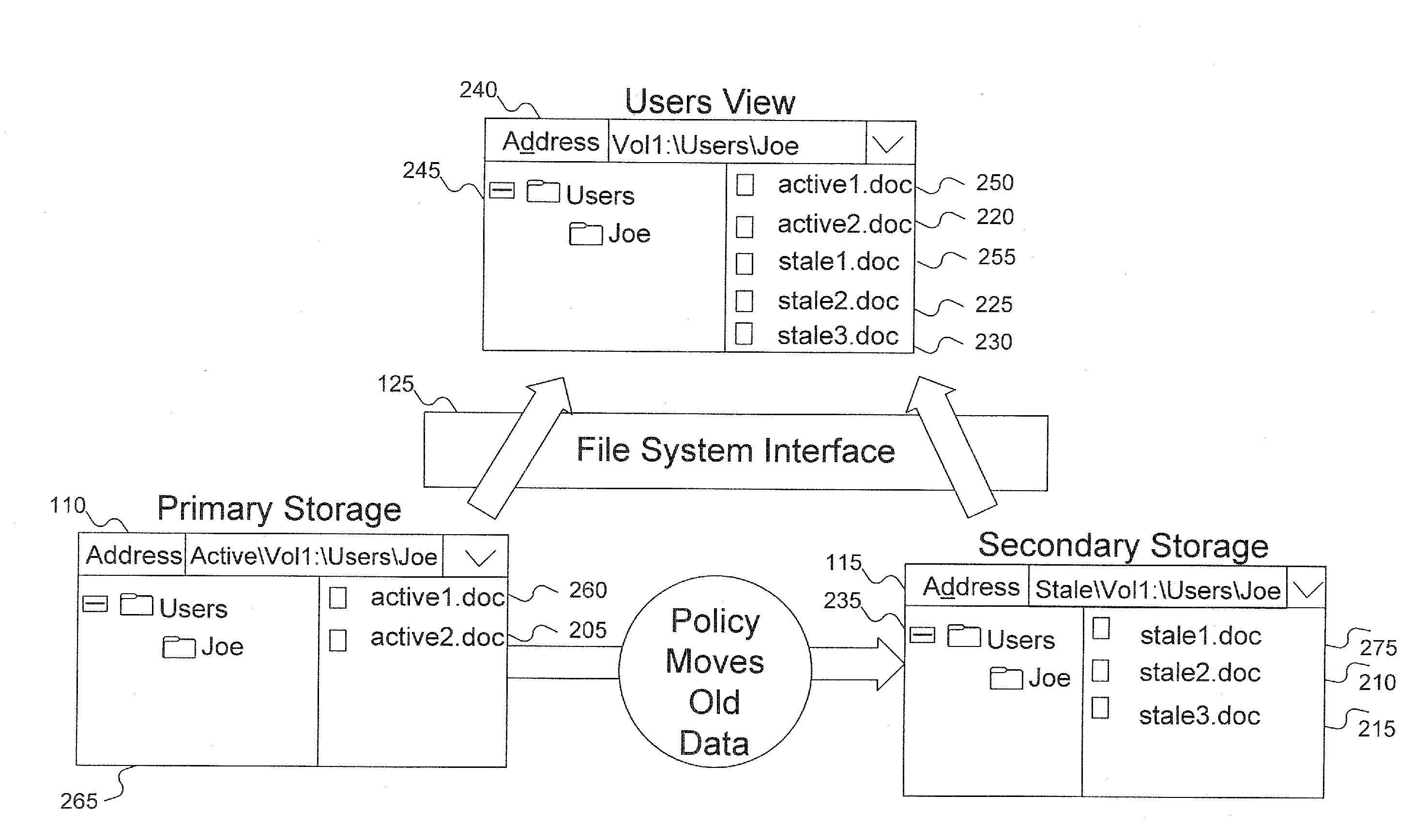
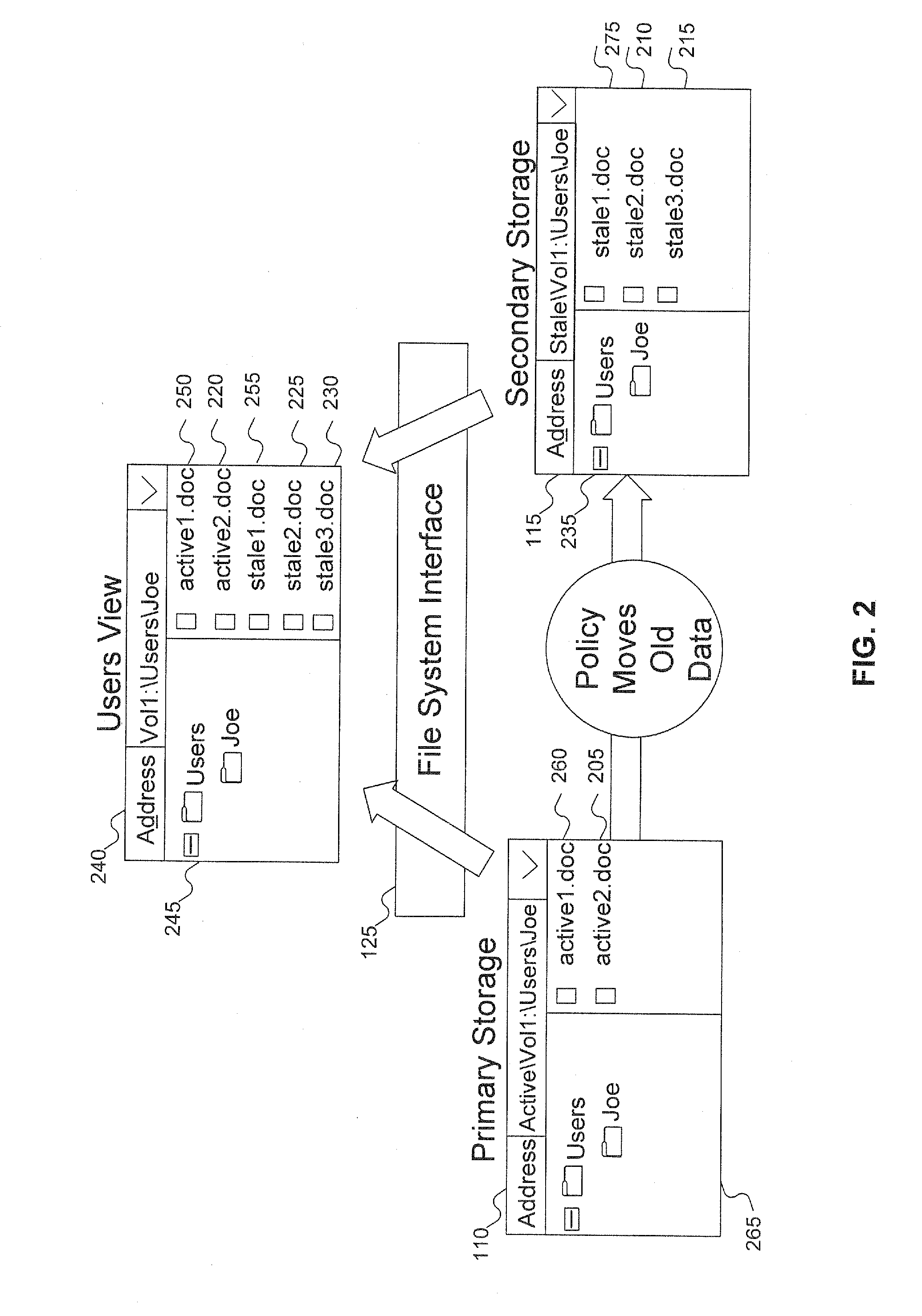
InactiveUS20070220029A1Guaranteed accuracyDigital data information retrievalDigital data processing detailsShadow volumeData file
Data partitioned onto two or more storage devices is presented to a user as if the data resided on a single storage area. Data is divided between the storage areas based on policies. Data on the primary storage can utilize frequent back up or other storage management to ensure the accuracy of the data. The data on the secondary storage can employ other data management than the data management for the primary storage. The subdirectory structure is replicated in each area so a data file can be located in either physical area. This allows data files to migrate between the storage areas based on policy.
Owner:NOVELL INTPROP HLDG
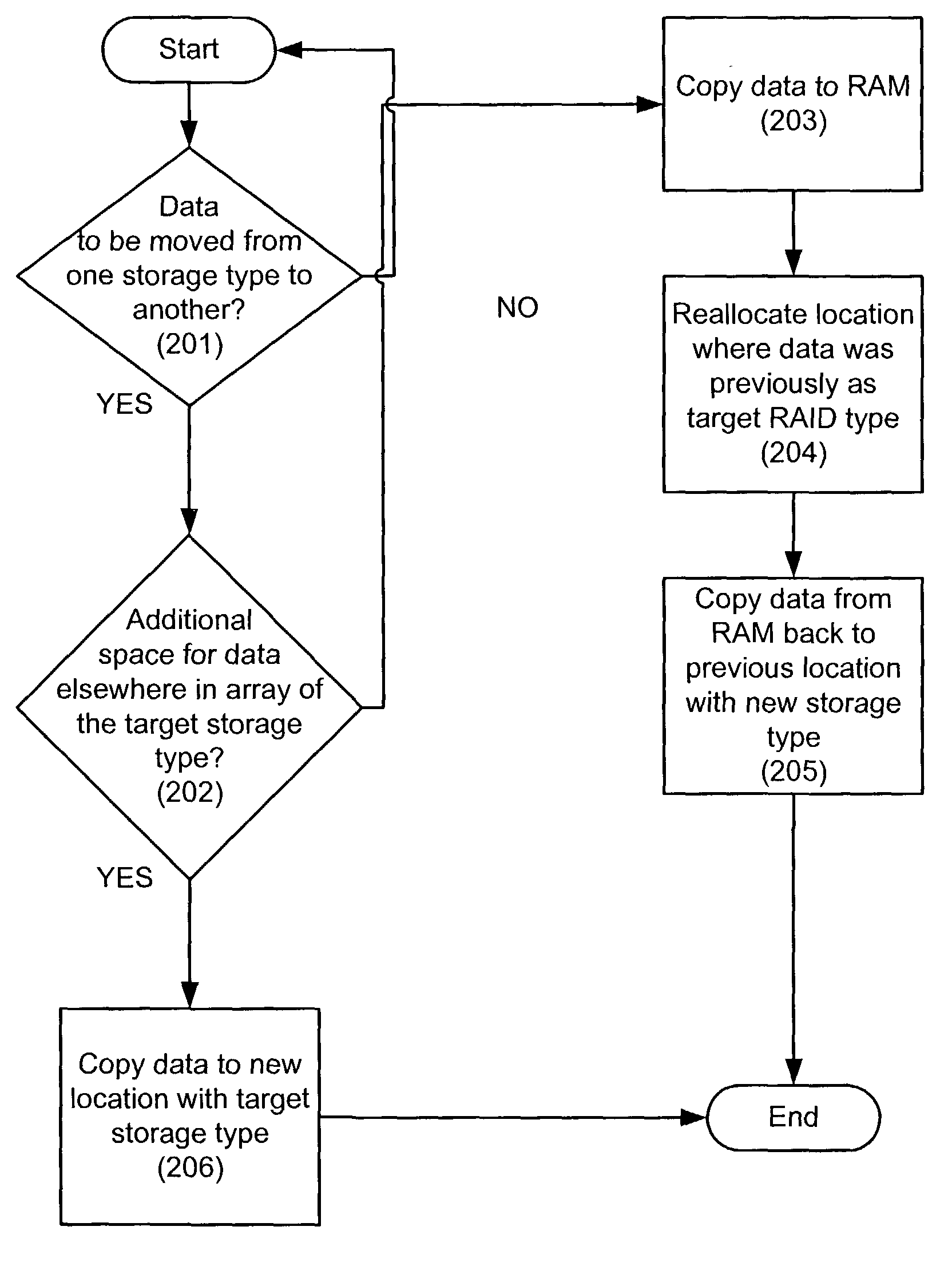
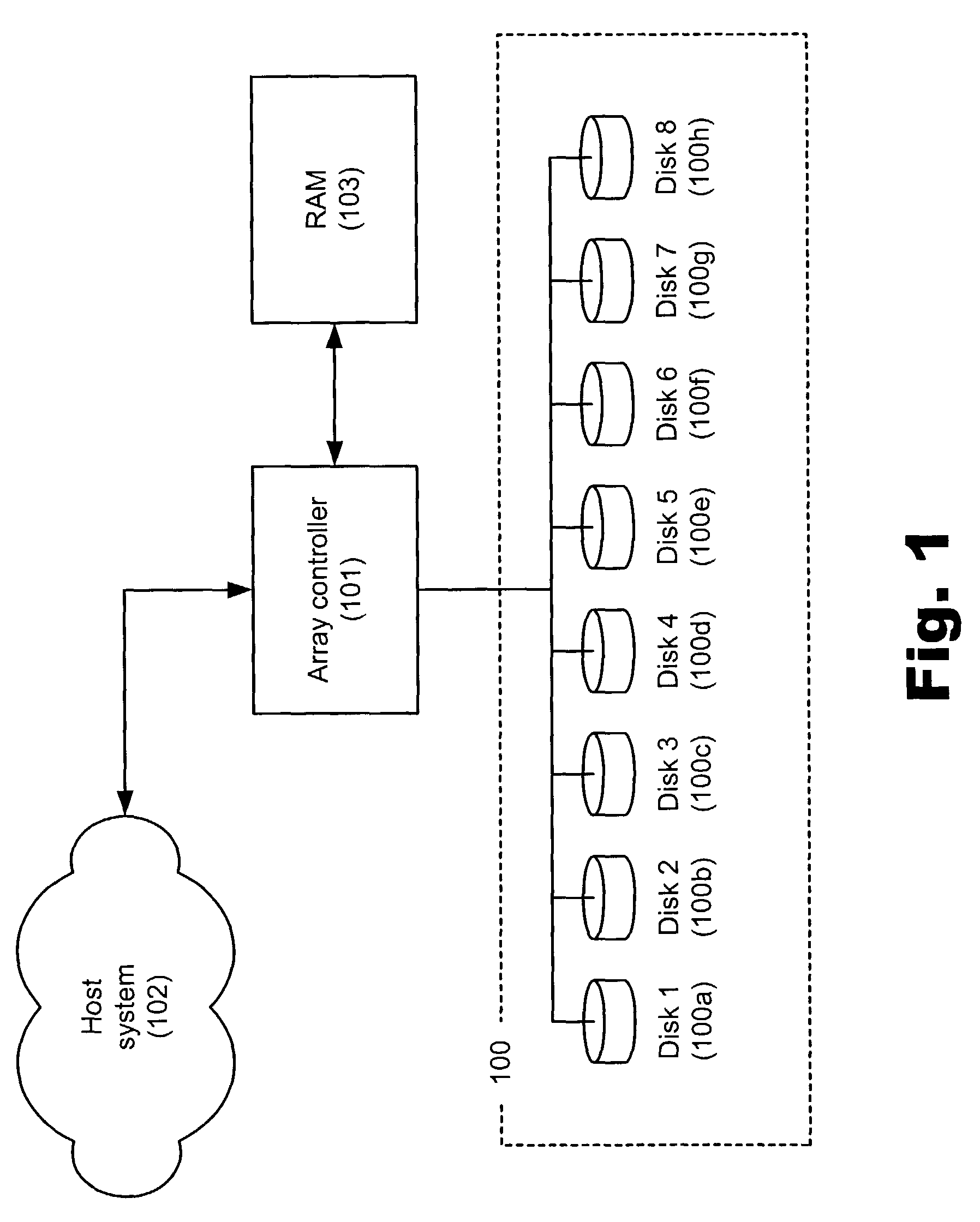
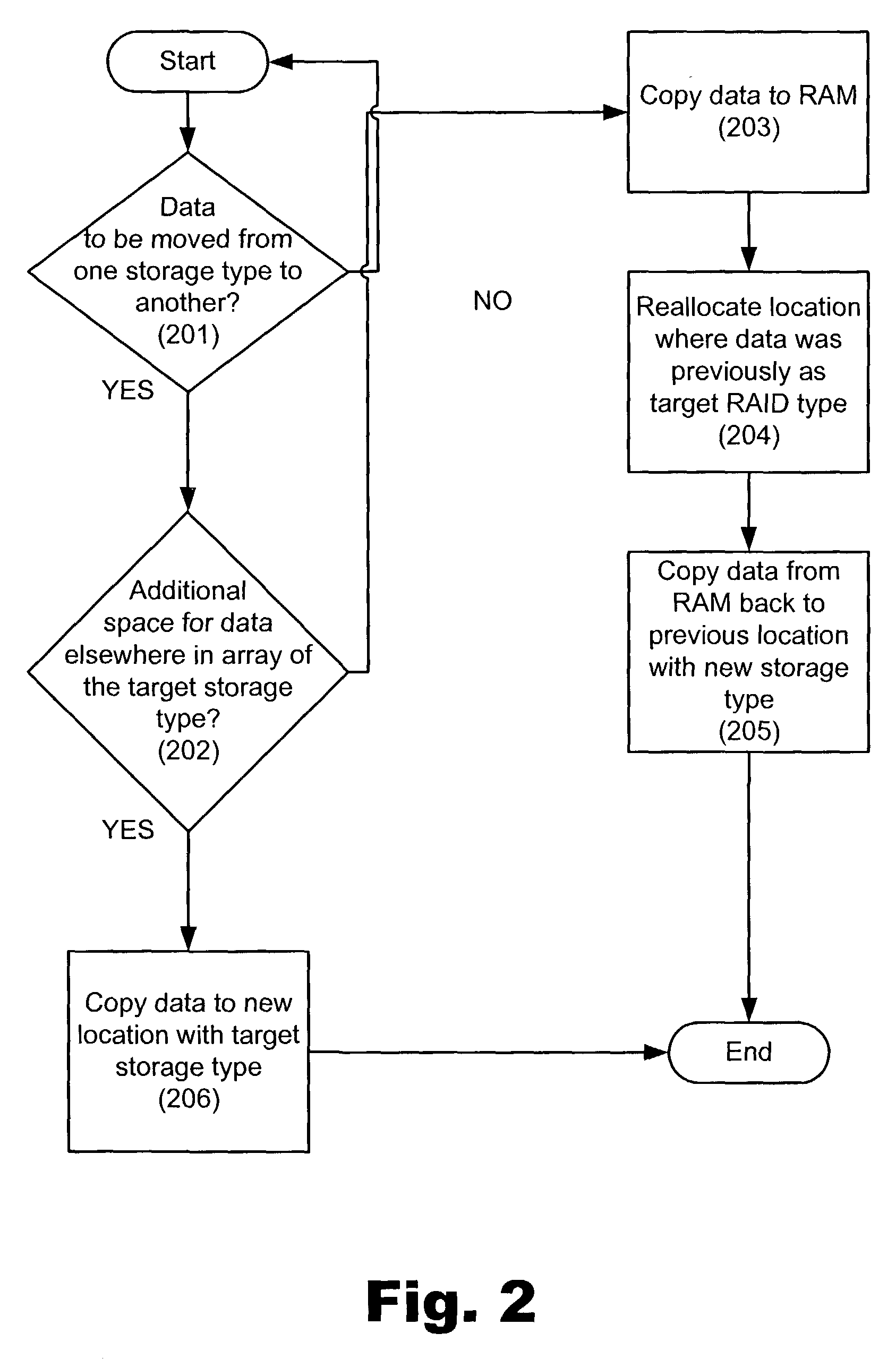
Manipulating data in a data storage device using an auxiliary memory device
ActiveUS7383379B2Balance performanceInput/output to record carriersMemory systemsAuxiliary memoryDisk array
A data storage device having, for example, a disk array comprising a plurality of independent disks, an array controller for controlling the array and an auxiliary memory device connected to the disk array and array controller for temporarily storing data being moved within the array or being changed from a first data storage type to a second data storage type within the array.
Owner:HTC CORP
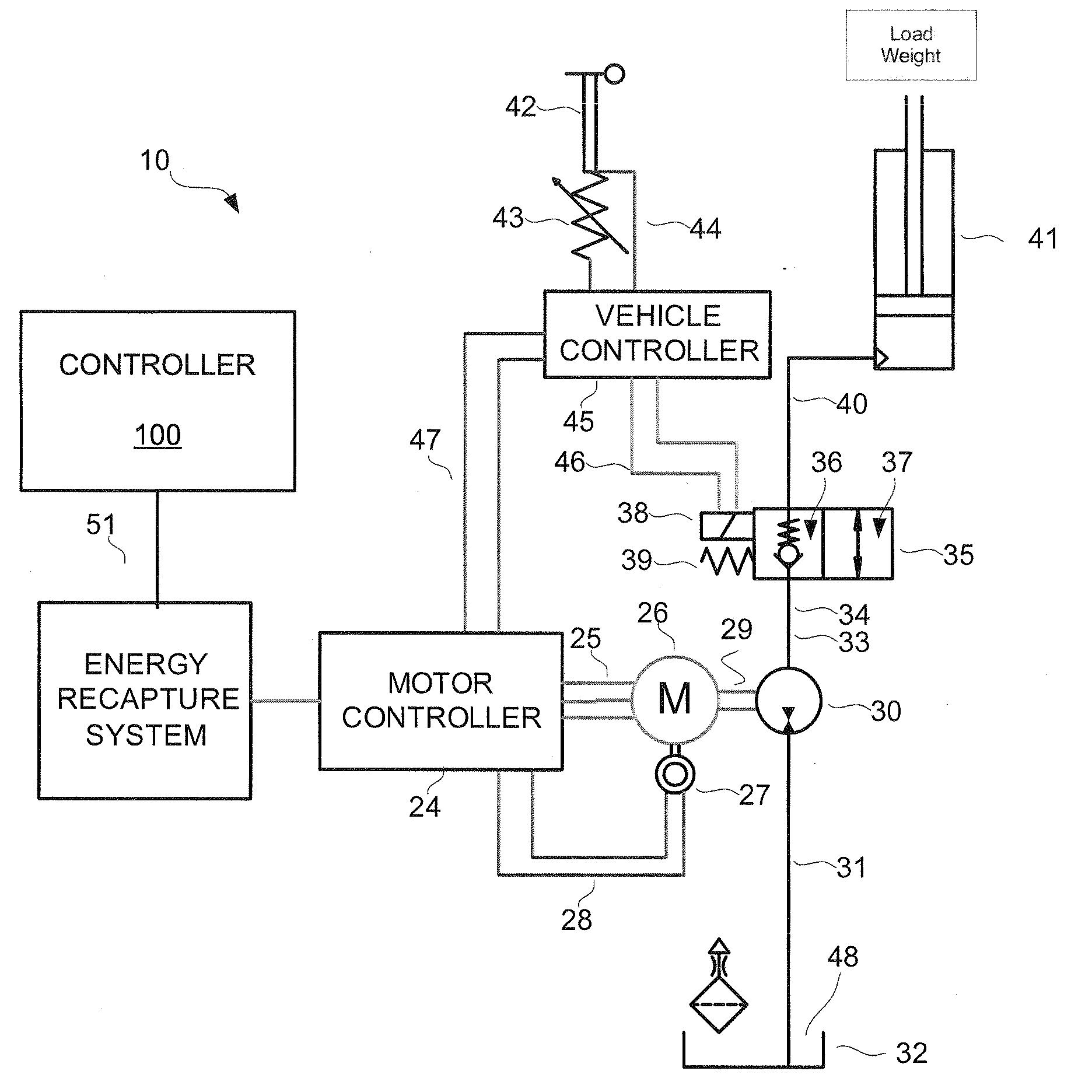
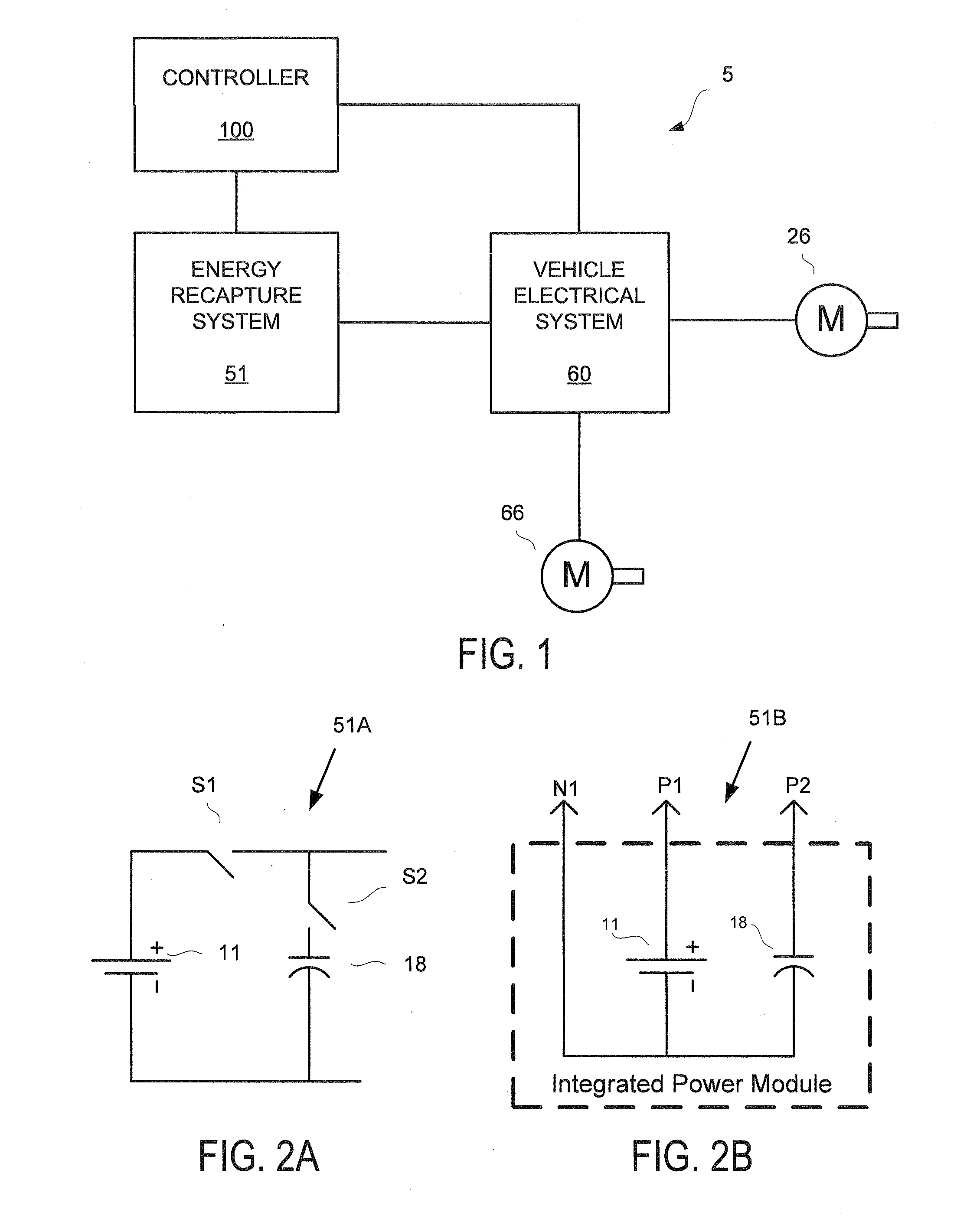
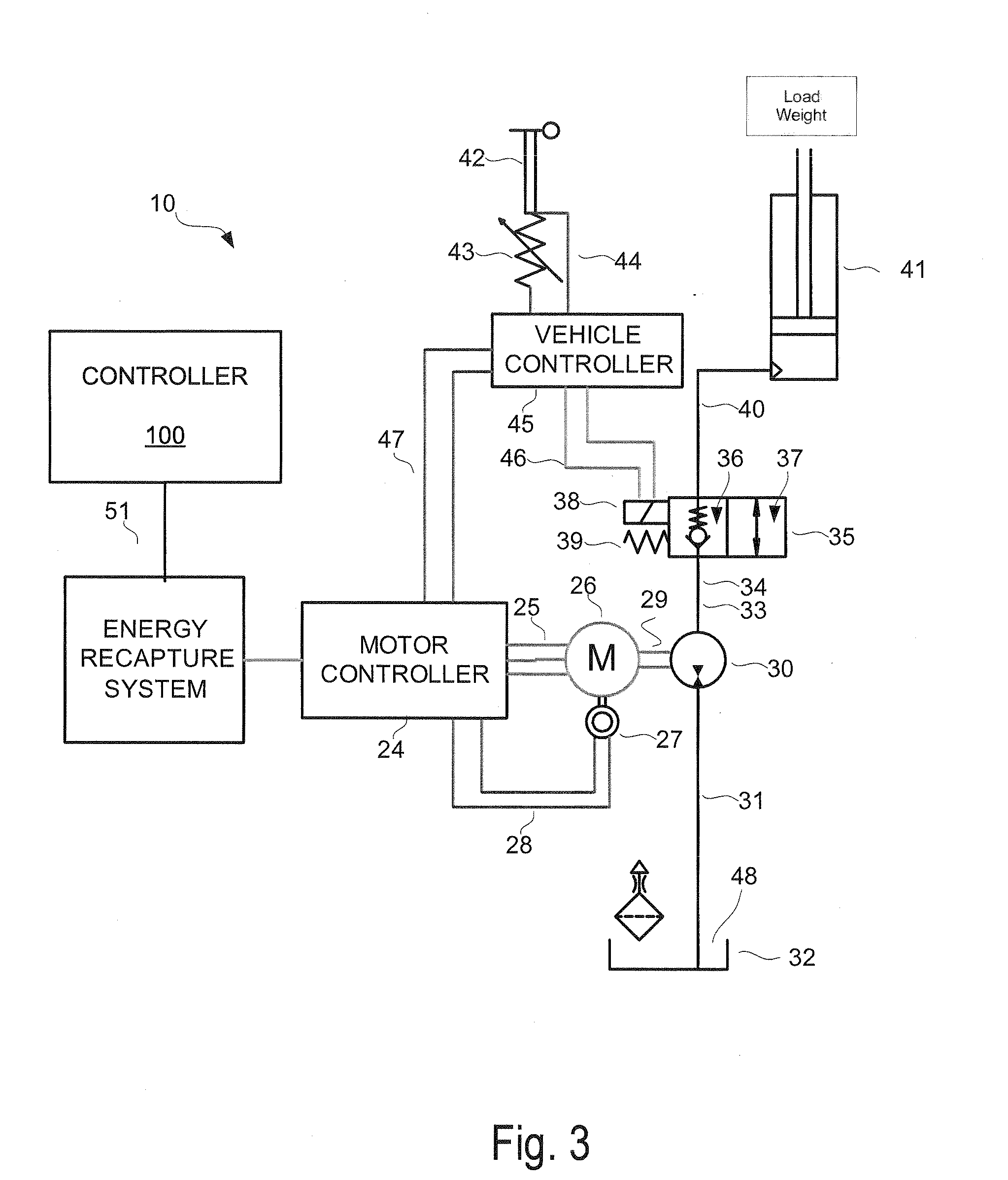
Energy recapture for an industrial vehicle
ActiveUS20080290842A1Readily apparentBatteries circuit arrangementsElectrodynamic brake systemsAuxiliary memoryEnergy recovery
A system for capturing regenerative energy includes a battery configured to provide power for a traction motor and other operations of a vehicle and a capacitor connected to the battery. An auxiliary motor is configured to operate as a generator during a regenerative energy operation. The system further includes a controller configured to direct the regenerative energy to the capacitor during the regenerative energy operation and discharge the capacitor to provide power to the traction motor or for the other operations of the vehicle.
Owner:HYSTER YALE GRP
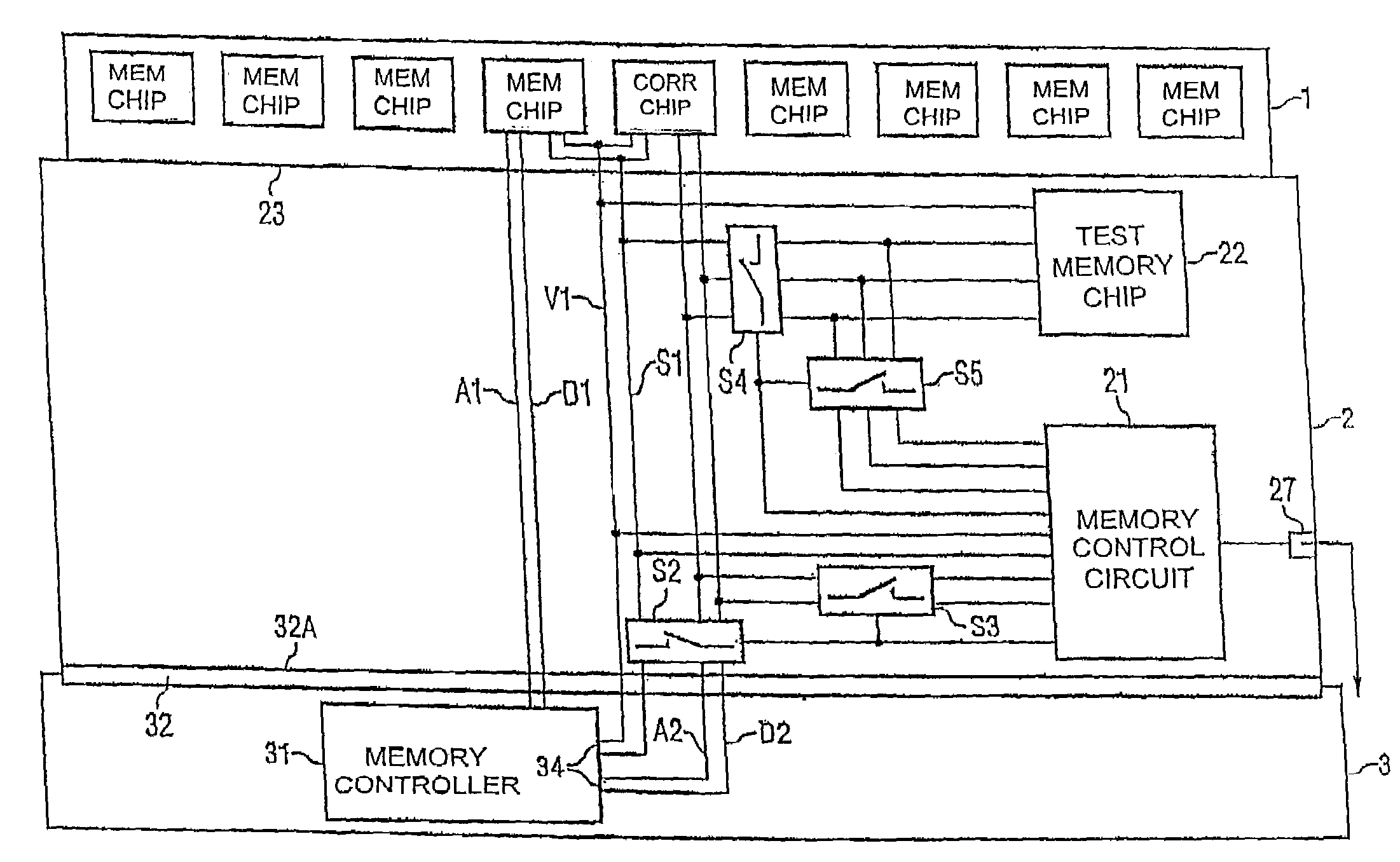
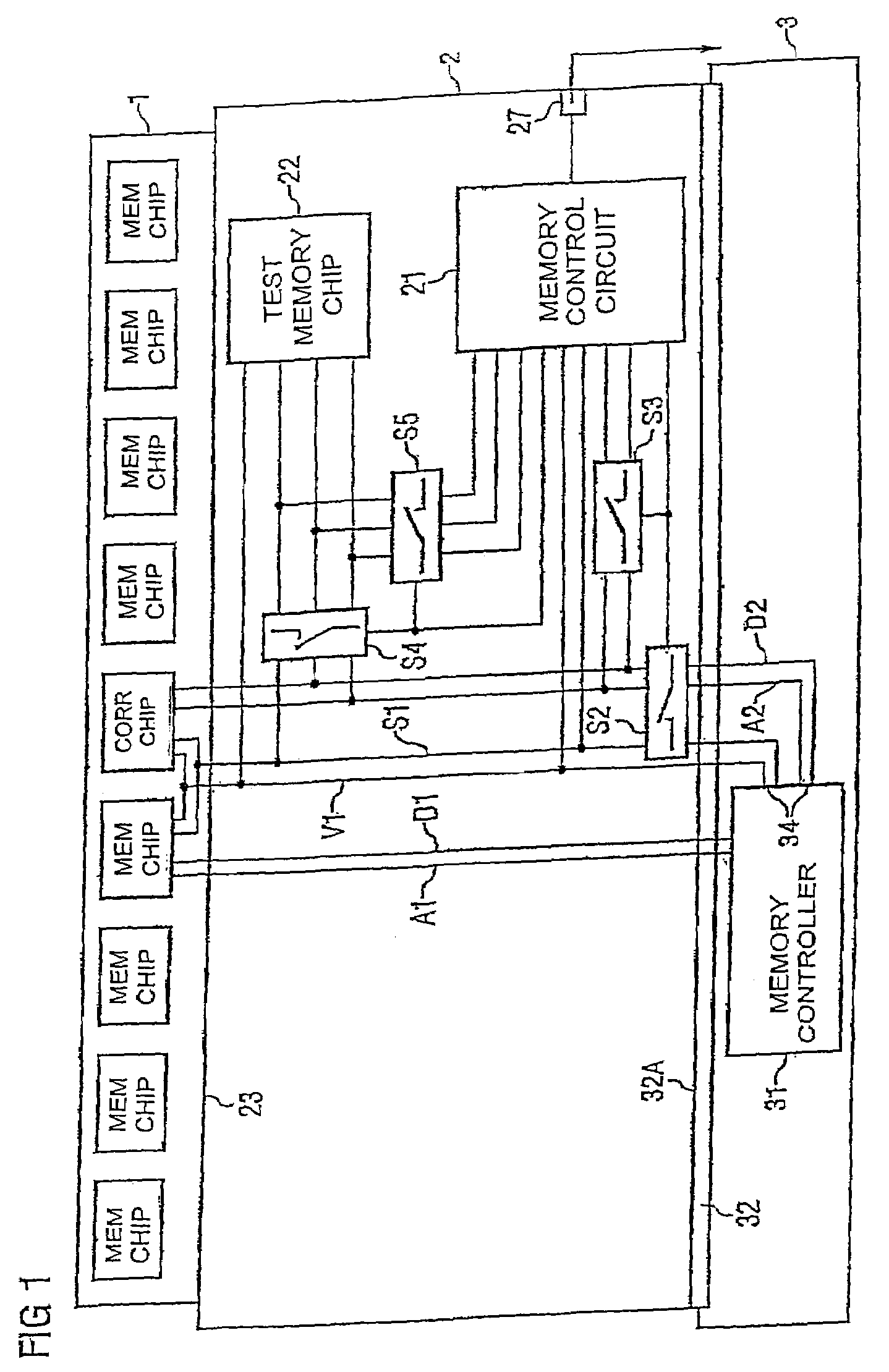
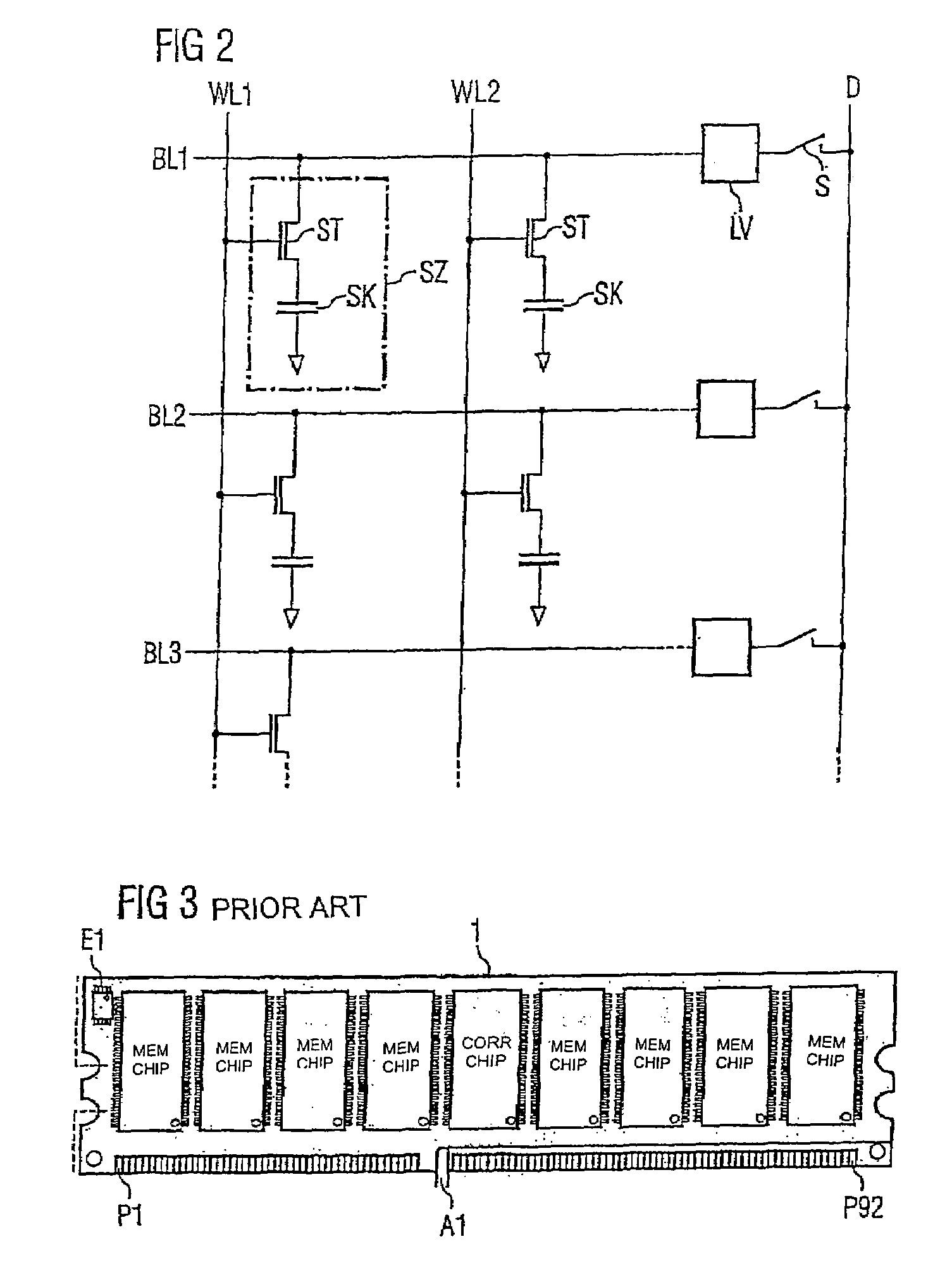
Method for testing a memory chip and test arrangement
InactiveUS7272757B2Accurate identificationQuick identificationElectronic circuit testingDigital storageMemory chipAuxiliary memory
A test arrangement with a test memory chip and a control device is provided. Error correction data are stored in the test memory chip with the aid of the control device. In the case of an error event, it is ascertained whether the error occurred on the error correction chip. If so, the memory controller compares the data stored in the error correction chip with the data of the auxiliary memory. The address of the error correction chip can be deduced from the address of the auxiliary memory, thereby enabling unambiguous addressing of a defective memory cell of the error correction chip.
Owner:POLARIS INNOVATIONS LTD
Auxiliary method and auxiliary system of intelligent refrigerator
ActiveCN104361041AImprove usabilityImprove practicalityDomestic cooling apparatusLighting and heating apparatusNetwork connectionAuxiliary memory
The invention discloses an auxiliary method of an intelligent refrigerator. The auxiliary method can be used in food material management, recipe recommendation, purchase assistance, and the like. The invention further discloses an auxiliary system of the intelligent refrigerator. The auxiliary system consists of embedded equipment, a server and mobile equipment, wherein the embedded equipment is embedded into the outer side of a refrigerator door. In the embedded equipment, food material information is written into the system in modes of manual operation, bar codes and camera acquisition. The embedded equipment is connected with the server through a network and is used for performing high-precision recognition and other processing; the mobile equipment is interconnected with the server and is used for acquiring system information; system auxiliary information, that is, shortage alert made according to the number of the food materials, is fed back to the embedded equipment and the mobile equipment. The auxiliary method has the advantages of low cost, low power consumption, high use easiness and the like.
Owner:SOUTH CHINA UNIV OF TECH
Method and system of clock with adaptive cache replacement and temporal filtering
InactiveUS20060069876A1Amenable to implementationImprove performanceMemory architecture accessing/allocationMemory systemsData retrievalParallel computing
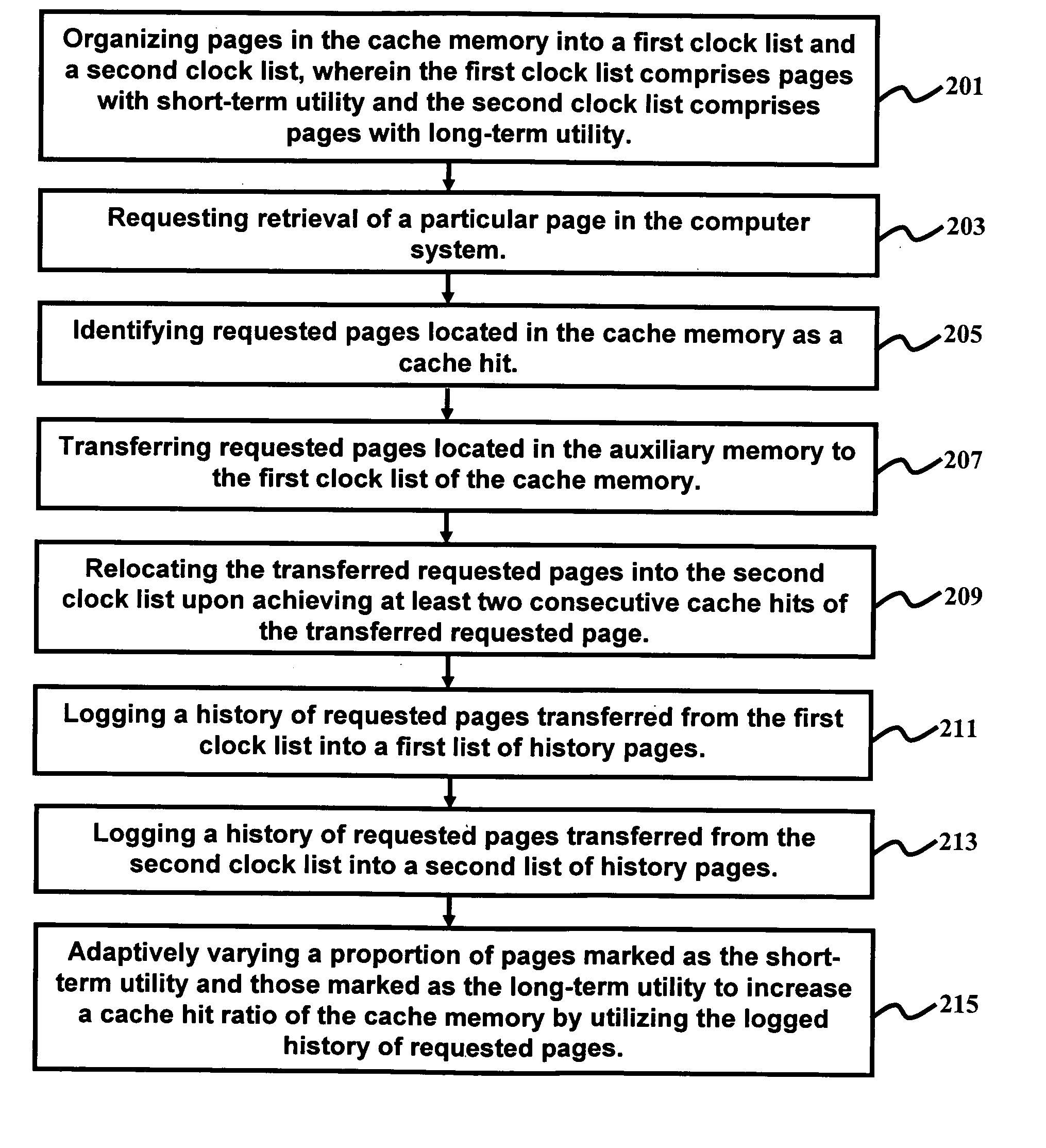
A method and system of managing data retrieval in a computer comprising a cache memory and auxiliary memory comprises organizing pages in the cache memory into a first and second clock list, wherein the first clock list comprises pages with short-term utility and the second clock list comprises pages with long-term utility; requesting retrieval of a particular page in the computer; identifying requested pages located in the cache memory as a cache hit; transferring requested pages located in the auxiliary memory to the first clock list; relocating the transferred requested pages into the second clock list upon achieving at least two consecutive cache hits of the transferred requested page; logging a history of pages evicted from the cache memory; and adaptively varying a proportion of pages marked as short and long-term utility to increase a cache hit ratio of the cache memory by utilizing the logged history of evicted pages.
Owner:IBM CORP
Methods and systems for providing predictive maintenance, preventative maintenance, and/or failure isolation in a tape storage subsystem
ActiveUS20050052772A1Input/output to record carriersFilamentary/web record carriersMagnetic tapeAuxiliary memory
A system and method of operating a storage system is provided. The storage system includes a tape cartridge having a magnetic tape medium and a tape drive for reading and writing data to the magnetic tape medium of the tape cartridge. Performance data associated with specific operating loci (e.g., bands, directions, tracks, segments, etc.) of the tape drive and tape medium are collected, analyzed, and stored, allowing for analysis and detection of trends over time. In one example, tape usage events are monitored and when they cross a threshold the system may remove particular tapes in a preventative maintenance approach to reduce system outage. Performance data is collected and analyzed with a portion of the performance data being saved to emulated medium auxiliary memory (EMAM) on the magnetic tape, and a portion of the of the performance data saved in non-volatile storage in the drive.
Owner:QUANTUM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com