Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
457 results about "System verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
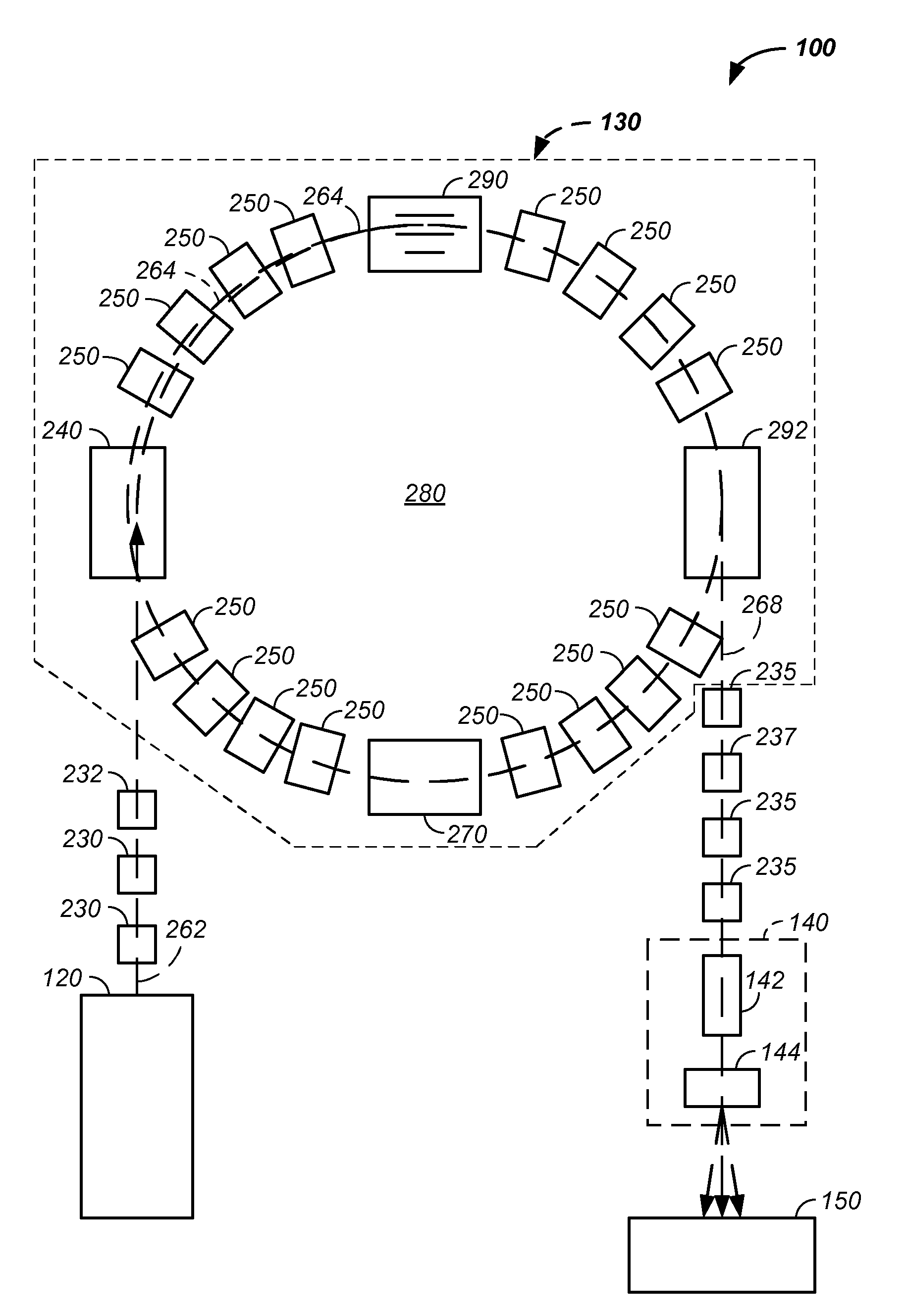
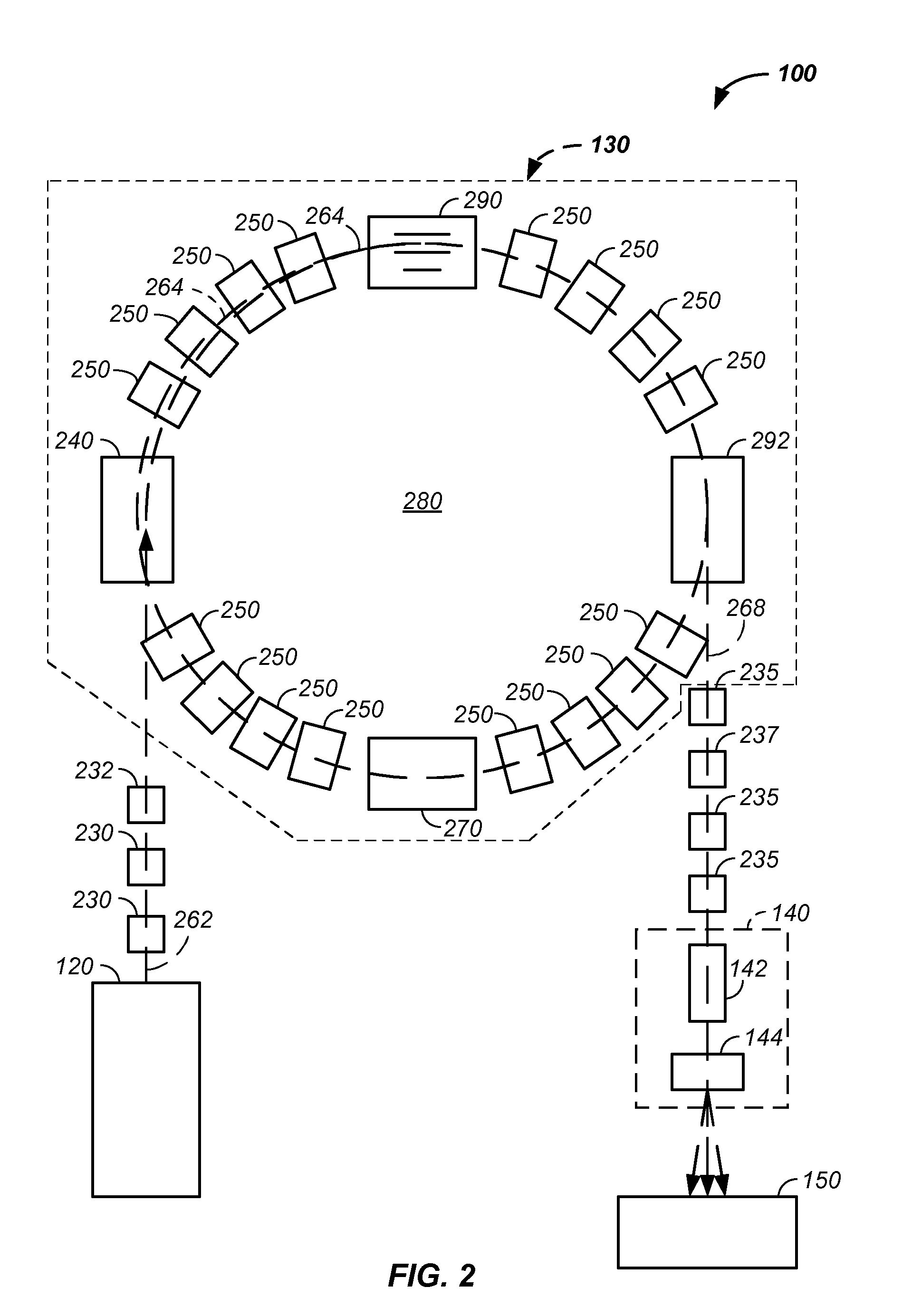
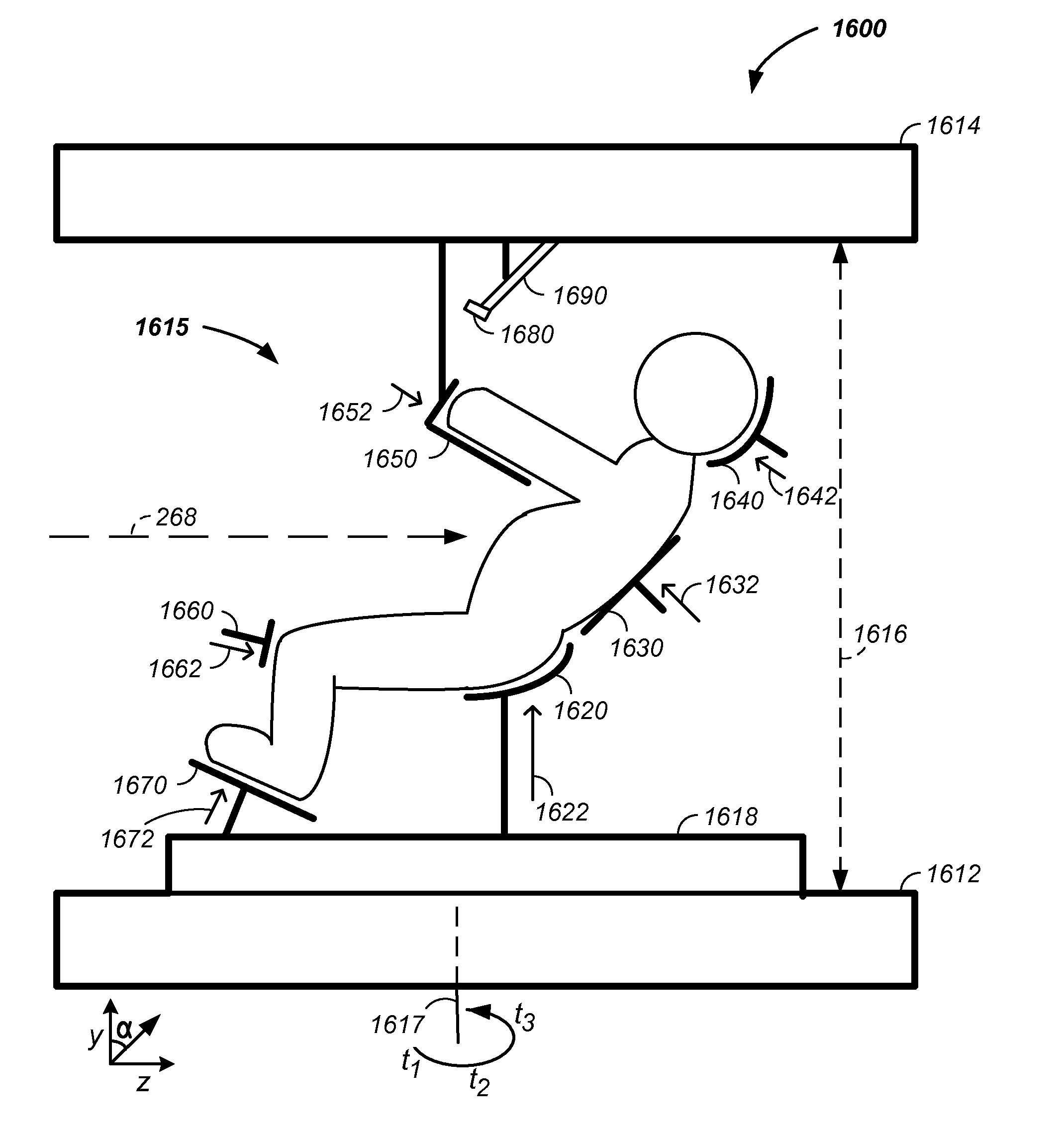
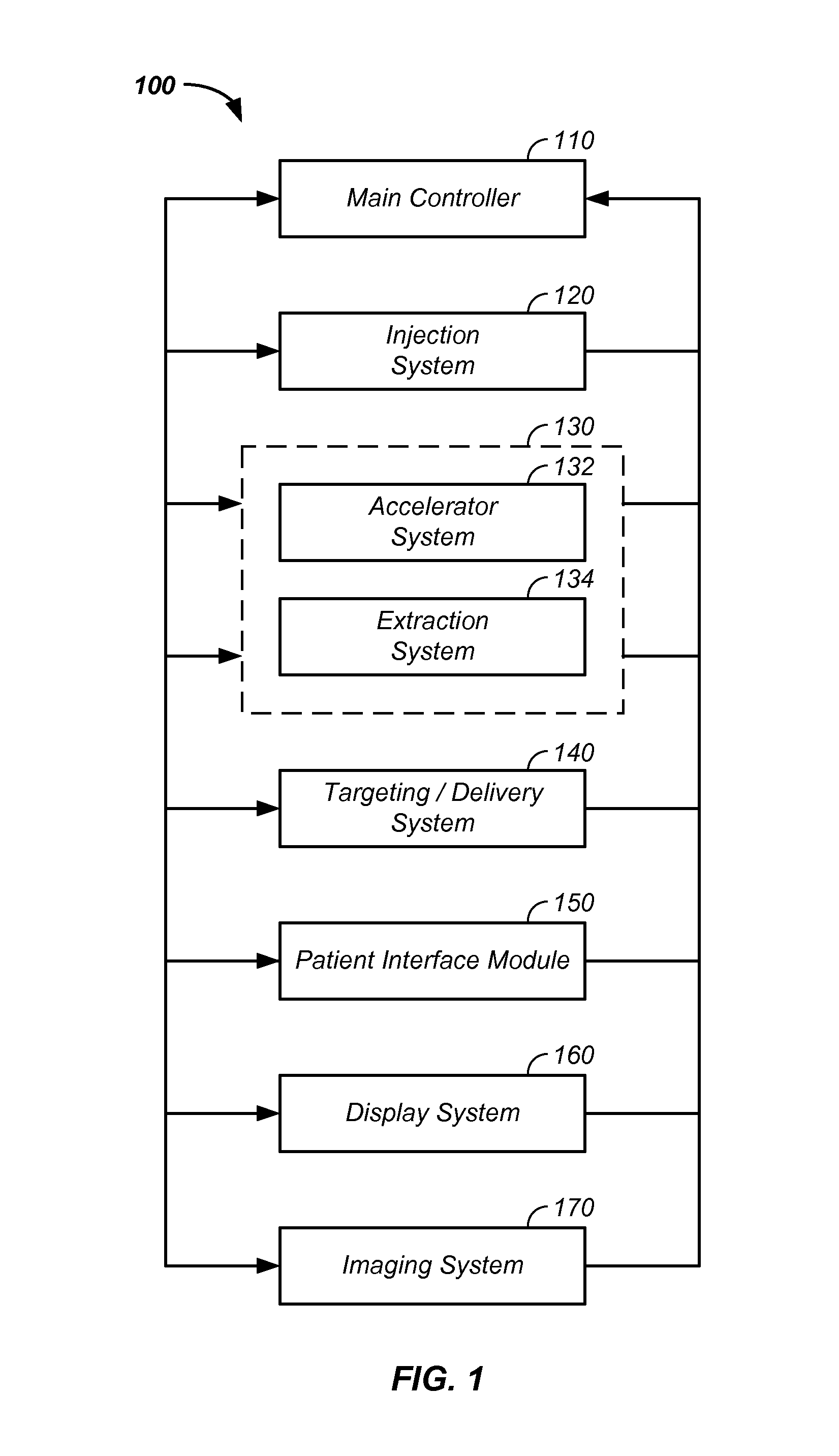
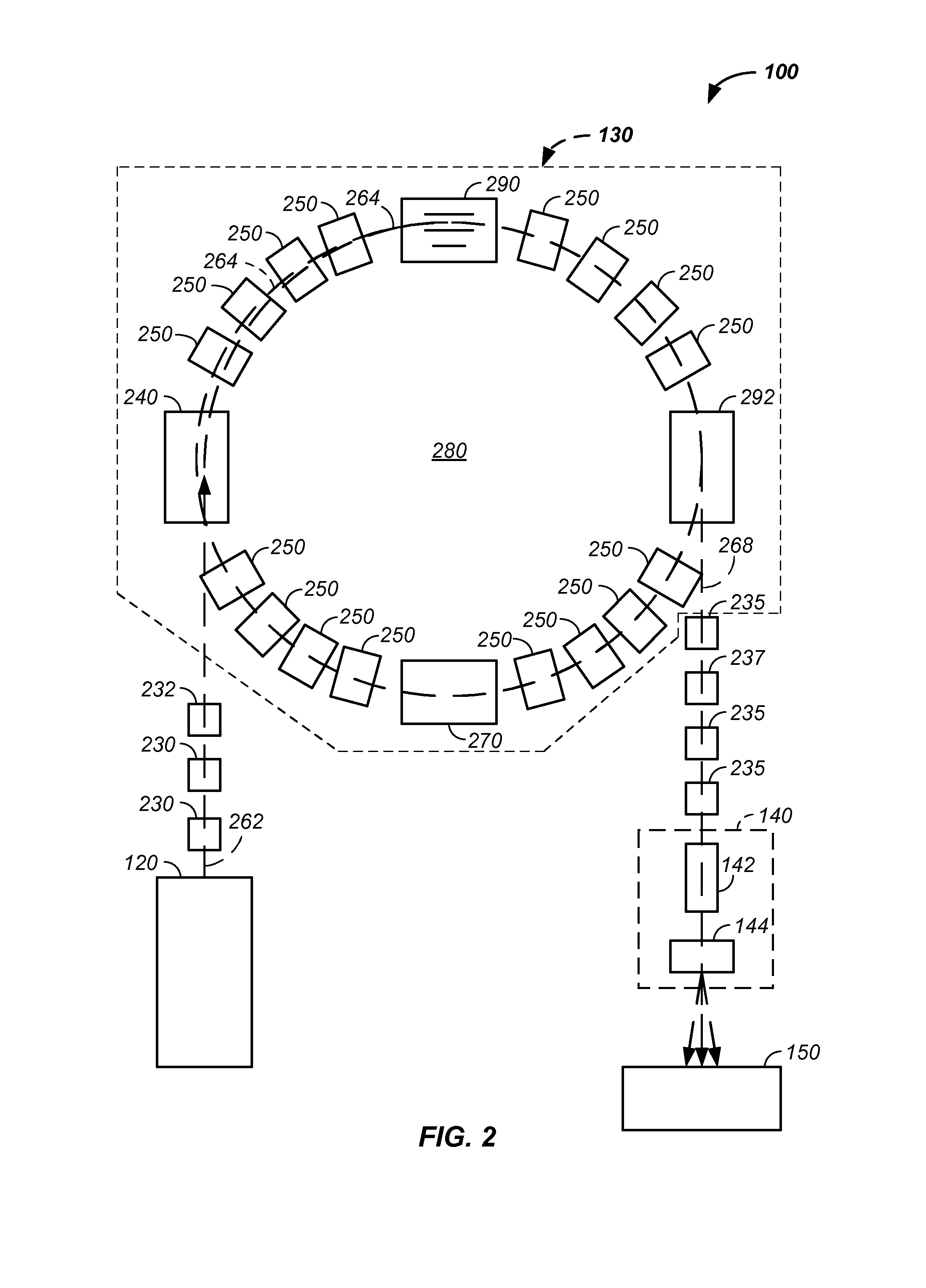
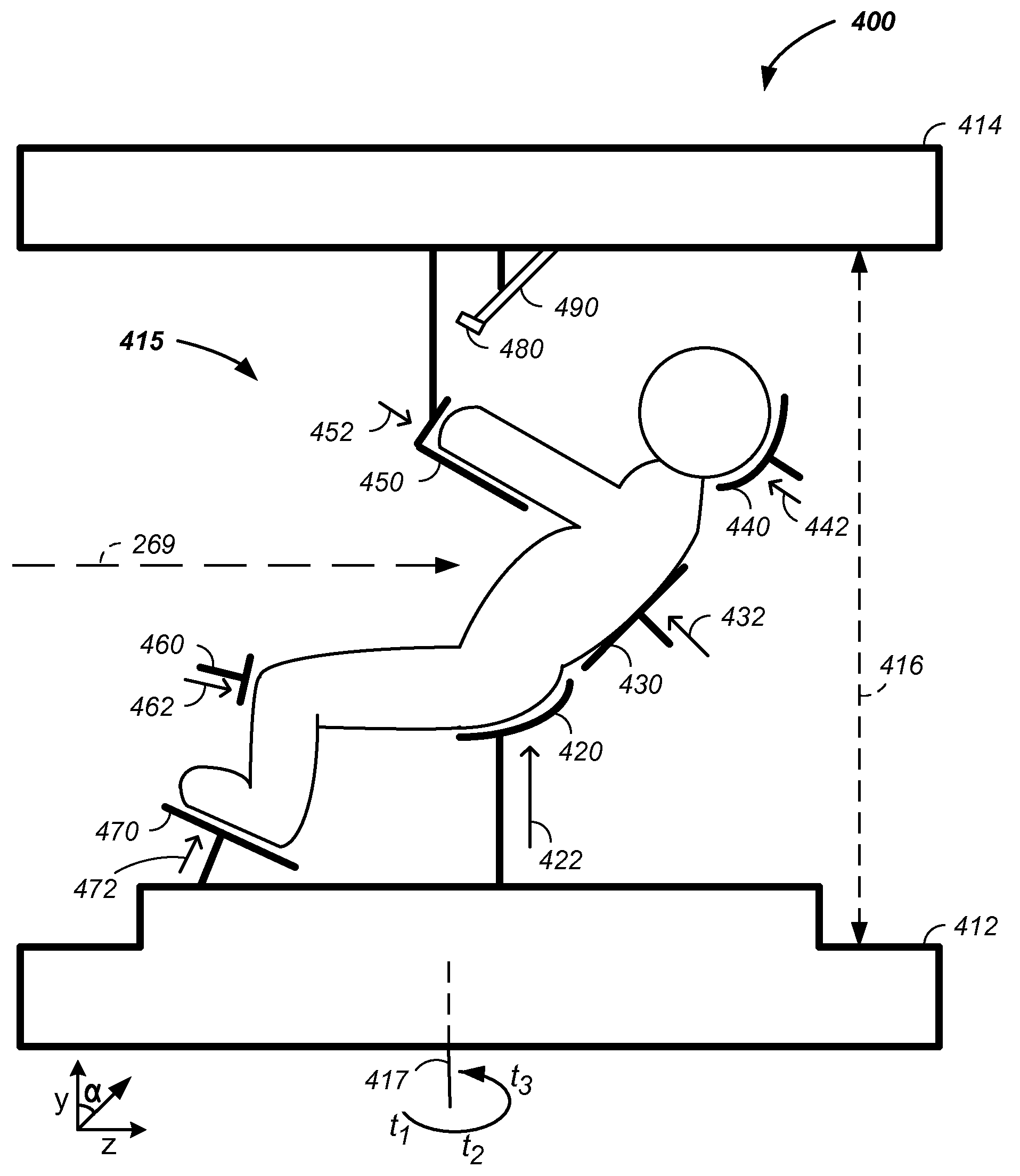
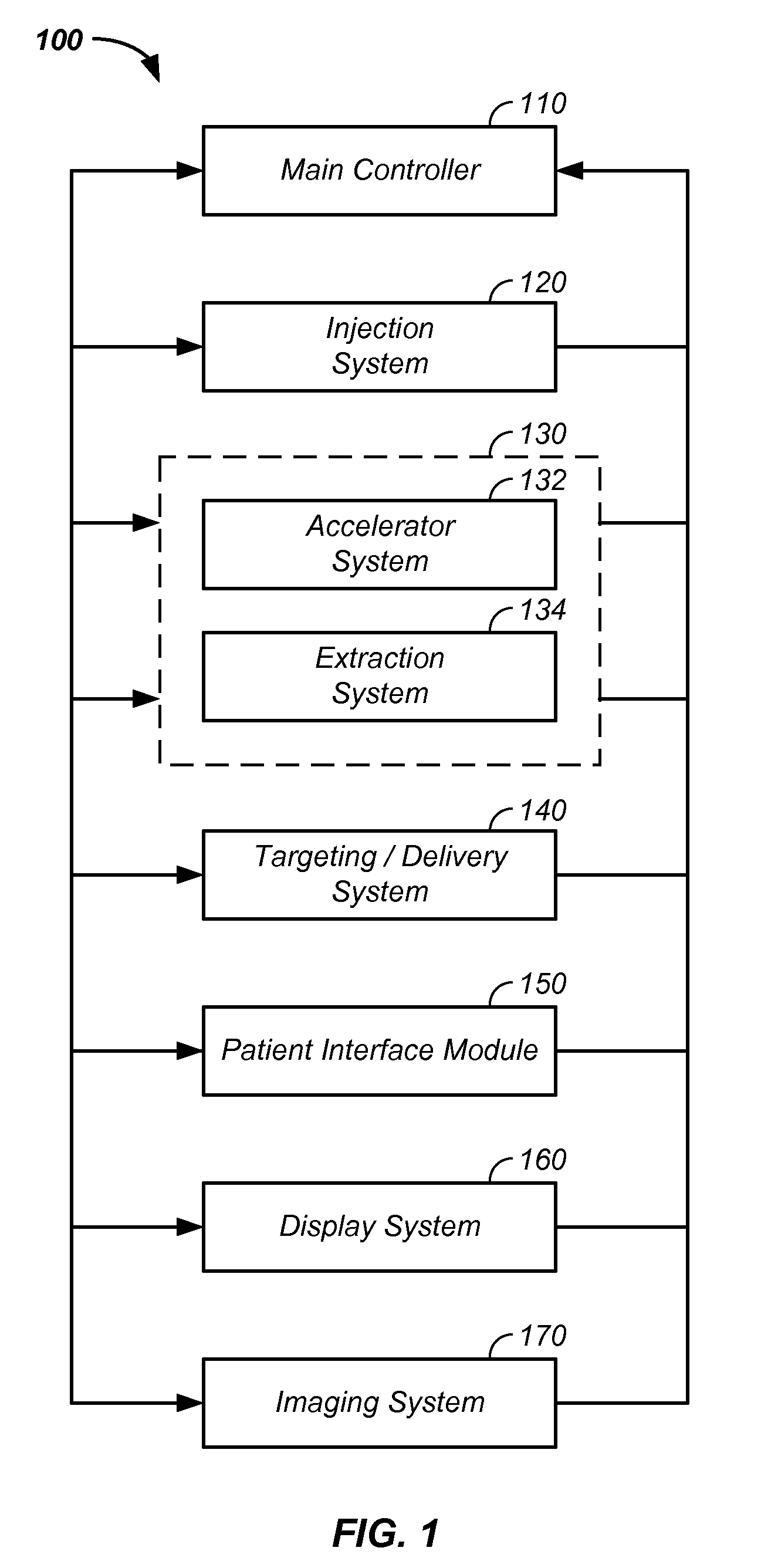
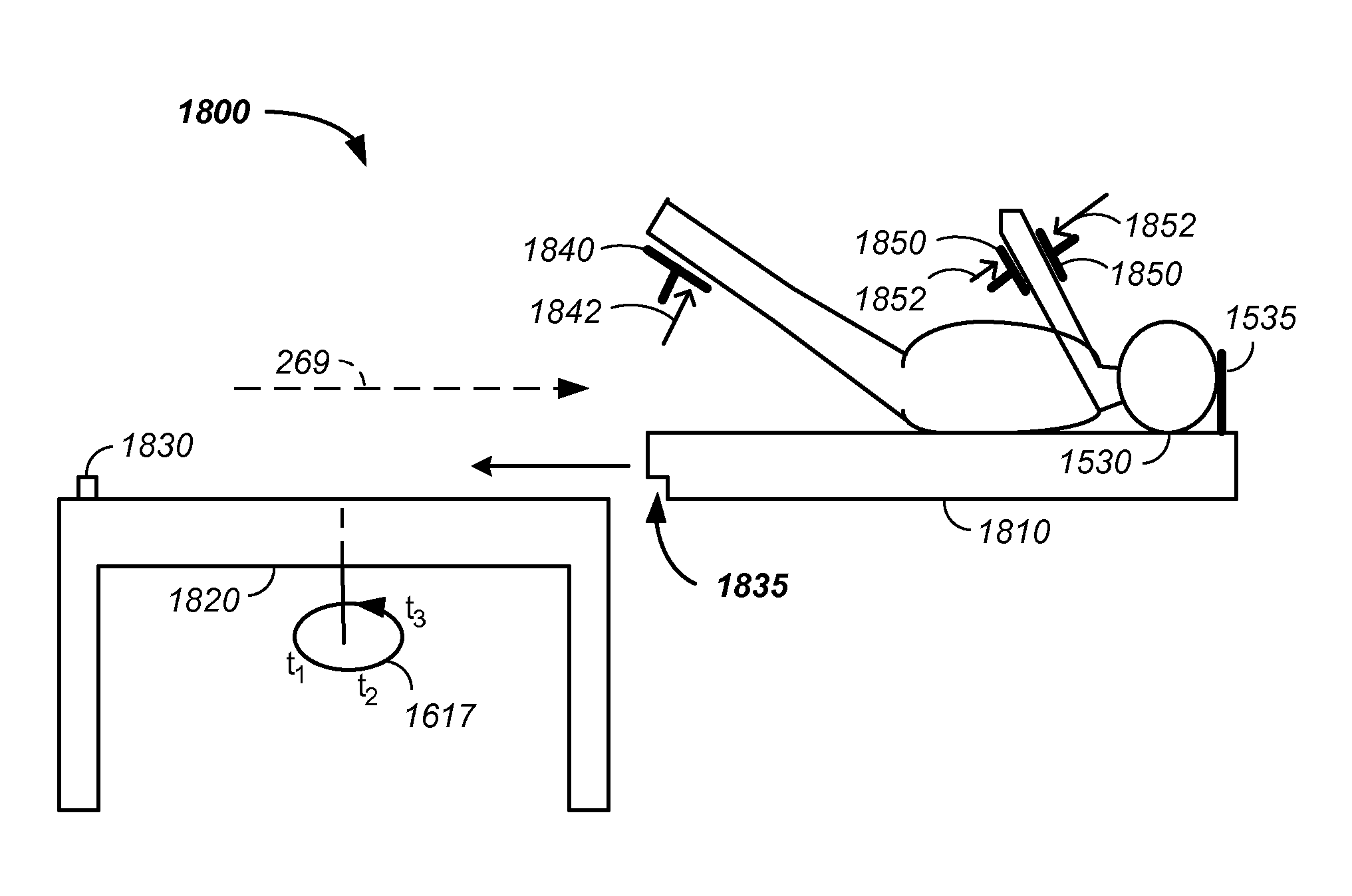
Charged particle cancer therapy and patient positioning method and apparatus
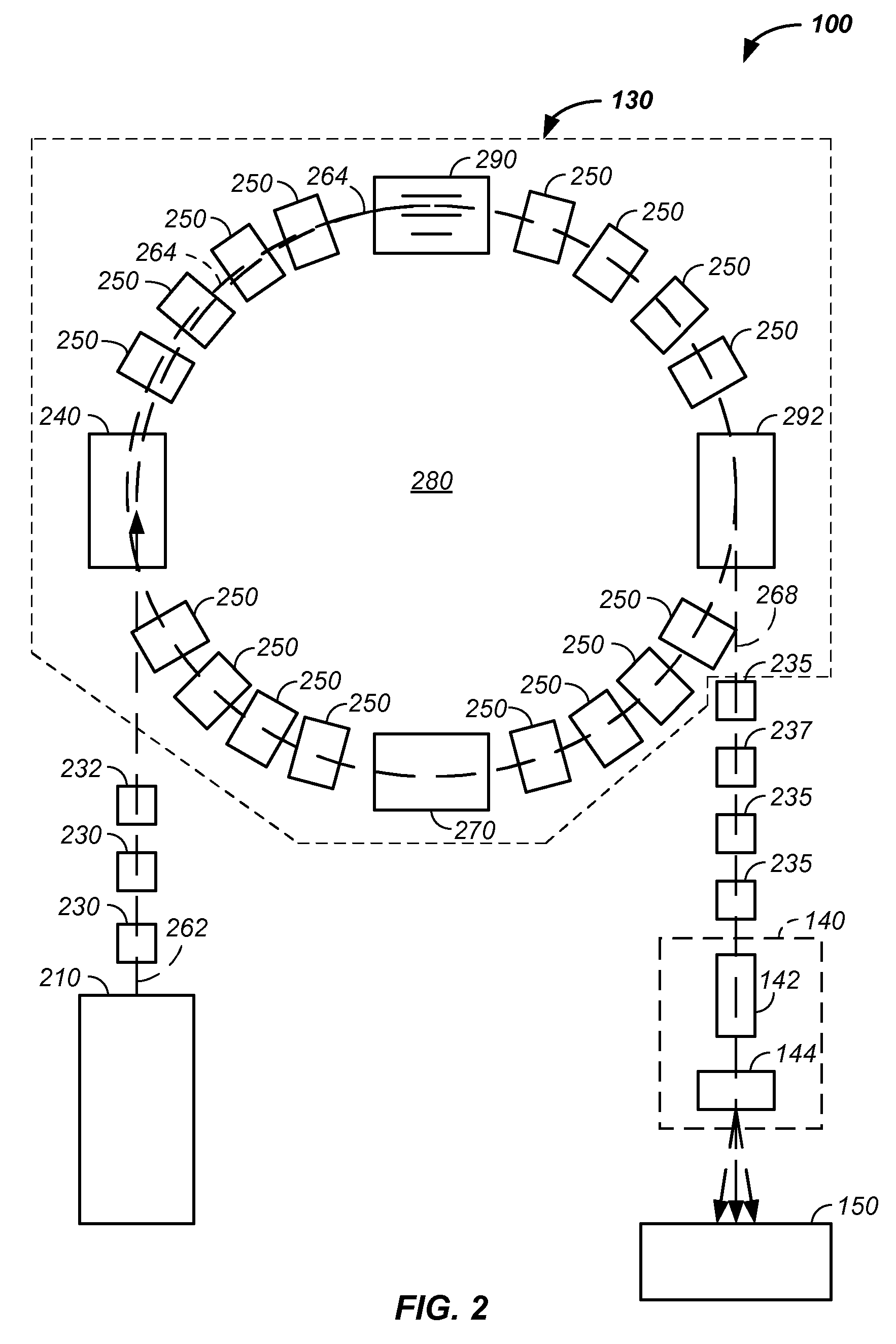
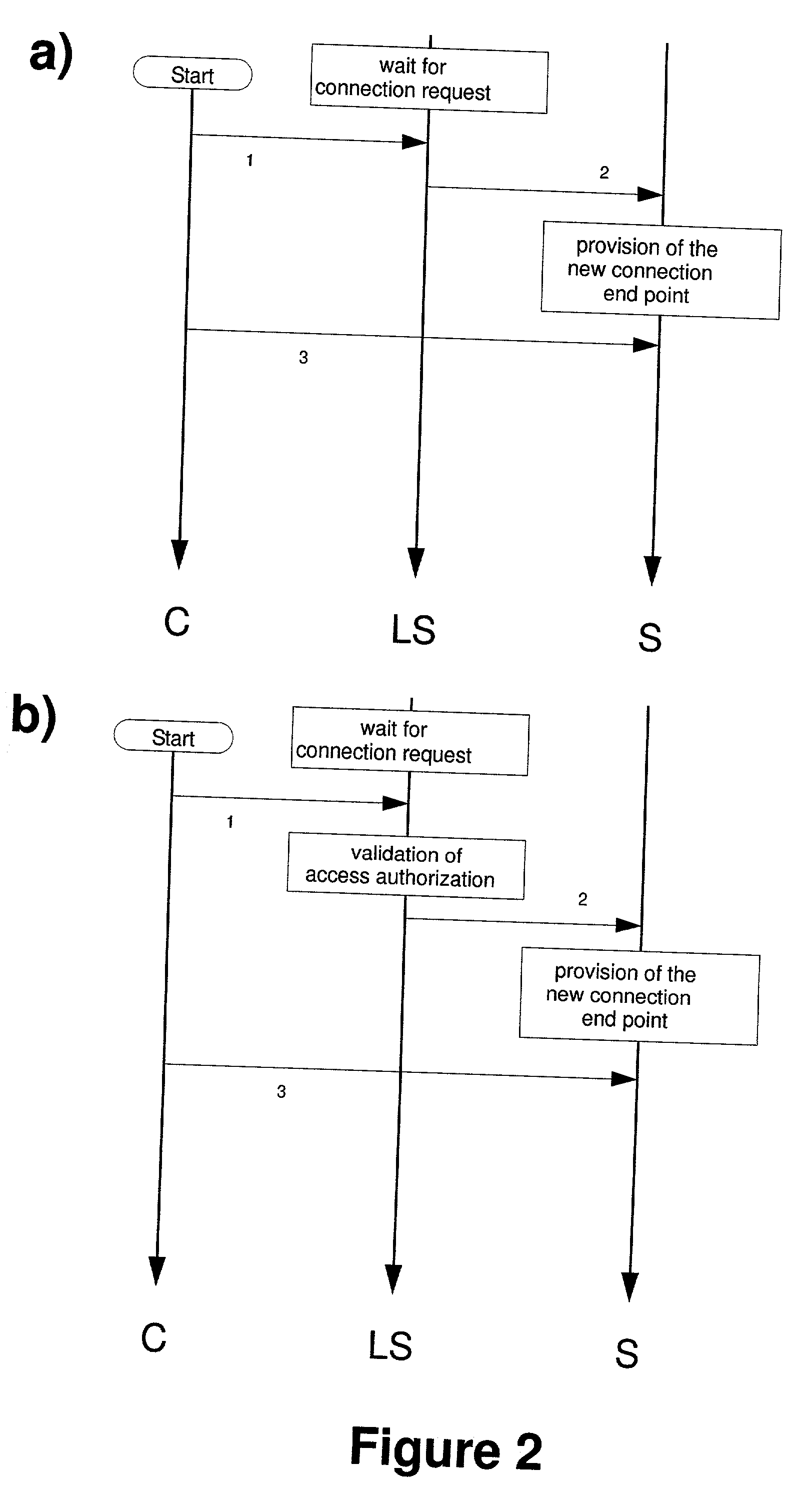
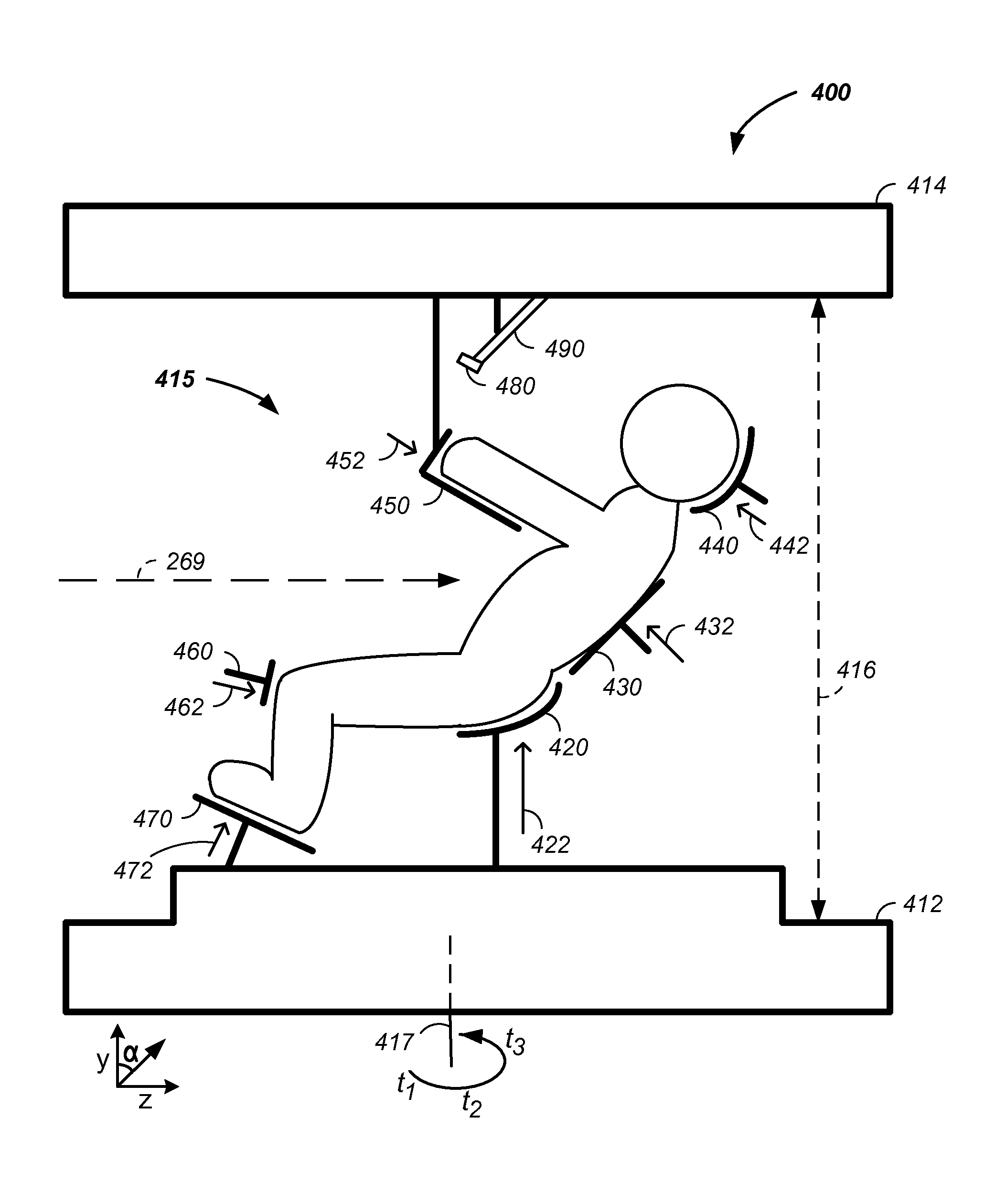
The invention comprises a laying, semi-vertical, or seated patient positioning, alignment, and / or control method and apparatus used in conjunction with multi-axis charged particle or proton beam radiation therapy of cancerous tumors. Patient positioning constraints are used to maintain the patient in a treatment position, including one or more of: a seat support, a back support, a head support, an arm support, a knee support, and a foot support. One or more of the positioning constraints are movable and / or under computer control for rapid positioning and / or immobilization of the patient. The system optionally uses an X-ray beam that lies in substantially the same path as a proton beam path of a particle beam cancer therapy system. The generated image is usable for: fine tuning body alignment relative to the proton beam path, to control the proton beam path to accurately and precisely target the tumor, and / or in system verification and validation.
Owner:BALAKIN ANDREY VLADIMIROVICH +1
Patient positioning method and apparatus used in conjunction with a charged particle cancer therapy system
InactiveUS20090314960A1Chemical conversion by chemical reactionX-ray/gamma-ray/particle-irradiation therapySystem verificationFoot supports
The invention comprises a semi-vertical or seated patient positioning, alignment, and / or control method and apparatus used in conjunction with multi-axis charged particle or proton beam radiation therapy of cancerous tumors. Patient positioning constraints are used to maintain the patient in a treatment position, including one or more of: a seat support, a back support, a head support, an arm support, a knee support, and a foot support. One or more of the positioning constraints are movable and / or under computer control for rapid positioning and / or immobilization of the patient. The system optionally uses an X-ray beam that lies in substantially the same path as a proton beam path of a particle beam cancer therapy system. The generated image is usable for: fine tuning body alignment relative to the proton beam path, to control the proton beam path to accurately and precisely target the tumor, and / or in system verification and validation.
Owner:BALAKIN VLADIMIR
Semi-vertical positioning method and apparatus used in conjunction with a charged particle cancer therapy system
The invention comprises a semi-vertical patient positioning, alignment, and / or control method and apparatus used in conjunction with charged particle or proton beam radiation therapy of cancerous tumors. Patient positioning constraints are used to maintain the patient in a treatment position, including one or more of: a seat support, a back support, a head support, an arm support, a knee support, and a foot support. One or more of the positioning constraints are movable and / or under computer control for rapid positioning and / or immobilization of the patient. The system optionally uses an X-ray beam that lies in substantially the same path as a proton beam path of a particle beam cancer therapy system. The generated image is usable for: fine tuning body alignment relative to the proton beam path, to control the proton beam path to accurately and precisely target the tumor, and / or in system verification and validation.
Owner:BALAKIN ANDREY VLADIMIROVICH +1
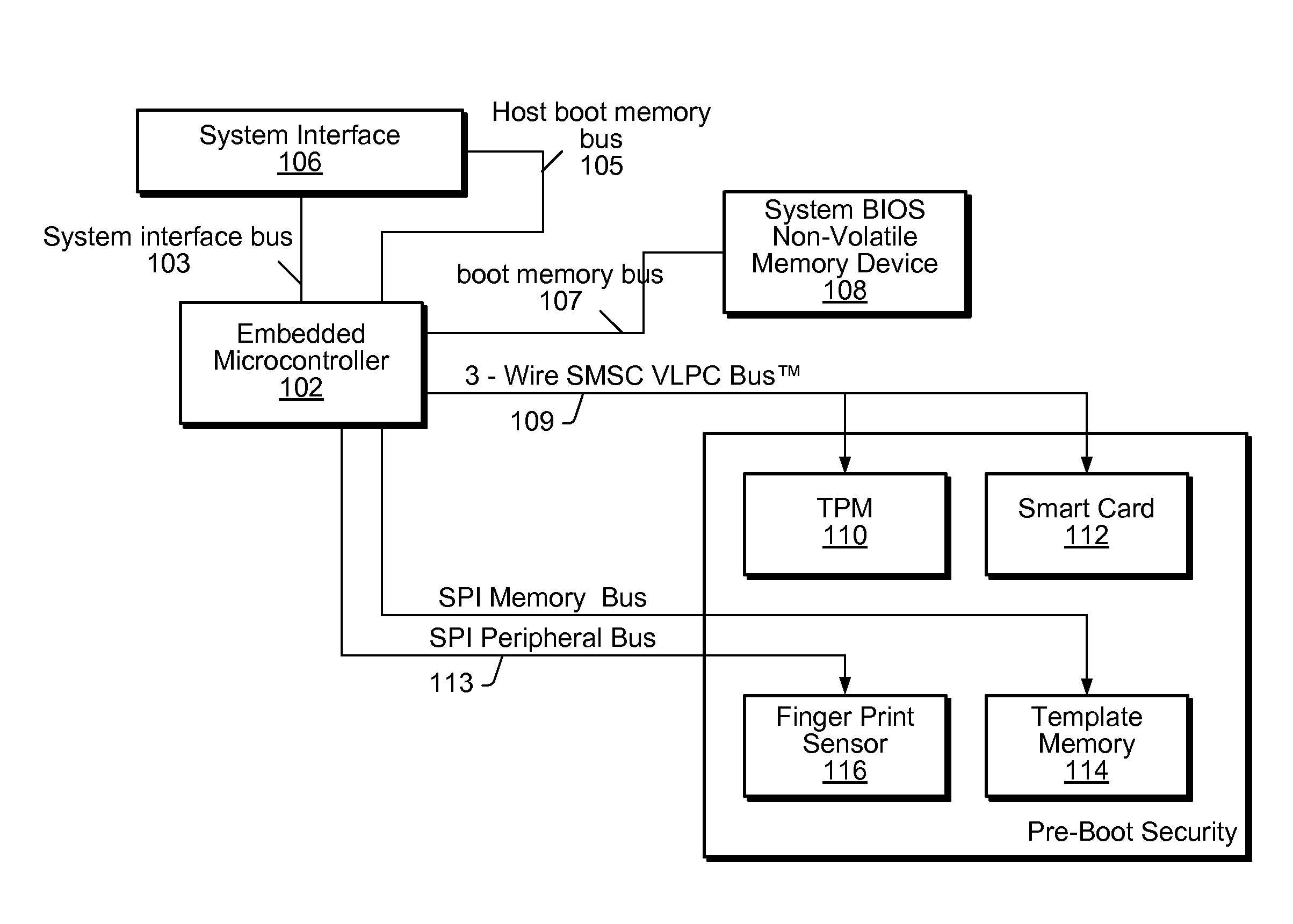
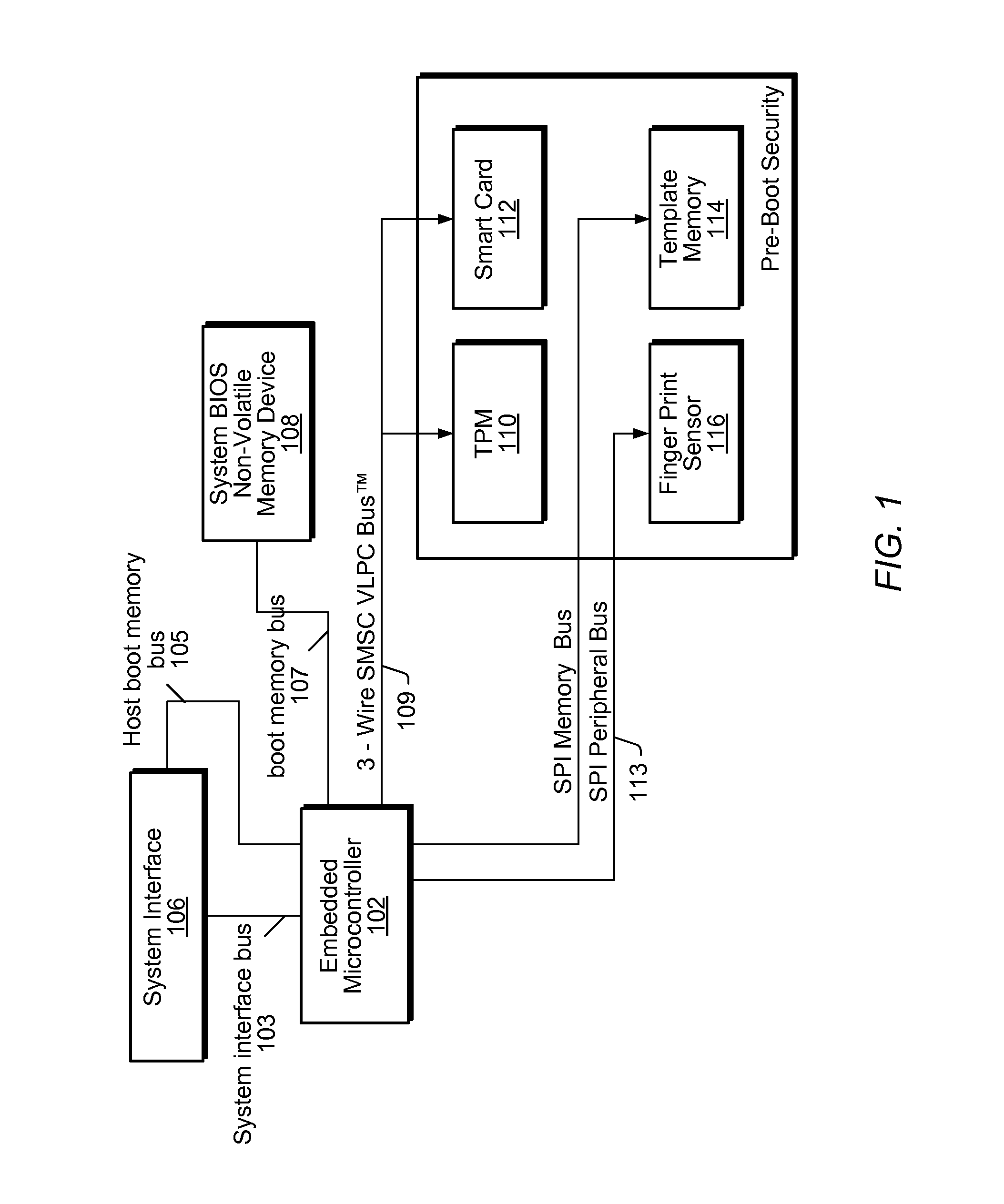
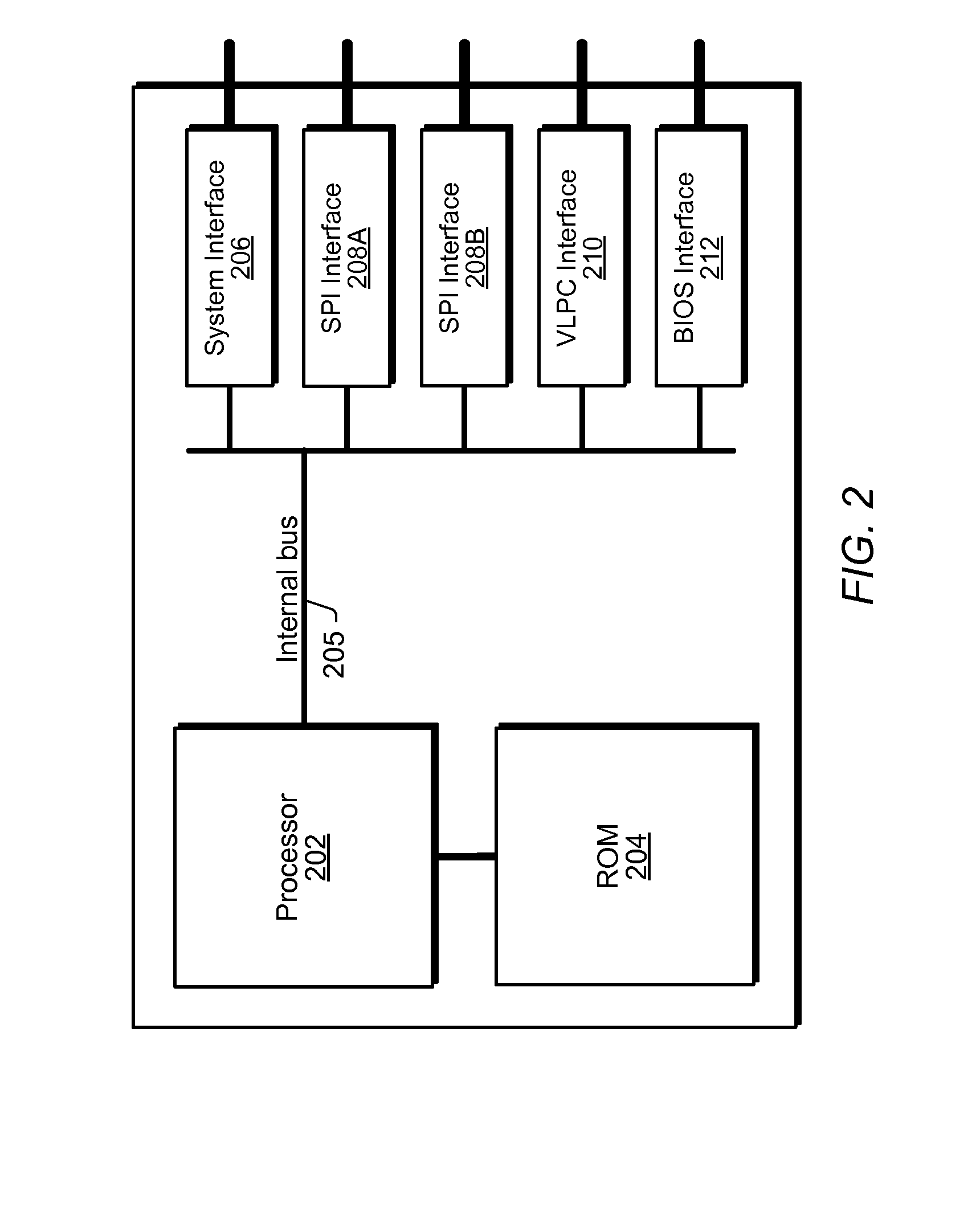
Enhancing Security of a System Via Access by an Embedded Controller to A Secure Storage Device
ActiveUS20090327678A1Improve securityVolume/mass flow measurementAnalogue secracy/subscription systemsMicrocontrollerSystem verification
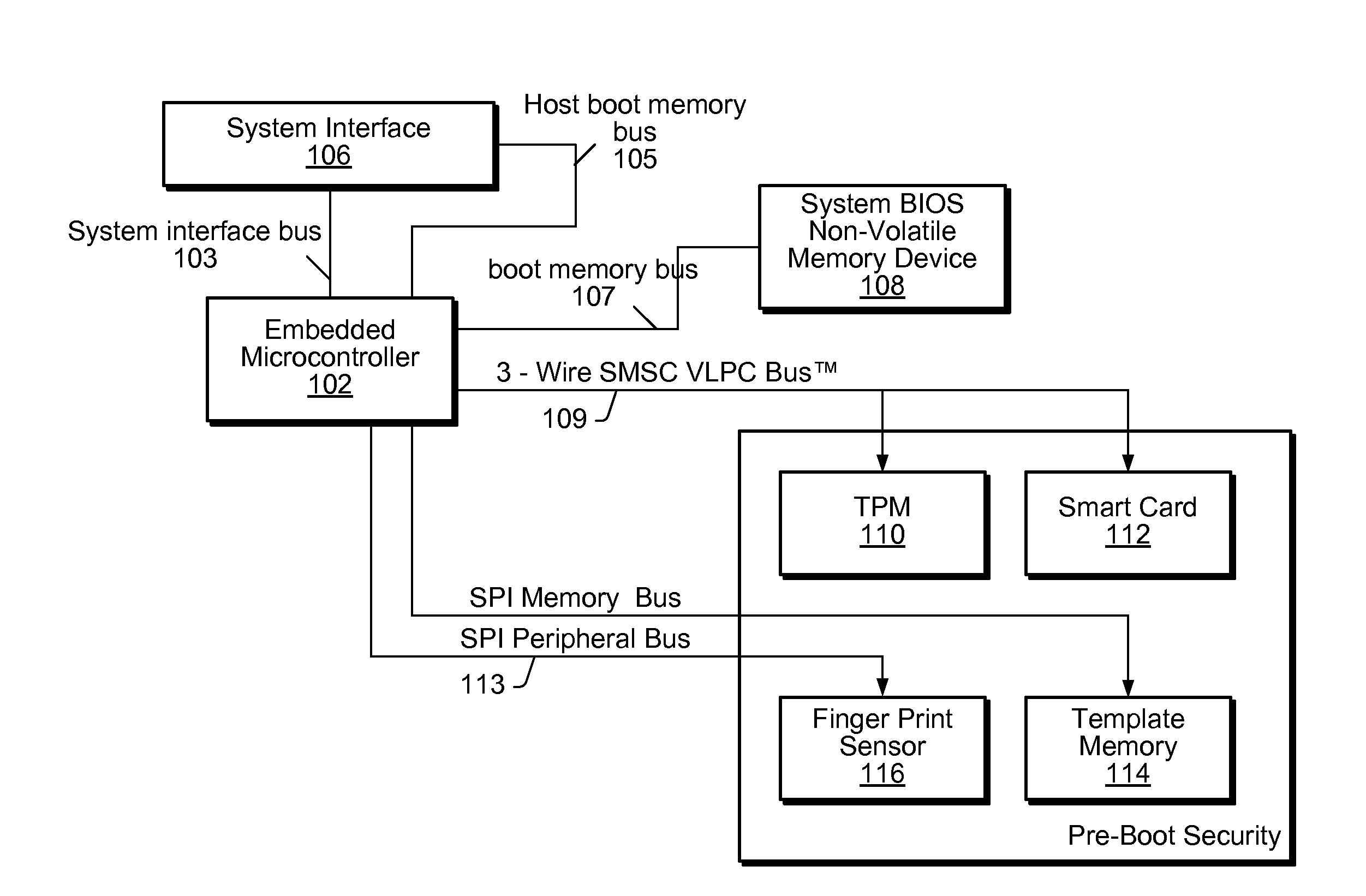
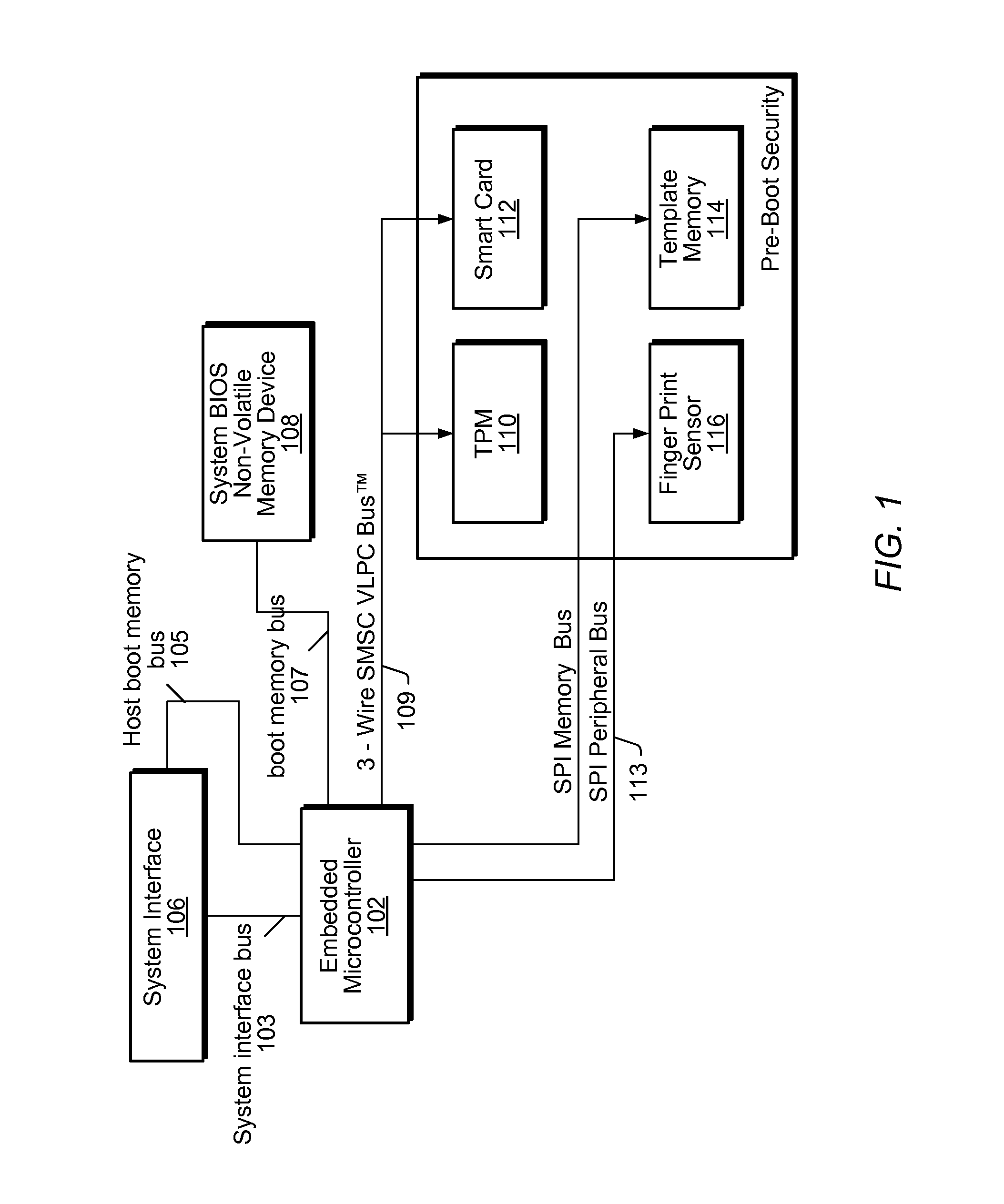
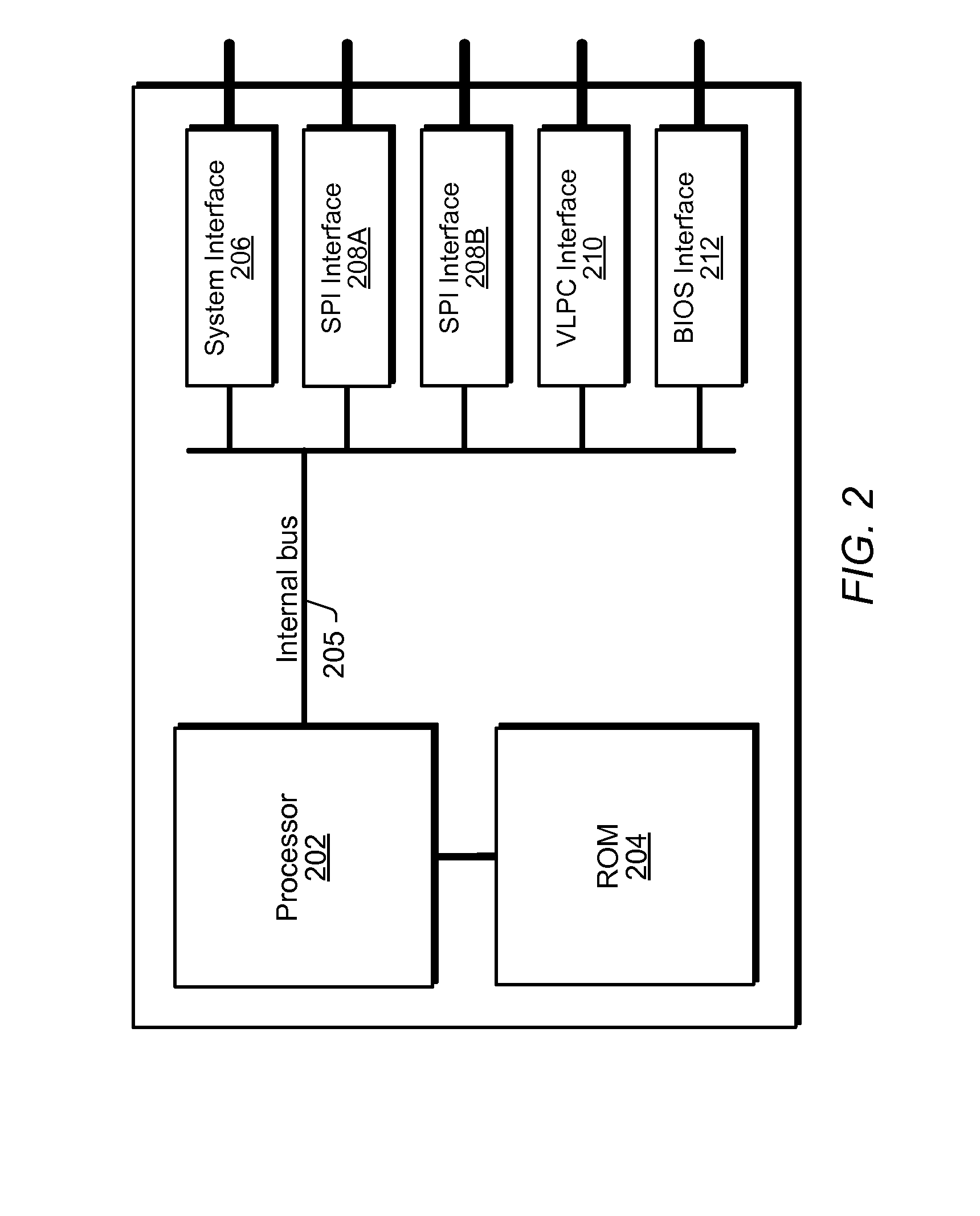
System and method for performing pre-boot security verification in a system that includes a host processor and memory, an embedded microcontroller with an auxiliary memory, e.g., an on-chip ROM, or memory controlled to prohibit user-tampering with the contents of the memory, and one or more pre-boot security components coupled to the embedded microcontroller. Upon power-up, but before host processor boot-up, the embedded microcontroller accesses the auxiliary memory and executes the program instructions to verify system security using the one or more pre-boot security components. The one or more pre-boot security components includes at least one identity verification component, e.g., a smart card, or a biometric sensor, e.g., a fingerprint sensor, a retinal scanner, and / or a voiceprint sensor, etc., and / or at least one system verification component, e.g., TPM, to query the system for system state information, and verify that the system has not been compromised.
Owner:MICROCHIP TECH INC
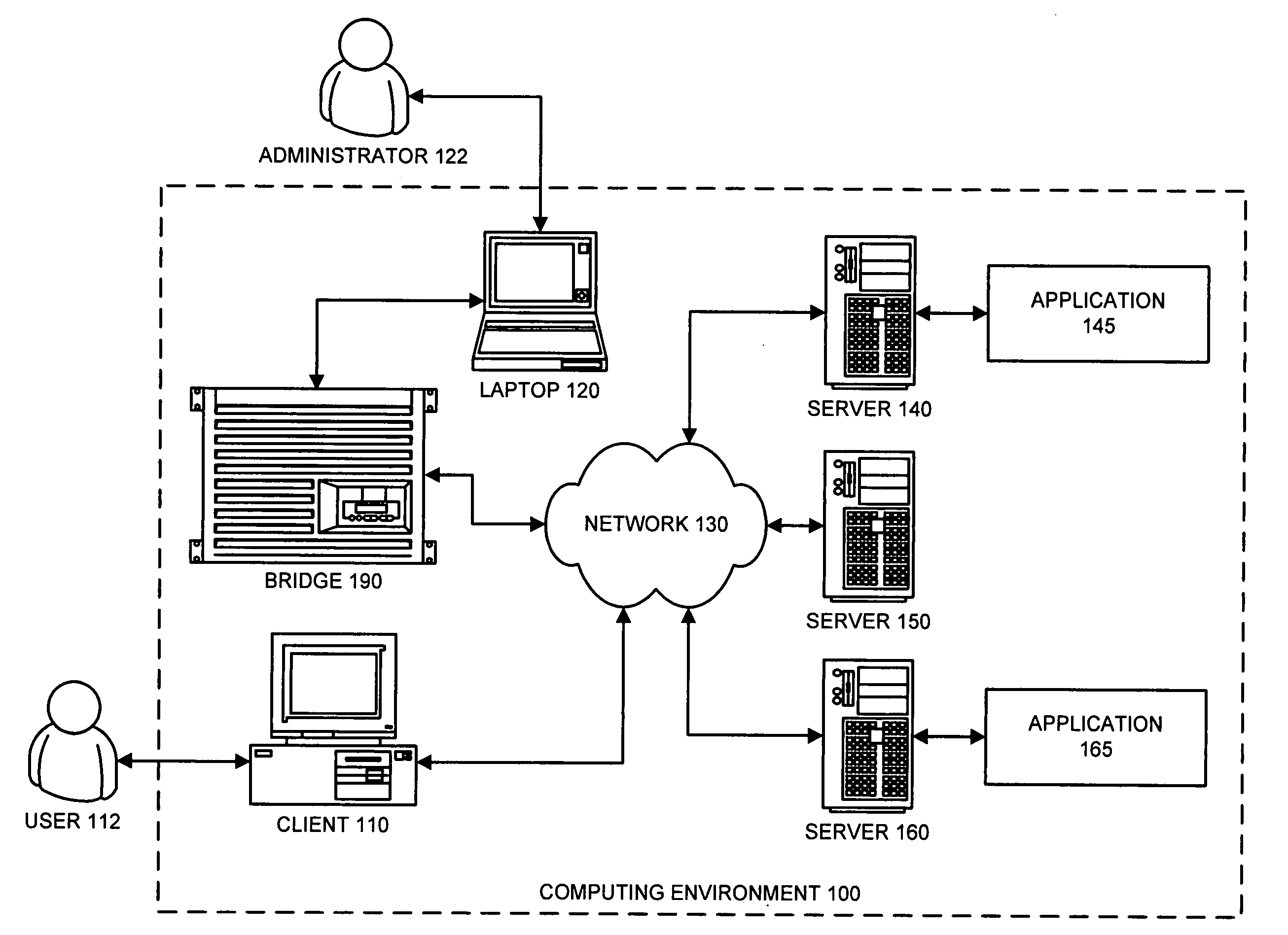
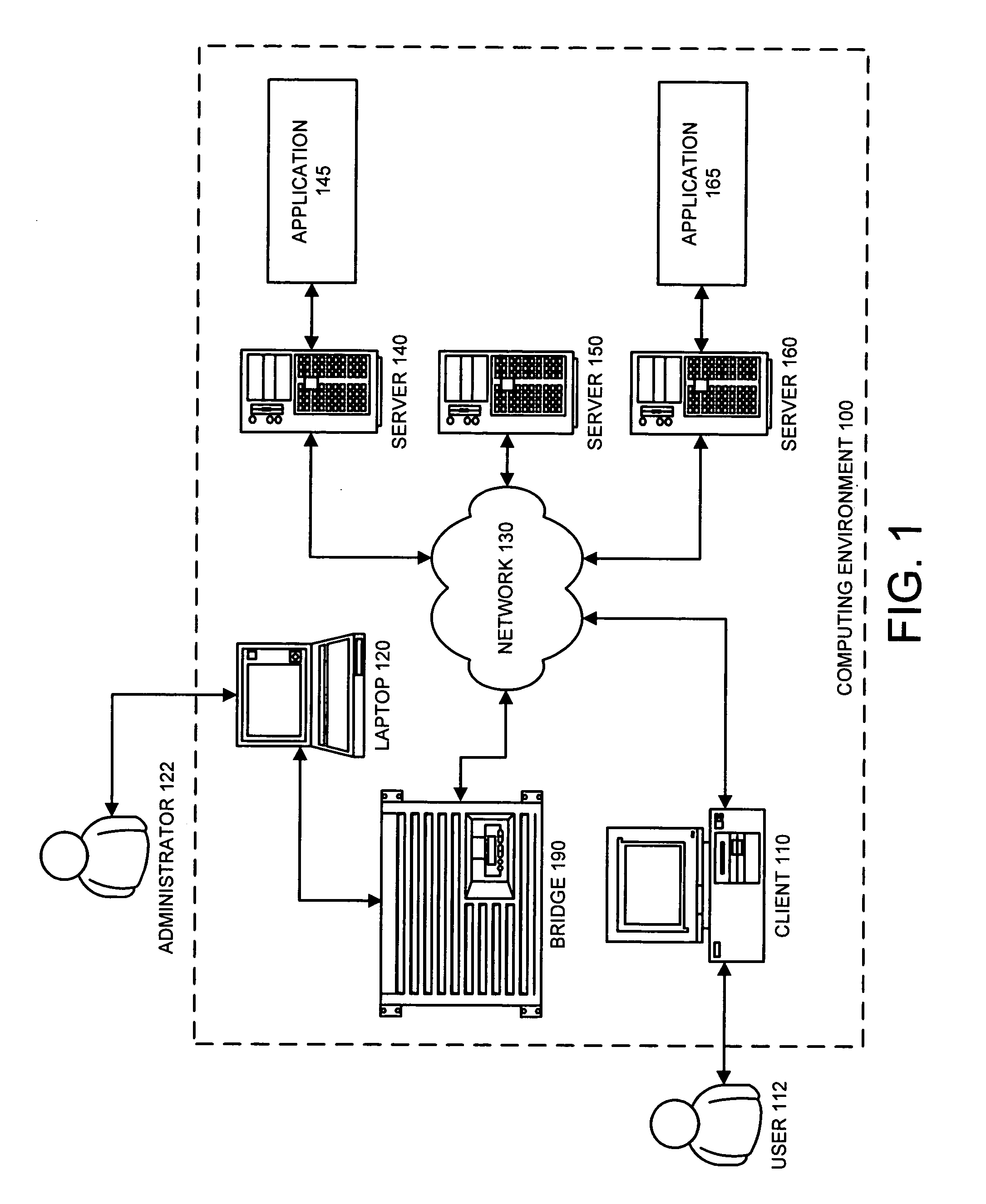
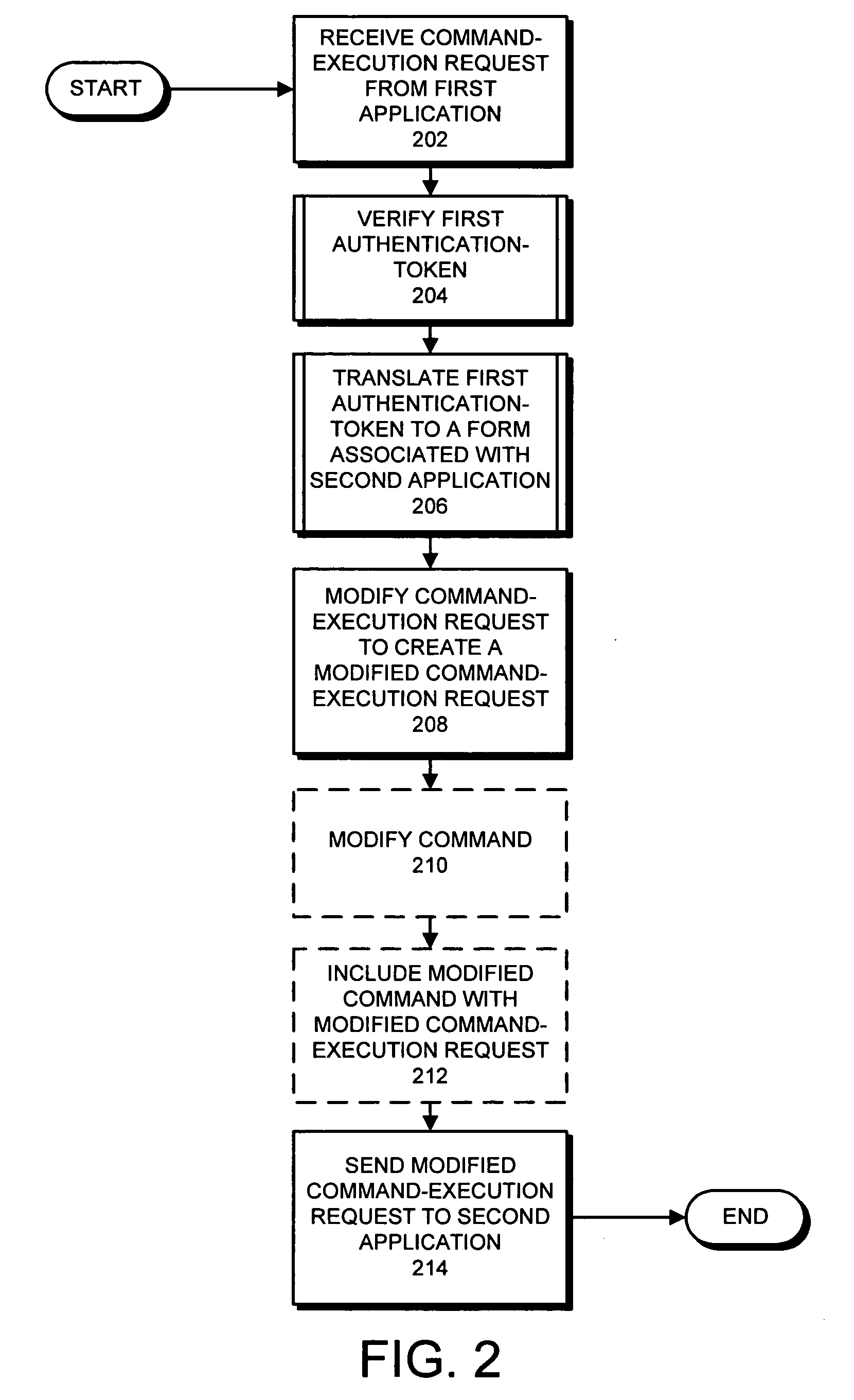
Method and apparatus for converting authentication-tokens to facilitate interactions between applications
ActiveUS20080046715A1Digital data authenticationSecuring communicationComputer scienceAuthentication
One embodiment of the present invention provides a system that converts authentication-tokens to facilitate interactions between applications. During operation, the system receives a command-execution request from a first application, wherein the command-execution request specifies a command to execute on a second application. Subsequently, the system verifies a first authentication-token included with the command-execution request. Next, the system translates the first authentication-token into a form associated with the second application to produce a second authentication-token. The system then modifies the command-execution request by replacing the first authentication-token with the second-authentication-token to create a modified command-execution request. Then, the system sends the modified command-execution request to the second application.
Owner:INTUIT INC
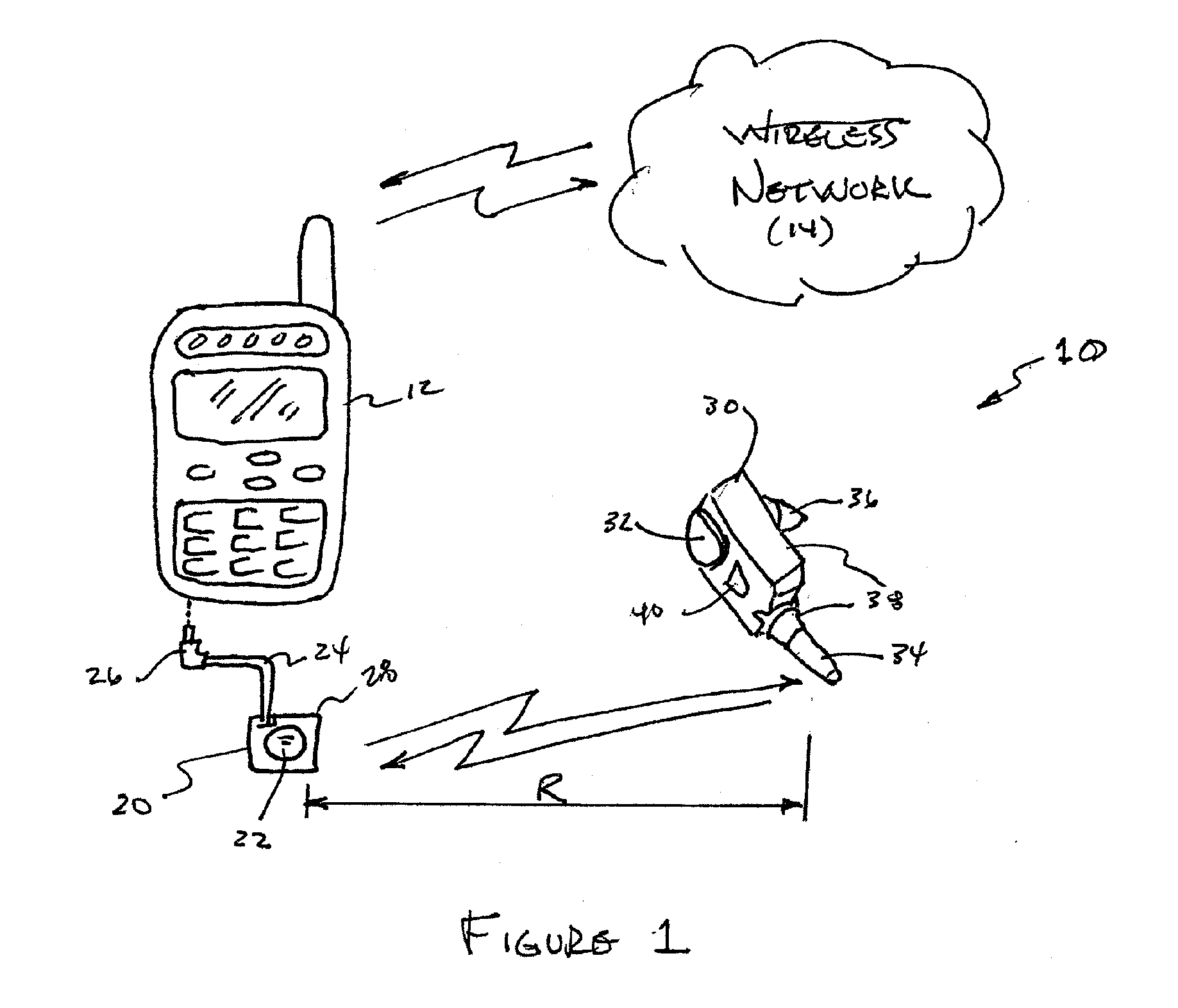
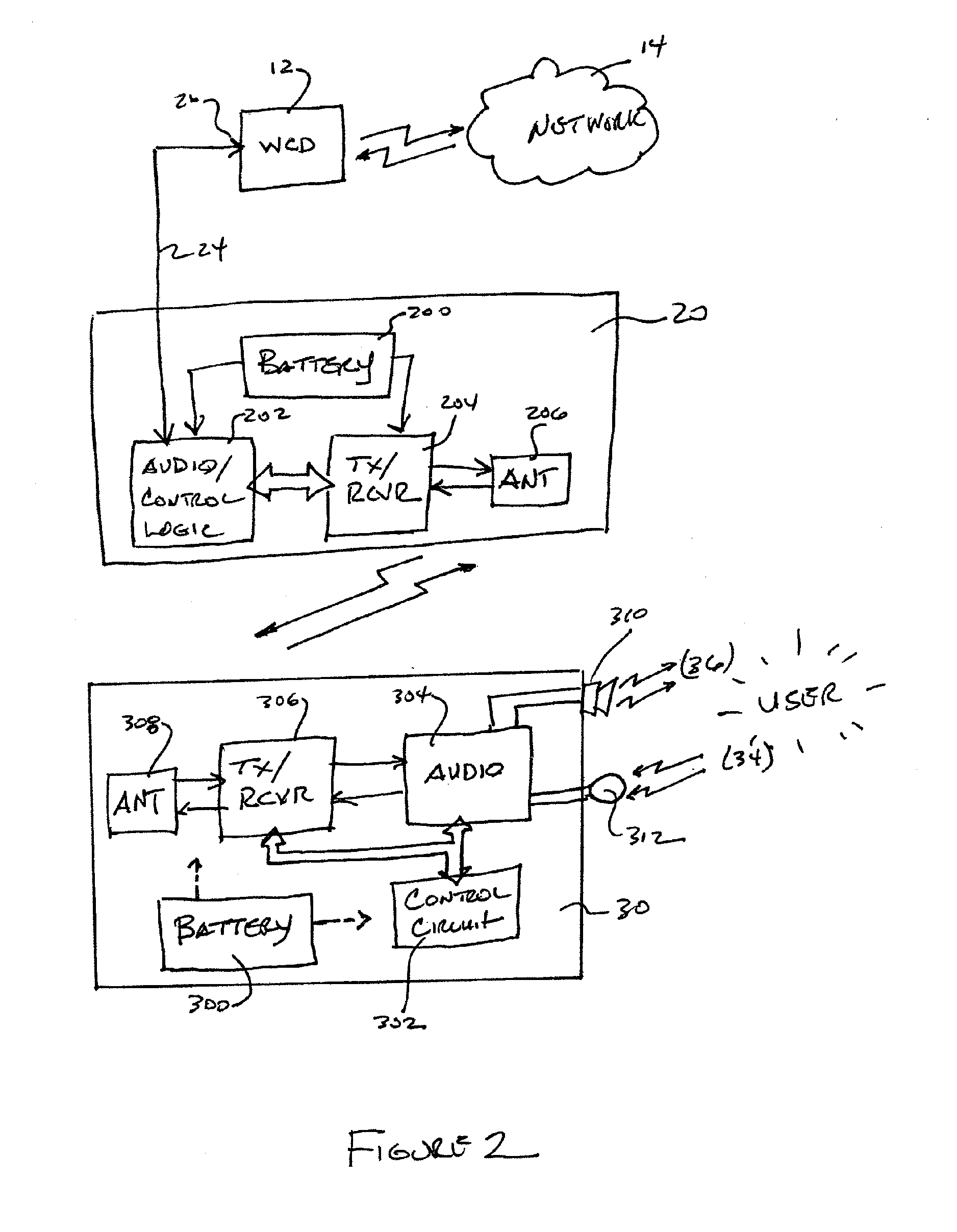
An Adaptive Wireless Headset System
The present invention is directed to a method for pairing a wireless headset and a dongle. The method includes the step of inserting a headset battery into the wireless headset. The headset is configured to retrieve a headset identification key in response to the headset battery insertion. A dongle battery is inserted into a dongle within a predetermined period of time after inserting the headset battery into the wireless headset. The dongle is configured to retrieve a dongle identification key in response to the dongle battery being inserted. Handshaking transmissions are exchanged between the wireless headset and the dongle, wherein the headset random identification key is combined with the dongle random identification key to form a system verification key, the system verification key being employed by the wireless headset and the dongle to code and decode transmissions between the wireless headset and the dongle.
Owner:THE CHAMBERLAIN GRP INC
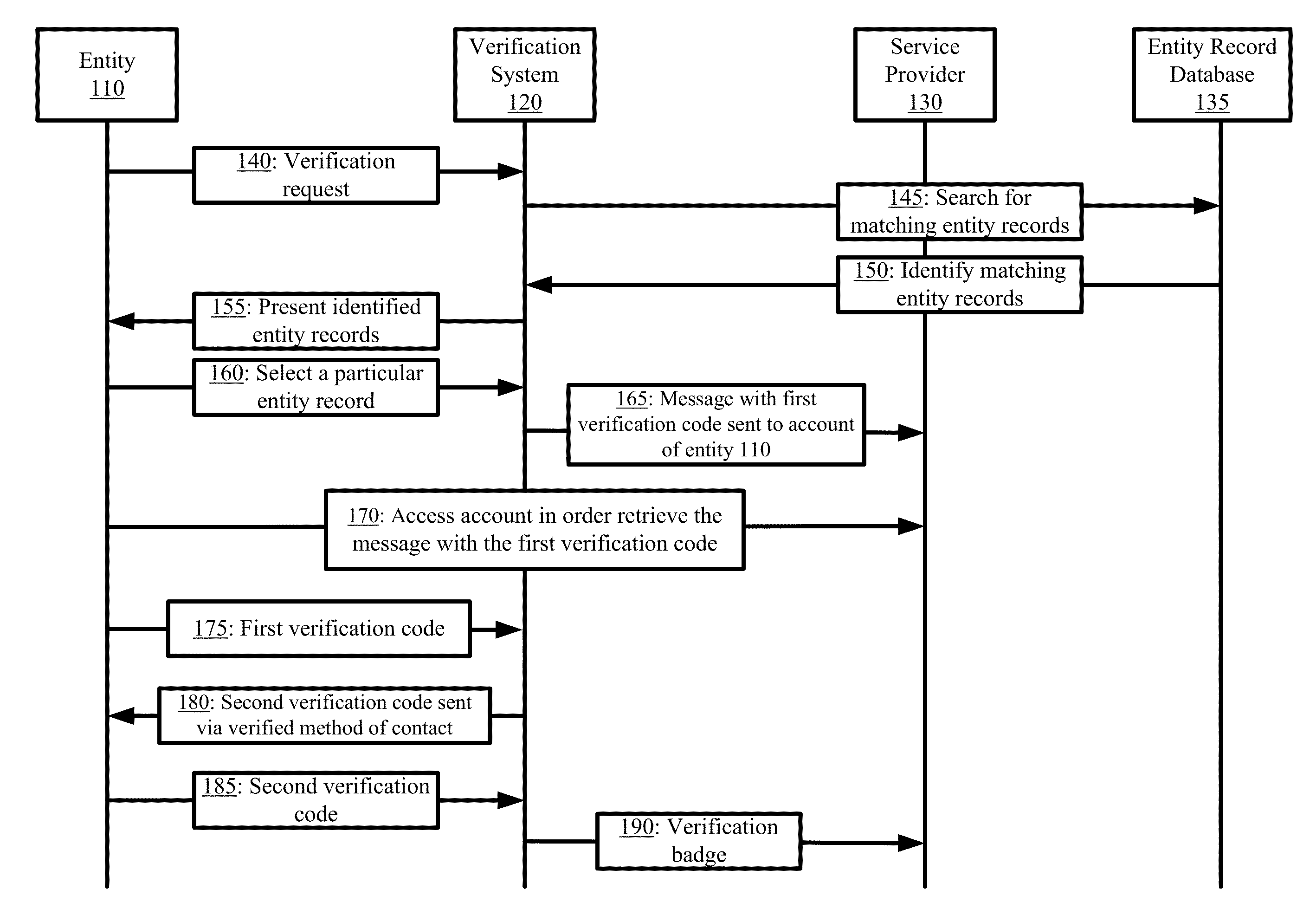
Automated Entity Verification
ActiveUS20130013553A1Big impactMinimal interactionData processing applicationsDigital data processing detailsComputer securityProgramming language
Some embodiments provide a verification system for automated verification of entities. The verification system automatedly verifies entities using a two part verification campaign. One part verifies that the entity is the true owner of the entity account to be verified. This verification step involves (1) the entity receiving a verification code at the entity account and returning the verification code to the verification system, (2) the entity associating an account that it has registered at a service provider to an account that the verification system has registered at the service provider, (3) both. Another part verifies the entity can respond to communications that are sent to methods of contact that have been previously verified as belonging to the entity. The verification system submits a first communication with a code using a verified method of contact. The verification system then monitors for a second communication to be returned with the code.
Owner:DUN & BRADSTREET EMERGING BUSINESSES
Charged particle cancer therapy and patient positioning method and apparatus
The invention comprises a laying, semi-vertical, or seated patient positioning, alignment, and / or control method and apparatus used in conjunction with multi-axis charged particle or proton beam radiation therapy of cancerous tumors. Patient positioning constraints are used to maintain the patient in a treatment position, including one or more of: a seat support, a back support, a head support, an arm support, a knee support, and a foot support. One or more of the positioning constraints are movable and / or under computer control for rapid positioning and / or immobilization of the patient. The system optionally uses an X-ray beam that lies in substantially the same path as a proton beam path of a particle beam cancer therapy system. The generated image is usable for: fine tuning body alignment relative to the proton beam path, to control the proton beam path to accurately and precisely target the tumor, and / or in system verification and validation.
Owner:BALAKIN ANDREY VLADIMIROVICH +1
Invisible services
InactiveUS20020194505A1Digital data processing detailsMultiple digital computer combinationsClient-sidePort scan
The presented inventions concern communication systems with services. The services provided by the presented systems are invisible to port scans, allowing security critical data to be stored on units without any permanently open connection endpoints. Existing network systems according to the client / server-principle require the permanent provision of open connection endpoints to be accessible on a 24h base. The large number of services implies a large number of open connection endpoints, where each open connection endpoint presents a potential point-of-attack for malicious clients. The object of the present invention is to securely provide services in communication systems. The present invention overcomes the prior art by triggerable invisible services, which during normal operation do not provide any permanently open connection endpoint. Connection endpoints are only opened after prior client authentication and authorization validated by an independent logon sub-system. Connection endpoints can be opened for previously authenticated and authorized clients either on the service side during a predefined short time interval or on the client side. If opened on the client side, the invisible service is triggered to initiate the connection build-up to the open connection endpoint on the client side. Services opening temporary connection endpoints are for port scan during normal operation invisible. Services connecting to connection endpoints opened on the client side, at no time provide any open connection endpoints and are therefore for port scan absolutely invisible. In networks on the base of TCP / IP the id of an opened connection endpoint (port) may be selected pseudo or absolutely randomly. In addition, it is possible to dynamically select the service unit out of a set of multiple service units in dependence of the actual system load distribution "load balancing", connection quality, geographical, topological or other criteria. After the establishment of a connection between an invisible service and a client, both partners may authenticate each other using random access data (tickets).
Owner:MUSCHENBORN HANS JOACHIM
Semi-vertical positioning method and apparatus used in conjunction with a charged particle cancer therapy system
The invention comprises a semi-vertical patient positioning, alignment, and / or control method and apparatus used in conjunction with charged particle or proton beam radiation therapy of cancerous tumors. Patient positioning constraints are used to maintain the patient in a treatment position, including one or more of: a seat support, a back support, a head support, an arm support, a knee support, and a foot support. One or more of the positioning constraints are movable and / or under computer control for rapid positioning and / or immobilization of the patient. The system optionally uses an X-ray beam that lies in substantially the same path as a proton beam path of a particle beam cancer therapy system. The generated image is usable for: fine tuning body alignment relative to the proton beam path, to control the proton beam path to accurately and precisely target the tumor, and / or in system verification and validation.
Owner:BALAKIN ANDREY VLADIMIROVICH +1
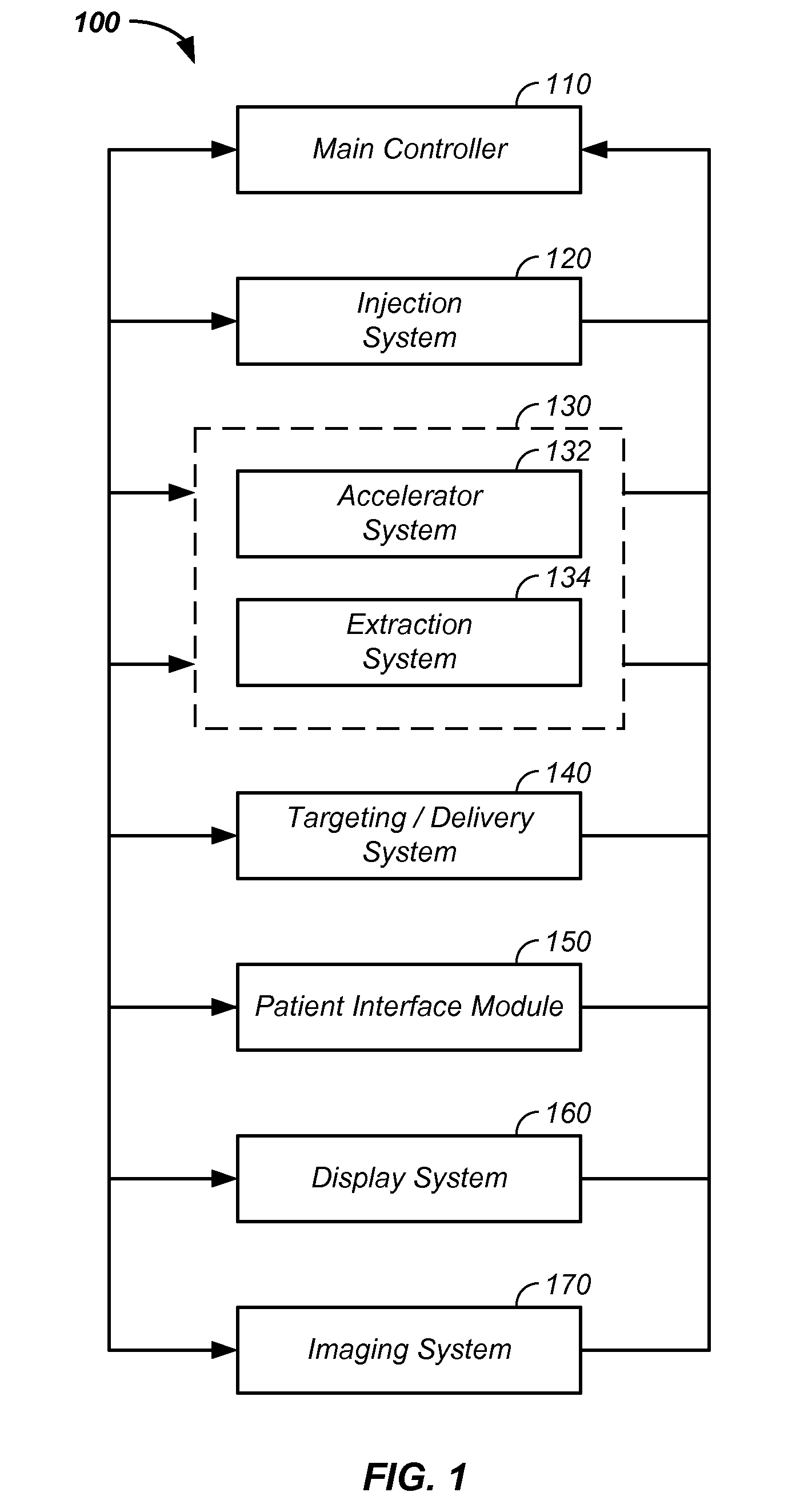
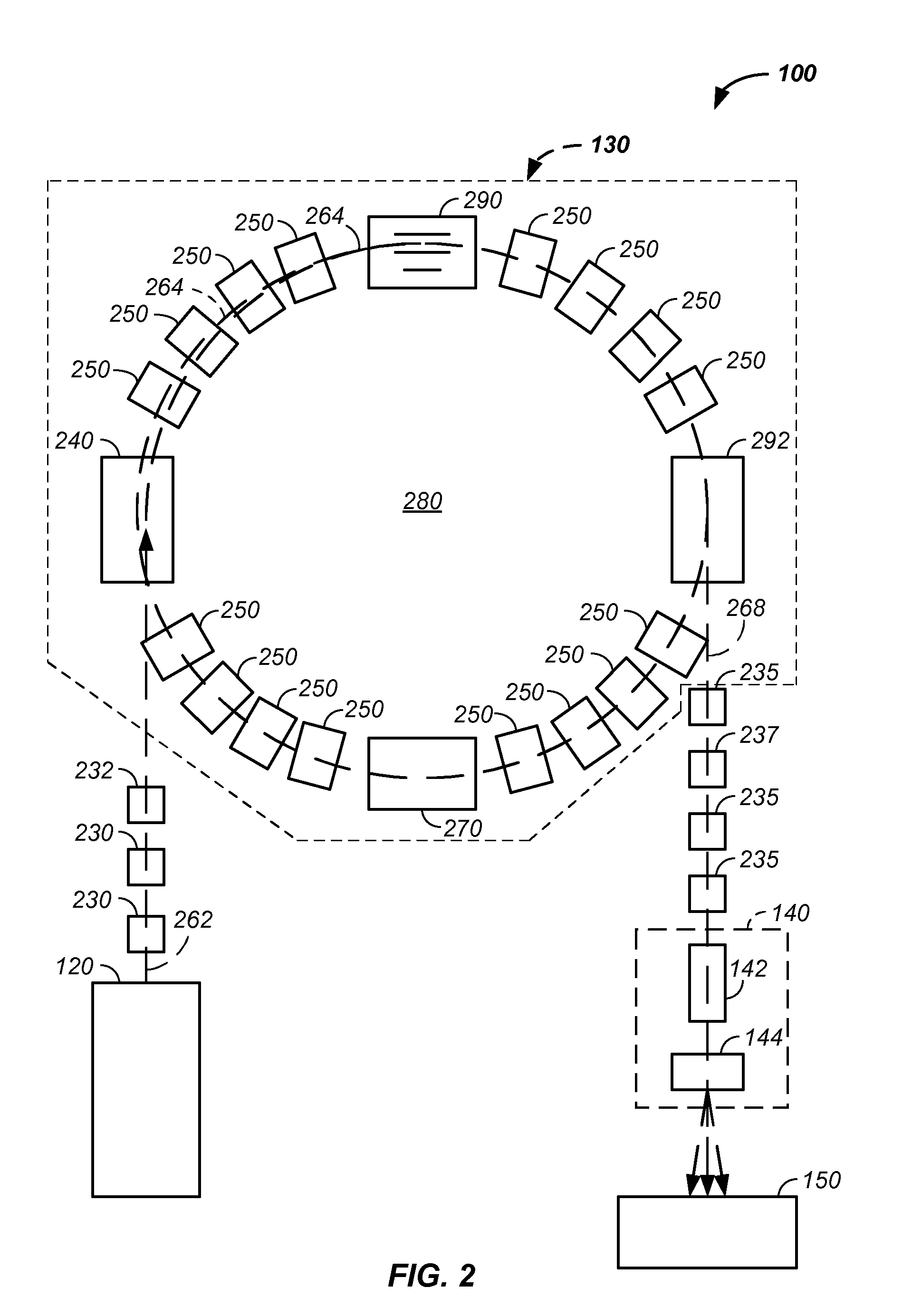
Multi-processor system verification circuitry
ActiveUS7469273B2Improve rendering capabilitiesImprove fault coverageFunctional testingMultiple digital computer combinationsCoprocessorSystem verification
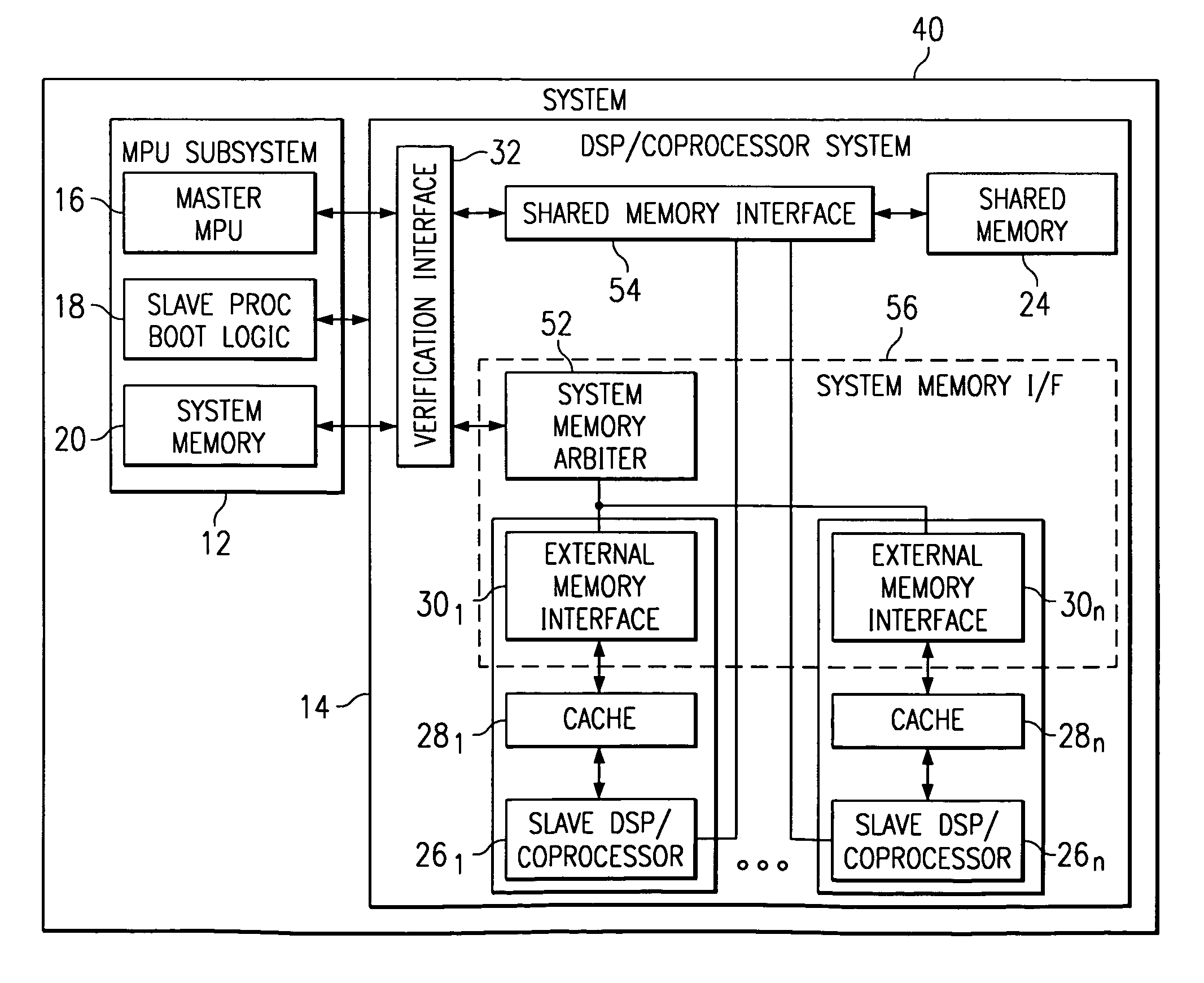
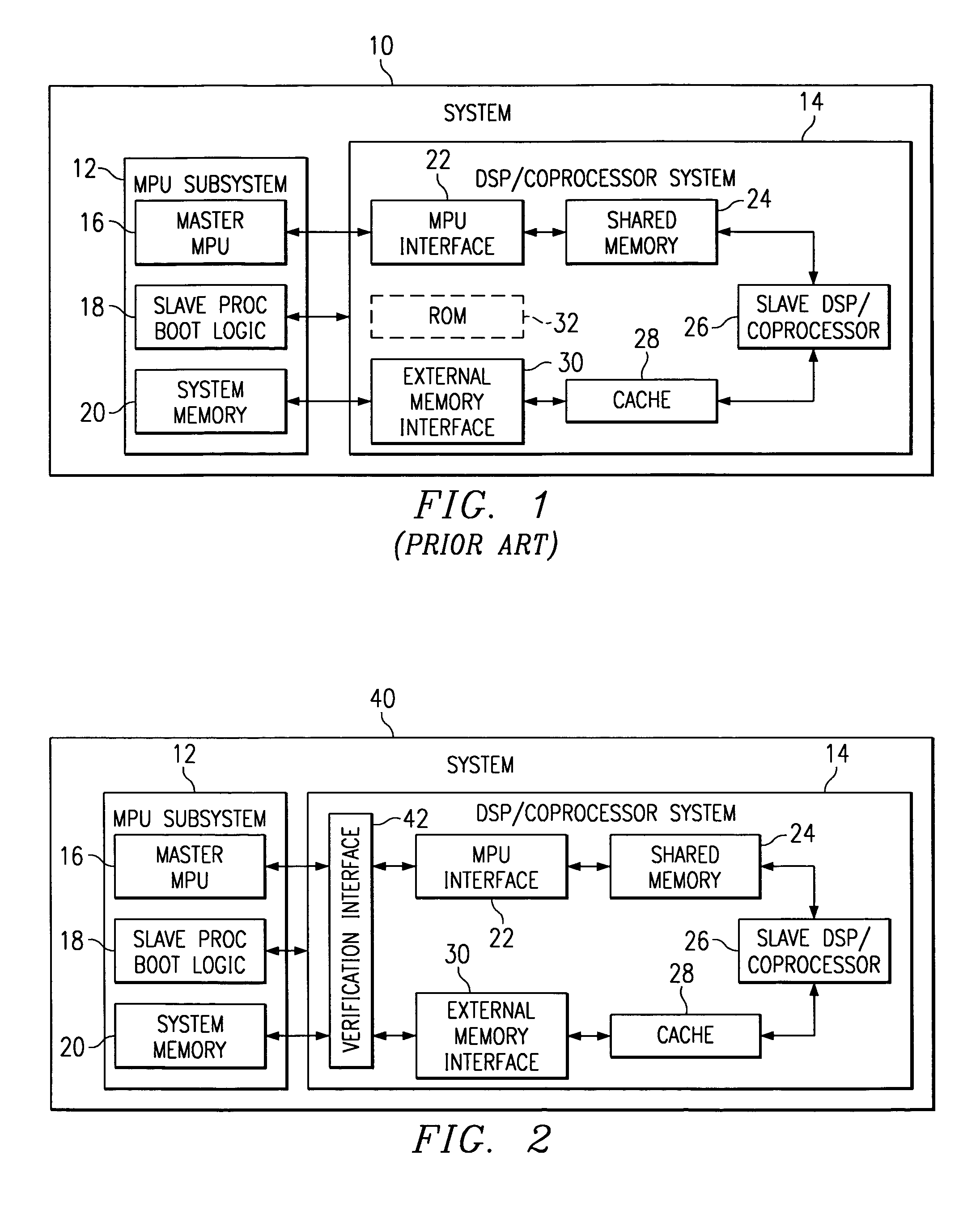
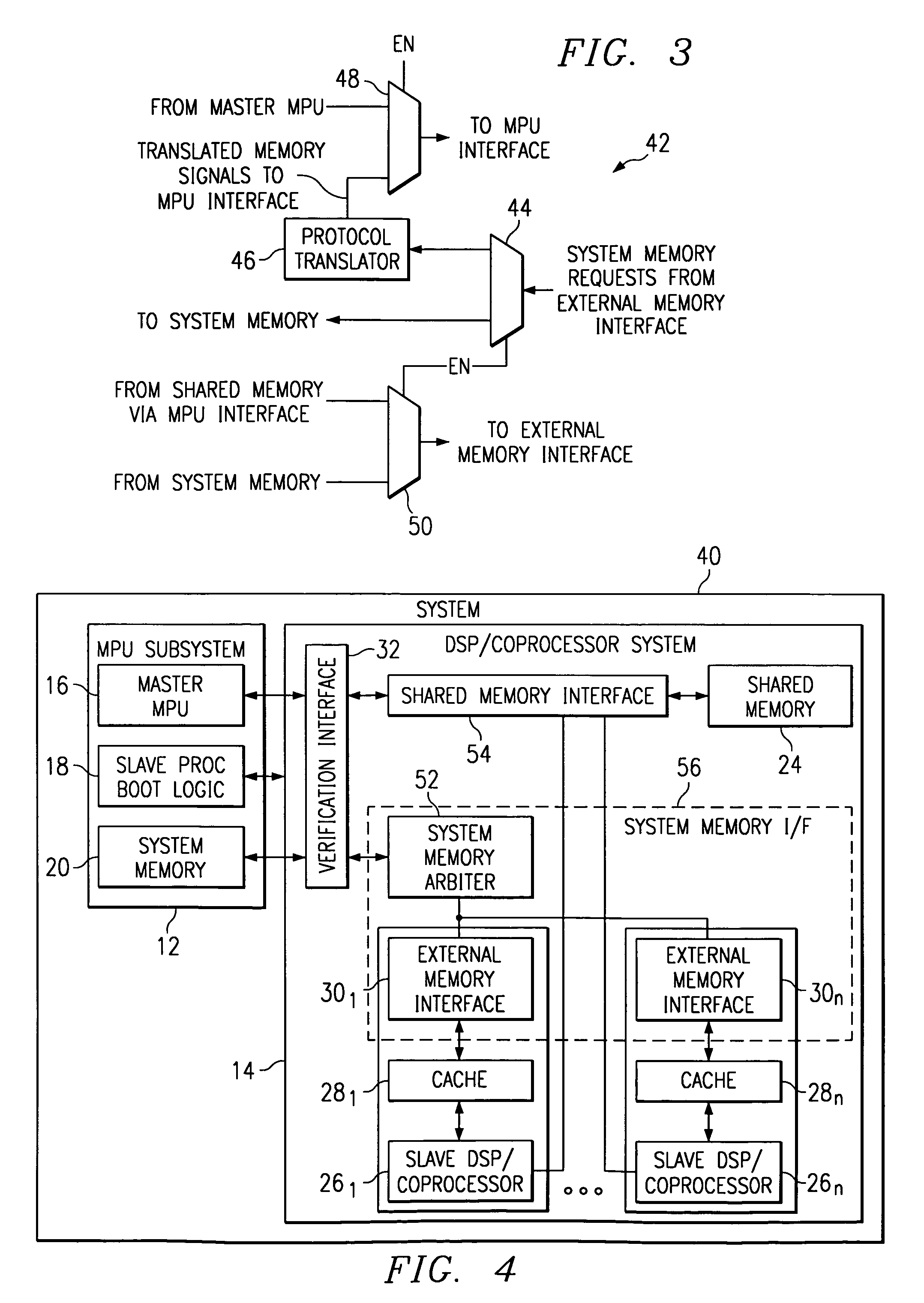
A multiprocessor system (40) includes a MPU subsystem (12), with master MPU (16) and shared memory (24), and a DSP / Coprocessor subsystem (14), with one or more slave DSP / Coprocessors (26). The system memory (20) is accessed by each DSP / Coprocessor subsystem (14) through a cache (28) and external memory interface (30). A verification interface (42) is used in verification mode to isolate the DSP / Coprocessor subsystem (14) from the MPU subsystem (12) and to translate system memory requests from the external memory interfaces (30) (through an arbiter (52), where multiple external memory interfaces are used) to a protocol which can be used to access the data from the shared memory (24).
Owner:TEXAS INSTR INC
Real-time simulation validation system and method for communication system integrated circuit design
InactiveCN101504690AEasy to findEasy to moveSpecial data processing applicationsSystem verificationComputer architecture
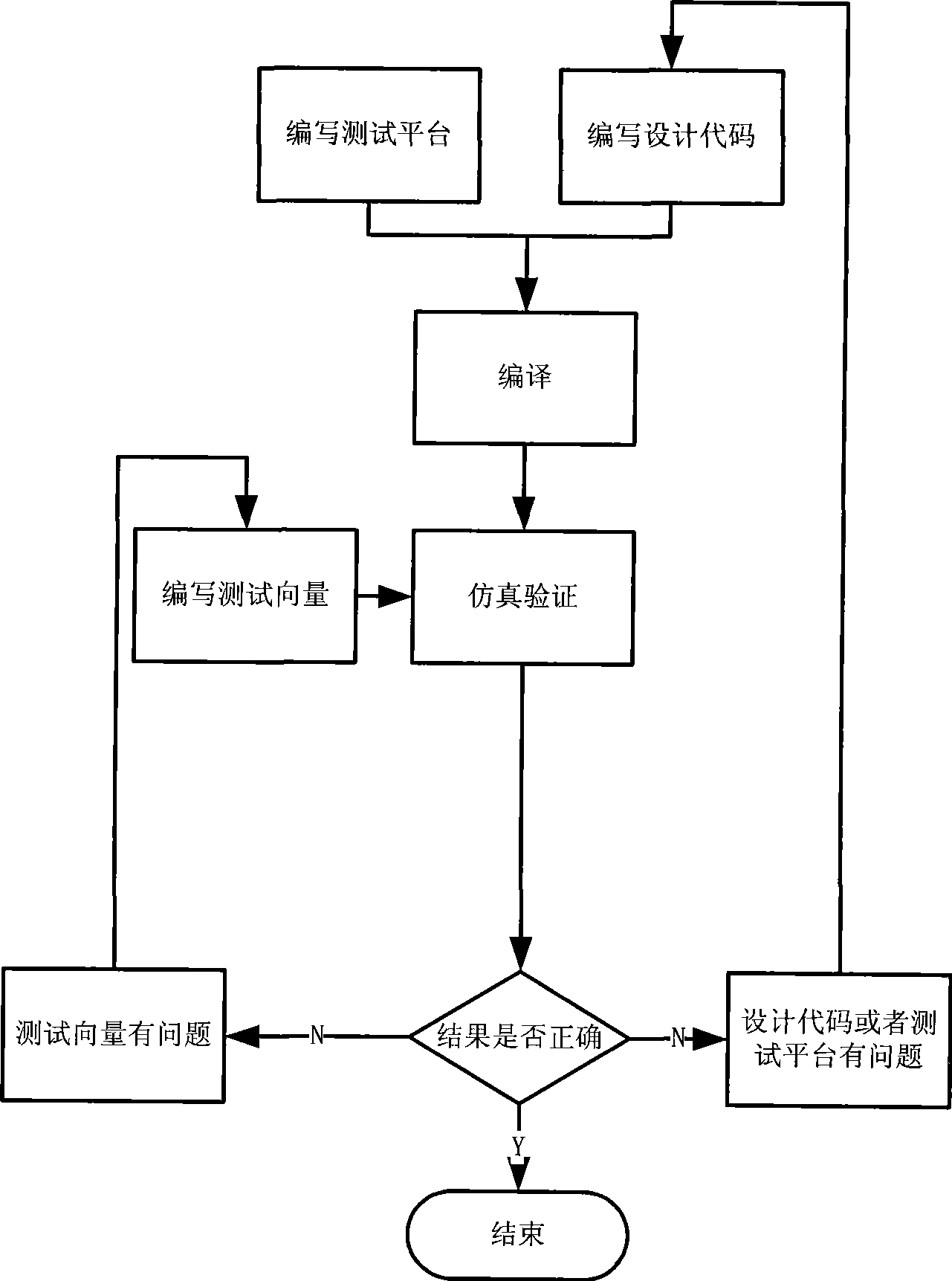
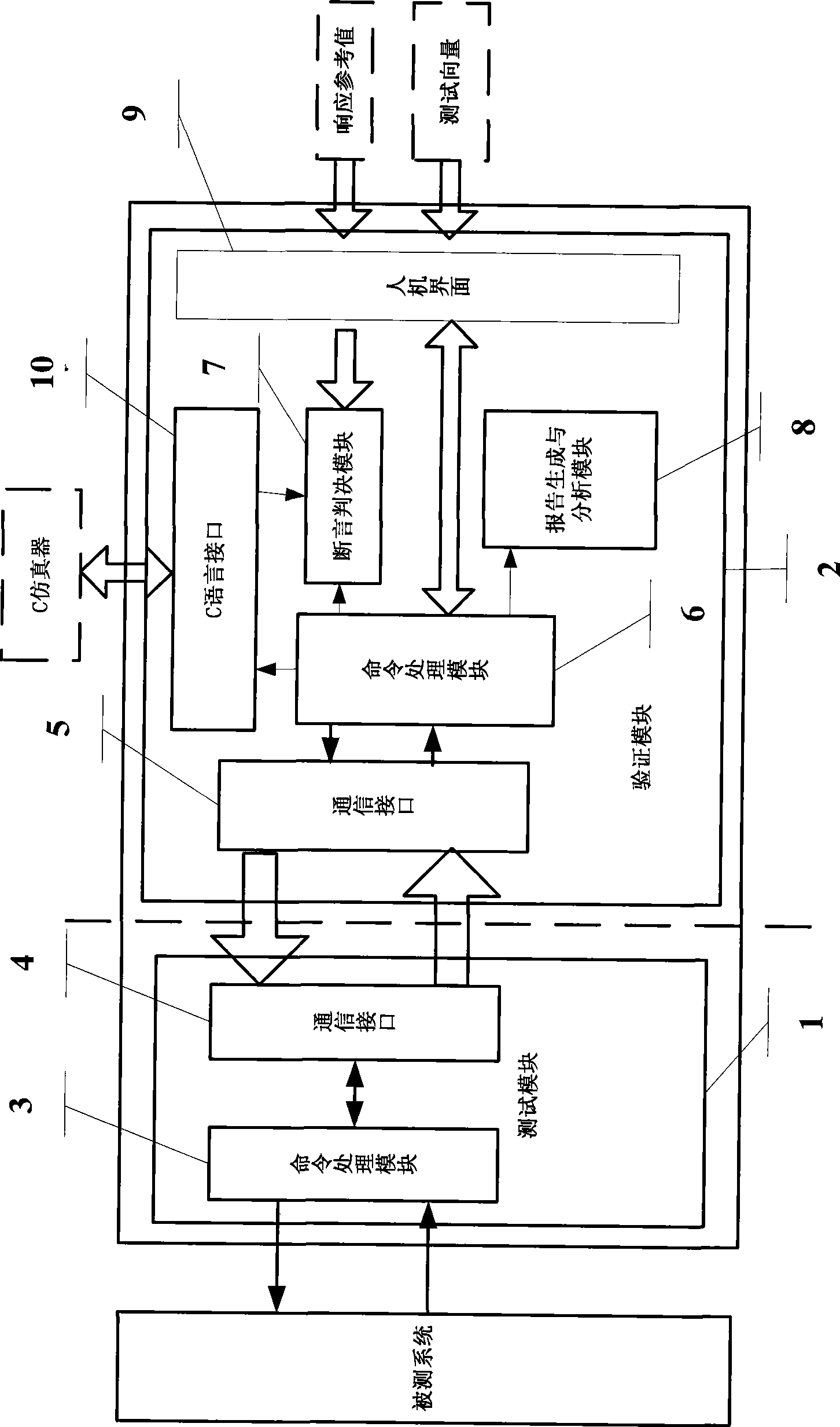
The invention provides a real-time simulation verification system and a real-time simulation verification method for the design of an integrated circuit of a communication system, which are used for the verification of the design of the integrated circuit of the communication system. The system and the method can be used for real-time verification of the front end and the rear end in the design of the integrated circuit of the communication system. The system and the method comprise that: a test module generates excitation data with the frame format required by a tested system by calling a related task, collects response regenerated by the tested system, compares the response value and the reference value in a verification module, and obtains a verification conclusion, and the two modules are communicated with each other in the mode of text. The system and the method can be transplanted into different system verifications as required aiming at communication systems with fixed frame format, and simultaneously the system changes the execution sequence of basic steps of verification, can be operated in real time, and reduces the time required by simulation verification. Moreover, the system not only can be applied to the simulation verification of a simple system provided with a standard serial port but also can be applied to the simulation verification of a large-scale complex communication system of a navigation receiver.
Owner:BEIHANG UNIV
A method and system for generating a picture verification code
InactiveCN102298763AIncrease the difficulty of recognitionReduce difficultyUser identity/authority verificationImage data processing detailsPattern recognitionSystem verification
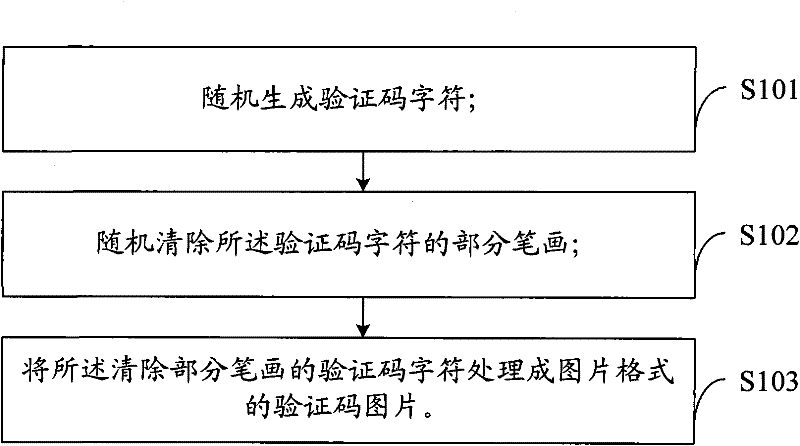
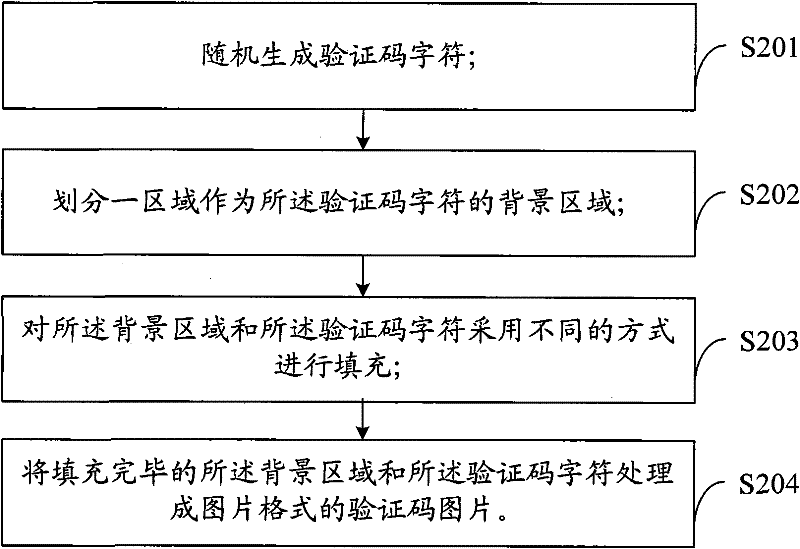
The invention is applicable to the technical field of verification code generation, and provides a method and system for generating a picture verification code. The method comprises the following steps: randomly generating verification code characters; randomly clearing part of the strokes of the verification code characters; processing the verification code characters whose partial strokes are removed into picture format verification code pictures. The method also includes the following steps: randomly generating verification code characters; dividing an area as the background area of the verification code characters; filling the background region and the verification code characters in different ways; The background area and the verification code characters are processed into a verification code picture in picture format. The invention enables the verification code generated by the method for generating the picture verification code provided by the invention to reduce the difficulty of human eye recognition while increasing the difficulty of machine recognition.
Owner:TENCENT TECH (BEIJING) CO LTD
Technique for optical inspection system verification
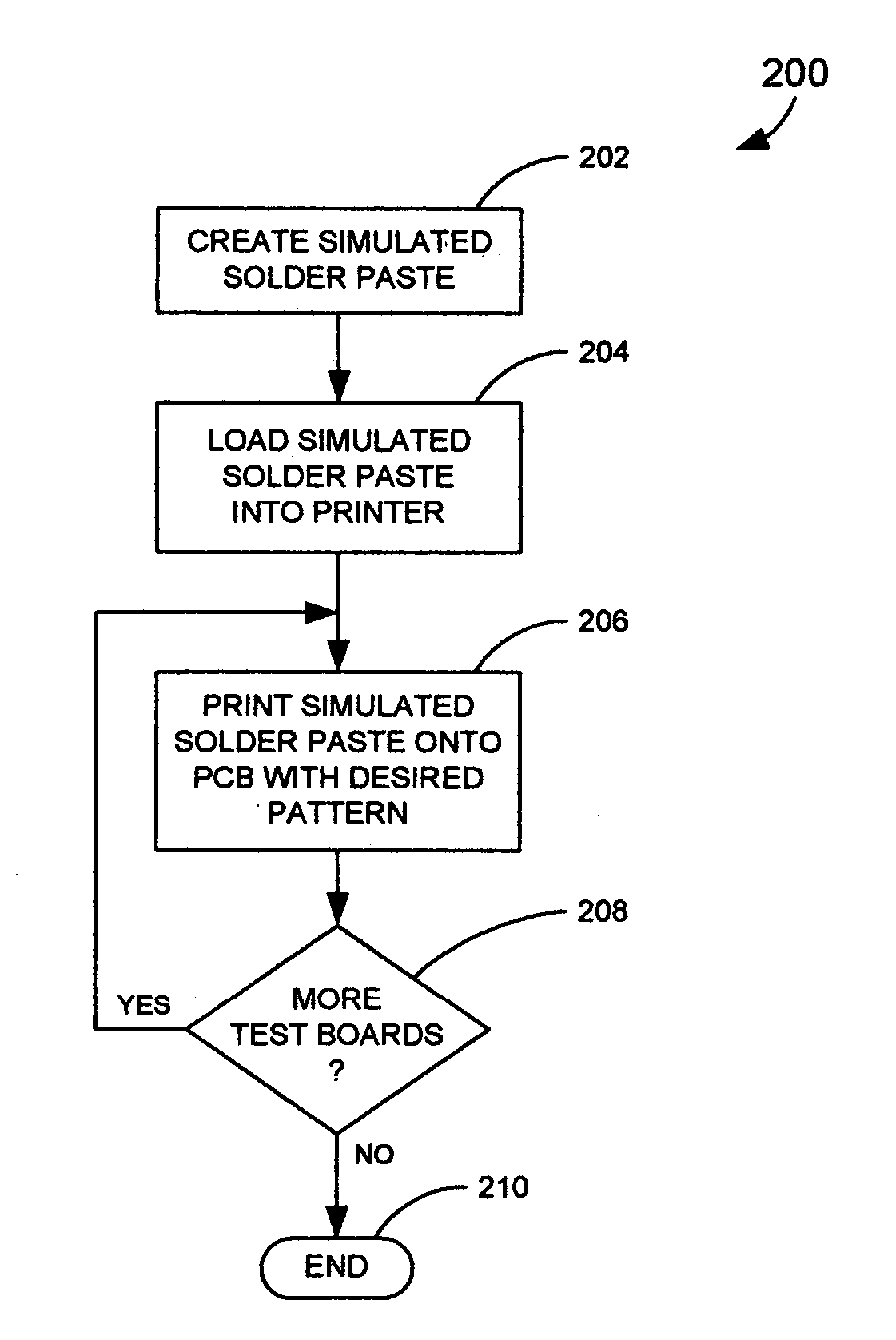
A technique for optical inspection verification implements a number of steps. Initially, a simulated solder paste material, including a solder powder and an organic resin, is provided. Next, the simulated solder paste material is printed in a desired pattern on a base material to provide a reference test board. Then, the test board is cured to stabilize the simulated solder paste material. Next, the test board is utilized to train the optical inspection system to reject defective product.
Owner:DELPHI TECH INC
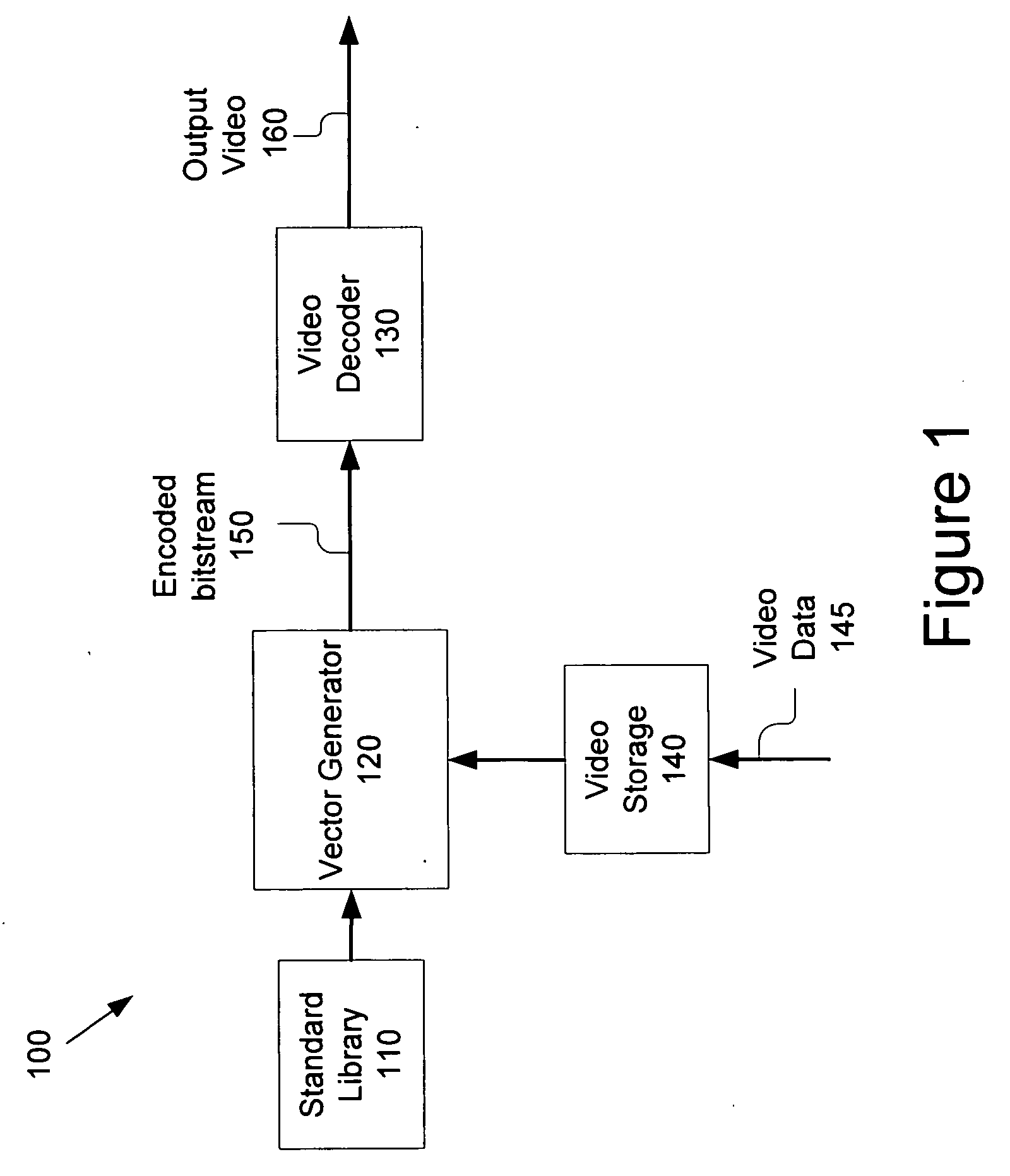
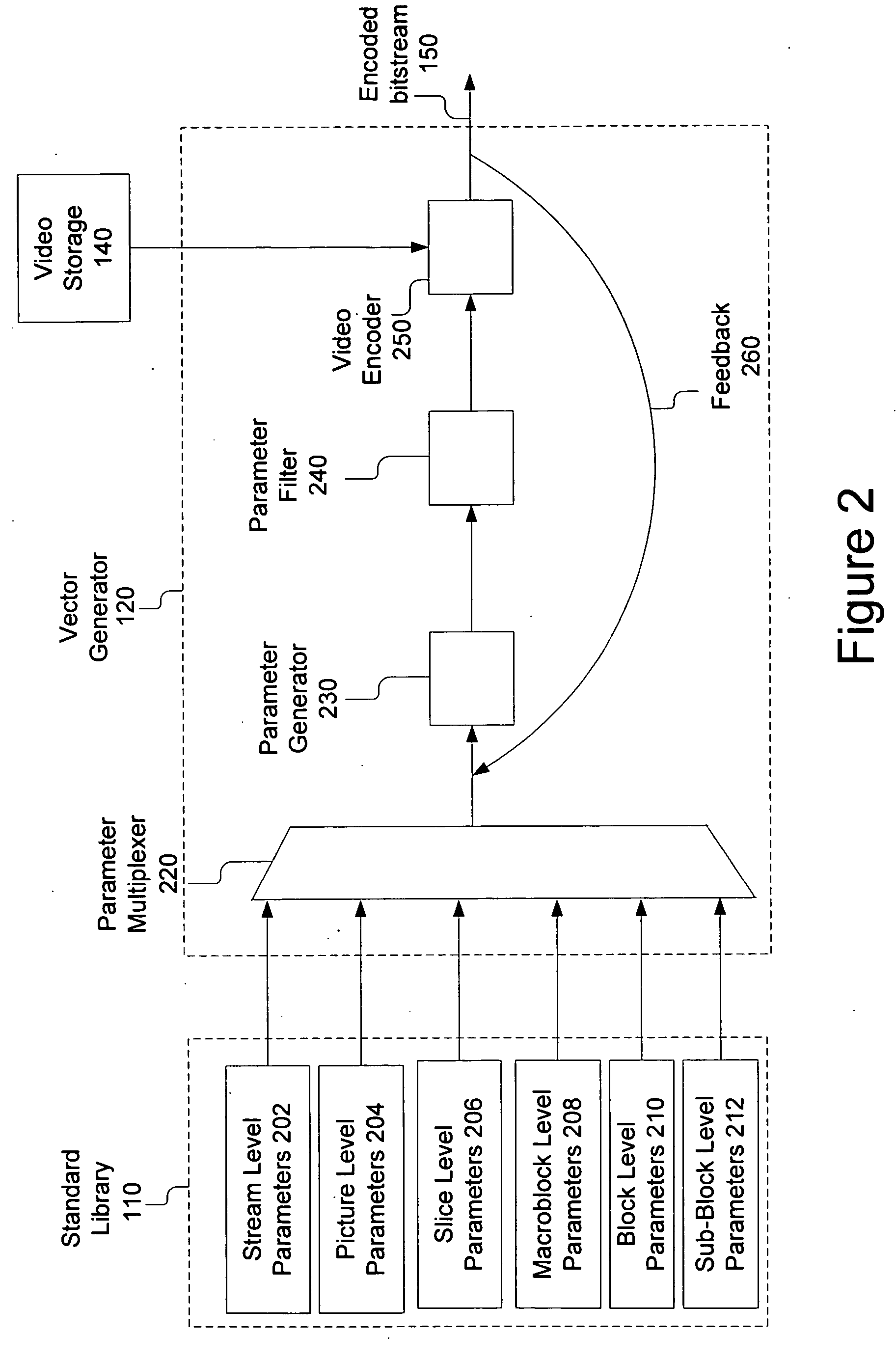
Automated test vector generation for complicated video system verification
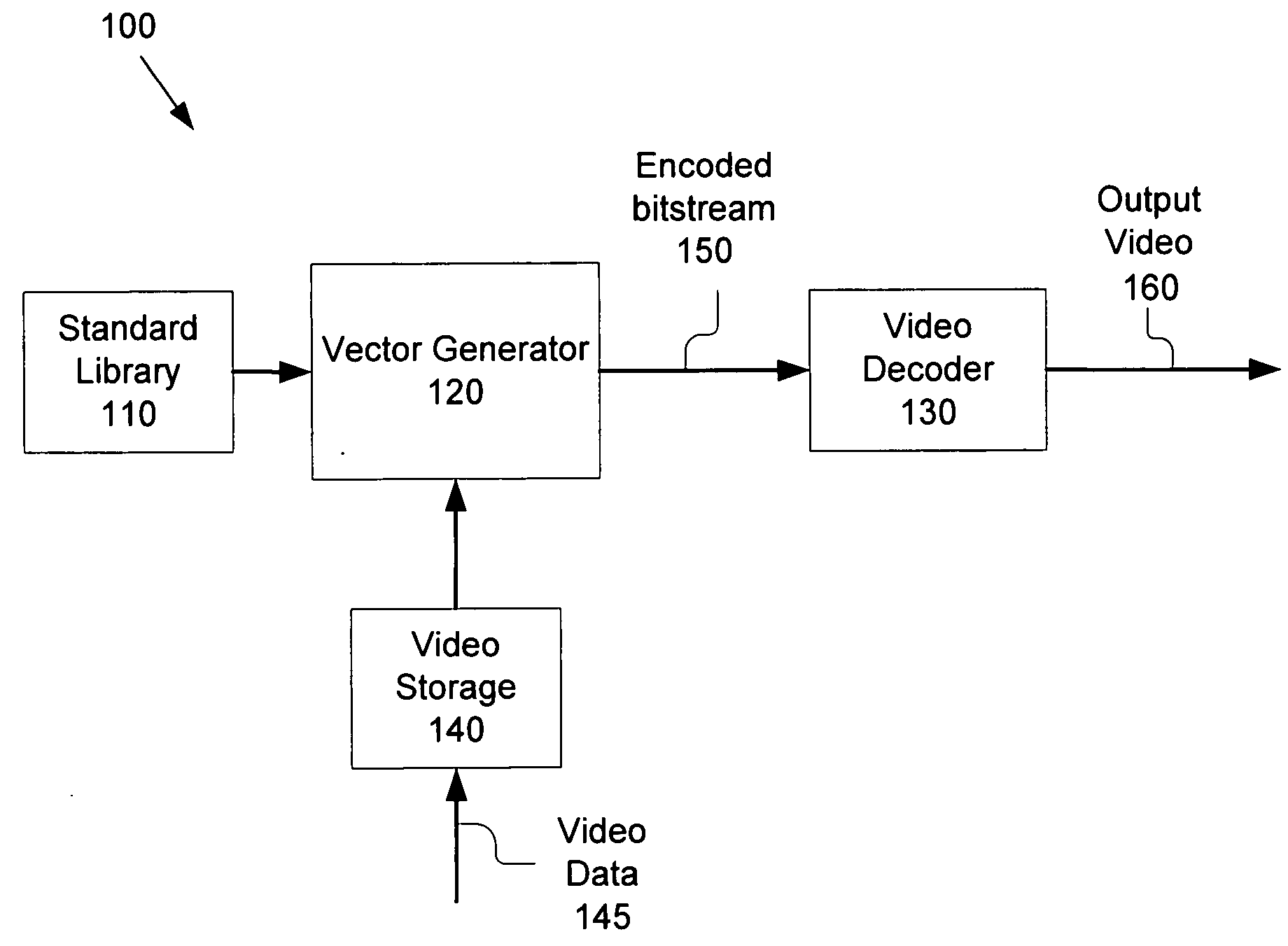
InactiveUS20060126725A1Color television with pulse code modulationColor television with bandwidth reductionSystem verificationVideo encoding
According to one embodiment, the present invention generates a test vector for verification of a video encoder or decoder by encoding video data using a permissible combination of parameters. One embodiment of the present invention provides for verification of a video decoder by performing at least one video decoding operation and comparing a resulting partially or fully decoded test vector to an expected value. Another embodiment of the present invention provides for verification of a video encoder by performing at least one video encoding operation using a selected combination of parameters, and comparing a resulting partially or fully encoded test vector to an expected value.
Owner:MICRONAS
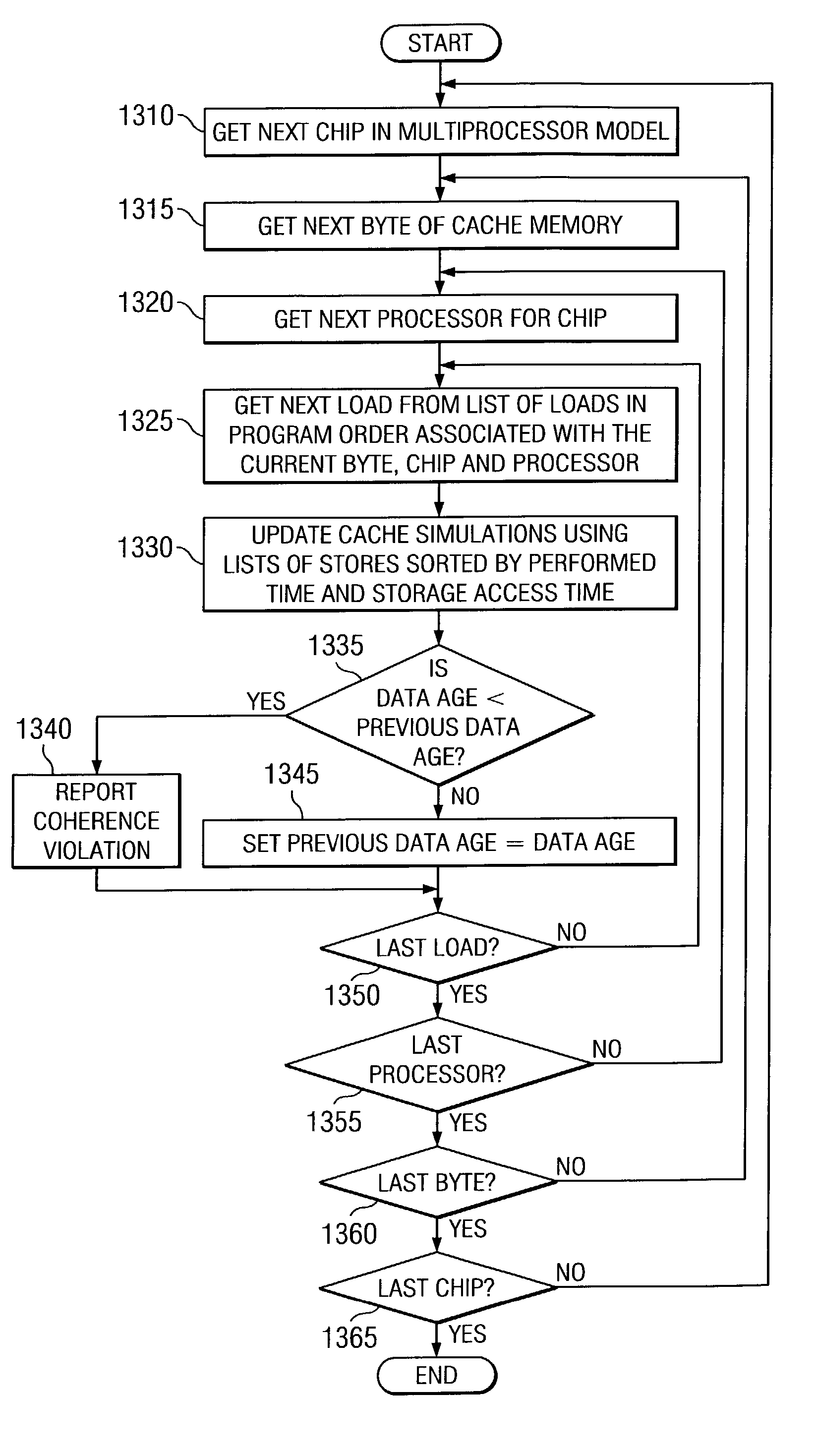
Method and apparatus for verification of coherence for shared cache components in a system verification environment
InactiveUS7000079B2Memory architecture accessing/allocationError detection/correctionSystem verificationParallel computing
A method and apparatus for verification of coherence for shared cache components in a system verification environment are provided. With the method and apparatus, stores to the cache are applied to a cache functional simulator in the order that they occur in the trace information from the canonical tracers. However, rather than updating the cache simulator with the actual data stored, the performed time of the store event is applied to the simulator as data. The cache simulator stores the latest performed time for each byte of each cache line in the simulated cache, in an associated data structure. For each load event that is encountered in the trace information for a byte, a comparison is made between a global expected data age of the data in the cache and the performed time associated with the byte. If the data age in the simulated cache for the byte is less than the global expected data age, i.e. a latest previously encountered data age, then a cache coherence violation has occurred.
Owner:IBM CORP
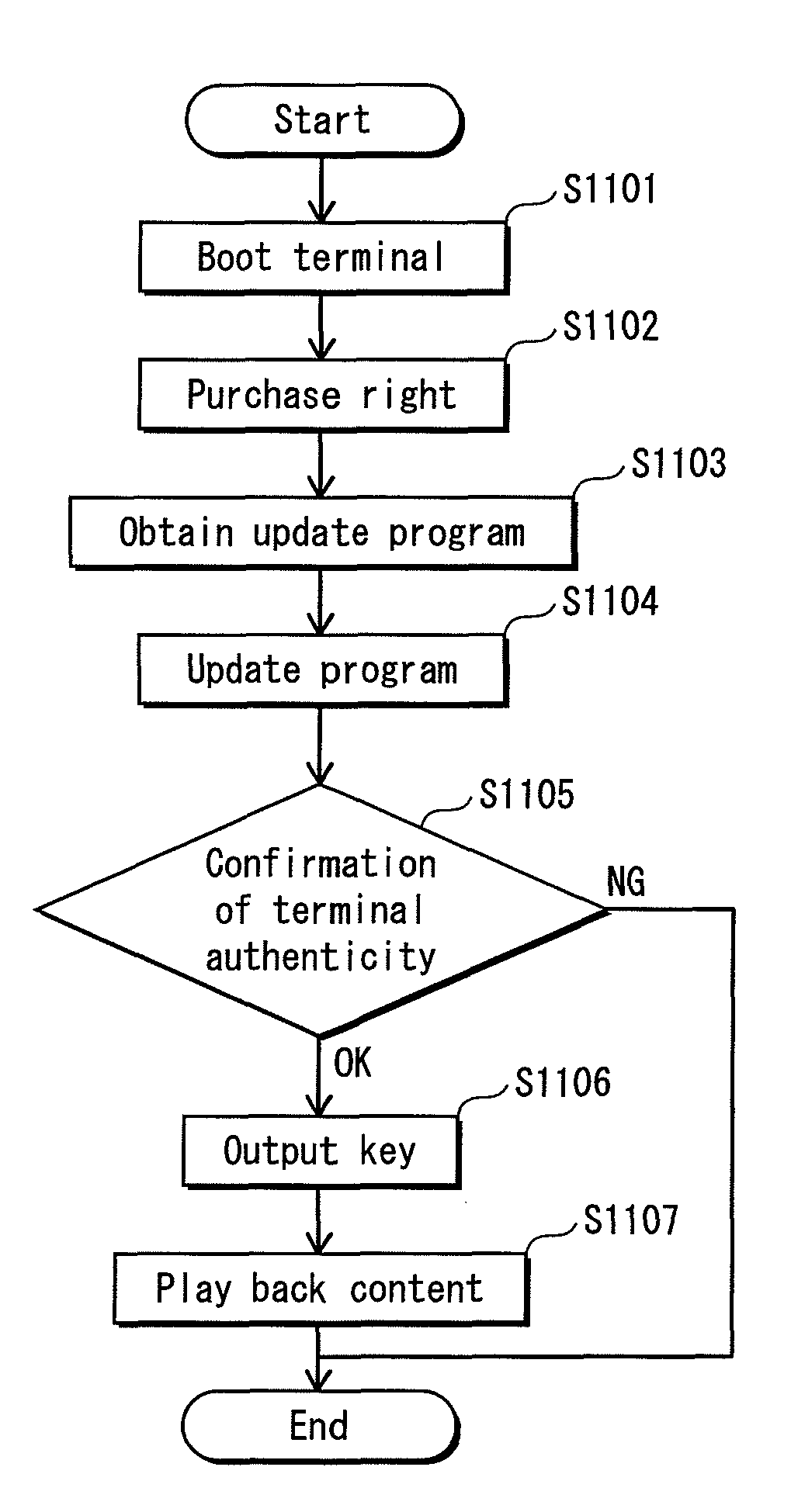
Certifying device, verifying device, verifying system, computer program and integrated circuit
InactiveUS8296561B2Increase authenticityDigital data protectionDigital data authenticationSystem verificationSoftware engineering
An authentication system verifies an authentic computer program, certifies the authenticity itself, and verifies a certification. The authentication system includes a terminal (e.g., requesting device) and a card (e.g., verifying device). The card stores secret information to be used by the terminal, and an update program for the terminal. The card verifies authenticity of the terminal using information obtained from the terminal. When it judges that the terminal is authentic, the card outputs the secret information to the terminal. When it judges that the terminal is not authentic, the card outputs the update program. The terminal is forced to update the program when it attempts to use the secret information.
Owner:SOVEREIGN PEAK VENTURES LLC
Logic verification system and method
InactiveCN1725188AReduce duplication of development workImprove development efficiencyDetecting faulty computer hardwareSystem verificationValidation methods
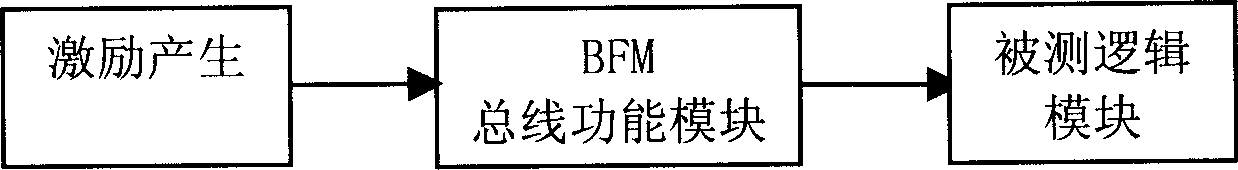
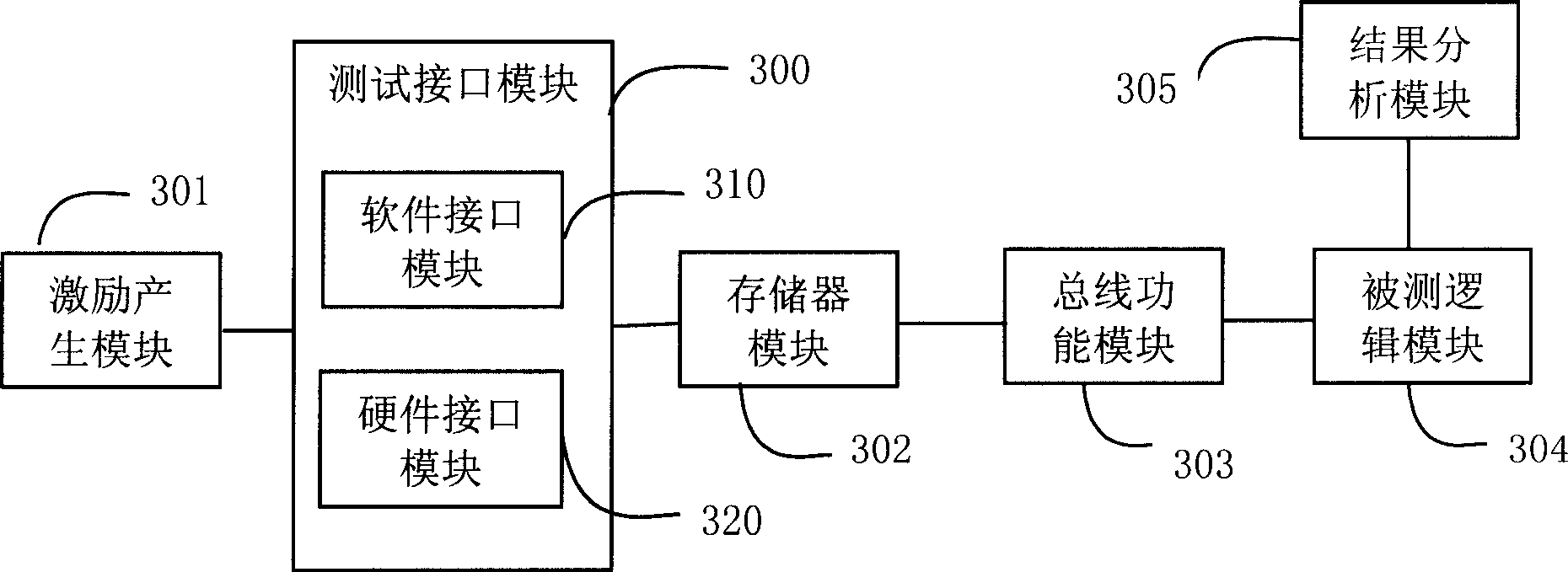
This invention discloses a logic verification system including an excitation generating module, a tested logic module, a result analysis module, a test interface module, a storage module a bus functional module realized by hardware. A method for logic verification includes: generating exciting data necessary for test, writing the exciting data into the needed verified logic chips via different interfaces when carrying out emulation and hardware system verification verifying if the logic is correct based on the output result of the logic chips.
Owner:HUAWEI TECH CO LTD
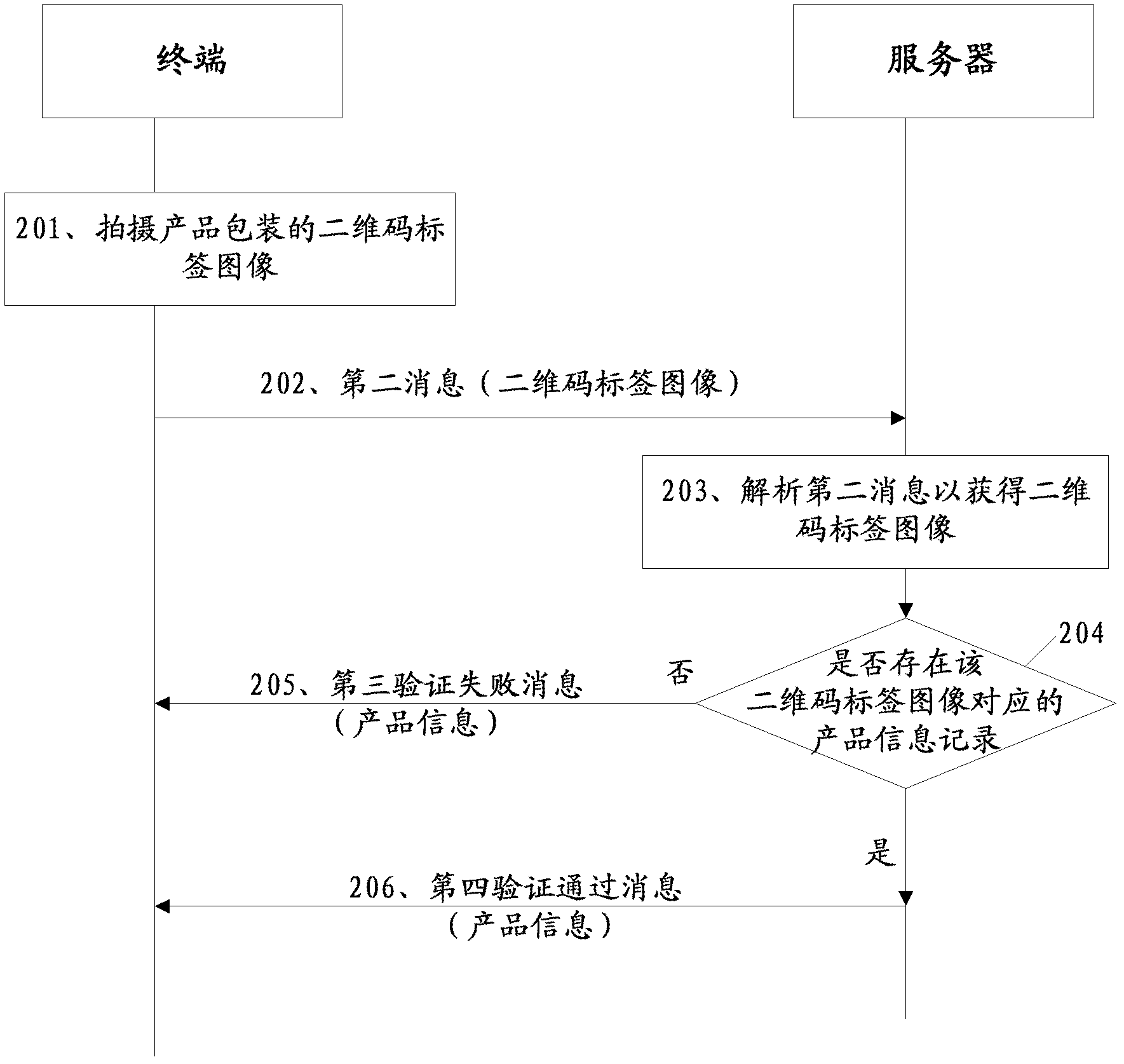
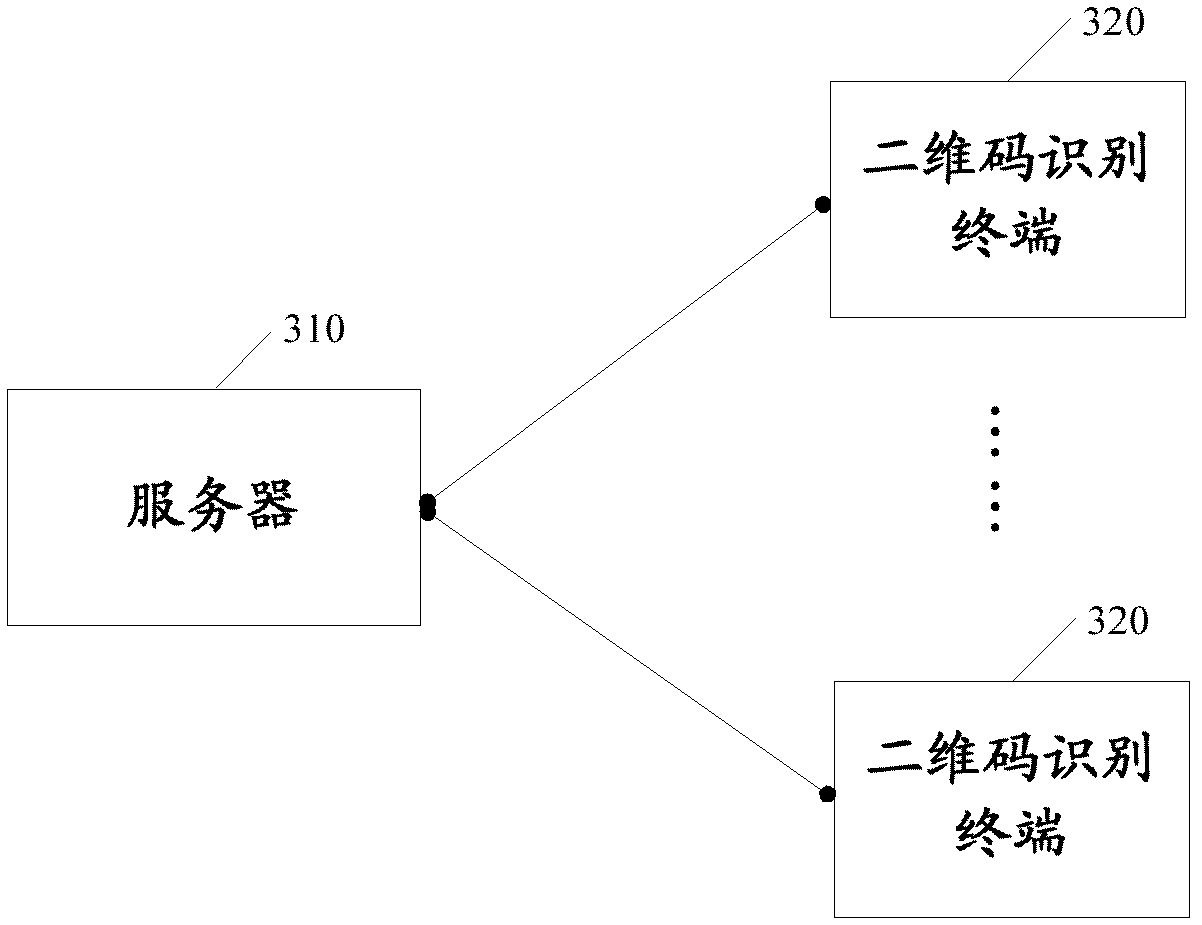
A label verification method and system
InactiveCN102289651ACommerceSensing by electromagnetic radiationSystem verificationSoftware engineering
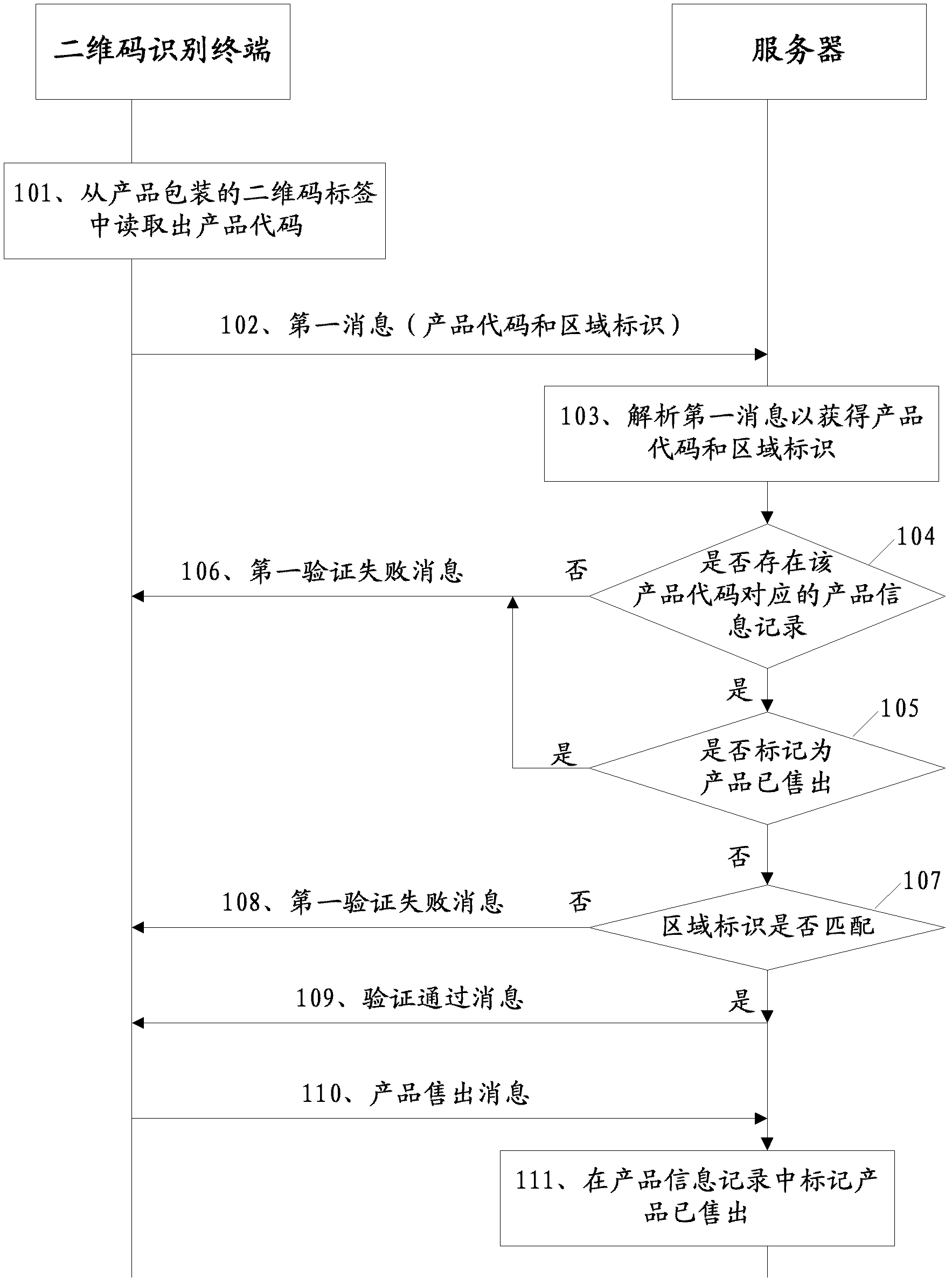
The embodiment of the invention discloses a label verification method and system. In one of the schemes, the two-dimensional code identification terminal reads the product code from the two-dimensional code label of the product package; sends to the server a message carrying the product code and the area identification corresponding to the area where the two-dimensional code identification terminal is located; Based on this, the server performs relevant verification and feeds back the verification results. This mechanism can be applied to authenticity identification and "false goods" identification in the process of product sales. The technical solution provided by the embodiment of the present invention is beneficial to improve the anti-counterfeiting and anti-"smuggling" capabilities of the product. The solution provided by the embodiment of the present invention.
Owner:SHENZHEN BEAUTY STAR
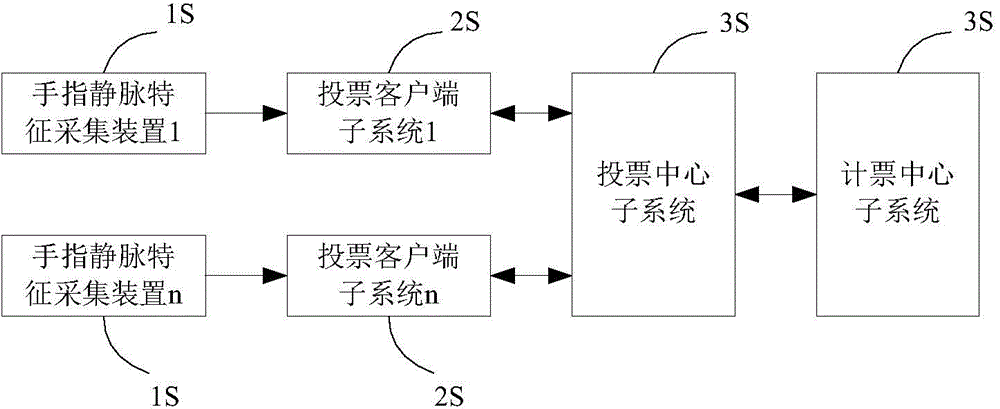
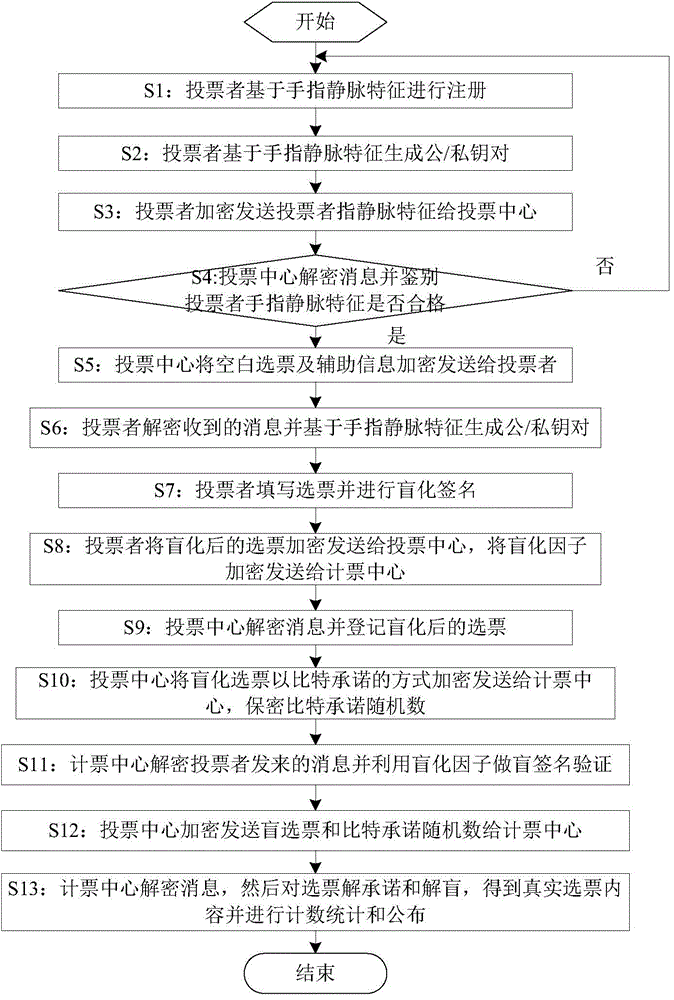
Electronic voting system based on finger vein feature recognition
ActiveCN104392534ASafe Finger Vein AuthenticationImprove ease of useVoting apparatusCharacter and pattern recognitionSystem verificationEngineering
The invention discloses an electronic voting system based on finger vein feature recognition. The system comprises a finger vein feature acquisition device, a voting client sub-system, a voting center sub-system and a vote counting center sub-system. The finger vein image of a voter is acquired by the finger vein feature acquisition device, the voter is registered in the voting center sub-system by the finger vein feature, the legality of the voter is verified by the voting center sub-system, and the vote is issued to the voter if the voter is qualified. A biological characteristic public / private key pair of the voter can be generated by software of the voting client sub-system, and the voting process is realized by the interaction of security protocols such as certificate signing among the voting client sub-system, the voting center sub-system and the vote counting center sub-system. Compared with other electronic voting systems, the system enables a finger vein feature recognition technology to be introduced, and the finger vein feature recognition technology replaces ways such as passwords and digital certificates and takes part in the network identity authentication and the voting process, so that the safety and use convenience of the system are improved; the electronic voting system based on finger vein feature recognition also has anonymity, transparency and openness.
Owner:SOUTHWEST JIAOTONG UNIV
Enhancing security of a system via access by an embedded controller to a secure storage device
ActiveUS7917741B2Improve securityVolume/mass flow measurementAnalogue secracy/subscription systemsMicrocontrollerSystem verification
System and method for performing pre-boot security verification in a system that includes a host processor and memory, an embedded microcontroller with an auxiliary memory, e.g., an on-chip ROM, or memory controlled to prohibit user-tampering with the contents of the memory, and one or more pre-boot security components coupled to the embedded microcontroller. Upon power-up, but before host processor boot-up, the embedded microcontroller accesses the auxiliary memory and executes the program instructions to verify system security using the one or more pre-boot security components. The one or more pre-boot security components includes at least one identity verification component, e.g., a smart card, or a biometric sensor, e.g., a fingerprint sensor, a retinal scanner, and / or a voiceprint sensor, etc., and / or at least one system verification component, e.g., TPM, to query the system for system state information, and verify that the system has not been compromised.
Owner:MICROCHIP TECH INC
Simulation method and system for simulating real network environment based on virtualization, electronic equipment and storage medium
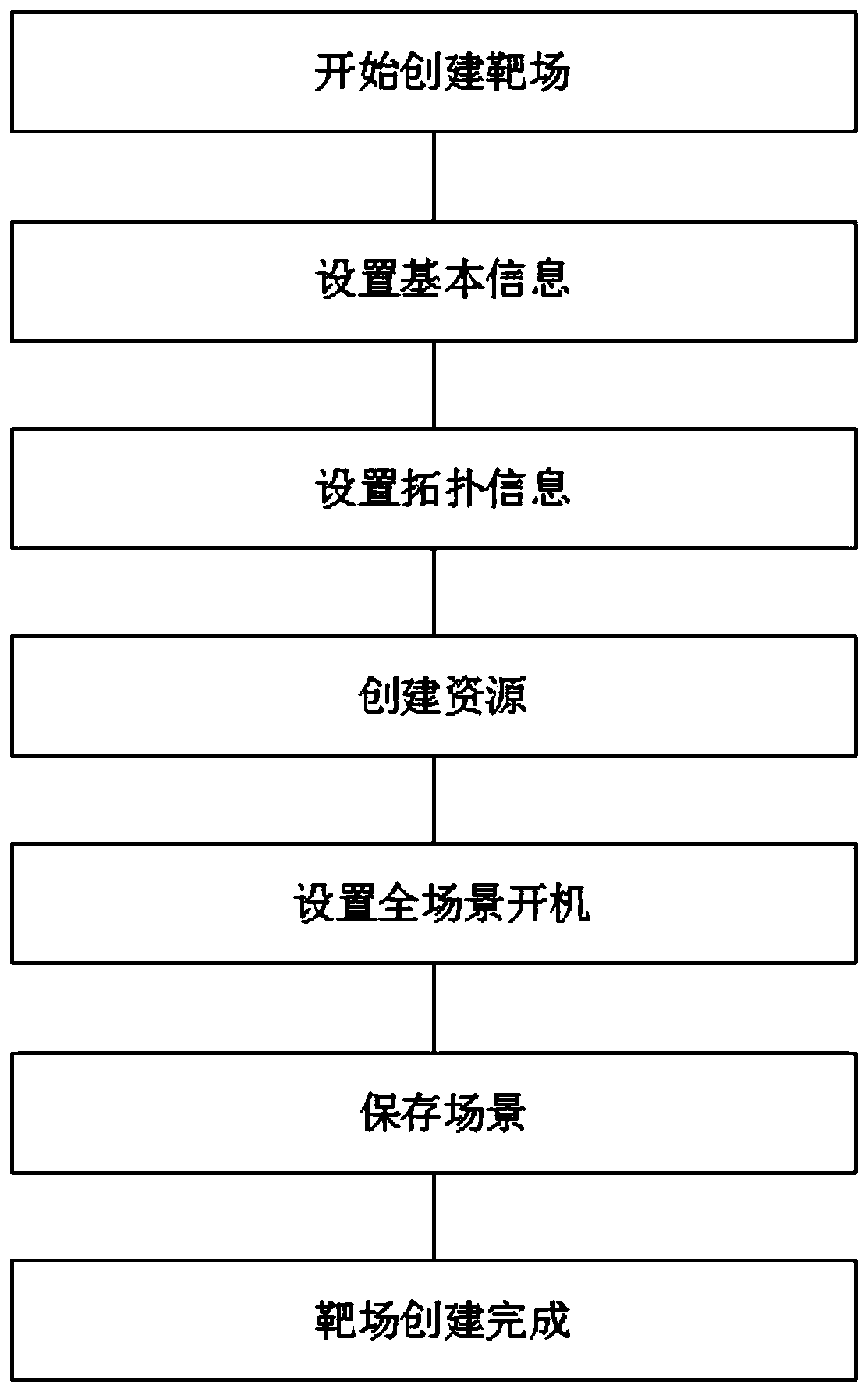
PendingCN111555913AMeet different application requirementsImprove weak linksData switching networksSoftware simulation/interpretation/emulationVirtualizationSystem verification
The invention relates to the technical field of virtual network simulation, in particular to a simulation method and system for simulating a real network environment based on virtualization, electronic equipment and a storage medium. The simulation method comprises the following steps: starting to create a target range; setting basic information; setting topology information; creating resources; setting full-scene startup; storing the scene; and completing shoot range creation. According to the simulation method and system for simulating the real network environment based on virtualization, the electronic equipment and the storage medium, network attack and defense parameters such as a topological structure, the number of nodes and rule parameters can be configured according to needs; multi-mode drilling can be carried out to meet different application requirements, including red and blue confrontation, individual soldier drilling and equipment system verification; in the drilling process, the target range can support rapid deployment of different attack and defense scenes in the aspects of operation resources and management resources, so that safety evaluation is conducted on thetarget range in an omnibearing mode, and weak links are perfected in an emphasized mode.
Owner:BEIJING SAFE CODE TECH
Gate-level power consumption analysis device and gate-level power consumption analysis method based on hardware platform
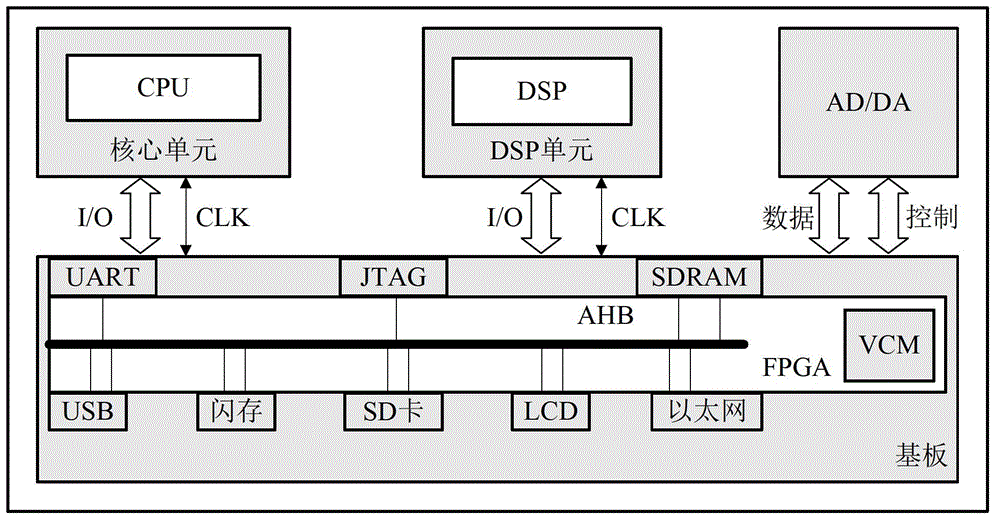
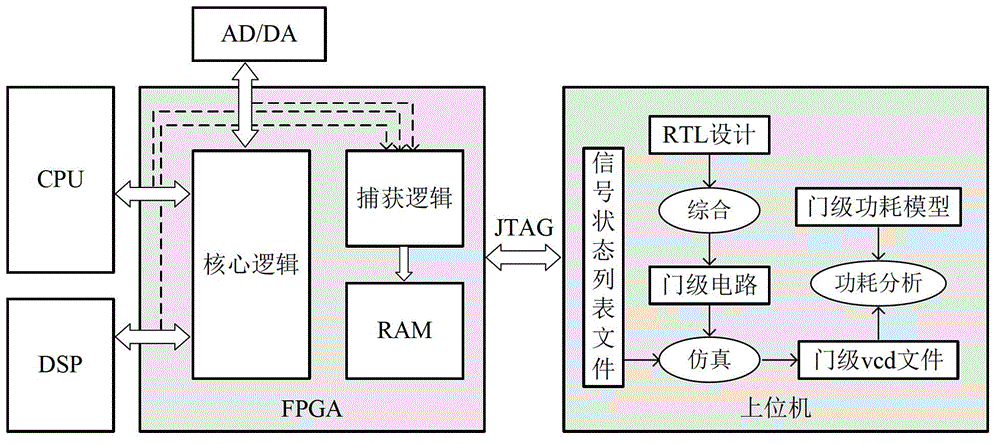
ActiveCN102866291AEstimate power consumption levels in real timeIncrease success rateElectric devicesElectric power measurementSystem verificationComputer module
A gate-level power consumption analysis device comprises a vector capture module, a control module, a storage module and a power consumption analysis module, wherein the vector capture module, the control module and the storage module are arranged on a hardware platform, and the power consumption analysis module is arranged in a principal computer; the control module supplies a clock control signal to the work and the signal capture of the hardware platform, the vector capture module captures a real-time signal state under the clock control, the storage module is used for storing a captured signal, and the power consumption analysis module generates a gate-level waveform conversion file according to the captured signal, establishing a gate-level power consumption model and completing the power consumption analysis. Correspondently, the invention also provides a power consumption analysis method based on an on-chip system verification platform. The power consumption analysis device can evaluate the running state of the entire system before the realization of the rear end of a system on chip (SoC), can estimate the power consumption level of a tested module in real time and finally gives an entire performance index of the system. The success rate of a SoC disposable chip can be greatly improved.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
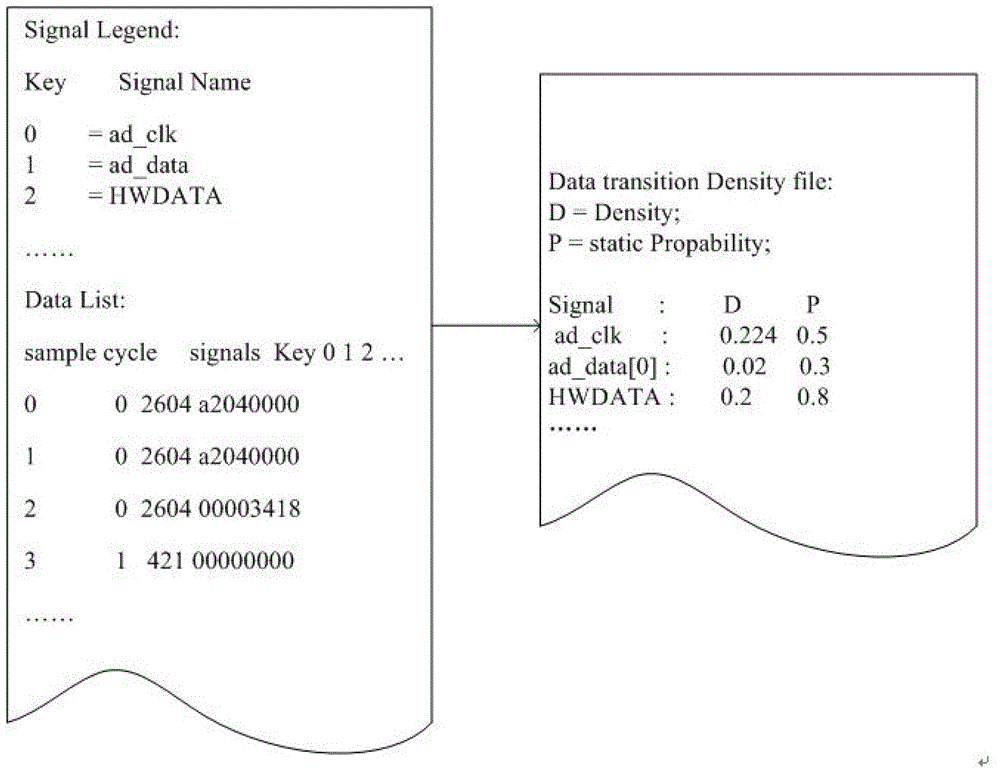
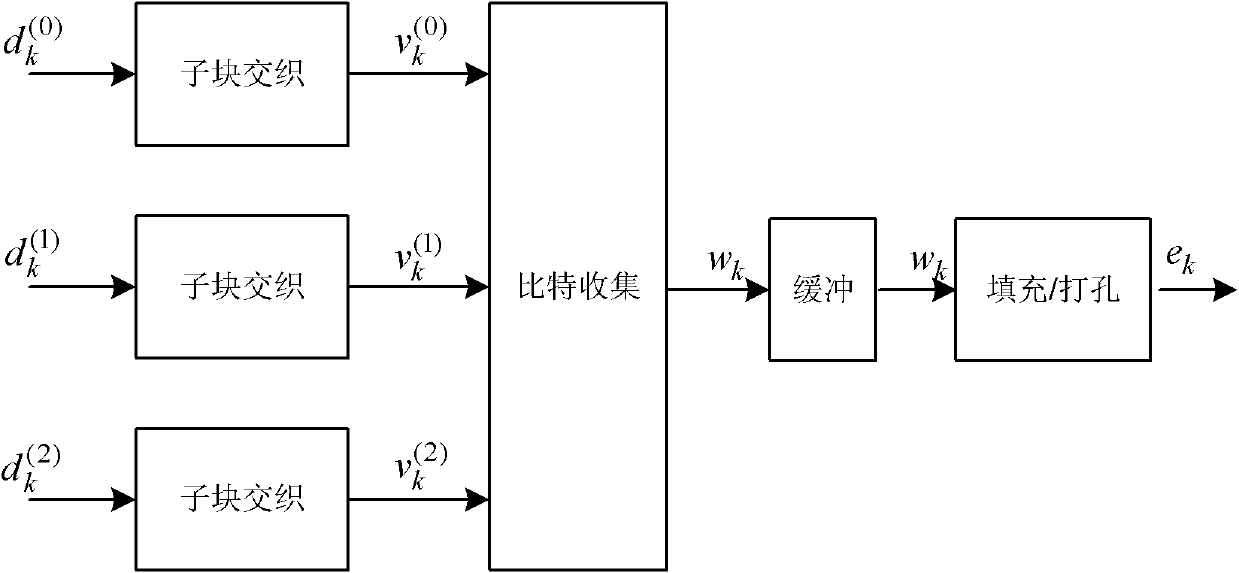
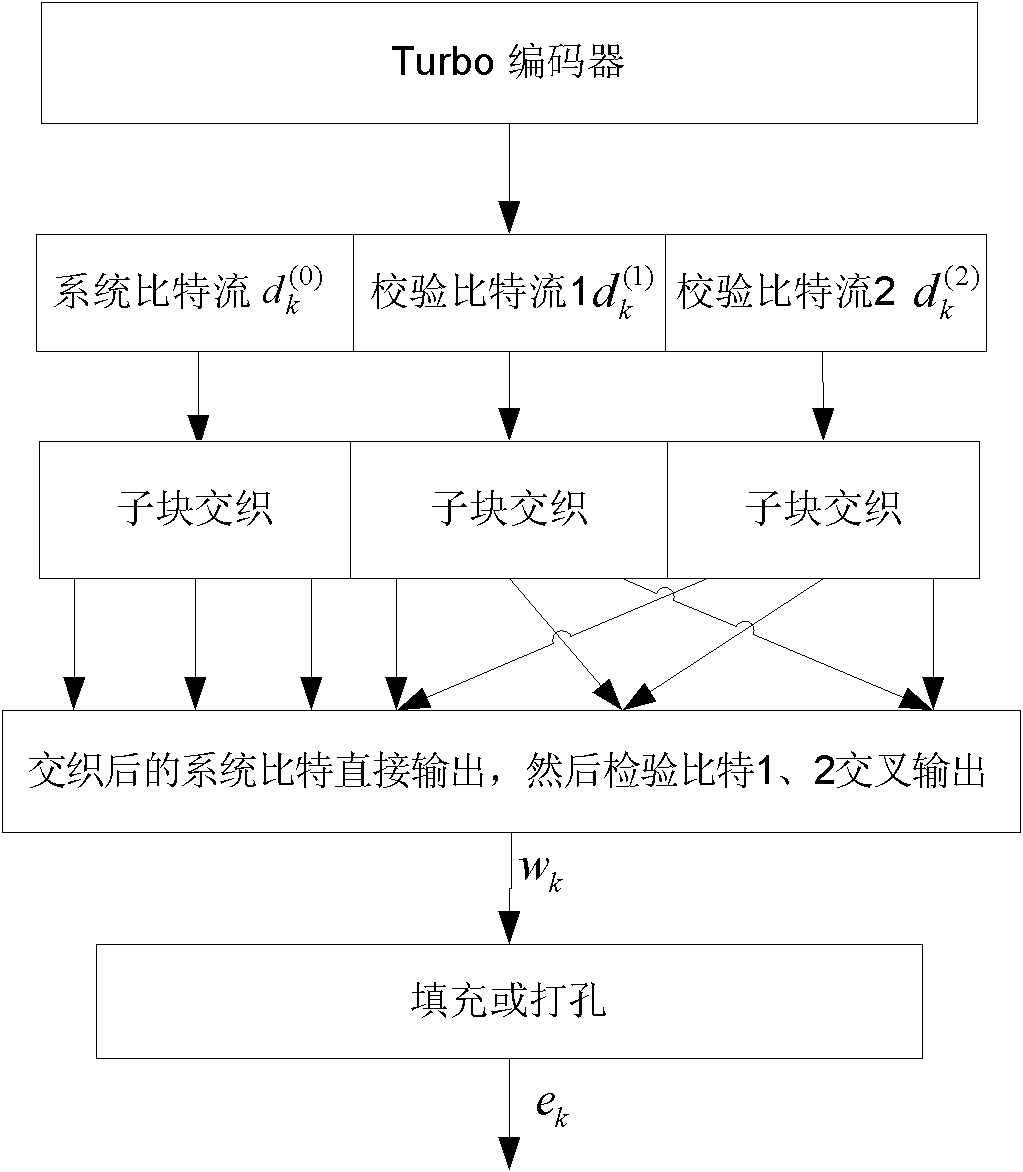
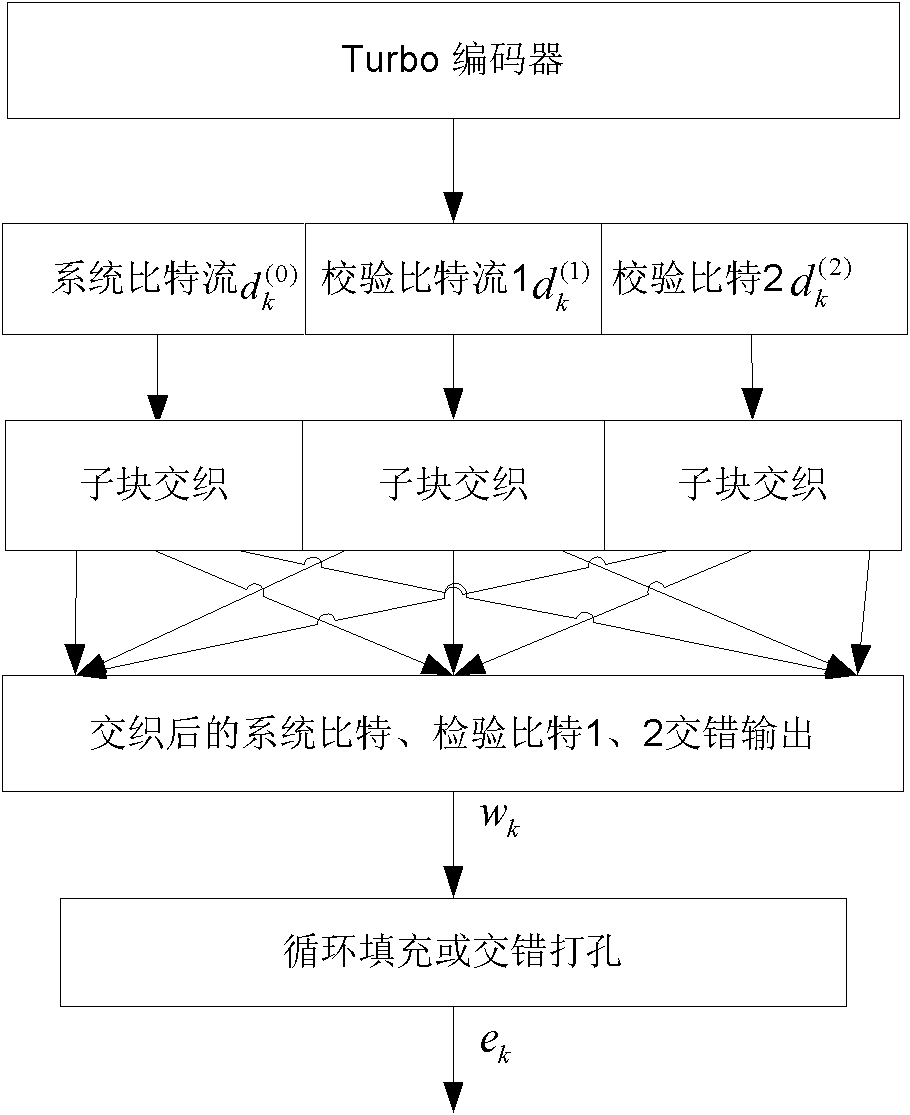
Rate matching method in LTE (Long Term Evolution) downlink system
InactiveCN102325000AImprove realizabilityReduce complexityError preventionSystem verificationPunching
The invention discloses a rate matching method in an LTE (Long Term Evolution) downlink system, wherein specific to a 3GPP (The 3rd Generation Partnership Project) LTE downlink system, a transmission channel model based on Turbo codes is proposed, and circulatory filling and interlaced punching are adopted in the rate matching method in the LTE downlink system. In the invention, the rate matchingmethod comprises the steps of: firstly, performing bit collection by adopting a system-verification information bit stream interlaced combination method, and then adding or removing a corresponding number of bits to obtain corresponding code rate by adopting a circulatory filling or interlaced punching method specific to the collected bit stream, thereby realizing rate matching. Experimental tests show that compared with the traditional LET rate matching method, the rate matching method disclosed by the invention can be used for effectively increasing a false bit error rate (BER) performance.In addition, the rate matching method in the LET downlink system has the advantages that the positioning and deleting of dummy bits are omitted, the computational complexity is lowered, and the realizability of an algorithm on software and hardware is increased.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
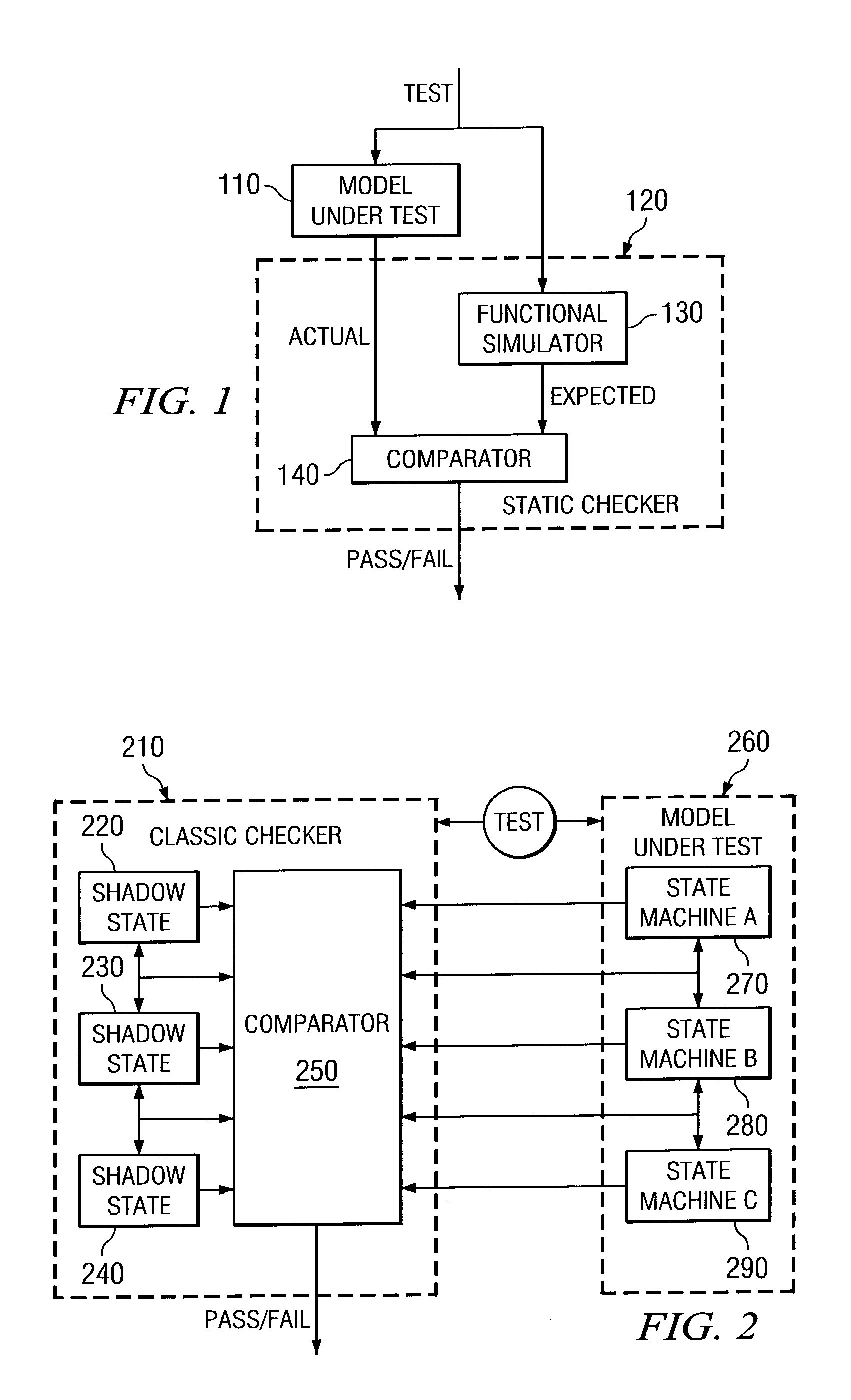
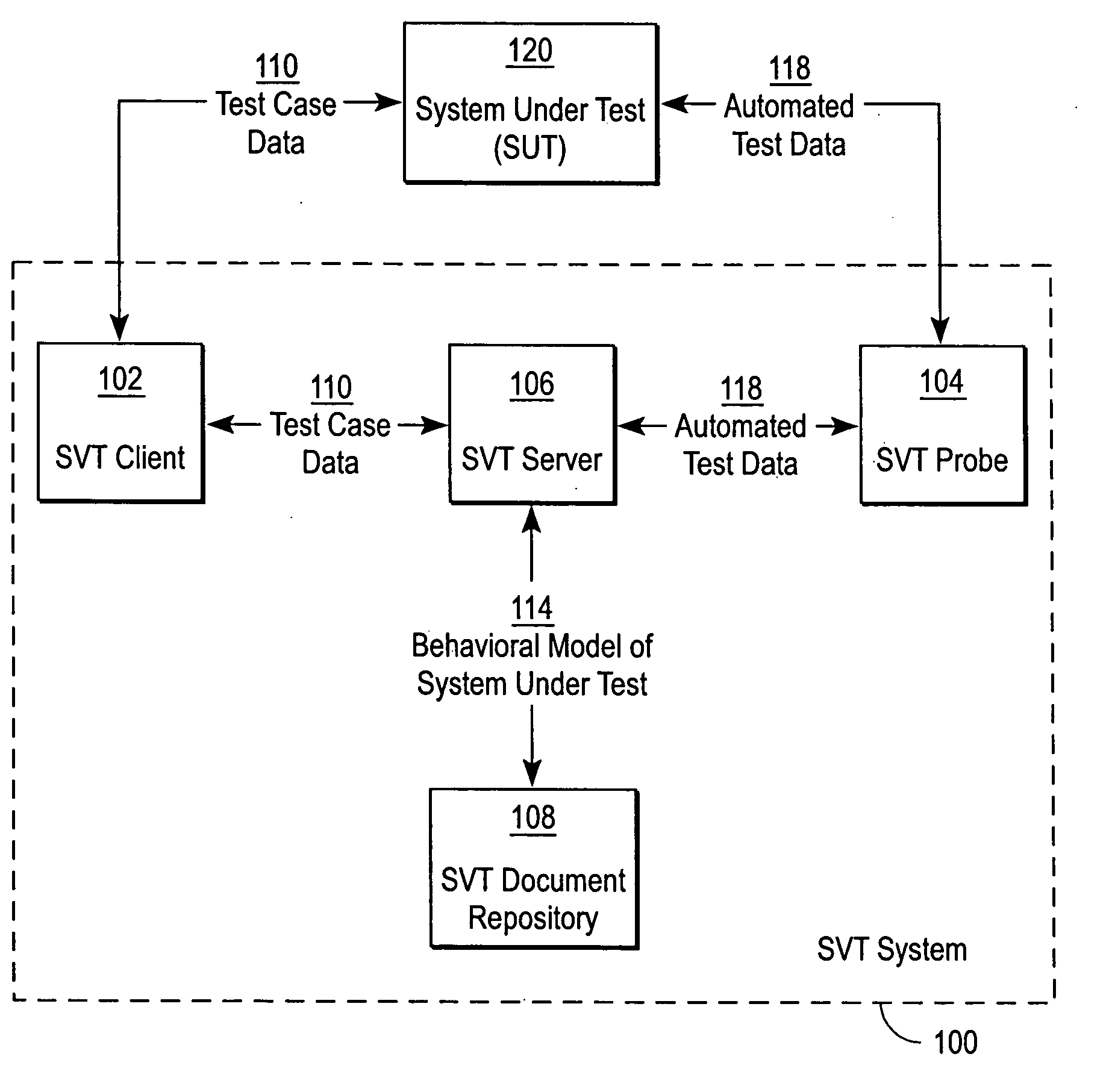
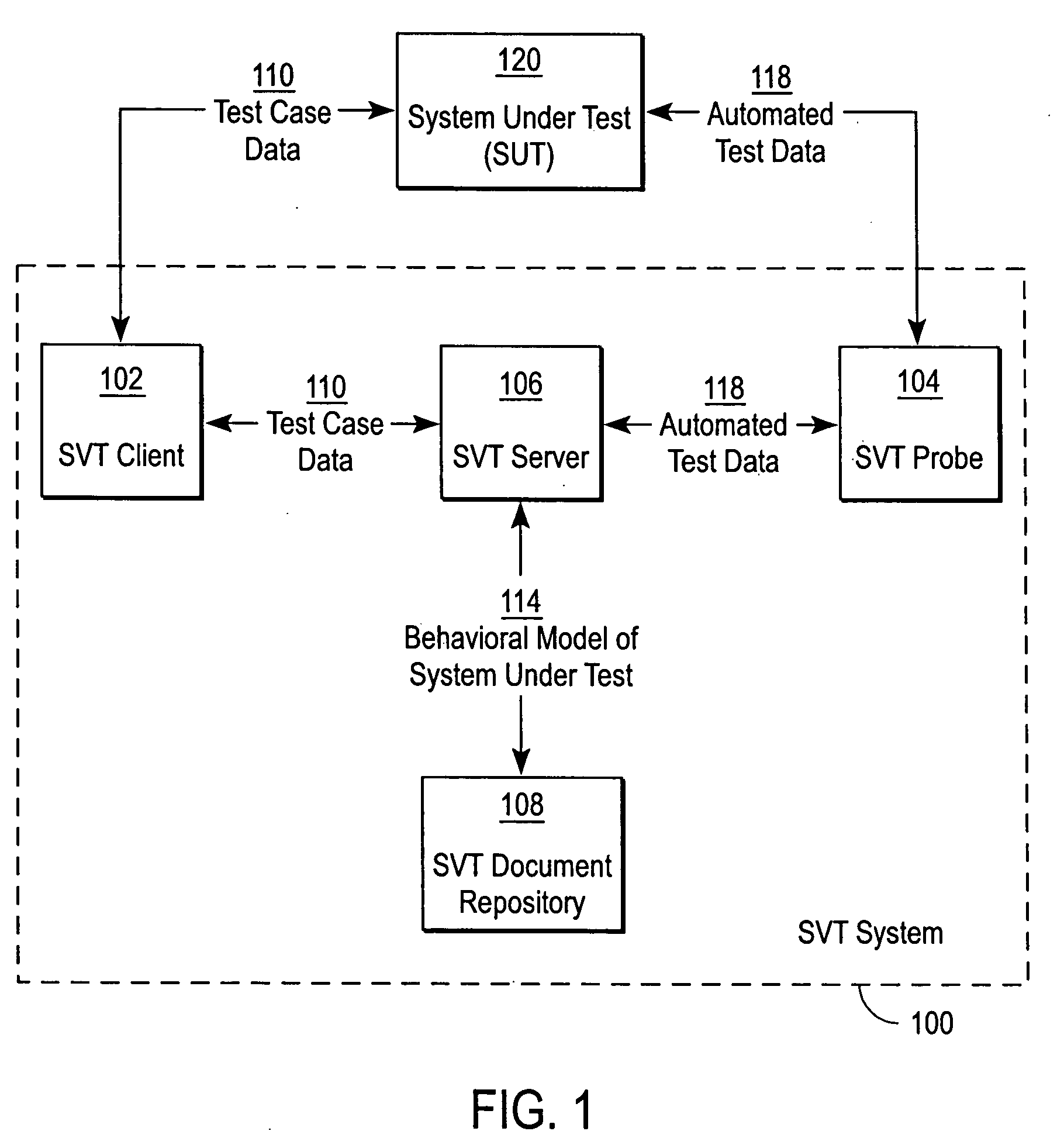
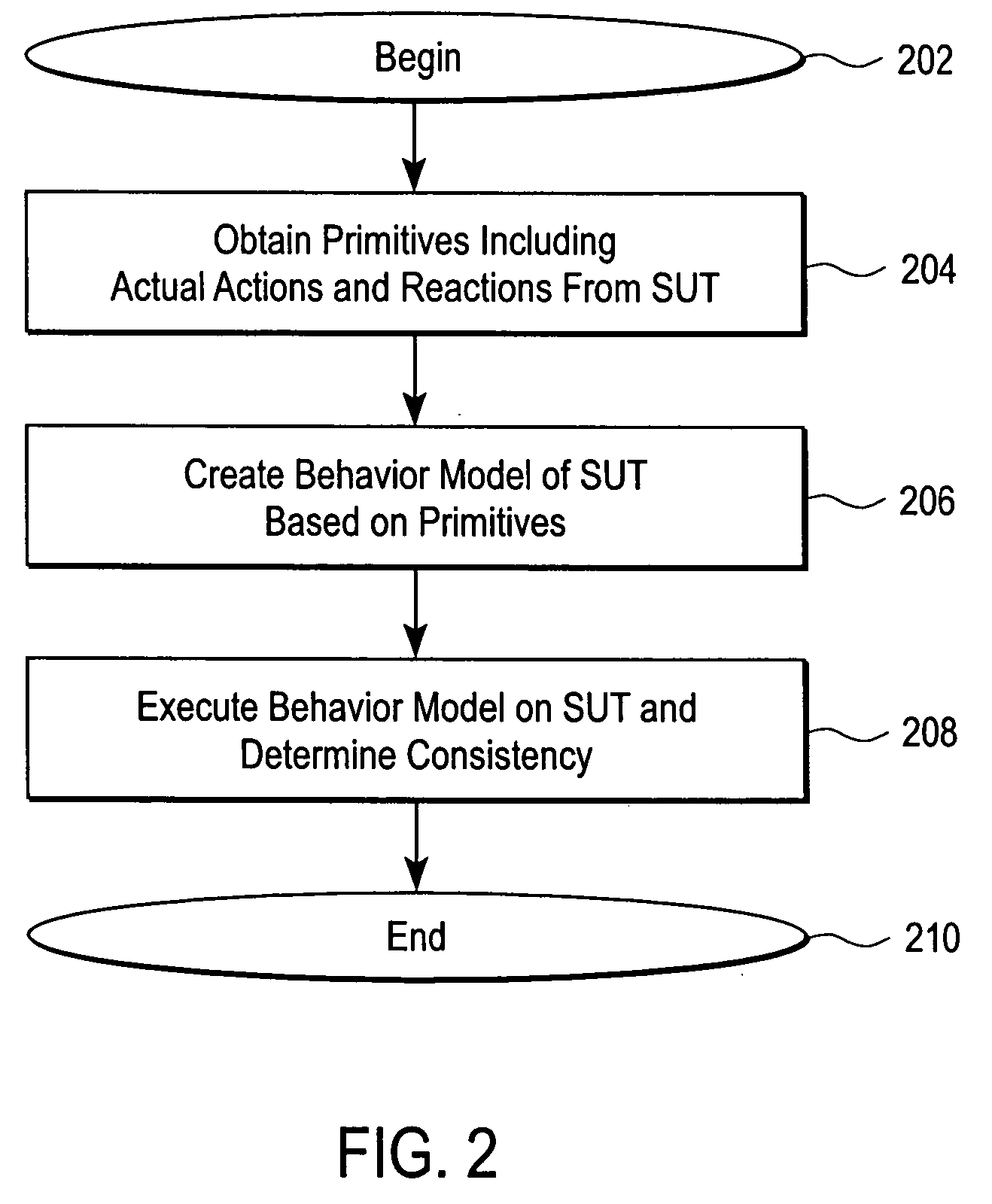
System verification test using a behavior model
ActiveUS20060161508A1Increase coverageLess testingElectronic circuit testingError detection/correctionSystem verificationTheoretical computer science
The present invention provides a system verification system that automatically generates a behavior model modeling the system under test in terms of actions of a test case and a range of expected reactions corresponding to those actions. In this regard, the system verification system obtains a set of actions and individual reactions corresponding to the actions from a plurality of runs of a test case for the system under test, and automatically generates the behavior model representing the system under test in terms of the set of actions and a range of expected reactions each range corresponding one of the actions. The range of expected reactions generalizes and includes all or most of the individual reactions corresponding to said one of the actions.
Owner:SPIRENT COMM
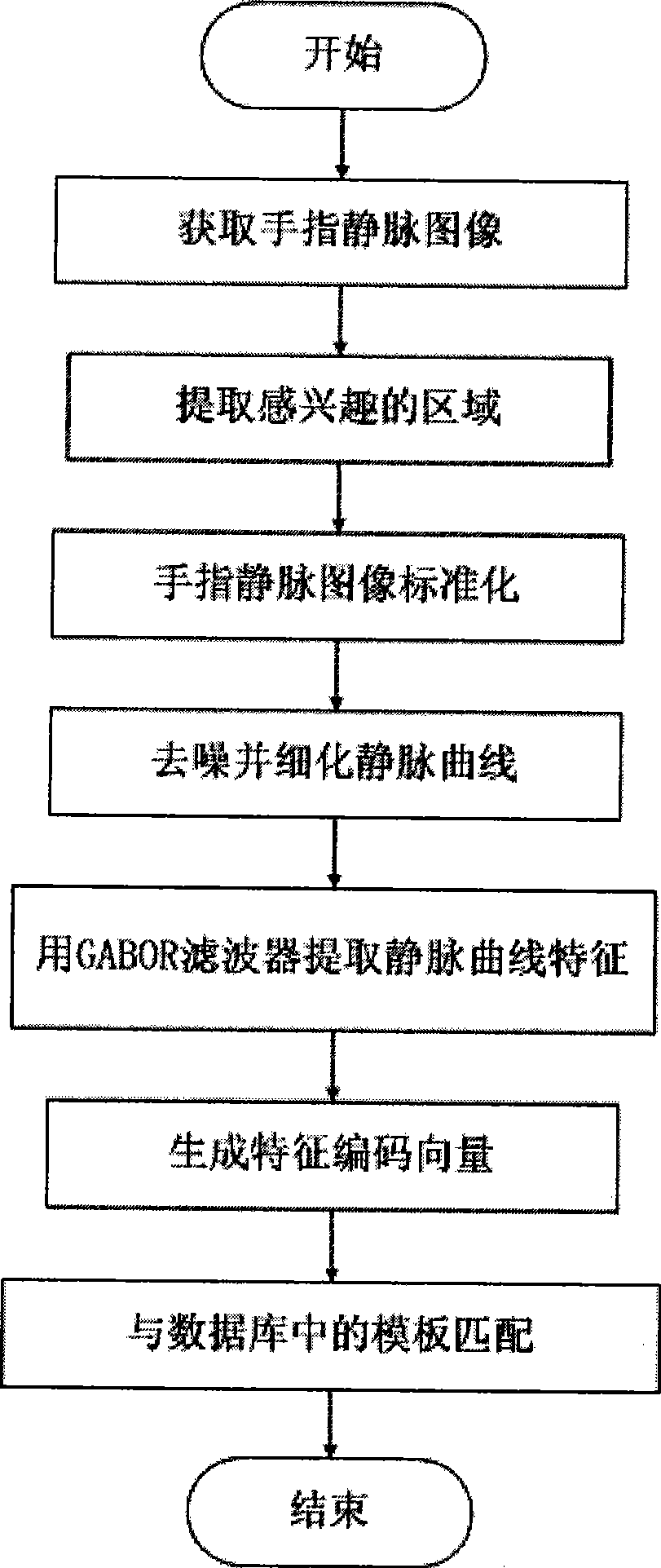
Finger vein recognition system
InactiveCN101477622AAvoid breakingEnsure convenienceCharacter and pattern recognitionVeinFinger vein recognition
The invention discloses a finger vein recognizing system which belongs to the technical field of biometric identification. The invention further discloses equipment which comprises a finger vein image collecting device, an image processing device and an image recognizing and storing device. The image collecting device is connected with the image processing device through a USB interface, and the image processing device is connected with the mage recognizing and storing device through the USB interface. The finger vein recognizing system comprises two modes: an authentication mode and a recognition mode, wherein, the authentication mode is used for verifying whether a person to be verified is a designated person or not, that is, a user first selects a corresponding user number when the system verification is performed; after finger vein images of the person to be verified are collected, a comparison is made between the finger vein images and the template which is stored in a database and corresponds to the user number, so that whether the user is valid or not can be determined; the recognition mode is used for verifying which registered person the person to be verified is, that is, a comparison is made between finger vein image characteristics of the user and the template of the user in the database; and then a template number with the greatest similarity is found, so as to determine the identity of the person to be verified.
Owner:SHANDONG UNIV
Logic design segmentation method and system
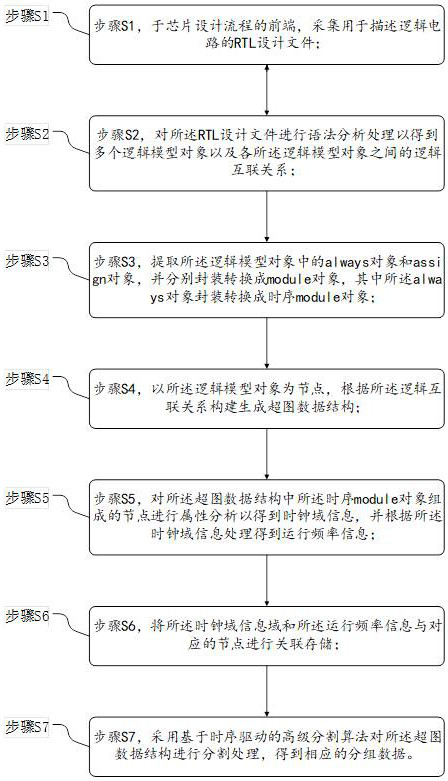
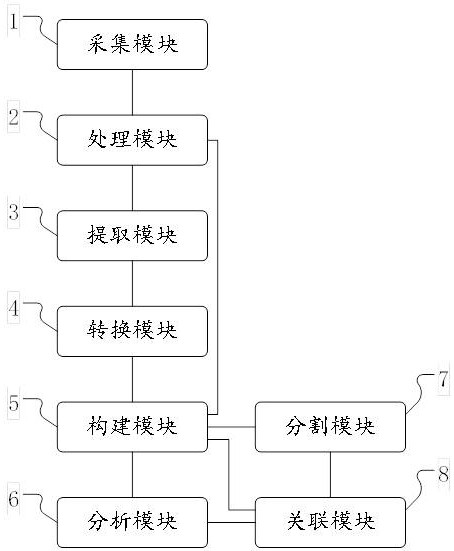
ActiveCN112257369AAccelerate the process of front-end functional verificationAccelerate time to marketCAD circuit designSpecial data processing applicationsInformation processingSystem verification
The embodiment of the invention provides a logic design segmentation method and system, and belongs to the technical field of logic array prototype system verification, and the method specifically comprises the steps: collecting an RTL design file for describing a logic circuit; performing grammatical analysis processing on the RTL design file, extracting an always object and an assign object in the logic model object, respectively packaging, constructing and generating a hypergraph data structure, performing attribute analysis, processing according to the clock domain information to obtain operation frequency information, and performing associated storage on the clock domain information domain and the operation frequency information and corresponding nodes; and performing segmentation processing to obtain corresponding grouped data. By means of the processing scheme, other processing at the back end of the process is not affected, the segmentation duration is shortened, the segmentation efficiency is improved, meanwhile, efficient, reasonable and correct segmentation processing is conducted on the chip design logic content, the performance and efficiency of design segmentation aregreatly improved, then the process of user front-end function verification is accelerated, and the appearance of integrated circuit products is accelerated.
Owner:S2C
Method and system for secure user identification
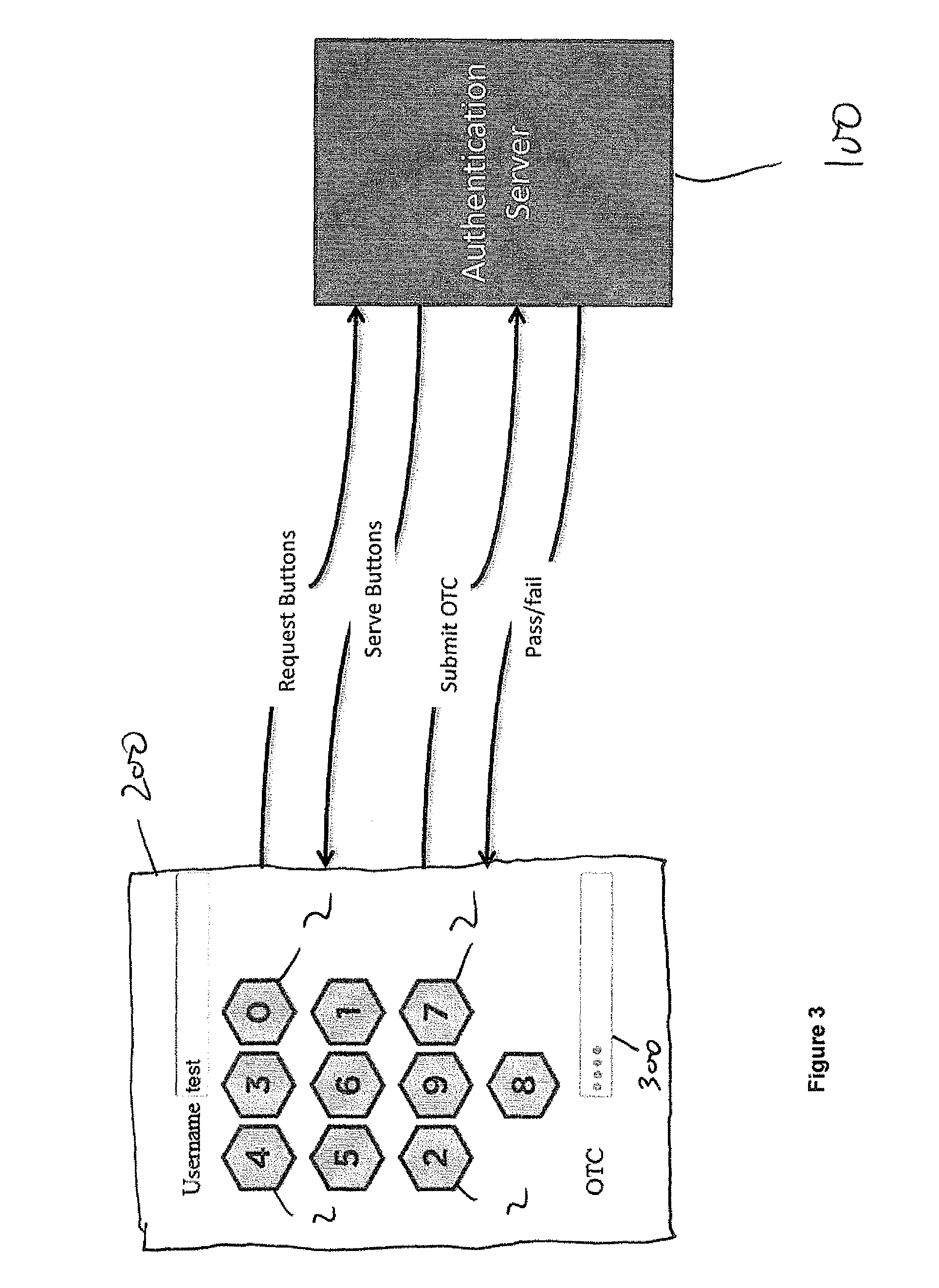
ActiveUS20150134526A1Process safetyReduce riskAcutation objectsFinanceComputerized systemDisplay device
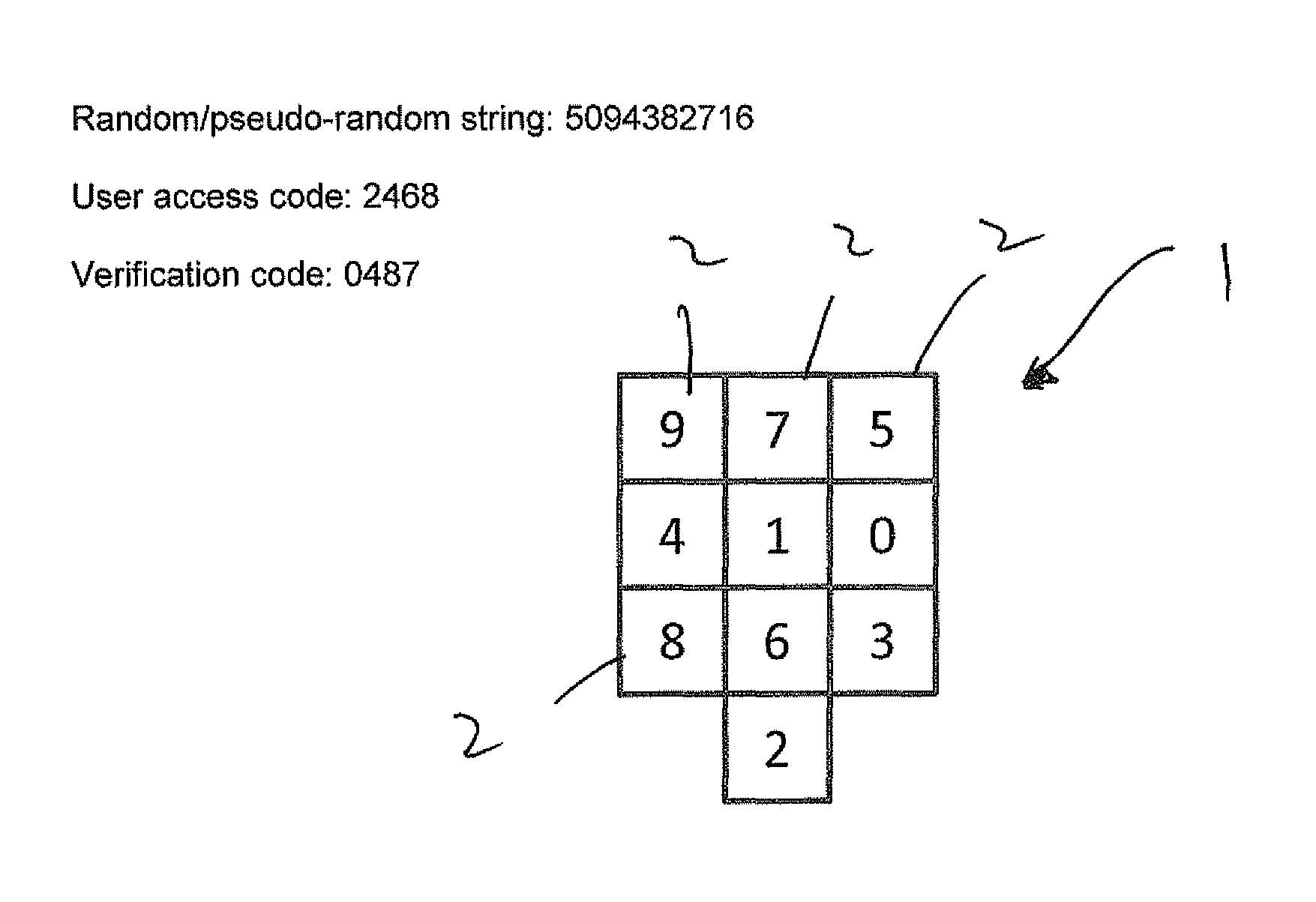
There is disclosed a method and system for verifying an identity of a user to a computer system. The user is assigned a user access code in the form of an invariant string of integers from 0 to 9, with length no greater than ten. The user access code is stored in the computer system; the computer system generates a ten-digit random or pseudo-random non-repeating string of the integers 0 to 9, the string having 1st to 10th positions each with a unique integer and having respective positional values 1 to 10; and the computer system performs a predetermined algorithm to combine the user access code and the random or pseudo-random string, thereby to determine a one-time verification code in the form of a string of the same length as the user access code. The computer system also generates 1st to 10th cells, the cells having respective locational values 1 to 10; populates the cells with the integers of the non-repeating string such that the locational value of each cell corresponds to the integer it contains combined with the random or pseudo-random string using the same predetermined algorithm as used previously; and displays the cells on a display. A user uses an input device of the computer system to select, in order, the cells on the display that contain the integers constituting the user access code. Each act of selection returns the locational value of the selected cell, thereby to generate a one-time transaction code comprising a string of integers from 0 to 9 having the same length as the user access code. The computer system then compares the verification code with the one-time transaction code and makes a successful identity verification if the verification code matches the one-time transaction code.
Owner:SWIVEL SECURE LTD
Method and system for completing a transaction between a customer and a merchant
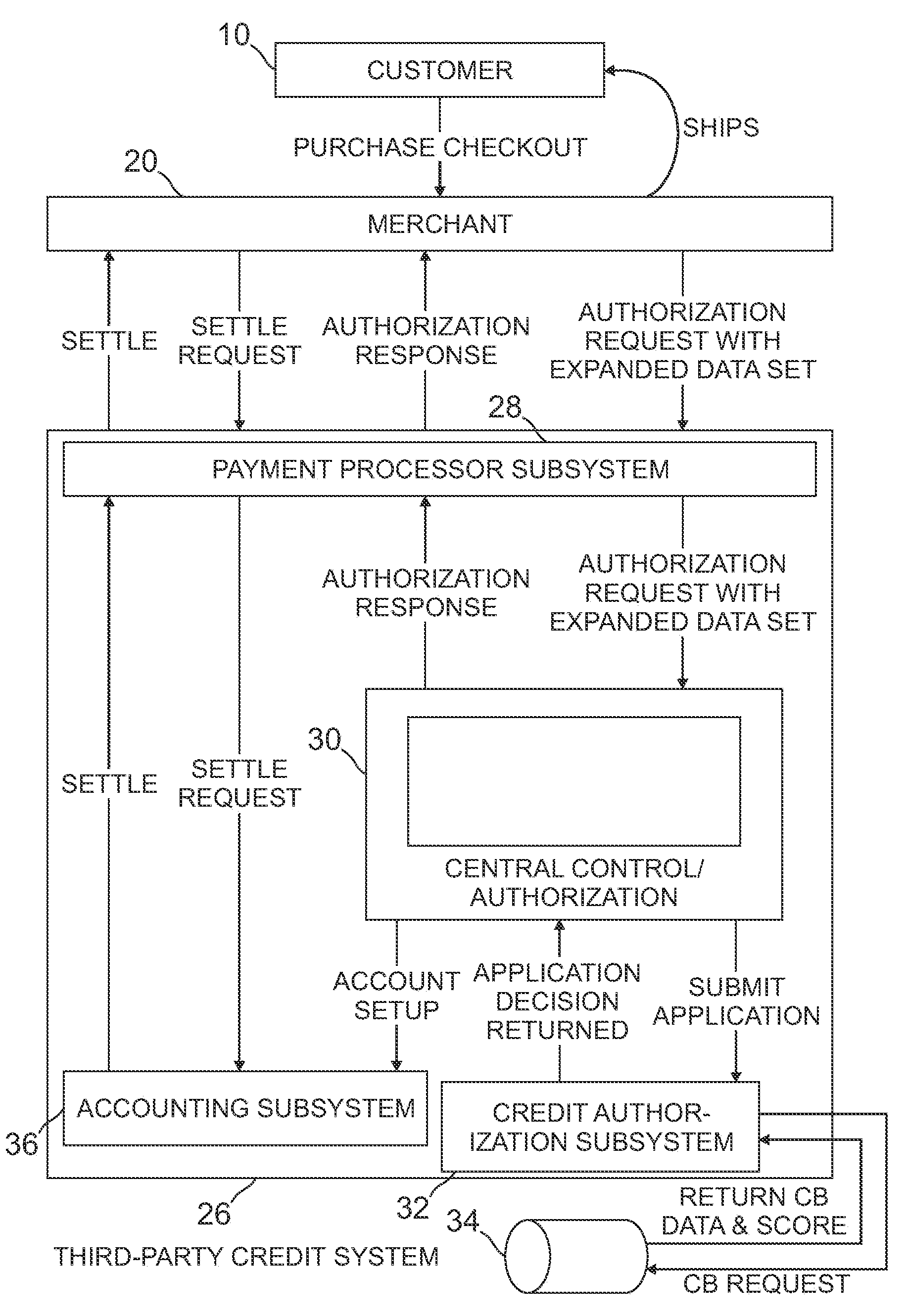
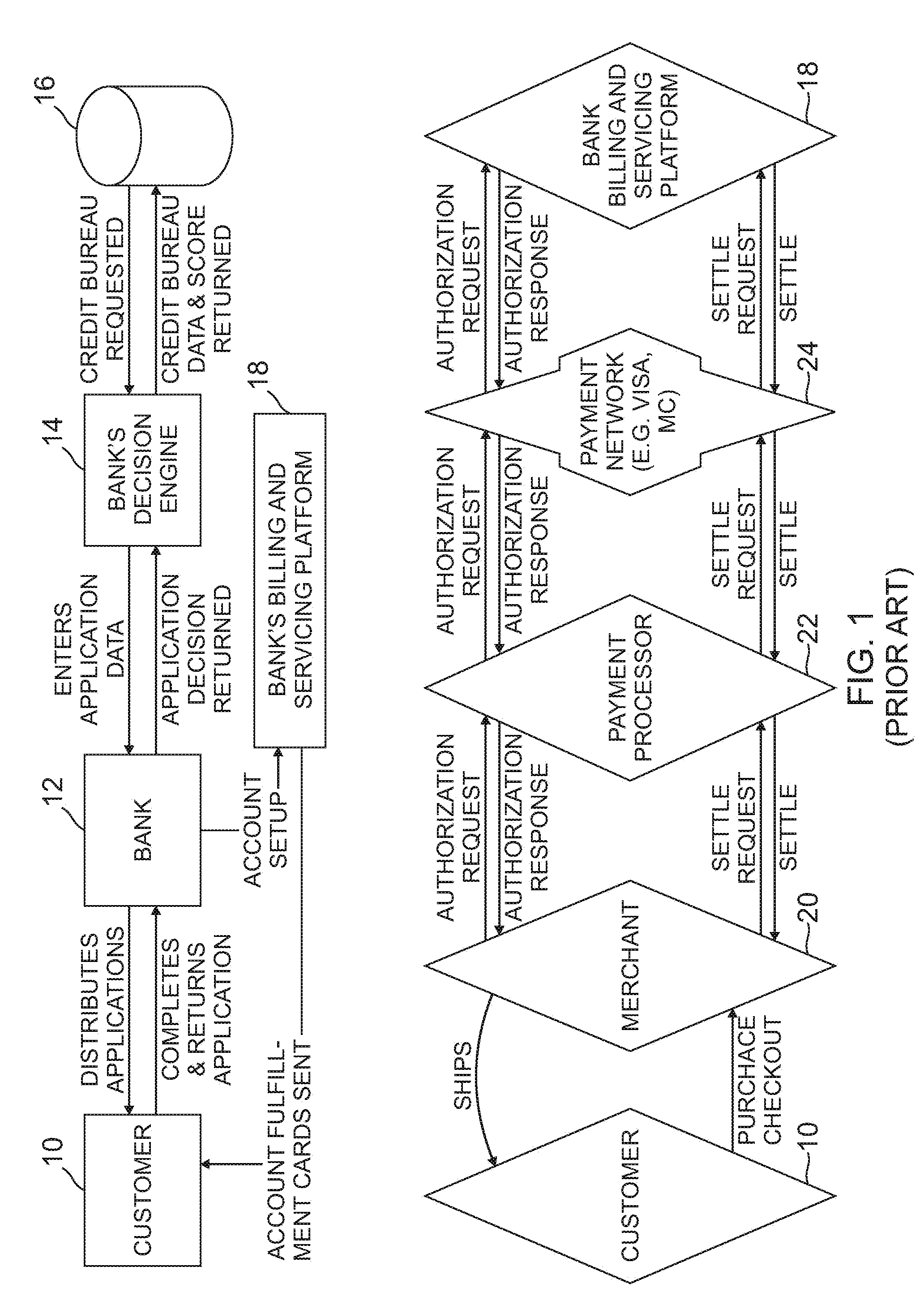
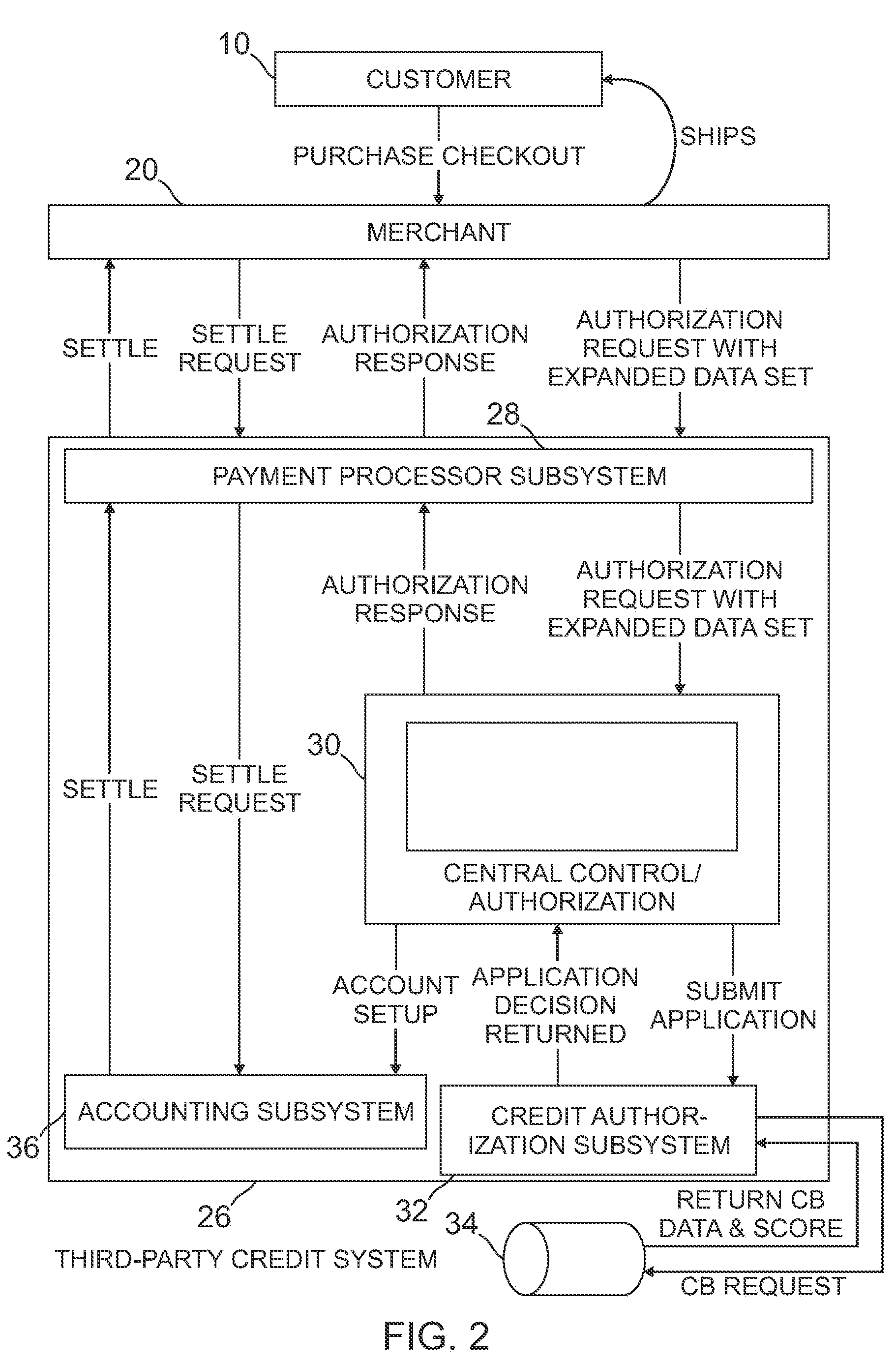
InactiveUS20110125619A1Economic and risk mitigation efficiencyOvercome deficienciesComplete banking machinesFinanceAuthorizationDatabase
A computer-implemented method for completing a transaction between a customer and at least one merchant receives, by a transaction system, an authorization request including customer data and transaction specific data from the merchant, wherein, prior to the authorization request, the customer is unknown to the transaction system; authenticates the customer by the transaction system based at least in part upon at least one of the following: at least a portion of the customer data, at least a portion of the transaction specific data or any combination thereof; authorizes the transaction by the transaction system based at least in part upon at least one of the following: at least a portion of the customer data, at least a portion of the transaction specific data or any combination thereof; and communicates the authorization response to the merchant during the transaction. An apparatus for implementing the method is disclosed.
Owner:PAYPAL INC
Processing technology digital planning method and software platform
InactiveCN112712303AReduce processingRealize the digitalization of the whole processDigital data information retrievalResourcesDimensional simulationMachine parts
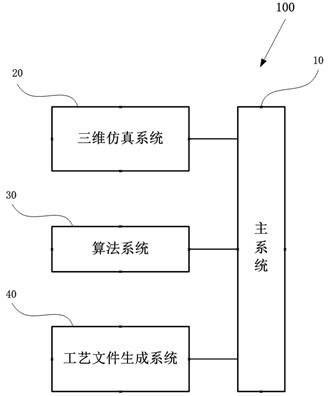
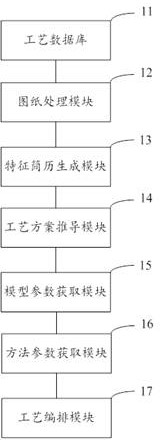
The invention provides a machining process digital planning method and a software platform, and belongs to the field of part machining. The method comprises the steps that a main system obtains a machining drawing of a to-be-machined part, and generates a feature resume corresponding to the features of the to-be-machined part; the three-dimensional simulation system generates at least one process method modeling corresponding to the to-be-processed part according to the feature resume and the process method of the process database, and performs interference verification; the algorithm system performs operation on features in the feature resume according to a preset algorithm, and performs screening on process method modeling verified by the three-dimensional simulation system to obtain a theoretical processing flow; the three-dimensional simulation system performs virtual debugging according to the theoretical processing flow to obtain a current processing flow; and the process file generation system outputs a target process file which is provided for the machine tool and corresponds to the to-be-machined part according to the current machining process. By means of the processing scheme, information is digitalized from the process design source, and full-process digitalized and intelligent machining is achieved.
Owner:SHANGHAI SMARTSTATE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com