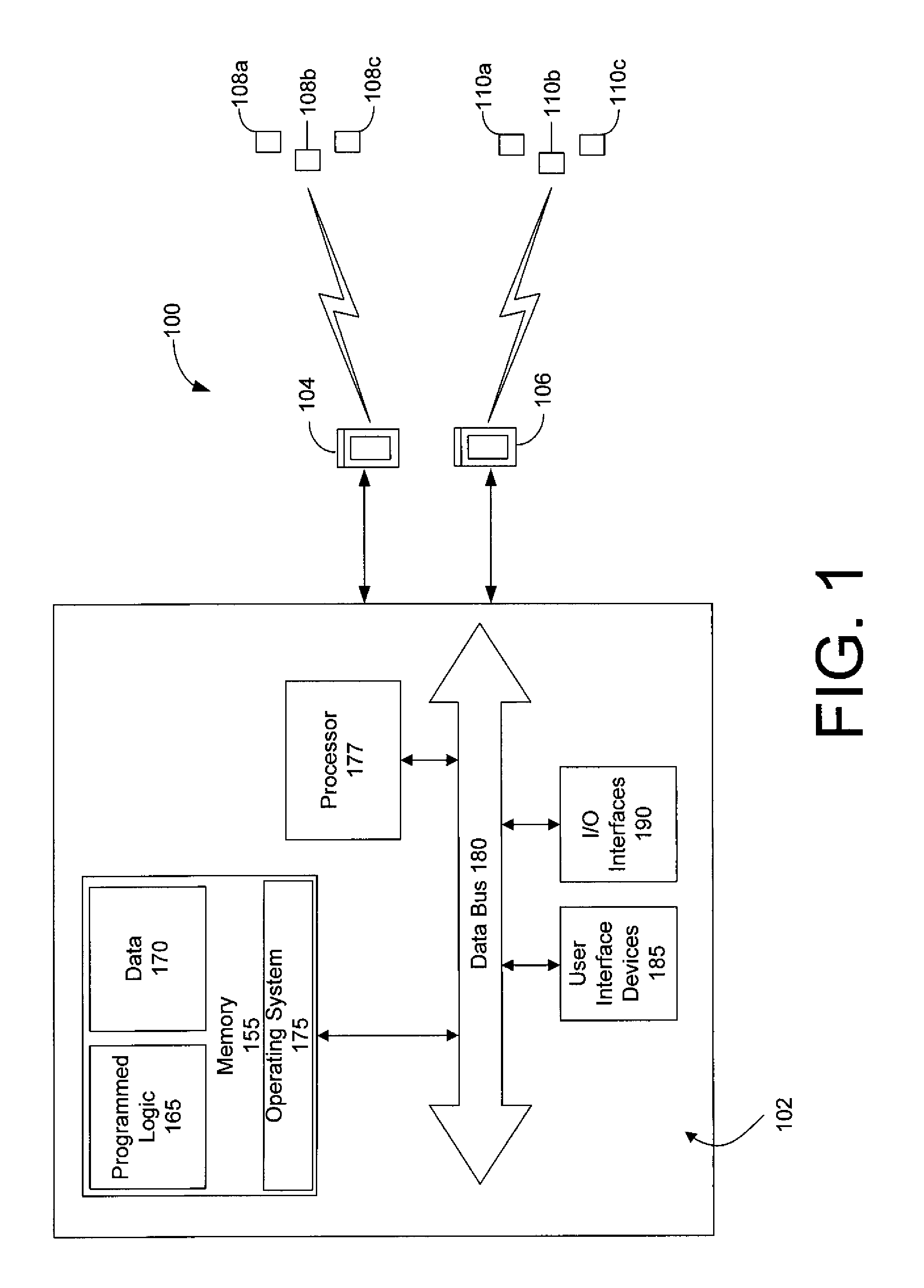
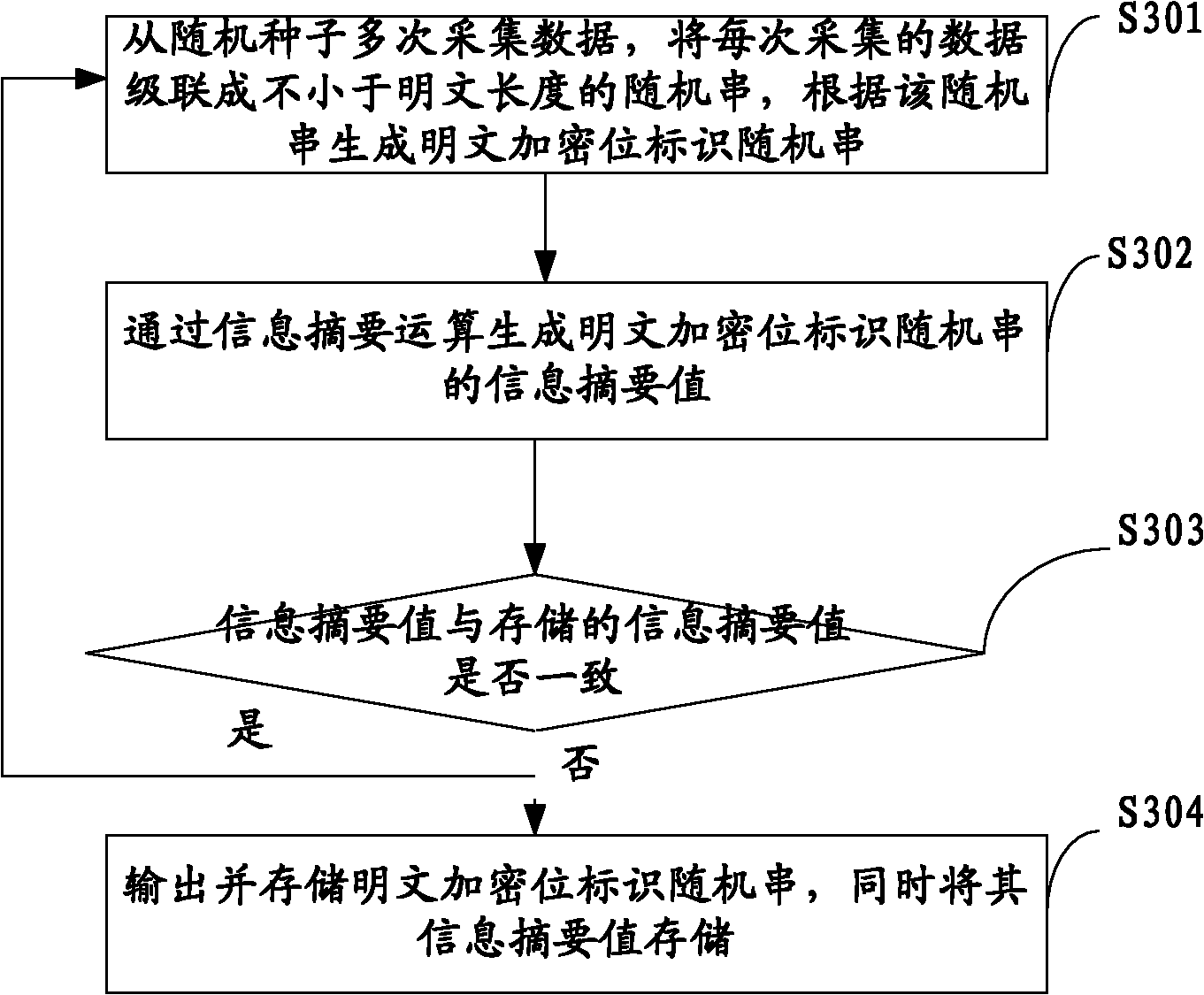
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
279 results about "Random string" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Rechargeable battery pack and operating system
InactiveUS7941865B2Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
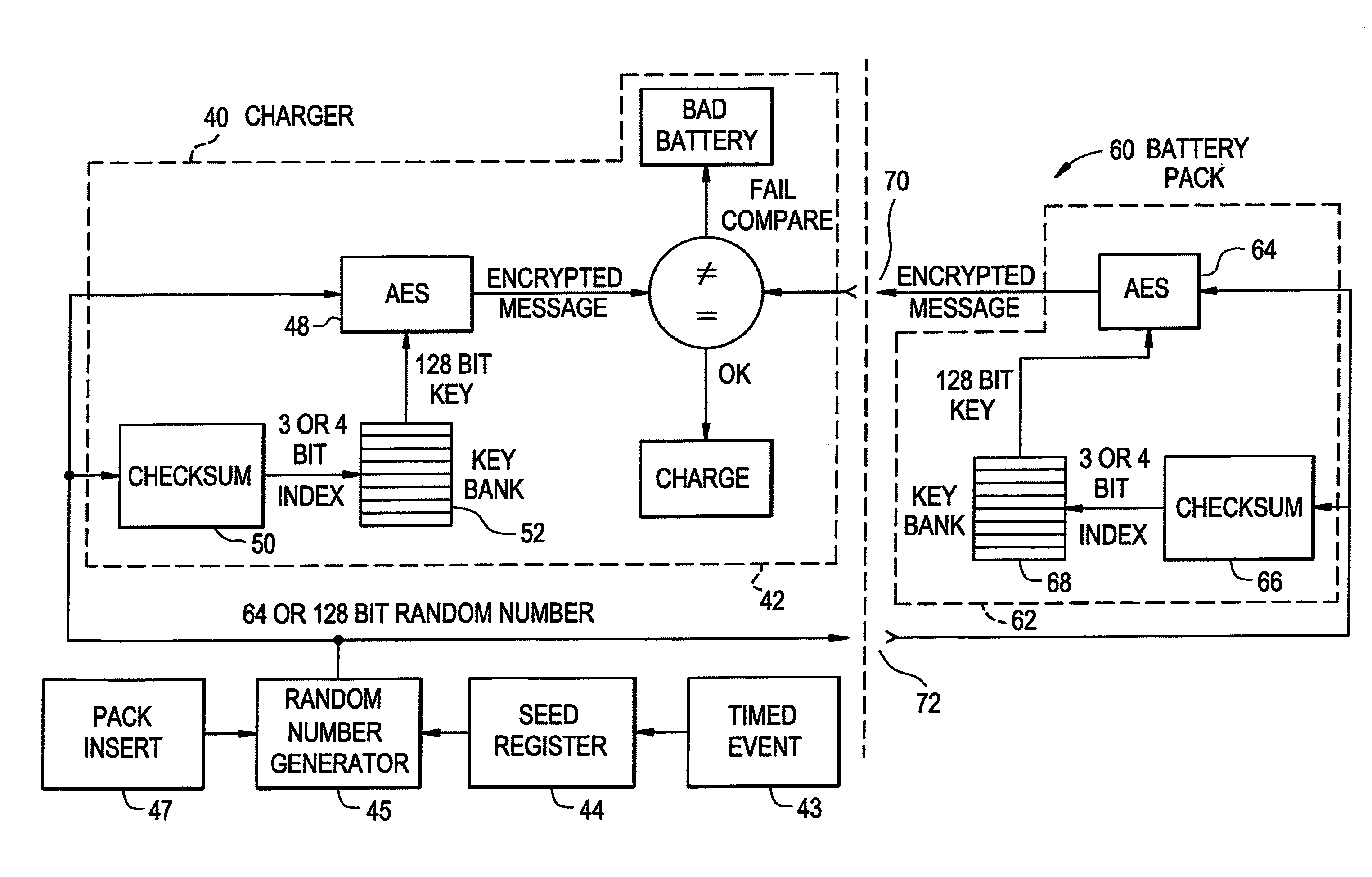
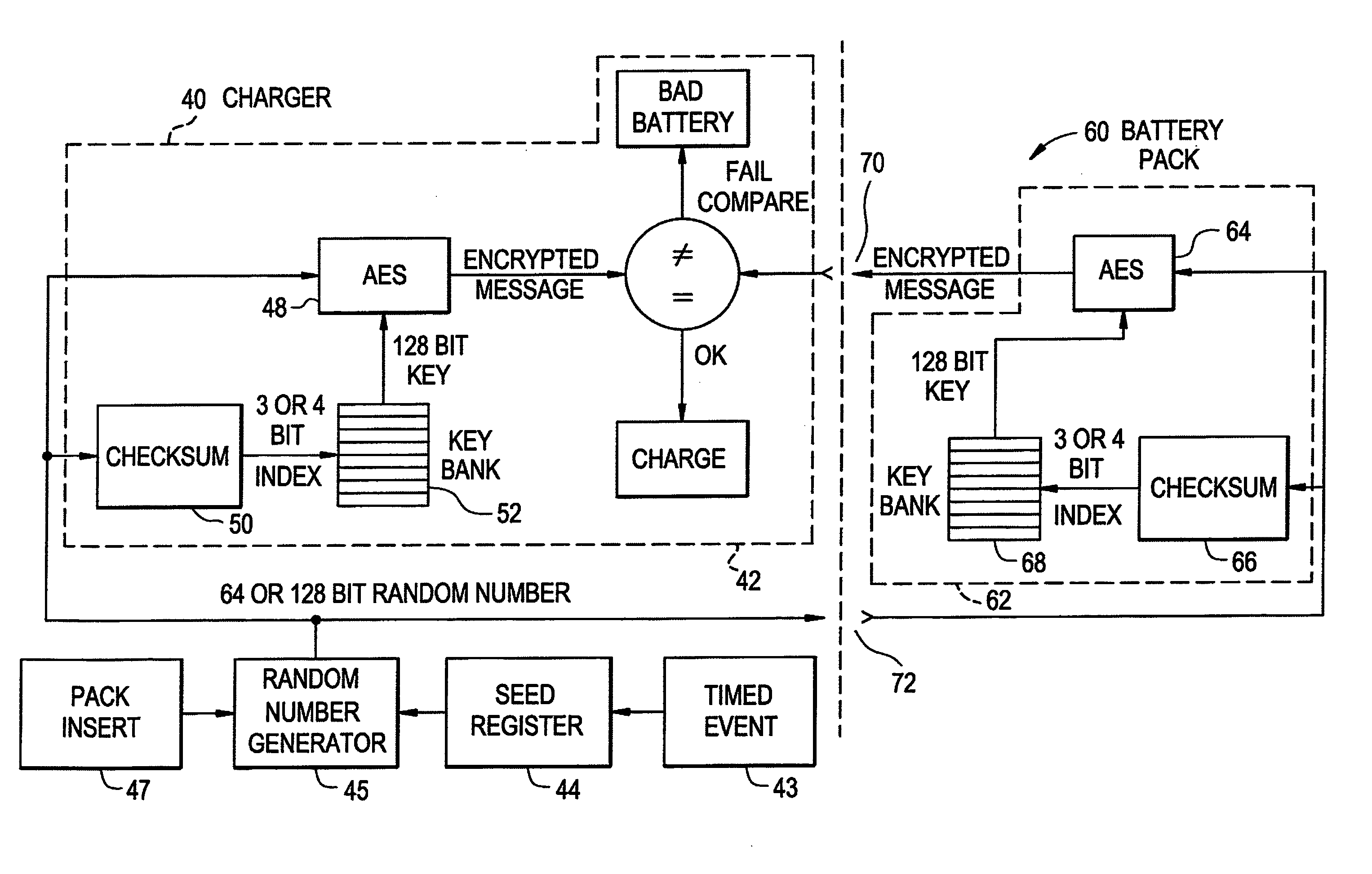
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
Asymmetric encryption block chain identity information authentication method and device
ActiveCN106100847AImprove convenienceImprove authentication securityKey distribution for secure communicationUser identity/authority verificationRandom stringEncryption
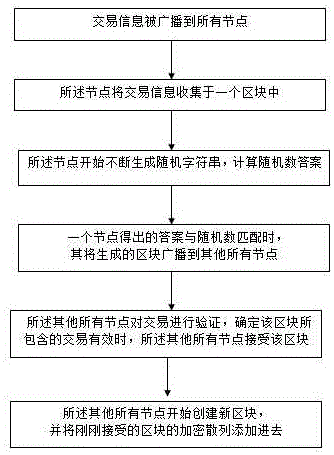
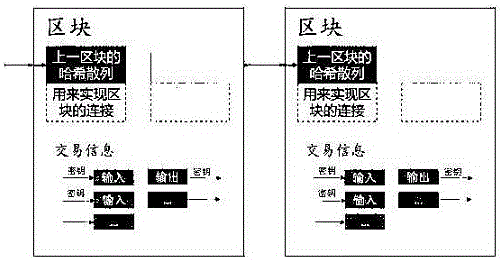
The invention discloses an asymmetric encryption block chain identity information authentication method, which is characterized by comprising the following steps that: transaction information is broadcasted to all the nodes; the node collects the transaction information in one block; the node starts to continually generate random character strings, and calculates a random number answer; when the answer obtained by one node is matched with a random number, the node broadcasts the generated block to all the other nodes; and all the other nodes authenticate the transaction, and accept the block when confirming that the transaction contained in the block is valid. All the other nodes start to create a new block, and add an encryption hash of the block accepted just now. The blocks are randomly hashed and chained together to form a block chain. The encryption hash formed by the previous block is used for connecting the blocks together, and arranging the blocks according to an order of past transaction. After the block chain is chained together with the previous block, transaction can be further confirmed.
Owner:惠众商务顾问(北京)有限公司
Network user identification verification method, server and client terminal
ActiveCN101465735AImprove securityAvoid the problem of being easily intercepted by hacker softwareUser identity/authority verificationCiphertextValidation methods
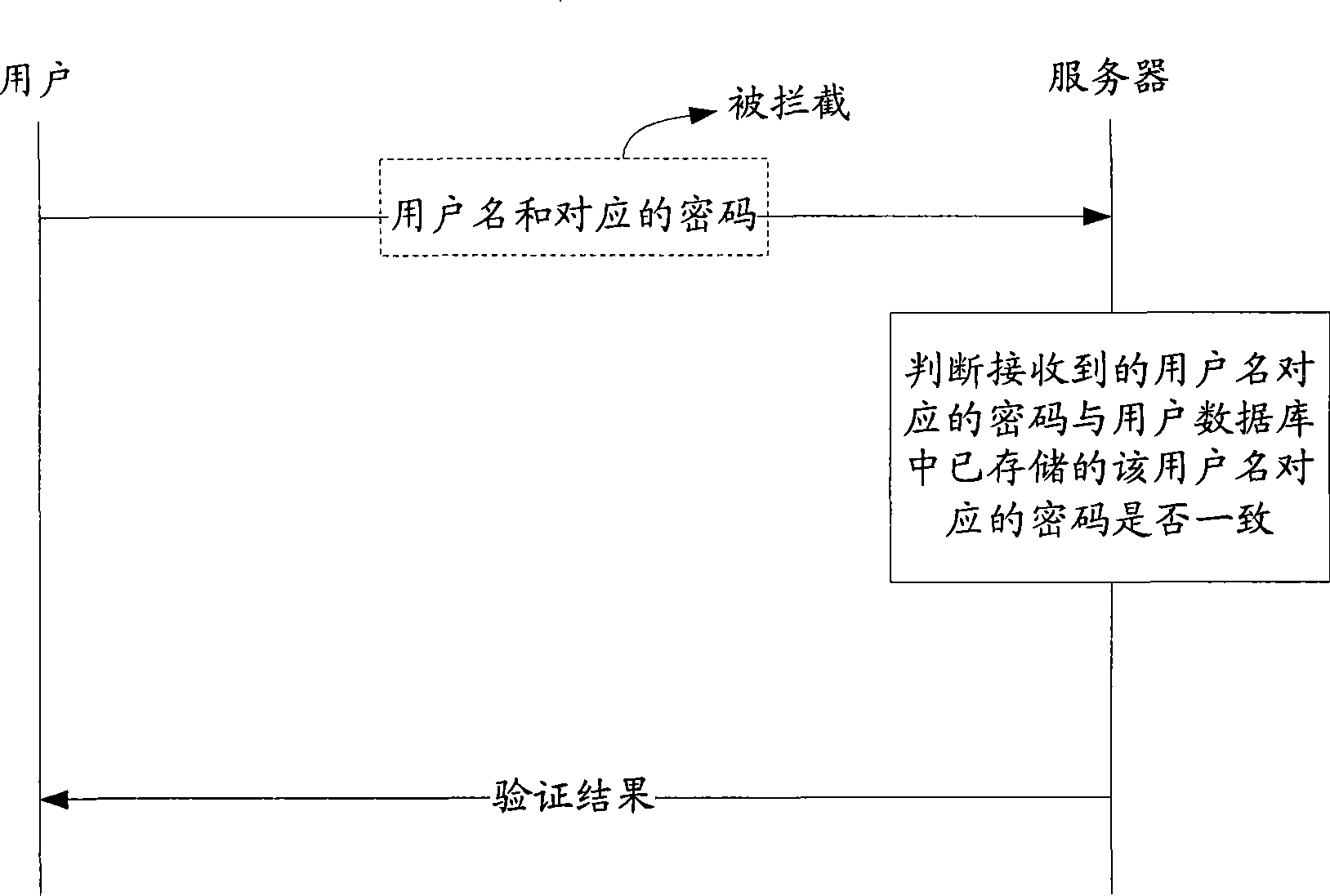
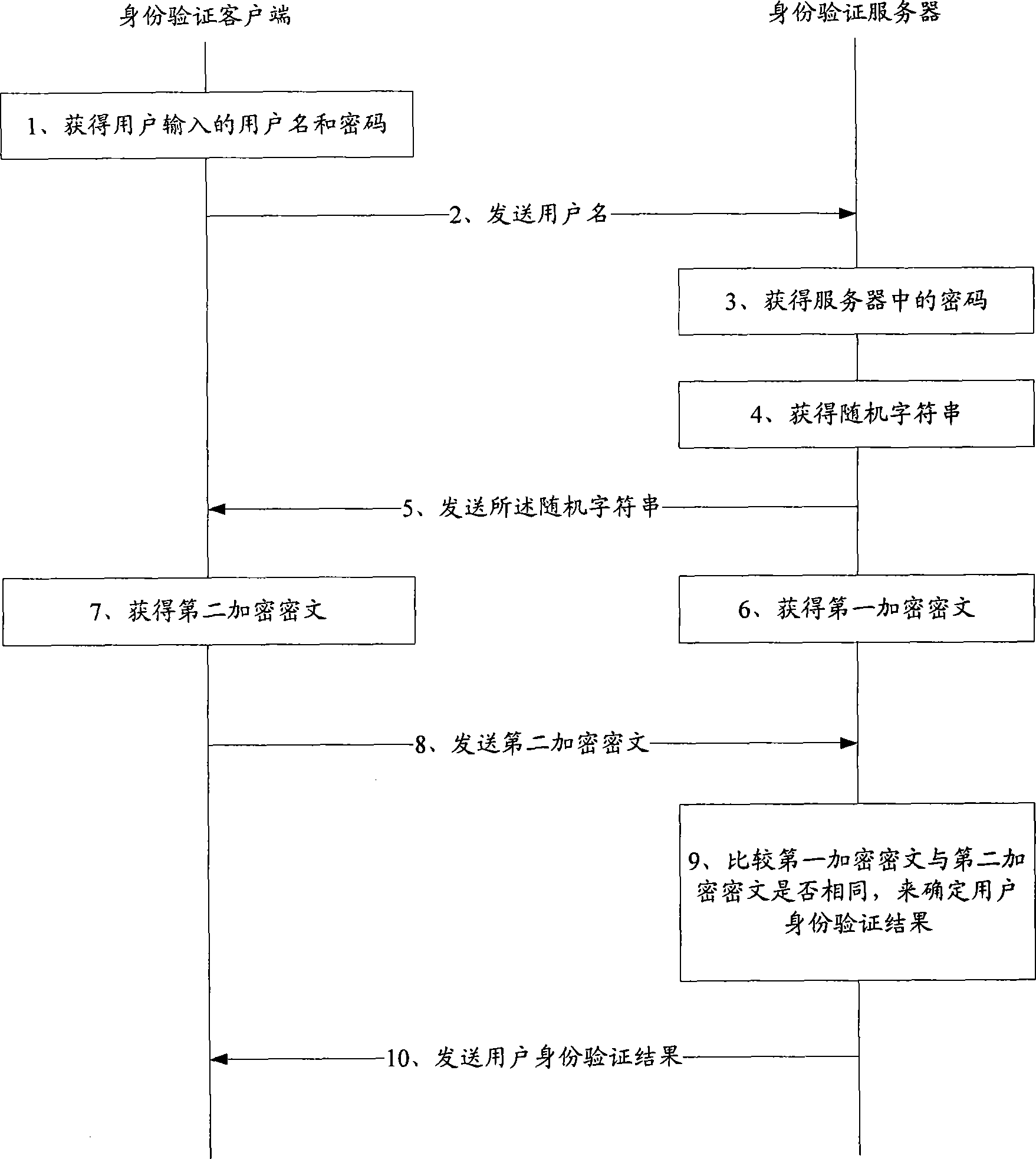
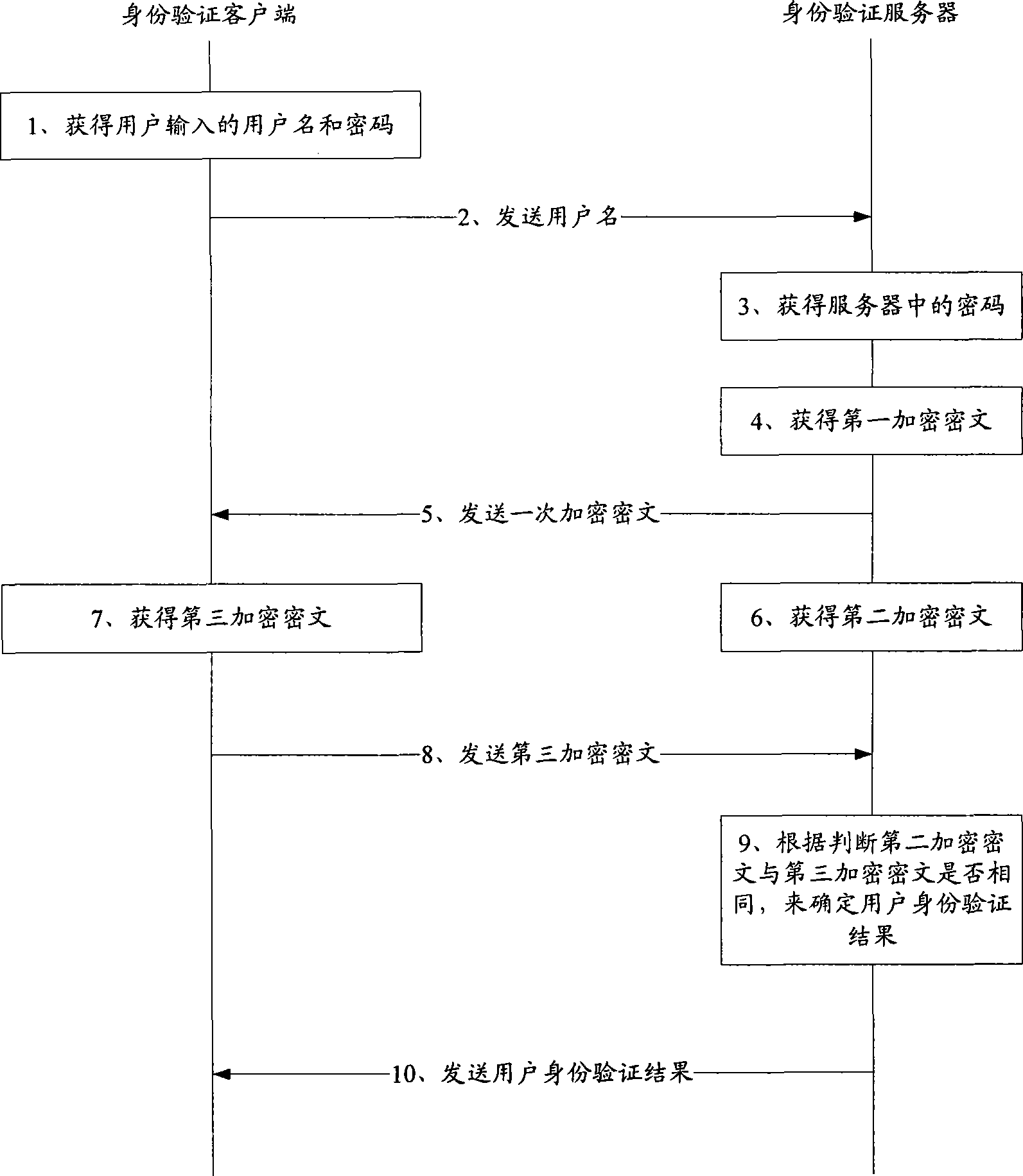
The invention discloses a network user identity authentication method, a server and a client, which solve the problem that user ID and password inputted by a user can be possibly intercepted and used illegally in network transmission process in the prior art. The identity authentication method includes that an identity authentication server receives a user ID sent from a client, and searches the password corresponding to the sent user ID in the corresponding relation of user ID and password; then the identity authentication server sends a random character string to the identity authentication client and encrypts the random character string to acquire a first encrypted cryptograph based on the searched password; the identity authentication server receives a second encrypted cryptograph sent from the identity authentication client; the identity authentication client encrypts a random character string based on the password inputted by user, so as to acquire the second encrypted cryptograph; the consistency of the first encrypted cryptograph and the second encrypted cryptograph is judged to determine the identity authentication result of the network user.
Owner:PEKING UNIV +2
Embedded synchronous random disposable code identification method and system
InactiveUS7043635B1Improve security levelImprove securityAcutation objectsError preventionComputer hardwareRandom string
A method and system for secure identification of a person in an electronic communications environment, wherein a host computer is adapted to be able to communicate with a specific electronic communications device operated by the person. The person is issued with a mask code, known only to the person and stored in the host computer, but never transmitted electronically there between. When the person is required to identify him- or herself to the host computer, the host computer transmits a pseudo-random string to the specific electronic communications device, whereupon the mask code must be applied to the pseudo-random string according to predetermined rules so as to generate a volatile identification code which is then transmitted back to the host computer. Positive identification is achieved when the volatile identification code matches a volatile identification code generated within the host computer by applying the mask code stored therein to the pseudo-random string. In this way, a person's mask code is never transmitted electronically and is therefore relatively safe from interception, and the volatile identification code will be different for each different pseudo-random string, thus making a fraudulently intercepted communication meaningless.
Owner:SWIVEL SECURE LTD
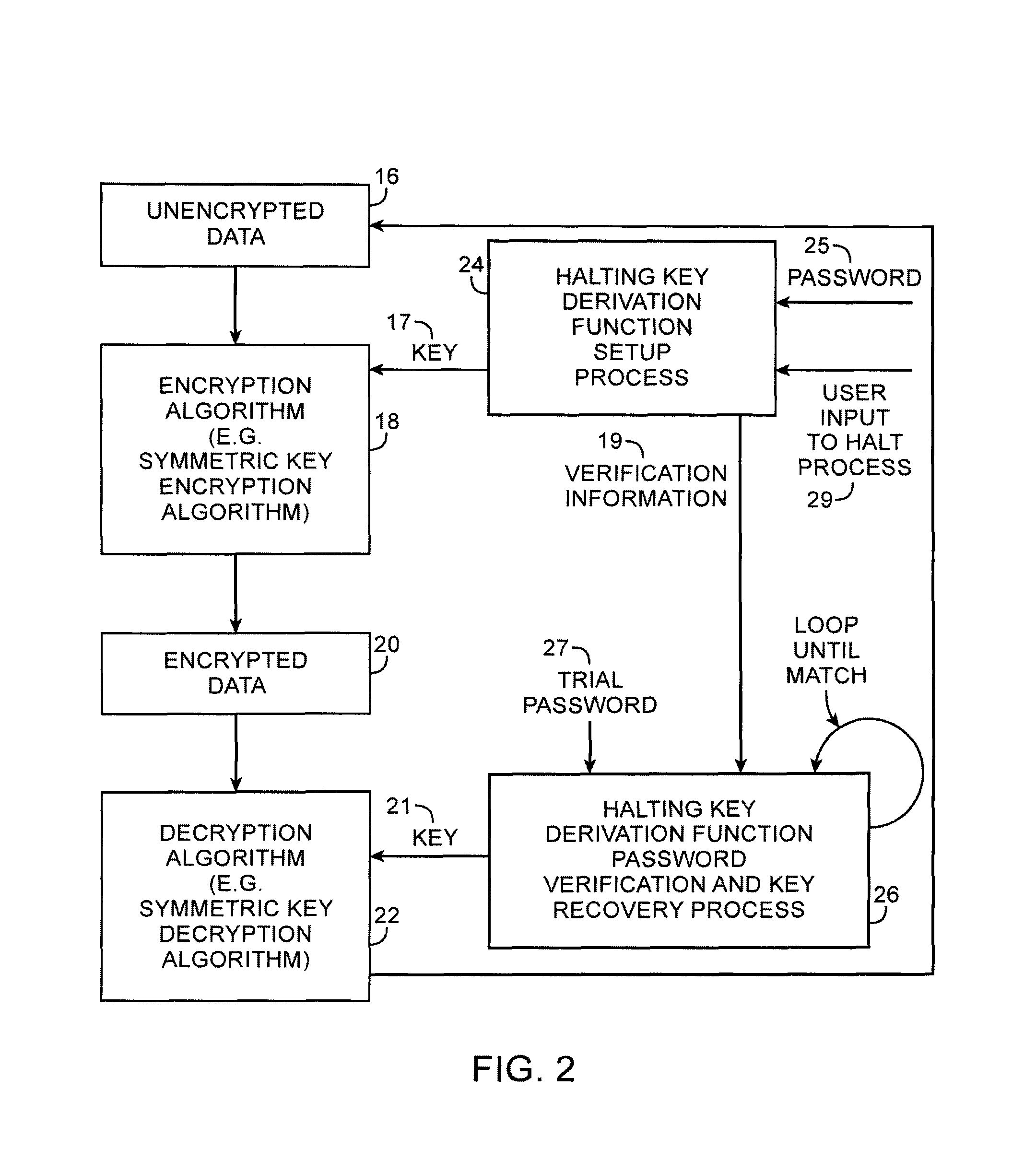
Cryptographic system with halting key derivation function capabilities
ActiveUS8254571B1Key distribution for secure communicationDigital data processing detailsUser inputPassword
A halting key derivation function is provided. A setup process scrambles a user-supplied password and a random string in a loop. When the loop is halted by user input, the setup process may generate verification information and a cryptographic key. The key may be used to encrypt data. During a subsequent password verification and key recovery process, the verification information is retrieved, a user-supplied trial password obtained, and both are used together to recover the key using a loop computation. During the loop, the verification process repeatedly tests the results produced by the looping scrambling function against the verification information. In case of match, the trial password is correct and a cryptographic key matching the key produced by the setup process may be generated and used for data decryption. As long as there is no match, the loop may continue indefinitely until interrupted exogenously, such as by user input.
Owner:MICRO FOCUS LLC
Network for improved verification speed with tamper resistant data
ActiveUS20200162264A1Efficient cross-shard transactionsEfficient atomic broadcastSpecial service provision for substationCryptography processingTamper resistanceComputer network
A method is disclosed. The method includes: a) receiving node identifiers from nodes of a plurality of nodes in a computer network; b) determining a plurality of node committees in a sampler graph comprising a plurality of nodes, wherein the node is present in a node committee in the plurality of node committees; c) and i) generating a random string; ii) performing a proof of work process using the random string and a hash function; iii) if the proof of work process yields a solution that is acceptable, then broadcasting the solution to all other nodes in the plurality of nodes, wherein the other nodes verify the solution; and iv) if the other nodes verify the solution, the node is elected to a subcommittee for the node committee, wherein the subcommittee updates the sampler graph; and d) repeating steps b) and c) until a leader committee is determined.
Owner:VISA INT SERVICE ASSOC +1
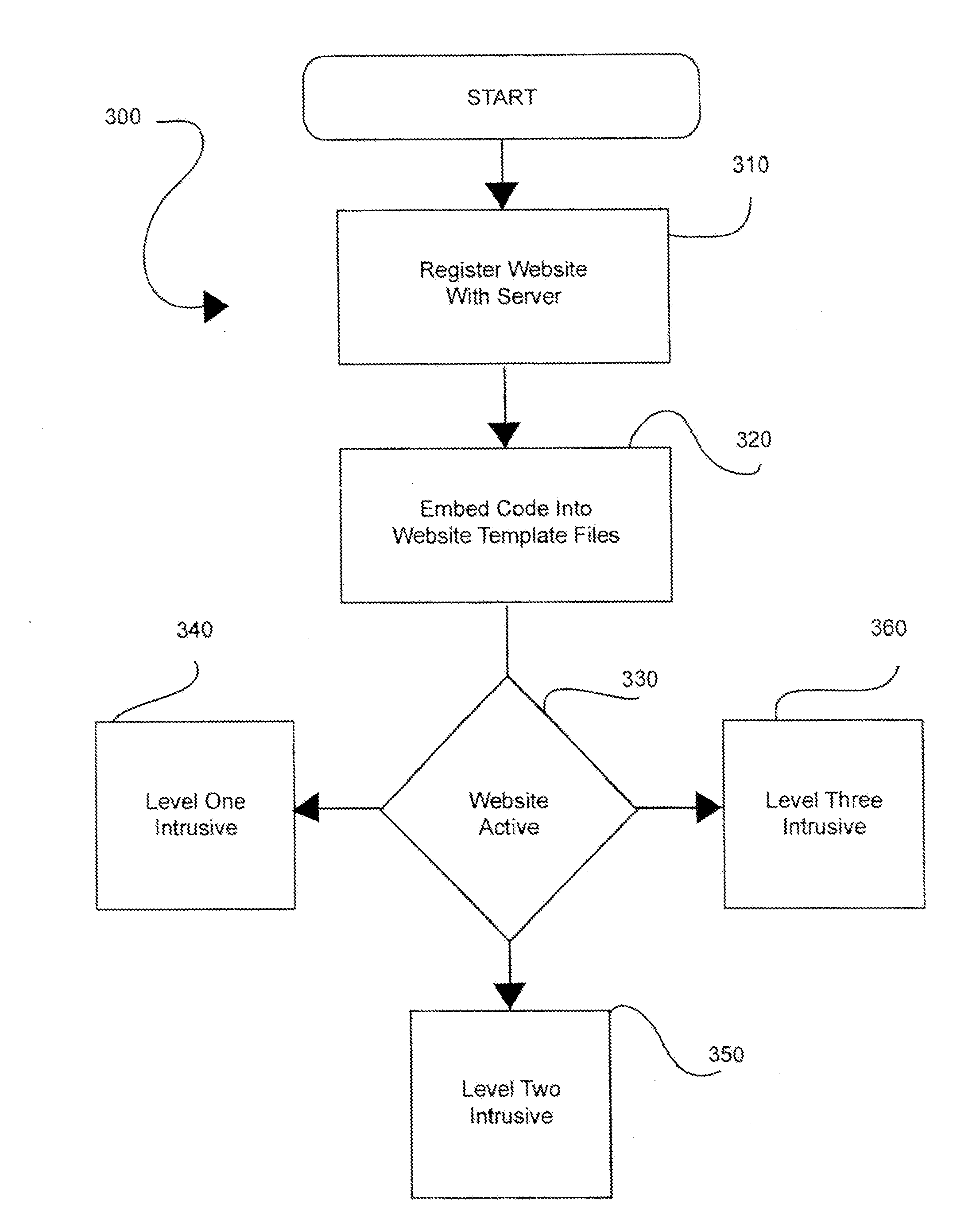
Method and system for collaborative or crowdsourced tagging of images
InactiveUS20120203651A1Lower potentialDigital data processing detailsWebsite content managementRandom stringWorld Wide Web
A method for tagging images comprises embedding a code into a template file of a website, executing the code to activate the image by overlaying a tagging interface on the image, placing a tag within the image, and storing a copy of the tag in a database supported by a remote server. A unique random string of characters is generated as a function name before data is posted to the remote server and on response executes a string function to allow the tag to be displayed on the website and the copy of the tag be posted to the remote server while maintain system security.
Owner:EMMAACTIVE ADVERTISING
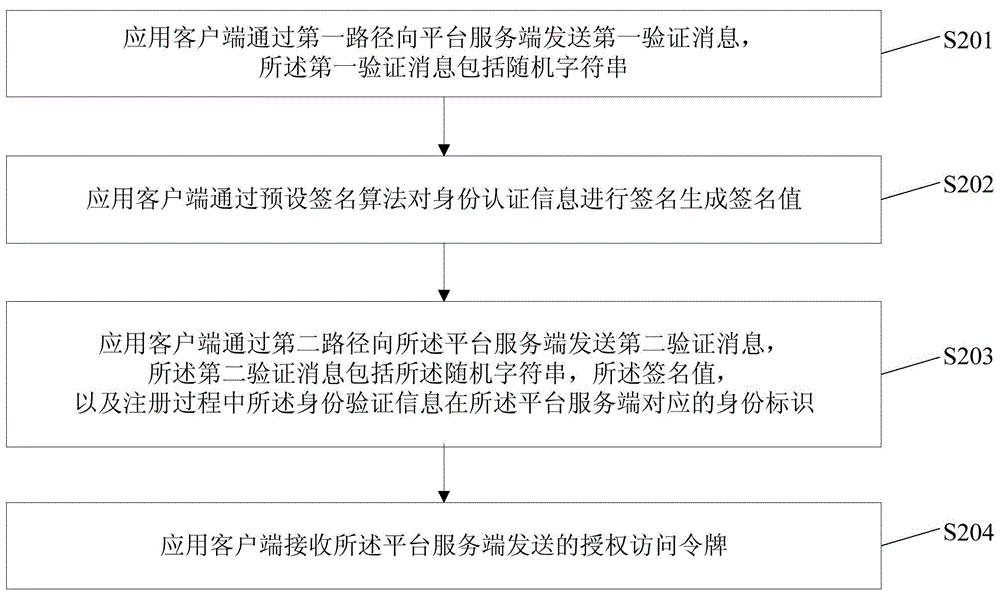
Platform authorization method, platform server side, application client side and system
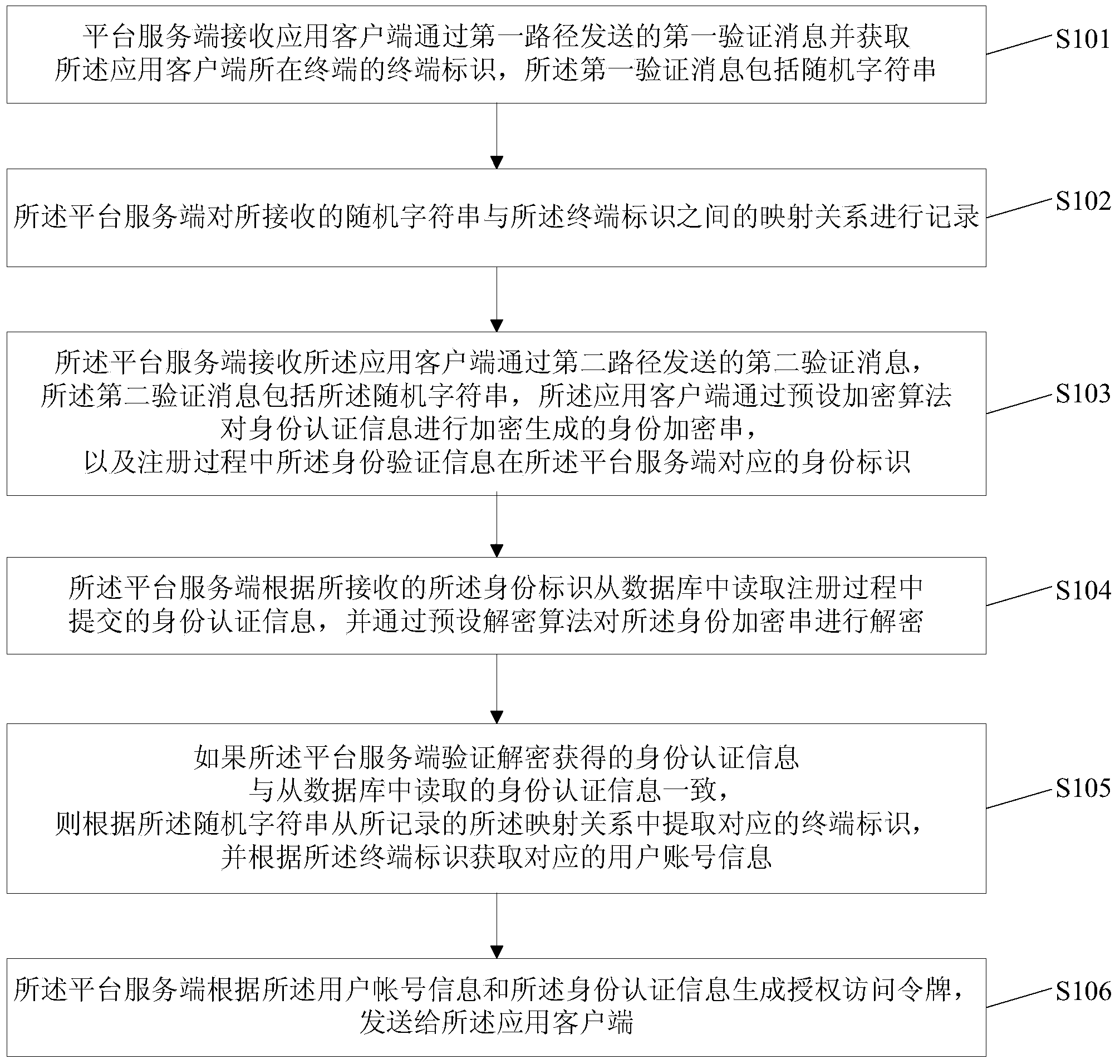
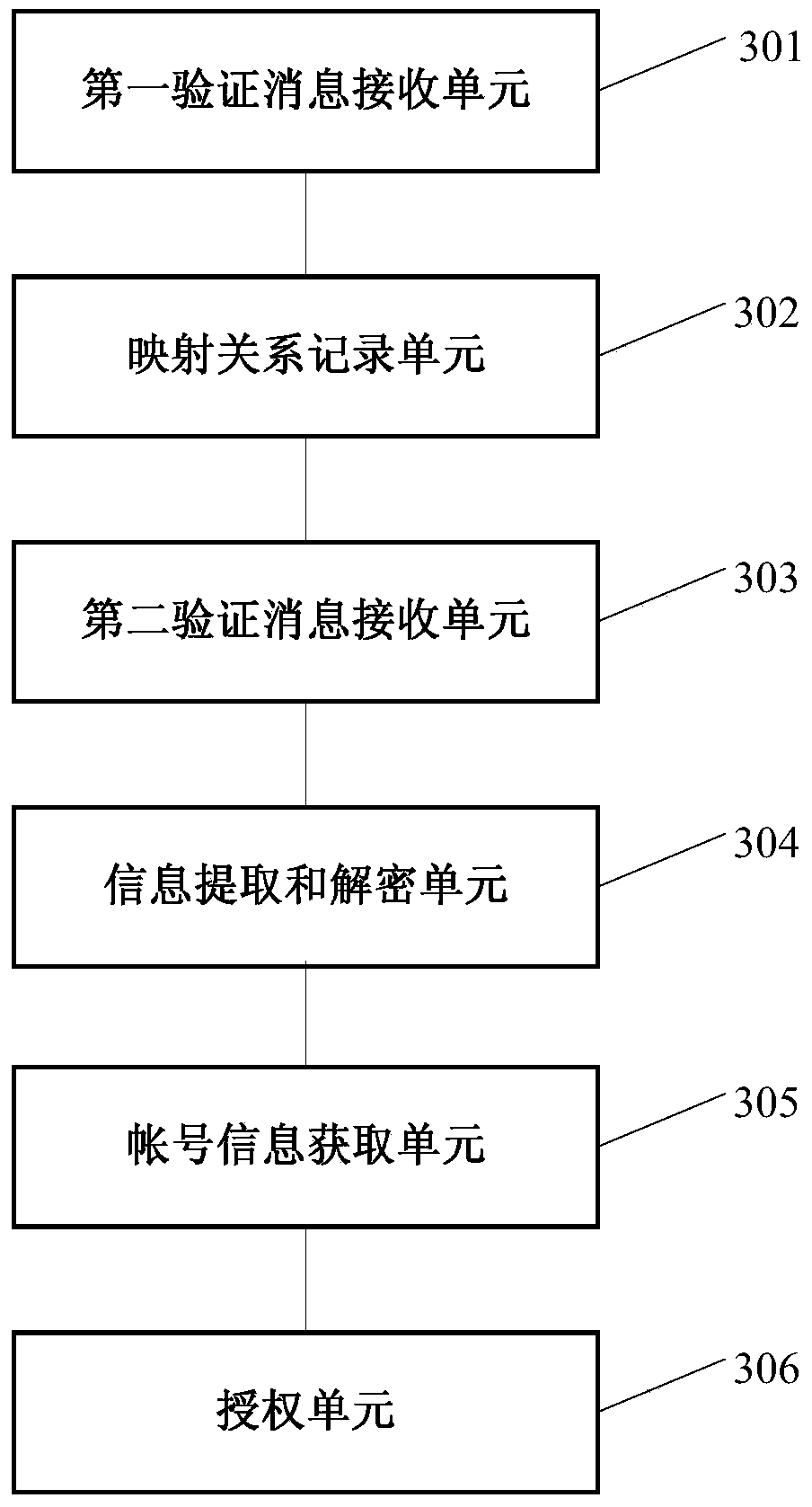
The embodiment of the invention discloses a platform authorization method, a platform server side, an application client side and a system. The method includes receiving a first verification message sent by the application client side through a first path and obtaining terminal identification of the terminal of the application client side; recording the mapping relationship between the received random strings and the terminal identification; receiving a second verification message sent by the application client side through a second path; reading identity authentication information submitted in a registration process from a database according to the received identification, decrypting and verifying encrypted identity strings, extracting the corresponding terminal identification from the recorded mapping relationship if the consistency is determined, and obtaining corresponding user account information according to the terminal identification; generating an authorized access token according to the user account information and the identity authentication information and sending the authorized access token to the application client side. The platform authorization method, the platform server side, the application client side and the system enable a user to have no awareness of the authorization process and can further improve the security of the authorization.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Data encryption, decryption and transmission methods and systems
InactiveCN105591737AIncrease the difficulty of crackingImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareOriginal data
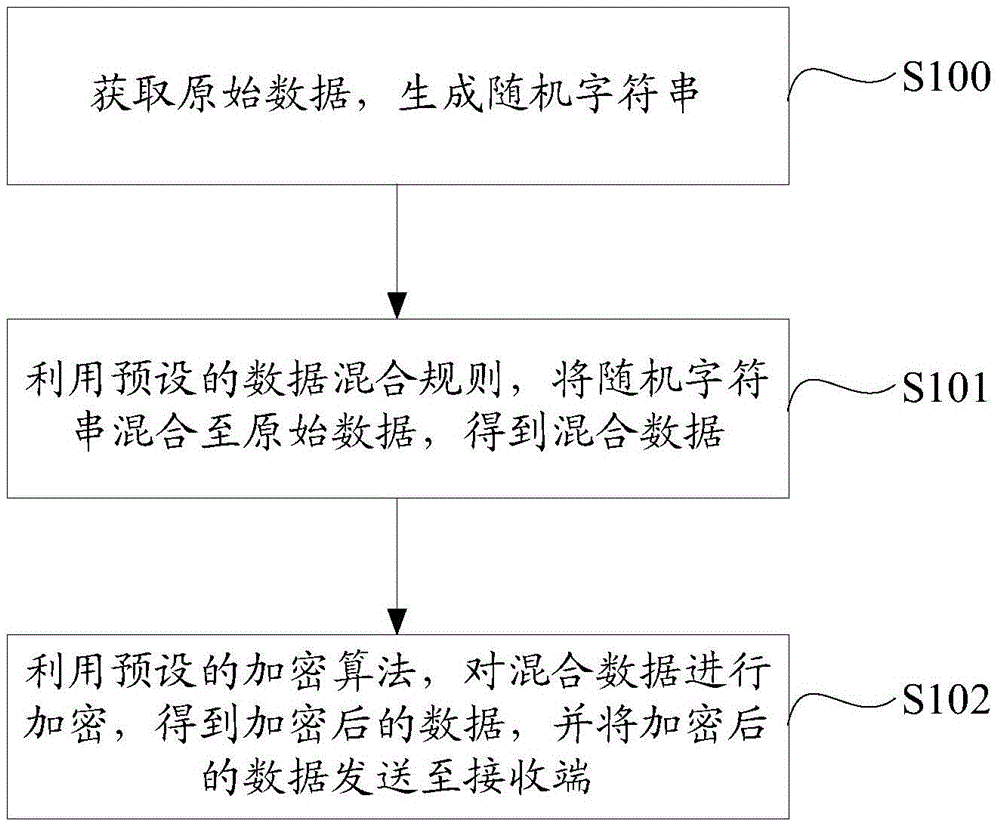
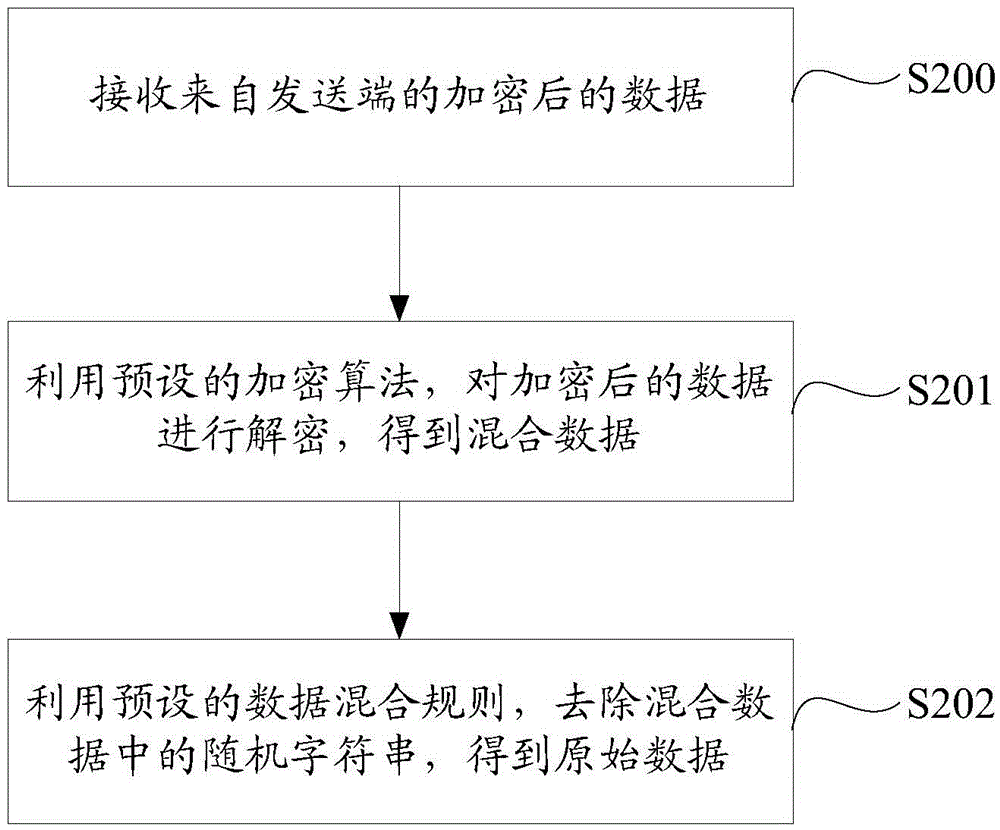
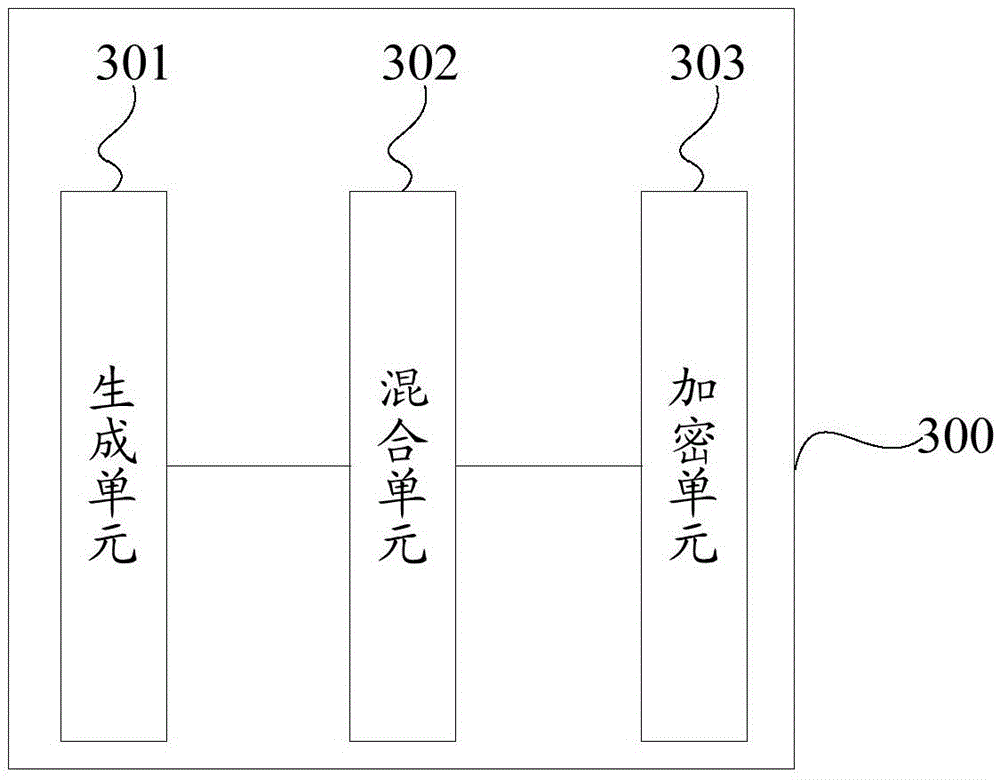
The invention discloses data encryption, decryption and transmission methods and systems. The data encryption method comprises the steps of: obtaining original data, and generating a random character string; utilizing a preset data mixing rule, mixing the random character string to the original data, and obtaining mixed data; and utilizing a preset encryption algorithm to encrypt the mixed data, obtaining encrypted data, and sending the encrypted data to a receiving end. According to the invention, for either a symmetric encryption mode or an asymmetric encryption mode, dual insurance by the random character string and an encryption key exists, and even if the same secret key is used to encrypt the same original data, different encrypted data is obtained because of the adding of the random character string, so that the decryption difficulty of the encrypted data is enhanced, and the safety of the encrypted data is further improved.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
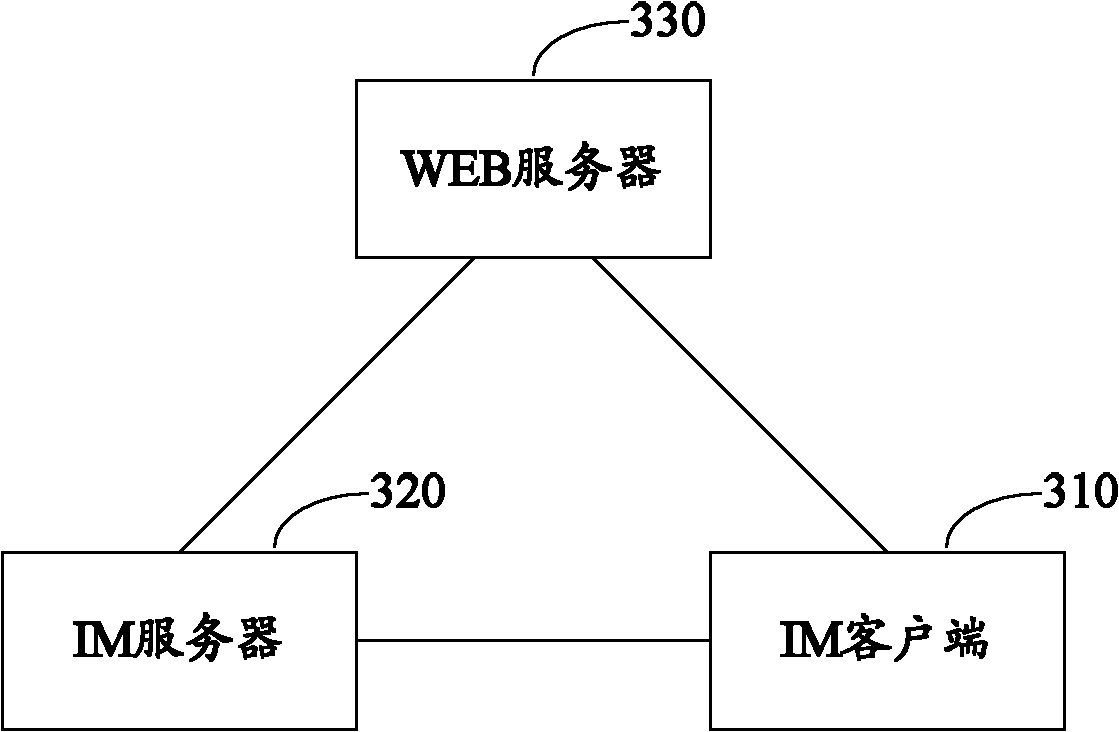
Login verification method, system and instant messaging (IM) server
ActiveCN102651739AImprove login securityEnsure safetyData switching networksValidation methodsWeb service
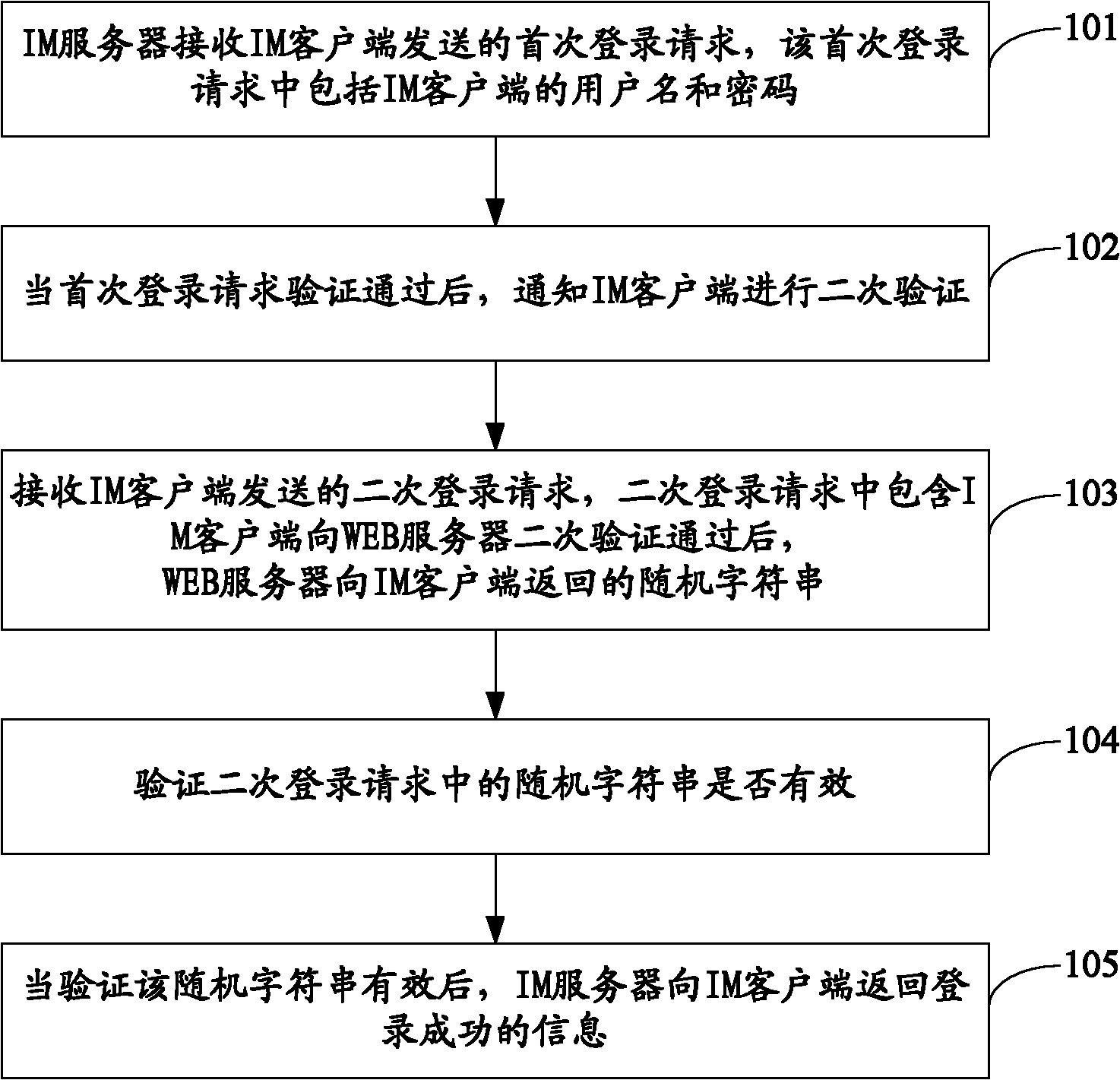
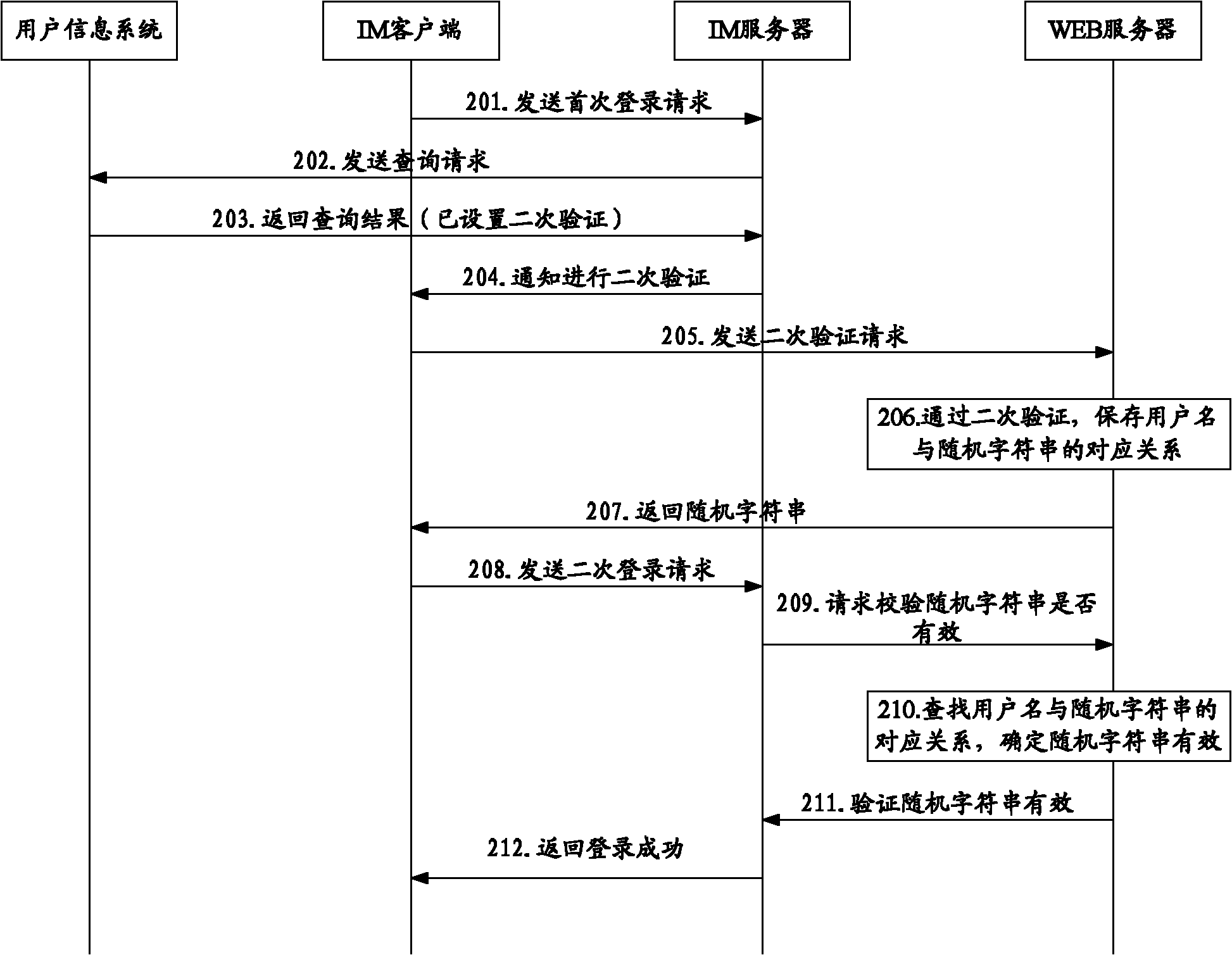
The embodiment of the invention discloses a login verification method, a system and an instant messaging (IM) server. The method comprises the following steps that: the IM server receives first-time login requests sent by an IM client, and the first-time login requests comprise user names and passwords of the IM client; when the first-time login request verification is passed, the IM client is notified to carry out second-time verification; the second-time login requests sent by the IM client is received, the second-time login requests comprise random character strings returned by a web server to the IM client after the second-time verification of the IM client to the web server is passed; whether the random character strings in the second-time login requests are valid or not is verified; and when verification results show that the random character strings are valid, the IM server returns the login successful information to the IM client. Because of the introduction of the second-time verification process in the embodiment of the invention, only the login security of users is improved.
Owner:ALIBABA GRP HLDG LTD
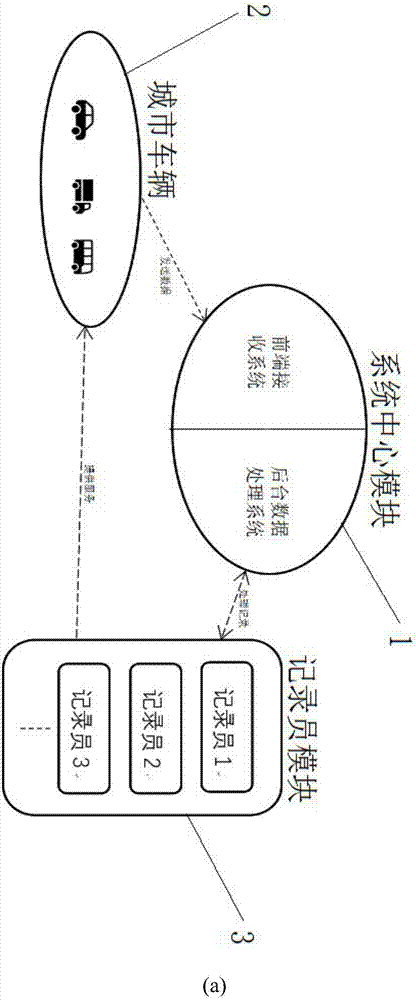
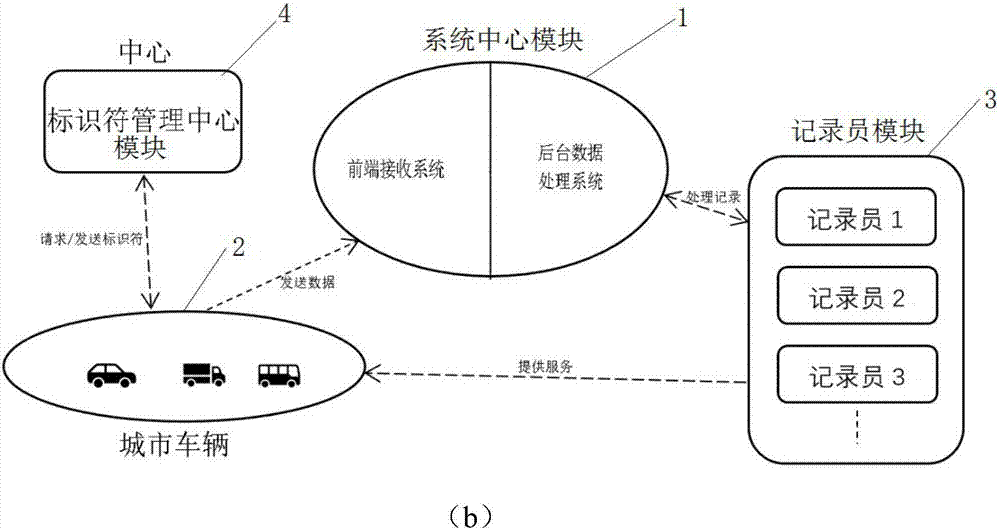
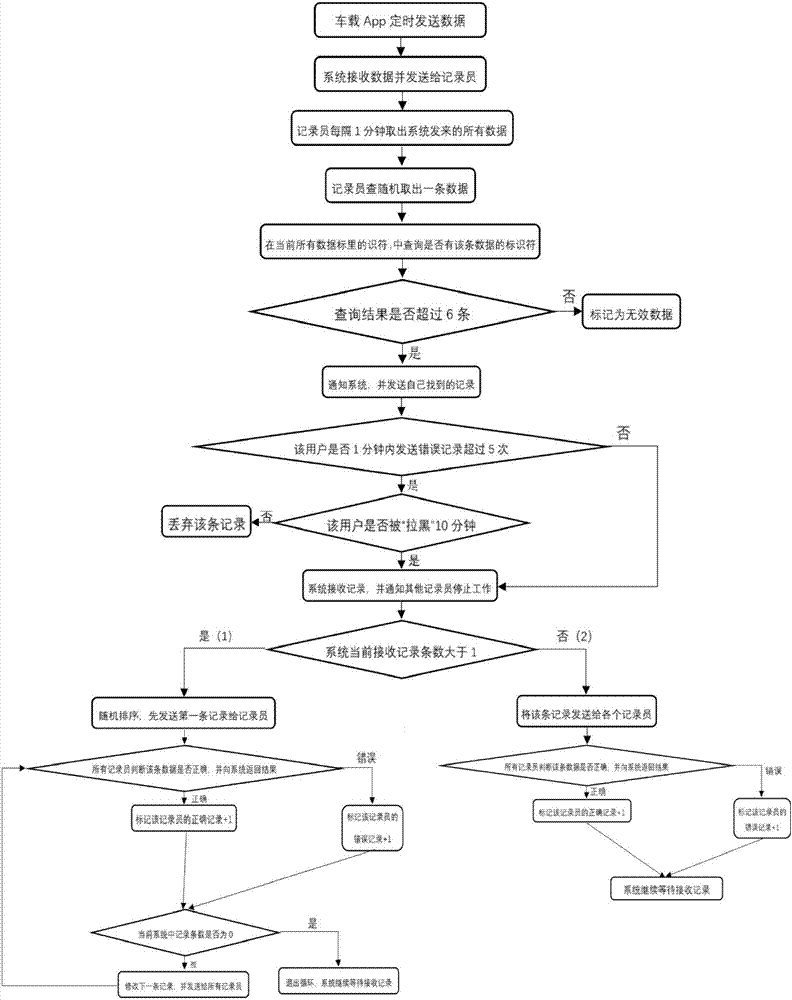
Urban real-time traffic system and method capable of realizing privacy protection based on block chains
ActiveCN107067720ARealize privacy protectionMap real-time traffic conditionsDetection of traffic movementConfidentialityPrivacy protection
The invention relates to two systems which are an urban real-time traffic system capable of realizing privacy protection based on block chains of a public chain and an urban real-time traffic system capable of realizing vehicle monitoring based on block chains of a private chain. The urban real-time traffic system capable of realizing privacy protection based on the block chains of the public chain comprises a system center module, urban vehicles and a recorder module. The urban real-time traffic system capable of realizing vehicle monitoring based on the block chains of the private chain is additionally provided with a center which is responsible for managing identifiers of the vehicles. According to the invention, the block chain is adopted as a core technology, a record book of the block chain is utilized to store and record driving records of each automobile in a distributed manner, each automobile is recorded by adopting a mode of the automobile identifier in the record book, each identifier generates a random character string by adopting an encryption algorithm and varies in a timed manner, and privacy protection for an automobile owner or vehicle monitoring is realized according to the confidentiality of the identifiers. The recorder draws real-time traffic conditions according to data of the record book.
Owner:CHENGDU UNIV OF INFORMATION TECH
Rechargeable battery pack and operating system
InactiveUS20080037779A1Data stream serial/continuous modificationVolume/mass flow measurementOperational systemData stream
A method and system for authenticating a smart battery having a smart battery and an electronic device. Both the device and the smart battery generate encrypted random strings using key material based by A / D noise bits as a seed value. A pseudo random number is generated from the A / D noise that is transmitted to both the electronic device and the smart battery. The pseudo random number is used by both devices as a key index to select one of a plurality of keys stored in separate key libraries. The keys, or key material, is used to execute an encryption algorithm. The two encryption data streams are then compared to authenticate the smart battery.
Owner:BLACK & DECKER INC
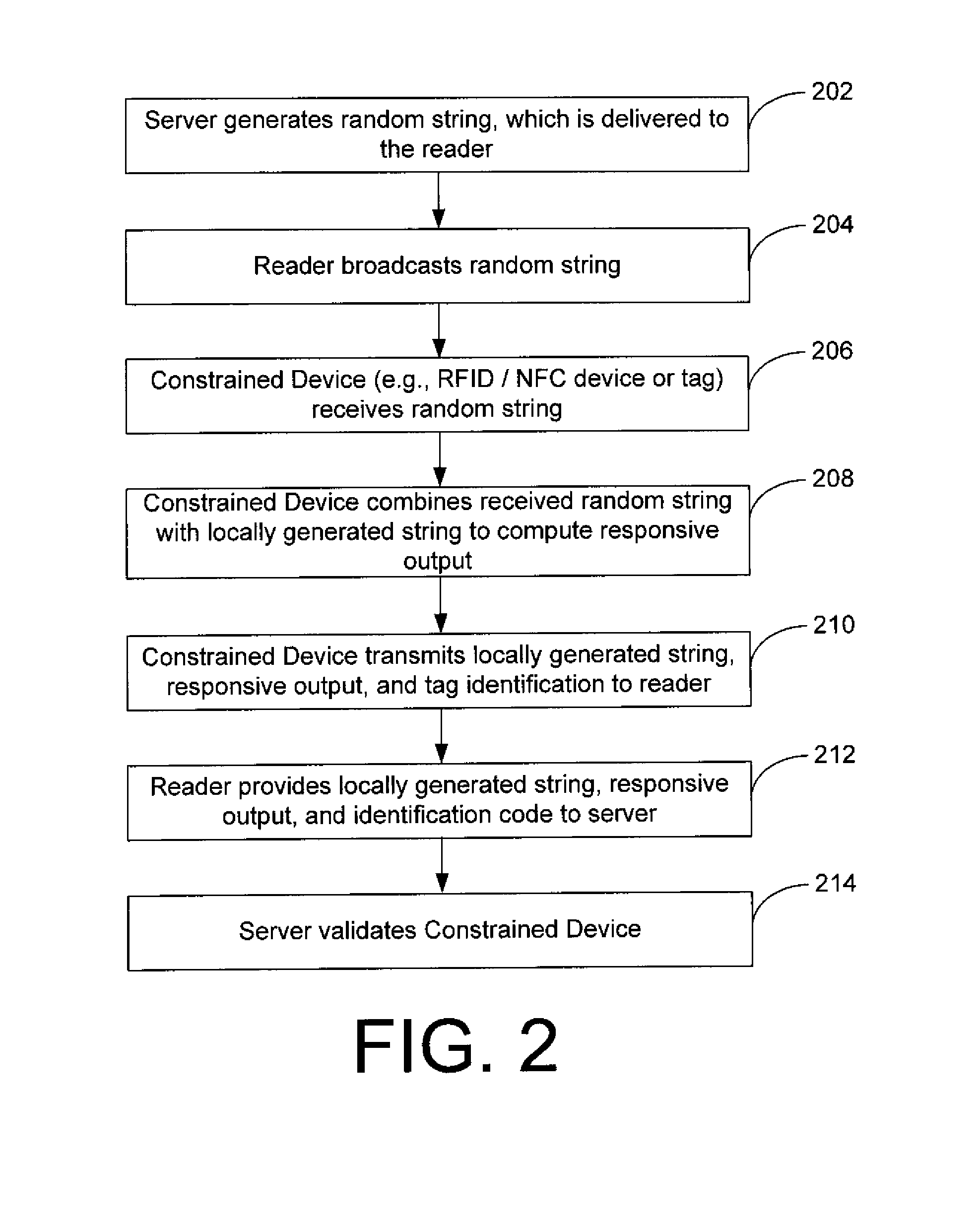
Systems, Methods, and Computer Program Products for Secure Optimistic Mechanisms for Constrained Devices
InactiveUS20140019759A1User identity/authority verificationSecurity arrangementDeterministic functionRandom string
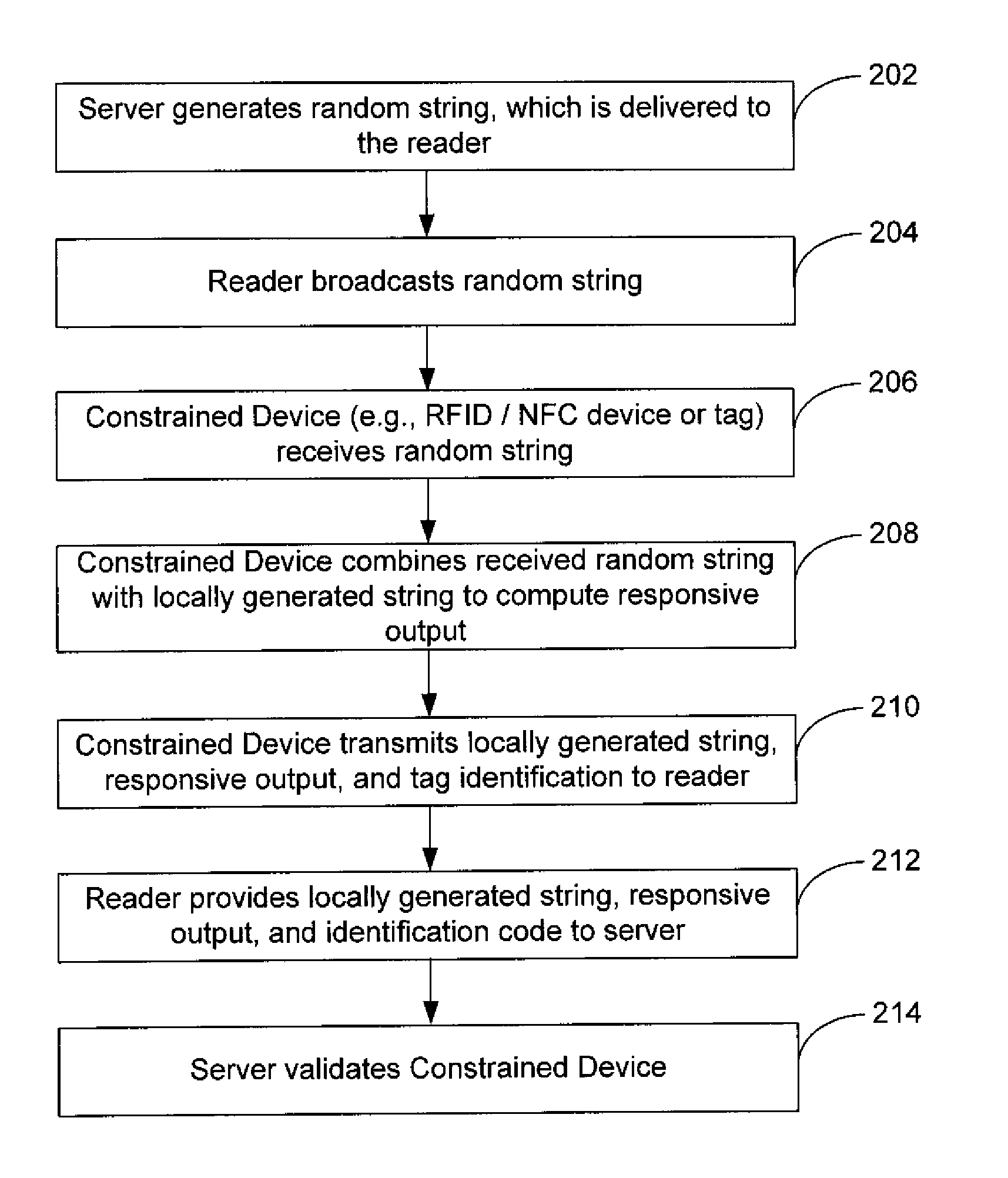
Embodiments of the invention may provide for systems and methods for secure authentication. The systems and methods may include receiving, by a constrained device, a random string transmitted from a server; determining, by the constrained device, a responsive output by evaluating a first deterministic function based upon the received random string, a locally generated string and a first private key stored on the constrained device; and transmitting at least one portion of the responsive output and the locally generated string from the constrained device to a server. The systems and methods may also include determining, by the server, a validation output by evaluating a second deterministic function based upon the random string, the locally generated string, and a second private key of a plurality of private keys stored on the server; and authenticating the constrained device based upon the server matching the transmitted at least one portion of the responsive output to at least a portion of the validation output.
Owner:FLORIDA STATE UNIV RES FOUND INC
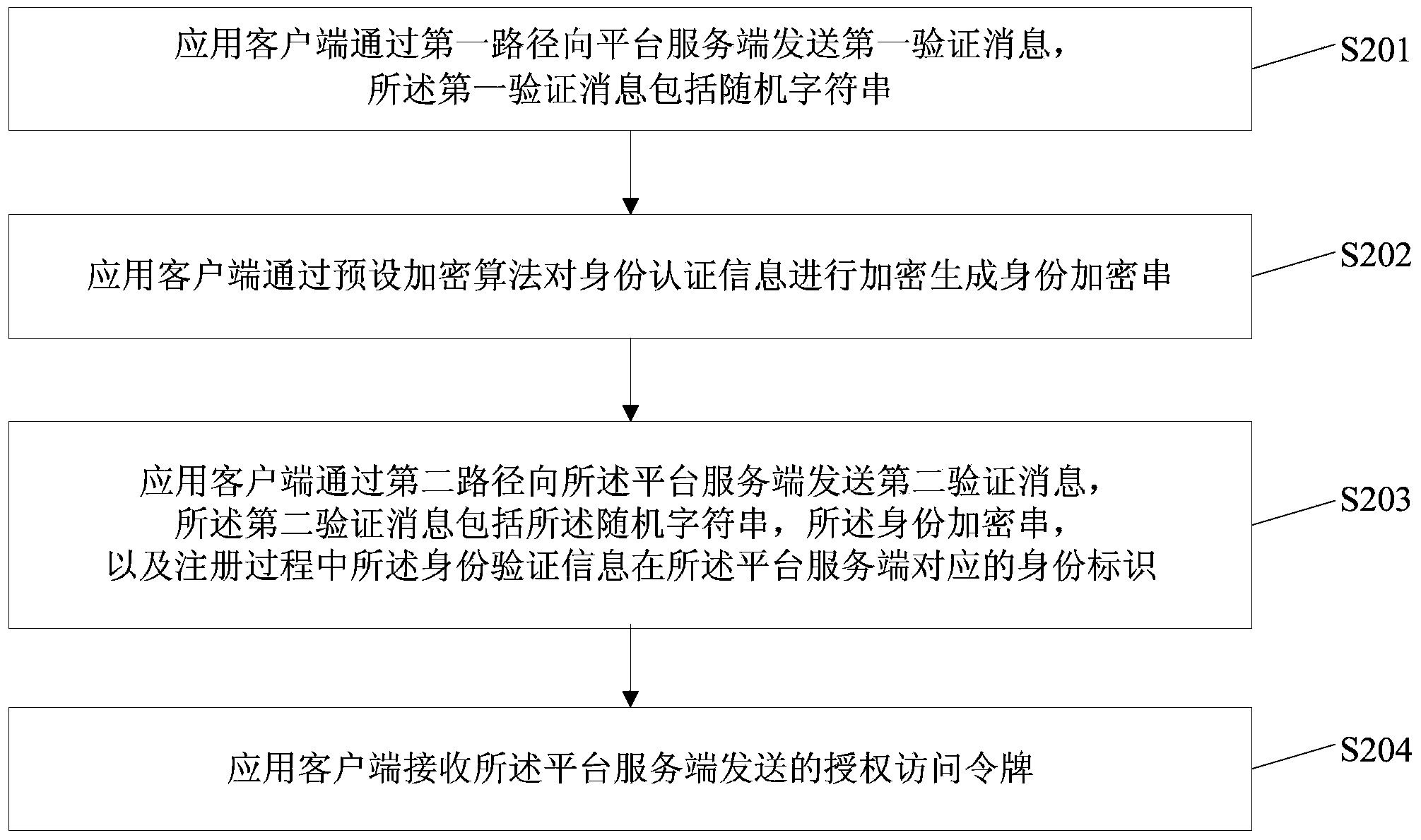
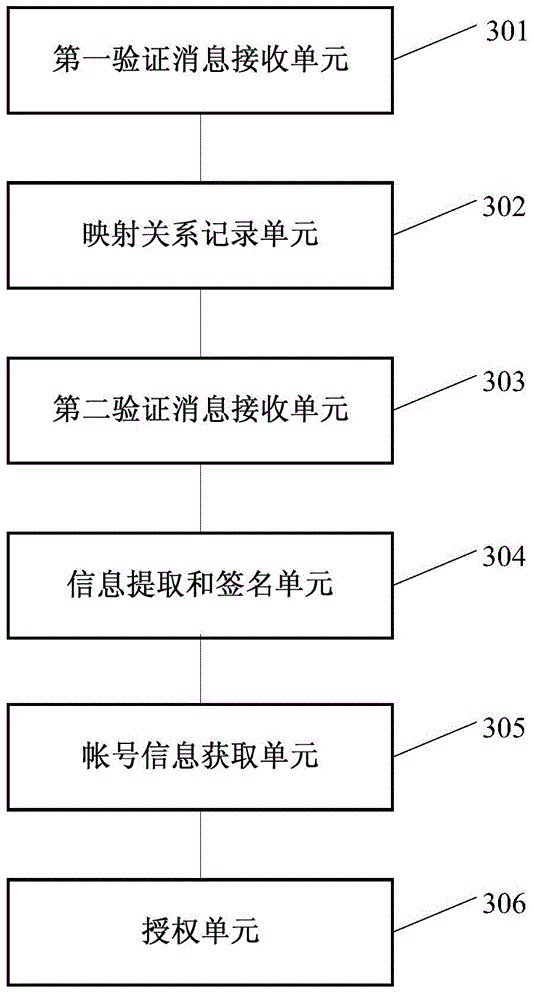
Platform authorization method, platform service side, application client side and system
The embodiment of the invention discloses a platform authorization method, a platform service side, an application client side and a system. The platform authorization method comprises the following steps: a first validation message sent by the application client side through a first pathway is received and a terminal identifier is acquired; the mapping relation between received random character strings and the terminal identifier is recorded; a second validation message sent by the application client side through a second pathway is received; identity certification information submitted during a registration process is read from a data base according to an identity identifier; signature is conducted on the extracted identity certification information; if a generated signature value is consistent with a received signature value, a corresponding terminal identifier is extracted from the recorded mapping relation according to the random character strings; corresponding information on a user account is acquired according to the terminal identifier; an authorized access token is generated according to the information on the user account and the identity identification information; the authorized access token is sent to the application client side. According to the technical scheme provided by the embodiment of the invention, the user cannot perceive the authorization process and the authorization safety can be further improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
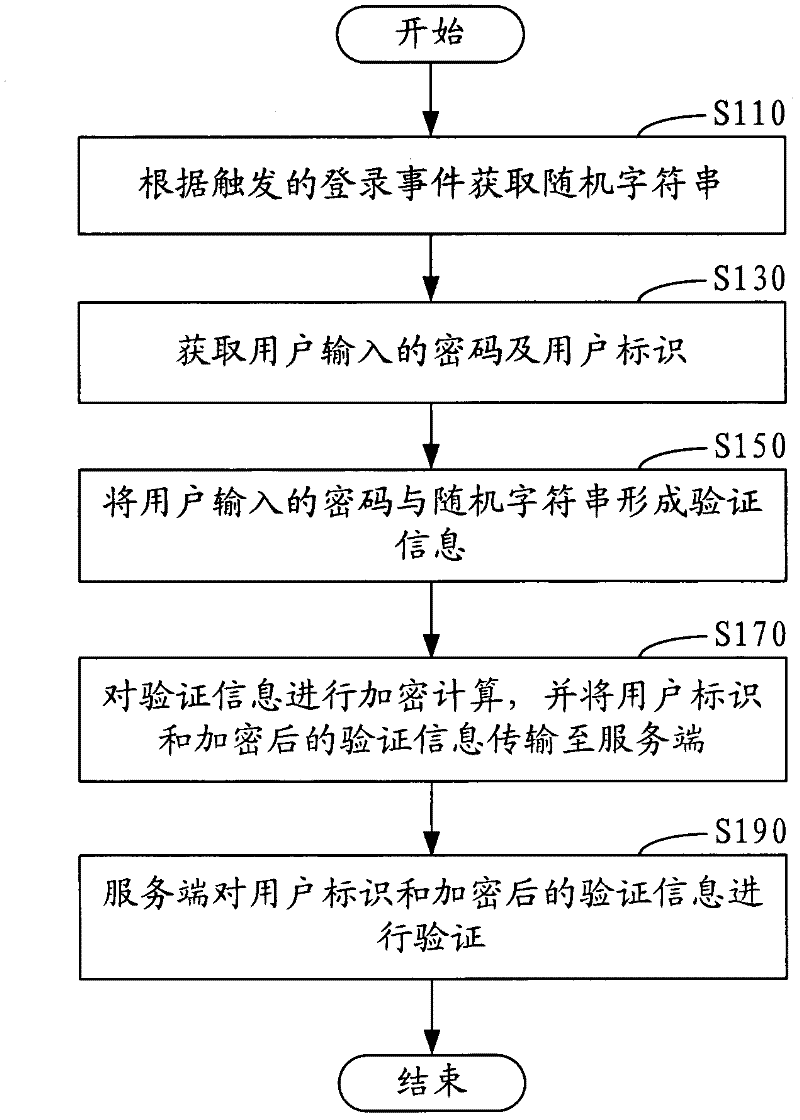
Password authentication method in network application and system
InactiveCN102316112ACrack reductionReduces the possibility of crackingDigital data authenticationTransmissionUser inputPassword
The invention relates to a password authentication method in network application and a system. The method comprises the following steps that: a random character string is obtained according to a triggered login event; a password input by a user and user identification are obtained; the password input by the user and the random character string form authentication information; the authentication information is encrypted, and the user identification and the encrypted authentication information are transmitted to a server; and the server authenticates the user identification and the encrypted authentication information. In the password authentication method and the system, disclosed by the invention, since the password input by the user and the obtained random character string form the authentication information and the encrypted authentication information is transmitted to the server, the security during password authentication is improved and the situation that the authentication information is intercepted by malicious software during transmission is avoided; and since the random character string is added into the authentication information and the encryption is conducted, the probability that the authentication information is cracked violently is greatly reduced.
Owner:李建成
Data collection and remote control method and system
InactiveCN108965447AFully automatic sendingAutomatic receivingNatural language data processingTransmissionRemote controlData acquisition
The invention relates to the field of network communication, and provides a data collection and remote control method aiming at the problem that during existing data collection and remote control, release and subscription of a subject need predetermined parameters. The method comprises the steps as follows: an equipment end and a control end are connected with an MQTT server; the equipment end submits an own machine code and a random character string to the control end to perform binding storage; the equipment end releases a message to the MQTT server by using a fixed prefix and the own machine code as a release subject, and the control end subscribes to the message from the MQTT server by using the fixed prefix and a wildcard character as a subscription subject; and the equipment subscribes to the message from the MQTT server by using the own machine code and the random character string as the subscription subject, the control end releases the message to the MQTT server by using the subscription subject of the equipment as a release subject, and the MQTT server automatically pushes the message according to the subscription subject and the release subject. The method and the systemprovided by the invention are applicable to data collection and remote control of the intelligent equipment.
Owner:四川爱创科技有限公司
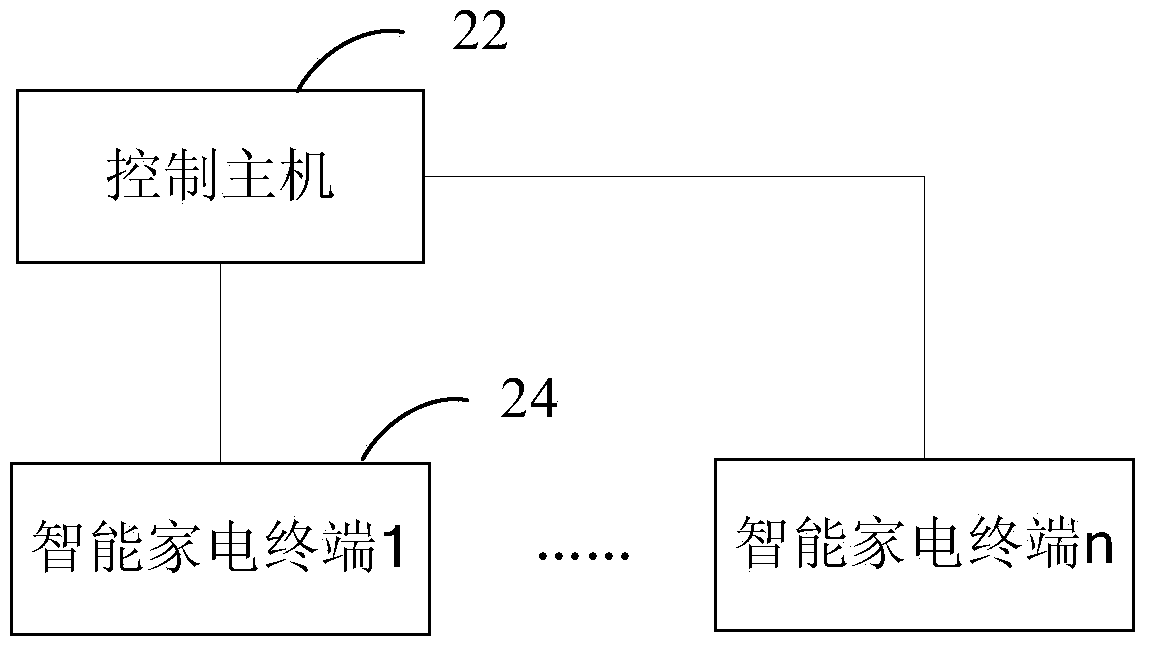
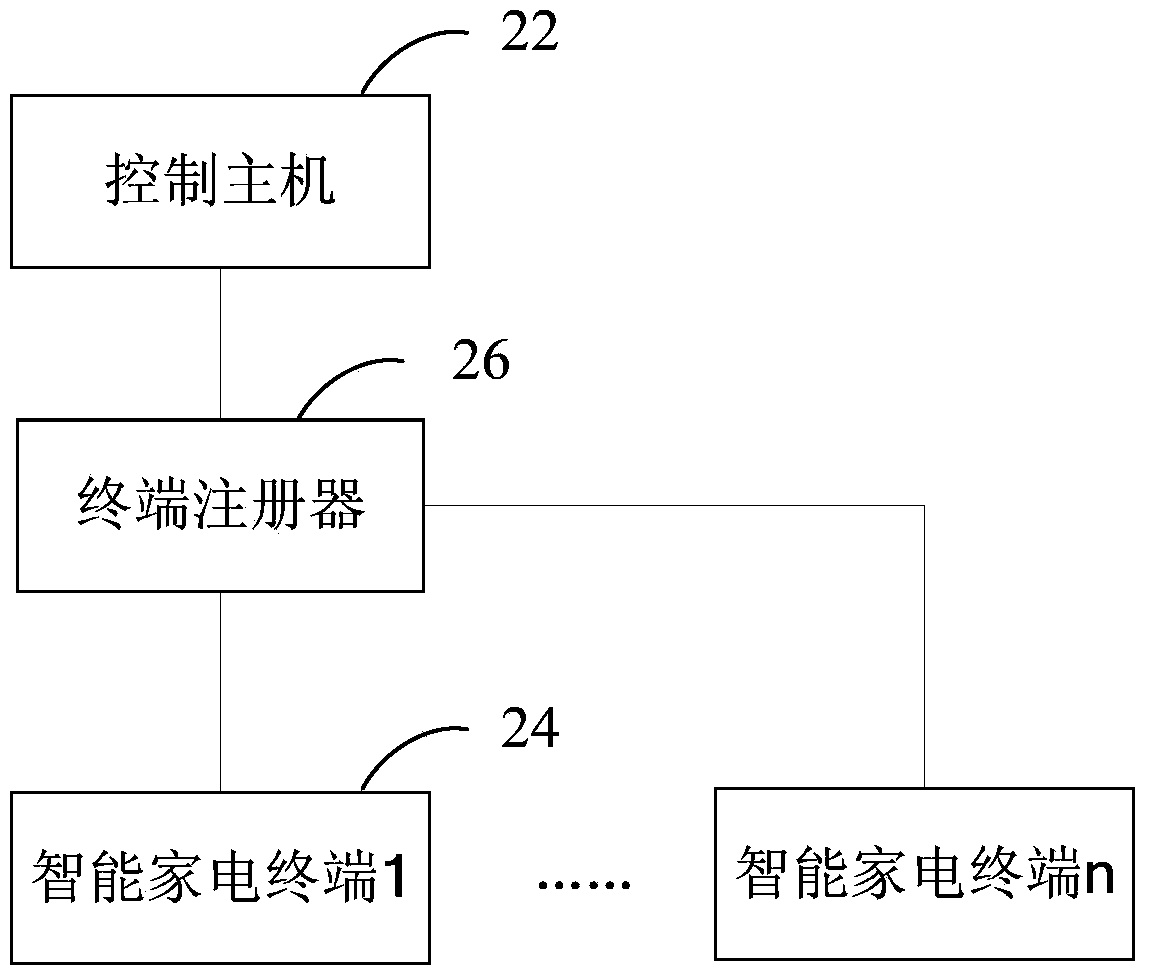
Intelligent household appliance system secret key control method and intelligent household appliance system
InactiveCN103763107AEnsure safetyKey distribution for secure communicationUser identity/authority verificationComputer terminalRandom string
The invention provides an intelligent household appliance system secret key control method and an intelligent household appliance system. The method comprises the steps that a control host generates random character strings at certain time intervals, the random character strings are used as a new secret key to be sent to an intelligent household appliance terminal, the intelligent household appliance terminal updates a local communication secret key of the terminal after receiving the new secret key, and sends a confirmation message to the control host, and the control host synchronously updates the locally-saved communication secret key of the intelligent household appliance terminal after receiving the confirmation message. Therefore, synchronous dynamic secret key updating between the control host and the intelligent household appliance terminal in the intelligent household appliance system can be achieved, communication can be achieved between the control host and the intelligent household appliance terminal without the need that a user manually inputs the secret key, using is convenient, specific secret key information does not need to be managed manually, the system changes automatically and dynamically, each terminal secret key is independent, each secret key is formed by dynamically-generated long character strings, the possibility that the secret keys are guessed does not exist, and communication safety can be ensured.
Owner:刘文军
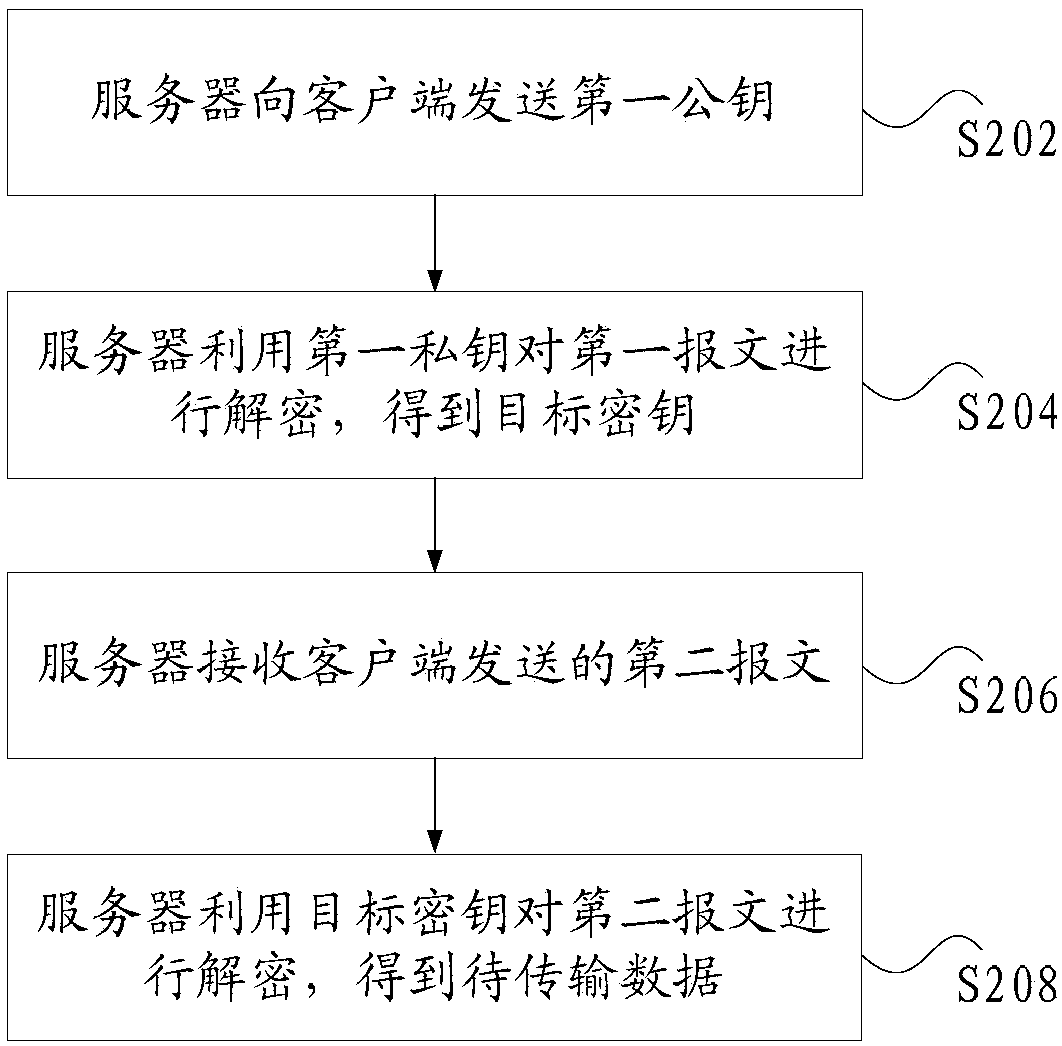
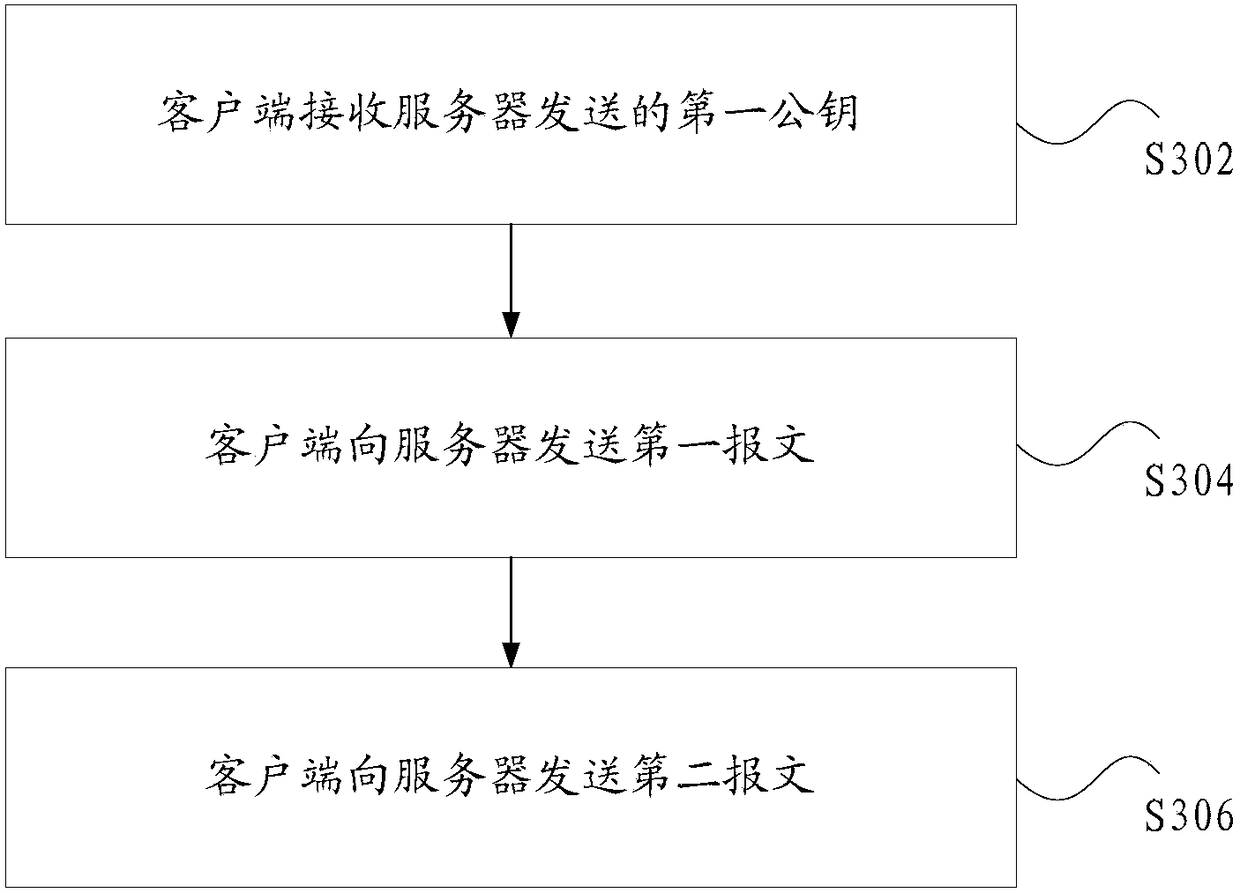
Data transmission method and device
InactiveCN108347419AEnsure safetyImprove securityKey distribution for secure communicationCiphertextClient-side
The invention discloses a data transmission method and device. The data transmission method comprises the following steps: a server sends a first public key to a client; the server uses a first private key to decrypt a first message to obtain a target key, wherein the first public key and the first private key are a pair of keys, the first message is obtained through encrypting the target key withthe first public key by the client, and the target key is generated according to a random string sent by the server; the server receives a second message sent by the client, wherein the second message comprises the encrypted data obtained through encrypting first data with the target key by the client and second data, and the data to be transmitted includes the first data and the second data, wherein the first data is data that needs to be encrypted during the data transmission process, and the second data is data that does not need to be encrypted during the data transmission process; and the server uses the target key to decrypt the second message to obtain the data to be transmitted. The data transmission method and device solves the technical problem of low data transmission securityin the prior art.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Voice access control and quiet environment monitoring method and system
ActiveCN106251874AImprove efficiencyImprove accuracySpeech recognitionComputer hardwareMedia access control
The invention discloses a voice access control and quiet environment monitoring method on the basis of end point detection, speaker segment clustering and voiceprint identification and a system. According to the voice access control and quiet environment monitoring method, an access control mode on the basis of voice identification replaces a traditional door lock key mode, the identification content employs a random character string mode to further enhance safety. The brand new automatic quiet environment monitoring method and the system are advantaged in that management on the quiet environment taking student dormitories for example is convenient, a traditional time-consuming labor-consuming method requiring teachers to do dormitory check by themselves can be replaced, the voice access control and quiet environment monitoring method is convenient and reliable, and reliable guarantee is provided for rest quality of students.
Owner:SHENZHEN EAGLESOUL EDUCATION SERVICE CO LTD
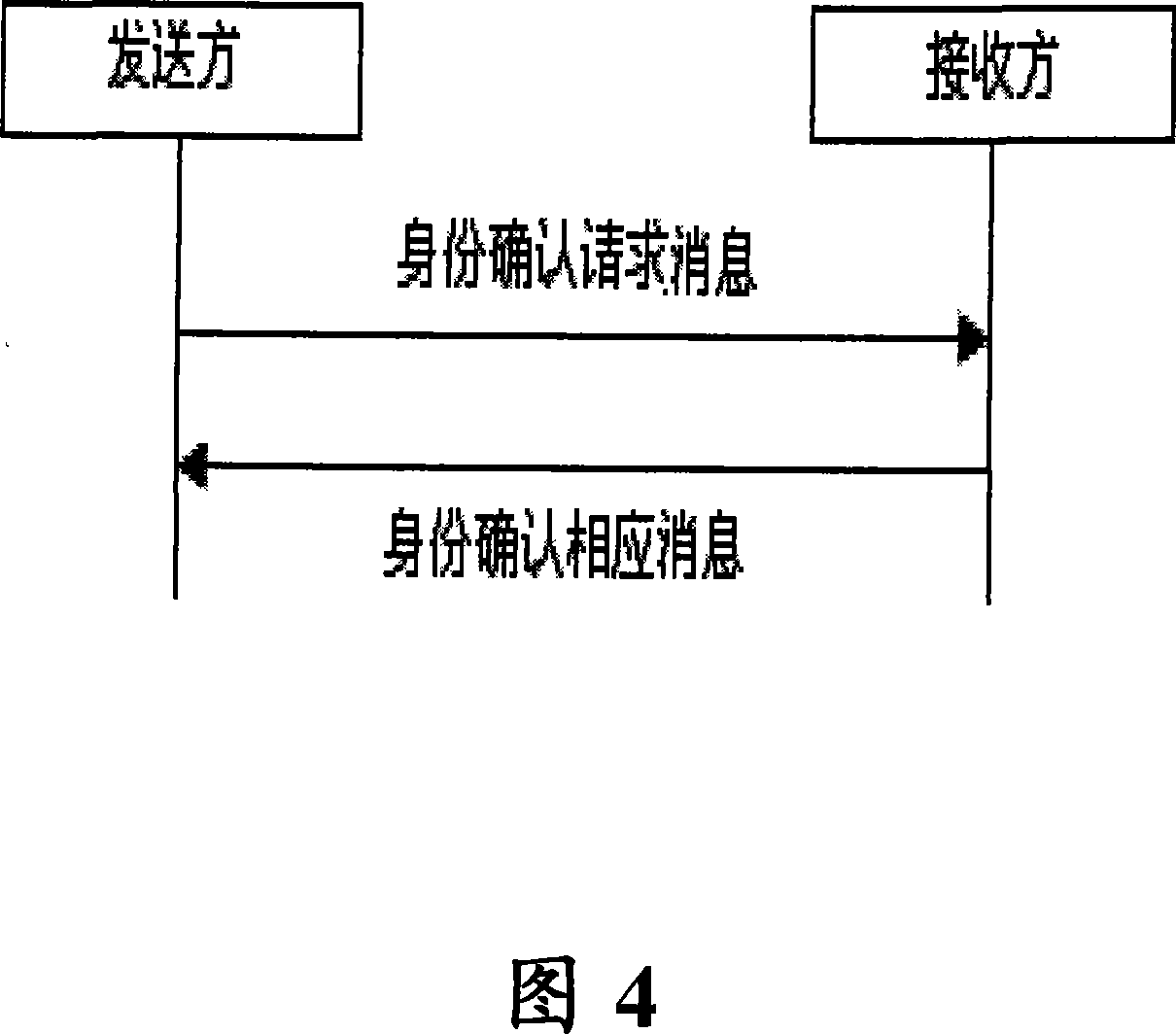
Method and system for confirming terminal identity in mobile terminal communication
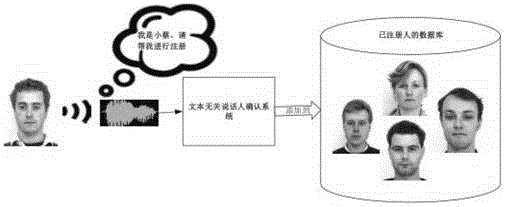
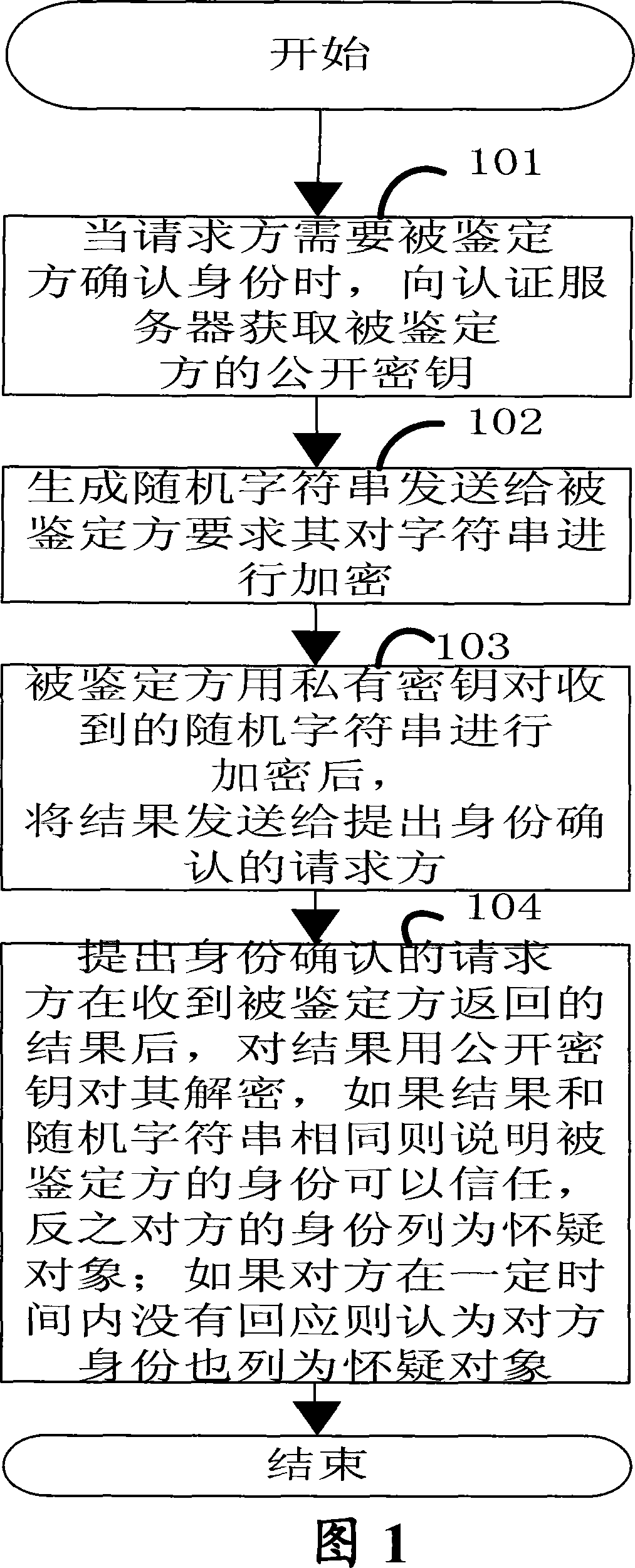
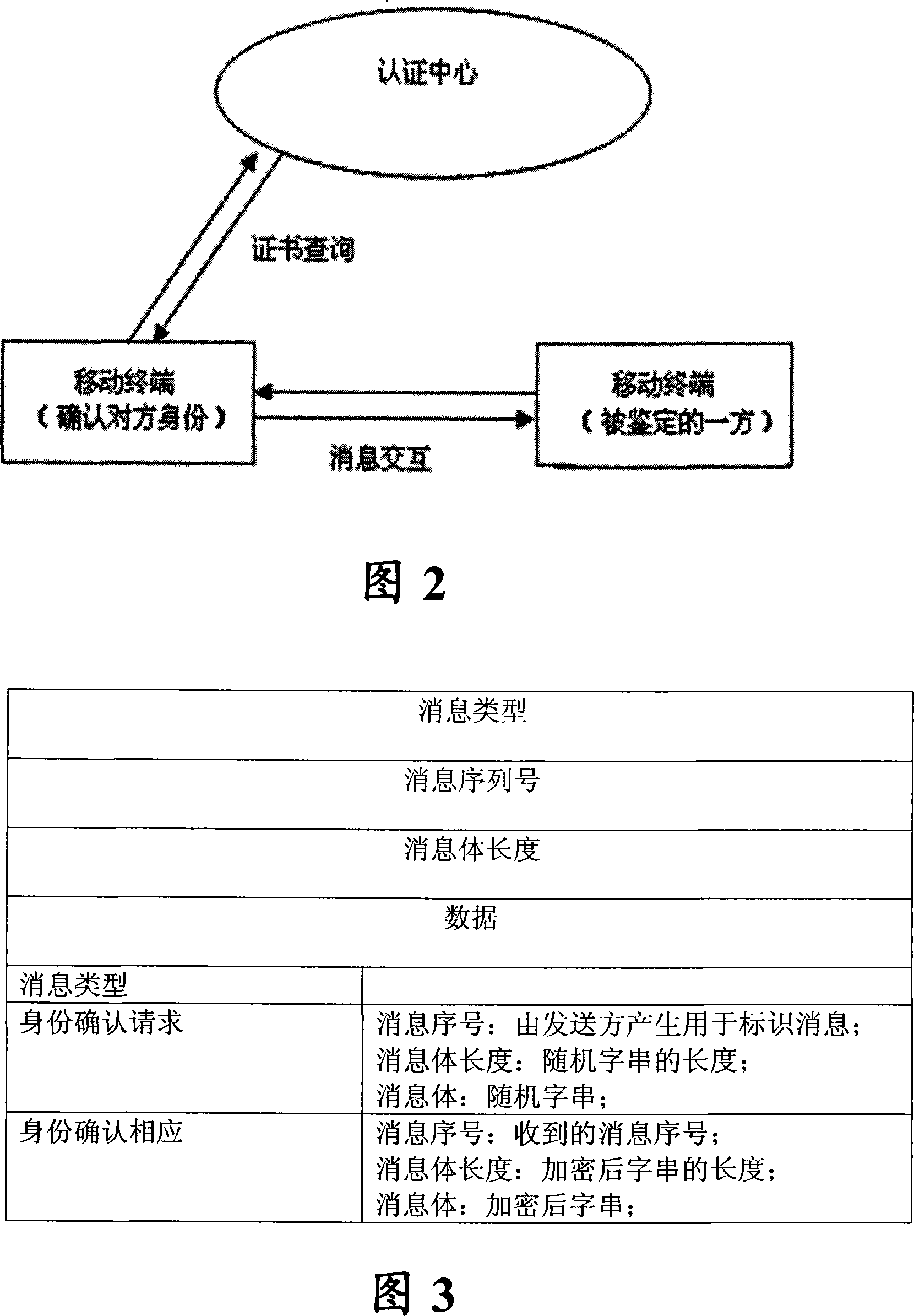
InactiveCN101083843ATo achieve the purpose of confirming identityUser identity/authority verificationRadio/inductive link selection arrangementsRandom stringStatus changed
The present invention discloses a method of terminal identification in mobile communication, it includes following aspects. (1) The mobile terminal would use the asymmetric key algorithm; the requester who requests the confirmation of identity would receive the public key from the authentication center server, then produce the random string, and then send it to the identified party to ask it encrypt the string. (2) The identified party would encrypt the received random string using the private key, and then send the result to the requester. (3) After the requester receives the result returned by the identified party, the result would be decrypted by the obtained public key. If the result is the same as the random string, identified party would be trusted; if not, the identified party would be listed as a suspected target. The present invention solves the problem that how the mobile communication terminal could ask for identity verification at any time during the whole process from the establishment of communication to the end of communication.
Owner:ZTE CORP
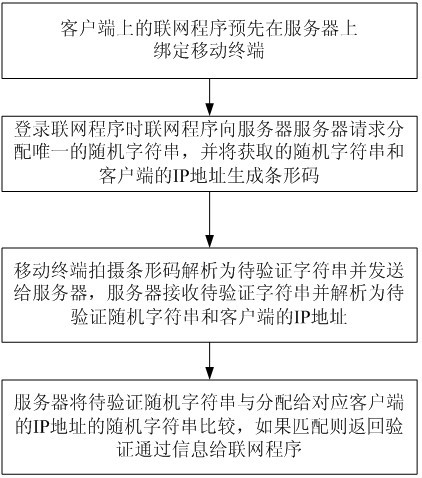
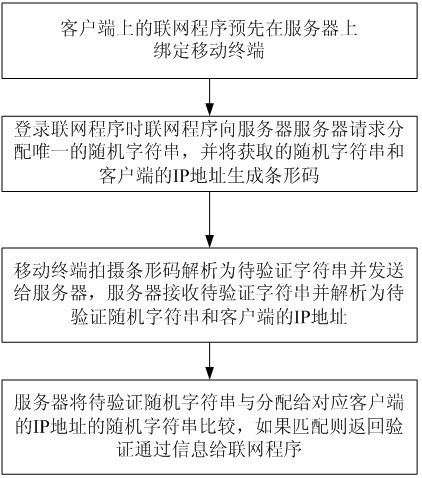
Networking program user authentication method based on mobile terminal
InactiveCN102624687ARealize verificationVerification is simple and reliableTransmissionUser verificationIp address
The invention discloses a networking program user authentication method based on a mobile terminal. The networking program user authentication method includes the implementation steps: 1) binding the mobile terminal on a server by a networking program on a client in advance; 2) sending a request for distributing a unique random character string to a server by the networking program when the networking program is logged in, and generating a barcode by the aid of the acquired random character string and an IP (internet protocol) address of the client; 3) shooting the barcode by the mobile terminal, analyzing the barcode to generate a character string to be authenticated, transmitting the character string to be authenticated to the server, receiving the character string to be authenticated by the server, and analyzing the character string to be authenticated into a random character string to be authenticated and an IP address, to be authenticated, of the client; and 4) comparing the random character string to be authenticated with the random character string distributed to the corresponding IP address of the client, and returning authentication passing information to the networking program if the random character string to be authenticated matches with the random character strings distributed to the corresponding IP address of the client. The networking program user authentication method has the advantages that users of the networking program can be authenticated, authentication is simple and reliable, and utilization is convenient.
Owner:苏州奇可思信息科技有限公司
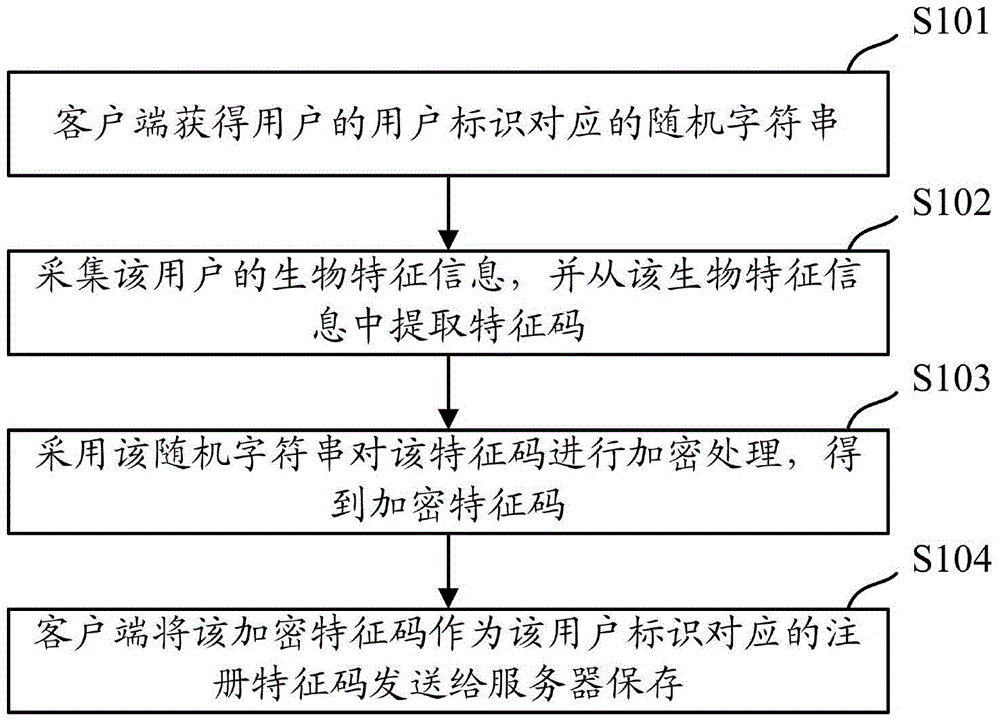
On-line registration and authentication method and apparatus
The invention discloses an on-line registration and authentication method and apparatus, and solves the problem that when biological characteristics are employed for on-line authentication in the prior art, the biological characteristic information can be easily stolen and is low in security. During registration, a client obtains random string corresponding to a subscriber's ID, acquires the biological characteristic information and extracts a characteristic code therefrom. The characteristic code is encrypted through the random strings to obtain an encrypted characteristic code, and the encrypted characteristic code serves as register characteristic code corresponding to the subscriber's ID and is sent to the server for storing. Since the characteristic code that the client sent during registration is encrypted, an attacker can not easily decrypt the characteristic code and obtain the original characteristic code even if the characteristic code is stolen by the attacker. The security of biological characteristic information is effectively improved.
Owner:ADVANCED NEW TECH CO LTD
System and method using temporary identity for authentication with session initiation protocol
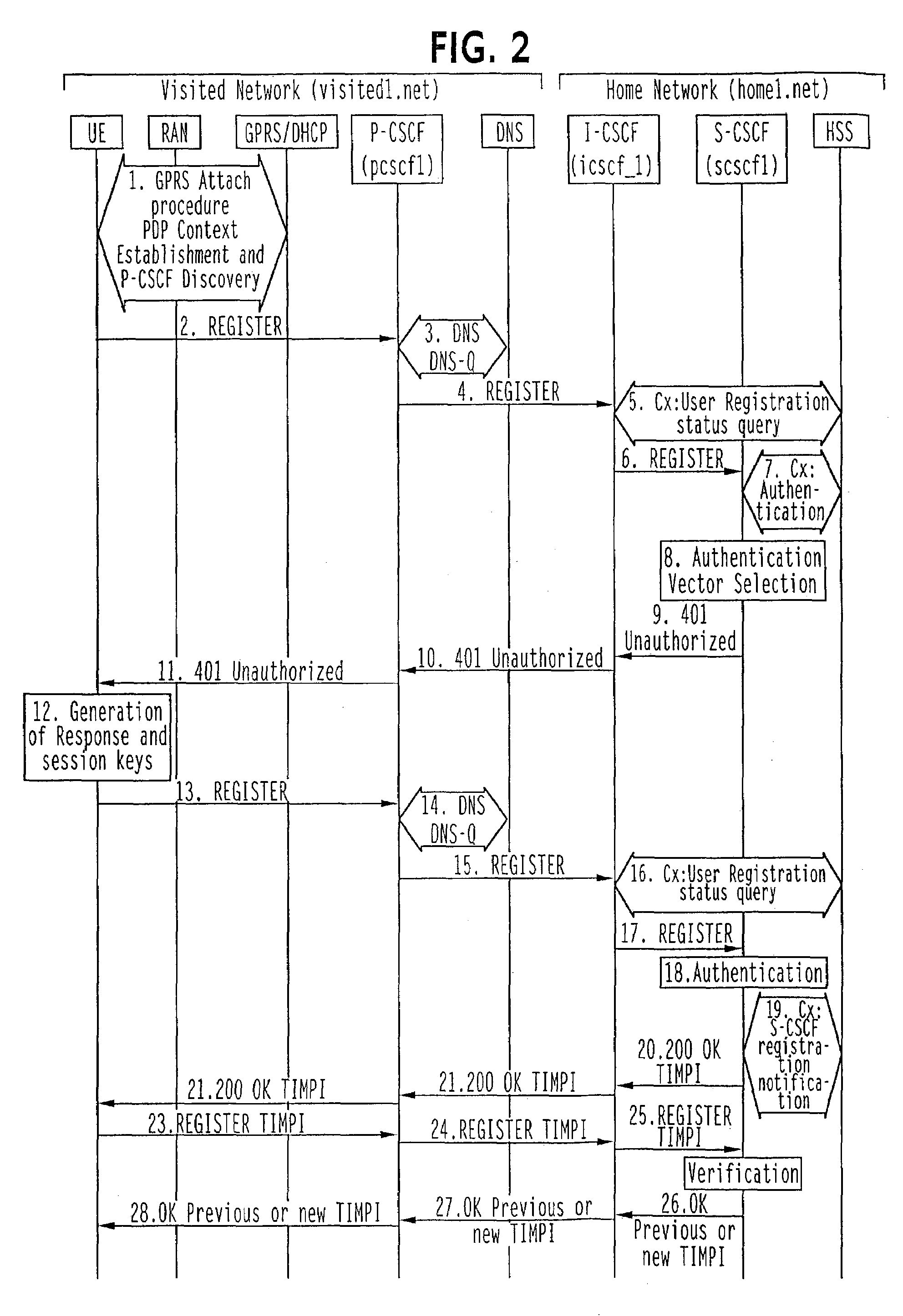
InactiveUS7624266B2User identity/authority verificationWireless network protocolsSession Initiation ProtocolCommunications system
A communication method and a communication system providing services for subscribers having private identities is disclosed. The method includes receiving at a network element (S-CSCF) a communication from user equipment (UE) including a private identity of the subscriber and assigning a random string to the private identity.
Owner:NOKIA CORP
Method and device for dynamically encrypting data, computer equipment and storage media
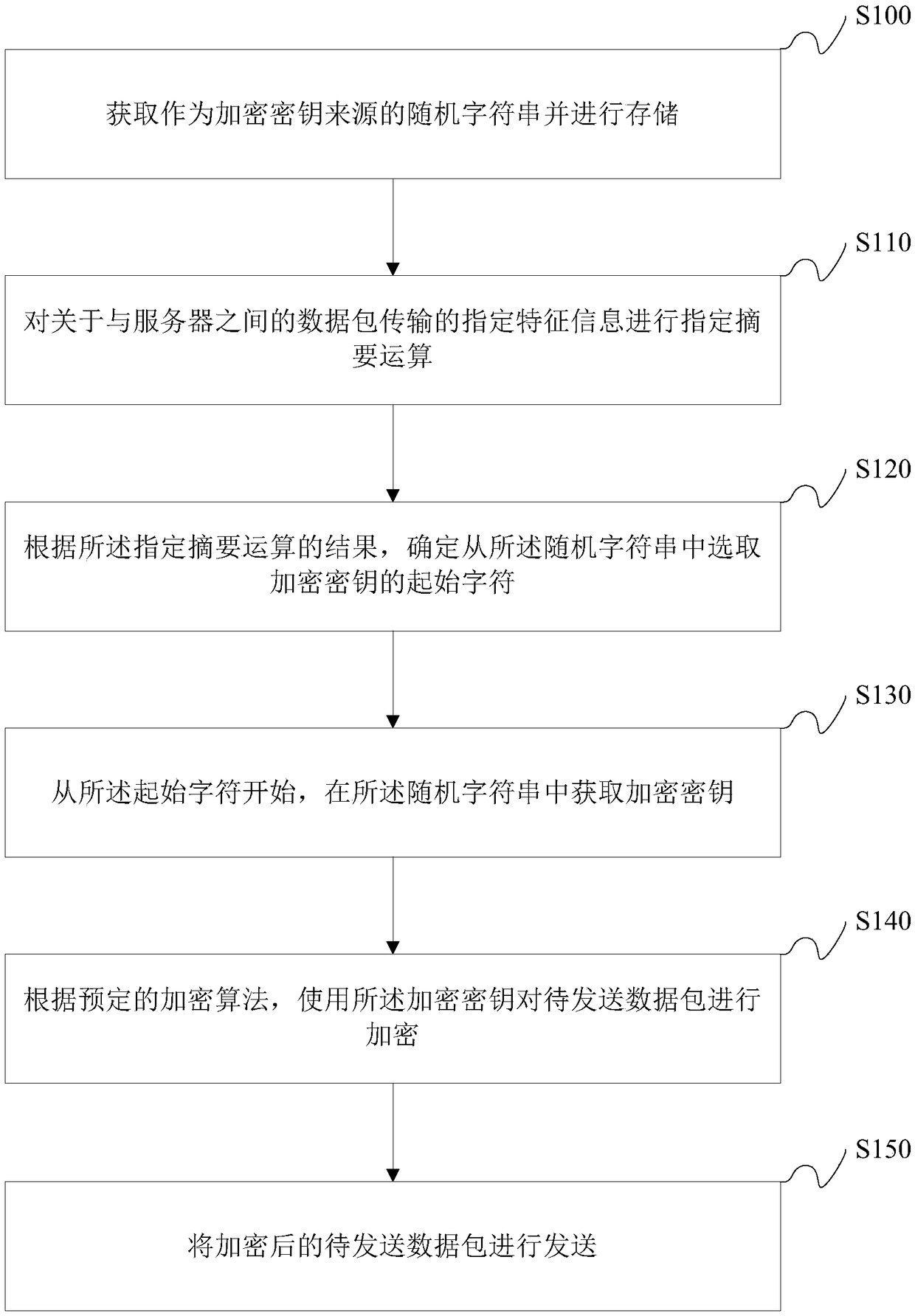
ActiveCN109150499AImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareRandom string
The invention discloses a method and device for dynamically encrypting data, computer equipment and storage media. The method includes obtaining random strings which are taken as the source of encryption keys to perform storing; performing specified digest operation on the specified characteristic information transmitted by data packets between servers; determining starting characters of the encryption keys selected from the random strings according to results operated by specified digests; starting from the starting characters to obtain the encryption keys from the random strings; performingencryption on to-be-sent data packets by using the encryption keys according to a predetermined encryption algorithm; and sending the encrypted to-be-sent data packets. The method enhances the security of data encryption.
Owner:深圳市迷你玩科技有限公司
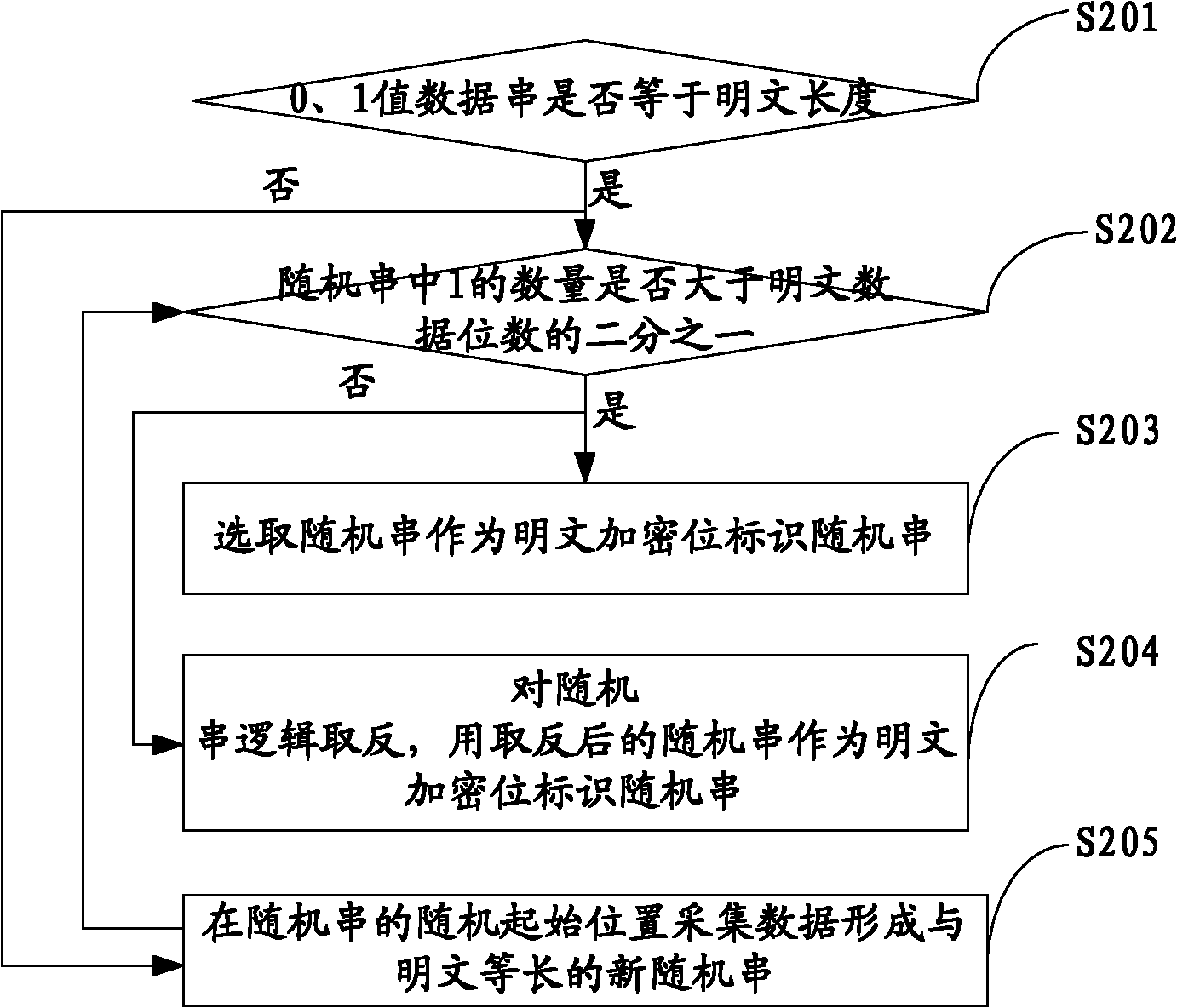
Methods and devices for selectively encrypting and decrypting data
ActiveCN102012993AWithout sacrificing protection strengthFast encryption and decryptionComputer security arrangementsSecuring communicationComputer hardwarePlaintext
Owner:BIGKNOW (BEIJING) DATA TECH CO LTD
user identification system
InactiveCN102281142ASafe and convenient authentication methodEasy to useUser identity/authority verificationApplication serverIdentity recognition
The invention discloses a user identification system, comprising the following steps: the user inserts a USB KEY, the client sends an authentication request to the authentication server; the authentication server receives the request and generates a random character string X; the authentication server sends X to the client ; The client uses the first algorithm to calculate the information + X in the USB KEY, and the calculation result is Rh; the client sends Rh to the authentication server; the authentication server uses the first algorithm to store the information + X in the user's USB KEY The operation result is Rh1; the authentication server compares Rh and Rh1, and if they are consistent, the verification is successful; the comparison result is sent to the application server, and the application server judges whether the user can log in according to the comparison result. The invention eliminates the system security problem caused by the traditional login mode of "user name + password", and ensures the security and accuracy of identity authentication.
Owner:JURONG SHENGSHI SOFTWARE
System and method for user login and tracking
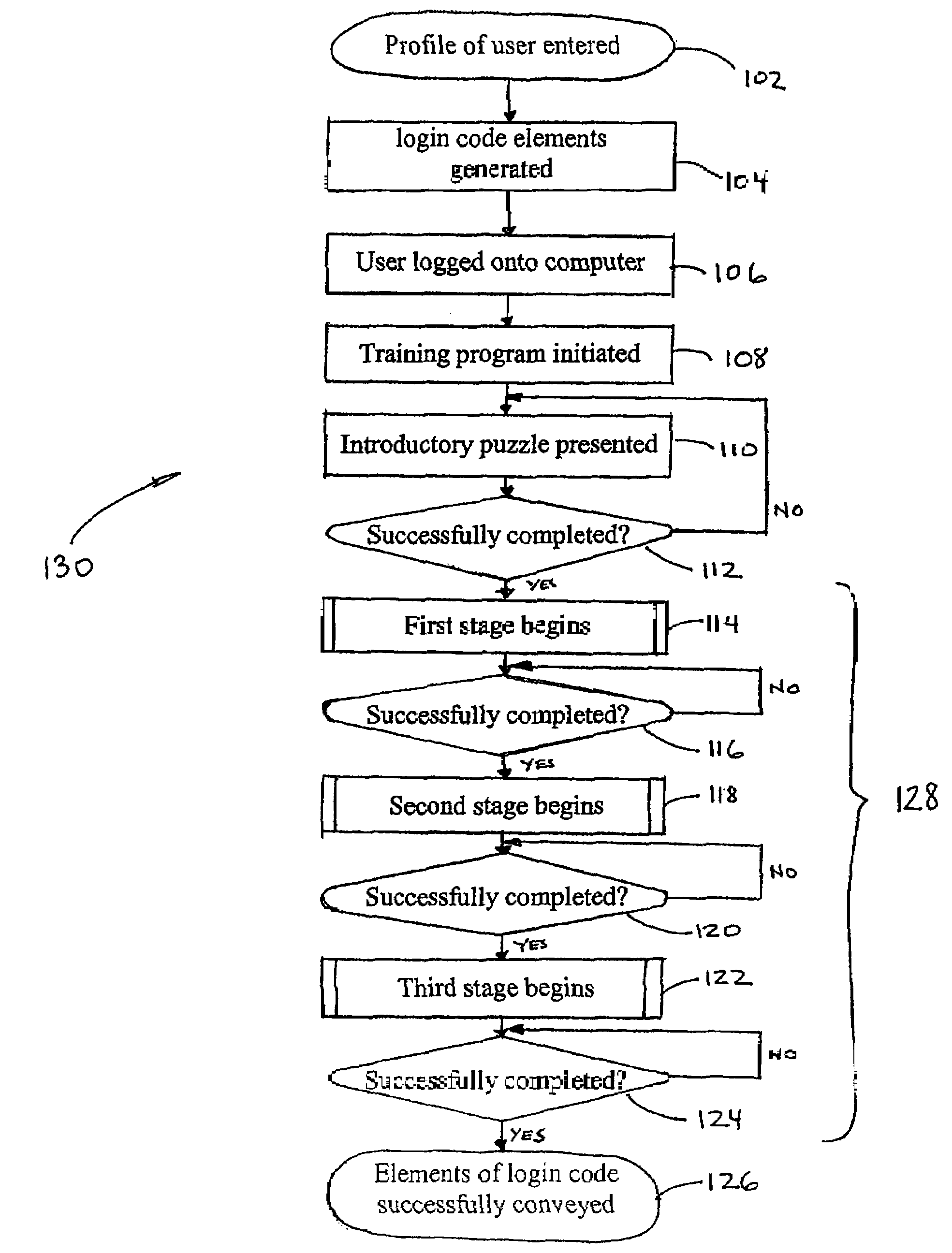
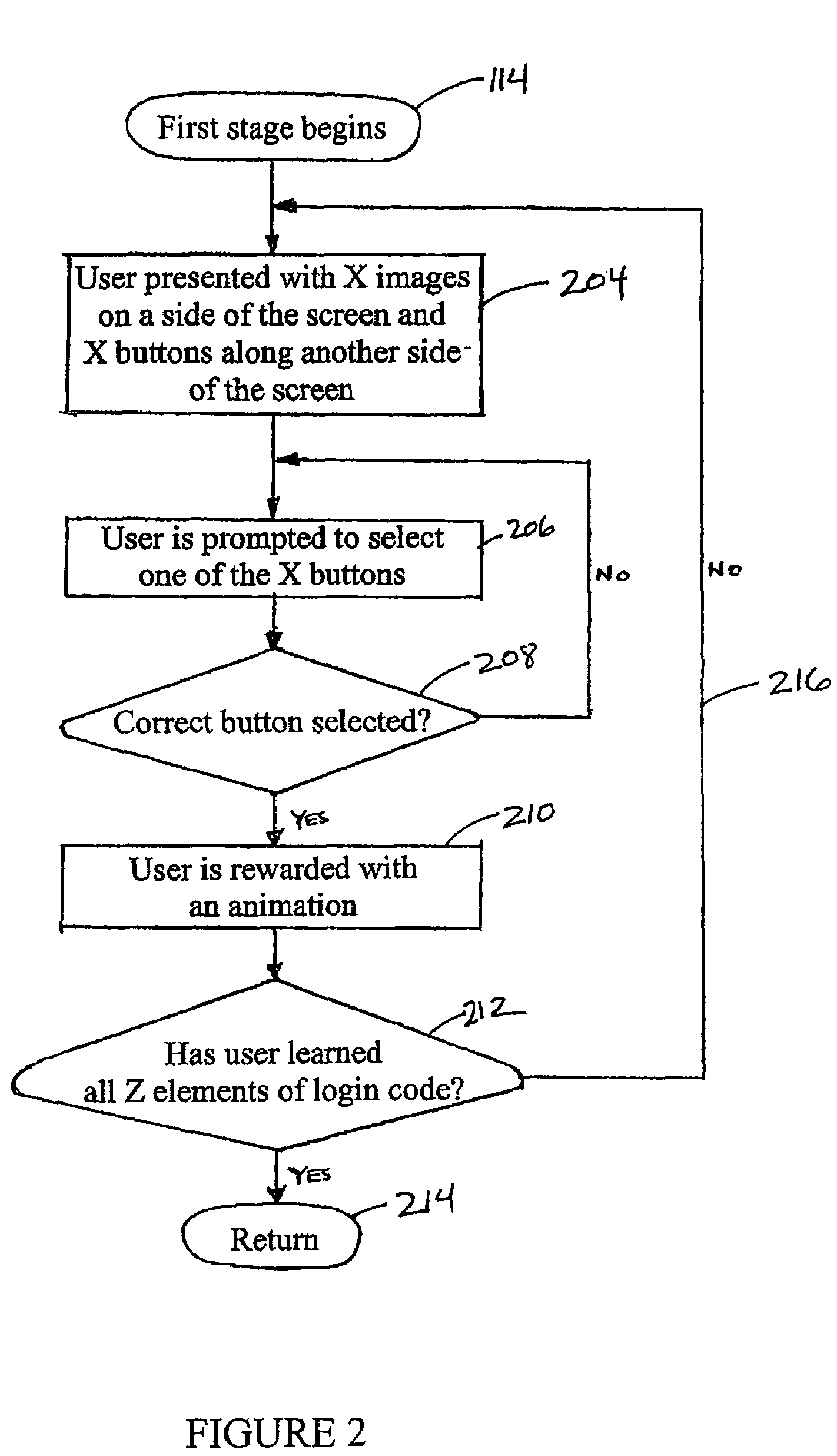
ActiveUS7653931B1Digital data processing detailsUser identity/authority verificationProgramming languageCoded element
The disclosure provides for systems that generate random strings of objects corresponding to elements of a login code. The disclosure also provides for methods for training individuals in remembering the elements of the login code. Those login code elements, in certain embodiments, are taught to its user by way of a puzzle or game-like environment. That game-like environment, in one embodiment, does not require the use of language-based instructions, which make learning the elements of the login code simple and easy for a wide range and variety of persons. In addition, the login code elements are taught to its user, in certain embodiments, by way of a multi-staged training process, wherein each stage includes a plurality of training sessions. Those training sessions may use a process of spatial and visual recognition. That process may help assist a login code user to remember the elements of the code even if the login code is only periodically used.
Owner:MIND RES INST
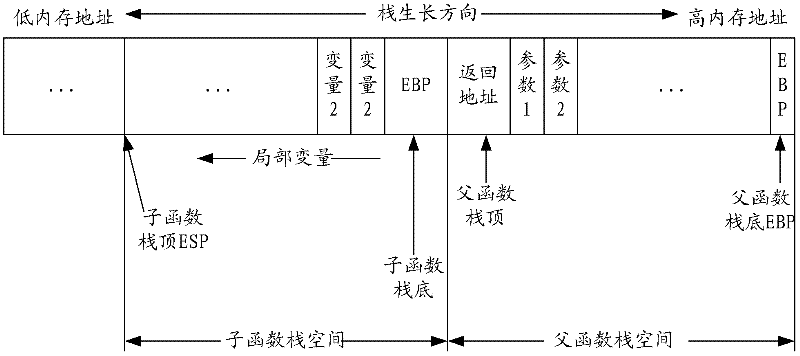
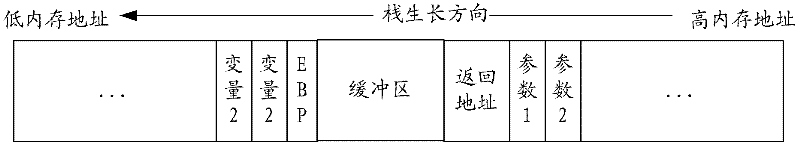
A stack overflow protection method and device
InactiveCN102298677AImprove protectionEasy to getPlatform integrity maintainanceRandom stringStack overflow
The invention provides a stack overflow protection method, by inserting a buffer into the stack, and filling the buffer with filling characters in the format of "fixed character string + random character string" or "random character string+fixed character string" String, and check the filling value in the buffer when the stack is released, which solves the problem of poor defense against stack overflow vulnerabilities, thereby reducing the risk of attackers using stack overflow vulnerabilities to damage the system. The invention also includes a stack overflow protection device.
Owner:RAISECOM TECH
Method for protecting passwords using patterns
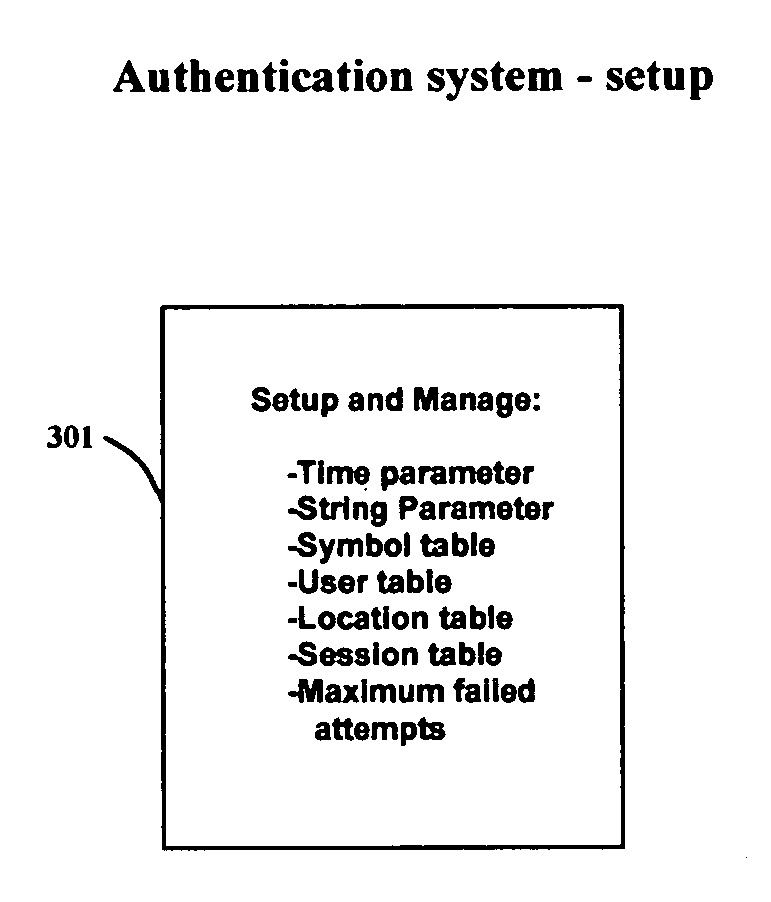
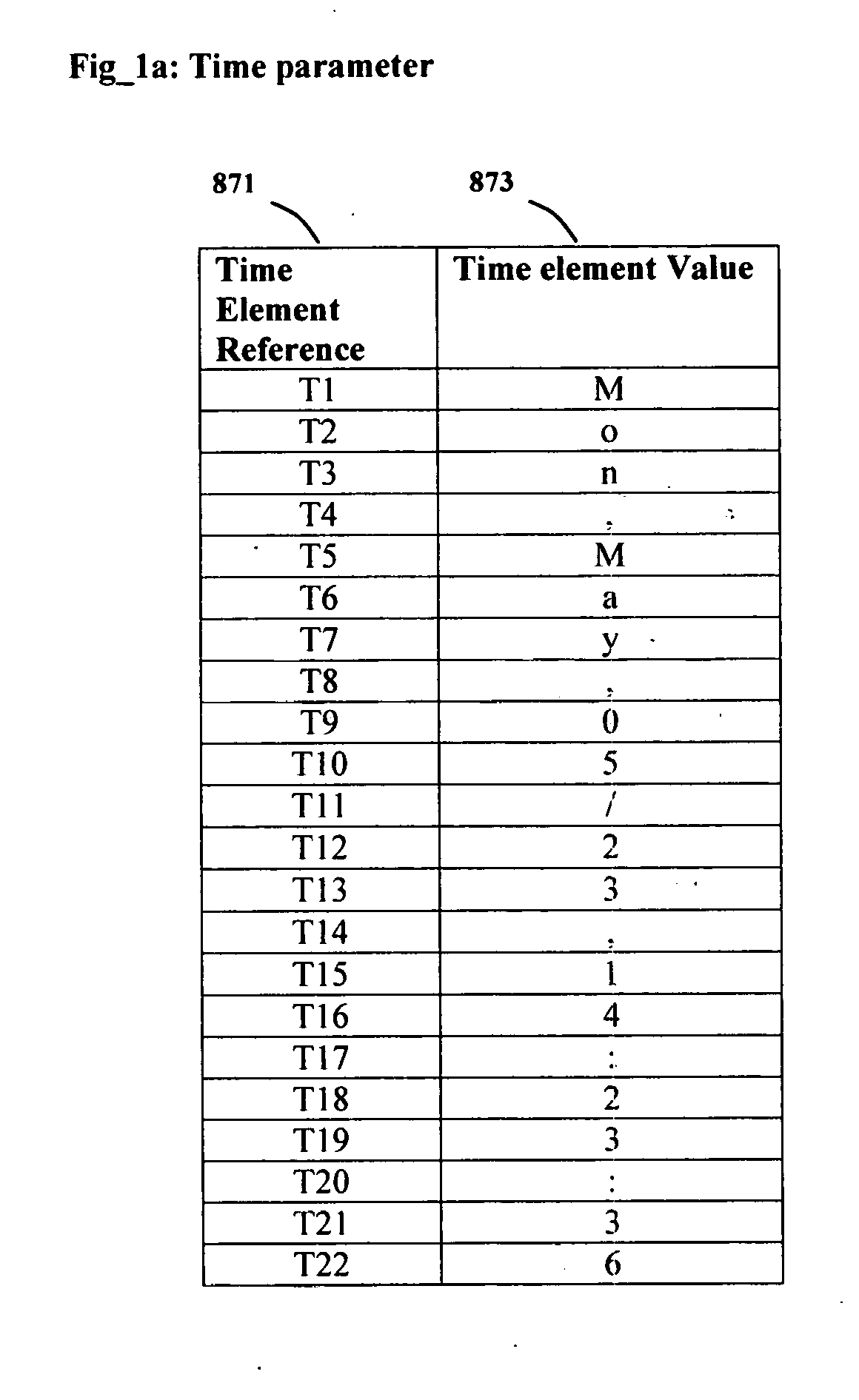
PendingUS20100180324A1Digital data processing detailsMultiple digital computer combinationsAs elementPassword
A method, system and computer program for protecting the password by limiting the password's validity to the user's active session. The present invention provides for password to automatically change for each session and only the user will be able to construct the valid password for the session. The user provides to the authentication system, a password pattern, embedding symbols in to a string. The embedded symbols are substituted by elements of parameters. The parameter elements and the symbols that represent them are defined by the authenticating system. The parameters contain either time driven or random string of characters and digits as elements. The user builds a password using the values of the elements in the session parameters and the user's password pattern's memory hint recalled from memory. The authenticating system generates the valid password for the session using the password pattern the user has provided. If the users built password matches the authenticating system generated password, secured access is allowed otherwise access is denied.
Owner:KARUR RANGAN
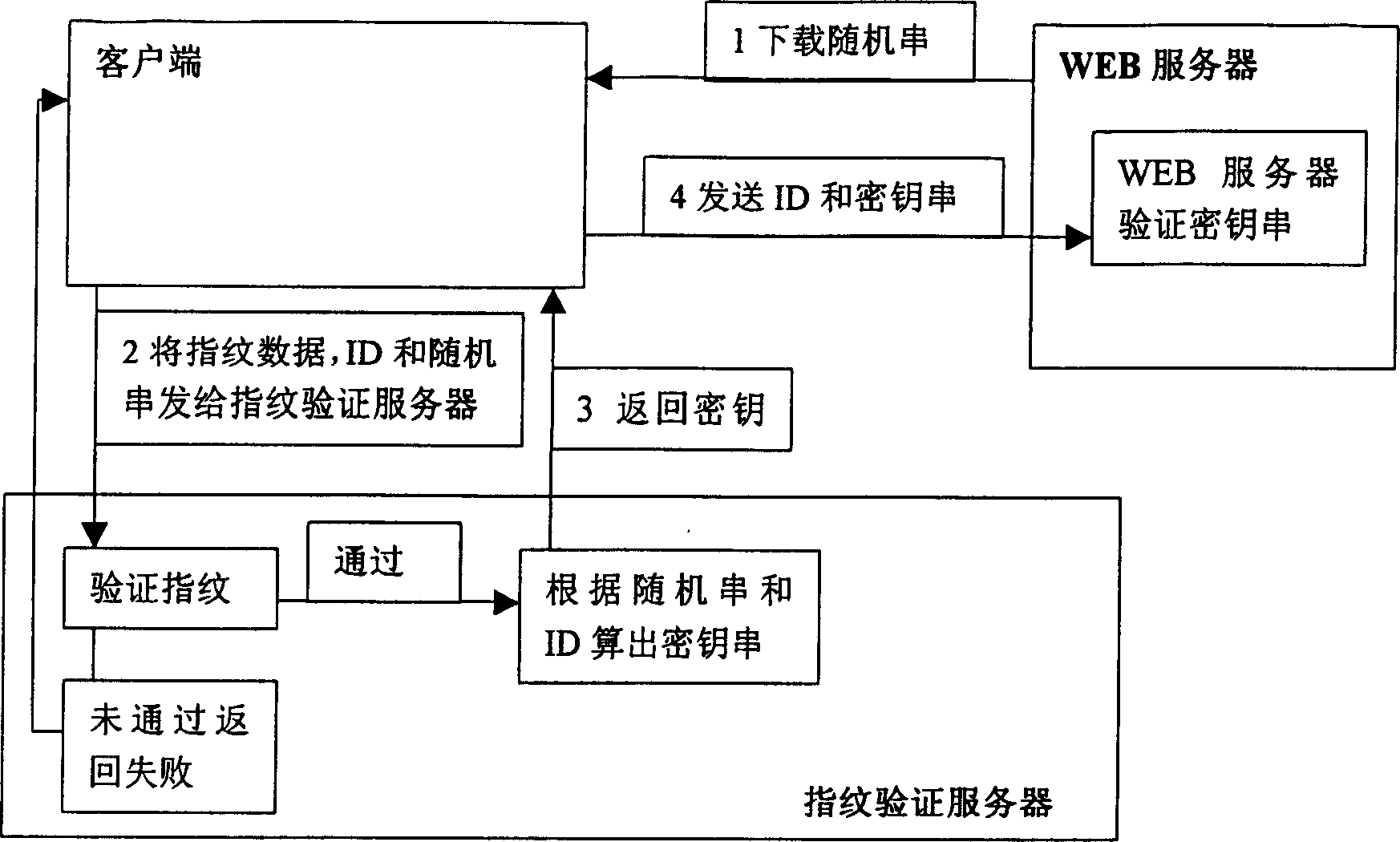
Dynamic cipher network identification system based on fingerprint and realizing method thereof
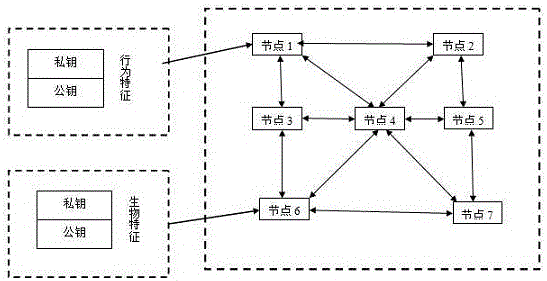
InactiveCN1674500ARandomFlexible and convenient to useMultiple keys/algorithms usageUser identity/authority verificationFeature extractionClient-side
The present invention relates to a fingerprint based dynamic cipher network identity authentication system and its implementation method. Said invention includes fingerprint identification server mounted in the system and customer machine matched with fingerprint collector. Its implementation method includes the following steps: the fingerprint identification server can down-send a random character string to customer terminal and is used for receiving fingerprint identification request, after the fingerprint identification is passed, the dynamic cipher can be sent to the customer sending request, the customer terminal can acquire fingerprint and make characteristic extraction, and can send the extracted characteristics, user ID and a random character string to server and use dynamic cipher back-transferred by server so as to implement logging.
Owner:XIAN QINGSONG TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com