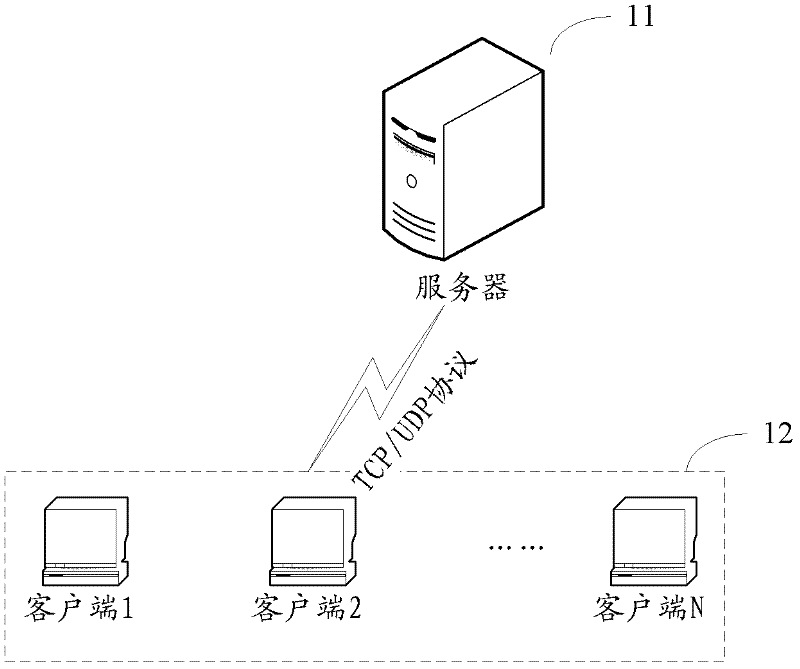
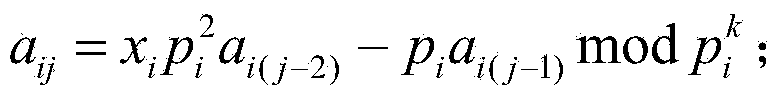Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
129results about How to "Fast encryption and decryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
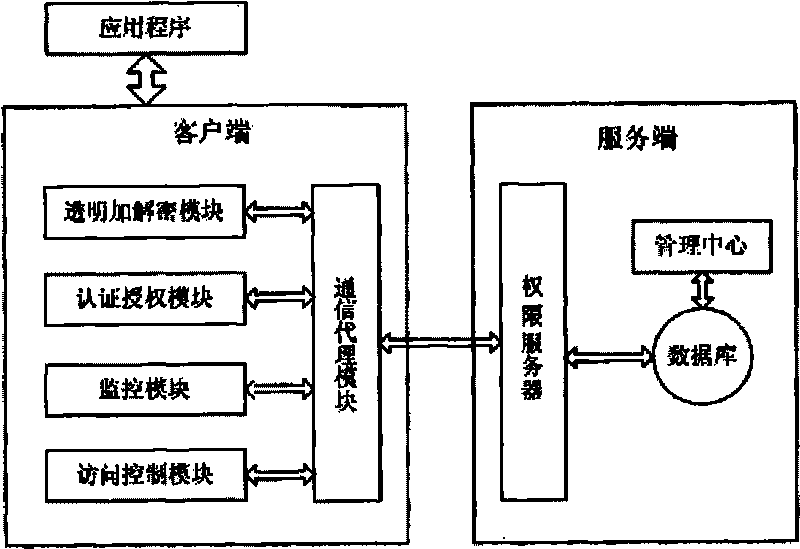
Digital content safeguard system based on transparent encryption and decryption method thereof
InactiveCN101729550AThe encryption method is safe and efficientImprove securityKey distribution for secure communicationProgram/content distribution protectionOperational systemCiphertext
The invention belongs to the field of information safety, providing a digital content safeguard system based on transparent encryption and decryption. The system comprises a transparent encryption and decryption module, an access control module, a monitoring module, a certificate authority module, a communication proxy module, a management center and a permission server module, wherein the transparent encryption and decryption module, the access control module and the monitoring module are on a client side, and the management center and the permission server module are on a server side; the client side and the server side are connected by the communication proxy module and the permission server module. Aiming at the safeguard system, the invention provides a dynamic encryption and decryption method which carries out encryption and access control to digital content as well as opens, reads and writes cipher texts. The method realizes transparent encryption and decryption to the digital content by realizing filtering driving on the bottom layer of an operating system and records an intact log to all operation of a user, thus improving system safety, and greatly improving encryption and decryption speed. Compared with the existing like products, the system of the invention has the advantages of safe and efficient encryption mode, fine grit access control, perfect log audit function and convenient and efficient management mode.
Owner:NORTHWEST UNIV(CN)
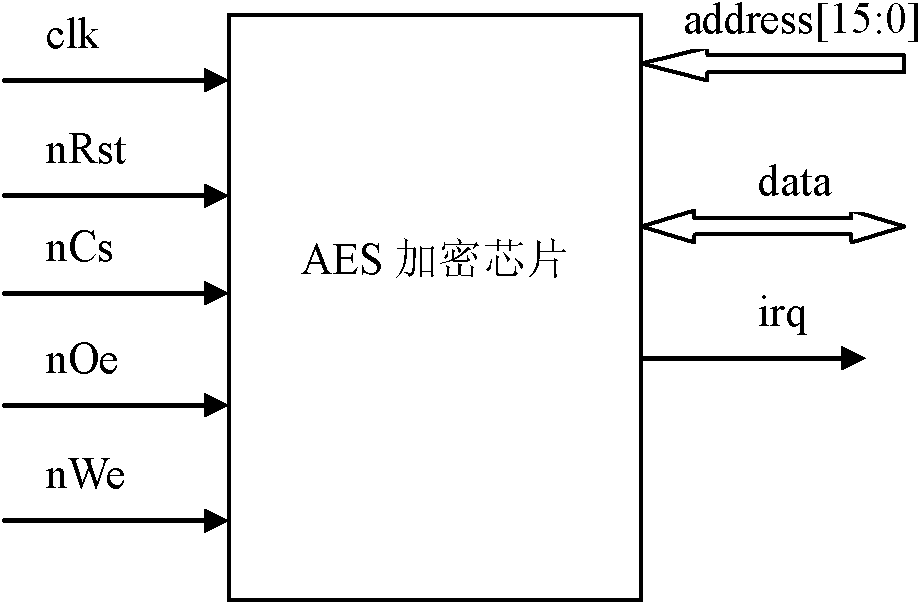
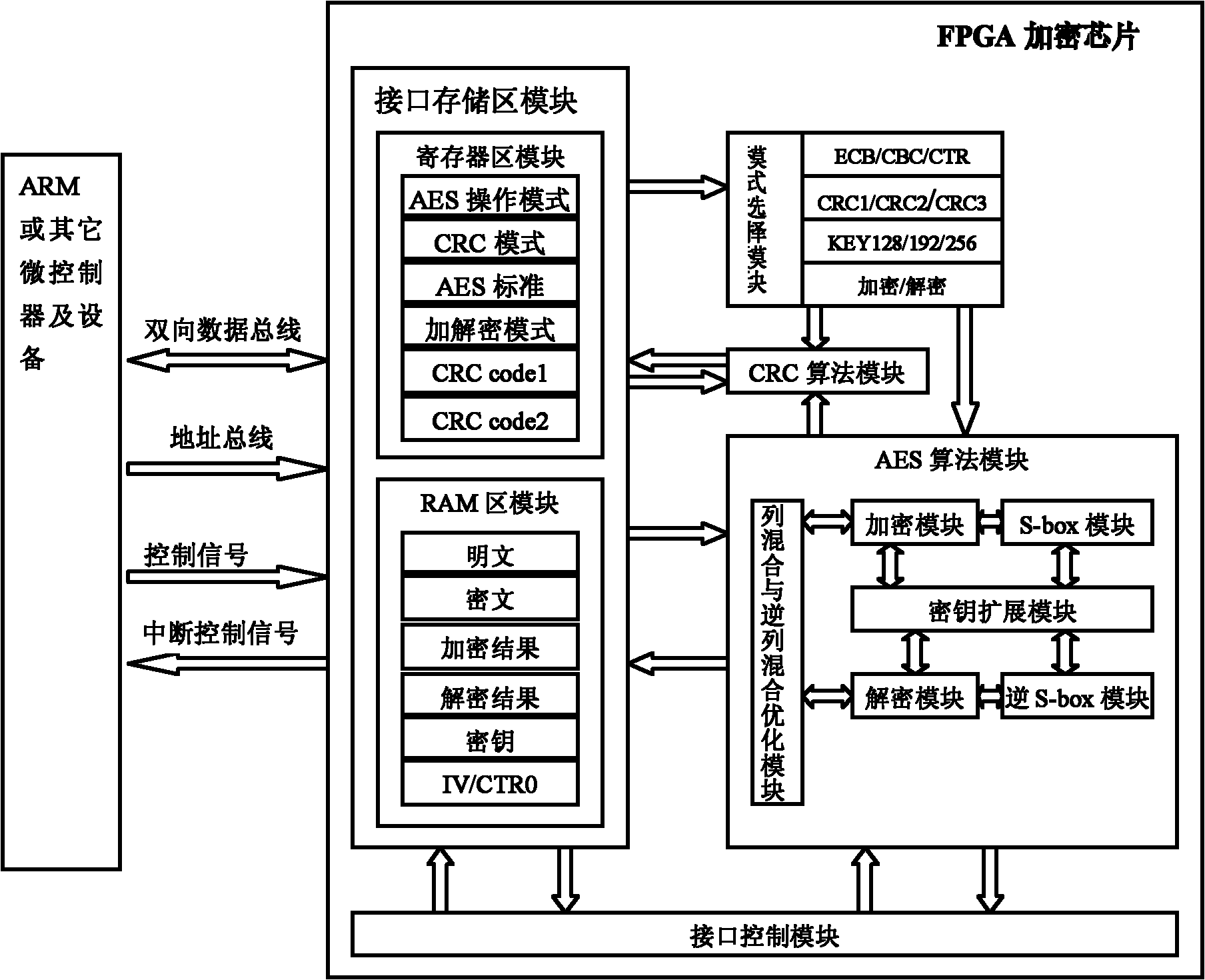
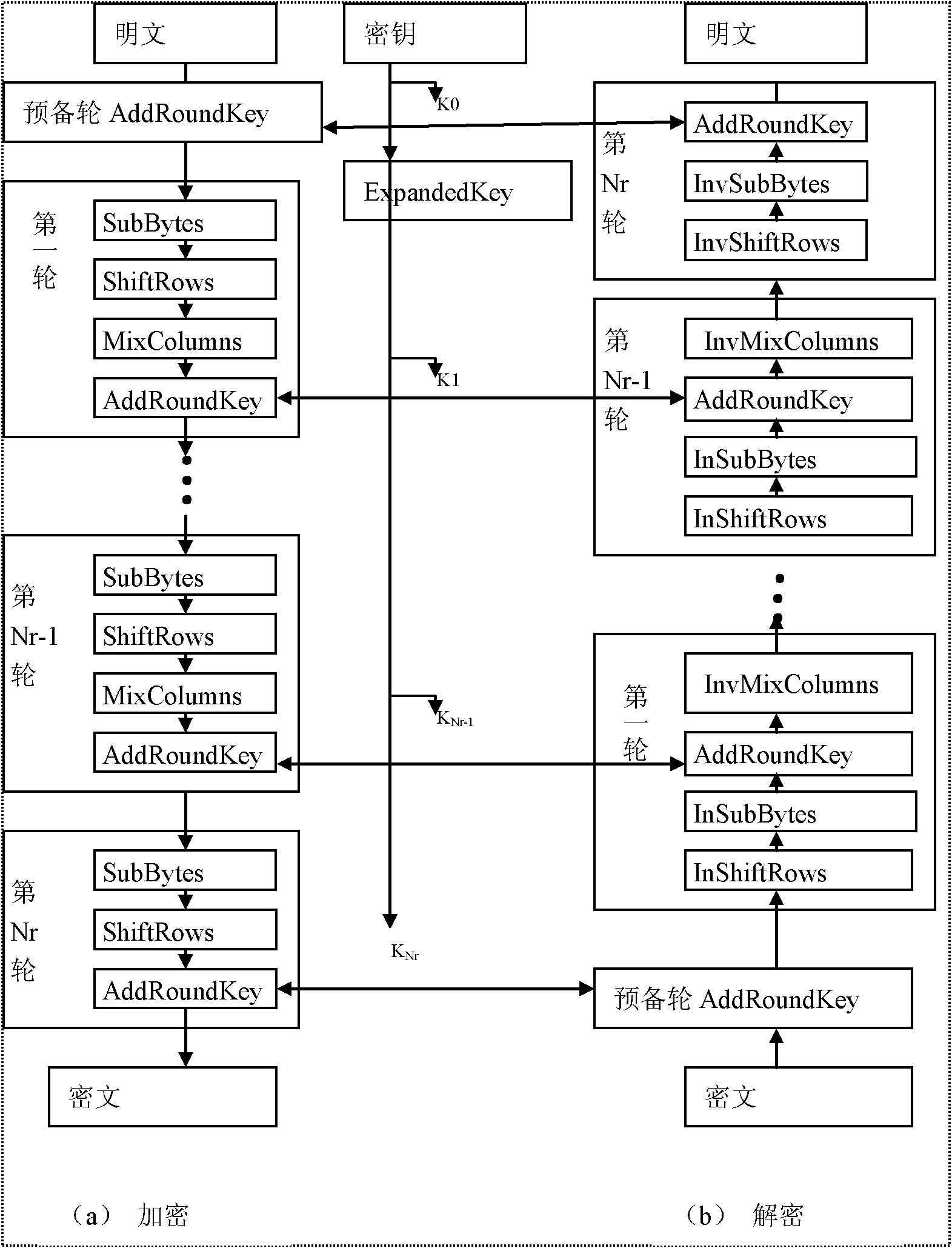
Method for designing AES (Advanced Encryption Standard) encryption chip based on FPGA (Field Programmable Gate Array) and embedded encryption system
InactiveCN102223228AFlexible useReduce areaEncryption apparatus with shift registers/memoriesInformation technologyEncryption system
The invention discloses a method for designing an AES (Advanced Encryption Standard) encryption chip based on an FPGA (Field Programmable Gate Array), which is designed for aiming at the requirement of an embedded system. The AES encryption chip not only can be used in a manner of a solid chip but also used in a manner of a software module. Three operation modes of ECB (Electronic Code Book), CBC (Cipher Block Chaining) and CTR (Counter Technical Requirement) are supported simultaneously. All standards of the AES can be encrypted and decrypted. The byte replacement and the key expansion are carried out by using a look-up table optimization algorithm. A column mixed optimization structure is provided. Device resources are saved while the operation speed is ensured. An RAM (Random-Access Memory) can be configured as a cache of information and a key through double ports of the FPGA. A problem for storing a time sequence and data of other devices or equipment and the FPGA is resolved. Safe and reliable communication with an FPGA interface joins CRC (Cyclic Redundancy Check) error detection in a manner of a memory bus. The AES encryption chip has the advantages of high safety, high encryption and decryption speeds, low device resource requirement, low cost and the like. The AES encryption chip can be widely used in information technology industries of intelligent card systems, ATMs (Automatic Teller Machines), wireless local area networks, wireless sensor networks and the like.
Owner:BEIHANG UNIV
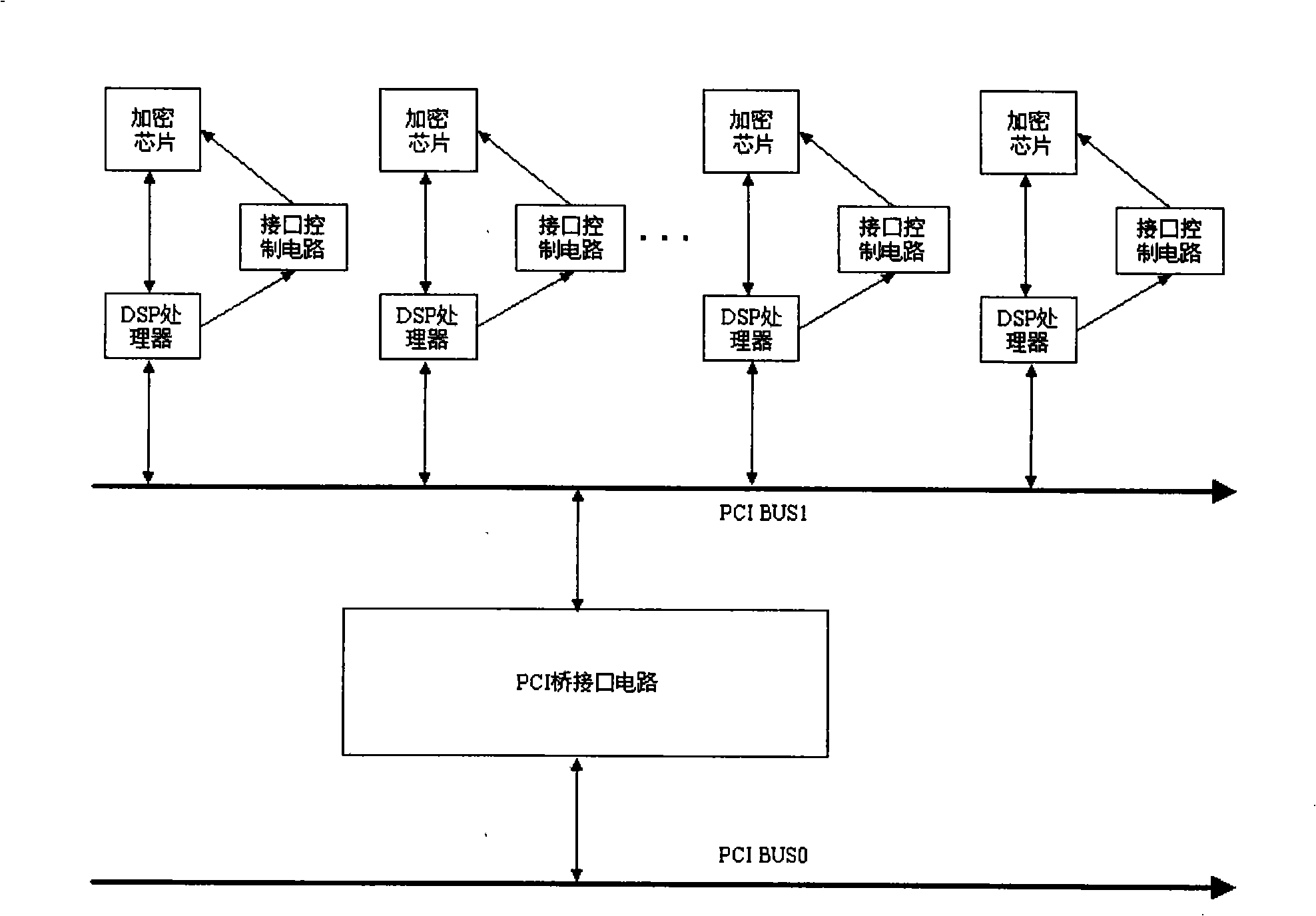
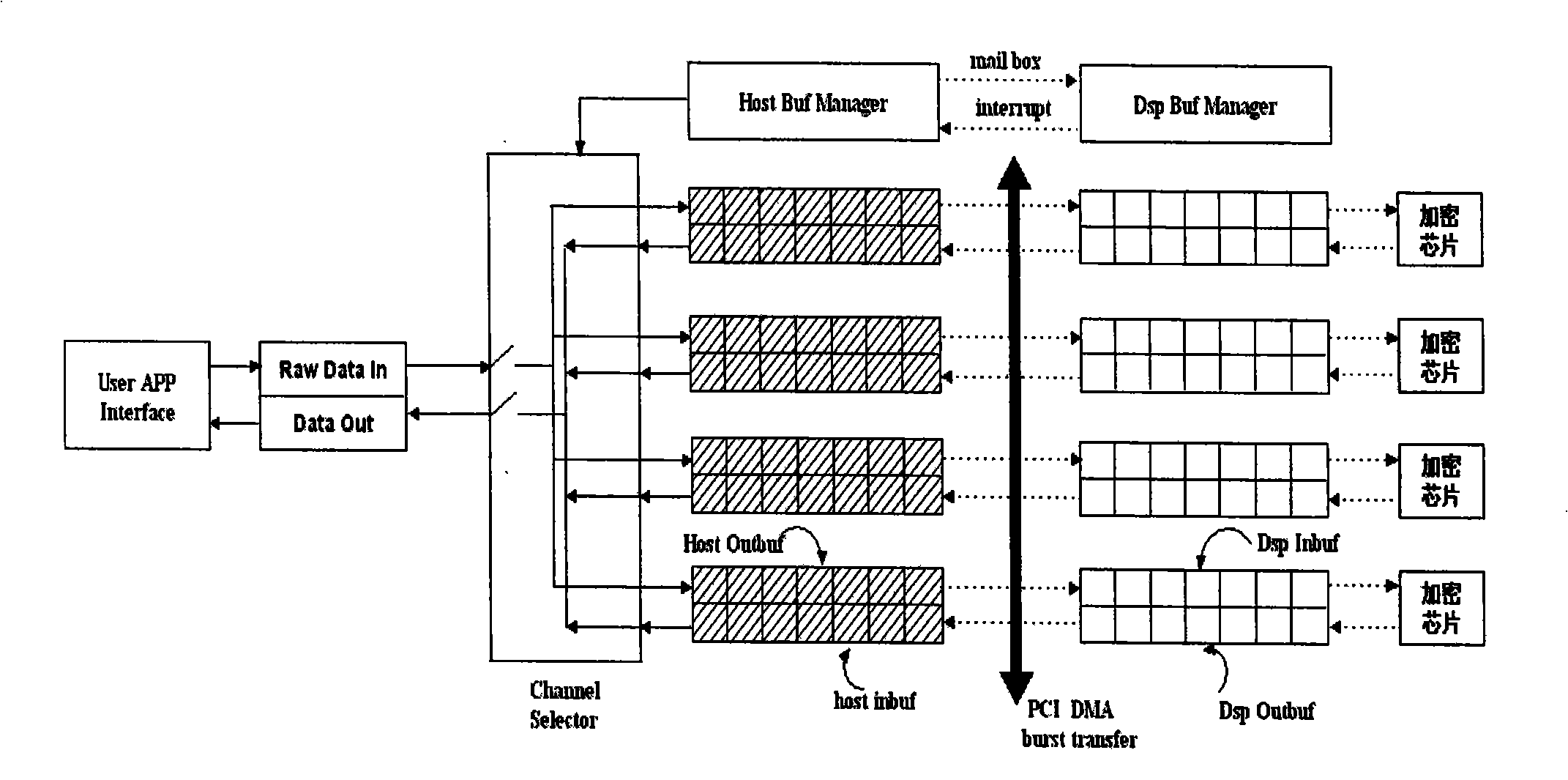
Method for parallel data processing adopting multi- password chip
InactiveCN101290569AFast encryption and decryptionAvoid resourcesConcurrent instruction executionSecuring communicationPasswordDsp processor
The invention relates to a data encryption and decryption technology, in particular to a method adopting the parallel data processing of multi-crypto chips to improve the encryption and decryption speed of a system. A parallel data processing unit for the multi-crypto chips and a high-speed encryption method for the data have the following advantages that: the operation of the system does not occupy extra resource of a main CPU, all the encryption and decryption operations are performed in a DSP processor, and the extreme improvement of the encryption and decryption speed is realized through the parallel processing of a plurality of crypto chips and the DSP.
Owner:STATE GRID ELECTRIC POWER RES INST +1
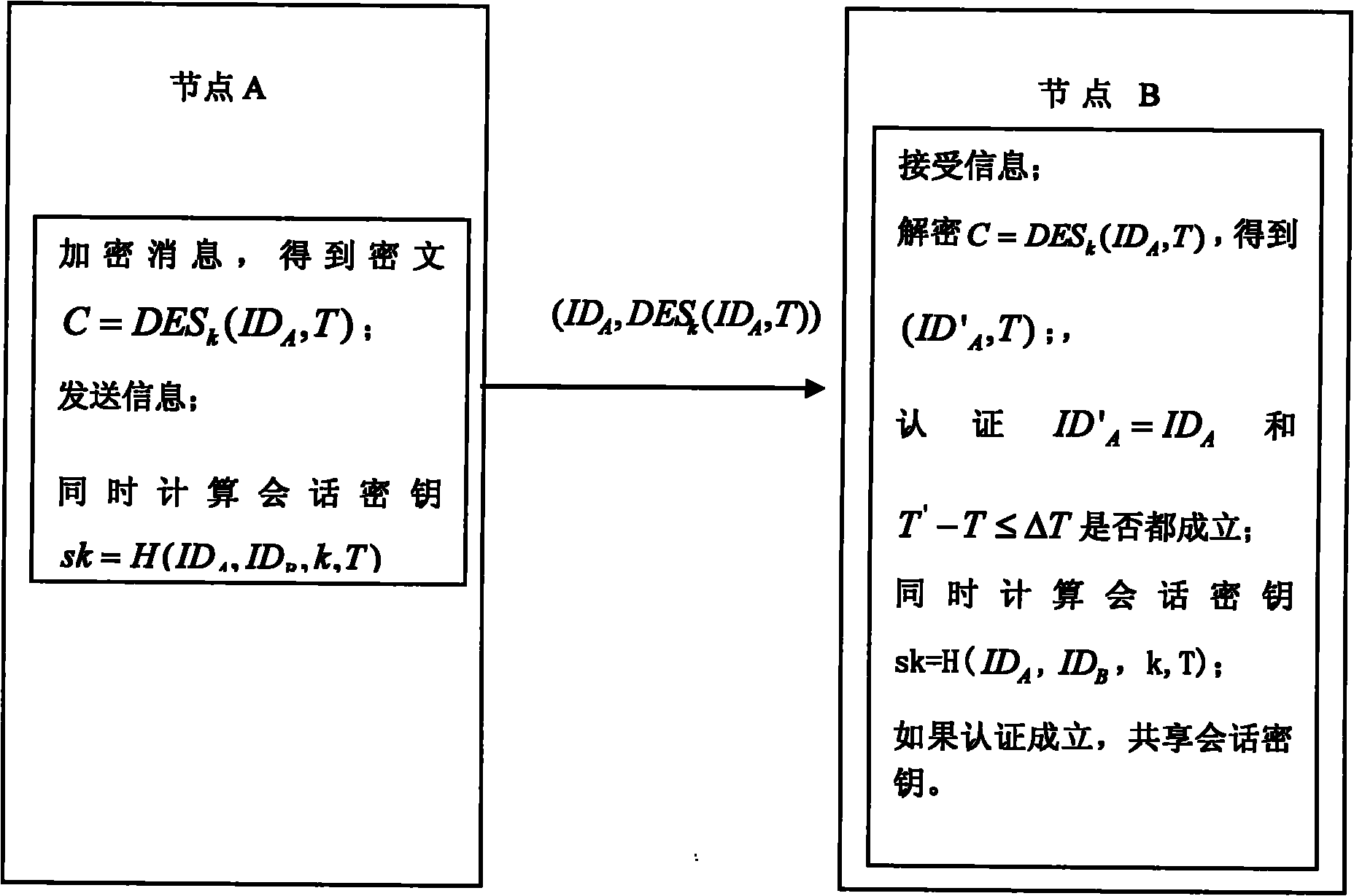
Weak authentication and key agreement method based on symmetrical password
ActiveCN101917270AHigh speedShorten the lengthKey distribution for secure communicationUser identity/authority verificationCiphertextPassword
The invention discloses a weak authentication and key agreement method based on a symmetrical password, comprising the following steps: 1) presetting a long-term shared secret key k between any two network node equipment A and B; 2) respectively arranging a clock on a node A and a node B, wherein, the error between each clock and standard time does not exceed T0 second; 3) internally installing an encryption algorithm E between the node A and the node B; and 4) building an authentication and session key between the node A and the node B by utilizing the encryption algorithm E and the long-term shared secret key k. The method of the invention has low energy-consumption computation and communication, rapid execution speed and high authentication efficiency, and is suitable for resource-restricted communication environments. As the invention uses a symmetric cryptographic algorithm DES or AES, the difficult degree that opponents capture authentication message to obtain the long-term shared key or a ciphertext is relative to the difficult degree of decoding the DES or AES algorithm, thus ensuring the safety of the ciphertext and the key.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Data encryption transmission method and system
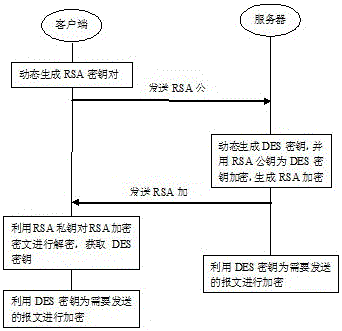
InactiveCN102333093AImprove securityFast encryption and decryptionEncryption apparatus with shift registers/memoriesUser identity/authority verificationCiphertextNetwork communication
The invention is applicable to the field of network communication, and provides a data encryption transmission method and system. The data encryption transmission method comprises the following steps: A. a server dynamically generates a DES (data encryption standard) key based on a data encryption algorithm (DEA), and encrypts the DES key by an RSA (Rivest, Shamir and Adleman) public key which is dynamically generated by a client side so as to generate an RSA encrypted ciphertext; B. the client side decrypts the received RSA encrypted ciphertext so as to obtain the DES key; and C. a message transferred between the server and the client side is compressed according to a ZLIB algorithm, and then the DES key encrypts the compressed message. The data encryption transmission method has the beneficial effects that the RSA and DES encryption algorithms are combined together, namely the message is encrypted according to the DES algorithm and meanwhile the DES key is encrypted according to the RSA algorithm so as to integrate the advantage of fast encryption and decryption speed of the DES algorithm and the advantage of high safety of the RSA algorithm; and meanwhile the message is compressed according to the ZLIB algorithm so as to realize safe and efficient data encryption transmission.
Owner:SHENZHEN SEG SCI NAVIGATIONS CO LTD
Cloud computing based password service system
InactiveCN104202421AImprove work efficiencyFast encryption and decryptionUser identity/authority verificationData processingKey management
The invention discloses a cloud computing based password service system comprising a physical layer, a computing resource layer, a service layer and an application layer. The physical layer is used for describing its hardware architecture and functions of its parts. The computing resource layer is used for describing its modules and functions of the modules. The service layer is used for describing password operation software and a password computing application interface. The application layer is used for describing various password services provided. Compared with the prior art, the system has the advantages that the techniques such as the cryptographic techniques, the Hadoop technology and the parallel computing technology are adopted, password services such as file encryption, data encryption, key management and identity authentication are provided, safeguarding efficiency can be significantly improved, data processing speed, encryption speed and decryption speed are higher, and data security is effectively protected for cloud computing.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
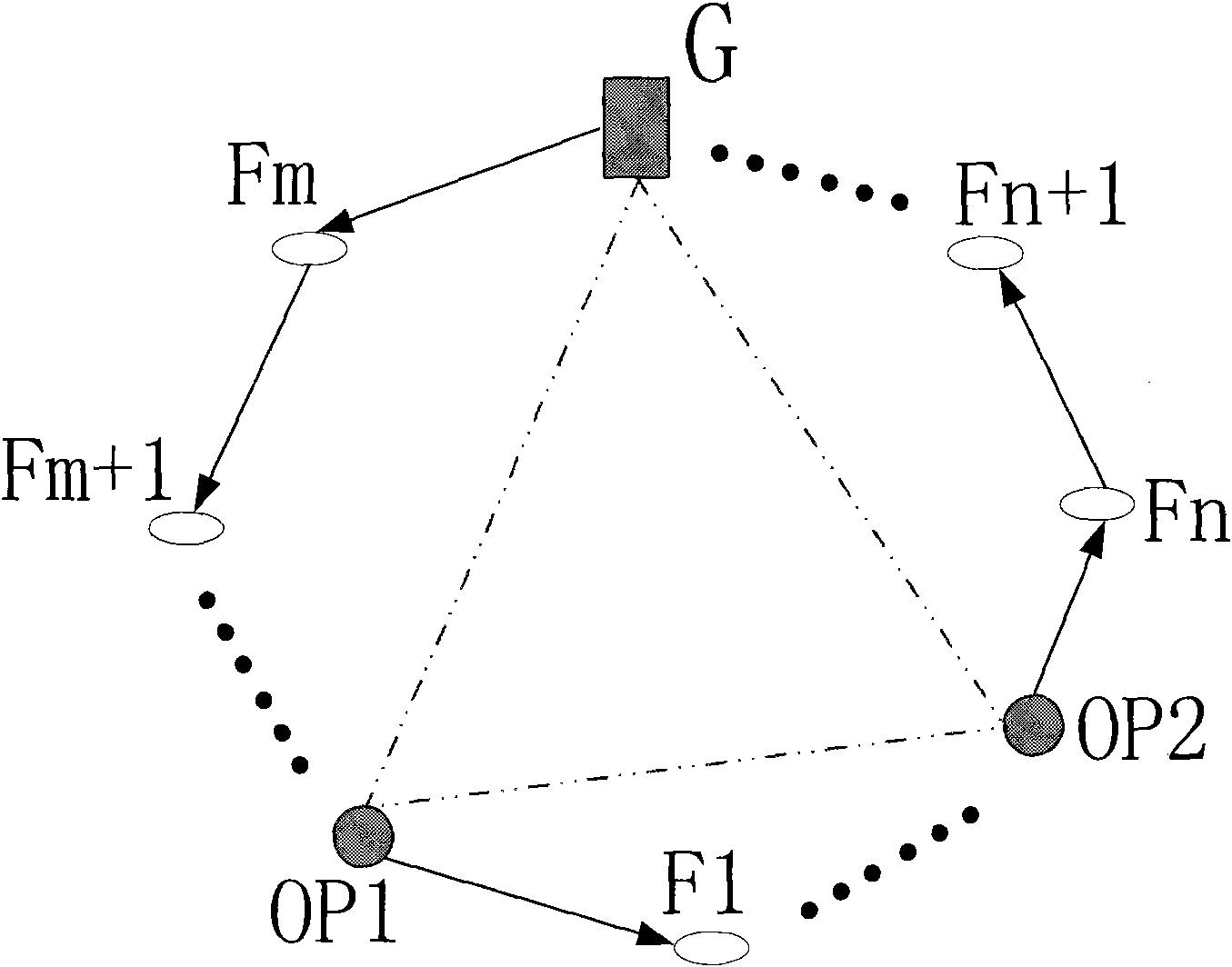
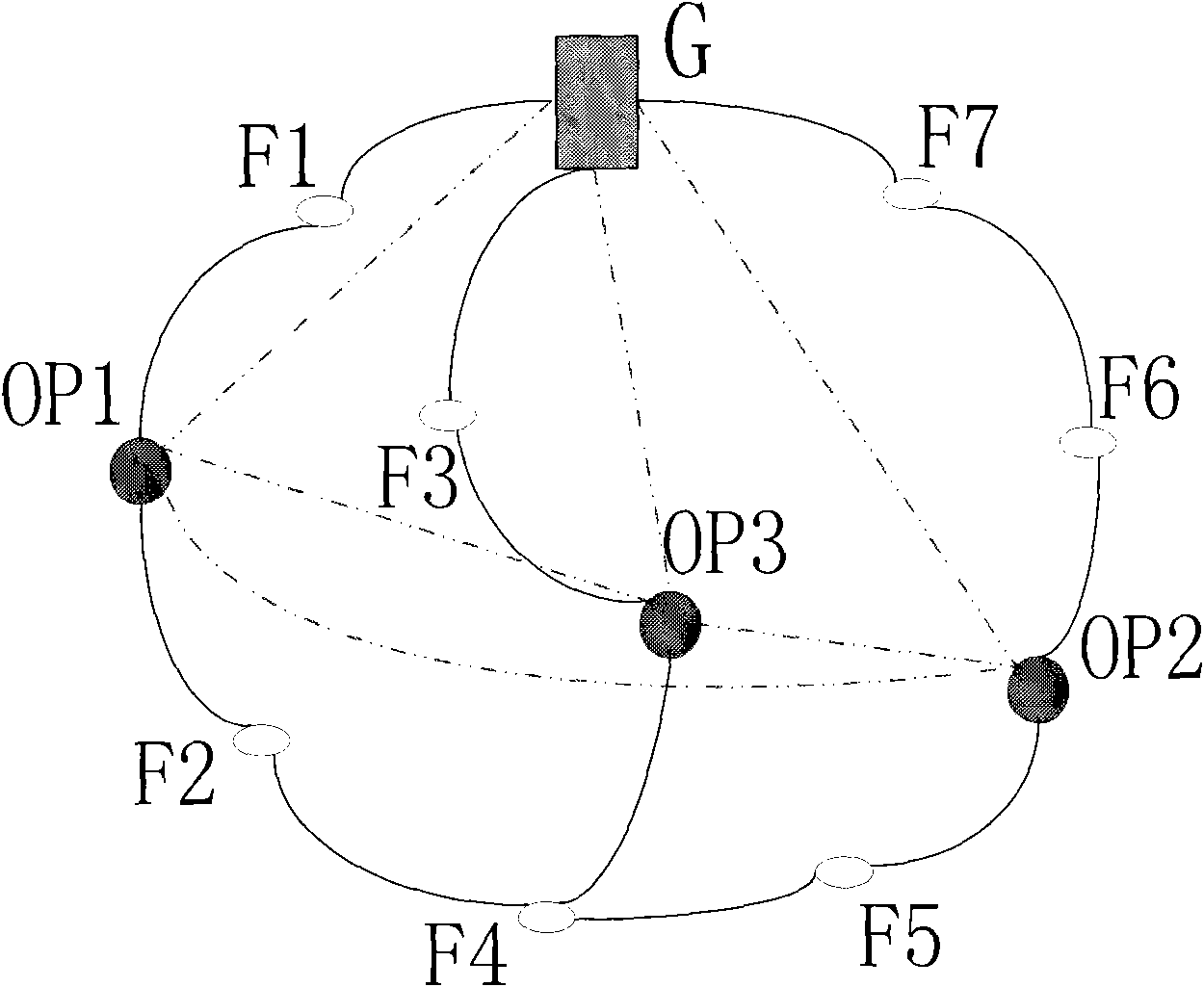
Method for hierarchichal onion rings routing
InactiveCN101635918APrevent intersection attacksReduce tamperingSecurity arrangementSecure communicationWireless mesh network
The invention discloses a method for hierarchichal onion rings routing. The nodes in a wireless Mesh network are divided into a gateway G, trusted nodes OP (Onion Proxy) and normal nodes Fi, wherein, the trusted nodes OP and the gateway G are induction nodes; the trusted nodes OP serve the function of selecting a route during the initialization of the ring; and the assembly of all the trusted nodes OP and the gateway G constitutes an anonymous assembly. The onion routing of the network is divided into two loop layers, wherein, the first route layer is a loop route consisting of the non-adjacent trusted nodes OP and the gateway G of the anonymous assembly; and the second route layer is a loop route formed by filling normal nodes Fi among the trusted nodes OP, and the second route layer is randomly selected by the trusted nodes OP and the gateway during the initialization. Accordingly, the anonymous and secure communication in the Mesh network can be achieved by the layered loops of the onion rings route. By using the layered onion rings communication protocol and allowing the trusted nodes OP and the gateway of the anonymous assembly to select the route together, the invention can effectively mix up the paths and prevent the intersection attacks, thereby reducing the computation, alleviating the load of the gateway, accelerating the ring construction, preferably utilizing the network resources to reduce delay.
Owner:XIDIAN UNIV
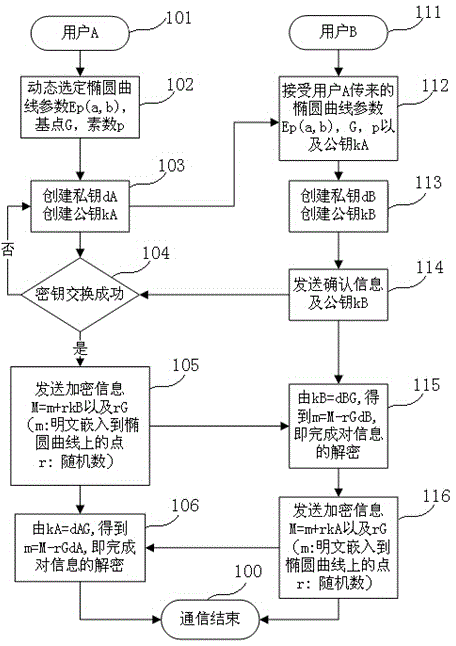
Mobile Internet information communication encryption method based on GMB algorithm
InactiveCN104468125AGood effectFast operationKey distribution for secure communicationUser identity/authority verificationEngineeringCommon key
The invention discloses a mobile Internet information communication encryption method based on the GMB algorithm. A user A sends an encrypted message to a user B through a mobile terminal and establishes an elliptic curve dynamically according to the SM2 elliptic curve public key cryptography algorithm, the user A sends parameters relevant to the public key and elliptic curve to the user B, the user B generates a public key kB by means of the parameters relevant to the elliptic curve sent by the user A, and then communication encryption / decryption is conducted. According to the method, Miller-Rabin algorithm underlayer optimization is conducted with the Montgomery algorithm, a good effect is obtained in terms of prime number testing optimal selection, the window size can be controlled flexibly with the sliding window algorithm, elliptic curve point multiplication speed and encryption / decryption speed are increased greatly through salutatory binary string computation, and mobile Internet communication encryption / decryption can be achieved quickly, safely and reliably by means of the asymmetrical secret key algorithm and symmetric secret key algorithm.
Owner:JIANGXI BITCARE INFORMATION TECH
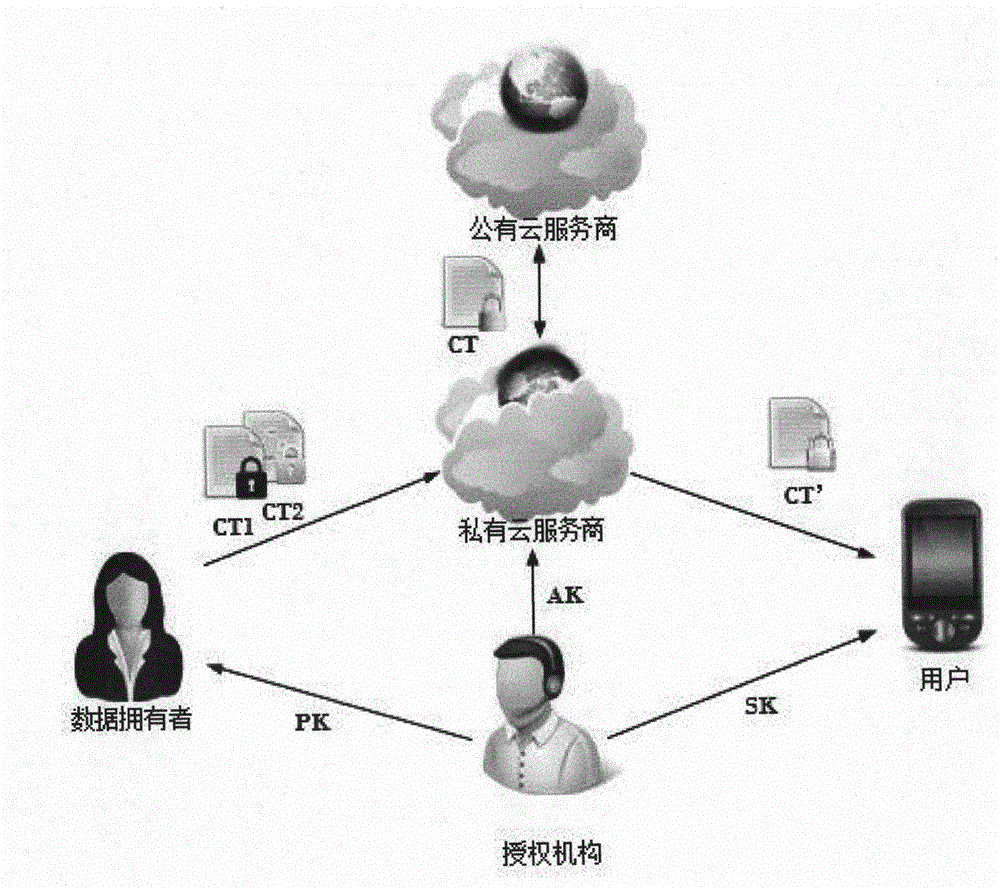
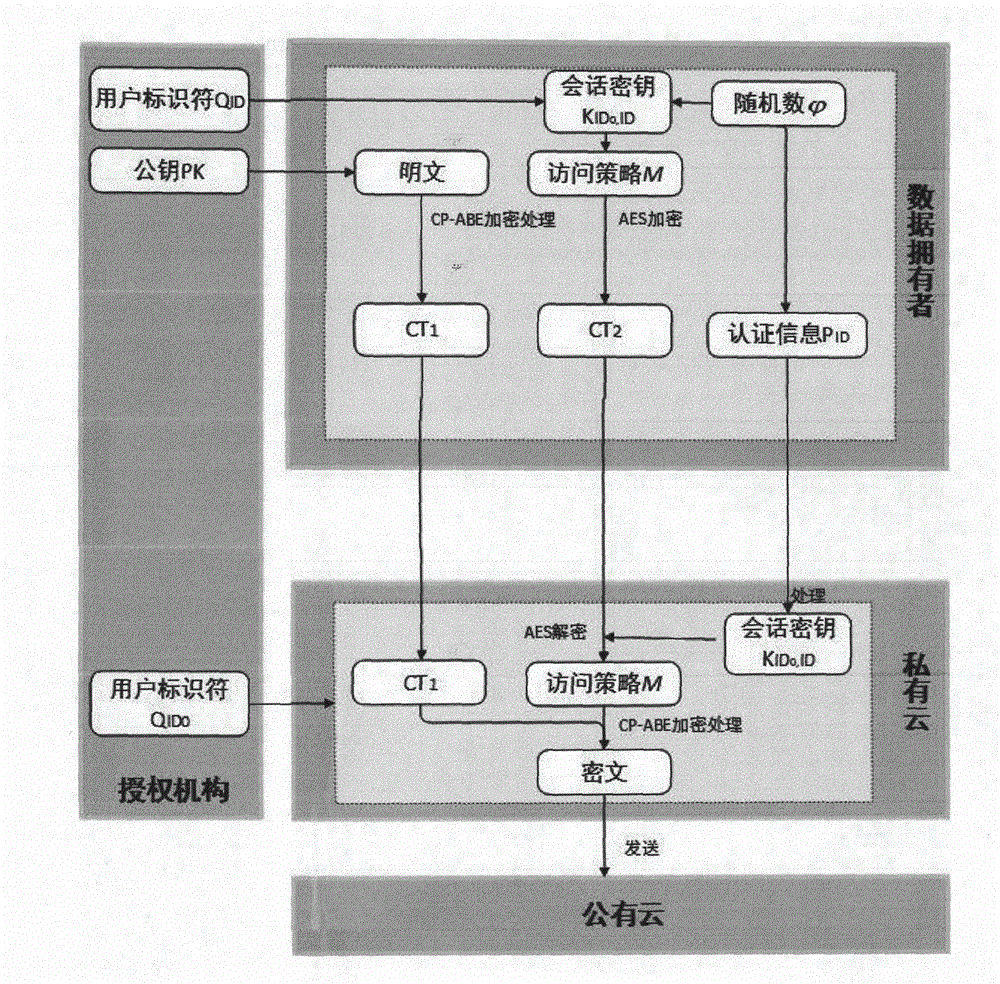
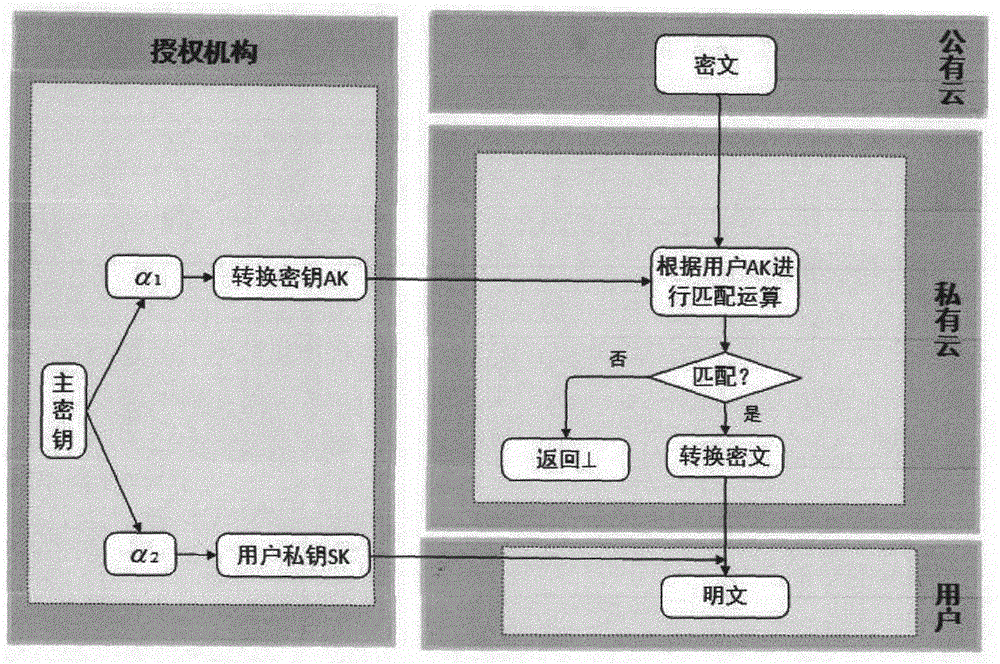
Safe data sharing method suitable for hybrid cloud environment
ActiveCN105897812AComputing securityEasy to operateUser identity/authority verificationDecompositionCiphertext
A safe data sharing method suitable for a hybrid cloud environment is disclosed and comprises the following steps: a system is initialized; a secret key is generated by an authorization mechanism, a data owner encrypts a file so as to generate a data ciphertext and a middle ciphertext of a secret key ciphertext, the data ciphertext is directly uploaded to a public cloud without being processed via a private cloud, the middle ciphertext of the secret key ciphertext is uploaded to the private cloud, the private cloud processes the middle ciphertext and generates the same into a complete secret key ciphertext, ciphertext conversion is conducted via the private cloud, and user data of a mobile terminal is decrypted. According to the method, in the hybrid cloud environment, data is ciphered and shared based on ciphertext strategy attributes; with limited computation and storage capability of the mobile terminal taken into consideration, the private cloud as a proxy can safely take over part of complex ciphering and deciphering tasks via use of secret key decomposition technologies and secret key negotiation technologies on a precondition that data safety is ensured, a computation burden and storage demand of the mobile terminal can be reduced, and a reliable method is provided for protecting and sharing data of the mobile terminal in a highly efficient and safe manner.
Owner:HANGZHOU YUANTIAO TECH CO LTD
Method and system for monitoring and diagnosing large scale equipment remotely
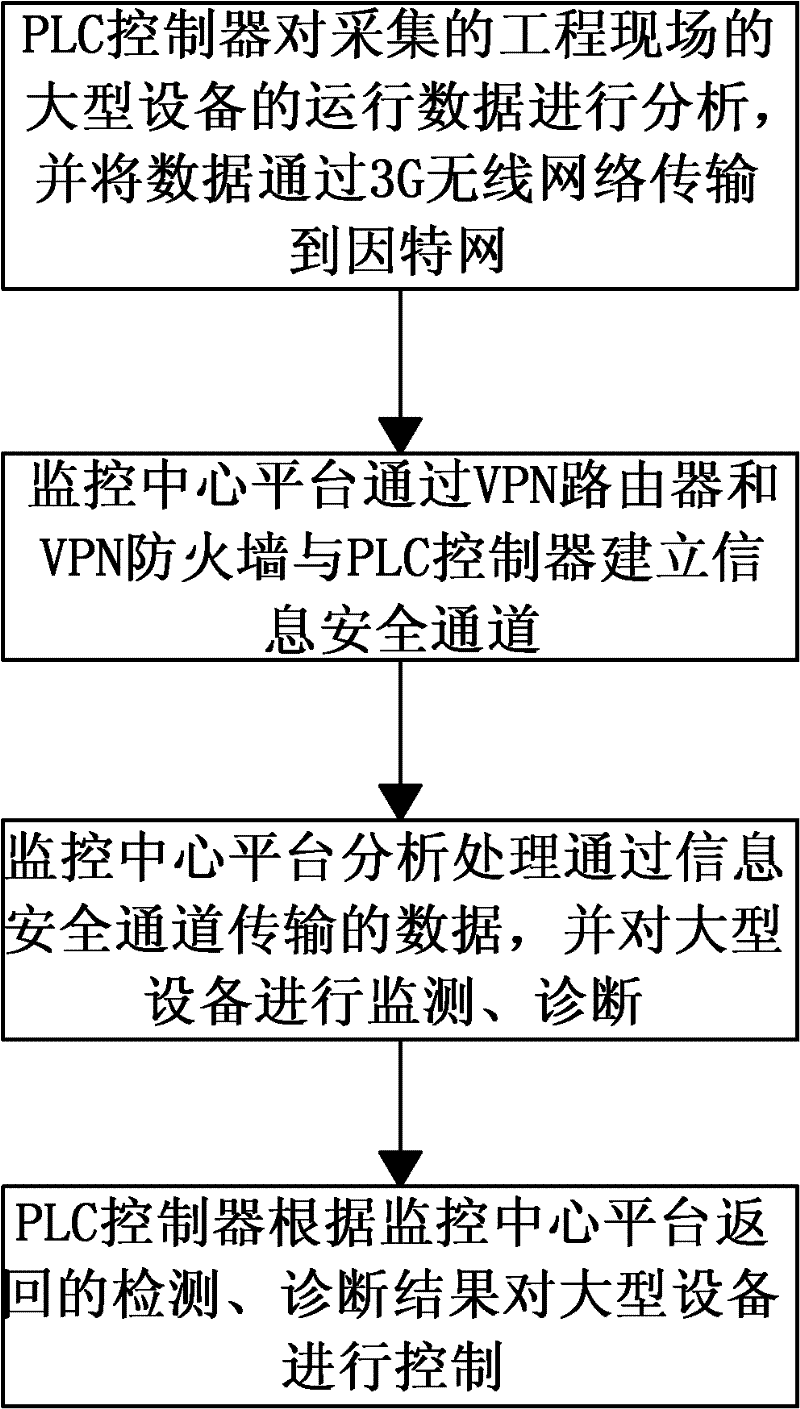
InactiveCN102393715ASolve the speed problemSolve process problemsProgramme total factory controlPrivate networkProgrammable logic controller
The invention discloses a method and a system for monitoring and diagnosing large scale equipment remotely. The method comprises the steps as follows: firstly, a PLC (Programmable Logic Controller) analyzes collected running data of the large scale equipment on an engineering site, and transmits the data to an internet by a 3G (the third generation telecommunication) wireless network; secondly, a monitoring center platform builds a safe information channel with the PLC by a VPN (Virtual Private Network) router and a VPN fire bulkhead; thirdly, the monitoring center platform analyzes and processes data passing by the safe information channel, and monitors and diagnoses the large scale equipment; and fourthly, the PLC controls the large scale equipment according to the detection and diagnosis results sent back by the monitoring center platform. The method and the system can enhance the data transmission rate and improves the data transmission safety.
Owner:HUADIAN HEAVY IND CO LTD
Methods and devices for selectively encrypting and decrypting data
ActiveCN102012993AWithout sacrificing protection strengthFast encryption and decryptionComputer security arrangementsSecuring communicationComputer hardwarePlaintext
Owner:BIGKNOW (BEIJING) DATA TECH CO LTD
Vehicle data transmission method and system
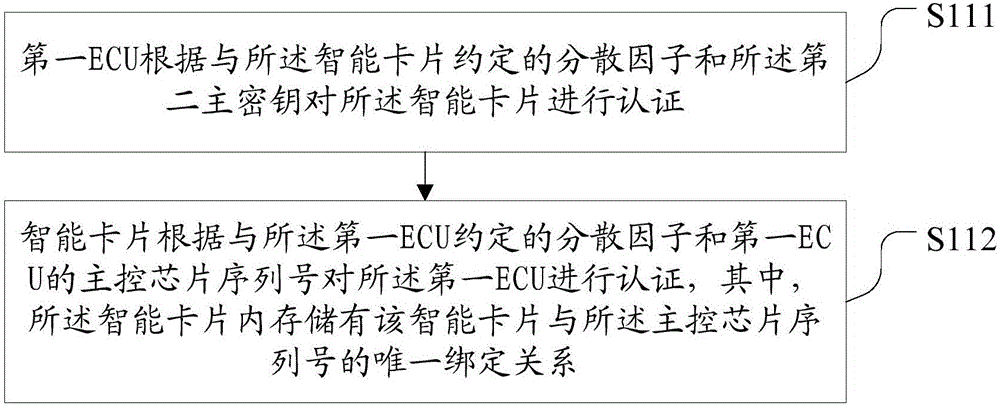
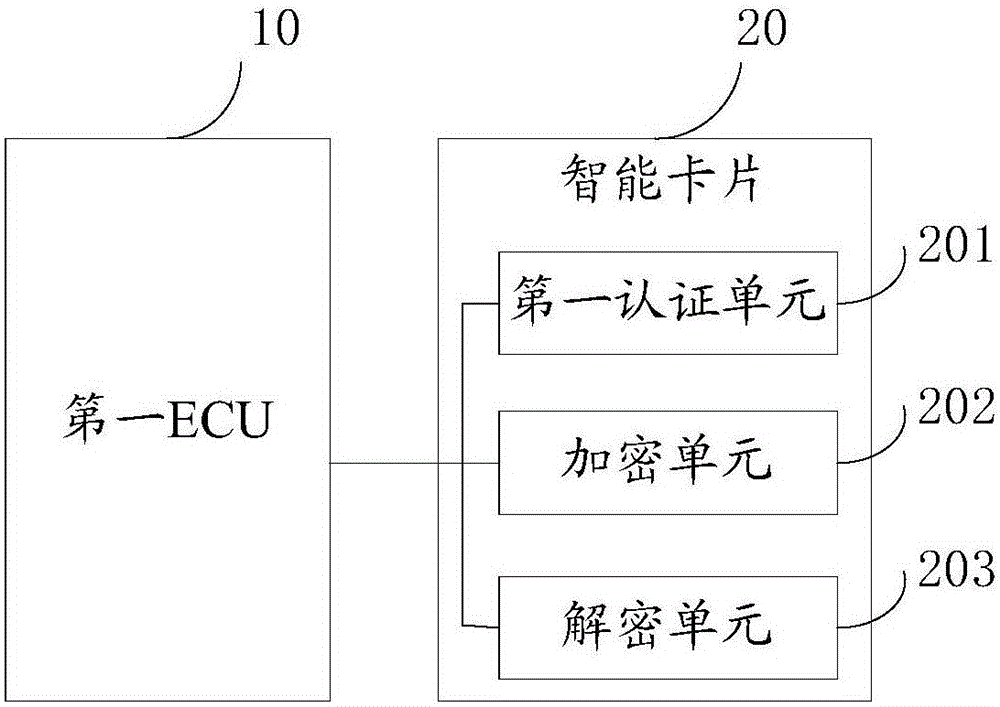
ActiveCN106549940ARealize encryption and decryptionFast encryption and decryptionTransmissionThird partySmart card
The invention discloses a vehicle data transmission method and system. The method comprises the steps of establishing an authentication relationship between a first electronic control unit ECU and a corresponding smart card; when the first ECU transmits a CAN message to a second ECU, sending the CAN message sent by the first ECU to the smart card for encryption, and sending the encrypted CAN message to a bus; and when the encrypted CAN message transmitted on the bus is received, sending the received encrypted CAN message, by the first ECU, to the smart card for decryption and taking data returned by the smart card as valid data. According to the method and the system, in a mode of employing the smart card, the CAN message information of a whole vehicle is encrypted with relatively low cost, the CAN message can be encrypted and decrypted rapidly, the transmission timeliness demand of the data is ensured, the possibility of taking the CAN message information as an attack by an ECU subcontractor is reduced to the greatest extent, and a CAN message protocol is effectively prevented from being utilized by a third party to attack a car.
Owner:三六零数字安全科技集团有限公司
A mobile terminal file encryption and decryption system and method based on a hardware encryption TF card
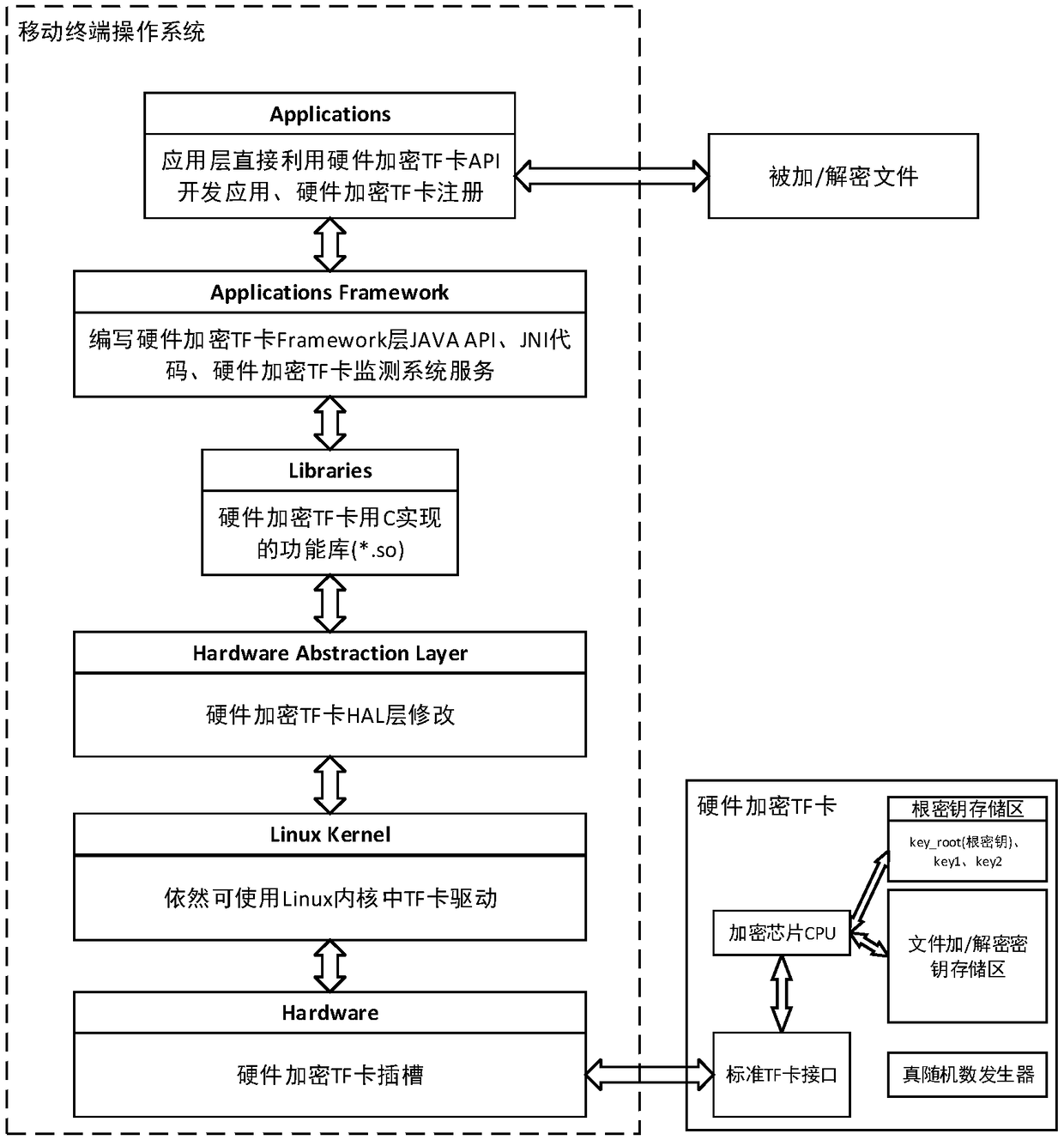
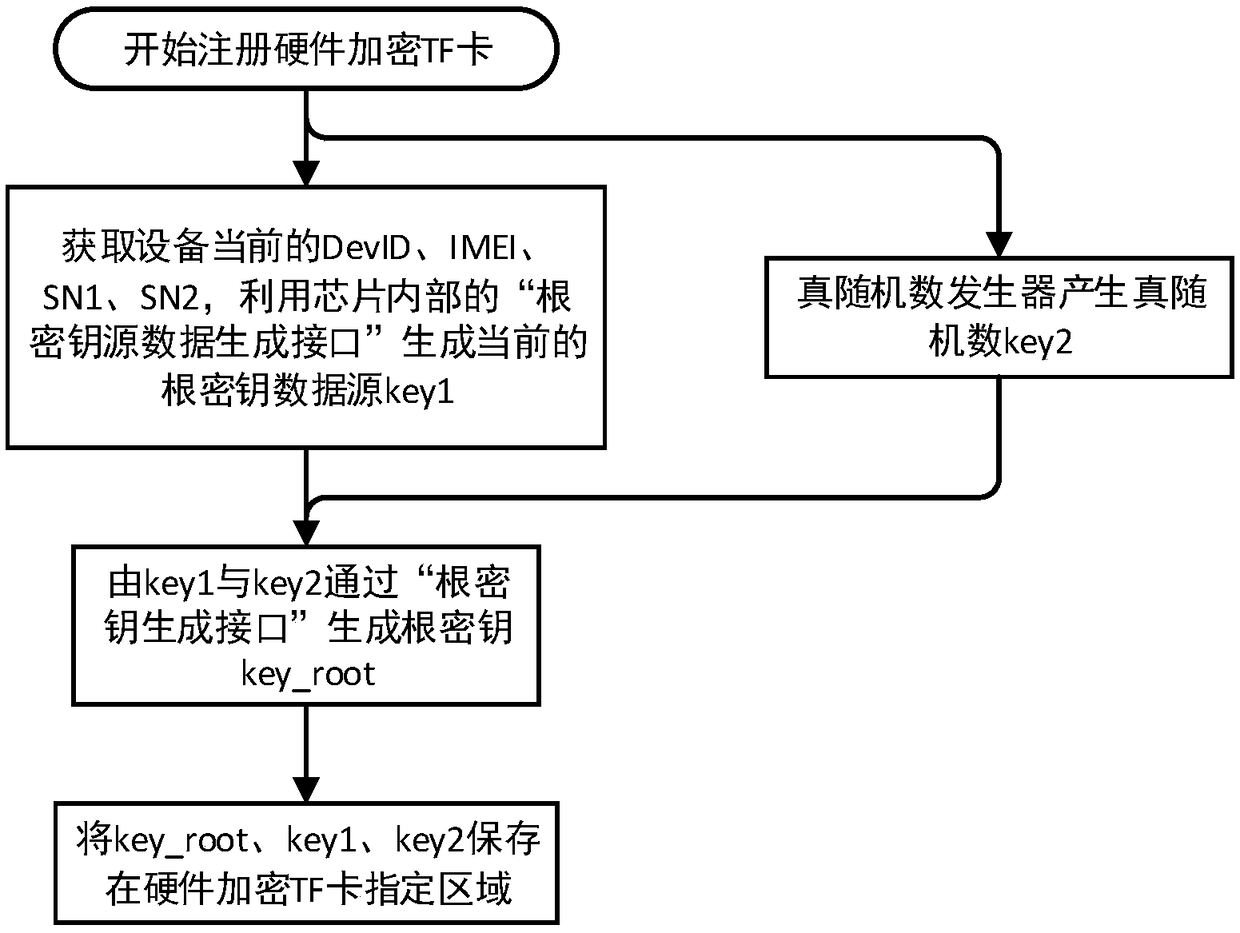
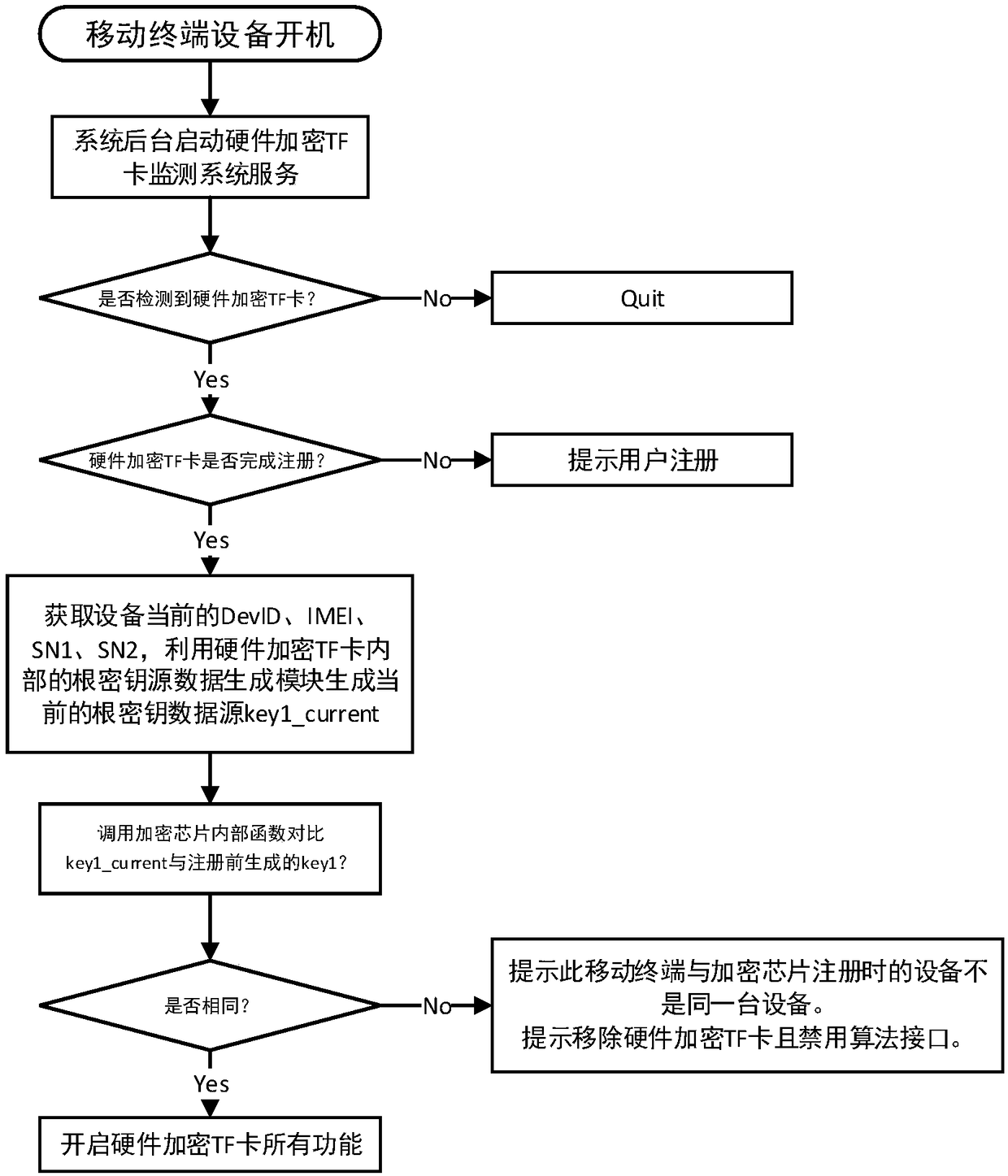
ActiveCN108959982AOperational Status SupervisionGuaranteed uptimeInternal/peripheral component protectionMemory chipMonitoring system
The invention provides a mobile terminal file encryption and decryption system and method based on a hardware encryption TF card, which relate to the technical field of information security. The fileencryption and decryption method is applied to a file encryption and decryption system. The system comprises: an operating system bottom support framework for a hardware encrypted TF card, a hardwareencrypted TF card monitoring system service, an application layer registration, and a hardware encrypted TF card system. The method comprises: the hardware encryption TF card is configured to encryptthe device according to the device DevID of the mobile terminal, the IMEI of the SIM card, the SN of the memory chip and the SN of the hardware encrypted TF card are used as parameters, and the true random number generated in the hardware encrypted TF card is used as a key to carry out AES encryption to generate a hardware encrypted TF card root key, which is a key bound with the mobile device andis responsible for encrypting and decrypting the file header information of the mobile terminal. The file encryption and decryption method and system provided by the embodiment of the invention effectively guarantee the information security, and ensure that user data and privacy are not disclosed.
Owner:江苏北弓智能科技有限公司
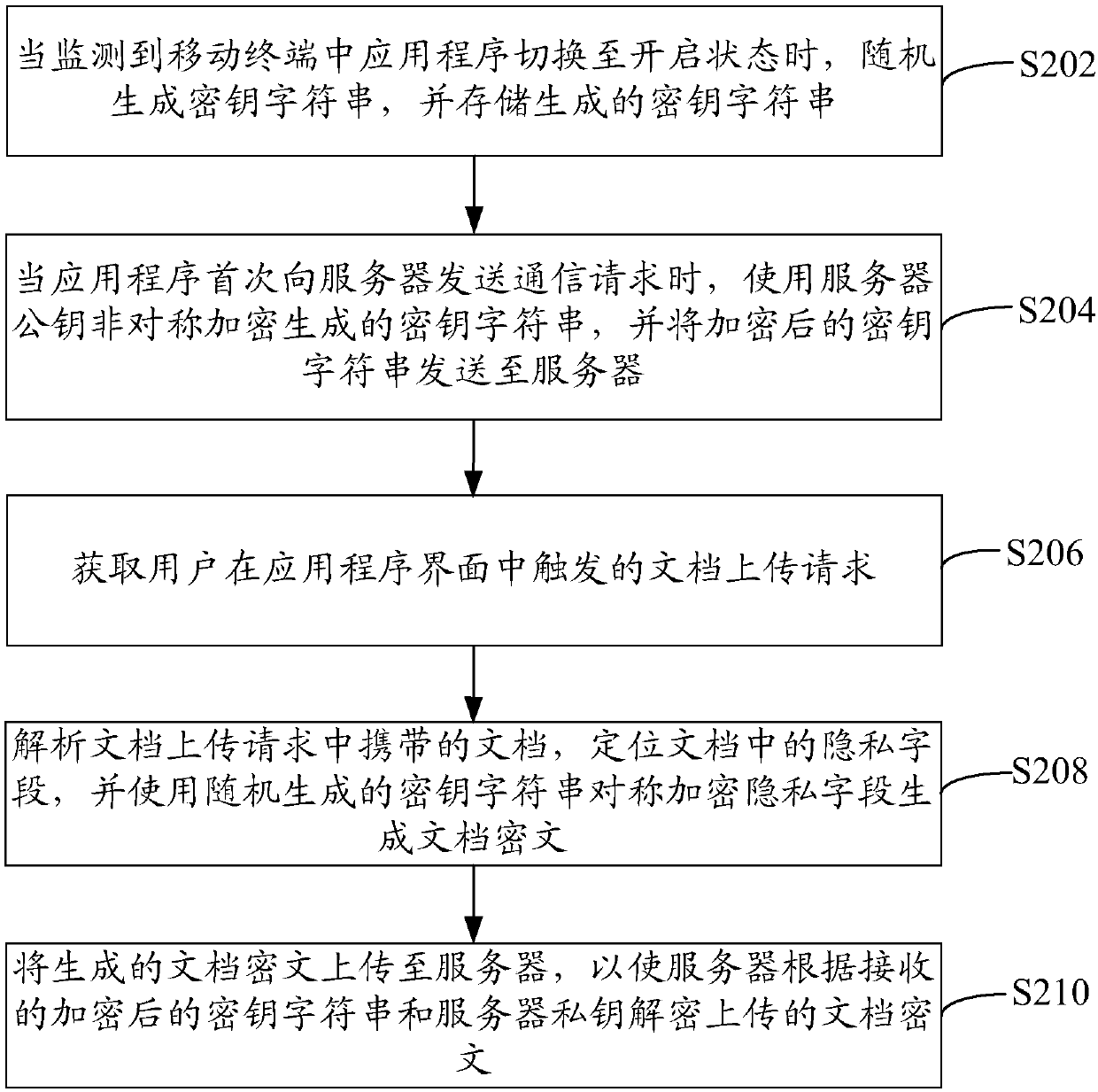
Method and apparatus for encrypting information, computer device, and storage medium
InactiveCN107666479ASafe and reliable cloud transmissionSafe and reliable storageTransmissionCiphertextDocumentation
The invention relates to a method for encrypting information. The method comprises the following steps that: when an application program in a mobile terminal is monitored to be switched in an on state, a secret key character string is generated randomly and the generated secret key character string is stored; when the application program sends a communication request to a server for the first time, the generated secret key character string is encrypted asymmetrically by using a server public key published by the server in advance and the encrypted secret key character string is sent to the server; a document uploading request triggered by a user in the application program interface is obtained; a document carried by the document uploading request is analyzed, a privacy field in the document is localized, and the privacy filed is encrypted symmetrically by using a secret key character string generated randomly to generate a document ciphertext; and the generated document ciphertext is uploaded to the server, so that the server decrypts the uploaded document ciphertext based on the received encrypted secret key character string and a server private key. With the method provided by the invention, the information decryption and encryption processing efficiency is increased and the safety is enhanced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
System for controlling ink quantity reset of ink box and ink quantity reset method
The invention provides a system for controlling ink quantity reset of an ink box and an ink quantity reset method. The ink box comprises a control module with a built-in storage unit and a communication module with a built-in storage unit; a printer performs read-write operation on the communication module, and stores ink box identification information and ink quantity information in the storage unit of the communication module; and the communication module comprises a data encryption / decryption module, and encrypts / decrypts the data exchanged by the printer and the communication module. In the ink quantity reset method, the control module determines whether to reset according to the identification bit; when the reset is needed, the control module acquires a bus control right, blocks the communication between the printer and the communication module through a resistor, and resets the data of bytes of the ink quantity of the corresponding ink box in the communication module; and when the printer rereads the ink box information, because the data of the ink quantity of the corresponding ink box are reset, personal computer (PC) monitoring software displays that the ink quantity of the corresponding ink box is already fully filled. The method improves the use efficiency of printer consumables, and reduces the environmental pollution.
Owner:CRM ICBG (WUXI) CO LTD
Multivariable public key encryption method
ActiveCN103973439AShorten the lengthEasy to managePublic key for secure communicationPlaintextProbabilistic encryption
The invention discloses a multivariable public key encryption method. According to the multivariable public key encryption method, when a key is generated, a matrix is constructed according to an iterative method, the length of the key is greatly reduced, and the key can be managed conveniently; a probability encryption method is adopted, random parameters are introduced into encryption, the random parameters must be solved by a deciphering party through a deciphering process, the random parameters take part in decryption of a plaintext, the plaintext can be deciphered only under the condition that the random parameters are known, the difficulty of ciphertext decryption by an attacker is increased, ciphertexts are different even if public keys are the same, the public keys can be released in the forms such as telephone numbers, and encryption security is improved; based on the combinatorial optimization difficulty and multivariable quadratic polynomial, attack of a quantum computer can be resisted, both the encryption speed and the decryption speed are high, and the method can be applied to mobile terminals such as mobile phones; based on calculation on a finite field, the calculation process is simplified; the addition homomorphism and the subtraction homomorphism are achieved, the multiplication homomorphism can be achieved under special conditions, and the method can be applied to the newly-developed fields such as cloud computing.
Owner:HUAZHONG UNIV OF SCI & TECH
Encryption method based on cycle queue shift rule
InactiveCN101237321AFast encryption and decryptionSimple transformationMultiple keys/algorithms usageTransformation matrixLow speed
The invention relates to an encryption method based on circular queue shifting rule. The method comprises the following steps: a plaintext information matrix is taken; a random integer sequence is created; a matrix transformation frequency is input by a user; a random number is taken out from the random integer sequence and is rounded; circular queue shifting of one row or one column of the transformation matrix is carried out according to a set remainder rule; a cipher text matrix is obtained after repeated transformations; finally, all transformation operation processes are recorded as sub keys which are arranged in turn to obtain a key. The encryption method, which belongs to a classic permutation encryption, adopts basic shifting operation and realizes quick enciphering process and deciphering process by means of less resource; meanwhile, the method solves the problems of the prior shifting encryption method such as low encryption intensity, low speed and poor operability; moreover, the encryption method which has the advantages of high encryption speed, simple implementation, high encryption intensity, excellent safety and a wide application scope is suitable to be used in software implementation and hardware implementation.
Owner:NORTHWEST A & F UNIV
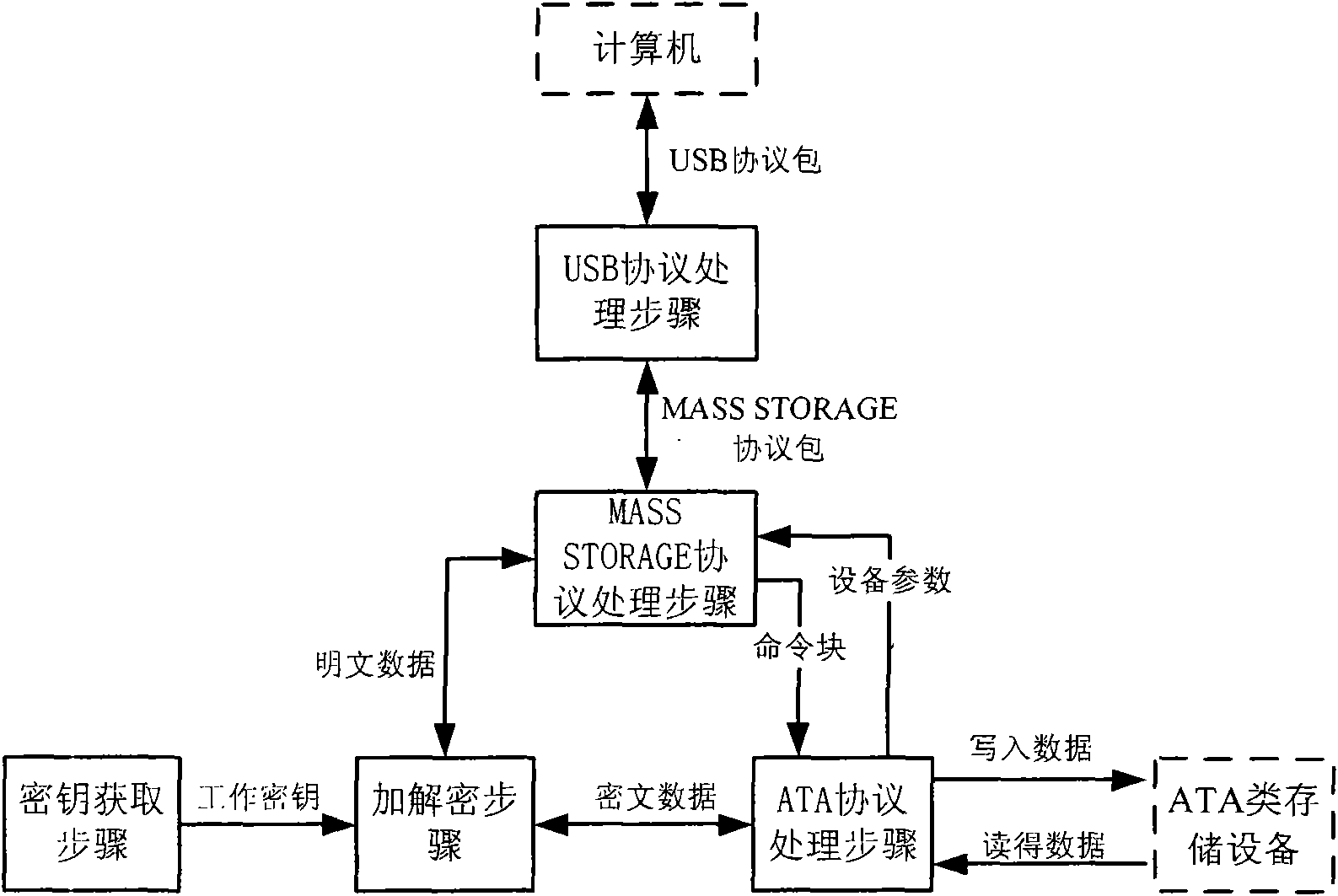
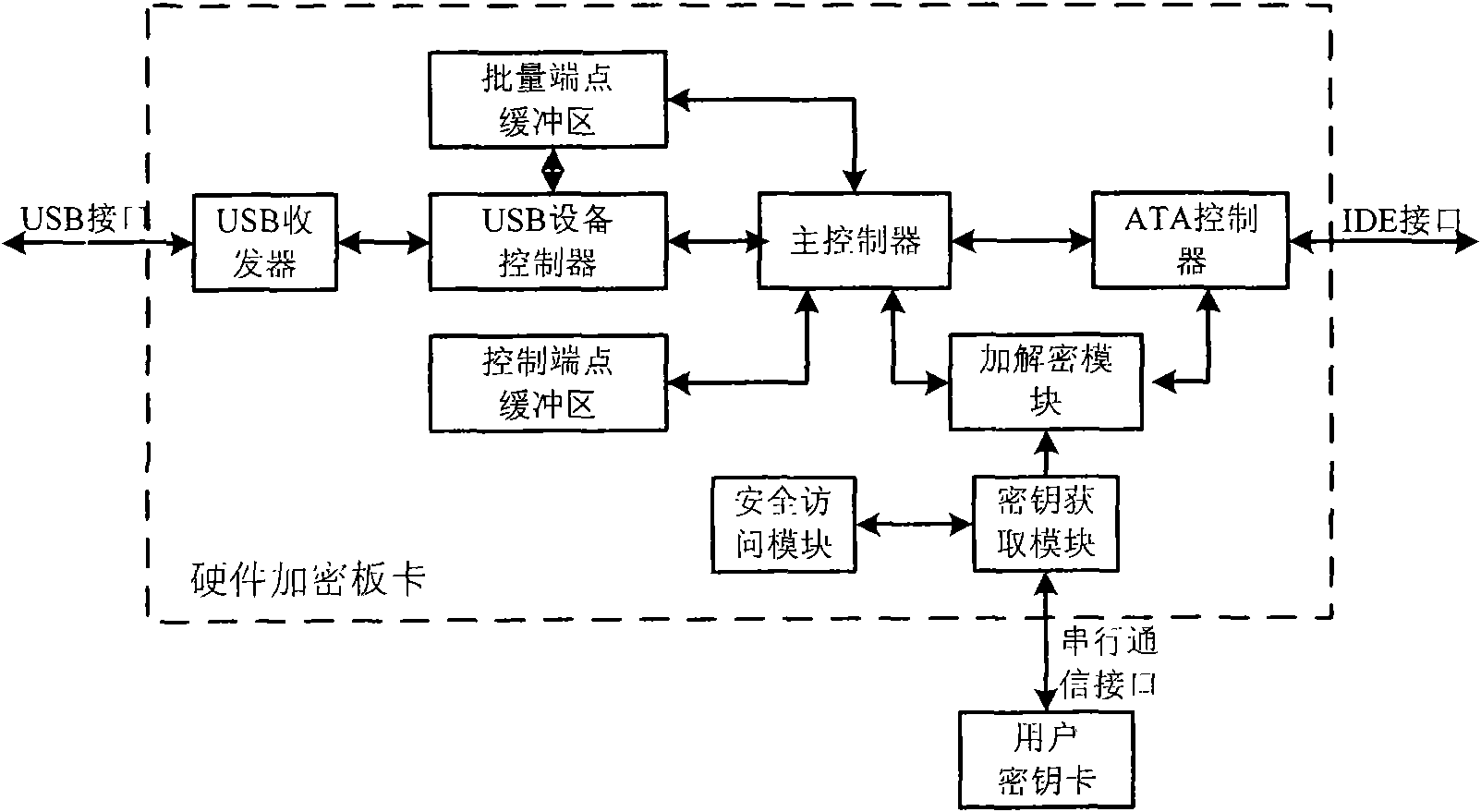
Method and device for encrypting data in ATA memory device with USB interface
InactiveCN101551784AFast encryption and decryptionImprove securityUnauthorized memory use protectionOperational systemEncryption decryption
The invention relates to a method and a device for encrypting data in an ATA memory device with a USB interface. Based on the conventional ATA memory device, the device for encrypting data consisting of a user card and a hardware encryption board card encrypts data transmitted between the memory device and a USB host, thereby achieving the aim for encrypting the data in the memory device. The device for encrypting data consists of a user secret key card and a hardware encryption bard card; and the hardware encryption bard card consist of a USB transreceiver, a USB equipment controller, a control endpoint buffer area, a batch endpoint buffer area, a main controller, an encryption-decryption module, an ATA controller, a secret key acquisition module and a safe access module. The invention has the advantages that the secret key is directly read by the encryption device, without using a computer connected with the memory, thereby ensuring high security; in addition, the data can be encrypted and decrypted at high speed without using an operation system; and moreover, the secret key is stored in a special hardware secret key memory card, and the secret key and the protected data are independently stored, thereby ensuring the security of the data.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
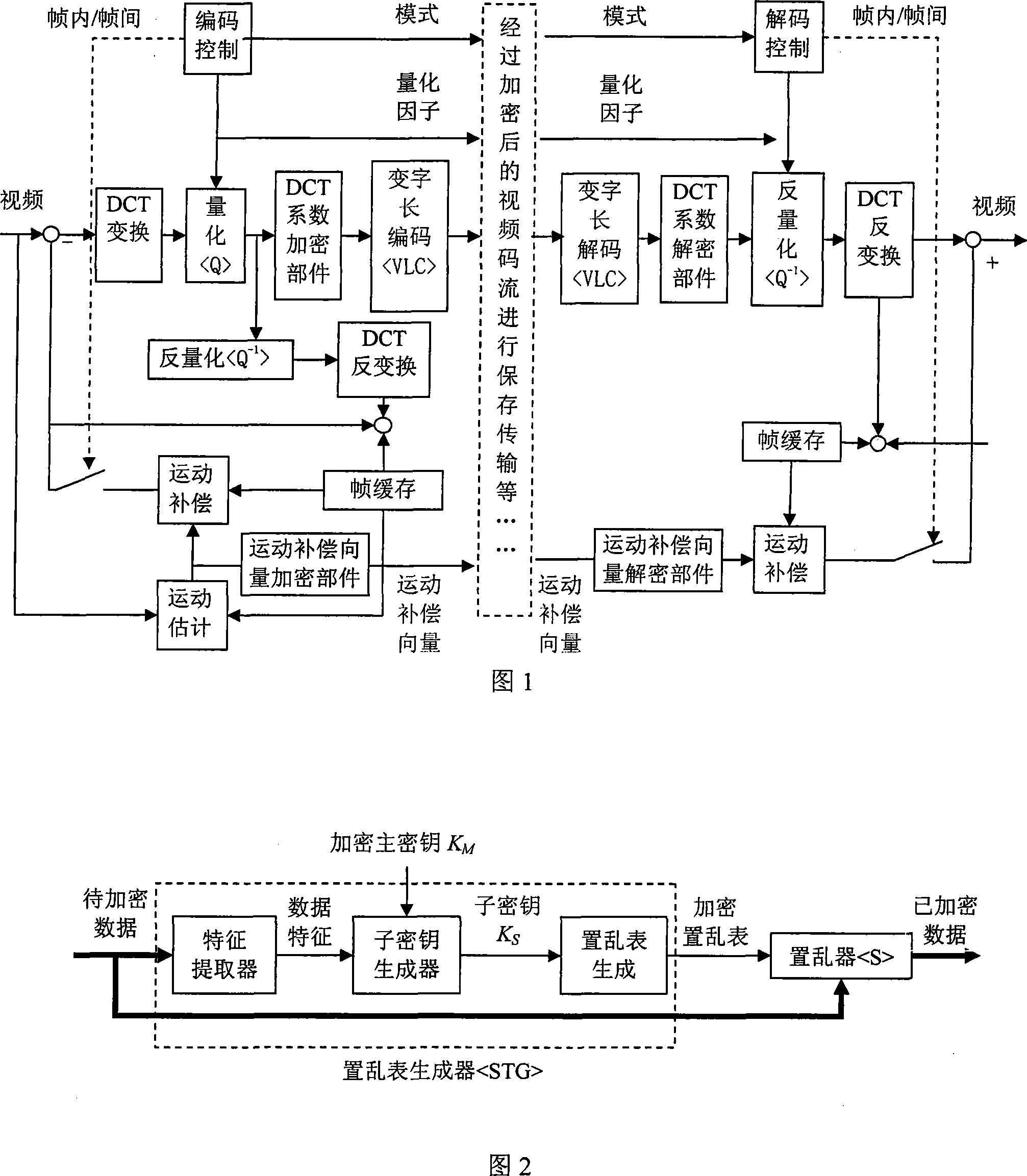
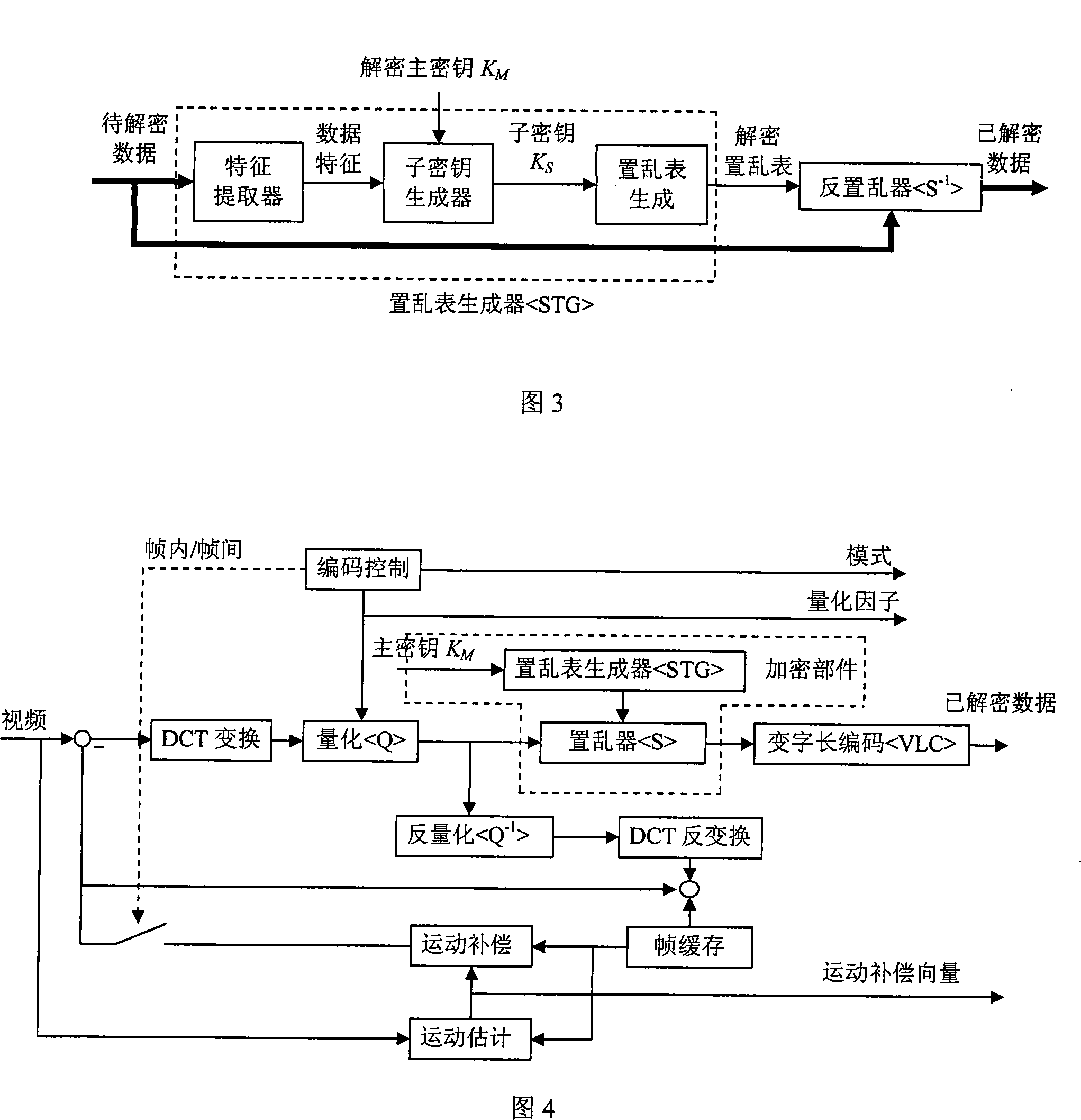
Video data enciphering/deciphering method
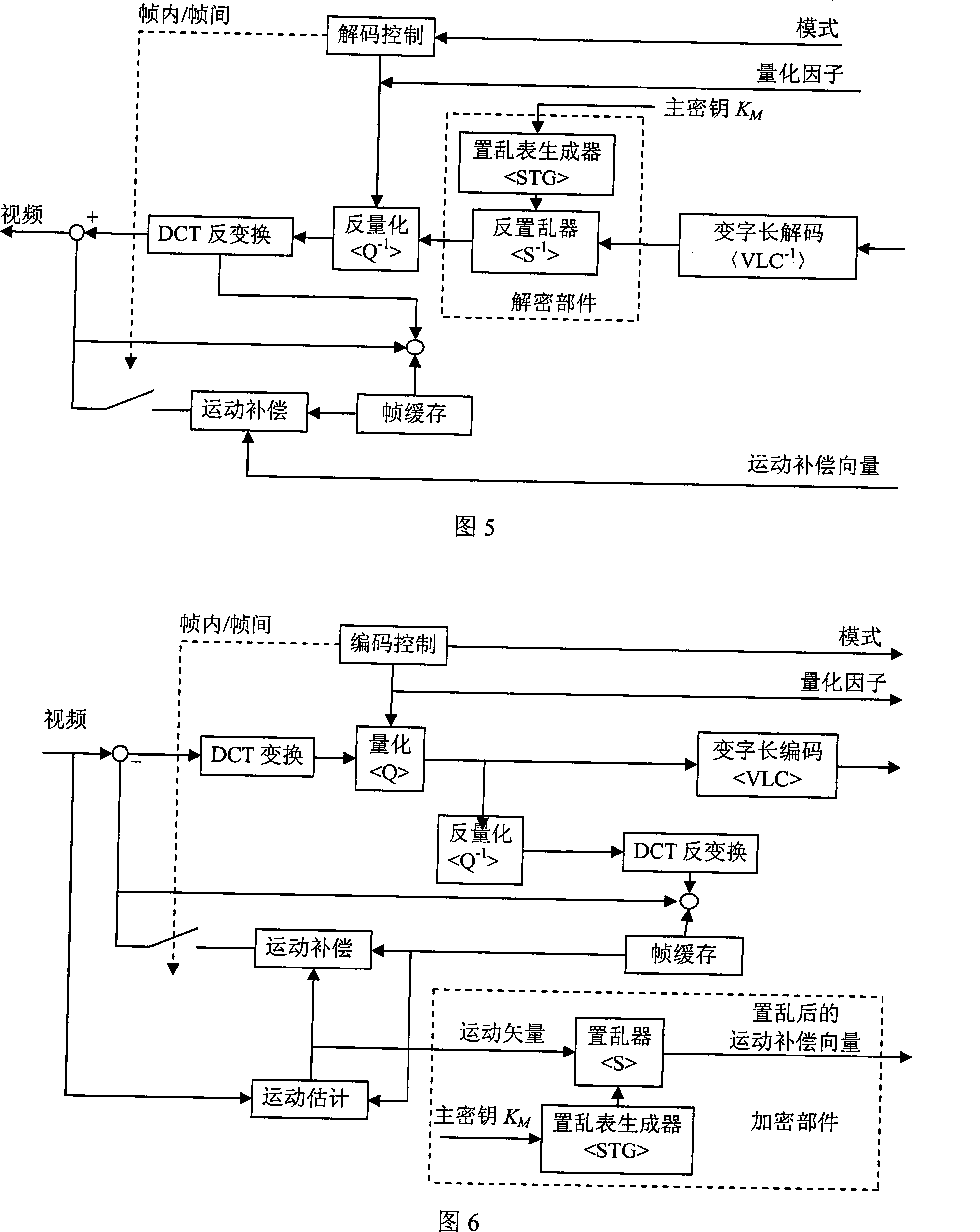
InactiveCN101247520AGuaranteed real-timeFast encryption and decryptionPulse modulation television signal transmissionTwo-way working systemsDigital videoVideo image
A method for ciphering / deciphering the video data is characterized in that the ciphering component is embedded in the encoding process and adopts a strategy of grouping scrambling for ciphering the DCT coefficient of the digital video data. The deciphering data is embedded into the decoding process and adopts an inverse scrambling strategy which is reverse to the ciphering for deciphering the DCT coefficient of the digital video data. The frame movement compensating of the digital video can be simultaneously executed with scrambling to obtain a higher security. The invention embeds the ciphering / deciphering into the coding / decoding process and has the advantages of high ciphering speed and low actualizing difficulty. The technique of dynamic key is adopted and the invention has strong clear text attacking resistance. The effect of the ciphering / deciphering method of the invention is reduced to the minimum. The quality of the deciphered vide image does not have any loss compared with the video image before ciphering.
Owner:BEIHANG UNIV
Hand-held equipment data encryption and decryption method and hand-held equipment peripheral equipment thereof
InactiveCN102332077APracticalAvoid the risk of being easily decryptedDigital data protectionSecurity arrangementComputer hardwareEngineering
The invention relates to a hand-held equipment data encryption and decryption method and hand-held equipment peripheral equipment with encryption and decryption functions. In the hand-held equipment data encryption and decryption method, the hand-held equipment peripheral equipment with the encryption and decryption functions is used for encrypting and decrypting private data in the hand-held equipment, when the encryption and the decryption are completed, the hand-held equipment peripheral equipment with the encryption and decryption functions can be physically separated from the hand-held equipment, when the hand-held equipment is not connected with the hand-held equipment peripheral equipment with the encryption and decryption functions, the private data in the hand-held equipment can not be encrypted, and the encrypted data can not be decrypted, so the security of the encrypted data is ensured. A key used during the encryption and the decryption is stored in the hand-held equipment peripheral equipment with the encryption and decryption functions and is bound with the hand-held equipment peripheral equipment, and the security and the uniqueness of the encryption key are ensured.
Owner:NATIONZ TECH INC
Teledata transmission content encrypting system and method based on RFID (radio frequency identification)-SIM (subscriber identity module) card
InactiveCN102231883AFast encryption and decryptionSecurity arrangementAuthentication serverPacket data transmission
The invention relates to a teledata transmission content encrypting system and method based on an RFID (radio frequency identification)-SIM (subscriber identity module) card in the technical field of wireless communication. The system comprises a server and an RFID-SIM card, wherein the server contains a server roof certificate and a system user personalized certificate, and the RFID-SIM card contains a service certificate and a personalized certificate. The RFID-SIM card sends short messages with encrypted data to a short message authentication server through a common wireless network provided by an operator, and the short message authentication server also sends the short messages with encrypted data to the RFID-SIM card through the common wireless network provided by the operator in the same way. By utilizing the system and method provided by the invention, the defects of symmetric encryption and asymmetric encryption in the prior art can be overcome, and more comprehensive compressing-encrypting-envelope packet data transmission can be realized.
Owner:SHANGHAI COS SOFTWARE CO LTD +1
Management-use separated computer encryption lock
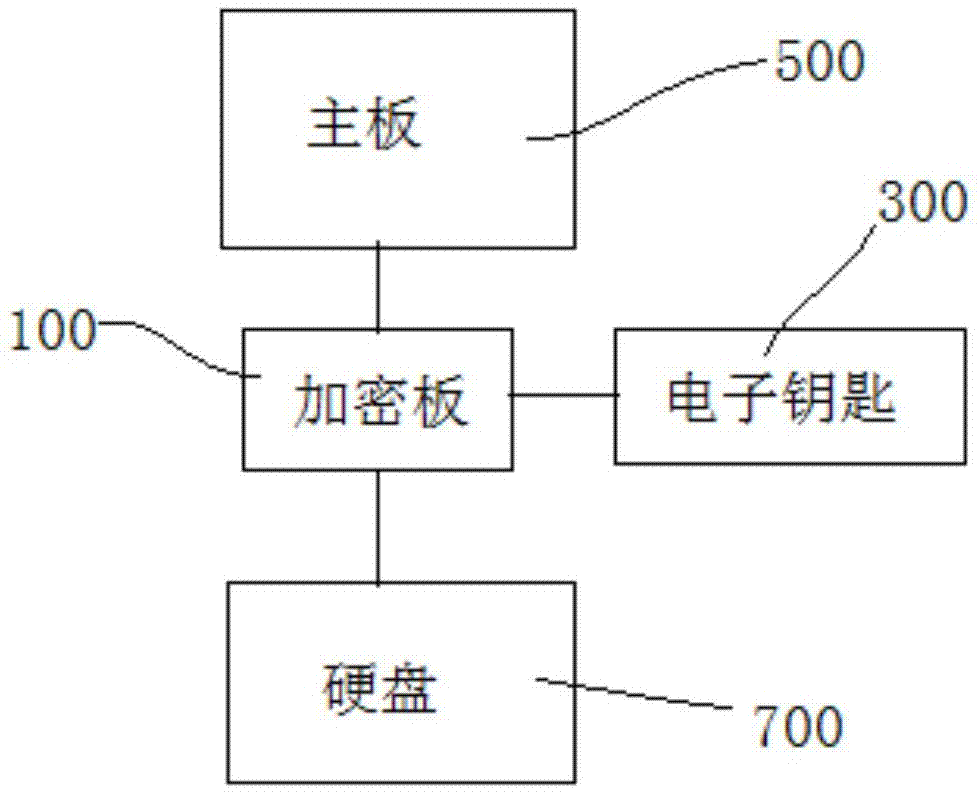
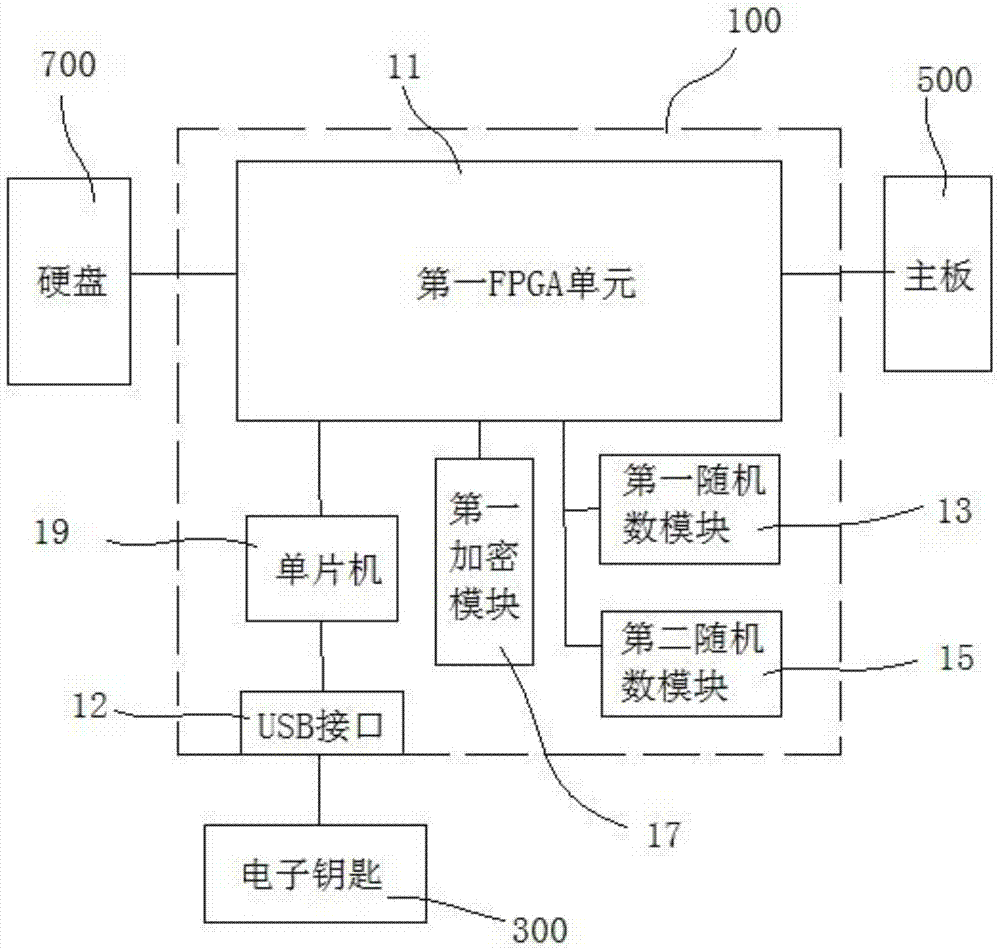
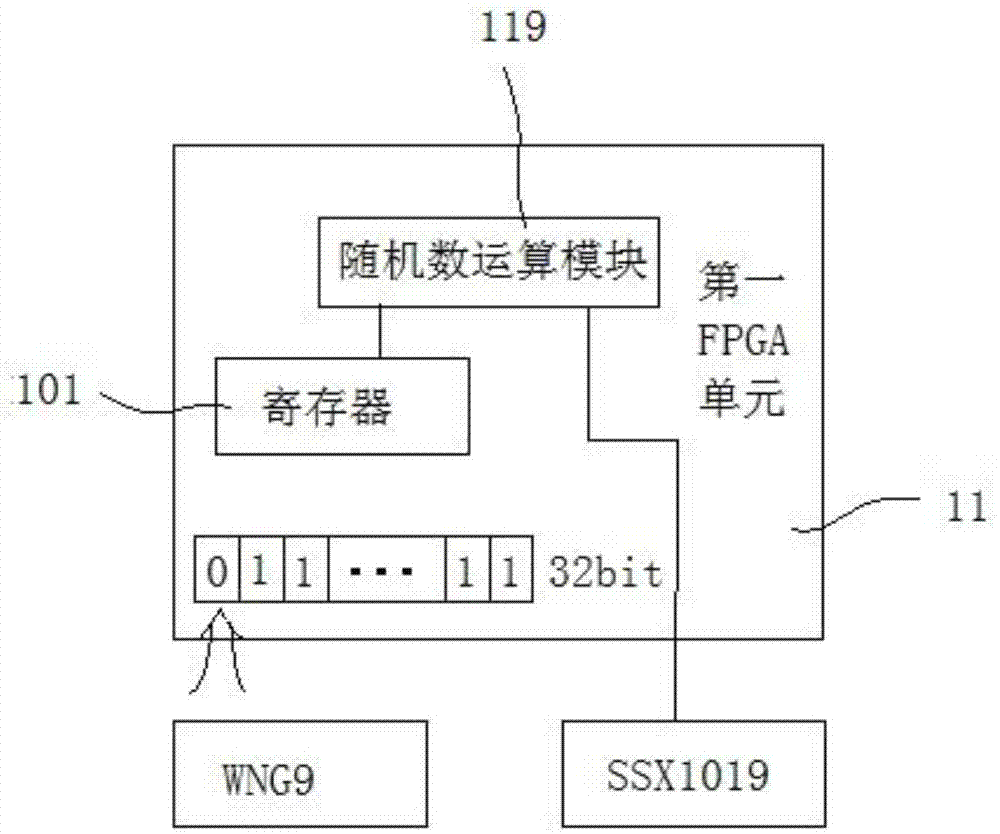
PendingCN106897640AImprove securityPrevent copyingInternal/peripheral component protectionDigital data authenticationConfidentialitySoftware engineering
A management-use separated computer encryption lock includes an encryption board inserted between a main board and a hard disk of a computer; an electronic key which is inserted in the encryption board and can perform real-time identity authentication with the encryption board; the electronic key and the encryption board perform real-time identity authentication and firmware anti-copy detection, and perform encryption on data accessing between the electronic key and the encryption board; after identity authentication and firmware anti-copy detection is completed, the electronic key combines a part of user key lists stored in an inner part and a part of user key lists of the encryption board, and a part of user keys are randomly selected from the key lists according to different storage partitions of the hard disk to perform encryption on data accessing the hard disk. The security of the computer encryption lock is high, the firmware will not be copied, encrypted data in the hard disk and electronic key and encryption board communication data are encrypted and will not be cracked, and the confidentiality is high.
Owner:SHENZHEN ZHENHUA MICROELECTRONICS +1
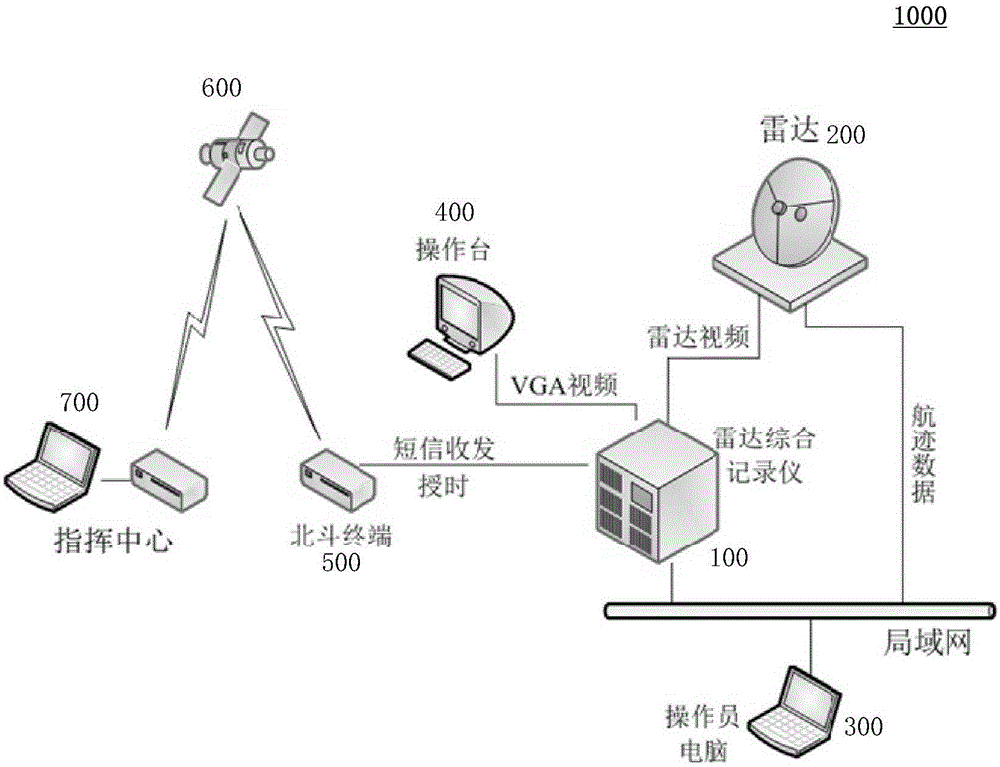
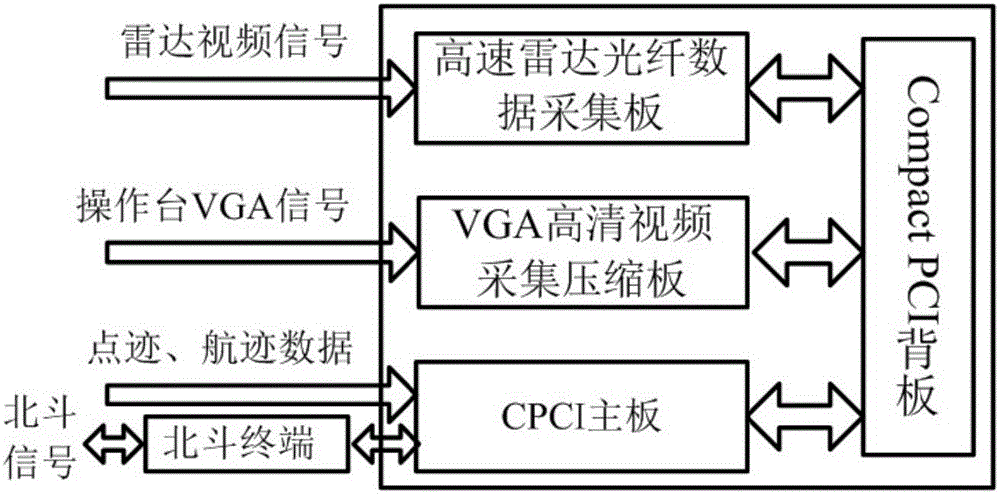
Radar comprehensive recorder and radar data recording method
ActiveCN105759247AFast encryption and decryptionAchieve interactionWave based measurement systemsNetworked Transport of RTCM via Internet ProtocolRadar
Provided are a radar comprehensive recorder and a radar data recording method. The radar comprehensive recorder comprises a radar optical fiber data acquisition board used for receiving radar video data, a video acquisition card used for processing operation station VGA output data, a network card used for receiving track data, a solid-state disk used for storing the radar video data, the VGA output data and the track data, a processor, and a memory which stores a program, wherein the program, when executed by the processor, can operate to acquire the radar video data from the radar optical fiber data acquisition board, acquire the operation station VGA output data from the video acquisition card and acquire the track data from the network card and store the data in the solid-state disk. Radar original video, target plot, target track, work status, operator manual operation command and other data can be transmitted based on an optical fiber, a video acquisition card and a network and can be acquired, recorded and stored in parallel, comprehensive analysis of radar data and track data is facilitated, radar operator's operation of the data is supervised, and the data security is ensured.
Owner:北京源仪迅驰科技有限公司
Long repeating data encryption and transmission method and system
InactiveCN106453391AImprove securityFast encryption and decryptionKey distribution for secure communicationUser identity/authority verificationTimestampPassword
The invention discloses a long repeating data encryption and transmission method and a long repeating data encryption and transmission system, and belongs to the field of data encryption. The method comprises the following steps: a server receives and detects a login message from a client, wherein the login message comprises a user name, a password, a timestamp and a RSA public key of the client; the server dynamically generates a data encryption algorithm data encryption standard (DES) secret key, encrypts the DES secret key by using the RSA public key dynamically generated by the client, and thus generates a RSA encrypted ciphertext; the client decrypts the received RSA encrypted ciphertext and acquires the DES secret key; the client empties RSA secret key pairs; a message transmitted between the server and the client is compressed by using a RLE algorithm, and the compressed message is encrypted by using the DES secret key; and the client / server decrypts the received message by using the DES secret key, and decompresses the decrypted message by using the RLE algorithm.
Owner:BEIHAI HESI TECH
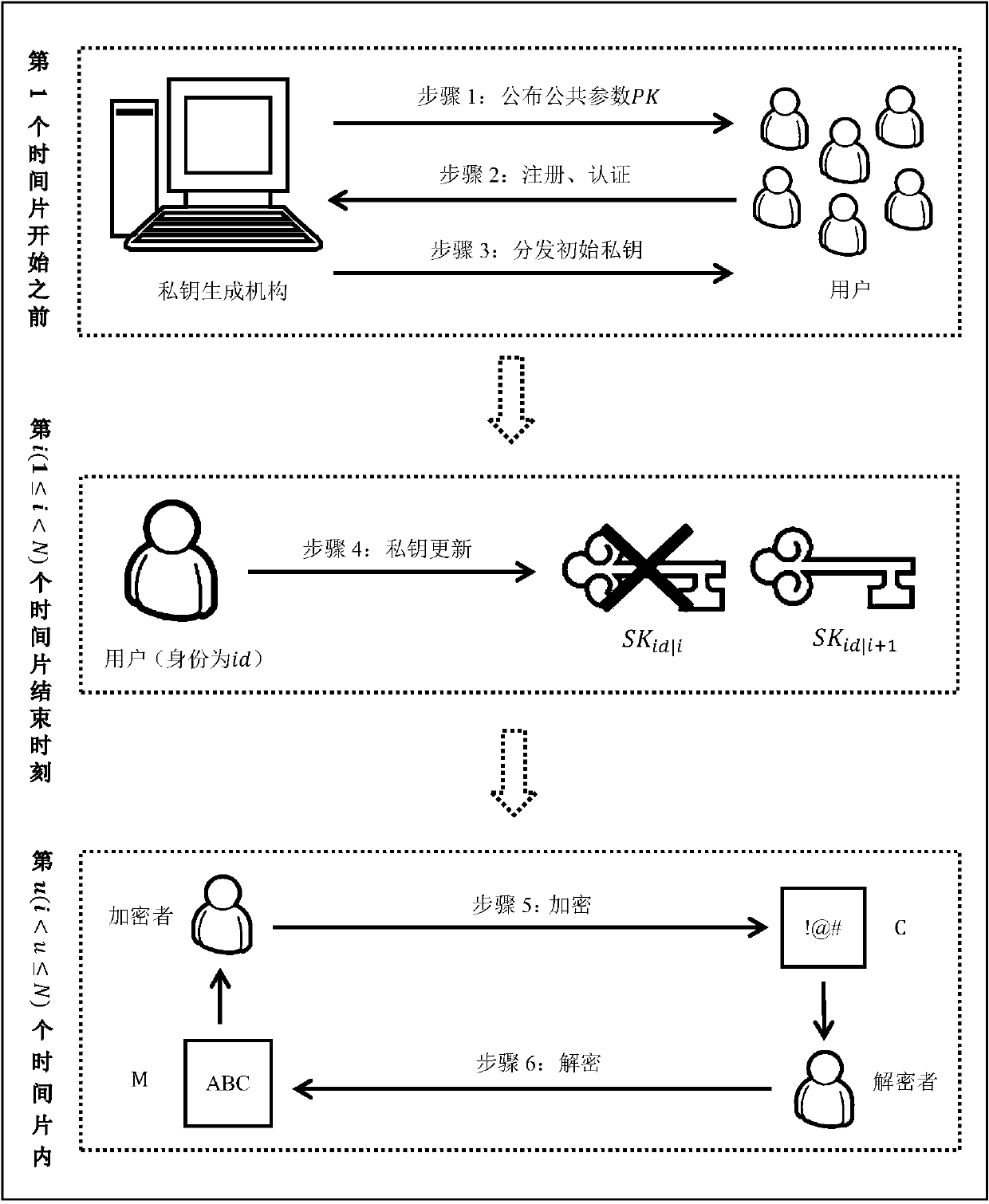
Short ciphertext identity-based encryption method satisfying forward security
ActiveCN104796260AReduce lossesReduce the burden onPublic key for secure communicationUser identity/authority verificationCiphertextAuthentication
The invention discloses a short ciphertext identity-based encryption method satisfying forward security. The short ciphertext identity-based encryption method includes six steps of 1) initializing a private key generating mechanism; 2) registering and authenticating users; 3) generating and issuing initial private keys; 4) updating the private keys; 5) encrypting; 6) decrypting. On the basis of the identity-based encryption mechanism, forward security is realized, the users can independently update private keys, loss caused by revealing of the private keys can be effectively reduced, and the short ciphertext identity-based encryption method is applicable to the communication encryption solution scheme in the open network environment and non-secure devices. In addition, ciphertext is short and fixed in length, encryption and decryption cost low, authentication link is omitted for decryption, and encryption and decryption are high in efficiency, so that the short ciphertext identity-based encryption method has wider application range in actual application.
Owner:BEIHANG UNIV +1
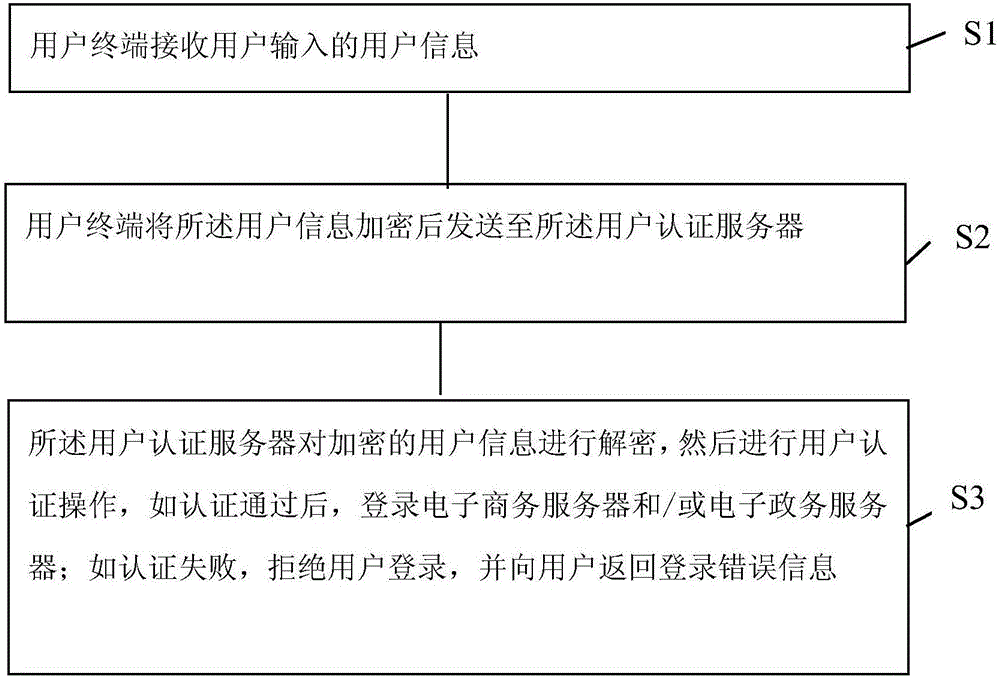
Data processing method of E-commerce and government affairs system
InactiveCN106230842AFast encryption and decryptionImprove securityBuying/selling/leasing transactionsTransmissionUser inputUser authentication
The invention provides a data processing method of an E-commerce and government affairs system. The data processing method includes the steps of a user terminal receiving user information input by a user, the user terminal encrypting the user information and then sending the user information to a user authentication server, the user authentication server decrypting the encrypted user information, conducting user authentication, logging an E-commerce server and / or electronic government affairs server if authentication succeeds, rejecting log-in of the user, if authentication fails, and returning log-in error information to the user. The invention provides an integrated e-commerce and government affairs system, which allows a user to log in an E-government server or a business server according to the user's choice or default and allows switching between the two servers without reconfirming the user's identity. The invention also provides an encryption and decryption algorithm for a user's terminal. The encryption and decryption speed is increased by converting a string into a plurality of integers and hiding the integers in a matrix. The system security is improved.
Owner:张家口乐淘商贸有限公司
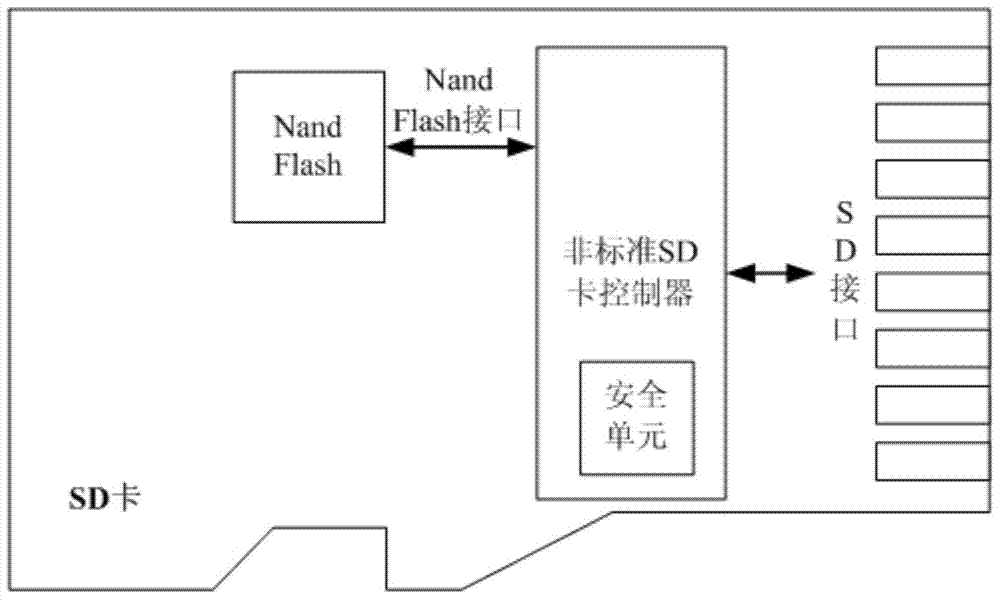
Data flow encryption SD card
ActiveCN103903042AFast encryption and decryptionEasy to useDigital data protectionRecord carriers used with machinesMass storageMemory cards
A data flow encryption SD card comprises a security chip. An SD memory card slave interface, various public key and private key encryption and decryption algorithms, various grouped data encryption and decryption algorithms, an embedded memorizer and an SD or eMMC main control interface are integrated on the security chip. The security chip is connected with an SD interface for being connected with an SD host through the SD memory card slave interface. The SD or eMMC main control interface is connected with a standard SD / eMMC controller for operating a nonvolatile memorizer. The standard SD / eMMC controller is connected with the nonvolatile memorizer for achieving the SD card large-capacity memory function through a NandFlash interface. The data flow encryption SD card has the advantages of being high in encryption and decryption speed, safe to use, low in cost and large in memory capacity.
Owner:HANGZHOU SYNOCHIP DATA SECURITY TECH CO LTD
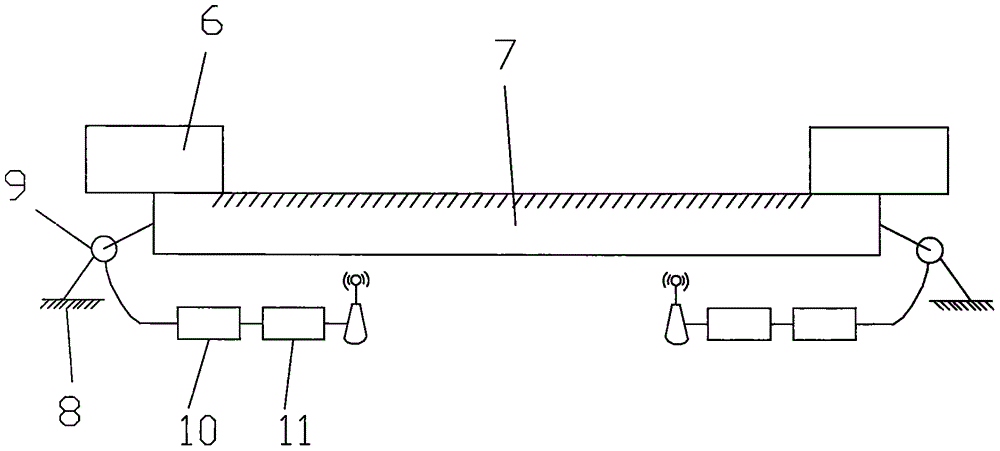
Composite sensor for 10kV distribution cable partial discharge online monitoring and positioning system
InactiveCN105699860AEnsure safetyReduce complexityTesting dielectric strengthFault location by conductor typesElectric cablesField coil
The invention discloses a composite sensor for a 10kV power distribution cable partial discharge on-line monitoring and positioning system, comprising an insulating shell, an electric field coil frame, an electric field coil, a magnetic field coil frame and a magnetic field coil, and the electric field coil frame and the magnetic field coil frame are arranged in the insulating shell Inside, the electric field coil is evenly wound on the electric field coil frame, and the magnetic field coil is evenly wound on the magnetic field coil frame. The composite sensor for the 10kV distribution cable partial discharge on-line monitoring and positioning system can not only detect high-frequency partial discharge signals, It can also locate the discharge source, which effectively improves the accuracy and reliability of positioning while reducing the complexity of the system.
Owner:友铂空天动力(深圳)有限公司
Image encryption and decryption method and image encryption and decryption system
PendingCN112636895ASave storage spaceSave resourcesKey distribution for secure communicationSecuring communication by chaotic signalsEncryption decryptionComputer vision
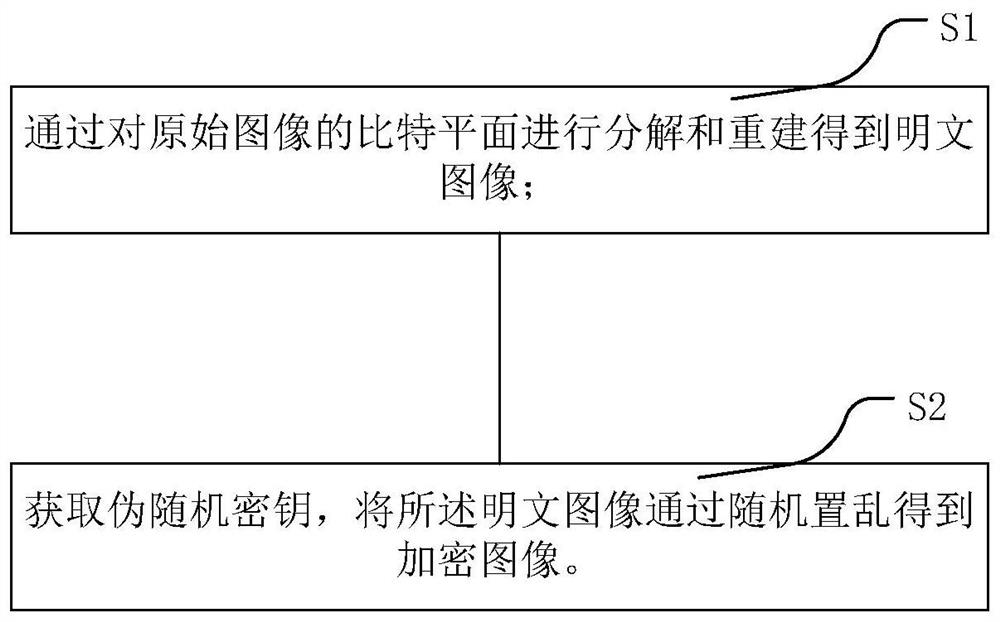
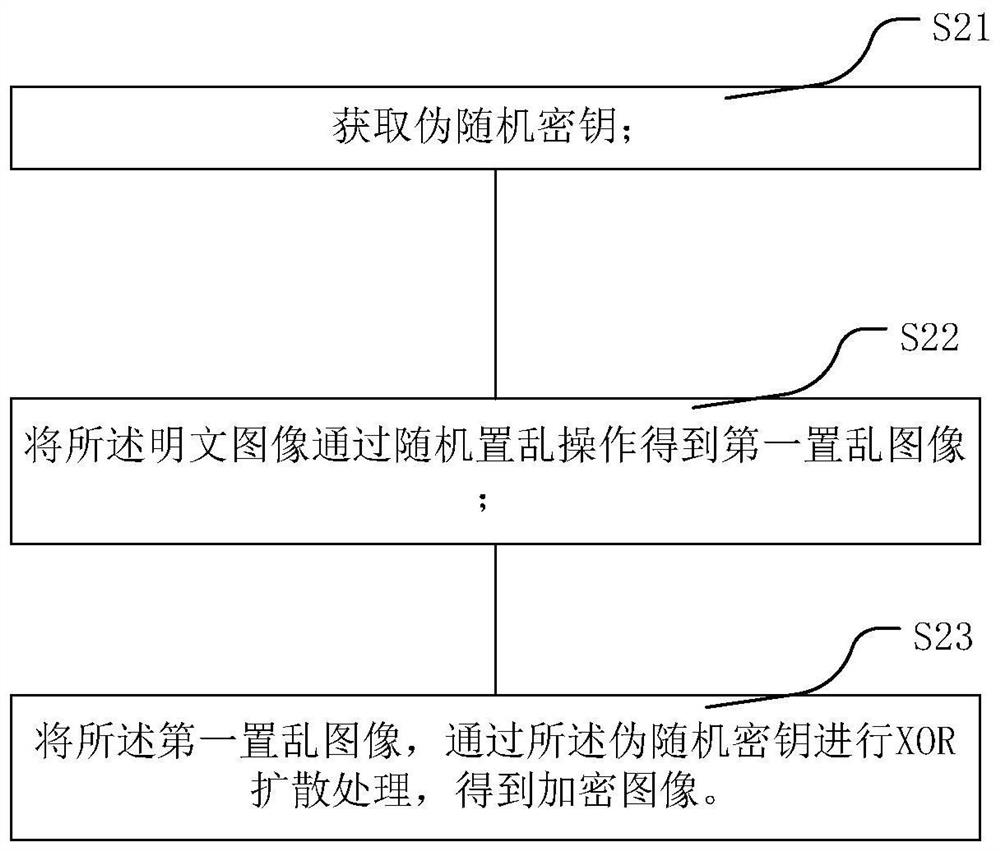
The invention relates to an image encryption and decryption method and an image encryption and decryption system. The invention discloses an image encryption and decryption method, and the method comprises an image encryption operation step: S1, carrying out the decomposition and reconstruction of a bit plane of an original image, and obtaining a plaintext image; and S2, acquiring a pseudo-random key, and randomly scrambling the plaintext image to obtain an encrypted image. According to the image encryption and decryption method provided by the invention, the encrypted image obtained by using the encryption operation is subjected to security analysis and differential attack resistance analysis, so that the effectiveness of the algorithm is ensured, and the pixel correlation of the encrypted image tends to 0. Compared with an existing encryption algorithm in performance, a result obtained by feedback proves that the encrypted image obtained by using the image encryption method provided by the invention is excellent in safety performance.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Information security chip for Internet of Things
ActiveCN109818745AFast encryption and decryptionReduce chip areaEncryption apparatus with shift registers/memoriesPublic key for secure communicationKey generationInternet of Things
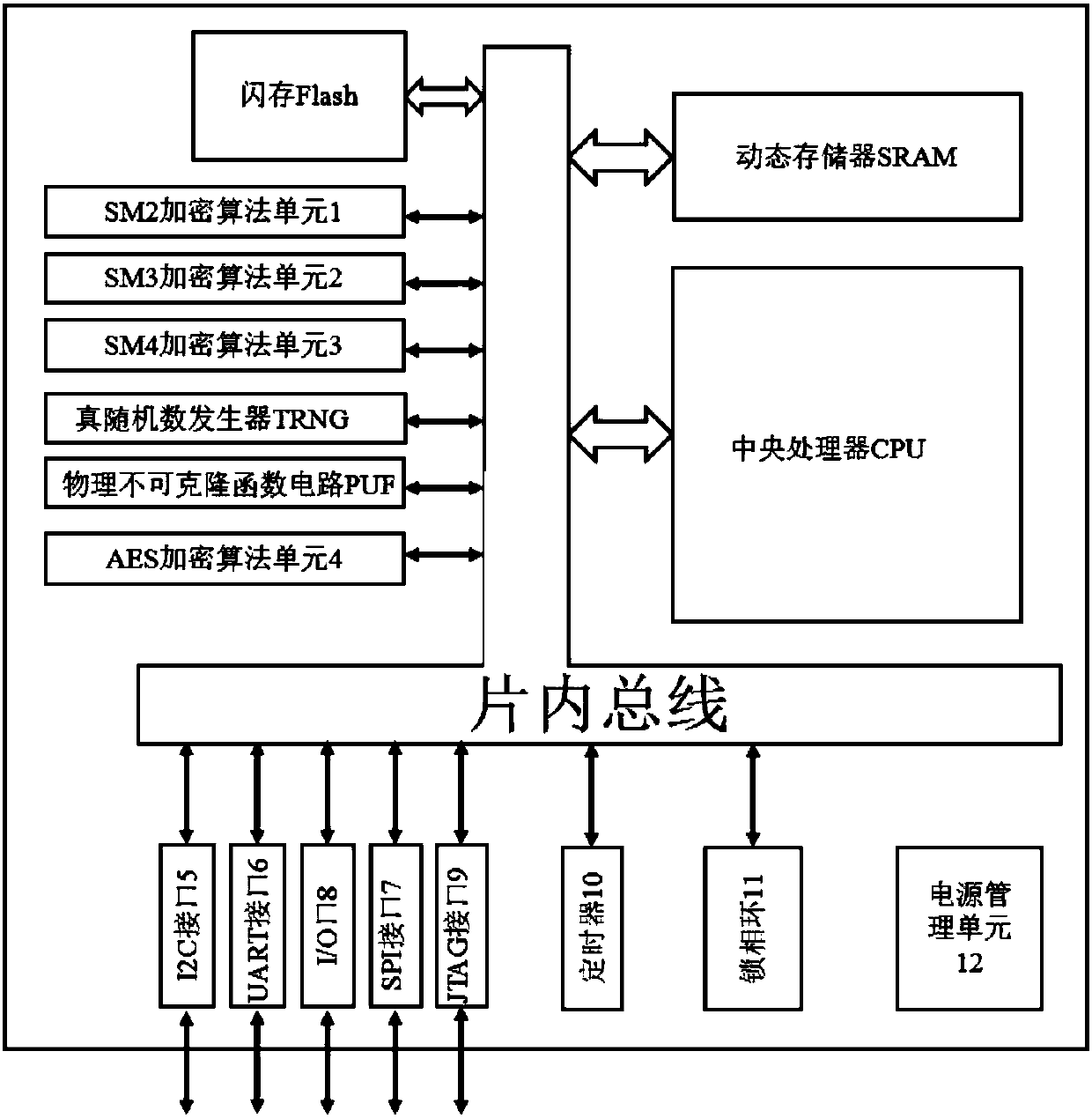
The invention discloses an information security chip of the Internet of Things. The chip comprises a central processor, a dynamic memory, a flash memory, an SM2 encryption algorithm unit, an SM3 encryption algorithm unit, an SM4 encryption algorithm unit, an AES encryption algorithm unit, a true random number generator, a physical unclonable function circuit, an I2C interface, a UART interface, anSPI interface, an I / O interface, a JTAG interface and a timer which are interconnected through an on-chip bus. The true random number generator is used for generating true random numbers; The physical unclonable function circuit is used for chip authentication and key generation, when a key needs to be used, a true random number generated by the true random number generator is input into the physical unclonable function circuit through an on-chip bus, the physical unclonable function circuit outputs a unique response sequence, and the response sequence is the key. The encryption and decryption operation speed is high, the hardware resource consumption is low, the power consumption is low, the secret key cannot be copied and stolen, and the security and anti-counterfeiting level is high.
Owner:佛山芯珠微电子有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com