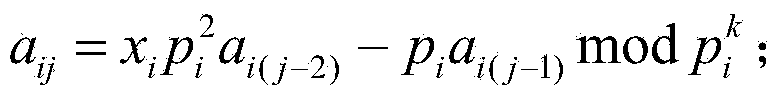Multivariable public key encryption method
A multi-variable public key and encryption method technology, applied in the field of multi-variable public key encryption, can solve the problems of long key and inconvenient key management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0067] The random parameter ε is obtained through the decryption method, and the method includes the following steps:
[0068] (1) Generate a key. Further include the following steps:
[0069] (1-1) Construct a k×n-dimensional full-rank matrix A in an iterative manner. Further include the following steps:
[0070] (1-1-1) Determine k=2.
[0071] (1-1-2) Select finite field Z, and 2 integers p in finite field Z 1 ,p 2 .
[0072] (1-1-3) Select the following integers on the finite field Z: (β 11 ,β 12 ), (β 21 ,β 22 ) and (x 1 ,x 2 ). Order a 11 = β 11 p 1 , a 12 = β 12 p 1 2 , a 21 = β 21 p 2 , a 22 = β 22 p 2 2 .
[0073] (1-1-4) Construction matrix A=(a ij ), wherein,...
Embodiment 2
[0102] The random parameter ε is obtained through a synchronous method. This method includes the following steps:
[0103] (1) Generate a key. Further include the following steps:
[0104] (1-1) Construct a k×n-dimensional full-rank matrix A in an iterative manner. Further include the following steps:
[0105] (1-1-1) Determine k=2.
[0106] (1-1-2) Select finite field Z, and 2 integers p in finite field Z 1 ,p 2 .
[0107] (1-1-3) Select the following integers on the finite field Z: (β 11 ,β 12 ), (β 21 ,β 22 ) and (x 1 ,x 2 ). Order a 11 = β 11 ,a 12 = β 12 p 1 ,a 21 = β 21 ,a 22 = β 22 p 2 .
[0108] (1-1-4) Construction matrix A=(a ij ), wherein, when i=1,2, j=1,...,n, j>2, a ij = x i p i 2 a i ( j - 2 ...
Embodiment 3
[0136] This method comprises the steps:
[0137] (1) Generate a key. Further include the following steps:
[0138] (1-1) Construct a k×n-dimensional full-rank matrix A in an iterative manner. Further include the following steps:
[0139] (1-1-1) Determine k=2, n=4.
[0140] (1-1-2) Select the finite field Z, and 2 integer numbers p in the finite field Z 1 = 3,p 2 =7.
[0141] (1-1-3) Select the following integers on the finite field Z: β 11 =28,β 12 =10,β 21 =345,β 22 =52,x 1 =5,x 2 =9. Order a 11 = β 11 p 1 =84, a 21 = β 21 p 2 =2415, a 22 = β 22 p 2 2 = 2548 .
[0142] (1-1-4) Construction matrix A=(a ij ), wherein, i=1,2, j=1,...,4, when j>2, a ij = x i p i 2 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com