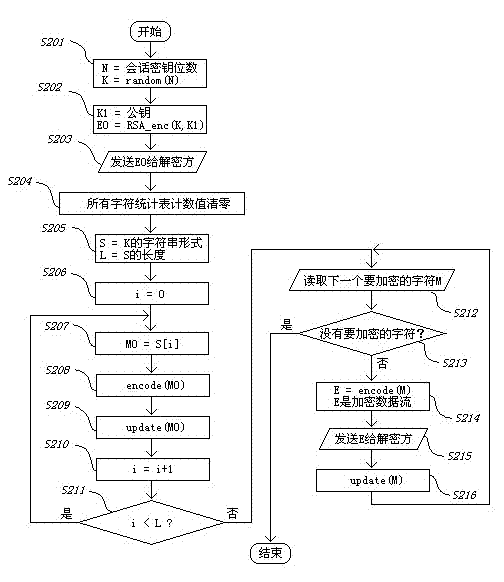
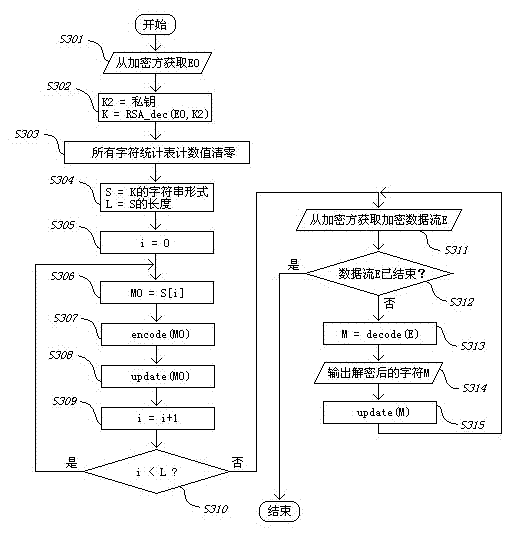
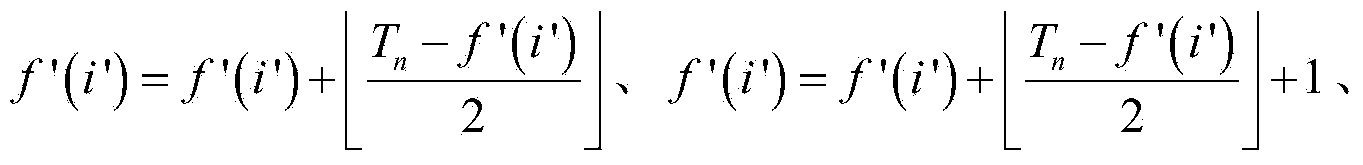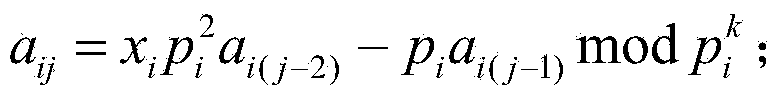Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
101results about How to "Improve encryption security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
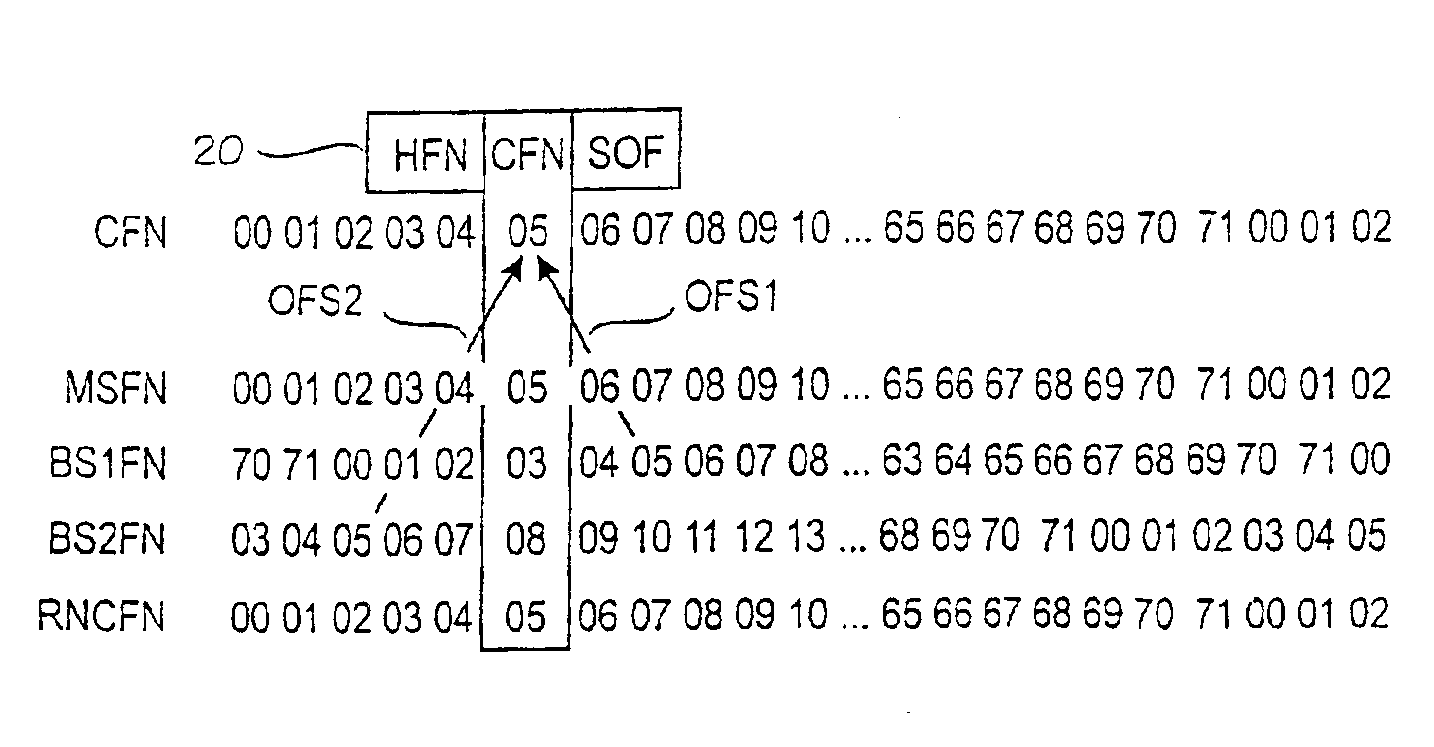
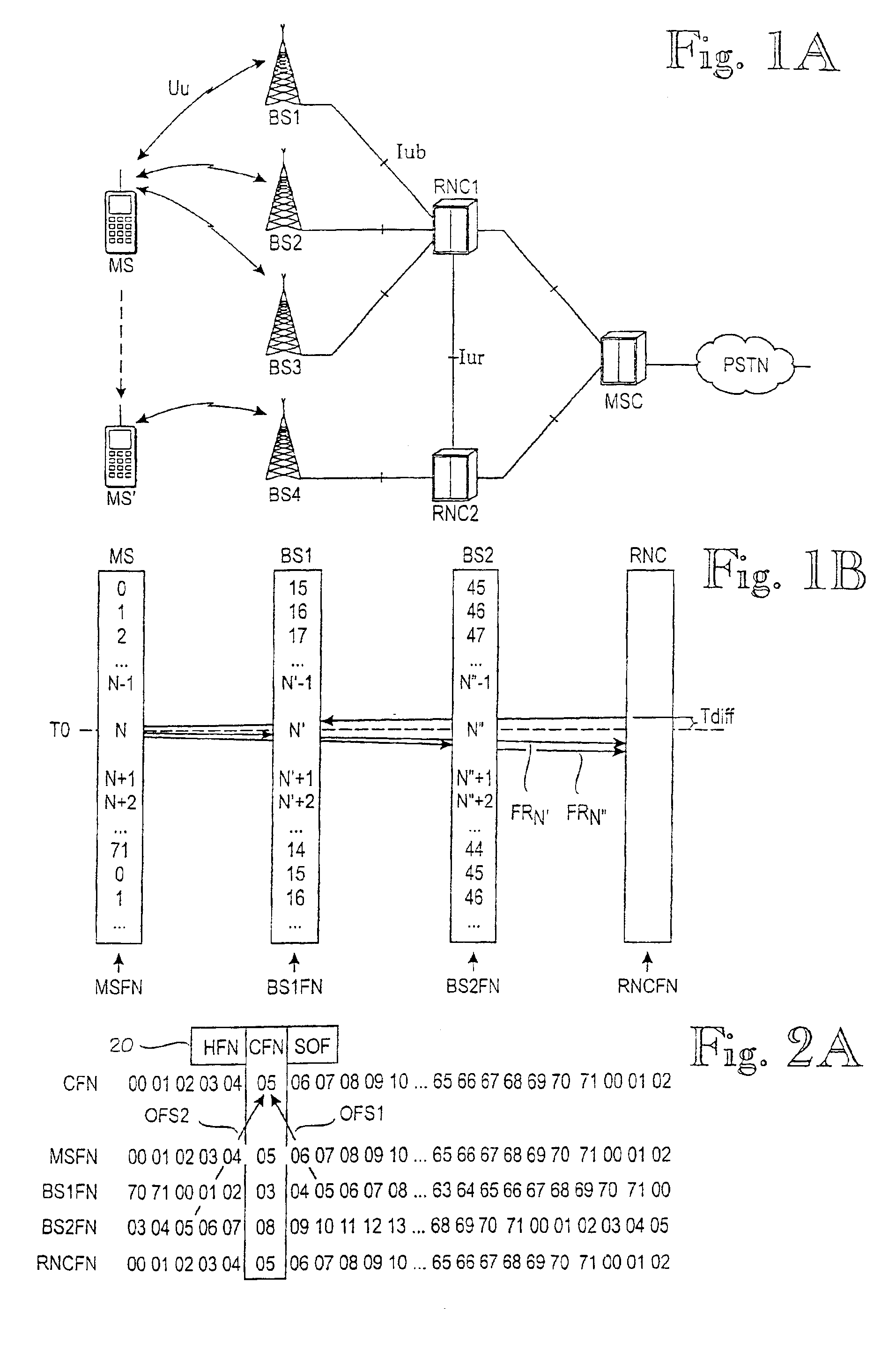
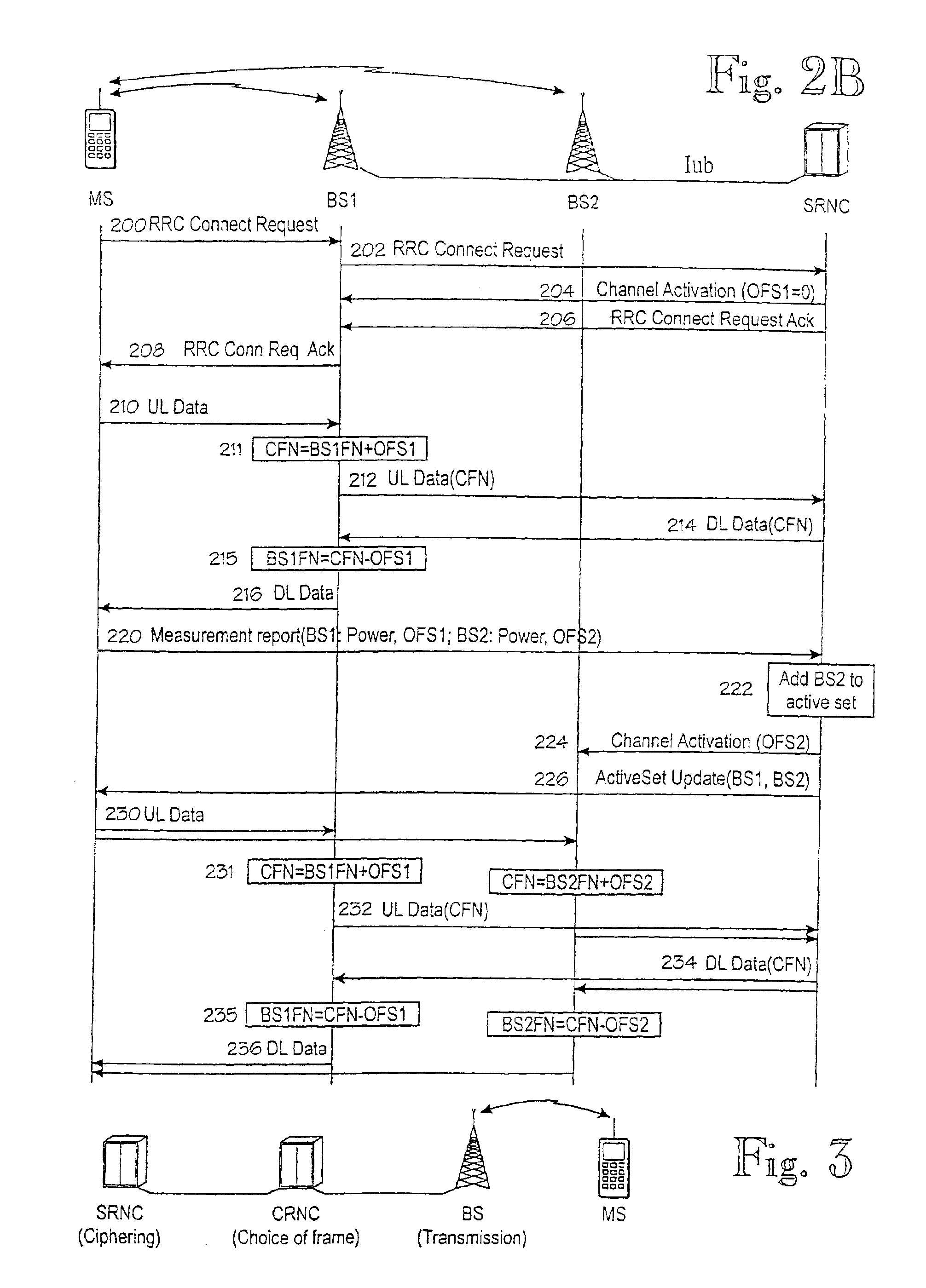
Frame synchronization mechanism
InactiveUS7085294B2Improve encryption securityWeaken ciphering securitySynchronisation arrangementTime-division multiplexRadio networksTelecommunications network
A mechanism for synchronizing transmission of frames in a telecommunications network including a mobile station, a radio network controller, at least one base station. The mobile station and each base station have a corresponding timing reference. The mechanism includes or performs the steps of establishing a connection-specific timing reference which is common to all nodes involved in the connection; determining, for the base stations an offset between the timing reference of the base station in question and the CFN; and using the offset in the base stations, to compensate for the difference between the timing references.
Owner:SISVEL INT
Data encrypting method and device and data decrypting method and device
ActiveCN105760765ARealize multi-dimensional encryptionAvoid crackingEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOriginal data
The invention relates to the field of data encrypting and decrypting, in particular to a data encrypting method and device and a data decrypting method and device.The data encrypting method comprises the steps that at first, an encryption key and original data are obtained; then, an encryption rule is selected from a preset encryption rule base; the encryption key is adopted for encrypting the original data according to the encryption rule to obtain intermediate data; then, identification information corresponding to the encryption rule is obtained; finally, the intermediate data and the identification information are packaged to generate encrypted data.Compared with the prior art, encryption information does not only depend on the carrier key, the encryption rule is selectively used, and the encryption rule is encrypted; meanwhile, in the file transmitting process, only the identification information of the encryption rule exists in the transmission information, and the specific content of the encryption rule does not exist, so that multi-dimensional encryption is achieved, the encryption means is more complex, the key can not be decrypted easily, and encryption safety is higher.
Owner:BEIJING SEEYON INTERNET SOFTWARE CORP
Internet picture transparent and safe transmission method based on chaotic encryption
ActiveCN103427979AImprove efficiencyImprove encryption securitySecuring communicationUser inputInternet users
The present invention relates to an internet picture transparent and safe transmission method based on chaotic encryption, and provides a chaotic digital image encryption transmission solution scheme which supports the automatic generation of a secret key and is fully transparent to the internet user operation. According to the internet picture transparent and safe transmission method based on the chaotic encryption, a browser client utilizes a JavaScript program to automatically map, calculate and obtain two key Logistic chaotic secret key parameters according to the information, such as the usernames, password Hash values, etc. inputted by the internet valid users, to realize the safe and transparent encryption and transmission on the to-be-uploaded pictures of users; a server terminal can query a user database according to the registered username to obtain the password Hash value of a user, so that a same chaotic random sequence can be obtained, and finally the encrypted pictures uploaded by the user can be decrypted; on the contrary, when the user registers validly to require the server pictures, the JavaScript program can automatically carry out the chaotic secret key parameter calculation and chaotic decryption operations at a browser terminal. According to the scheme of the present invention, the balance problem among the security, the encryption efficiency, the secret key management and the like of the internet picture transmission can be solved effectively.
Owner:ZHEJIANG UNIV OF TECH
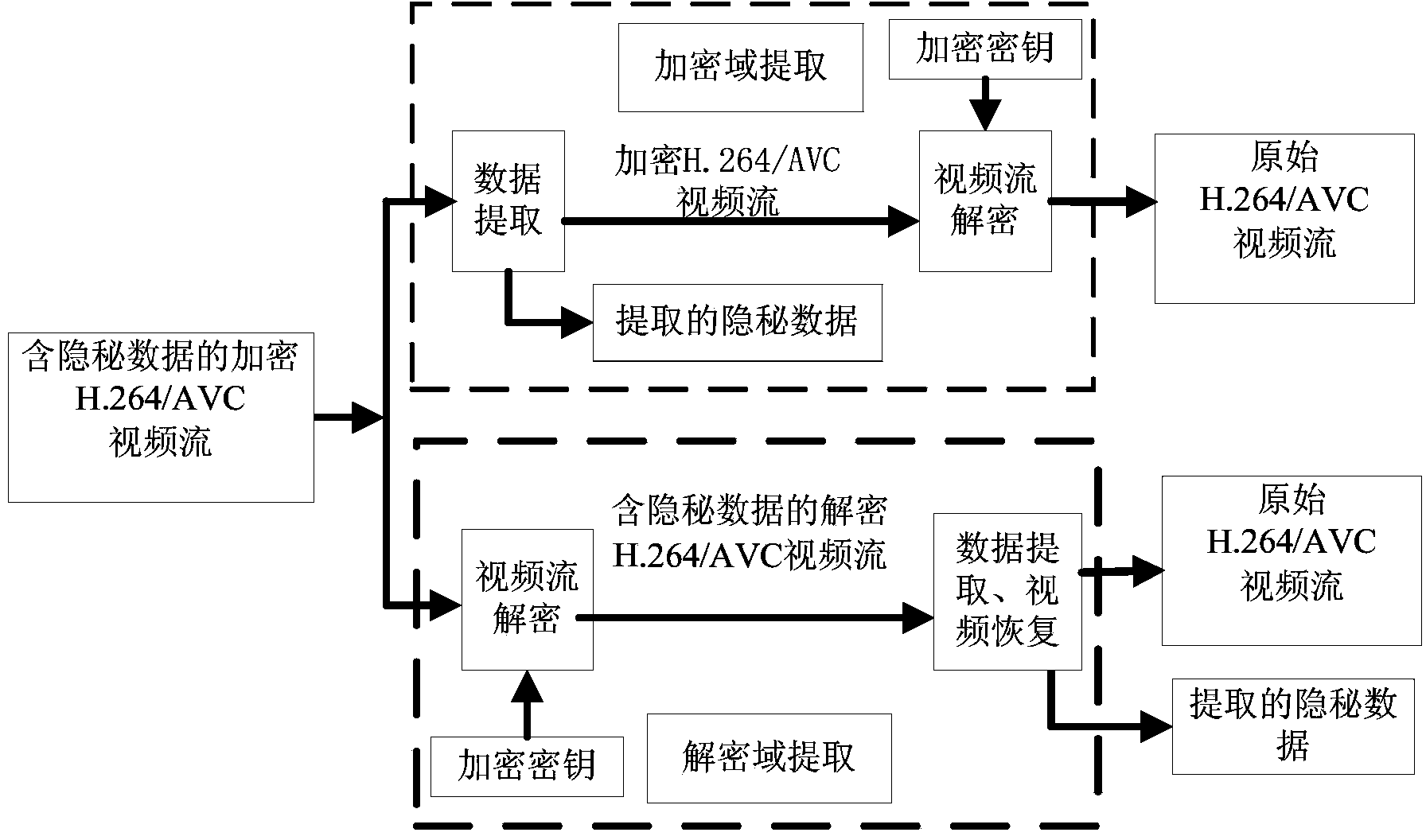
Encryption domain H.264/AVC video reversible data hiding method
ActiveCN103826128AMeet application needsLittle impact on code rateDigital video signal modificationComputation complexityData expansion
The invention discloses an encryption domain H.264 / AVC video reversible data hiding method. Under the premise that the encryption domain H.264 / AVC video reversible data hiding method is compatible with an H.264 / AVC video compressed encoding standard, code words of prediction modes, Exp-Golomb code words of motion vector difference and sign bits of residual error coefficients are selected to be encrypted, computation complexity is low, the application demands of real-time videos are met, and encryption safety is high. Meanwhile, influences of encryption on the code rate of code streams of H.264 / AVC videos are quite small, and the problem of data expansion in the video encryption process is solved. A data hiding person can embed private information in the H.264 / AVC videos of an encryption domain directly, and thus the problems of video content safety and privacy disclosure can be solved effectively. The hidden data can be extracted effectively from the encryption domain and can also be extracted effectively from a decryption domain, namely, data extraction and data decryption are separated completely, and practicality is high. In addition, the encryption domain H.264 / AVC video reversible data hiding method is completely revisable, and original videos can be restored without damage after the hidden information is decrypted and extracted.
Owner:NINGBO UNIVERSITY OF TECHNOLOGY
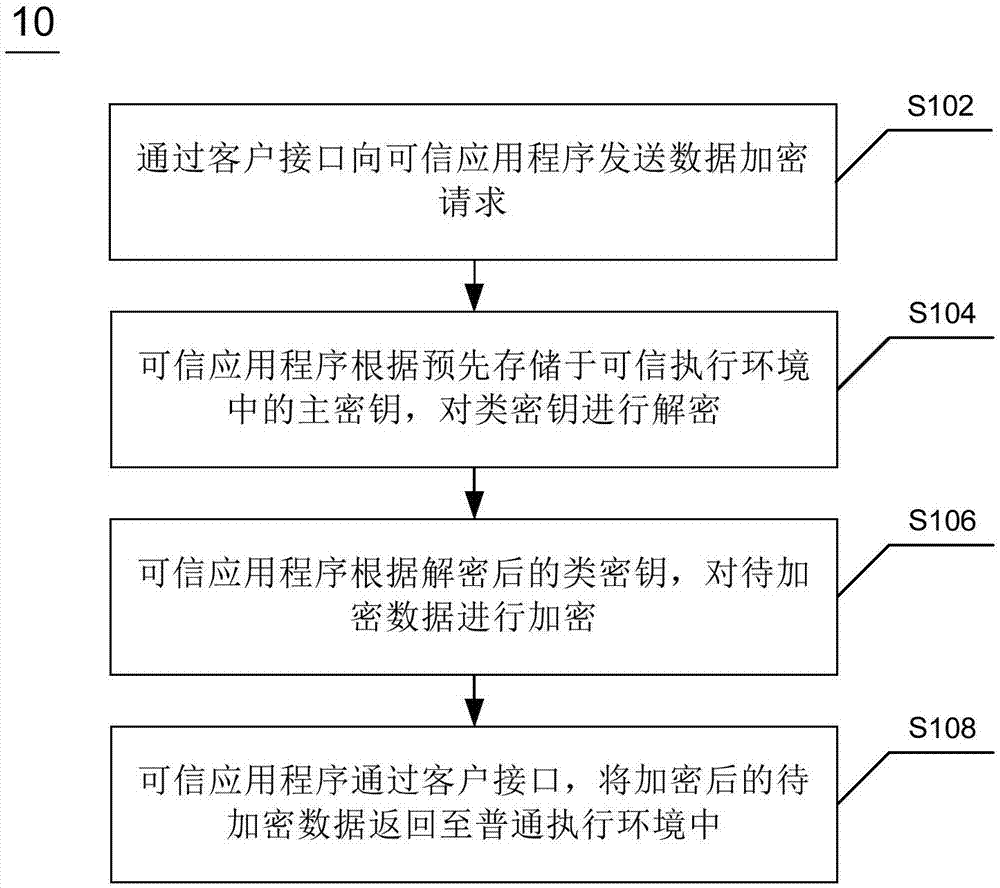
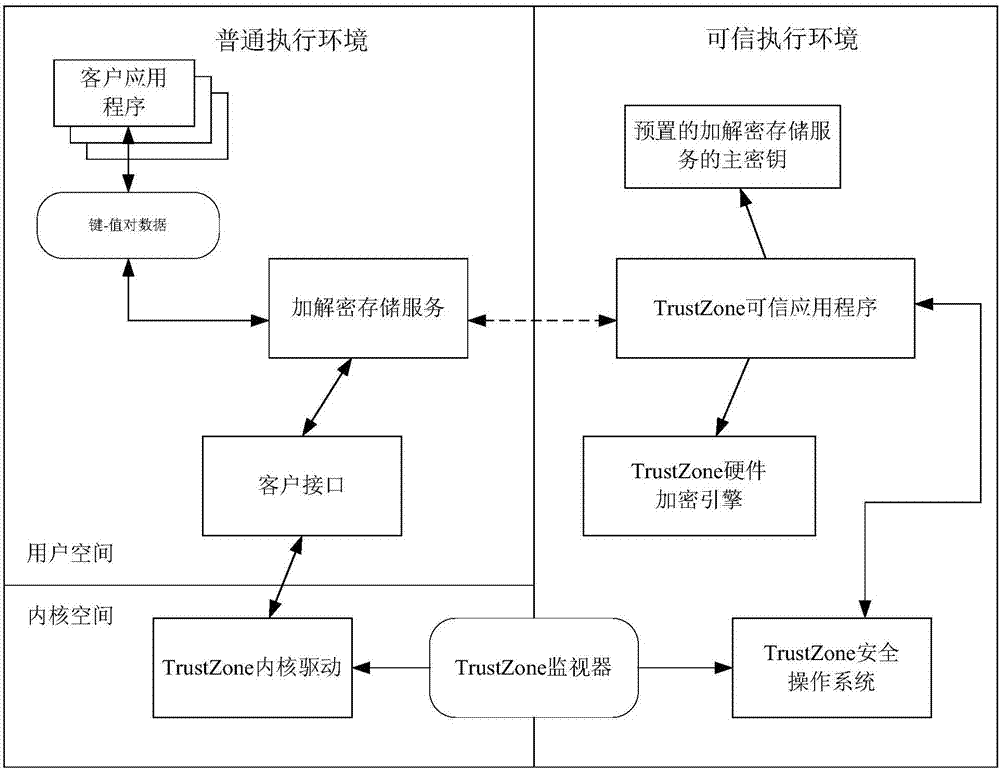
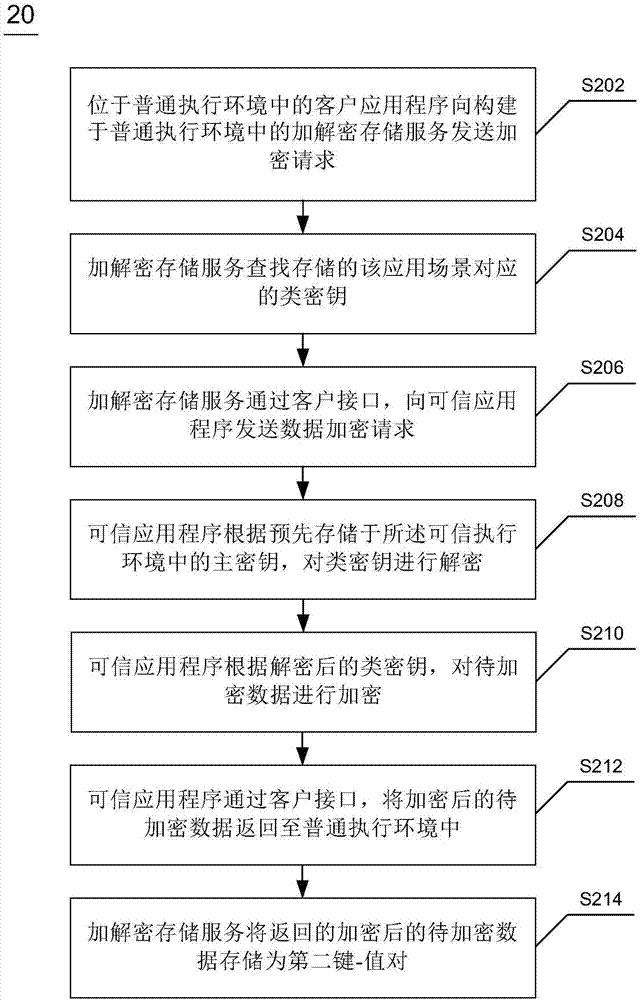
TrustZone-based data encryption and decryption methods and apparatuses, and terminal device
ActiveCN106997439AImprove encryption securityImprove securityKey distribution for secure communicationDigital data protectionTerminal equipmentXML Encryption
The invention discloses TrustZone-based data encryption and decryption methods and apparatuses, and a terminal device. The encryption method comprises the steps of sending a data encryption request to a trusted application in a trusted execution environment through a client interface between a general execution environment and the trusted execution environment, wherein the data encryption request comprises a class key and to-be-encrypted data; decrypting the class key according to a main key pre-stored in the trusted execution environment by the trusted application; encrypting the to-be-encrypted data according to the decrypted class key by the trusted application; and returning the encrypted to-be-encrypted data to the general execution environment through the client interface by the trusted application. The encryption method has high security performance and expandability.
Owner:北京元心君盛科技有限公司
Chaos synchronization encrypting/decrypting method and device using data compression encoding
ActiveCN102904717AImprove encryption securityKey distribution for secure communicationPublic key for secure communicationData compressionKey size
The invention discloses a chaos synchronization encrypting / decrypting method and device using data compression encoding. The device comprises a random number generator, a public key cryptography encipher, a public key cryptography decipher, a dynamical probability counter, an entropy encoder and an entropy decoder. The method comprises the steps of taking the entropy encoder and the dynamical probability counter used for the data compression as a chaotic dynamics system; enabling a compression coding process to form a chaotic cryptology encryption process; combining the public key cryptography encipher with the chaotic dynamics system, wherein after a randomly generated session key is encrypted in an asymmetrical encryption manner by a sender, the session key is sent to a receiver; initializing the respective chaotic dynamics system through the respective session key the sender and the receiver so that the system states of the sender and the receiver are synchronous; carrying out data compression encoding through the initialized system by the sender; and carrying out data uncompressing through a system with consistent state by the receiver. The method and the device provided by the invention support overlong session key and improve the encryption safety; and simultaneously, the encryption speed is not affected by the key length.
Owner:SOUTH CHINA UNIV OF TECH
Method and apparatus for encrypting information, computer device, and storage medium
InactiveCN107666479ASafe and reliable cloud transmissionSafe and reliable storageTransmissionCiphertextDocumentation
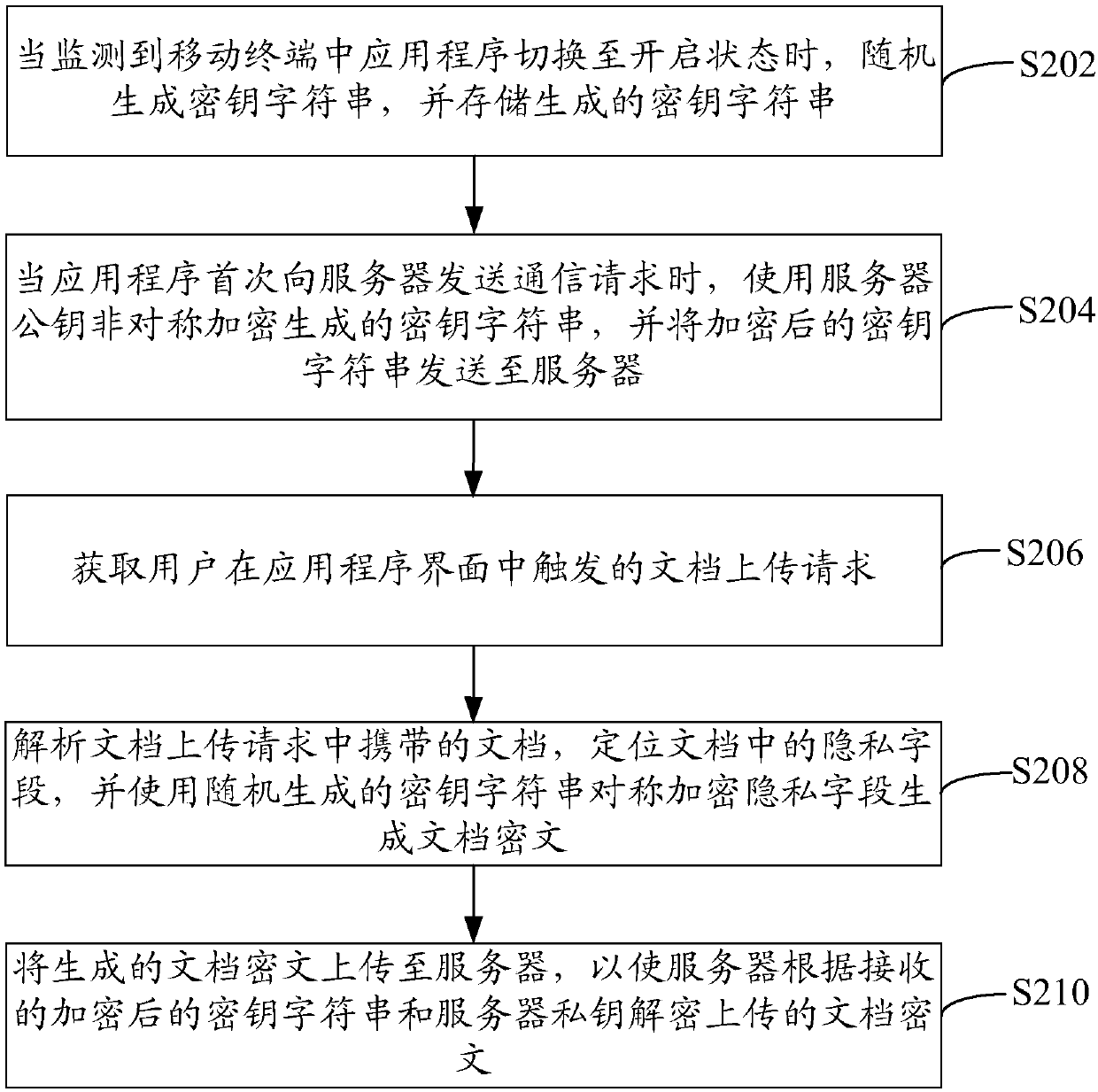
The invention relates to a method for encrypting information. The method comprises the following steps that: when an application program in a mobile terminal is monitored to be switched in an on state, a secret key character string is generated randomly and the generated secret key character string is stored; when the application program sends a communication request to a server for the first time, the generated secret key character string is encrypted asymmetrically by using a server public key published by the server in advance and the encrypted secret key character string is sent to the server; a document uploading request triggered by a user in the application program interface is obtained; a document carried by the document uploading request is analyzed, a privacy field in the document is localized, and the privacy filed is encrypted symmetrically by using a secret key character string generated randomly to generate a document ciphertext; and the generated document ciphertext is uploaded to the server, so that the server decrypts the uploaded document ciphertext based on the received encrypted secret key character string and a server private key. With the method provided by the invention, the information decryption and encryption processing efficiency is increased and the safety is enhanced.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Image encryption method and device
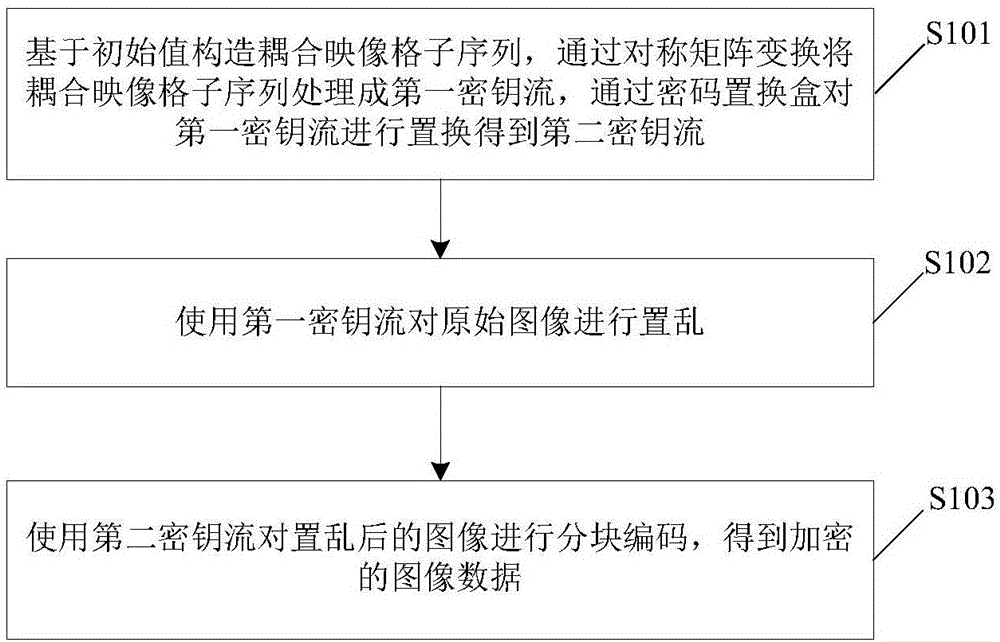
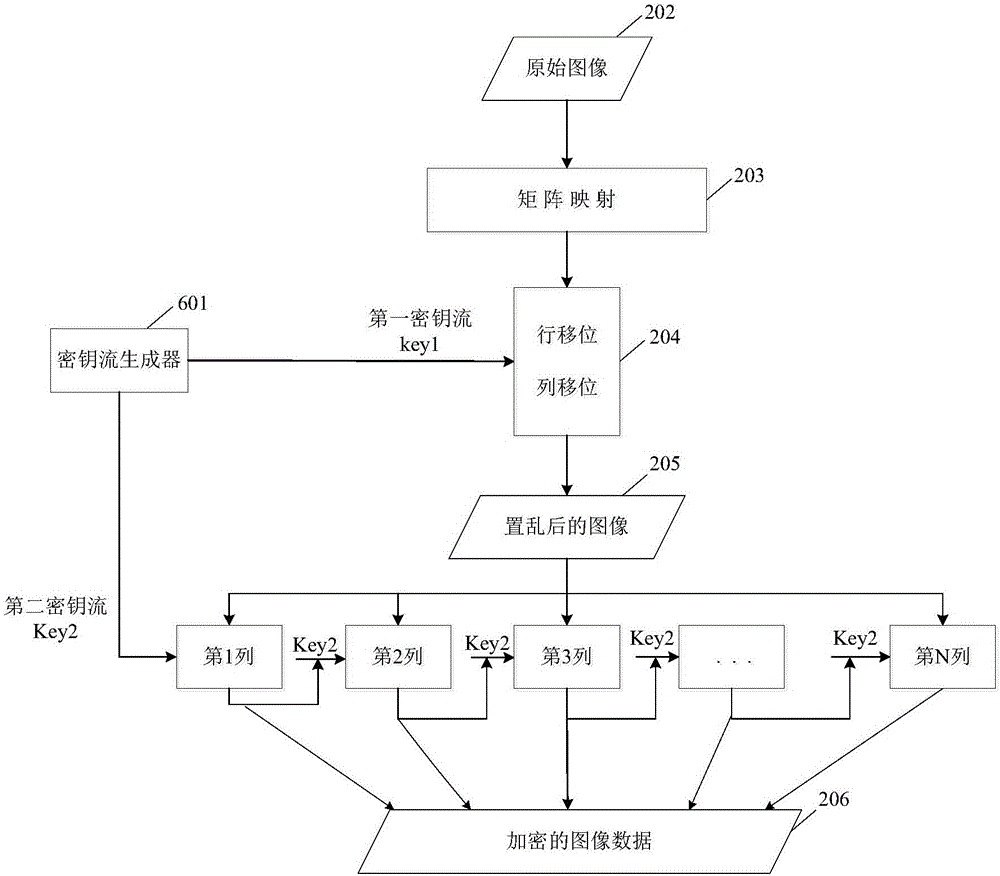
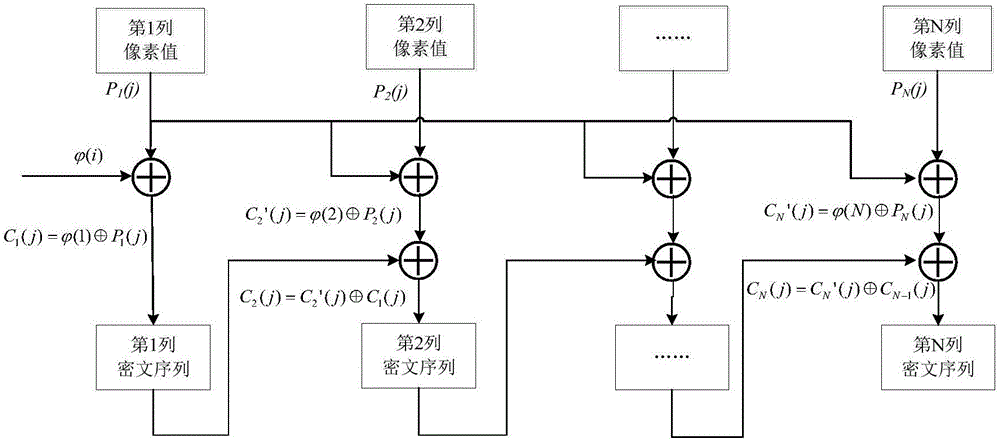
ActiveCN106407824AReduce computational complexityImprove encryption securityEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareComputation complexity
The invention relates to an image encryption method, an image encryption device, a key stream generation method and a key stream generator. The image encryption method comprises following steps of constructing a coupling image grid sequence based on the initial value, processing the coupling image grid sequence to be a first key stream by means of symmetric matrix transformation, replacing the first key stream through a password displacement box to obtain a second key stream, scrambling the original image by means of the first key stream, carrying out block encoding to the scrambled image by means of the second key stream, and obtaining the encrypted image data. According to the invention, the scrambling operation encryption method and the block encoding encryption method are combined, the encryption safety is improved, and the computation complexity of the encryption operation is well reduced; different key streams are used in the scrambling operation and the block encoding; compared with a method that a single key stream is used, the image encryption method is advantaged in that the encryption safety is higher.
Owner:CHONGQING UNIV OF EDUCATION
Multivariable public key encryption method
ActiveCN103973439AShorten the lengthEasy to managePublic key for secure communicationPlaintextProbabilistic encryption
The invention discloses a multivariable public key encryption method. According to the multivariable public key encryption method, when a key is generated, a matrix is constructed according to an iterative method, the length of the key is greatly reduced, and the key can be managed conveniently; a probability encryption method is adopted, random parameters are introduced into encryption, the random parameters must be solved by a deciphering party through a deciphering process, the random parameters take part in decryption of a plaintext, the plaintext can be deciphered only under the condition that the random parameters are known, the difficulty of ciphertext decryption by an attacker is increased, ciphertexts are different even if public keys are the same, the public keys can be released in the forms such as telephone numbers, and encryption security is improved; based on the combinatorial optimization difficulty and multivariable quadratic polynomial, attack of a quantum computer can be resisted, both the encryption speed and the decryption speed are high, and the method can be applied to mobile terminals such as mobile phones; based on calculation on a finite field, the calculation process is simplified; the addition homomorphism and the subtraction homomorphism are achieved, the multiplication homomorphism can be achieved under special conditions, and the method can be applied to the newly-developed fields such as cloud computing.
Owner:HUAZHONG UNIV OF SCI & TECH
Video encryption algorithm based on new spatiotemporal chaos system
ActiveCN104093029AImprove encryption securityGuaranteed rate controlDigital video signal modificationPseudorandom sequenceChaotic systems
The invention relates to an H.264 video encryption algorithm based on a spatiotemporal chaos system and belongs to the technical field of multimedia information security. The H.264 video encryption algorithm is provided to solve the problem that the requirements for real time performance, high security and low complexity cannot be met easily by an existing H.264 video encryption algorithm. A compound chaos cryptographic algorithm is constructed by designing a complex spatiotemporal chaos system model, and a more secure encryption pseudorandom sequence hard to crack is designed and generated. Meanwhile, by selecting an encryption control technology, intra-frame and inter-frame prediction modes, the residual data scanning sequence before coding of a CAVLC coding process and multiple key data in coding are encrypted. Theoretical analysis and experimental results show that the algorithm is high in encryption speed and security and small in influence on the compression ratio, the video format is kept being free of damage, and the algorithm has extensive application prospects and practical value.
Owner:HARBIN INST OF TECH AT WEIHAI
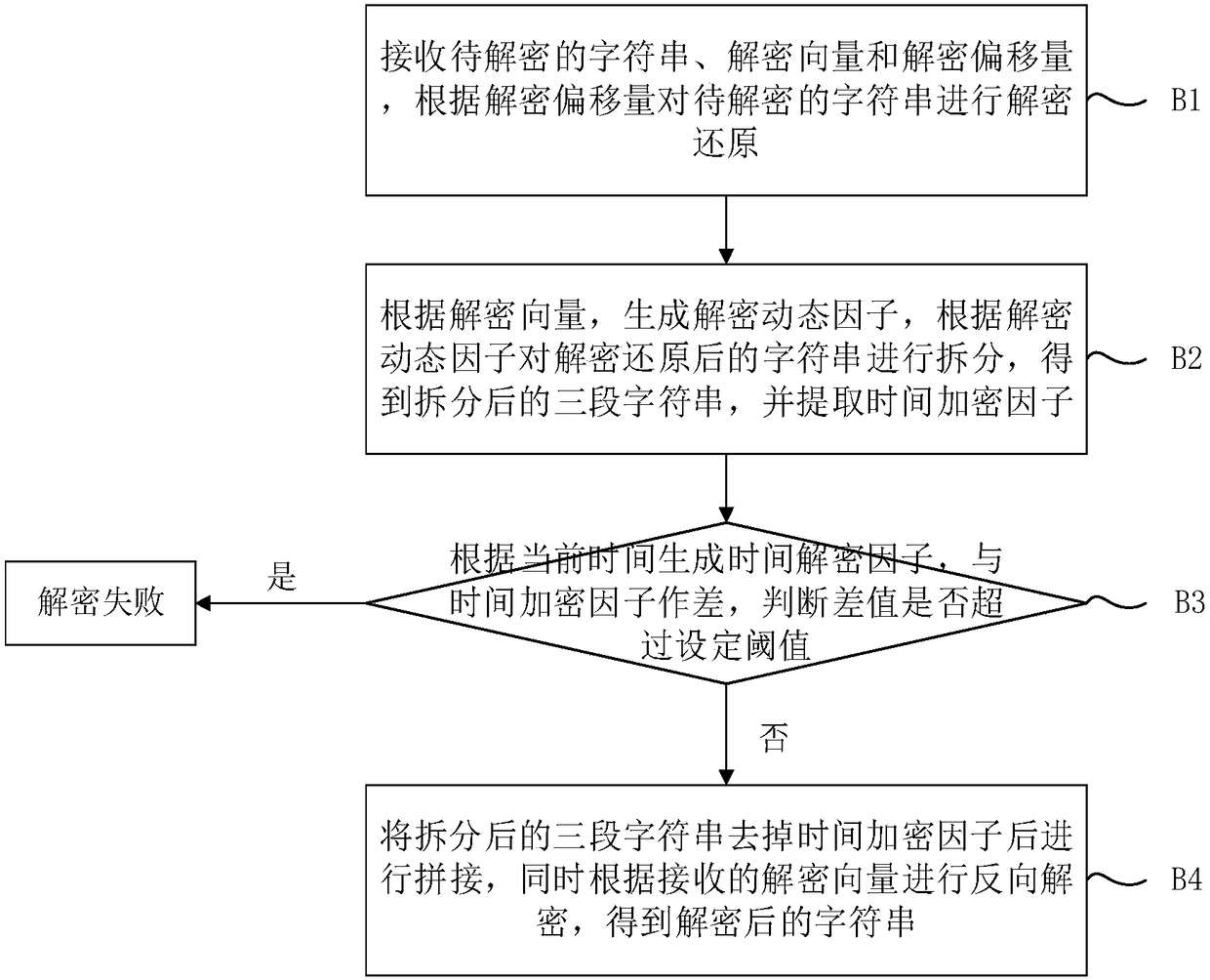
High security character string symmetrical encryption and decryption method
ActiveCN108173640AProtection securityImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareEncryption
The invention relates to a high security character string symmetrical encryption and decryption method. The encryption method comprises the steps of receiving a to-be-encrypted character string, an encryption vector and encryption offset; generating an encryption dynamic factor according to the encryption vector, and splitting the to-be-encrypted character string, thereby obtaining two sections ofsplit character strings; and generating a time encryption factor according to current time, adding the time encryption factor to the two sections of split character strings, combining the split character strings, and encrypting the combined character string according to the encryption offset, thereby obtaining the encrypted character string. The decryption method is reverse operation of the encryption method. Difference is calculated through utilization of a current time decryption factor and the time encryption factor extracted after the split is carried out. Decryption is carried out if a difference value does not exceed a threshold. Decryption failure is returned if the difference value exceeds the threshold. Compared with the prior art, the methods have the advantages that the security performance is high, the exhaustion break is prevented, and the break difficulty is high.
Owner:上海高顿教育科技有限公司
Chaotic encryption method for voice information
ActiveCN106375079AGood pseudorandomnessExtended cycleSecuring communication by chaotic signalsPlaintextComputer hardware
The invention discloses a chaotic encryption method for voice information. The method is characterized in comprising the steps of 1), establishing a dynamic variable parameter composite chaotic system and generating a real-value chaotic sequence of which length is the same to that of a plaintext voice sequence through utilization of the system; 2), carrying out binarization processing on the real-value chaotic sequence, thereby obtaining a chaotic key sequence of which length is the same to that of the plaintext voice sequence; and 3), through combination of the chaotic key sequence, carrying out bit-by-bit exclusive or operation on the plaintext voice sequence, thereby obtaining a ciphertext. According to the method, under limited calculation precision, the chaotic sequence with good pseudo-randomness can be generated, the valid precision effect is reduced, and a chaotic sequence cycle is prolonged; and through adoption of a chaotic system cascading mode, the encryption security is improved, a sufficient key space can be generated, and an exhaustive attack can be resisted effectively.
Owner:HUAQIAO UNIVERSITY
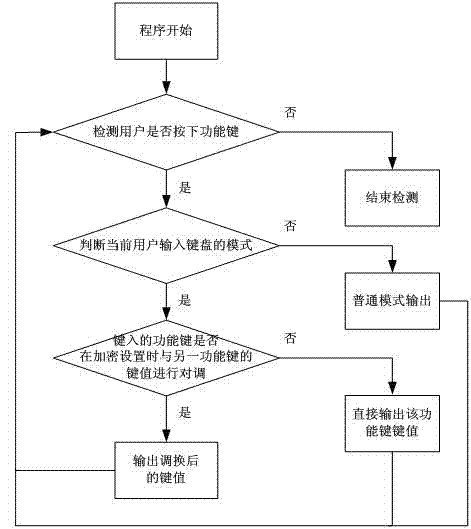
Keyboard input encryption method and mobile terminal thereof
InactiveCN102880305AImprove encryption securityPrevent snoopingInternal/peripheral component protectionInput/output processes for data processingTerminal equipmentProcessing element
The invention discloses a keyboard input encryption method and terminal equipment thereof. The mobile terminal comprises an encryption setting module, a resetting encryption setting module, an encryption input module and a central processing unit. The method comprises the following steps of: (a) detecting whether a user presses a functional key, and if the user presses the functional key, executing the next step, otherwise, ending the detection; (b) judging a mode of the current user input keyboard by a system, if the mode is a common mode, directly outputting a typed functional key value through a keyboard, and if the mode is an encryption input mode, executing the next step; (c) judging whether the typed functional key value is exchanged with a key value of another functional key during encryption, if so, executing the next step, otherwise, directly outputting the functional key value; and (d) outputting the exchanged key value, and returning to the step (a). Aiming at a situation that a user uses mobile phone application to input sensitive information under a complicated environment, the encryption security of an input method is realized; a phenomenon that sensitive information acquired by the user is pried is avoided; fund loss of the user is prevented; and therefore, the user can securely execute relevant operation with a mobile phone, and the security of the mobile phone is also improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
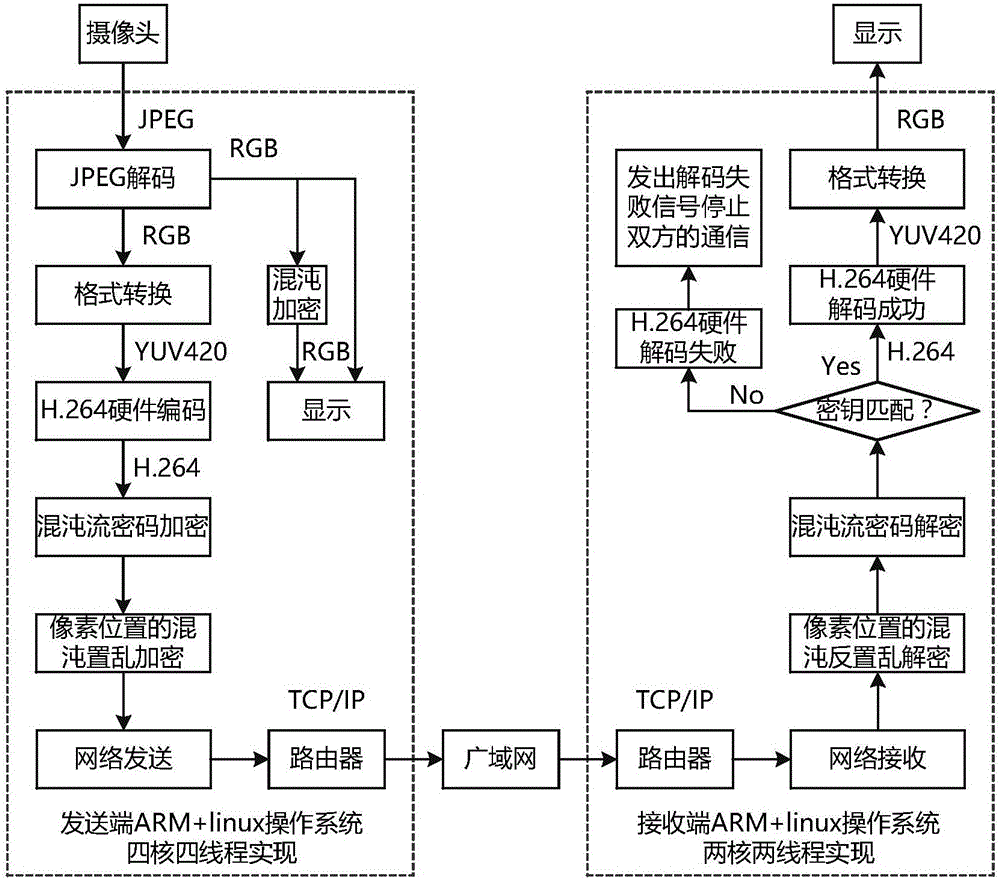
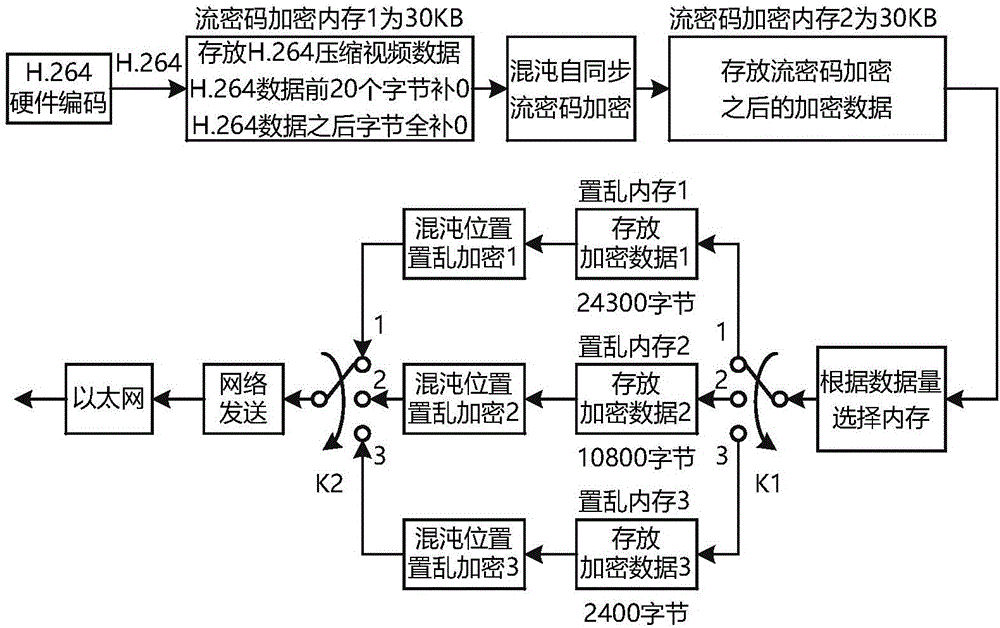
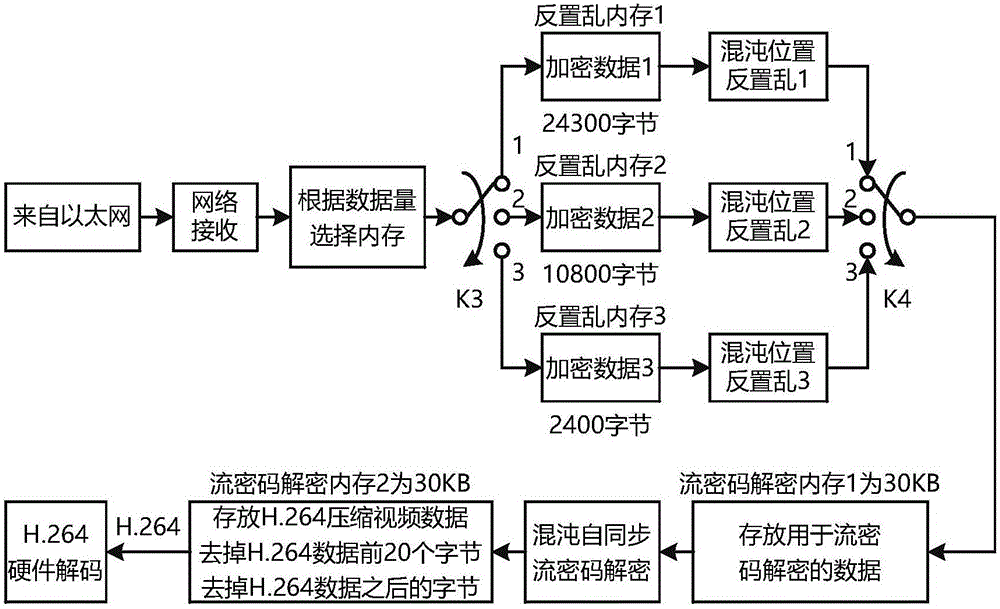
Encrypted embedded video chaotic secret communication method after H.264 coding
ActiveCN105791853AImprove coding efficiencyReduce redundancyDigital video signal modificationSelective content distributionEncryption systemComputer hardware
The invention discloses an encrypted embedded video chaotic secret communication method after H.264 coding. The encrypted embedded video chaotic secret communication method comprises the following steps of S1, at a transmitting end, performing H.264 hardware coding, chaotic flow password encryption, pixel-position chaotic scrambling encryption, network transmission and wide-area network transmission on video data; and S2, at a receiving end, receiving encrypted video data through the network, finishing pixel-position chaotic descrambling decryption and chaotic flow cipher decryption, realizing H.264 hardware decoding on the condition that a password matches, and stopping communication between the transmitting end and the receiving end after H.264 hardware decoding failure on the condition that password mismatching occurs. The encrypted embedded video chaotic secret communication method has double encryptions, namely chaotic flow password encryption and chaotic position scrambling encryption. The double encryptions are performed after H.264 coding compression. The encrypted embedded video chaotic secret communication method has advantages of realizing no damage of original video correlation, improving coding efficiency, reducing data redundancy, and realizing high real-time performance and high safety of an encryption system.
Owner:GUANGDONG UNIV OF TECH
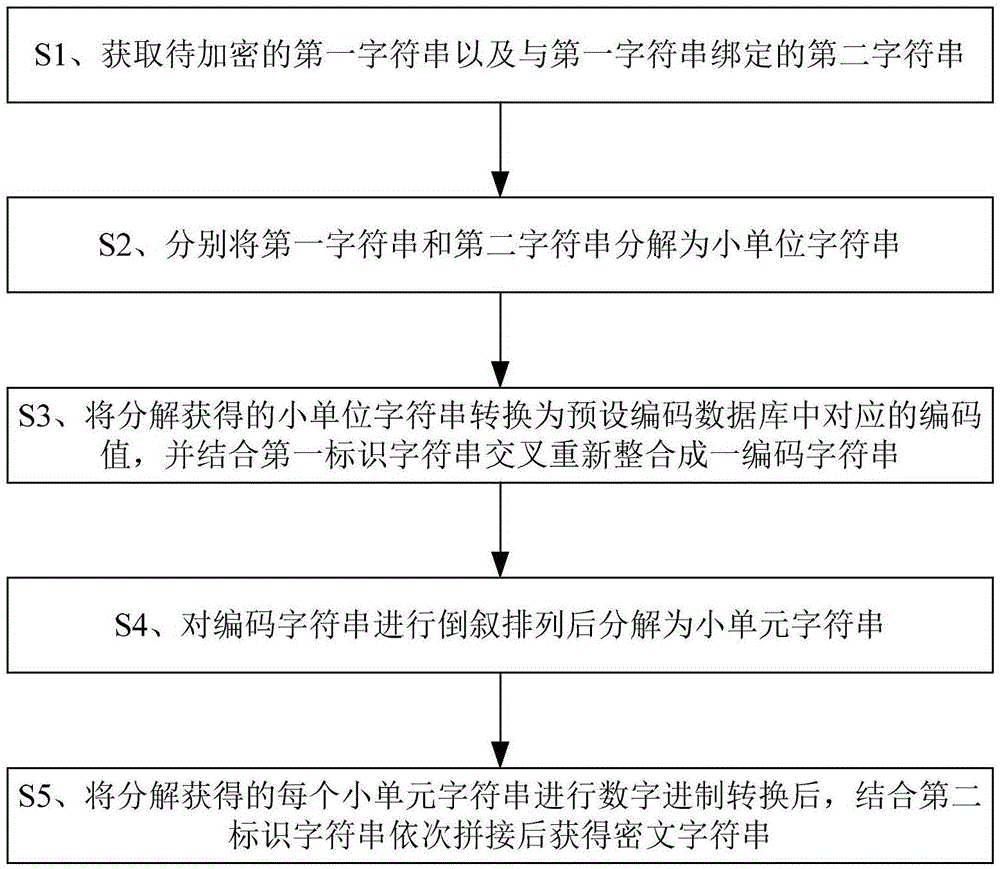
Reverse reconstruction encryption method
ActiveCN105656626AIncrease the difficulty of crackingImprove encryption securityDigital data protectionSecuring communicationCiphertextAlgorithm
The invention discloses a reverse reconstruction encryption method. The method comprises the steps of 1, acquiring a first character string to be encrypted and a second character string bound with the first character string; 2, decomposing the first character string and the second character string into subsection character strings; 3, converting the subsection character strings obtained through decomposition into corresponding coded values in a preset encoding database, and obtaining an encoding character string through intersection and reintegration according to a first identification character string; 4, conducting flashback arrangement on the encoding character string, and then decomposing the encoding character string into subsection character strings; 5, conducting digital decimal-binary conversion on each subsection character string obtained through decomposition, and then obtaining an ciphertext character string through sequential splicing of a second identification character string. The method is large in cracking difficulty and high in encryption safety and can be widely applied to the data encryption field.
Owner:陈剑辉
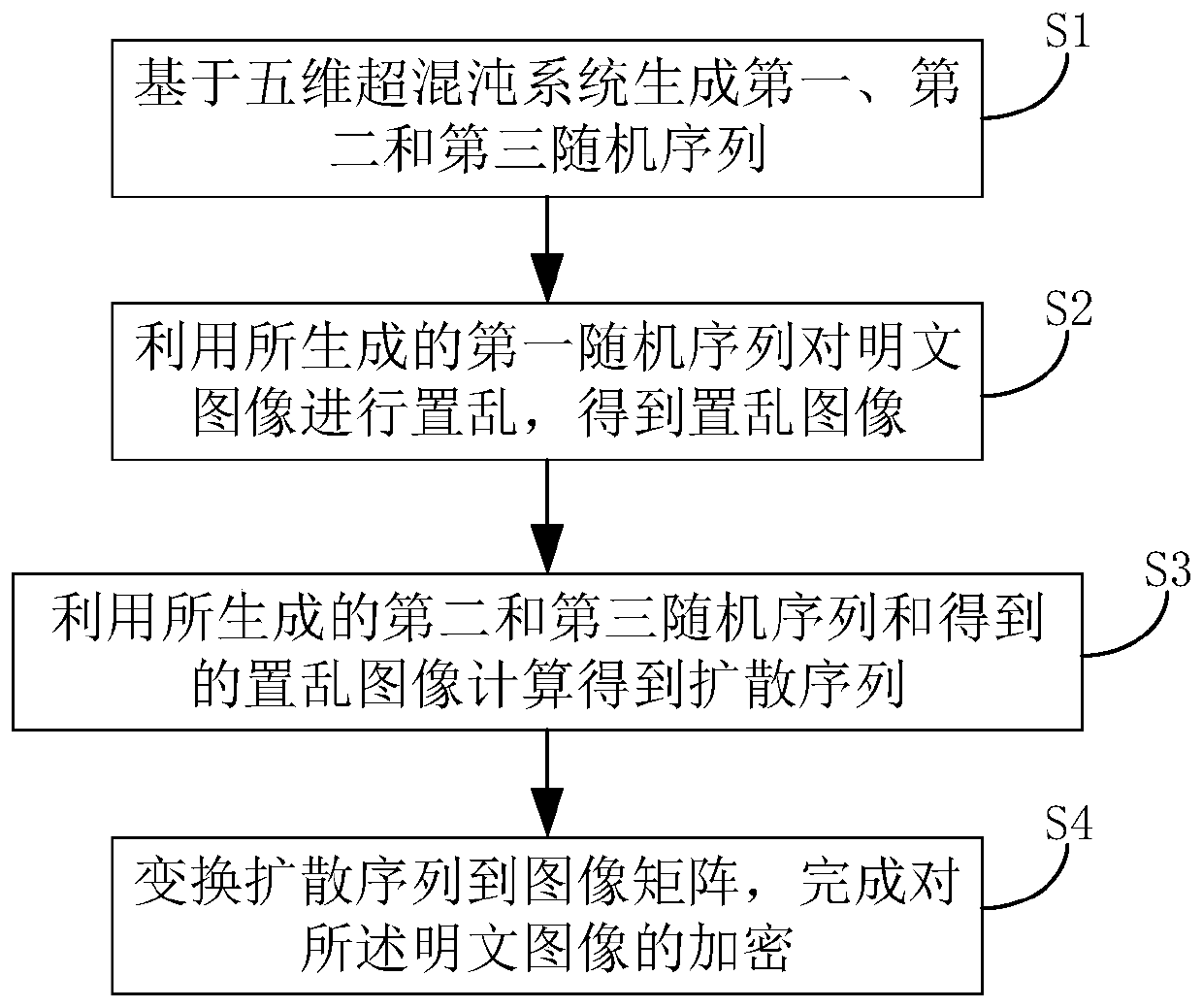
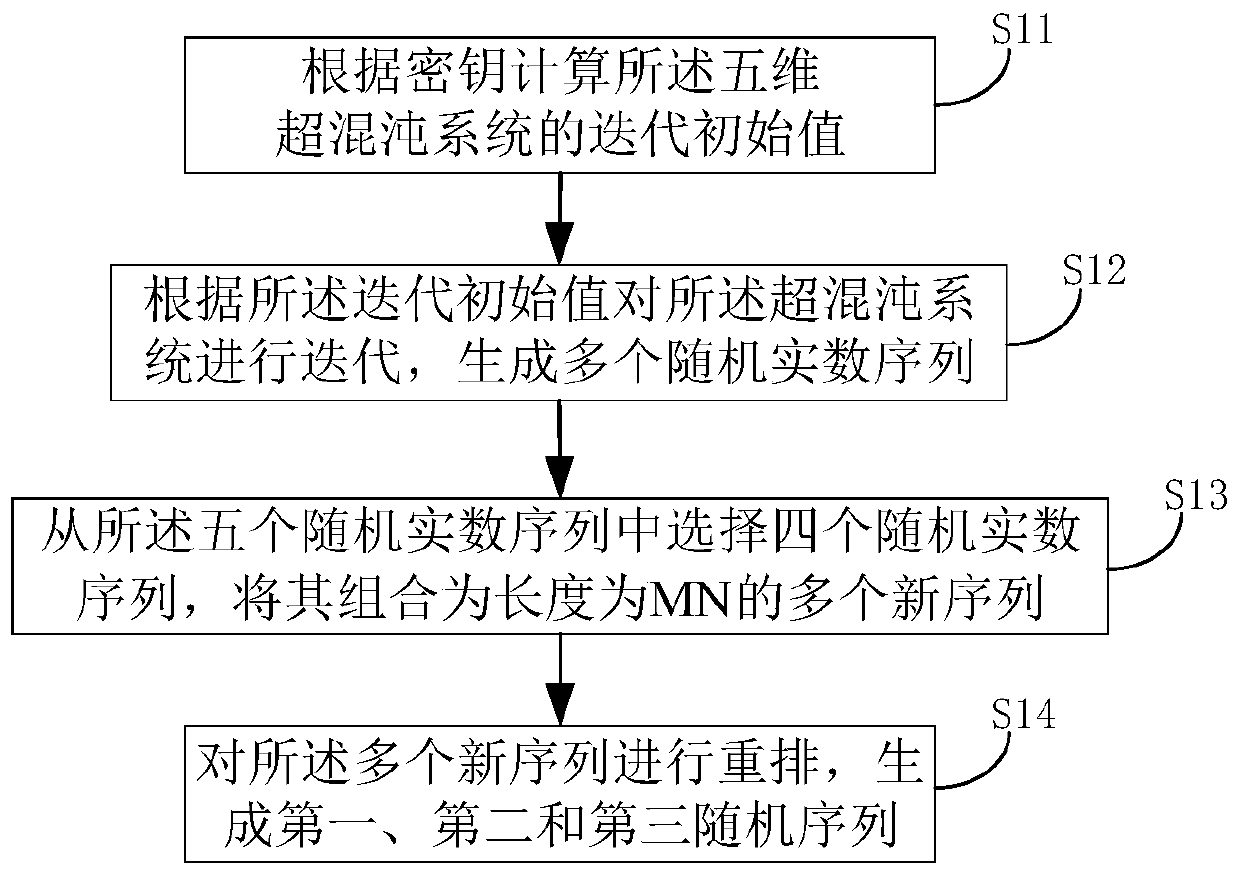
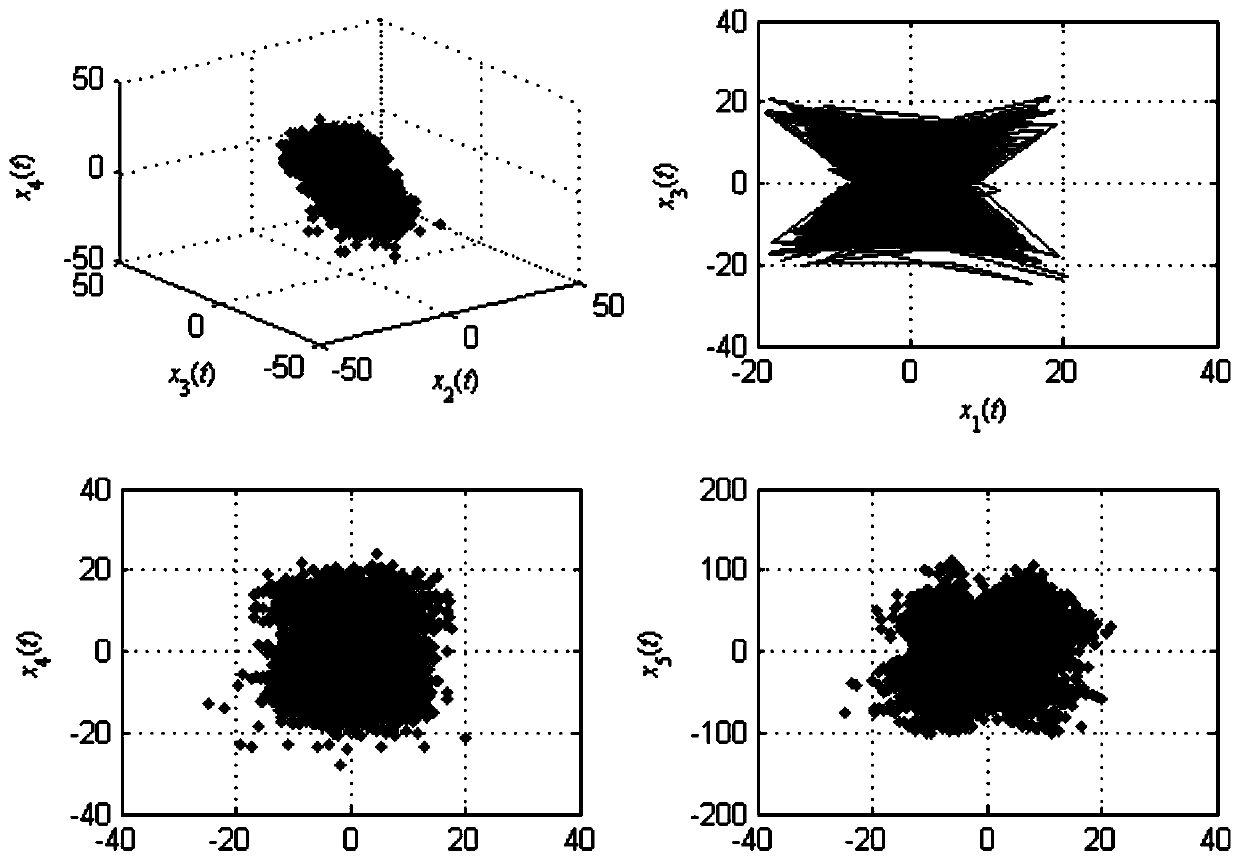
Image encryption method based on a five-dimensional hyper-chaotic system
InactiveCN109803063AImprove encryption securityImprove pseudo-randomnessSecuring communicationPictoral communicationPlaintextPattern recognition
The invention relates to an image encryption method based on a five-dimensional hyper-chaotic system. The method comprises the steps of generating a first random sequence, a second random sequence anda third random sequence based on the five-dimensional hyper-chaotic system; Scrambling the plaintext image by using the generated first random sequence to obtain a scrambled image; Calculating to obtain a diffusion sequence by using the generated second and third random sequences and the obtained scrambled image; And transforming the diffusion sequence to an image matrix to complete encryption ofthe image. According to the embodiment of the invention, based on the five-dimensional hyper-chaotic system, the pseudo-randomness of the sequence and the scrambling effect of the image are improvedthrough the new chaotic sequence generation method and the new image scrambling method, so that the image has higher encryption security.
Owner:FUQING BRANCH OF FUJIAN NORMAL UNIV
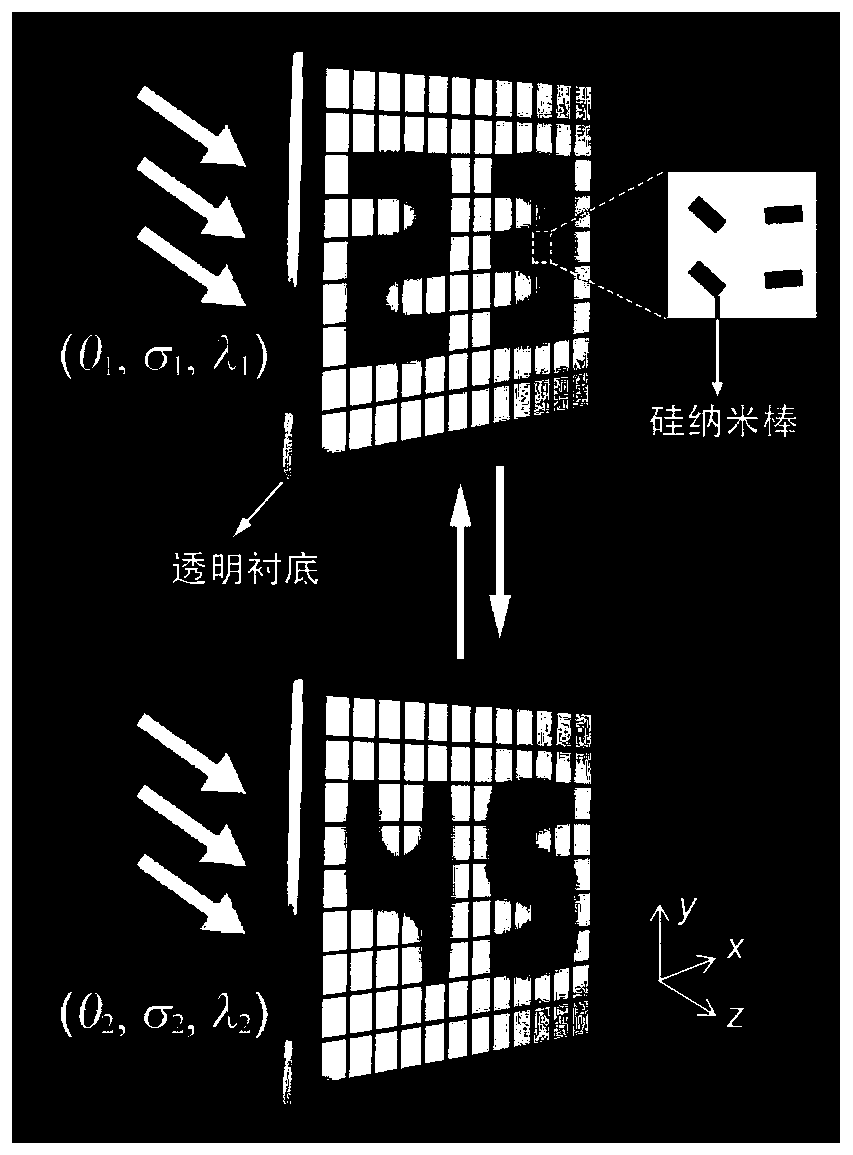
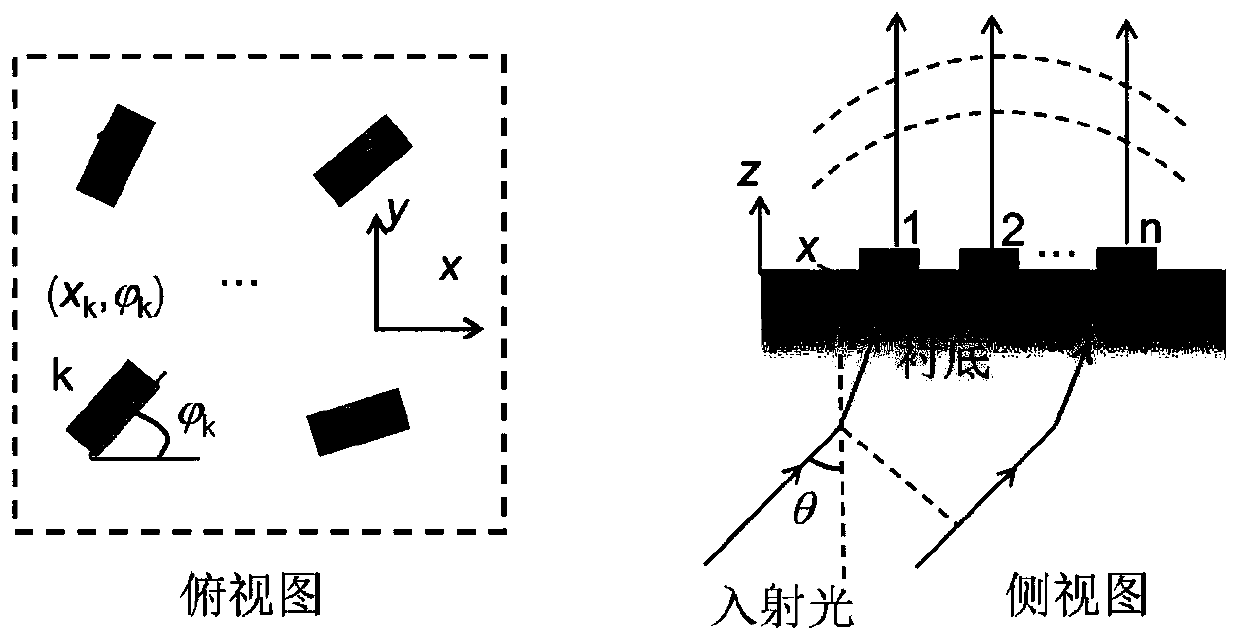
Metasurface structure design method realizing multi-dimensional optically manipulative image transformation
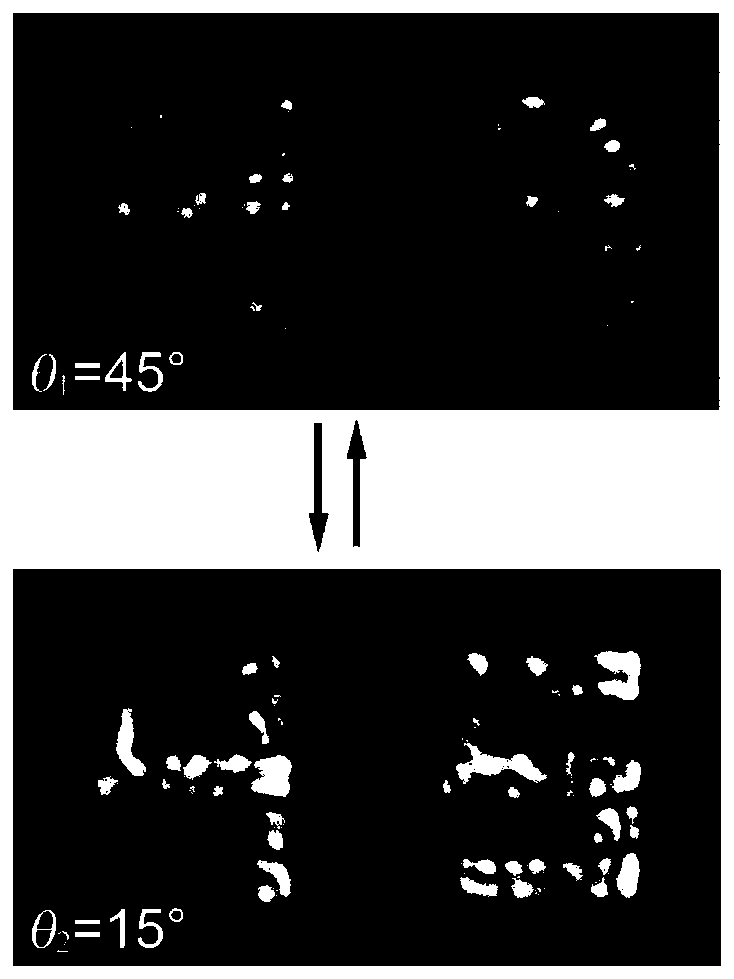
InactiveCN110133758AImplement image transformation operationsAvoid crosstalkPolarising elementsLength waveMulti dimensional
The present invention relates to the technical field of optical devices based on an artificial metasurface structure, more specifically, the invention relates to a metasurface structure design methodrealizing multi-dimensional optically manipulative image transformation. A metasurface structure composed of structural units is constructed on a transparent substrate; pixels of the metasurface structure are formed by the coherent interference among the structural units; a Jones matrix J is obtained for the structural unit with a rotation angle of phi; according to the incident light acting on the structural unit, a scattering factor of the incident light is obtained on the basis of the Jones matrix J of the structural unit; considering the pixels composed of the n structural units, when theincident light is incident on the transparent substrate at the incident angle theta, the wavelength lambda and the polarization state sigma, the intensity of the pixels of the metasurface is formed bythe coherent interference of all the structural units; and the multi-dimensional optically manipulative image transformation function of the metasurface structure is realized. The invention can realize the image transformation with any multi-dimensional optical parameters and solves the image crosstalk problem.
Owner:SUN YAT SEN UNIV
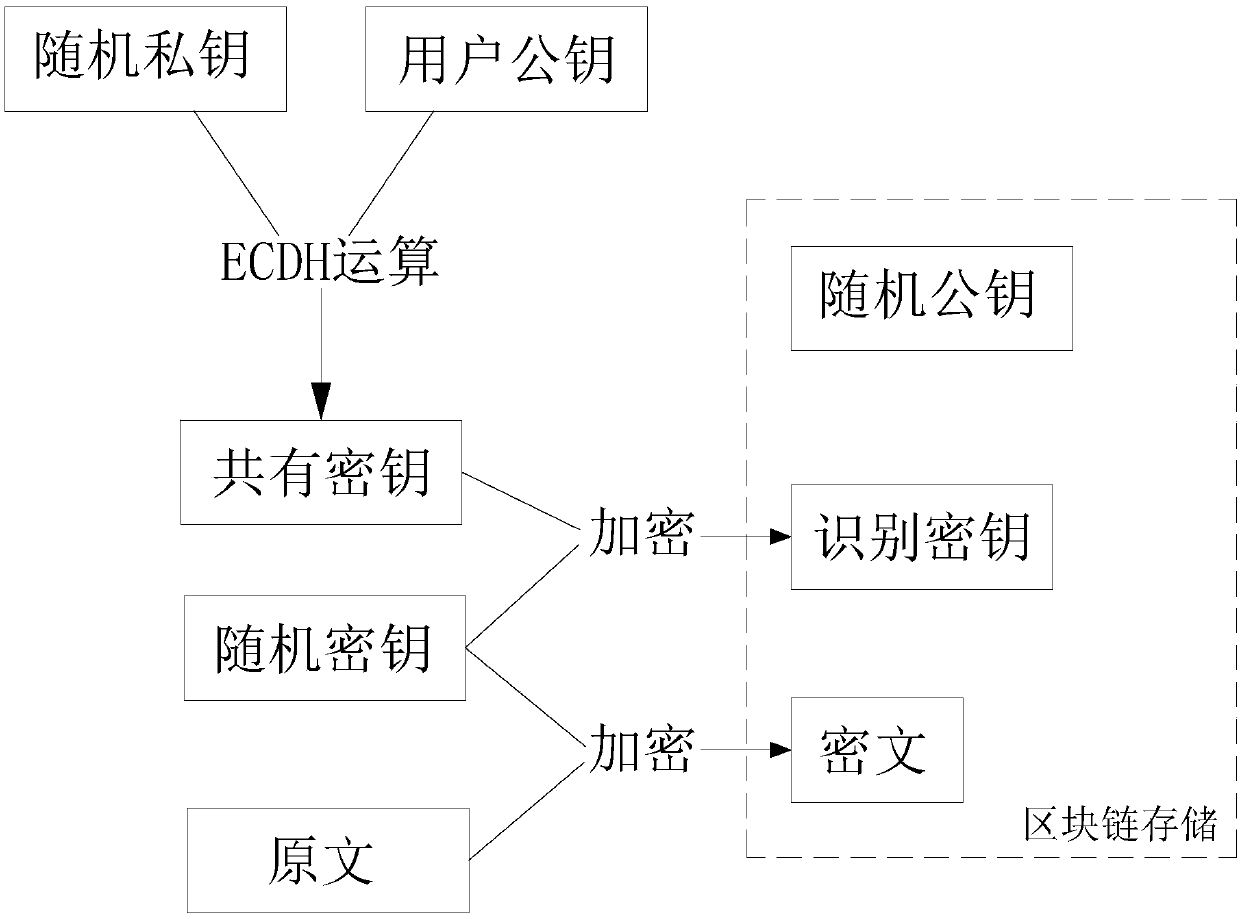
Block-chain information encryption method, decryption method, storage method and device
ActiveCN109543434AExtensive social functionsImprove encryption securityDigital data protectionBlockchainKey generation
The invention relates to a block chain information encryption method, a decryption method, a storage method and device. The block chain information encryption method is used for encrypting multi-userinteractive information. The block chain information encryption method comprises the following steps: an original encryption step of encrypting the original text by a random key to obtain a ciphertext; A key generation step of generating a pair of random public keys and a random private key, and then calculating the random private keys with more than one user public keys by using an encryption algorithm to obtain separate common keys respectively; A secondary encryption step of separately encrypting the random key through each common key to obtain a separate identification key; wherein, the user public key, the common key and the identification key are one-to-one correspondence. The invention can realize the secrecy and decryption of multi-user interactive forms such as group chat, forum,micro-blog, etc., so that more extensive social function can be realized on the block chain, high encryption security can be achieved, and good user experience can be maintained at the same time.
Owner:深圳市墨者安全科技有限公司
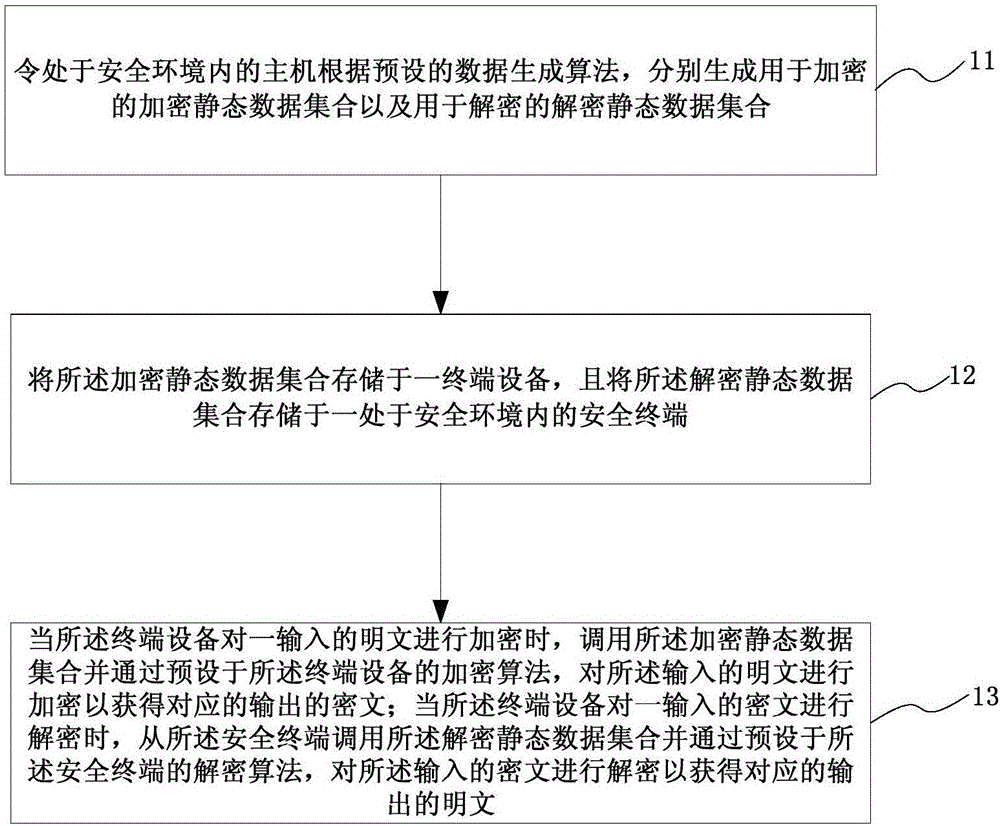
Safety operation method and system based on white box encryption
ActiveCN106603224ASmall static data volumeImprove operational efficiencyEncryption apparatus with shift registers/memoriesEncryptionStatic data
The invention provides a safety operation method and system based on white box encryption. The corresponding encryption algorithm and the decryption algorithm are matched by employing a series of static data as fixed input, lightweight safety operation can be realized, the volume of the static data is small, the operation efficiency is high, and relatively high encryption security can be obtained in a white box attack environment with limited calculating resources.
Owner:TONGJI UNIV
Voice communication information source encryption system for mobile terminal
InactiveCN107786574AImplement encryptionPrevent intrusionTransmissionSecurity arrangementModem deviceVoice communication
The invention discloses a voice communication information source encryption system for a mobile terminal, comprising an analog-digital converter and a data encryption and decryption and phonological modem, wherein the analog-digital converter is used for converting an audio analog signal generated by a voice collector into voice data, or used for converting the audio data undergoing phonological encoding into an audio analog signal; the data encryption and decryption and phonological modem comprises a voice digital coding and decoding module, a security kernel module and a phonological modulation and demodulation module, wherein the voice digital coding and decoding module is used for performing digital voice compression on the converted audio data, the security kernel module is used for performing digital hardware encryption on the audio data subjected to digital voice compression, and the phonological modulation and demodulation module is used for performing phonological encoding onthe audio data subjected to digital hardware encryption. According to the invention, under the condition of not changing the voice communication procedure of the existing mobile terminal, voice communication information source encryption of the mobile terminal is realized, the encryption security is high, and the applicability is wide.
Owner:河南芯盾网安科技发展有限公司
Attack verification and protection method and device for SM2 signature algorithm
ActiveCN109600232AImprove encryption securityKey distribution for secure communicationUser identity/authority verificationValidation methodsInjection attacks
The invention discloses an attack verification and protection method and device for an SM2 signature algorithm. According to the attack verification method, an error injection attack is carried out atan addition position of an SM2 signature algorithm, and the protection method protects an addition and subtraction process in which a random number k participates. The attack verification device forthe SM2 signature algorithm comprises an attack module, and a protection device for the SM2 signature algorithm comprises a protection module. The invention discovers that the protection measures in the prior art ignore the protection of the random number k when s is calculated, regardless of the original formula k-r*dA, or a deformed r + k, an addition and subtraction process in which a random number k participates exists. The existing protection technology does not protect this, so that the existing SM2 encryption algorithm has certain risk vulnerabilities, and the protection method providedby the invention can effectively resist corresponding attack means and prevent information leakage.
Owner:北京智慧云测科技有限公司 +1
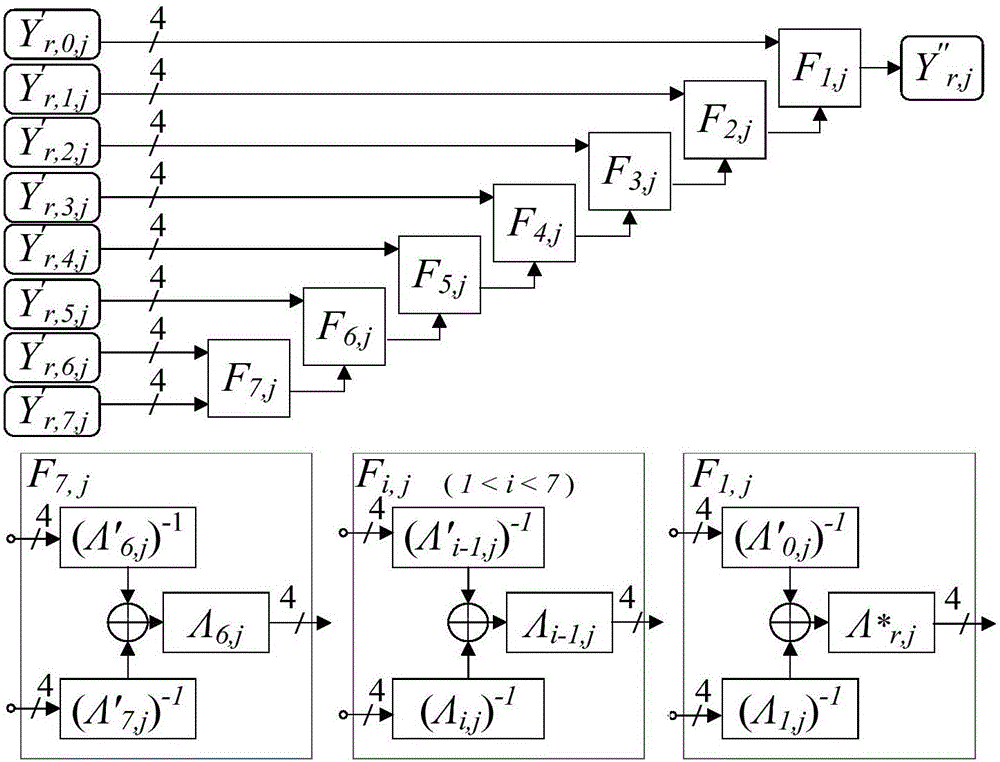
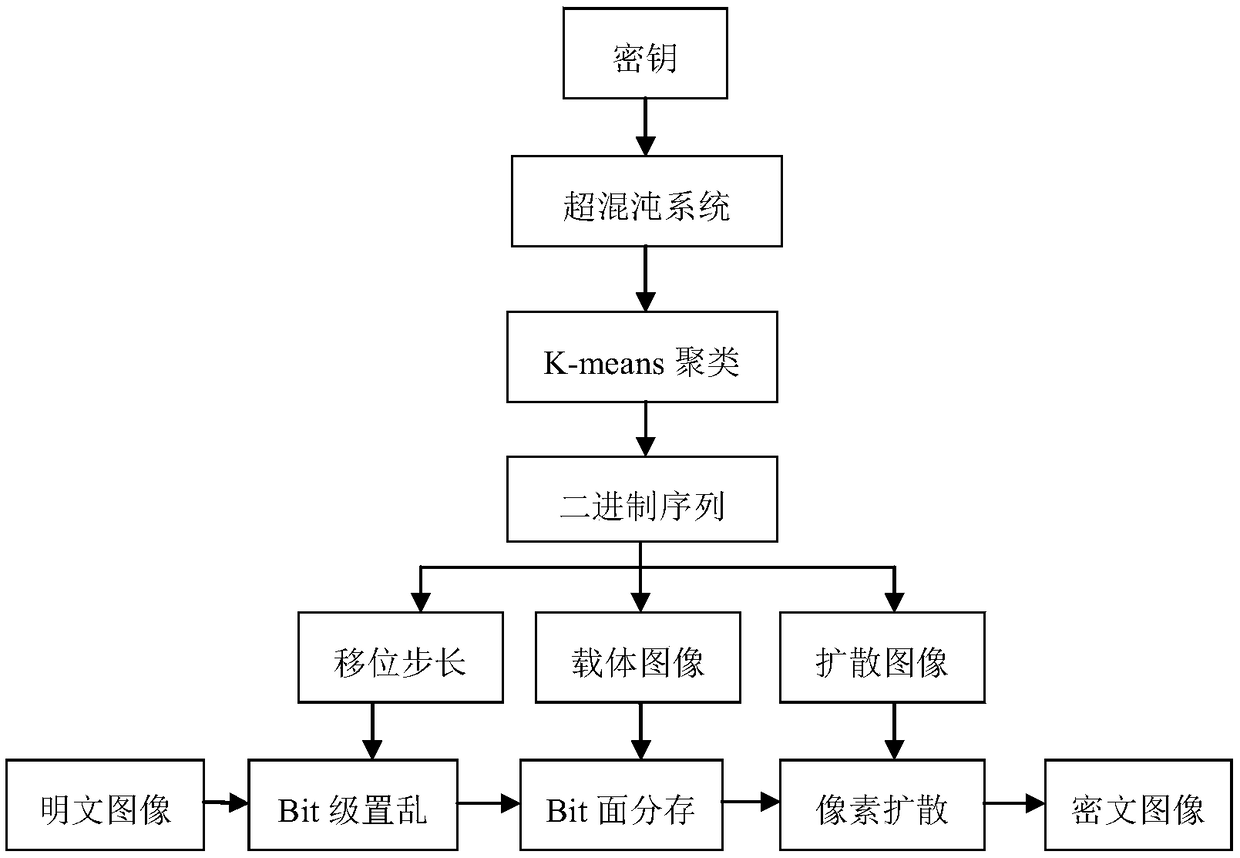
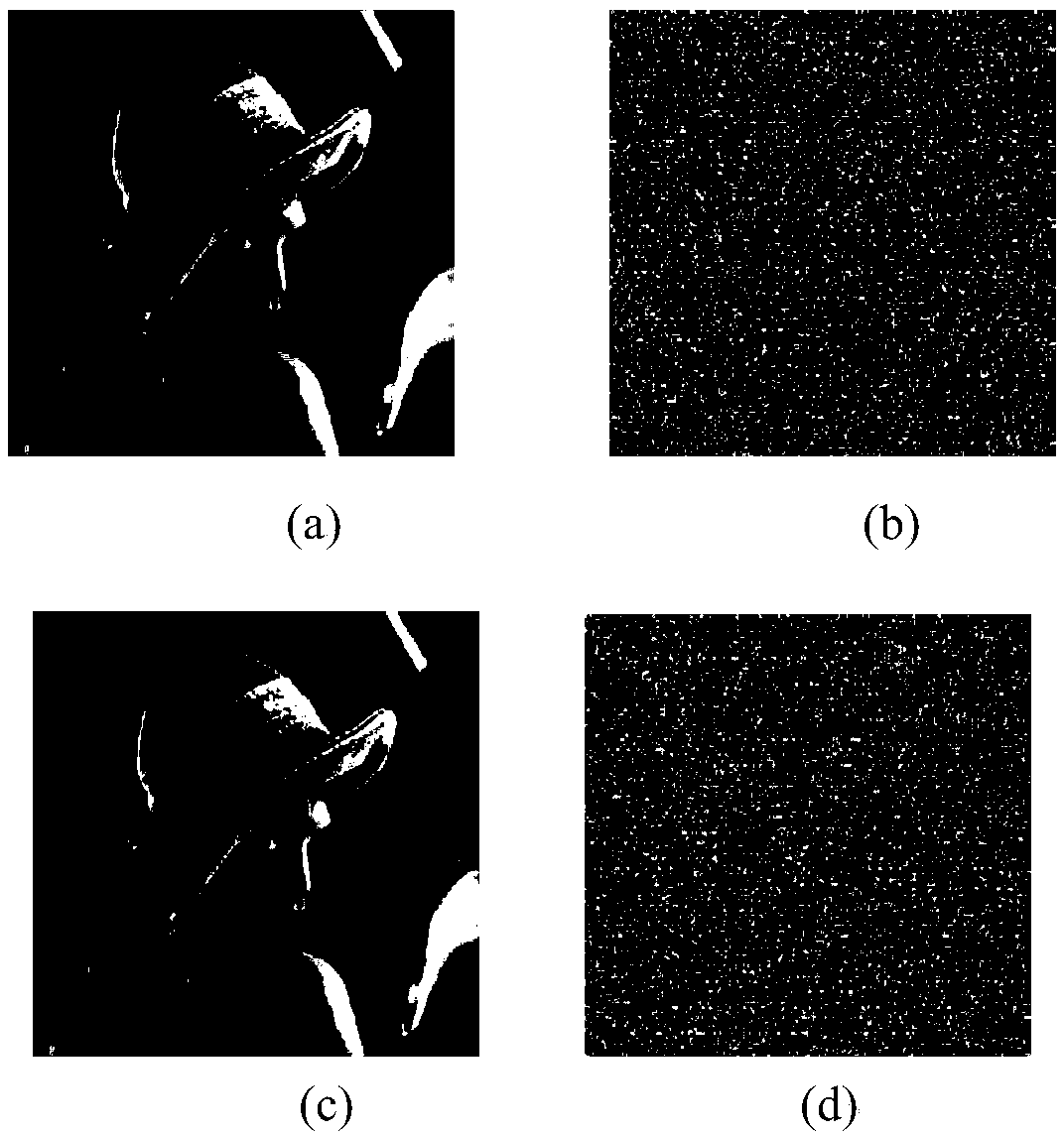
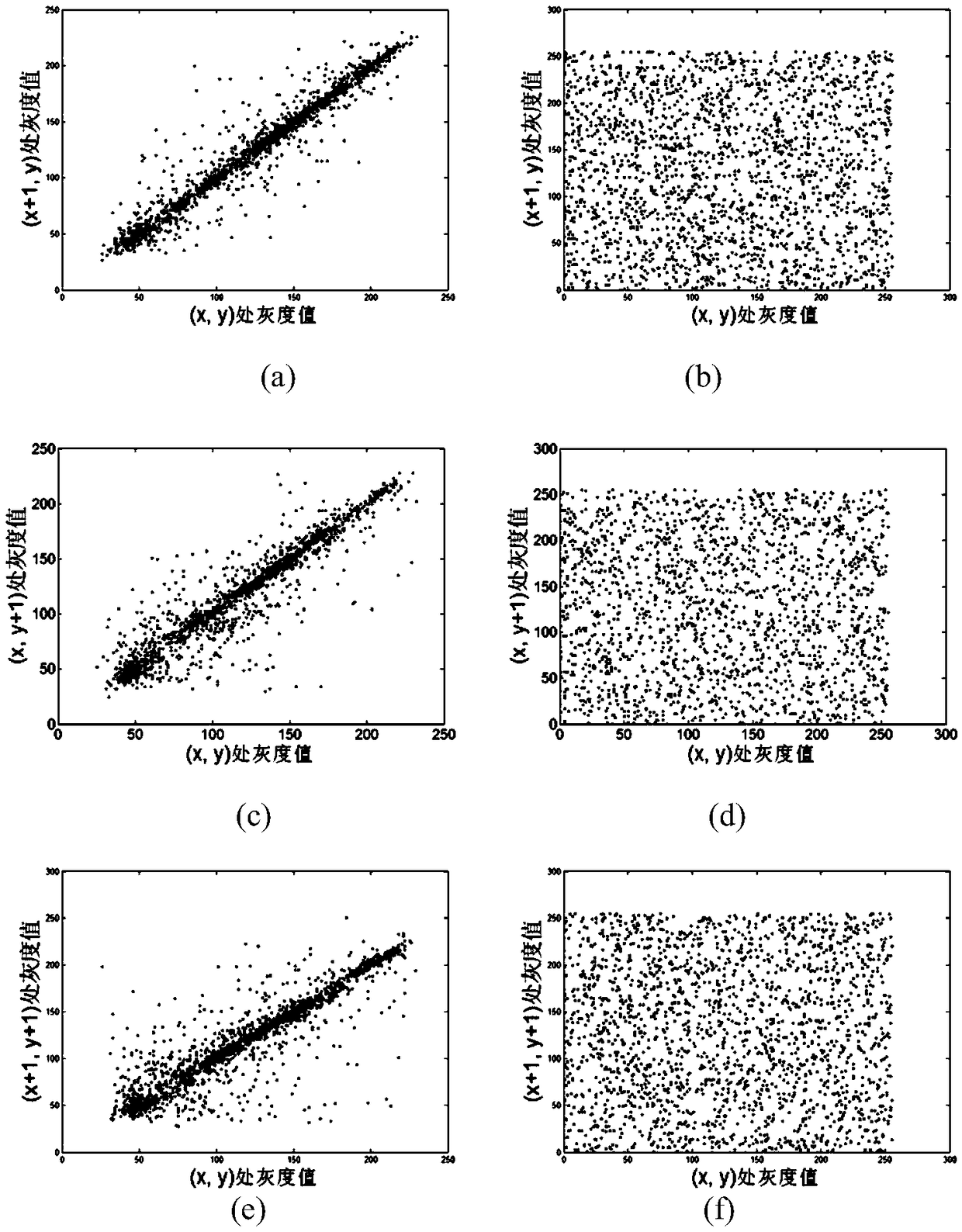
An image encryption method based on four-dimensional Chen's hyperchaotic system and K-means clustering
ActiveCN109376793AGood pseudorandomnessImprove performanceCharacter and pattern recognitionDigital data protectionImaging processingCiphertext
The invention relates to the field of image processing, in particular to an image encryption method based on four-dimensional Chen's hyperchaotic system and K-means clustering. The invention adopts high-dimensional continuous hyperchaotic system-four-dimensional Chen's system to generate chaotic sequence, ensures that the algorithm has larger key space, and adopts K-Means clustering algorithm is used to process the chaotic sequences generated by Chen's system, and the binary sequences with good pseudo-random performance are obtained (through US NIST statistical test). Secondly, according to the property of bit-plane decomposition of plaintext image, an efficient scrambling algorithm is designed, and an intermediate result sharing link is added between scrambling and spreading to improve the encryption security. Finally, the traditional linear diffusion function is improved and the diffusion matrix generated by the pseudo-random binary sequence is used to perform linear bidirectional diffusion on the pixels of the initial ciphertext, which further improves the performance of the system against the attack of differential analysis.
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY
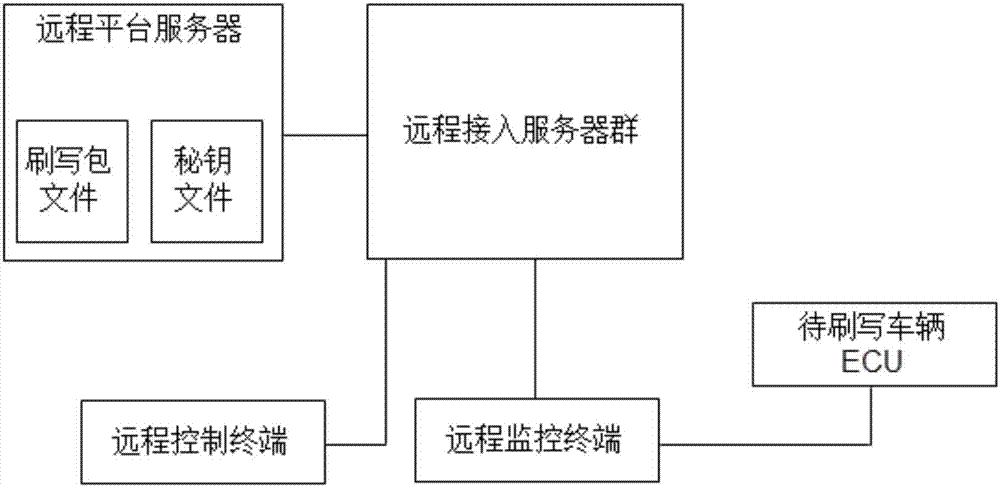
Vehicle ECU file safe writing method and system
ActiveCN107273749ARealize dynamic encryptionImprove securityDigital data protectionPlatform integrity maintainanceRemote controlComputer terminal
The invention relates to a vehicle ECU file safe writing method. A remote platform server is used for seeking a to-be-wrote vehicle and sending a writing package file and a secret key file to a remote monitoring terminal, real-time checking is conducted on the writing package file and the secret key file stored in the remote monitoring terminal in real time before writing and during writing, and a writing control command is sent through a remote control terminal. The invention further provides a vehicle ECU file safe writing system based on the method, the system includes the remote monitoring terminal connected with an ECU of the to-be-wrote vehicle, the remote monitoring terminal is connected with the remote platform server through a remote access server cluster, and the remote access server cluster is connected with the remote control terminal. According to the method and the system, safe and reliable ECU file writing is conducted on vehicles in batch in a remote environment, the situation that the vehicles are centralized to one place for writing is avoided at the same time, and a large amount of manpower and financial resources are saved for after-sale maintenance of vehicle factories and suppliers.
Owner:WUHAN INTEST ELECTRONICS TECH
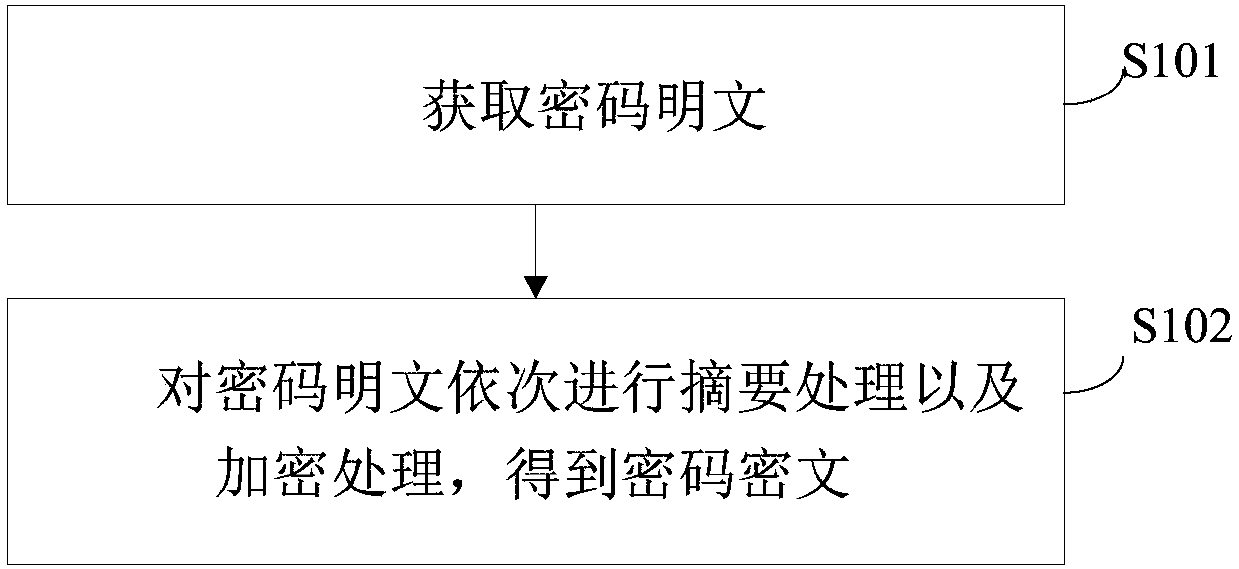
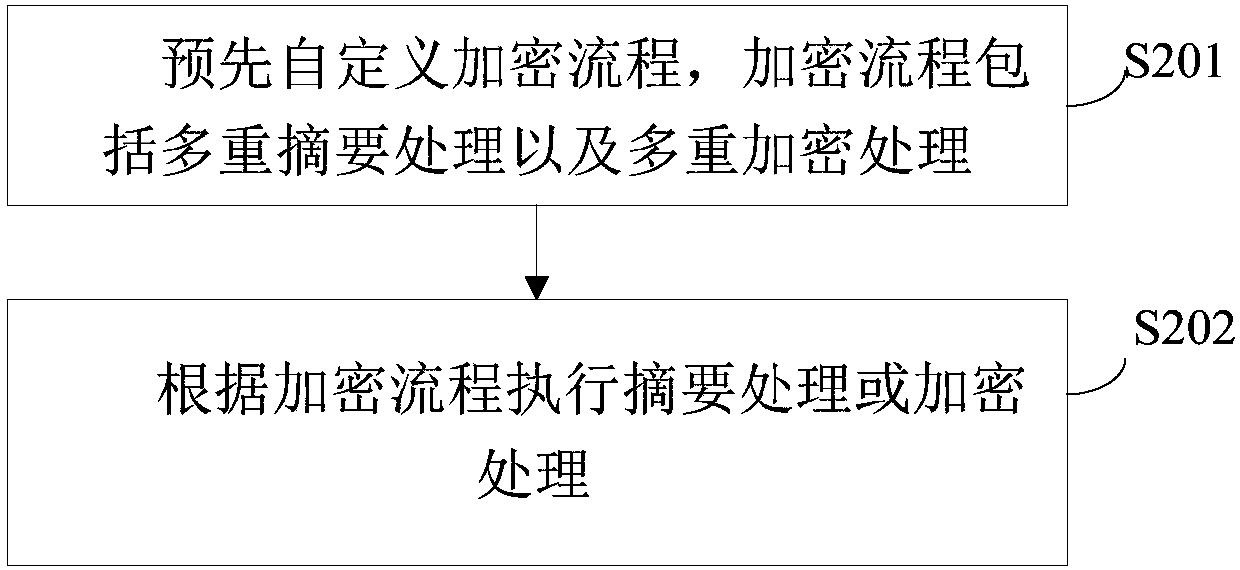
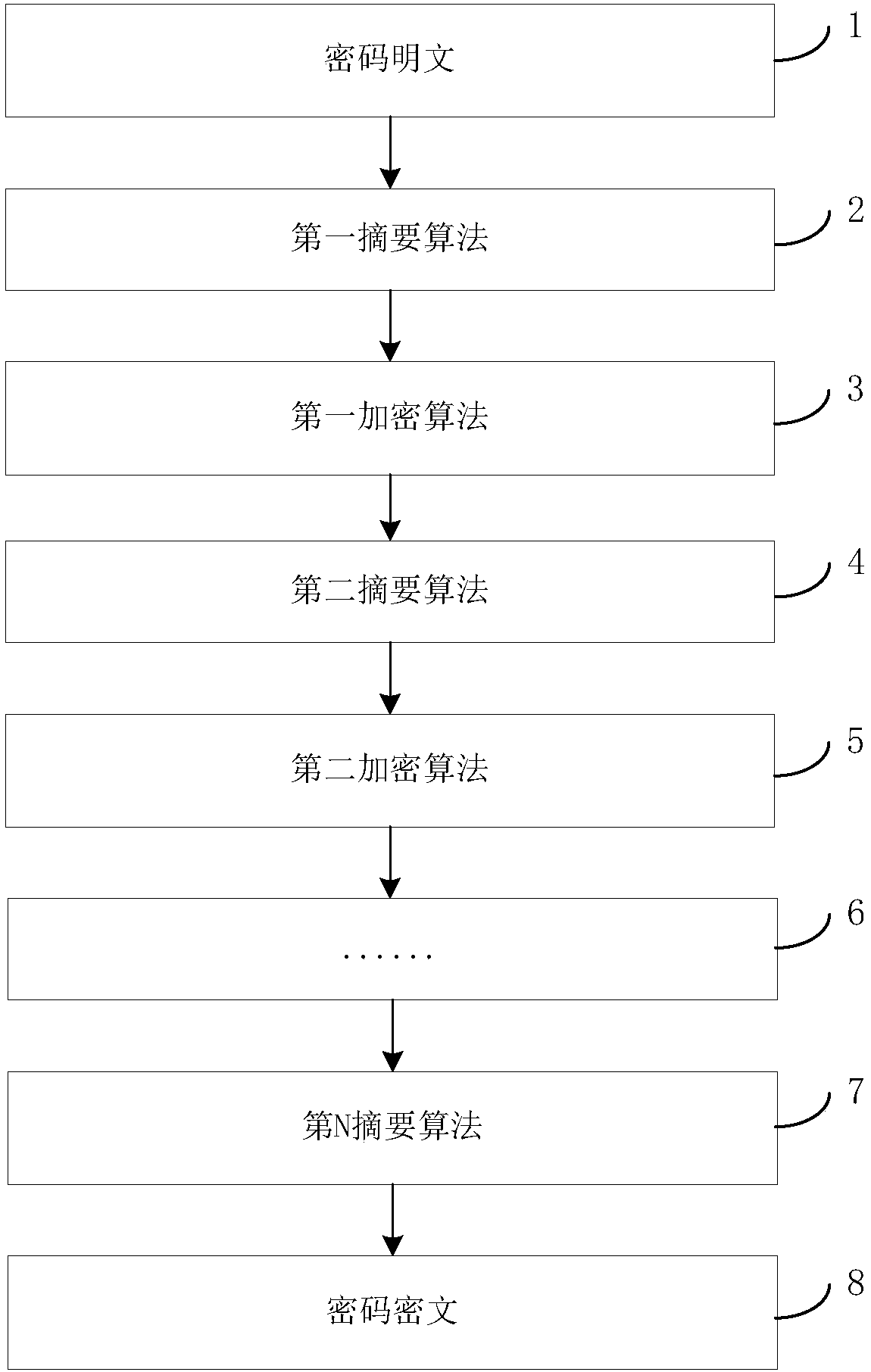
Security encryption method and system
InactiveCN107563211AImprove encryption securityDigital data protectionDigital data authenticationPlaintextPassword
The invention provides a security encryption method and system, and relates to the technical field of encryption. The method includes the steps that a password plaintext is acquired; abstract processing and encryption processing are conducted on the password plaintext according to a preset rule, and a password ciphertext is obtained. The encryption safety is improved through a self-defined multi-abstract algorithm and an encryption algorithm.
Owner:LOTUS TECH BEIJING CO LTD
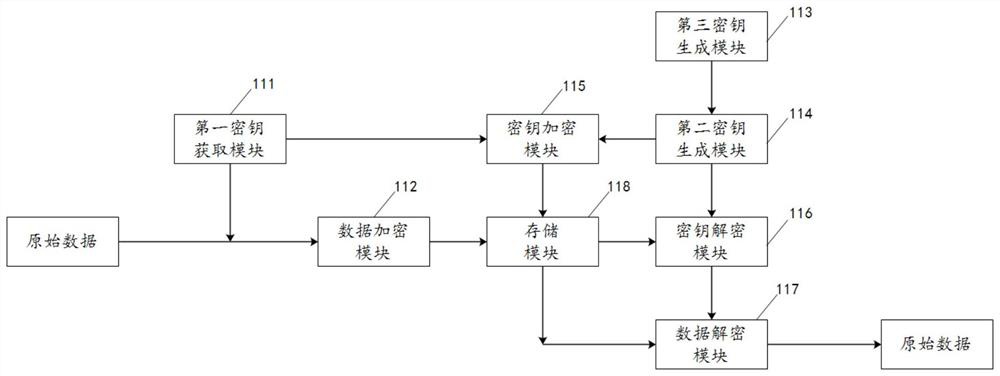
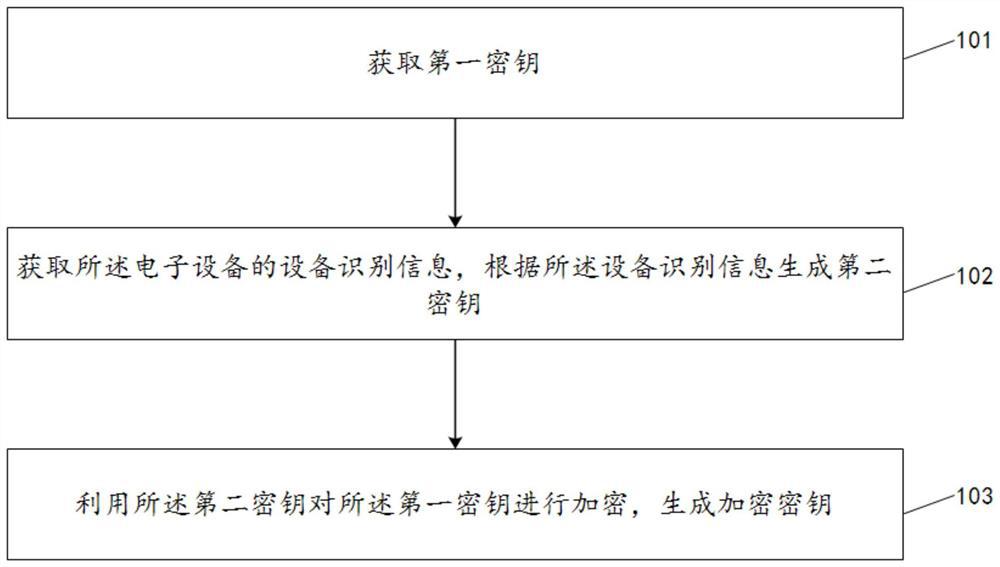
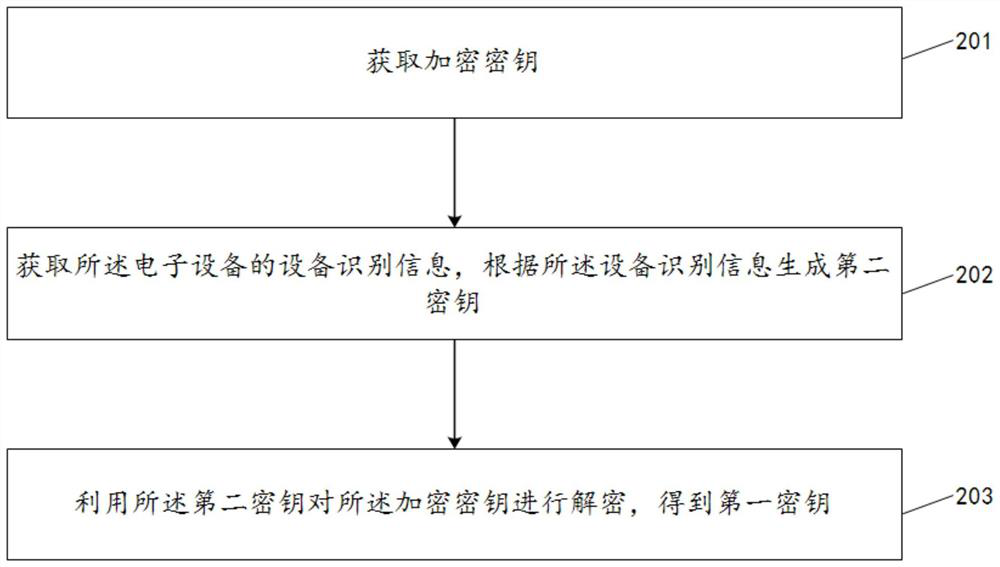
Key encryption method, key decryption method, data encryption method and data decryption method
PendingCN112953707AEnsure safetyImprove encryption securityKey distribution for secure communicationUser identity/authority verificationEngineeringData decryption
The invention discloses a key encryption method, a key decryption method, a data encryption method and a data decryption method. The key encryption method comprises the following steps: acquiring a first key and equipment identification information of the electronic equipment, generating a second key according to the equipment identification information, encrypting the first key by using the second key, and generating an encrypted key. In the embodiment of the invention, the first key is encrypted by using the equipment identification information, so that the security of the first key can be effectively ensured, and the security of data encryption is improved; and meanwhile, the first key is encrypted by using the equipment identification information, and the encryption security of the first key is greatly improved based on the uniqueness of the equipment identification information.
Owner:ZTE CORP
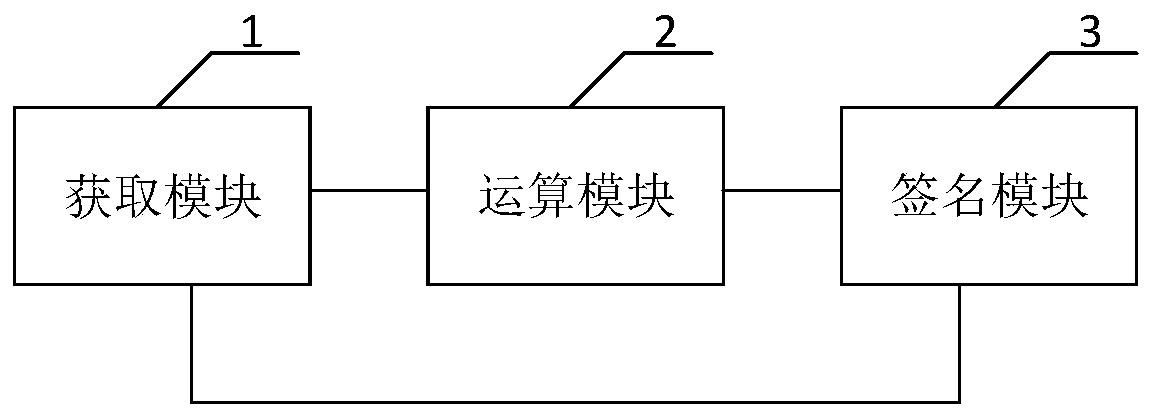
Data signature method, system and device
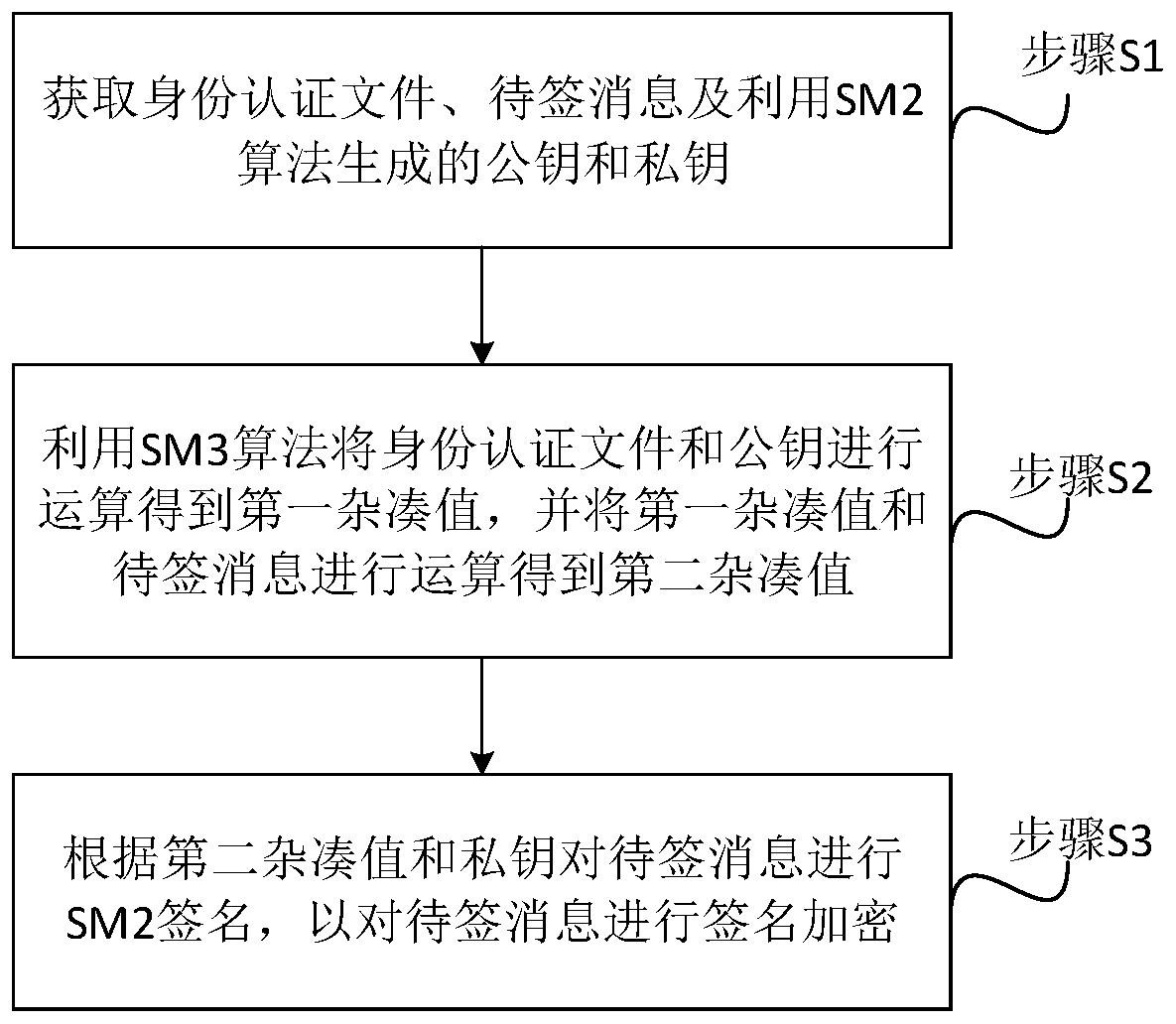
ActiveCN110932868AImprove encryption securityDifficult to solvePublic key for secure communicationUser identity/authority verificationTheoretical computer scienceAuthentication
The invention discloses a data signature method. Firstly, an identity authentication file, a to-be-signed message and a public key and a private key which are generated by utilizing an SM2 algorithm are acquired; the identity authentication file and the public key are operated through an SM3 algorithm to obtain a first hash value, the first hash value and the to-be-signed message are operated to obtain a second hash value, and finally SM2 signature is conducted on the to-be-signed message according to the second hash value and the private key so that signature encryption can be conducted on the to-be-signed message. Visibly, the signature encryption of the to-be-signed message is realized by adopting multiple operations of the SM2 algorithm and the SM3 algorithm, and the solving difficultyof the algorithm is relatively high, so that the data encryption security is improved. The invention further discloses a data signature system and device which have the same beneficial effects as thedata signature method.
Owner:INSPUR BUSINESS MACHINE CO LTD
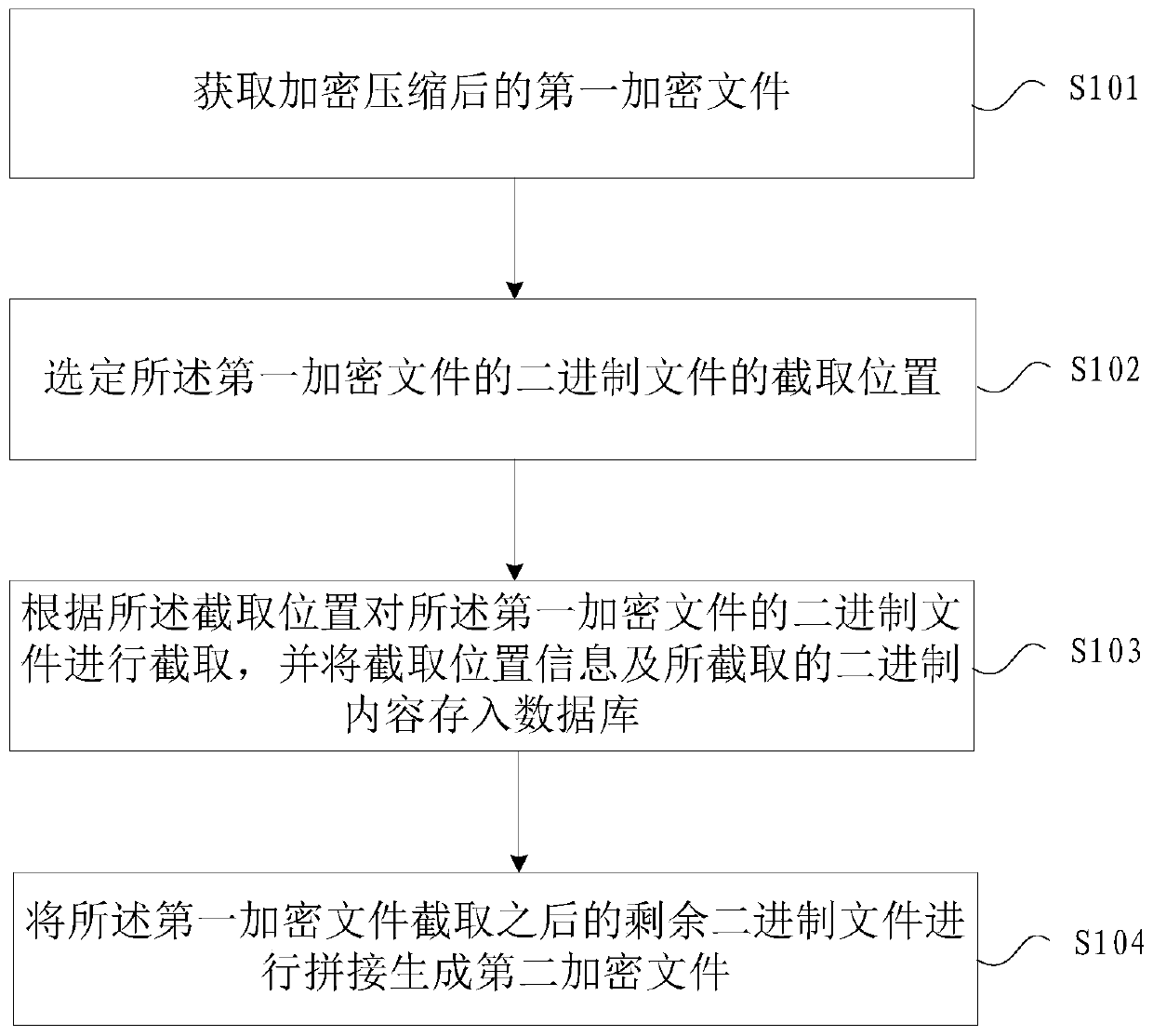
File encryption method and device
PendingCN111552938AFix security issuesSolve complexityDigital data protectionDigital data authenticationEncryptionData library
Embodiments of the invention provide a file encryption method and device. The method comprises the steps of obtaining an encrypted and compressed first encrypted file; selecting an interception position of a binary file of the first encrypted file; intercepting a binary file of the first encrypted file according to the interception position, and storing interception position information and intercepted binary content into a database; and splicing the remaining binary files after the first encrypted file is intercepted to generate a second encrypted file. According to the embodiment of the invention, the binary file of the first encrypted file is subjected to position interception and storage, so that the problem of relatively low file encryption security in related technologies can be solved, and the effect of improving the security of the encrypted file is achieved.
Owner:SHANGHAI MININGLAMP ARTIFICIAL INTELLIGENCE GRP CO LTD
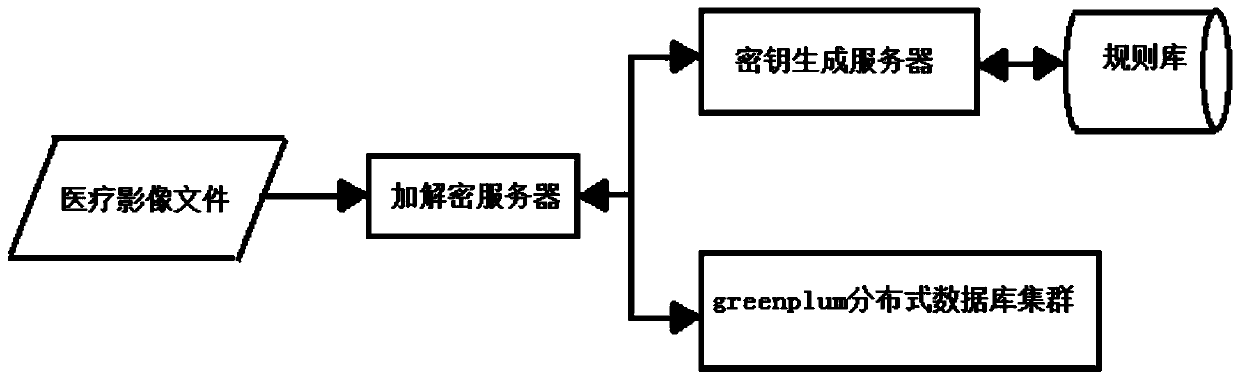
Medical image file segmentation encryption and decryption system and method based on greenplum
InactiveCN110990877AImprove reliabilityImprove encryption securityDigital data protectionMedical imagesKey storageKey generation
The invention discloses a medical image file segmentation encryption and decryption system and method based on greenplum and relates to the technical field of computers. The medical image file segmentation encryption and decryption system comprises an encryption and decryption server used for encrypting or decrypting a received medical image file; a rule base used for storing a secret key generation rule and a segmentation ID generation rule; a key generation server used for generating a key and a segment ID according to metadata information given by the encryption and decryption server and the key generation rule and the segment ID generation rule obtained from the rule base and returning the key and the segment ID to the encryption and decryption server; a greenplum distributed databasecluster used for storing the generated secret key and the segment ID. According to the invention, sensitive information in the medical image file is encrypted in a segmented manner by utilizing a datasegmented encryption means based on the segmented ID, and only the sensitive information in the medical image file is encrypted instead of the whole file, so that the encryption and decryption efficiency can be improved, and meanwhile, the encryption security of the medical image file and the reliability of key storage are improved.
Owner:中电健康云科技有限公司
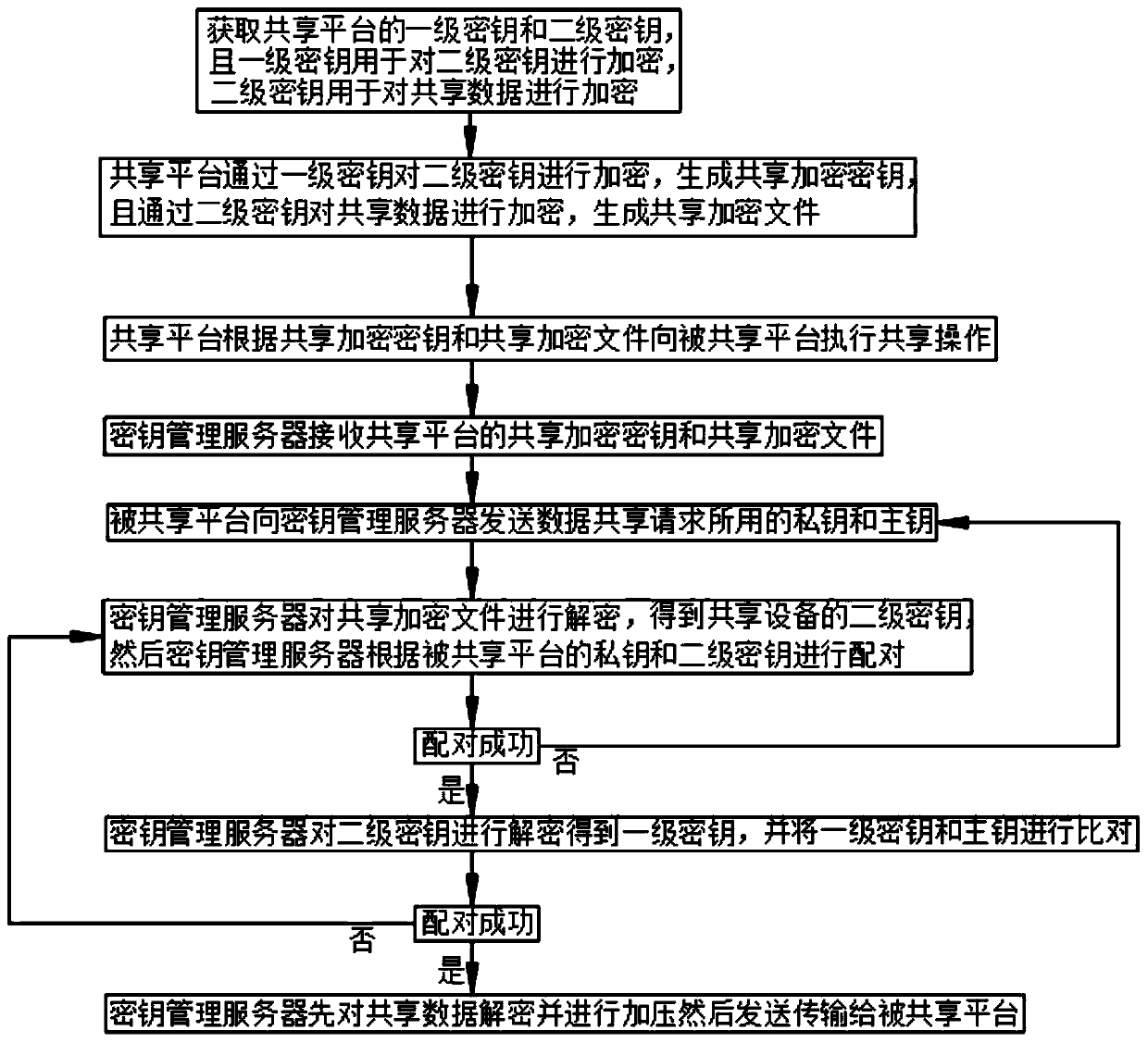
Method for realizing data cross-platform sharing by configuring key pair
ActiveCN111342961AImprove securityImprove user experienceKey distribution for secure communicationEngineeringData sharing
The invention discloses a method for realizing data cross-platform sharing by configuring a key pair in the technical field of data cross-platform sharing. The sharing platform encrypts the second-level key through the first-level key, generates a shared encryption key, encrypts the shared data through the secondary key, and generates shared encrypted files; the shared platform sends a private keyand a main key used by the data sharing request to the key management server; the private key of the shared platform are paired with the secondary key by the key management server; the key managementserver decrypts the second-level key to obtain a first-level key, compares the first-level secret key with the main key; and if not, the key management server decrypts the shared data, compresses thedecrypted shared data and then transmits the compressed shared data to the shared platform, so that different platforms realize cross-platform data sharing of the shared data by configuring key pairs, mutual independence of data sharing among different platforms can be ensured, and relatively high data sharing security is achieved.
Owner:贵州弈趣云创科技有限公司
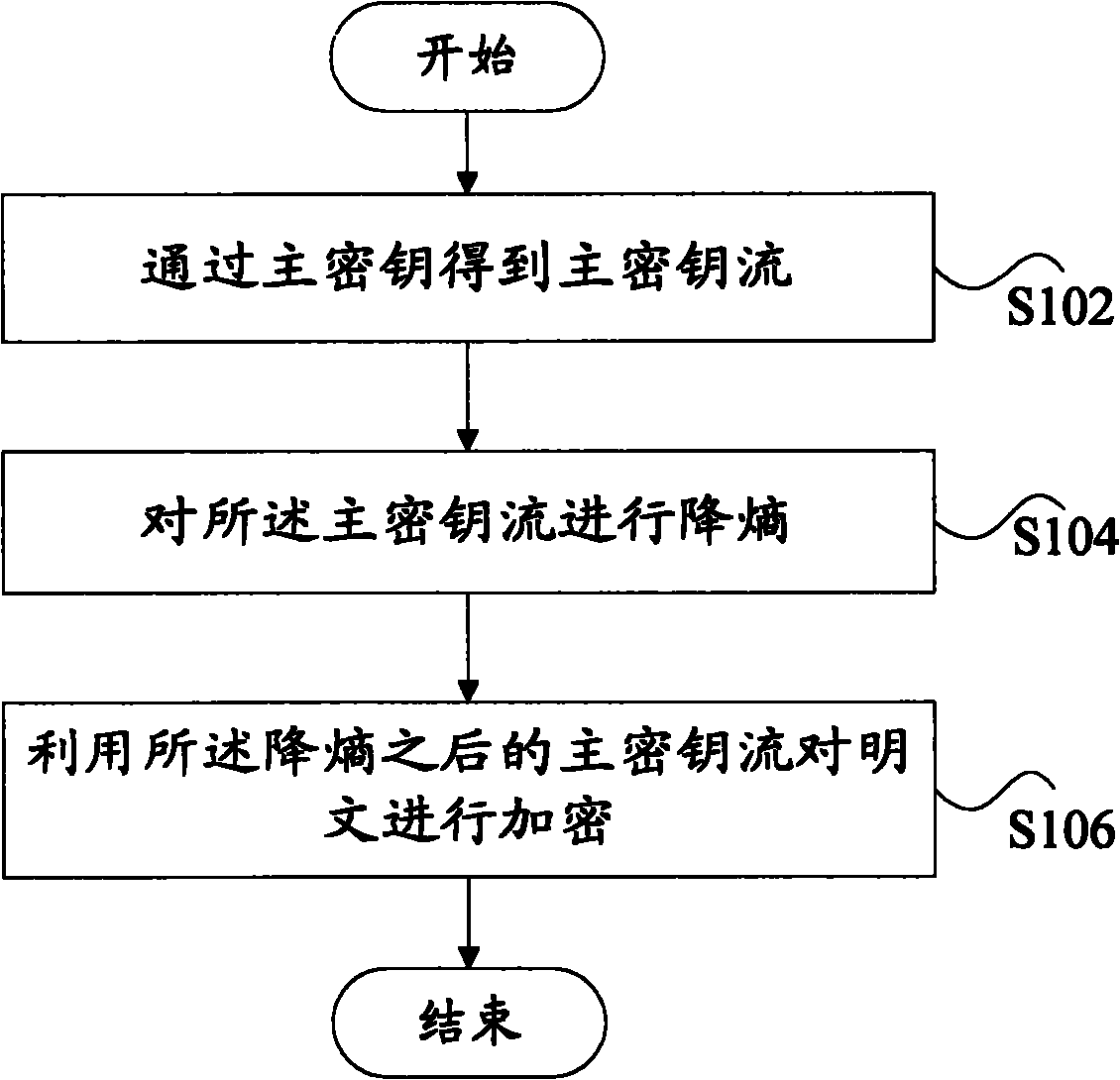
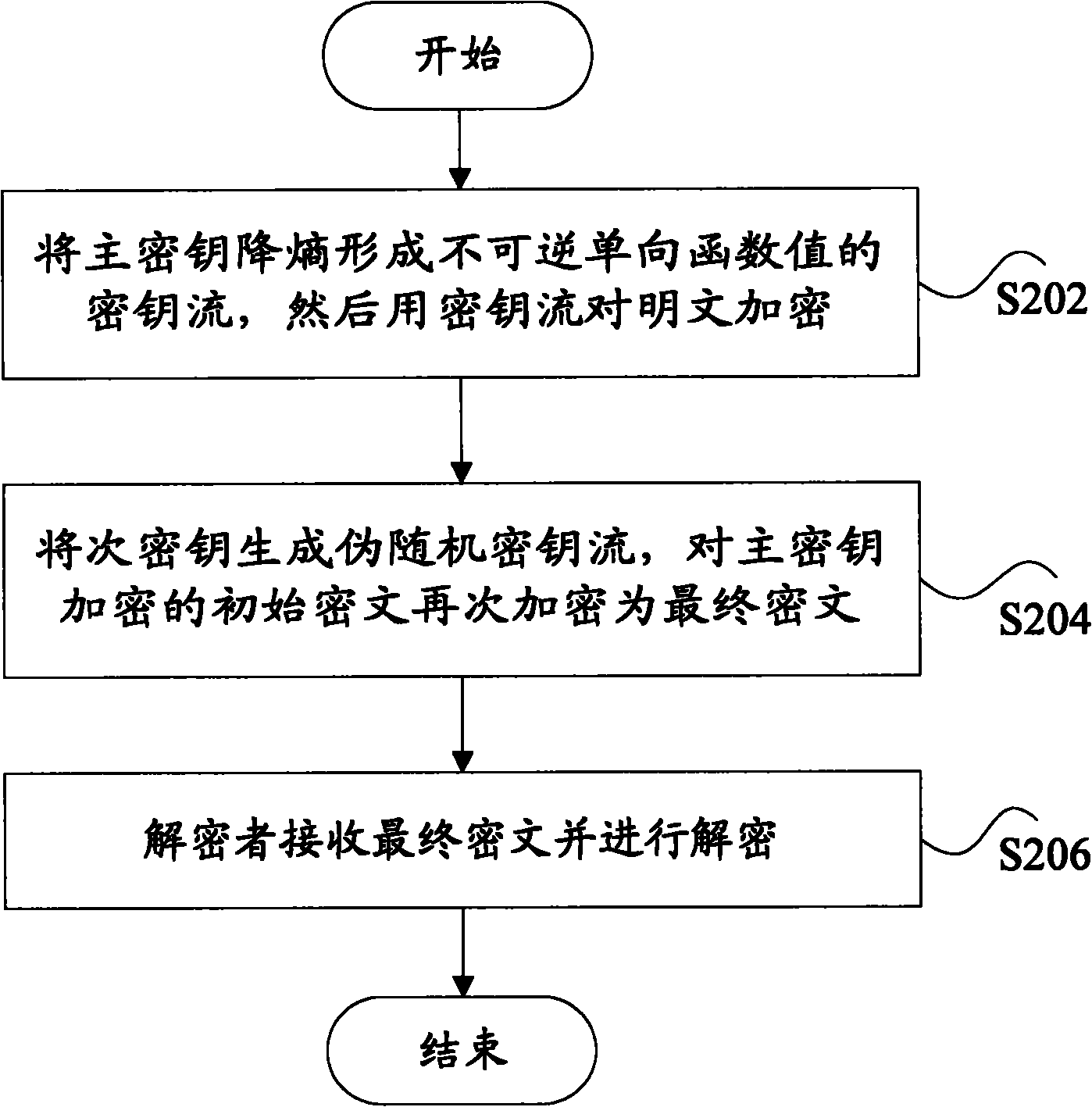
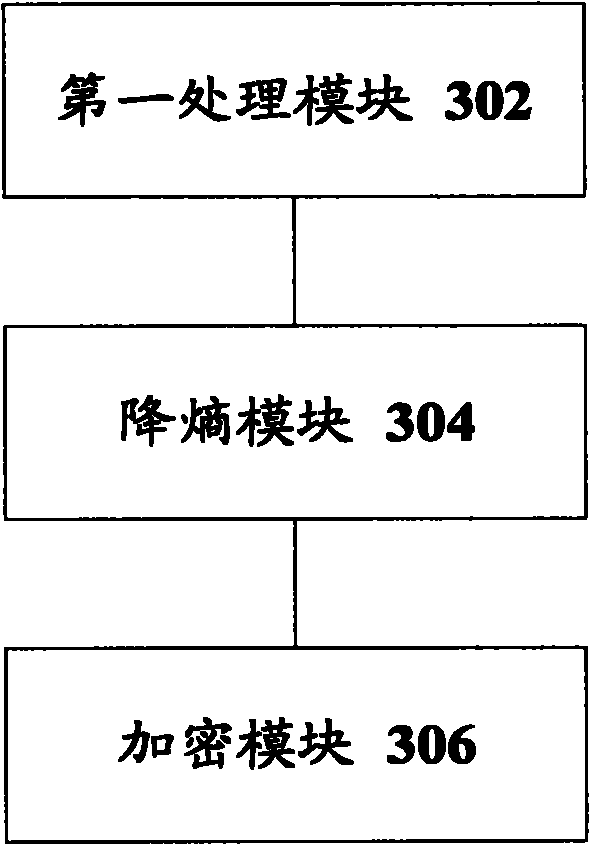
Encrypting method and device
InactiveCN102377562ASolve the problem of insufficient securityImprove encryption securityKey distribution for secure communicationEntropy reductionPlaintext
The invention discloses an encrypting method and an encrypting device. The encrypting method comprises the following steps of: acquiring a master key stream through a master key; performing entropy reduction on the master key stream; and encrypting a plain text by using the master key stream subjected to the entropy reduction. By the encrypting method and the encrypting device, the encrypting safety can be improved.
Owner:程碧波
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com