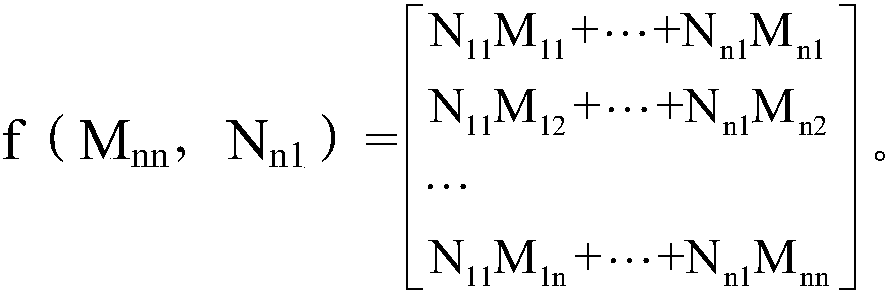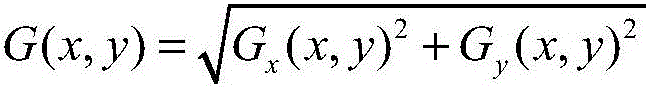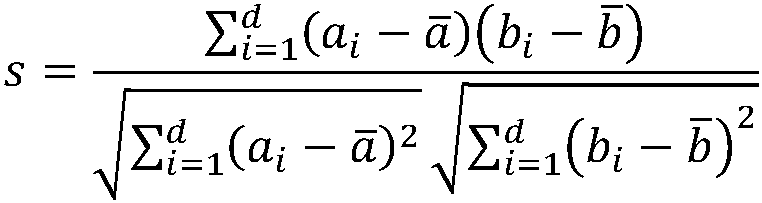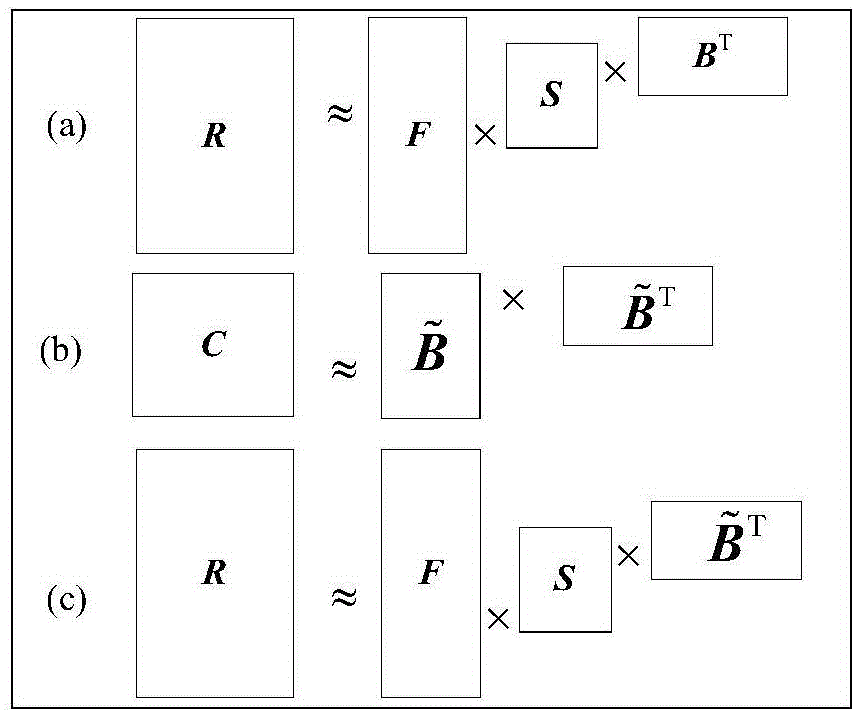Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
182 results about "Symmetric matrix" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
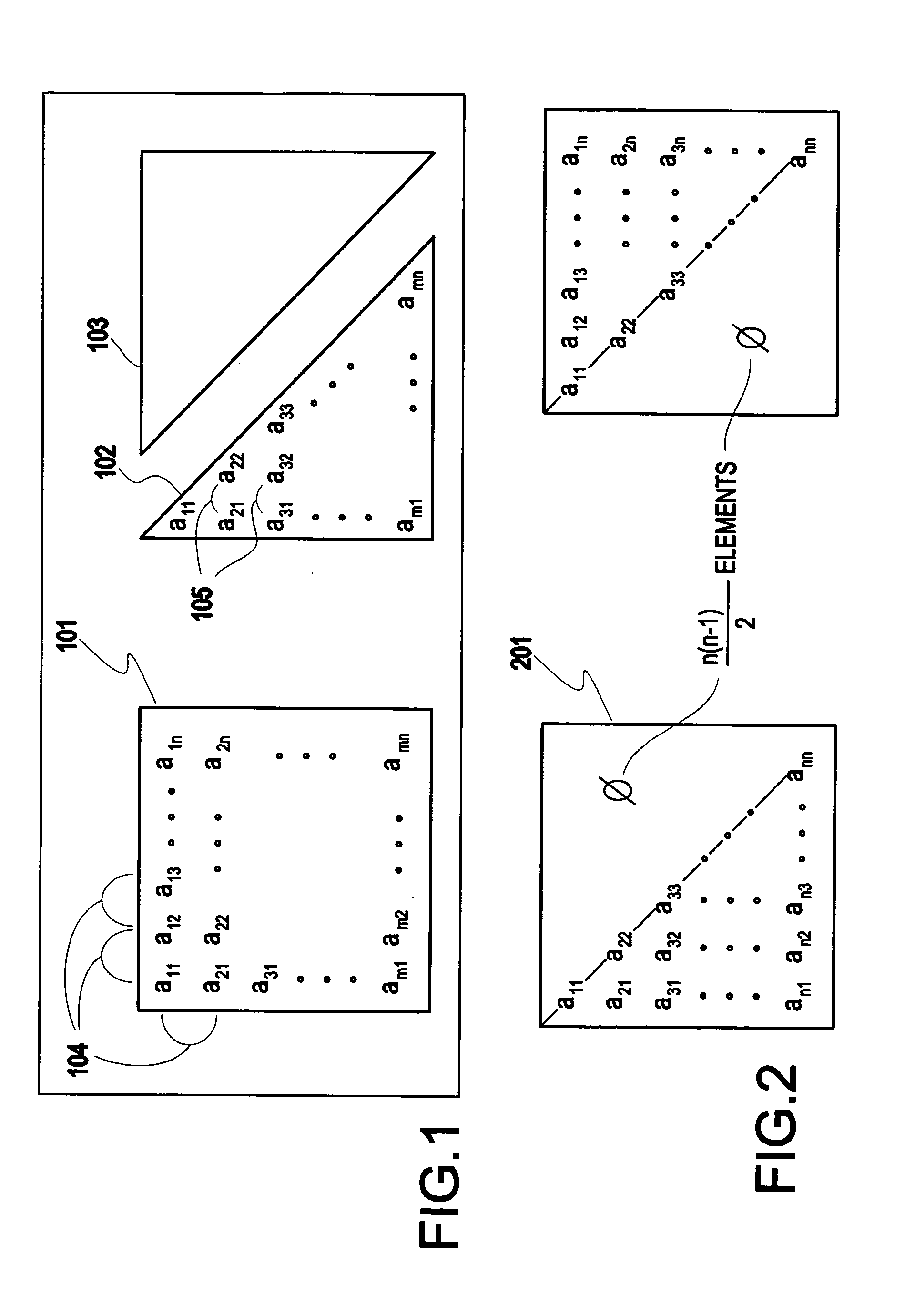
In linear algebra, a symmetric matrix is a square matrix that is equal to its transpose. Formally, Because equal matrices have equal dimensions, only square matrices can be symmetric. The entries of a symmetric matrix are symmetric with respect to the main diagonal. So if aᵢⱼ denotes the entry in the i-th row and j-th column then for all indices i and j. Every square diagonal matrix is symmetric, since all off-diagonal elements are zero.
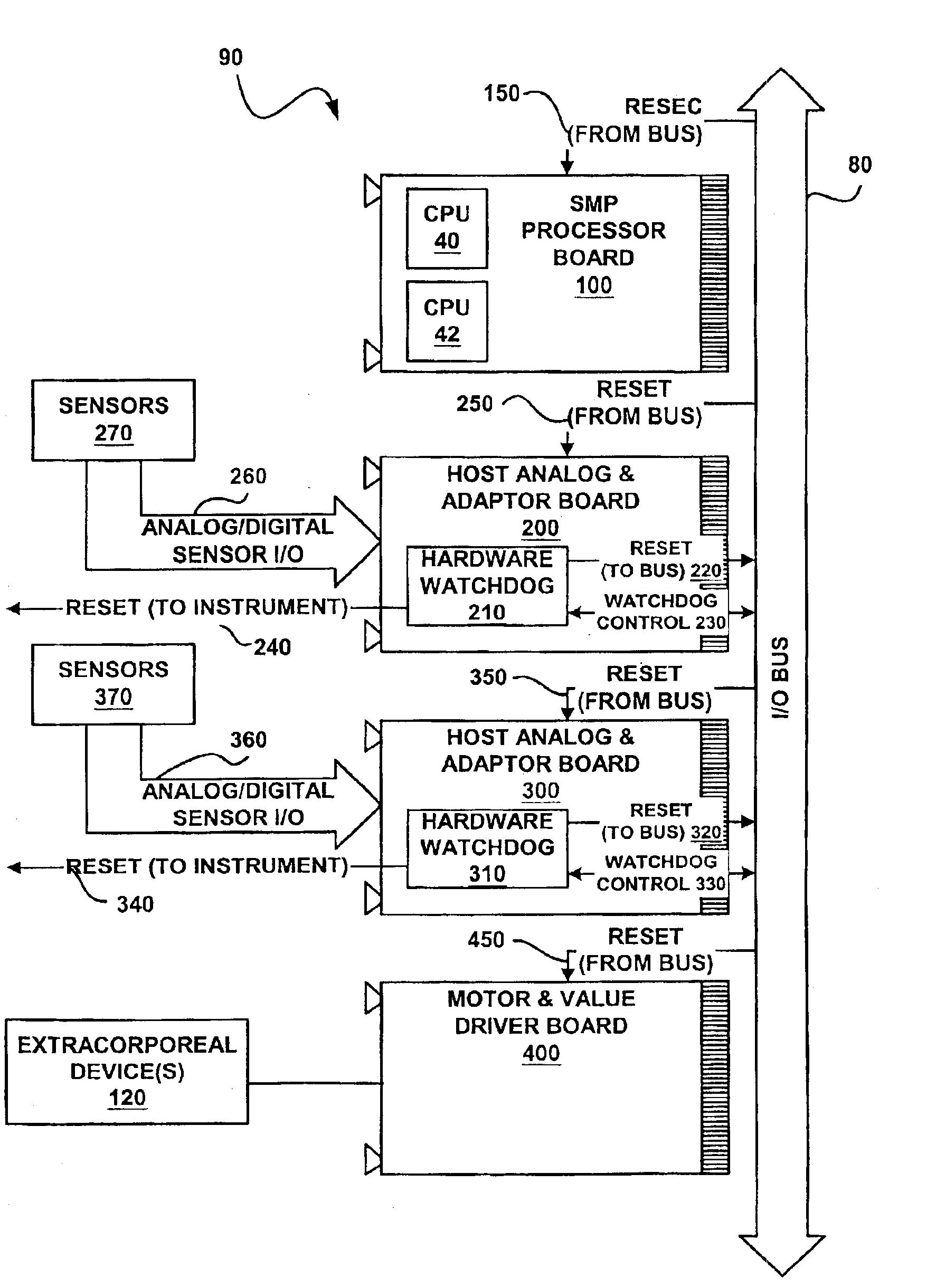
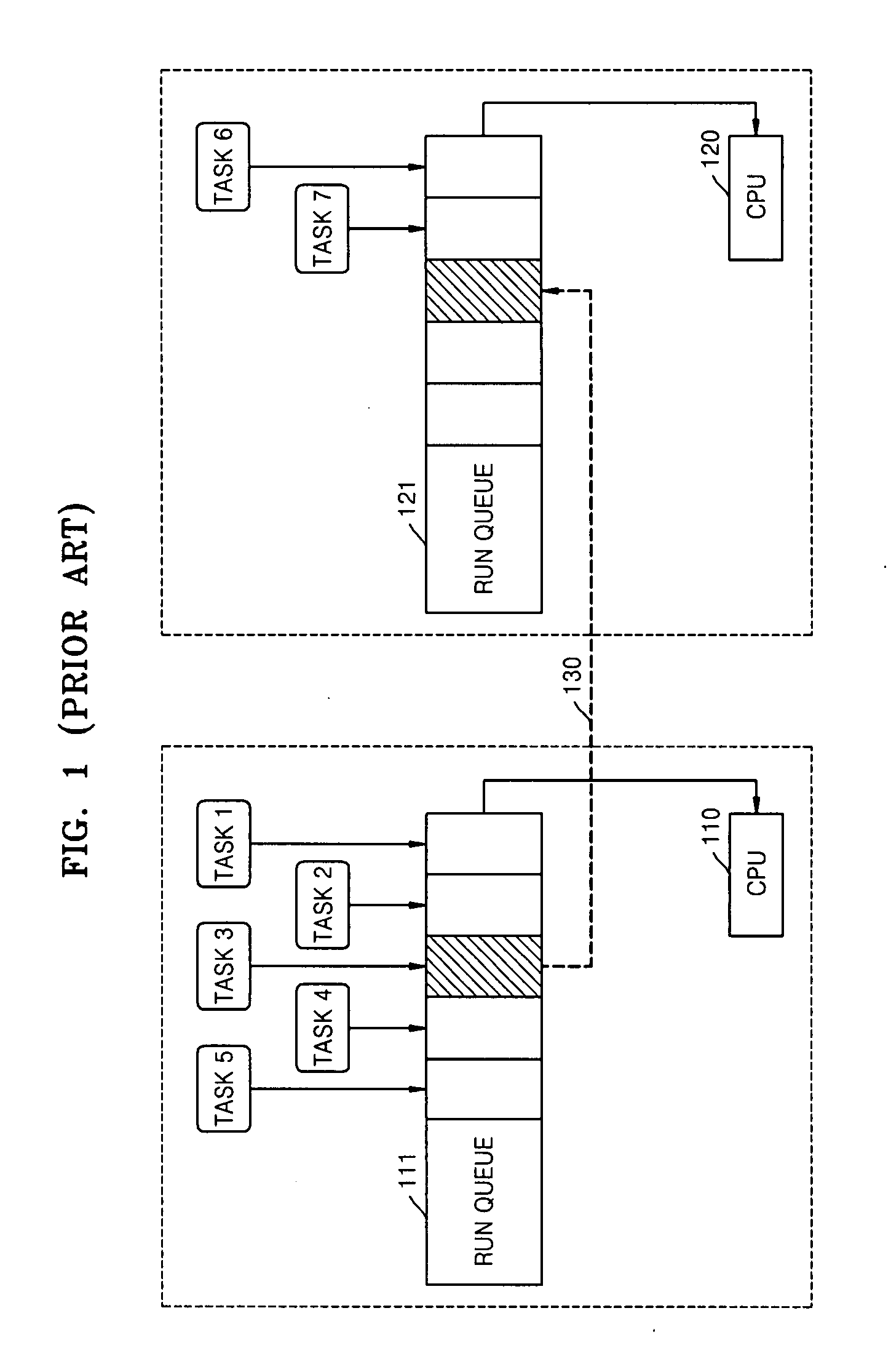
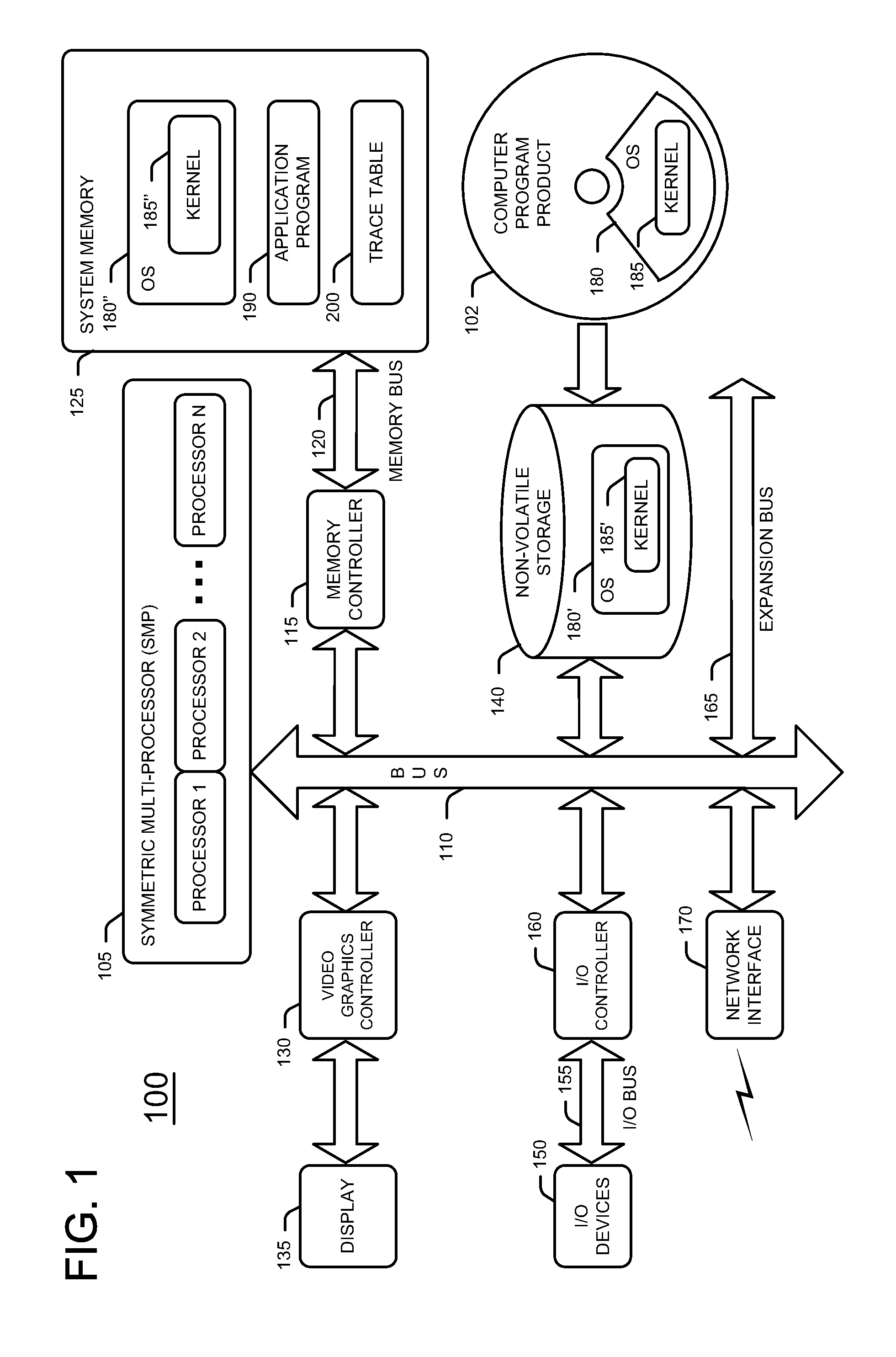
Dialysis machine with symmetric multi-processing (SMP) control system and method of operation
InactiveUS6868309B1Low costImprove performanceMechanical/radiation/invasive therapiesLevel controlControl systemSingle point of failure
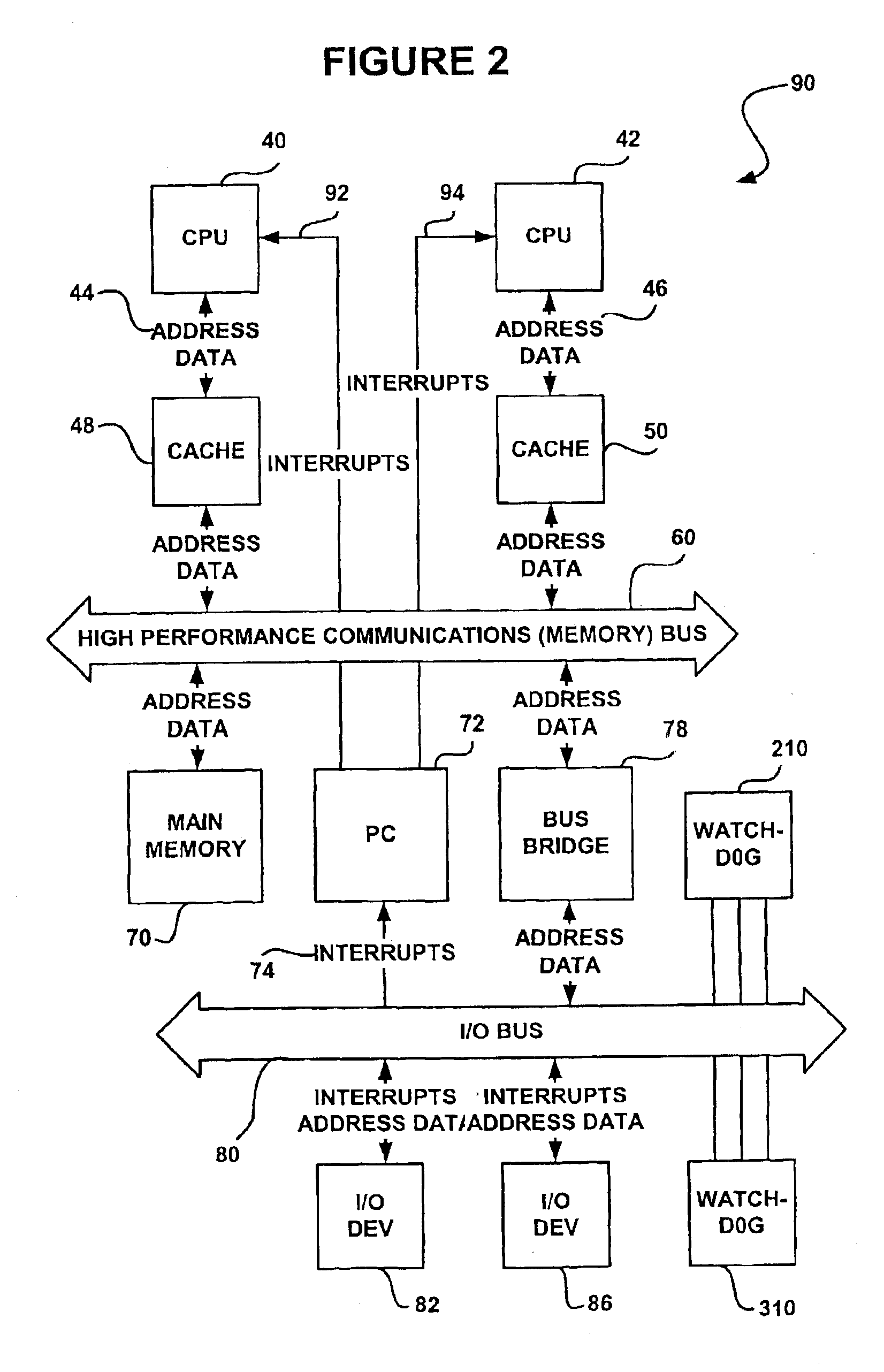
A method and control system computing platform for a dialysis machine that uses Symmetric Multi-Processing (SMP) architecture. The SMP architecture tightly couples multiple (e.g., 2) independent processors by sharing memory between the processors. A single shared memory is used by both processors in order to facilitate communication between the processors and reduce cost by eliminating the expense of redundant memory. In this way, the two, or in general “N” processors, increase processor throughput by allowing the execution of N processes in parallel while without requiring extra memory and without having a single point of failure in the computer. In the event of a bus failure on the circuit card, the computer is reset using distributed hardware watchdogs. The watchdog reset signal is also sent to the hardware components of the dialysis machine in order to place the system in a safe.
Owner:BAXTER INT INC +2
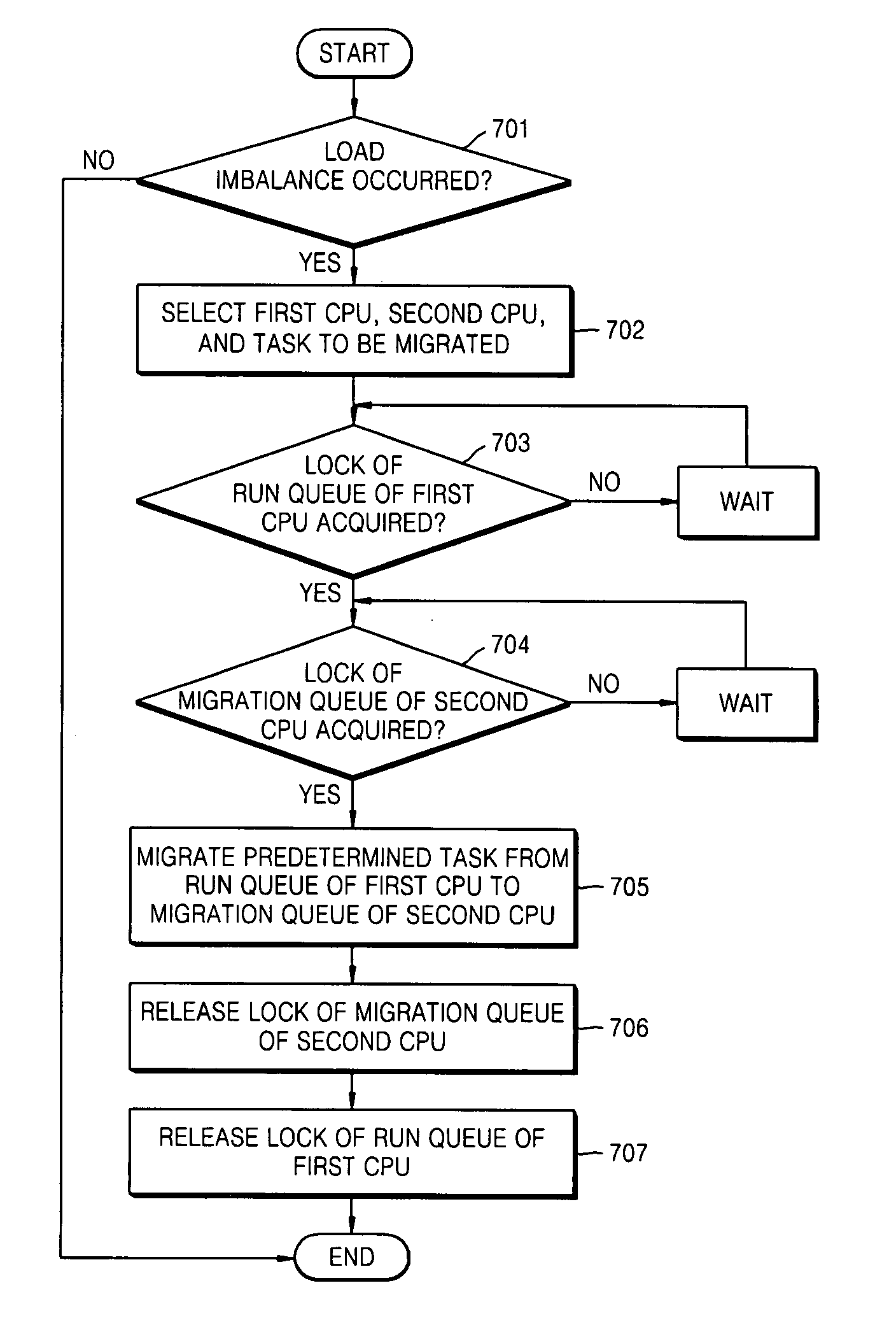
Load balancing method and apparatus in symmetric multi-processor system
InactiveUS20090019449A1Prevents delay in response timeLong waiting timeResource allocationMemory systemsSymmetric matrixSymmetric multiprocessing
Provided are a load balancing method and a load balancing apparatus in a symmetric multi-processor system. The load balancing method includes selecting at least two processors based on a load between a plurality of processors, from among the plurality of processors, migrating a predetermined task stored in a run queue of a first processor to a migration queue of a second processor, and migrating the predetermined task stored in the migration queue of the second processor to a run queue of the second processor. Accordingly, a run queue of a processor is not blocked while migrating a task, an immediate response of the run queue is possible, and a waiting time of a scheduler is reduced. Consequently, the scheduler can speedily perform context switching, and thus performance of the entire operating system is improved.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and structure for improving processing efficiency in parallel processing machines for rectangular and triangular matrix routines
InactiveUS20060265445A1Reduce storageImprove efficiencyData mergingComplex mathematical operationsDistributed memoryData preparation
A computerized method (and structure) of linear algebra processing on a computer having a plurality of processors for parallel processing, includes, for a matrix having elements originally stored in a memory in a rectangular matrix AR or especially of one of a triangular matrix AT format and a symmetric matrix AS format, distributing data of the rectangular AR or triangular or symmetric matrix (AT, AS) from the memory to the plurality of processors in such a manner that keeps all submatrices of AR or substantially only essential data of the triangular matrix AT or symmetric matrix AS is represented in the distributed memories of the processors as contiguous atomic units for the processing. The linear algebra processing done on the processors with distributed memories requires that submatrices be sent and received as contiguous atomic units based on the prescribed block cyclic data layouts of the linear algebra processing. This computerized method (and structure) defines all of its submatrices as these contiguous atomic units, thereby avoiding extra data preparation before each send and after each receive. The essential data or AT or AS is that data of the triangular or symmetric matrix that is minimally necessary for maintaining the full information content of the triangular AT or symmetric matrix AS.
Owner:IBM CORP
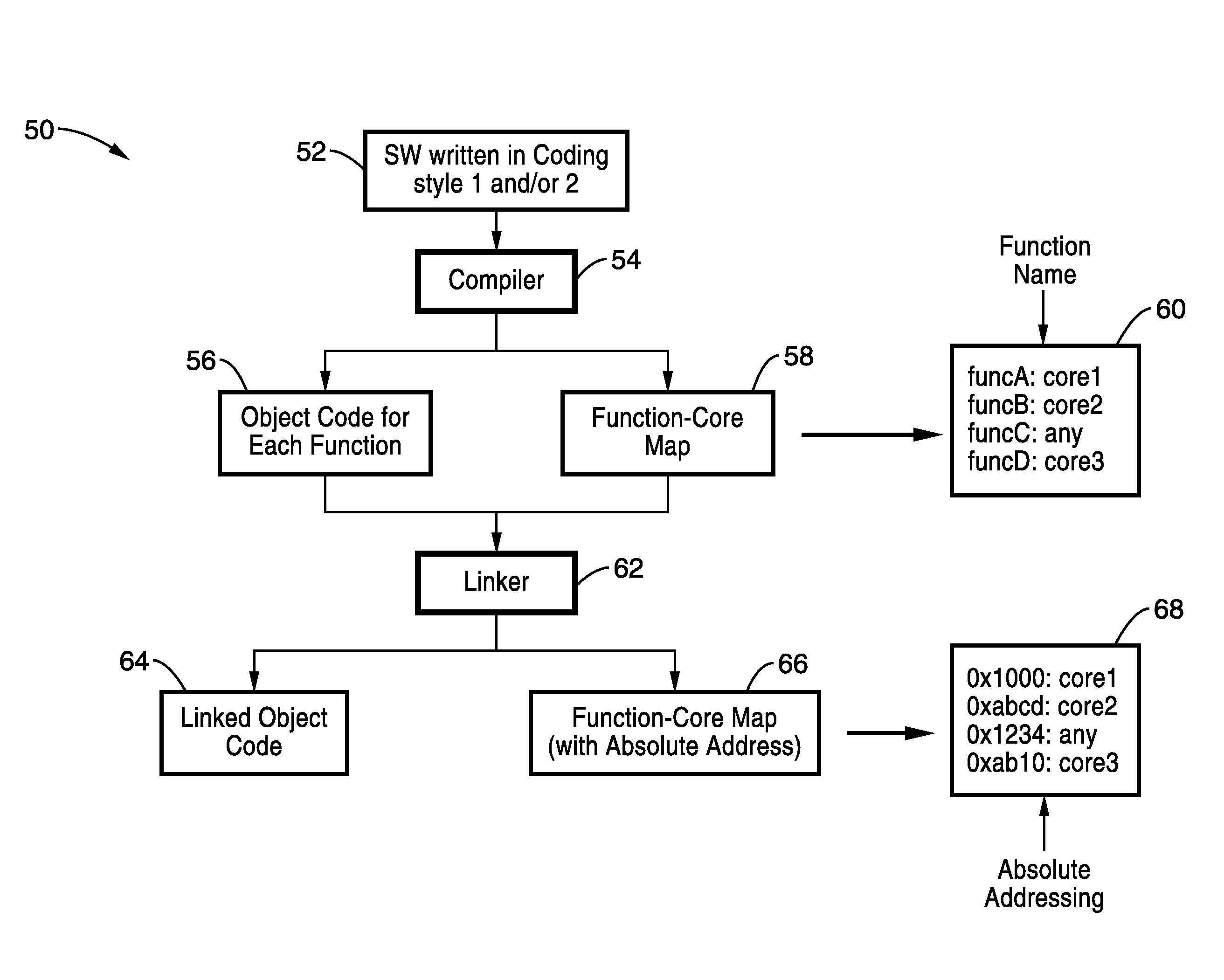
Symmetric multi-processor operating system for asymmetric multi-processor architecture
InactiveUS20100242014A1Maximum reusabilityDevelopment effortEnergy efficient ICTProgram control using stored programsOperational systemMulti processor
A method and system for supporting multi-processing within an asymmetric processor architecture in which processors support different processor specific functionality. Instruction sets within processors having different functionalities are modified so that a portion of the functionality of these processors overlaps within a common set of instructions. Code generation for the multi-processor system (e.g., compiler, assembler, and / or linker) is performed in a manner to allow the binary code to be generated for execution on these diverse processors, and the execution of generic tasks, using the shared instructions, on any of the processors within the multiple processors. Processor specific tasks are only executed by the processors having the associated processor specific functionality. Source code directives are exemplified for aiding the compiler or assembler in properly creating binary code for the diverse processors. The invention can reduce processor computation requirements, reduce software latency, and increase system responsiveness.
Owner:SONY CORP +1
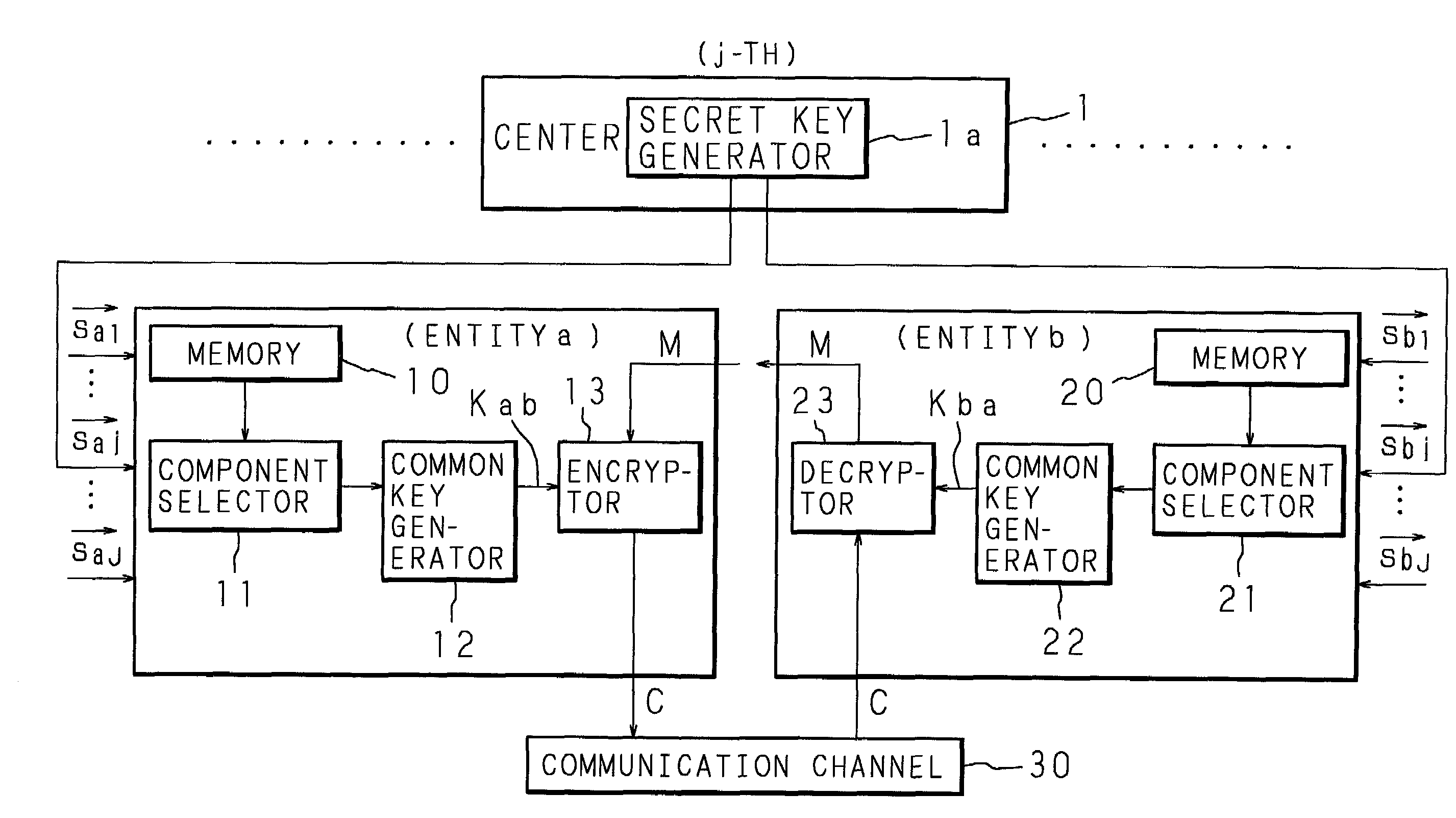
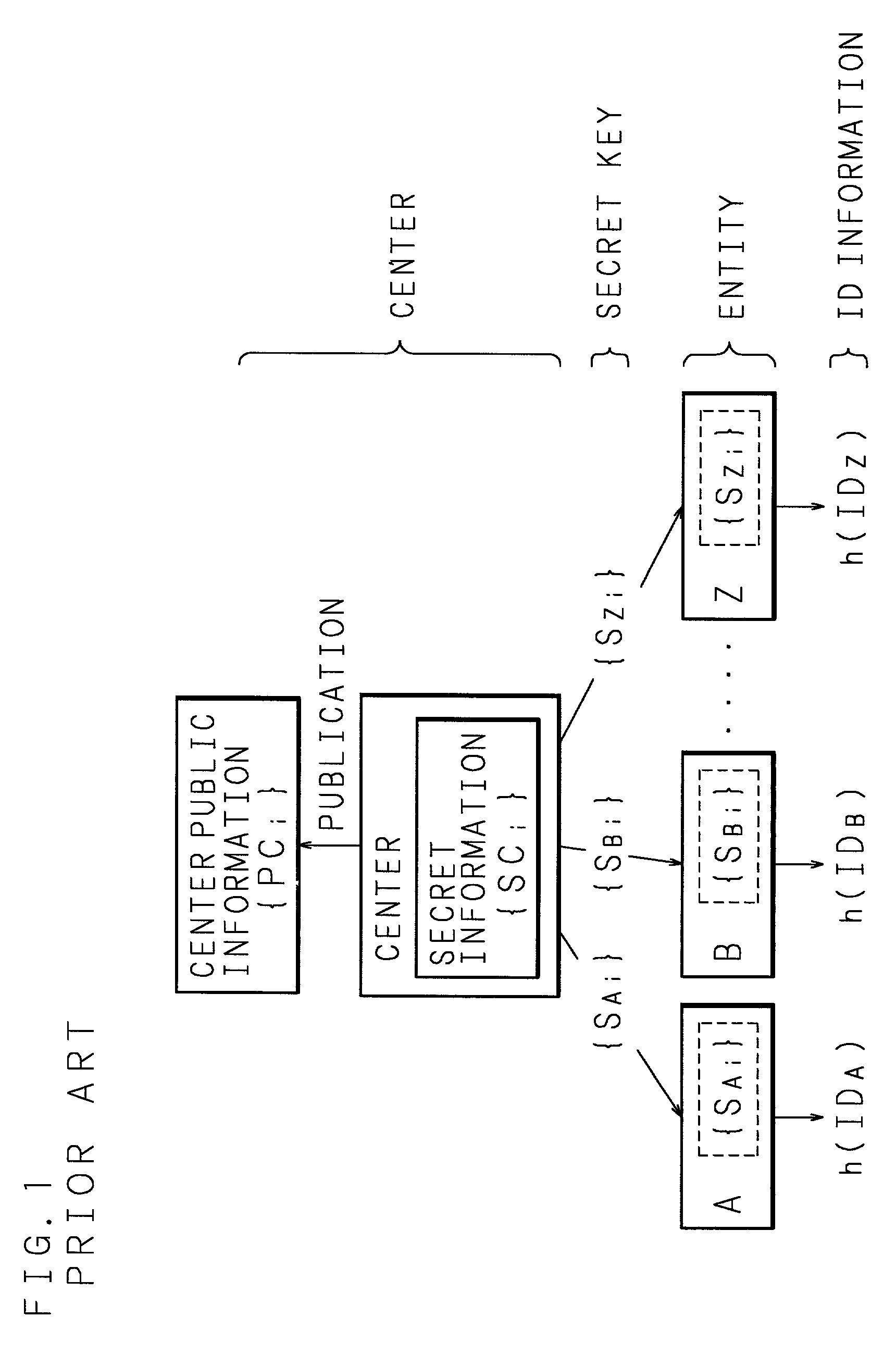
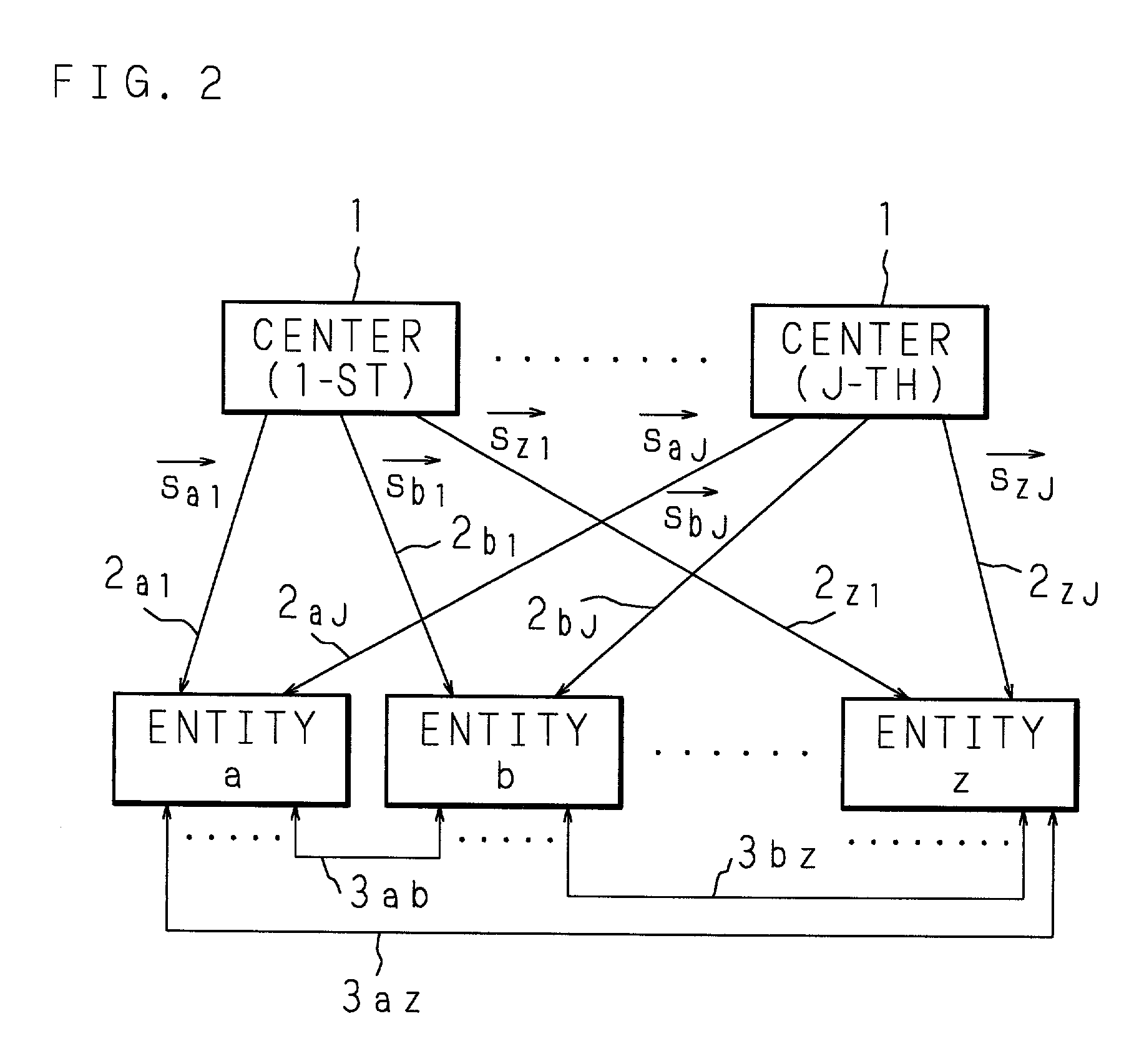
Secret key generating method, common key generating method, encryption method, cryptographic communication method and cryptographic communication system
InactiveUS6996724B2Increase speedReduce attackKey distribution for secure communicationUnauthorized memory use protectionComputer hardwareCommunications system
At the time when generating a secret key of each entity by using each divided identification information (ID division vector) obtained by dividing identification information (ID vector) of each entity into a plurality of blocks and by using a secret symmetric matrix of each key generating agency (center), a part of the components of the symmetric matrix is extracted in accordance with each divided identification information (ID division vector) so that the extracted components are synthesized with a random number particular to each entity so as to generate a secret key of each entity.
Owner:MURATA MASCH LTD +2
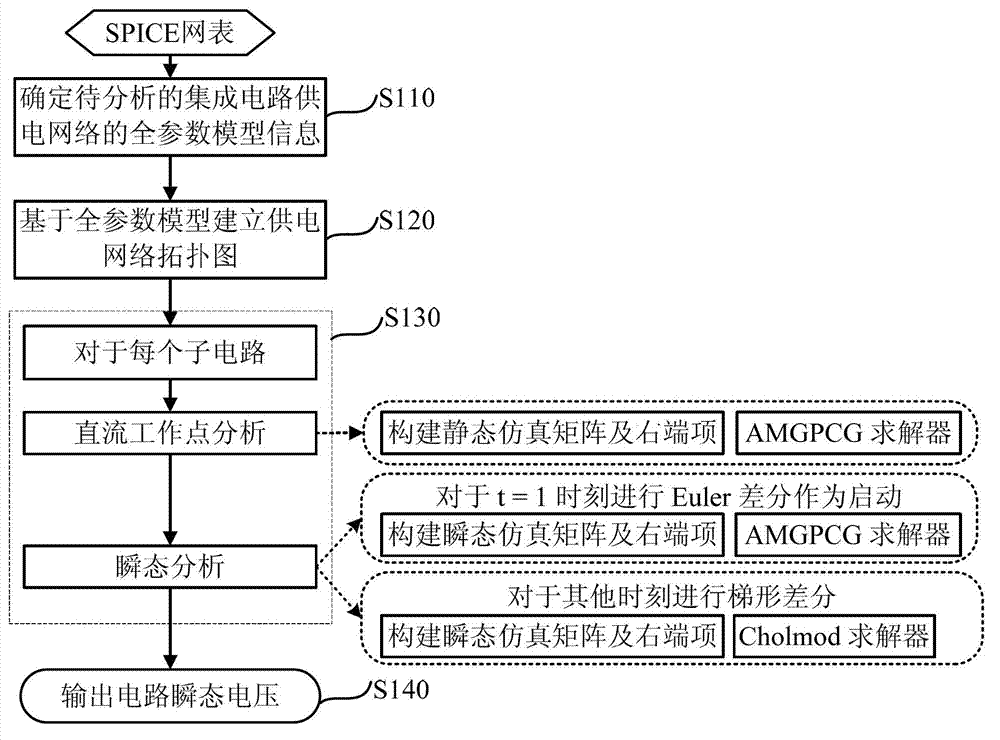
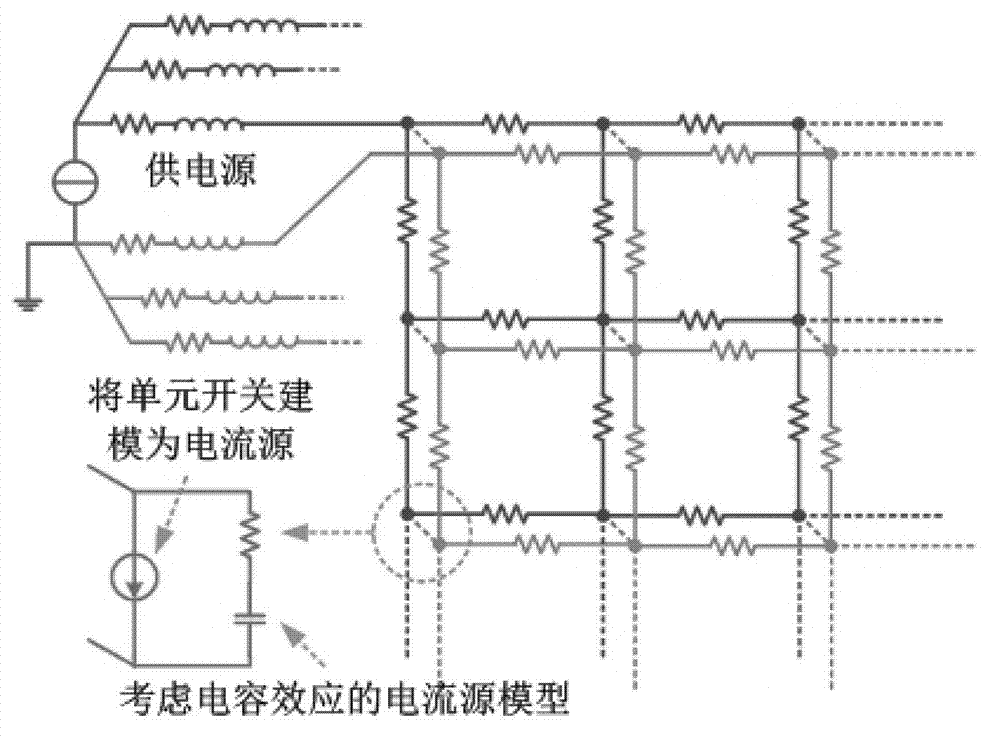
Transient analysis method and transient analysis system under integrated circuit power supply network full-parameter model
InactiveCN103207941AFast and accurate transient voltage drop analysisIncreased memory consumptionSpecial data processing applicationsTransient analysisEngineering
The invention discloses a transient analysis method under an integrated circuit power supply network full-parameter model. The method comprises the following steps: a determining step of determining the full-parameter model information of a to-be-analyzed integrated circuit power supply network; an establishing step of establishing a power supply network topological graph comprising a plurality of independent sub-circuits based on the full-parameter model information; and an analysis step of in parallel carrying out direct current working site analysis and transient analysis on each sub-circuit of the power supply topological graph to obtain the circuit node voltage distribution graph at each moment of each sub-circuit. As for a full-parameter circuit model, the invention establishes a linear system capable of adopting a symmetric matrix solver, and adopts a direct solver and an iterative solver in a hybrid manner according to the characteristics of problem solving. The method and system disclosed by the invention can be applied to carrying out fast and precise transient voltage drop analysis on the power supply network under the full-parameter model in formats such as an SPICE (Simulation Program with Integrated Circuit Emphasis) net-list form, especially on the aspect of memory consumption, and the system is improved to a great extent in comparison with the original emulator.
Owner:TSINGHUA UNIV
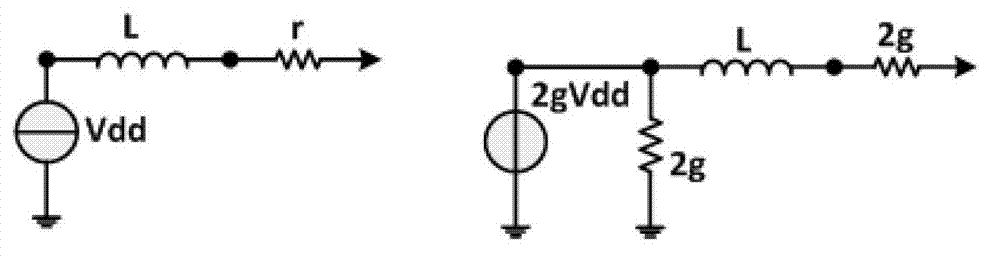
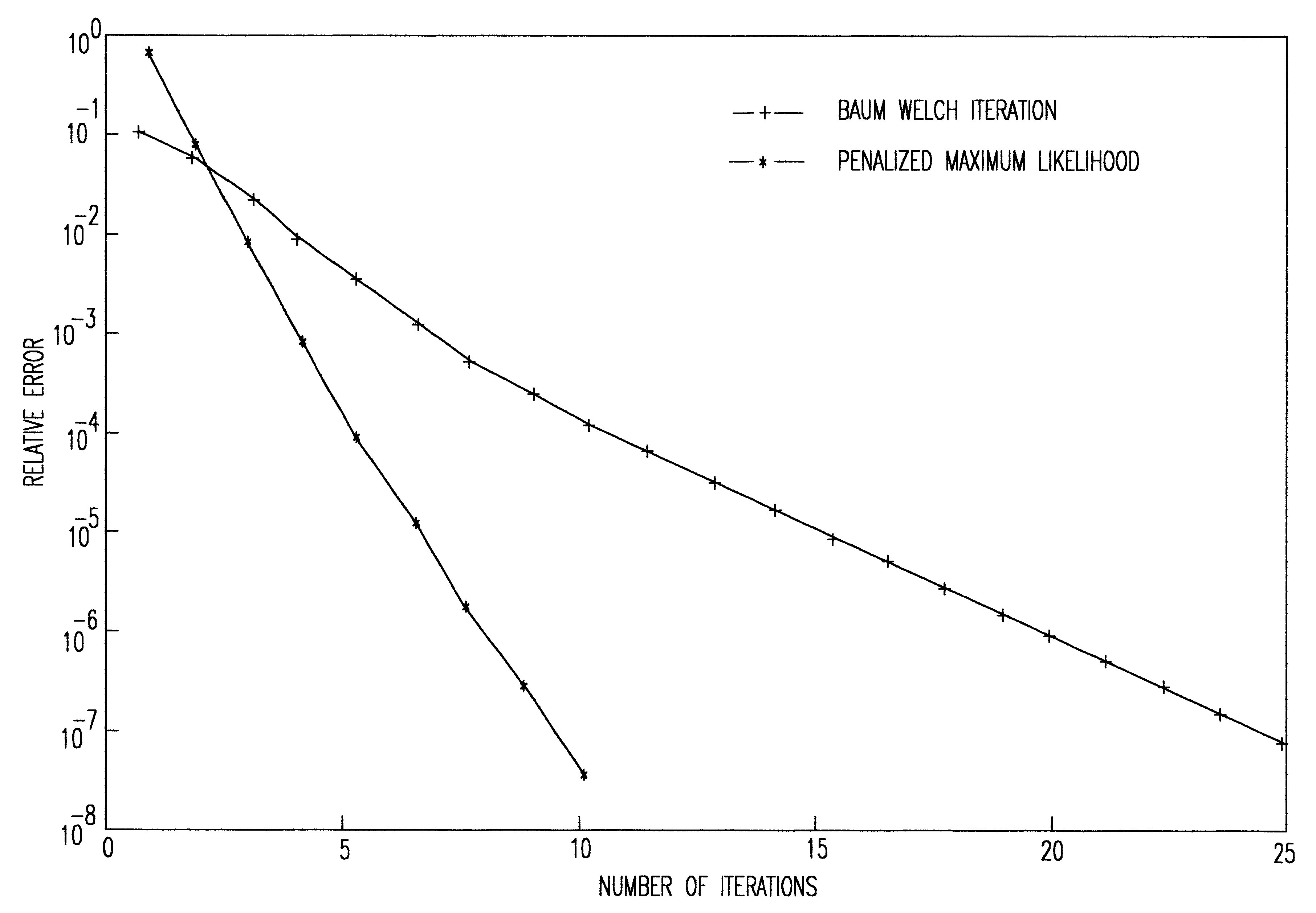
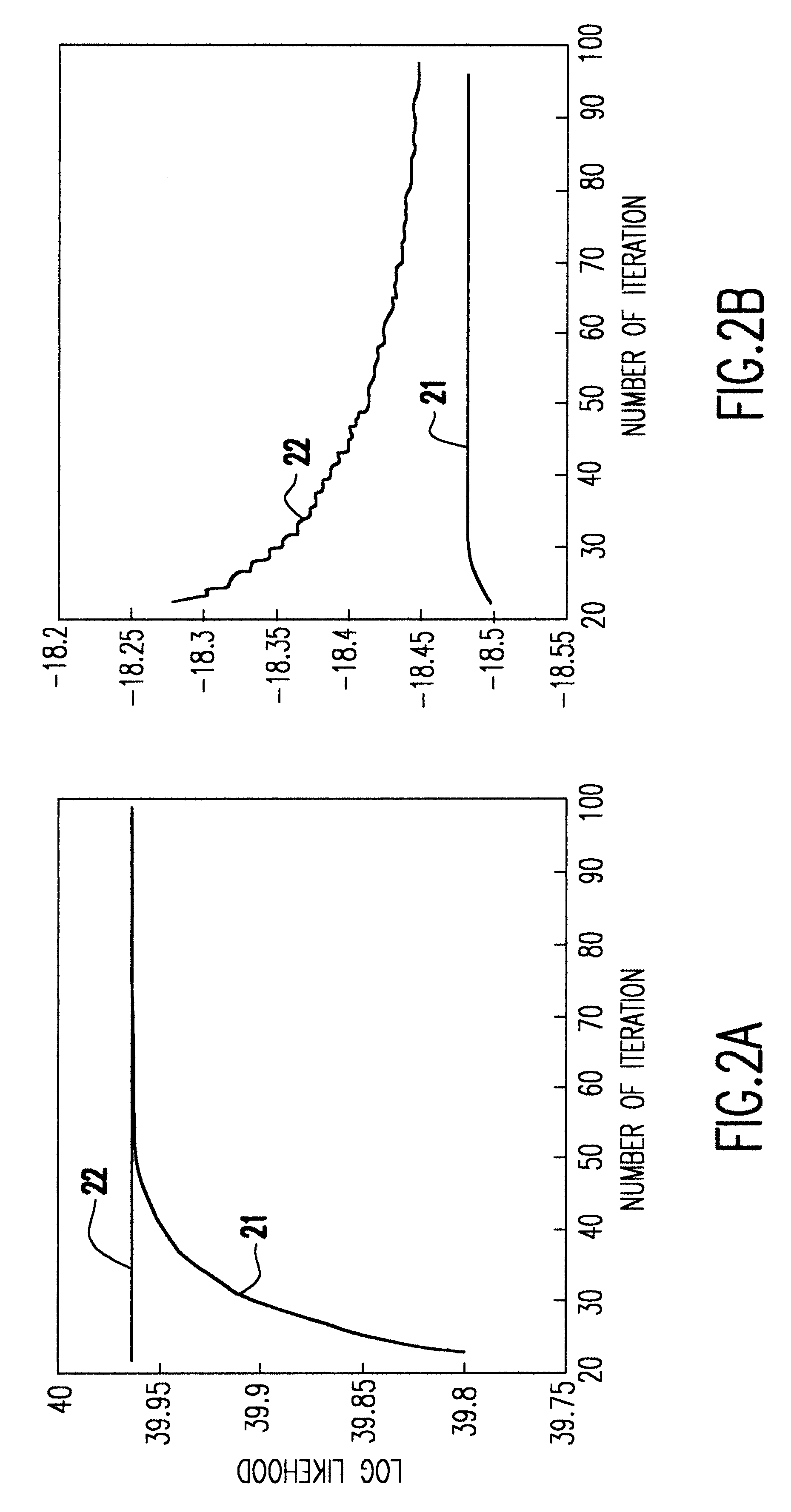
Penalized maximum likelihood estimation methods, the baum welch algorithm and diagonal balancing of symmetric matrices for the training of acoustic models in speech recognition
A nonparametric family of density functions formed by histogram estimators for modeling acoustic vectors are used in automatic recognition of speech. A Gaussian kernel is set forth in the density estimator. When the densities are found for all the basic sounds in a training stage, an acoustic vector is assigned to a phoneme label corresponding to the highest likelihood for the basis of the decoding of acoustic vectors into text.
Owner:IBM CORP
Method and node for generating distributed rivest shamir adleman signature in ad-hoc network
ActiveUS20080181413A1Communication securityKey distribution for secure communicationPublic key for secure communicationSelf-organizing networkSymmetric matrix
A distributed Rivest Shamir Adleman (RSA) signature generation method in an ad-hoc network and a node of an ad-hoc network. The distributed RSA signature generation method in an ad-hoc network includes distributing key share information, which is generated using a maximum distance separable (MDS) code and a random symmetric matrix, to a plurality of nodes; generating, in a fewer number of nodes than the plurality of nodes, a partial signature using the distributed key share information; transmitting the partial signature to a signature generation node; and generating an RSA signature using the partial signature, in the signature generation node.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and node for generating distributed Rivest Shamir Adleman signature in ad-hoc network
ActiveUS8645698B2Key distribution for secure communicationPublic key for secure communicationSelf-organizing networkSymmetric matrix
Owner:SAMSUNG ELECTRONICS CO LTD
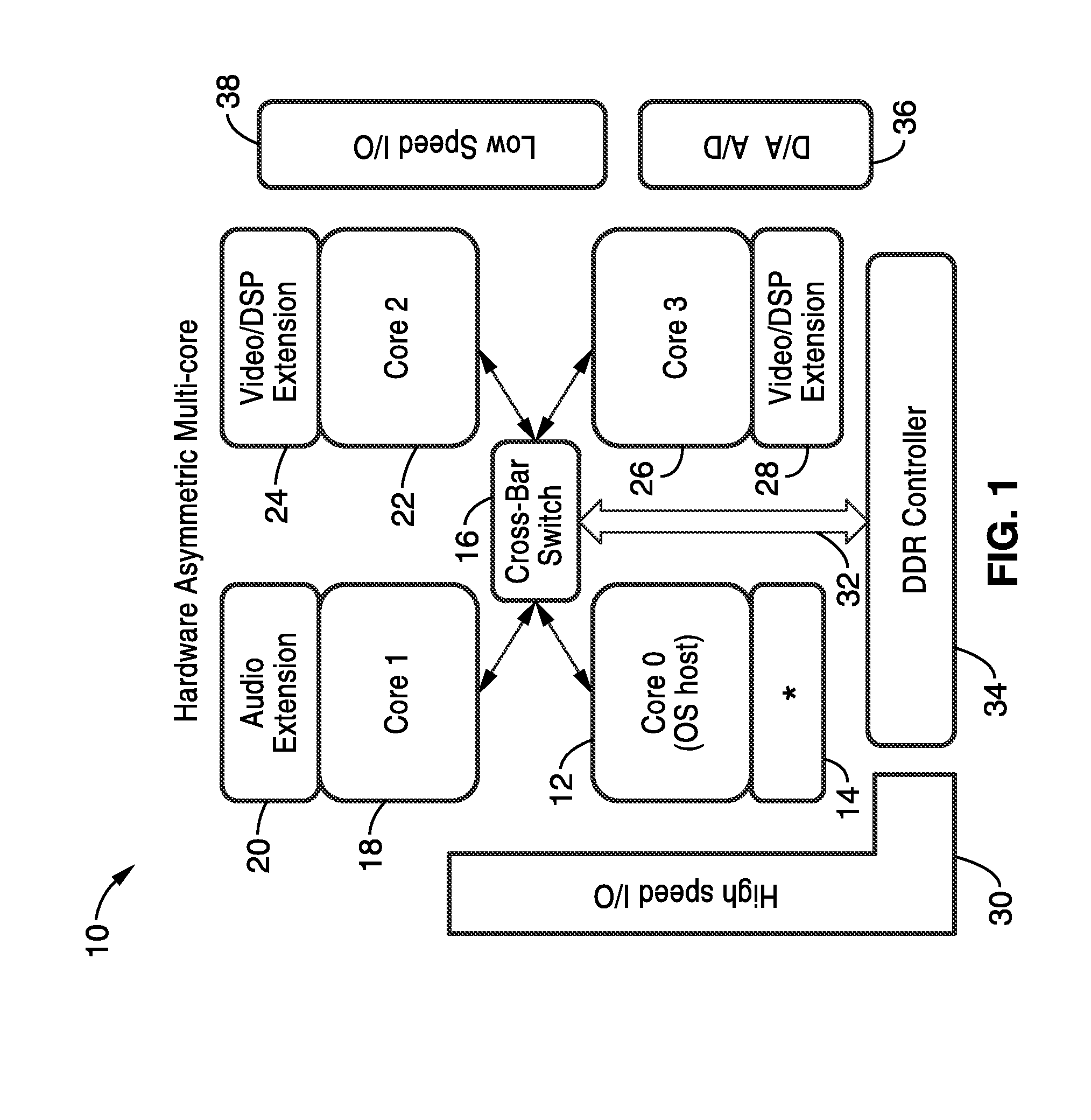
Anti-interference system-on-chip and method of intelligent antenna based on FPGA (Field Programmable Gate Array)
InactiveCN102170302AOvercome costsOvercoming integratioDiversity/multi-antenna systemsTransmitter/receiver shaping networksDigital signal processingInterference resistance
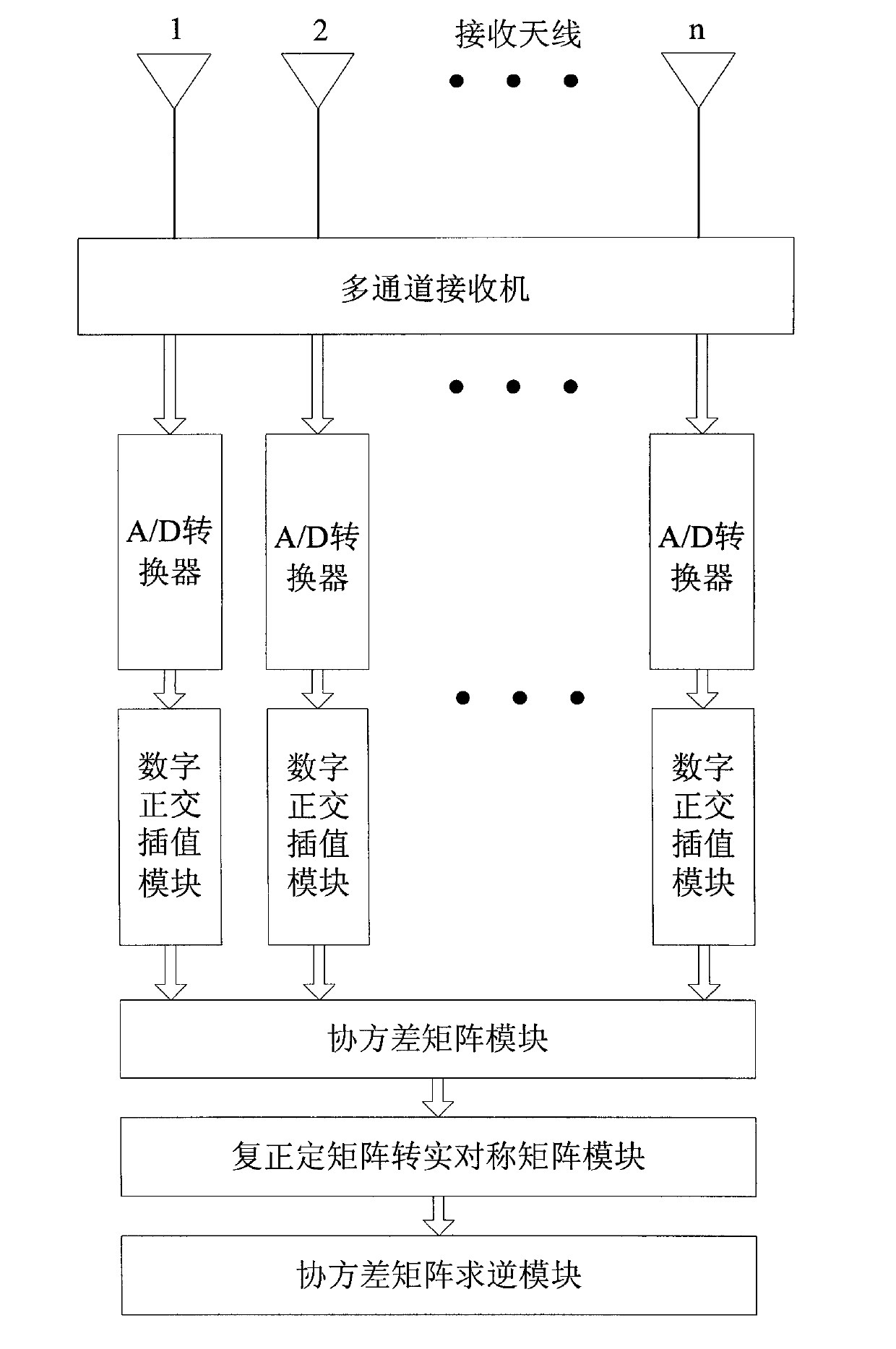
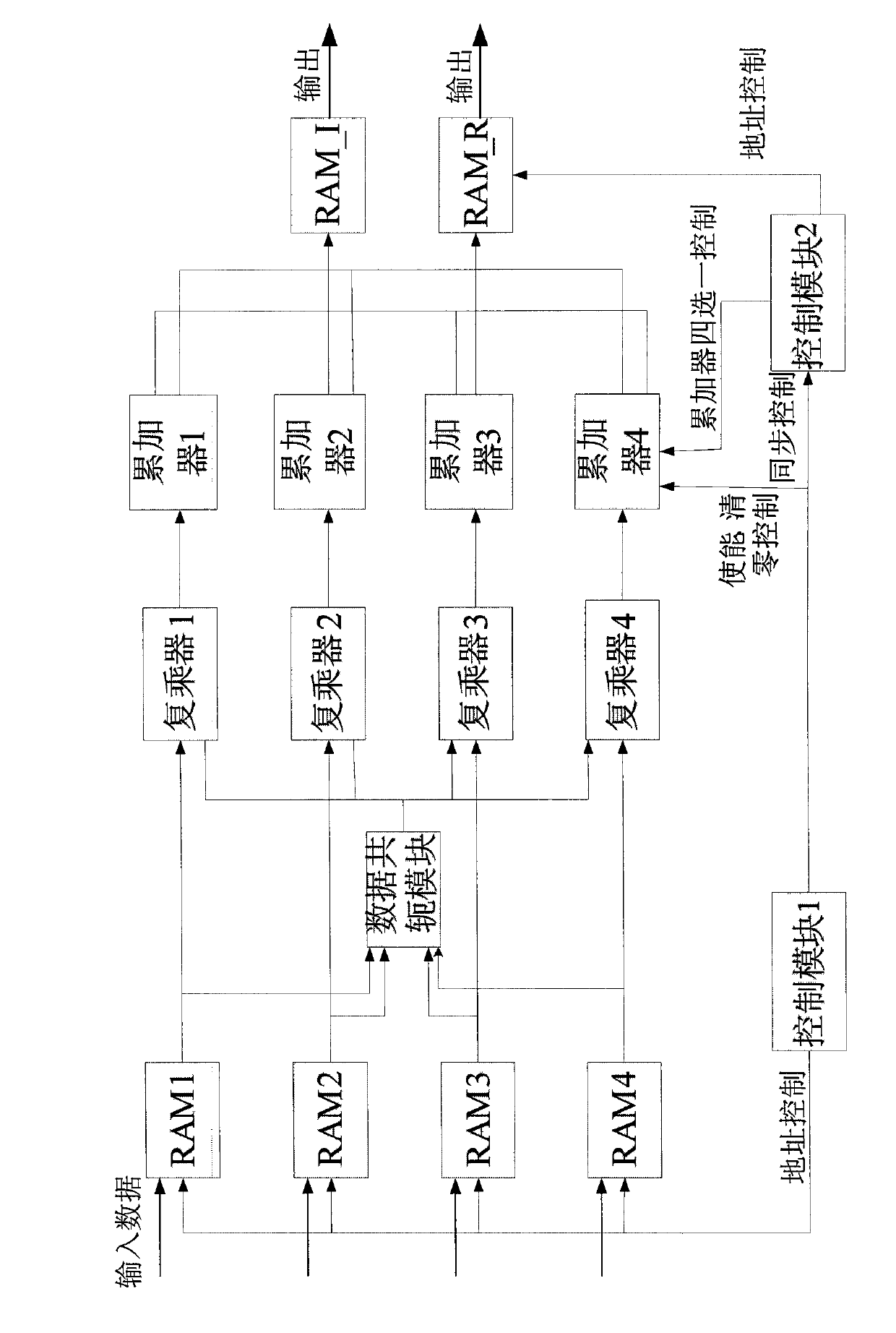
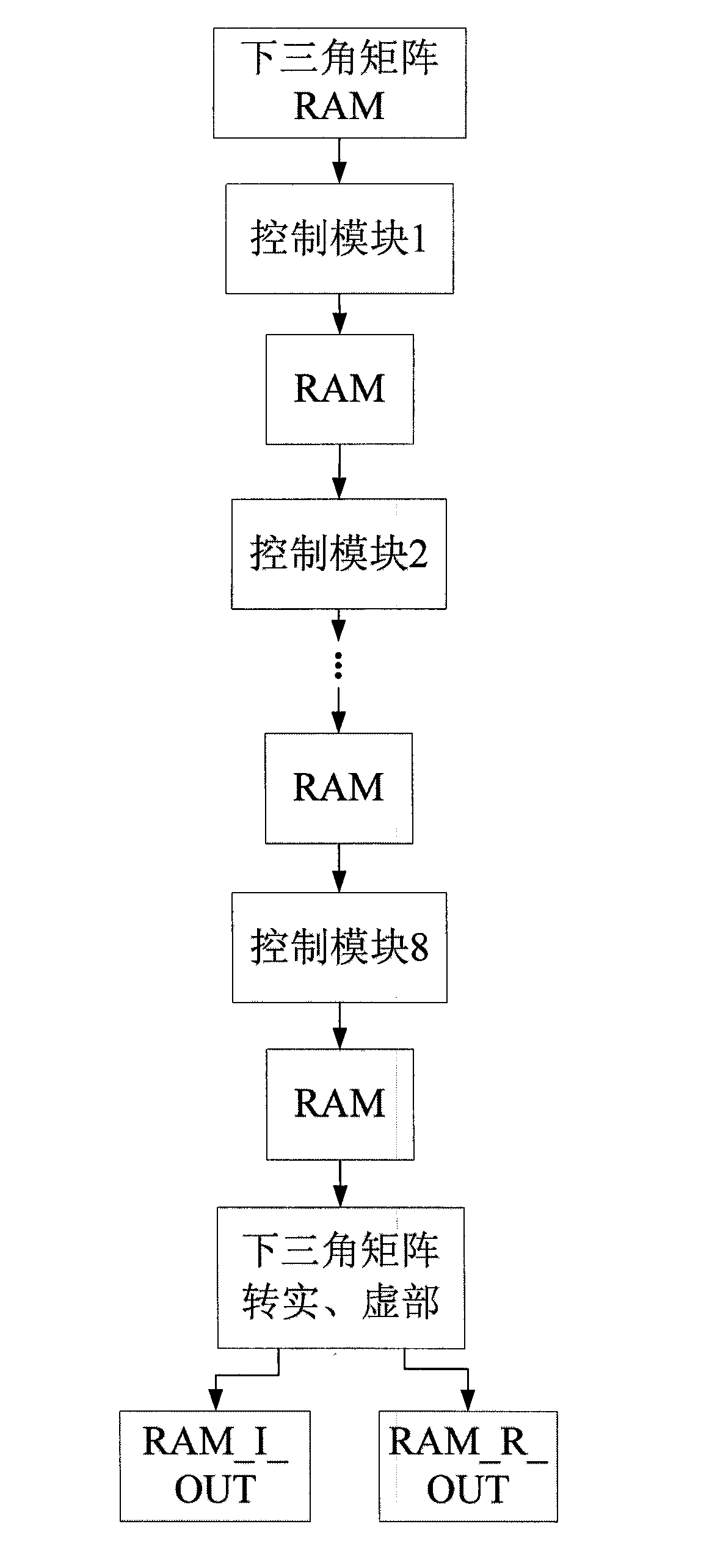
The invention provides an anti-interference system-on-chip and method for an intelligent antenna based on an FPGA (Field Programmable Gate Array). The anti-interference system-on-chip for the intelligent antenna based on the FPGA comprises a receiving antenna, a multi-channel receiver, an A / D (Analog-to-Digital) converter, a digital orthogonal interpolation module, a covariance matrix module, a complex positive definite Hermite matrix to real symmetric matrix module and a covariance matrix inversion module. In the invention, the anti-interference method for the intelligent antenna based on the FPGA comprises the following specific steps of: 1, data receiving; 2, digital orthogonal interpolation; 3, covariance matrix data calculation; 4, complex positive definite Hermite matrix to real symmetric matrix; and 5, covariance matrix inversion. By using the invention, the real-time and fast anti-interference of the intelligent antenna is realized under the situation that interference exists in a communication channel, and thus, the problems of poor instantaneity, high hardware cost, low integration degree and incapability of parallel processing in an anti-interference system for the intelligent antenna based on (Digital Signal Processing) are solved.
Owner:XIDIAN UNIV
Fast singular value decomposition for expediting computer analysis system and application thereof
ActiveUS20090265404A1Increase computing speedSimple processDigital computer detailsCharacter and pattern recognitionSingular value decompositionAlgorithm
The present invention uses a computer analysis system of a fast singular value decomposition to overcome the bottleneck of a traditional singular value decomposition that takes much computing time for decomposing a huge number of objects, and the invention can also process a matrix in any form without being limited to symmetric matrixes only. The decomposition and subgroup concept of the fast singular value decomposition works together with the decomposition of a variance matrix and the adjustment of an average vector of a column vector are used for optimizing the singular value decomposition to improve the overall computing speed of the computer analysis system.
Owner:PHISON ELECTRONICS
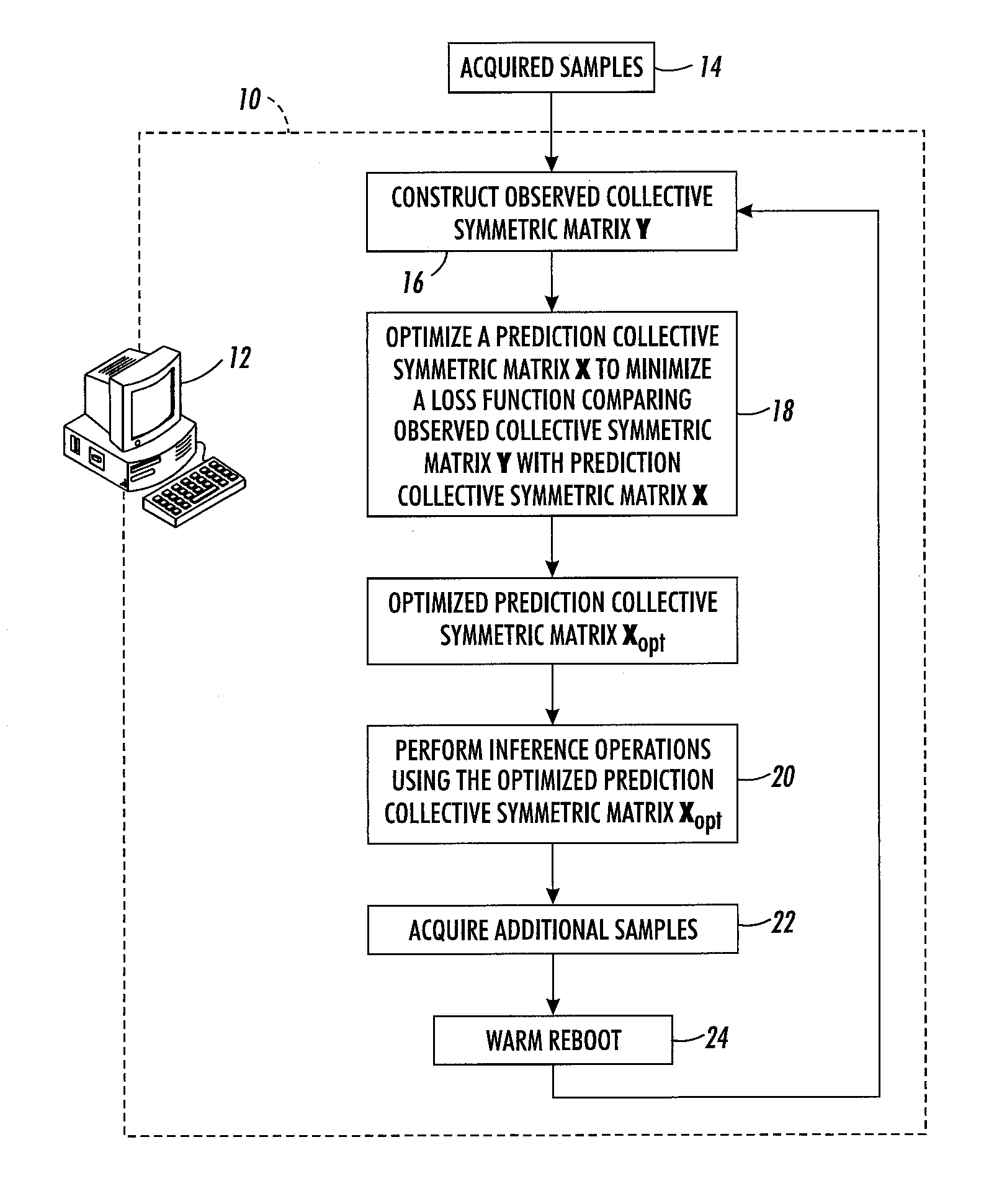
Convex collective matrix factorization
A method operates on observed relationship data between pairs of entities of a set of entities including entities of at least two (and optionally at least three) different entity types. An observed collective symmetric matrix is constructed in which element (n,m)=element (m,n) stores the observed relationship between entities indexed n and m when the observed relationship data includes this observed relationship. A prediction collective symmetric matrix is optimized in order to minimize a loss function comparing the observed collective symmetric matrix and the prediction collective symmetric matrix. A relationship between two entities of the set of entities is predicted using the optimized prediction collective symmetric matrix. Entities of the same entity type may be indexed using a contiguous set of indices such that the entity type maps to a contiguous set of rows and corresponding contiguous set of columns in the observed collective symmetric matrix.
Owner:XEROX CORP
Computing method applied to symmetric matrix and vector multiplication
ActiveCN107590106AImprove computing efficiencyReduce wasteComplex mathematical operationsDiagonalParallel processing
The invention discloses a computing method applied to a symmetric matrix and vector multiplication. The method is used for computing the product of the (n1xn1) symmetric matrix and n1-dimensional column vectors, wherein first, the (n1xn1) symmetric matrix and the n1-dimensional column vectors are partitioned, and microscale data extension is performed on matrix blocks on diagonal lines of the (n1xn1) symmetric matrix after partitioning to turn the matrix blocks into symmetric matrix blocks; then the n1-dimensional column vectors are partitioned, an intermediate data block is computed accordingto the matrix after partitioning, and a final result vector is computed according to the intermediate data block. Through the computing method applied to the symmetric matrix and the vector multiplication, on the premise of performing parallel processing on the symmetric matrix, waste of storage space by the symmetric matrix can be reduced, and the computing efficiency of the symmetric matrix andthe vector multiplication can be improved.
Owner:SUZHOU RICORE IC TECH LTD
Method and structure for a hybrid full-packed storage format as a single rectangular format data structure
InactiveUS20060173947A1Improve performanceSave memory spaceComputation using non-contact making devicesComplex mathematical operationsAlgorithmSymmetric matrix
A method (and structure) of linear algebra processing, includes processing a (real or complex) matrix data having elements originally stored in one of a triangular format and a symmetric matrix format in a subroutine designed to process matrix data in a full format. The processing uses a hybrid full packed data structure, which provides a rectangular space characteristic of the full format. The rectangular space is defined by a leading dimension (LD). Inside of the rectangular space are stored a plurality of entities that include all elements of the matrix data originally stored in the triangular or symmetric format.
Owner:IBM CORP
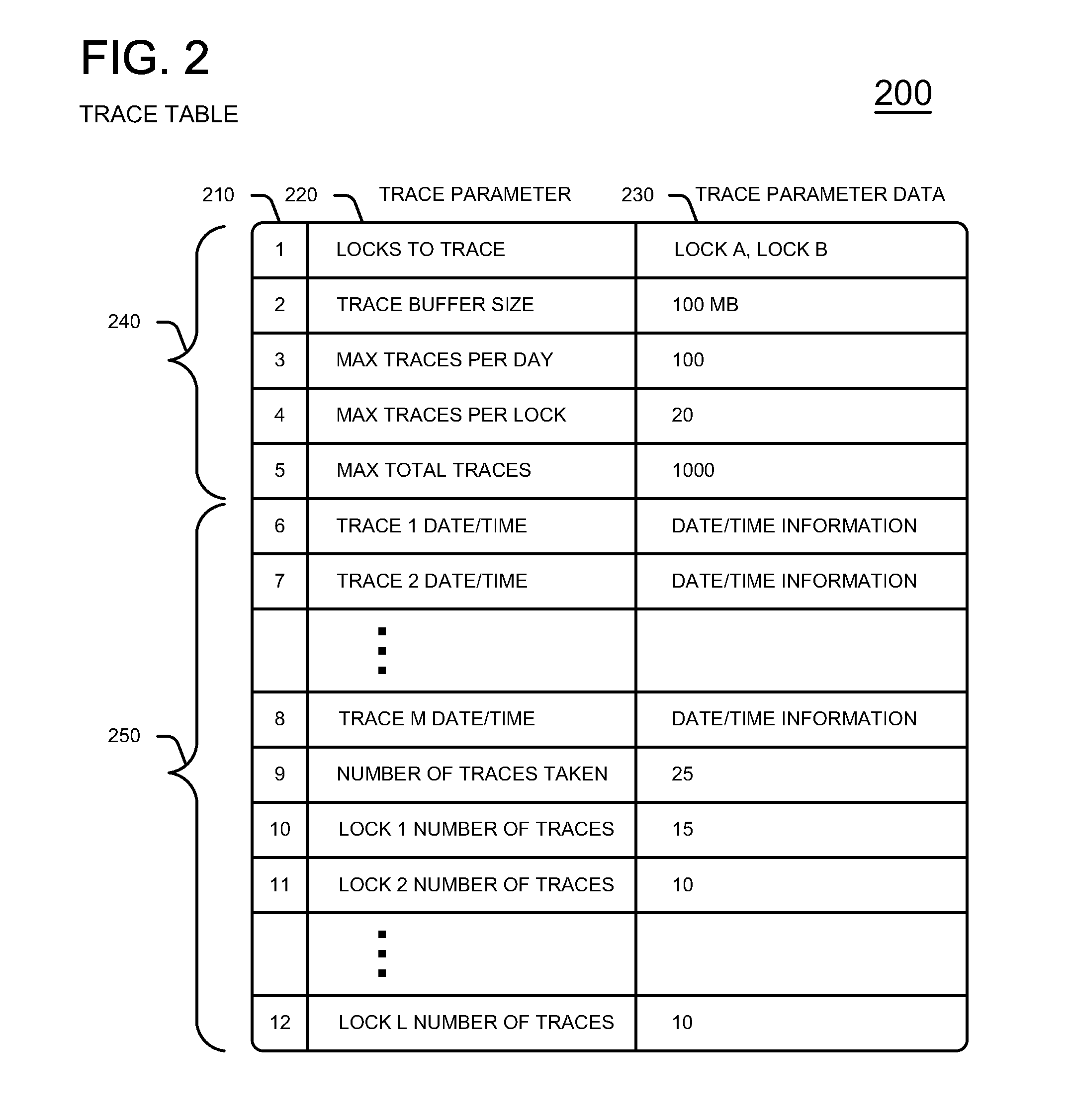
Symmetric multi-processor lock tracing
InactiveUS20110113406A1Error detection/correctionDigital computer detailsMemory addressOperational system
A symmetric multi-processor SMP system includes an SMP processor and operating system OS software that performs automatic SMP lock tracing analysis on an executing application program. System administrators, users or other entities initiate an automatic SMP lock tracing analysis. A particular thread of the executing application program requests and obtains a lock for a memory address pointer. A subsequent thread requests the same memory address pointer lock prior to the particular thread release of that lock. The subsequent thread begins to spin waiting for the release of that address pointer lock. When the subsequent thread reaches a predetermined maximum amount of wait time, MAXSPIN, a lock testing tool in the kernel of the OS detects the MAXSPIN condition. The OS performs a test to determine if the subsequent thread and address pointer lock meet the list of criteria set during initiation of the automatic lock trace method. The OS initiates an SMP lock trace capture automatically if all criteria or the arguments of the lock trace method are met. System administrators, software programmers, users or other entities interpret the results of the SMP lock tracing method that the OS stores in a trace table to determine performance improvements for the executing application program.
Owner:IBM CORP
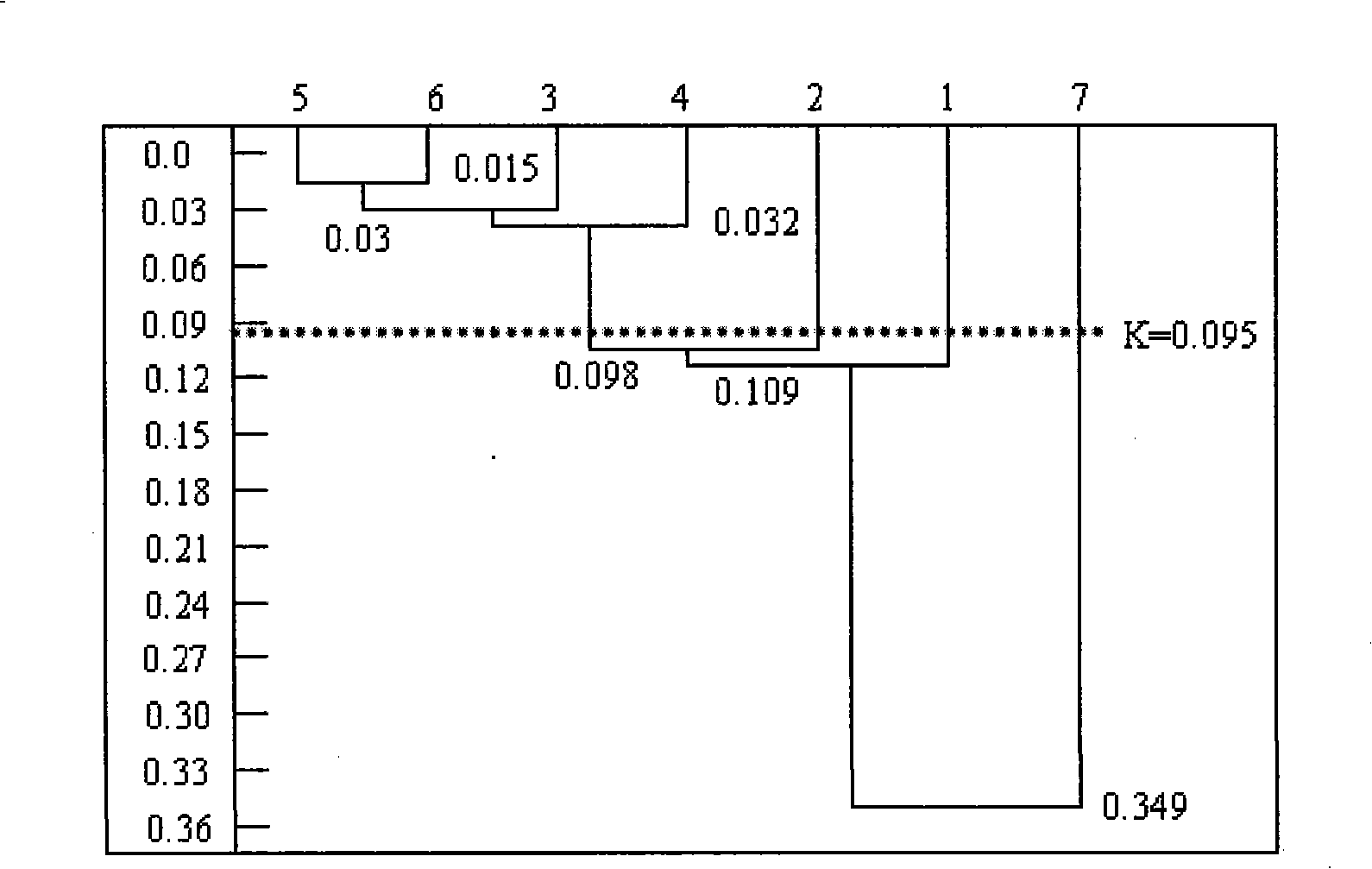
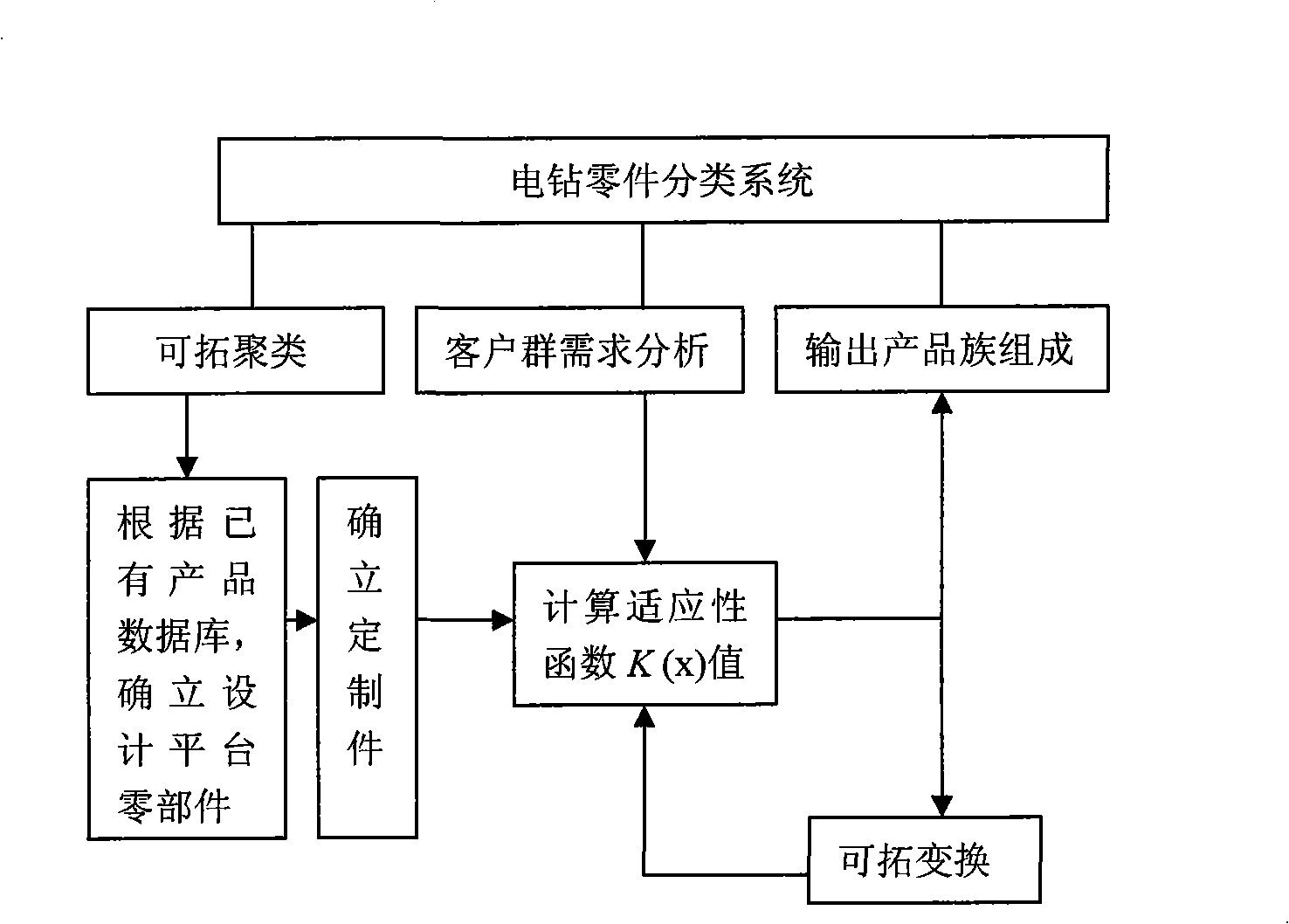
Part classification method based on developable clustering
ActiveCN101315644AReduce human interventionFacilitate sorting of structural featuresSpecial data processing applicationsClassification methodsSymmetric matrix
The invention relates to a parts classification method based on expansible cluster, which comprises the following steps: 1) the node domain of the structural characteristic of parts is extracted; 2) the characteristic variable numerical value v and the interval V of the parts are determined; 3) the distance formula of each part structure is established; 4) the structural relevancy T(i, j) of parts Ri and Rj is determined; 5) numerical analysis is carried out to a symmetric matrix M; 6) the average relevancy numerical value of cluster analysis is established; 7) the n minus 2 symmetric matrix is obtained by utilizing the algorithm process of step 5) to the newly formed n minus 1 symmetric matrix, the processes are circulated, and when the minimum relevancy is more than K value, the cluster process is terminated and a unique cluster result is obtained: the category of products and the parts of each category. The invention provides a part classification method based on the expansible cluster, which has clear relevancy analysis, high classification efficiency and high accuracy.
Owner:ZHEJIANG UNIV OF TECH
Pedestrian detection feature extraction method in road traffic auxiliary driving environment
InactiveCN106446792AThe detection process is fastDetection speedScene recognitionBiometric pattern recognitionSupport vector machine svm classifierFeature vector
The invention discloses a pedestrian detection feature extraction method in a road traffic auxiliary driving environment. The pedestrian detection feature extraction method comprises the following steps of S1, establishing a positive sample library and a negative sample library used for training, and performing normalization processing; S2, calculating two layers of HOG feature vectors of each image from the sample library images; S3, combining all feature vectors of positive and negative samples into an HOG feature matrix V for the first layer HOG feature vector v calculated in the step S2; S4, performing symmetrical feature calculation on the second layer HOG feature vector w calculated in the step S2, extracting an HOG symmetrical feature vector s, and combining HOG symmetrical feature vectors of all sample images into a symmetric matrix S; S5, performing serial connection on obtained two feature matrixes V' and S, and combining into a new feature matrix Q; S6, using the feature matrix Q to train a support vector machine (SVM) classifier; and S7, adopting the SVM linear classifier to detect traffic road images. The pedestrian detection feature extraction method has the advantages of simple principle, easy realization, high detection speed, high accuracy and the like.
Owner:DALIAN ROILAND SCI & TECH CO LTD
Metrology imaging targets having reflection-symmetric pairs of reflection-asymmetric structures
ActiveUS10190979B2Scattering properties measurementsPhotomechanical exposure apparatusMetrologyEngineering
Metrology targets, design files, and design and production methods thereof are provided. Metrology targets comprising at least one reflection-symmetric pair of reflection-asymmetric structures are disclosed. The structures may or may not be periodic, may comprise a plurality of unevenly-spaced target elements, which may or may not be segmented. The asymmetry may be with respect to target element segmentation or structural dimensions. Also, target design files and metrology measurements of the various metrology targets are disclosed.
Owner:KLA CORP
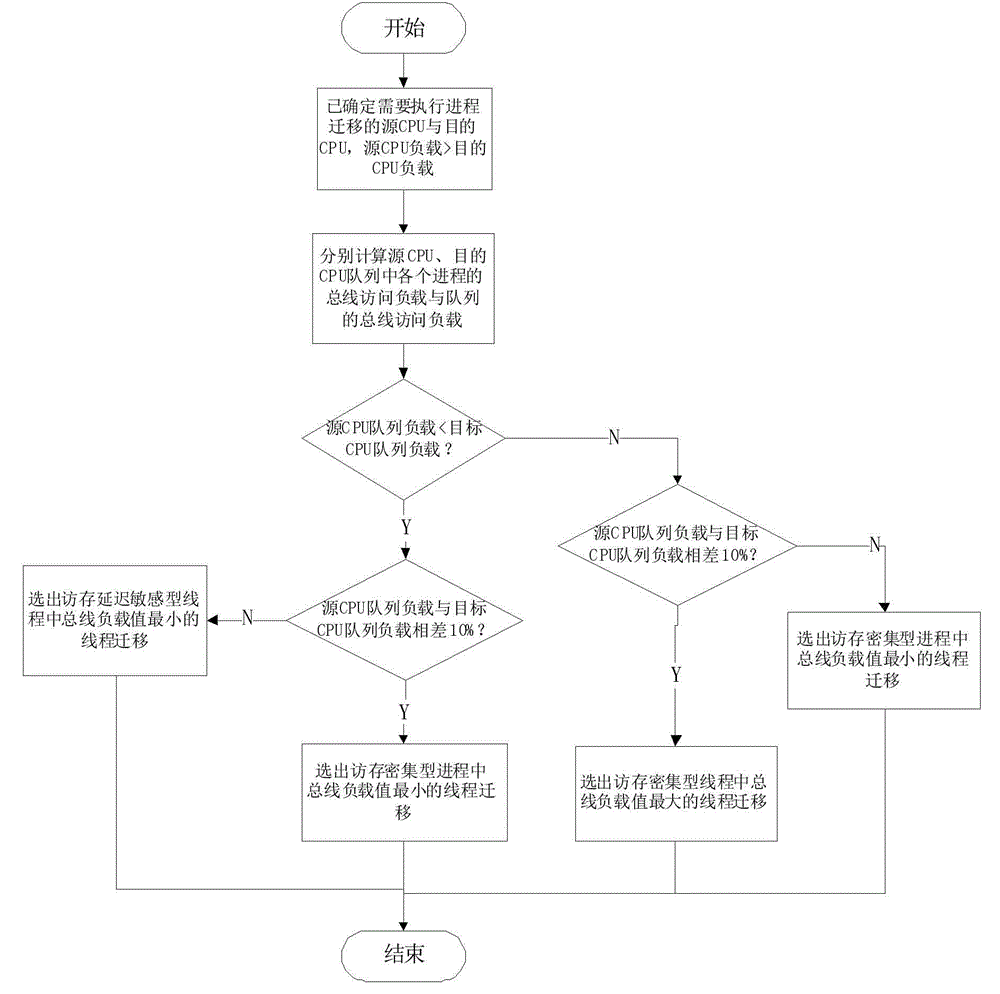
Task scheduling optimizing method based on SMP (symmetric multi-processing) system
ActiveCN104679593ASolve the problem of resource utilizationIncrease profitProgram initiation/switchingResource allocationCpu loadSymmetric matrix
The invention discloses a task scheduling optimizing method based on an SMP (symmetric multi-processing) system. The task scheduling optimizing method specifically comprises the following steps of firstly, dividing the accessing types; according to the accessing intensity on a memory or a bus, dividing a to-be-scheduled thread into an accessing delay sensitive type and an accessing intensive type; accessing the thread bandwidth, namely the bus accessing rate of the thread in the running process is obtained by a built-in hardware property counting function of a processor; equalizing and optimizing a load, wherein the load is equalized by a calling function according to a scheduling domain; according to the use conditions of the bus bandwidth, dividing an SMP task scheduling optimizing strategy into two parts, namely a property technical sampling module and a bus accessing load equalizing module. Compared with the prior art, the task scheduling optimizing method based on the SMP system has the advantages that the use of the bus bandwidth is optimized on the basis of no influence on the CPU (central processing unit) load equalizing effect of the original algorithm, the effective utilization rate of the bus is improved, the practicality is high, and the method is suitable for being popularized.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
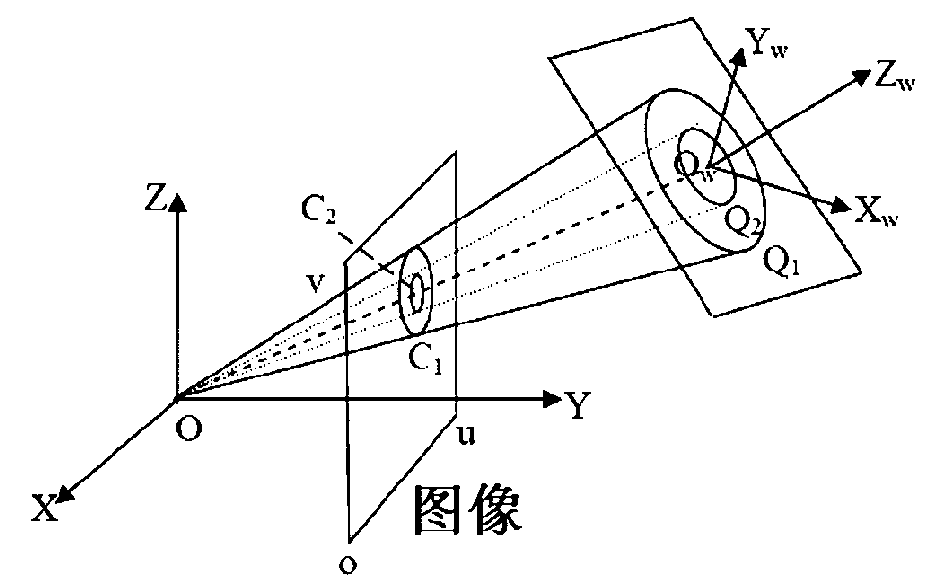
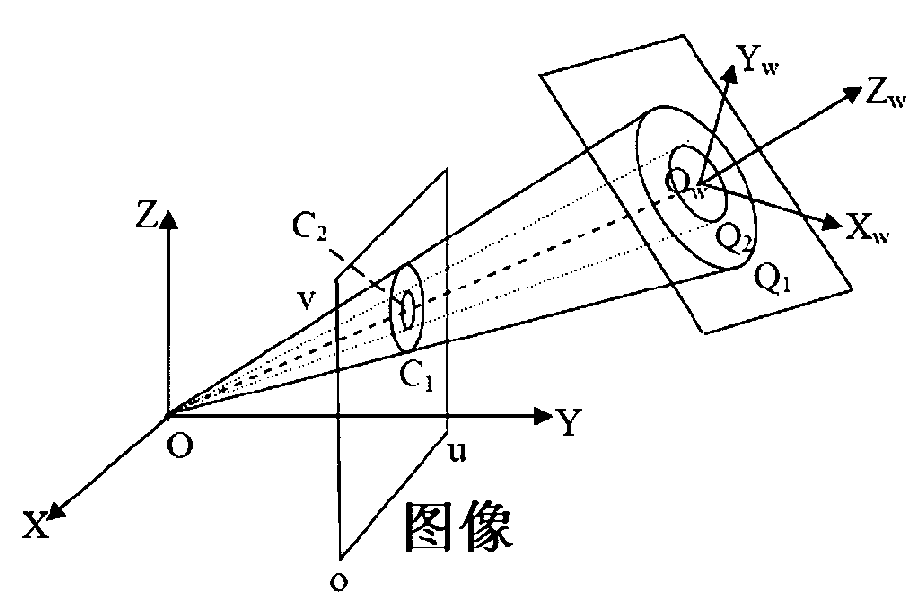
Method for calibrating camera by utilizing concentric circles
InactiveCN101783018AEasy and accurate calibrationRealize CalibrationImage analysisAutonomous Navigation SystemImaging processing
The invention discloses a method for calibrating camera by utilizing concentric circles, and belongs to the technical field of image processing, which comprises the following steps: pasting white paper on a horizontally even panel to prepare a calibration object; acquiring three initial images; fitting according to an elliptical point set to obtain an elliptical image matrix; and obtaining a projection equation of a circle by adopting projective transformation, calculating circle center projection of two concentric circles according to a correlation of a projection equation of the concentric circles, and obtaining a symmetrical matrix according to the circle center projection so as to obtain an internal parameter matrix of the camera and complete the internal parameter calibration of the camera. The method avoids an error caused by a mode that the internal parameters of the camera are determined by calculating imaginary circular points, and a linear method is adopted to simply, conveniently and accurately calibrate all the internal parameters of the camera (including a principal point position, an aspect ratio and an obliquity factor). The method is suitable for vision-based autonomous navigation system and non-contact industrial detection.
Owner:SHANGHAI JIAO TONG UNIV
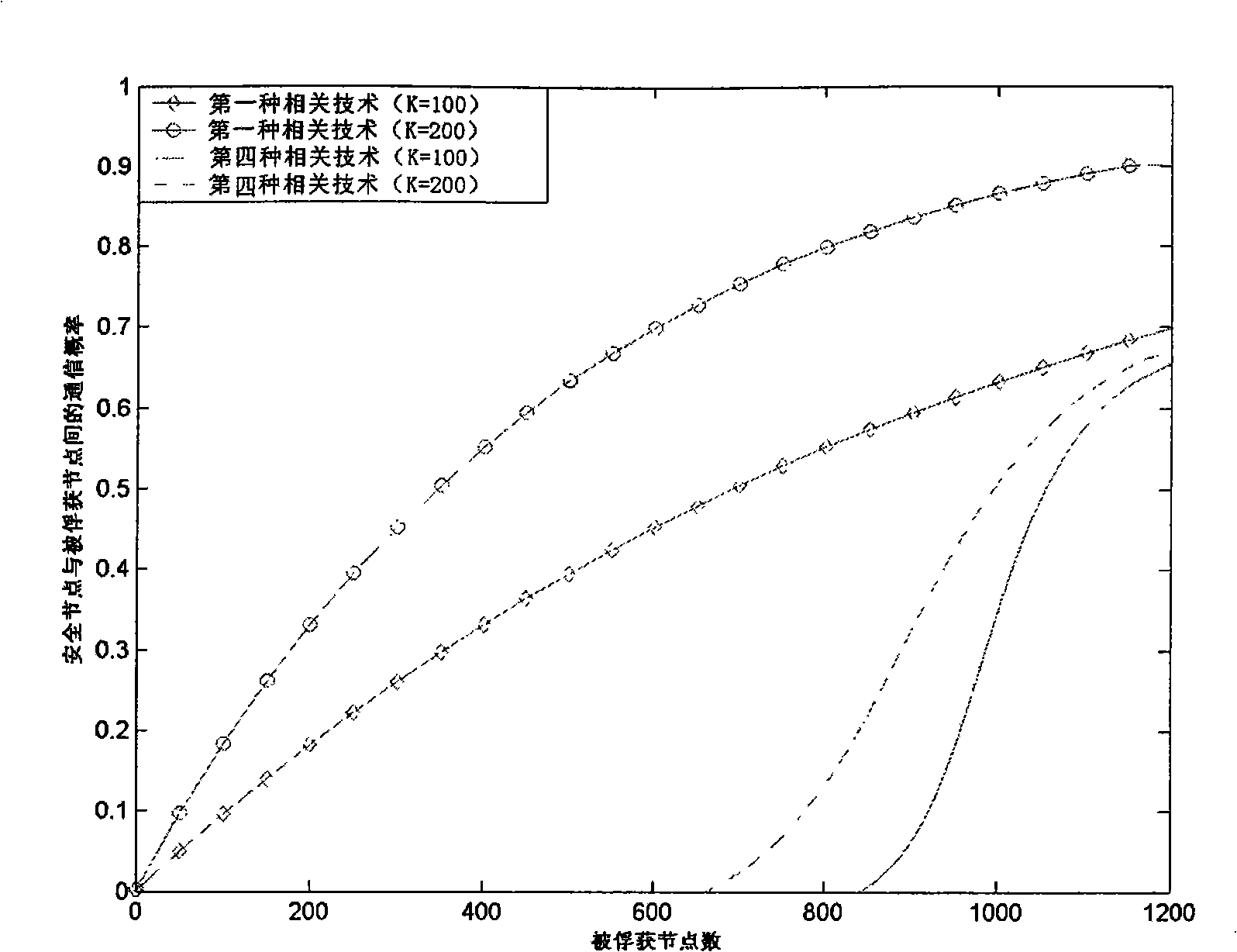
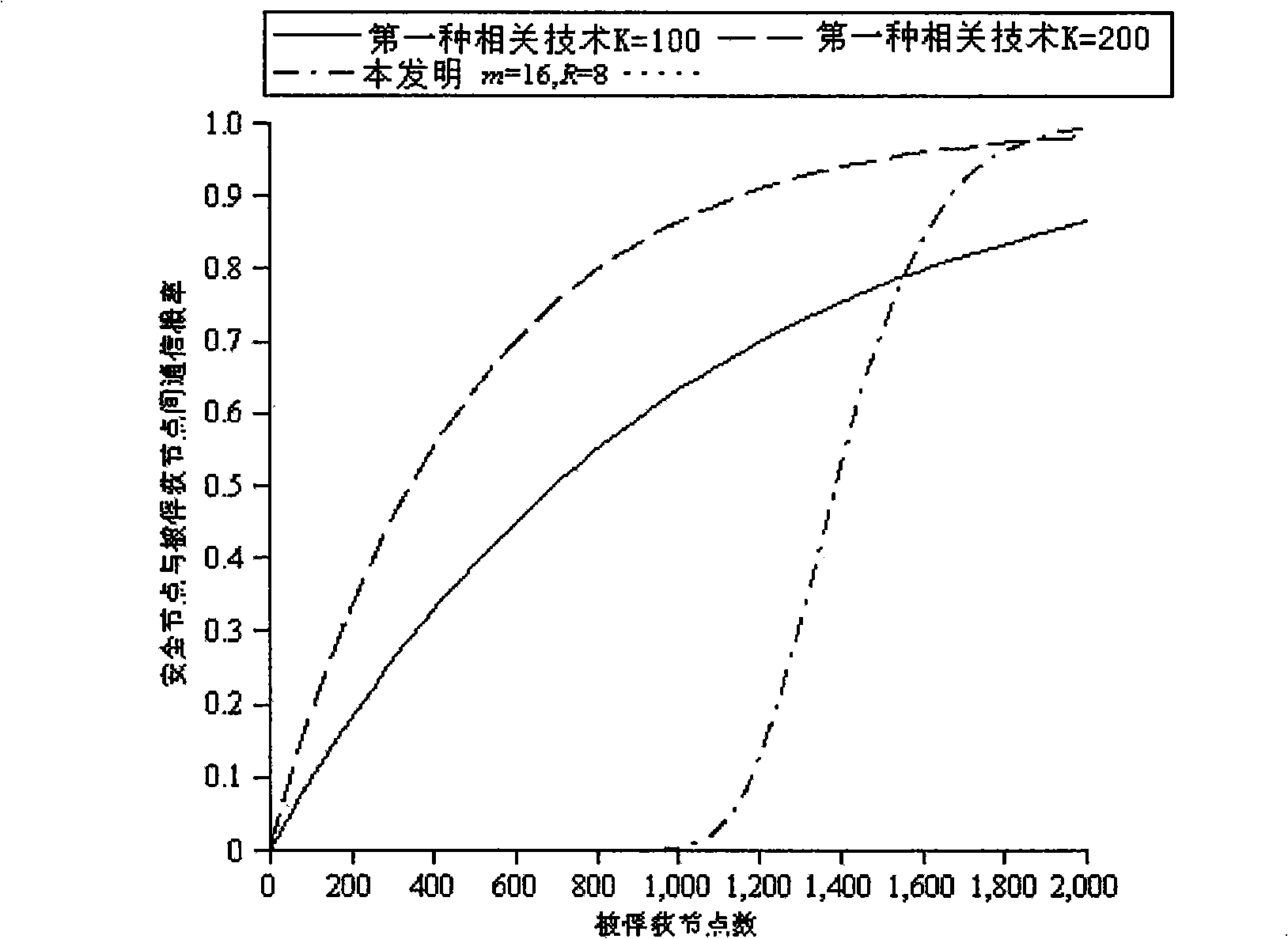
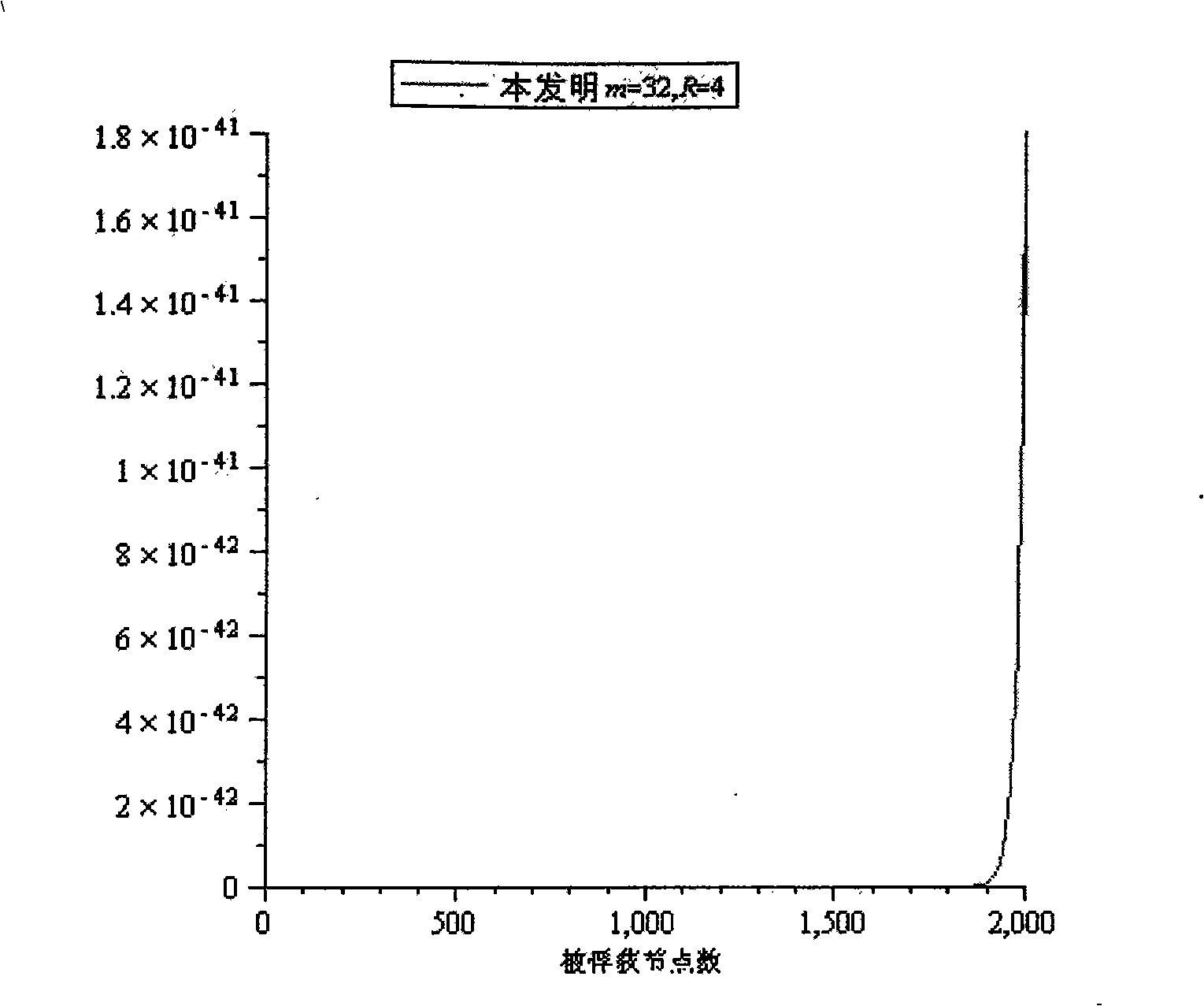
Method for pre-distributing wireless sensor network cipher key
The invention relate to a wireless sensor network key pre-distribution method, which comprises the following steps: step S001: disposition server generating R upper triangular matrixes G and R diagonal matrixes D at random on the finite field GF (q); step S002: generating R groups of real symmetric matrixes K; step S003: saving the ID of every node, row vector seed gir, column vector; step S004: starting base station, and clustering networking; step S005: discovering the shared secret key pair corresponding to secret key space between nodes by pre-distributing secret key; step S006: distributing cluster secret keys with cluster head towards inner-cluster by the constructed shared secret key pair between nodes; step S007: expanding the secret key space dimension. The invention achieves lower node capacity, communication complexity and calculation complexity while ensuring the network completely is communicated; and has higher node anti-capture capability.
Owner:SOUTHEAST UNIV
Brain function magnetic resonance image classification-oriented TSK fuzzy system modeling method
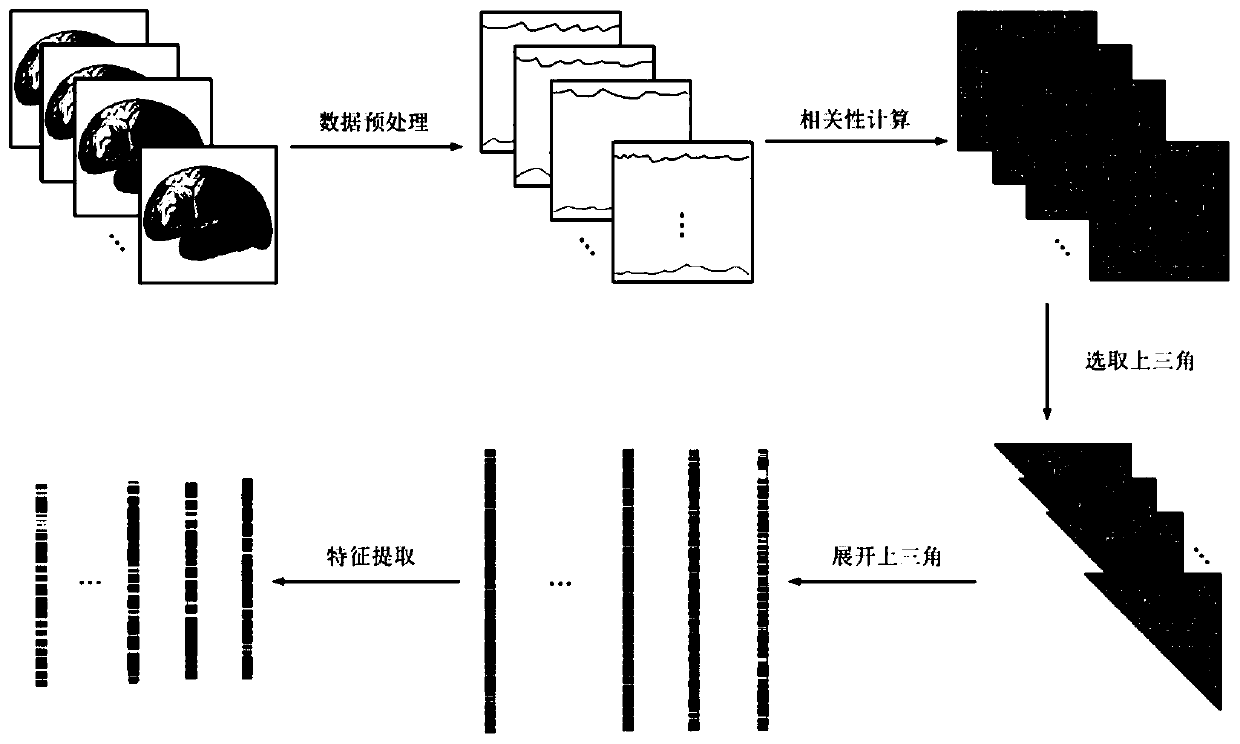
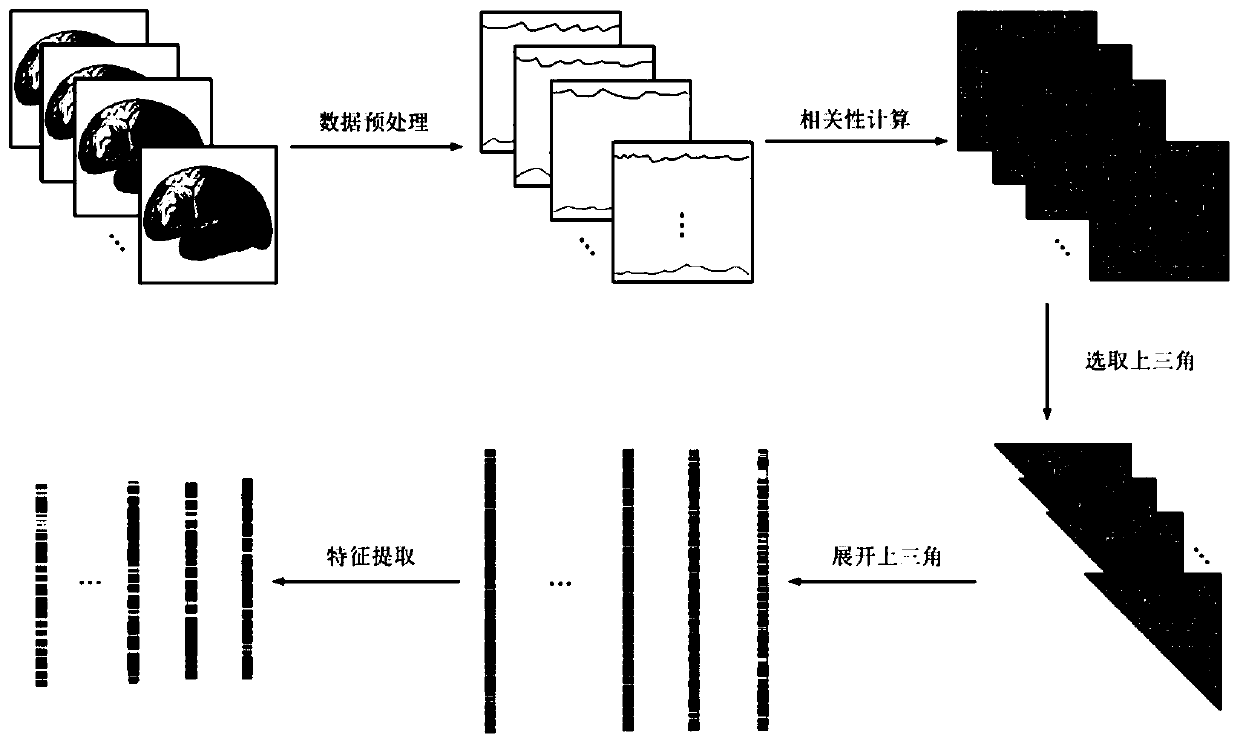
ActiveCN109993230AImprove interpretabilityImprove accuracyInternal combustion piston enginesRecognition of medical/anatomical patternsSpearman's rank correlation coefficientEuclidean vector
The invention relates to a TSK fuzzy system modeling method for brain function magnetic resonance image classification, and belongs to the technical field of image processing. The method comprises thefollowing steps: S1, preprocessing a brain function magnetic resonance image; s2, calculating a Pearson correlation coefficient among the brain regions to obtain a symmetric matrix, taking a triangleon the symmetric matrix to unfold according to lines to obtain a sample feature vector, and representing the data of one picture by each column of the sample feature vector; s3, carrying out featureextraction on the sample feature vectors; and S4, constructing a classifier to classify the brain function magnetic resonance images, and solving a model used by the classifier by adopting an alternating optimization algorithm to complete image classification. According to the method, the nonlinear classifier is constructed based on the TSK fuzzy system, the correlation between the features is represented by using the undirected graph, and the brain function magnetic resonance images can be accurately classified.
Owner:JIANGNAN UNIV
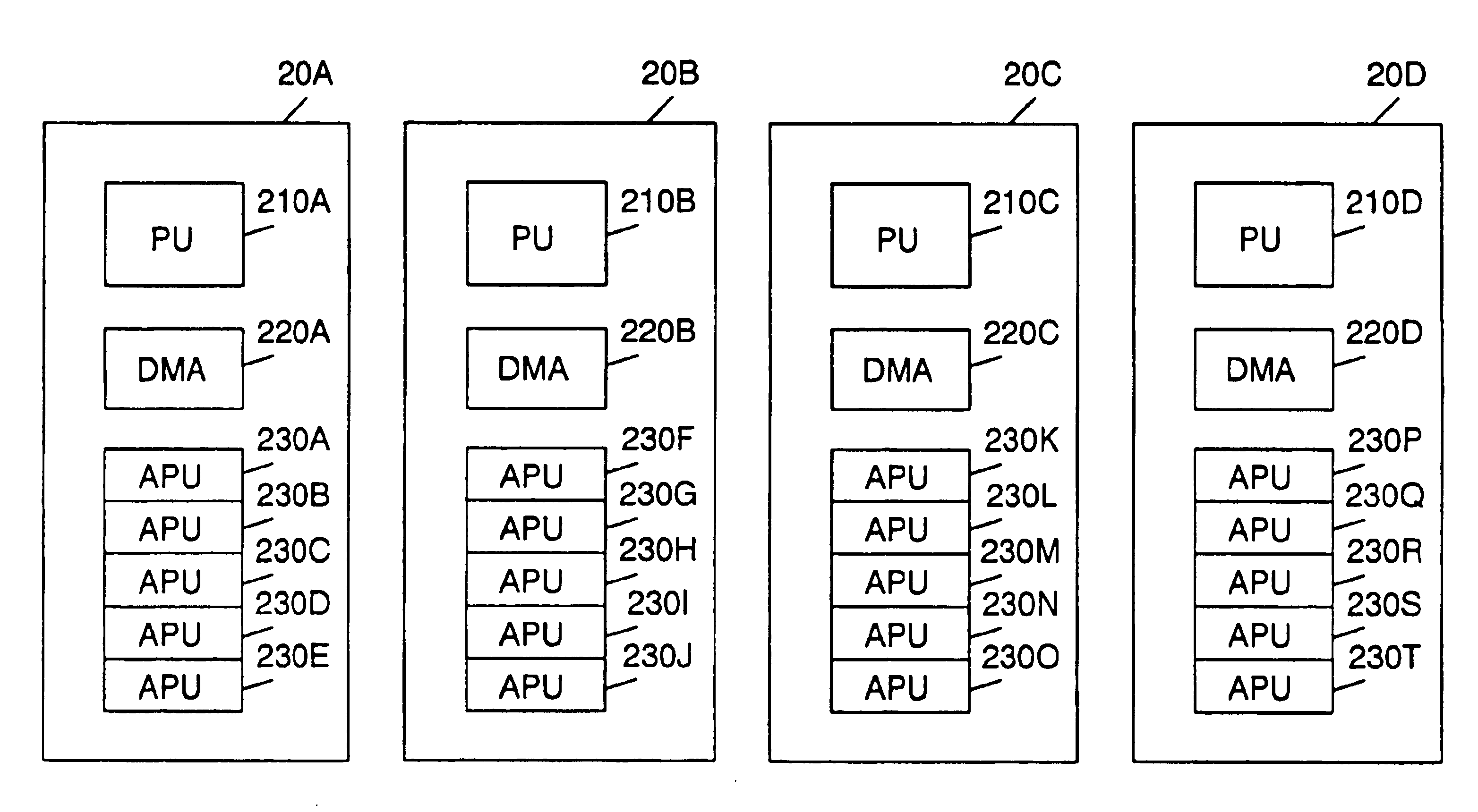
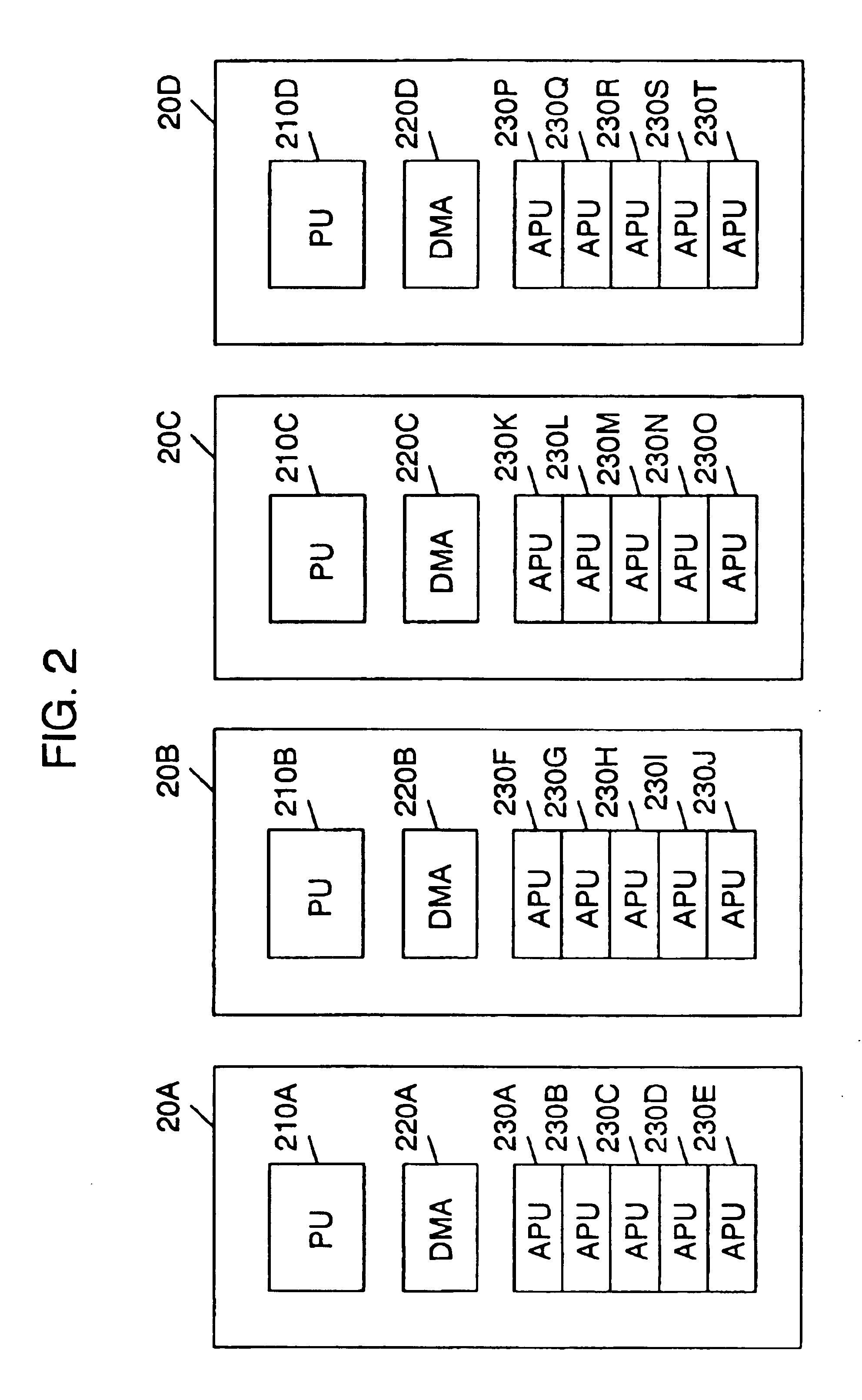
Symmetric multi-processing system utilizing a DMAC to allow address translation for attached processors
InactiveUS6907477B2Memory architecture accessing/allocationOperational speed enhancementDirect memory accessProcessing element
A method and system for attached processing units accessing a shared memory in an SMT system. In one embodiment, a system comprises a shared memory. The system further comprises a plurality of processing elements coupled to the shared memory. Each of the plurality of processing elements comprises a processing unit, a direct memory access controller and a plurality of attached processing units. Each direct memory access controller comprises an address translation mechanism thereby enabling each associated attached processing unit to access the shared memory in a restricted manner without an address translation mechanism. Each attached processing unit is configured to issue a request to an associated direct memory access controller to access the shared memory specifying a range of addresses to be accessed as virtual addresses. The associated direct memory access controller is configured to translate the range of virtual addresses into an associated range of physical addresses.
Owner:IBM CORP
Symmetrical matrix representation of dipole UWB antenna
InactiveUS20090256767A1Easily and simply mass productionIncrease productionSimultaneous aerial operationsAntenna feed intermediatesDipole antennaSymmetric matrix
A symmetrical matrix representation of dipole UWB antenna, mounted on a substrate and attachable to a wireless communication apparatus, comprises a first radiation arm, said first radiation arm comprising a first feed point, a first branch, a second branch, and a third branch, said first branch, said second branch, and said third branch are spaced in parallel, said first feed point and said second branch are aligned; and a second radiation arm, said second radiation arm comprising a second feed point, a fourth branch, a fifth branch, and a sixth branch, said fourth branch, said fifth branch, and said sixth branch are spaced in parallel, said first feed point and said second branch are aligned; wherein said first feed point and said second feed point are interconnected to a wireless communication apparatus.
Owner:KINSUN INDS
Transductive low-rank tensor discrimination analysis method
InactiveCN107609580ACharacter and pattern recognitionComplex mathematical operationsPattern recognitionAnalysis method
The invention discloses a transductive low-rank tensor discrimination analysis method, which comprises the following steps that: N image sets are given, and image set data matrix which is greater than1 and less than N in the data matrixes of the N image sets gives category labeling information, and N feature matrixes extracted by the N image sets are mapped into points on a Grassmann manifold; each point on the Grassmann manifold which represents an image set feature matrix is mapped to a symmetric space to form N b-order symmetric matrices; the N b-order symmetric matrices are combined to form a tensor; a target function is constructed for solving the discrimination low-rank representation matrix of the tensor; and an iterative convergence threshold value algorithm is adopted to solve the target function to obtain the discrimination low-rank representation matrix of the tensor. By use of the method, a situation that original image set data is directly taken as the input tensor is avoided, and calculation is carried out through transformation to Euclidean space through one piece of mapping on the basis of similarity between points on the Grassmann manifold so as to form the tensor.
Owner:TIANJIN UNIV
Knowledge assisted space-time adaptive processing method integrating generalized symmetrical structure information
InactiveCN104215939AReduce demandEasy to detectWave based measurement systemsAlgorithmSpace-time adaptive processing
The invention provides a knowledge assisted space-time adaptive processing method integrating generalized symmetrical structure information. The knowledge assisted space-time adaptive processing method integrating the generalized symmetrical structure information comprises steps of (1) performing linear transformation through an unitary transformation matrix and transforming an original space-time adaptive processing problem to be in a form which is equivalent to the original space-time adaptive processing problem to enable a covariance matrix of the original space-time adaptive processing problem to be transferred into a real symmetric matrix in the same dimension from a generalized symmetric matrix; (2) obtaining an estimation of the transformed covariance matrix according to sample data; (3) solving an optimal real symmetric estimation of a prior covariance matrix under the minimum Euclidean distance; (4) solving a minimum mean square error estimation through a generalized linear combination and convex combination method in combination with training samples and the prior covariance matrix; (5) obtaining detector forms under part of uniform model and random non-uniform model assumption according to a two-step design and achieving target detection. The knowledge assisted space-time adaptive processing method integrating the generalized symmetrical structure information has the advantages of effectively reducing demanded quantity of the training samples during covariance matrix estimation in the space-time adaptive processing, remarkably improving the detector performances and being simple in achievement.
Owner:BEIHANG UNIV
Large-scale heterogeneous data oriented co-clustering method
ActiveCN104636454AJoint Clustering FastReduce sparsityWeb data indexingRelational databasesEntity typeDecomposition
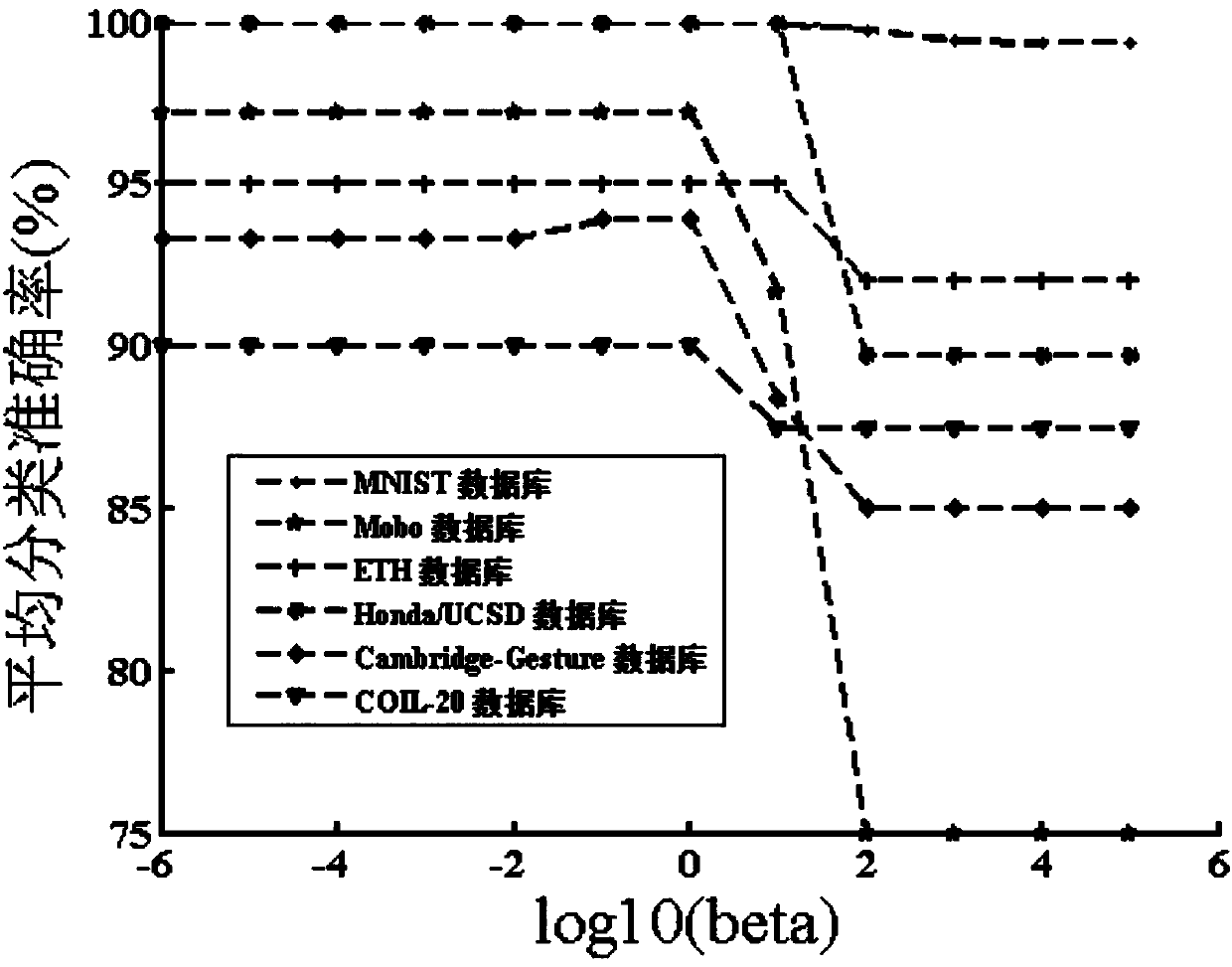
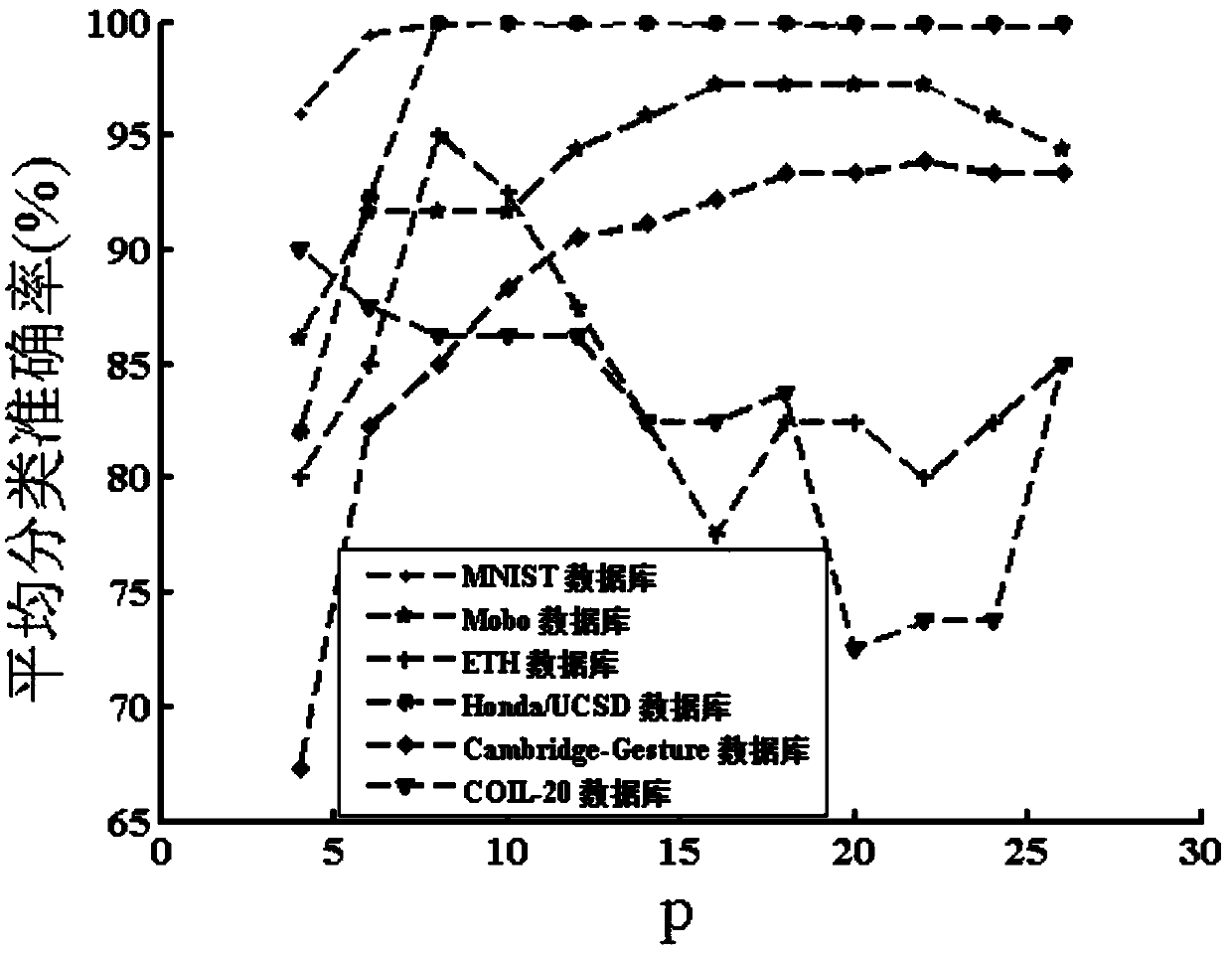
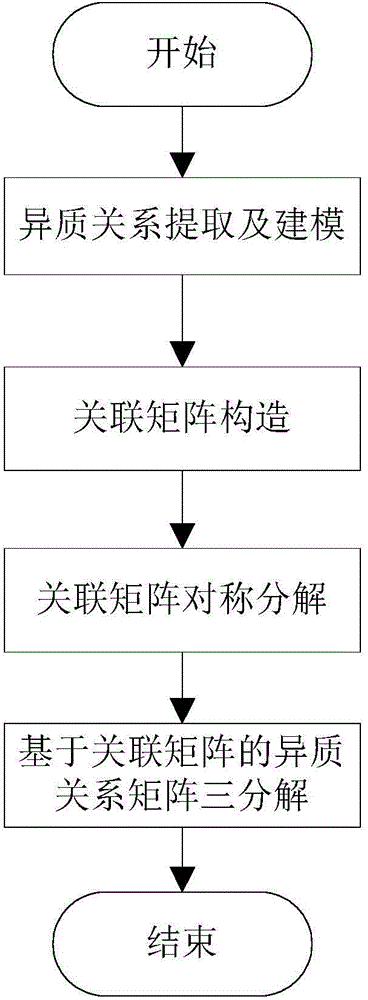
The invention discloses a large-scale heterogeneous data oriented co-clustering method. The method comprises the following steps that entities and a heterogeneous relation between the entities are extracted from the heterogeneous data to obtain a heterogeneous relation matrix; the entity X2 of the small scale is selected from two corresponding entities in the heterogeneous relation matrix, and an incidence matrix is set according to an incidence relation of the entity X2; a symmetric matrix sparse decomposition method is adopted to decompose the incidence matrix to obtain a clustering instruction matrix B corresponding to the entity X2; the matrix B is used as an input, tri-decomposition is carried out on heterogeneous relation moment R to obtain a clustering instruction matrix corresponding to an entity X1, and entity type division is achieved through the clustering instruction matrix corresponding to the entity X1 and the clustering instruction matrix corresponding to the entity X2. According to the method, sparsity of the matrixes can be reduced, and the accuracy of the co-clustering method is improved.
Owner:HARBIN ENG UNIV
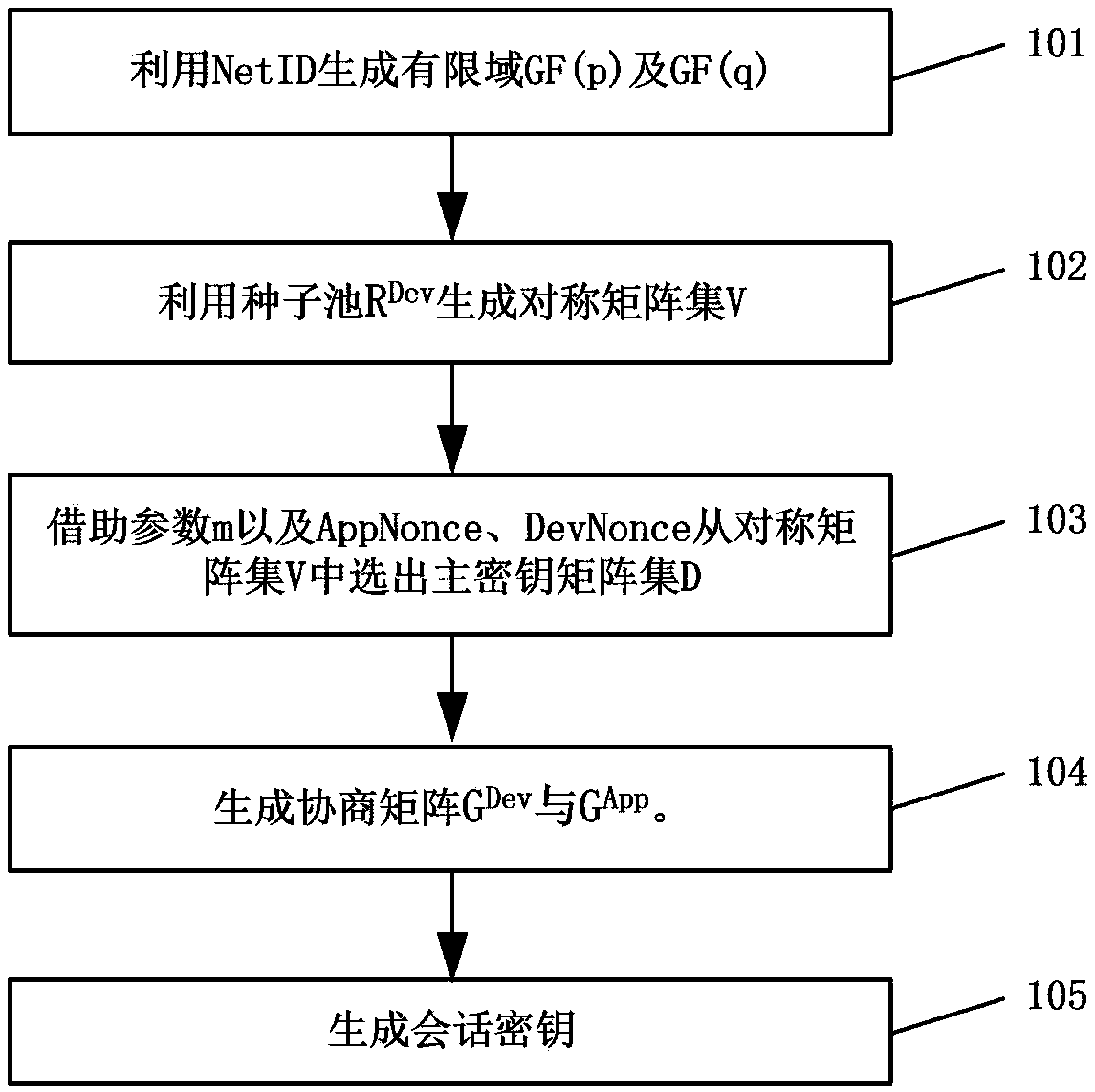
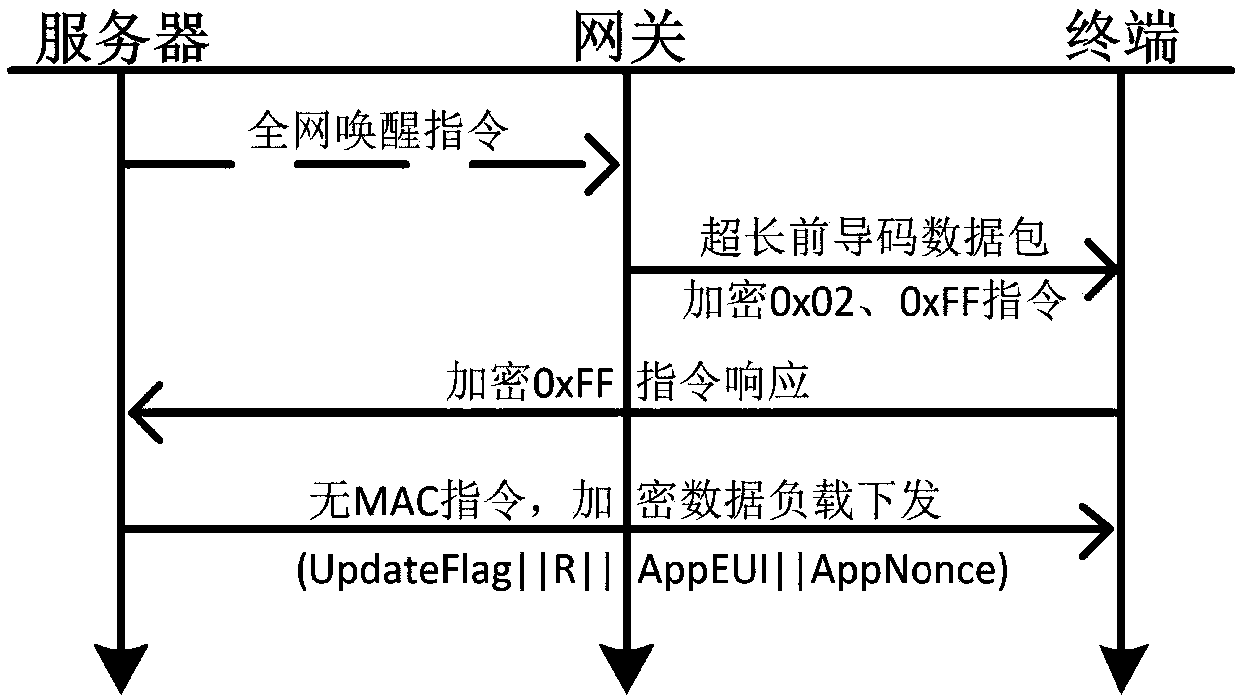
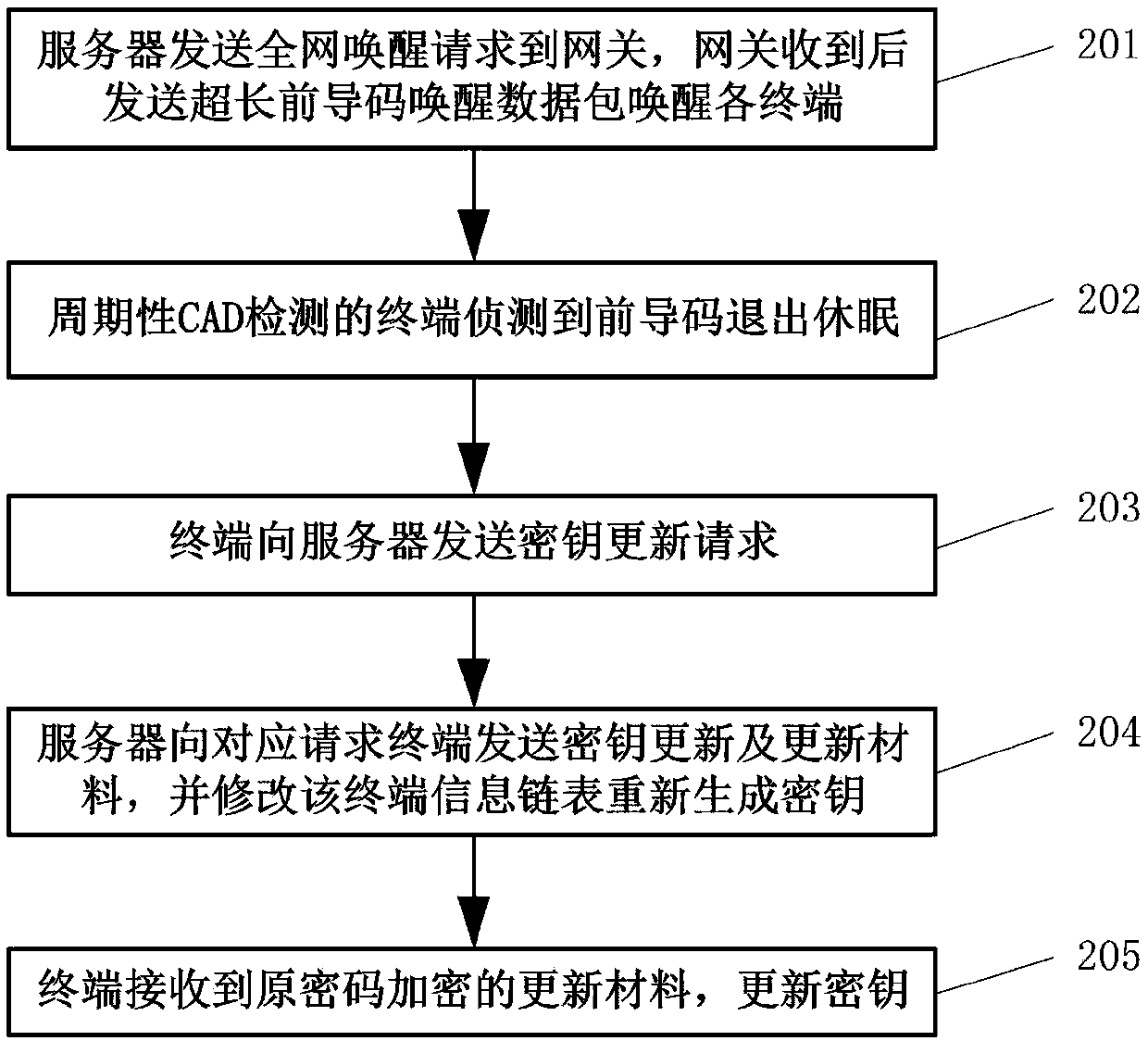
Matrix type key management method for LoRaWAN
ActiveCN107846280AImprove securityGuaranteed CompatibilityPower managementKey distribution for secure communicationRandom Number SeedRadio frequency
The invention relates to a matrix type key management method for LoRaWAN, and belongs to the field of the wireless wide area network. The method comprises the following steps: generating a symmetrix matrix of the key computation by using a random number seed pool R and a line limit number M, and accomplishing the negotiation in the key establishment with the help of the existing AppEUI, AppNonce and DevNonce in the LoRa access interaction message; generating the auxiliary material required by the individual key by using the specific message content of the LoRa and the character thereof; computing by using the matrix type matrix to obtain the AppSKey and NwkSKey required by the LoRa; and realizing the key update based on the WOR function by using the specific CAD mode of the LoRa radio frequency chip. Through the method disclosed by the invention, the conflict between the improved Blom key management key and the LoRa protocol is solved, and the security of the LoRa network has a certainimprovement.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method for solving node impedance matrix of electric system on basis of Gaussian elimination method of sparse symmetric matrix technology
InactiveCN104714928AReduce invalid calculationsReduce calculationComplex mathematical operationsNODALElectric power system
The invention belongs to the field of power system analysis and computing and discloses a method for solving a node impedance matrix of an electric system on the basis of a Gaussian elimination method of a sparse symmetric matrix technology. The method mainly comprises the following steps that a node admittance matrix Y is formed; the matrix Y and a matrix En form an augmented matrix Bn=[YEn]; elimination is carried out on the matrix Bn according to the spare symmetry to obtain Bn(n-1)'=[Y(n-1)'En(n-1)']; according to Y(n-1)'Zn=En(n-1)', sparseness and symmetry, elements above and on the left of a diagonal element Znn of a matrix Zn are solved; a matrix Y(k-1)' is obtained according to the Y(n-1)'; elements above and on the left of a diagonal element Zkk of the matrix Zk are obtained according to Y(k-1)'Zk=Ek(k-1)', sparseness and symmetry. By the utilization of the symmetric sparseness, all invalid computation of the previous generation process is avoided, and computation of about 50% of nonzero elements is reduced; by the utilization of the characteristics of the E matrix element structure and the sparseness of upper triangle elements, the elements of the matrix Zk are obtained in a back substitution mode according to a symmetry mode, and back substitution computation is greatly accelerated. The method can check IEEE-30, -57 and -118 node systems and the like, and the computation speed for the IEEE-118 node system can be improved by 96-97% compared with a traditional Gaussian elimination method and an LDU triangular decomposition method.
Owner:NANCHANG UNIV
Cipherkey setting method of heterogeneous wireless sensor network
InactiveCN102651864AImprove securityReduce storage consumptionNetwork topologiesSecurity arrangementLine sensorHash function
The invention relates to a cipherkey setting method of a heterogeneous wireless sensor network. The method comprises the following steps: step1, three layers of heterogeneous network structures are built; step2, a plurality of t-order symmetric binary polynomials are generated on a galois field GF (q), and S t-order symmetric binary polynomials form an N*N symmetric matrix A; each strong-capacity node stores a certain row vector j of an upper triangular matrix and a column vector j of a corresponding lower triangular matrix, meanwhile, the row number j of the certain row vector j is used as an ID number to be stored, and a Hash function is stored; step3, the cipherkeys of the strong-capacity nodes (H-sensor) and common sensor nodes (L-sensor) are pre-distributed; step4, the session cipherkeys among the strong-capacity nodes (H-sensor) are generated; and step5, the session cipherkeys of the strong-capacity nodes (H-sensor) and the common sensor nodes (L-sensor) are generated. Compared with the prior art, the method has the advantages that the relationship between the energy consumption and the safety of the wireless sensor network are further balanced; and on the basis that the storage consumption of the whole network is reduced, the safety of the network is increased, and the network nodes realize a 100-percent ability to resist capture attack.
Owner:FOSHAN DIXINGWEI AUTOMATION EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com