Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
150results about How to "Reduce storage consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
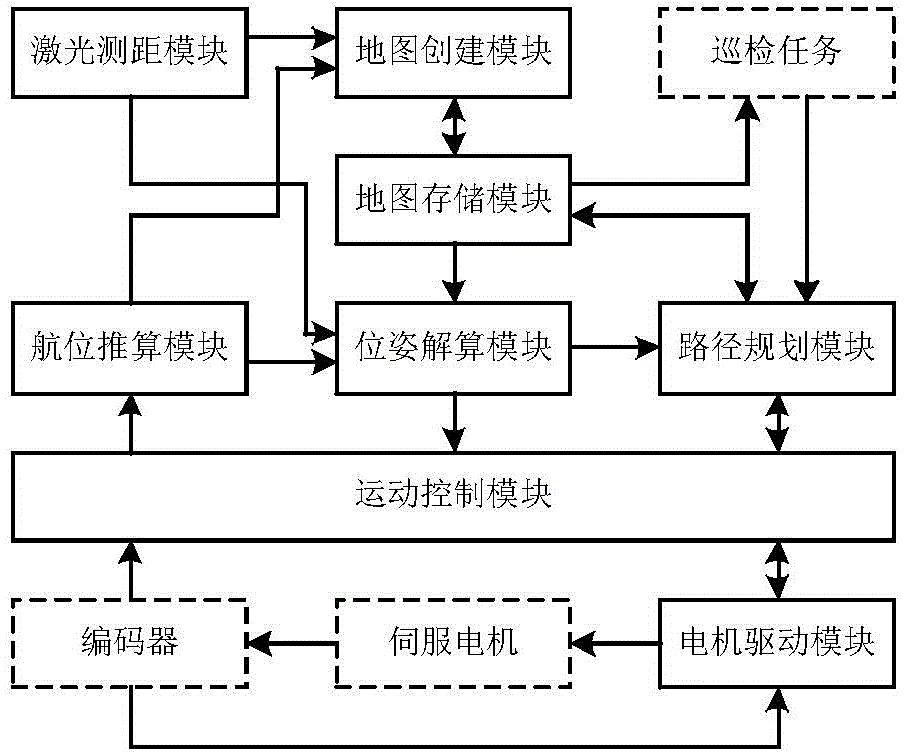
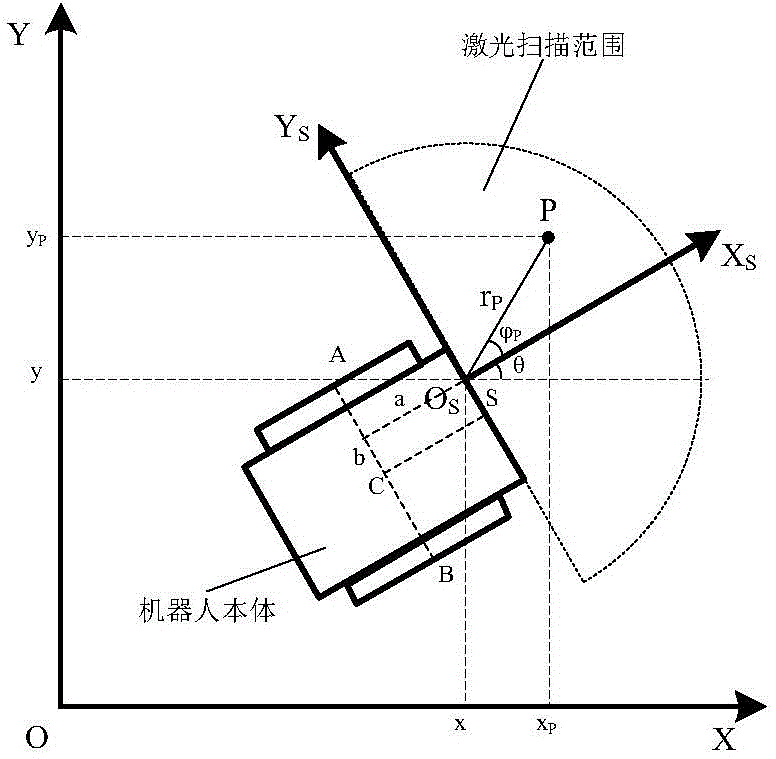
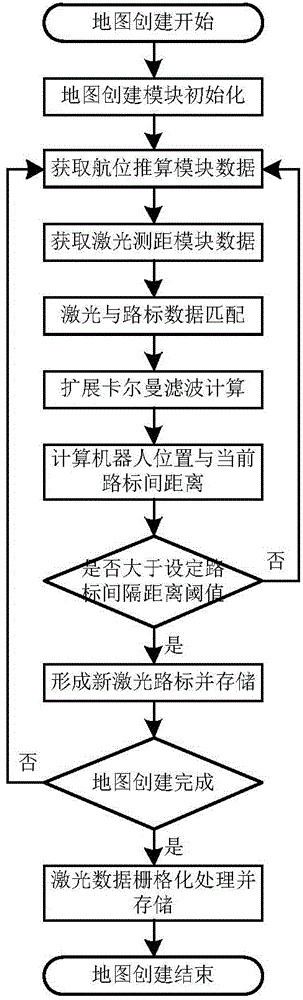
Transformer station inspection tour robot positioning navigation system and method
ActiveCN104914865APrecise positioningGuaranteed real-timeNavigational calculation instrumentsData visualisationLaser rangingTransformer
The invention discloses a transformer station inspection tour robot positioning navigation system and a method. Confidence obtained by a laser range finding module and a dead reckoning module is outputted to a map creation module and a pose resolving module; the map creation module creates a laser road sign map and a laser grid map which show a robot operation environment and are inputted into a map storage module for storage; the posture resolving module utilizes map data in the map storage module and output data of the dead reckoning module to perform real-time calculation on the current position and the posture of the robot and accesses the obtained posture data into a path planning module and a motion control module; the path planning module generates robot operation path data which is outputted to the motion control module; the motion control module generates motion control quantity according to the current position and posture data of the robot and the path planning data, and then is driven to execute by a motor. The transformer station inspection tour robot positioning navigation system realizes the accuracy positioning of the inspection tour robot in the transformer station.
Owner:STATE GRID INTELLIGENCE TECH CO LTD
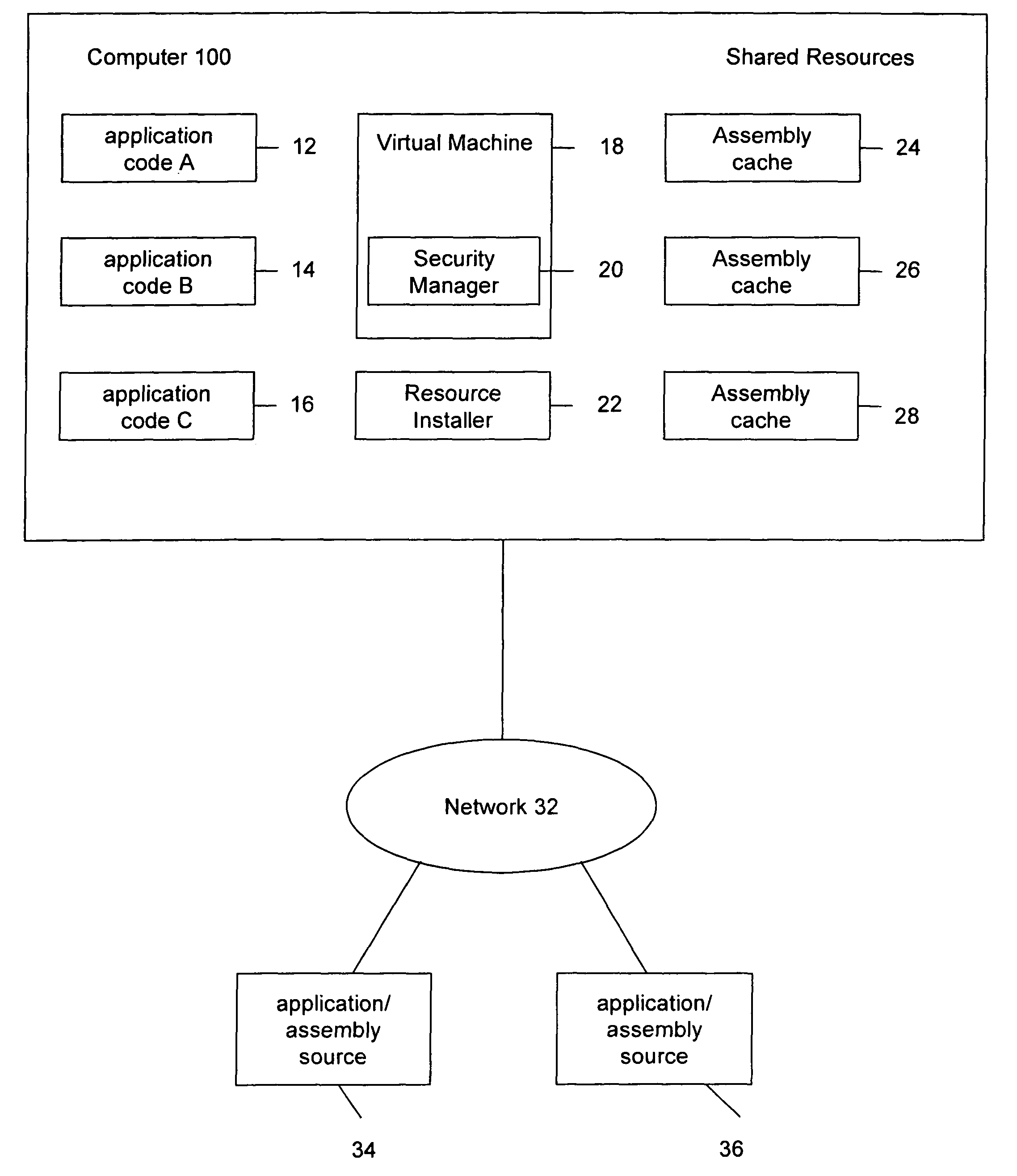
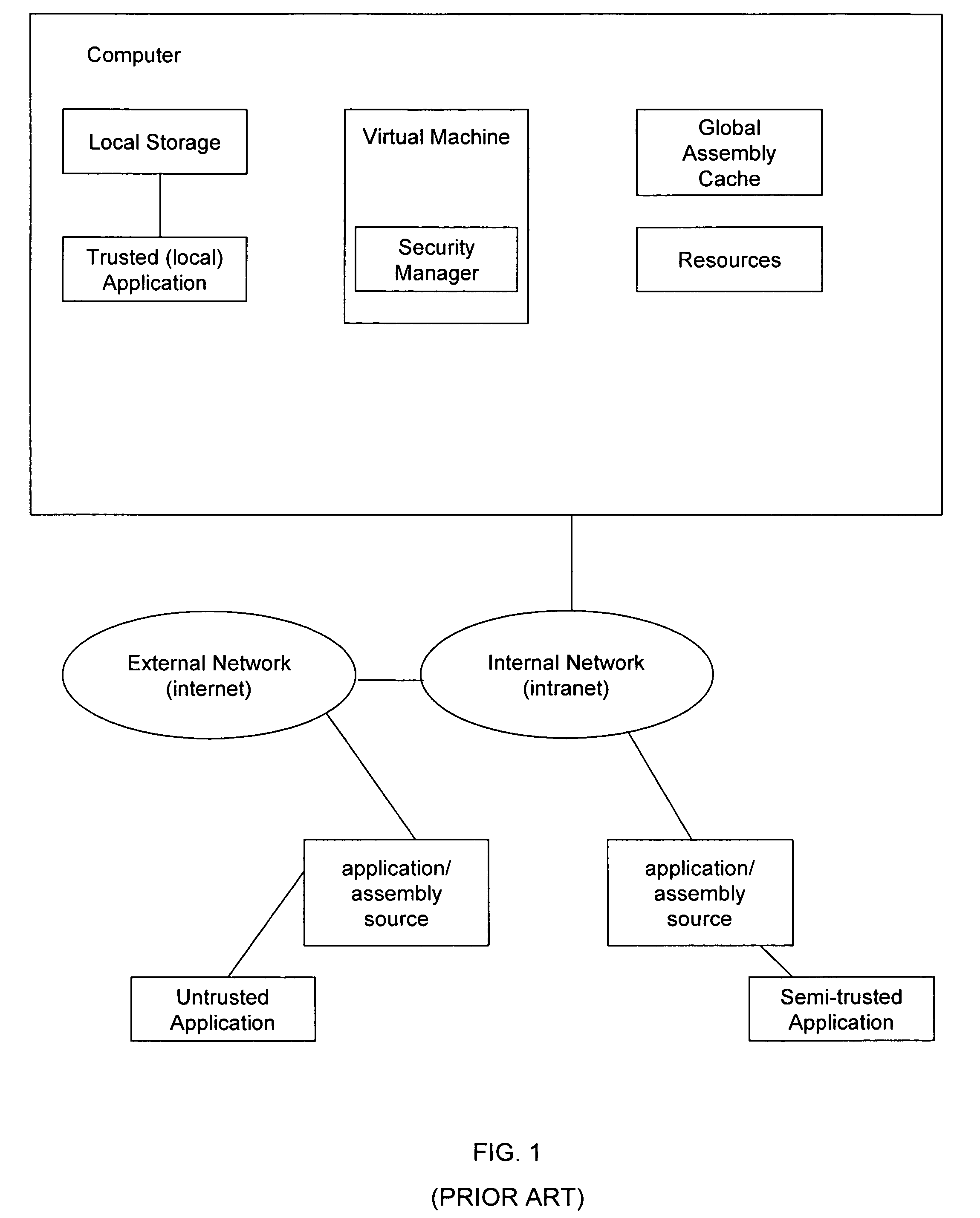
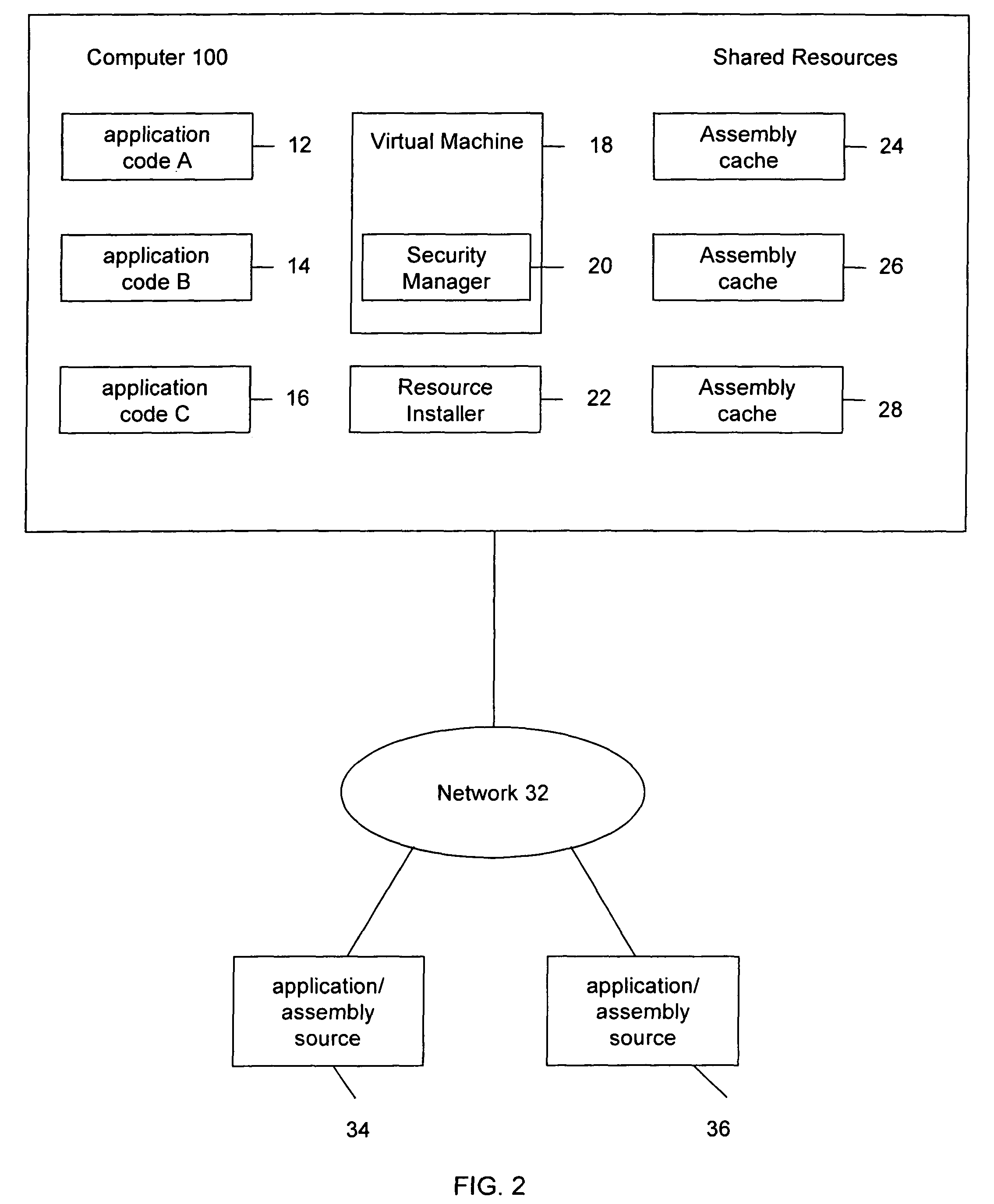
System and method for applying security policies on multiple assembly caches
ActiveUS7823186B2Reducing storage consumptionLimited informationPlatform integrity maintainanceTransmissionSecurity policyApplication software
The invention relates to a system and method for providing multiple assembly caches for storing shared application resources. Each assembly cache may be associated with a different security policies, locations, internal structures and management. An application may be determined to have access to an assembly cache based on the permission and security policy of the application and security policy of the assembly cache. Additionally, one or more assembly caches may have other policies for cache retention, resolution, and creation.
Owner:ORACLE INT CORP
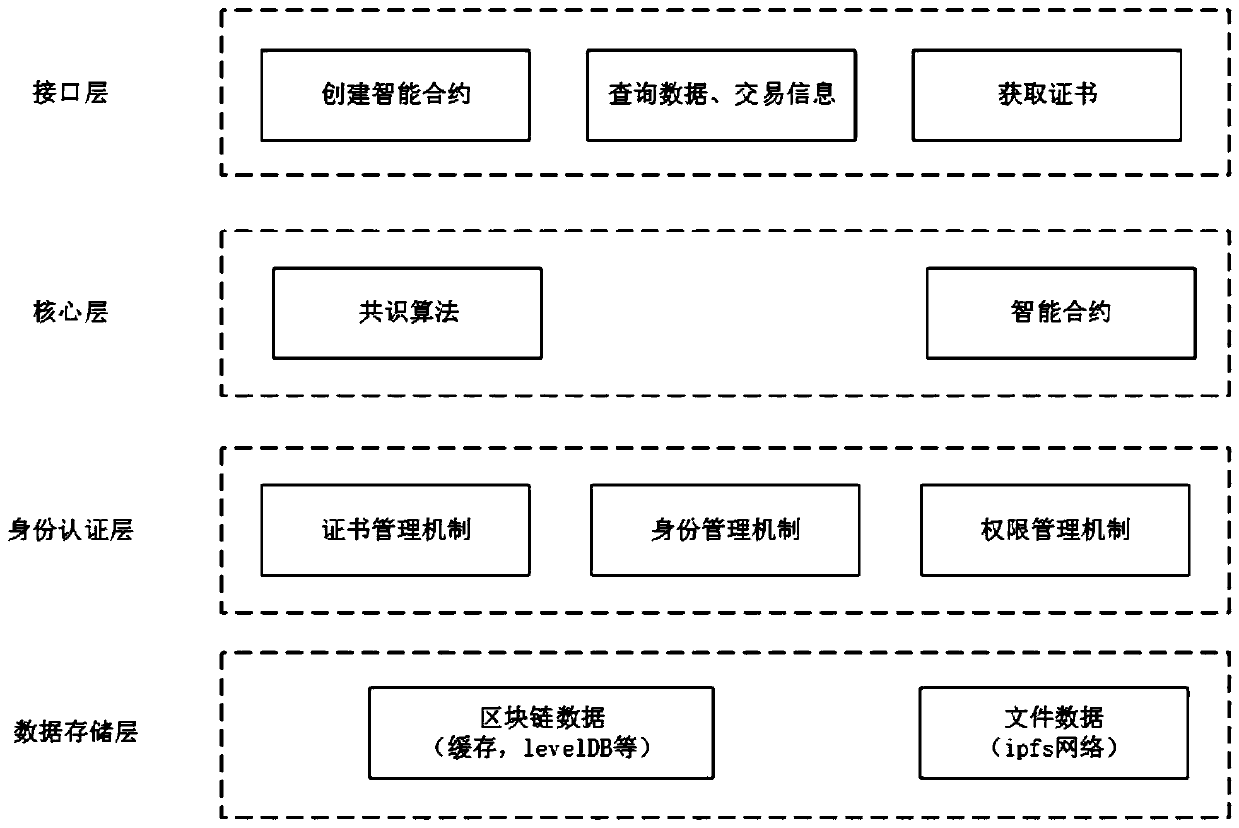
Data sharing solution based on a block chain technology
ActiveCN109871669AReduce storage consumptionDigital data authenticationTransmissionImproved algorithmAuthorization
The invention belongs to the field of resource aggregation, and particularly relates to a block chain technology-based data sharing solution, which comprises the following steps of: data model architecture design; business intelligent contract design; authority management and identity authentication design; access control mechanism design; data storage structure design. According to the multi-layer block chain model supporting massive data hierarchical authorization transactions, an offline storage mode is adopted, so that the storage space consumption of the block chain is greatly reduced. Comparison experiments verify that the Ethereum data model has great advantages in the aspects of data storage and access control compared with bit coins. An alliance chain consensus algorithm based ona message queue kafka and a private chain consensus algorithm based on an improved PBFT algorithm are provided.
Owner:HARBIN ENG UNIV
Image recognition method and system based on edge geometric features
ActiveCN103793712AMeet the high-speed real-time requirements of grabbing operationsImprove stabilityCharacter and pattern recognitionMinimum bounding rectangleEdge based
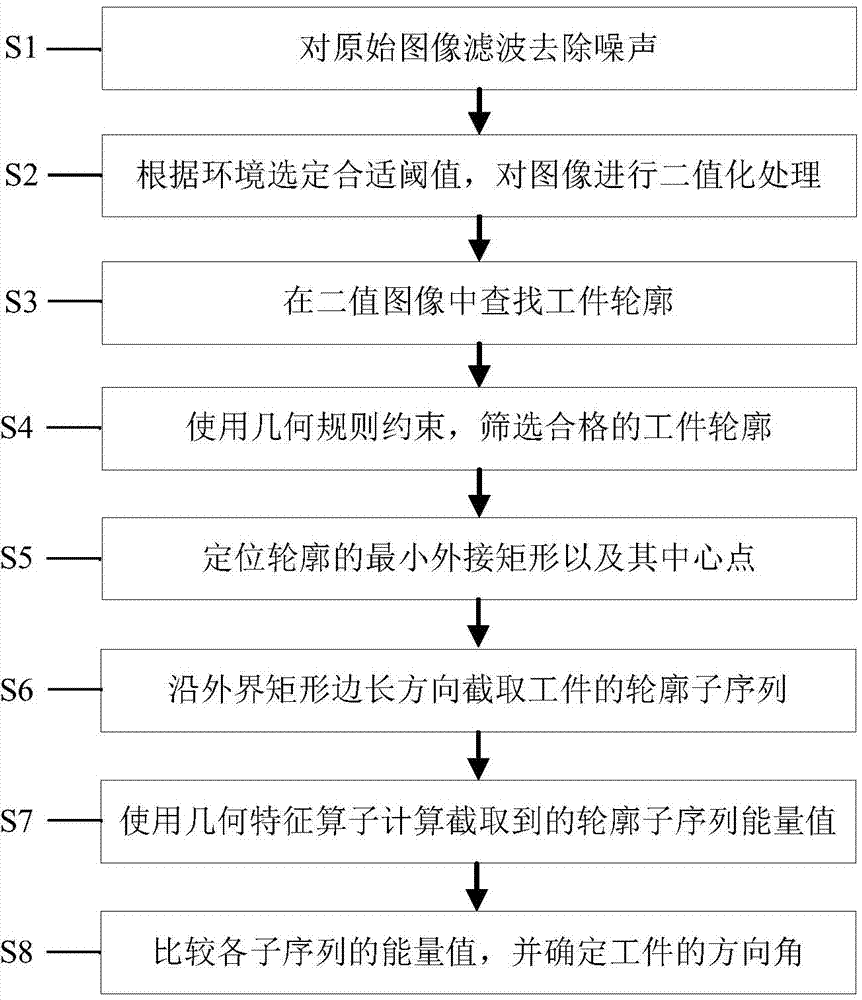
The invention discloses an image recognition method based on edge geometric features. The image recognition method based on the edge geometric features comprises the steps that filtering processing is carried out on an original image of a workpiece; binarization processing is carried out on the image after the filter processing; the image after the binarization processing is searched to obtain a contour sequence set; a qualified workpiece contour is screened out of the contour sequence set; a minimum enclosing rectangle of the workpiece contour is determined, and the central point of the workpiece contour is determined; four subsequences of the workpiece contour are intercepted in the directions of the four edges of the minimum enclosing rectangle; energy values of all the four subsequences are calculated by using edge geometric feature operators; the subsequence with the maximum energy value in the four subsequences is determined, and direction angles of the workpiece are determined. The invention further provides a corresponding image recognition system. According to the image recognition method and system based on the edge geometric features, a template database of workpieces does not need to be established, storage consumption is lowered, calculation time is reduced, the requirement for high speed real-time performance can be met, and meanwhile the image recognition method and system have high fast recognition capability.
Owner:HUAZHONG UNIV OF SCI & TECH
A sparse convolutional neural network accelerator and an implementation method
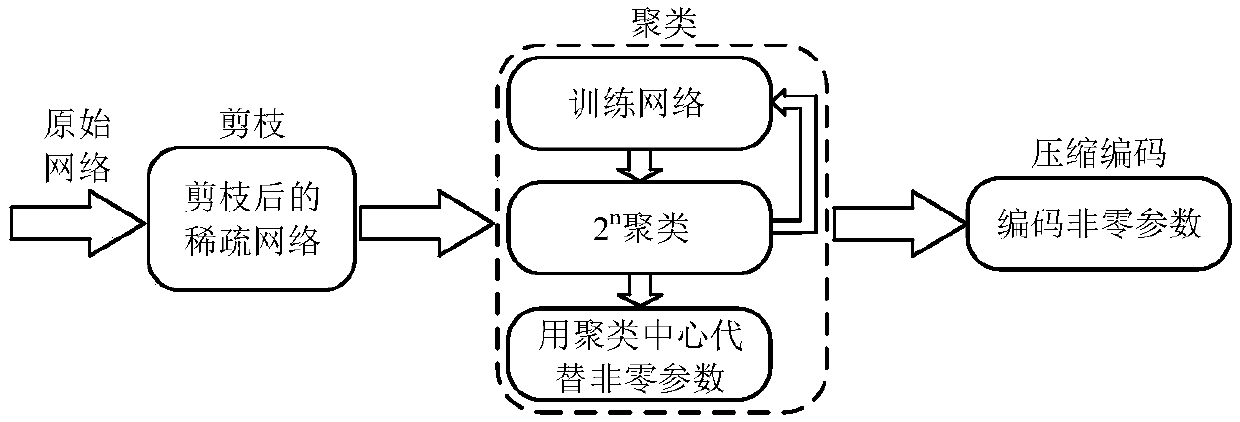
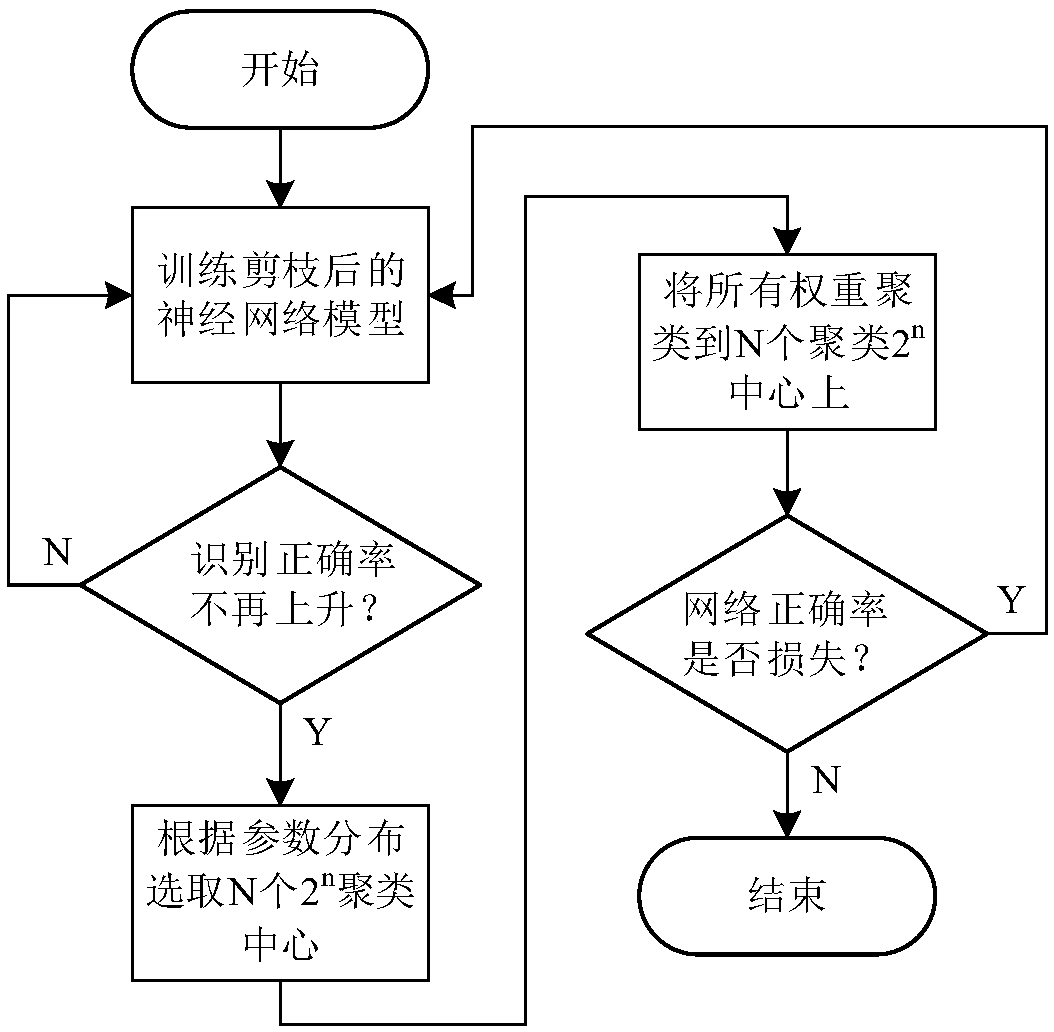
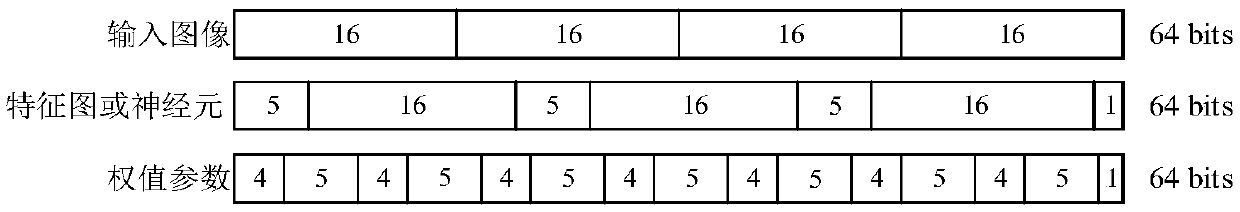
ActiveCN109635944ASimplify complexitySave storage resourcesNeural architecturesPhysical realisationEngineeringNeuron
The invention relates to a sparse convolutional neural network accelerator and a realization method, and the method comprises the steps: reading the connection weight of a sparse network in an off-chip DRAM into a weight input buffer area, decoding the connection weight through a weight decoding unit, and storing the connection weight in a weight on-chip global buffer area; Reading neurons into aneuron input buffer area, decoding the read neurons through a neuron decoding unit, and storing the decoded neurons in a neuron on-chip global buffer area; Determining a calculation mode of the PE calculation unit array according to the configuration parameters of the current layer of the neural network, and sending neurons and connection weights which are arranged after decoding to a PE calculation unit; Calculating the product of the neuron and the connection weight; In the accelerator, the multipliers in the PE units are all replaced by the shifters, and all basic modules can be configuredaccording to network calculation and hardware resources, so that the accelerator has the advantages of high speed, low power consumption, small resource occupation and high data utilization rate.
Owner:XI AN JIAOTONG UNIV
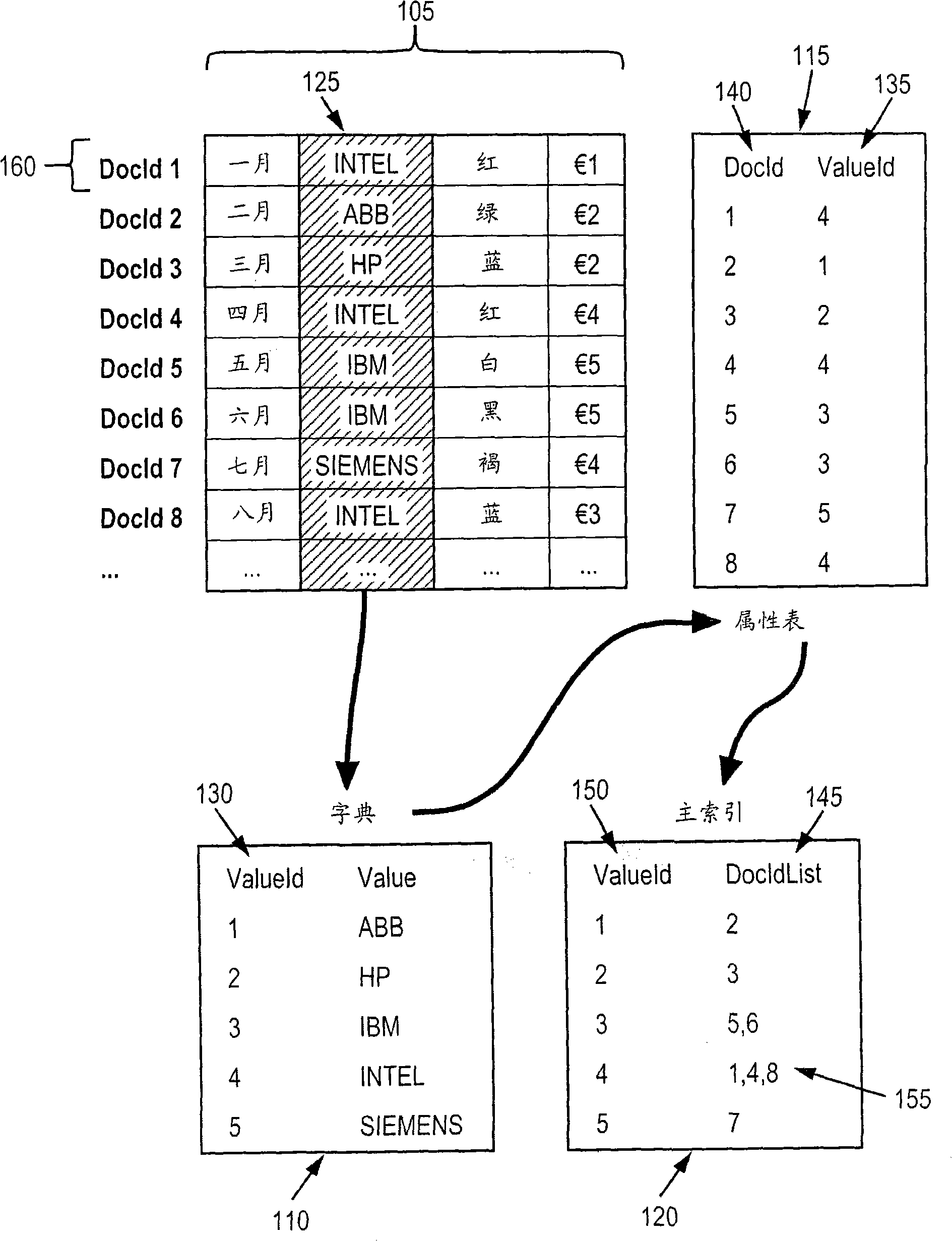
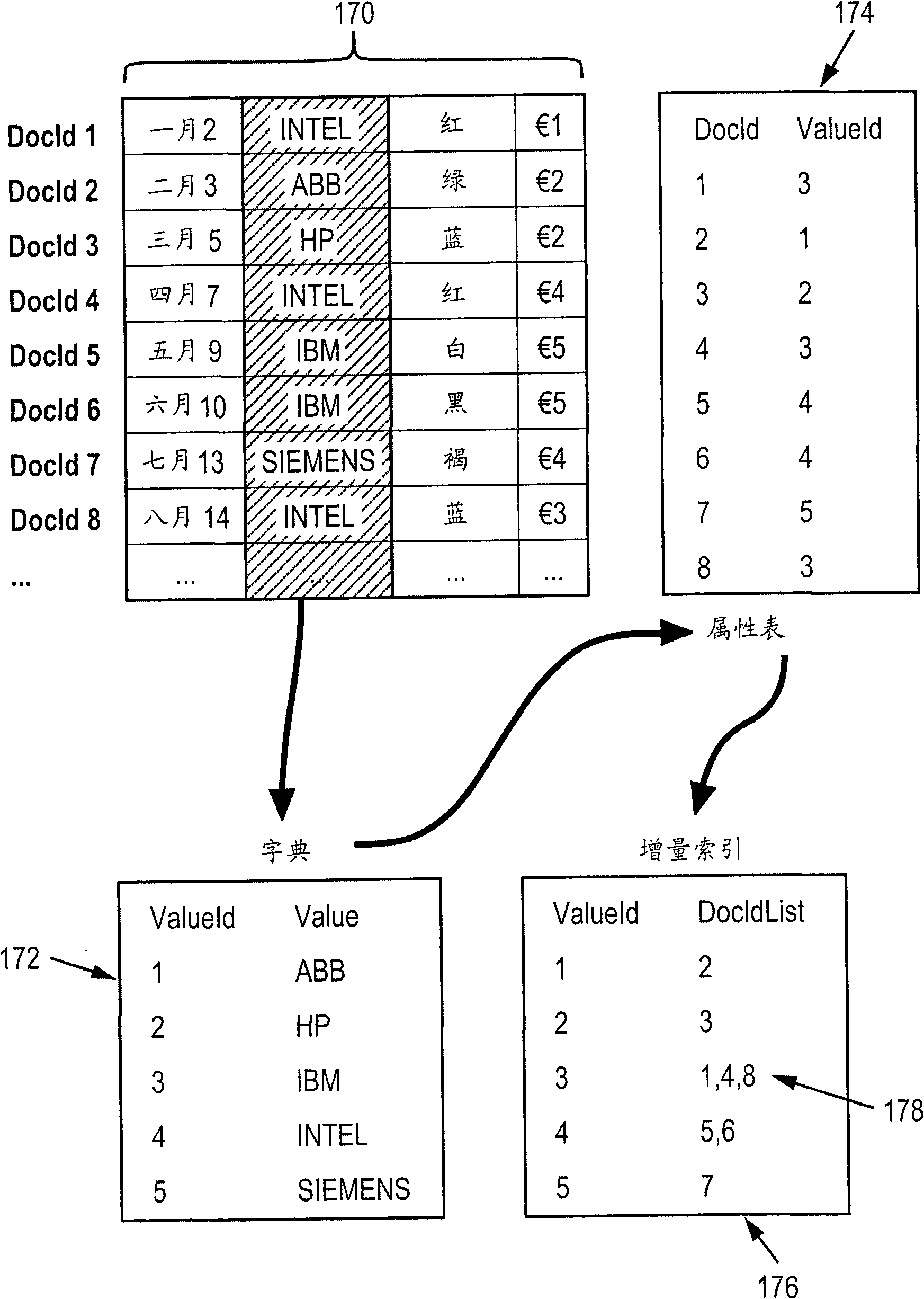
Block compression of tables with repeated values
ActiveCN101311930ALow costReduce capacityCode conversionSpecial data processing applicationsComputer scienceComputer program
Methods and apparatus, including computer program products, for block compression of tables with repeated values. In general, value identifiers representing a compressed column of data may be sorted to render repeated values contiguous, and block dictionaries may be generated. A block dictionary may be generated for each block of value identifiers. Each block dictionary may include a list of block identifiers, where each block identifier is associated with a value identifier and there is a block identifier for each unique value in a block. Blocks may have standard sizes and block dictionaries may be reused for multiple blocks.
Owner:SAP AG
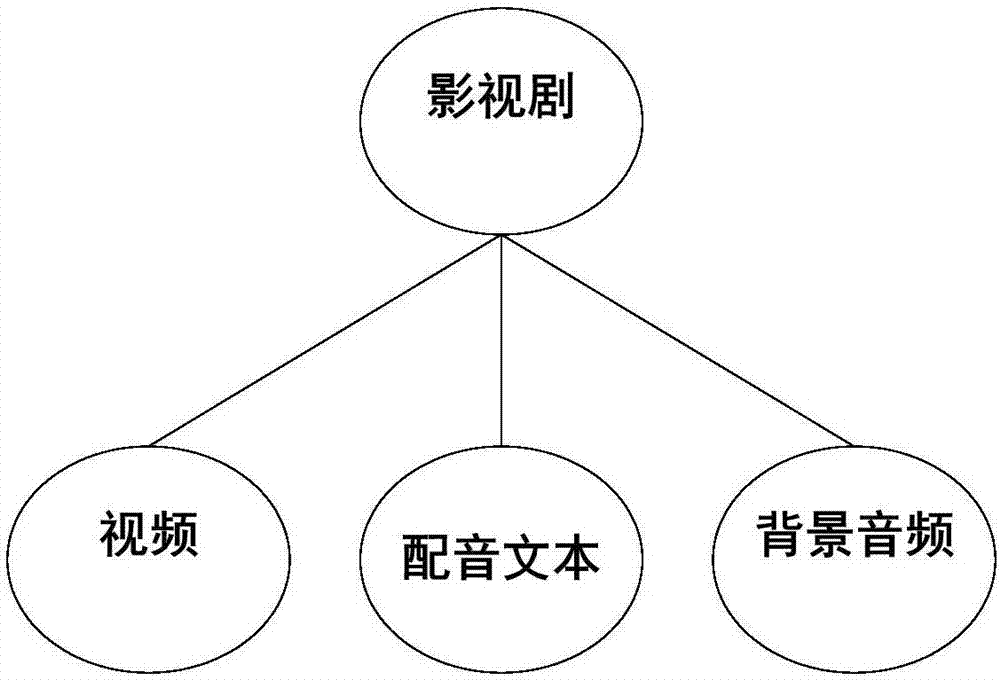
Multimedia playing method and apparatus, and multimedia storage method
InactiveCN107172449AReduce storage consumptionMeet personalized appreciation needsSelective content distributionSpeech synthesisPersonalizationMultimedia storage
The invention discloses a multimedia playing method. The method comprises the following steps: S1, obtaining multimedia file information and dub configuration determined by a user, wherein the file information comprises a multimedia video, a background audio and storage information of a dub text, and the dub configuration comprises vocal print features of roles; S2, obtaining the multimedia video, the background audio and the dub text according to the file information; S3, generating dub audio according to the dub text and the dub configuration, wherein the vocal print features of roles in the dub audio are consistent with the vocal print features of roles in the dub configuration; S4, synthesizing the dub audio and the background audio into the multimedia audio; and S5, synchronously playing the multimedia video and the multimedia audio. The invention further discloses a multimedia playing apparatus and a multimedia storage method. By adoption of the multimedia playing method, the storage resources occupied by the multimedia can be greatly reduced on one hand, and on the other hand, the role dub can be adjusted according to the user demands, thereby satisfying the individual appreciation demands of the users.
Owner:WHALEY TECH CO LTD
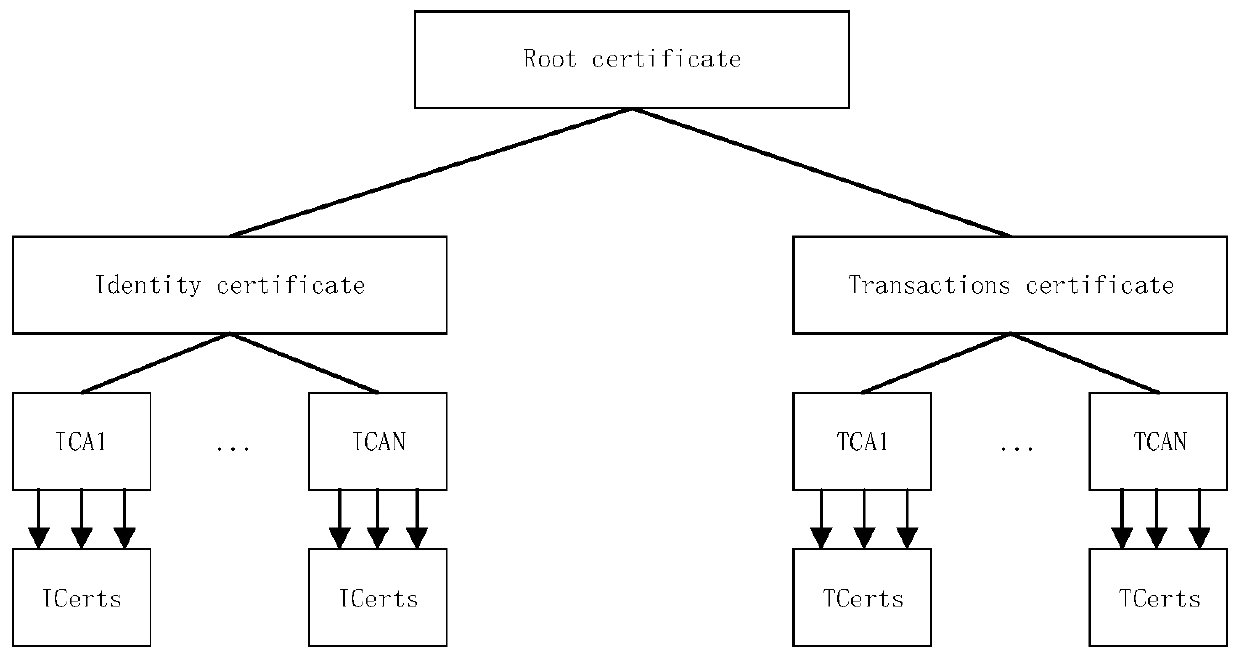
System and method for blockchain based cross entity certification
PendingCN111316303AReduce complexityReduce security risksFinancePublic key for secure communicationBlockchainComputer program
The invention provides a method, system, and device for blockchain based cross entity certification. The device comprises computer program encoded in a computer storage medium. The method comprises the following steps: obtaining, from a blockchain, a blockchain transaction including an authentication request of a first entity for authenticating a user, the authentication request including a decentralized identifier (DID) of the user; in response to determining that the first entity is allowed to access authentication information of the user endorsed by a second entity, obtaining an authentication result of the second entity to the user in response to the obtained blockchain transaction, the authentication result being associated with the decentralized identifier; generating different blockchain transactions including the authentication result; and sending the different blockchain transactions to blockchain nodes so as to add the different blockchain transactions to the blockchain.
Owner:ADVANCED NEW TECH CO LTD
Spatial-temporal index constructing method oriented to massive track point data
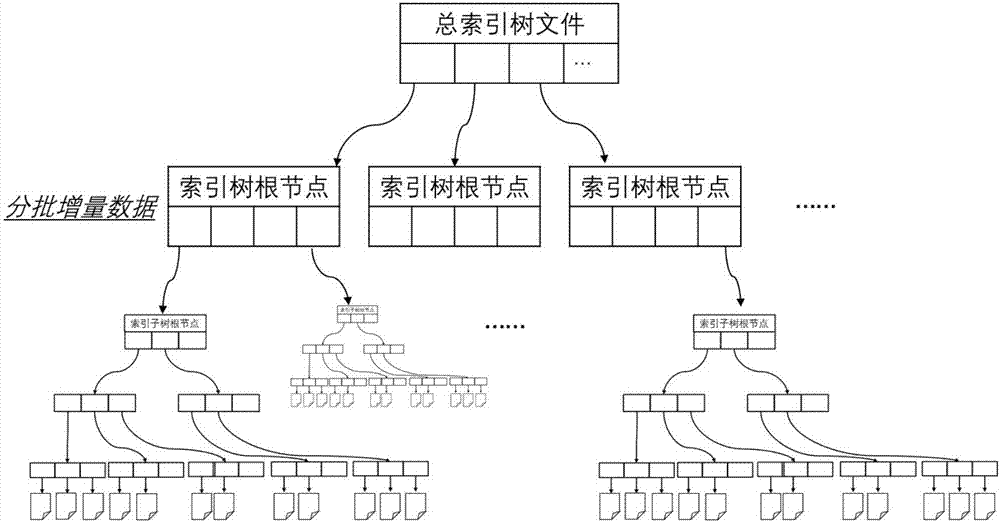
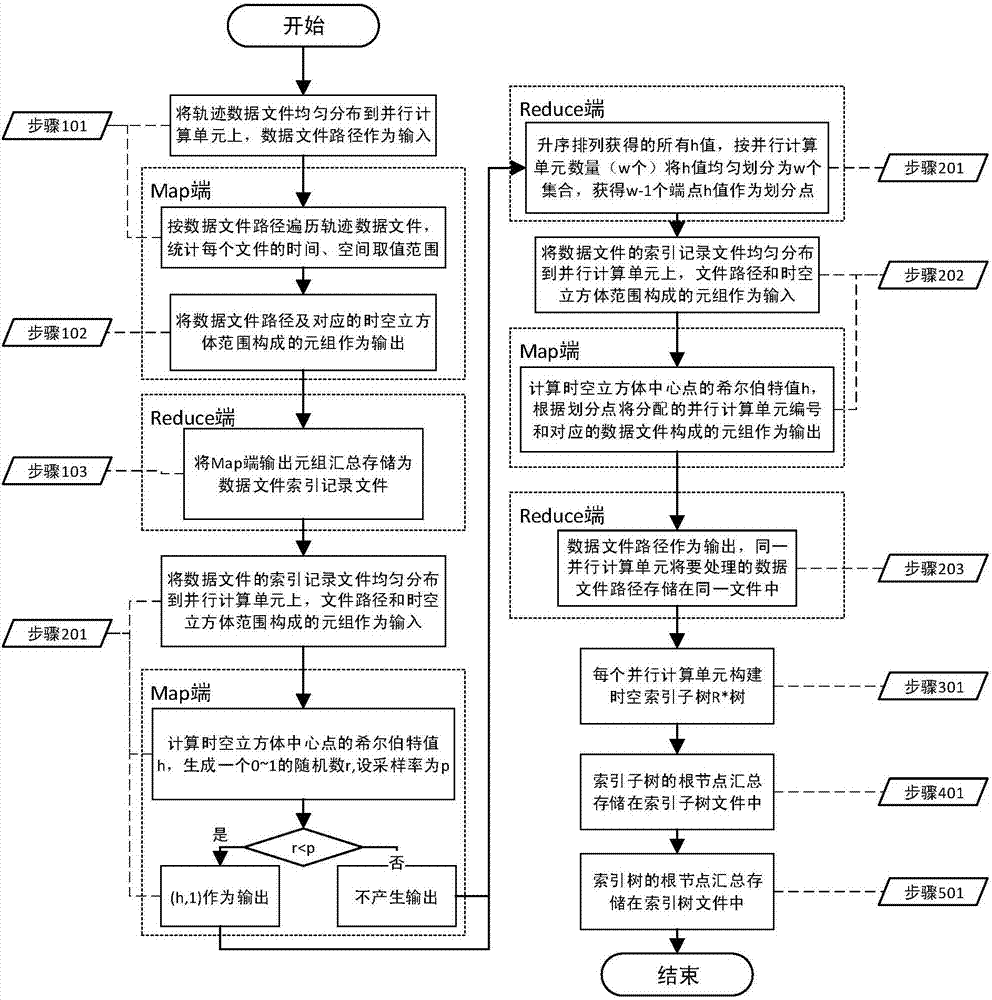
ActiveCN107220285AReduce the chance of tiltingReduce storage consumptionSpecial data processing applicationsExtensibilityData file
The invention relates to a parallel spatial-temporal index constructing method oriented to massive track point data. According to the spatial-temporal index constructing method oriented to the massive track point data, with a track point data file being an index unit, the storage consumption of an index is lowered, so that an index structure has high expandability; meanwhile, by utilizing a Hilbert curve to divide a data file, compared with other modes from multi-dimension to one-dimension mapping, since the Hilbert curve has an excellent space filling characteristic, the dividing effect is better, and the probability of the occurrence of data skew can be lowered.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Power distribution method and power distribution device for downlink of low-earth-orbit satellite
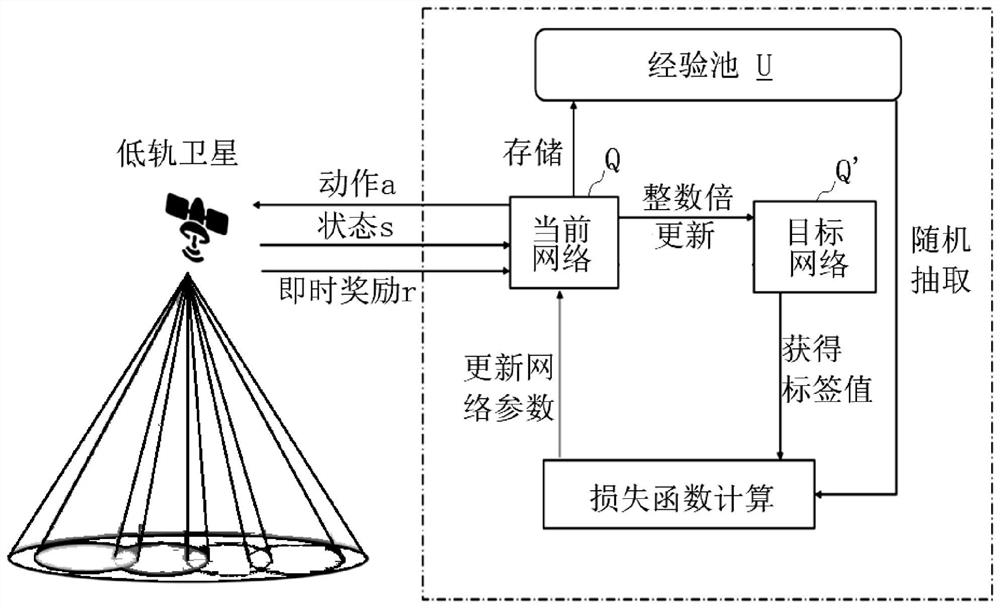
ActiveCN111867104ASolve the problem of low capacityAccelerating the Convergence Speed of Reinforcement LearningTransmission path divisionCriteria allocationFrequency spectrumSpectral efficiency
The invention provides a power distribution method for the downlink of a low-orbit satellite. The method comprises the steps of: initializing the low-orbit satellite, and building a Markov decision process; observing the current state St; randomly selecting an action or selecting an optimal action according to the probability of an exploration factor; obtaining a new state St+1 and the instant reward rt of the current state St according to an action at, and storing the (st, at, rt, st+1) tetrad into an experience pool; under the condition that a cycle period is greater than a training number,training a current network; under the condition that the current time slot is integer multiples of the updating frequency of a target network, updating parameters of the target network; adding 1 to the current time slot; repeating the above steps until the current time slot is greater than a time slot counter, setting the current time slot to be 1 and adding 1 to the count of the cycle period; andrepeating the steps until the cycle period is greater than the training network period number. According to the distribution method, a deep reinforcement learning algorithm is adopted to dynamicallydistribute the subcarrier power of the multi-beam low-orbit satellite, so that the capacity of the low-orbit satellite is maximized, and the spectral efficiency is improved.
Owner:SHANGHAI INST OF MICROSYSTEM & INFORMATION TECH CHINESE ACAD OF SCI
URL merging processing method and device
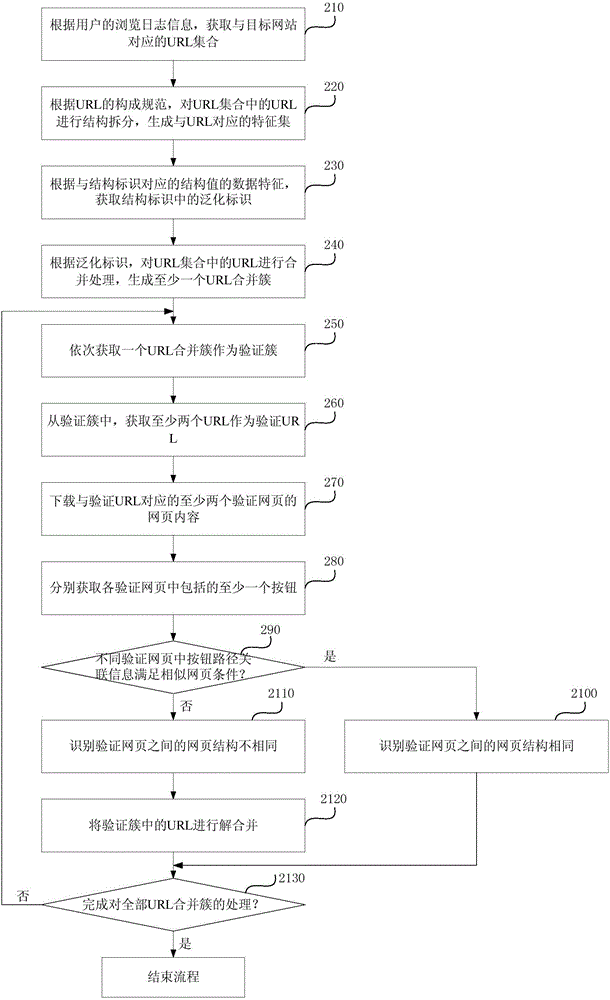
ActiveCN106095979ASimple and fast sorting and merging technologyReduce bandwidthSpecial data processing applicationsUniform resource locatorData mining
The embodiment of the invention discloses a URL merging processing method and device. The method comprises the steps that a URL set corresponding to a target website is obtained; structure splitting is conducted on URLs in the URL set according to composition specifications of the URLs to generate a characteristic set corresponding to the URLs; generalization identifiers in structure identifiers are obtained according to data characteristics of structure values corresponding to the structure identifiers contained in the characteristic set; merging processing is conducted on the URLs in the URL set according to the generalization identifiers to generate at least one URL merging cluster. According to the technical scheme, the URL merging processing method and device can achieve the technical effect of merging the URLs corresponding to web pages with the similar structures, bandwidth is greatly decreased, storage consumption is greatly reduced, and a more simple, convenient and rapid mode is provided for sorting and merging technologies of the web pages.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Method and device for rapidly processing XML (Extensible Markup Language) compressed data
ActiveCN102073663AReduce storage consumptionSave parsingSpecial data processing applicationsStructure of Management InformationExtensible markup
The invention provides a method and connector for rapidly reading XML (Extensible Markup Language) compressed data. XML compressed data are converted into hybrid data type objects to generate a message sequence including the hybrid data type objects, wherein the hybrid data type adopts a mode of data type marks and data storage part. Correspondingly, the invention provides a method and device forrapidly processing the XML compressed data. The method comprises the steps of: generating a message sequence comprising the hybrid data type objects through converting the XML compressed data into the hybrid data type objects; searching corresponding data processing logic according to the read hybrid data type objects in the message sequence and converting hybrid data, and transmitting the converted data to the searched data processing logic. Through the hybrid data types and the flow read interface, for the XML structure information and some types of data, the read original compressed data are directly transmitted, thus the operation consumption and the storage consumption caused by character string operation are saved.
Owner:NEW FOUNDER HLDG DEV LLC +2
Iris image quality cascade type evaluation method
ActiveCN105117705AImprove recognition efficiencyReduce quality evaluation timeCharacter and pattern recognitionEnergy gradientPeak value
The invention discloses an iris image quality cascade type evaluation method. The method includes following steps: S1, measuring and calculating the relative position between a light source image point and a pupil in an iris image, determining whether strabismus exists, determining the image fails to satisfy the quality requirement if yes, and continuing if not; S2, detecting the availability of an iris in the iris image according to a grayscale classification statistical method, determining whether the availability is qualified, determining the image fails to satisfy the quality requirement if not, and continuing if yes; S3, measuring and calculating the local energy gradient in the iris image, determining whether defocus blur exists, determining the image fails to satisfy the quality requirement if yes, and continuing if not; and S4, determining whether motion blur exists according to a circular gradient peak value detection method, determining the image fails to satisfy the quality requirement if yes, and determining the image satisfies the quality requirement if not. According to the technical scheme, the design of a multi-thread assembly line is facilitated, the quality evaluation time is effectively reduced, the storage consumption is reduced, and the iris recognition efficiency is improved.
Owner:BEIJING INST OF RADIO METROLOGY & MEASUREMENT
Image signature generating method and image verifying method and device
ActiveCN103871044AAvoid interferenceImprove anti-interference abilityImage analysisPattern recognitionValidation methods
The invention provides an image signature generating method and an image verifying method and device. The image signature generating method comprises the steps that characteristic data of multiclass characteristics of an image are extracted, the multiclass characteristics are divided into at least three classes, including at least one class of overall characteristics and at least one class of local characteristics, the extracted different classes of the characteristics contain different image content information amount, and an image signature is generated based on the extracted characteristic data of the multiclass characteristics. The image signature generating method can fully describe the image content information and save storage space. The image verifying method and the device can effectively avoid the interference of image coding and editing tools on image repeatability judging.
Owner:ALIBABA GRP HLDG LTD
Method for strengthening infrared focal plane array image
InactiveCN101567080AEnhance detailsInhibition effectImage enhancementImaging processingExternal storage
The invention discloses a method for strengthening an infrared focal plane array image, pertains to the field of infrared focal plane detector, particularly relates to the hardware realization of a specified image processing algorithm, and aims at extending image gray value and increasing computerization speed under the condition of limited FPGA storage resource. The method comprises the steps of median filtering, sub-point access and sub-section extension. The median filter adopted by the method eliminates spiced salt noise in the image and the sub-section extension effectively strengthens the detailed part of the dark image area. The algorithm requires no external memory, has low requirement for the FPGA storage resource and good real-time property and can effectively fit the high requirement of the infrared focal plane detector to image strengthening processing.
Owner:HUAZHONG UNIV OF SCI & TECH
Method for guiding video coding by utilizing scene semantic segmentation result
ActiveCN112004085AIncrease the compression factorReduce storage consumptionImage enhancementImage analysisPattern recognitionComputer graphics (images)
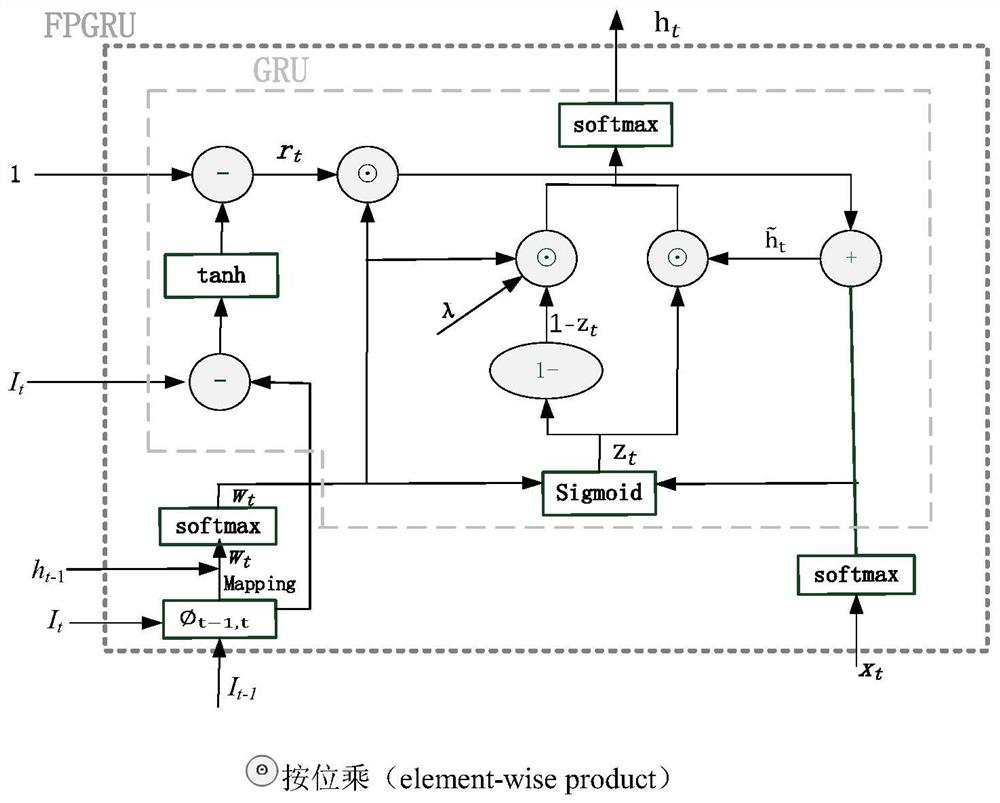
The invention provides a method for guiding video coding by utilizing a semantic segmentation result. Firstly, on the basis of an image semantic segmentation result, inter-frame optical flow estimation is combined, semantic segmentation of a video flow sequence is achieved in a mode that a plurality of flow propagation gating circulation units are connected in series, and the precision and speed of video semantic segmentation are improved. Furthermore, the video semantic segmentation result is applied to adaptive video coding under the guidance of scene content classification;, the target category and motion characteristics in the video content can be effectively utilized to realize self-adaptive quantization, low-rate compression is carried out on key objects and motion targets, high-ratecompression is carried out on non-key objects, the storage consumption and bandwidth occupation of the video are reduced, and effective reference is provided for video coding compression, especiallyapplication in the monitoring field.
Owner:BEIHANG UNIV
Increment study classification method under limited storage resources
InactiveCN101604394AEasy to identifyEffective studyCharacter and pattern recognitionMinimum distance classifierMisclassification error
The invention provides an increment study classification method under limited storage resources, which belongs to the technical field of pattern recognition. The method adopts a minimum distance classifier and comprises the following concrete steps: firstly, pre-classifying new samples, adding the new samples which are correctly pre-classified to the corresponding subset of the classifier, adding the new samples which are wrongly pre-classified to the set of wrong samples, and carrying out K-mean clustering on the samples in the set of wrong samples; then respectively selecting representative samples for each subset in the classifier and the set of wrong samples, adding the subsets in the set of wrong samples to the classifier after selection, and updating the classifier; and finally, adopting the updated classifier to classify the new samples. In the invention, by selecting the representative samples, not only the studied knowledge is saved, but also the new knowledge is acquired, and higher sample recognizing accuracy is achieved on the basis of reducing the storage cost and calculating the cost.
Owner:HUAZHONG UNIV OF SCI & TECH
Medical CT image storage and retrieval method based on random forest hash
ActiveCN109166615AImprove generalization abilityFast trainingStill image data indexingFile access structuresUser inputMedical diagnosis
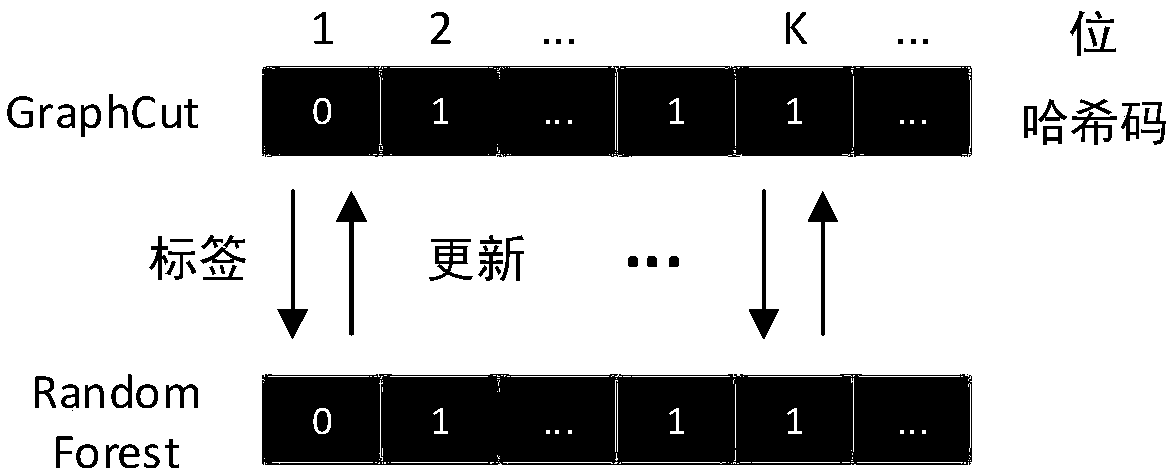
The invention claims a medical CT image efficient storage and retrieval method based on random forest hash learning. According to the method, a random forest hash model is trained with a medical CT image set, and the model and a hash code library corresponding to an image library are stored. When a user enters a new image that needs to be retrieved, the model maps the image to a hash code; K hashcodes nearest to the hash code are retrieved in the hash code library; and the K hash codes are decoded and reconstructed into an image through a maximum compatible rule defined by the decision pathsof a tree, and the image is returned to the user. With the method implemented, the retrieval speed of images can be effectively improved, and the storage space of the images is greatly saved; the medical diagnosis of doctors can be facilitated; the workload of the doctors can be reduced; work efficiency can be improved; and the utilization rate of hospital storage devices can be improved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Intelligent gas water heater diagnostic system
ActiveCN107965918AReduce difficultyShorter troubleshooting cyclesFluid heatersDiagnostic systemFuel gas
The invention relates to an intelligent gas water heater diagnostic system which is characterized in that the intelligent gas water heater diagnostic system comprises an analysis diagnostic module, awireless communication module and a remote service center; the analysis diagnostic module is connected with a controller of a gas water heater and can collect and detect operational parameters of thegas water heater in real time; the wireless communication module is connected with the analysis diagnostic module; and the analysis diagnostic module can collect the operational parameters of the gaswater heater in real time, divides failures of the gas water heater into at least two categories, namely, non-serious safe failures and serious safe failures according to the real-time operational parameters of the gas water heater, and then carries out treatment according to the two categories of failures correspondingly. Compared with the prior art, the intelligent gas water heater diagnostic system has the advantages that a user can check specific running conditions of the gas water heater through the analysis diagnostic module, and carries out simple operation according to a diagnostic result of the analysis diagnostic module, so that the difficulty of handling a part of failures of the gas water heater by the user voluntarily is lowered, the failure handling cycle is shortened substantially, the user is prevented from getting into a panic, and the number of times of on-site repair by service technicians is reduced.
Owner:NINGBO FOTILE KITCHEN WARE CO LTD
Signature verification method based on Gaussian sampling
ActiveCN104038347AImprove execution efficiencySmall amount of calculationUser identity/authority verificationGaussian samplingCipher
The invention discloses a signature verification method based on Gaussian sampling. The problem that an existing signature technology based on Gaussian sampling is low in execution efficiency when the modulus is not the power of two is mainly solved. The signature verification method based on Gaussian sampling comprises the steps that (1) parameters are selected, a key production algorithm is used for generating a signature key sk and a verification key vk; (2) the signature key sk is used for generating a trap door matrix R' of an expanding matrix AM; (3) the trap door matrix R' of the expanding matrix AM is used for signing a selected signature message M to obtain the signature sign; (4) the verification key vk is used for verifying the validity of the signature sign. According to the signature verification method, the calculated amount of the signature verification method based on Gaussian sampling is greatly reduced through an aspherical basic Gaussian sampling algorithm, and the signature verification method can be used for generation of signature in public key codes based on grids and personal private keys in encryption based on identities.
Owner:XIDIAN UNIV
Method for identifying graphic connection relationship between units in hierarchical layout verification
InactiveCN102402630AReduce complexityReduce data volumeSpecial data processing applicationsGraphicsComputer architecture
The invention relates to a method for identifying a graphic connection relationship between units in hierarchical layout verification, and belongs to the field of semiconductor integrated circuit design automation. A high-efficiency solution is provided for identification operation of the connection relationship between graphs of two units in the hierarchical layout verification. Most data in the units of a semiconductor integrated circuit design layout is rectangular units which are orthogonal to a coordinate axis; and the traditional method comprises the following steps of: converting polygons in the units into edges, and identifying the connection relationship between graphic units by an edge-based scanning line method, so that data quantity is doubled and efficiency is low. In order to solve the problem, the scanning line method taking a rectangle as a unit is provided, so that the number of data units is greatly reduced, and operating efficiency is obviously improved.
Owner:北京华大九天科技股份有限公司
Method for protecting data integrity of memory
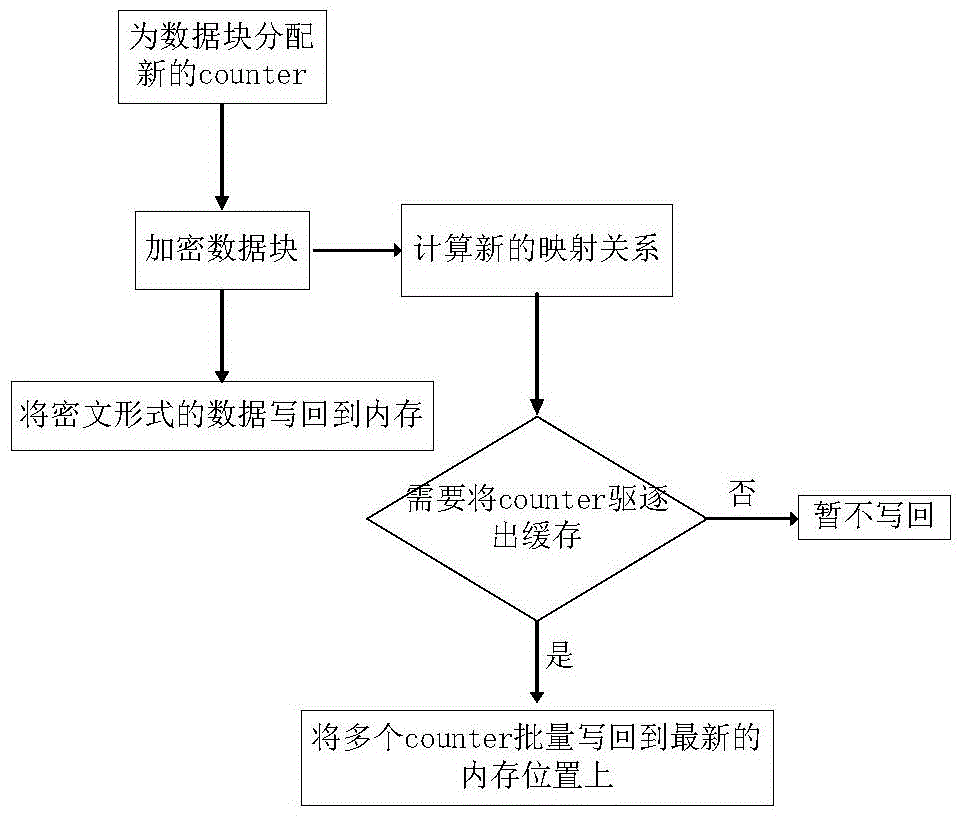
InactiveCN104463020AReduce consumptionReduce performance degradationMemory adressing/allocation/relocationDigital data protectionComputer hardwareData integrity
The invention provides a method for protecting data integrity of a memory. The method comprises the steps of first, generating a new counter to be allocated to a data block when a system needs to write the data block back to the memory; encrypting the data block through a counter mode encryption method; inputting addresses of the obtained cryptograph data block and the data block to an MAC function with a secrete key, wherein the MAC function will generate an output; determining a storage position of the counter in the memory according to the output of the MAC function. Compared with a traditional memory data integrity protection scheme, the same or superior memory data integrity protection can be provided with low storage space consumption and small occupation of computing resources.
Owner:DALIAN UNIV OF TECH
Method and device for realizing counting of independent user number
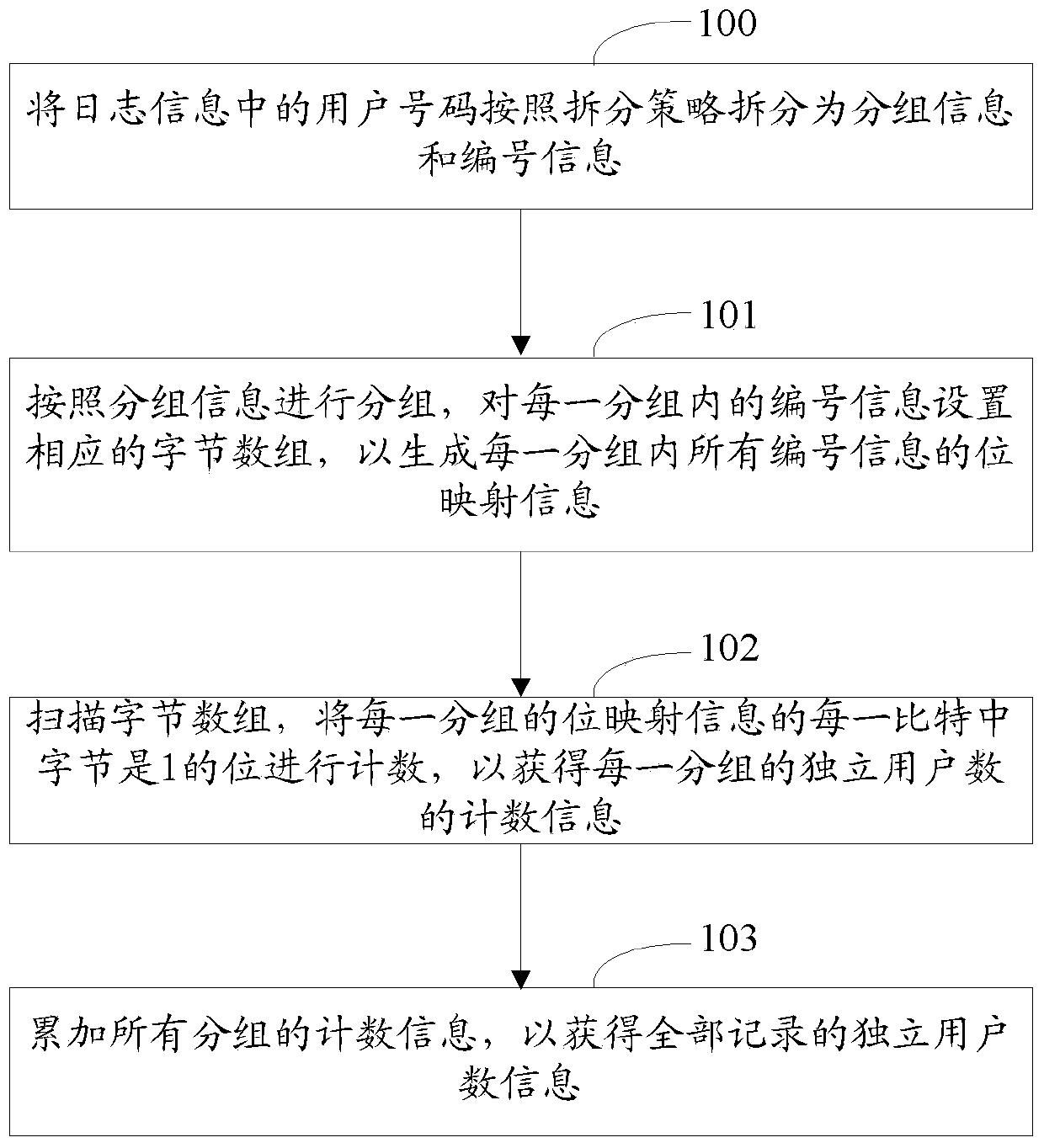
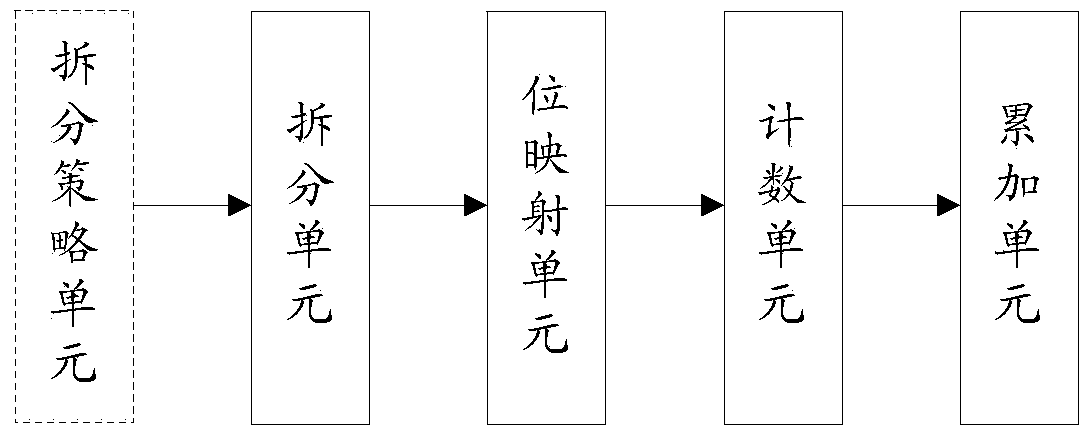
InactiveCN103746851AReduce storage consumptionStatistical speed controllableData switching networksBand countsArray data structure
The invention discloses a method and a device for realizing counting of an independent user number. The method comprises the steps of splitting user numbers in logo information into grouping information and number information according to a splitting strategy; grouping according to the grouping information, setting a corresponding byte array for the number information in each group, to generate bit mapping information of all number information in each group; scanning the byte arrays and counting each bit with each bit byte being 1 of the bit mapping information in each group to obtain counting information of independent user number of each group; accumulating the counting information of all groups to obtain the independent user number information of all records. A controllable counting speed is realized by splitting the user numbers, the number information in the groups can be subjected to bit mapping, the aim of realizing the counting of the independent user number without sequencing is realized, counting is performed by counting the byte bit of 1 in the arrays instead of sequence changing, and the storage space consumption of data sequencing is saved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Convolutional neural network based on 1T1R and operation method thereof
ActiveCN110852429AImprove accuracyReduce power consumptionRead-only memoriesPhysical realisationSynaptic weightEngineering
The invention discloses a convolutional neural network based on 1T1R and an operation method thereof. The convolutional neural network comprises an input module, a convolution calculation module, a pooling calculation module and a full connection calculation module. the convolution calculation module, the pooling calculation module and the full-connection calculation module are all composed of 1T1R arrays, synaptic weight information can be stored in situ, fusion of calculation and storage is achieved, consumption of data interaction is omitted, the calculation time is greatly shortened, and meanwhile energy consumption is reduced. Besides, bidirectional gradual change adjustment of the conductance value of the memristor is realized by regulating and controlling the gate voltage of a transistor in the 1T1R device; in this way, in the process of achieving conductivity reduction, the 1T1R device does not need to be operated to the lowest conductivity state again, the target conductivitycan be achieved by directly adjusting the grid voltage of the transistor in the 1T1R device, and power consumption is low.
Owner:HUAZHONG UNIV OF SCI & TECH
Overlay network-oriented lightweight in-band network telemetering method and device and storage medium
ActiveCN112702330AReduce monitoring overheadReduce storage consumptionData switching networksSoftware simulation/interpretation/emulationPathPingData pack
The invention discloses an overlay network-oriented lightweight in-band network telemetering method and the method comprises the following steps: S1, packaging an IP message, so as to obtain a detection data packet so that the detection data packet sequentially collects the ID of underlay equipment along the way and the link state information of an equipment port side; S2, analyzing the detection data packet; S3, starting to traverse by taking any equipment in the Overlay network as a root node to obtain a non-overlapping detection path; S4, performing control according to the detection path in the step S3 to obtain a customized detection data packet forwarding path; and S5, after the detection data packet reaches the end point, storing and querying the acquired network monitoring information. The invention also provides an overlay network-oriented lightweight in-band network telemetering device and a storage medium, and lightweight Overlay network monitoring can be realized with lower overhead.
Owner:PURPLE MOUNTAIN LAB
Internet of things perception data sharing transaction platform, control method, equipment and terminal
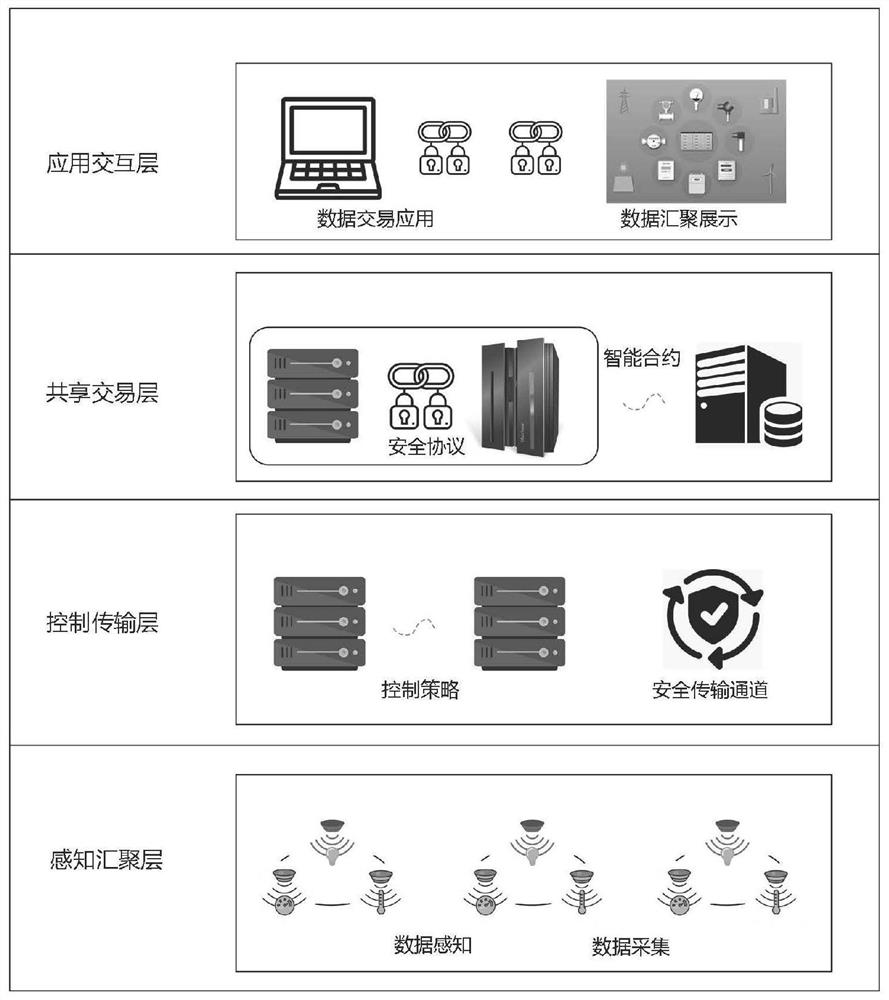
PendingCN113783696ASupport intelligenceSupport collaborative developmentKey distribution for secure communicationFinanceThe InternetData access
The invention belongs to the technical field of communication network security, and discloses an Internet of Things perception data sharing transaction platform, a control method, equipment and a terminal, and the Internet of Things perception data sharing transaction platform comprises a perception convergence layer, a control transmission layer, a sharing transaction layer, an application interaction layer, a blockchain bottom layer platform, a blockchain network and a blockchain bottom layer architecture. According to the invention, based on a cloud-fog mixed structure data architecture, perception data in the same management domain is collected, encrypted and published by using edge fog nodes, and a cloud server is used as a transfer point to store transaction data, so a decentralized and extensible identity management, credible authentication and data transaction environment is realized; fog nodes and data consumers responsible for sensing equipment management join an alliance chain, a trusted center does not need to be selected to organize transactions, platform nodes do not need to carry out peer-to-peer free transaction negotiation, data security sharing is realized by utilizing flexible autonomy of an intelligent contract and real-time adjustment of cloud server data access authority, and the method has the advantage of transaction traceability.
Owner:XIDIAN UNIV
Cipherkey setting method of heterogeneous wireless sensor network
InactiveCN102651864AImprove securityReduce storage consumptionNetwork topologiesSecurity arrangementLine sensorHash function
The invention relates to a cipherkey setting method of a heterogeneous wireless sensor network. The method comprises the following steps: step1, three layers of heterogeneous network structures are built; step2, a plurality of t-order symmetric binary polynomials are generated on a galois field GF (q), and S t-order symmetric binary polynomials form an N*N symmetric matrix A; each strong-capacity node stores a certain row vector j of an upper triangular matrix and a column vector j of a corresponding lower triangular matrix, meanwhile, the row number j of the certain row vector j is used as an ID number to be stored, and a Hash function is stored; step3, the cipherkeys of the strong-capacity nodes (H-sensor) and common sensor nodes (L-sensor) are pre-distributed; step4, the session cipherkeys among the strong-capacity nodes (H-sensor) are generated; and step5, the session cipherkeys of the strong-capacity nodes (H-sensor) and the common sensor nodes (L-sensor) are generated. Compared with the prior art, the method has the advantages that the relationship between the energy consumption and the safety of the wireless sensor network are further balanced; and on the basis that the storage consumption of the whole network is reduced, the safety of the network is increased, and the network nodes realize a 100-percent ability to resist capture attack.
Owner:FOSHAN DIXINGWEI AUTOMATION EQUIP CO LTD
Rapid ship target detection method, storage medium and computing equipment
PendingCN111914924AGood precisionEfficient removalCharacter and pattern recognitionNeural architecturesData setComputer science
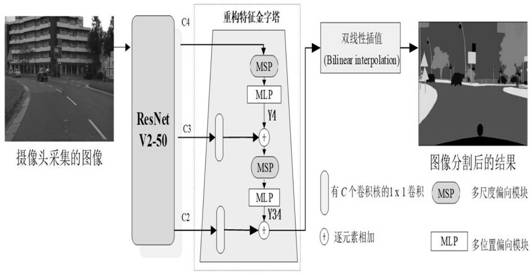
The invention discloses a rapid ship target detection method, a storage medium and computing equipment, and the method comprises the steps: establishing a feature pyramid full-convolution network anda double-branch module which sequentially comprise an input layer, a feature extraction layer, a feature fusion layer and an output layer, determining a ship data set, inputting a generated training set into the built feature pyramid full-convolution network, and generating a target detection result. According to the method, the ship in the image can be rapidly and accurately detected; and the detection result is accurate and rapid, the requirement on embedded equipment is low, and the method has very high practical application value in various aspects such as military affairs, civil use and the like.
Owner:XIDIAN UNIV
Multi-document machine reading understanding method based on hash learning
PendingCN111460176AImprove accuracyReduce storage consumptionNatural language data processingNeural architecturesAttention modelData mining
The invention discloses a multi-document machine reading understanding method based on hash learning. The method can achieve the effects of high prediction accuracy and low memory overhead in an online multi-document reading understanding scene. According to the method, a hash learning-based multi-document reading understanding model is trained; during machine online prediction, firstly, a pre-trained self-attention model is used for extracting text feature information of a problem and a document, then binary matrix representations corresponding to the documents are calculated, answers and probabilities of the documents are predicated by using a dynamic pointer decoder, probabilities that the documents contain correct answers are also predicated, all the answers are sequenced by combiningthe two probabilities, and the foremost answer is selected and output. The multi-document dynamic pointer decoder considers semantic information of other documents when predicting answers to each document, so that the model accuracy is improved. During model prediction, binary matrix representations of all documents are stored in a memory, so that the storage cost is reduced.
Owner:NANJING UNIV
Language learning method and system based on video dubbing and pronunciation correction training
ActiveCN111462553ASolve the boringSolve the problem that most people dare not speak the languageTelevision system detailsSpeech analysisDegree of similarityVerbal learning
The invention discloses a language learning method and system based on video dubbing and pronunciation correction training. The method comprises the steps of: displaying a to-be-dubbed video selectedby a user; generating a subtitle list of the to-be-dubbed video after acquiring a dubbing starting trigger signal of the user; receiving a subtitle sentence selected by a user, playing a video picturecorresponding to the subtitle sentence, and collecting the dubbing content of the user; comparing the phoneme of the dubbing content with a standard phoneme, and calculating a first score; calculating the similarity between the dubbing content and the video original pronunciation to serve as a second score; calculating an evaluation score of each dubbing content based on the first score and the second score; generating a video dubbing report based on the evaluation scores of all the subtitle sentences; and extracting words to be enhanced in the video dubbing report, and entering a pronunciation correction mode. According to the invention, the user can learn whenever and wherever, the problems that the user is afraid to speak the language and the pronunciation is inaccurate are solved, andthe accuracy of dubbing evaluation is improved.
Owner:杭州菲助科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com