Method for protecting data integrity of memory
A data integrity and memory technology, applied in digital data protection, internal/peripheral computer component protection, memory address/allocation/relocation, etc., can solve the problem of occupying system computing resources, spending a lot of time on integrity verification, and other issues to achieve the effect of reducing storage space consumption, small negative impact, and reducing system performance degradation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings. The specific implementation process is as follows, combined with figure 1 , 2 and 3:
[0029] When the CPU reads a block of data from memory:
[0030] ①The system reads the data block in ciphertext form from the memory;
[0031] ②If the counter of this data block is in the on-chip counter cache, go to ④;
[0032] ③If the counter of this data block is not in the on-chip counter cache, calculate the position of the counter in the memory, and read the counter from the memory;
[0033] ④ Apply the counter mode encryption method to decrypt the data block;
[0034] ⑤The program ends.
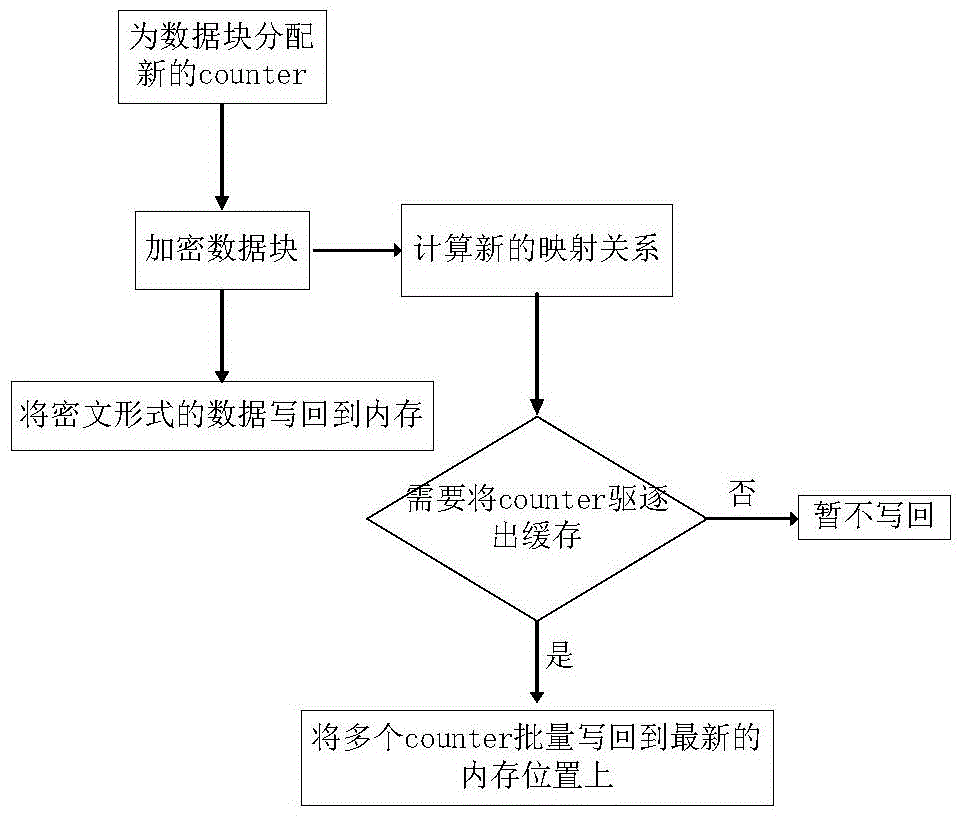
[0035] When the CPU writes a block of data back to memory:
[0036] ①The system allocates the latest counter for the data block that needs to be written back;
[0037] ② Apply the counter mode encryption method to encrypt the data block;
[0038] ③ Calculate the storage location of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com