Reverse reconstruction encryption method
An encryption method and string technology, applied in the field of information security, can solve the problems of low security and easy to be cracked, and achieve the effect of high encryption security and great difficulty in cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
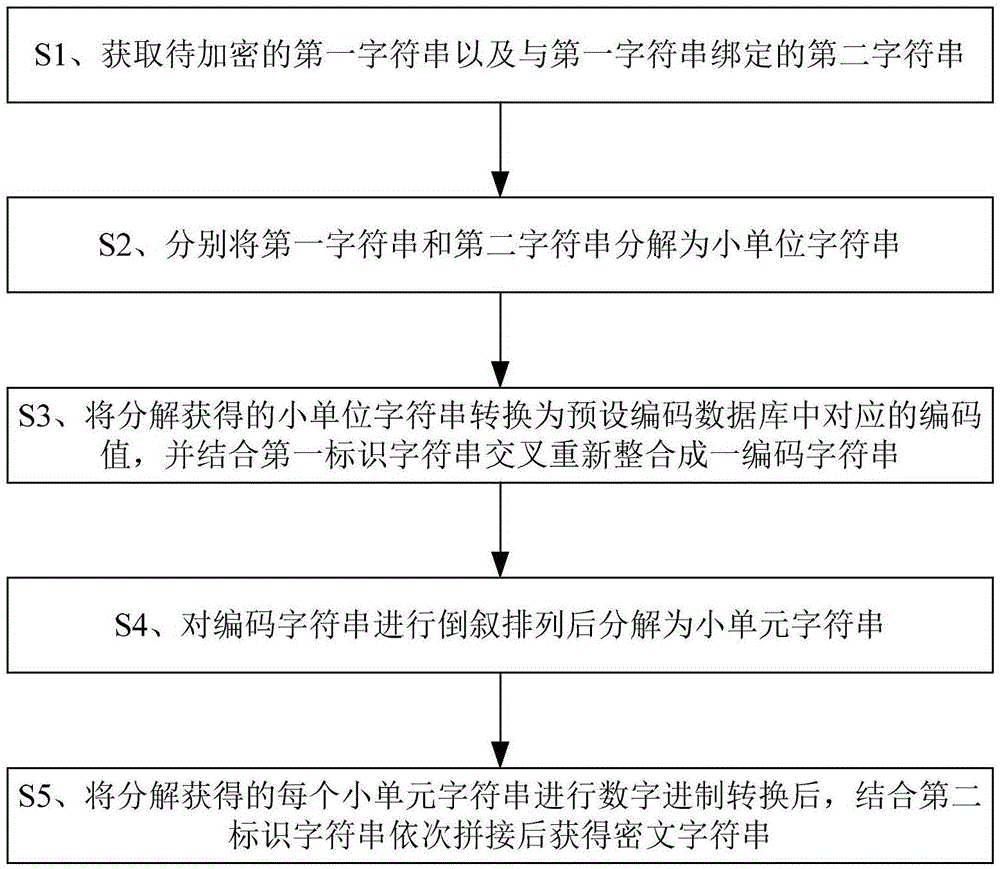
[0046] refer to figure 1 , the reverse reassembly encryption method, including steps:
[0047] S1. Obtain the first character string to be encrypted and the second character string bound to the first character string; the first character string generally refers to character strings such as passwords, and the second character string generally refers to the user name and account number bound to the password and so on.
[0048] S2. Decompose the first character string and the second character string into small unit character strings according to the first step length parameter and the second step length parameter; when decomposing, use a loop statement to intercept the corresponding character string from the left according to the value of the step length parameter The number of digits is used as a small unit string. For example, if the value of the step parameter is 2, 2 characters are intercepted each time as the small unit string; generally speaking, it is recommended to use 1...
Embodiment 2
[0055] This embodiment is a detailed example of Embodiment 1, specifically as follows:
[0056] In this embodiment, the first character string to be encrypted is called an encrypted character string, and the second character string bound to the first character string is called a bound character string, both of which are as follows:
[0057] The encrypted string is: admin;
[0058] Bind string: username;
[0059] The first step length parameter is the encrypted string decomposition step size: 1;
[0060] The second step size parameter is the binding string decomposition step size: 2;
[0061] The third step length parameter is flashback interception step size: 1;
[0062] The fourth step length parameter refers to the length of each character unit intercepted during the final recombination, also known as "gene length", and its value is 5;
[0063] The first identification string mark1 is: 999;
[0064] The second identification string mark2 is: ggg;
[0065] The character...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com