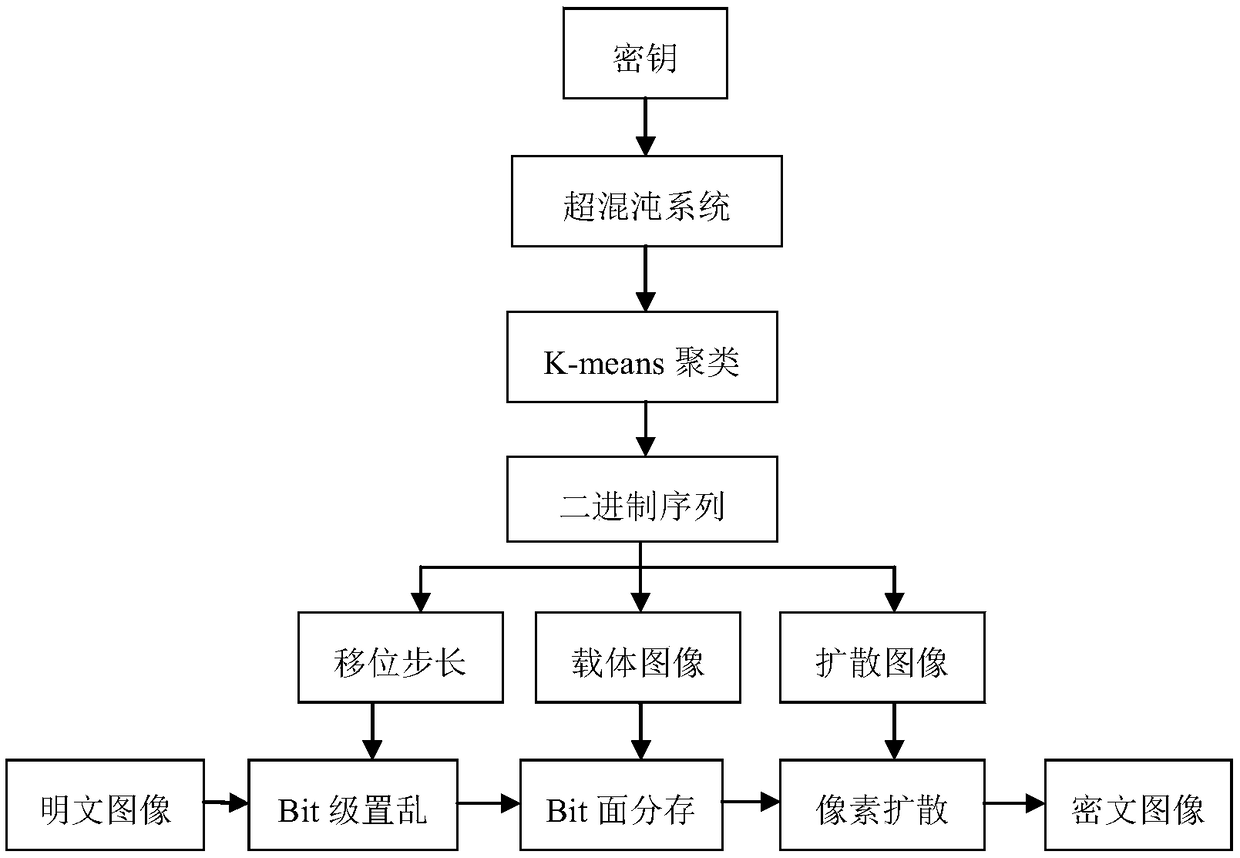
An image encryption method based on four-dimensional Chen's hyperchaotic system and K-means clustering
A technology of k-means clustering and encryption method, which is applied in the field of image processing, can solve the problems of encryption security improvement, secret key deciphering, high space-time complexity, etc., to achieve large key space, improve performance, and enhance encryption security. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
experiment example
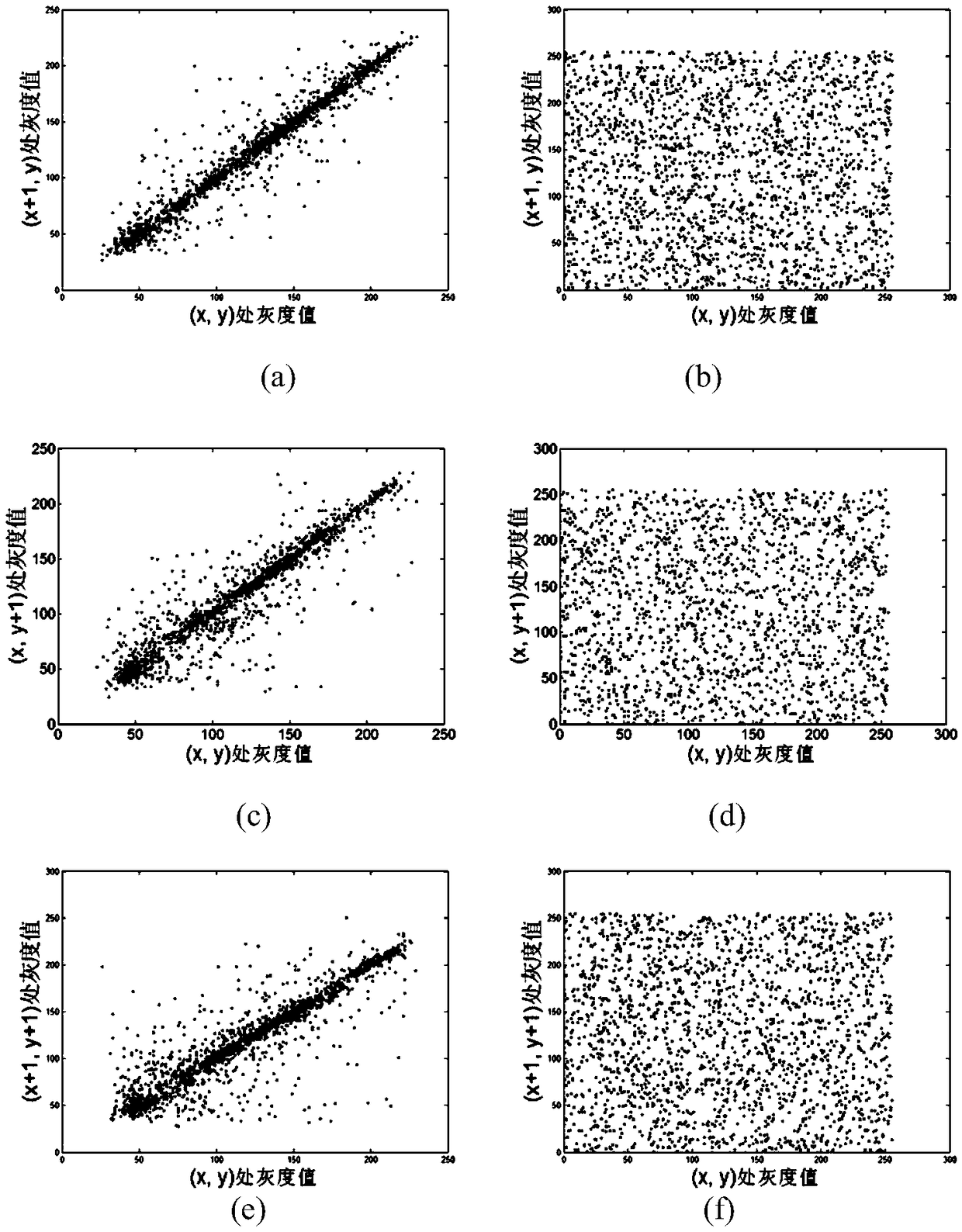
[0092] (1) US NIST statistical test. Utilize the common standard US NIST statistical test group to pseudo-random binary sequence B={b 1 ,b 2 ,b 3 ,...,b 4L-1 ,b 4L} for randomness testing. Let sequence length L=1000000, significant level α=0.01, Table 1 lists the statistical test results. It can be seen that sequence B passes all the statistical tests well, indicating that it has good pseudo-random performance.
[0093] Table 1 NIST statistical test results for binary sequence B
[0094]
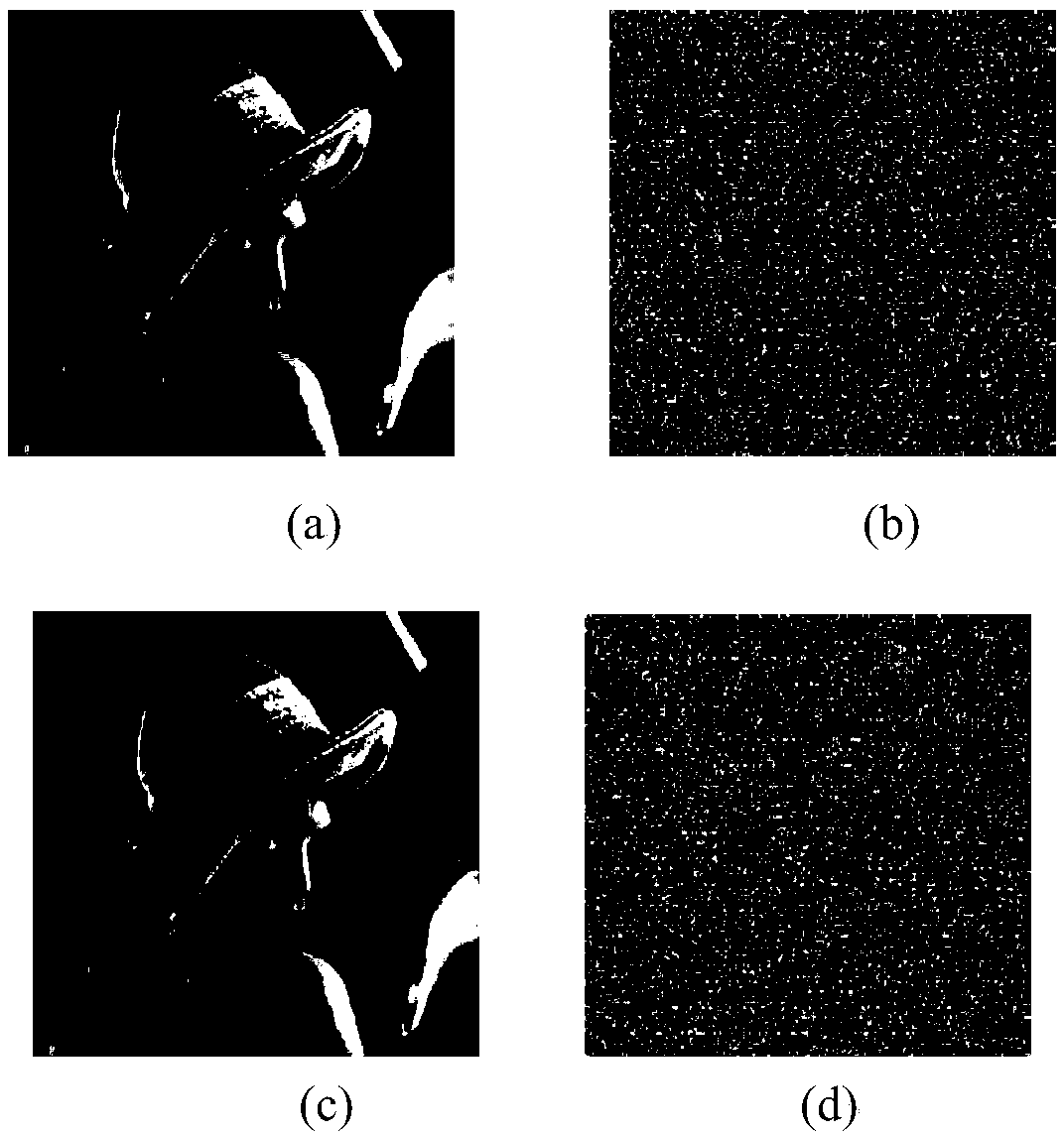
[0095] (2) Secret key sensitivity experiment. Set the secret key to x 0 =-0.1,y 0 =0.1,z 0 =-0.1,w 0 =0.1, for the plaintext image Lena( figure 2 a) Encrypt to get the ciphertext image ( figure 2 b). Then use two sets of secret keys to decrypt the ciphertext image. Among them, the first group is the original secret key, and the second group is the x in the original secret key 0 perform a 10 -14 A small disturbance of the level, that is, x 0 =-0.1+10 14 . figure 2 a ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com