Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
63results about How to "Reduce tampering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electronic signature method, device, device and medium
ActiveCN109472166AReduce tamperingReduce riskFinanceDigital data protectionThird partySignature file
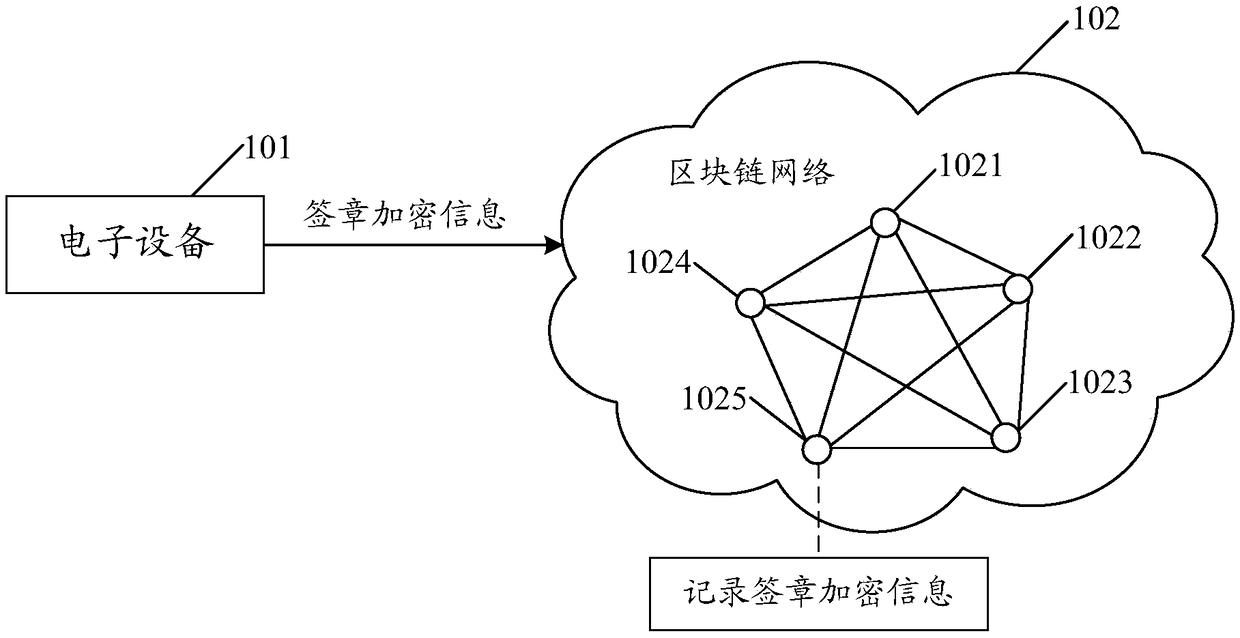
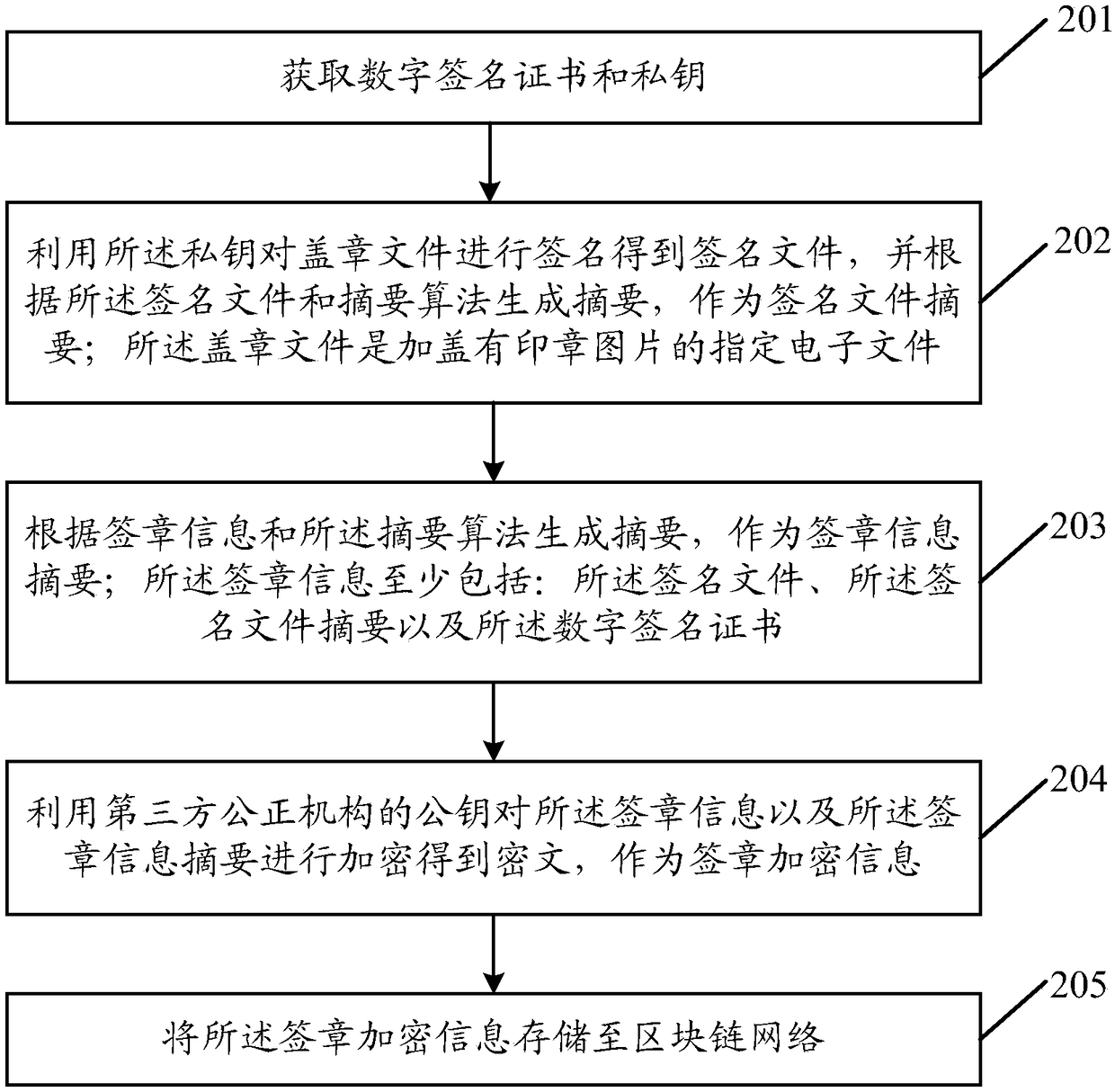
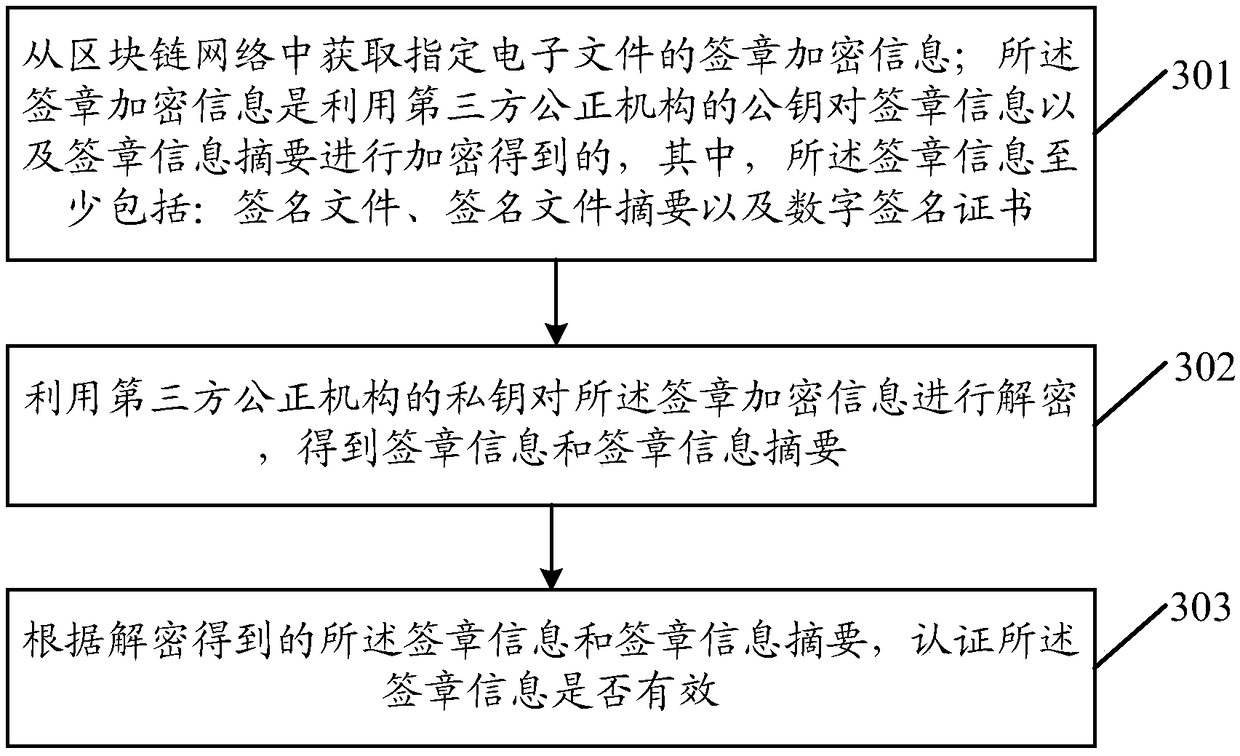
An embodiment of the application discloses an electronic signature method. An electronic device signs a seal file by using a private key to obtain a signature file, and generates a signature file digest according to a digest algorithm and the signature file. A signature information digest is generated according to the signature information and the digest algorithm. The signature information includes at least a signature file, a signature file digest and a digital signature certificate. The signature encryption information is generated by encrypting the signature information and the signature information digest with the public key of the third party fair organization, and the signature encryption information is stored in the block chain network. The signature encryption information is generated by encrypting the necessary information generated in the process of electronic signature with the public key of the third party fair organization, which ensures that other organizations or individuals except the third party fair organization can not decrypt the signature encryption information privately, and reduces the risk of information being tampered with or stolen; The signature encryption information is stored in the block chain network with anti-tamper mechanism, which ensures the authenticity and security of the information.
Owner:HUNDSUN TECH
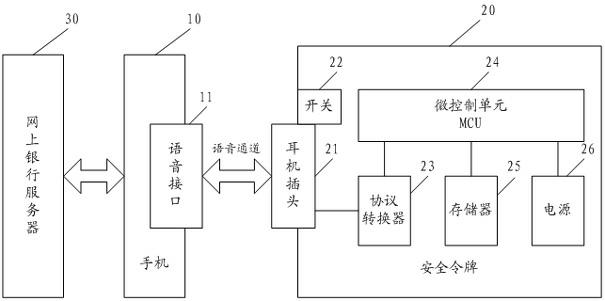
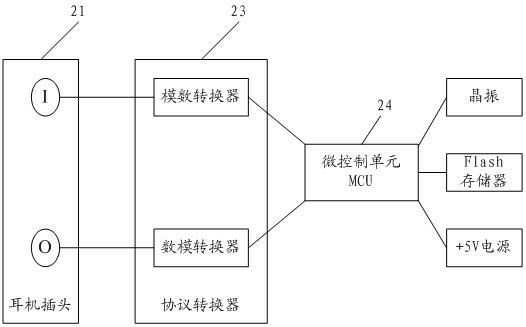
Security control method and security control system of mobile payment
InactiveCN102254264AImprove general performanceReduce tamperingPayment architectureSecuring communicationMobile paymentSecurity token
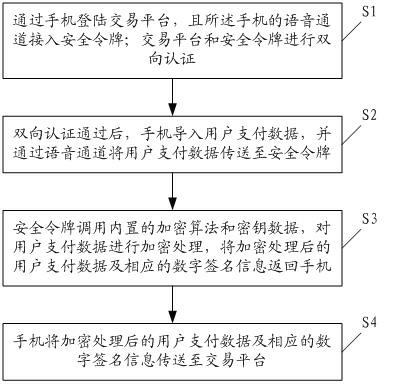
The invention discloses a security control method and a security control system of mobile payment. The method comprises the following steps that: a transaction platform is logged in through a mobile phone, and a voice channel of the mobile phone accesses a security token; the transaction platform and the security token carry out two-way authentication; after the two-way authentication passes, the mobile phone imports user payment data and transmits the user payment data to the security token through the voice channel; the security token calls an encryption algorithm and key data, which are arranged in the security token, encrypts the user payment data, and returns the encrypted user payment data and corresponding digital signing information to the mobile phone; and the mobile phone transmits the encrypted user payment data and the corresponding digital signing information to the transaction platform. By adoption of the embodiment of the invention, risks on faking of the user identity, falsification of transaction information and theft of account assets can be reduced, and the security of the mobile payment is improved.
Owner:GRG BAKING EQUIP CO LTD
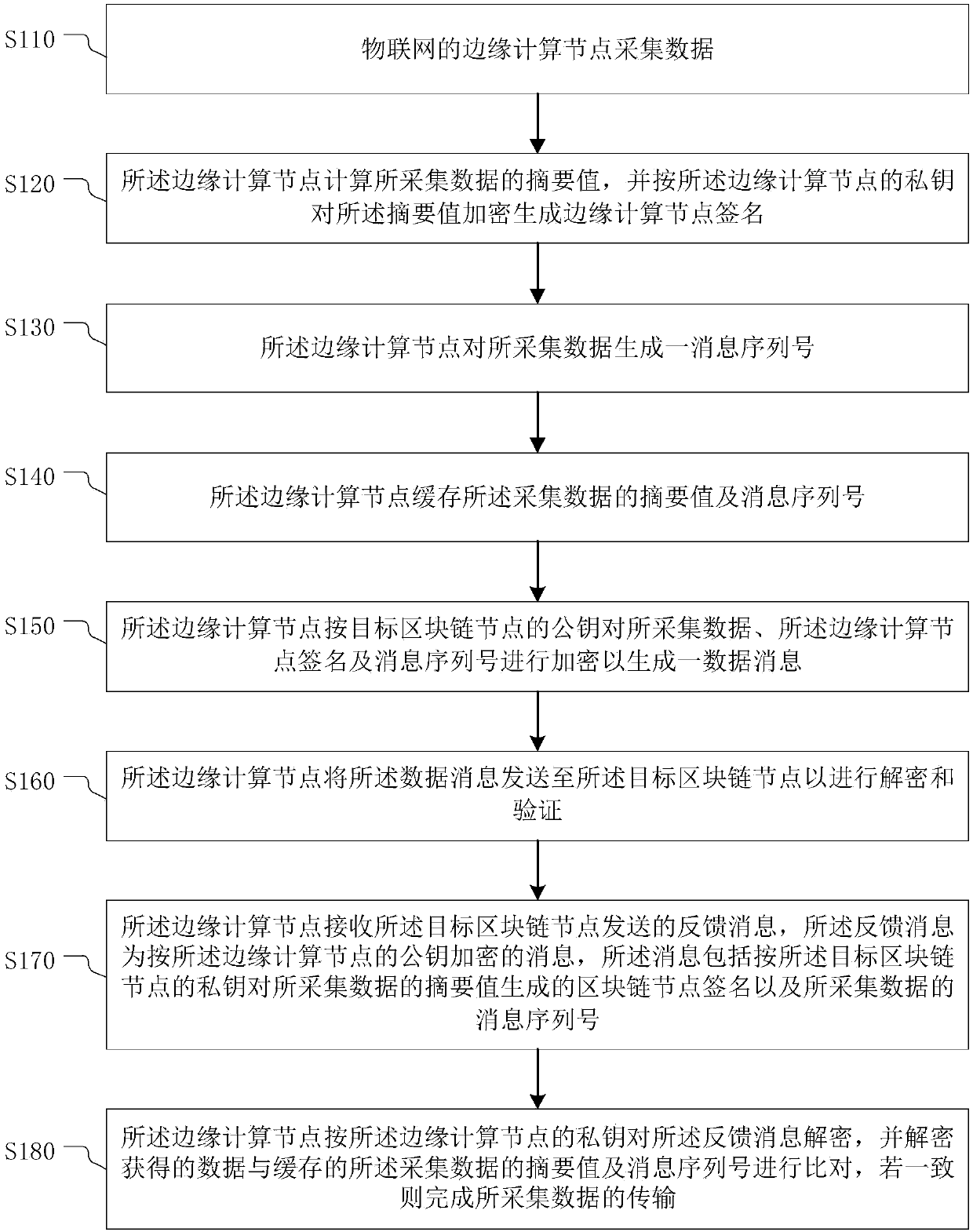
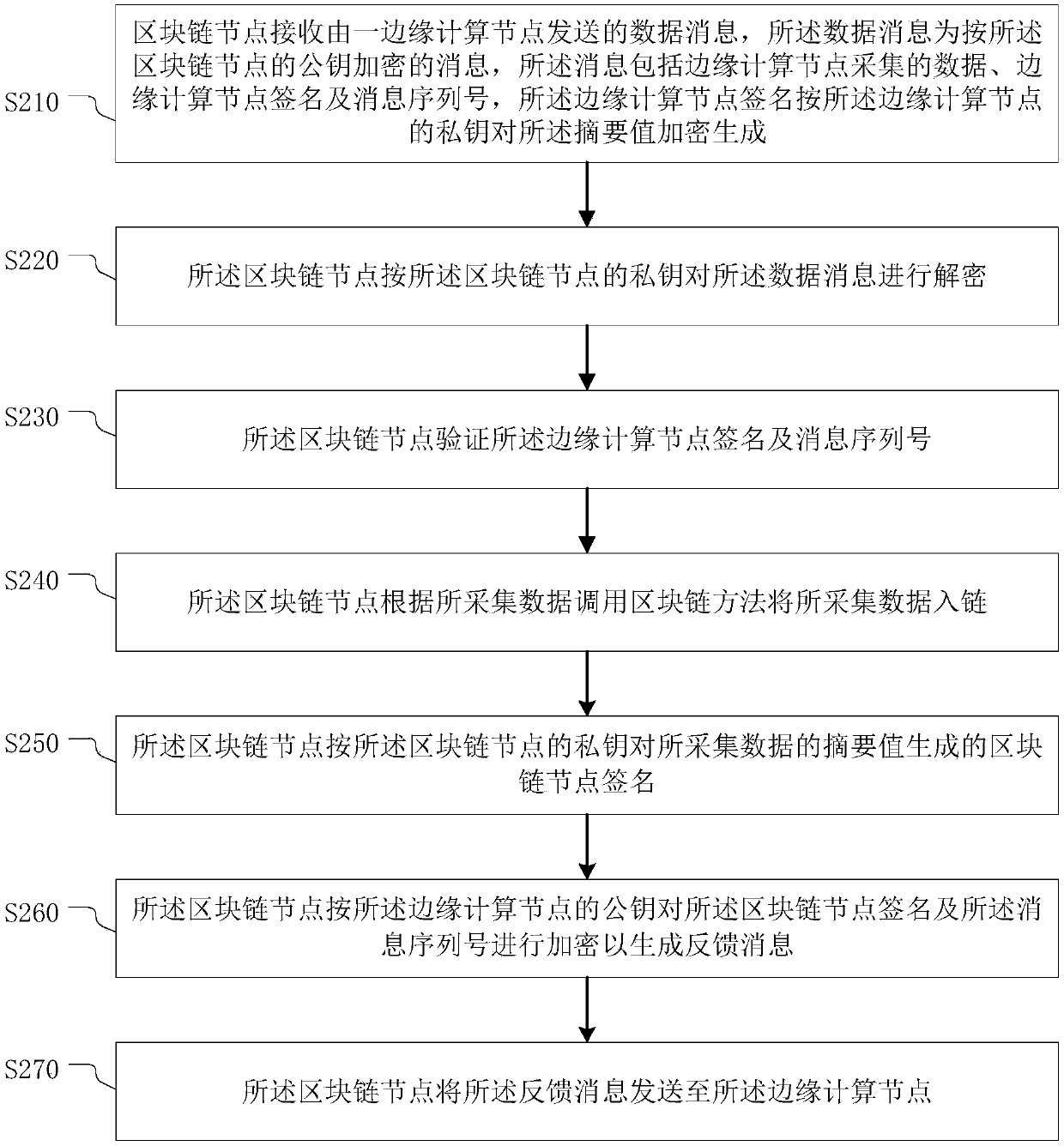
Trusted data transmission method and system, electronic equipment and storage medium
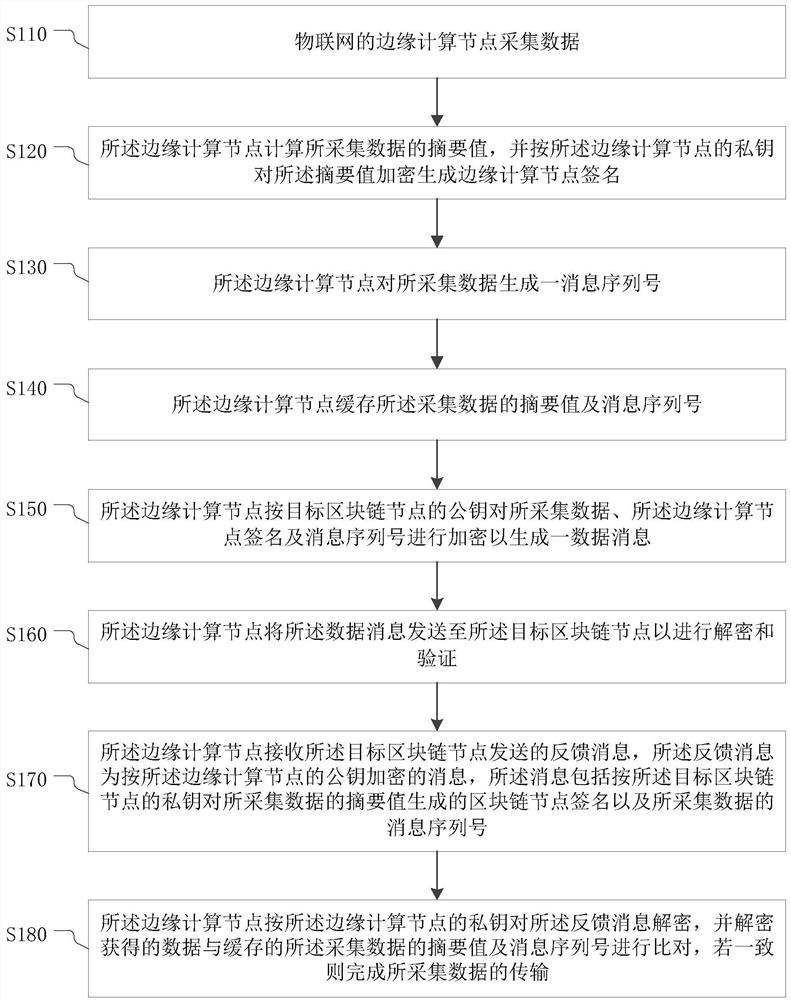
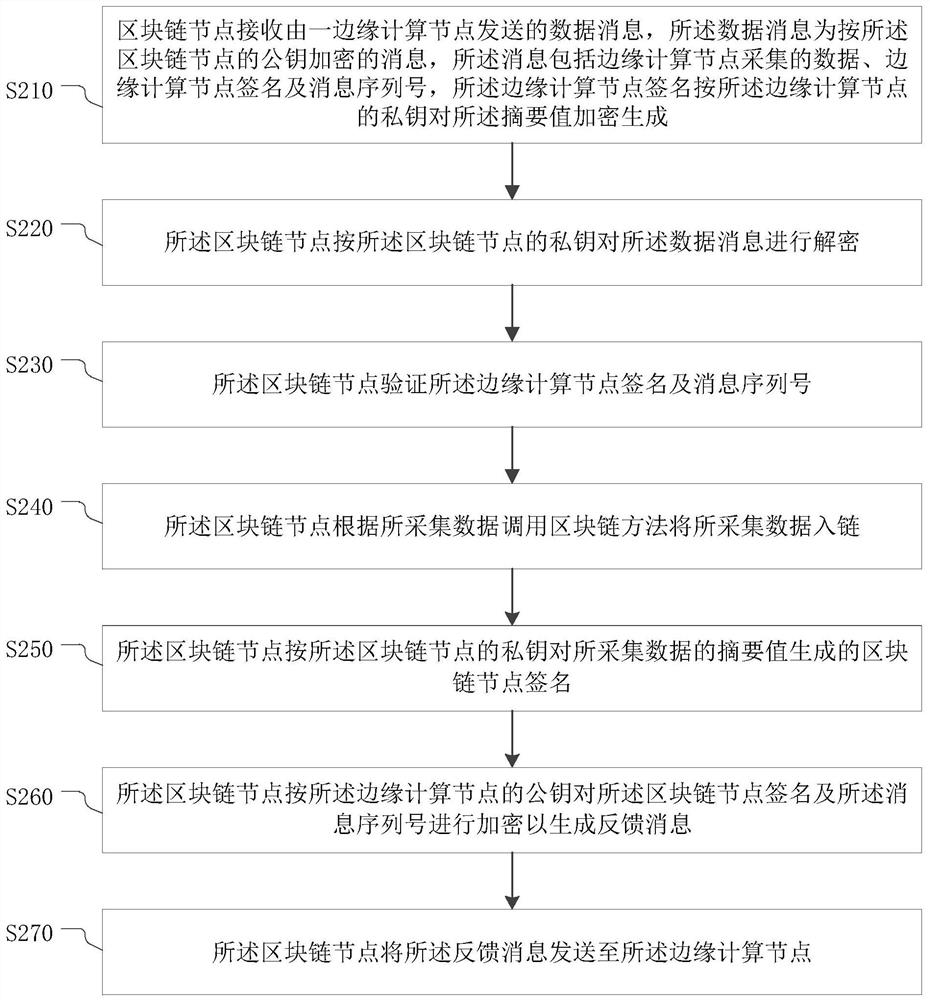
PendingCN110535647AReduce message lossReduce message tamperingPublic key for secure communicationUser identity/authority verificationComputer securityData messages
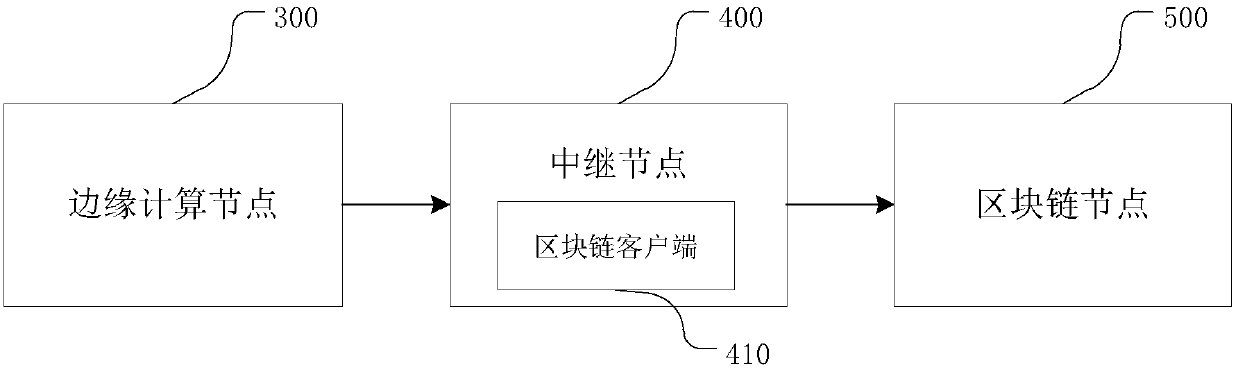
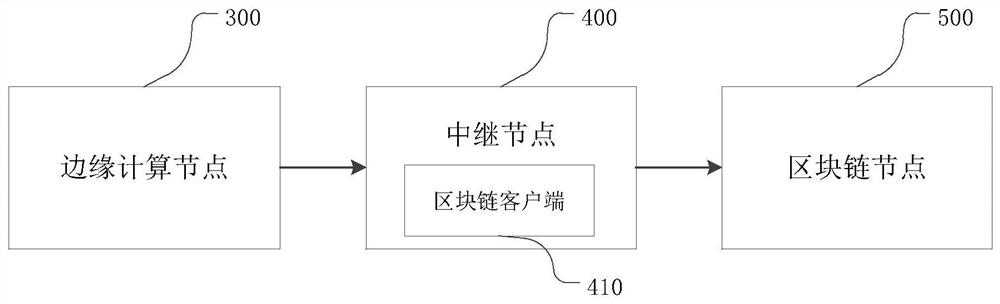
The invention provides a trusted data transmission method and a system, electronic equipment and a storage medium. The trusted data transmission method comprises the following steps: acquiring data; calculating an abstract value of the collected data, and encrypting the abstract value according to a private key of the edge computing node to generate an edge computing node signature; generating a message serial number for the acquired data; caching the abstract value and the message serial number of the acquired data; generating a data message according to the public key of the target blockchain node; sending the data message to the target blockchain node for decryption and verification; receiving a feedback message sent by the target blockchain node; and decrypting the feedback message according to the private key of the edge computing node, comparing the decrypted data with the cached abstract value and message serial number of the acquired data, and if the decrypted data is consistent with the cached abstract value and message serial number of the acquired data, finishing the transmission of the acquired data. According to the method and the device provided by the invention, thesecurity of message transmission between the Internet-of-thingsInternet-of-things and the blockchain can be realized.
Owner:上海诚频信息科技合伙企业(有限合伙)
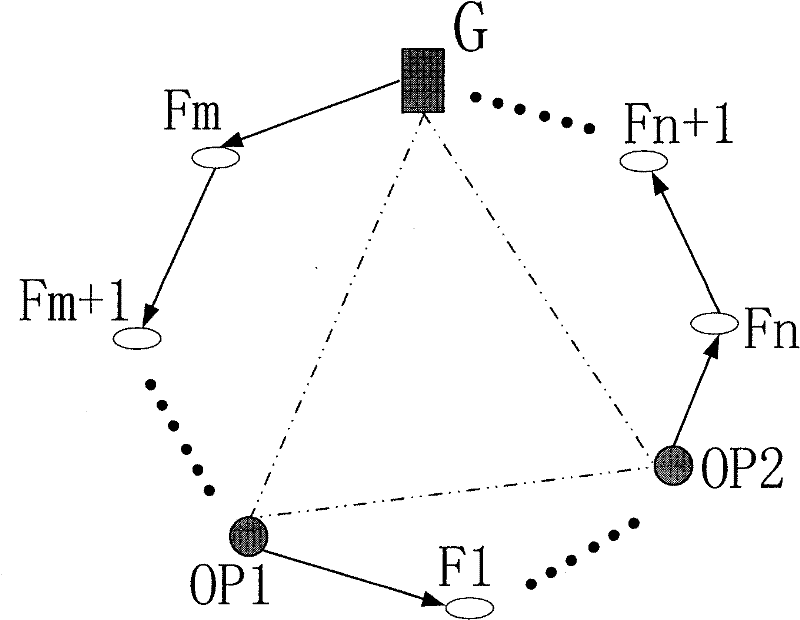
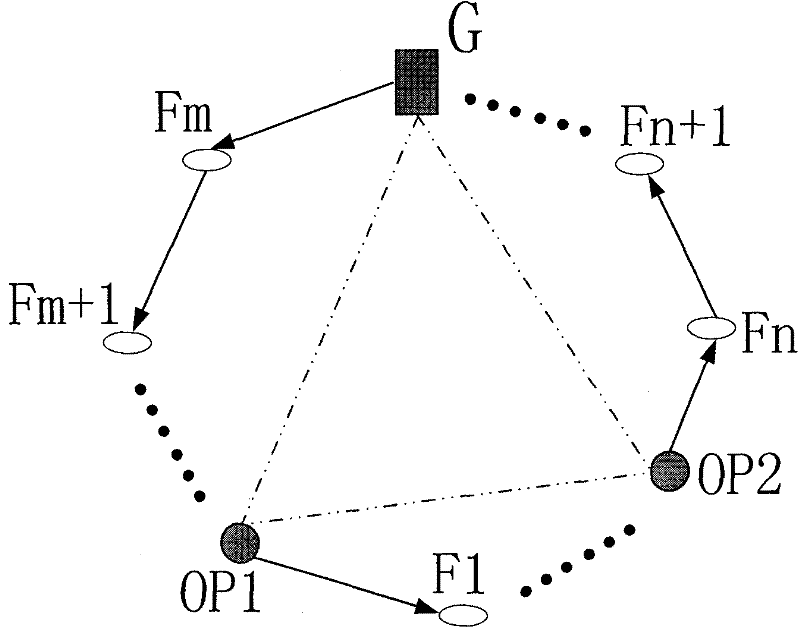
Method for hierarchichal onion rings routing
InactiveCN101635918APrevent intersection attacksReduce tamperingSecurity arrangementSecure communicationWireless mesh network
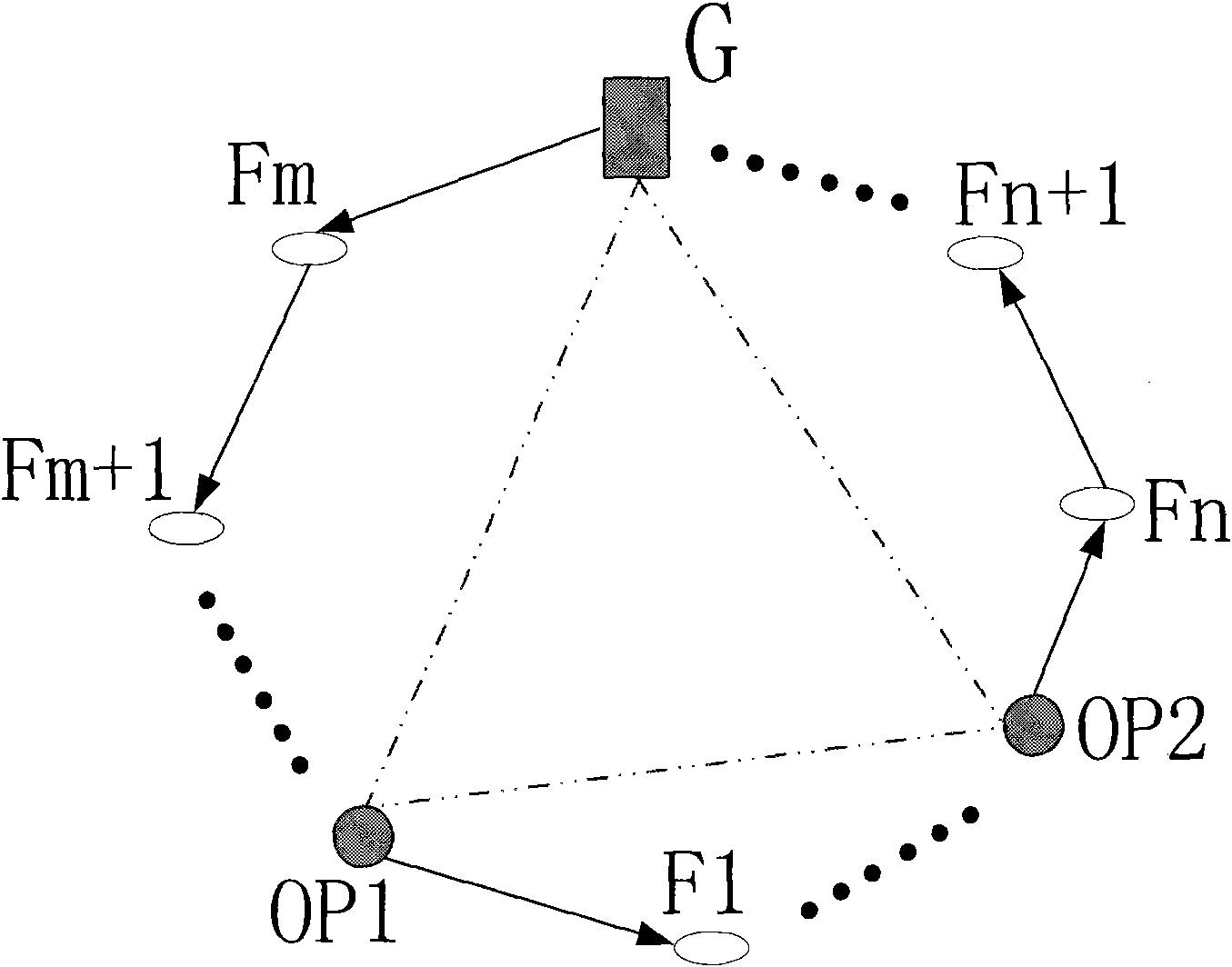
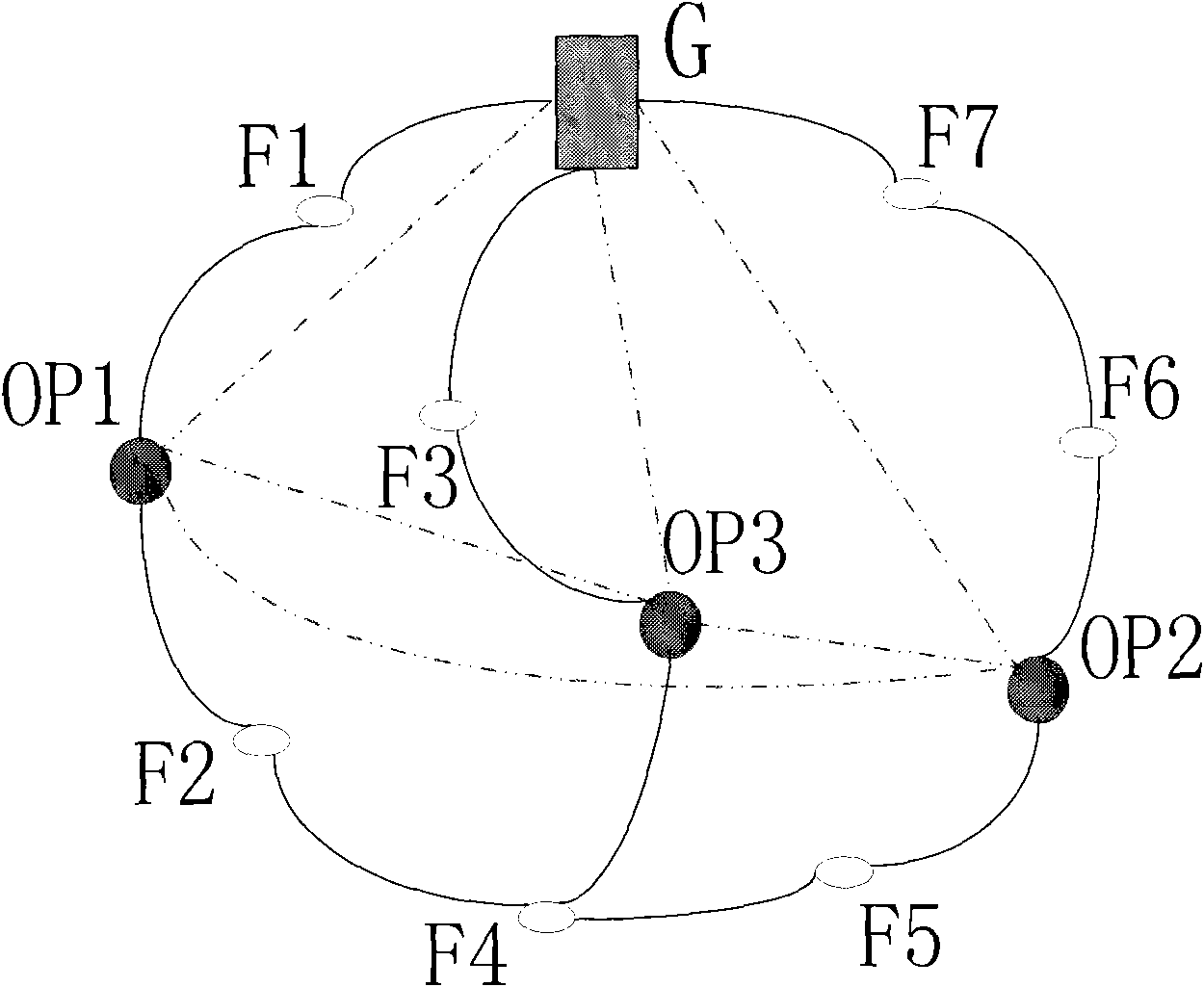
The invention discloses a method for hierarchichal onion rings routing. The nodes in a wireless Mesh network are divided into a gateway G, trusted nodes OP (Onion Proxy) and normal nodes Fi, wherein, the trusted nodes OP and the gateway G are induction nodes; the trusted nodes OP serve the function of selecting a route during the initialization of the ring; and the assembly of all the trusted nodes OP and the gateway G constitutes an anonymous assembly. The onion routing of the network is divided into two loop layers, wherein, the first route layer is a loop route consisting of the non-adjacent trusted nodes OP and the gateway G of the anonymous assembly; and the second route layer is a loop route formed by filling normal nodes Fi among the trusted nodes OP, and the second route layer is randomly selected by the trusted nodes OP and the gateway during the initialization. Accordingly, the anonymous and secure communication in the Mesh network can be achieved by the layered loops of the onion rings route. By using the layered onion rings communication protocol and allowing the trusted nodes OP and the gateway of the anonymous assembly to select the route together, the invention can effectively mix up the paths and prevent the intersection attacks, thereby reducing the computation, alleviating the load of the gateway, accelerating the ring construction, preferably utilizing the network resources to reduce delay.
Owner:XIDIAN UNIV
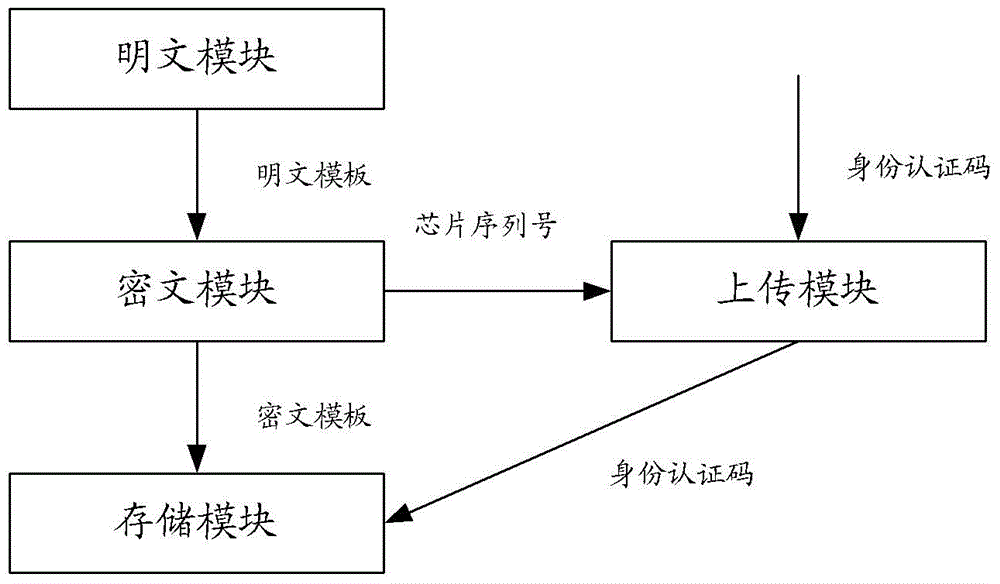
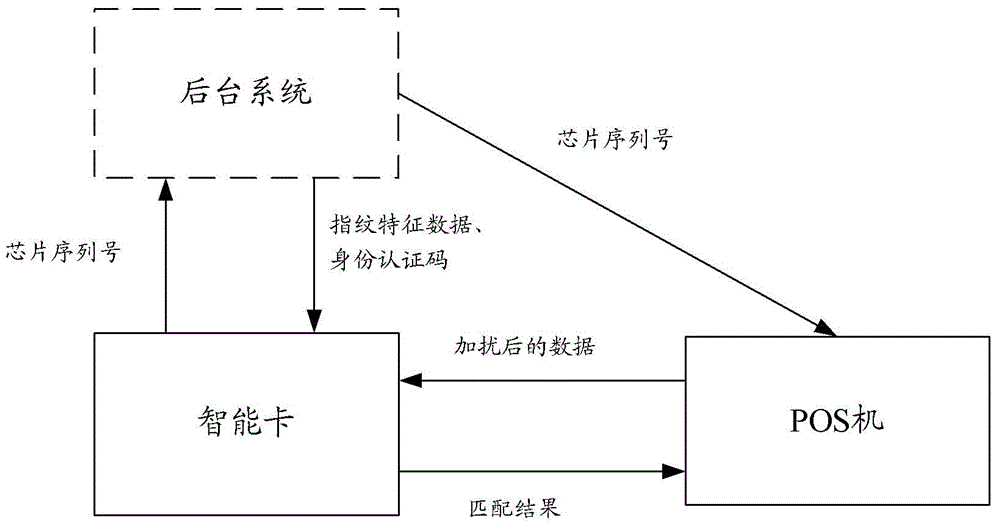
Fingerprint authentication method and system and fingerprint template encrypting device
ActiveCN104408356AReduce tamperingReduce counterfeitingDigital data authenticationPoint-of-sale network systemsCiphertextSmart card
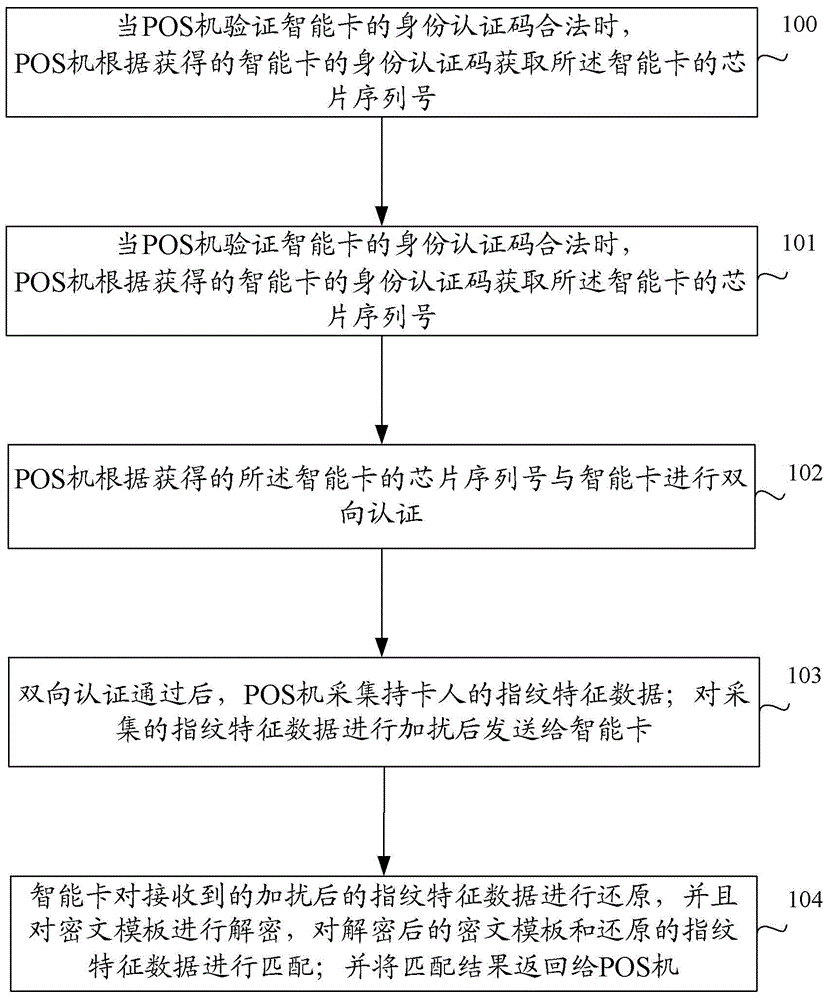
The invention discloses fingerprint authentication method and system and a fingerprint template encrypting device. The method comprises the following steps: processing fingerprint characteristics data from a background system by a smart card to produce a ciphertext template; acquiring a chip serial number of the smart card by a POS machine according to the acquired identity of the smart card when verifying the validity of the identity authorization code of the smart card by the POS machine; performing double authorization according to the acquired chip serial number of the smart card and the smart card; acquiring the fingerprint characteristics data of a card holder by the POS machine after the passing the double authorization; scrambling the acquired fingerprint characteristics data and then sending to the smart card; recovering the received scrambled fingerprint characteristics data by the smart card; decrypting the ciphertext template; matching the decrypted ciphertext template and the recovered fingerprint characteristics data; returning the matching result to the POS machine. According to the technical scheme, the method has the advantages that the possibility that a fingerprint template is tampered or forged is reduced, and the safety of the fingerprint authorization system is improved.
Owner:北京大唐智能卡技术有限公司
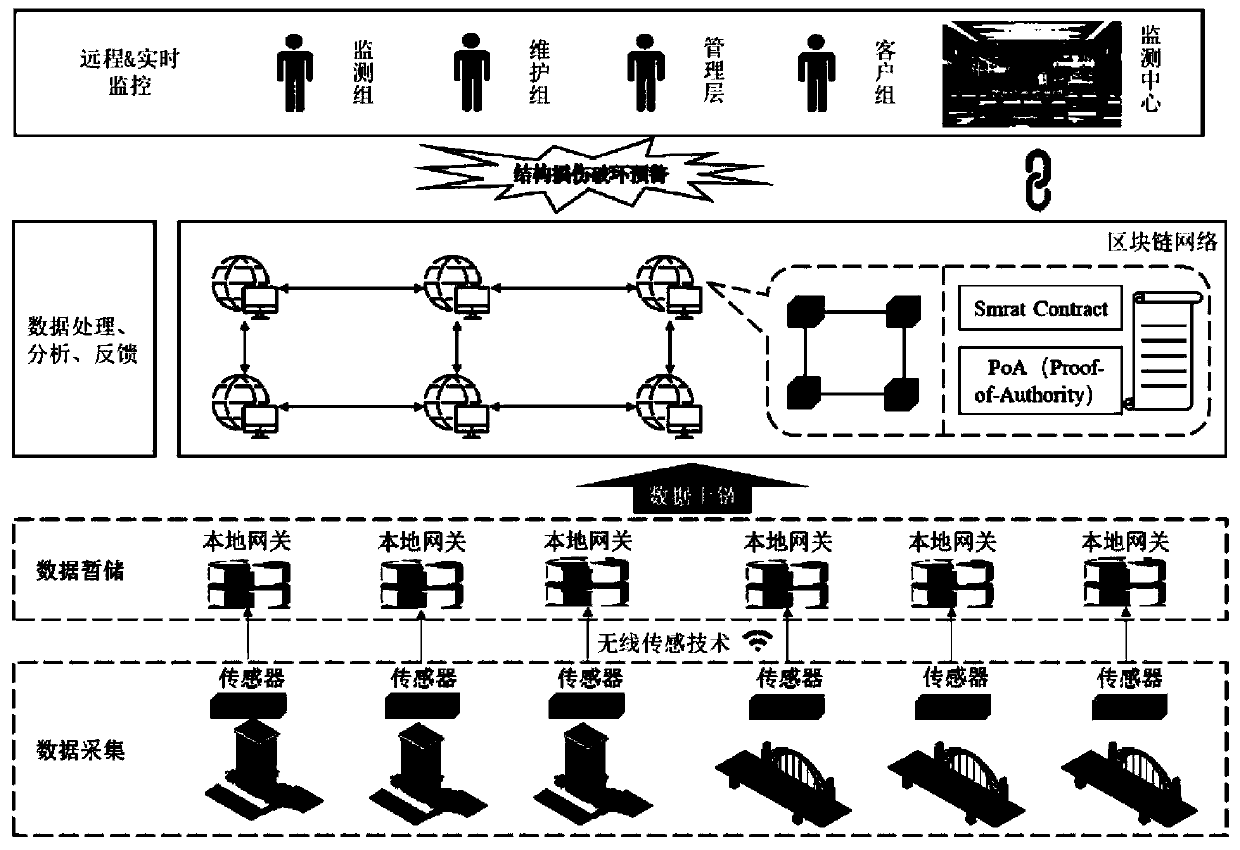
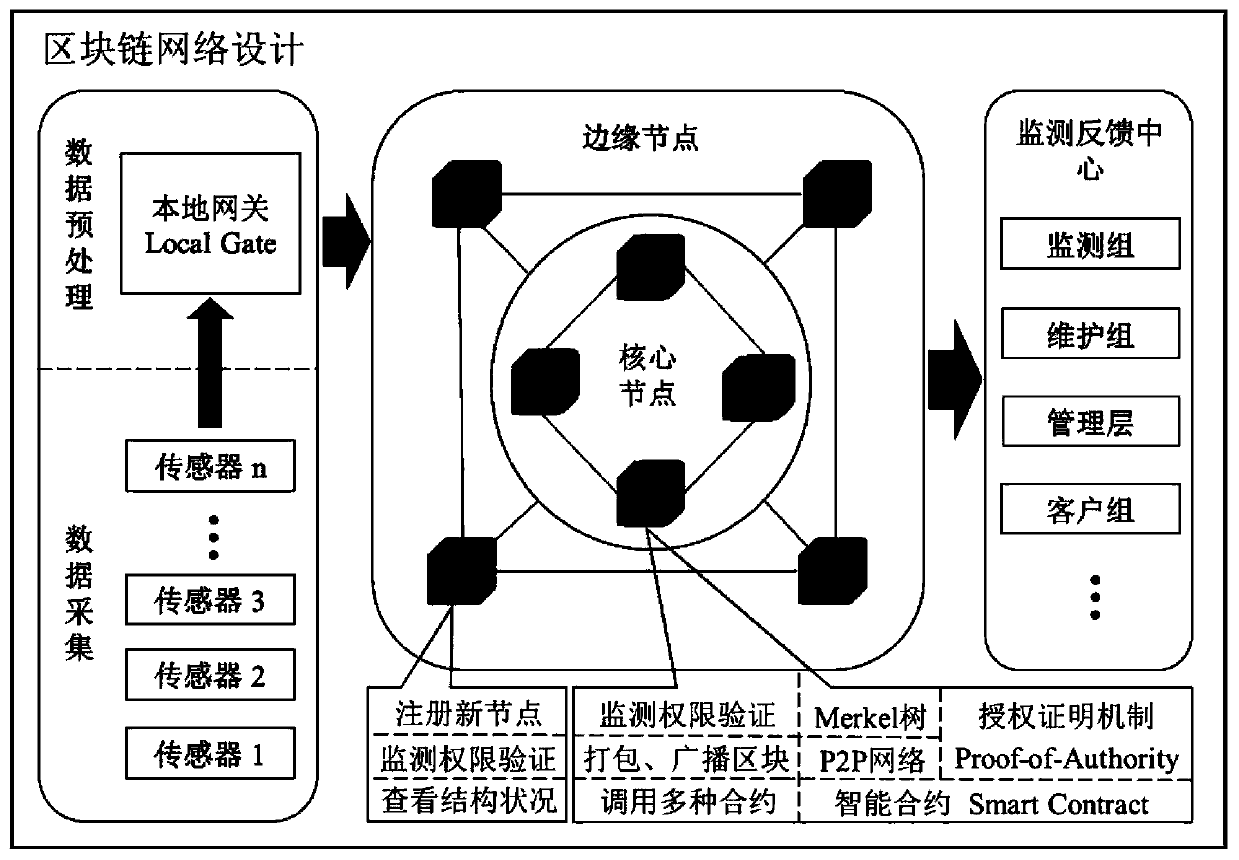
System and method for structure health monitoring based on block chain technology and smart contract
PendingCN111125468AGuarantee safe and reliableSolve the problem of mutual mistrustData processing applicationsOther databases browsing/visualisationOriginal dataData acquisition
The invention provides a system and a method for structural health monitoring based on a block chain technology and a smart contract. The system comprises a data acquisition module, a data temporary storage and transmission module, a data analysis module and an intelligent monitoring module; the data acquisition module comprises a sensor and a digital camera which are arranged on a building structure, and the sensor and the digital camera are used for acquiring original data; the data temporary storage and transmission module comprises a local gateway, and the local gateway is in wireless connection with the data acquisition module and the data analysis module; and the data analysis module comprises a block chain network system and the health monitoring smart contract deployed in the blockchain network system. The information among the participants is accurate, efficient and shared, and the operation efficiency of the whole system is improved from the perspective of data management and application. The structure health monitoring system is effectively prevented from being paralyzed under the condition of a server fault or a network fault.
Owner:TIANJIN UNIV
Operation management method for base station equipment and base station equipment
ActiveCN108566653AGuaranteed service qualityReduce tamperingWireless communicationResource useBase station
The embodiment of the invention provides an operation management method for base station equipment and the base station equipment and relates to the technical field of communication. According to theembodiment of the invention, distributed storage can be carried out on recorded resource usage amount of the base station equipment, so the data security and accuracy are improved. The method comprises the steps that target base station equipment receives communication requests of terminals in a first preset time period; the target base station equipment records operation information of the targetbase station equipment when the target base station equipment provides communication service for the communication requests; the target base station equipment sends the operation information to the other base station equipment in a preset area, thereby enabling the other target base station equipment in the preset area to update operation bills stored in the base station equipment; and the targetbase station equipment determines the resource usage amount of the target base station equipment in the first preset time period according to the operation bills stored in the base station equipmentwithin the preset area through utilization of a consensus mechanism. The method is applied to the operation management of the base station equipment.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD +2
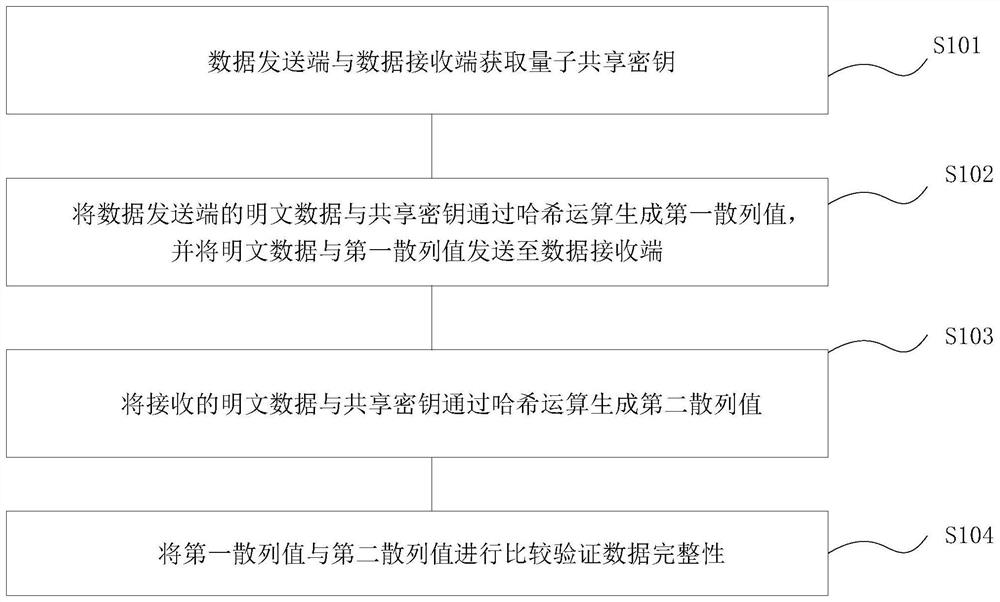
Data integrity rapid authentication method and system based on quantum secret communication, terminal and storage medium
PendingCN111726224AImprove integrityFast implementation of integrity verificationKey distribution for secure communicationComputer networkData integrity
The invention provides a data integrity rapid authentication method and system based on quantum secret communication, a terminal and a storage medium. The method comprises the steps that a data sending end and a data receiving end obtain a quantum shared key; the plaintext data of the data sending end and the shared key are subjected to hash operation to generate a first hash value, and the plaintext data and the first hash value are sent to the data receiving end; hash operation is performed on the received plaintext data and the shared key to generate a second hash value; the first hash value is compared with the second hash value to verify data integrity. According to the invention, a quantum key is used to replace a traditional key to carry out hash operation so as to carry out data integrity verification; according to the method, the risk that the hash function is cracked when data integrity verification is carried out can be reduced, authentication needs to be carried out on thetwo communication ends during data communication to ensure authenticity and integrity of data, rapid authentication needs to be carried out during large-scale communication, and data integrity and authenticity verification can be rapidly achieved by adopting the quantum key to carry out hash operation.
Owner:BEIJING INFORMATION SCI & TECH UNIV
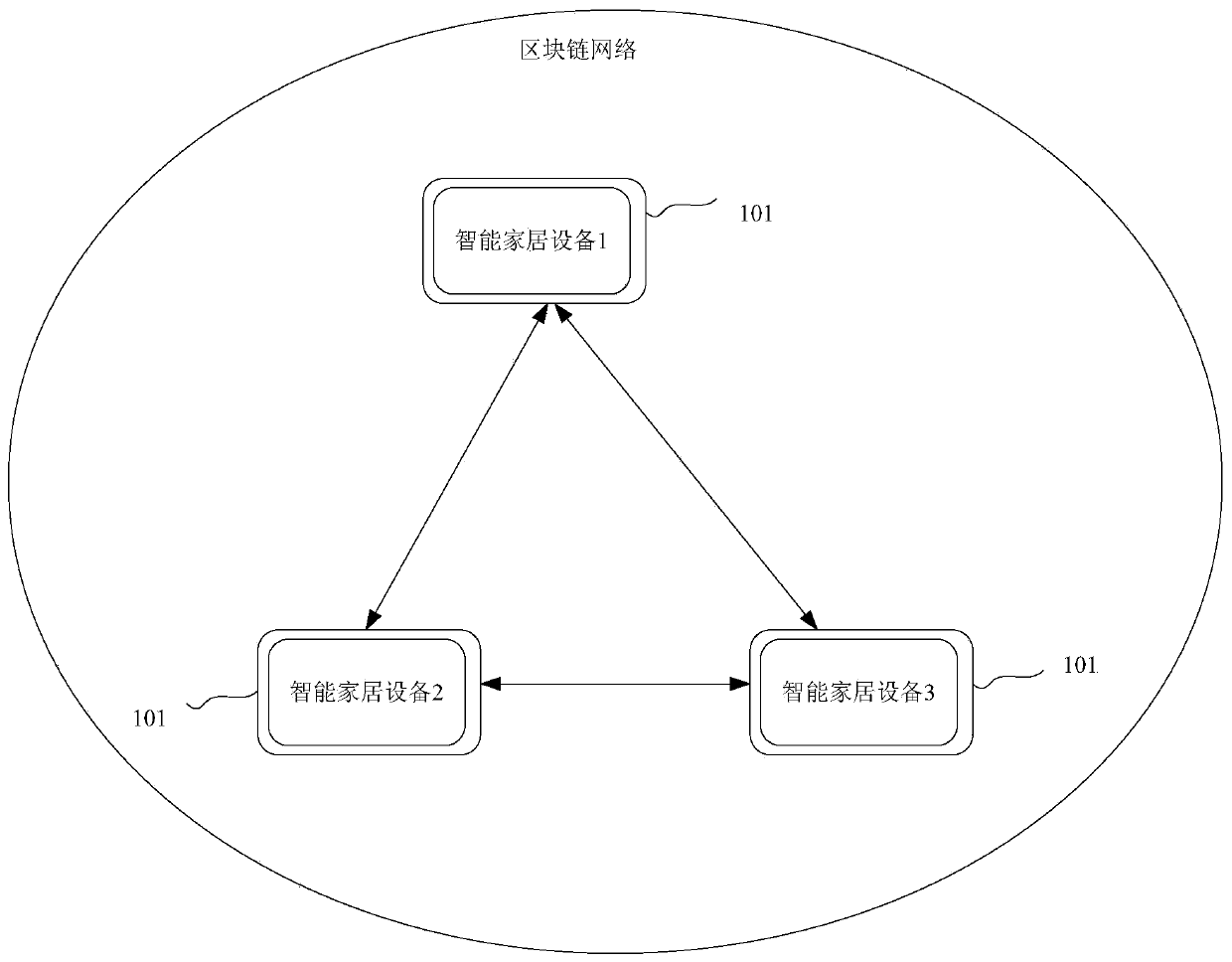
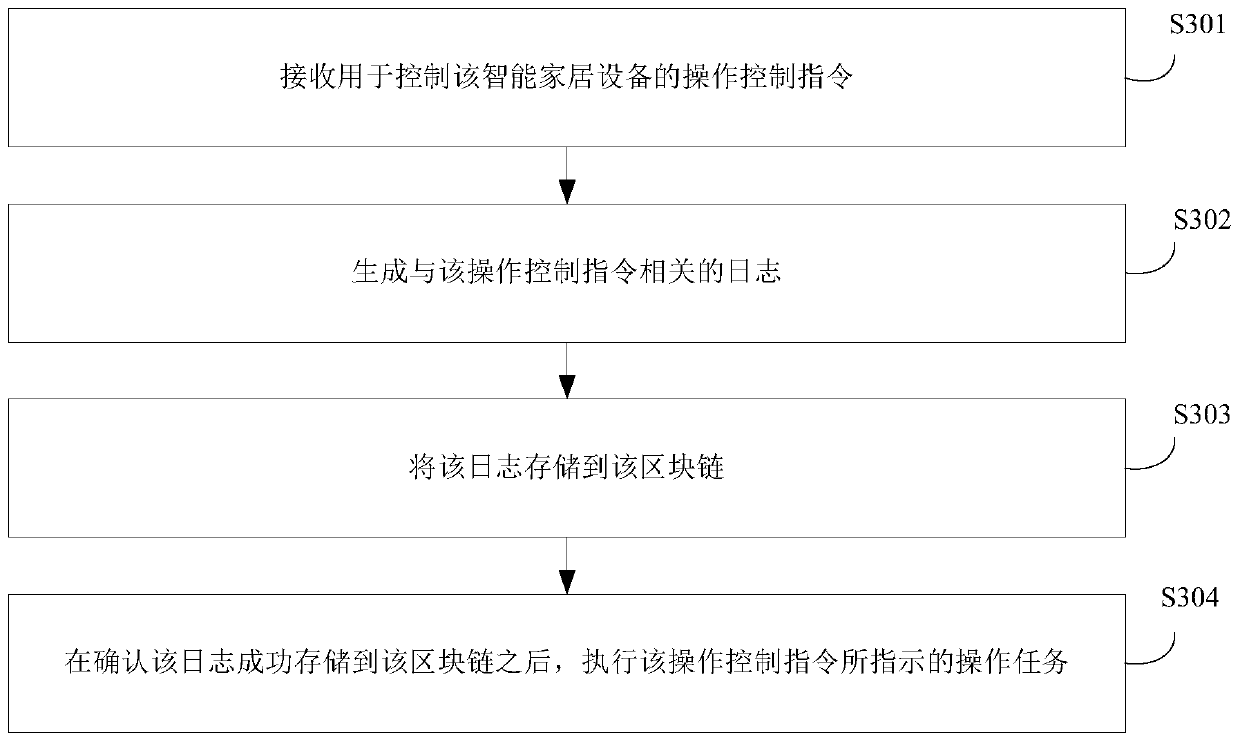
Operation control method and device for smart home equipment, equipment and storage medium
ActiveCN110719203AImprove securityPrevent tamperingComputer controlTotal factory controlComputer hardwareEmbedded system
The invention discloses an operation control method, device and equipment of smart home equipment and a storage medium, the method is applied to the smart home equipment, the smart home equipment is anode forming a block chain, and the method comprises the following steps: receiving an operation control instruction for controlling the smart home equipment; generating a log related to the operation control instruction; storing the log in the block chain; and after it is confirmed that the log is successfully stored in the blockchain, executing an operation task indicated by the operation control instruction. According to the scheme, the situation that the log of the smart home device is lost or deleted can be reduced, and the security of the log is improved.
Owner:TENCENT CLOUD COMPUTING BEIJING CO LTD
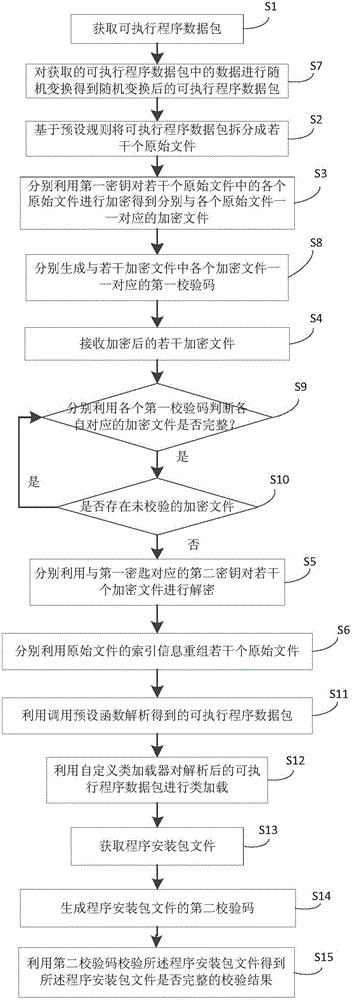
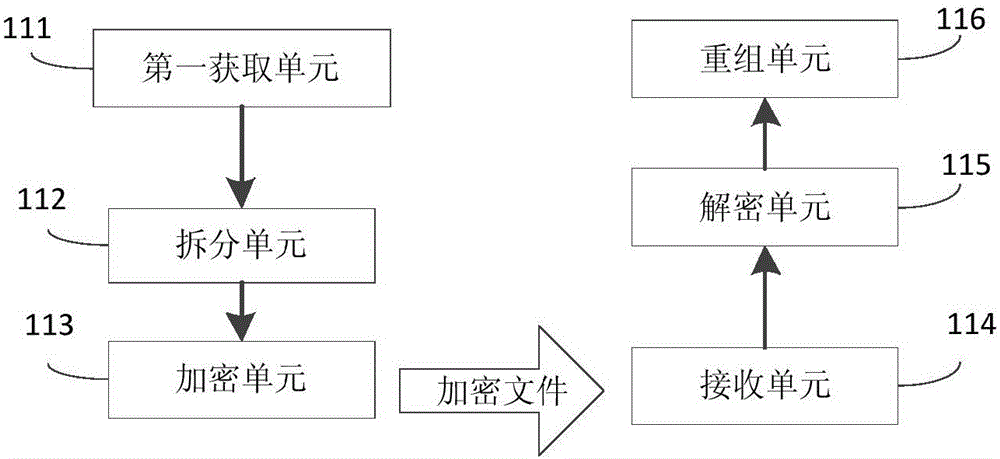
Method and device for encryption/decryption of executable program data package
ActiveCN106055936AGuaranteed confidentialityPrevent malicious crackingDigital data protectionProgram/content distribution protectionMultiple encryptionNetwork packet
The invention provides a method and device for encryption / decryption of an executable program data package. The method comprises the steps that the executable program data package is acquired; based on preset rules, the executable program data package is divided into multiple original documents; a first secret key is used to encrypt the multiple original documents respectively, so that encryption documents which have one-to-one correspondence relations with each original document respectively can be obtained; the multiple encrypted encryption documents are received; a second secret key corresponding to the first secret key is used to decrypt the multiple encryption documents respectively, so that the multiple original documents which have the one-to-one correspondence relations with the encryption documents can be obtained; and index information of the original documents are used respectively to reform the multiple original documents, so that the executable program data package can be obtained. The method and the device provided by the invention have the advantages that vicious decryption of the executable program data package caused by theft of a single secret key in the executable program data package can be prevented; a probability of the vicious decryption of an application program can be reduced; and data safety of the application program can be enhanced.
Owner:SHENZHEN UNIV
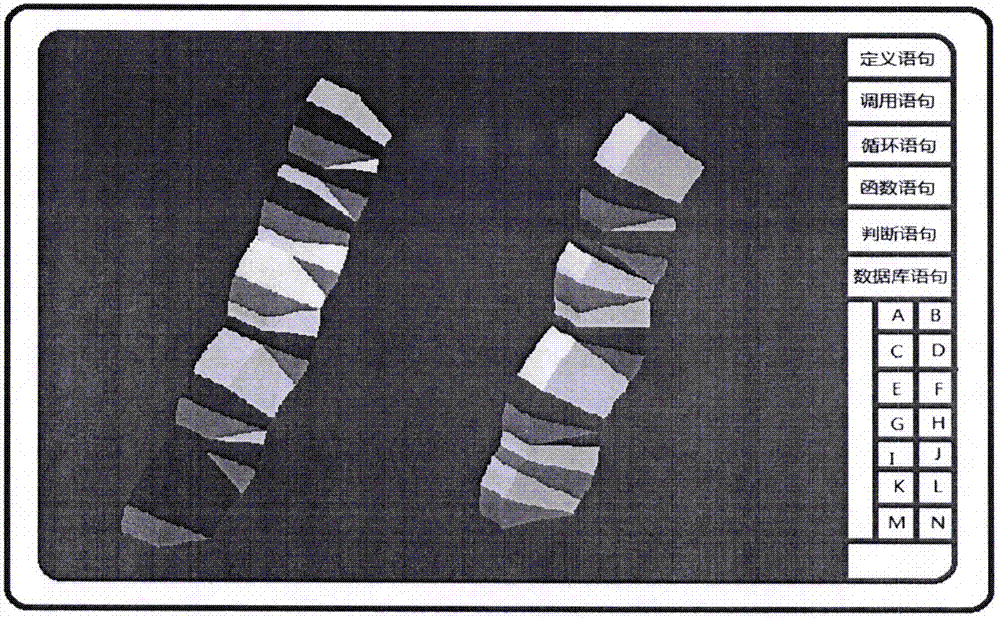
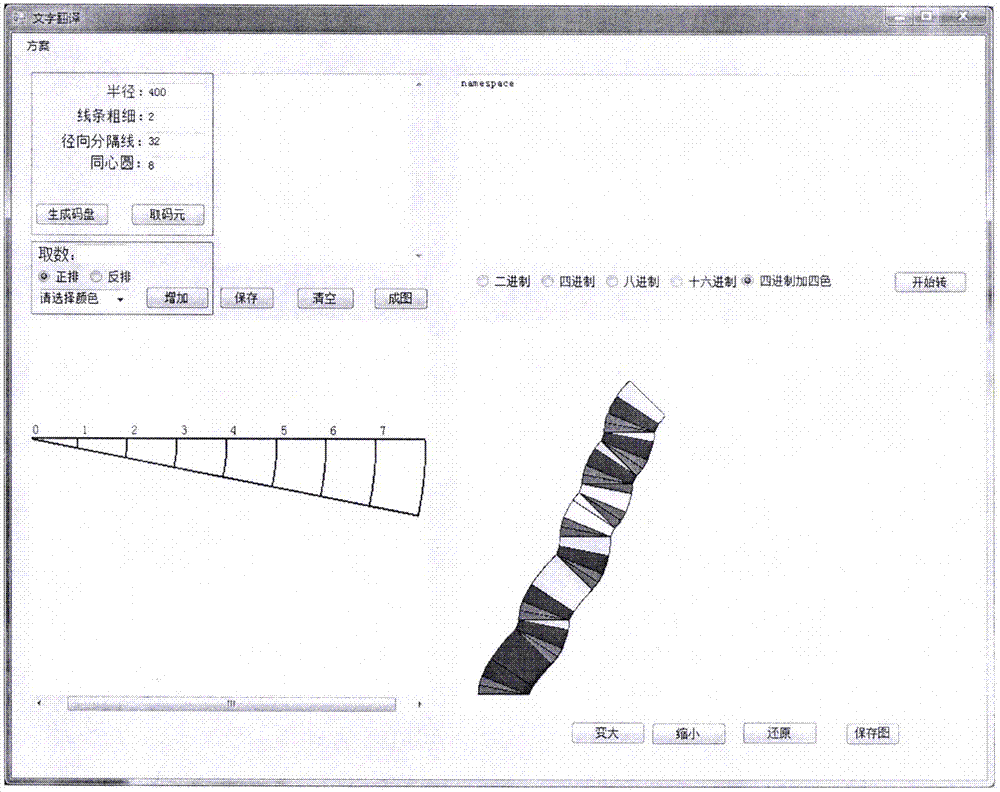
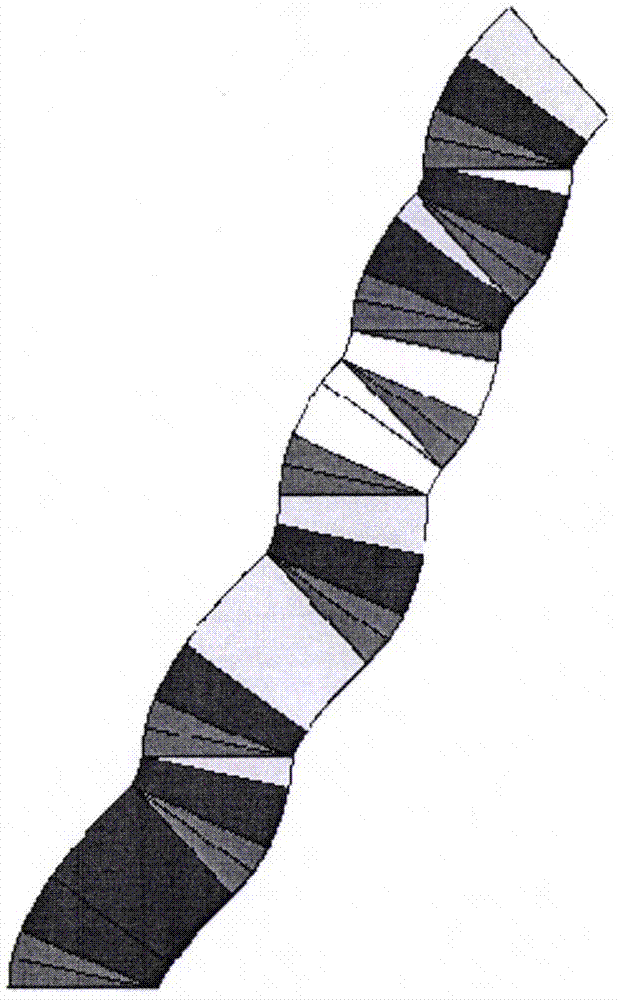
Visual three-dimensional code touch screen compiler and programming technique
ActiveCN105446747AReduce errorsImprove programming efficiencyVisual/graphical programmingCompiler constructionGeometric programmingProgram security
The invention discloses a visual three-dimensional code touch screen compiler product and its programming technique. According to the invention, visual geometric programming and three-dimensional code programming are realized; a programmer can finish programming work by one-hand or two-hand touch screen operation, therefore the workload of the programmer is greatly reduced; and the programming work is driven to humanized and intelligentized development. The built-in technologies of the new type geometric decoder and three-dimensional compiler of the invention comprise: generating a code plate and selecting a code element, coding a rule, information expression, hexadecimal number expression, conversion of digital and geometric codes, plane code to three-dimensional code, and so on; the functions of the compiler comprise: a touch screen function, program three-dimensional coding, a three-dimensional code paraphrasing function, an intelligent detection function, an automatic code storage function, an automatic connection function of three-dimensional code chains, and so on. According to the invention, the program code is converted into a shape code; a new pattern is provided for the security operation of the program; each code chain is not divided, so there is no leak for an external virus program to implant; the program is effectively prevented from being tampered and attached; and the program security is improved.
Owner:JIANGSU FIGURE CODE INFORMATION TECH LTD
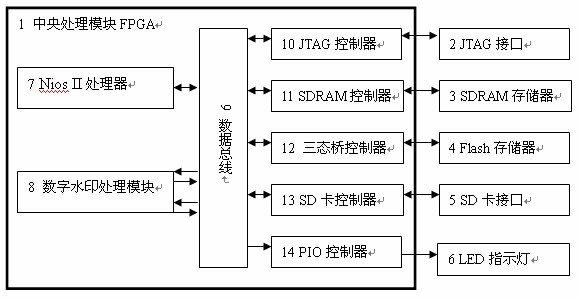
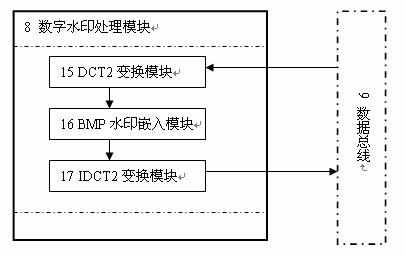
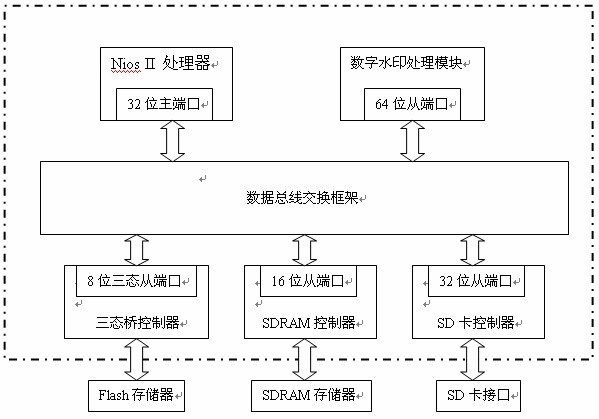
Digital watermarking processing method for BMP image
InactiveCN102402780AShorten the propagation pathReduce the chance of tamperingImage data processing detailsImage storageDigital watermarking
The invention relates to a digital watermarking processing method for a BMP (bitmap) image, which belongs to the technical field of computer application. The method comprises the following steps of: firstly, building three folders in an SD card; next, automatically loading programs cured in an Flash memory by the digital watermarking processing system for BMP image after startup, and transmitting image data to a digital watermarking processing module for processing through an SDRAM (Synchronous Dynamic Random Access Memory) controller and a data bus; then, caching the BMP image data with watermarking information to an SDRAM memory through the data bus and the SDRAM controller; finally, writing the image data to the SD card in an SD card interface through the SDRAM controller, the data bus and the SD card controller, storing the BMP image embedded with the watermarking information, after storing, lighting up an LED indication lamp and finishing processing. The method is fast for processing speed, small in volume, simple, portable and convenient to timely execute copyright protection on the obtained original image information.
Owner:KUNMING UNIV OF SCI & TECH
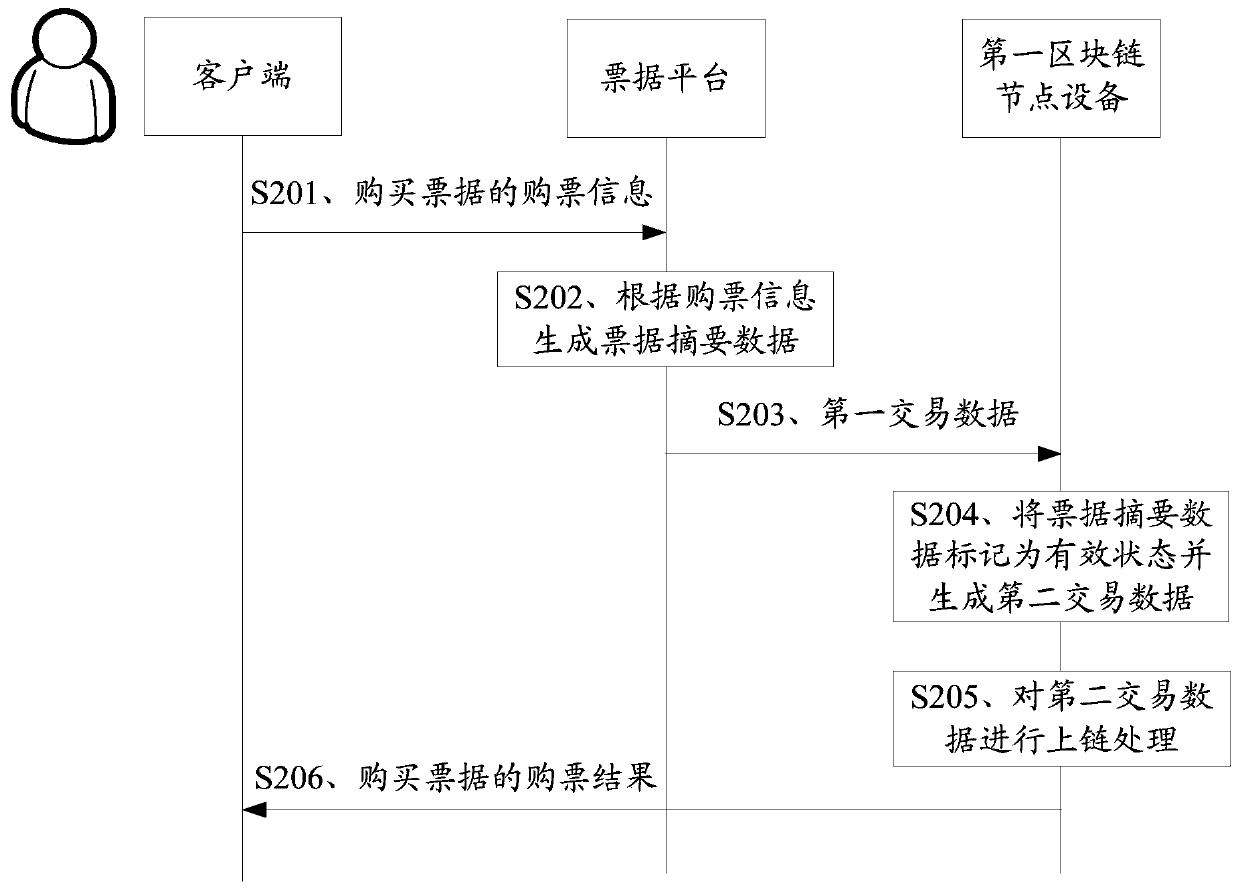
Bill data processing method and device, and medium
PendingCN110866755AIncrease credibilityImprove claims efficiencyDatabase distribution/replicationPayment protocolsThird partyTransaction data
The embodiment of the invention provides a bill data processing method and device and a medium. The method is applied to first block chain node equipment, and comprises the following steps: receivingfirst transaction data sent by a bill platform, the first transaction data comprising bill abstract data of a purchased bill, target contract information address information, a bill platform identifier and a target user identifier; searching bill contract information from the block chain according to the target contract information address information, and verifying the bill platform identifier according to the searched bill contract information; if the verification is passed, adding a mark to the abstract data, and packaging the mark, the abstract data and the target user identifier to obtainsecond transaction data; and performing uplink processing on the second transaction data. Based on the bill data processing method provided by the embodiment of the invention, the refunding and altering claim settlement can be automatically executed without the participation of a third party, the claim settlement efficiency is improved, and the credibility of a bill platform is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
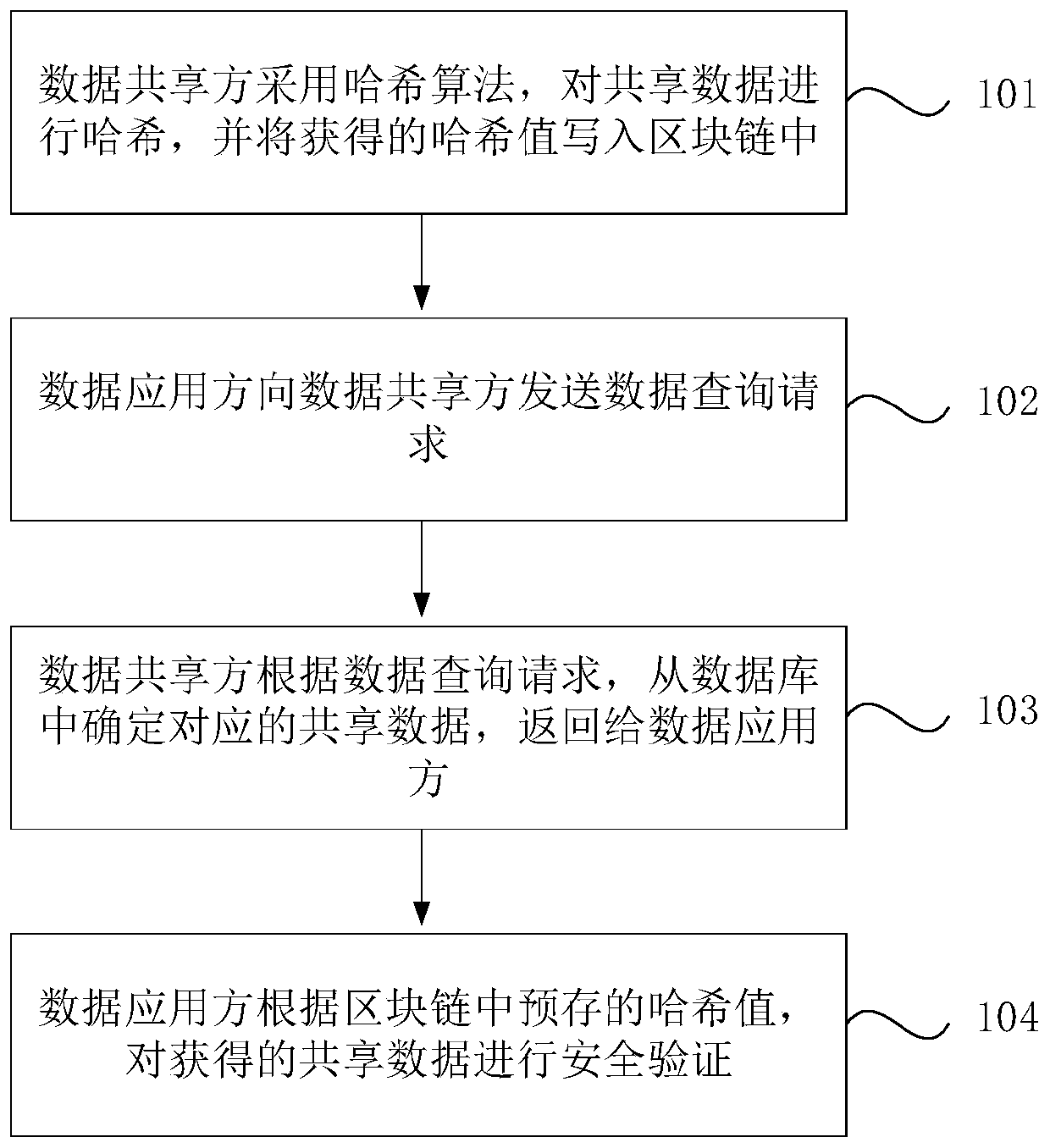
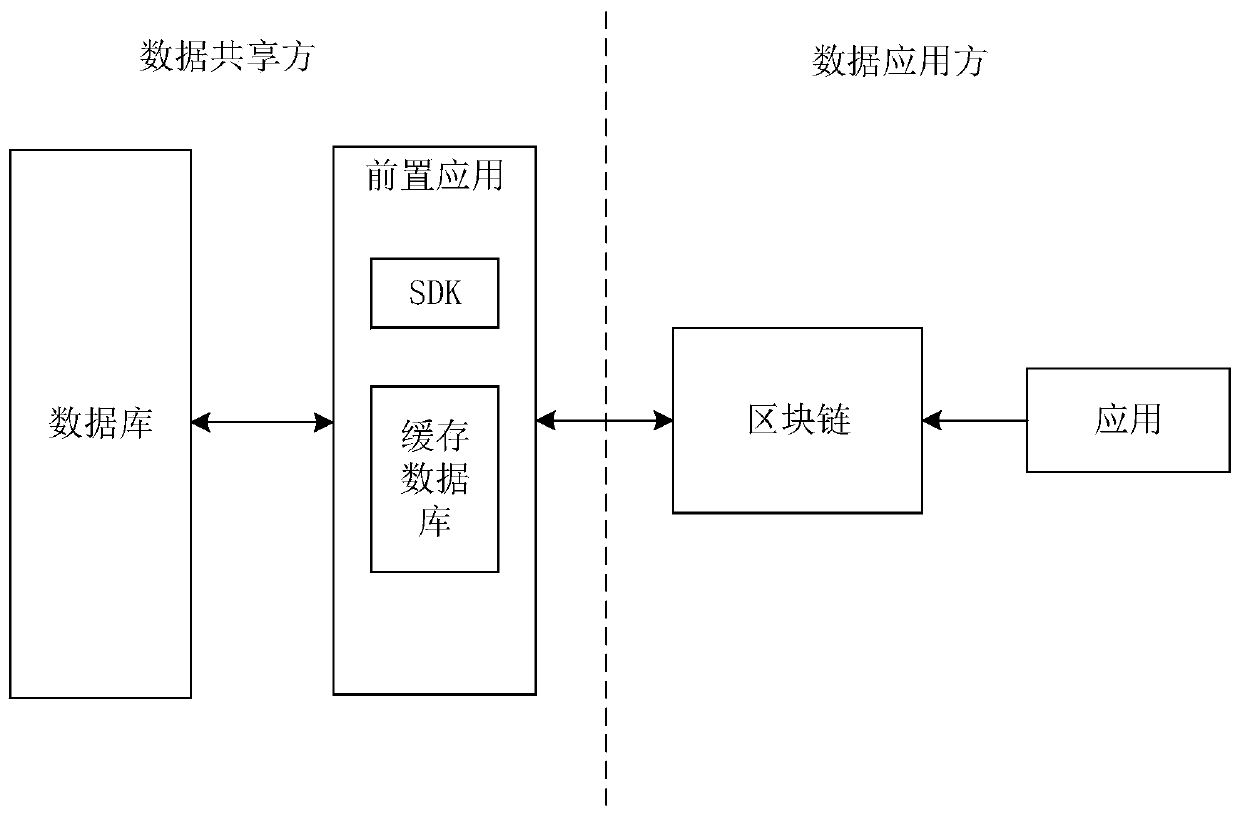
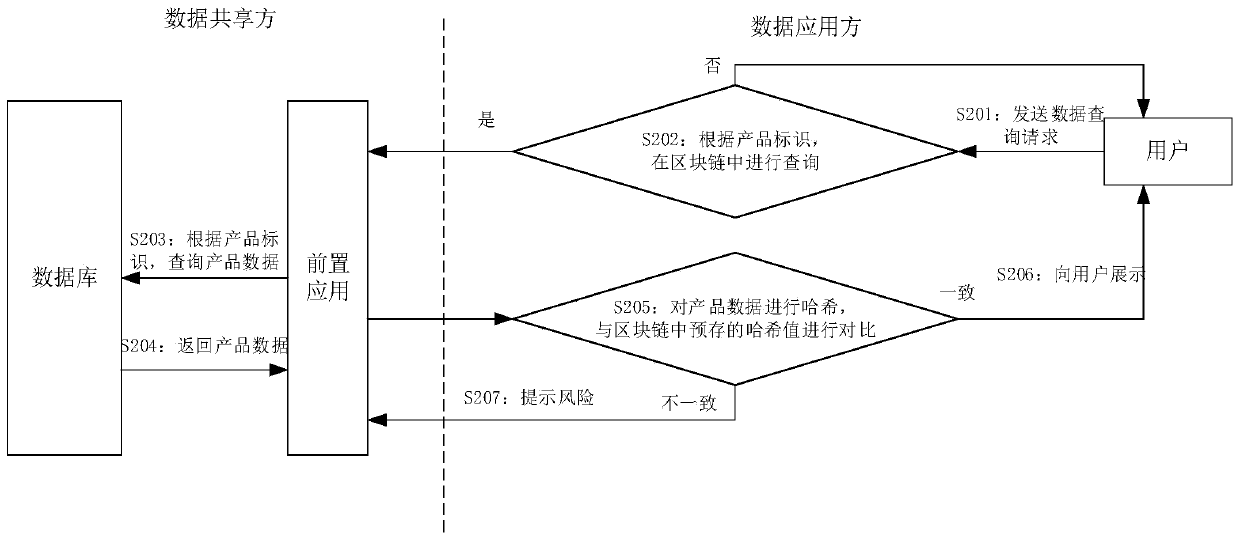
Data security sharing method and device based on block chain, and medium
PendingCN111224786AEnsure safetyReduce workloadUser identity/authority verificationDigital data protectionComputer networkEngineering
The invention discloses a data security sharing method and device based on a block chain, and a medium. The method comprises, by a data application party, sending a data query request to a data sharing party; according to the received shared data corresponding to the data query request, adopting a hash algorithm to hash the shared data; and matching the obtained hash value with a hash value pre-written into a block chain by the data sharing party so as to carry out security verification on the shared data. The hash value of the shared data is pre-stored in the block chain, so that the data application party can verify the acquired shared data to ensure the security of data sharing.
Owner:SHANDONG LANGCHAO YUNTOU INFORMATION TECH CO LTD
Perception layer data fidelity method for local area Internet of Things
InactiveCN110474921AAuthentication is trustedNo risk of tamperingTransmissionSecurity arrangementAuthenticationInternet of Things
The invention relates to a perception layer data fidelity method for a local area internet of things. The perception layer data fidelity method comprises the steps that a trusted execution environmentprocessor is arranged between a sensing node and a gateway in the local area Internet of Things, and the trusted execution environment processor can be used for intercepting a risk sensing node witha suspected identity before sensing data collected by the sensing node passes through the gateway, wherein the trusted execution environment processor is configured to extract an identity attribute set of the sensing node before the sensing node accesses the gateway, and the identity attribute set is used for identifying the identity of the sensing node. The identity authentication of the sensingnode is carried out in a trusted execution environment, and the trusted execution environment is a completely trusted part in the network and can be responsible for sensitive operations such as identity authentication, so that the identity authentication of the sensing node is completely trusted in the trusted execution environment.
Owner:CHINA UNIV OF PETROLEUM (BEIJING)
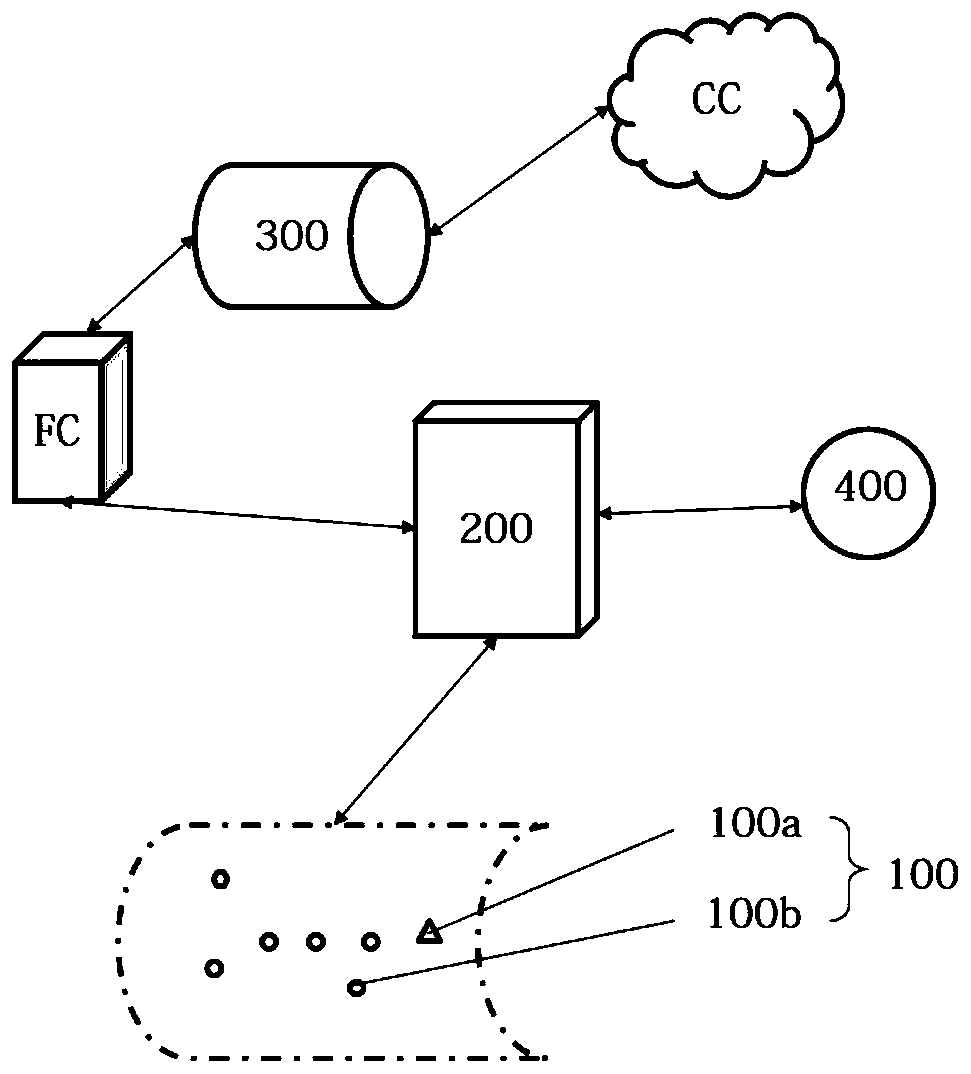
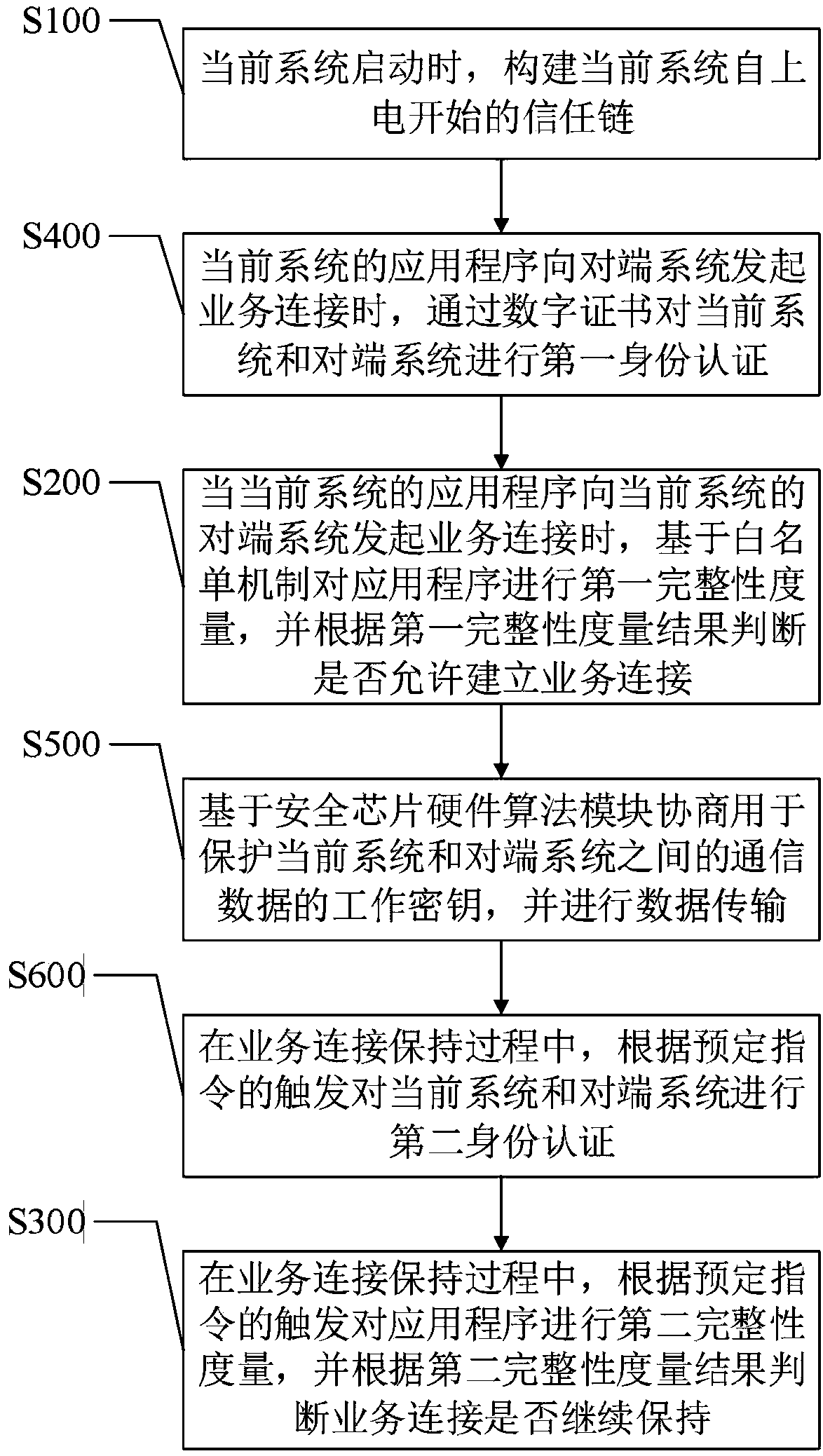
Trusted network communication method and device based on safety chip hardware algorithm module
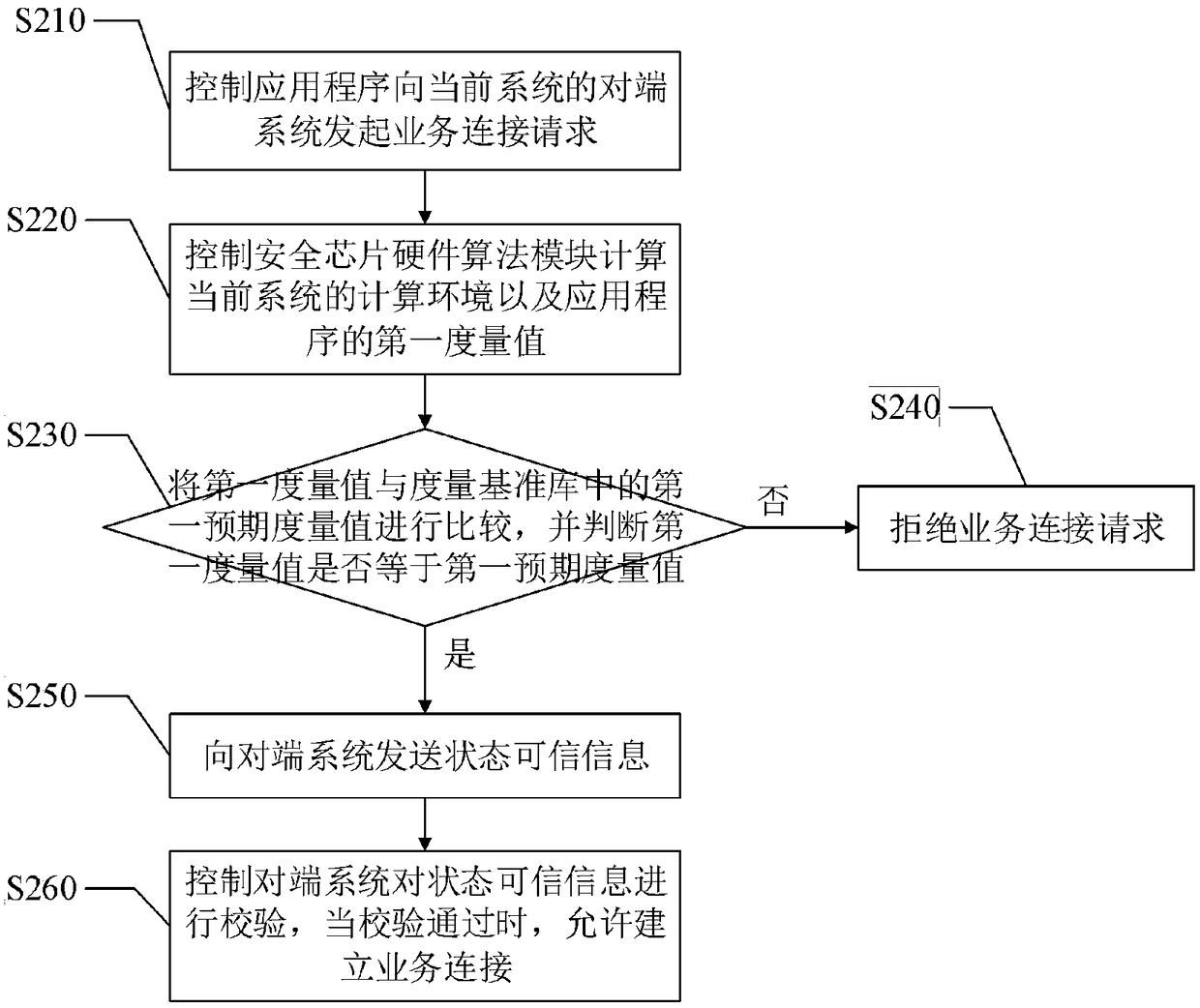
InactiveCN108632243AImprove securityIncrease credibilityKey distribution for secure communicationUser identity/authority verificationElectricityPrimary station
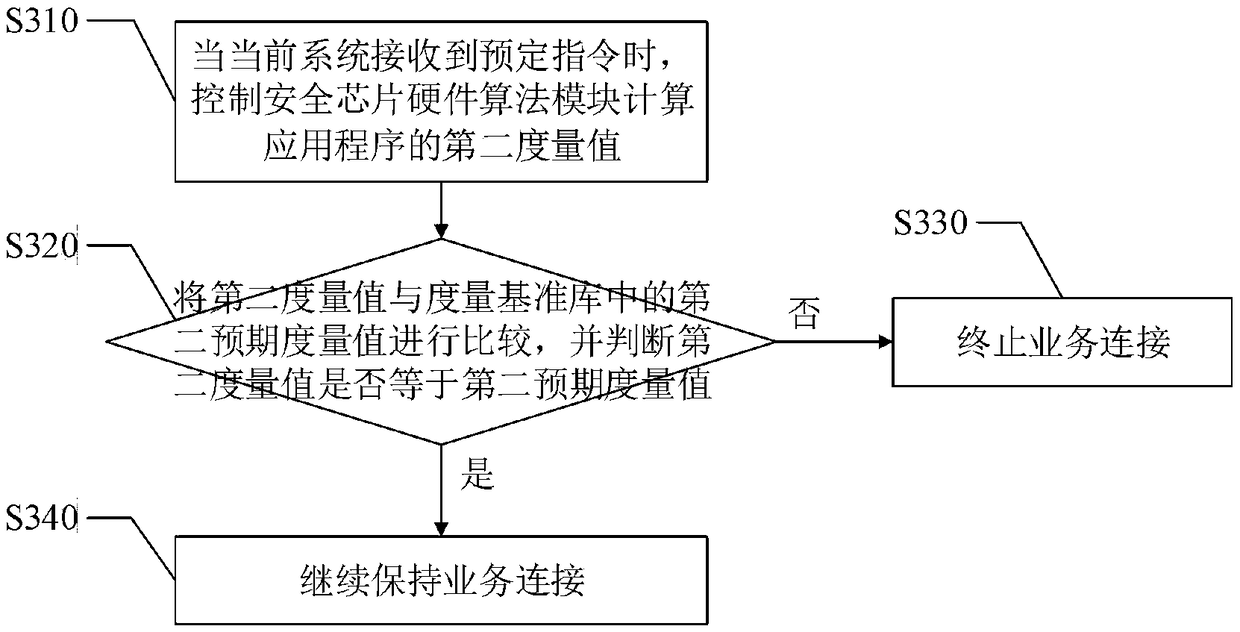
The invention discloses a trusted network communication method and device based on a safety chip hardware algorithm module. The method comprises the following steps of when a system is started, constructing the trust chain of a current system from the beginning of power on; when the application program of the current system initiates service connection to the opposite end system of the current system, carrying out first integrity measurement on the application program based on a whitelist mechanism, and according to a first integrity measurement result, determining whether the service connection is allowed to establish; and during a service connection maintenance process, carrying out a second integrity measurement on the application program based on the triggering of a predetermined instruction, and according to a second integrity measurement result, determining whether the service connection is continuously maintained. When the application program initiates the service connection tothe opposite end system, the first integrity measurement is performed, and during the service connection maintenance process, the second integrity measurement is performed so as to reduce a possibility that transmission data between a terminal system and a main station system is stolen, and improve the safety and the credibility of the method.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
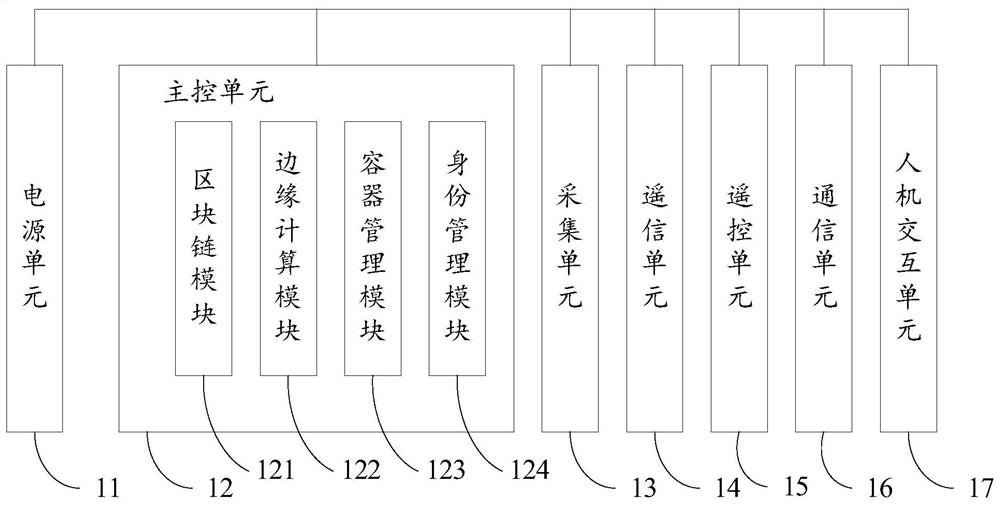
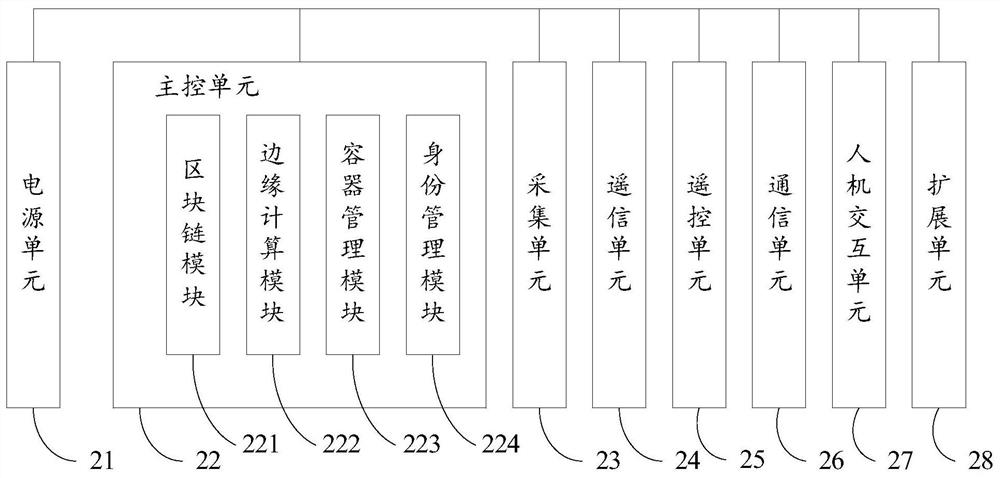
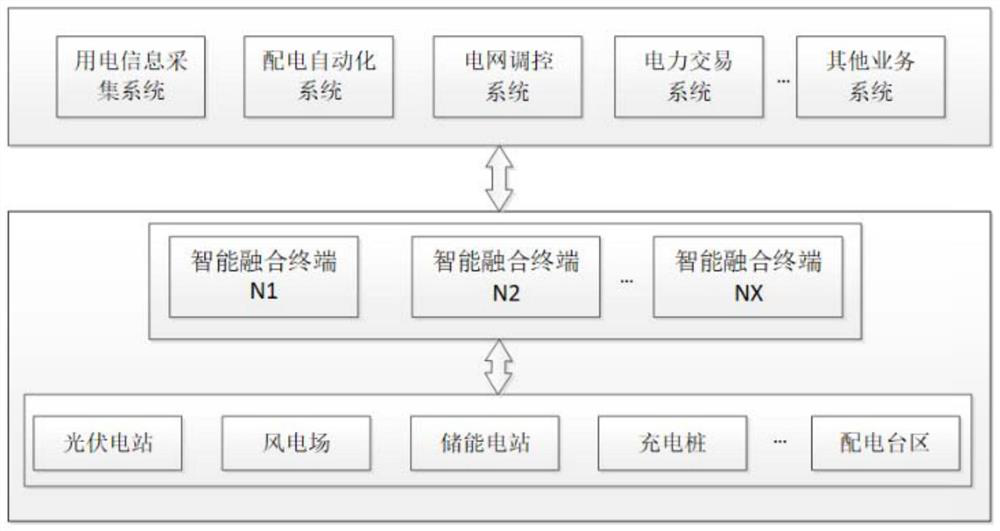
Intelligent fusion terminal based on block chain
InactiveCN112383141AReduce tamperingReduce riskCircuit arrangementsSustainable buildingsCommunication unitRemote control
The invention discloses an intelligent fusion terminal based on a block chain. The intelligent fusion terminal comprises a power supply unit, a main control unit, an acquisition unit, a remote signaling unit, a remote control unit, a communication unit and a human-computer interaction unit, and the main control unit comprises a block chain module, an edge calculation module, a container managementmodule and an identity management module. The intelligent fusion terminal based on the block chain provided by the invention can be used as an edge node of the block chain to realize uplink evidencestorage and data processing from a data source, so that the risk that the data is tampered and abused is effectively reduced, and the reliability and safety of the data are ensured.
Owner:STATE GRID BLOCKCHAIN TECH (BEIJING) CO LTD +1
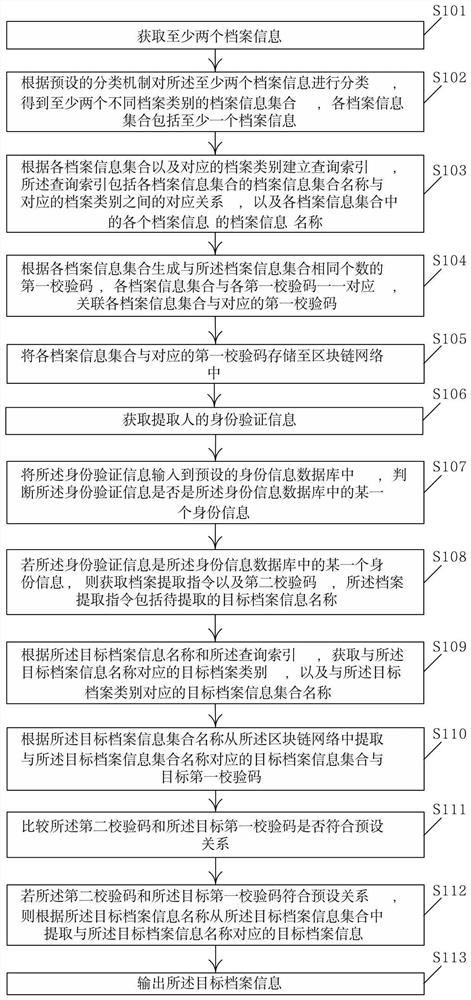
Archive management method based on block chain
PendingCN111611460AImprove securityReduce the possibility of illegal theftDigital data protectionDigital data authenticationCheck digitEngineering
The invention relates to an archive management method based on a block chain. The method comprises the steps of obtaining at least two pieces of archive information, classifying the archive information and establishing a query index; storing the classified archive information and the generated corresponding first check code into a block chain network; when the archive information is extracted, obtaining identity verification information of an extractor; after the identity verification is passed, obtaining an archive extraction instruction and a second check code; extracting a related target archive information set and a target first check code from the block chain network according to the archive extraction instruction; comparing whether the second check code and the target first check code meet a preset relationship or not; and if yes, obtaining and outputting target archive information. According to the archive management method based on the block chain, the possibility that the archive information is illegally stolen, tampered and damaged can be effectively reduced, and the safety of archive management is effectively improved.
Owner:ZHEJIANG GUANGSHA COLLEGE OF APPLIED CONSTRTECH
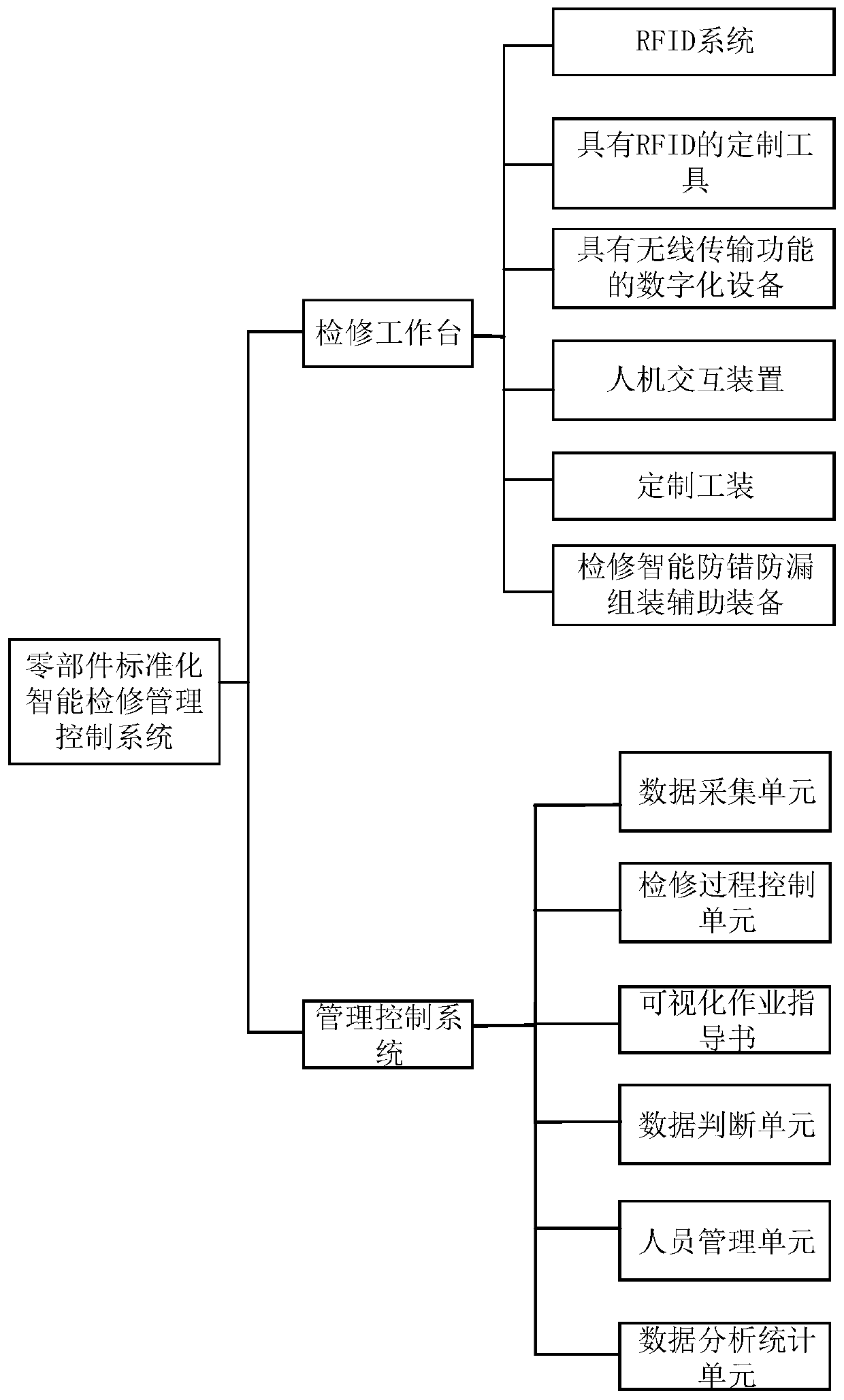
Standardized intelligent maintenance management control system for parts
ActiveCN109784767ASelf-repairImprove maintenance levelCo-operative working arrangementsResourcesEngineeringHuman–computer interaction
The invention discloses a standardized intelligent maintenance management control system for parts, and belongs to the technical field of maintenance control of parts. The system comprises at least one maintenance workbench and a management control system. The maintenance workbench comprises a customization tool with an RFID function, an RFID system, man-machine interaction equipment, digital equipment with an infinite transmission system, maintenance intelligent error-proof and leakage-proof assembly auxiliary equipment and a customization tool. The management control system comprises a process control unit, a visual operation instruction, a data acquisition unit, a data judgment unit, a personnel management unit and a data analysis and statistics unit. Monitoring and control of the partmaintenance process can be achieved, it is guaranteed that maintenance of the parts is executed according to the standardized process, meanwhile, work of operators can be monitored, all data in the maintenance process can be recorded, and standardized value maintenance and life cycle management of the parts are achieved.
Owner:睿惟智(上海)科技有限公司
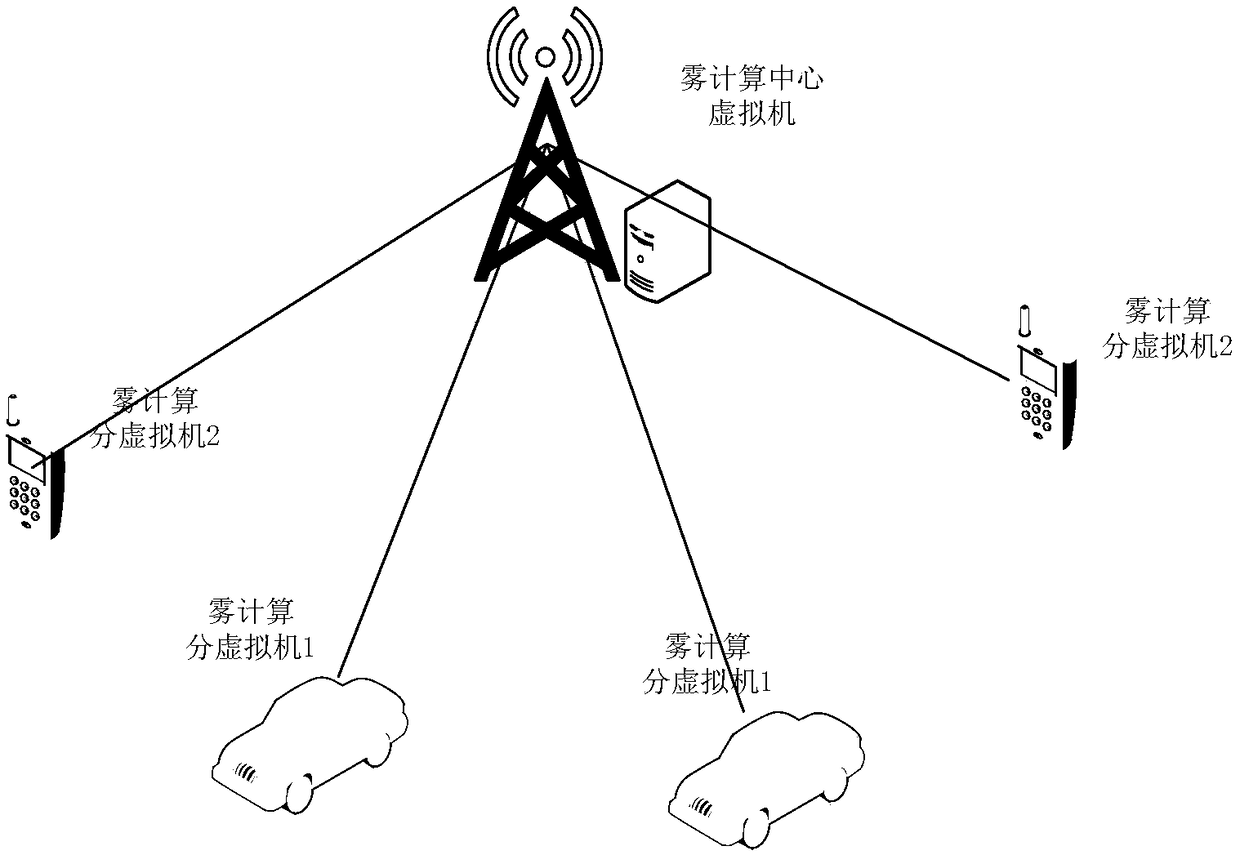
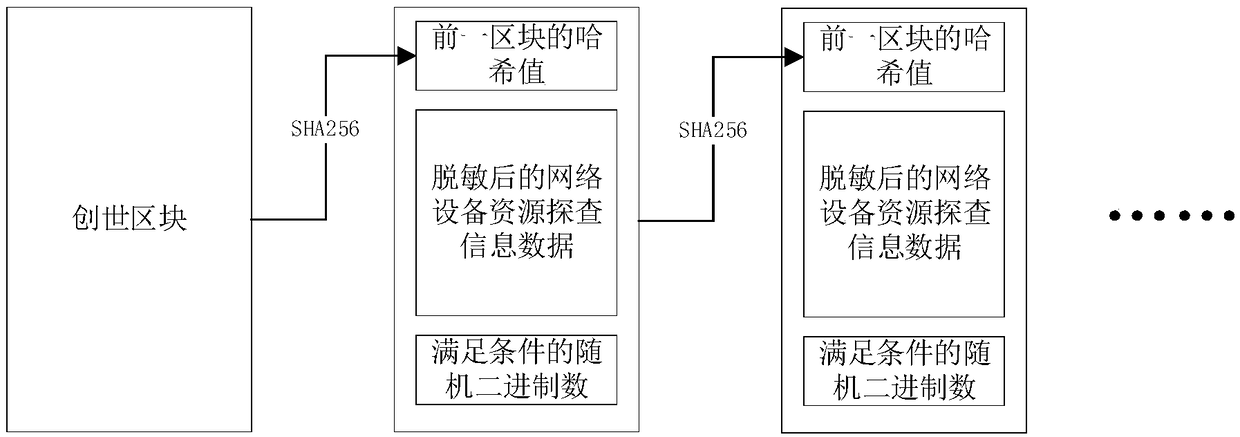
Tamper-proofing storage system of network device resource exploration information and control method thereof
ActiveCN109195160AReduce tamperingRealize decentralized storageEncryption apparatus with shift registers/memoriesSecurity arrangementTamper resistanceBlockchain
The present invention provides a tamper-proofing storage system of network device resource exploration information and a control method thereof, and relates to the field of information safety. The system comprises a base station and a plurality of intelligent devices connected with the base station, the base station and the intelligent devices are all provided with fog computing programs, the basestation is provided with a fog computing center virtual machine, the intelligent devices are provided with a plurality of fog computing sub virtual machines, the sub virtual machines are managed by the center virtual machine, and the center virtual machine and the sub virtual machines are all provided with data packet analysis programs. The tamper-proofing storage system of network device resource exploration information and the control method thereof reduce the computing amount of the base station, improve the large-scale data processing capacity and provide enough computing power for the blockchain technology.
Owner:SHANGHAI JIAO TONG UNIV
Intelligent contract information flow integrity verification method and system based on type detection
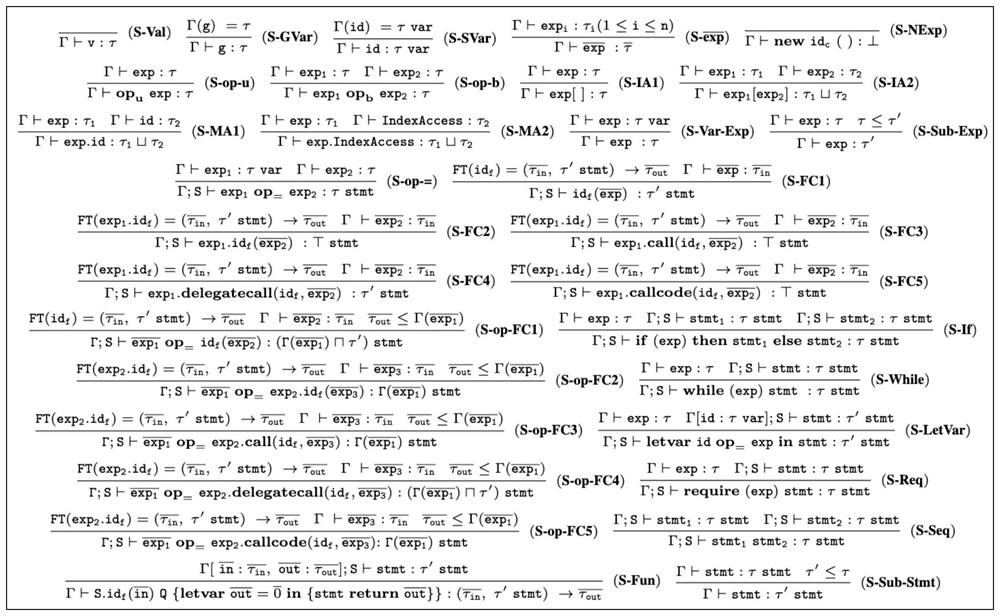
PendingCN113051624AReduce the probability of credible information being tampered withReduce tamperingDigital data protectionSecurity informationValidator
The invention discloses an intelligent contract information flow integrity verification method and system based on type detection, and belongs to the field of block chains and information security. The method can be used for solving the problem of potential information tampering of the smart contract in an Ethereum block chain environment. The method comprises the following steps: constructing formalized grammar and semantics for a smart contract programming language; constructing a security type system STC of the smart contract, wherein the STC is used for detecting the integrity of information flow of the smart contract; and constructing a type verifier STV based on an intelligent contract type system STC, and searching optimal security type allocation automatically for state variables of the intelligent contract. According to the method, formalized grammar and semantics of the smart contract are given, meanwhile, the advantages of type detection in security information flow check are combined, the information flow integrity of source codes of the smart contract can be effectively analyzed and verified, and the probability that credible information is tampered in the running process of the smart contract is reduced.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
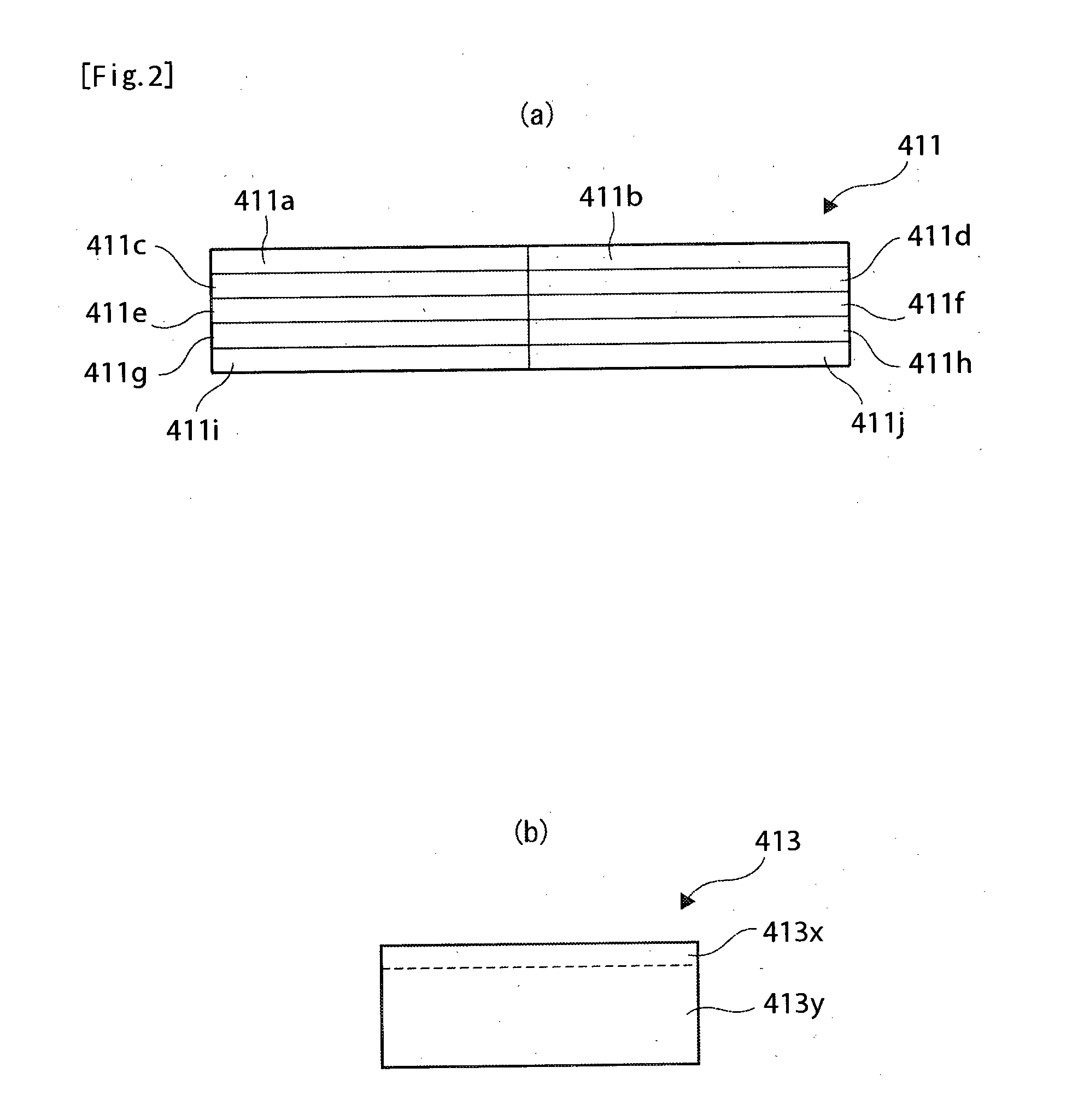
Fiscal Printer
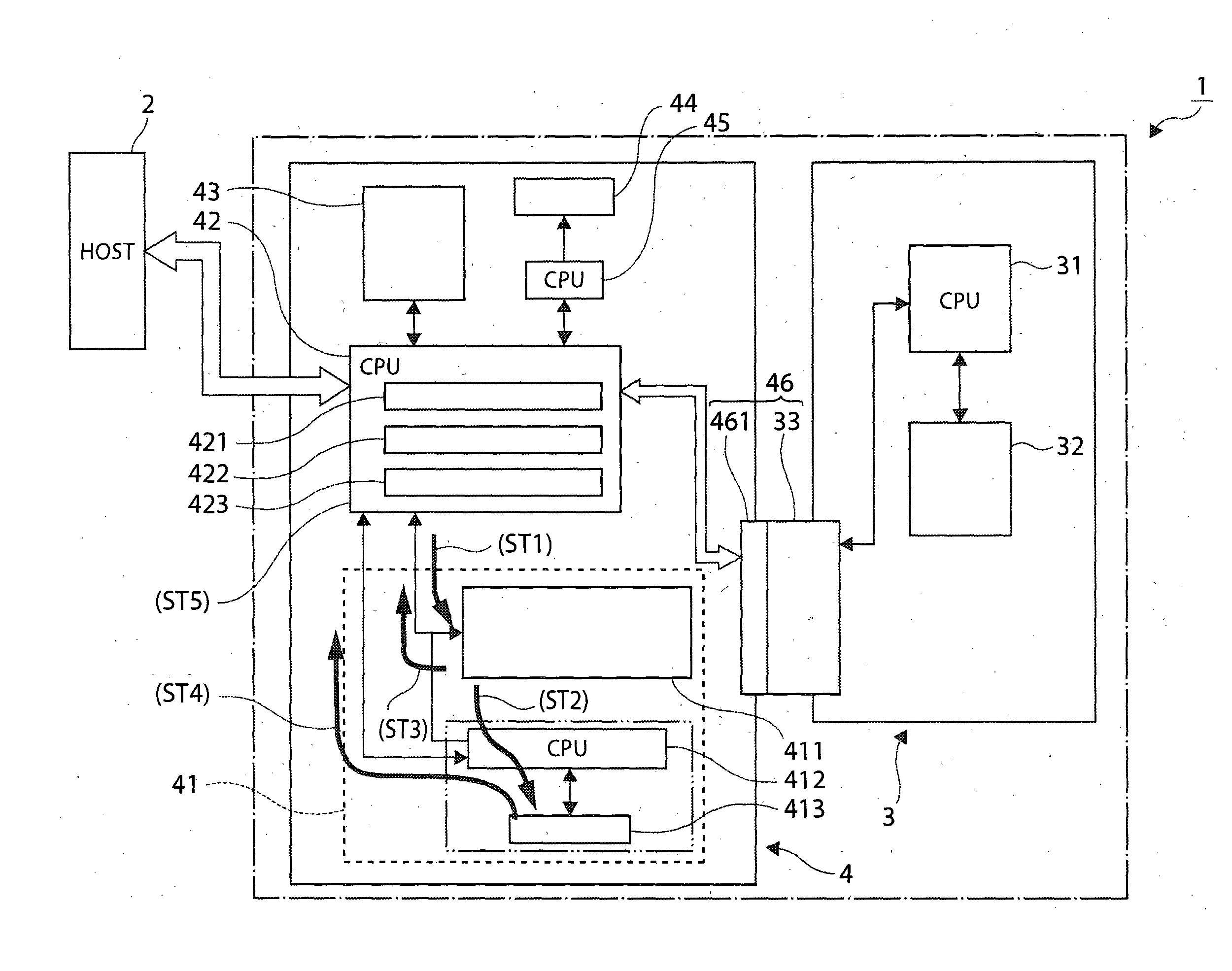
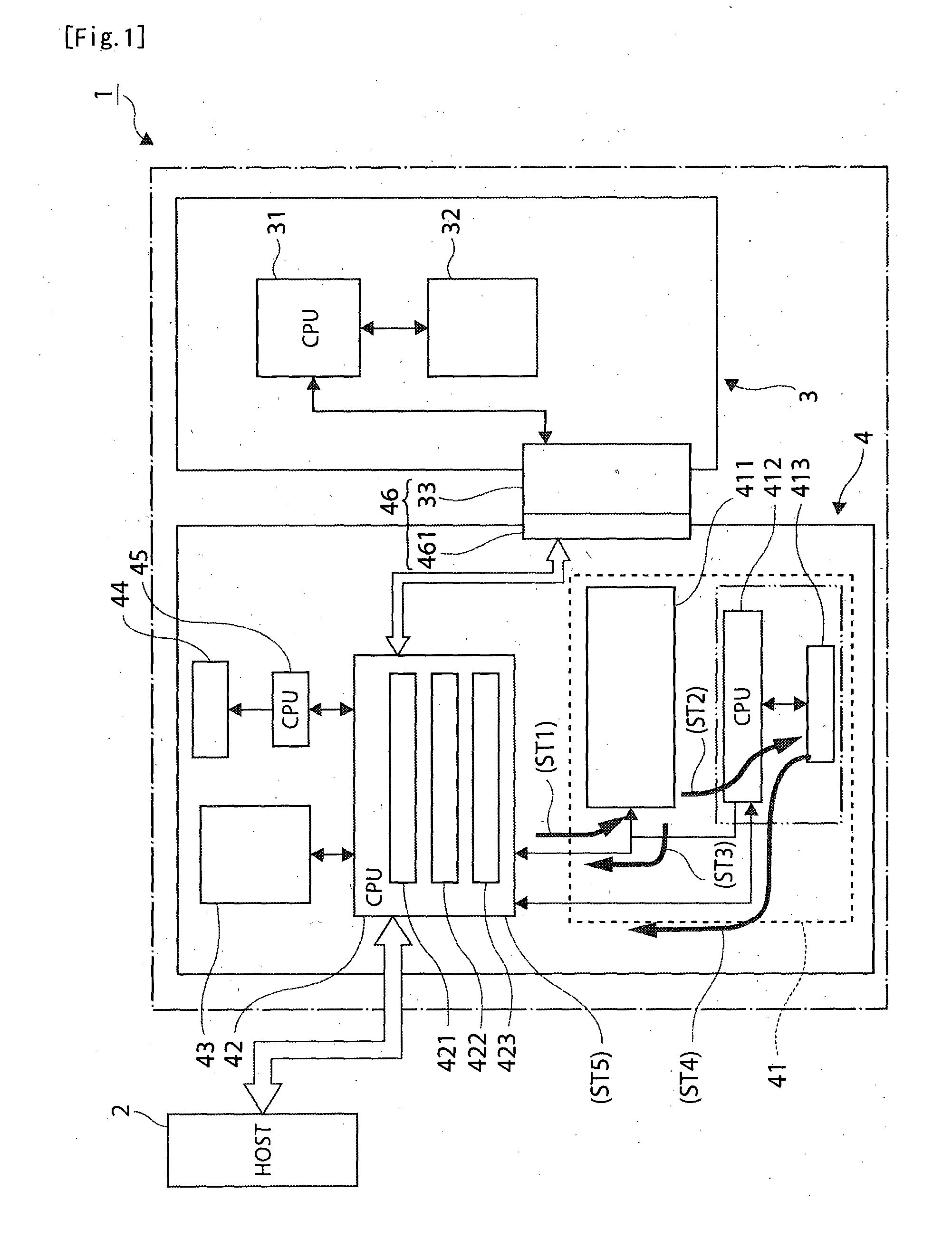
InactiveUS20130293918A1Reduce tamperingDecrease in writing speedDigital data protectionCash registersHash tableMemory control
Tampering with fiscal information written to memory can be detected without reducing the write speed. When fiscal information is written to first memory unit 411 by means of a fiscal control CPU 42 , a memory control CPU 412 writes a first hash value corresponding to the fiscal information in second memory unit 413. When fiscal information is read from the first memory unit 411, the fiscal control CPU 42 reads the first hash value from the second memory unit 413 through the memory control CPU 412, compares the first hash value with a second hash value calculated from the fiscal information read from first memory unit 411, and detects tampering with the fiscal information.
Owner:SEIKO EPSON CORP
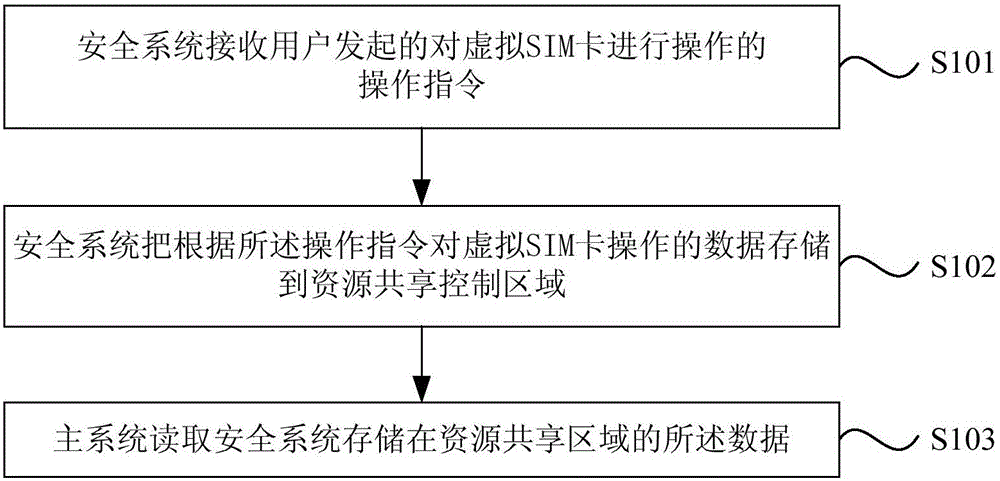
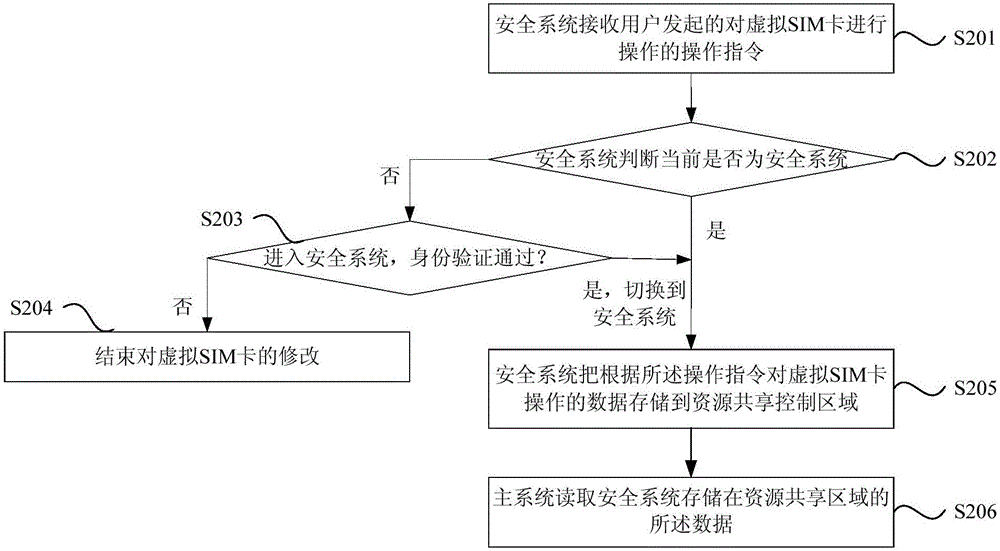
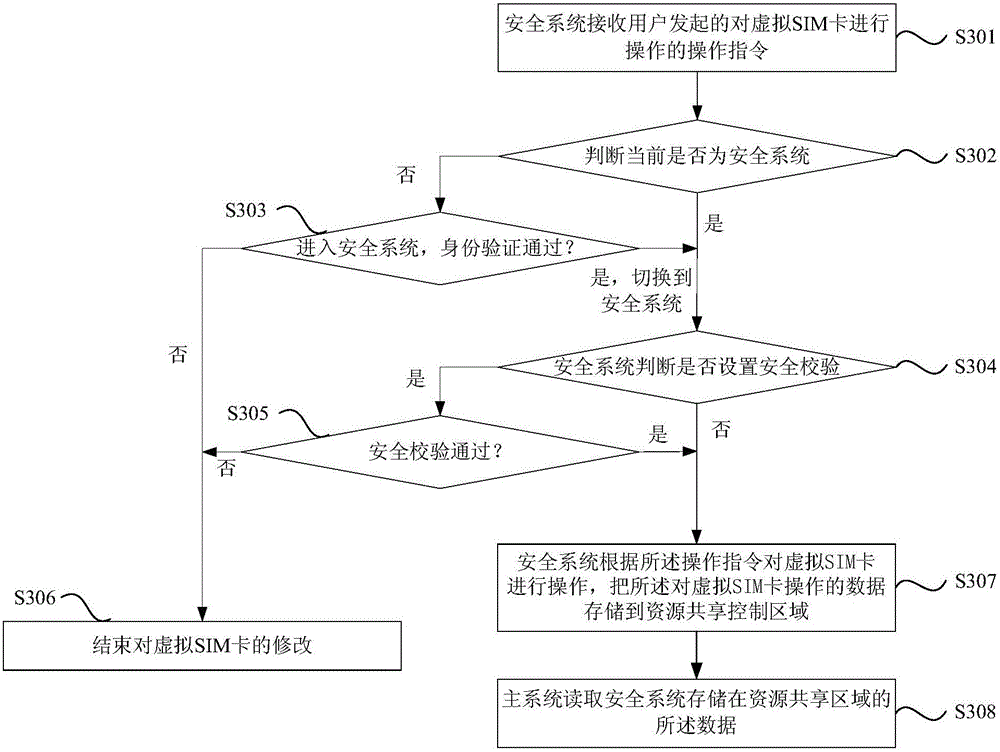
Virtual SIM card information storage method and system
ActiveCN105873018ATechnical securityReduce tamperingSecurity arrangementNetwork data managementControl areaData storing
The invention discloses a virtual SIM card information storage method and system. The method comprises the steps that a, a security system receives an operation instruction initiated by a user for operation on a virtual SIM card; b, the security system stores data about operation on the virtual SIM card according to the operation instruction to a resource sharing control area; c, a main system reads the data stored by the security system to the resource sharing control area; the security system and the main system are two secure systems isolated by hardware, and the resource sharing control area is arranged between the security system and the main system; the main system only has a reading right on the resource sharing control area without a modification right. In combination with the secure two-system technology, the virtual SIM card technology is more secure and reliable, and the risks that user information in the virtual SIM card is tampered and property is subjected to loss are reduced.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Method for hierarchichal onion rings routing
InactiveCN101635918BPrevent intersection attacksReduce tamperingSecurity arrangementSecure communicationComputer network
The invention discloses a method for hierarchical onion rings routing. The nodes in a wireless Mesh network are divided into a gateway G, trusted nodes OP (Onion Proxy) and normal nodes Fi, wherein, the trusted nodes OP and the gateway G are induction nodes; the trusted nodes OP serve the function of selecting a route during the initialization of the ring; and the assembly of all the trusted nodes OP and the gateway G constitutes an anonymous assembly. The onion routing of the network is divided into two loop layers, wherein, the first route layer is a loop route consisting of the non-adjacent trusted nodes OP and the gateway G of the anonymous assembly; and the second route layer is a loop route formed by filling normal nodes F among the trusted nodes OP, and the second route layer is randomly selected by the trusted nodes OP and the gateway during the initialization. Accordingly, the anonymous and secure communication in the Mesh network can be achieved by the layered loops of the onion rings route. By using the layered onion rings communication protocol and allowing the trusted nodes OP and the gateway of the anonymous assembly to select the route together, the invention can effectively mix up the paths and prevent the intersection attacks, thereby reducing the computation, alleviating the load of the gateway, accelerating the ring construction, preferably utilizing the network resources to reduce delay.
Owner:XIDIAN UNIV
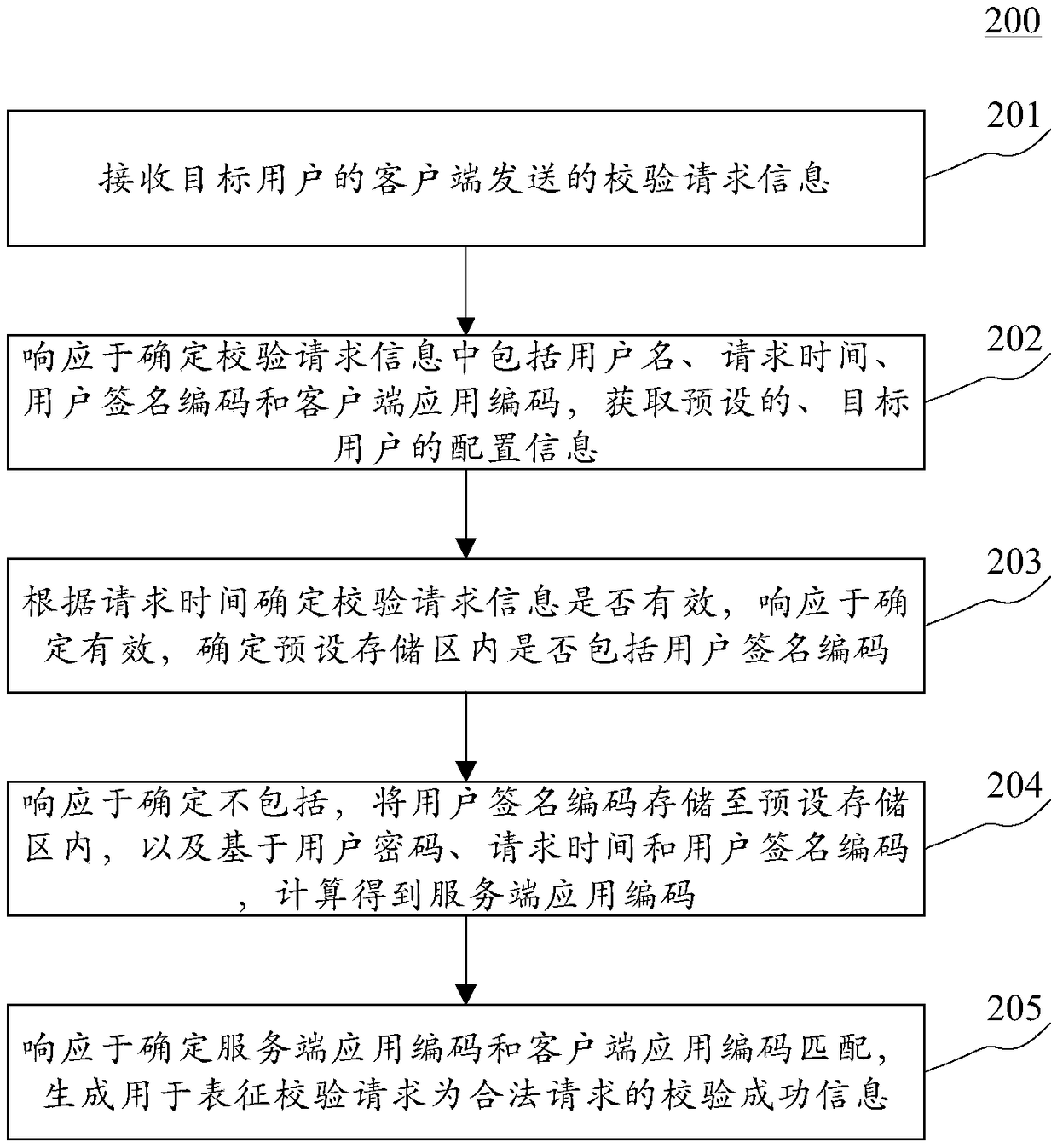
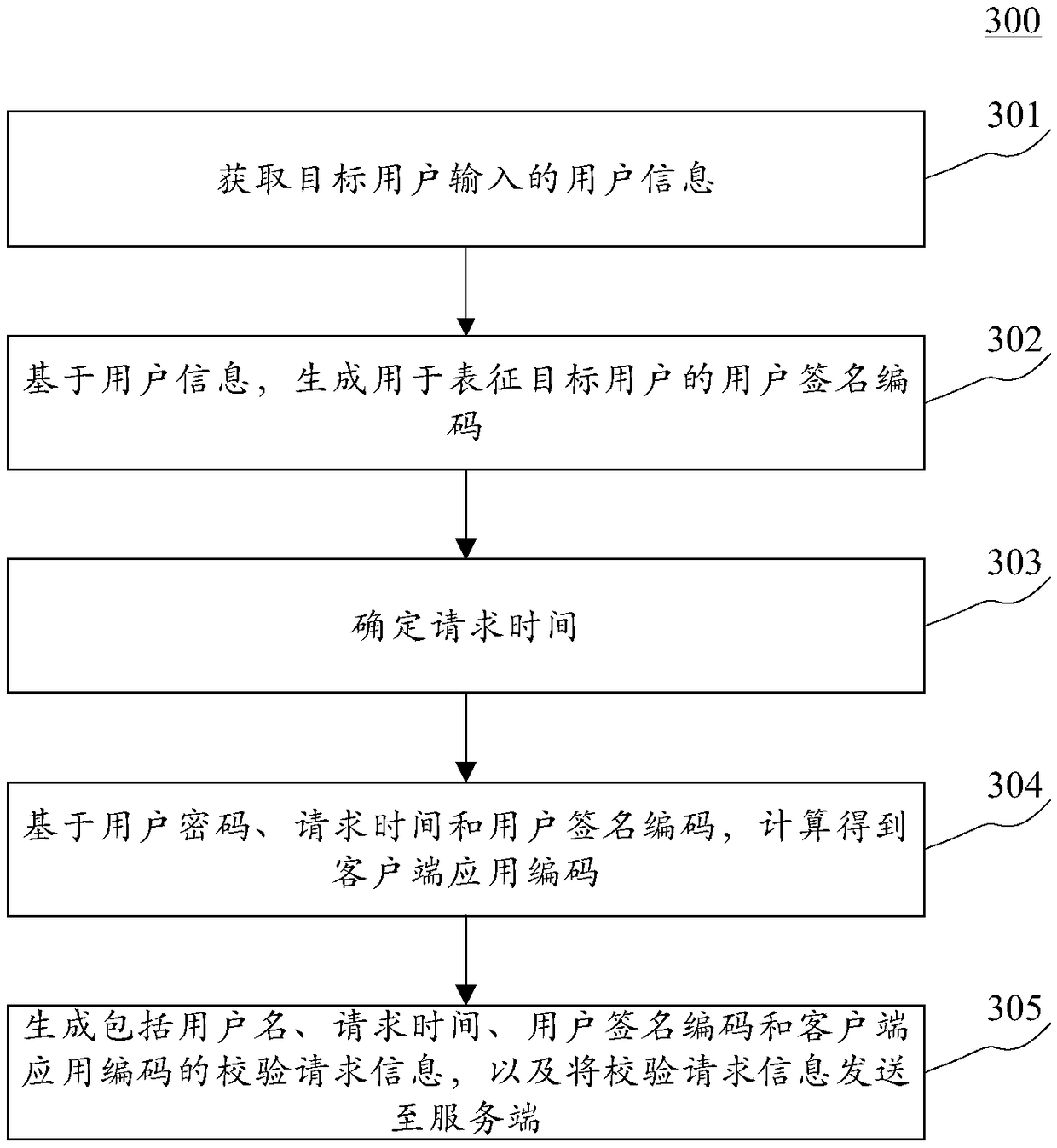
Method and device for processing information
The invention discloses a method and device for processing information. The method comprises receiving verification request information sent by the client of a target user; responding to the fact thatthe verification request information comprises a user name, a request time, a user signature code and a client application code, and acquiring the preset configuration information of the target user;determining whether the verification request information is valid or not according to the request time, and responding to the determination that the verification request information is valid, determining whether the preset storage area comprises the user signature code; responding to the determination that the user signature code is not included, and storing the user signature code into the preset storage area, and calculating to obtain the server application code based on the user password, the request time and the user signature code; and responding to the determination that the server application code is matched with the client application code, and generating verification success information which is used for representing the verification request as a legal request. According to the embodiment, the risk that the information sent by the client side is tampered or intercepted is reduced.
Owner:XIAMEN ANSCEN NETWORK TECH CO LTD
Trusted data transmission method and system, electronic equipment and storage medium
The invention provides a credible data transmission method and system, electronic equipment and a storage medium. The credible data transmission method comprises: collecting data; calculating an abstract value of the collected data, and encrypting the abstract value according to a private key of the edge computing node to generate an edge computing node signature; generating a message serial number for the collected data; caching an abstract value and a message serial number of the collected data; generating a data message according to the public key of the target block chain node; sending the data message to the target block chain node for decryption and verification; receiving a feedback message sent by the target block chain node; and decrypting the feedback message according to the private key of the edge computing node, comparing the decrypted data with the cached abstract value and message serial number of the collected data, and if the decrypted data are consistent with the cached abstract value and message serial number of the collected data, completing the transmission of the collected data. According to the method and the device provided by the invention, the security of message transmission between the Internet of Things and the block chain can be realized.
Owner:ROOTCLOUD TECH CO LTD
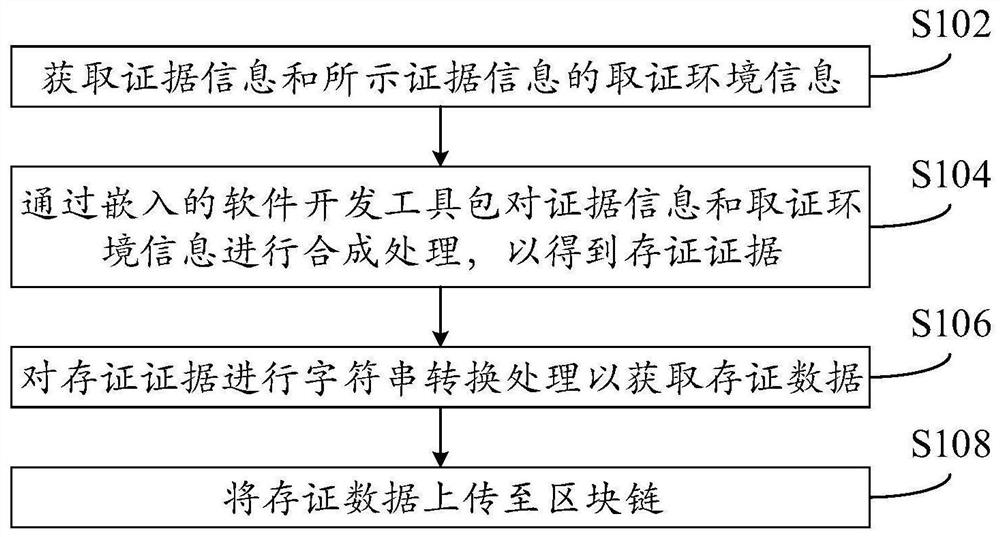
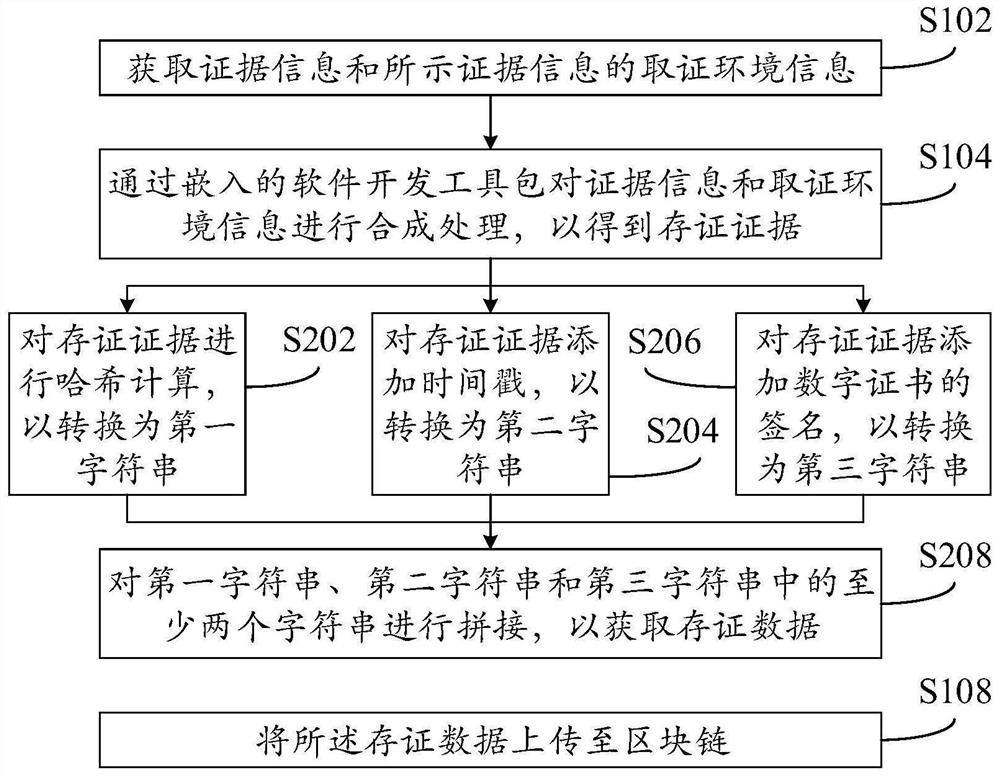
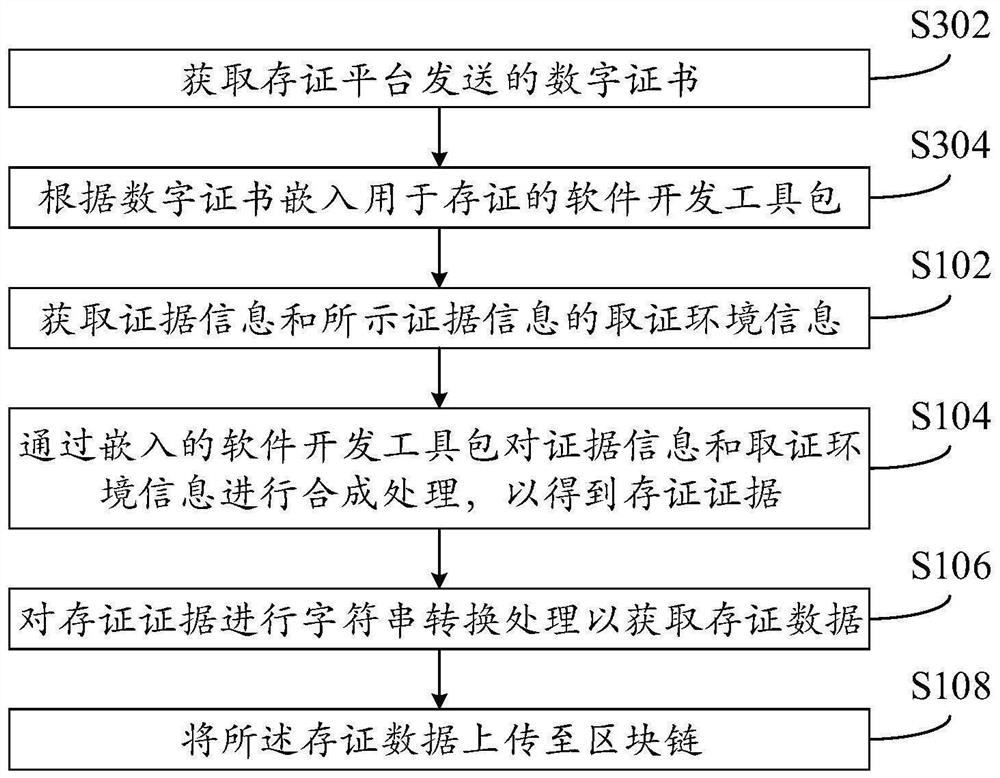
Electronic evidence data processing method, device, electronic equipment and storage medium
PendingCN112733167AGuaranteed privacySecure tenureData processing applicationsDigital data protectionEngineeringEmbedded software
The invention provides an electronic evidence data processing method, a device, electronic equipment and a storage medium, and relates to the technical field of block chains. The electronic evidence data processing method comprises the steps of collecting the evidence information and evidence obtaining environment information of the evidence information; synthesizing the evidence information and the evidence obtaining environment information through an embedded software development kit to obtain evidence storage evidences; performing character string conversion processing on the evidence storage evidence to obtain evidence storage data; and uploading the evidence storage data to the block chain. Through the technical scheme of the invention, the probability that the evidence storage data is tampered or leaked is reduced, and the privacy and ownership relationship of the evidence storage data are guaranteed.
Owner:JD DIGITS HAIYI INFORMATION TECHNOLOGY CO LTD +1
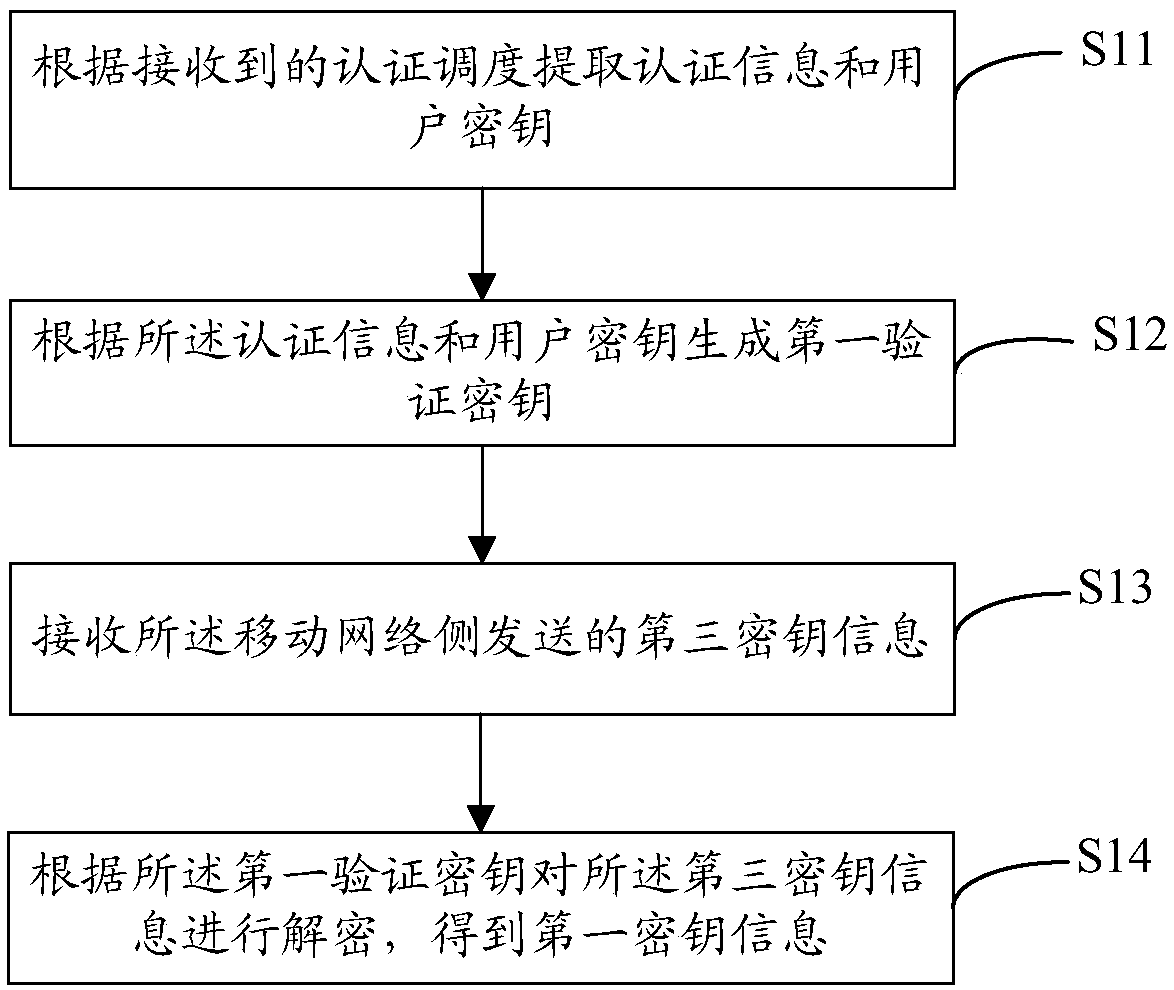
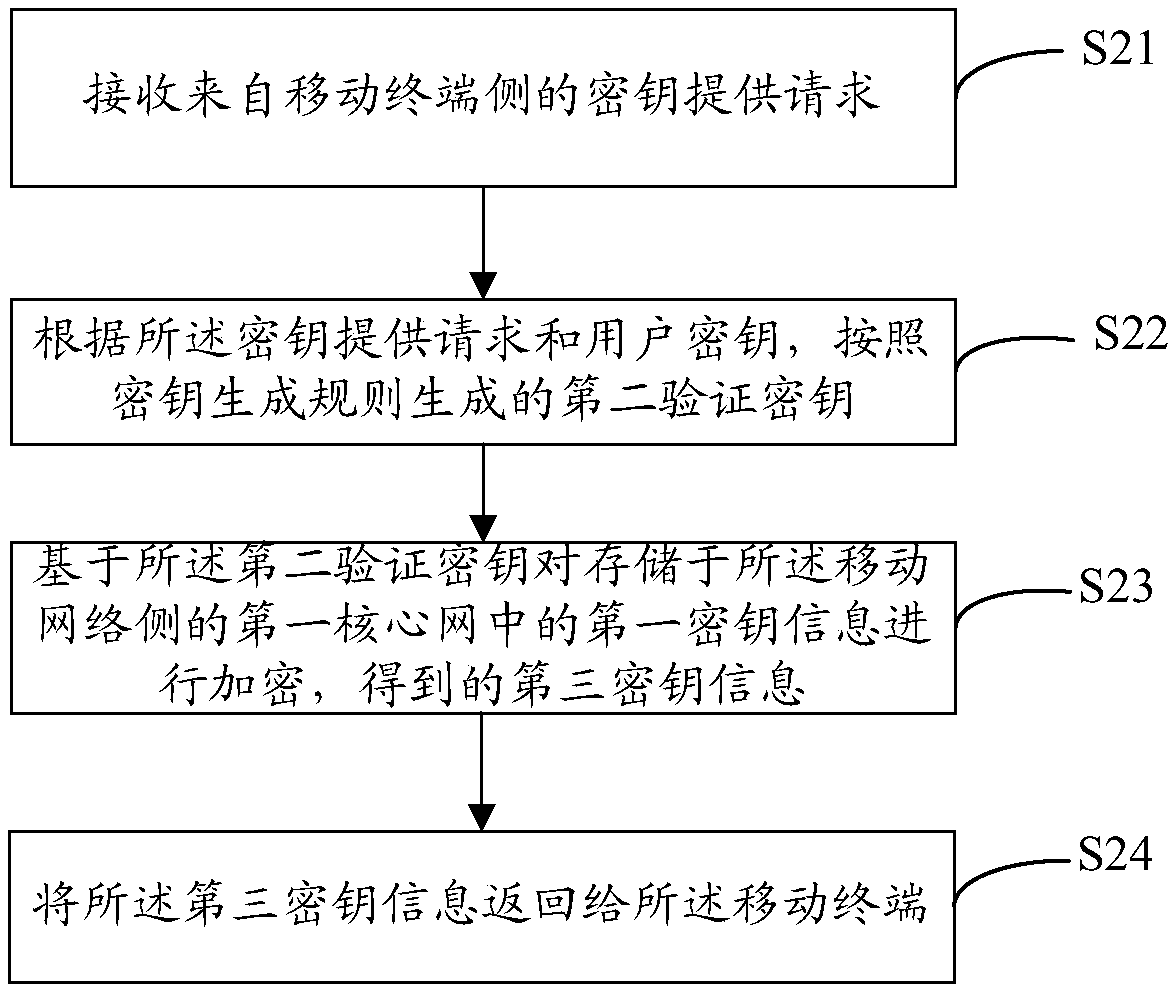
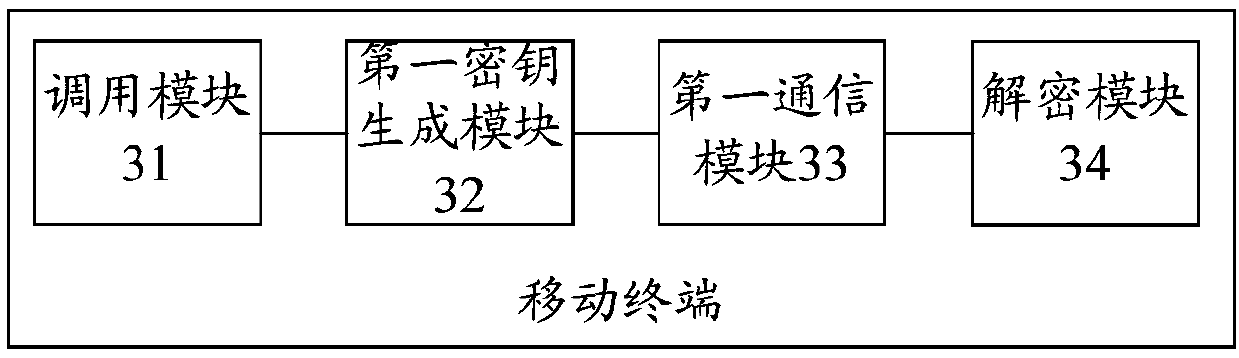
Key distribution method and device, mobile terminal, communication equipment and storage medium
PendingCN110536289AGuaranteed real-time updatesReduce tamperingKey distribution for secure communicationUser identity/authority verificationKey distributionMobile Web
The embodiment of the invention provides a key distribution method and device, a mobile terminal, communication equipment and a storage medium. The method comprises the following steps: extracting authentication information and a user key according to received authentication scheduling; generating a first verification key according to a key generation rule; and returning an authentication responsemessage to the mobile network side, after receiving the authentication response message, enabling the mobile network side to send the authentication response message; acquiring corresponding authentication information and a user key to generate a second verification key; encrypting the first secret key information; obtaining a third secret key and returning the third secret key to the mobile terminal; and enabling the mobile terminal to decrypt the third key information according to the first verification key. According to the method and the system, the security problem of the mobile terminalwhen the mobile terminal accesses the mobile network is solved by issuing the secret key based on the mutual mode, the real-time updating of the secret key is ensured, the tampering of the secret keyis reduced, the security is further improved, and the security performance of the system is also greatly improved.
Owner:ZTE CORP
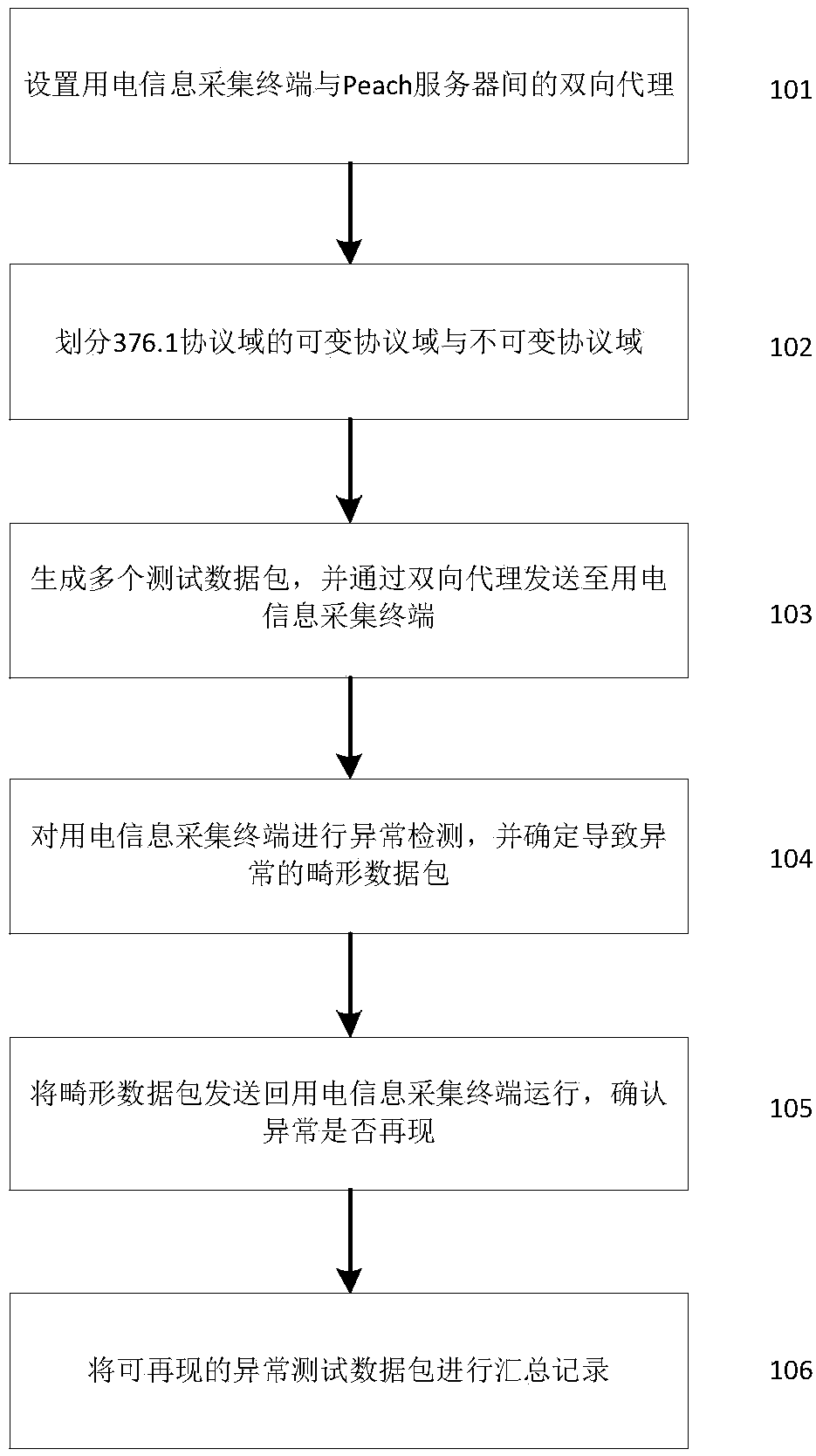
Fuzz testing method and system suitable for 376.1 protocol safety defect detection
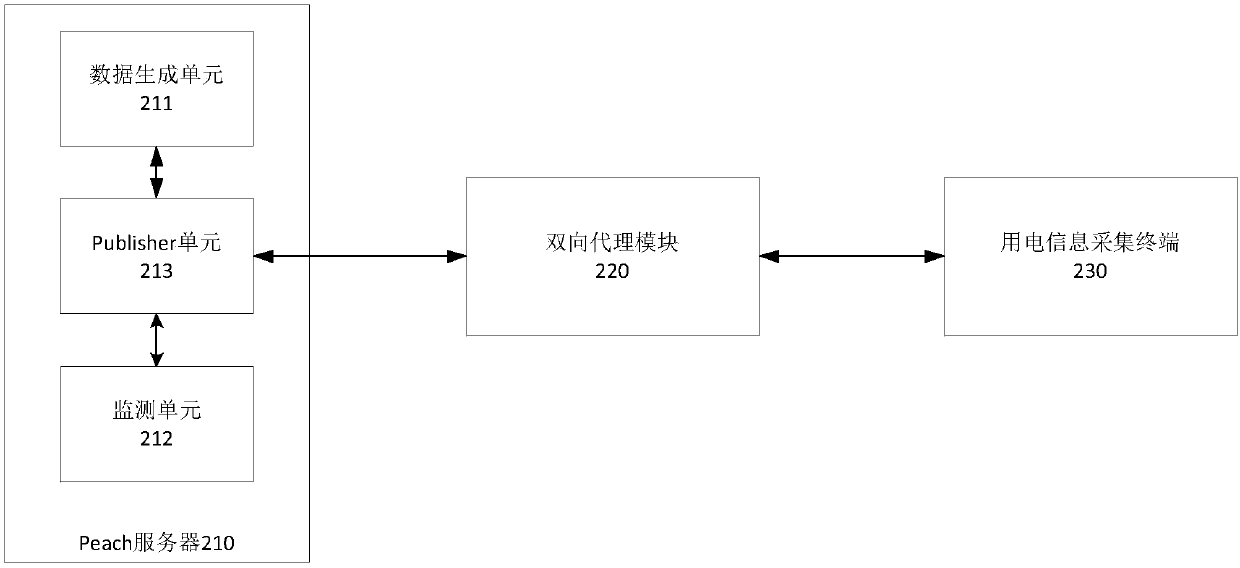
The invention discloses a fuzz testing method and system suitable for 376.1 protocol safety defect detection. The method comprises the following steps: setting bidirectional proxy between a power-using information acquisition terminal and a Peach server, wherein the Peach server generates a testing data packet and sends to the power-using information acquisition terminal through the bidirectionalproxy to perform the testing; monitoring an abnormal situation of the power-using information acquisition terminal; sending the monitored abnormal distortion data packet to the power-using informationacquisition terminal to perform the reproduction, recording the reproducible data packet for the subsequent analysis; the system comprises the Peach server and a bidirectional proxy module, wherein the bidirectional proxy module sends the data packet received from the Peach server to the power-using information acquisition terminal from a fixed port; the Peach server comprises a data generation unit, a monitoring unit and a Publisher unit, and is used for generating the testing data and sending the testing data to the power-using information acquisition terminal through the bidirectional proxy module, and performing the monitoring.
Owner:STATE GRID CORP OF CHINA +1
Archive data protection method based on block chain
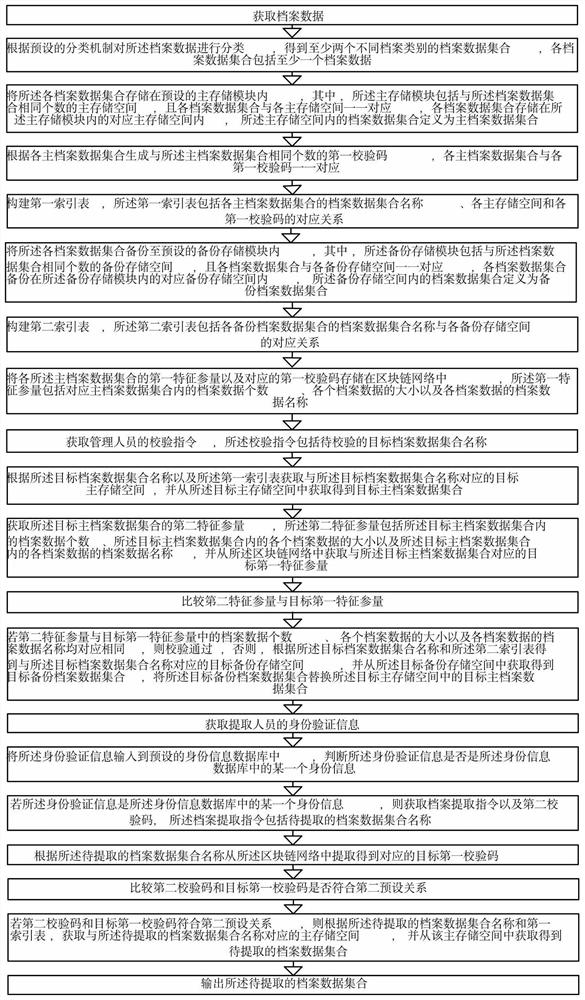
ActiveCN111611459AGuaranteed reliabilityEnsure safetyDatabase distribution/replicationDigital data protectionData ingestionData set
The invention relates to an archive data protection method based on a block chain. The method comprises the steps of obtaining archive data, classifying the archive data to obtain at least two archivedata sets, storing and backing up to the corresponding storage space; storing the first characteristic parameter of each archive data set in a block chain network, obtaining an actual second characteristic parameter according to the target archive data set, obtaining a first characteristic parameter from the block chain network; verifying according to the first characteristic parameter and the second characteristic parameter; and if the archive data set stored in the backup space does not pass the verification, replacing the archive data set in the corresponding main storage space with the archive data set stored in the backup space; when the archive data are extracted, firstly carrying out identity verification, then comparing related verification codes; and after the archive data passesthe verification, obtaining and outputting a to-be-extracted archive data set. The archive data protection method can effectively reduce the possibility that the archive data are illegally stolen, tampered and destroyed, and effectively improve the security of archive data management.
Owner:ZHEJIANG GUANGSHA COLLEGE OF APPLIED CONSTRTECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com