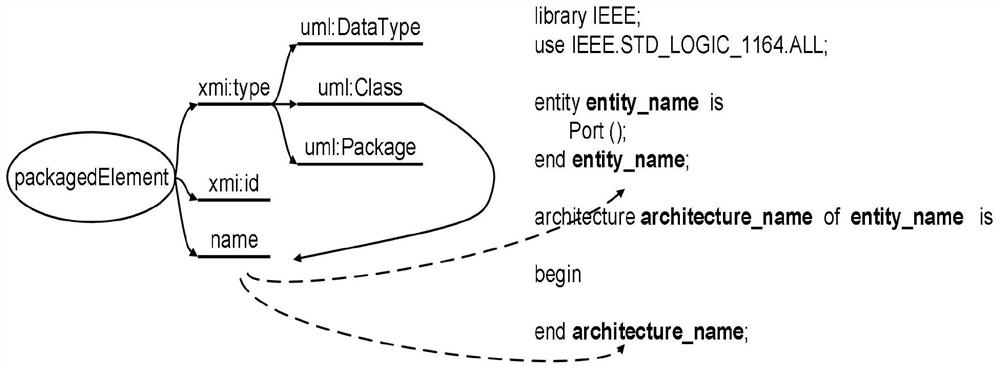
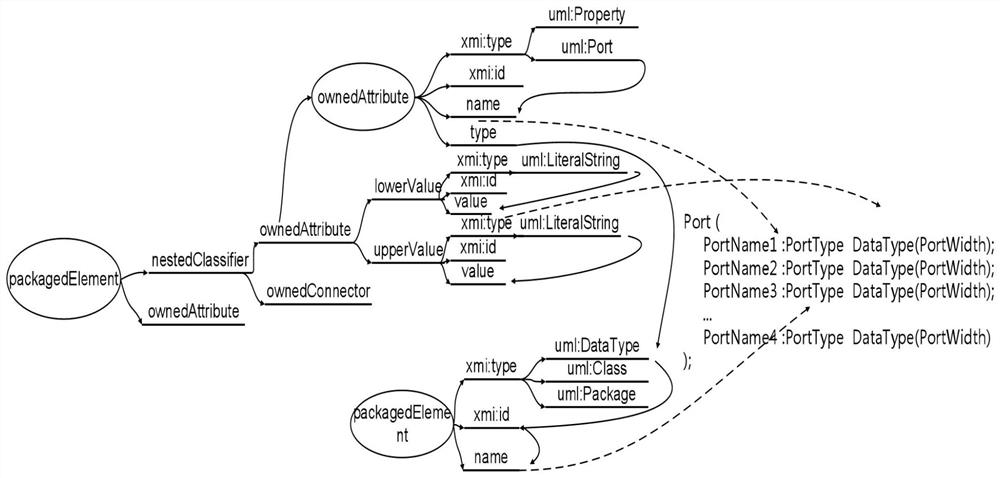
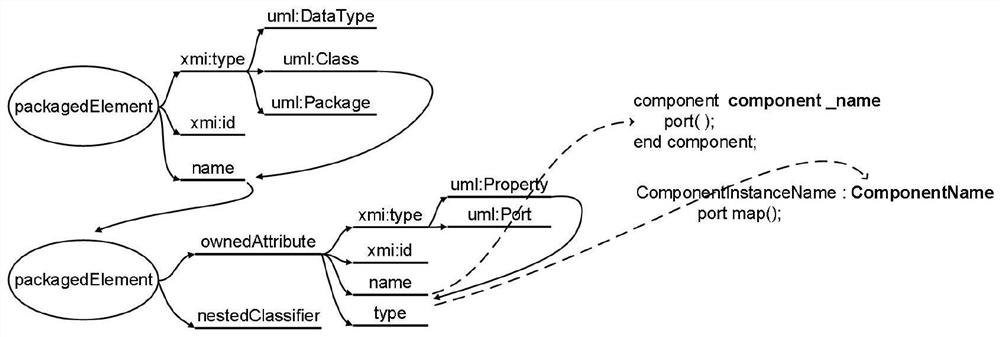
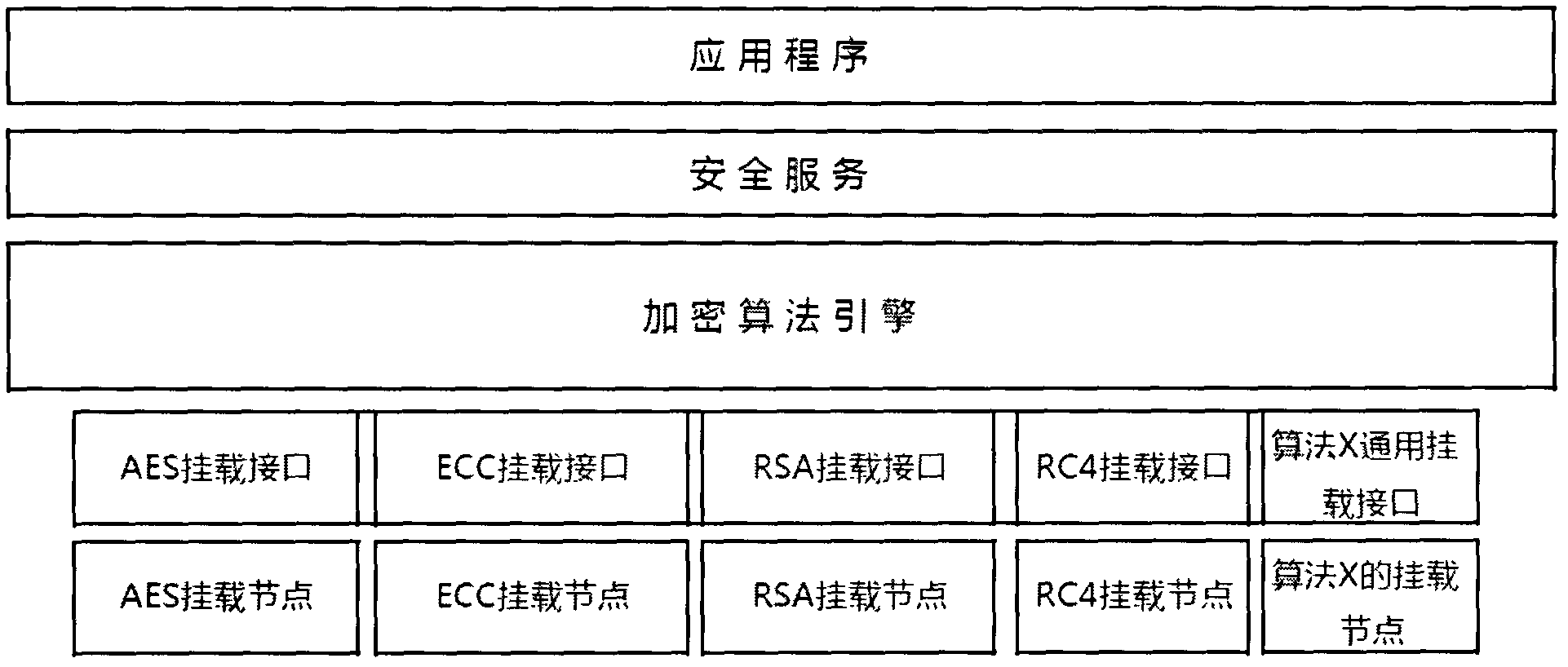
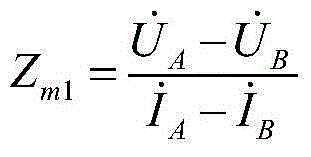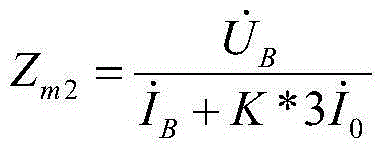Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
63 results about "Hardware algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
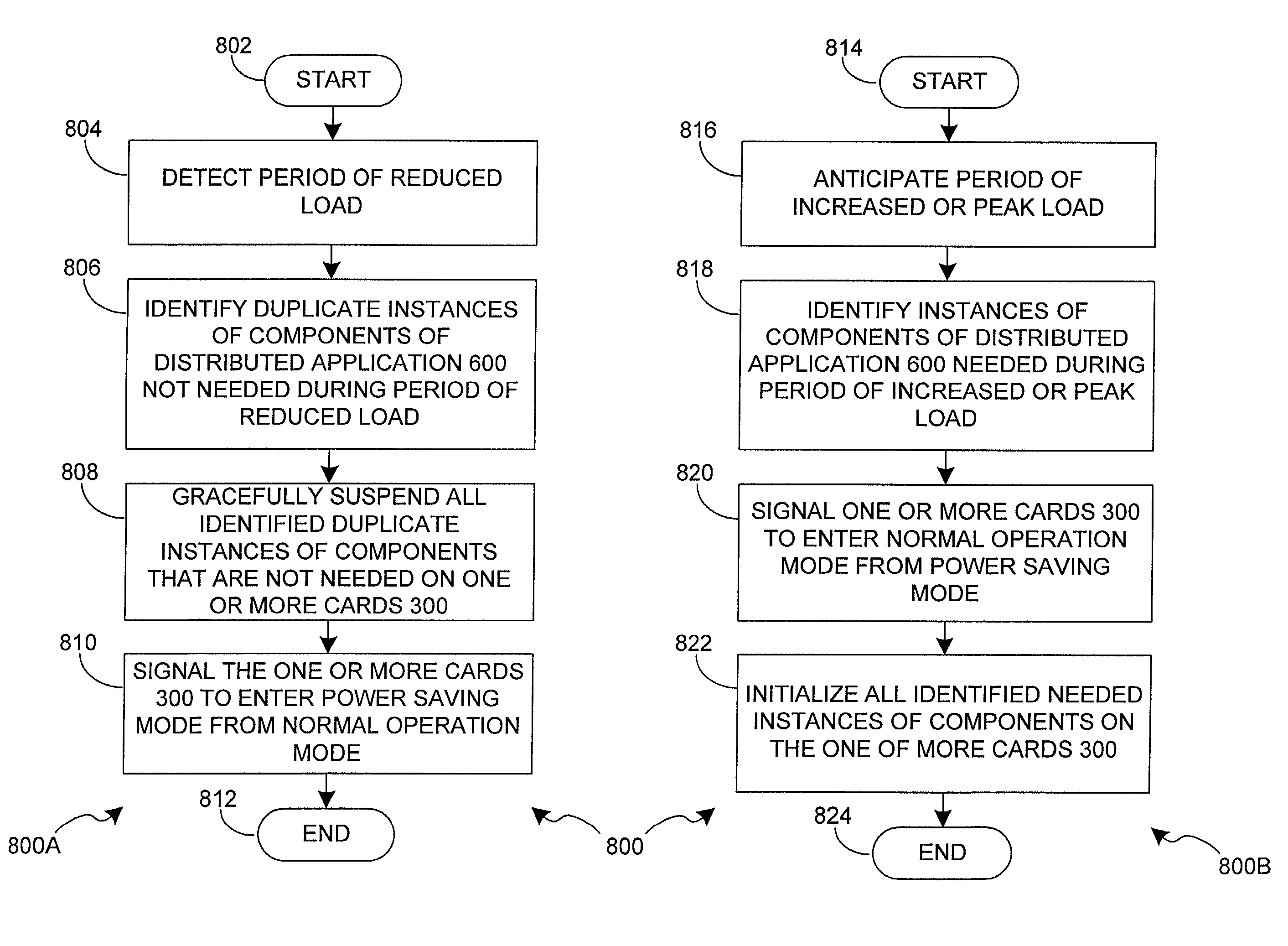
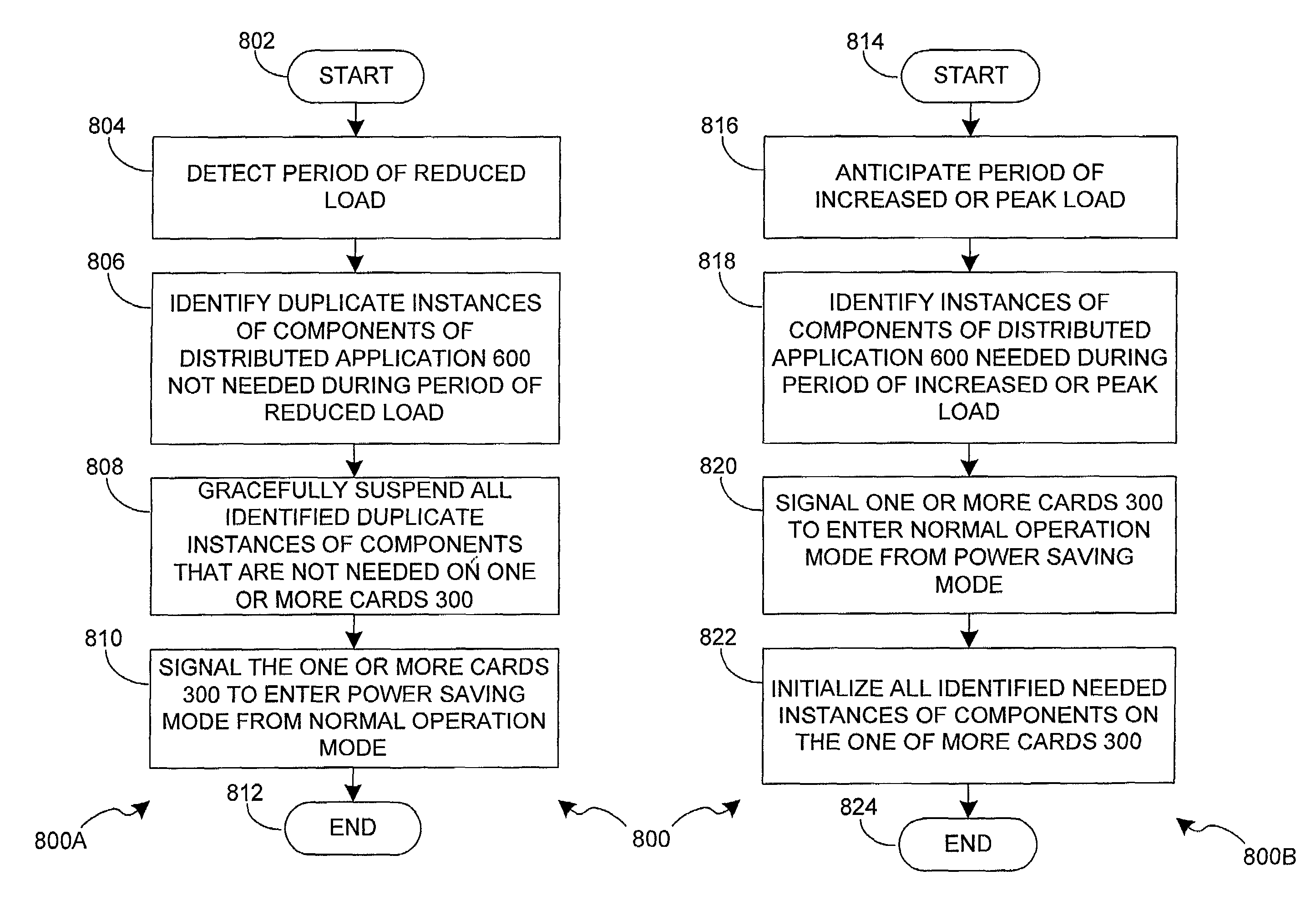
System and method for intelligent control of power consumption of distributed services during periods when power consumption must be reduced
InactiveUS7043650B2Minimum power consumptionIncrease redundancyEnergy efficient ICTVolume/mass flow measurementControl powerComputerized system
A system and method intelligently control power consumption of distributed services using a computer system that provides independent computing elements each capable of entering a power saving mode. In accordance with the present invention, three different algorithms are disclosed. The first algorithm is a reduced load power saving algorithm. As the load decreases, duplicate instances of services can be gracefully suspended and the host processor cards hosting these instances can enter a power saving mode. The second algorithm is a priority-based power consumption reduction algorithm. If power consumption must be reduced, services having less of a contribution to revenue are suspended before components that having a higher contribution to revenue. The third algorithm is a minimal power-consuming redundant computing hardware algorithm that allows a “cold spare” host processing card to be pressed into service if another card fails.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
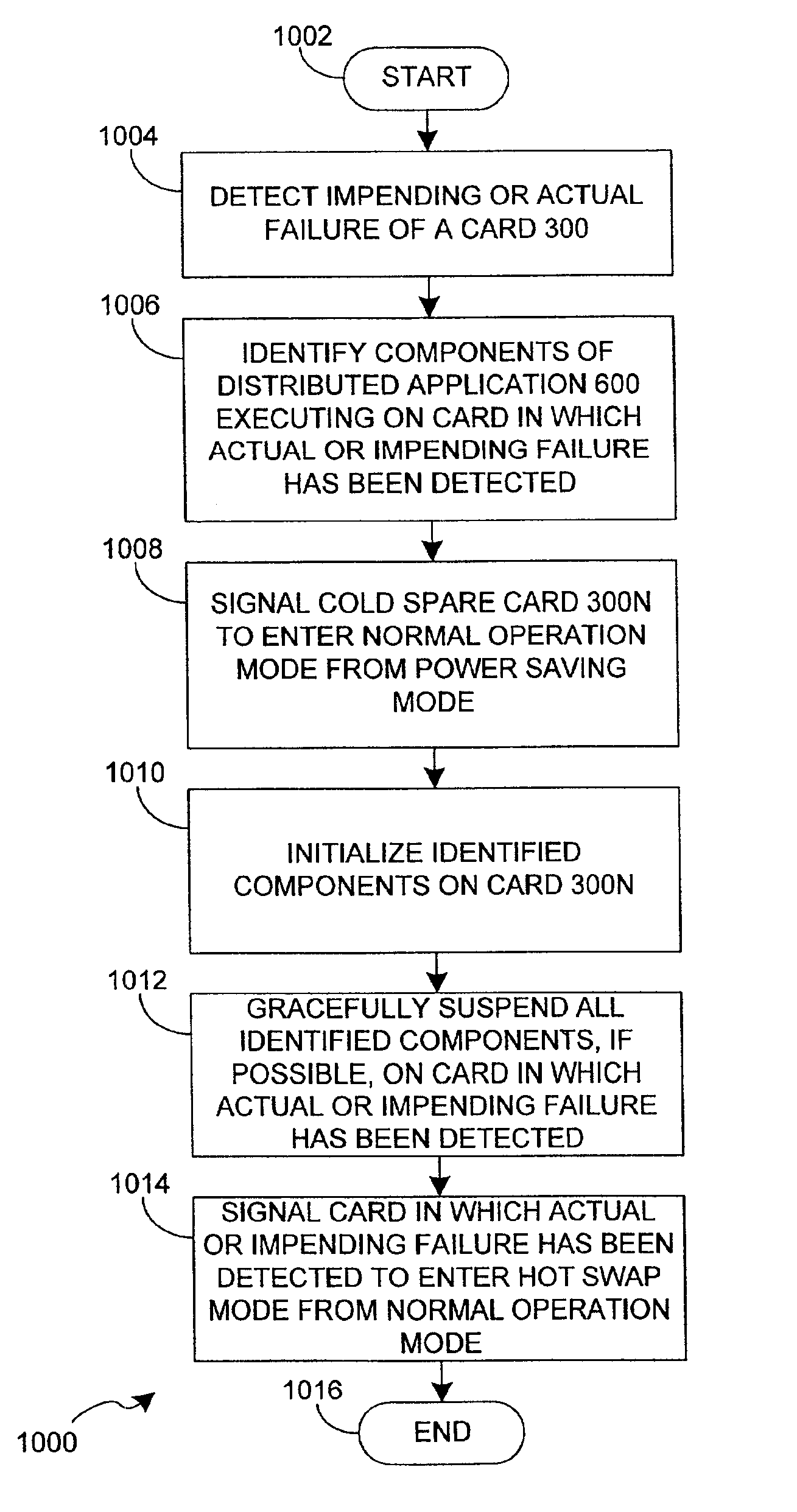
System and method for providing minimal power-consuming redundant computing hardware for distributed services
InactiveUS6957353B2Minimum power consumptionIncrease redundancyEnergy efficient ICTVolume/mass flow measurementControl powerDistributed services
A system and method to intelligently control power consumption of distributed services using a computer system that provides independent computing elements each capable of entering a power saving mode. The first algorithm is a reduced load power saving algorithm. As the load decreases, duplicate instances of services can be gracefully suspended and the host processor cards hosting these instances can enter a power saving mode. The second algorithm is a priority-based power consumption reduction algorithm. If power consumption must be reduced, services having less of a contribution to revenue are suspended before components that having a higher contribution to revenue. The third algorithm is a minimal power-consuming redundant computing hardware algorithm that allows a “cold spare” host processor card to be pressed into service if another card fails.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
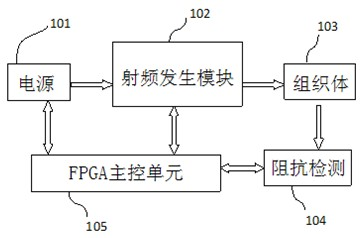
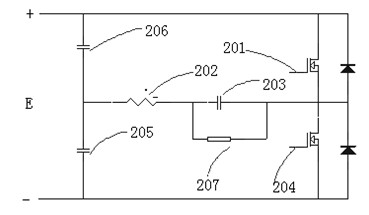
High-frequency electrotome generator based on FPGA (Field Programmable Gata Array)
InactiveCN102641152AEasy to controlQuick responseSurgical instruments for heatingEngineeringReturn channel
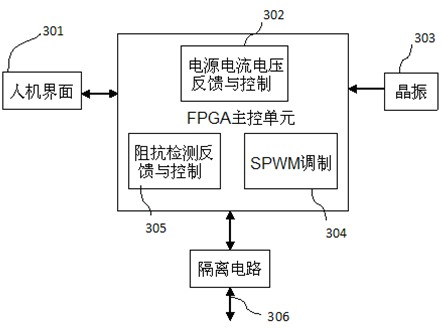
The invention relates to a high-frequency electrotome generator based on an FPGA (Field Programmable Gata Array). A power supply provides direct-current voltage signals to a radio frequency generation module; the direct-current voltage signals are subjected to resonant amplification of the radio frequency generation module and rectification of a half bridge circuit to be changed to high-voltage alternating-current radio frequency singles to be output, and then the output signals are transmitted to a biological organization by a radiation electrode and a backward channel; an impedance detection unit is used for detecting the impedance of the biological organization and transmitting impedance parameters to an FPGA main control unit; according to the impedance parameters, the FPGA main control unit regulates the duty ratio of SPWM (Sinusoidal Pulse Width Modulation) waves in real time; and then the SPWM waves are output to the radio frequency generation module. A controller disclosed by the invention can realize accurate control and is high in response speed, easy to modify, capable of programming in situ, strong in universality and stable in performance; and more importantly, by virtue of the large-scale FPGA, a microprocessor, a special hardware algorithm unit, a special waveform generation unit and a signal acquisition and processing unit are all integrated on a single chip, so that the high-frequency electrotome generator becomes a special integral electronic control system.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
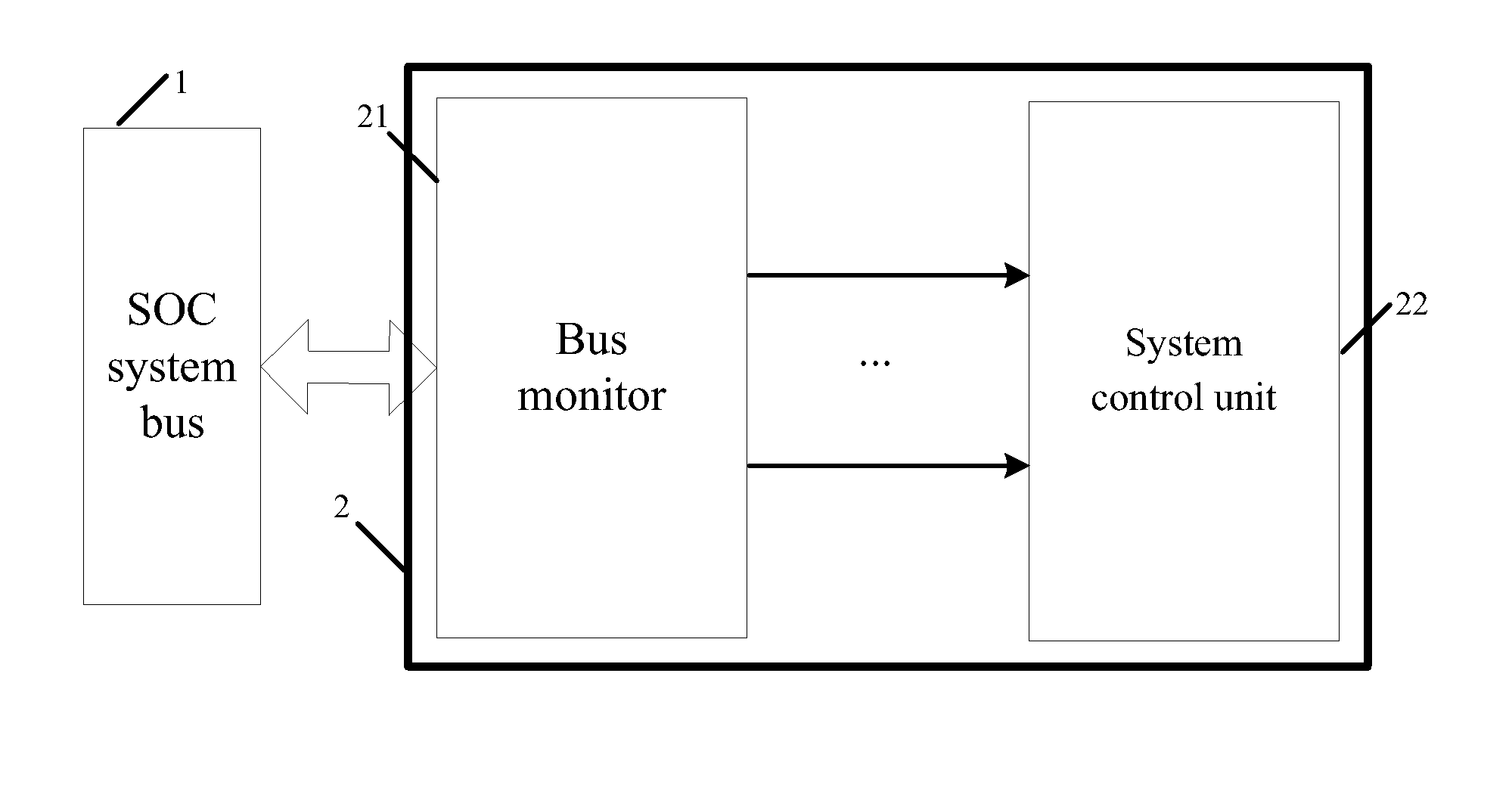
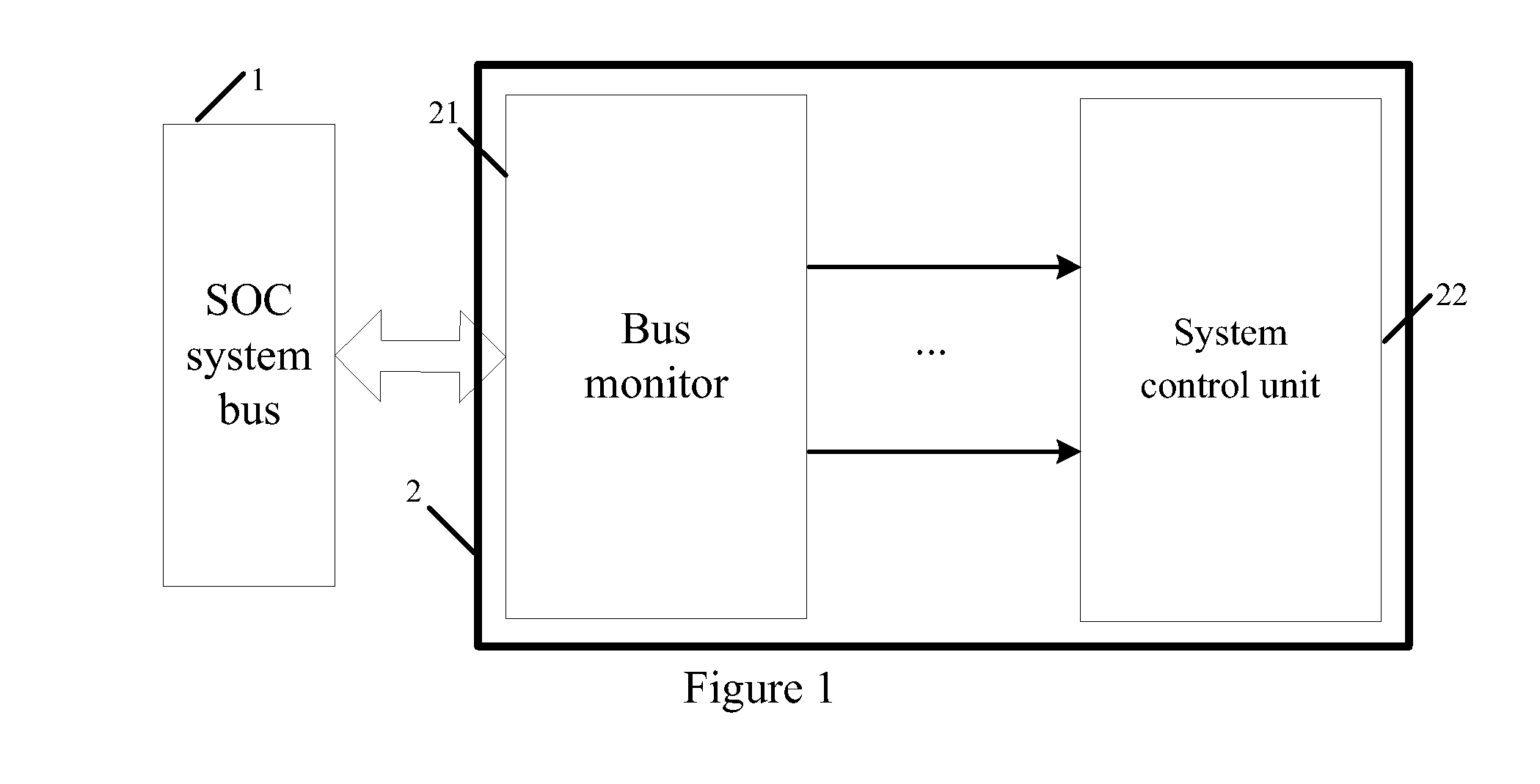
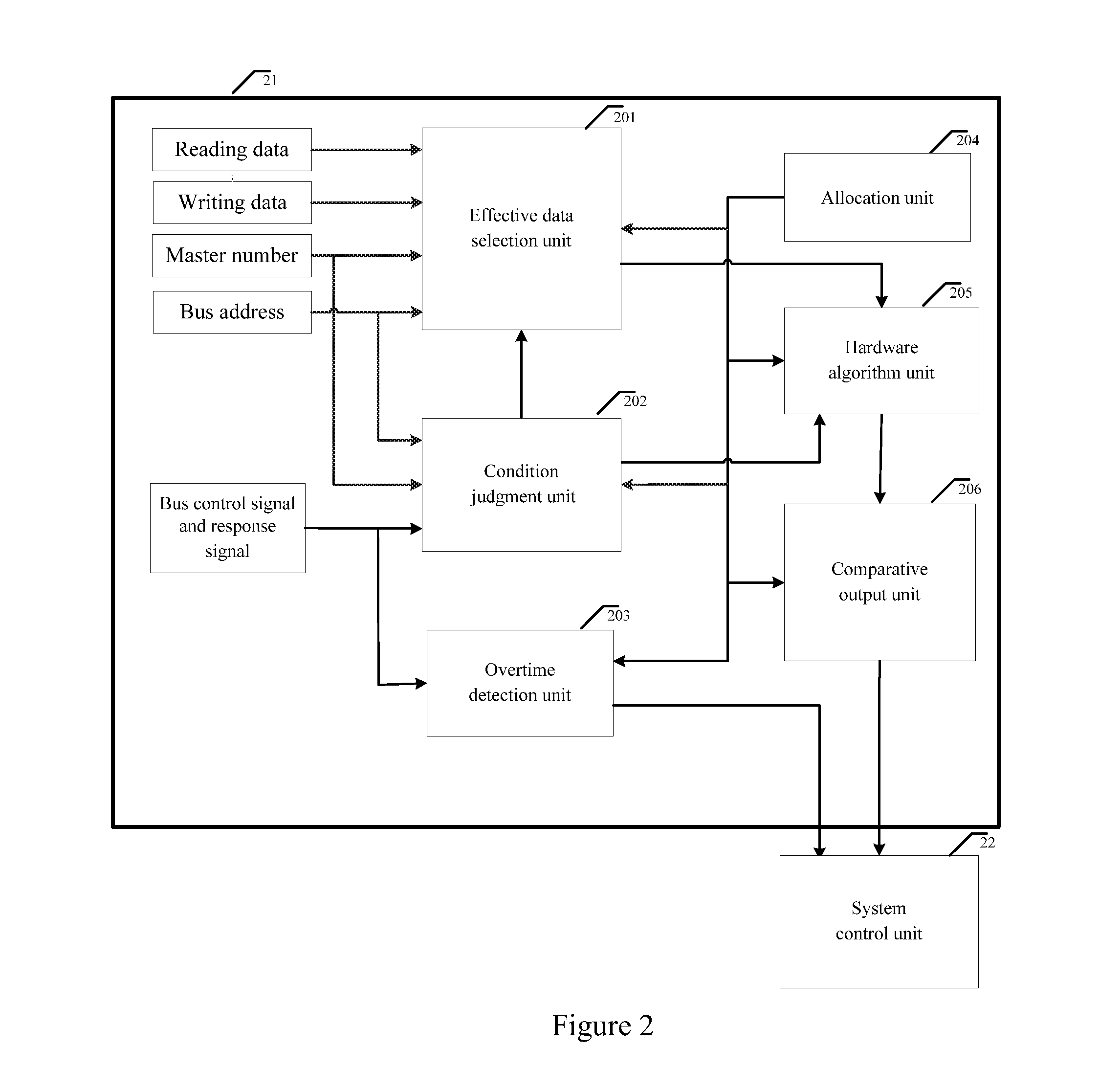
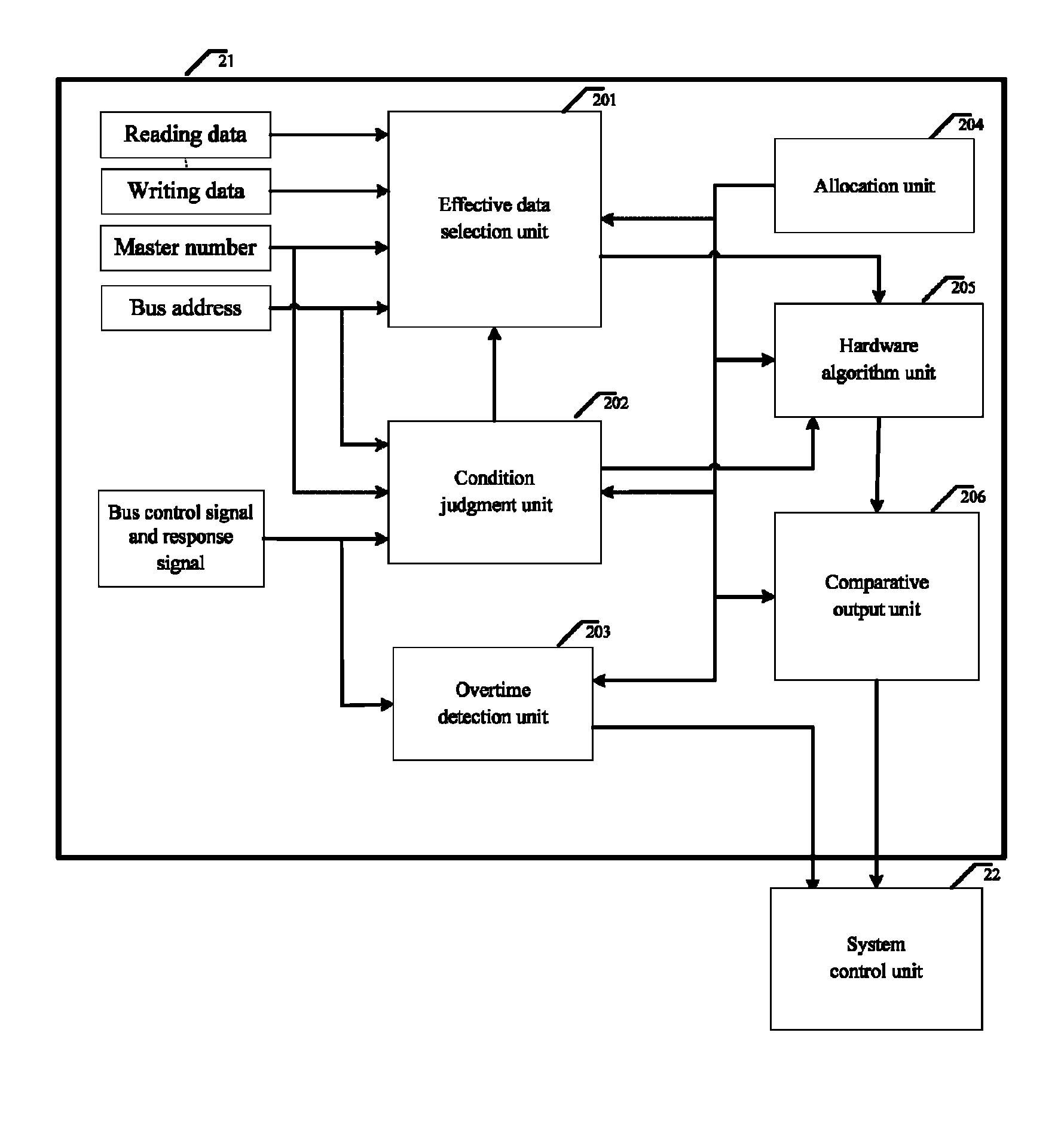
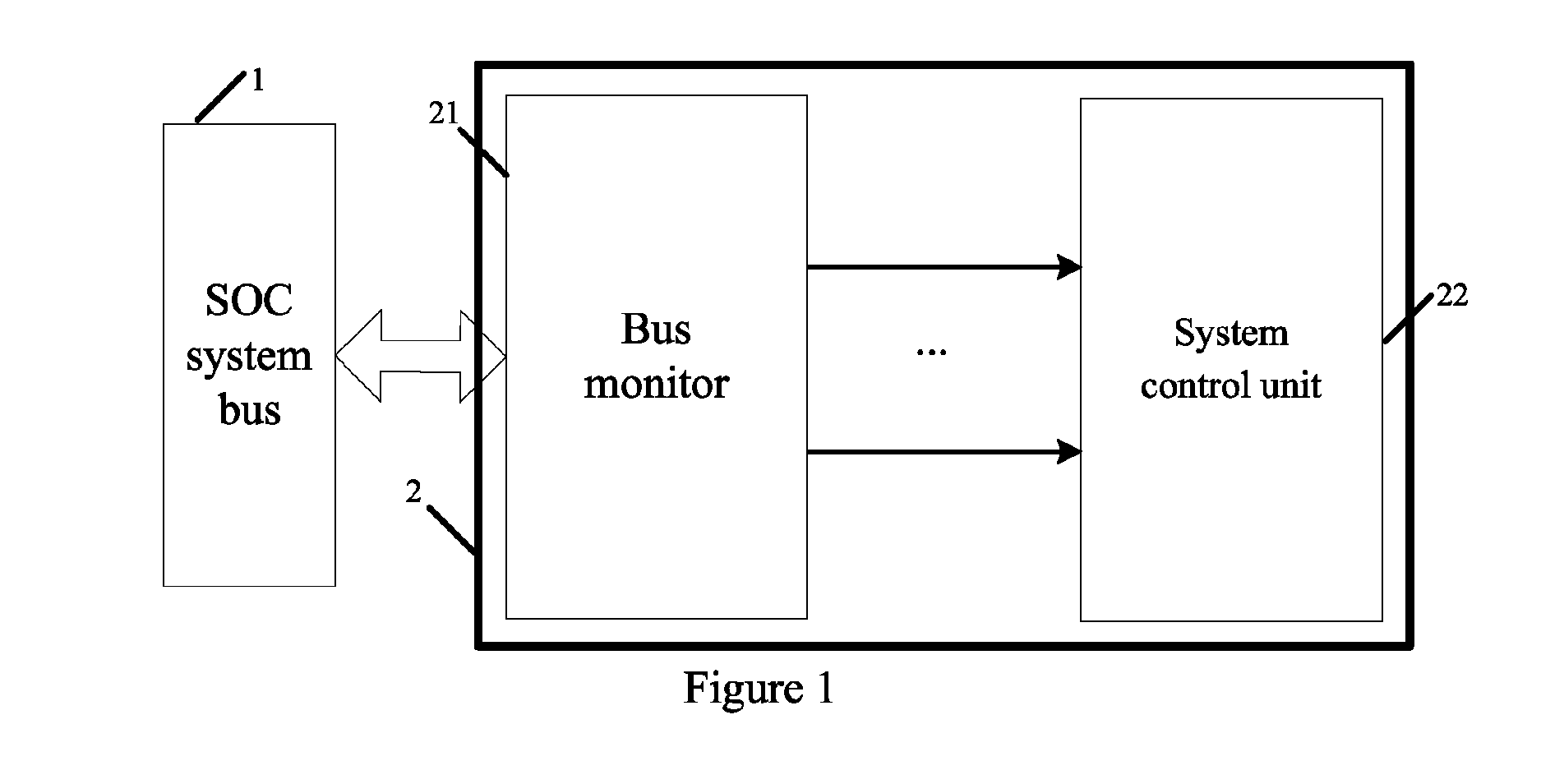
Bus monitor for enhancing soc system security and realization method thereof
InactiveUS20130219452A1Improve information securityInformation leakageMemory loss protectionError detection/correctionClassified informationData selection
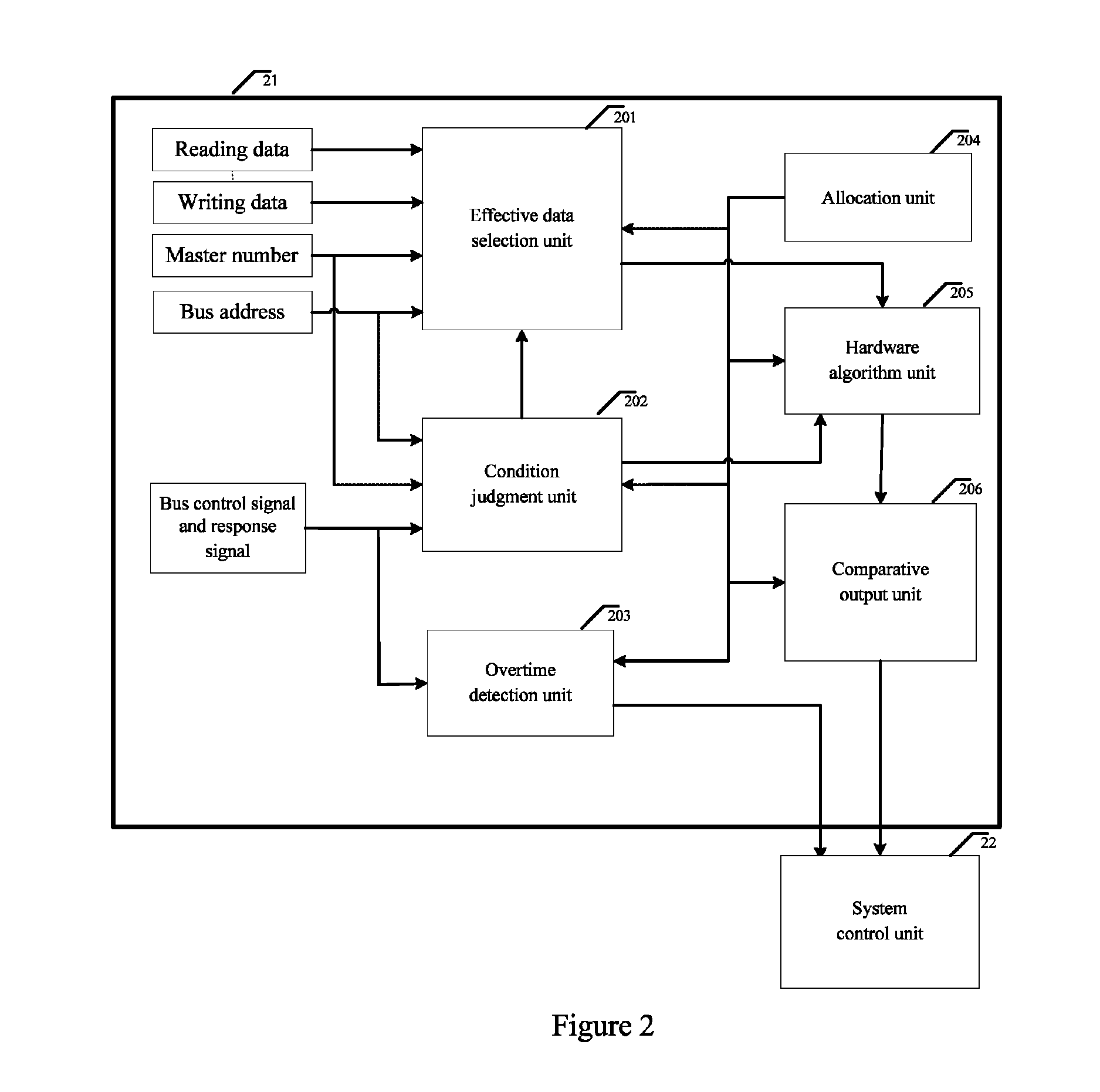
The present invention discloses a bus monitor for enhancing SOC system security and a realization method thereof. The bus monitor disposed between a system bus and a system control unit includes a configuration unit, a condition judgment unit, an effective data selection unit, a hardware algorithm unit and a comparative output unit. Without affecting the bus access efficiency, the present invention provides the method capable of immediately monitoring the bus behavior, and the detection system notices whether a particular bus access serial behavior is changed due to an accidental fault or intentional attacking fault. If the particular bus access serial behavior is changed, the present invention warns the system to adopt a suitable security measure to prevent the security hidden trouble and leakage of classified information due to the incorrect system security process.
Owner:SHENZHEN STATE MICRO TECH CO LTD
System and method for intelligent control of power consumption of distributed services during periods of reduced load
InactiveUS7203846B2Minimum power consumptionIncrease redundancyEnergy efficient ICTVolume/mass flow measurementControl powerComputerized system
A system and method intelligently control power consumption of distributed services using a computer system that provides independent computing elements each capable of entering a power saving mode. In accordance with the present invention, three different algorithms are disclosed. The first algorithm is a reduced load power saving algorithm. As the load decreases, duplicate instances of services can be gracefully suspended and the host processor cards hosting these instances can enter a power saving mode. The second algorithm is a priority-based power consumption reduction algorithm. If power consumption must be reduced, services having less of a contribution to revenue are suspended before components that having a higher contribution to revenue. The third algorithm is a minimal power-consuming redundant computing hardware algorithm that allows a “cold spare” host processing card to be pressed into service if another card fails.
Owner:HEWLETT PACKARD DEV CO LP
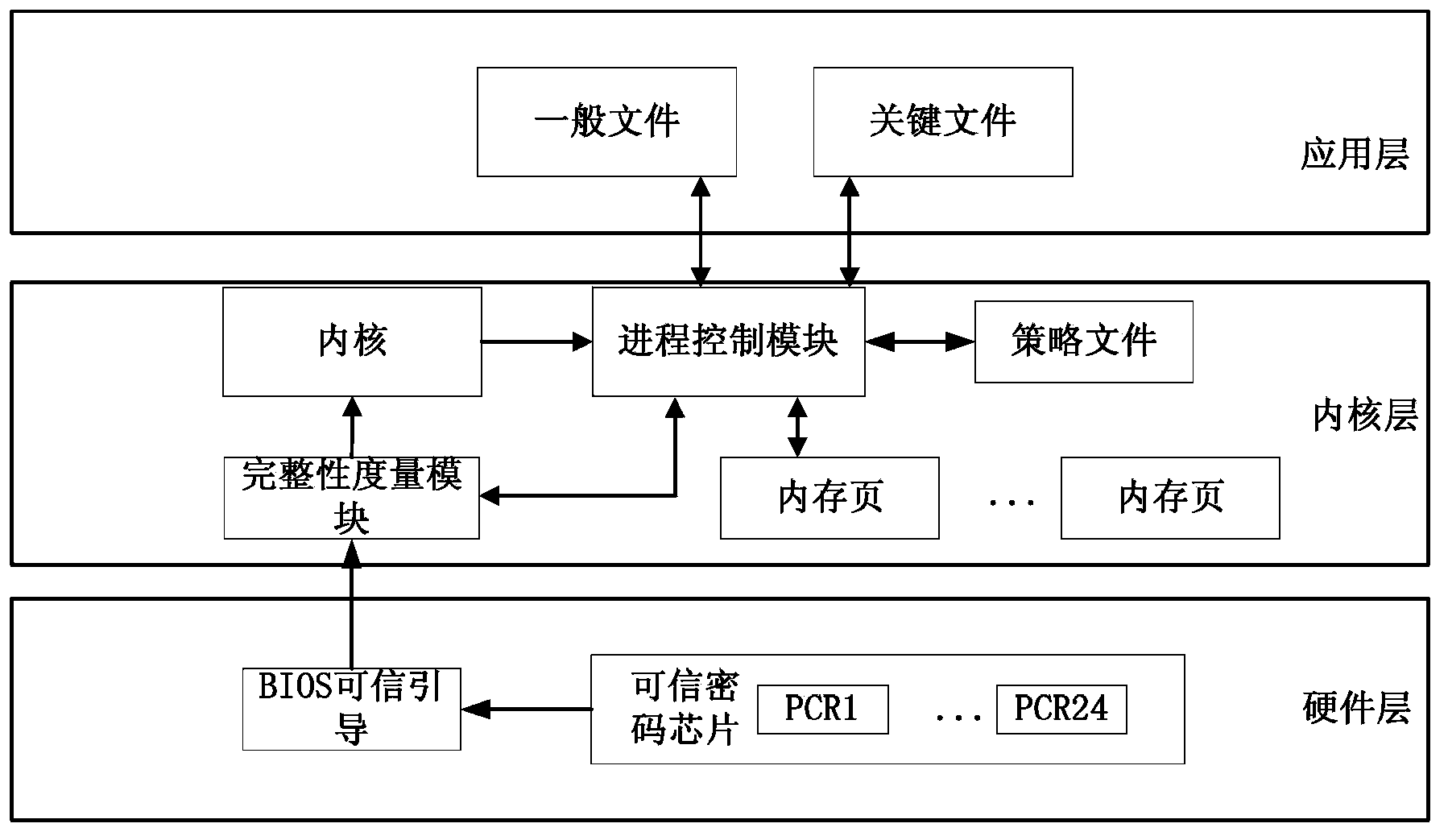
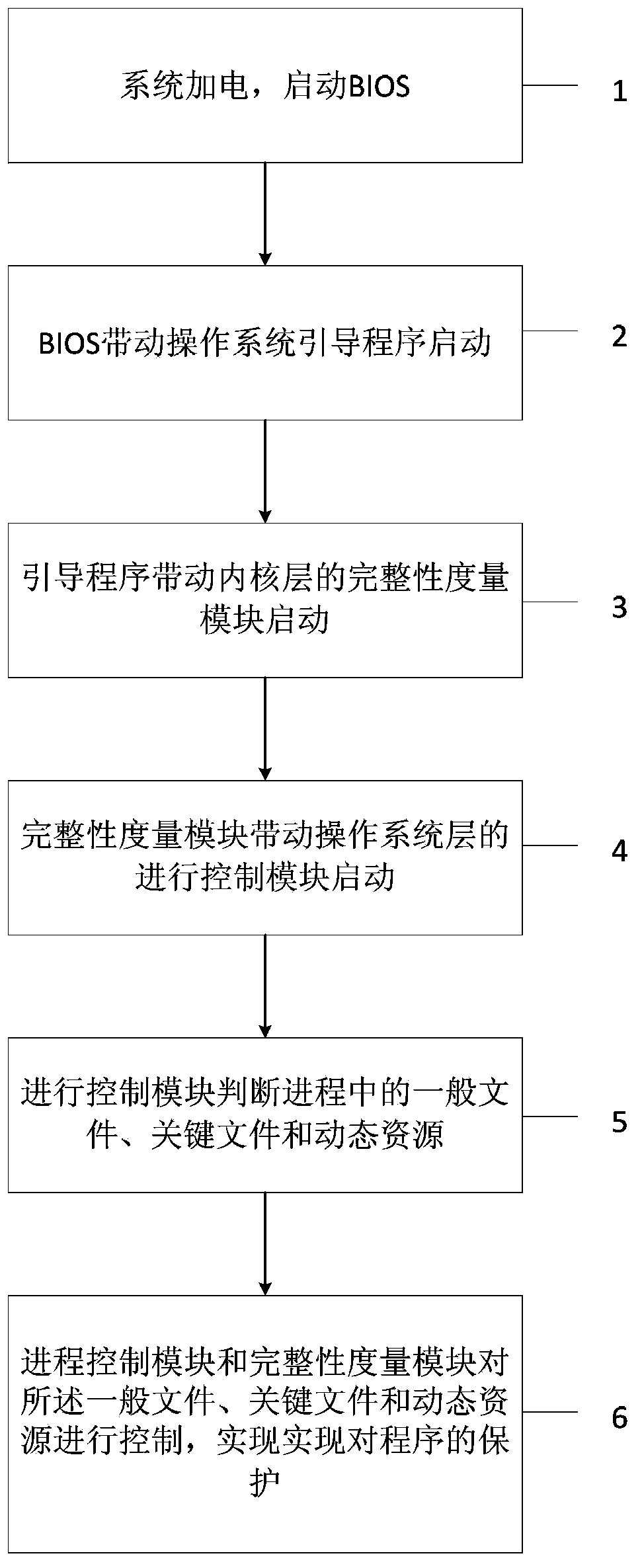
Dependable computing based process control method
ActiveCN103455756AAvoid destructionGuaranteed uptimePlatform integrity maintainanceOperational systemDynamic resource
The invention provides a dependable computing based process control method. The process control method includes that a system is powered and a BIOS (basic input / output system) is started; the BIOS drives an operating system bootstrap program to start; the bootstrap program drives an integrity measurement module in an inner nuclear layer to start; the integrity measurement module drives a process control module in an operating system layer to start; the process control module is used for judging ordinary files, critical files and dynamic resources in process; the process control module and the integrity measurement module are used for controlling the ordinary files, the critical files and the dynamic resources to realize protection of the program. By the method, the files related to process operation are subjected to protection based on the dependable computing platform hardware algorithm, static files and the dynamic files are protected, permission of accessed files and mapping relation label pages are defended, and protective means are stereo and include the aspects of direct encryption storage, and inputting credibility quantity into a dependable computing platform register and the like, so that the process can be effectively controlled.
Owner:STATE GRID CORP OF CHINA +5
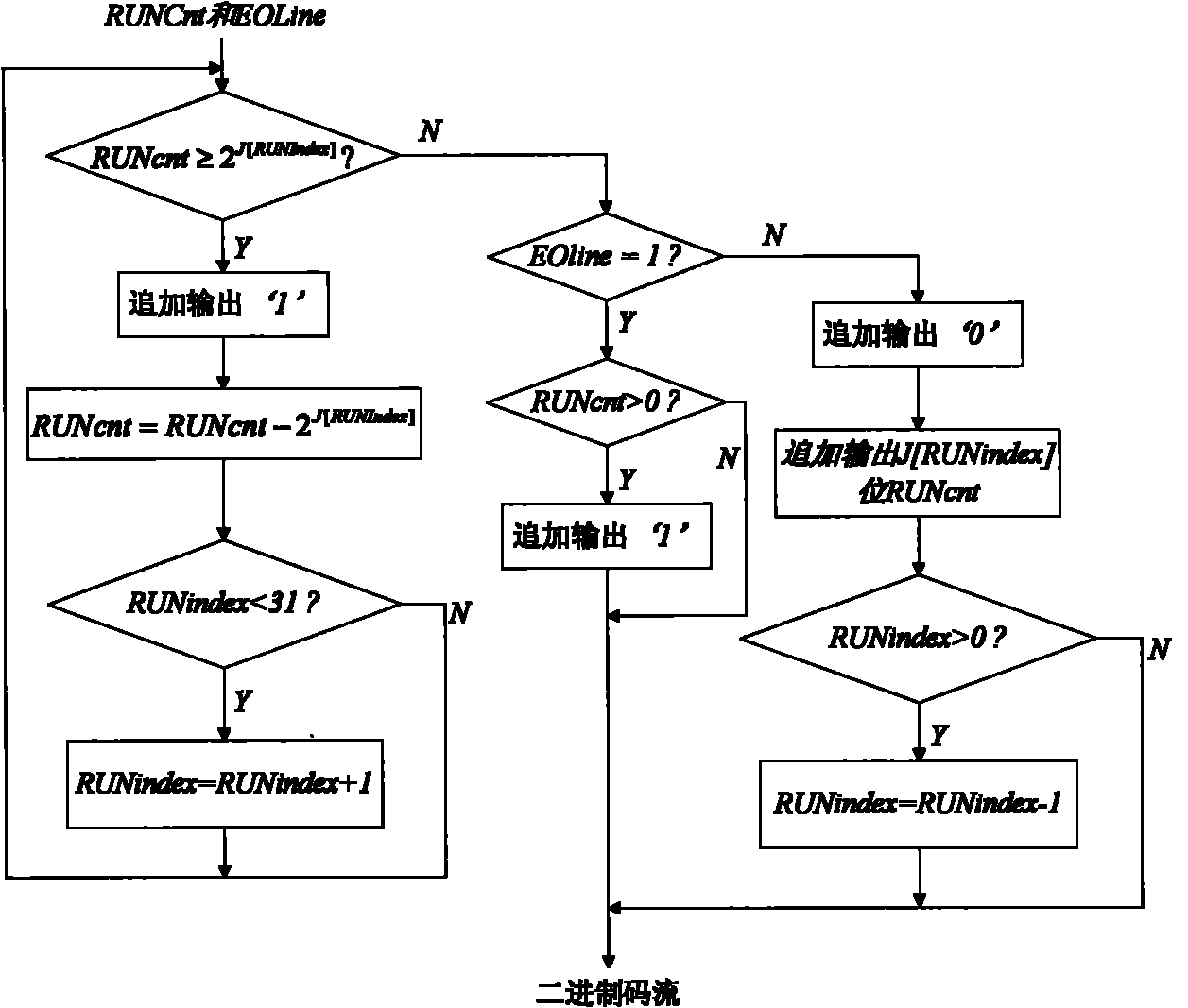
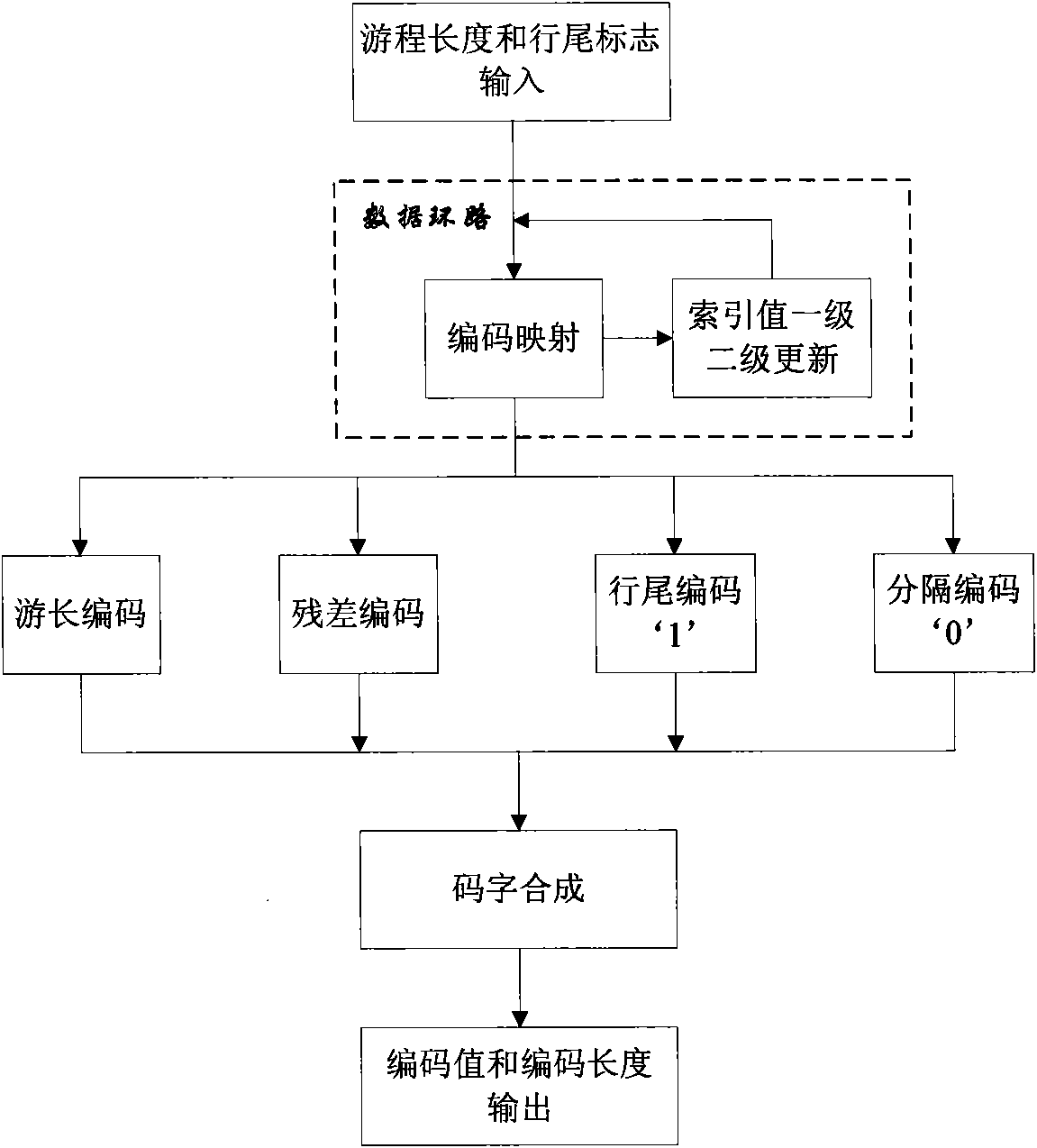
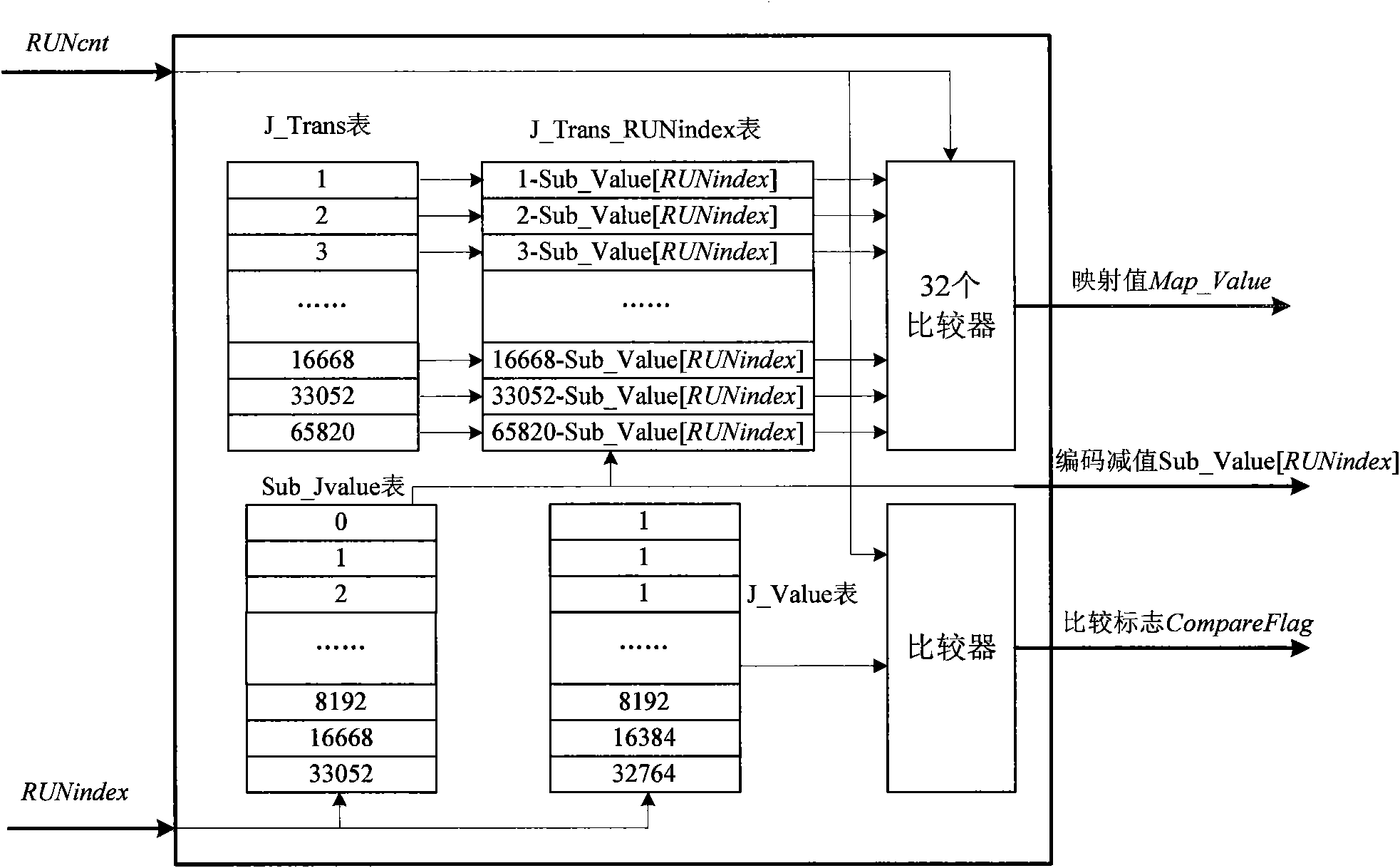
JPEG-LS run length coding hardware implementation method
InactiveCN101783953AWith full pipelineImprove real-time performanceTelevision systemsDigital video signal modificationComputer architectureFpga implementations
The invention discloses a JPEG-LS run length coding hardware implementation method which improves and optimizes the standard procedure of JPEG-LS run length coding, introduces coding mapping operation, implements coding by comparing a table look-up operation pipeline, and solves cycle coding in multiple clock cycles in an original algorithm; in addition, since only residual coding adopts index value RUN index single-cycle update operation and tour length coding and residual coding adopt index value RUNindex two-cycle update operation, coding speed is improved. The method is completely implemented by FPGA, has the advantages of full pipeline and good real time property, and can be applied to hardware algorithm of JPEG-LS lossless and near lossless compression.
Owner:BEIJING RES INST OF SPATIAL MECHANICAL & ELECTRICAL TECH
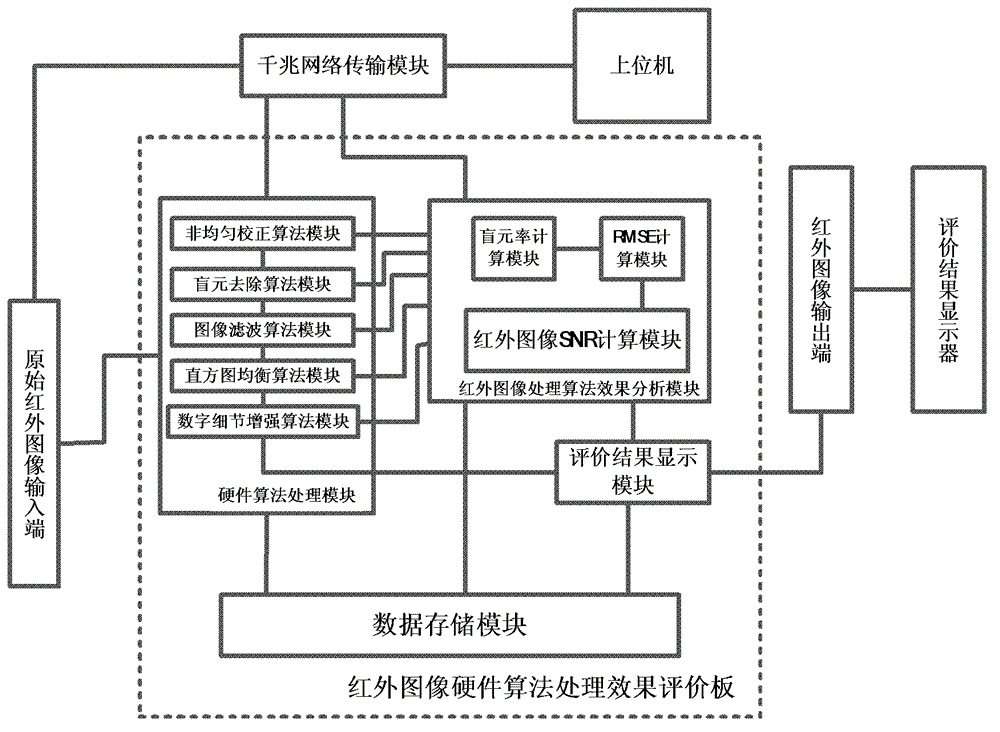
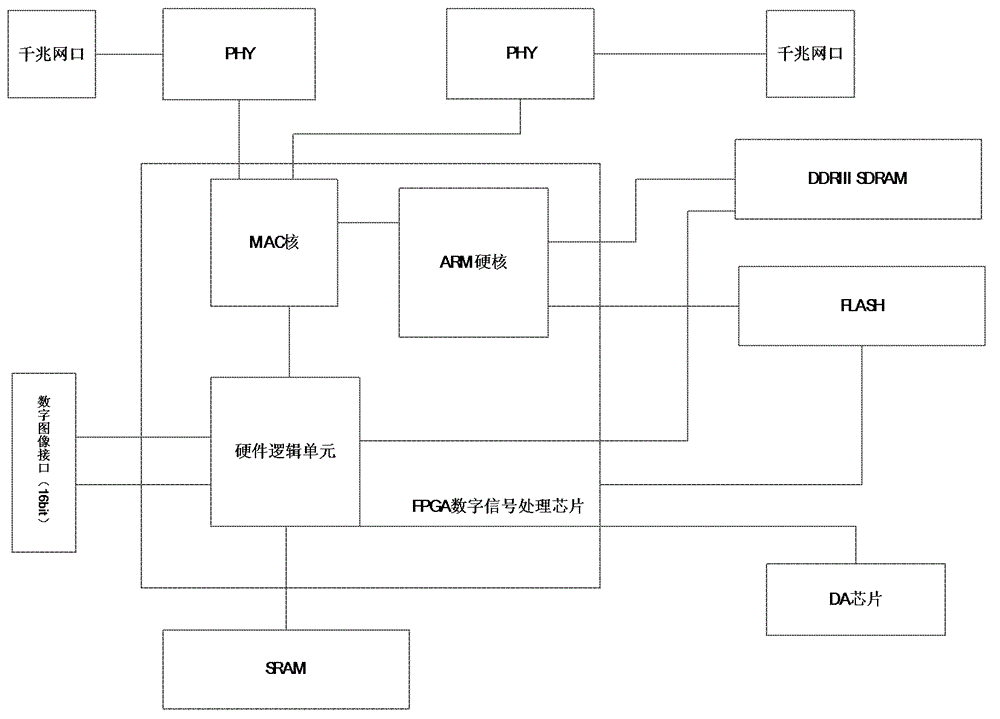
Infrared image based hardware processing algorithm effectiveness performance evaluation device and method
InactiveCN104424383AEasy to handleEasy to carryImage enhancementSpecial data processing applicationsComputer hardwareDisplay device
The invention discloses an infrared image based hardware processing algorithm effectiveness performance evaluation device and method. The infrared image based hardware processing algorithm effectiveness performance evaluation device is formed by an original infrared image input end, a gigabit network transmission module, an infrared image hardware algorithm processing performance evaluation board, an infrared image output end and an evaluation result display. The infrared image based hardware processing algorithm effectiveness performance evaluation method comprises transmitting an original infrared image into an upper computer and the infrared image hardware algorithm processing performance evaluation board; determining the performance evaluation index information of the infrared image after processing through the infrared image hardware algorithm processing performance evaluation board; displaying an evaluation result through the evaluation result display. According to the infrared image based hardware processing algorithm effectiveness performance evaluation device and method, the effect of the infrared image after the processing of different hardware algorithms can be objectively evaluated, the comparison can be performed on the infrared image after the processing by the algorithm in the upper computer and the hardware algorithm in the infrared image hardware algorithm processing performance evaluation board, and designers can further optimize and improve the hardware algorithms of the infrared image processing algorithm according to the comparison of the two processing results.
Owner:NANJING UNIV OF SCI & TECH
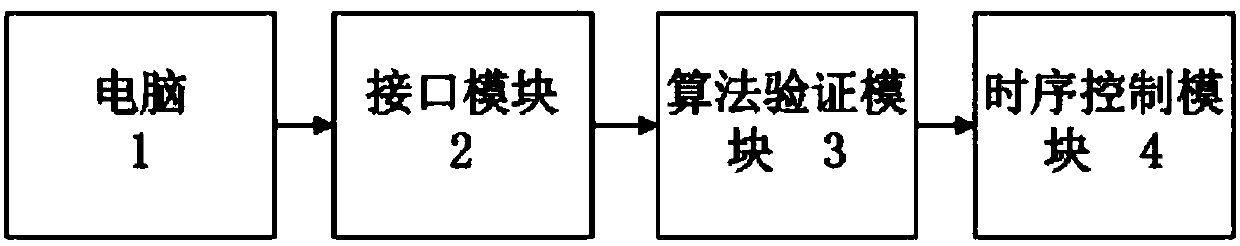
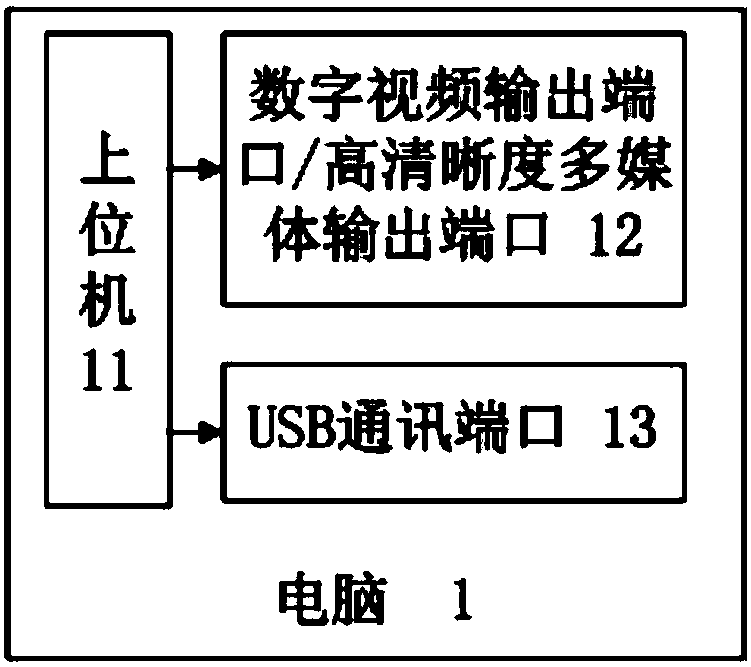
Algorithm verification platform and method
ActiveCN107734323AVerification of the actual improvement effectTelevision systemsVideo imageImaging data
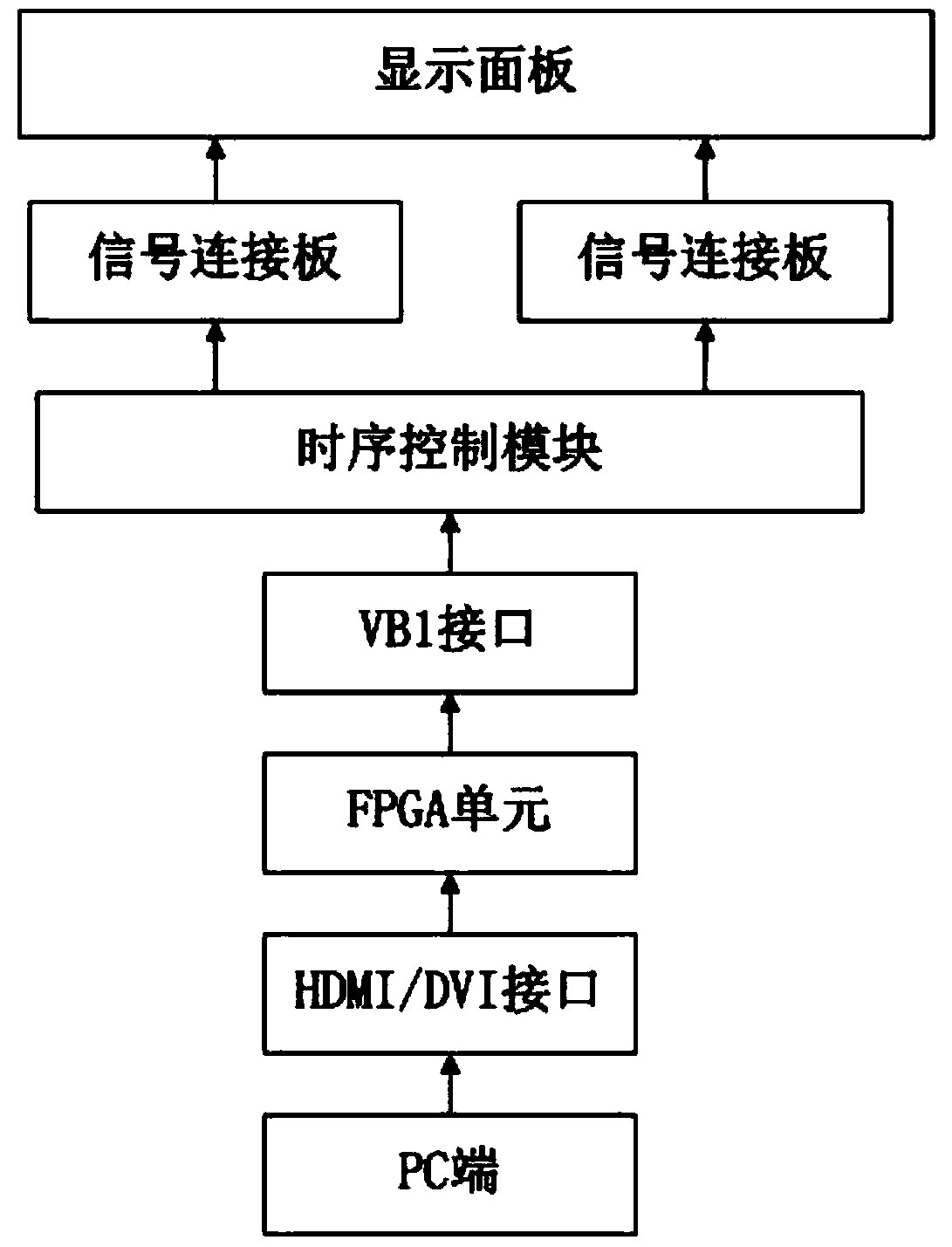
The invention provides an algorithm verification platform and method. The platform comprises a computer, an algorithm verification module, and a sequential control module; the computer outputs testingvideo image data and frame-extracting interval parameter, refreshing frequency of a display panel and an output selection parameter to the algorithm verification module; the algorithm verification module performs frame extraction on the testing video image data according to the frame-extraction interval parameter to obtain the second video image data, and processes the second video image data according to a preset video image hardware algorithm to obtain the third video image data, and encodes the second or the third video image according to the selection output parameter and then outputtingthe encoded second or third video image data to the sequential control module; the sequential control module controls the display panel to display the corresponding video image. The verification platform provided by the invention can verify the actual improvement effect on the display panel by the video image hardware algorithm without performing the frequency lowering output on the second or third video image data.
Owner:SHENZHEN CHINA STAR OPTOELECTRONICS TECH CO LTD
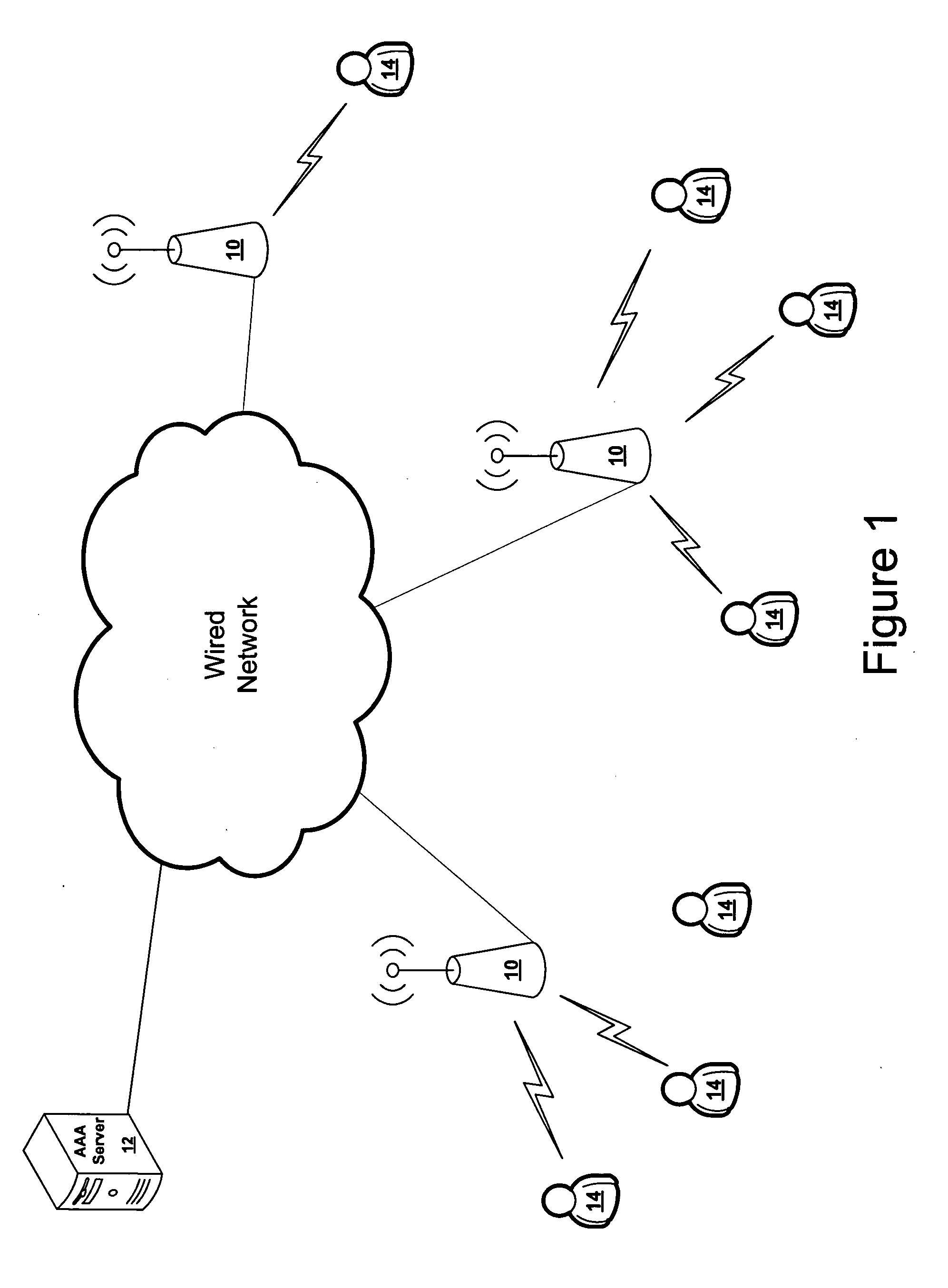
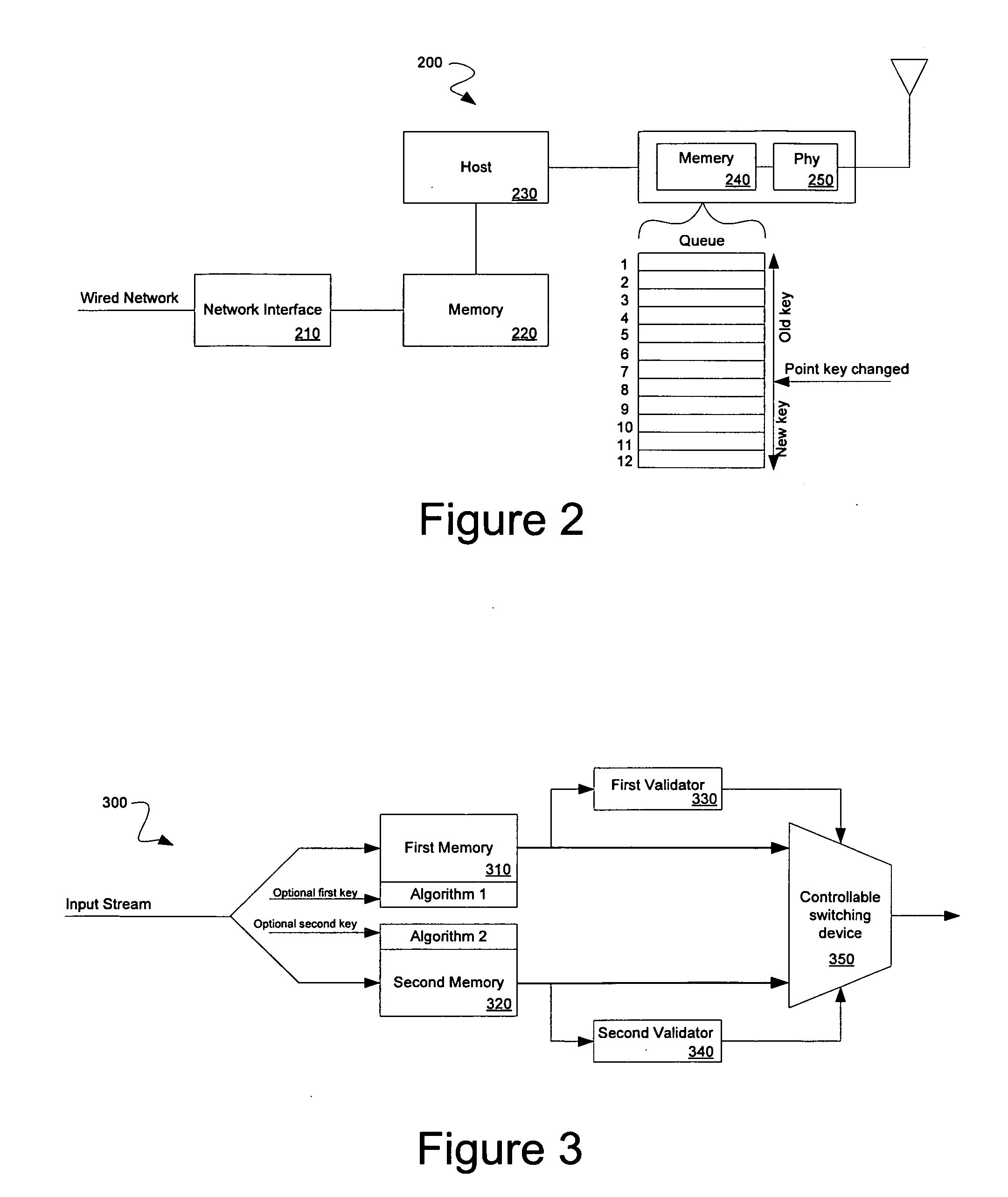
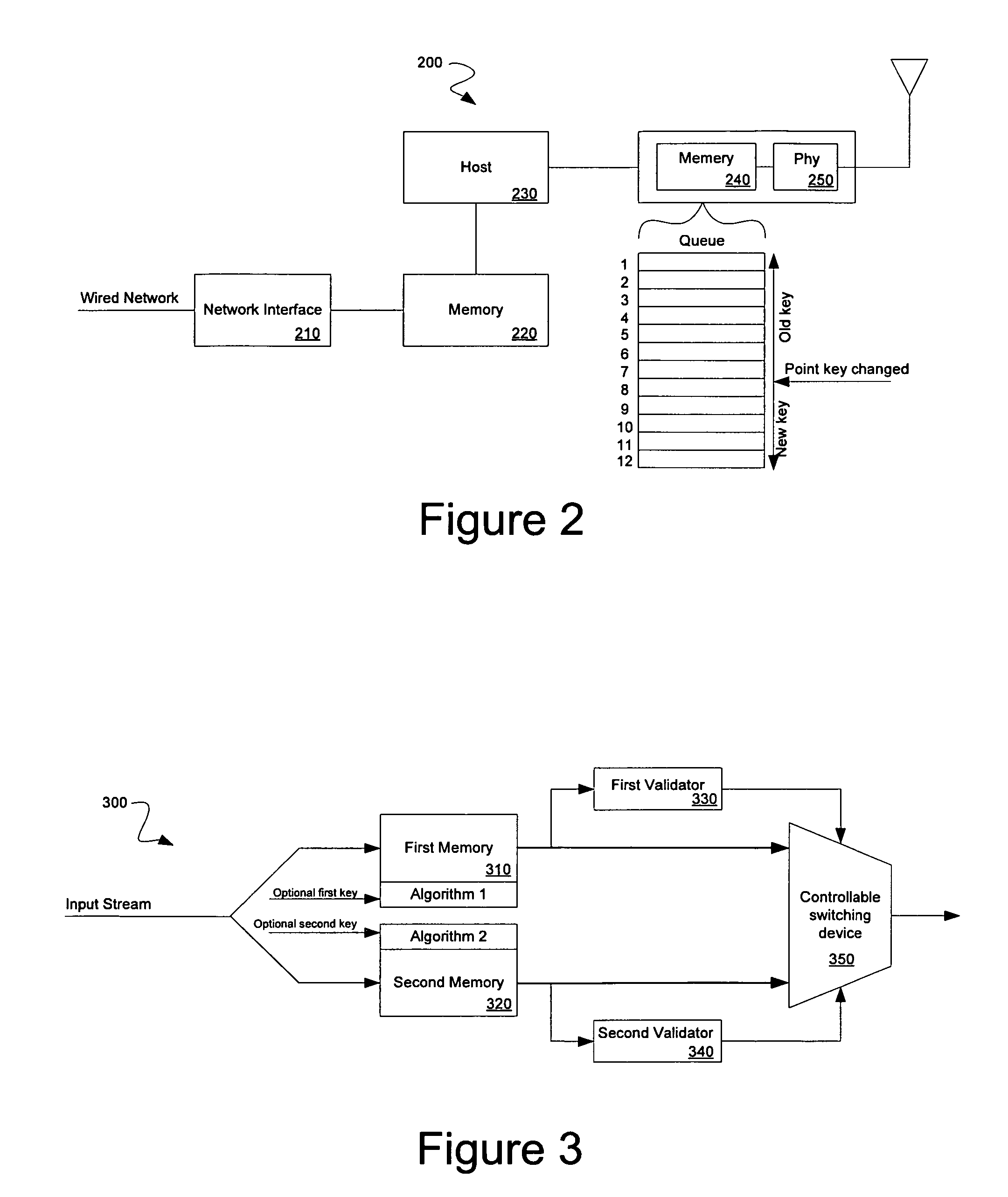
Parallel cipher operations using a single data pass
ActiveUS20070064934A1Improve latencyImprove system throughputDigital data processing detailsUser identity/authority verificationComputer hardwareParallel algorithm
Multiple cipher hardware algorithms are run in parallel over an input stream. For example, one algorithm can process the input stream using an old cipher key while a parallel algorithm processes the input stream using the current cipher key. Alternatively, multiple cipher operations can be performed in parallel enabling a receiver to determine which cipher algorithm was employed in encrypting a data packet.
Owner:CISCO TECH INC
Hardware Algorithm for Complex-Valued Exponentiation and Logarithm Using Simplified Sub-Steps
PendingUS20210109712A1More circuitryReduce the amount requiredDigital data processing detailsData conversionAlgorithmParallel computing
A method of generating complex exponentiation and logarithms in hardware is described that uses half the number of bits of lookup tables as the state-of-the-art. By splitting up each of the iterations into more simplified stages or using more iterations, the amount of precomputed information that must be held by the circuitry is reduced. This allows synthesis tools to take this more succinct logical description of the algorithm and make it into efficient gate level logic for fabrication into more compact integrated circuitry.
Owner:ULTRALEAP LTD
Full impedance distance protection method based on FPGA
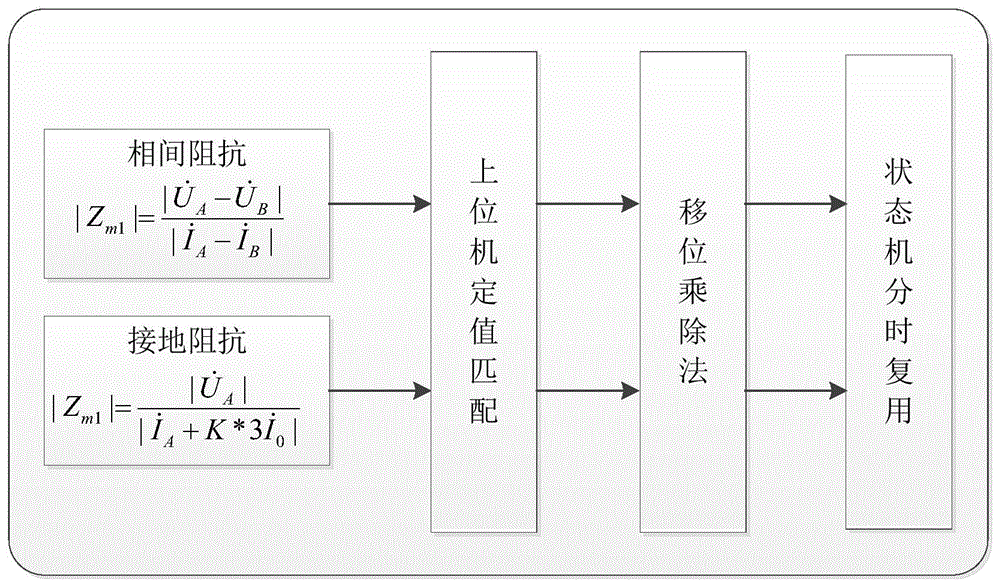
InactiveCN104578010AProcessing speedEnsure safetyResistance/reactance/impedenceEmergency protective circuit arrangementsTime-division multiplexingSimulation testing
The invention relates to a full impedance distance protection method based on an FPGA. The method includes the steps of 1 calculating impedance protection, 2 adopting an upper computer for definite value matching, 3 adopting a shifting multiplication and division method, 4 adopting a state machine for time division multiplexing, 5 testing the impedance protection characteristic and 6 carrying out simulation testing. Based on a hardware platform of the FPGA, the FPGA is used for calculating the processing speed of improving the hardware protection logic in parallel at high speed to ensure the safety and reliability of motions. By the adoption of a full impedance distance protection hardware algorithm based on the FPGA, judgment processes of starting elements such as positive sequence voltage, negative sequence voltage and currents are reduced, and real-time calculation and logical judgment are carried out to further protect the reliability of relay protection motions.
Owner:STATE GRID CORP OF CHINA +2
Smart card system
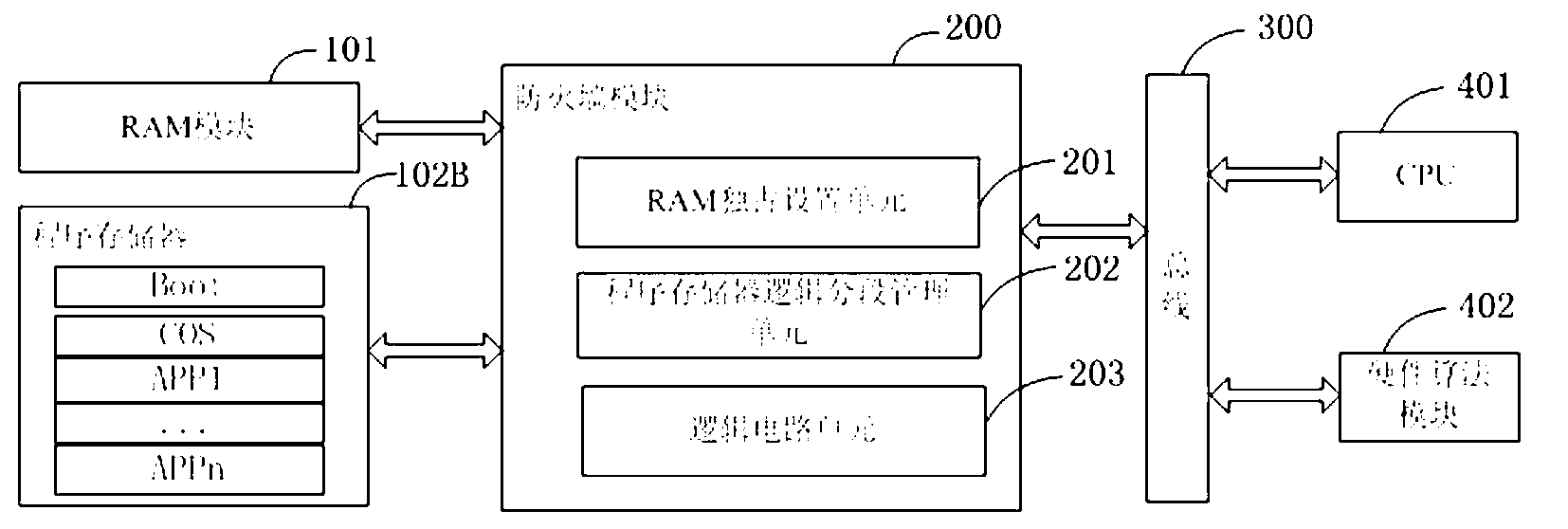
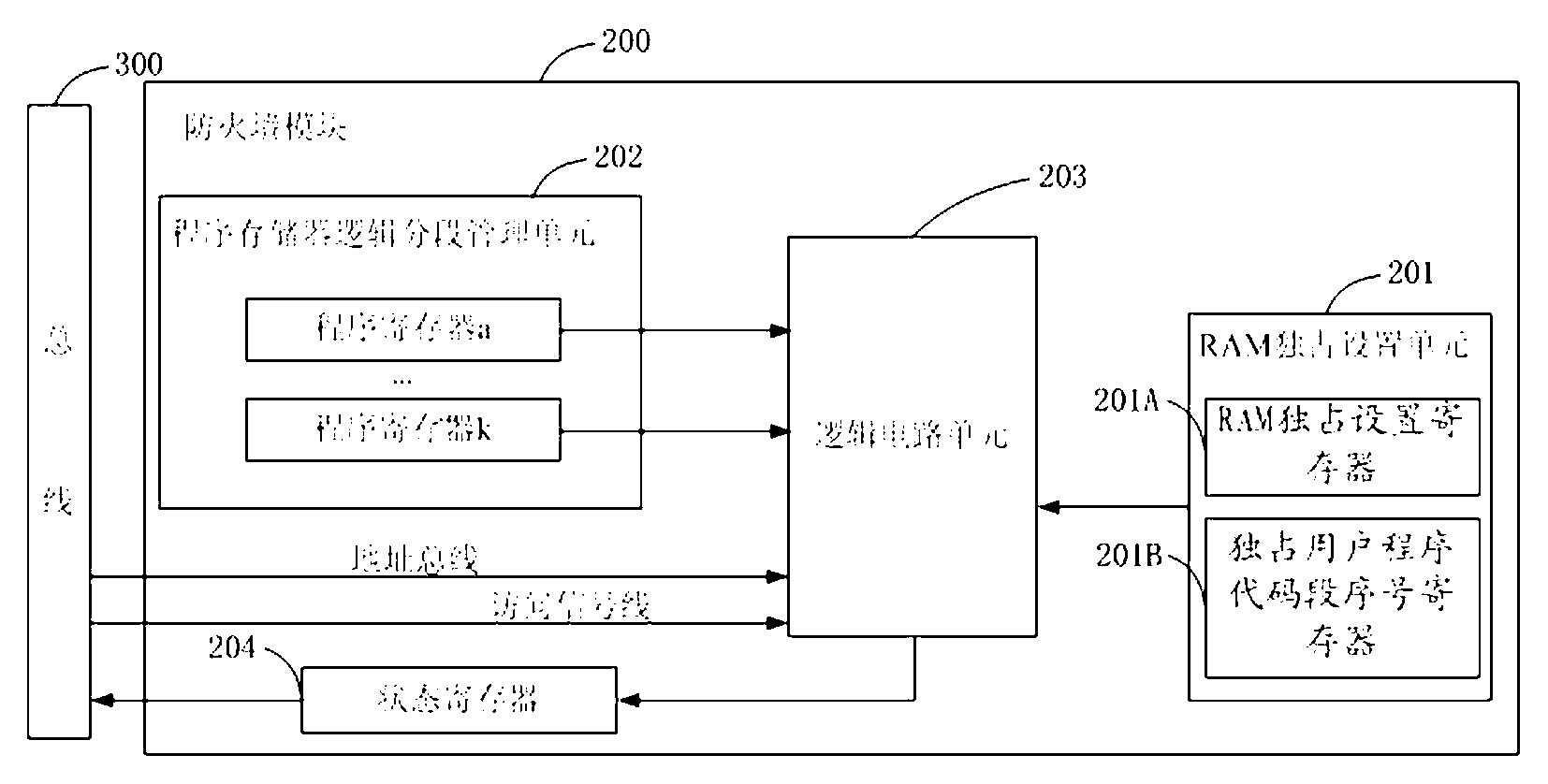
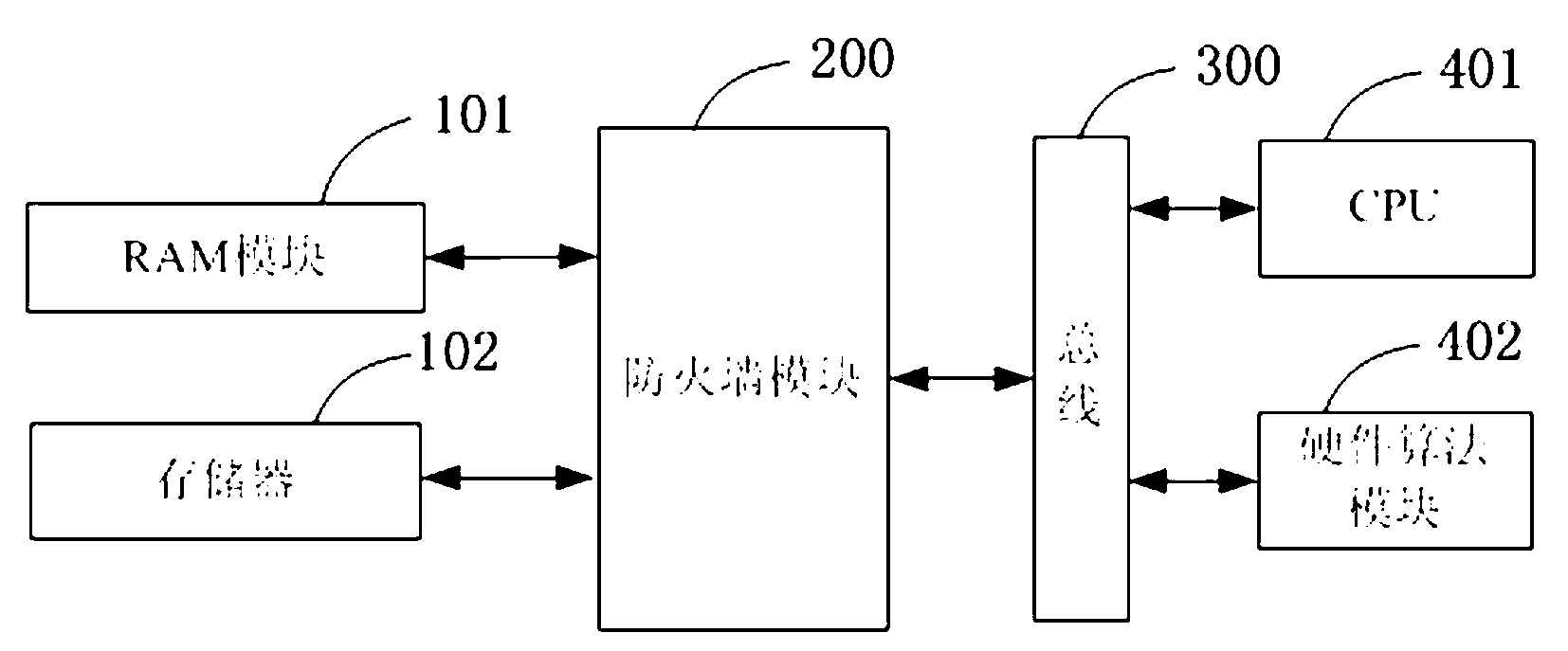
ActiveCN103136571AImprove operational efficiencyGuaranteed uptimeRecord carriers used with machinesRandom access memorySmart card
The invention relates to a smart card system which comprises a central processing unit (CPU), a hardware algorithm module used for algorithm calculation, a memorizer used for storing program and data, a random access memory (RAM) and a firewall module, wherein the RAM module is used for providing algorithm running space as ordinary RAM used for a central processor unit (CPU) for a smart card hardware algorithm module. The firewall module is used for providing safeguard for a smart card algorithm RAM module. Due to the smart card system, in the process of algorithm running, only the hardware algorithm module accounts for the RAM. On the one hand, efficiency of the algorithm running is greatly improved, on the other hand, only the hardware algorithm module can read middle results of the algorithm running, and therefore the hacktivism that an illegal program uses CPU to maliciously read the results of the algorithm running to speculate a secret key or algorithm implementation is eliminated, and absolutely reliability of the hardware algorithm module is ensured.
Owner:NATIONZ TECH INC
High-speed parallel processing architecture for data center
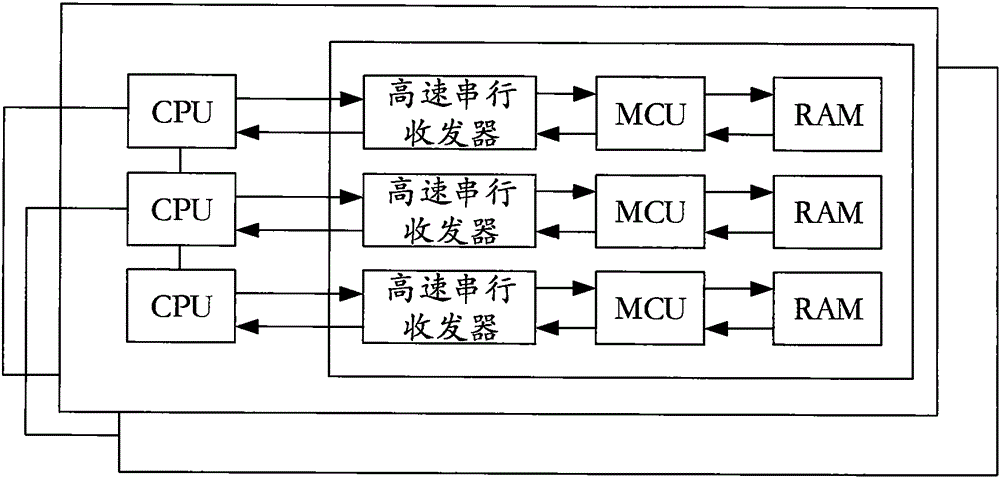
ActiveCN105045761AEasy to handleReduce Scheduling LatencyDigital computer detailsElectric digital data processingFpga architectureTransceiver
The present invention relates to the field of data processing, and discloses a high-speed parallel processing architecture for a data center. The high-speed parallel processing architecture comprises a plurality of processing boards, and is characterized in that each processing board comprises at least two transceivers, at least one FPGA programmable logic chip and at least two processors (CPUs), wherein the CPUs are connected with with the FPGA chip through CPU high-speed serial interfaces; and a plurality of high-speed serial transceiver cores and a plurality of corresponding coprocessors (MCUs) are arranged in the FPGA chip; a plurality of embedded memories corresponding to each coprocessor MCU are embedded into the FPGA ; and each embedded memory is configured to be in a dual-port mode capable of reading and writing. According to the high-speed parallel processing architecture, an embedded CPU+FPGA architecture is realized; high-speed parallel hardware algorithms are realized, so that processing ability of basic computing elements is greatly improved, and system schedule delay is reduced.
Owner:厦门中源能链科技有限公司
Self-calibration method for ray collimator and system thereof
ActiveCN109431534AEnsure normal communicationEasy to debugTomographyDiaphragms for radiation diagnosticsX-rayComputer science
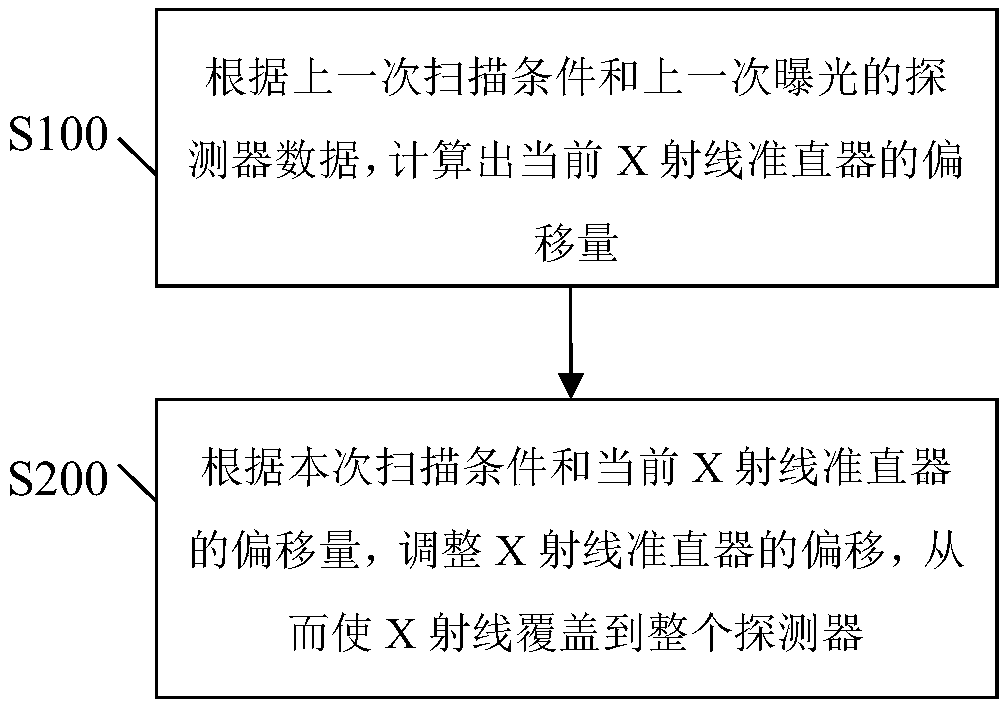
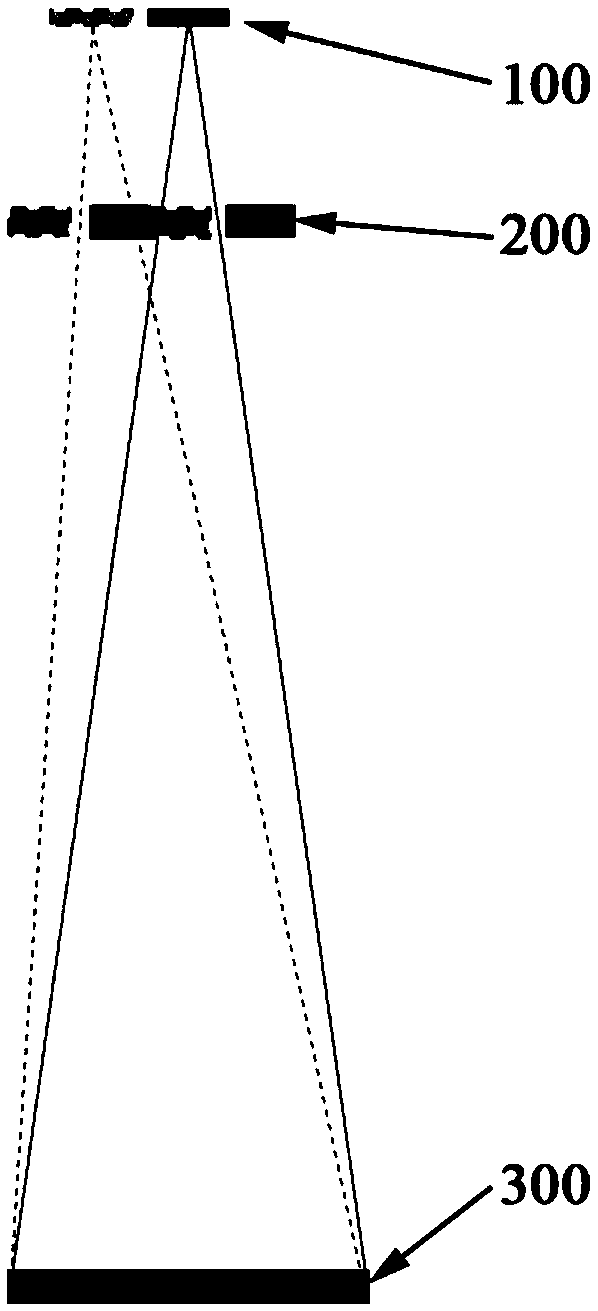
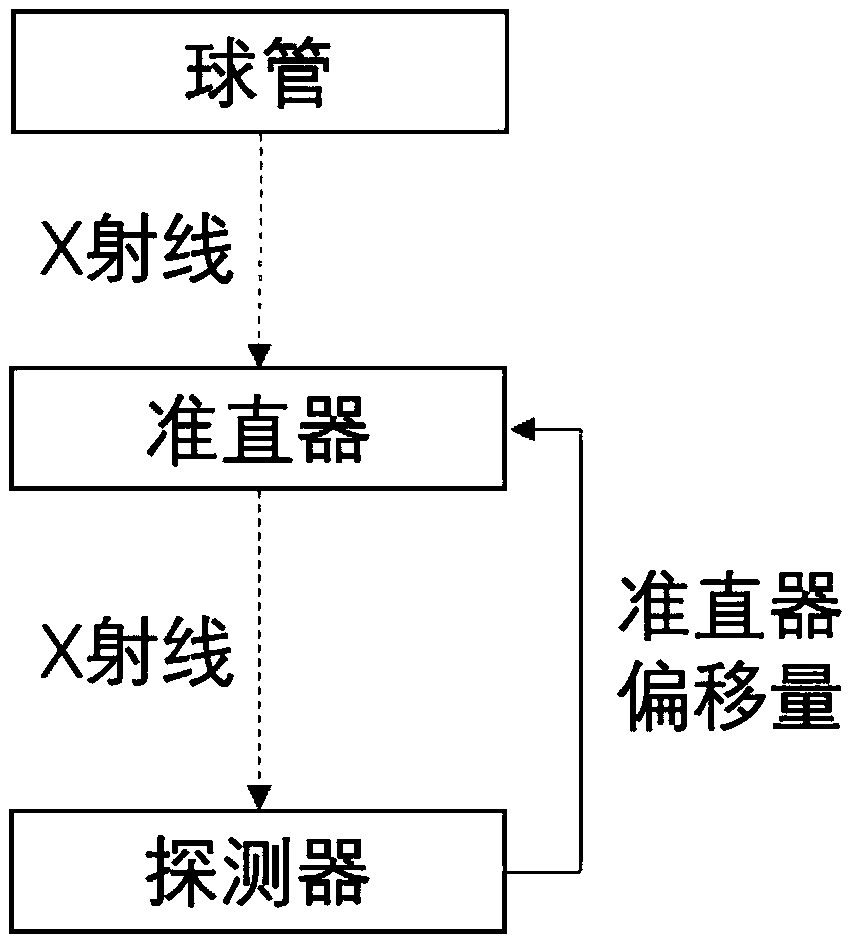
The invention discloses a self-calibration method for a ray collimator and a system thereof. The method comprises the steps of calculating an offset of a current X-ray collimator according to a previous scanning condition and detector data of previous exposure; according to the current scanning condition and the offset of the current X-ray collimator, adjusting the offset of the X-ray collimator,so that X-rays cover an entire detector. Since all calibration methods can be implemented by software of a reconstruction machine, there is no need to increase the hardware cost to ensure communication between the detector and the collimator, and hardware algorithm integration is also not needed. The difficulty of developing the software on the reconstruction machine is easier and simpler than implementing of a dynamic tracking algorithm on the hardware, the system is also easy to debug, and the probability of errors can be greatly reduced.
Owner:SHENZHEN ANKE HIGH TECH CO LTD
Virtually photographing method of mobile phone
InactiveCN102088514ARealize the dreamy photo effectImprove execution efficiencySubstation equipmentComputer graphics (images)Imaging data
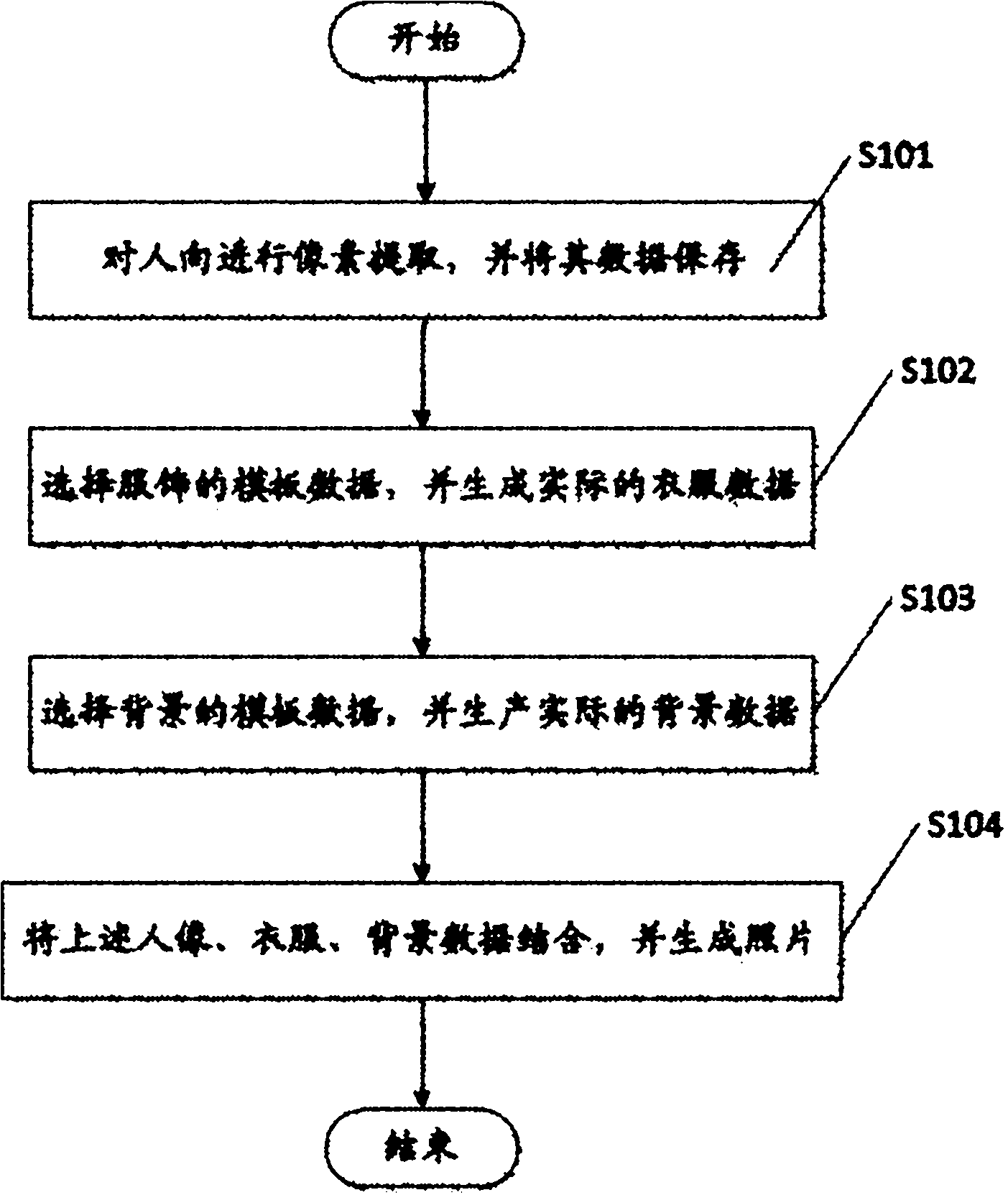
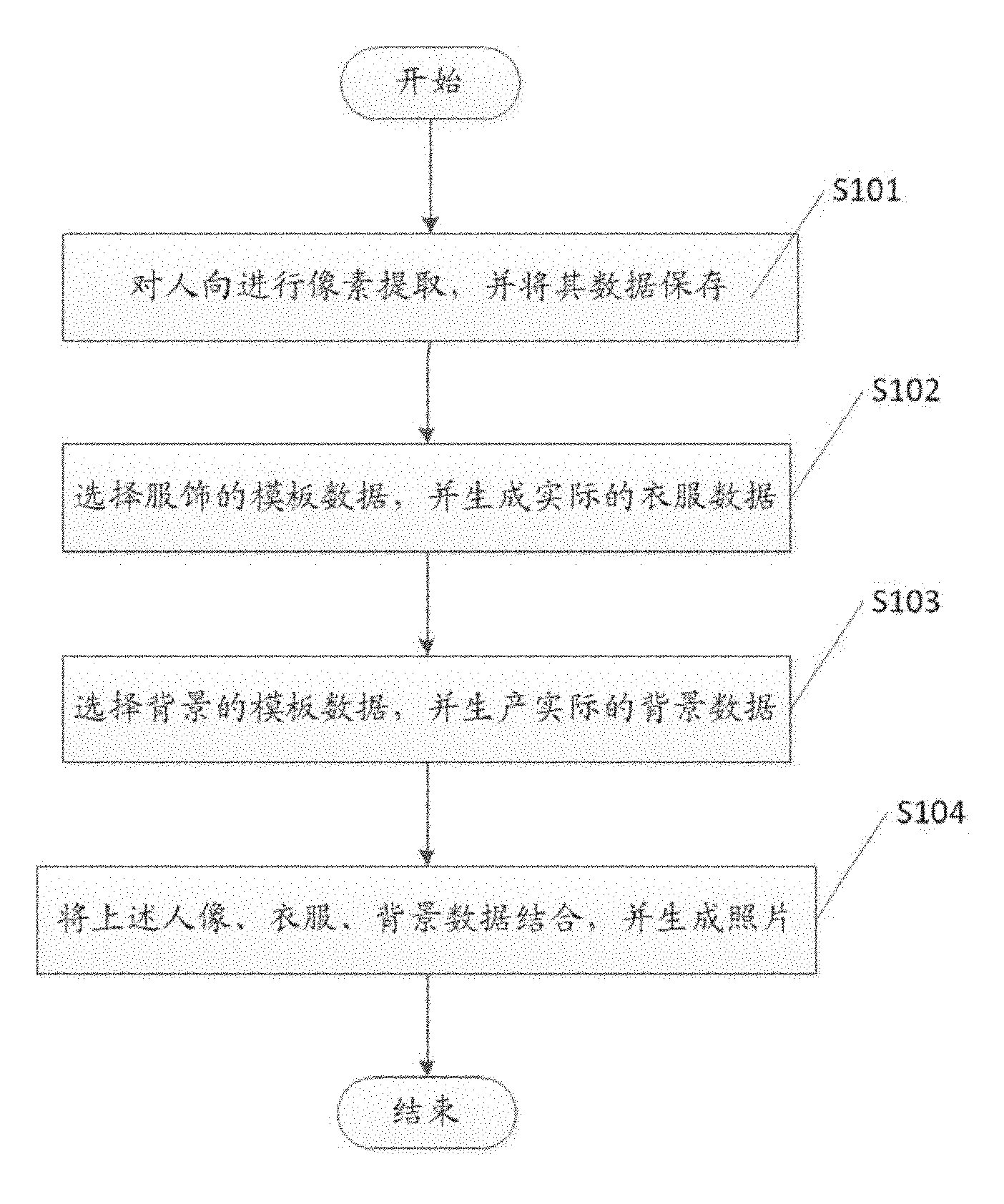
The invention discloses a virtually photographing method of a mobile phone. The virtually photographing method comprises the following steps: (1) extracting pixels of a portrait image, and storing the portrait image data; (2) selecting template data of clothes, and generating the actual clothes data; (3) selecting template data of a background, and generating the actual background data; and (4) combining the portrait image data, the clothes data and the background data and generating a photograph. Based on the above design, various kinds of virtual photographing effects can be obtained by using the mobile phone, and the method has the advantage of high execution efficiency by adopting a hardware algorithm.
Owner:HUAQIN TECH CO LTD
Similarity measurement hardware accelerating method based on rapid normalized cross correlation method
ActiveCN104657553ASuitable for hardware implementationReduce operationSpecial data processing applicationsProduction lineCorrelation coefficient
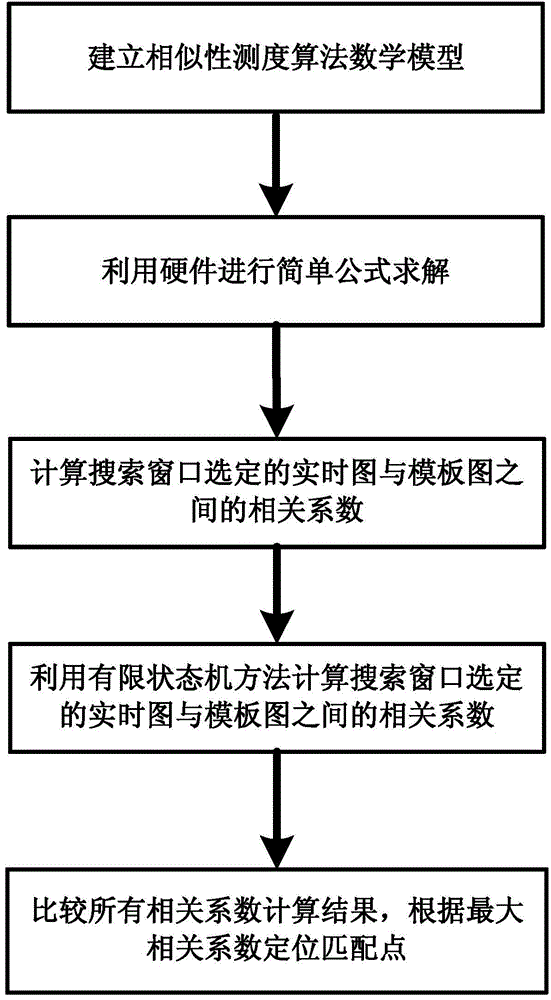
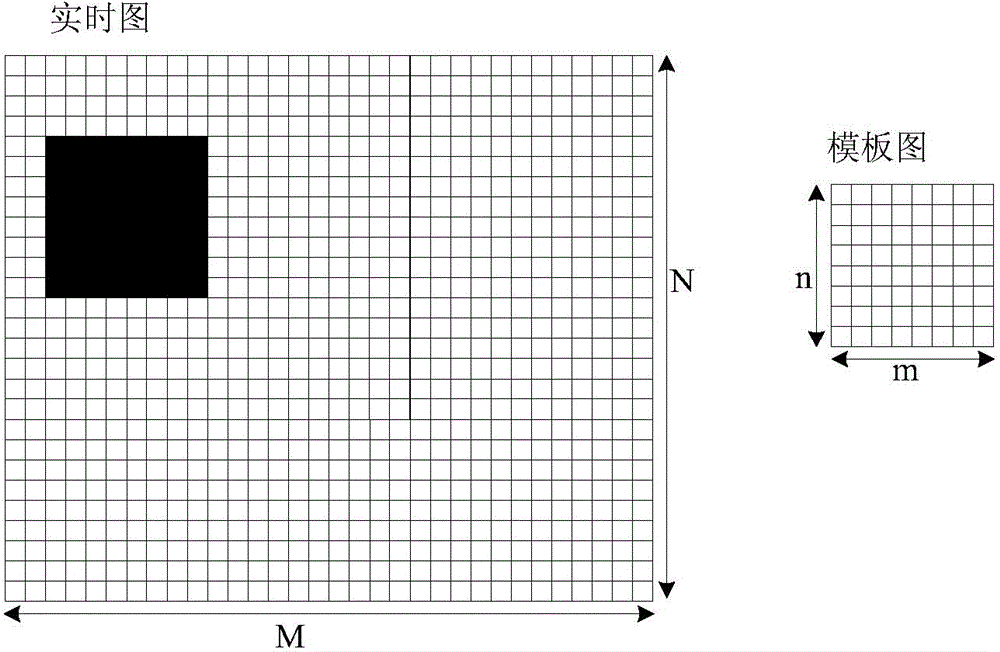
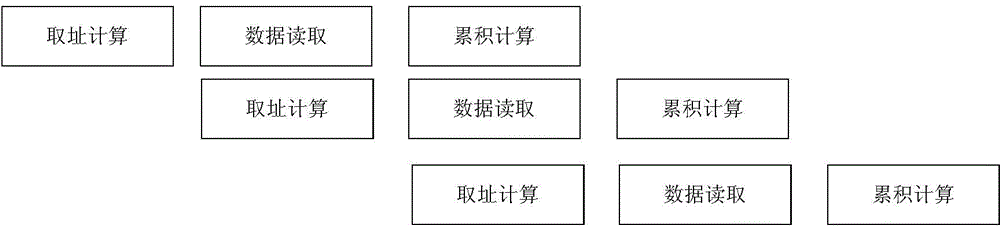
The invention provides a similarity measurement hardware accelerating method based on a rapid normalized cross correlation method. The similarity measurement hardware accelerating method comprises the following steps of firstly establishing a mathematic model of correlation coefficients between a real-time image and a template image; then performing a hardware algorithm design by use of a two-layer production line, and calculating the correlation coefficients between the real-time image selected by a search window and the template image; after all the correlation coefficients between the real-time image selected by the search window and the template image are calculated, and finding out the maximal value of the correlation coefficients and the horizontal coordinate and longitudinal coordinate of the top left corner of the corresponding search window in a real-time image coordinate system, wherein the selected region corresponding to the search window is a matched region. According to the method, the hardware resource cost is reasonably controlled, 100M requirement is met under Xilinx Virtex5-XC5VFX100T, similarity matching calculation for a 80*64 real-time image and a 25*25 template image only needs 3.5ms, and thus the algorithm speed is greatly improved.
Owner:BEIJING AEROSPACE AUTOMATIC CONTROL RES INST +1
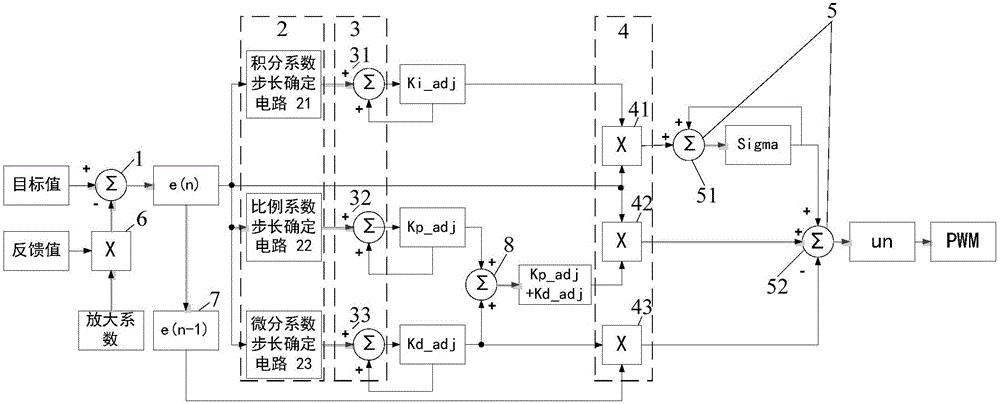
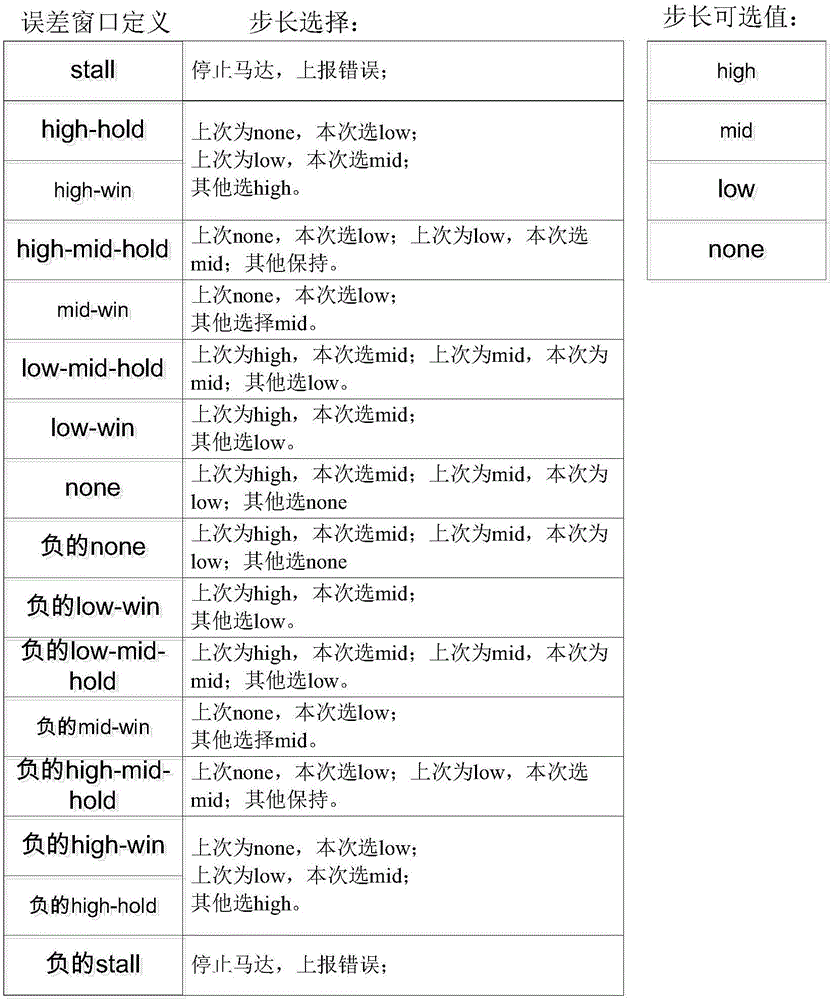
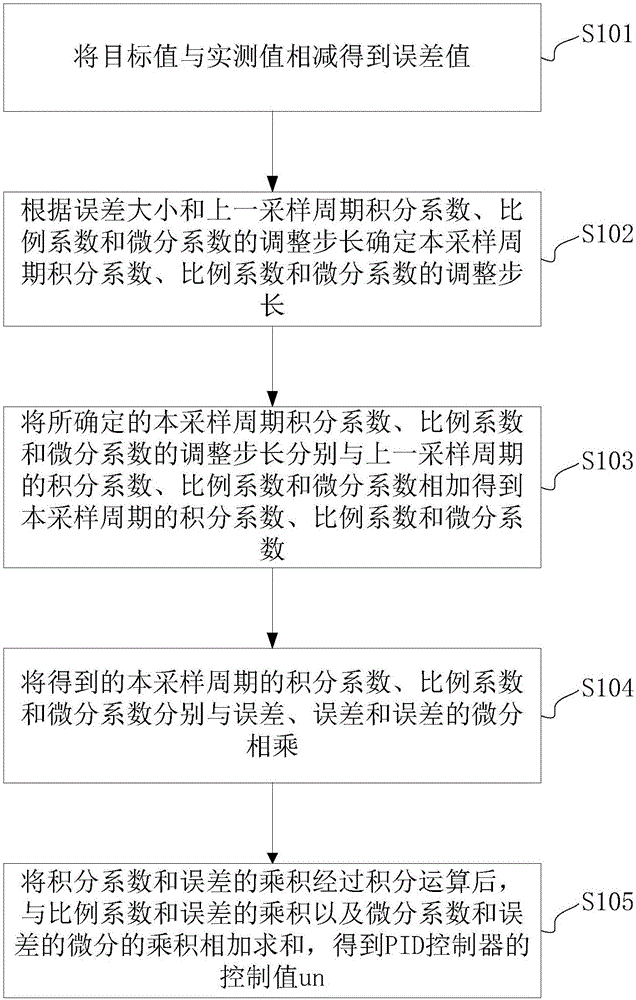
Adaptive hardware PID controller for controlling motor and control method of adaptive hardware PID controller
ActiveCN106712652AEasy to controlSmall scaleElectric motor controlGeneral control strategiesDifferential coefficientEngineering
The invention discloses an adaptive hardware PID controller for controlling a motor and a control method of the adaptive hardware PID controller. The adaptive hardware PID controller comprises a first adder, a PID coefficient adjustment step length determining circuit, an adder group, a multiplier group and a second adder. The method comprises the following steps of subtracting a measured value from a target value; determining three coefficient adjustment step lengths according to the error magnitude and three coefficient adjustment step lengths of the previous period; adding the determined three coefficient step lengths to three coefficients of the previous period separately to obtain three coefficients of the period; multiplying the obtained three coefficients of the period with the error, error and differential of the error; and carrying out integral operation on the product of an integral coefficient and the error and then adding the product of a proportion coefficient and the error and the product of the integral coefficient and the differential of the error to obtain a control value. The adaptive hardware PID controller is widely applicable to various motor control scenes; and the motor is more accurately controlled by adopting different coefficients at different stages, control on the motor is completed through a pure hardware algorithm and the calculation speed is very high.
Owner:北京鸿智电通科技有限公司
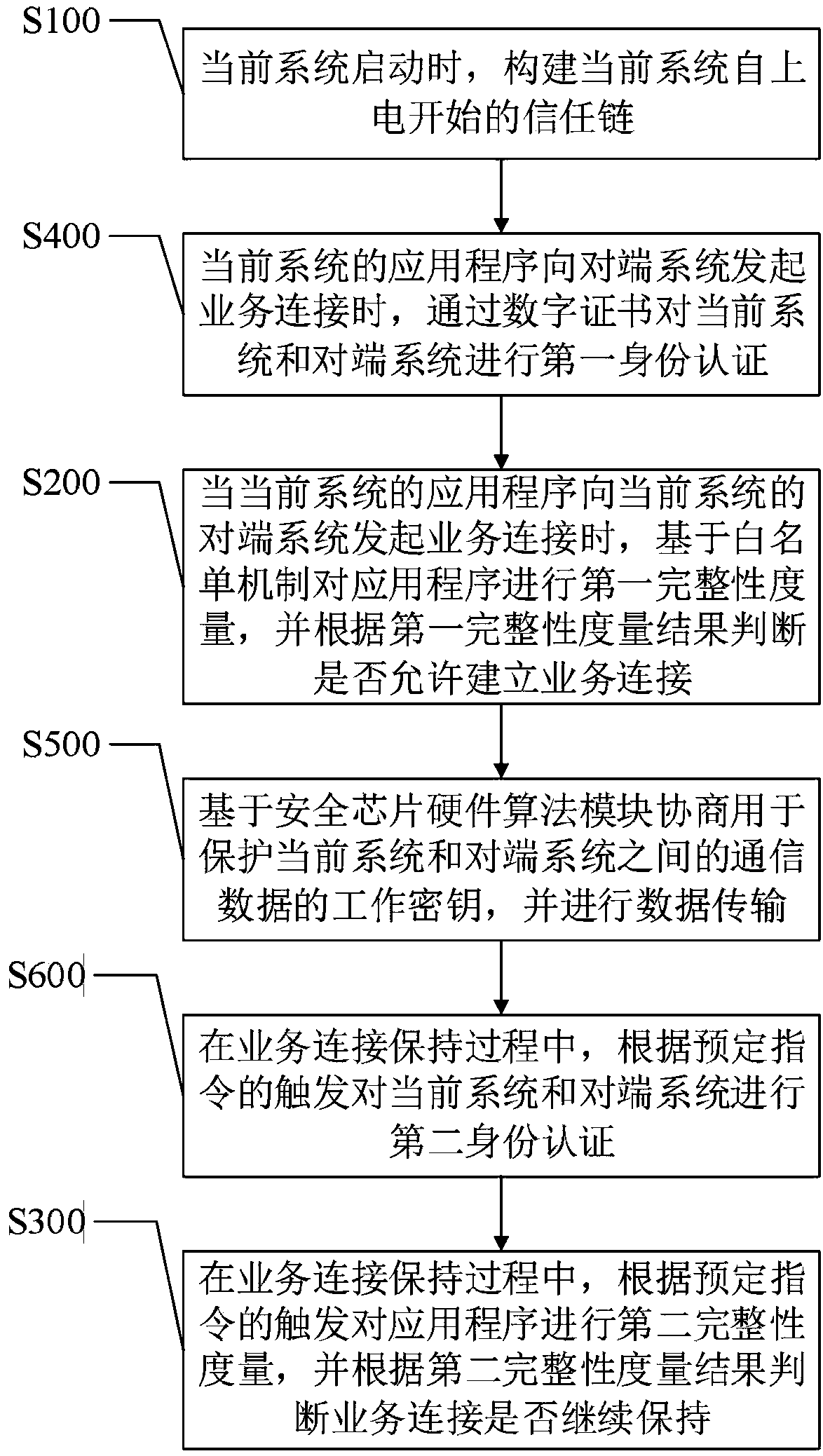
Trusted network communication method and device based on safety chip hardware algorithm module
InactiveCN108632243AImprove securityIncrease credibilityKey distribution for secure communicationUser identity/authority verificationElectricityPrimary station
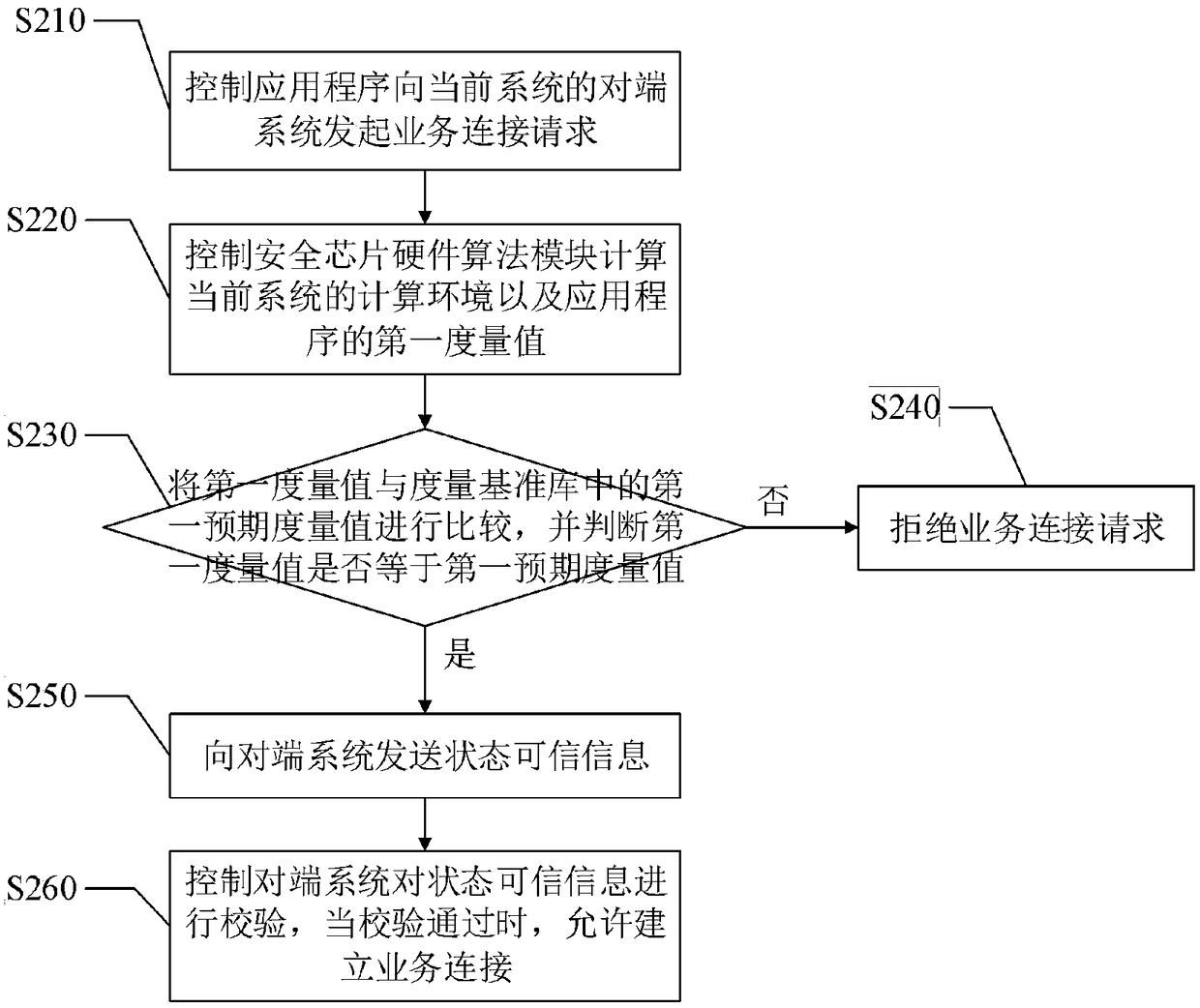
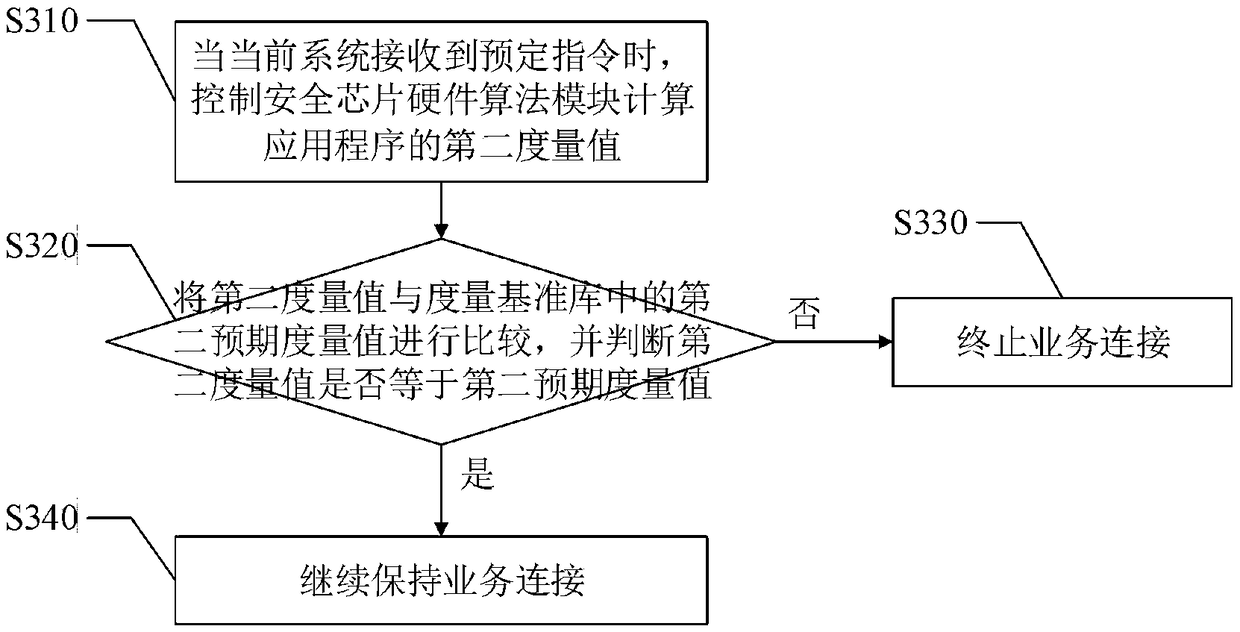
The invention discloses a trusted network communication method and device based on a safety chip hardware algorithm module. The method comprises the following steps of when a system is started, constructing the trust chain of a current system from the beginning of power on; when the application program of the current system initiates service connection to the opposite end system of the current system, carrying out first integrity measurement on the application program based on a whitelist mechanism, and according to a first integrity measurement result, determining whether the service connection is allowed to establish; and during a service connection maintenance process, carrying out a second integrity measurement on the application program based on the triggering of a predetermined instruction, and according to a second integrity measurement result, determining whether the service connection is continuously maintained. When the application program initiates the service connection tothe opposite end system, the first integrity measurement is performed, and during the service connection maintenance process, the second integrity measurement is performed so as to reduce a possibility that transmission data between a terminal system and a main station system is stolen, and improve the safety and the credibility of the method.
Owner:GLOBAL ENERGY INTERCONNECTION RES INST CO LTD +3
Infrared image super-resolution reconstruction method based on structural transformation self-similarity
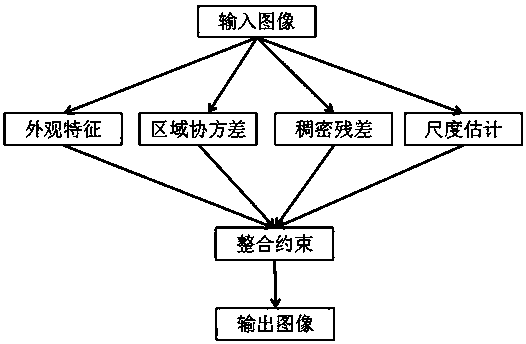
InactiveCN108090870AReduce redundant informationHigh-resolutionGeometric image transformationResource utilizationReconstruction method
The present invention discloses an infrared image super-resolution reconstruction method based on a structural transformation self-similarity. The method comprises the steps of calculating an appearance feature cost function and analyzing the structure information of an image block, calculating an area covariance cost function and analyzing image area structure information, calculating a dense residual cost function and reducing the redundancy of a reconstruction process, calculating a scale cost function and restraining loss information of a high-resolution image, and integrating and restraining appearance characteristics, a regional covariance, a dense residual error and scale estimation. According to the method, more image details can be retained, the amount of loss in the transmissionprocess of an image signal is reduced, and the transmission load is reduced. The resolution of the image can be effectively improved, the computational power consumption of a hardware algorithm can bereduced, the resource utilization of the image signal is improved, and the visual quality of the image is effectively improved.
Owner:SUZHOU CHANGFENG AVIATION ELECTRONICS
Parallel cipher operations using a single data pass
ActiveUS7995753B2Digital data processing detailsUser identity/authority verificationComputer hardwareParallel algorithm
Multiple cipher hardware algorithms are run in parallel over an input stream. For example, one algorithm can process the input stream using an old cipher key while a parallel algorithm processes the input stream using the current cipher key. Alternatively, multiple cipher operations can be performed in parallel enabling a receiver to determine which cipher algorithm was employed in encrypting a data packet.
Owner:CISCO TECH INC
Ethernet controller security enhancement design method
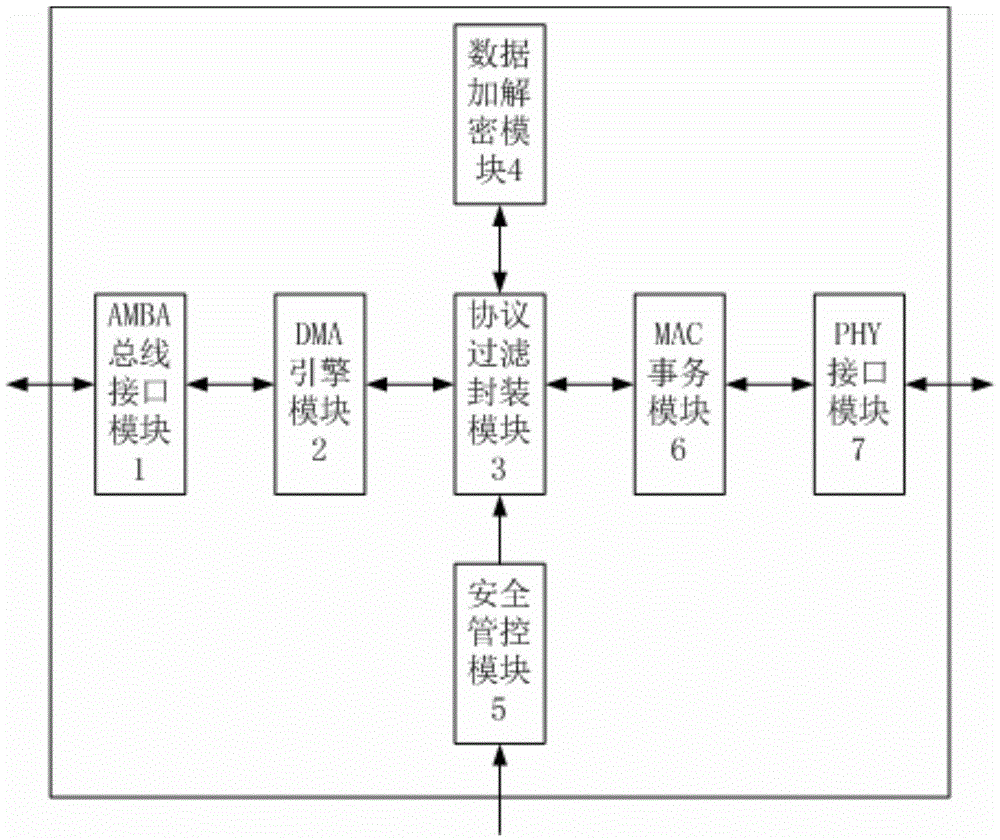
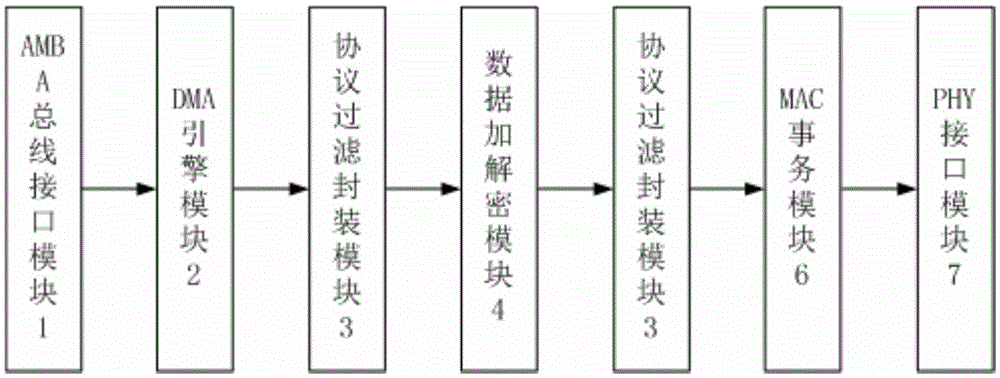
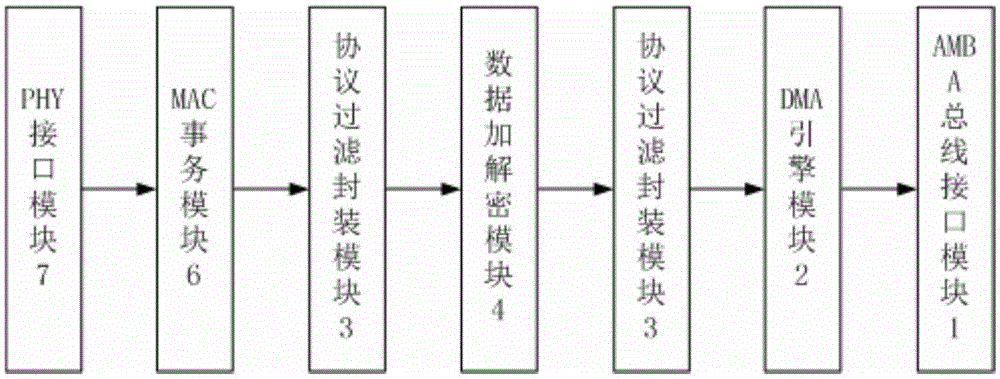
The invention provides an Ethernet controller security enhancement design method. An Ethernet controller performs the following operations in an encryption and decryption mode: carrying out control flow and data flow communication with an external host system through an AMBA bus interface module; realizing transmission of data used for access configuration of different buses in the sending and receiving directions through a DMA engine module; parsing and filtering Ethernet frame data in the sending and receiving directions through a protocol filtering and encapsulating module; sending link layer or network layer protocol data needing encryption and decryption to a data encryption and decryption module, and re-encapsulating the returned data; using a hardware algorithm to process the data through the data encryption and decryption module; sending and receiving data buffer through an MAC transaction module; and carrying out data communication with an external PHY chip through a PHY interface module.
Owner:JIANGNAN INST OF COMPUTING TECH
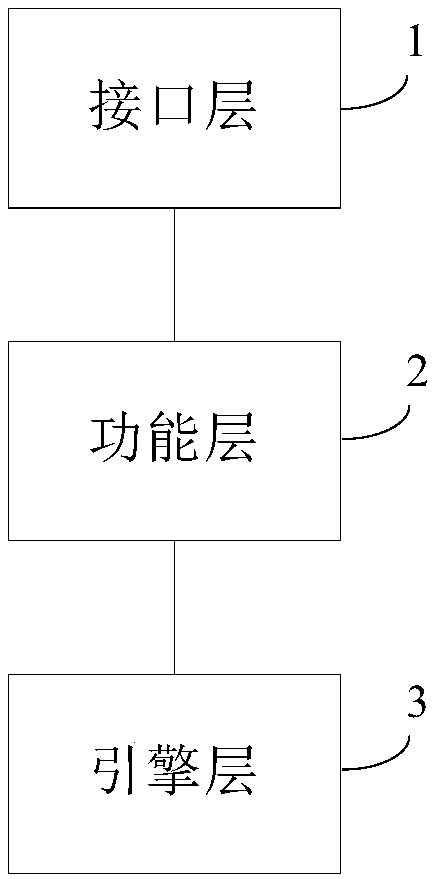
A security network middleware for identity authentication, and a method and apparatus for implementing the same
ActiveCN109492359APrevent Malicious UsePrevent theftDigital data protectionDigital data authenticationCheck markThird party
The invention discloses a security network middleware for identity authentication, a method and apparatus for implementing the same. The middleware comprises an interface layer, a function layer and an engine layer. The interface layer is located on top of the function layer and is used for providing a channel for the client to call the middleware. The function layer is located on top of the engine layer, and is used for providing service interface to the interface layer, and is responsible for service realization of the middleware. The service includes signature, check mark, encryption and decryption. The engine layer comprises a national secret algorithm engine, an OpenSSL algorithm engine and a hardware algorithm engine. The middleware of the application is a front terminal of the authentication platform for collecting user information, which provides protection for safely collecting user identity information and avoids malicious use of the user identity information after the third-party network application collects the user identity information. At the same time, the user identity information is avoided to be stolen in the transmission process from the client to the authentication platform and from the authentication platform to the third-party network application.
Owner:北京庚金科技有限公司
Bus monitor for enhancing SOC system security and realization method thereof
InactiveUS8601536B2Improve information securityEffective expansionMemory loss protectionError detection/correctionClassified informationData selection
The present invention discloses a bus monitor for enhancing SOC system security and a realization method thereof. The bus monitor disposed between a system bus and a system control unit includes a configuration unit, a condition judgment unit, an effective data selection unit, a hardware algorithm unit and a comparative output unit. Without affecting the bus access efficiency, the present invention provides the method capable of immediately monitoring the bus behavior, and the detection system notices whether a particular bus access serial behavior is changed due to an accidental fault or intentional attacking fault. If the particular bus access serial behavior is changed, the present invention warns the system to adopt a suitable security measure to prevent the security hidden trouble and leakage of classified information due to the incorrect system security process.
Owner:SHENZHEN STATE MICRO TECH CO LTD
Method for manufacturing and verifying offline burning mirror image of NAND memory
ActiveCN111966369ARealize one-click generationImprove programming efficiencyRedundant data error correctionSoftware deploymentComputer hardwareEngineering
The invention provides a method for manufacturing and verifying an offline burning mirror image of an NAND memory. The invention relates to the technical field of vehicle-mounted storage equipment. Corresponding software processing is carried out on different partitions of a finally generated mirror image, and therefore one-key generation of an offline mirror image can be realized; once an original mirror image is input, software can automatically generate an offline mirror image file according to the actual partition configuration of the Nandflash; in this way, mirror image generation completely does not depend on operation of a Nandflash controller and a Nandflash corresponding file system. The mirror image programming of the Nandflash can be realized without electrifying a machine; theburning efficiency of a production line is greatly improved; through a software simulation hardware algorithm and improvement of an existing file system offline mirror image manufacturing tool, full automation of offline mirror image manufacturing is achieved, one-time offline programming is conducted through a programmer, a mirror image verification mechanism is added, and the correctness of an offline mirror image is verified through a method of reading back the offline mirror image and comparing source data.
Owner:YANFENG VISTEON ELECTRONICS TECH NANJING
Hardware algorithm model construction method based on SysML
ActiveCN112395818AImprove efficiencyThe implementation method is simpleCAD circuit designSpecial data processing applicationsAlgorithmTransformation of text
The invention discloses a hardware algorithm model construction method based on SysML, and relates to the technical field of modeling simulation. The method comprises the following steps: establishinga module definition graph and an internal module graph of a hardware algorithm through SysML; storing the module definition graph and the internal module graph as a first text, and determining corresponding relationships between the module definition graph and the first text and between the internal module graph and the first text; extracting a first text by using a KMP algorithm and determininga mapping rule of the first text and the VHDL meta-model; and calling the VHDL meta-model, and converting the first text into a second text of the VHDL language according to the mapping rule. According to the method, the model is converted into the VHDL language for hardware algorithm model construction, the hardware modeling efficiency is improved, the problem that various models are difficult tounify in the complex product modeling process is solved, and the method is simple, convenient and easy to implement.
Owner:BEIJING INFORMATION SCI & TECH UNIV
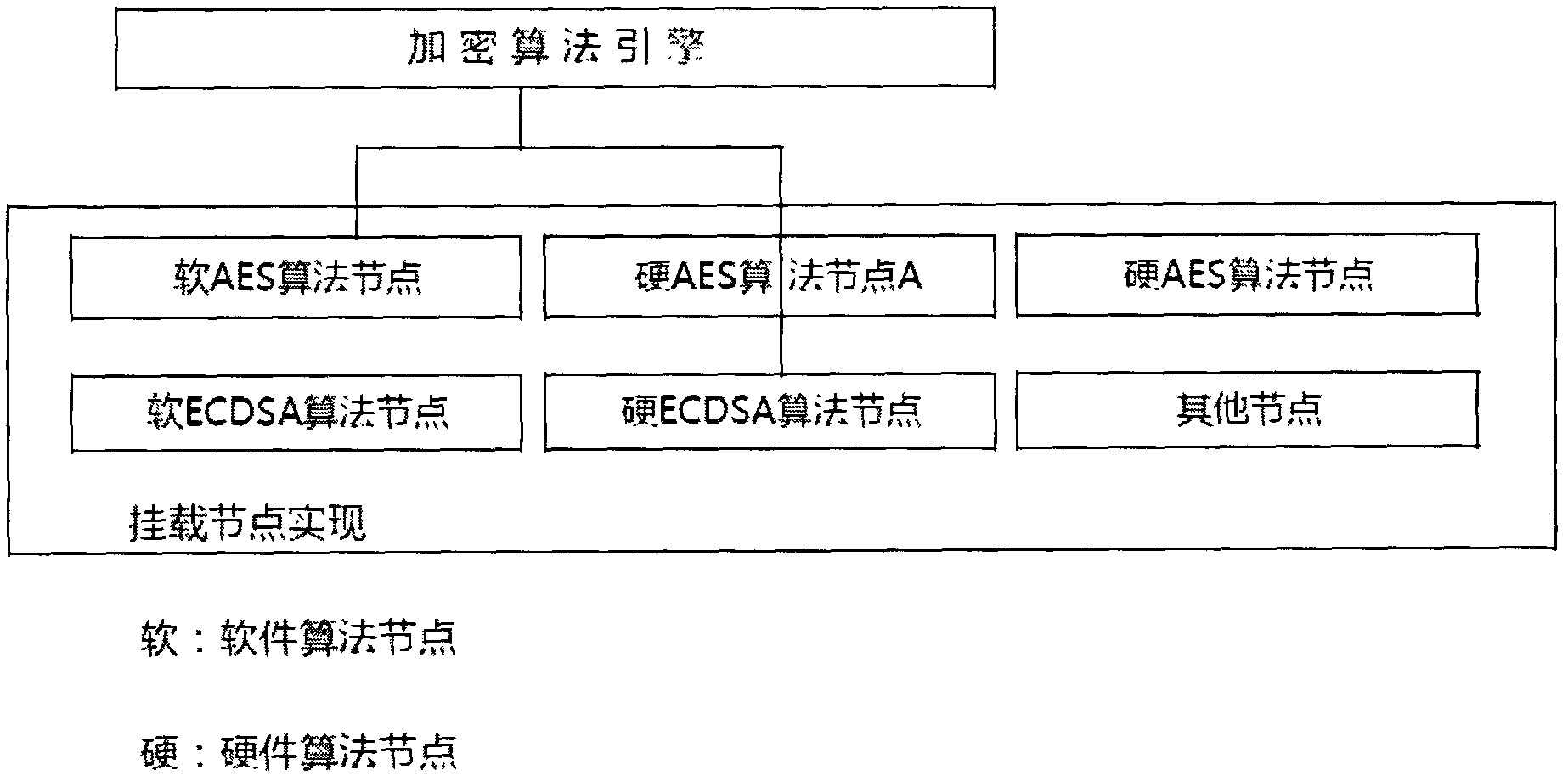
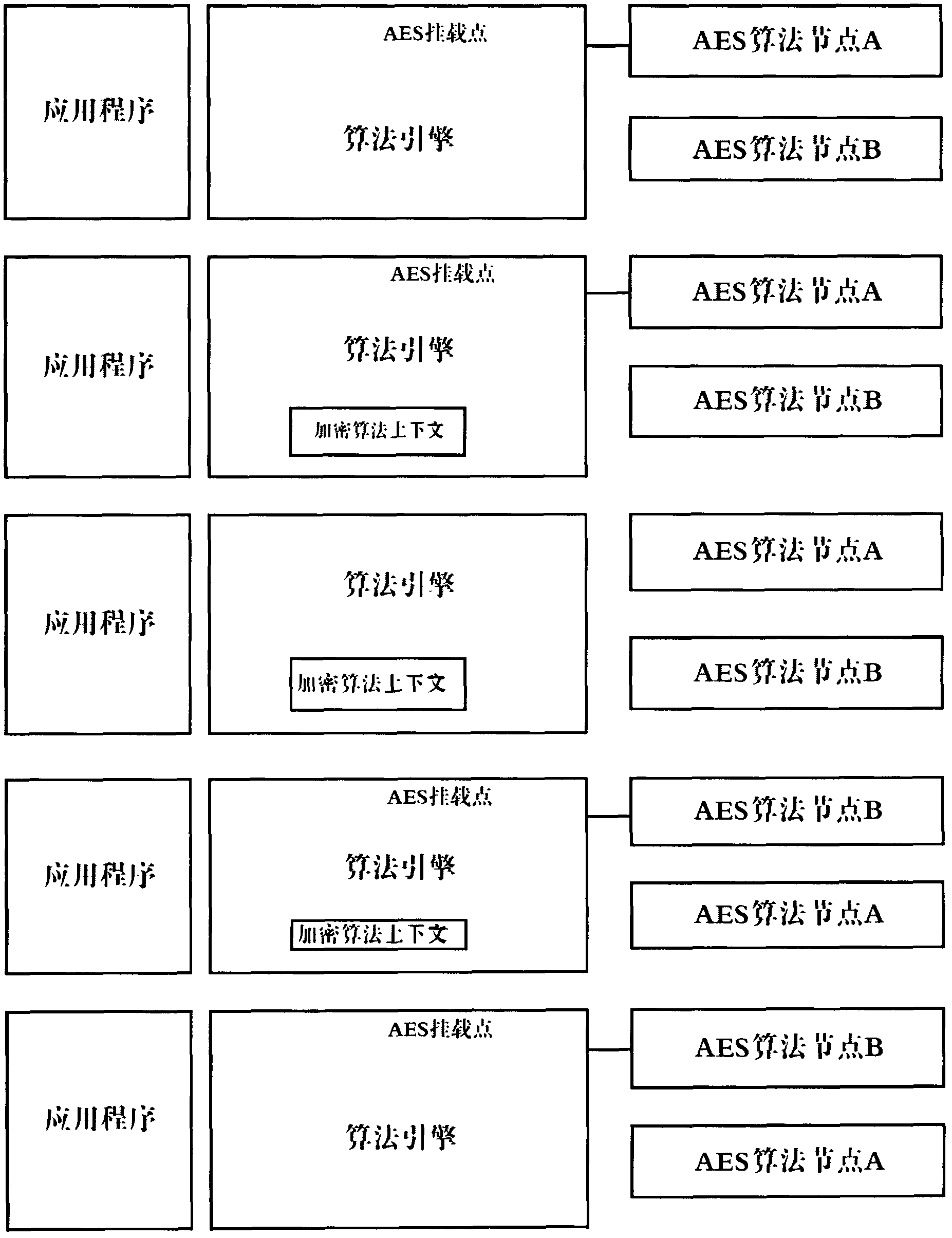
Hanging type encryption algorithm engine system and use method thereof
InactiveCN102426636AImprove service qualityImprove mean time between failuresPlatform integrity maintainanceComputer hardwareSystem maintenance
The invention provides a hanging type encryption algorithm engine system, which comprises a plurality of encryption algorithm nodes complying with a same interface definition and is characterized in that the algorithm nodes can be dynamically switched by a hanging type encryption algorithm engine; the hanging type encryption algorithm engine comprises a plurality of nodes of a uniform algorithm; and the encryption algorithm nodes are hung into the engine system through a uniform packaging interface. The hanging type encryption algorithm engine system has the beneficial effects that: 1) the resistance for bypass attack is combined with a traditional resisting mode and the effect is better; 2) the service quality of equipment is promoted, the continuous usage of the equipment is ensured, an average fault interval of the equipment is greatly increased, and the system diagnosis can be performed when the following system maintenance is carried out; 3) the developing efficiency is increased; and 4) the portability of a program is increased, and a new hardware algorithm node can be supported in the manner of slightly modifying and configuring an algorithm engine part.
Owner:绚视软件科技(上海)有限公司
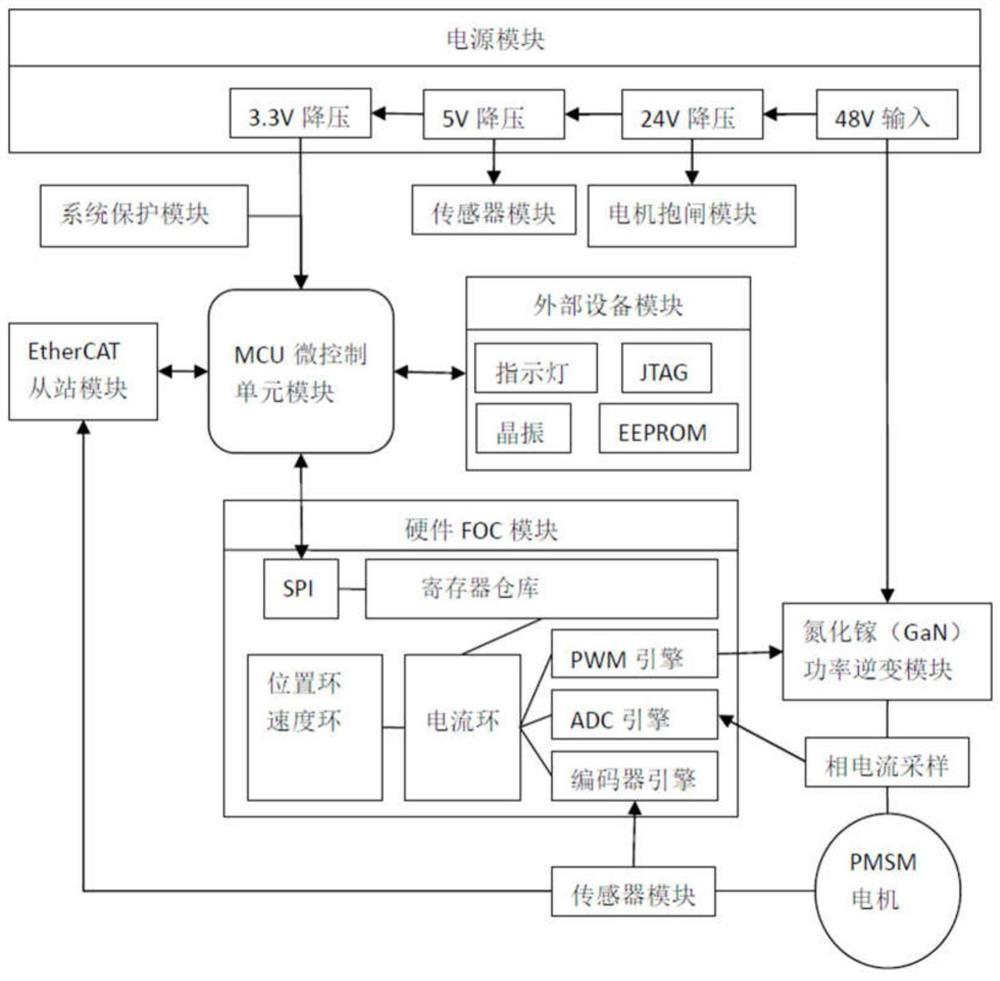
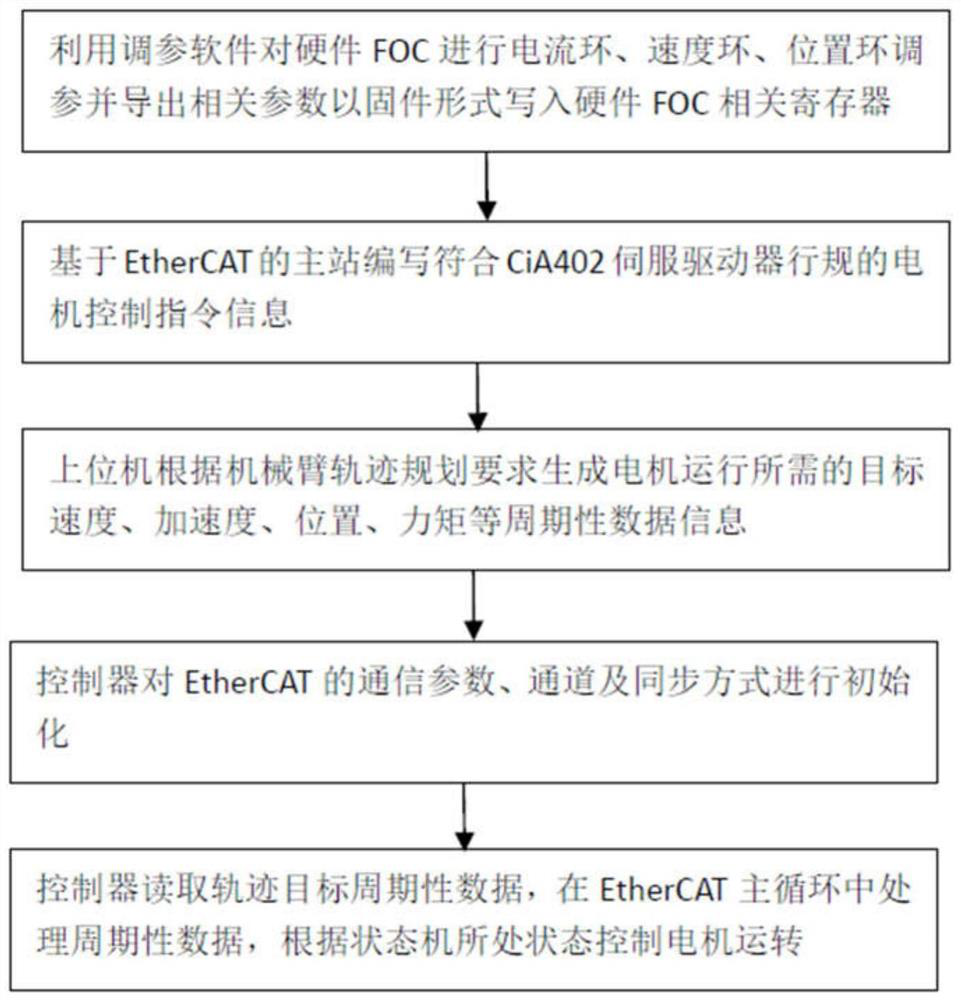
Cooperative robot driver based on EtherCAT, hardware FOC and gallium nitride power tube and control method
PendingCN114865958AIncrease pressureGuaranteed uptimeSingle motor speed/torque controlEmergency protective circuit arrangementsMicrocontrollerHemt circuits
The invention discloses a collaborative robot driver based on EtherCAT, hardware FOC and a gallium nitride power transistor and a control method. The driver comprises an MCU microcontroller unit module, an EtherCAT slave station module, a hardware FOC module, a gallium nitride power inversion module, a sensor module, a system protection module, a motor band-type brake module, a power supply module and an external equipment module which are connected with one another. Wherein the MCU microcontroller unit module comprises a minimum peripheral circuit and is responsible for EtherCAT protocol stack processing and hardware FOC related register configuration. The hardware FOC module is responsible for hardware execution of a current loop, a speed loop and a position loop. According to the invention, a highly integrated hardware FOC algorithm and a gallium nitride (GaN) power transistor are adopted, and an EtherCAT bus is adopted to carry out data communication, so that the driver layout space is smaller, the energy consumption is lower, the real-time performance is better, the communication rate is higher, and the inversion efficiency and the precision stability are also higher.
Owner:浙江环动机器人关节科技股份有限公司
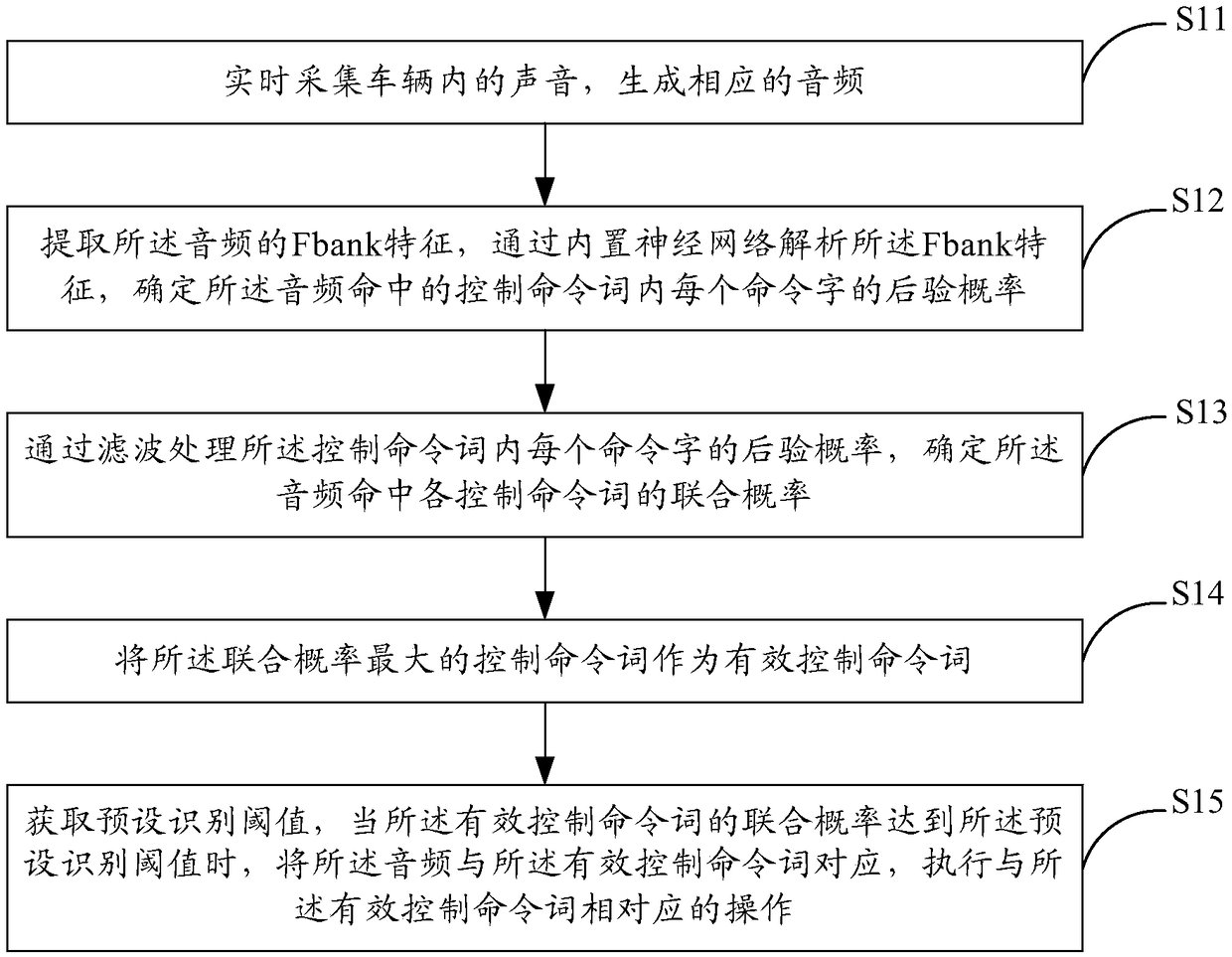
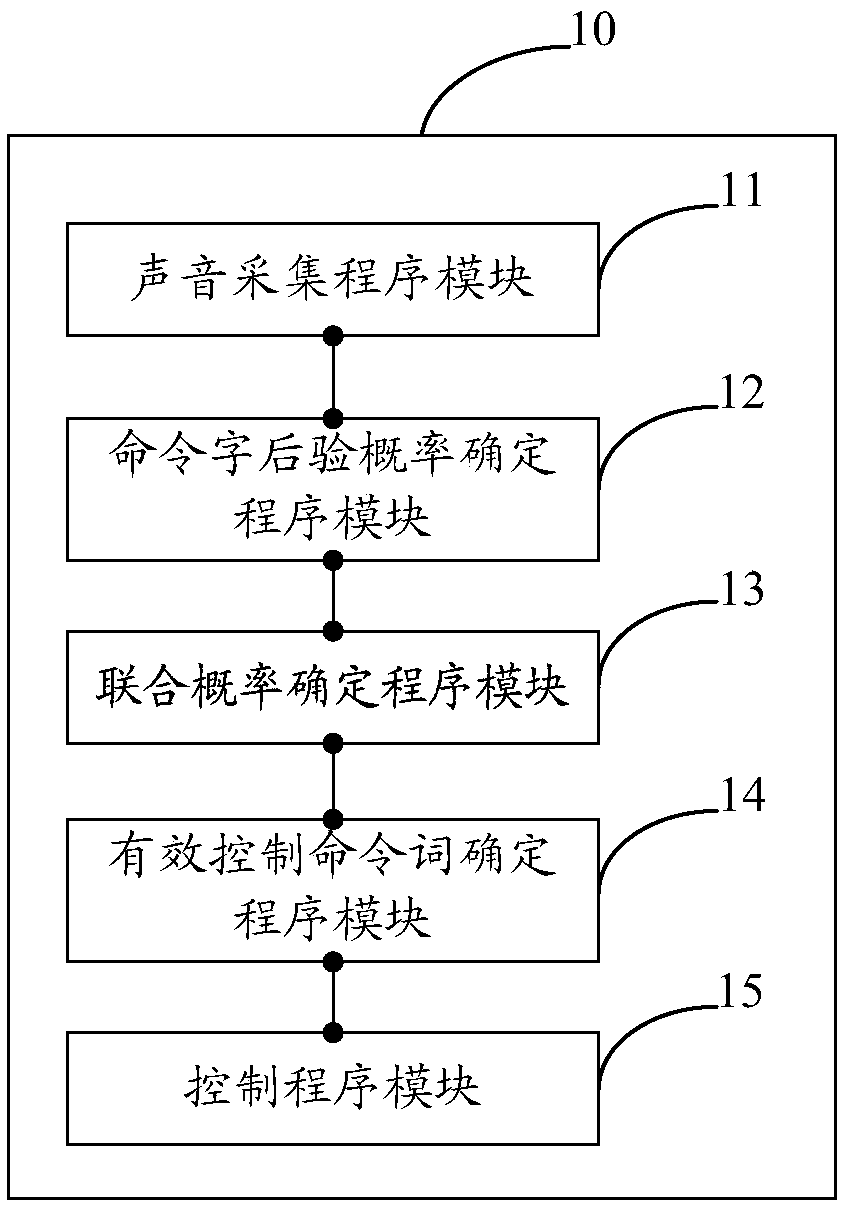
Voice control method and system for traffic recorder
An embodiment of the present invention provides a voice control method for a traffic recorder. The method comprises the following steps of: collecting sound in a vehicle in real time to generate corresponding audio; the Fbank feature of audio is extracted, and the Fbank feature is analyzed by built-in neural network to determine the posterior probability of each command word in the control commandword hit by audio. The posterior probability of each command word in the control command word is filtered to determine the joint probability of hitting each control command word. The control commandword with the highest joint probability is regarded as the effective control command word. When the joint probability of the effective control command word reaches the preset recognition threshold, the audio is associated with the effective control command word, and an operation corresponding to the effective control command word is performed. Embodiments of the present invention also provide a voice control system for a traffic recorder. The embodiment of the invention reduces the computation amount by extracting the Fbank characteristics of the collected audio, and saves the occupation of the memory and the hardware algorithm because the decoding is not performed.
Owner:AISPEECH CO LTD
Soft and hard synergic dynamic load storage method
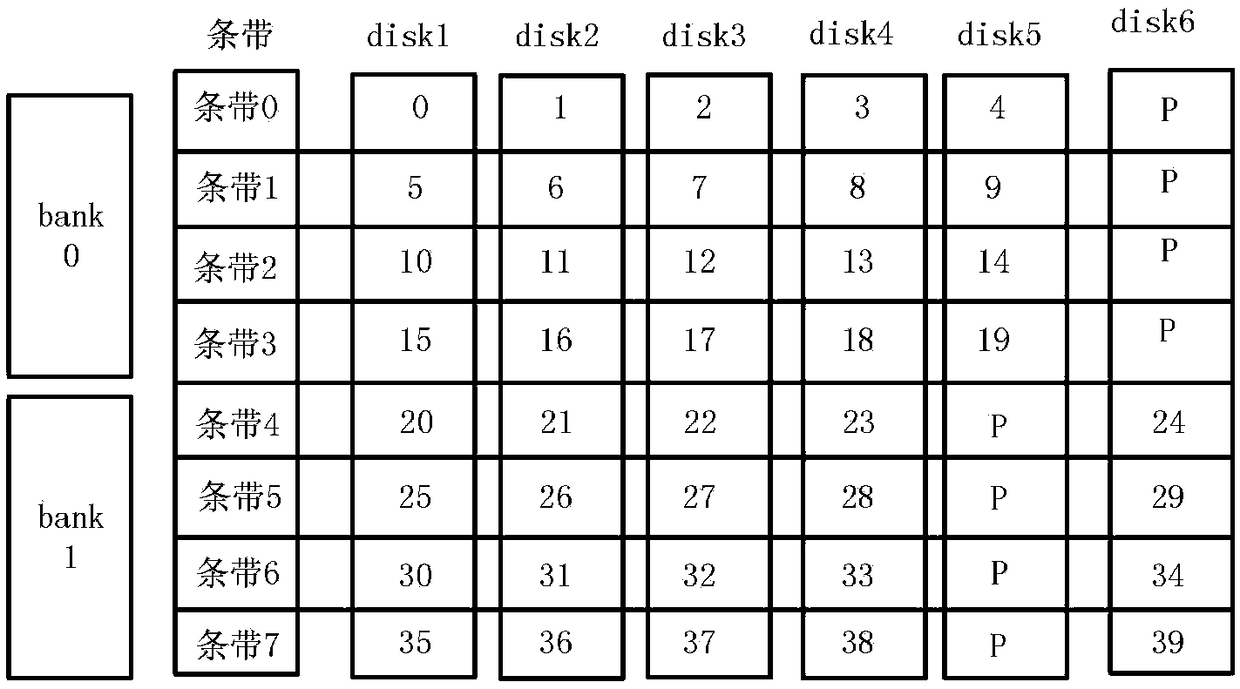
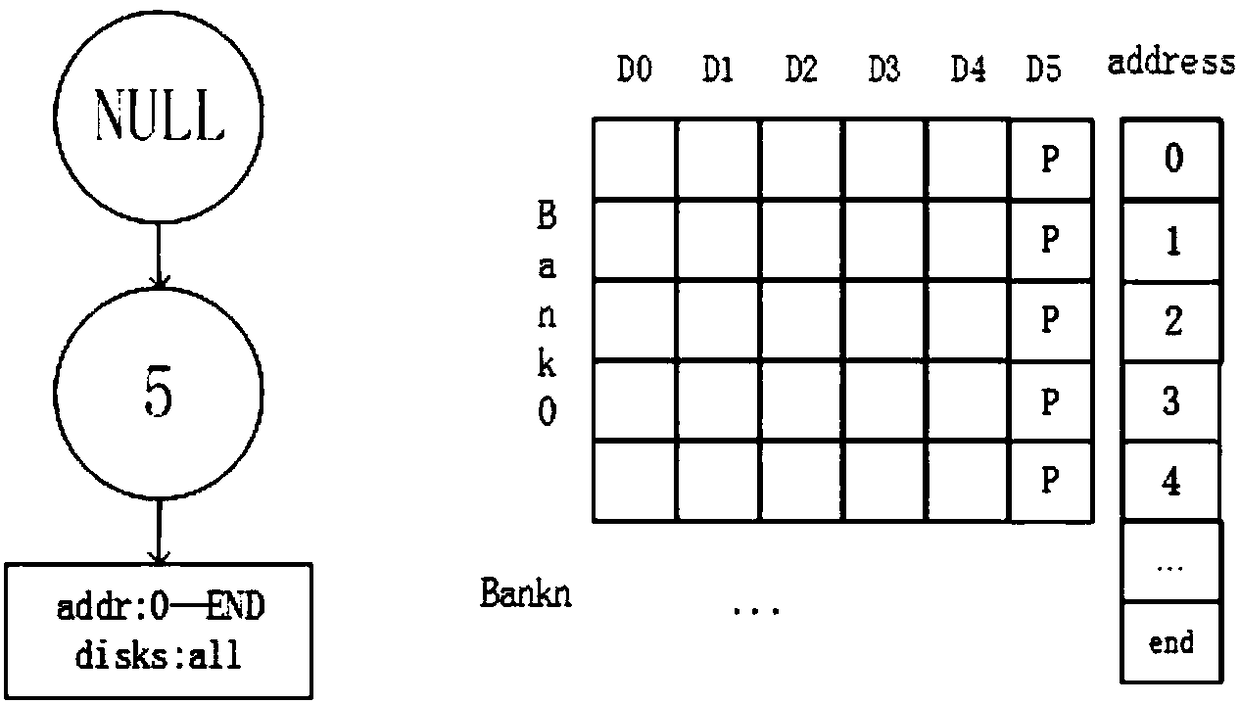
ActiveCN108920101AReduce energy consumptionReduce cooling costsInput/output to record carriersRAIDDisk layout
The invention discloses a soft and hard synergic dynamic load storage method. The method comprises the steps of adopting a cold and hot tree in a data disk layout for recording disk strips, and dynamically allocating the disk strips. The energy is saved on the condition that the requirement for data transmission bandwidth is met, the xor computing part which is originally conducted through a CPU is achieved through an FPGA hardware algorithm, and the method is very suitable for a large-sized storage system for dynamic load change. According to the method, a novel disk layout mode is adopted and combined with hardware to be in charge of dynamic storage in the software and hardware combination mode, an opened disk is more reasonably utilized, the extra energy consumption brought by conversion of the disk is reduced, the address computing part is achieved through a software algorithm, the xor computing part is achieved through hardware, the disk energy consumption and the CPU resource when the data is stored are reduced, and the performance of an entire RAID storage framework is improved.
Owner:HEBEI UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com