Ethernet controller security enhancement design method
A design method, Ethernet technology, applied in the field of electronic information, can solve problems such as high CPU usage and occupation of system resources, and achieve the effect of not occupying system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the content of the present invention clearer and easier to understand, the content of the present invention will be described in detail below in conjunction with specific embodiments and accompanying drawings.
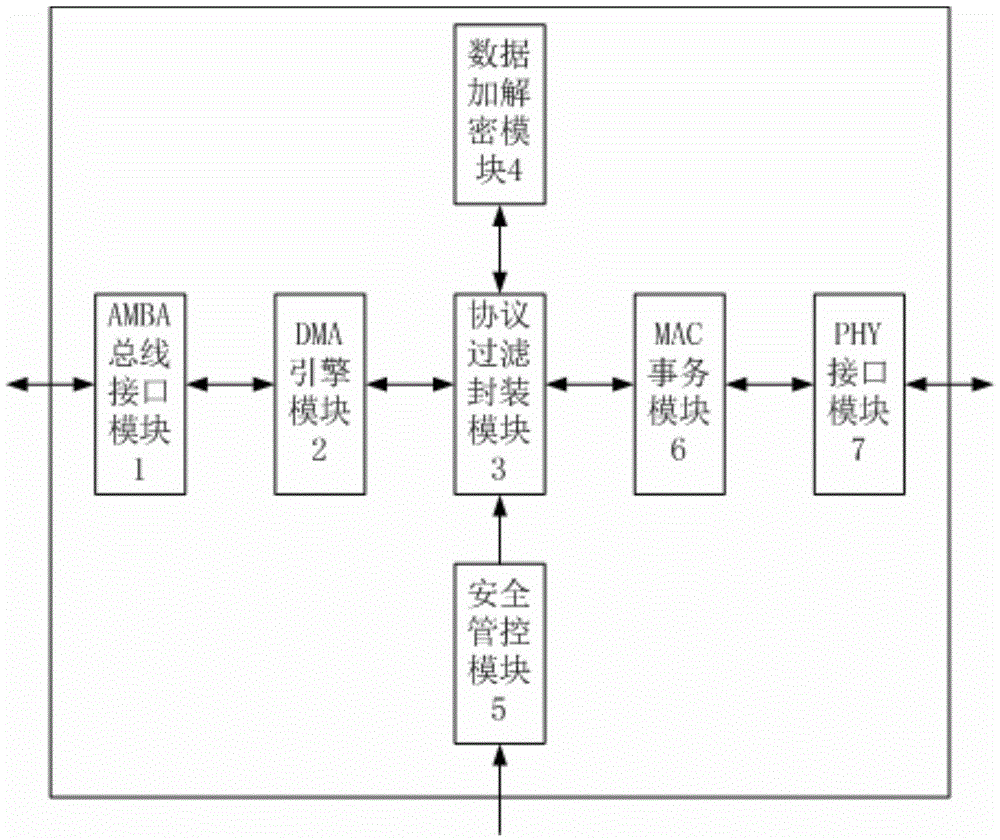
[0027] The working mode of the Ethernet controller is pre-configured through the security control module (for example, the working mode includes normal mode, disabled mode and encryption and decryption mode).
[0028] Wherein, the Ethernet controller does not perform encryption and decryption processing of the network protocol in the normal mode.
[0029] In an example where there is a disabled mode, the Ethernet controller may only support system IO access in the disabled mode and not respond to other configuration operations issued by the system.
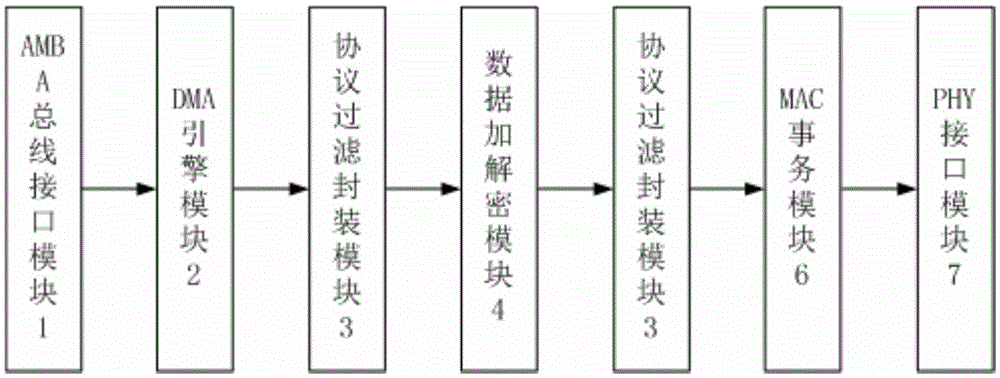
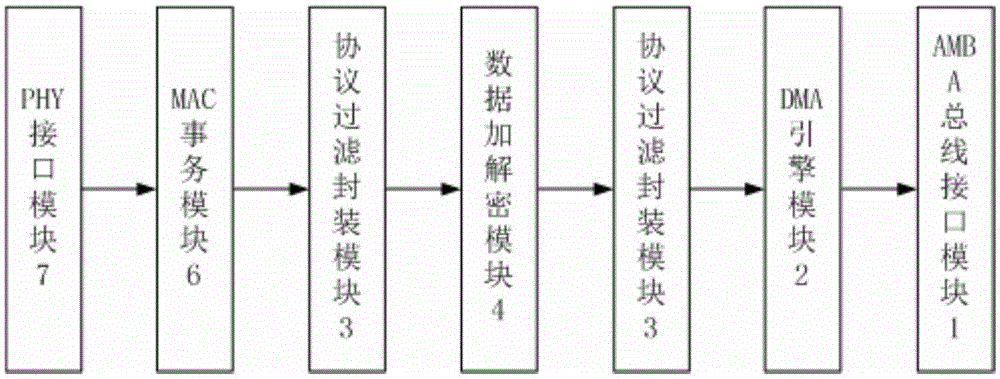
[0030] Moreover, under the encryption and decryption mode, the Ethernet controller carries out control flow and data flow communication with the external host system through the AMBA bus interface m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com