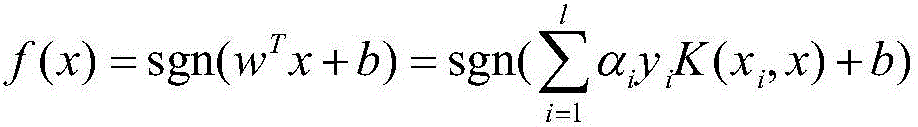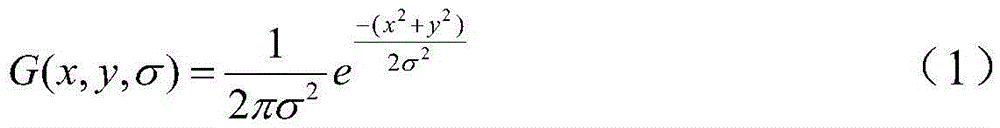Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1110 results about "Similarity matching" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
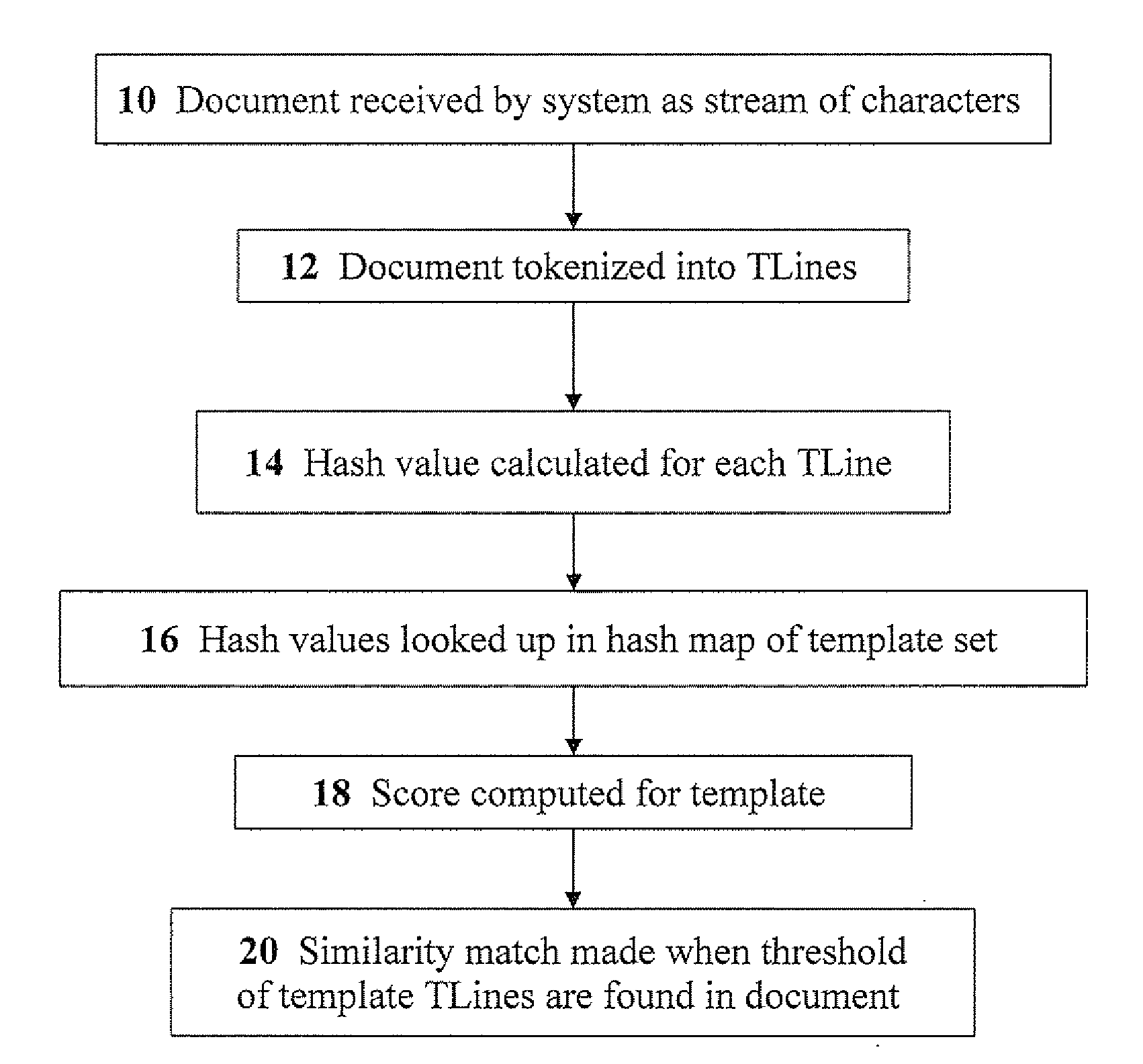
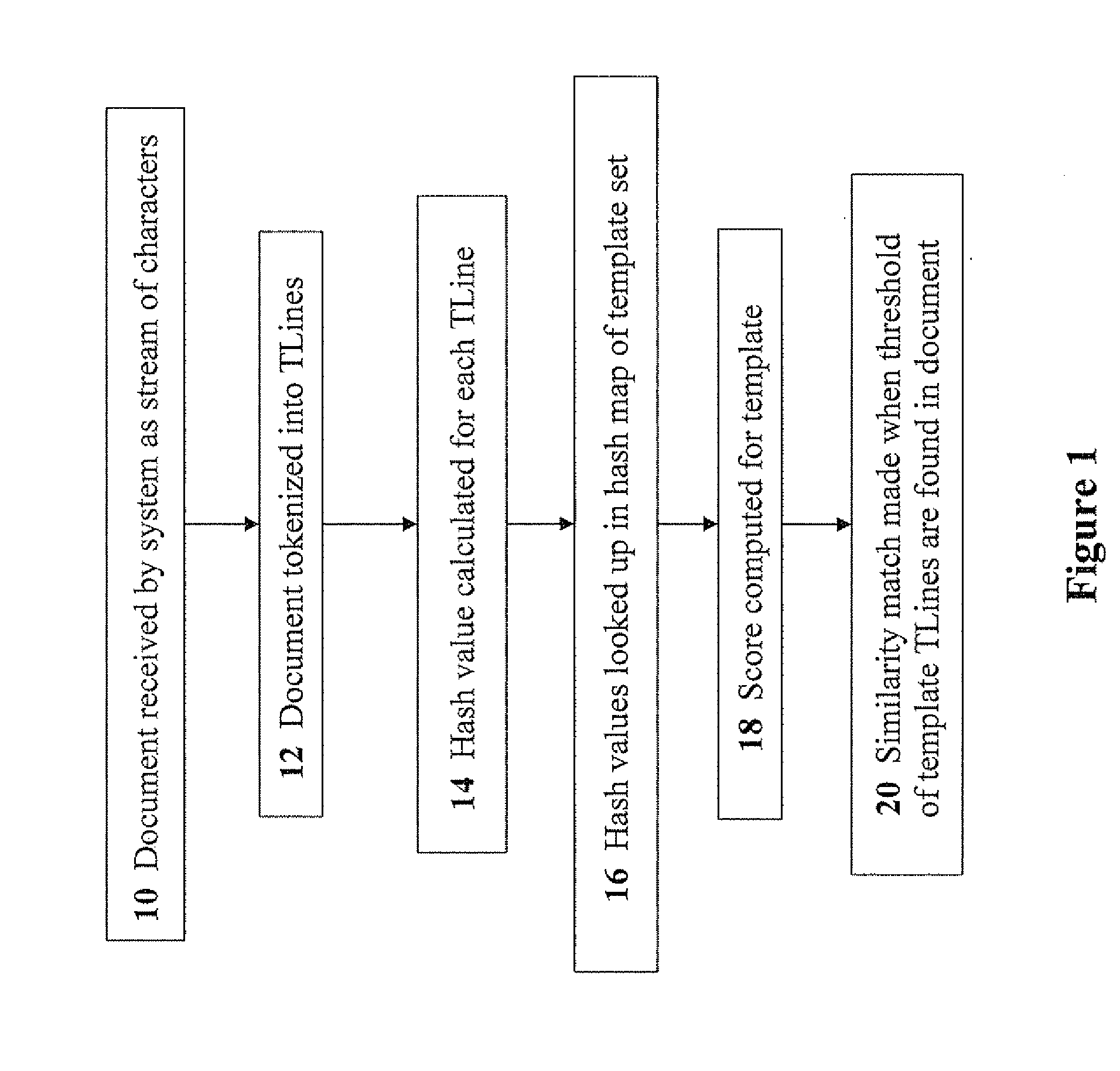
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Similarity matching. a technique for identify conceptual categories. Users are given a set of topics, and they are asked to rate the similarity of pairs of topics (on some scale, e.g. 1 to 10).
Fuzzy hash of behavioral results
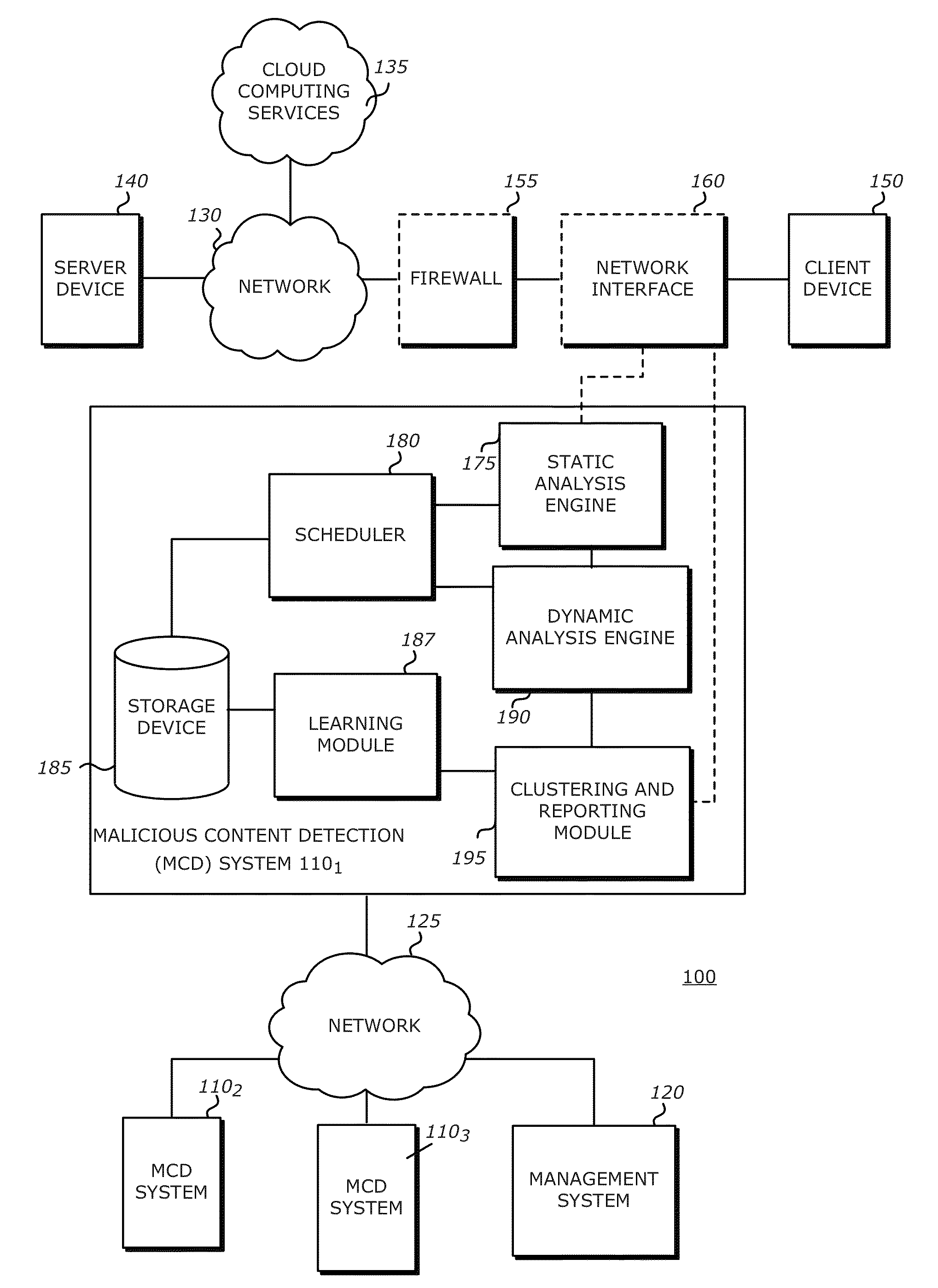
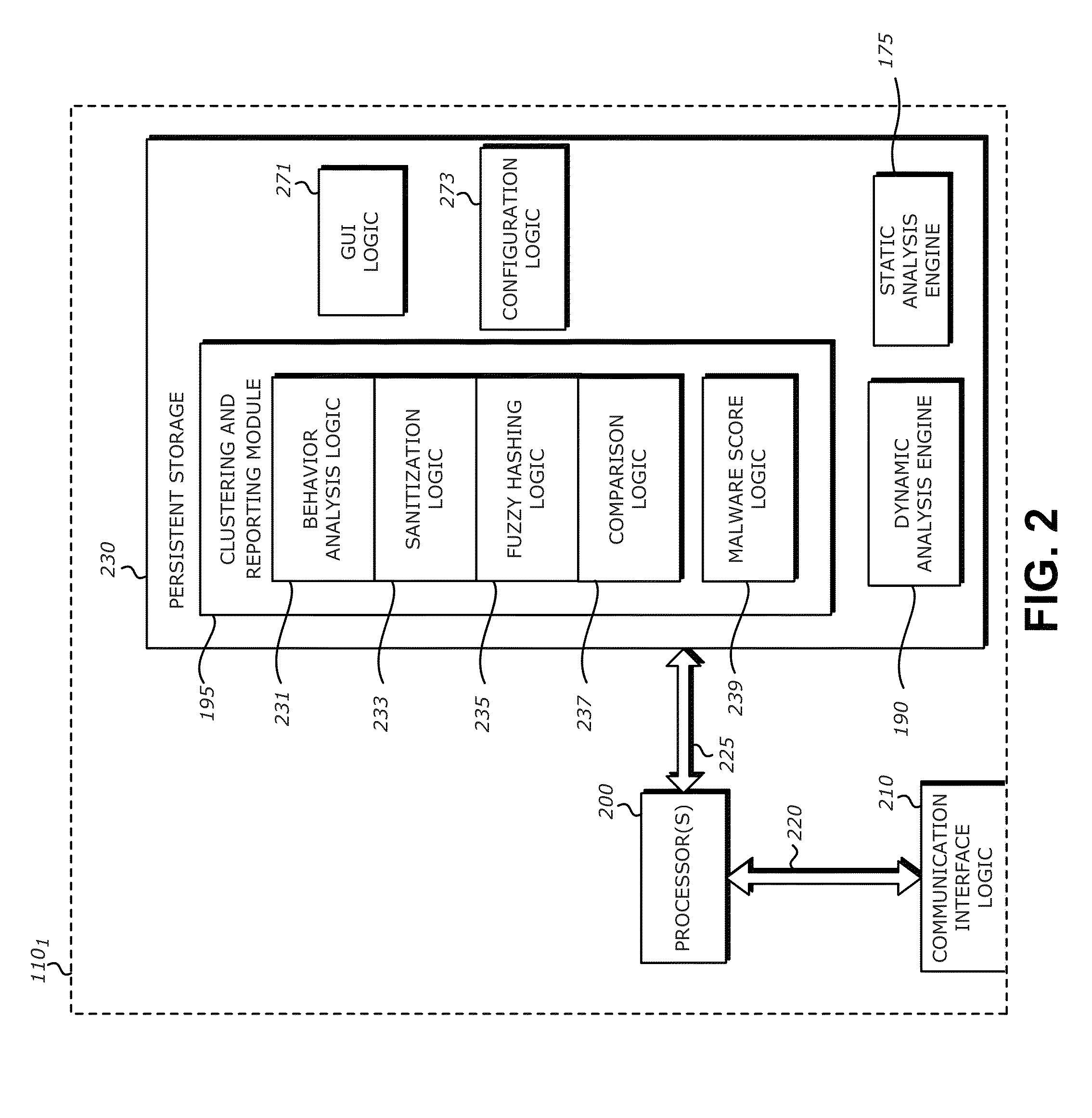
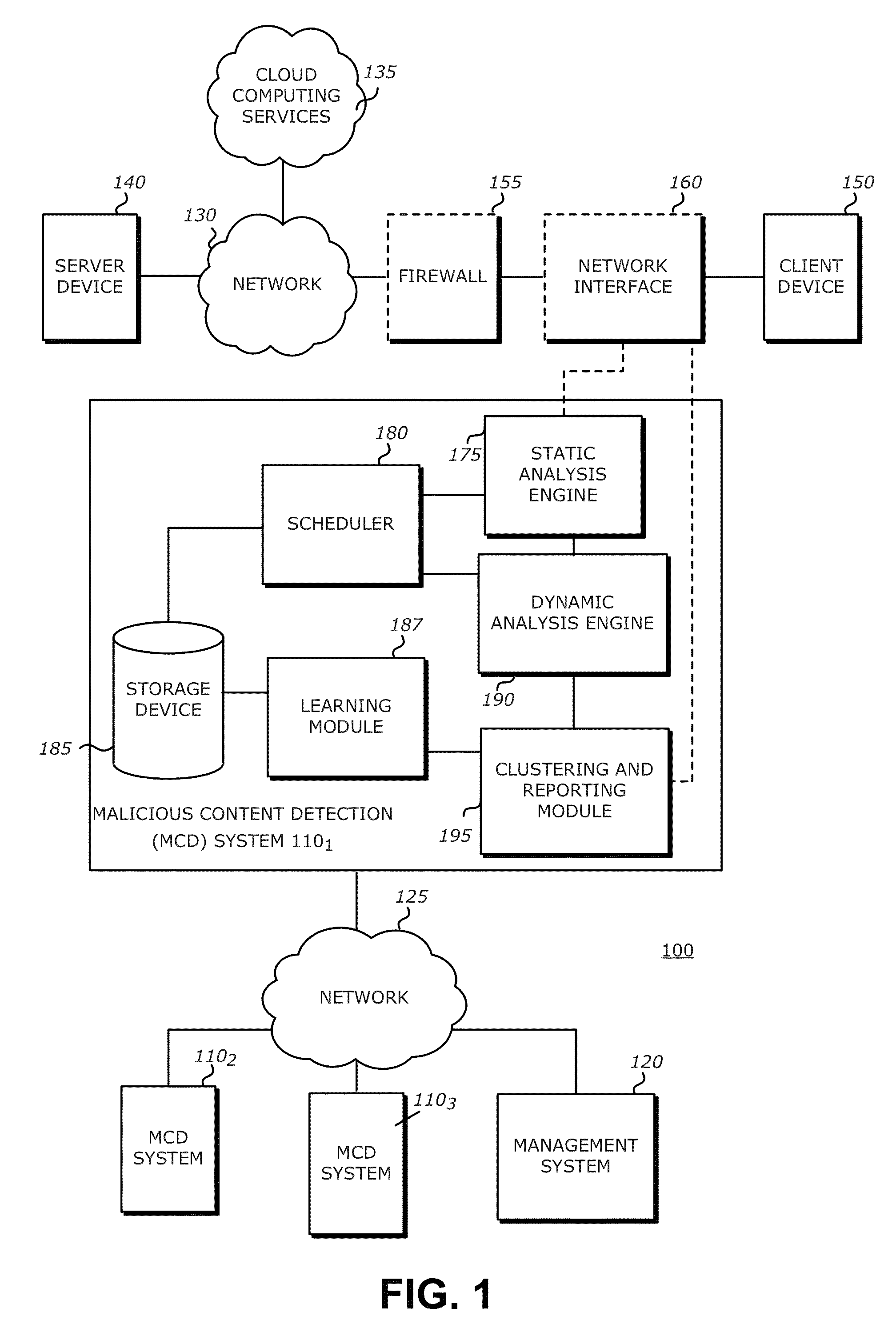
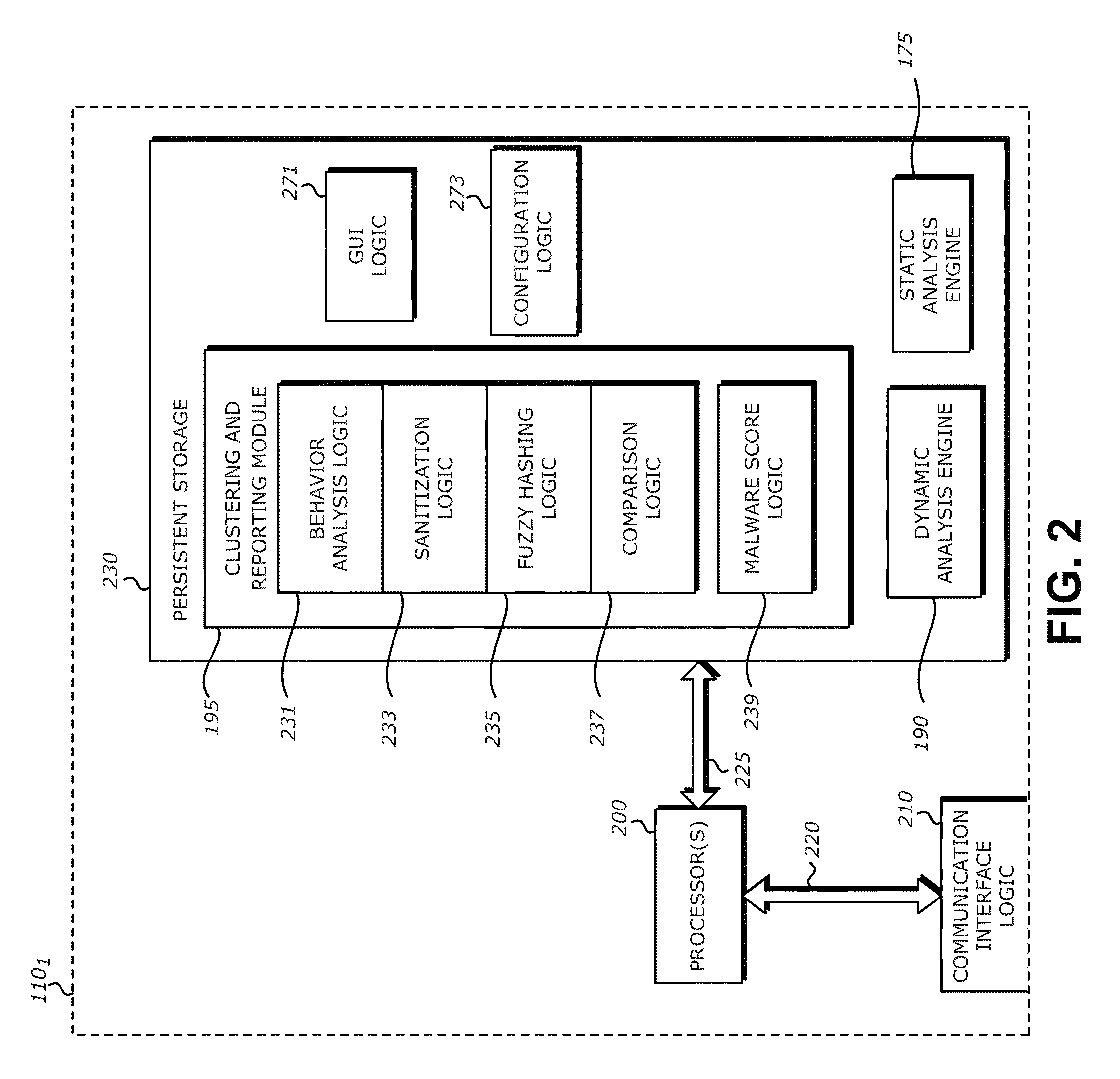
A computerized method is described in which a received object is analyzed by a malicious content detection (MCD) system to determine whether the object is malware or non-malware. The analysis may include the generation of a fuzzy hash based on a collection of behaviors for the received object. The fuzzy hash may be used by the MCD system to determine the similarity of the received object with one or more objects in previously classified / analyzed clusters. Upon detection of a “similar” object, the suspect object may be associated with the cluster and classified based on information attached to the cluster. This similarity matching provides 1) greater flexibility in analyzing potential malware objects, which may share multiple characteristics and behaviors but are also slightly different from previously classified objects and 2) a more efficient technique for classifying / assigning attributes to objects.
Owner:FIREEYE SECURITY HLDG US LLC +1
Fuzzy hash of behavioral results
A computerized method is described in which a received object is analyzed by a malicious content detection (MCD) system to determine whether the object is malware or non-malware. The analysis may include the generation of a fuzzy hash based on a collection of behaviors for the received object. The fuzzy hash may be used by the MCD system to determine the similarity of the received object with one or more objects in previously classified / analyzed clusters. Upon detection of a “similar” object, the suspect object may be associated with the cluster and classified based on information attached to the cluster. This similarity matching provides 1) greater flexibility in analyzing potential malware objects, which may share multiple characteristics and behaviors but are also slightly different from previously classified objects and 2) a more efficient technique for classifying / assigning attributes to objects.
Owner:FIREEYE SECURITY HLDG US LLC +1
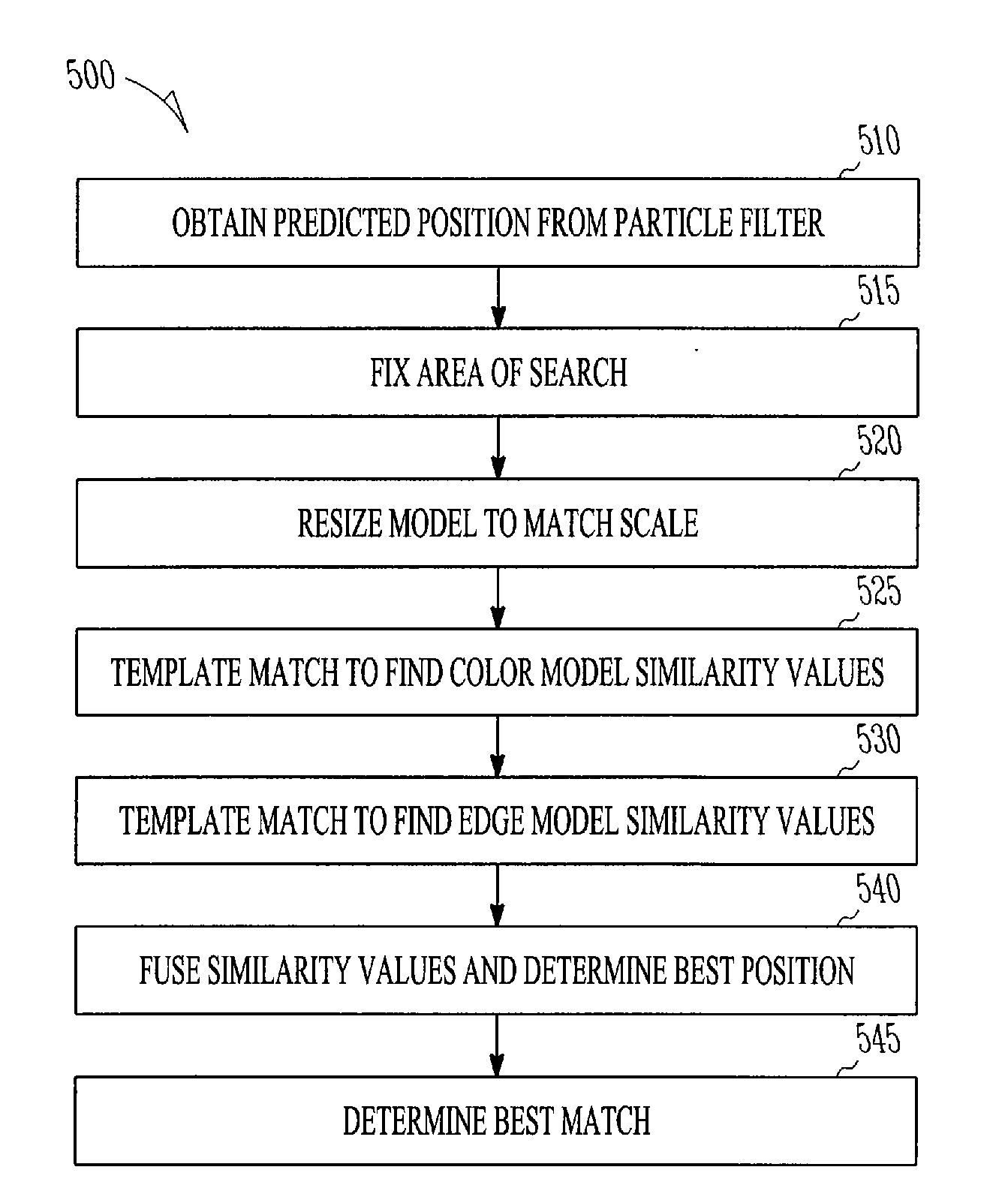
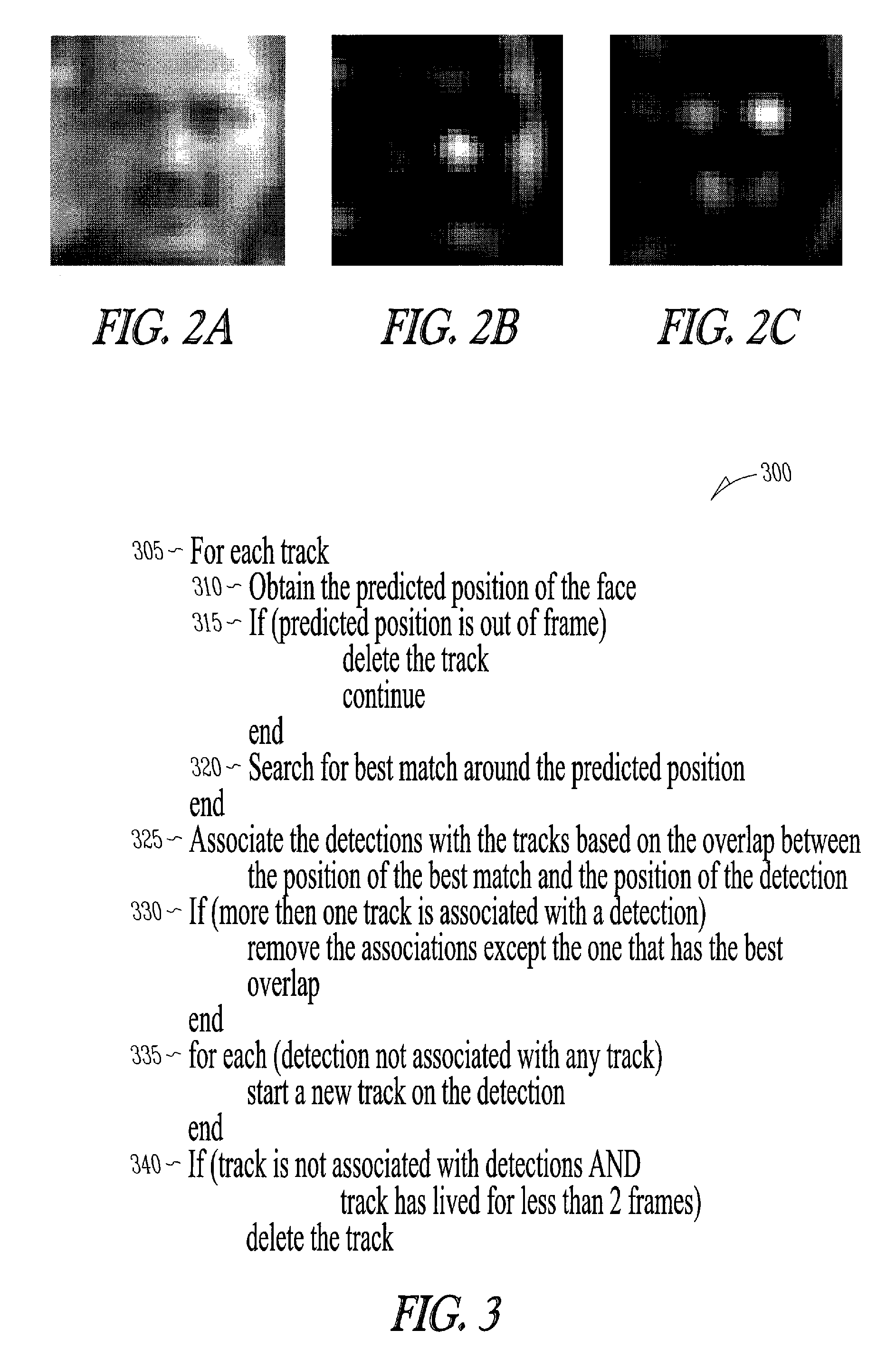
Multi-pose fac tracking using multiple appearance models
A system and method are provided for tracking a face moving through multiple frames of a video sequence. A predicted position of a face in a video frame is obtained. Similarity matching for both a color model and an edge model are performed to derive correlation values for each about the predicted position. The correlation values are then combined to determine a best position and scale match to track a face in the video.
Owner:HONEYWELL INT INC
Human face similarity degree matching method and device
InactiveCN101510257AGood compatibilityCharacter and pattern recognitionFeature dataDegree of similarity
The embodiment of the invention provides a human face similarity matching method which comprises the following steps of: obtaining a first human face image; extracting the feature data of a plurality of key points in the first human face image and a stored second human face image; searching a matched key point in the key points of the second human face image for each key point of the first human face image; calculating the score of the similarity between the key point of the first human face image and the key point of the second human face image matching with the key point of the first human face image; and inosculating each key point of the first human face image with the similarity score of the key point of the second human face image to judge whether the two are matched with each other.
Owner:HUAWEI TECH CO LTD +1
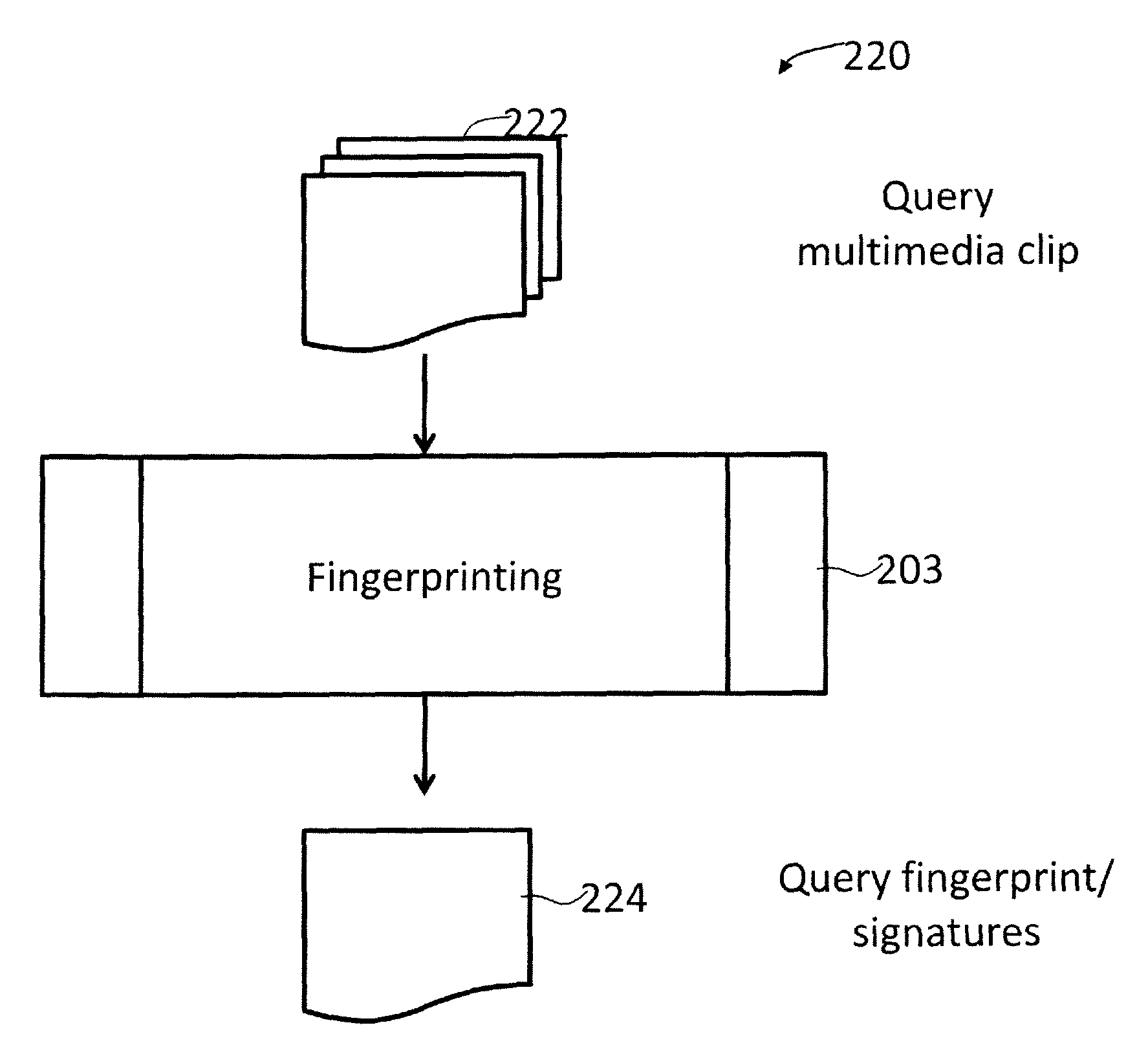
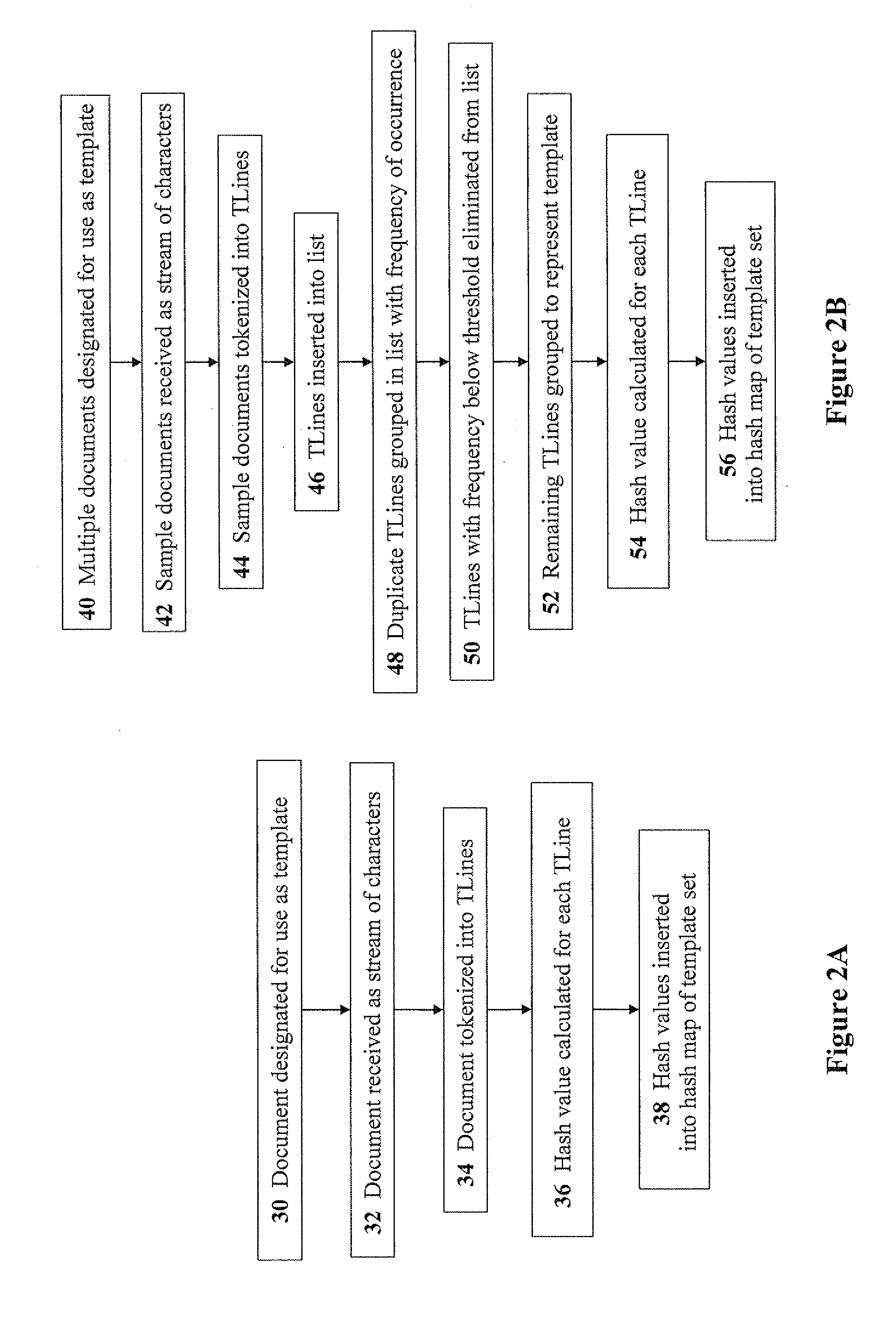
Scalable, adaptable, and manageable system for multimedia identification
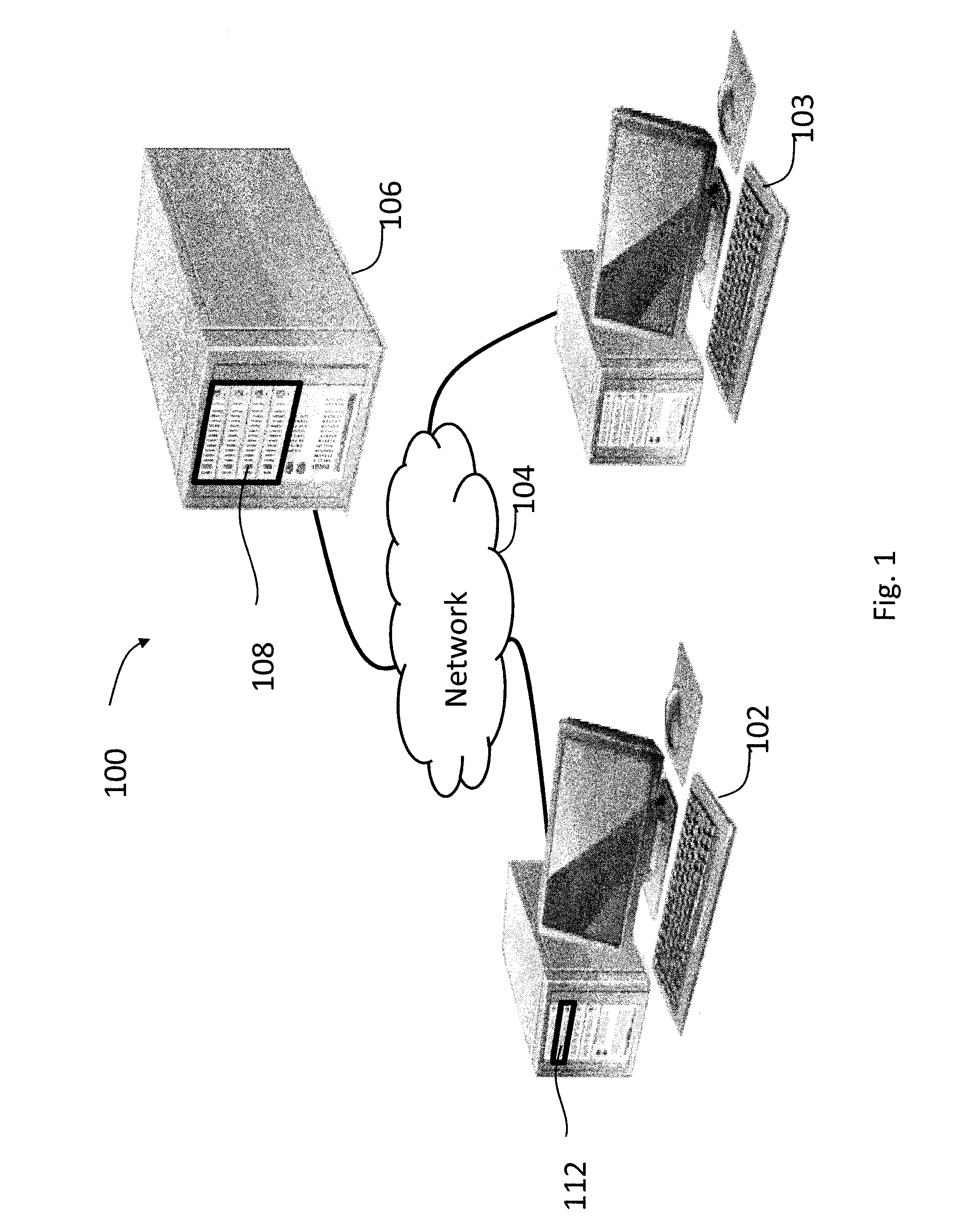
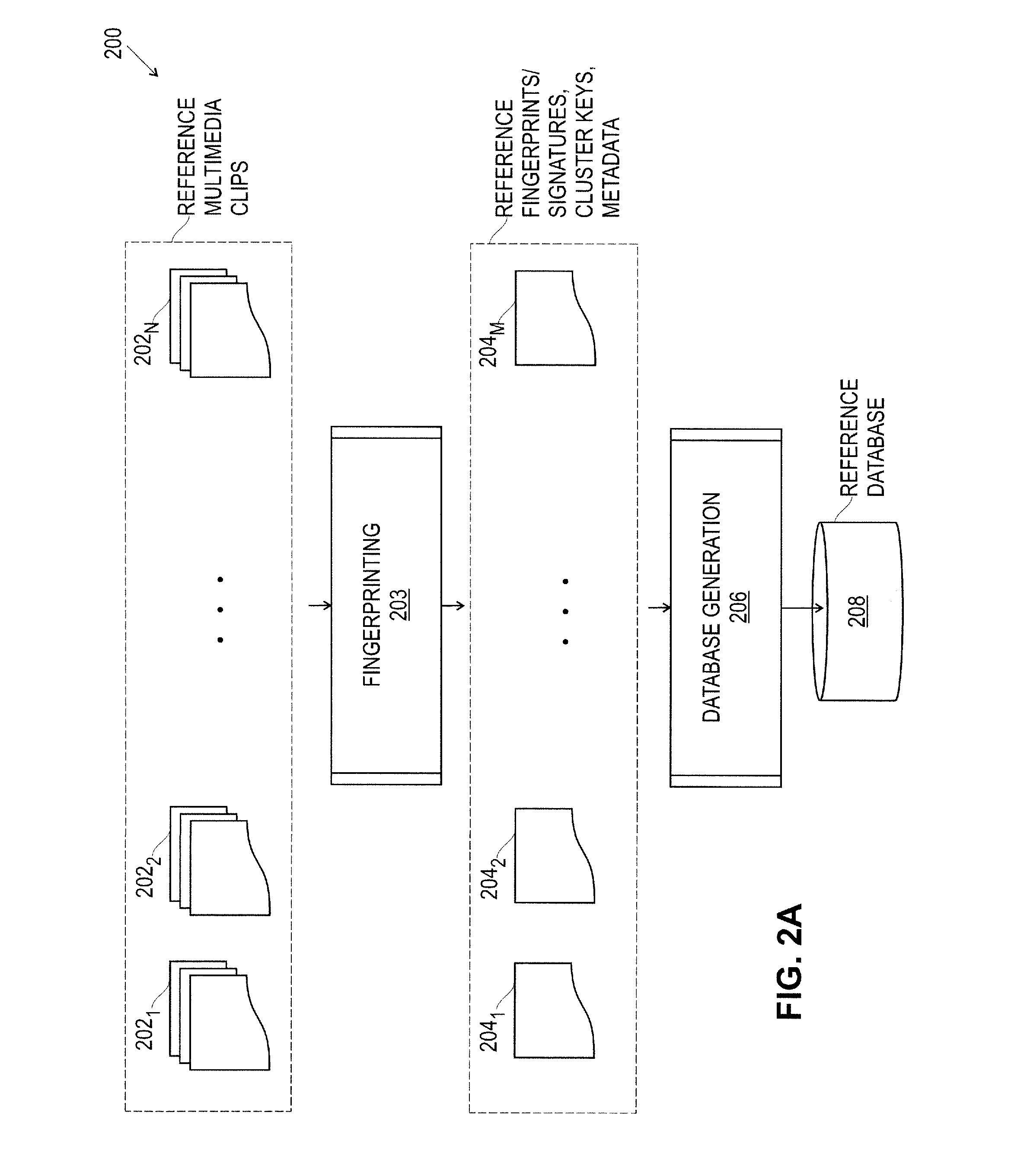
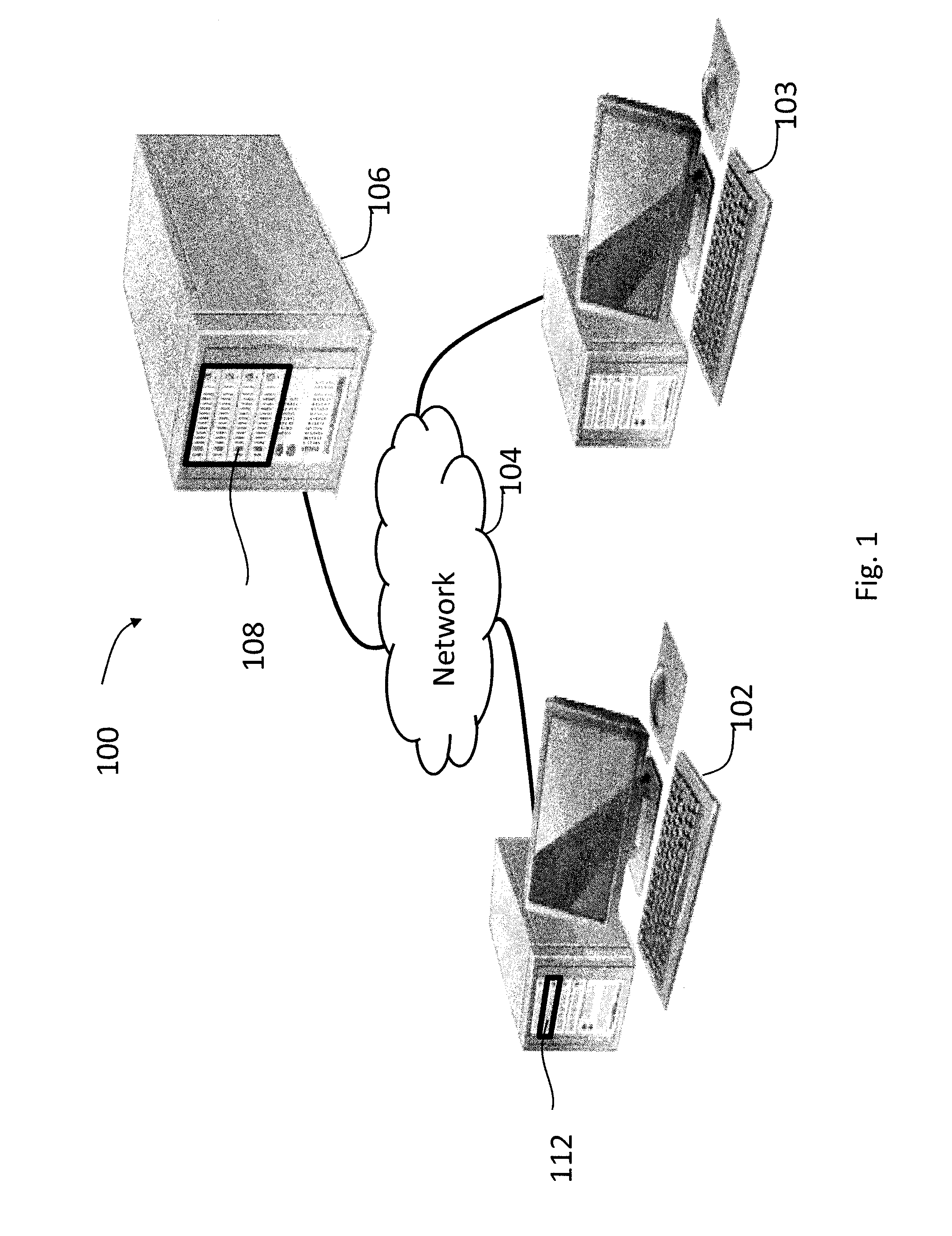
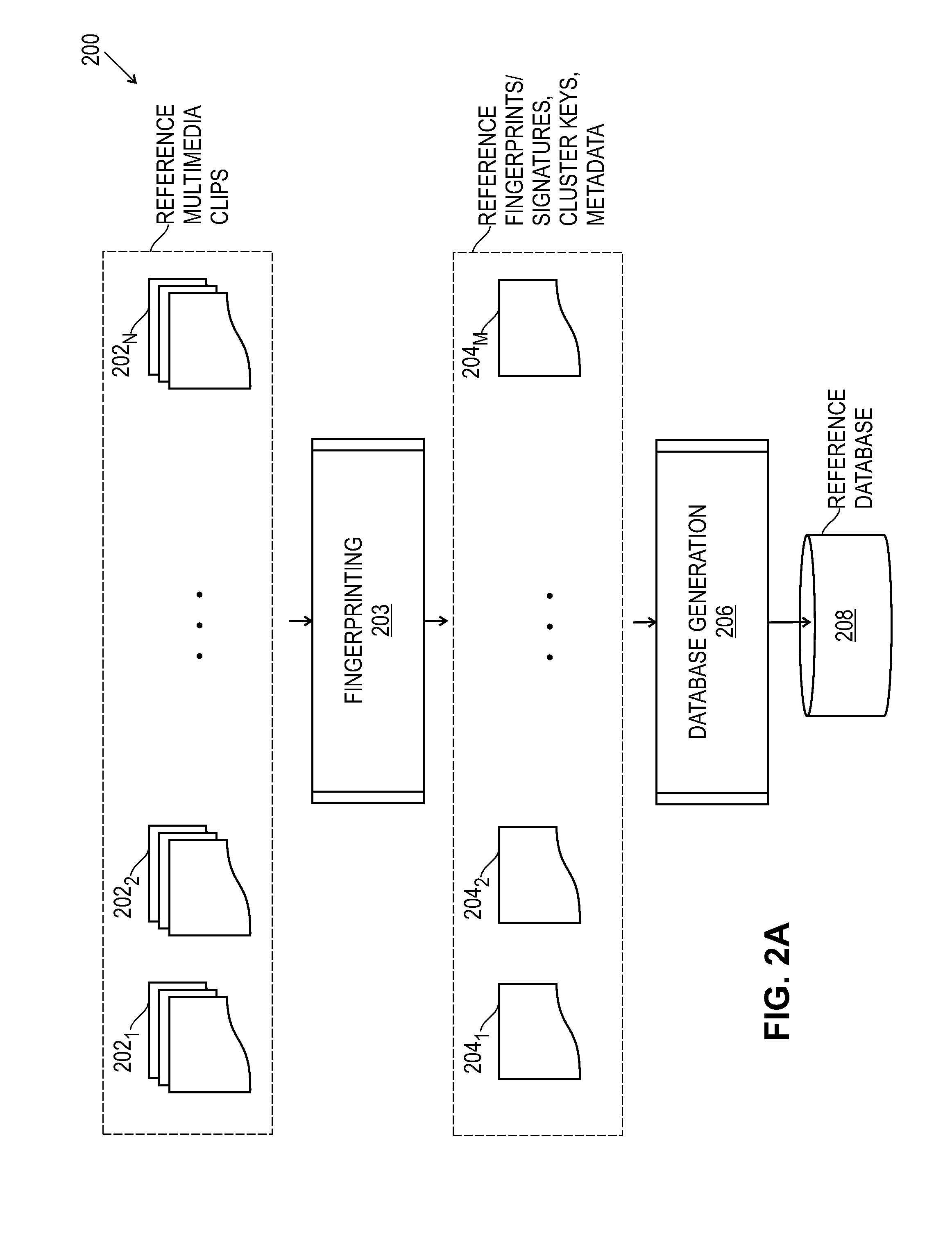
An architecture for a multimedia search system is described. To perform similarity matching of multimedia query frames against reference content, reference database comprising of a cluster index using cluster keys to perform similarity matching and a multimedia index to perform sequence matching is built. Methods to update and maintain the reference database that enables addition and removal of the multimedia contents, including portions of multimedia content, from the reference database in a running system are described. Hierarchical multi-level partitioning methods to organize the reference database are presented. Smart partitioning of the reference multimedia content according to the nature of the multimedia content, and according to the popularity among the social media, that supports scalable fast multimedia identification is also presented. A caching mechanism for multimedia search queries in a centralized or in a decentralized distributed system and a client based local multimedia search system enabling multimedia tracking are described.
Owner:ROKU INCORPORATED
Scalable, Adaptable, and Manageable System for Multimedia Identification
An architecture for a multimedia search system is described. To perform similarity matching of multimedia query frames against reference content, reference database comprising of a cluster index using cluster keys to perform similarity matching and a multimedia index to perform sequence matching is built. Methods to update and maintain the reference database that enables addition and removal of the multimedia contents, including portions of multimedia content, from the reference database in a running system are described. Hierarchical multi-level partitioning methods to organize the reference database are presented. Smart partitioning of the reference multimedia content according to the nature of the multimedia content, and according to the popularity among the social media, that supports scalable fast multimedia identification is also presented. A caching mechanism for multimedia search queries in a centralized or in a decentralized distributed system and a client based local multimedia search system enabling multimedia tracking are described.
Owner:ROKU INCORPORATED
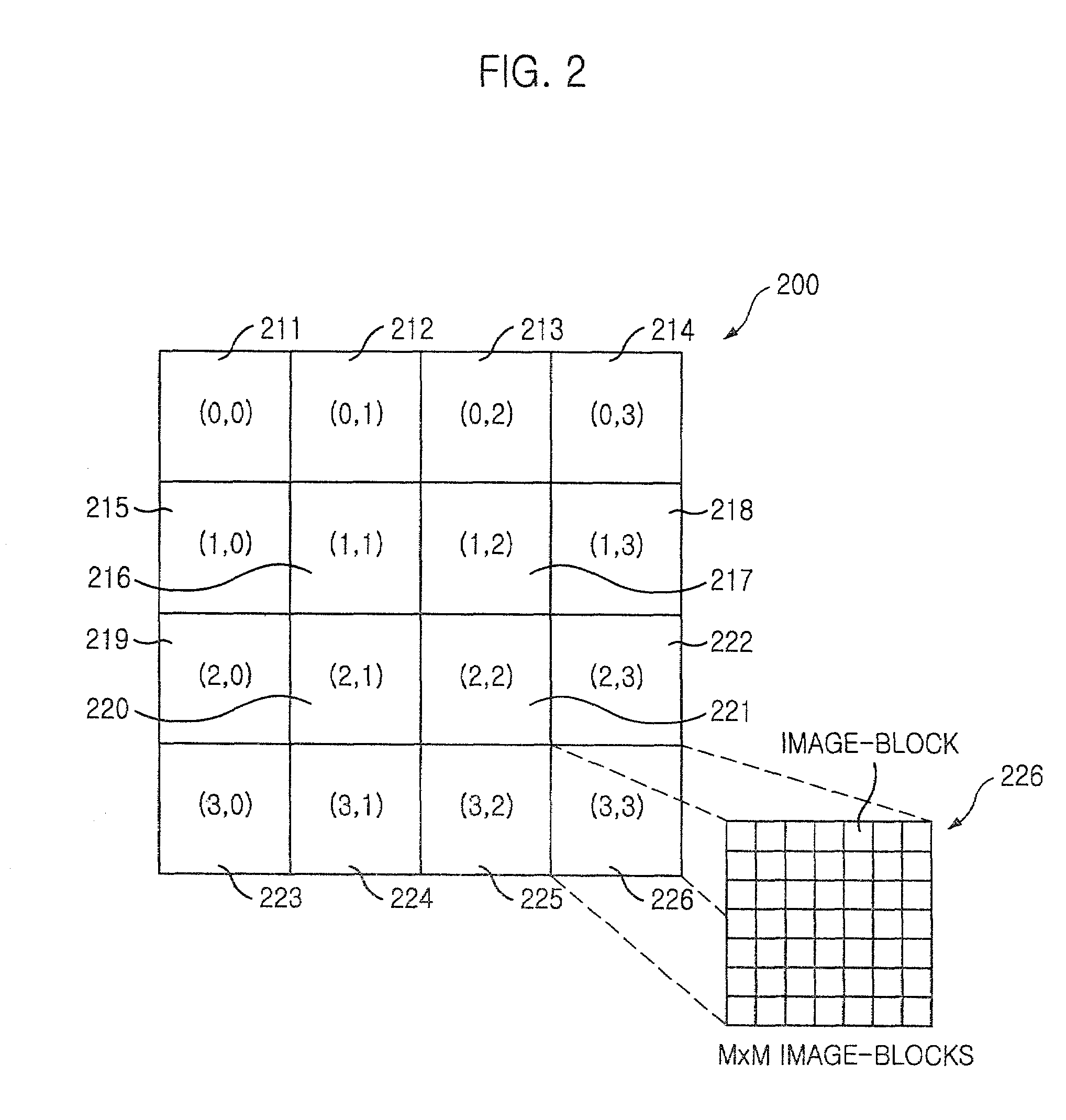
Non-linear quantization and similarity matching methods for retrieving image data
InactiveUS7295718B2Improve accuracyImprove retrieval speedImage enhancementDigital data information retrievalHistogramImaging data
A method for constructing a database having image information representing a plurality of images including the steps of: a) calculating L×5 number of normalized edge histogram bins to generate L number of edge histograms of a target image, wherein each edge histogram has five normalized edge histogram bins and represents a spatial distribution of five reference edges in a sub-image and L is a positive integer, wherein the reference edges include four directional edges and a non-directional edge; b) non-linearly quantizing the L×5 number of normalized edge histogram bins to generate L×5 number of quantization index values for the target image; c) storing the L×5 number of quantization index values to the database; and d) repeating the steps a) to c) until all of the stored images are processed to thereby construct the database having the image information.
Owner:ELECTRONICS & TELECOMM RES INST
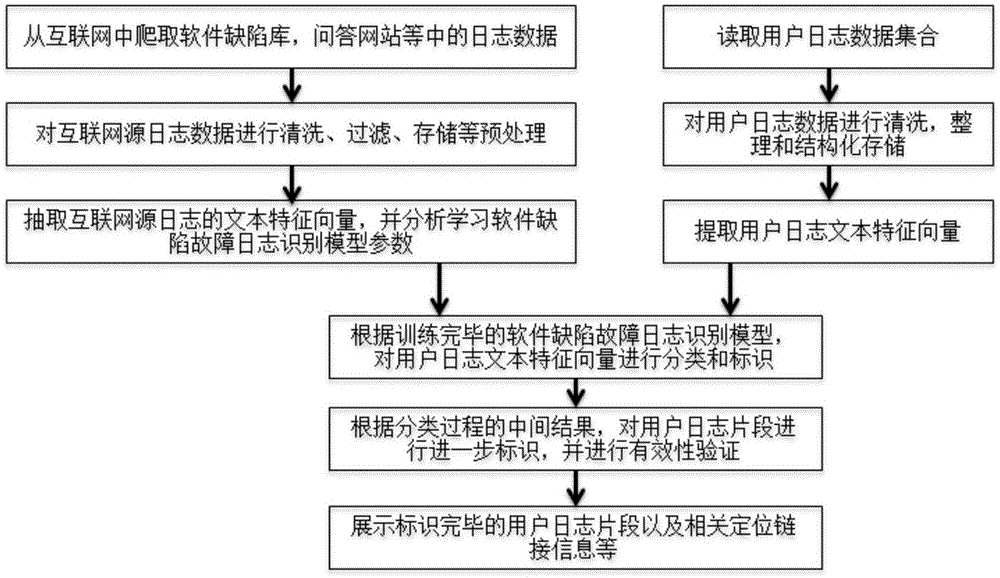
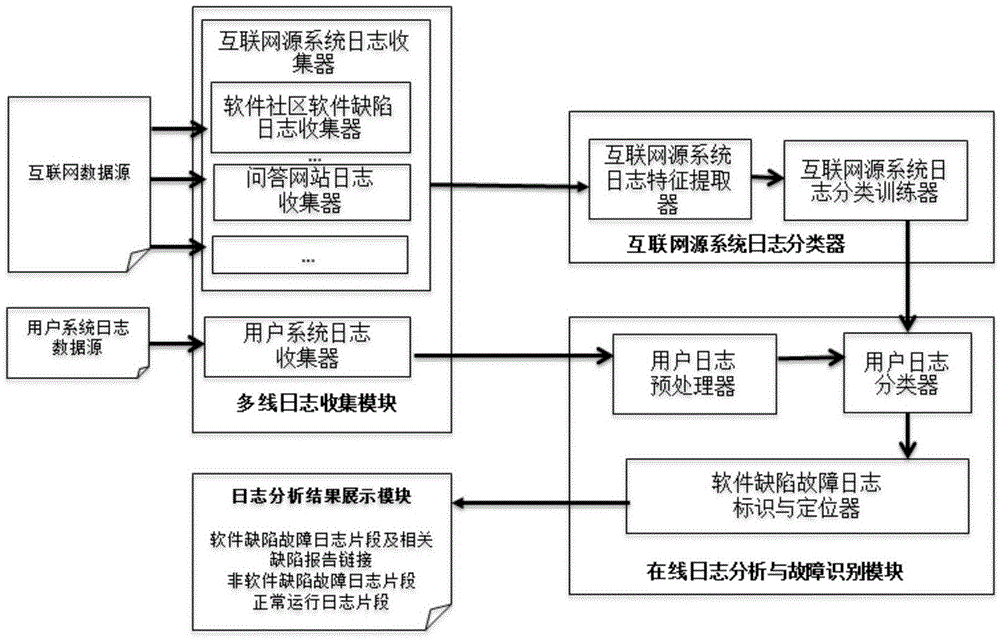
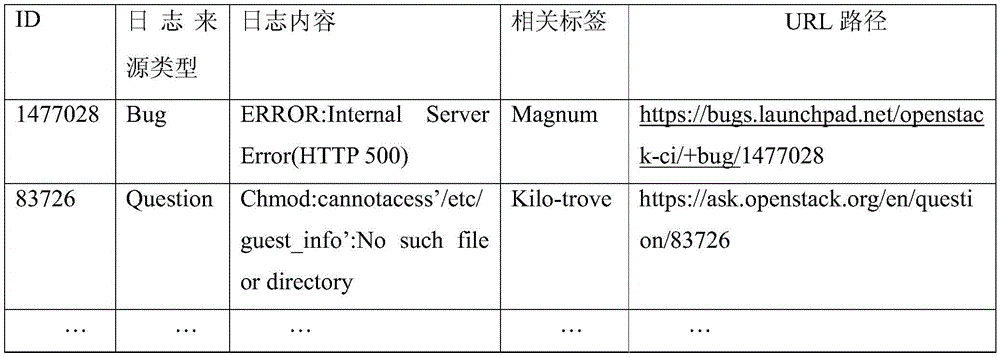
Internet log data-based software defect failure recognition method and system
ActiveCN105653444AExpand log data sourcesStrong expandabilitySoftware testing/debuggingThe InternetUsability
The invention discloses an internet log data-based software defect failure recognition method and system. The method comprises the following steps: in allusion to internet source system log data and user system source log data, taking the internet source system log data as a training set and extracting features from the training set, and generating a software defect failure log recognition prediction model through machine learning or similarity matching; and analyzing and recognizing the user system source log data to obtain log fragments which represent software defect failures, so as to a software defect failure types in allusion to user system logs. A cloud computing system failure recognition system comprises a multi-line log collection module, an internet source system log classifier and an online log analysis and failure recognition module. According to the method and system disclosed in the invention, the failures, caused by software defects, massive log information recognition can be realized, the failure reasons can be rapidly positioned, the failures during the operation can be recognized and the failure types can be diagnosed, so that the reliability and usability of the cloud computing system can be improved.
Owner:PEKING UNIV
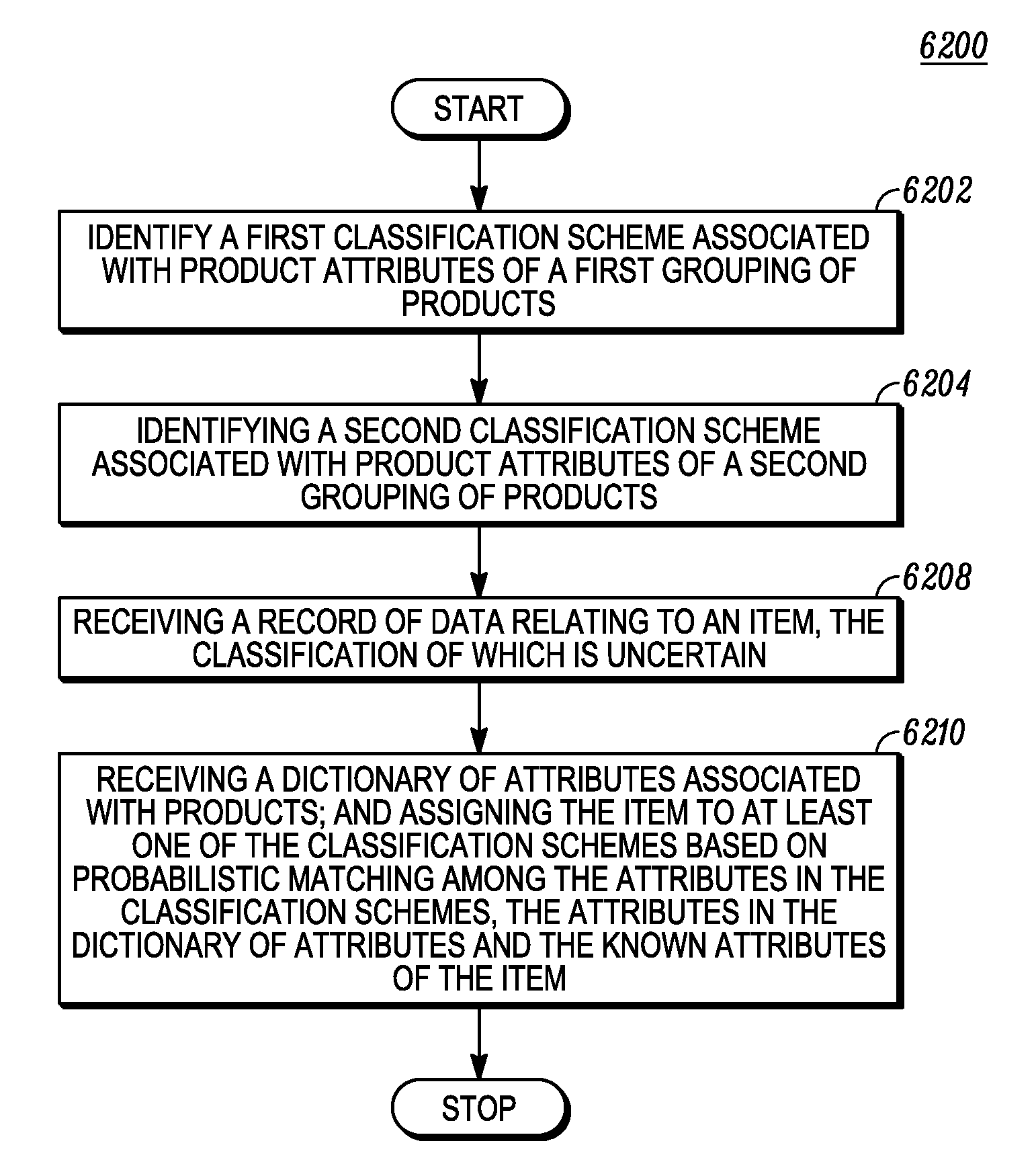
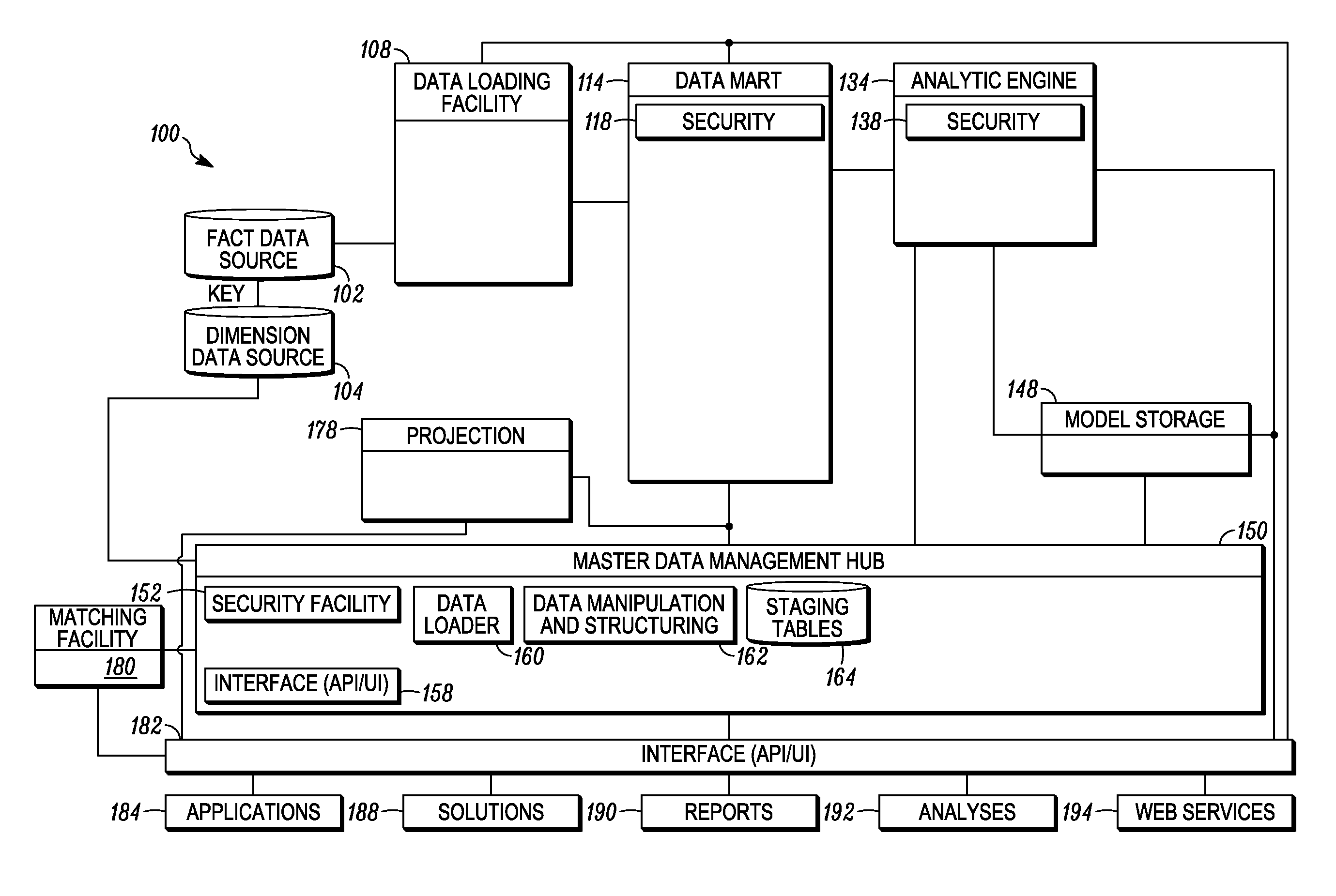
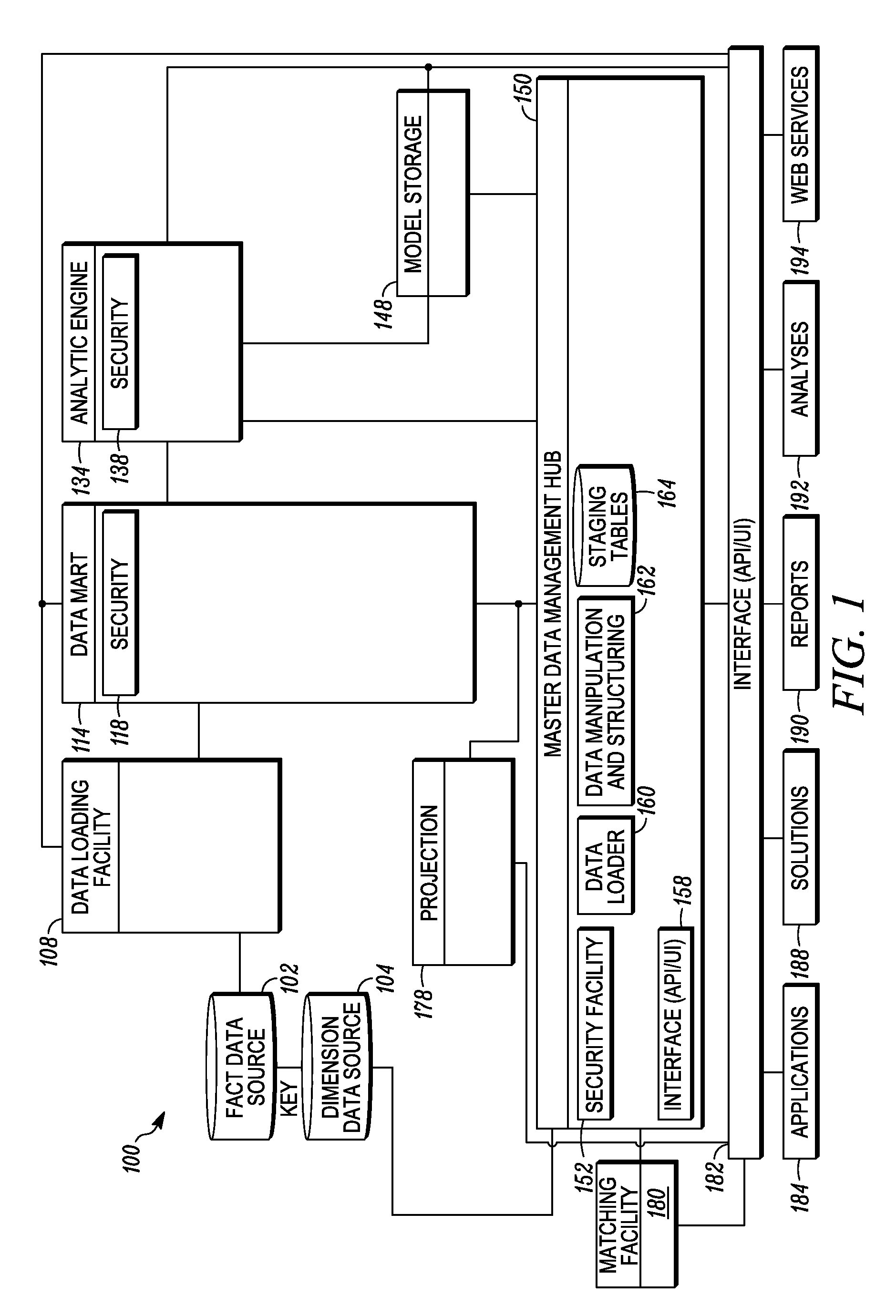
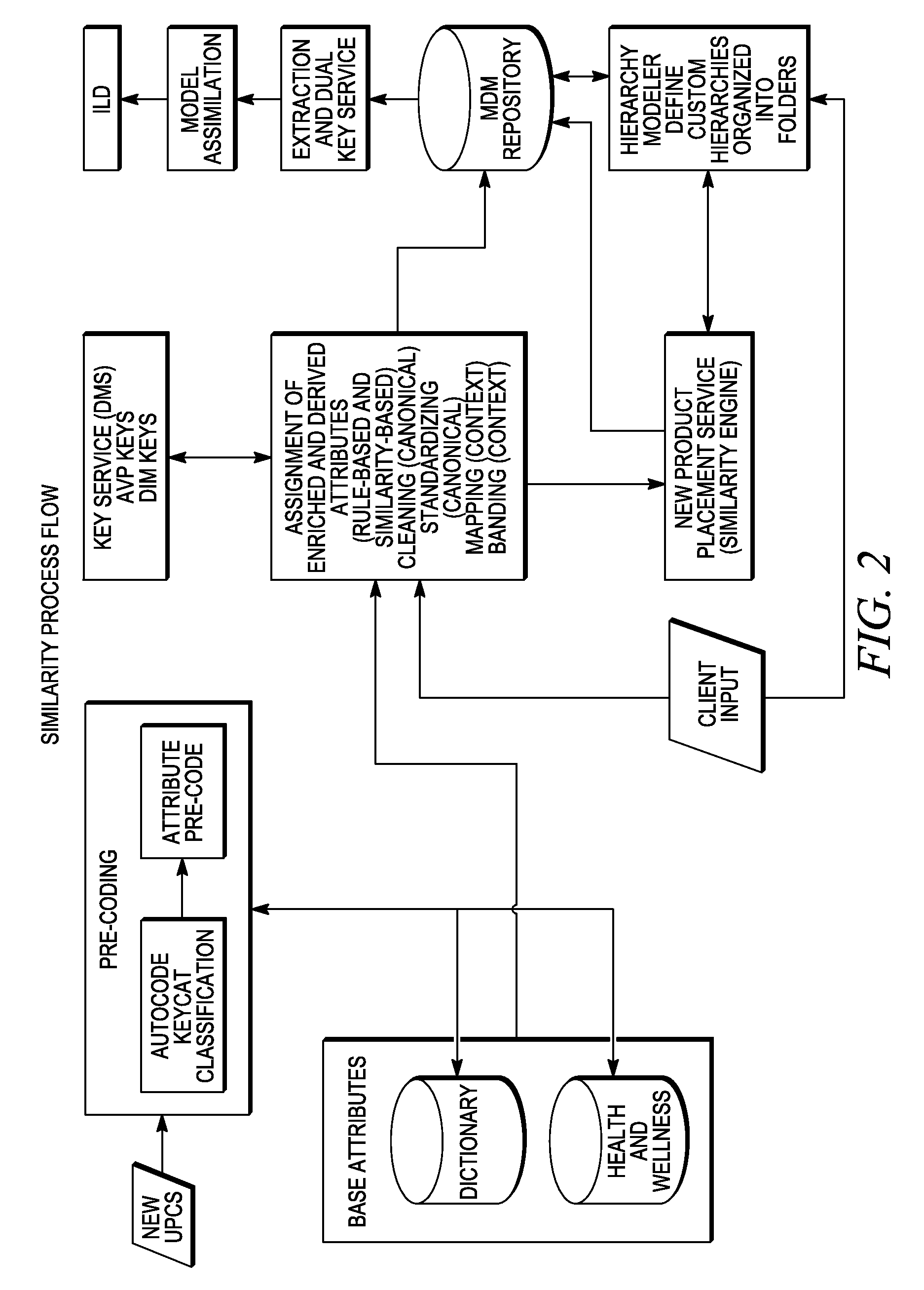
Similarity matching of products based on multiple classification schemes
In embodiments of the present invention improved capabilities are described for identifying a first classification scheme associated with product attributes of a first grouping of products, identifying a second classification scheme associated with product attributes of a second grouping of products, and receiving a record of data relating to an item, the classification of which is uncertain. It may also involve receiving a dictionary of attributes associated with products and assigning the item to at least one of the classification schemes based on probabilistic matching among the attributes in the classification schemes, the attributes in the dictionary of attributes and the known attributes of the item.
Owner:INFORMATION RESOURCES
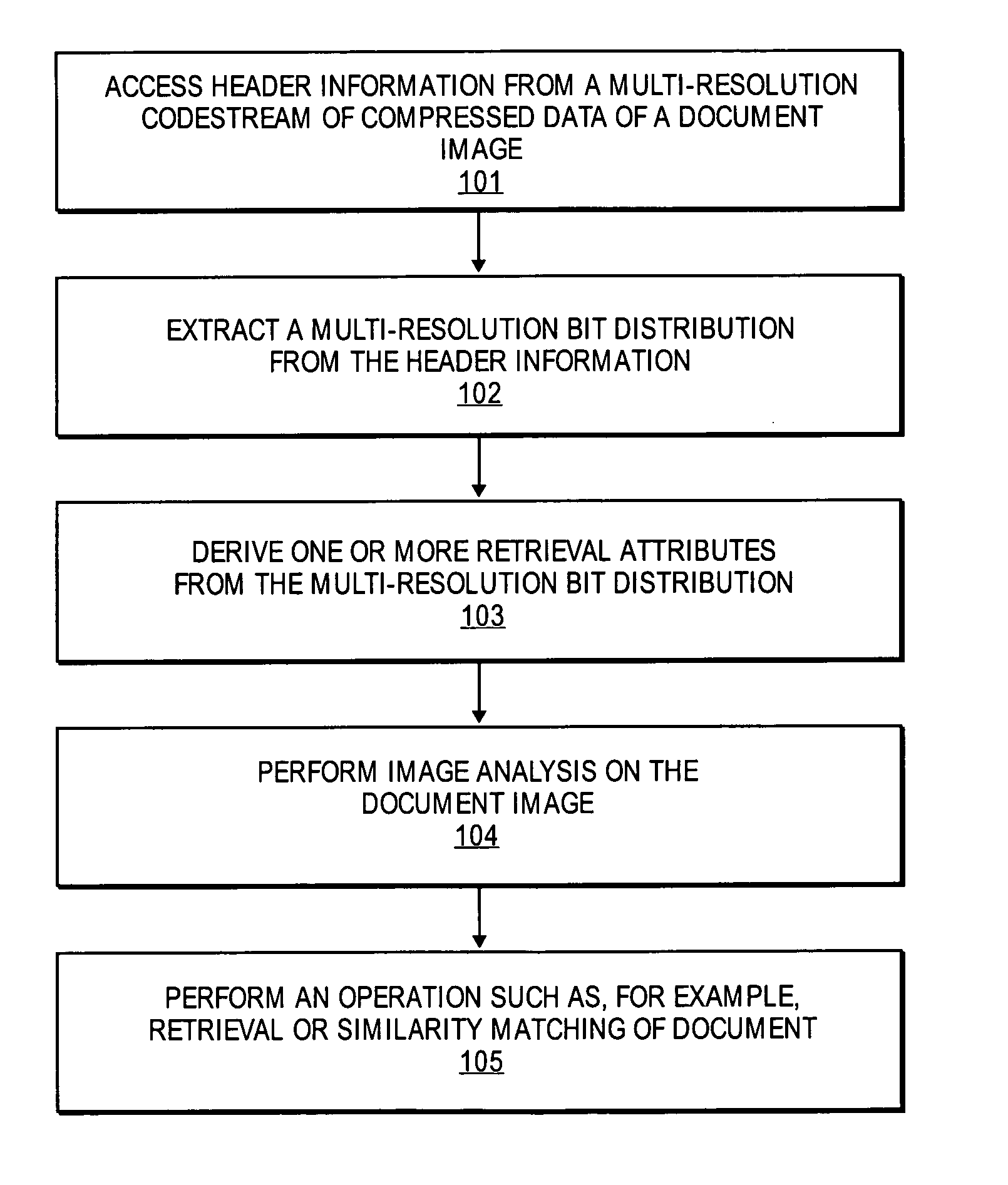
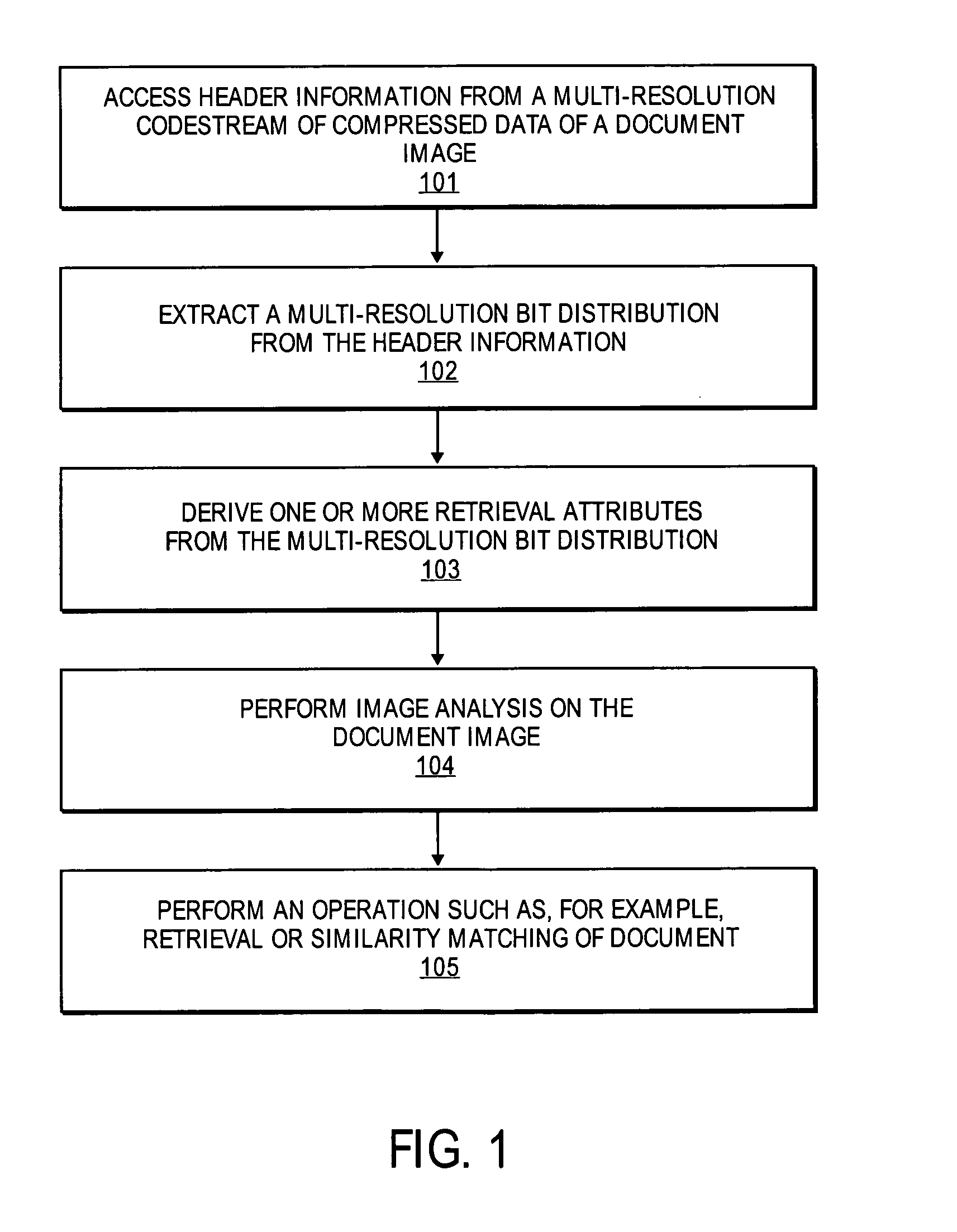
Features for retrieval and similarity matching of documents from the JPEG 2000-compressed domain
InactiveUS20050100219A1Digital data information retrievalImage analysisImaging processingImaging analysis
A method and apparatus for image processing is described. In one embodiment, the method comprises accessing header data from a multi-resolution codestream of compressed data of a first document image, deriving one or more retrieval attributes from the header information, and performing image analysis between the first document image and a second document image based on the one or more retrieval attributes.
Owner:RICOH KK
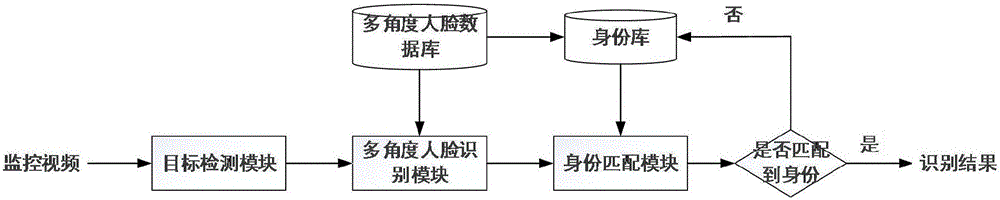
Surveillance video character identity identification system and method thereof fusing facial multi-angle feature
ActiveCN106503687AAchieve integrationRealize early warningCharacter and pattern recognitionFeature vectorIntegrated monitoring
Owner:山东心法科技有限公司
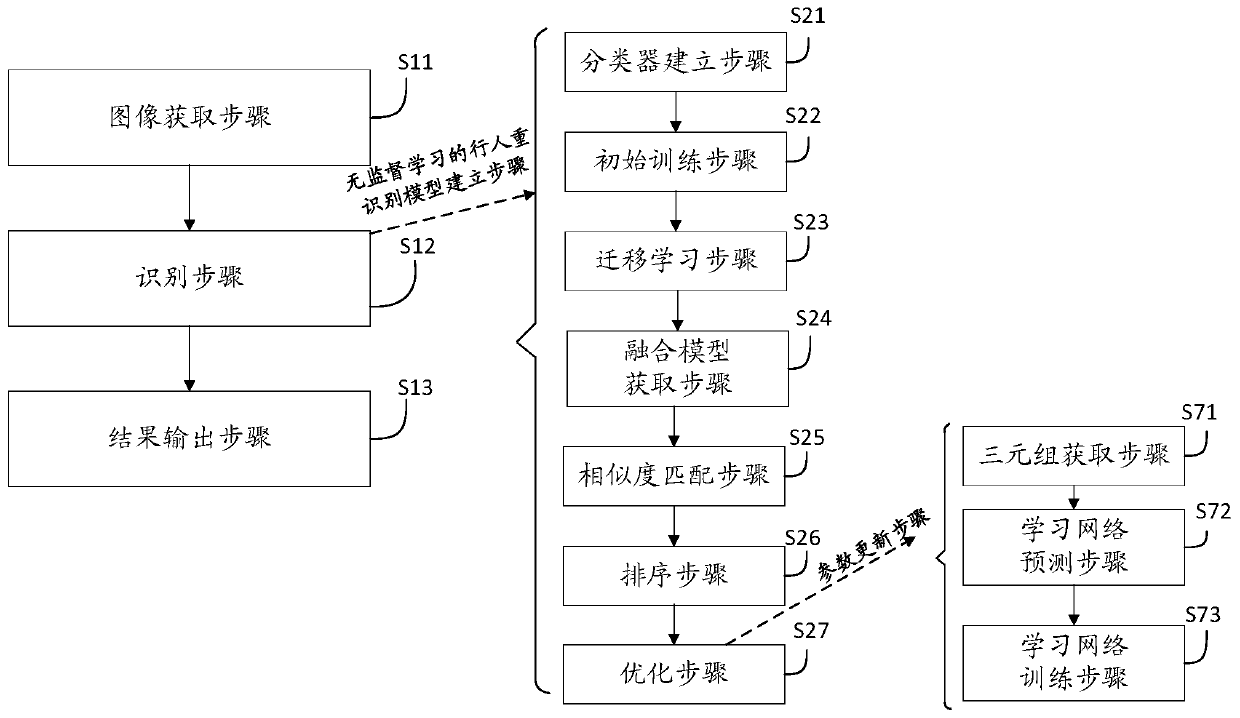
Pedestrian re-identification method and device based on unsupervised learning and medium
InactiveCN110263697AClose to realizationRealization of re-identificationBiometric pattern recognitionNeural architecturesData setSpeed learning
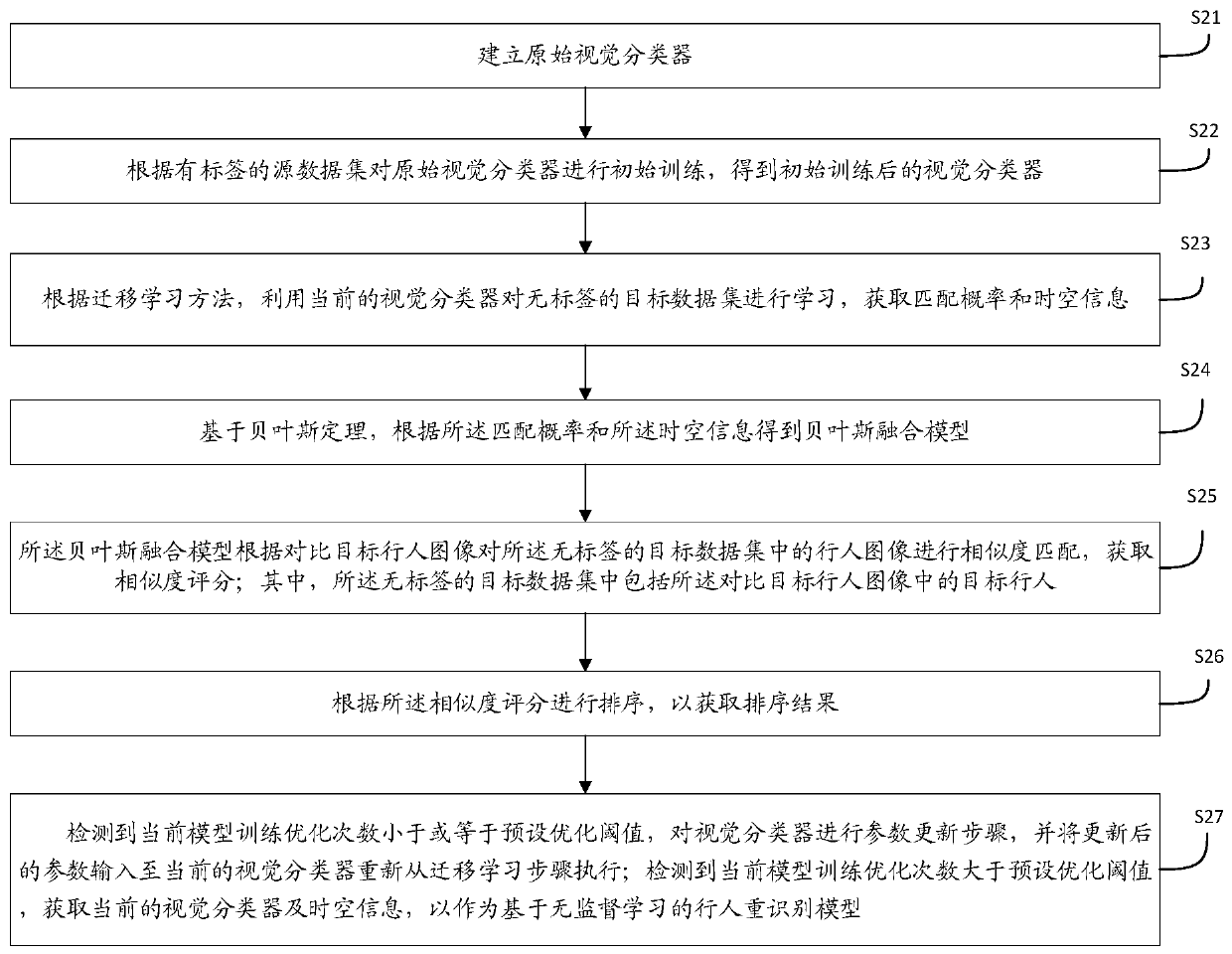
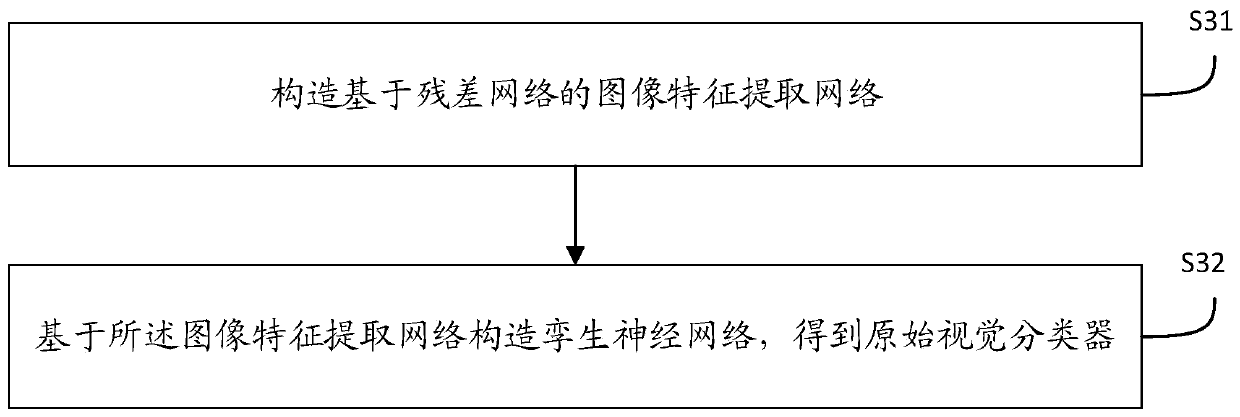
The invention discloses a pedestrian re-identification method and device based on unsupervised learning and a medium, and the method comprises the steps: obtaining a target image and a comparison image, and identifying whether a pedestrian exists in the target image in the comparison image through a pedestrian re-identification model based on unsupervised learning; outputting a recognition result; establishing a pedestrian re-identification model: carrying out initial training on the visual classifier according to the labeled source data set to obtain a visual classifier; learning the label-free target data set by using the vision classifier after initial training to obtain a matching probability and space-time information; obtaining a Bayesian fusion model according to the matching probability and the space-time information; carrying out similarity matching on pedestrian images in the unlabeled target data set by the Bayesian fusion model according to the comparison target pedestrian images to obtain a similarity score; sorting the similarity scores according to a preset threshold value to obtain a sorting result; when it is detected that the current model training optimization frequency is smaller than or equal to a preset optimization threshold value, performing parameter updating on the visual classifier.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Text information similarity matching method and device, computer device and storage medium
InactiveCN108628825AHigh precisionImprove efficiencyNatural language data processingSpecial data processing applicationsCosine similarityAlgorithm
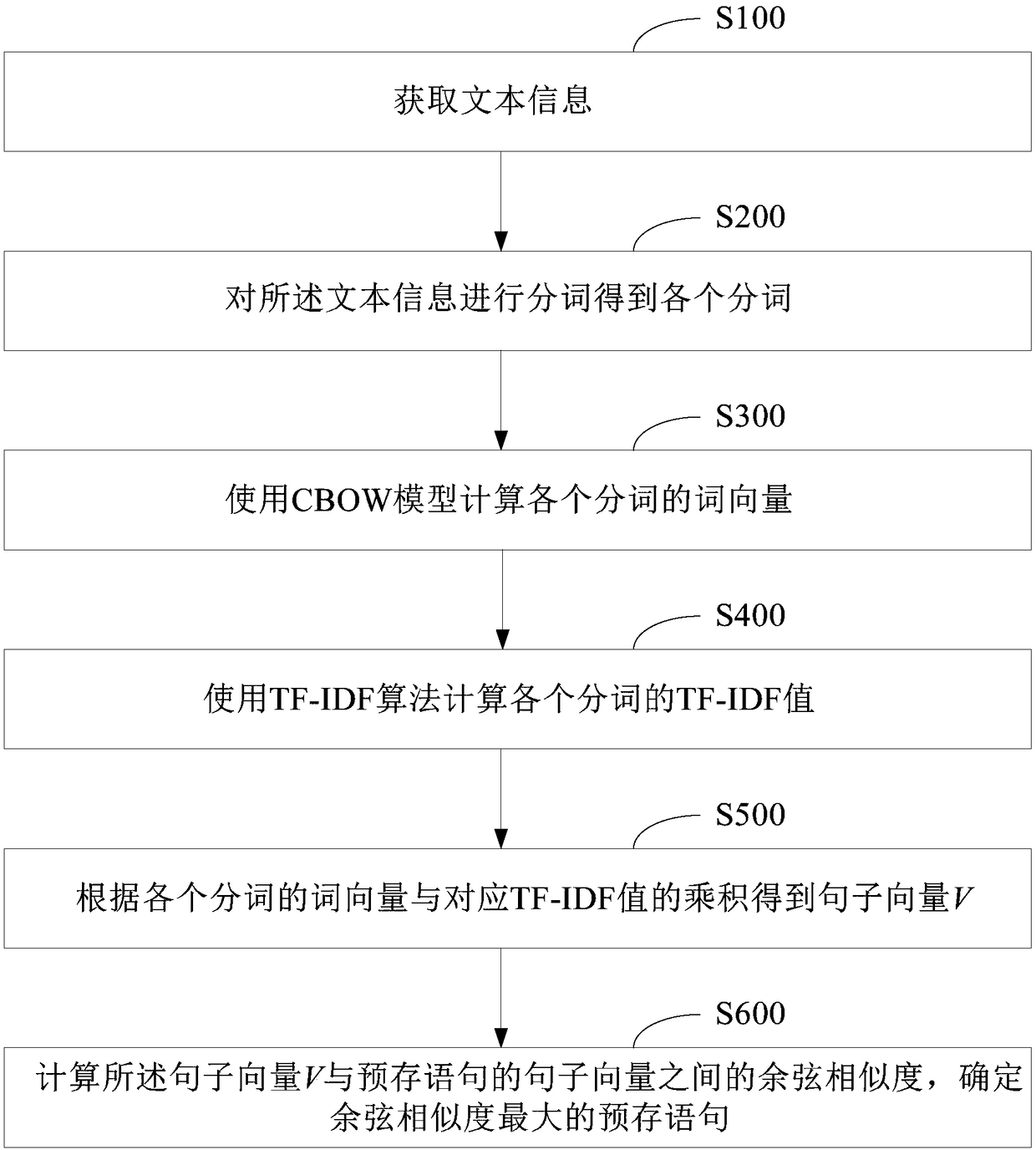
The invention provides a text information similarity matching method and device on the basis of TF-IDF. The method includes the steps of acquiring text information; performing word segmentation on thetext information to obtain word segments w1, w2, ..., wn-1 and wn; using a CBOW model for calculating word vectors V(w1), V(w2), ..., V(wn-1) and V(wn) of the word segments respectively; using the TF-IDF algorithm for calculating TF-IDF values k1, k2, ..., kn-1 and kn of the word segments respectively; according to products of the word vectors of the word segments and the corresponding TF-IDF values, obtaining a sentence vector V; calculating the cosine similarity between the sentence vector V and sentence vectors of pre-stored statements, and determining the pre-stored statement with the maximum cosine similarity. Through the process above, the pre-stored statement which is the most similar to the text information can be found, the accuracy of problem recognition can be improved in the aspects of robot dialogue, information classification and the like, and therefore the dialogue efficiency or the classification efficiency is improved. A computer device and a storage medium are also provided.
Owner:PING AN TECH (SHENZHEN) CO LTD
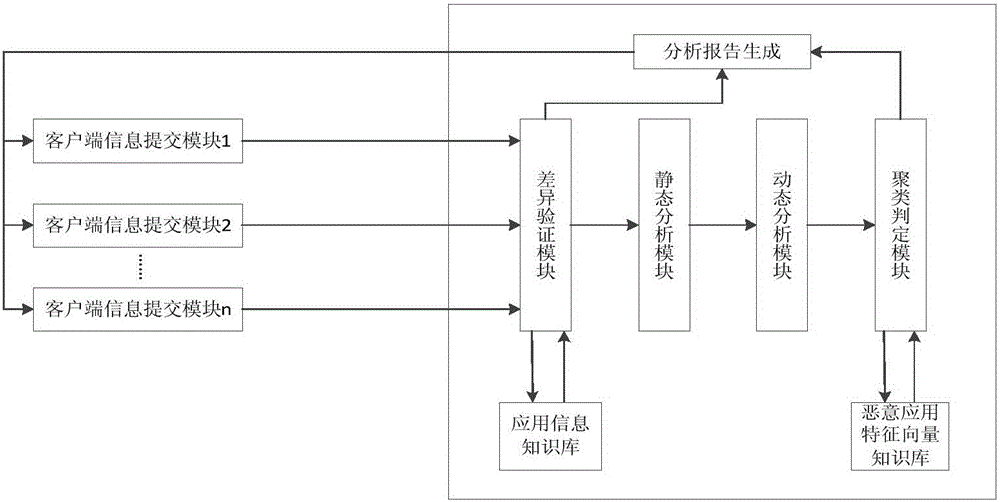
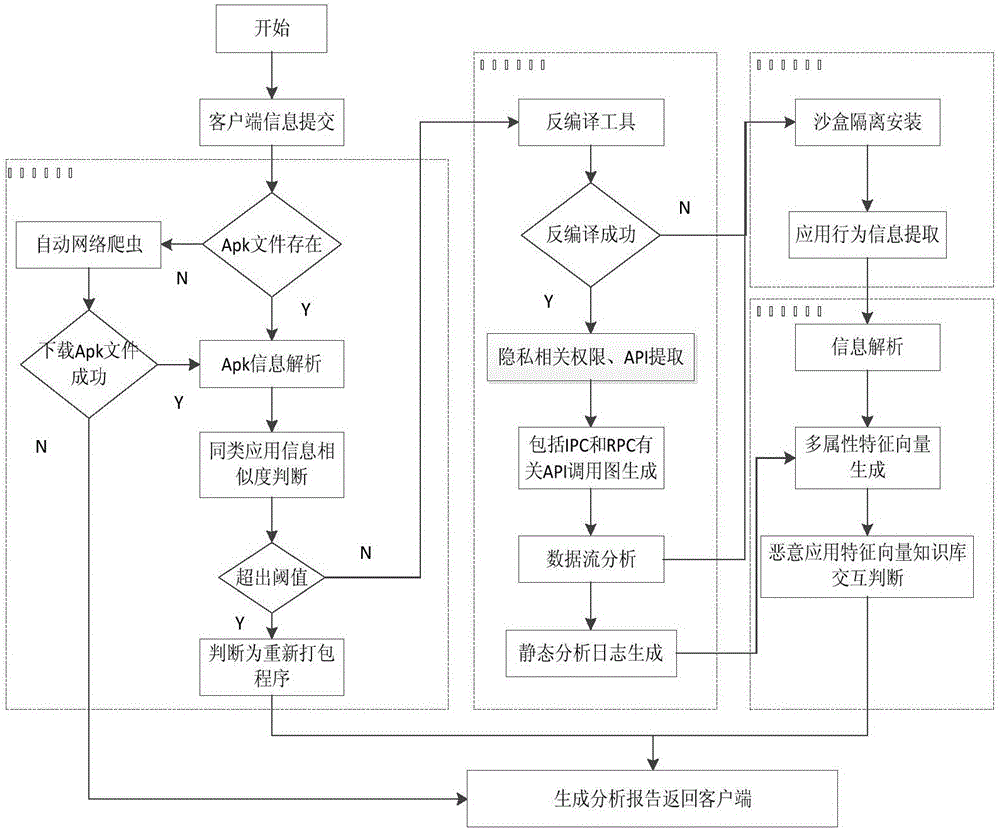
Precaution method for Android malicious application program based on code behavior similarity matching
InactiveCN105893848AGuaranteed high coverageEasy to detectPlatform integrity maintainanceSystem callApplication software
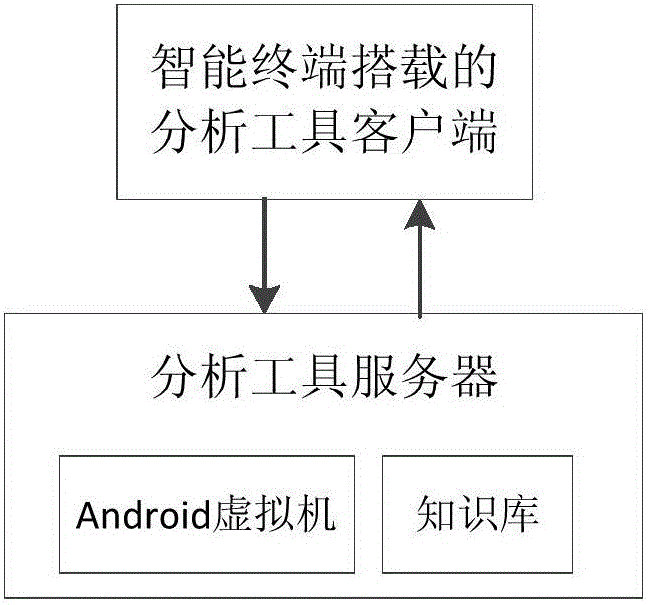
The invention discloses a precaution method for an Android malicious application program based on code behavior similarity matching. The method comprises the following steps: establishing an application information knowledge base; detecting a repacked malicious program by comparing the characteristics of a homonymic program in the application information knowledge base by a difference verifying module; performing high coverage analysis on an application code by a static analysis module and extracting the permission related to privacy information and API calling information; simulating the program running in a sandbox by a dynamic analysis module, detecting the system calling and the LKM parameter related to the calling, and tracking the specific behavior of recording application; to constructing a multi-dimensional feature vector by utilizing log information through a clustering judging module, performing similarity matching on each feature vector of the malicious application and judging the attribution of the application. According to the method, The light client and heavy server system design is adopted, the client is responsible for lightweight information extraction, the server is responsible for heavy data analysis, and the method can effectively adapt to the reality of resource shortage of electric quantity, operation, storage and the like of the intelligent terminal.
Owner:NANJING UNIV OF POSTS & TELECOMM
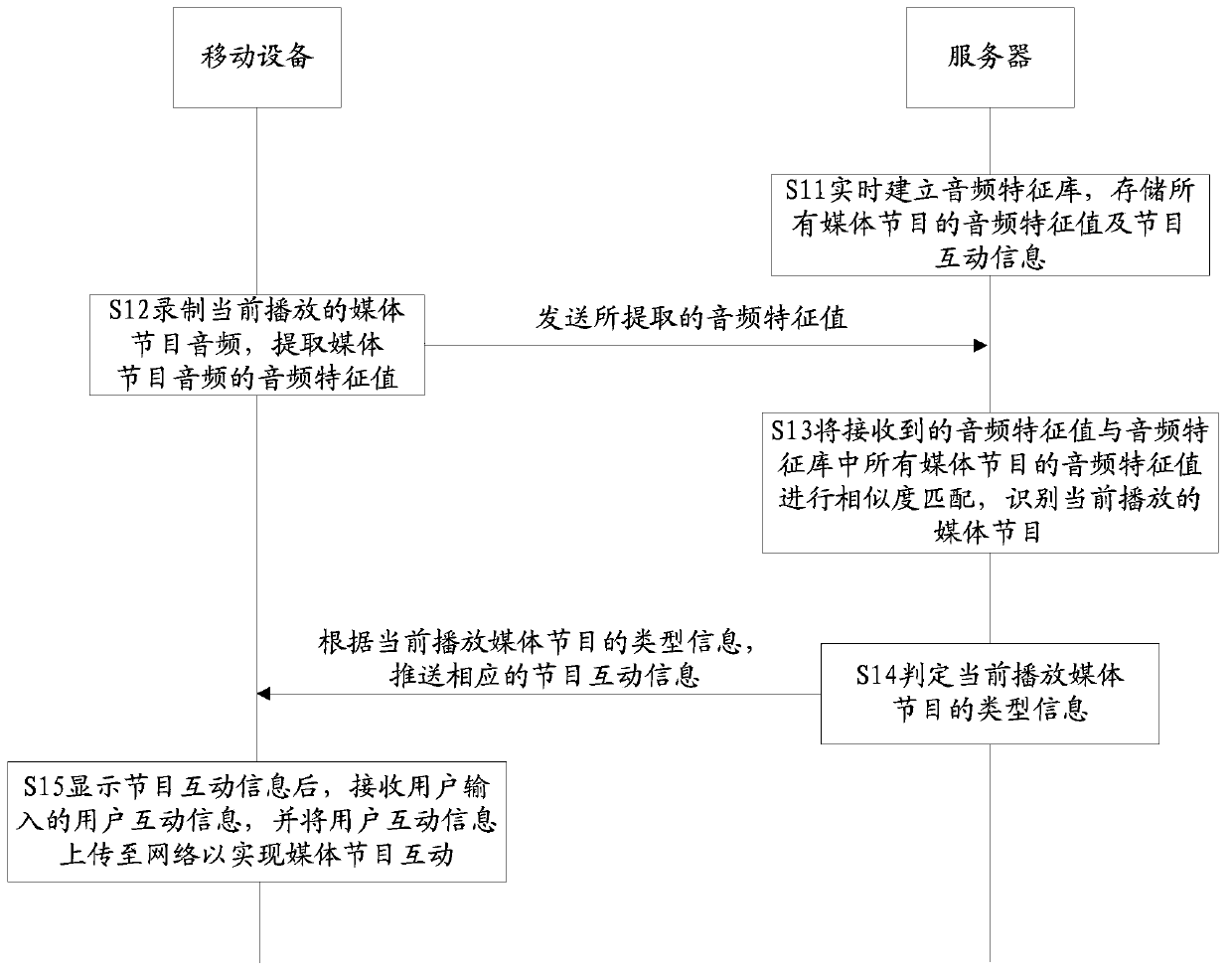
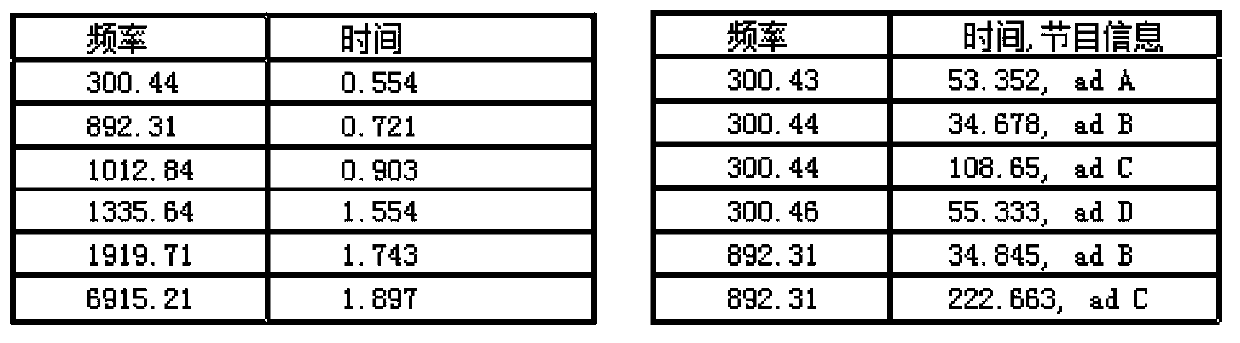
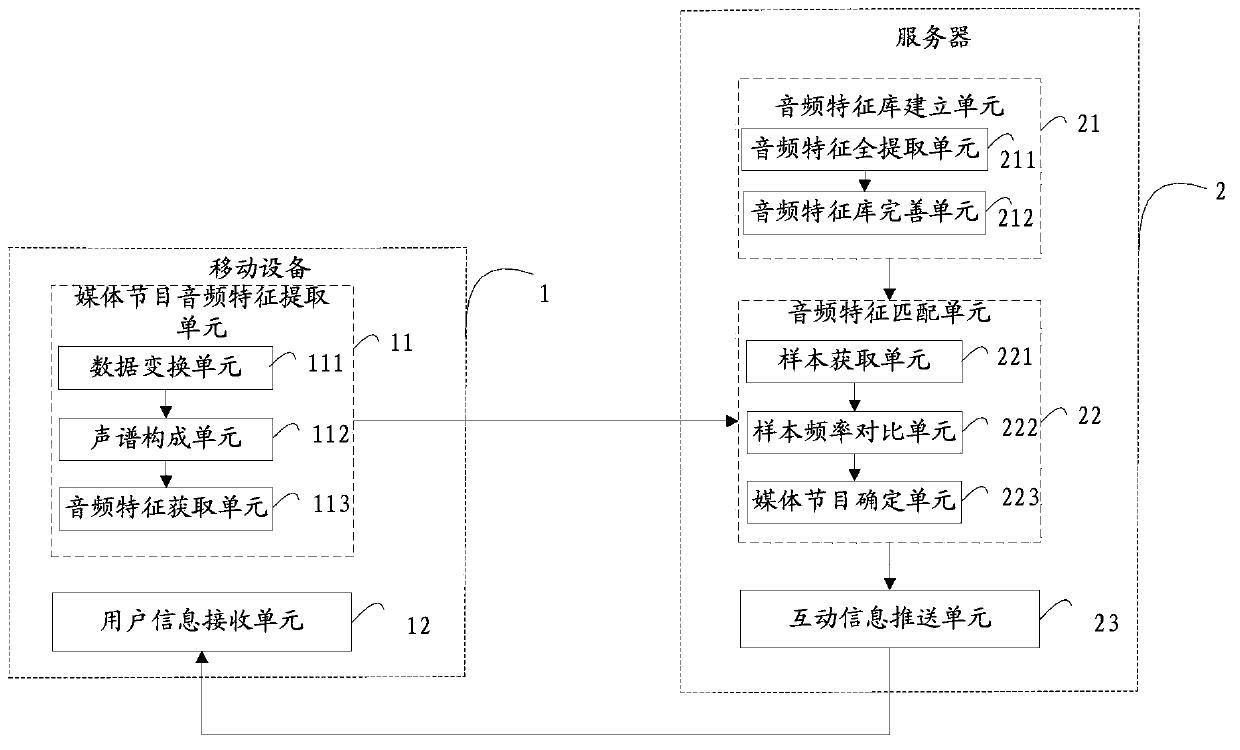
Media program interaction method and system
InactiveCN103402118AThe identification method is accurateQuick feedbackSelective content distributionInteraction systemsApplication areas
The invention provides a media program interaction method and system and is applicable to the field of multimedia application. The media program interaction method comprises the following steps: establishing an audio feature library by a server in real time; storing audio feature values and program interactive information of all media programs; recording an audio of a currently-played media program through a mobile device; extracting the audio feature values of the audio of the media program, and sending the extracted audio feature value to the server; carrying out similarity matching on the received audio feature value and the audio feature values of all the media programs in the audio feature library by the server, so as to identify the currently-played media program; and judging the type information of the currently-played media program by the server, and pushing the corresponding program interactive information to the mobile device according to the type information of the currently-played media program. With the adoption of the media program interaction method and the media program interaction system provided by the invention, the media program interactive information watched by a user can be accurately and rapidly fed back to the user. The media program interaction method and the media program interaction system provided by the invention have the advantages of large amount of the interactive information, various types and better user experience; and the various demands of the user can be met.
Owner:TCL CORPORATION
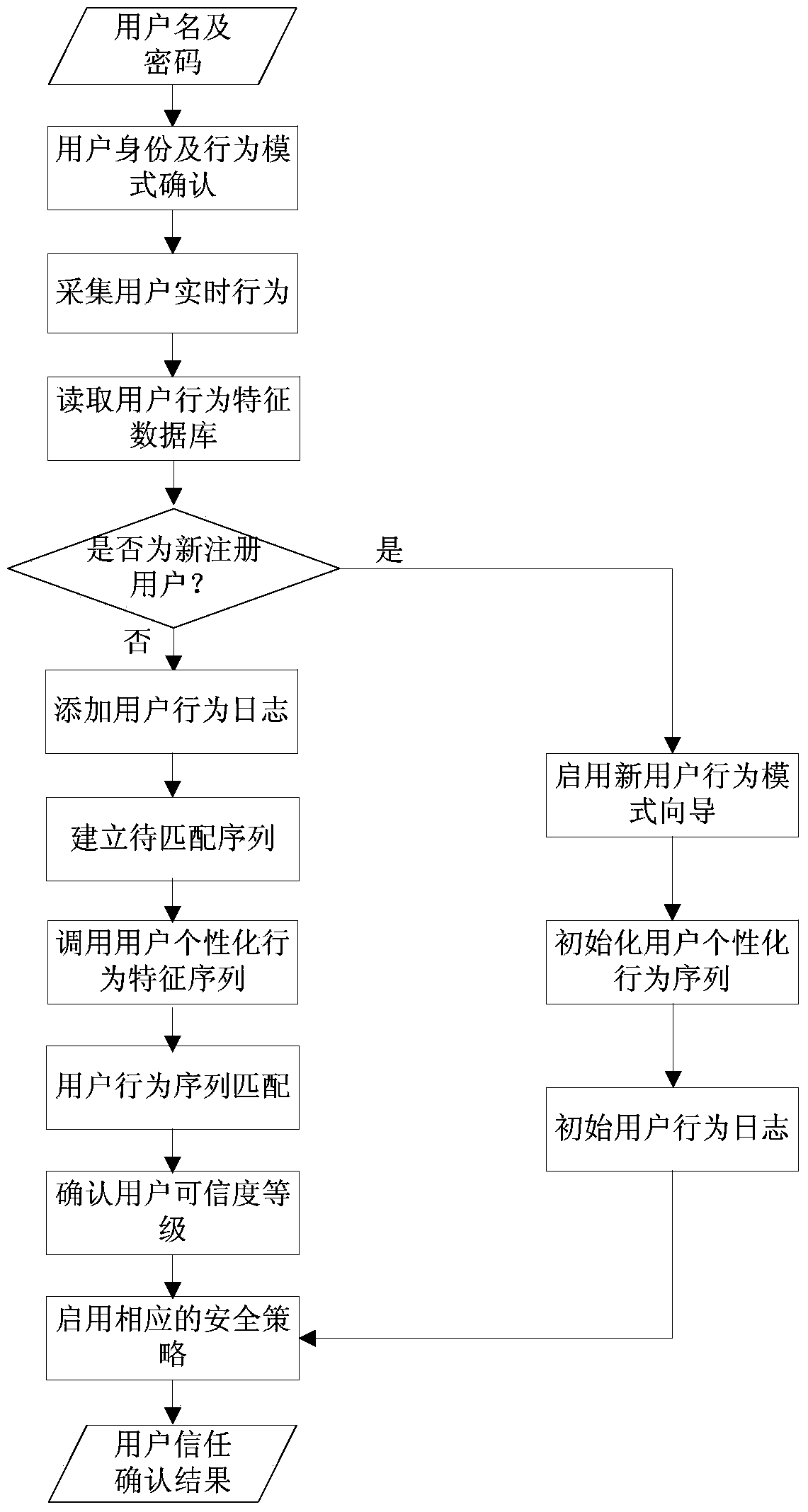
User credibility authentication system and method based on user behaviors
ActiveCN103646197AGuarantee property securityImprove accuracyDigital data authenticationPersonalizationAuthentication system
The invention discloses a user credibility authentication system and method based on user behaviors. The system comprises a user identity and behavior model determination module, a user behavior collection module, a user behavior mining module, a user behavior sequence matching and credibility authentication module and a local security policy module. The method comprises the steps as follows: the user behavior mining module performs behavior mining on user behavior logs; a personal user behavior characteristic sequence is established; the user behavior sequence matching and credibility authentication module performs sequence similarity calculation on the personal user behavior characteristic sequence and a to-be-matched sequence, so that a user credibility grade is obtained, and a corresponding security policy is started using. According to the invention, a sequence pattern mining manner is adopted to collect real-time user behaviors so as to establish the to-be-matched sequence, the similarity matching of the behavior sequence is performed, accordingly, the real-time user behaviors are subjected to credibility authentication, the accurate rate of authentication is improved, and enterprise and personal property safety is guaranteed.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
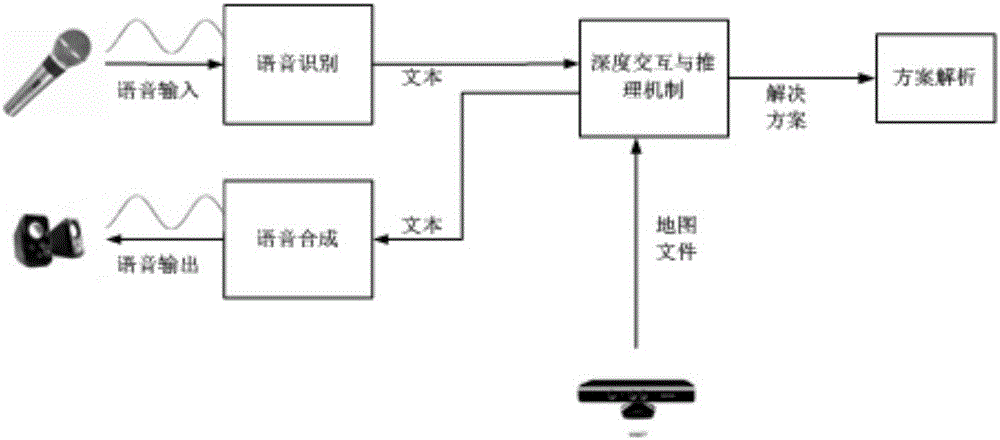
Natural language-based robot deep interacting and reasoning method and device
ActiveCN106056207AImprove recognition rateNarrow searchSemantic analysisCharacter and pattern recognitionWork taskSpeech identification
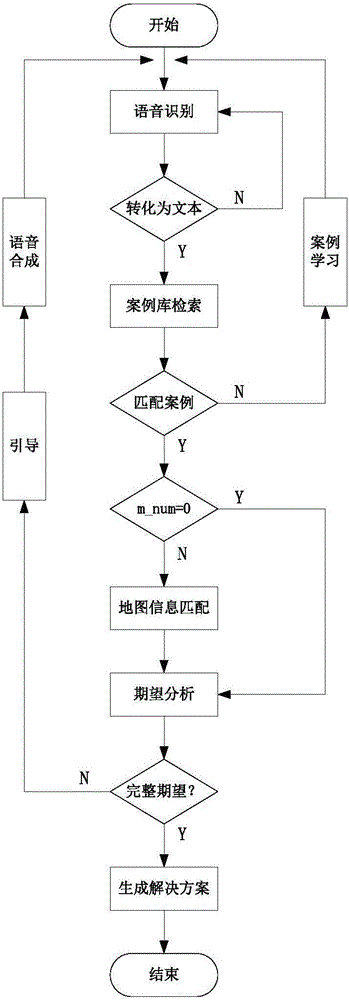
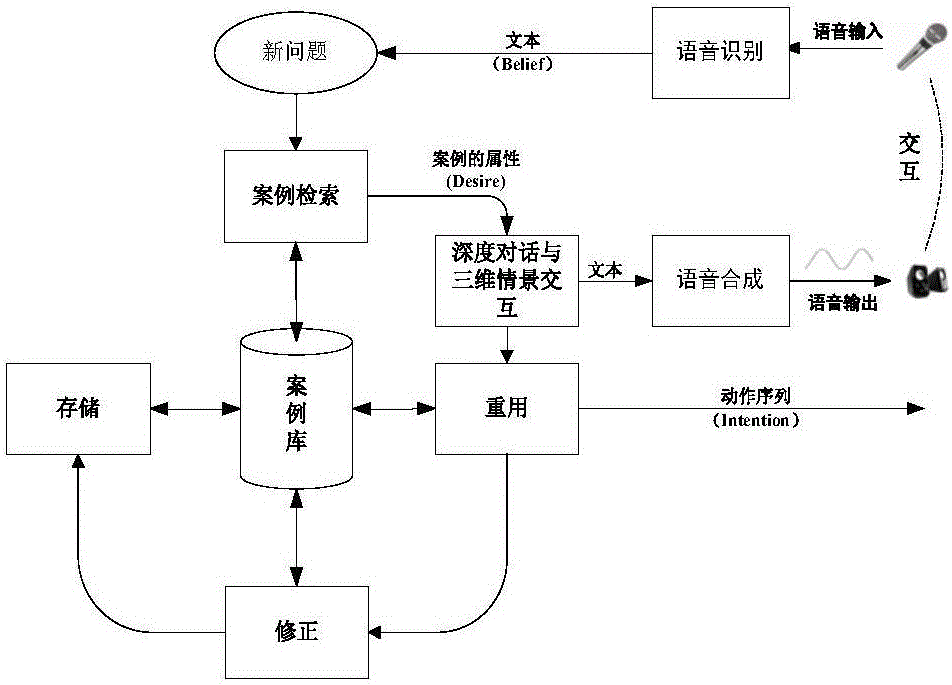
The present invention discloses a natural language-based robot deep interacting and reasoning method and device. The method comprises 1) a speech identification step of receiving the user speech input, and processing an input signal to obtain the text information; 2) a case attribute obtaining step of carrying out the participle processing on the text obtained in the step 1), and then carrying out the similarity matching on the text after participle and the cases in a case base to extract the attributes of the cases; 3) a deep dialogue and three dimensional scene interaction step of if the intention of the user obtained according to the case attributes extracted in the step 2) is not complete, repeatedly guiding a user by combining a real-time map file obtained by a Kinect sensor until the complete intention is obtained, and then generating a solution scheme aiming at a working task of the user complete intention; a speech synthesis step of displaying the obtained solution scheme in a text format, synthesizing the speech, and feeding back to the user via a sound device. During an interaction process of the present invention, a robot and the user both use a natural language.
Owner:WUHAN UNIV OF SCI & TECH
Secure image retrieval method based on homomorphic encryption
ActiveCN103744976ADoes not affect retrieval performanceCharacter and pattern recognitionComputer security arrangementsImage retrievalImaging Feature
The invention relates to a secure image retrieval method based on homomorphic encryption. The secure image retrieval method includes: firstly, extracting features, such as colors, textures, shapes and the like and reducing dimensions of the image features by a LPP method; secondly, protecting the image features by a Paillier homomorphic encryption algorithm; thirdly, conducting similarity matching of the image features which are encrypted and sending back retrieval results of K images with highest similarity to users. The secure image retrieval method is based on a CBIR structure and adopts a homomorphic encryption technology, so decryption is not needed and direct similarity measurement of the image features which are encrypted can be realized by using by using the homomorphic features of the Paillier encryption algorithm. Accordingly, the problem that the direct retrieval of the image features which are encrypted cannot be realized by the prior retrieval method can be solved. Experiment results prove that the retrieval results of the secure image retrieval method is consistent with the retrieval results of a plaintext CBIR method in the prior art under the condition of ensuring the security of image information, so that the encryption cannot influence the image retrieval performance.
Owner:数安信(北京)科技有限公司
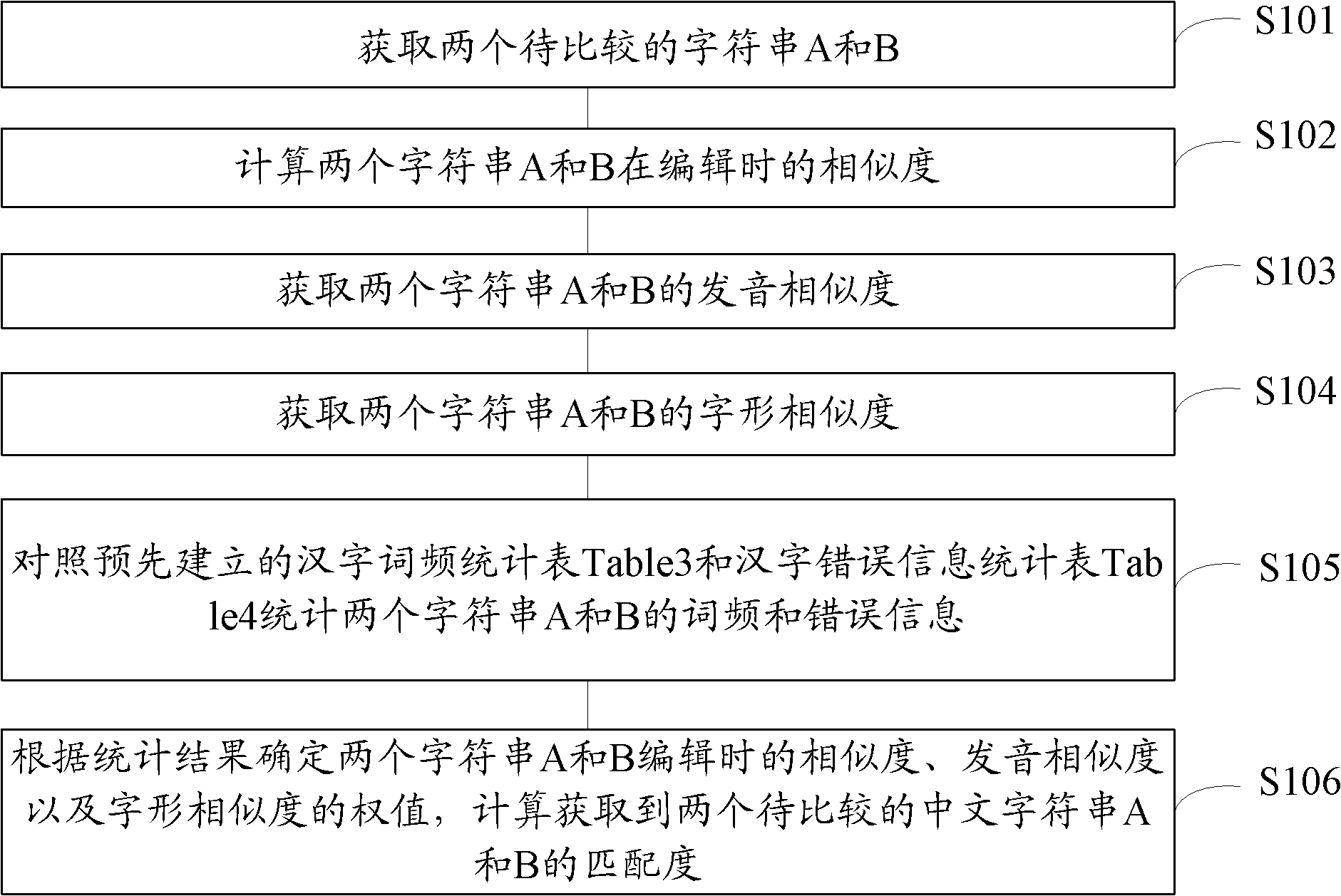
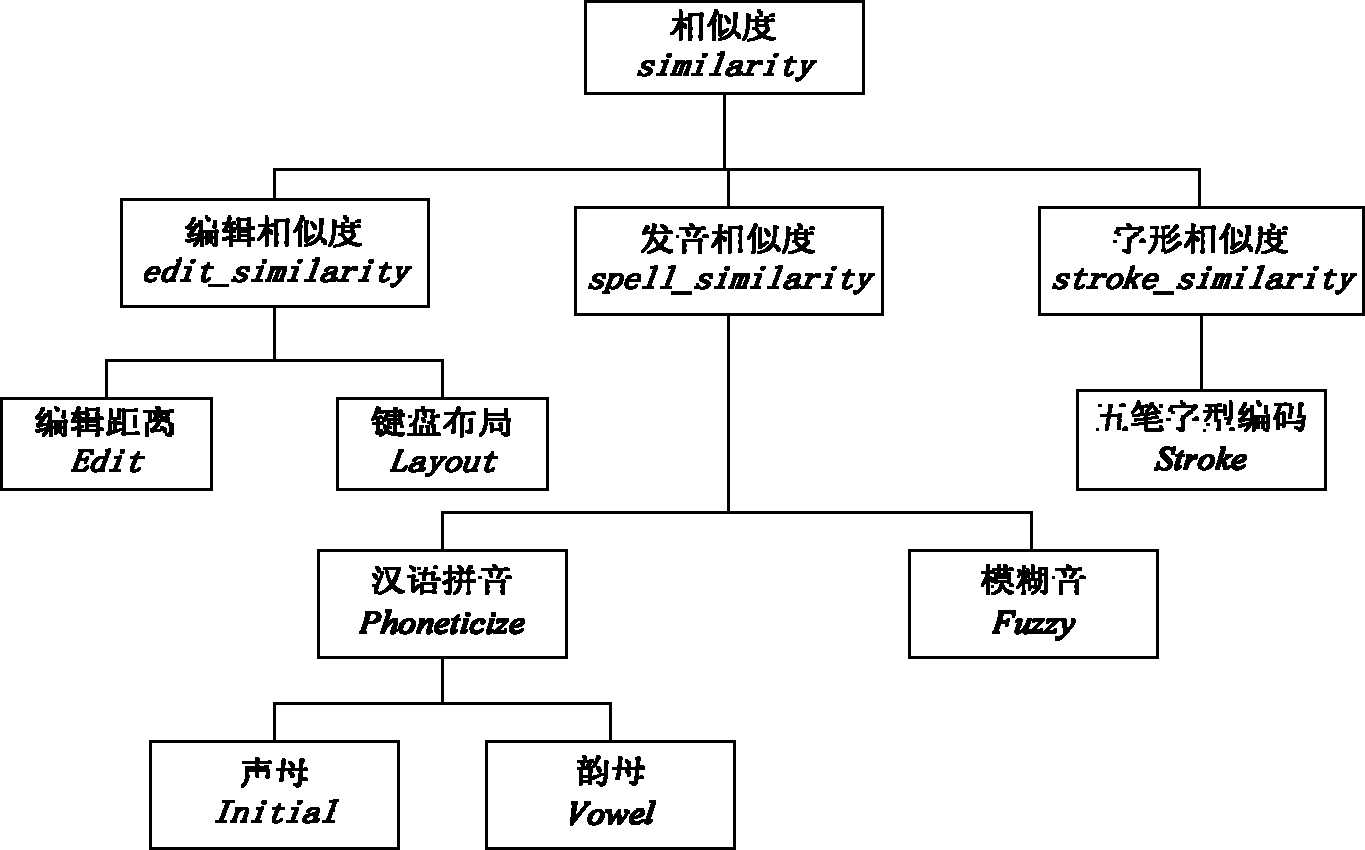
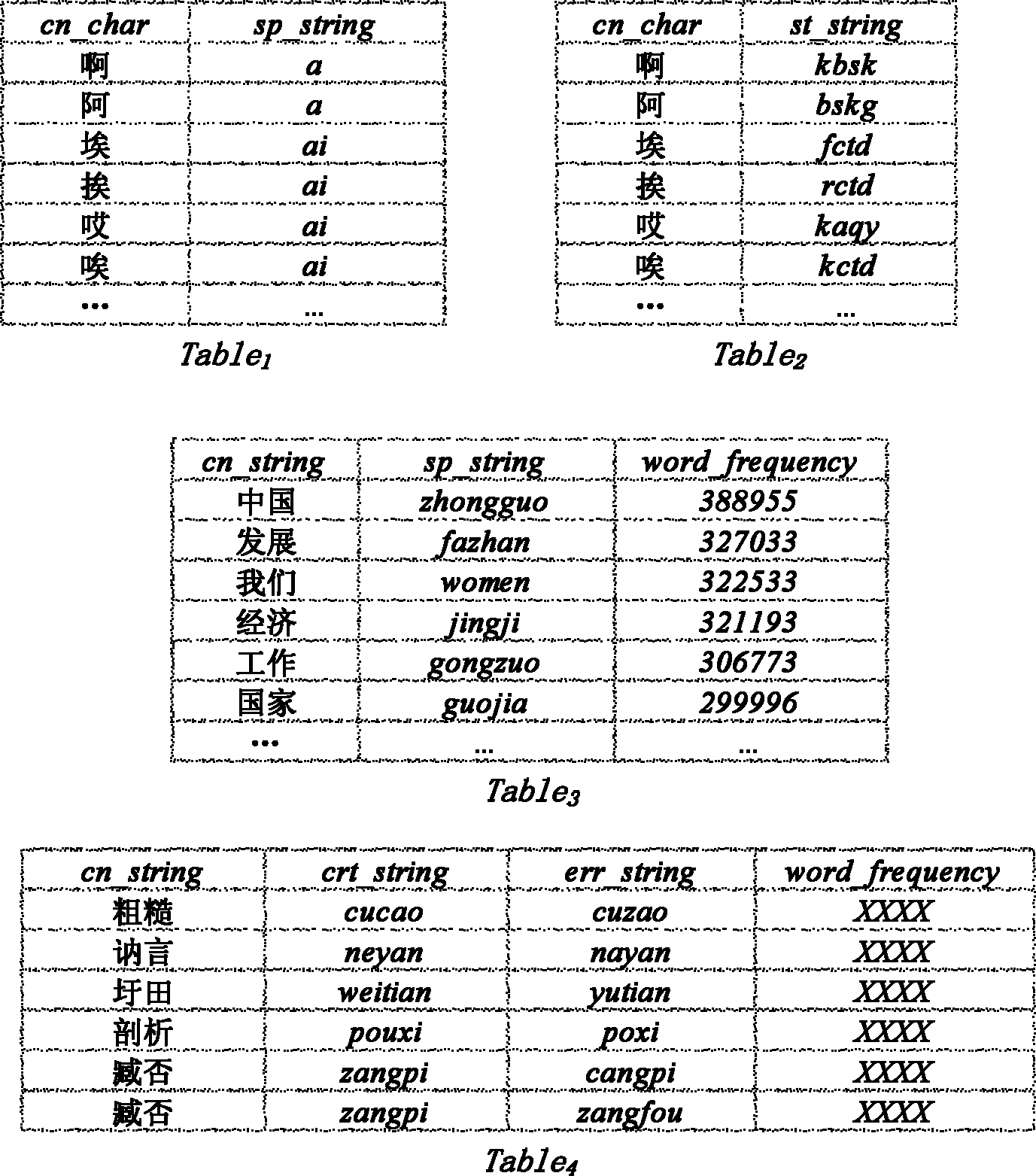
Method for matching Chinese similarity
The invention provides a method for matching Chinese similarity. An edit distance formula and a keyboard fingering rule are used to obtain the edition similarity of the corresponding pinyin of Chinese, namely, whether the Chinese and the pinyin are easily mixed up during edition is reflected; the pronunciation rules of the initial consonant and the final sound of Chinese characters are used for obtaining the initial consonant similarity and the final sound similarity of character strings; and common fuzzy tones in dialects or common pronunciation are combined to calculate the pronunciation similarity among character strings. Because the Chinese character pattern is one of the most important characteristics of Chinese, character pattern coding namely the Five-stroke Method coding is used for calculating the character pattern similarity among character strings; information is collected and calculated at the same time for updating data; and the above similarities are combined to obtain the whole similarity of Chinese word, various factors, such as Chinese spelling custom, user input custom, keyboard layout, mandarin pronunciation rules, dialects, common wrong pronunciation, Chinese character patterns and the like are fully considered, the statistical regularity is combined, and the similarity among Chinese words is comprehensively evaluated.
Owner:TSINGHUA UNIV
Self-adaptation camouflage design method based on background
InactiveCN104318570AHigh synthesis efficiencyQuality assuranceImage analysisTexturing/coloringCluster algorithmSelf adaptive
The invention discloses a self-adaptation camouflage design method based on a background. According to the method, on the basis of a texture synthesis algorithm based on pixels, a whole camouflage image is synthesized pixel by pixel; in the synthesis process, a self coding algorithm is adopted to extract a texture primitive containing background sample complete texture features, and a neighborhood of the pixels to be synthesized is determined; by means of the neighboring correlation principle and a helix supplement search mechanism, a neighborhood matched with a target pixel neighborhood is searched for in a background sample; similarity matching is carried out through a pixel and texture similarity matching rule, pixels in the neighborhoods which are most similar in the sample are selected to serve as synthesis pixels, pixels of a target image are synthesized according to the sequence of scanning lines, and after synthesis, color quantization is carried out on the image by means of the clustering algorithm to generate a final camouflage image. By means of the method, similar camouflage images can be synthesized quickly according to the background, and the application aim of quickly camouflaging a target in a self-adaptation mode can be achieved.
Owner:SHENYANG JIANZHU UNIVERSITY
Methods for document-to-template matching for data-leak prevention
ActiveUS20100254615A1Memory loss protectionDigital data processing detailsTemplate matchingTemplate based
Owner:CHECK POINT SOFTWARE TECH LTD
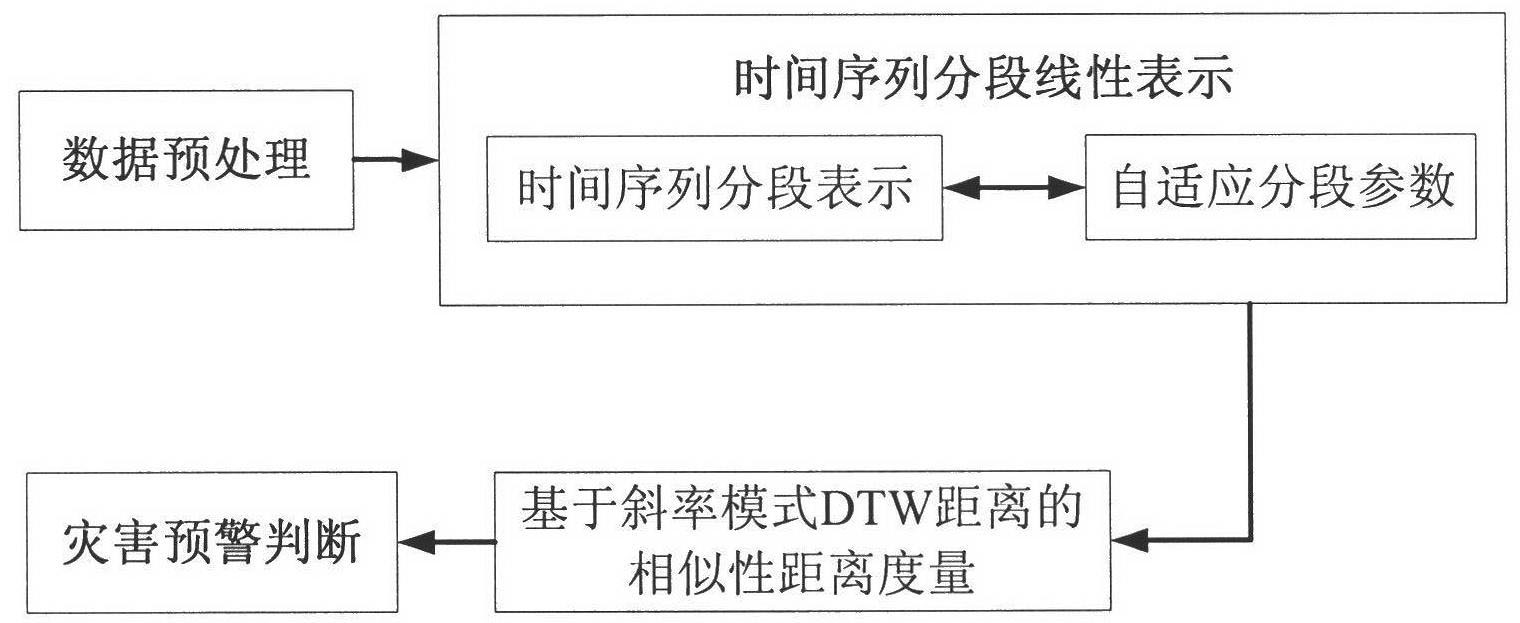
Time sequence analysis-based storm surge disaster early warning system
The invention discloses a time sequence analysis-based storm surge disaster early warning system, which comprises a database server, an early warning prediction model analysis module, an assistant decision making system, a Web server and a management user, wherein the database server stores historical monitoring data, real-time monitoring data, basic geographic information data, emergency plan data, related calculation model data and early warning data; the monitoring data and the early warning data are time sequence data; the early warning prediction model analysis module is mainly used for preprocessing the data, piecewise linearly expressing the time sequence data to fulfill dimension reduction and compression aims, performing similarity matching on the time sequence data and the historical monitoring data, and performing disaster early warning according to a similarity matching result; and the assistant decision making system displays assistant decision making information on the basis of geographical graphic information, and displays the assistant decision making information to a client of the management user through the deployed Web server.
Owner:SHANGHAI OCEAN UNIV
Multi-scale generative adversarial network-based shielded pedestrian re-identification method
ActiveCN110135366AQuality improvementReduce distractionsBiometric pattern recognitionNeural architecturesDiscriminatorVisual technology
The invention discloses a multi-scale generative adversarial network-based shielded pedestrian re-identification method, and relates to a computer vision technology. The method comprises the followingsteps of preparing a pedestrian image training set; designing and training a multi-scale generative adversarial network, with the network comprising a multi-scale generator and a discriminator, withthe multi-scale generator being capable of performing a de-occlusion operation on the random occlusion area to generate a high-quality reconstructed graph; enabling a discriminator to distinguish whether the input image is a real image or a generated image; generating an expanded pedestrian image training set by using the trained multi-scale generator; designing and training a classification recognition network, wherein the network is used for performing identity classification on the input pedestrian images; and extracting features of the pedestrian images by using the trained classificationand recognition network and carrying out similarity matching.
Owner:XIAMEN UNIV
Key point positioning method and terminal
ActiveCN105512627AHigh precisionReduce processing difficultyCharacter and pattern recognitionComputer terminalFace perception
The embodiment of the invention discloses a key point positioning method and a terminal. The method comprises the steps of detecting a target object as a face image during the collecting process of the target object; generating a target detecting region on the face image of the i frame for human face recognition and location according to a preset configuration and annotating the target detecting region, wherein i is larger than or equal to 1; when i is larger than 1, estimating the key point information of a human face based on the face image of the i frame according to the similarity matching strategy between a previous frame and the current frame so as to obtain the category of the human face for the face image of the i frame; according to the category of the human face for the face image of the i frame, determining a first initial shape out of a plurality of preset candidate initial shapes; and calculating the position of an initial face key point in the face image of the i frame according to the target detecting region and the first initial shape.
Owner:TENCENT TECH (SHENZHEN) CO LTD
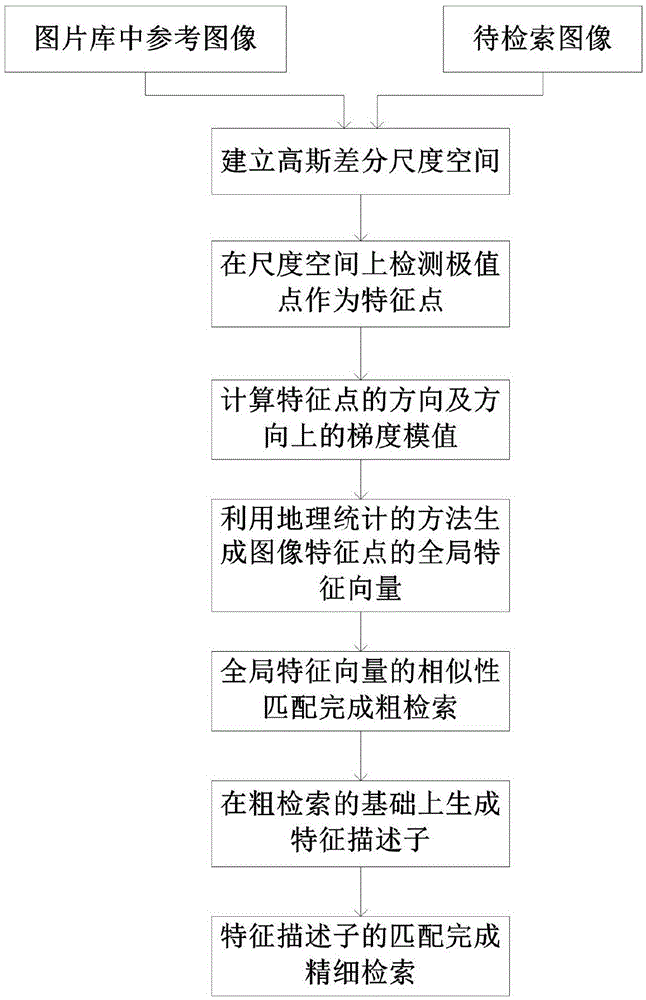
Efficient image retrieval method based on improved SIFT (scale invariant feature transform) feature
ActiveCN105550381AApplicable Image Infringement Review RequirementsSpecial data processing applicationsFeature vectorImaging processing
The invention discloses an efficient image retrieval method based on an improved SIFT (scale invariant feature transform) feature, relates to the field of image processing and computer vision and belongs to a content-based image retrieval method. The method comprises the steps of establishing a gauss difference scale space, taking scale space detection extreme points as feature points, calculating the direction of the feature points and gradient module values in the direction, generating a global feature vector of the image feature points through a geographical statistical method, conducting global feature vector similarity matching to finish rough retrieval, generating feature descriptors on the basis of rough retrieval, and conducting feature descriptor matching to finish accurate retrieval. The novel image retrieval method is superior to a traditional SIFT algorithm, and is more suitable for requirements of image infringement examination in digital prints than an existing retrieval algorithm.
Owner:BEIJING UNIV OF TECH
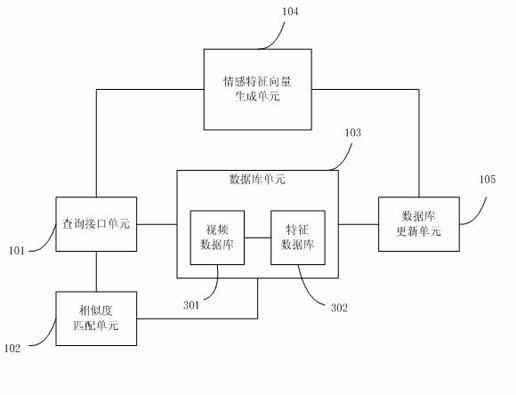
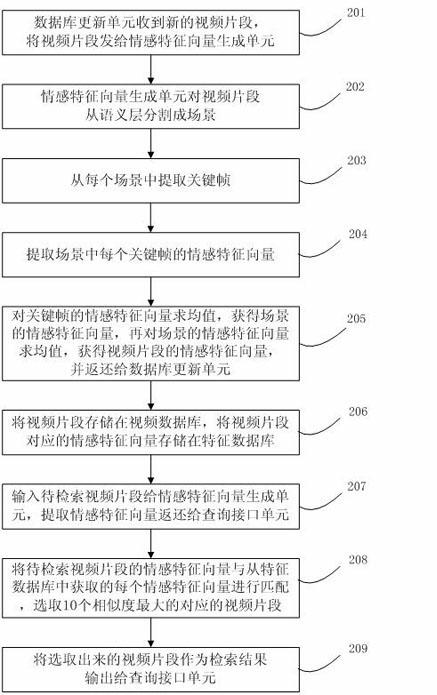
Video retrieval method and system
InactiveCN102117313AFully consider the fuzzy characteristicsAddressing the Semantic GapSpecial data processing applicationsVideo retrievalComputer graphics (images)
The invention discloses a video retrieval method and a video retrieval system. The video retrieval method comprises the following steps of: storing video clips into a video database, extracting corresponding affective characteristic vectors of each video clip, and storing the extracted affective characteristic vectors into a characteristic database; inputting the video clip to be retrieved, and extracting the affective characteristic vector of the video clip to be retrieved; matching the affective characteristic vector of the video clip to be retrieved with each affective characteristic vector in the characteristic database, calculating similarities between the affective characteristic vector of the video clip to be retrieved and each affective characteristic vector in the characteristic database, sequencing the similarities, and selecting a preset number of video clips with the greatest similarities; and outputting the selected video clips as retrieval results. By the technical scheme provided by the invention, the problems of affective characteristic extraction of the video clips and video content similarity matching can be solved, and the retrieval of video contents is realized by high-level semantics.
Owner:TVMINING BEIJING MEDIA TECH
Method for capturing human motion by aid of fused depth images and three-dimensional models
InactiveCN104268138ALarge range of activitiesNot many performance venues are requiredImage analysisCharacter and pattern recognitionHuman bodyHuman motion
The invention relates to a method for capturing human motion by the aid of fused depth images and three-dimensional models. By the aid of the method, problems of adhesion requirement on mark points, inconvenience in interaction and easiness in confusing and shielding the mark points of a method for optically capturing motion can be solved. The method includes acquiring depth information of human actions; removing backgrounds of motion objects; acquiring complete depth information of the human actions; converting the complete depth information of the human actions into three-dimensional point-cloud information of human bodies; acquiring three-dimensional human action models; establishing databases; enabling the databases to be in one-to-one correspondence with data of human action skeleton databases; extracting depth information of to-be-identified human actions to build the three-dimensional models; then matching the similarity of the three-dimensional models with the similarity of human actions in the databases of the three-dimensional models; outputting human action skeletons according to similarity sequences. The human action skeletons are motion capturing results. The method has the advantages that sensors or added mark points can be omitted on the human bodies, the method is easy to implement, motion sequences are matched with one another by the aid of a regular time wrapping process, the matching precision of each two sequences can be improved, the matching time can be greatly shortened, and the motion capturing speed and the motion capturing precision can be guaranteed.
Owner:XIAN TECH UNIV
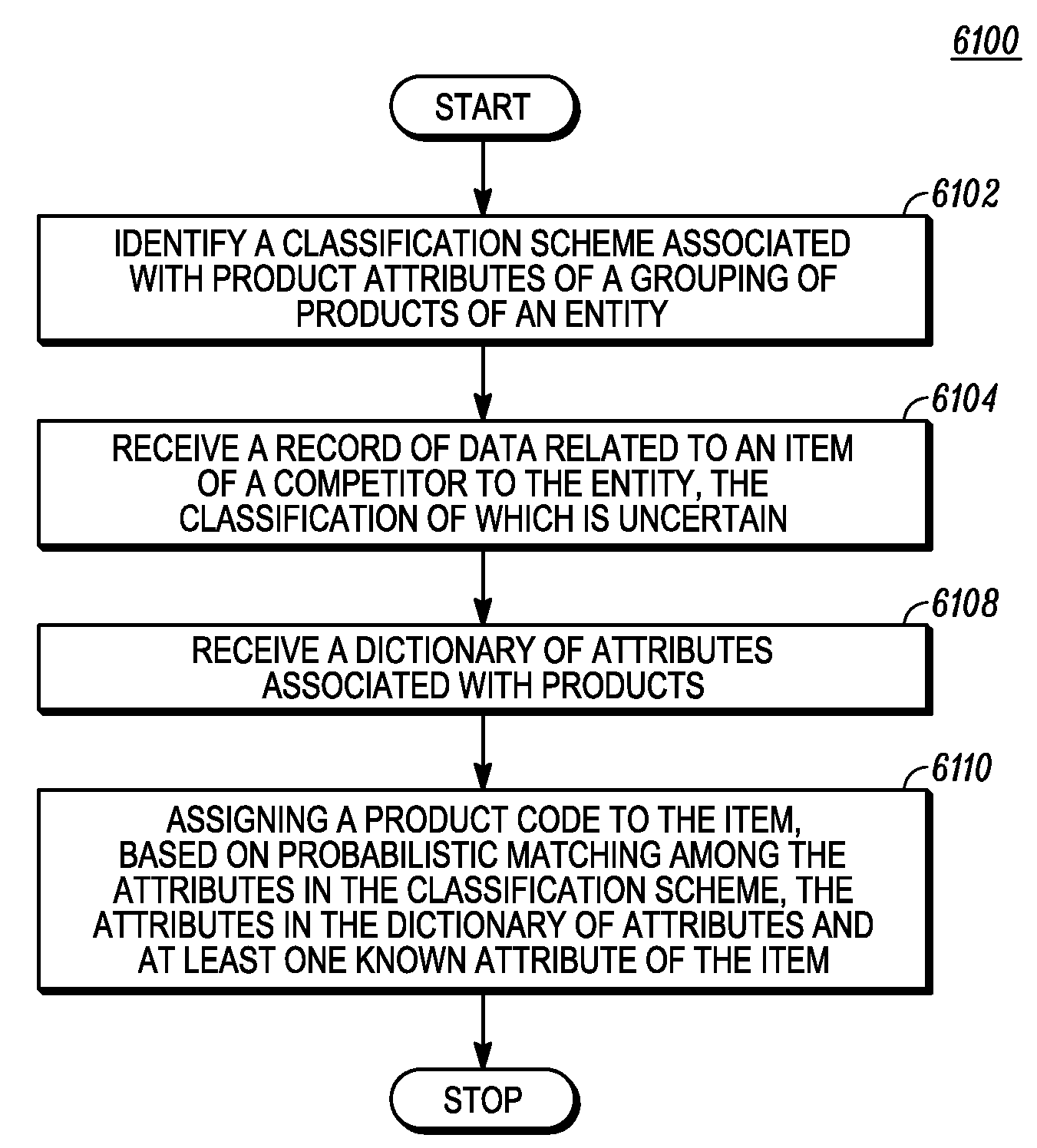
Similarity matching of a competitor's products
In embodiments of the present invention improved capabilities are described for identifying a classification scheme associated with product attributes of a grouping of products of an entity, receiving a record of data relating to an item of a competitor to the entity, the classification of which is uncertain, receiving a dictionary of attributes associated with products, and assigning a product code to the item, based on probabilistic matching among the attributes in the classification scheme, the attributes in the dictionary of attributes and at least one known attribute of the item.
Owner:INFORMATION RESOURCES
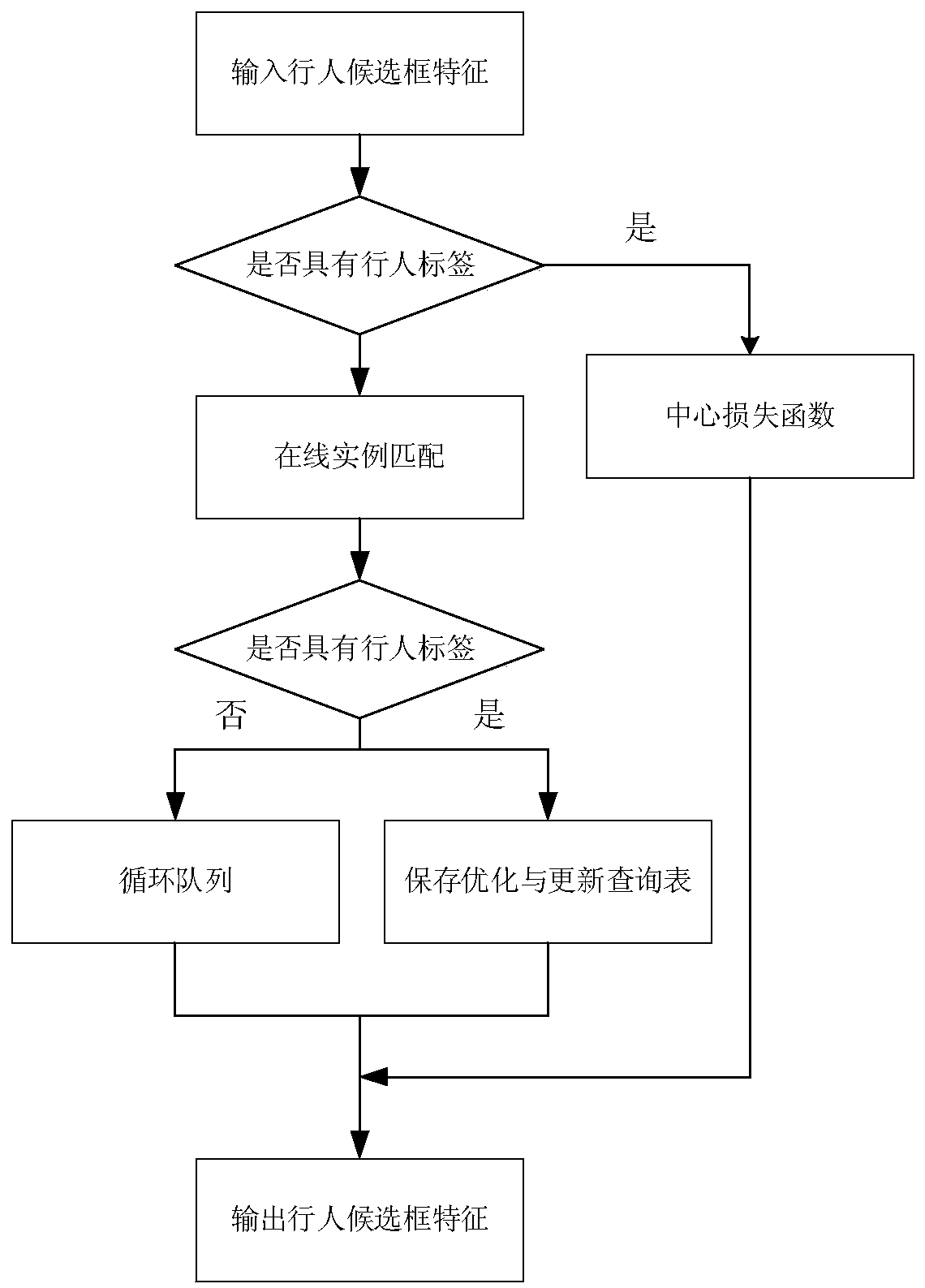
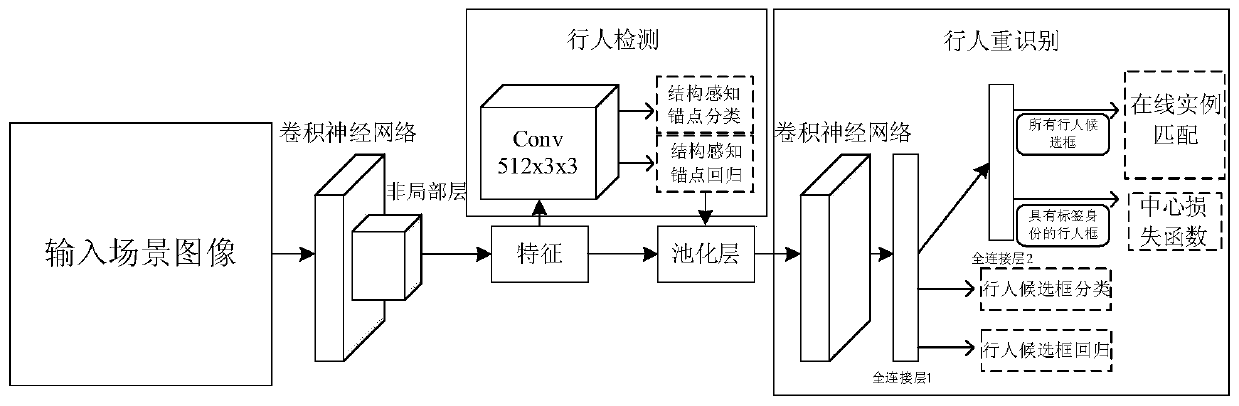
A pedestrian searching method and device based on structural perception self-attention and online instance aggregation matching
ActiveCN109948425AHigh precisionImprove efficiencyInternal combustion piston enginesCharacter and pattern recognitionNerve networkVisual technology
The invention discloses a pedestrian searching method and device based on structural perception self-attention and online instance aggregation matching, and belongs to the technical field of computervision technology processing. The method comprises the following steps: firstly, in a training phase, combining a convolutional neural network with a non-local layer; carrying out feature extraction on an input whole scene image to obtain feature representation of the scene image, designing structure-perceived anchor points for a special object of a pedestrian, improving the performance of a detection framework, framing the detected pedestrian into the same size, then sending the pedestrian into a pedestrian re-identification network, and carrying out training, storage, optimization and updating of pedestrian features with tags. In the model testing stage, the trained non-local convolutional neural network is used for carrying out pedestrian detection on an input scene image, and after a pedestrian frame is detected, a target pedestrian image is used for carrying out special similarity matching sorting and retrieval. Pedestrian detection and re-identification can be carried out on large-scale real scene images at the same time, and the method plays an important role in the security and protection fields of urban monitoring and the like.
Owner:CHINA UNIV OF MINING & TECH
Similarity matching of a competitor's products
In embodiments of the present invention improved capabilities are described for identifying a classification scheme associated with product attributes of a grouping of products of an entity, receiving a record of data relating to an item of a competitor to the entity, the classification of which is uncertain, receiving a dictionary of attributes associated with products, and assigning a product code to the item, based on probabilistic matching among the attributes in the classification scheme, the attributes in the dictionary of attributes and at least one known attribute of the item.
Owner:INFORMATION RESOURCES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com