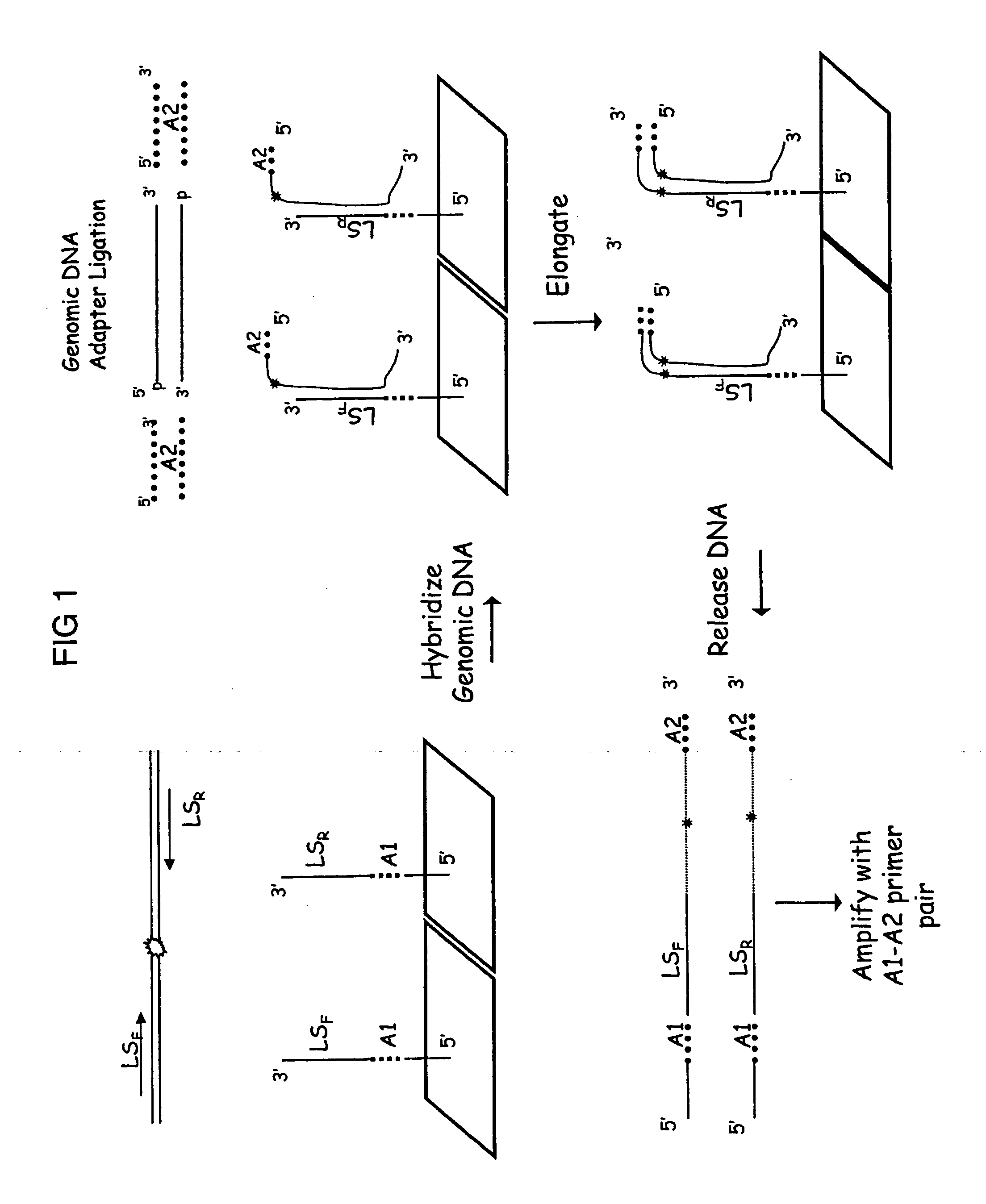
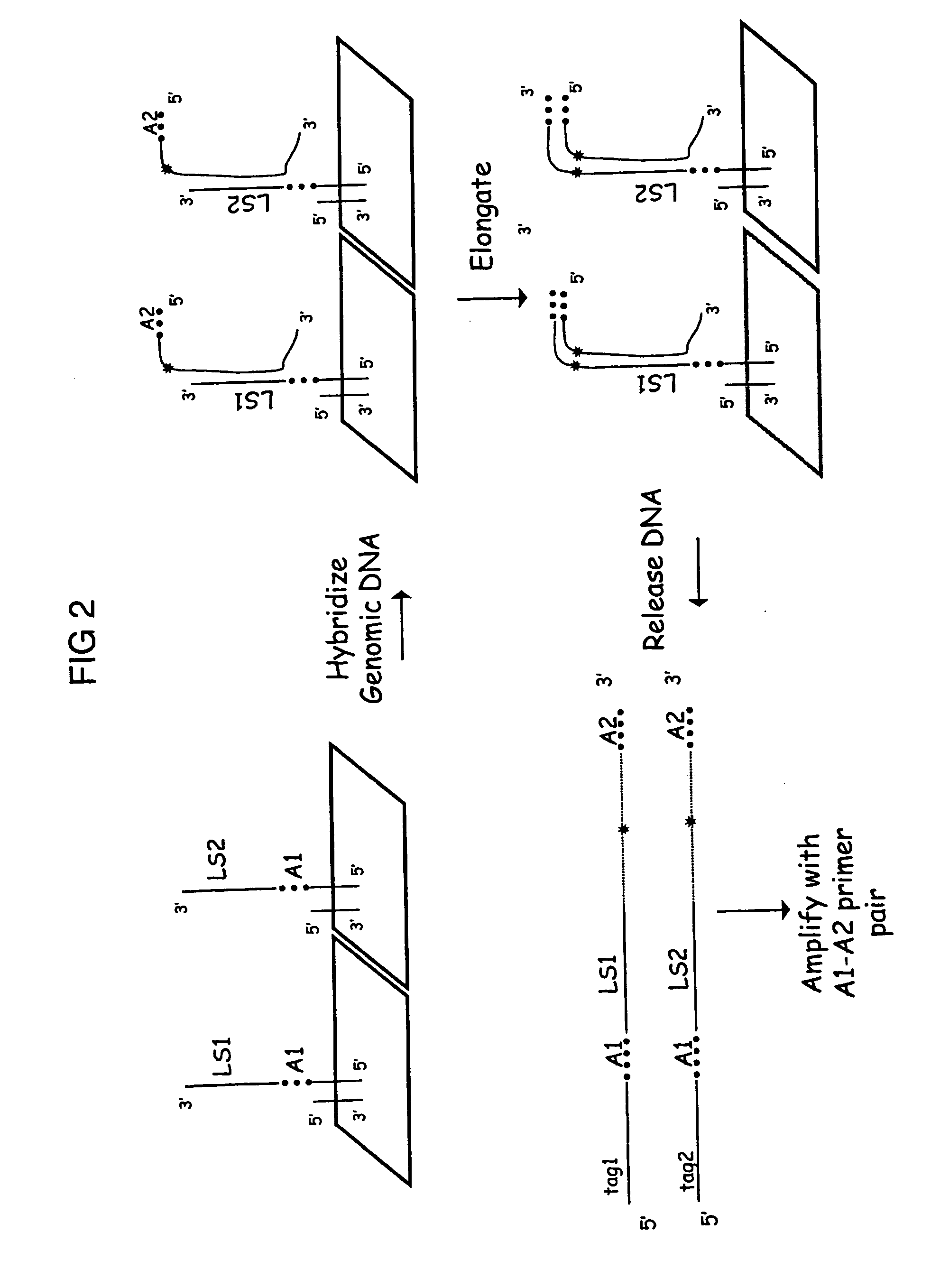
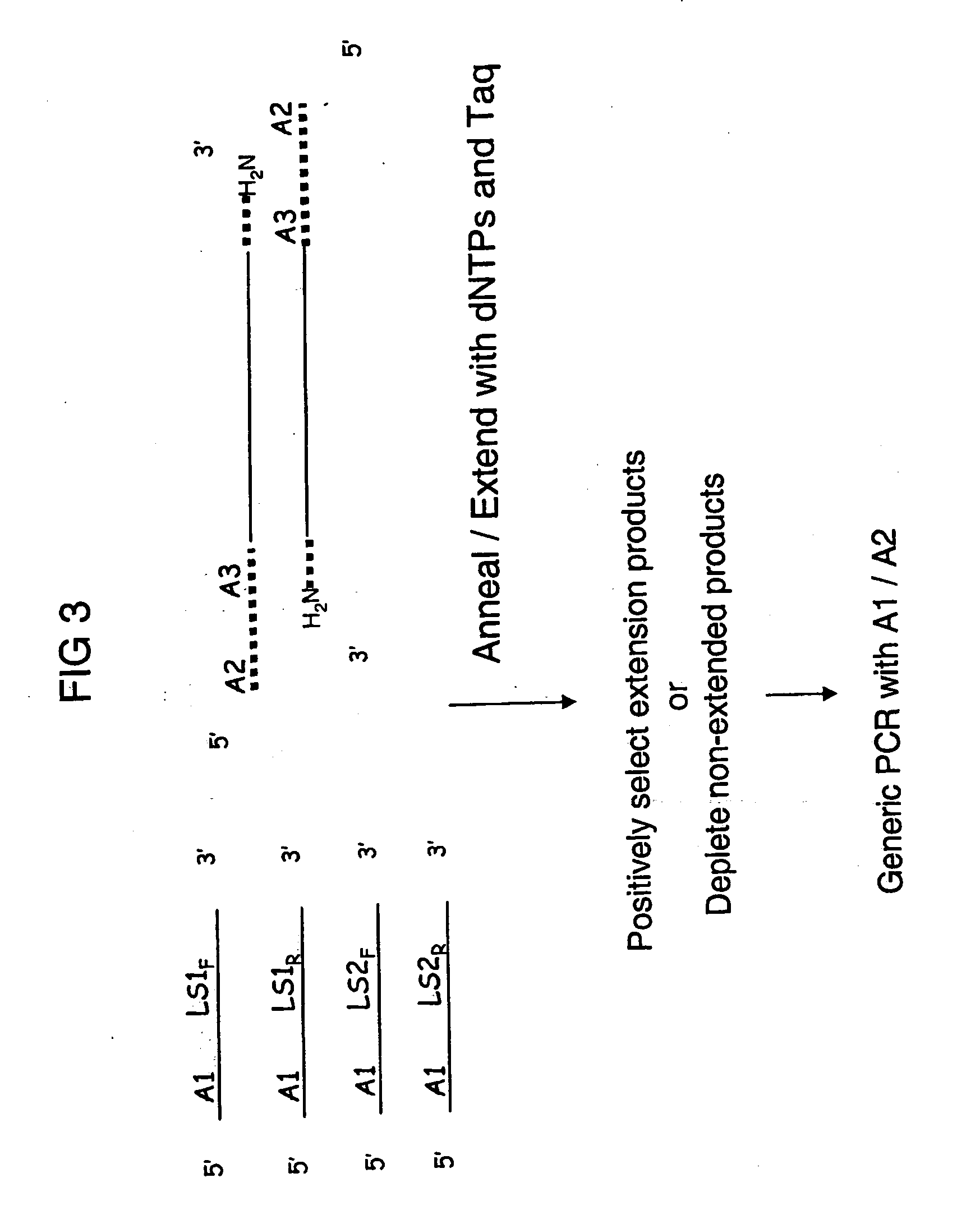
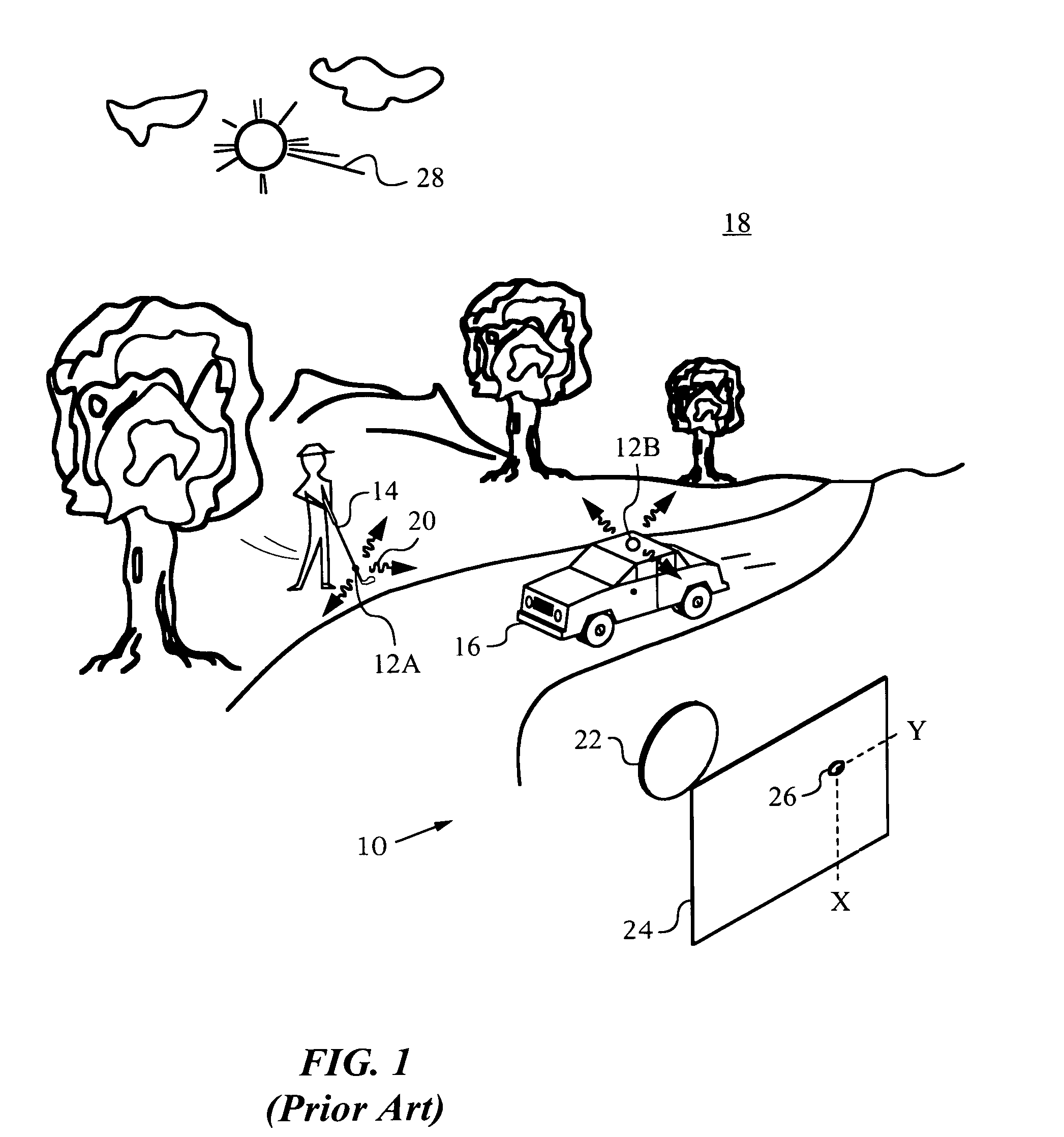
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
327 results about "Sequence pattern" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Methods for genotyping selected polymorphism
InactiveUS20050142577A1Sugar derivativesMicrobiological testing/measurementDegenerate oligonucleotideGene
Methods for genotyping polymorphisms using a locus specific primer that is complementary to a region near a selected polymorphism are described. Methods for synthesizing pools of locus specific primers that incorporate some degenerate positions are also disclosed. A plurality of different sequence capture probes are synthesized simultaneously using degenerate oligonucleotide synthesis. The sequence of the locus specific regions of the capture probes are related in that they have some bases that are identical in each sequence in the plurality of sequences and positions that vary from one locus specific region to another. The sequences are selected based on proximity to a polymorphism of interest and because they conform to a similar sequence pattern.
Owner:AFFYMETRIX INC
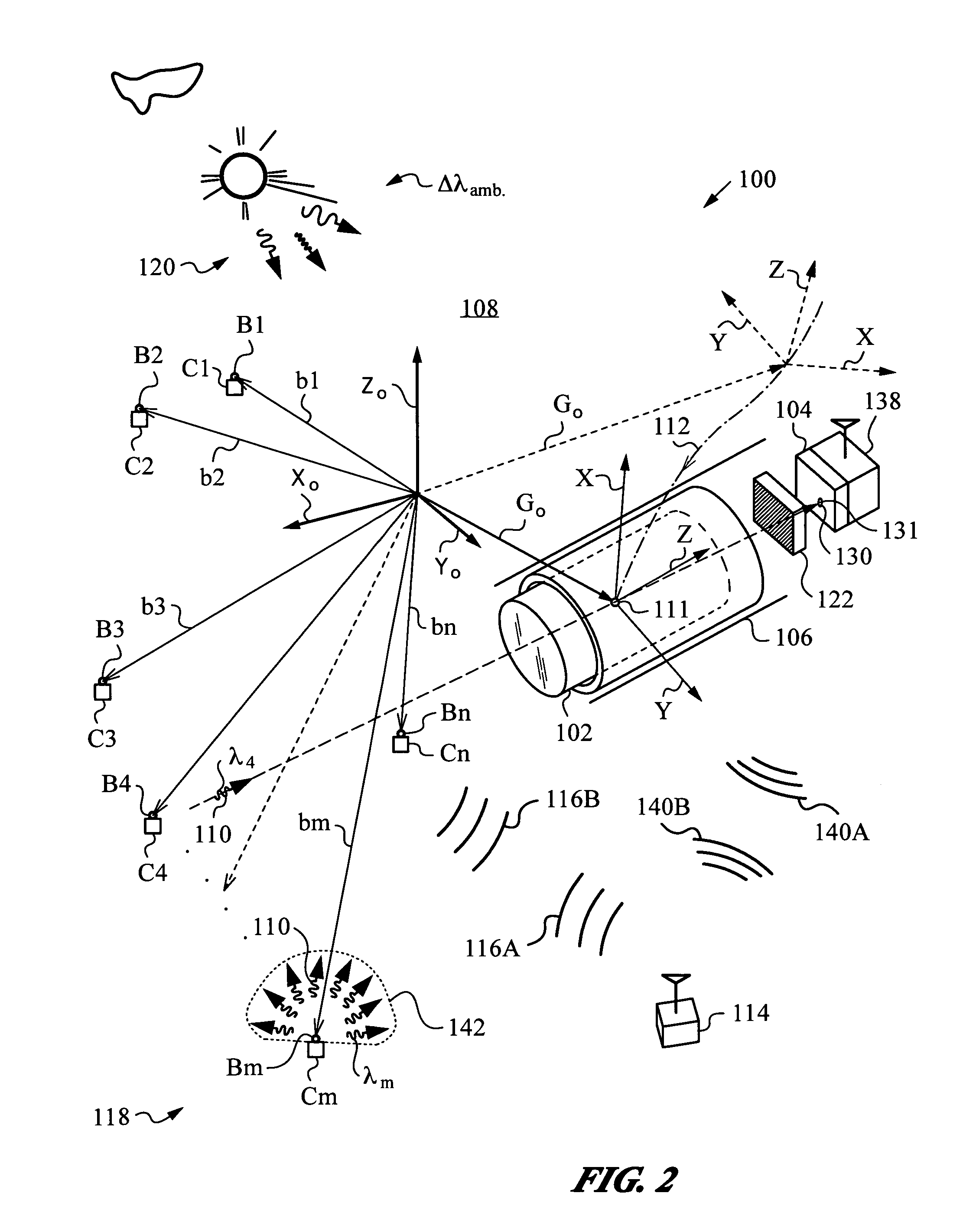
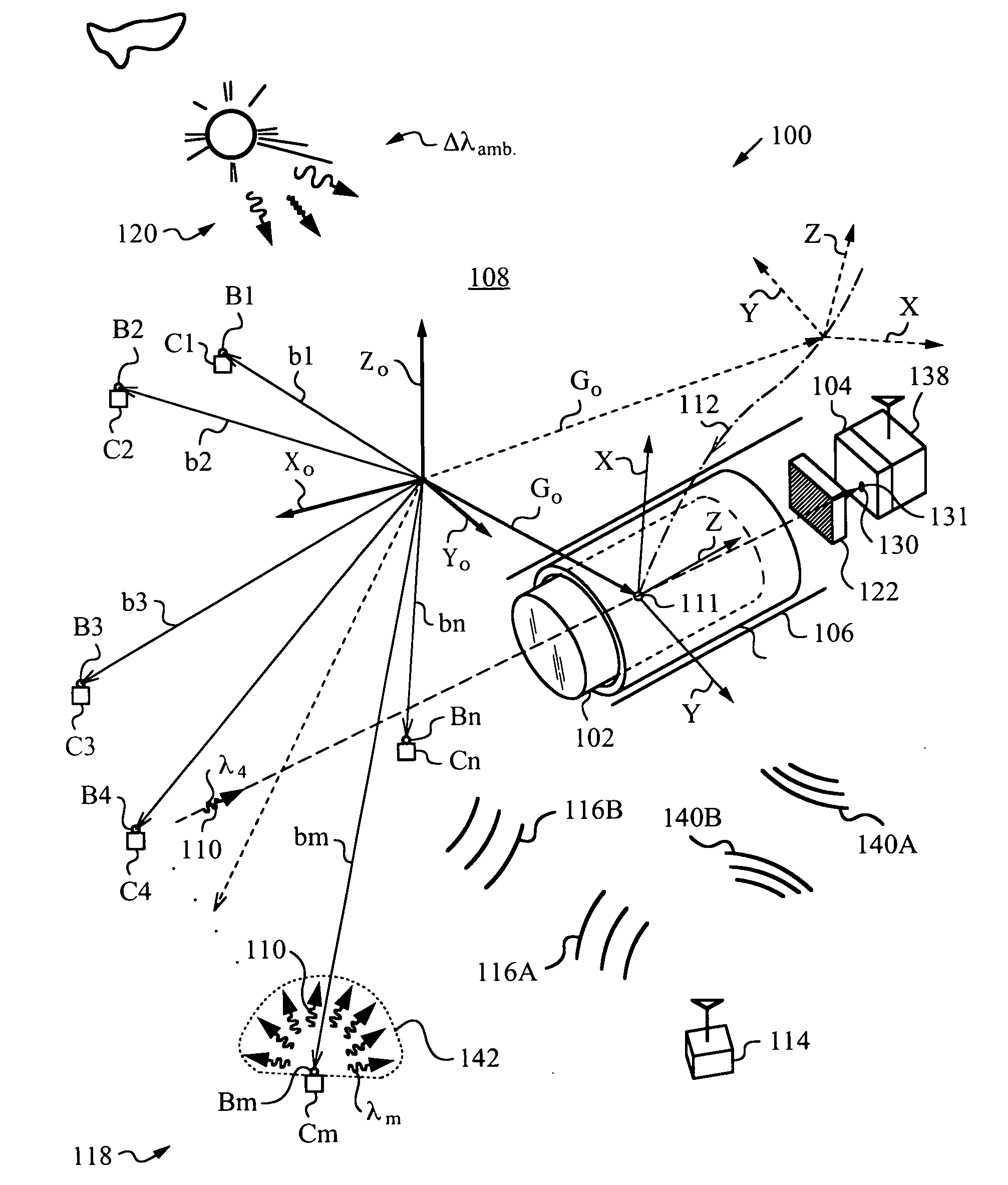
Optical navigation apparatus using fixed beacons and a centroid sensing device
The present invention relates to an optical navigation system for determining a pose, which includes the position and orientation of an object in an environment. The optical navigation system uses a number of beacons affixed at known locations in the environment to provide electromagnetic radiation in a sequenced pattern. An on-board optic images the radiation from the beacons onto an on-board centroid sensing device to obtain an imaged distribution of the radiation on the on-board centroid sensing device. The centroid sensing device determines the centroid of the imaged distribution and provides centroid information to a navigation unit for determining the pose of the object from the centroid. The navigation system is particularly well-suited for navigating hand-held objects.
Owner:ELECTRONICS SCRIPTING PRODS
Electronic device and method for switching between locked state and unlocked state
InactiveUS20090289916A1Digital data authenticationInput/output processes for data processingComputer scienceSequence pattern
A method for switching an electronic device with a touch sensitive display between a locked state and an unlocked state. The method includes receiving multiple contacts with respect to multiple predefined areas of the touch-sensitive display; detecting a sequence pattern in response to receiving the multiple contacts; determining if the recognized sequence pattern matches a predefined sequence pattern; and switching the electronic device to the unlocked state in response to determining that the recognized sequence pattern matches the predefined sequence pattern, so as to allow the electronic device to be manipulated in the unlocked state. An electronic device using the method is provided.
Owner:HON HAI PRECISION IND CO LTD
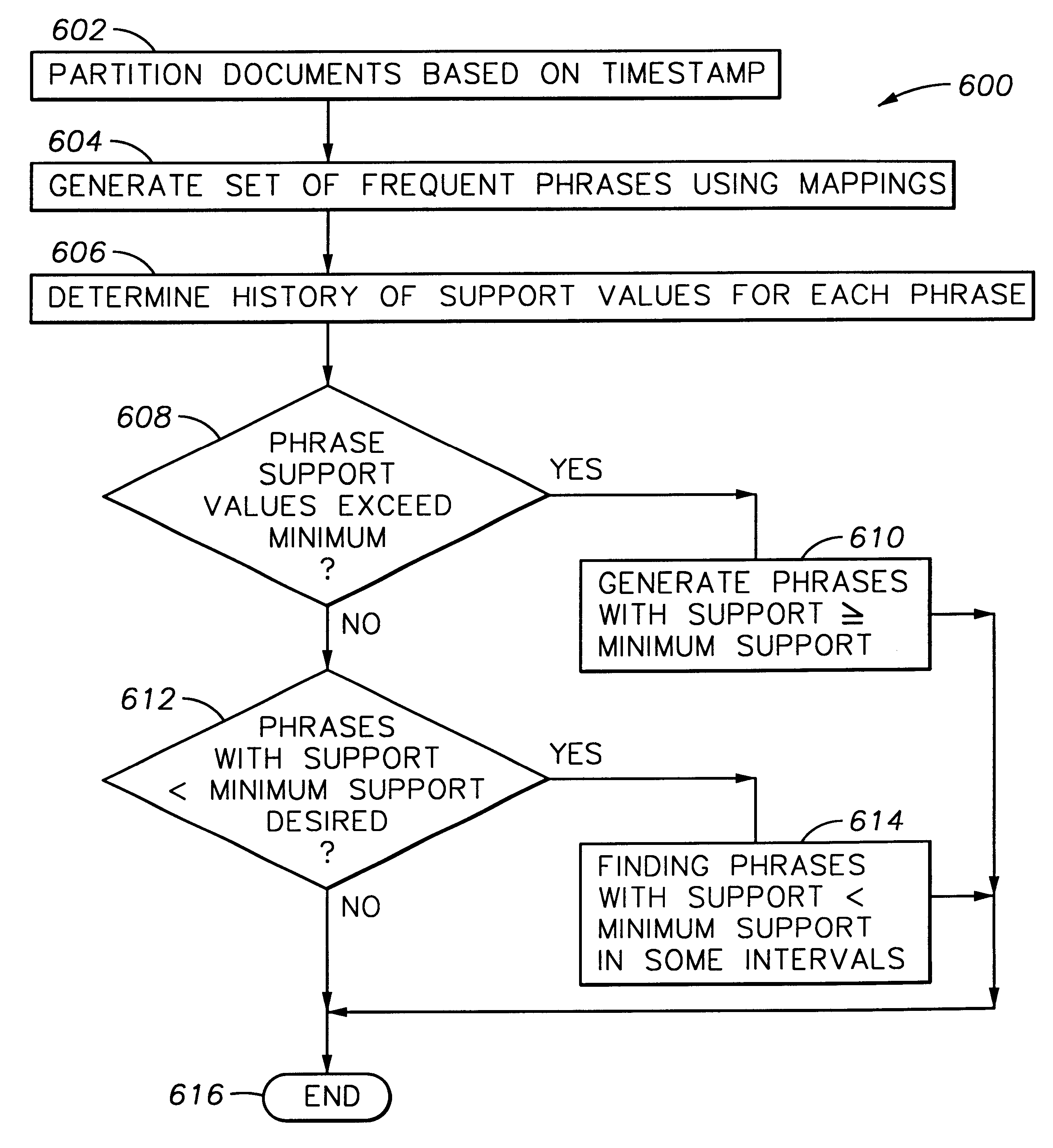
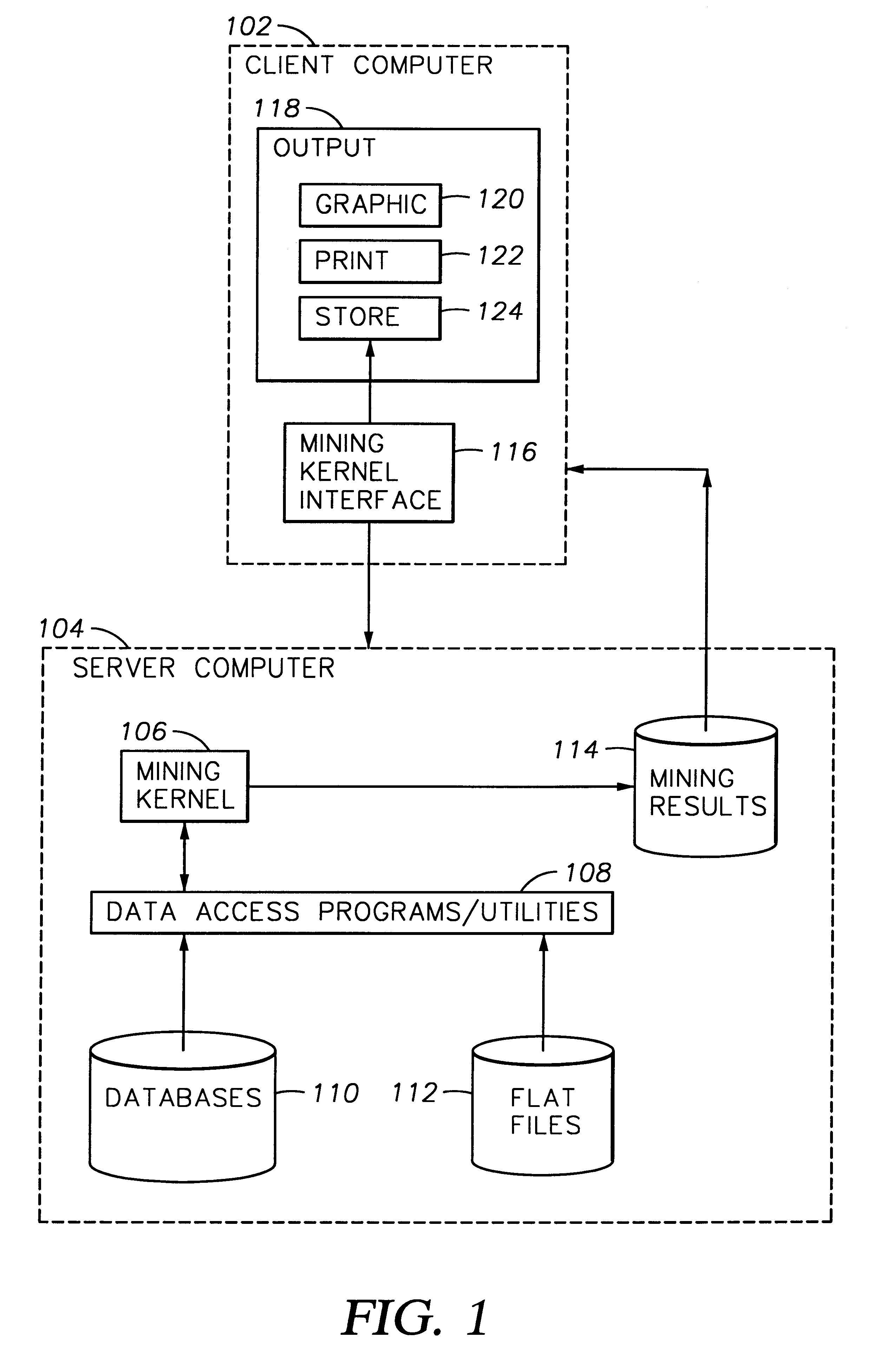
Method and apparatus for partitioning a database upon a timestamp, support values for phrases and generating a history of frequently occurring phrases
A method and apparatus for mining text databases, employing sequential pattern phrase identification and shape queries, to discover trends. The method passes over a desired database using a dynamically generated shape query. Documents within the database are selected based on specific classifications and user defined partitions. Once a partition is specified, transaction IDs are assigned to the words in the text documents depending on their placement within each document. The transaction IDs encode both the position of each word within the document as well as representing sentence, paragraph, and section breaks, and are represented in one embodiment as long integers with the sentence boundaries. A maximum and minimum gap between words in the phrases and the minimum support all phrases must meet for the selected time period may be specified. A generalized sequential pattern method is used to generate those phrases in each partition that meet the minimum support threshold. The shape query engine takes the set of phrases for the partition of interest and selects those that match a given shape query. A query may take the form of requesting a trend such as "recent upwards trend", "recent spikes in usage", "downward trends", and "resurgence of usage". Once the phrases matching the shape query are found, they are presented to the user.
Owner:GLOBALFOUNDRIES INC
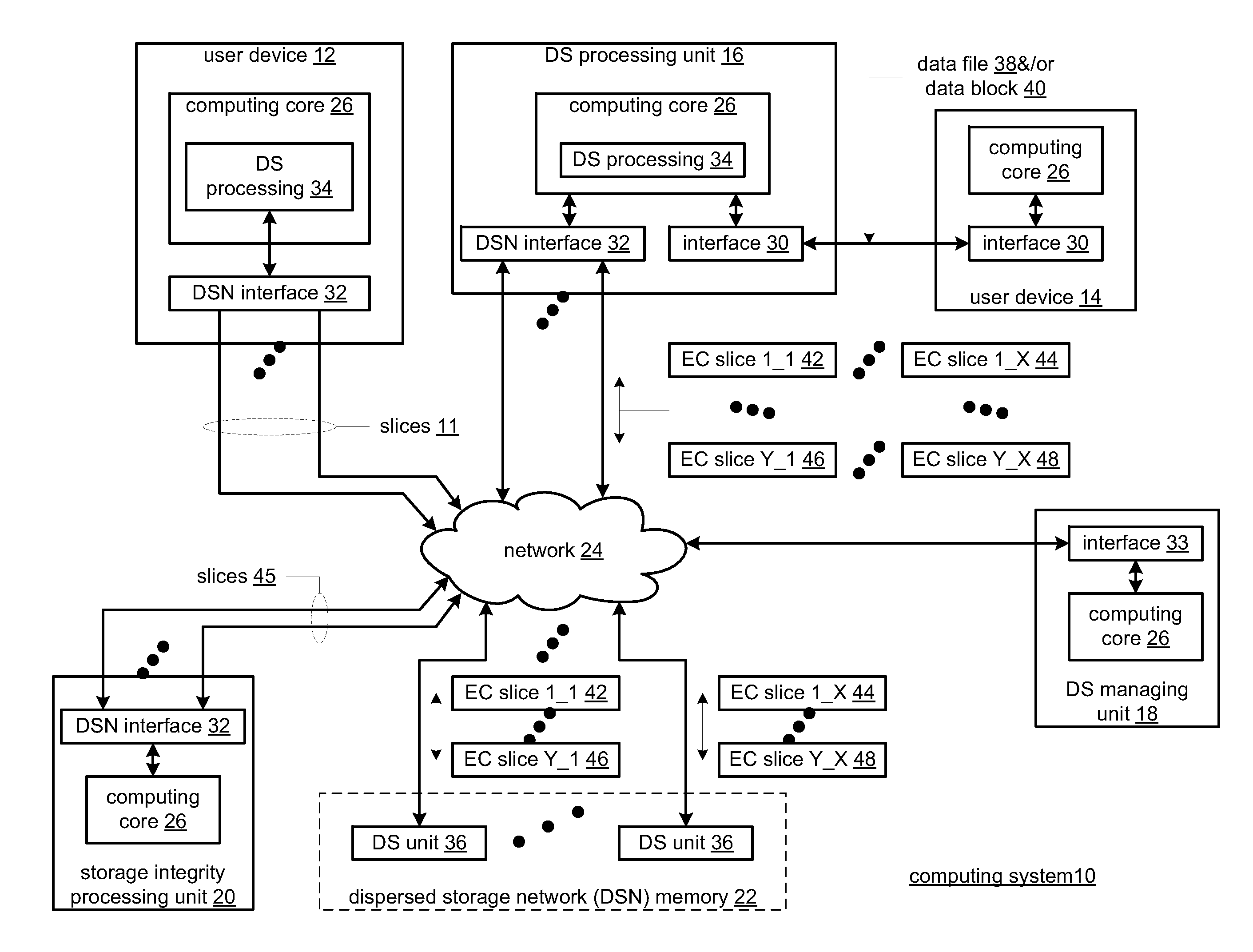
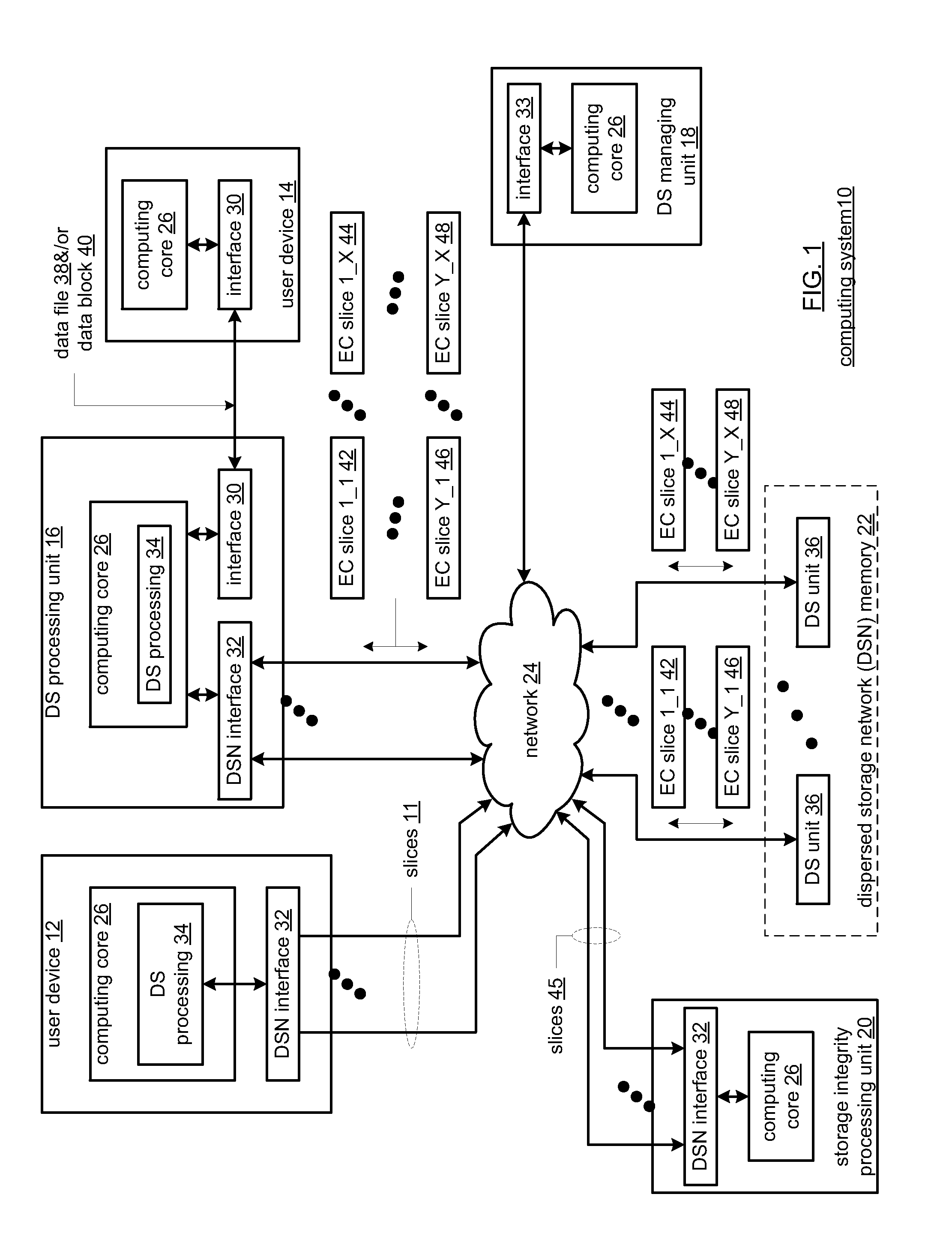
Distributed storage network for modification of a data object
In a dispersed storage network, data objects are dispersed storage error encoded into pluralities of sets of encoded data slices that are each stored in corresponding sets of storage units. To recover a data object, a read threshold number of encoded data slices from each set of encoded data slices of the plurality of sets of encoded data slices are required. Upon determining that an update is available for the storage units, a dispersed storage managing unit determines an updating sequence pattern that ensures that while one or more storage units are taken off line for the update, a sufficient number of storage units remain on line such that at least the read threshold number of encoded data slices are available for each set of encoded data slices.
Owner:PURE STORAGE
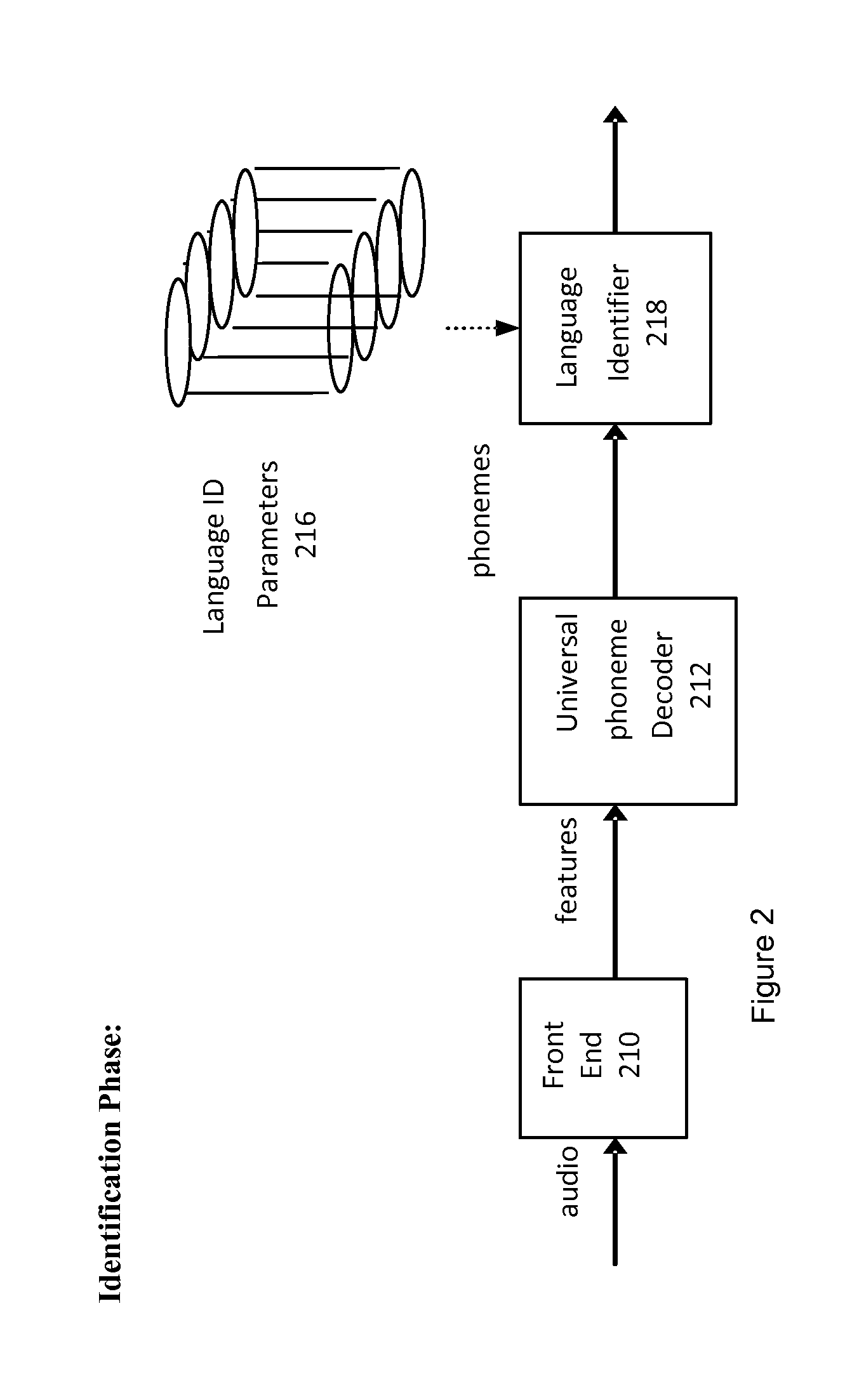
Automatic spoken language identification based on phoneme sequence patterns
ActiveUS20110035219A1Digital data processing detailsNatural language data processingSpoken languageRunning time
A language identification system that includes a universal phoneme decoder (UPD) is described. The UPD contains a universal phoneme set representing both 1) all phonemes occurring in the set of two or more spoken languages, and 2) captures phoneme correspondences across languages, such that a set of unique phoneme patterns and probabilities are calculated in order to identify a most likely phoneme occurring each time in the audio files in the set of two or more potential languages in which the UPD was trained on. Each statistical language models (SLM) uses the set of unique phoneme patterns created for each language in the set to distinguish between spoken human languages in the set of languages. The run-time language identifier module identifies a particular human language being spoken by utilizing the linguistic probabilities supplied by the one or more SLMs that are based on the set of unique phoneme patterns created for each language.
Owner:LONGSAND
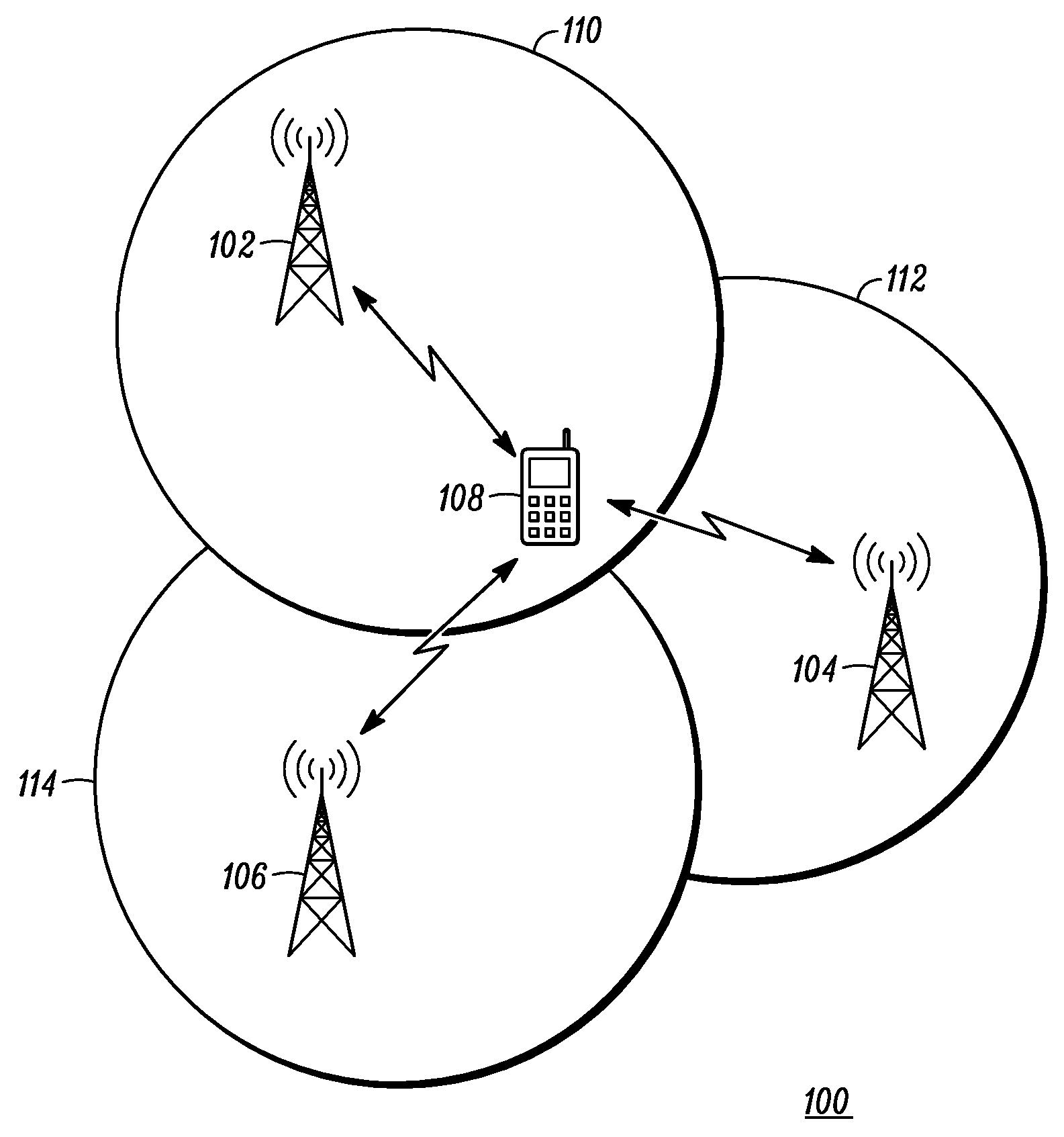
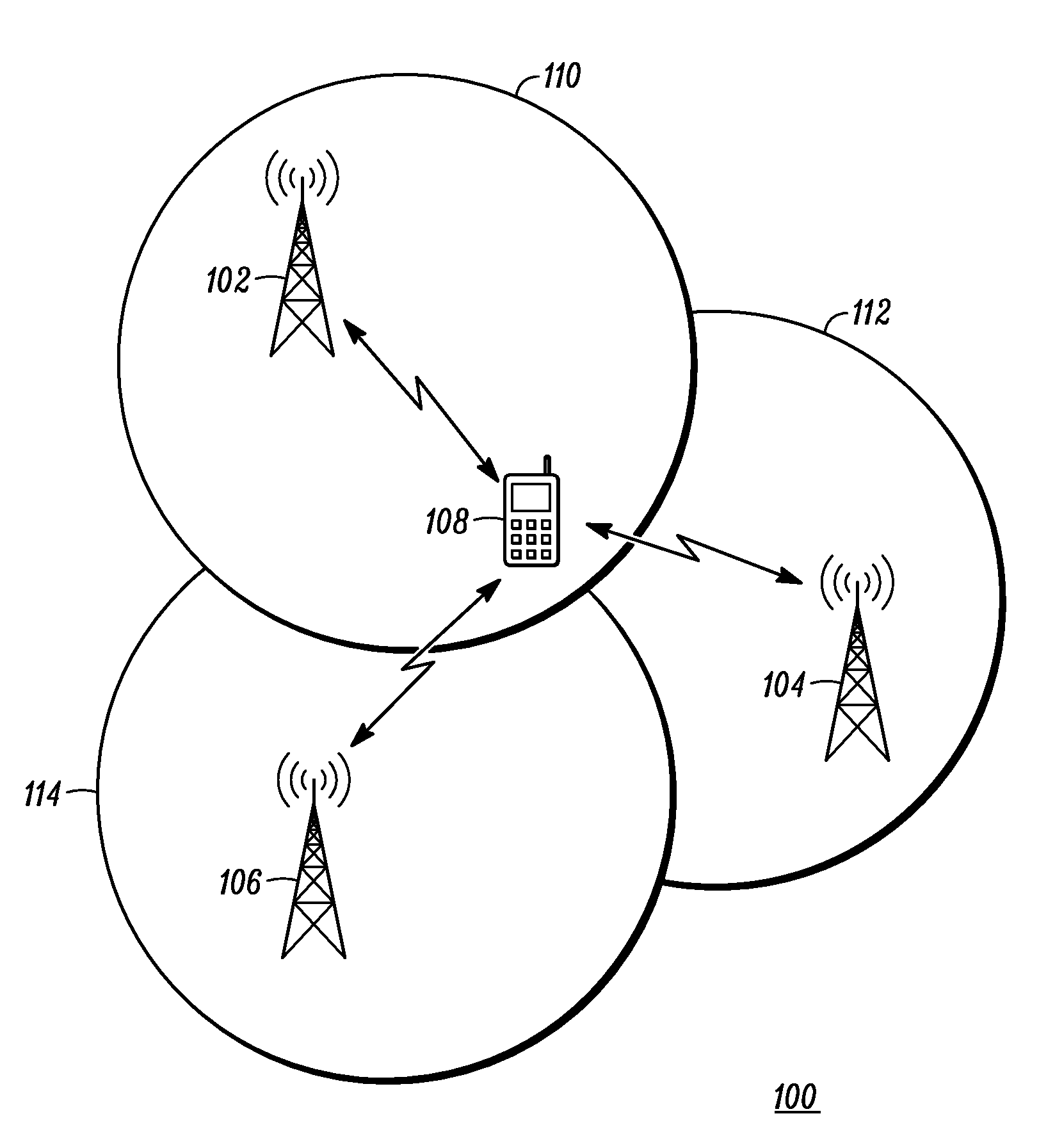
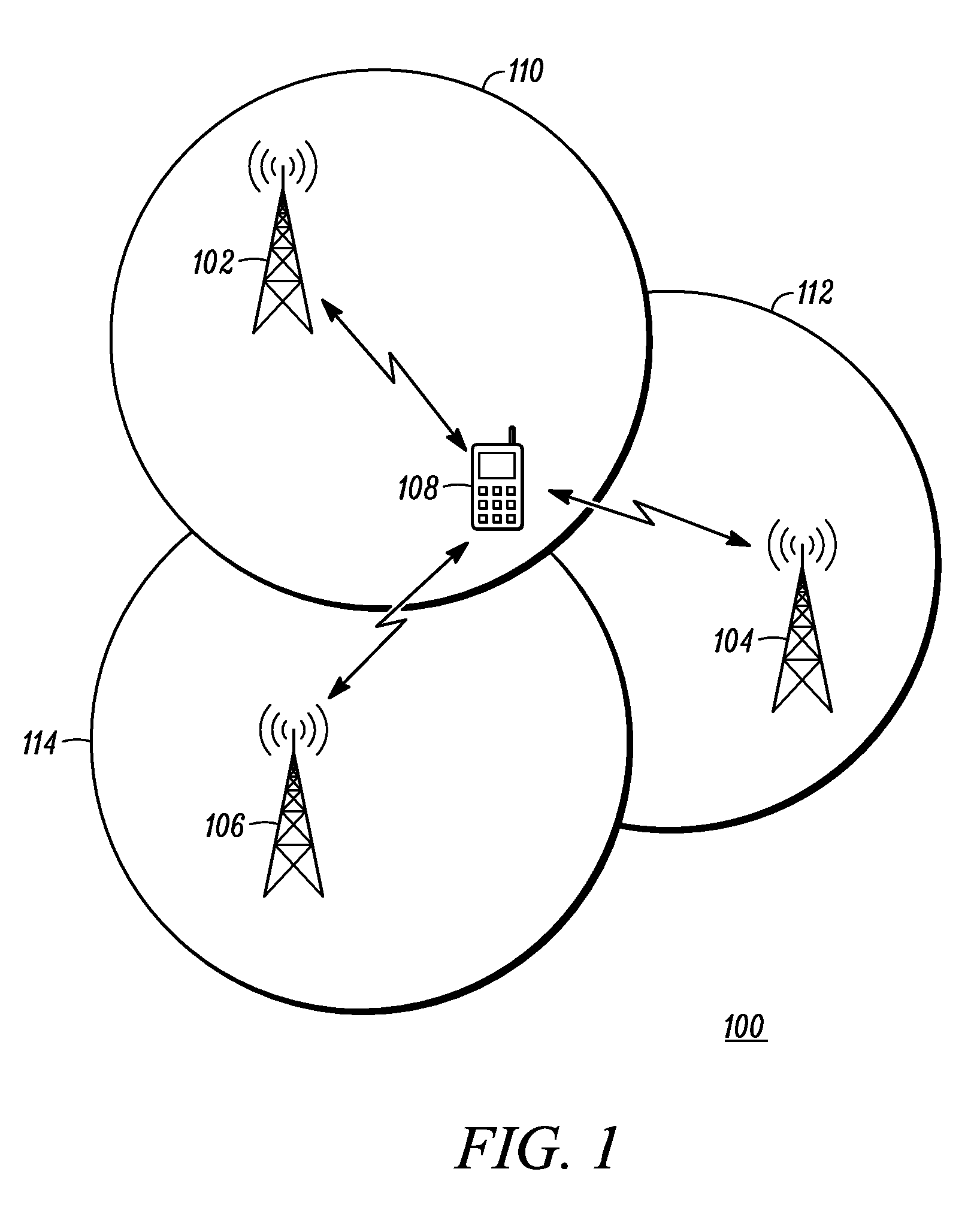
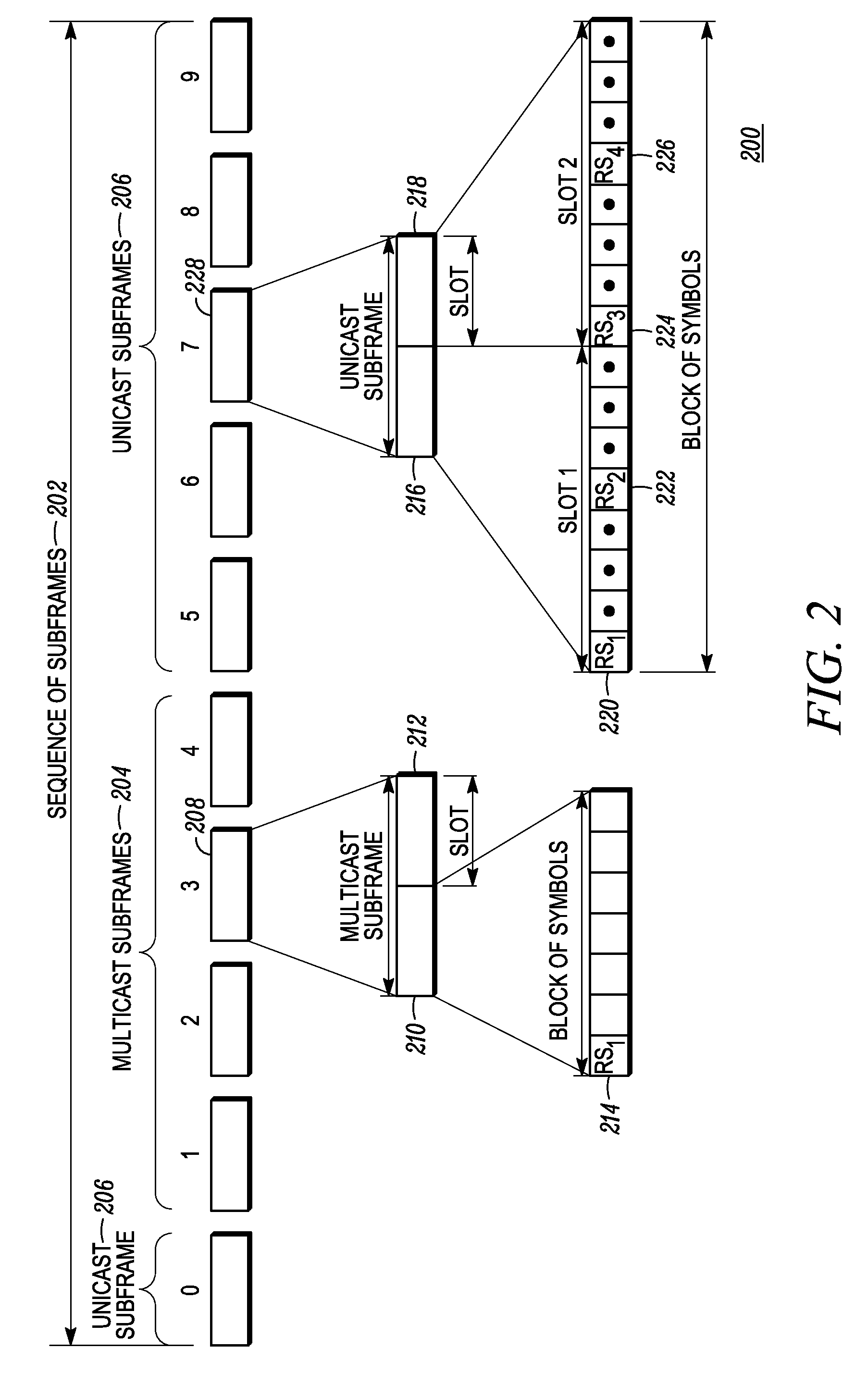
Method and apparatus for performing mobility measurements in a communication network
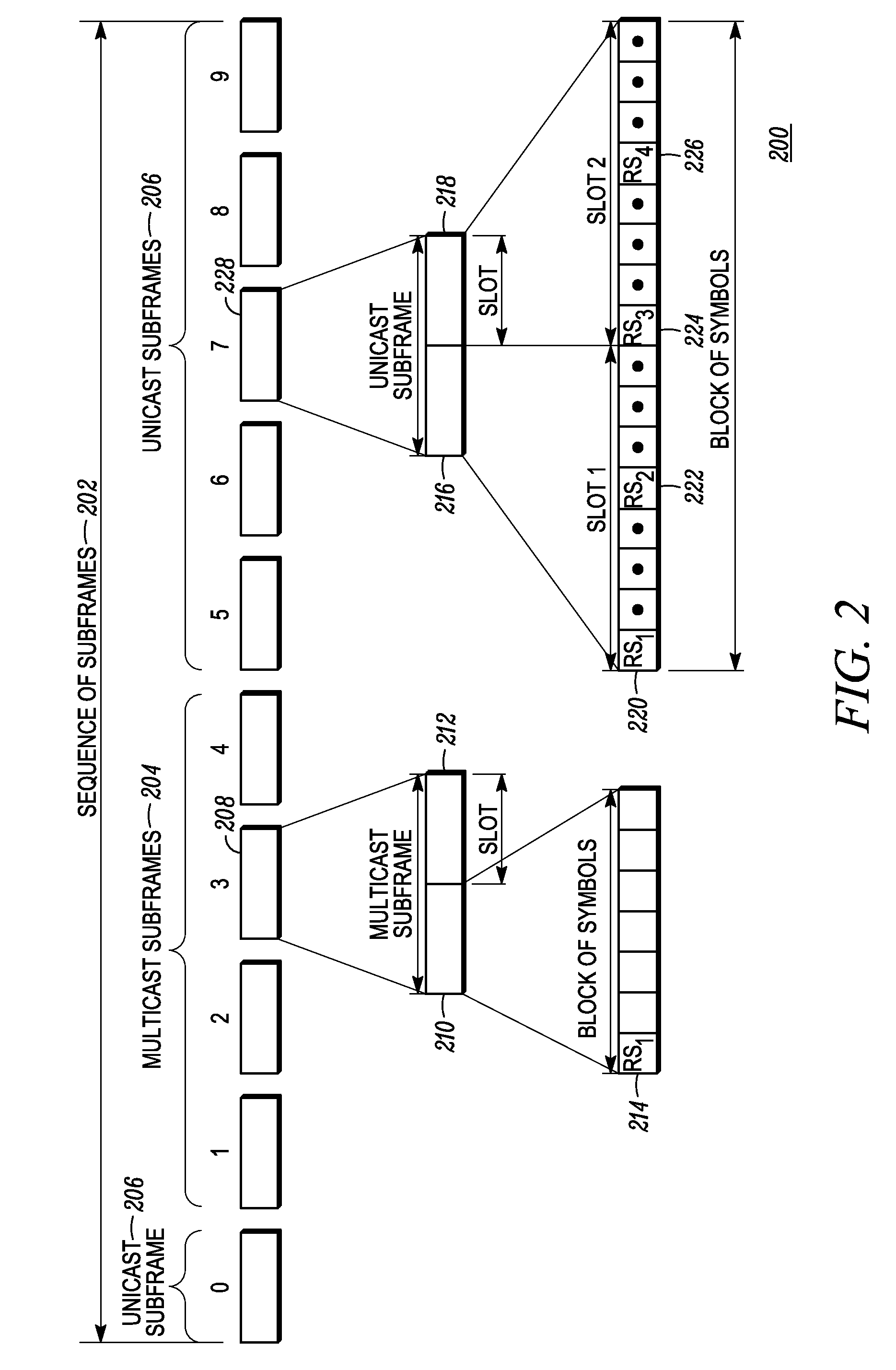
A method and apparatus for performing mobility measurement in a communication network (100) is described. The method comprises of receiving a subframe sequence pattern from a node in the communication network (100). The subframe sequence pattern indicates types of subframes being transmitted by a neighboring cell node (104) in a neighboring cell (112). The method includes receiving a subframe from a sequence of subframes transmitted by the neighboring cell node (104) in the neighboring cell (112), and determining that the received subframe is a multicast subframe based on the subframe sequence pattern. The method then includes performing a single cell-specific reference symbol measurement in response to determining that the received subframe is the multicast subframe.
Owner:GOOGLE TECH HLDG LLC
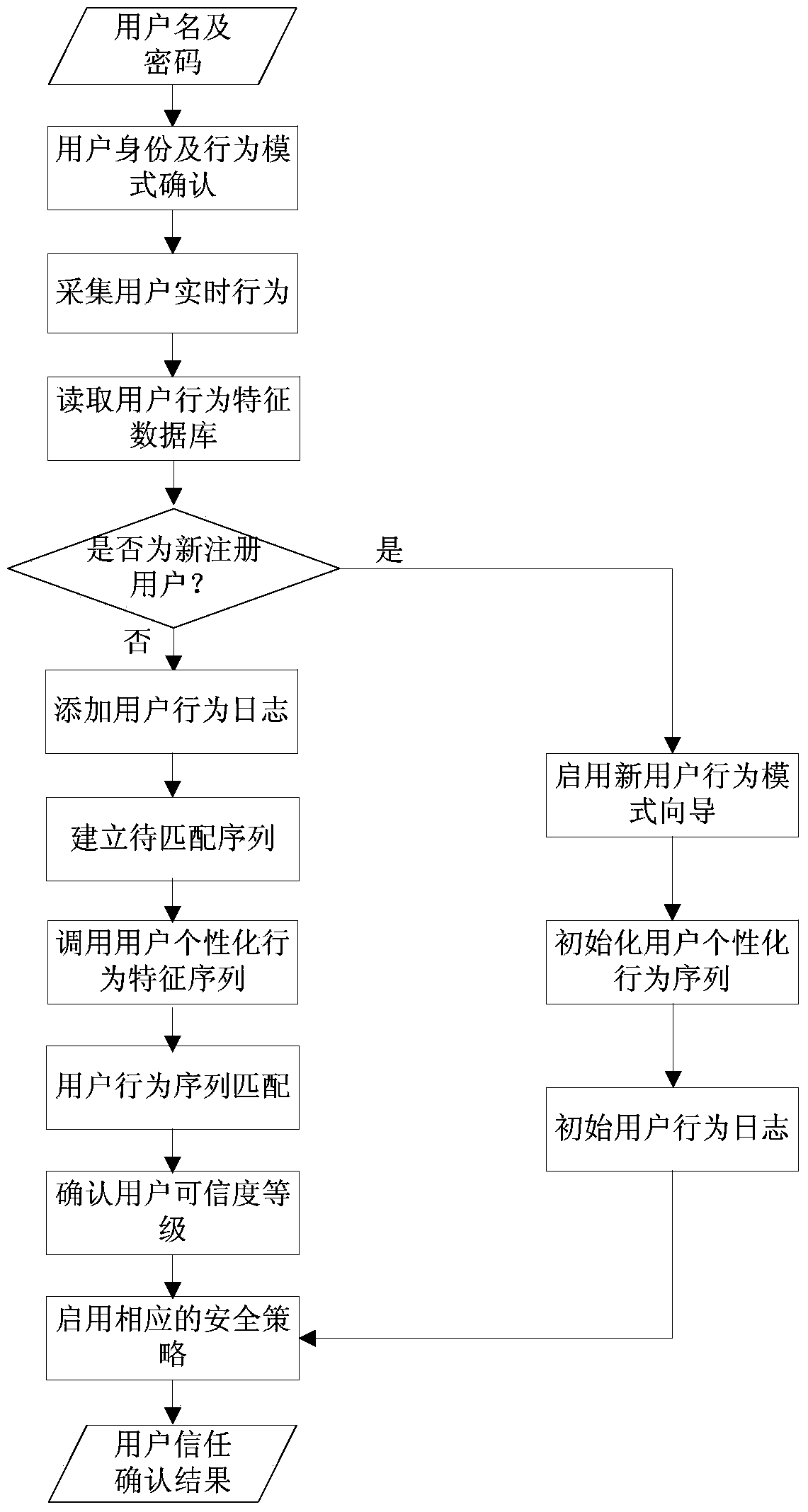
User credibility authentication system and method based on user behaviors
ActiveCN103646197AGuarantee property securityImprove accuracyDigital data authenticationPersonalizationAuthentication system
The invention discloses a user credibility authentication system and method based on user behaviors. The system comprises a user identity and behavior model determination module, a user behavior collection module, a user behavior mining module, a user behavior sequence matching and credibility authentication module and a local security policy module. The method comprises the steps as follows: the user behavior mining module performs behavior mining on user behavior logs; a personal user behavior characteristic sequence is established; the user behavior sequence matching and credibility authentication module performs sequence similarity calculation on the personal user behavior characteristic sequence and a to-be-matched sequence, so that a user credibility grade is obtained, and a corresponding security policy is started using. According to the invention, a sequence pattern mining manner is adopted to collect real-time user behaviors so as to establish the to-be-matched sequence, the similarity matching of the behavior sequence is performed, accordingly, the real-time user behaviors are subjected to credibility authentication, the accurate rate of authentication is improved, and enterprise and personal property safety is guaranteed.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
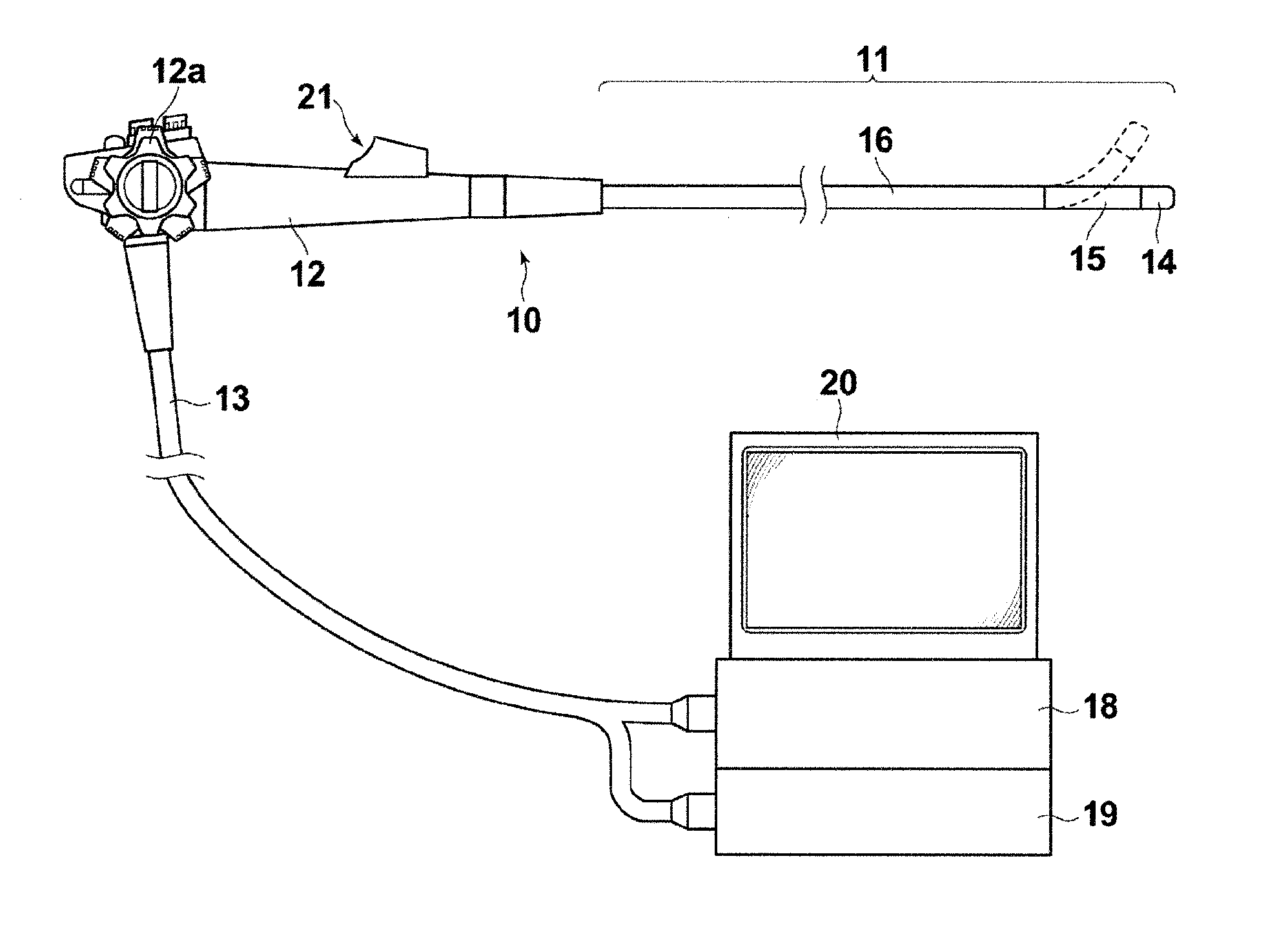
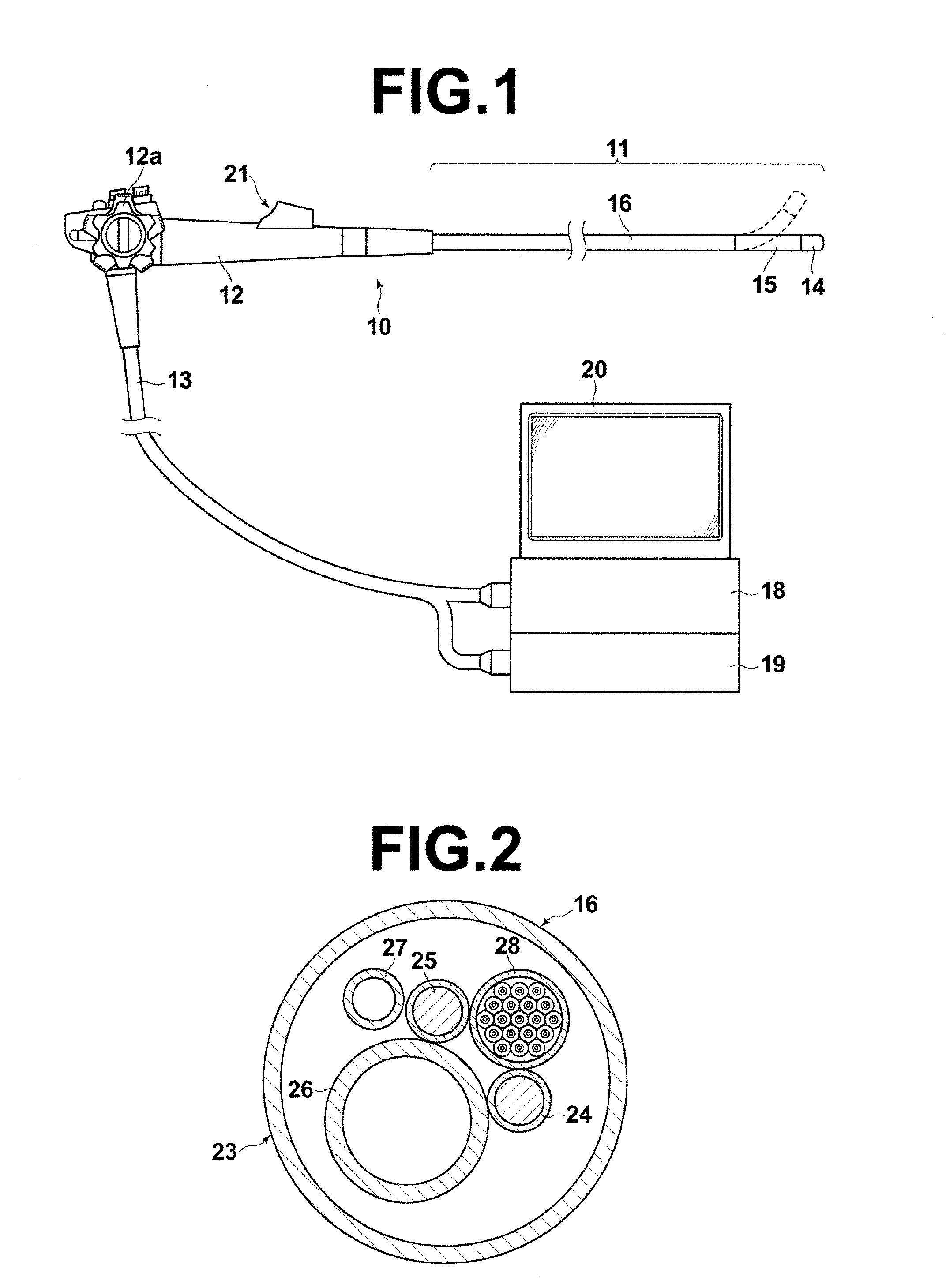
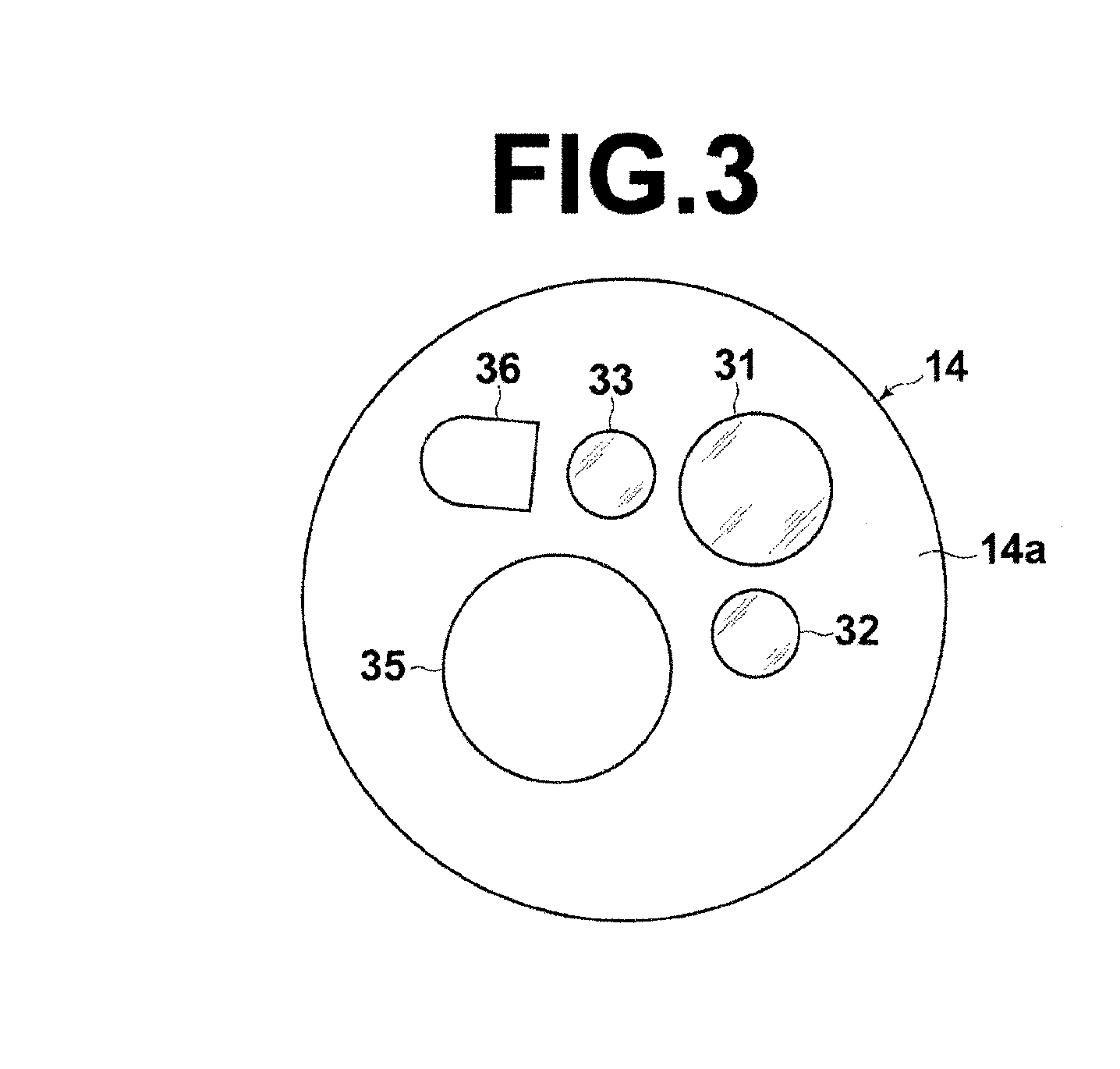
Endoscope system
InactiveUS20140354788A1Eliminate needReduce the burden onTelevision system detailsSurgeryImaging conditionControl signal
An endoscope unit includes a sequence pattern setting section in which a combination of sequence pattern which includes a plurality of parameters, each corresponding to imaging conditions of the image sensor on a frame-by-frame basis according to the type of the light source and control signal is set, an imaging condition setting section in which imaging conditions corresponding to each parameter are set, and an imaging control section that obtains the sequence pattern based on a control signal outputted from a control section of a processor unit, reads out the imaging conditions corresponding to each parameter included in the sequence pattern from the imaging condition setting section, and controls the imaging operation of the image sensor on a frame-by-frame basis based on the imaging conditions.
Owner:FUJIFILM CORP
Self-Compacting Pattern Indexer: Storing, Indexing and Accessing Information in a Graph-Like Data Structure
ActiveUS20090112905A1Digital data information retrievalDigital data processing detailsGraphicsSearch data structure
An indexing system uses a graph-like data structure that clusters features indexes together. The minimum atomic value in the data structure is represented as a leaf node which is either a single feature index or a sequence of two or more feature indexes when a minimum sequence length is imposed. Root nodes are formed as clustered collections of leaf nodes and / or other root nodes. Context nodes are formed from root nodes that are associated with content that is being indexed. Links between a root node and other nodes each include a sequence order value that is used to maintain the sequencing order for feature indexes relative to the root node. The collection of nodes forms a graph-like data structure, where each context node is indexed according to the sequenced pattern of feature indexes. Clusters can be split, merged, and promoted to increase the efficiency in searching the data structure.
Owner:MICROSOFT TECH LICENSING LLC
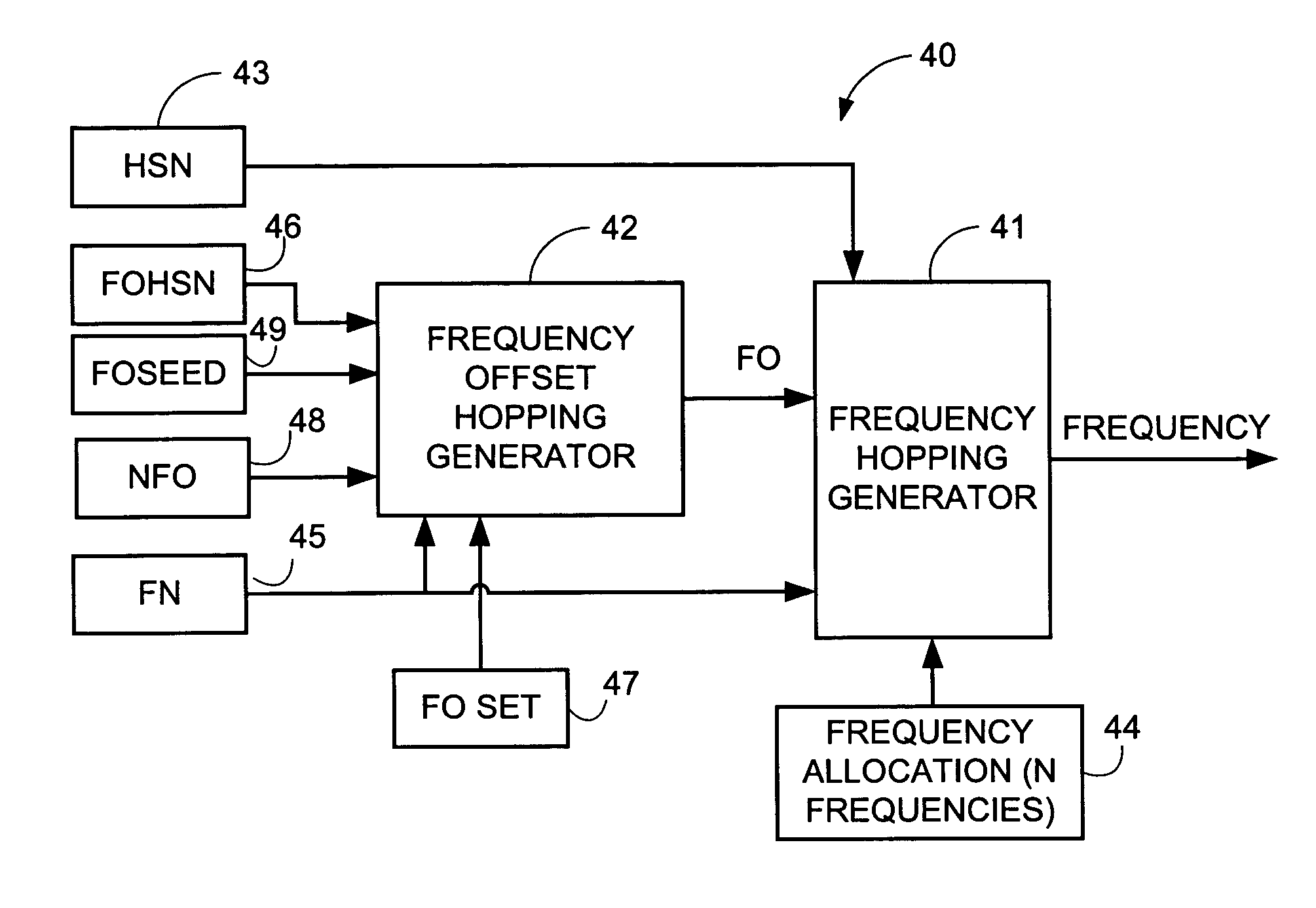
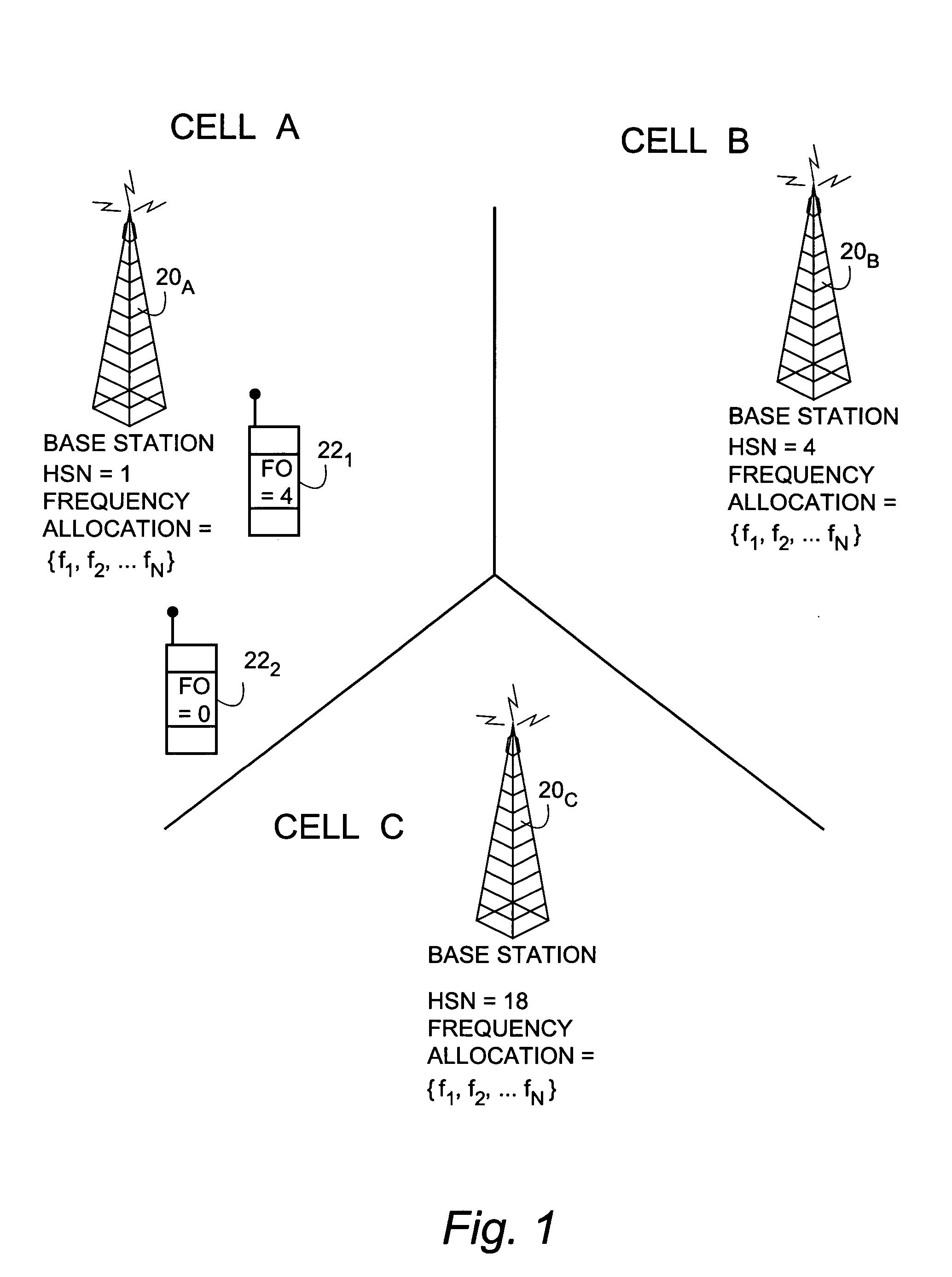
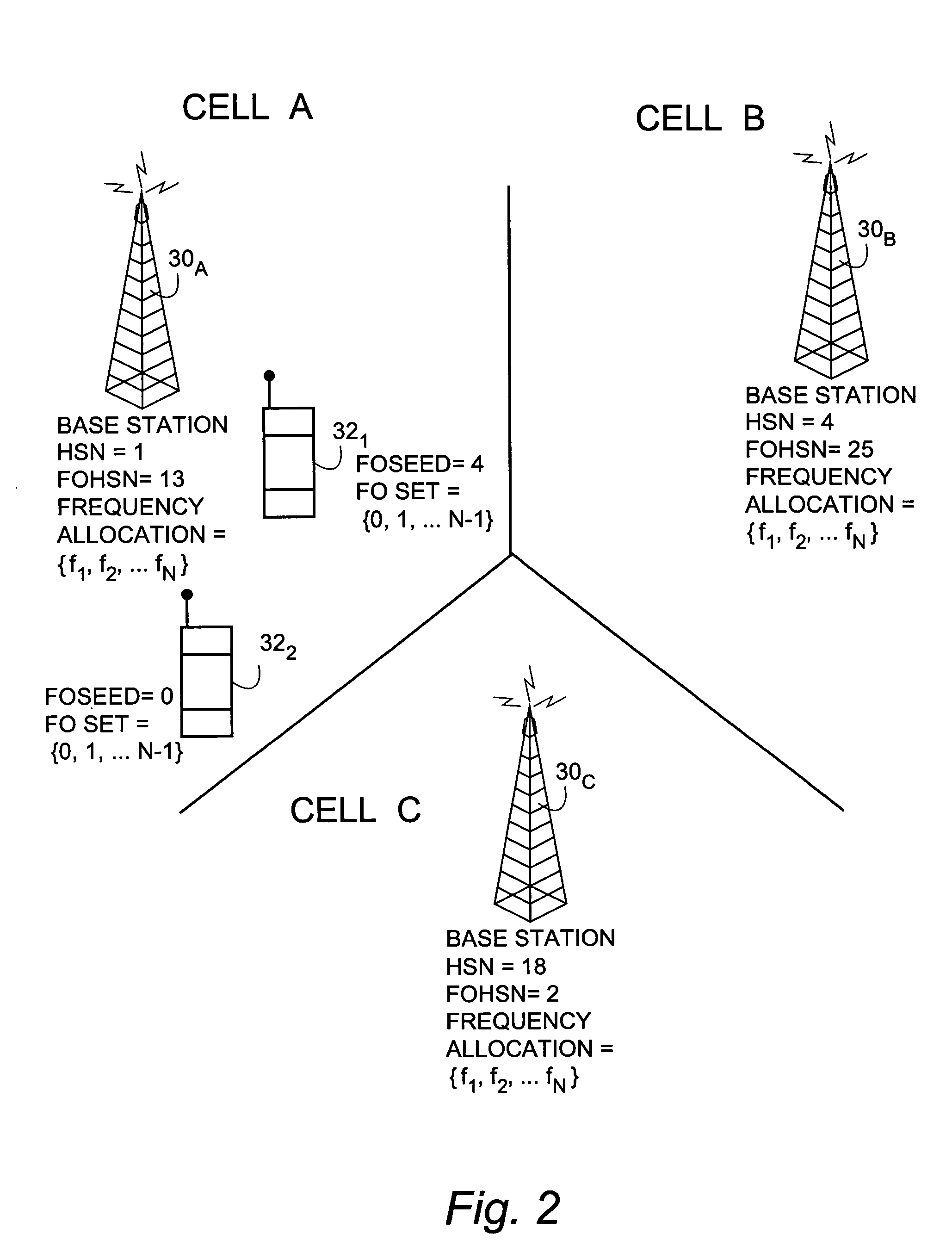
Frequency offset hopping for telecommunications
A frequency hopping sequence generator system (40) for use in a radio telecommunications system utilizes variable frequency offsets (FO) to determine a frequency hopping sequence for use in communication between a mobile station and a network node. The frequency hopping sequence generator comprises a frequency offset hopping generator (42) which chooses the variable frequency offsets so that the frequency hopping sequence provides intra-cell interference diversity. For each mobile station, the frequency offset hopping generator determines a frequency offset index (FOI) which is mapped to one of plural possible frequency offsets (FO). The frequency offset index (and thus the corresponding frequency offset) is determined to provide the frequency hopping sequence with both interference diversity and orthogonality. The frequency offset index has a first component and a second component. The first component of the frequency offset index is an inter-cell component that provides, e.g., collision diversity between FO hopping sequences that are not orthogonal. The second component is an intra-cell component that provides orthogonal (non-colliding) sequences with a variable difference between two sequences. The intra-cell component sub-generator can operate in either a “short sequences” mode or a “long sequences” mode. The long sequences mode renders adjacent frequency collision rates between two sequences with equal FOHSN independent of the choice of the two different FOSEEDs selected. On the other hand, the short sequences mode yields higher collision rates between certain pairs than between other pairs.
Owner:TELEFON AB LM ERICSSON (PUBL)
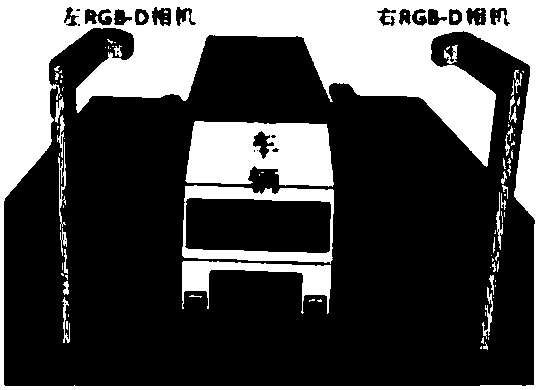
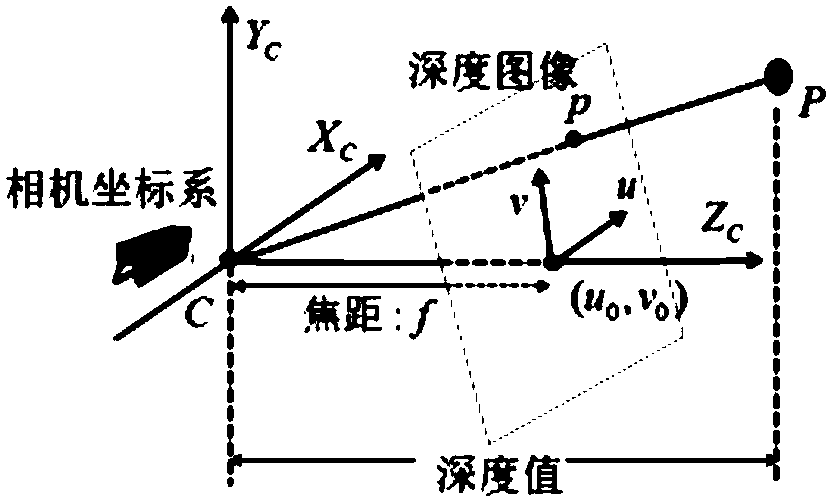
Measuring method for length, width and height of vehicle based on RGB-D camera
InactiveCN108550143ARealize 3D measurementRealize the solutionImage enhancementImage analysisGraphicsPoint cloud
The invention discloses a measuring method for length, width and height of a vehicle based on an RGB-D camera. The method comprises the steps of acquiring a clear vehicle image in a camera short-distance mounting manner, calibrating the camera according to a calibrating method based on a disappearing point, obtaining an internal parameter and an external parameter of the camera, realizing three-dimensional point cloud conversion of a vehicle target in a world coordinate system through a camera depth image solution, and acquiring three-dimensional coordinate information of the external surfaceof the vehicle; acquiring the three-dimensional coordinate of the external surface of the vehicle by means of prior knowledge and an image processing method, splicing a vehicle image according to sequence patterns in a vehicle motion process through a registering method, and realizing three-dimensional measurement to the profile of the vehicle. The measuring method overcomes defects of high equipment requirement and tedious operation in a traditional method and realizes high calibration precision. The actual displacement of the vehicle is comprehensively analyzed through a matching relation ofpoints which correspond with the same position of the vehicle in the image sequence, thereby realizing relatively high registering precision. The measuring method further has advantages of realizingaccurate splicing of the vehicle side surfaces, reducing vehicle length measurement error and improving accuracy in splicing the vehicle side surfaces.
Owner:CHANGAN UNIV
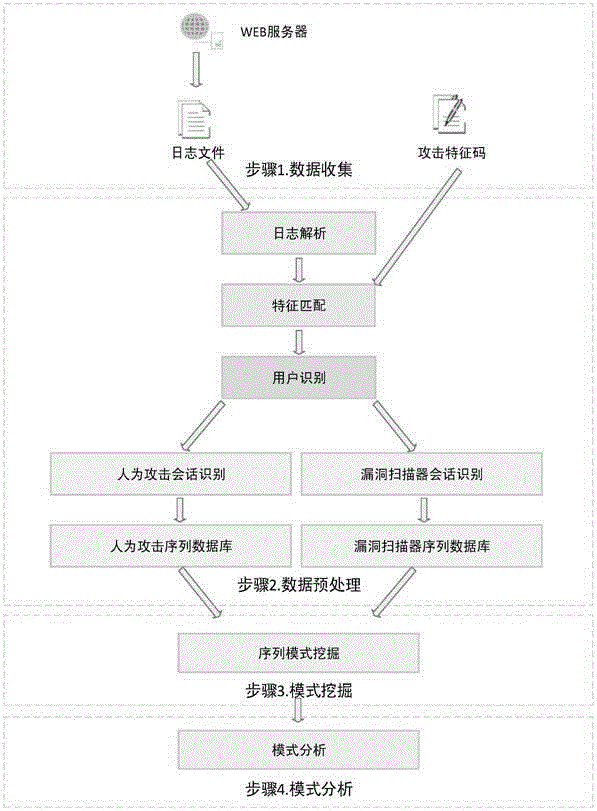
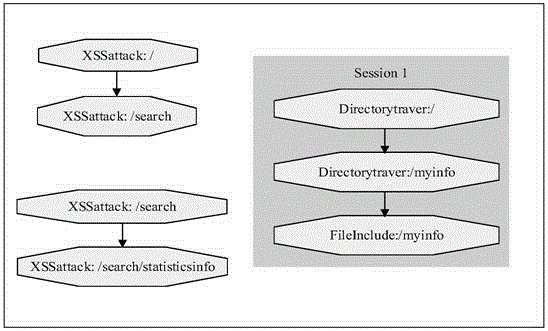
Method for mining attack frequent sequence mode from Web log
ActiveCN105721427ATransmissionSpecial data processing applicationsSequence databaseUniform resource locator
The invention relates to data mining in the field of network security and especially relates to a method for mining an attack frequent sequence mode from a Web log. The method comprises the following steps: collecting website access log files, website information and attack feature codes; analyzing a website log structure, matching analyzed URLs with the collected attack feature codes, obtaining attack records, and clearing up the URLs; performing user identification on attack log data and distinguishing manual attacks and attacks of a loophole scanner; respectively performing session identification to obtain a sequence database of the manual attacks and a sequence database of the loophole scanner; converting a character string database into a digital database, and respectively mining a frequent sequence of the sequence database by use of a sequence mode mining method; and maximizing the frequent sequence obtained through mining and converting a sequence mode into visual figure language. The process is indicated in the first graph. The method provided by the invention can realize visualization of an attack mode and explores a scanning sequence in the loophole scanner.
Owner:HUNAN UNIV
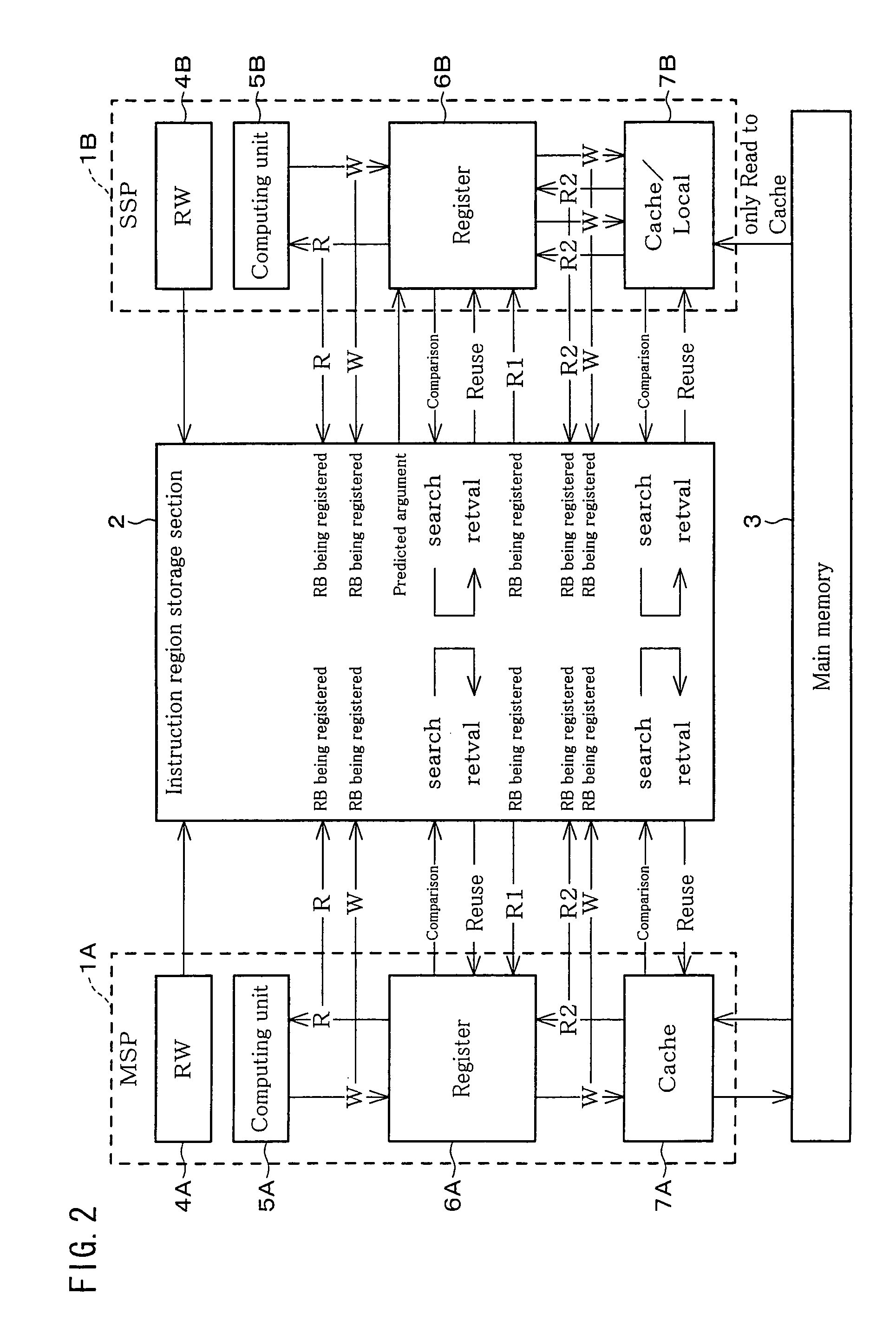
Data processing device for implementing instruction reuse, and digital data storage medium for storing a data processing program for implementing instruction reuse
ActiveUS8055885B2Improve forecast accuracyProgram control using stored programsDigital computer detailsComputer architectureEngineering
A method and apparatus is provided for significantly speeding-up program execution in a data processing device. The data processing device is provided with a specialized instruction region storage section comprising content addressable memory (CAM) and random access memory (RAM) that operatively functions as an instruction sequence reuse table which is capable of registering / storing sequences of program instructions and corresponding instruction sequence output data as input / output (I / O) groups for potential future use in place of re-executing identical portions of program code. The data processing device includes at least one instruction stream processor which includes a computing unit for executing instructions and a dependency relationship analysis unit or “reuse window” unit (RW) that analyzes instruction sequence patterns from regions of instructions stored in a main memory to determine if the patterns can be divided up into smaller partitions that have no interdependencies and hence are potential candidates for reuse.
Owner:JAPAN SCI & TECH CORP
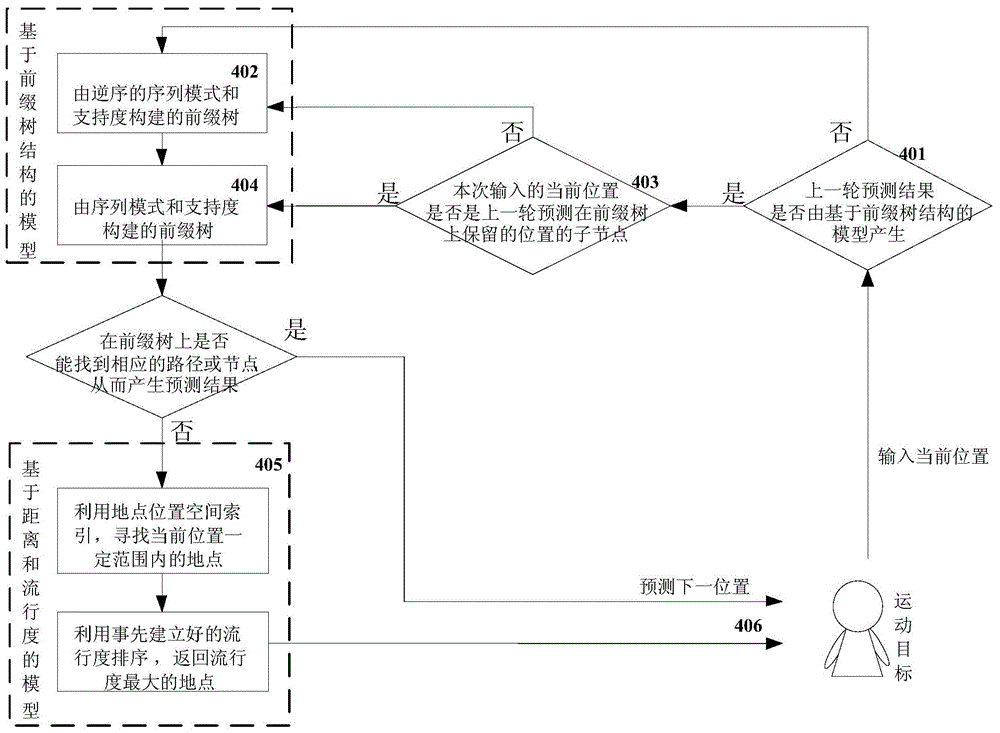
On-line position prediction method based on mass of space trajectory excavation
ActiveCN104462190AImprove accuracySpecial data processing applicationsGeographic siteComputation complexity
The invention relates to an on-line position prediction method based on mass of space trajectory excavation and belongs to the field of space trajectory excavation. The method comprises the steps of firstly, excavating frequent sequential patterns from the mass of space trajectory excavation, secondly, using the sequence patterns to establish a model based on a prefix tree structure, thirdly, establishing a model based on distance and popularity to solve the zero frequency problem, and finally, using the established predication models to predict the next position of a moving target according to the current trajectory information of the moving target. The accuracy of the prediction method is improved greatly compared with the existing methods, the calculation complexity is low, real-time prediction can be carried out on the position of the moving target, only the position information of the moving target is needed, and therefore the on-line position prediction method based on mass of space trajectory excavation can be widely applied to the fields such as intelligent traffic and services based on geographic positions.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
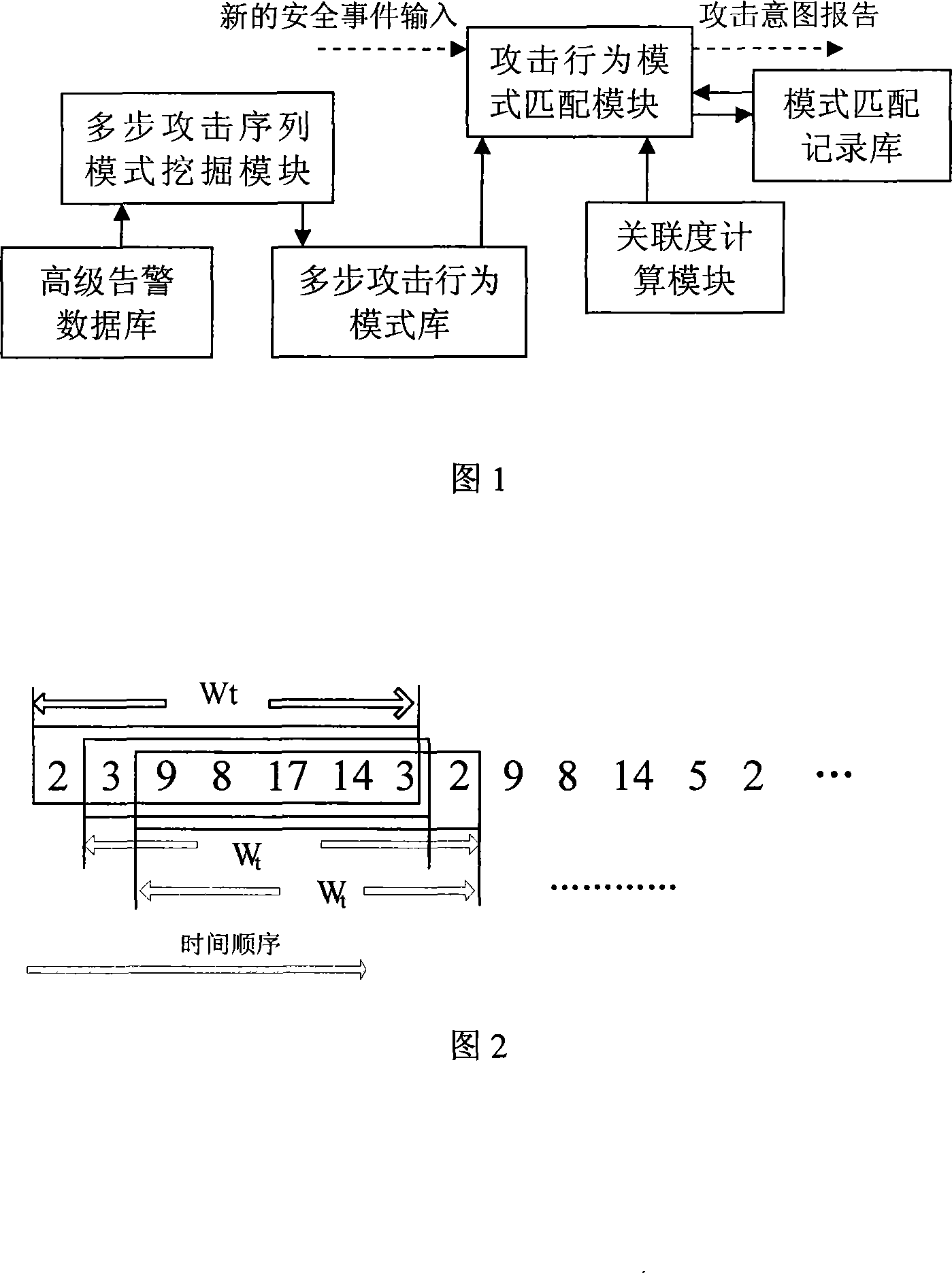
Online recognition method for network multi-step attack intension
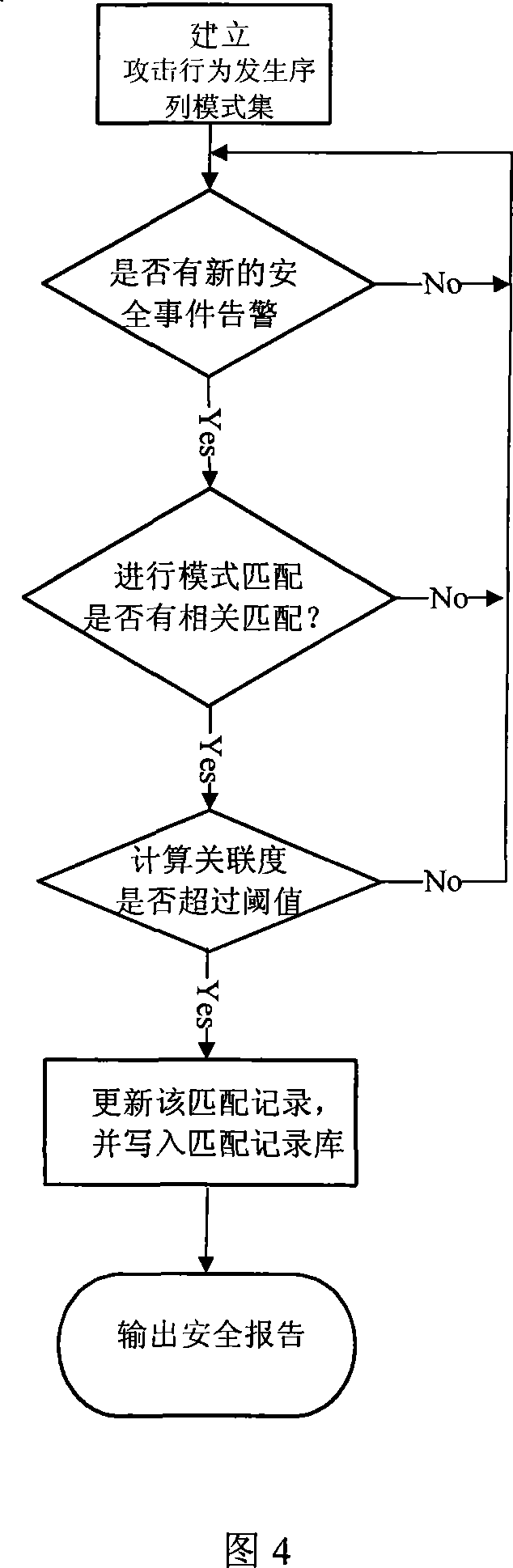
InactiveCN101242278AReal-time online detectionSecuring communicationPattern matchingDegree of association
The invention provides an online identification method for a network multi-step attacking intention, wherein the method extracts characters of the received security incident warning message, carries out a pattern matching based on a character and attacking action happening sequence pattern collection. If the pattern matching is success, degree of association between fore and aft security incident warning messages according to the pattern matching is computed, and the network multi-step attacking relation between the security incident warning messages is recorded based on a compared result of the degree of association and a threshold value thereof. The invention filters the security incident with pattern matching but without association relation by computing the degree of association, and the real time online detect is realized by real time reporting a matching process and result.
Owner:HUAZHONG UNIV OF SCI & TECH
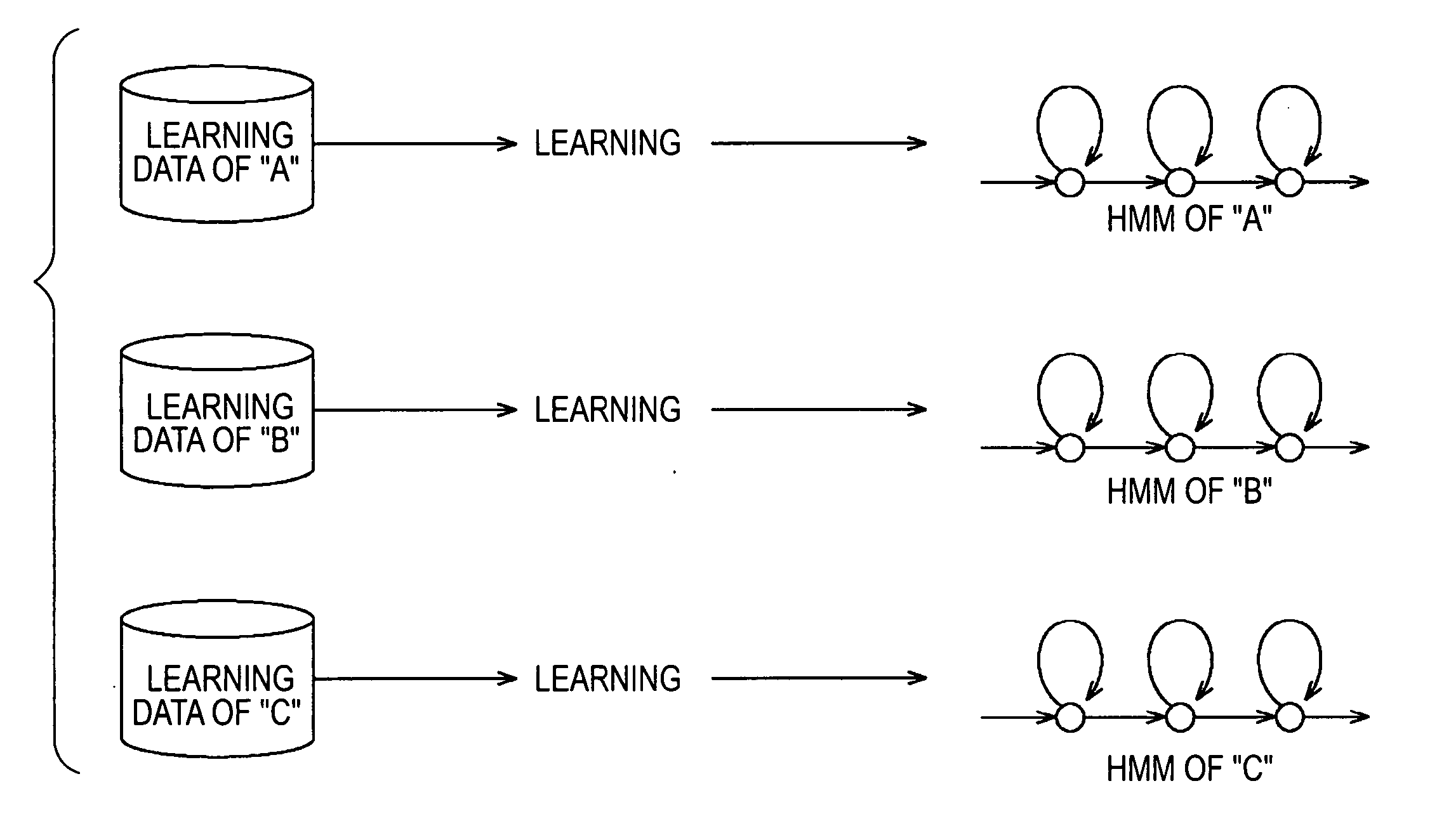
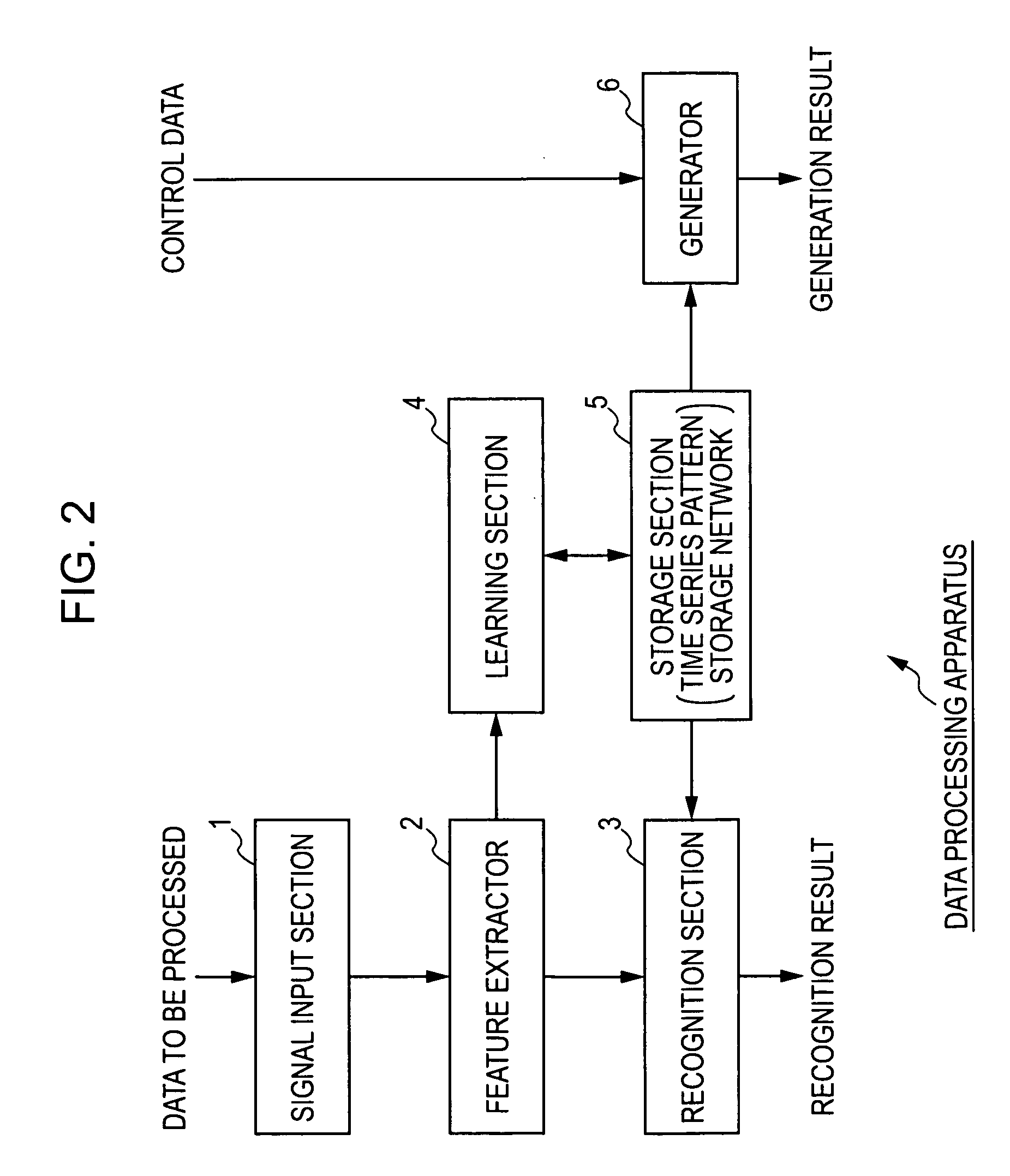
Method and apparatus for learning data, method and apparatus for recognizing data, method and apparatus for generating data, and computer program
A learning apparatus for learning time series data, includes a learning unit for updating, in a self-organizing manner based on an observed value of the time series data, a time series pattern storage network including a plurality of nodes, each node having a time series pattern model representing a time series pattern of the time series data.
Owner:SONY CORP
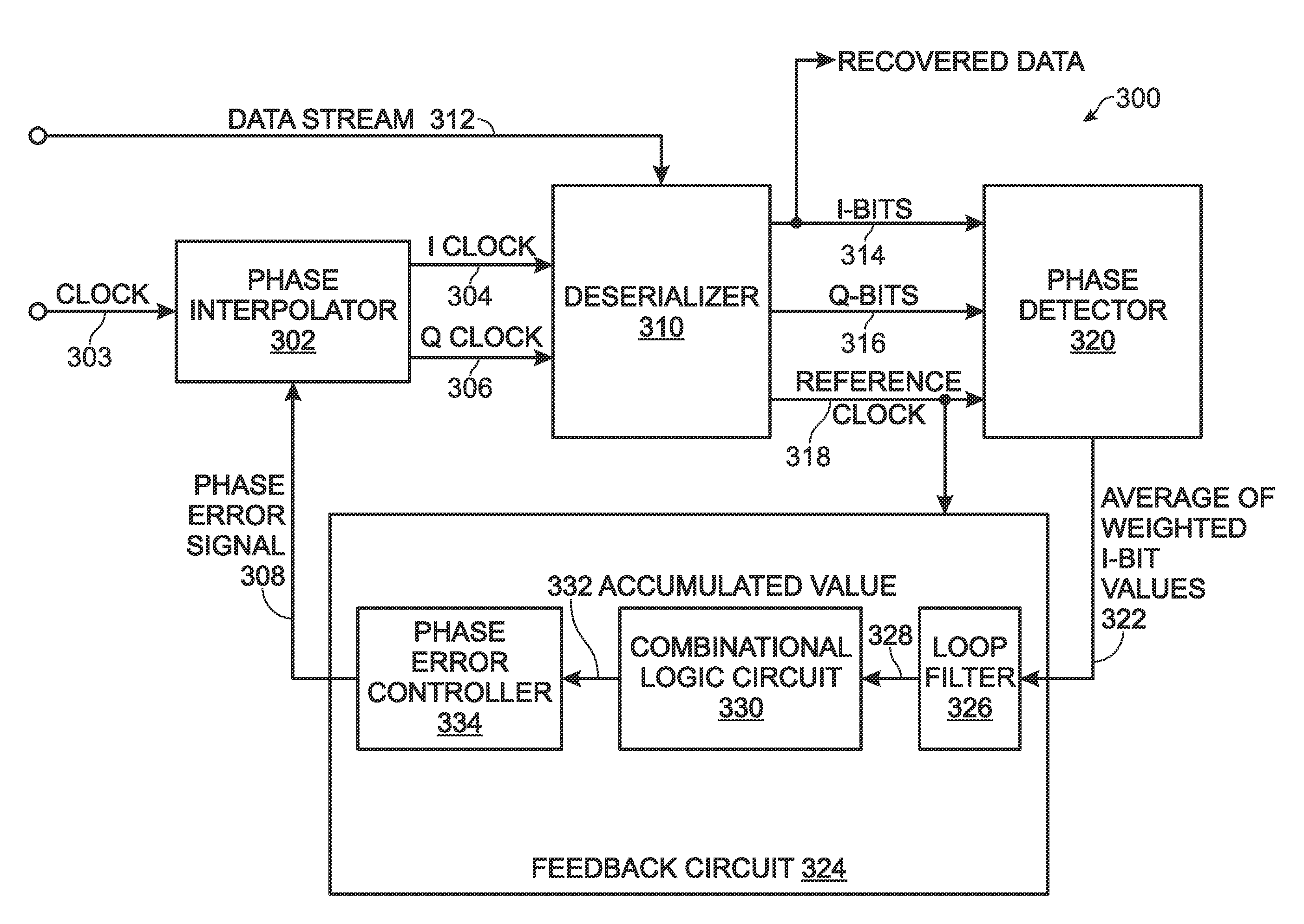
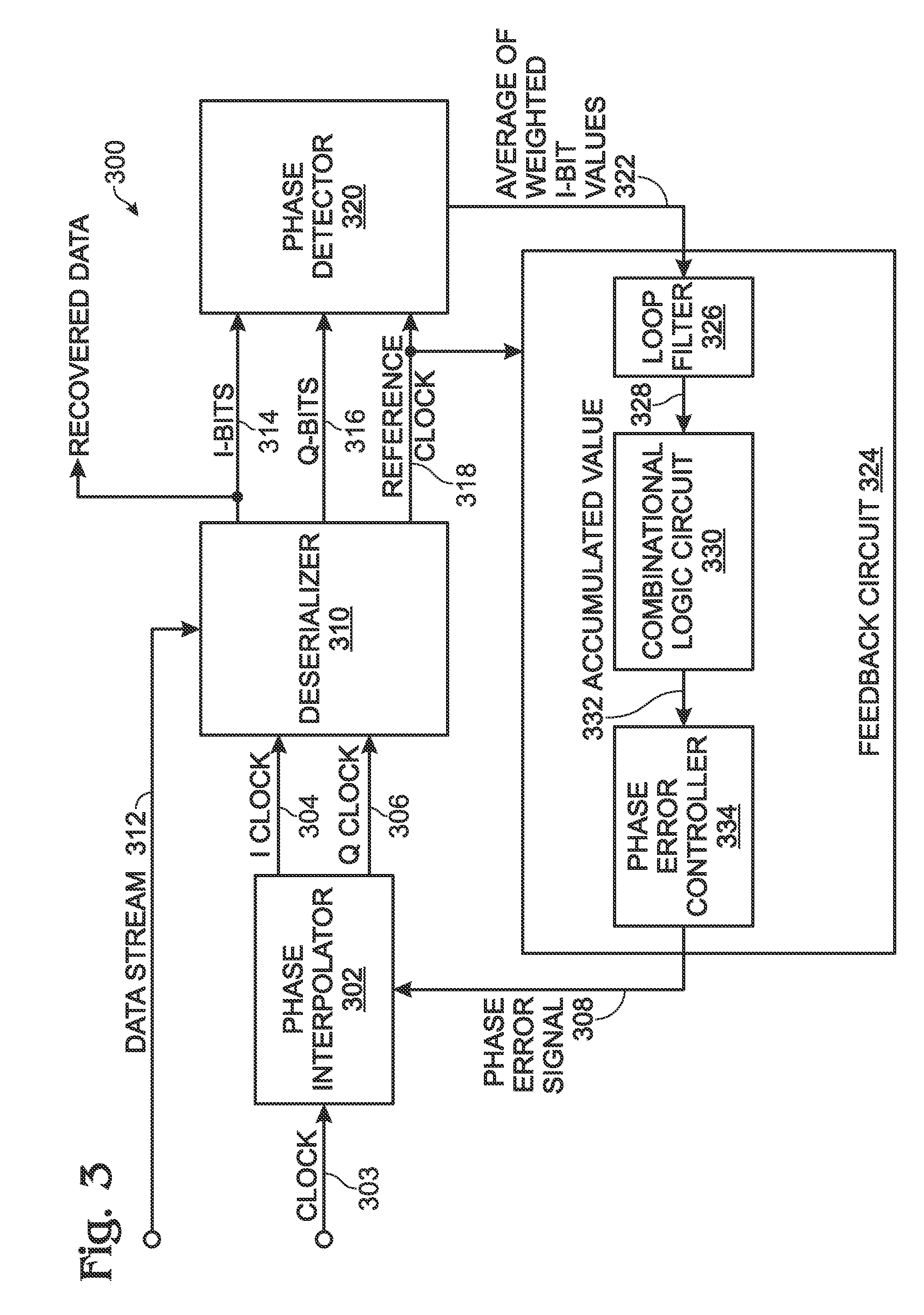
ISI Pattern-Weighted Early-Late Phase Detector with Jitter Correction
ActiveUS20090296867A1Reduce the impactReduce probabilityError preventionLine-faulsts/interference reductionLate phasePhase detector
An inter-symbol interference (ISI) pattern-weighted early-late phase detector is provided. I and Q clocks are generated. The I clock frequency is divided by n, creating a reference clock. A serial data stream is sequentially sampled with the I clock, and with Q clocks having fixed and varied phase delays from the I clock, creating digital I-bit and Q-bit values. The I-bit values and Q-bit values are segmented into n-bit digital words. I clock phase corrections are identified and a modulation factor is determined in response to comparing Q-bit values sampled by the varied delay Q clock. Also identified are bit sequence patterns associated with each I-bit value. Each I-bit value is weighted in response to the identified bit sequence pattern and the identified I clock phase correction. The modulation factor is applied to the weighted average, and I and Q clock phase error signal are generated.
Owner:MACOM CONNECTIVITY SOLUTIONS LLC
Frequent pattern extraction apparatus frequent pattern extraction method and program
ActiveUS20130179381A1Digital data information retrievalKnowledge representationDegree of similaritySequence pattern
There is provided a frequent pattern extraction apparatus. In the apparatus, time series data for an item operation is divided into a plurality of item operation sets. Using a set degree of similarity between the item operation sets, an abstract item operation set is generated. A pattern of sequences that frequently appear is extracted from the sequences in the abstract item operation set. Using the pattern of sequences that frequently appear, an item as well as an item operation are recommended to a user.
Owner:CANON KK
Method for extracting network interactive behavioral pattern and analyzing similarity
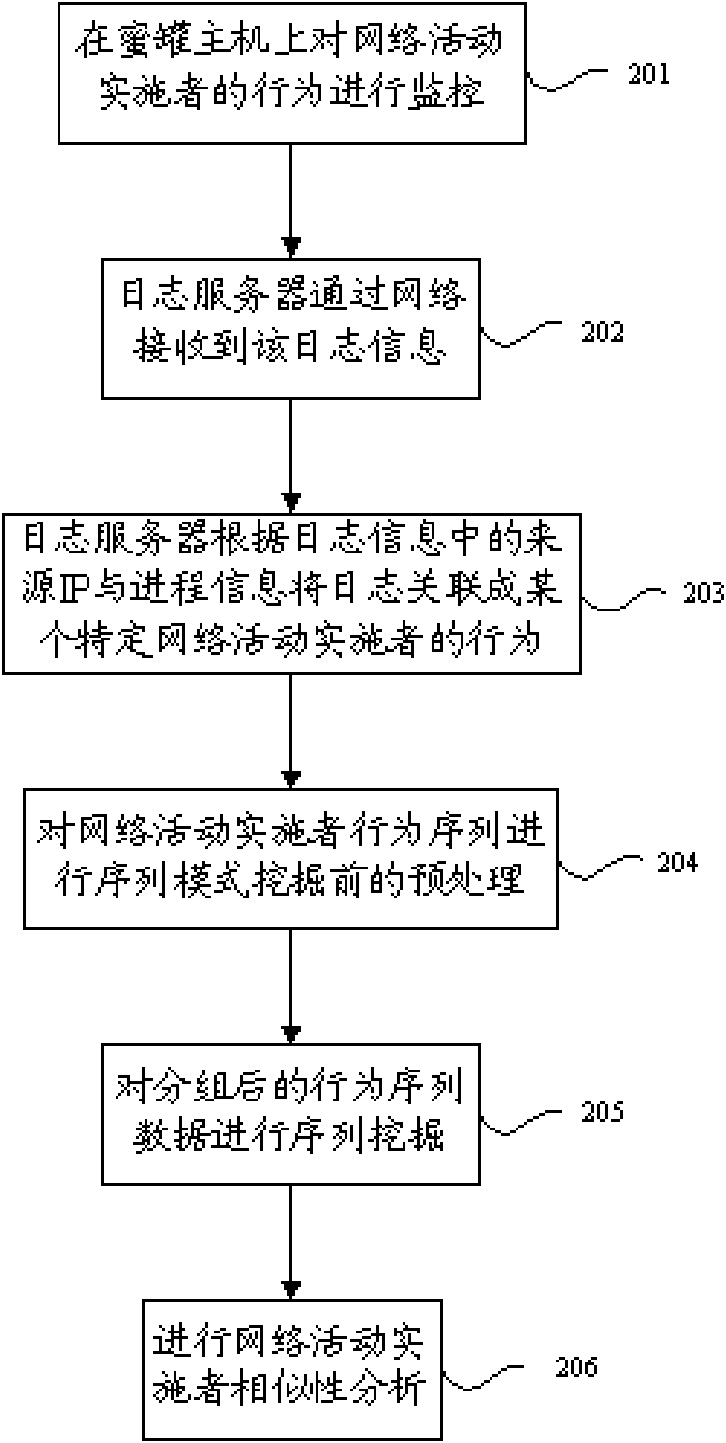
InactiveCN101582817ATimely cyber attackRespond in a timely mannerData switching networksSpecial data processing applicationsNetwork activityEngineering
The invention discloses a method for extracting a network interactive behavioral pattern and analyzing similarity, which comprises the following steps: the behavior of a network activity implementer is monitored on a honey-pot host computer; the captured journal information is transmitted to a journal server; the journal server associates journals to a behavior sequence belonging to a particular network activity implementer according to the source address and the process information in the journal information; the behavior sequence of the network activity implementer is pretreated before sequence pattern excavation; the behavior sequence data of the pretreated network activity implementer is processed by the sequence excavation; and the similarity between the network activity implementers is analyzed. By analyzing the similarity between the different network activity implementers, the network activity implementers are deeply associated and researched, which has a certain help for judging the purpose of the network activity implementers, adopting corresponding counter-measure for behaviors such as network attack and the like and obtaining the evidence of network attack.
Owner:HUAZHONG UNIV OF SCI & TECH
Software security flaw detection method based on sequential pattern mining
InactiveCN101710378AImprove detection efficiencyReduce the false negative rate of vulnerability detectionPlatform integrity maintainanceSpecial data processing applicationsSequence databaseSoftware system
The invention provides a software security flaw detection method based on sequential pattern mining. Firstly, a great quantity of relevant operation sequence data of a detected software security flaw is used for building a relevant operation sequence database of the security flaw; then, a closed sequential pattern mining arithmetic in the data mining is used to mine frequently appearing relevant operation sequence of the flaw; the mined frequently appearing relevant operation sequence of the flaw is used for detecting the security flaw of the current software system so as to lower flaw detection missing report rate as well as improve security flaw detection efficiency. Along with the accumulation of flaw data, the advantage of high security flaw detection efficiency of the invention is more outstanding.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +2
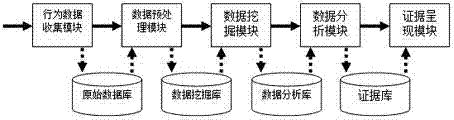
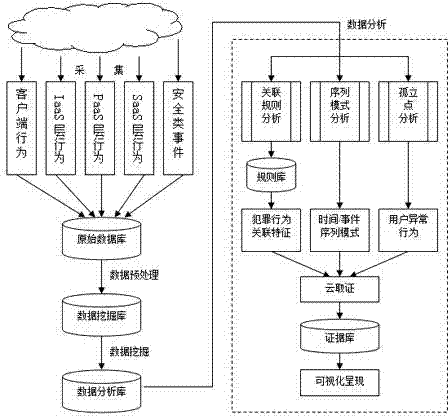
Dynamic user behavior-based cloud forensics method and dynamic user behavior-based cloud forensics system
The invention discloses a dynamic user behavior-based cloud forensics method and a dynamic user behavior-based cloud forensics system; the formalized definition of dynamic user behavior is put forward as basis; and the method comprises the steps of: collecting dynamic user behavior and behavior data, and storing the behavior data as primary evidence data; carrying out data integration, data cleaning and data mining to form forensic analysis data, and storing the forensic analysis data into a data analysis library (key value database); using Map Reduce to carry out correlation analysis, sequence pattern analysis and isolated point analysis on the forensic analysis data, and digging out the potential user behavior patterns and the possible aggressive behavior to form forensic evidence; and displaying the forensic evidence in a visual way. The high performance computing power of cloud computing and large-scale distributed-memory environment are applied into computer forensic analysis, so that various problems in cloud computing forensics can be solved.
Owner:INSPUR GROUP CO LTD
Optical navigation apparatus using fixed beacons and a centroid sensing device
The present invention relates to an optical navigation system for determining at least one parameter of a pose, which includes the position and orientation of an object in an environment. The optical navigation system uses a number of beacons affixed at known locations in the environment to provide electromagnetic radiation in a sequenced pattern. An on-board optic images the radiation from the beacons onto an on-board centroid sensing device to obtain an imaged distribution of the radiation on the on-board centroid sensing device. The centroid sensing device determines the centroid of the imaged distribution and provides centroid information to a navigation unit for determining at least one parameter of the pose of the object from the centroid. The navigation system is particularly well-suited for navigating hand-held objects.
Owner:ELECTRONICS SCRIPTING PRODS
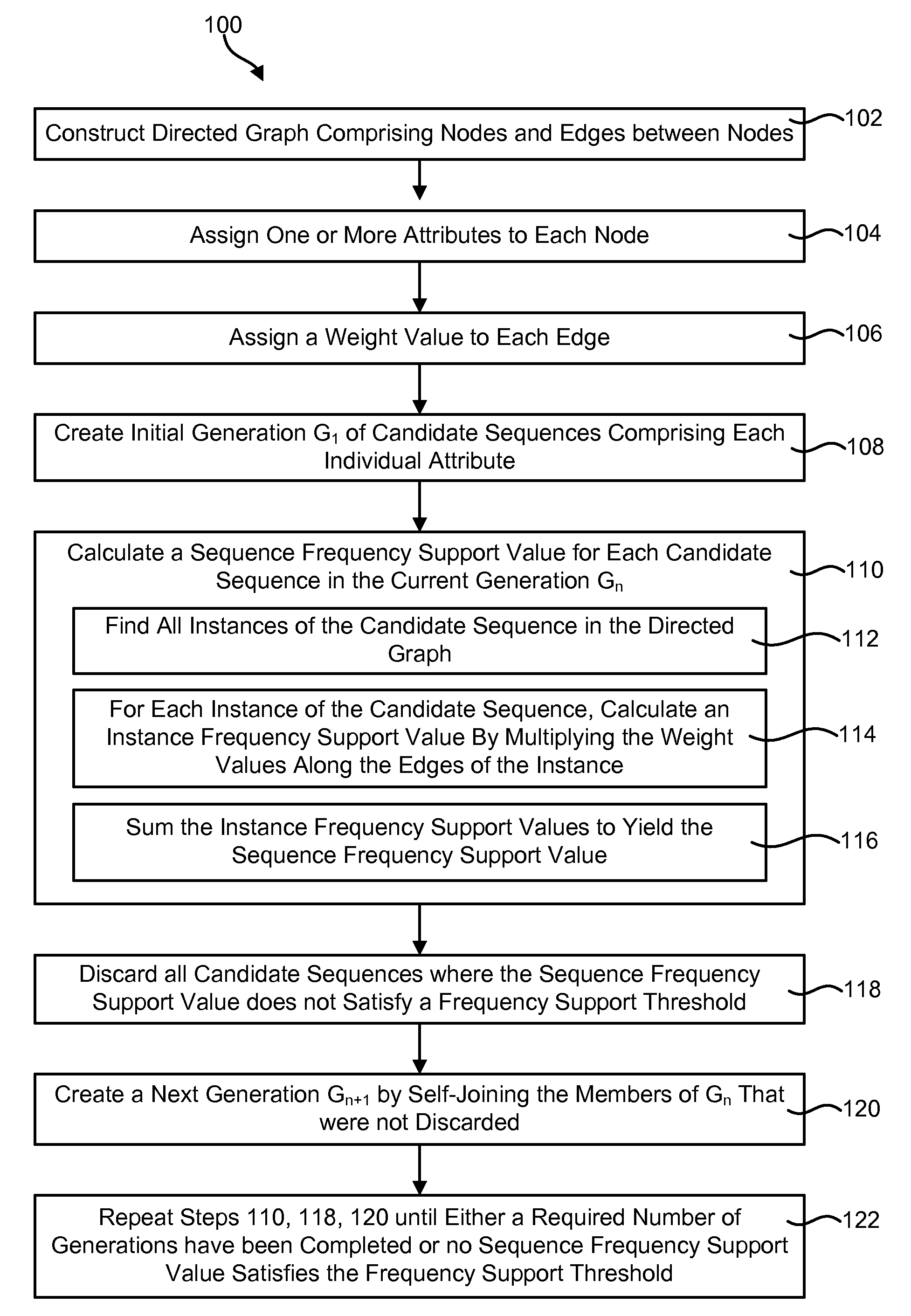
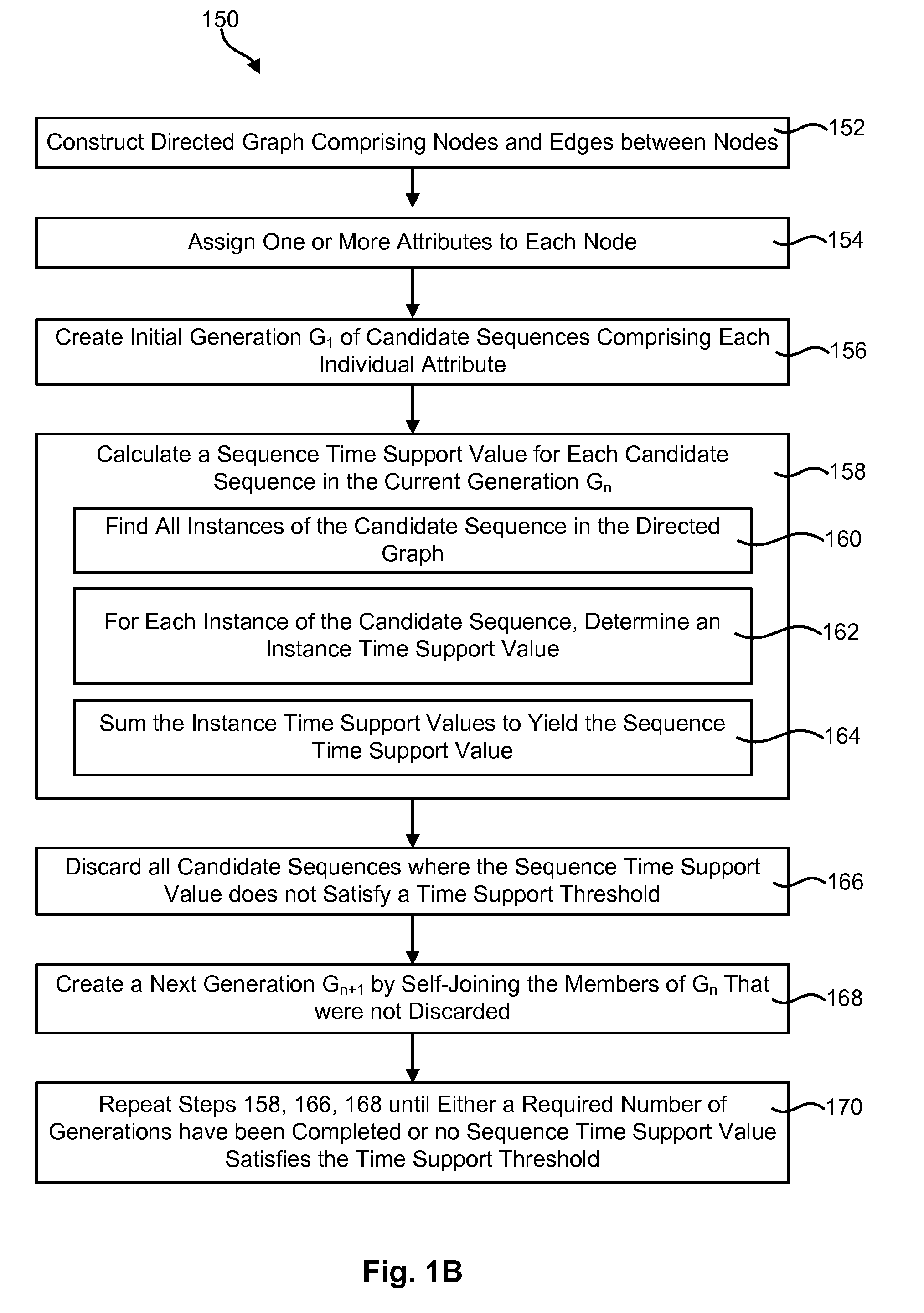
Mining sequential patterns in weighted directed graphs
A method for finding sequential patterns of attributes in a directed graph includes constructing a directed graph comprising multiple nodes and edges between the nodes. Each of the nodes may be assigned one or more attributes. Similarly, each of the edges may be assigned a weight value which may indicate the probably the edge will be traversed during traversal of the directed graph. The method may further include finding sequences of attributes in the directed graph that have some minimum amount of frequency and / or time support. In performing this step, the frequency support of each individual instance of a sequence of attributes may be calculated by multiplying the weight values along the edge or edges of the instance. A corresponding apparatus and computer program product are also disclosed and claimed herein.
Owner:IBM CORP
On-line character detection method based on machine vision and system thereof
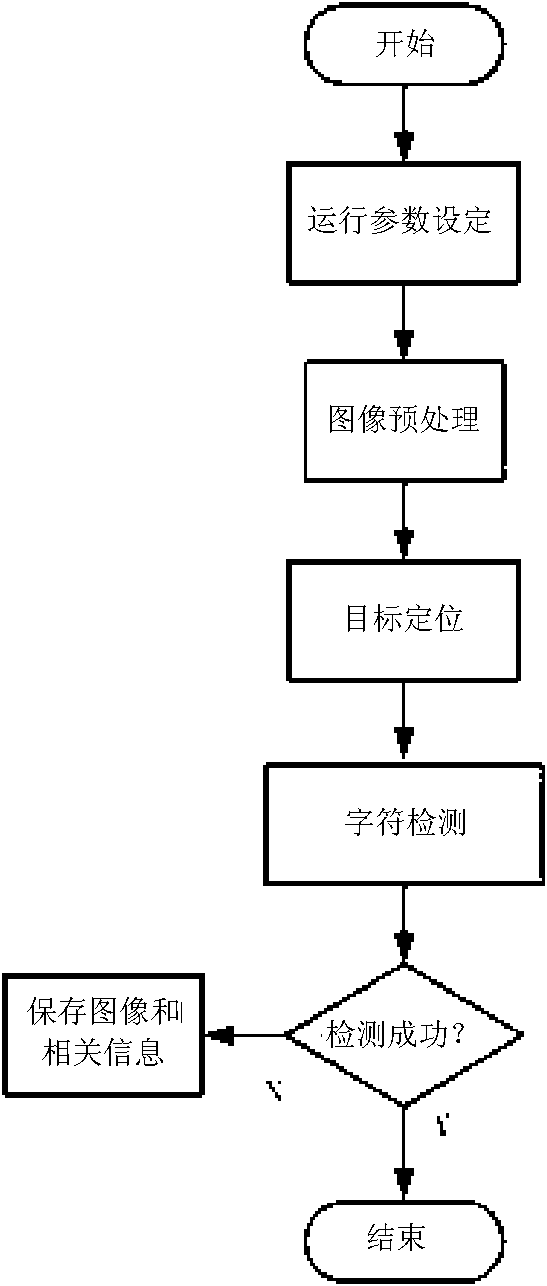
InactiveCN101576956AEfficient extractionEfficient online detectionCharacter and pattern recognitionPattern recognitionMachine vision
The invention belongs to the technical field of automatic detection and relates to an on-line character detection method based on machine vision. The detection method comprises a plurality of software modules including an image pre-treatment software module, a target extraction software module, a type matrix extraction software module, a character sequence mode generation software module, a character detection software module and so on. The above modules are combined together to form two independent flows including a production establishment operation flow and a character real-time detection flow. The invention synchronously provides an on-line detection system for realizing the detection method. The detection system and method provided in the invention have strong robustness, are capable of effectively reducing the influence of image variations, such as brightness, contrast, quality, character stroke, rotation, scale and the like, caused by environment or other factors, and are capable of realizing fast and correct character region location and high-efficiency and real-time charter on-line detection.
Owner:TIANJIN PUDA SOFTWARE TECH
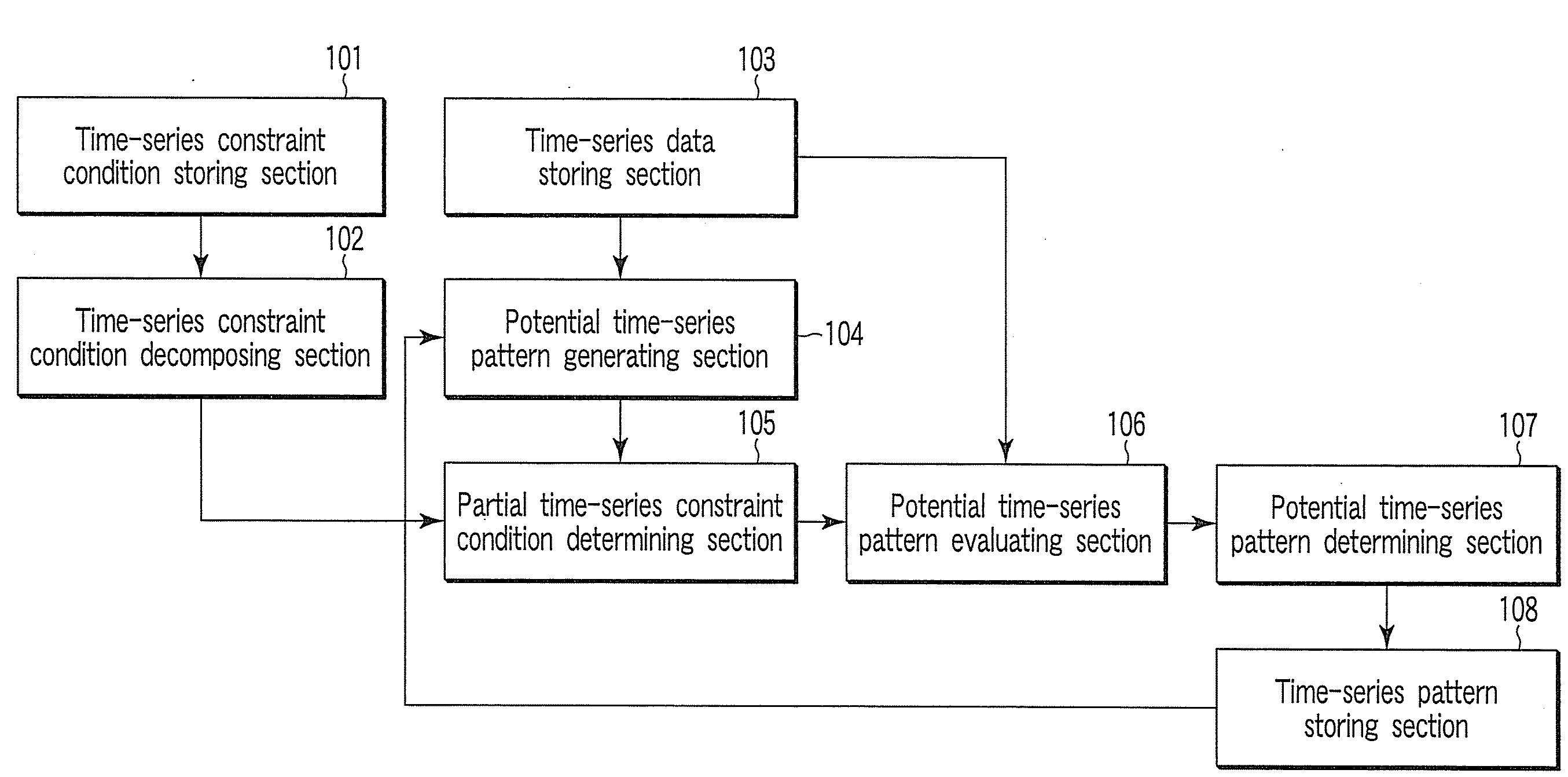
Time-series pattern finding apparatus, method and program
InactiveUS20080222109A1Evaluation of blood vesselsCharacter and pattern recognitionFrequency of occurrenceSequence pattern
A time-series pattern finding apparatus, includes decomposing unit decomposing a condition, which indicates a condition of time-series relationship between first elements each defined as including first events each including an attribute and an attribute value of the attribute, into a partial condition, determining unit determining whether the partial condition holds for each potential events, each potential characteristic event sets, and each potential time-series patterns, calculating unit calculating frequency of occurrence in the time-series data items only for fourth events in the potential events, first sets in the potential characteristic event sets, and first patterns in the potential time-series patterns, which satisfy the partial condition, and extracting unit extracting a potential event, a potential event set and a potential time-series pattern from the fourth events, the first sets and the first patterns, respectively, based on the frequency of occurrence not less than a threshold value, as a time-series pattern.
Owner:KK TOSHIBA +1
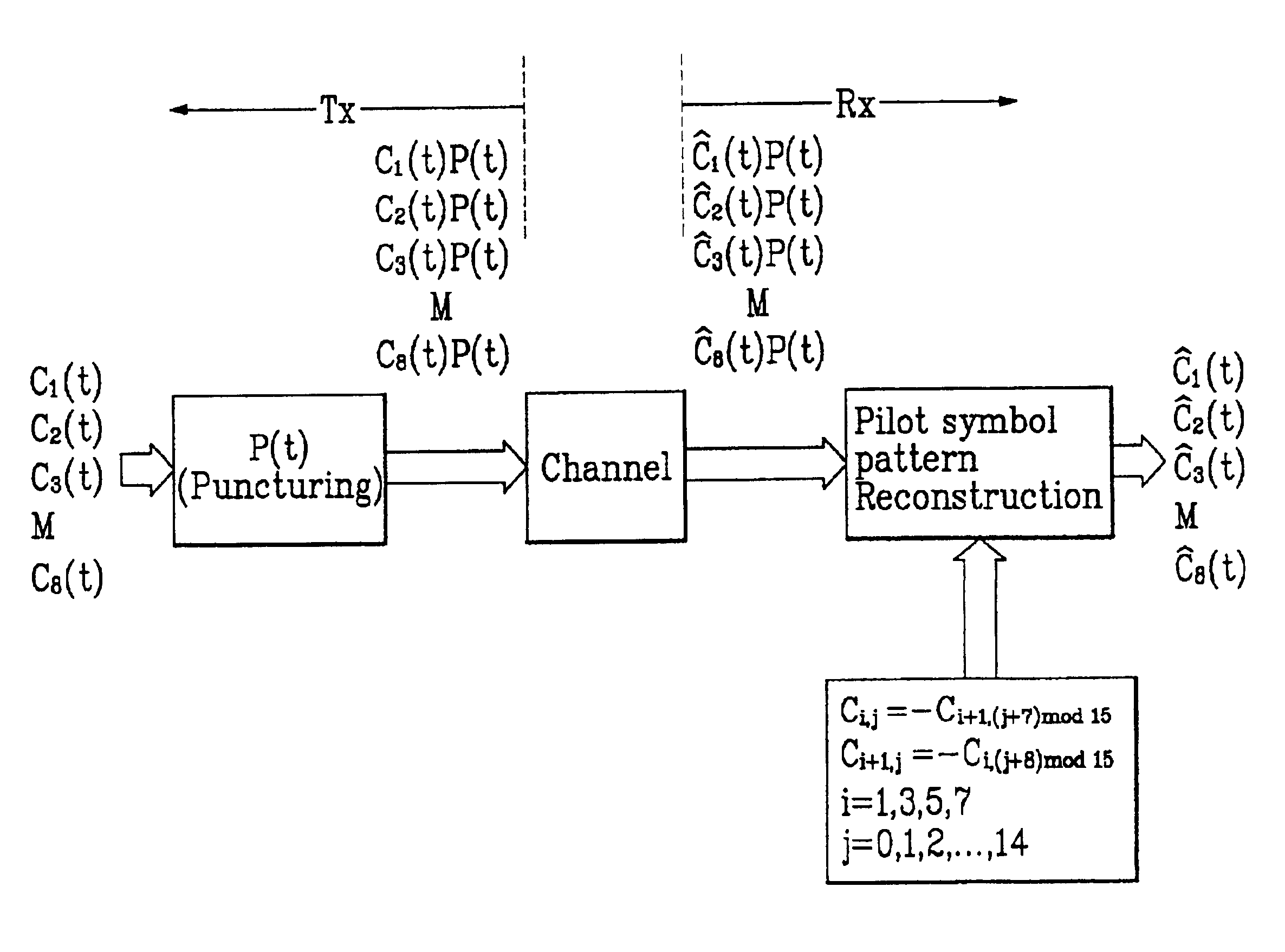
Method for synchronizing frame by using pilot pattern in compressed mode
InactiveUS6947476B2Good synchronizationSynchronisation arrangementTime-division multiplexCommunications systemMobile communication systems
Method for synchronizing frames by using pilot patterns in a compressed mode. In a case a W-CDMA mobile communication system is operated in a compressed mode, the present invention permits to restore perfect frame synchronization words in frames by using dedicated pilot sequence pattern, and achieve frame synchronization by using correlation of the restored frame synchronization words, even if all the 15 slots of one frame are not transmitted.
Owner:LG ELECTRONICS INC
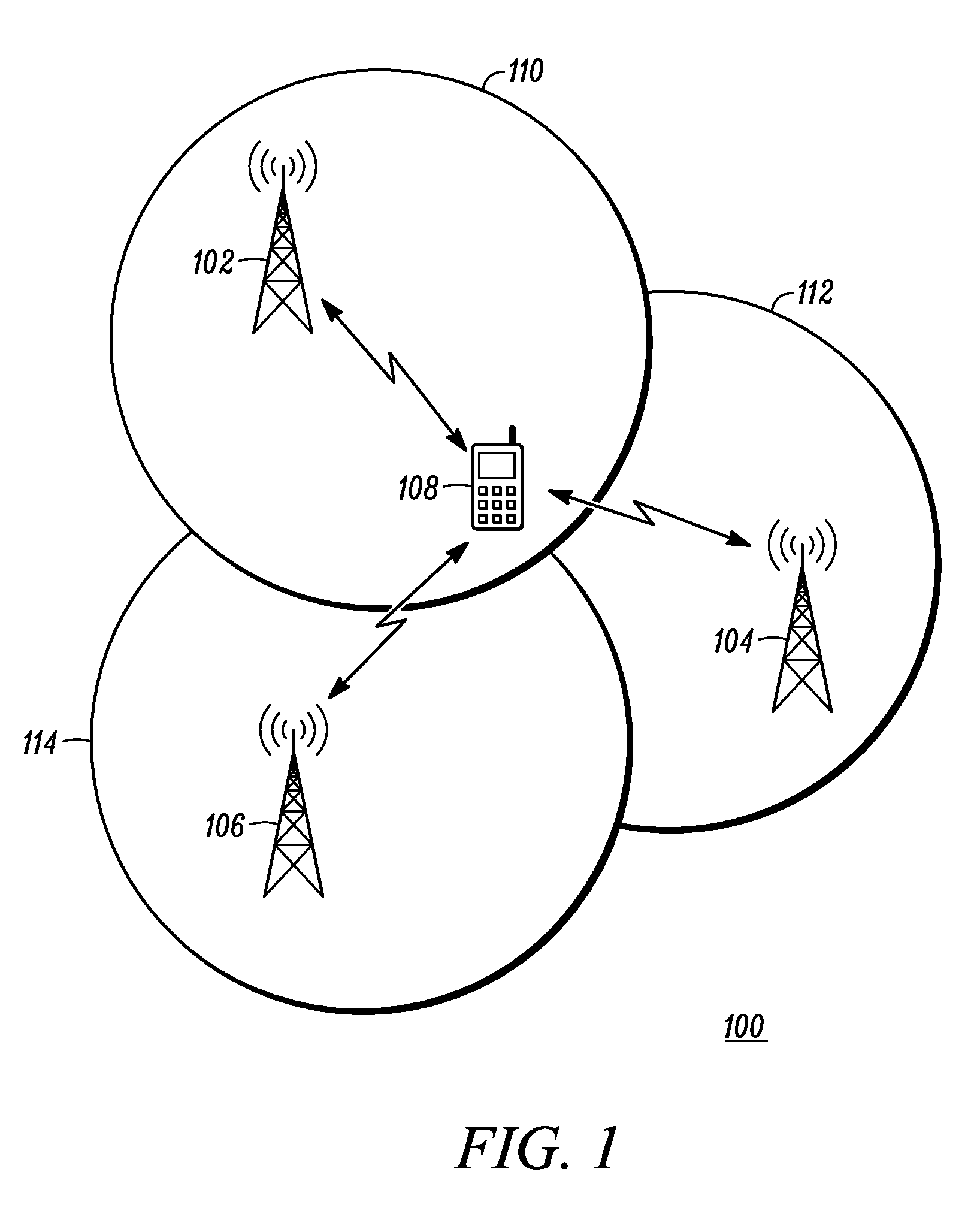
Method and apparatus for performing mobility measurements in a communication network
ActiveUS7920494B2Error preventionFrequency-division multiplex detailsCell specificTelecommunications
A method and apparatus for performing mobility measurement in a communication network (100) is described. The method includes of receiving a subframe sequence pattern from a node in the communication network (100). The subframe sequence pattern indicates types of subframes being transmitted by a neighboring cell node (104) in a neighboring cell (112). The method includes receiving a subframe from a sequence of subframes transmitted by the neighboring cell node (104) in the neighboring cell (112), and determining that the received subframe is a multicast subframe based on the subframe sequence pattern. The method then includes performing a single cell-specific reference symbol measurement in response to determining that the received subframe is the multicast subframe.
Owner:GOOGLE TECH HLDG LLC
Method and system for network micro flow control
ActiveUS9419902B1Reduce buffering needReduce needSpecial service provision for substationDistributed computingSequence pattern
The present technology pertains to unilaterally interleaving individual data packets of long bursts of multi-packet messages in various sequence patterns to be sent to one or more receivers over a network. Before determining a pattern, the sending device attempts to reduce the transmission length of the long bursts of the data packets into multiple chunks. Subsequently, the sending device generates a sequence pattern of the individual data packets and consecutively transmits these packets to their respective receivers. The determined sequence pattern may be based upon outbound limits at the sender, inbound limits at the one or more receivers, and various transmission priorities. Moreover, the sender may limit the data flow of any message transmission. The present technology does not require feedback from the network's components or from the network itself to micro flow control the individual data packets.
Owner:GOOGLE LLC
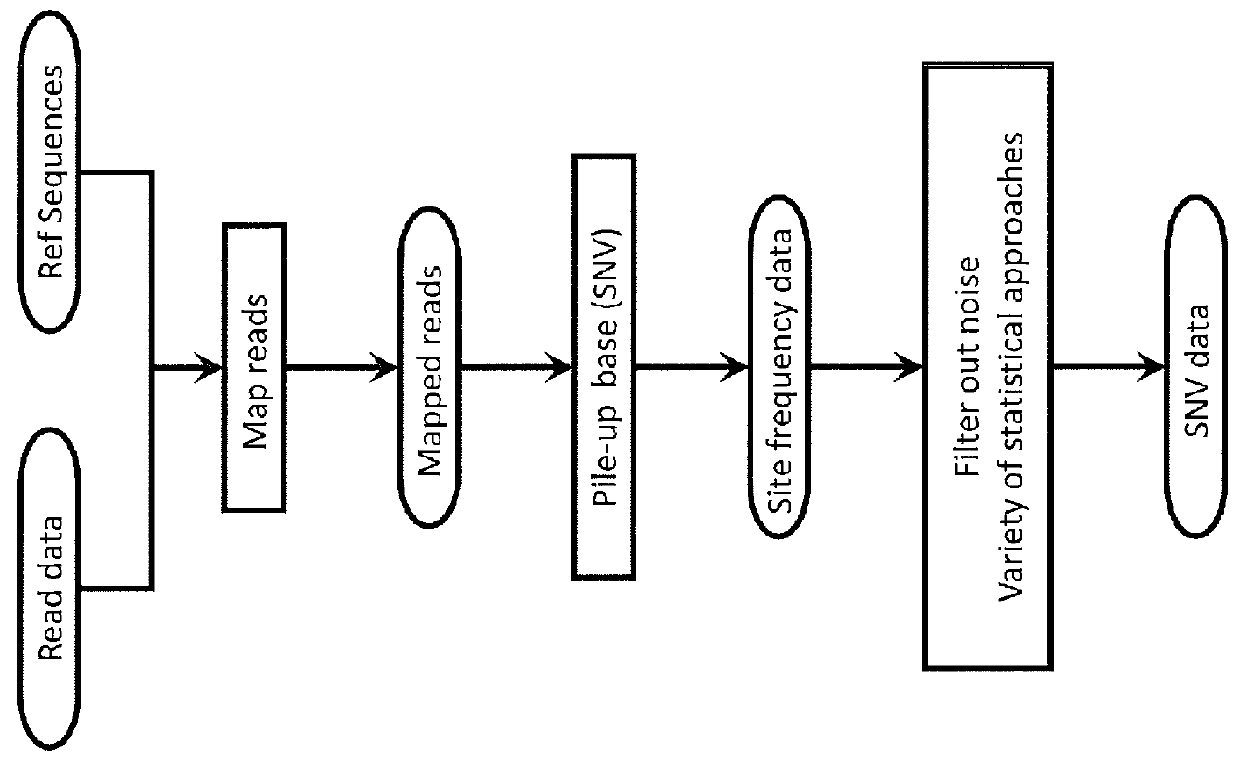
System and Method for Detecting Population Variation from Nucleic Acid Sequencing Data
InactiveUS20160034638A1Microbiological testing/measurementProteomicsPopulation variationNucleic acid sequencing
The present invention relates to a method of identifying genetic variants within a population of sequences. The method includes the steps of aligning a set of sequence data reads to reference sequences, dividing reference sequences into multiple tracks of overlapping regions of analysis (ROAs), partitioning each read into a ROA, identifying a plurality of sequence patterns in the reads, setting a sequence pattern frequency threshold value, eliminating any sequence pattern that has a value below the frequency threshold value forming a plurality of dictionaries from the sequence patterns having a value above the frequency threshold value, and cross-validating sequence patterns via partial sequence assembly. The method may optionally include amending the reference sequences used in iterative re-alignment of sequence data.
Owner:UNIVERSITY OF ROCHESTER
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com