Method for extracting network interactive behavioral pattern and analyzing similarity
A similarity analysis, network interaction technology, applied in the field of computer network security, can solve the problem of inability to analyze the relationship between different sources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
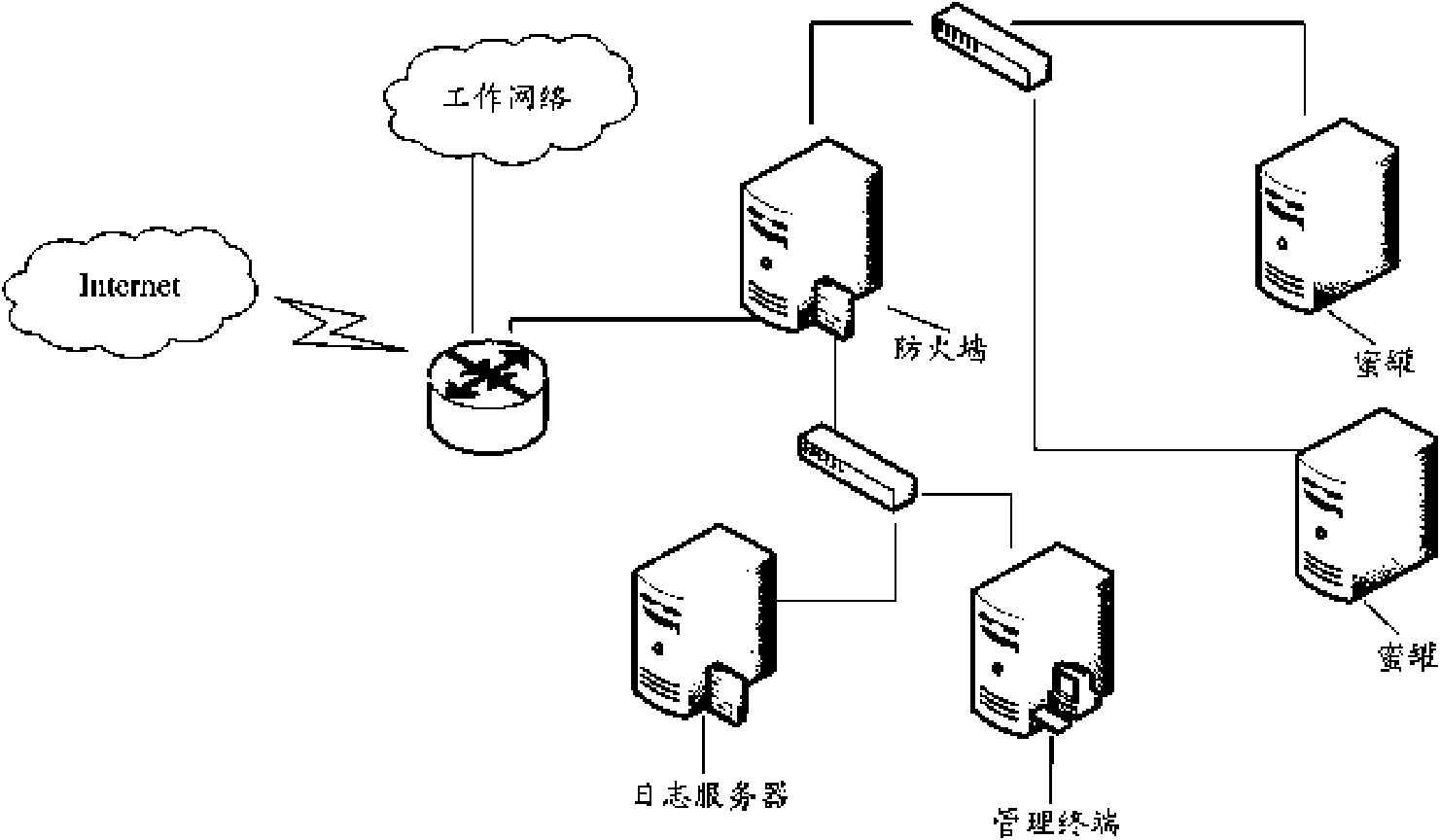
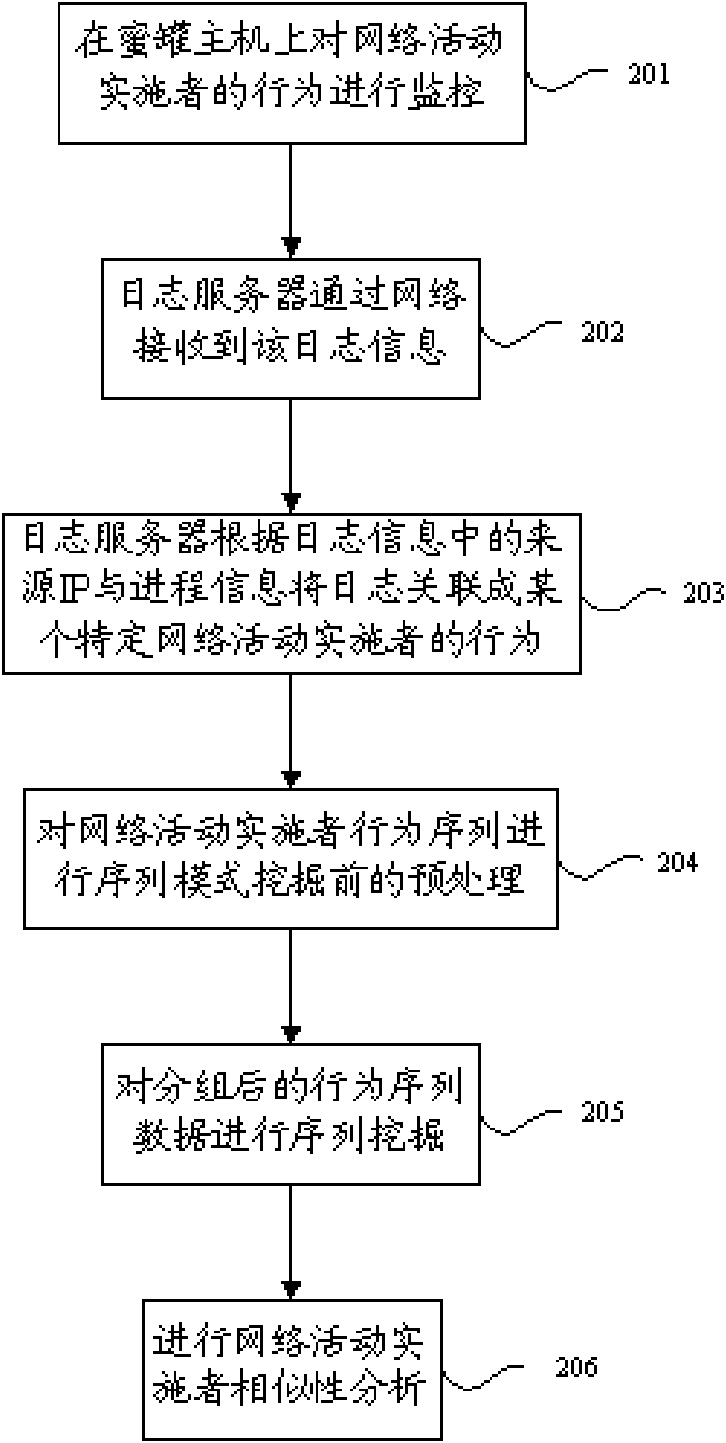
[0028] The embodiment of the present invention adopts a mechanism for similarity analysis of network activity implementers. On the framework of the honeypot system, by analyzing various interactive data captured by the honeypot system, using the sequential pattern technology in data mining, a large number of The behavioral feature sequence pattern of the network activity implementer is excavated from the complex log records, and each network activity implementer who has performed suspicious behavior on the honeypot is defined according to the behavior feature sequence pattern, and each network activity to be defined Actors are defined in the vector space, and the similarity between different network activity performers is quantitatively analyzed using the similarity analysis principle in the vector space model. By analyzing the similarities between different network activity implementers, it is possible to carry out deeper association and research on network activity implemente...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com