Method for mining attack frequent sequence mode from Web log
A frequent sequence and sequential pattern mining technology, applied in the field of Web security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] The hardware environment of the present invention is mainly a PC host. Among them, the CPU of the PC host is Intel(R) Core(TM) i5-4570, 3.20GHz, the memory is 4GB RAM, and the 64-bit operating system.
[0045] The software implementation of the present invention takes Windows7 as a platform, and is developed using the Java language under the Eclipse environment. Graphical display with the help of Graphviz tool. The Java version is 1.8.0_40, the Eclipse version is 4.4.2, and the Graphviz version is 2.37.
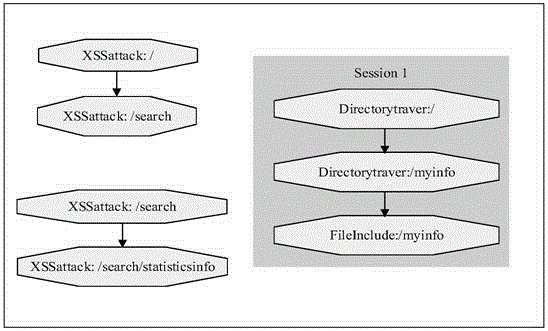
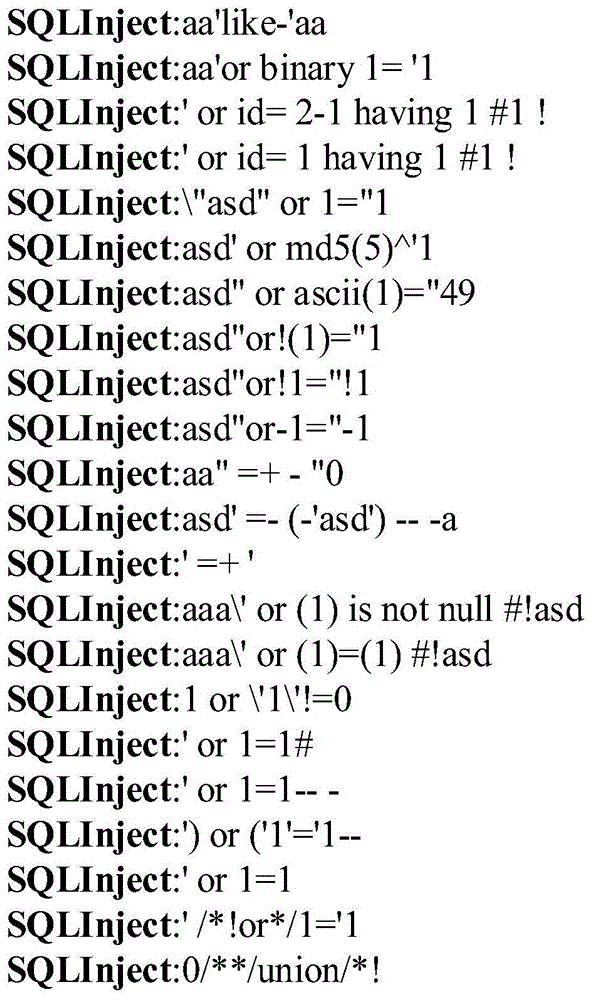
[0046] The experimental data is the Nginx server access log, and its format is visitor IP, authorized user, time, HTTP request, status code, size of transmitted data, upper-level path, and user agent. Specific examples are as follows: Figure 4 shown.
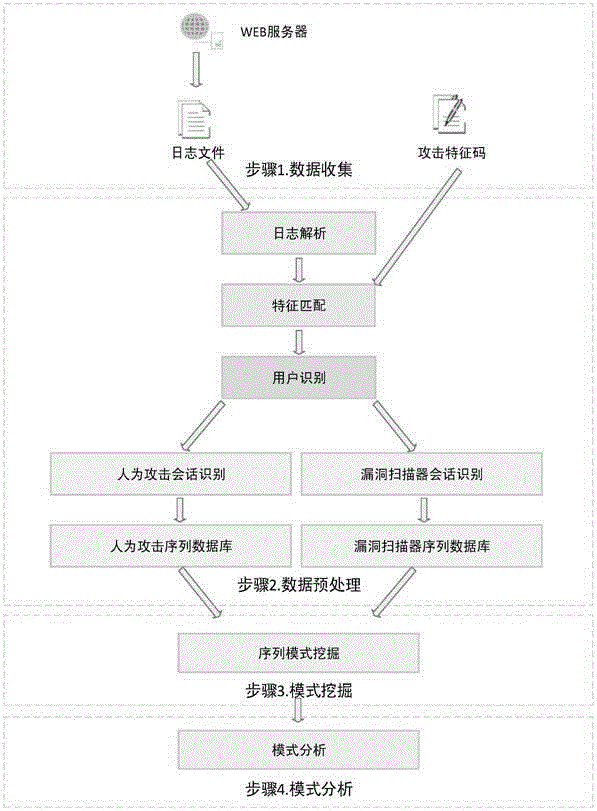
[0047] The operation is mainly divided into two parts, the first part is the log data preprocessing part, and the second part is the data mining and graphical display part.
[0048] 1. Preprocessing part
[0049] (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com