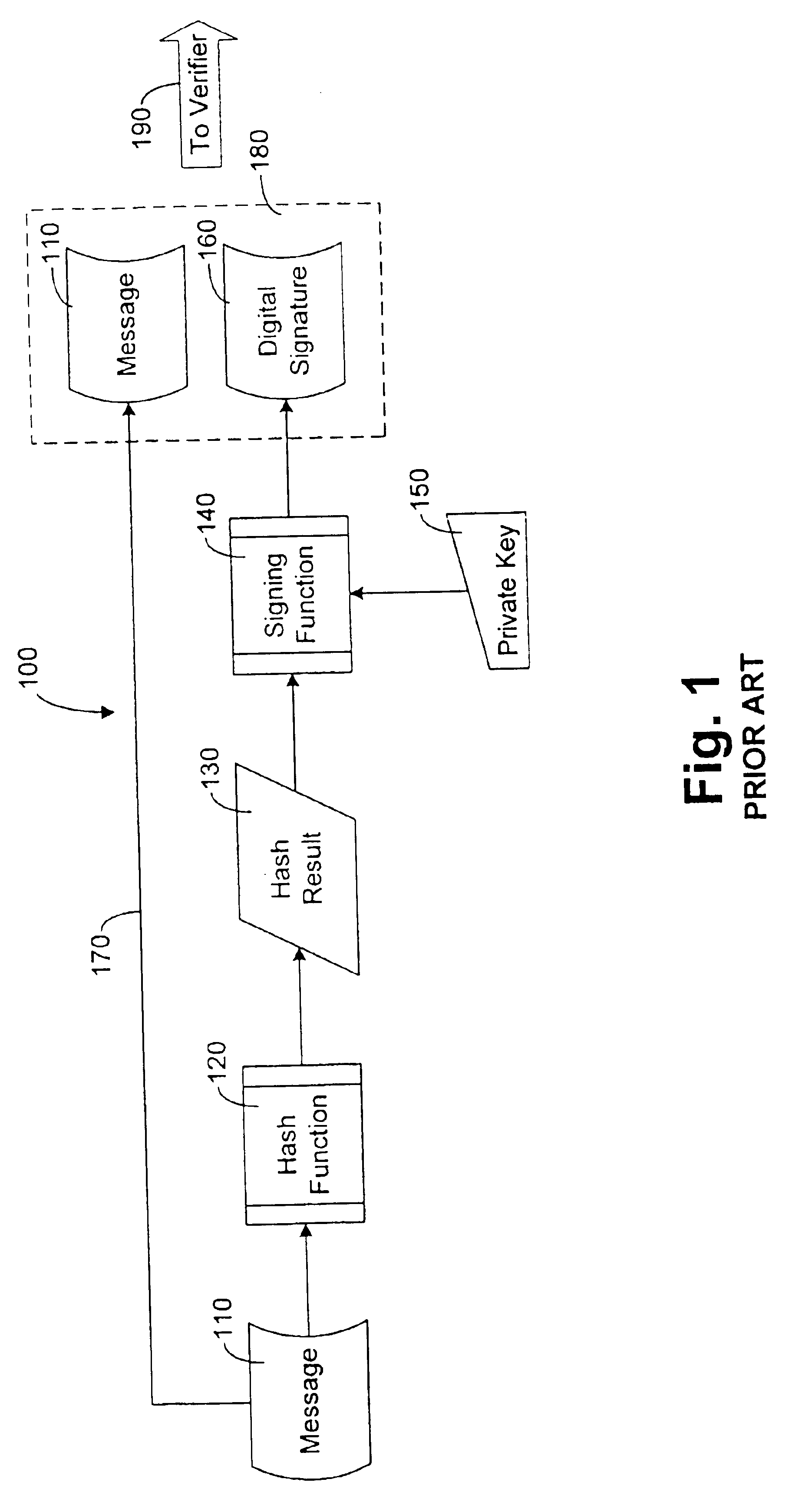
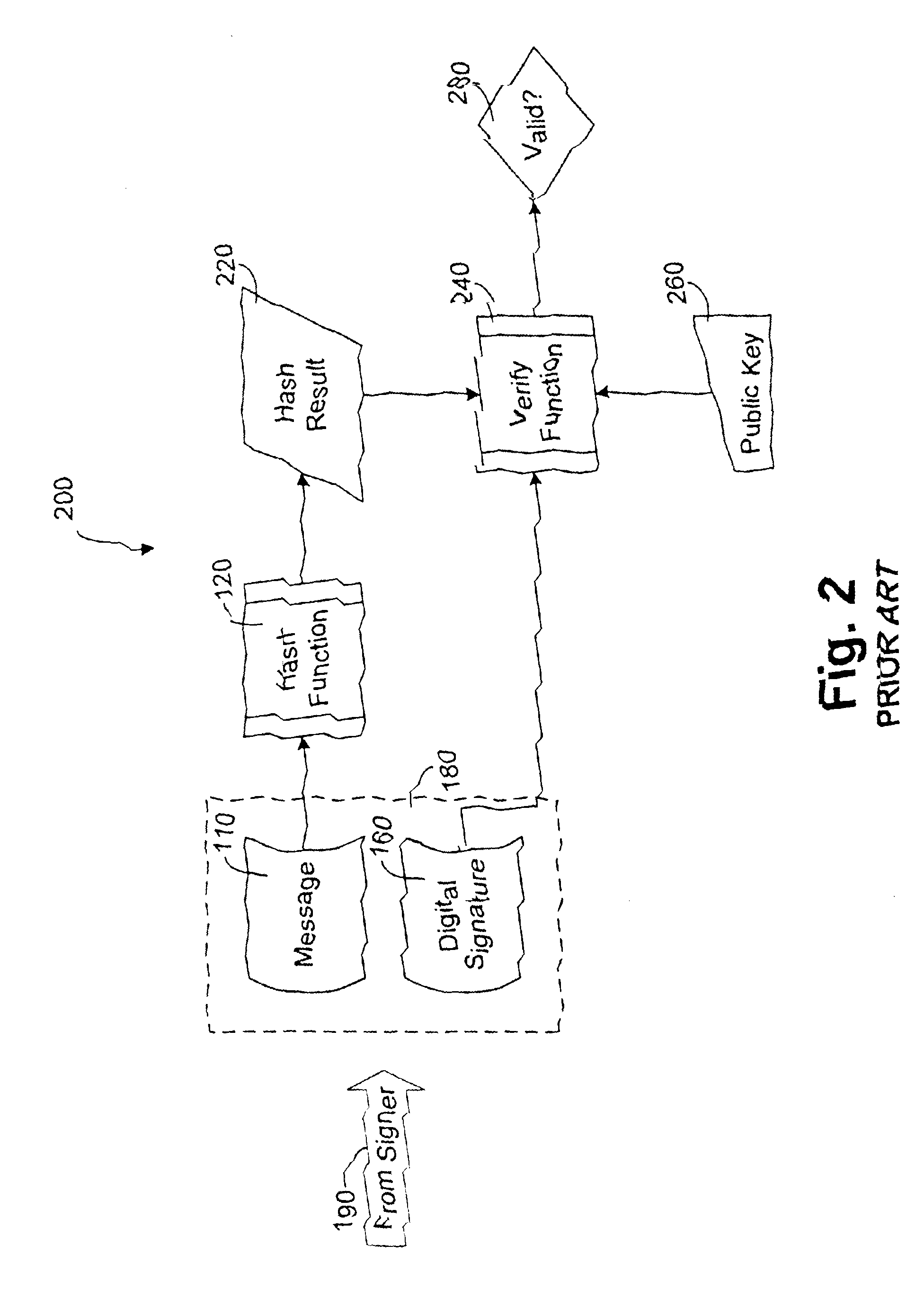
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
392 results about "Signature file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
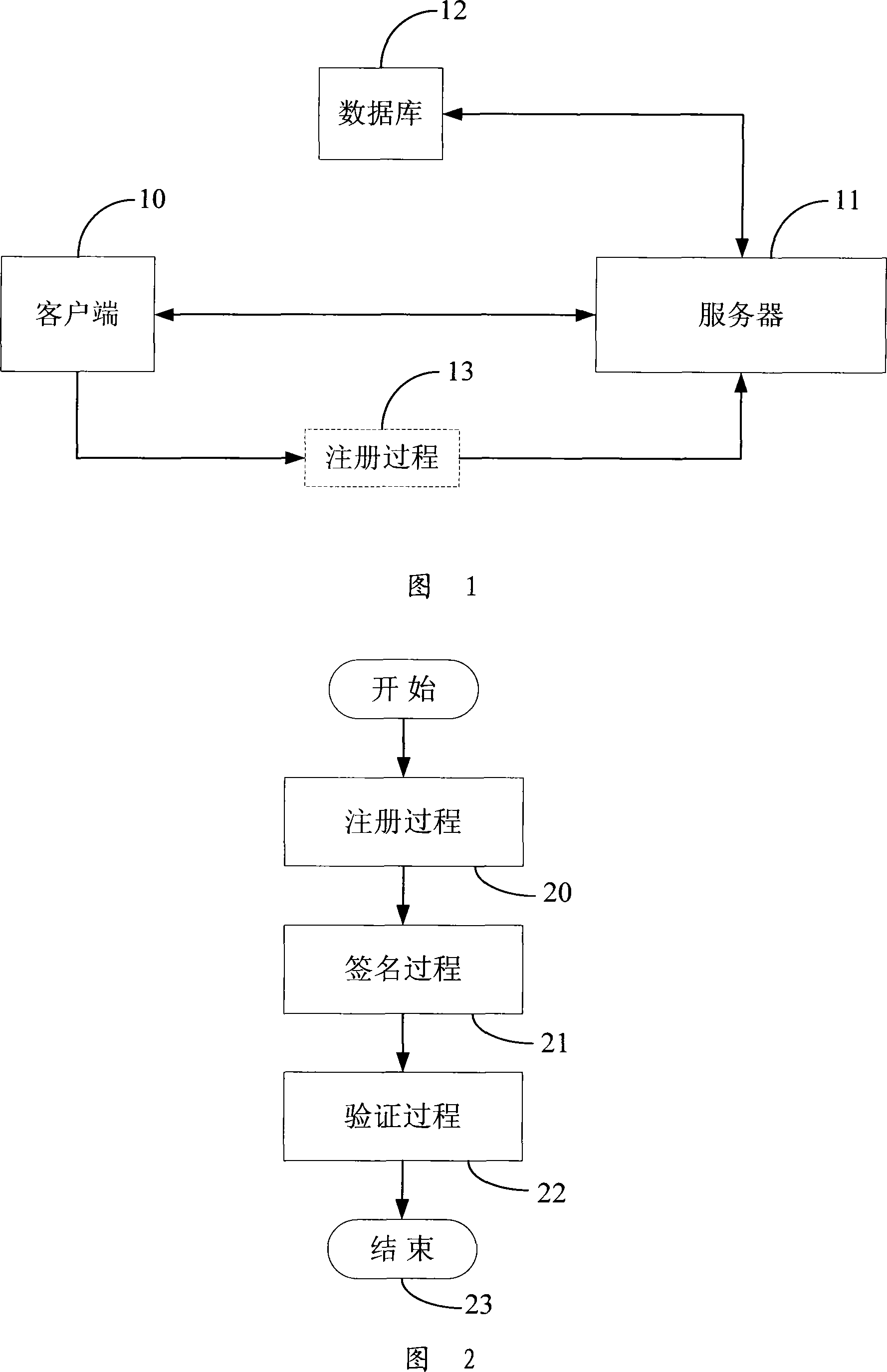
A signature file describes the namespaces, modules, types, and members in the corresponding implementation file. You use the information in a signature file to specify what parts of the code in the corresponding implementation file can be accessed from code outside the implementation file, and what parts are internal to the implementation file.
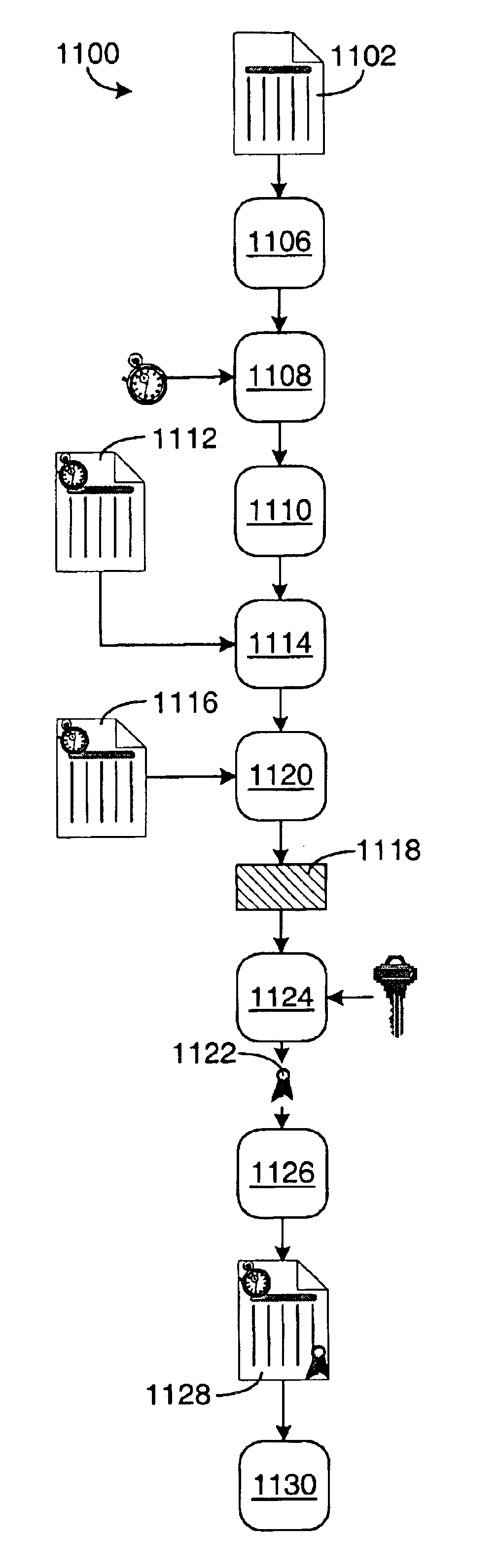
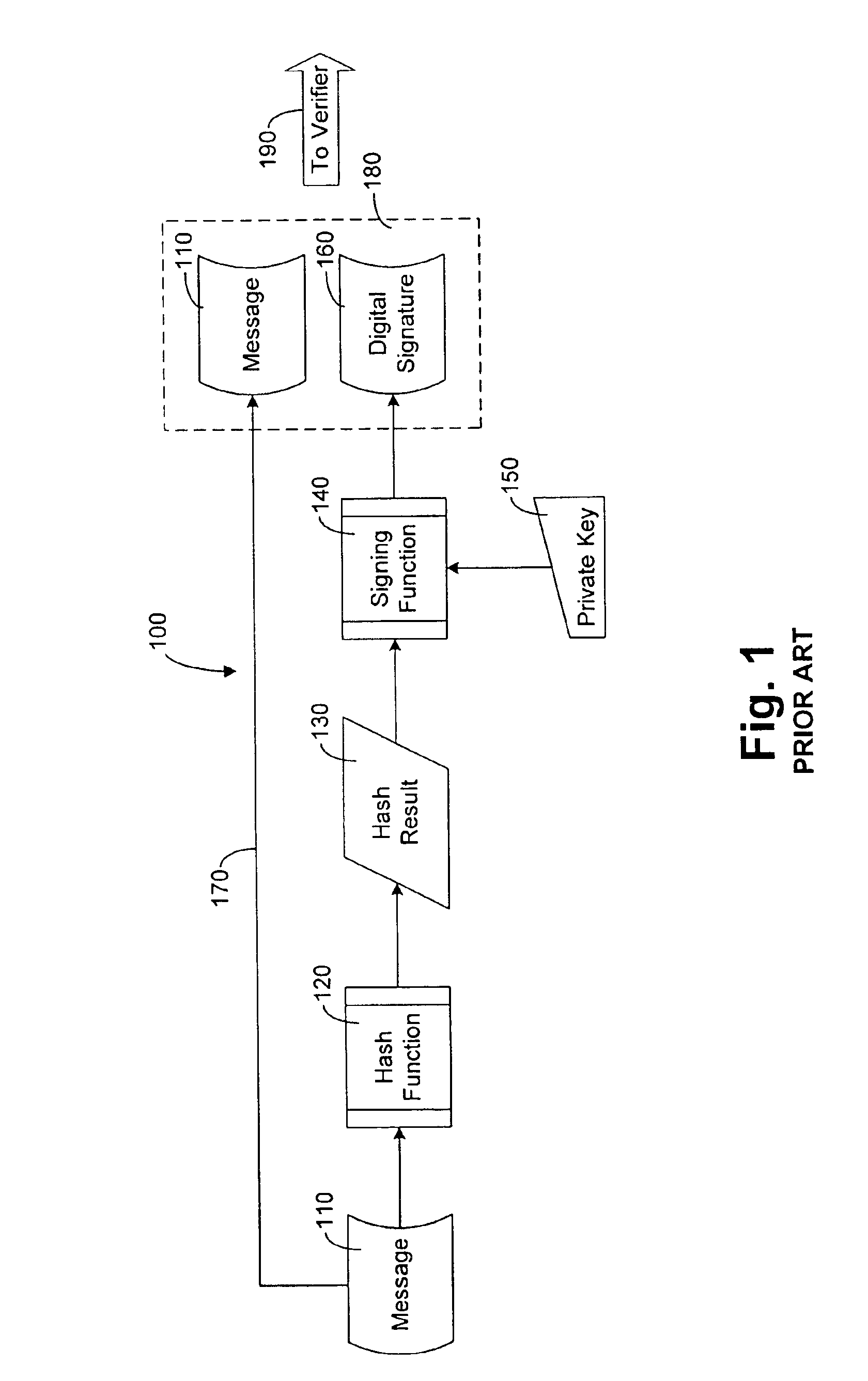
Personal computer system and methods for proving dates in digital data files
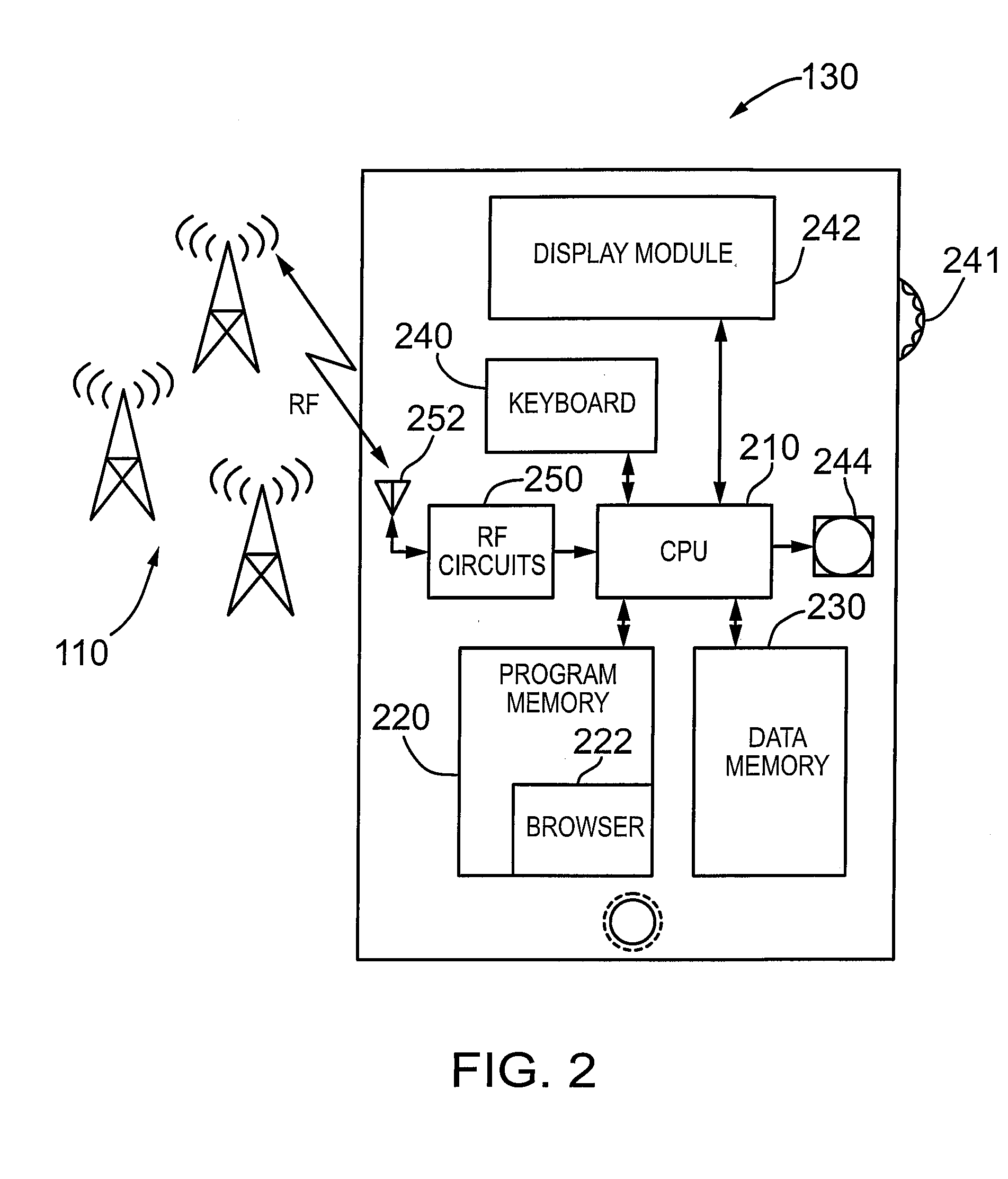
InactiveUS6898709B1Prevent fraudDigital data processing detailsUser identity/authority verificationDigital dataReal-time clock
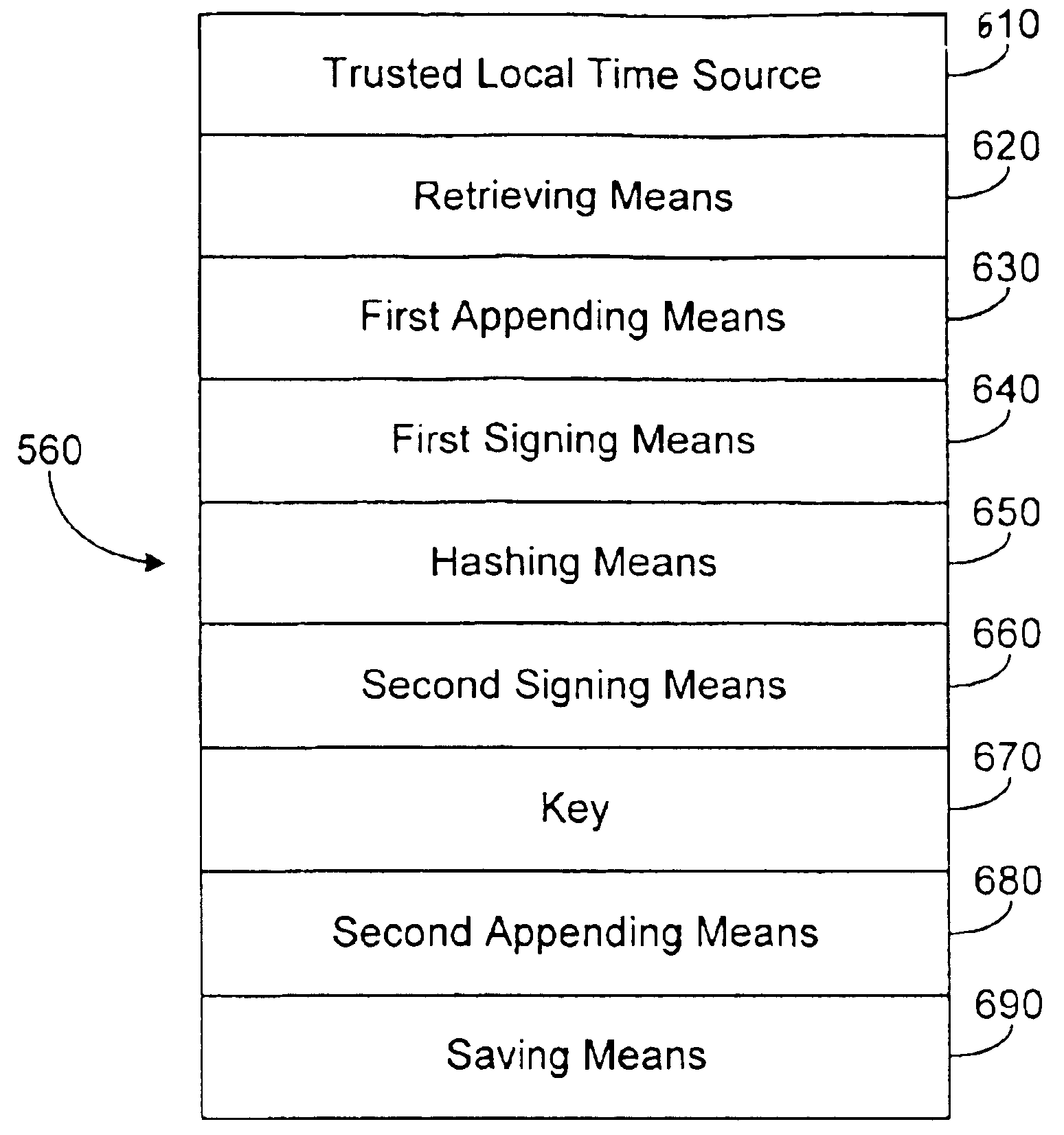
A personal computer (PC) system and methods for proving dates of digital data files, which are accessed, created, modified, received, or transmitted by the PC includes a trusted time source in a tamperproof environment, a first subsystem for saving the file at a moment in time, a second subsystem for retrieving from the trusted time source a date and a time corresponding to the moment in time, a third subsystem for appending the date and the time retrieved from the trusted time source to the saved file, a fourth subsystem for signing the saved file with the date and the time retrieved from the trusted time source appended thereto, a fifth subsystem means for hashing the signed file to produce a digest, a sixth subsystem for signing the digest with a key to produce a certificate, a seventh subsystem for appending the certificate to the saved file, and an eighth subsystem for saving the file with the certificate appended thereto. The trusted time source is a real time clock, which is not resettable, is independent of any system clock of the PC, and is installed locally relative to the PC.
Owner:TIME CERTAIN
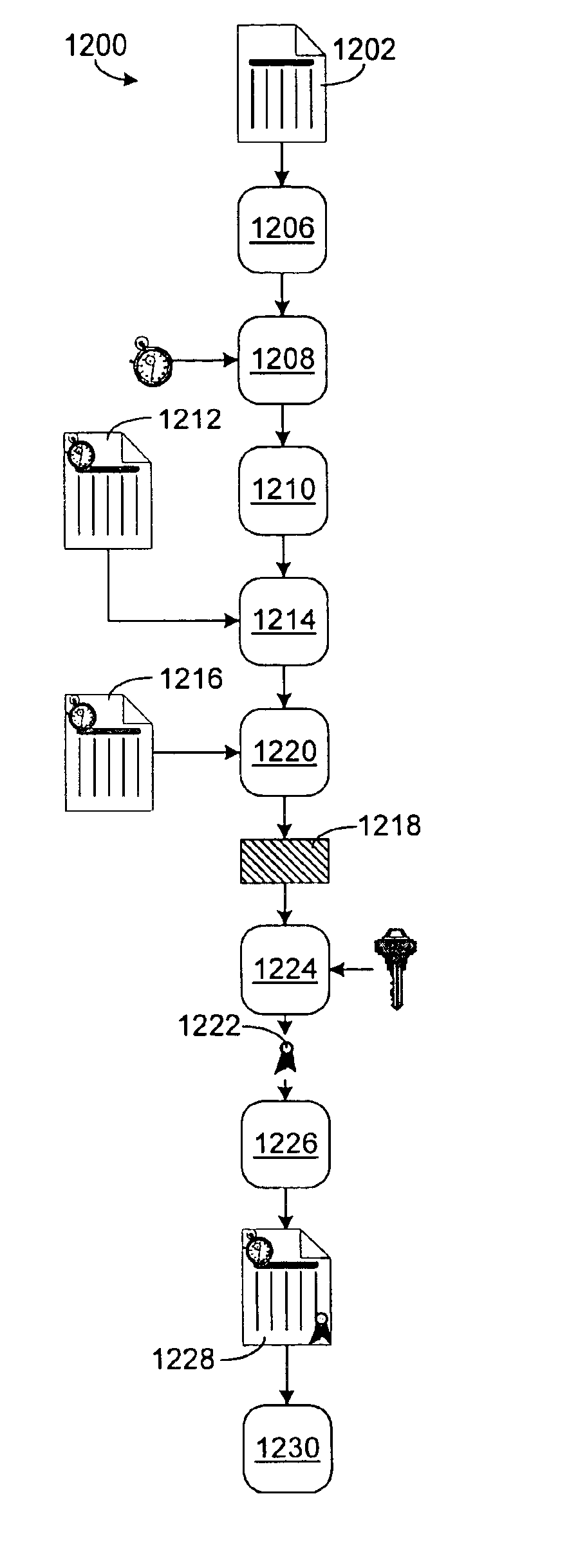
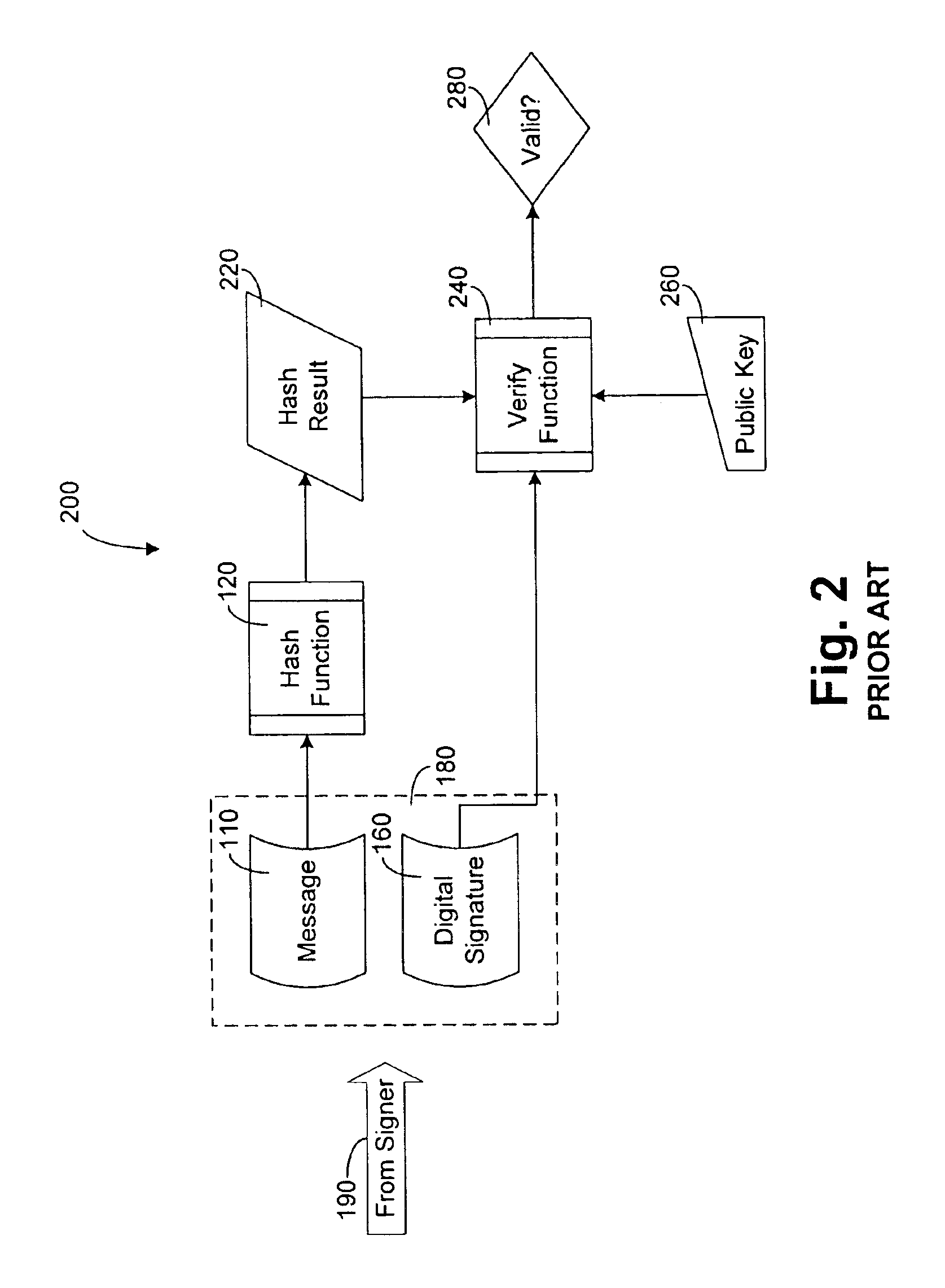
Method and system for determining and maintaining trust in digital data files with certifiable time
InactiveUS6895507B1Prevent fraudDigital data processing detailsUser identity/authority verificationDigital dataSignature file
A system and methods for proving dates of digital data files, which are accessed, created, modified, received, or transmitted by a computer includes a trusted time source in a tamperproof environment, a first subsystem for saving the file at a moment in time, a second subsystem for retrieving from the trusted time source a date and a time corresponding to the moment in time, a third subsystem for appending the date and the time retrieved from the trusted time source to the saved file, a fourth subsystem for signing the saved file with the date and the time retrieved from the trusted time source appended thereto, a fifth subsystem for hashing the signed file to produce a digest, a sixth subsystem for signing the digest with a key to produce a certificate, a seventh subsystem for appending the certificate to the saved file, and an eighth subsystem for saving the file with the certificate appended thereto. The trusted time source is a real time clock, which is not resettable, is independent of any system clock of the computer, and is installed locally relative to the computer.
Owner:TIME CERTAIN
Method and apparatus for checkout transition in an e-commerce application
ActiveUS20090187820A1Natural language data processingBuying/selling/leasing transactionsWeb siteSignature file
A method and apparatus for transcoding content or elements of a webpage received at a client device, for example, a mobile communication device or other type of networked device. The apparatus includes a transcoding engine which is configured to transcode webpage content during a secure end-to-end connection between a client device and a website without the use of a proxy. According to an embodiment, the transcoding engine resides on the client, and is implemented as a plug-in to the browser, and transcoding instructions are provided to the client device by way of the signature file(s) each time the plug-in is invoked. The client device uses the transcoding instructions to manipulate the secure response from the secure server, for example, to transcode the response to a format suitable for display on the client device.
Owner:MALIKIE INNOVATIONS LTD
Method and system for determining and maintaining trust in digital image files with certifiable time
InactiveUS6948069B1Prevent fraudDigital data processing detailsPublic key for secure communicationReal-time clockDigital imaging
A system and methods for proving dates of digital-imaging files, which are accessed, created, modified, received, saved, or transmitted by a computer includes a trusted time source in a tamperproof environment, a first subsystem for saving the file at a moment in time, a second subsystem for retrieving from the trusted time source a date and a time corresponding to the moment in time, a third subsystem for appending the date and the time retrieved from the trusted time source to the saved file, a fourth subsystem for signing the saved file with the date and the time retrieved from the trusted time source appended thereto, a fifth subsystem for hashing the signed file to produce a digest, a sixth subsystem for signing the digest with a key to produce a certificate, a seventh subsystem for appending the certificate to the saved file, and an eighth subsystem for saving the file with the certificate appended thereto. The trusted time source is a real time clock, which is not resettable, is independent of any system clock of the computer, and is installed locally relative to the computer.
Owner:TIME CERTAIN
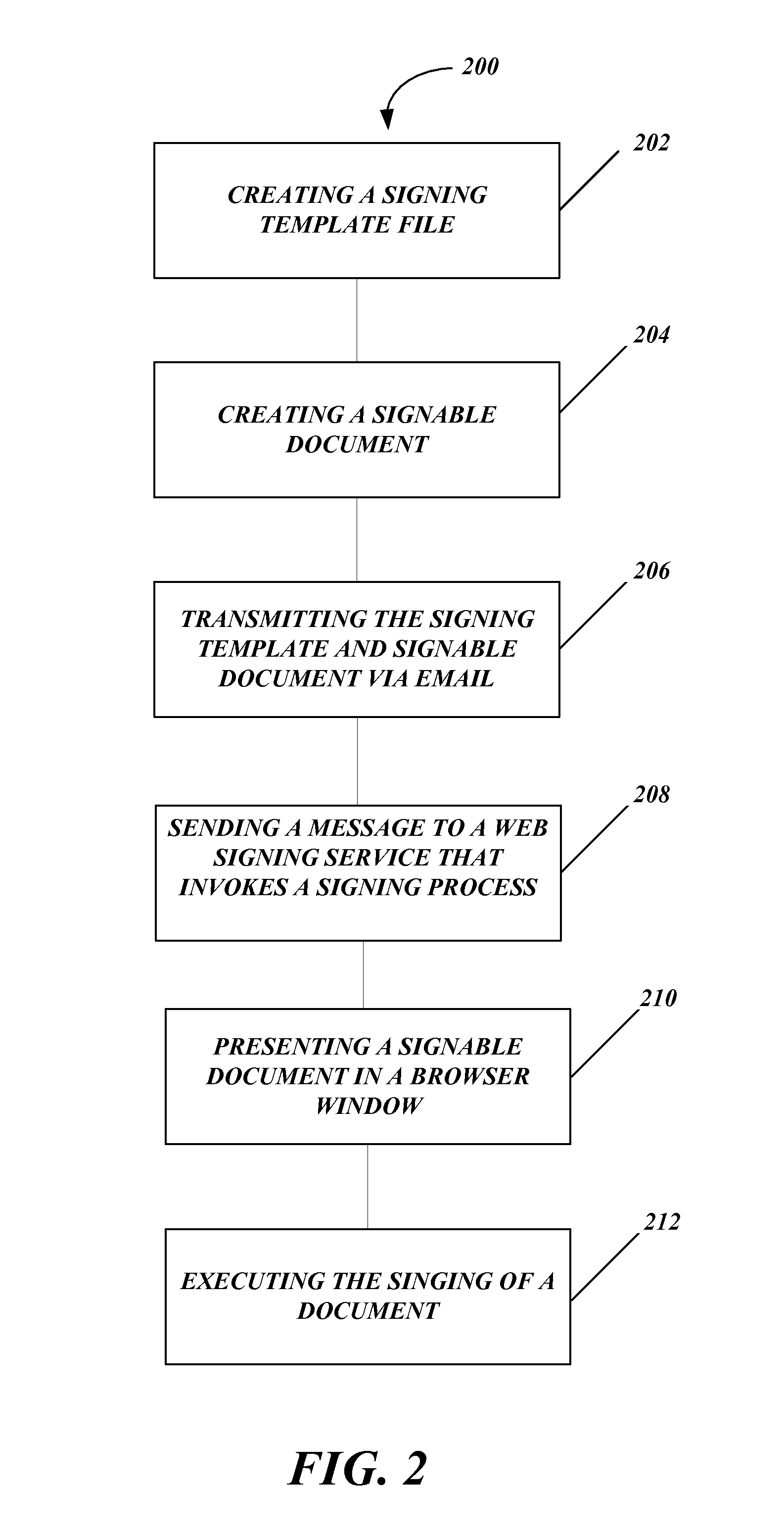
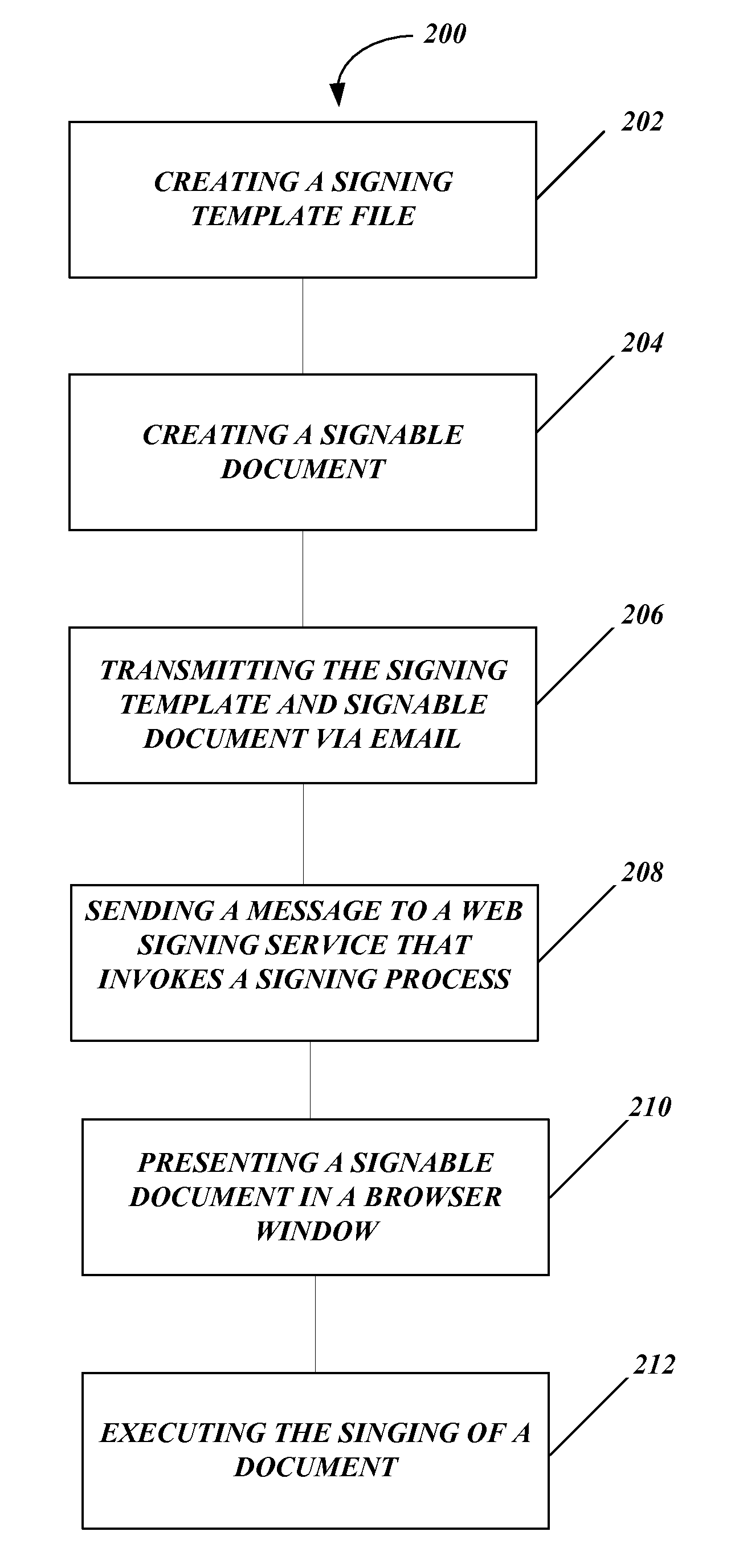
Systems and methods for distributed electronic signature documents
ActiveUS20090024912A1Digital data protectionNatural language data processingSignature fileDocument preparation
Systems and methods for distributed electronic signature documents. A method for distributed electronic signature documents includes creating a signing template that contains information about how a signable document is to be signed. A signable document is created to be distributed to a signer for signing. The signable document is electronically transmitted to the signer. A message is sent using an activatable control in the signing document to a web signing server to invoke the signing process. A browser window is opened on a signer's computer in order to execute the signing process.
Owner:DOCUSIGN
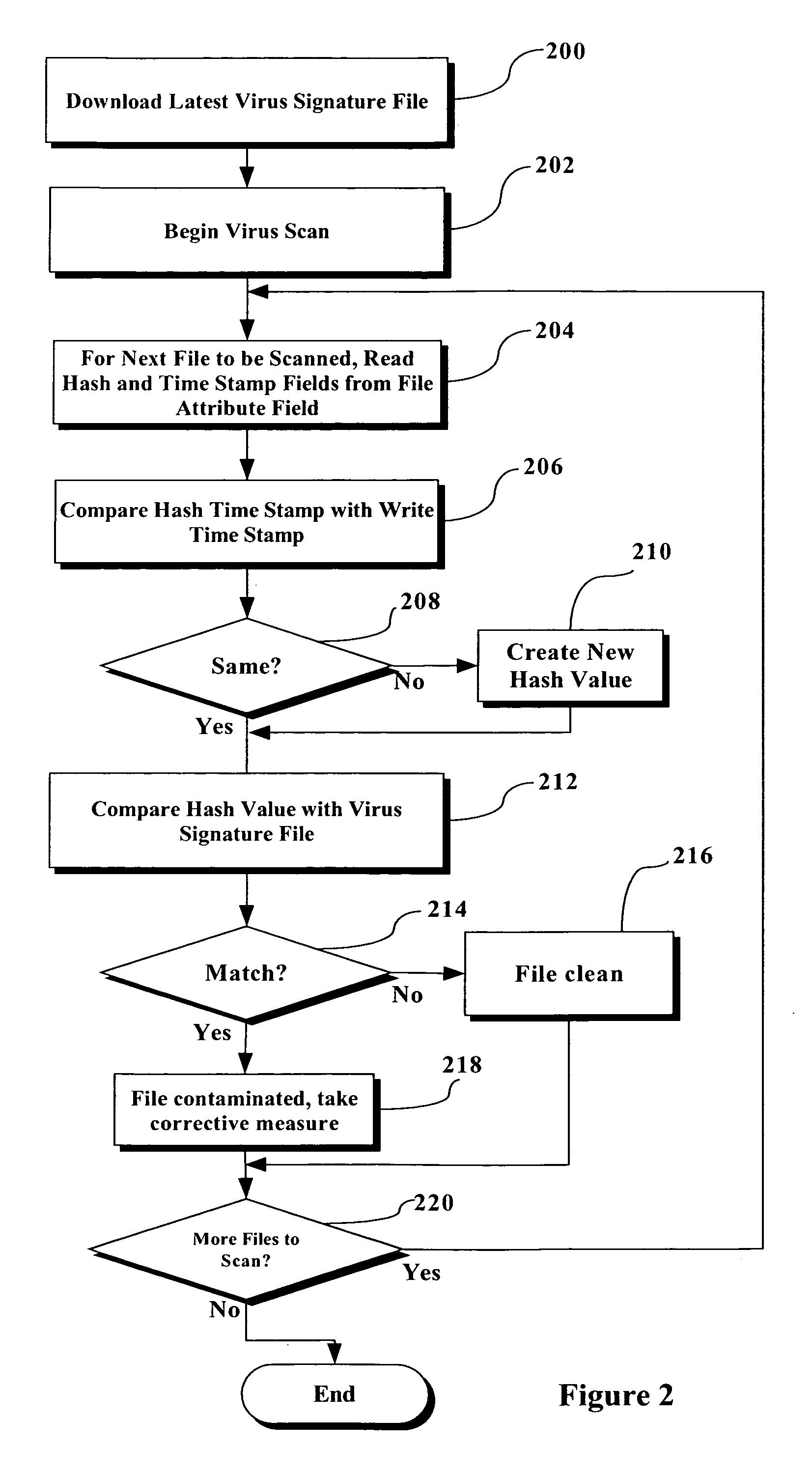
Rapid virus scan using file signature created during file write
ActiveUS20060143713A1Amount of timeMemory loss protectionDetecting faulty computer hardwareSignature fileVirus
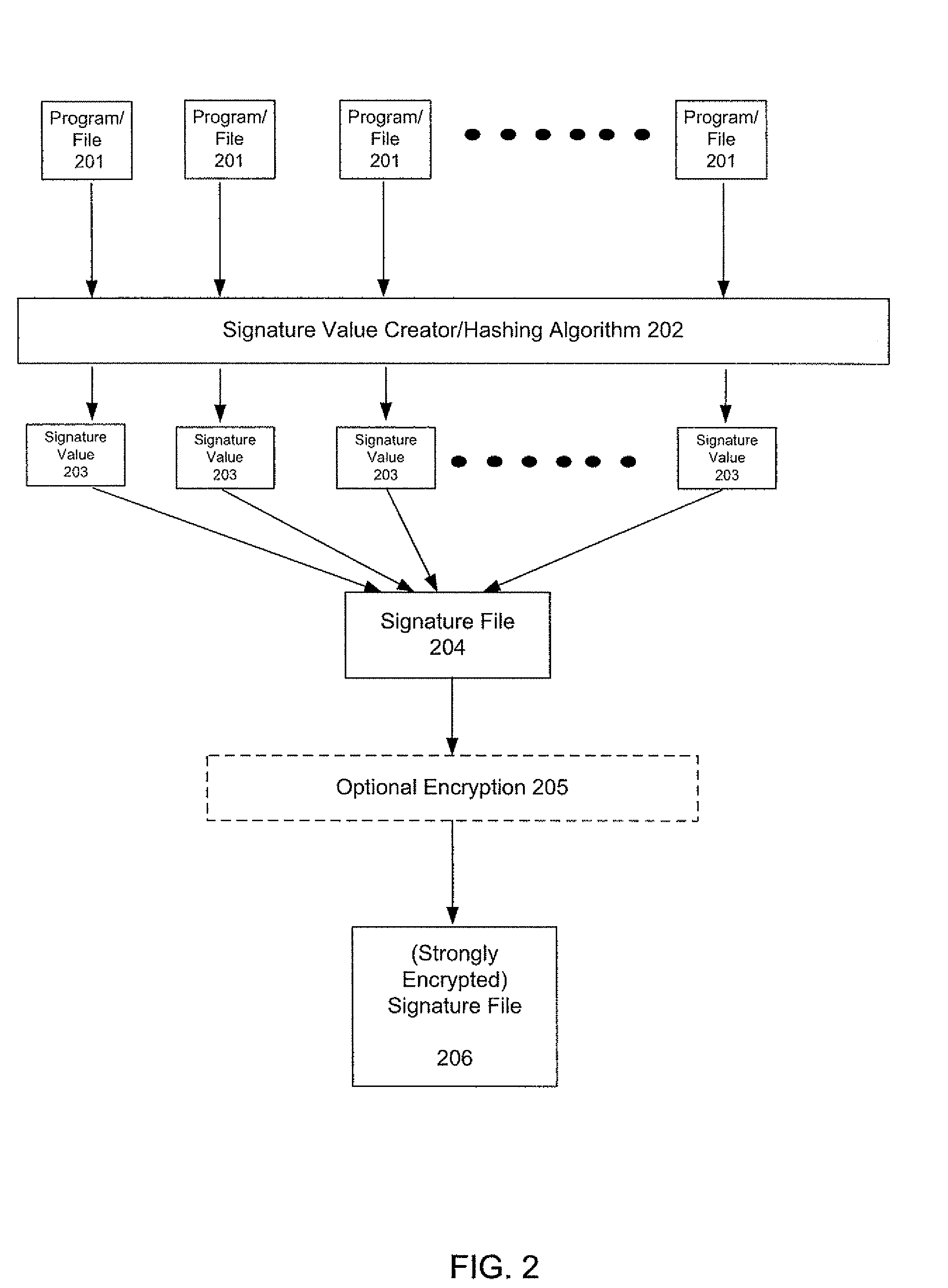
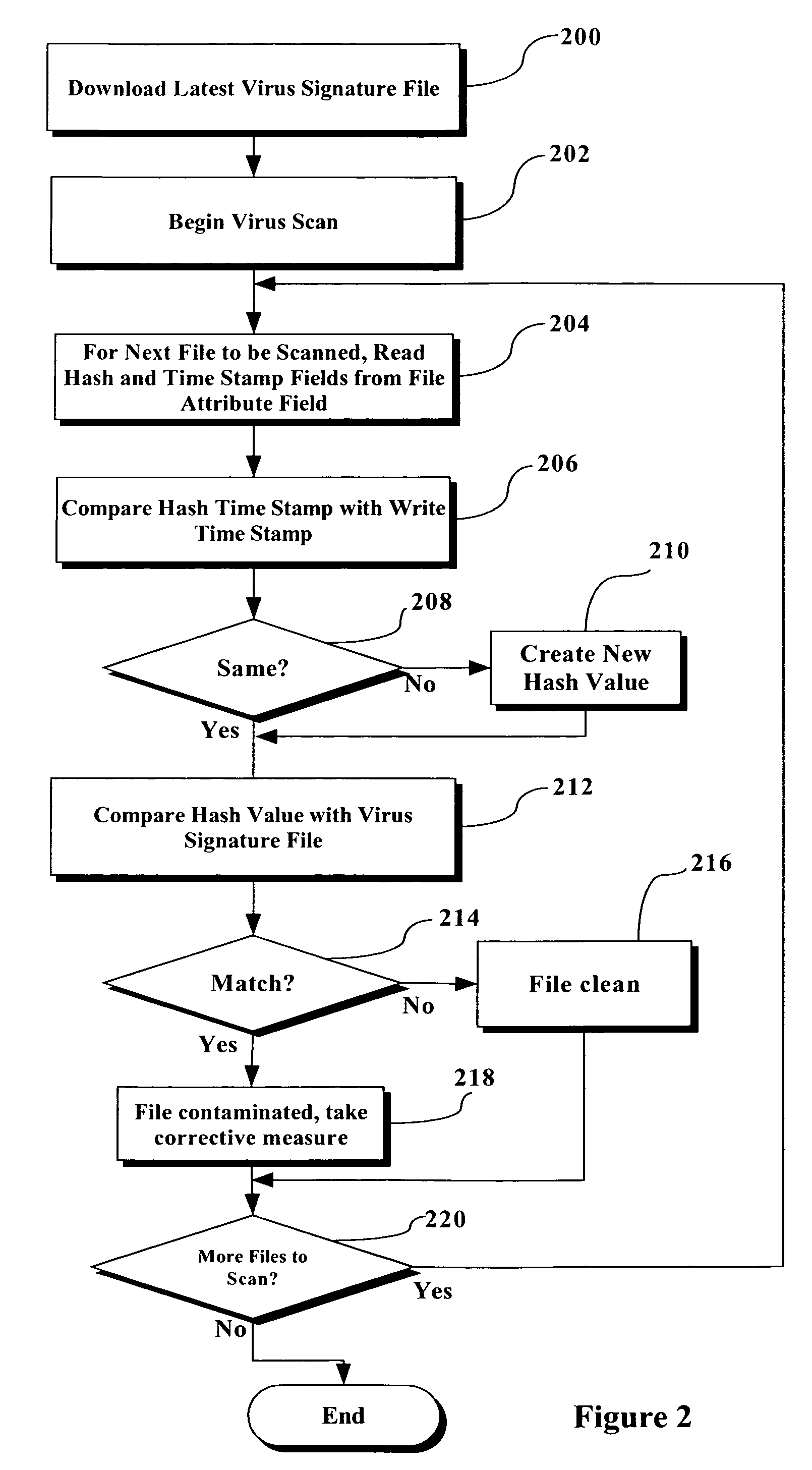
A procedure and implementations thereof are disclosed that significantly reduce the amount of time necessary to perform a virus scan. A file signature is created each time a file is modified (i.e., with each “file write” to that file). The file signature is inserted, with a date stamp, into the file attributes. The virus scan program checks the previously-created file signature against the virus signature file instead of creating the file signature for every file during the virus scan. Checks to ensure that the file signature is secure, and is valid and up to date, are also implemented. Only if the file signature is not valid and up-to-date does the virus scan program create a new file signature at the time of the running of the virus scan.
Owner:LENOVO PC INT
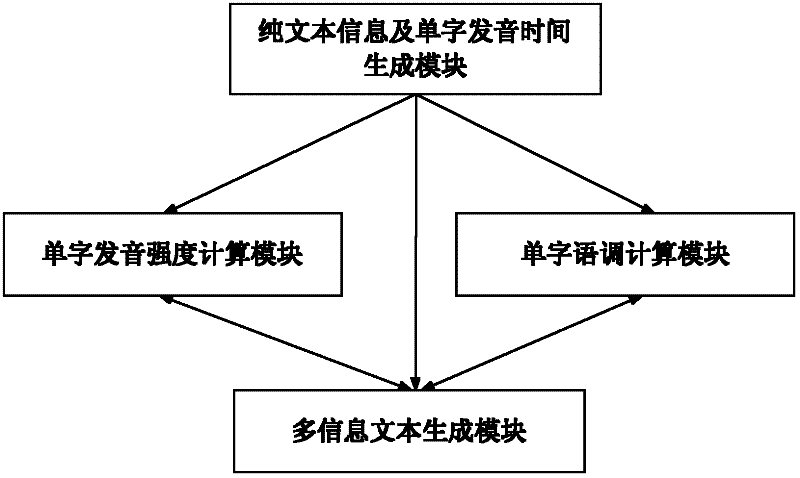
Device and method for acquiring speech recognition multi-information text
The invention provides a device and a method for acquiring a speech recognition multi-information text. After a speech audio frequency is converted into pure text information by speech recognition, individual character pronunciation speed, individual character pronunciation strength and individual character pronunciation intonation in the speech audio frequency are integrated into the initially-generated pure text information in a certain expression way to generate multi-information text information. The device and the method for acquiring the speech recognition multi-information text can be widely used for information release platforms such as micro blogs, short messages, signature files and the like.
Owner:SHANGHAI GUOKE ELECTRONICS
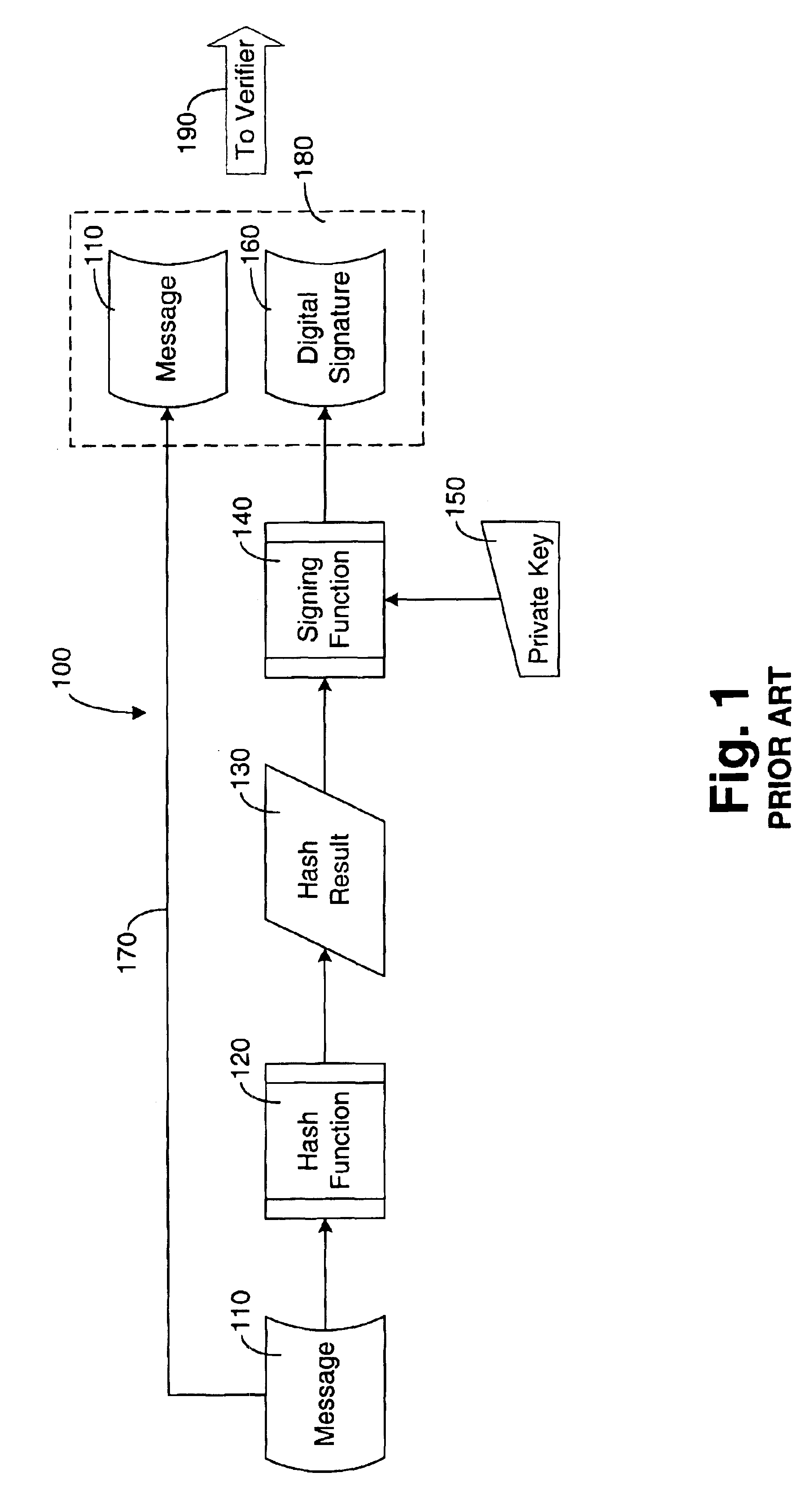
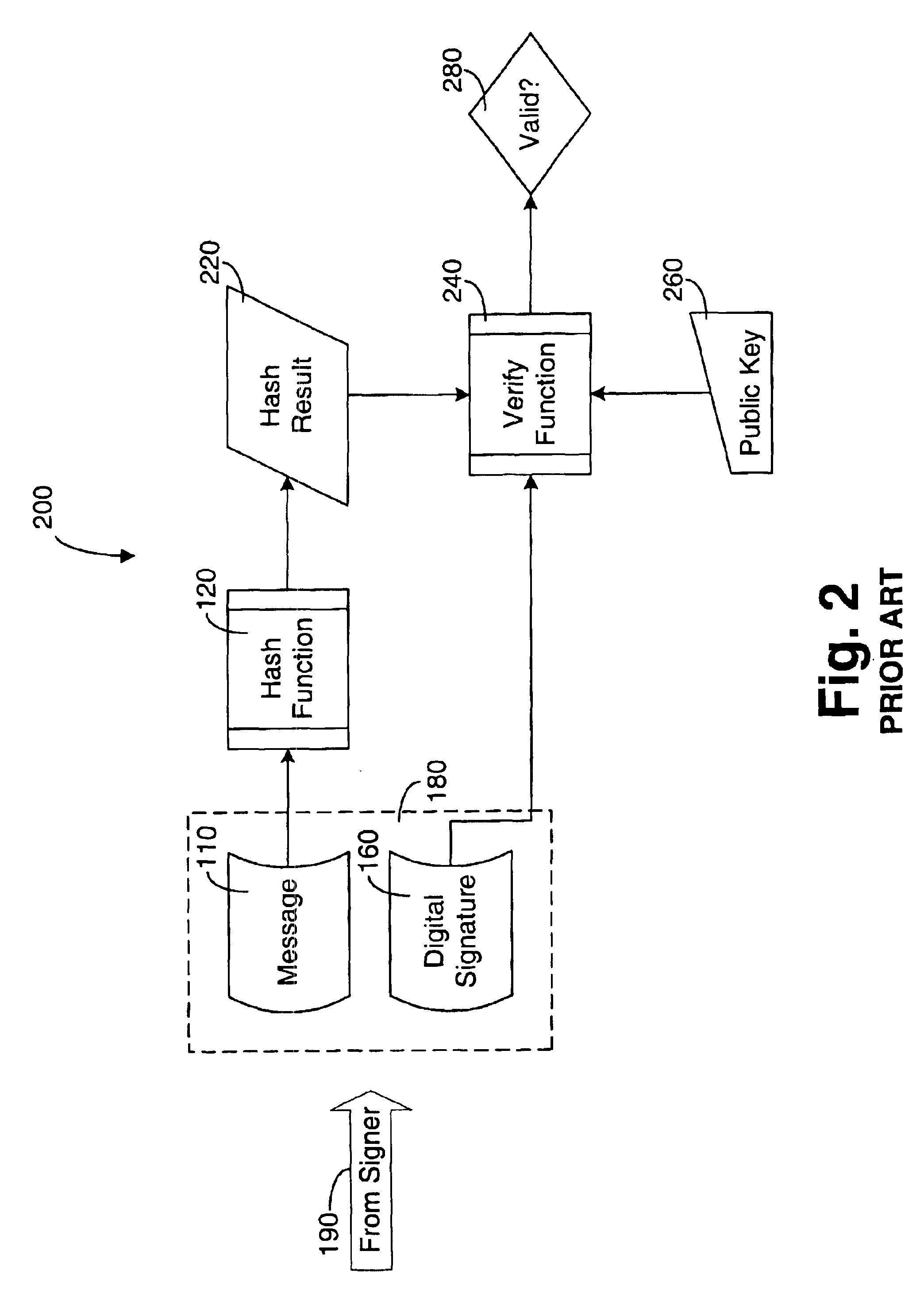
Digital signature system, digital signature method, digital signature mediation method, digital signature mediation system, information terminal and storage medium
InactiveUS6990585B2User identity/authority verificationUnauthorized memory use protectionDigital signatureComputer terminal
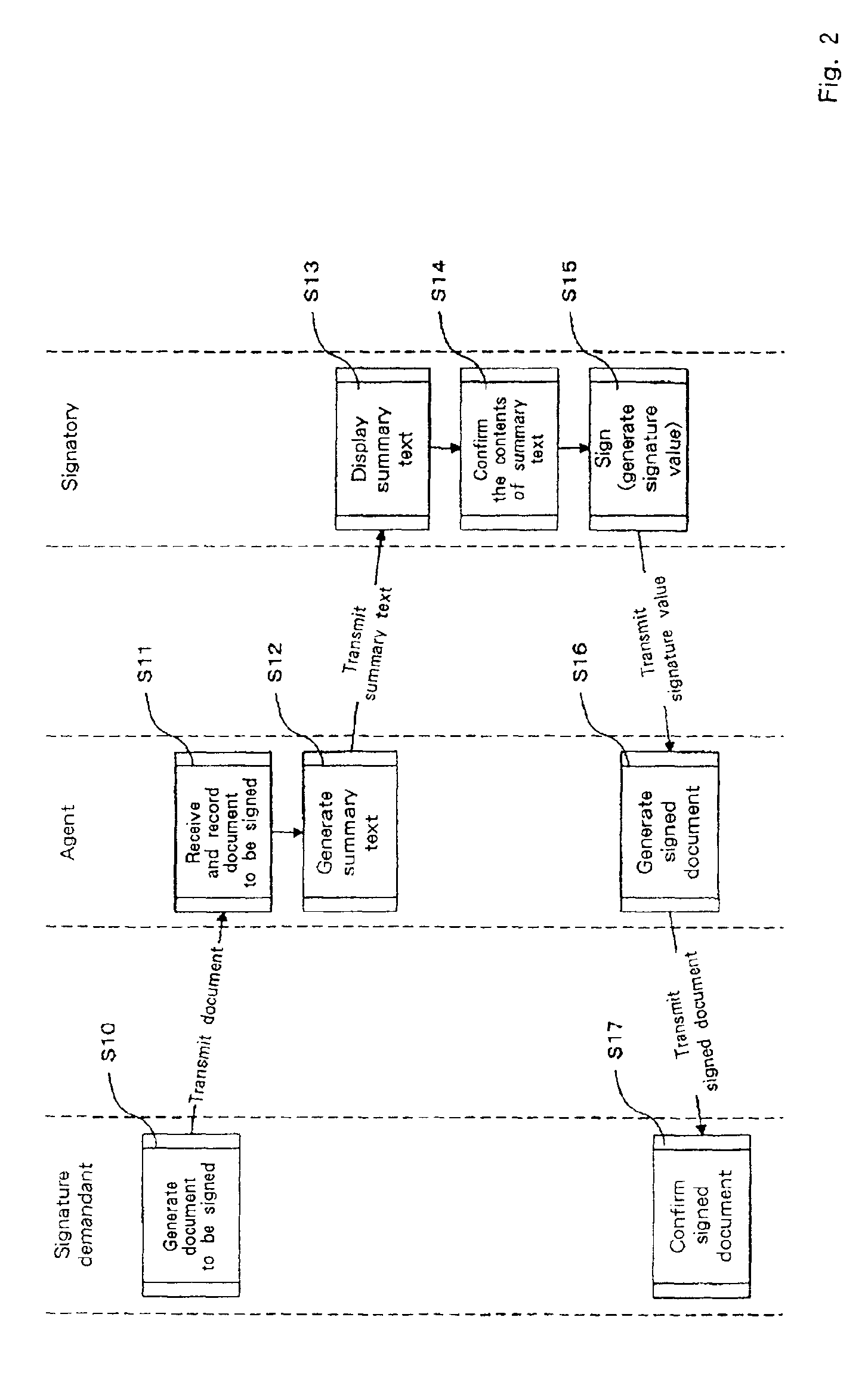
The present invention provides digital signature techniques using an information terminal, such as a portable terminal, having limited calculation resources. In one embodiment, a signature demandant generates a document to be signed, and an agent receives this document. The agent generates summary text for this document, and transmits the summary text to a signatory, and the signatory displays the summary text using his or her information terminal. The signatory confirms the contents, employs a private key stored in his or her terminal to sign (encrypt) the summary text. The signatory thereafter transmits a signature value to the agent, who generates a signed document that includes the signature value. Finally, the signature demandant verifies (decrypts) the received signed document using the public key of the signatory and confirms the contents.
Owner:IBM CORP
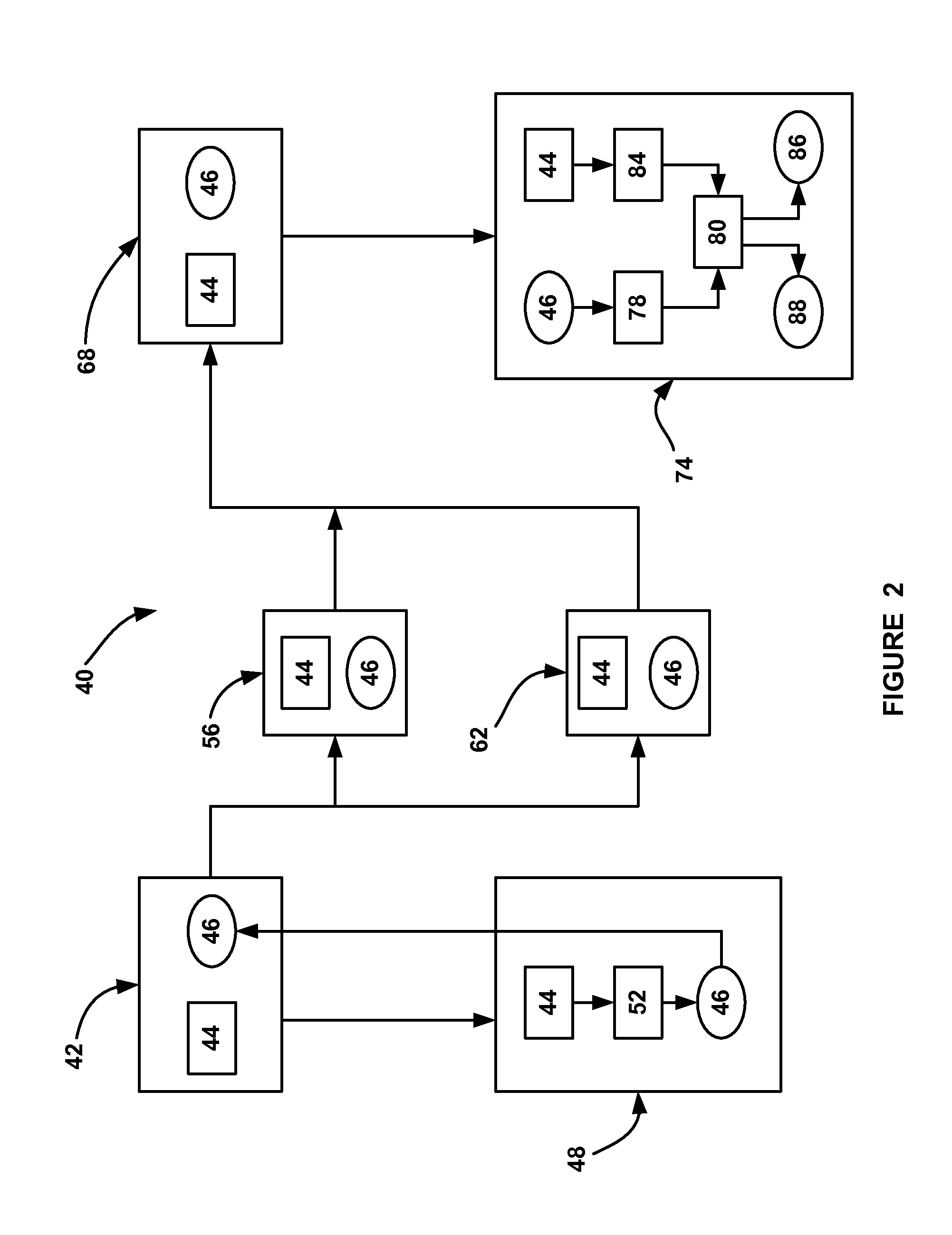
Digital signature method, digital signature system and quantum key card
ActiveCN106357396AFix security issuesReduce the risk of being crackedKey distribution for secure communicationUser identity/authority verificationSignature fileDigital signature
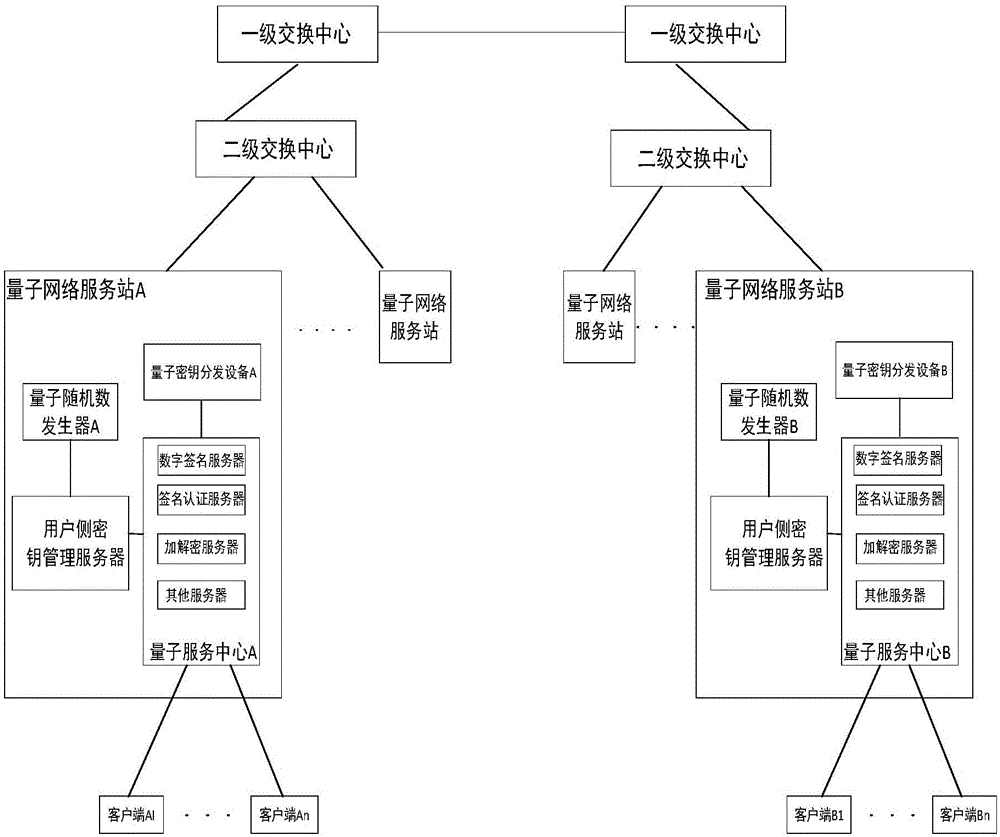
The invention discloses a digital signature method, a digital signature system and a quantum key card. The digital signature system comprises quantum network service stations, signature client sides, authentication client sides and quantum key cards, wherein the quantum network service stations are configured on the network side, and the signature client sides and the authentication client sides are configured on the user side. The digital signature method includes that a true random number is generated on the network side and then stored in the corresponding quantum key card and on the network side respectively to form a corresponding user-side key; the quantum key card matching with the signature client side uses the stored user-side key to generate a signature file, the signature file is sent to the authentication client side via the signature client side, and the authentication client side sends the received signature file to the current quantum network service station, acquires the corresponding user-side key from the network side to perform signature authentication on the signature file and sends signature authentication results to the corresponding authentication client side. The digital signature method, the digital signature system and the quantum key card have the advantage that key seeds are stored in the quantum key cards and the quantum network service stations, so that the problems of access use and safety of quantum network terminals are solved.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
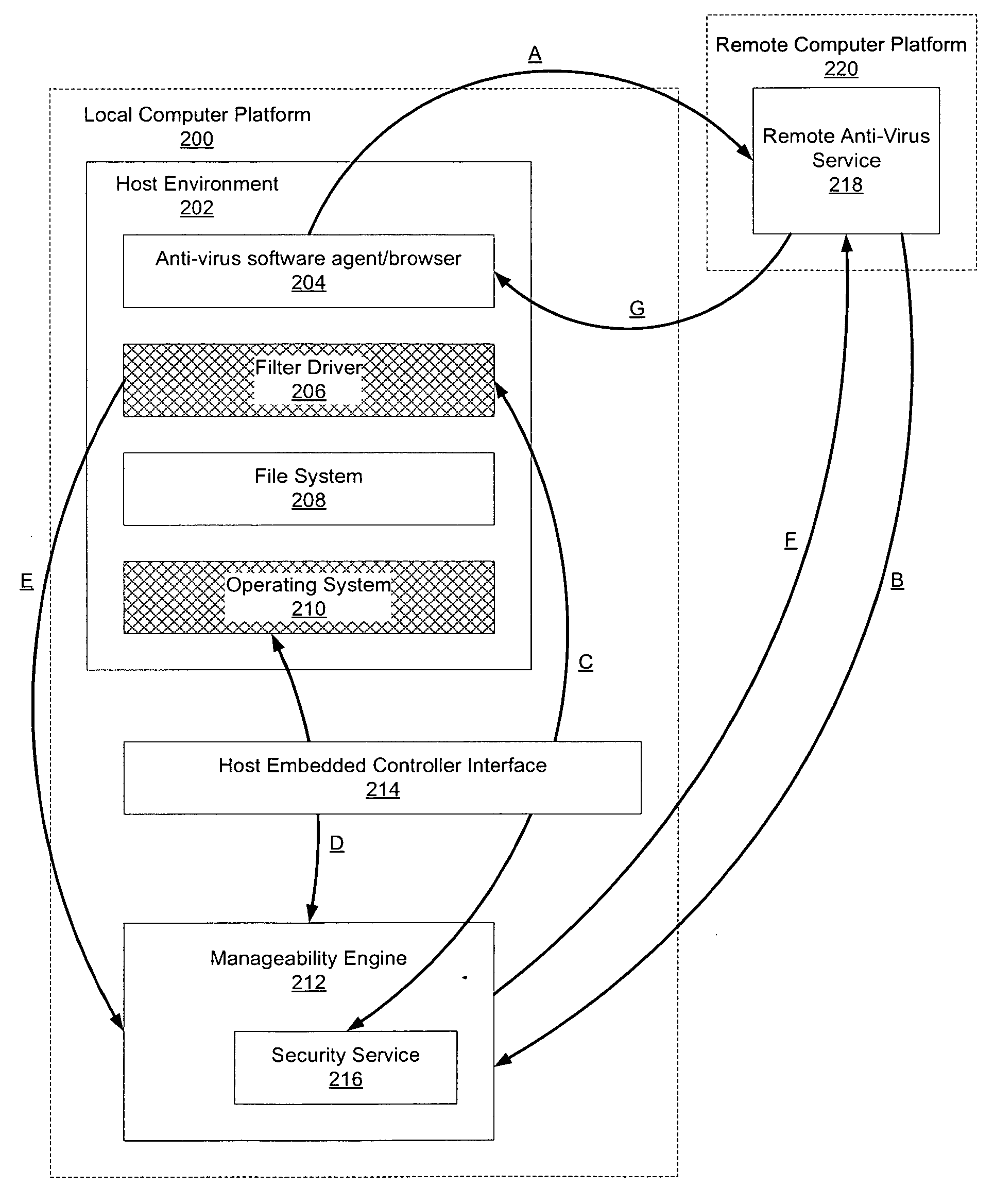
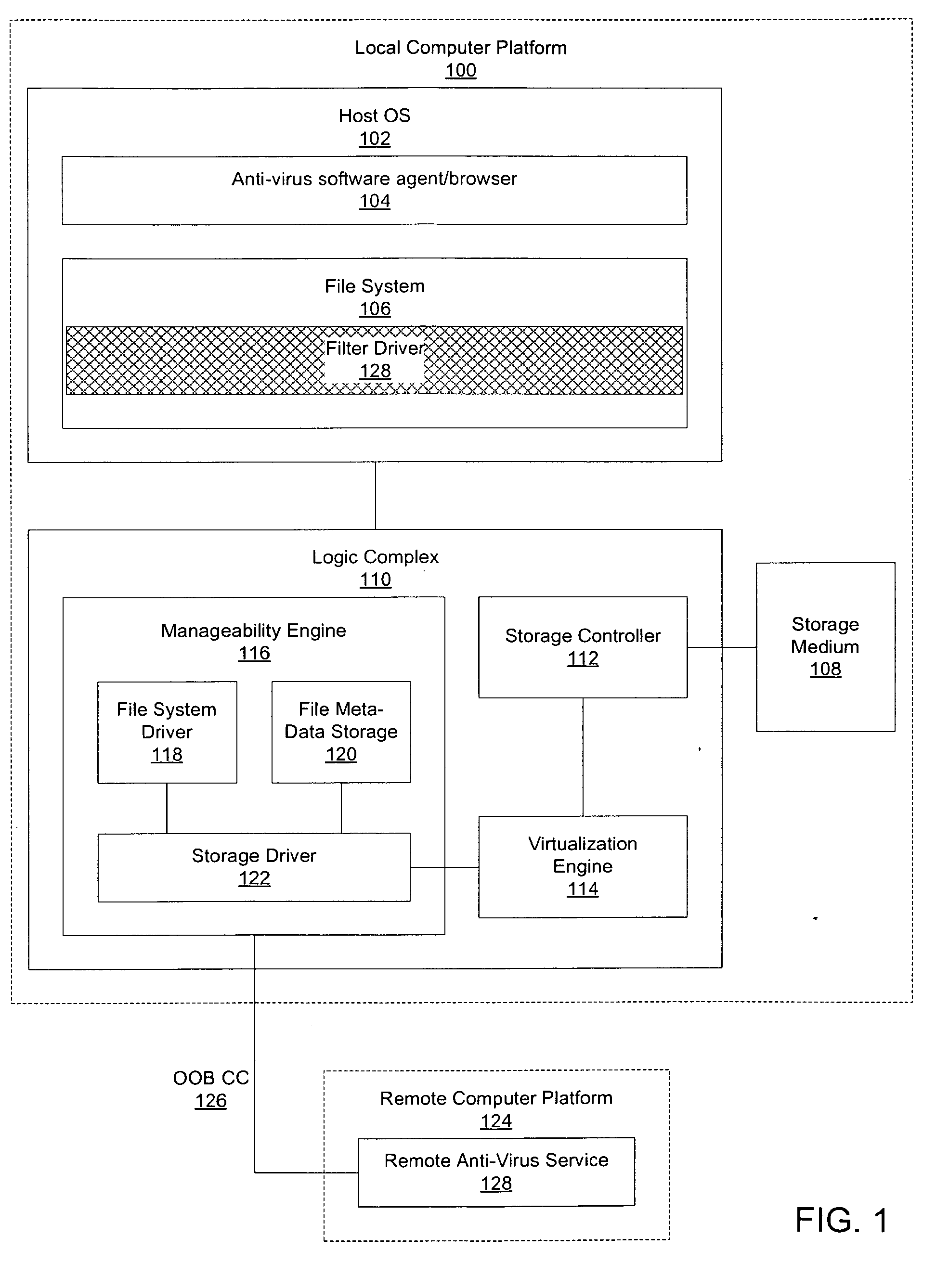
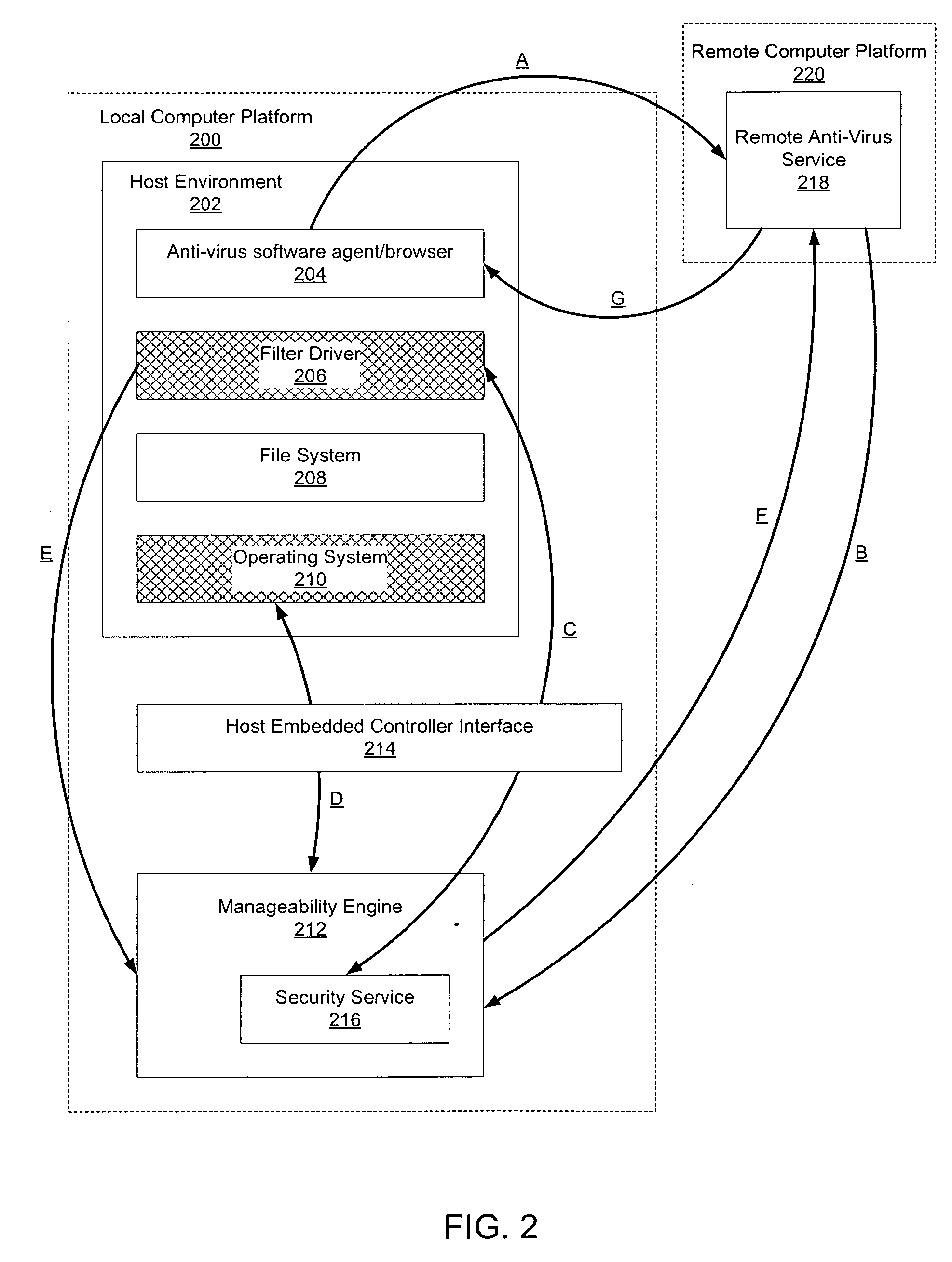
Hardware-based anti-virus scan service
A device, system, and method are disclosed. In an embodiment, the device includes a storage medium to store files. The device also includes a manageability engine. The manageability engine accesses a virus signature file. The manageability engine then performs an anti-virus scan using patterns in the signature file to compare to one or more of the files. The manageability engine then reports the results of the scan to an external agent.
Owner:INTEL CORP
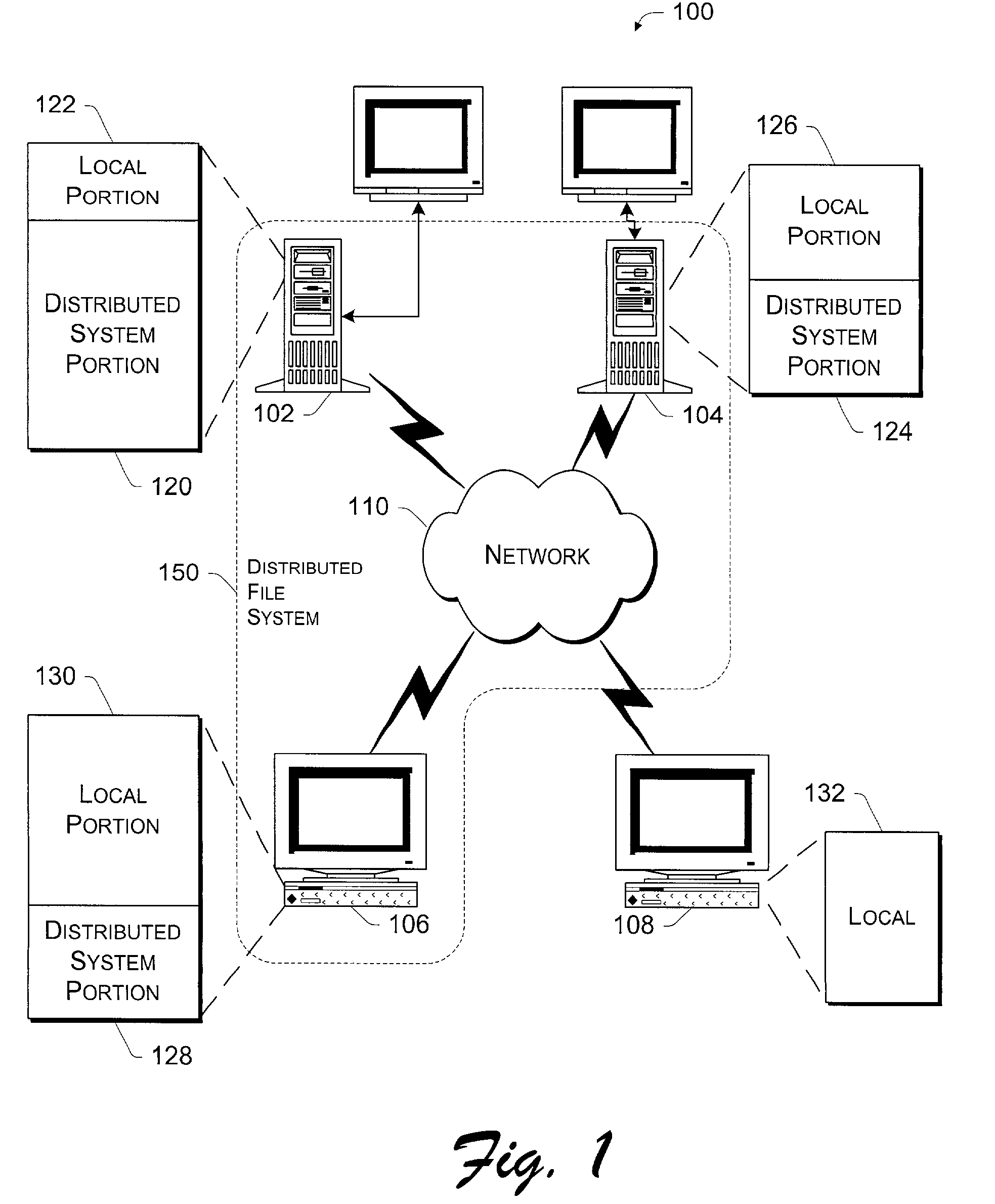
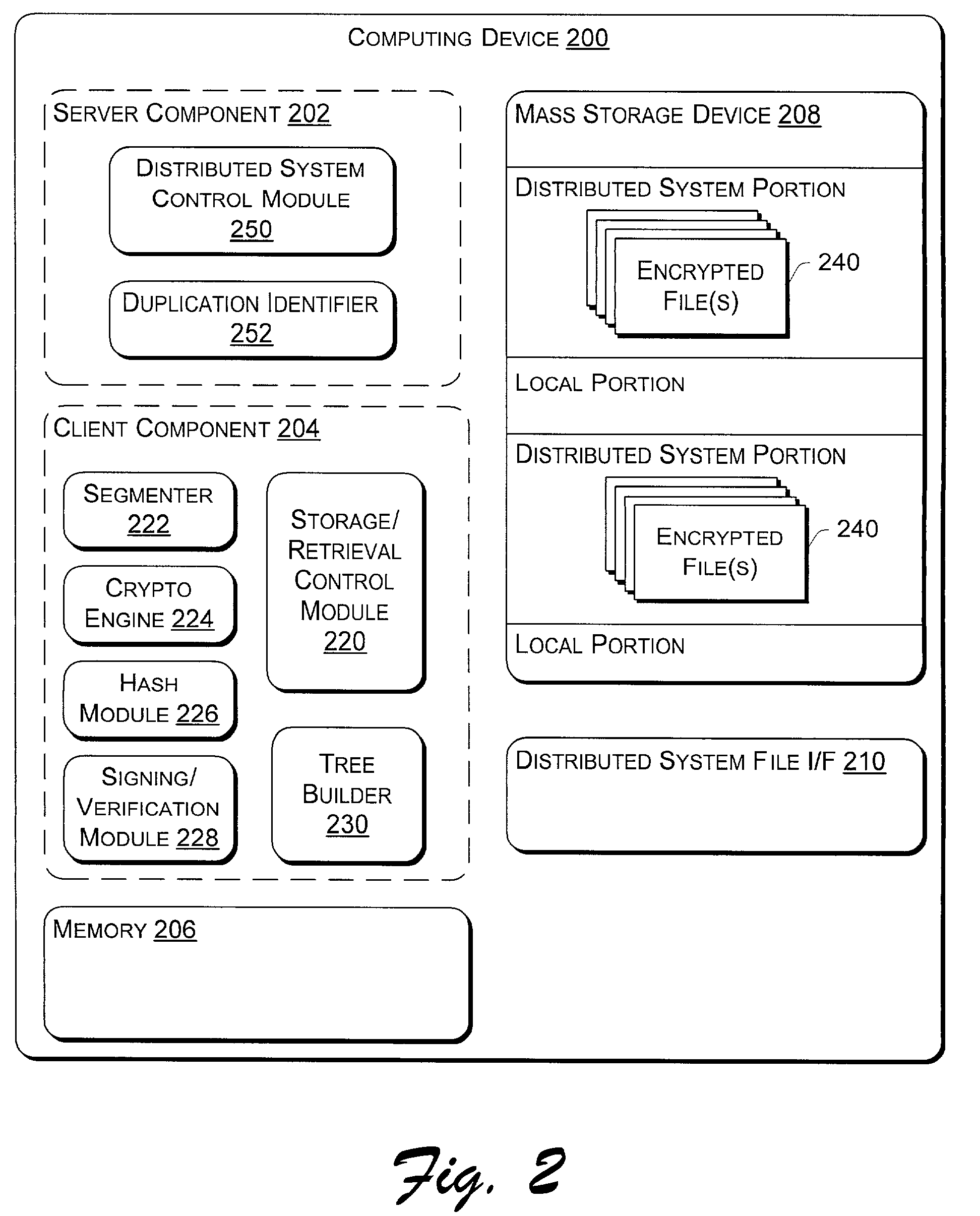
On-disk file format for serverless distributed file system with signed manifest of file modifications
InactiveUS7478243B2Error preventionUser identity/authority verificationSignature fileDistributed File System
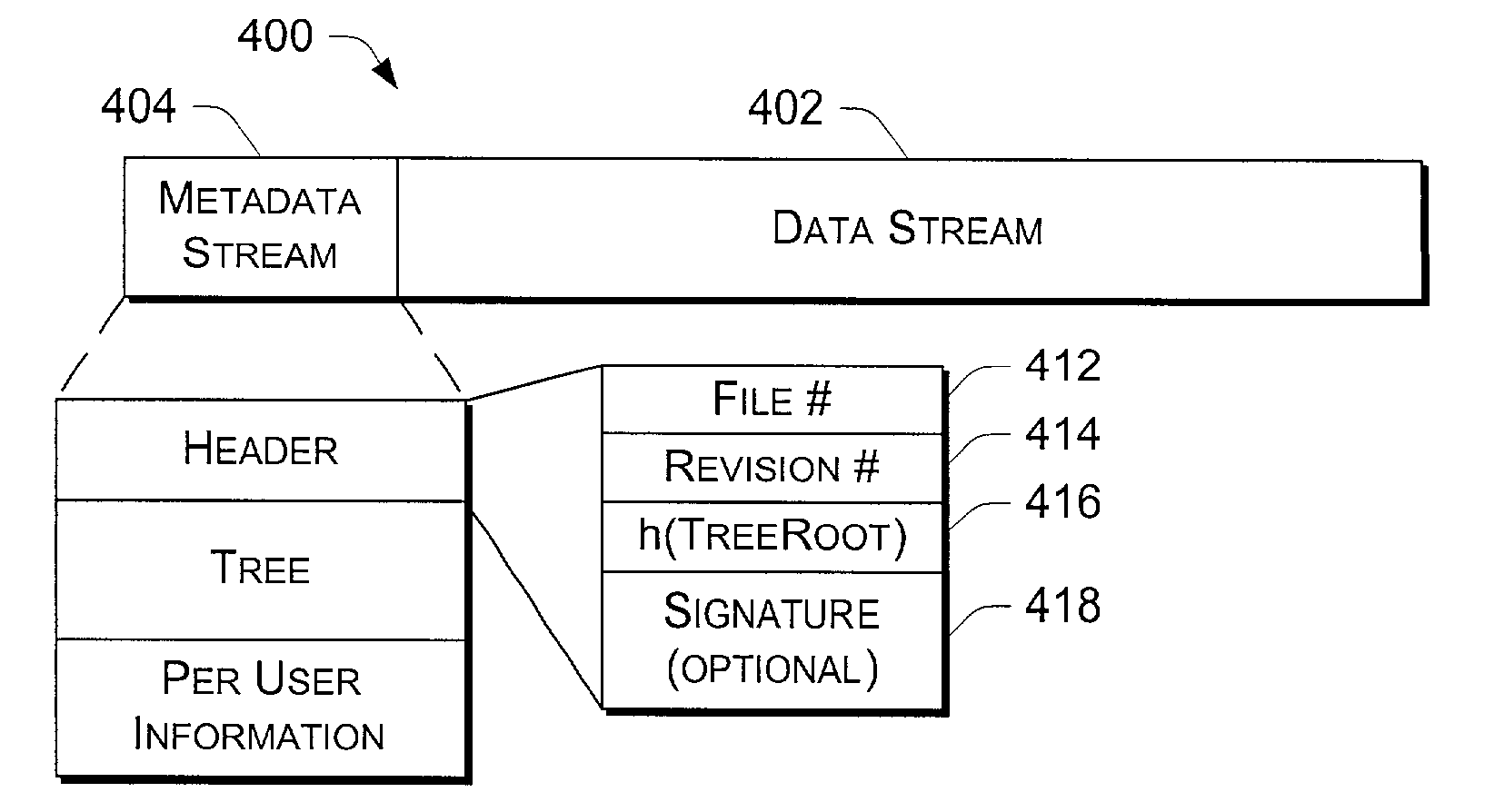
In a serverless distributed file system, the writer of a file can provide file authentication information to a verifying machine without having to compute a new digital signature every time a written file is closed. Periodically, the writer compiles a list of the hash values of all files that have been written over a recent interval, computes a hash of the list, and signs the hash. This signed list of hash values is known as a manifest, akin to a shipping manifest that enumerates the items in a shipment. The advantage of using a signed manifest is that the writer need only perform a single signature computation in order to authenticate the writes to multiple files, rather than having to compute a separate signature for each file, as it would if a signature were embedded in each file.
Owner:MICROSOFT TECH LICENSING LLC
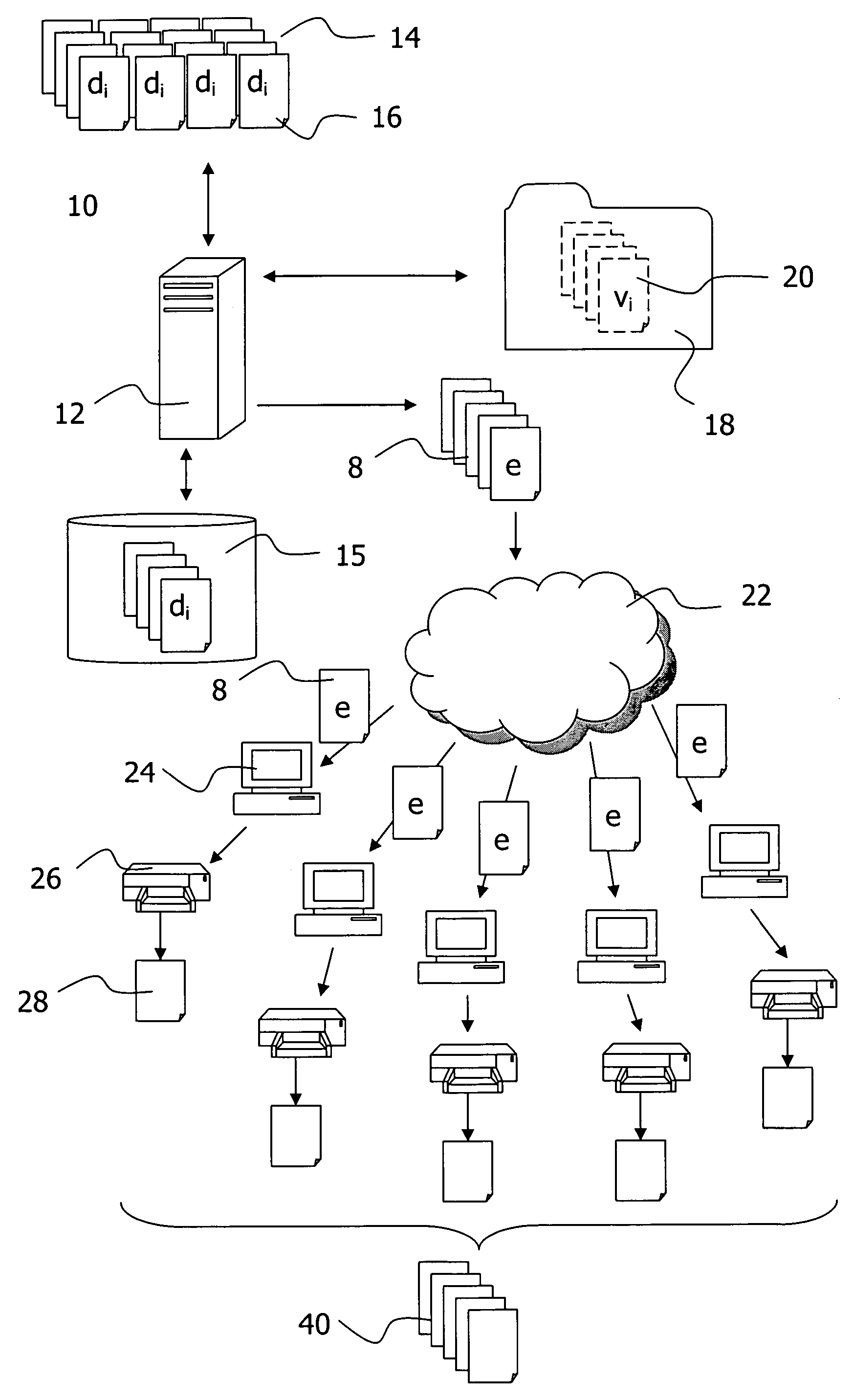
Creation of electronically processable signature files
InactiveUS7685516B2Easy to operateTo offer comfortNatural language data processingSpecial data processing applicationsBatch processingSignature file
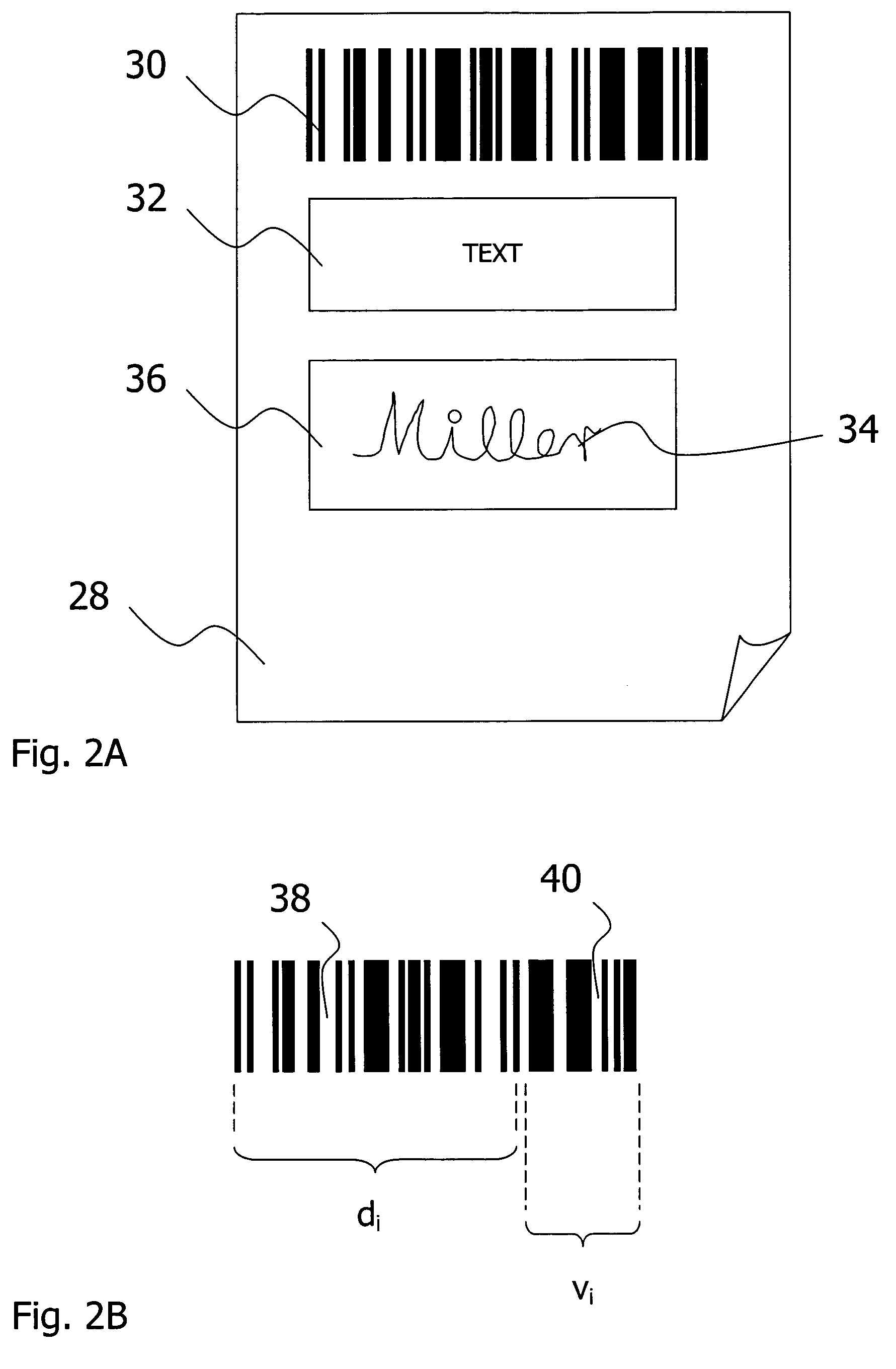
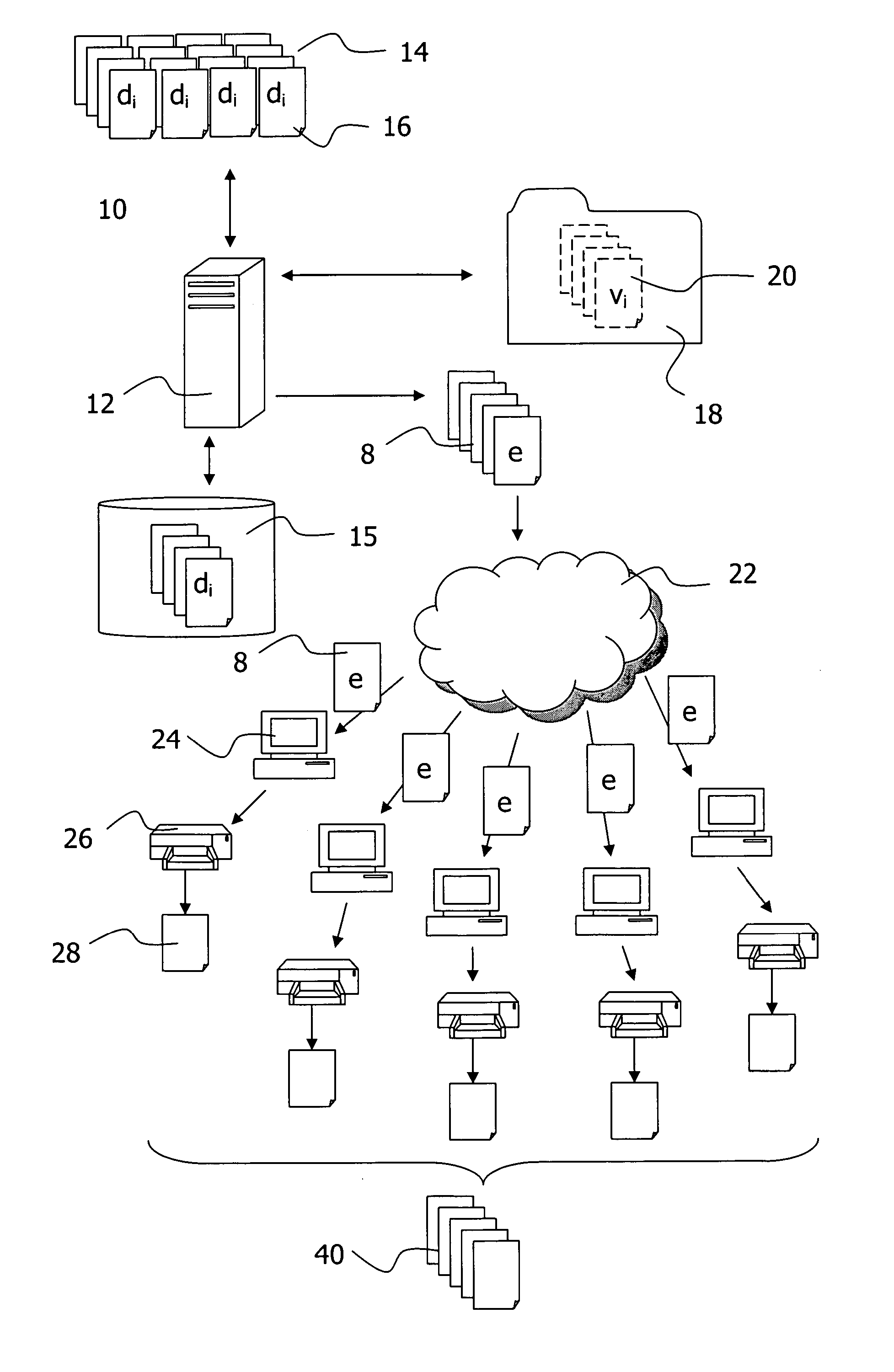
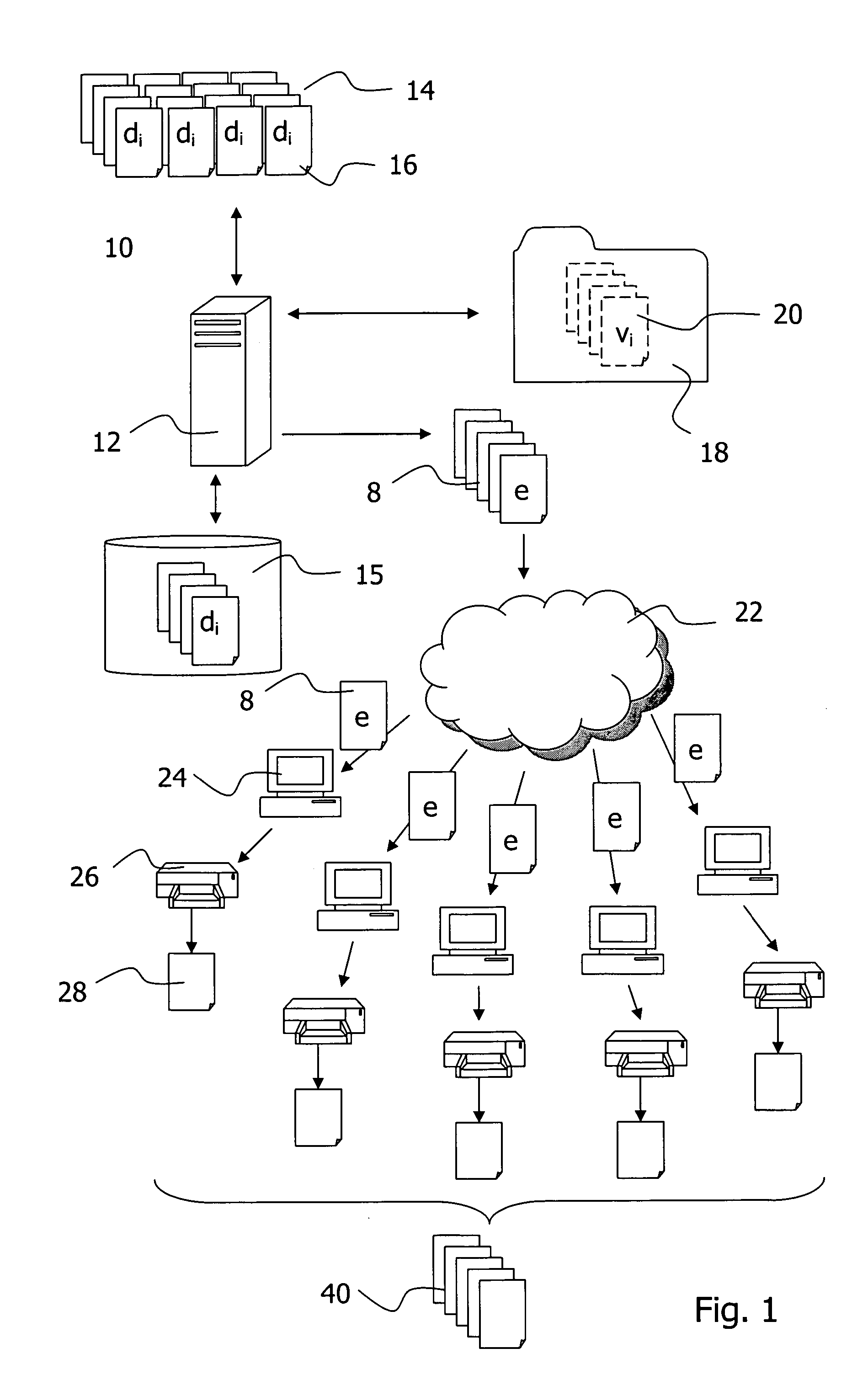
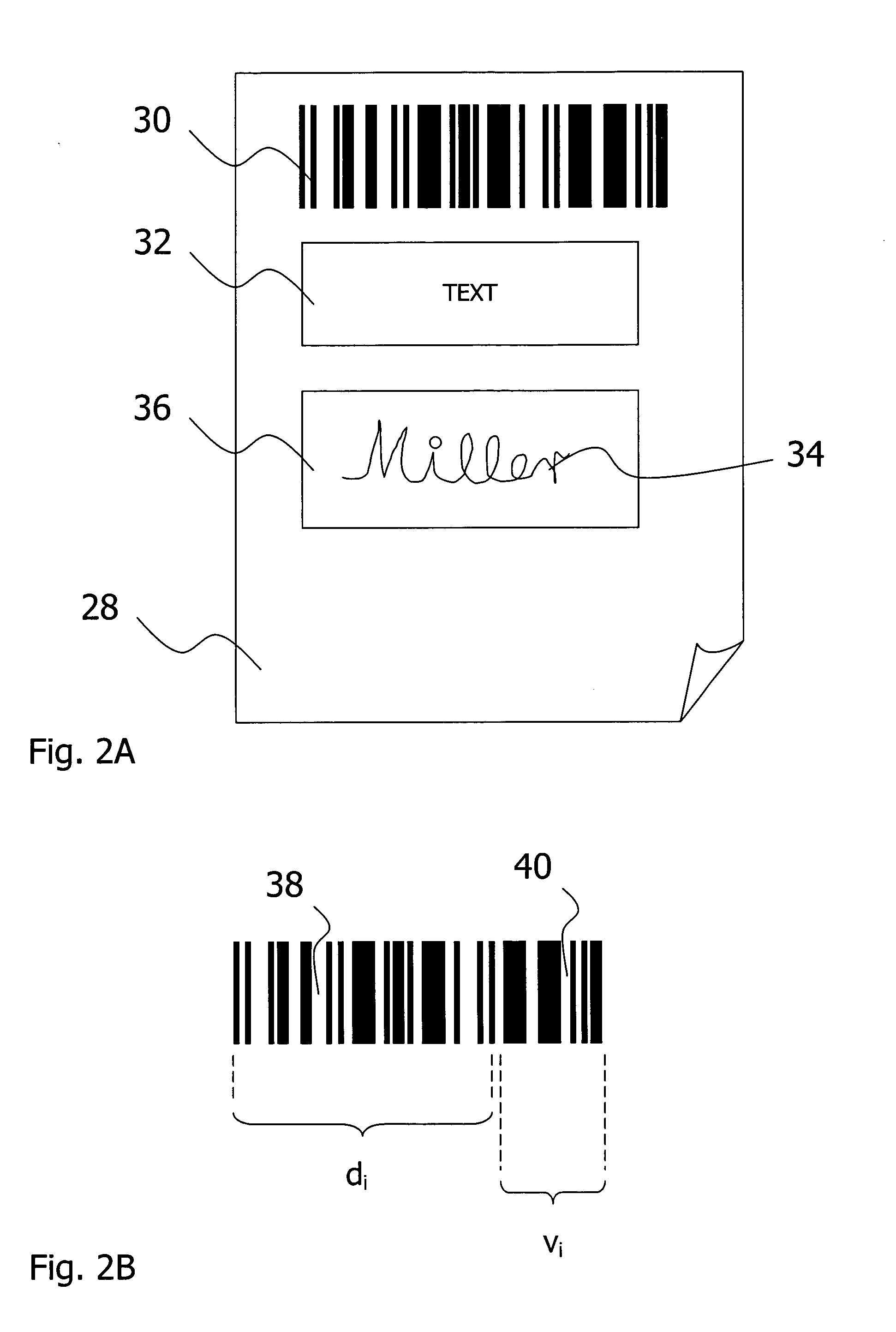
The invention relates to aspects in connection with the automatic generation and processing of signature files. The signature files are generated in paper form on the basis of documents (28) that comprise a personal signature (34) and also control information items (30) assigned to the signature (34) and / or the documents (28). The documents in paper form (28) are scanned in within the scope of a batch processing operation in order to generate signature files that contain the personal signatures (34) in an electronically processable form and also representations of the respectively assigned control information items (30). The control information items (30) contained in a signature file are identified and interpreted document-wise. Then the signature files are automatically processed as a function of the content of the assigned control information items (30).
Owner:UBS BUSINESS SOLUTIONS AG
Digital signature method based on CSK
ActiveCN101282222AAvoid attackImprove security levelPublic key for secure communicationUser identity/authority verificationWeb siteSignature file
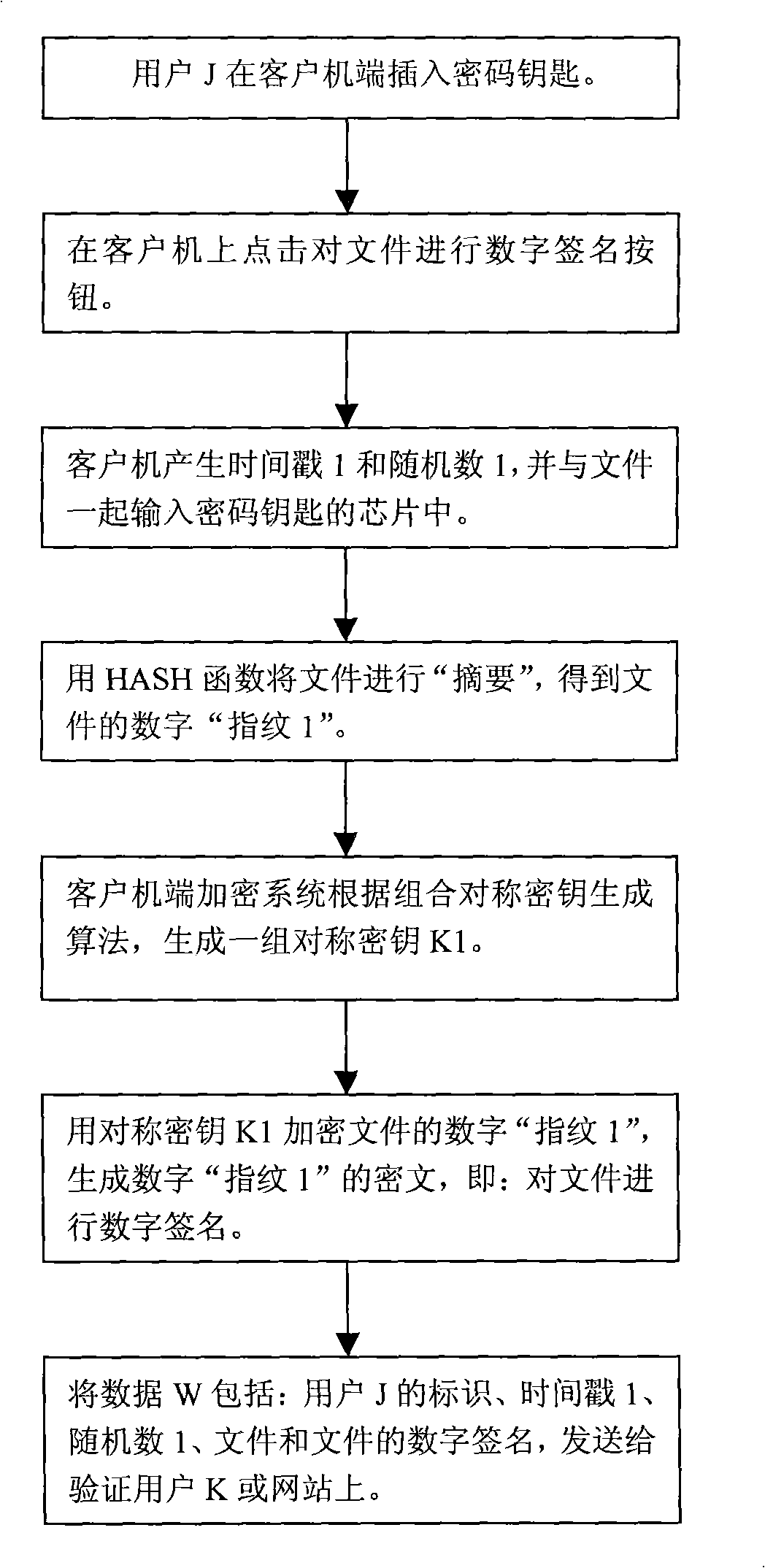
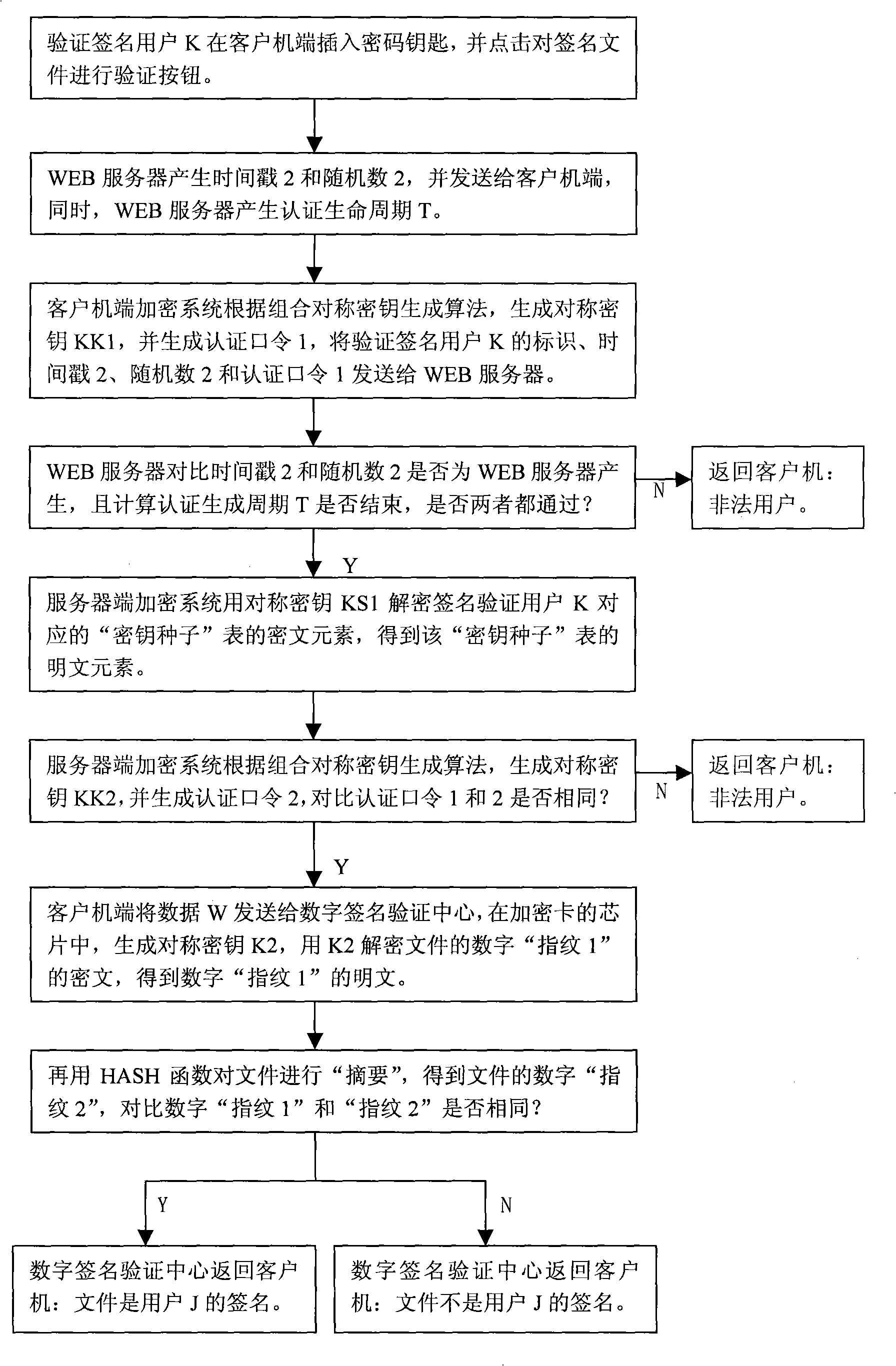
A digital signature method based on CSK establishes a digital signature checking center on the website for checking the signature file. A client computer is established with a ciphering system and a digital signature protocol. Each subscriber is distributed with a hardware device of the cipher key. A signature subscriber uses the cipher key for executing digital signature to the file. The digital signature protocol adopts a combined symmetrical cipher technique for executing digital signature to the file and realizes that the signature cipher is different each time. A signature checking subscriber also uses a cipher key for checking the signature file. The digital signature checking center firstly checks the identity of the signature checking subscriber, and subsequently executes the checking to the signature file. The identity checking protocol and the digital signature checking protocol are all completed with a combined symmetrical key technique thereby realizing the digital signature of the file and the checking to the signature file.
Owner:胡祥义
Method and system for linking certificates to signed files
InactiveUS20070168657A1User identity/authority verificationDigital data protectionSignature fileDigital signature
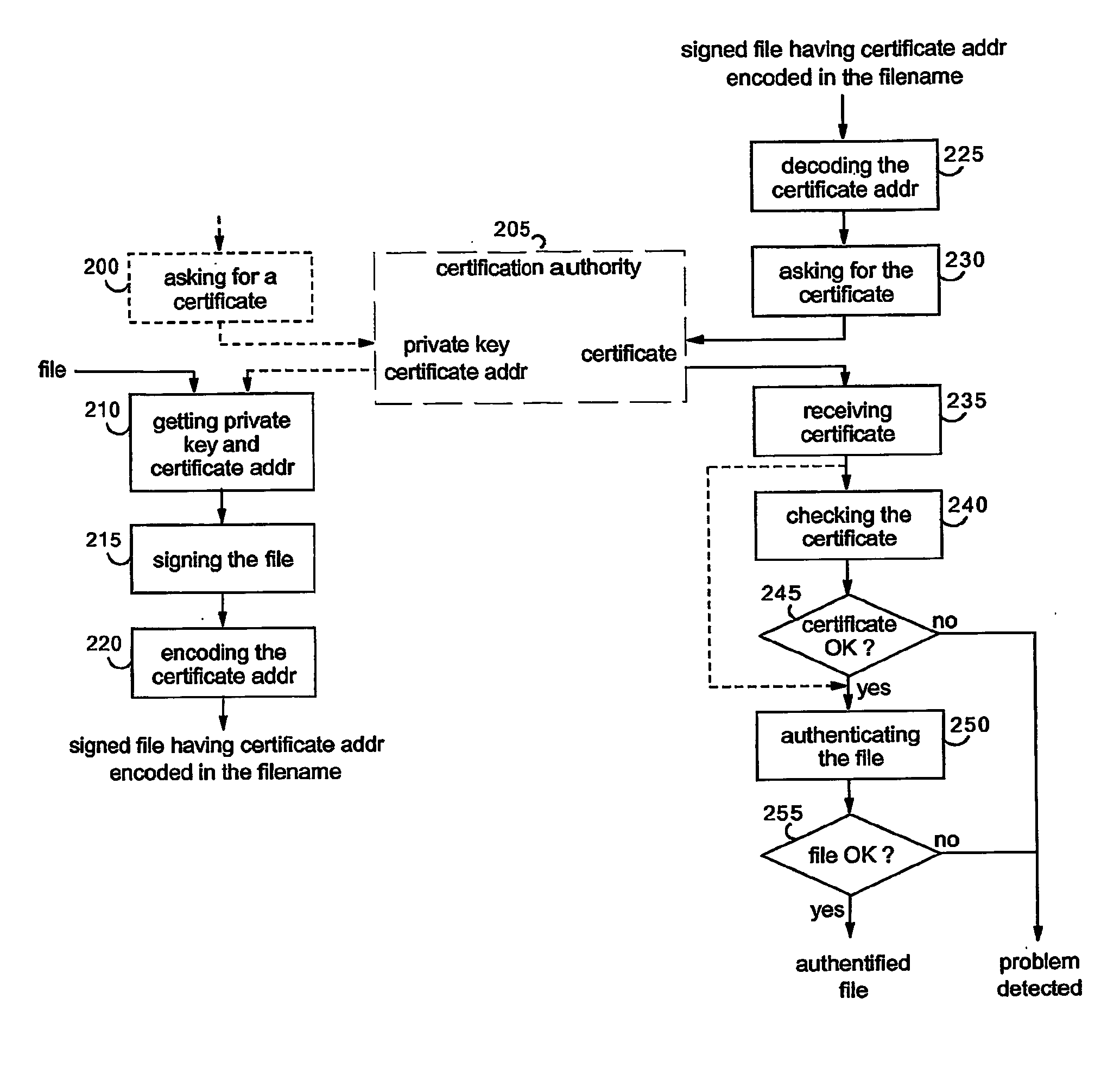
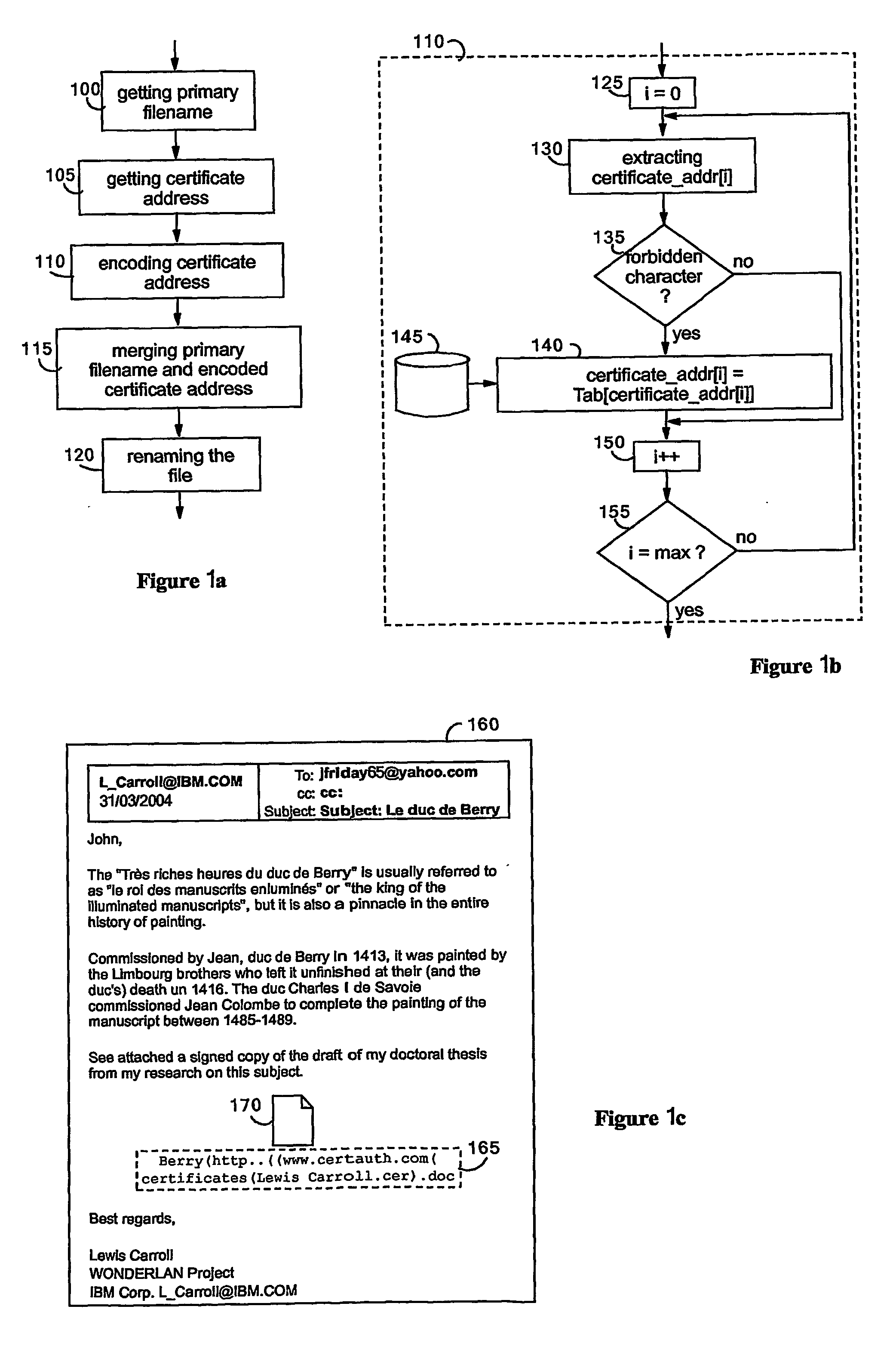
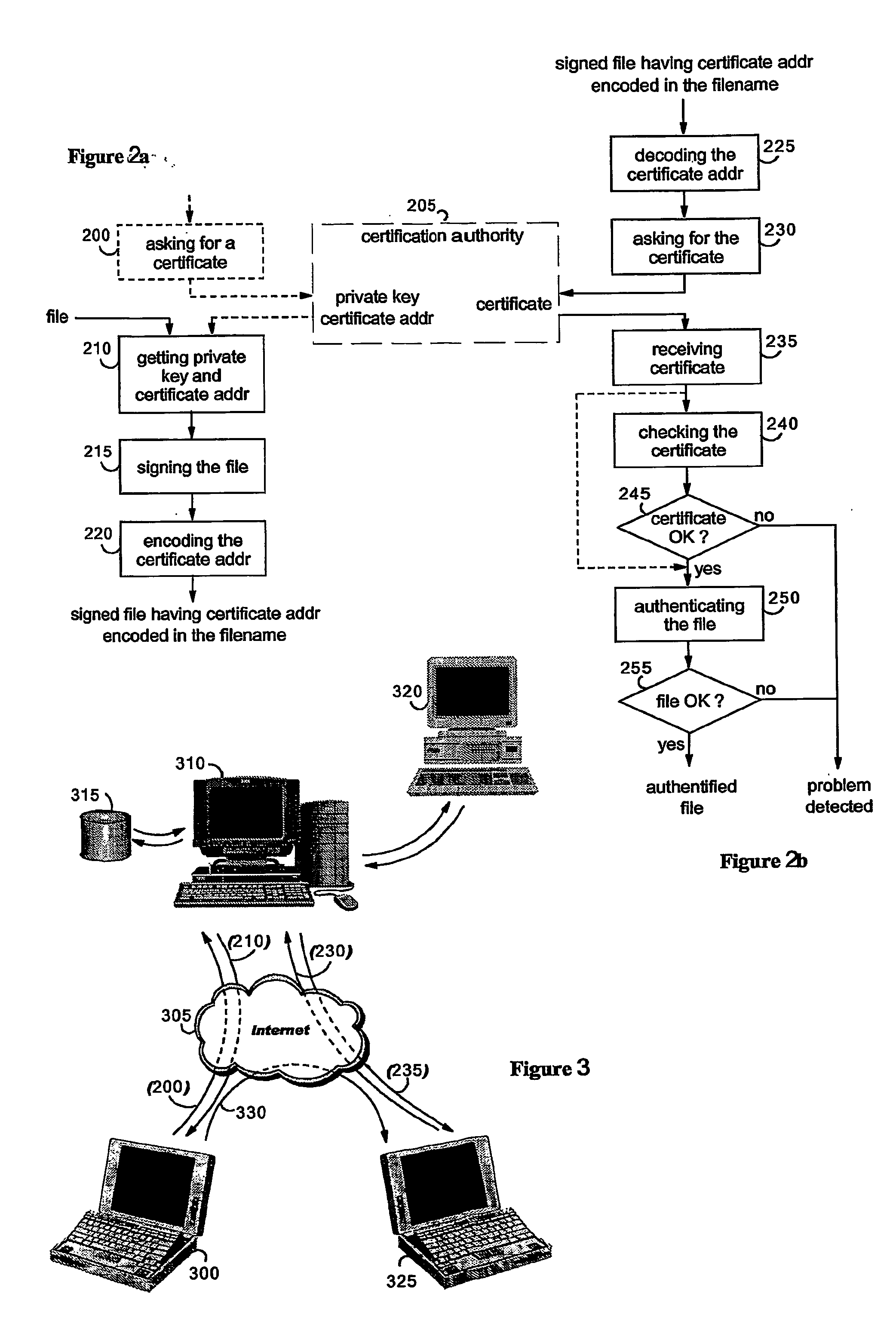
A method for processing a file having an existing filename. A private key associated with a digital certificate and a certificate address from which the digital certificate may be accessed are received from a certification authority (CA) who issued the digital certificate. A digital signature is generated based on the file and the received private key. The digital certificate includes a public key associated with the private key such that the generated digital signature can be verified through use of the public key. The file is signed with the generated digital signature The received certificate address is encoded to generate an encoded address. The existing filename and the encoded address are merged to generate a new filename. The file is renamed with the new filename. The renamed file may be authenticated by verifying the digital signature via execution of an authentication algorithm in conjunction with the public key.
Owner:KYNDRYL INC
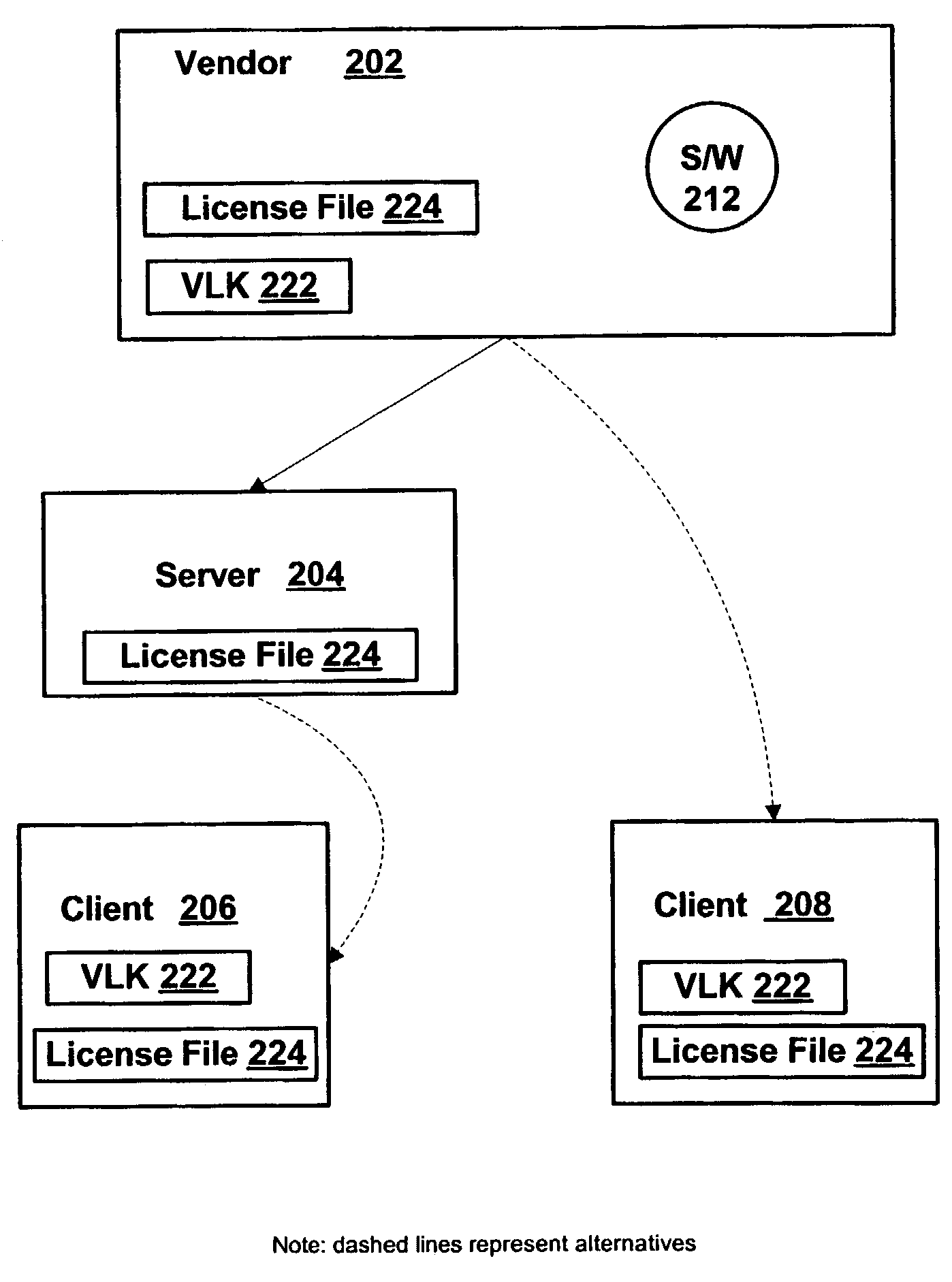
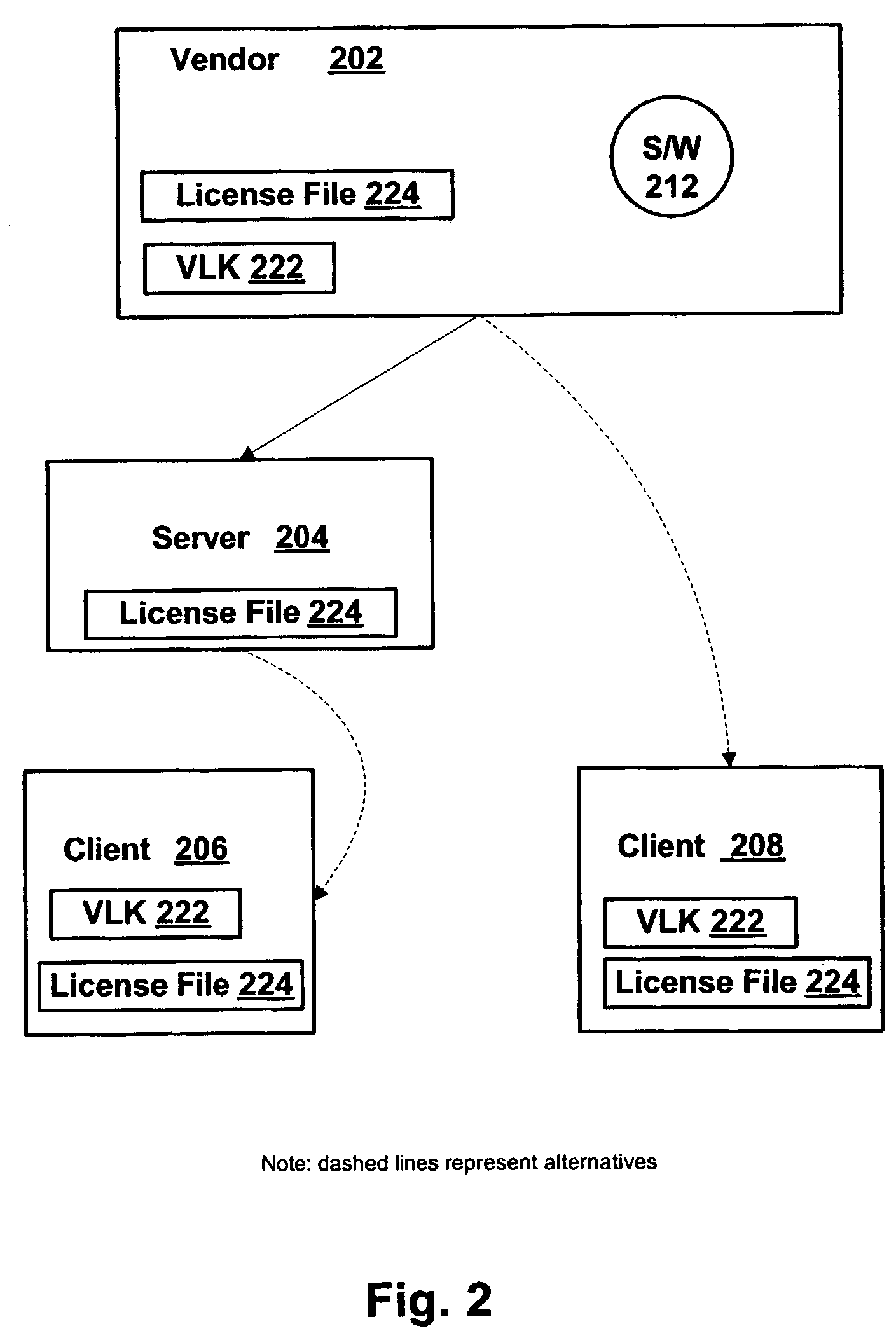
Systems and methods for deterring software piracy in a volume license environment
ActiveUS7356709B2Digital data processing detailsUnauthorized memory use protectionComputer hardwareSignature file
A unique volume license key (VLK) is provided to a volume license holder. A signed file containing the VLK and the data derived from volume license holder's submitted computing environment information is provided to the volume license holder along with the licensed software. The license file is stored in a central location, such as on an installation server, or locally on client machines, in a rather large file of any type. Upon logon, the license file is read, the data authenticated and the system is activated. If license data cannot be authenticated, a connected system either fully functions in grace period or run in reduced functionality mode until authentication succeeds. If the system is disconnected, the system is functional only with disconnected features until it joins a network again. In a completely off-line installation, the license file is generated by the volume license holder using software vendor assigned specific VLK and software vendor provided security hardware device. The distribution methods of software package, the VLK, and the license file can be flexible, including, but not limited to, single or multiple media.
Owner:MICROSOFT TECH LICENSING LLC
System and method for monitoring and recognizing broadcast data
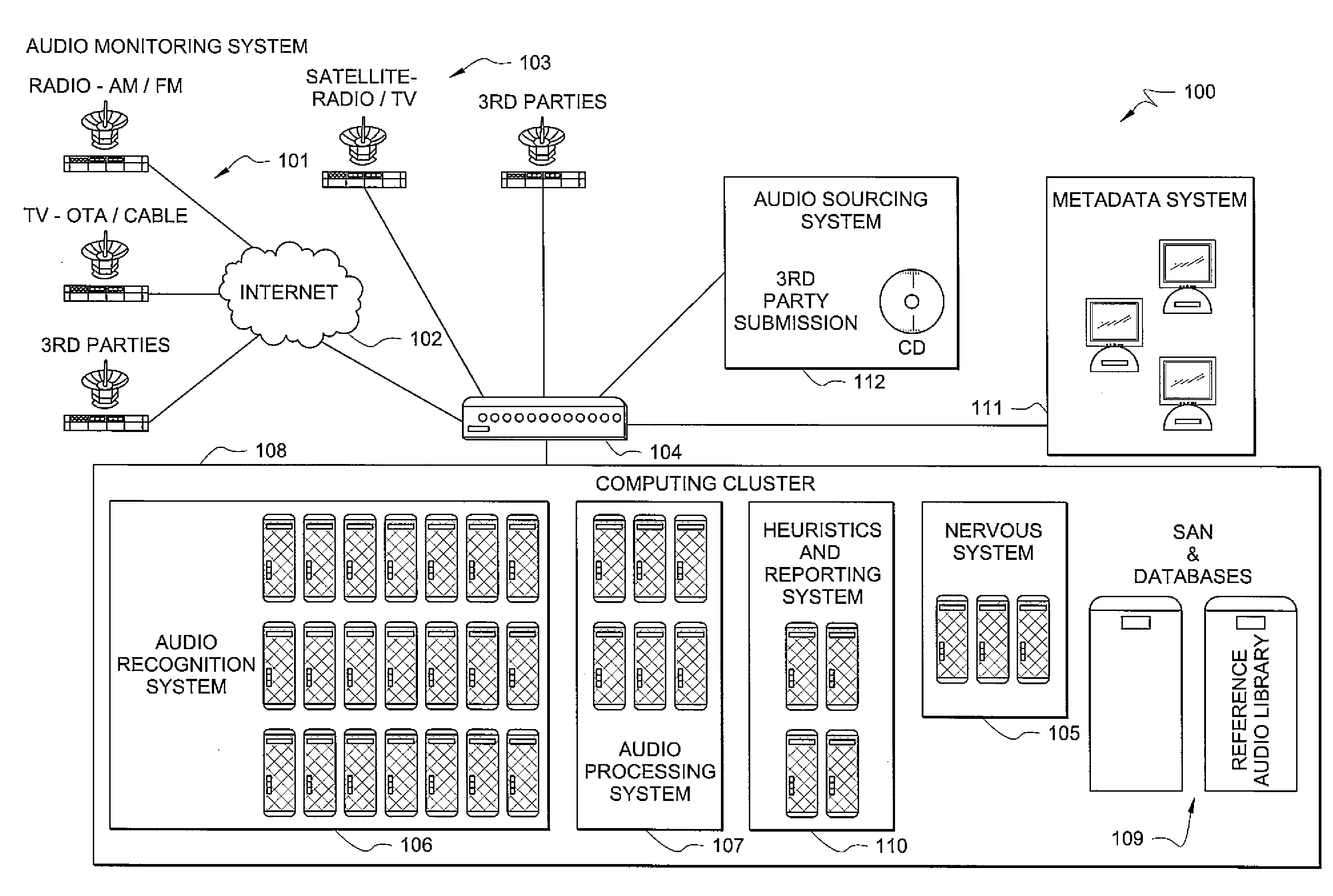
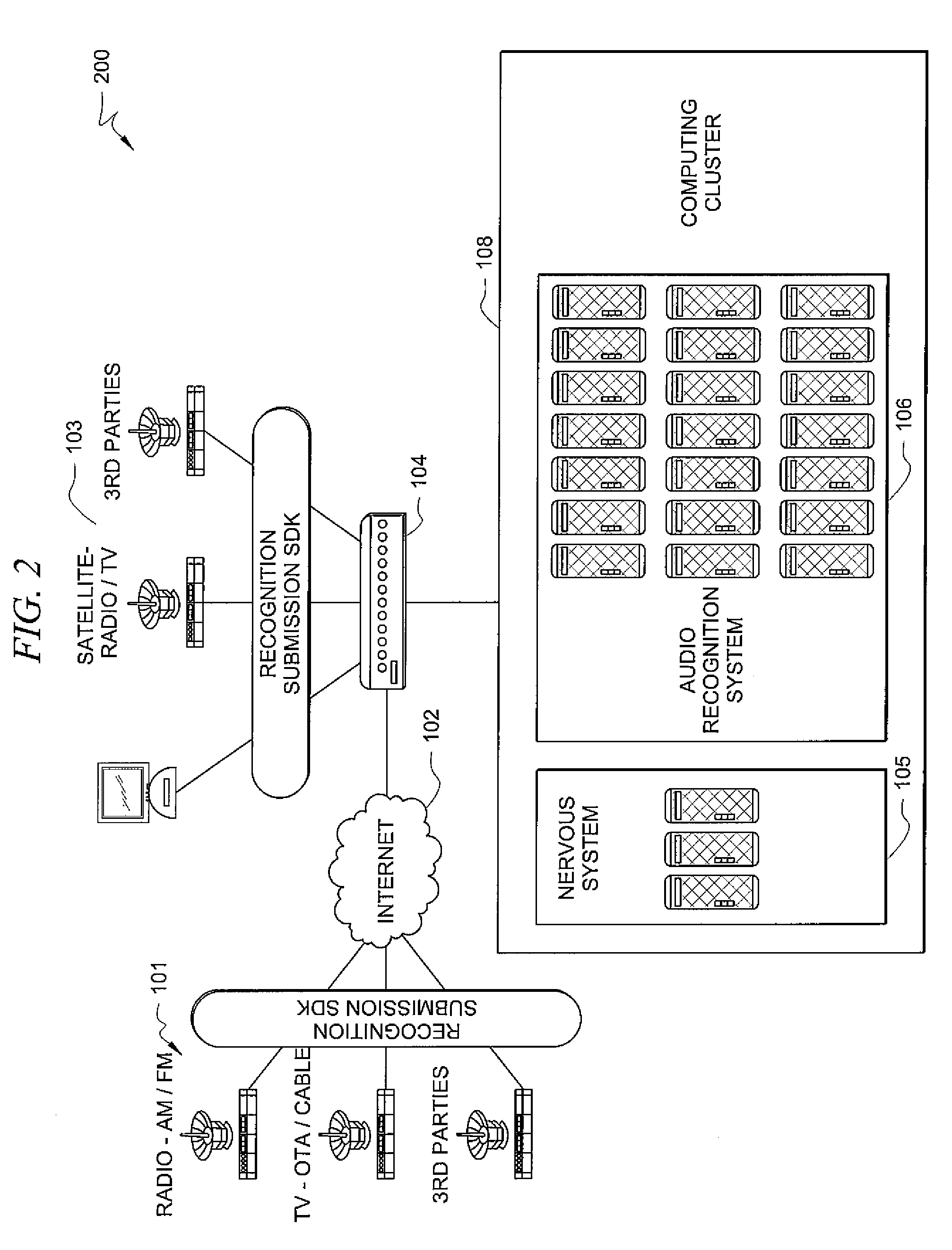
ActiveUS20080208851A1Digital data processing detailsSpecific information broadcast systemsSignature fileHeuristic
A system for monitoring and recognizing audio broadcasts is described. The system includes a plurality of geographically distributed monitoring stations, each of the monitoring stations receiving unknown audio data from a plurality of audio broadcasts. A recognition system receives the unknown audio data from the plurality of monitoring stations and compares the unknown audio data against a database of signature files. The database of signature files, or index sets, corresponds to a library of known audio files, such that the recognition system is able to identify known audio files in the unknown audio stream as a result of the comparison. The system further includes a nervous system able to monitor and configure the plurality of monitoring stations and the recognition system, and a heuristics and reporting system able to analyze the results of the comparison performed by the recognition system and use metadata associated with each of the known audio files to generate a report of the contents of plurality of audio broadcasts.
Owner:LANDMARK DIGITAL SERVICES
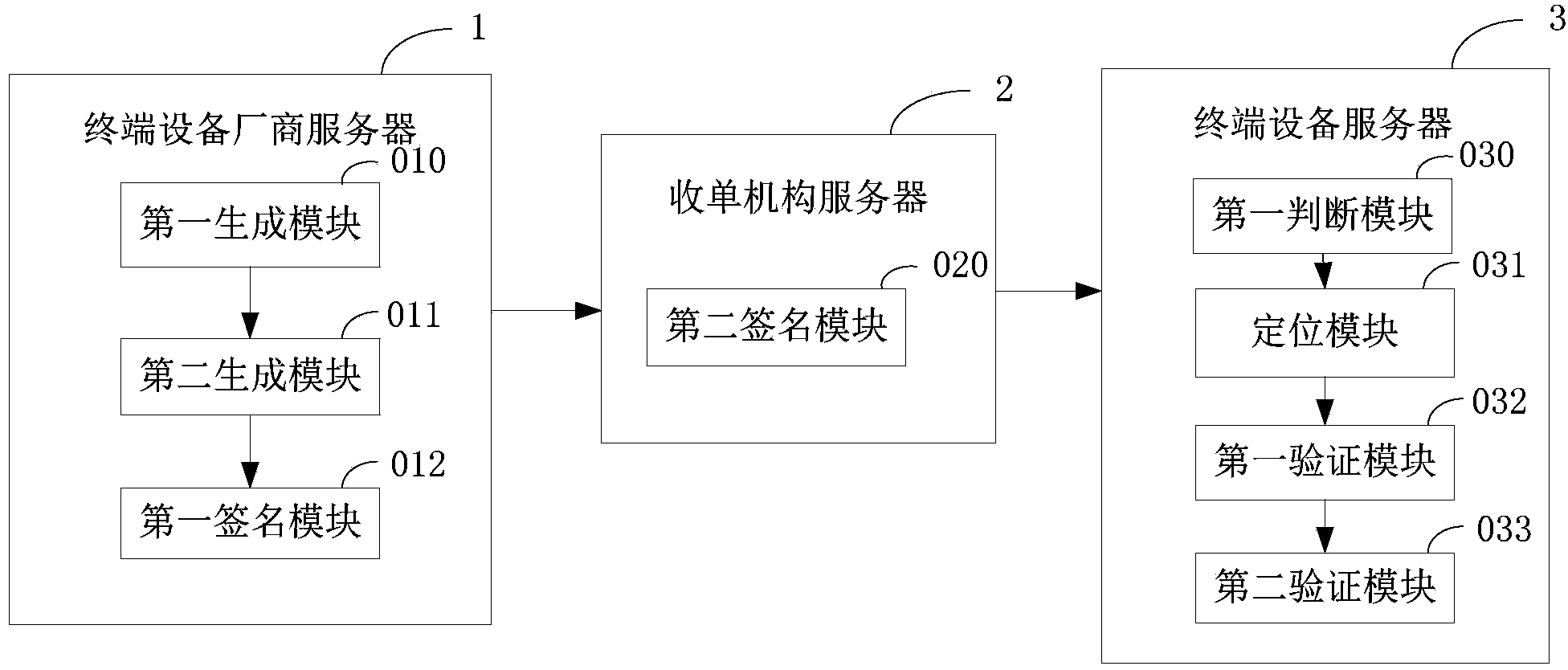
Multi-party authorized APK signature method and system
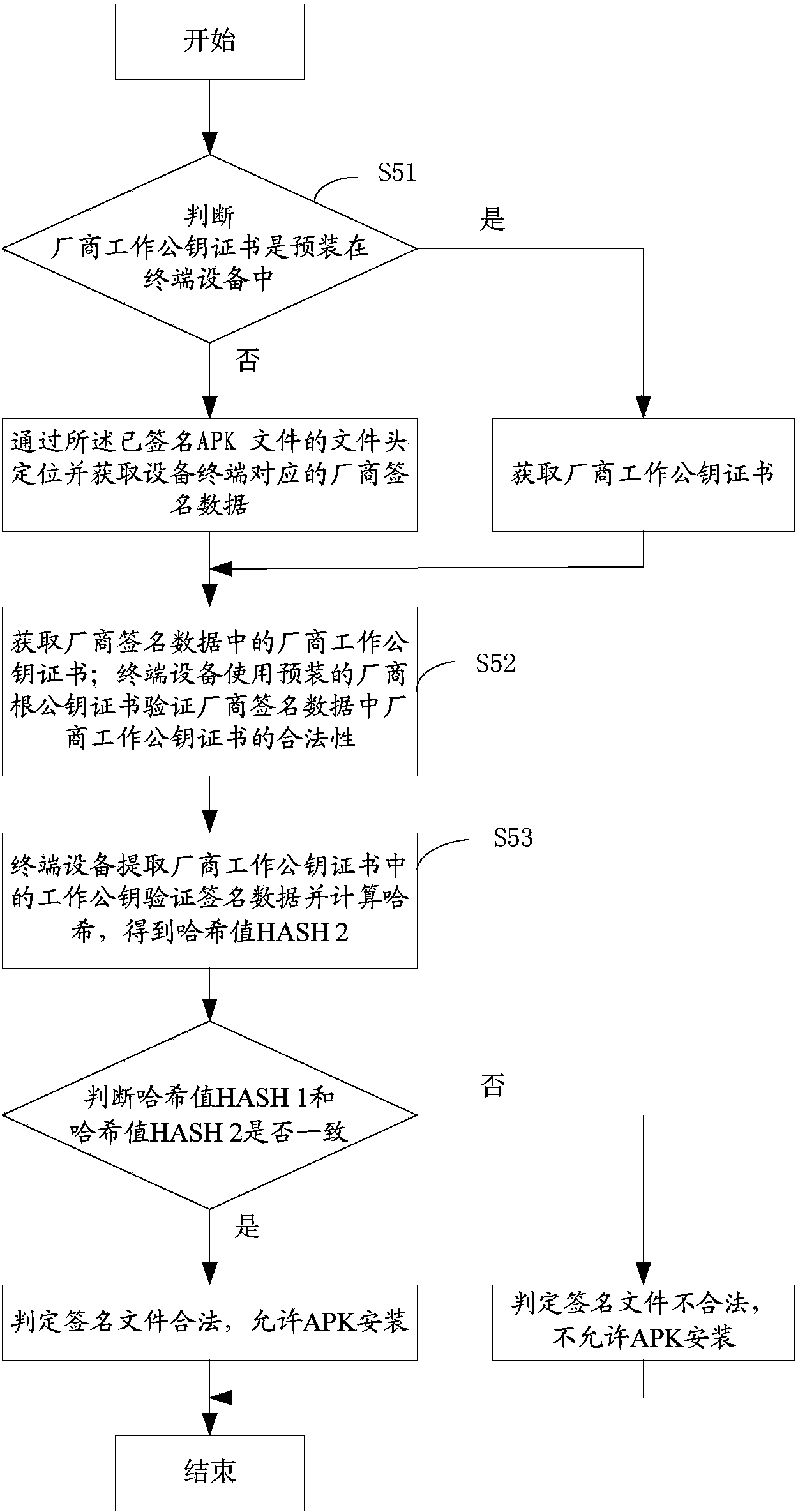
ActiveCN103944903AIntegrity guaranteedGuaranteed legalityComputer security arrangementsCash registersSignature fileTerminal equipment
The invention provides a multi-party authorized APK signature method and system. The multi-party authorized APK signature method includes the steps that different terminal device manufacturer signature servers conduct signature on signed data containing an original ARK file through respective work key pairs to generate different terminal device manufacturer signature data, and manufacturer work public key certificates are put into the terminal device manufacturer signature data or are preinstalled in terminal devices; an acquirer signature server combines the different terminal device manufacturer signature data in the form of DER according to the sequence of signature time to form a signed APK file; the signed APK file comprises the original APK file and a signature file header, the signature file header comprises a file for marking the files subjected to signature operation and a file for marking the numbers of the corresponding manufacturer signature data of the different terminals and marking the specific positions of the corresponding manufacturer signature data of the different terminals in the signed APK file; the terminal devices acquire the signed APK file and conduct verification after judging that the manufacturer signature data generated by the corresponding terminal device manufacturers of the terminal devices exist in the signed APK file, and after the verification is successful, installation and operation are allowed.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
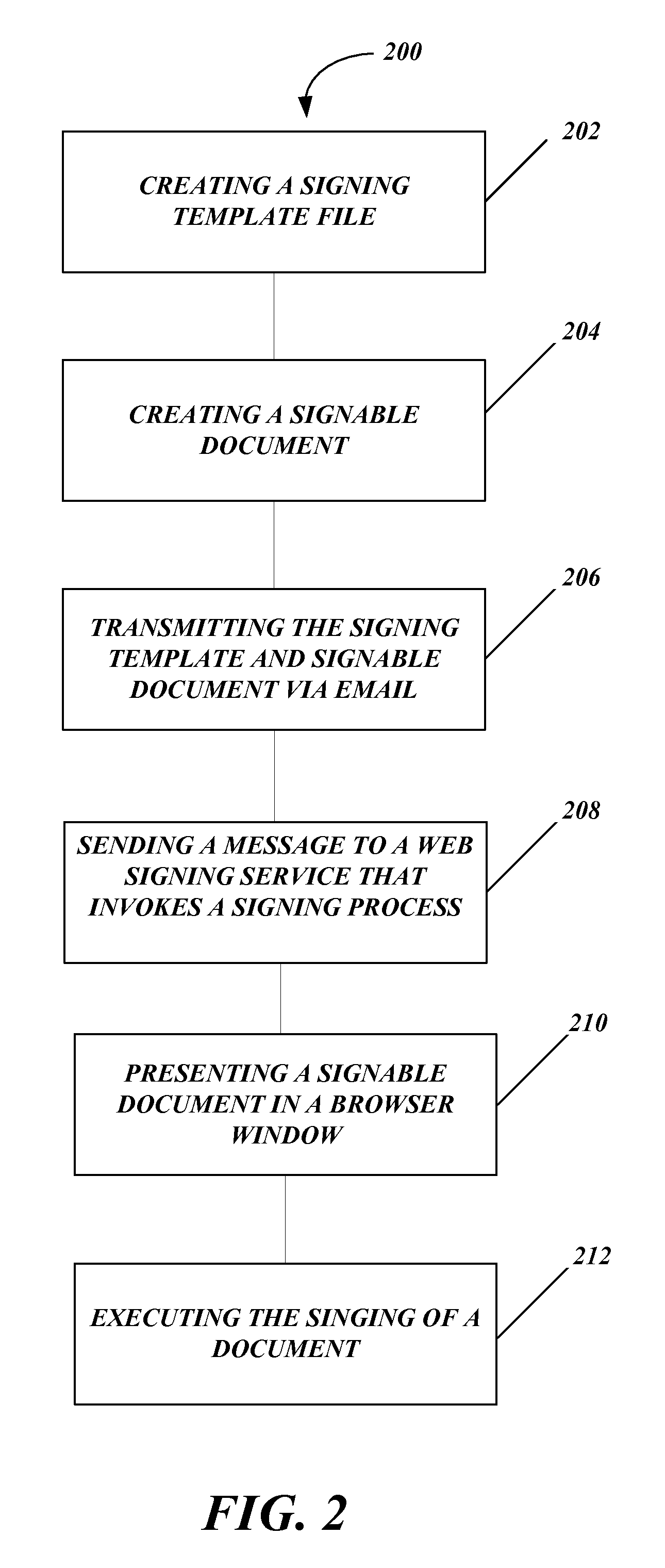
Systems and methods for distributed electronic signature documents
ActiveUS8949706B2User identity/authority verificationDigital data protectionSignature fileDocument preparation
Systems and methods for distributed electronic signature documents. A method for distributed electronic signature documents includes creating a signing template that contains information about how a signable document is to be signed. A signable document is created to be distributed to a signer for signing. The signable document is electronically transmitted to the signer. A message is sent using an activatable control in the signing document to a web signing server to invoke the signing process. A browser window is opened on a signer's computer in order to execute the signing process.
Owner:DOCUSIGN
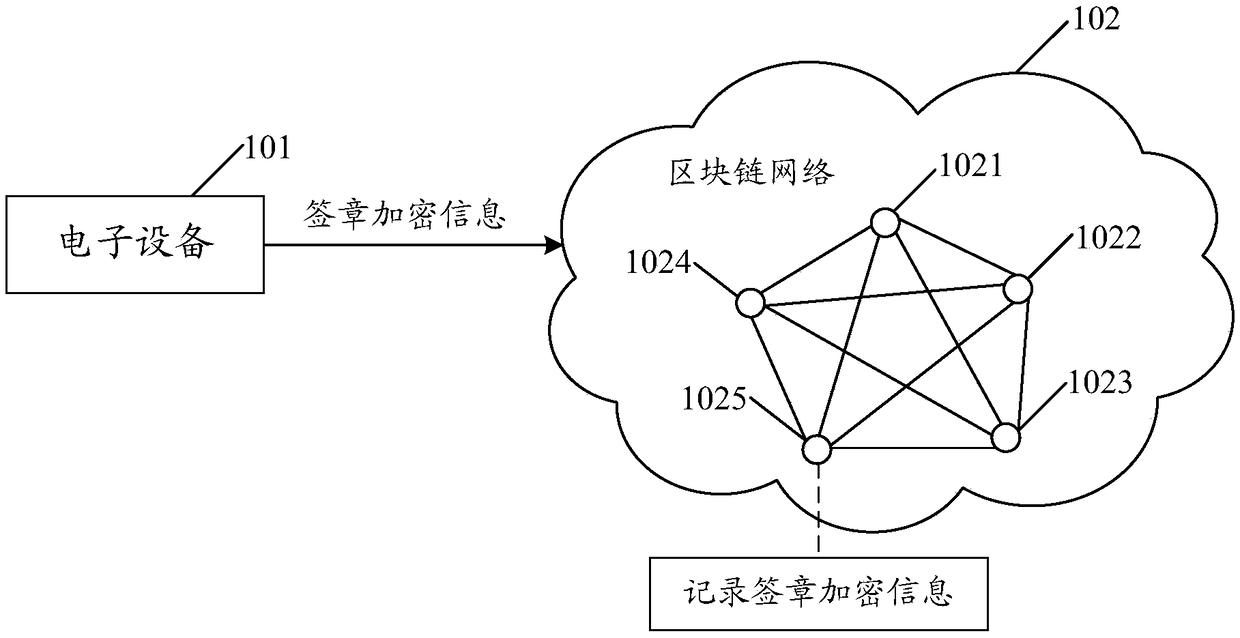
Electronic signature method, device, device and medium
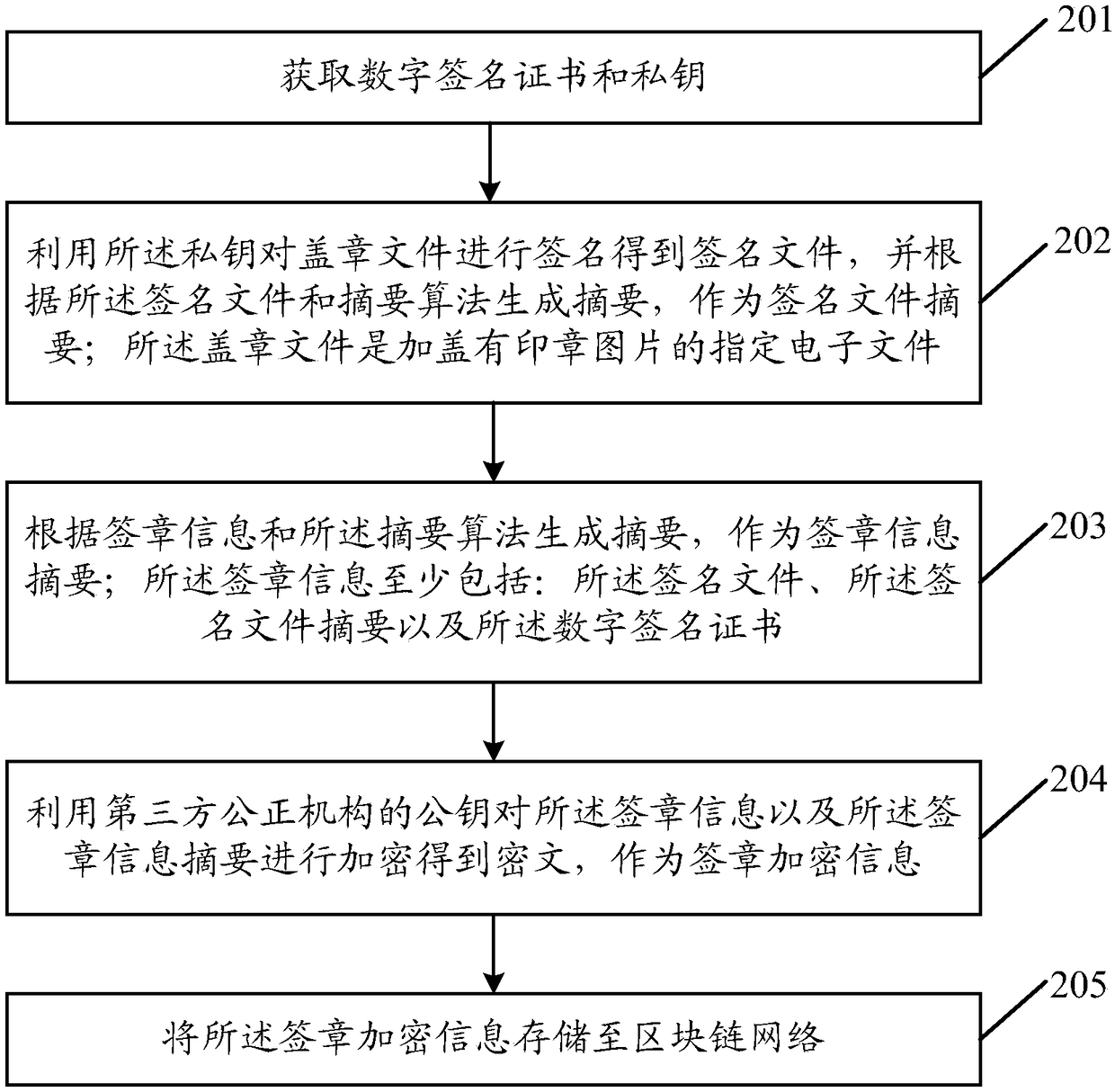
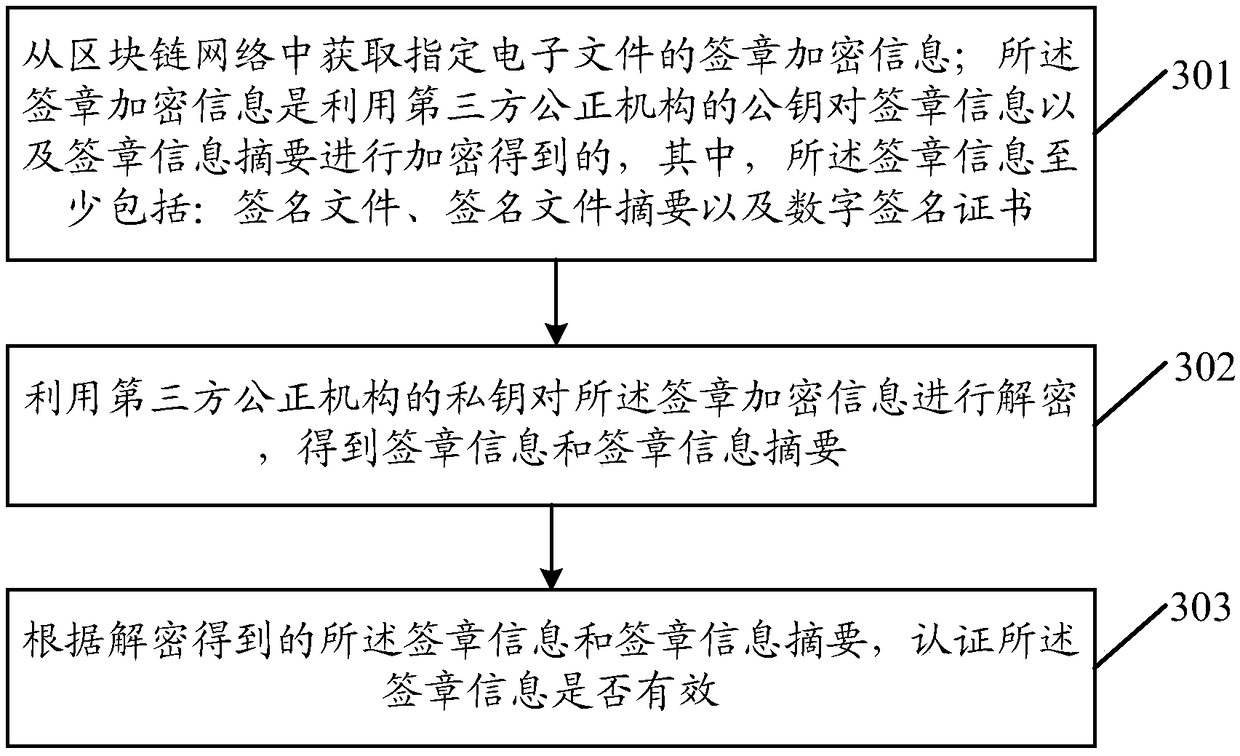
ActiveCN109472166AReduce tamperingReduce riskFinanceDigital data protectionThird partySignature file
An embodiment of the application discloses an electronic signature method. An electronic device signs a seal file by using a private key to obtain a signature file, and generates a signature file digest according to a digest algorithm and the signature file. A signature information digest is generated according to the signature information and the digest algorithm. The signature information includes at least a signature file, a signature file digest and a digital signature certificate. The signature encryption information is generated by encrypting the signature information and the signature information digest with the public key of the third party fair organization, and the signature encryption information is stored in the block chain network. The signature encryption information is generated by encrypting the necessary information generated in the process of electronic signature with the public key of the third party fair organization, which ensures that other organizations or individuals except the third party fair organization can not decrypt the signature encryption information privately, and reduces the risk of information being tampered with or stolen; The signature encryption information is stored in the block chain network with anti-tamper mechanism, which ensures the authenticity and security of the information.
Owner:HUNDSUN TECH
Object anti-counterfeiting method and system
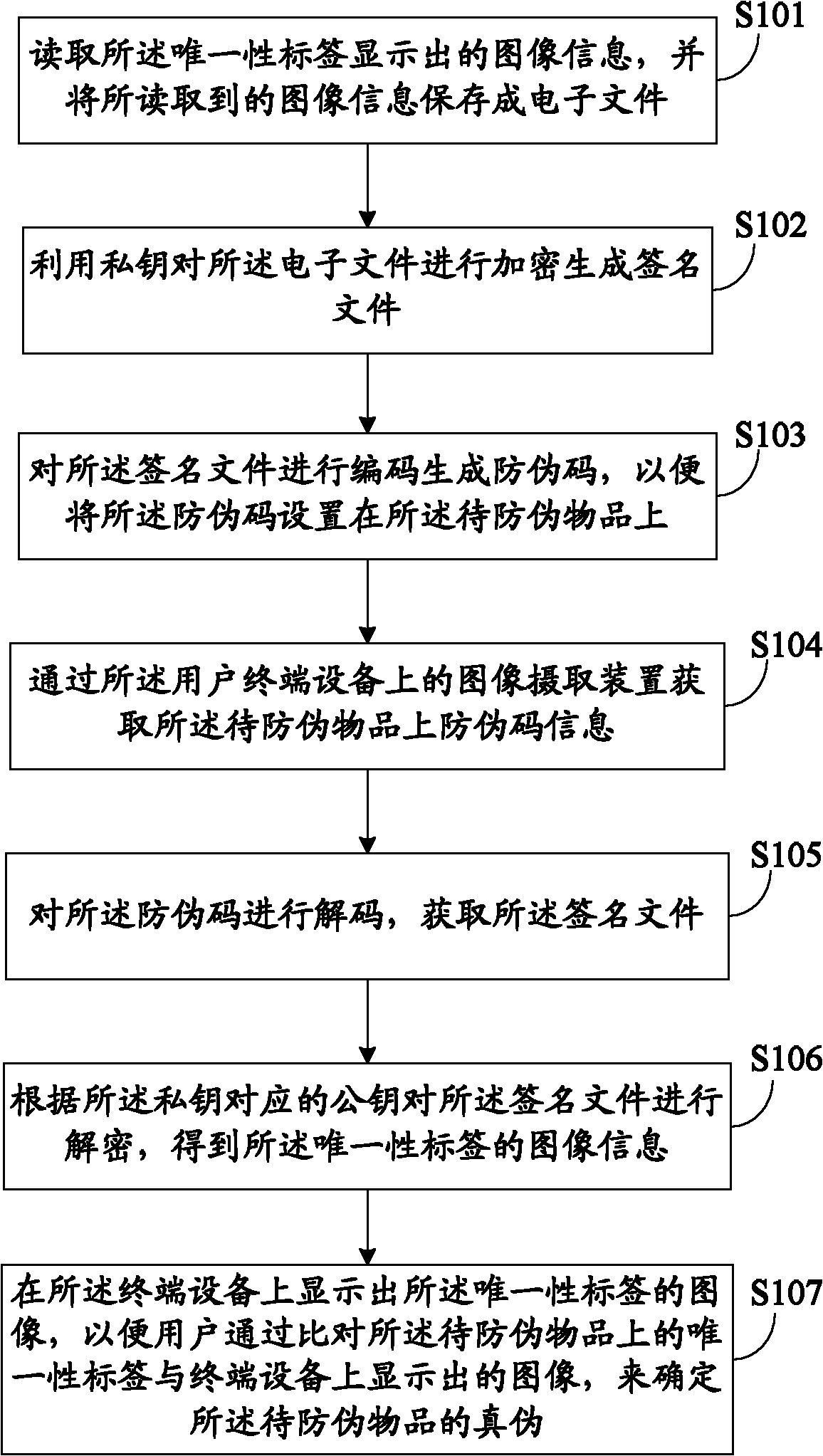
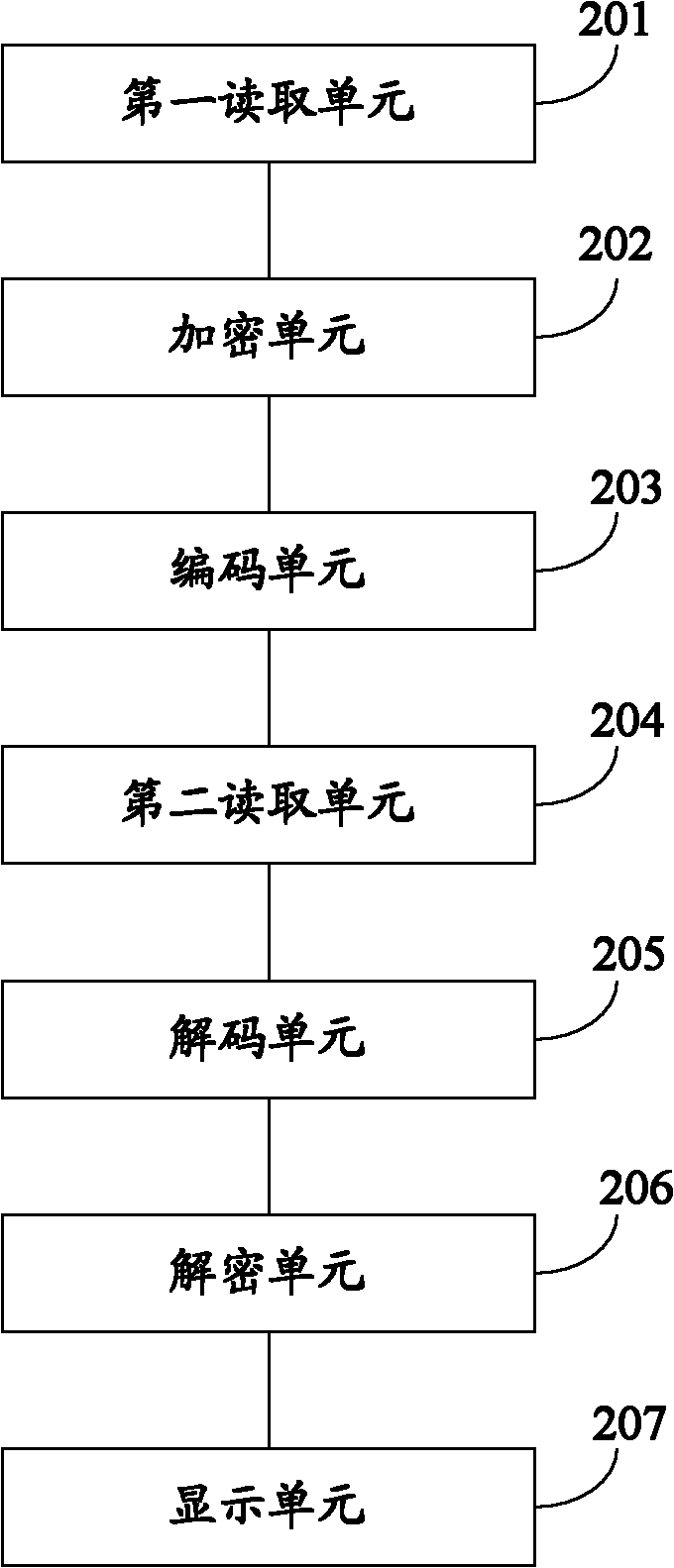
InactiveCN102201100ANon-reproducibleIncrease the difficulty of copyingUser identity/authority verificationCommerceSignature fileTerminal equipment
The invention discloses an object anti-counterfeiting method and system. The method comprises the following steps of: firstly, setting a label on an object to be anti-counterfeited, wherein the label is provided with uniqueness; reading image information displayed by the uniqueness label when anti-counterfeiting verification is carried out, and encrypting the label by utilizing a private key to generate a signature file; encoding the signature file to generate an anti-counterfeiting code so as to set the anti-counterfeiting code on the object to be anti-counterfeited; obtaining anti-counterfeiting information on the object to be anti-counterfeited through an image capturing device on a user terminal device when the truth and false of the object to be anti-counterfeited need to be verified; decoding the anti-counterfeiting code to obtain the signature file; and decrypting the signature file according to public key information corresponding to the private key to obtain and display the image information of the uniqueness label. By adopting the object anti-counterfeiting method and system, the anti-counterfeiting effect can be improved.
Owner:朱清明 +1
Automated analysis of collected field data for error detection
ActiveUS20070256114A1Facilitate data communicationAnalogue secracy/subscription systemsNon-redundant fault processingSignature fileField data
Included are embodiments of a method for detecting errors in a set top terminal (STT). At least one embodiment of a method includes receiving error data related to at least one error that occurred in at least one STT and comparing the received error data to at least one signature file, the at least one signature file including a pattern related to at least one documented error. Additional embodiments of the method may also include in response to determining that the received error data does not match the pattern related to at least one documented error, creating a new signature file, the new signature file including at least one pattern associated with the received error data.
Owner:SYNAMEDIA LTD
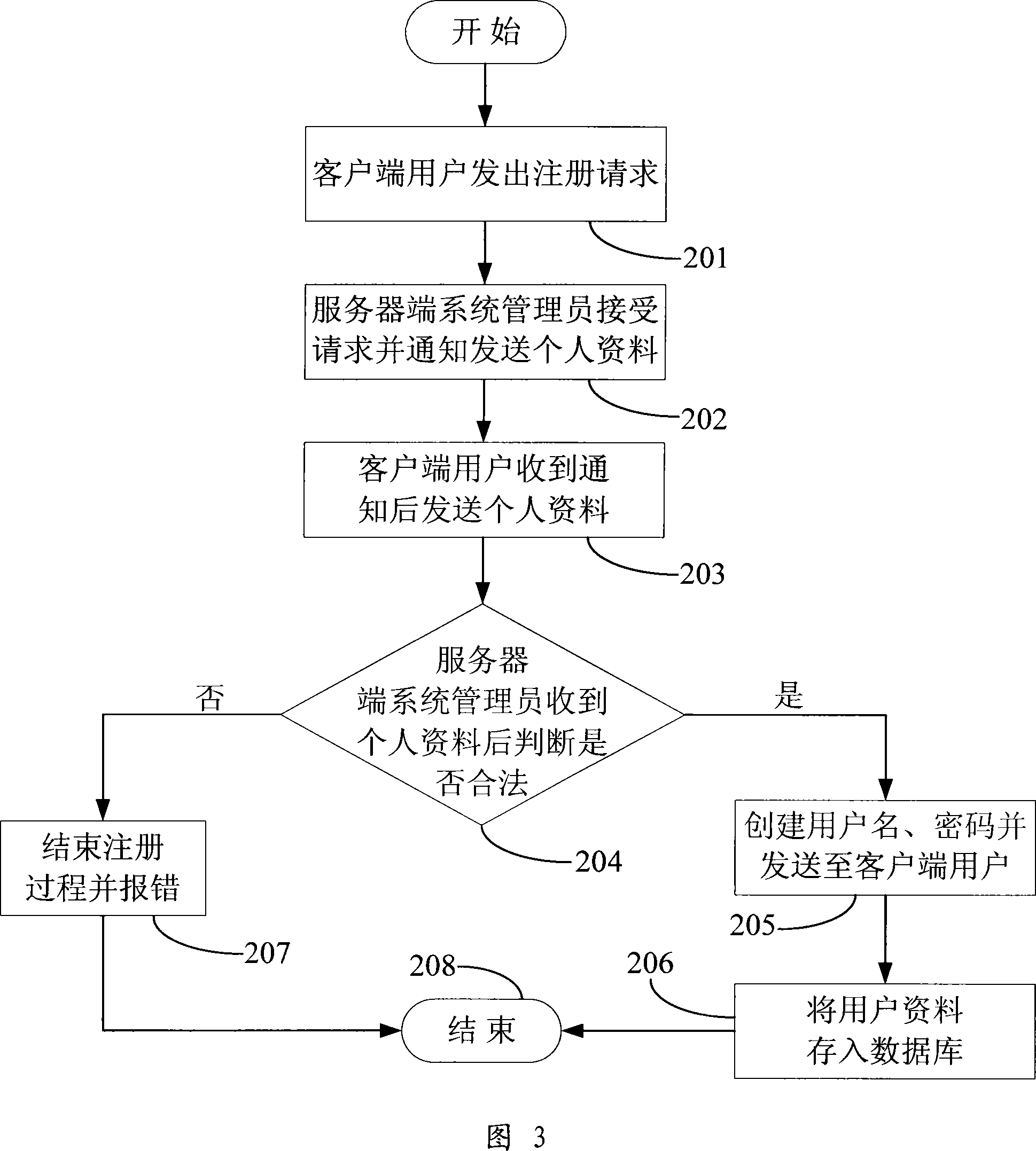
Intelligent terminal application program installing file networking digital signature method
ActiveCN103036894ARisk of preventing signing and passing signature authenticationSolve the legality checkUser identity/authority verificationSignature fileSource Data Verification
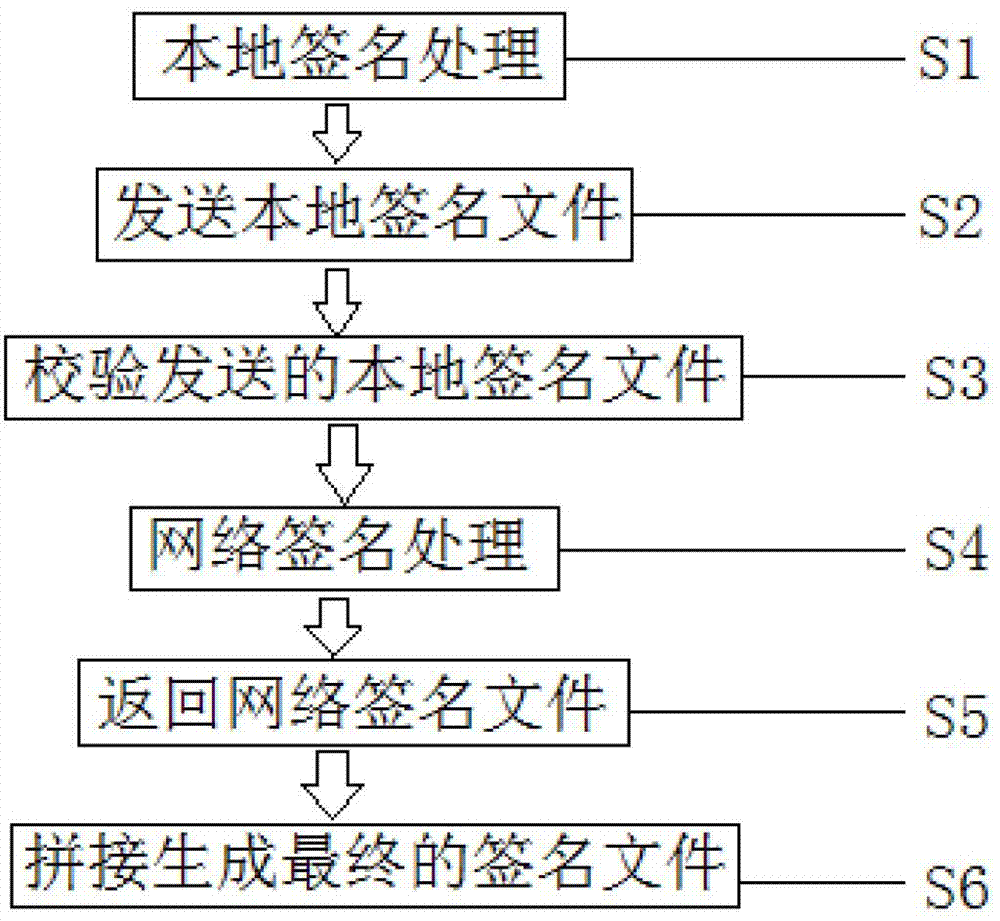
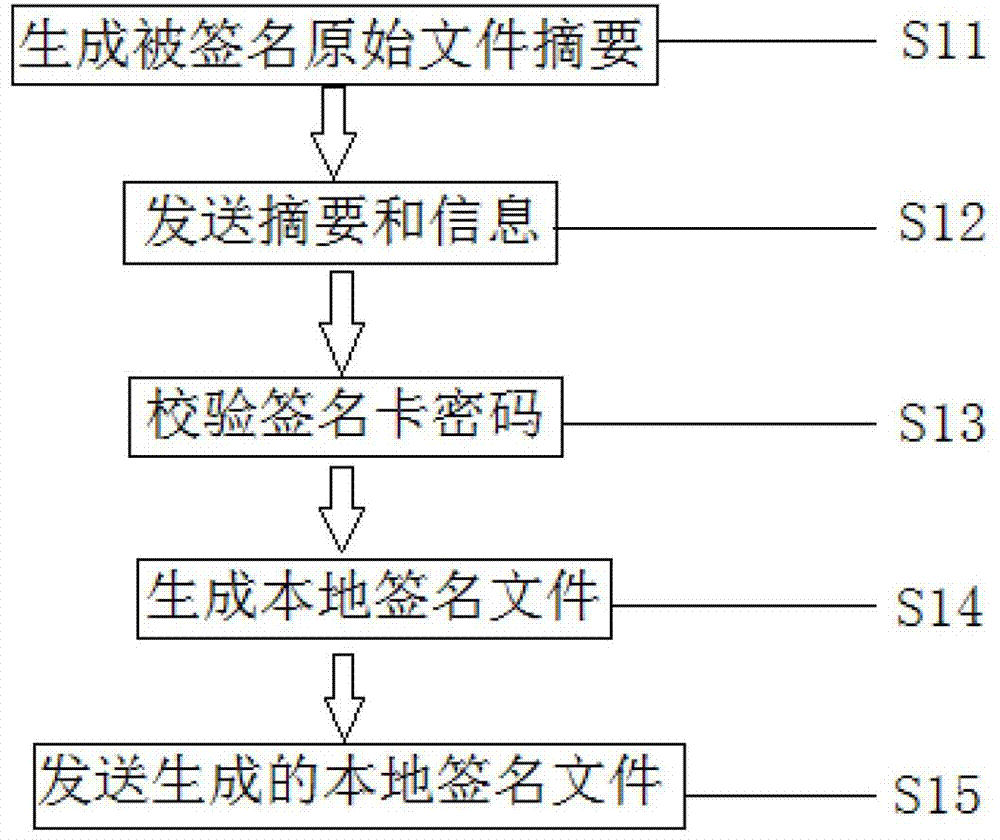
The invention relates to an intelligent terminal application program installing file networking digital signature method. A developer uses a local signature card to sign a to-be-signed source file to generate a local signature file with a local end signature tool. The local signature file is sent to a signature server. After the local signature file passes data verification of the signature server, the local signature file is sent to a network signature terminal, a network signature card of a manufacturer is used for signature, a network signature file is generated and is sent back to the signature server, and network signature file is sent to the local end signature tool to generate a final signature file. Private key data is stored in the signature card and cannot be read, a private key of the signature card can be used for signature only after code verification is passed, the storing and using safety of the private key is improved, a signature server end verifies local signature data accuracy, local certificate validity, developer identity legality, and the manufacturer can authorize and control signature authority limit.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
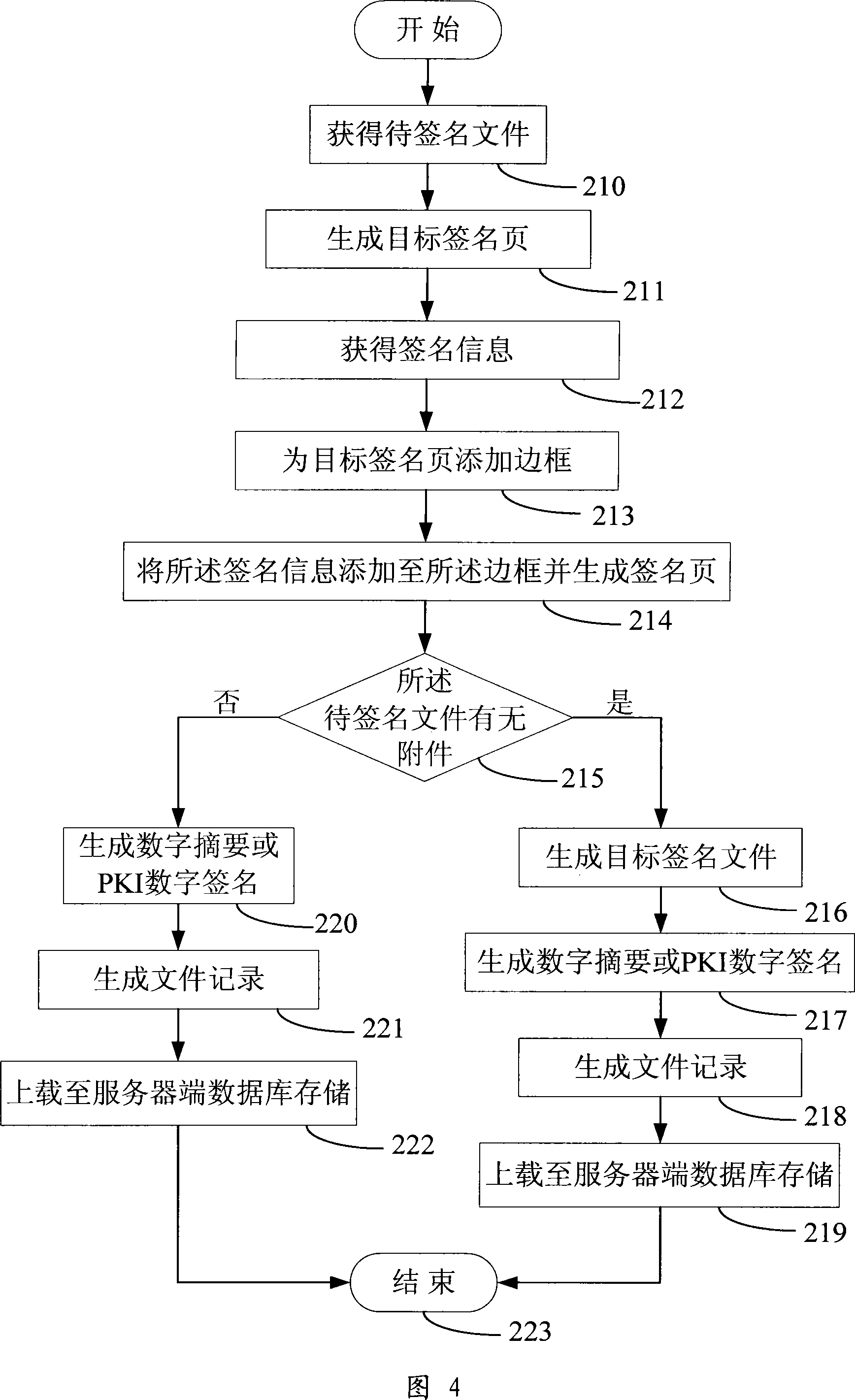
Electronic signature method
InactiveCN101089880ARealize visualizationGuaranteed reliabilityTransmissionInstrumentsSignature fileElectronic signature
Owner:王少波
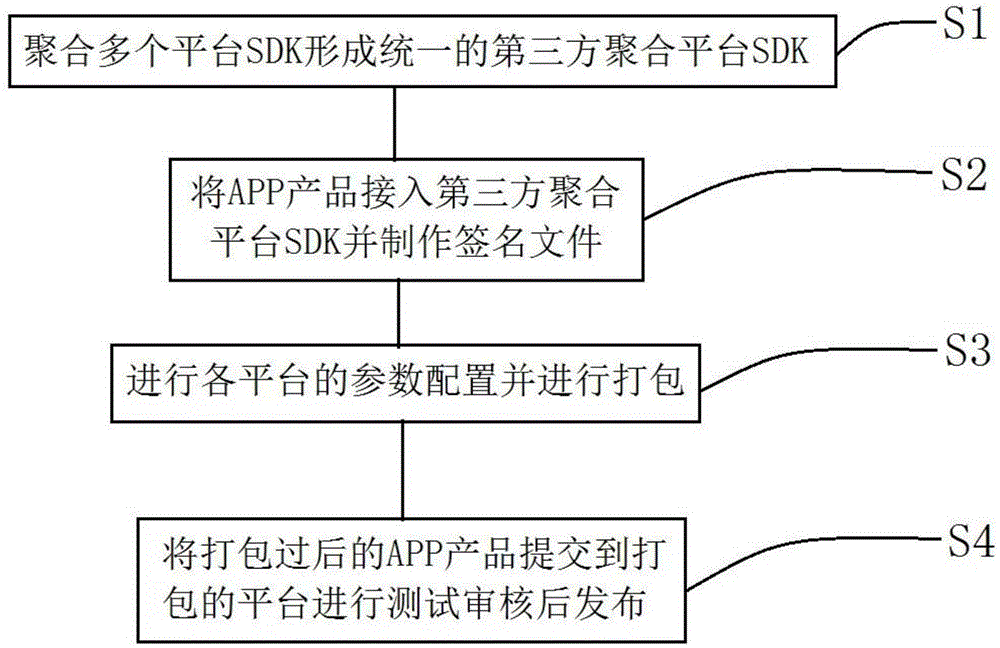
APP-product multi-platform release method
InactiveCN105323285AImprove docking efficiencyEasy to choose promotionTransmissionSpecific program execution arrangementsThird partySignature file
The invention discloses an APP-product multi-platform release method. The APP-product multi-platform release method comprises the following steps of polymerizing a plurality of platform SDKs to form a uniform third party polymerization platform SDK; connecting an APP product into the third party polymerization platform SDK and making a signature file; carrying out parameter configuration of each platform and carrying out packing; submitting the packed APP product to a packing platform so as to carry out testing and checking and then releasing. By using the APP-product multi-platform release method, an APP product developer can complete SDK butt joint and release of the multiple platforms through once access so that the APP product developer does not need to select the platform to carry out SDK butt joint and release for several times; an access period is short and platform SDK butt joint and release efficiency of the APP product are increased.
Owner:SHANGHAI ZHIYOU NETWORK TECH CO LTD
External interface access control for medical systems
A method and system of controlling access to a system in a medical environment is provided. The method includes calculating a signature value for at least one file usable with the medical system, transferring the calculated signature value to a signature file, and providing at least one signature value in the signature file and at least one associated file to a file system configured to be received by the medical system. At least one signature value and at least one associated file are inspected by the medical system to verify the associated file is a known medical software application asset. The medical system comprises an input / output data port configured to receive the external memory storage device, and an operating system capable of reading medical system data from and writing medical system data to the memory storage device.
Owner:JOHNSON & JOHNSON SURGICAL VISION INC
Systems and methods for computer security
InactiveUS20050235164A1Maintaining computer securityMaintain securityMemory loss protectionUser identity/authority verificationSignature fileClient-side
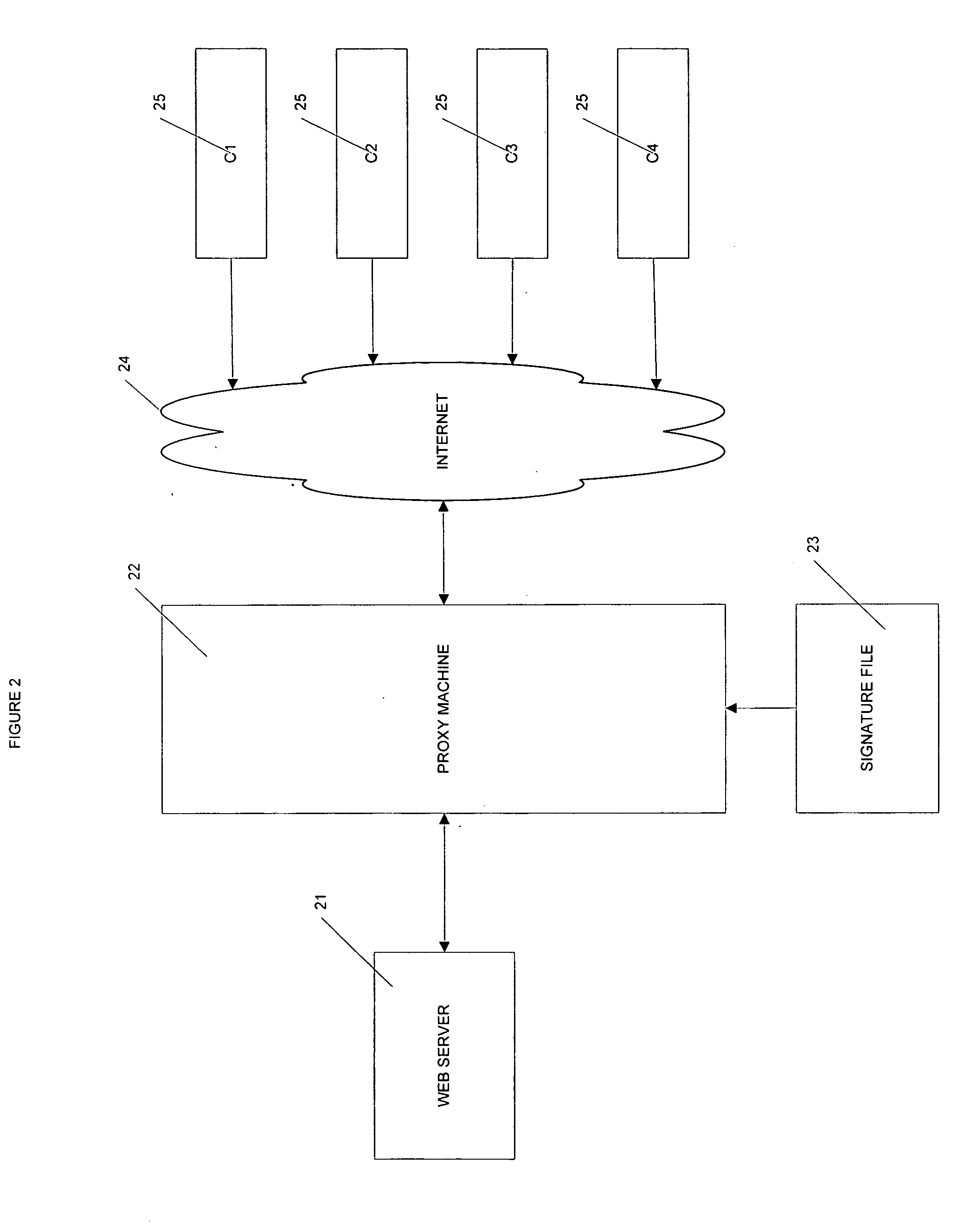
A method and system for maintaining computer security including providing a signature file; receiving an incoming message from at least one client computer; comparing the received incoming message with the signature file to determine whether the incoming message is malicious; and blocking the incoming messages determined to be malicious from reaching a web server.
Owner:GOOGLE LLC
Rapid virus scan using file signature created during file write
A procedure and implementations thereof are disclosed that significantly reduce the amount of time necessary to perform a virus scan. A file signature is created each time a file is modified (i.e., with each “file write” to that file). The file signature is inserted, with a date stamp, into the file attributes. The virus scan program checks the previously-created file signature against the virus signature file instead of creating the file signature for every file during the virus scan. Checks to ensure that the file signature is secure, and is valid and up to date, are also implemented. Only if the file signature is not valid and up-to-date does the virus scan program create a new file signature at the time of the running of the virus scan.
Owner:LENOVO PC INT
Methods to provide digital signature to secure flash programming function
InactiveUS20130111212A1User identity/authority verificationDigital data protectionSignature fileDigital signature
A method for providing digital signatures for authenticating the source and content of binary files which are flash programmed into automotive embedded controllers. A piece of electronic content is digitally signed on a signing server by creating a hash value and encrypting it using the signer's private key. The content file and digital signature files are then delivered using one of several alternative approaches to a programming tool, which in turn loads the content and signature files onto the controller on which the content will execute. The controller verifies the content by decrypting the signature file to restore the hash value, and comparing the decrypted hash value to a hash value calculated from the content itself. Multiple signature files for a piece of content are supported.
Owner:GM GLOBAL TECH OPERATIONS LLC
Electronic signing mobile terminal, system and method
ActiveCN1980121AImprove confidentialitySynchronising transmission/receiving encryption devicesRadio/inductive link selection arrangementsSignature fileElectronic signature
Based on STK program and digit certificate, which represents identity of owner of mobile terminal, the mobile terminal carries out electronic signature for signature file. Being accorded with stipulation of electronic signature raw, electronic signature possesses force of law identical to handwritten signature and stamp.
Owner:BEIJING SURSEN INT TECH CO LTD
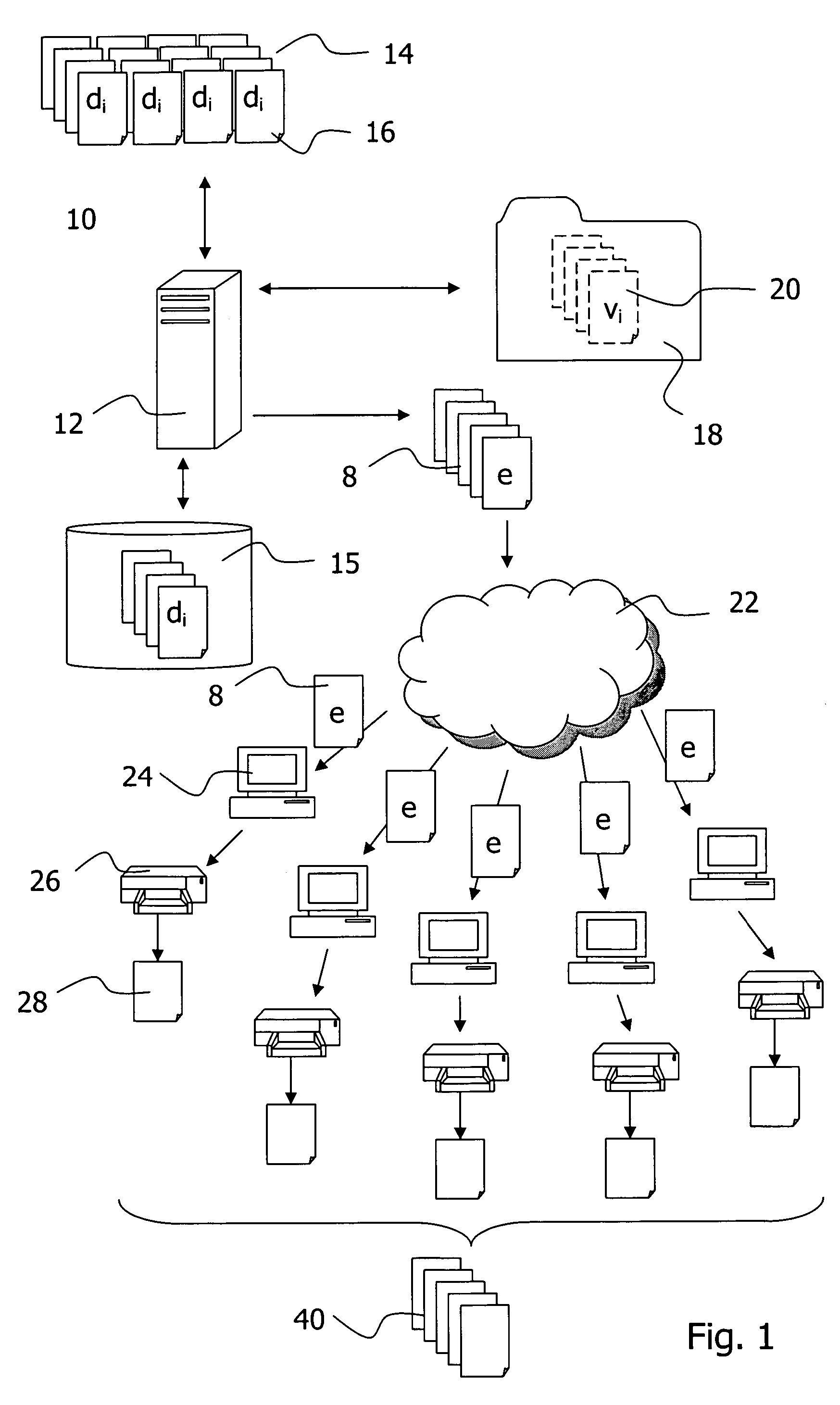
Creation of electronically processable signature files
InactiveUS20050262339A1Easy to operateTo offer comfortNatural language data processingSpecial data processing applicationsBatch processingSignature file
The invention relates to aspects in connection with the automatic generation and processing of signature files. The signature files are generated in paper form on the basis of documents (28) that comprise a personal signature (34) and also control information items (30) assigned to the signature (34) and / or the documents (28). The documents in paper form (28) are scanned in within the scope of a batch processing operation in order to generate signature files that contain the personal signatures (34) in an electronically processable form and also representations of the respectively assigned control information items (30). The control information items (30) contained in a signature file are identified and interpreted document-wise. Then the signature files are automatically processed as a function of the content of the assigned control information items (30).
Owner:UBS BUSINESS SOLUTIONS AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com