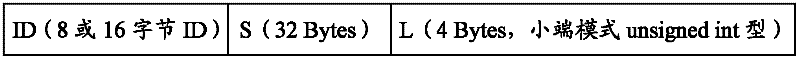Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
47results about How to "Reduce the risk of being cracked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
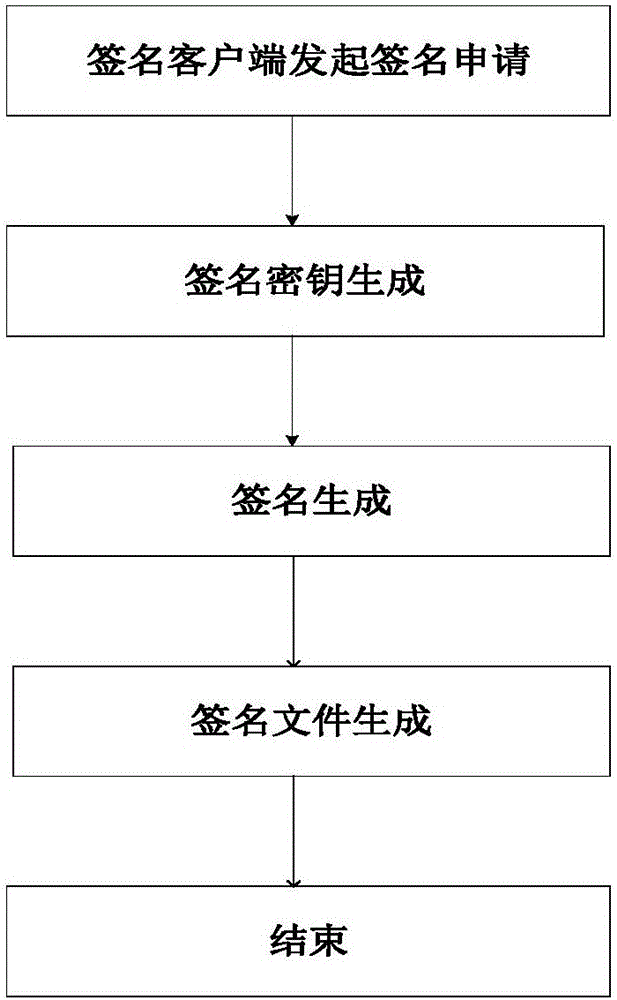
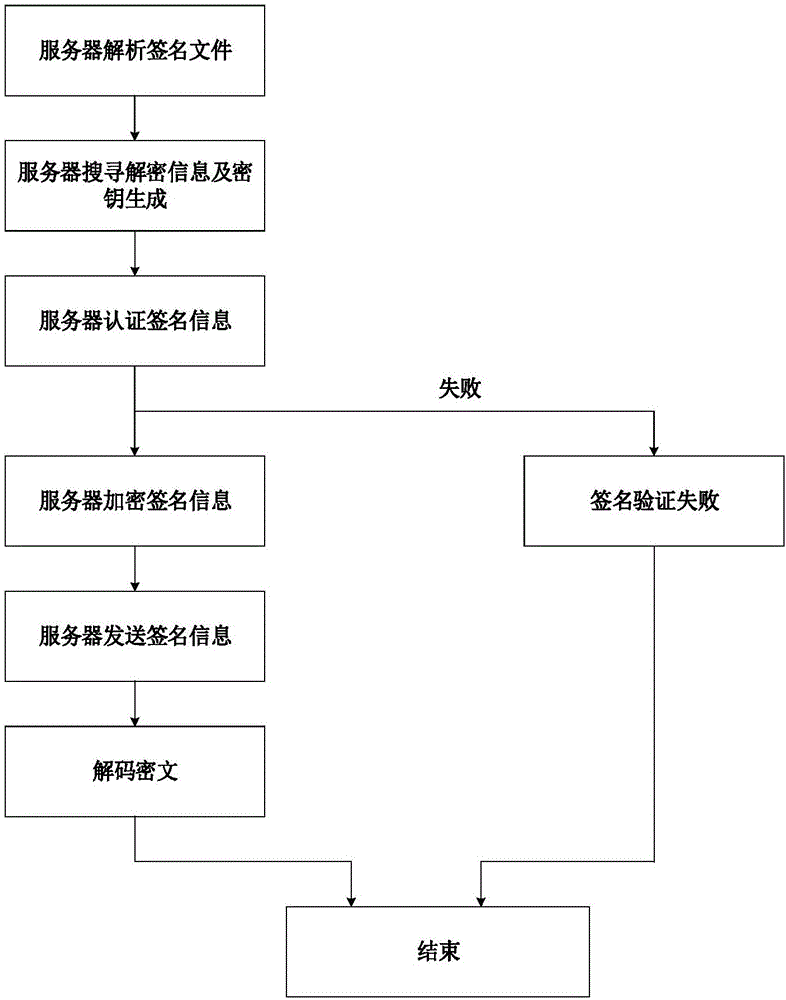
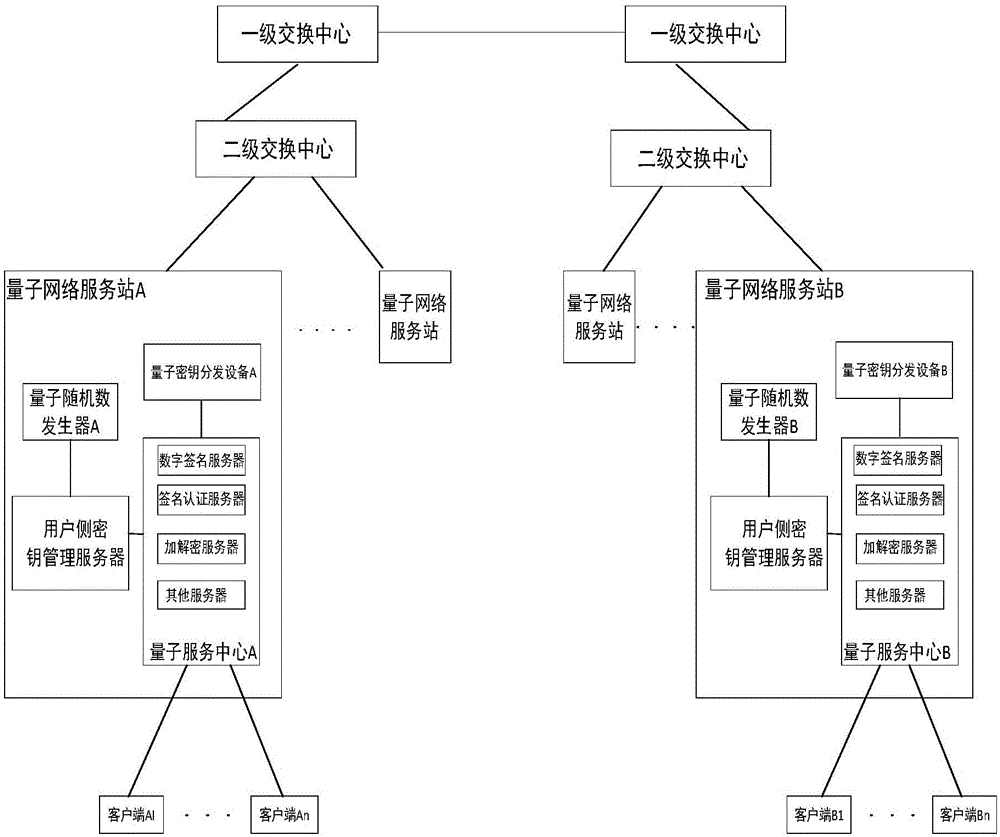
Digital signature method, digital signature system and quantum key card
ActiveCN106357396AFix security issuesReduce the risk of being crackedKey distribution for secure communicationUser identity/authority verificationSignature fileDigital signature
The invention discloses a digital signature method, a digital signature system and a quantum key card. The digital signature system comprises quantum network service stations, signature client sides, authentication client sides and quantum key cards, wherein the quantum network service stations are configured on the network side, and the signature client sides and the authentication client sides are configured on the user side. The digital signature method includes that a true random number is generated on the network side and then stored in the corresponding quantum key card and on the network side respectively to form a corresponding user-side key; the quantum key card matching with the signature client side uses the stored user-side key to generate a signature file, the signature file is sent to the authentication client side via the signature client side, and the authentication client side sends the received signature file to the current quantum network service station, acquires the corresponding user-side key from the network side to perform signature authentication on the signature file and sends signature authentication results to the corresponding authentication client side. The digital signature method, the digital signature system and the quantum key card have the advantage that key seeds are stored in the quantum key cards and the quantum network service stations, so that the problems of access use and safety of quantum network terminals are solved.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
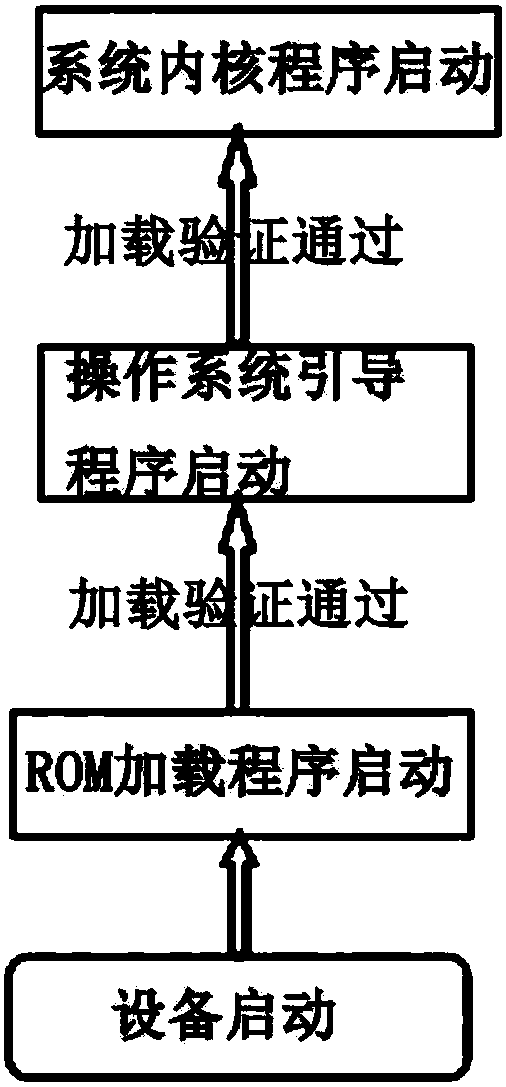
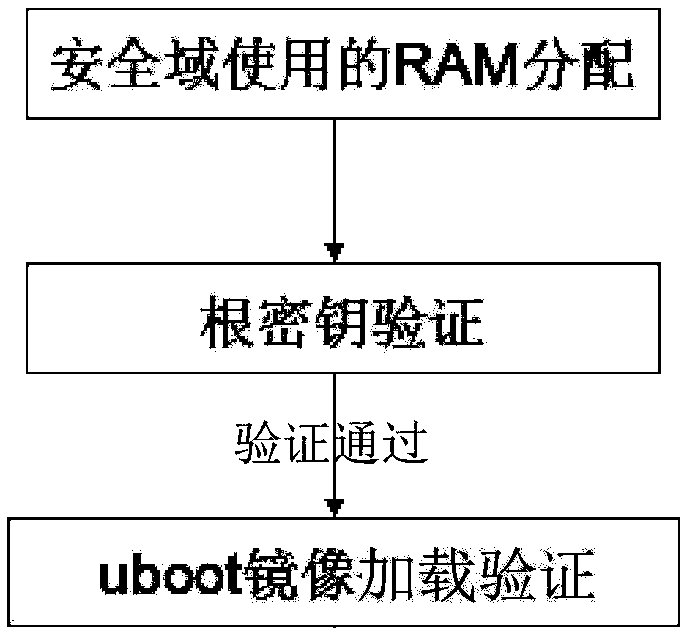
Trusted booting method based on TrustZone system
InactiveCN108287999AReduce the risk of being crackedReduce difficultyPlatform integrity maintainanceBootingSecurity domain
The invention discloses a trusted booting method based on a TrustZone system. The system is based on a system supporting a TrustZone technology, equipment of the system at least comprises memorizers,and the memorizers at least comprise an ROM and an RAM located in a security domain and a memorizer located in a generic domain. The method comprises the steps that S1, the system is started; S2, an ROM loading program located in the ROM is started; S3, loading verification is conducted on a bootstrap program of an operating system by the ROM loading program, and if the verification is passed, thebootstrap program of the operating system is started; S4, loading verification is conducted on a kernel program of the operating system by the bootstrap program of the operating system, and if the verification is passed, the kernel program of the operating system is started. According to the method, the trusted booted process of the system is deployed by using hardware technology characteristicsof a system on chip (SOC) of ARM, no additional trusted chip or trusted calculation module is needed, and cracked risks are reduced; the difficulty of circuit designing and the product cost are reduced.
Owner:XIAMEN YAXON NETWORKS CO LTD
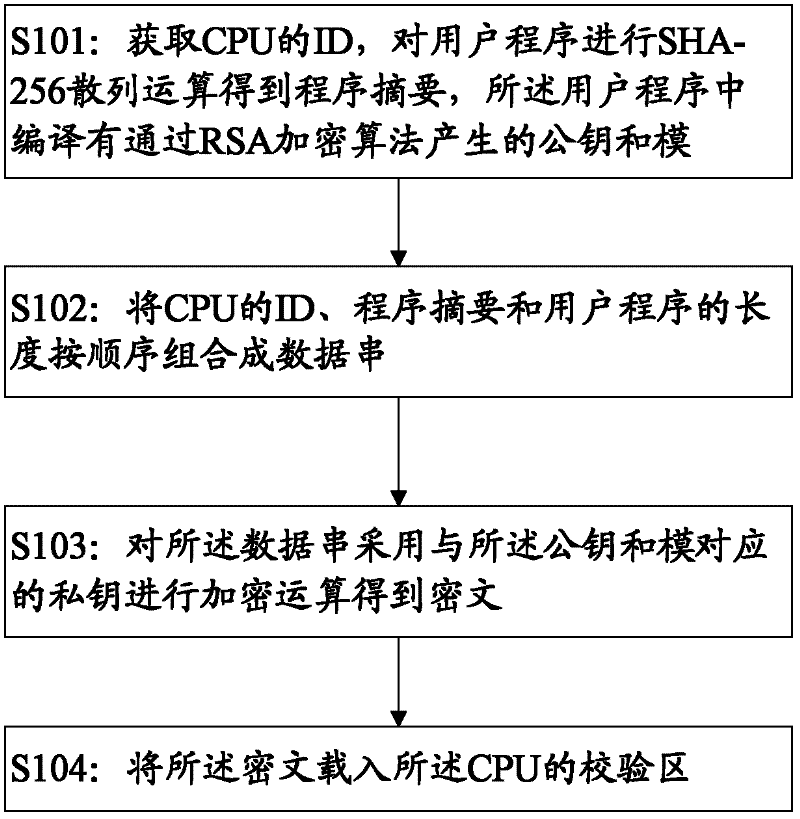
Method and device for signing user program and method and device for verifying signature of user program
ActiveCN102609665AReduce the risk of being brute-forcedPrevent malicious tamperingDigital data protectionProgram/content distribution protectionCiphertextBrute-force attack
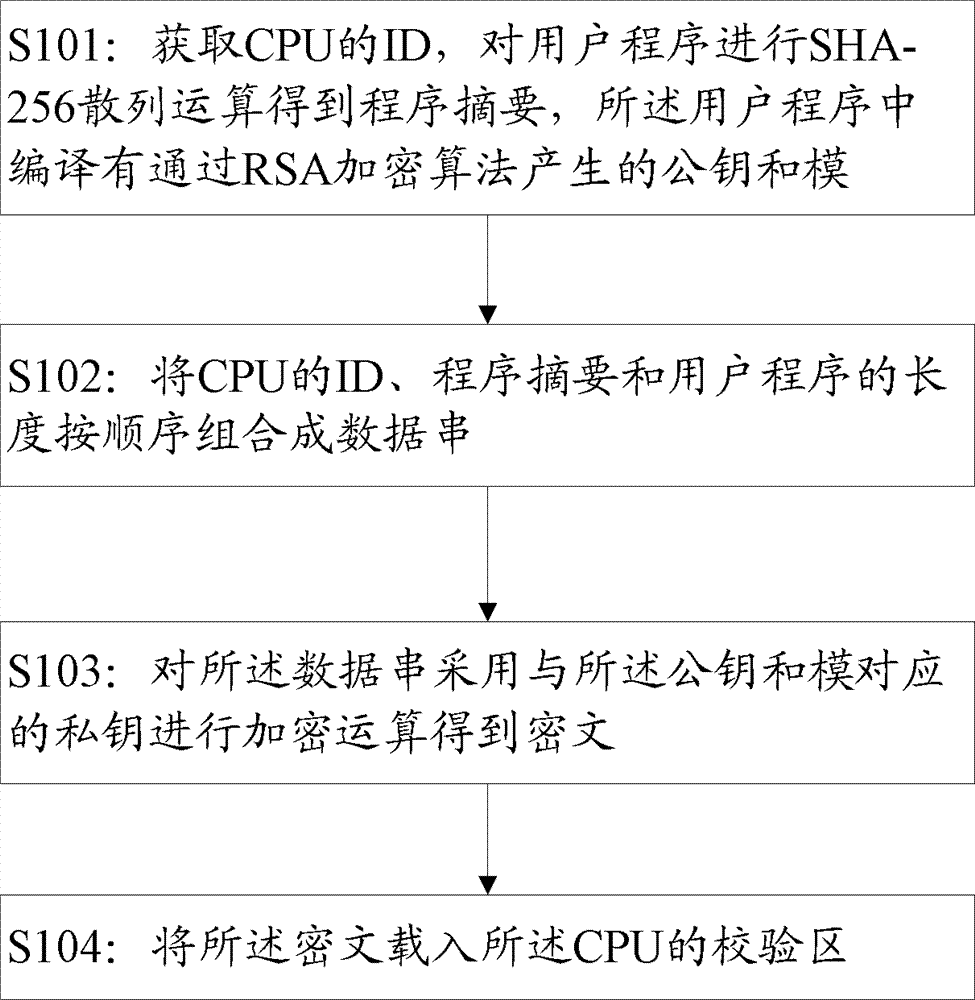
The invention discloses a method and a device for signing a user program verifying signature of the user program. The method for signing the user program includes steps of acquiring ID (identity) of a CPU (central processing unit), computing the user program by SHA-256 hash operation to obtain a program digest, compiling a public key and a module generated through RSA (Ron Rivest,Adi Shamirh and Len Adleman) encryption algorithm into the user program; combining the ID of the CPU, the program digest and the length of the user program in sequence to form a data string; operating the data string by a private key corresponding to the public key and the module to obtain ciphertext; and loading the ciphertext into a check area of the CPU. By combining with the RSA algorithm and the SHA algorithm to process the user program and integrating with the ID of the CPU to be a part of the signature, the user program must be restarted by being strictly subjected to the signature verifying process matched with the signature, risk in brute force attack to the user program is greatly reduced, and the user program can be effectively protected from being tampered or stolen maliciously.
Owner:恒鸿达科技有限公司
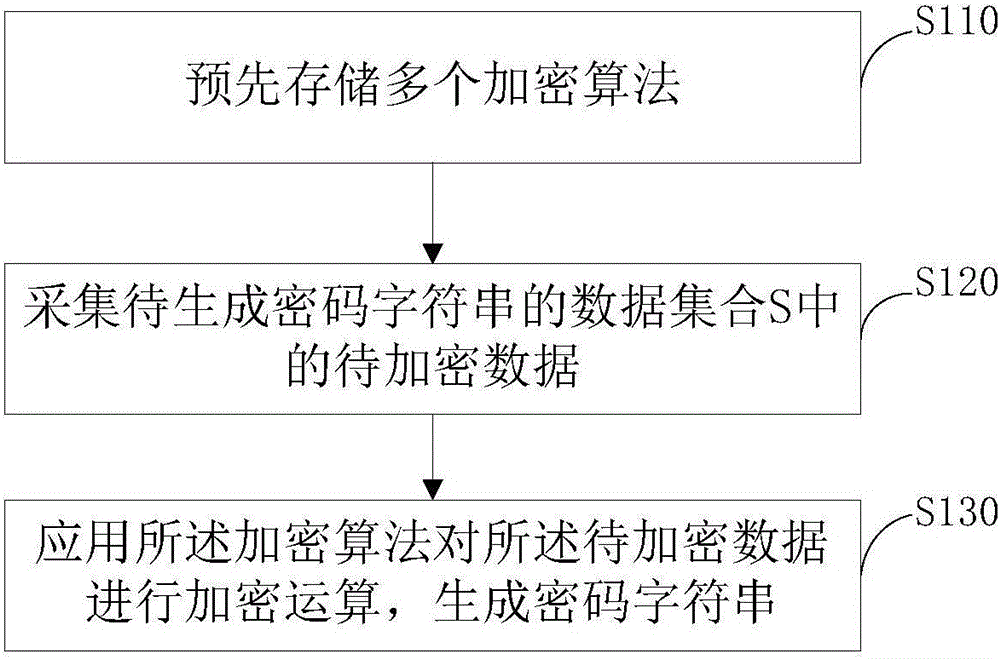
Cipher character string generation method and apparatus
InactiveCN106204038AOvercoming repetitivenessOvercome the flaws that are easy to be crackedPayment protocolsMultiple encryptionData set
The invention provides a cipher character string generation method. The method comprises the following steps: prestoring multiple encryption algorithms; acquiring data to be encrypted in a data set S of cipher character strings to be generated; and by use of the encryption algorithms, performing encryption operation on the data to be encrypted so as to generate the cipher character strings. According to the embodiments of the invention, the cipher character strings are generated through arrangement of the multiple encryption algorithms, and the method and apparatus have the positive effects of reducing the risk of cracking the cipher character strings and improving the security of the cipher character string.
Owner:GUANGZHOU ZHENGFENG ELECTRON TECH CO LTD
Verification code image generating method and device and verification method and device
ActiveCN103902875AReduce the success rate of machine recognitionReduce the risk of being crackedDigital data authenticationValidation methodsNetwork security
The invention provides a verification code image generating method and device and a verification method and device. The verification code image generating method and device and the verification method and device aim to lower the success rate of automatic identification of a machine. The verification code image generating method comprises the steps of generating a texture image, determining the position of a verification code, and modifying the pixel value of the texture image at the position of the verification code to obtain a verification code image. The verification code image generating method has the advantages that the success rate of automatic identification of a machine can be lowered, the risk that the verification code is cracked is lowered, and the network security is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
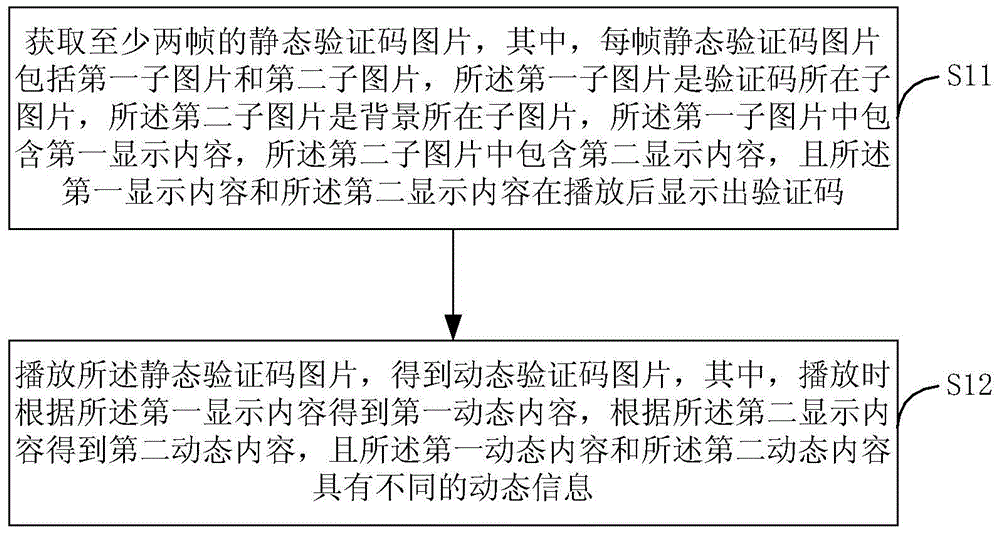
Generation method and device of dynamic verification code pictures and verification method and device of dynamic verification code pictures
ActiveCN103886243AReduced risk of crackingLower success rateDigital data authenticationProgramming languageValidation methods
The invention provides a generation method and device of dynamic verification code pictures and a verification method and device of the dynamic verification code pictures in order to reduce the success rate of automatic identification through a machine. The generation method of the dynamic verification code pictures includes the steps that at least two frames of static verification code pictures are acquired, wherein in each frame of static verification code picture, a verification code is displayed after first display content and second display content are played; the static verification code pictures are played, and the dynamic verification code pictures are obtained, wherein in the playing process, first dynamic content is obtained according to the first display content, second dynamic content is obtained according to the second display content, and the first dynamic content and the second dynamic content contain different kinds of dynamic information. Through the method, the success rate of automatic identification through a machine can be lowered, the risk that verification codes are cracked is reduced, and the safety of a network is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
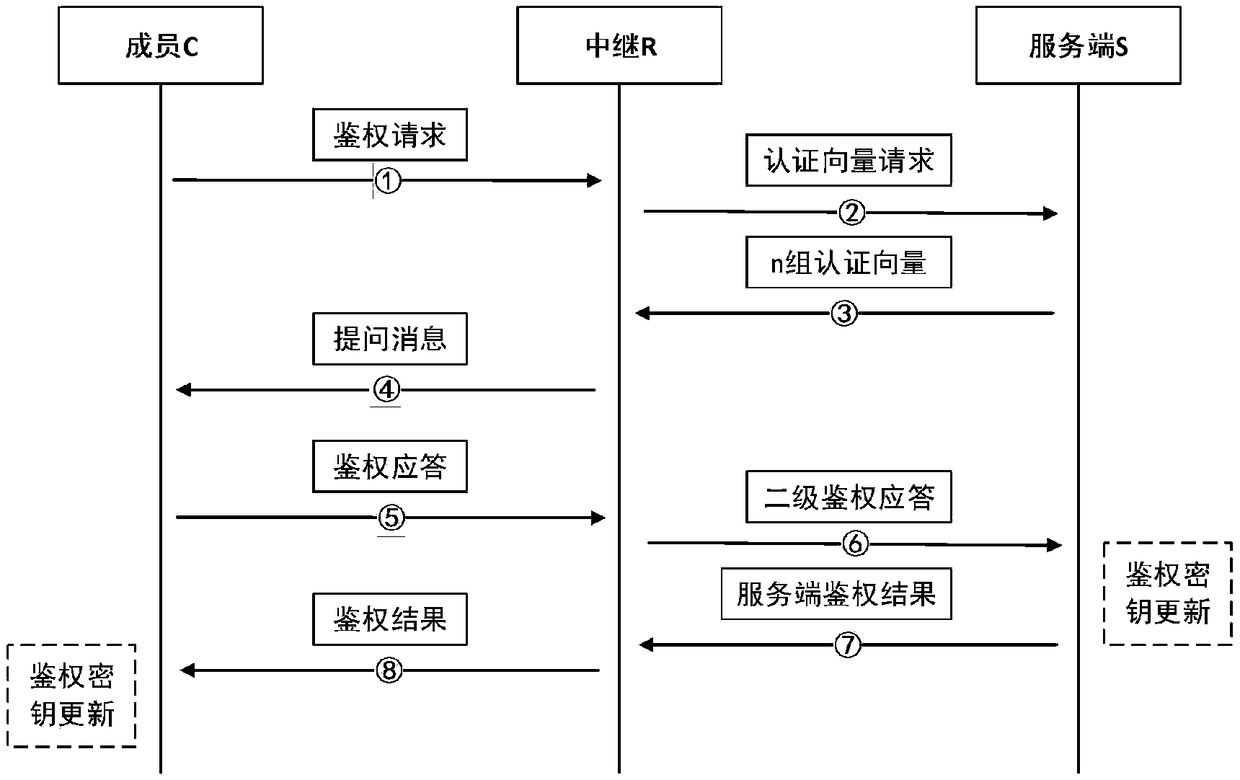
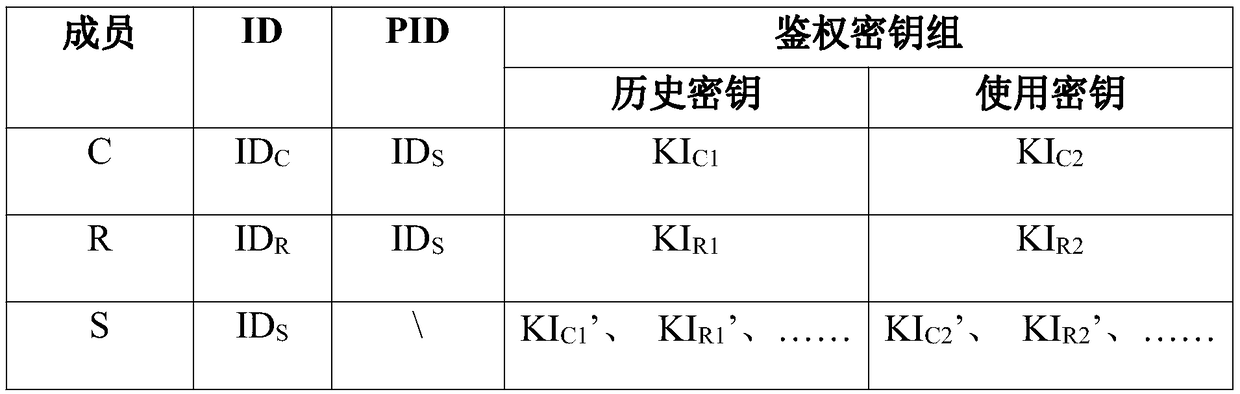
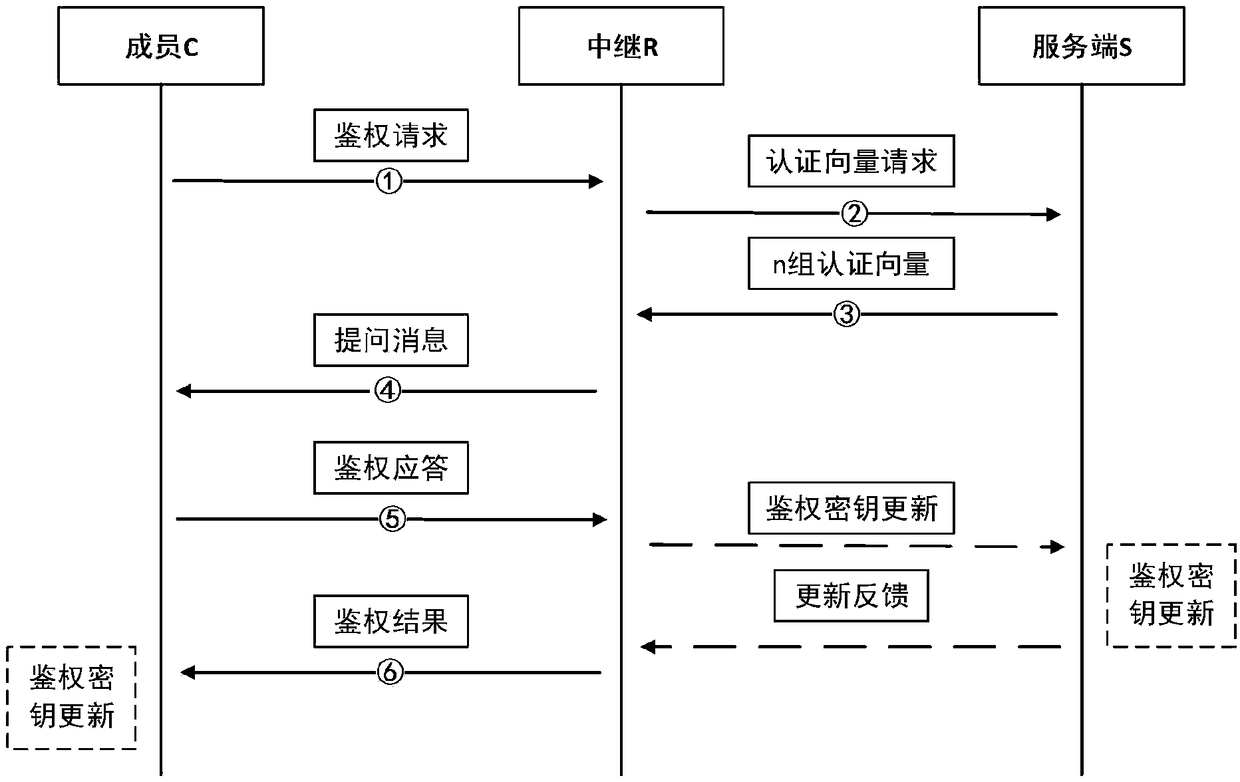
AKA identity authentication system and method based on symmetric key pool and cross-relay
ActiveCN108712252AEnsure safetyImprove securityKey distribution for secure communicationAuthentication systemKey generation
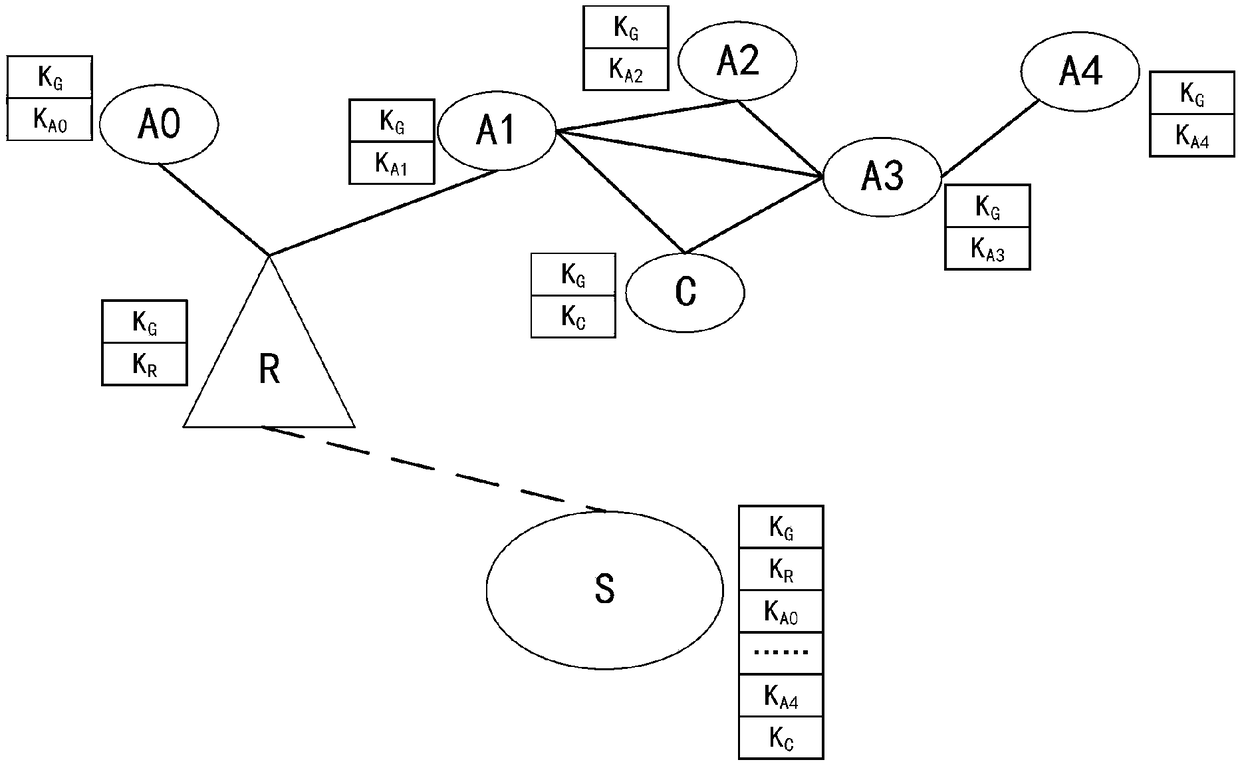
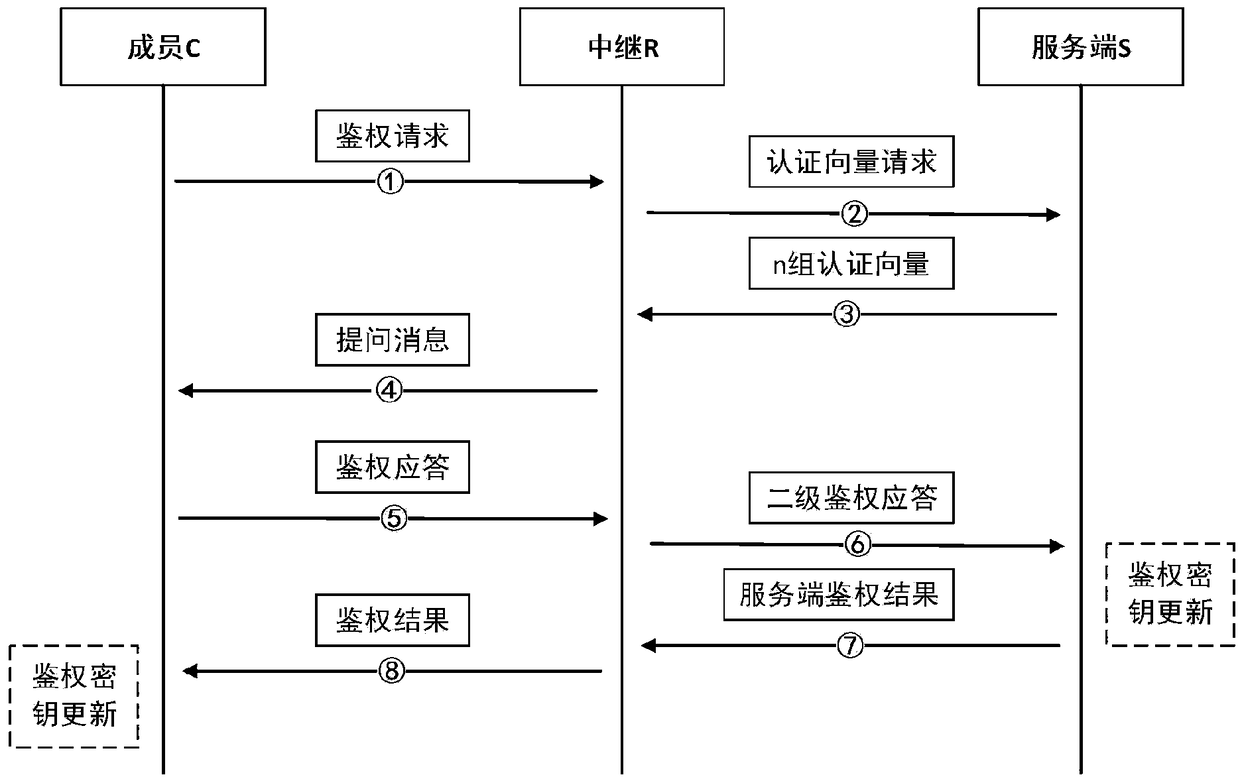
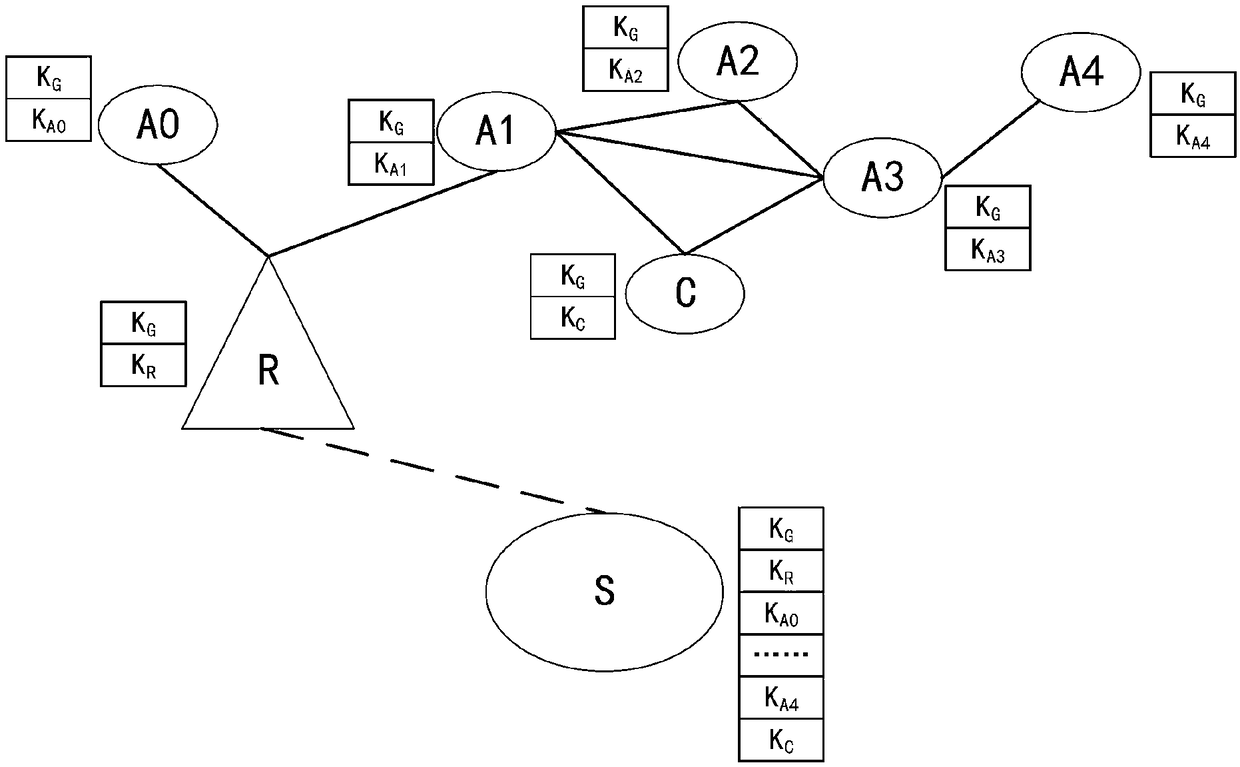
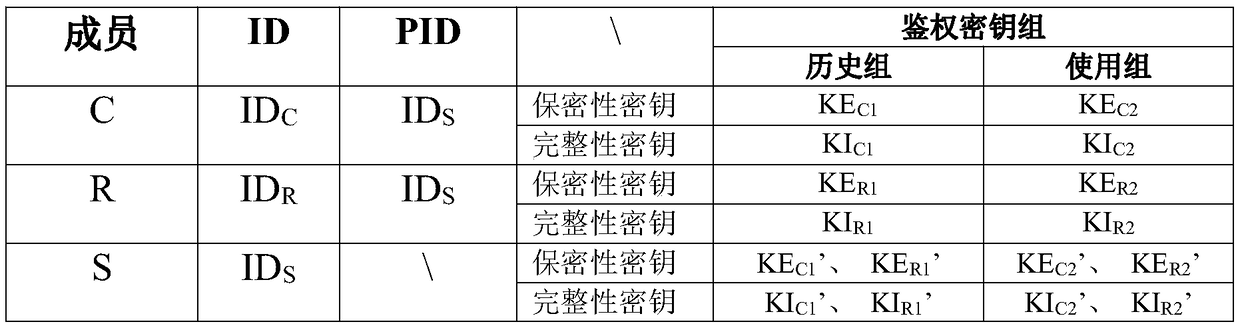
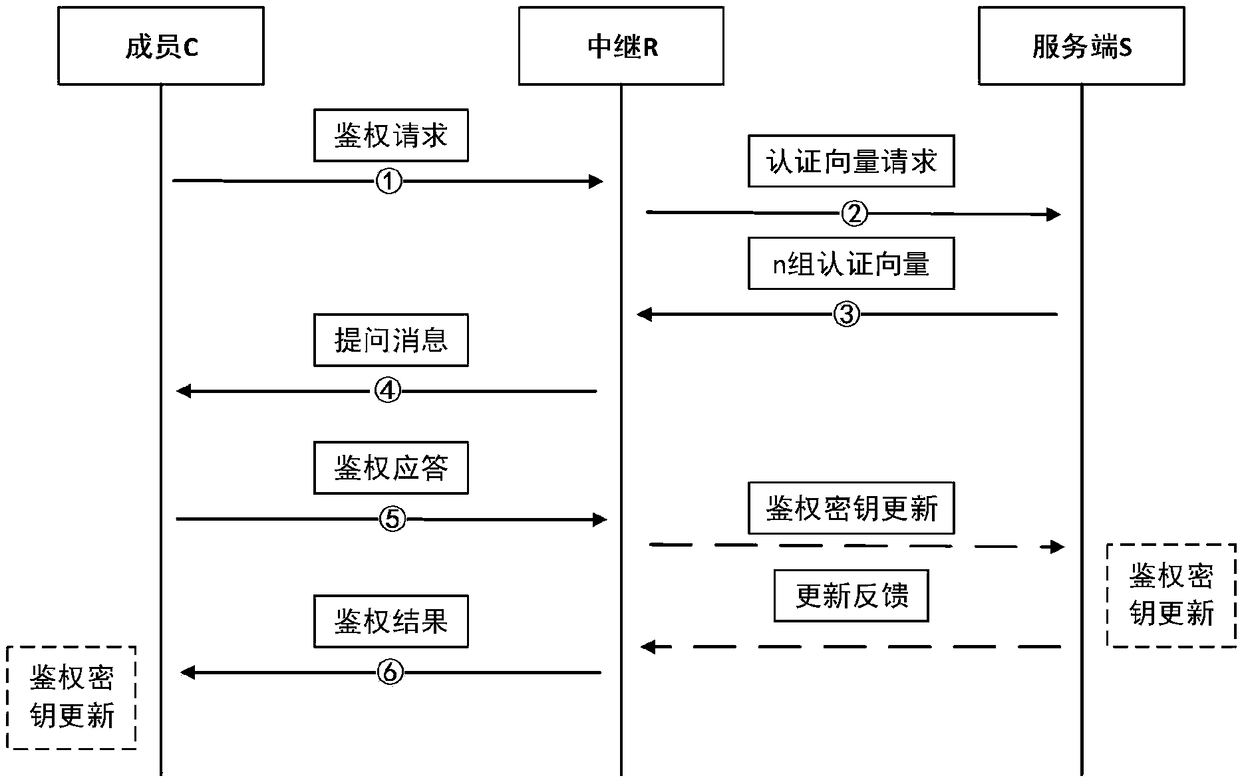
The invention discloses an AKA identity authentication system and method based on a symmetric key pool and a cross-relay. The AKA identity authentication system comprises a member participating in AKAidentity authentication, a relay and a server, wherein the member, the relay and the server share a group key pool; the member and the relay are further respectively provided with private key pools for generating authentication keys, and the member and the relay independently share the private key pools with the server; the member and the relay negotiate a corresponding pointer address in an AKAidentity authentication process, and generates a first negotiation key between the member and the relay in combination with the respective group key pools; the member and the server also share the corresponding pointer address in the AKA identity authentication process and generate a second negotiation key between the member and the server in combination with the respective authentication keys. Byadoption of the AKA identity authentication system and method disclosed by the invention, the security of communication can be further improved.
Owner:RUBAN QUANTUM TECH CO LTD
Improved AKA identity authentication system and method based on symmetric secret key pool and relay communication
ActiveCN108964888AImprove securityIncrease capacityKey distribution for secure communicationPhotonic quantum communicationAuthentication systemRelay
The invention discloses an improved AKA identity authentication system and method based on a symmetric secret key pool and relay communication. The AKA identity authentication system comprises a member participating in AKA identity authentication, a relay and a server. The member, the relay and the server share a group secret key pool. The member and the relay use a secret key seed from the groupsecret key pool and combine with a random number parameter to calculate and acquire a negotiation secret key between the member and the relay in an AKA identity authentication process, wherein the random number parameter is correspondingly obtained by using a pointer address A in the group secret key pool. In the AKA identity authentication process, the relay acquires the pointer address A throughthe server, and the member acquires a parameter for generating the pointer address A from the server via the relay, and generates the pointer address A by using the parameter. In the invention, the safety of communication can be further increased.
Owner:RUBAN QUANTUM TECH CO LTD
Key exchange method for communication of automobile electronic control unit
InactiveCN110492995AShort service lifePhenomena of avoiding attacksKey distribution for secure communicationPublic key for secure communicationComputer hardwareKey exchange
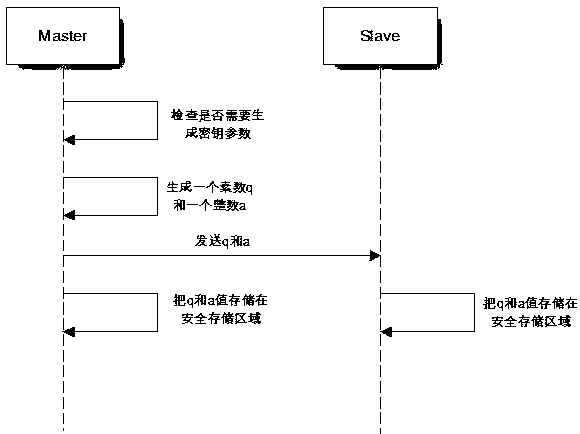
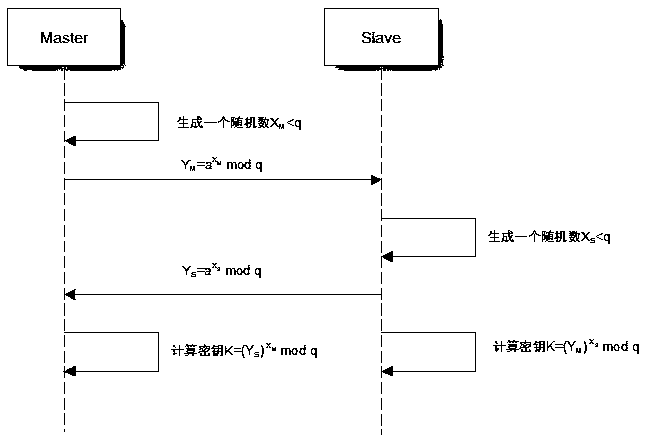
The invention relates to a key exchange method for automobile electronic control unit communication, which comprises the following steps that 1, an encryption object is selected, and a plurality of electronic control units are classified into a Master and a Slave; 2, a system is initialized, the Slave is accessed to the Master, and the Master checks whether a key parameter needs to be generated ornot; if so, a key parameter is generated, and simultaneously the key parameter is stored into safe storage areas of the Master and the Slave; if not, the originally generated key parameters are used;3, a secret key is generated in real time, after the vehicle is ignited each time, the Master and the Slave respectively generate a random number, and the secret key is generated according to secretkey parameters and the random numbers; and step 4, data encryption: the Master encrypts the communication data needing to be sent to the Slave through the secret key, and the Slave encrypts the communication data needing to be sent to the Master through the secret key. The secret key exchange method for automobile electronic control unit communication is low in encryption cost, does not need to establish a special server to store the secret key, is low in secret key leakage risk, and has very high safety.
Owner:HUIZHOU DESAY SV INTELLIGENT TRANSPORTATION TECH INST CO LTD
Encryption method, decryption method and electronic equipment
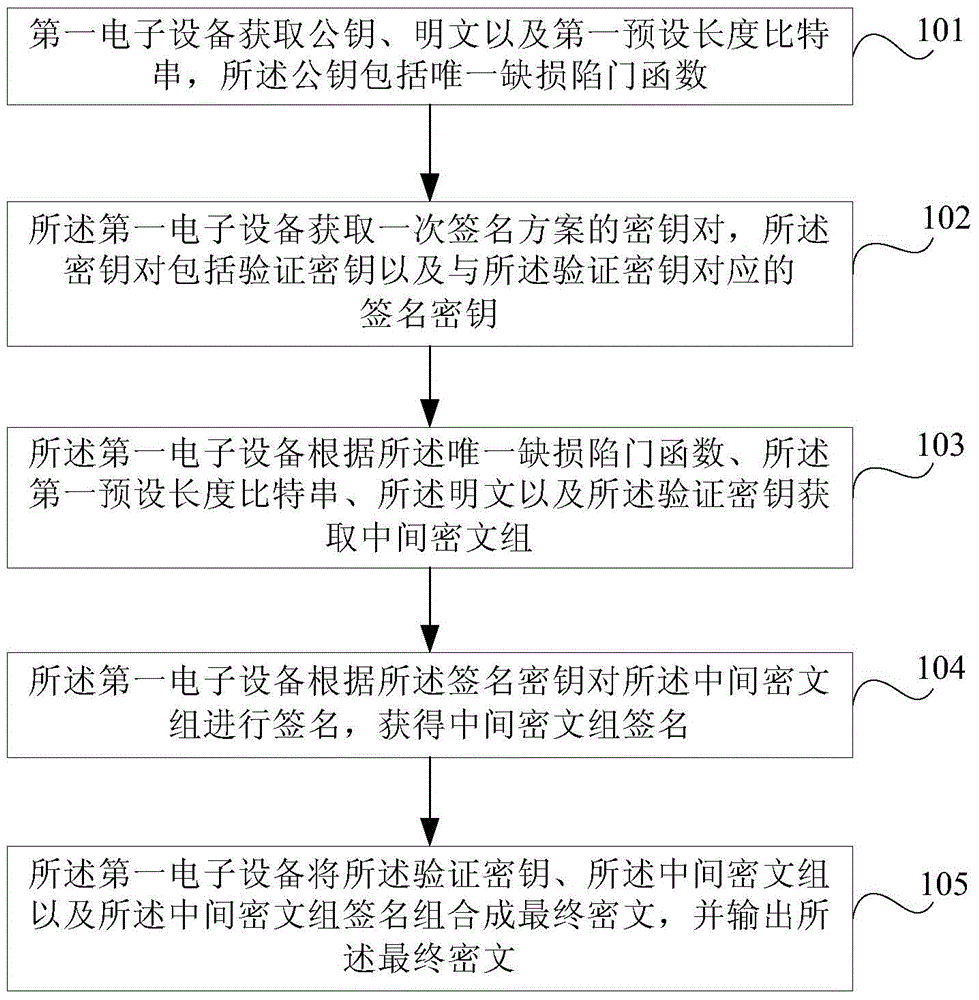
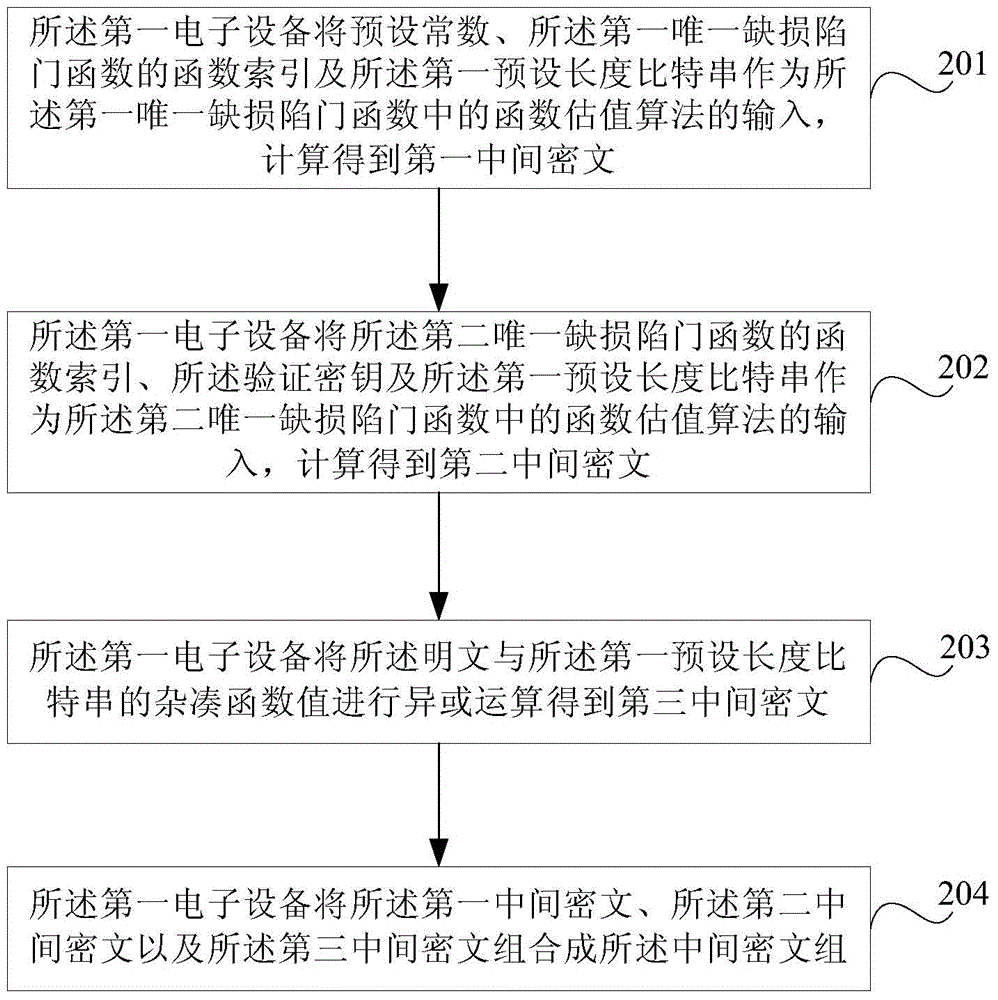
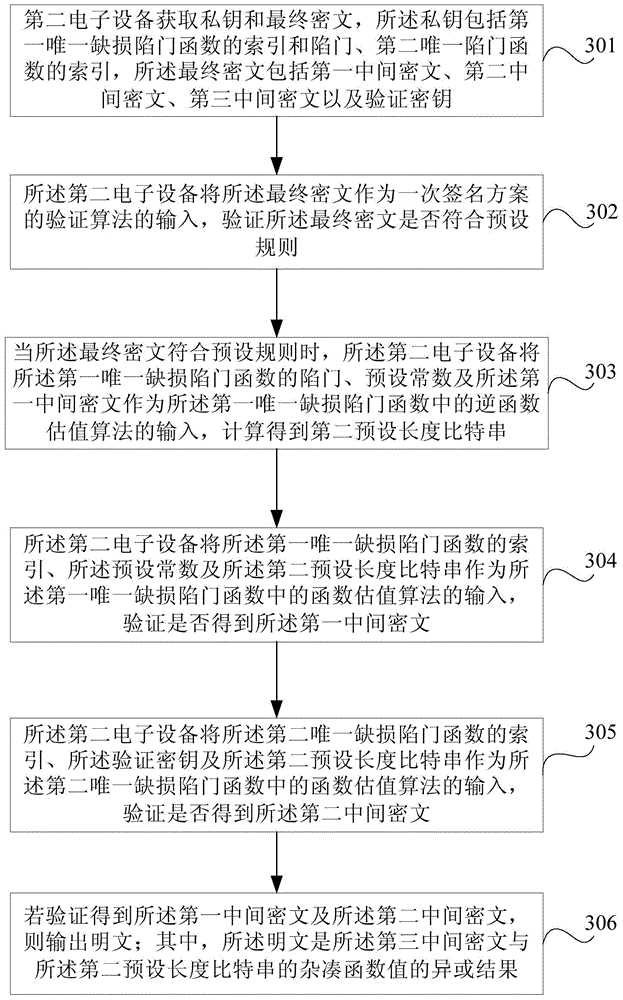
ActiveCN105227308AReduce the risk of being crackedUser identity/authority verificationPlaintextChosen-ciphertext attack
Embodiments of the invention provide an encryption method, a decryption method and electronic equipment. The method comprises steps of acquiring a public key, a plaintext and a first bit string of a preset length through first electronic equipment, wherein the public key comprises the only defect trapdoor function; acquiring a key pair of a one-time signature scheme by the first electronic equipment, wherein the public pair comprises a verification secret key and a signature secret key corresponding to the verification secret key; acquiring a middle cryptograph set according to the only defect trapdoor function, the first bit string of the preset length, the plaintext and the verification secret key; signing the middle cryptograph set by the first electronic equipment according to the signature secret key, and acquiring a signature of the middle cryptograph set; and forming a final cryptograph by combing the verification secret key, the middle cryptograph set and the signature of the middle cryptograph set, and outputting the final cryptograph. Therefore, anti-selection cryptograph attack is achieved.
Owner:HONOR DEVICE CO LTD
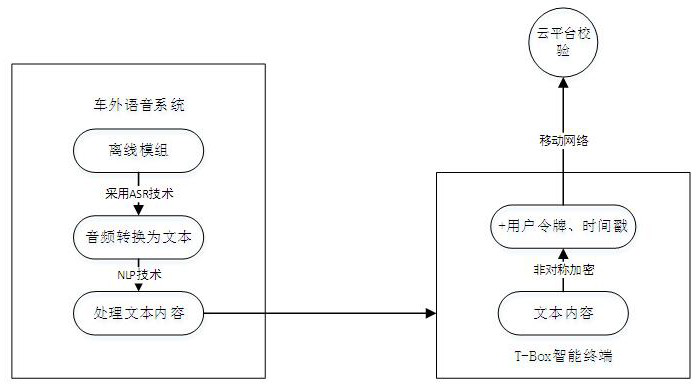
Method and system for unlocking and starting vehicle based on voice system outside vehicle
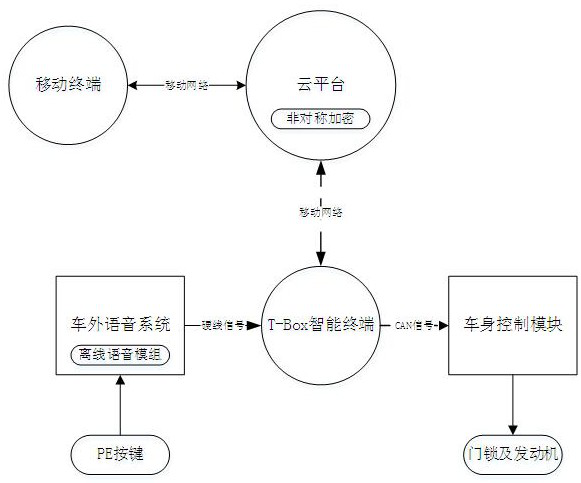
PendingCN113823018AReduce the risk of being crackedImprove anti-theft performanceIndividual entry/exit registersIntelligent NetworkIn vehicle
The invention discloses a method and a system for unlocking and starting a vehicle based on an out-of-vehicle voice system, and relates to the field of intelligent networked vehicles. The system comprises a cloud platform used for generating and verifying a random secret key for vehicle identity authentication; intelligent mobile equipment which communicates with the cloud platform through a communication network and requests to generate a visible random secret key; a pickup which is arranged in a key of the PE door handle and serves as a wake-up source of a voice system outside the automobile; an out-of-vehicle voice system which is used for processing a random secret key input by out-of-vehicle voice, and an offline module of the out-of-vehicle voice system transmits the random secret key to the T-Box vehicle-mounted intelligent terminal; the T-Box vehicle-mounted intelligent terminal transmits the received random secret key to the cloud platform for verification; the vehicle body control module receives a signal transmitted by the T-Box through a CAN signal and is used for giving vehicle unlocking and ignition authority.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD
Anti-shearing reinforcement device and method for concrete box girder web
ActiveCN109537478ASolve the problem of excessive main tensile stressAvoid corrosionBridge erection/assemblyBridge strengtheningPre stressRebar
The invention relates to an anti-shearing reinforcement device and method for a concrete box girder web. In order to solve the problem that in existing engineering technologies, the concrete box girder web has cracking inclined cracks and insufficient anti-shearing bearing capacity, an external vertical prestressing tendon reinforcement device and method are provided. The device comprises groove-shaped steel, L-shaped steel, vertical prestressing tendons, wedge-shaped steel cushion blocks and an anti-corrosion coating at the outer side of the web. The groove-shaped steel is horizontally fixedto the junction of the upper end of the web and a top plate in the girder length direction. The L-shaped steel (6) is horizontally fixed to the lower end of the web in the girder length direction andis parallel to the groove-shaped steel (5). The vertical prestressing tendons are vertically mounted on the groove-shaped steel and the L-shaped steel, and it is ensured that the vertical prestressingtendons are parallel to the plane of the web. According to the anti-shearing reinforcement device and method, the web is connected with the top plate and a bottom plate through finish rolling twistedsteel, the force transmission path is definite, the risk that web concrete is pulled broken is reduced, and meanwhile, midspan deformation is reduced; the problem of insufficient main tensile stressof the web concrete is effectively solved, and the situations of continuous extension of the inclined cracks of the web or new inclined cracks are prevented.
Owner:BEIJING UNIV OF TECH
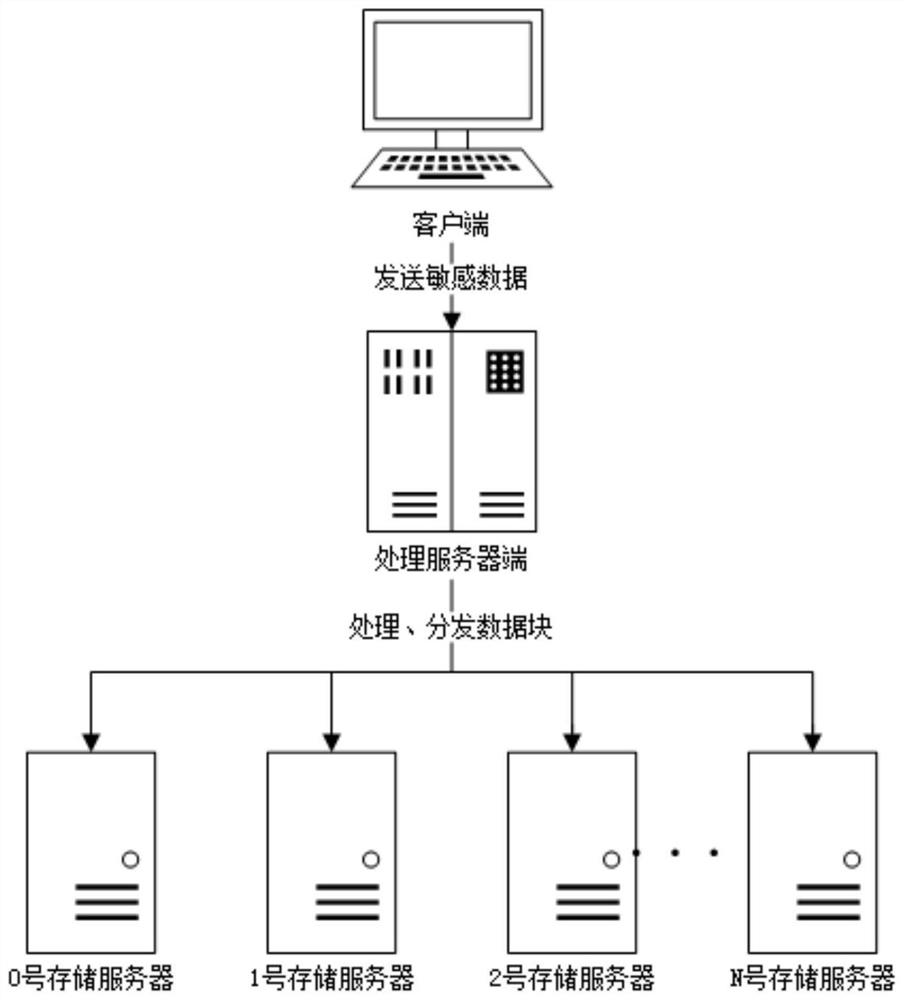
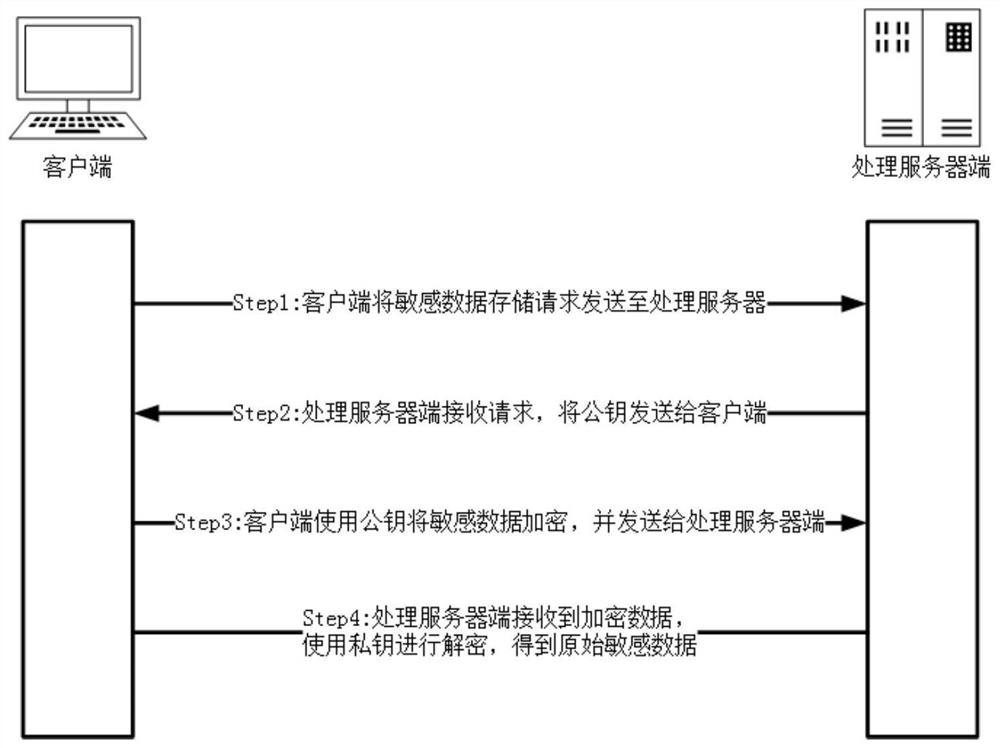
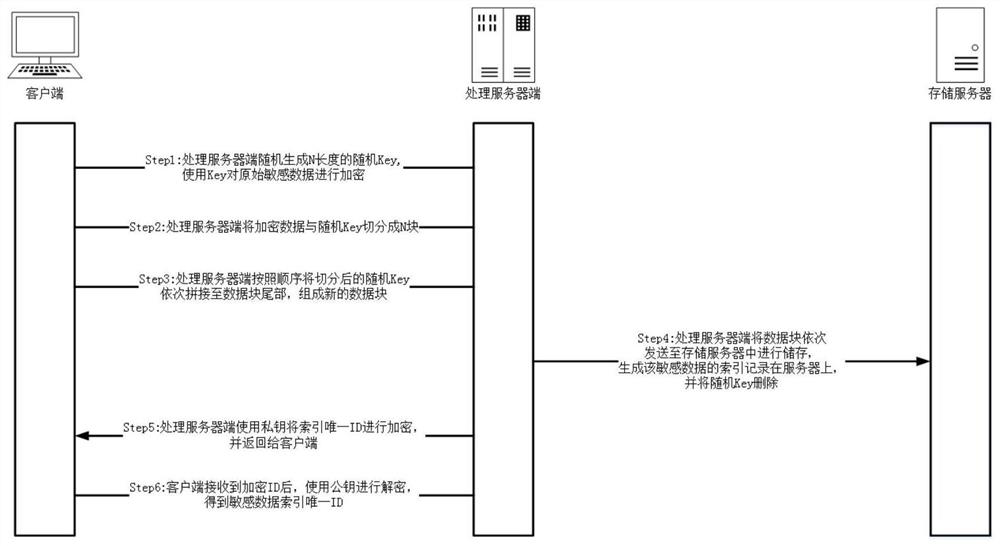
Safe discrete storage method for sensitive data
PendingCN111709040AReduce the risk of being crackedImprove securityDigital data protectionSpecial data processing applicationsEngineeringServer-side
Owner:江苏智先生信息科技有限公司
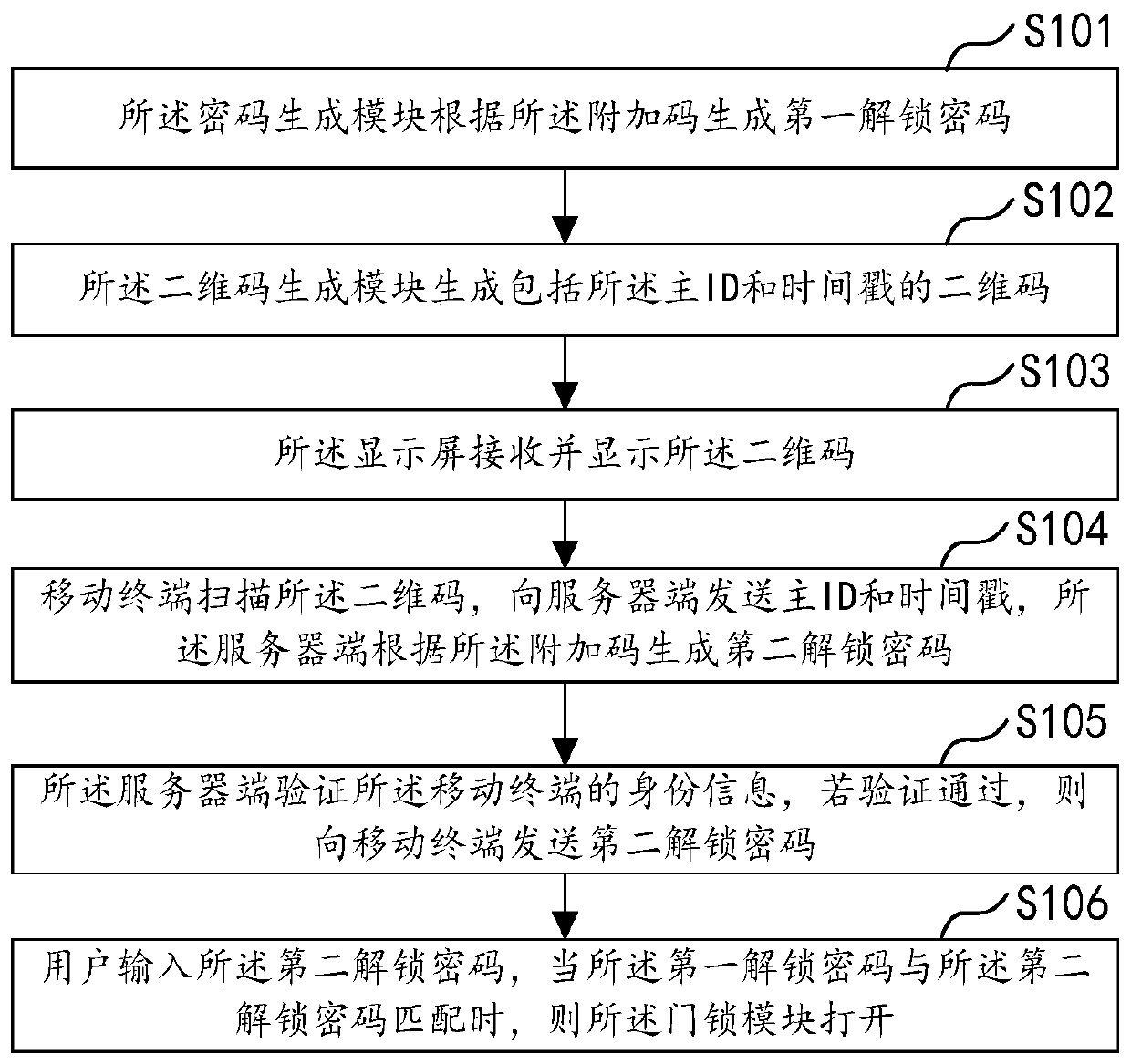
Dynamic password door opening method and door lock
PendingCN110910544AImprove securityReduce the risk of being crackedIndividual entry/exit registersTimestampPassword
The invention discloses a dynamic password door opening method and a door lock, wherein the dynamic password door opening method comprises the following steps that a password generation module generates a first unlocking password according to an additional code; a two-dimensional code generation module generates a two-dimensional code comprising a main ID and a timestamp; a display screen receivesand displays the two-dimensional code; a mobile terminal scans the two-dimensional code and sends the main ID and the timestamp to a server side, and the server side generates a second unlocking password according to the additional code; the server side verifies the identity information of the mobile terminal, and sends a second unlocking password to the mobile terminal if the verification passes; and a user inputs the second unlocking password, and when the first unlocking password is matched with the second unlocking password, a door lock module is opened.
Owner:深圳市深华方科技有限公司
Express cabinet door lock opening method and device and express cabinet
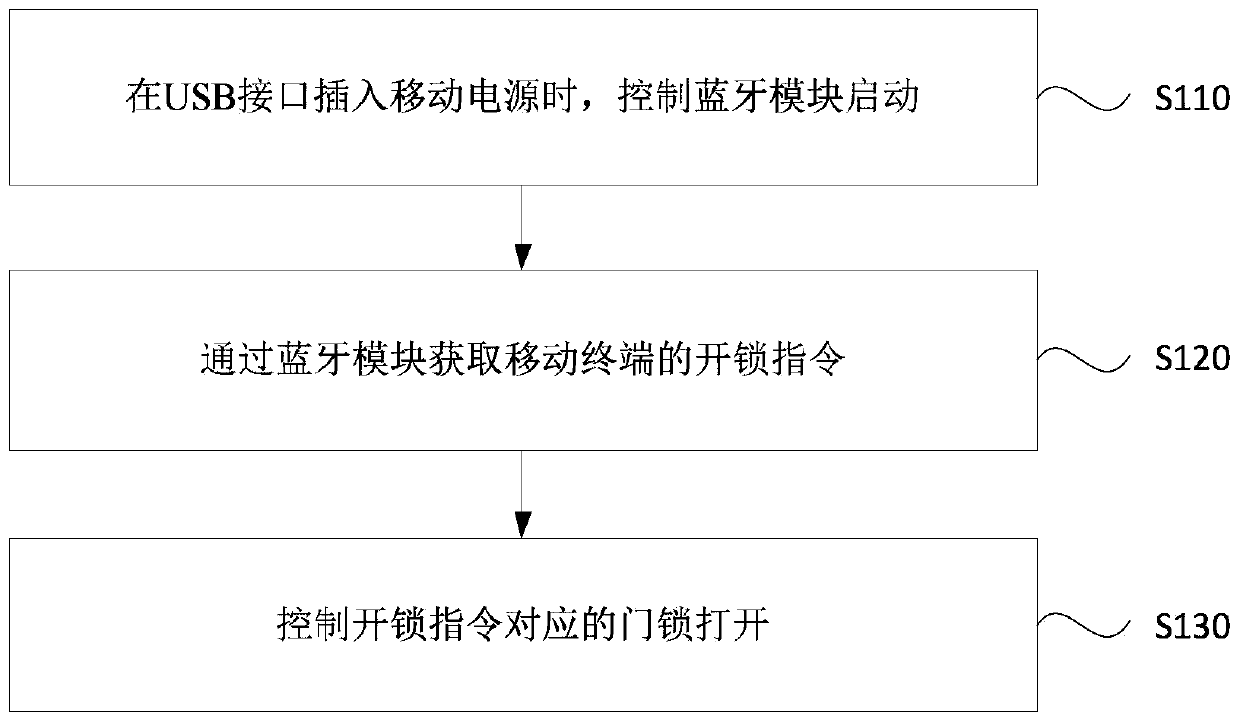
InactiveCN111080864AImprove operation and maintenance processing efficiencyAvoid working all the timeApparatus for meter-controlled dispensingIndividual entry/exit registersEngineeringUSB
The embodiment of the invention discloses an express cabinet door lock opening method and device and an express cabinet. The express cabinet comprises a Bluetooth module and a USB interface. The express cabinet door lock opening method comprises the following steps: when a mobile power source is inserted into the USB interface, the Bluetooth module is controlled to be started; an unlocking instruction of a mobile terminal is acquired through the Bluetooth module; and a door lock corresponding to the unlocking instruction is controlled to be opened. According to the technical scheme provided bythe embodiment of the invention, the Bluetooth module and the USB interface are additionally arranged in the express cabinet, so that when the express cabinet breaks down, the mobile terminal can send an unlocking instruction to the express cabinet through the Bluetooth module, and then the operation and maintenance processing efficiency of the express cabinet can be improved.
Owner:SHENZHEN HIVE BOX TECHNOLOGY CO LTD
Encryption method, decryption method and system
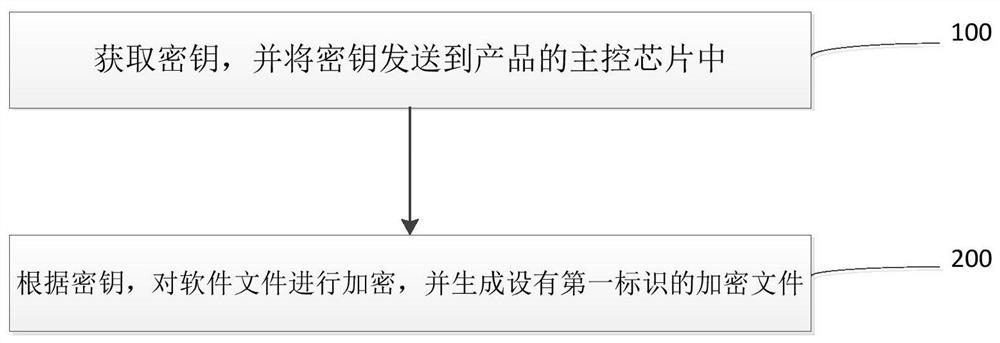
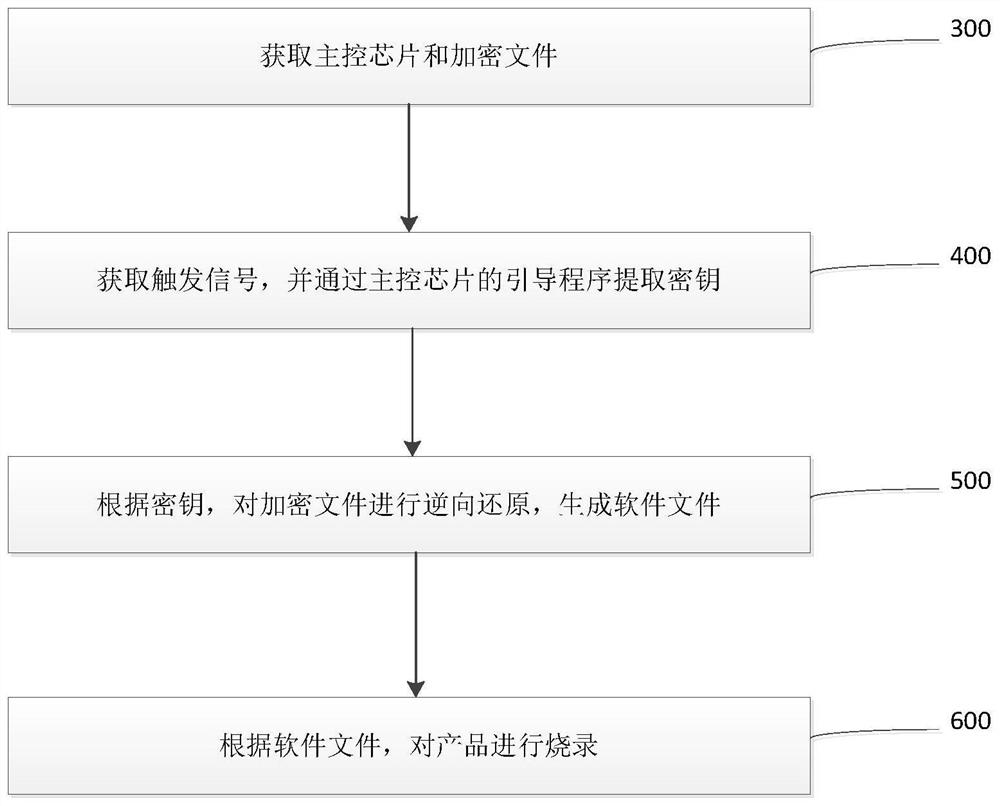
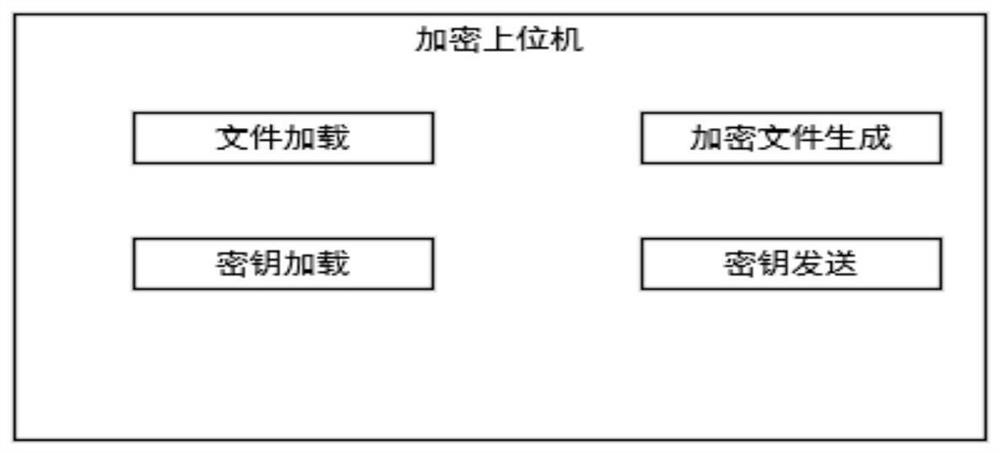
PendingCN113806774AImprove securityReduce the risk of being crackedDigital data protectionSoftware deploymentSoftware engineeringEncryption
The invention relates to an encryption method, a decryption method and a system, which are applied to software product burning, and the method comprises the following steps: obtaining a secret key, and sending the secret key to a main control chip of a product; and encrypting a software file according to the key, and generating an encrypted file with a first identifier. The invention has the beneficial effects that the software file is encrypted, so that the security of the file is improved, the cracking risk is greatly reduced, and the software file can be effectively prevented from being monitored and cracked.
Owner:HUIZHOU DESAY BATTERY
Data processing method and electronic device
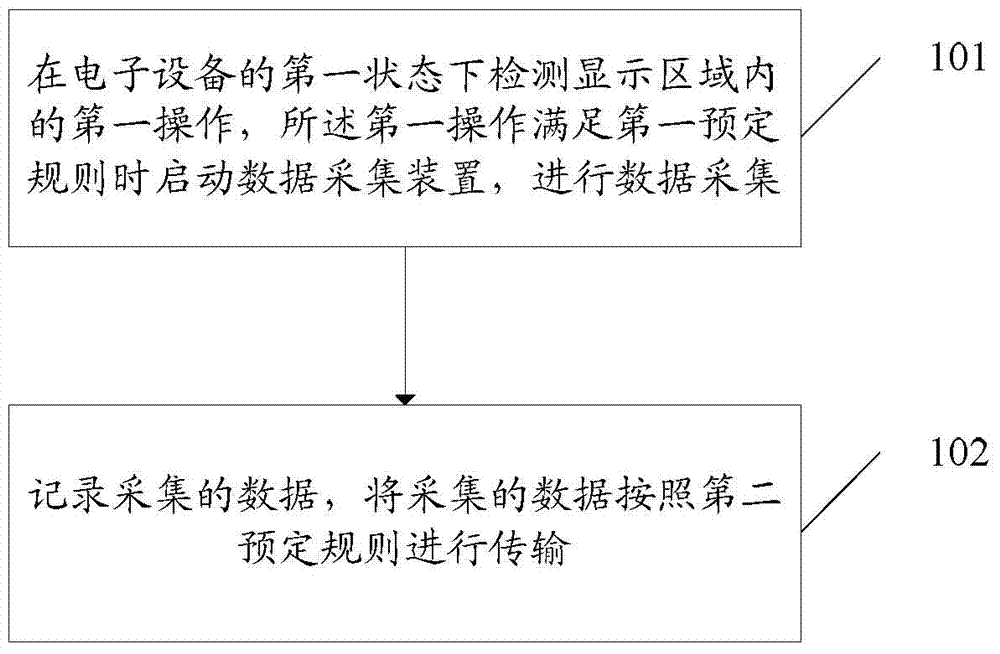
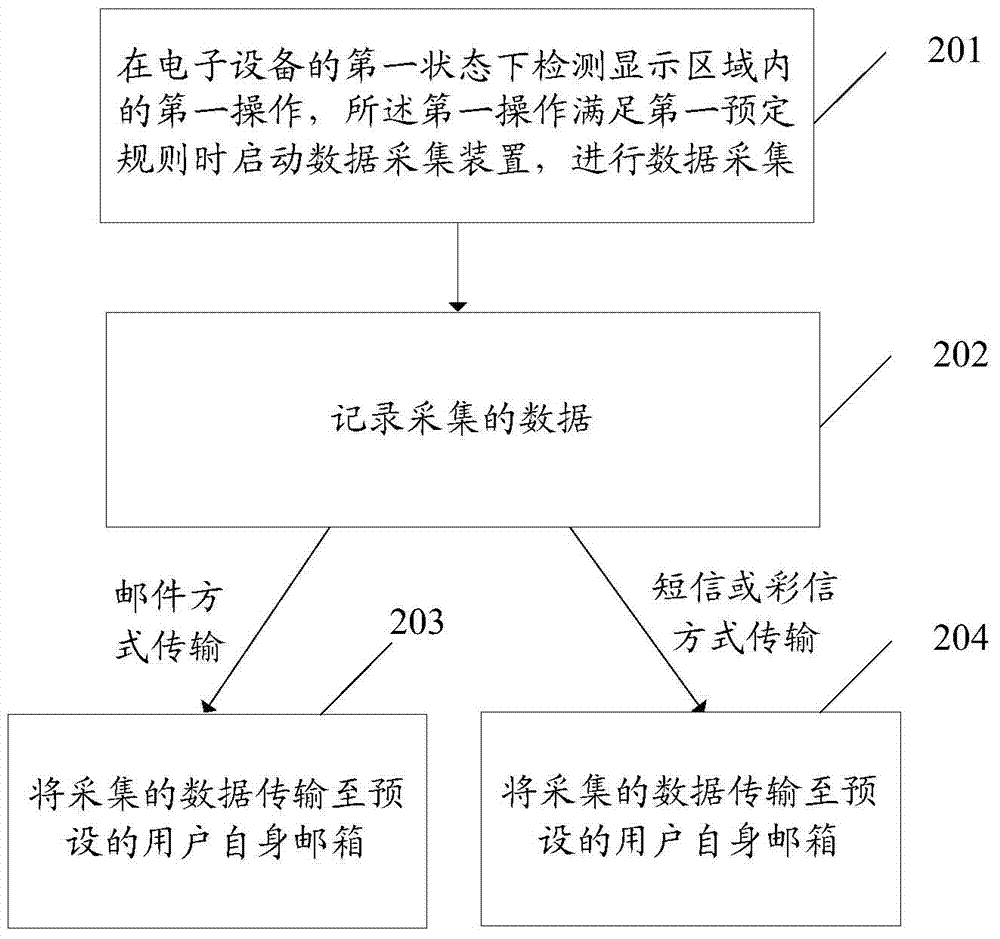
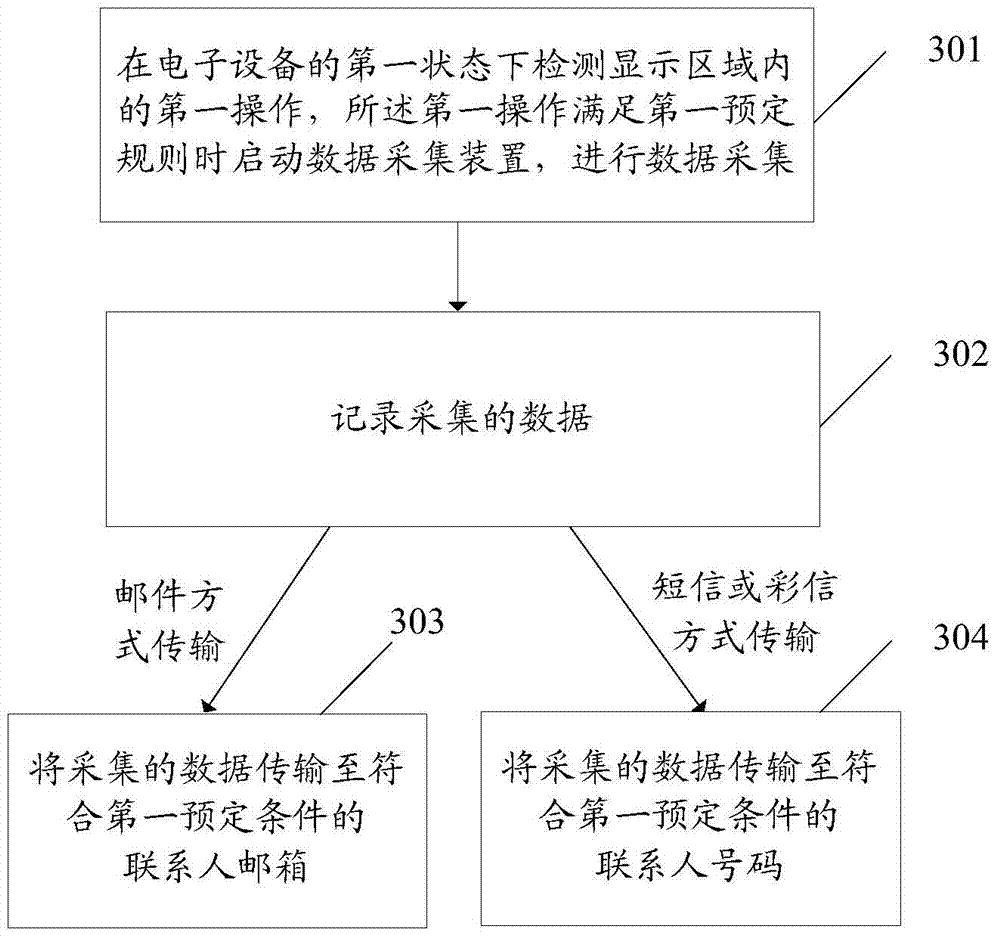
InactiveCN104750635AImprove privacy and security protectionReduce the risk of being crackedElectric digital data processingData acquisitionComputer engineering
The invention discloses a data processing method and an electronic device. The electronic device comprises a display unit which is provided with a display area. The data processing method includes: detecting a first operation in the display area under the first state of the electronic device, starting a data acquisition unit when the first operation meets a first preset rule, and performing data acquisition; recording the acquired data and transmitting the acquired data according to a second preset rule.
Owner:LENOVO (BEIJING) CO LTD
Improved AKA identity authentication system and method based on symmetric key pool and cross-relay
ActiveCN108768661AImprove securityIncrease the difficultyKey distribution for secure communicationUser identity/authority verificationAuthentication systemKey generation
The invention discloses an improved AKA identity authentication system and method based on a symmetric key pool and a cross-relay. The AKA identity authentication system comprises a member, a relay and a server which participate in AKA identity authentication. The system is characterized in that the member, the relay and the server share a group key pool; the member and the relay are further respectively provided with a private key pool used for generating an authentication key, and the member and the relay independently share the private key pool with the server; the member and the relay share a corresponding pointer address in an AKA identity authentication process, and then a first negotiation key between the member and the relay is generated by combining the respective group key poolsof the member and the relay; the member and the server share the corresponding pointer address in the AKA identity authentication process, and then a second negotiation key between the member and theserver is generated by combining the respective authentication keys of the member and the server. According to the system and the method, the safety of communication can be further improved.
Owner:RUBAN QUANTUM TECH CO LTD
Anti-quantum computing RFID authentication method and system based on asymmetric key pool and IBS
ActiveCN110768782AEnsure safetySmall amount of calculationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesRfid authenticationInternet privacy
The invention relates to an anti-quantum computing RFID authentication method based on an asymmetric key pool and an IBS. The participants comprise an authentication party and a request party which interact in an RFID mode. Each participant is configured with a key fob; an authentication party public key, a pointer address, an IBS signature public and private key pair, an IBS signature random number, an IBS signature parameter and an identity parameter issued by the authentication party are stored in a key card of the request party, and the identity parameter comprises an identity number of the request party, the request party public and private key pair and an offset public key. By adopting the method, the storage cost in the key fob of the requester can be reduced, and the security in the authentication interaction process of the requester and the requester can be improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
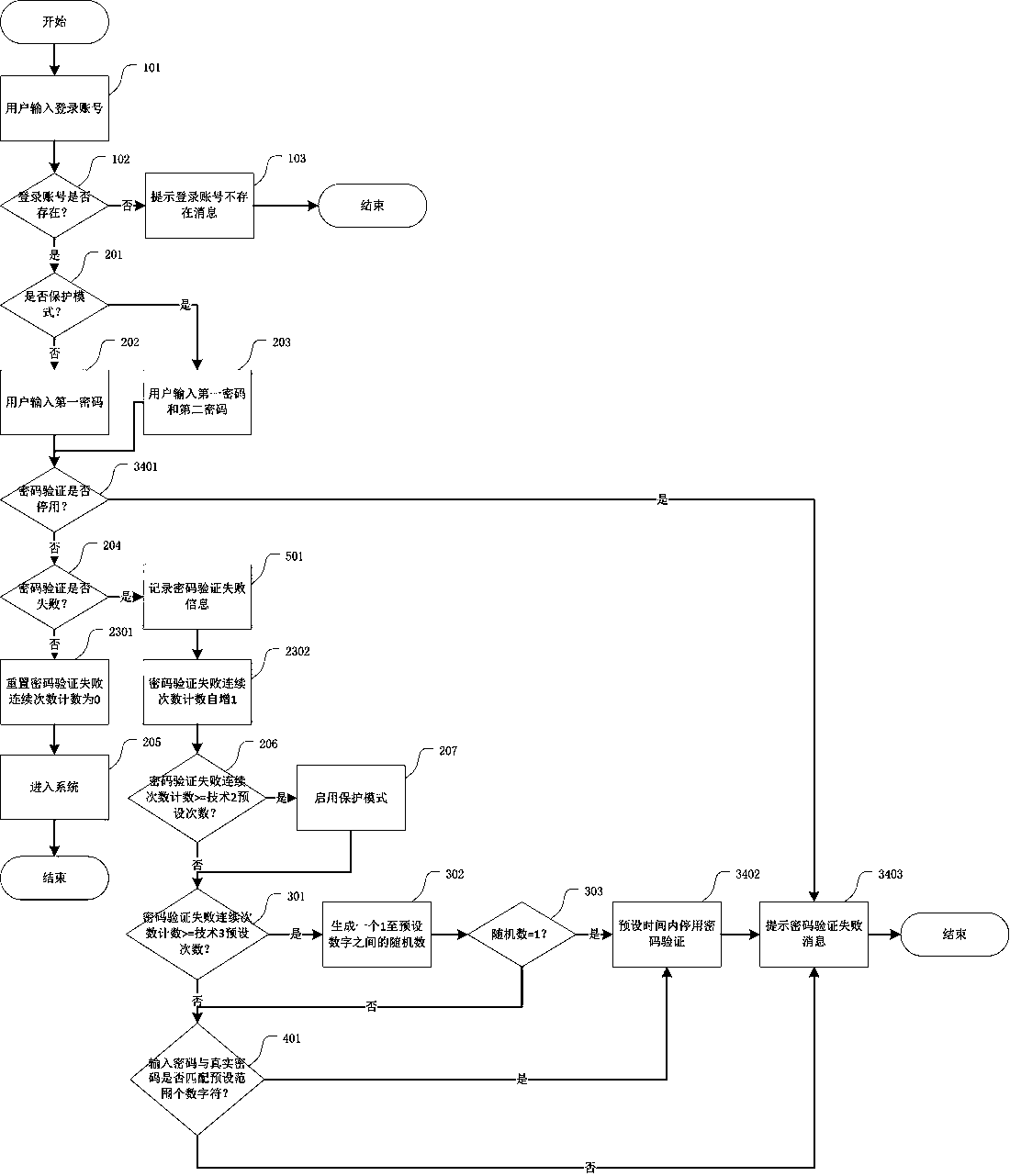
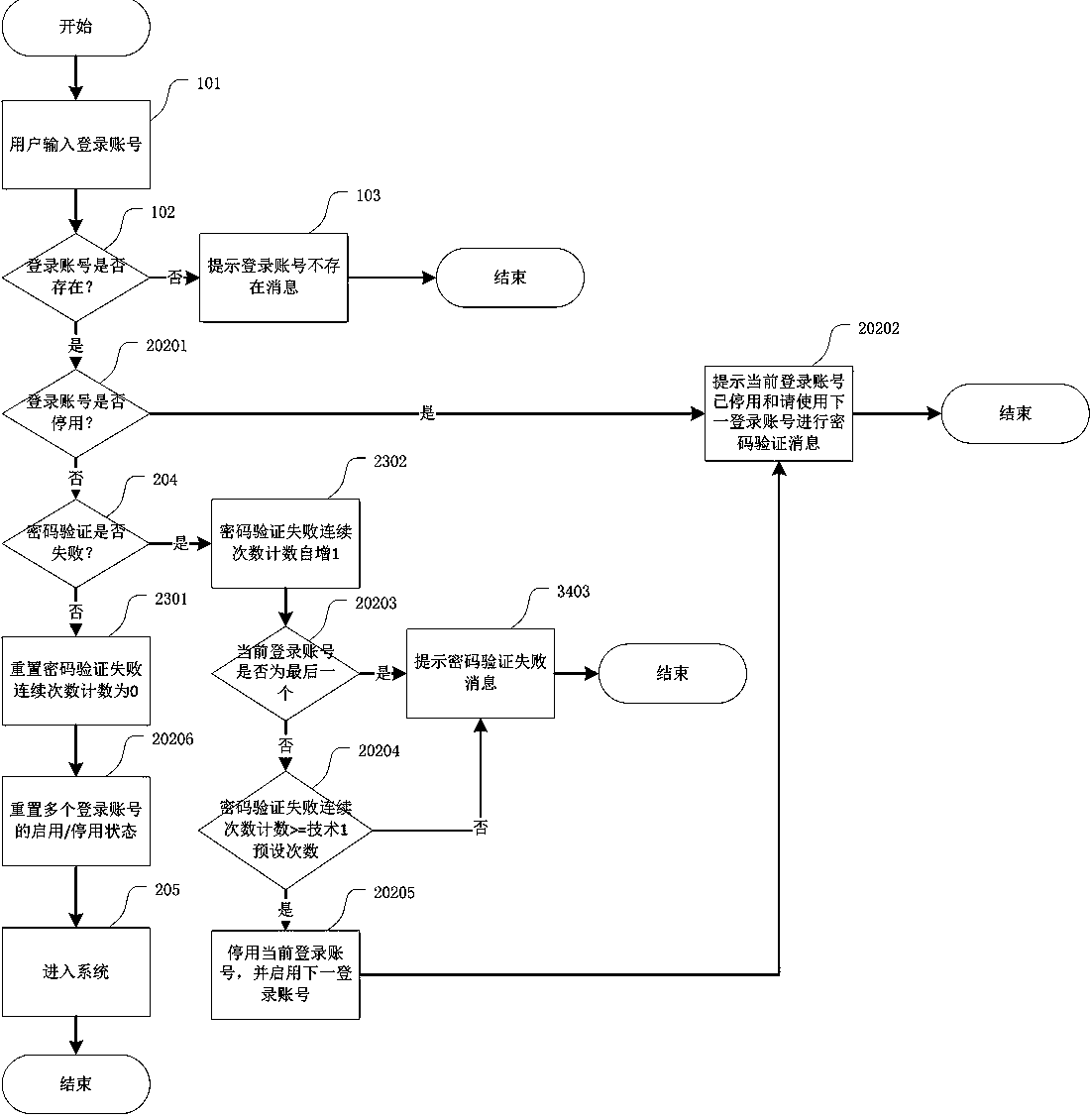
Password authentication method and system
InactiveCN108429758AImprove securityReduce the risk of being crackedTransmissionAuthentication systemTime based
The invention provides a password authentication method and system, and particularly relates to a password authentication method and system capable of realizing any one of or a technology of multipleof ''allowing alteration of a login account, simultaneously submitting multiple passwords for authentication, authenticating a password which is not used within a period of time based on a certain probability, authenticating a password which is not used within a period of time when characters in an input password are matched with characters in a real password within an appointed range and recording and counting password authentication failure information''. The password authentication method and the password authentication system effectively prevent such a situation that an illegal user cracksan account password, so that the account security is improved, and the user experience cannot be reduced.
Owner:易胜燕
Method and device for controlling encryption lock
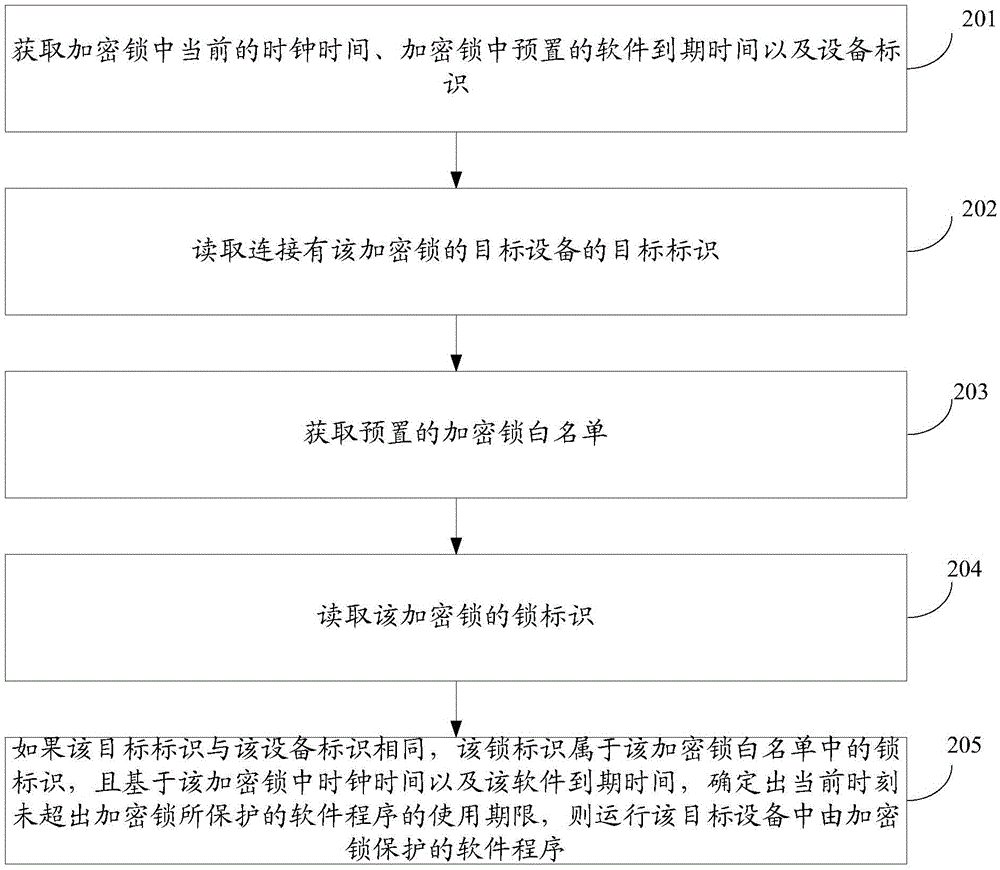
InactiveCN105468937AReduce the risk of being crackedImprove securityProgram/content distribution protectionExpiration TimeSoftware
Embodiments of the invention provide a method and a device for controlling an encryption lock. The method comprises the following steps of obtaining current clock time in the encryption lock, preset software expiration time in the encryption lock and a device identifier, wherein the device identifier is preset in the encryption lock and is an identifier of a device associated with the encryption lock; reading a target identifier of a target device connected to the encryption lock; and running a software program protected by the encryption lock if determining that the target identifier is the same as the device identifier and the current moment does not exceed the service life of software protected by the encryption lock based on the clock time in the encryption clock and the software expiration time. According to the method and the device, the risk of cracking of the encryption lock can be reduced and a condition that software resources protected by the encryption lock are stolen is reduced.
Owner:BEIJING FOREVER TECH
Expansion card, encryption card, mobile terminal, communication data receiving and transmitting method and equipment
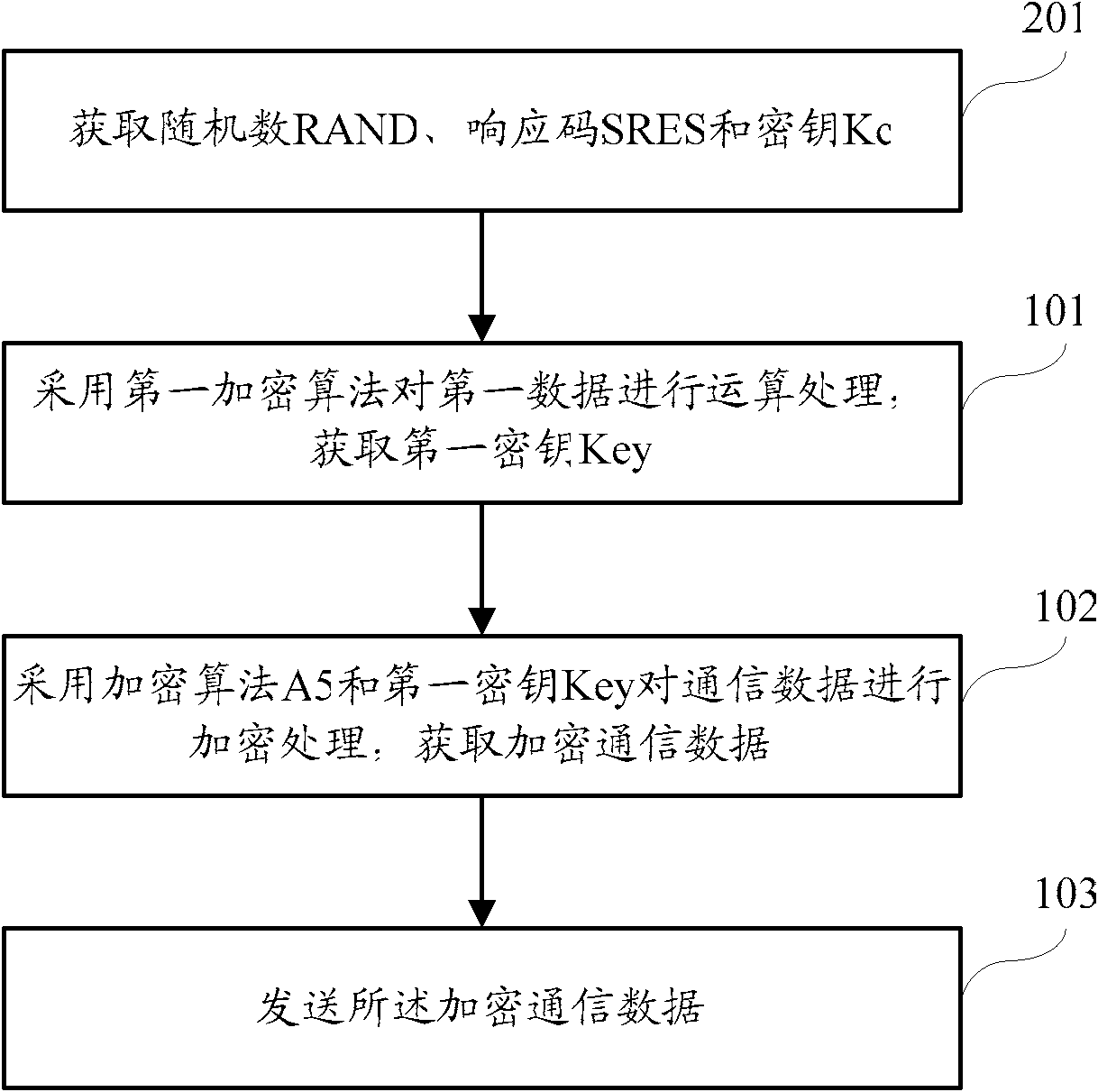
InactiveCN102158861AReduce the risk of being crackedAvoid Complex RetrofitsSecurity arrangementExpansion cardElectricity
The invention discloses an expansion card, an encryption card, a mobile terminal, communication data receiving and transmitting method and equipment. The expansion card is used for being electrically connected with a receiving and transmitting unit of the mobile terminal and an SIM card respectively. First encryption algorithm is adopted to perform algorithm processing on first data to obtain a first cryptographic key; the first cryptographic key is transmitted to the receiving and transmitting unit; and the first data comprises at least one of a cryptographic key Kc obtained from the SIM card and a response code SRES and a random number RAND obtained from the receiving and transmitting unit. The mobile terminal comprises the receiving and transmitting unit, the SIM card and the expansion card, wherein the expansion card is electrically connected with the receiving and transmitting unit and the SIM card respectively. The invention is beneficial to improving the transmission security of communication data between the mobile terminal and a base station.
Owner:北京钱袋宝支付技术有限公司
Authorization management method and system
ActiveCN108848064BReduce the risk of being crackedAvoid the disadvantages of increased management costsKey distribution for secure communicationCiphertextSoftware engineering
Owner:WUHAN JIULE TECH
Class AKA identity authentication system and method based on symmetric secret key pool and cross relay
ActiveCN108965243AEnsure safetyImprove securityKey distribution for secure communicationUser identity/authority verificationAuthentication systemKey generation
The invention discloses a class AKA identity authentication system and method based on a symmetric secret key pool and a cross relay. An AKA identity authentication system comprises a member participating in AKA identity authentication, a relay and a server. The system is characterized in that the member, the relay and the server share a group secret key pool; the member and the relay have privatesecret key pools used for generating authentication secret keys, and the member and the relay independently share the private secret key pools with the server; the member and the relay share a corresponding pointer address in an AKA identity authentication process, and then combine the respective group secret key pool to generate a first negotiation secret key between the member and the relay; and the member and the server also share the corresponding pointer address in the AKA identity authentication process, and combine the respective authentication secret key to generate a second negotiation secret key between the member and the server. The system and the method can be used to further increase the safety of communication.
Owner:RUBAN QUANTUM TECH CO LTD
Information security verification method, device and equipment and storage medium
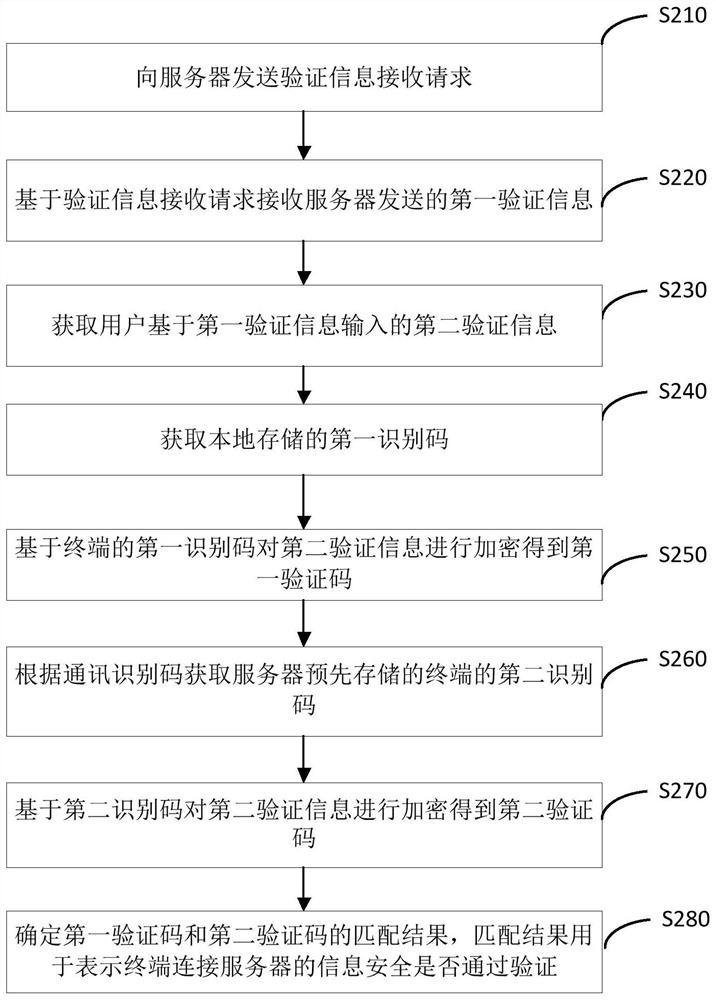
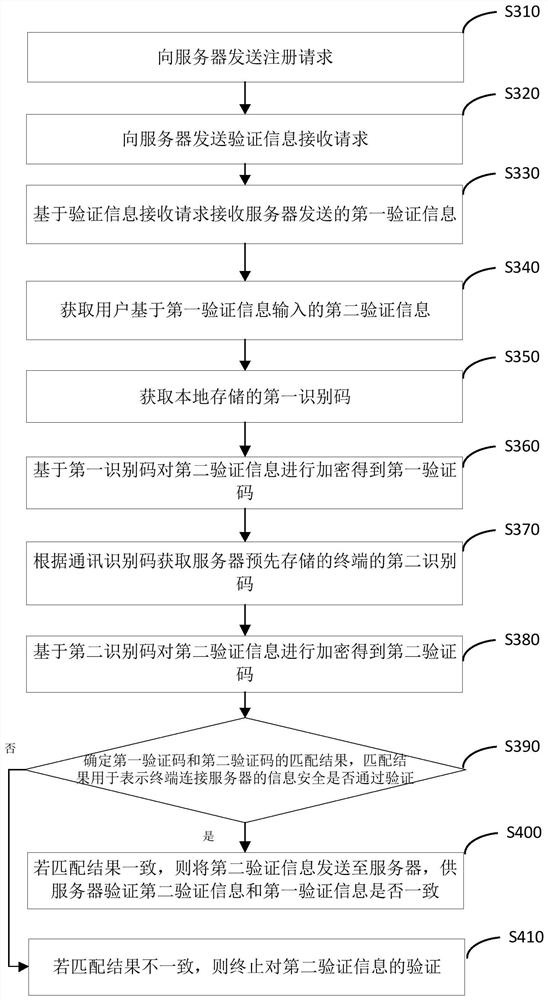
PendingCN111741469AAvoid behaviors that pass validationReduce the risk of being crackedSecurity arrangementComputer hardwareCommunications security
The invention relates to the technical field of communication security, and provides an information security verification method and device, equipment and a storage medium. The method comprises the following steps: sending a verification information receiving request to a server, wherein the verification information receiving request comprises a communication identification code of a terminal; receiving first verification information sent by the server based on the verification information receiving request; obtaining second verification information input by the user based on the first verification information; obtaining a first identification code stored locally; encrypting the second verification information based on the first identification code to obtain a first verification code; acquiring a second identification code pre-stored by the server based on the communication identification code; encrypting the second verification information based on the second identification code to obtain a second verification code; and determining a matching result of the first verification code and the second verification code, wherein the matching result indicates whether the information security of the terminal connected with the server passes the verification. By adopting the method, loss caused by verification information leakage and communication identification code leakage can be avoided, and the risk that the identification code is cracked in the verification process is reduced.
Owner:SHANGHAI WINGTECH ELECTRONICS TECH
Transformation encryption algorithm based on generation of random bit sequence
ActiveCN112887079AImprove confidentialityReduce the risk of crackingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringMultiple encryption
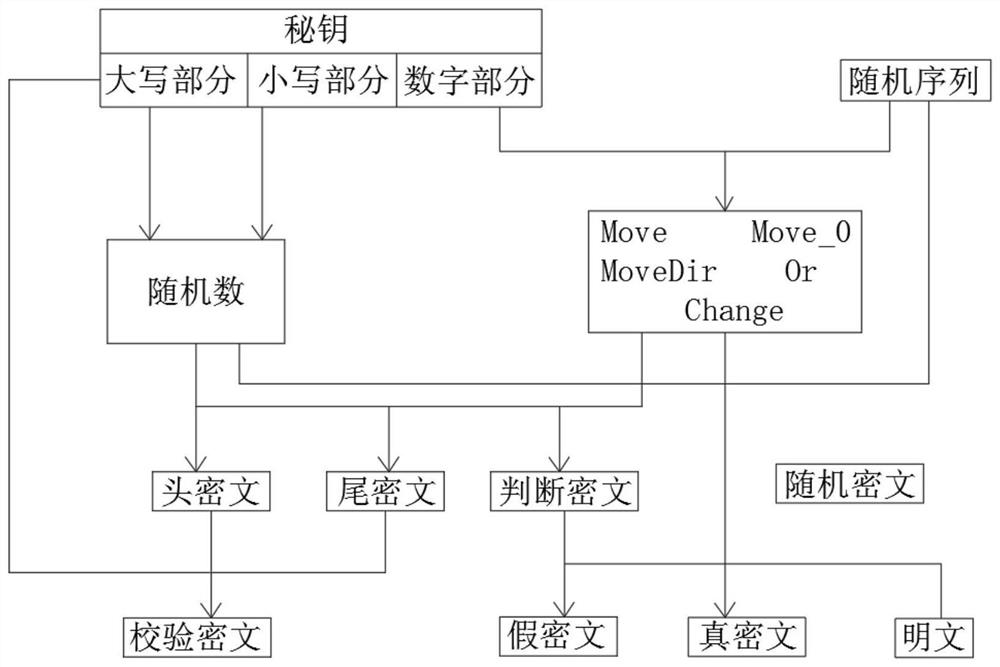
The invention discloses a transformation encryption algorithm generated based on a section of random bit sequence, and relates to the technical field of bit sequence generation, and the transformation encryption algorithm generated based on the section of random bit sequence comprises the following specific steps: 1, generating a random ciphertext; 2, encrypting a random 10-bit bit stream Y by a secret key digital part; 3, generating a header ciphertext; 4, generating a tail ciphertext; 5, generating a check code and a check ciphertext; 6, generating a true ciphertext; 7, generating a false ciphertext; 8, generating a judgment ciphertext; 9, generating a final ciphertext, wherein the random ciphertext in the step 1 is composed of two characters. According to the transformation encryption algorithm generated based on the random bit sequence, multiple encryption can be carried out, the confidentiality of the ciphertext can be improved, the cracking risk can be reduced, the security can be improved on the basis of a traditional method without too much overhead, the use cost can be saved, and popularization is convenient.
Owner:CHINA UNIV OF PETROLEUM (EAST CHINA)
Method and device for signing user program and method and device for verifying signature of user program
ActiveCN102609665BReduce the risk of being brute-forcedPrevent theftDigital data protectionDigital data authenticationCiphertextBrute-force attack
The invention discloses a method and a device for signing a user program verifying signature of the user program. The method for signing the user program includes steps of acquiring ID (identity) of a CPU (central processing unit), computing the user program by SHA-256 hash operation to obtain a program digest, compiling a public key and a module generated through RSA (Ron Rivest,Adi Shamirh and Len Adleman) encryption algorithm into the user program; combining the ID of the CPU, the program digest and the length of the user program in sequence to form a data string; operating the data string by a private key corresponding to the public key and the module to obtain ciphertext; and loading the ciphertext into a check area of the CPU. By combining with the RSA algorithm and the SHA algorithm to process the user program and integrating with the ID of the CPU to be a part of the signature, the user program must be restarted by being strictly subjected to the signature verifying process matched with the signature, risk in brute force attack to the user program is greatly reduced, and the user program can be effectively protected from being tampered or stolen maliciously.
Owner:恒鸿达科技有限公司
Information security protection method, device, electronic equipment and storage medium
PendingCN112597528AIncrease the credit verification processReduce the risk of being crackedDigital data protectionDigital data authenticationResource poolEngineering
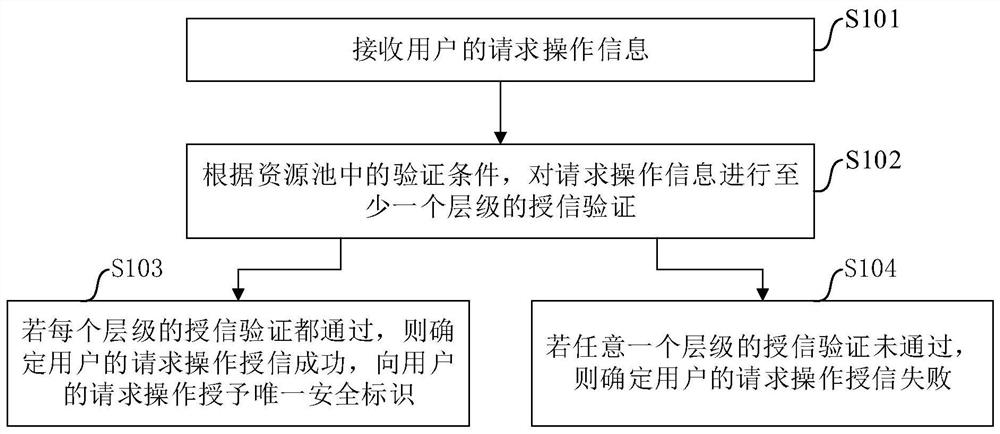
The invention provides an information security protection method, a device, electronic equipment and a storage medium. The information security protection method comprises the steps of receiving the request operation information of a user; according to a verification condition in the resource pool, performing credit granting verification of at least one level on the request operation information;if the credit granting verification of each level is passed, determining that the credit granting of the request operation of the user is successful, and granting a unique security identifier to the request operation of the user; if the credit granting verification of any level is not passed, determining that the request operation of the user fails in credit granting; wherein the at least one hierarchy comprises a behavior layer, performing credit granting verification of the at least one hierarchy on the request operation information according to a verification condition in the resource pool,and the method comprises the steps of determining whether an operation behavior in the request operation information is matched with a pre-registered operation type in a database or not; if so, determining that the credit granting verification of the behavior layer is passed; and if not, determining that the credit granting verification of the behavior layer does not pass. The method is helpful for improving the security level of the system.
Owner:BEIJING JINFENG HUINENG TECH CO LTD +2
Symmetrical key pool and relay communication-based quasi authentication and key agreement (AKA) identity authentication system and method
ActiveCN108737091AEnsure safetyImprove securityKey distribution for secure communicationAuthentication systemRepeater
Owner:RUBAN QUANTUM TECH CO LTD
Method and device for generating dynamic verification code pictures and verification method and device
ActiveCN103886243BReduce the risk of being crackedReduce the recognition success rateDigital data authenticationProgramming languageValidation methods
The invention provides a generation method and device of dynamic verification code pictures and a verification method and device of the dynamic verification code pictures in order to reduce the success rate of automatic identification through a machine. The generation method of the dynamic verification code pictures includes the steps that at least two frames of static verification code pictures are acquired, wherein in each frame of static verification code picture, a verification code is displayed after first display content and second display content are played; the static verification code pictures are played, and the dynamic verification code pictures are obtained, wherein in the playing process, first dynamic content is obtained according to the first display content, second dynamic content is obtained according to the second display content, and the first dynamic content and the second dynamic content contain different kinds of dynamic information. Through the method, the success rate of automatic identification through a machine can be lowered, the risk that verification codes are cracked is reduced, and the safety of a network is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com