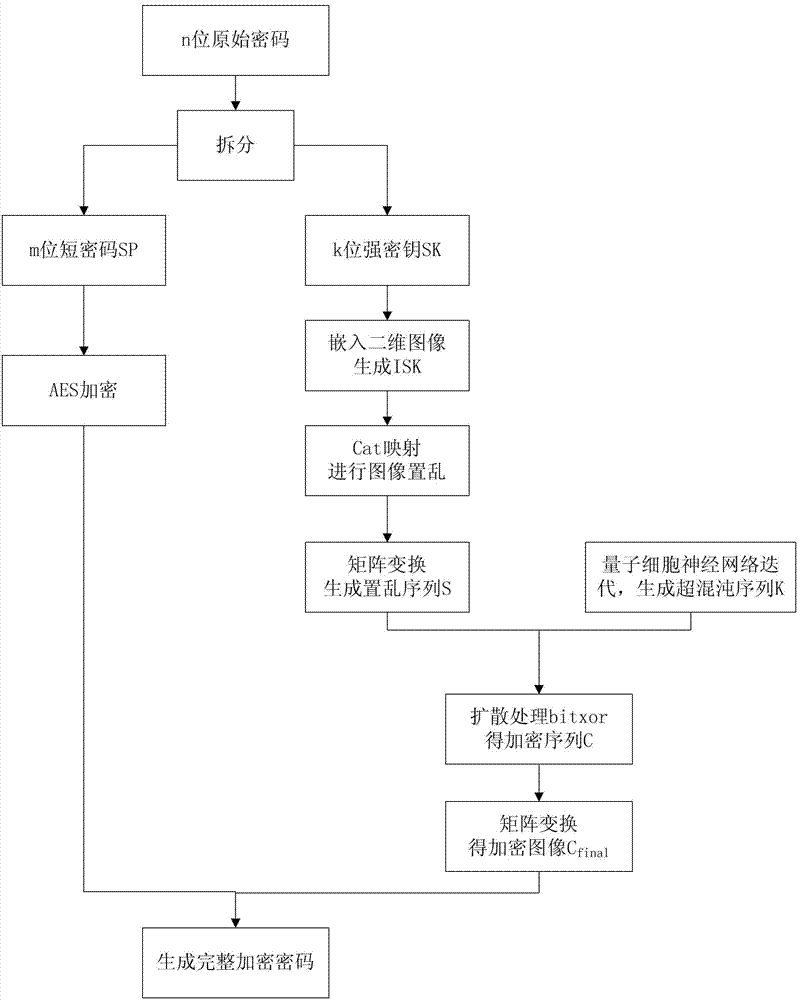
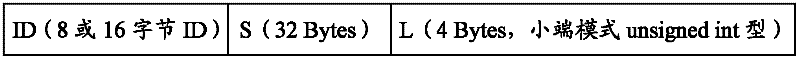Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
150 results about "Brute-force attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In cryptography, a brute-force attack consists of an attacker submitting many passwords or passphrases with the hope of eventually guessing correctly. The attacker systematically checks all possible passwords and passphrases until the correct one is found. Alternatively, the attacker can attempt to guess the key which is typically created from the password using a key derivation function. This is known as an exhaustive key search.
Secure authentication systems and methods
InactiveUS7383570B2Digital data processing detailsUser identity/authority verificationBrute forcePassword
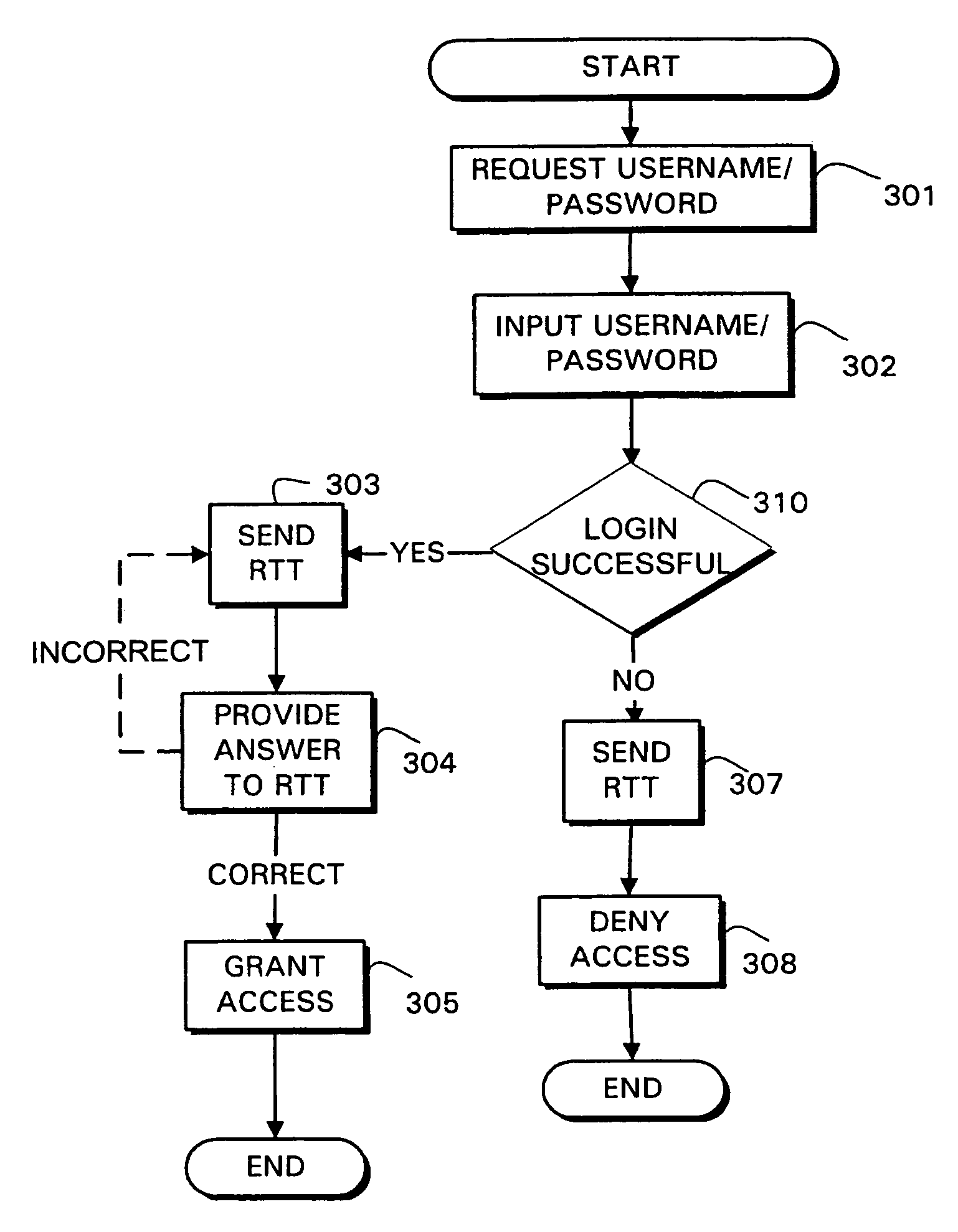
Systems and methods are provided for authentication by combining a Reverse Turing Test (RTT) with password-based user authentication protocols to provide improved resistance to brute force attacks. In accordance with one embodiment of the invention, a method is provided for user authentication, the method including receiving a username / password pair associated with a user; requesting one or more responses to a first Reverse Turing Test (RTT); and granting access to the user if a valid response to the first RTT is received and the username / password pair is valid.
Owner:INTERTRUST TECH CORP
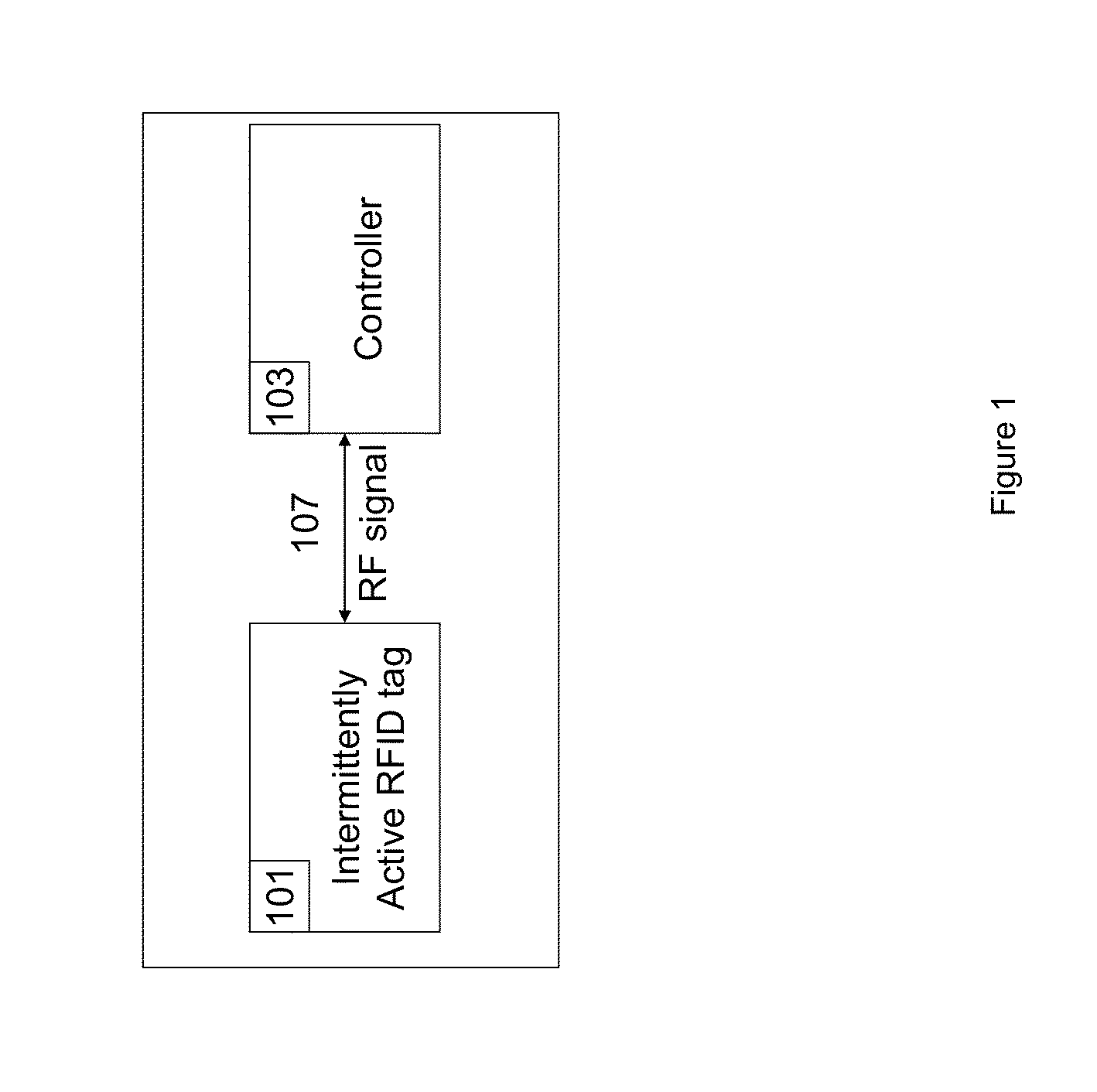
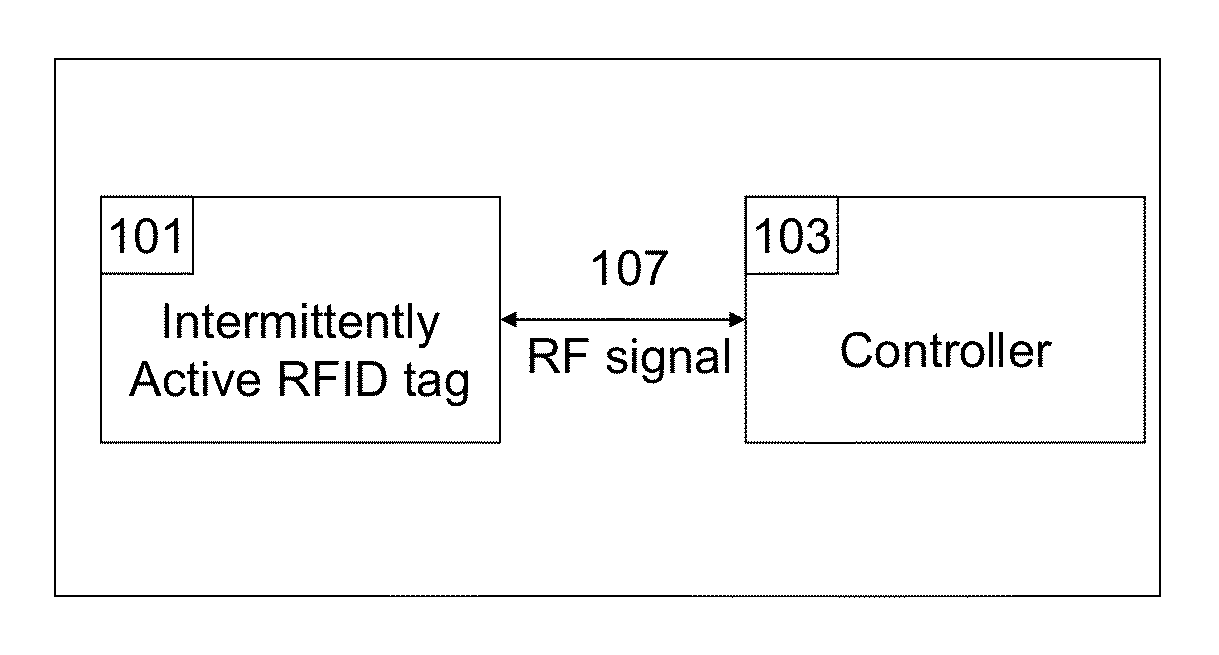
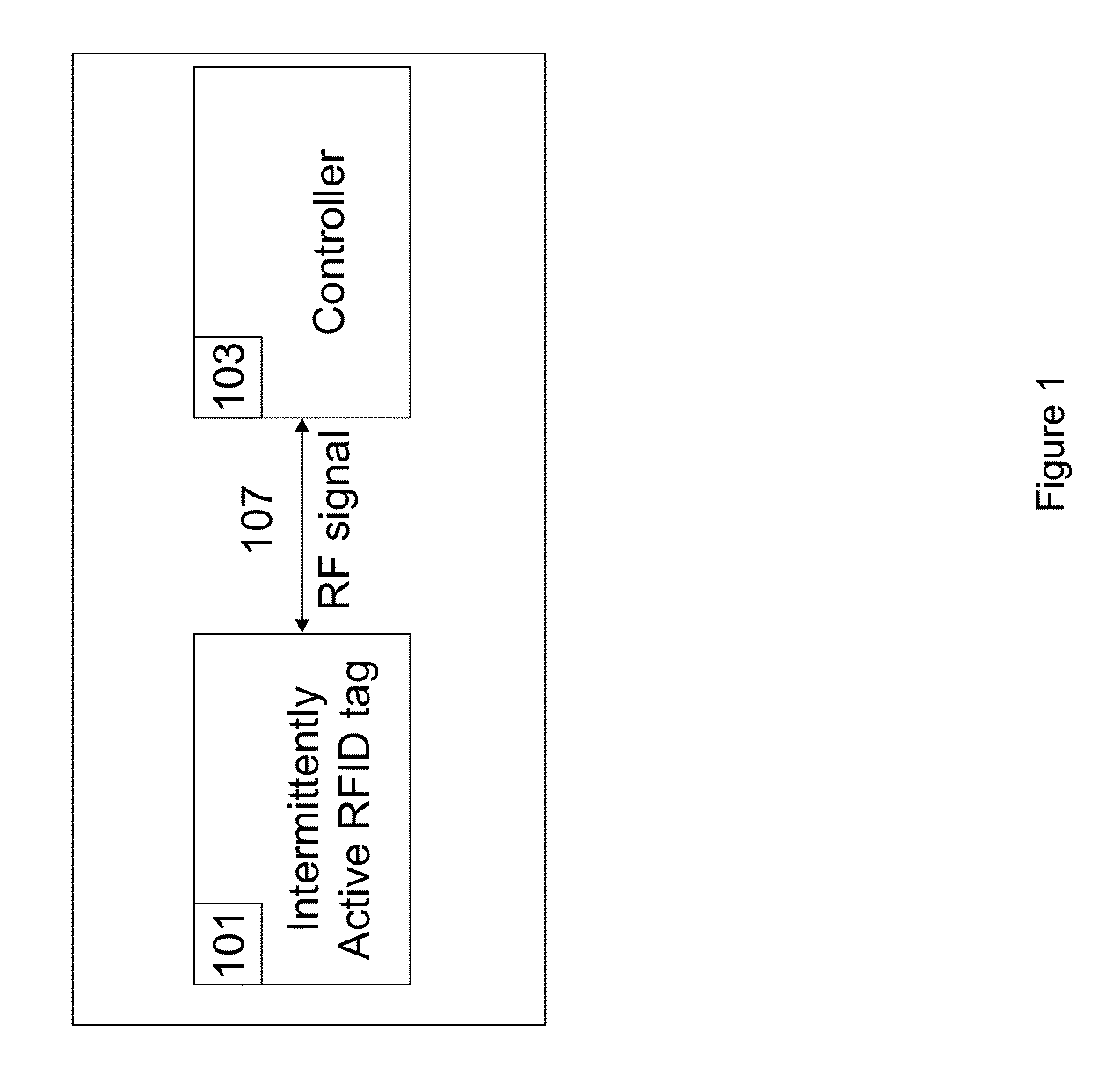
Apparatus and method for locating, tracking, controlling and recognizing tagged objects using active RFID technology
InactiveUS20140240088A1Avoid disturbanceEasy to changeProgramme controlElectric signal transmission systemsThe InternetUSB
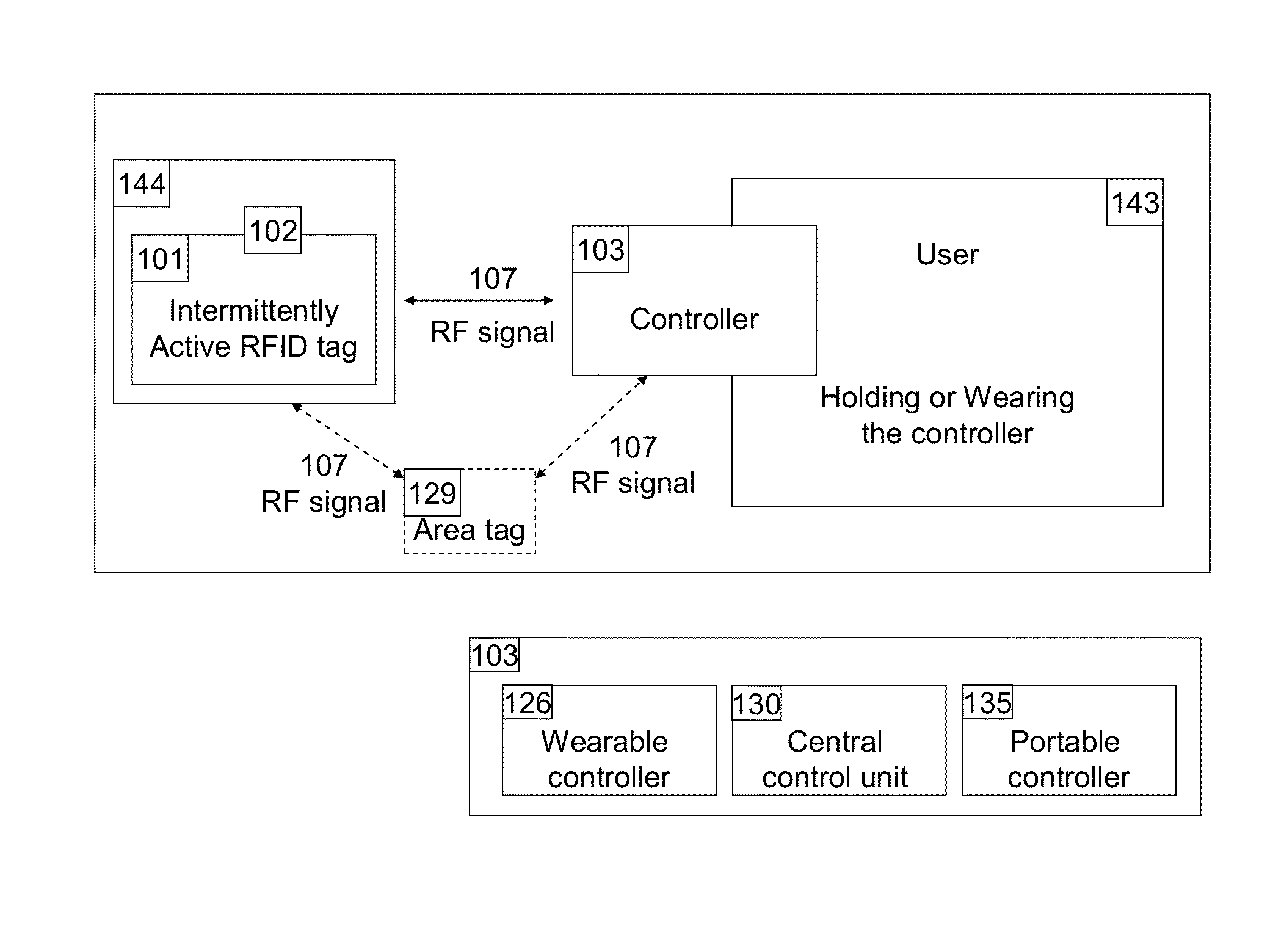
A real-time automated data security system protects both data and devices from loss, theft, and unauthorized access or activity. A miniature active RFID circuit is embodied in tags, area tags, controllers, USB sticks and a universal interface software for computers (i.e., Java), smart phones, and gateway boxes written to interface with the system. These devices are customizable and can link in arrays to cover large areas, use sensors, and scale up in module configurations to meet any need. The system is independent of electricity, GPS, satellites, the Internet, other software, and IT personnel. Its novel software, inside the tags, area tags and controllers is inaccessible and cannot be copied. Wireless transmissions are encrypted to military grade levels and packets are never repeated, making it unhackable, even by brute force attack. A unique battery-conserving protocol ensures good range and long battery life. The system has the ability to ignore copied packages or relaying by attackers, and to prevent of unauthorized access to USB sticks by proximity checks to the active RFID circuit.
Owner:ROBINETTE JAMIE +1
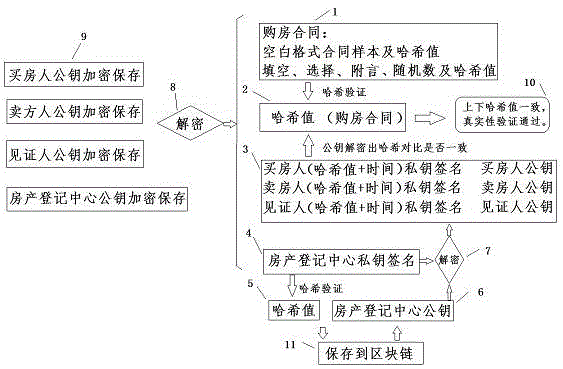
Block chain information archiving and privacy protection method
ActiveCN105610578APrevent tamperingEasy retrievalKey distribution for secure communicationThird partyPrivacy protection
The invention discloses a block chain information archiving and privacy protection method. The block chain information archiving and privacy protection method comprises the steps of adding random number generation Hash values to information needing archiving; then signing by an interest-related person or a eyewitness and generating Hash values; and finally recording at a block chain. Some information needing archiving is formatting and separable formatting information and self-filling information respectively stored and subjected to Hash verification, such as gap-filling information, selection information, postscript information, random number information (for preventing brute force attack). Data which are encrypted by using a public key only can be decrypted by a relevant person who knows the original information by using a private key; a third party verifies true and false of the information; and the encrypted information can be disclosed for a judicial institution if judiciary involvement is needed.
Owner:苏州交链科技有限公司 +1
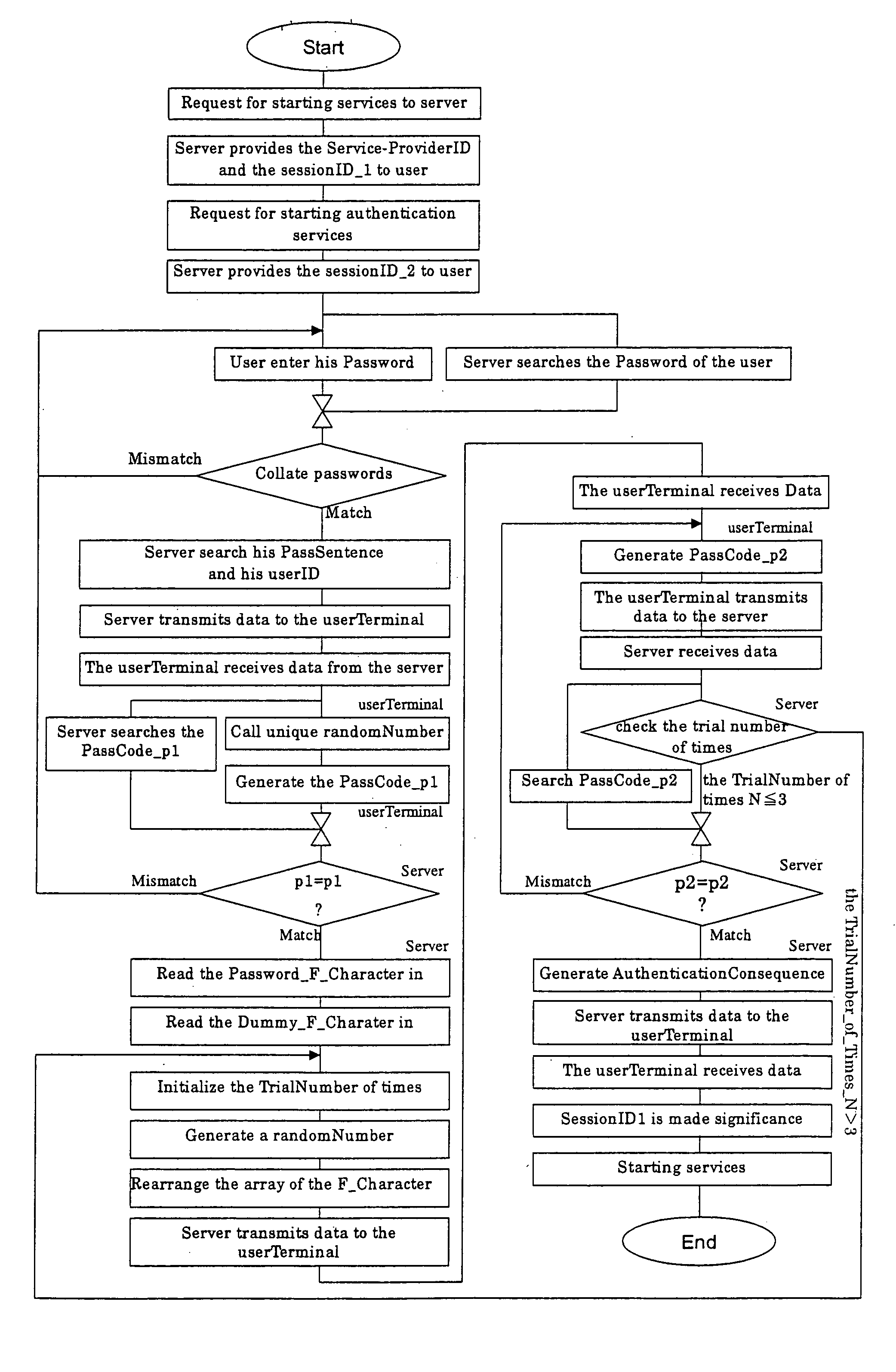
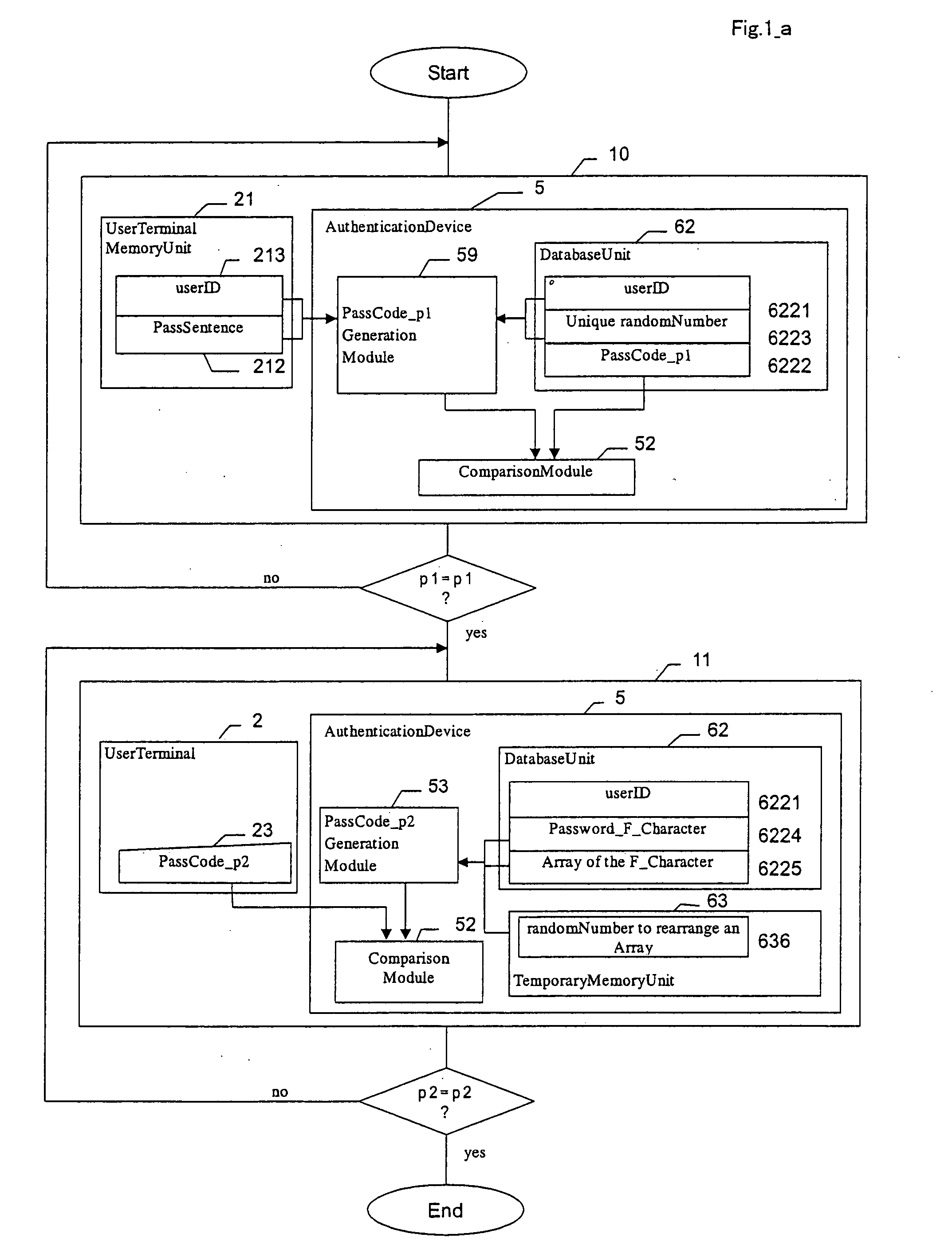
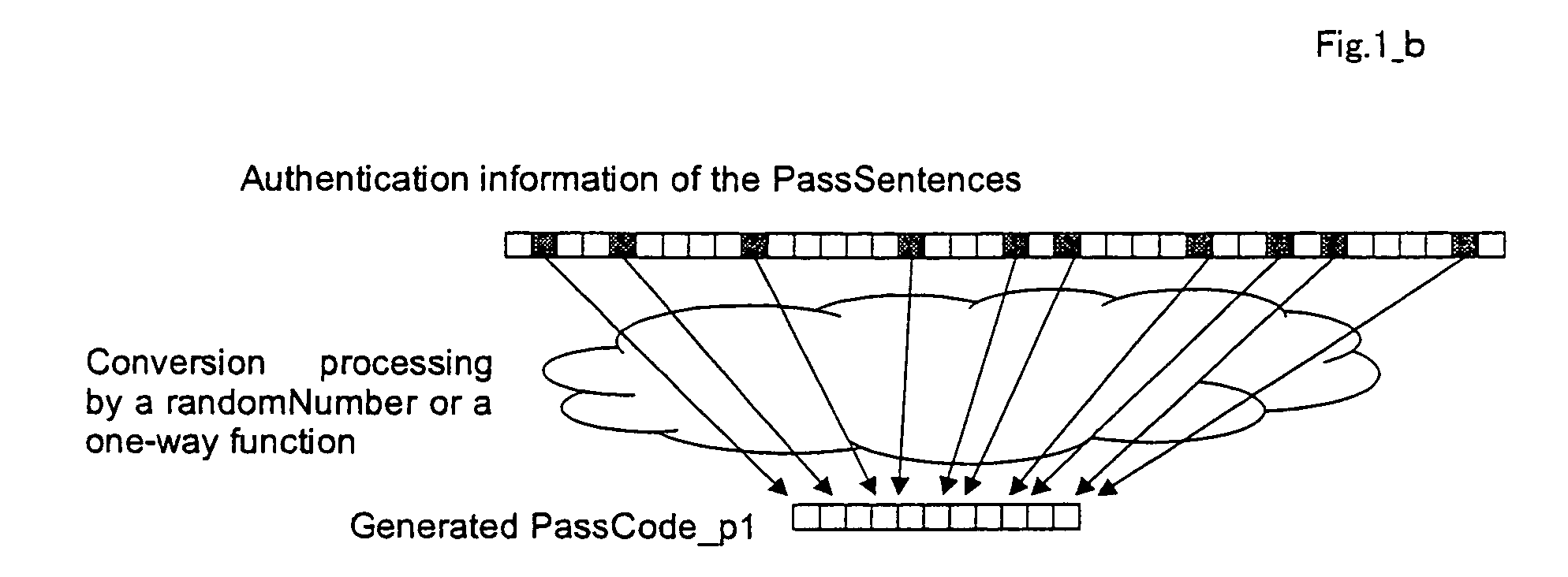
Authenticating method
InactiveUS20050144484A1Inhibition of reproductionDigital data processing detailsUnauthorized memory use protectionUser authenticationBrute-force attack
All conceivable problems associated with user authentication can be coped with at least individually by preventing spoofing as the result of leakage of authentication information through interception of communications, monitoring, stealthy glance, brute-force attack, and beyond the control of the user and outside the system, duplication and forgery of authentication information by carrying out an “authentication method that can cope with every possible problem in relation to authentication, excluding monitoring” and an “authentication method authentication having the possibility of spoofing by the authenticating side though there is no danger of monitoring and he possibility of spoofing as the result of theft of authentication information from the authentication device” in two stages in one user authentication processing, and “preventing spoofing by the authenticating side and as the result of theft of authentication information from the authentication device by establishing a collatable and irreversible relationship between the authentication information issued by the user and the authentication information registered in the authentication device” in the latter authentication method.
Owner:WAKAYAMA HIRONORI
Methods and systems for secure user authentication
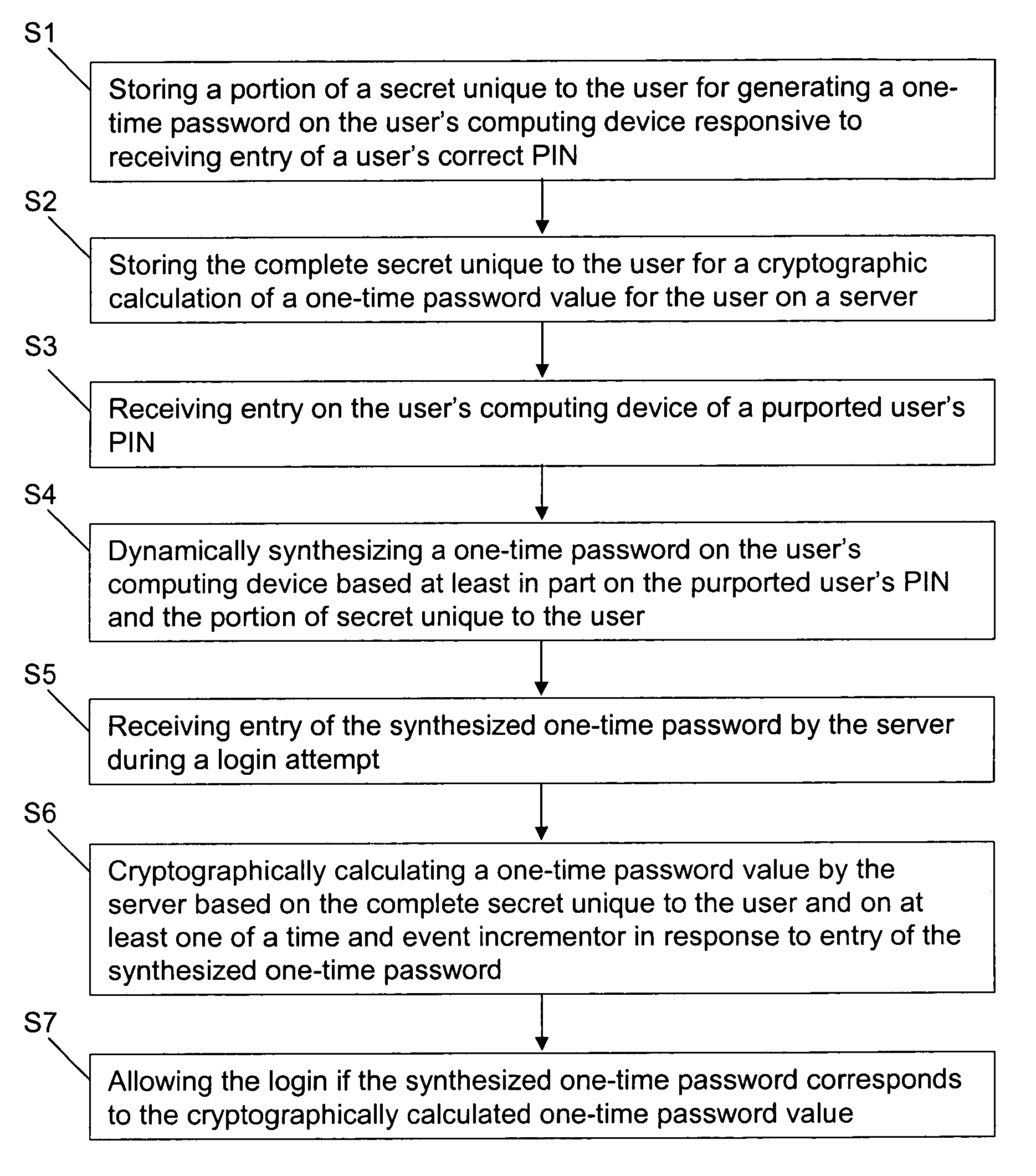
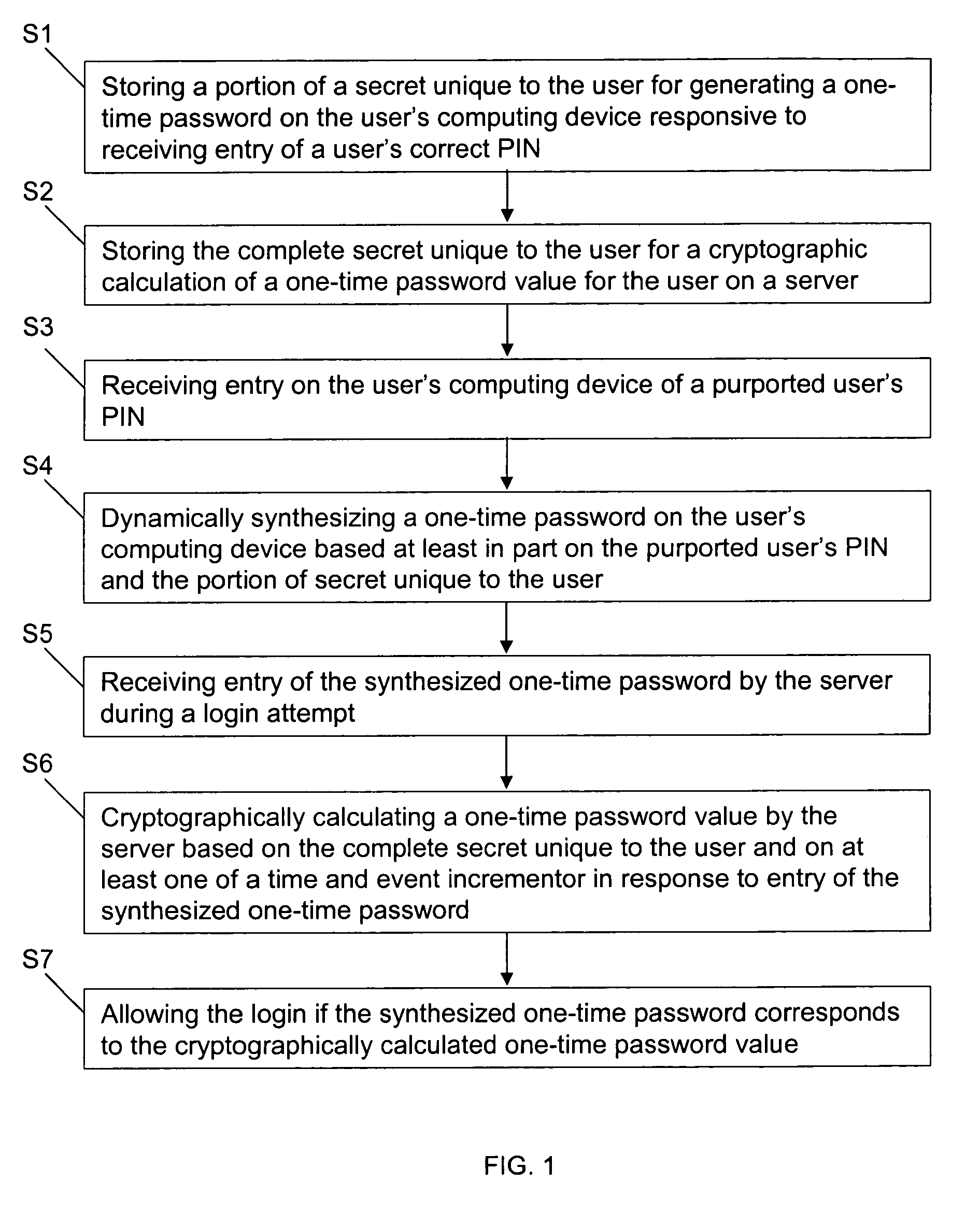
ActiveUS7904946B1Reduce in quantityDefeat threatDigital data processing detailsMultiple digital computer combinationsBrute forceUser authentication
Methods and systems for secure user authentication utilizes OTP generation and validation techniques in which the shared secret for generating the OTP is not stored in the user's mobile device but instead is dynamically synthesized based on a PIN that activates the OTP generation and the personalized OTP data. The client software has no knowledge of what the correct PIN should be and always generates a normal looking OTP based on whatever PIN is entered, and the only way to learn whether or not the OTP is correct is to submit it during user login. By limiting the number of failed login attempts before the account is locked, brute-force attacks via the online channel will fail, and further, brute-force attacks to uncover the correct PIN for generating the correct OTP offline will also fail even if a hacker steals the user's mobile device and extracts the data inside for offline hacking, because there is nothing on the client that contains the PIN or encrypted by the PIN.
Owner:CITICORP CREDIT SERVICES INC (USA)
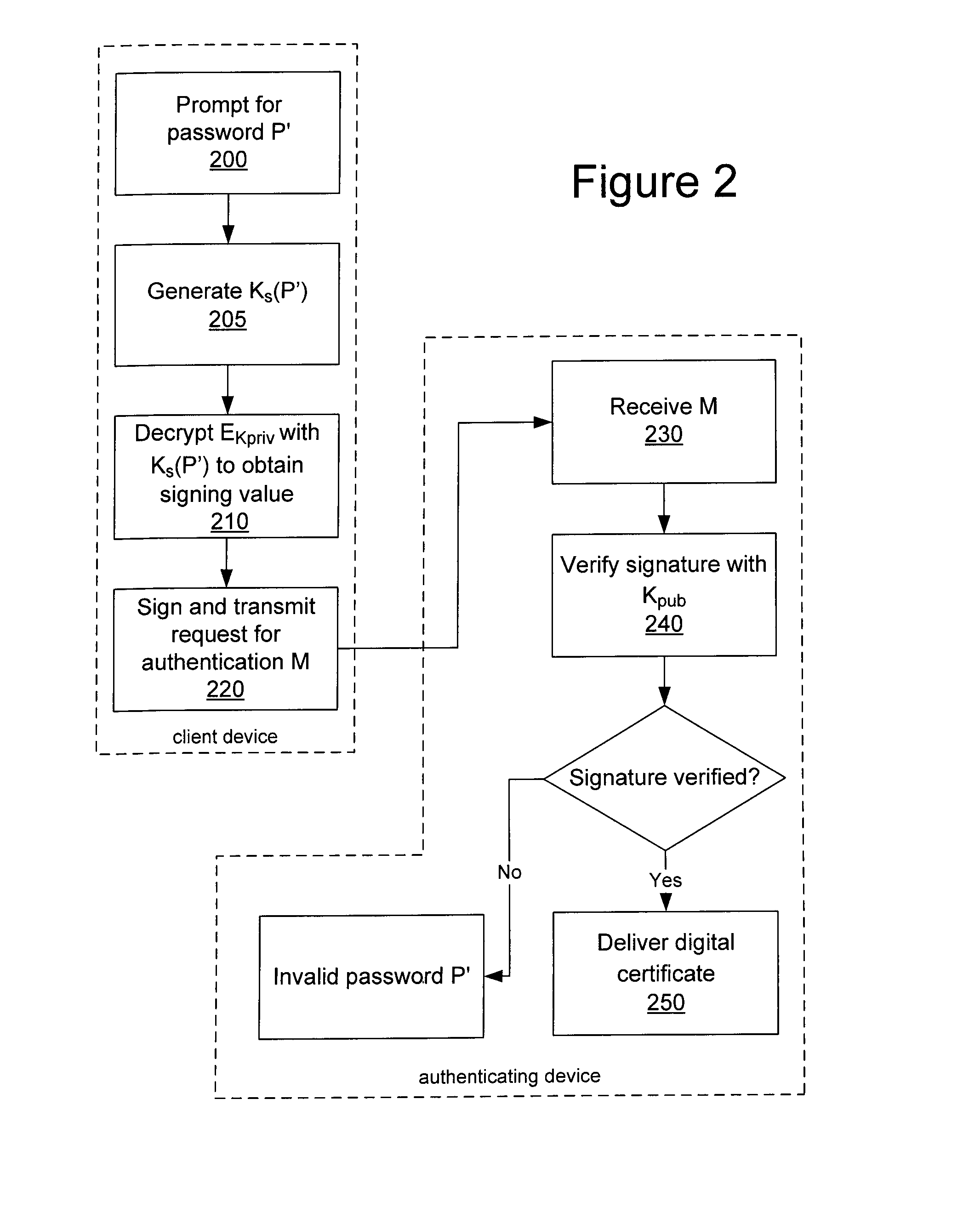
System and method for protecting a password against brute force attacks
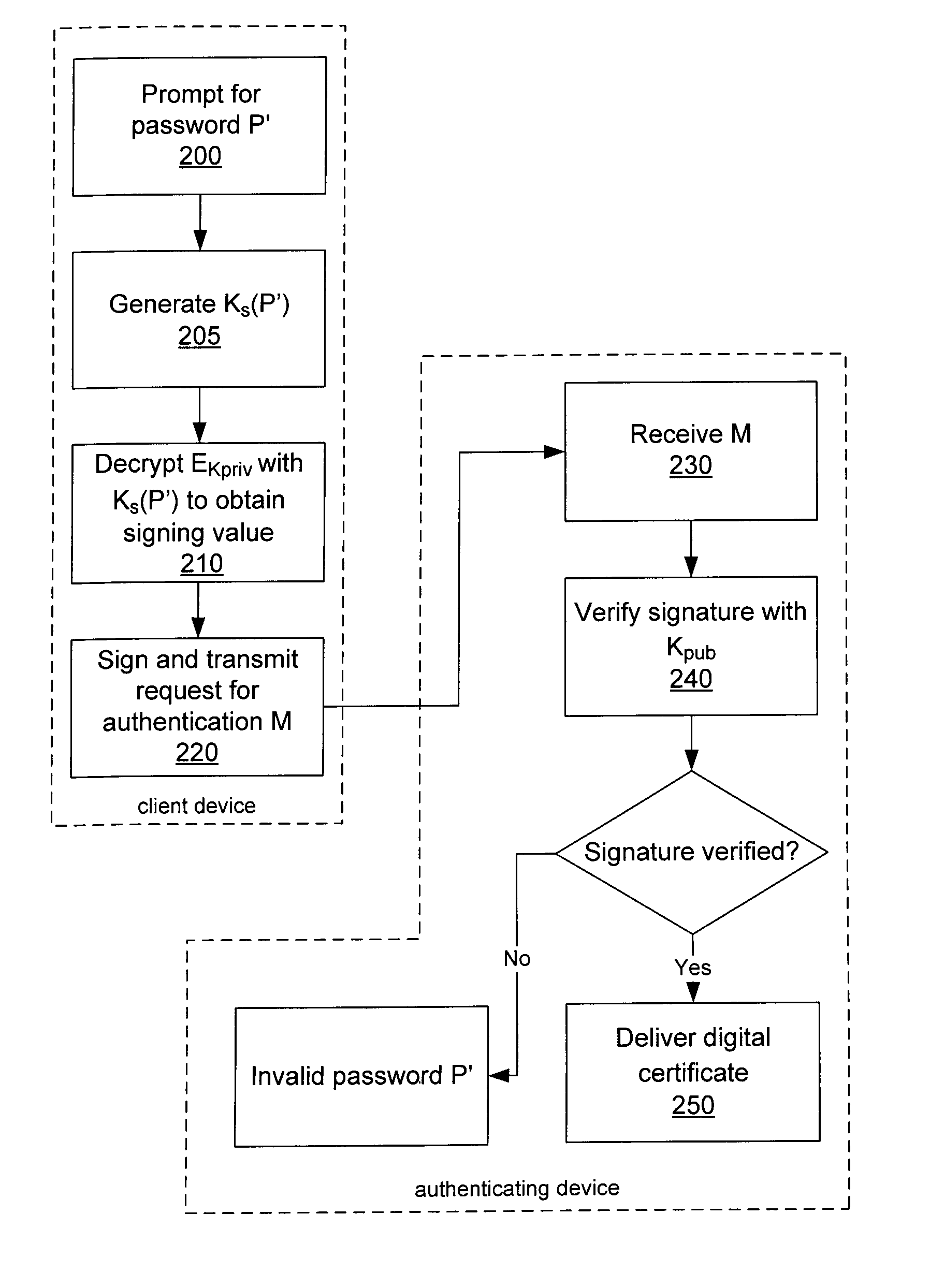
ActiveUS20080120504A1User identity/authority verificationCryptographic attack countermeasuresBrute forcePassword
In a system and method for authenticating a client device by an authentication device, the client device user is assigned a PIN generated by the authentication device. The user provides the PIN and a password to the client device, from which the client device generates a symmetric key and further generates a public / private key pair. The private key is encrypted using the symmetric key and stored in encrypted form only. The public key and a message authentication code generated from the PIN are provided to the authentication device, which stores the public key. Subsequently, when the user seeks to be authenticated, the user enters a password at the client device, which is used to generate a symmetric key to decrypt the encrypted private key. A message to the authentication device is signed using the resultant value. The authentication device uses the public key to verify the signature of the message.
Owner:MALIKIE INNOVATIONS LTD
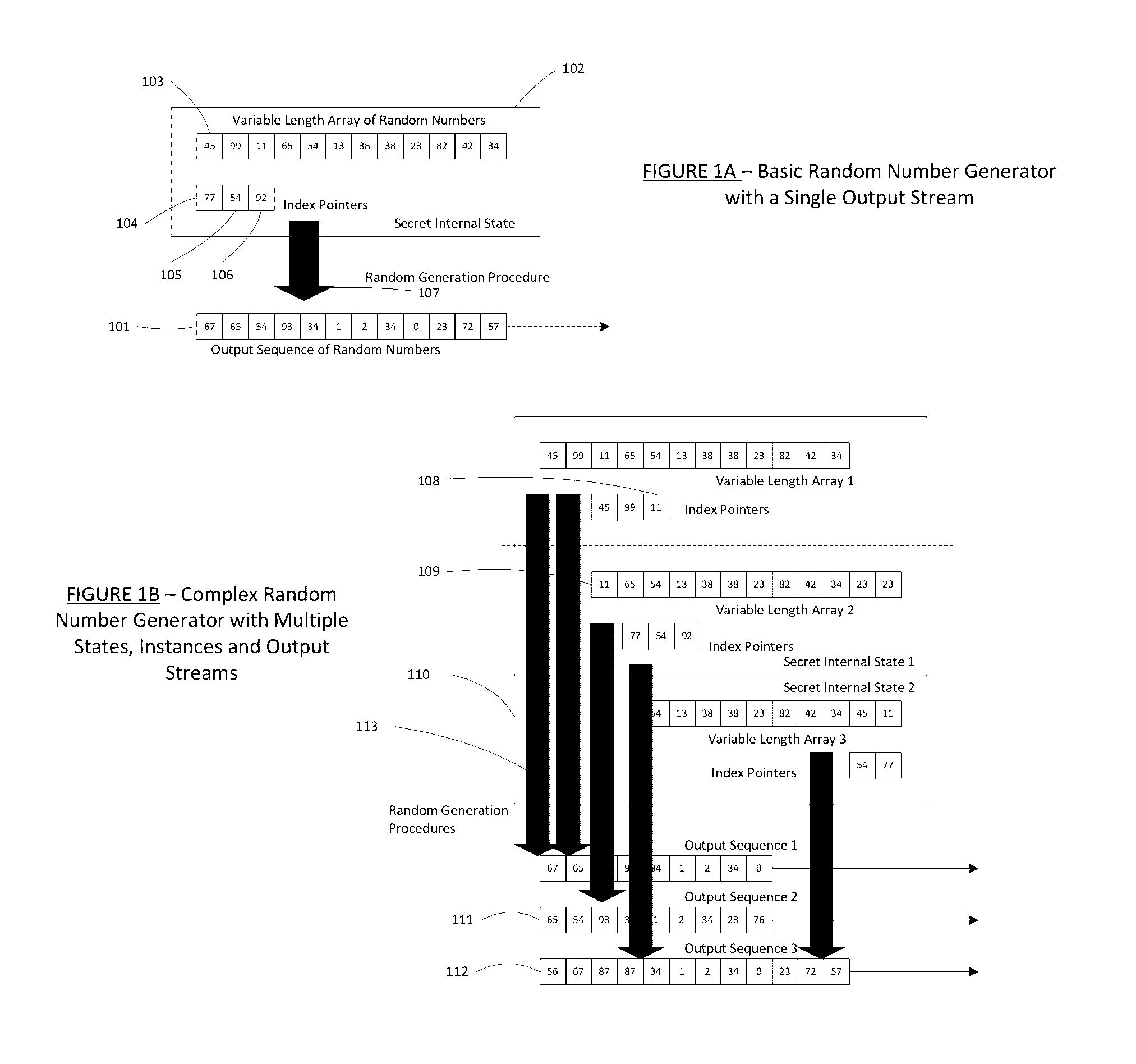
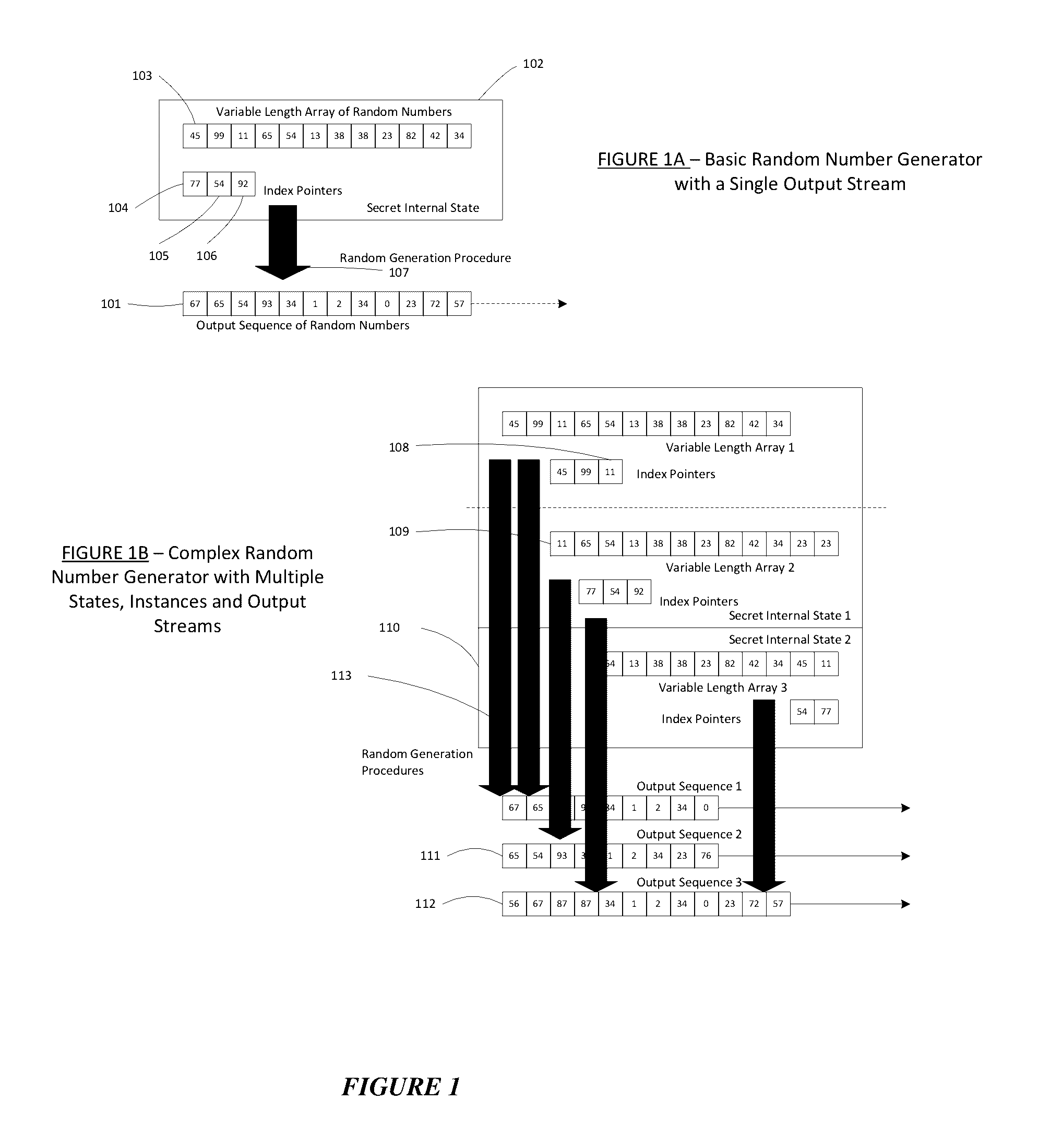
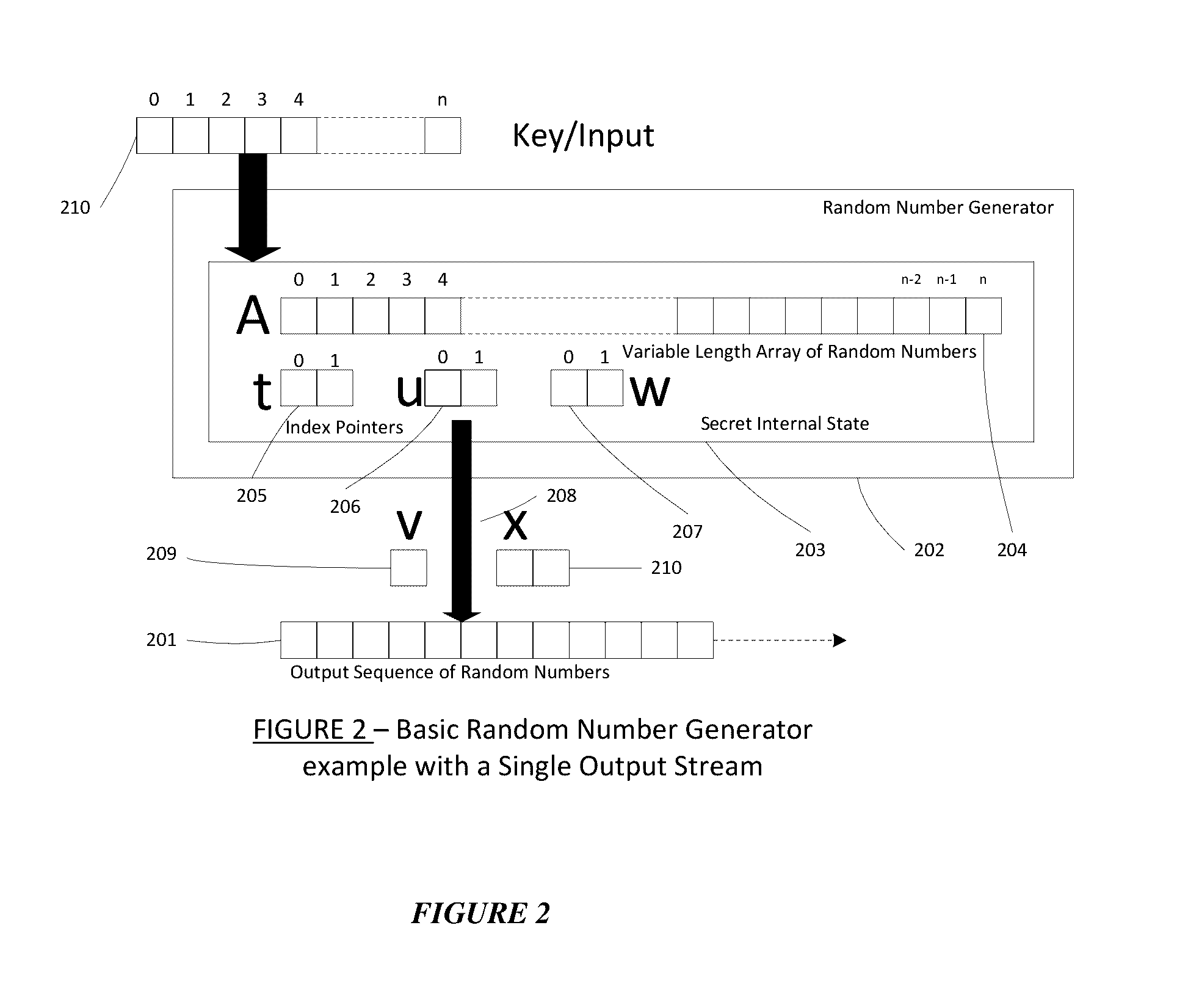
Method for a Dynamic Perpetual Encryption Cryptosystem
A dynamic computer communication security encryption method or system using an initial seed key and multiple random number generators of a specific design, whereby a sequence of independent random entropy values is produced by one set of random number generators and encrypted along with the message stream using the initial seed key, or the output of a second set of random number generators initialized with the initial seed key, and following the subsequent transmission of the variable encrypted entropy / message block, the entropy values are used to symmetrically or identically augment or increase the current uncertainty or entropy of the cryptosystem at both the sender and the receiver, prior to the next encryption block operation. The encryption process effectively entailing the use of multiple encryption ciphers, and the entropy augmentation process entailing the encryption or application of various logical mathematical operations on the already dynamic but deterministic internal state values of the second set of random number generators, effectively altering their deterministic outputs in a random probabilistic manner.Random length message value sequences from one or more data sources is combined with one or more random length entropy value sequences from an independent source, following which the entropy “updates” may also be used to alter, or change any cryptosystem variable, value or component in a randomly determined manner. In addition, whilst ensuring synchronization, the random entropy sequences also serve to “pollute” the cipher-stream and thereby hinder most current forms of cryptanalysis, whilst simultaneously injecting additional entropy into the cryptographic system and allowing for its propagation to affect any connected system nodes, and thereby introducing unpredictable entropy into the system pseudorandom number generator outputs, and thereby ensuring the perpetual generation of unpredictable random numbers.Super-encryption mechanics are independent of the user data, simple, fast and efficient, and can incorporate compression, error correction and asymmetric encryption authentication routines. But most importantly, super-encryption ensures resistance to brute force attacks (not possible to verify if a message was even sent), an ability to exceed “perfect secrecy” requirements, and an improvement on previous super-encipherment design, since overhead can be dramatically reduced from 100% overhead.Communication links previously established by system nodes with central authorities may be used for secure node authentication and registration, whilst allowing the central authority to broker and synchronize communication channels and providing mutual authentication and other security functions between the system nodes.
Owner:FIGUEIRA HELDER SILVESTRE PAIVA
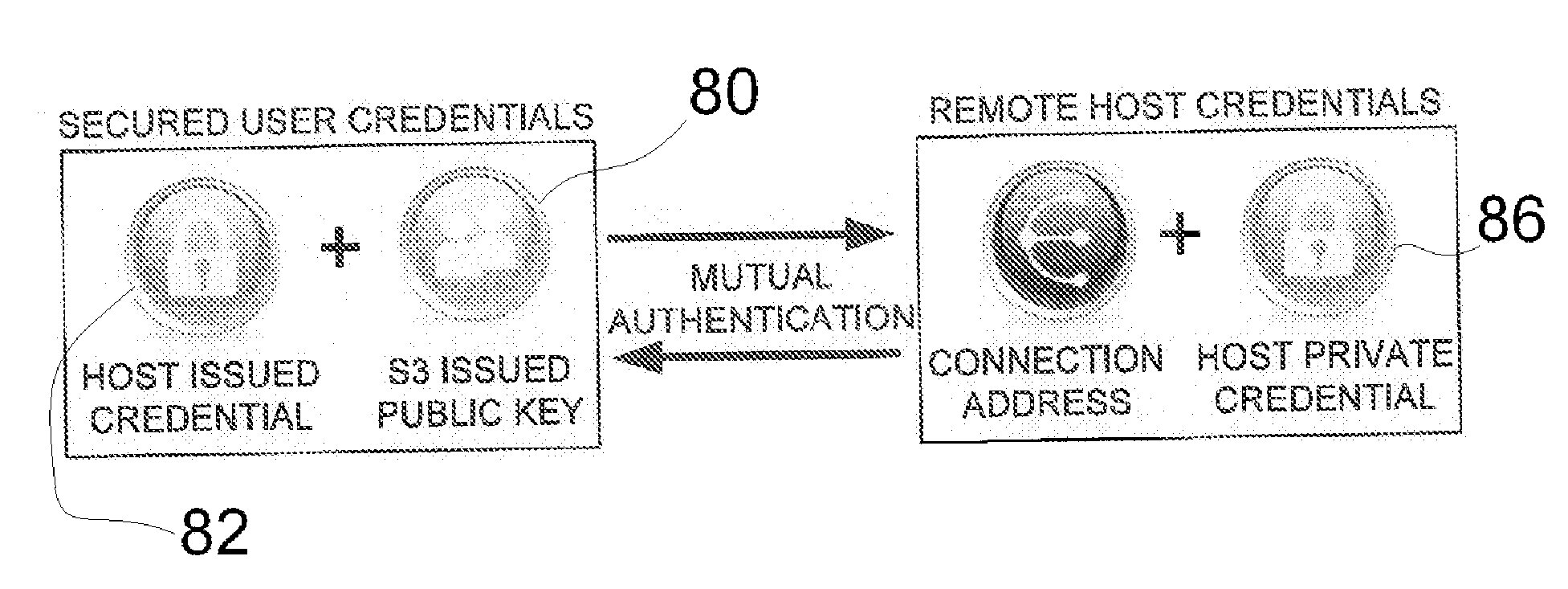
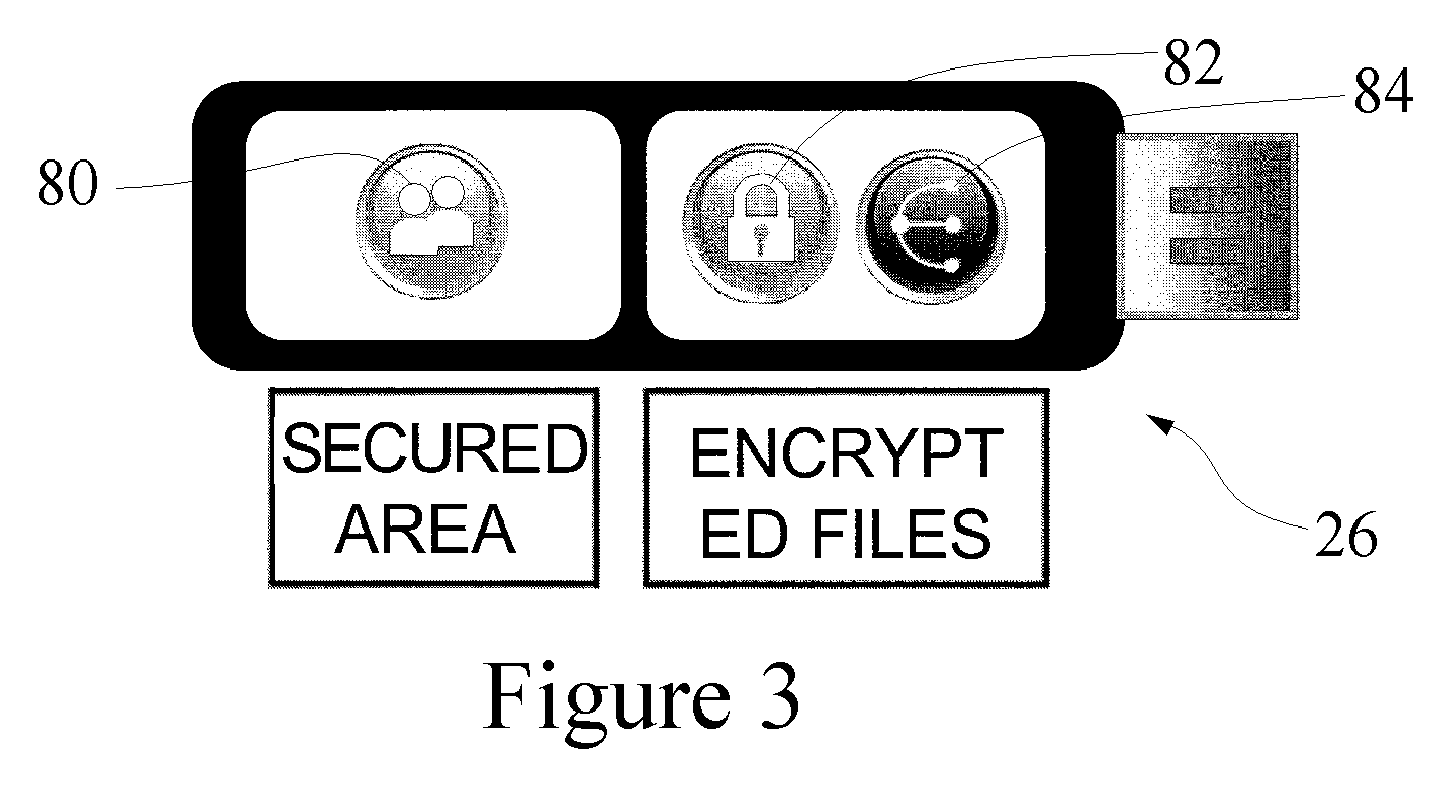
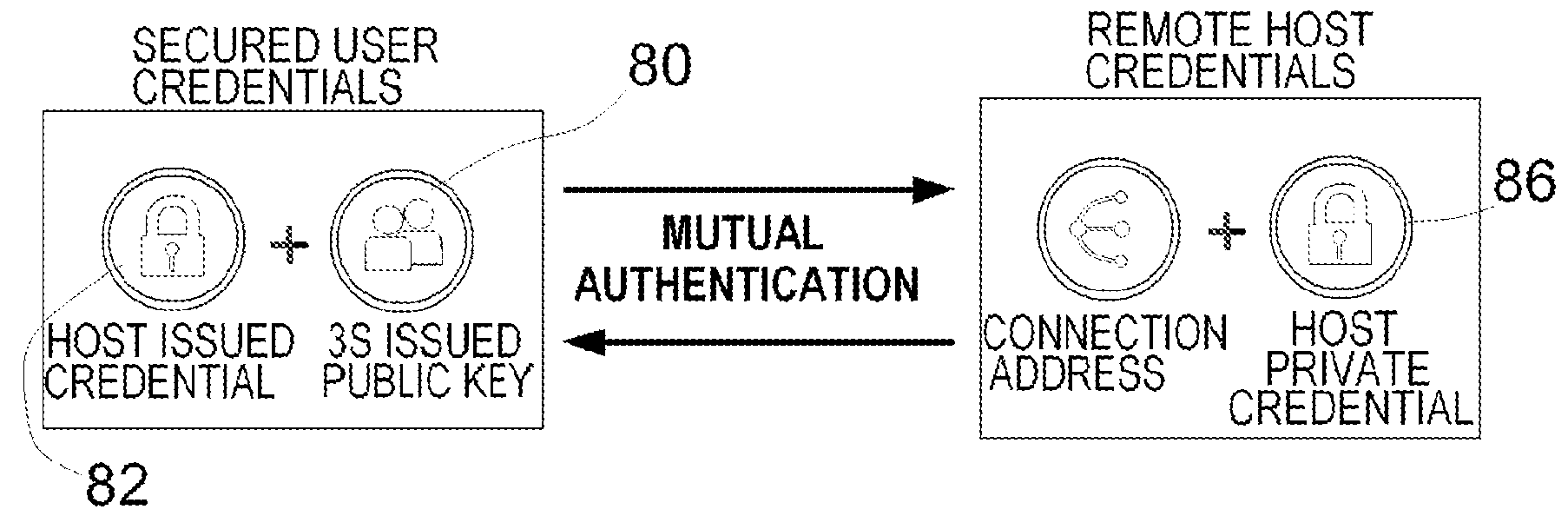
Token based two factor authentication and virtual private networking system for network management and security and online third party multiple network management method
InactiveUS20070186099A1Efficient and effectiveNetwork topologiesDigital data authenticationBrute forcePrivate network
A two-factor network authentication system uses “something you know” in the form of a password / Pin and “something you have” in the form of a key token. The password is encrypted in a secure area of the USB device and is protected from brute force attacks. The key token includes authentication credentials. Users cannot authenticate without the key token. Four distinct authentication elements that the must be present. The first element is a global unique identifier that is unique to each key. The second is a private credential generated from the online service provider that is stored in a secure area of the USB device. The third element is a connection profile that is generated from the online service provider. The fourth element is a credential that is securely stored with the online service provider. The first two elements create a unique user identity. The second two elements create mutual authentication.
Owner:DIRECTPOINTE
Secure Authentication Systems and Methods
InactiveUS20080016551A1Digital data processing detailsUser identity/authority verificationBrute forceInternet privacy
Systems and methods are provided for authentication by combining a Reverse Turing Test (RTT) with password-based user authentication protocols to provide improved resistance to brute force attacks. In accordance with one embodiment of the invention, a method is provided for user authentication, the method including receiving a username / password pair associated with a user; requesting one or more responses to a first Reverse Turing Test (RTT); and granting access to the user if a valid response to the first RTT is received and the username / password pair is valid.
Owner:INTERTRUST TECH CORP
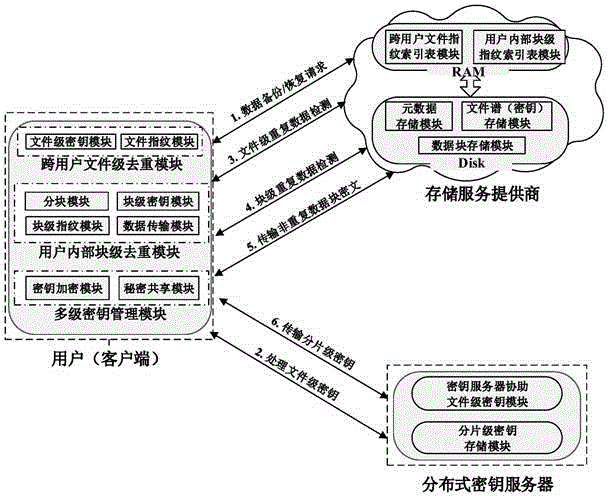
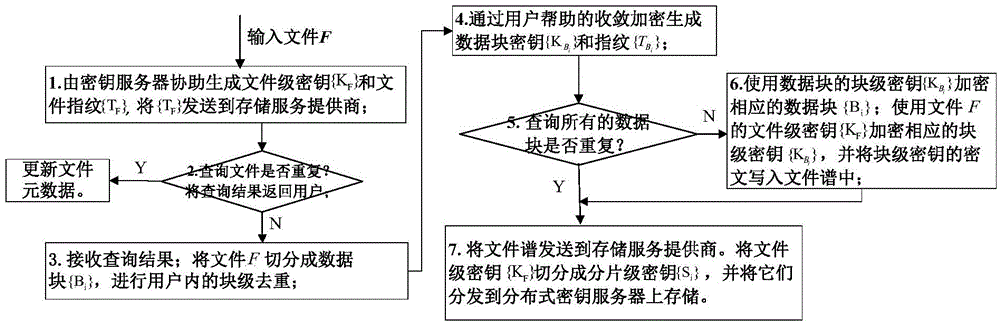
Efficient and safe data deduplication method and efficient and safe data deduplication system based on user perception
ActiveCN104917609AResistance to brute force attacksGuaranteed confidentialityKey distribution for secure communicationSpecial data processing applicationsBrute forceConfidentiality
The invention provides an efficient and safe data deduplication method based on user perception, which comprises the steps that a client adopts key server assisted Hash-based convergence encryption to carry out file-level data deduplication across users; if duplication does not exists in files, user assisted convergence encryption is adopted to carry out block-level deduplication inside the users; and multilevel key management is adopted, a file-level secret key is used to encrypt a block-level secret key, the file-level secret key is segmented into fragment-level secret keys by using secret sharing, and the fragment-level secret keys are stored in a distributed key server. The invention further provides an efficient and safe data deduplication system based on user perception. According to the invention, random information is added through adopting key server assisted Hash-based convergence encryption in a file level and adopting user assisted convergence encryption in a block level, thereby enabling file-level secret keys and block-level secret keys of users to be randomized, being capable of effectively resisting brute force attacks of opponents, and ensuring the data confidentiality and the safety of the users; and the multilevel key management scheme is adopted to ensure the safety of secret keys, and the secret key space overhead is reduced.
Owner:HUAZHONG UNIV OF SCI & TECH
Methods and systems for unilateral authentication of messages
InactiveUS7134019B2Optimization mechanismUser identity/authority verificationSecret communicationBrute forceAuthentication
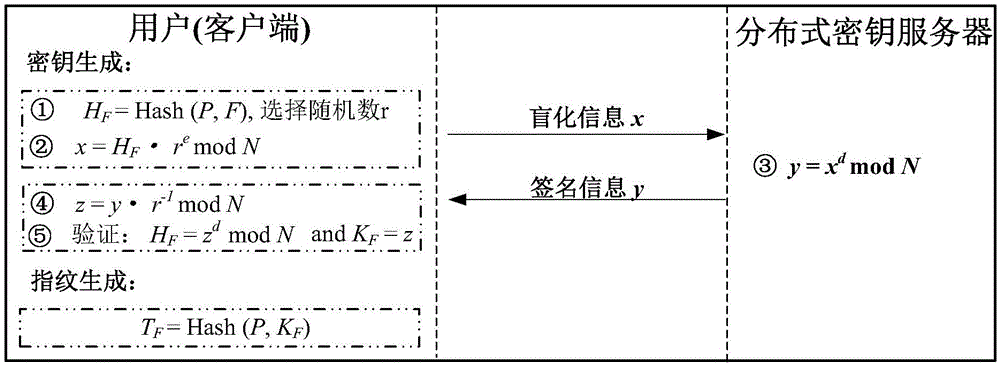
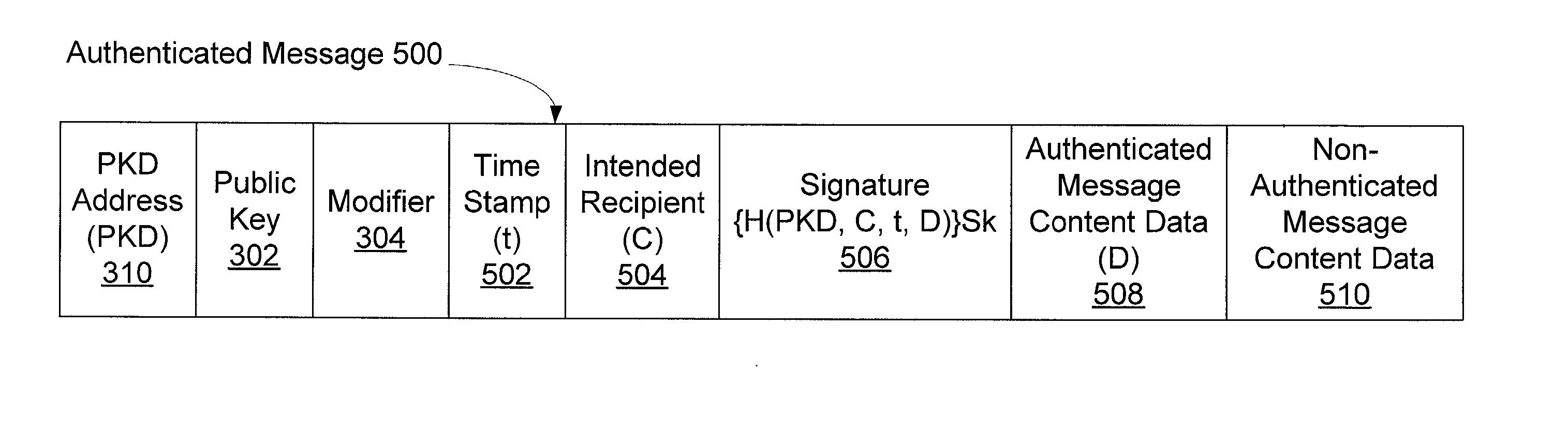
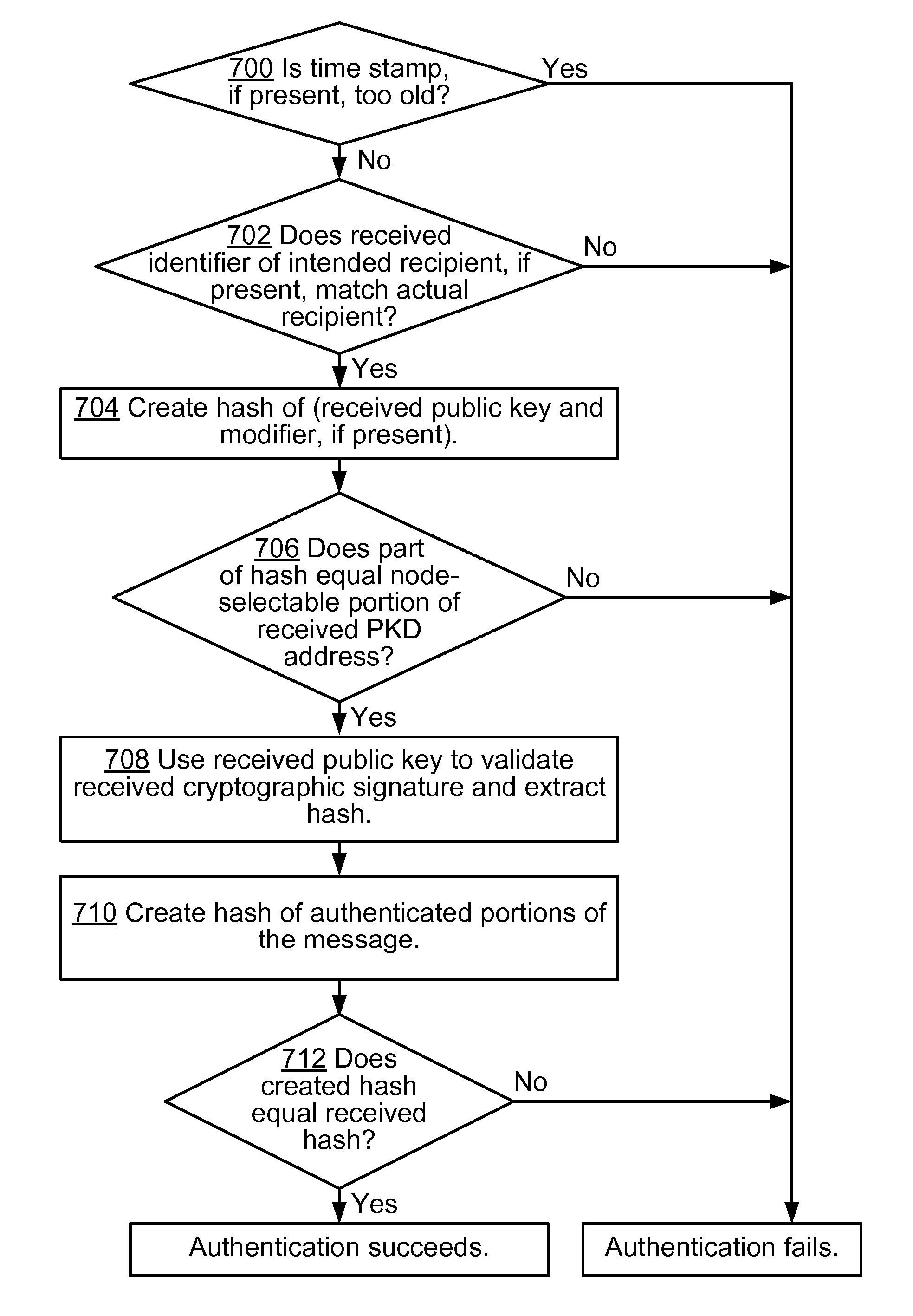
Disclosed is an authentication mechanism that enables an information recipient to ascertain that the information comes from the sender it purports to be from. This mechanism integrates a private / public key pair with selection by the sender of a portion of its address. The sender derives its address from its public key, for example, by using a hash of the key. The recipient verifies the association between the address and the sender's private key. The recipient may retrieve the key from an insecure resource and know that it has the correct key because only that key can produce the sender's address in the message. The hash may be made larger than the sender-selectable portion of the address. The recipient may cache public key / address pairs and use the cache to detect brute force attacks and to survive denial of service attacks. The mechanism may be used to optimize security negotiation algorithms.
Owner:MICROSOFT TECH LICENSING LLC
Unlocking method and system for smart mobile terminal
InactiveCN103677644AIncrease password spacePassword space improvedDigital data authenticationInput/output processes for data processingKey pressingPassword
The invention discloses an unlocking system for a mobile terminal. The system comprises a function setting module, a dynamic keyboard claiming module, an unlocking module and a function verification module. An unlocking method for the mobile terminal includes the steps of 1, setting the finger sliding directions corresponding to digital passwords and digital keys; 2, performing unlocking and 3 performing verification. The unlocking method and system for the mobile terminal are high in applicability, the digital passwords which are popular among most users are still used, the continuous sliding unlocking function is added on the basis that user habits are not changed, operation is simple, convincement and rapid, and user experience is good. The unlocking method and system for the mobile terminal are extremely high in safety, the corresponding sliding directions of fingers on the digital keys are added on the basis of the traditional digital passwords, password space is increased greatly so as to lower brute force attack risks, meanwhile, a dynamic claiming digital keyboard is used for preventing smudge attacks, and the safety is further improved.
Owner:BEIHANG UNIV
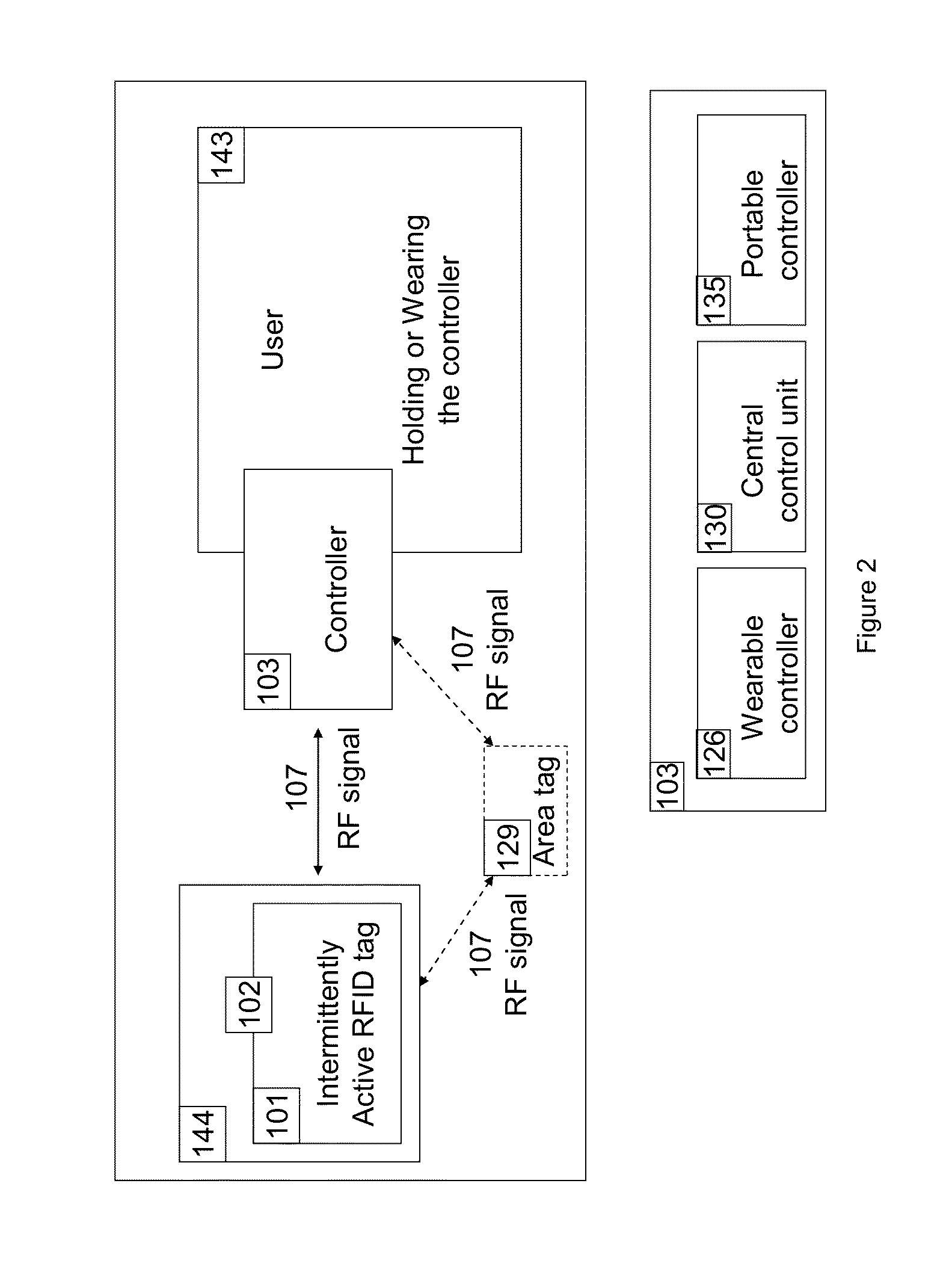
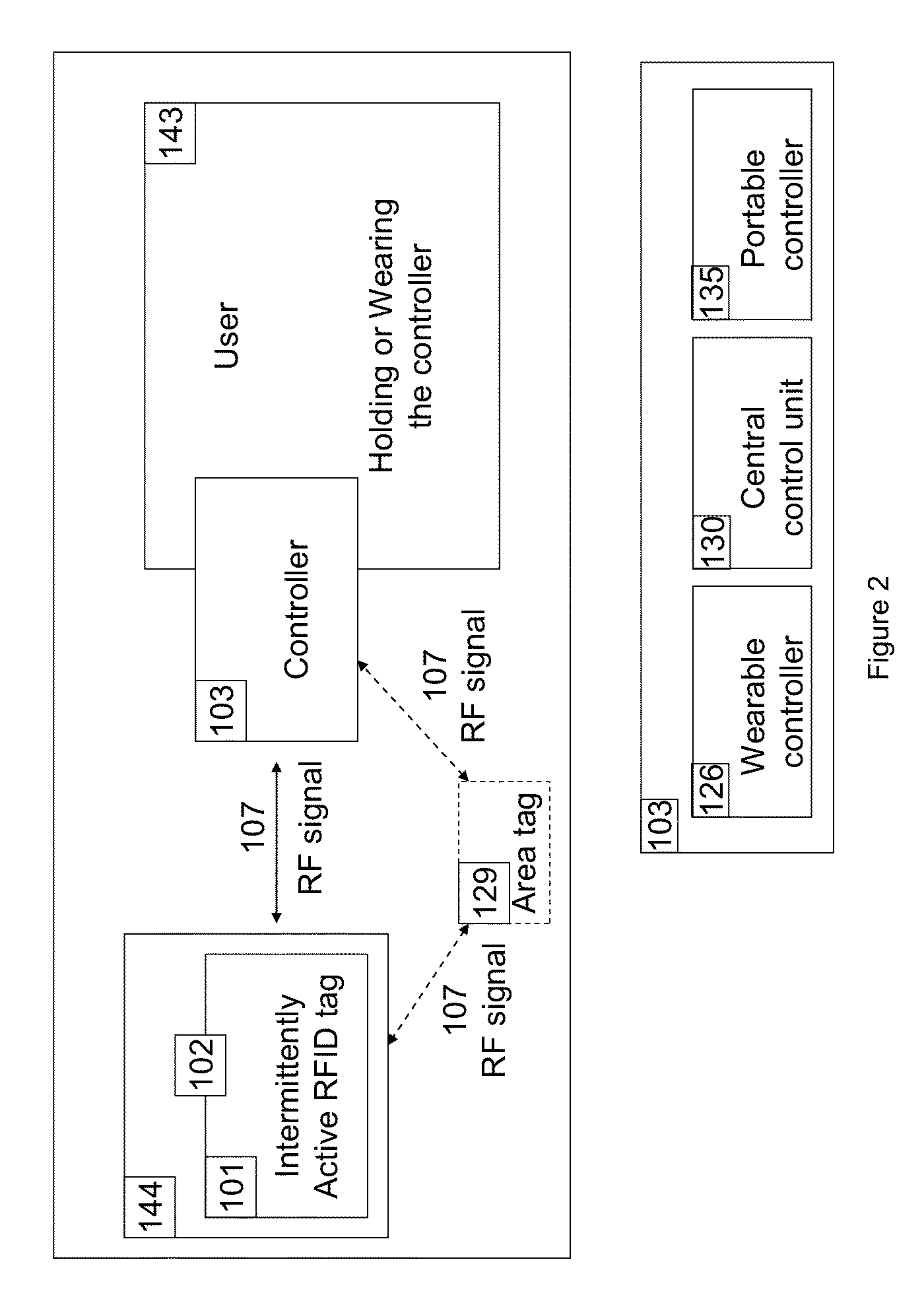
Apparatus and method for locating, tracking, controlling and recognizing tagged objects using active RFID technology
InactiveUS9311586B2Avoid disturbanceEasy to changeProgramme controlComputer controlData packThe Internet
A real-time automated data security system protects both data and devices from loss, theft, and unauthorized access or activity. A miniature active RFID circuit is embodied in tags, area tags, controllers, USB sticks and a universal interface software for computers (i.e., Java), smart phones, and gateway boxes written to interface with the system. These devices are customizable and can link in arrays to cover large areas, use sensors, and scale up in module configurations to meet any need. The system is independent of electricity, GPS, satellites, the Internet, other software, and IT personnel. Its novel software, inside the tags, area tags and controllers is inaccessible and cannot be copied. Wireless transmissions are encrypted to military grade levels and packets are never repeated, making it unhackable, even by brute force attack. A unique battery-conserving protocol ensures good range and long battery life. The system has the ability to ignore copied packages or relaying by attackers, and to prevent of unauthorized access to USB sticks by proximity checks to the active RFID circuit.
Owner:ROBINETTE JAMIE +1
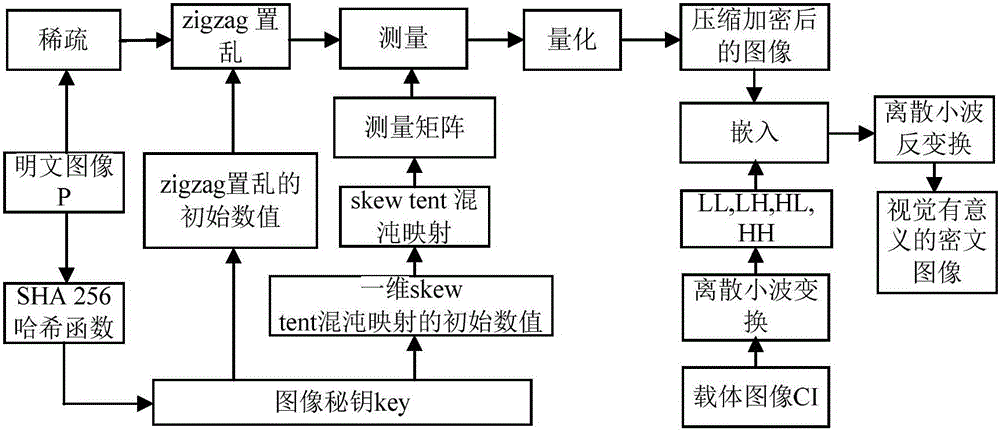
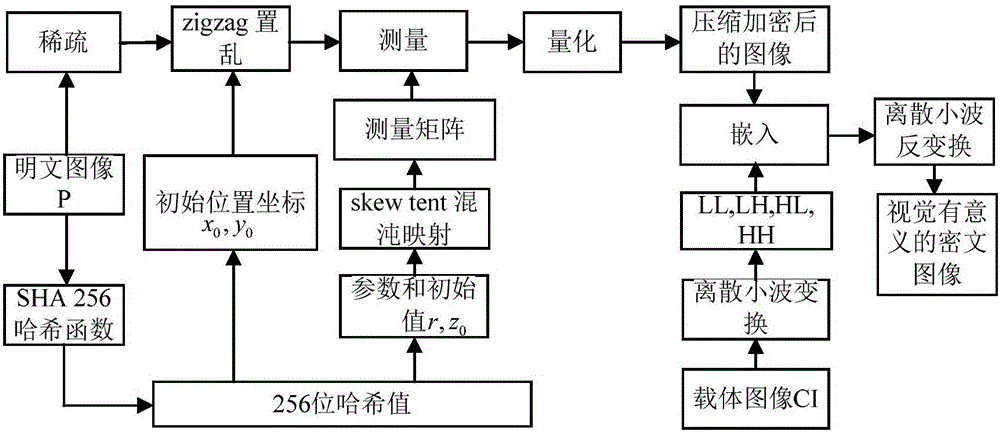
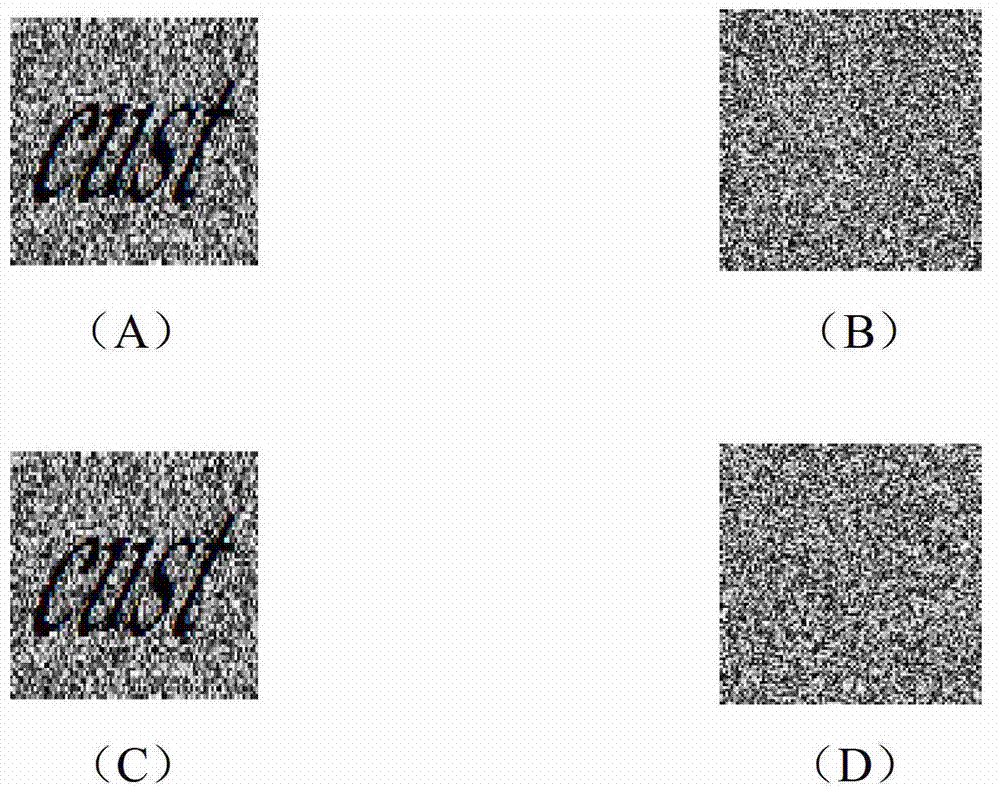
Image encryption method and image decryption method with visual security and data security based on compressed sensing
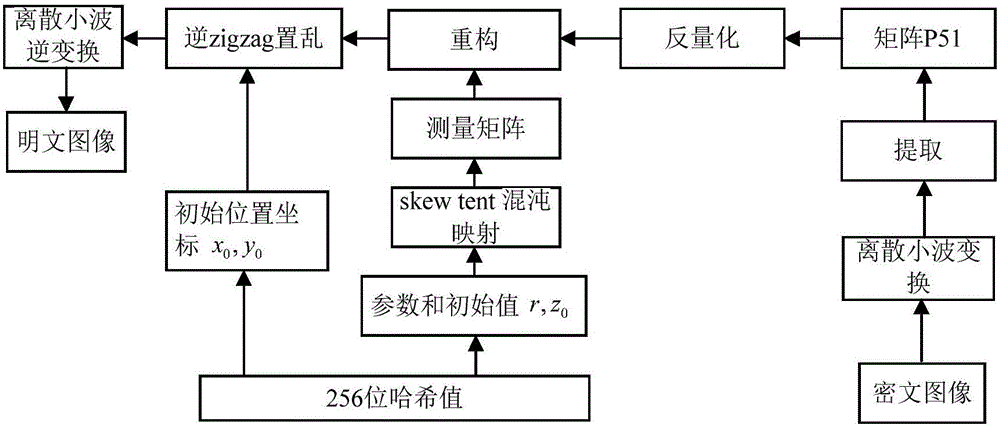
ActiveCN106600518AIncrease spaceEnhanced resistance to brute force attacksImage data processing detailsChosen-plaintext attackHash function
The invention relates to an image encryption method and an image decryption method with visual security and data security based on compressed sensing. The image encryption method comprises the steps of: firstly, utilizing an SHA 256 hash function to obtain a 256-bit hash value of a plaintext image as an image secret key, and calculating initial numerical values of one-dimensional skew tent chaotic mapping and zigzag scrambling; carrying out sparse processing on the plaintext image, and carrying out zigzag scrambling on a coefficient matrix; and then utilizing the one-dimensional skew tent chaotic mapping to generate a measurement matrix, measuring and quantifying a scrambling matrix to obtain a compressed and encrypted image, and embedding the image into a carrier image with visual significance to obtain a final ciphertext image with visual significance. The image encryption method realizes the visual security and data security of the plaintext image, has large secret key space, is highly sensitive to plaintext, has higher capacity of resisting brute-force attack, chosen-plaintext attack and known-plaintext attack, does not need an additional storage space, and can transmit and store the ciphertext image quickly and effectively.
Owner:HENAN UNIVERSITY
Method and apparatus for using navigation signal information for geoencryption to enhance security
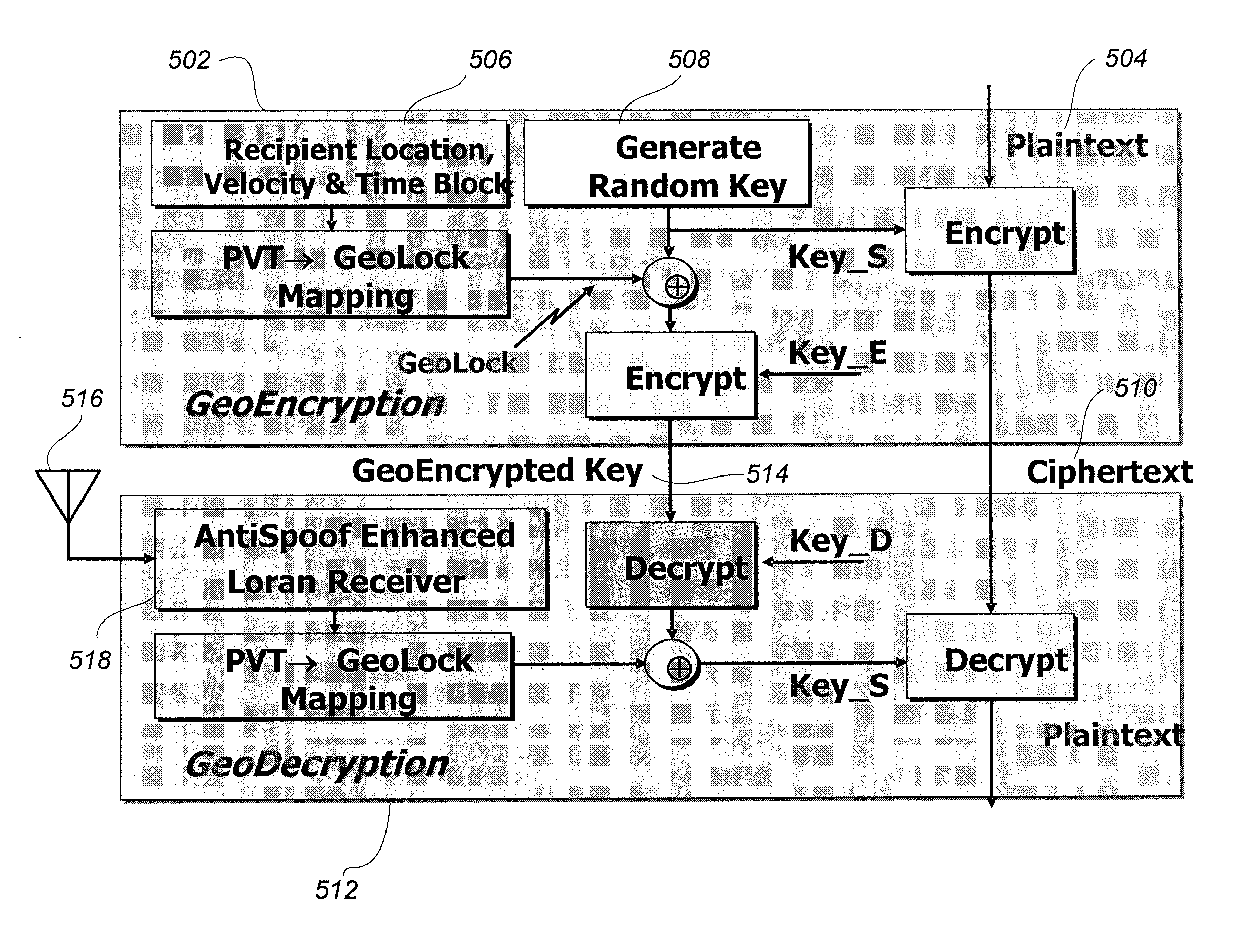
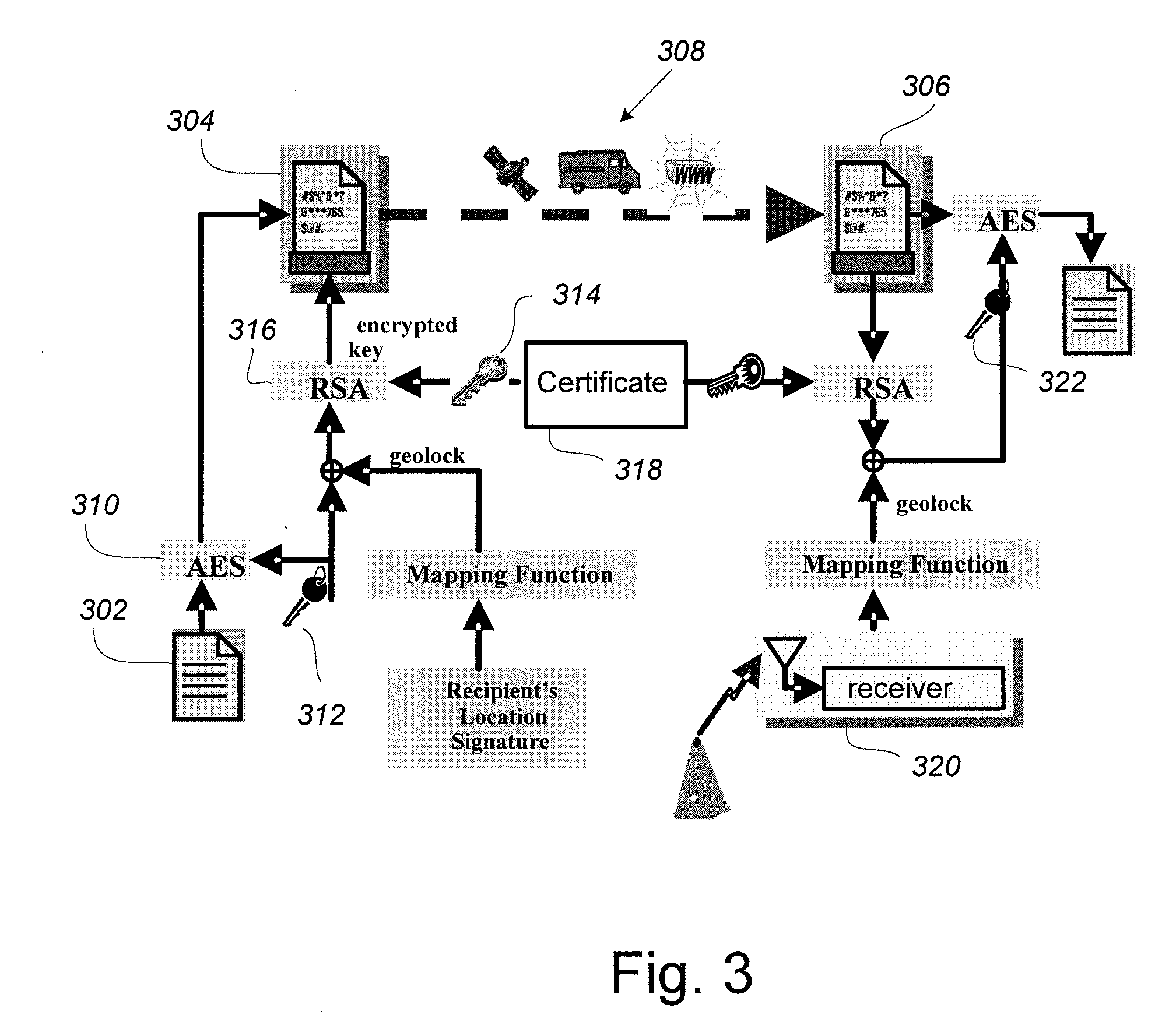
ActiveUS20090316900A1Increase entropyError detection/correctionVolume/mass flow measurementComputer hardwareSignal envelope
A data encryption and decryption system securely geoencrypts data using location-dependent navigation signals. To increase the entropy of the cryptographic key to guard against a brute-force attack, geoencryption is made to depend on largely time-independent characteristics of the navigation signals that are not easily spoofed, including the time difference of arrival, the envelope-to-cycle difference, the differential signal-to-noise, the signal envelope shape, and the directions of arrival of the navigation signal set.
Owner:SANDFORD UNIV +1
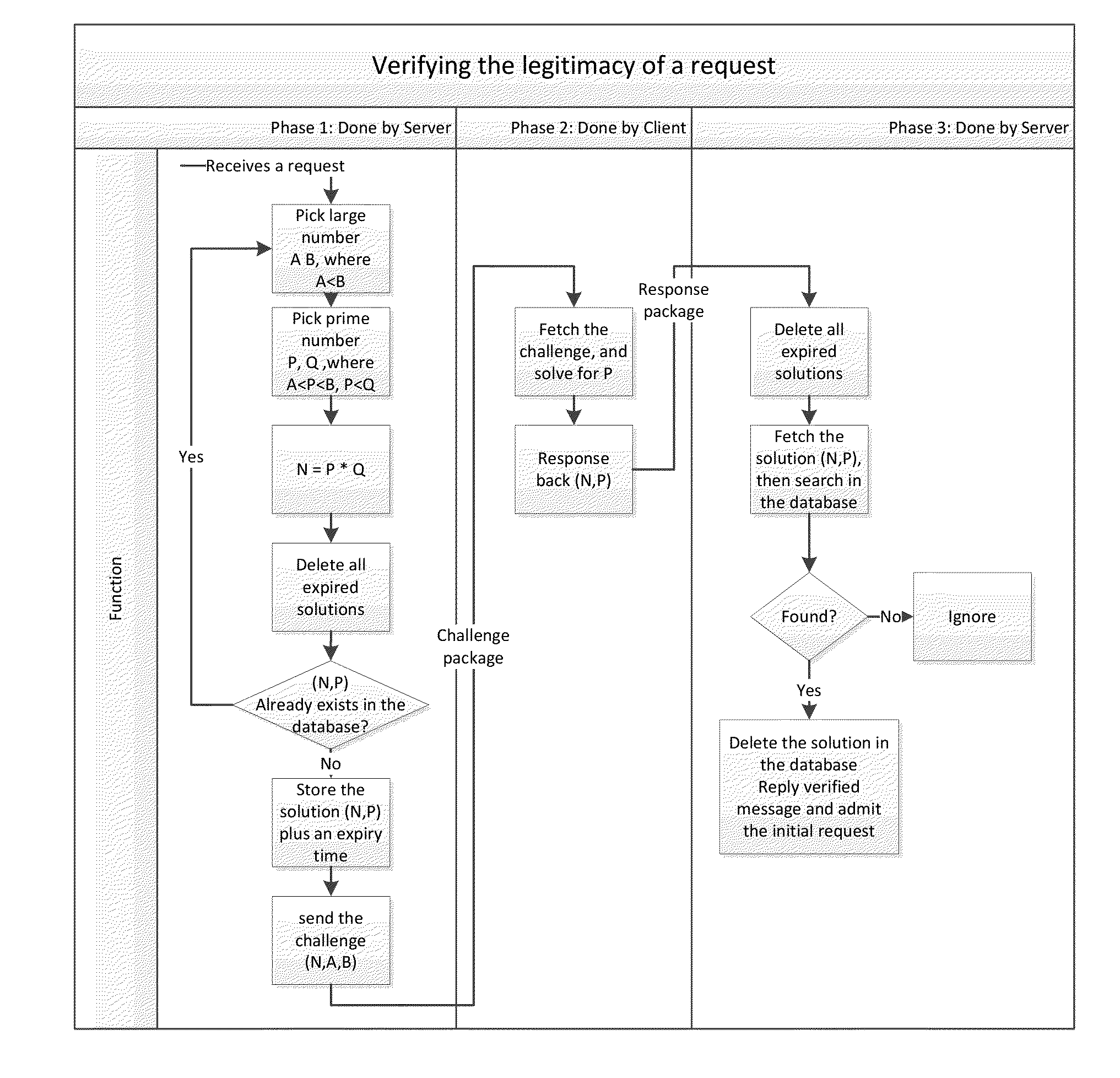
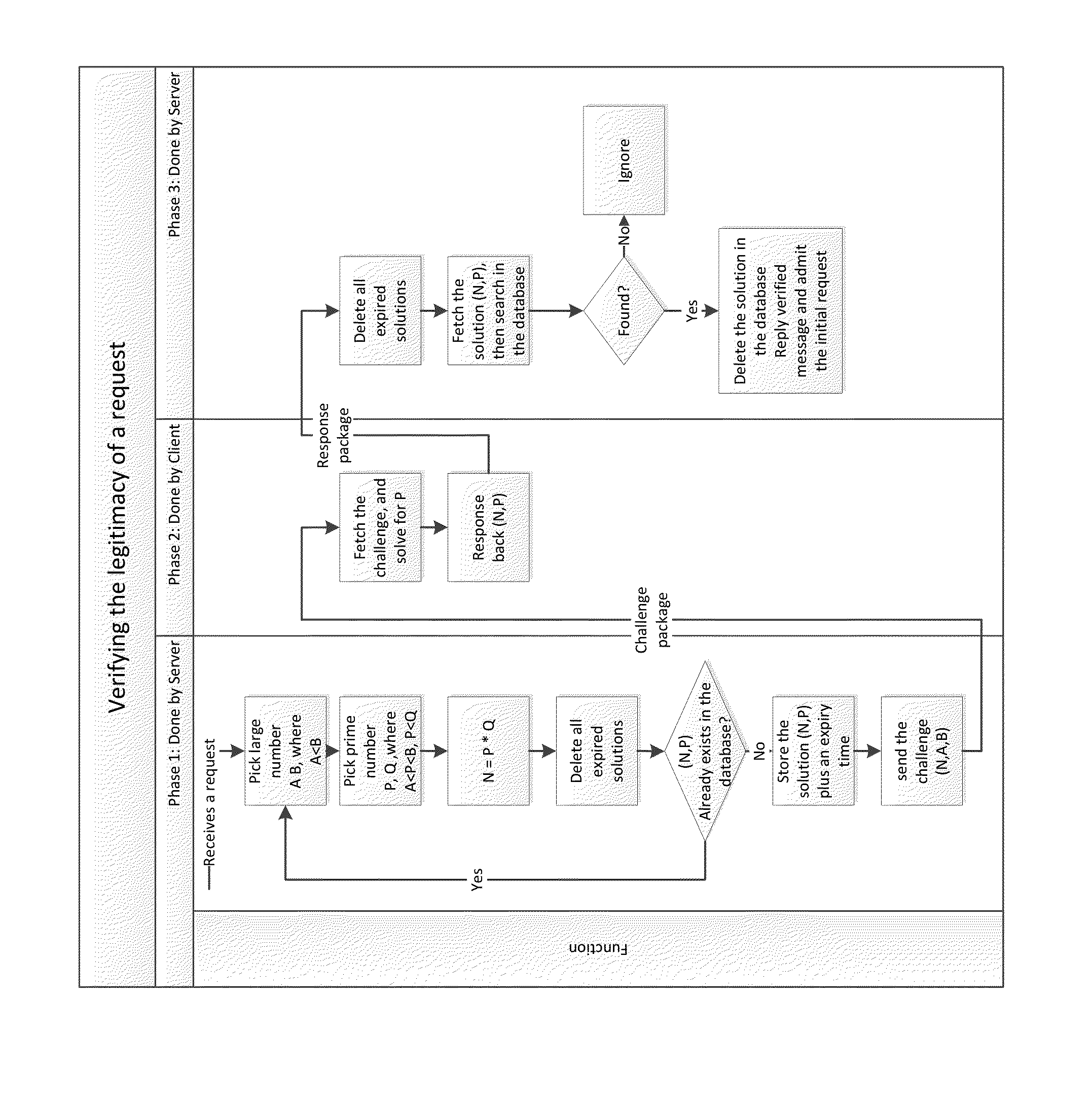
System and method for verifying the legitimacy of requests sent from clients to server
InactiveUS20140380418A1Preventing brute force attack against passwordImprove reliabilityDigital data processing detailsMultiple digital computer combinationsBrute forceComputation complexity
Disclosed herein are method and system that can be used for: preventing brute force attacks against passwords; preventing denial of service attacks by flooding; restricting bots from spamming emails, registering resources, and collecting sensitive information; and possibly in other challenge-response tests. It also can be used to replace CAPTCHA in some situations, with advantages of better reliability and spares human participation during the process. This present invention considers a request as legitimate when the requesting client has paid certain amount of computation resource required by the server, in exchange for the server to admit the request. It performs a challenge-response test. The subject challenged is the sincerity of the client to make that request, which is measured by computation resources the client willing to spend in exchange for the service provided by the server. The invention also gives a method to control and guarantee the computation complexity of the challenge problem of the test.
Owner:WANG HAOXU
Back-end matching method supporting front-end knowledge-based probabilistic authentication systems for enhanced credential security
ActiveUS20150341327A1Digital data processing detailsUser identity/authority verificationBrute forceMatching methods
A party can authenticate itself by interacting with multiple servers without revealing the shared secret to any of the involved parties. The stored shared secret is strengthened and broken into shares and saved on the servers. The shared secret is safe against offline brute force attack unless all servers where the shares are stored are compromised. The compromise of any single server, or multiple servers—but less than the maximum number—will not allow the attacker to do a brute force analysis on the shared secret. This back end security enhancement is suitable for probabilistic front end authentication algorithms.
Owner:AUTHERNATIVE INC
Methods and systems for authenticating messages
InactiveUS7409544B2Lower administrativeReduce communication overheadUser identity/authority verificationComputer hardwareBrute force
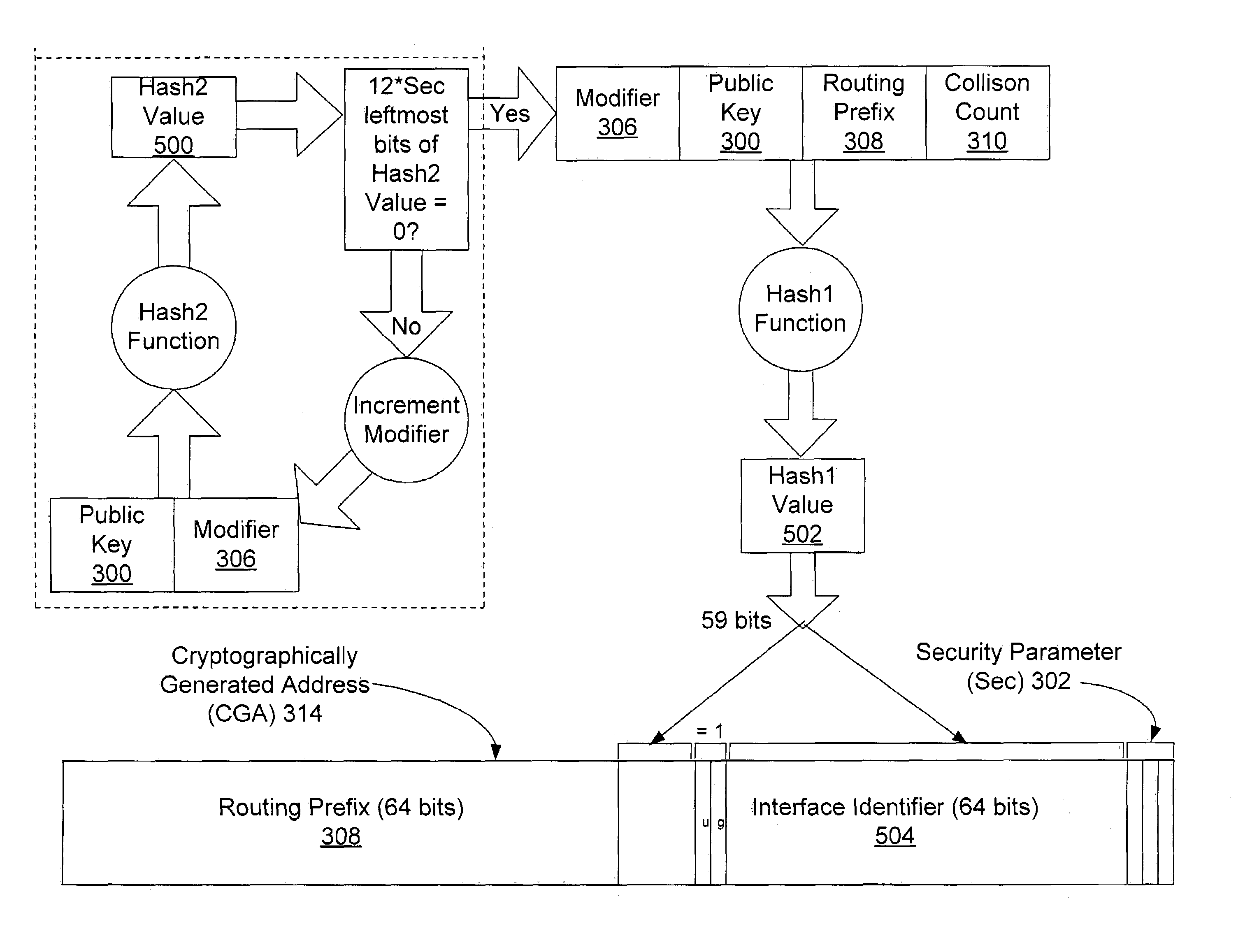
Disclosed is an authentication mechanism that provides much of the security of heavyweight authentication mechanisms, but with lower administrative and communicative overhead while at the same time not being limited to a 64-bit limit on the length of a cryptographic hash value. Removal of this limitation is achieved by increasing the cost of both address generation and brute-force attacks by the same parameterized factor while keeping the cost of address use and verification constant. The address owner computes two hash values using its public key and other parameters. The first hash value is used by the owner to derive its network address. The purpose of the second hash is to artificially increase that computational complexity of generating new addresses and, consequently, the cost of brute-force attacks. As another measure against brute-force attacks, the routing prefix (i.e., the non-node selectable portion) of the address is included in the first hash input.
Owner:MICROSOFT TECH LICENSING LLC
Methods and Systems for Unilateral Authentication of Messages
InactiveUS20070061574A1User identity/authority verificationNetwork data managementBrute forceAuthentication
Disclosed is an authentication mechanism that enables an information recipient to ascertain that the information comes from the sender it purports to be from. This mechanism integrates a private / public key pair with selection by the sender of a portion of its address. The sender derives its address from its public key, for example, by using a hash of the key. The recipient verifies the association between the address and the sender's private key. The recipient may retrieve the key from an insecure resource and know that it has the correct key because only that key can produce the sender's address in the message. The hash may be made larger than the sender-selectable portion of the address. The recipient may cache public key / address pairs and use the cache to detect brute force attacks and to survive denial of service attacks. The mechanism may be used to optimize security negotiation algorithms.
Owner:MICROSOFT TECH LICENSING LLC
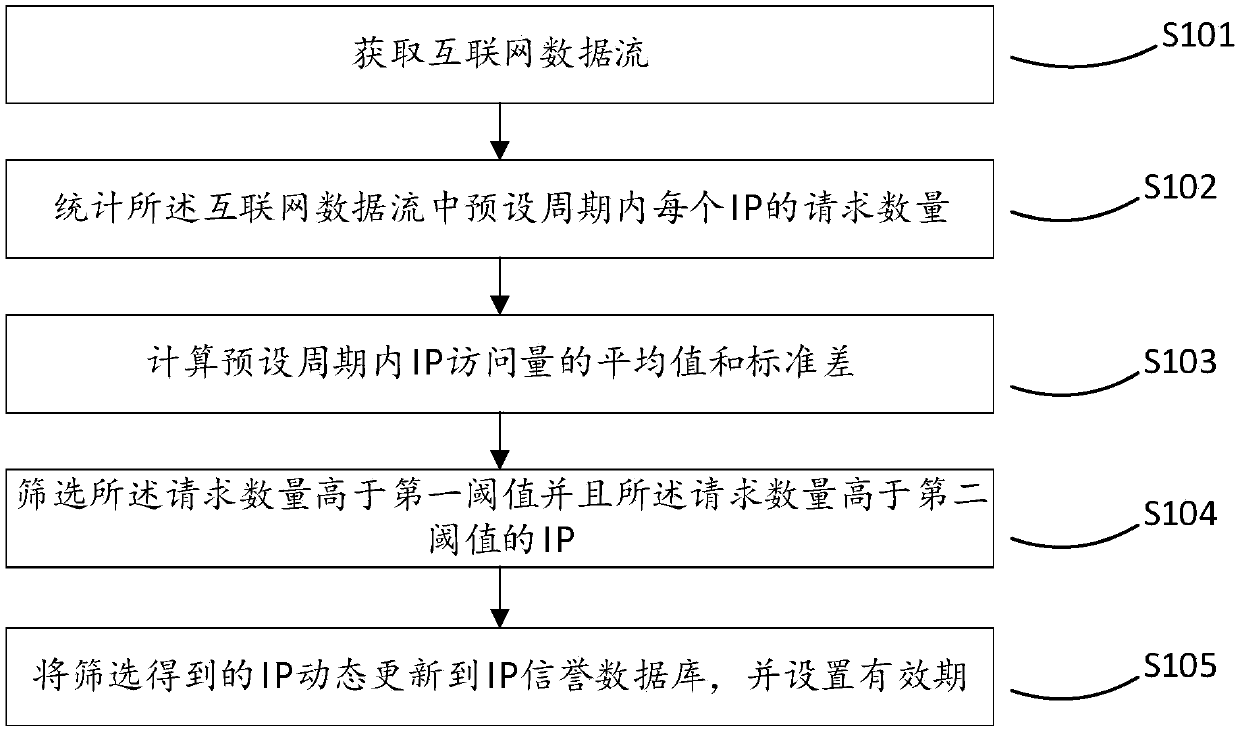
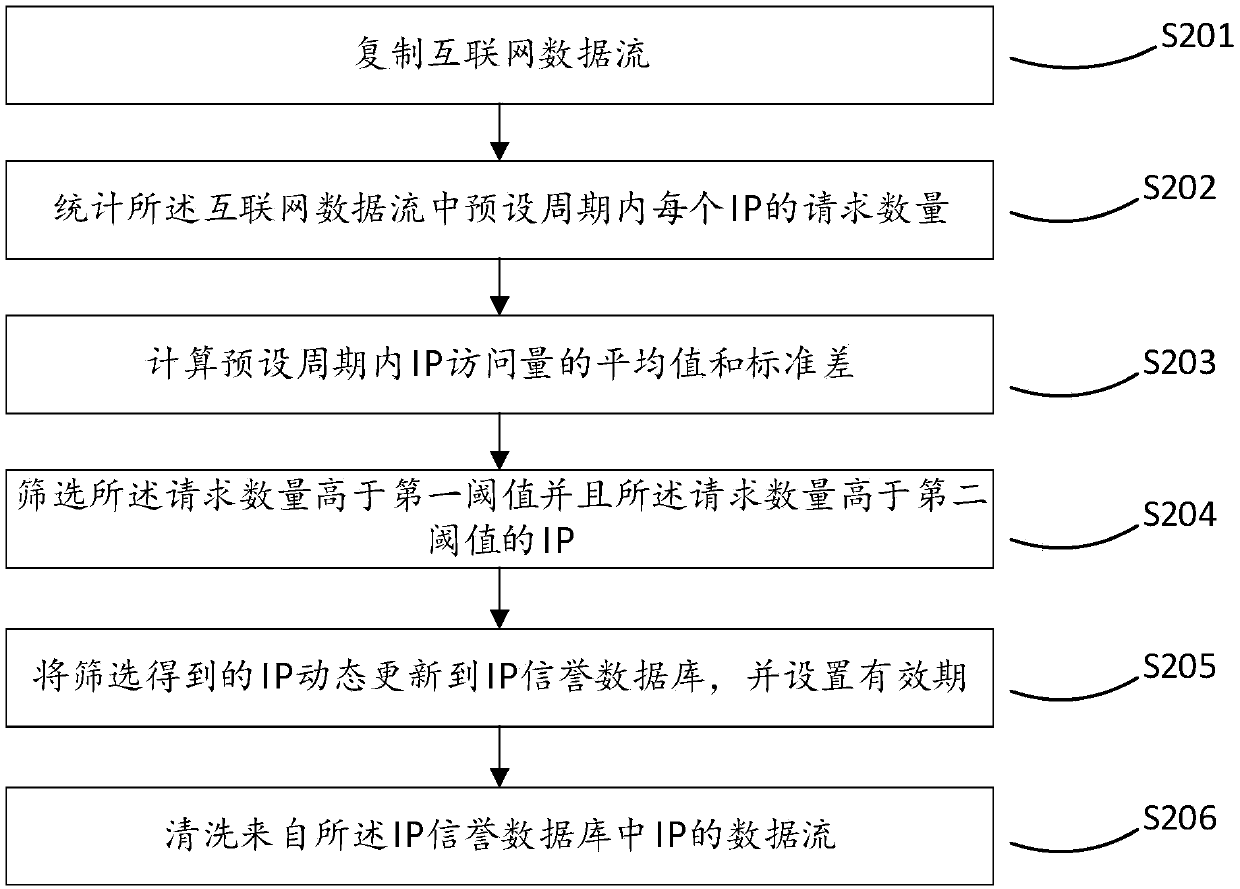
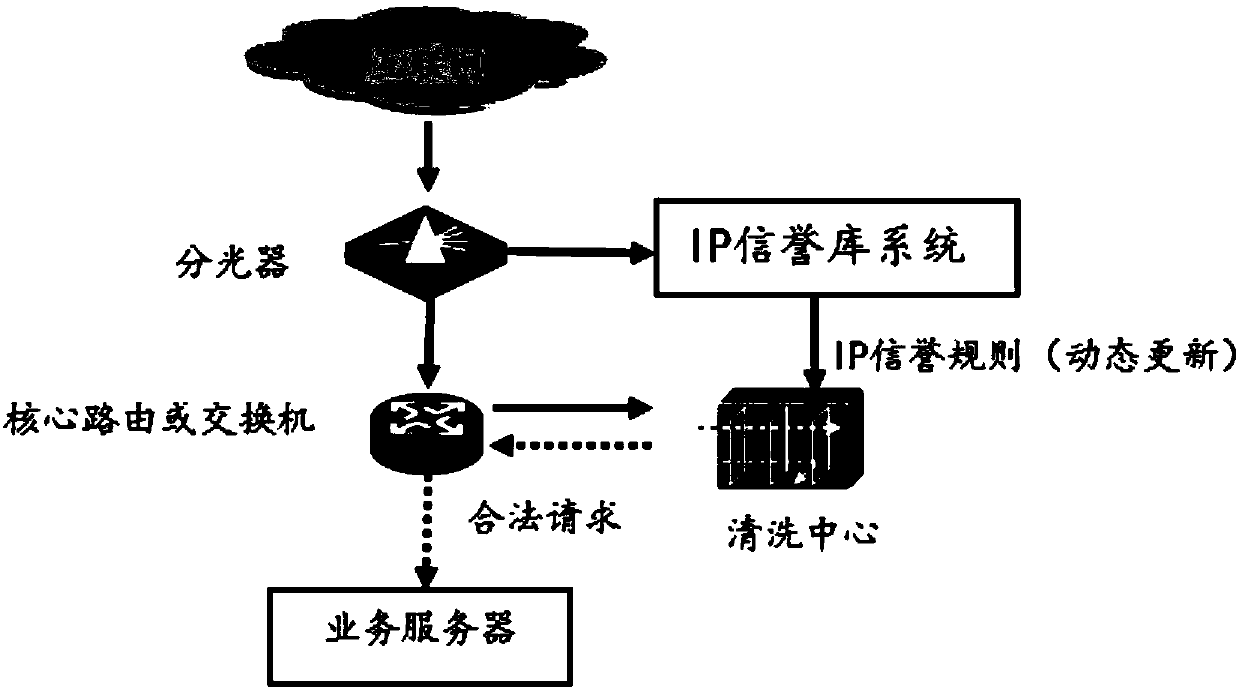
Network security protection method and system based on IP address security credibility
The invention relates to a network security protection method and system based on the IP address security credibility. The network security protection method comprises the steps of: obtaining an internet mirror image data flow, counting and calculating the request numbers of IP addresses in the mirror image data flow and the arithmetic statistical values of the request numbers, furthermore, determining a threshold value condition based on the normal access volume and the arithmetic statistical values of the request numbers, screening the IP addresses, the request numbers of which satisfy the threshold value condition, dynamically updating the IP addresses to an IP address credibility database, and cleaning the data flow of the IP addresses from the IP address credibility database. Continuously malicious behaviours that a single access accords with normal request characteristics, such as DDoS attacks, CC attacks, library hit attacks, piracy crawler grabbed contents and brute force attacks, can be effectively protected; and thus, the security assurance of the internet and application layers can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
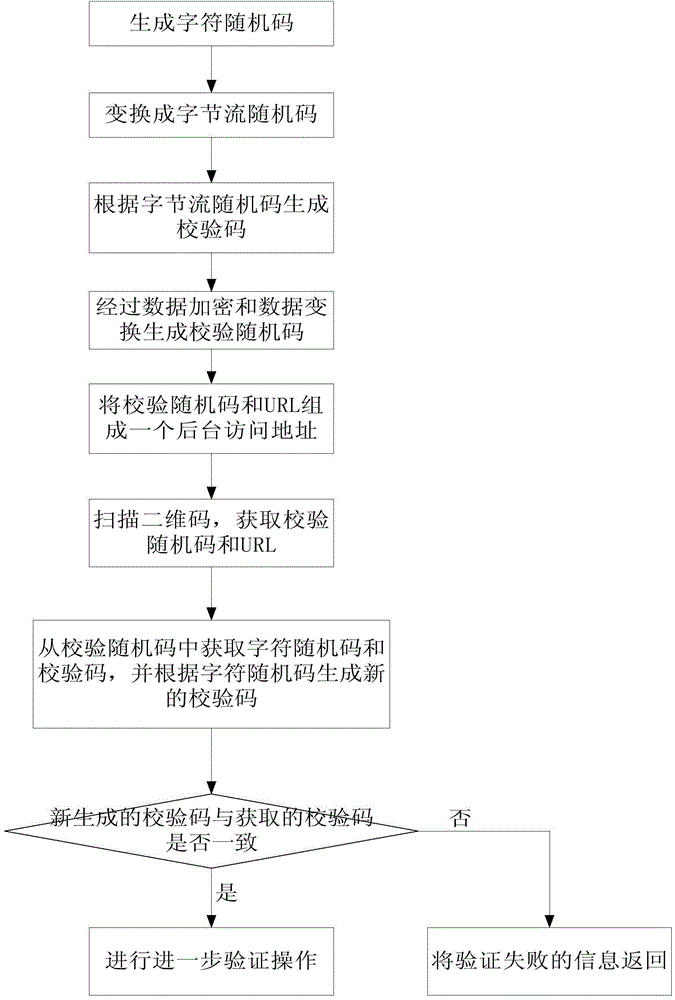
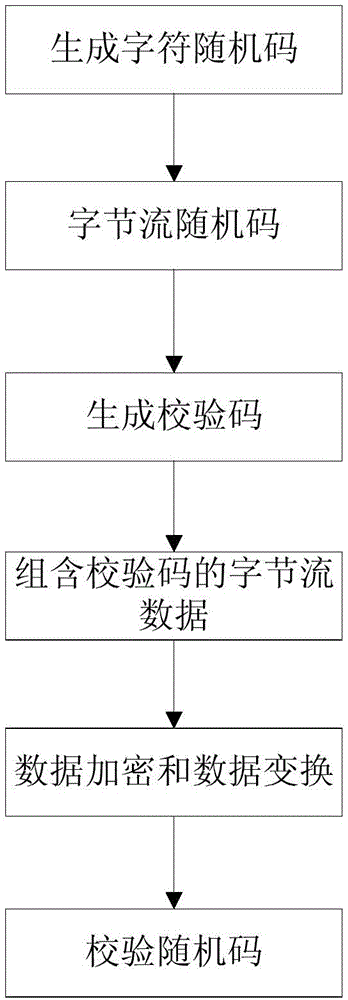
Data identification method for two-dimension code safety verification
ActiveCN104835046AAvoid paralysisComputer security arrangementsCommerceAlgorithmTheoretical computer science
Owner:SIGMATRIX TECH CO LTD
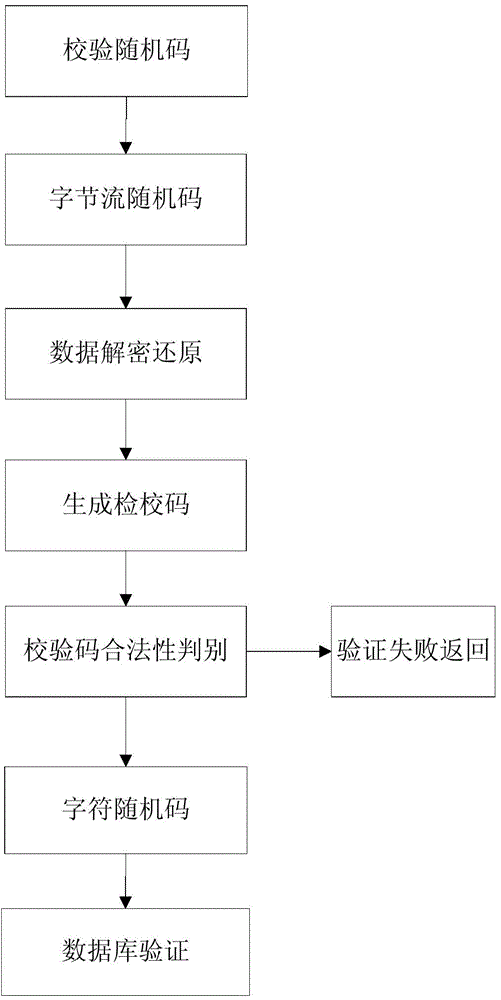
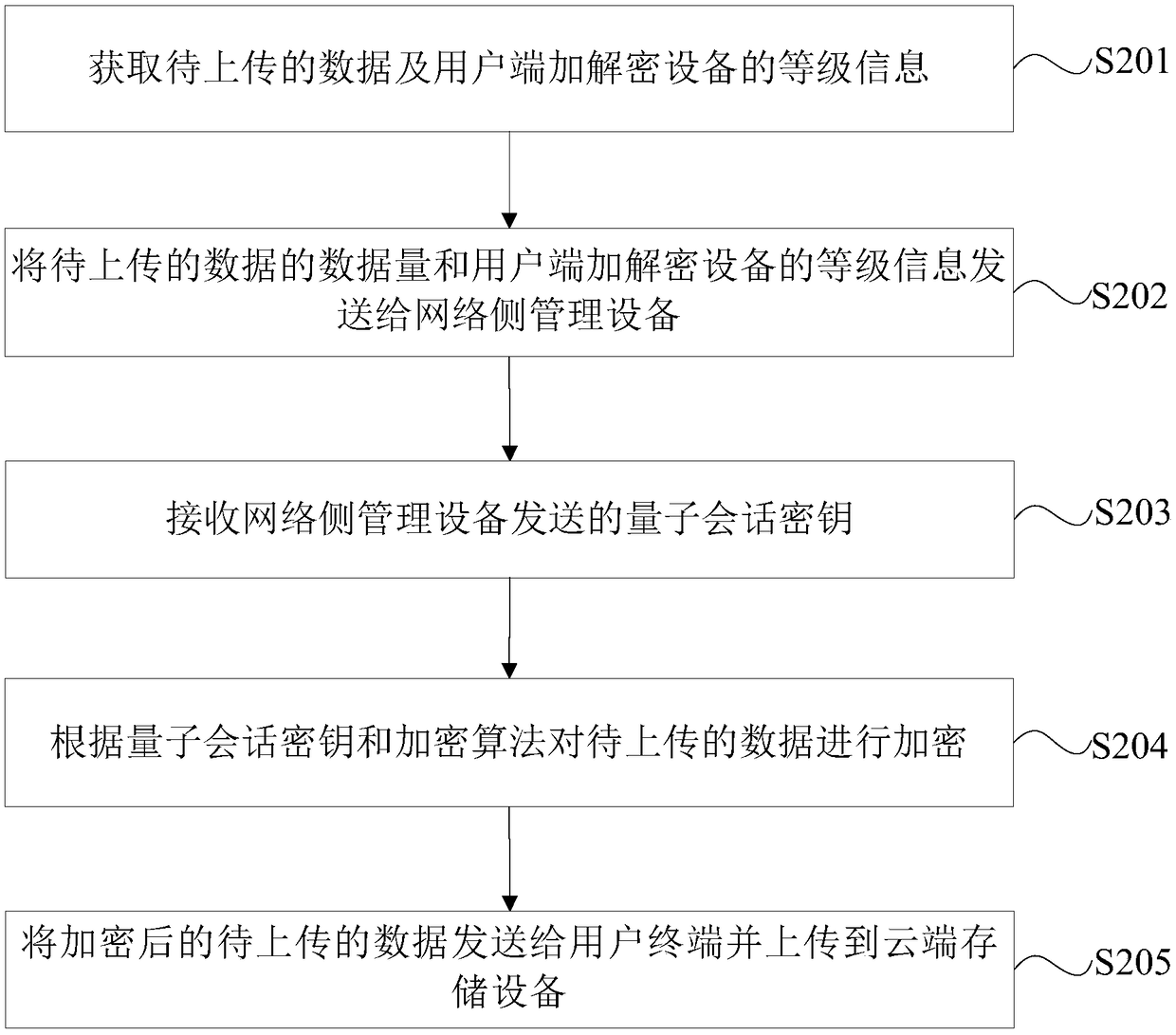
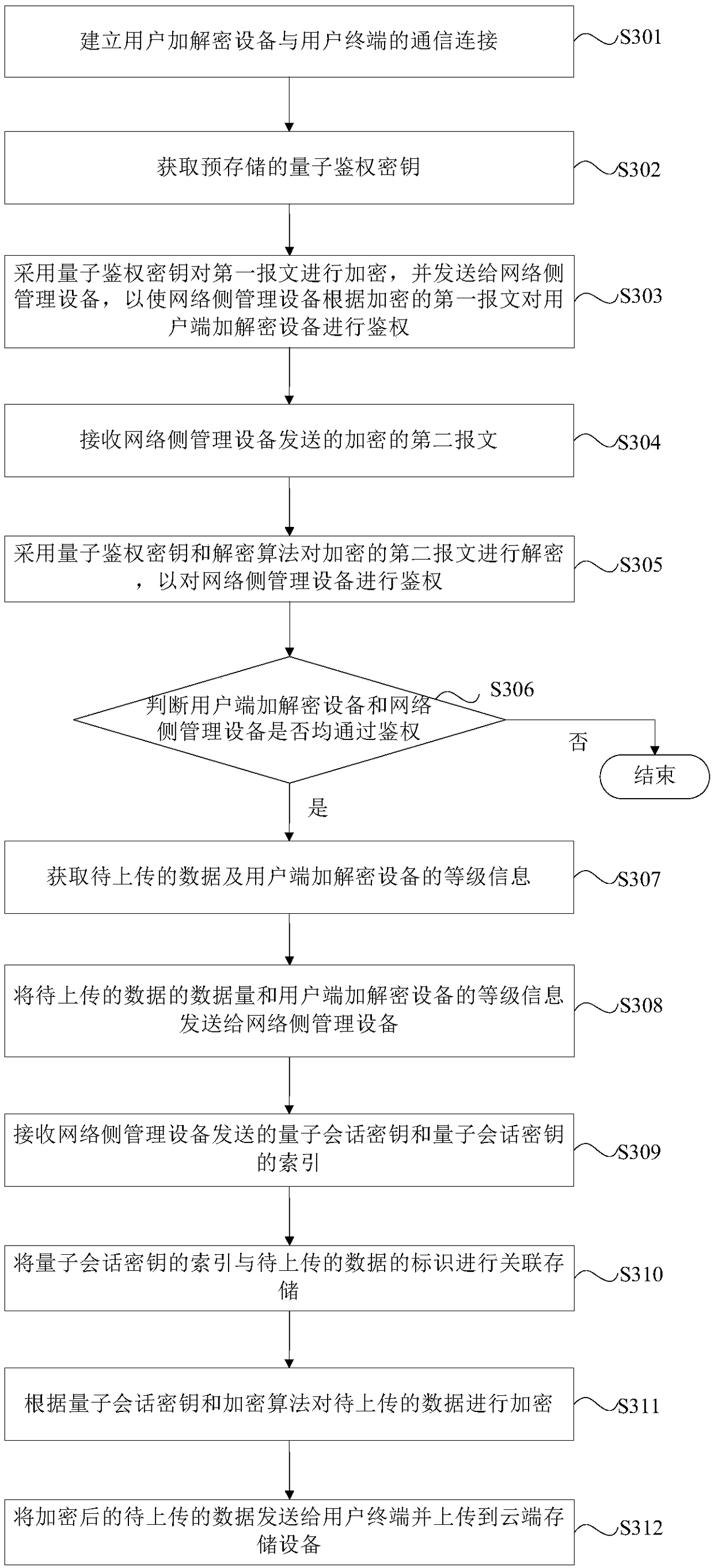
Cloud data access method, device and equipment, and computer readable storage medium
ActiveCN109150835APrevent leakageMeet individual needsKey distribution for secure communicationPersonalizationAccess method
The invention provides a cloud data access method, device and equipment, and a computer readable storage medium. The method comprises the following steps of acquiring data to be uploaded and the levelinformation of a user side encryption and decryption device; sending the data amount of the data to be uploaded and the level information of the user side encryption and decryption device to a network side management device; receiving a quantum session key sent by the network side management device; encrypting the data to be uploaded according to the quantum session key and an encryption algorithm; and sending the encrypted data to be uploaded to a user terminal and uploading to a cloud storage device. Through using the anti-quantum-attack characteristic of a quantum key, cloud storage data can be prevented from being obtained through a brute force attack, collision, and the like. The safety of cloud storage data is effectively protected and information leakage is prevented. A more safe encryption service can be provided for a high-priority user and sensitive data to meet the personalized need of the user.
Owner:CAS QUANTUM NETWORK CO LTD
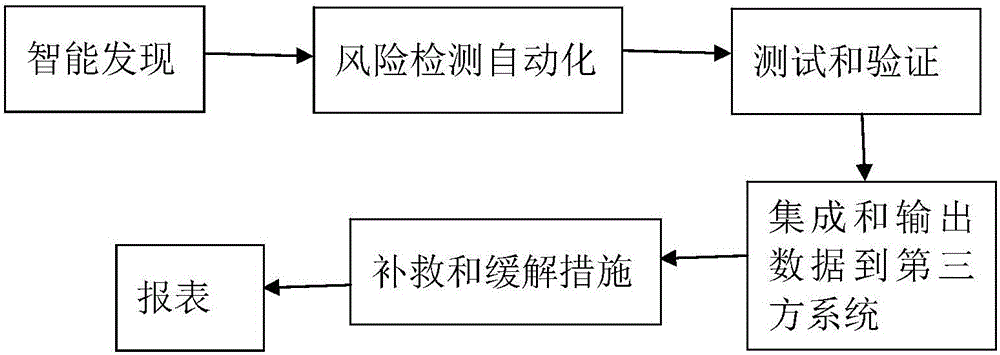
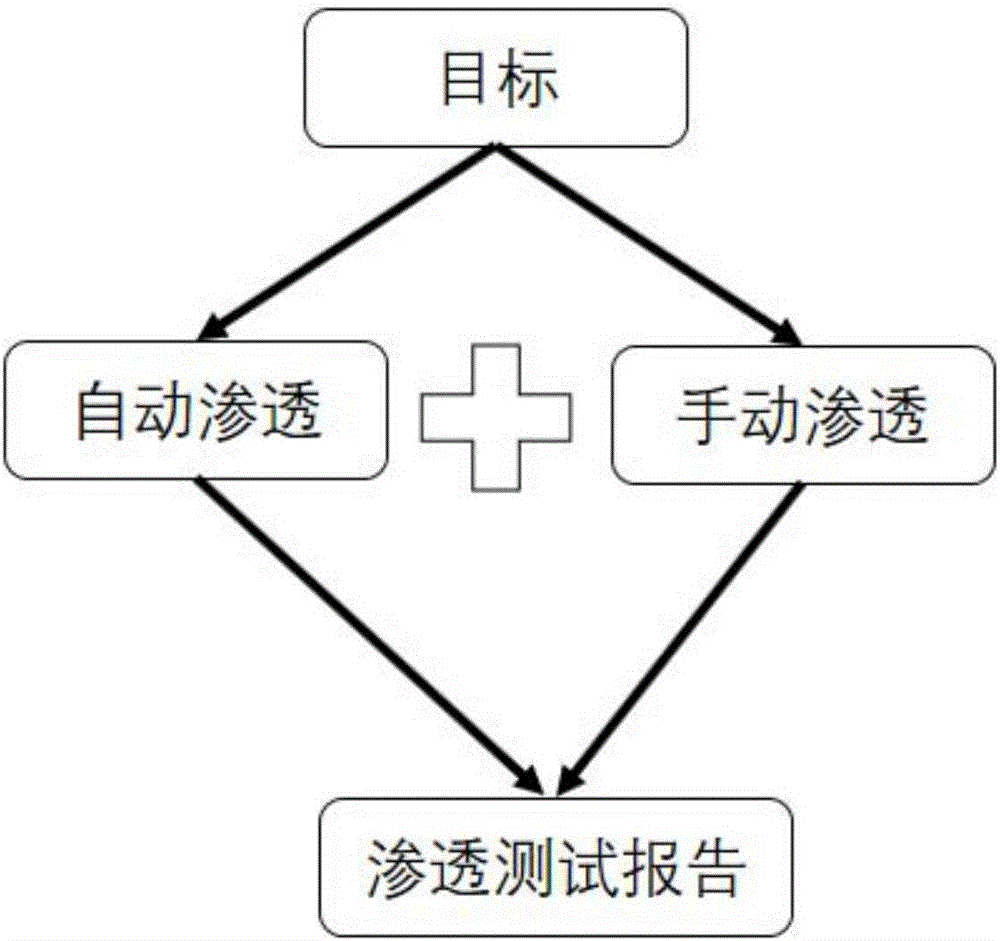
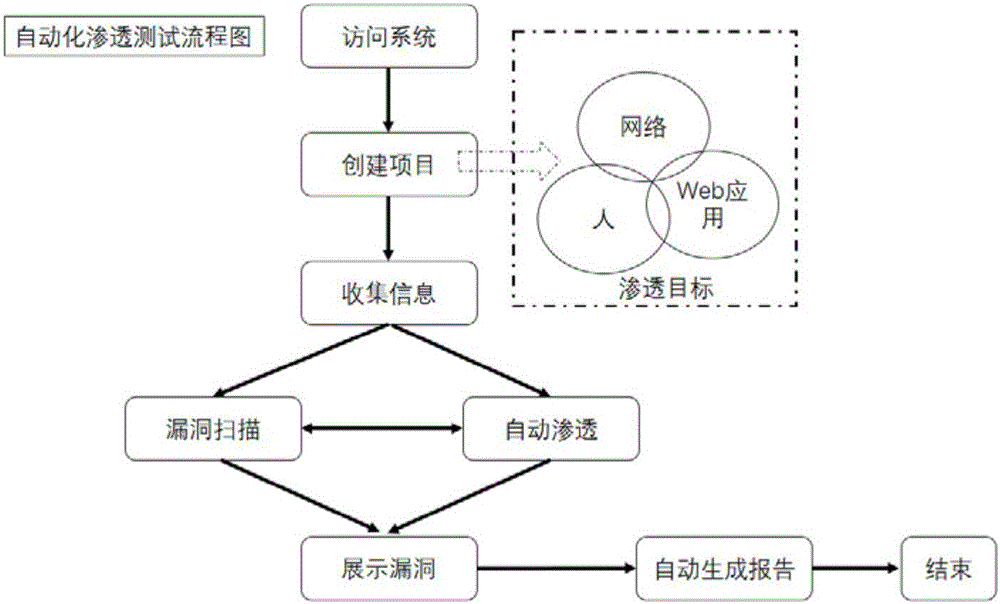
Automatic penetration testing method and system
InactiveCN105827642ARaise security awarenessImprove inspection efficiencyData switching networksEngineeringVulnerability
The invention discloses an automated penetration testing method and system, including an automatic penetration method and a manual penetration method; in the manual penetration method, it is necessary to select a penetration mode for automatic penetration; the penetration mode includes loophole penetration, brute force cracking, and WEB penetration and social engineering tests. The present invention has the advantages of loophole hazard display, comprehensive coverage inspection, and automatic penetration. By utilizing the discovered loopholes, the present invention displays the hazards caused by the loopholes, deters development and operation and maintenance personnel, forms indirect security awareness education for them, and improves personnel security. Security awareness; comprehensive coverage inspection, through security inspection of networks, applications, and personnel; through automated penetration, improve the efficiency and comprehensiveness of security personnel inspections.
Owner:SHENZHEN ANLUO TECH CO LTD
Multiple uncertainty encryption system with misleading function
The invention discloses a multiple uncertainty encryption system with a misleading function, which aims at attacks such as rubber-hose attacks, key stealing, brute force attacks and the like. Multiple encryption is performed, and an algorithm and encryption multiplicity are uncertain, so the system has multiple uncertainty, a password analyzer cannot perform analysis, and even though the brute force attacks are adopted, a plaintext obtained only by incomplete single decryption is meaningless. The encryption multiplicity of the algorithm, encryption algorithms of each layer and keys of each layer are all uncertain, and are all included in a structural master key. The multiple uncertainty makes securer the algorithm. The system is required to comprise an improved one-time pad mechanism, and one-time pad has high reversibility, so the encryption system can obtain pseudo keys in two ways to mislead and confuse the password analyzer, and has high value in military affairs and special occasions.
Owner:桂林轻鸿科技有限公司
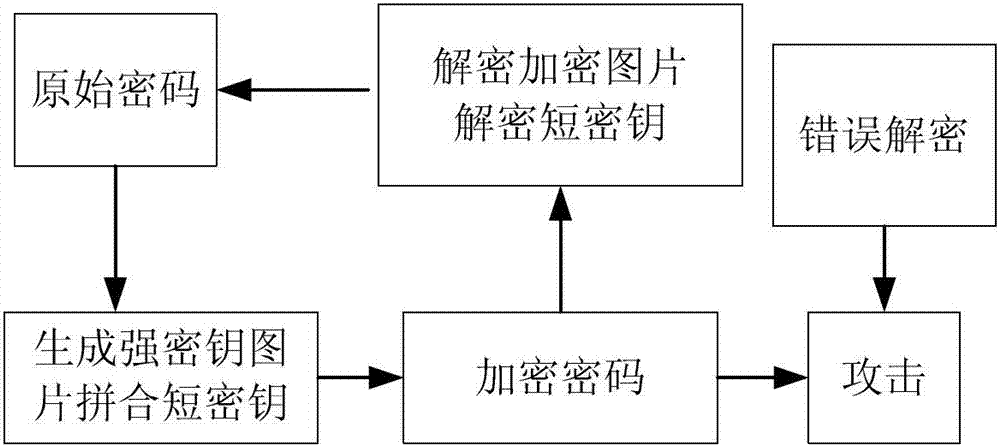
Hyper-chaos encryption method for weak password based on quantum cellular neural network
InactiveCN102904710AEasy to rememberImprove securityEncryption apparatus with shift registers/memoriesBrute forcePassword
The invention relates to a hyper-chaos encryption method for a weak password based on a quantum cellular neural network, which belongs to the field of the information security technology. The method provided by the invention solves the problem that the existing password system is limited by limited key space so that the safety of the system is difficult to guarantee when running into brute-force attacks. The encryption method provided by the invention combines the hyper-chaos characteristic of the quantum cellular neural network with the advantages of human brain identification; the safe password is divided into two parts, wherein one part is translated into the picture form; in terms of an initial value and extremely sensitive characteristics of a control parameter, images are encrypted by using the high complexity of the hyper-chaos system; the other part of secret key is encrypted by using an AES (Advanced Encryption Standard) encryption method; and the two parts form a safe password for encrypting the data. The encryption method provided by the invention has great key space; the ability resisting to brute force attack is obviously strengthened; the calculated quantity in the encryption process is reduced when less password number is used; and the encryption method has the characteristics of high safety and convenience for remembering by a user.
Owner:CHANGCHUN UNIV OF SCI & TECH
Token based two factor authentication and virtual private networking system for network management and security and online third party multiple network management method
InactiveUS20100191960A1Efficient and effectiveDigital data processing detailsUser identity/authority verificationPrivate networkNetworked system
Owner:DIRECTPOINTE
Method and device for signing user program and method and device for verifying signature of user program
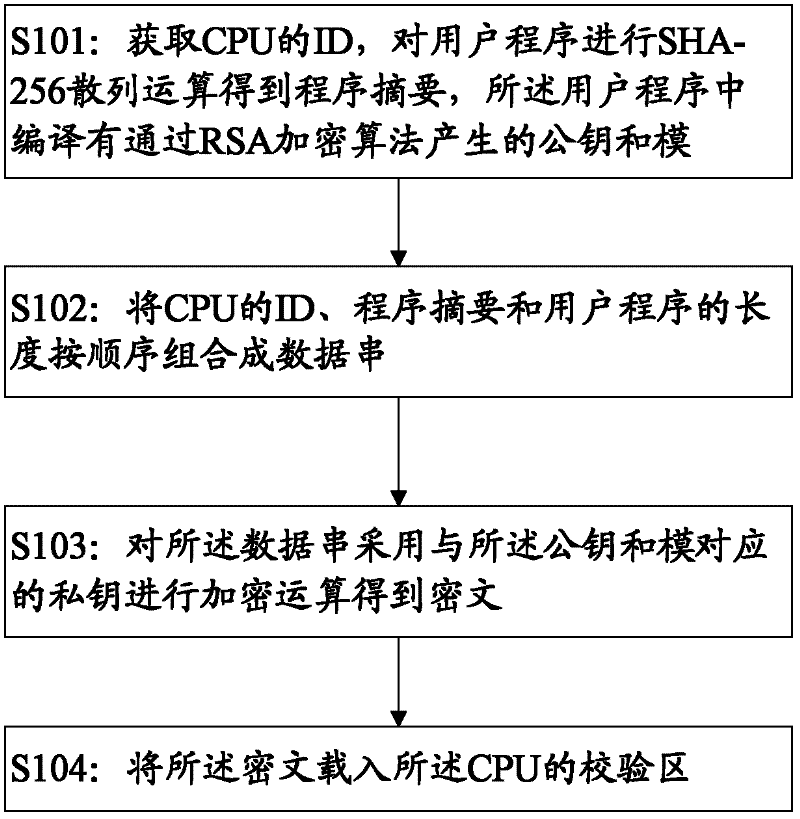
ActiveCN102609665AReduce the risk of being brute-forcedPrevent malicious tamperingDigital data protectionProgram/content distribution protectionCiphertextBrute-force attack
The invention discloses a method and a device for signing a user program verifying signature of the user program. The method for signing the user program includes steps of acquiring ID (identity) of a CPU (central processing unit), computing the user program by SHA-256 hash operation to obtain a program digest, compiling a public key and a module generated through RSA (Ron Rivest,Adi Shamirh and Len Adleman) encryption algorithm into the user program; combining the ID of the CPU, the program digest and the length of the user program in sequence to form a data string; operating the data string by a private key corresponding to the public key and the module to obtain ciphertext; and loading the ciphertext into a check area of the CPU. By combining with the RSA algorithm and the SHA algorithm to process the user program and integrating with the ID of the CPU to be a part of the signature, the user program must be restarted by being strictly subjected to the signature verifying process matched with the signature, risk in brute force attack to the user program is greatly reduced, and the user program can be effectively protected from being tampered or stolen maliciously.
Owner:恒鸿达科技有限公司
Key storage method
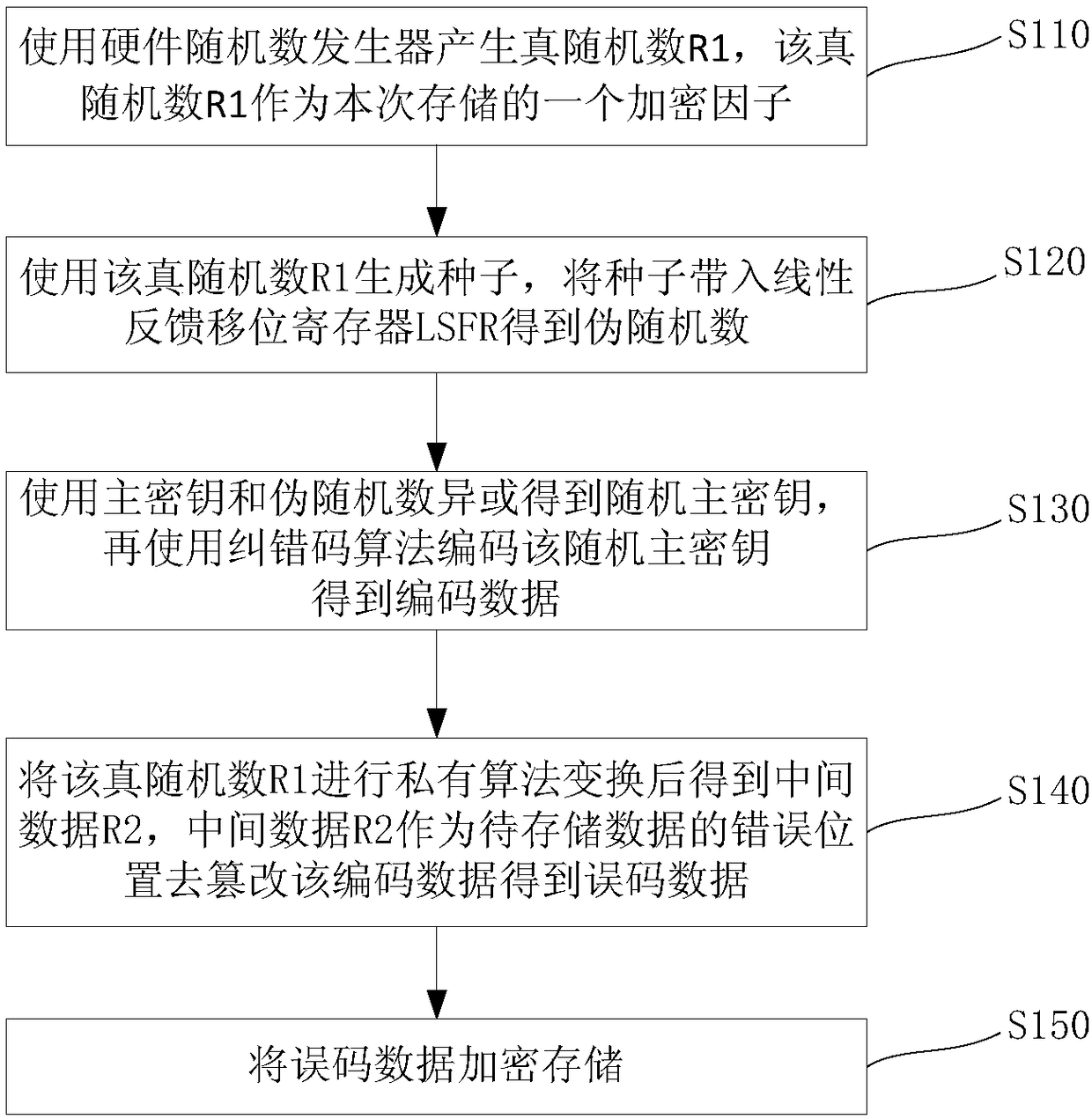
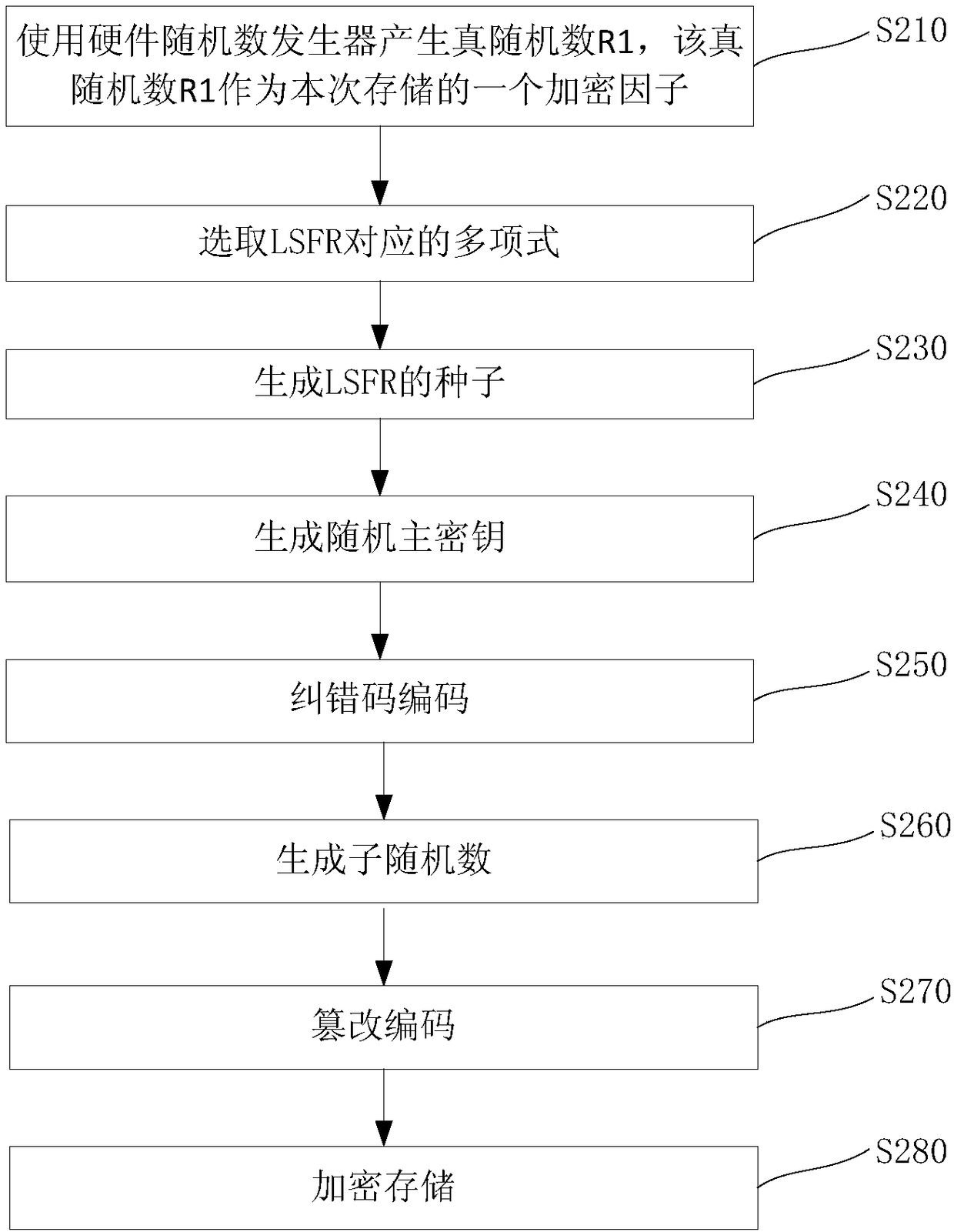
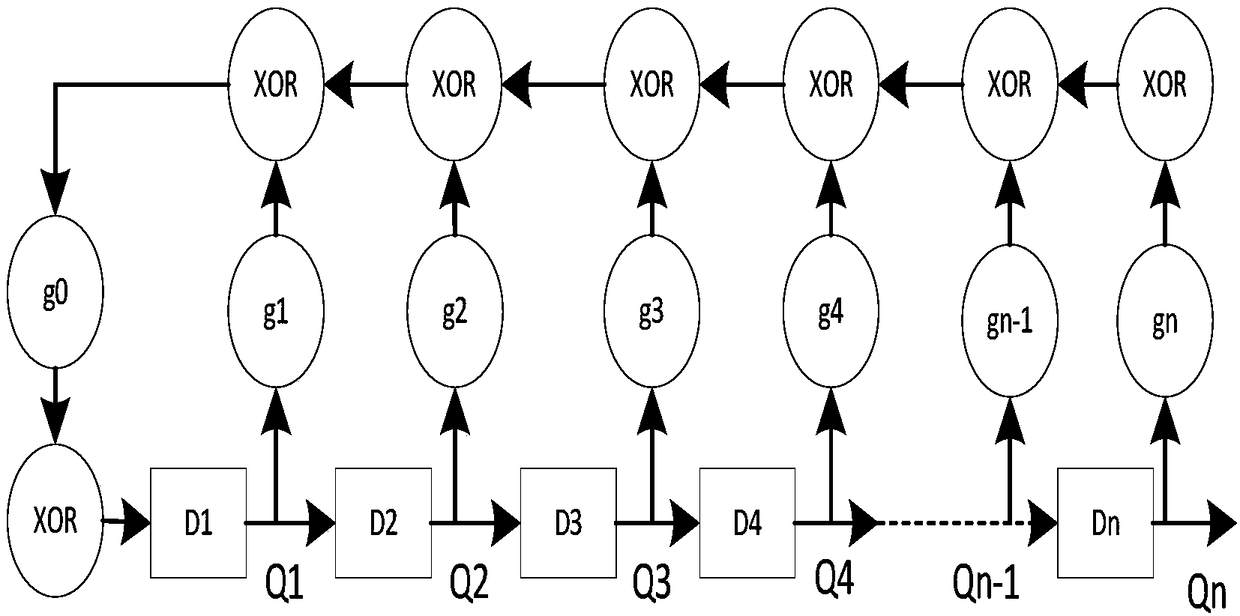
InactiveCN108259162AHigh strengthSafe storageKey distribution for secure communicationDigital data protectionAlgorithm transformationBrute force
The invention relates to a key storage method. The method comprises the following steps: generating a true random number by using a hardware random number generator, wherein the true random number isused as an encryption factor of the present storage; generating a seed by using the true random number, and substituting the seed into a linear feedback shift register to obtain a pseudo random number; performing an xor operation on a master key and the pseudo random number to obtain a random master key, and then encoding the random master key by using an error correcting code algorithm to obtainencoded data; performing private algorithm transformation on the true random number to obtain intermediate data, wherein the intermediate data are used as error locations of data to be stored to tamper the encoded data to obtain error code data; and performing encrypted storage on the error code data. According to the key storage method provided by the invention, the generated random number is hidden in the data to be protected, thereby improving the intensity of data randomization. In the case of limited storage resources, in order to prevent brute force attacks after ciphertext leakage, thedata are mixed with error codes, and the data are encrypted by using a private algorithm, so that the key storage is more secure.
Owner:AEROSPACE INFORMATION
Method for Preventing Information Leaks on the Stack Smashing Protector Technique
InactiveUS20160028767A1Negligible overheadMemory loss protectionError detection/correctionComputer hardwareBrute force
A method for hardening the Stack-Smashing Protector (SSP) technique which prevents information leaking of the protecting guard is disclosed. The reference stack guard secret value is renewed at one or more selected time points during the execution of the application. The technique is non-intrusive and has a negligible run-time cost (both spatial and temporal). The technique reuses the SSP infrastructure, and does not need to recompile the code or modify the binary image of the application. The method prevents any kind of brute force attacks against the SSP technique and most memory leaks affecting the canary guard.
Owner:RIPOLL JOSE ISMAEL +1
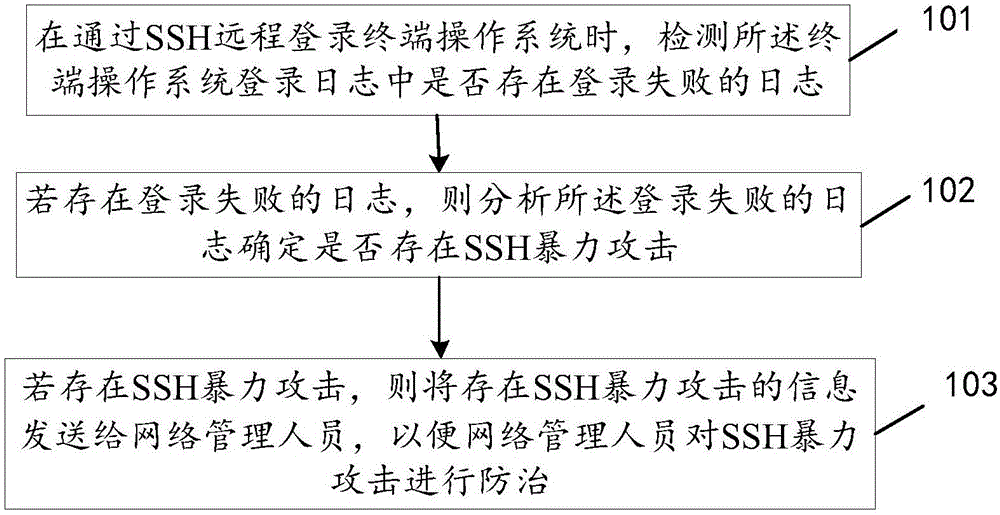
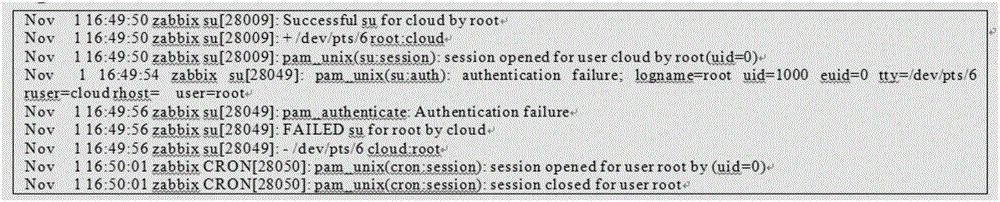
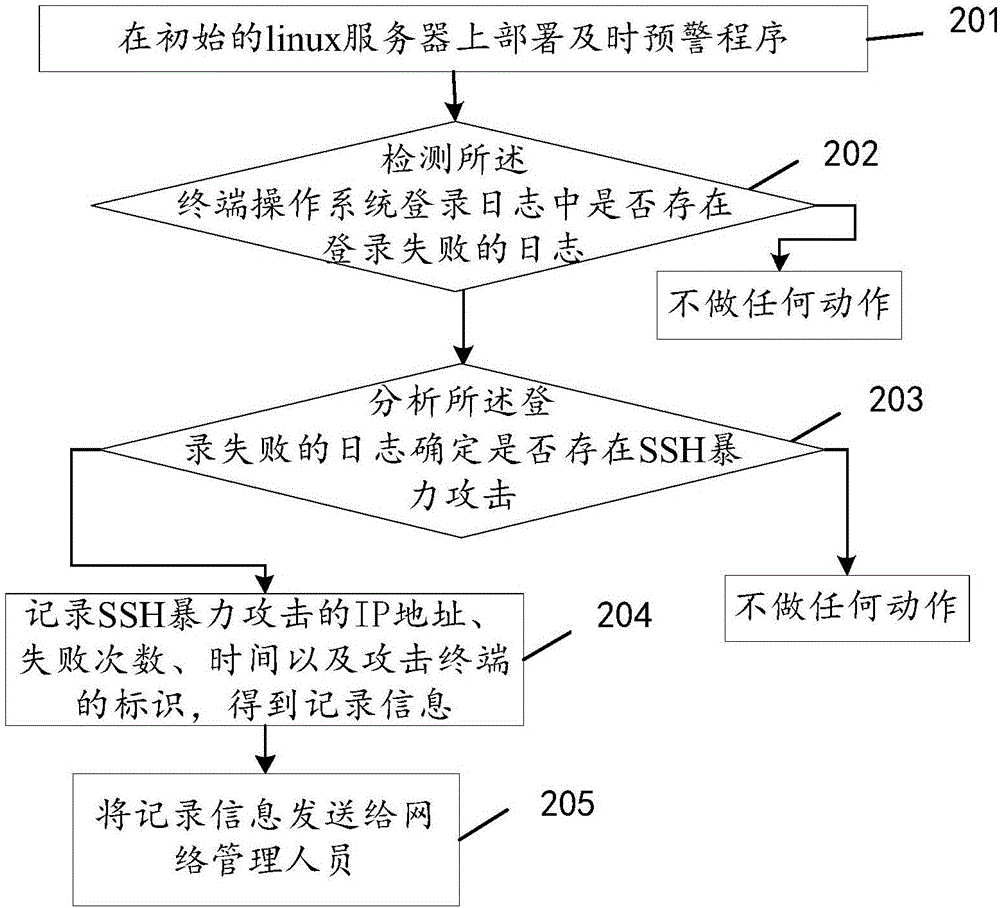
Early warning method and device of network attack
InactiveCN106656640ATimely and effective preventive measuresEffective Prevention and Control MeasuresData switching networksOperational systemNetwork management
The invention discloses an early warning method and device of a network attack, relates to the technical field of network safety and mainly aims at solving the problems that an operating system when suffering from a malicious SSH brute force attack cannot percept the attack and efficient controlling measures cannot be taken in time and efficiently for the operating system which suffers from the SSH brute force attack. The main technical scheme comprises the steps of detecting whether a log about login failure exists in a login log of a terminal operating system when remotely logging in the terminal operating system through a secure shell protocol (SSH); if the log about the login failure exists, analyzing the log about the login failure to determine whether an SSH brute force attack exists; if the SSH brute force attack exists, sending information indicating the existence of the SSH brute force attack to a network manager so as to enable the network manager to prevent the SSH brute force attack conveniently. The early warning method and device of the network attack are mainly used in an SSH brute force attack early warning process.
Owner:BEIJING SENSESHIELD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com