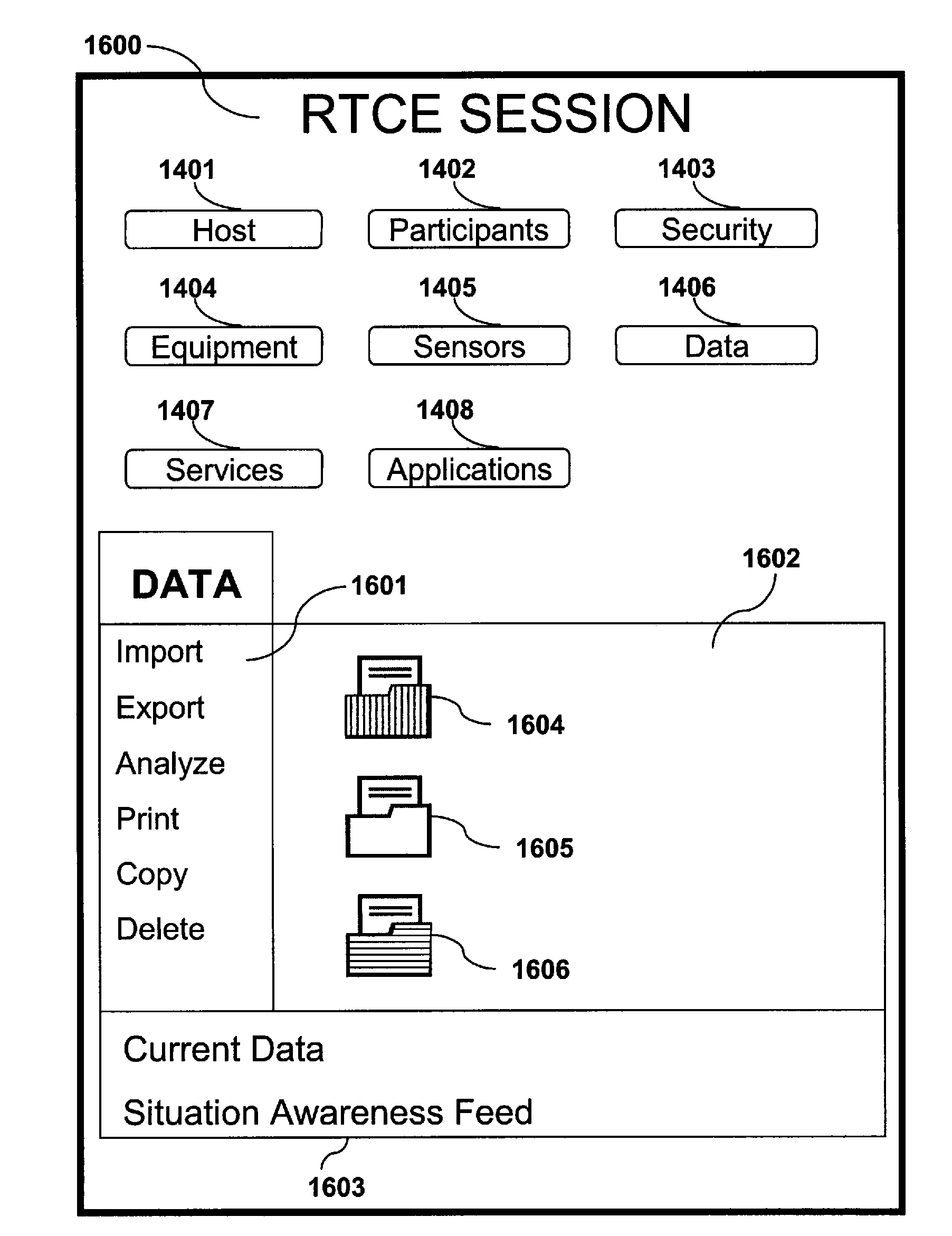
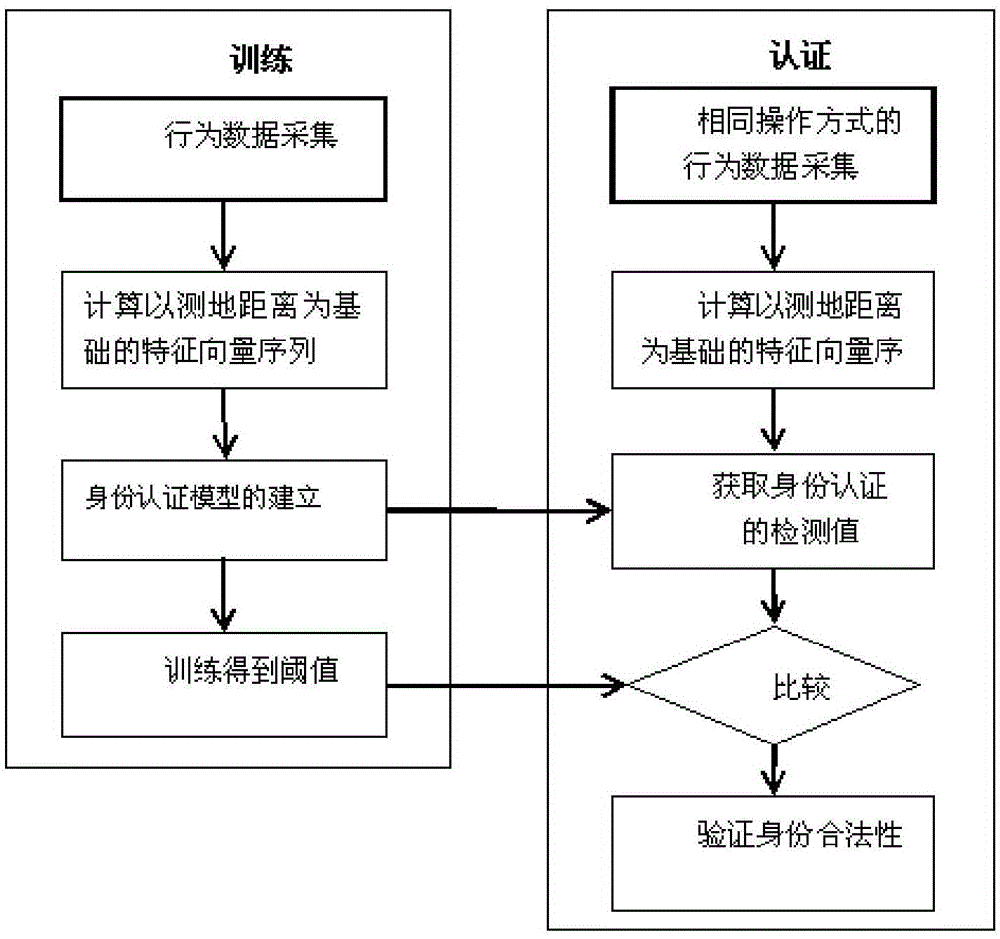
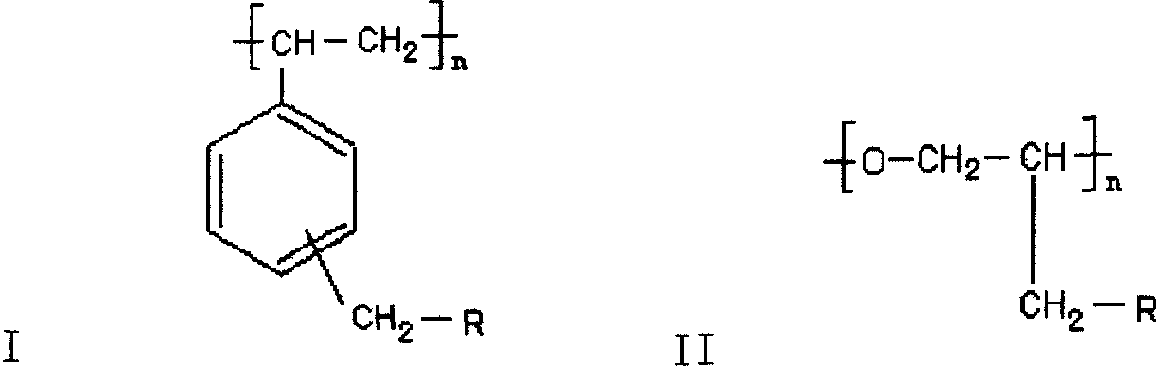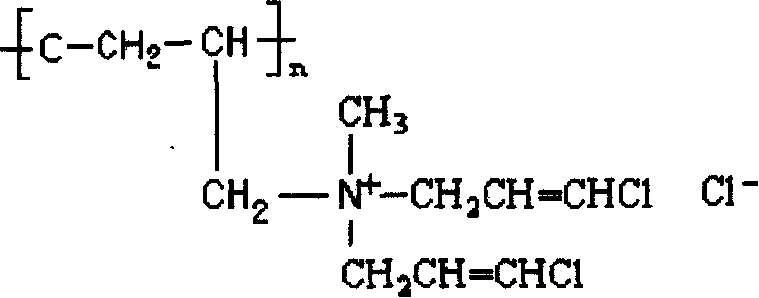Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
406results about How to "Lower success rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
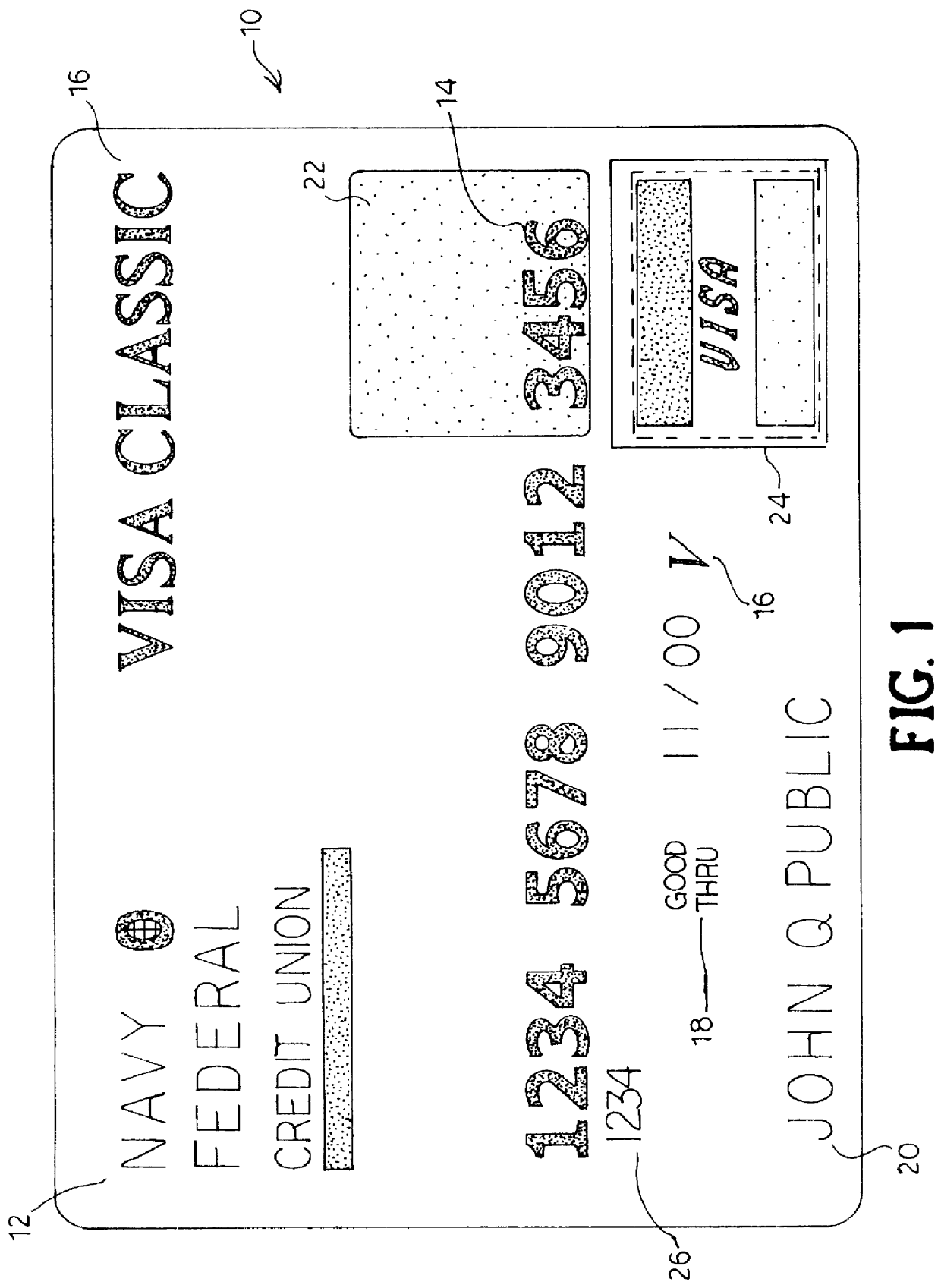
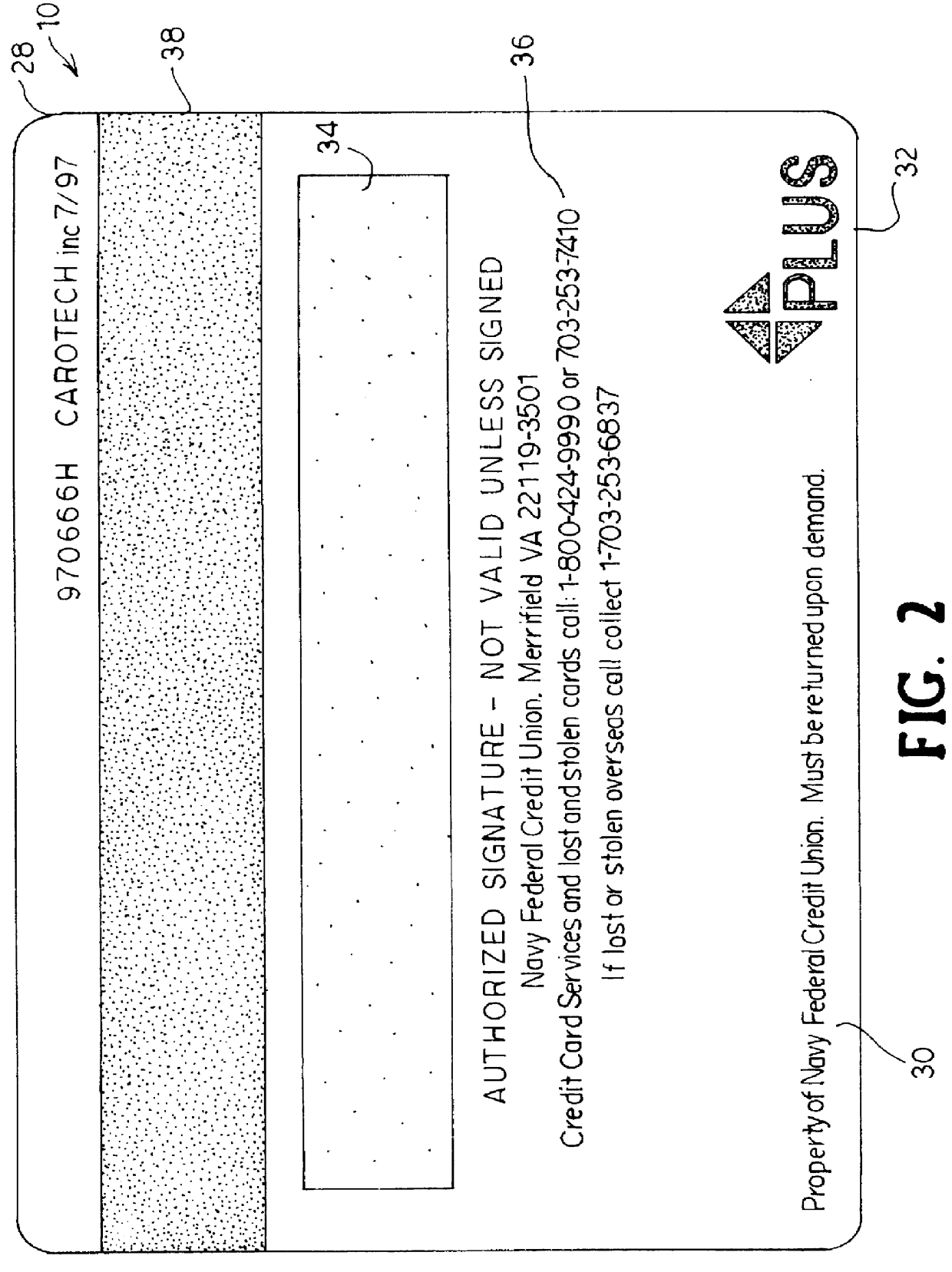
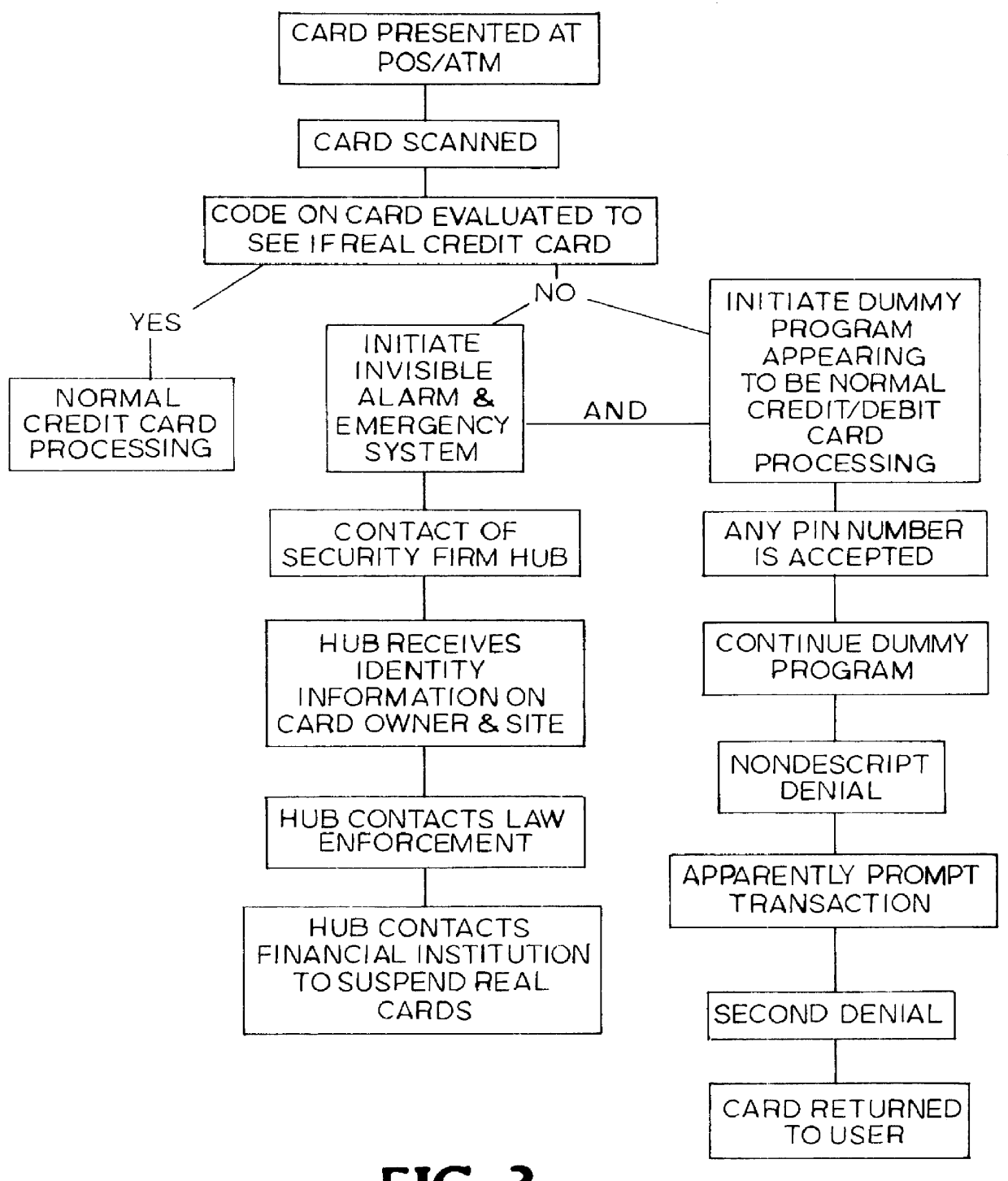
Security card and system for use thereof
InactiveUS6068184AIncreased peace of mindLower success rateComplete banking machinesFinanceCredit cardEmergency situations
A security card system that includes a security card having an appearance like a real credit card or other bank card, and a security network that contains a security firm that enrolls persons in the system who have been provided with a security card by a card-issuing institution, and uses the security network for responding to emergency calls initiated by use of the security card, reports fraud, and in general, implements an emergency system and acts as a theft deterrent.
Owner:BARNETT DONALD A
Gaming device having skill/perceived skill bonus round
InactiveUS7175524B2Maximum achievable awardLower success rateApparatus for meter-controlled dispensingVideo gamesSkill setsEngineering
Owner:IGT
Implantable cardioverter-defibrillator including arrhythmia detection criteria
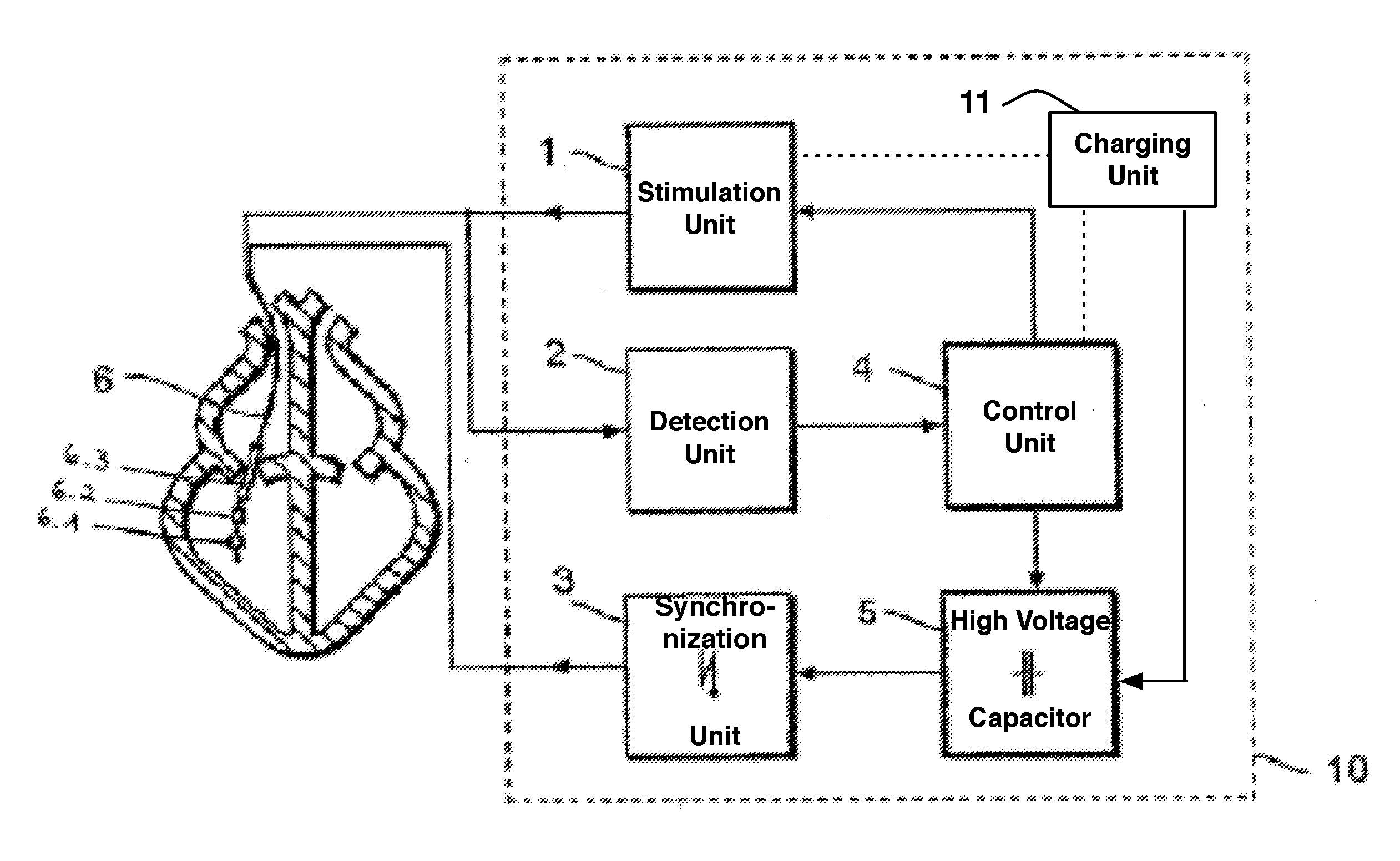
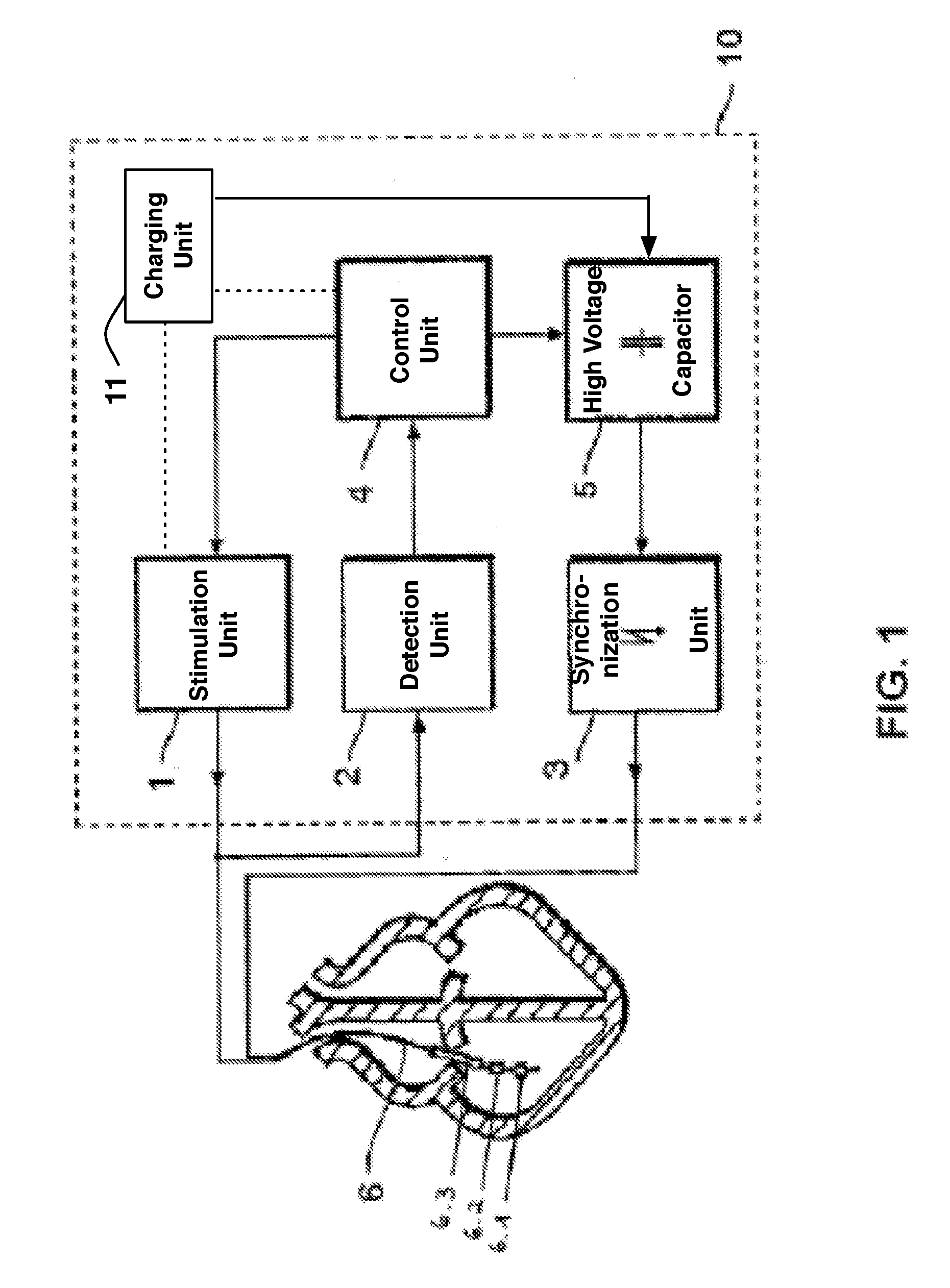
ActiveUS9393436B2Improve reliabilityLower success rateHeart defibrillatorsMedicineHigh voltage capacitors
An implantable cardioverter-defibrillator system that includes at least one or more stimulation units, one or more detection units, one or more control units, two or more electrode poles and one or more high voltage capacitors. The at least one control unit is connected with the at least one stimulation unit, and the at least one control unit is connected with at the least one detection unit. The two or more electrode poles are in contact with body tissue, and the one or more high voltage capacitors are charged by at least one charging unit, wherein the at least one charging unit is connected to the at least one control unit.
Owner:BIOTRONIK SE & CO KG
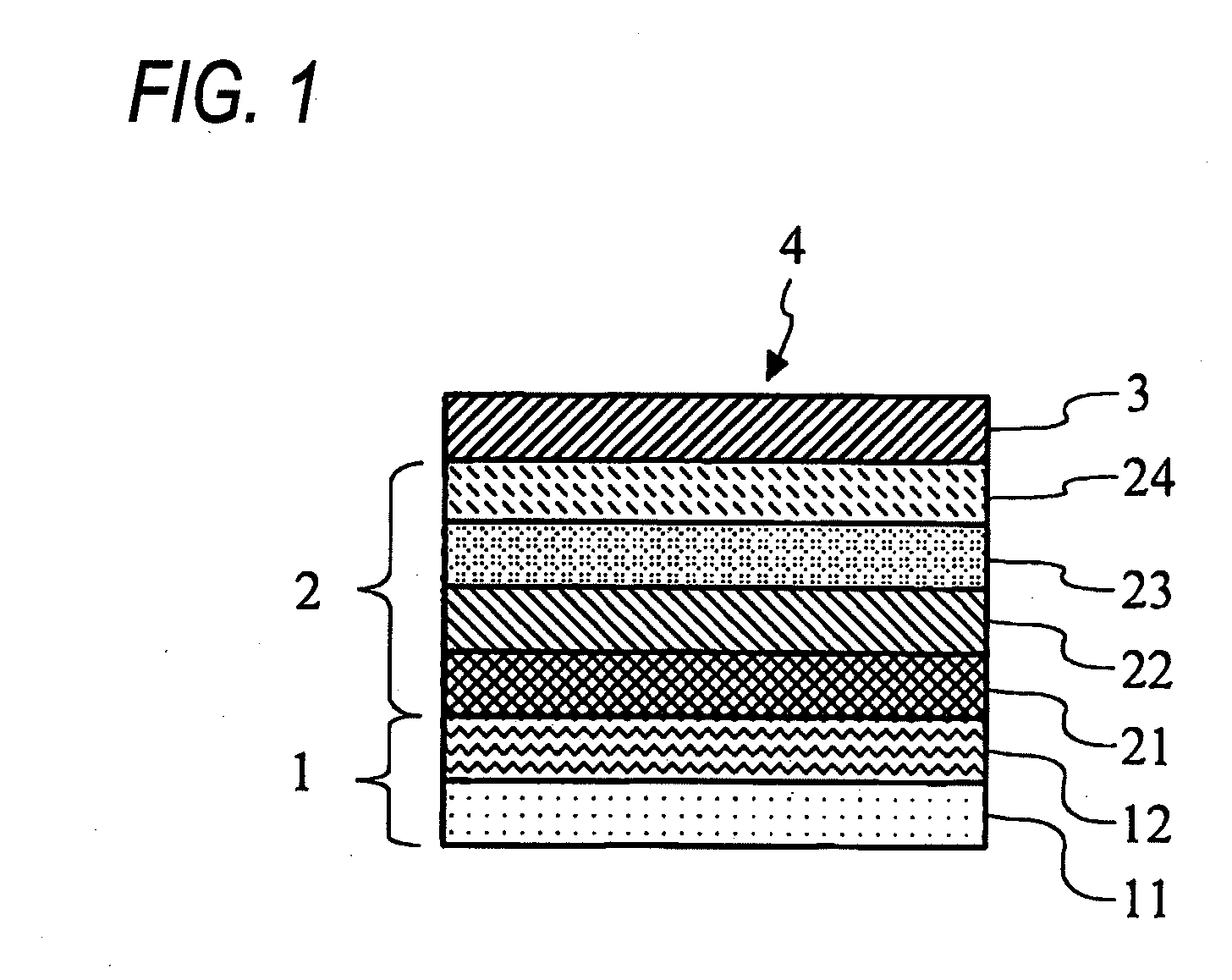
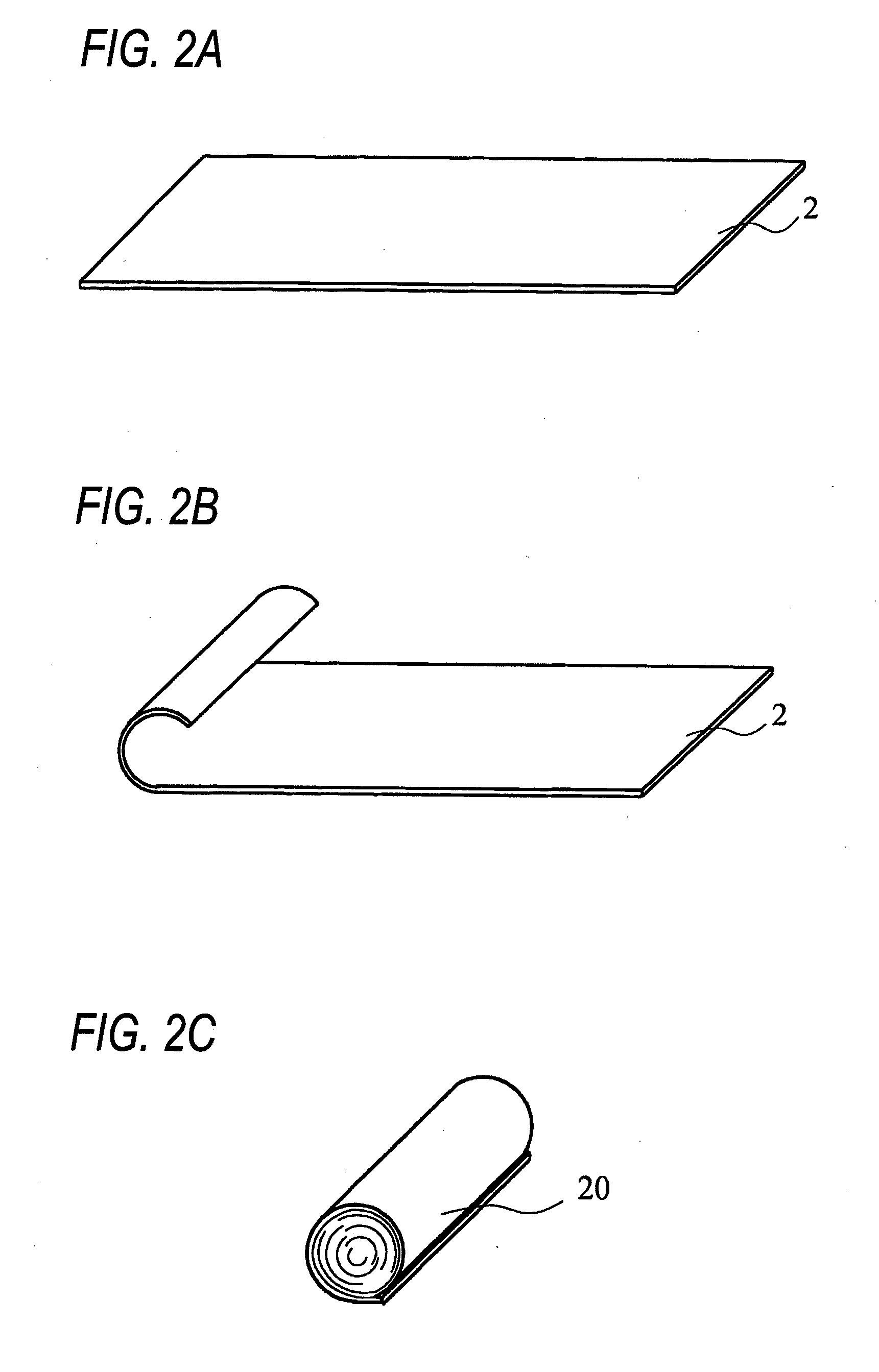
Die attach film-provided dicing tape and production process of semiconductor device
InactiveUS20100279491A1Efficient productionImprove productivityAdhesive articlesSynthetic resin layered productsDicing tapeDevice material
The present invention provides a die attach film-provided dicing tape, which includes a dicing tape, a supporting tape and a die attach film laminated in this order, wherein the supporting tape is a tape having a self-rolling peelability, and a process for producing a semiconductor device by using the die attach film-provided dicing tape.
Owner:NITTO DENKO CORP
Gaming device having skill/perceived skill bonus round
InactiveUS20050026664A1Easy to convertMaximum achievable awardApparatus for meter-controlled dispensingVideo gamesSkill setsHuman–computer interaction
Owner:IGT
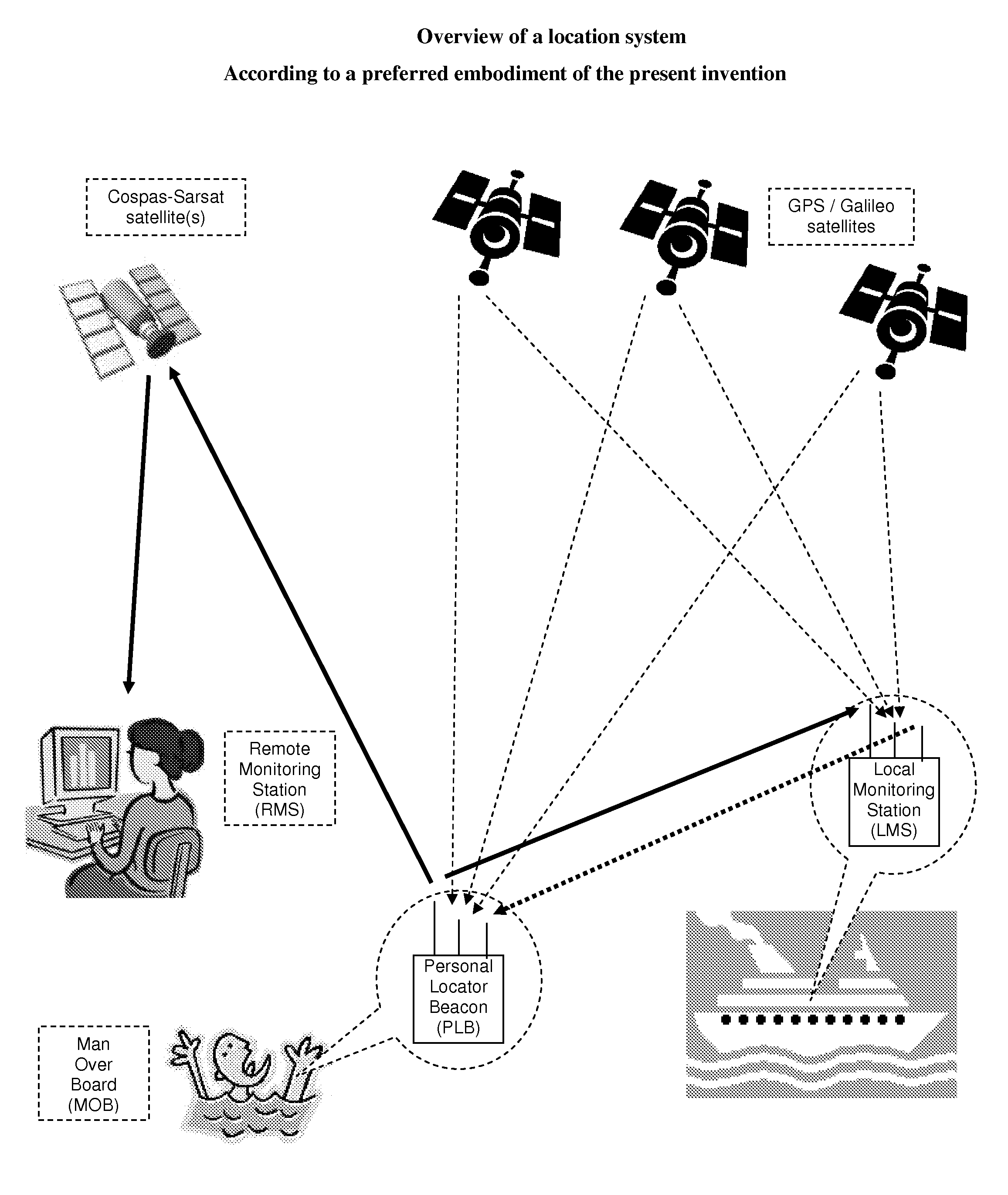
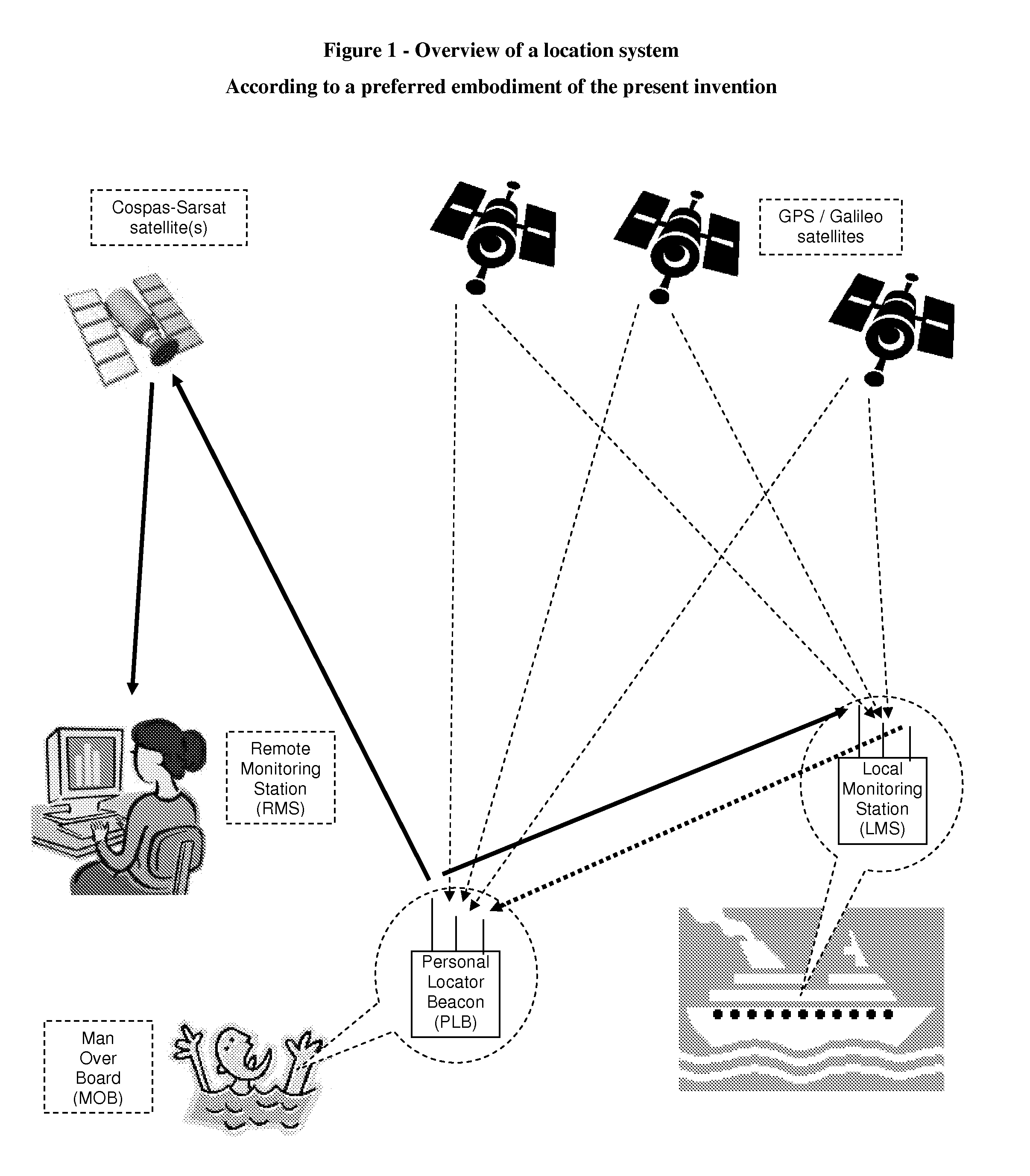
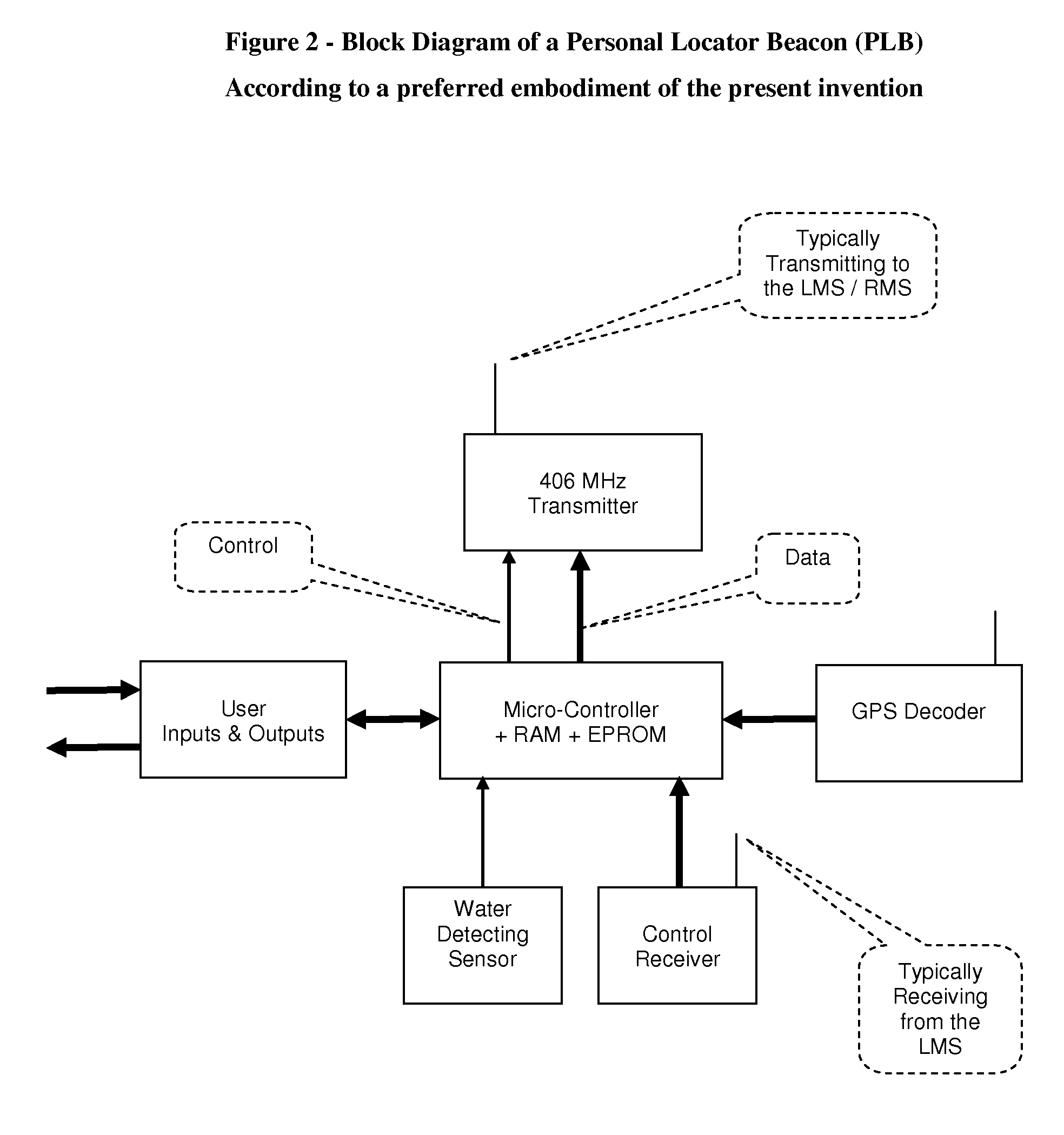
Dual mode personal locator beacon
ActiveUS7492251B1Decrease transmission repetition rateLong PLBDirection finders using radio wavesTelephonic communicationDual modeOperation mode
A Personal Locator Beacon (PLB), supporting two operation modes local monitoring and remote monitoring. The apparatus includes a PLB that supports the present operation mode, as well as a local monitoring mode, employing the same transmitter, and automatically switching between modes. Upon activation, the PLB first tries to communicate with a local monitoring station, at a low transmission power, and at a high repetition rate, in purpose of dealing with the PLB call locally, without involving the remote monitoring station. Then, if not acknowledged by a local monitoring station, the PLB increases its transmission power, enabling access to a remote monitoring station. In a preferred embodiment, the PLB is carried by a person onboard a vessel, to alarm upon a Man Overboard (MOB) accident, the local monitoring station is installed onboard the same vessel, and the remote monitoring station is part of a satellite Search and Rescue (SAR) system, as Cospas-Sarsat.
Owner:MOBIT TELECOM
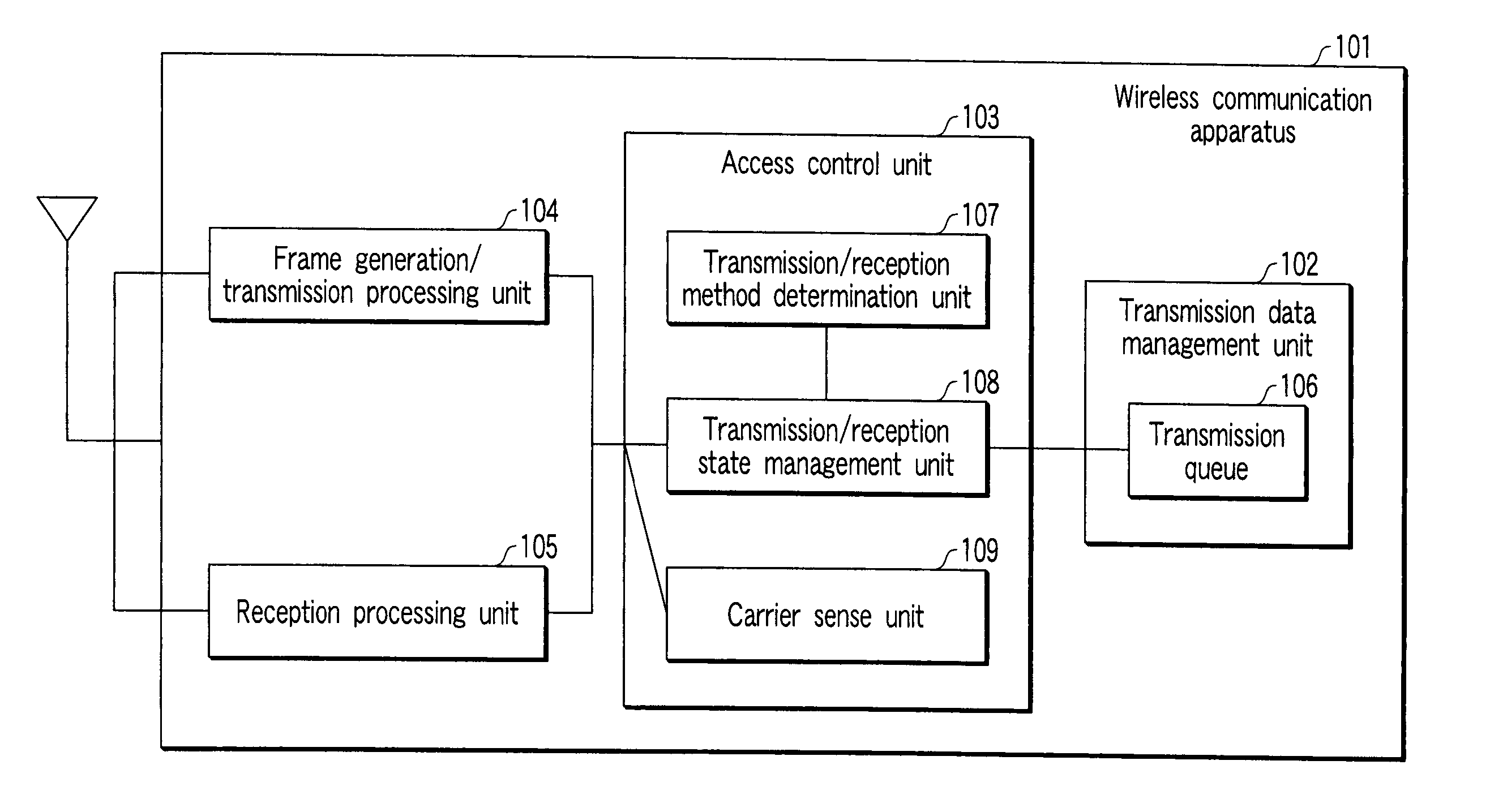
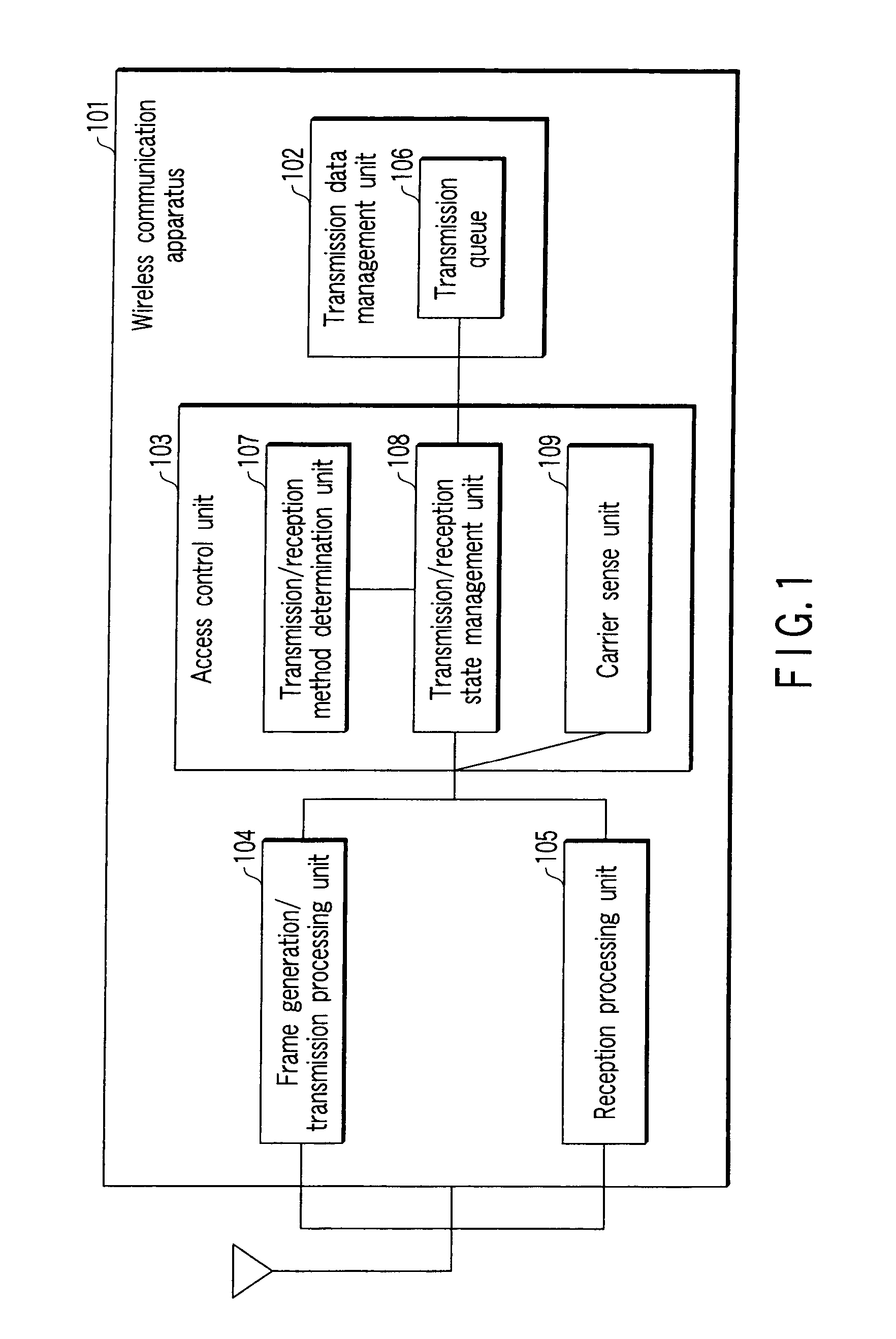
Wireless communication apparatus and method
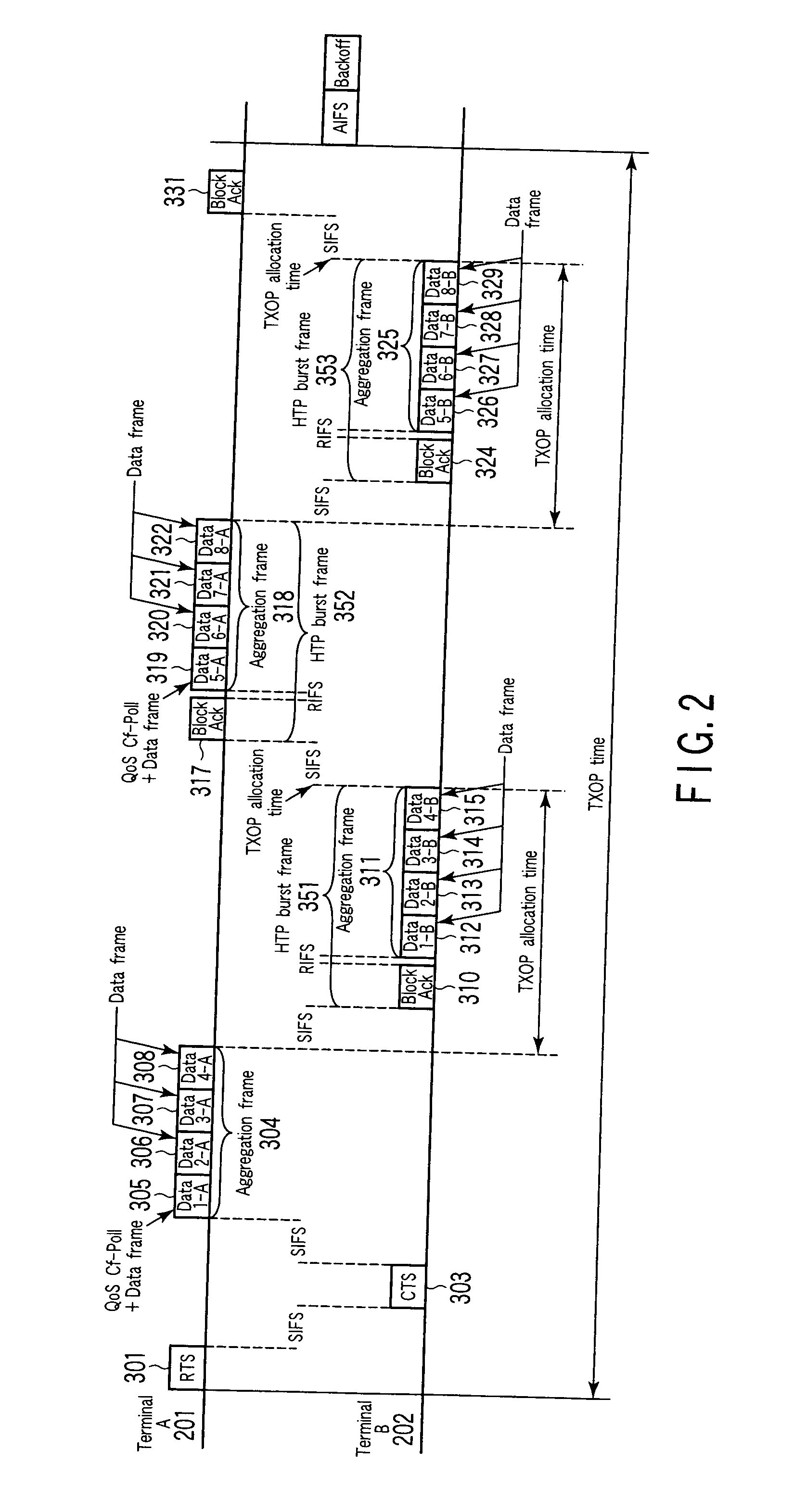
ActiveUS20080002615A1Improve transmission success rateReduce transmissionError preventionNetwork traffic/resource managementComputer hardwareData transmission
A wireless communication apparatus performs bi-directional communication with an initiator. The apparatus is allocated an allocation period for data transmission from the initiator. The apparatus includes means for generating a first physical frame including an acknowledgement frame with respect to data received from the initiator, and generating a second physical frame in which a plurality of transmission data frames addressed to the initiator are aggregated. The apparatus also includes means for transmitting the first physical frame at a first transmission rate and the second physical frame at a second transmission rate, during the allocation period.
Owner:PALMIRA WIRELESS AG
Method and system for reading information at network resource site, and searching engine
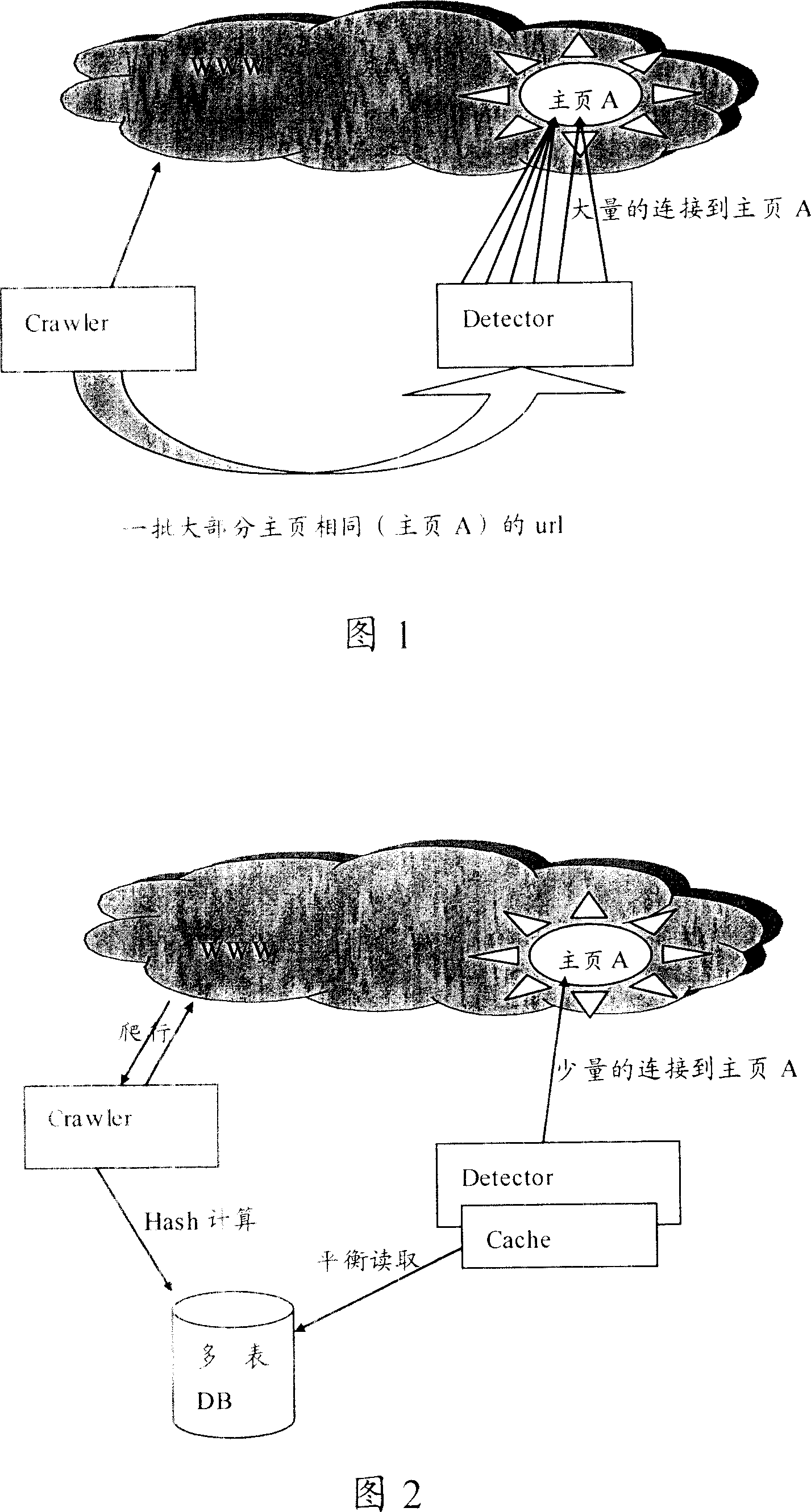
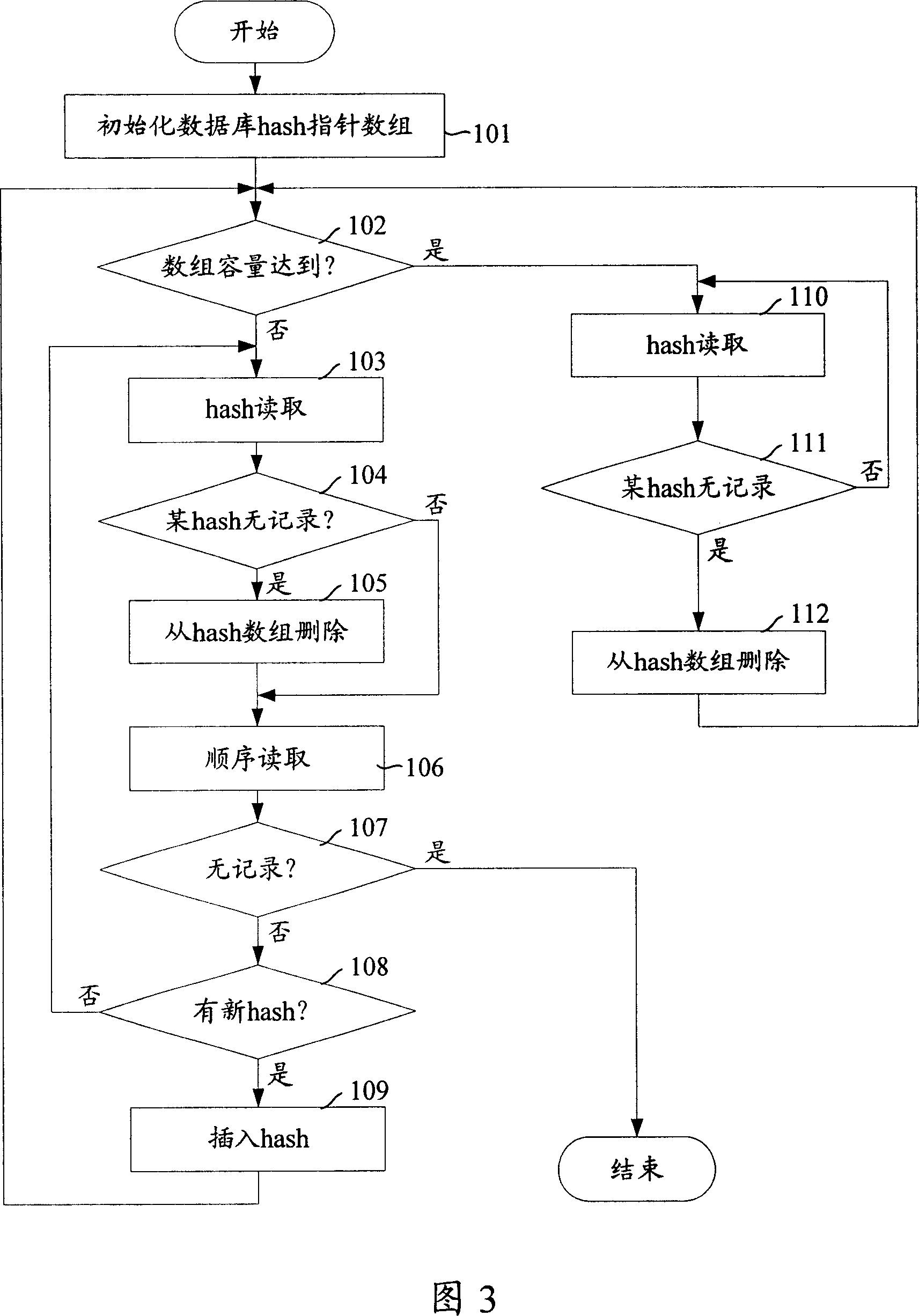
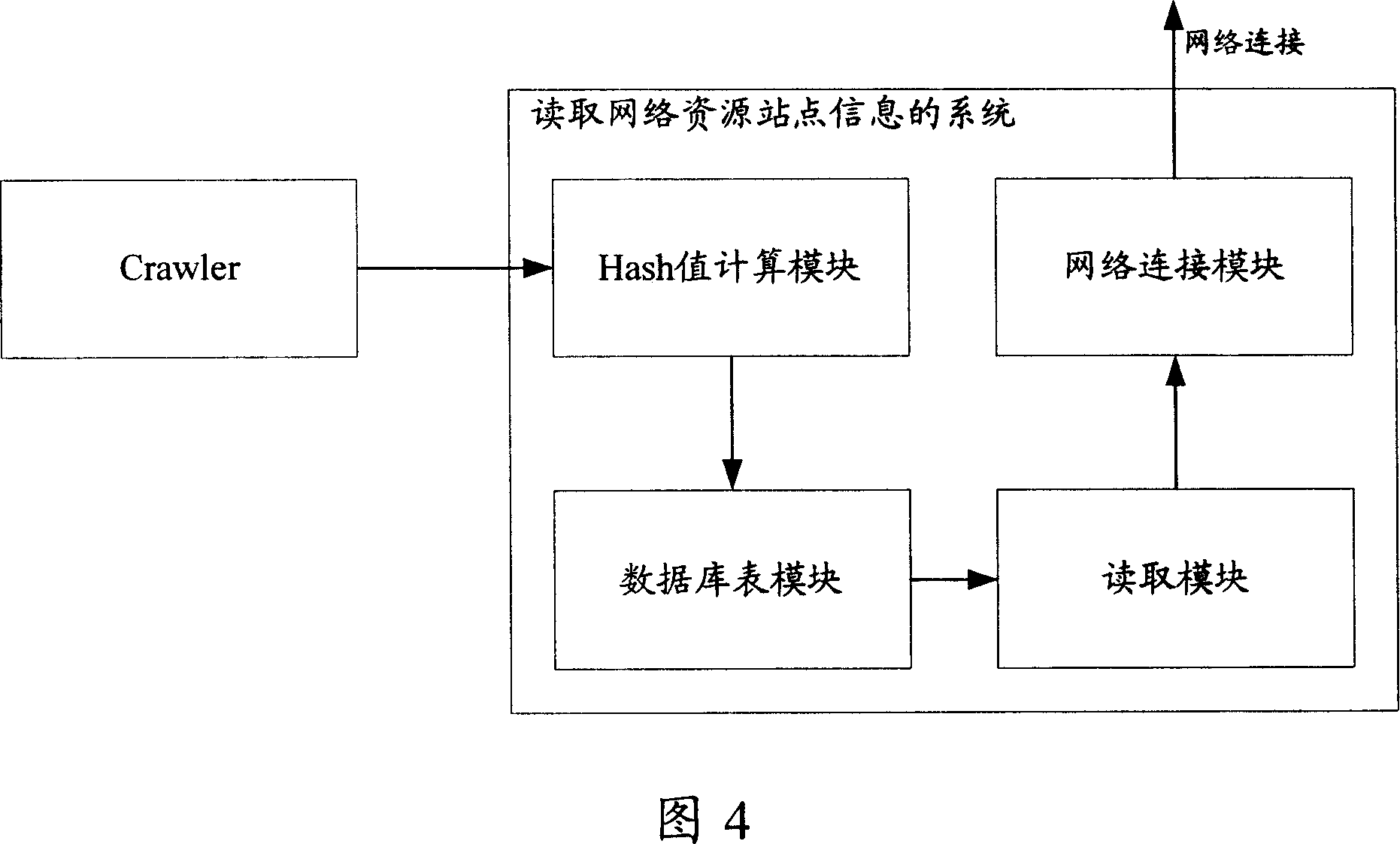
ActiveCN101004740ASolve the Detector concurrencySolve efficiency problemsSpecial data processing applicationsComputer hardwareArray data structure
A method for fetching information of network resource station includes obtaining hash value by calculation and storing obtained hash valve into databank table, initializing hash pointer array, carrying out sequential fetching on databank table, setting a corresponding pointer array to be zero if hash array is not existed in a certain record and executing hash fetching step if hash array volume is on preset top limit or otherwise executing sequential fetching, carrying hash fetching on databank table and executing sequential fetching if fetching record of certain hash value is blank or otherwise executing hash fetching.
Owner:SHENZHEN SHI JI GUANG SU INFORMATION TECH
Perturb voltage as a decreasing non-linear function of converter power
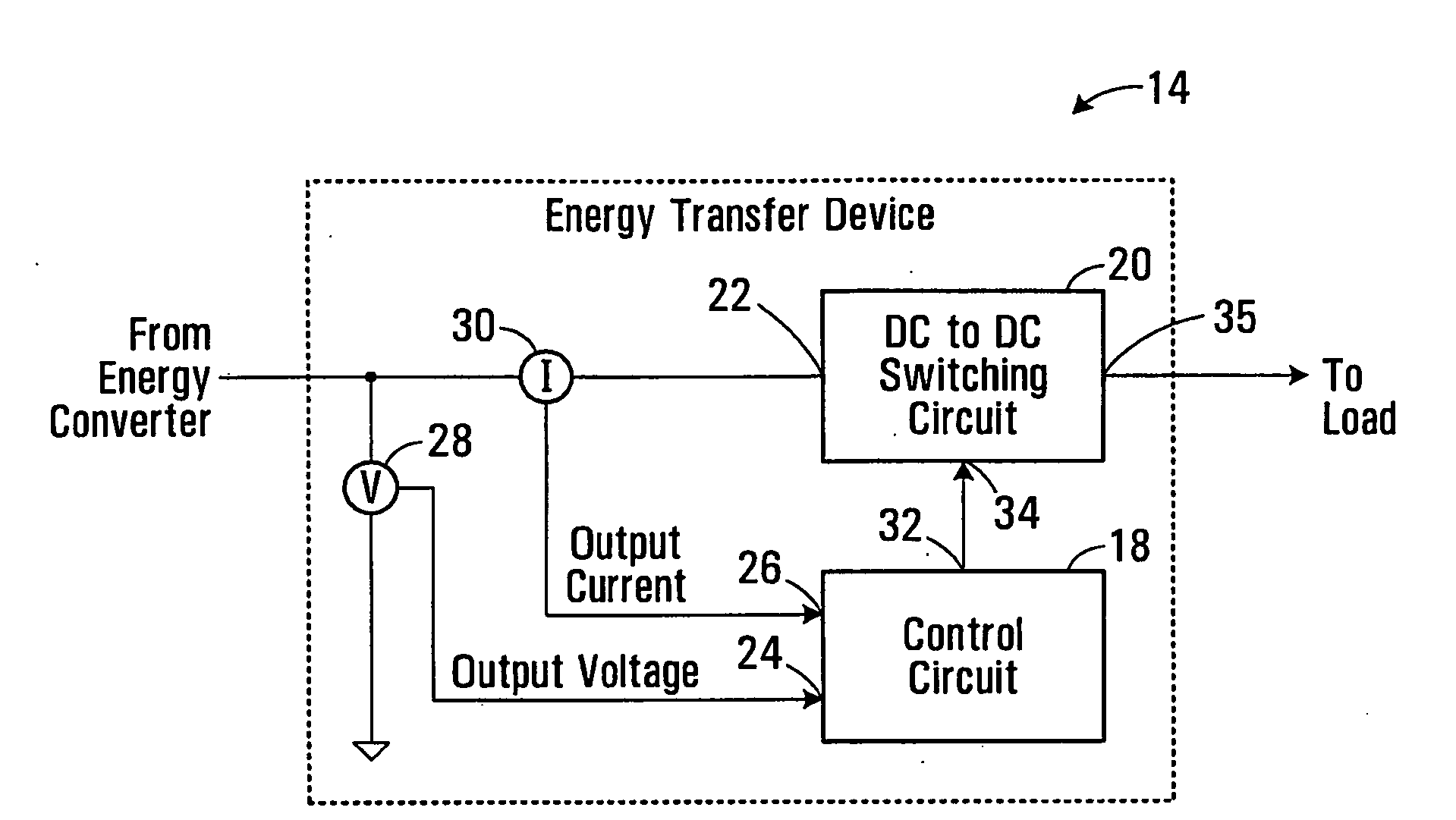
ActiveUS20100176771A1Lower success rateAc network voltage adjustmentElectric variable regulationTransverterEngineering
Methods, apparatus and media for controlling a switching circuit controlling an amount of power drawn from an energy converter, to optimize the amount of power drawn from the energy converter. An output voltage and an output current of the energy converter are measured to produce signals representing converter output voltage and current. Converter power is calculated from the product of the converter output voltage and current. A perturb voltage is calculated as a decreasing nonlinear function of the converter power. A new reference voltage signal representing a desired converter output voltage is produced in response to a previous reference voltage signal and the perturb voltage. The reference voltage signal is used by the switching circuit to adjust the power drawn from the converter to achieve the desired converter output voltage.
Owner:SCHNEIDER ELECTRIC SOLAR INVERTERS USA
Transcleral opthalmic illumination method and system
InactiveUS20070159600A1Low success rateIncrease efficiencySurgical instrument detailsOthalmoscopesRetina/choroidOphthalmoscopes
A method and apparatus for illuminating the interior of the eye through the sclera without any contact to the eye. The apparatus contains a lamp element and optics that focus the light on the eye sclera. One or more fiber optics bundles may be used to convey the light from the light source close to the illuminated eye, ending with condensing optical elements. Alternatively, light could be conveyed by sharing the optics of an imaging system. It is useful for observing or imaging the interior of the eye, the retina, or the choroid. The observation or the imaging of the interior of the eye, the retina, or the choroid by applying the disclosed illumination method can be done in conjunction with any system that includes optics for that purpose, e.g., fundus cameras and ophthalmoscopes, without using those systems' illumination elements.
Owner:MEDIBELL MEDICAL VISION TECH
Diagnosis and monitoring of renal failure using peptide biomarkers
InactiveUS20100190164A1Failure incidentLower success rateSugar derivativesPeptide/protein ingredientsUrologyPeptide
Methods for the determination of renal failure, especially chronic renal failure and acute kidney injury, by measurement of peptide or protein biomarkers are described. The methods are useful to determine stages of renal failure, especially the early stages such as stage 1, 2, and 3 of chronic renal failure and stages R and I of acute kidney injury. Furthermore there are described peptides and test kits used in the invention. The described methods are intended to replace or complement the measurement of creatinine and / or cystatin C and / or NGAL for diagnosis of renal failure.
Owner:PXBIOSCI
Network dynamic service monitoring method and apparatus
ActiveCN104811344AAvoid wastingAvoid bad judgmentCommerceData switching networksFailure rateWorkload
The invention discloses a network dynamic service monitoring method. The method comprises the following steps: extracting already finished network service data in a specific period from a network service data record as historical service data, adjusting and calculating a success rate reference value to obtain an adjusting success rate reference value in accordance with the success rate reference value or a failure rate reference value which is obtained according to the historical service data, and determining whether the adjusting success rate reference value is smaller than or equal to a preset fluctuation ratio alarm threshold; or performing adjustment and calculation on the failure rate reference value to obtain an adjusting failure rate reference value, and determining whether the adjusting failure rate reference value is greater than the preset fluctuation ratio alarm threshold; if so, determining that severe abnormities occur in network services within a monitoring period; and determining the severity of the severe abnormities through severity scores. By using the dynamic service monitoring method, the network service monitoring accuracy and flexibility are improved, and the manual processing workload generated due to false reporting is effectively reduced.
Owner:ADVANCED NEW TECH CO LTD
Event reminding method and device
InactiveCN104158955AIncrease success rateLower success rateSubstation equipmentOffice automationComputer engineeringComputer terminal
Owner:XIAOMI INC
Secure messaging
ActiveUS20130275758A1Improve the level ofReduce consumptionKey distribution for secure communicationUser identity/authority verificationPrivate communicationOff the shelf
Given the rise in popularity of communicating personal, private, sensitive, or vital peer-to-peer or peer-to-group information over insecure text messaging infrastructure, it would be highly desirable to provide a lightweight solution that enables the exchange of information in a secure manner. The non-limiting technology herein provides systems and methods for the exchange of cryptographic material that can be used to encipher message-oriented communications between at least two peer devices. Once the cryptographic material is exchanged between cooperating peers, this lightweight solution can be used by common off the shelf hardware such as smartphones, tablets, feature phones, or special purpose machine to machine devices for private communications, such as command and control, location services, etc. using insecure voice or data communication paths, such as SMS.
Owner:GLOBAL INTEGRITY INC
Optical Under-Sampling And Reconstruction Of Sparse Multiband Signals
InactiveUS20110123192A1Efficient reconstructionImprove signal-to-noise ratioAnalogue/digital conversionTime-division optical multiplex systemsReconstruction methodComb generator
A scheme for reconstructing multiband signals that occupy a small part of a given broad frequency range under the constraint of a small number of sampling channels. The multirate sampling scheme (MRS) entails gathering samples at several different rates whose sum is significantly lower than the Nyquist sampling rate. The number of channels does not depend on any characteristics of a signal. The reconstruction method may or may not rely on the synchronization between different sampling channels. The scheme can be implemented easily with optical sampling systems. The optical pulses required for the under-sampling are generated by a combination of an electrical comb generator and an electro-absorption optical modulator
Owner:TECHNION RES & DEV FOUND LTD
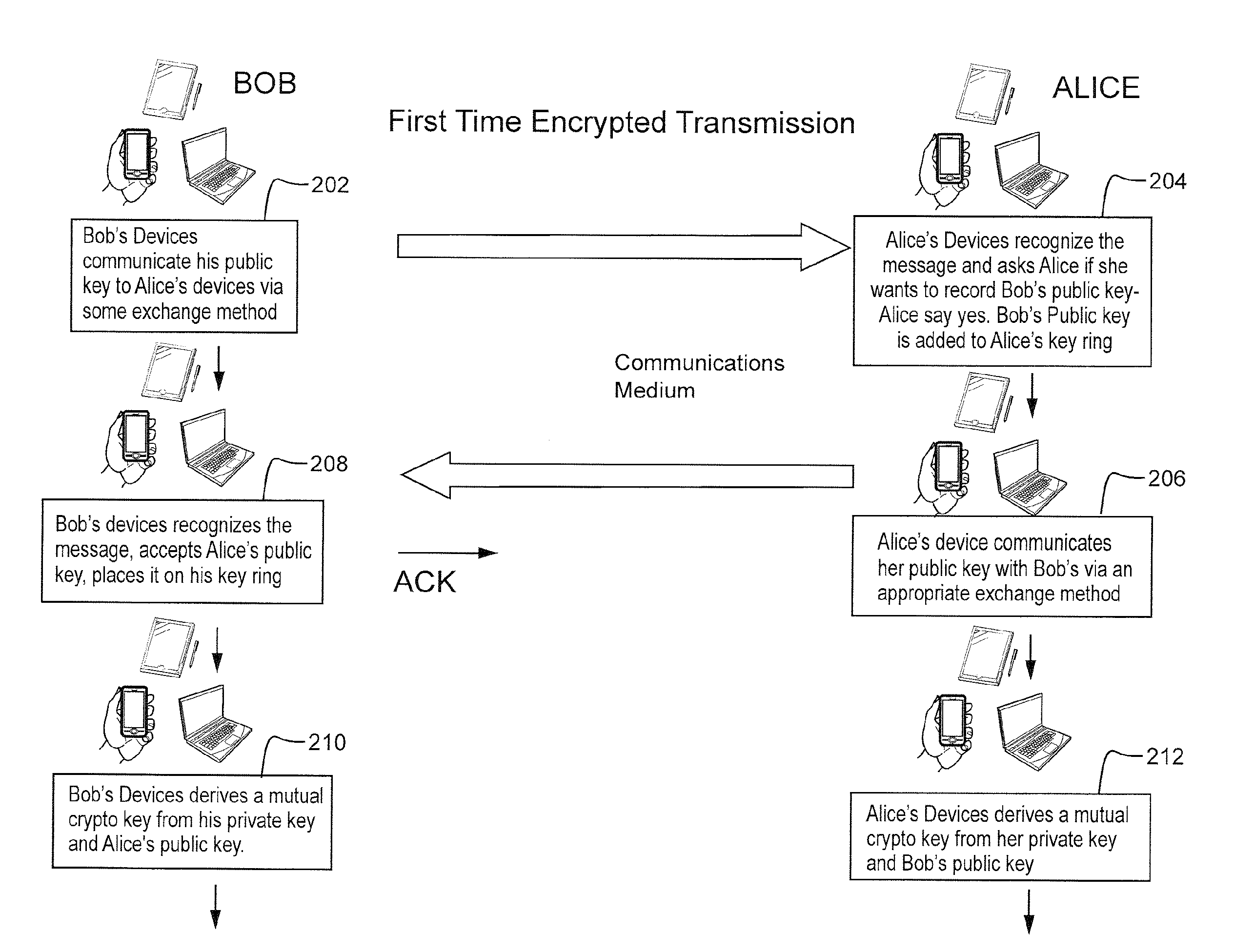
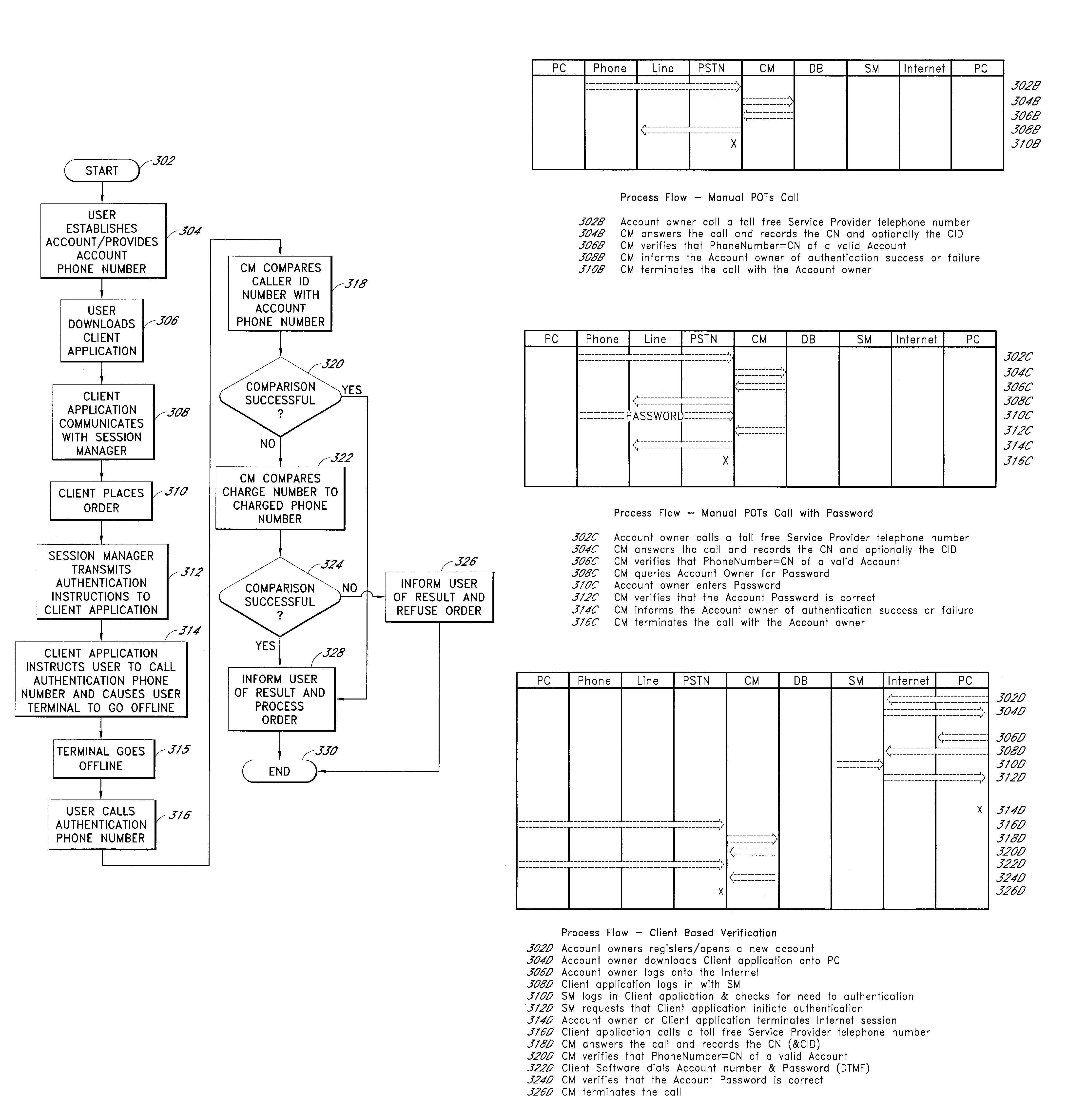
Apparatus and methods for telecommunication authentication
InactiveUS7460653B2Lower success rateReduce morbidityInterconnection arrangementsAutomatic call-answering/message-recording/conversation-recordingUser authenticationComputer science
The present invention is related to telecommunications, and in particular to systems and methods of using telecommunication services for user authentication. Account information is stored for a user, the account information including at least a first phone number associated with the user. A user order is received. A verification phone call is received from the user, the call including charge phone number information. The charge number information is compared to the first phone number to authenticate that the user is associated with the first phone number. Based at least in part on the comparison, the user order is selectively caused to be fulfilled.
Owner:CALLWAVE COMM
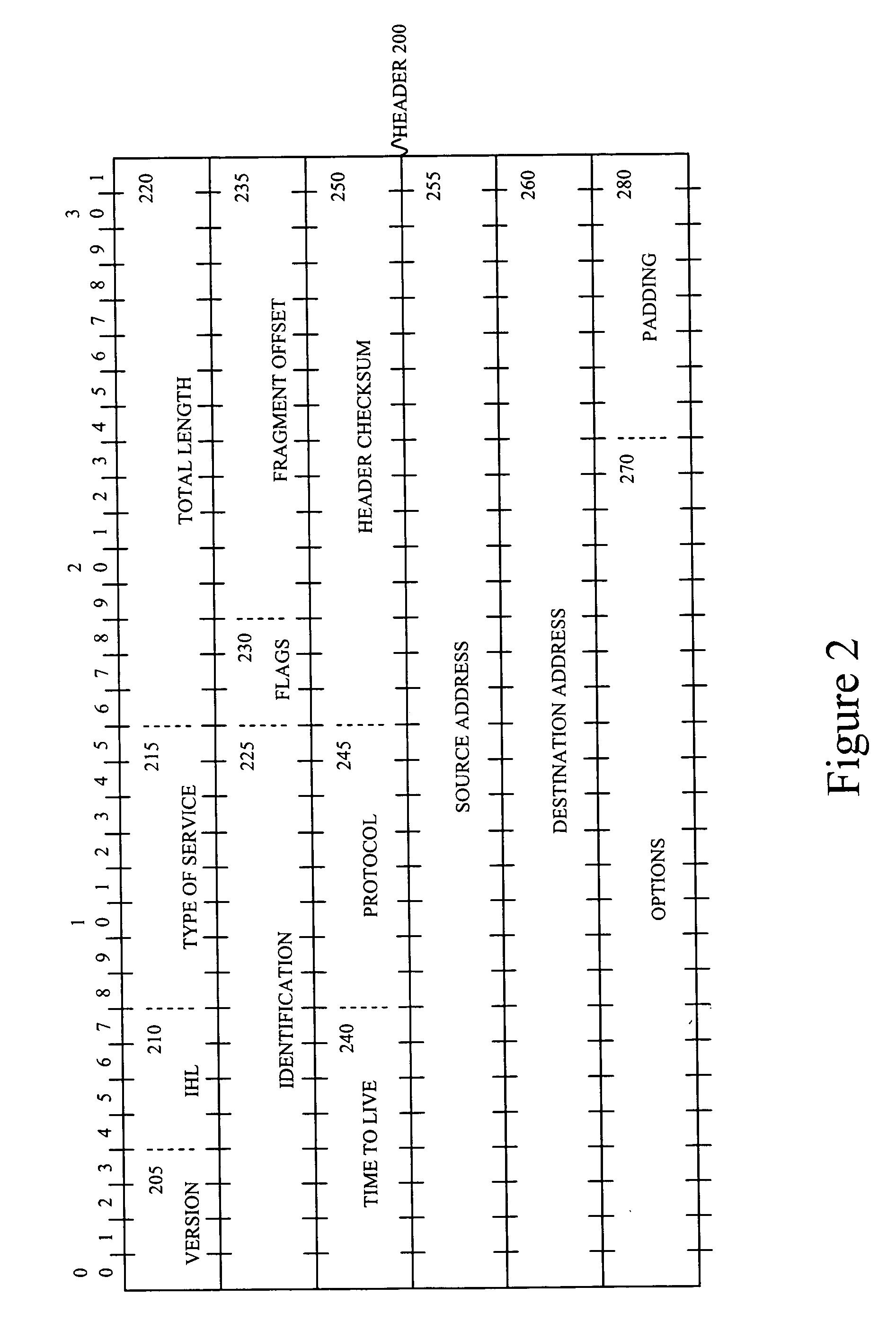
Means of mitigating denial of service attacks on IP fragmentation in high performance IPsec gateways
InactiveUS20070143598A1Lower success rateReduce probabilityMemory loss protectionError detection/correctionIPsecIP fragmentation
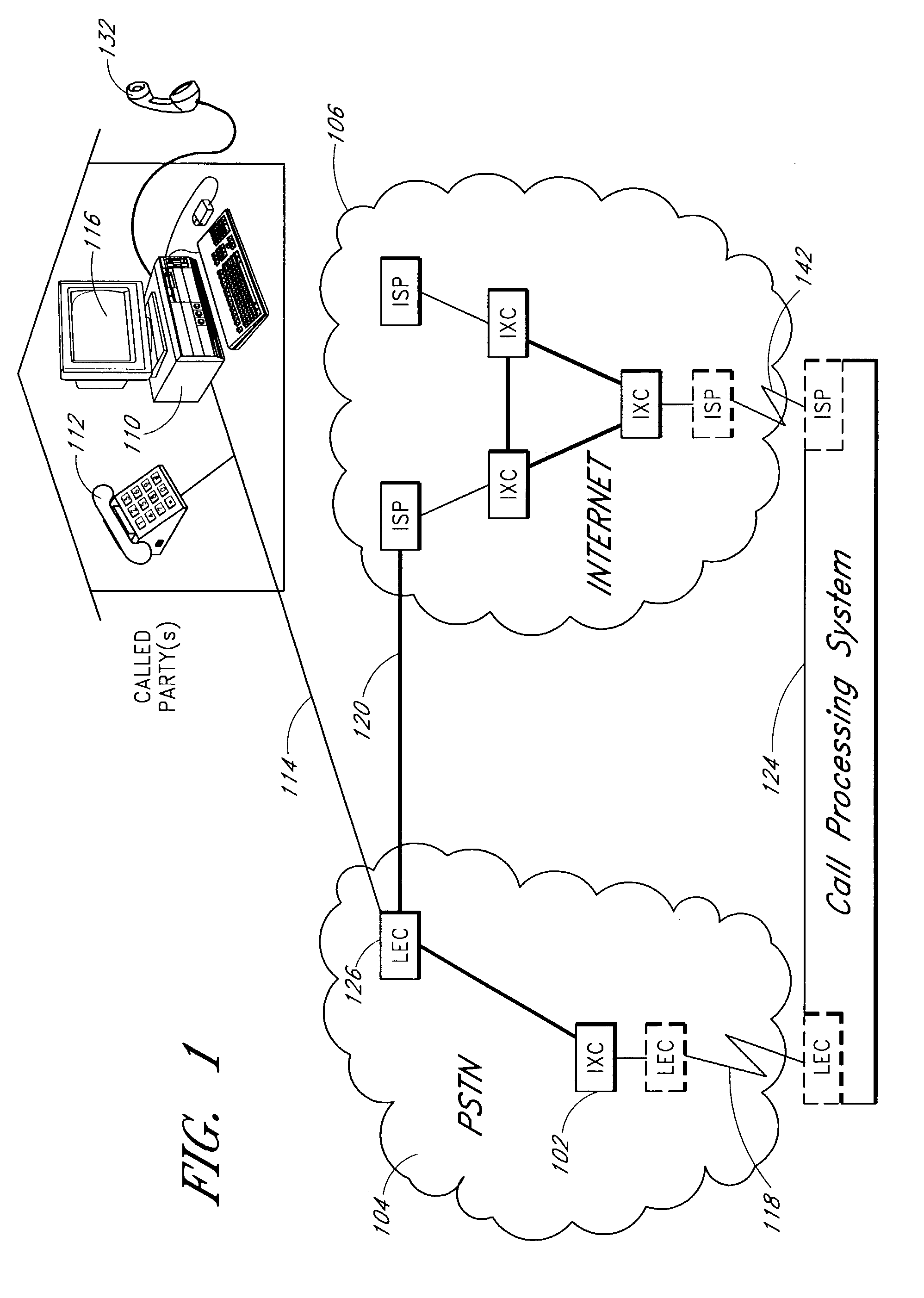
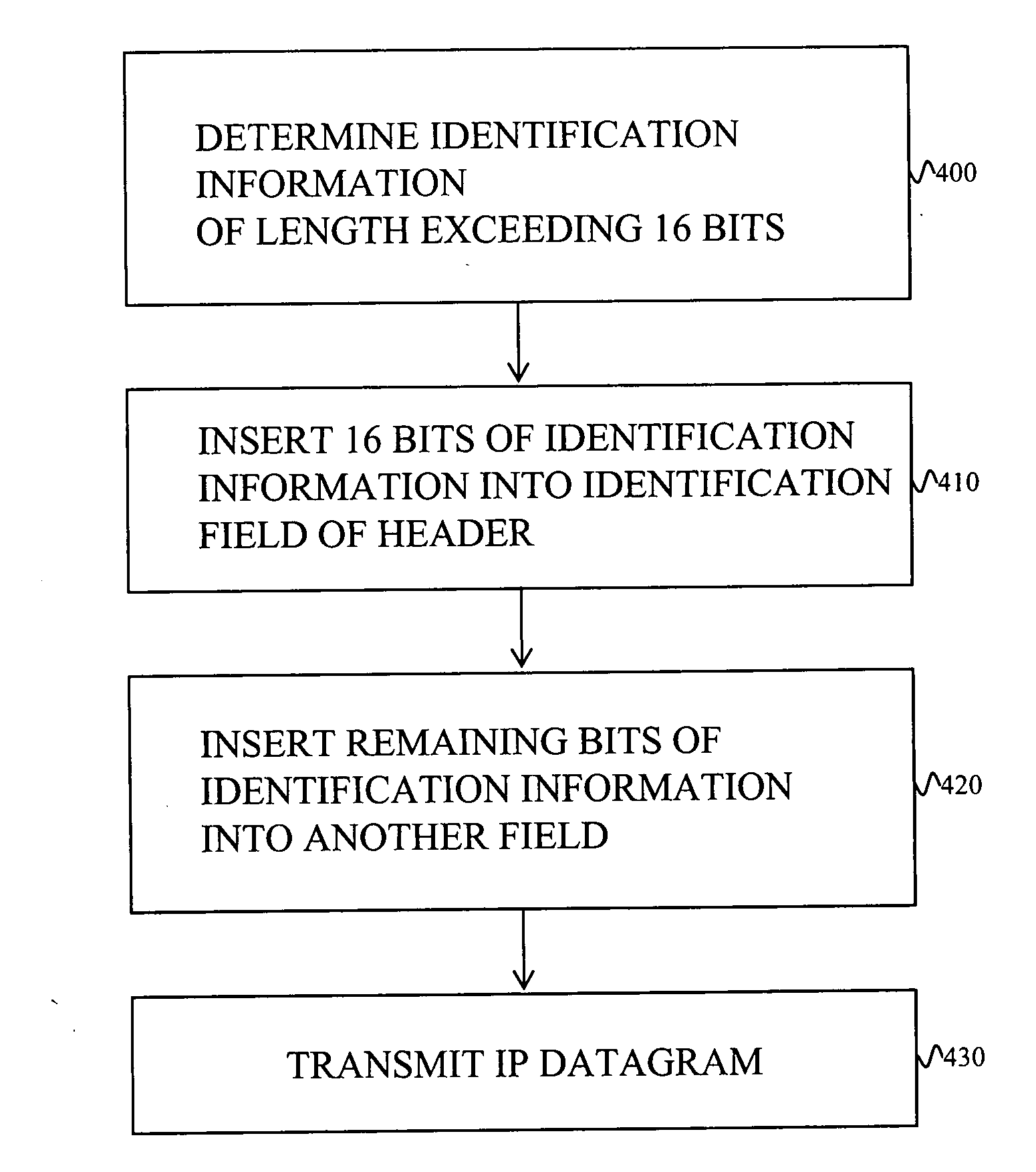
Embodiments of the invention reduce the probability of success of a DOS attack on a node receiving packets by decreasing the probability of random collisions of packets sent by a malicious user with those sent by honest users. The probability of random collisions may be reduced in one class of embodiments of the invention by supplementing the identification field of the IP header of each transmitted packet with at least one bit from another field of the header. The probability of random collisions may be reduced in another class of embodiments of the invention by ensuring that packets sent from a transmitting IPsec node to a receiving IPsec node are not fragmented.
Owner:RAYTHEON BBN TECH CORP +1
Calculating method and device for payment route
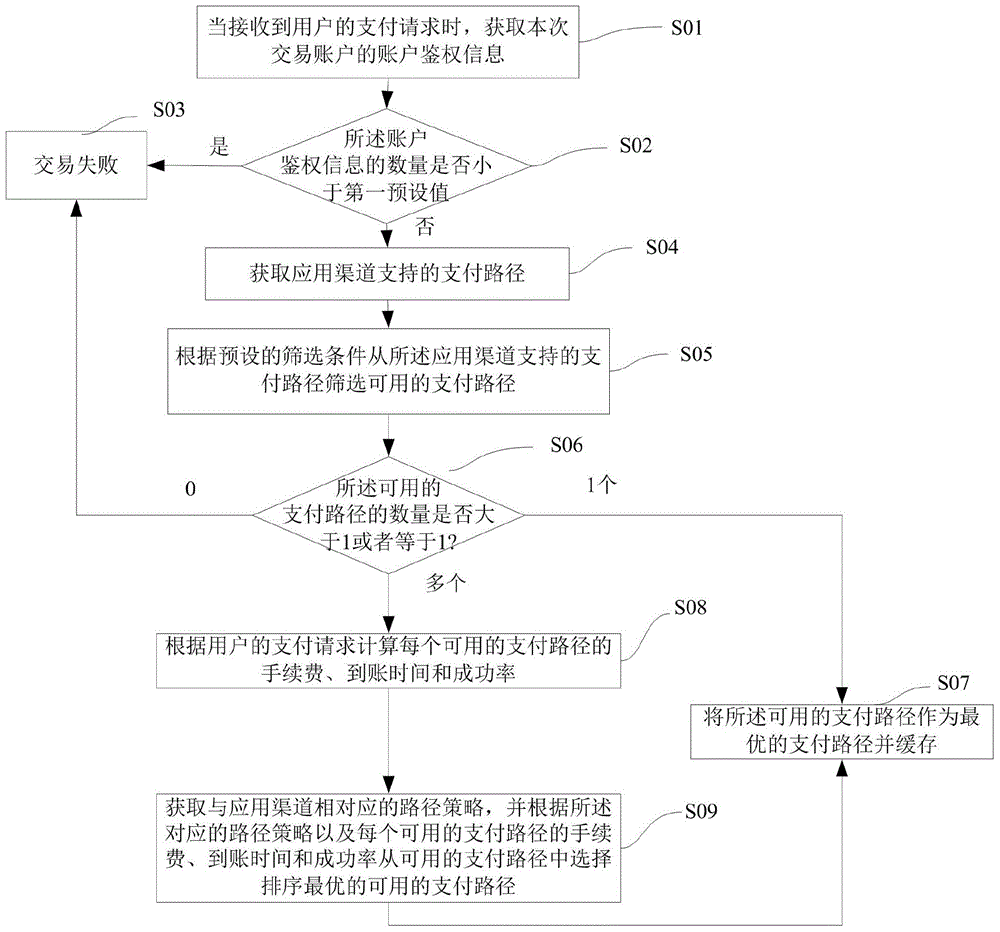
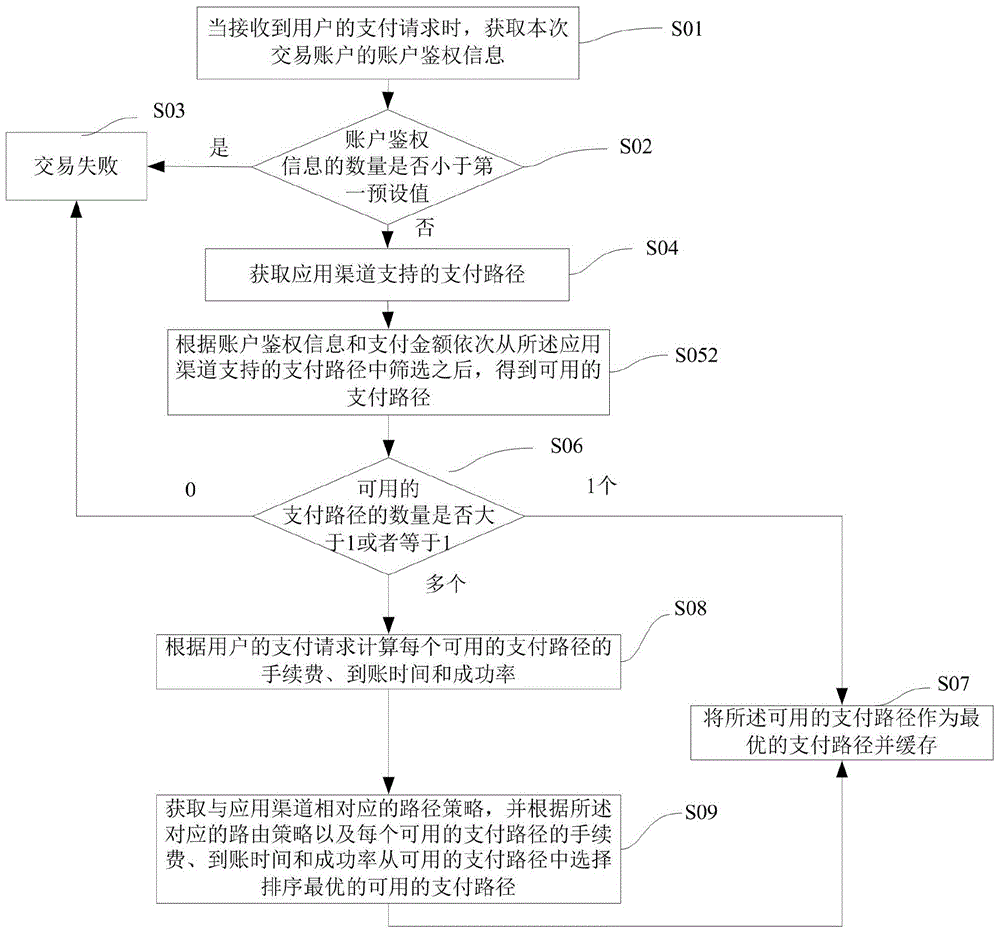
InactiveCN105205653ASuit one's needsReduce operating costsPayment schemes/modelsPaymentComputer science
The invention provides a calculating method and device for a payment route. The calculating method comprises the following steps that when the number of available payment routes is larger than 1, a handling charge, the time for funds to an account and the success rate of each available payment route are calculated according to a payment request of a user; a route strategy corresponding to an application channel is acquired, the payment route which is optimal in the rank is selected from the available payment routes according to the corresponding route strategy and the handling charge, the time for the funds to the account and the success rate of each available payment route to serve as the optimal payment route and cached. According to the calculating method for the payment route, the payment efficiency is higher, the success rate is higher, and meanwhile the requirements of the user can also be met.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method of and apparatus for transferring data
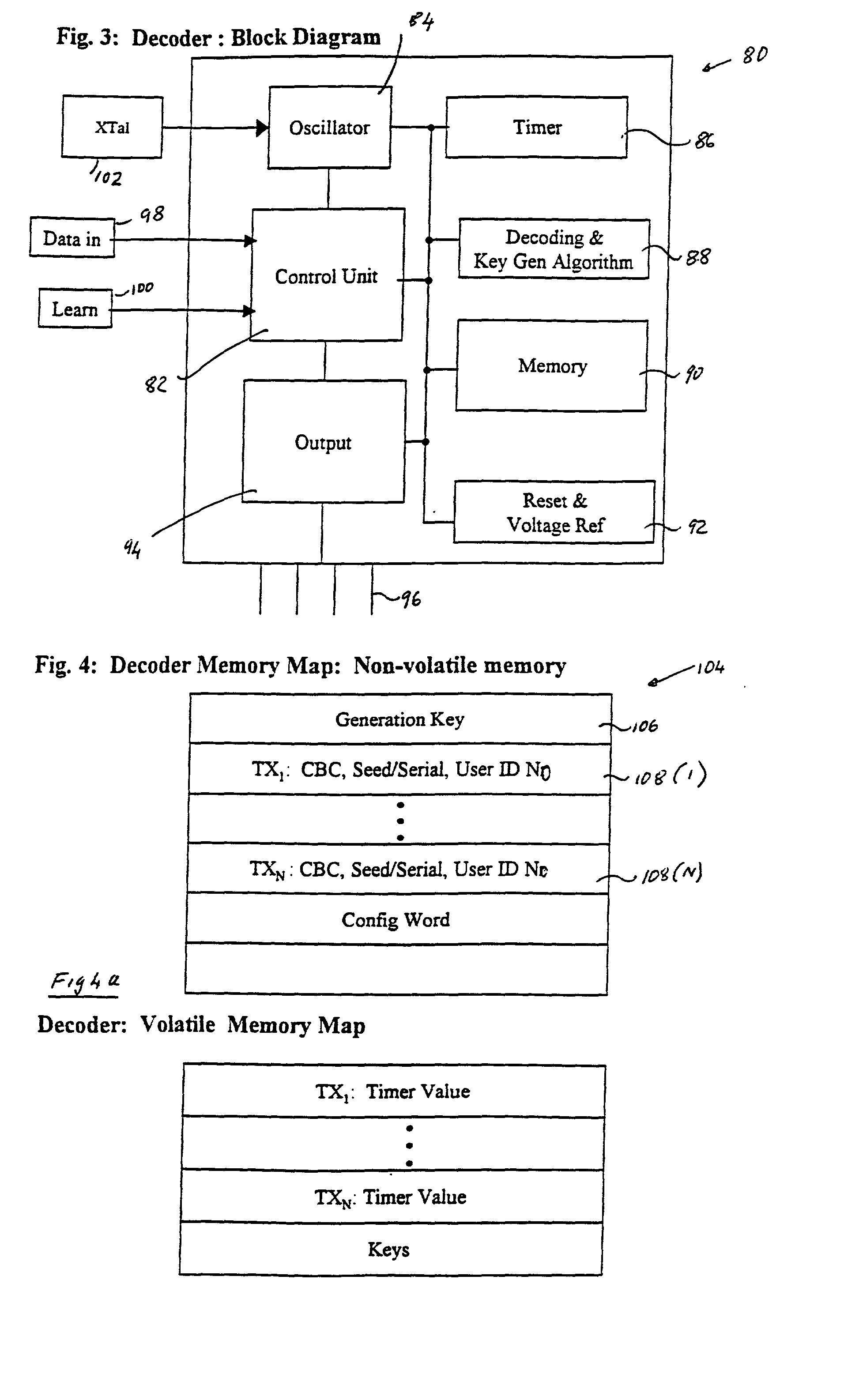
ActiveUS20020110242A1ProbabilityReduce probabilityVolume/mass flow measurementUser identity/authority verificationTransmitterReceiver
A method of securely transferring data from a transmitter to a receiver which includes the steps of at the transmitter encrypting data which at least in part is based on timer information at the transmitter, to form a transmission word, transmitting the transmission word to the receiver, at the receiver decrypting the transmission word, validating the transmission word by comparing the transmitted timer information to predetermined information at the receiver; and when a valid transmission word is received adjusting the said predetermined information.
Owner:MICROCHIP TECH INC +2
Communications Control Method And Apparatus
InactiveUS20080139167A1Exposure was also limitedLower success rateCalling susbscriber number recording/indicationChaos modelsCognitionCommunication control
A communications controller is provided for empowering the user of a communications device, such as a telephone or other device, to assume control over incoming communications. Each originator of a communication is identified by unique identification information as information associated with an incoming communication. The user of a receiving communication device selects one of a plurality of different priority levels for a particular originator of a communication. The user also selects block time intervals for each priority to indicate times during which communication will not be passed to user's communications device or other appropriate action is to be taken. When that particular originator of a communication initiates a communication to the user, the user's communication controller determines the originator's identification information and recalls the priority and corresponding blocking time interval for that particular identity. The communication is accordingly permitted to alert the user or blocked with the exception of conditional filtering. Conditional filtering permits the originator of a communication to send a conditional communication along with situational awareness information that is processed specifically for the particular situation. Conditional filtering includes the case of an emergency communication that would override normal communication control. A cognition engine is used to support conditional communication along with an event session. Intelligent data is created and used to support said event sessions.
Owner:AZOS AI
Multifocal correction providing improved quality of vision
ActiveUS8894203B2Eliminating and minimizing visibilityAdd depthEye treatmentIntraocular lensVisibilityImaging quality
Owner:BRADLEY ARTHUR +2
Mobile terminal user identity authentication method based on multi-finger touch behavior characteristics
ActiveCN105068743AEasy to realize identificationImmutableDigital data authenticationInput/output processes for data processingFeature vectorSupport vector machine classifier
The present invention discloses a smart mobile terminal authentication method based on multi-finger touch behavior characteristics. The method comprises a first step of obtaining touch screen operating information of a user through multi-finger touch screen operation, the multi-finger touch screen operation being touch screen sliding of multiple fingers at a together-put state; a second step of extracting a physiological feature and a behavior feather of a touch screen from the user touch screen operation information, and combining the above feathers as one feature vector; a third step of training a probabilistic neural network classifier and a support vector machine classifier by using the above combined feather vector, to generate a training model of valid users; and a fourth step of collecting touch screen operation information of test users, processing the information according to the second step to obtain combined feature vectors of the touch screen operation of the test users, and putting the combined feature vectors into the two classifiers to compare with the training model of the valid users, thus to obtain classifying results if the test users are valid users.
Owner:XI AN JIAOTONG UNIV
Method for cultivating plant tissue under non-aseptic condition
InactiveCN1628507AReduce pollutionReduce decompositionPlant tissue cultureHorticulture methodsPlant tissueCulture mediums
The invention provides a method for cultivating plant tissue under non-aseptic condition, wherein the whole procedure of plant tissue cultivation is conducted under the natural ambient condition of non-asepsis, the method consists of adding disinfection and bactericidal agent into the culture media, preparing bacterium suppression culture media, inoculating under the natural ambient condition of non-asepsis, and placing the culture material in natural ambient condition meeting plant tissue culture.
Owner:单文修
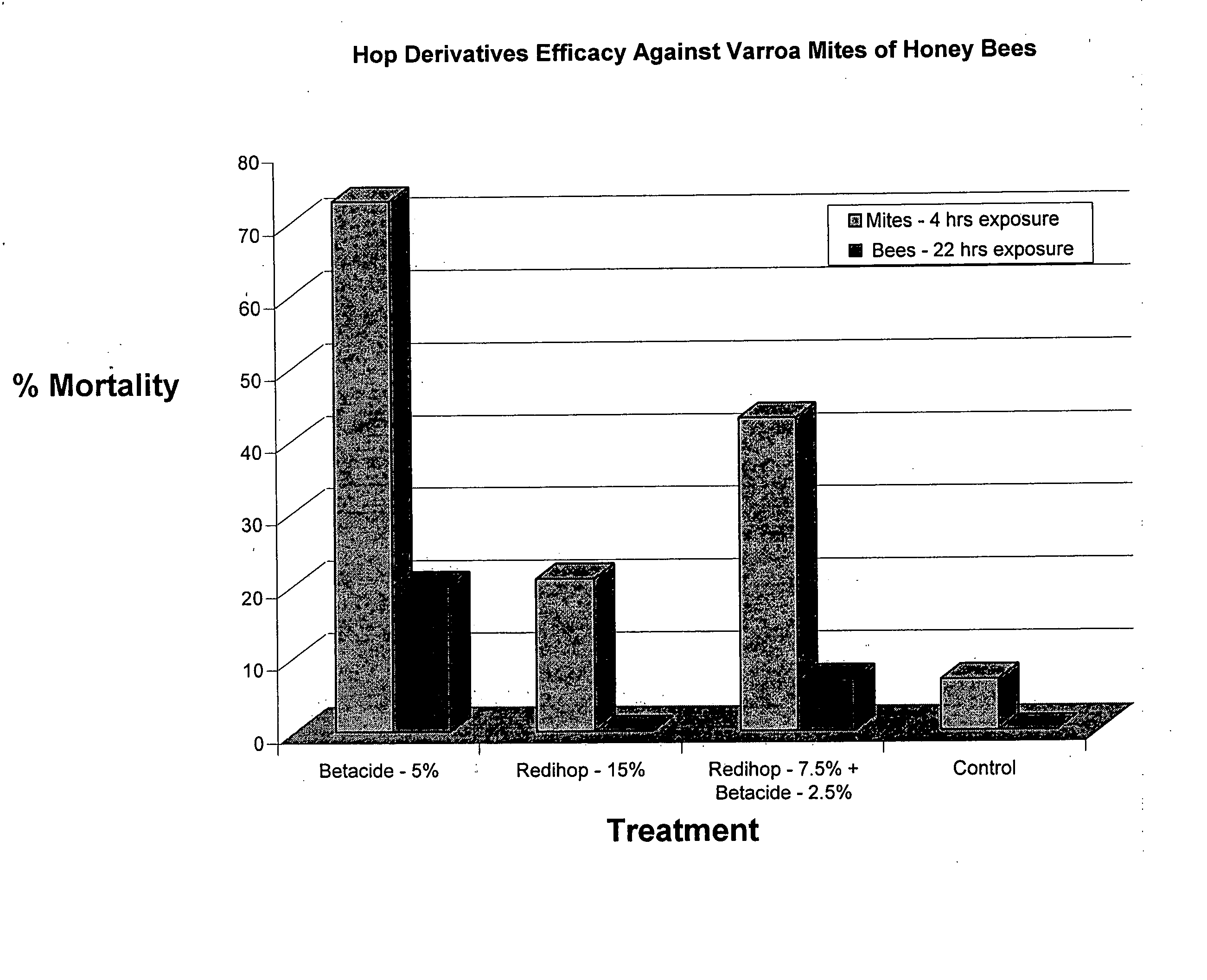
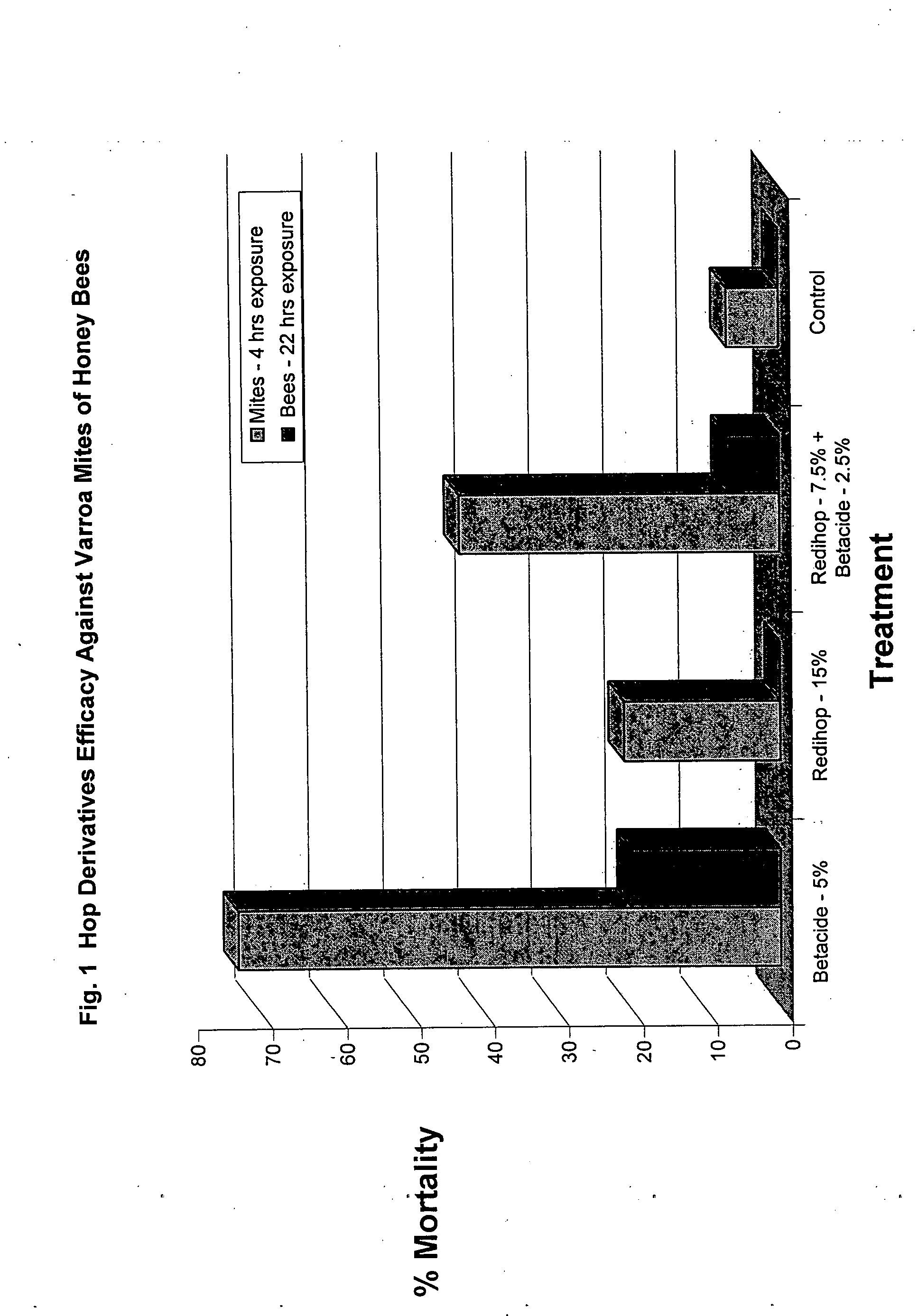
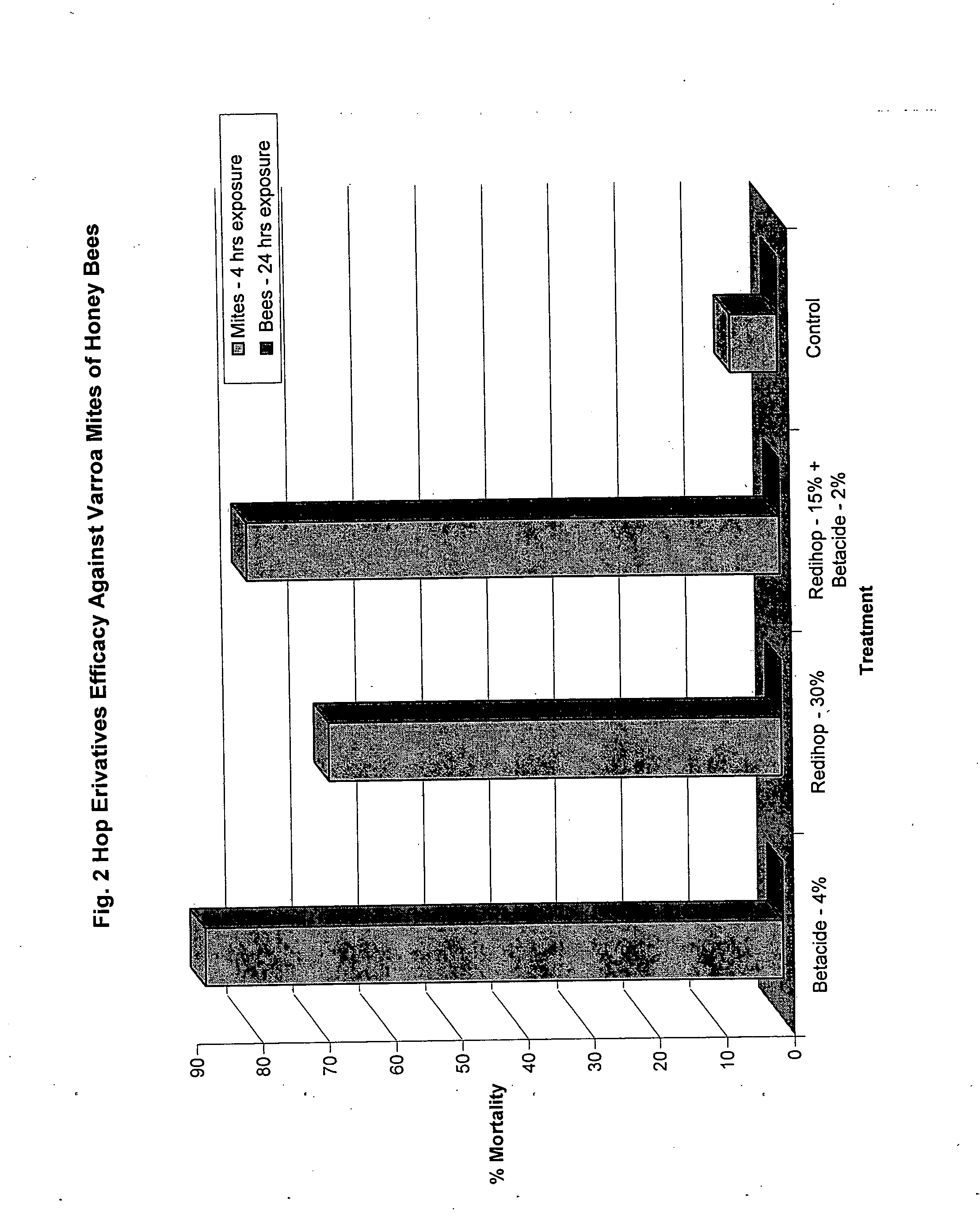
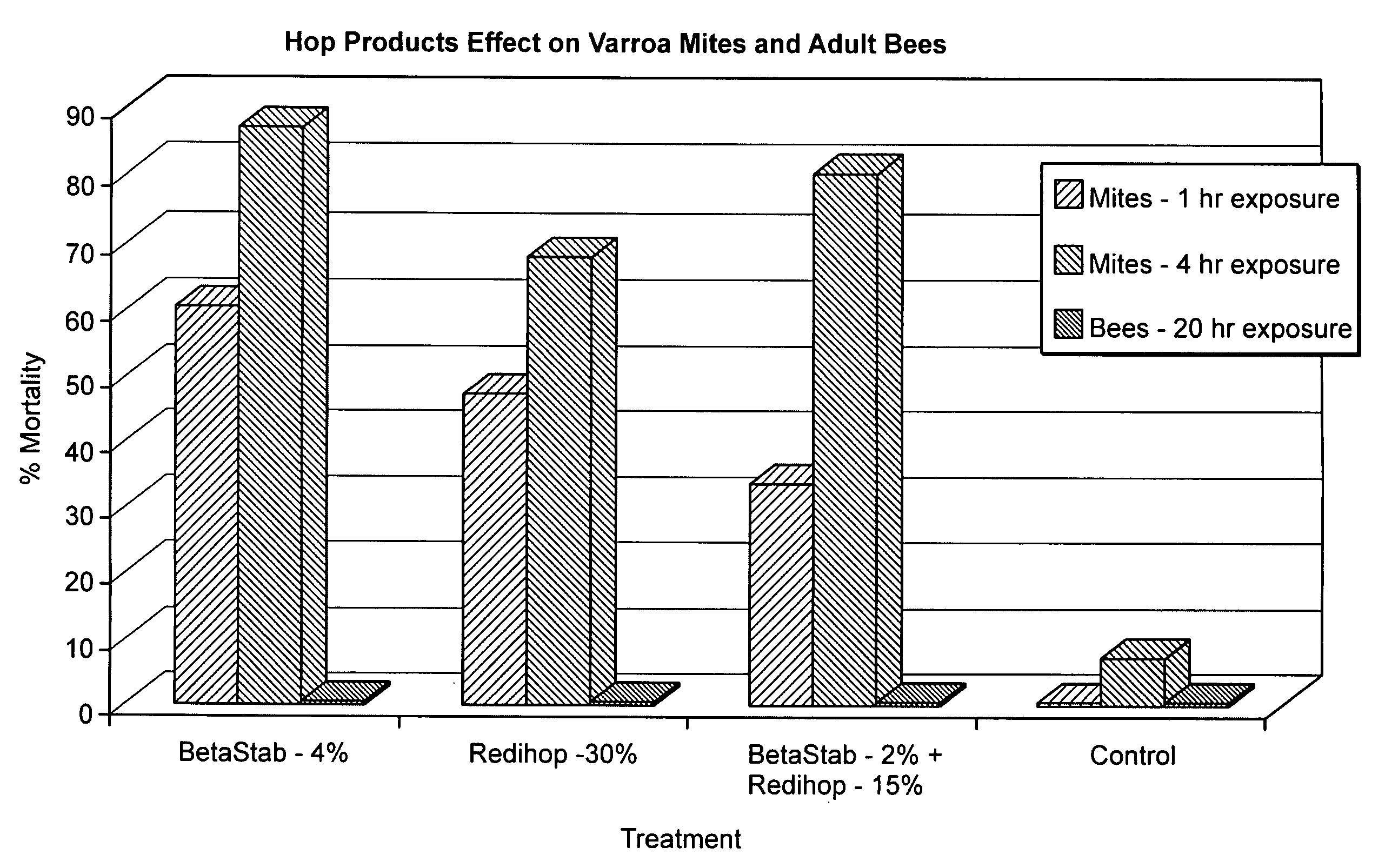
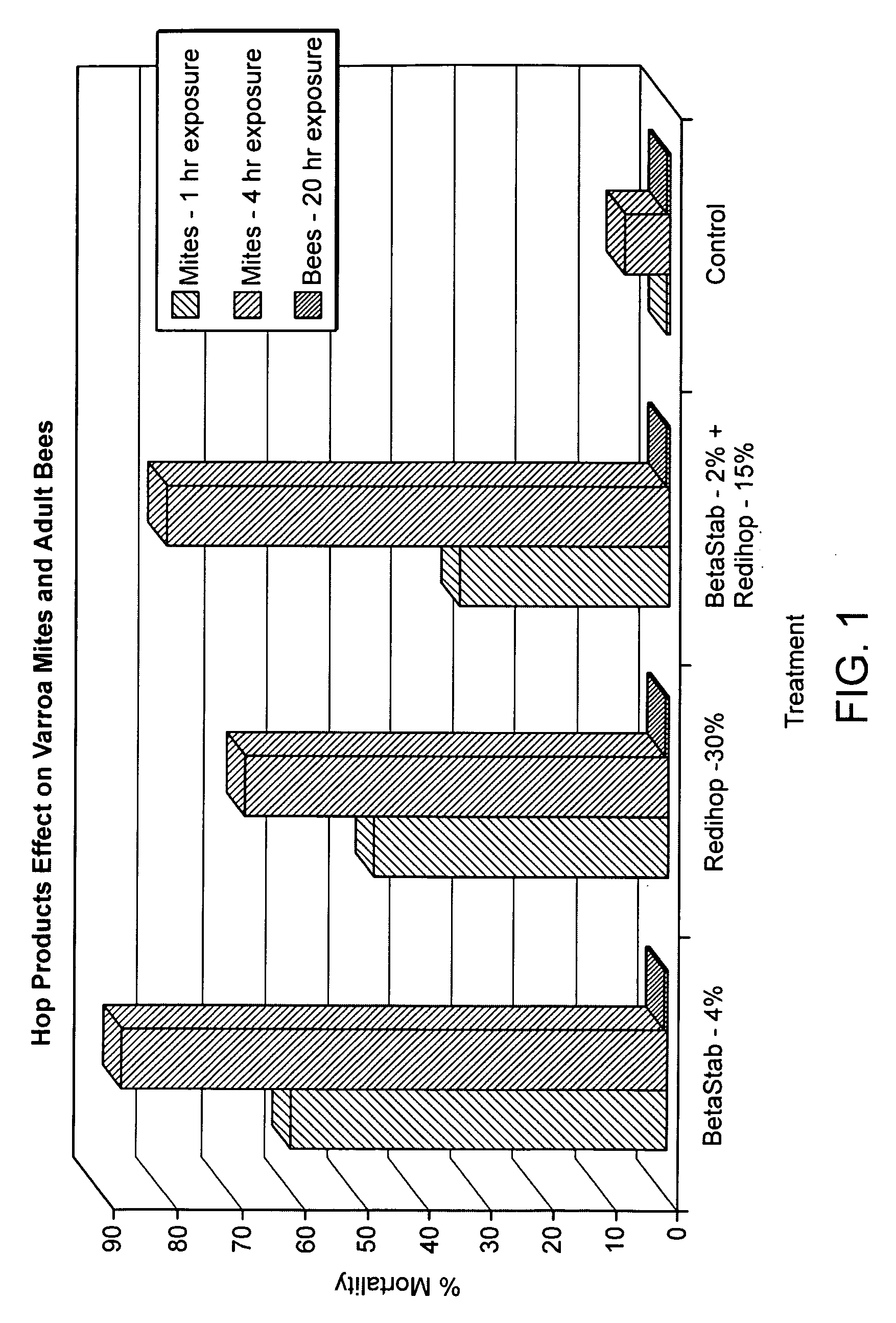
Compositions and methods for controlling a honey bee parasitic mite
ActiveUS20080026673A1Avoid survivalSlowing and stabilizing growthBiocideAntiparasitic agentsMite InfestationsToxicology
As described below, the present invention provides methods and compositions for controlling a honey bee parasitic mite. In addition, the invention features compositions useful for the treatment or prevention of a parasitic mite infestation in a honey bee hive.
Owner:JOHN I HAAS
Brute force attack prevention method, device and system
ActiveCN106161395AImprove the efficiency of brute force crackingTimely defenseTransmissionComputer securityBrute force
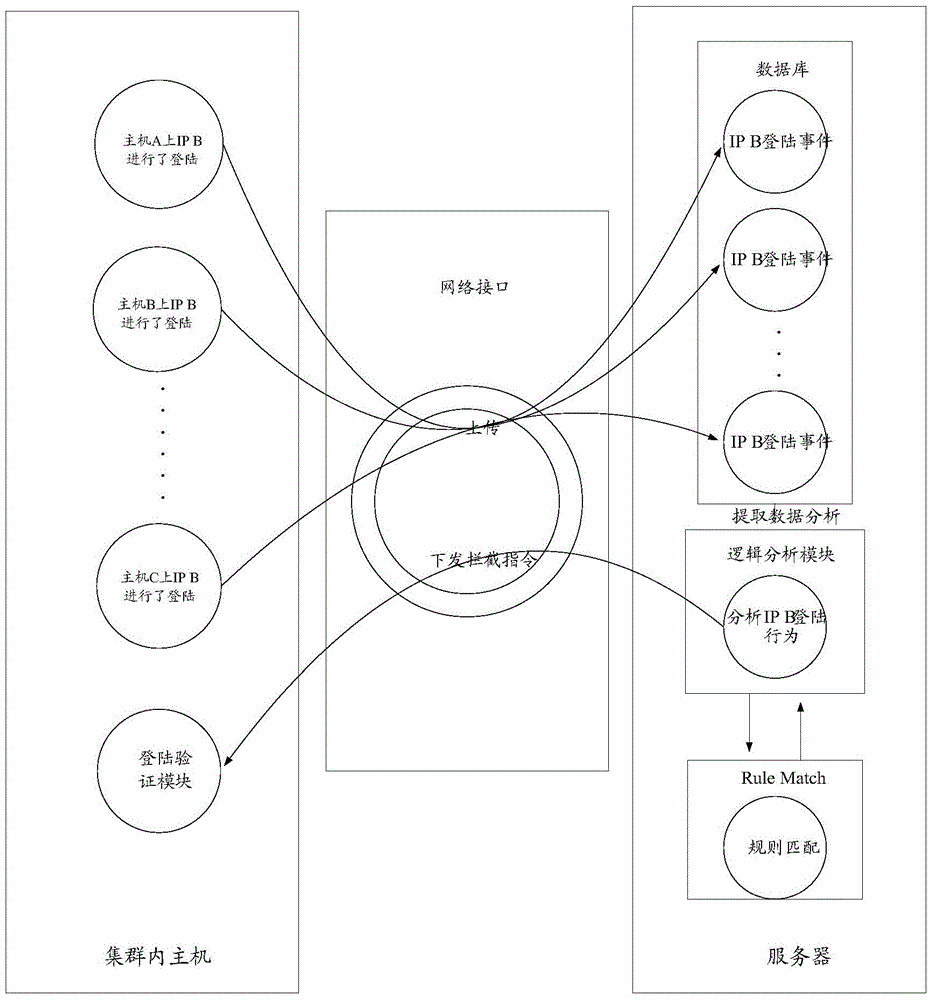
The invention discloses a brute force attack prevention method, device and system. The method, the device and the system are used for improving the brute force attack prevention efficiency of cluster hosts. The method comprises the steps that a server carries out analysis and rule matching on each piece of login information each time after the login information reported by one host in a cluster is received; indicating interception of a login user corresponding to the host reporting any one piece of login information when it is judged that brute force attack behaviors are generated based on any one piece of login information; and directly indicating interception of the login user corresponding to any one host when the login information which is reported by any one host in the cluster and is similar to the login information is further received. In this way, the brute force attack prevention efficiency of the cluster hosts is improved, the hosts in the whole cluster can defense malicious attackers timely, the mutual brute force attacks of the hosts in the cluster are effectively prevented, the realization cost is low, and the realization is easy.
Owner:ALIBABA GRP HLDG LTD
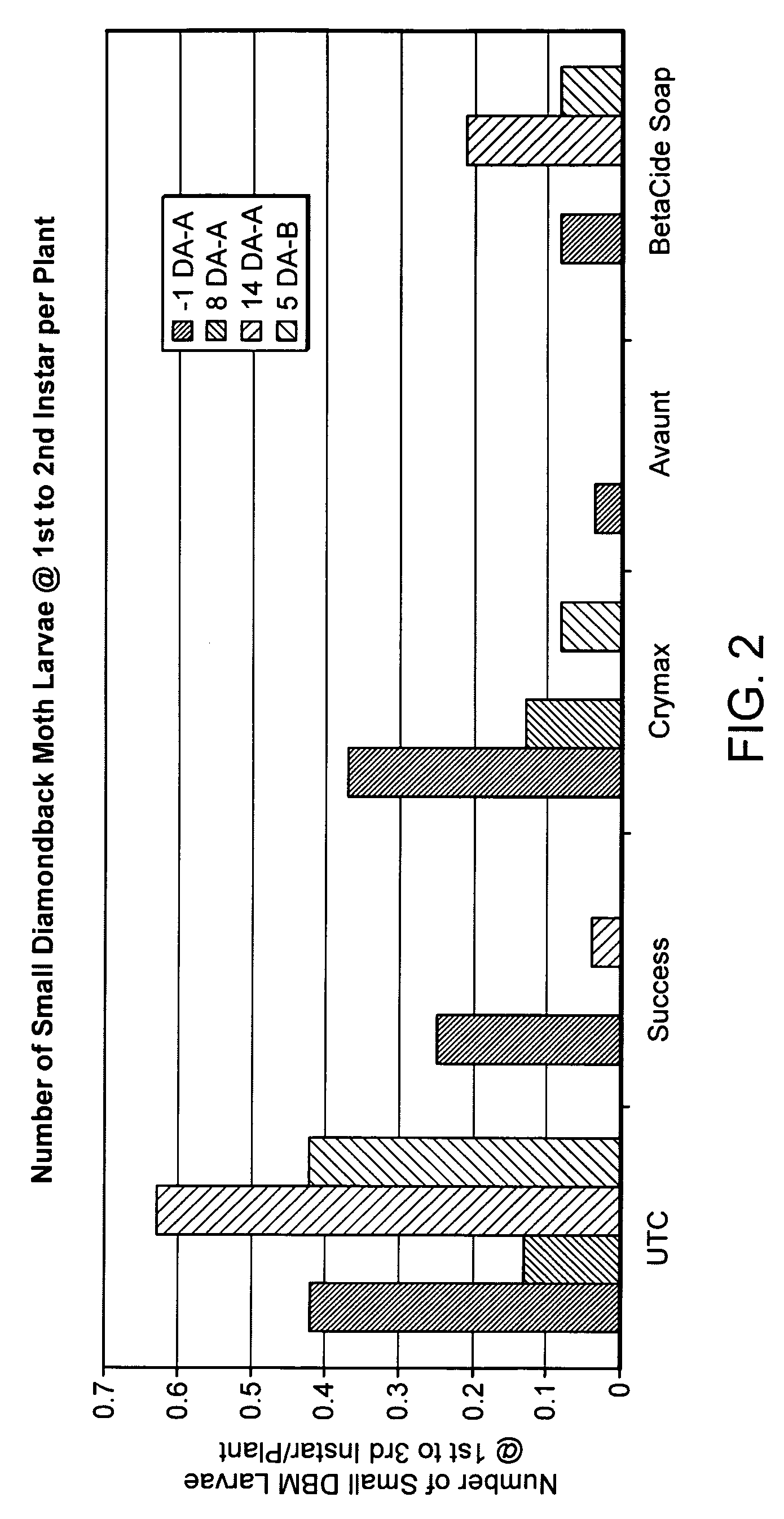
Compositions and methods for inhibiting a honey bee pathogen infection or controlling a hive infestation
InactiveUS20090104288A1Lower success rateOptimize allocationBiocideAnimal repellantsPaenibacillus larvaePsocoptera
The present invention is directed to methods and compositions to prevent or treat a honey bee pathogen infection (e.g., Melissococcus plutonis, Paenibacillus larvae, Ascosphaera apis). Specifically, the invention provides for the treatment or prevention of European or American foulbrood or chalkbrood. In addition, the invention provides methods for controlling Varroa mites that can weaken a hive or act as vectors for bacterial diseases. In further embodiments, the invention provides for the treatment or prevention of hive infestations with Lepidopteran pests, such as the wax moth (Galleria mellonella).
Owner:JOHN I HAAS
Credibility Token System for Over The Air Multi-programming of a Wireless Device and Method of Operation
ActiveUS20160007198A1Improve protectionData SecurityService provisioningUser identity/authority verificationNetwork packetData storing
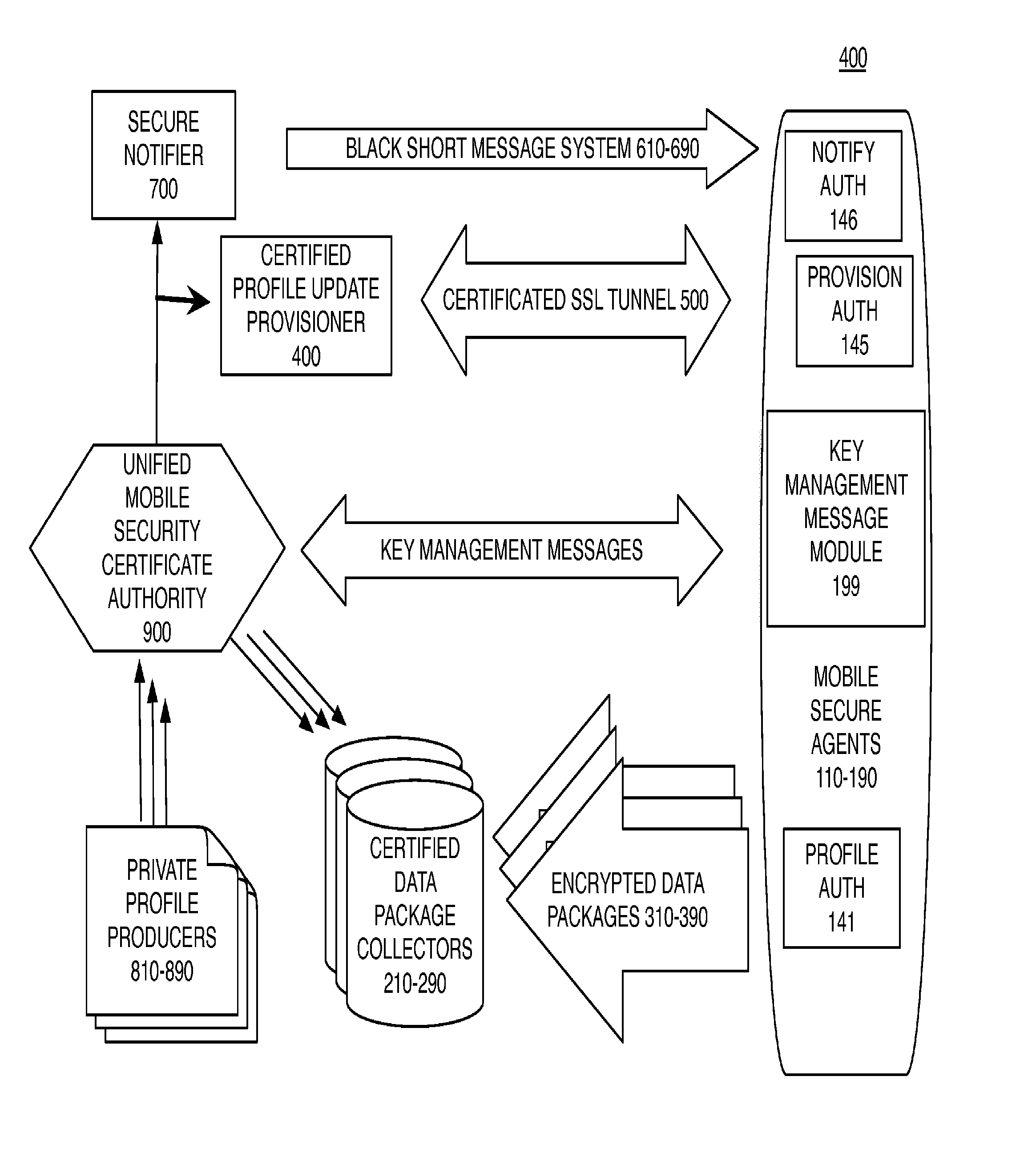
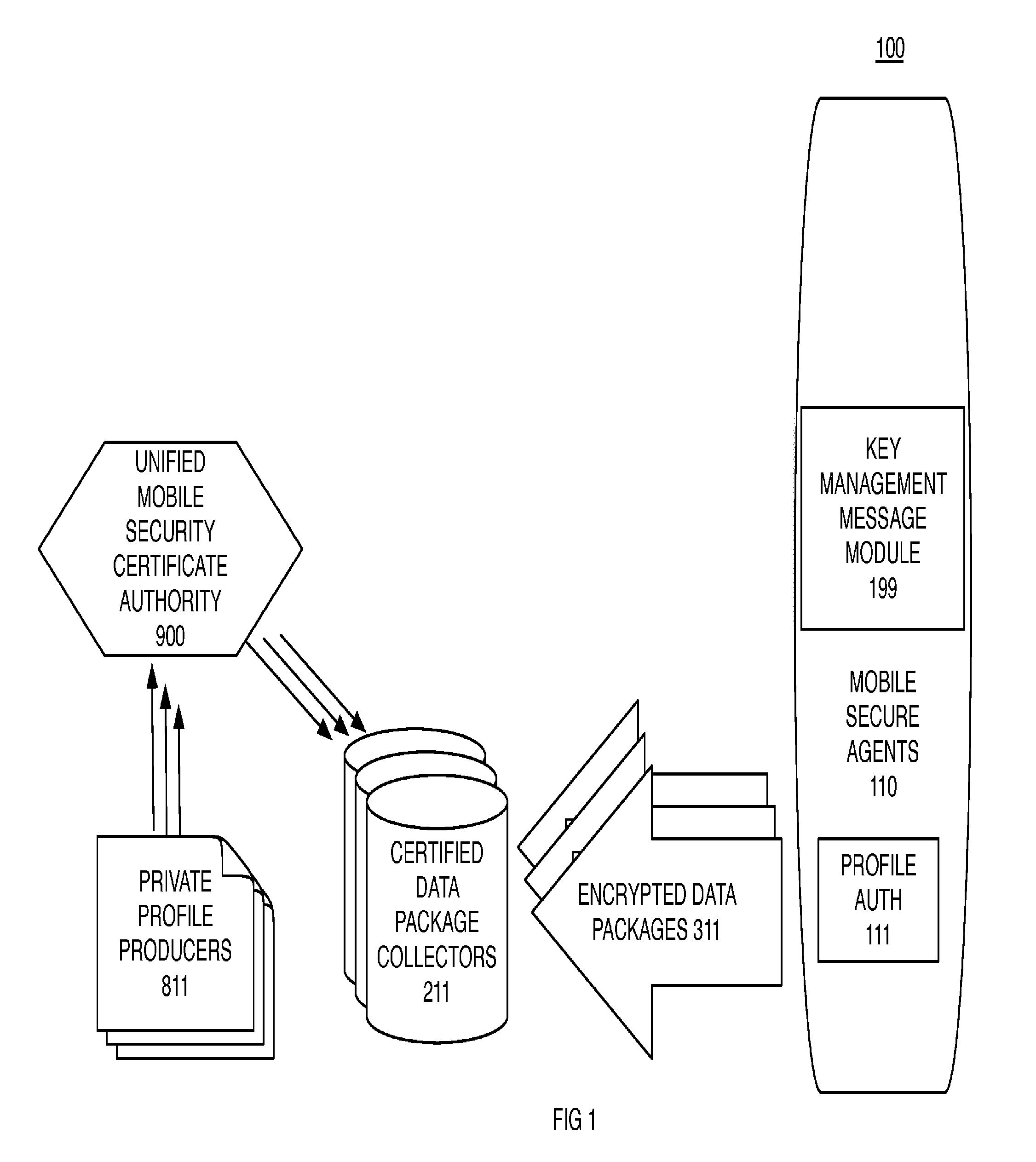
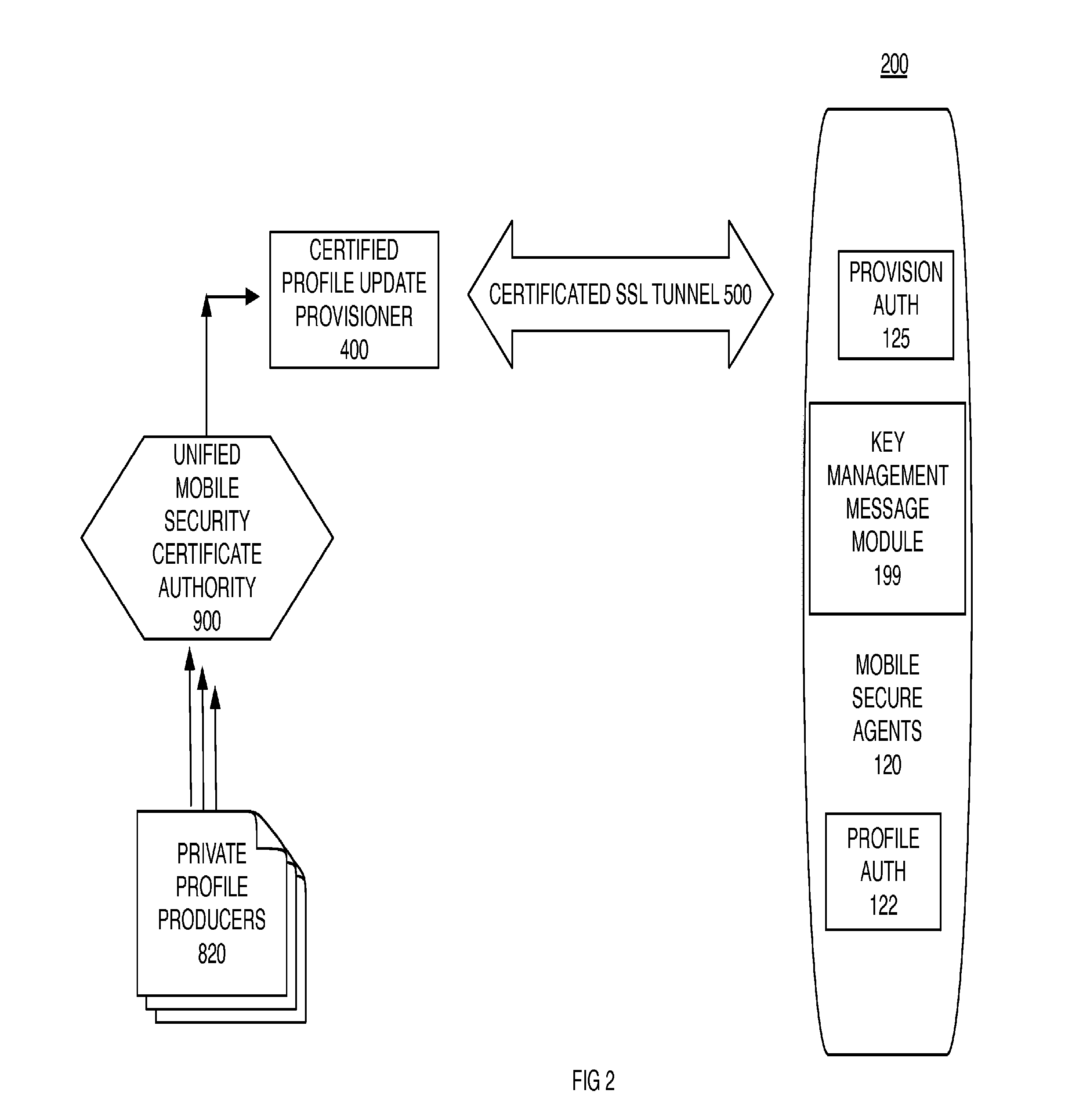
A mobile secure agent on a wireless device executes co-resident authenticated data collection profiles provisioned by private profile producers. Each wireless device has a MAC address that is transformed into a credibility token which is included in a notification to execute or update a data collection profile. The credibility token may also include attributes of location current or stored data. Each wireless device retains location history data transformed by encryption or by hashing. Each data package can only be transmitted to a collector certificated by the same private profile producer. Update profiles are signed and provisioned through a tunnel initiated from the mobile secure agent. A Certificate Authority provides libraries, anchors, and certificates in a key management message module to each mobile secure agent which enables revocation and replacement of certificates. Data stored in this way may only be transmitted to one destination per profile.
Owner:AT&T MOBILITY IP LLC
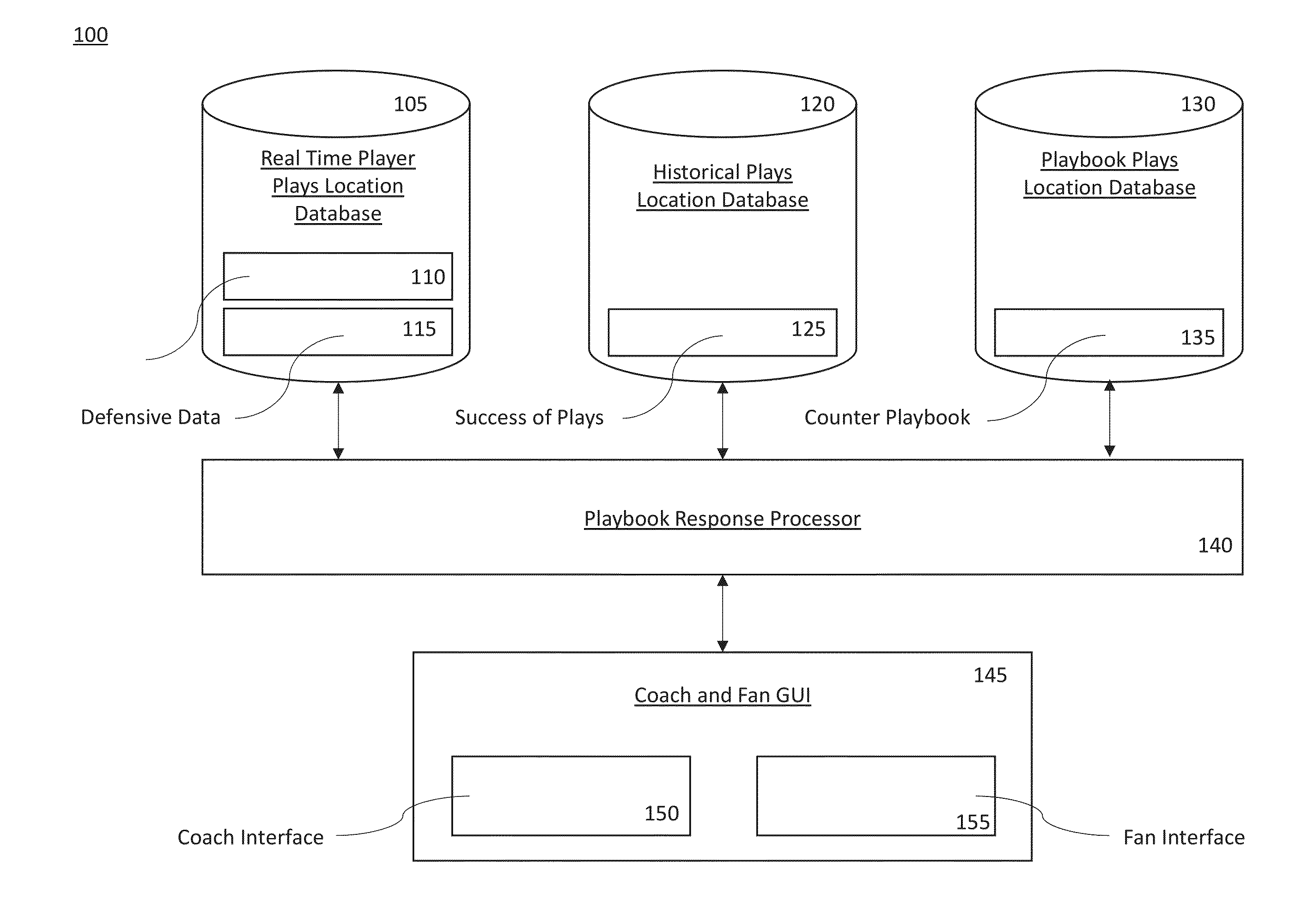
Playbook processor
ActiveUS20160008693A1High success rateLower success rateCharacter and pattern recognitionSport apparatusData scienceMultimedia
Owner:PROSPORTS TECH
Method and system for providing positioning service
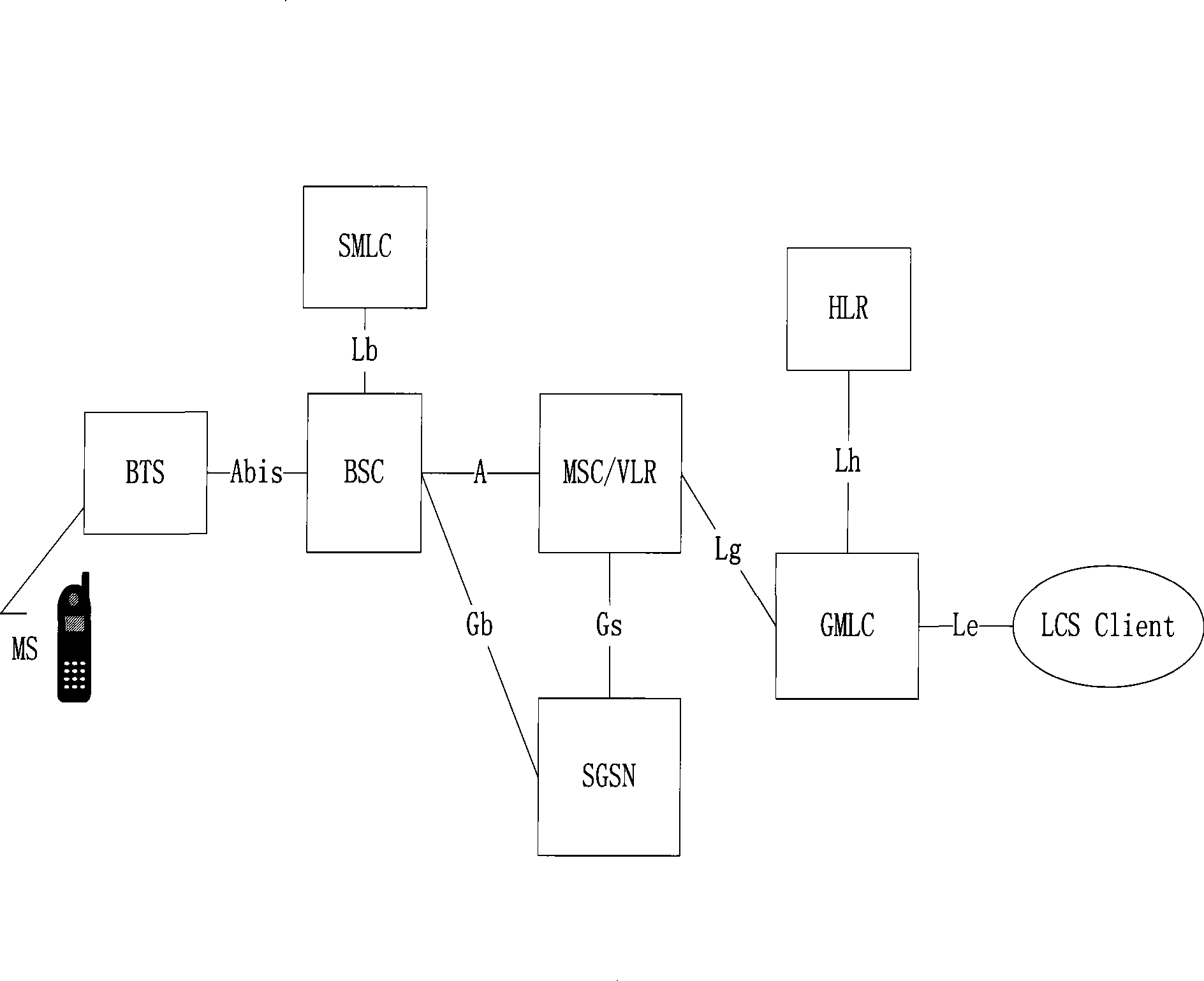
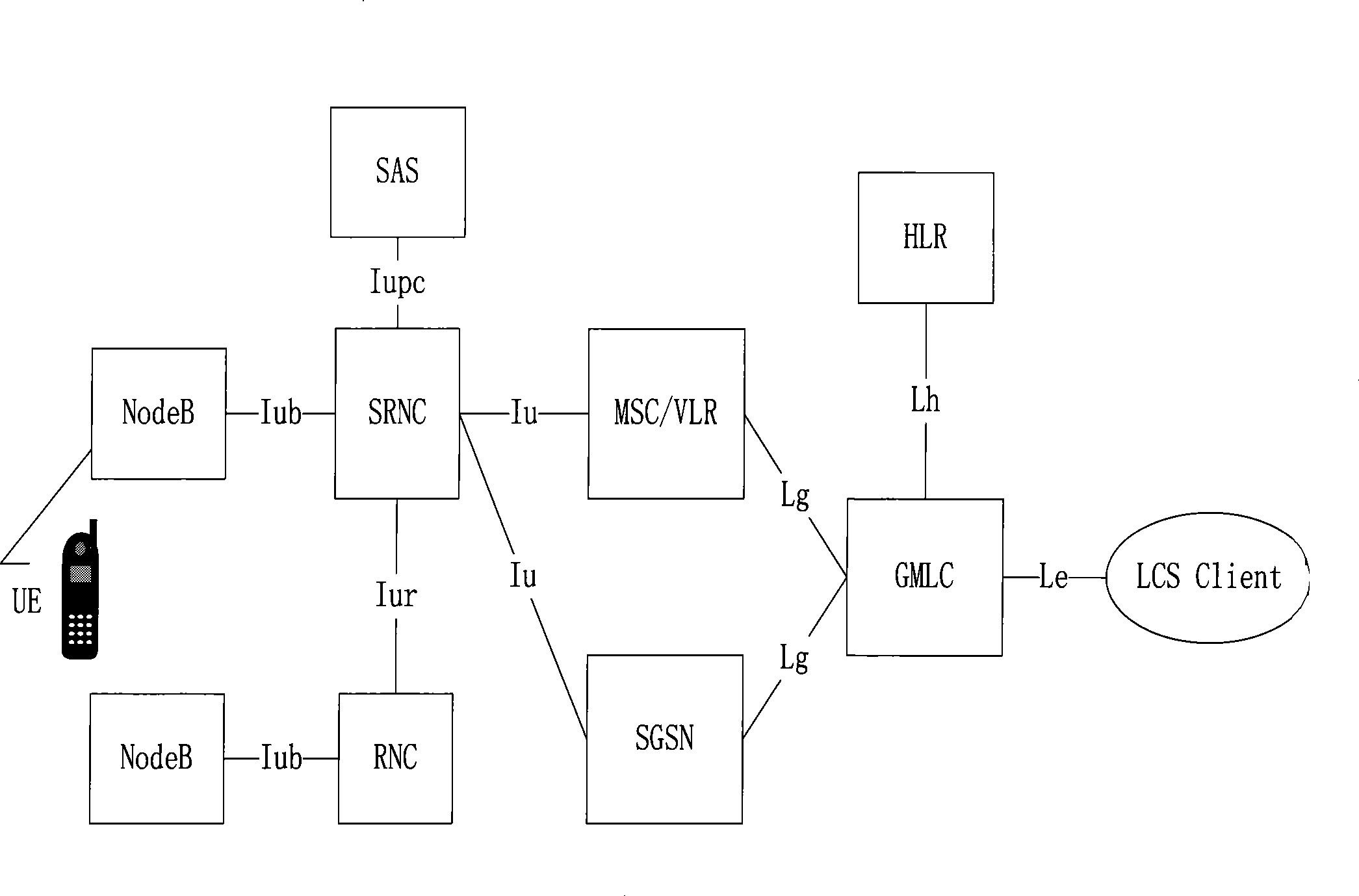
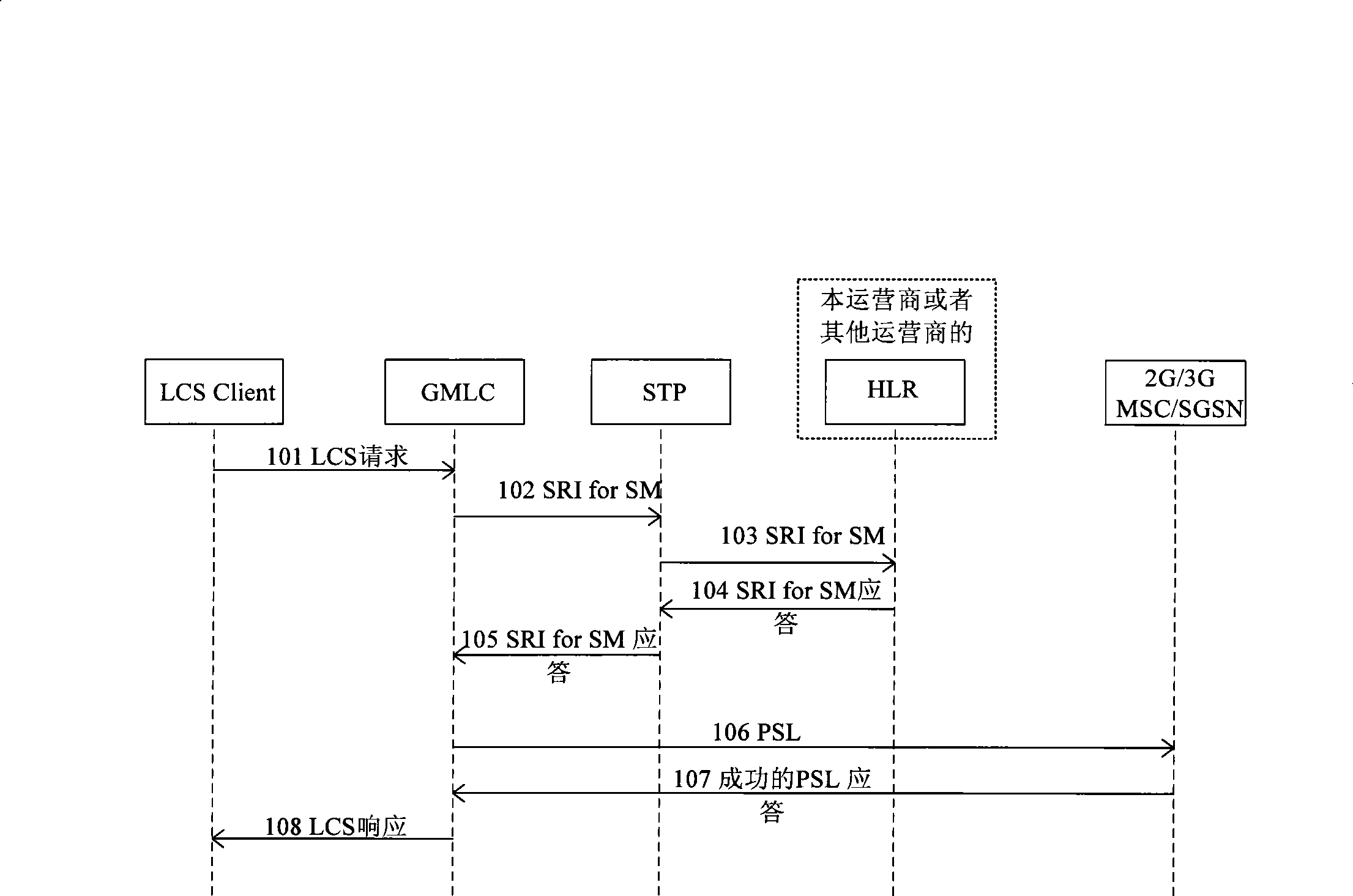
ActiveCN101478741AImprove reliabilityLower success rateNetwork data managementAccess networkThird generation
The invention provides a method and a system for realizing positioning service. The method comprises the following procedures: after receiving the positioning request of an LCS client, GMLC judges the positioned UE identification type, sends the corresponding information to HLR according to the result and receives the responding information which carries along with routing information and comes from HLR; the GMLC sends PSL information to the corresponding MSC or SGSN according to the current routing information of the positioned UE, and carries out different positioning business operations to obtain the position information about the positioned UE which is then sent to the LCS client according to the corresponding information content of the PSL information. The technique scheme of the invention has the advantages of avoiding the reduction of business success rate in the 2G / 3G hybrid network owing to the failure of PSL information which is caused by access network, satisfying the needs of various operators. The technique scheme can achieve the function of effectively obtaining the position of user in the 2G / 3G hybrid network with a number portability strategy.
Owner:ZTE CORP
High-strength Halbach permanent magnet array rotor structure
ActiveCN109713819AReduce stressHigh mechanical strengthMagnetic circuit rotating partsManufacturing stator/rotor bodiesPhysicsAxial flux
The invention discloses a high-strength Halbach permanent magnet array rotor structure, which belongs to the technical field of an axial flux permanent magnet motor. The structure includes a permanentmagnet fixation pin supporting inner fixing ring, a circumferentially-distributed segmental Halbach permanent magnet array, a rotor magnetic conductive back yoke sleeving a rotating shaft, and a U-shaped supporting outer fixing ring; and two side surfaces of each of permanent magnets of the Halbach permanent magnet array are provided with semi-circular grooves used for inserting pins during assembly, the magnet fixation pin supporting inner fixing ring, the rotor magnetic conductive back yoke, and the U-shaped supporting outer fixing ring are fastened and connected to form a rotor disc through threaded holes disposed respectively and axially, and two adjacent sector-shaped permanent magnet blocks are radially fixed on the rotor disc by radial pin holes formed by the semi-circular grooves.A Halbach permanent magnet array rotor disclosed by the invention has the characteristics of high permanent magnet excitation efficiency, high structural strength and good installation manufacturability, and is suitable for application occasions such as high-speed axial magnetic field permanent magnet motor drive and propulsion.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com