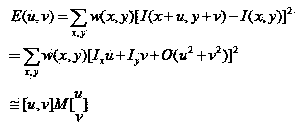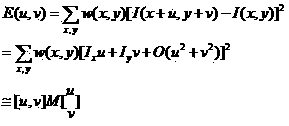Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
131results about How to "Immutable" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
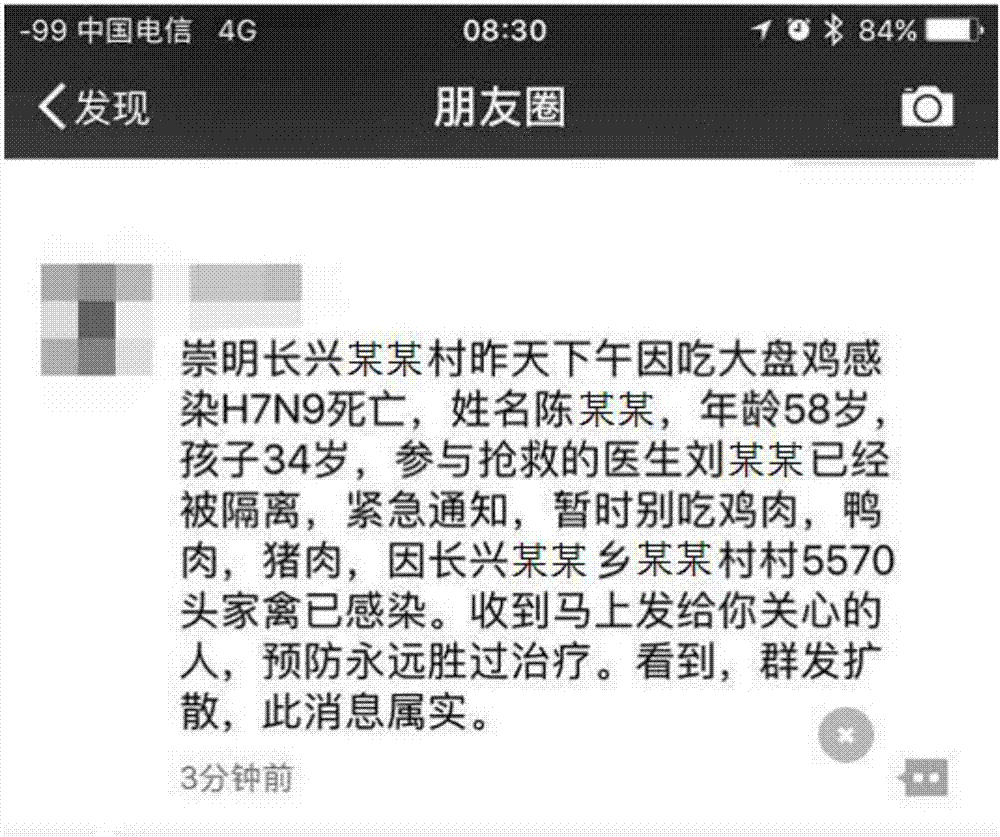
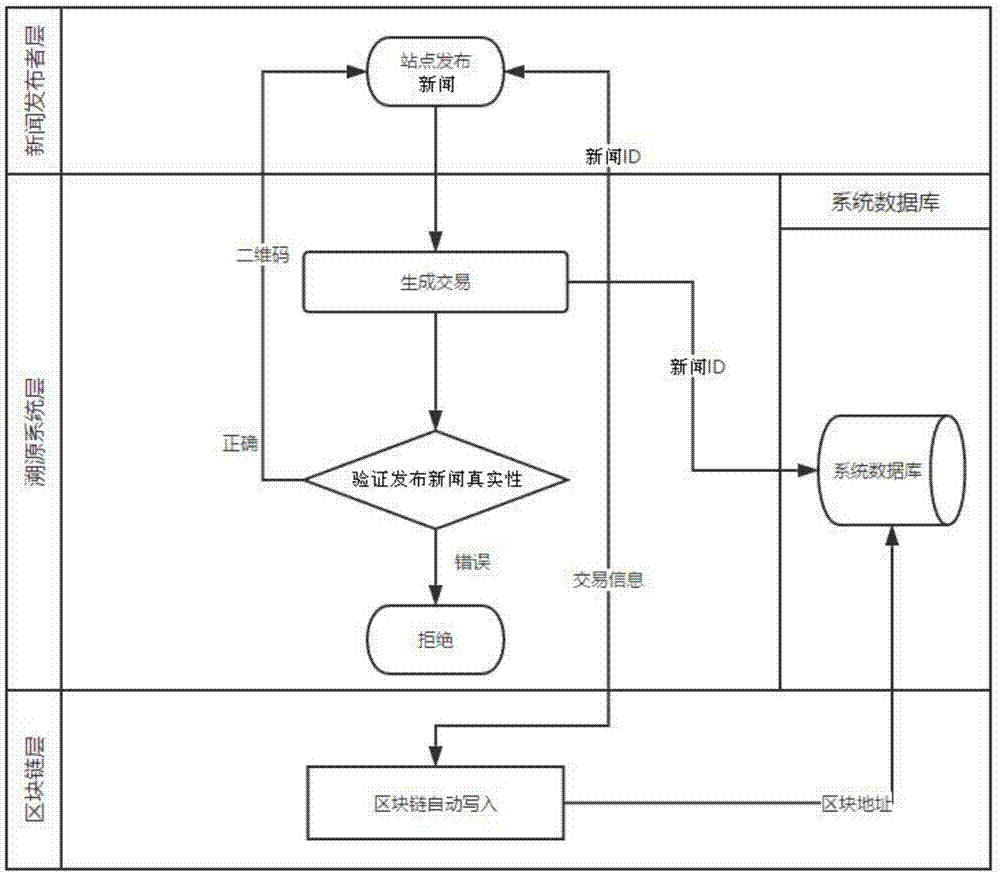
Block chain-based information-authenticating and source-tracing method and system
InactiveCN107316239AAchieve authenticationRealize traceabilityFinanceDigital data protectionVoucherSource tracing
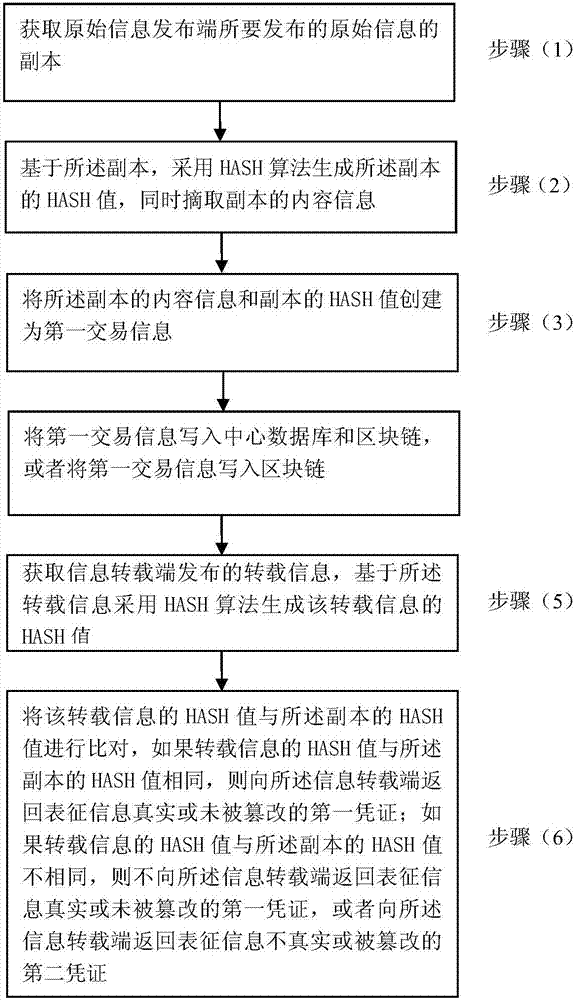
The invention discloses a block chain-based information-authenticating and source-tracing method. The method comprises the steps of (1) acquiring the copy of the original information to be issued by an original information publishing end; (2) generating the hash value of the copy and picking the content information of the copy at the same time; (3) creating the first transaction information based on the content information of the copy and the hash value of the copy; (4) writing the first transaction information into a center database and a block chain, or writing the first transaction information into the block chain; (5) acquiring the transshipment information released by a information transshipment end, and generating the hash value of the transshipment information; (6) comparing the hash value of the transshipment information with the hash value of the copy; if the two hash values are the same, returning a first voucher for representing the information to be true or non-tampered; if the two hash values are not the same, not returning the first voucher or returning a second voucher for representing the information to be not true or tampered. The invention further discloses a corresponding system. According to the invention, the information authentication and the source tracing can be reliably realized.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
Image detection method for detecting foreign matter at bottom of vehicle
ActiveCN103984961AMeet the needs of real-time detectionReliable detection methodImage analysisCharacter and pattern recognitionForeign matterImage detection
The invention relates to an image detection method for detecting foreign matter at the bottom of a vehicle. The method sequentially includes the following steps of image input, image registration, binary image acquisition and foreign matter detection. The method can be used for fast recognizing whether the bottom of the vehicle going in or out of a barrier gate carries foreign matter or not, a vehicle chassis image provided by a vehicle chassis imaging system is subjected to signal analysis and processing, a real-time reliable foreign matter detection method is provided for detection of the chassis of the vehicle, and therefore the foreign matter at the bottom of the chassis of the vehicle can be fast, accurately and efficiently detected, the detecting accuracy is improved, interference of manual operation and environment changes is eradicated, and the requirement for real-time detection of the bottom of the vehicle in the security and prevention market in China is met. The time needed for recognition is no longer than five seconds, and the recognition efficiency is high.
Owner:CHENGDU XIWU SECURITY SYST ALLIANCE
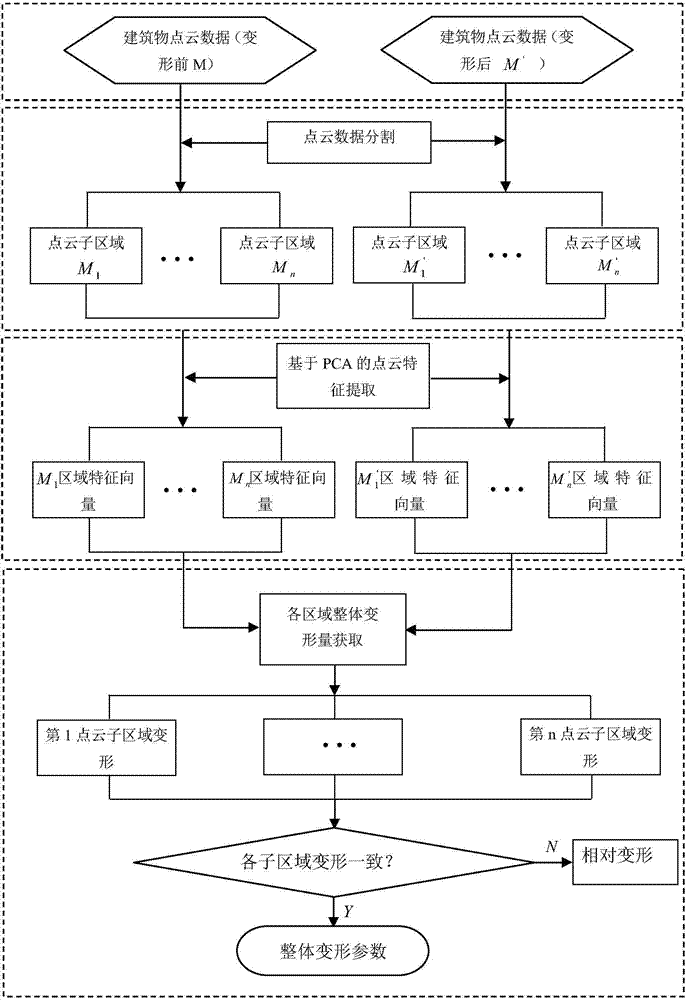
Building overall-deformation monitoring method based on three-dimensional laser scanning technology
The invention discloses a building overall-deformation monitoring method based on a three-dimensional laser scanning technology. The method includes the following steps: obtaining building point cloud data, segmenting the point cloud data, regularizing the data, performing deformation analysis on a point cloud model and judging a building overall-deformation condition. The building overall-deformation monitoring method based on the three-dimensional laser scanning technology is capable of rapidly extracting three-dimensional space characteristics of the point cloud model from the building mass point cloud data and the space characteristics have rotation and translation invariance so that attitude of the building in a three-dimensional space can be expressed uniquely and according to the variance condition of the three-dimensional space characteristics of the building point cloud model, the overall deformation condition of the building, such as sedimentation, inclination and rotation and the like in the three-dimensional space can be analyzed and judged. The building overall-deformation monitoring method based on the three-dimensional laser scanning technology makes full use of complete point cloud data of the surface of the building to analyze the overall deformation condition of the building and the measurement and analysis technology based on faces effectively prevents locality and one-sidedness brought by a deformation analysis result in traditional deformation monitoring based on points.
Owner:SHANDONG JIAOTONG UNIV
Commodity anti-counterfeit traceability method and device based on block chain, and node of block chain
ActiveCN109034851AReliable anti-counterfeiting traceability informationImmutableCo-operative working arrangementsCommerceClient-sideBlockchain
The invention relates to the technical field of commodity anti-counterfeiting traceability, in particular to a commodity anti-counterfeiting traceability method based on a block chain and a device thereof, a block chain node. The method comprises the following steps: receiving the two-dimensional code information of the commodity sent by the client, wherein the two-dimensional code information isused for indicating to skip to the anti-counterfeiting traceability page, and the anti-counterfeiting traceability page records the information of each link of the commodity; the hash value to be verified being calculated according to the information of each link in the anti-counterfeiting traceability page. Each block chain node stores a hash list recording the true hash value of each commodity,and the hash list has been verified by the block chain consensus. Whether there is a true hash value corresponding to the hash value to be verified in the traversal hash list; if yes, returning the commodity verification success information to the client; if not, the merchandise verification failure information is returned to the client. Because the block chain has the characteristics of non-tampering, decentralization and high transparency, it can provide reliable anti-counterfeiting traceability information.
Owner:SHENZHEN GENUINE INNOVATIVE TECH CO LTD
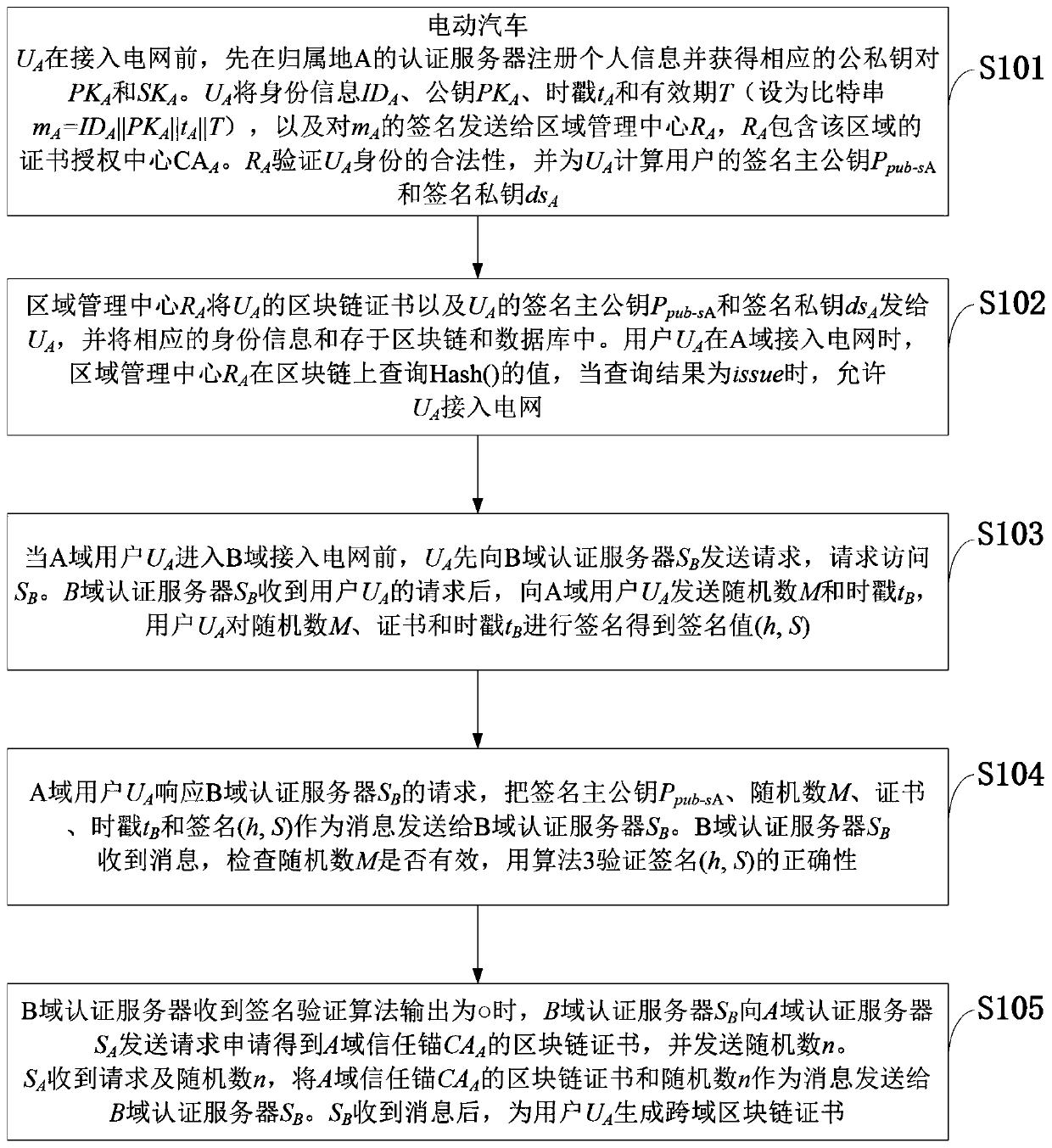
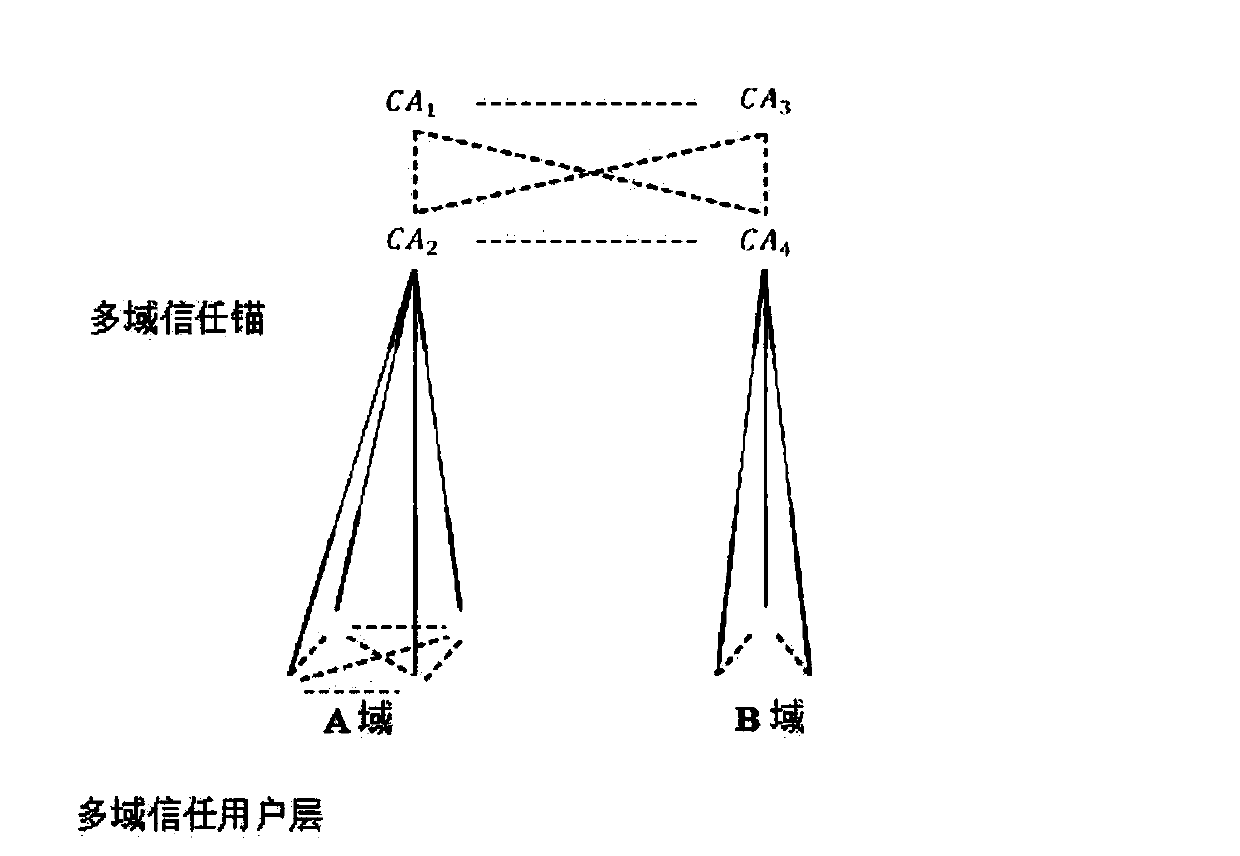
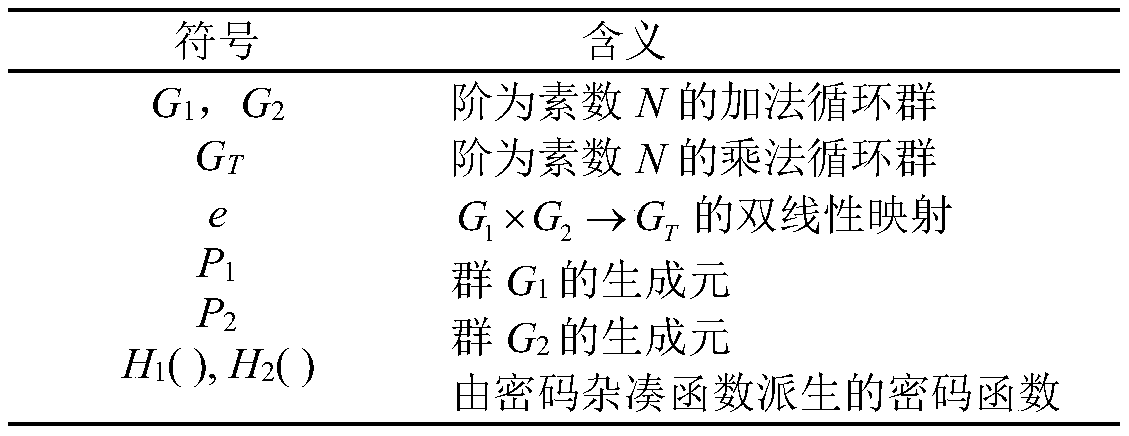
V2G network cross-domain authentication method based on alliance block chain and information data processing terminal
ActiveCN109743172AWith decentralizationAchieve traceabilityUser identity/authority verificationEngineeringElectric network
The invention belongs to the technical field of confidential or secure communication, and discloses a V2G network cross-domain authentication method based on an alliance block chain and an informationdata processing terminal. For the security threat that the electric vehicle joins a power grid V2G network, a V2G network cross-domain authentication scheme based on an alliance block chain is provided; A V2G network trust model and a system architecture are designed, and a specific scheme is described in detail. Signature and authentication of the method both adopt the latest national password standard SM9 cryptographic algorithm; The characteristic that the block chain technology is not easy to tamper is utilized, the Hash algorithm is used for verifying the certificate, and the signature and verification times of the public key algorithm are reduced, so that the efficiency is high, and the expandability is high. The introduction of the block chain technology provides a new idea and method for solving the security problem of the smart power grid. The invention provides a high-performance cross-domain authentication scheme in a V2G network by utilizing a block chain technology and anSM9 digital signature algorithm.
Owner:ELECTRIC POWER RESEARCH INSTITUTE OF STATE GRID SHANDONG ELECTRIC POWER COMPANY
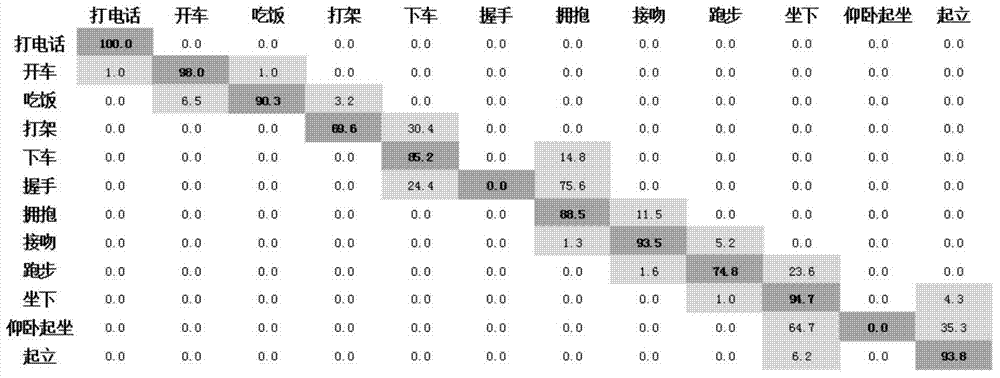
Video human action reorganization method based on sparse subspace clustering
InactiveCN104732208AImprove performanceIncreased overall recognition accuracyCharacter and pattern recognitionFeature extractionThree-dimensional space
The invention belongs to computer visual pattern recognition and a video picture processing method. The computer visual pattern recognition and the video picture processing method comprise the steps that establishing a three-dimensional space-time sub-frame cube in a video human action reorganization model, establishing a human action characteristic space, conducting the clustering processing, updating labels, extracting the three-dimensional space-time sub-frame cube in the video human action reorganization model and the human action reorganization from monitoring video, extracting human action characteristic, confirming category of human sub-action in each video and classifying and merging on videos with sub-category labels. According to the computer visual pattern recognition and the video picture processing method, the highest identification accuracy is improved by 16.5% compared with the current international Hollywood2 human action database. Thus, the video human action reorganization method has the advantages that human action characteristic with higher distinguishing ability, adaptability, universality and invariance property can be extracted automatically, the overfitting phenomenon and the gradient diffusion problem in the neural network are lowered, and the accuracy of human action reorganization in a complex environment is improved effectively; the computer visual pattern recognition and the video picture processing method can be applied to the on-site video surveillance and video content retrieval widely.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Food safety risk traceability analysis system and method based on block chain
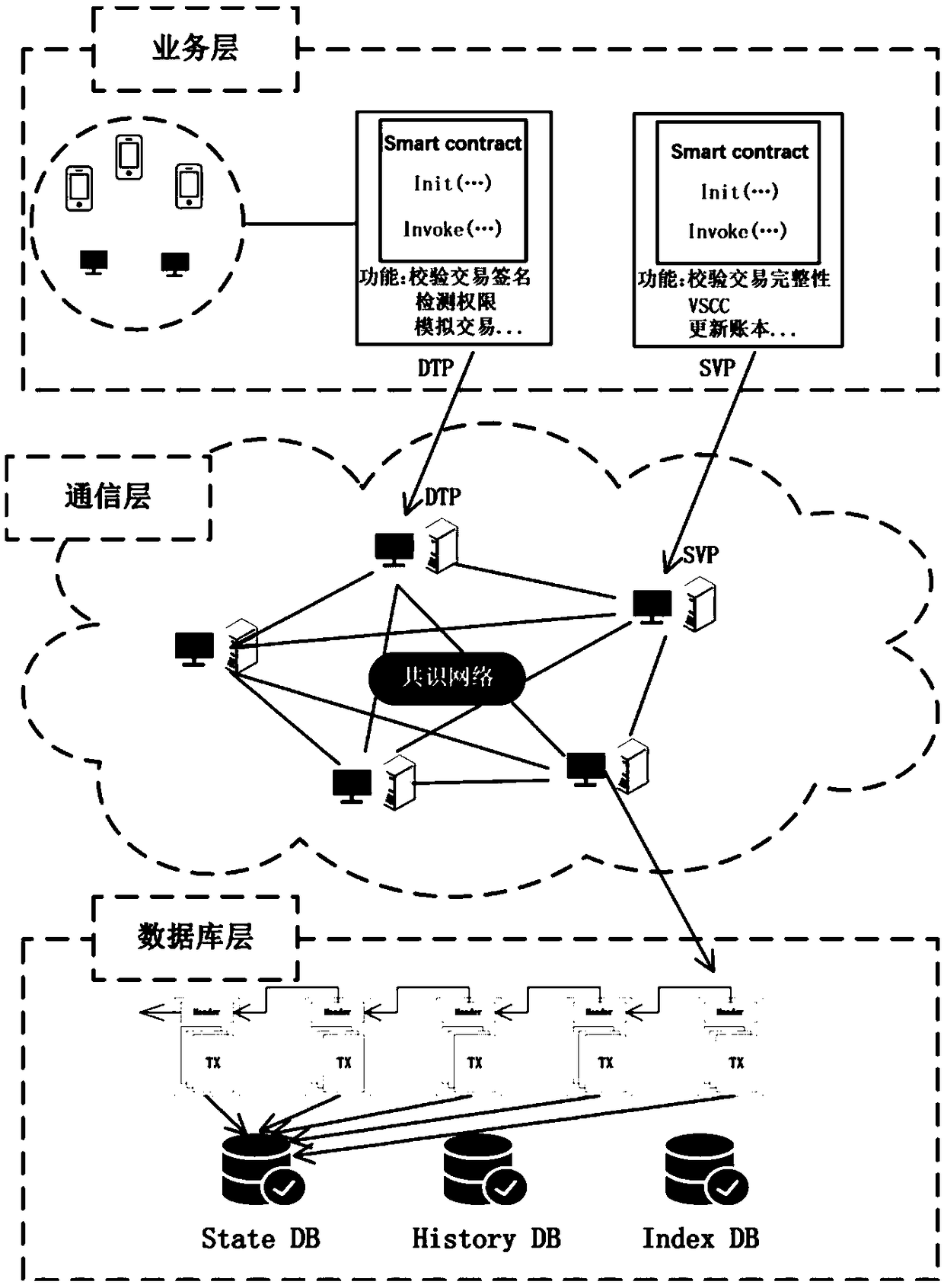
The invention relates to a food safety risk traceability analysis method and a system based on a block chain. The block chain technology is applied to a database layer and a communication layer of thesystem, and the visualization technology is applied to a service layer of the system. Data upload requires the initiator's digital signature to ensure that the data is not tampered with and that thedata is stored in the block chain. Data access is controlled by permissions to access data in the chunk chain by executing smart contracts. Use Force-Directed Graph and flow maps show the food risk traceability process. When tracing the source of food safety risk, the user can trace the source of food safety risk through Force-Directed Graph Drills up to trace the source, then down to track the flow of food, Force-Directed Graph drill-through operations are shown in conjunction with a flow map in which arrows indicate the flow direction of risky foods, where different shades of color representdifferent degrees of risk flow. The invention not only solves the problems of unsafe storage of the traditional food traceability data and the vulnerability of the central database, but also providesa friendly visual interaction interface for users.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
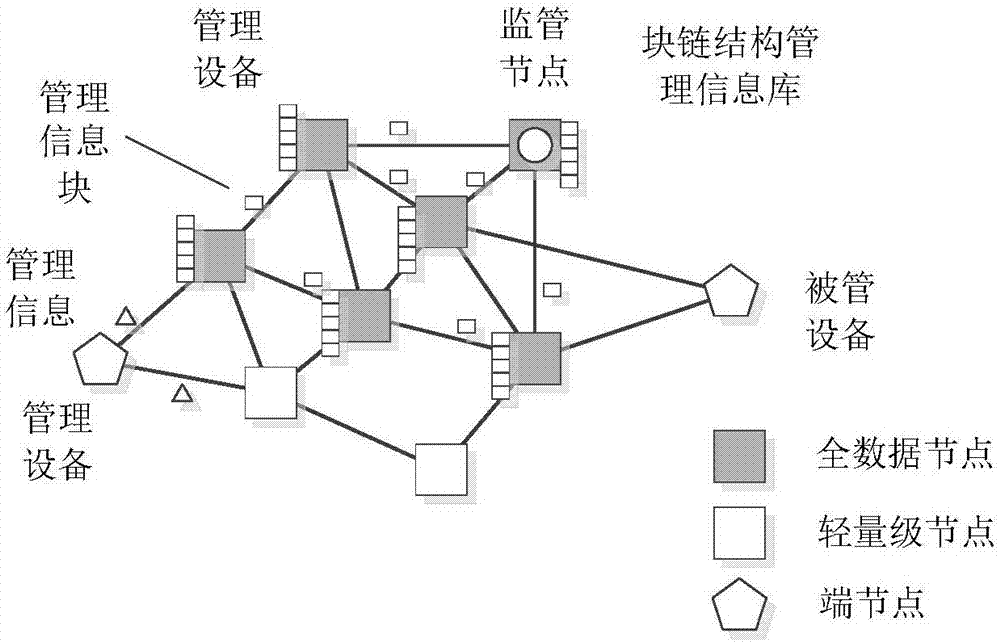
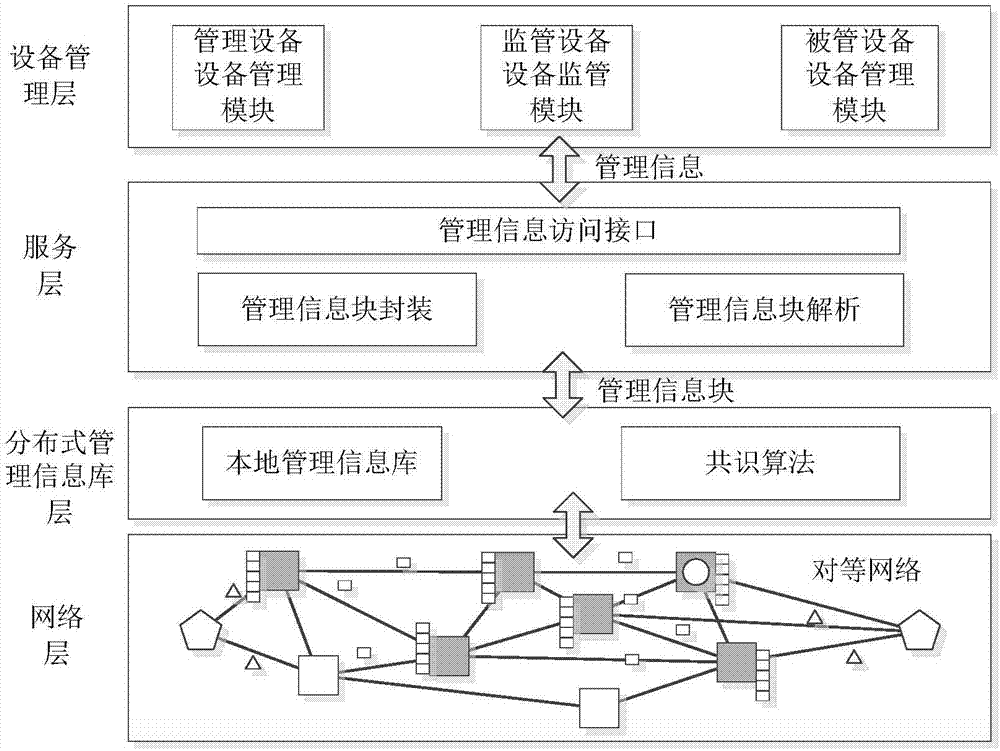
Trusted device management method based on decentralized network
ActiveCN106911513AGuaranteed not to be tampered withSecure tamperingUser identity/authority verificationData switching networksManagement information baseAsynchronous communication
The invention relates to the field of device networking management, and provides a trusted device management method based on a decentralized network. According to the method, a distributed decentralized network is adopted, and coupling between a management device and a managed device is eliminated. Encrypted management commands and management data are utilized. The managed device actively or passively acquires a management instruction from the distributed network, and furthermore feedback information is written, thereby realizing asynchronous communication between the management device and the managed device. A target node according to the invention acquires management information through a lightweight node, wherein the lightweight node filters local node information; the information which matches the address of the target node is forwarded to the target node; and the target node verifies an information signature by means of a source node public key, decrypts a session key through a local private key and decrypts a message, thereby acquiring management information and processing.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
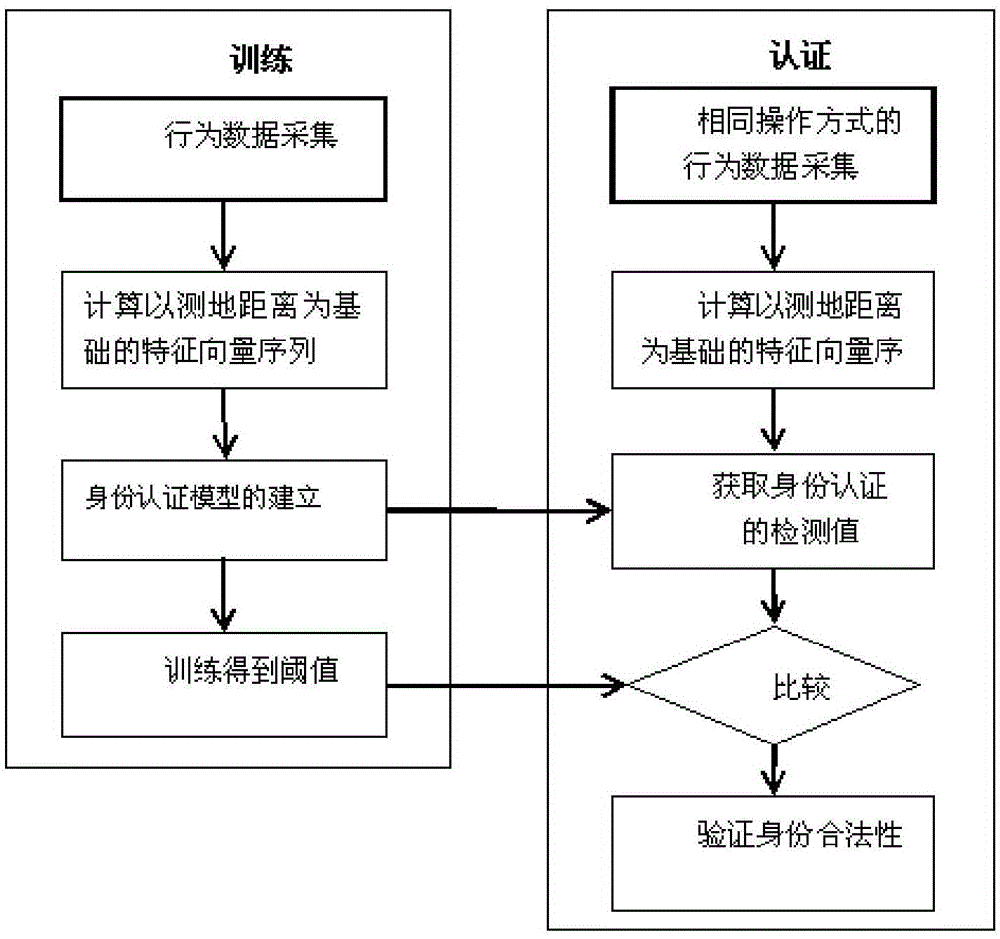
Mobile terminal user identity authentication method based on multi-finger touch behavior characteristics
ActiveCN105068743AEasy to realize identificationImmutableDigital data authenticationInput/output processes for data processingFeature vectorSupport vector machine classifier
The present invention discloses a smart mobile terminal authentication method based on multi-finger touch behavior characteristics. The method comprises a first step of obtaining touch screen operating information of a user through multi-finger touch screen operation, the multi-finger touch screen operation being touch screen sliding of multiple fingers at a together-put state; a second step of extracting a physiological feature and a behavior feather of a touch screen from the user touch screen operation information, and combining the above feathers as one feature vector; a third step of training a probabilistic neural network classifier and a support vector machine classifier by using the above combined feather vector, to generate a training model of valid users; and a fourth step of collecting touch screen operation information of test users, processing the information according to the second step to obtain combined feature vectors of the touch screen operation of the test users, and putting the combined feature vectors into the two classifiers to compare with the training model of the valid users, thus to obtain classifying results if the test users are valid users.
Owner:XI AN JIAOTONG UNIV
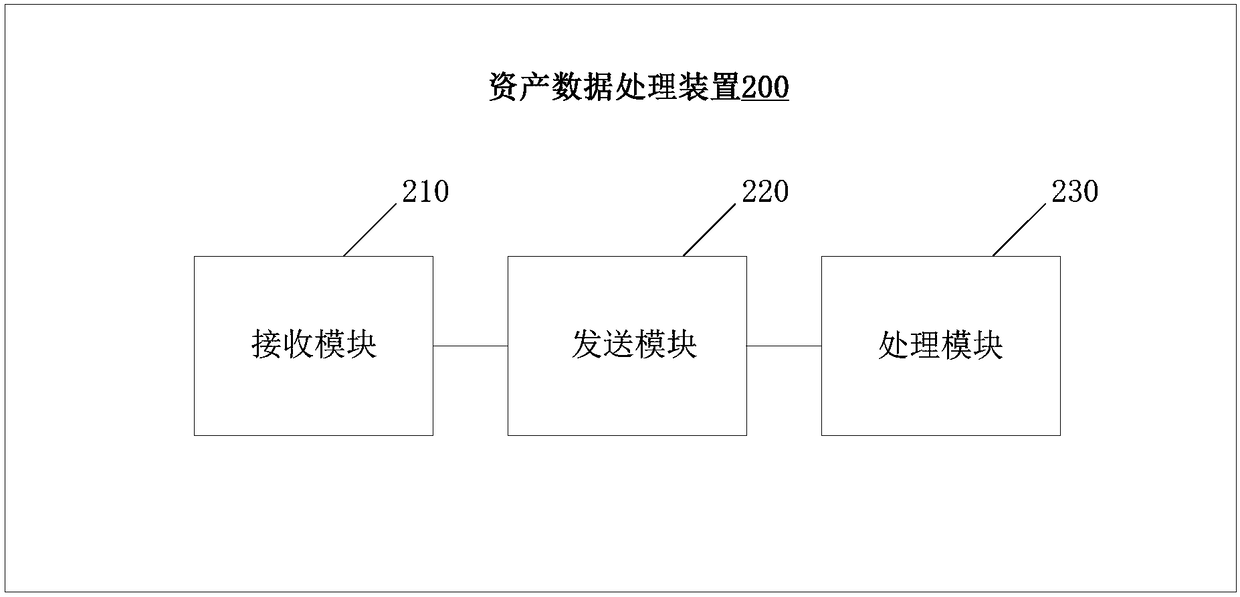
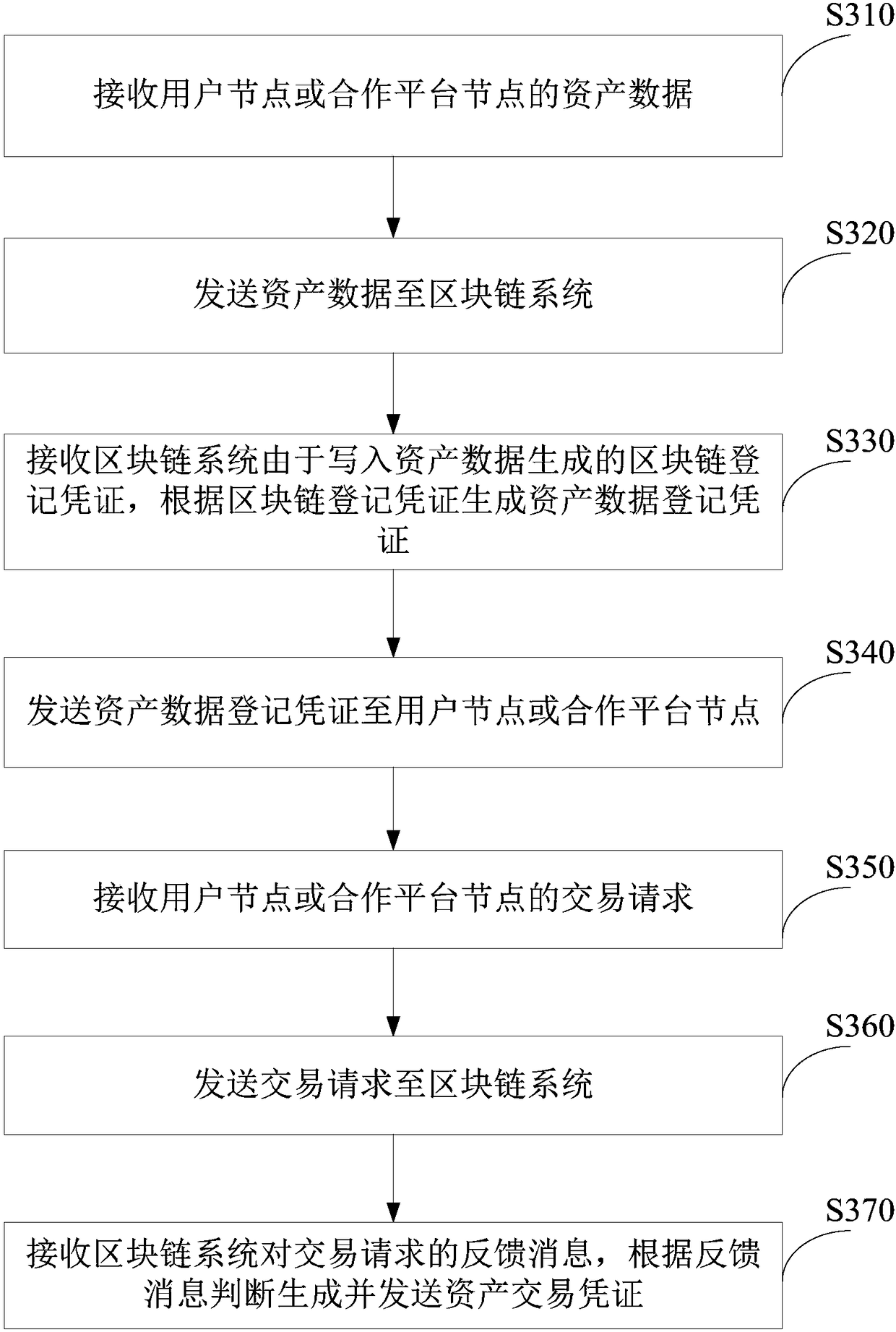
Asset data processing apparatus and method
InactiveCN108154439AImmutableAsset registration is safe, open and transparentFinanceData registrationBlockchain
The present invention provides an asset data processing apparatus and method. The apparatus comprises: a receiving unit, a sending unit and a processing unit. The receiving unit is configured to receive asset data of a user node or a cooperation platform node; the sending unit is configured to send asset data to a blockchain system; and the processing unit is configured to receive the blockchain registration certificate of the blockchain system generated due to writing of asset data, and generate the asset data registration certificate according to the blockchain registration certificate. Thesending unit is further configured to send the asset data registration certificate to the user node or the cooperation platform node; the receiving unit is further configured to receive a transactionrequest of the user node or the cooperation platform node; the sending unit is further configured to send the transaction request to the blockchain system; and the processing unit is further configured to receive a feedback message from the blockchain system to the transaction request, and according to the feedback message, determine whether to generate and send the asset transaction certificate.
Owner:北京金股链科技有限公司
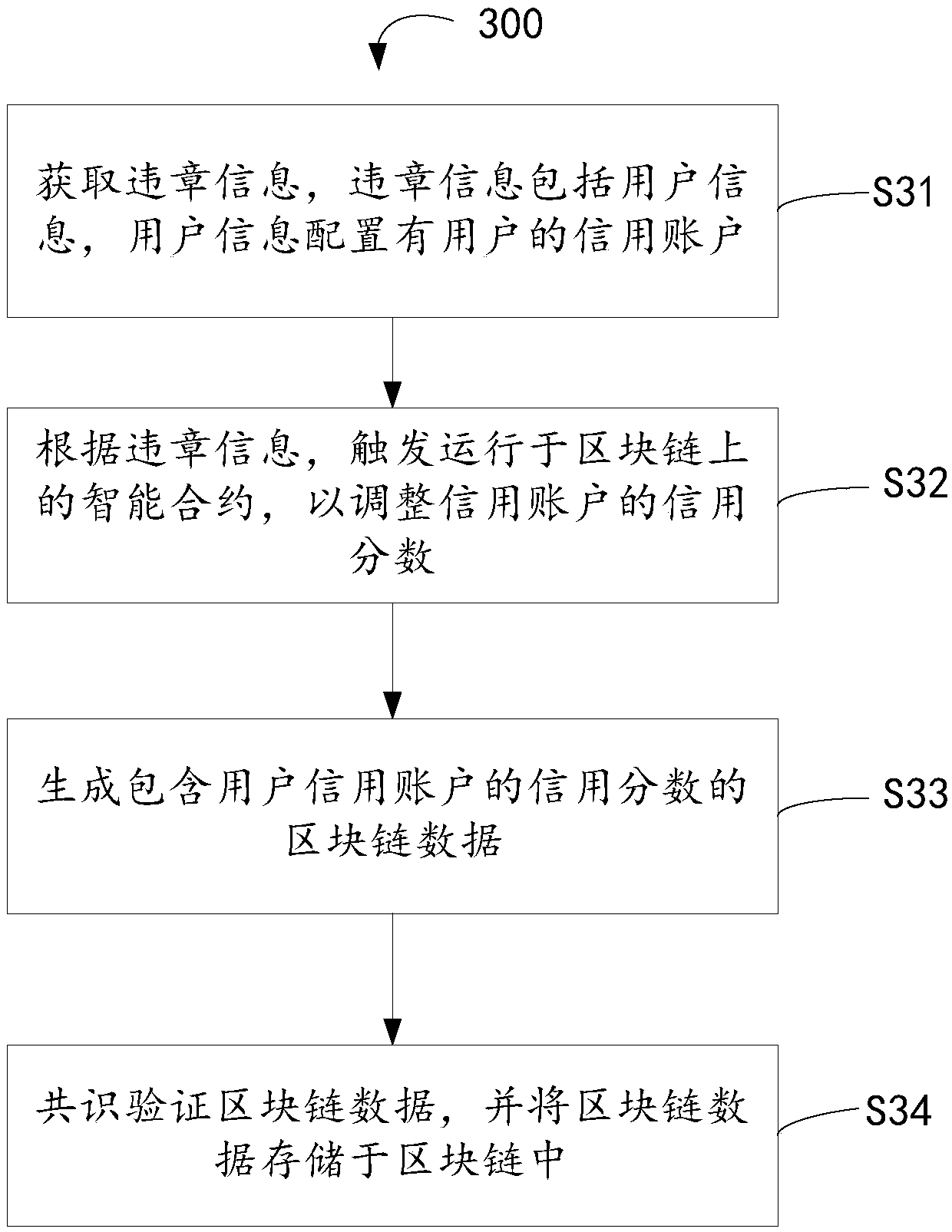
Parking credit adjustment method and device based on block chain, and electronic device
InactiveCN109086619AImmutableWith decentralizationData processing applicationsDigital data protectionSmart contractUser information
The invention relates to the technical field of a block chain, in particular to a parking credit adjustment method based on a block chain, a device thereof and an electronic device. The parking creditadjustment method based on the block chain comprises the following steps: obtaining illegal information, wherein the illegal information includes user information, and the user information is configured with the user's credit account; triggering an intelligent contract running on the block chain to adjust the credit score of the credit account according to the violation information; generating block chain data containing credit scores of a user's credit account; validating the block chain data by consensus and storing the block chain data in the block chain. Because the block chain has the characteristics of non-tampering, decentralization and high transparency, which can provide reliable and highly transparent parking credit.
Owner:广东天泽汇通科技有限公司
Commodity integration method based on block chain and device thereof, and node of block chain
InactiveCN109146573AImmutableImprove points versatilityDiscounts/incentivesPayment protocolsSoftware engineeringSmart contract
The invention relates to the technical field of block chain, in particular to a commodity integration method based on block chain and a device thereof, and a block chain node. The method comprises thefollowing steps of: acquiring an integral storage request, wherein the integral storage request carries integral information; executing an intelligent contract according to the point storage requestto calculate a point value corresponding to the user identity information; packaging a plurality of integration information belonging to user identity information and integral values corresponding tothe integration information with the same integration valid period into block data; the block data being sent to the consensus node so that the consensus node verifies the block data. On the one hand,block chains can provide reliable integration information because of their untampered, decentralized and highly transparent characteristics. On the other hand, it adopts unified rules to calculate the integral value, which means that the integral between different merchants can be exchanged peer to peer, so as to improve the universality of the integral and expand the scope of use of the integral.
Owner:SHENZHEN GENUINE INNOVATIVE TECH CO LTD
Electronic evidence storage method based on block chain smart contract
ActiveCN110223068ARealize the core logic functionTransparent deposit processElectronic credentialsTransmissionTamper resistanceEvidence analysis
The invention requests to protect an electronic evidence storage method based on a block chain smart contract, and the method comprises the steps: carrying out the evidence storage through the smart contract by a evidence storage person, carrying out the query of evidence information through the smart contract by a verification person, carrying out the evidence downloading through the smart contract by a researcher, and carrying out the uploading of an evidence analysis result through the smart contract. The smart contract is a key logic module for realizing the method and exchanges data withthe block chain, so that the integrity, the verifiability and the tamper resistance of the electronic evidence are ensured. And meanwhile, all data operations are recorded on the block chain, so thatthe traceability of the electronic evidence is realized.
Owner:广东灏昌商业保理有限公司
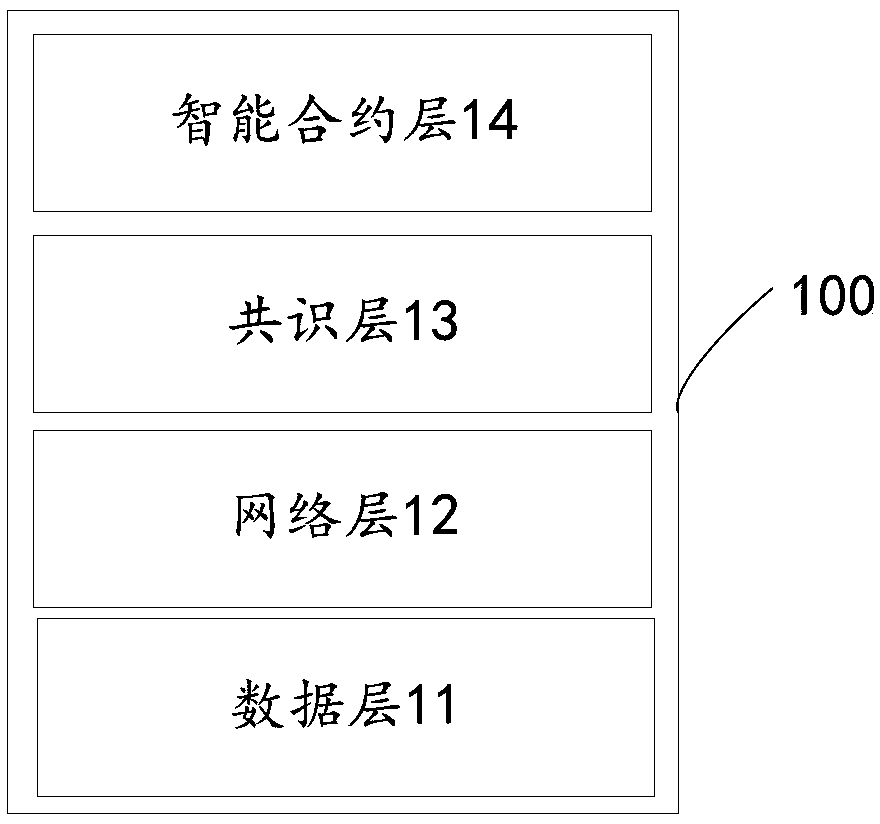
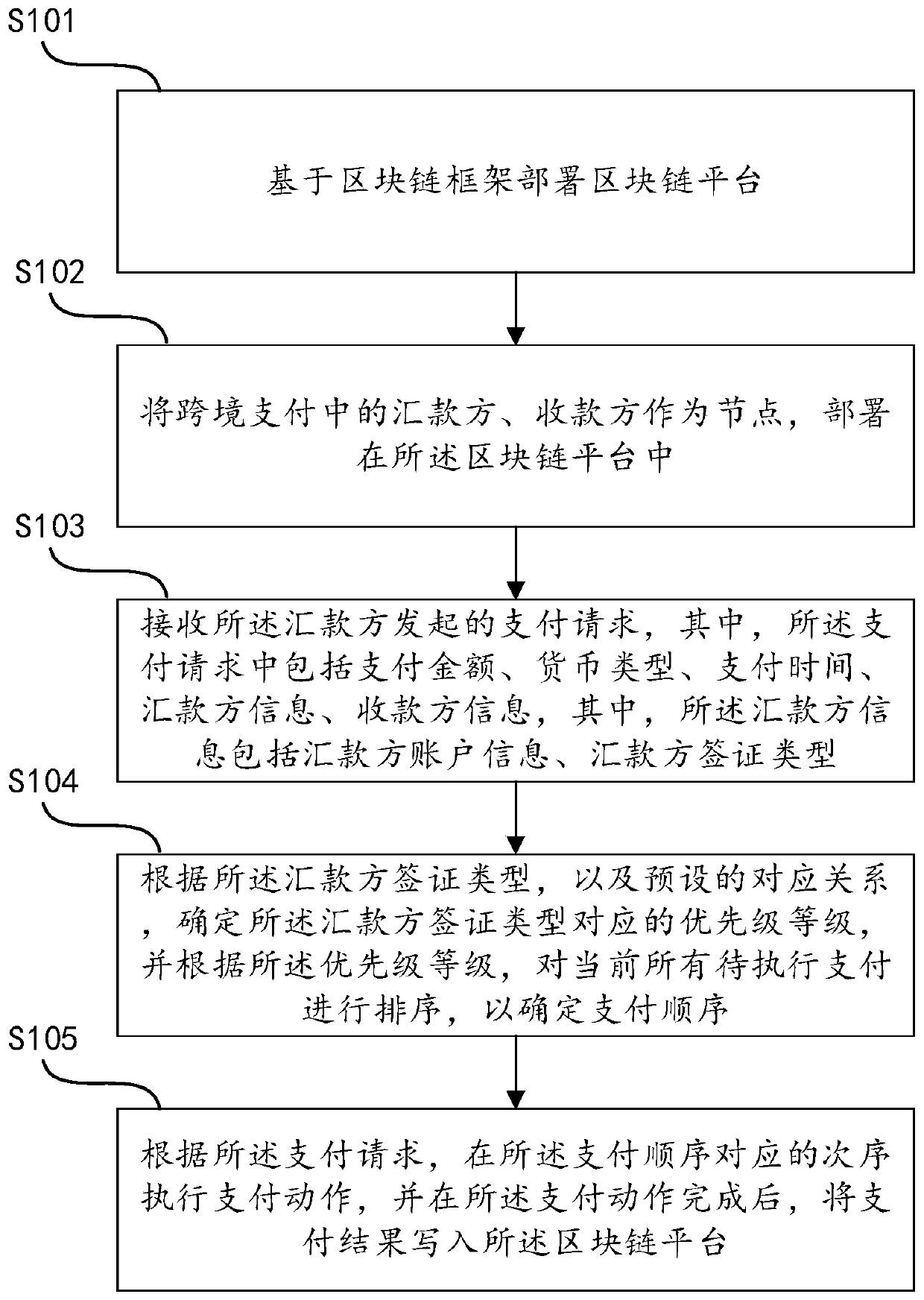
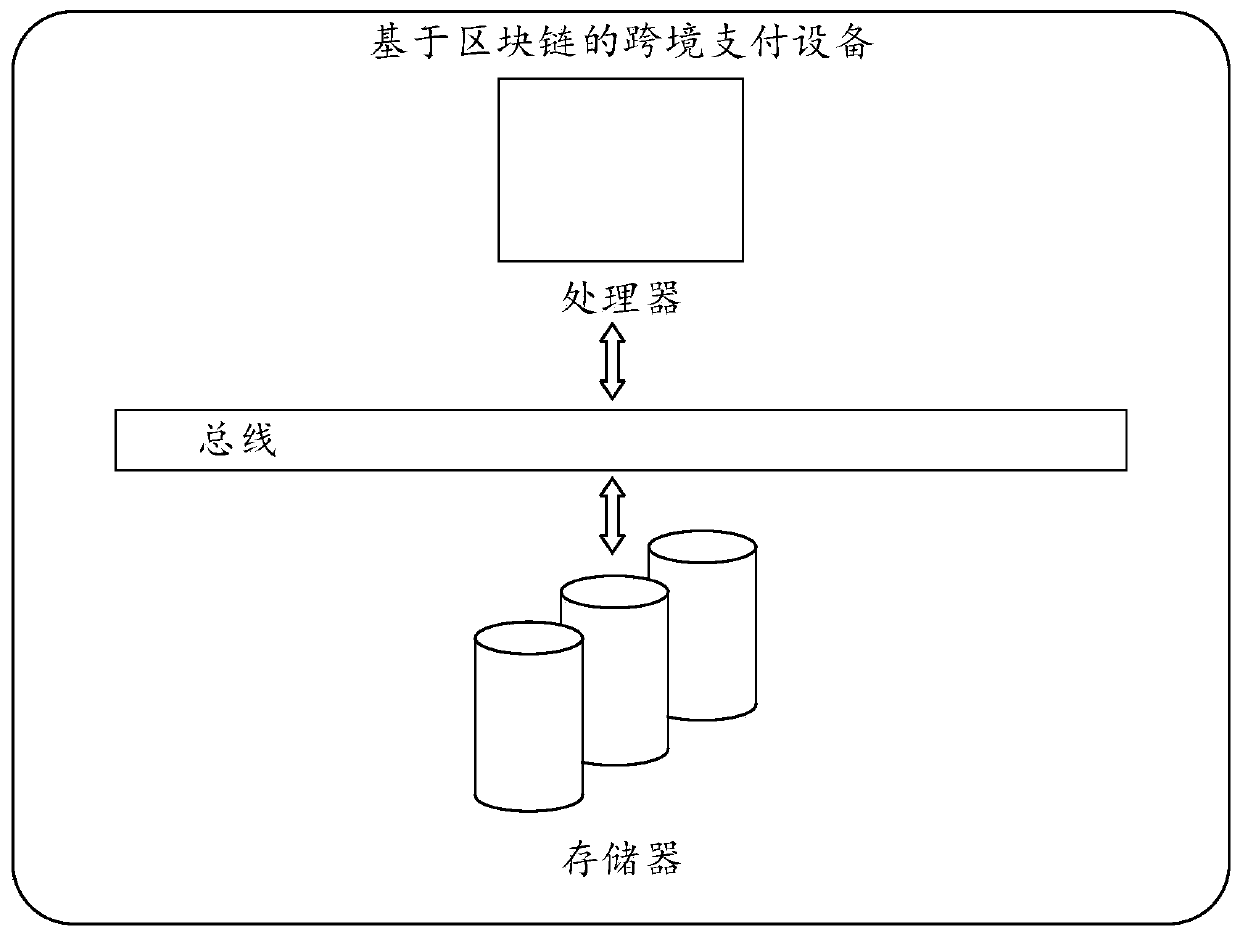
Cross-border payment method and device based on blockchain, and medium
PendingCN111008825AImmutableGuaranteed reliabilityPayment circuitsPayment schemes/modelsTamper resistanceDistributed data store
The invention discloses a cross-border payment method and device based on a block chain and a medium. The method comprises the steps of receiving a payment request initiated by a remittance party , wherein the payment request comprises remittance party information, and the remittance party information comprises a remittance party visa type; determining a priority level corresponding to the remittance party visa type according to the remittance party visa type and a preset corresponding relationship, and sorting all current to-be-executed payments according to the priority level; and accordingto the payment request, executing a payment action in an order corresponding to the payment order, and writing a payment result into a block chain platform. Typical characteristics of the block chaintechnology are integrated innovation of information technologies such as distributed data storage, point-to-point transmission, a trust consensus algorithm, an encryption algorithm and the like, and the block chain technology has the characteristics of generalization, trust consensus, information tamper resistance, openness and the like, and is suitable for being applied to payment services requiring high mutual trust of two transaction parties. The efficiency is improved, and a user can complete a cross-border payment service without waiting for too long time.
Owner:浪潮云洲工业互联网有限公司
Commodity information maintenance method based on block chain, block chain node and system thereof
InactiveCN109102308AImmutableWith decentralizationPayment protocolsBuying/selling/leasing transactionsDigital signatureBlockchain
The invention relates to the technical field of a block chain, in particular to a commodity information maintenance method based on a block chain, a block chain node and a system thereof. The method comprises: receiving a commodity purchase success request sent by a common node, wherein the commodity purchase success request comprises a commodity name, a number and a digital signature; the digitalsignature is generated by a private key; the public key generated by the private key is broadcasted in a block chain; and the block chain stores a commodity list list of the relationship between eachcommodity name, the number and the purchase status; verifying the digital signature against the public key; when the digital signature is legal, the purchase status corresponding to the commodity name being set to the purchased status in the commodity list list, the commodity list list being updated, and the updated commodity list list being packaged into block data; the block data being sent tothe consensus node so that the consensus node verifies the block data. Because the block chain has the characteristics of non-tampering, decentralization and high transparency, which can provide reliable commodity information.
Owner:SHENZHEN GENUINE INNOVATIVE TECH CO LTD
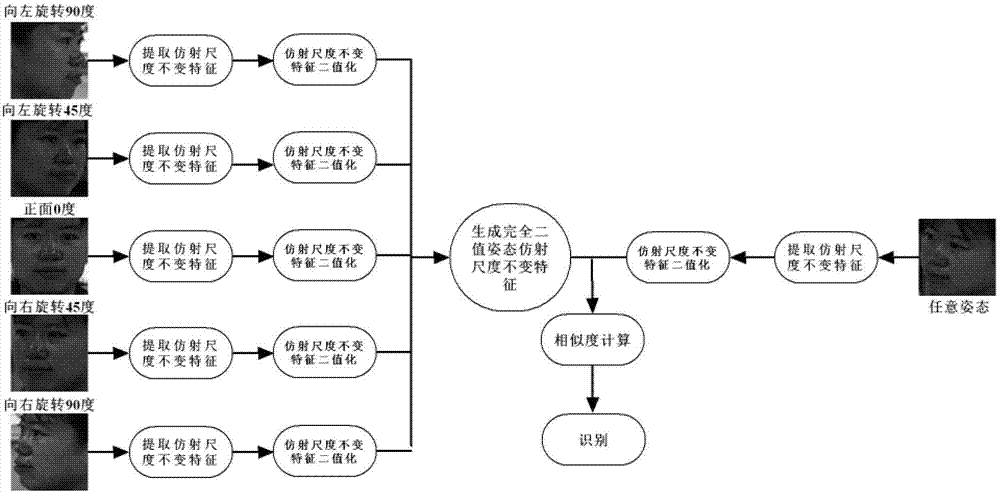
Total posture face identification method based on complete binary posture affinity scale invariant features
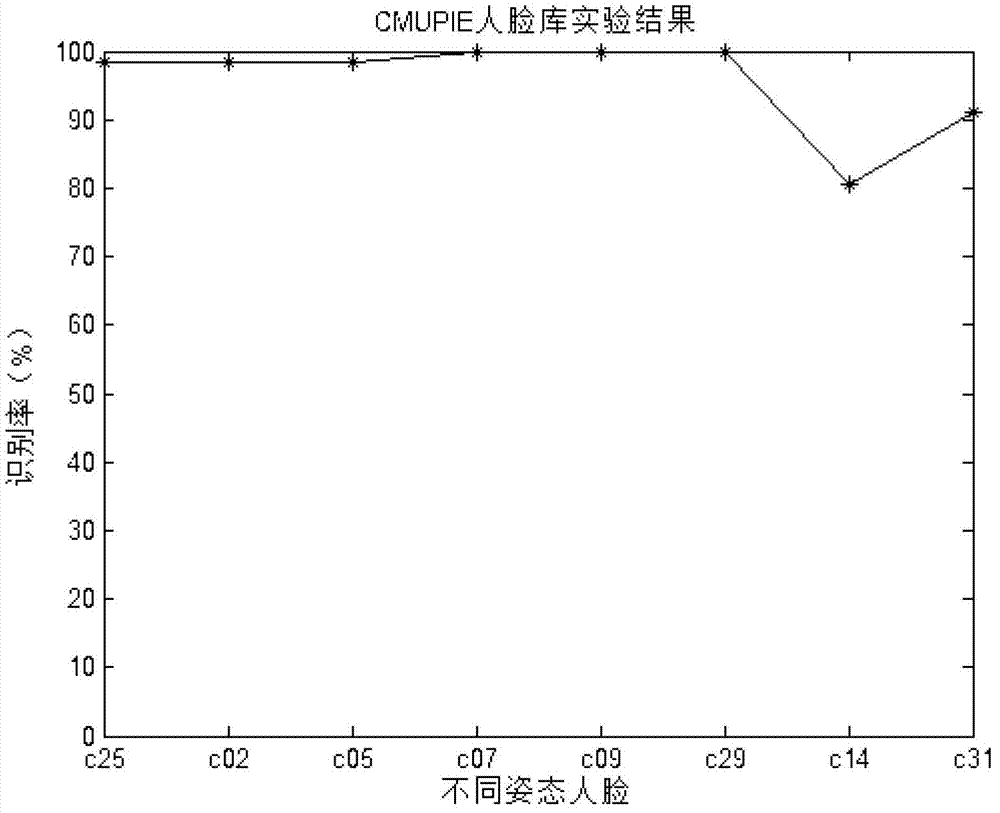
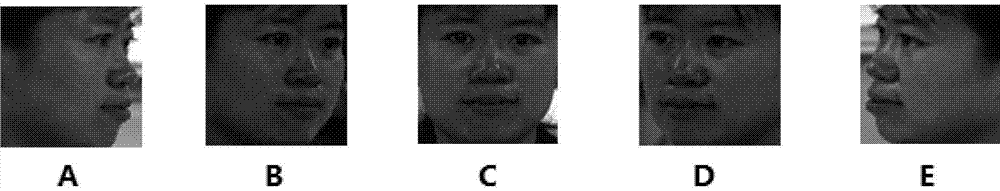
ActiveCN103295002AReduce computational complexitySave storage spaceCharacter and pattern recognitionComputation complexitySimulation training
Disclosed is a total posture face identification method based on complete binary posture affinity scale invariant features. By the method, identification of faces with total posture variations (from horizontal 90-degree left turning to horizontal 90-degree right turning, head raising and head lowering) can be achieved. Experiments analysis shows that affinity scale invariant features are invariant to faces turning in a plane and invariant to faces turning within 25 degrees in a plane, and accordingly the method acquires multiple face images of specific postures, extracts affinity scale invariant features of the face images, and combines the features to generate complete binary posture affinity scale invariant features so as to realize invariance to total posture face turning. The method needs no simulation training, so that the method is much better than methods based on models in terms of computation complexity. Meanwhile, for conditions with large posture variations, the identification performance is much better than traditional methods based on features. The method has certain application value and significance.
Owner:BEIJING UNIV OF TECH
Method for storing and inquiring identity information of sale merchandise
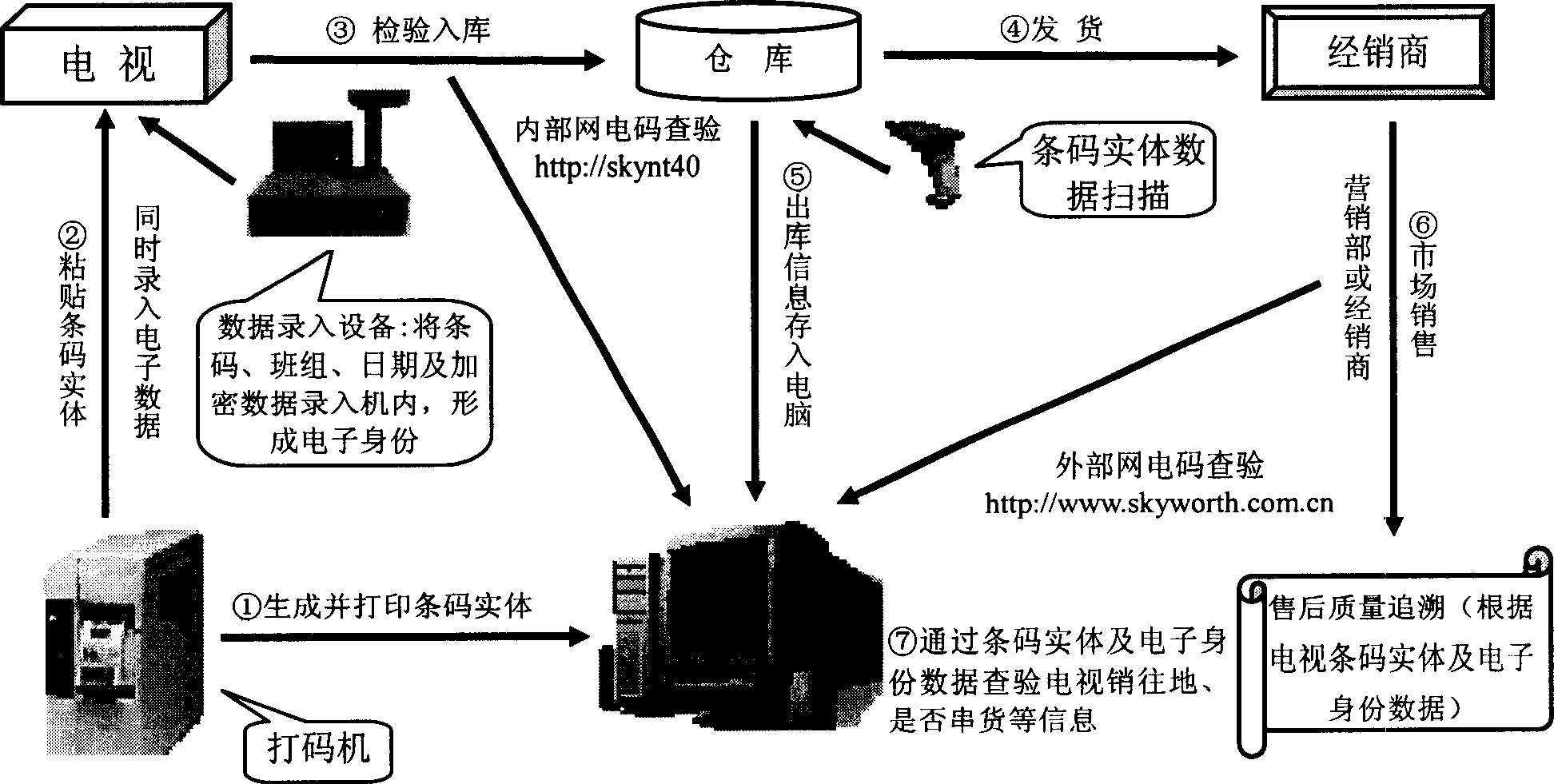
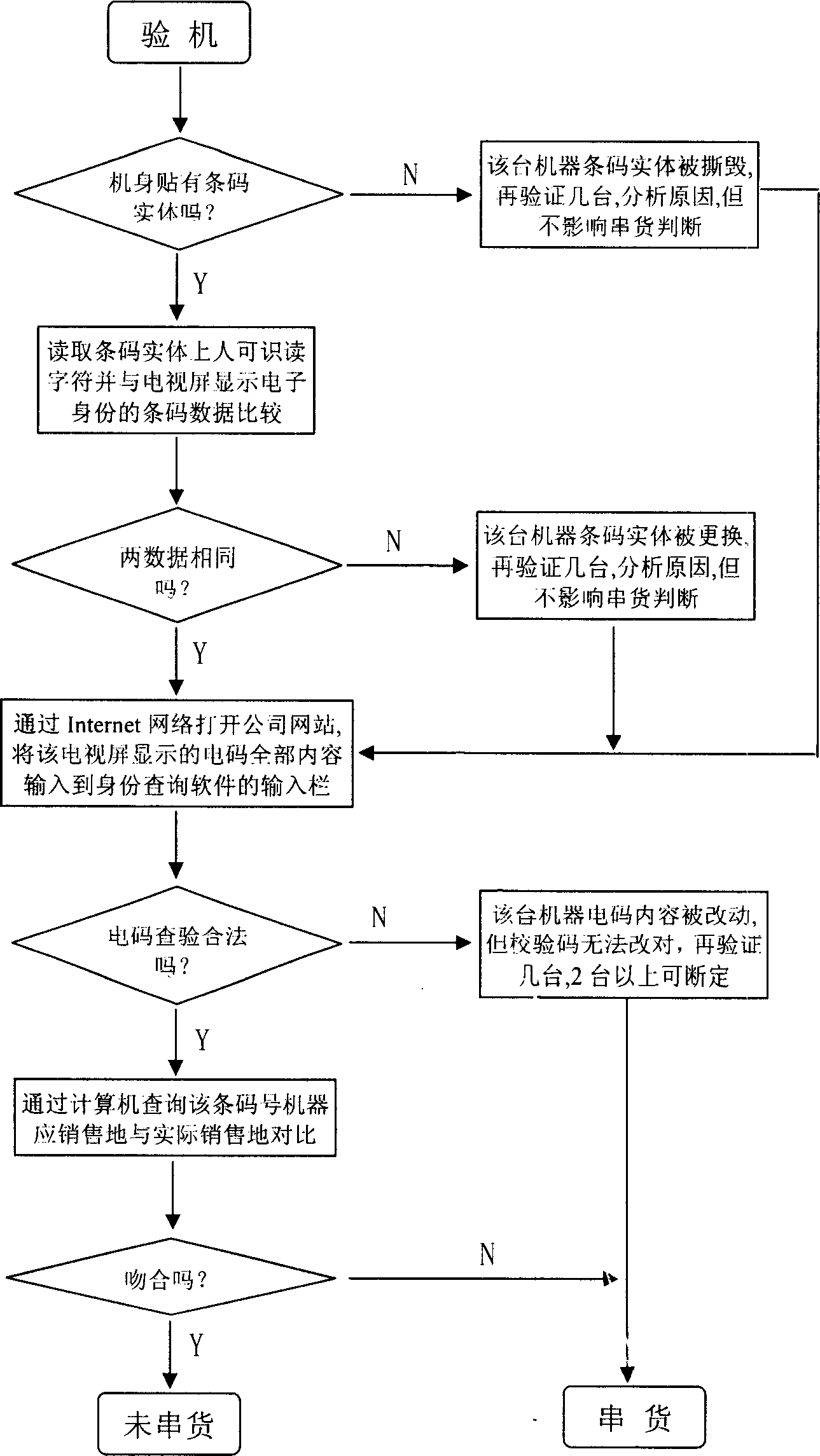
InactiveCN1734450AAccurate authenticationPrevent cross-sellingSensing record carriersSpecial data processing applicationsModel NumberComputer science
The invention discloses an identity information storing and checking method of sales commodity, which comprises the following steps: a) sticking bar code on the commodity or package, whose basic information concludes commodity type+key component number +product sequence; b) transforming null symbol to datum of bar code and superimposing the group product and daily date datum of the commodity; c) disposing the datum with superimposing the step b) to obtain electric identity information encryptedly; d) inputting the information to storage unit of specific commodity; e) recording the information of electric identity, sales address where the commodity post and transportation in the computer datum.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
Bionic vision transformation-based image RSTN (rotation, scaling, translation and noise) invariant attributive feature extraction and recognition method
ActiveCN105809173AThe RSTN invariant property hasInvariant properties haveCharacter and pattern recognitionFeature extractionImage resolution
The invention discloses a bionic vision transformation-based image RSTN (rotation, scaling, translation and noise) invariant attributive feature extraction and recognition method. The method includes the following steps: 1) gray processing is performed on an original image, and the size of the image is reset by using a bilinear interpolation method; 2) the directional edge of the target image is detected based on a Gabor and bipolar filter F-based filter-filter filter, so that an edge image E can be obtained; 3) the spatial resolution pitch detection value of the edge image E is calculated, so that a first-stage output image S1 is obtained; and 4) directional edge detection mentioned in the step 2) and spatial resolution pitch detection mentioned in the step 3) are performed on the first-stage output image S1 again, so that a second-stage feature output image S2 can be obtained, and invariant attributive features can be obtained. According to the method of the invention, a human visual perception mechanism is simulated, and bionic vision transformation-based RSTN invariant attributive features are used in combination, and therefore, the accuracy of image recognition can be improved, and robustness to noises is enhanced.
Owner:CENT SOUTH UNIV
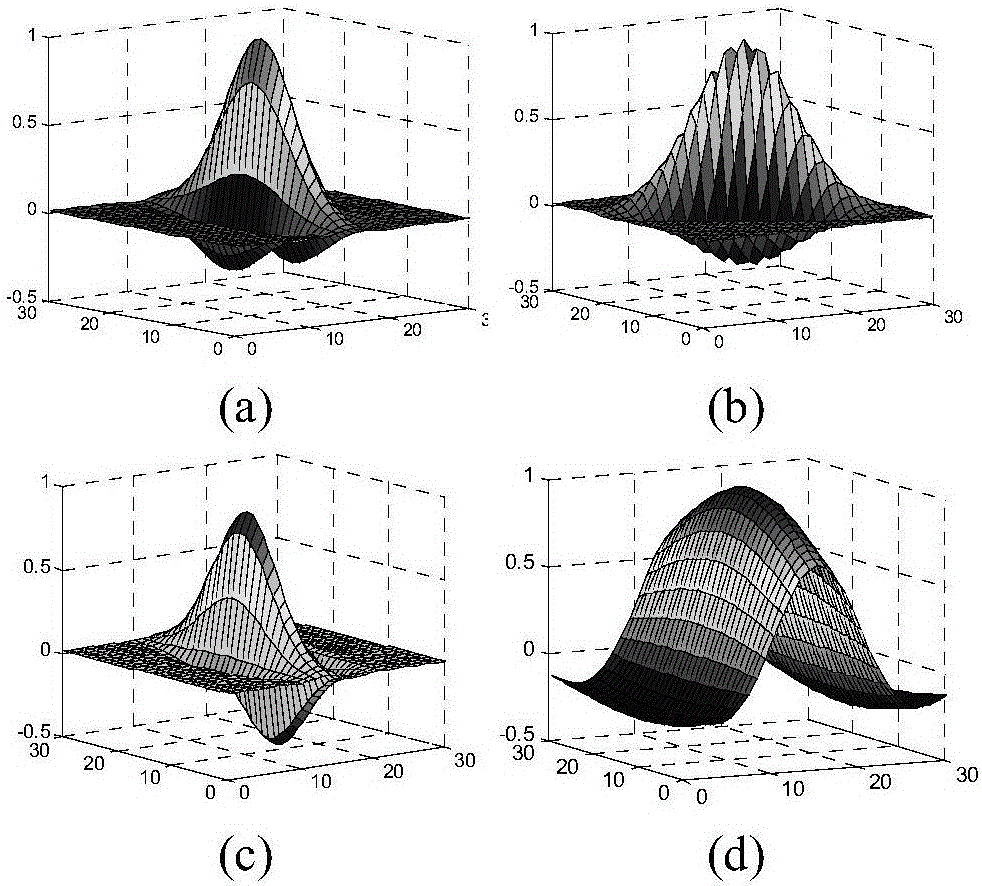
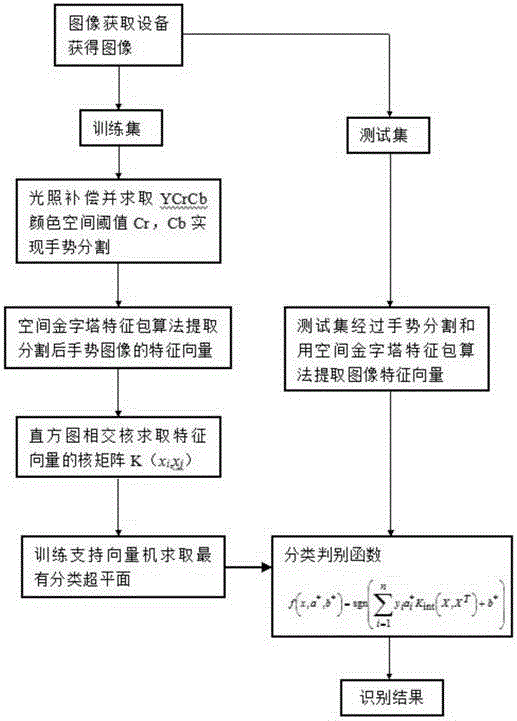
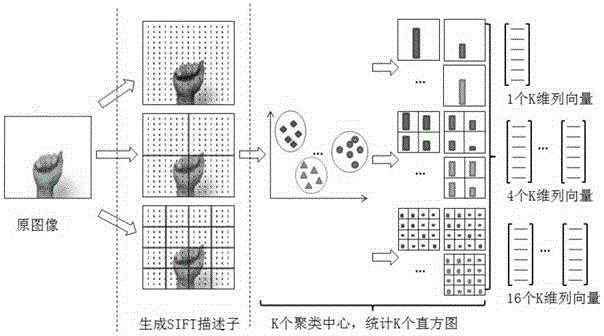
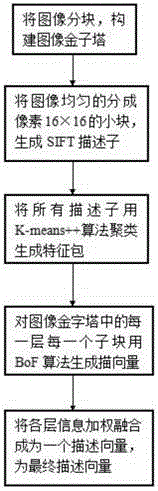
Gesture recognition method based on image space pyramid bag of features
InactiveCN104156690AAccurate descriptionImprove recognition rateCharacter and pattern recognitionFeature vectorBag of features
The invention relates to a gesture recognition method based on an image space pyramid bag of features. The method comprises the following steps of carrying out gesture division of an image with a gesture; extracting and describing features of the divided gesture image; using extracted features to train a histogram intersection core support vector machine; obtaining a gesture type to which a feature vector of the gesture image belongs according to the support vector machine, in order to achieve gesture recognition. The method combines a space pyramid algorithm and a bag of features algorithm, and describes features of overall quantity and distribution of feature points of the gesture image. By means of the histogram intersection core support vector machine, classification of gesture features is achieved, and gesture recognition is achieved further. In addition, the rate of recognizing gestures of multiple similar types is improved.
Owner:LIAONING UNIVERSITY OF PETROLEUM AND CHEMICAL TECHNOLOGY
Robust tracking method of target in airport monitoring video
InactiveCN101877134ASingular value unchangedStrong ability to resist noiseImage analysisClosed circuit television systemsSingular value decompositionFeature vector
The invention relates to a robust tracking method of target in an airport monitoring video, which combines singular value decomposition (SVD) and particle filtering target tracking technology. The method comprises the following steps: step 100: initiating, generating particle swarm containing N particles, carrying out SVD for the tracked target, and establishing template model; step 200: forecasting state by forecasting position of the target in current frame based on position of the target in a prior frame; step 300: updating particle weight, carrying out SVD for candidate image area, establishing feature vector, and comparing similarity of the candidate area and the template by using least squares criterion to be weight of the particle; step 400: re-sampling particle, keeping particles with larger weight, discarding particles with smaller weight, enabling particles with larger weight to derive new particles to keep total number N of particles unchanged, and transferring new particles and the next frame of image to step 200 for circulation operation; and step 500: outputting result, and weighting all particles and weight of all particles to obtain position of the target in current frame. The invention solves problems of complicated scene, frequent illumination change, serious interference caused by background analogue and the like of existing airport monitoring video, and meets requirements of robustness and accuracy in monitoring and tracking process.
Owner:BEIHANG UNIV
Image matching method based on corner point and single-line segment marshalling feature description operator
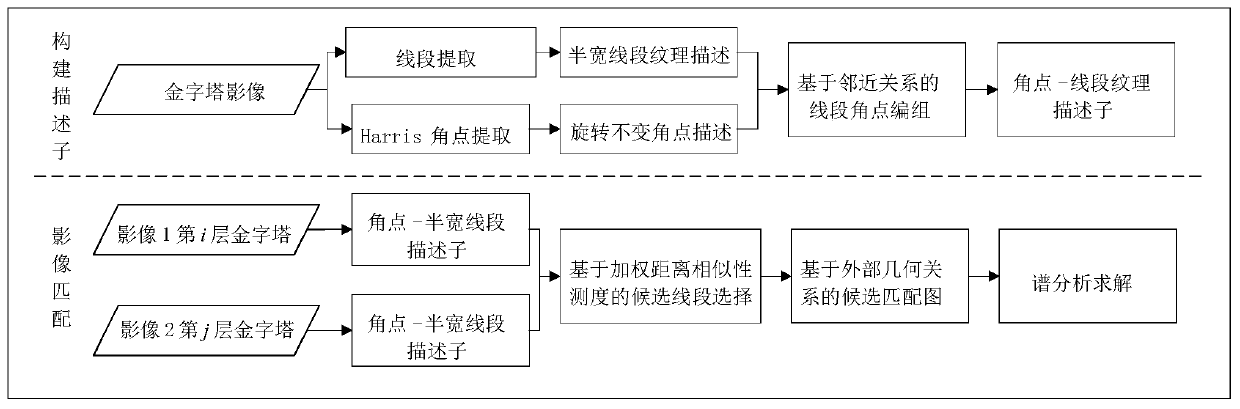
ActiveCN110490913AReduce time complexitySmooth rotationImage analysisShortest distanceRotational invariance
The invention discloses an image matching method based on a corner point and single-line segment marshalling feature description operator. The method comprises the following steps: firstly, extractingline segments and Harris corner points from an image; constructing a line segment, searching and grouping the line segment, constructing an angular point-single line segment texture descriptor with scale, rotation and illumination invariance by using a detected angular point and the line segment, the Harris angular point having the advantage of rotation invariance, and the line segment adopting ahalf-width descriptor can improve the reliability in a parallax change scene; performing spatial weighted shortest distance measurement to obtain a local matching result; finally, determining the candidate matching of each line segment, establishing a matching matrix and solving a global matching result through spectral analysis. The image matching description operator has the characteristics ofscale, rotation and illumination invariance. According to the invention, image pyramids are respectively established for three-dimensional images. The pyramids on different layers are matched one byone, so that the scale influence can be eliminated. The defects of large marshalling calculation amount and long consumed time in multi-line-segment matching can be overcome.
Owner:HUAZHONG NORMAL UNIV
Improved method for jitter quantisation and watermark modulation
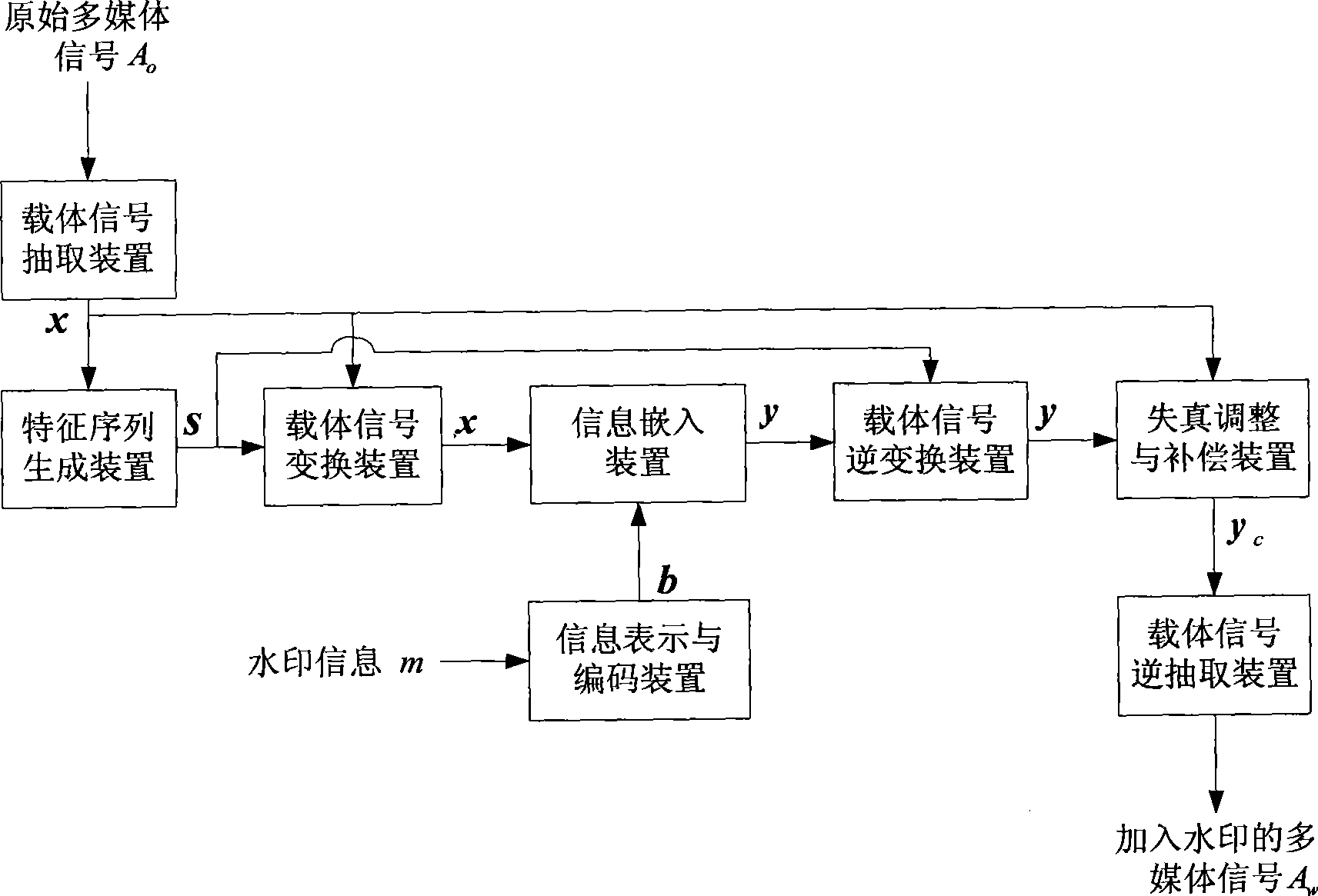
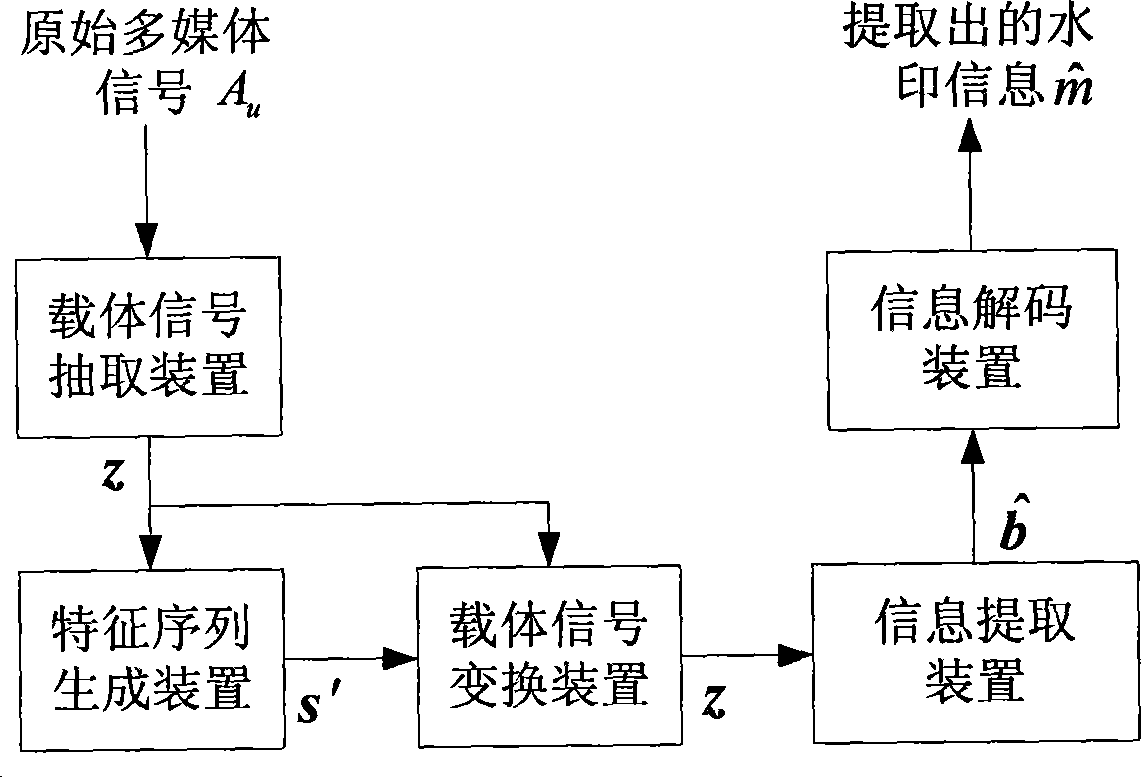
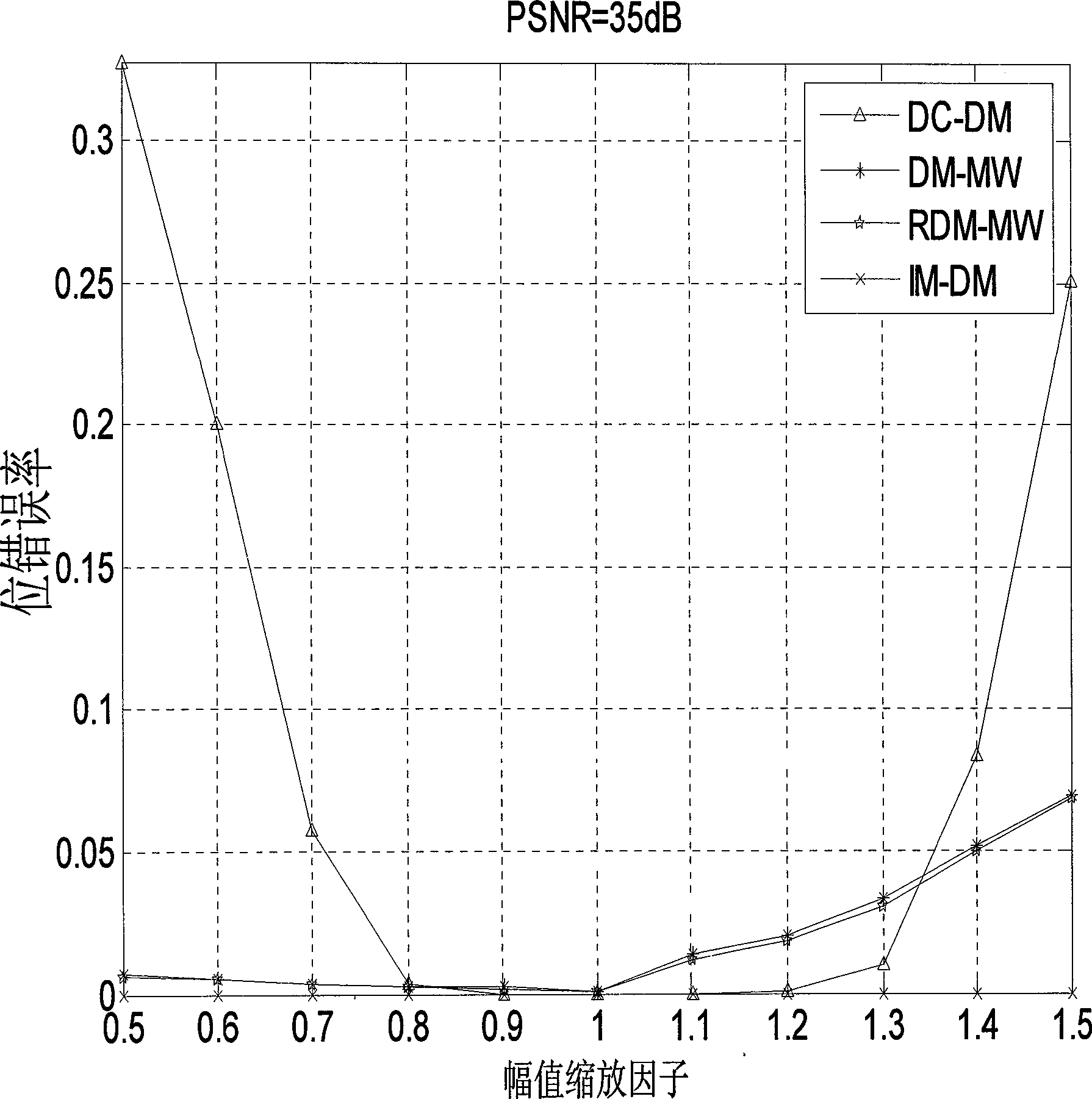
InactiveCN101452564AZero error rateImmutableImage codingImage data processing detailsOriginal dataCarrier signal
The invention relates to an improved dither modulation (DM) watermarking method and belongs to the technical field of digital watermarks. Compared with a statistical watermarking method of known carrier signal such as spread spectrum watermarking, original DM has the advantages of higher watermark capacity and has the disadvantage of high sensitivity to amplitude scaling attack. The invention constructs a signal invariable relative to the scaling for quantification by using a method which comprises: extracting from original content a statistical characteristic sequence which has a characteristic of scaling with original data according to the same scale factor; and obtaining the signal invariable relative to the amplitude scaling by dividing a carrier signal by the introduced characteristic sequence correspondingly. Watermark embedment and detection operation are both carried out on the newly constructed signal. The method improves the robustness of watermarks to amplitude scaling greatly and obtains watermarking performance similar to the original STDM watermarking in other aspects.
Owner:YANGZHOU UNIV
Ganoderma lucidum product, its production method and edible method
InactiveCN102860500AHigh content of ingredientsPromote absorptionFood preparationPlant ingredientsGanoderma lucidumPrimordium
The invention discloses a ganoderma lucidum product, its production method and edible method, belonging to the field of medicinal and health food. The product comprises ganoderma lucidum fruit body and ganoderma lucidum primordium that breed spores to maturity but do not release the spores yet as raw materials, wherein the raw materials have highest content of ganoderma lucidum beneficial ingredients and are most easily adsorbed. The raw materials are subject to washing, cutting and drying to prepare the product. The edible method of the product is characterized by chewing the product in the mouth, chewing out most beneficial ingredients and absorbing a part by the mouth, and swallowing the rest. By swallowing, the effective ingredients which are chewed out are easily digested and absorbed by the stomach and intestine. The production of the product is conducted at a low temperature which is a means for preventing the growth of bacteria and satisfies the requirement of keeping ganoderma lucidum beneficial ingredients. According to the production method disclosed herein, the natural beneficial ingredients of ganoderma lucidum can be completely kept, and especially immune protein of ganoderma lucidum is kept. The product disclosed herein has the characteristics of complete components, good efficiency, rapid absorption, and low cost.
Owner:何松庆
Internet-of-things and block chain-based green asset management system
InactiveCN108681887AWith traceable verificationImmutableFinanceOffice automationBusiness efficiencyOpen platform
The invention discloses an internet-of-things and block chain-based green asset management system. For target groups such as banks, manufacturers, dealers, factors and securities traders, while integrated green asset management is realized, the aspects of deployment security capability, network security management control, data security management control and the like are normalized by high standards to ensure secure and ordered work of businesses; and a secure, efficient and controllable green asset management system and an open platform are provided. According to the internet-of-things and block chain-based green asset management system, the quick bank loan can be realized; product design and management of asset securitization are facilitated; debts of core enterprises are reduced; the timeliness, security and the like of return funds are guaranteed; the business efficiency is greatly improved; and the labor and time costs can be reduced.
Owner:杭州阳光智联科技有限公司
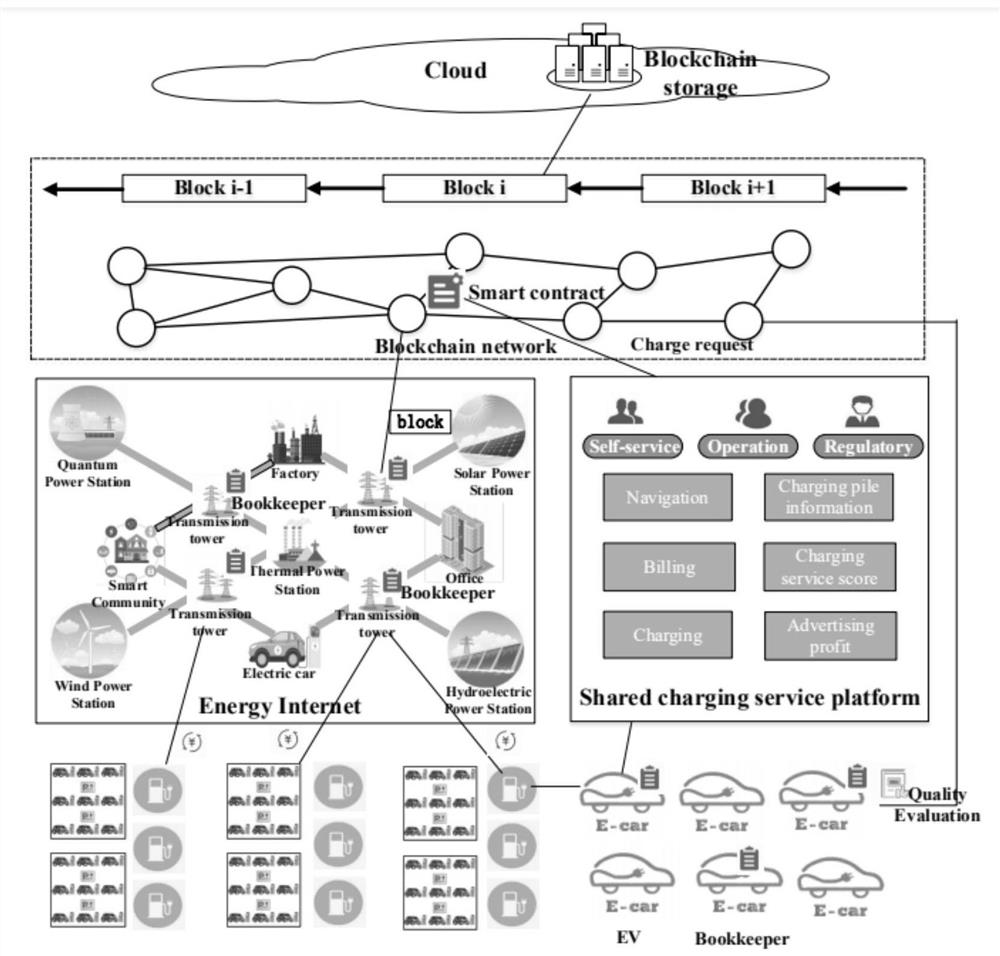
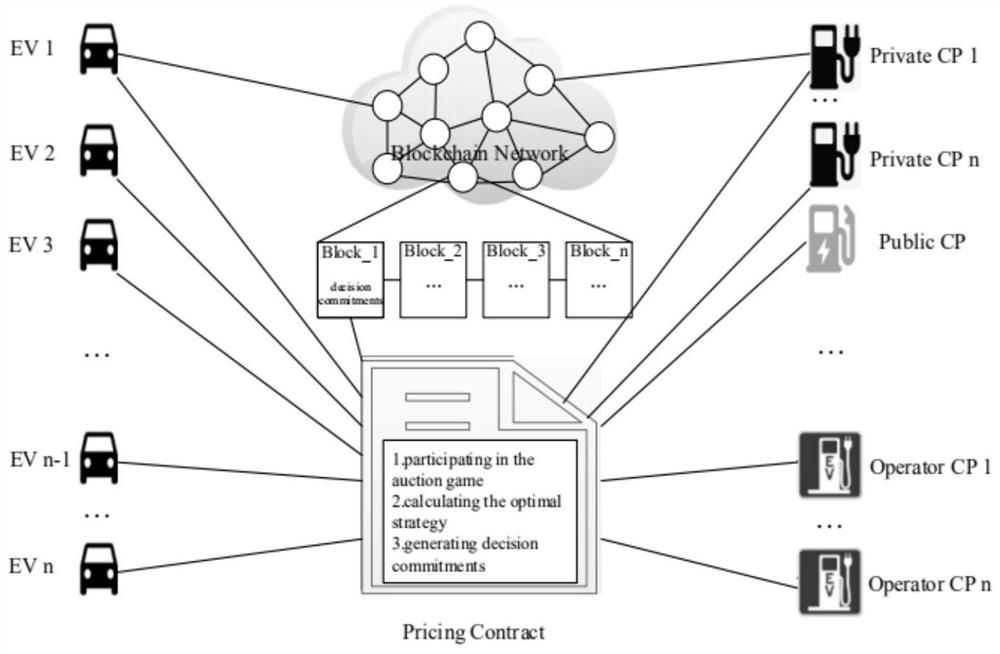
Block chain-based electric vehicle shared charging credible system and method
ActiveCN112765656AWith decentralizationAnonymityDigital data information retrievalFinanceEngineeringElectric vehicle
The invention discloses a block chain-based electric vehicle shared charging credible system and method. The system comprises a private pile owner, a charging pile operator, an electric vehicle user, a shared charging service platform and a trusted environment of a block chain network. Pointers are added for a block structure for rapid search, multi-party contracts are automatically executed to achieve contract content of safe calculation, and a reputation-based incentive mechanism for high-quality charging service is provided. And a shared charging multi-party participation trust environment is established from three aspects of secure storage, secure calculation and secure excitation.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
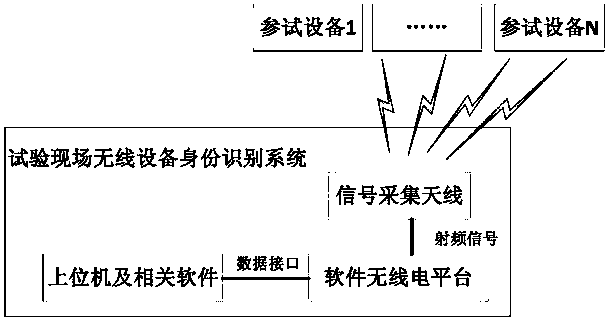
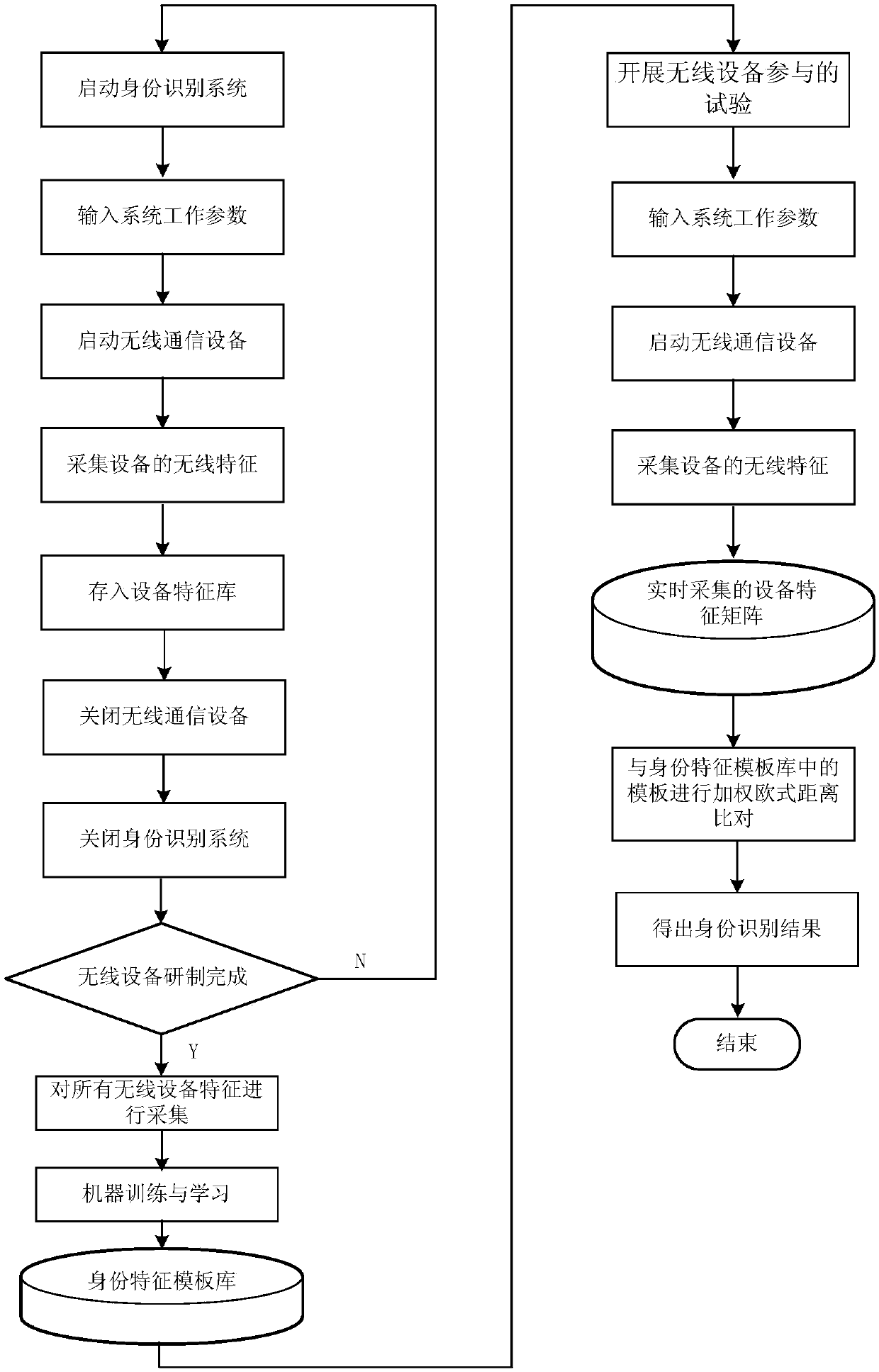
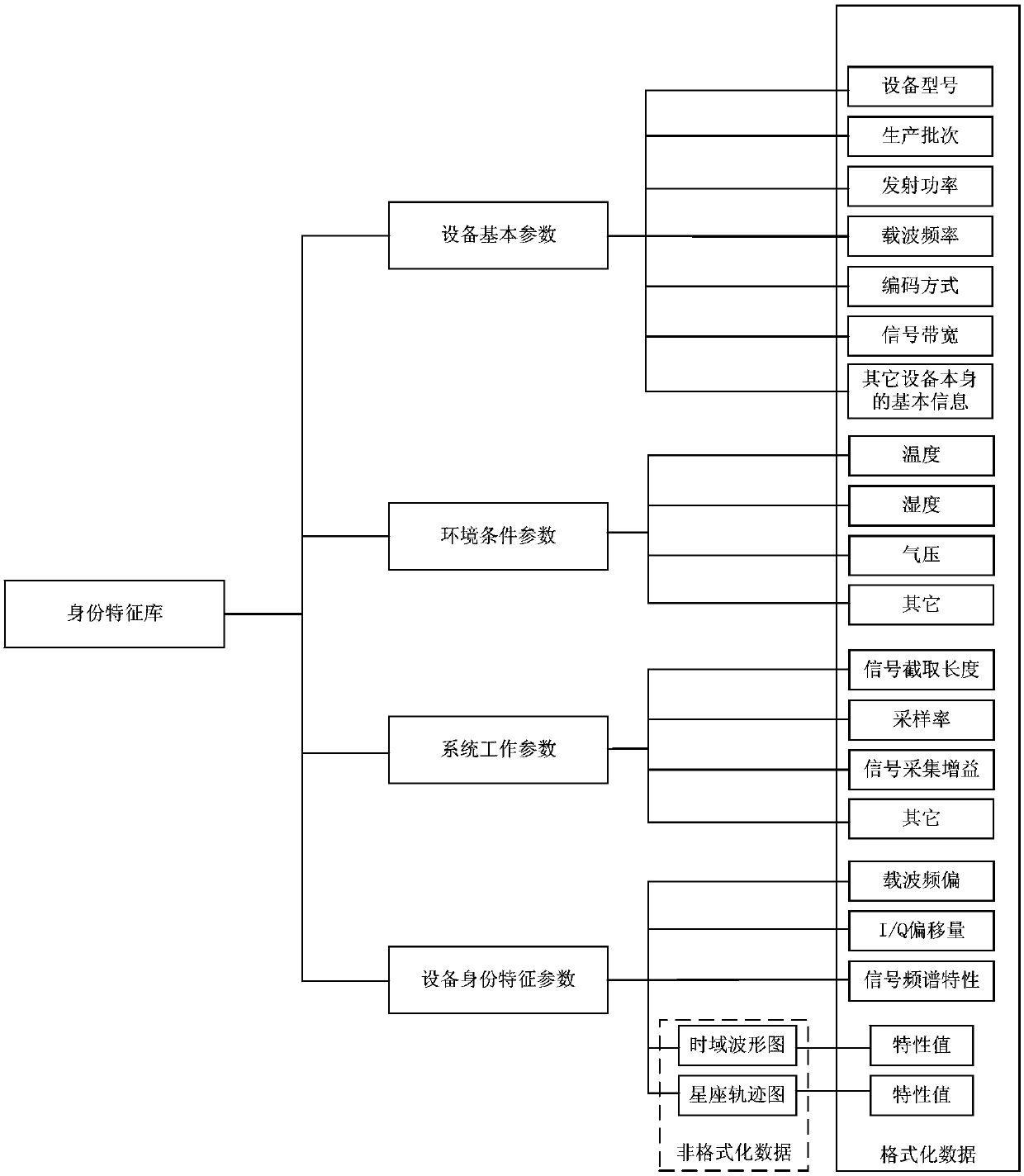
Test site wireless equipment identity recognition system and method
ActiveCN107944513AReduce workloadQuick recognitionCo-operative working arrangementsCharacter and pattern recognitionWireless transmissionIdentity recognition
The invention provides a test site wireless equipment identity recognition system and method. The test site wireless equipment identity recognition system comprises a signal acquisition antenna, a software radio platform, an upper computer and an identity management software system. The wireless fingerprint characteristics of the equipment are repetitively acquired for multiple times in the production link of the wireless equipment to form a sample database, and the wireless equipment fingerprint characteristics of the test equipment are acquired in real time in the test link of the wireless equipment to be compared with the characteristics in the sample database so as to obtain the identity information of the test equipment. Identity recognition and authentication can be rapidly and safely performed on the test wireless transmission electronic equipment in test so as to have great use value.
Owner:CHINA ACAD OF LAUNCH VEHICLE TECH
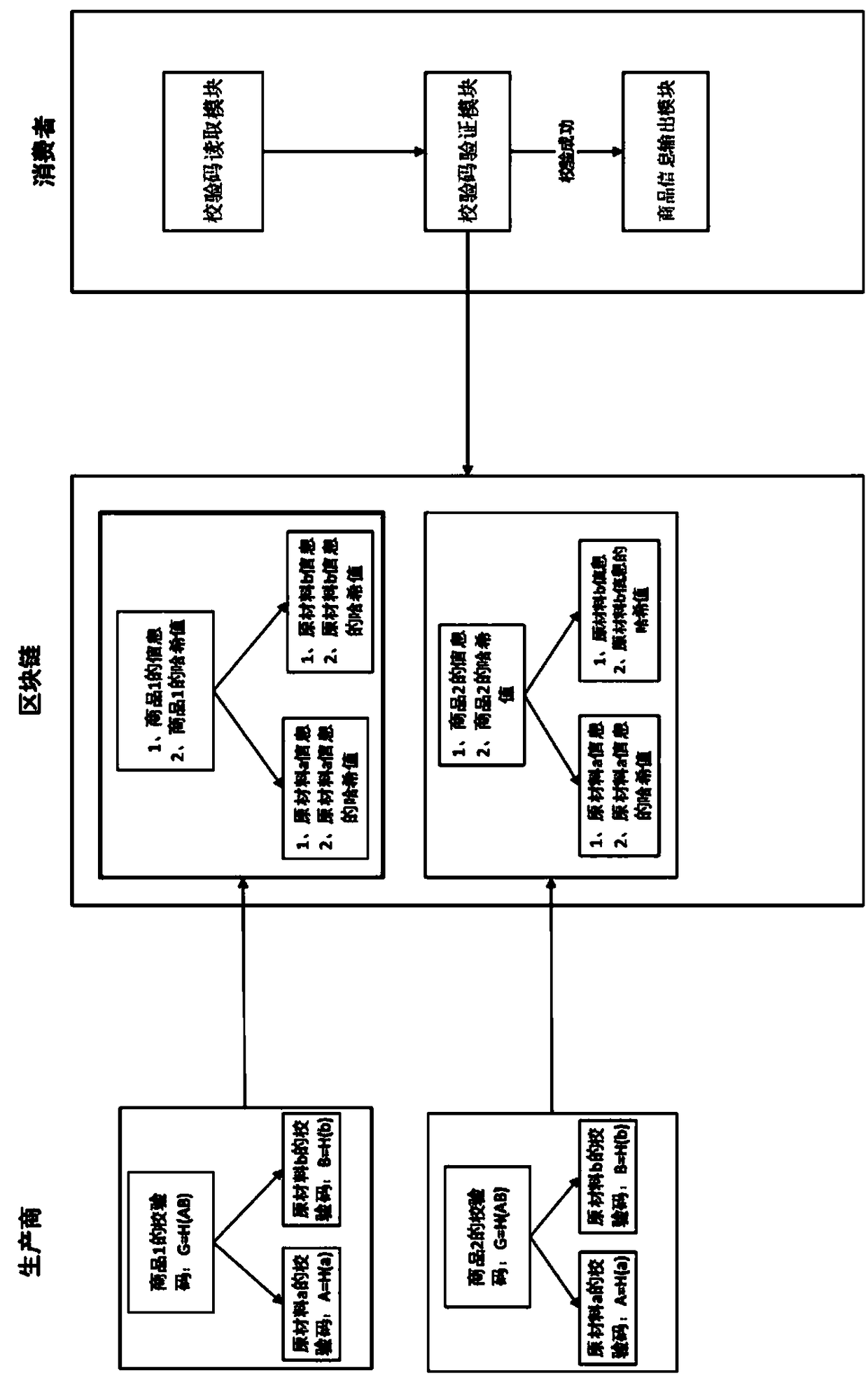
Commodity anti-counterfeiting method and system based on block chain
InactiveCN109146528AOpenWith transparencyCo-operative working arrangementsCommerceComputer scienceData preservation
The invention provides a commodity anti-counterfeiting method and a commodity anti-counterfeiting system based on a block chain, including a commodity information generation module, a commodity information storage module, a check code reading module, a verification code verification module and a commodity information output module, wherein a unified commodity anti-counterfeit system is built by using safe and reliable block chain technology, the establishment of the system will not overthrow the traditional anti-counterfeiting design, nor need to change the habits of consumers, but renovate the original bottom anti-counterfeiting framework into a system based on the block chain design, and store the data in the block chain, so that the information of the uplink can not be tampered with andcounterfeited, according to the characteristic, the reliability of the commodity information is ensured.
Owner:郑州信大壹密科技有限公司
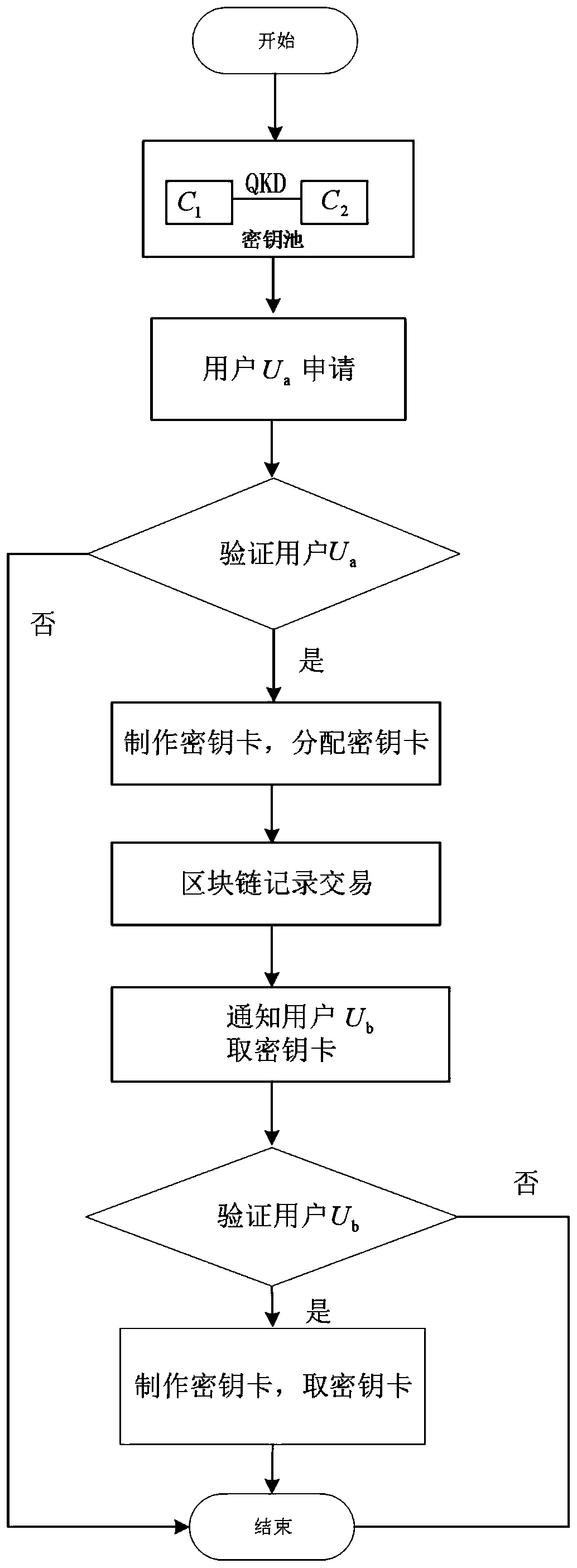
Quantum key distribution method based on block chain
ActiveCN110932855AImprove distribution efficiencyEasy to implementKey distribution for secure communicationFinancePhysicsKey generation
The invention discloses a quantum key distribution method based on a block chain, which comprises the following steps that two key pools separated from two places exist, the configurations of the twokey pools are the same and are connected through public quantum channels, a quantum key distribution (QKD) protocol is called to generate key streams, and the key streams are respectively stored in corresponding positions of the two key pools; wherein the two key pools are respectively connected with respective key pool managers, and the key pool managers are used for managing the key pools, updating storage addresses in the key pools and being responsible for contacting with users; wherein the two key pool managers are connected with a block chain, and the block chain is used for recording transactions between users and the key pool managers. The invention aims to solve the problem that the existing quantum key generation and distribution efficiency is low, and improve the key distribution efficiency under the condition of ensuring the key generation and distribution safety.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
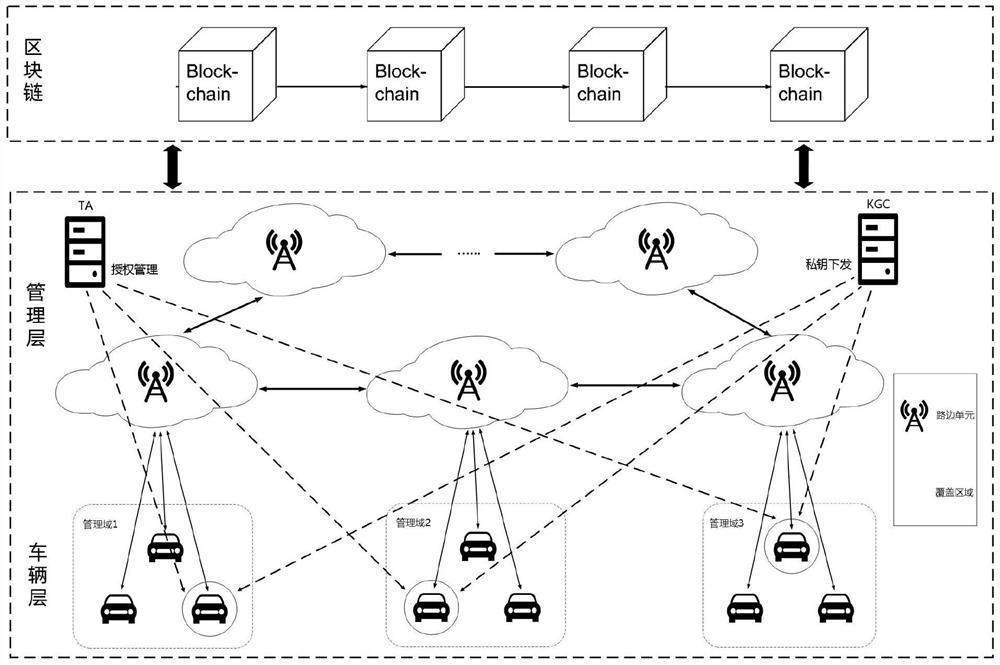
Internet of vehicles identity management system and management method based on block chain and identification password
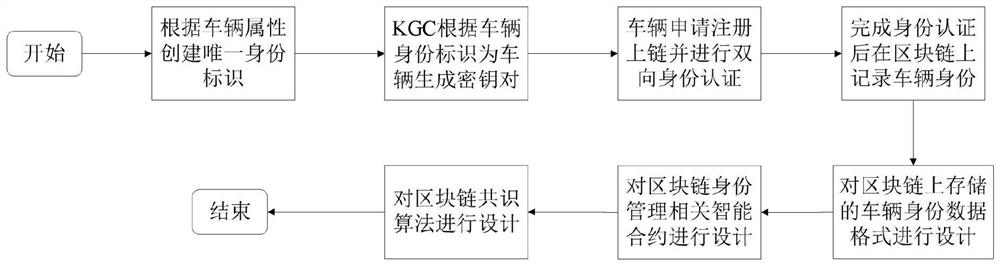
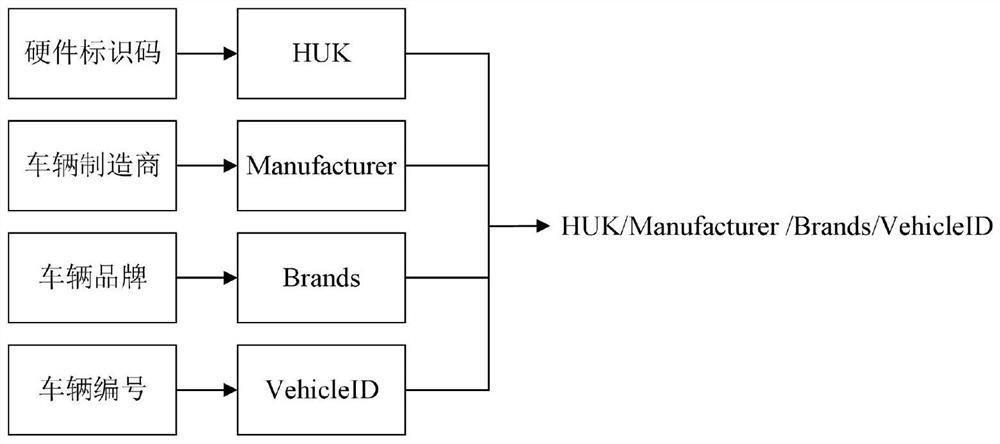
PendingCN114125773ASatisfy uniqueness and distinguishabilityOmit certificate interactionParticular environment based servicesUser identity/authority verificationBlockchainAuthorization
The invention discloses an Internet of Vehicles identity management system and management method based on a block chain and an identification password, and the system comprises a block chain layer, a management layer and a sensing layer, and the block chain layer interacts with a vehicle, a trusted authorization mechanism, a roadside unit and a key generation center, and completes the identity management, data management and behavior monitoring of the vehicle. According to the invention, a decentralized identity management platform is constructed among the vehicle enterprises by adopting the alliance chain, the vehicle identity authentication process and the identity format of uplink storage are unified, and cross-domain authentication is conveniently realized; a certificate-based authentication mode in a traditional public key password scheme is simplified through a lightweight two-way identity authentication mechanism based on an identification password technology; the MPT is adopted to construct the block chain node, and the storage form of the vehicle information in the MPT is designed according to the form of the key-value pair, so that the vehicle information can be quickly positioned and searched, and the on-chain query speed is increased.
Owner:SHANGHAI JIAO TONG UNIV
Commodity information generation method based on block chain, block chain node and system thereof
InactiveCN109272383AImmutableTrustless transactionsFinanceBuying/selling/leasing transactionsSmart contractOperating system
The invention relates to the technical field of block chain, in particular to a commodity information generation method based on block chain, a block chain node and a system thereof. The method comprises the following steps of: receiving a business request sent by an ordinary node; selecting and executing a corresponding type of intelligent contract to generate commodity information according to arequest type of a commercial request, wherein the request type of the commercial request includes a purchase request or a selling request, and the purchase request or the selling request are all matched with each type of intelligent contract; generating block data containing commodity information; sending the Block data to the consensus node so that the consensus node verifies the block data. Because the block chain has the characteristics of non-tampering, decentralization and high transparency, it can provide a decentralized and highly transparent transaction mode. Moreover, the block chaincontains purchase requests and sale requests, which should have their own types of smart contracts, whether purchasing goods or selling goods, which can automatically achieve and facilitate the transaction, thereby improving the efficiency of the transaction.
Owner:SHENZHEN GENUINE INNOVATIVE TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com