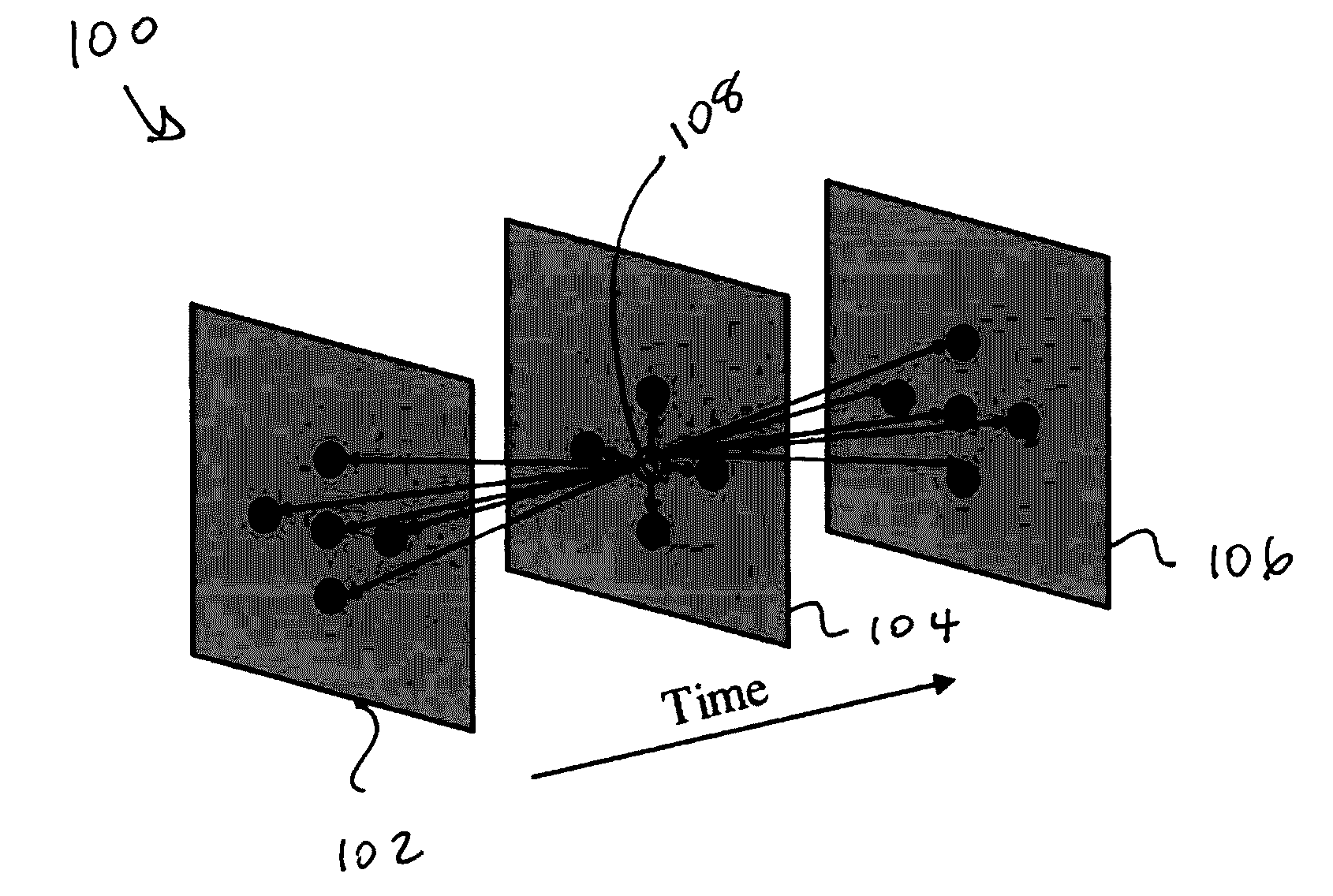
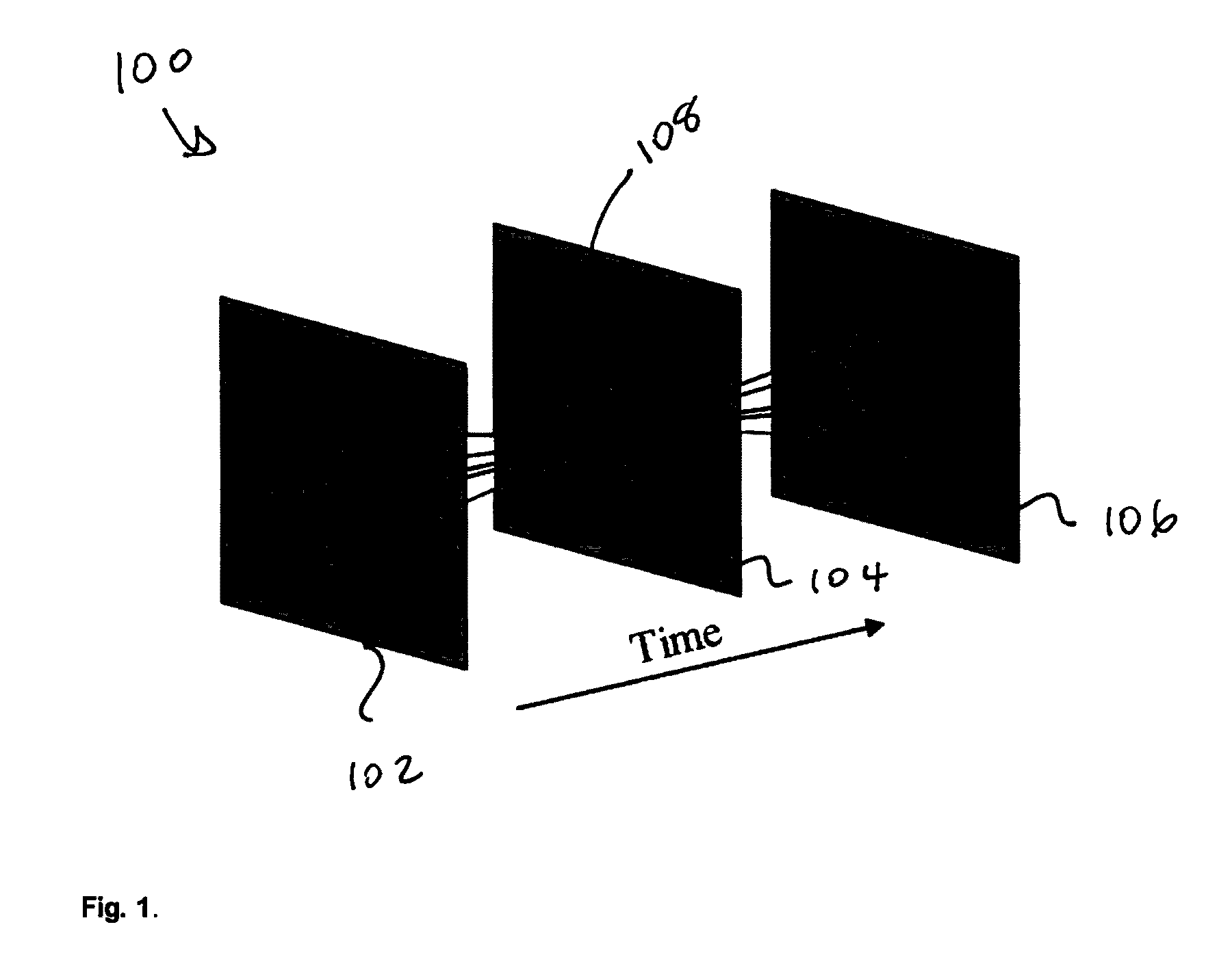
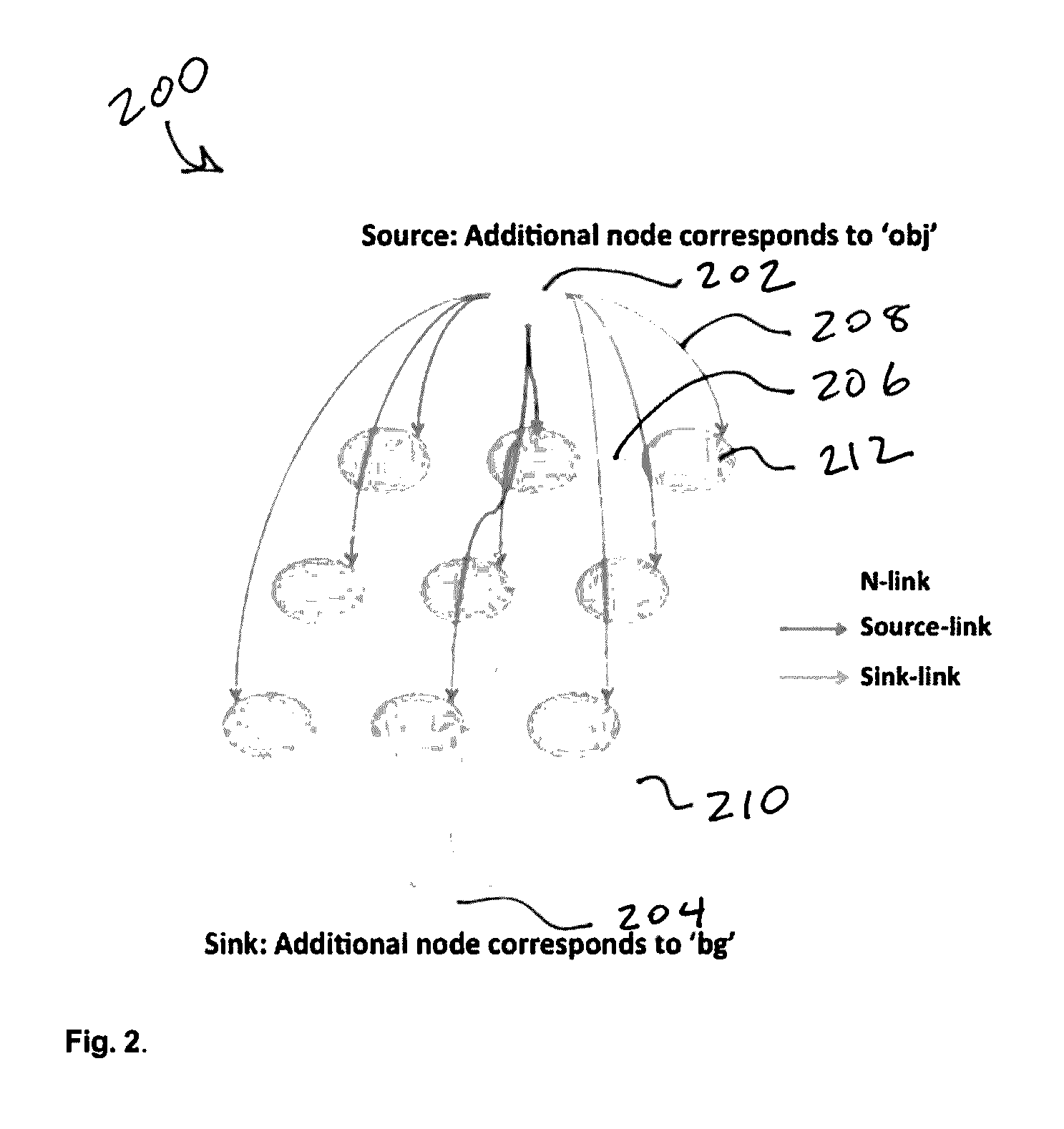
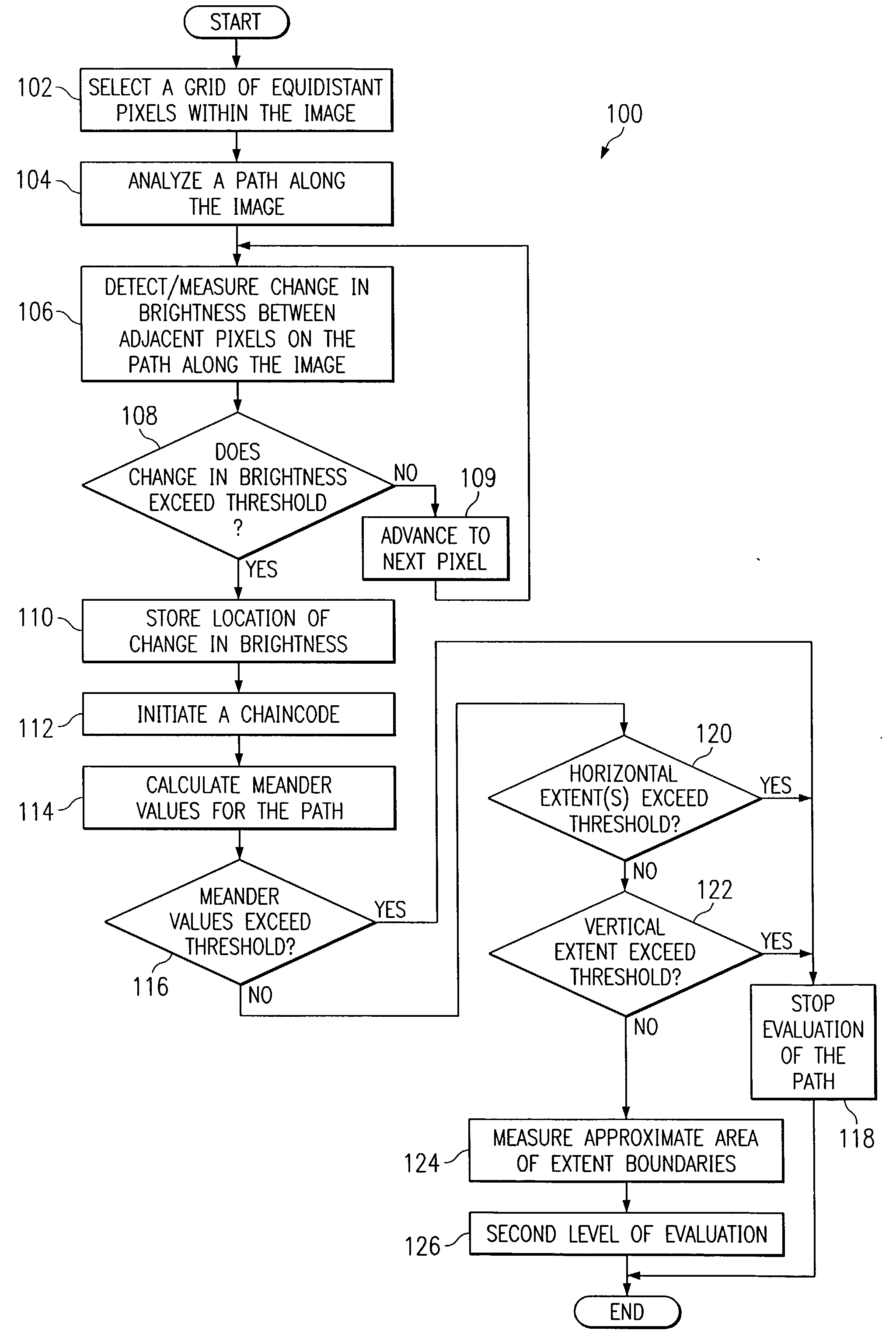
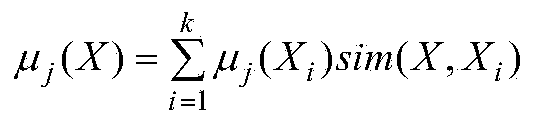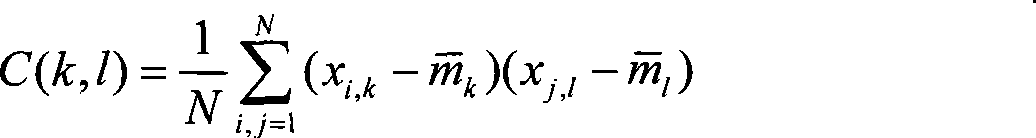Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1423 results about "Characteristic space" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
According to the OSHA reg, a defined space has the following three characteristics: Large enough and configured so an employee can bodily enter and perform assigned work. Limited or restricted means for entry and exit. Not designed for continuous employee occupancy.
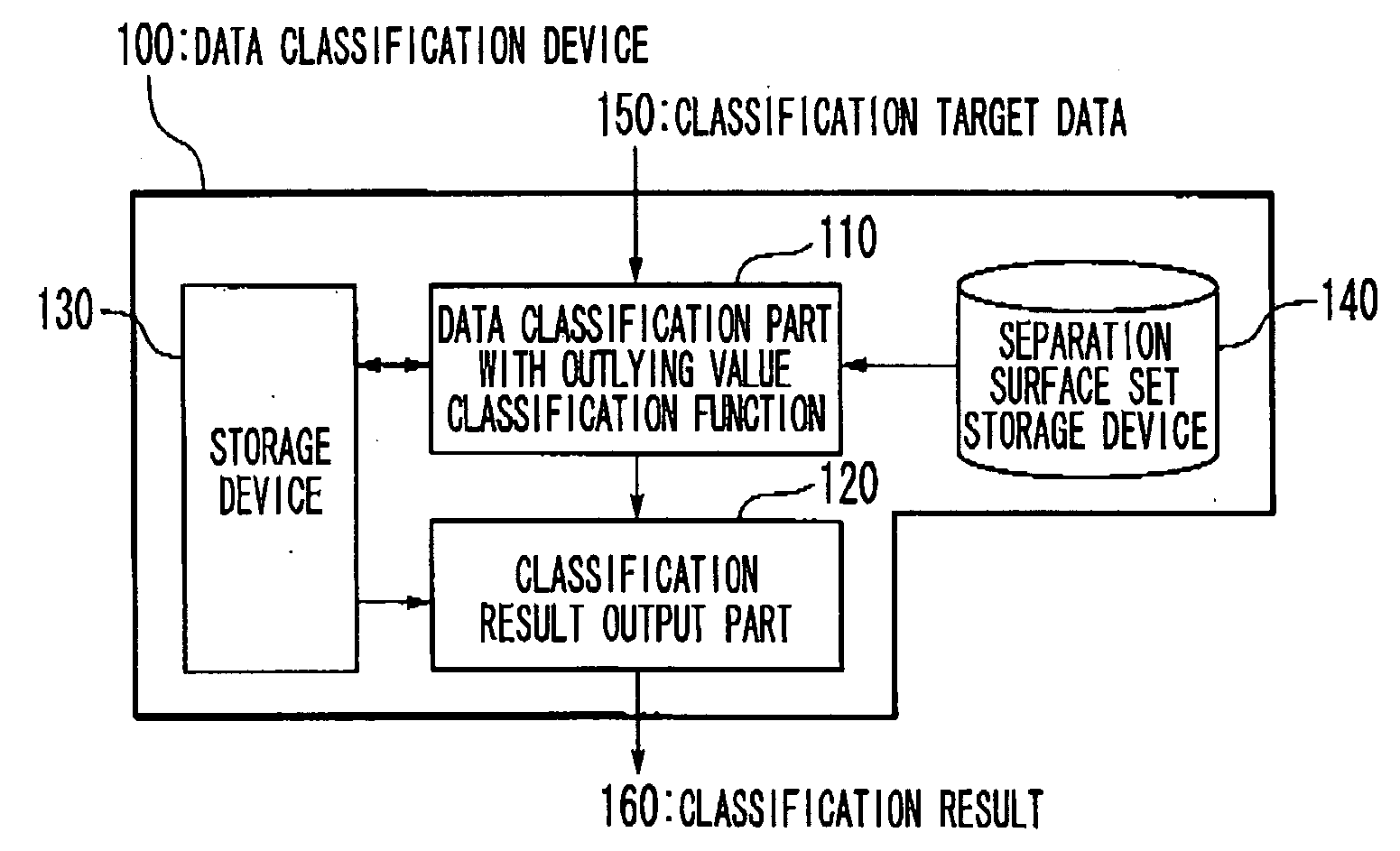
Data classification method and data classification device
ActiveUS20100250542A1Improve reliabilityHigh data reliabilityDigital data processing detailsKernel methodsAlgorithmCharacteristic space
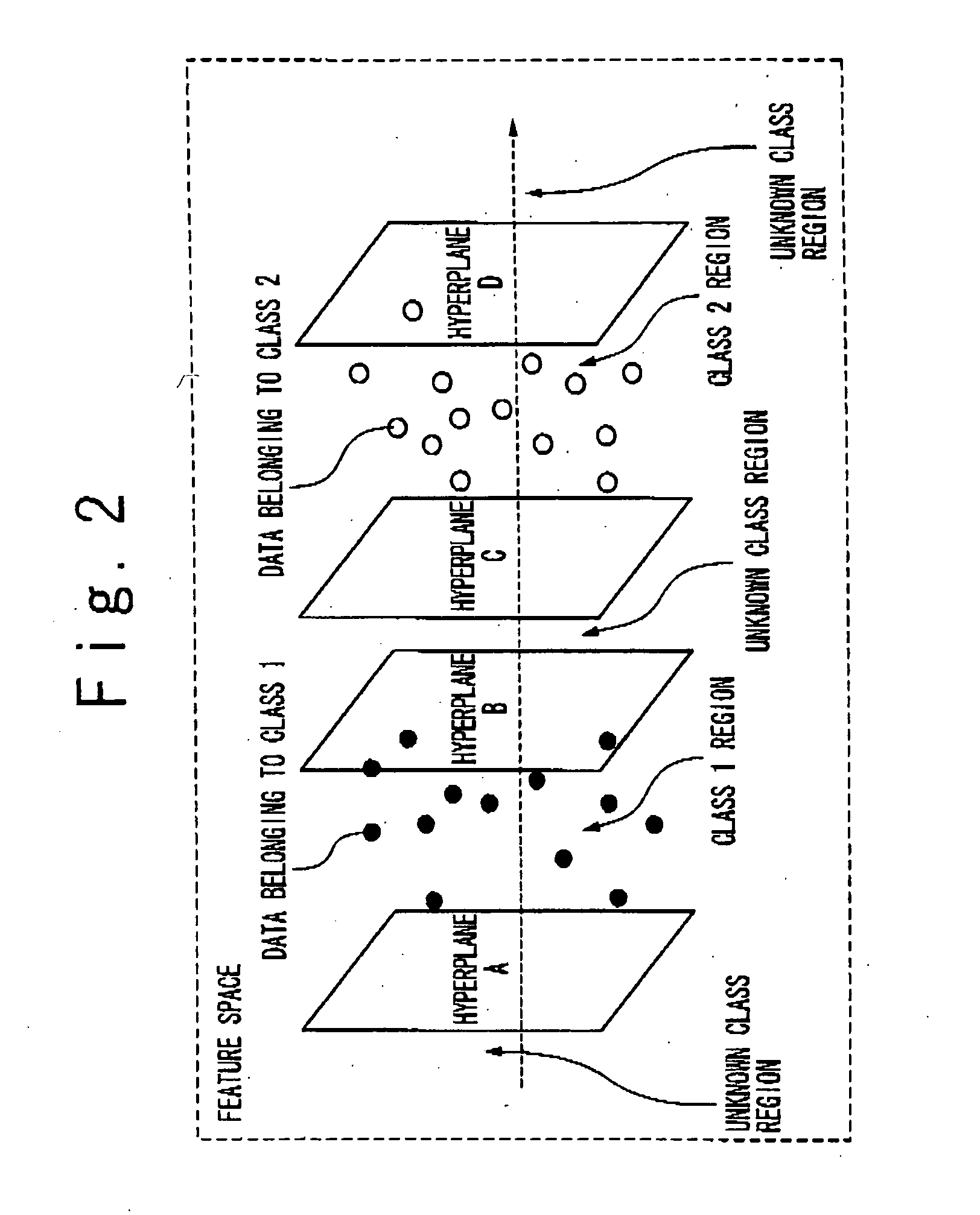
A separation surface set storage part stores information defining a plurality of separation surfaces which separate a feature space into at least one known class region respectively corresponding to at least one known class and an unknown class region. Each of the at least one known class region is separated from outside region by more than one of the plurality of separation surfaces which do not intersect to each other. A data classification apparatus determine a classification of a classification target data whose inner product in the feature space is calculable by calculating to which region of the at least one known class region and the unknown class region determined by the information stored in the separation surface set storage part the classification target data belongs. A method and apparatus for data classification which can simultaneously perform identification and outlying value classification with high reliability in a same procedure are provided.
Owner:NEC CORP
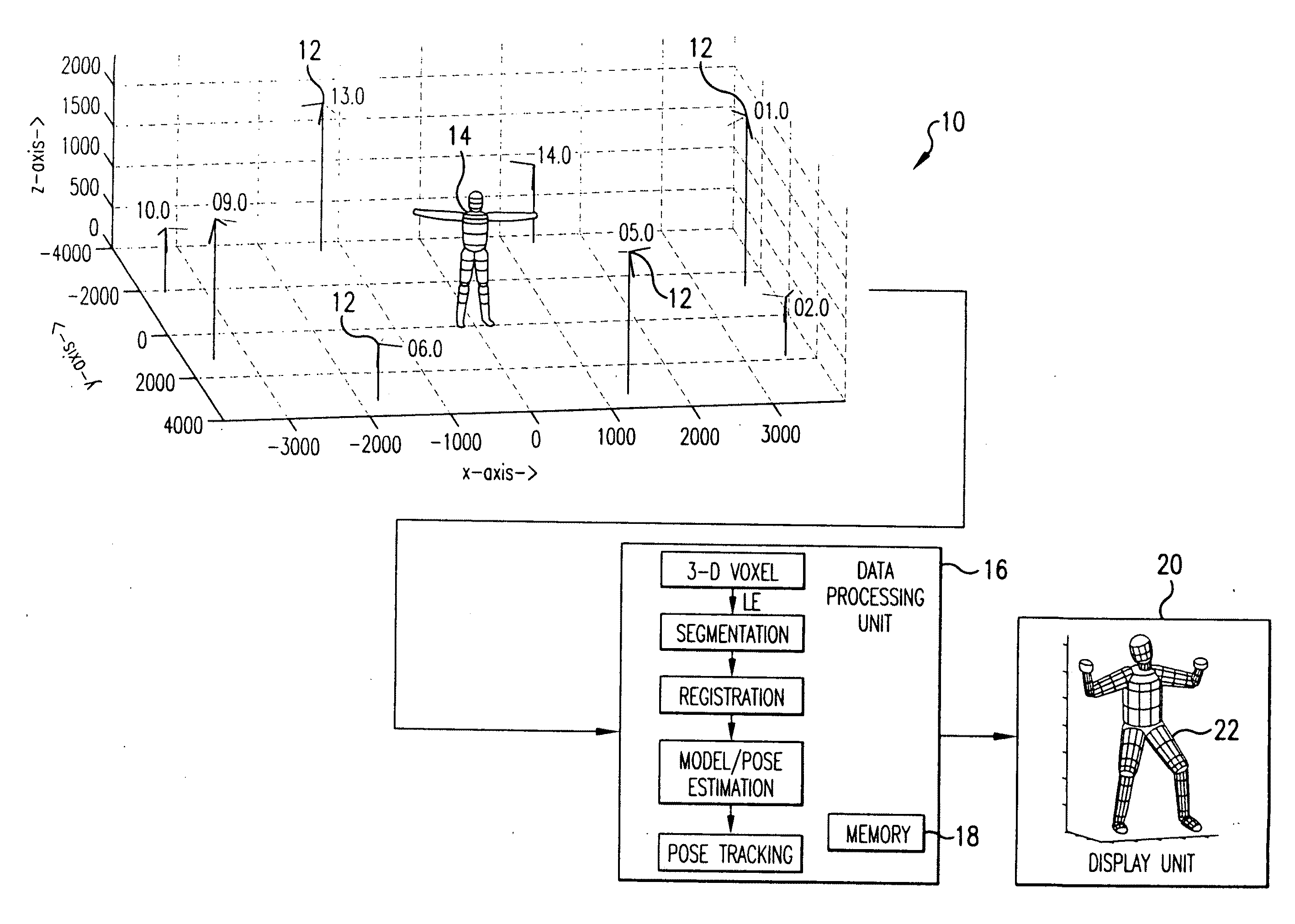
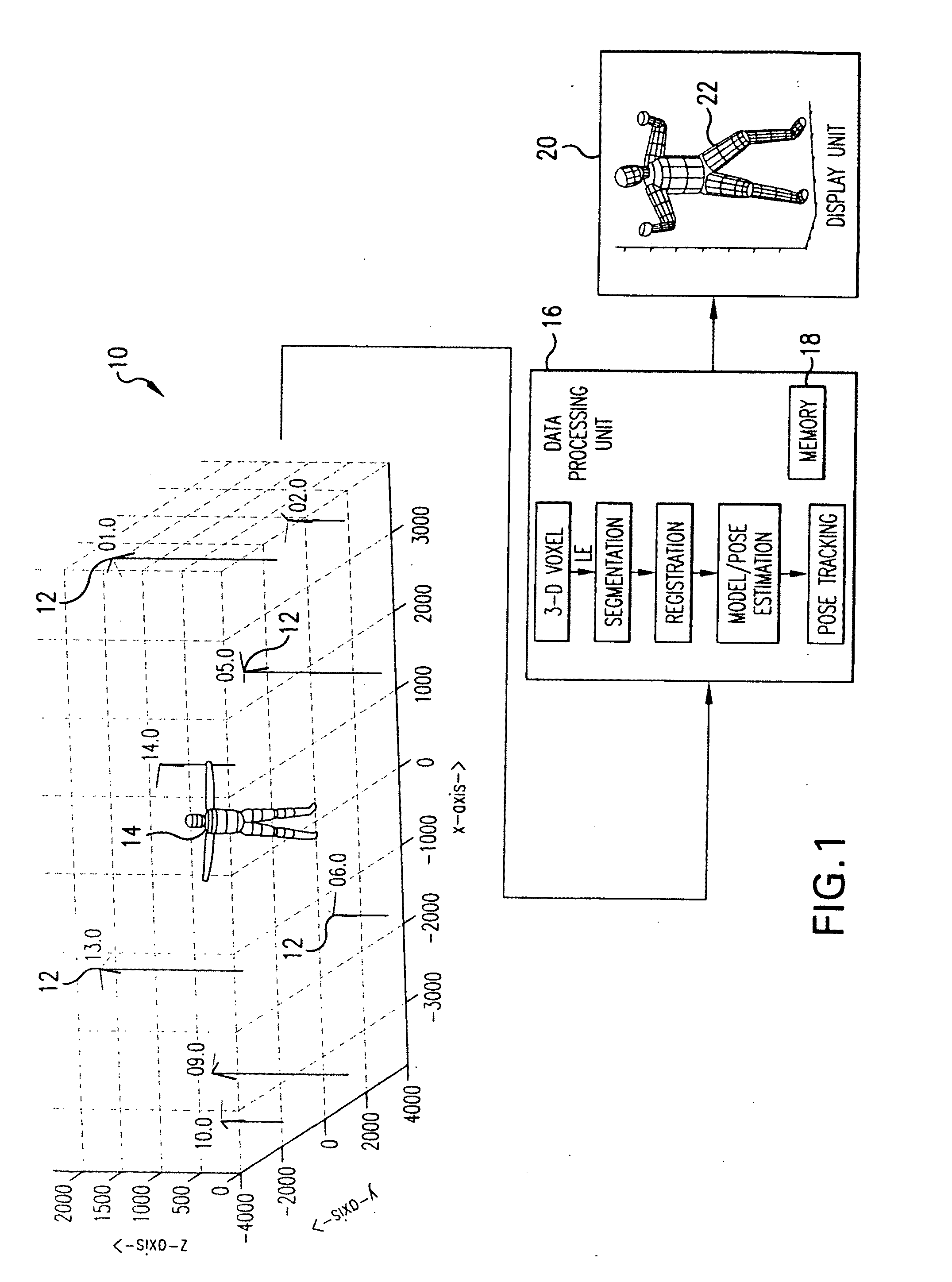
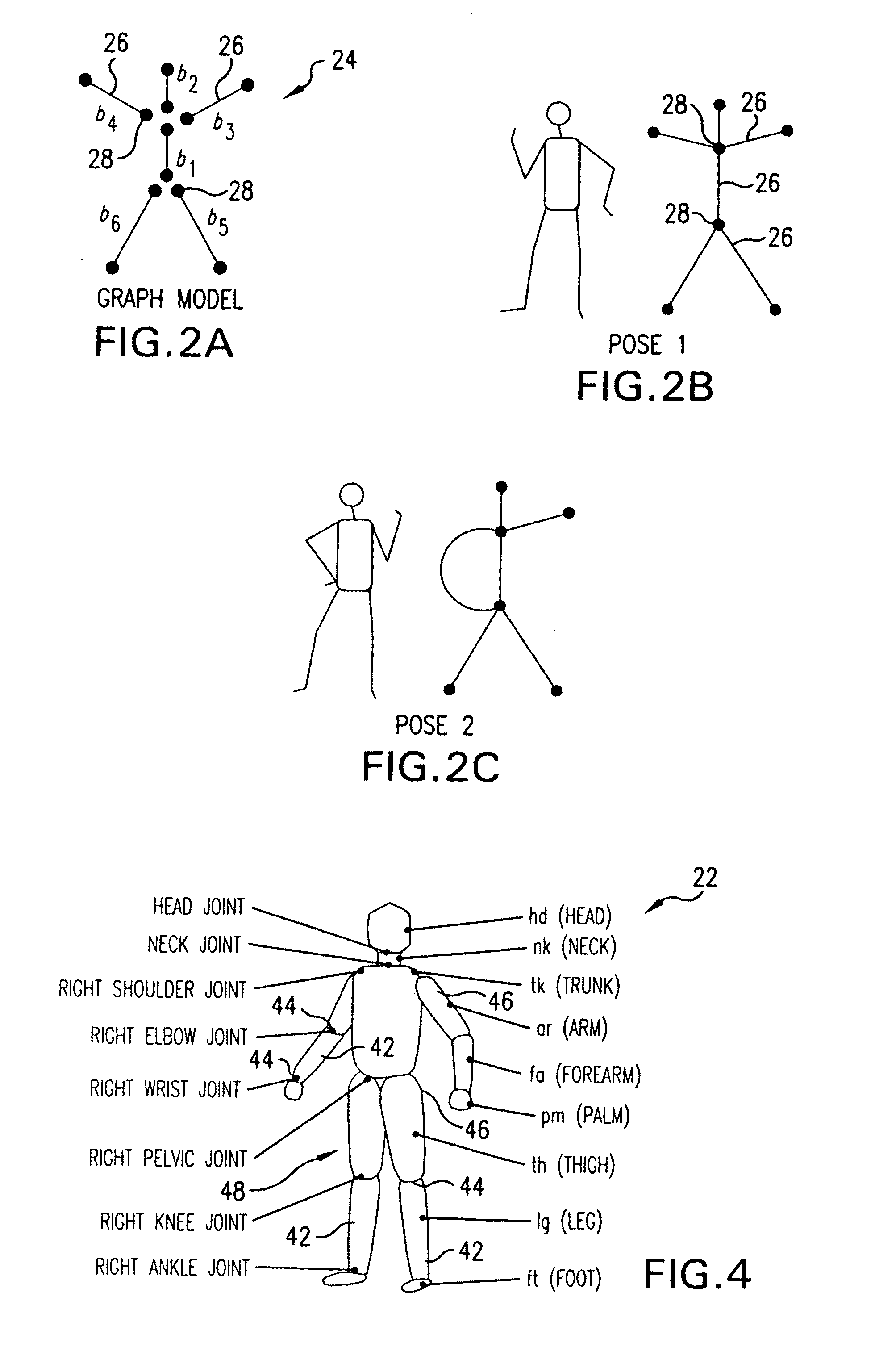
Method and system for markerless motion capture using multiple cameras
InactiveUS20090232353A1Accurate estimateAccurate presentationImage enhancementDetails involving processing stepsProbabilistic methodVoxel
Completely automated end-to-end method and system for markerless motion capture performs segmentation of articulating objects in Laplacian Eigenspace and is applicable to handling of the poses of some complexity. 3D voxel representation of acquired images are mapped to a higher dimensional space (k), where k depends on the number of articulated chains of the subject body, so as to extract the 1-D representations of the articulating chains. A bottom-up approach is suggested in order to build a parametric (spline-based) representation of a general articulated body in the high dimensional space followed by a top-down probabilistic approach that registers the segments to an average human body model. The parameters of the model are further optimized using the segmented and registered voxels.
Owner:UNIV OF MARYLAND
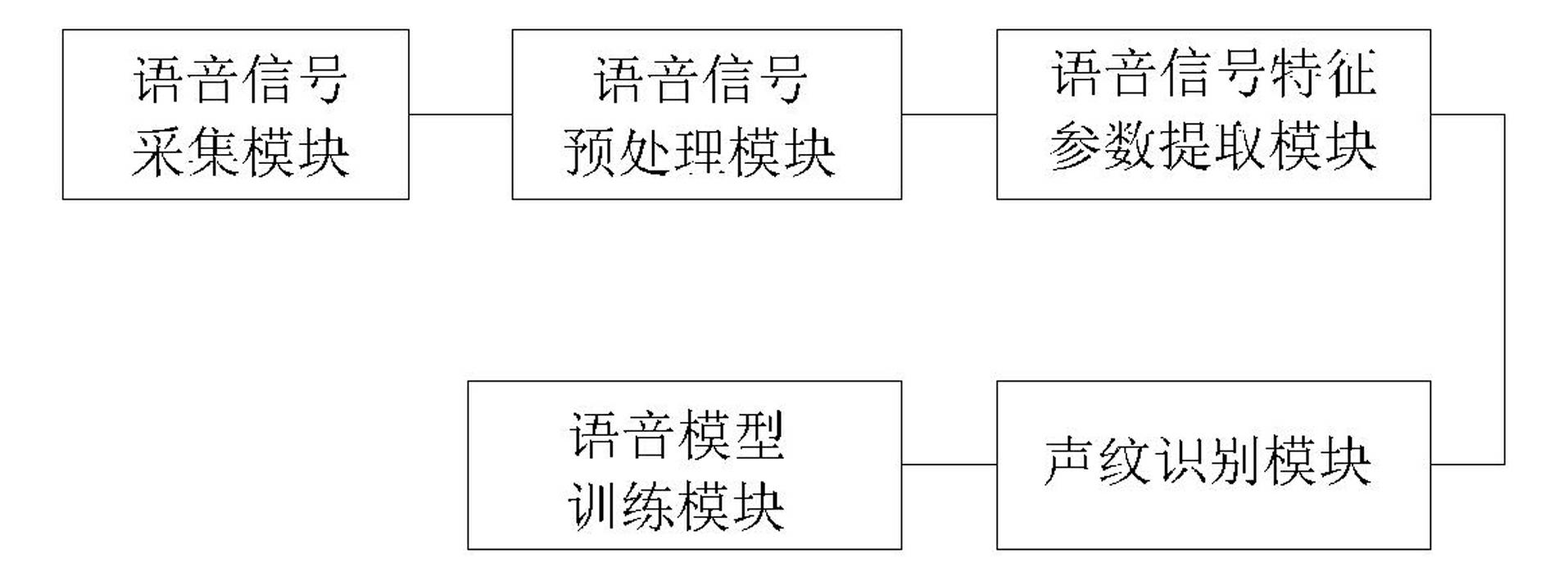
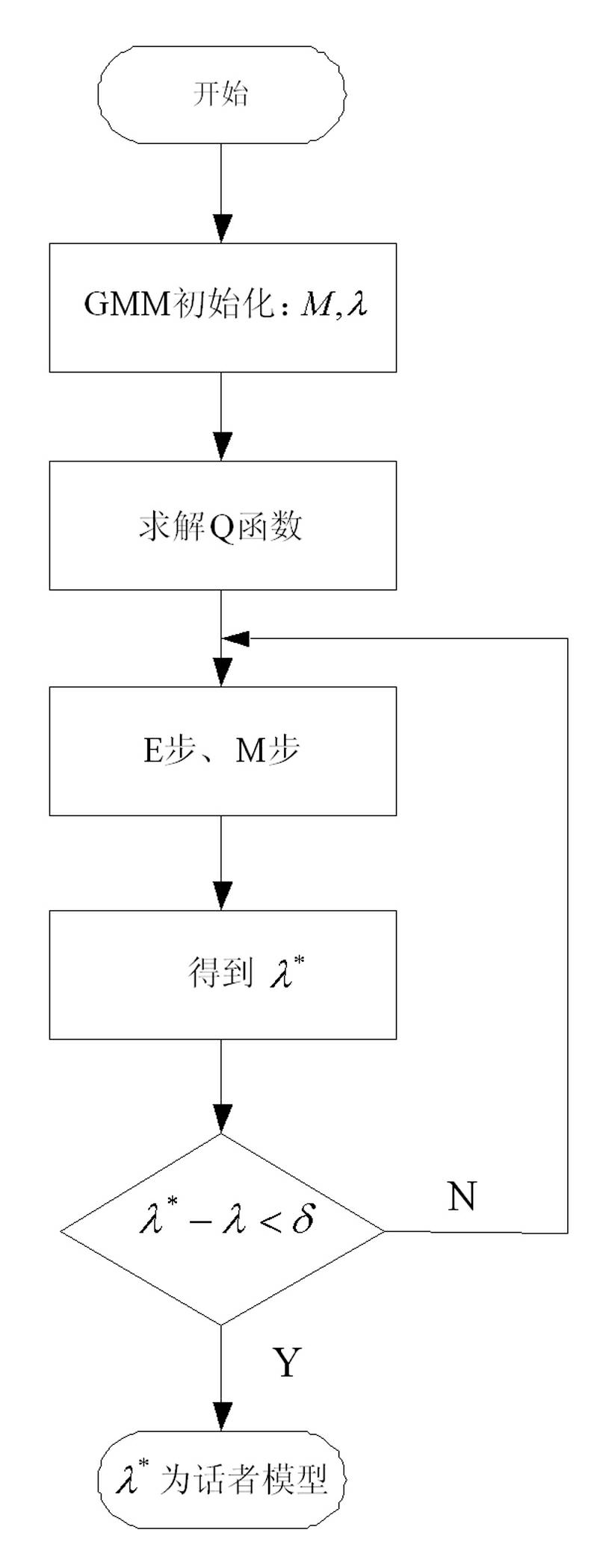
Voiceprint identification method based on Gauss mixing model and system thereof
InactiveCN102324232AGood estimateEasy to trainSpeech recognitionMel-frequency cepstrumNormal density
The invention provides a voiceprint identification method based on a Gauss mixing model and a system thereof. The method comprises the following steps: voice signal acquisition; voice signal pretreatment; voice signal characteristic parameter extraction: employing a Mel Frequency Cepstrum Coefficient (MFCC), wherein an order number of the MFCC usually is 12-16; model training: employing an EM algorithm to train a Gauss mixing model (GMM) for a voice signal characteristic parameter of a speaker, wherein a k-means algorithm is selected as a parameter initialization method of the model; voiceprint identification: comparing a collected voice signal characteristic parameter to be identified with an established speaker voice model, carrying out determination according to a maximum posterior probability method, and if a corresponding speaker model enables a speaker voice characteristic vector X to be identified to has maximum posterior probability, identifying the speaker. According to the method, the Gauss mixing model based on probability statistics is employed, characteristic distribution of the speaker in characteristic space can be reflected well, a probability density function is common, a parameter in the model is easy to estimate and train, and the method has good identification performance and anti-noise capability.
Owner:LIAONING UNIVERSITY OF TECHNOLOGY
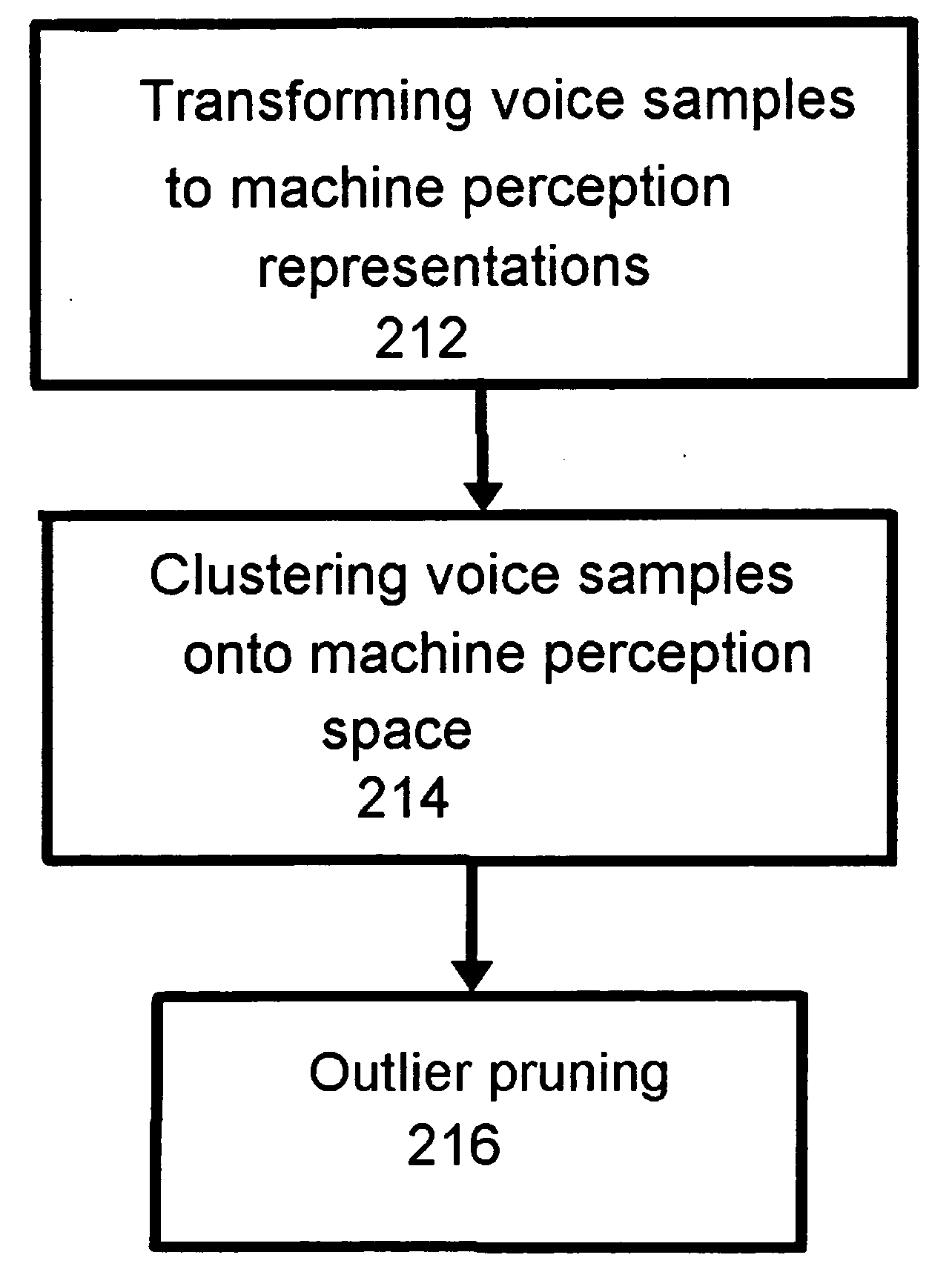
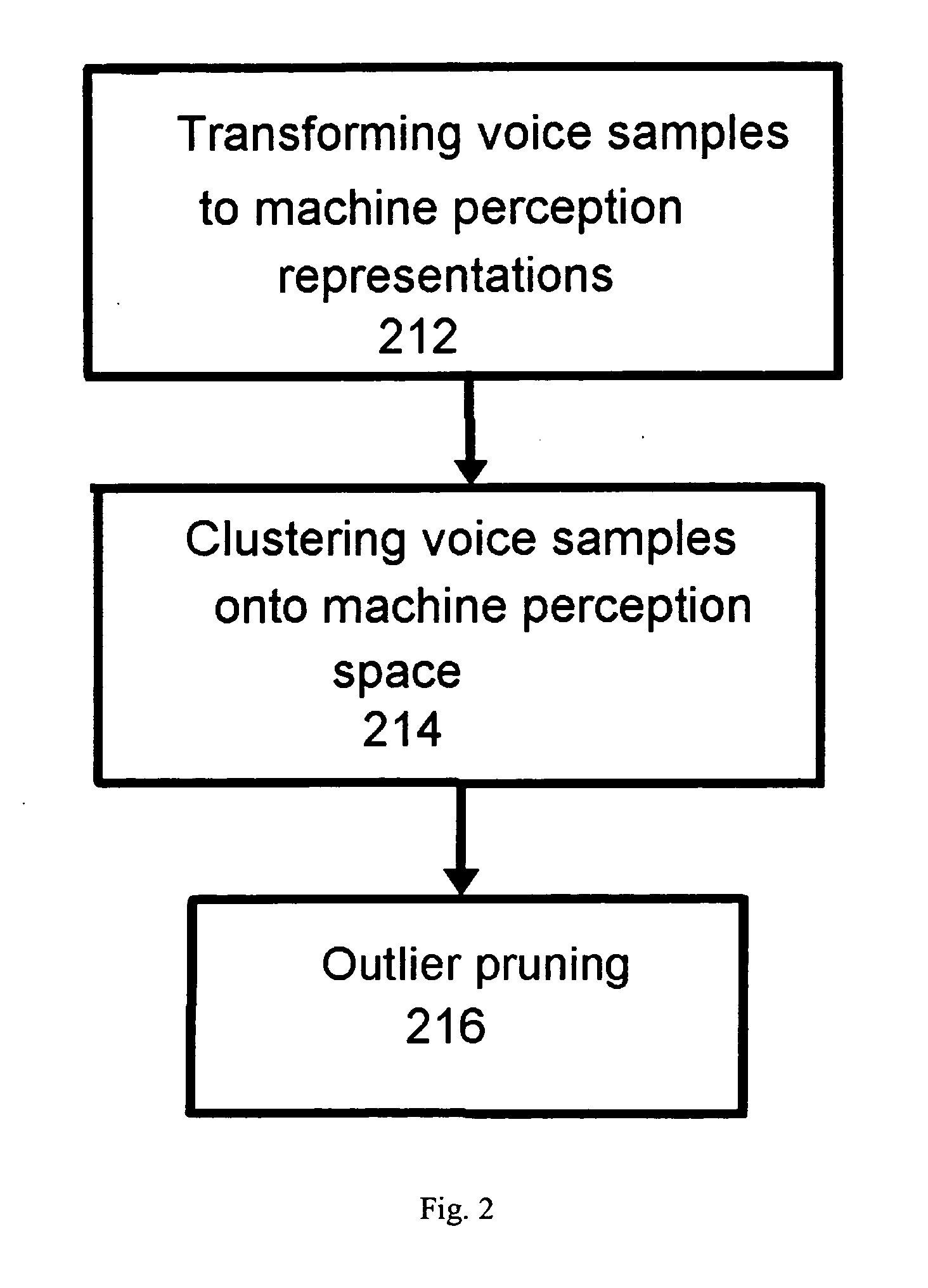
Methods and apparatus related to pruning for concatenative text-to-speech synthesis
InactiveUS20080091428A1Speech recognitionSpeech synthesisSingular value decompositionCharacteristic space
The present invention provides, among other things, automatic identification of near-redundant units in a large TTS voice table, identifying which units are distinctive enough to keep and which units are sufficiently redundant to discard. According to an aspect of the invention, pruning is treated as a clustering problem in a suitable feature space. All instances of a given unit (e.g. word or characters expressed as Unicode strings) are mapped onto the feature space, and cluster units in that space using a suitable similarity measure. Since all units in a given cluster are, by construction, closely related from the point of view of the measure used, they are suitably redundant and can be replaced by a single instance. The disclosed method can detect near-redundancy in TTS units in a completely unsupervised manner, based on an original feature extraction and clustering strategy. Each unit can be processed in parallel, and the algorithm is totally scalable, with a pruning factor determinable by a user through the near-redundancy criterion. In an exemplary implementation, a matrix-style modal analysis via Singular Value Decomposition (SVD) is performed on the matrix of the observed instances for the given word unit, resulting in each row of the matrix associated with a feature vector, which can then be clustered using an appropriate closeness measure. Pruning results by mapping each instance to the centroid of its cluster.
Owner:APPLE INC
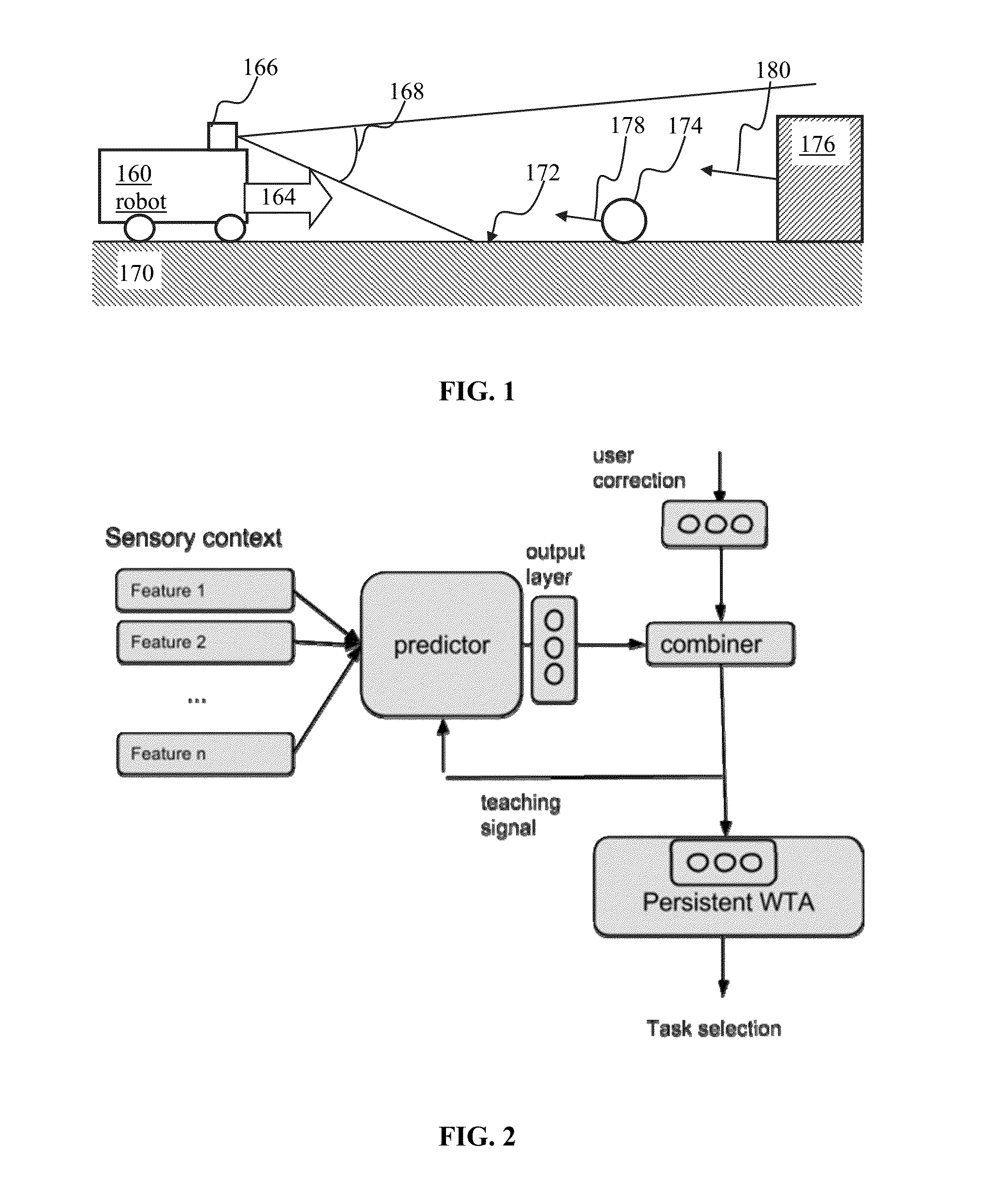
Apparatus and methods for training of robots
ActiveUS20160096272A1Programme-controlled manipulatorAutonomous decision making processVision basedCharacteristic space
A random k-nearest neighbors (RKNN) approach may be used for regression / classification model wherein the input includes the k closest training examples in the feature space. The RKNN process may utilize video images as input in order to predict motor command for controlling navigation of a robot. In some implementations of robotic vision based navigation, the input space may be highly dimensional and highly redundant. When visual inputs are augmented with data of another modality that is characterized by fewer dimensions (e.g., audio), the visual data may overwhelm lower-dimension data. The RKNN process may partition available data into subsets comprising a given number of samples from the lower-dimension data. Outputs associated with individual subsets may be combined (e.g., averaged). Selection of number of neighbors, subset size and / or number of subsets may be used to trade-off between speed and accuracy of the prediction.
Owner:BRAIN CORP
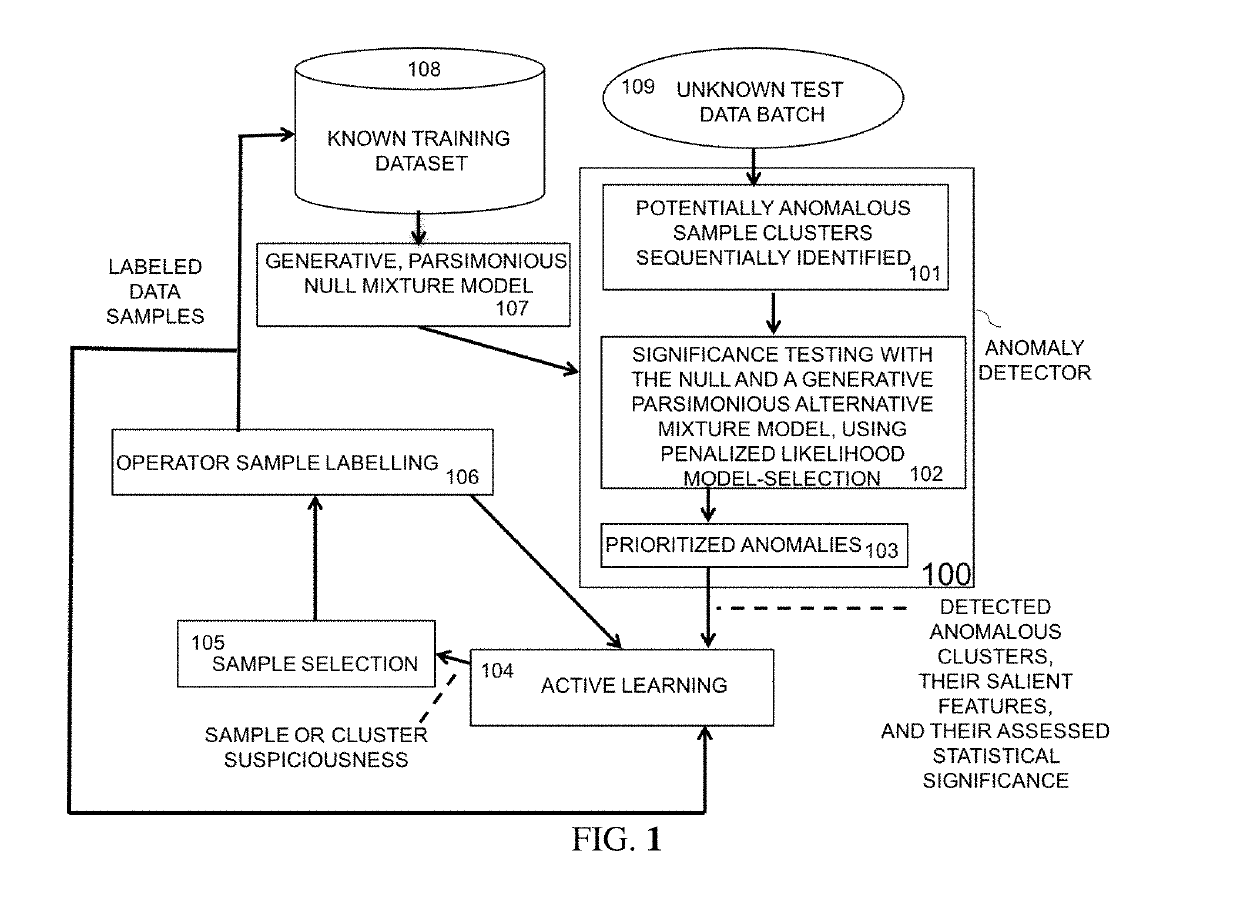
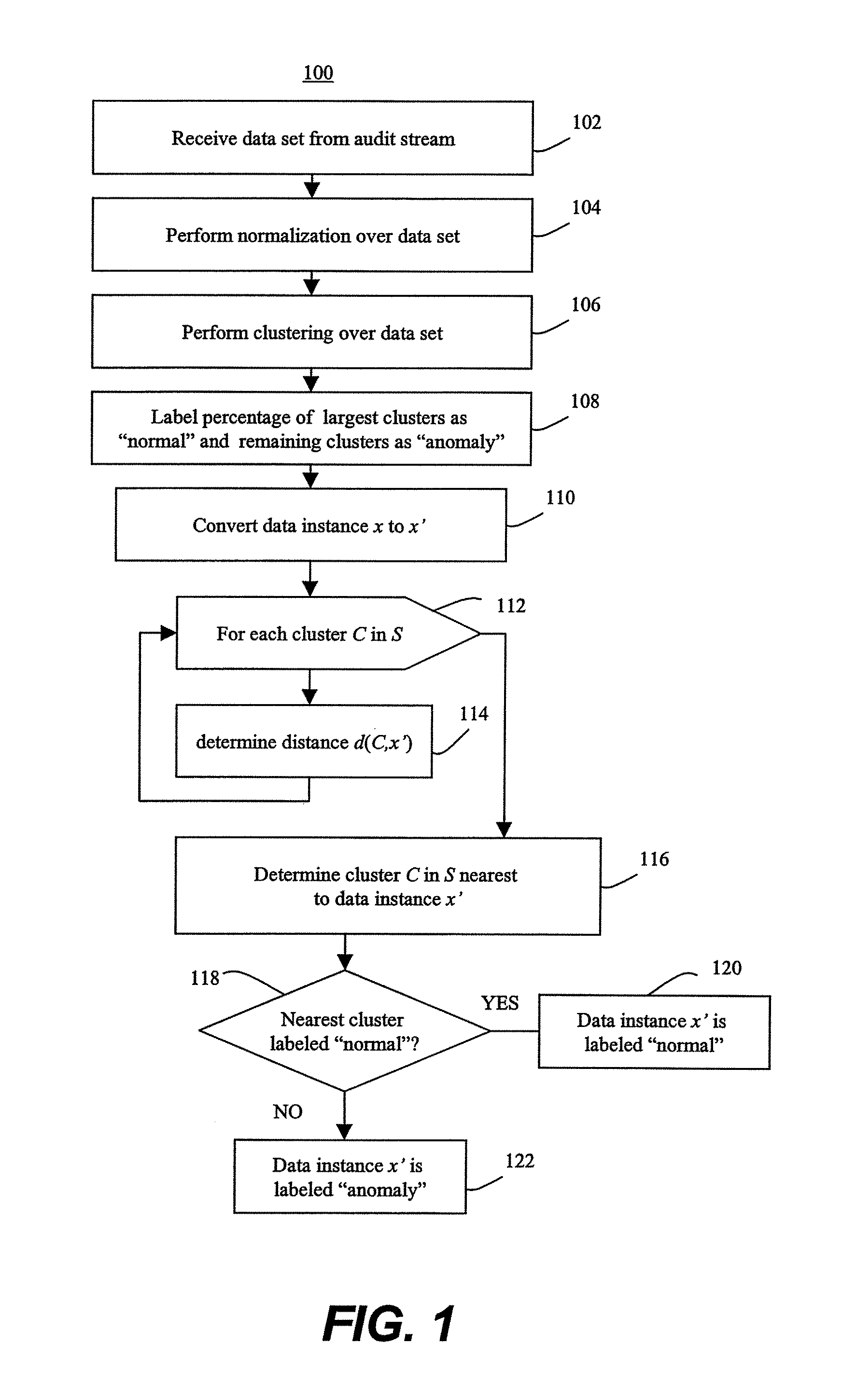
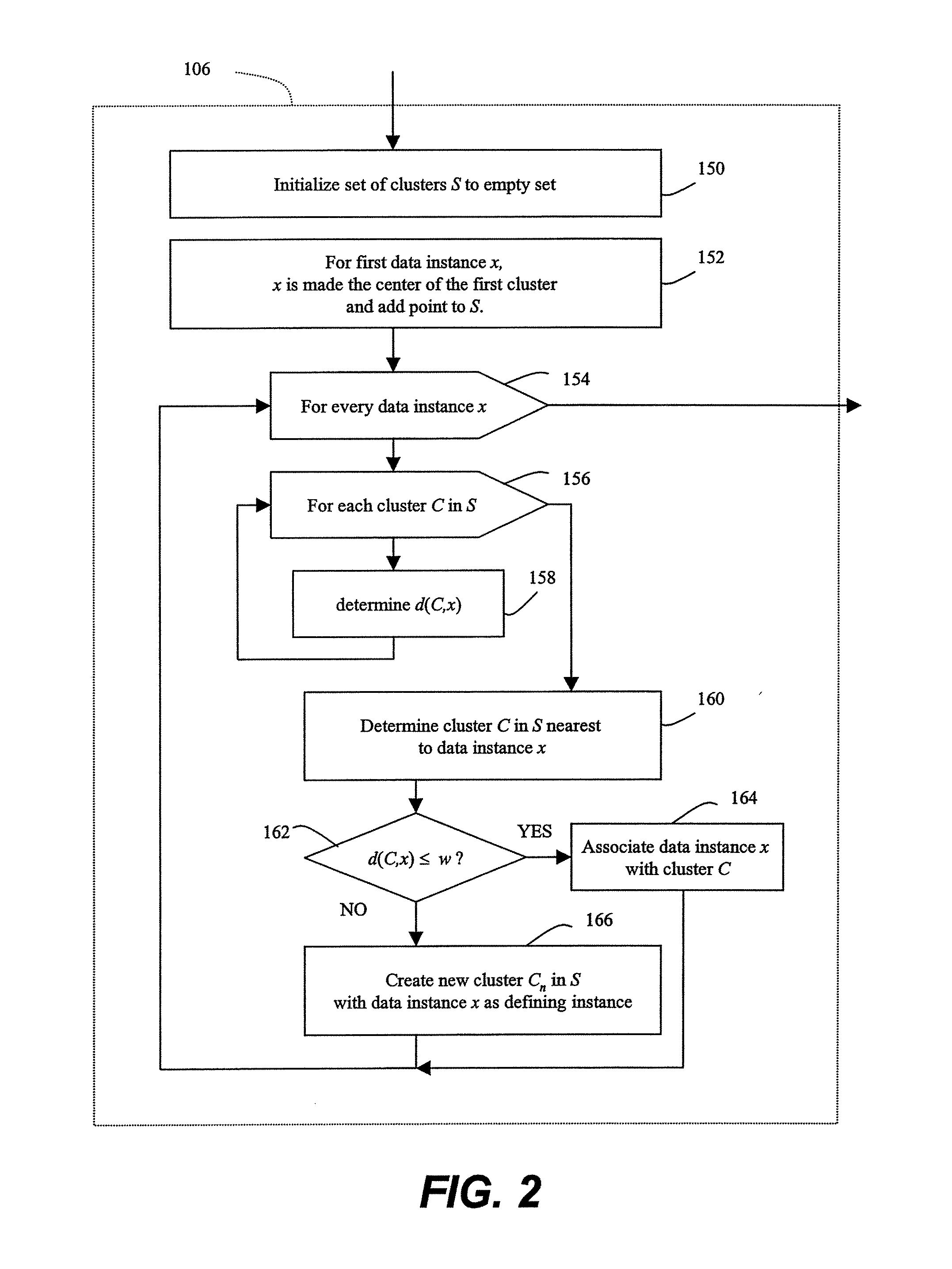
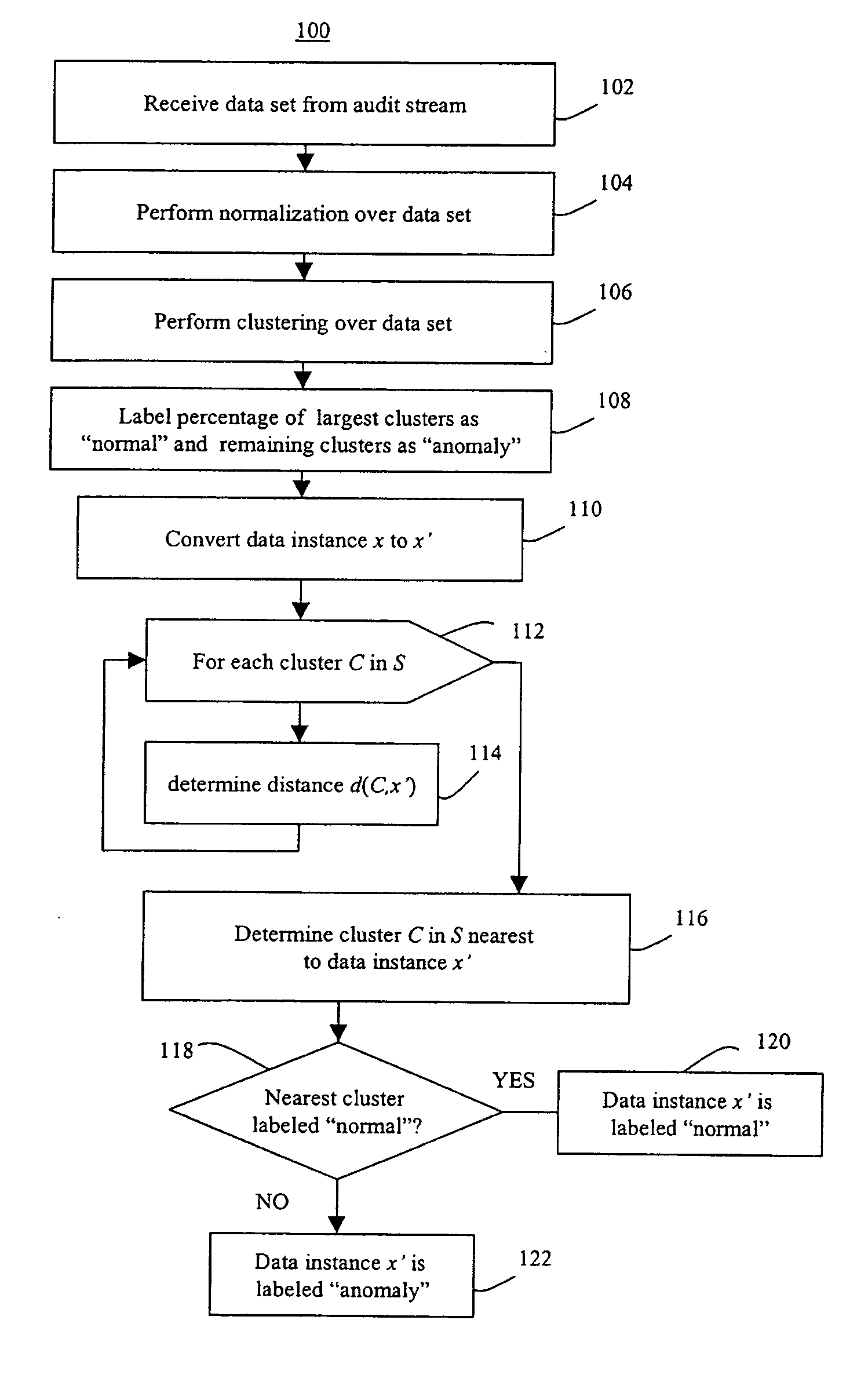
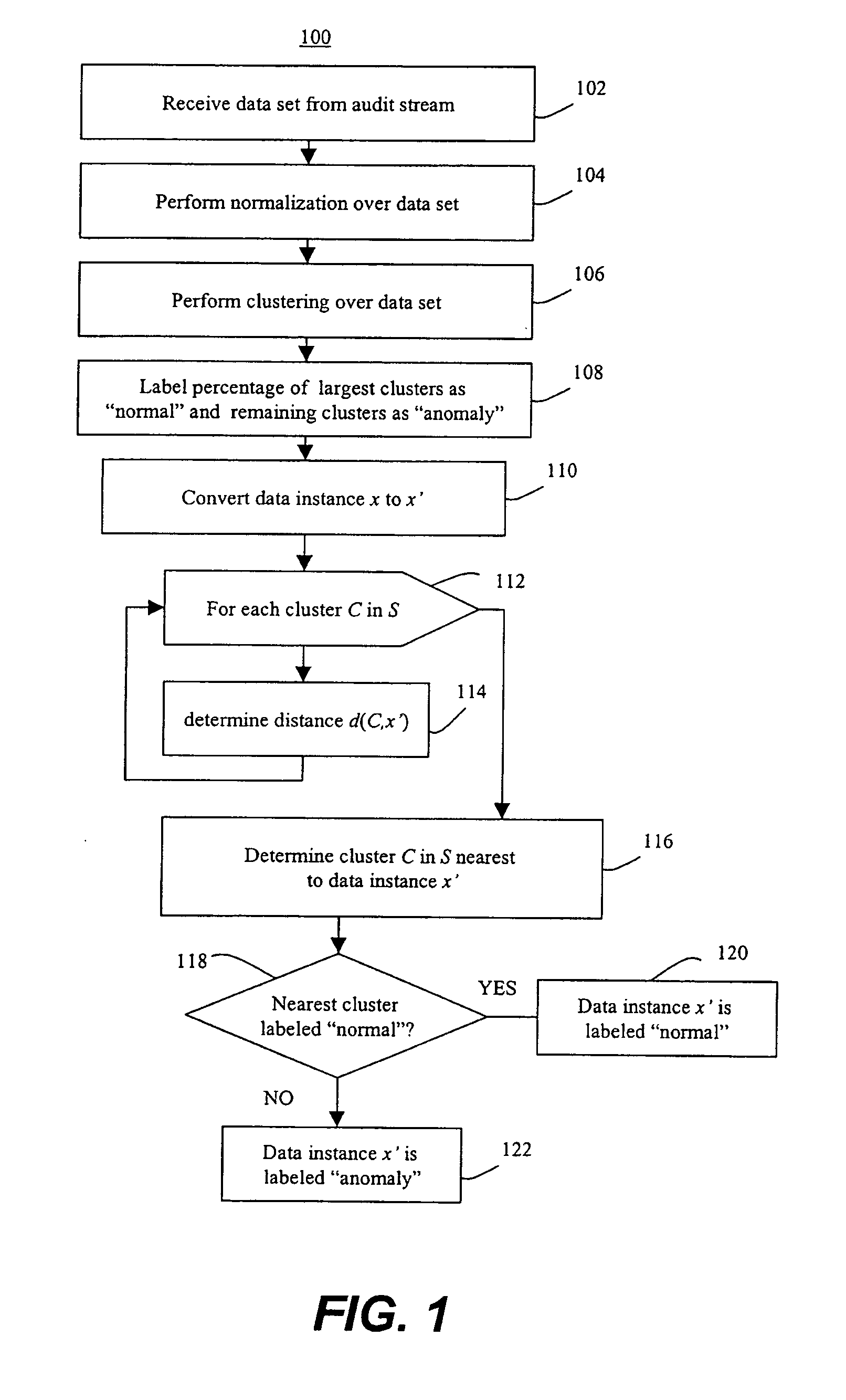
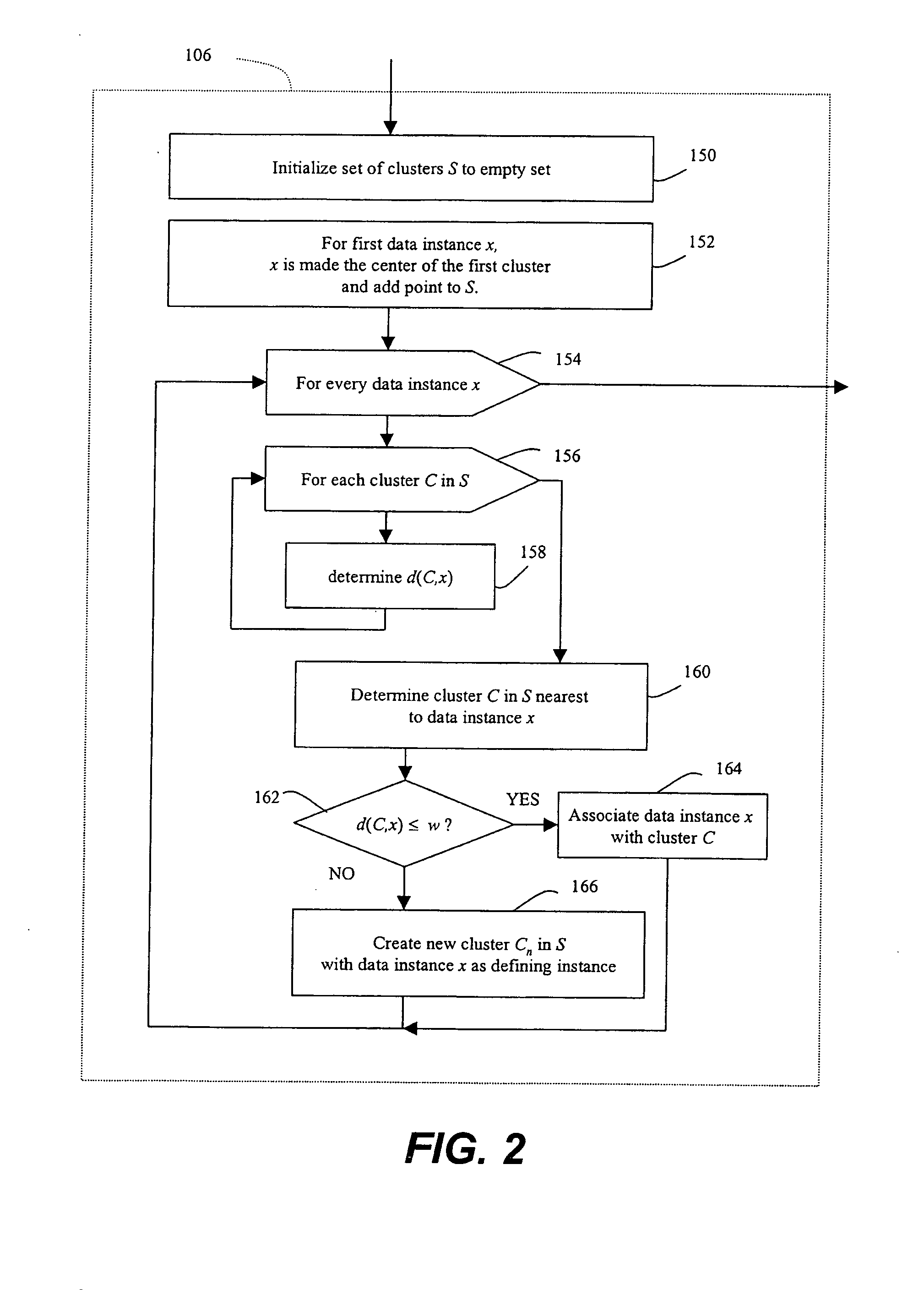
Prioritized detection and classification of clusters of anomalous samples on high-dimensional continuous and mixed discrete/continuous feature spaces
ActiveUS20190188212A1Maximizes confidenceMinimum entropyKernel methodsRelational databasesData classAnomaly detection
This patent concerns novel technology for detection of zero-day data classes for domains with high-dimensional mixed continuous / discrete feature spaces, including Internet traffic. Assume there is a known-class database available for learning a null hypothesis that a given new batch of unlabeled data does not contain any data from unknown / anomalous classes. A novel and effective generalization of previous parsimonious mixture and topic modeling methods is developed. The novel unsupervised anomaly detector (AD) acts on a new unlabeled batch of data to either identify the statistically significant anomalous classes latently present therein or reject the alternative hypothesis that the new batch contains any anomalous classes. The present AD invention can be applied in an on-line setting. Labeling (by a human expert or by other means) of anomalous clusters provides new supervised data that can be used to adapt an actively learned classifier whose objective is to discriminate all the classes.
Owner:ANOMALEE INC
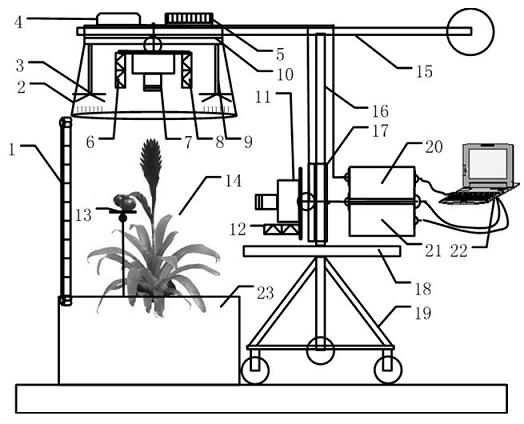
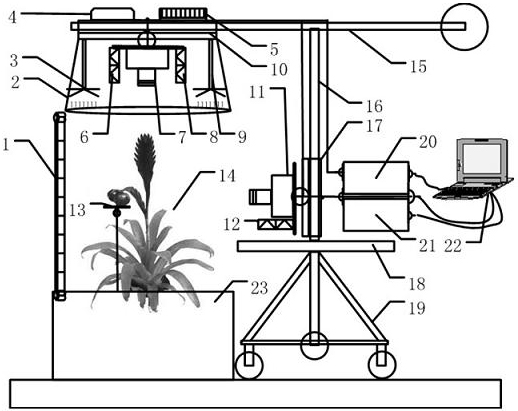
Nondestructive detection device and method for facility crop growth information
ActiveCN102384767AGrasp the state of growthImprove acquisitionMeasurement devicesPotassiumCharacteristic space
The invention discloses a nondestructive detection device and a nondestructive detection method for facility crop growth information, and belongs to the technical field of monitoring of facility crops. The device comprises a growth information sensing system, an electric control mechanical rocker arm and a control computer; the control computer drives the electric control mechanical rocker arm to be positioned at a detection position, and controls the growth information sensing system; reflection spectrums of nitrogen, phosphorus, potassium and moisture of crops, multispectral images, canopy temperature characteristic, multispectral morphological characteristics of canopies, stalks, plants and fruits, fruit quality information, and information of environmental illumination, temperature and humidity are acquired by using a multispectral imager and sensors of infrared temperature, irradiance, environmental temperature and humidity and load; nutrient and moisture characteristic spaces are acquired by optimizing and compensating the nutrient and moisture characteristics of the crops; and growth vigor information of canopy area, stalk thickness, fruit quality, plant height and the like is acquired by extracting the multispectral morphological characteristics of the crops, and comprehensive acquisition and nondestructive detection of the growth information of the crops are realized by combining nutrient, moisture and growth vigor characteristics.
Owner:JIANGSU UNIV
Methods of unsupervised anomaly detection using a geometric framework
ActiveUS8544087B1New typeEasy to operateMemory loss protectionError detection/correctionFrequency spectrumAlgorithm
A method for unsupervised anomaly detection, which are algorithms that are designed to process unlabeled data. Data elements are mapped to a feature space which is typically a vector space . Anomalies are detected by determining which points lies in sparse regions of the feature space. Two feature maps are used for mapping data elements to a feature apace. A first map is a data-dependent normalization feature map which we apply to network connections. A second feature map is a spectrum kernel which we apply to system call traces.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
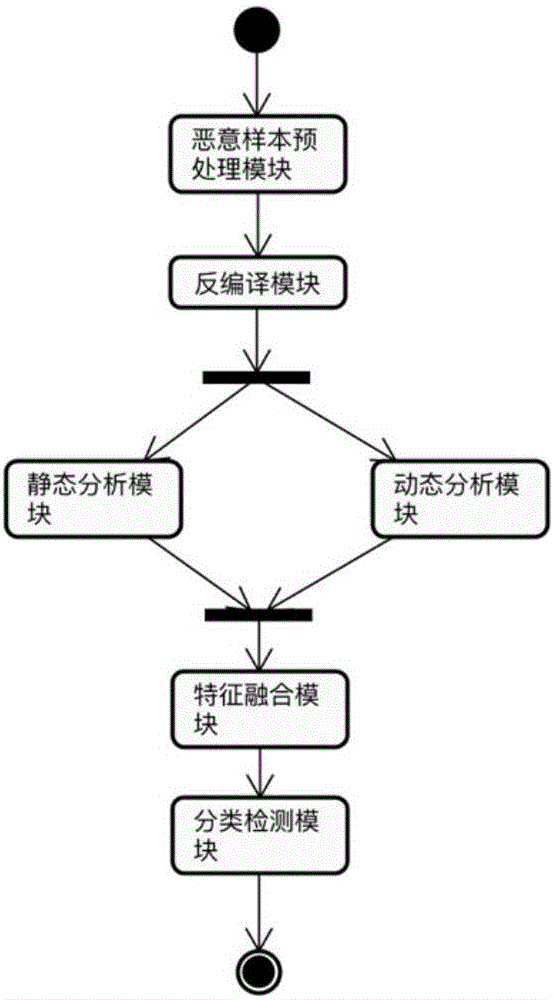
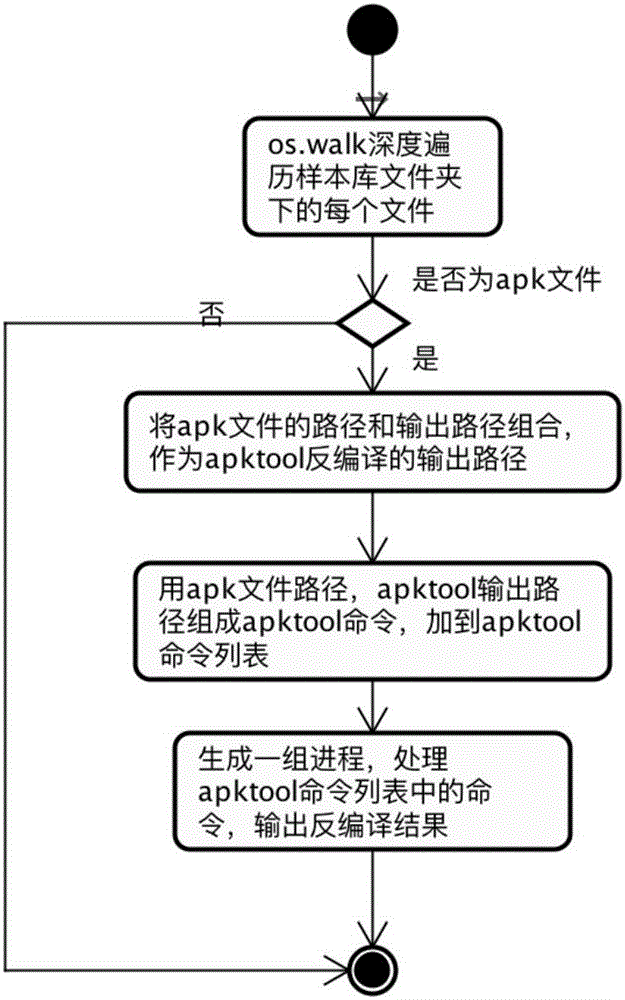
Android malicious application detection method and system based on multi-feature fusion
ActiveCN107180192AImprove detection accuracyReflect malicious appsCharacter and pattern recognitionPlatform integrity maintainanceFeature vectorAnalytical problem
The invention discloses an Android malicious application detection method and system based on multi-feature fusion. The method comprises the following steps that: carrying out decompilation on an Android application sample to obtain a decompilation file; extracting static features from the decompilation file; operating the Android application sample in an Android simulator to extract dynamic features; carrying out feature mapping on the static features and the dynamic features by the text Hash mapping part of a locality sensitive Hash algorithm, mapping to a low-dimensional feature space to obtain a fused feature vector; and on the basis of the fused feature vector, utilizing a machine learning classification algorithm to train to obtain a classifier, and utilizing the classifier to carry out classification detection. By use of the method, the high-dimensional feature analysis problem of a malicious code rare sample family can be solved, and detection accuracy is improved.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Gesture identification method and gesture identification system
InactiveCN104680127AAvoid interferenceHigh precisionCharacter and pattern recognitionPoint sequencePrincipal component analysis
The invention discloses a gesture identification method and a gesture identification system, wherein the method comprises the following steps: step S1, a gesture detecting step: detecting a gesture in video stream in real time, marking a region in which the gesture is detected as an interested region; step S2, a gesture segmenting step: processing the interested region by utilizing skin color segmentation, and then performing edge detecting and outline extracting to obtain a point sequence of a hand-shaped outline; step S3, a gesture identifying step: firstly extracting a Fourier descriptor of the hand-shaped outline and then mapping the Fourier descriptor to a new vector of a characteristic space by utilizing PCA (principal components analysis), comparing the distance between the new vector and a gesture clustering center obtained by training, and judging a gesture type represented by the vector. The gesture identification method and the gesture identification system disclosed by the invention can improve the gesture identification accuracy and the gesture identification efficiency, and can effectively avoid background color interference.
Owner:WINGTECH COMM
Multi-behavior process monitoring method based on pivot analysis and vectorial data description support
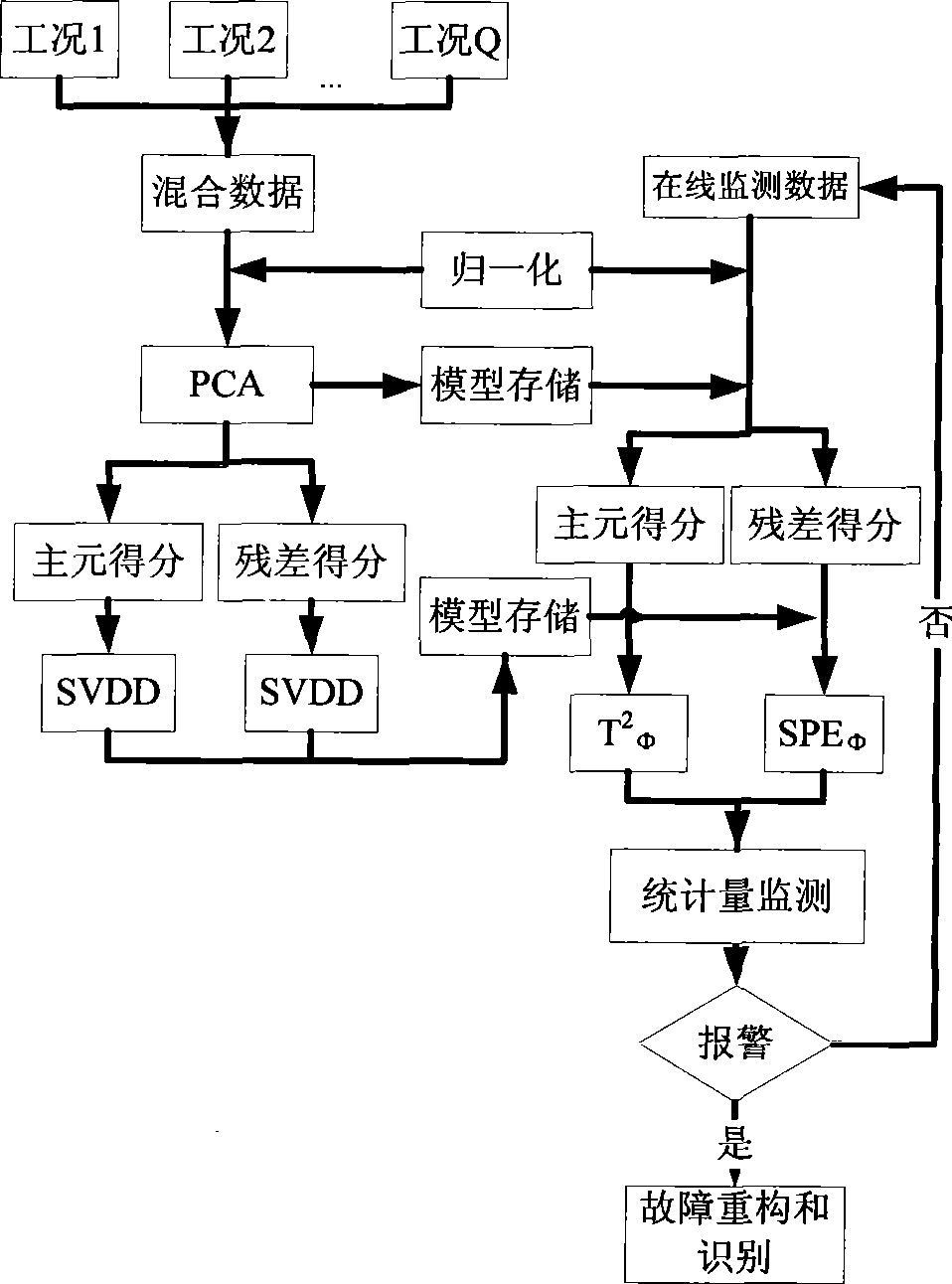
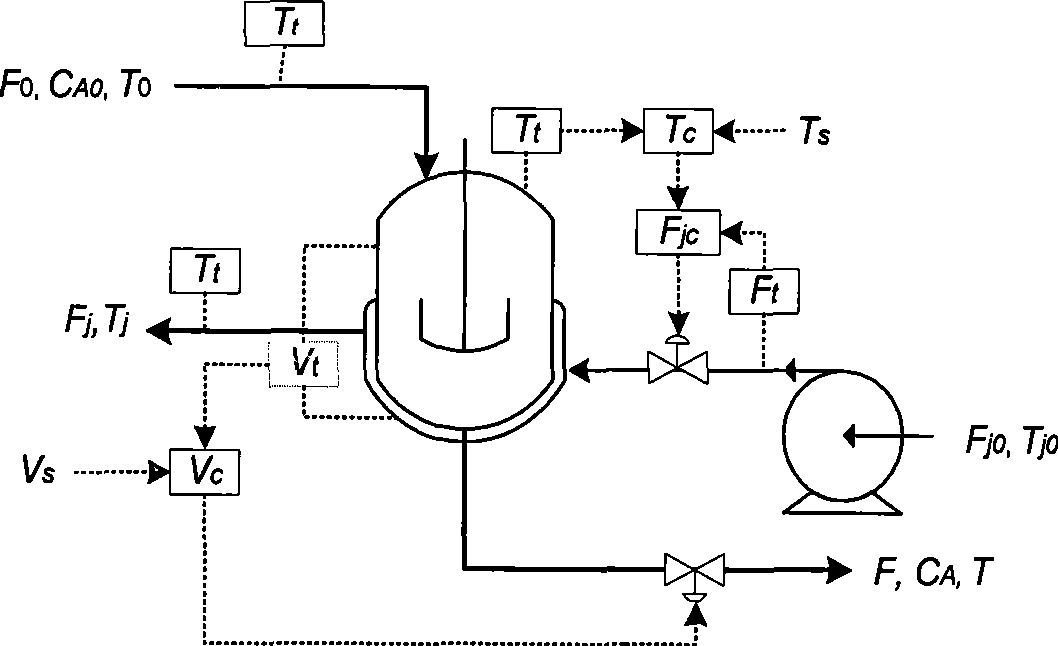
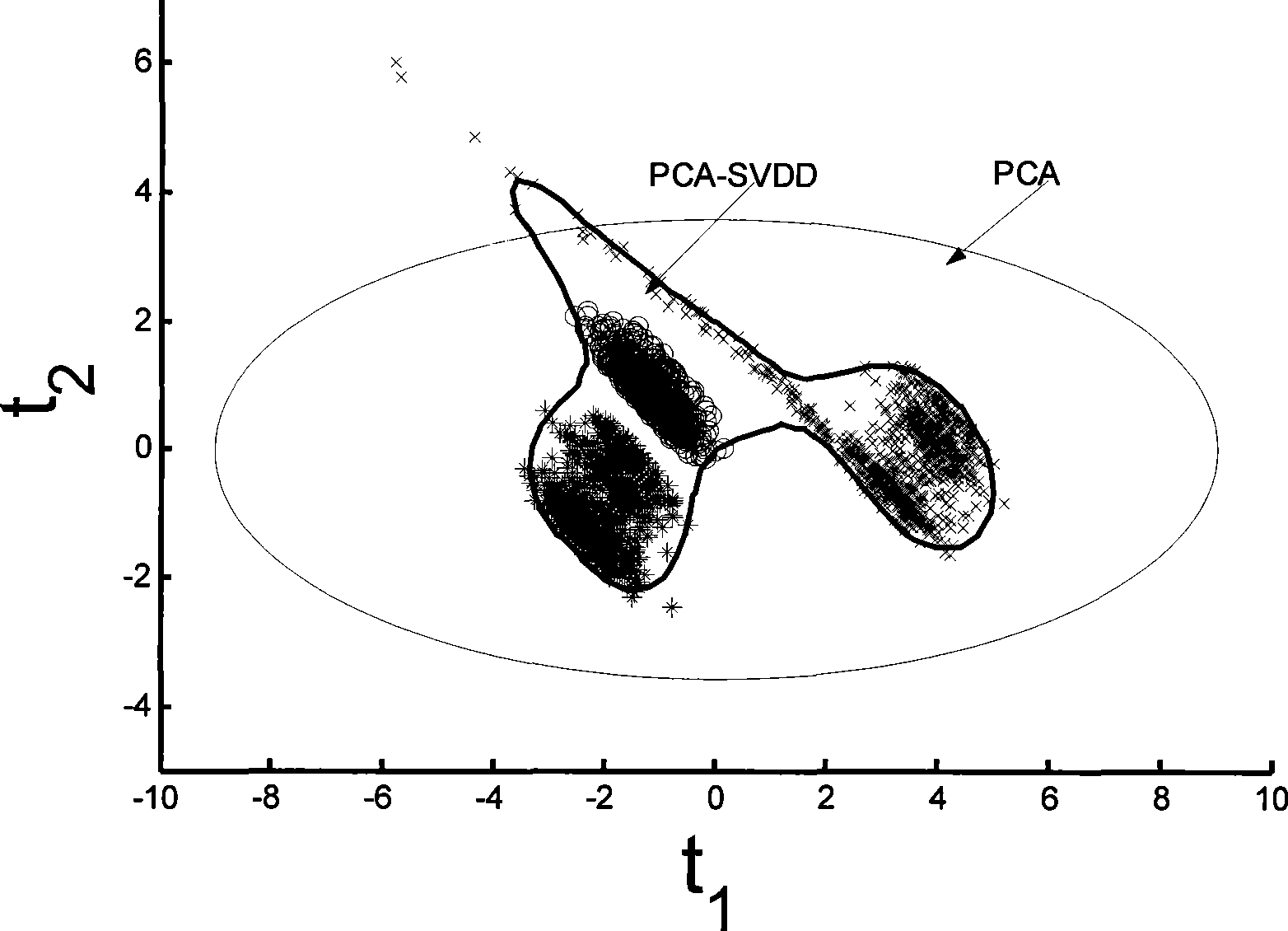
InactiveCN101458522ATighten statistical limitsHigh sensitivityTotal factory controlProgramme total factory controlData descriptionPrincipal component analysis
The invention discloses a multi-operating process monitor method based on principal component analysis and support vectors data. The method establishes a uniform PCA model to various operating mixed data firstly, puts score vectors of principal component space and residual space to high dimension characteristic space. Two new statistics are established in the characteristic space for monitoring the principal component space and residual space. When the process goes wrong, a fault reconstruction method based on SVDD identifies fault. The method establishes two SVDD statistics monitor model to various operating based that the principal analysis method is used for reducing process variable dimension, reduces statistics limit of processing monitor, increases sensitivity of processing monitoring. In addition, the invention provides a fault reconstruction and identifying method aiming at detected process fault which can locate source of fault commendably, is benefit to removing fault as soon as possible, returns process to normal operation.
Owner:ZHEJIANG UNIV
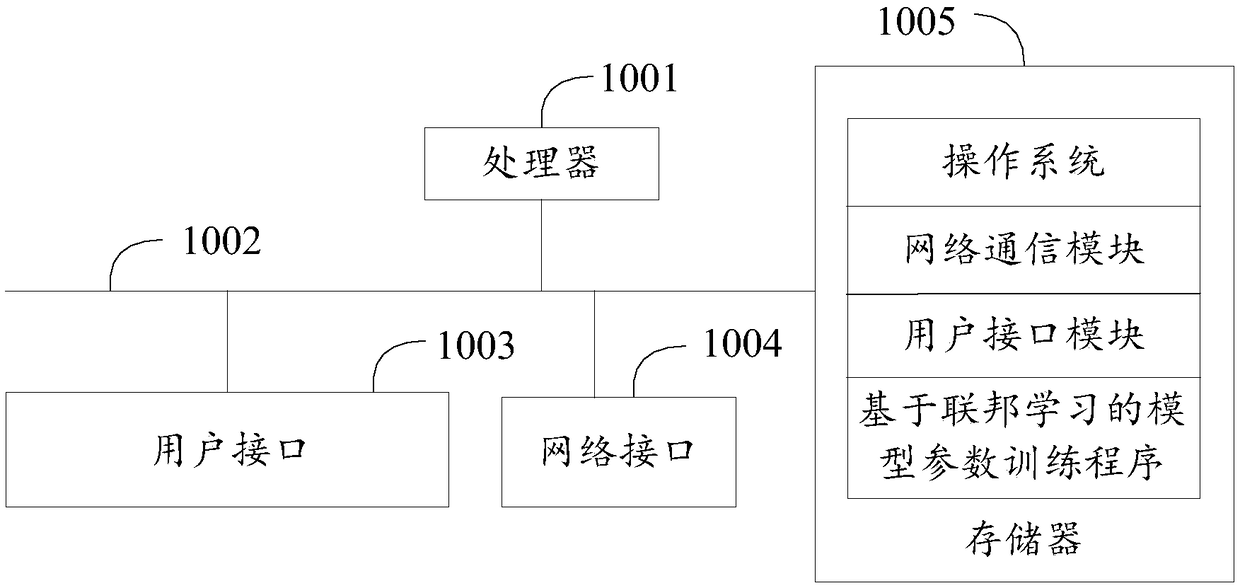
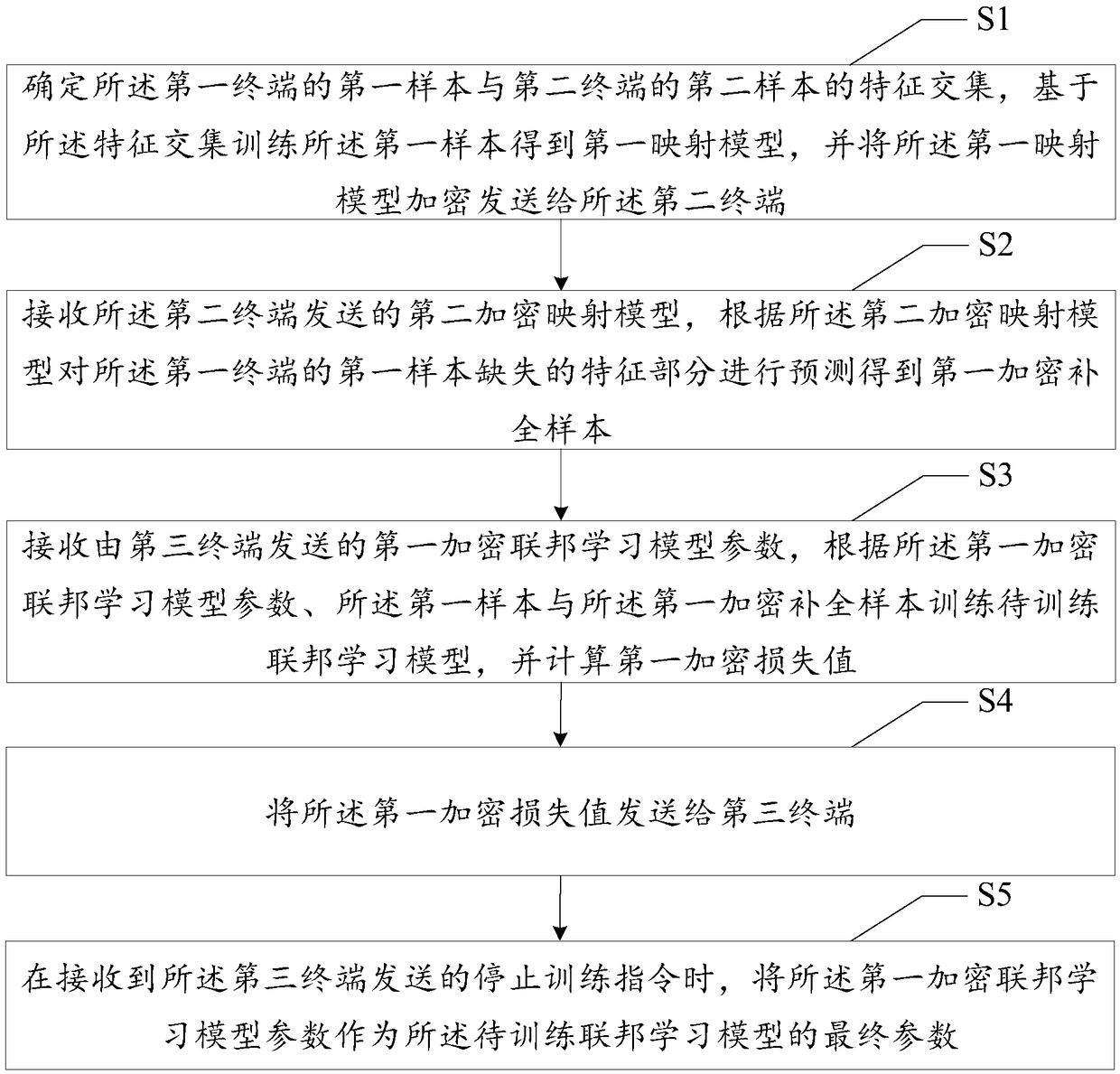
Model parameter training method, terminal, system and medium based on federated learning
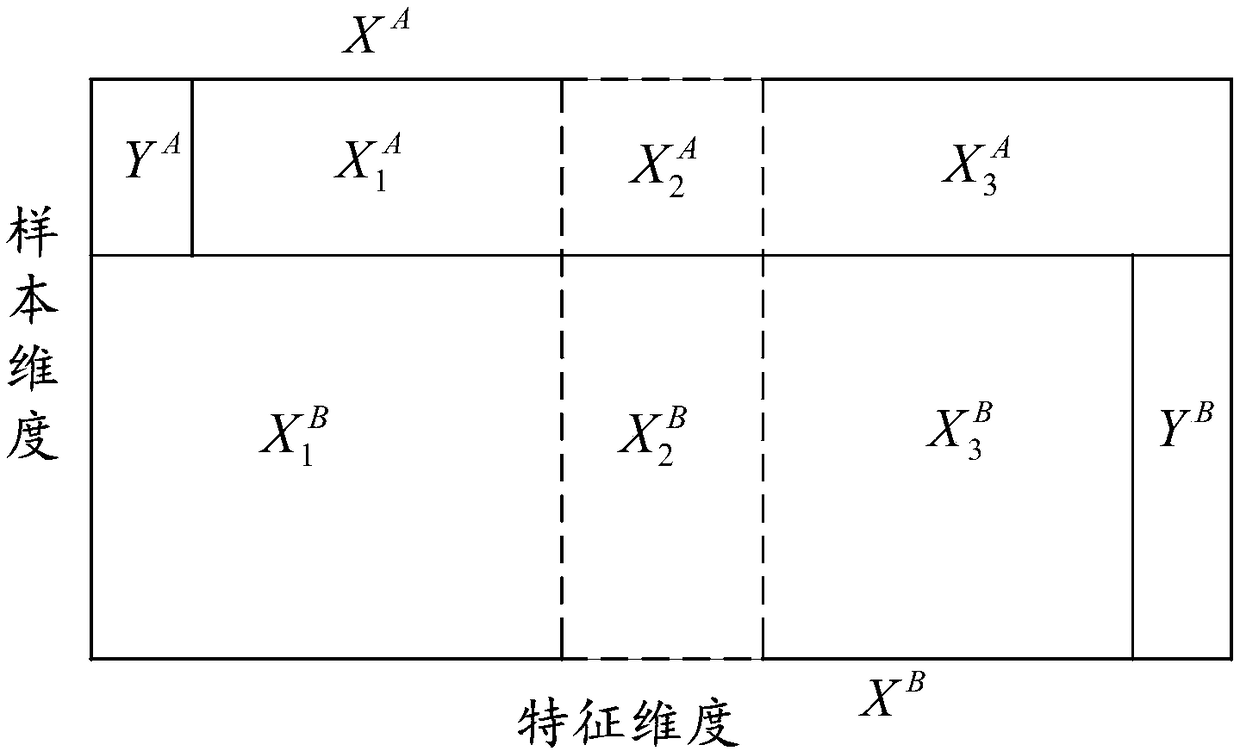
ActiveCN109492420AImprove predictive abilityFeature Space ExpansionEnsemble learningCharacter and pattern recognitionCharacteristic spaceModel parameters
The invention discloses a model parameter training method based on federal learning, a terminal, a system and a medium, and the method comprises the steps: determining a feature intersection of a first sample of a first terminal and a second sample of a second terminal, training the first sample based on the feature intersection to obtain a first mapping model, and sending the first mapping modelto the second terminal; receiving a second encryption mapping model sent by a second terminal, and predicting the missing feature part of the first sample to obtain a first encryption completion sample; receiving a first encrypted federal learning model parameter sent by a third terminal, training a to-be-trained federal learning model according to the first encrypted federal learning model parameter, and calculating a first encryption loss value; sending the first encryption loss value to a third terminal; and when a training stopping instruction sent by the third terminal is received, takingthe first encrypted federal learning model parameter as a final parameter of the federal learning model to be trained. According to the invention, the characteristic space of two federated parties isexpanded by using transfer learning, and the prediction capability of the federated model is improved.
Owner:WEBANK (CHINA)
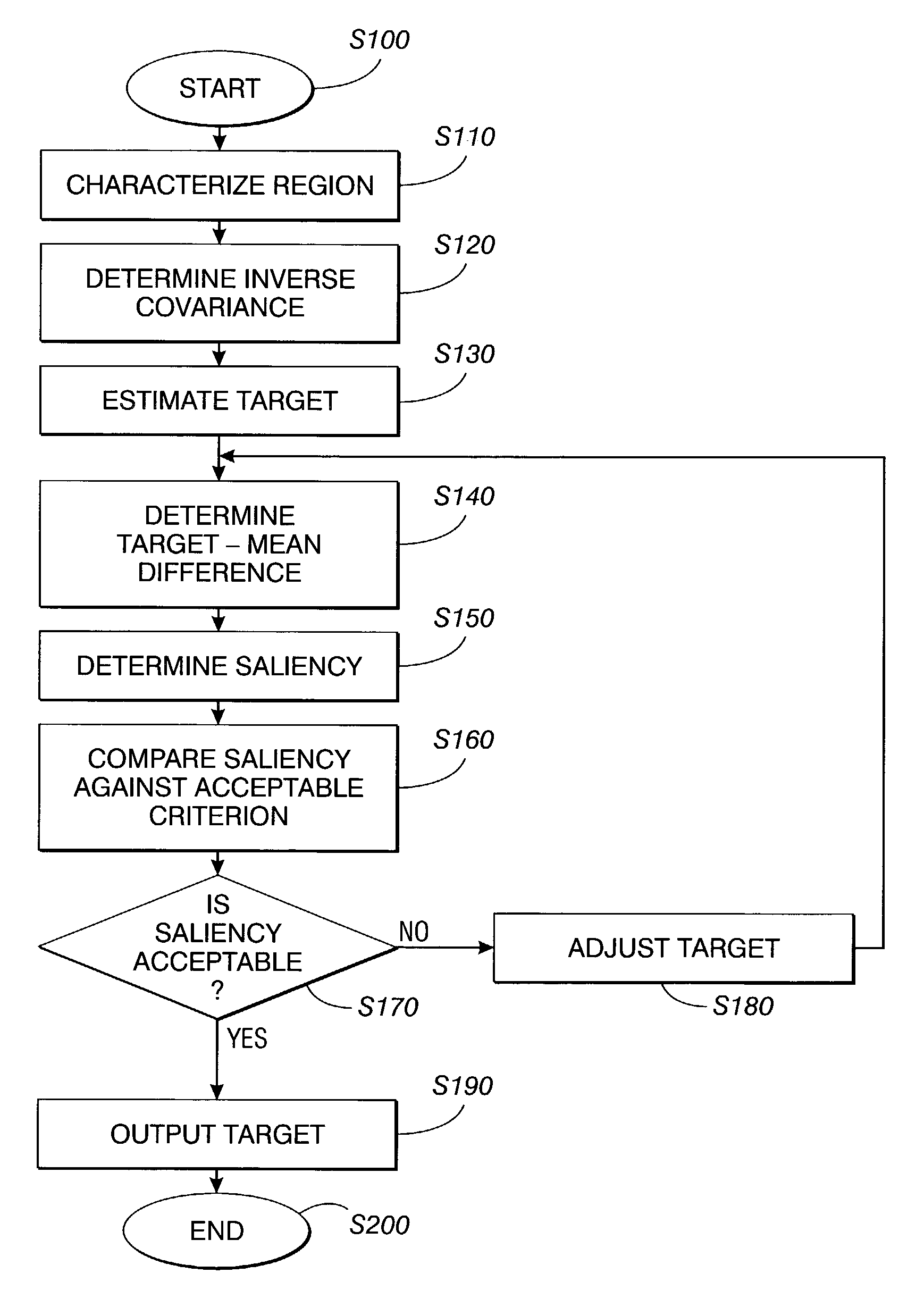
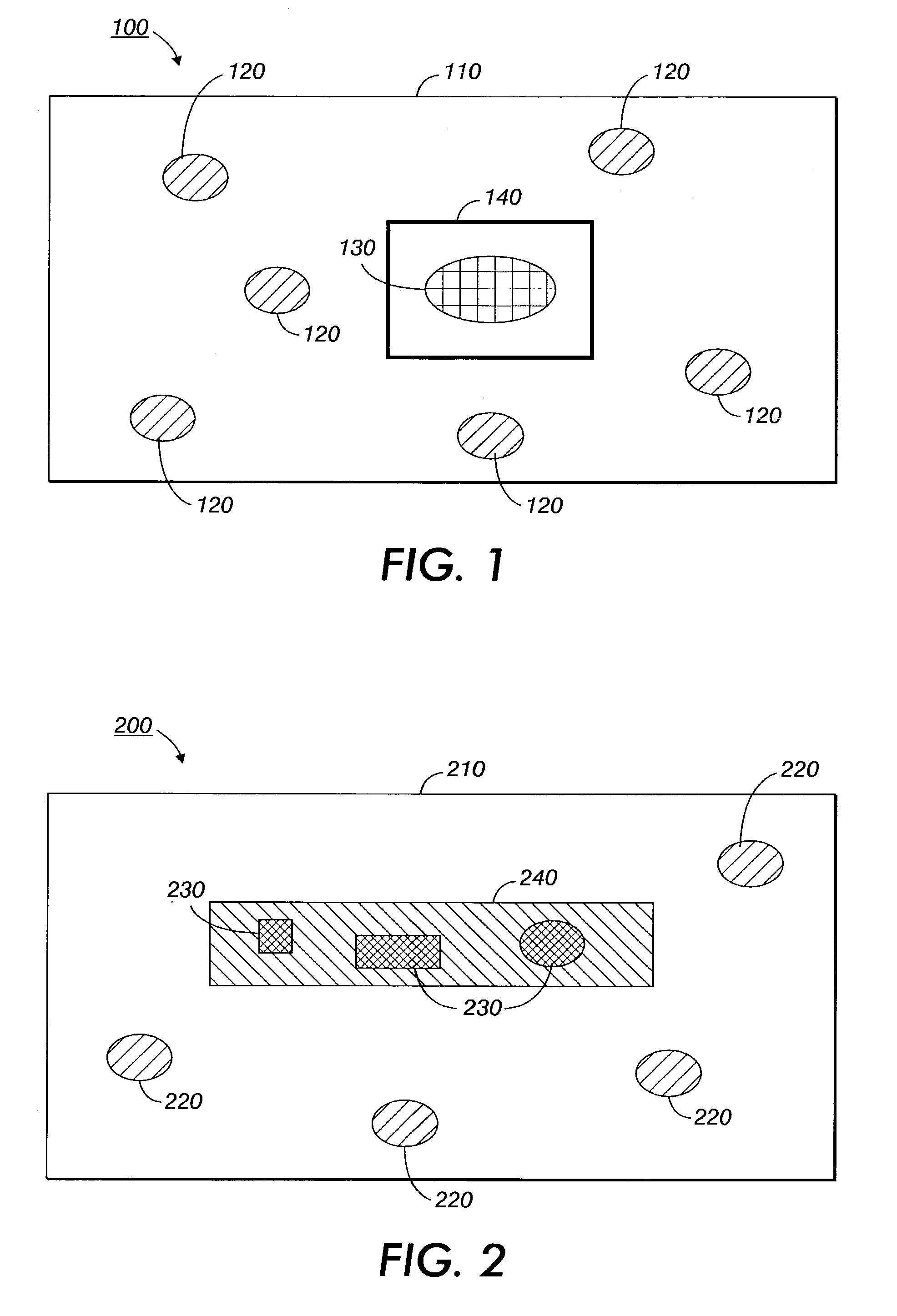
Systems and method for automatically choosing visual characteristics to highlight a target against a background
InactiveUS7130461B2Facilitate a viewer to distinguishMitigate attention-diverting influenceImage enhancementImage analysisCharacteristic spaceCovariance
A method for choosing visual characteristics of a characteristic space within a region includes calculating a mean characteristic of the region, determining a covariance of the region, inverting the covariance to produce an inverse covariance, estimating a target characteristic, determining a difference between the mean characteristic and the target characteristic transposing the difference to produce a difference transpose, determining a saliency from a product of the difference transpose multiplied by the inverse covariance multiplied by the difference, comparing the saliency to an acceptance criterion to yield one of an acceptance if the saliency satisfies the acceptance criterion and a rejection otherwise, adjusting the target characteristic and repeating the determining a difference, transposing the difference, determining a saliency and comparing the saliency steps if the comparing yields the rejection, and outputting the target characteristic if the comparing yields the acceptance.
Owner:XEROX CORP
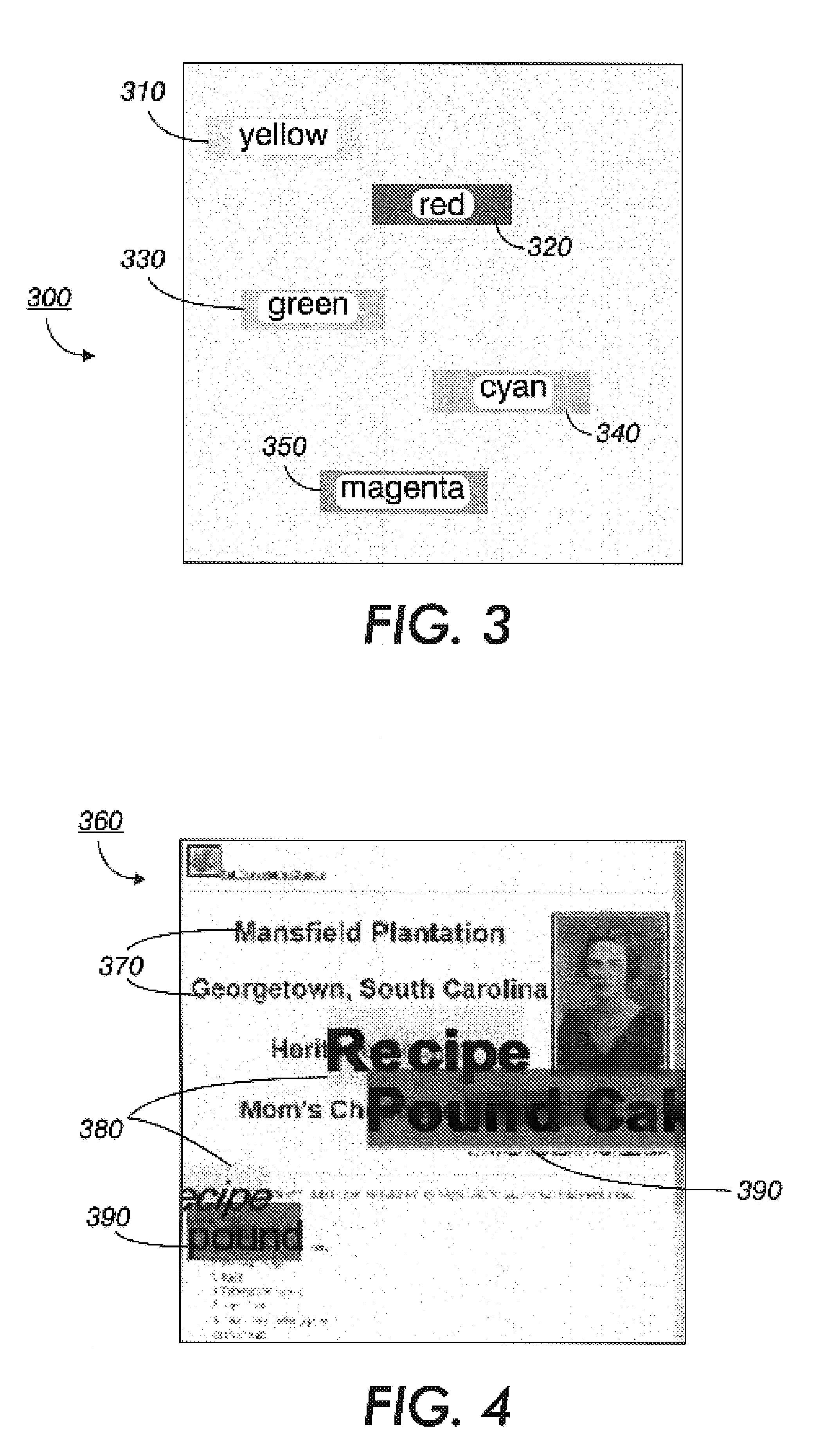
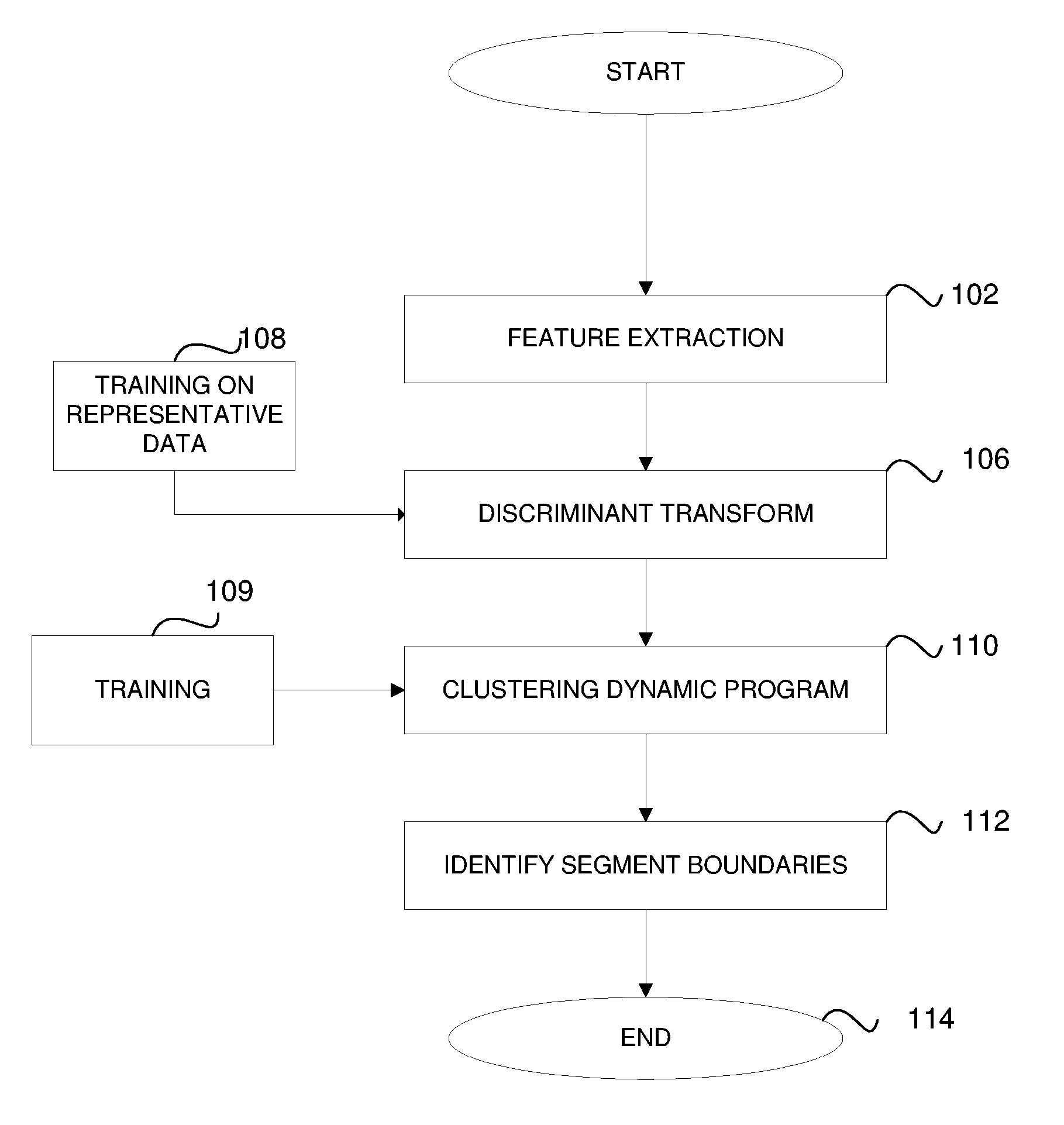
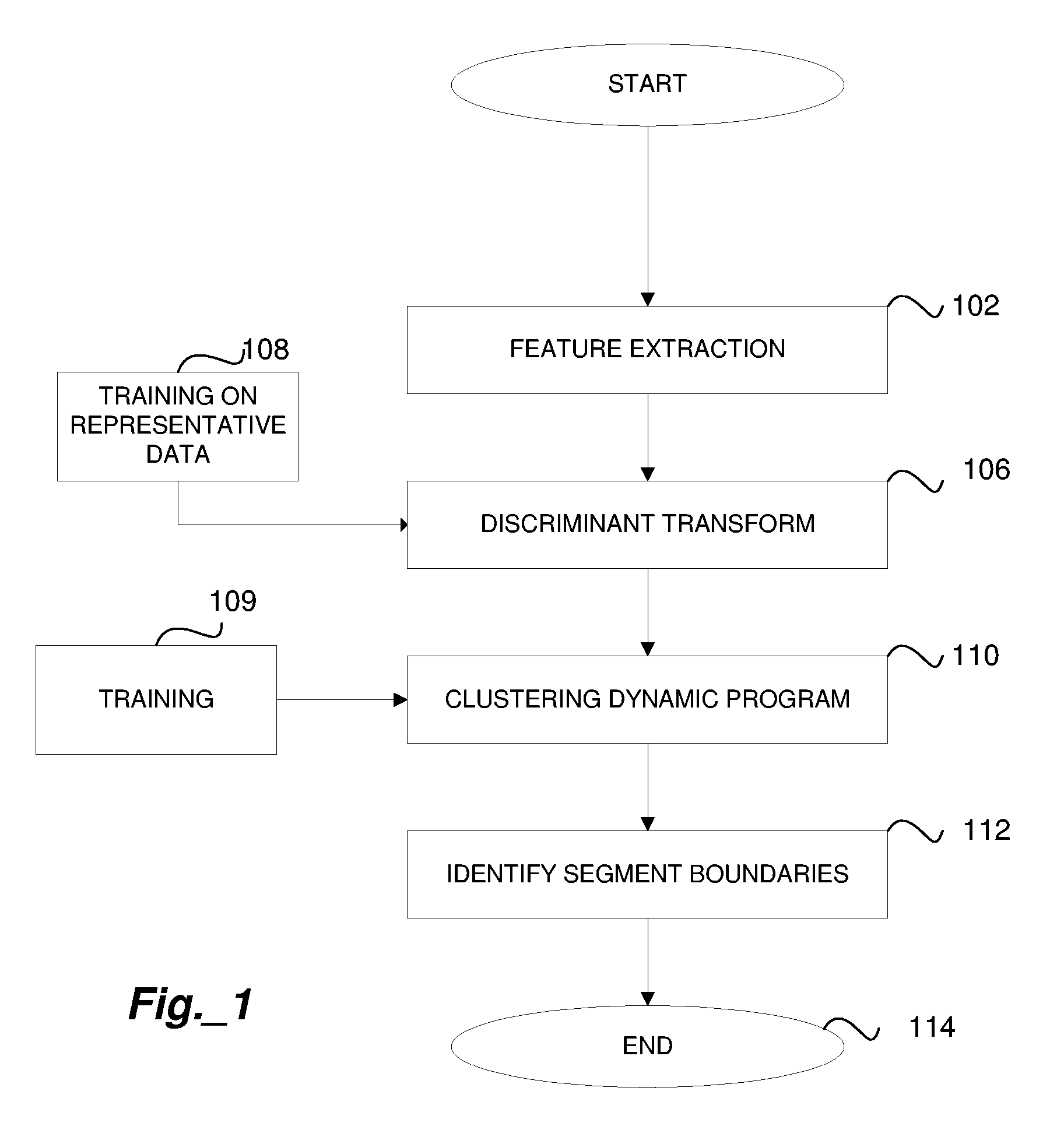
Method for Segmenting Audio Signals
ActiveUS20060085188A1Easy to separateGain controlDigital data processing detailsCharacteristic spaceDynamic programming
An input signal is converted to a feature-space representation. The feature-space representation is projected onto a discriminant subspace using a linear discriminant analysis transform to enhance the separation of feature clusters. Dynamic programming is used to find global changes to derive optimal cluster boundaries. The cluster boundaries are used to identify the segments of the audio signal.
Owner:CREATIVE TECH CORP
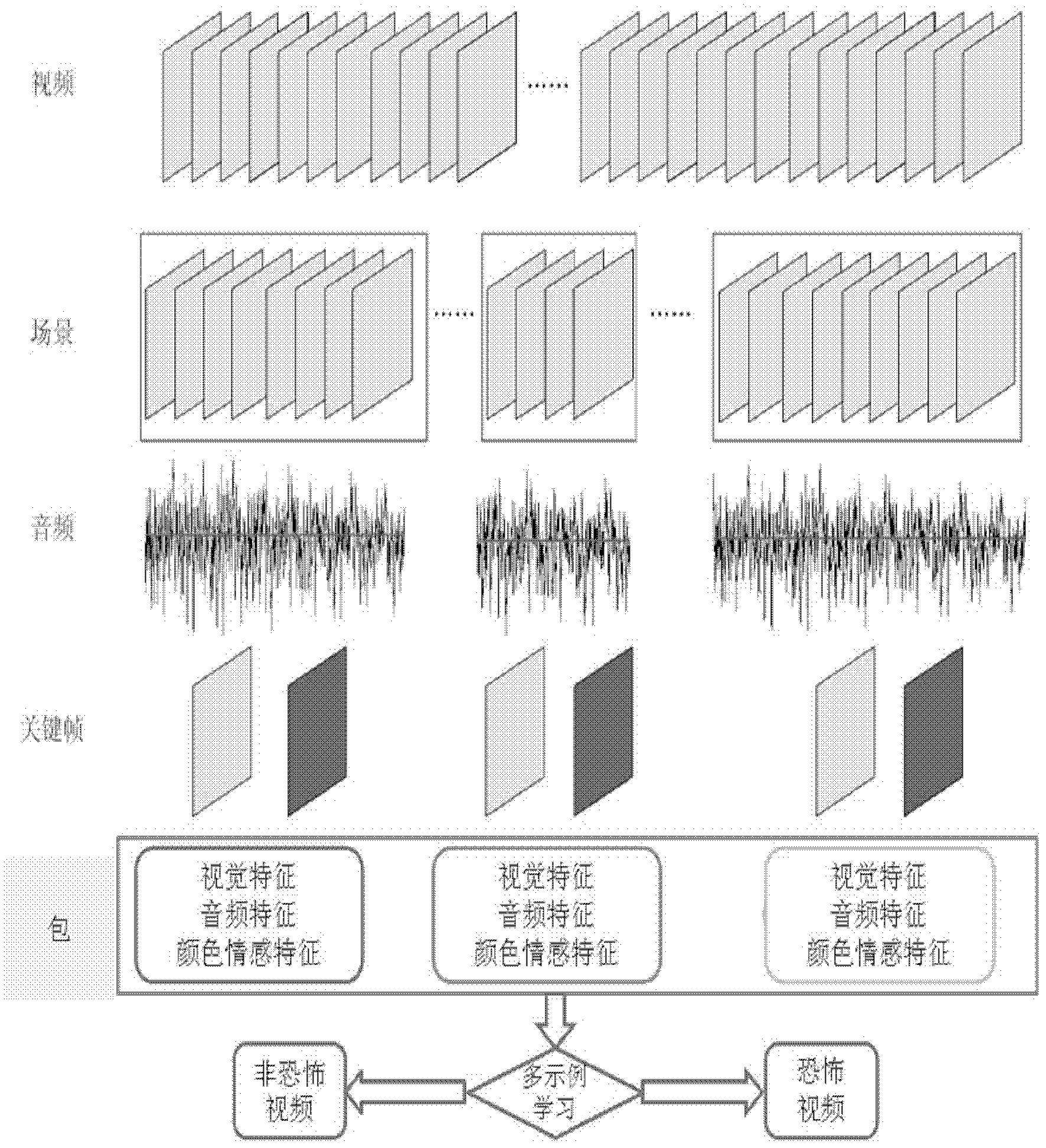
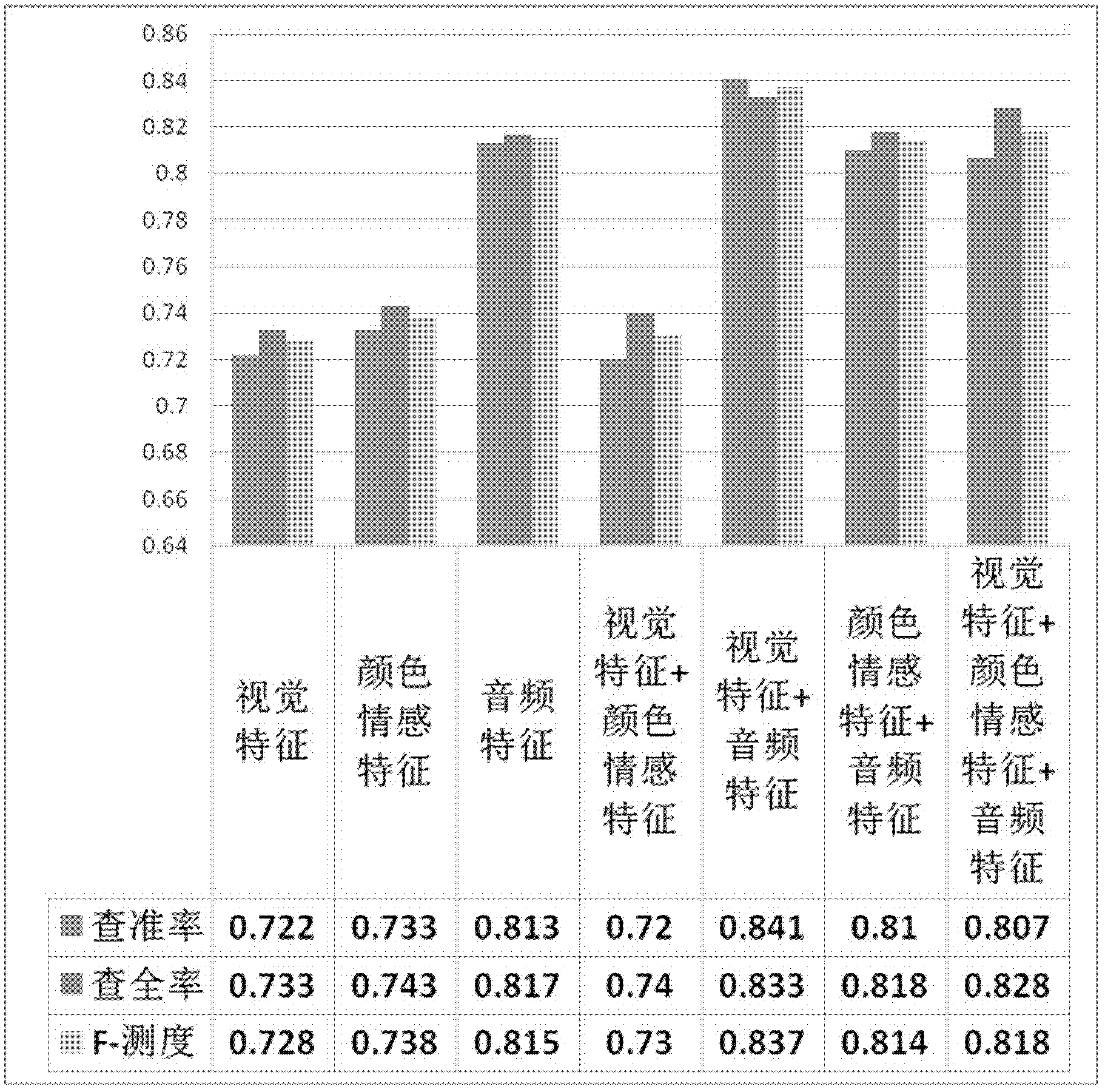
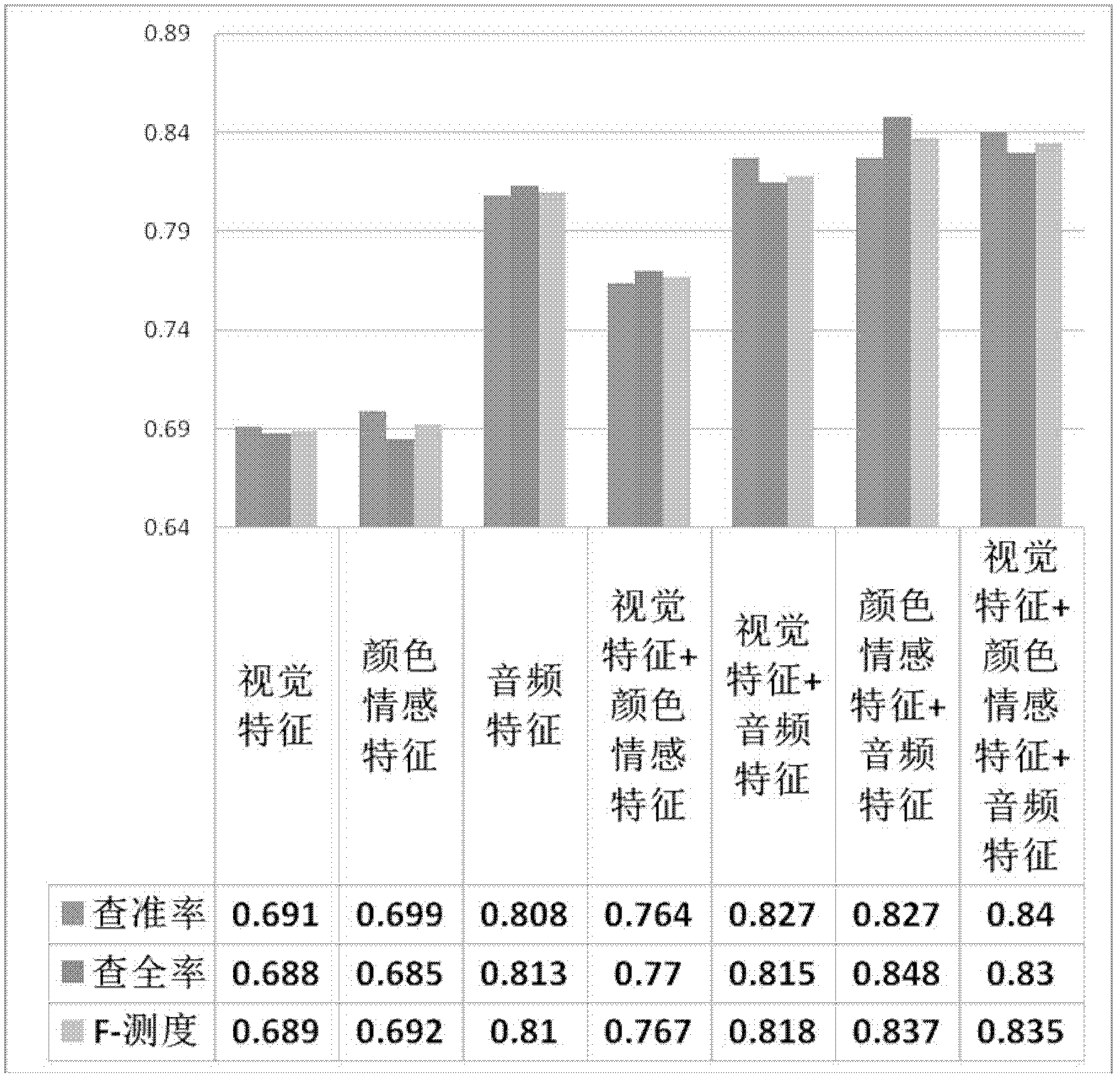
Multi-examples-learning-based method for identifying horror video scene
The invention discloses a multi-examples-learning-based method for identifying a horror video scene. The multi-examples-learning-based method comprises the following steps of: carrying out shot segmentation and key frame selection on a video scene, wherein the video scene corresponds to a multi-examples learning bag, and a shot corresponds to the examples in the bag; respectively extracting visual characteristics, audio characteristics and color affective characteristics on the basis of the shot and a key frame to form a characteristic space; training a corresponding multi-examples learning classifier in the characteristic space; structurally analyzing a video sample to be tested, and extracting related characteristics; and predicting the category, namely horror or non-horror, of the video sample through the trained classifier. According to the invention, the novel color affective characteristics are provided and applied to the method for identifying the horror video scene, and the multi-examples-learning-based method has wide application prospect.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
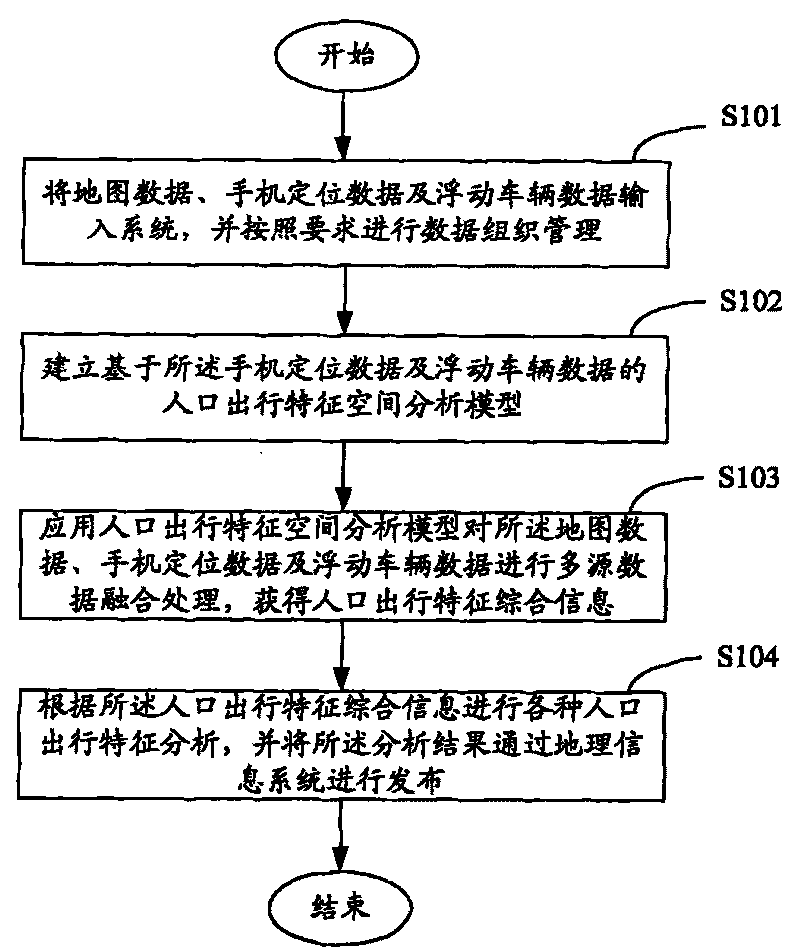
Modeling method of characteristics of population space-time dynamic moving based on multisource data fusion
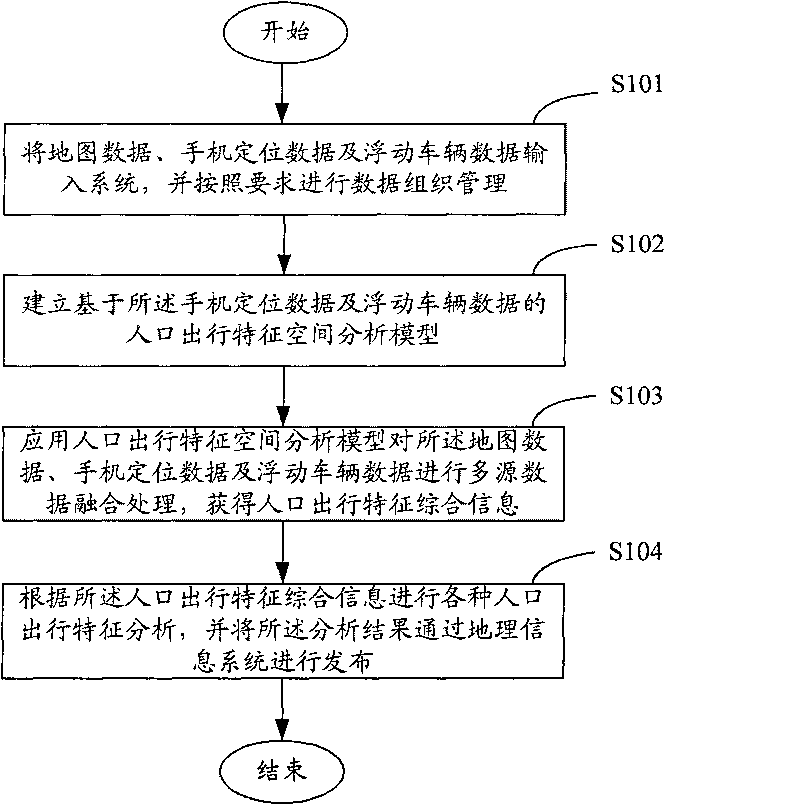
InactiveCN101694706ABig amount of dataQuality improvementData processing applicationsDetection of traffic movementSimulationCharacteristic space
The invention provides a modeling method of the characteristics of population space-time dynamic moving based on multisource data fusion. The modeling method comprises: A. inputting map data, mobile phone locating data and floating vehicle data into a system and managing data organization according to requirements; B. establishing a spatial analysis model of the characteristics of population moving based on the mobile phone locating data and the floating vehicle data; C. applying the spatial analysis model of the characteristics of the population moving to carry out multisource data fusion of the map data, the mobile phone locating data and the floating vehicle data to obtain integrated information of the characteristics of the population moving; and D. analyzing the characteristics of various population moving according to the integrated information of the characteristics of the population moving and publishing an analyzed result by the geographic information system. The modeling method can acquire data of urban population space-time dynamic distribution and moving characteristics with large data amount, high quality and space-time characteristics, obtain basis of accurate population distribution and population moving characteristics, and provide decision-making supports for urban planning, land use planning, transportation planning and the like.
Owner:SHENZHEN INST OF ADVANCED TECH
Methods of unsupervised anomaly detection using a geometric framework
InactiveUS20150058982A1Easy to operateMemory loss protectionError detection/correctionFir systemFrequency spectrum
A method for unsupervised anomaly detection, which are algorithms that are designed to process unlabeled data. Data elements are mapped to a feature space which is typically a vector space d. Anomalies are detected by determining which points lies in sparse regions of the feature space. Two feature maps are used for mapping data elements to a feature apace. A first map is a data-dependent normalization feature map which we apply to network connections. A second feature map is a spectrum kernel which we apply to system call traces.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
Rapid image retrieval method based on supervised topology keeping hash
ActiveCN105069173AStrong semantic expression abilityStrong intra-class differential expression abilityStill image data retrievalCharacter and pattern recognitionFeature extractionAlgorithm
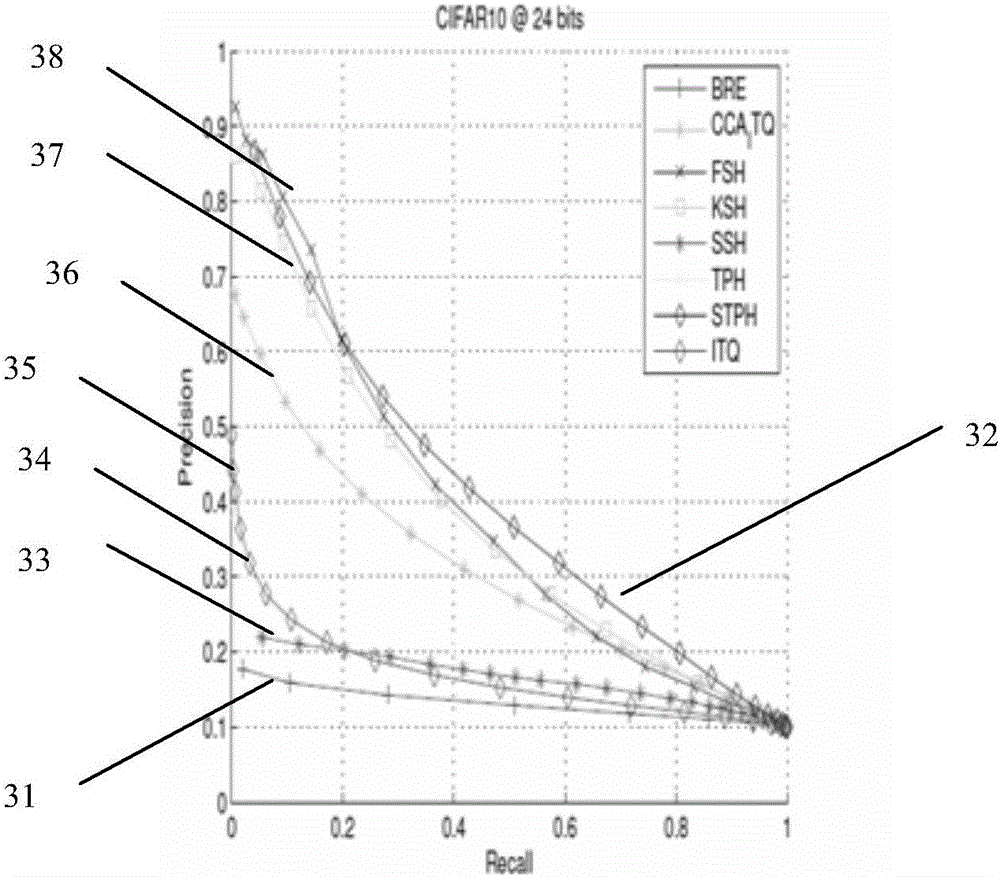
The invention discloses a rapid image retrieval method based on supervised topology keeping hash. The method includes the steps of S1, extracting features of obtained training images and inquiry images, converting feature spaces into new nuclear spaces, and obtaining nuclear space representation of each image; S3, conducting binary coding on the training images and the inquiry images; S4, conducting image retrieval through binary codes. For solving the rapid image retrieval problem, hash coding is studied in the nuclear space with higher expression capacity, supervise information and topology keeping information are added in the hash mapping matrix studying process, a studied mapping matrix has higher semantic expression capacity and higher within-cluster variation expression capacity, and therefore the studied binary codes are more suitable for image retrieval tasks, retrieval accuracy is improved, and retrieval result sequencing is optimized.
Owner:天津中科智能识别有限公司
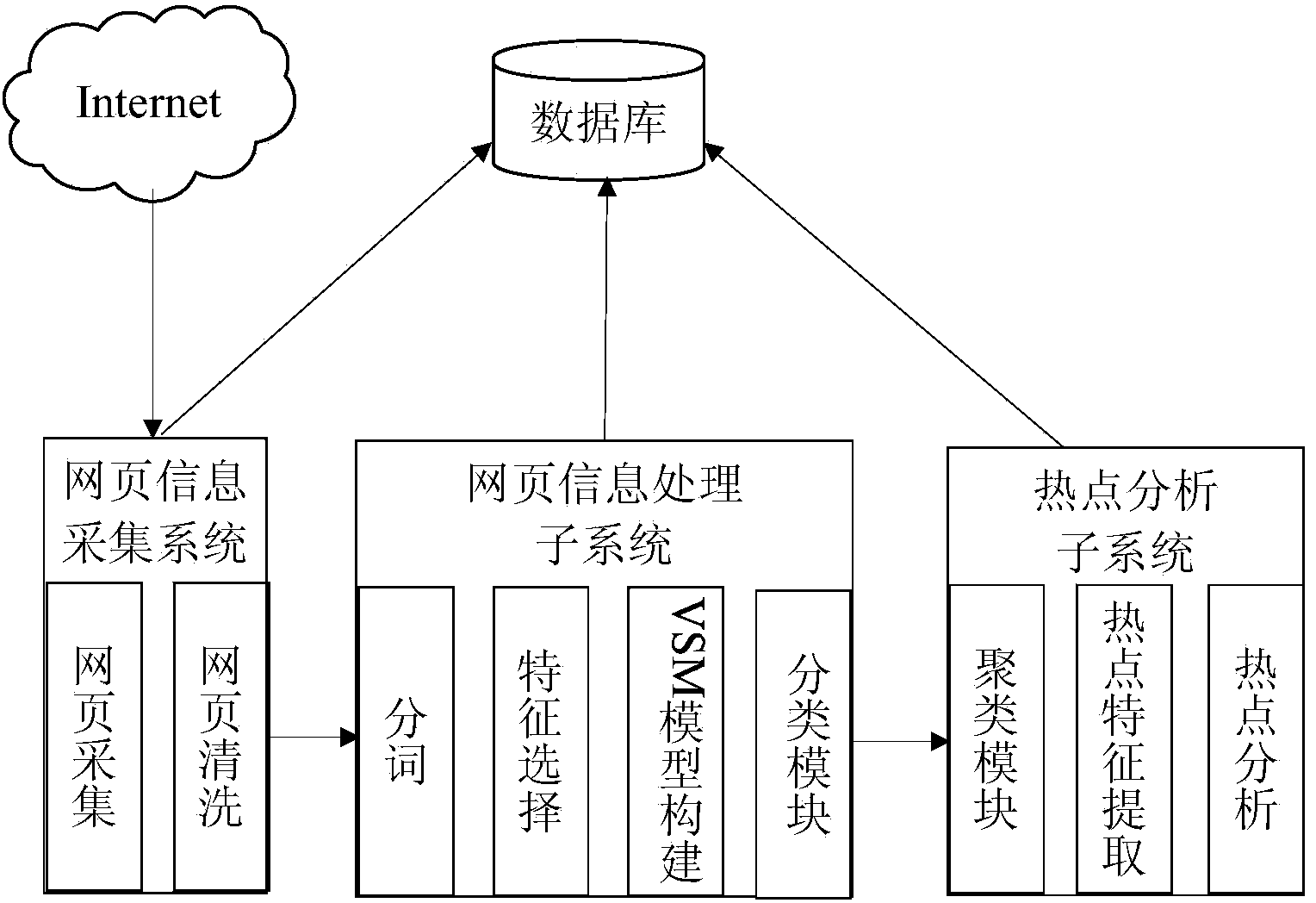
Network hot event detection method based on text classification and clustering analysis
ActiveCN104239436AImprove efficiencyImprove accuracySpecial data processing applicationsText database clustering/classificationFeature extractionText categorization
The invention discloses a network hot event detection method based on text classification and clustering analysis. The method solves the problem that the efficiency and accuracy rate of the existing network hot event detection method based on clustering analysis need to be improved. The method comprises the steps that feature words are respectively selected for various classes of files through feature extraction and feature selection by utilizing a training corpus; each training text and test text are represented as vectors in all of the feature spaces by utilizing a vector space model method, and the weight of each dimension of the vectors is determined by utilizing a TF-IDF (term frequency-inverse document frequency) method, and then each test text is classified; the classified test texts in different classes are respectively subjected to clustering analysis, so the hot cluster of each class is obtained, the feature word representing the hot event is obtained through further analysis, and then the word property and other aspects of each feature word are analyzed; the description of each hot event is generated by utilizing relevant language knowledge and necessary linguistic organization. With the network hot event detection method based on text classification and clustering analysis, the detection efficiency and accuracy rate of hot events can be effectively improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method for sorting and processing internet public feelings information
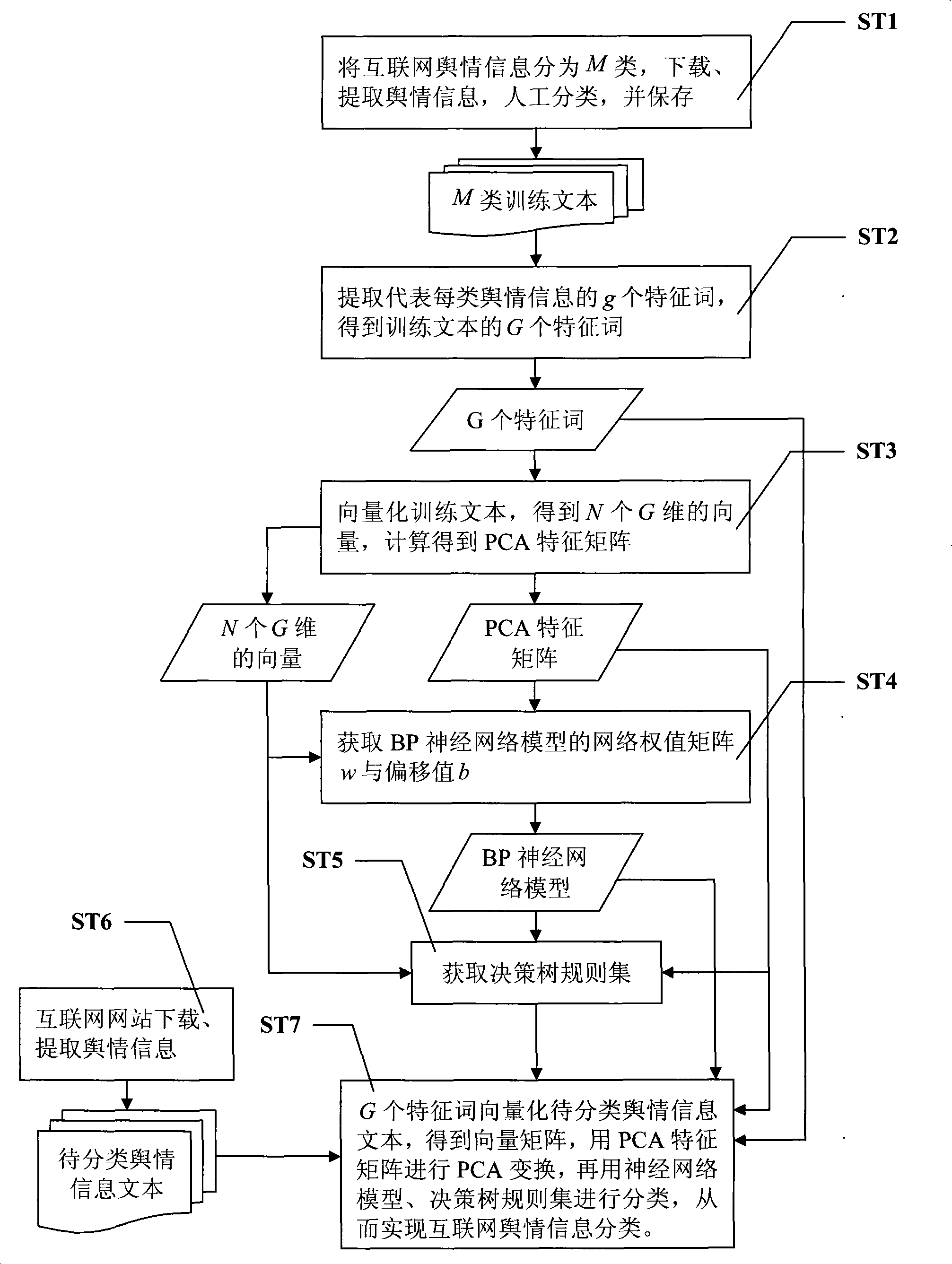
InactiveCN101414300ASolve the shortcomings of inaccurate classificationReduce dimensionalityPhysical realisationSpecial data processing applicationsAlgorithmCharacteristic space
The invention discloses a classified processing method of internet public information. The method comprises the following steps: selecting a classified public information text as a training text, and parsing words; selecting and screening nouns and verbs, acquiring feature words by extraction, vectorizing the training text, then acquiring a PCA transformation feature matrix, a BP neural network model, and a decision tree rule; performing dimension reduction on vectors of the vector matrix of the public information text to be classified by the PCA transformation feature matrix, and transforming the vectors by the BP neural network model to obtain an output vector which has the same number of dimensions as the classified number, and then performing matching by the decision tree rule, and determining that the public information text to be classified belongs to the public information category marked by the rule if the matching is successful. As the PCA transformation converts a feature word space related to a high dimension into a low-dimensional orthogonal feature space, the disadvantage of inaccurate classification is solved; meanwhile, the decision tree rule is used for classification without data similarity comparison so that a plurality of data sources can be processed in a short time.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Wavelet-based clustering method for managing spatial data in very large databases
InactiveUS6882997B1Successfully handleData processing applicationsDigital data processing detailsSatelliteWavelet transform
The method termed WaveCluster for mining spatial data. WaveCluster considers spatial data as a multidimensional signals and applies wavelet transforms, a signal-processing technique, to convert the spatial data into the frequency domain. The wavelet transforms produce a transformed space where natural clusters in the data become more distinguishable. The method quantizes a feature space to determine cells of the feature space, assigns objects to the cells, applies a wavelet transform on the quantized feature space to obtain a transformed feature space, finds connected clusters in sub bands at different levels of the transformed feature space, assigns labels to the cells, creates a look-up table, and maps the objects to the clusters. The method can manage spatial data in a two-dimensional feature space. The method also is applicable to a feature space that is made up of an image taken by a satellite.
Owner:RES FOUND OF SUNY AT BUFFALO THE
Graph-based framework for video object segmentation and extraction in feature space
ActiveUS20160379055A1Reducing inter-class connectivityComparable and good performanceCharacter and pattern recognitionTemporal informationGraphics
A method for graph-based spatiotemporal video segmentation and automatic target object extraction in high-dimensional feature space includes using a processor to automatically analyze an entire volumetric video sequence; using the processor to construct a high-dimensional feature space that includes color, motion, time, and location information so that pixels in the entire volumetric video sequence are reorganized according to their unique and distinguishable feature vectors; using the processor to create a graph model that fuses the appearance, spatial, and temporal information of all pixels of the video sequence in the high-dimensional feature space; and using the processor to group pixels in the graph model that are inherently similar and assign the same labels to them to form semantic spatiotemporal key segments.
Owner:KODAK ALARIS INC
System and method for analyzing a contour of an image by applying a sobel operator thereto
ActiveUS20050002570A1Accurate analysisImage enhancementImage analysisAngular degreesCharacteristic space
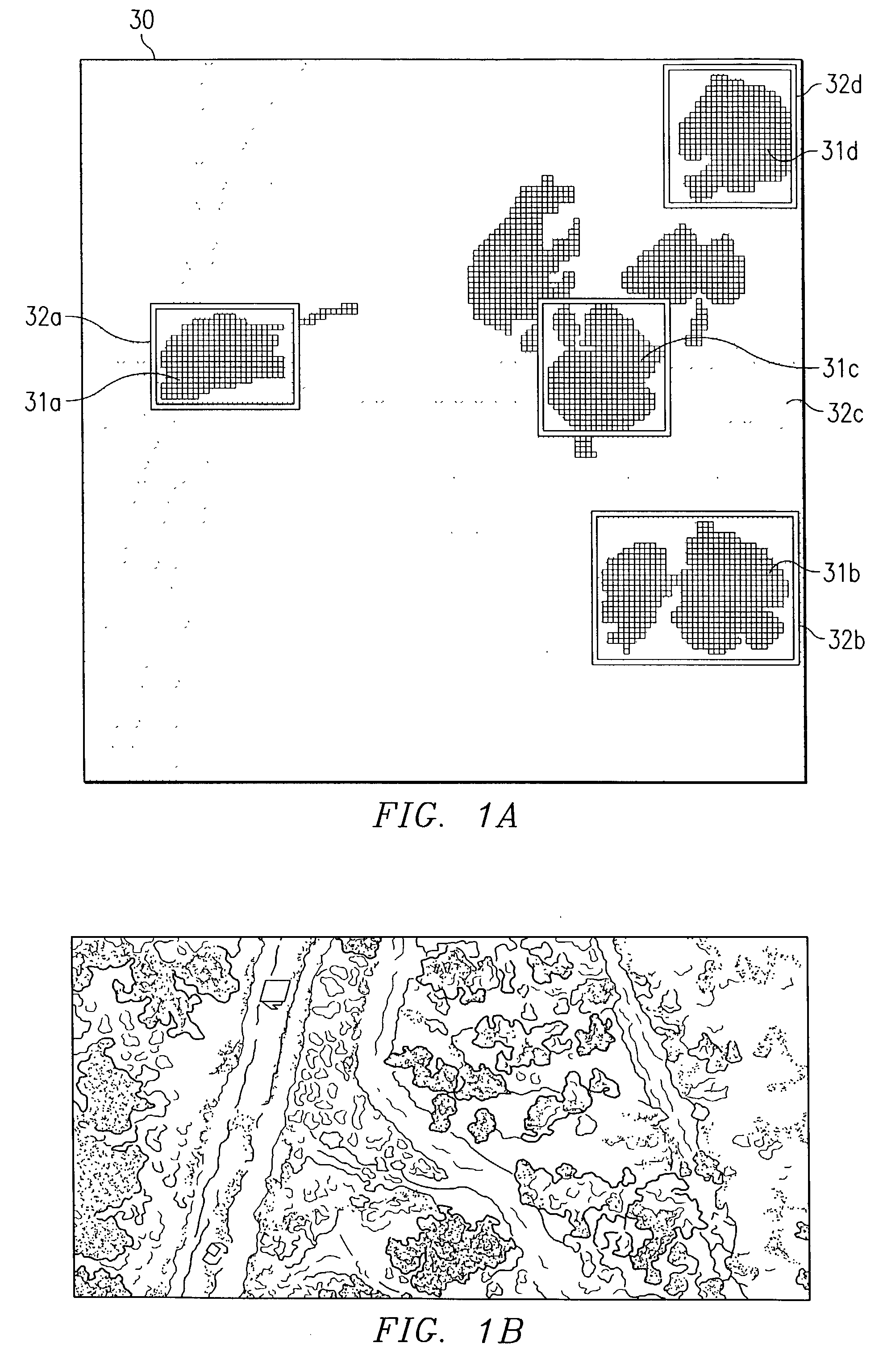
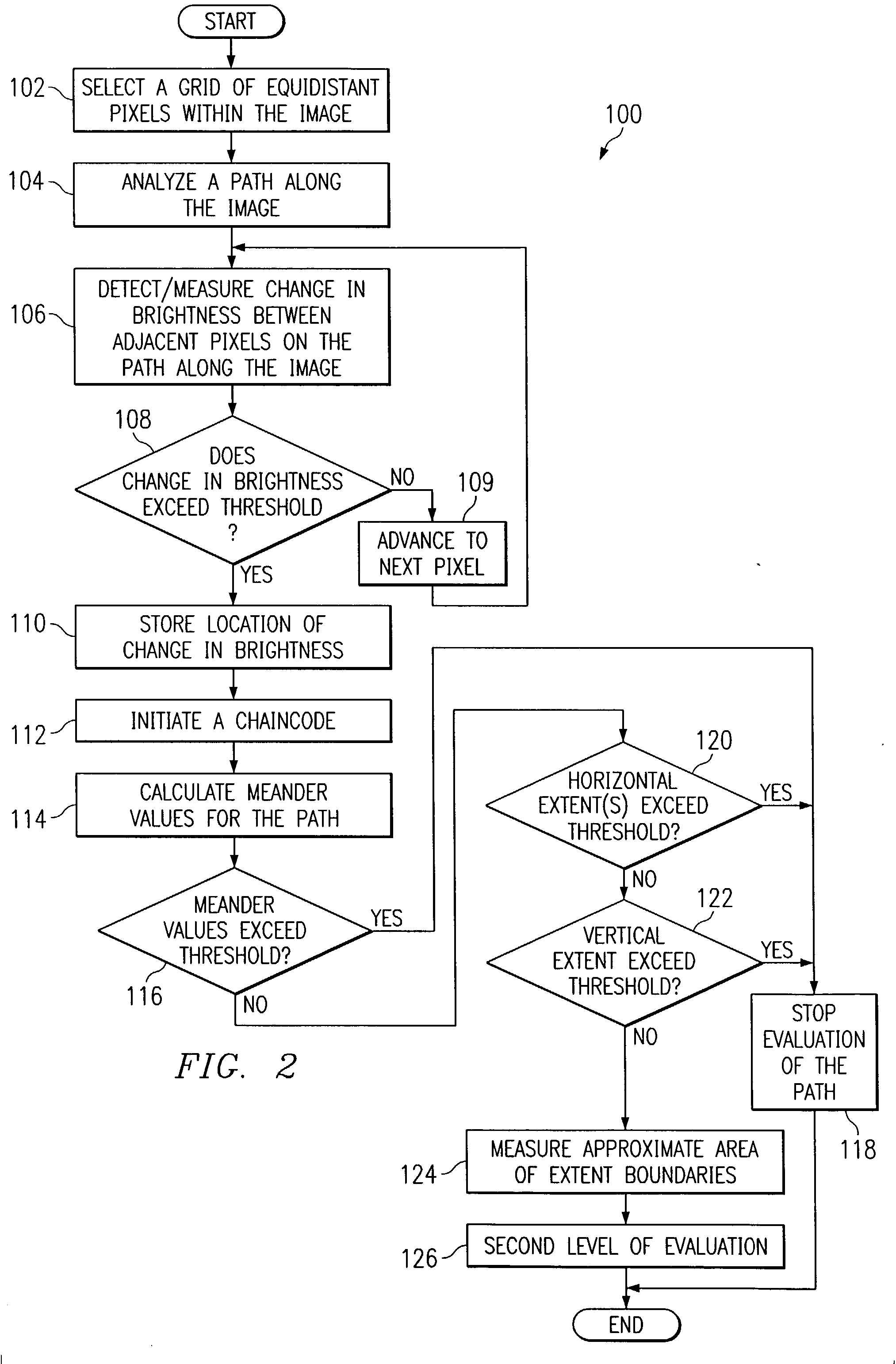
The present invention includes a method for analyzing an image wherein elements defining a path within a two-dimensional image are received from a prescreener. A Sobel operator may be applied to the region around each of the elements of the chain to obtain a corresponding array of gradient directions. An angle correction may be applied to any of the gradient directions that goes beyond the highest value (in radian measure; the Pi −Pi transition), to obtain an array of gradient directions free of any artificial jumps in value. The gradient direction array (Sobel chaincode) can have its bandwidth taken to determine a single number of straightness so as to identify extremely straight edges, (manmade objects) from less straight edges (natural objects). A similar process can be used to analyze contours for straight sections, which are also parallel. These two and other filters applied to the gradient array can be part of a feature suite, for feature space analysis.
Owner:NORTHROP GRUMMAN SYST CORP
System and method for vascular segmentation by Monte-Carlo sampling
InactiveUS7715626B2Reduce in quantityIssue to overcomeImage enhancementImage analysisCharacteristic spaceDigital image
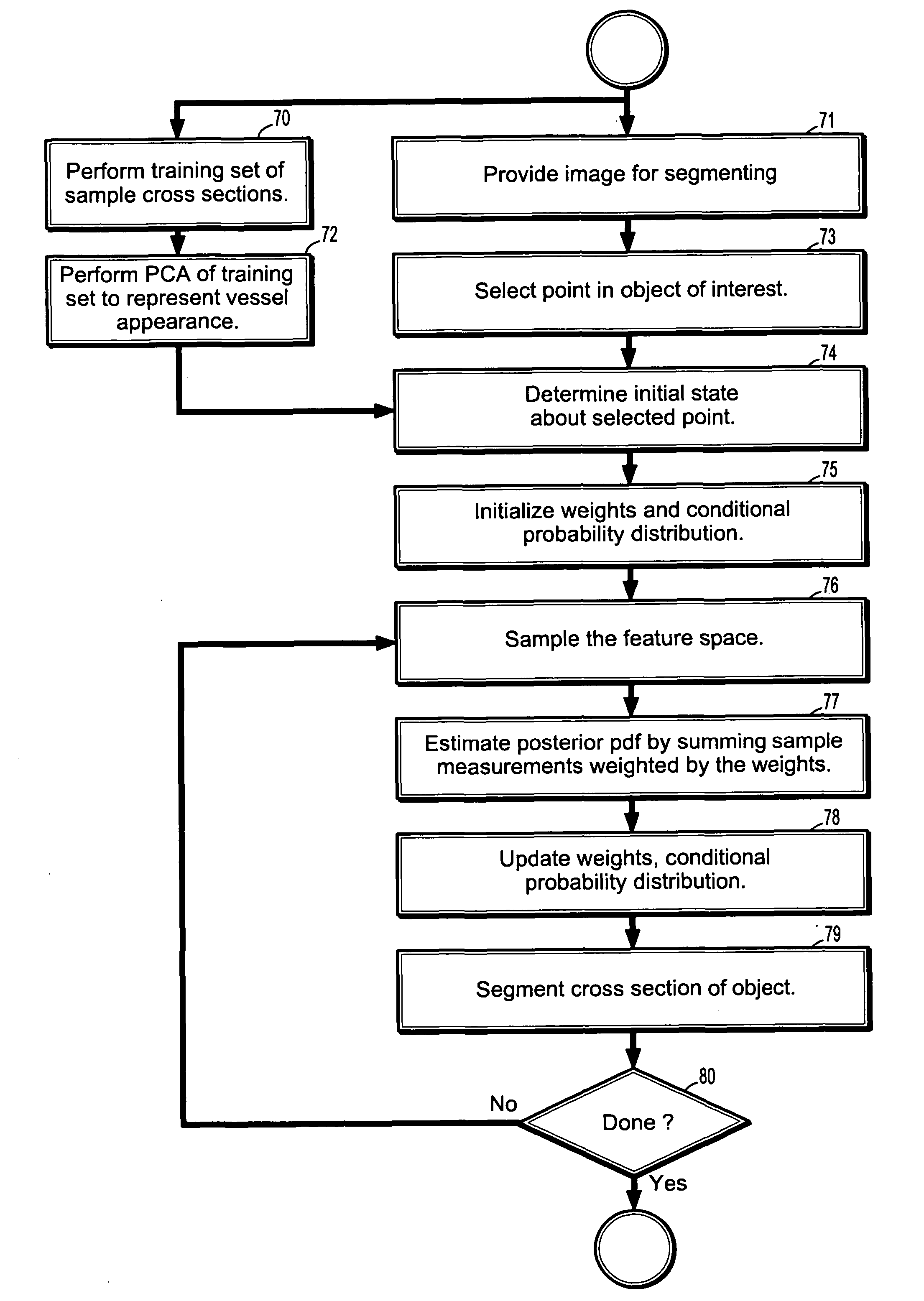
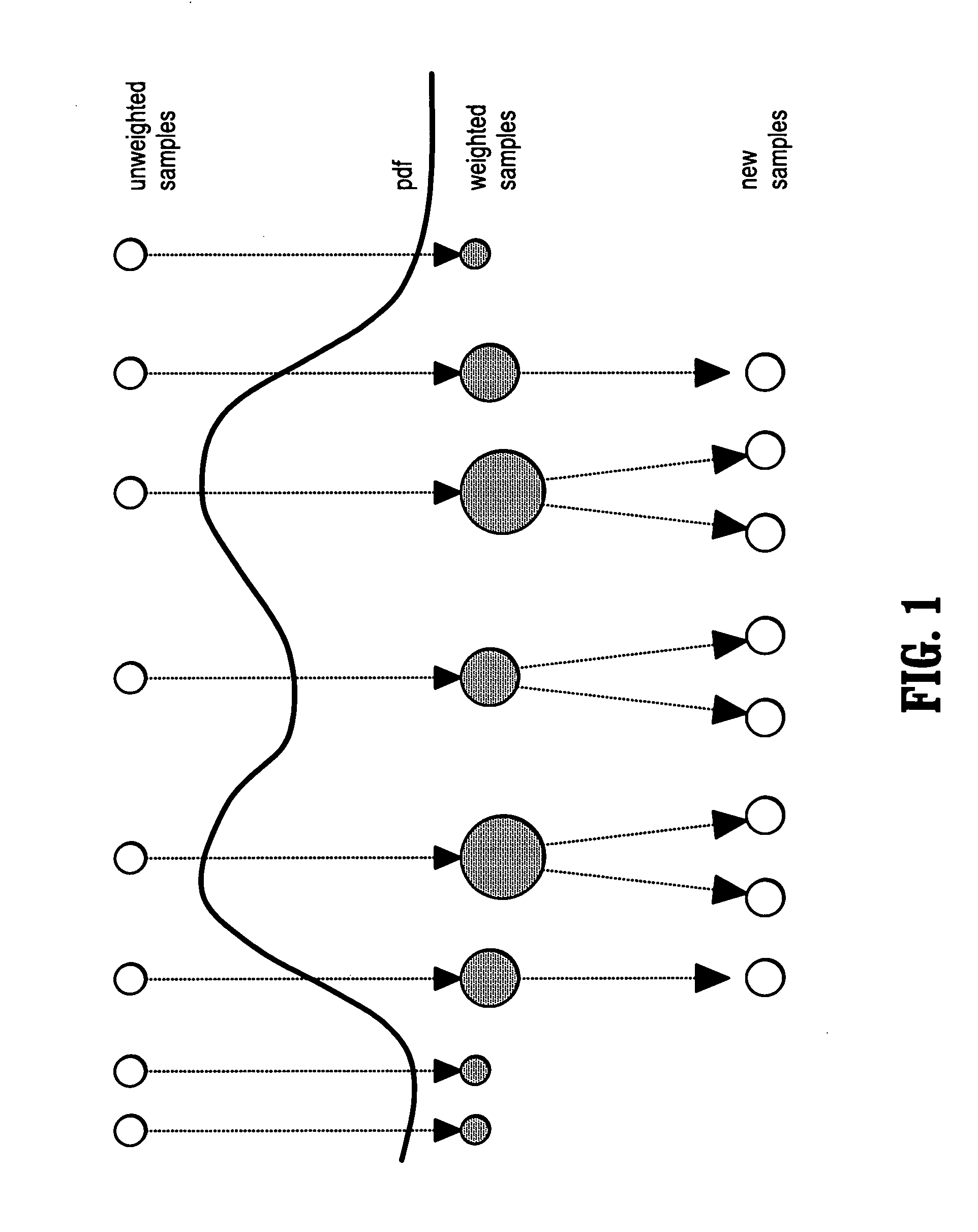
A method of segmenting tubular structures in digital images includes selecting a point in an image of a tubular object to be segmented, defining an initial state of the selected point, initializing measurement weights, a conditional probability distribution and a prior probability distribution of a feature space of the initial state, sampling the feature space from the prior probability distribution, estimating a posterior probability distribution by summing sample measurements weighted by the measurement weights, and segmenting a cross section of the tubular object from the posterior probability distribution.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
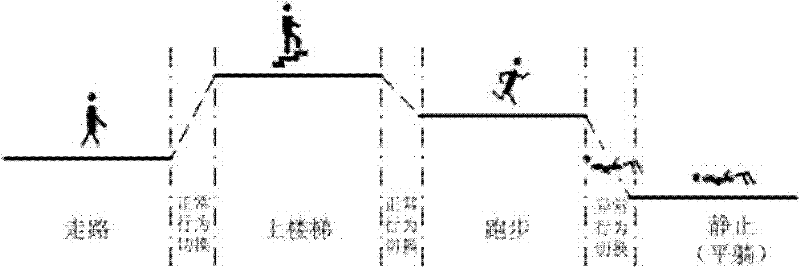
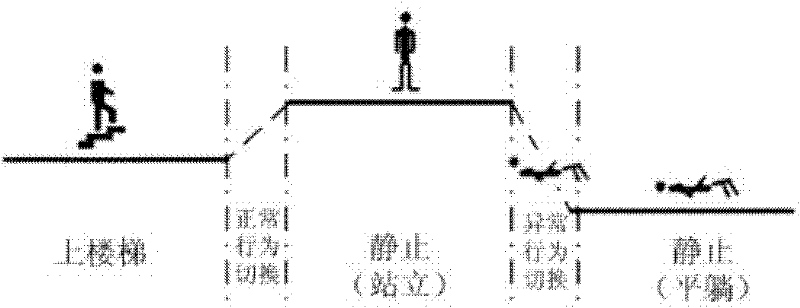
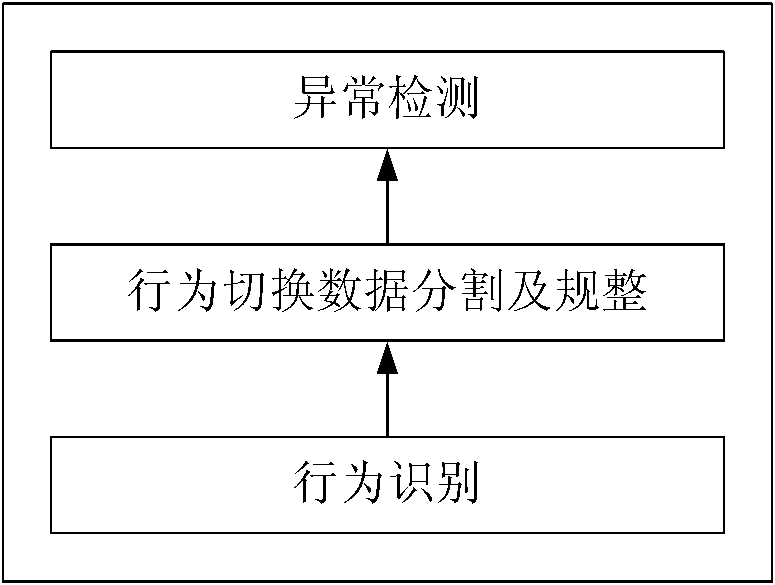
Method and device for detecting tumbling
ActiveCN102302370AReduce complexityEffective filteringDiagnostic recording/measuringSensorsFeature vectorCharacteristic space
The invention provides a method and device for detecting tumbling. The method provided by the invention comprises the steps of: firstly, collecting behavioral data of a user; secondly, identifying behavior of the user according to the behavioral data of the user; thirdly, segmenting out behavioral switching data from the collected data according to a behavioral identification result, and warping the behavioral switching data into equilong characteristic vectors; and fourthly, performing tumbling detection according to the warped characteristic vectors. According to the method and device provided by the invention, tumbling detection is performed on the basis of behavioral switching, a great amount of normal behavioral data can be filtered, the complexity of a feature space is reduced, the separating capacity of models is enhanced, and the model detection rate is improved.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
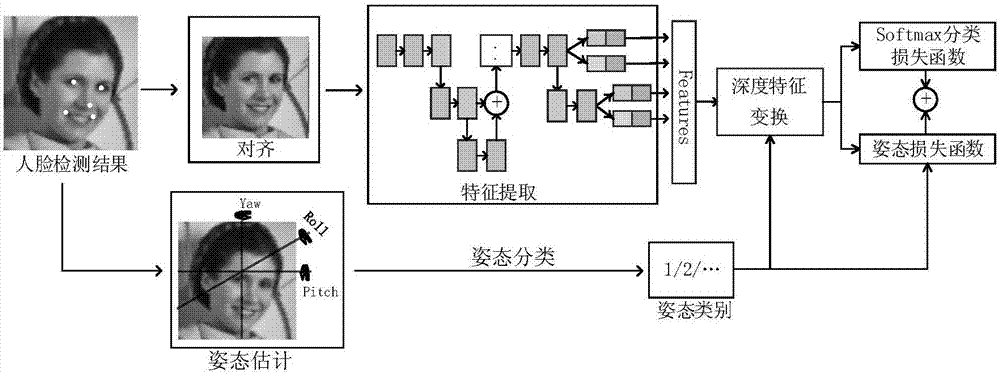
Face recognition method based on deep transformation learning in unconstrained scene
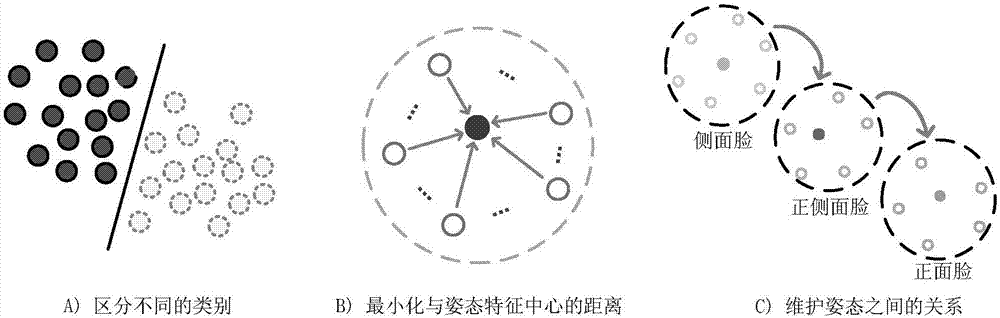
ActiveCN107506717AEnhancing Feature Transformation LearningImprove robustnessCharacter and pattern recognitionNeural learning methodsCrucial pointCharacteristic space
The invention discloses a face recognition method based on deep transformation learning in an unconstrained scene. The method comprises the following steps: obtaining a face image and detecting face key points; carrying out transformation on the face image through face alignment, and in the alignment process, minimizing the distance between the detected key points and predefined key points; carrying out face attitude estimation and carrying out classification on the attitude estimation results; separating multiple sample face attitudes into different classes; carrying out attitude transformation, and converting non-front face features into front face features and calculating attitude transformation loss; and updating network parameters through a deep transformation learning method until meeting threshold requirements, and then, quitting. The method proposes feature transformation in a neural network and transform features of different attitudes into a shared linear feature space; by calculating attitude loss and learning attitude center and attitude transformation, simple class change is obtained; and the method can enhance feature transformation learning and improve robustness and differentiable deep function.
Owner:唐晖
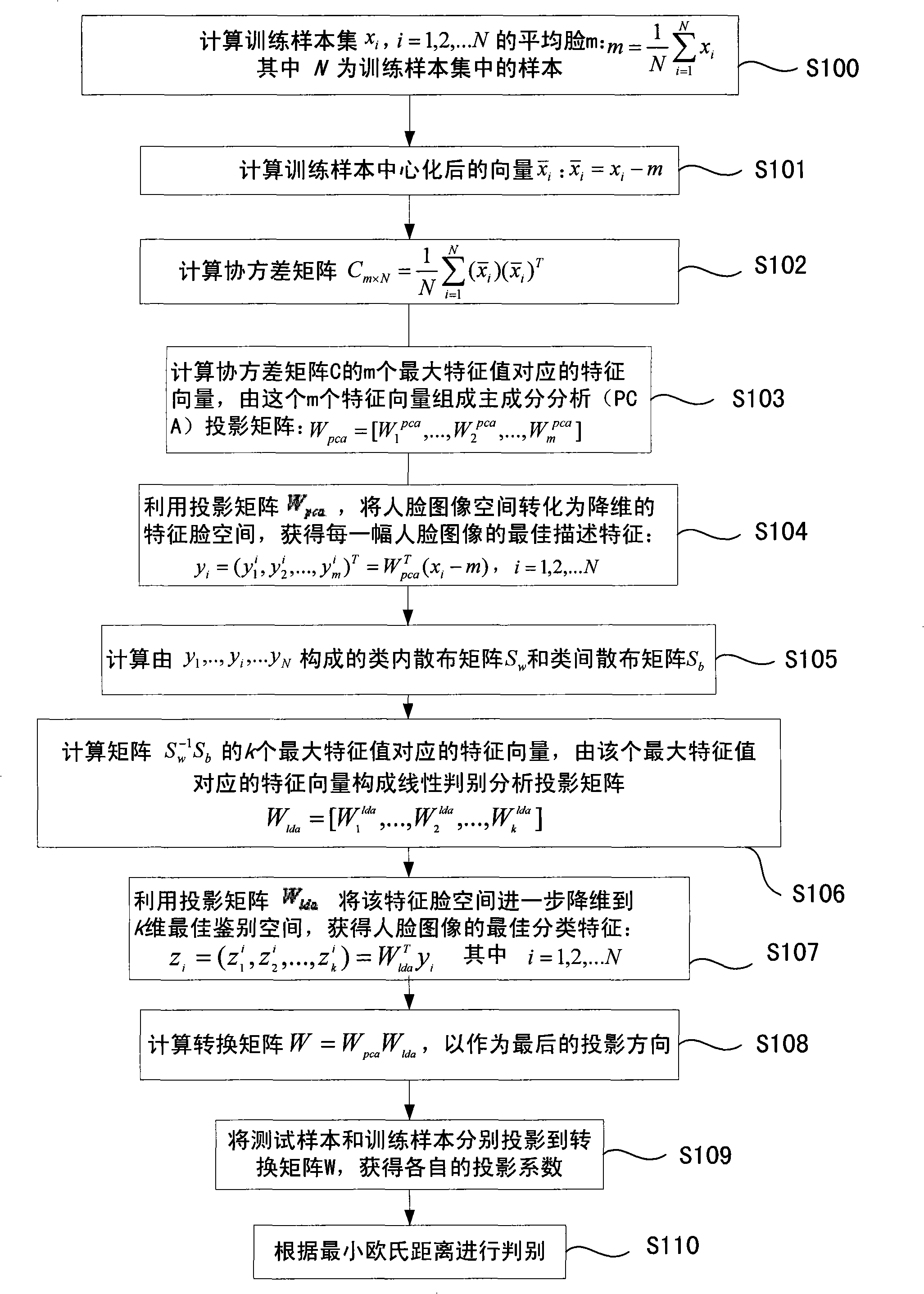
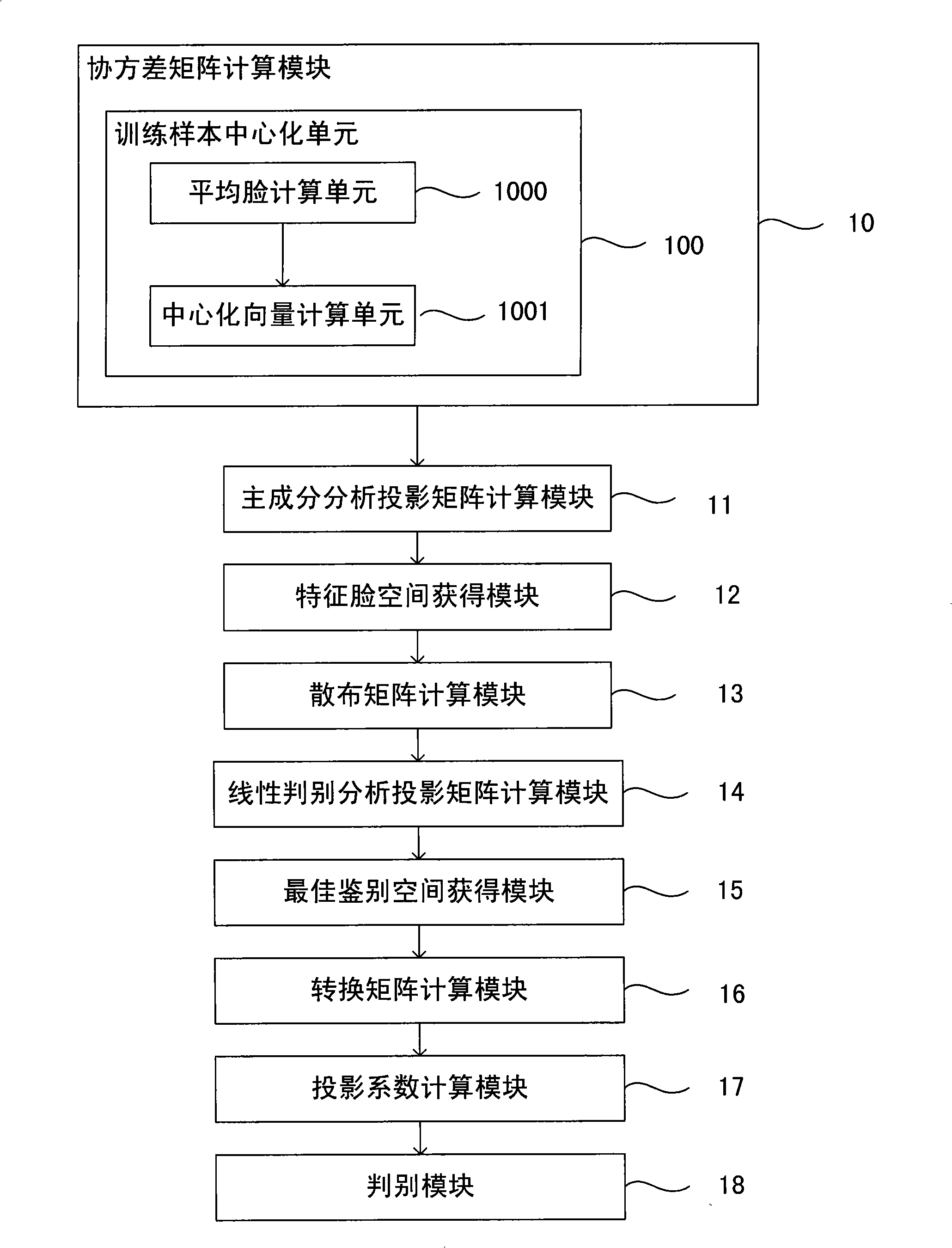
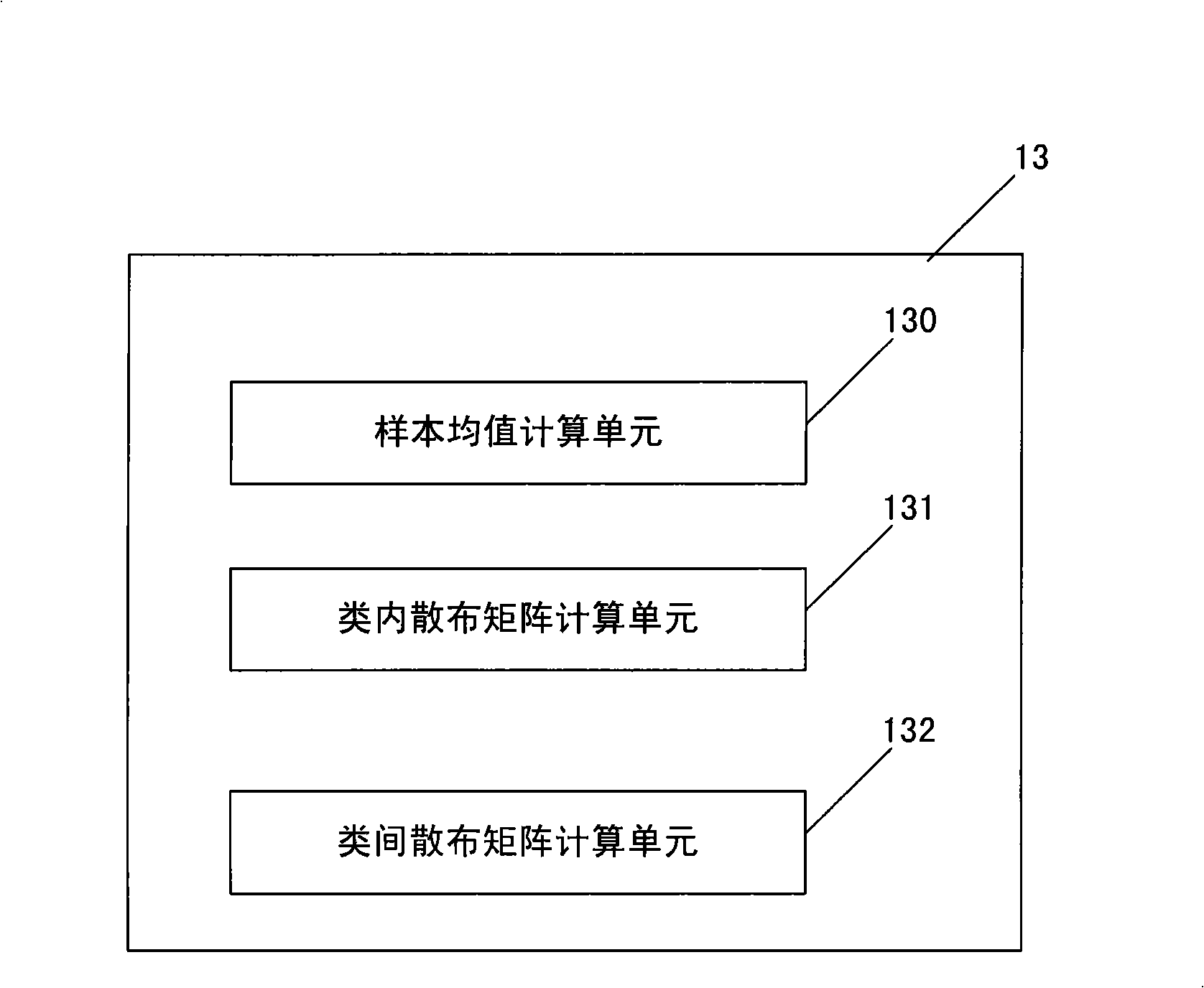
Optimized human face recognition method and apparatus
InactiveCN101329724AReduce dimensionalityImprove recognition rateCharacter and pattern recognitionPrincipal component analysisCharacteristic space
The invention discloses an optimized face recognition method and a device thereof, which improve the rate of facial image recognition. The technical proposal is that: the method and the device combine principal component analysis and linear discriminant analysis to solve the recognition problem; namely, the principal component analysis is carried out first before the conduction of the linear discriminant analysis so as to obtain relatively low dimensional space, then the space is utilized to carry out the linear discriminant analysis, and therefore, an intra-class dispersion matrix can not be caused and the process of the linear discrimination is effective. The invention firstly adopts the principal component analysis to obtain the best feature description, based on which, optimum identifying features are obtained by adopting the linear discriminant analysis, thereby greatly reducing the space dimension of facial features; finally, a minimum distance method is adopted to carry out classification and identification and therefore the rate of recognizing human faces is evidently increased. The method and the device of the invention are applied to face recognition.
Owner:上海天冠卫视技术研究所 +1
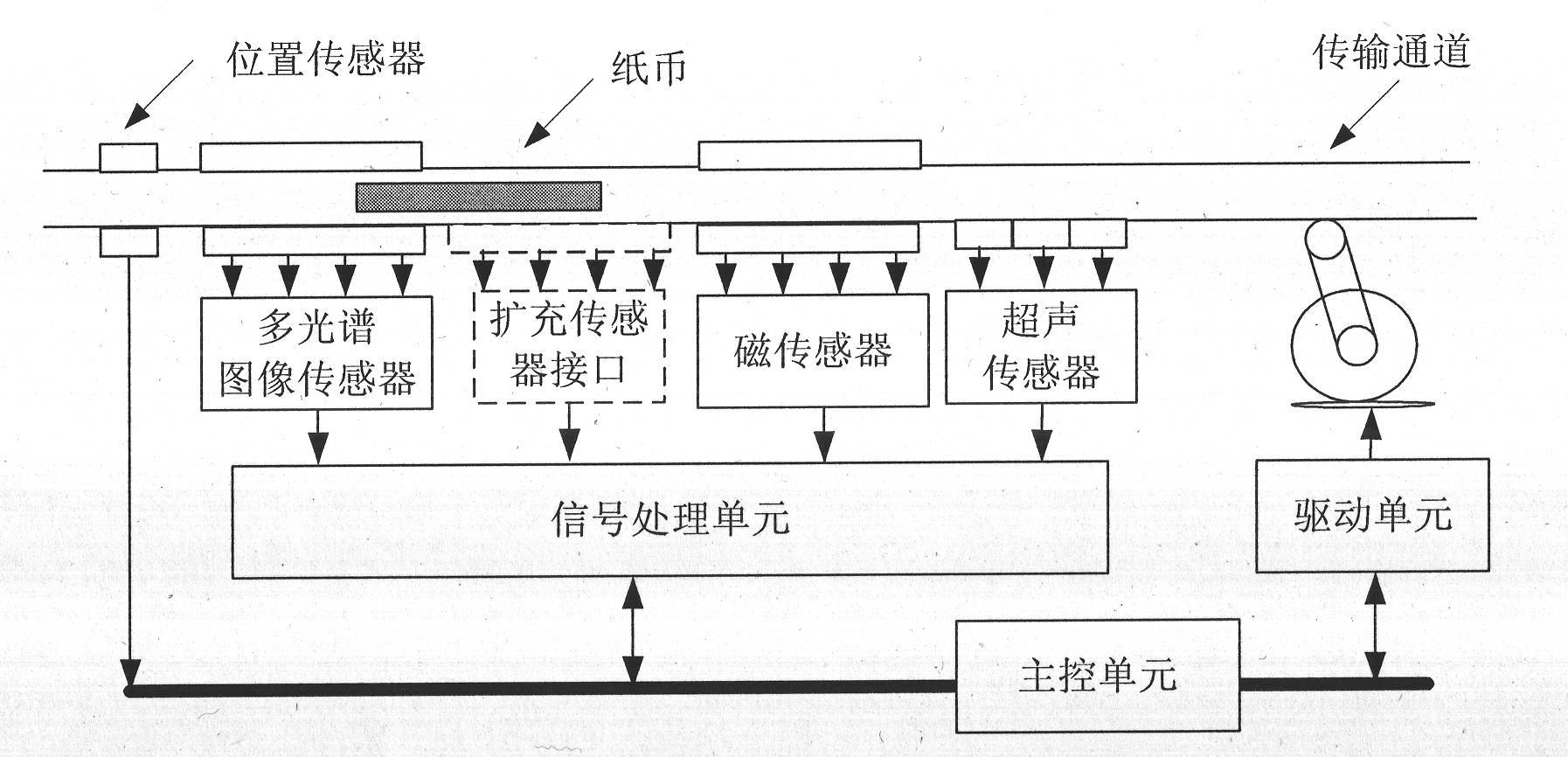
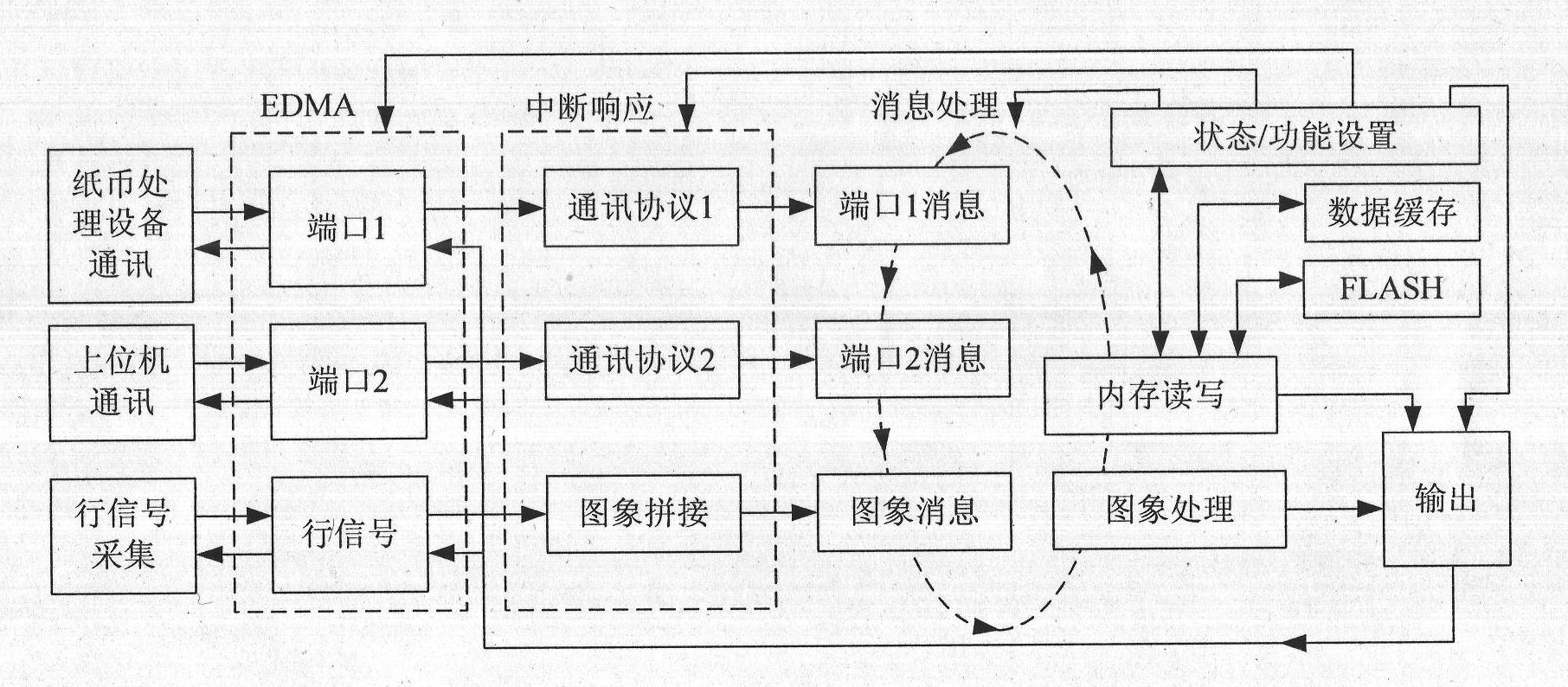
Method and device for distinguishing false money by imaging paper money through multimodal information fusion
InactiveCN102136166ARealize acquisitionImplement refactoringCoin testingPaper-money testing devicesAlgorithmSimulation
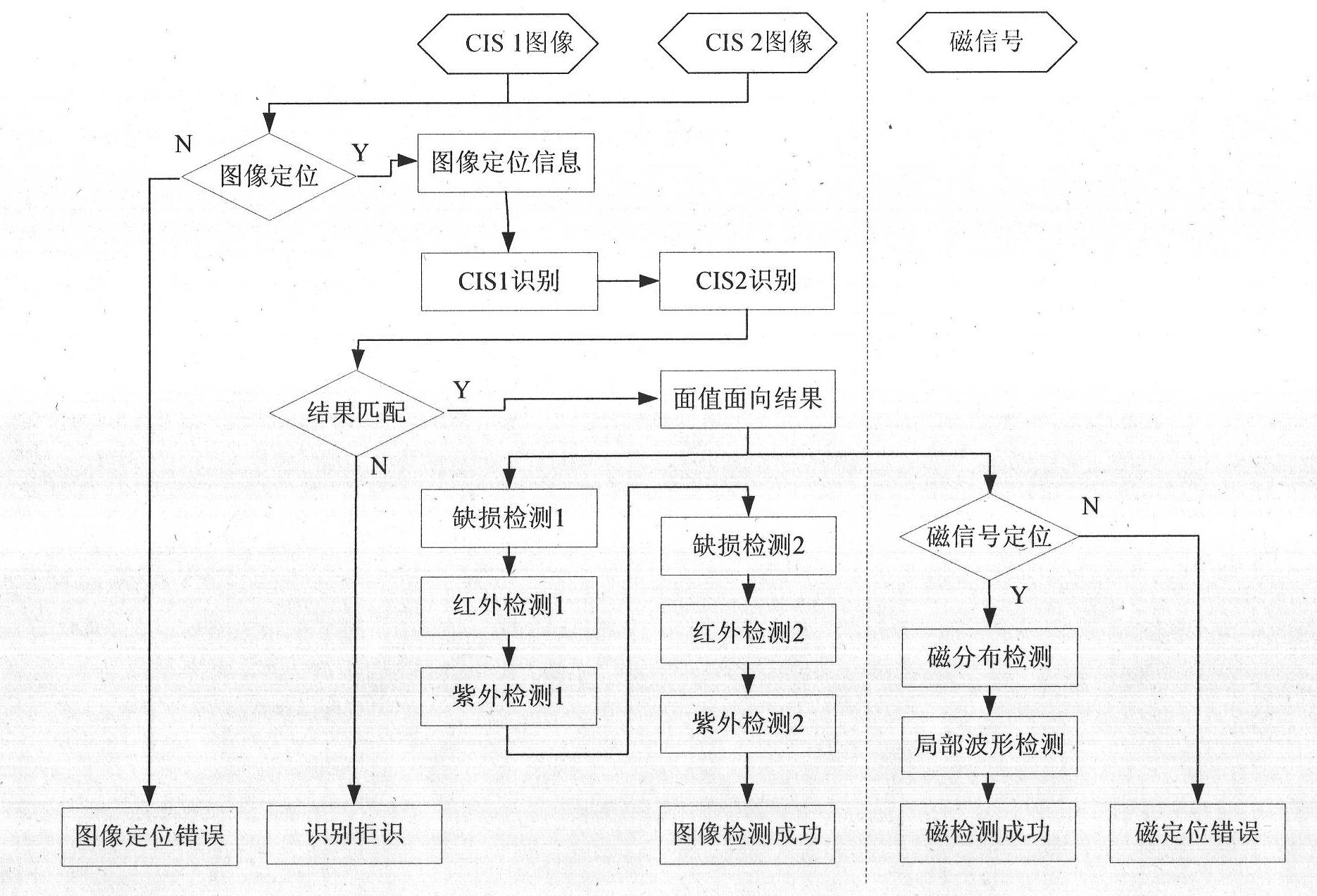
The invention provides a method and a device for distinguishing false money by imaging paper money through multimodal information fusion, which overcome the limitation of the conventional method and achieve high reliability. The device for distinguishing the false money by imaging the paper money through the multimodal information fusion consists of a sensor, a signal processing unit, a master control unit, a driving unit and a transmission passage, wherein the master control unit is connected with the position sensor, the signal processing unit and the driving unit respectively; and the driving unit is connected with the transmission passage. The method comprises the following steps of: acquiring the multimodal characteristics of the paper money; fitting the process that a person senses the false distinguishing characteristics of the paper money by a plurality of characteristic extracting methods, and constructing a multimodal characteristic space; and using a targeted matching and comparing algorithm for different anti-counterfeiting characteristics. By using the method and the device, paper money stained damage and anti-counterfeiting characteristic abnormality are distinguished according to a model, and by a multi-classifier fusion method, the limitation of the conventional method is effectively overcome, and the false paper money distinguishing with high reliability is realized.
Owner:HARBIN INST OF TECH
Agricultural drought grade monitoring method based on temperature vegetation drought index (TVDI)
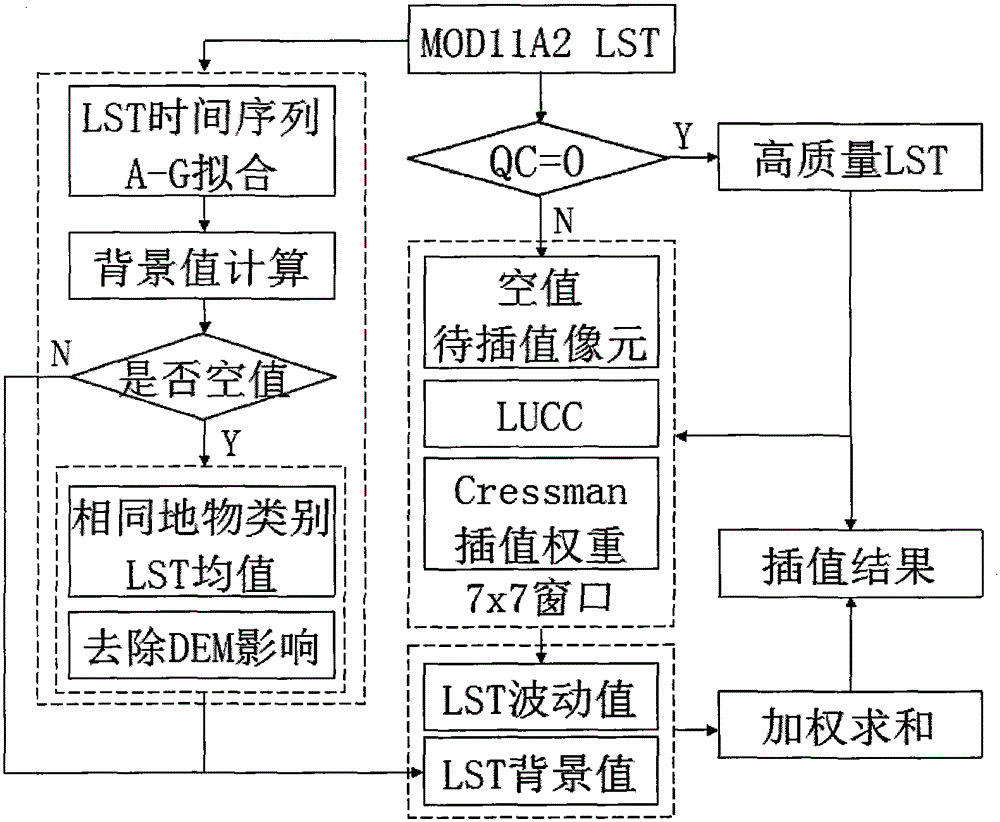
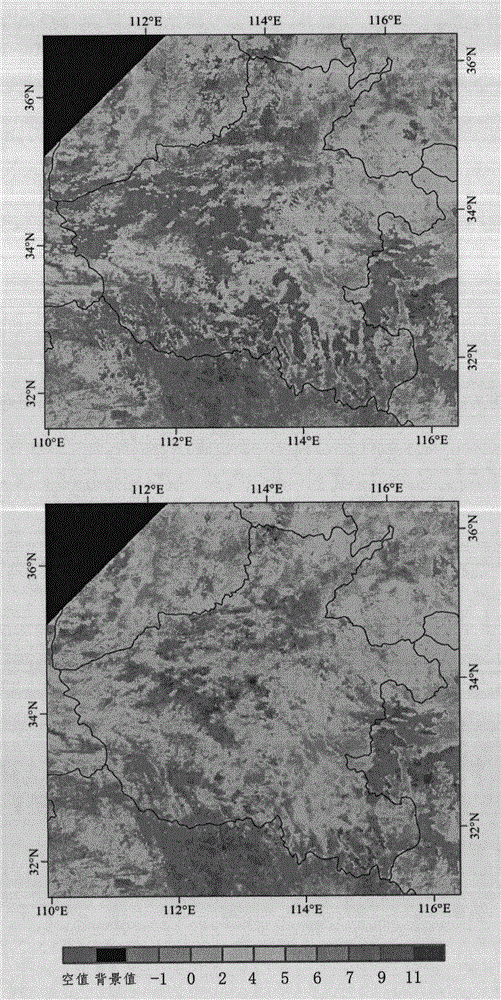
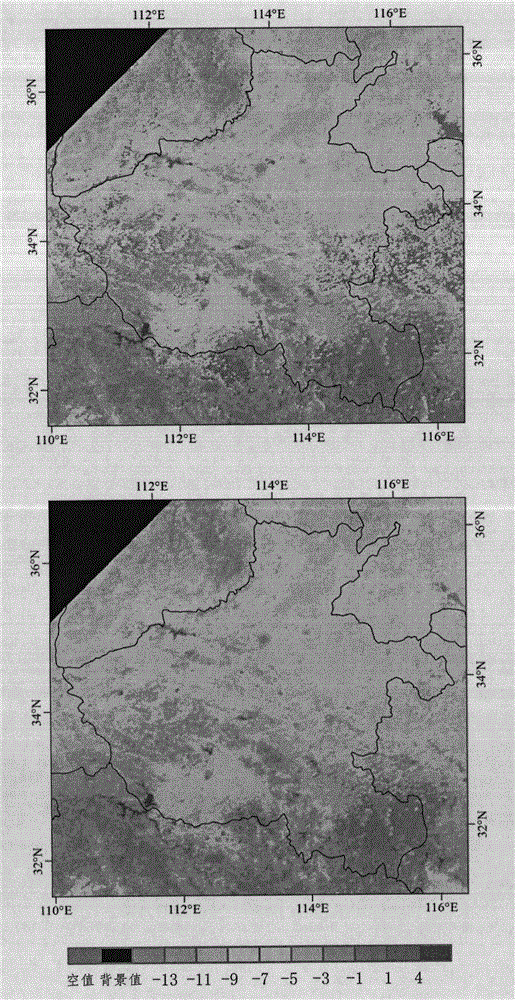
The invention discloses an agricultural drought grade monitoring method based on a temperature vegetation drought index (TVDI). The method comprises the following steps of: 1, data preparation; 2, land surface temperature (LST) data reconstruction; 3, construction of crop plantation area normalized difference vegetation index-land surface temperature (NDVI-LST) feature space; 4, TVDI calculation; and 5, drought grade monitoring based on the TVDI. The invention brings forward an LST data reconstruction method based on multi-year background values and area fluctuation values, a cultivated land area multi-year NDVI-LST feature space is constructed for crops, the TVDI is calculated, a crop drought grade monitoring model based on a supervision classification idea is designed for drought grade remote sensing monitoring, the model can quite accurately reflect drought threat degrees of the crops under difference conditions in real time, and the method has great significance in monitoring, early warning and prevention of agricultural disasters.
Owner:BEIJING NORMAL UNIVERSITY +1
Target detection performance optimization method
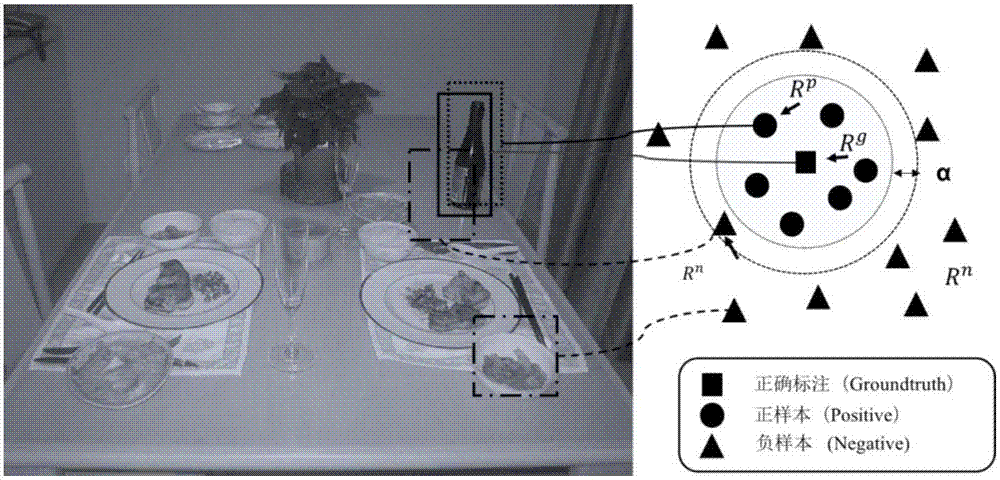
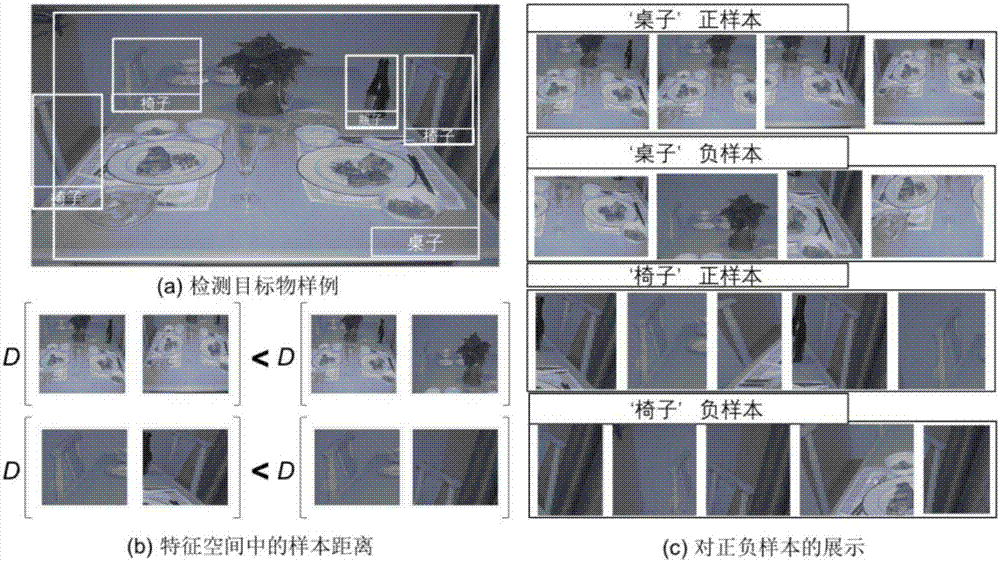
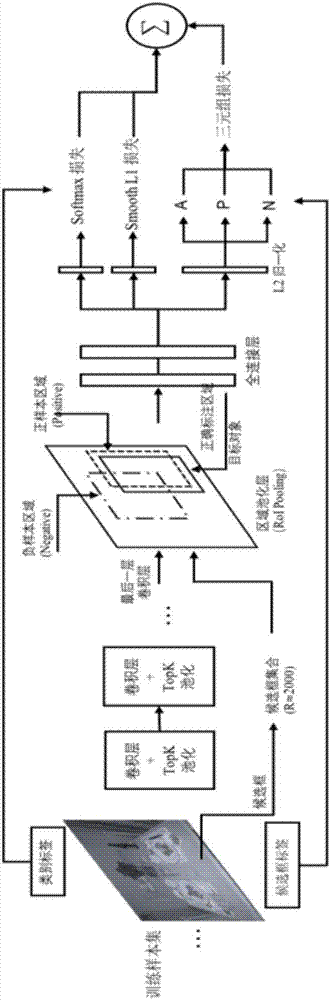
ActiveCN106934346AEasy to detectEasy characteristic distributionCharacter and pattern recognitionNeural architecturesCharacteristic spaceErrors and residuals
The invention discloses a target detection performance optimization method. The method comprises the steps that in the training process of a detection model, metric learning is used for adjusting distribution of samples in a characteristic space to generate characteristics with higher discrimination; a deep neural network corresponding to metric learning is in iteration training, and a candidate box used in each iteration is determined through united overlapping of IoU information and has the positional relation that identical target object distances meet a certain constraint condition and different target distances meet a certain constraint condition; whether the characteristics of a candidate box target generated in each turn of iteration training meet a similarity constraint condition or not is checked; if yes, the detection model does not generate loss in this iteration, and output errors corresponding to all layers in a reverse propagation network are not needed; and during testing, a picture to be detected and a candidate box set of the picture are input into the detection model obtained after training to obtain target object coordinate and category information output by the detection model. Through the method, detection capability can be improved, and detection performance can be optimized.
Owner:PEKING UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com