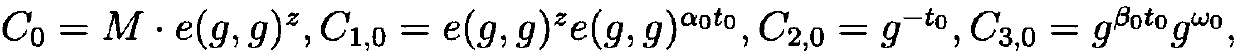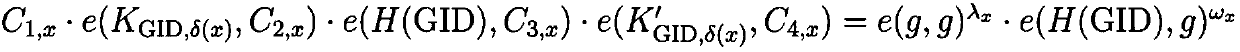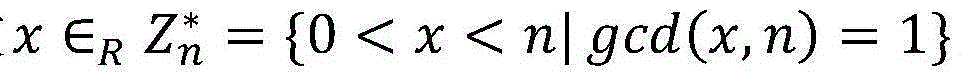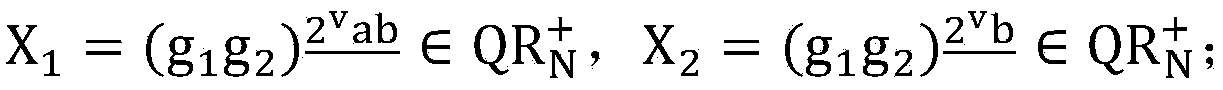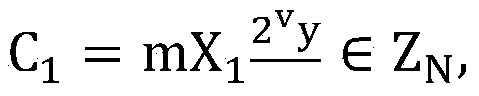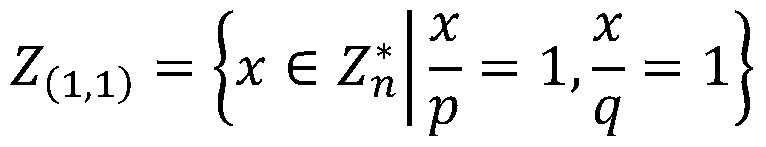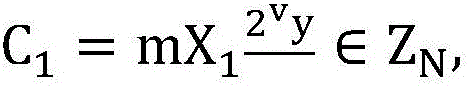Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Chosen-ciphertext attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A chosen-ciphertext attack (CCA) is an attack model for cryptanalysis where the cryptanalyst can gather information by obtaining the decryptions of chosen ciphertexts. From these pieces of information the adversary can attempt to recover the hidden secret key used for decryption.
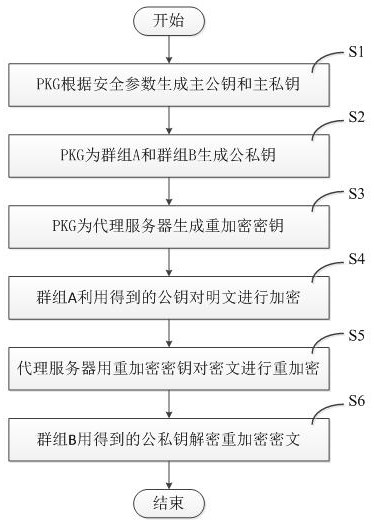
A method for realizing identity-based broadcast encryption by ciphertext-policy attribute-based encryption
ActiveCN104135473AShorten the development cycleReduce system loadPublic key for secure communicationPlaintextAttribute-based encryption
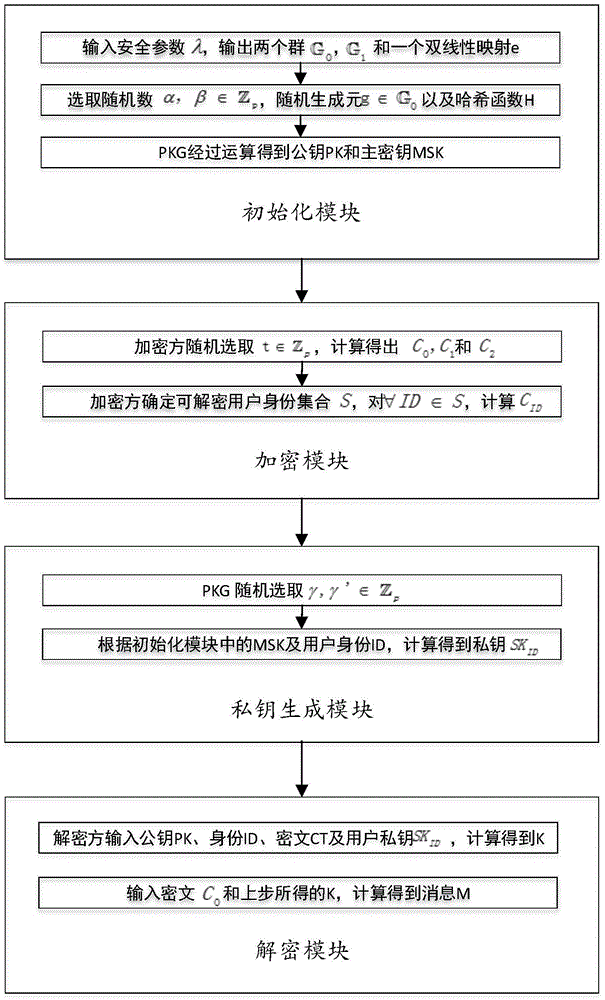
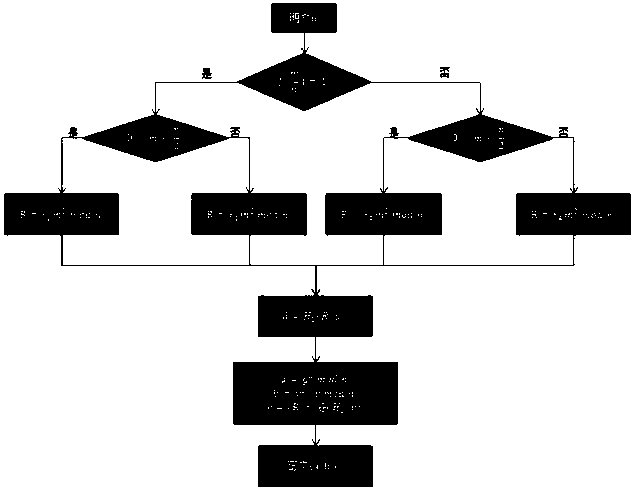
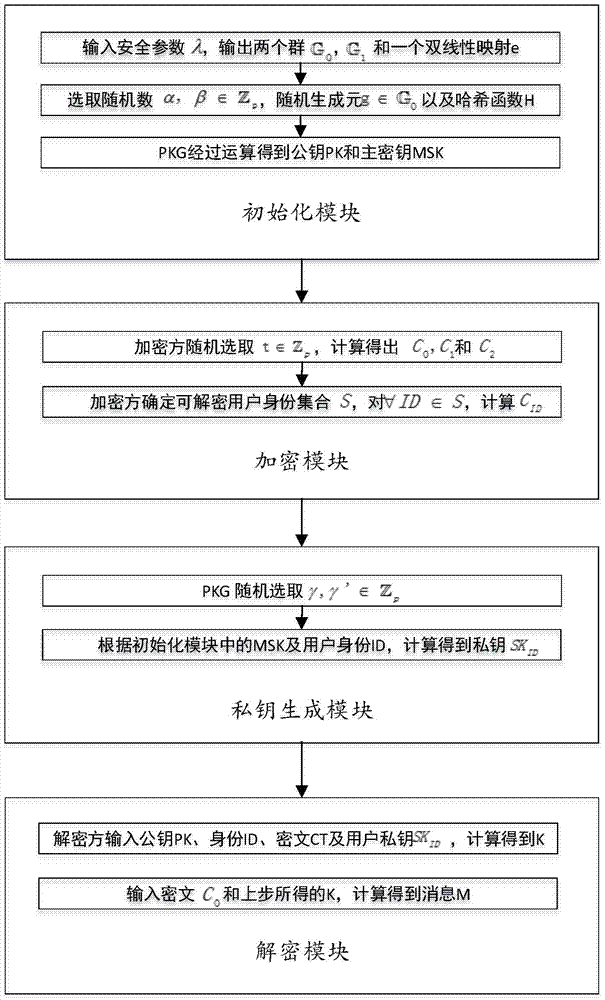
There is provided a method for realizing identity-based broadcast encryption by ciphertext-policy attribute-based encryption. The steps of the method are as follows: in step 1, a PKG (Private Key Generator) inputs a safety coefficient of a system to output an initialization parameter; in step 2, the PKG runs a random number generation algorithm to choose a random number required for the system; in step 3, the PKG executes operation to obtain a public key and a master secret key; in step 4, an encrypting party chooses the random number and completes operation to output a part of ciphertext; in step 5, the encrypting party executes calculation according to a set of identities of decrypting users to obtain the remaining part of the ciphertext; in step 6, the PKG runs a random number generation algorithm to obtain a random parameter; in step 7, the PKG executes calculation according to the master secret key and the identity of the user to obtain a private key SKID; in step 8, a decrypting party conforming to requirement is able to execute calculation according to the private key and the ciphertext to obtain K; and in step 9, the decrypting user is able to output correct plaintext by executing calculation according to the K. According to the invention, a development cycle and system load are reduced greatly, and chosen ciphertext attack can be resisted, which ensures safety and effectiveness of the scheme.
Owner:BEIHANG UNIV
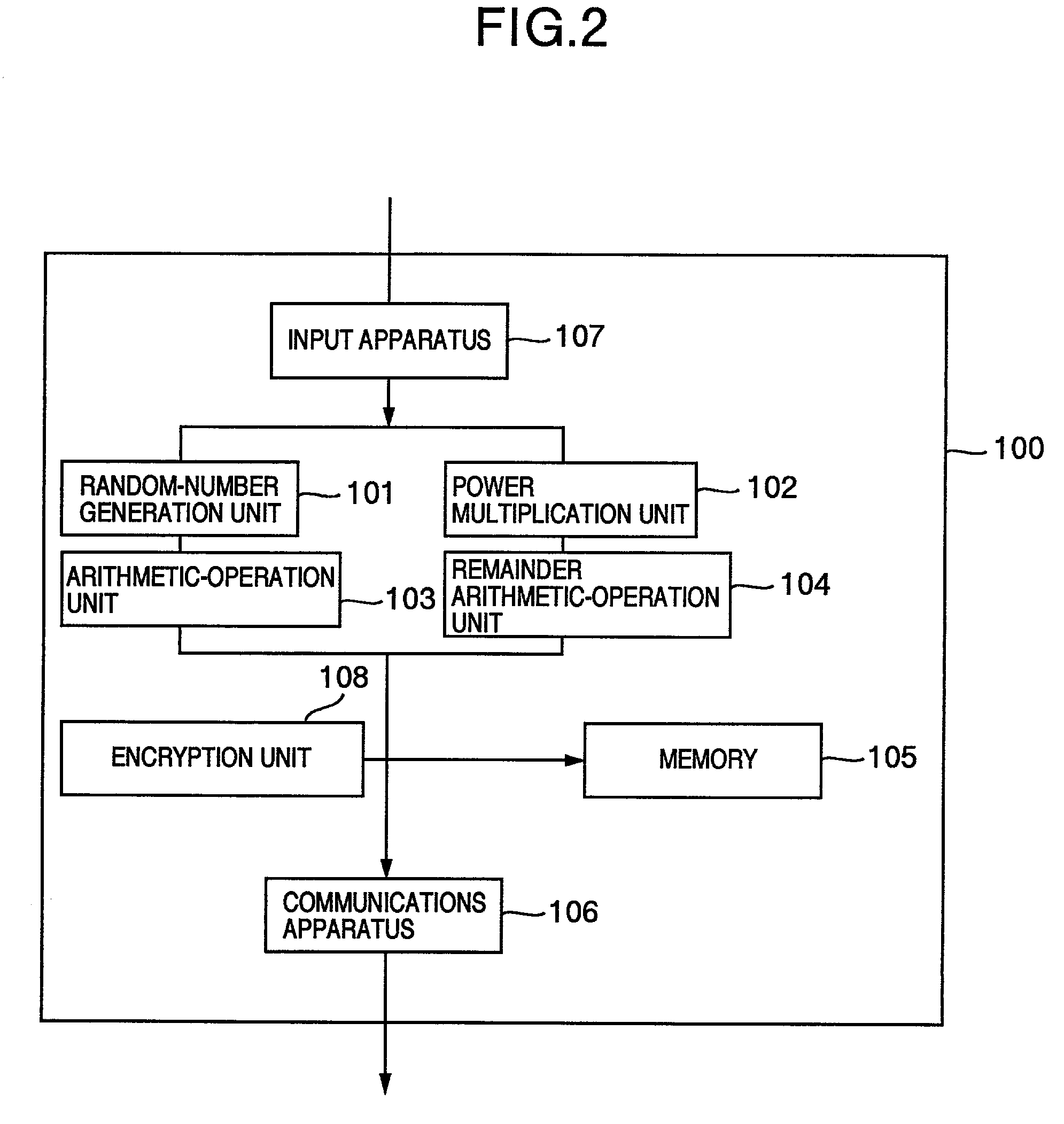
Method of a public key encryption and a cypher communication both secure against a chosen-ciphertext attack
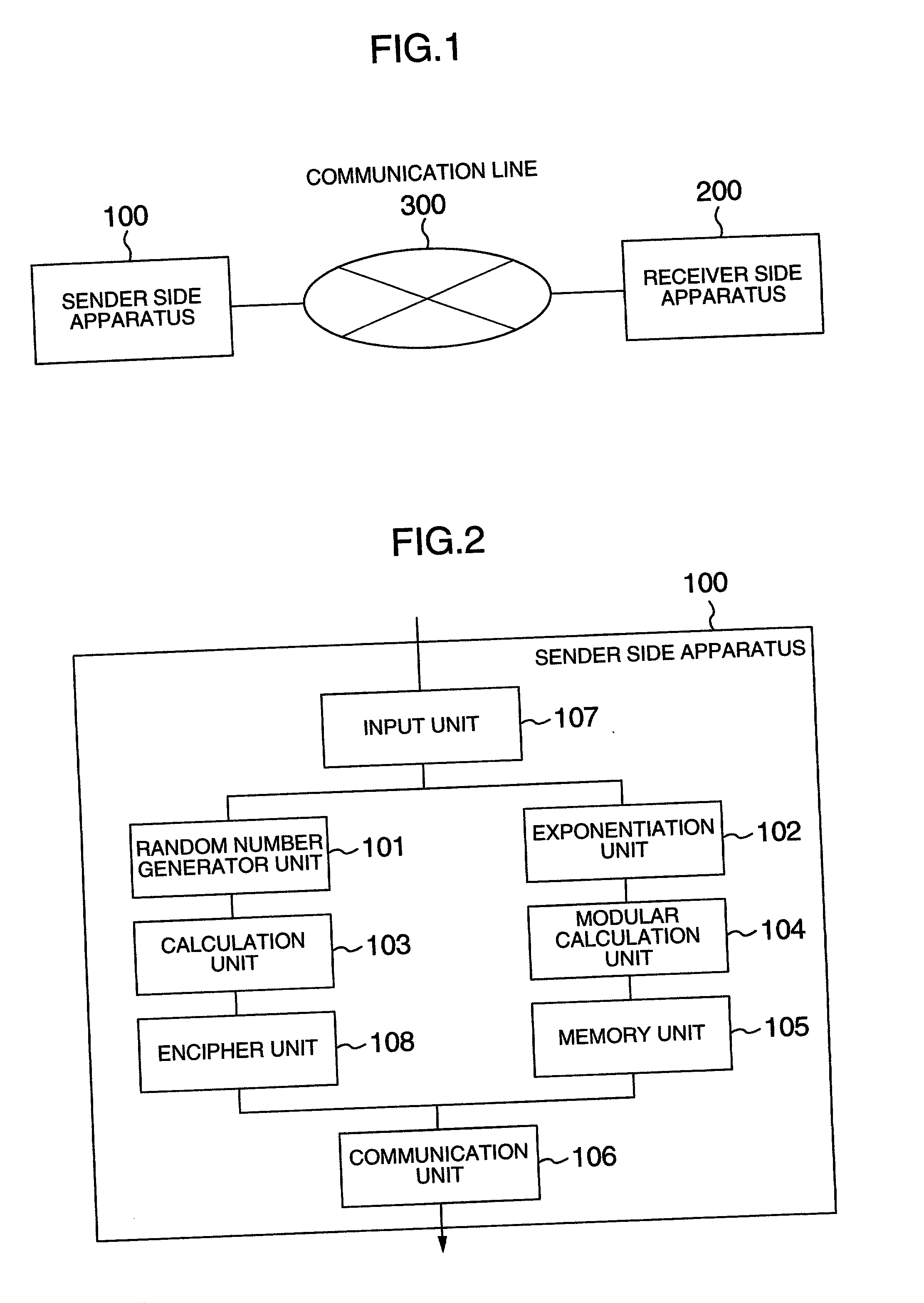
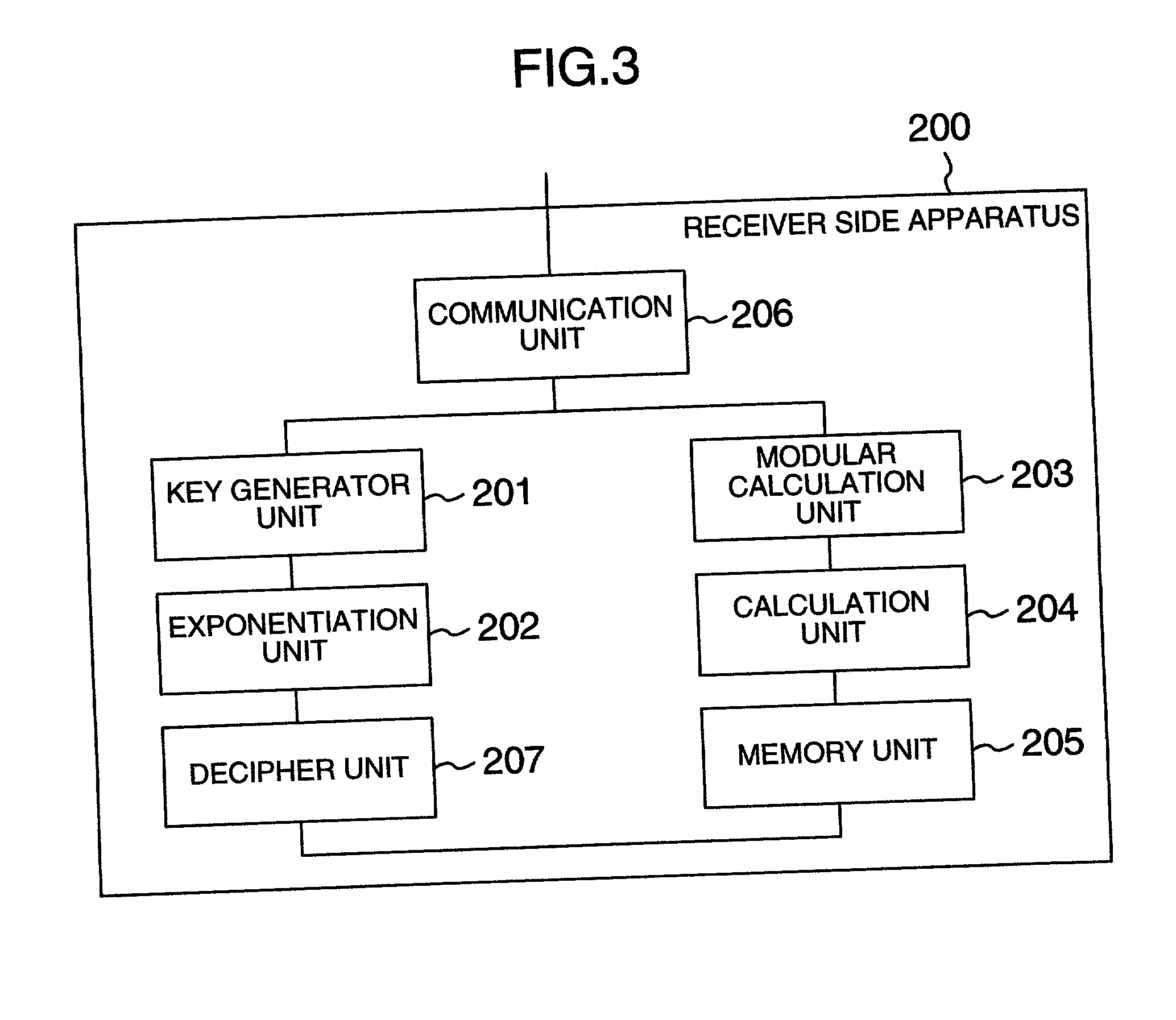
InactiveUS7164765B2High speed machiningSmall loadPublic key for secure communicationSecret communicationPlaintextChosen-ciphertext attack
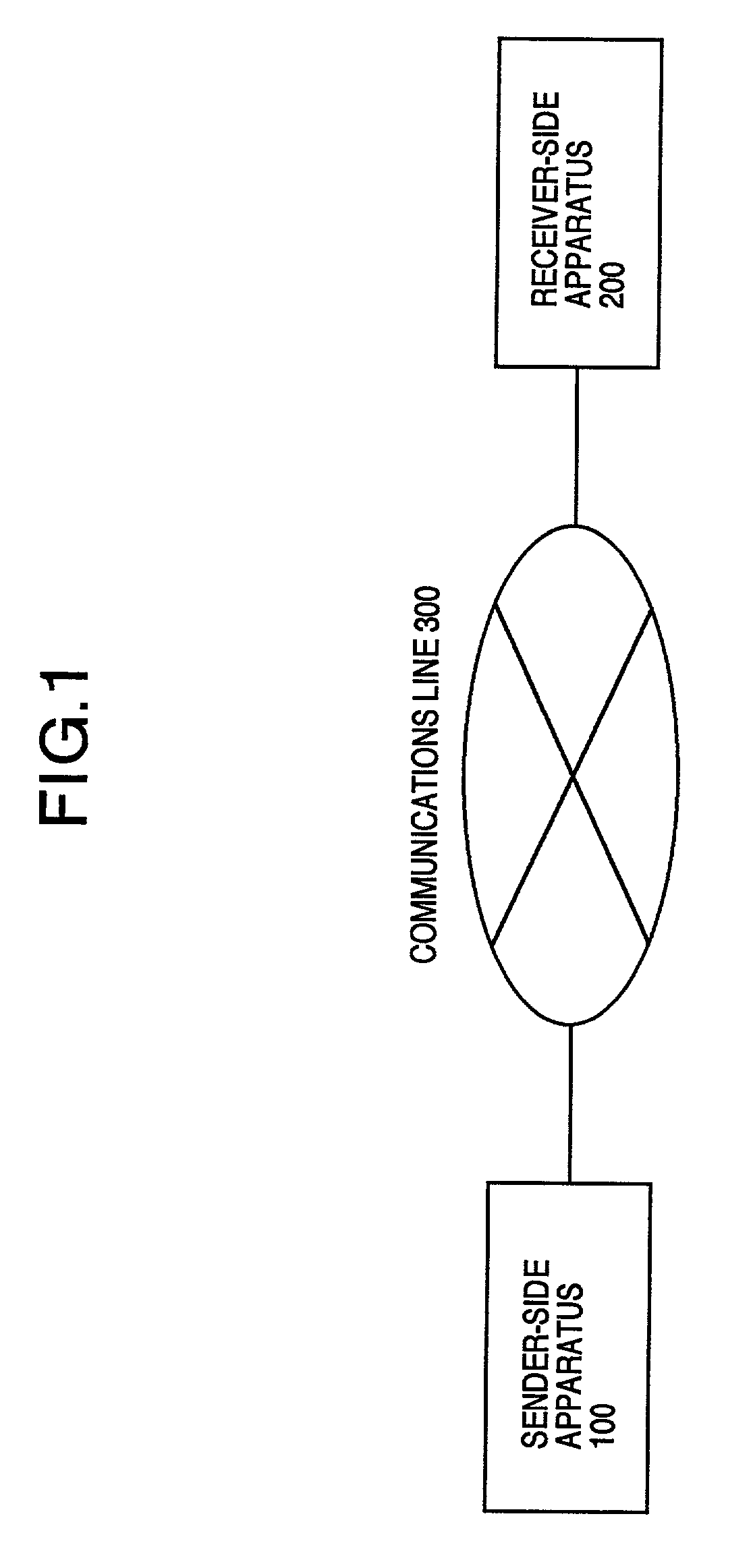
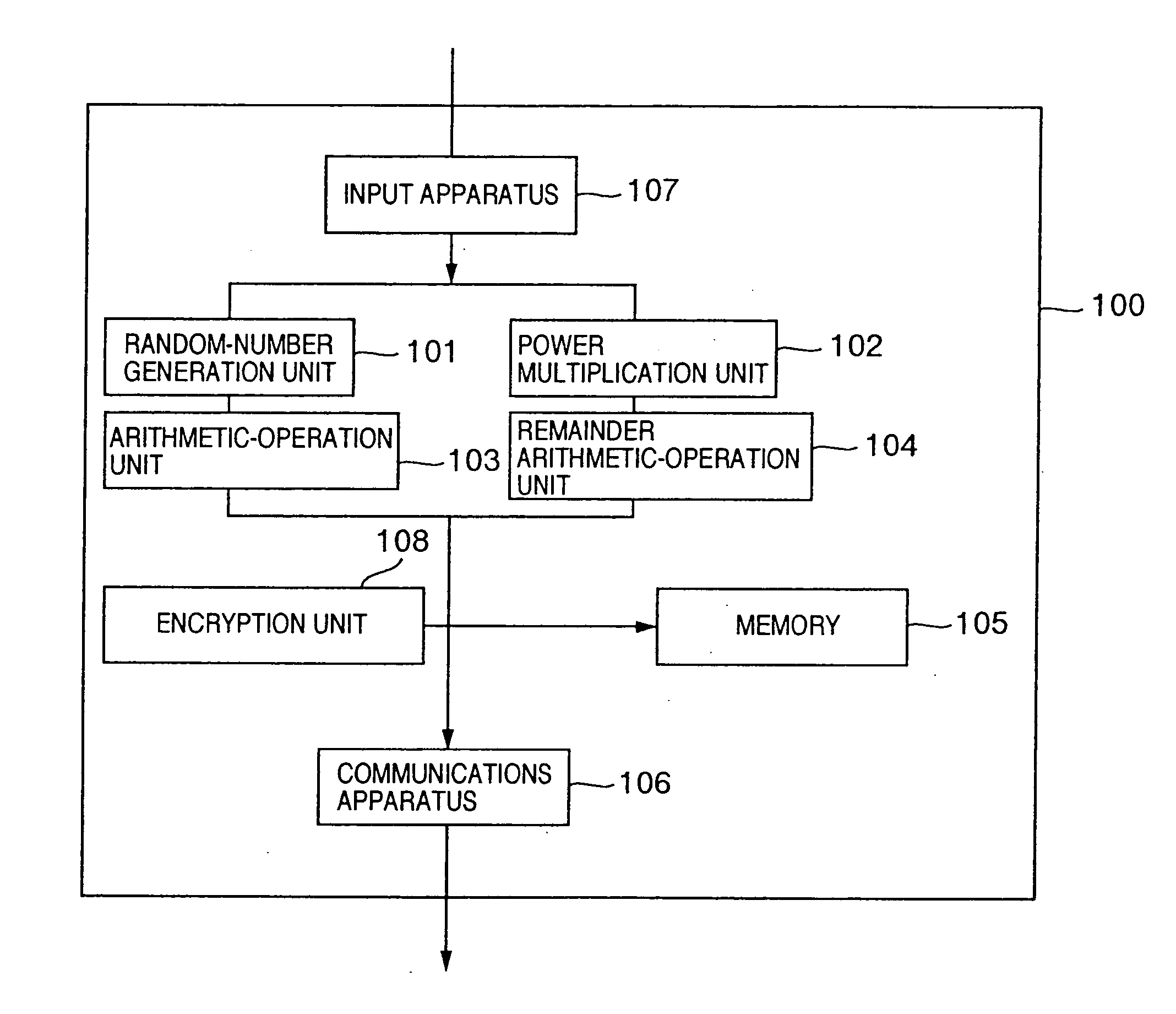
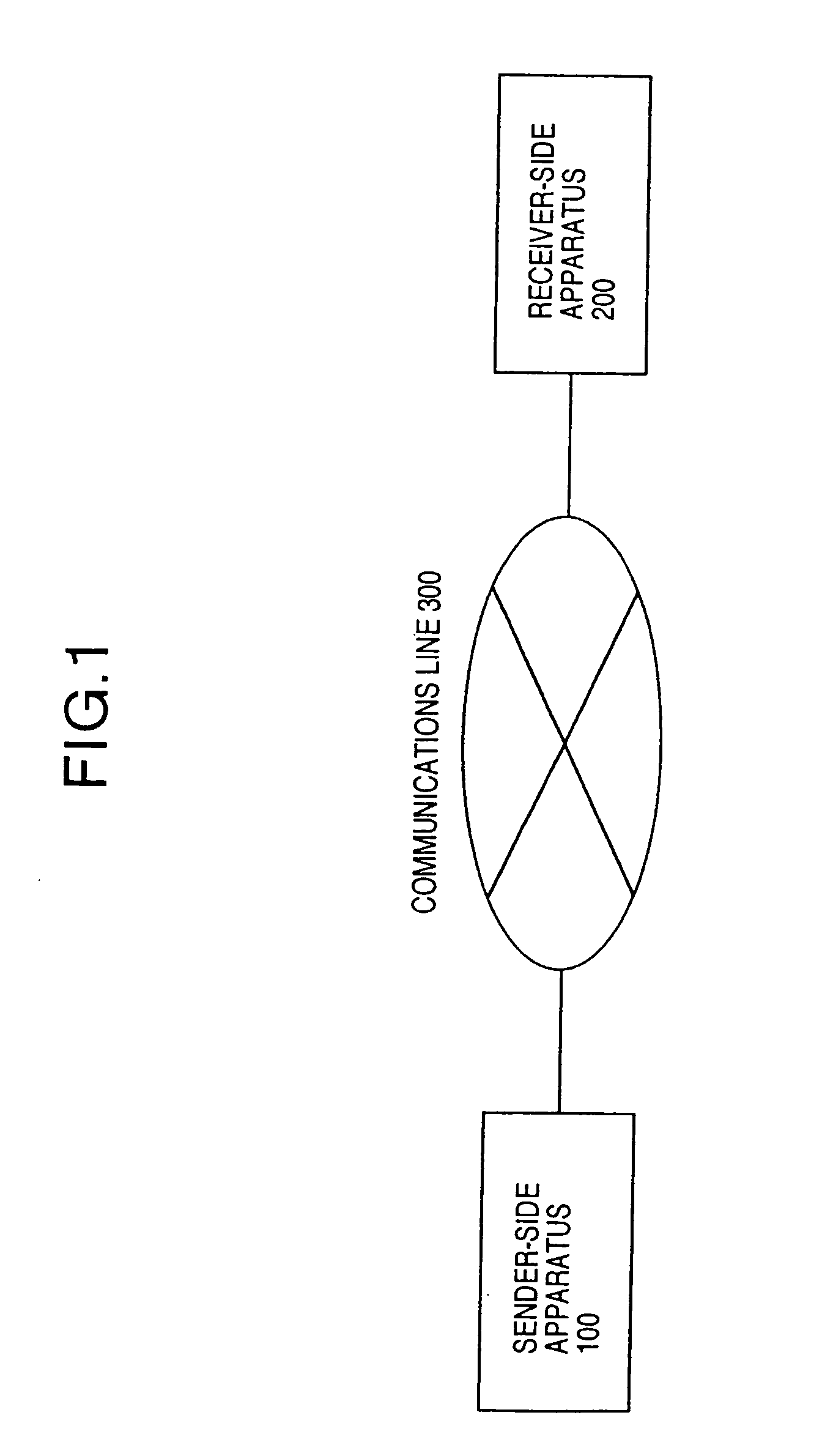
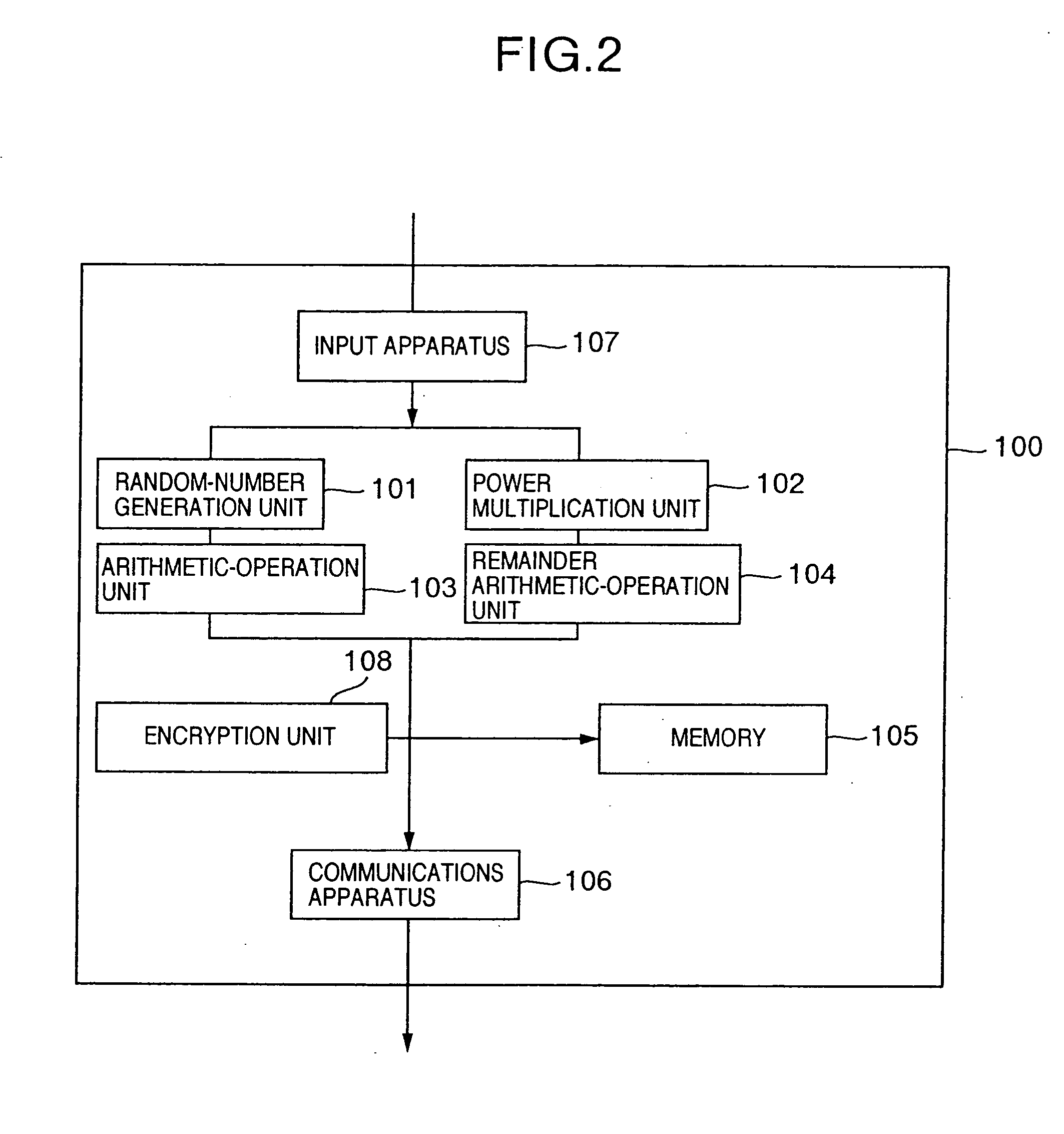
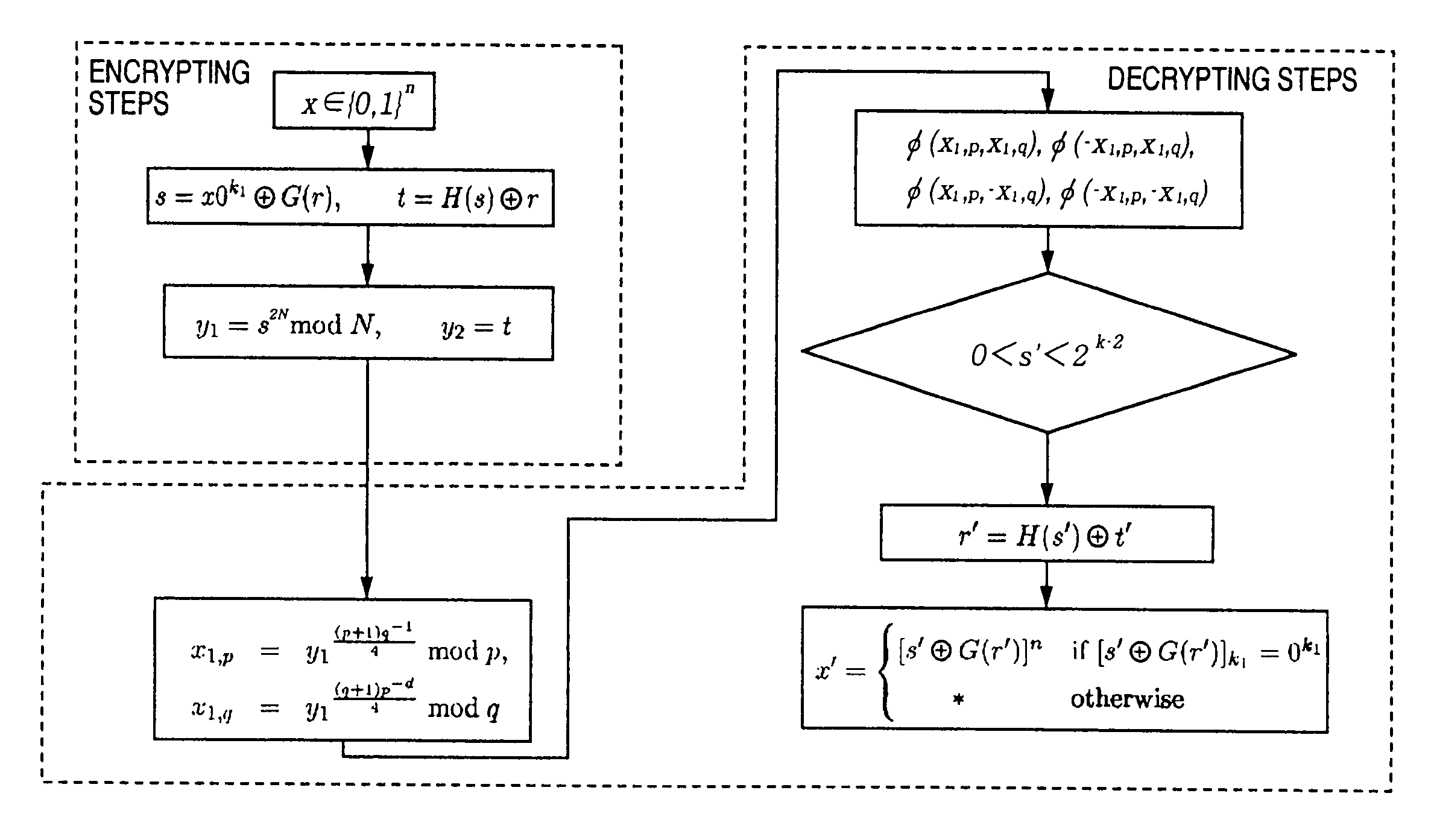
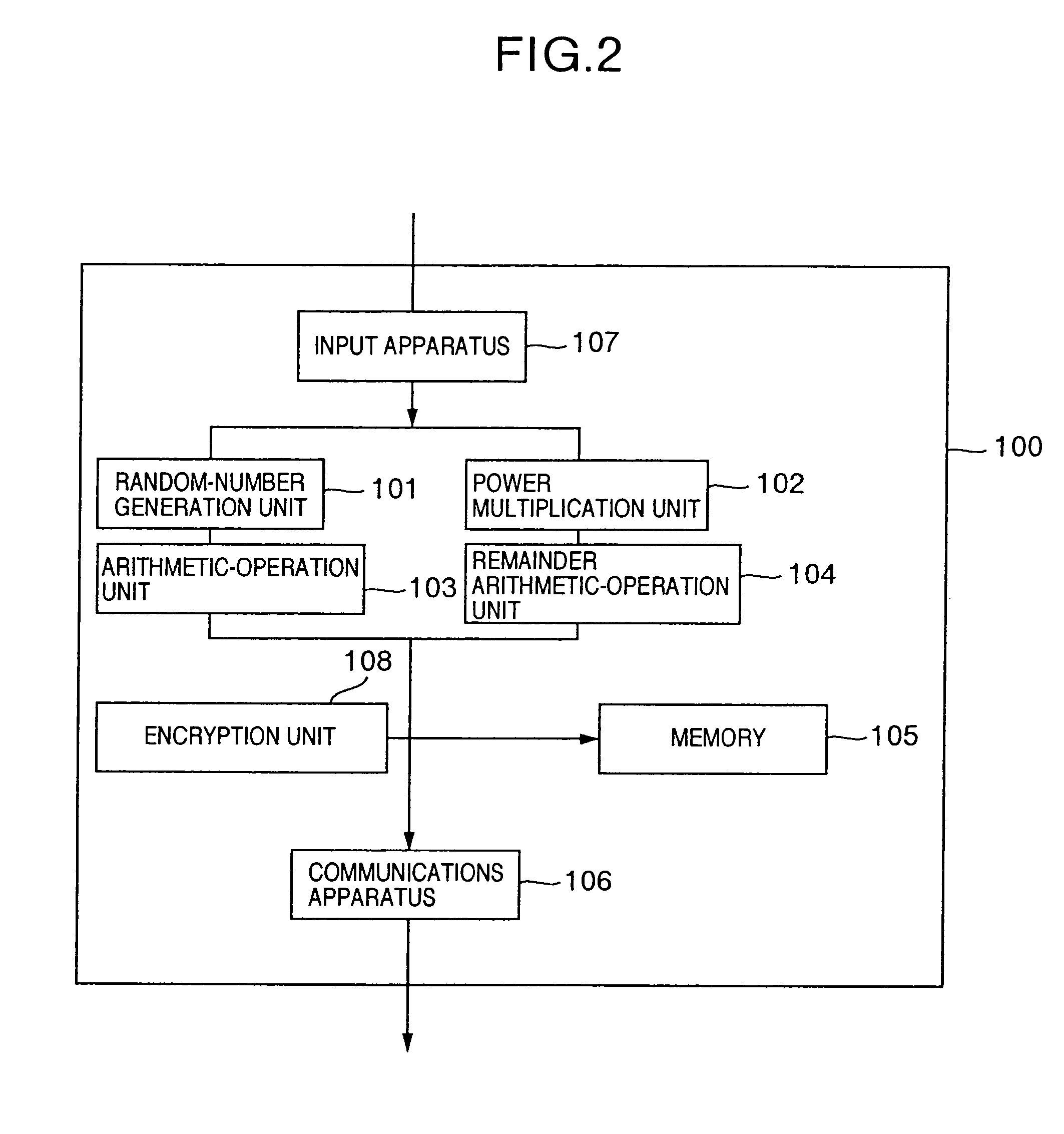
The public-key encryption method uses the sender-side apparatus by the creator of a ciphertest and creates the ciphertext of a plaintext x (ε{0, 1}n) in y1=f (x0k1G(r)), y2=H (x0k1G(r))r with respect to the published trapdoor-equipped unidirectional function f and the random functions G, H. Meanwhile, the receiver of the ciphertext, who has received the ciphertext by the receiver-side apparatus via the communications line, performs the decryption processing with the use of f−1, i.e., the secret key, in accordance with the steps inverse to those of the encryption processing.
Owner:HITACHI LTD
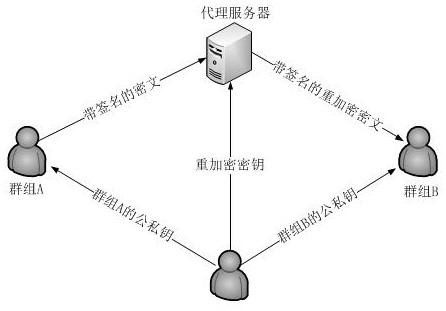
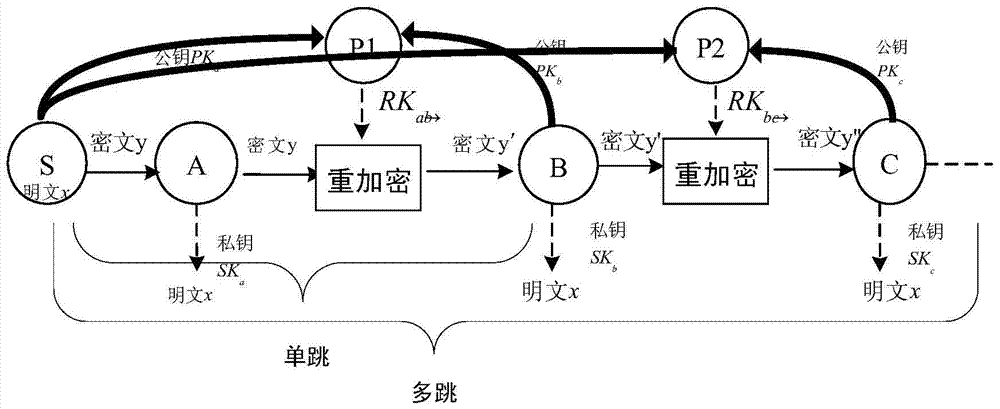
Agent re-encryption method used for group traffic
InactiveCN103888249AImprove securityResistant to Collusion AttacksSpecial service provision for substationKey distribution for secure communicationPlaintextHash function
The invention provides an agent re-encryption method used for group traffic. The method comprises the following steps: step one: a sender sets safety parameters and broadcasts the safety parameters to all users; step two: a private key is independently selected, and a public key is generated according to the private key and the public key is disclosed; step three: a Hash function operation and a bilinear pairing operation are performed on a clear text to be encrypted according to the safety parameters and the public key of a principal so that a first-level cipher text is generated; step four: a re-encryption secrete key is generated by the sender according to the safety parameters and the public key of an agent and the re-encryption secrete key is sent to the third part agent; step five: the first-level cipher text is re-encrypted by the third part agent according to the re-encryption secrete key so that a second-level cipher text is generated and sent to the agent; and step six: the principal and the agent are respectively decrypted according to the private key so that the clear text is acquired. According to the method, chosen cipher text attack safety can be achieved, the secret key can be completely disclosed via agent re-encryption and the agent re-encryption secret key is generated by the sender so that collusive attack can be resisted and safety of the clear text can be enhanced.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
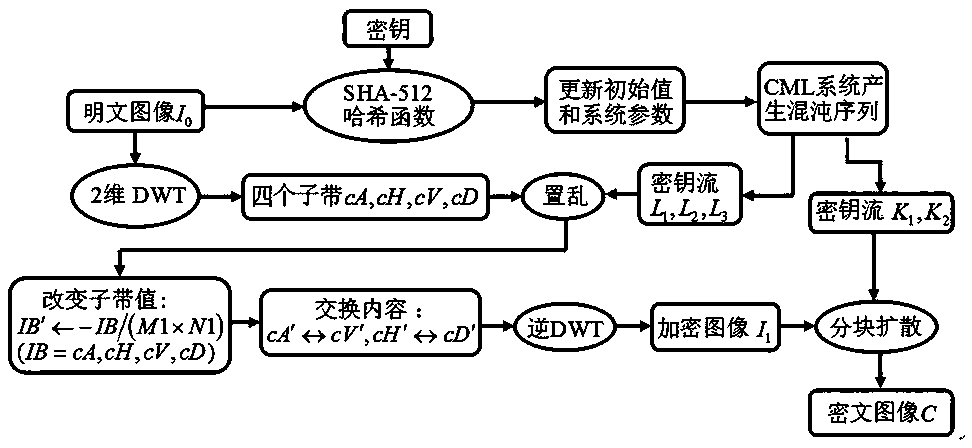
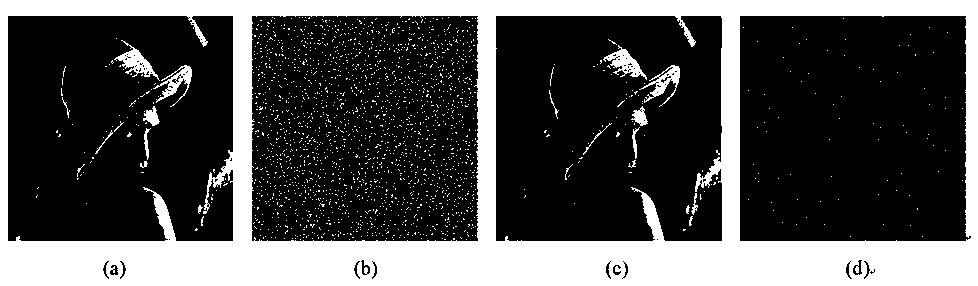
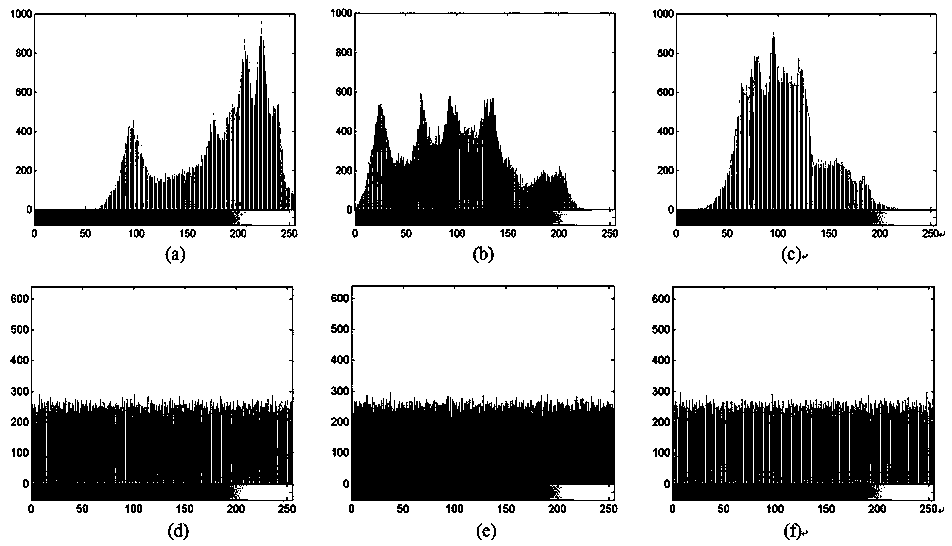
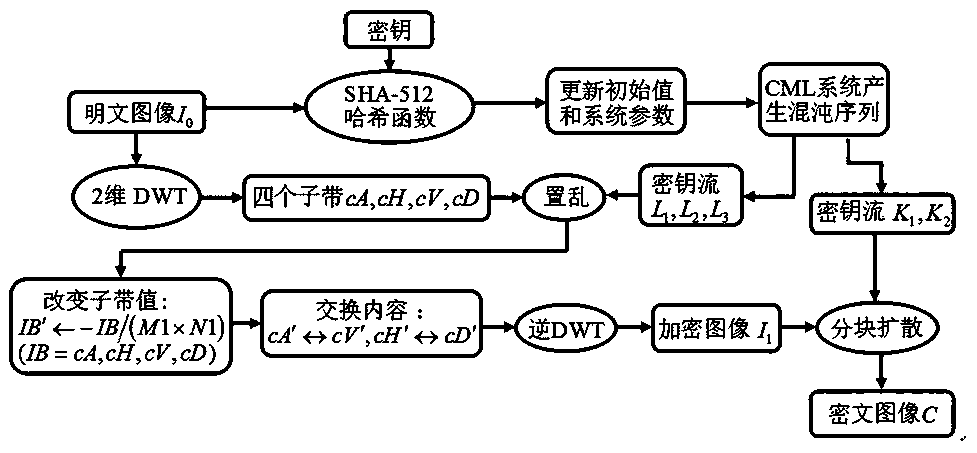
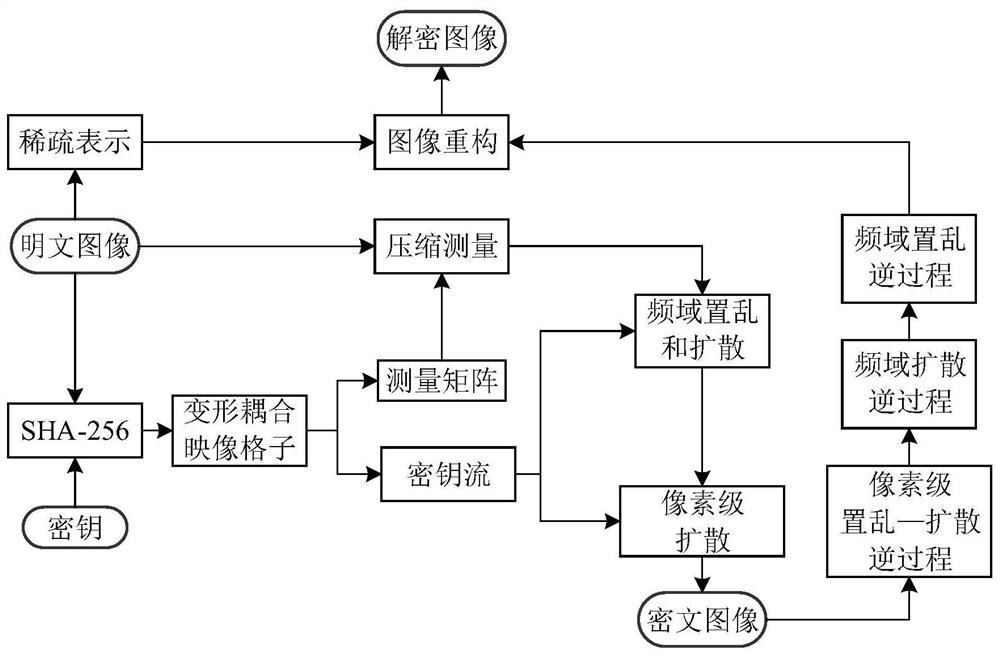
Color image encryption method based on compressed sensing and deformation coupling mapping lattices
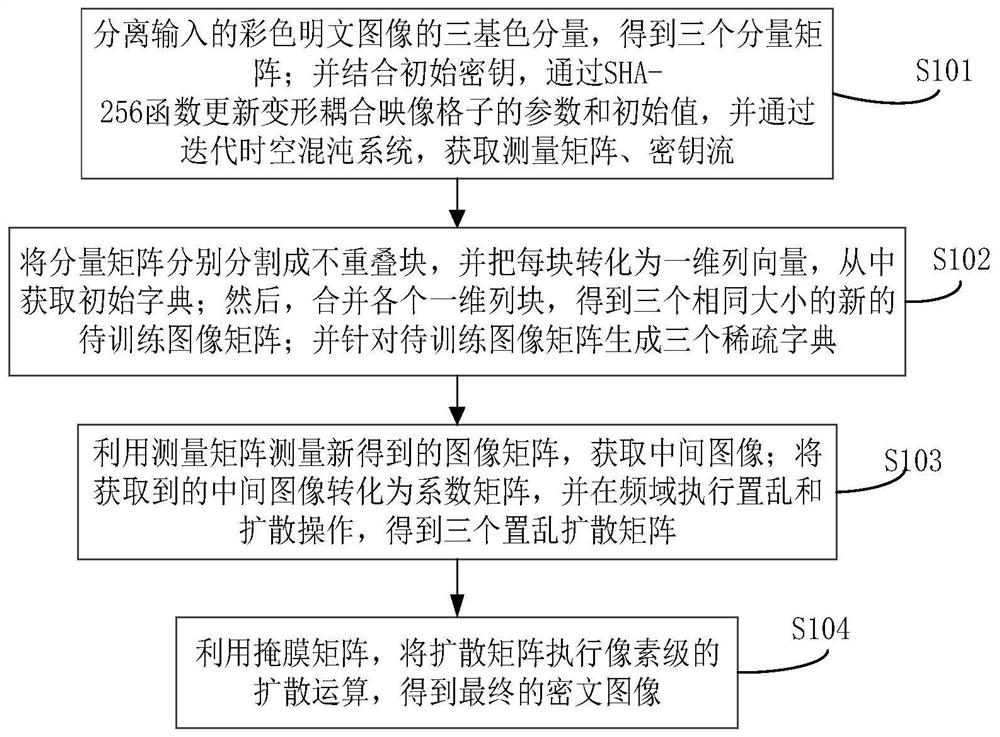
ActiveCN111327900AReduce sizeEasy to compressSecuring communication by chaotic signalsDigital video signal modificationPlaintextIntermediate image
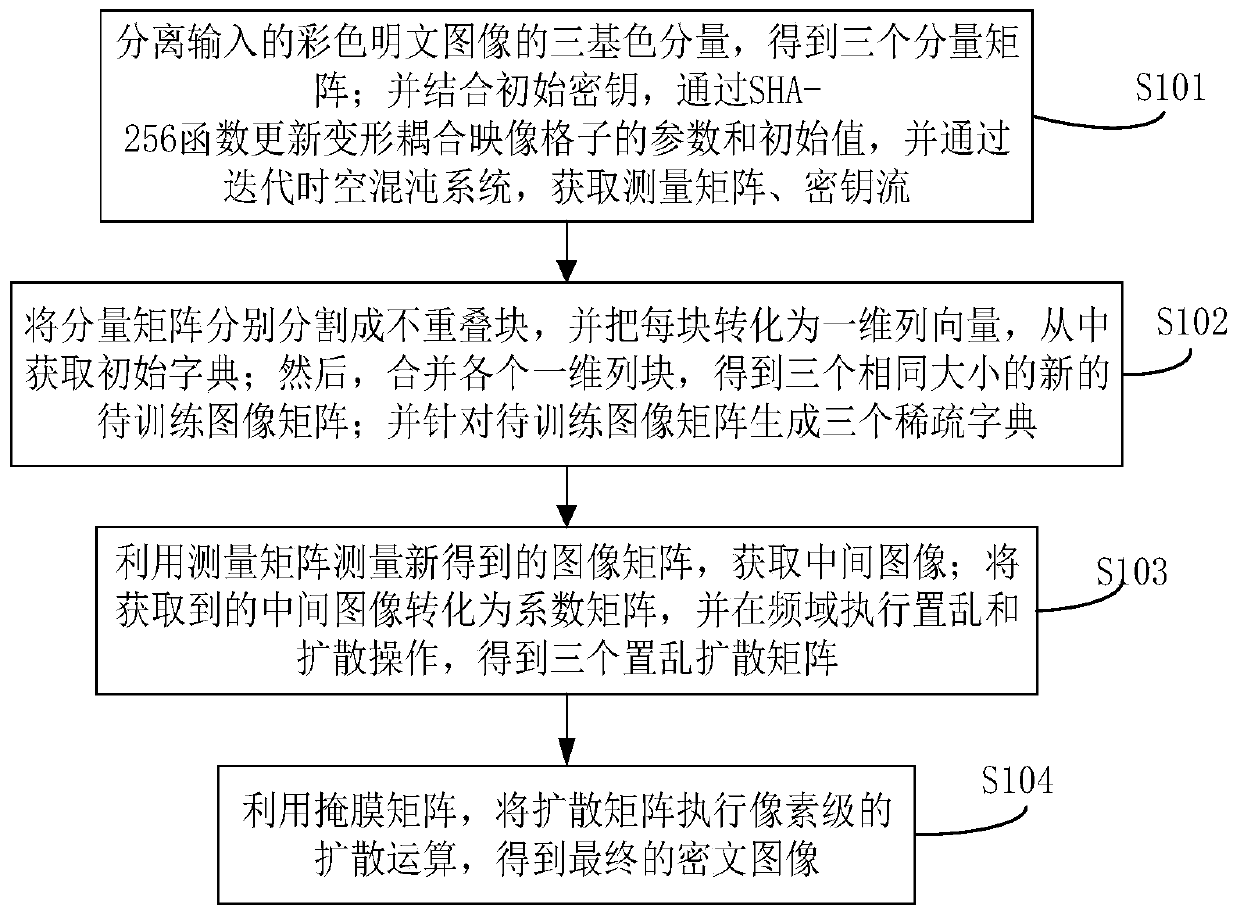
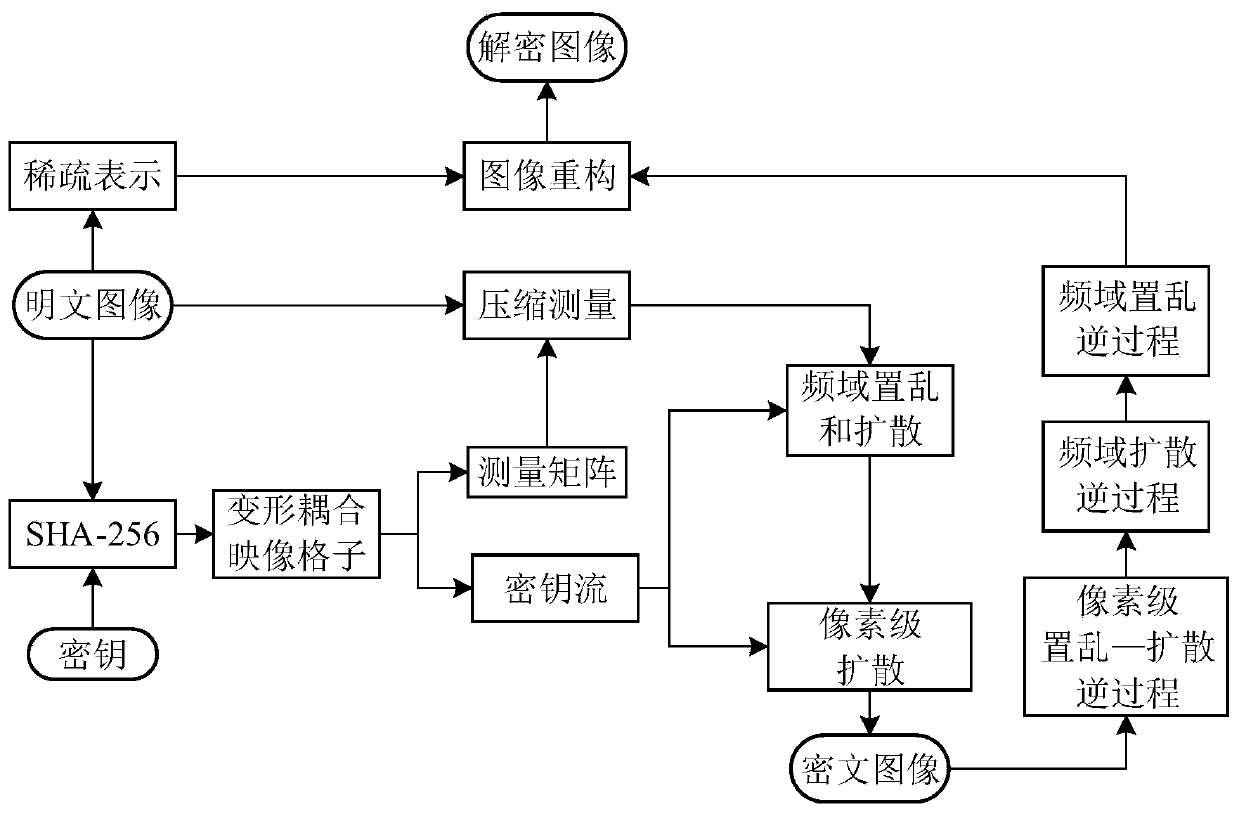
The invention belongs to the technical field of information security, and particularly relates to a color image encryption method based on compressed sensing and deformation coupling mapping lattices,which comprises the following steps: separating three primary color components of a color plaintext image to obtain a component matrix; updating parameters and initial values of the deformation coupling image grids through an SHA-256 function in combination with the initial key, and obtaining a measurement matrix and a key stream through an iterative space-time chaotic system; segmenting the component matrix and obtaining a new image matrix; generating a sparse dictionary for the new image matrix; measuring a new image by using the measurement matrix to obtain an intermediate image; converting the intermediate image into a coefficient matrix, and executing scrambling and diffusion operations in a frequency domain to obtain a scrambling diffusion matrix; and performing pixel-level diffusion operation on the scrambling diffusion matrix by using the key stream matrix to obtain a final ciphertext image. Statistics, known and selected plaintexts, selected ciphertext attacks and the like are effectively resisted, the safety and the encryption effect are improved, and the method has a good application prospect.
Owner:HENAN UNIVERSITY
Color image encryption method based on hybrid domain and LSS type coupled map lattice
ActiveCN108566501ANo lossGood encryptionImage data processing detailsSecuring communication by chaotic signalsChosen-plaintext attackPattern recognition
The invention belongs to the technical field of information security and particularly relates to a color image encryption method based on a hybrid domain and an LSS type coupled map lattice. The method comprises the steps of inputting a color plaintext image, separating red, green and blue three primary color components of the plaintext image to obtain corresponding three matrixes, generating a parameter and an initial value of the LSS type coupled map lattice through combination of a key, and generating key streams through utilization of the LSS type coupled map lattice; carrying out two-dimensional discrete wavelet transform on the three matrixes to obtain three groups of sub-bands; keeping a high and low frequency sub-band unchanged, scrambling the other sub-bands through utilization ofthe key streams, and shrinking the scrambled sub-bands; switching the content of the shrunk sub-bands; carrying out the two-dimensional discrete wavelet transform on the three groups of sub-bands toobtain three encryption components; and blocking the three encryption components, and carrying out bit level diffusion operation on the blocked matrixes through utilization of the key streams to obtain a ciphertext image. According to the method, statistics attacks, known and chosen plaintext attacks and chosen ciphertext attacks can be effectively resisted.
Owner:HENAN UNIVERSITY
Method for enhancing security of public key encryption schemas
InactiveUS7424114B2Key distribution for secure communicationMultiple keys/algorithms usageDeterministic encryptionChosen-ciphertext attack
There exist numerous public key probabilistic encryption algorithms. Most of these algorithms do not have a maximum security level against someone capable of chosen ciphertext attacks. The disclosed method provides a construct to enhance the security of any public key probabilistic or deterministic encryption algorithm to achieve an optimal security level.
Owner:GEMPLU
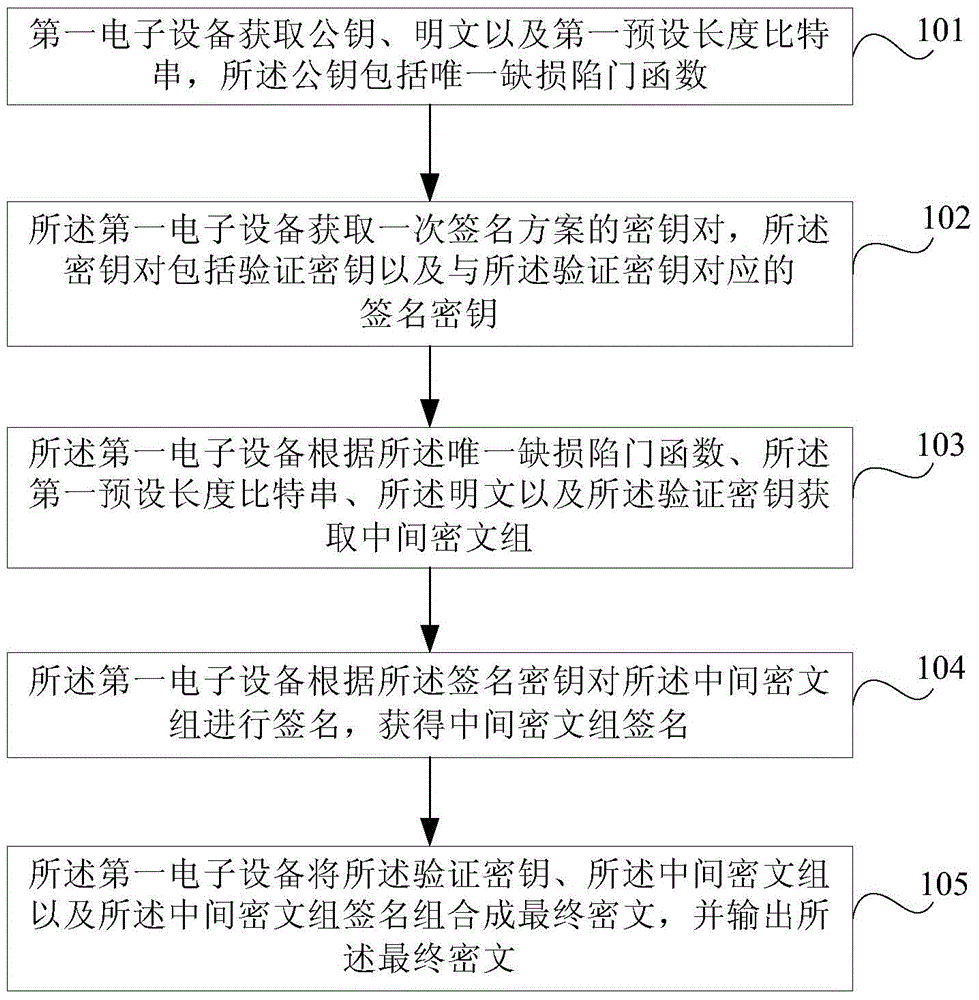
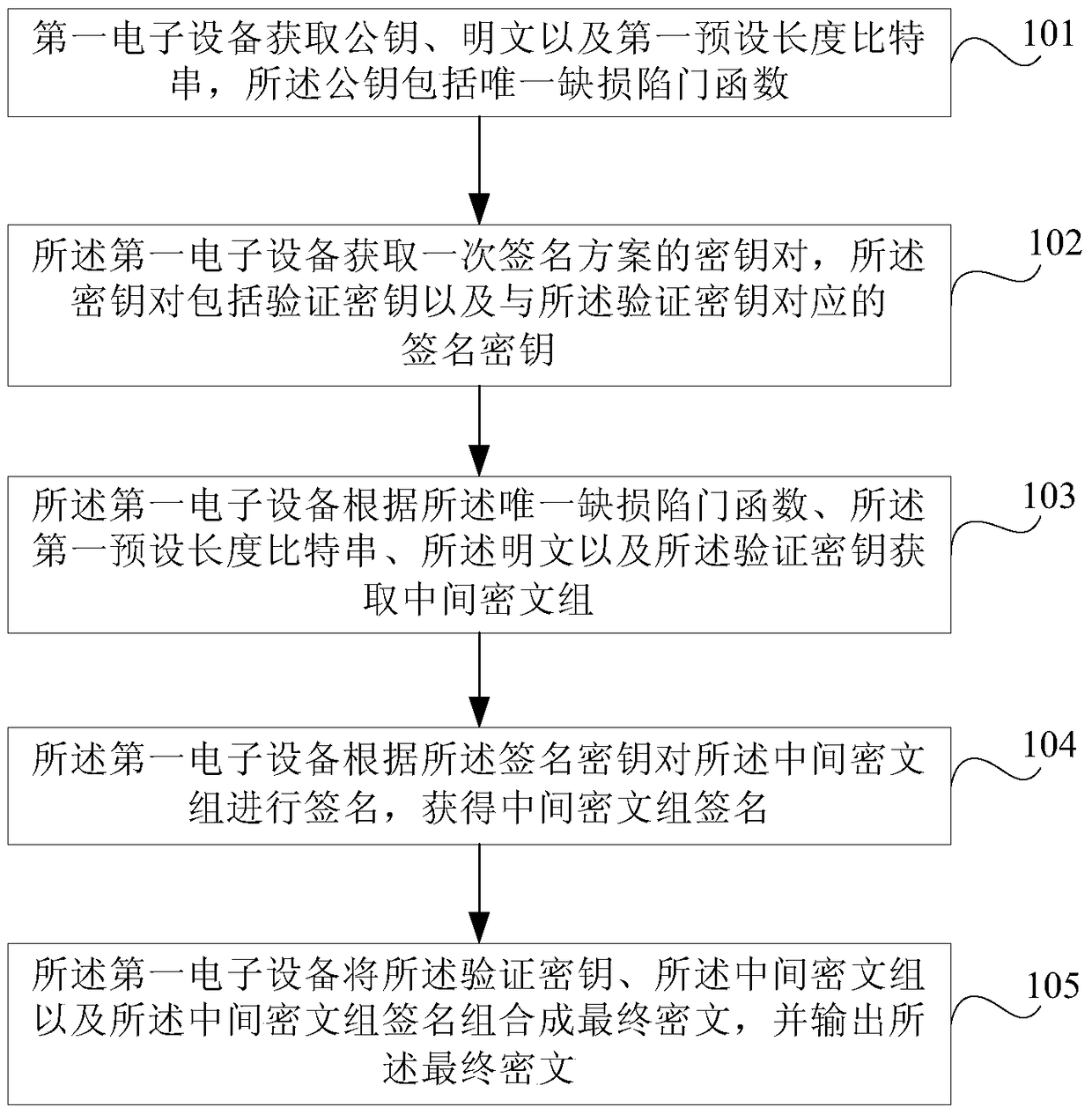
Encryption method, decryption method and electronic equipment
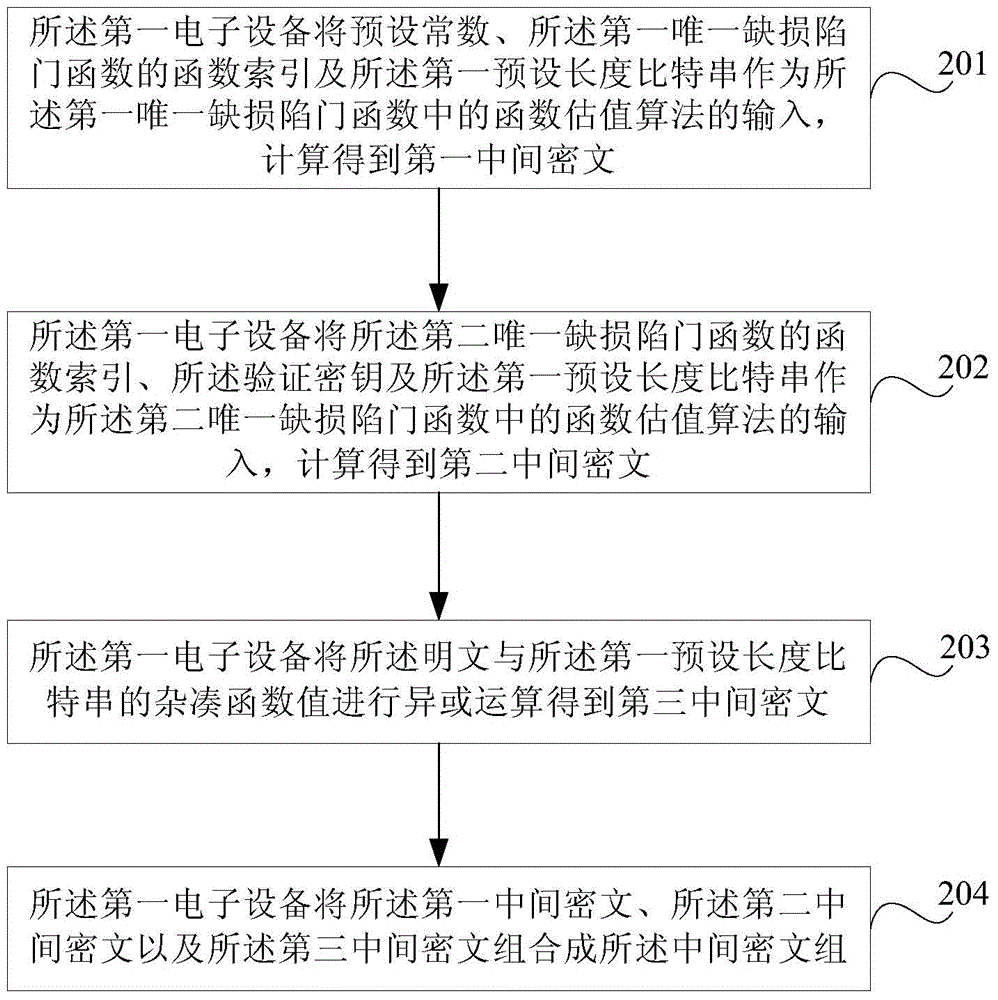
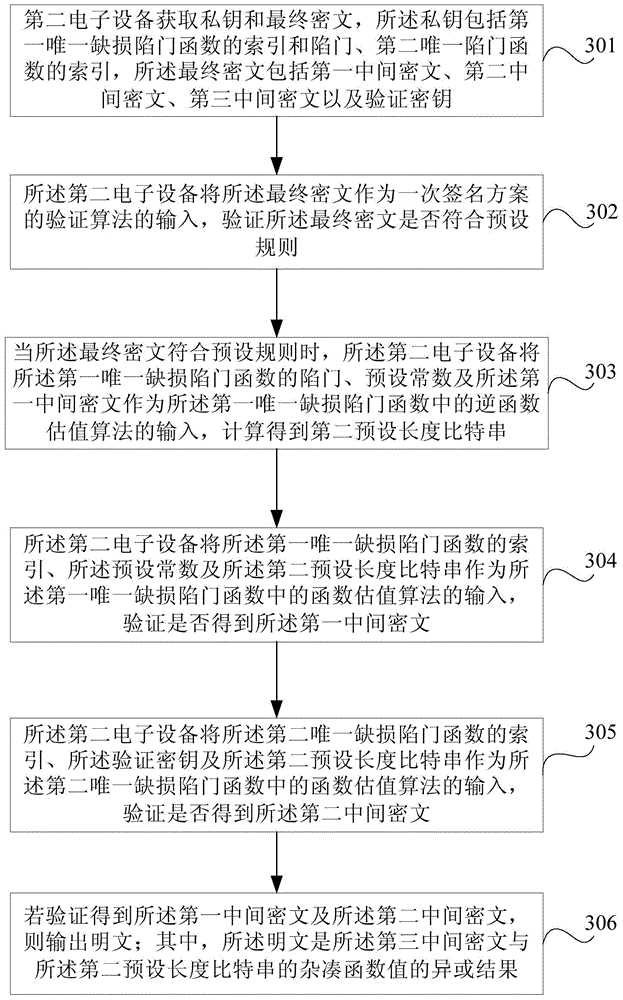
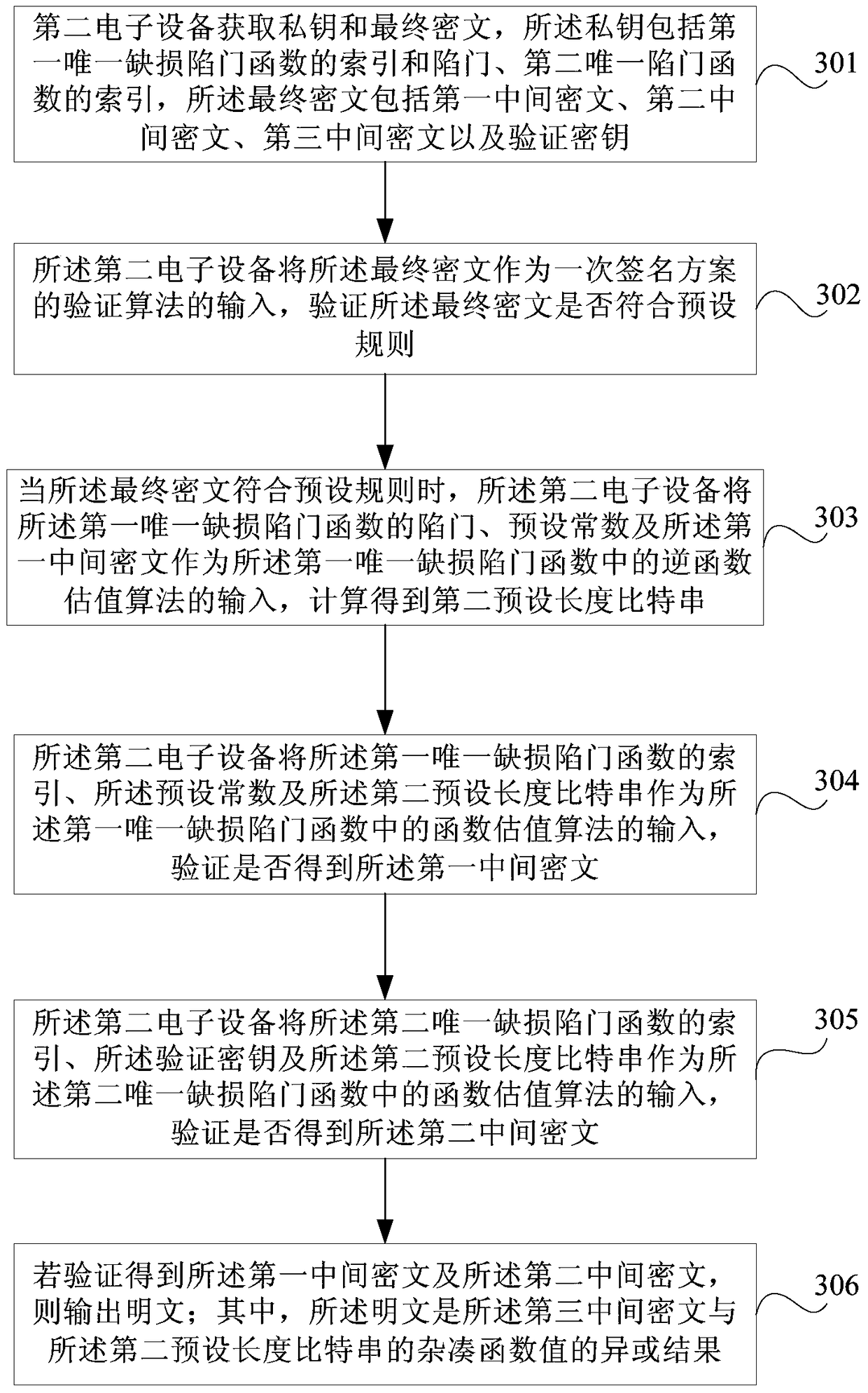
ActiveCN105227308AReduce the risk of being crackedUser identity/authority verificationPlaintextChosen-ciphertext attack
Embodiments of the invention provide an encryption method, a decryption method and electronic equipment. The method comprises steps of acquiring a public key, a plaintext and a first bit string of a preset length through first electronic equipment, wherein the public key comprises the only defect trapdoor function; acquiring a key pair of a one-time signature scheme by the first electronic equipment, wherein the public pair comprises a verification secret key and a signature secret key corresponding to the verification secret key; acquiring a middle cryptograph set according to the only defect trapdoor function, the first bit string of the preset length, the plaintext and the verification secret key; signing the middle cryptograph set by the first electronic equipment according to the signature secret key, and acquiring a signature of the middle cryptograph set; and forming a final cryptograph by combing the verification secret key, the middle cryptograph set and the signature of the middle cryptograph set, and outputting the final cryptograph. Therefore, anti-selection cryptograph attack is achieved.
Owner:HONOR DEVICE CO LTD
Public-key cryptographic schemes secure against an adaptive chosen ciphertext attack in the standard model
InactiveUS20020146117A1Key distribution for secure communicationPublic key for secure communicationPlaintextCiphertext-only attack
A public-key cryptographic scheme of high efficiency capable of verifying security in a standard model. In order to retain security against adaptive chosen ciphertext attacks, a ciphertext is generated by a combination of a plaintext and random numbers so that an illegal ciphertext input to a (simulated) deciphering oracle is rejected.
Owner:HITACHI LTD
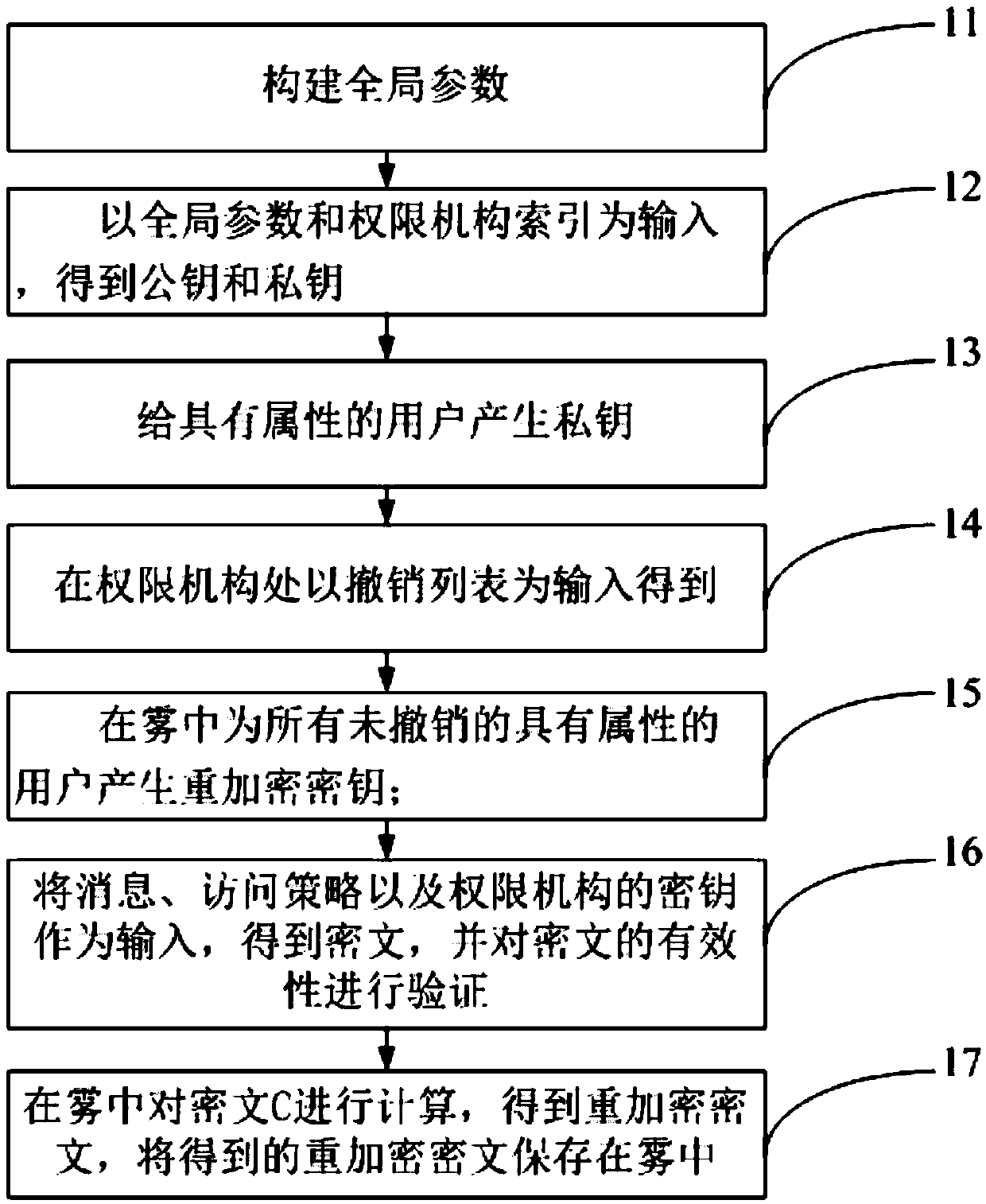
Secure revocable multi-center large attribute domain attribute-based encryption method in fog computing
ActiveCN108763944AEfficient undoSecurity against chosen ciphertext attacksDigital data protectionTransmissionAttribute-based encryptionFog computing
The invention provides a secure revocable multi-center large attribute domain attribute-based encryption method in fog computing, belonging to the field of encryption. The method includes the following steps: constructing a global parameter Param; taking the global parameter Param and an authority theta index as the input to obtain a public key PKtheta and a private key SKtheta; generating a private key SKGID, att for a user GID with an attribute expressed by a FORMULA (as shown in the original specification); taking a revocation list (RL) as the input at the authority theta to obtain {KUtheta, N}, and generating a re-encrypted key RKtheta for all unrevoked users with the attribute T(att)=theta in fog; taking a message M, an access policy (A, delta) and the key PKtheta of the authority asthe input to obtain a ciphertext C, and verifying the validity of the ciphertext C; and calculating the ciphertext C in fog to obtain a re-encrypted ciphertext C', and storing the obtained re-encrypted ciphertext in fog. The flexible fine-grained access control in fog computing can be implemented, and large attribute domains can be supported to meet various requirements in practical applications of fog computing, so that the scheme of the invention is applicable to the efficient revocation for the keys of resource-constrained devices in fog computing, and has the security of resisting chosen-ciphertext attacks.
Owner:金华航大北斗应用技术有限公司
A plaintext-associated fractional order chaotic image encryption method
The invention provides a plaintext-associated fractional order chaotic image encryption method. Firstly, the adopted chaotic system is a four-dimensional fractional order chaotic system, and comparedwith the chaotic system, the chaotic system is more complex in dynamic characteristic, larger in key space and more advantageous in encryption. Secondly, for most existing plaintext association encryption algorithms, the algorithm is only related to plaintext in a diffusion stage or a scrambling stage; in order to further improve the plaintext attack resistance, the image encryption method provided by the invention not only relates to image pixel diffusion and plaintext, but also relates to image position scrambling and plaintext, the image pixel diffusion adopts a secondary key plaintext association encryption algorithm, and the image position scrambling adopts a plaintext association image encryption algorithm. Experimental simulation shows that the method not only can well resist statistical property analysis, but also can effectively resist plaintext selection attacks and ciphertext selection attacks.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Encryption and decryption method based on coupling and self-triggering cellular automata
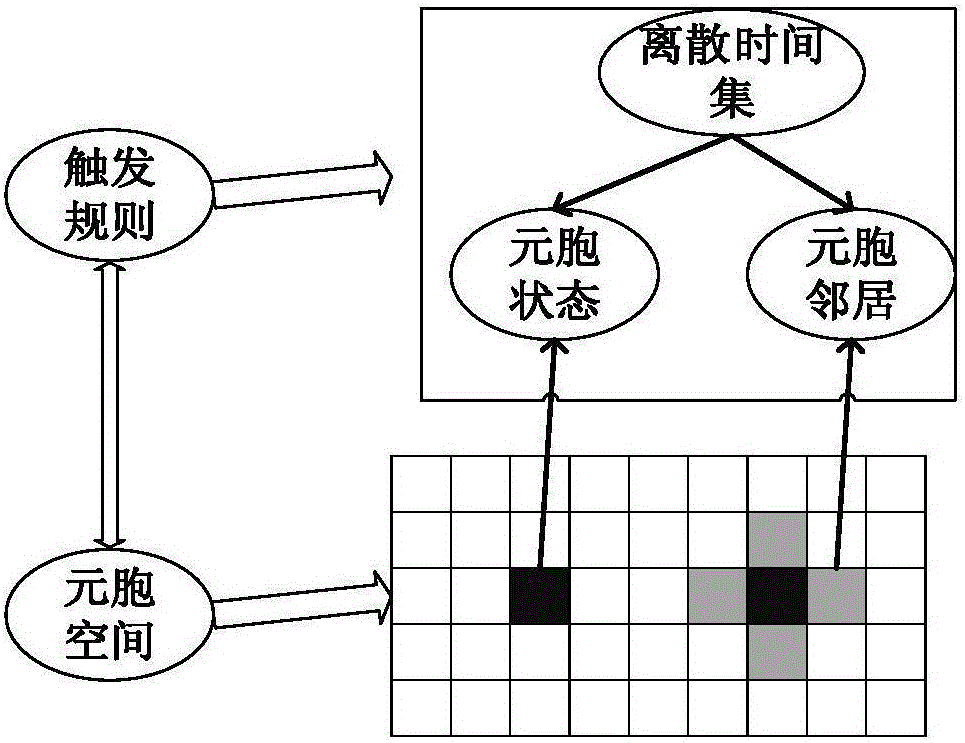
InactiveCN105099654ASimple local actionIntrinsic parallelismComputing modelsSecuring communicationCellular automationCoupling
The invention discloses an encryption and decryption method based on coupling and self-triggering cellular automata. The encryption and decryption method comprises: according to the properties of the coupling and self-triggering cellular automata, adopting n interactional cellular automata as an entirety, and constructing an encryption and decryption system of coupling and self-triggering cellular automata. A simulation experiment result indicates that the algorithm greatly improves the key space and effectively prevents brute force attack; and meanwhile, when a random number is introduced in an encryption process to prevent an attacker from obtaining an exclusive plaintext and ciphertext pair, so that known plaintext attach and selective ciphertext attach are effectively prevented.
Owner:NANJING UNIV OF SCI & TECH
Data encryption method based on dual difficulties
ActiveCN105049208AImprove securityKey distribution for secure communicationUser identity/authority verificationChosen-plaintext attackHypothesis
Provided is a verifiable public key encryption method. The encryption method includes steps: initialization, encryption, and decryption. In terms of security, the method has a mathematics hypothesis with dual difficulties referring to factorization and Diffie-Hellman problem. In other words, an attacker has to simultaneously solve the mathematical problem of the two calculations if he wants to crack the encryption method. The encryption method is designed by partly employing the concept of the trapdoor one-way function, the method has semantic security and can resist chosen plaintext attack and chosen ciphertext attack, and good practical values are provided.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Method for encrypting public key in signed quadratic residue class group
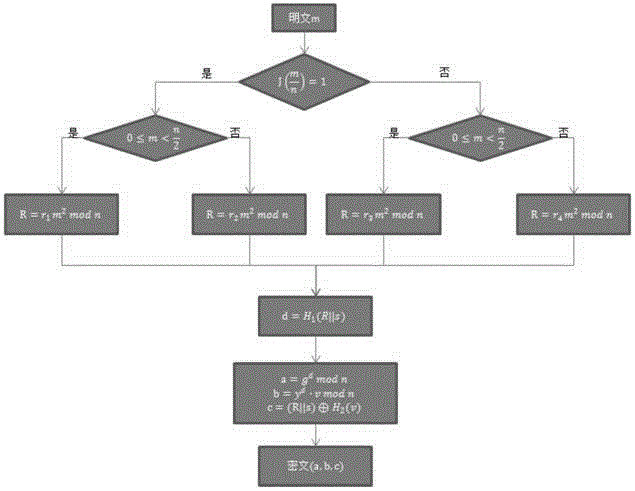
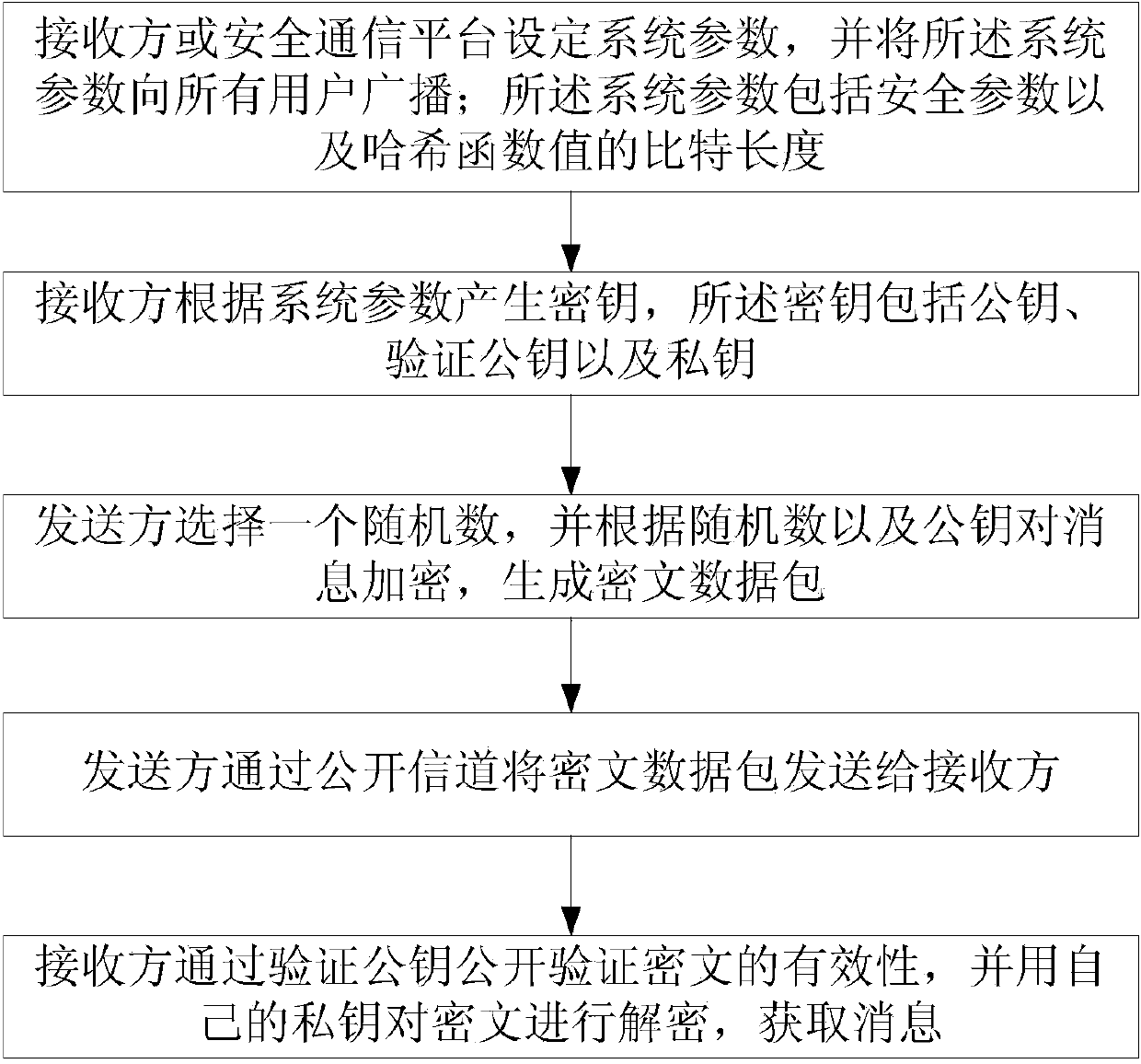
InactiveCN104184581AMake it publicly verifiableSatisfy confidentialityPublic key for secure communicationNetwork packetConfidentiality
The invention discloses a method for encrypting a public key in a signed quadratic residue class group. The method comprises the steps of 1, setting system parameters; 2, generating a secret key; 3, selecting a random number by a sender, carrying out encryption on a message, and generating a ciphertext data packet; 4, sending the ciphertext data packet to a receiver by the sender through a public channel; and 5, verifying the effectiveness of the ciphertext after the receiver receives the ciphertext data packet, decrypting the ciphertext data packet by using a private key, and acquiring the message. The method disclosed by the invention satisfies the confidentiality, the integrity and the chosen-ciphertext attack security simultaneously, and realizes public verification of the ciphertext legitimacy; the method does not use bilinear pairings and one-time signatures which are time-consuming, so that defects of other public key encryption methods in which the ciphertext legitimacy is verified by using the bilinear pairings and the one-time signatures are overcome, thereby having higher computational efficiency and higher practical values.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Method of a public key encryption and a cypher communication both secure against a chosen-ciphertext attack
InactiveUS20070177727A1Small loadIncrease in sizePublic key for secure communicationSecret communicationPlaintextChosen-ciphertext attack
The public-key encryption method uses the sender-side apparatus by the creator of a ciphertest and creates the ciphertext of a plaintext x (∈ {0, 1}n), in y1=f (x0k1G(r)), y2=H (x0k1G(r))r with respect to the published trapdoor-equipped unidirectional function f and the random functions G, H. Meanwhile, the receiver of the ciphertext, who has received the ciphertext by the receiver-side apparatus via the communications line, performs the decryption processing with the use of f−1, i.e., the secret key, in accordance with the steps inverse to those of the encryption processing.
Owner:HITACHI LTD
Dual scrambling image encryption method based on AFD adaptive decomposition
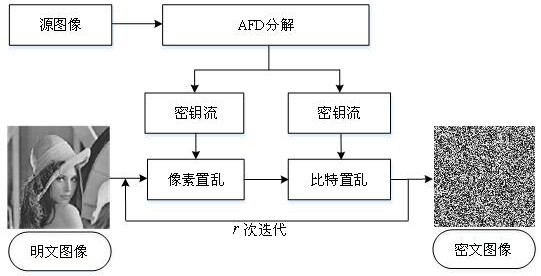
ActiveCN113344762AImplement one-time padImprove robustnessDigital data protectionImage data processing detailsAlgorithmKeystream
The invention relates to a pixel position and bit dual scrambling image encryption method based on AFD adaptive decomposition, which comprises the following steps: firstly, performing adaptive decomposition on a source image through an AFD method to generate two groups of key streams, and then performing pixel position scrambling and pixel bit scrambling operations on a plaintext image. The source image adopted by the method can be any image on the network or a newly generated image, the size of the source image is kept consistent with that of a plaintext image, the obtained encrypted image can efficiently resist selected plaintext attack, selected ciphertext attack and statistical attack, meanwhile, the invention has high robustness to noise attack and shearing attack. The method can indirectly realize the one-time pad encryption effect, further improves the security and robustness of the encrypted image, and can be applied to the fields of image security and image secret communication.
Owner:TAIYUAN UNIV OF TECH
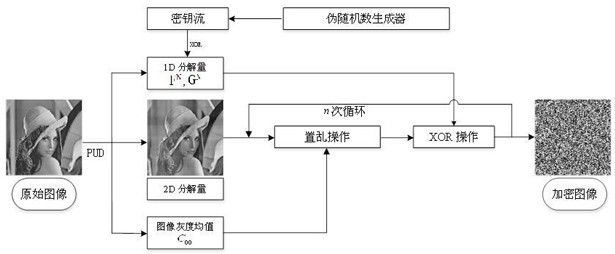
Plaintext related image encryption method based on PUD adaptive decomposition
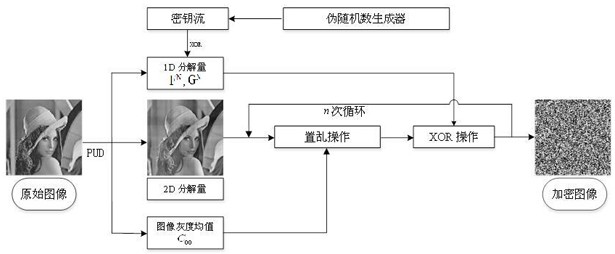
ActiveCN112261239AImprove robustnessImprove securityKey distribution for secure communicationCryptographic attack countermeasuresPlaintextAlgorithm
The invention relates to a plaintext related image encryption method based on PUD adaptive decomposition, and the method comprises the steps: carrying out the adaptive PUD decomposition of a plaintextimage, and carrying out the scrambling diffusion of a decomposed two-dimensional component. According to the method, the adopted encryption key is related to the plaintext, the obtained encrypted image can efficiently resist the attack of the selected plaintext and the attack of the selected ciphertext; meanwhile, the robustness in the aspects of filtering noise attacks, shearing attacks and differential attacks is high, and the security and robustness of the encrypted image are further improved. The method can be applied to the fields of image security and image secret communication.
Owner:TAIYUAN UNIV OF TECH
Method of a public key encryption and a cypher communication both secure against a chosen-ciphertext attack
InactiveUS7649991B2Small loadIncrease in sizePublic key for secure communicationSecret communicationPlaintextChosen-ciphertext attack
The public-key encryption method uses the sender-side apparatus by the creator of a ciphertest and creates the ciphertext of a plaintext x (ε{0, 1}n), in y1=f(x0k1G(r)), y2=H(x0k1G(r))r with respect to the published trapdoor-equipped unidirectional function f and the random functions G, H. Meanwhile, the receiver of the ciphertext, who has received the ciphertext by the receiver-side apparatus via the communications line, performs the decryption processing with the use of f−1, i.e., the secret key, in accordance with the steps inverse to those of the encryption processing.
Owner:HITACHI LTD
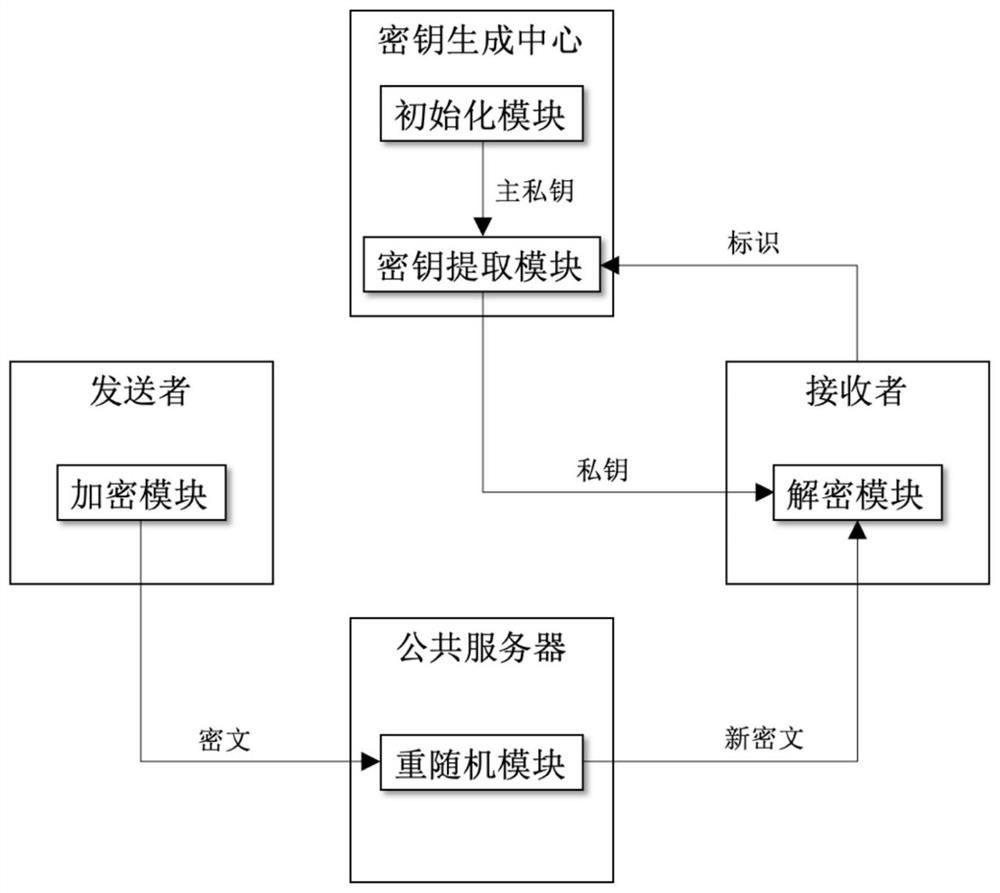
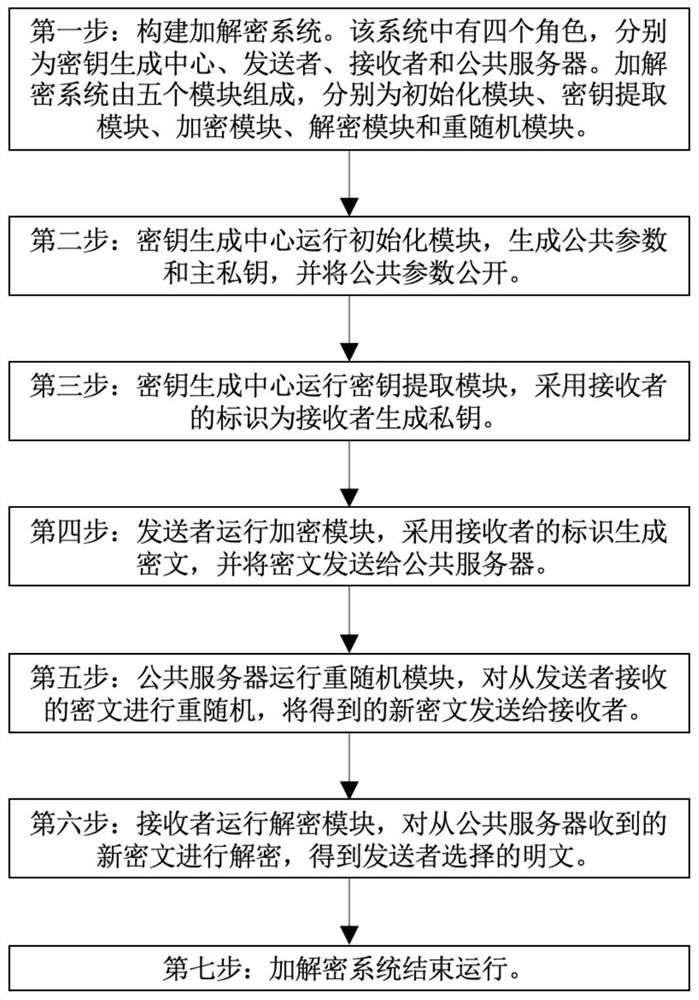
Rerandomizable identifier encryption and decryption method
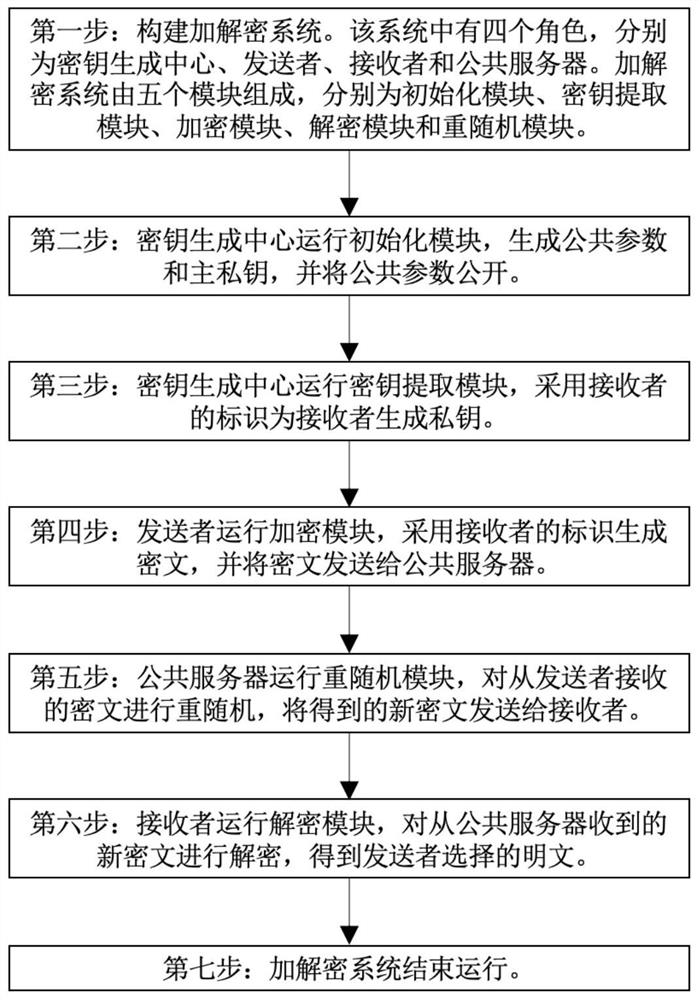
ActiveCN111756539AAddress security flawsPublic key for secure communicationUser identity/authority verificationEngineeringChosen-ciphertext attack
The invention discloses a rerandomizable identifier encryption and decryption method, and aims to solve the security defect of an existing rerandomizable identifier encryption and decryption method. According to the invention, the technical scheme is that the method comprises the steps: constructing an encryption and decryption system composed of an initialization module, a key extraction module,an encryption module, a decryption module and a re-random module; enabling the key generation center to operate the initialization module, generating a public parameter and a main private key, and disclosing the public parameter; enabling the key generation center to operate a key extraction module, and generating a private key for the receiver by adopting the identifier id of the receiver; enabling a sender to operate the encryption module, generating a ciphertext C by adopting the identifier id of the receiver, and sending the ciphertext C to the public server; enabling a public server to operate a re-randomization module to re-randomize the C, and sending the new ciphertext C' to a receiver; and enabling a receiver to operate the decryption module to decrypt the C'. According to the invention, the replayable selective ciphertext attack based on the identifier can be resisted, and the operation of the rerandom module does not need the identifier of a receiver, so the distribution ofthe identifier is avoided.
Owner:NAT UNIV OF DEFENSE TECH
A plaintext-related image encryption method based on pud adaptive decomposition
ActiveCN112261239BImprove robustnessImprove securityKey distribution for secure communicationCryptographic attack countermeasuresChosen-plaintext attackAlgorithm
The invention relates to a plaintext-related image encryption method based on PUD adaptive decomposition, which performs adaptive PUD decomposition on plaintext images, and performs scrambling-diffusion operations on decomposed two-dimensional components. The encryption key used in this method is related to the plaintext, and the obtained encrypted image can efficiently resist chosen plaintext attack and chosen ciphertext attack, and has strong robustness against filtering noise attack, clipping attack and differential attack, further improving The security and robustness of encrypted images can be applied in the fields of image security and image confidential communication.
Owner:TAIYUAN UNIV OF TECH
Color Image Encryption Method Based on Mixed Domain and LSS Type Coupled Mapping Lattice
ActiveCN108566501BNo lossGood encryptionImage data processing detailsSecuring communication by chaotic signalsChosen-plaintext attackAlgorithm
The invention belongs to the technical field of information security and particularly relates to a color image encryption method based on a hybrid domain and an LSS type coupled map lattice. The method comprises the steps of inputting a color plaintext image, separating red, green and blue three primary color components of the plaintext image to obtain corresponding three matrixes, generating a parameter and an initial value of the LSS type coupled map lattice through combination of a key, and generating key streams through utilization of the LSS type coupled map lattice; carrying out two-dimensional discrete wavelet transform on the three matrixes to obtain three groups of sub-bands; keeping a high and low frequency sub-band unchanged, scrambling the other sub-bands through utilization ofthe key streams, and shrinking the scrambled sub-bands; switching the content of the shrunk sub-bands; carrying out the two-dimensional discrete wavelet transform on the three groups of sub-bands toobtain three encryption components; and blocking the three encryption components, and carrying out bit level diffusion operation on the blocked matrixes through utilization of the key streams to obtain a ciphertext image. According to the method, statistics attacks, known and chosen plaintext attacks and chosen ciphertext attacks can be effectively resisted.
Owner:HENAN UNIVERSITY
Data Encryption Method Based on Double Difficulty
ActiveCN105049208BImprove securityKey distribution for secure communicationUser identity/authority verificationChosen-plaintext attackHypothesis
Provided is a verifiable public key encryption method. The encryption method includes steps: initialization, encryption, and decryption. In terms of security, the method has a mathematics hypothesis with dual difficulties referring to factorization and Diffie-Hellman problem. In other words, an attacker has to simultaneously solve the mathematical problem of the two calculations if he wants to crack the encryption method. The encryption method is designed by partly employing the concept of the trapdoor one-way function, the method has semantic security and can resist chosen plaintext attack and chosen ciphertext attack, and good practical values are provided.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
A Method for Realizing Identity-Based Broadcast Encryption by Attribute-Based Encryption of Ciphertext Policy
ActiveCN104135473BShorten the development cycleReduce system loadPublic key for secure communicationPlaintextAttribute-based encryption
There is provided a method for realizing identity-based broadcast encryption by ciphertext-policy attribute-based encryption. The steps of the method are as follows: in step 1, a PKG (Private Key Generator) inputs a safety coefficient of a system to output an initialization parameter; in step 2, the PKG runs a random number generation algorithm to choose a random number required for the system; in step 3, the PKG executes operation to obtain a public key and a master secret key; in step 4, an encrypting party chooses the random number and completes operation to output a part of ciphertext; in step 5, the encrypting party executes calculation according to a set of identities of decrypting users to obtain the remaining part of the ciphertext; in step 6, the PKG runs a random number generation algorithm to obtain a random parameter; in step 7, the PKG executes calculation according to the master secret key and the identity of the user to obtain a private key SKID; in step 8, a decrypting party conforming to requirement is able to execute calculation according to the private key and the ciphertext to obtain K; and in step 9, the decrypting user is able to output correct plaintext by executing calculation according to the K. According to the invention, a development cycle and system load are reduced greatly, and chosen ciphertext attack can be resisted, which ensures safety and effectiveness of the scheme.
Owner:BEIHANG UNIV
An Intergroup Proxy Re-encryption Method Resistant to Selected Ciphertext Attacks
ActiveCN106713349BReduce computational complexityReduce complexityTransmissionRandom oracleComputation complexity
The present invention discloses an inter-group proxy re-encryption method capable of resisting selected ciphertext attack. A ciphertext is re-encrypted through proxy, a decryption capability is designated based on the group, and any member in the group can decrypt the ciphertext independently, so that the method is more flexible than an individual-based proxy re-encryption method. A reliable, convenient data sharing manner is provided for cloud storage. The calculation complexity of a licensor and a licensee is relatively low, and encryption and decryption can be performed conveniently. Particularly, compared with existing inter-group proxy re-encryption methods, the method has the advantage that the calculation complexity in the key generation phase is lower. A primary strong unforgeable signature is added when the ciphertext is generated, so that the ciphertext and the re-encrypted ciphertext cannot be tampered. Finally, if a dual linear Diffie_Hellman assumption is valid, the selected ciphertext attack is resisted in a random oracle model.
Owner:郑州埃文计算机科技有限公司
A Public Key Encryption Method in Signed Quadratic Residue Groups
InactiveCN104184581BMake it publicly verifiableSatisfy confidentialityPublic key for secure communicationNetwork packetConfidentiality
The invention discloses a method for encrypting a public key in a signed quadratic residue class group. The method comprises the steps of 1, setting system parameters; 2, generating a secret key; 3, selecting a random number by a sender, carrying out encryption on a message, and generating a ciphertext data packet; 4, sending the ciphertext data packet to a receiver by the sender through a public channel; and 5, verifying the effectiveness of the ciphertext after the receiver receives the ciphertext data packet, decrypting the ciphertext data packet by using a private key, and acquiring the message. The method disclosed by the invention satisfies the confidentiality, the integrity and the chosen-ciphertext attack security simultaneously, and realizes public verification of the ciphertext legitimacy; the method does not use bilinear pairings and one-time signatures which are time-consuming, so that defects of other public key encryption methods in which the ciphertext legitimacy is verified by using the bilinear pairings and the one-time signatures are overcome, thereby having higher computational efficiency and higher practical values.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
A re-random identification encryption and decryption method
ActiveCN111756539BAddress security flawsPublic key for secure communicationUser identity/authority verificationComputer hardwareTheoretical computer science
The invention discloses a re-randomized identification encryption and decryption method, aiming to solve the security defect existing in the existing re-random identification encryption and decryption method. The technical solution is: build an encryption and decryption system consisting of an initialization module, a key extraction module, an encryption module, a decryption module and a rerandom module; the key generation center runs the initialization module, generates public parameters and master private keys, and makes the public parameters public ;The key generation center runs the key extraction module, uses the receiver's identification id to generate a private key for the receiver; the sender runs the encryption module, uses the receiver's identification id to generate ciphertext C, and sends C to the public server; the public server Run the re-random module to re-randomize C, and send the new ciphertext C' to the receiver; the receiver runs the decryption module to decrypt C'. The invention can resist the replayable selected ciphertext attack based on the logo, and the operation of the re-random module does not need the logo of the receiver, which avoids the distribution of the logo.
Owner:NAT UNIV OF DEFENSE TECH
SM2-based multi-receiver public key encryption method
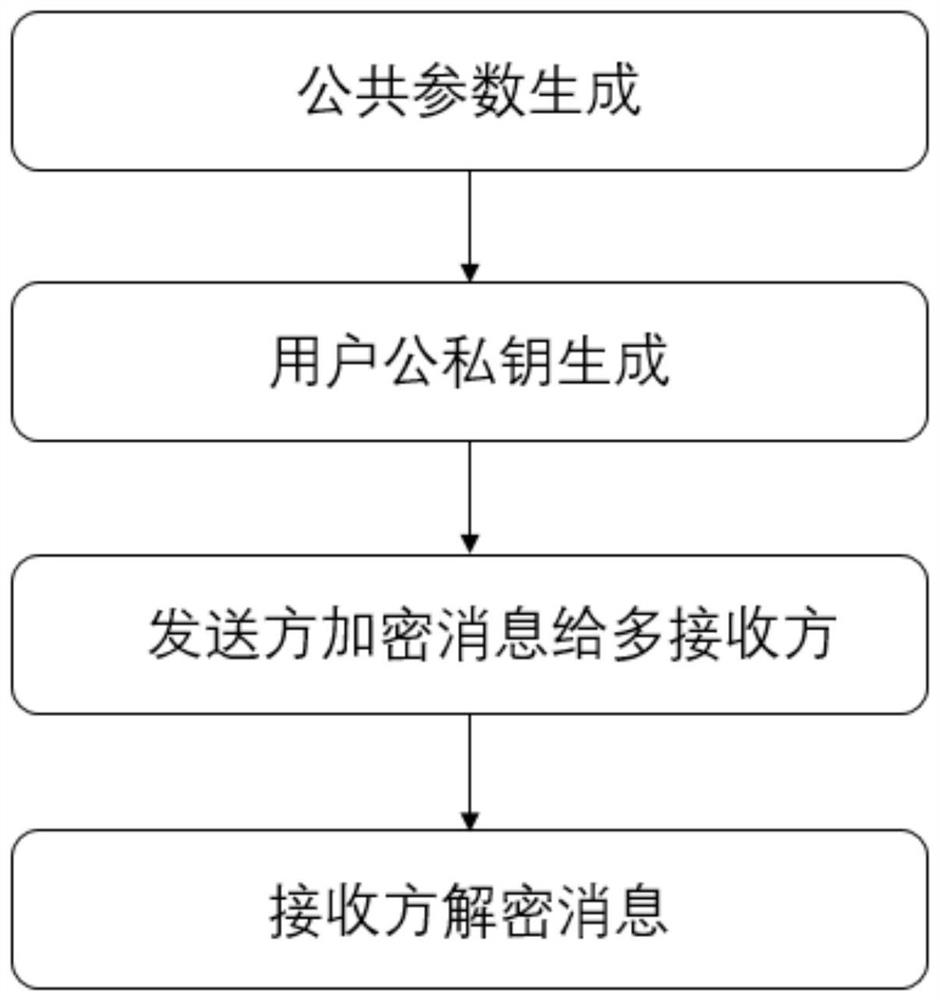
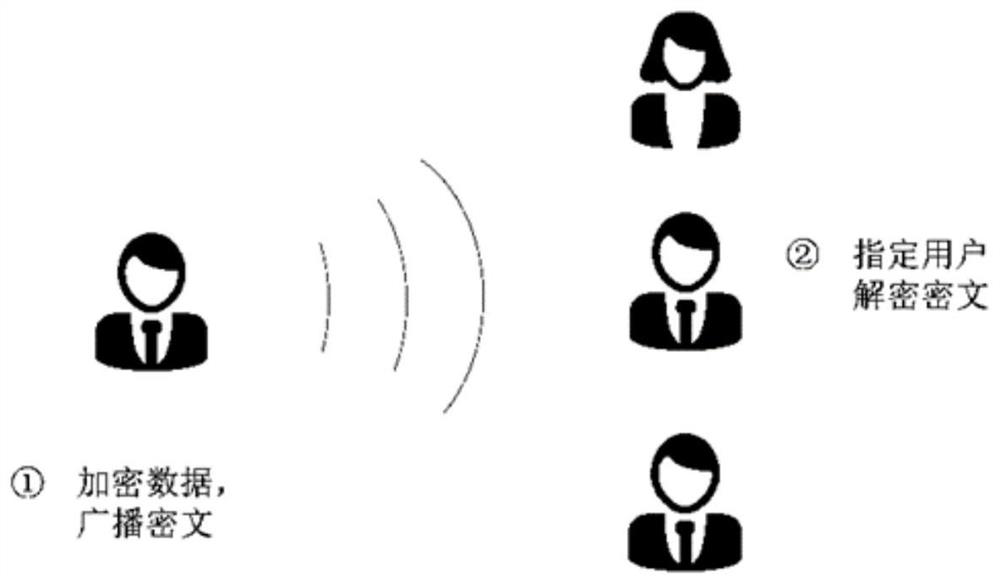
ActiveCN111865578AImprove encryption efficiencyReduced communication bandwidth requirementsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringCommunication bandwidth
The invention discloses a SM2-based multi-receiver public key encryption method. A traditional multi-receiver public key encryption method depends on a traditional public key encryption method, and has the defects of low encryption efficiency and high communication bandwidth requirement. Aiming at the defects, the invention provides the SM2-based multi-receiver public key encryption method for random number reuse, so that the method has the advantages of high encryption efficiency and low communication bandwidth requirement. A sender may encrypt a message into a ciphertext by using the method,and broadcasts the ciphertext to a plurality of receivers in a network; after receiving the ciphertext, the receivers can decrypt the ciphertext through a private key to obtain the message of the sender. According to the method, formalization proves that the safety of the RR-IND-CCA can be achieved, the calculated amount of the sender can be effectively reduced, and the actual work application requirements in the aspects of safety and efficiency are met.
Owner:JINAN UNIVERSITY
Combined image compression/encryption method based on compressed sensing
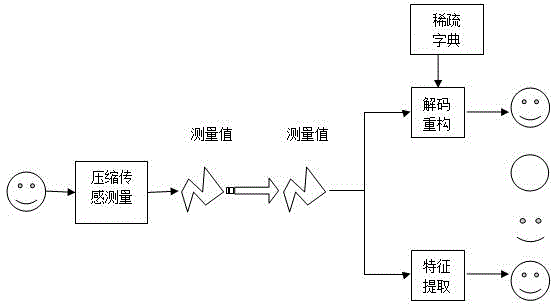
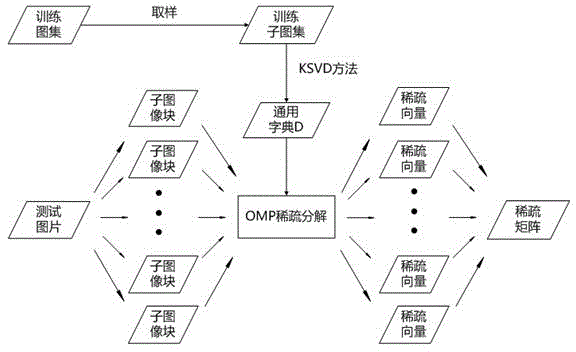
ActiveCN102891999BImprove rate-distortion performanceGood resistance to attackDigital video signal modificationChosen-plaintext attackAttack
The invention discloses a combined image compression / encryption method based on compressed sensing, which comprises the following steps of: firstly, a dictionary is formed by combining sub dictionaries obtained by classifying and training by combining a K-SVD method; secondly, an improved orthogonal matching pursuit algorithm is adopted in sparse coding; and finally, encryption is embedded in a compression process so that an encryption / compression algorithm of an image is realized. According to the invention, encryption and compression are tightly linked, therefore, on the premise of no basic influence to rate distortion performance, the attack resistance property and the stability of a system are further improved, the rate distortion performance of static image compression is superior to that of international main trend algorithms such as JEFG2000 and SPIHT at present, the image encryption performance is increased, and common attacks such as cipher text-only attack, chosen-ciphertext attack, known-plaintext attack and chosen-plaintext attack can be resisted. The invention can be used in image storage and transmission in the information security transmission fields such as internet, mobile telephones and video conferences.
Owner:瑞金市工业投资发展有限公司
Color Image Encryption Method Based on Compressed Sensing and Deformable Coupling Map Lattice
ActiveCN111327900BReduce sizeEasy to compressSecuring communication by chaotic signalsDigital video signal modificationPlaintextIntermediate image
The invention belongs to the technical field of information security, and in particular relates to a color image encryption method based on compressed sensing and deformable coupling image lattice, comprising: separating three primary color components of a color plaintext image to obtain a component matrix; combining with an initial key, through SHA-256 The function updates the parameters and initial values of the deformation coupling image lattice, obtains the measurement matrix and key stream by iterating the space-time chaotic system; divides the component matrix and obtains a new image matrix; generates a sparse dictionary for the new image matrix; uses the measurement matrix to measure the new image to obtain the intermediate image; transform the intermediate image into a coefficient matrix, perform scrambling and diffusion operations in the frequency domain to obtain a scrambled diffusion matrix; use the key stream matrix, perform pixel-level diffusion operations on the scrambled diffusion matrix, and obtain the final encryption text images. The invention effectively resists statistics, known and selected plaintext, selected ciphertext attacks, etc., improves security and encryption effect, and has good application prospect.
Owner:HENAN UNIVERSITY
Proxy re-encryption method for multicast communication
InactiveCN103888249BImprove securityResistant to Collusion AttacksSpecial service provision for substationKey distribution for secure communicationThird partyPlaintext
The invention provides a proxy re-encryption method for multicast communication, comprising the following steps: 1: the sender sets security parameters, and broadcasts the security parameters to all users; 2: independently selects a private key, and generates a public key according to the private key And make public the public key; 3: The sender performs hash function operation and bilinear pairing operation on the encrypted plaintext according to the security parameters and the public key of the agent to generate a first-level ciphertext; 4: The sender uses the security parameters and the proxy public key, generate a re-encryption key, and send it to the third-party agent; five: the third-party agent re-encrypts the first-level ciphertext according to the re-encryption key, generates a second-level ciphertext, and sends the second-level ciphertext to Agent; Six: The principal and the agent respectively decrypt according to the private key to obtain the plaintext. The invention can achieve the security of chosen ciphertext attack, and can be completely disclosed through the proxy re-encryption key, which is generated by the sender, which can resist collusion attack and improve the security of plaintext.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Encryption and decryption method and electronic device
ActiveCN105227308BReduce the risk of being crackedUser identity/authority verificationPlaintextChosen-ciphertext attack
Embodiments of the invention provide an encryption method, a decryption method and electronic equipment. The method comprises steps of acquiring a public key, a plaintext and a first bit string of a preset length through first electronic equipment, wherein the public key comprises the only defect trapdoor function; acquiring a key pair of a one-time signature scheme by the first electronic equipment, wherein the public pair comprises a verification secret key and a signature secret key corresponding to the verification secret key; acquiring a middle cryptograph set according to the only defect trapdoor function, the first bit string of the preset length, the plaintext and the verification secret key; signing the middle cryptograph set by the first electronic equipment according to the signature secret key, and acquiring a signature of the middle cryptograph set; and forming a final cryptograph by combing the verification secret key, the middle cryptograph set and the signature of the middle cryptograph set, and outputting the final cryptograph. Therefore, anti-selection cryptograph attack is achieved.
Owner:HONOR DEVICE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com