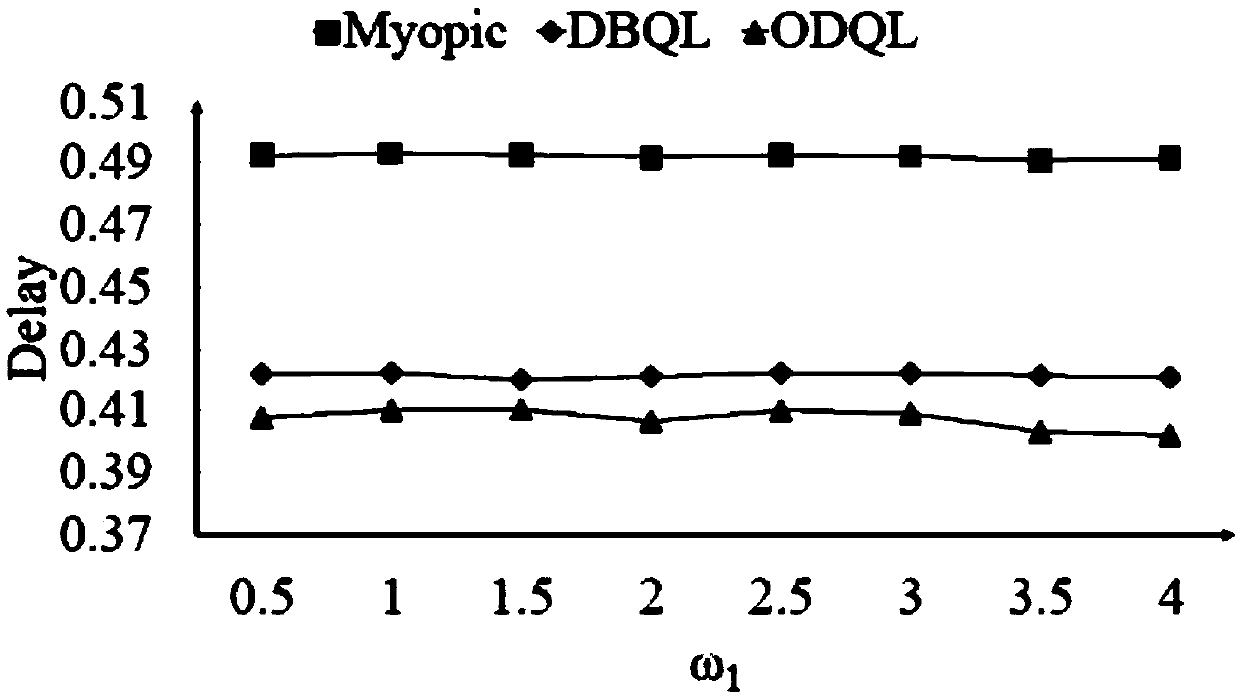
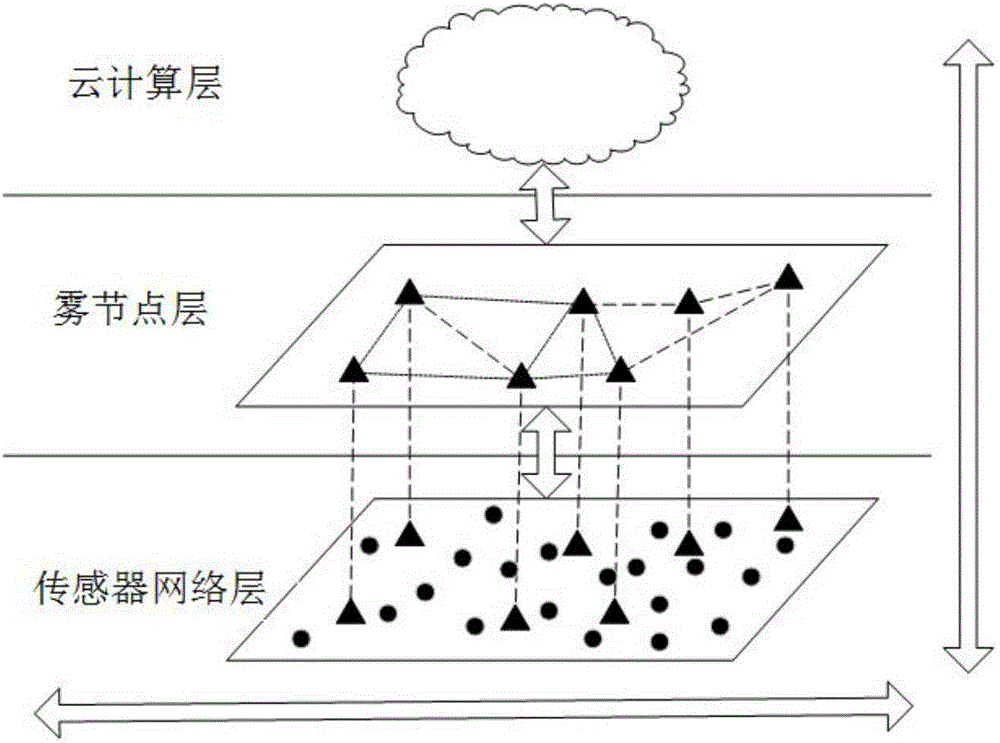
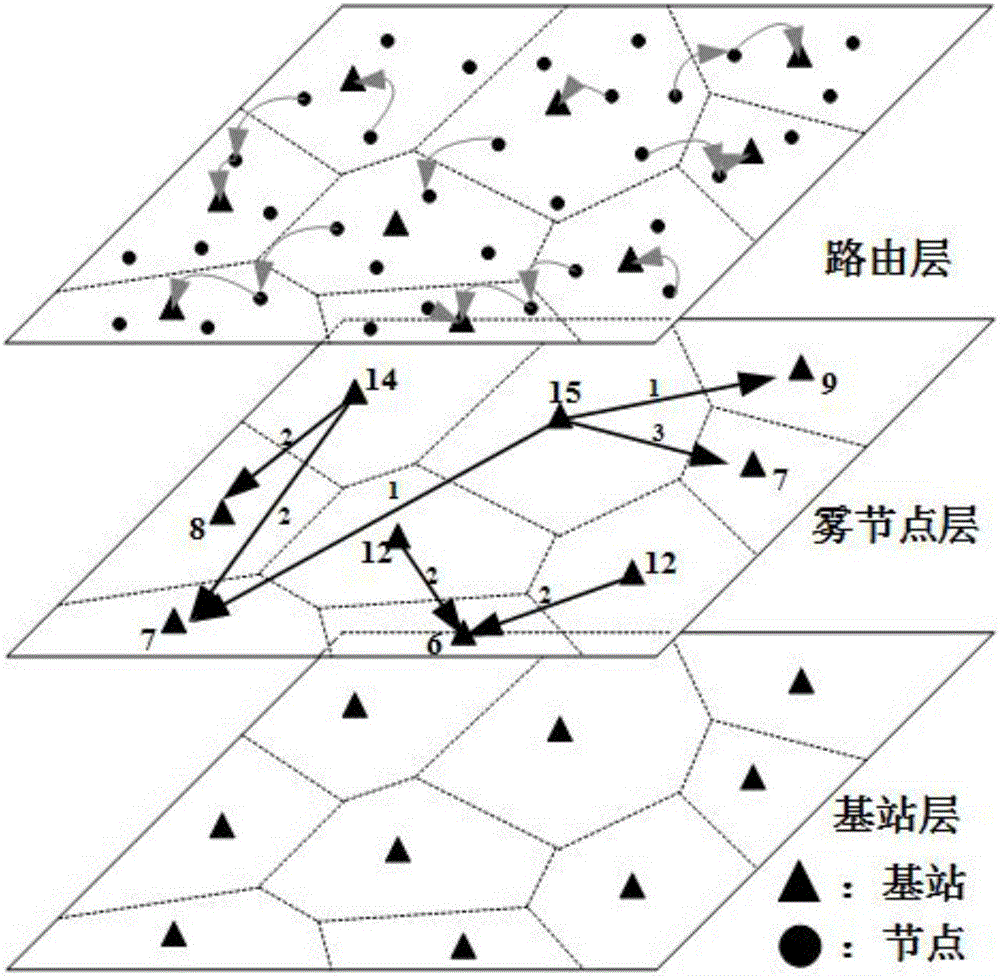
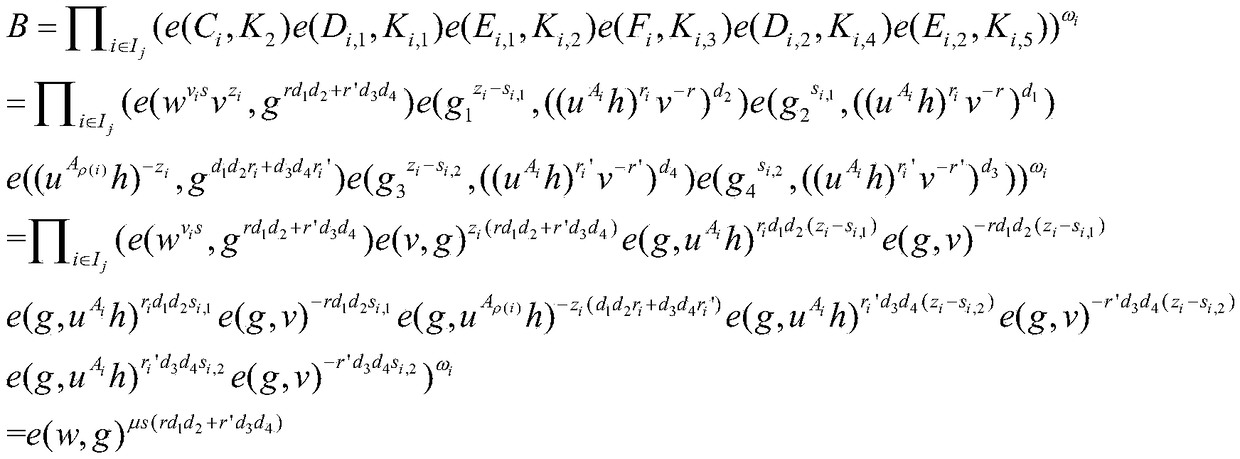Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
338 results about "Fog computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
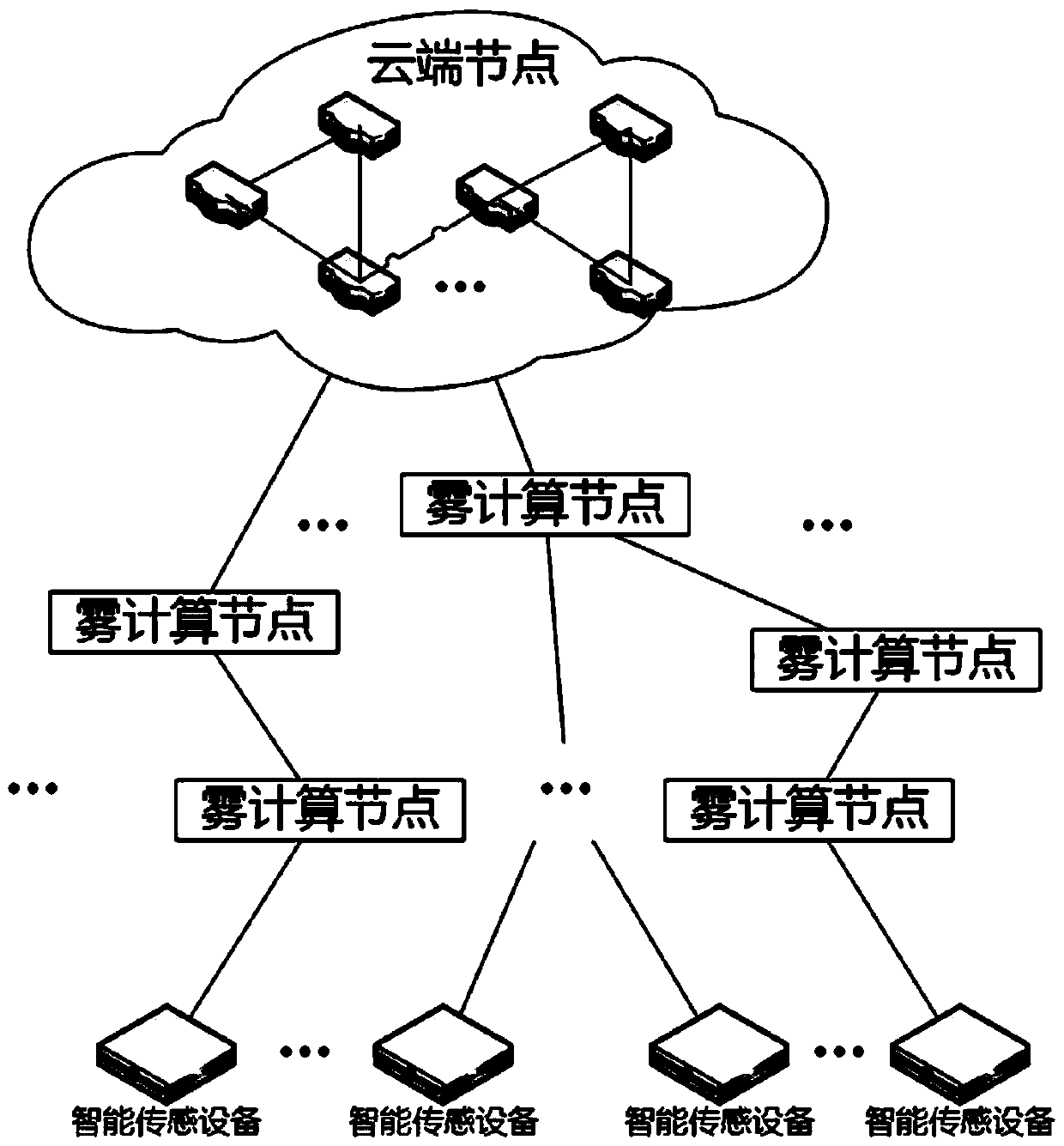
Fog computing or fog networking, also known as fogging, is an architecture that uses edge devices to carry out a substantial amount of computation, storage, and communication locally and routed over the internet backbone.
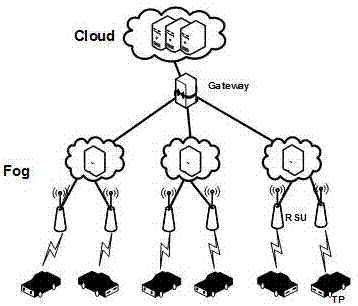
Internet of Vehicles deployment system based on fog computing
InactiveCN107071033AEasy accessEffective controlWireless commuication servicesTransmissionFog computingThe Internet
The invention discloses an Internet of Vehicles deployment system based on fog computing and relates to the field of Internet of Vehicles deployment and planning. A road side unit RSU collects vehicle traffic information and sends the information to fog equipment; the fog equipment processes and forwards the vehicle traffic information and temporarily stores the vehicle traffic information; and the fog equipment uploads the stored vehicle traffic information to a server cluster, and the server cluster controls the vehicle traffic information through computation and analysis of a big data result and makes a reasonable traffic strategy. According to the system, the fog equipment is introduced to the edge of the network, and meanwhile, the fog equipment temporarily computes and stores the vehicle traffic information, so that the bandwidth resources are saved and the data transfer rate is improved.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Internet of things network system using fog computing network
InactiveUS20160182639A1Easy to implementBroadband local area networksParticular environment based servicesFog computingComputer science
The present invention relates to an Internet of Things network system, and more particularly, to such an Internet of Things network system in which the installation and version management of an application of a virtual machine for operating a detection server device is performed through a fog computing network in response to a request from a manager so that an application specialized for the detection server device can be easily installed or managed through the fog computing network.
Owner:UNIV IND COOP GRP OF KYUNG HEE UNIV
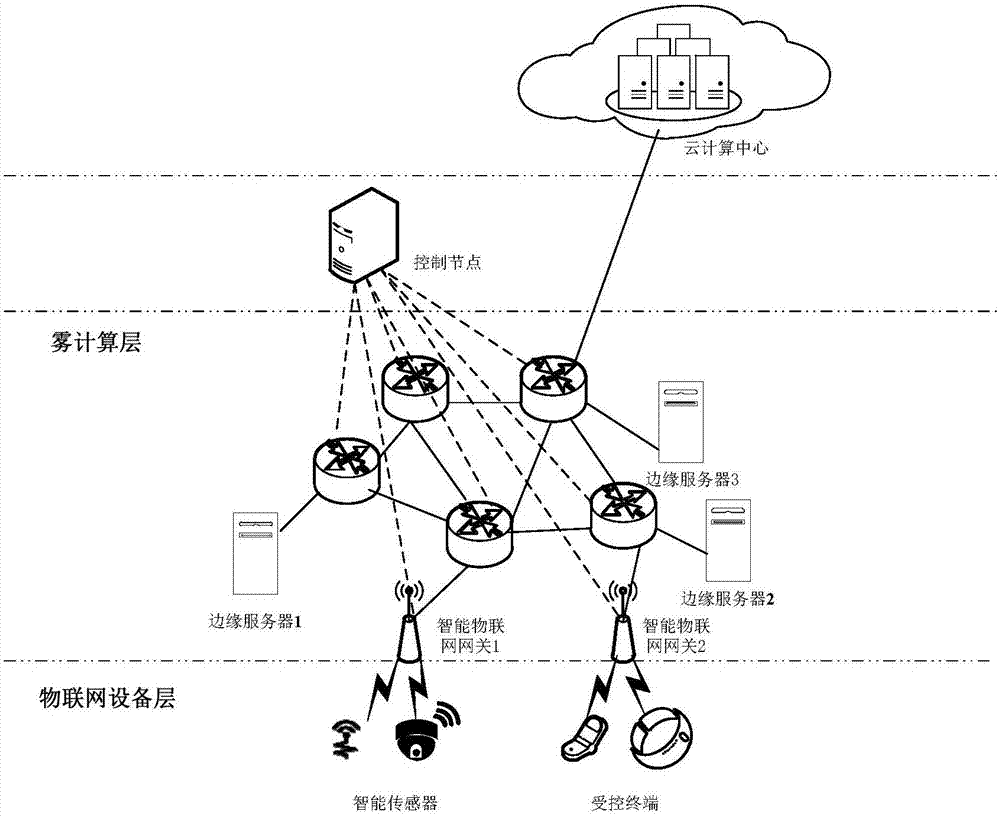
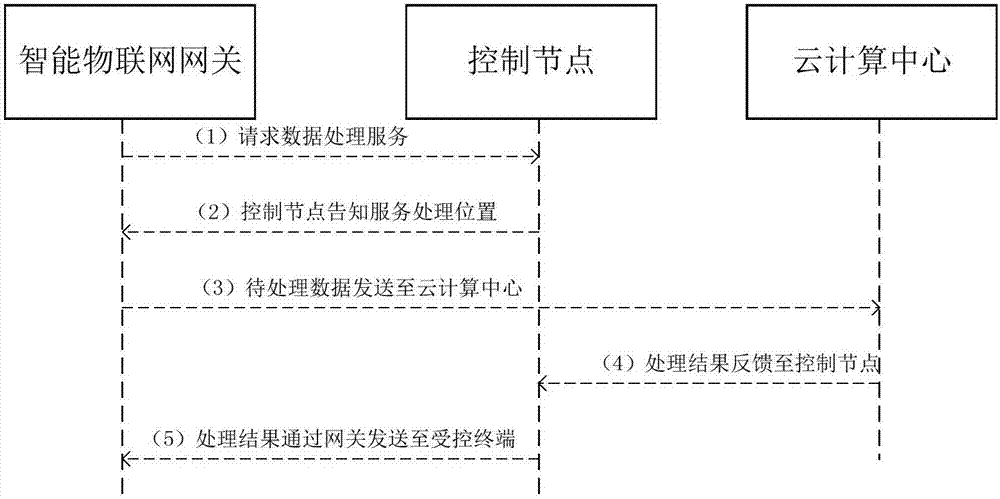
Architecture based on fog computing in SDN (Software Defined Network) and processing method thereof
The invention relates to an architecture based on fog computing in an SDN (Software Defined Network). The architecture comprises an Internet of Things equipment layer, a fog computing layer, a control node and a cloud computing center. A processing method of the architecture based on the fog computing in the SDN comprises the following steps: step (1), sending a request to the control node by an intelligent sensor via an intelligent Internet of Things gateway; step (2), if not being a delay-sensitive service, turning to step (3), otherwise turning to step (4); step (3), transmitting data to the cloud computing center by the control node, and feeding a result back to a controlled terminal by the cloud computing center; step (4), if a data processing service request is less than a threshold, turning to step (5), otherwise turning to step (6); step (5), searching a server occupancy table and processing the server occupancy table by selected edge servers and feeding the result back to the controlled terminal; and step (6), inquiring the server occupancy table, selecting the edge servers whose CPU utilization rate and memory usage are greater than the threshold by the control node, performing data processing by the plurality of selected edge servers, and returning a processing result to the controlled terminal.
Owner:XIDIAN UNIV
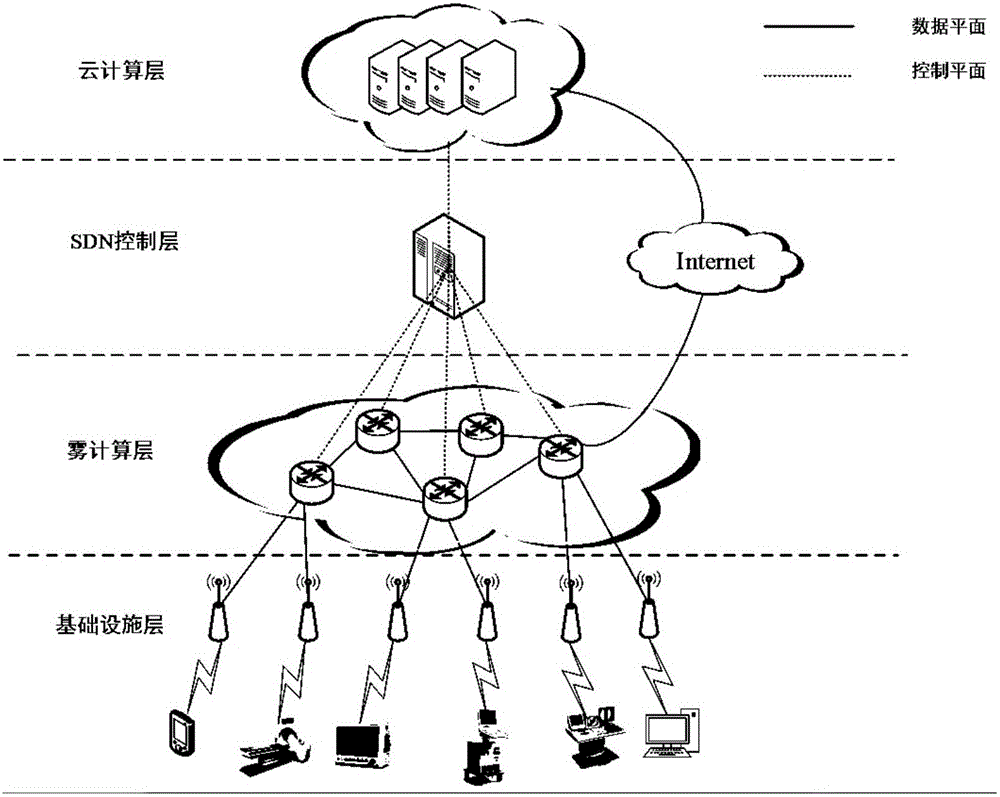
Cloud/fog hybrid network architecture based on SDN
The invention belongs to the technical field of a fog computing network, and particularly relates to a cloud / fog hybrid network architecture based on an SDN. The cloud / fog hybrid network architecture comprises an infrastructure layer, a fog computing layer, an SDN control layer and a cloud computing layer, wherein the infrastructure layer is used for sending a request of a user terminal and detection data of a medical device to the fog computing layer; the fog computing layer is connected with the infrastructure layer via an unshielded category 5e twisted pair, and is used for receiving and storing medical data uploaded by the user terminal, downloading an analysis result on a cloud server in an active caching manner, processing the medical data uploaded by a client according to the downloaded analysis result, and uploading the medical data to the cloud computing layer; the SDN control layer is connected with the fog computing layer via the unshielded category 5e twisted pair, and is used for controlling data forwarding of the fog computing layer; and the cloud computing layer is connected with the SDN control layer via an optical fiber, and is used for storing the collected medical data, carrying out analysis on the medical data, and processing the medical data received by the fog computing layer cooperatively with the fog computing layer.
Owner:XIDIAN UNIV
Personalized deep learning method for fog computing environment
ActiveCN107871164AEnsure safetySafeTransmissionPhysical realisationPersonalizationContinual improvement process
The invention discloses a personalized deep learning method for fog computing environment. A cloud node trains a general model through mass training data, the general model obtained by training is distributed to each fog computing node, the computation and storage ability of the fog computing node is used for training a deep leaning model which meets edge side industry requirements; data is collected from intelligent sensing equipment, and real-time reasoning is carried out on the fog computing node to output a result in real time; and errors which appear in reasoning are identified, the modelcan be continuously trained and optimized, the industrial personalized model can be selectively transmitted into the cloud, and meanwhile, the general model of the cloud is received and continuouslyimproved and optimized. Compared with the prior art, the method disclosed by the invention improves real-time business execution efficiency, meanwhile, the personalized deep learning method is storedin the fog computing node to guarantee the safety of the model, in addition, the model can be shared to the cloud according to the permission of the user, and therefore, the model exhibits openness.
Owner:山东浪潮创新创业科技有限公司
Tactile warning panel apparatus and system with smart technology
ActiveUS20170252256A1Enhancing urban mobilityImprove securitySingle unit pavingsCable installations in cable chambersElectricityTouch Perception
The present invention relates to tactile warning panels, and in particular to tactile warning panels that are designed and built with multifunction / multipurpose capabilities that serve the visually impaired and enable the deployment of smart city technology by integrating tactile warning systems and subsurface enclosures that can withstand pressures of five (5) tons up to and exceeding sixty (60) tons and incorporate small cells, beacons, sensors, Fog Computing, electric energy generation, rechargeable power supplies, wireless M2M communication and a plethora of other smart city technologies.
Owner:BRANDBUMPS
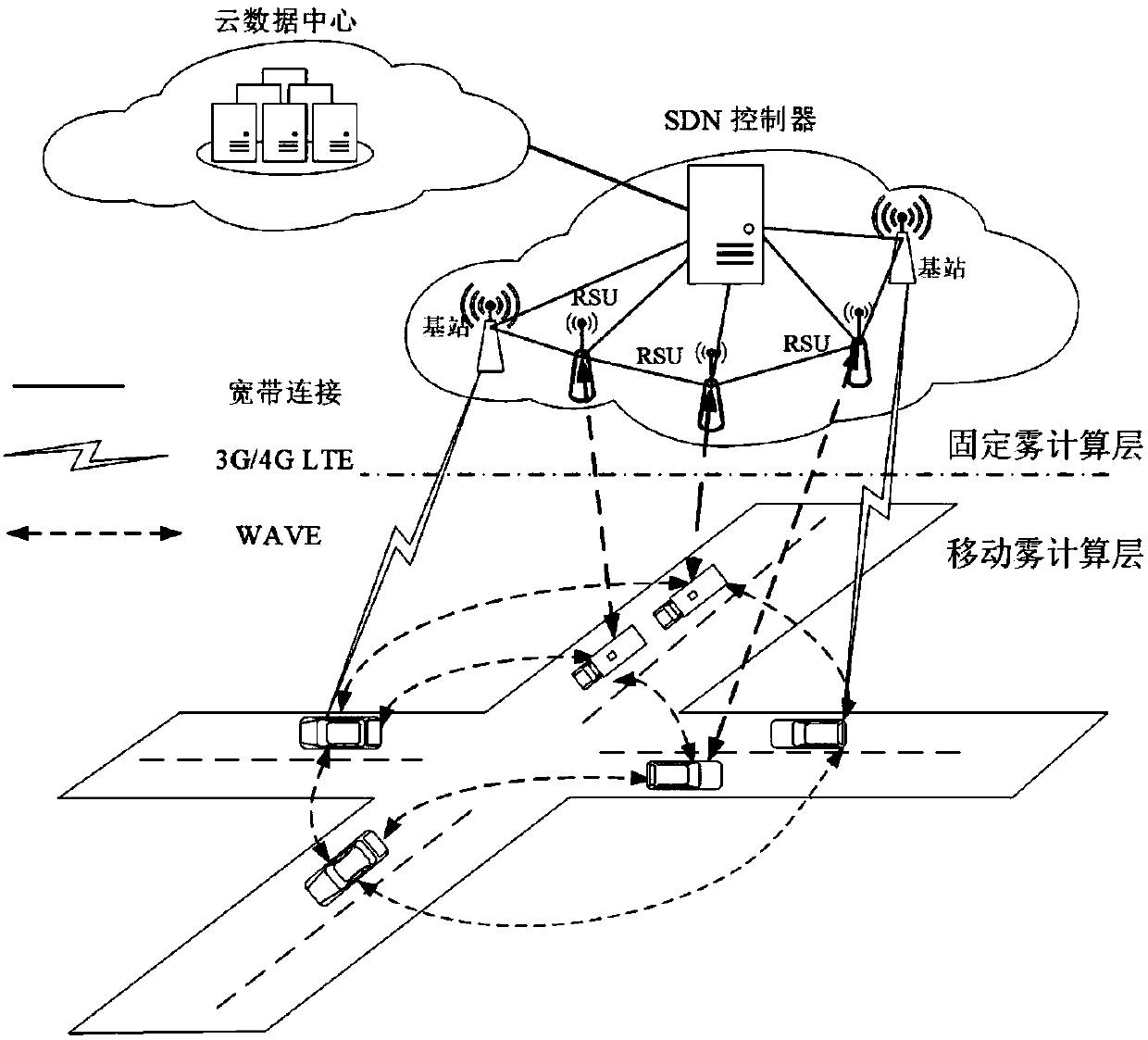
SDN and fog computing hybrid vehicular ad-hoc network system
InactiveCN108259573AIncrease resourcesImproved application service reliabilityParticular environment based servicesTransmissionMobile vehicleFog computing
The invention discloses an SDN and fog computing hybrid vehicular ad-hoc network system. The whole framework of the SDN and fog computing hybrid vehicular ad-hoc network system comprises a cloud computing layer, a fixed fog computing layer and a mobile fog computing layer; the cloud computing layer is composed of cloud servers; the fixed fog computing layer is composed of an SDN controller, a RSUand a base station; and the mobile fog computing layer is composed of running vehicles and vehicle-mounted mobile devices. The SDN and fog computing hybrid vehicular ad-hoc network system has the beneficial effects as follows: from the perspective of economics and application service reliability, as SDN and fog computing are mixed to consider roadside infrastructure, mobile vehicles, user terminals and the like as available processing nodes, resources such as computing, communication and network of the system are added; and due to adoption of a task distribution strategy, application service reliability is improved, and an extra cost consumption is avoided.
Owner:XIDIAN UNIV
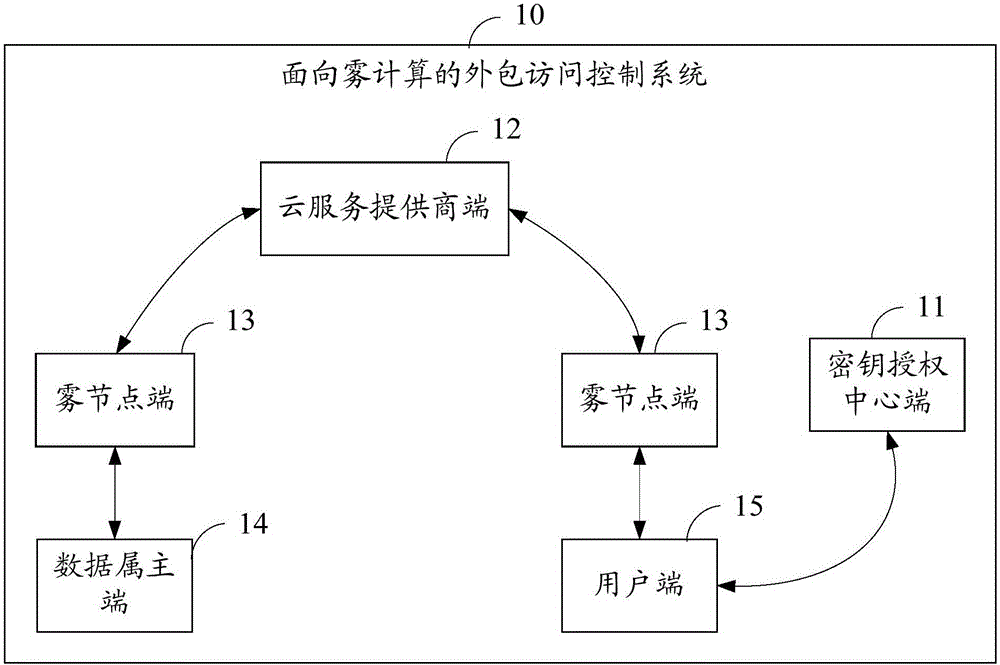
Outsourcing access control method and system aiming at fog computing
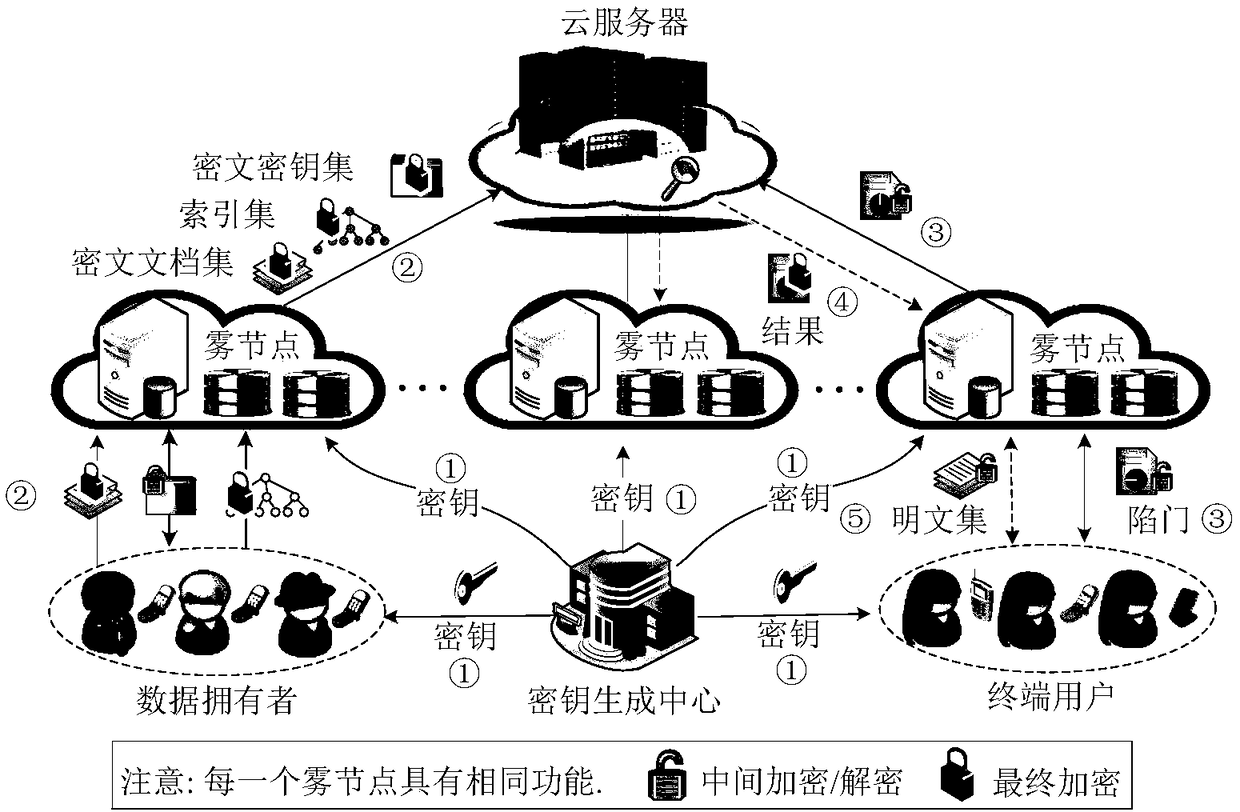
ActiveCN106357395AReduce computational overheadLighten the computational burdenKey distribution for secure communicationCiphertextFog computing
The invention belongs to the technical field of cloud storage services and provides an outsourcing access control method and system aiming at fog computing. The method includes: a key authorizing central terminal receives user registration and generates system parameters and a key for each user; a data owner terminal defines an access structural tree related to cipher text, generate cipher text unrelated to the access structural tree and transmits the generated cipher text to a fog node terminal; the fog node terminal generates cipher text related to the access structural tree, integrates all cipher text, and uploads the integrated cipher text to a cloud service provider terminal for storage; a user terminal accesses the cipher text stored at the cloud service provider terminal through the fog node terminal, the cipher text is decrypted to display plain text when the attribute set of the user terminal satisfies the access structural tree embedded into the cipher text. By the method, the computing burden of the data owner terminal can be lowered greatly, a user only needs to execute one bilinear-pair operation and two multiplication so as to successfully decrypt the cipher text, and the computing burden of the user is lowered greatly.
Owner:SHENZHEN UNIV
Lightweight privacy protection data multistage aggregation method based on fog computing
ActiveCN110536259AGuaranteed to proceed normallyReduce overheadParticular environment based servicesTransmissionComputer networkFog computing
The invention discloses a lightweight privacy protection data multistage aggregation method based on fog computing. Firstly, a power grid coverage area is divided into sub-areas; a fog node exists under each subarea; a plurality of intelligent electric meters exist under the fog node; the intelligent electric meter collects power consumption information of a user in real time and uploads an encrypted data generation report to the unique fog node in the subarea; the fog node collects power utilization data from all the intelligent electric meters in the sub-region, performs primary aggregation,generates a report and uploads the report to the cloud server; and the cloud server performs secondary aggregation on the data from all the fog nodes and generates a report, then decrypts and reads the aggregated data by using the key so as to control the power consumption, and the trusted institution is used for generating system parameters and registering the intelligent electric meter and thefog equipment in the data aggregation process. The method has the advantages of high flexibility, low calculation cost, high analysis speed, high precision and the like.
Owner:NANJING UNIV OF POSTS & TELECOMM
Intelligent power grid safety and privacy protection data aggregation method based on fog computing
ActiveCN110138538AIn line with regional divisionFlexible Power SchedulingKey distribution for secure communicationPublic key for secure communicationData aggregatorPrivacy protection
The invention provides an intelligent power grid security and privacy protection data aggregation method based on fog computing. The method comprises the following steps: acquiring, encrypting and uploading a user electricity consumption data report through an intelligent electric meter; performing fine-grained aggregation by using the fog nodes capable of mining local computing power and uploading the fine-grained aggregation to the cloud nodes; completing coarse-grained aggregated data through the cloud node and uploading the coarse-grained aggregated data to the electric power service mechanism; and finally collecting, processing and analyzing the coarse-grained aggregation data by a reliable power service mechanism, and generating a power dispatching scheme according to the analysis results. The method comprises the following specific steps: (1) initializing a system; (2) packaging an intelligent electric meter data report; (3) packaging a fog node fine-grained aggregation report;(4) packaging the coarse-grained aggregation report of the cloud node; and (5) reading the aggregation report by the power service mechanism. The method has the advantages that the security and integrity of user privacy data are protected, multi-resolution aggregation is carried out on the user privacy data, the transmission consumption is reduced, and flexible power dispatching is realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
Fog computing based road information service system and method during city traffic congestion
InactiveCN106548646ACalculation speedSave driving timeRoad vehicles traffic controlTraffic congestionFog computing
The invention discloses a fog computing based road information service system and method during city traffic congestion. The system comprises a vehicle-mounted intelligent terminal, a fog server, a roadside unit and a roadside cloud server module. The method comprises the following steps: 1, constructing a local area network; 2, positioning a vehicle; 3, sending a service request; 4, receiving the service request; 5, planning a driving route; and 6, feeding back an optimal path. According to the invention, the local area network is constructed by use of the fog server, real-time road condition information under jurisdiction is collected and is transmitted to the roadside unit governing the fog server, the roadside unit plans the driving route according to destination address information of the vehicle and the real-time road condition information, and the system and method are enabled to have the advantages of low delay, position perception, wider geographical distribution, suitability to more nodes and less driving time.
Owner:XIDIAN NINGBO INFORMATION TECH INST
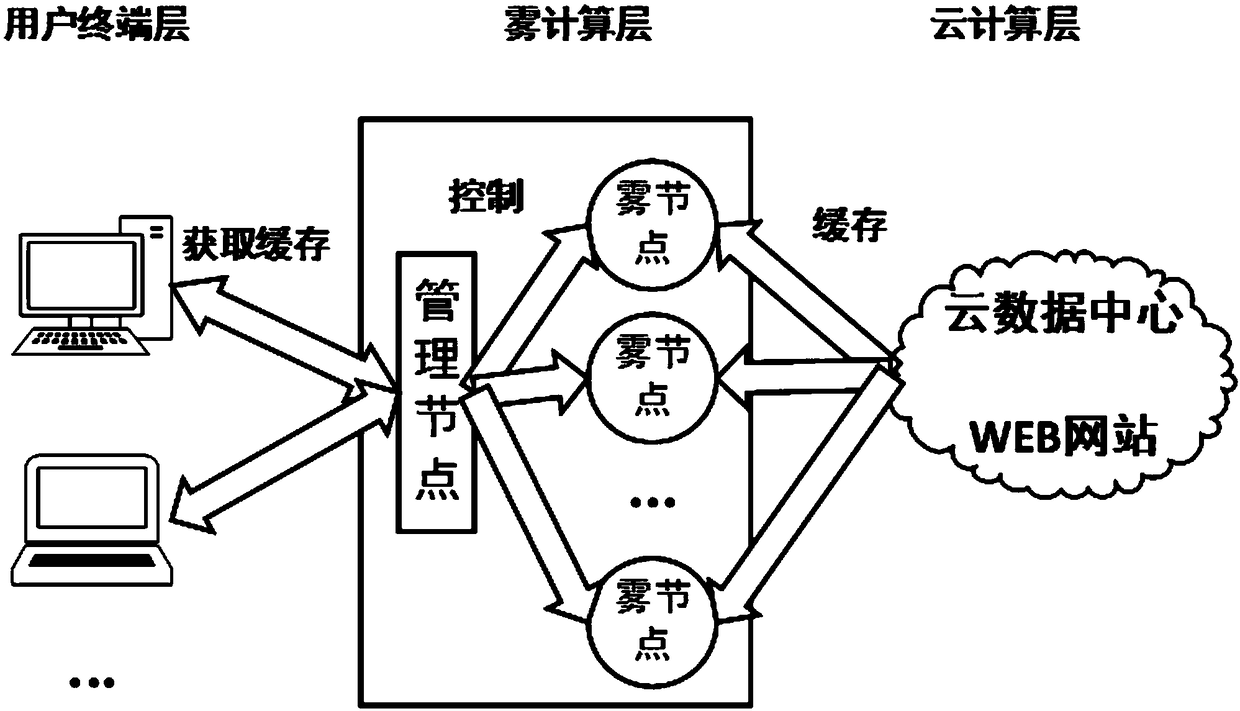
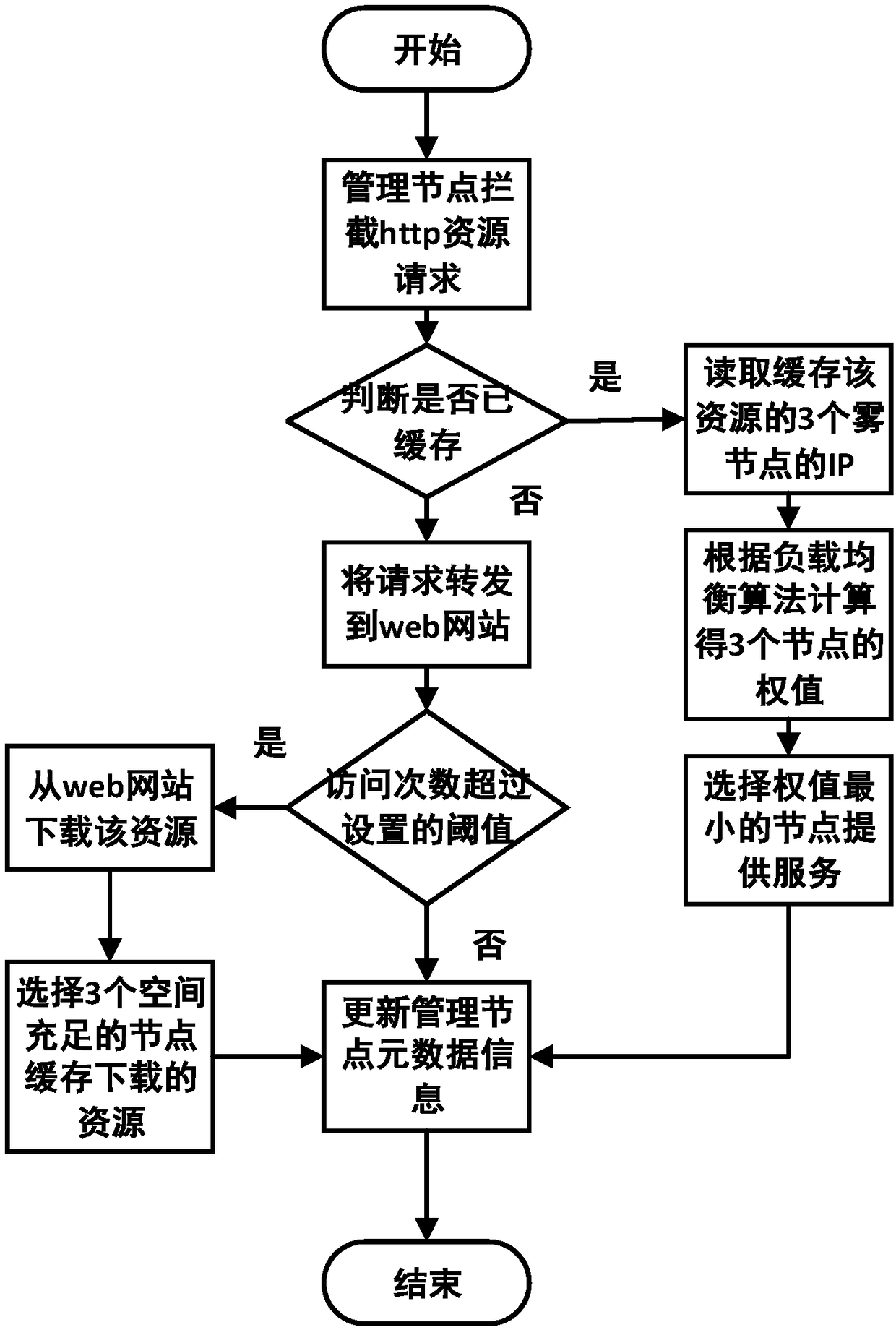
Method and system for reducing website access time delay by using caches in fog computing architecture
The invention relates to a method and system for reducing website access time delay by using caches in fog computing architecture. On the premise of not influencing normal running of a cloud data center website, fog nodes are used for caching static resources in a local area network to reduce the time delay of user access and improve the user experience. In the method and system, hot resources with the request quantity exceeding a threshold value set by the system are subjected to multi-copy caching in multiple fog nodes; when the resources need to be read, the most suitable fog node is selected to provide services according to the load balancing algorithm; cache management nodes are set to conduct record management on meta information of system cache resources.
Owner:SHANDONG UNIV
Fog computing task unloading method for Internet of Things
ActiveCN110098969AAchieve stabilityReduce latencyNetwork traffic/resource managementData switching networksThe InternetFog computing
The invention relates to a fog computing task unloading method for the Internet of Things, and belongs to the technical field of mobile communication. According to the method, bidirectional matching joint modeling are carried out task unloading decisions, transmission resource allocation and computing resource allocation, and FN and IoT equipment to minimize the total overhead problem of the system. Firstly, QoS requirements of the IoT equipment are analyzed based on an analytic hierarchy process, and priorities are established according to different QoS requirements of the IoT equipment; secondly, RB allocation is conducted on the IoT devices, and the number of RBs needed by every IoT equipment is determined; then, computing resource allocation is carried out, and the computing time delayis determined. Based thereon, a bi-directional matching game is established, and a stable association between the FN and the IoT device requesting offloading is determined. And finally, every IoT equipment makes an unloading decision according to the task local computing overhead and the task unloading computing overhead. According to the invention, the total time delay and the energy consumptioncost of the system are reduced, and the stability of IoT equipment association and the effectiveness of resource allocation are realized.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
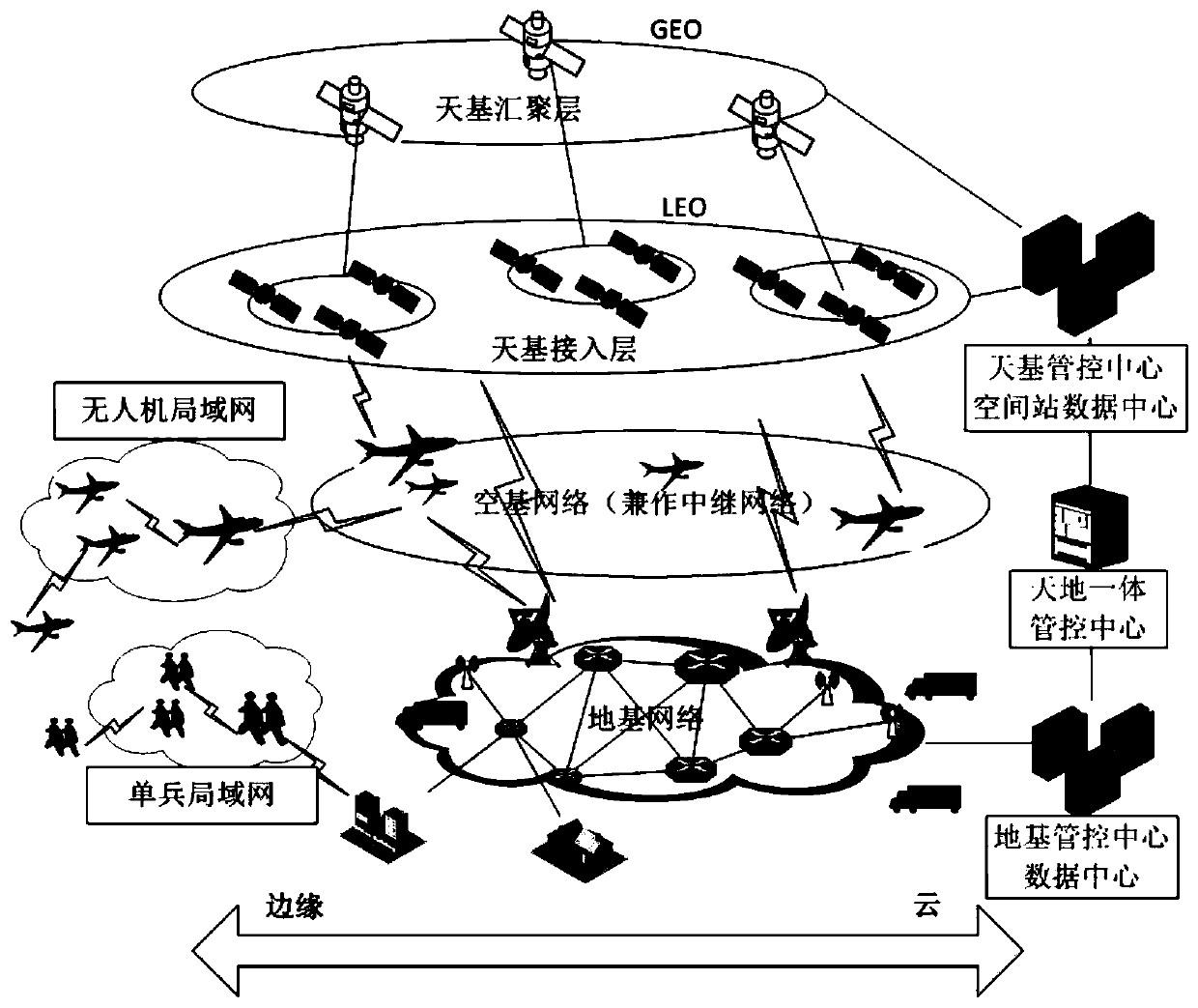
Fog computing-based spatial information network architecture and method, and readable storage medium
The invention discloses a fog computing-based spatial information network architecture, a fog computing-based spatial information network architecture method and a readable storage medium, and the architecture comprises a sensing layer which is used for collecting basic information of one or more applications in remote sensing, weather and positioning and sending the collected information to a cooperative processing layer; the cooperative processing layer used for co-processing the information acquired by the sensing layer; and an application service layer used for receiving the information processed by the sensing layer and the cooperative processing layer and providing comprehensive application services for space-based, space-based, sea-based and land-based users. According to the invention, distributed storage and distributed calculation can be provided, the network bandwidth can be saved, the CDN is optimized, the network bandwidth is saved, and the interaction rate is improved. Inaddition, the computing mode can be selected according to the content of the application service, the application service can be processed more quickly, and computing resources can be utilized to themaximum extent.
Owner:TECH & ENG CENT FOR SPACE UTILIZATION CHINESE ACAD OF SCI
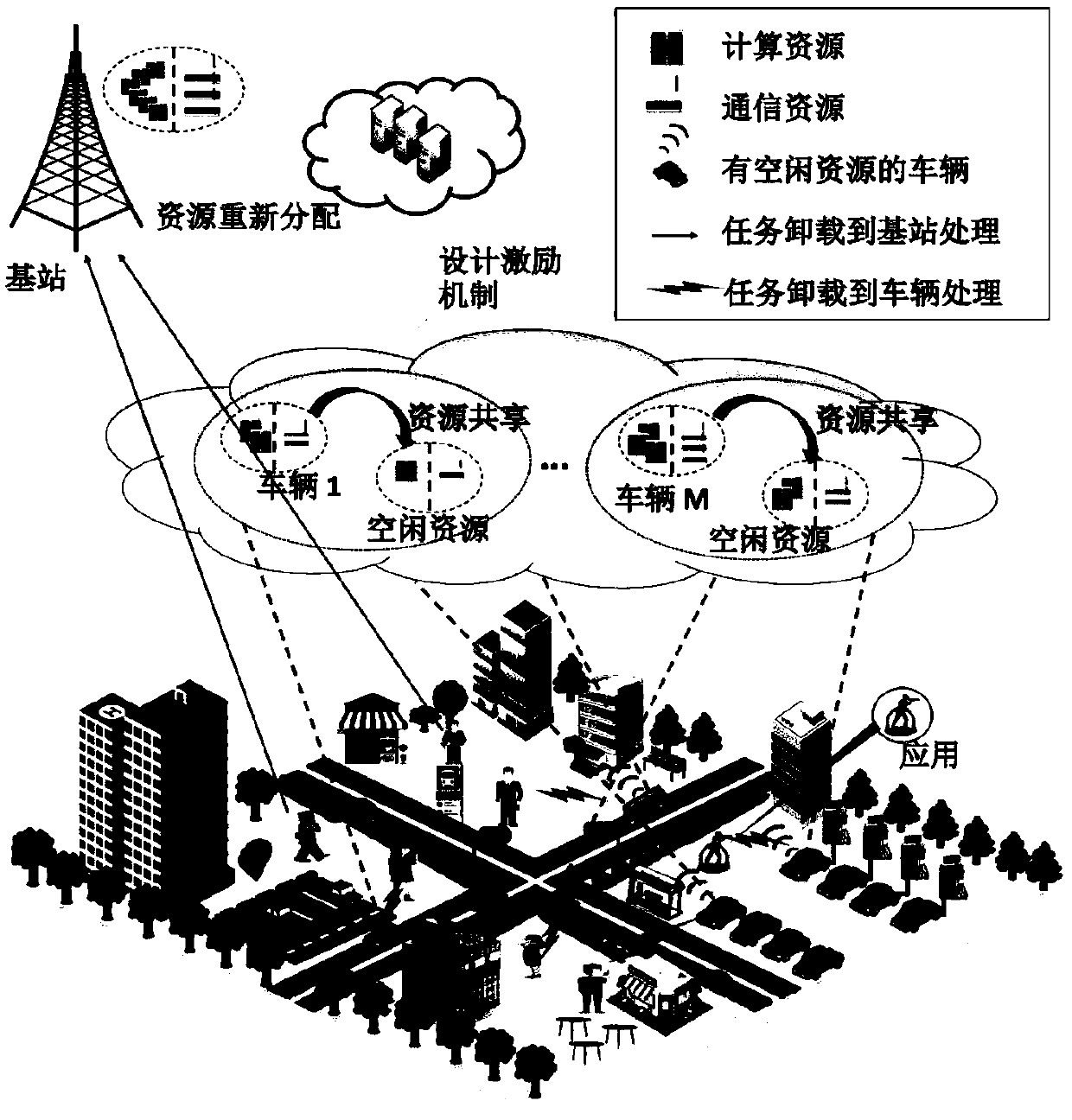
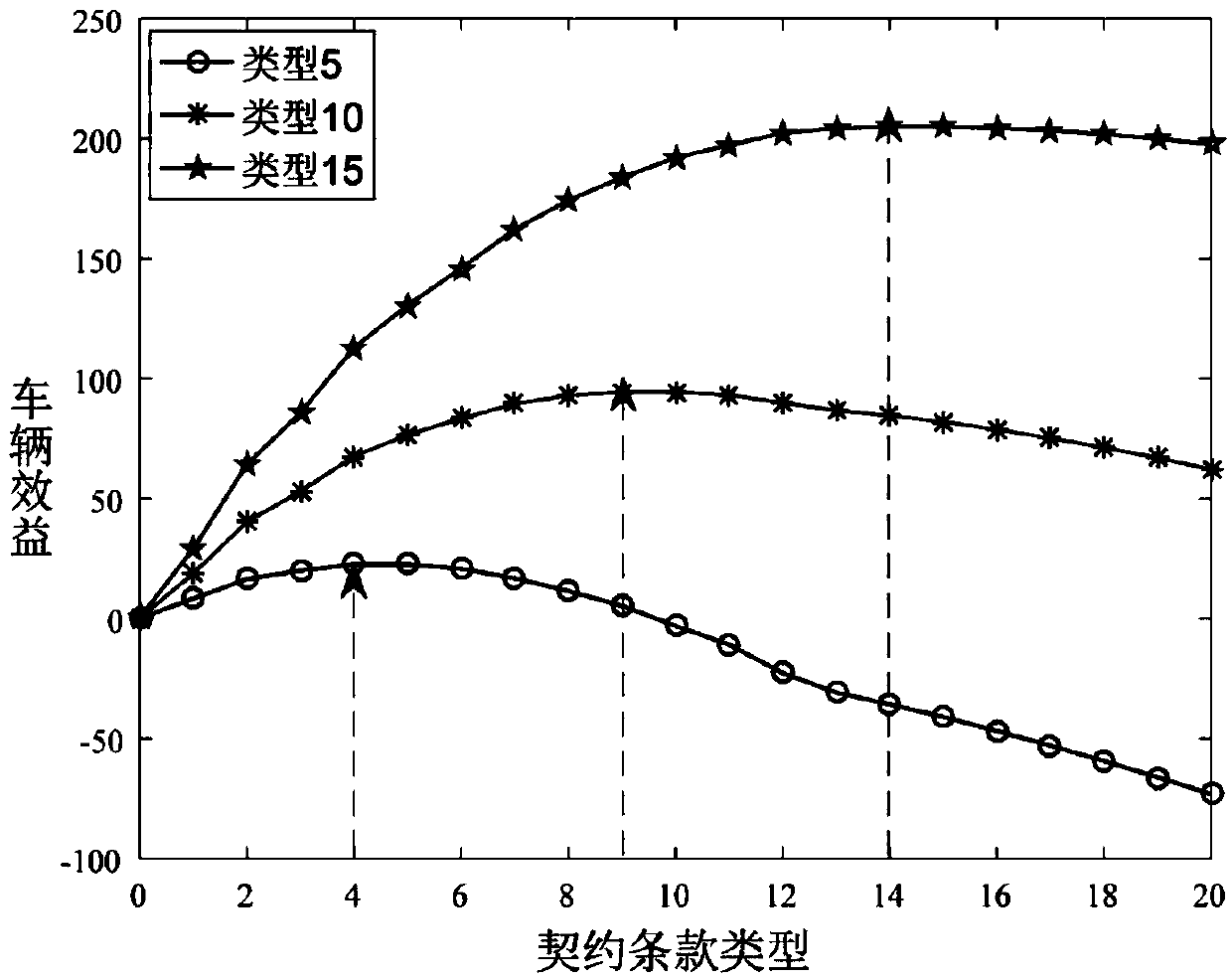
A computational resource allocation and task unloading scheme based on contract matching theory
ActiveCN109005057AHigh priceStable matchForecastingProgram loading/initiatingFog computingPhases of clinical research
The present invention relates to a resource allocation and task unloading scheme applied in fog computing, which unloads a computing task from a user equipment to a vehicle fog node by utilizing underutilized resources of a nearby vehicle. Through the study of contract theory and matching theory, an effective incentive mechanism and task allocation mechanism is provided. The contract theory-matching theory proposed in this paperis a two-stage optimization problem. In the first stage, this paper proposes an effective incentive mechanism based on contract theory to encourage vehicles to share resources. the expected utility of the base station is maximized by designing contracts for each vehicle type. In the second phase, the task assignment problem is transformed into a bilateral matching problem between the vehicle and the user equipment. The problem is solved by a price-based matching algorithm, which iteratively performs the process of 'applying' and 'raising the price' according tothe dynamic preference list, and finally obtains a stable match between the vehicle and the user.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
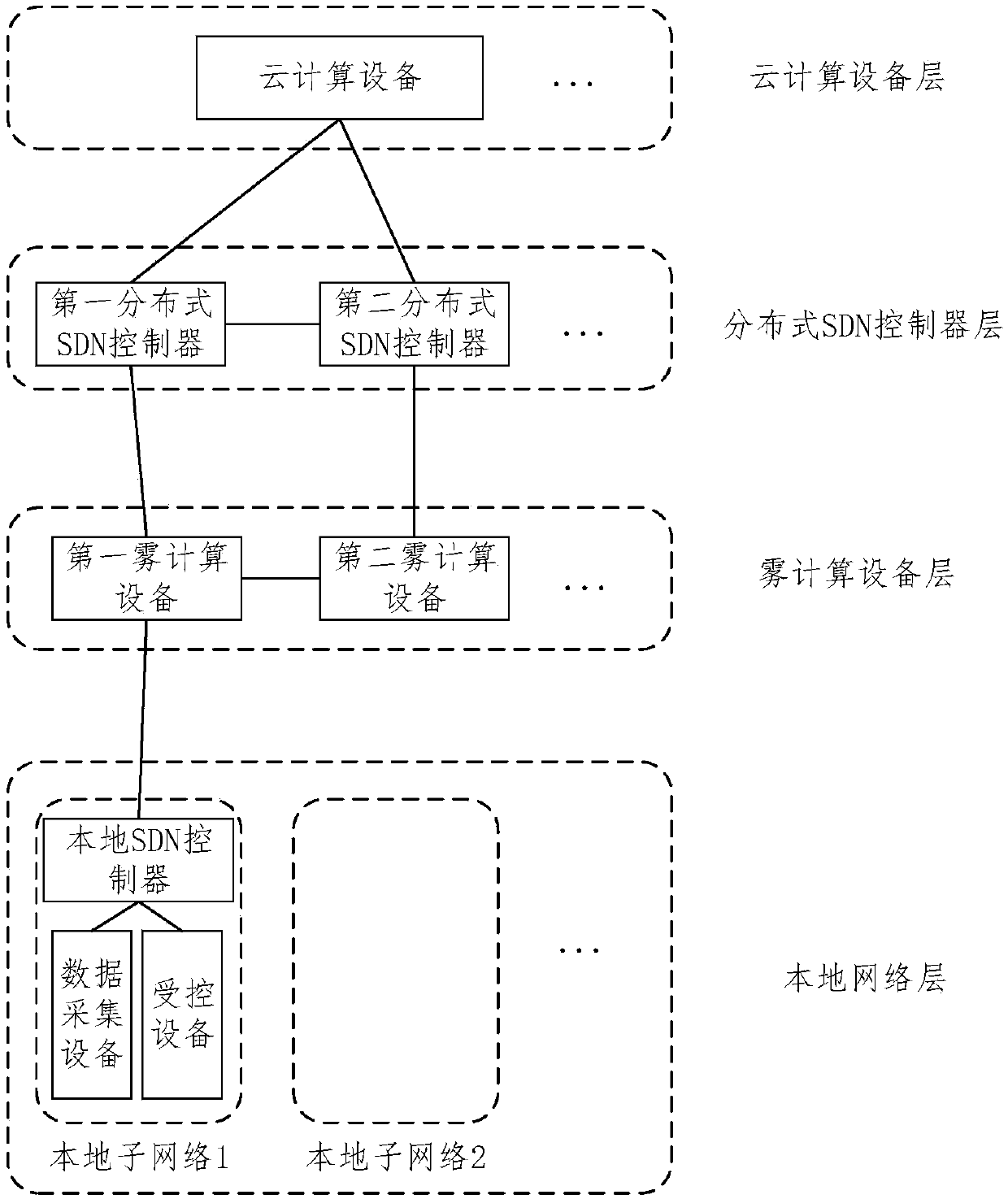
SDN-based Internet of Things fog computing network system and control method thereof
ActiveCN107948129AEnsure safetyImprove processing efficiencyData switching networksFog computingNetworked system
The invention provides an SDN-based Internet of Things fog computing network system and a control method thereof. The SDN-based Internet of Things fog computing network system comprises a local sub-network, fog computing equipment, distributed SDN controllers and cloud computing equipment, wherein the local sub-network comprises data acquisition equipment, controlled equipment and a local SDN controller, and the data acquisition equipment and the controlled equipment are each connected with the local SDN controller; and the distributed SDN controllers are used for verifying received request information sent by means of the local SDN controller, and sending request confirmation information to the fog computing equipment and the local SDN controller. The SDN-based Internet of Things fog computing network system and the control method thereof realize hierarchical authentication of accessed equipment and hierarchical processing of data through grading a network system, ensure the securityof the network, and improve the data processing efficiency and utilization rate of network resources.
Owner:BEIJING UNIV OF POSTS & TELECOMM
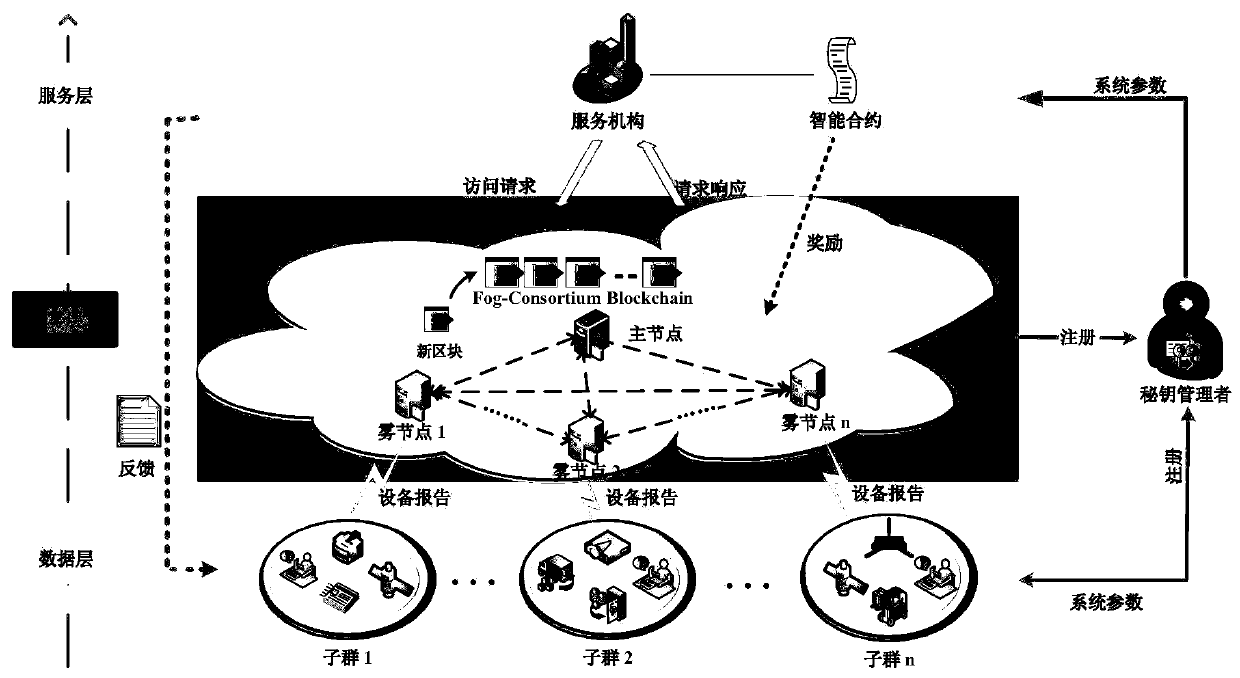
Security distributed aggregation and access system and method based on fog alliance chain
ActiveCN111372243AReduce transmission overheadResist curiosityPublic key for secure communicationSecurity arrangementData integrityConfidentiality
The invention discloses a security distributed aggregation and access system and method based on a fog alliance chain, and aims to solve the problem that most of current data aggregation schemes are designed based on a centralized mode, face single-point faults and tampering threats, and have security and performance improvement space. In order to solve the challenge, a distributed aggregation framework is designed in combination with fog computing and an alliance chain, single-point faults and tampering crisis are solved, and powerful support is provided for safe collection, communication andstorage of data. Meanwhile, a Paillier homomorphic algorithm of a threshold version is fused, a safe access control mechanism with a fault-tolerant function is designed, and confidentiality and privacy of data on a chain are guaranteed. Meanwhile, an efficient anonymous authentication method is provided, and identity privacy and data integrity can be guaranteed. Finally, the comparative analysisresult of the method and the existing method shows that the method can resist malicious attacks and ensure the system security, and compared with other existing methods, the method has lower calculation and communication costs.
Owner:NANJING UNIV OF POSTS & TELECOMM
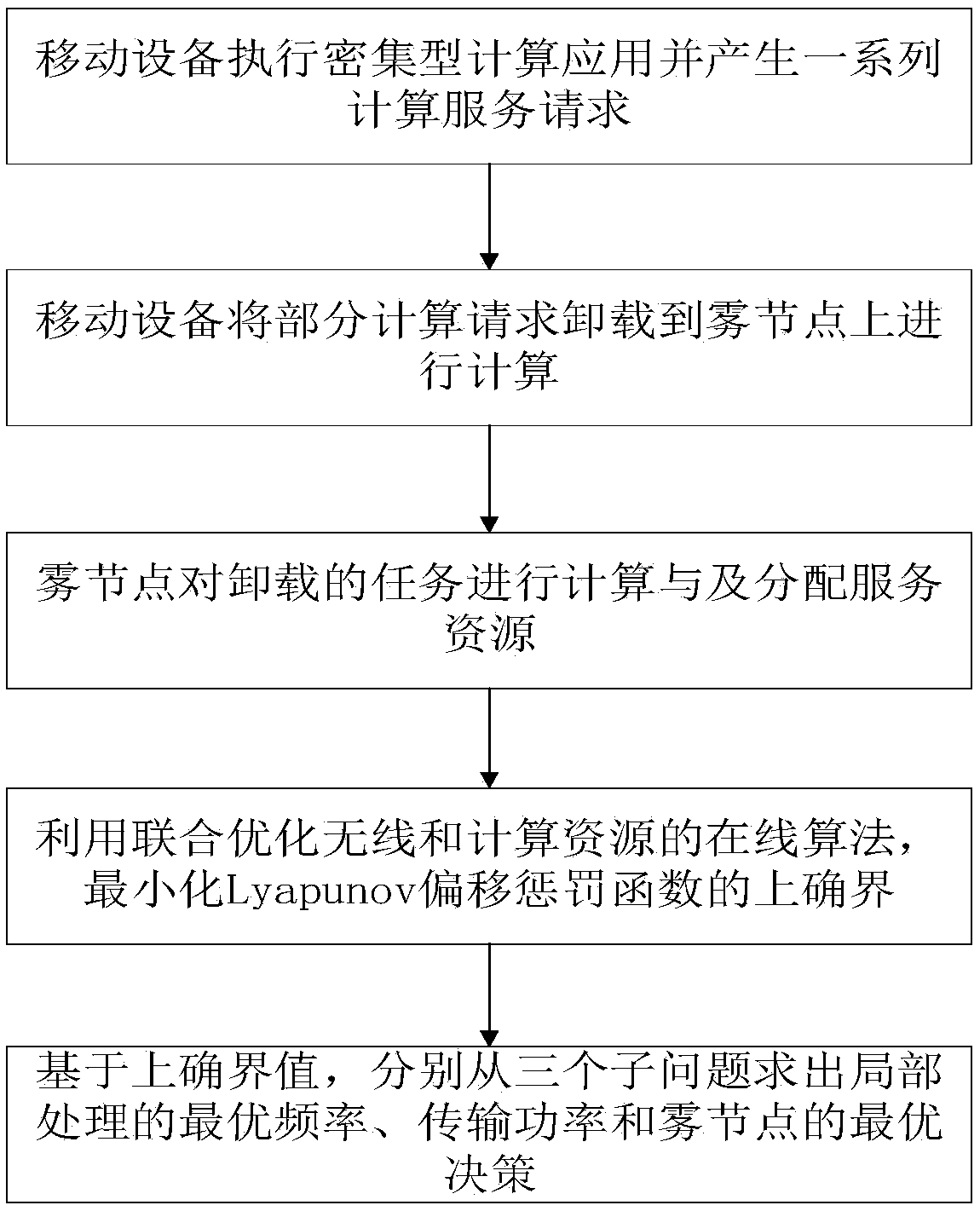
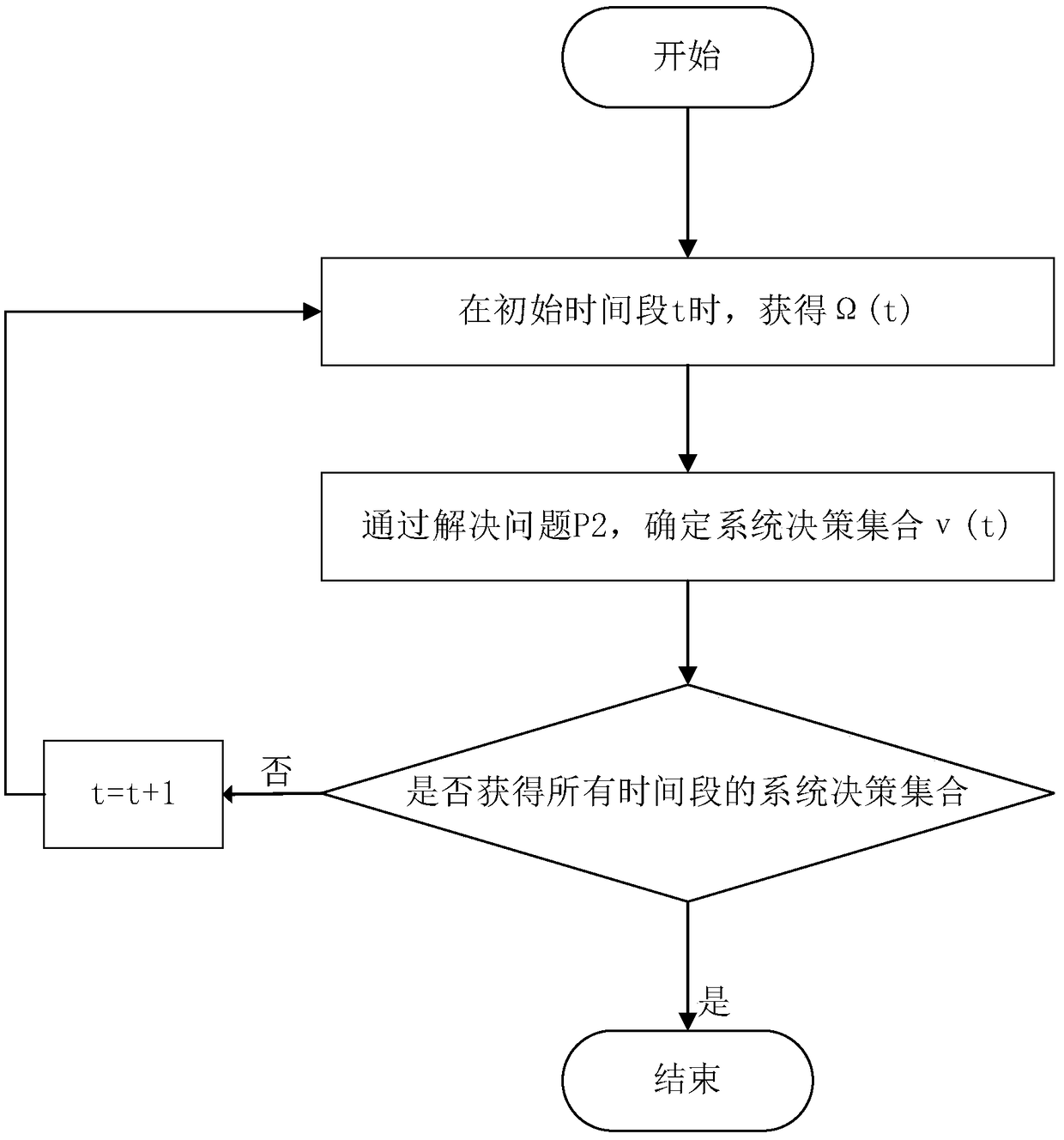
A dynamic unloading method of fog computation based on Lyapunov optimization
ActiveCN109343904AImprove performanceOptimum CPU cycle frequencyResource allocationProgram loading/initiatingLyapunov optimizationFog computing
The invention provides a dynamic unloading method of fog calculation based on optimization, belonging to the field of wireless network communication. The present invention divides the calculation request into a local calculation portion and a fog calculation portion. By offloading computationally intensive requests to fog nodes, application performance can be significantly improved. An online joint radio and computational resource algorithm based on Lyapunov optimization is used to derive the upper bound of Lyapunov migration penalty function. By minimizing the upper bound from the perspectiveof different decision variables, , the optimal CPU cycle frequency of local processor is obtained with a convex optimization method. By using the predefined offload priority function, the optimal transmission power of the optimal subchannel is obtained. On the fog node, the optimal request scheduling decision is obtained by absurdity proof.
Owner:YANSHAN UNIV
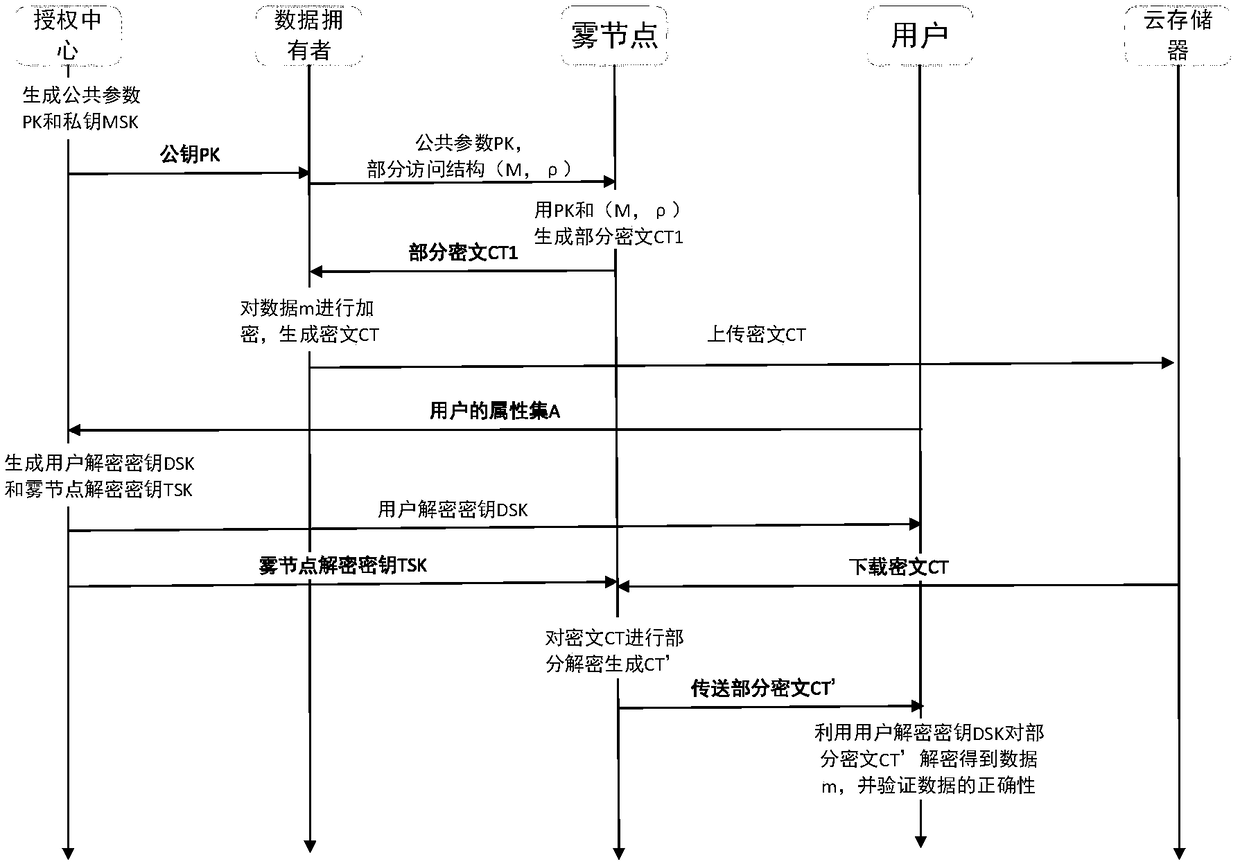
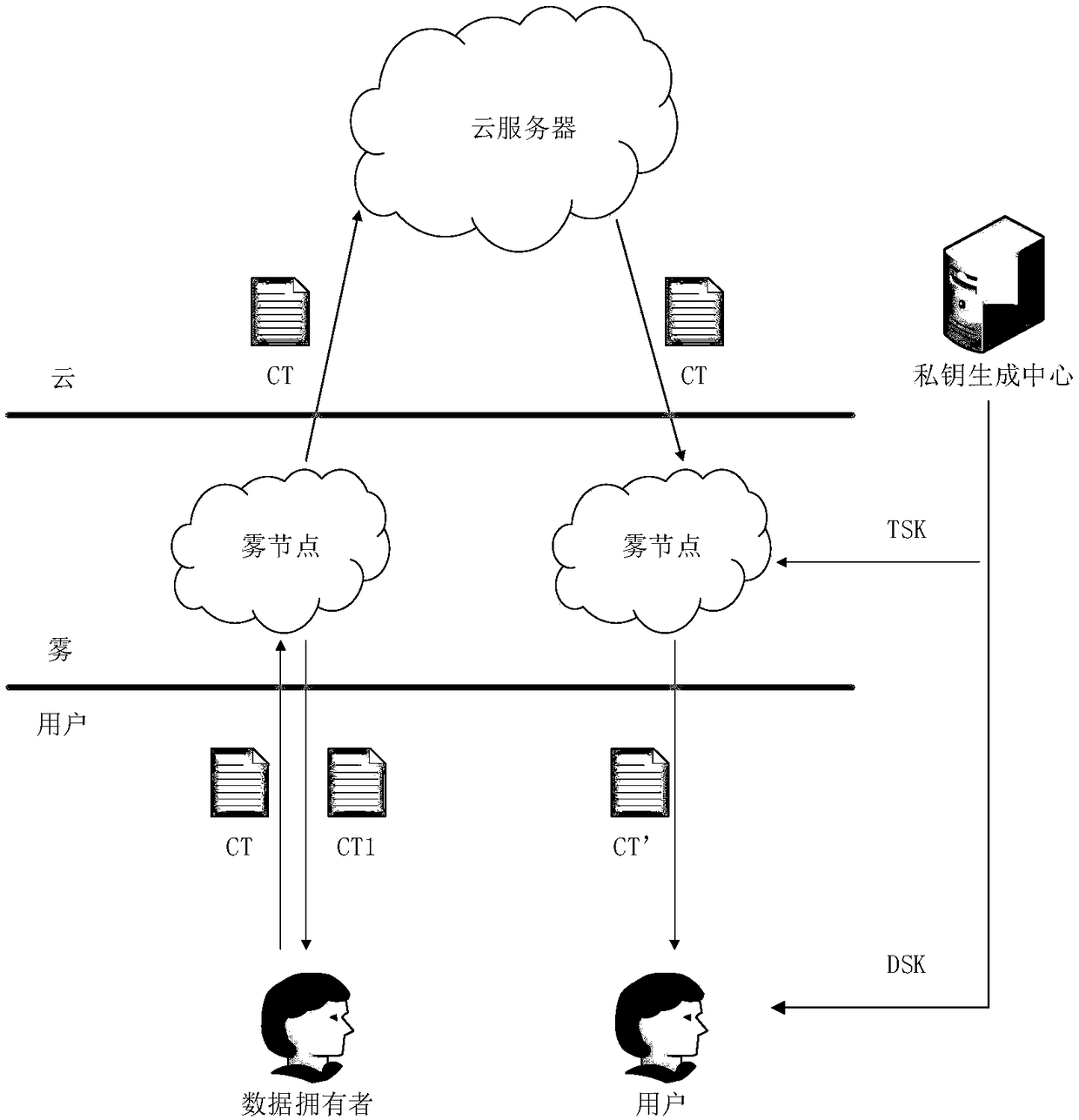
Method and device of achieving privacy protection based on CP-ABE ciphertext access control in fog computing environment
ActiveCN108881314AReduce the burden onShorten the timeKey distribution for secure communicationAccess structureCiphertext
The present invention discloses a method and a device of achieving privacy protection based on CP-ABE (Ciphertext-Policy ABE) ciphertext access control in a fog computing environment. A linear secretsharing matrix access structure based on LSSS is employed to support fine grit description of access user attributes and have a high computing efficiency. Part of computing is outsourced to a fog nodein the encryption and decryption phases to relieve the users' burden. By considering that an access structure possibly leaks users' privacy, the method introduces the technology of partially hiding the access structure so as to ensure the safety of user privacy. Finally, in order to verify whether the ciphertext is tampered or not in the transmission and outsourcing decryption processes, the ciphertext is verified to ensure the correctness of the ciphertext.
Owner:NANJING UNIV OF POSTS & TELECOMM
Rapid optimization method of Internet of Vehicle based on fog computing
ActiveCN107018031AImprove general performanceEasy to implementData switching networksWireless communicationNetwork deploymentNetwork link
The invention discloses a rapid optimization method of the Internet of Vehicle based on fog computing, and relates to the field of deployment and planning of the Internet of Vehicle. The optimization of a network topology structure is divided into two aspects; first of all, the network topology structure of nodes and links must be satisfied; secondly, aiming at an optimization target of the network, the requirement of the minimum total cost of network deployment must be satisfied; the problem of minimizing the cost of the entire network deployment is translated into the problem of the cost and minimum of the overall network link and network equipment; and the network is divided into three sections, the connection between a road-side unit (RSU) and fog equipment (fog), the connection between the fog equipment and a gateway (gw), and the connection between the gateway and cloud equipment; and a heuristic connection mode is used to minimize the total cost and optimize the network speed under the necessary condition of satisfying the network connection.
Owner:SHANDONG INSPUR SCI RES INST CO LTD
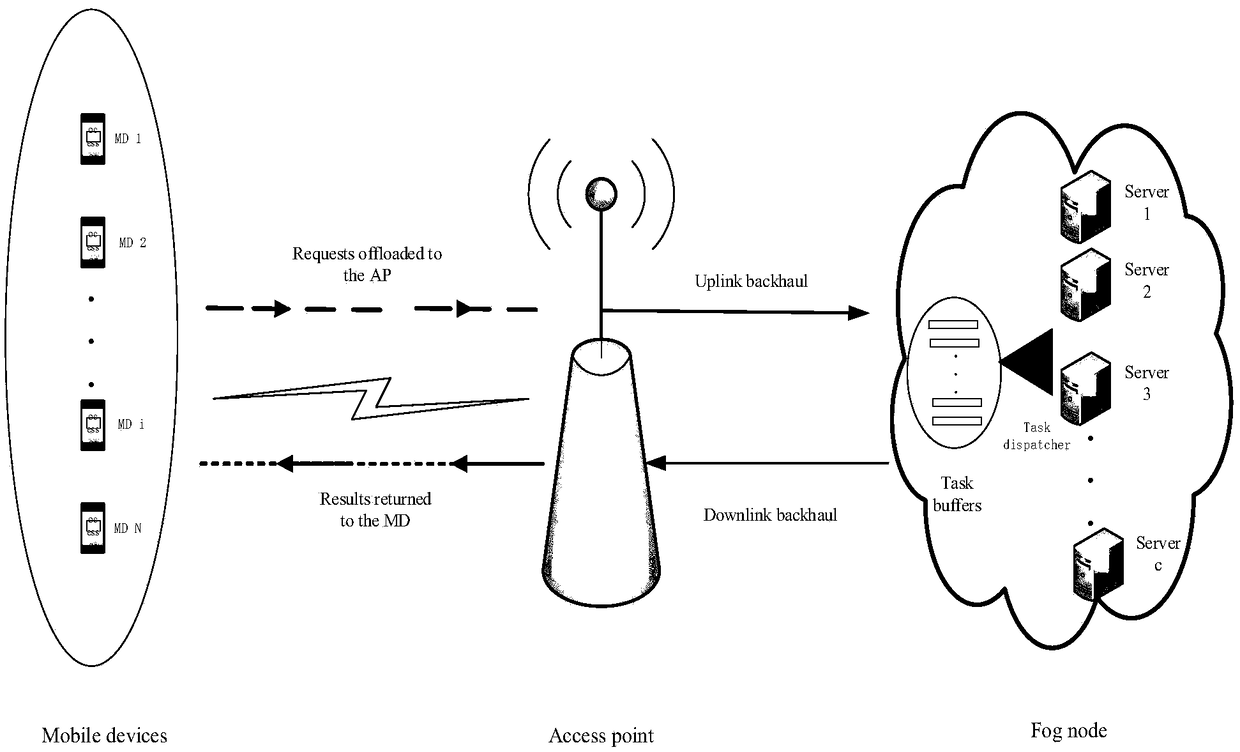
Optimization task unloading method based on network delay and resource management
The invention discloses an optimization task unloading method based on network time delay and resource management. The method comprises the steps that an optimization unloading PoW problem is studiedin a fusion blockchain and fog computing system based on node remaining resources and network time delay; in a network scene formed by a base station fog node, a fixed position fog node and a mobile fog node, the total duration required for unloading the PoW problem to various types of fog nodes is analyzed; the expenditure of the MUB is analyzed based on the remaining computing resources, storageresources and power resources of the network node and the social relationship between the nodes; an optimization task unloading scheme is provided based on node residual resources and network time delay, a mathematical optimization model is constructed by taking maximization of MUB income as a target, and the optimization model is solved by using an SA algorithm and a game theory; and finally, the superiority of the scheme is proved through analog simulation analysis. An intelligent task unloading mode of introducing artificial intelligence into the system is considered in future work.
Owner:CHONGQING VOCATIONAL INST OF ENG
Hidden data attack detection method based on fog computing and layered trust evaluation mechanism
ActiveCN108684038AReduce consumptionGuaranteed performanceNetwork topologiesTransmissionLine sensorWireless mesh network
The invention provides a hidden data attack detection method based on fog computing and a layered trust evaluation mechanism, and belongs to the field of network information safety, specifically a method for guaranteeing that node behaviors in wireless sensor networks (WSNs) are credible through the layered trust evaluation mechanism based on the fog computing, guaranteeing that nodes are credibleat a data level base on the above, i.e., detecting the attack performance of hidden data. According to the invention, the method enables the computing and storage task in the trust evaluation mechanism to be transferred to a fog layer, can remarkably reduce the network resources consumed by the trust evaluation mechanism, can maintain the network performances in a better way, and is superior in the expansibility of the trust evaluation mechanism. Meanwhile, the method can be applied to the dynamic and stationary WSNs, guarantees the trust state of the sensing nods at the data level, and prevents the hidden data attach from causing the economic loss of a sensing cloud application.
Owner:HUAQIAO UNIVERSITY
Self-adaptive container migration method under fog computing environment
ActiveCN108021451AReduce latencyReduce dimensionalityResource allocationEnergy efficient computingDimensionality reductionTime delays
The invention provides a self-adaptive container migration method under a fog computing environment. The method comprises the following steps that a container-based fog computing framework is established, wherein the container is located on a fog node, a mobile application is located on the body of a user body, and a task of the user is executed in the container; modeling is conducted on a targetmigration of the container under a fog computing scene, wherein the migration target comprises time delay, power consumption and migration cost; a state space and an action space are set, a reward function is defined, and a Q iterated function is set; dimensionality reduction is carried out on the state space through a deep neural network; dimensionality reduction of the action space is achieved through optimization of action selection; finally, a prototype of a self-adaptive migration system of the container is achieved, and the whole process is verified. By means of the provided self-adaptive container migration method under the fog computing environment, resources in fog computing can be better planned, the time delay between the user and the fog node is reduced, and the energy consumption expenditure of the fog node is reduced.
Owner:SHANGHAI JIAO TONG UNIV
Sensor cloud data transmission algorithm based on fog computing
InactiveCN106413024AImprove throughputMake the most of your communication capabilitiesNetwork topologiesTransmissionFog computingSensor node
The invention discloses a sensor cloud data transmission algorithm based on fog computing. The algorithm comprises the steps of 1), taking base stations of a sensor network layer as a fog node layer and generating Voronoi diagrams according to locations of the base stations; 2), carrying out statistics on the number of sensor nodes in various diagram regions, calculating a region node average number: the region node average=the total number of sensor nodes / the total number of the base stations, and analyzing call-in and call-out condition of the various diagram regions through combination of the region node average number; and 3), setting a scheduling algorithm among the regions. According to the algorithm, the base stations in the bottom layer network are taken as the fog nodes, the nodes cooperate with each other and are responsible for scheduling the nodes in the busy areas of the base stations to relatively idle areas, the communication capabilities among the fog nodes are utilized fully, the data is uniformly uploaded to an uploading cloud, and the network throughput is improved to the greatest extent.
Owner:HUAQIAO UNIVERSITY
Fine-grained searchable encryption method for fog computing
ActiveCN108156138ASolving Mobility IssuesSolve the delay problemKey distribution for secure communicationCiphertextFog computing
The invention discloses a fine-grained searchable encryption method for fog computing. A cloud-fog terminal user system structure is established by using the attribute encryption technology and the searchable encryption technology of a ciphertext strategy, a fog node serves as an agent to share the computing burden of a terminal user by using the attribute encryption technology and the searchableencryption technology of the ciphertext strategy, the terminal user can quickly generate a trap door and decryption ciphertext, therefore lightweight searchable encryption is achieved, meanwhile fine-grained access control is supported, only legitimate data users can perform ciphertext retrieval, the fine-grained searchable encryption method has a broad application prospect in actual scenes, fine-grained access control is achieved, only the legitimate data users can perform ciphertext retrieval, and the fine-grained searchable encryption method has a broad application prospect in actual scenes.
Owner:XIDIAN UNIV
Vehicle information secure collection method applicable to fog computing in intelligent traffic light system
ActiveCN106060148AEasy to controlStatistically accurateControlling traffic signalsTransmissionControl systemFog computing
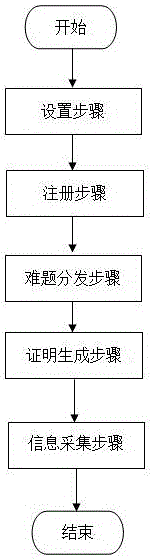
The invention discloses a vehicle information secure collection method applicable to fog computing in an intelligent traffic light system. The method comprises a setting step, a registering step, a difficulty distribution step, a certificate generation step and an information collection step. The method is characterized in that locations and the number of vehicles cannot be counterfeited; a fog computing device does not need too much computing and storage cost; the identity and location information of the vehicles will not be leaked to other vehicles and fog computing devices; the method is easy to deploy; and the vehicle information statistics is accurate.
Owner:浙江曲速科技有限公司
Internet of Things malicious traffic detection method based on fog computing platform
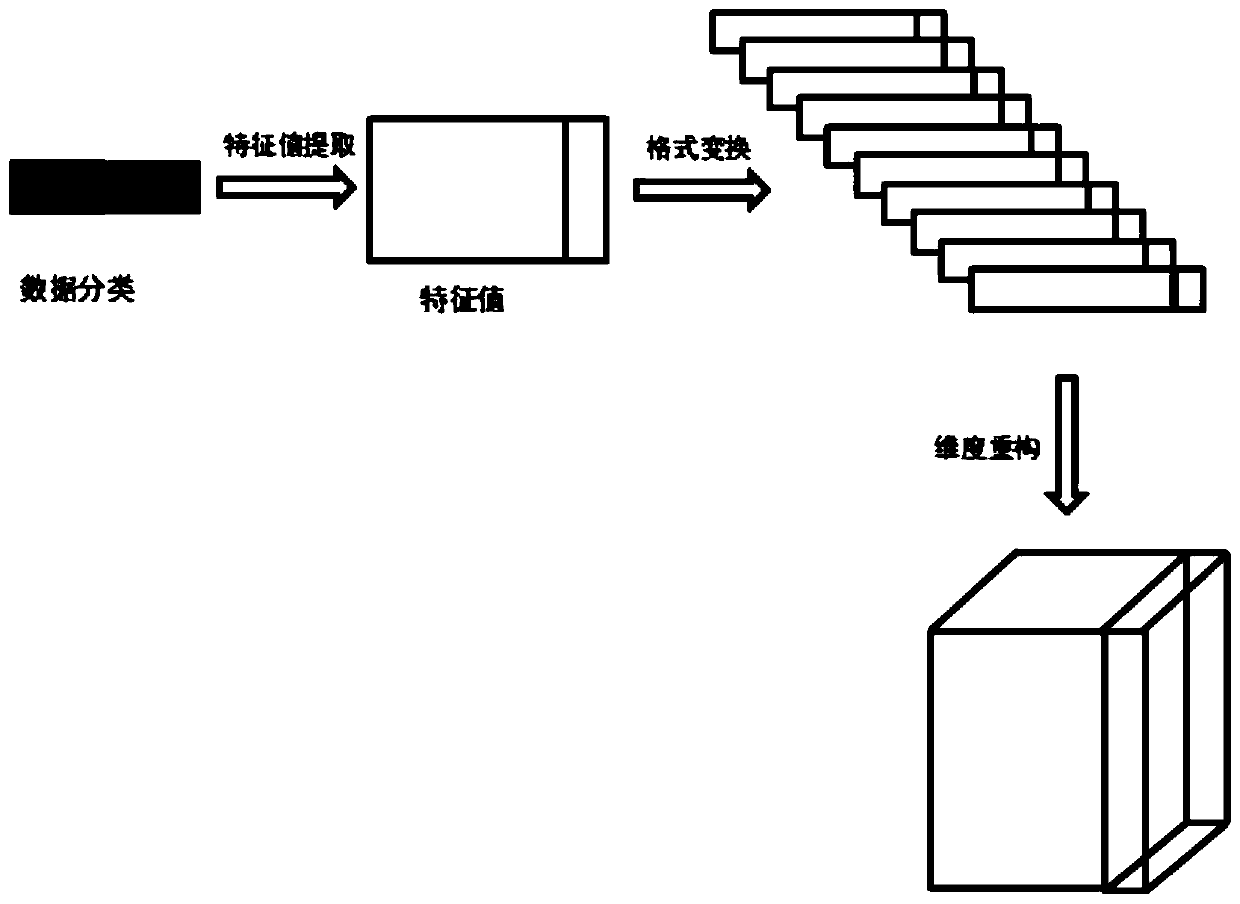
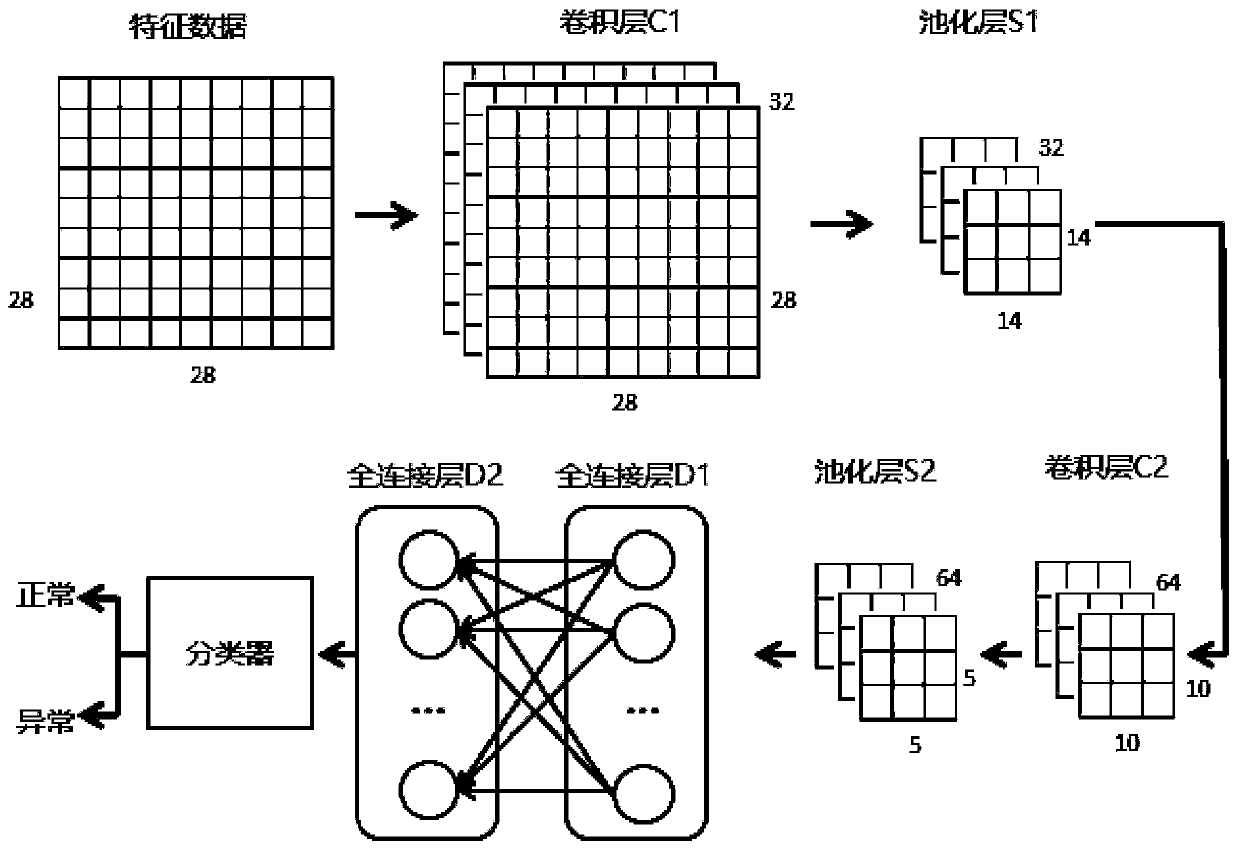
ActiveCN111510433AImprove recognition rateOvercoming delays and other issuesNeural architecturesTransmissionData packAttack
The invention relates to an Internet of Things malicious traffic detection method based on a fog computing platform, and the detection method is operated based on the fog computing platform, and comprises the steps: (1) building an experimental network, and building a feature extraction module which is used for collecting a traffic data packet of IoT equipment under jurisdiction; building a Miraibotnet environment, and obtaining a traffic data packet when a DDoS attack is initiated; (2) performing feature value classification and extraction on the traffic data packet by using a feature extraction module to generate feature data; (3) by a data processing module, performing data dimension reconstruction on the feature data; and (4) building a convolutional neural network on the fog computing node. According to the method, the convolutional neural network anomaly detection algorithm is transplanted to the field of IoT botnets, so that the identification rate of DDoS malicious traffic ofIoT equipment is improved; based on fog computing platform architecture construction, real-time detection of abnormal traffic of IoT equipment under jurisdiction is realized, and consequences of DDoSattacks are reduced.
Owner:SHANDONG UNIV
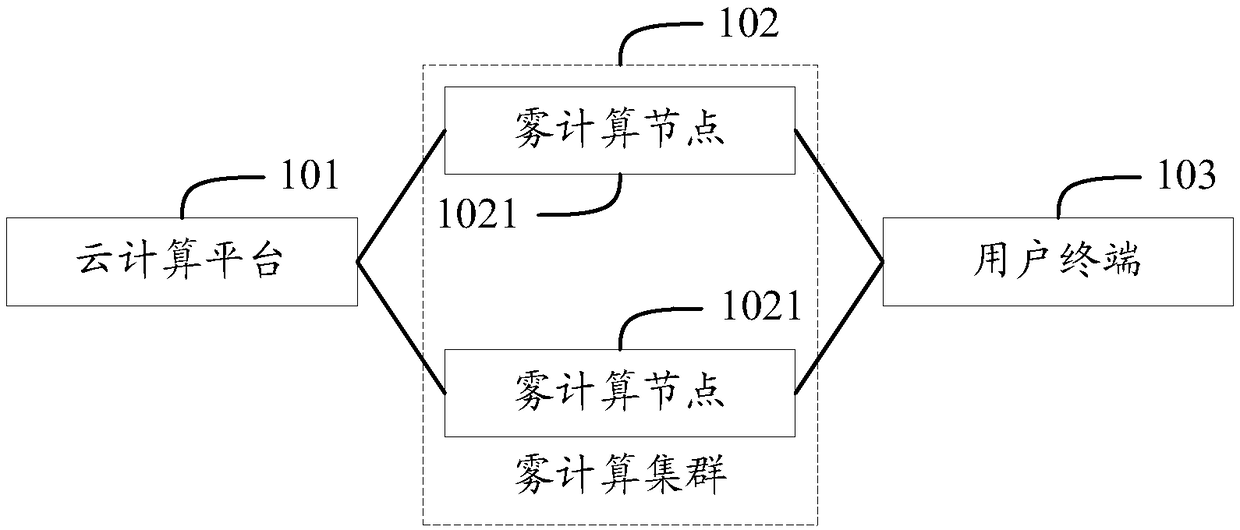
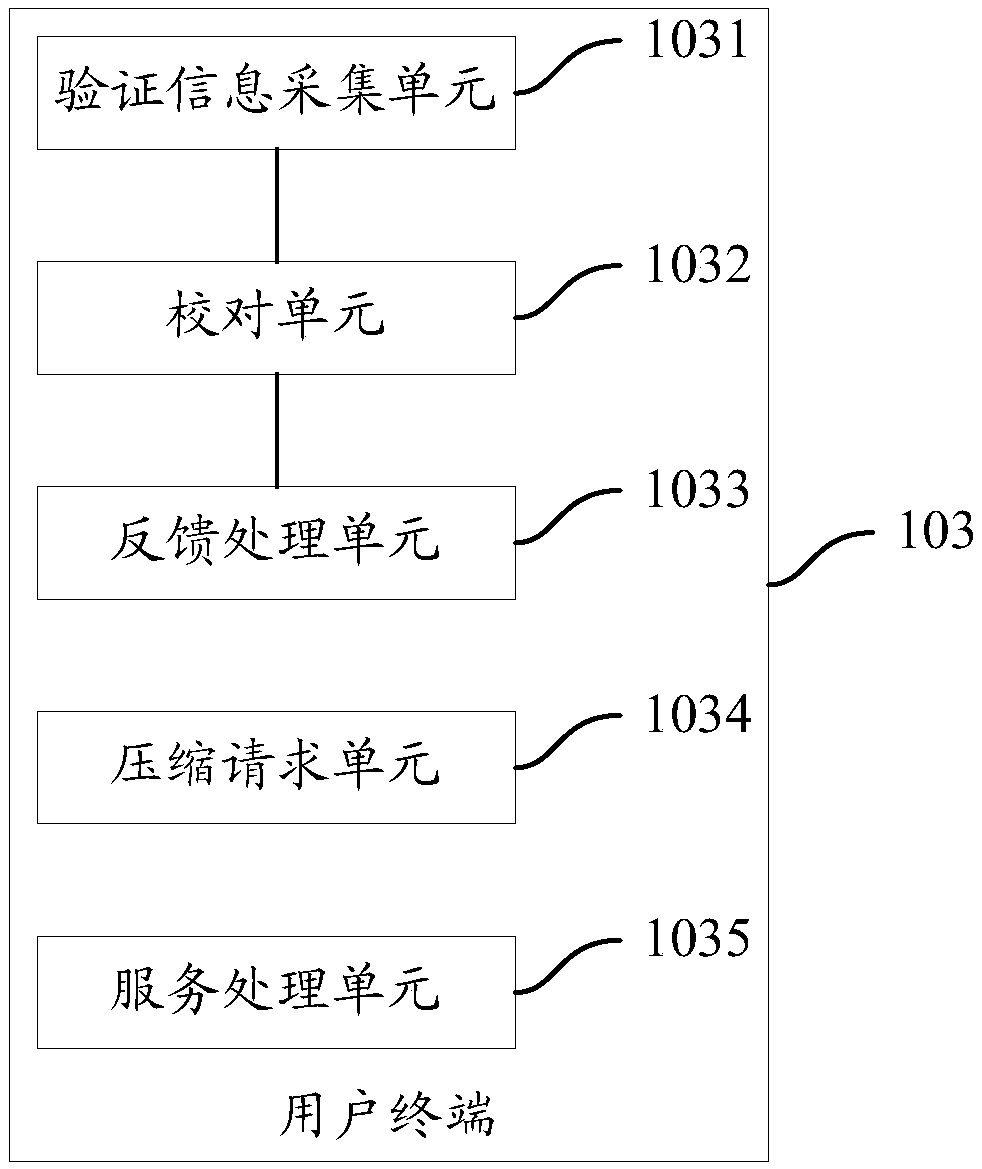
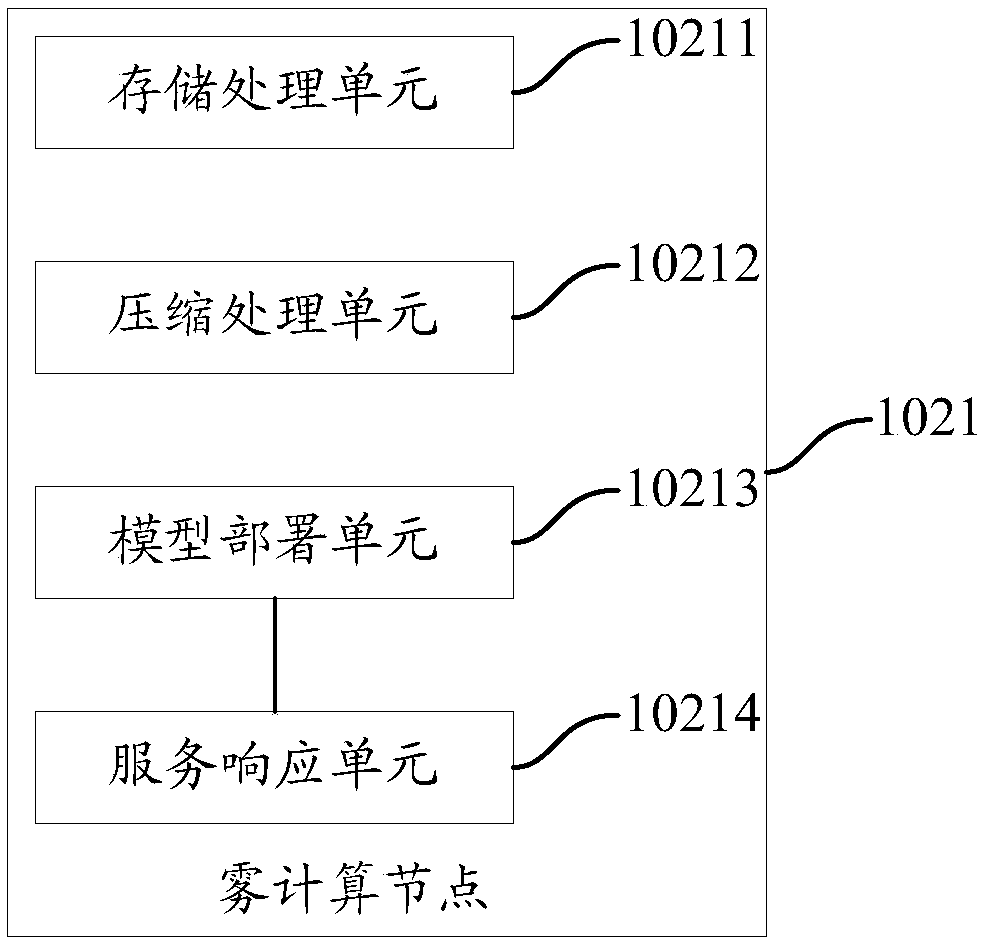
Artificial intelligence service system and method for realizing artificial intelligence service system
ActiveCN108667850ALow chance of malicious changesLess prone to data breachesComputing modelsCharacter and pattern recognitionData setAlgorithm
The invention provides an artificial intelligence service system and a method for realizing the artificial intelligence (AI) service system. The system comprises a cloud computing platform, a user terminal, and a fog computing cluster with a fog computing node; the cloud computing platform trains an AI model and issues the trained AI model to the fog computing node; the fog computing node performscompression processing on the AI model to form a target AI model when receiving the AI model; the target AI model is sent to the user terminal when a deployment request sent by the connected user terminal is received; the user terminal sends the deployment request to the connected fog computing node, receives and deploys the target AI model sent by the fog computing node, inputs a to-be-processeddata set into the target AI model, and receives a first processing result output by the AI model after processing the to-be-processed data set. Through the technical scheme provided by the invention,the AI service can be realized safer.
Owner:山东浪潮创新创业科技有限公司
Health monitoring system and method based on cloud resource low delay scheduling
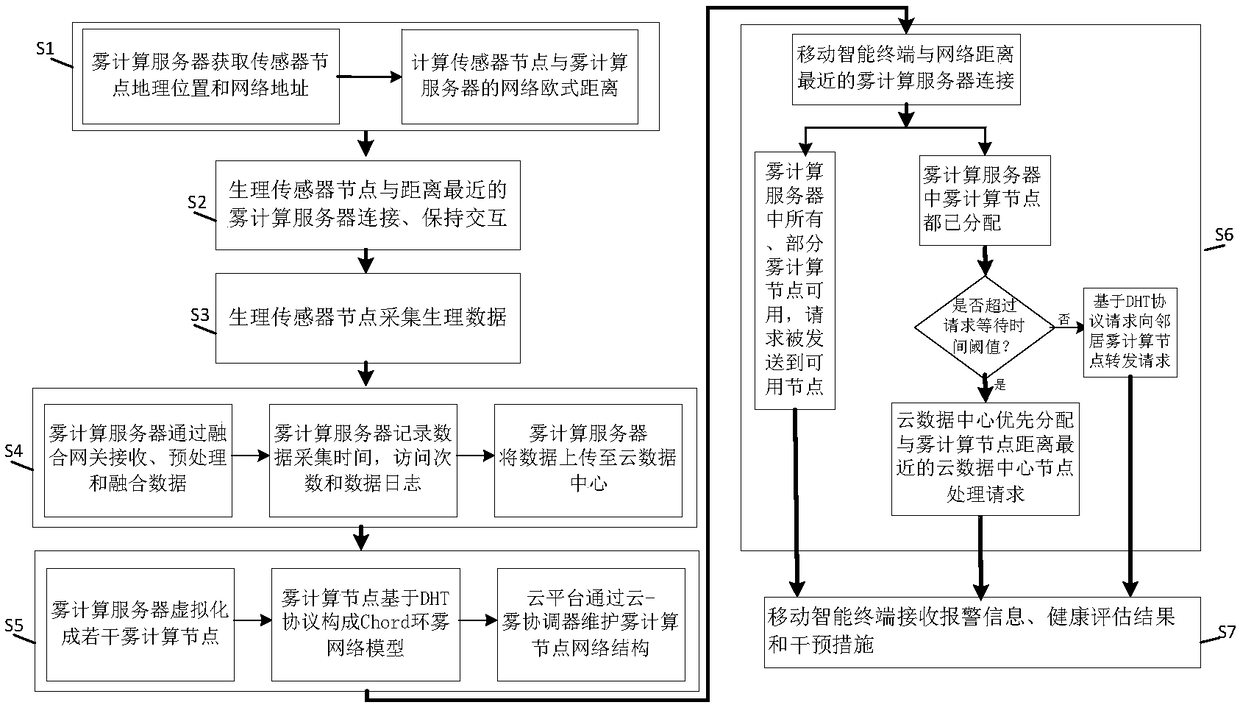
ActiveCN108597599AImprove experienceImprove real-time performanceMedical equipmentIntervention measuresFog computing
The invention discloses a health monitoring system based on cloud resource low delay scheduling. The system comprises a physiological sensor node, a fog computing server, a cloud data center and a mobile intelligent terminal. The invention further discloses a health monitoring method based on the cloud resource low delay scheduling. The physiological sensor node transmits physiological monitoringdata to the fog computing server with nearest network distance; the fog computing server is responsible for receiving, processing and merging data, and uploading the data to the cloud data center; themobile intelligent terminal is connected with the fog computing server with nearest network distance, receives intelligent alarm information, a health assessment result and an intervention measure; the fog computing server and a resource scheduling algorithm restrained based on a time threshold in the cloud data center process a request to ensure the low delay. The health monitoring system and method based on the cloud resource low delay scheduling have the advantages that the system is intelligent and front-end, the delay is low, the location awareness is strong, the limitations of physiological sensors in terms of energy and storage are overcome, the user experience is improved, and the method is conducive to finding problems and providing ambulance at the first time.
Owner:XIAMEN UNIV OF TECH
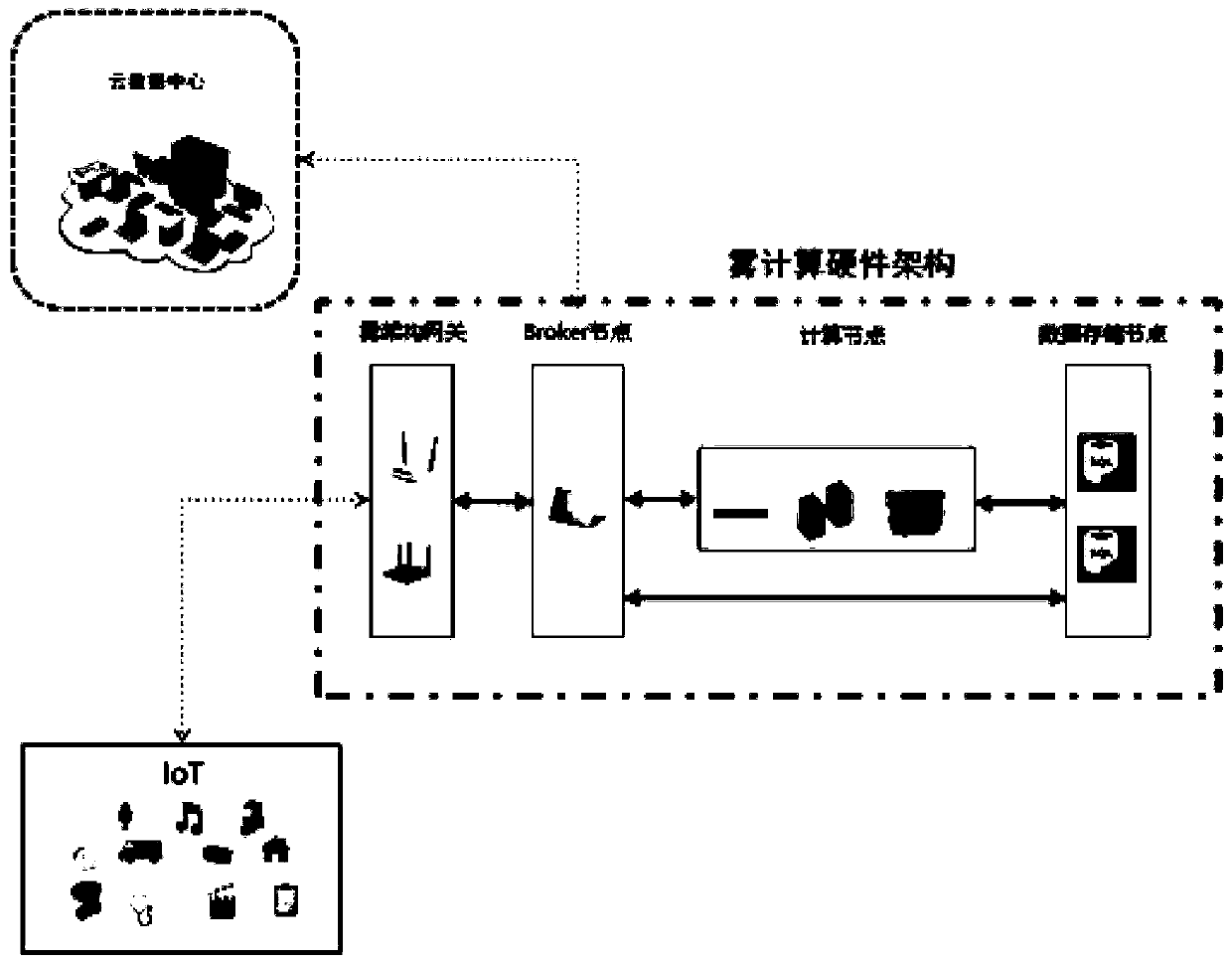
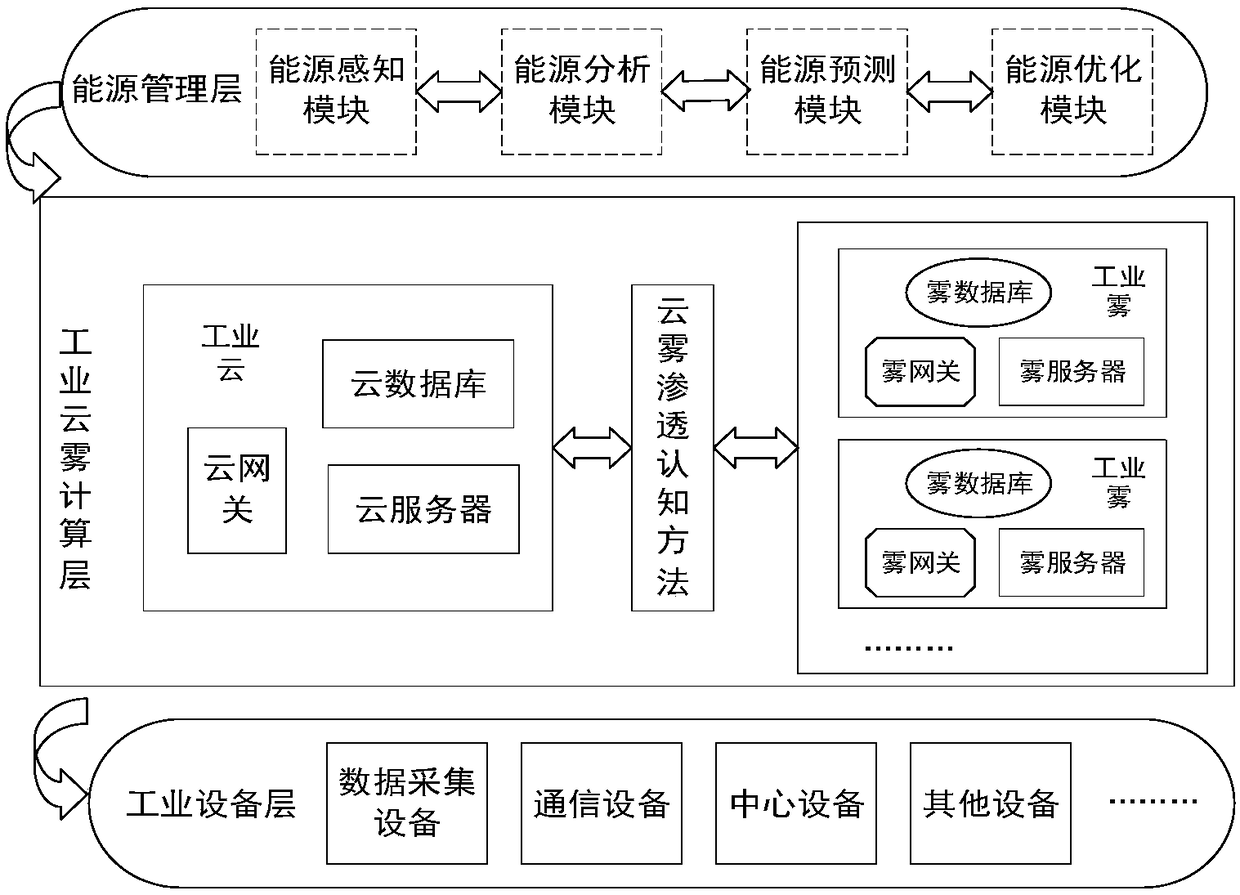
Cloud-fog integrated industrial Internet of Things cognitive energy management system and computing method
InactiveCN108156226AAlleviate the problem of limited resourcesAlleviate high latencyTransmissionInformation processingFog computing
The invention discloses a cloud-fog integrated industrial Internet of Things cognitive energy management system and computing method thereof, wherein a structure of the system comprises an industrialequipment layer, an industrial cloud-fog cognitive computing layer and an energy management layer. The industrial cloud-fog cognitive computing layer comprises industrial cloud computing and industrial fog computing; and the energy management layer, taken as a top layer of an architecture, takes charge of providing diversified energy management applications, and comprises an energy cognitive module, an energy analysis module, an energy prediction module and an energy optimization module. In the system and the method provided by the invention, by cloud computing, infinite resources can be provided for mitigating a problem of limitation of fog computing resources, problems of high delay, network congestion and low reliability caused by cloud computing can be mitigated through fog computing edge information processing capacity, cloud-fog integration is realized through construction of a penetration model between fog computing and cloud computing, under guidance of minimizing consumption of cloud-fog resources, an energy management service is allocated rationally between the cloud and the fog, rational and efficient utilization of the cloud-fog resources is realized, and consequently,efficient IIoT energy management is realized.
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com