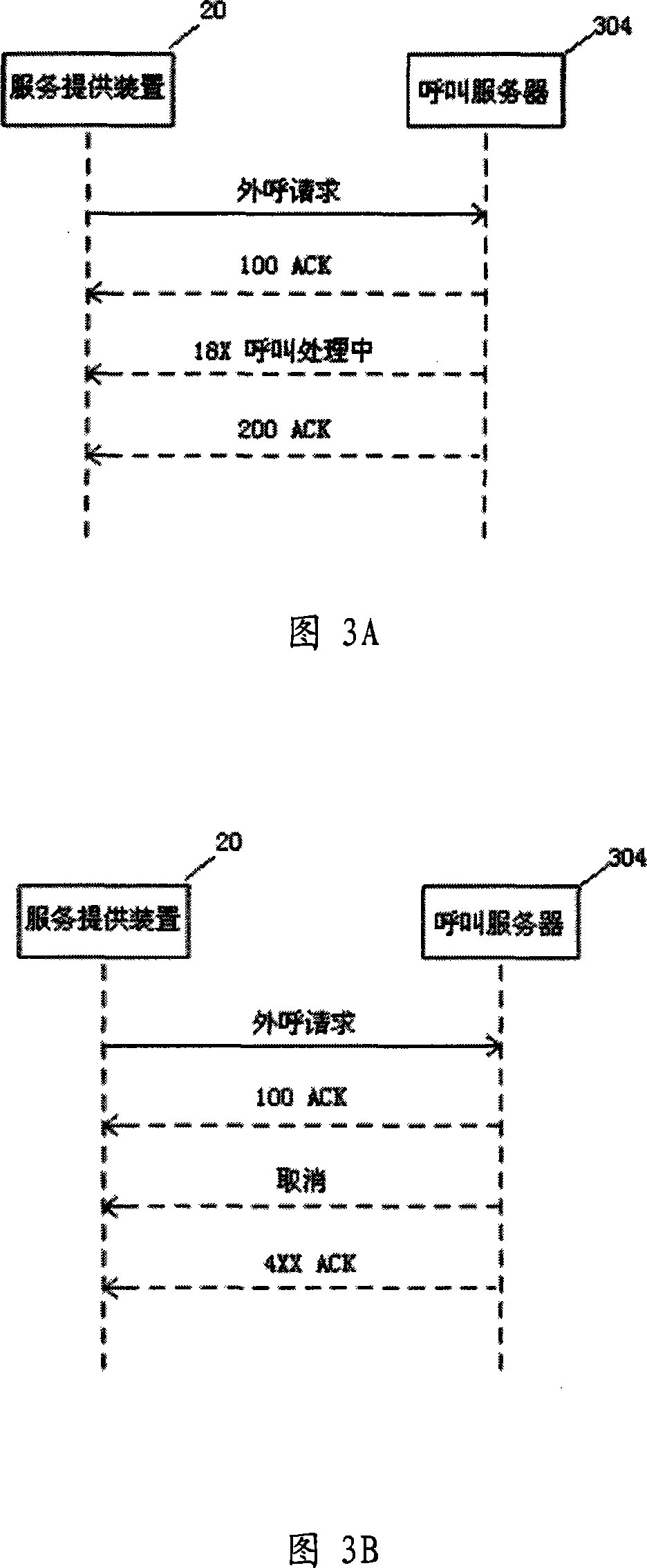
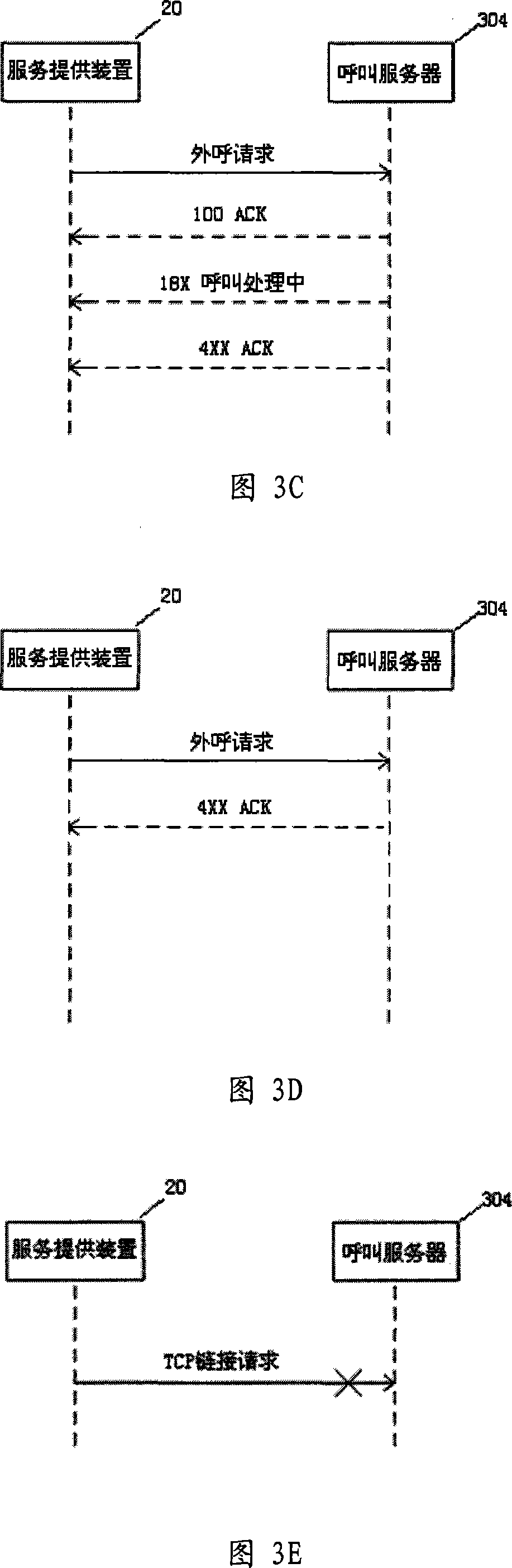
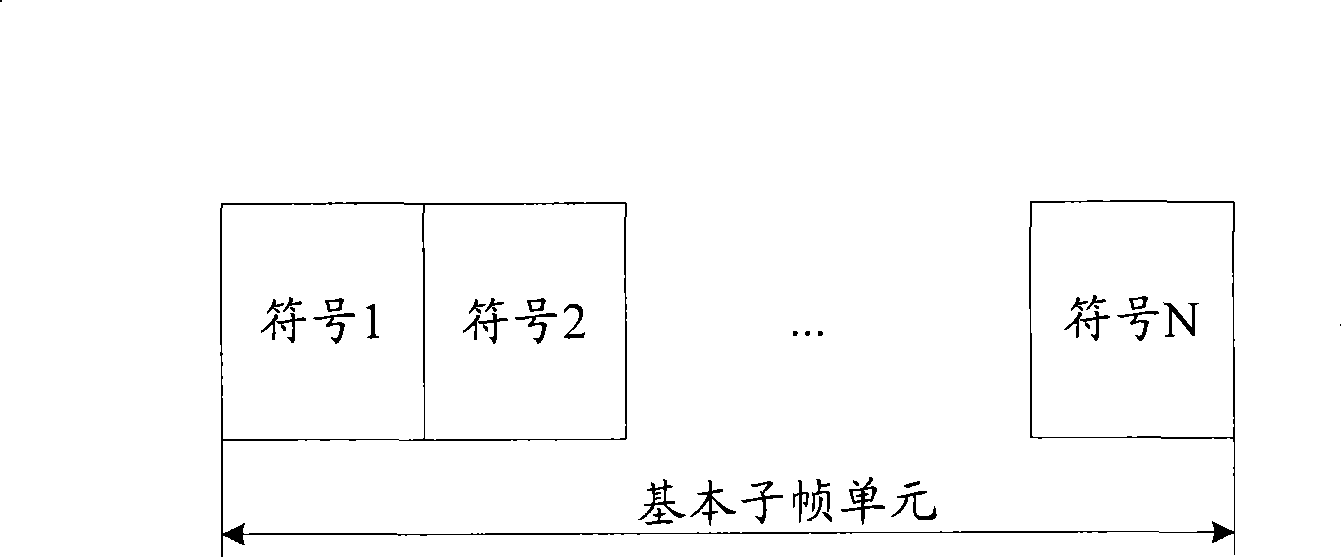
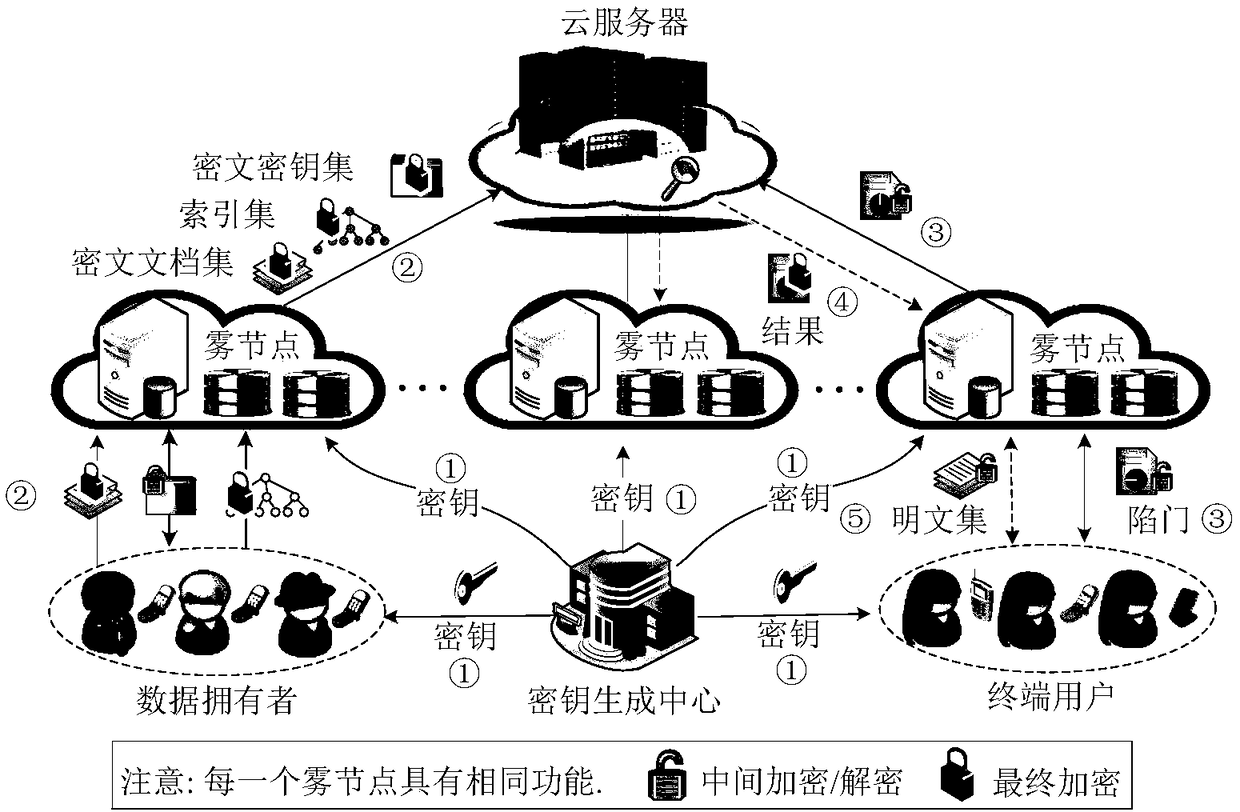
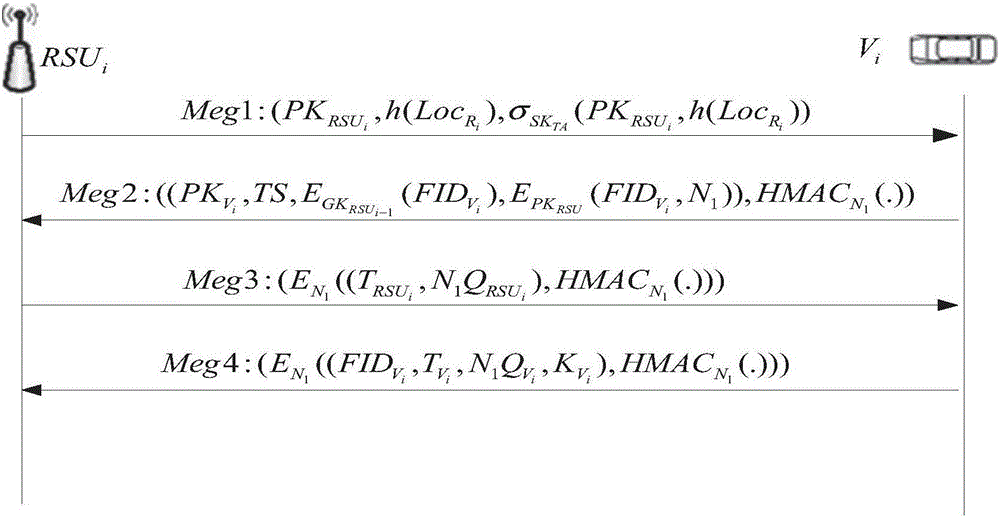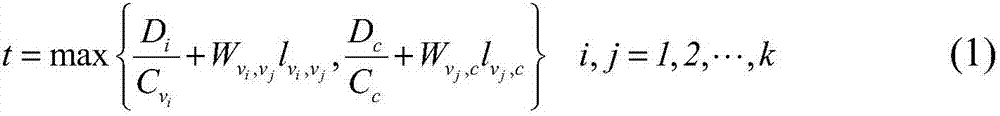Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
281results about How to "Solve the delay problem" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
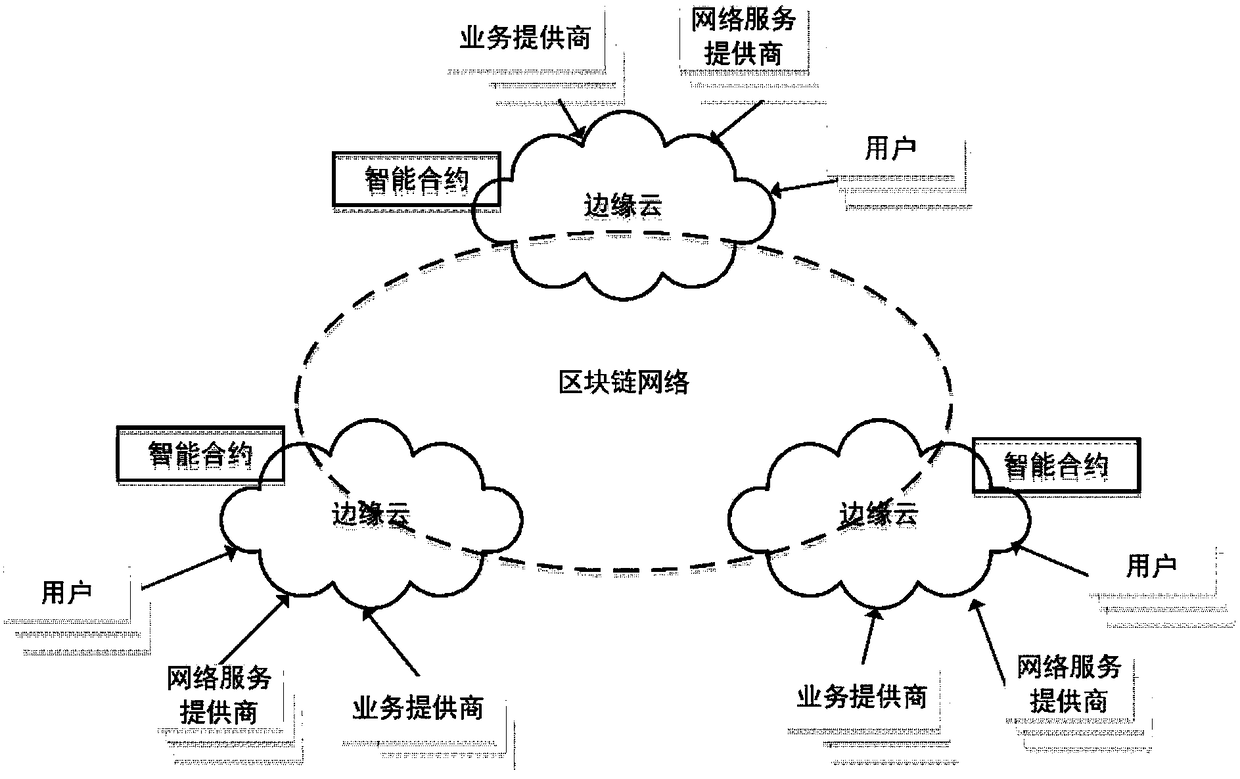
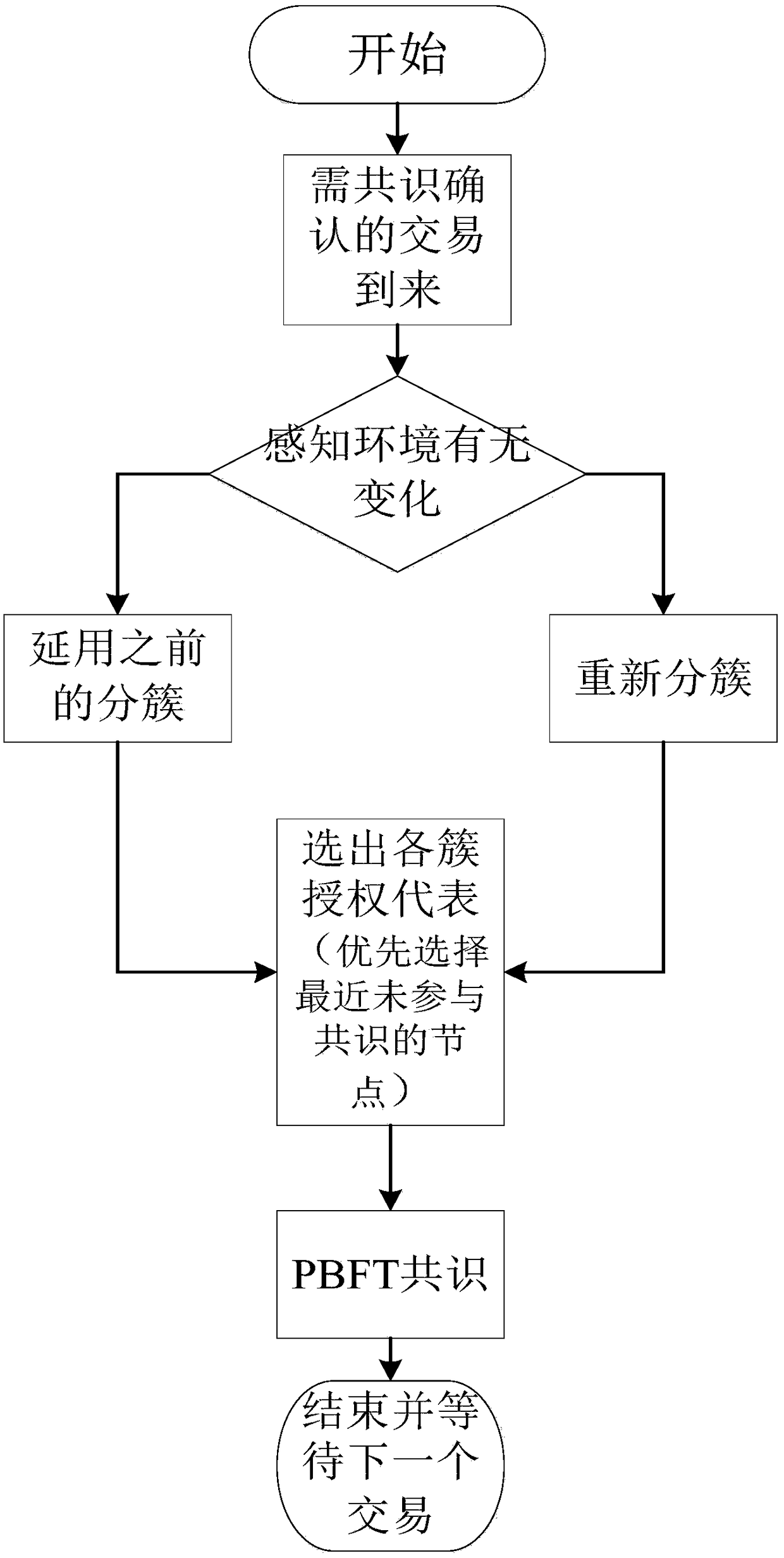
Block chain adaptive consensus method based on dynamic authorization and network environment perception
ActiveCN108616596ASolve low throughputSolve the delay problemFinanceDigital data protectionByzantine fault toleranceNODAL
The invention discloses a block chain adaptive consensus method based on dynamic authorization and network environment perception; the method comprises the following steps: 1, clustering block chain network nodes according to geological positions, and selecting one authorization representative from the same cluster; 2, allowing the authorization representatives selected from all clusters to form all consensus nodes that verify this transaction, wherein a Byzantium fault tolerance algorithm is employed among the consensus nodes so as to reach a consensus that whether this transaction is established or not; 3, adjusting or re-clustering according to network scale, topology, resource or business type changes; 4, updating authorization representatives in the next deal after one deal is verified. The advantages are that the method can set up a fast and credit synergy mechanism among distributed edge clouds based on block chain, so edge nodes can fast and effectively reach consensus withoutany trust basis, thus solving the low throughput, high time delay and low efficiency problems of a consensus algorithm that uses workload proves as representatives.
Owner:NANJING UNIV OF POSTS & TELECOMM
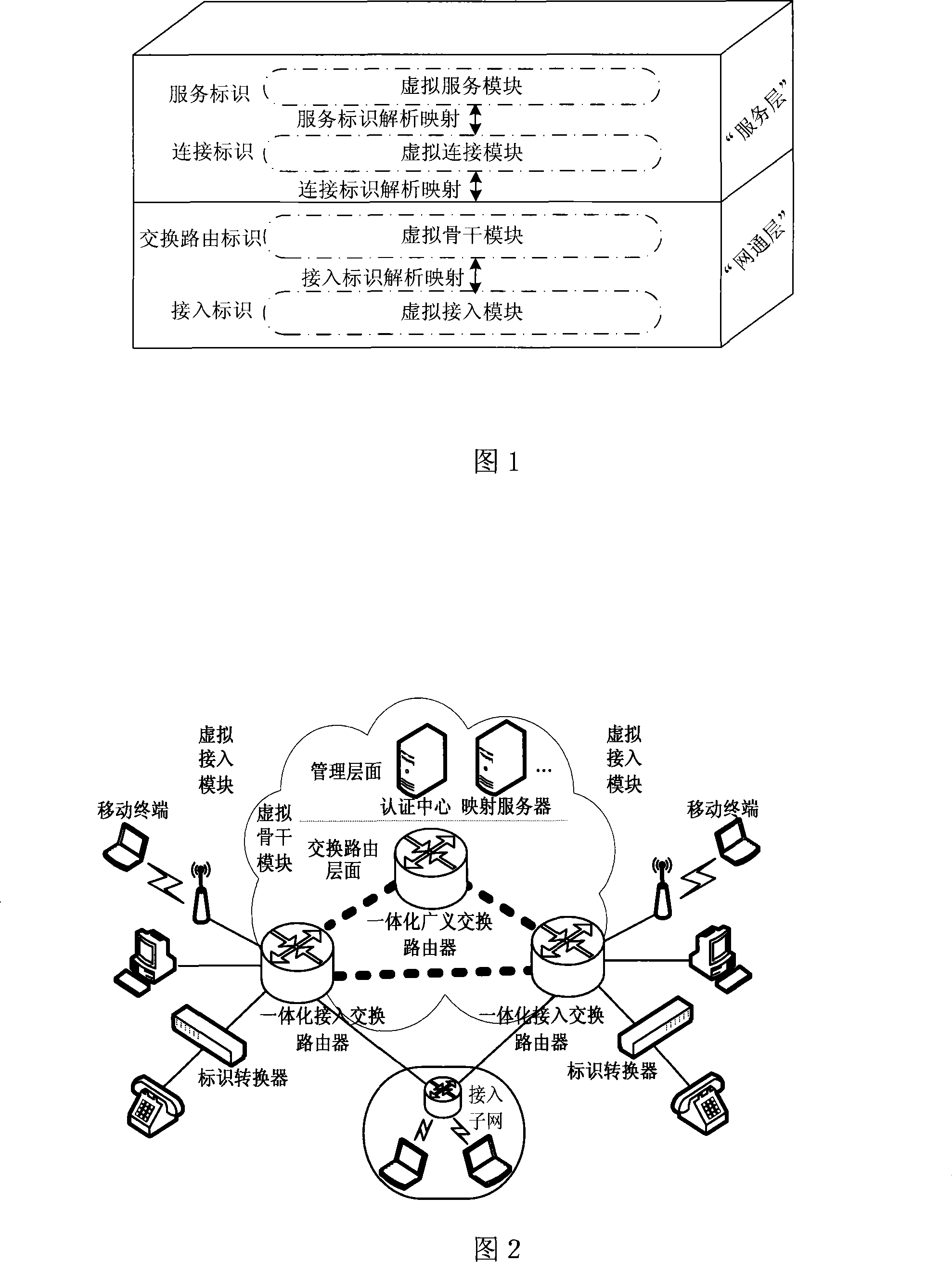
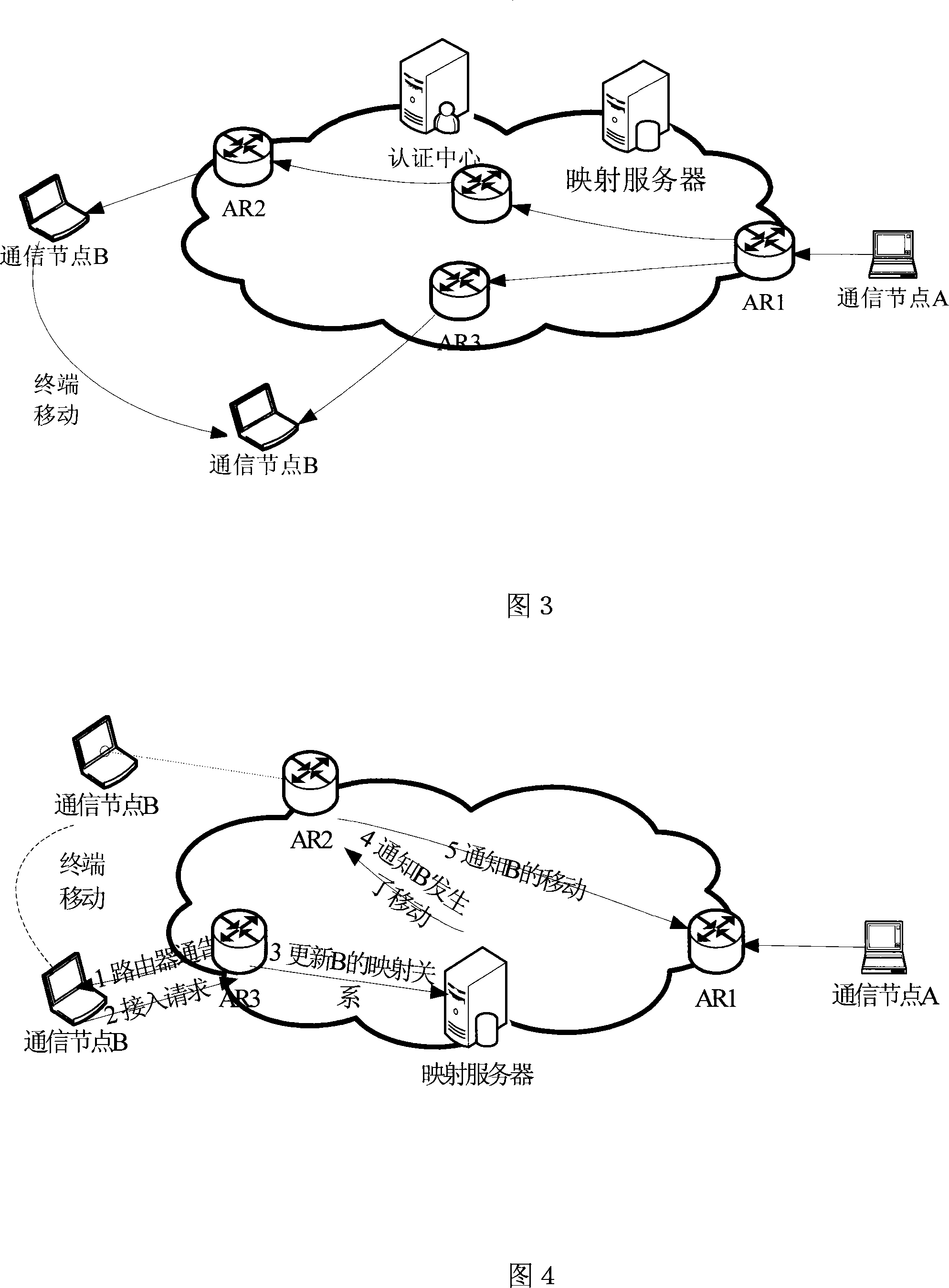
Method for implementing integrated network mobile switch management
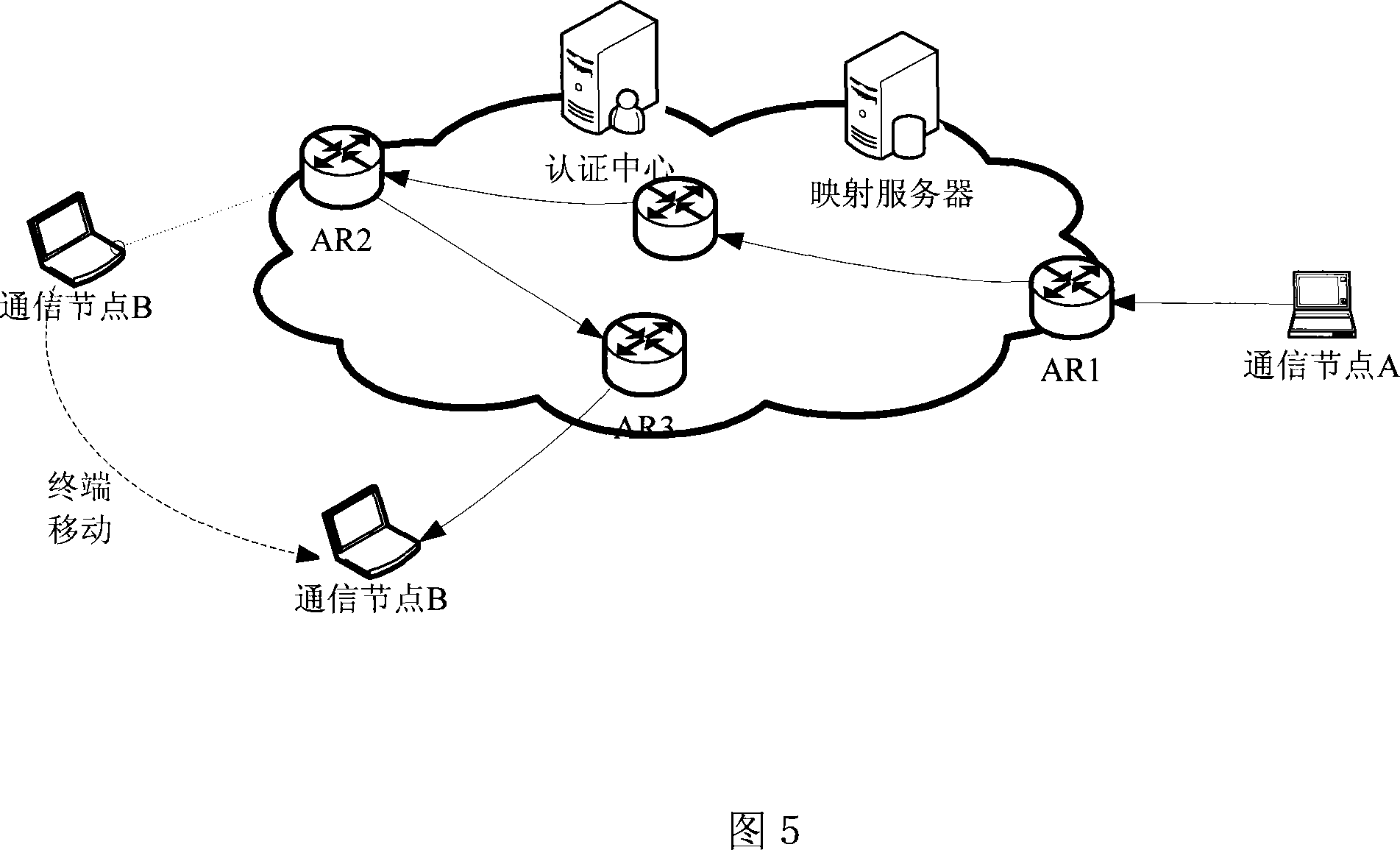
InactiveCN101119312AAchieve unitySolve the delay and packet loss rateRadio/inductive link selection arrangementsData switching networksService systemCommunication interface
The present invention relates to an integrated network moving and switching management method. The integrated network and common service system is a new network structure to overcome the disadvantages of the prior network art. The network can realize the service integration and network integration. The present invention is characterized in comprising an Internet, a mobile communication network, a communication node, a switch in exchange route, an authenticate center and a mapping server. The present invention has the following steps: the detecting and mapping exchanging step, the notice step and the step to prevent the route blackhole. The present invention sufficiently shows the unity of the communication interface of the customer terminal in the switching process. The present invention utilizes the network developing and exchanging of the route mark to solve the problems of time dragging and losing ratio in the communication switching process.
Owner:BEIJING JIAOTONG UNIV
System and method for guaranteeing distributed data processing consistency
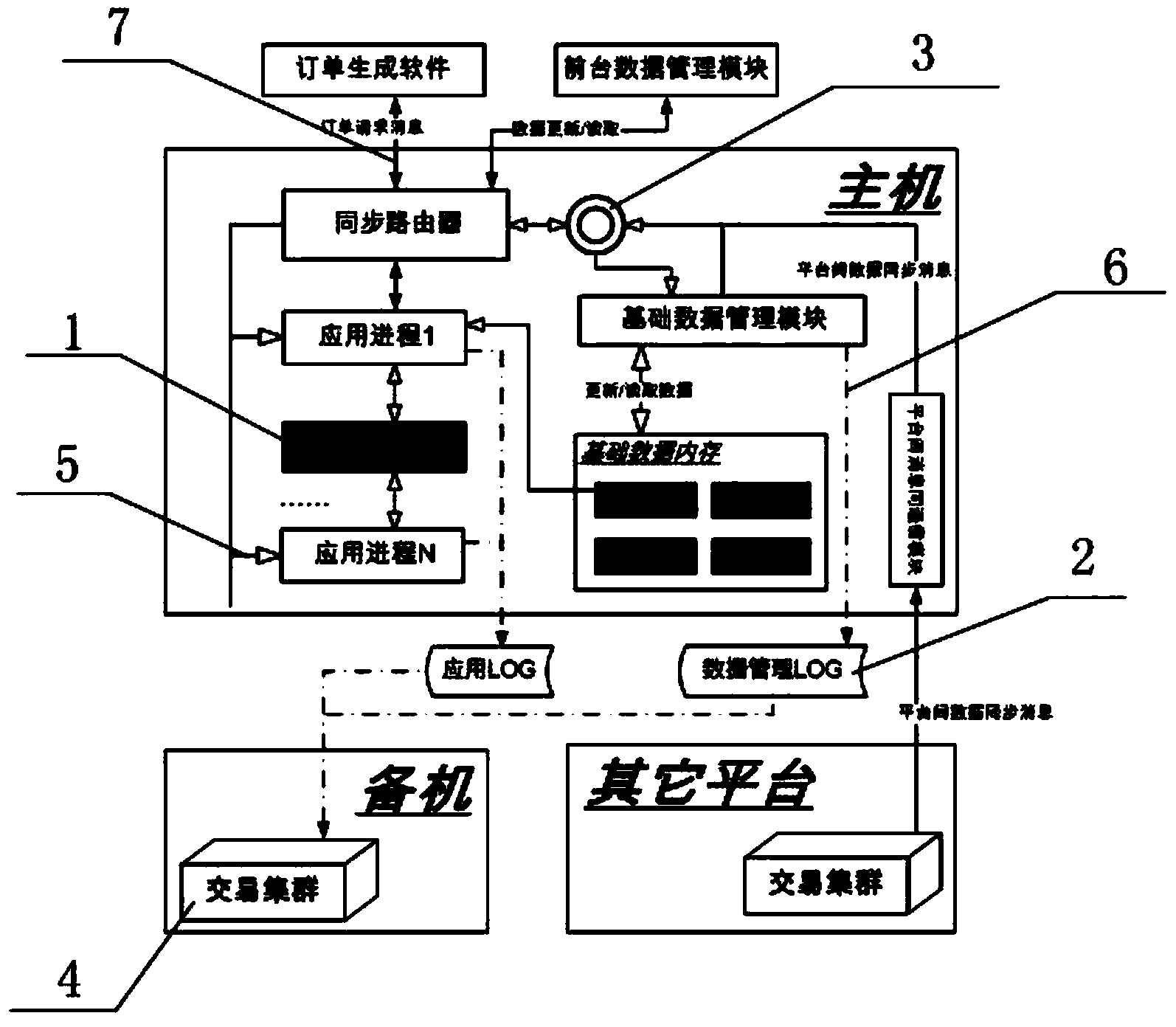
ActiveCN103647669AGuaranteed reliabilityReduce latencyData switching networksData memoryOrder processing
The invention relates to the distributed data processing technology field and particularly relates to a system and a method for guaranteeing distributed data processing consistency. The system comprises a computer transaction system platform. The computer transaction system platform comprises multiple transaction platforms for transaction business processing, a host in a transaction host is taken as a main node, other nodes are taken as standby transaction machines, the main node is for processing tasks of all orders and further for log record, maintenance and triggering basic data synchronization of secondary nodes, the secondary nodes do not carry out real-time order processing but realizes consistency with the main node through synchronization maintenance of basic data memory. Compared with the prior art, the system is advantaged in that a log structure with a message execution state is employed; a problem of time delay conflict of real-time reading and updating of the basic data of the transaction system can be solved; complexity of replay of the transaction system is reduced; consistency during data processing between platforms and switching between main and standby machines, system performance and reliability are improved.
Owner:SHANGHAI STOCK EXCHANGE
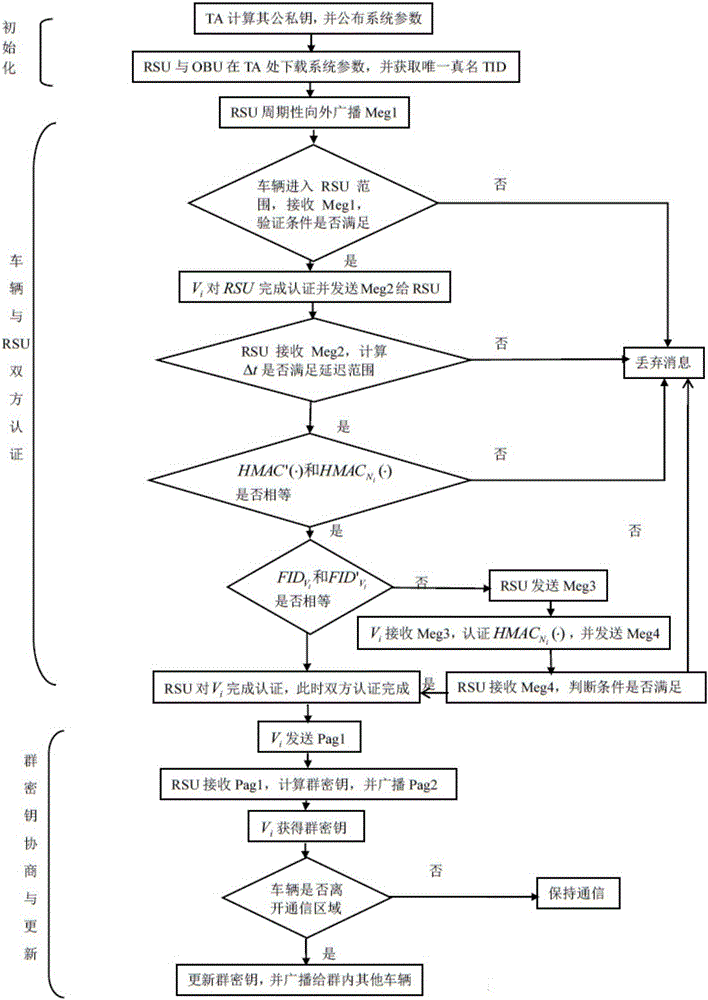
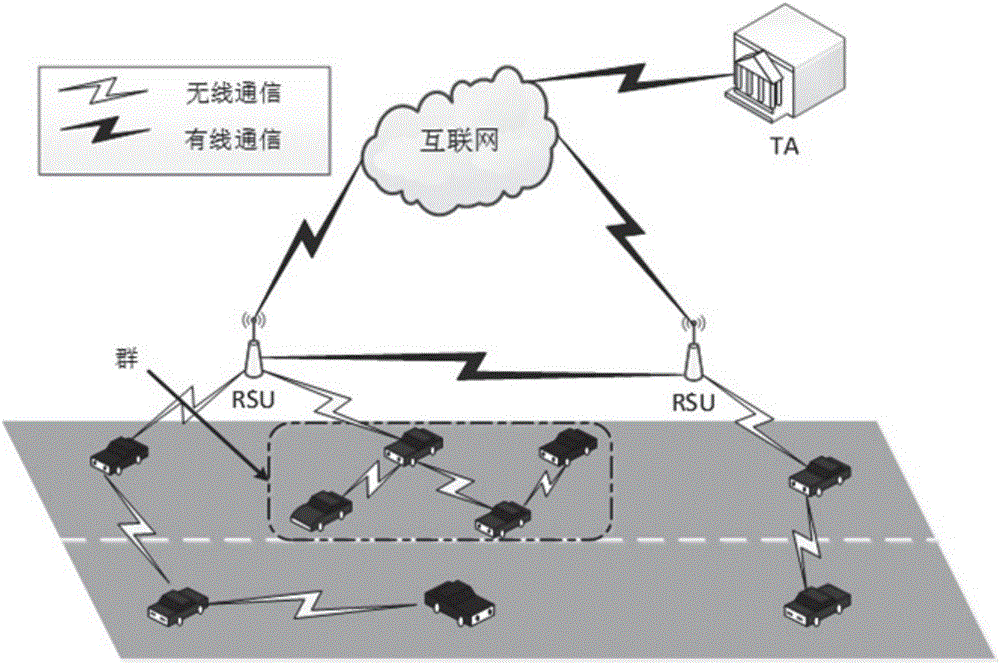
Method for designing vehicle network group negotiation communication protocol
InactiveCN106027233ASolve the delay problemFast authenticationKey distribution for secure communicationUser identity/authority verificationProtocol for Carrying Authentication for Network AccessVehicle networks
The invention discloses a method for designing a vehicle network group negotiation communication protocol, which includes the following steps: (1) first establish a system model; (2) system initialization; (3) both vehicle and roadside unit RSU authentication; ( 4) Negotiation and update of the group key; (5) Communication within the group mainly includes broadcast communication, communication between vehicles and RSUs, and one-to-one communication between vehicles. The present invention adopts a public key system without a certificate, and the communication process does not require the participation of a third-party TA, avoiding the time delay problem when the TA authenticates the certificate when the public key encryption system is used, and accelerates the authentication speed. Through the way of group key transmission, the number of authentications of legal vehicles is reduced. Using key agreement to generate keys instead of group leaders to distribute keys reduces the workload of group leaders and eliminates the possible single point of failure.
Owner:JIANGSU UNIV
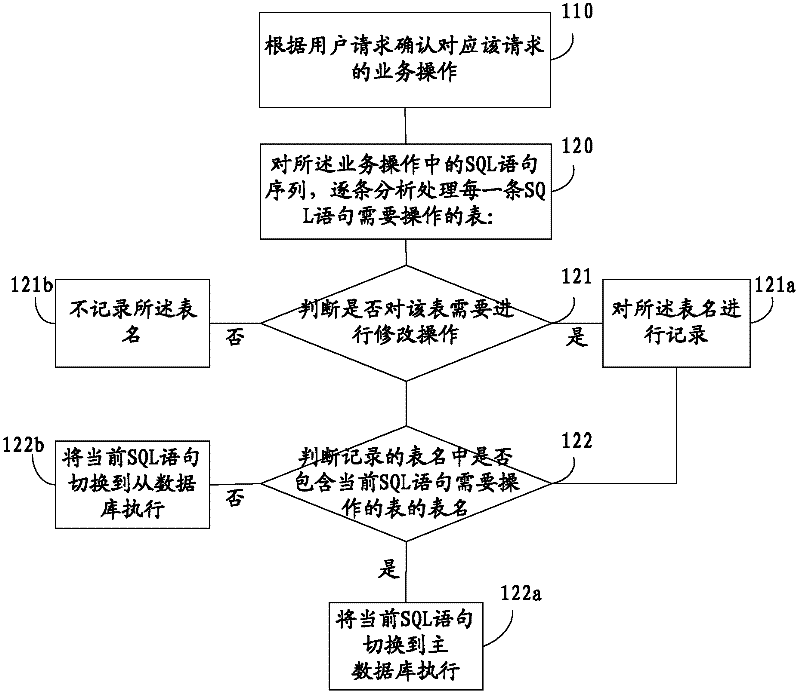
Reading and writing method and system of master slave separation database
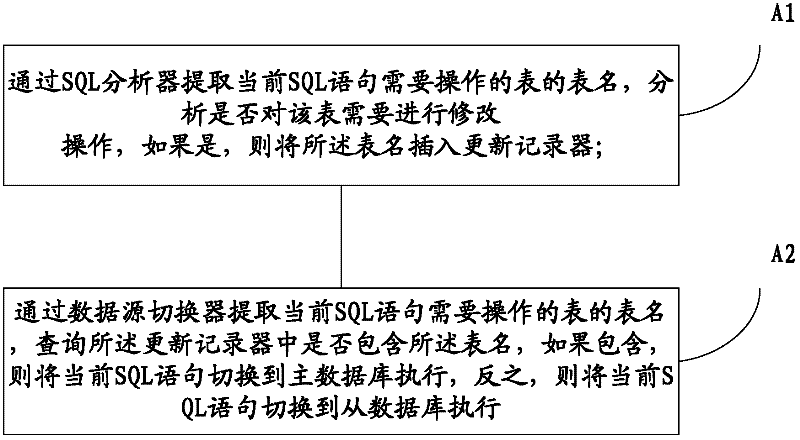
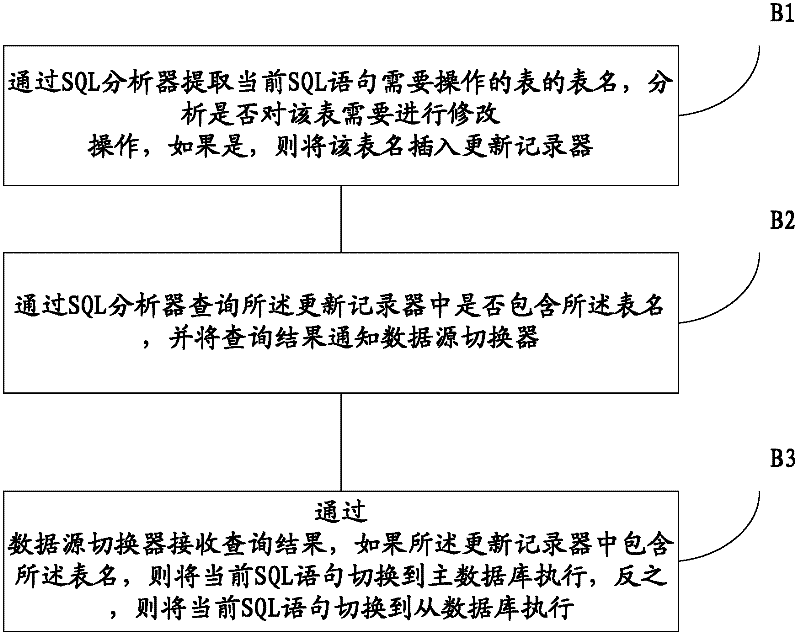
ActiveCN102402596ASolve the delay problemSpecial data processing applicationsSoftware engineeringSQL
The invention provides a reading and writing method and system of master slave separation database, referring to the field of database, wherein the method includes the steps of: confirming a corresponding business operation according to a user requirement; analyzing and processing a table of each SQL sentence to be operated in the business operation one by one; judging whether the table should be modified, if yes, recording the table name; judging whether the recorded table name includes the table name including the table of each SQL sentence to be operated, if yes, switching the current SQL sentence to the main database to execute. The table modified in the SQL sentence sequence of the business operation corresponding to the user requirement is recorded, and all the subsequent operations on the table are switched to the main database, so that the method does not need multiple complex designs and can simply and reliably avoid the synchronous time delay problem of the main slave database with a low cost.
Owner:BEIJING SOGOU TECHNOLOGY DEVELOPMENT CO LTD
Cloud computing network architecture and method for enhancing reliability of cloud network architecture
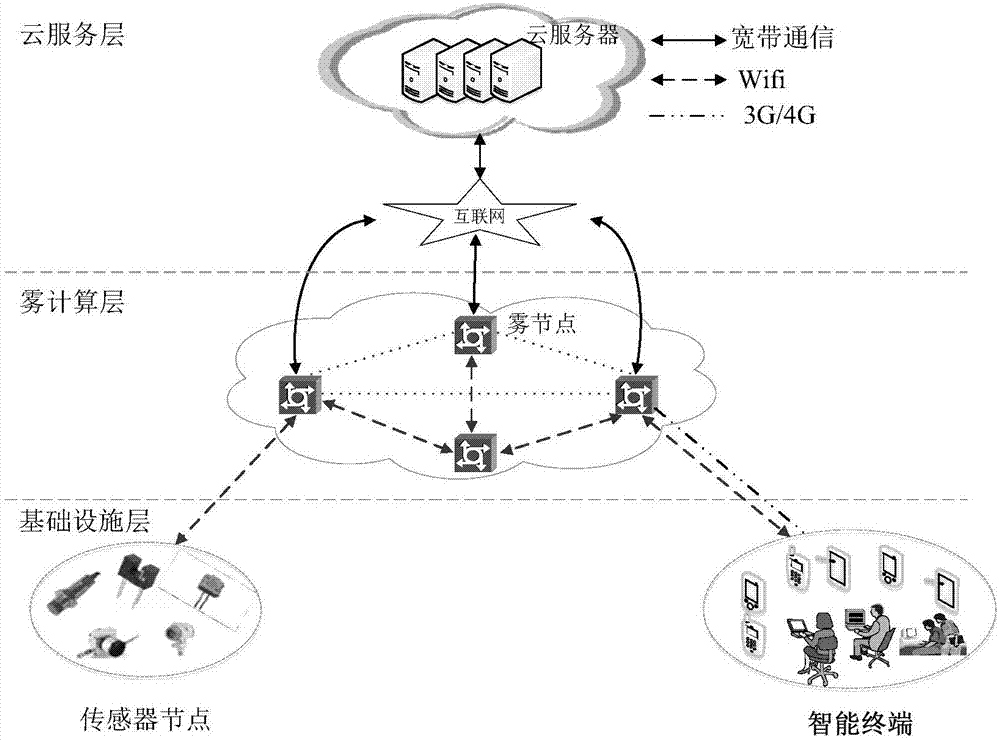
ActiveCN107493334ASolve the delay problemAddress reliabilityData switching networksTime delaysService layer
The invention relates to a cloud computing network architecture and a method for enhancing the reliability of the cloud network architecture. The cloud computing network architecture comprises an infrastructure layer, a fog computing layer and a cloud service layer. The method for enhancing the reliability of the cloud network architecture comprises the following steps: (1) constructing a weighted undirected graph of the cloud network architecture; (2) constructing a time delay optimization model of business processing in the cloud network architecture when the fog computing layer is not broken down; (3) constructing an average time delay optimization model of business processing in the cloud network architecture when the fog computing layer is broken down; and (4) constructing the time delay optimization strategy under the condition that the fog network is not broken down and constructing the average time delay optimization strategy under the condition that the fog network is broken down.
Owner:XIDIAN UNIV
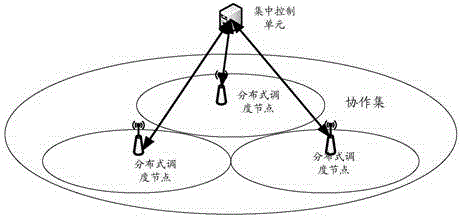
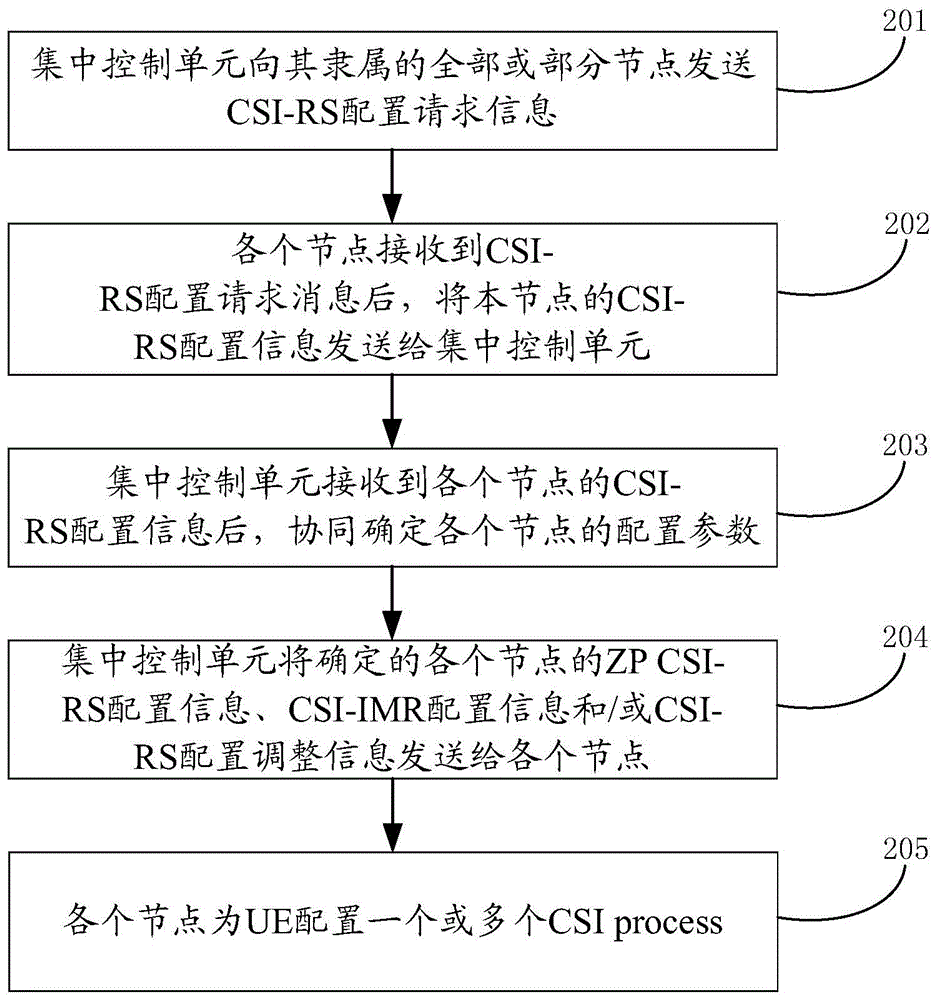
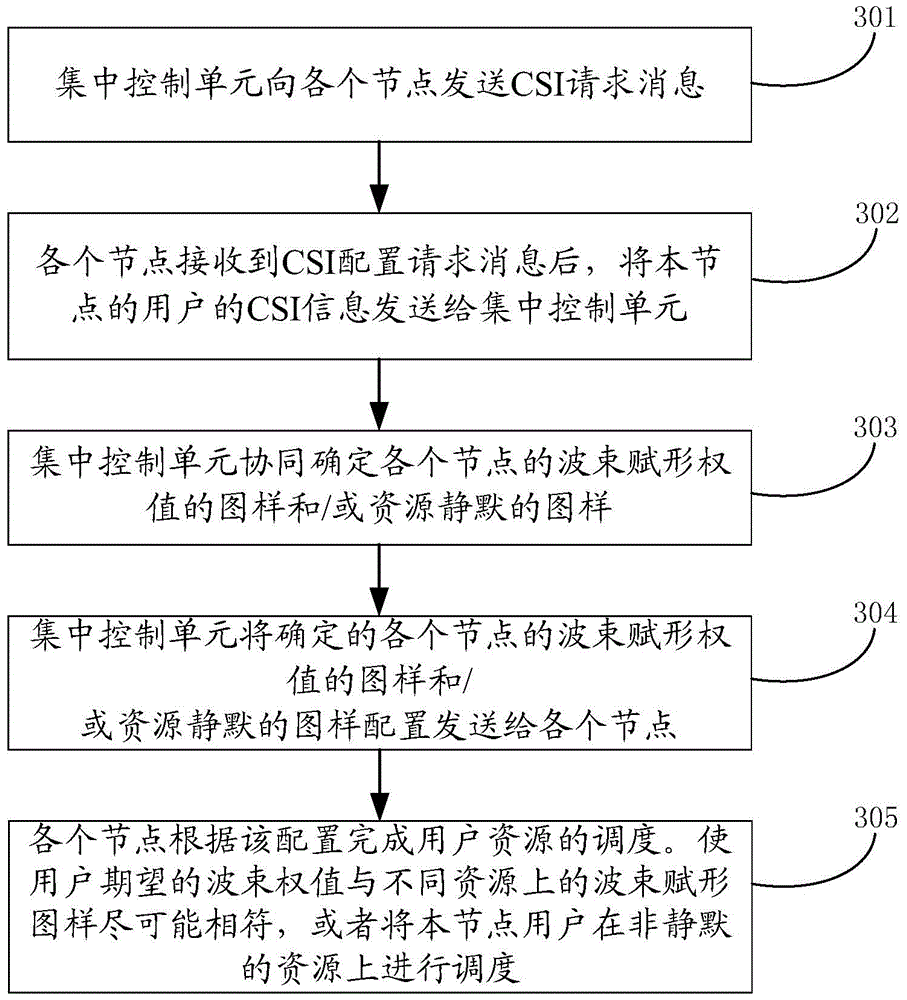
Dispatching configuring method and device
ActiveCN104469960ADoes not affect scheduling flexibilitySolve the delay problemSite diversityNetwork traffic/resource managementTime delaysEmbedded system
The invention discloses a dispatching configuring method. The dispatching configuring method comprises the steps that a centralized control unit configures coordination parameters of different nodes; and distributive dispatching units in the nodes dispatch user resources of the corresponding nodes. The invention further discloses a dispatching configuring device composed of a configuring unit and the dispatching units. The configuring unit is arranged in the centralized control unit and used for configuring the coordination parameters of the different nodes. The dispatching units are arranged in the modes and used for dispatching the user resources in the corresponding nodes. By means of the technical scheme, the non-coordination user time delay problem caused by backhaul transmission under the centralized dispatching mode is solved. Coordinative configuration is carried out on the relative half-static or slow changing parameters, and under the situation that system transmission is achieved, the user dispatching flexibility is not affected.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Hybrid spread spectrum communication system based on low density parity code (LDPC) encoding and method thereof
ActiveCN103701490ASolve the delay problemEasy to implementError preventionBurst errorFrequency offset
The invention discloses a hybrid spread spectrum communication system based on low density parity code (LDPC) encoding and a method thereof. The problems of leakage capture, high leakage capture probability, slow convergence of a phase-locked loop and low decoding performance of the existing synchronous capture method are mainly solved. The system comprises a transmitting part and a receiving part, wherein the transmitting part is used for carrying out pretreatment on original information; the pretreatment data are subjected to frequency hopping treatment and transmitted after being modulated and filtered by a base band; the receiving part is used for obtaining a synchronization point position and a frequency offset value in the received signal through synchronous capture, and intercepting useful data to carry out de-hopping according to the synchronization point position; the base band demodulates and filters; the filtering data are subjected to frequency offset compensation according to the frequency offset value; the data after frequency offset compensation are subjected to dispreading and frequency offset rectification; the frequency offset rectification data are decoded and the decoding result is output. The hybrid spread spectrum communication system has the advantages of being strong in burst error resisting ability, high in real-time synchronization capture speed, high in capture accuracy, high in convergence speed of the phase-locked loop, and good in decoding performance, and can be applied to reliable communication under the condition of very low powder spectral density.
Owner:XIDIAN UNIV
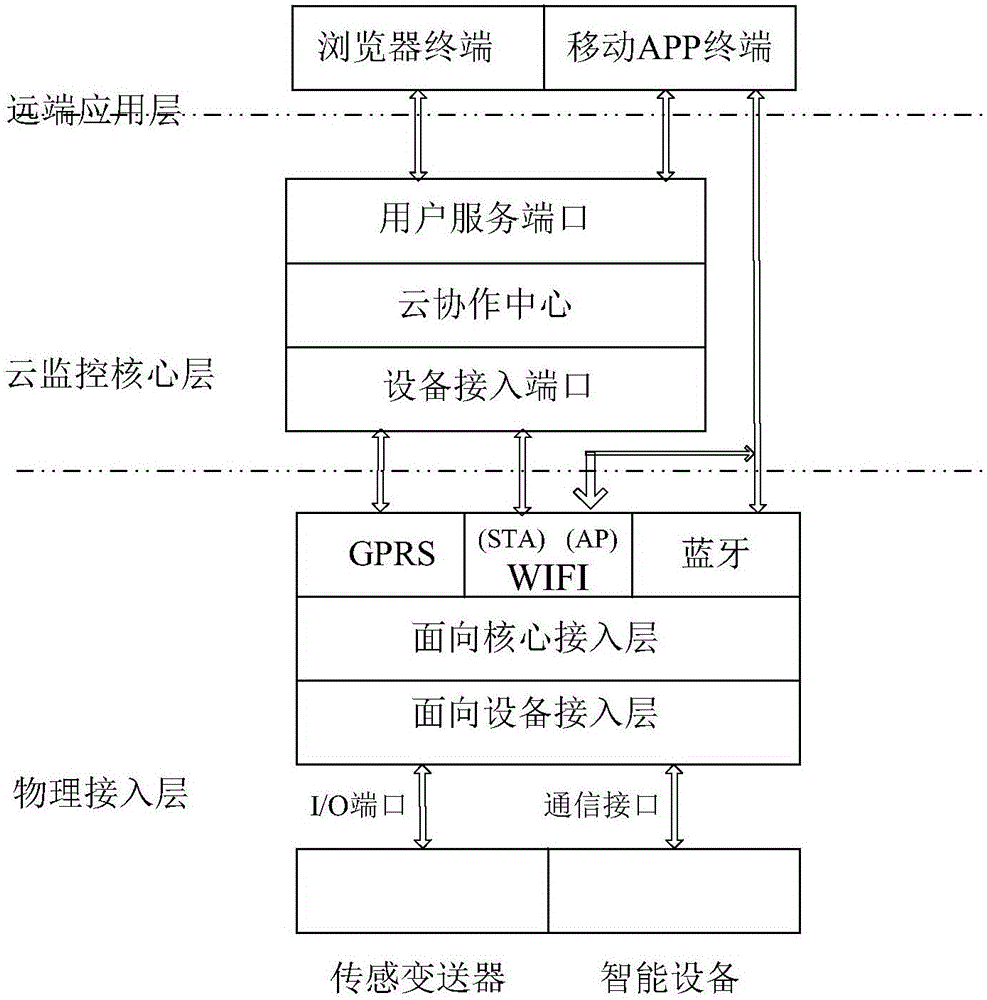
Cloud-cooperation general intelligent remote monitoring system
InactiveCN105717848ASolve local debuggingResolve escalationProgramme controlComputer controlRegister allocationMobile apps
A cloud cooperation general intelligent remote monitoring system, including a cloud collaboration center, a browser terminal, a mobile APP terminal, a remote maintenance terminal, user equipment, and a cloud cooperation general intelligent monitoring module; the cloud collaboration center consists of a cloud server, a cloud database, and a cloud monitoring platform The cloud monitoring platform is deployed on the cloud server, and the cloud collaboration center is connected to the general intelligent monitoring module of the cloud association through the Internet; the user equipment is connected to the general intelligent monitoring module of the cloud association; the general intelligent remote monitoring module of the cloud association is equipped with a device configuration information module , I / O configuration module, smart device configuration module, register configuration information module, I / O channel data detection module, RS485 communication interface detection module, RS232 communication interface detection module, CAN communication interface detection module, Ethernet communication interface detection module, Communication port data transparent transmission module, data packet module.
Owner:湖南云协智造信息科技有限公司 +1
Fault detection method of nonlinear network control system based on event triggering mechanism
ActiveCN108667673AIncreased failure sensitivityTroubleshooting fault detection issuesElectric testing/monitoringData switching networksEvent triggerSystem failure
The invention provides a fault detection method of a nonlinear network control system based on an event triggering mechanism, and relates to the technical field of network system fault detection. Themethod comprises the following steps: firstly, establishing a T-S fuzzy model of the nonlinear network control system, setting an event triggering condition, establishing a fuzzy fault detection filter model, establishing a fault weighting system, and then establishing a fault detection system model; selecting an appropriate residual evaluation function and a detection threshold according to the fault detection system model, and detecting whether a fault of the nonlinear network control system occurs; and finally, further designing a parameter matrix and an event triggering matrix of a fault detection filter according to the stability of the fault detection system and sufficient conditions of existence of the fault detection filter. By adoption of the fault detection method of the nonlinear network control system based on the event triggering mechanism provided by the invention, the robustness to external disturbance and communication delay is greatly improved, and the limited networkresources and computing resources can be saved by the application of the event triggering mechanism.
Owner:NORTHEASTERN UNIV
Implementation method of random access of carrier aggregation enhancement
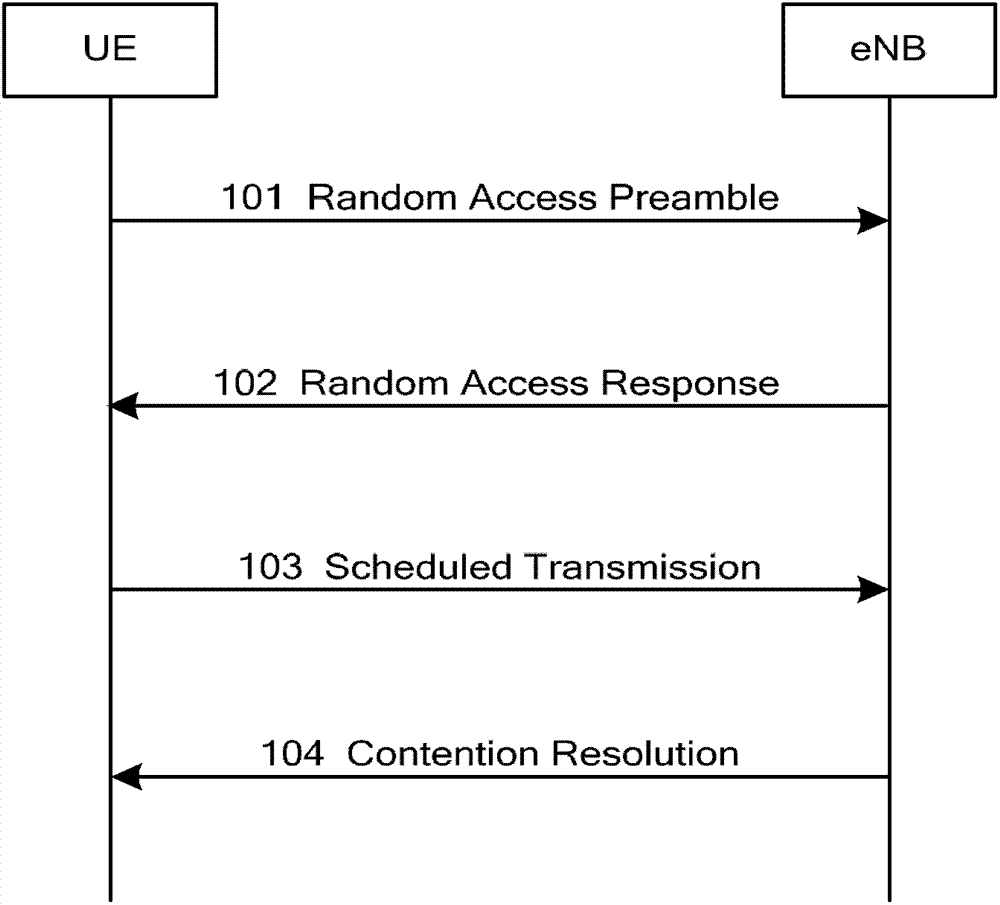
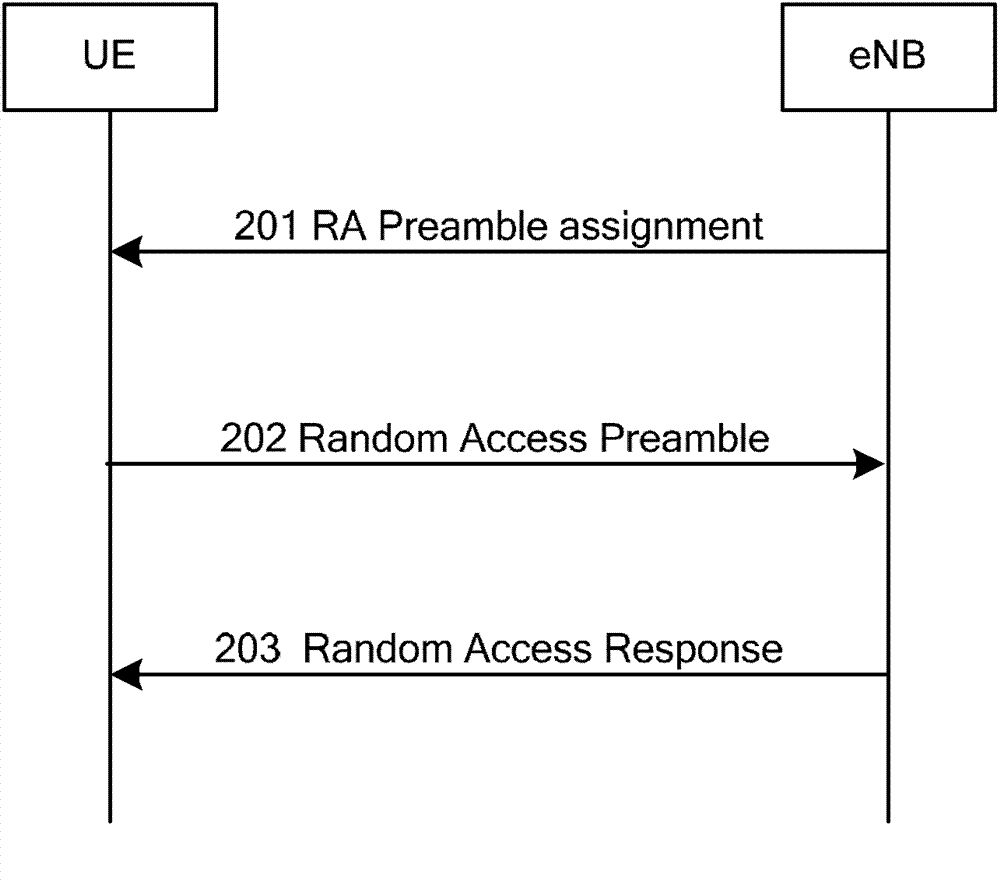
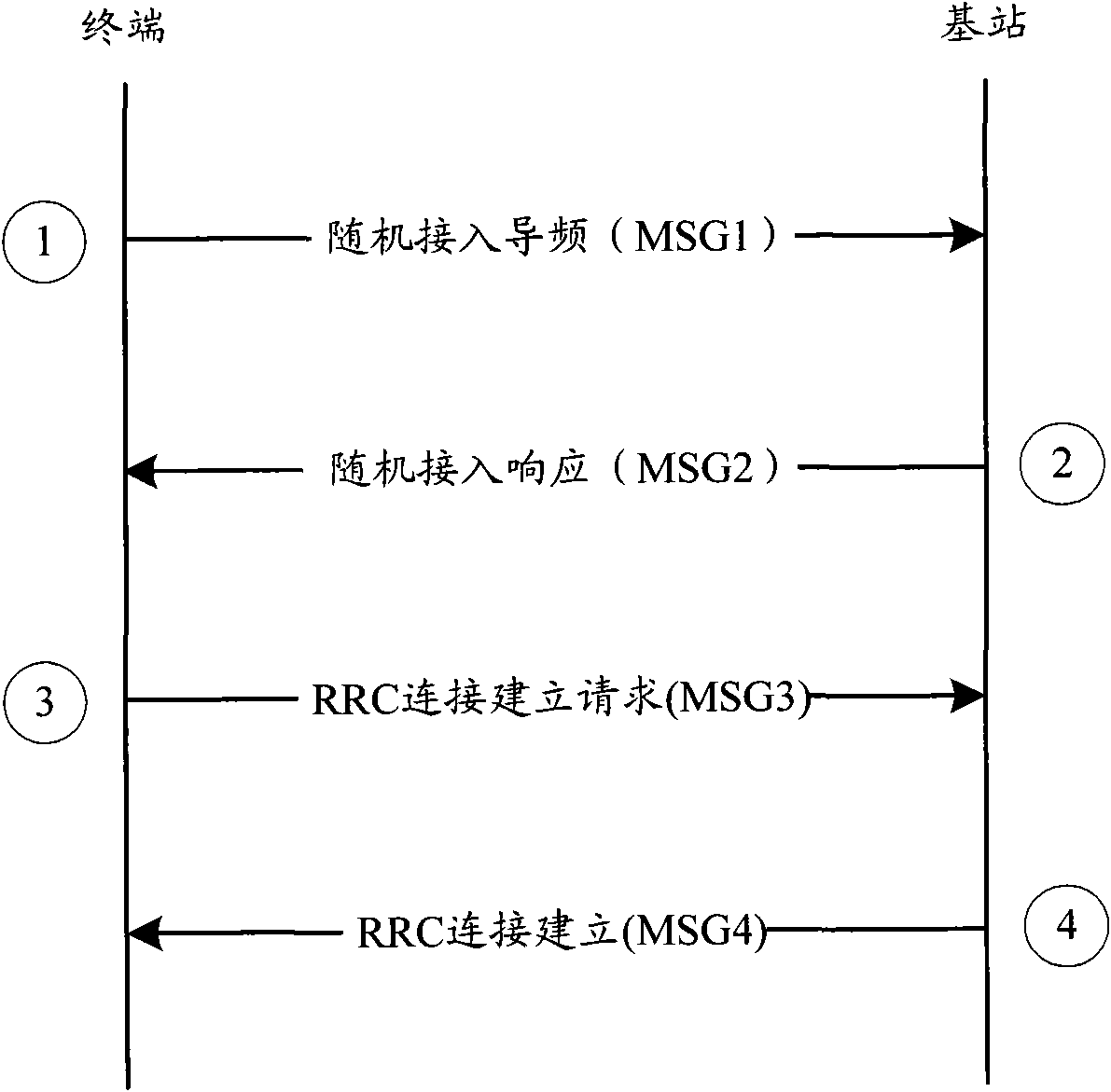
ActiveCN103096489AResolve UE conflictsSolve the delay problemWireless communicationCarrier signalTelecommunications
The invention provides an implementation method of random access of carrier aggregation enhancement. The implementation method of the random access of the carrier aggregation enhancement is applied to the situation that a cell carrying out random access to user equipment (UE) is not a primary service cell (PCell) and comprises the following steps: a network side chooses one secondary service cell (SCell) from a timing advance (TA) group of the UE according to dedicated lead code resources and / or load conditions, the network side indicates the lead code used by the UE to carry out random access and physical random access channel (PRACH) resource through physical downlink control channel (PDCCH) instructions on the chosen SCell scheduling cell, the UE transmits a specified lead code on the specified PRACH resources of the networks side, the network side receives the lead code on the specified PRACH resources, and therefore acquires the identifications of the UE, and the network side indicates to transmit the physical downlink shared channel (PDSCH) resource locations of corresponding TA information according to the non-competition mode random access process carried out by the UE.
Owner:POTEVIO INFORMATION TECH
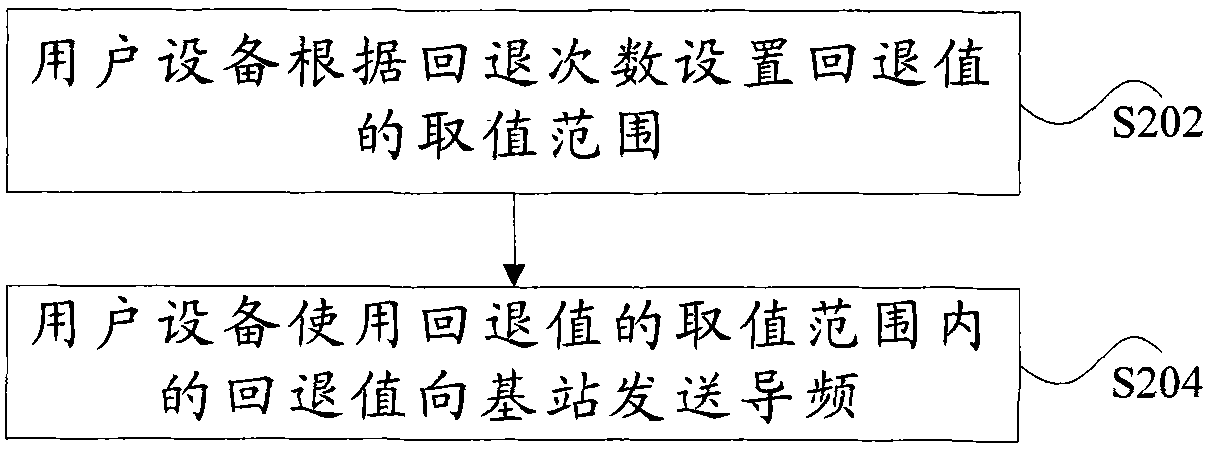
Access processing method and user equipment
InactiveCN102056322ASolve the delay problemAccess Latency ImprovementError prevention/detection by using return channelWireless communicationAccess timeUser equipment
The invention discloses an access processing method and user equipment. The method comprises the following steps that: the user equipment sets a value range of a backoff value according to a backoff frequency; and the user equipment transmits a pilot frequency to a base station by using the backoff value within the value range. Due to the invention, the problems of long access time delay and fairness absence in the access of the user equipment to a network of the prior art are solved, and the effects of improving the access time delay and enhancing the system performance are achieved.
Owner:ZTE CORP
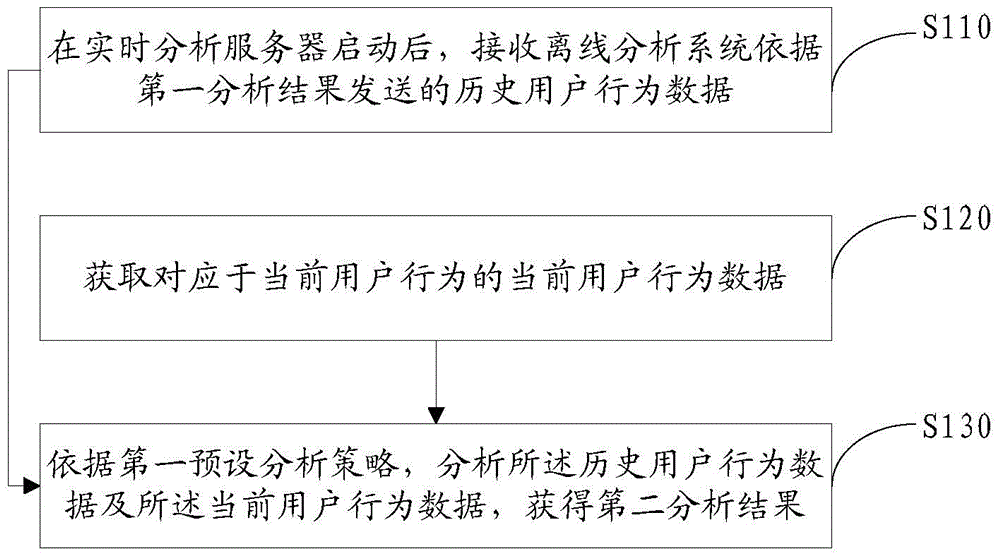
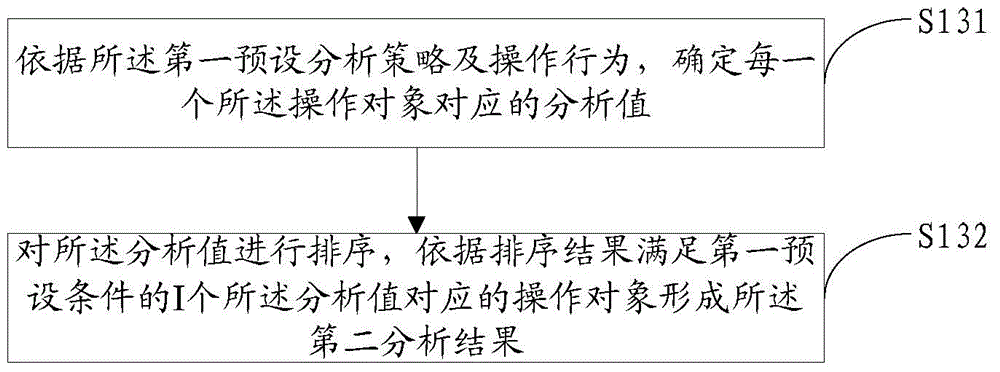
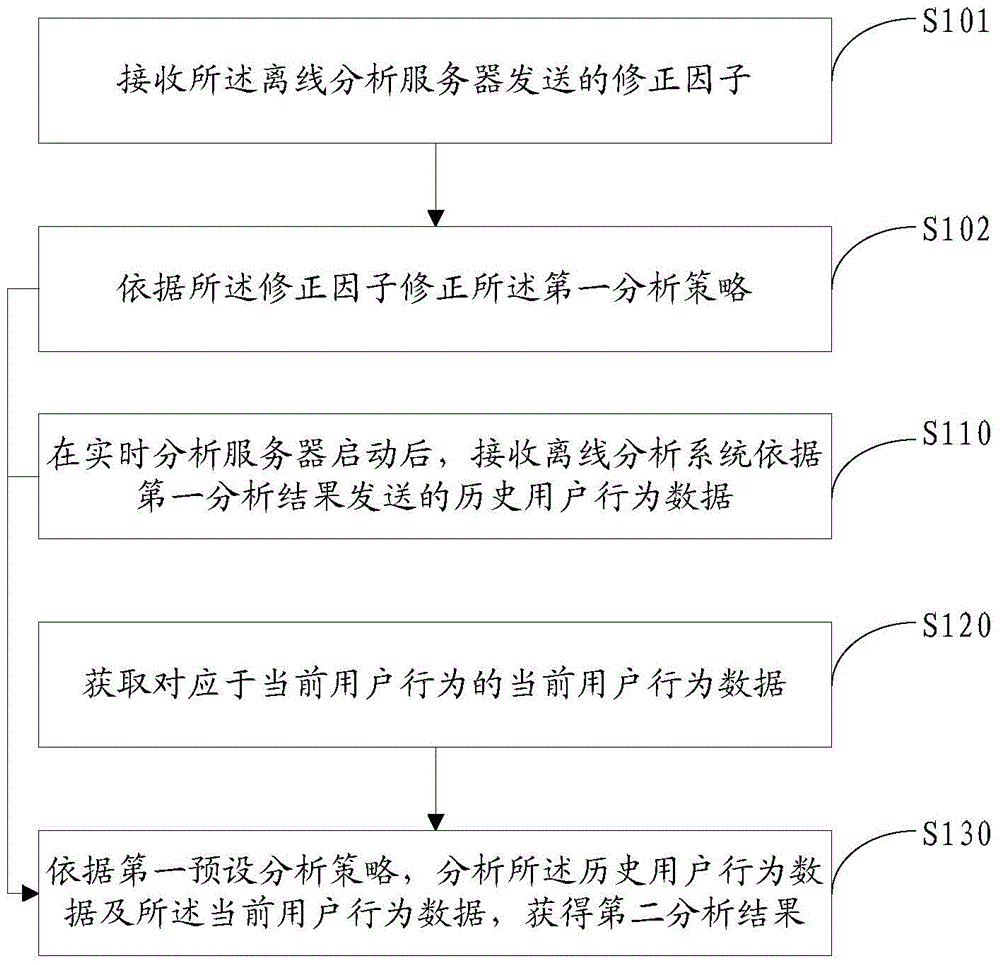
User behavior analysis method and servers
ActiveCN104834657AReduce time delayIncrease speedSpecial data processing applicationsBehavioral analyticsTime correlation
The invention discloses a user behavior analysis method and servers. The method comprises the steps of after booting a real-time analysis server, receiving historical user behavior data sent by an offline analysis server according to a first analysis result, wherein the first analysis result is an analysis result formed according to a first preset analysis strategy before the real-time analysis server boots; acquiring current user behavior data corresponding to current user behavior, wherein both the historical user behavior data and current user behavior data comprise user operations and operation objects which the user operations point at; and according to the first preset analysis strategy, analyzing the historical user behavior data and current user behavior data so as to obtain a second analysis result, wherein both the first analysis result and the second analysis result comprise at least one set of the operation objects, one operation object corresponds to at least two pieces of multimedia information, and the information content of the multimedia information corresponding to the same operation object has time correlation.
Owner:TENCENT TECH (BEIJING) CO LTD
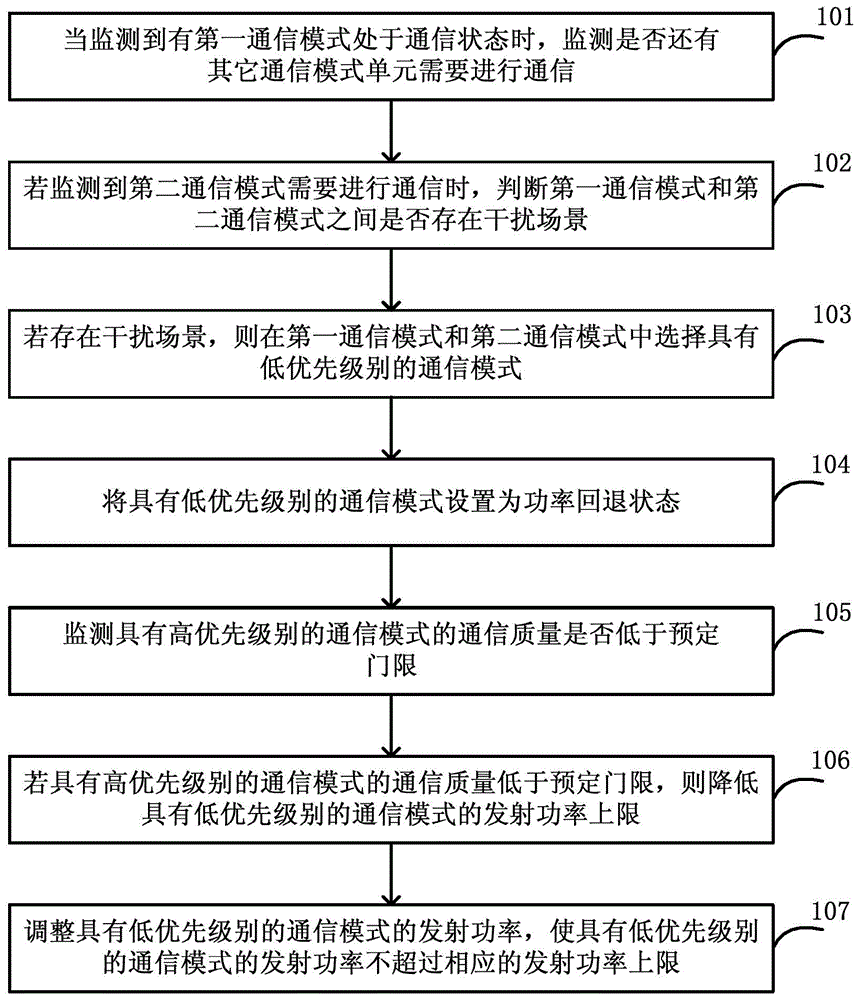
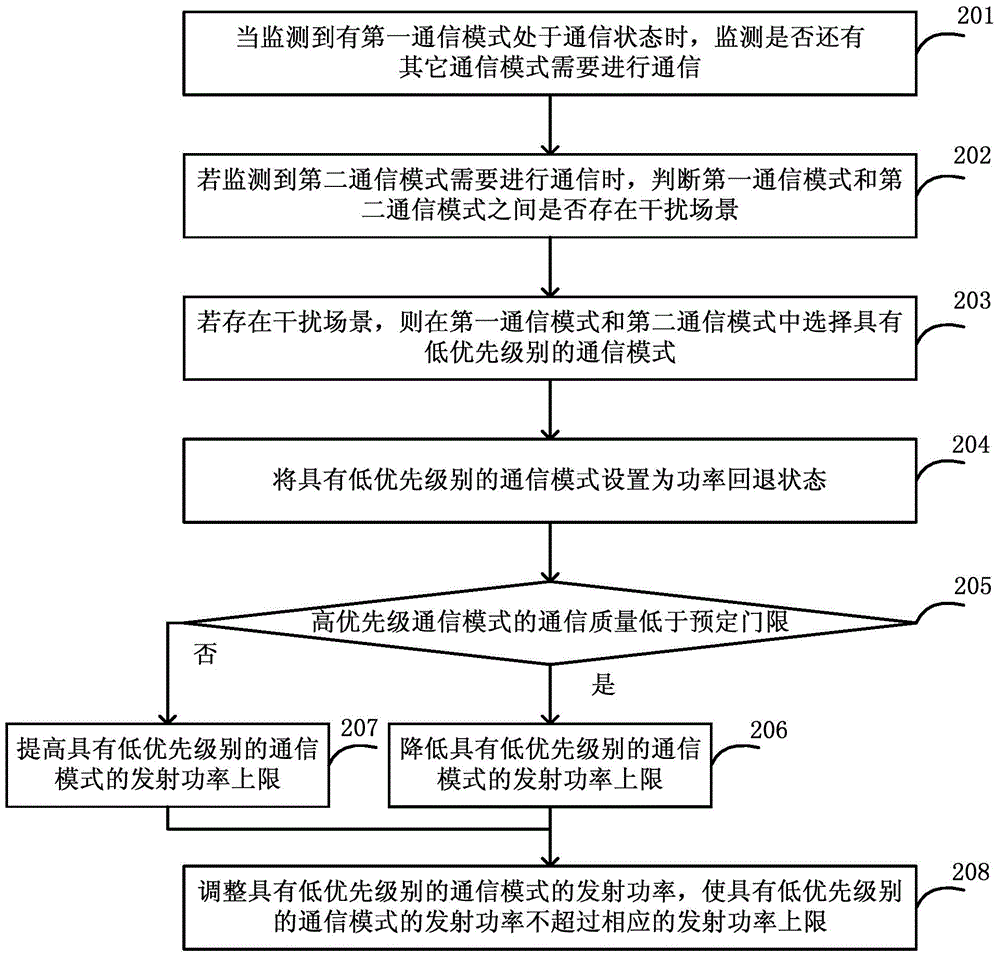
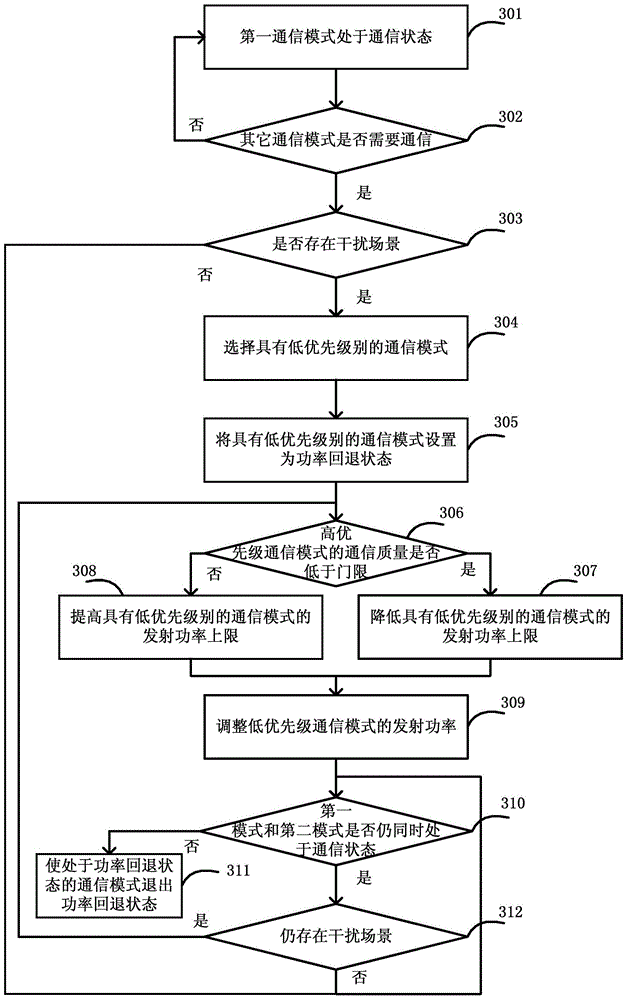
Method for achieving power control and user terminal
ActiveCN105263186AAvoid Latency IssuesImprove overall throughputPower managementTime delaysPower control
The invention discloses a method for achieving power control and a user terminal. The method comprises the following steps: after monitoring that a first communication mode is in a communication state, that a second communication mode requires communication, and judging that an interference scene exists between the first communication mode and the second communication mode, selecting a communication mode with a low priority level from the first communication mode and the second communication mode; setting the communication mode with the low priority level as a power backoff state; if the communication quality of the communication mode with a high priority level is lower than a preset threshold, reducing an upper limit of transmitting power of the communication mode with the low priority level; and adjusting the transmitting power of the communication mode with the low priority level, to prevent the transmitting power of the communication mode with the low priority level from exceeding the corresponding upper limit of transmitting power. Therefore, the time delay problem caused by service interruption / restart can be effectively avoided, and the concurrence of the communication modes can be guaranteed to the utmost, and the overall throughput of the system can be effectively improved.
Owner:CHINA TELECOM CORP LTD
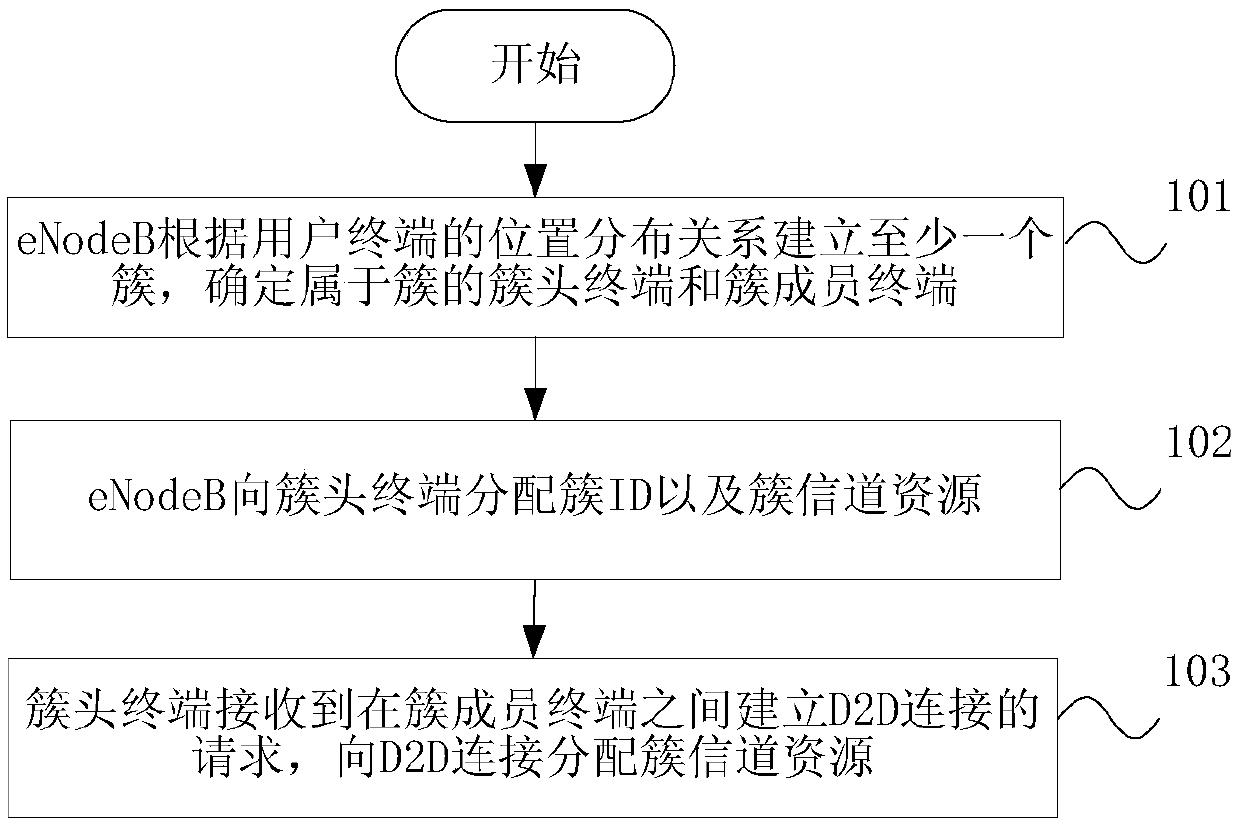
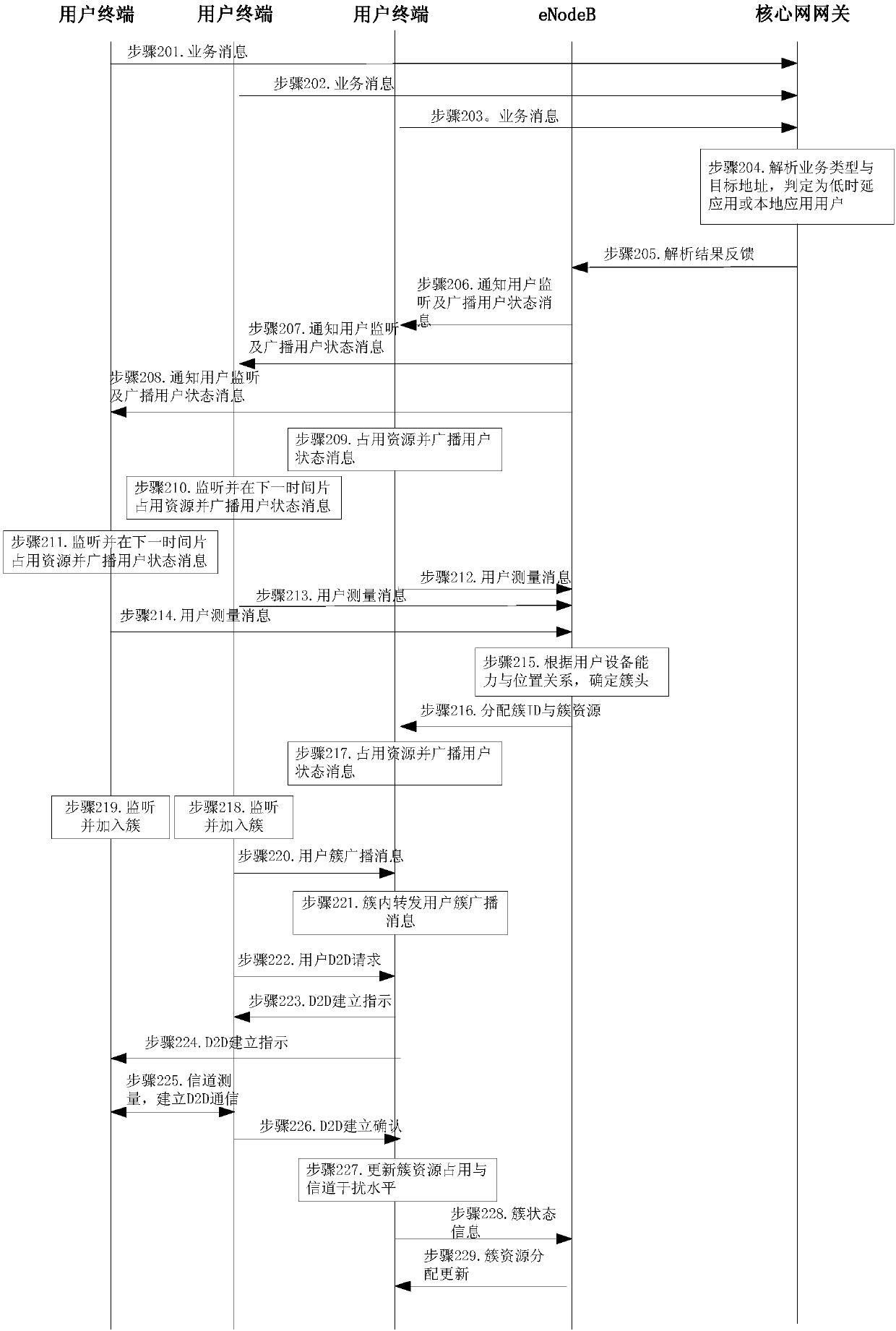
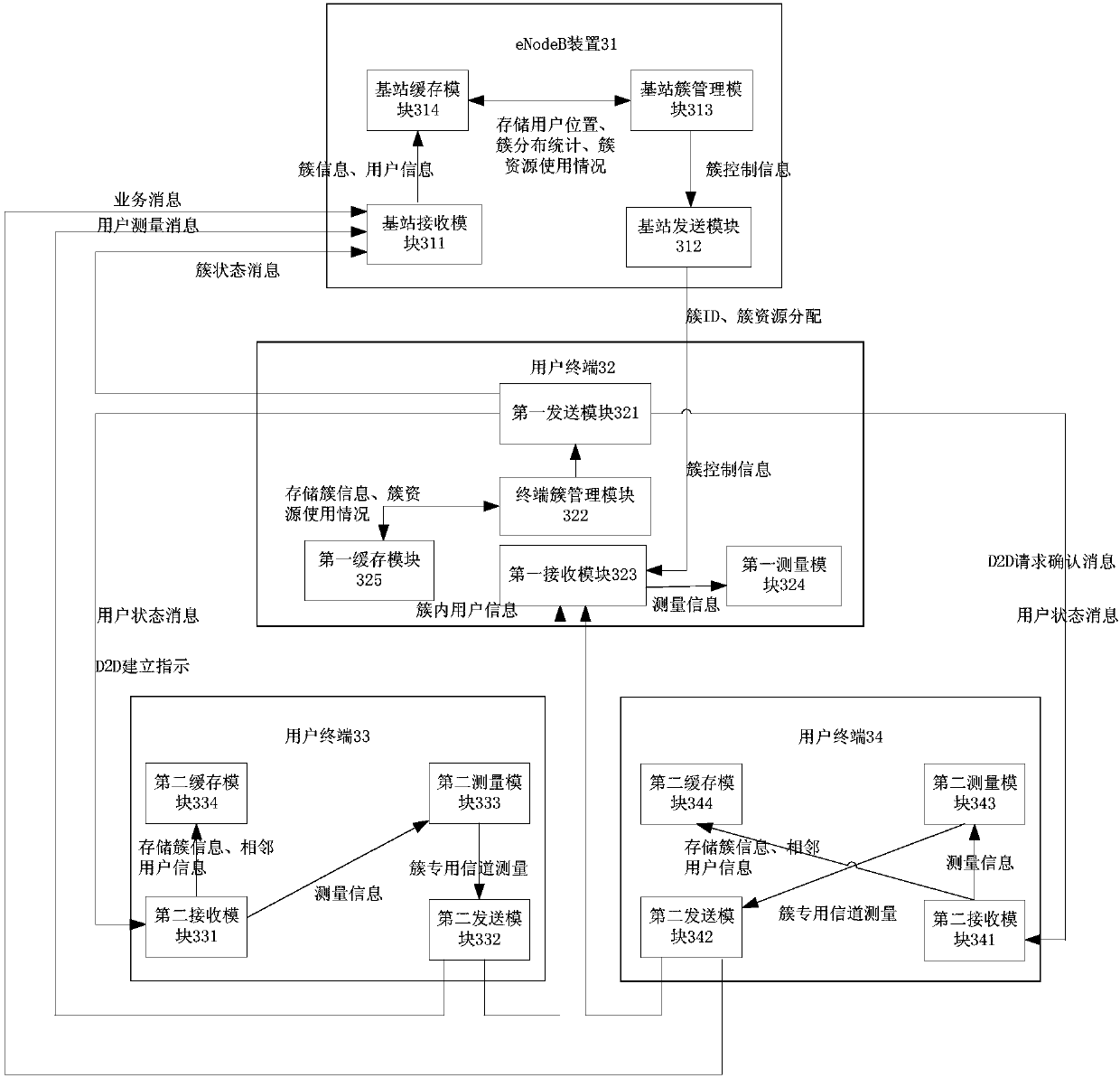
Cellular user clustering communication method and system as well as eNodeB and terminal
ActiveCN107734590ASolve the delay problemAddress reliabilityWireless communicationResource utilizationDirect communication
The invention discloses a cellular user clustering communication method and system, an eNodeB and a terminal and relates to the field of mobile communication. The method comprises the following stepsthat the eNodeB establishes at least one cluster according to the position distribution relationship of a user terminal and determines a cluster head terminal and cluster member terminals, which belong to the cluster; the eNodeB allocates a cluster ID and cluster channel resources to the cluster head terminal; and the cluster head terminal receives a request for establishing a D2D connection between the cluster member terminals and allocates the cluster channel resources to the D2D connection in order to enable the cluster member terminals to communicate through the cluster channel resources.According to the method, the system, the eNodeB and the terminal, the user terminals in a cell are divided into a plurality of user clusters according to the positions, the resources are allocated according to the clusters, the cluster head provides intra-cluster information aggregation broadcast and realizes direct communication of the intra-cluster users, autonomous clustering and device-to-device communication can be achieved, the requirements of services for transmission characteristics, such as communication delay and reliability, are met, and the resource utilization efficiency is improved.
Owner:CHINA TELECOM CORP LTD
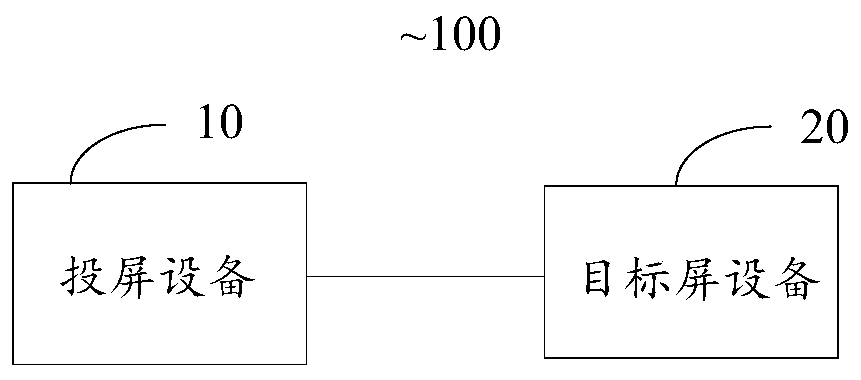
Screen projection method and system and storage device
ActiveCN109996097ASolve the delay problemControl congestionSelective content distributionData transmissionProjection system
The invention discloses a screen projection method, a screen projection system and a storage device, and the method comprises the steps: obtaining screen projection data, the screen projection data comprising a first type of screen projection data and / or a second type of screen projection data; transmitting the screen projection data to target screen equipment, therefore, the target screen devicereceives and displays the screen projection data, wherein the application layer is provided with at least a first transmission channel and a second transmission channel, the first type of screen projection data and the second type of screen projection data of the application layer are transmitted through the first transmission channel and the second transmission channel respectively, and the low-delay user datagram transmission protocol is used for transmitting the screen projection data on the transmission layer. In this way, the screen projection method and device can reduce the lagging in the screen projection process and improve the fluency.
Owner:GUANGZHOU HUYA INFORMATION TECH CO LTD
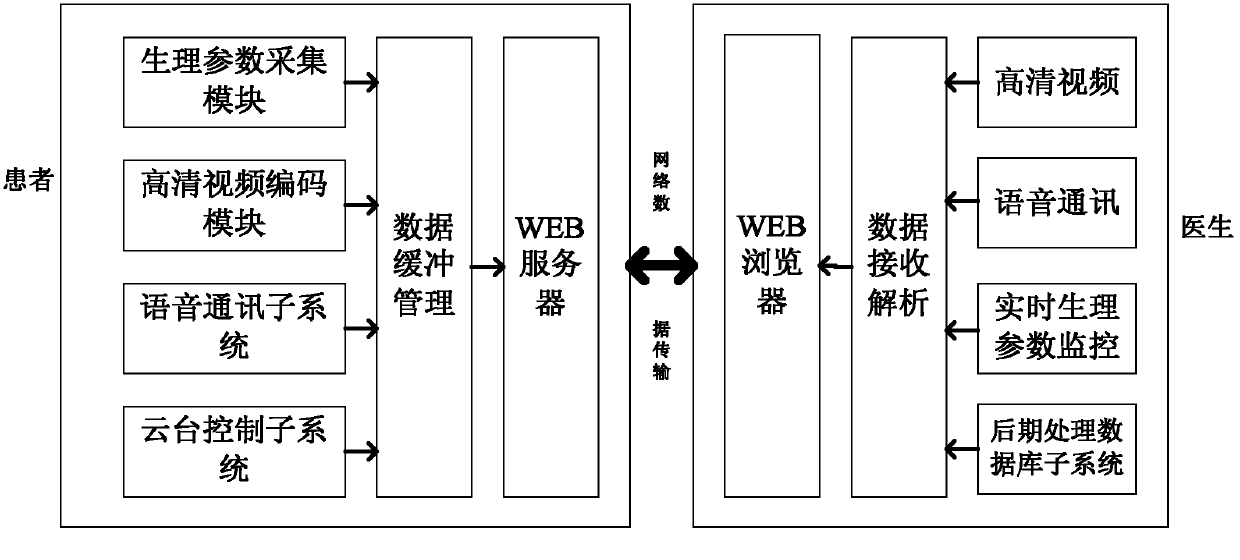
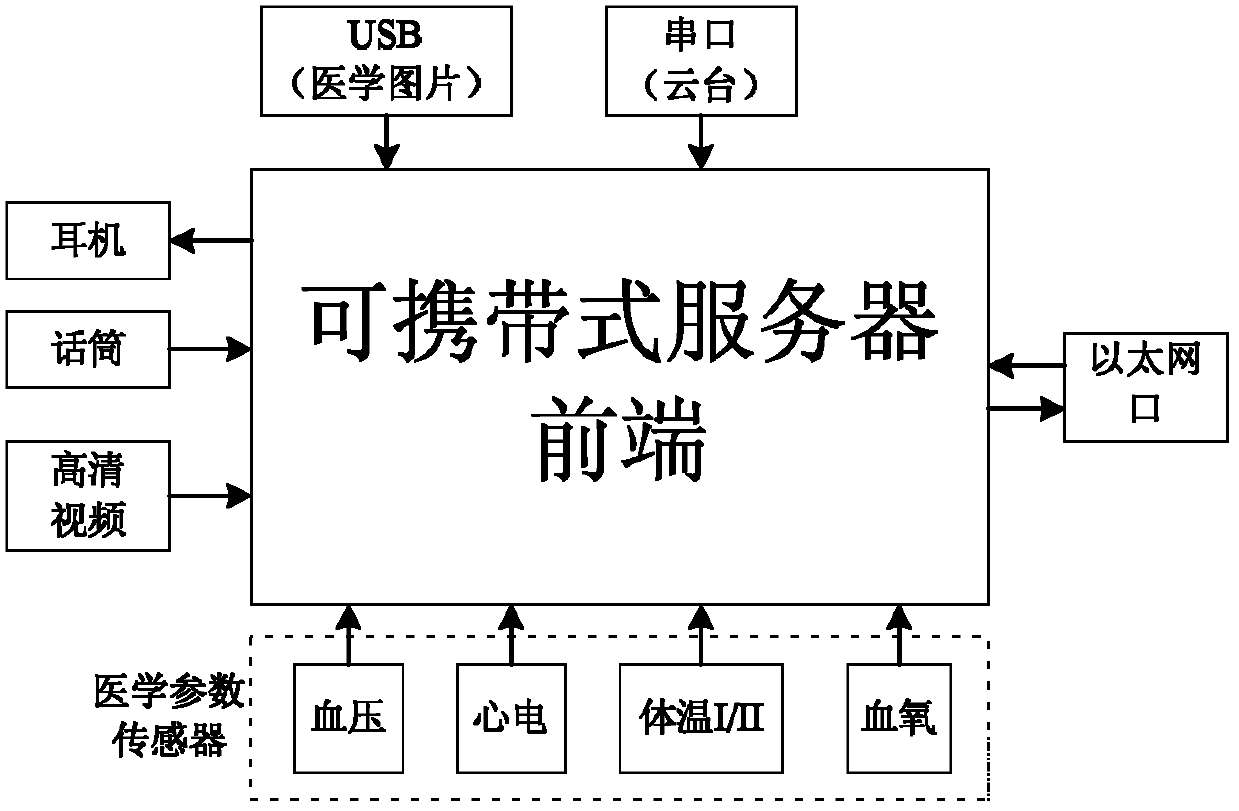
Webpage-based remote comprehensive diagnosis and treatment system
InactiveCN102609628AComprehensiveImprove communication qualitySpecial data processing applicationsWeb serviceTime delays
The invention discloses a webpage-based remote comprehensive diagnosis and treatment system, which comprises a server side and a client side. The server side is provided with a built-in WEB server, a high-definition video encoding module and a bidirectional voice communication subsystem. The built-in WEB server is used for acquiring various data, waits to be connected with users and realizes data transmission with the client side in a communication manner after being connected with the users successfully. The high-definition video encoding module completes acquisition and encoding of video data of the server side, wherein the encoding is completed by the aid of a hardware encoding chip. The bidirectional voice communication subsystem is mainly used for realizing communication between doctors and patients during the remote medical treatment process, realizing bidirectional voice cross-platform communication while solving the problems of noise and time delay in communication. The client side is a WEB-based high-definition video decoding client side. Compared with the conventional remote medical treatment system, the webpage-based remote comprehensive diagnosis and treatment system has the advantages of portability, easiness in use, high adaptability and communication quality and the like.
Owner:SHANGHAI JIAO TONG UNIV
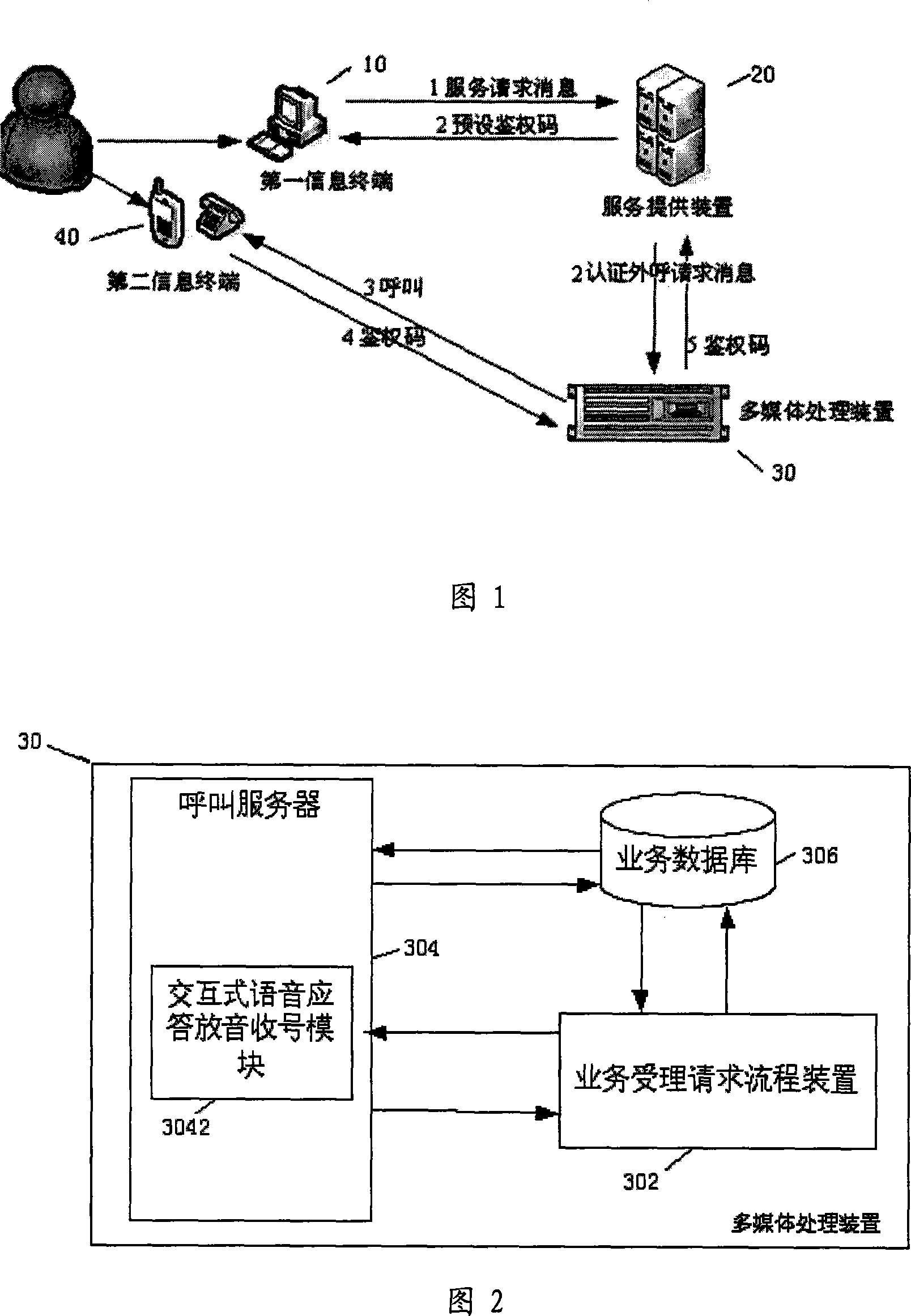
Authentication system and authentication method
InactiveCN101102324ASolve the problem of delay and lossThe implementation process is short and easyRadio/inductive link selection arrangementsSecuring communicationAuthentication systemService provision
The system comprises, a first information terminal, a service providing unit and an authentication code submitting unit. The first information terminal is used for receiving the service request message and sending the service request message to the service providing unit; the service providing unit is used for sending preset authentication code to the first information terminal, and sending the authentication out-calling request message to the authentication code providing unit, and after receiving the authentication code from the authentication code providing unit, and comparing the received authentication code with the preset authentication code, and according to the comparison result, deciding if providing service for the first information terminal; the authentication code providing unit is used for receiving the authentication out-calling message from said service providing unit and providing the authentication code for the service providing unit.
Owner:MDC TELECOM CO LTD
Terminal access method
InactiveCN101547496ASolve the delay problemSolve CP configuration problemsAssess restrictionMulti-frequency code systemsIdle timeAccess method
The invention discloses a terminal access method. The terminal access method comprises the following steps that: a base station configures and determines the specific composition structures of uplink and downlink subframes of a frame structure according to a cyclic prefix of a mobile communication system and sends the composition structure information of the uplink and downlink subframes to a terminal through a broadcasting message; and the terminal selects a particular uplink subframe to send the access information to the base station according to the composition structure information of the uplink and downlink subframes, wherein the frame structure comprises one or more downlink subframes and one or more uplink subframes. Each downlink subframe and each uplink subframe are formed by one or more basic subframe units and an idle time slot respectively. The method can meet the requirements of the IMT-Advanced on the systematic performance.
Owner:ZTE CORP
Fine-grained searchable encryption method for fog computing
ActiveCN108156138ASolving Mobility IssuesSolve the delay problemKey distribution for secure communicationCiphertextFog computing
The invention discloses a fine-grained searchable encryption method for fog computing. A cloud-fog terminal user system structure is established by using the attribute encryption technology and the searchable encryption technology of a ciphertext strategy, a fog node serves as an agent to share the computing burden of a terminal user by using the attribute encryption technology and the searchableencryption technology of the ciphertext strategy, the terminal user can quickly generate a trap door and decryption ciphertext, therefore lightweight searchable encryption is achieved, meanwhile fine-grained access control is supported, only legitimate data users can perform ciphertext retrieval, the fine-grained searchable encryption method has a broad application prospect in actual scenes, fine-grained access control is achieved, only the legitimate data users can perform ciphertext retrieval, and the fine-grained searchable encryption method has a broad application prospect in actual scenes.
Owner:XIDIAN UNIV
Vehicle networking communication optimization algorithm based on edge computing and Actor-Critic algorithm
ActiveCN109068391ASolve the problem of huge access volumeImprove utilization efficiencyParticular environment based servicesVehicle wireless communication serviceNon orthogonalReal-time computing
The invention relates to a method based on edge computing and an Actor-Critic algorithm. The specific steps are as follows: in the vehicle networking communication system, the user sequence is {1, 2,..., k,..., K}, and there are K users; the subchannel sequence is {1, 2,..., n,..., N} with N subchannels; fog access node sequence {1, 2,..., m,... M}, total M access nodes, computing power sequence of incoming nodes {1, 2,... Cm,..., cM}; task sequence {1, 2,... tk,..., tK} uploaded by user, total tK tasks; a non-orthogonal multiple access (NOMA) mode is adopted to connect the user to the vehiclenetworking communication system. The task uploaded by the user carries out edge calculation and returns the calculation result to the user; taking advantage of actor-Critic algorithm to optimize theresource allocation method and get the best resource allocation method. The invention combines the non-orthogonal multiple access, the edge calculation and the reinforcement learning, effectively solves the problem of huge access quantity existing in the vehicle networking, simultaneously reduces the time delay in the whole communication process, obtains the best resource distribution mode under different environments, and improves the energy utilization efficiency.
Owner:QINGDAO ACADEMY OF INTELLIGENT IND
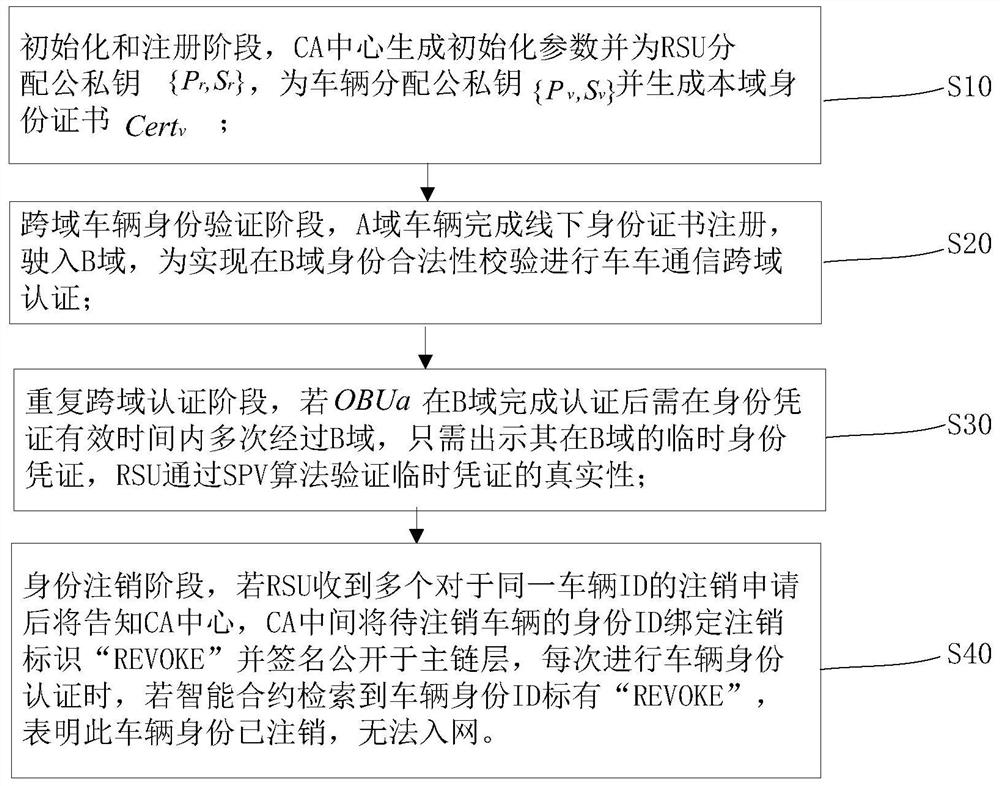
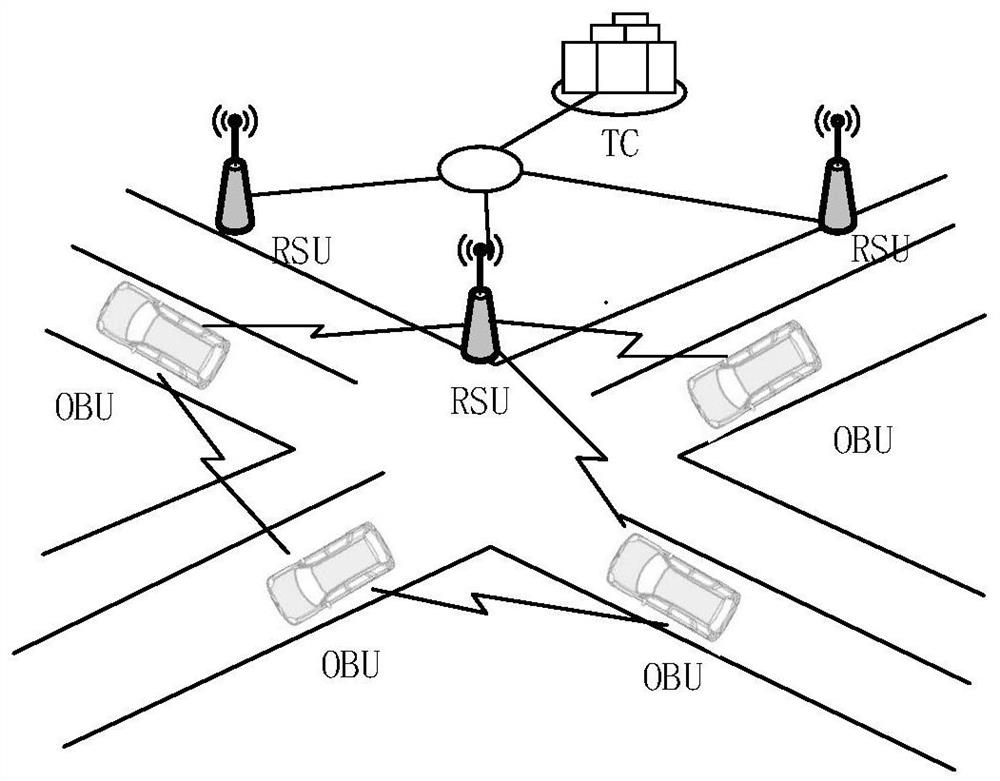
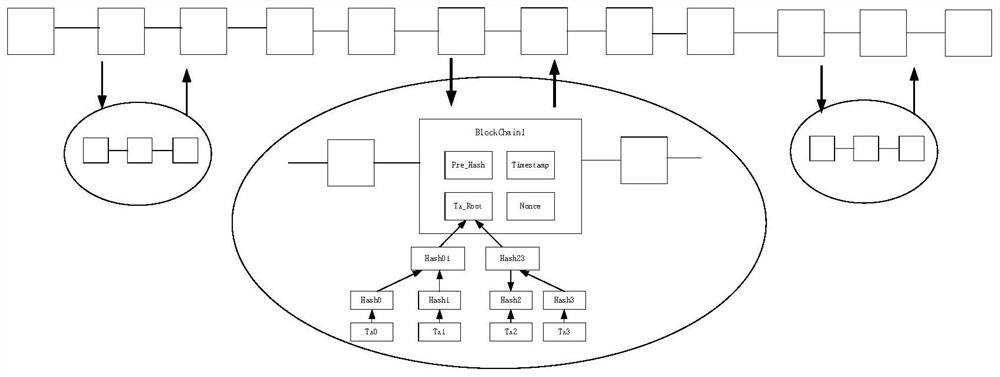
Internet of Vehicles cross-domain authentication method based on side chain technology trust model
ActiveCN112153608AMeet the needs of efficient cross-domain identity authenticationGuaranteed unforgeableEncryption apparatus with shift registers/memoriesParticular environment based servicesThe InternetEngineering
The invention provides an Internet of Vehicles cross-domain authentication method based on a side chain technology trust model. The Internet of Vehicles cross-domain authentication method comprises the following steps: S10, an initialization and registration stage; S20, a cross-domain vehicle identity verification stage; S30, repeating a cross-domain authentication stage; and S40, in an identity logout stage, if the RSU receives a plurality of logout applications for the same vehicle ID, informing a CA center of the logout applications, the CA center binding the identity ID of the vehicle to be logged out with a logout identifier 'REVOKE' and signing and disclosing the logout identifier 'REVOKE' in a main chain layer, and if the intelligent contract retrieves that the vehicle identity ID is marked with 'REVOKE', indicating that the vehicle identity is logout and cannot access a network. According to the Internet of Vehicles cross-domain authentication method based on the side chain technology trust model, the block chain side chain technology is innovatively applied to cross-domain identity authentication research of the Internet of Vehicles, and unforgeability, tamper resistance and traceability of vehicle identities are guaranteed through the characteristics of block chain distributed data storage and the like; the problem of centralized single-point failure of a cross-domainauthentication mechanism of the traditional Internet of Vehicles is solved.
Owner:NANTONG UNIVERSITY +1
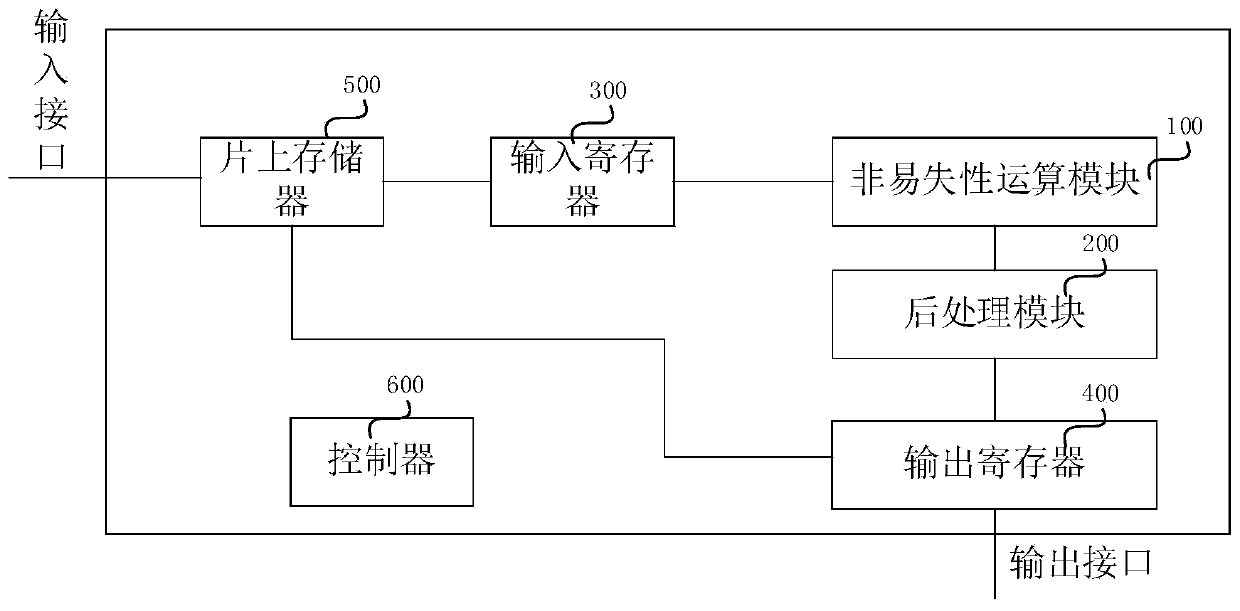
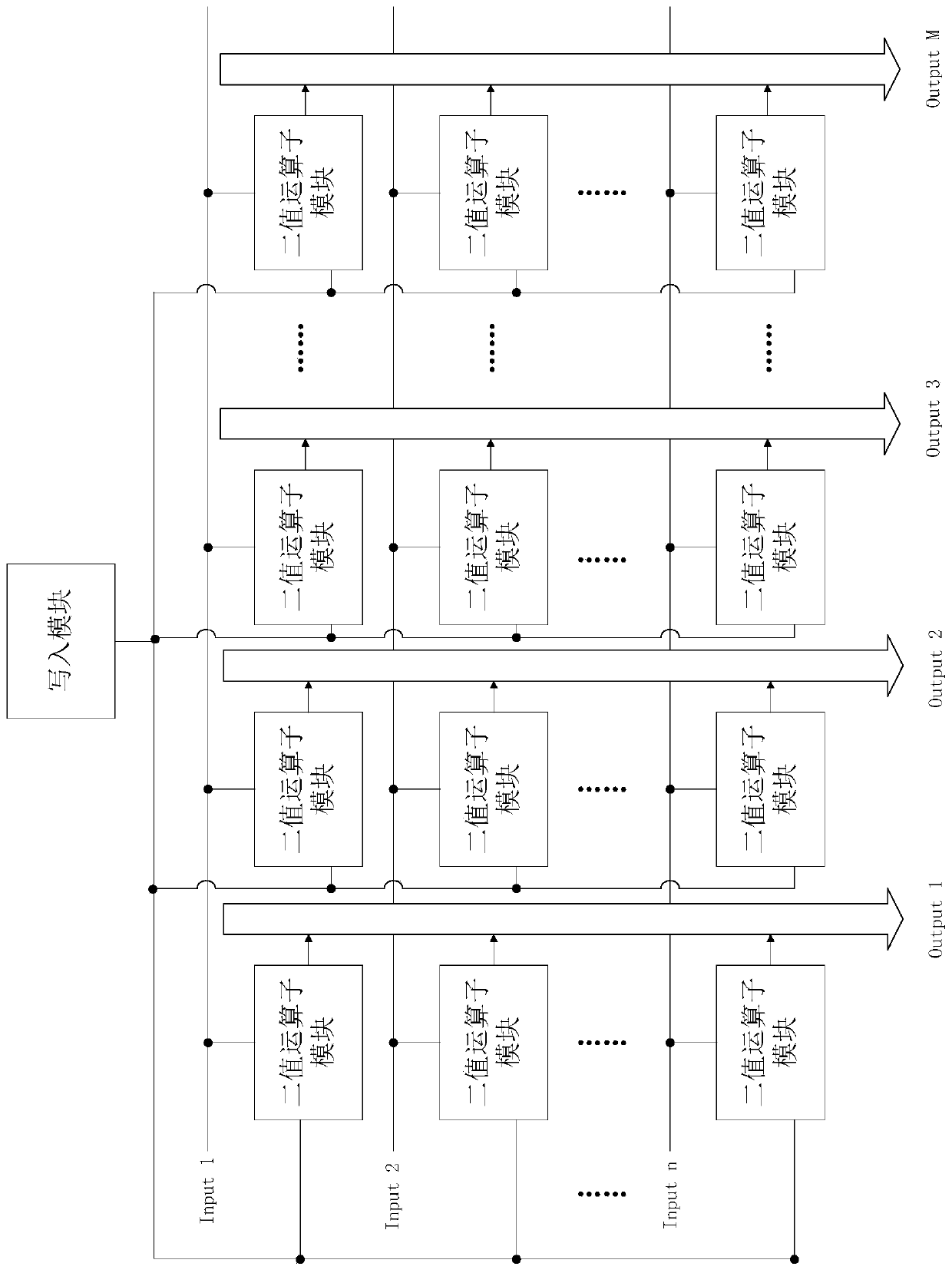
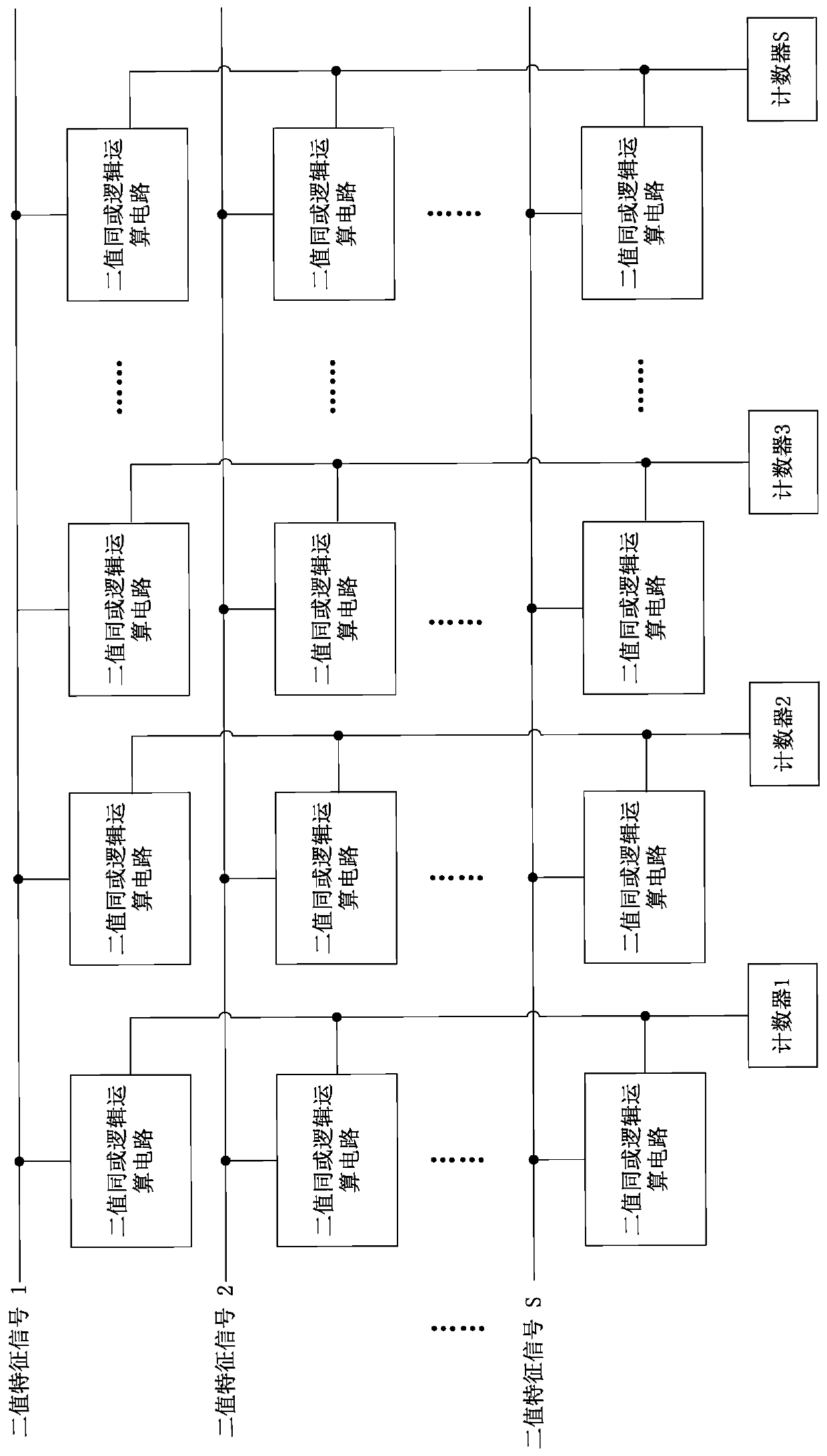
Chip for realizing binary neural network based on nonvolatile in-memory calculation and method
The invention provides a chip for realizing a binary neural network based on nonvolatile in-memory calculation and a method, and the chip comprises a nonvolatile operation module which is used for carrying out the matrix multiply-add operation on a first binary data packet received by the nonvolatile operation module and a second binary data packet pre-stored in the nonvolatile operation module, wherein the weight of the binary neural network is generally fixed during the reasoning process, and the input characteristics corresponding to each layer of neural network are generally changed alongwith the application. The weight of the binary neural network is used as the second binary data packet to be pre-stored in the nonvolatile operation module, and the input characteristics of the binaryneural network are loaded to the nonvolatile operation module, so that the matrix multiplication and addition operation can be realized in the nonvolatile operation module, and the problems of powerconsumption and time delay caused by data migration can be solved.
Owner:BEIHANG UNIV
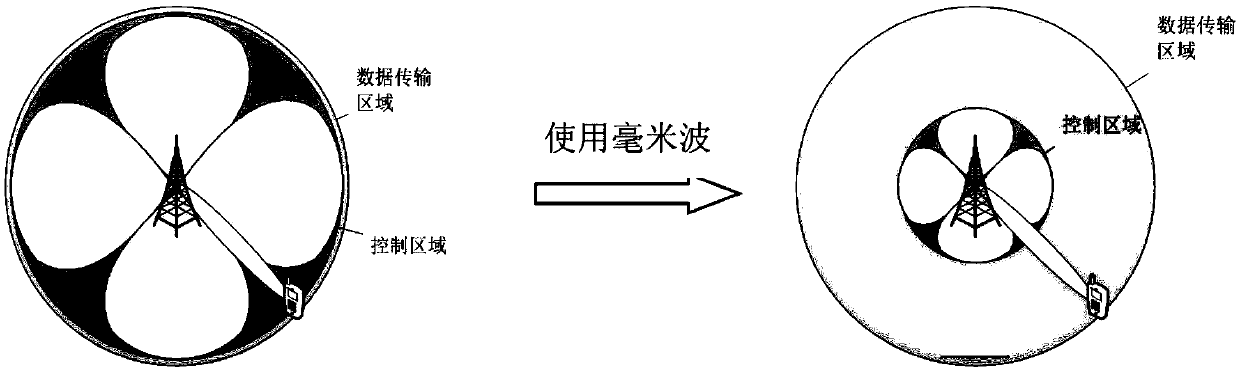
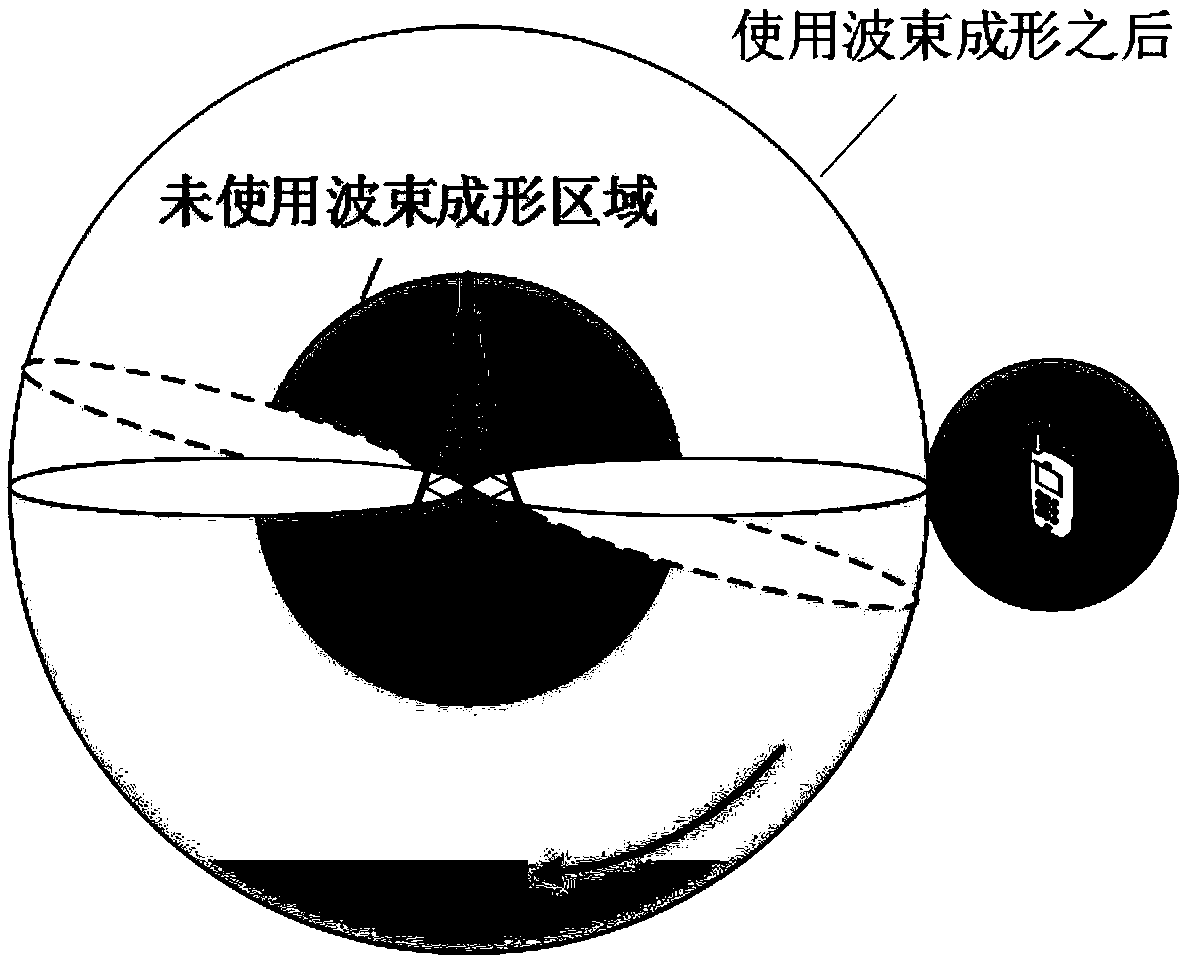
Beam optimization method based on user discovery stage in millimeter wave system
ActiveCN108964736AImprove performanceMaximum system capacitySpatial transmit diversityNetwork planningMillimeter wave communication systemsSystem capacity
The invention discloses a beam optimization method based on a user discovery stage in a millimeter wave system, comprising: modeling a millimeter wave communication system by adopting a random geometric method, and determining a path loss of the millimeter wave communication system and a beamforming gain model to obtain a receiving signal of the millimeter wave communication system; establishing coverage and capacity expressions of the millimeter wave communication system, comparing and analyzing the coverage performance of the system without considering interference and noise; determining therelationship between the capacity of the millimeter wave communication system and the search delay with the beam width as the intermediate quantity, optimizing the beam width to obtain the optimal system performance; using the beamforming technique in the user discovery phase of the millimeter wave to obtain the optimal beam width, and scanning the entire beam space for user search. By optimizingthe scanning beam width of the user discovery phase of the millimeter wave system, the invention solves the problem of the balance between the search delay and the system capacity, and obtains the optimal system performance, thereby saving the cost.
Owner:XI AN JIAOTONG UNIV
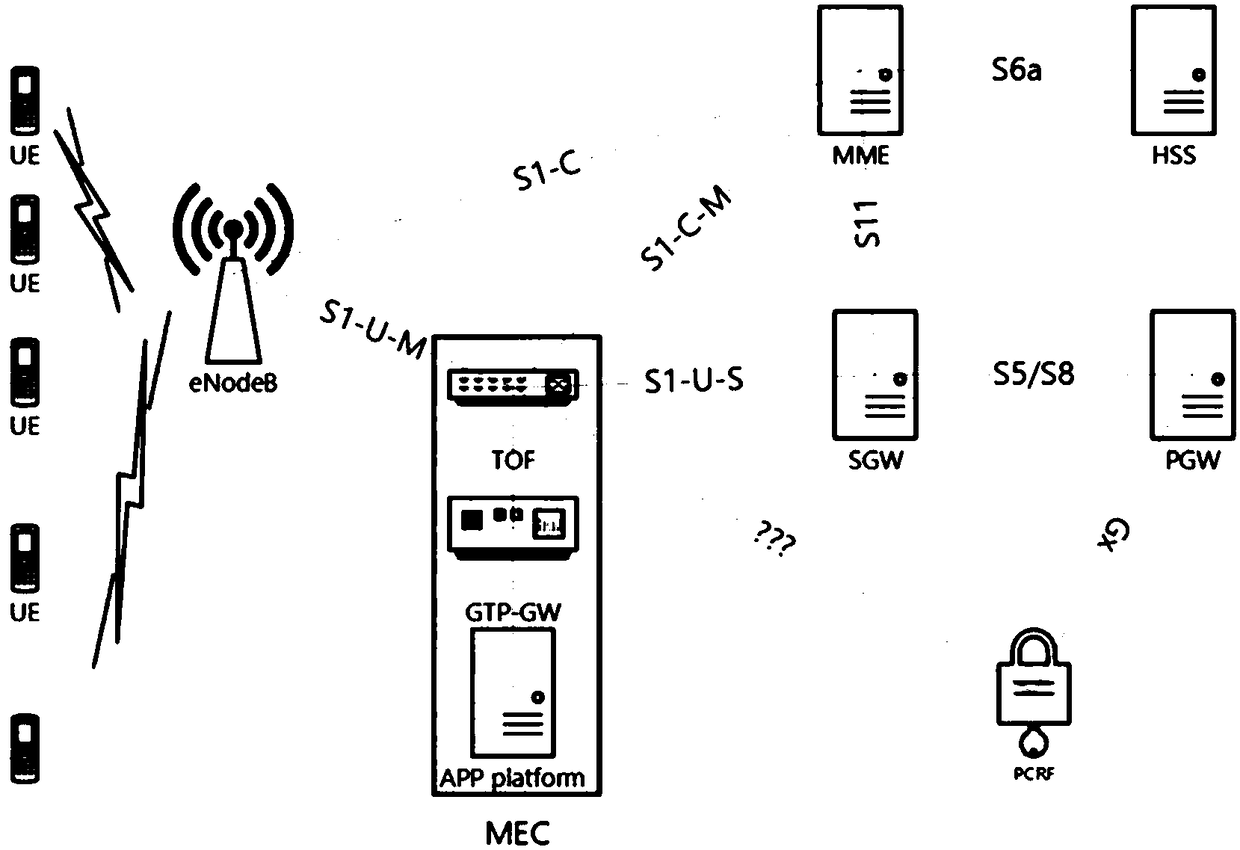
Mobile edge computing implementation method and system in Internet of vehicles
ActiveCN108881439AImprove network qualityEasy loadingNetwork traffic/resource managementParticular environment based servicesTraffic capacityThe Internet
Owner:BEIJING UNIV OF POSTS & TELECOMM
And inputting saturated automatic driving automovable path tracking control method
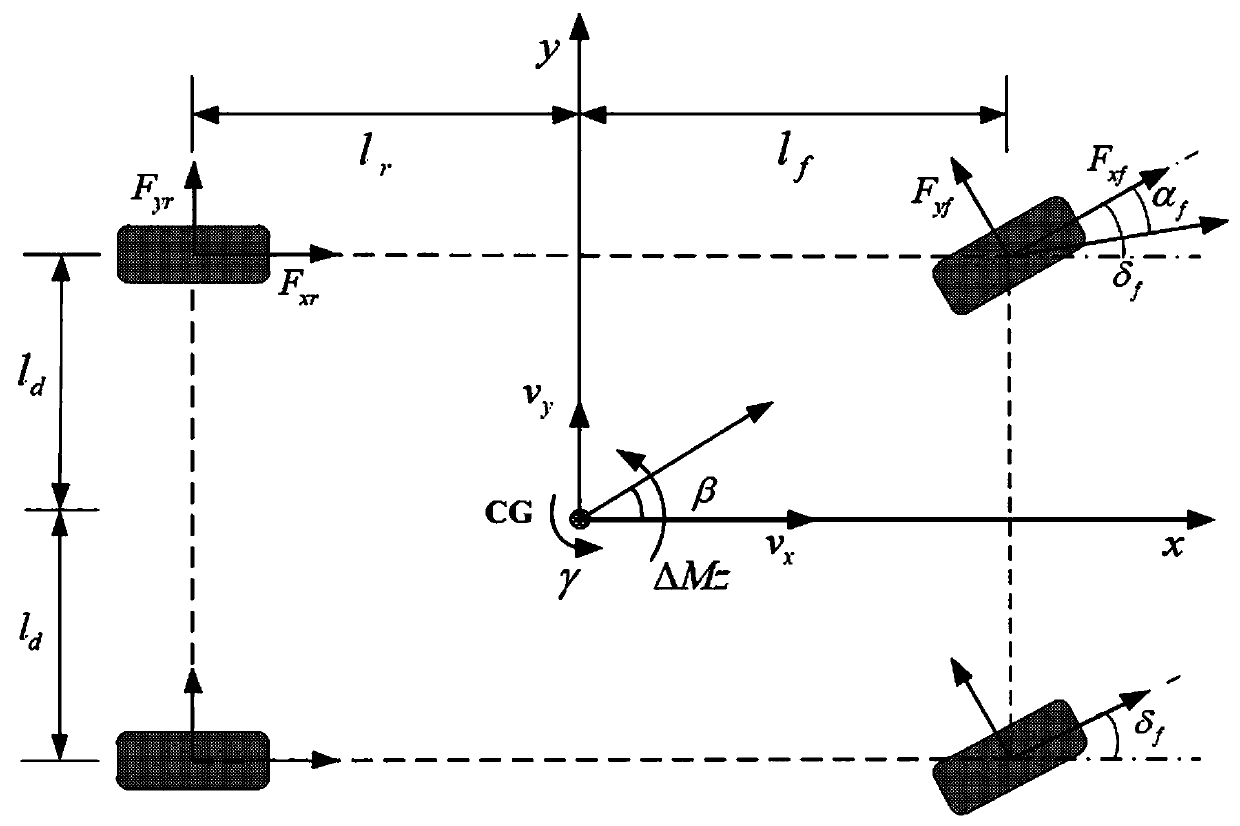
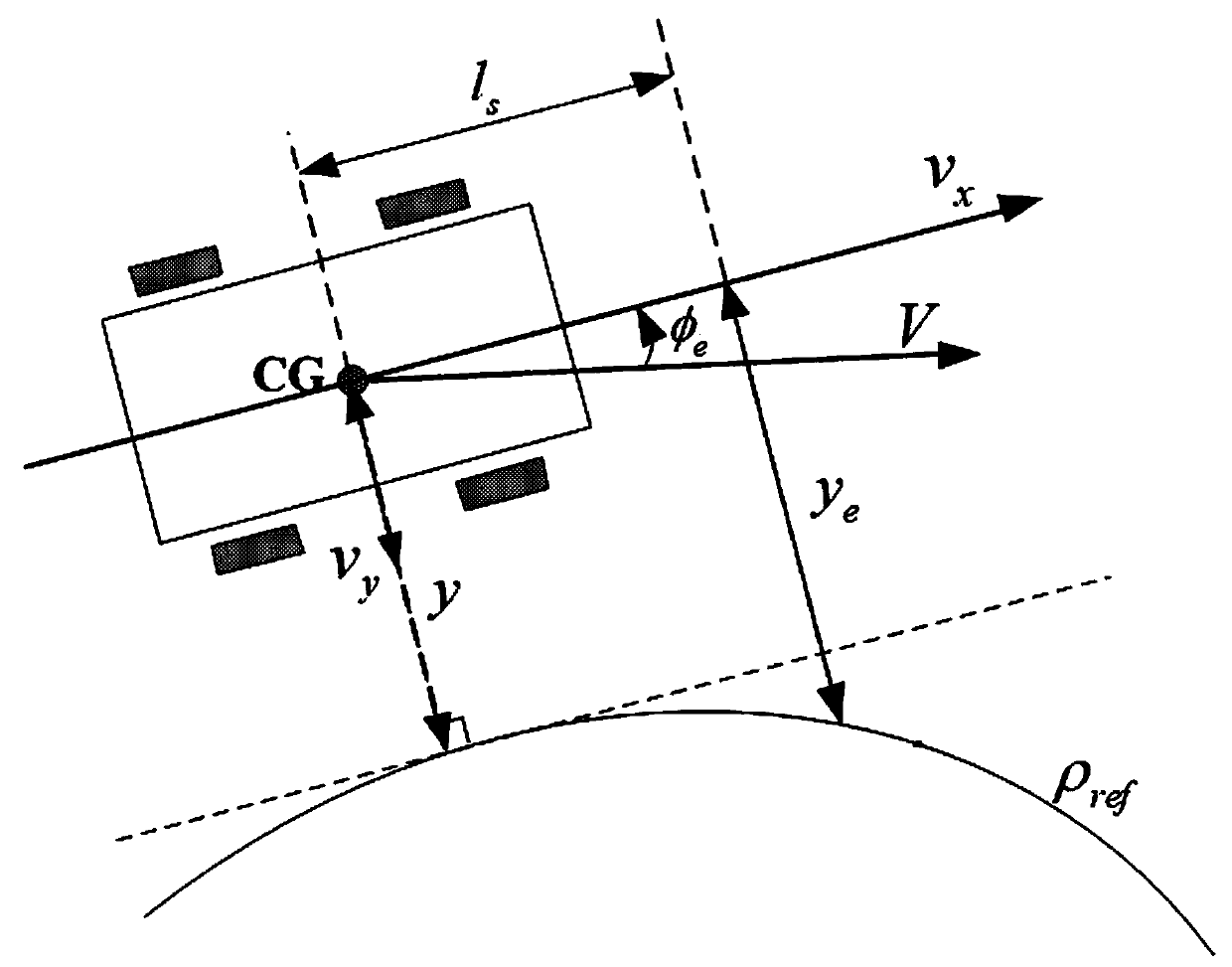
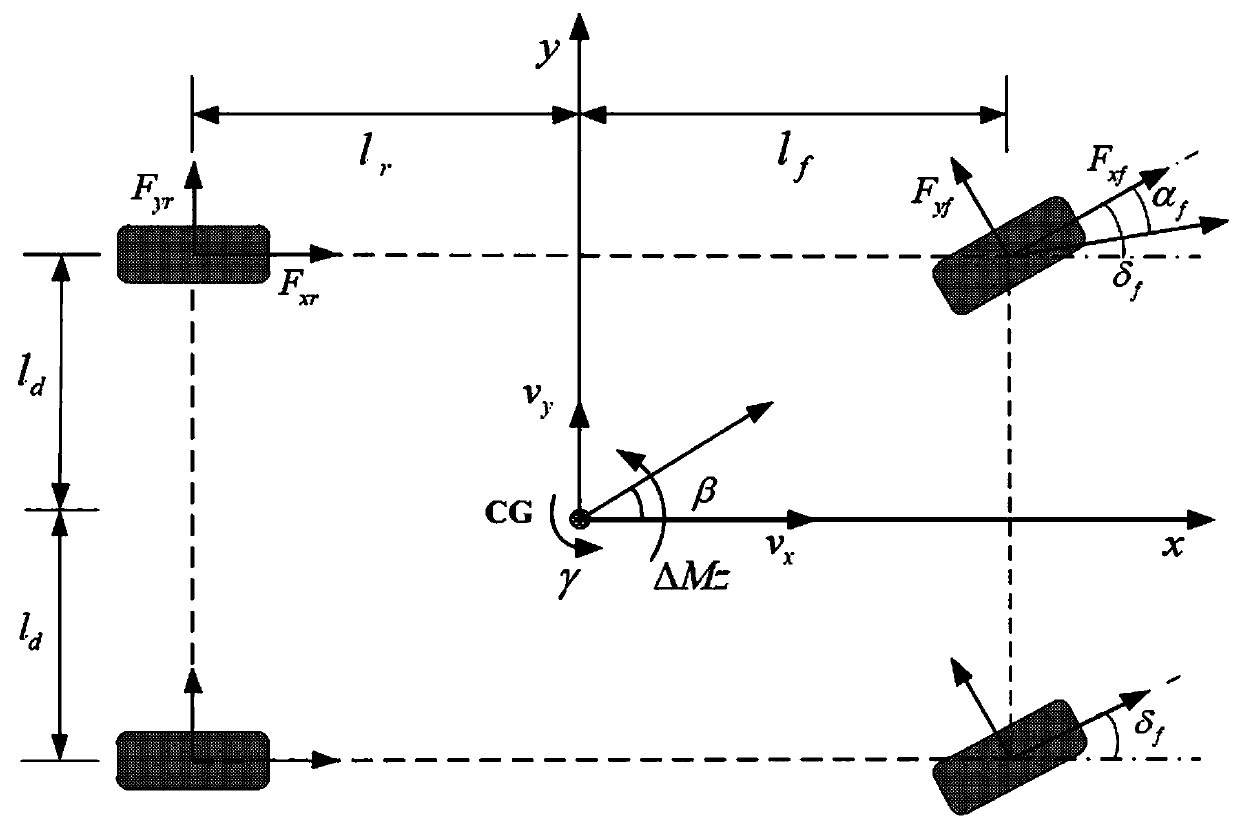
ActiveCN111176302ASolve the delay problemSolve the real problemVehicle condition input parametersPosition/course control in two dimensionsVehicle dynamicsFeedback controller
The invention relates to an input saturation automatic driving vehicle path tracking control method, which solves the problems of network time delay and input saturation of automatic driving vehicle path tracking control by designing a robust H-infinity path tracking controller, and improves the path tracking performance of a vehicle under extreme driving conditions. By adjusting the lateral speedand the yaw velocity of the vehicle, the operation stability of the vehicle is improved while automatic driving vehicle path tracking control is achieved. The robust H-infinity path tracking controlgain matrix of the autonomous vehicle can be obtained by solving a linear matrix inequality, and the calculation is simple and convenient. According to the path tracking control design, the uncertainty of a vehicle dynamic model and the influence of external disturbance are comprehensively considered, and the robustness of a path tracking control algorithm is improved. By designing the static output feedback controller, the cost of the control system is greatly reduced while ideal path tracking control is realized.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
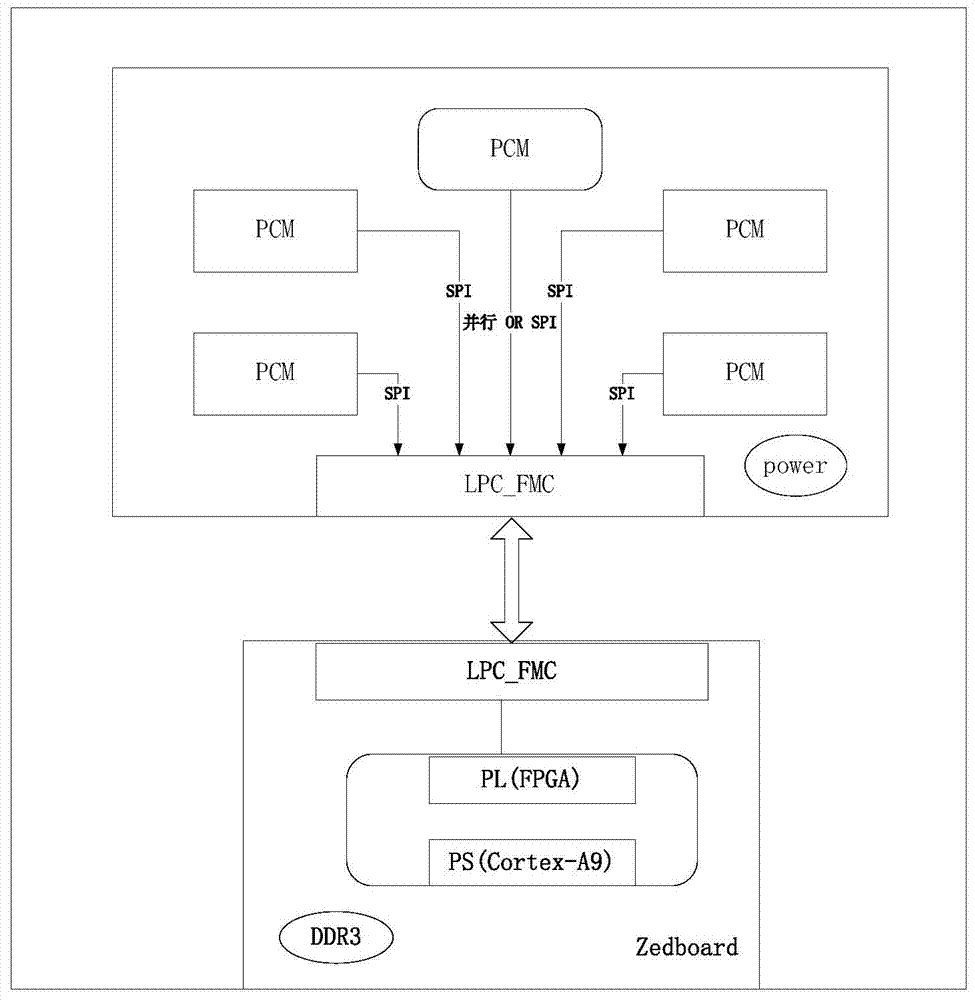
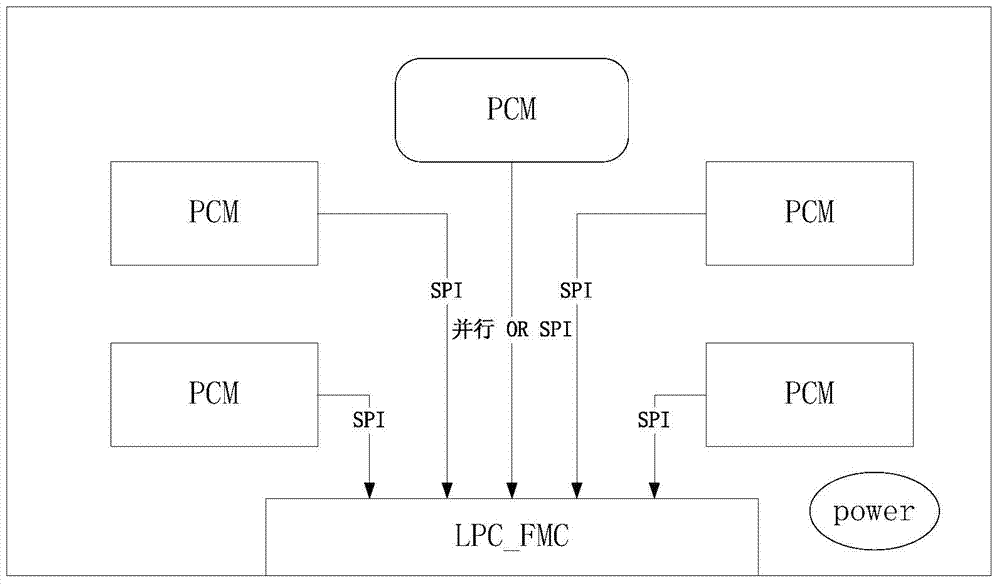
PCM FMC expansion board based on Zynq-7000 and working method of PCM FMC expansion board
InactiveCN103927276ASimple designImprove efficiencyInput/output to record carriersMemory adressing/allocation/relocationDual coreSingle chip
The invention discloses a PCM FMC expansion board based on Zynq-7000 and a working method of the PCM FMC expansion board. The PCM FMC expansion board comprises Zedboard development board based on Zynq-7000 and a PCM FMC expansion board body. The PCM FMC expansion board is characterized in that a plurality of PCMs a built in an FMC board, parts of the PCMs are connected to an FMC interface through SPI serial interfaces, and the other parts of PCMs are connected to the FMC interface through parallel interfaces. The Zedboard development board is characterized in that the Processing System of a dual-core ARM Cortex-A9 processor and Xilinx Programmable Logic are integrated in a single chip. The PCM FMC expansion board has the advantages that the PCM FMC expansion board can provide complex control ability of ARM and high-speed concurrent processing ability of FPGA.
Owner:SHANDONG UNIV
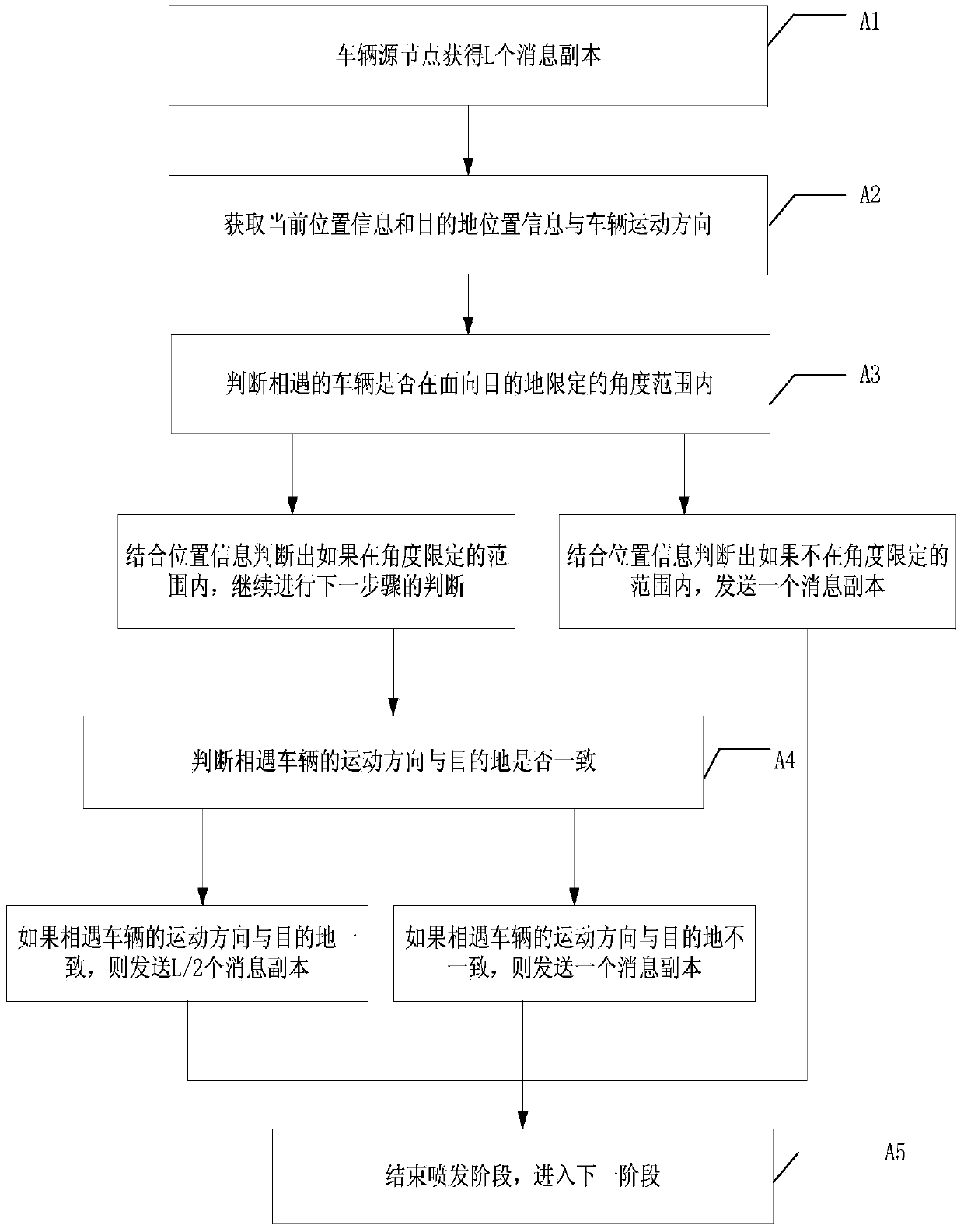
Multi-replication routing method for selecting eruption range in vehicular vdhoc networks
ActiveCN103763193AImprove delivery rateStrong performance such as reliabilityData switching networksDirectivityNODAL
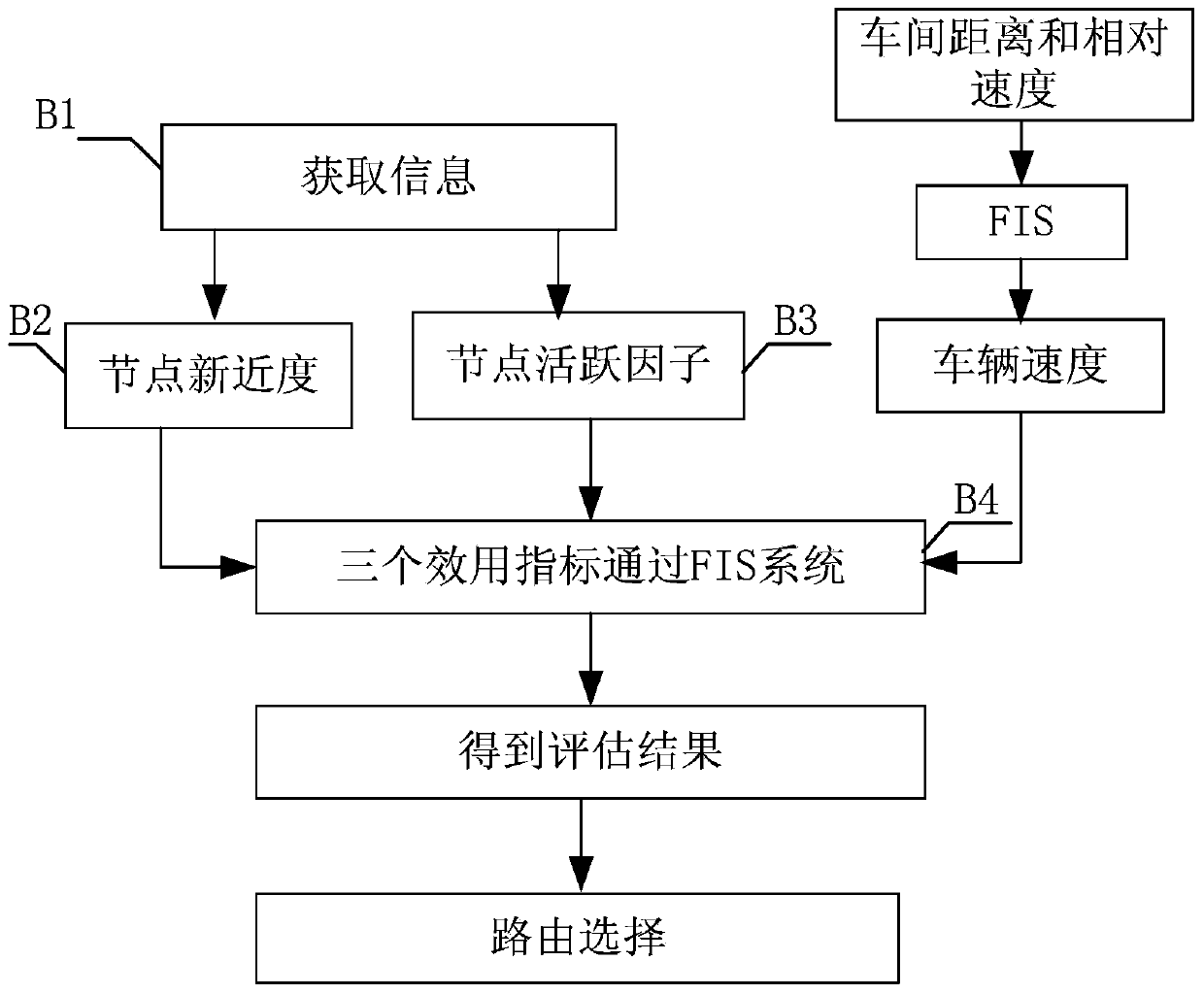
The invention discloses a multi-replication routing method for selecting an eruption range in vehicular vdhoc networks, and belongs to the technical field of the vehicular vdhoc networks. The multi-replication routing method for selecting the eruption range in the vehicular vdhoc networks comprises the steps that a method for limiting the multi-replication eruption range is adopted, message replications of different numbers are erupted in different ranges in different directions according to movement of a vehicle, and directivity of message transmission can be better; three node performance indexes are added, and neighbor nodes with best performance are selected to serve as forwarding nodes according to the node performance indexes through a fuzzy logic learning system; a cache scheduling strategy used for having control over jamming is adopted. According to the multi-replication routing method for selecting the eruption range in the vehicular vdhoc networks, the problem that network overheads are overlarge due to blind flooding of the message replication number in multi-replication routing is solved, and the problems that due to the fact that direct transmission is passively adopted, the delivery rate is low, and delay is large are solved; compared with a traditional method, timeliness, reliability and other performance are better, and the multi-replication routing method is more applicable to the vehicular vdhoc networks with high-dynamic topology.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
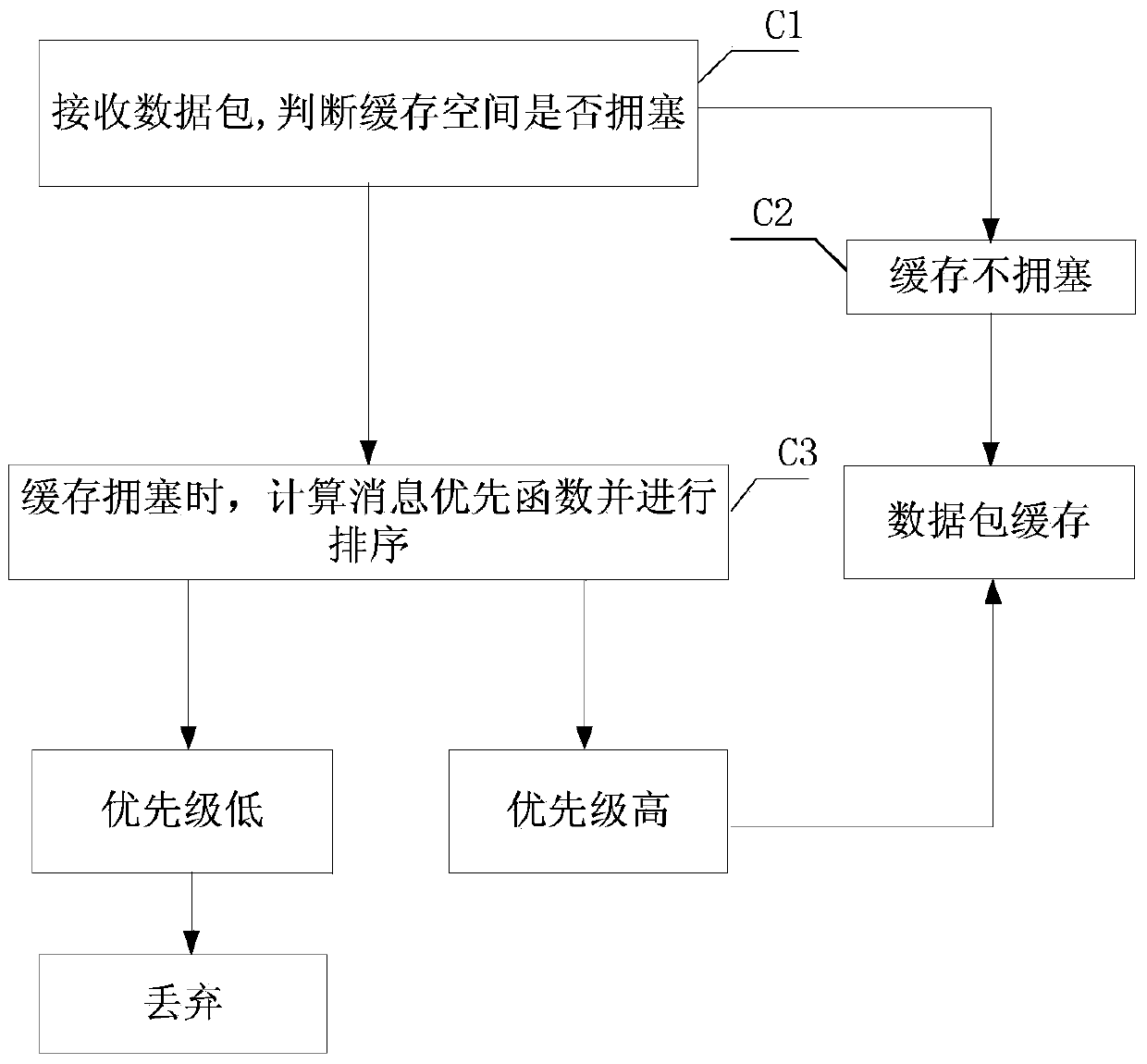
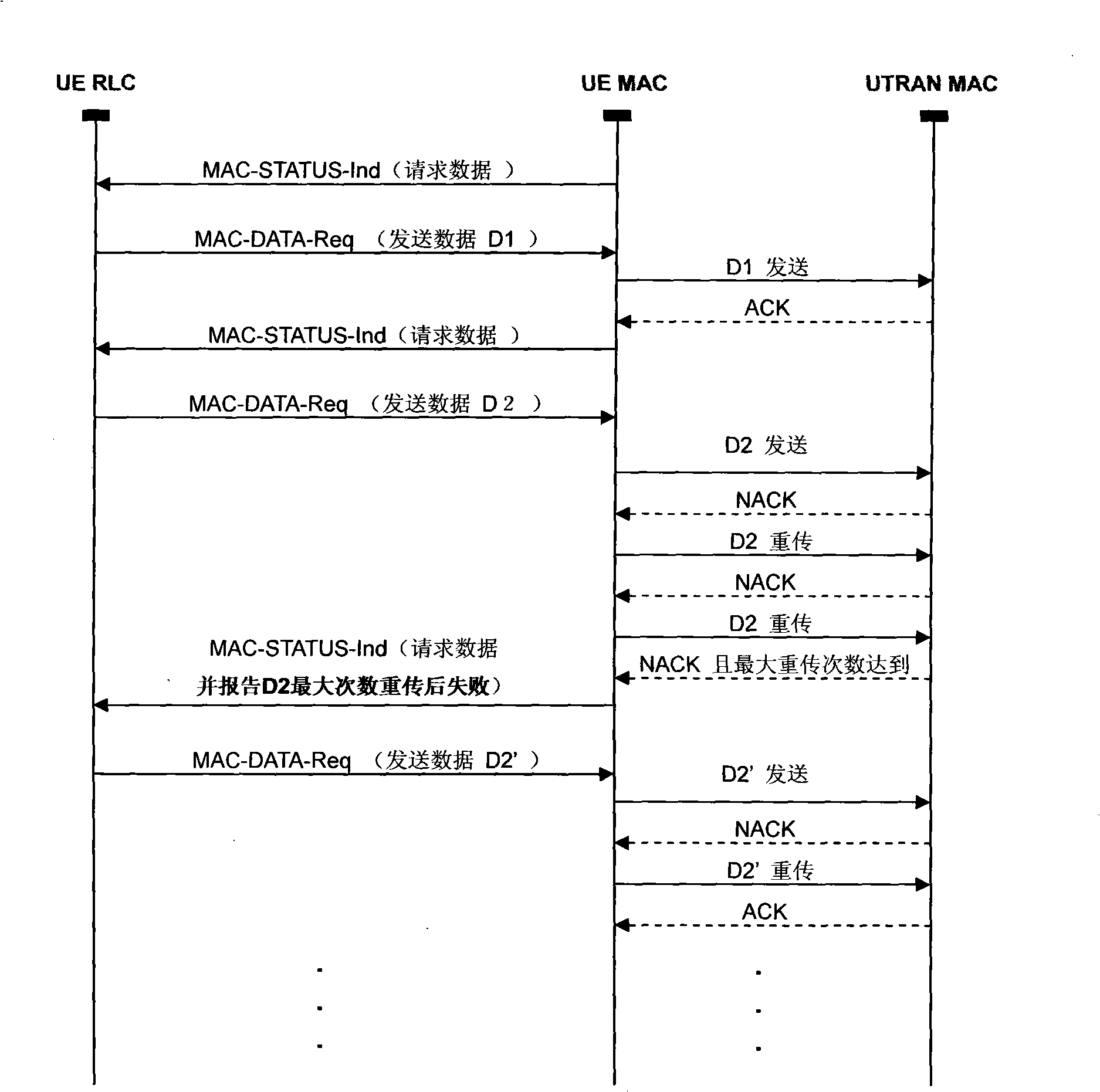
Method for reducing retransmission delay time of HSUPA data
InactiveCN101277250AReduce latencyResolution delayError prevention/detection by using return channelData switching by path configurationPre conditioningTime delays
The invention discloses a method for reducing HSUPA data retransmission time-delay. The method provides data transmission report in MAC layer to UE RLC by employing UE MAC, assistant processes data retransmission of RLC AM entity. Under the pre-condition of no-changing network side, no-adding interface, the method provided by the invention starts data retransmission in RLC layer in advance through carrying little bit of information in prior interface in suitable time, reduces HSUPA data transmission time-delay, and reduces pressure of data cushion in UE side factually. The method is easy to realized, and has strong practicability.
Owner:上海宇梦通信科技有限公司
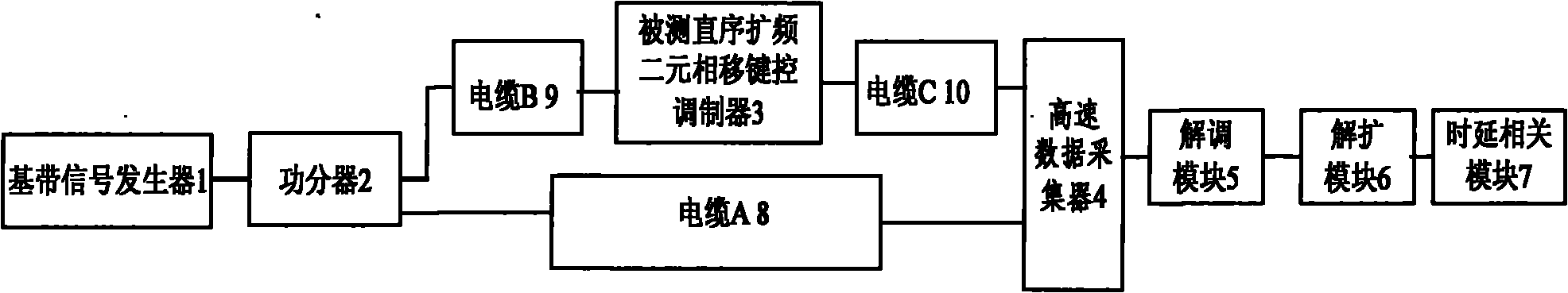
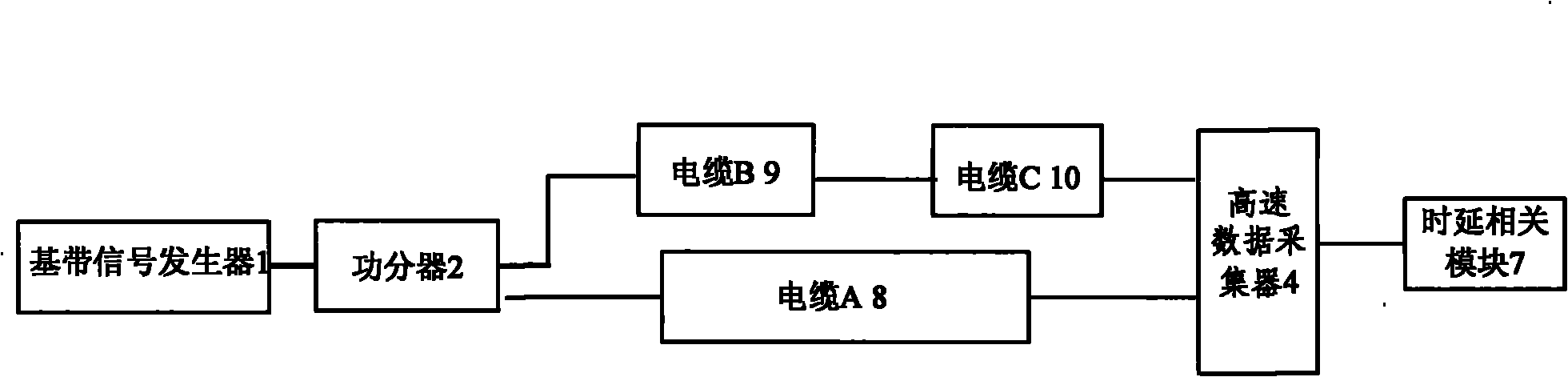
Method for measuring delay of direct sequence spread spectrum binary phase shift keying modulator
InactiveCN101902288AKeep latency informationSolve the delay problemTransmission monitoringDirect-sequence spread spectrumSignal generator
The invention discloses a method for measuring delay of a direct sequence spread spectrum binary phase shift keying modulator. Data despreading and demodulation and delay dependence are taken as cores, the delay measurement of input / output signals with different frequencies and different waveforms of the direct sequence spread spectrum binary phase shift keying modulator is converted into the delay measurement of signals with the same frequency and the same waveform, and is implemented by a created system. Digital signals are divided into two paths by a baseband signal generator (1) through apower divider (2), one path of digital signals pass through a direct sequence spread spectrum binary phase shift keying modulator (3) to be tested and enter a high-speed data acquisition unit (4), and the other path of digital signals are directly output by the power divider (2) to the high-speed data acquisition unit (4). A demodulation module (5) and a dispreading module (6) respectively perform demodulation and despreading processing on the acquired signals, and a delay-dependent module (7) calculates the delay of the two paths of signals. The method ensures that additional delay caused byhardware is not introduced in the measuring process, and can ensure the delay measuring accuracy less than 500ps when the sampling rate is 4GSa / s.
Owner:中国航天科工集团第二研究院二〇三所
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com