Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
185 results about "Keystream" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
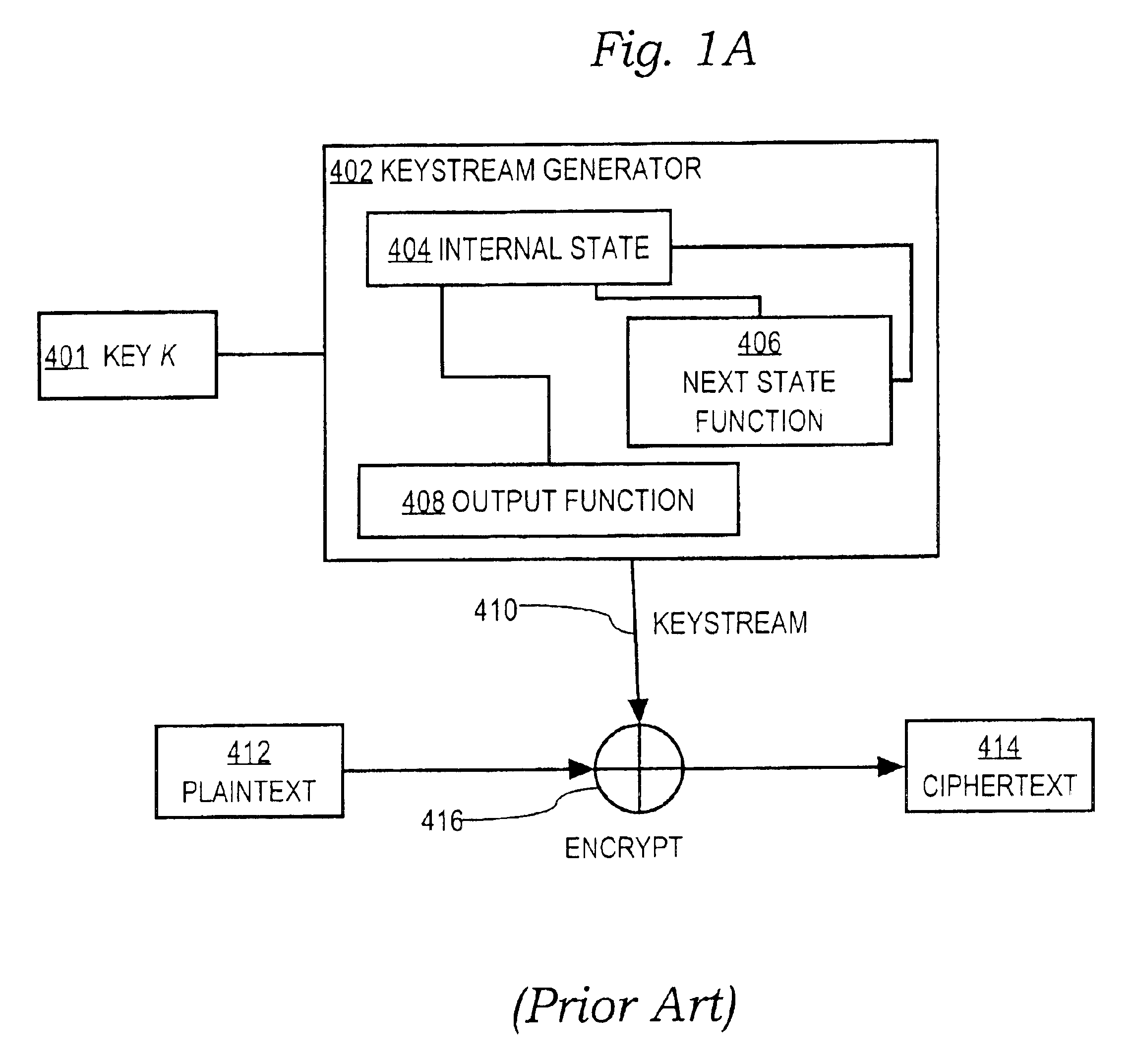
In cryptography, a keystream is a stream of random or pseudorandom characters that are combined with a plaintext message to produce an encrypted message (the ciphertext). The "characters" in the keystream can be bits, bytes, numbers or actual characters like A-Z depending on the usage case.
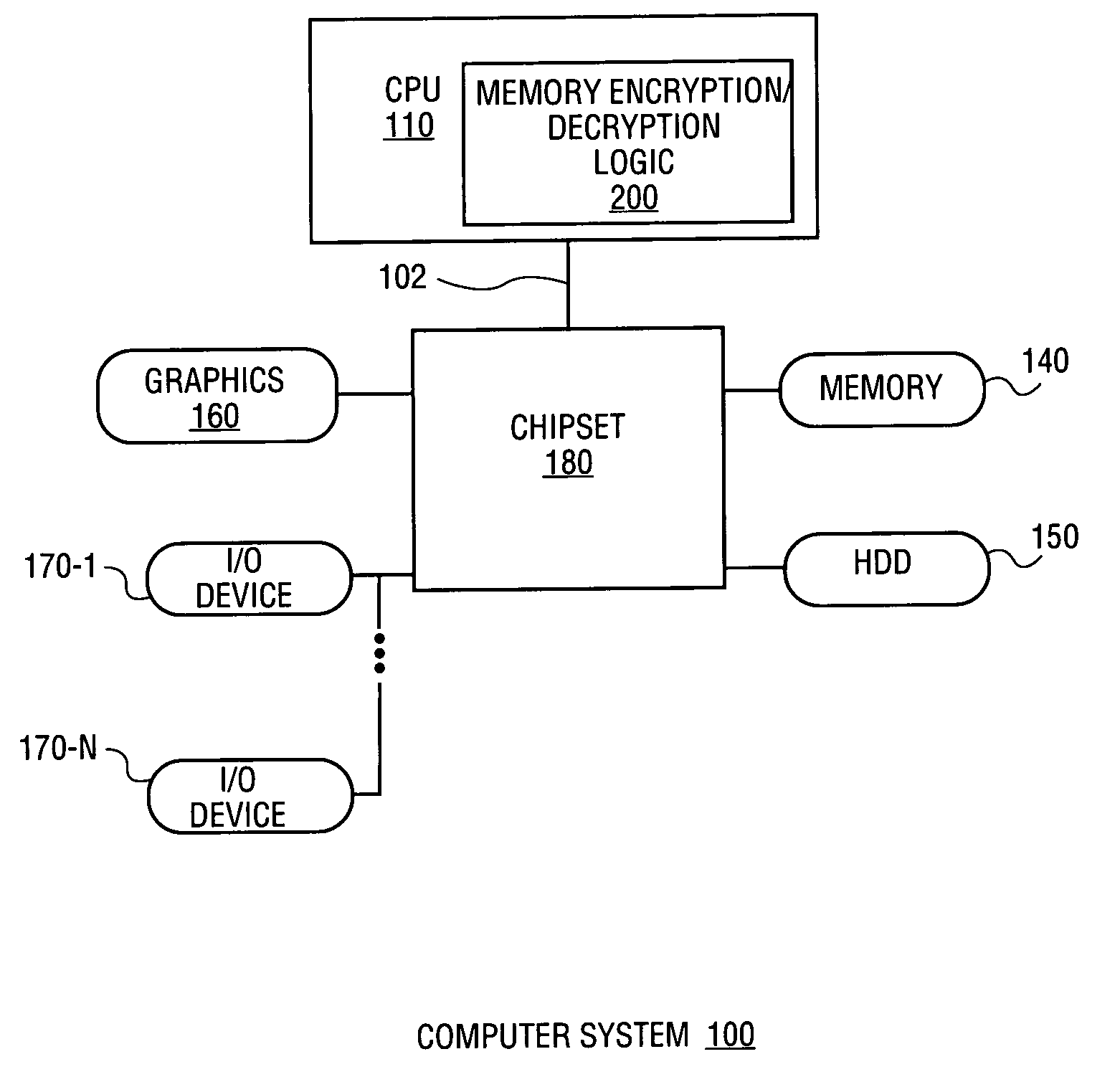
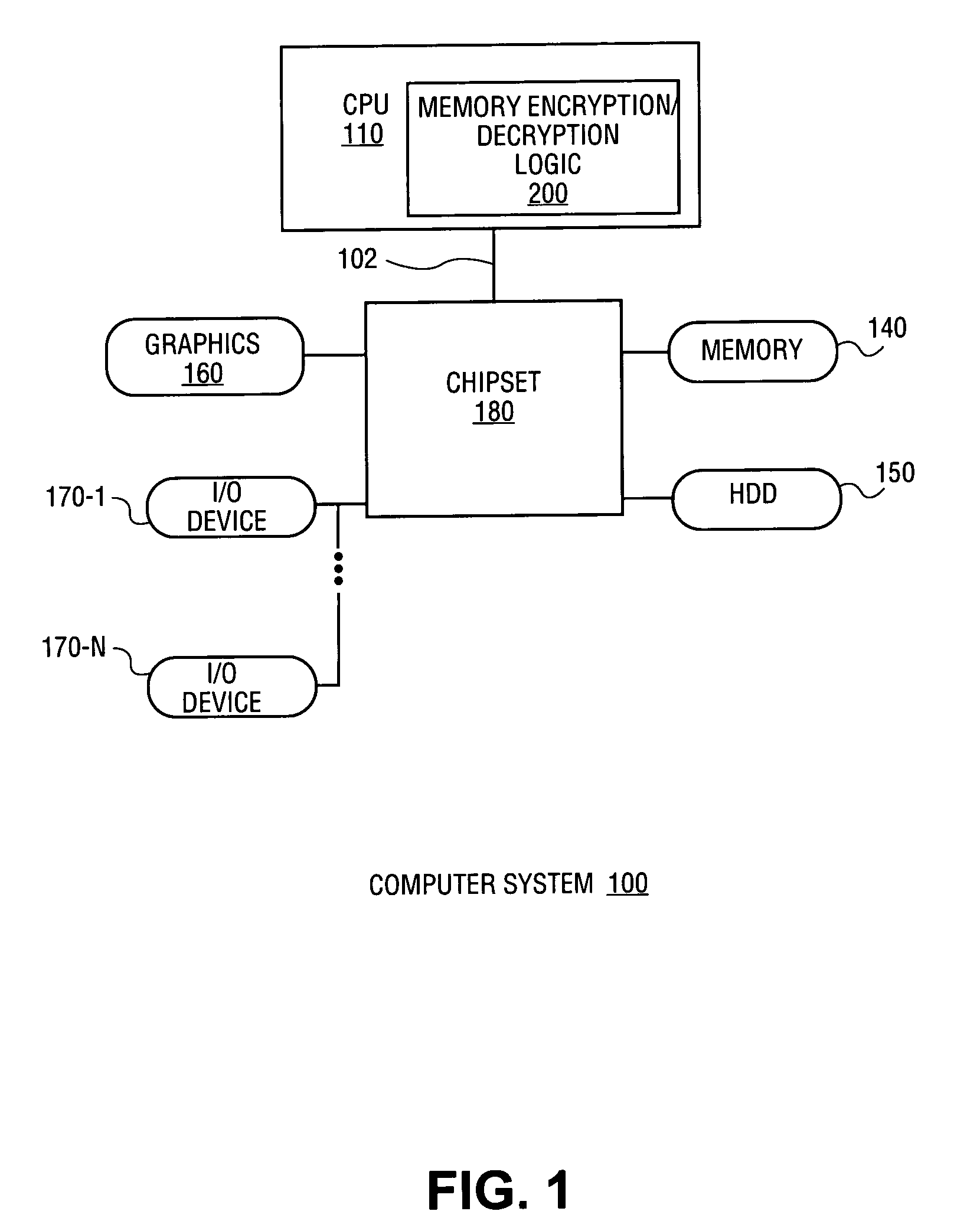
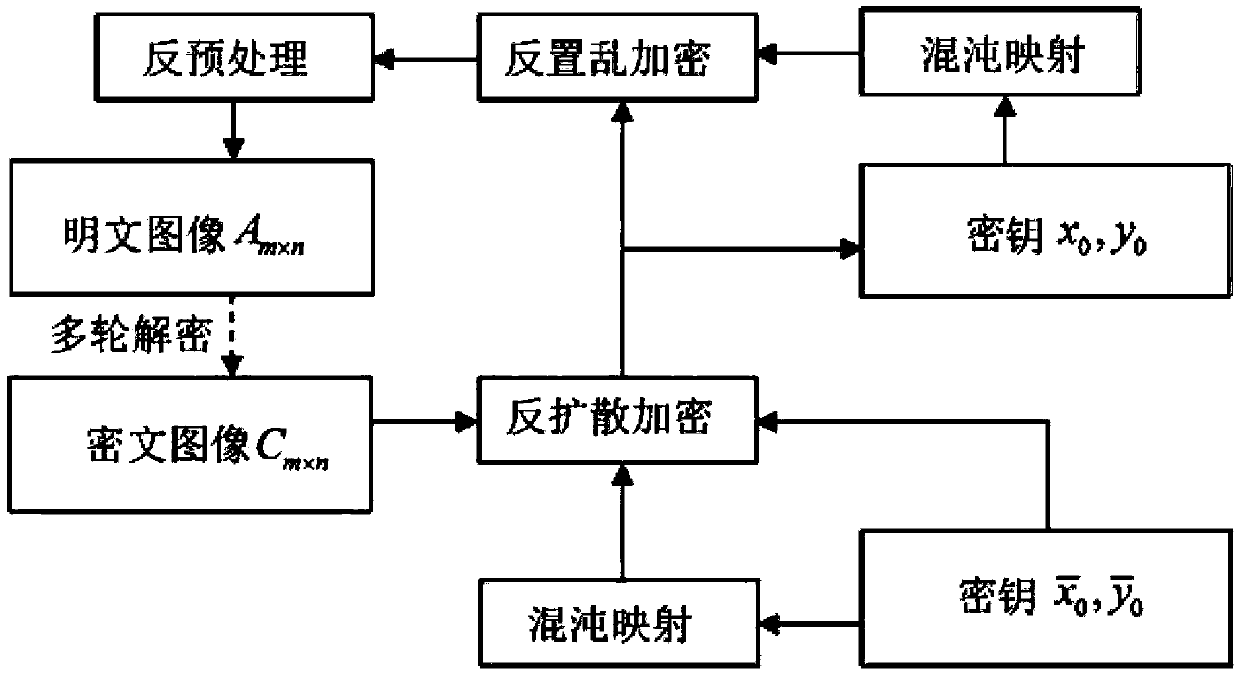
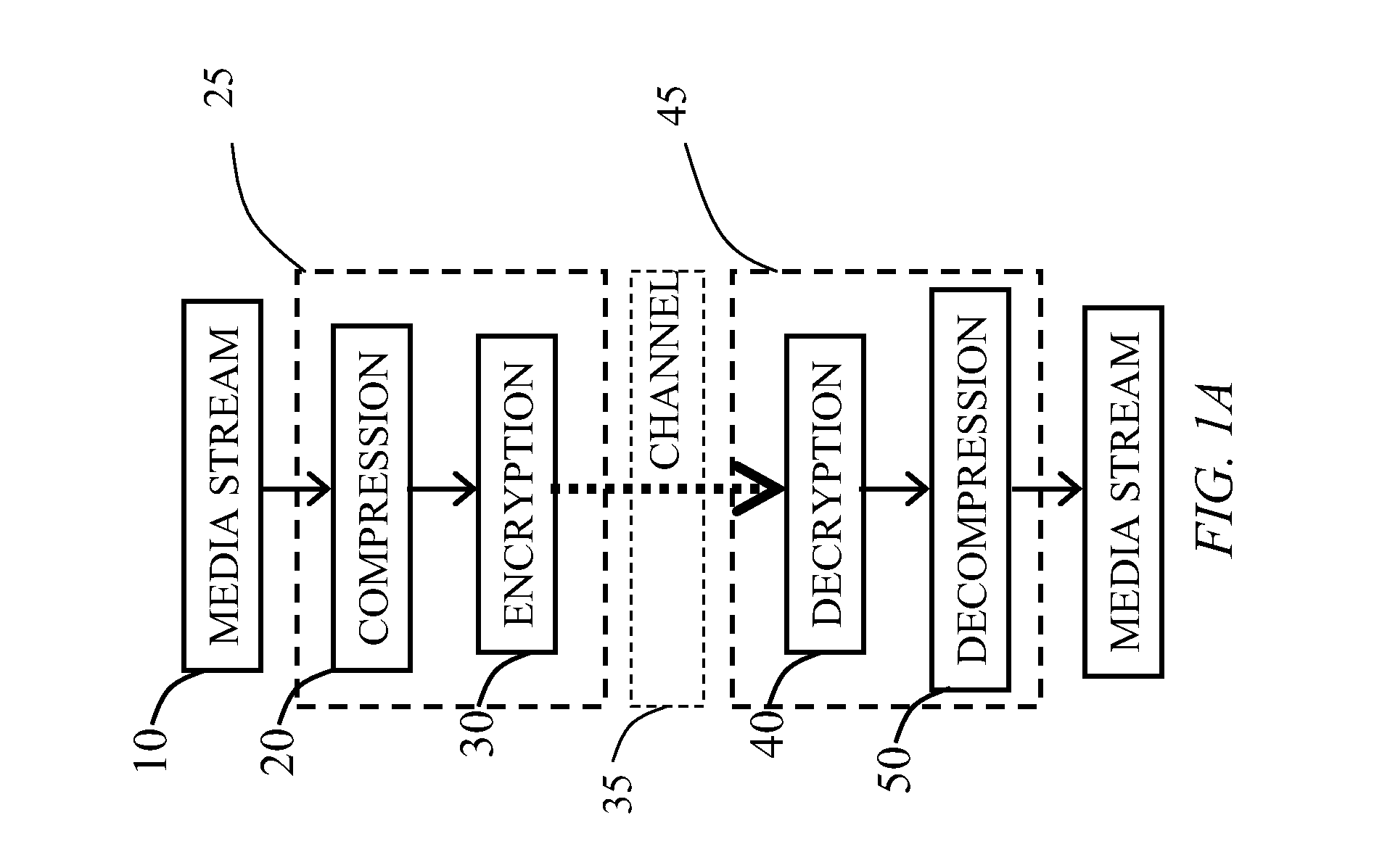
Apparatus and method for memory encryption with reduced decryption latency
InactiveUS7472285B2Memory adressing/allocation/relocationUnauthorized memory use protectionKeystreamData retrieval
Owner:INTEL CORP
Apparatus and method for memory encryption with reduced decryption latency
InactiveUS20050021986A1User identity/authority verificationMemory adressing/allocation/relocationKeystreamData retrieval
A method and apparatus for memory encryption with reduced decryption latency. In one embodiment, the method includes reading an encrypted data block from memory. During reading of the encrypted data block, a keystream used to encrypt the data block is regenerated according to one or more stored criteria of the encrypted data block. Once the encrypted data block is read, the encrypted data block is decrypted using the regenerated keystream. Accordingly, in one embodiment, encryption of either random access memory (RAM) or disk memory is performed. A keystream is regenerated during data retrieval such that once the data is received, the data may be decrypted using a single clock operation. As a result, memory encryption is performed without exacerbating memory latency between the processor and memory.
Owner:INTEL CORP
Reducing Security Protocol Overhead In Low Data Rate Applications Over A Wireless Link
InactiveUS20080044012A1Simplified low rate communicationEasy to processData stream serial/continuous modificationPublic key for secure communicationProtocol overheadLow data rate
A wireless communication module to provide security at a baseband layer is disclosed. A payload of plaintext may be divided into partitions. The module may use a block cipher such as the Advanced Encryption Standard (AES) algorithm to process a unique initiation vector (IV) for each partition so that each partition may be XORed with a key stream based on a respective IV, the result providing ciphertext. The IV may include a nonce, an upper level packet counter, a packet counter and a block counter. The state of the counters may be incremented in a predetermined pattern so as to provide a unique IV for use with each partition. The ciphertext may be transmitted in a packet with a security bit indicating that the payload is encrypted but omitting the nonce. Encrypted packets may include an integrity check value (ICV) to provide for integrity of the encrypted message.
Owner:NOKIA CORP
Color image encryption method based on cellular neural network hyperchaos and DNA sequence
The invention belongs to the technical field of information security, and particularly relates to a color image encryption method based on cellular neural network hyperchaos and a DNA sequence. The method provided by the invention comprises the steps of separating red, green and blue three primary color components of a color plaintext image; updating and generating parameters and initial values of a six-order cellular neural network hyperchaotic system and a Logistic-Sine mapping system through the plaintext image, respectively carrying out iterative operation on the two chaotic systems, and obtaining red, green and blue components of an encrypted image according to a DNA encoding rule and a DNA decoding rule; and finally, changing the pixel values of the encrypted image through key stream and a bitwise XOR operation to obtain a final ciphertext image. The decryption is a reverse operation of the encryption process. Compared with the existing image encryption method, the color image encryption method provided by the invention has the advantages of high security, good encryption effect, strong robustness, no information loss and the like, and thus being capable of being widely used in military, remote sensing, remote medical treatment, commerce and other fields.
Owner:FUDAN UNIV
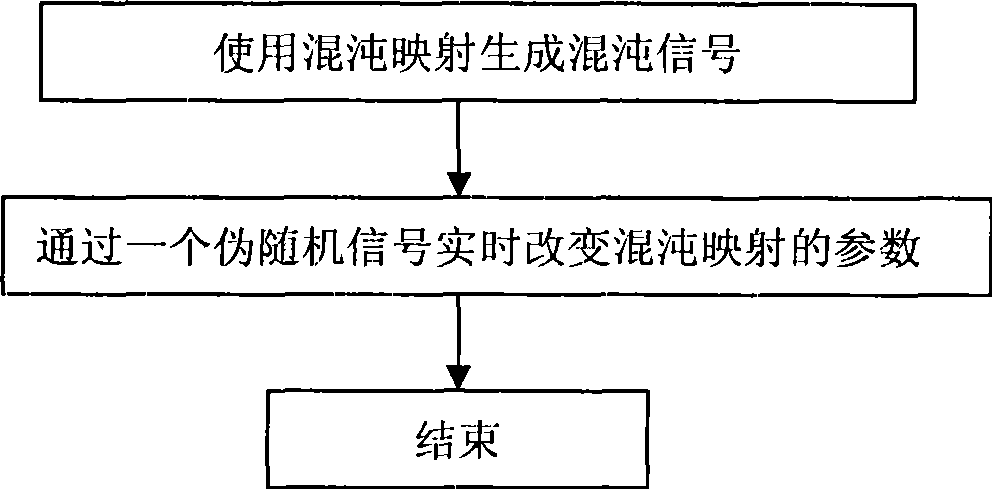
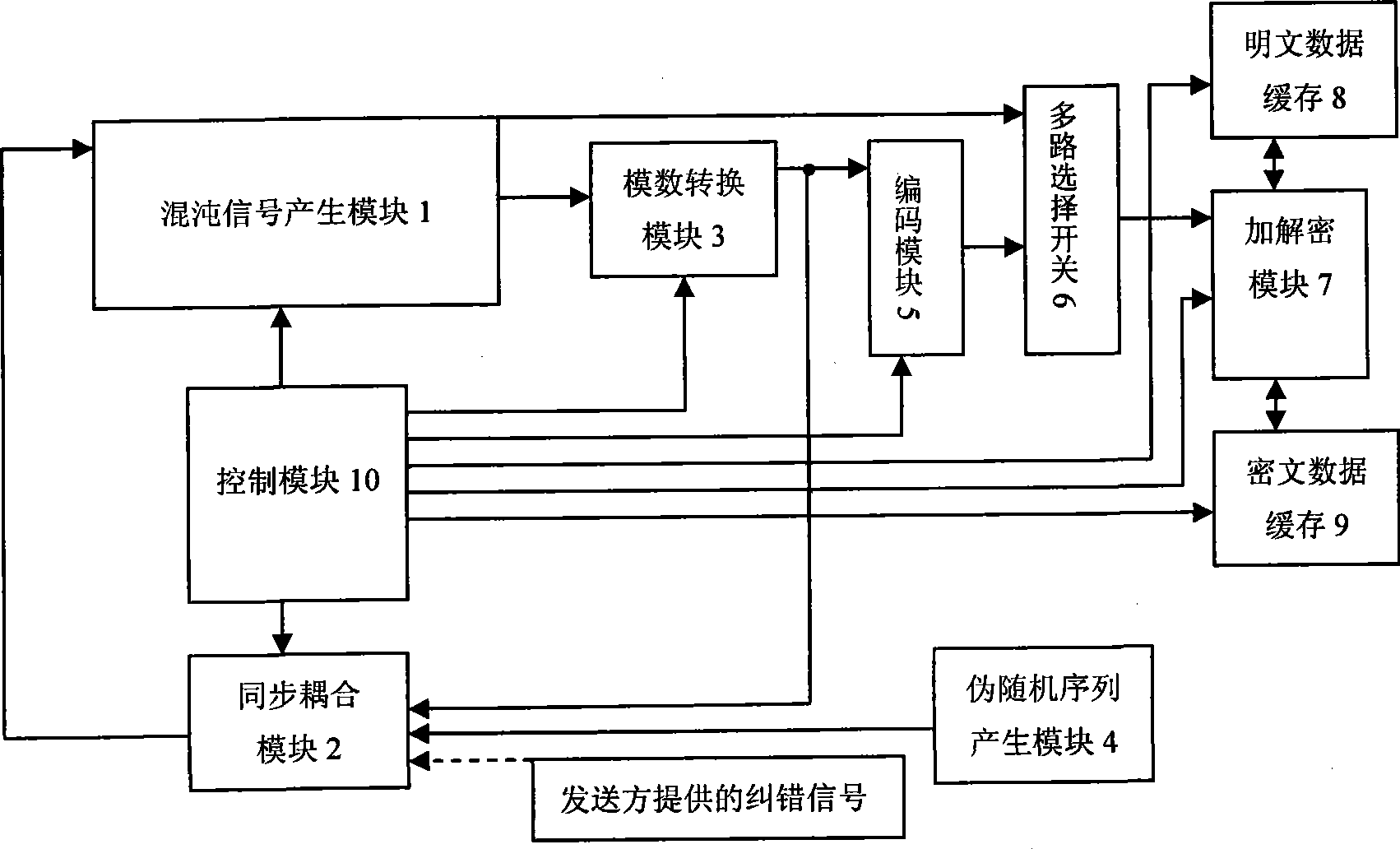
Method for generating variable parameter chaos signal and chaos secret communication system
InactiveCN101394266AIncreased complexityDefense analysisSecuring communicationComplex mathematical operationsCiphertextNonlinear prediction
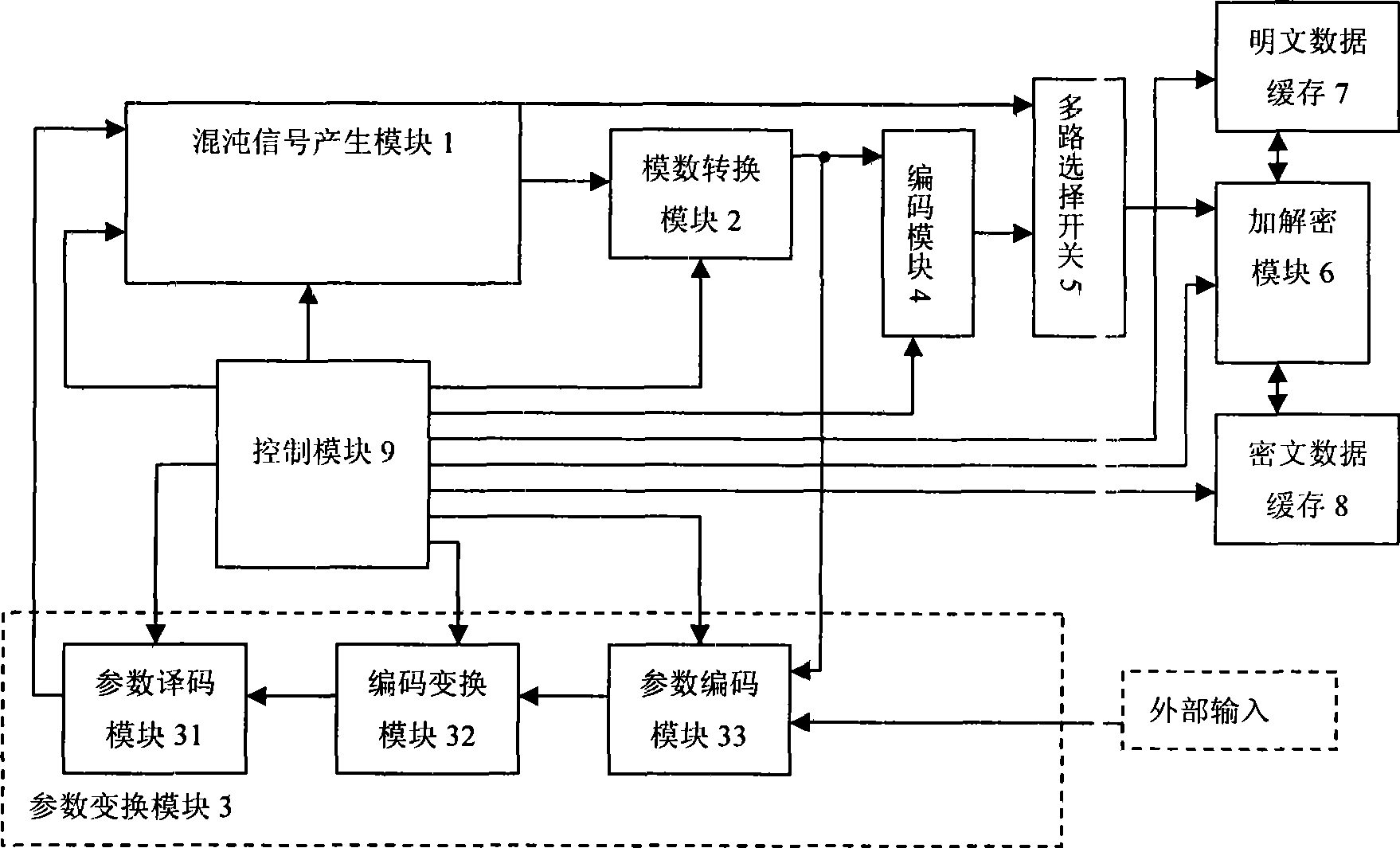
The invention discloses a method for generating a variable parameter chaotic signal, and a chaotic secure communication system. The method comprises the following steps: firstly, chaotic mapping is used to generate the chaotic signal; then a parameter set of the chaotic mapping is determined in advance, so as to process any pseudorandom signal, and enable the state of the pseudorandom signal and the elements of the parameter set to be in one-to-one correspondence; and a corresponding parameter is chosen to generate the variable parameter chaotic signal by chaotic mapping according to the state of the pseudorandom signal. The system comprises a chaotic signal generating module, an analog-to-digital conversion module, a parameter transformation module, a coding module, a multi-path choice switch, an encryption / decryption module, an encrypted message data cache, a plaintext data cache and a control module. The invention can increase the complexity of the output of the chaotic signal or a chaotic sequence, and effectively resist the analysis of the nonlinear prediction technology based on phase-space reconstruction. The output digital chaotic sequence can be taken as a pseudorandom number sequence or key stream to encrypt data; the output continuous chaotic signals can be used for designing a secret communication system based on chaos synchronization .
Owner:HUAZHONG UNIV OF SCI & TECH
Method and system for securely storing and transmitting data by applying a one-time pad
InactiveCN1593033ASimple methodEase of evaluationKey distribution for secure communicationData stream serial/continuous modificationPlaintextKeystream
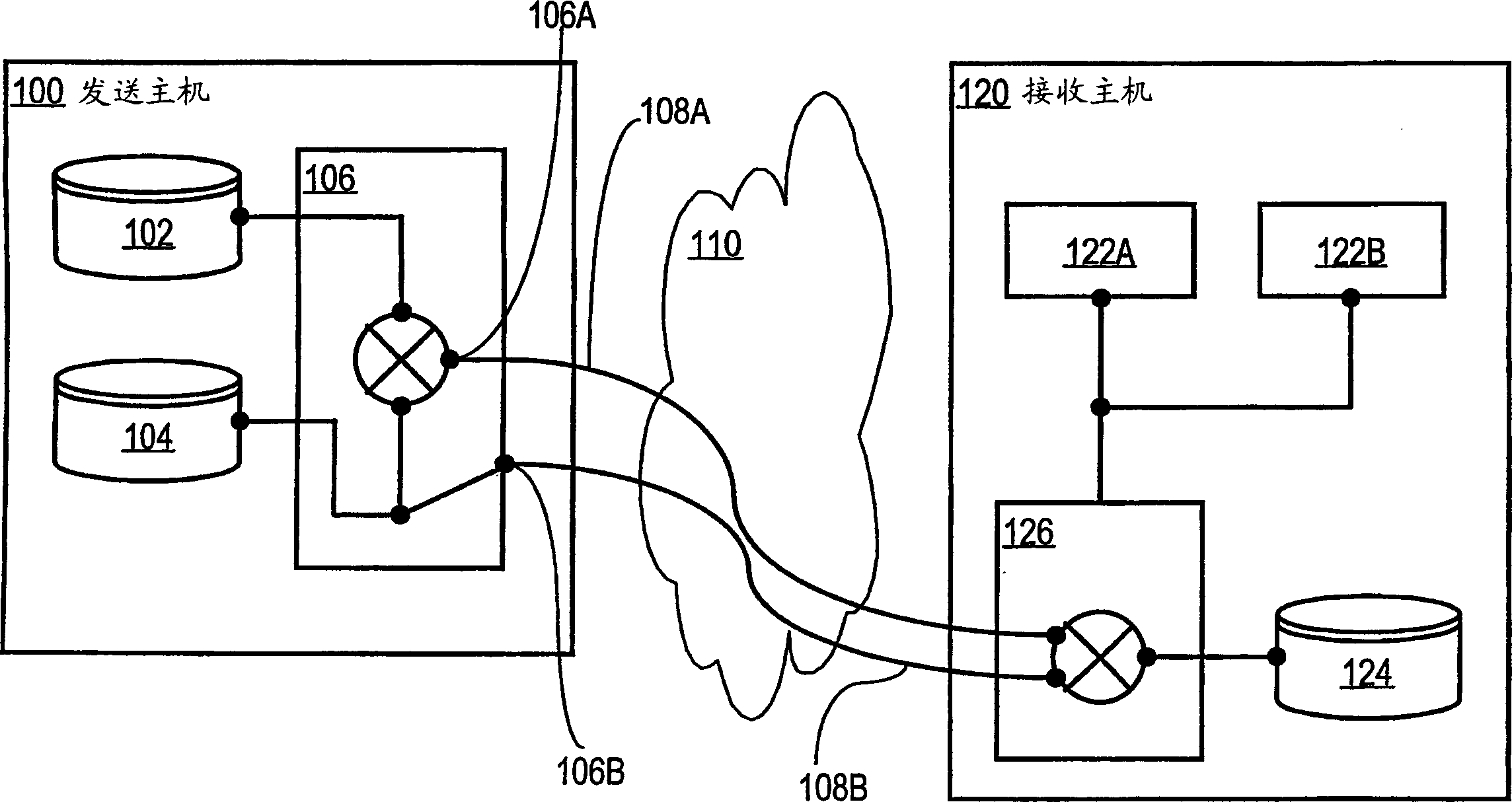
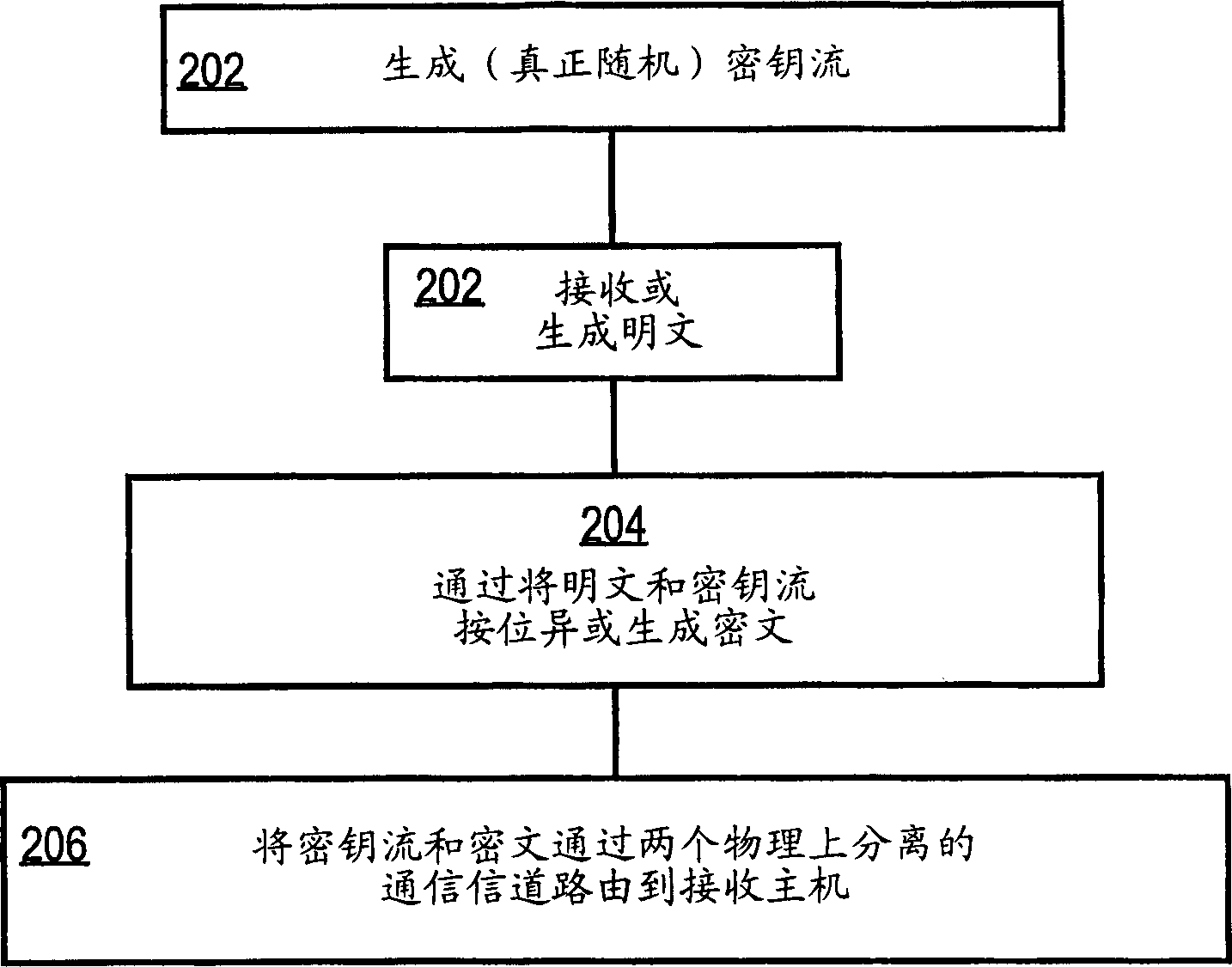
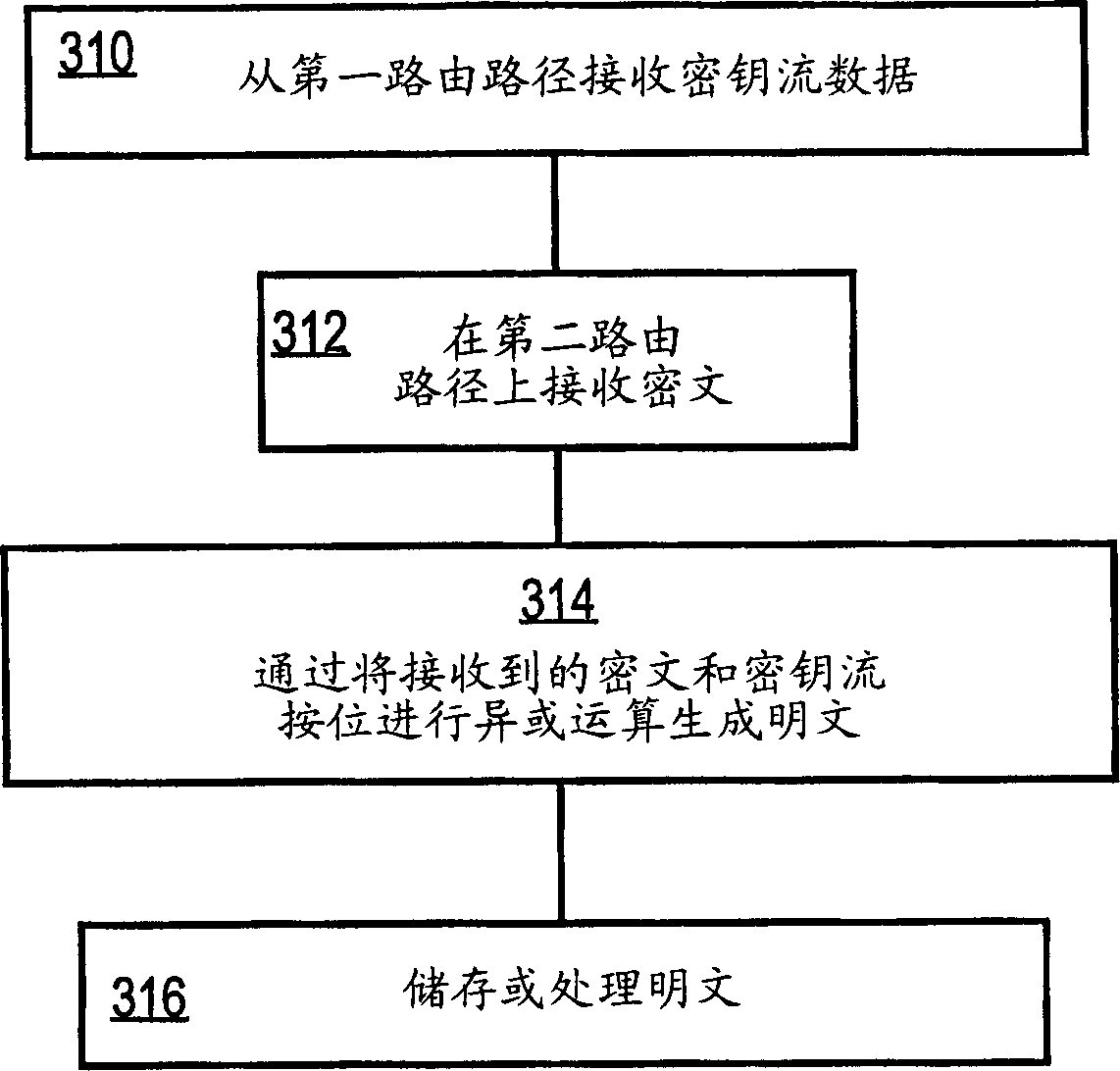
An approach for securely transmitting and storing data is described. A sending host generates a random sequence of characters as a keystream as a one-time pad. The keystream is bitwise combined with plaintext using an exclusive-OR operation to create ciphertext. The keystream and ciphertext are routed over physically separate communication paths to a receiving host, which decrypts by applying the keystream to the ciphertext using exclusive-OR, The separately routed paths may be established using MPLS labeling or strict route options.
Owner:CISCO TECH INC
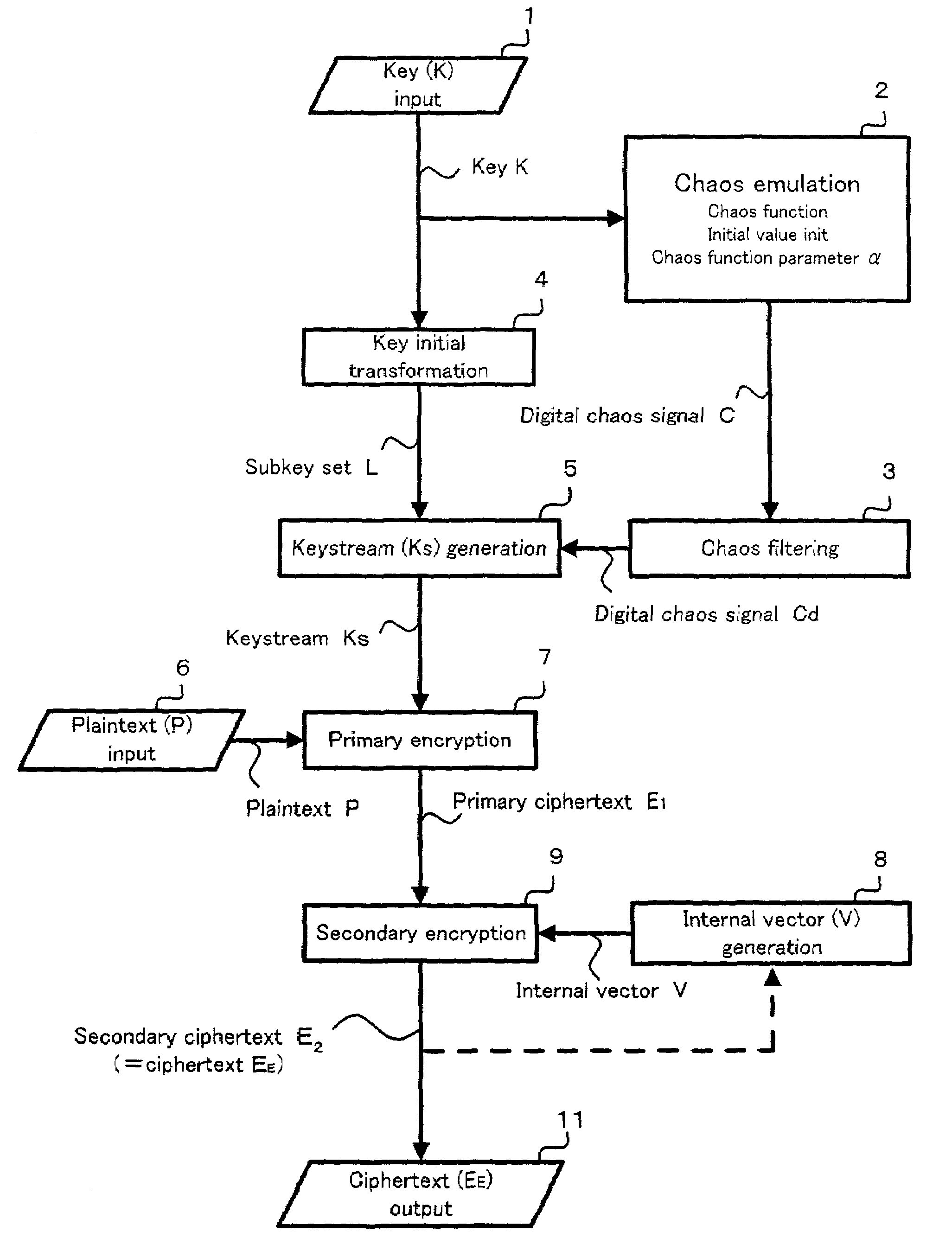
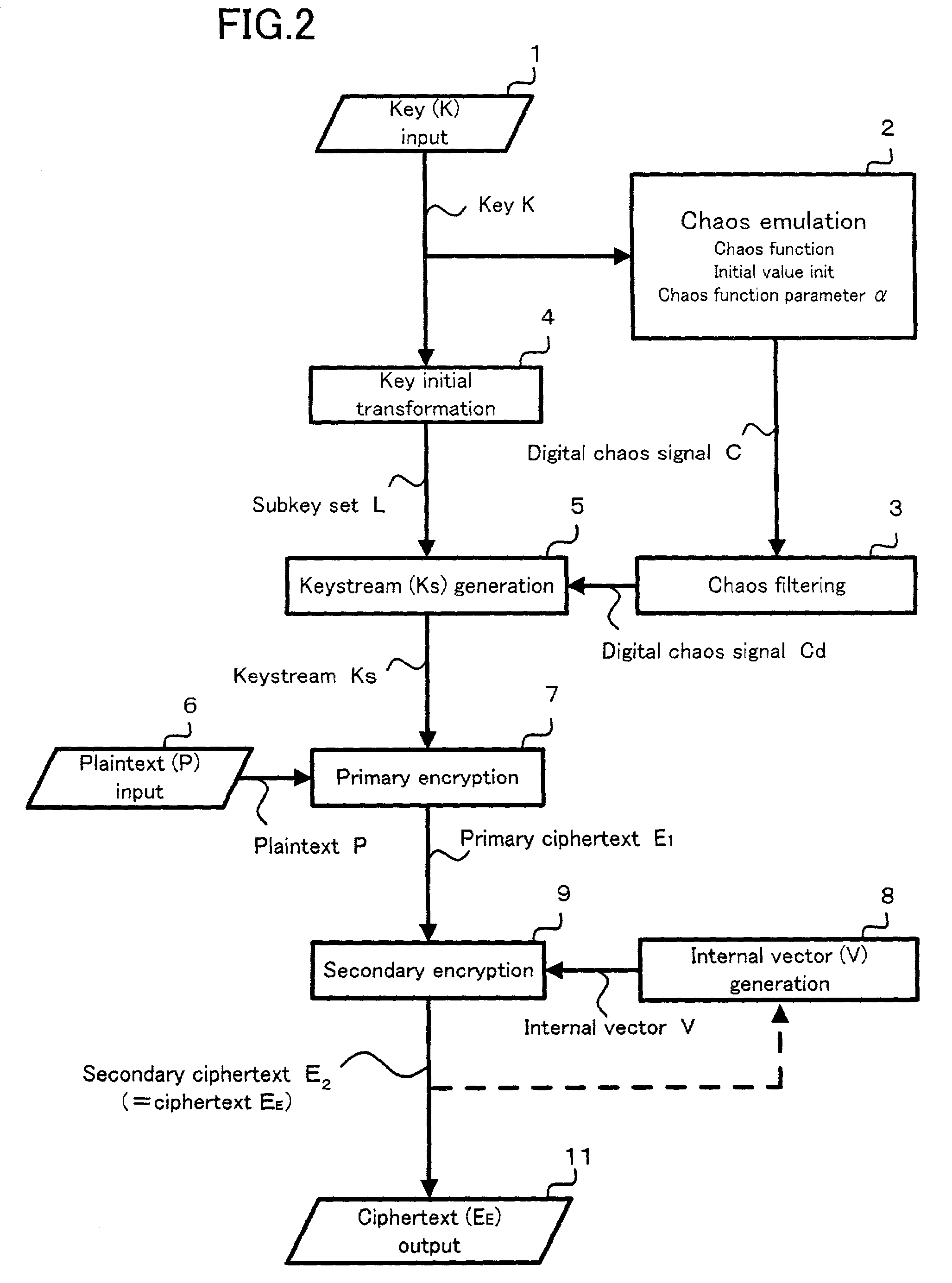
Encryption method, program for encryption, memory medium for storing the program, and encryption apparatus, as well as decryption method and decryption apparatus
InactiveUS7218733B2Easy loadingIncrease speedData stream serial/continuous modificationSecret communicationData spaceKeystream
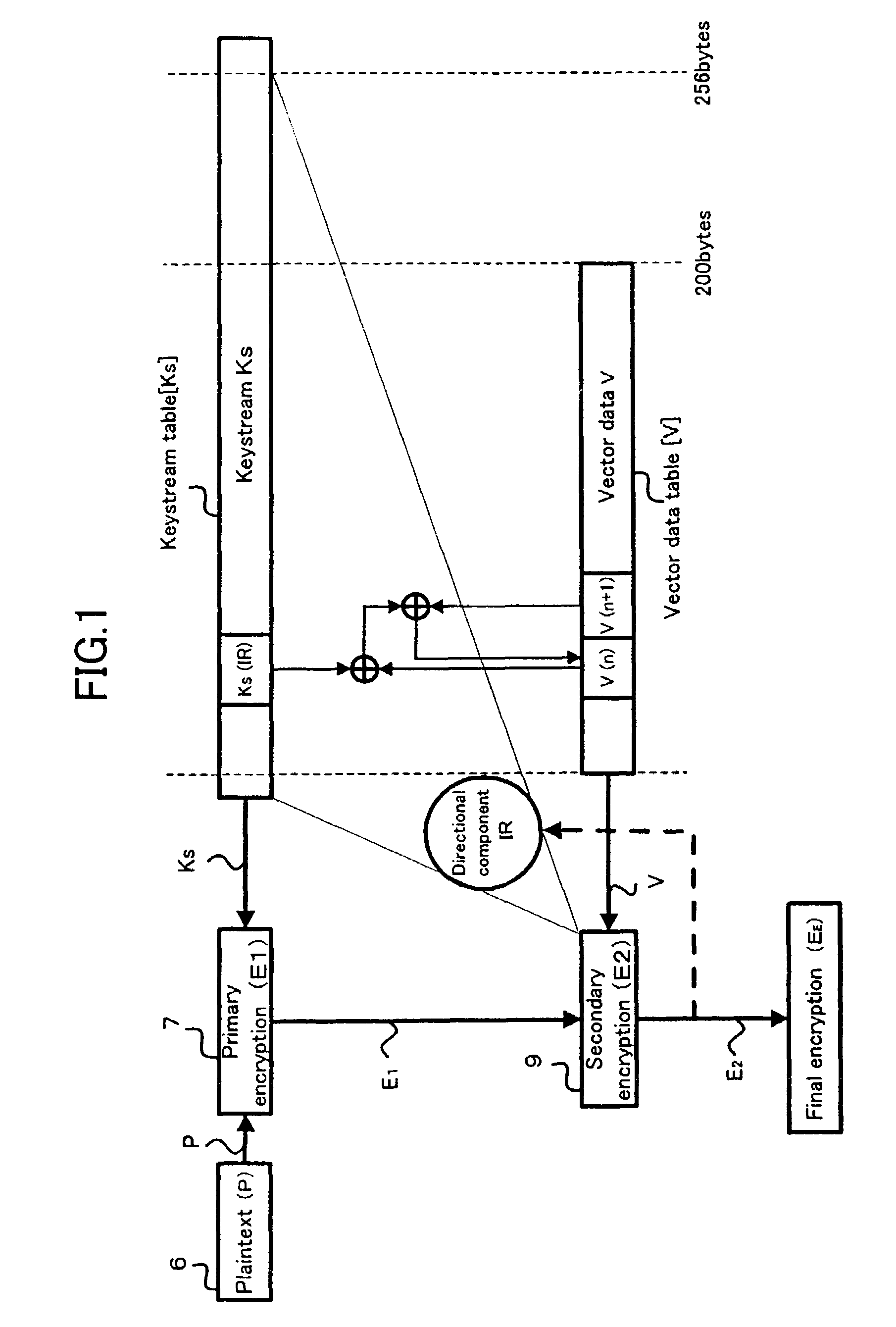
The present invention relates to a cryptosystem. A keystream table [Ks] is a virtual data space. Every data of 1 byte in a secondary ciphertext E2 provides a vector directional component IR. The data Ks (IR) in the keystream table [Ks] designated by the directional component IR of the vector is recognized as the quantitative component of the vector. By handling a secondary ciphertext E2 of 1 byte as the address in the keystream table [Ks], the secondary ciphertext E2 can be recognized as the directional component of the vector. A logical operation for the data Ks (IR) is performed, and the internal vector data V is sequentially replaced every 1 byte. An exclusive OR operation is performed between the internal vector data V and the primary ciphertext E1 for generating a secondary ciphertext E2.
Owner:C4 TECH
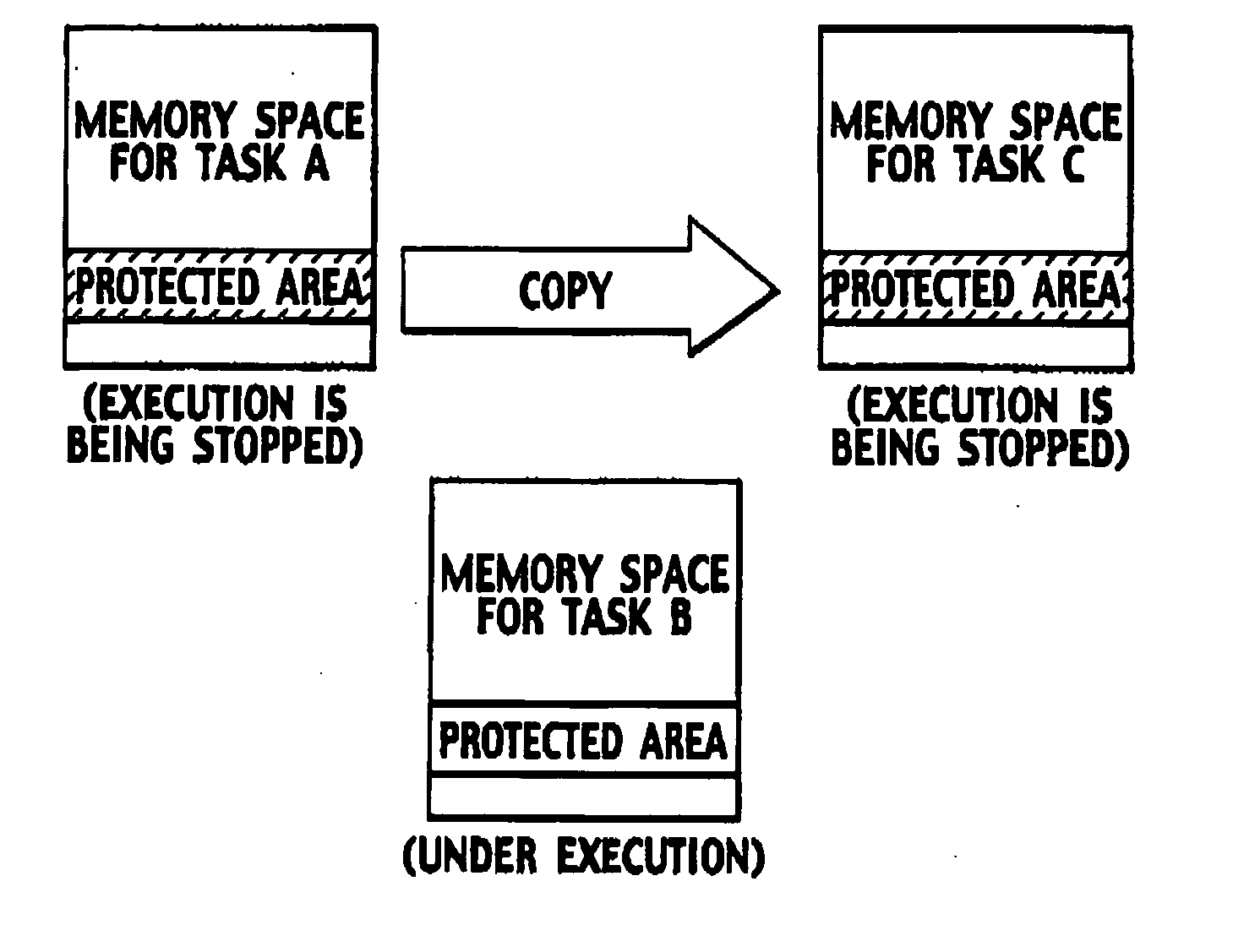
Multitask execution system
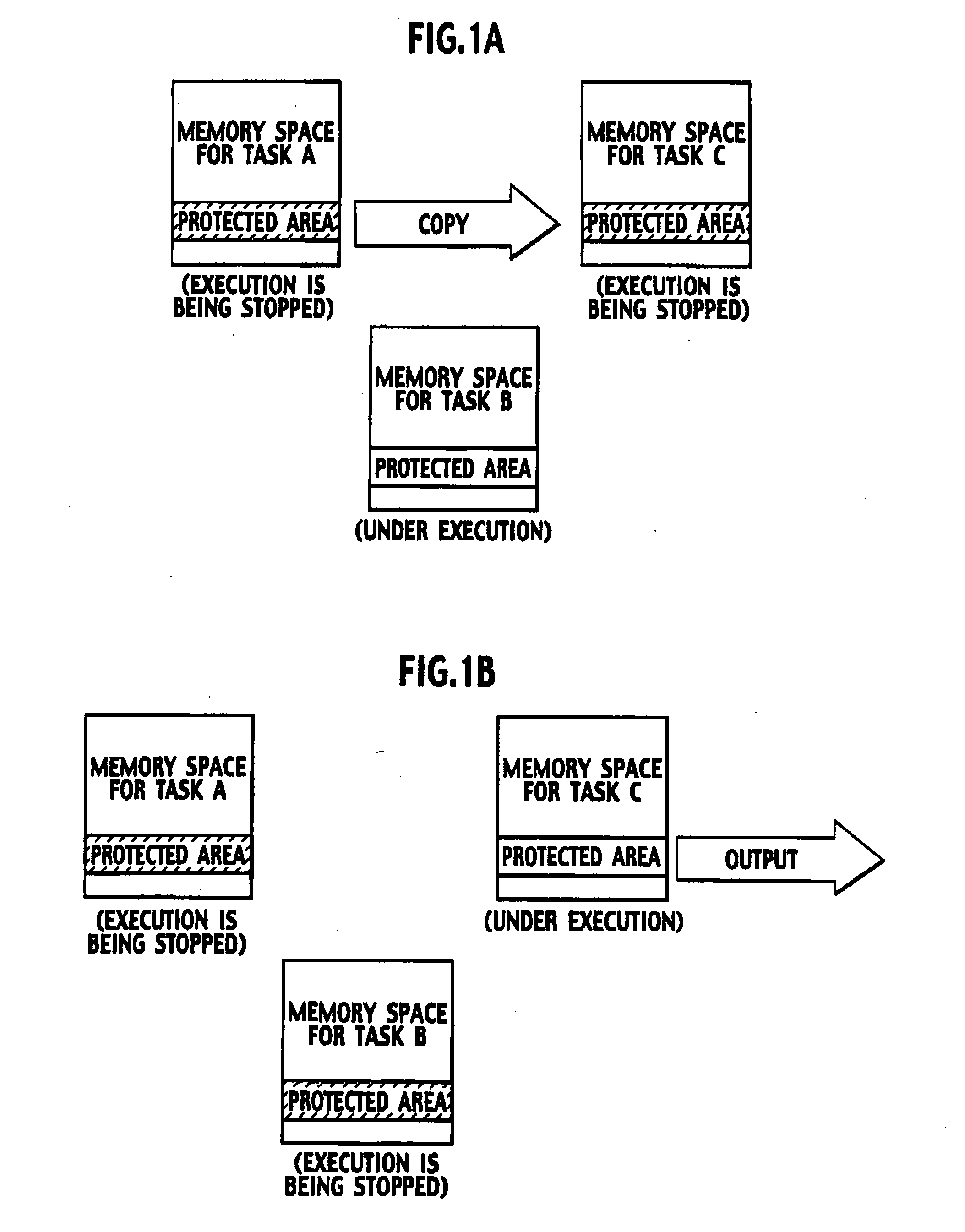
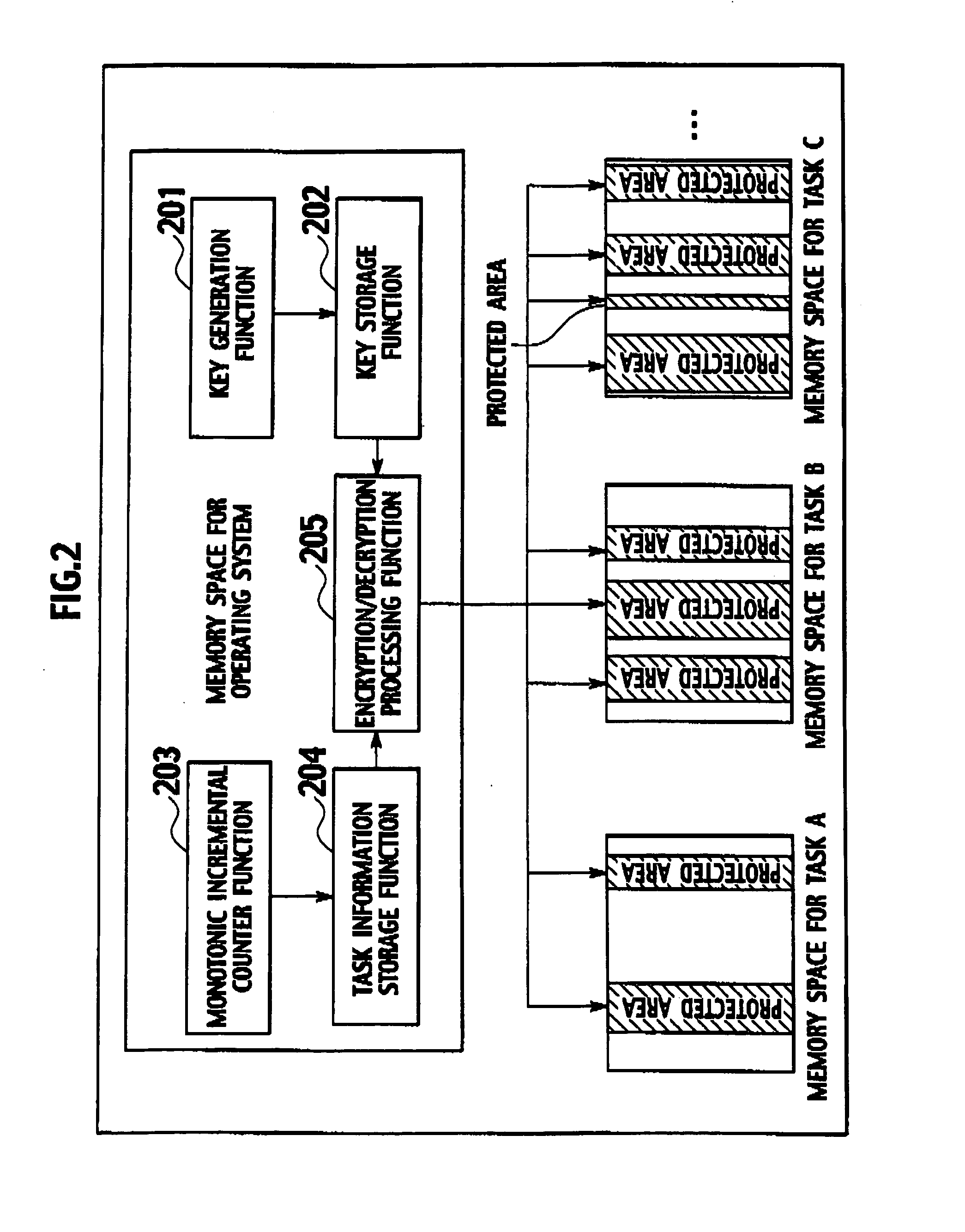
InactiveUS20060020941A1Protection is in progressMultiprogramming arrangementsDigital data protectionKeystreamData store
A multitask execution system executes a plurality of tasks in parallel. The multitask execution system includes an encryption processor configured to generate a key stream unique to each task, by using key data, a task ID for identifying each task, ad an output value, the number of the key data being smaller than the number of the plurality of tasks, the output value being output from a monotonic incremental counter when each task is generated, a value of the monotonic incremental counter configured to continue to be increased without being decreased, and to encrypt data stored in a protected area in a memory space for each task by using the generated key stream.
Owner:NTT DOCOMO INC
Digital image encryption method based on Cat mapping and hyper-chaos Lorenz system
InactiveCN103167213ASimple structureHigh speedSecuring communicationPictoral communicationKey sizeChosen-plaintext attack
The invention discloses a digital image encryption method based on a Cat mapping and hyper-chaos Lorenz system, and belongs to the field of image encryption. According to the digital image encryption method, a key length of an image encryption system is 247 digits and is higher than classical cryptography algorithms of the data encryption standard (DES, 56 digits), the advanced encryption standard (AES, the basic standard is 128 digits) and the international data encryption algorithm (IDEA, 128 digits). By introducing a secret key stream generative mechanism related to plaintexts, secret key streams are enabled to be related to both secret keys and the plaintexts, and even when the same diffusion secret keys are used to encrypt different plaintext images, the generated secret key streams are different. Therefore, the known-resistant / plaintext-selective attack capacity of the encryption system is obviously improved.
Owner:NORTHEASTERN UNIV
Stream cipher encryption method and apparatus that can efficiently seek to arbitrary locations in a key stream
InactiveUS6862354B1Computationally efficientSeek efficiencyData stream serial/continuous modificationSecret communicationComputer hardwareKeystream
A stream cipher encryption method and apparatus that can efficiently seek to arbitrary location in a keystream, and a method of generating an arbitrary segment of keystream.
Owner:CISCO TECH INC
Method and apparatus for composable block re-encryption of publicly distributed content
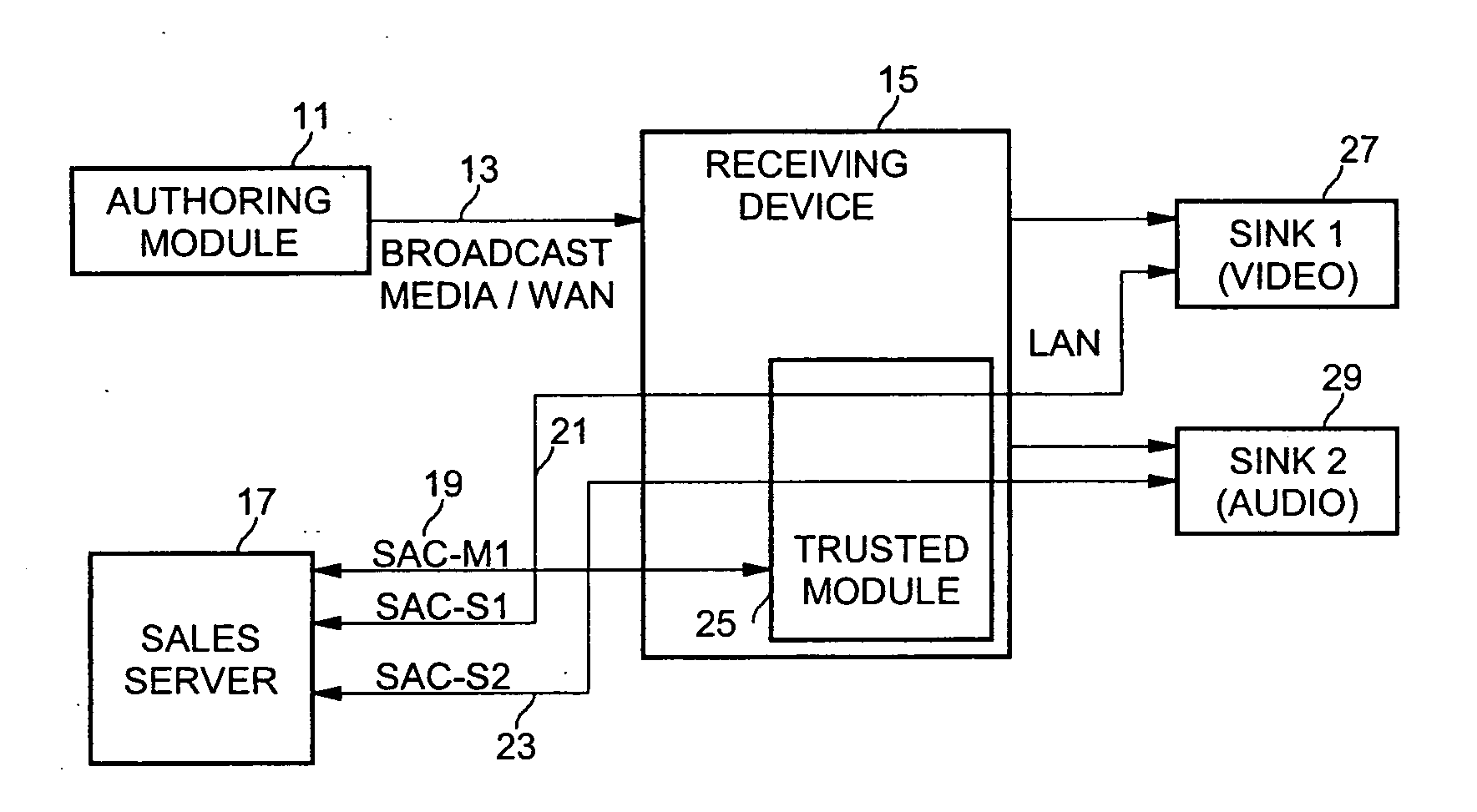
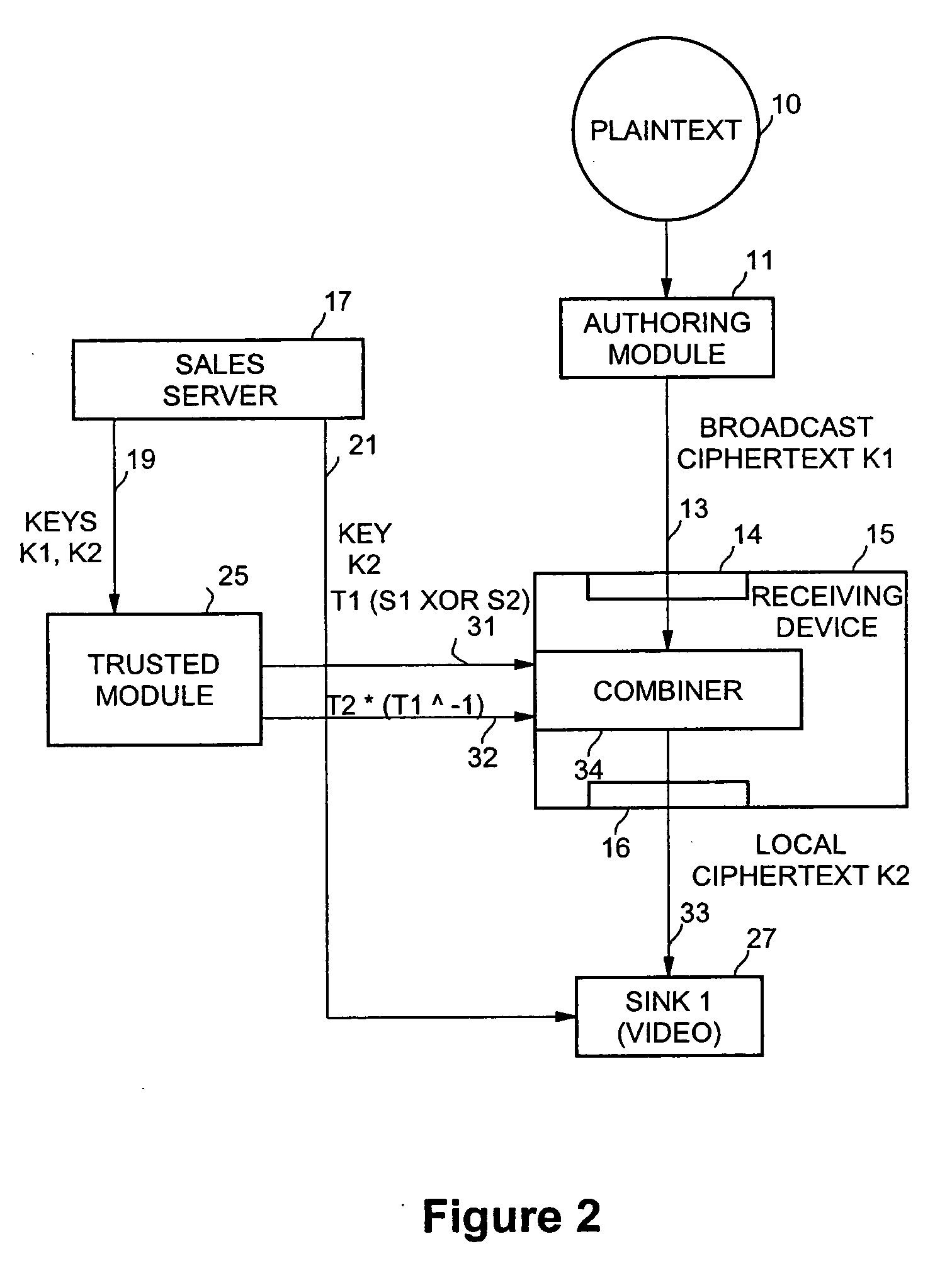
InactiveUS20060233363A1Key distribution for secure communicationData stream serial/continuous modificationSecure communicationKeystream
Secure communication from one encryption domain to another using a trusted module. In one embodiment, the invention includes receiving encrypted streamed content encrypted with a first key, generating a substitution key stream based on the first key and a second key, generating a transposition key stream based on the first and second keys, and simultaneously decrypting and re-encrypting the encrypted streamed content using a combination of the substitution and transposition streams to produce re-encrypted streamed content encrypted with the second key.
Owner:INTEL CORP
Pay per minute for DVB-H services
InactiveUS20070201695A1Digital data processing detailsUser identity/authority verificationData streamKeystream
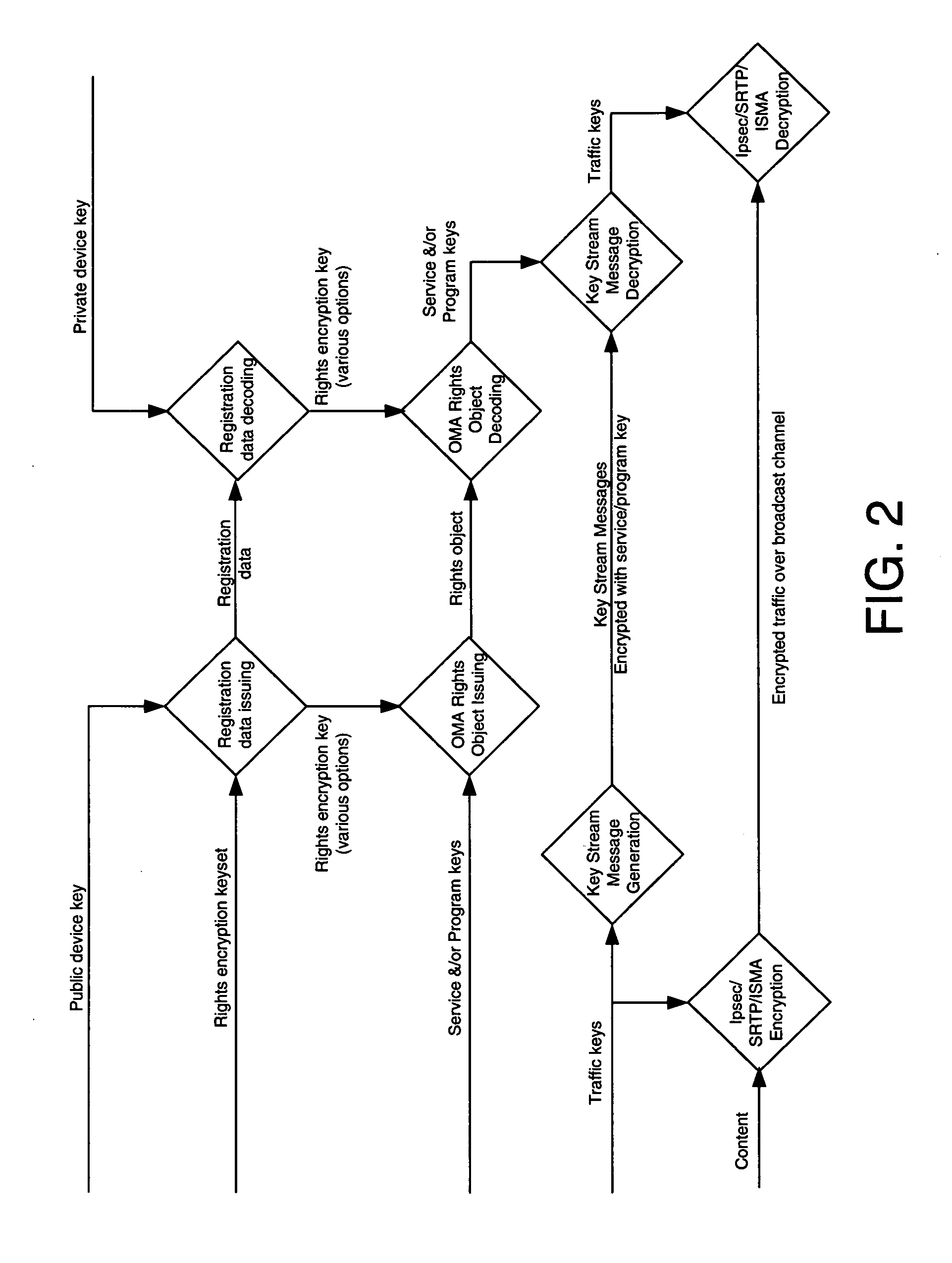
Provided are apparatuses, methods, and user interfaces for requesting access to a program or service, receiving the requested program or service and displaying the requested program or service at a user terminal. In one example, a request for a period of time for access to the program or service is transmitted from a user terminal via a broadcast network. The period of time may be converted to a key decryption count corresponding to the period of time and key interval, the key interval being a period of time separating adjacent key stream messages in a key stream corresponding to a content data stream for the program or service. The encrypted program or service may be decrypted at the user terminal based on the period of access, key interval, and / or key decryption count.
Owner:NOKIA CORP
Methods of encrypting and decrypting data and bus system using the methods
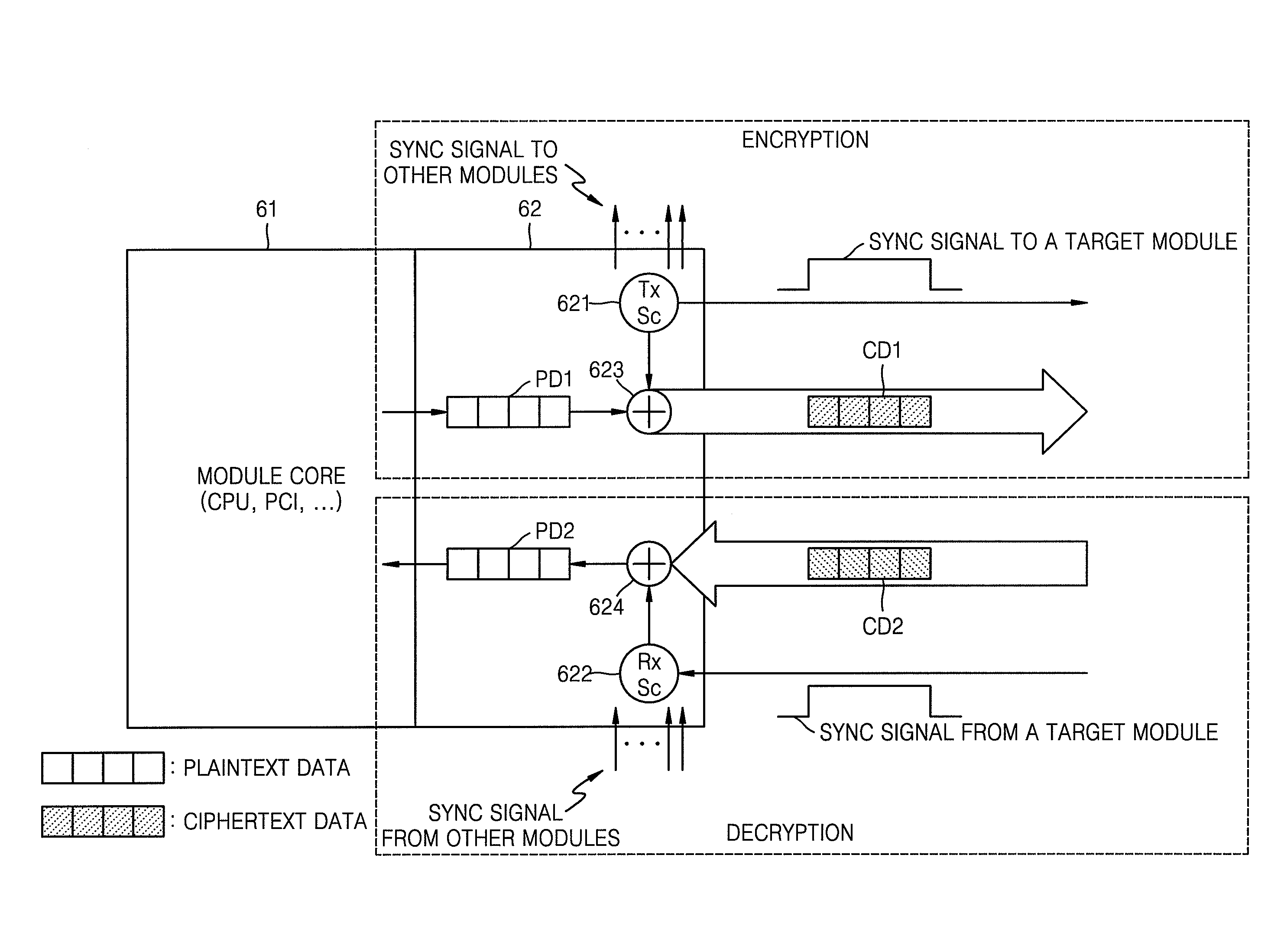
InactiveUS20080279371A1Secure transmissionSynchronising transmission/receiving encryption devicesData stream serial/continuous modificationComputer hardwareKeystream
Methods of encrypting and decrypting data, and a bus system using the methods are provided. The method of encrypting data includes: performing an operation on data that is to be transmitted through a bus with a key stream generated from a predetermined key so as to encrypt the data; transmitting the encrypted data to a predetermined module through the bus; and transmitting a synchronization signal that is logic high when the encrypted data is transmitted through the bus to the predetermined module. Therefore, an encryption speed is improved and encryption can be simply embodied so that security of data received from the bus can be improved.
Owner:SAMSUNG ELECTRONICS CO LTD
Hard-disc fan-area data enciphering and deciphering method and system
InactiveCN1936870AImprove securityPrevent leakageUnauthorized memory use protectionSecuring communicationProgrammable read-only memoryTransfer procedure
This invention discloses an encryption and decryption method for data in hardware. It consists of several steps: obtain the key by reading data from the ROM; obtain the original key by the expending mechanism; operate the logic address and the sequence number and shift the result to get the address key; encryption on the address key by the original key to form a key flow; encryption and decryption on transmitting data. This invention could enhance data security on storage device and protect them from missing.
Owner:ZHEJIANG XUNBO INFORMATION ENG
Secure distributed storage system and method
ActiveUS20110197056A1Less and less-robustProtect informationSecuring communicationOriginal dataKeystream
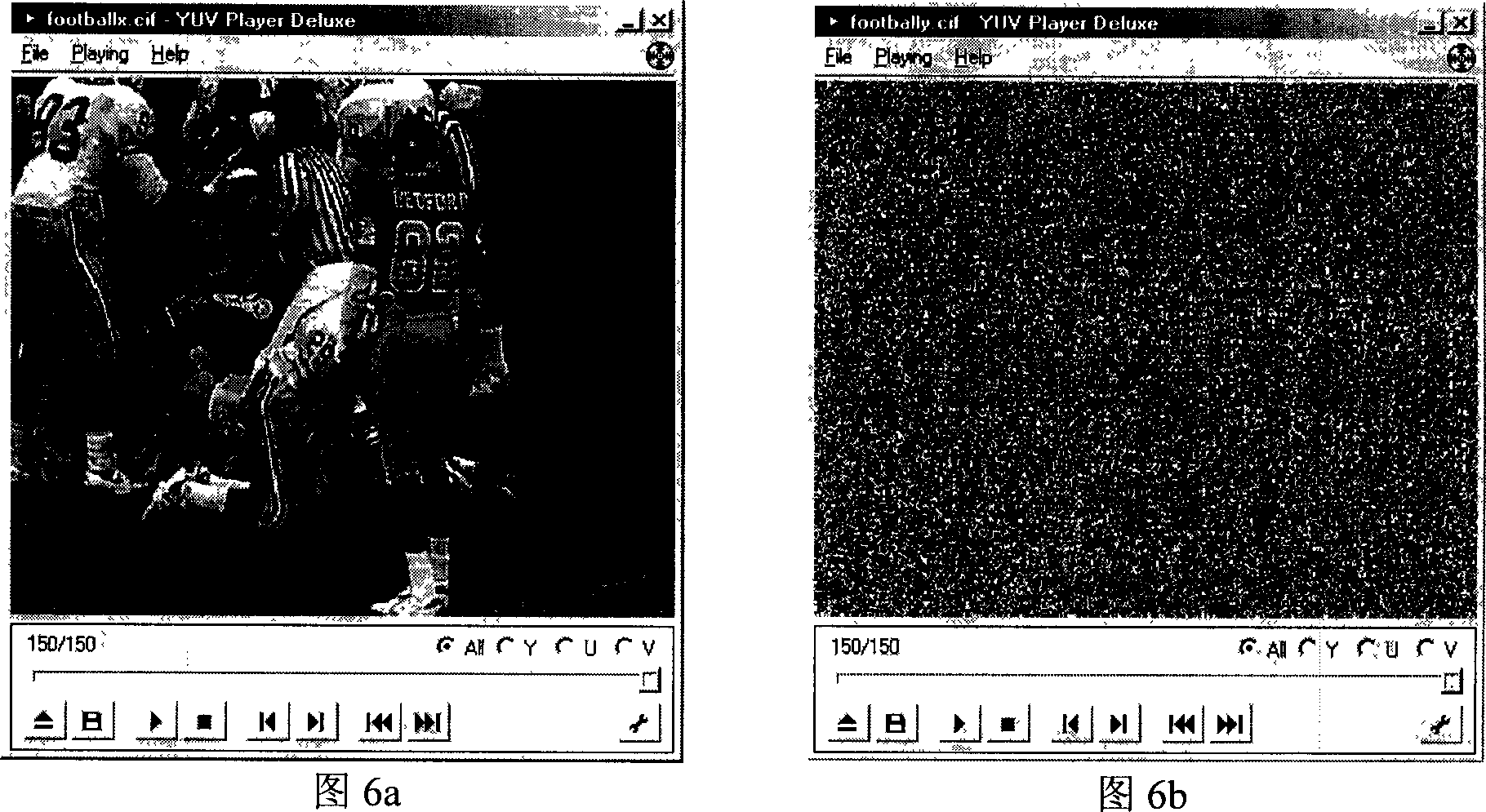
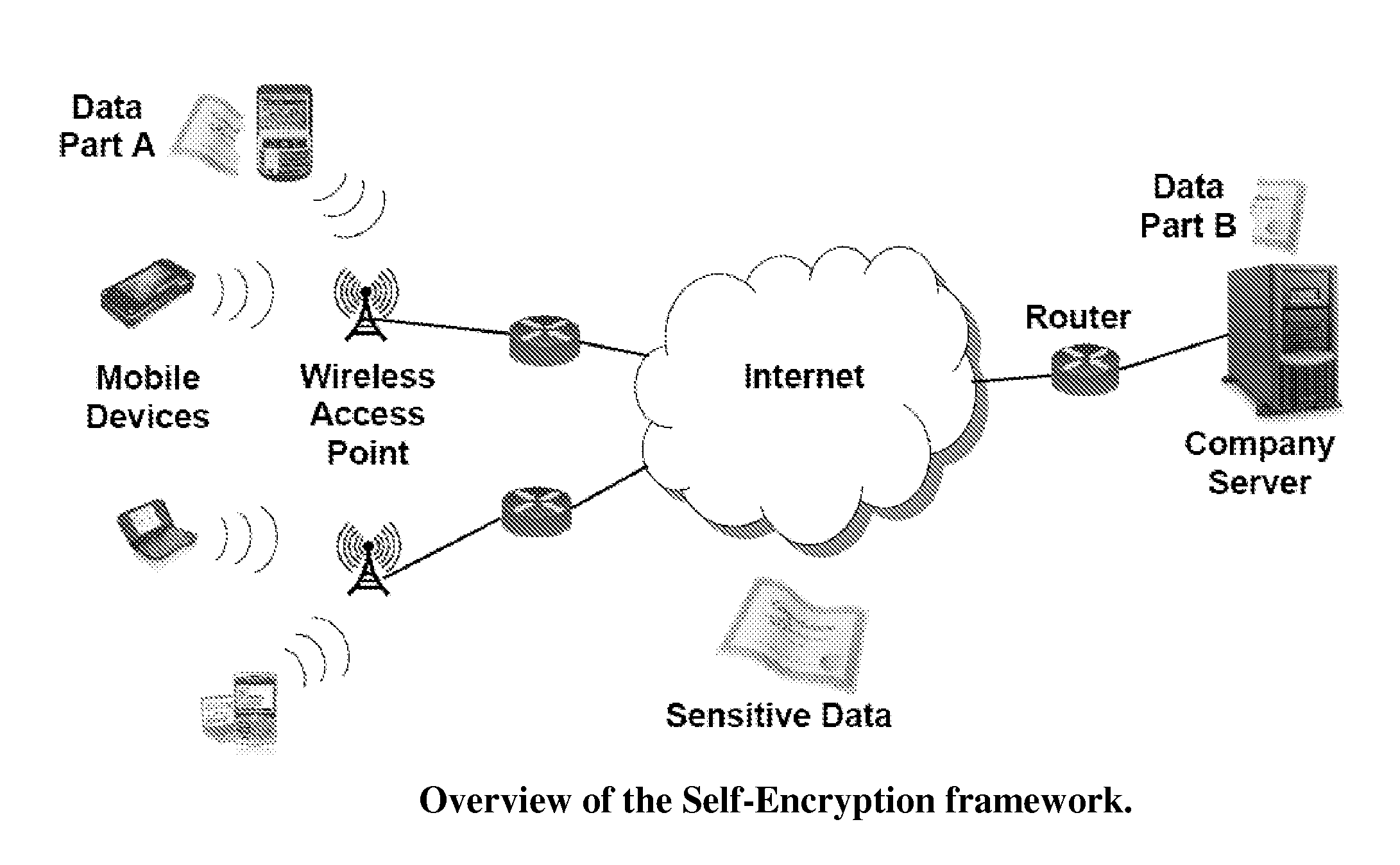
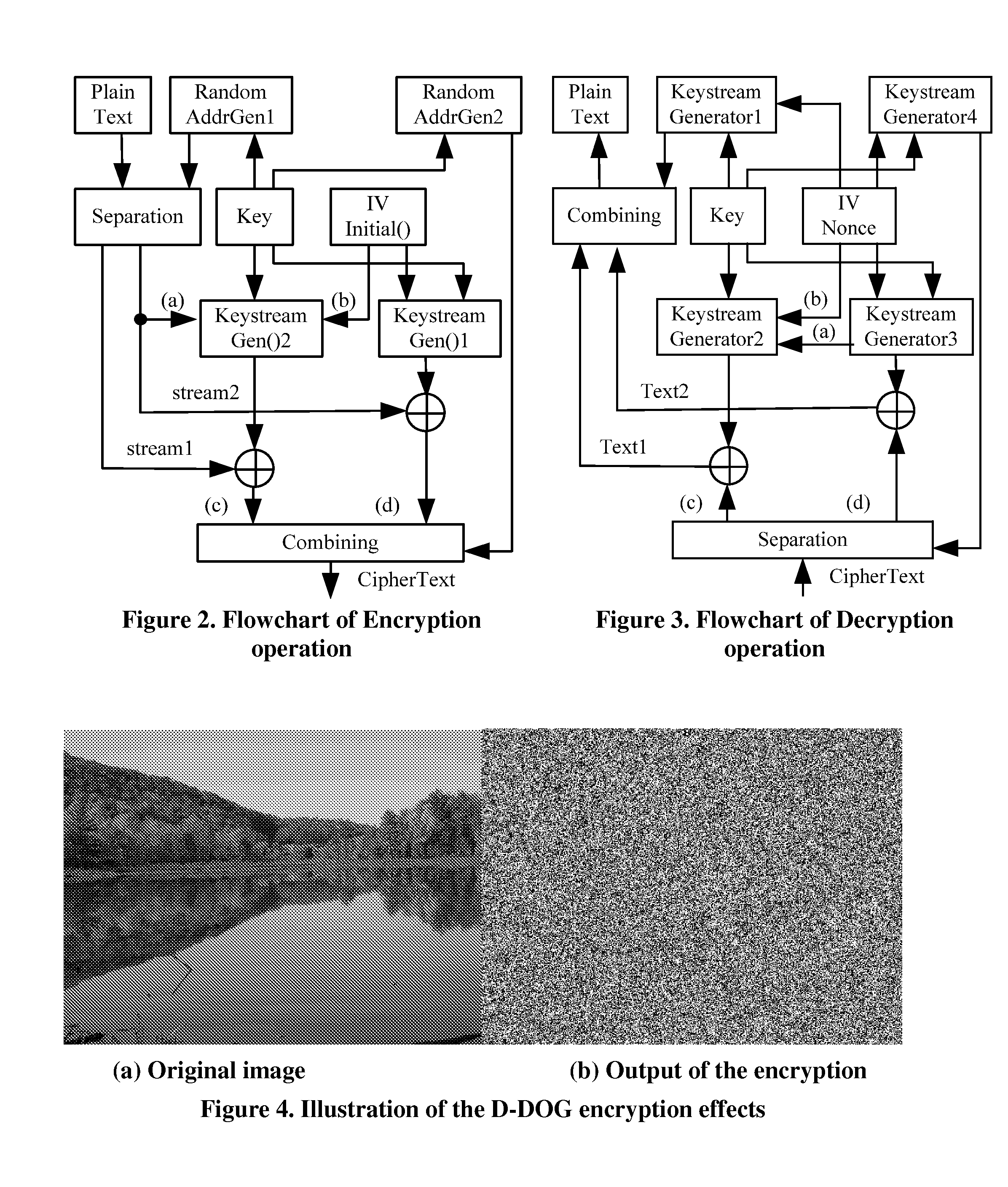
Moving from server-attached storage to distributed storage brings new vulnerabilities in creating a secure data storage and access facility. The Data Division and Out-of-order keystream Generation technique provides a cryptographic method to protect data in the distributed storage environments. In the technique, the Treating the data as a binary bit stream, our self-encryption (SE) scheme generates a keystream by randomly extracting bits from the stream. The length of the keystream depends on the user's security requirements. The bit stream is encrypted and the ciphertext is stored on the mobile device, whereas the keystream is stored separately. This makes it computationally not feasible to recover the original data stream from the ciphertext alone.
Owner:THE RES FOUND OF STATE UNIV OF NEW YORK
Method for password protection for constructing unidirectional hash function based on infinite dimension ultra-chaos
InactiveCN101237320AImprove scrambling performanceIncreased sensitivitySecuring communicationPlaintextHash function
The invention discloses a method for cryptoguard by utilization of infinite dimensional hyperchaos for construction of unilateral hash functions, wherein, a plaintext and a key are taken as initial values of two hyperchaos Chen systems provided with delay feedback at first; evolvement is performed according to characteristics of chaotic dynamics of the system; a final result of evolvement is quantized; the quantized value is substituted into key streams for iteration; confusion and diffusion of plaintext information and key information are realized, and a 128-bit Hash value of the plaintext with any length is generated on the basis of a cipher block chain mode. The method of the invention performs cryptoguard by construction of the Hash functions, fully utilizes signals generated by an infinite dimensional hyperchaos system to improve the scrambling performance of the signals and the sensitivity of parameters, and has stronger attack resistance and better safety to predicted attacks.
Owner:XIAN UNIV OF TECH
Method and system of document transmission
InactiveCN101202624AImprove securityThe transmission scheme is simple and easyData switching networksSecuring communicationTransport systemData stream
The invention discloses a document scrambling transmission system and a method. A transmitting terminal cuts the document to be transmitted into two parts that are an attribute description document and document content data. After the document content data is carried through slicing treatment, a cipher code flow is utilized to carry through scrambling treatment on the data slices; after the attribute description document is carried through the slicing treatment, the attribute description document slices and the data slices after being scrambled are carried through data packet sealing and then transmitted to a receiving terminal through a transmission network. Furthermore, before the slicing treatment is carried through on the attribute description document, the scrambling parameters that are not changed in the whole scrambling process are written in the attribute description document. The document transmission method and the system of the invention transmits the scrambled control words by a mode of ciphertext and transmits the document data by a scrambling data flow, thus leading the document transmission to have higher security.
Owner:新奇点智能科技集团有限公司
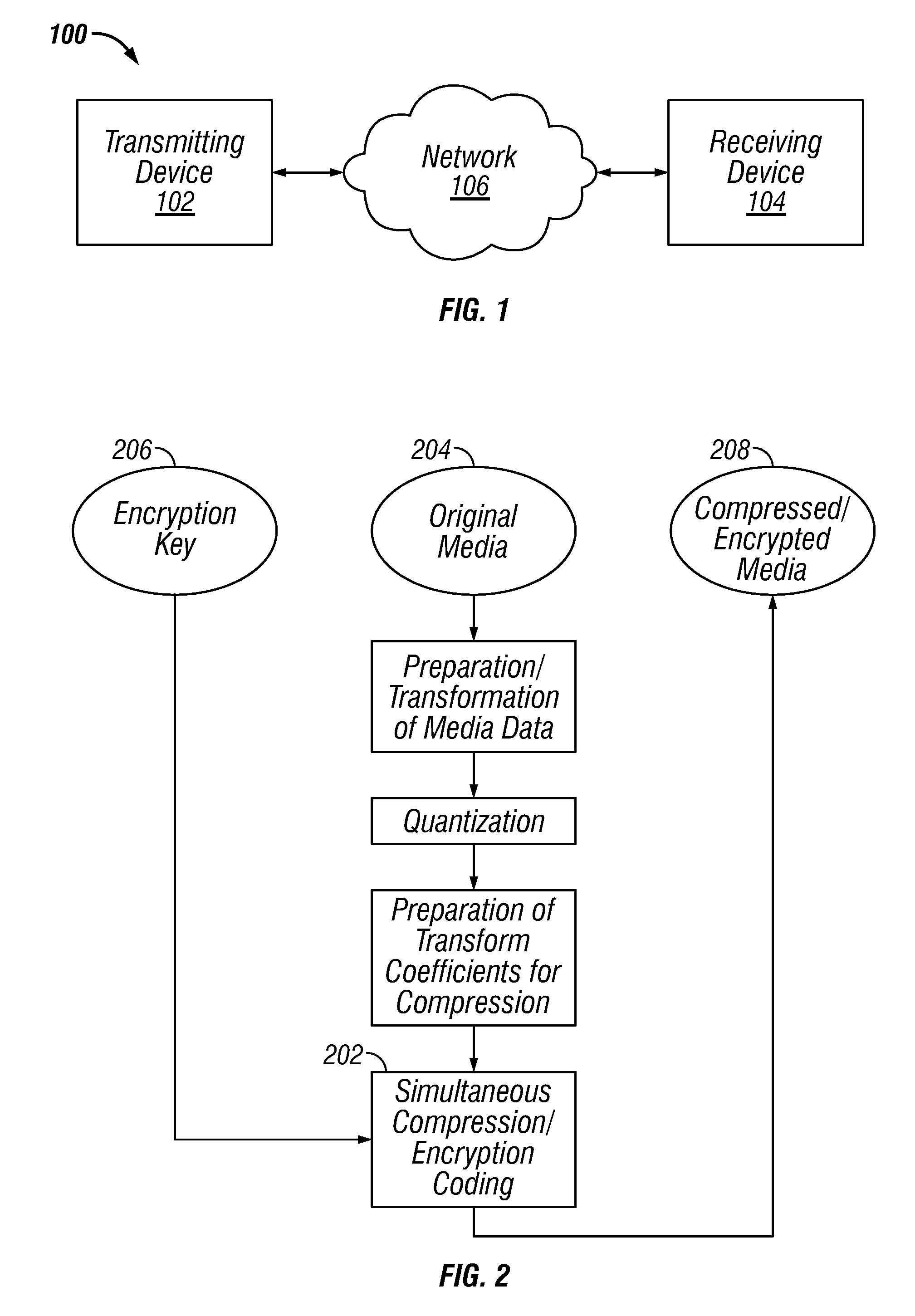
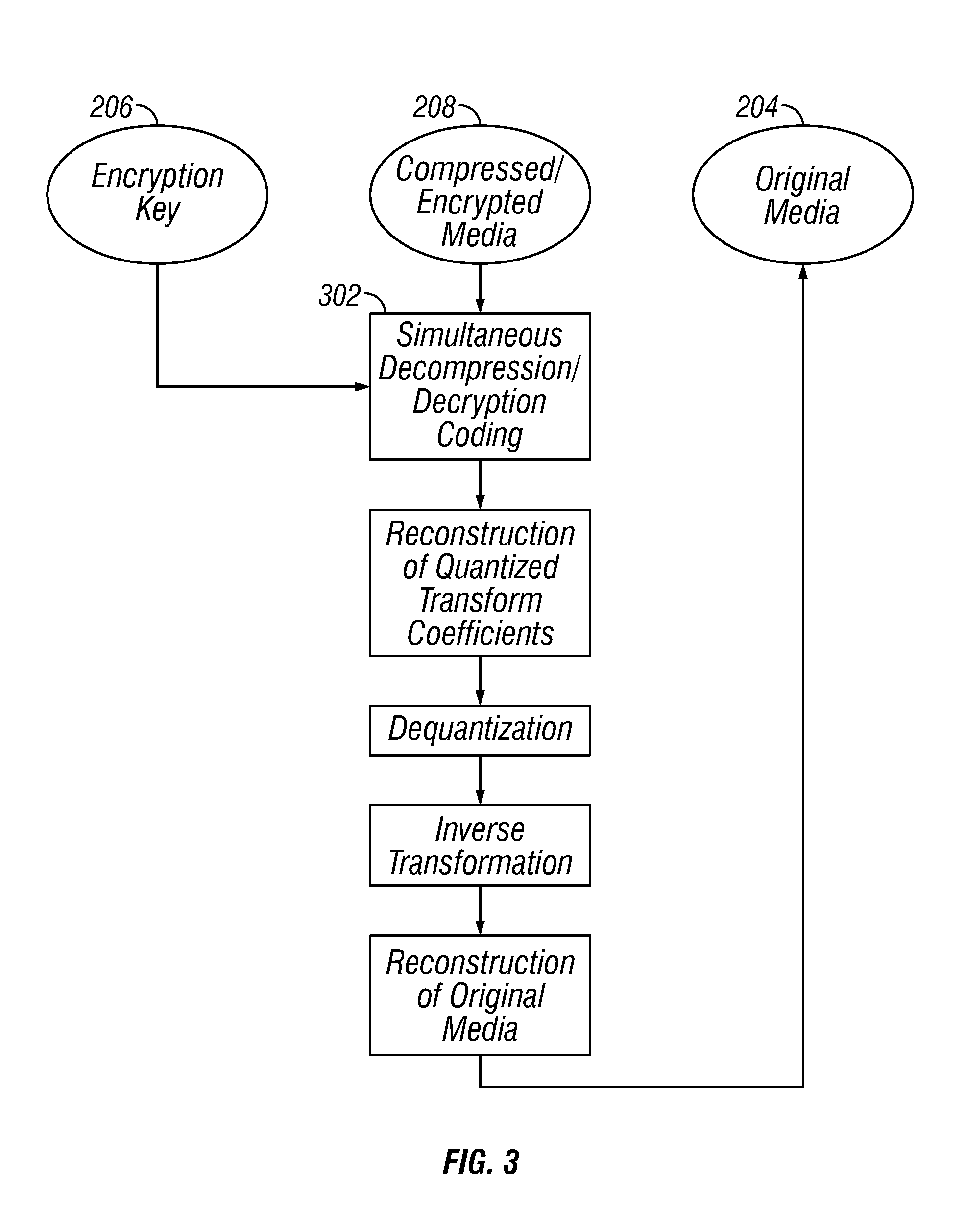
Systems and methods for simultaneous compression and encryption
ActiveUS20150086013A1Improve securityCompetitive compression ratioData stream serial/continuous modificationTelevision systemsDigital dataData segment
Embodiments of reversible systems and methods for fast, secure and efficient transmission, storage, and protection of digital multimedia are disclosed. The embodiments may have the ability to simultaneously compress and encrypt digital data in order to concurrently reduce data size and prevent reconstruction without the proper encryption key. Embodiments of a method may include pre-processing data to optimize the size of data segments to be compressed, transforming the data for improving the compressibility of the before-mentioned data segments, processing the data sequentially to generate predictive statistical models, encoding the data for simultaneously encrypting and compressing data segments using a keystream, and increasing both the compression ratio and security of these encoding processes using a block cipher. Embodiments of these methods may be suitable for use on both encrypted and unencrypted media.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Apparatus, system and method for detecting a loss of key stream synchronization in a communication system
InactiveUS7627121B1Use minimizedEasy to useSynchronising transmission/receiving encryption devicesData stream serial/continuous modificationCommunications systemKeystream
An apparatus, system and method provides an out-of-synchronization detection by using a network layer checksum. A process operating at an upper layer verifies that a checksum embedded in a network layer header is correct before encrypting and transmitting a data packet containing the header and a payload. The data packet is received through a wireless communication channel at a receiver and decrypted. A calculated checksum is calculated on the received payload at the receiver and compared to the received checksum embedded in the header. A key stream used at the receiver for decrypting the received encrypted data packets is determined to be out of synchronization with a key stream used at the transmitter to encrypt the data packets if the calculated checksum is not equal to the network layer checksum.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO +1
Novel image encryption method based on correlation between chaos and plaintext
InactiveCN105513002ABreak strong correlationImplement encryptionImage watermarkingPlaintextDiffusion
The invention provides a novel image encryption method based on correlation between chaos and plaintext. The method comprises the steps: carrying out row and column updating of a plaintext image A, and obtaining a processed image E; employing the modular operation of a gray level 256, changing the pixel sum of the image through the modular operation between rows and the modular operation between columns, and breaking the strong correlation between the adjacent rows and the adjacent columns of an original plaintext image; enabling the pixel sum s of the image E to serve as the feature of the image, extracting the feature of the image, participating the generation of a key stream, carrying out the second layer encryption through scrambling encryption, and obtaining an image Q; and solving a problem that a conventional algorithm employs the same key stream while encrypting different images. Through the gray value diffusion of the image, the method builds the mutual influence between two adjacent pixels, and a secret key directly participates in the output of a ciphertext image. In order to achieve an avalanche effect, the mutual influence between two adjacent pixels is built through the key stream. Meanwhile, a second group of secret keys are designed to participate in the output of the ciphertext image, thereby achieving the third layer encryption.
Owner:GUANGDONG OCEAN UNIVERSITY
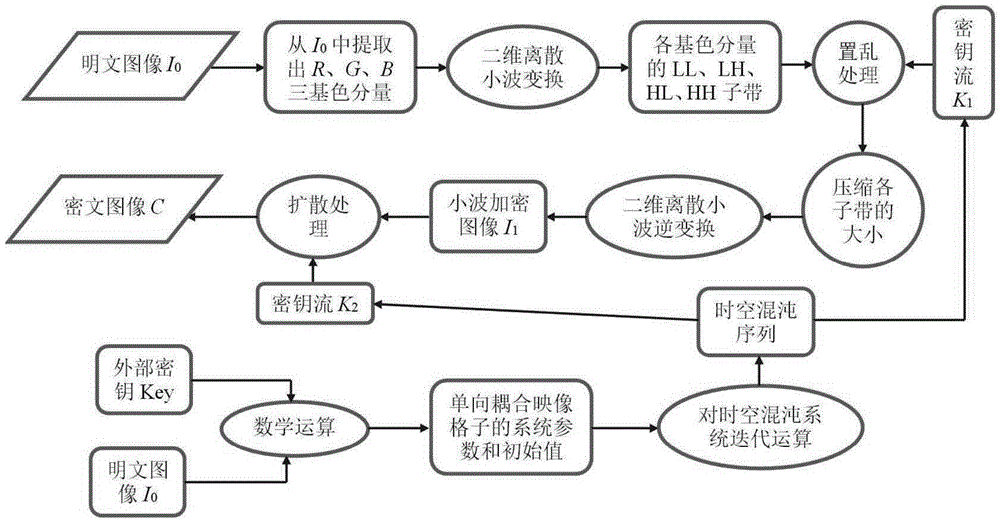
Color image lossless encryption method on basis of two-dimensional discrete wavelet transform and spatiotemporal chaos
The invention relates to a color image lossless encryption method on the basis of two-dimensional discrete wavelet transform and spatiotemporal chaos. The color image lossless encryption method comprises the following steps: separating three primary color components of a color plaintext image to obtain matrices IR0, IG0 and IB0; by utilizing an external key and combining the plaintext image, generating spatiotemporal chaos system parameters and initial values and carrying out iterative operation on a spatiotemporal chaos system to obtain key streams K1 and K2; carrying out two-dimensional discrete wavelet transform on the components IR0, IG0 and IB0 to obtain three groups of sub-bands; utilizing the key stream K1 to respectively carry out disorder processing on the three groups of sub-bands and compressing the sub-bands; respectively carrying out two-dimensional discrete wavelet transform on each group of processed sub-bands to obtain a wavelet encrypted image I1; utilizing the key stream K2 to carry out diffusion treatment on the image I1 to obtain a final ciphertext image C. Compared with an existing image encryption method, the color image lossless encryption method provided by the invention has the advantages of high safety, good encryption effect, lossless information, high encryption speed, high attack resistance and the like and can be widely applied to the fields of medicine, biological gene, military and the like.
Owner:HENAN UNIVERSITY
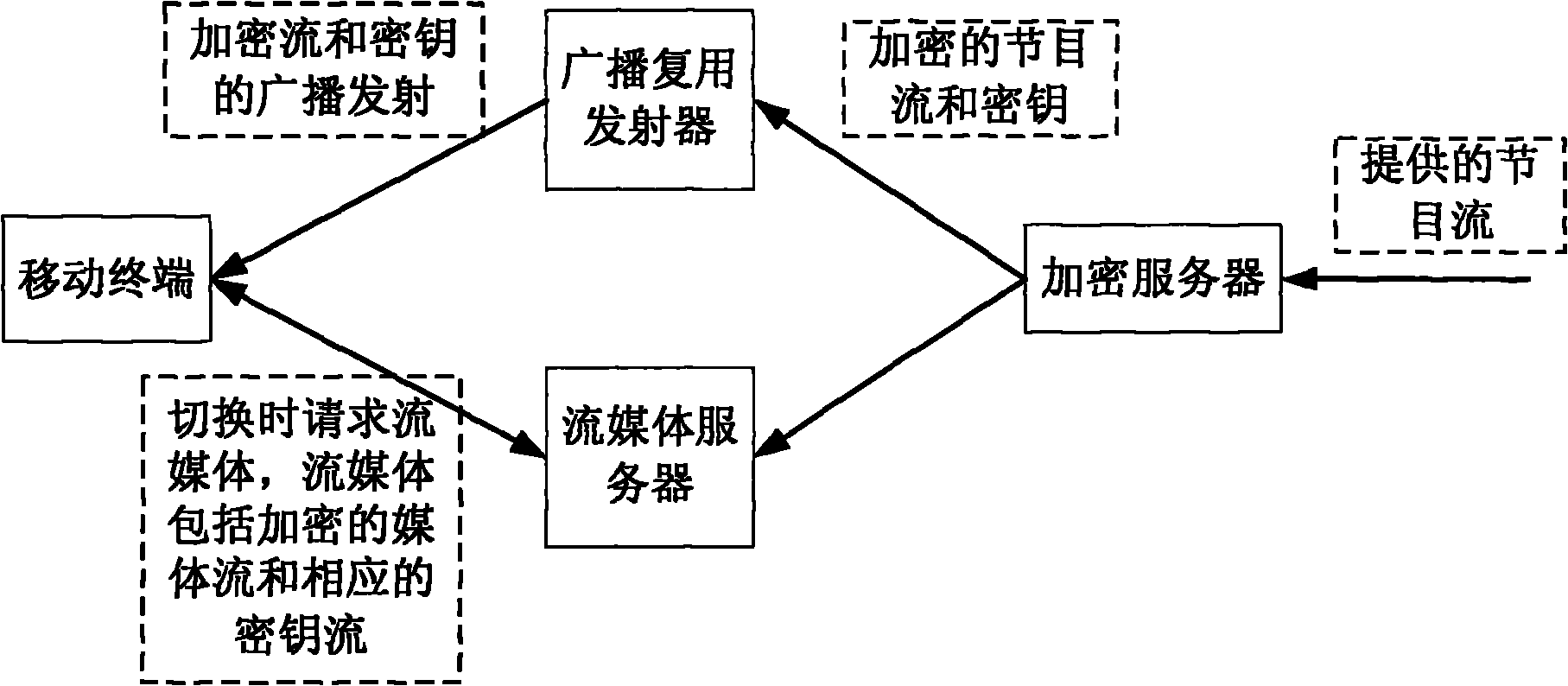
Method for encrypting transmission medium stream, encryption server and mobile terminal
InactiveCN101998384AReduce complexityReduce waiting timeSelective content distributionSecurity arrangementComputer hardwareMultiplexing
The invention provides a method for encrypting transmission medium stream, an encryption server and a mobile terminal. The method comprises the following steps that: 1, the encryption server generates a program key stream, encrypts a program data stream by using the program key stream and performs real-time transmission protocol (RTP) encapsulation to obtain an encrypted program data stream; 2, the encryption server encrypts and performs RTP encapsulation on the program key stream by utilizing a service key to obtain an encrypted key stream, wherein the encrypted key stream and the encrypted program data stream are synchronized through a time stamp; and 3, the encryption server sends the encrypted program data stream and the encrypted key stream to a broadcast multiplexing emitter which performs broadcast emission and a stream medium server which performs unicast transmission. The method can uniform the stream medium encryption and decryption modes in broadcast and unicast and facilitate reducing the complexity of the terminal and switching.
Owner:CHINA MOBILE COMM GRP CO LTD
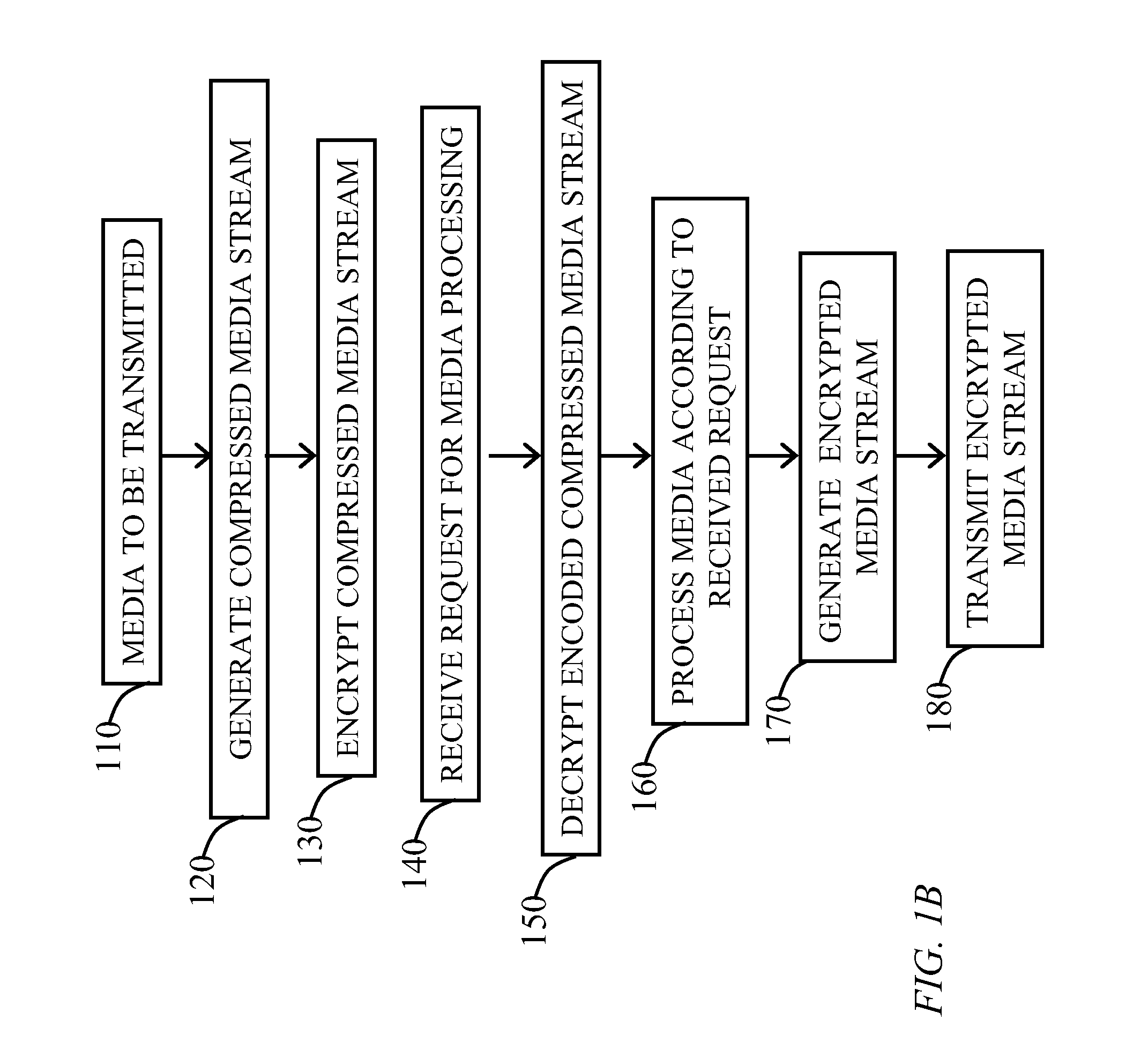
Media Processing Devices With Joint Encryption-Compression, Joint Decryption-Decompression, And Methods Thereof
InactiveUS20110191587A1User identity/authority verificationSelective content distributionKeystreamComputer science
In one embodiment, a method of adaptive media streaming includes receiving a cipher media stream at a media device. The cipher media stream is compliant with a media compression standard. The cipher media stream is decrypted and decoded using an inverse stream cipher algorithm and a compressed media stream is generated by combining the cipher media stream with a keystream.
Owner:FUTUREWEI TECH INC
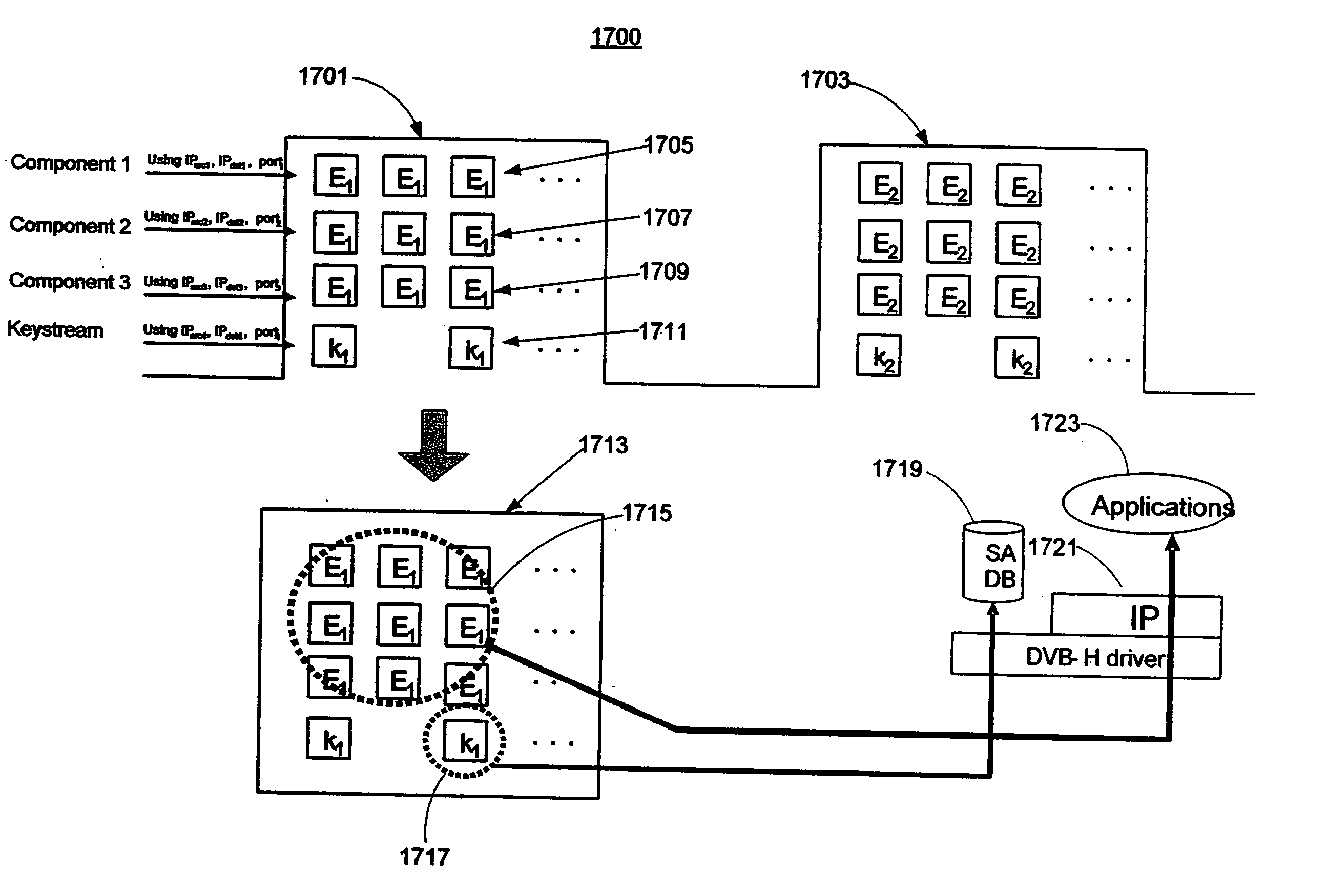
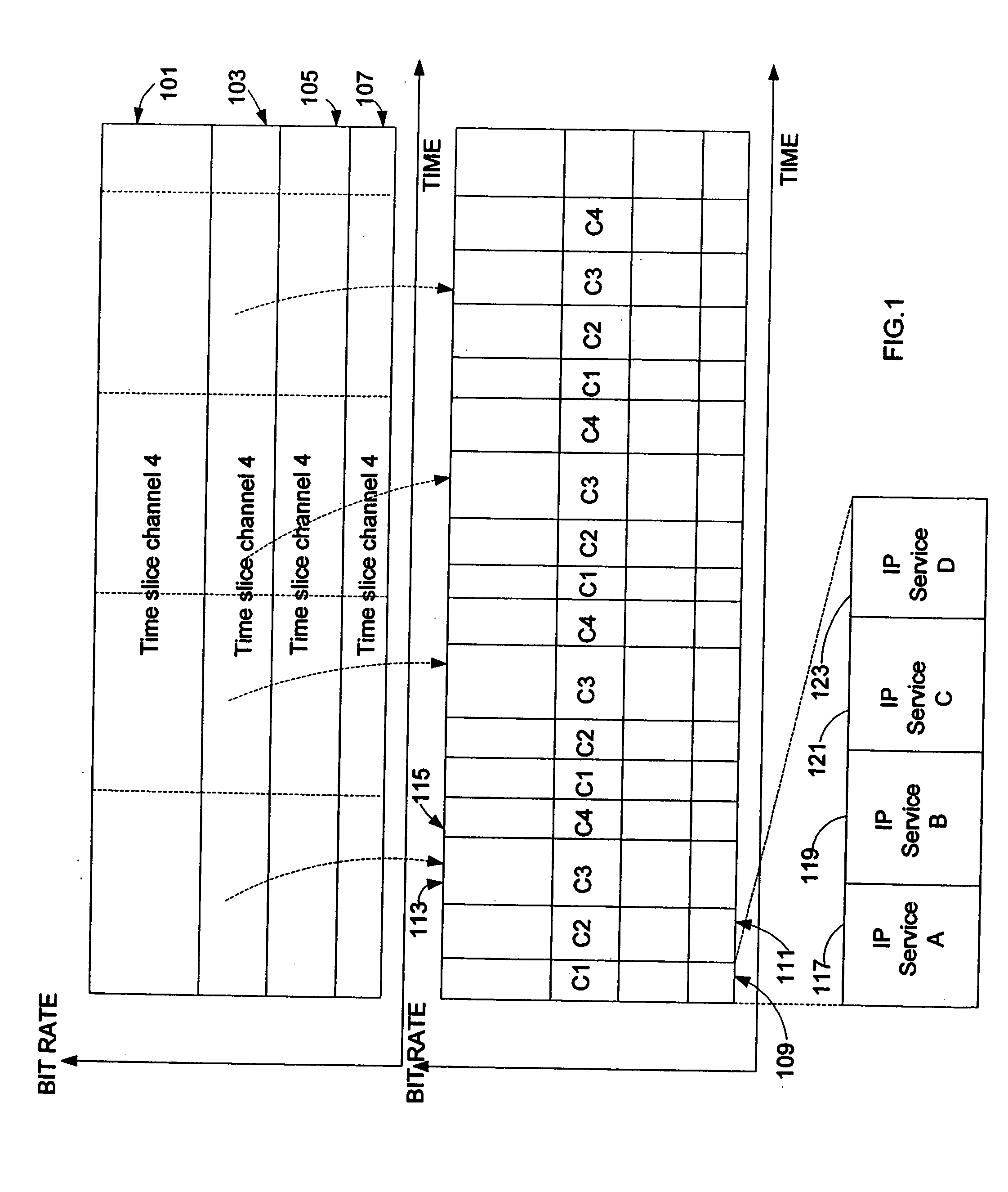
Method for receiving a time slice burst of data
InactiveUS20060034321A1Multiple keys/algorithms usagePublic key for secure communicationKeystreamDatagram
The present invention provides methods, apparatuses, and systems for delivering protected multi-media content to a receiving device. Protected multi-media content and key information are inserted in a same time slice burst. Multi-media content is processed into content datagrams, in which each content datagram is associated with a corresponding component. Key information may be processed as a keystream with key datagrams or may be included in one or more components. A content datagram may be encrypted with an associated key. A receiving device receives the time slice burst with the content datagrams and the key information. The receiving device subsequently decrypts the content datagrams with the key information. Key datagrams may be associated with a higher priority level than content datagrams. Consequently, a receiving device can process a key datagram in order to extract a key before routing associated content datagrams to a message stack.
Owner:NOKIA CORP
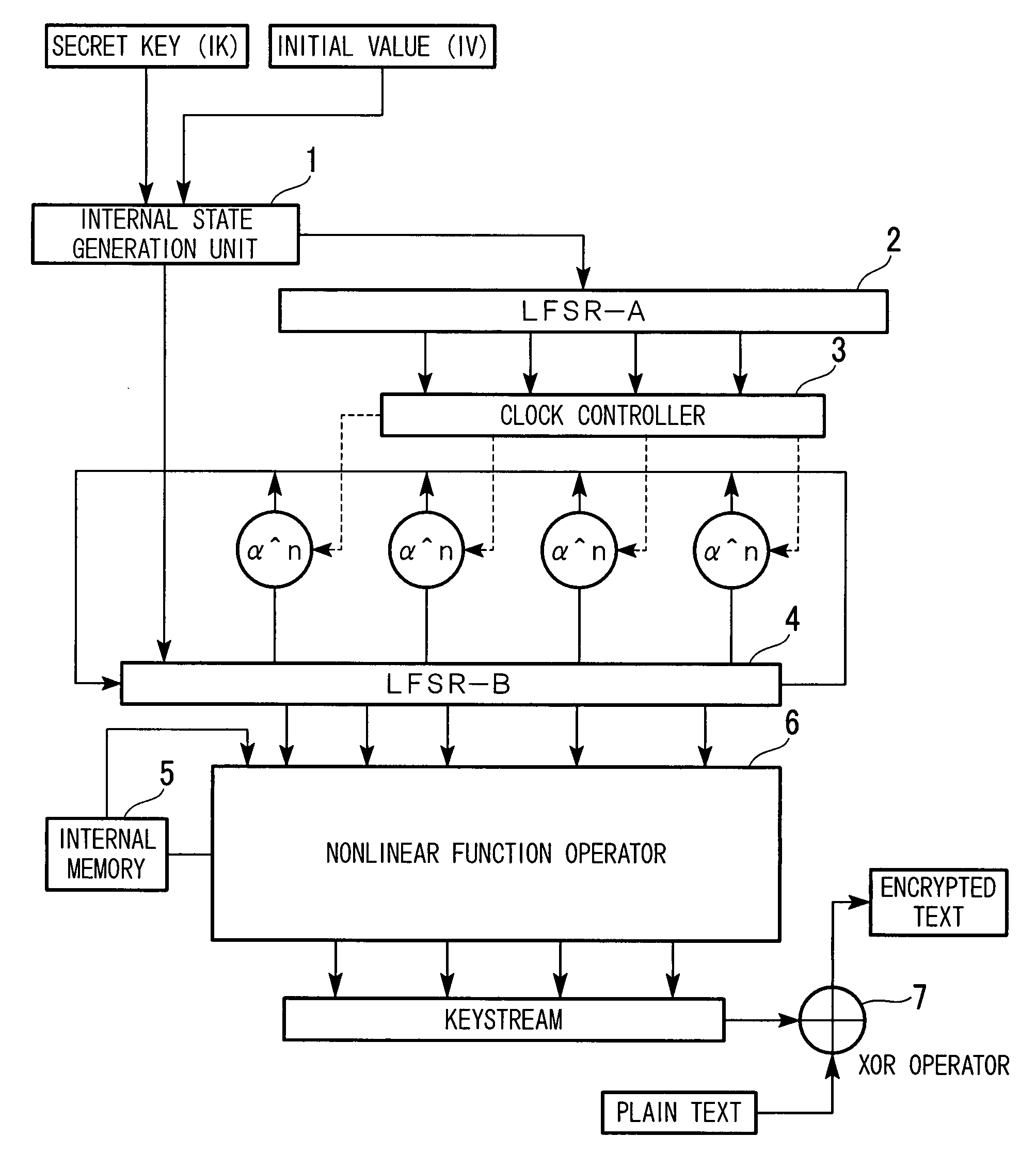
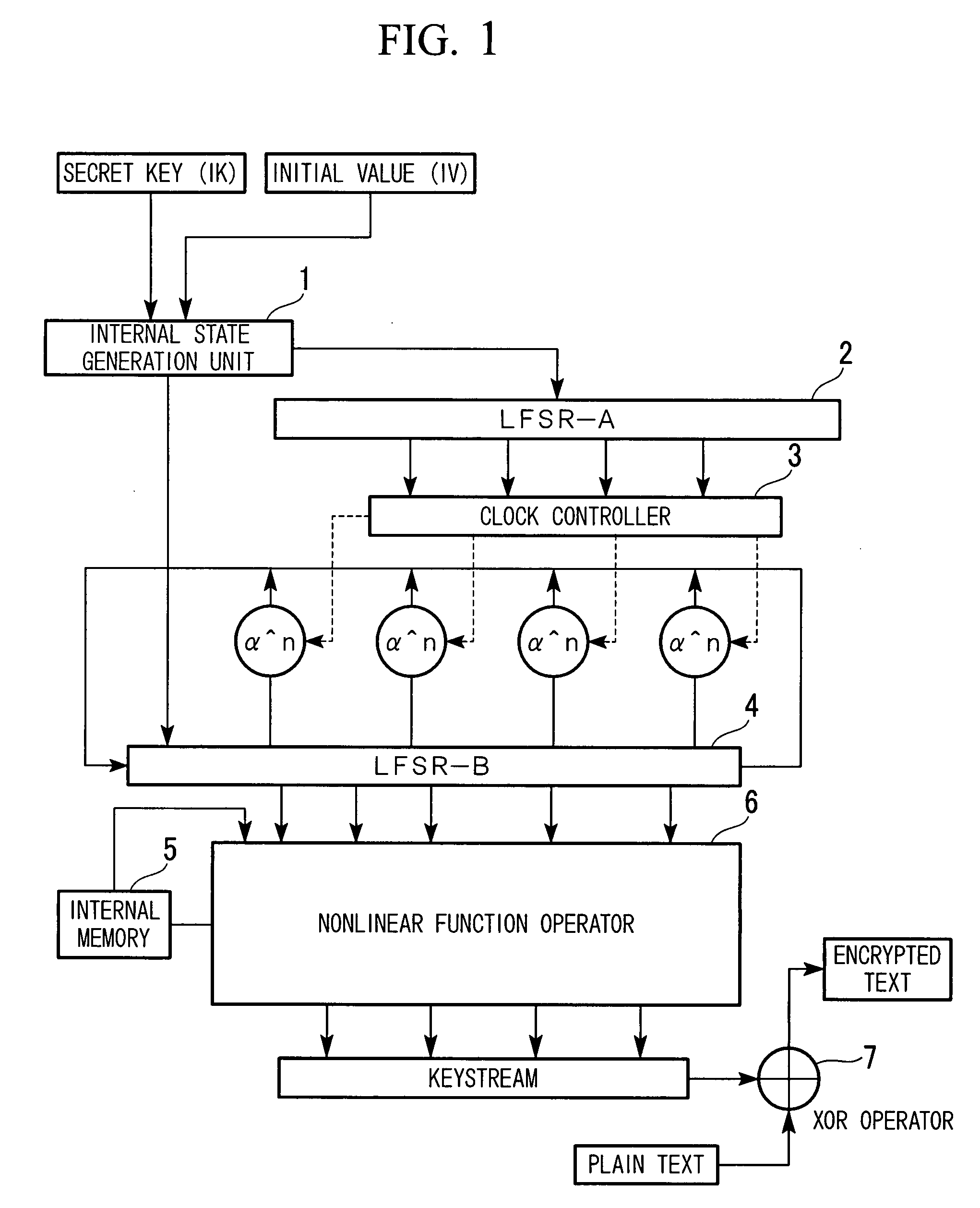
Keystream encryption device, method, and program
ActiveUS20070263861A1Efficient processingImprove securitySecret communicationSecuring communicationComputer hardwareKeystream
A stream encryption device generates a first pseudo random number sequence from key information, generates a second pseudo random number sequence according to clock control performed according to the first pseudo random number sequence, and subjects it to a nonlinear function calculation, thereby generating a key stream. The stream encryption device performs XOR operation with a plain text so as to create an encrypted text.
Owner:KDDI CORP
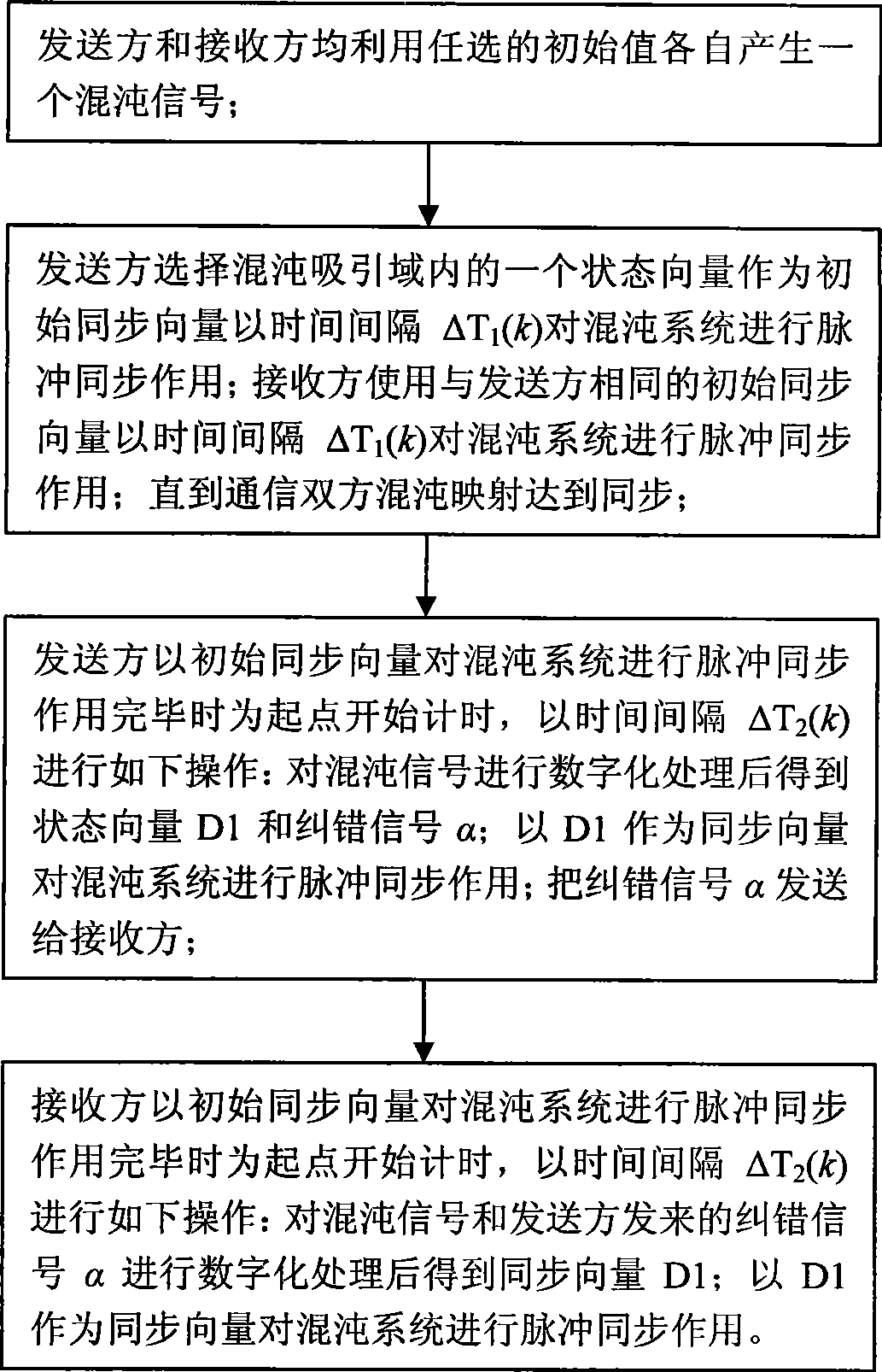
Encryption/decryption method and system based on chaos hybrid self-synchronizing method
InactiveCN101431400AReduce occupancyImprove securitySecuring communicationSynchronising arrangementCommunications systemKeystream
The objective of the invention is to provide a method of chaotic hybrid self-synchronization. Both communication sides get digital signal after sampling and analog-digital conversion of local continuous chaotic signal respectively at regular intervals. Sender executes pulse synchronization to continuous chaotic system with received digital signal and then transmits error correction signal including 1bit information to receiver. Receiver executes pulse synchronization to its continuous chaotic system with corrected digital signal. Continuous chaotic system at different location only need to transmit error correction information of 1bit to keep long period of steady synchronization through the synchronization method. Occupation rate to channel by redundant information fall to low and anti-attack ability of chaotic system is improved efficiently. The digital chaotic sequence output by chaotic system that synchronized through the invention can be used to encrypt data as pseudo-random sequence or key stream; the output continuous chaotic signal can be used to design encryption communication system that based on chaotic synchronization.
Owner:HUAZHONG UNIV OF SCI & TECH
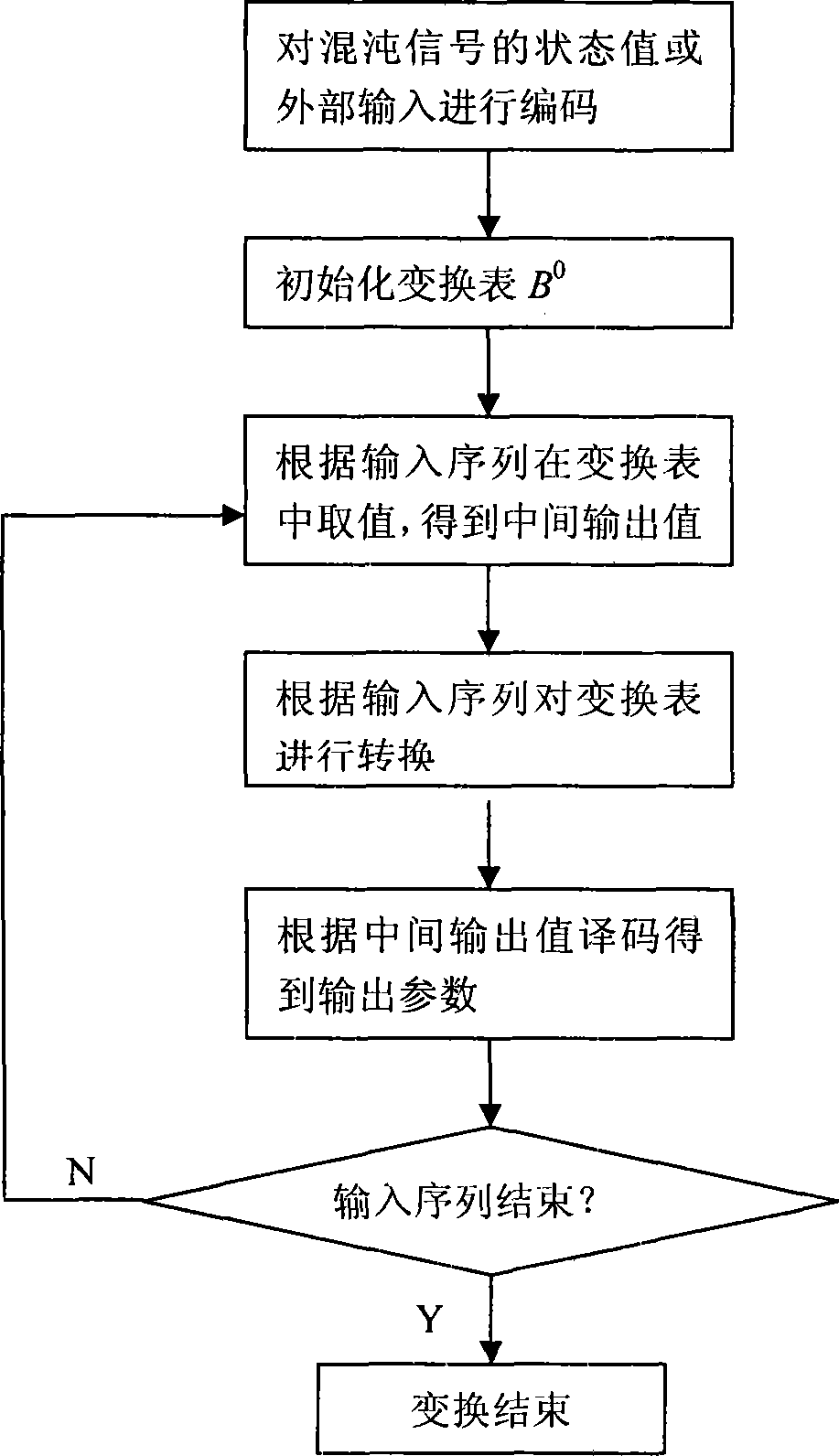
Word-oriented key stream generating method and encrypting method
InactiveCN101841415AIncrease randomnessAdd nonlinearityEncryption apparatus with shift registers/memoriesComputer hardwareKeystream
The invention discloses a word-oriented key stream generating method and an encrypting method. The key stream generating method comprises the steps of: generating, namely generating a source sequence and outputting the source sequence to a selecting step; selecting, namely selecting some bits in the source sequence to form four outputs, wherein three outputs are inputted to a mixing step, and another output is outputted to an outputting step; mixing, namely performing non-linear compression transformation on the three inputs to form an output; and outputting, namely receiving the output of the selecting step and the output of the mixing step and performing combined compression to obtain the key stream for outputting. The key stream sequence generated by the method has quite high randomness and non-linearity, and is much suitable to be quickly realized by software and hardware; and the encrypting method by using the key stream generated in the invention has higher security.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Monobase amorphous encryption
InactiveUS20080013720A1Good hashEasy to operateSecret communicationSecuring communicationMultiplexingGeneration process
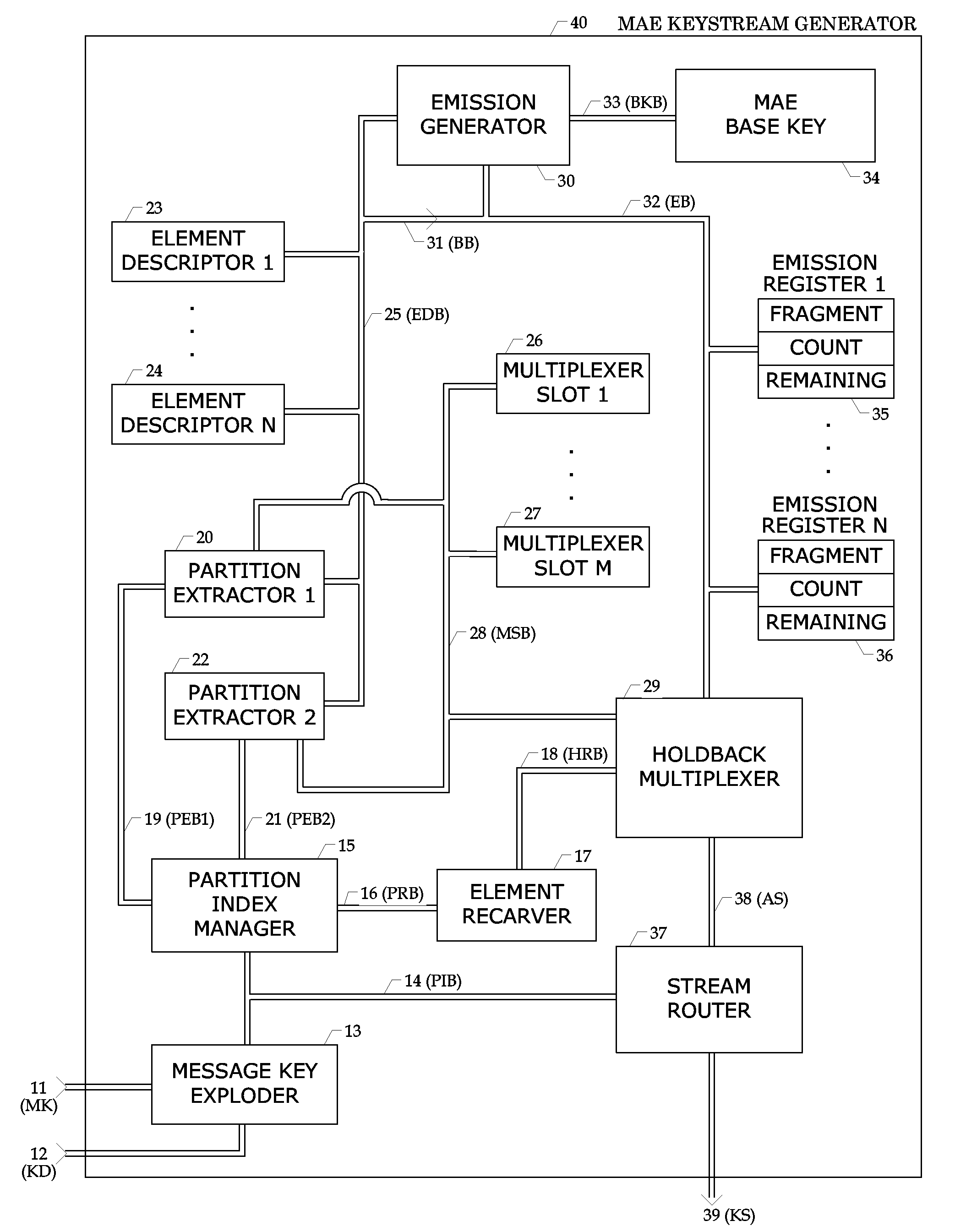
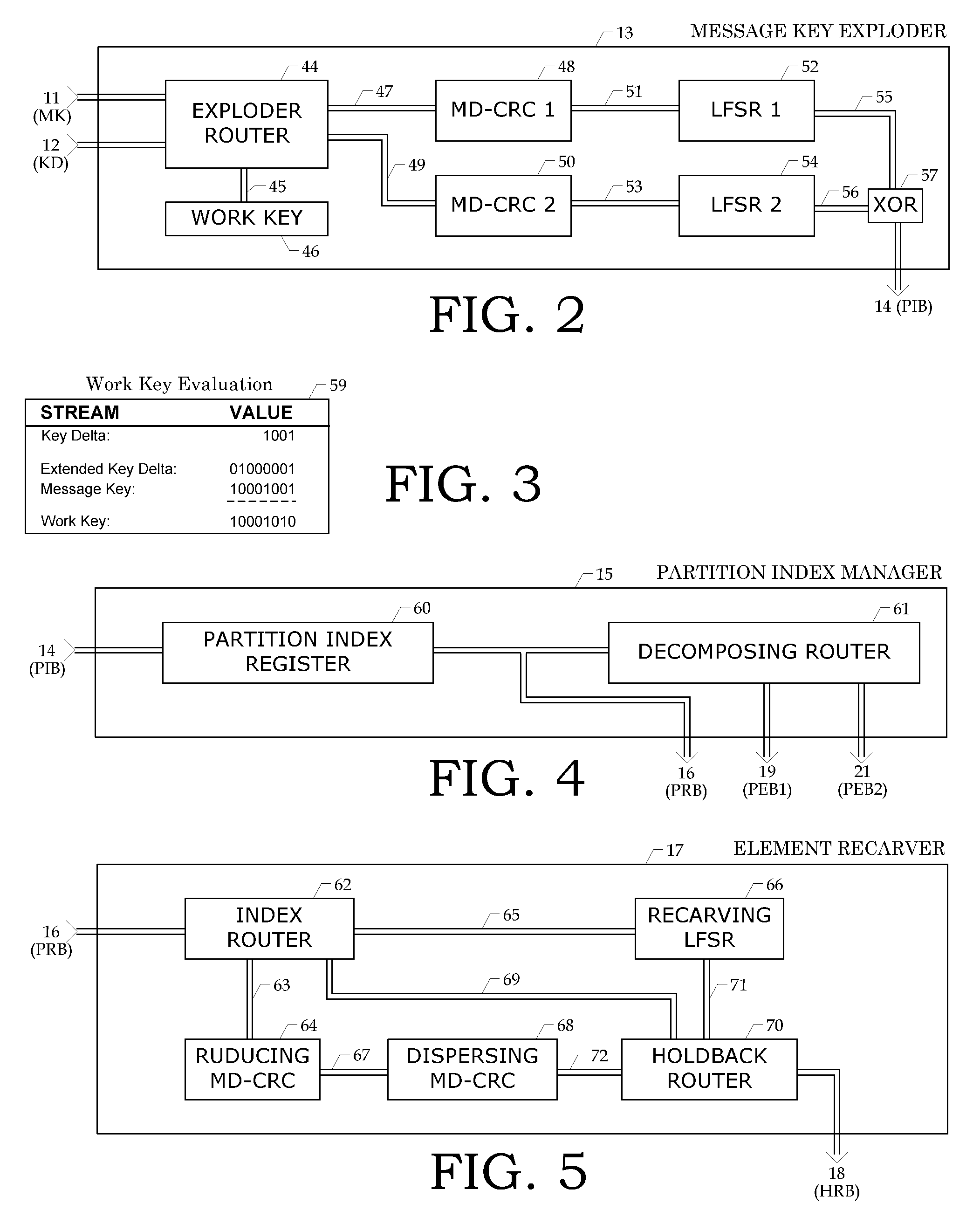
A cryptographically secure keystream generating process includes an expanding amorphous process. A seed key is expanded into a partition index that is carved into elements (parameters) by a parallelizable process. A dispersing value is derived from the partition index to de-cluster subsequent partition indexes. The process operates with constant entropy by “recarving” elements and employs block holdbacks for increased variance during multiplexing. Internal emissions are derived from the amorphous process itself, which provide secure random sources for subsequent use within the keystream generation process. Seed key expansion and dispersing value computation both use cyclic redundancy code evaluation employing multiple polynomials. A public (mono) base key family is defined with three preferred modes, two of which are specialized for software implementation. Two private base key embodiments are included that constantly morph the base key.
Owner:DEGELE STEVEN
Digital image feedback encryption method based on image network
ActiveCN107220923AIncreased complexityStrong pseudo-randomnessImage data processing detailsPlaintextDiffusion
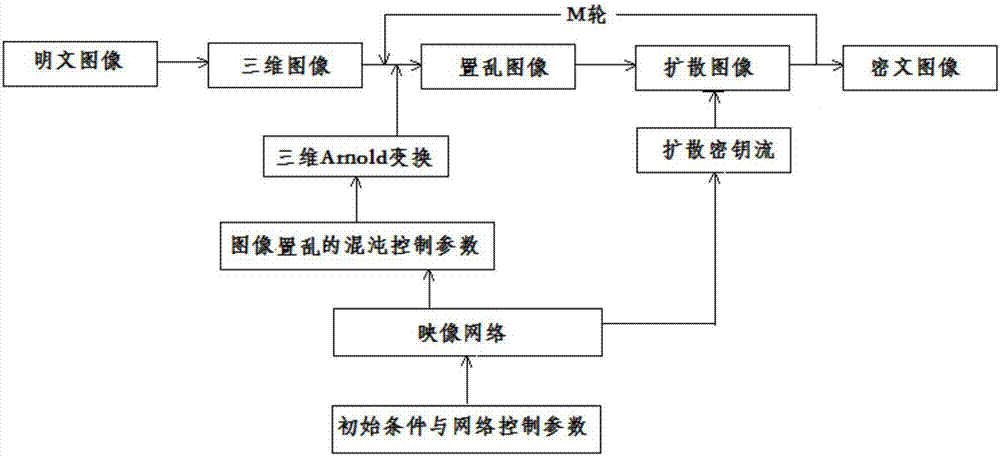
The invention discloses a digital image feedback encryption method based on an image network. The method comprises the following steps of processing a digital plaintext image; constructing the image network in which a node is a super-chaotic system and a non-neighbor connection mode is possessed; through three-dimensional Arnold, converting a scrambling image, wherein a scrambling matrix is driven by image-network space-time chaotic display and a current plaintext image; combining feedback information of the current plaintext image and a cryptograph image and carrying out image diffusion processing; alternatively operating scrambling and diffusion multiple times and acquiring the cryptograph image. In an encryption system, a scrambling-diffusion alternative-operated loop iteration structure is designed; during an encryption process, plaintext and cryptograph feedback mechanisms are introduced; and during each encryption, the used scrambling matrix and a secret key flow are dynamically changed and are different. An experiment result shows that the encryption method possesses high safety and high efficiency; and a capability of resisting various plaintext attacks, statistics attacks, violence attacks and difference attacks is high.
Owner:SHAANXI NORMAL UNIV
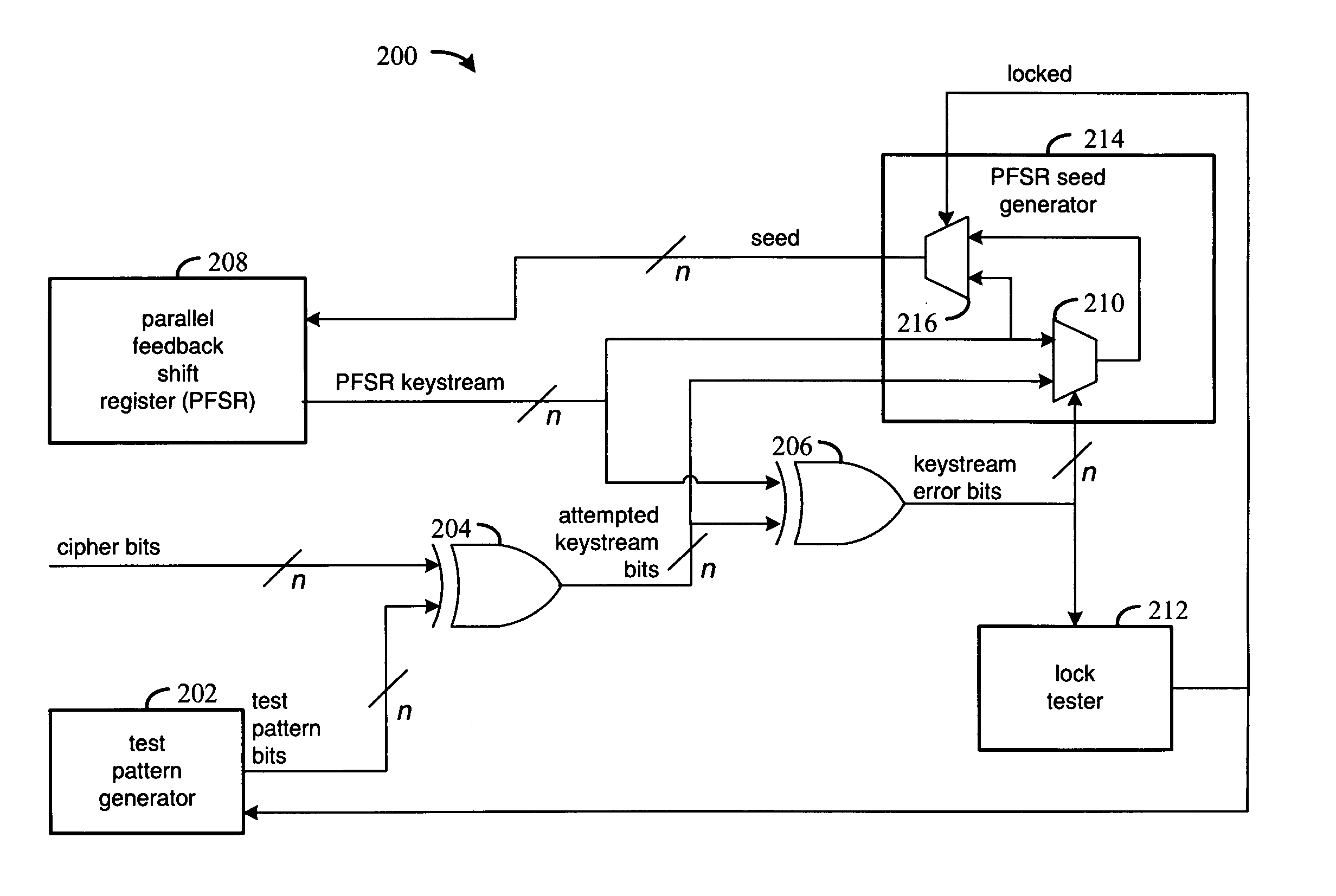
Parallel keystream decoder
ActiveUS7092906B1Data stream serial/continuous modificationComputer security arrangementsShift registerKeystream
Methods and circuitry are disclosed for decoding a keystream. A set of test bits is generated, and a set of attempted keystream bits are generated from differences between the test bits and an input set of cipher bits. A set of current keystream bits are generated from a current seed using a parallel feedback shift register, and the attempted keystream bits are compared to the current keystream bits. In response to attempted keystream bits being equal to the current keystream bits, the current keystream bits are fed back as a new current seed. In response to attempted keystream bits being not equal to the current keystream bits, the attempted keystream bits are fed back as the new current seed.
Owner:XILINX INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com