Color image lossless encryption method on basis of two-dimensional discrete wavelet transform and spatiotemporal chaos
A two-dimensional discrete wavelet, spatiotemporal chaotic technology, applied in image data processing, image data processing, instruments, etc., can solve problems such as weak security, complex data format and representation, and perception degradation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
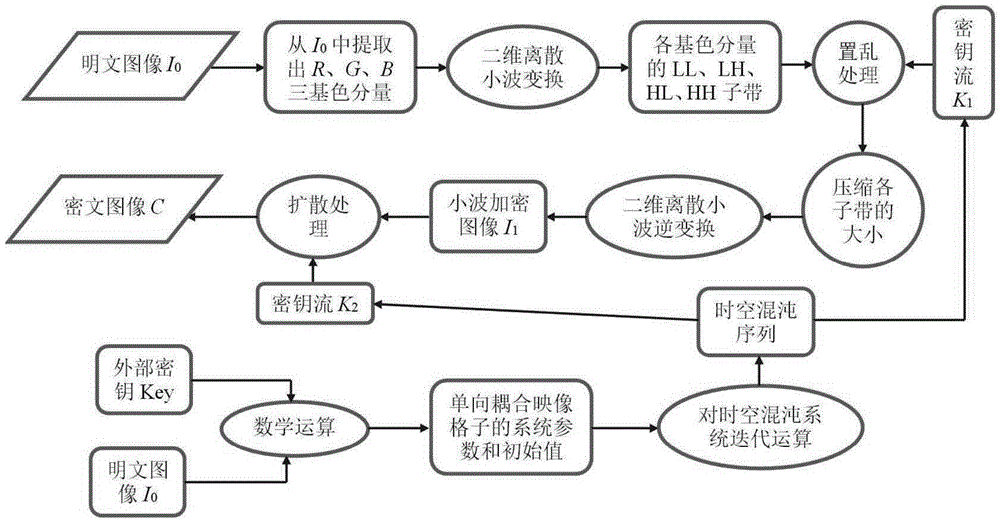
[0068] Embodiment one, see figure 1 As shown, a color image lossless encryption method based on two-dimensional discrete wavelet transform and space-time chaos includes the following steps:
[0069] Step 1. Input a color plaintext image I of size W×H 0 , separating the image I 0 The three primary color components of R, G, and B, get a component matrix IR with a size of W×H 0 , IG 0 and IB 0 ;
[0070] Step 2. Utilize the external key Key, and according to the plaintext image I 0 , to generate the system parameters and initial values of the one-way coupling map grid, and perform iterative operations on the space-time chaotic system to obtain the key stream K 1 and K 2 ;
[0071] Step 3. To the component matrix IR 0 , IG 0 and IB 0 Carry out two-dimensional discrete wavelet transform respectively to obtain subband groups with size m×n: {LL11, LH11, HL11, HH11}, {LL21, LH21, HL21, HH21} and {LL31, LH31, HL31, HH31}, each The subband group includes a low frequency su...
Embodiment 2
[0077] Embodiment 2 is basically the same as Embodiment 1, the difference is that in step 2, the iterative operation of the space-time chaotic system is performed using the following steps to obtain the key stream K 1 and K 2 :
[0078] Step 2.1. Set the length of the external key Key to 320 bits, and divide it into 40 blocks equally, that is, Key=B 1 B 2 B 3 …B 40 , according to the one-way coupled mapping lattice x n + 1 ( i ) = ( 1 - a ) [ 1 - ϵ x n 2 ( i ) ] + a [ 2 - ϵ x n 2 ( i ...
Embodiment 3
[0091] The third embodiment is basically the same as the second embodiment, the difference is: the system parameters a and ε and the initial value x in the step 2.1 k (0)(k=1,2,...,6) is calculated using the following formula:
[0092] x 1 ( 0 ) = mod ( ( B 1 ⊕ B 2 ⊕ B 3 ⊕ B 4 ⊕ B 5 + Σ i = 1 W / 2 Σ ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com