SM2-based multi-receiver public key encryption method
A public key encryption and receiver technology, applied in the field of information security, can solve the problems of low encryption efficiency and high communication bandwidth requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
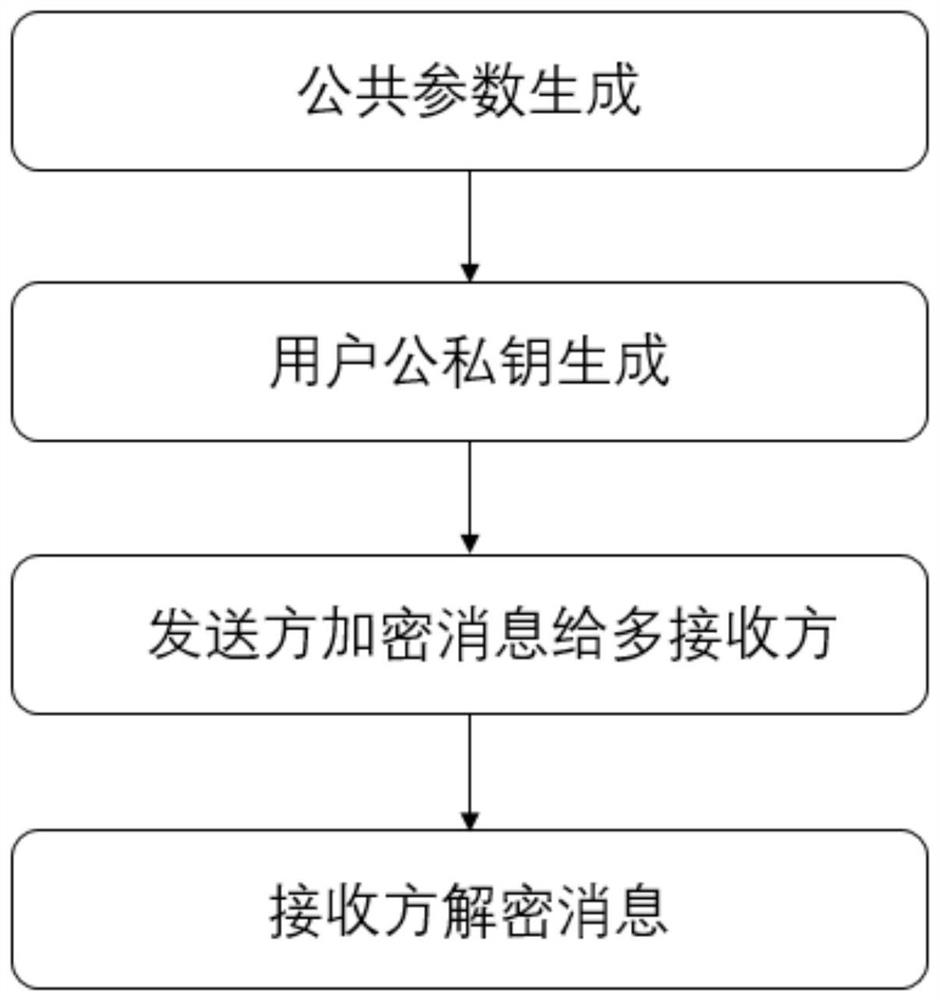
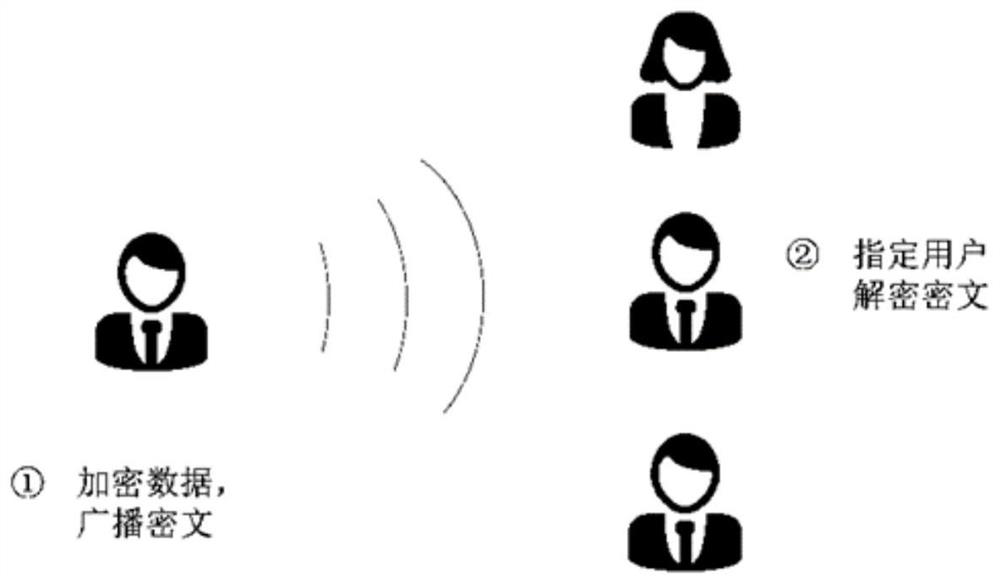
[0022] The SM2-based multi-recipient public key encryption method disclosed by the invention can be applied in the technical field of information security to encrypt and protect data. For example, when the sender needs to send secret information to multiple receivers in a one-to-many manner, the present invention can be used to encrypt the relevant data into ciphertext and broadcast it to multiple receivers. Each recipient obtains the corresponding ciphertext, and relies on its own private key to perform decryption operations to obtain the corresponding secret information, so as to carry out safe data sharing on the premise of ensuring user data security and efficiency.
[0023] Combine below figure 1 The specific process of an SM2-based multi-receiver public key encryption method disclosed in this embodiment will be described in detail.
[0024] A multi-recipient public key encryption method based on SM2 (the use case is shown as figure 2 shown), which mainly includes two ...
Embodiment 2
[0030] An SM2-based multi-recipient public key encryption method disclosed in the present invention can be applied to data encryption protection on a block chain. For example, in the blockchain system of the financial industry, users only want to share asset information and asset transaction information with some designated partners for commercial sharing. The present invention can be used to encrypt relevant data and then broadcast and upload it to the blockchain system. Each partner, as the recipient, obtains the corresponding user's ciphertext on the blockchain, and relies on its own private key to decrypt the operation to obtain the user's asset information, so as to carry out safe data sharing on the premise of ensuring the security of user data.
[0031] Combine below figure 1 The specific process of an SM2-based multi-receiver public key encryption method disclosed in this embodiment will be described in detail.
[0032] A multi-recipient public key encryption method b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com