Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35results about How to "Address security flaws" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for constructing certificateless public key cryptography
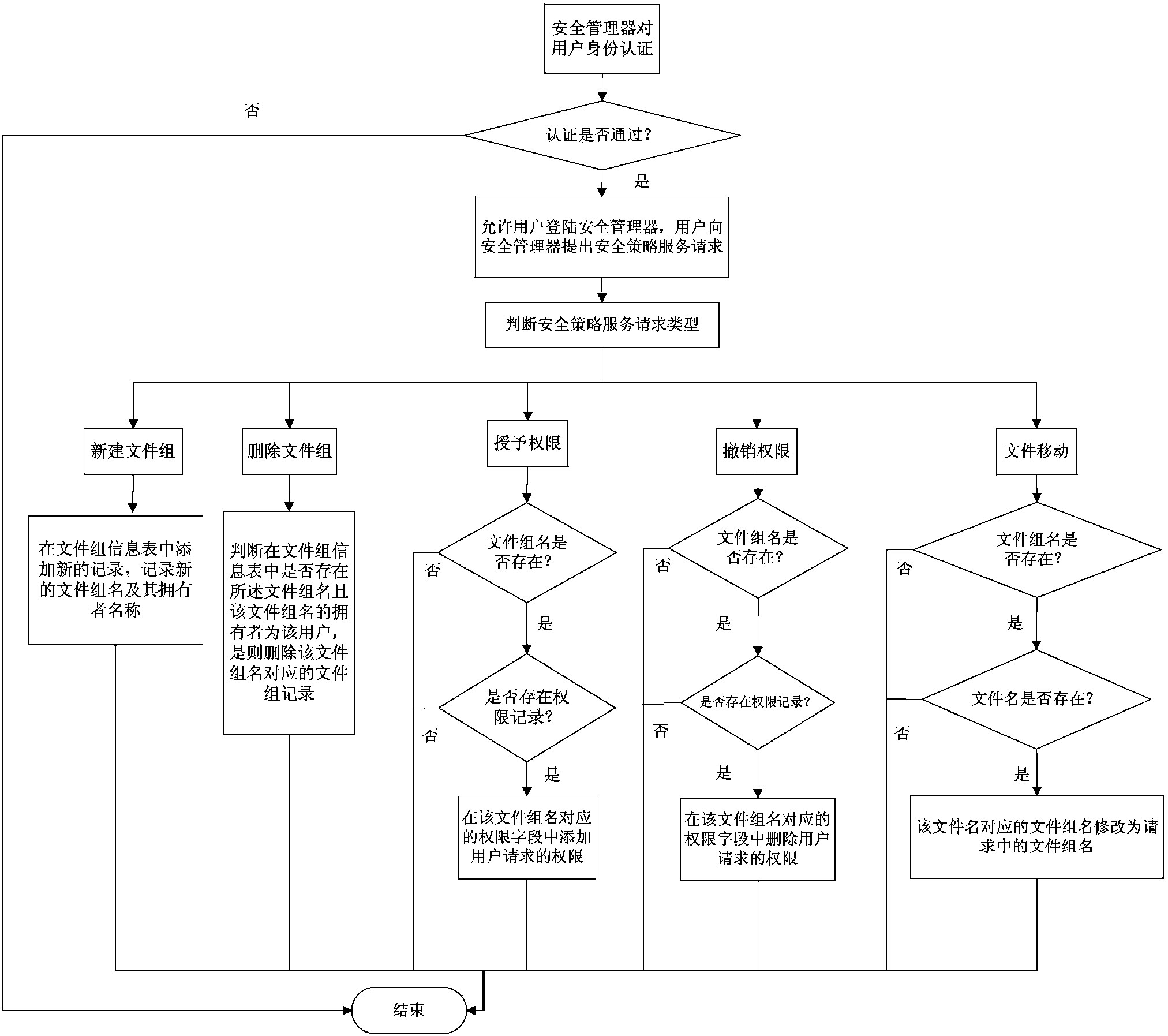
InactiveCN102201920AAddress security flawsImprove securityPublic key for secure communicationUser identity/authority verificationValidation methodsKey generation
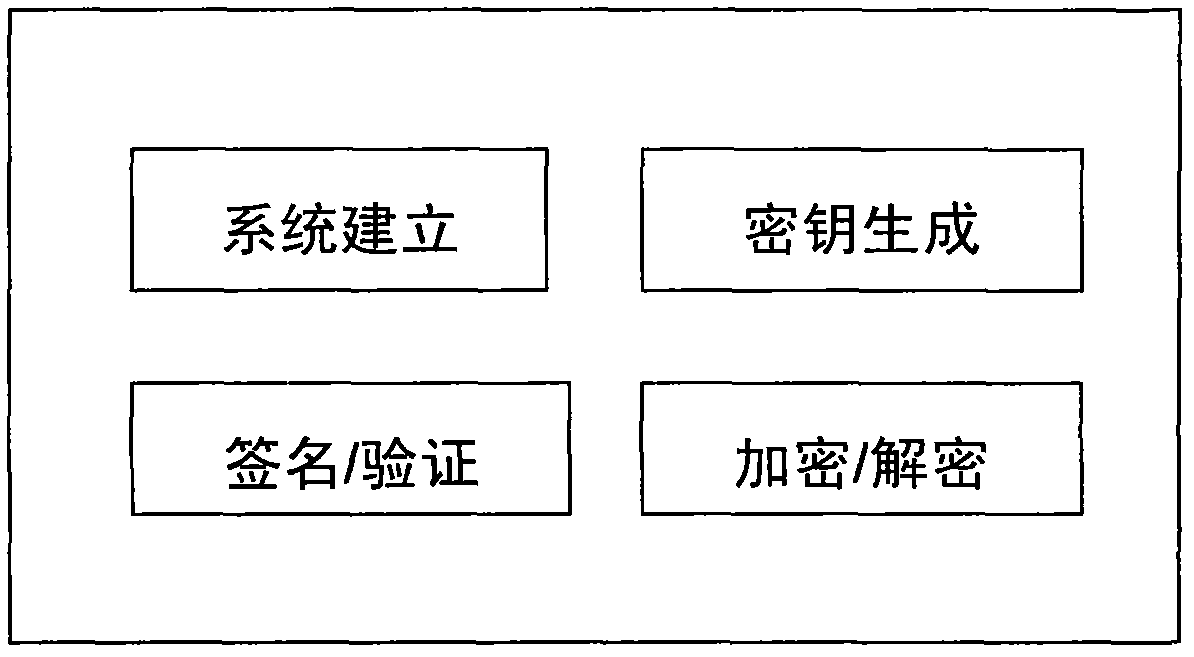
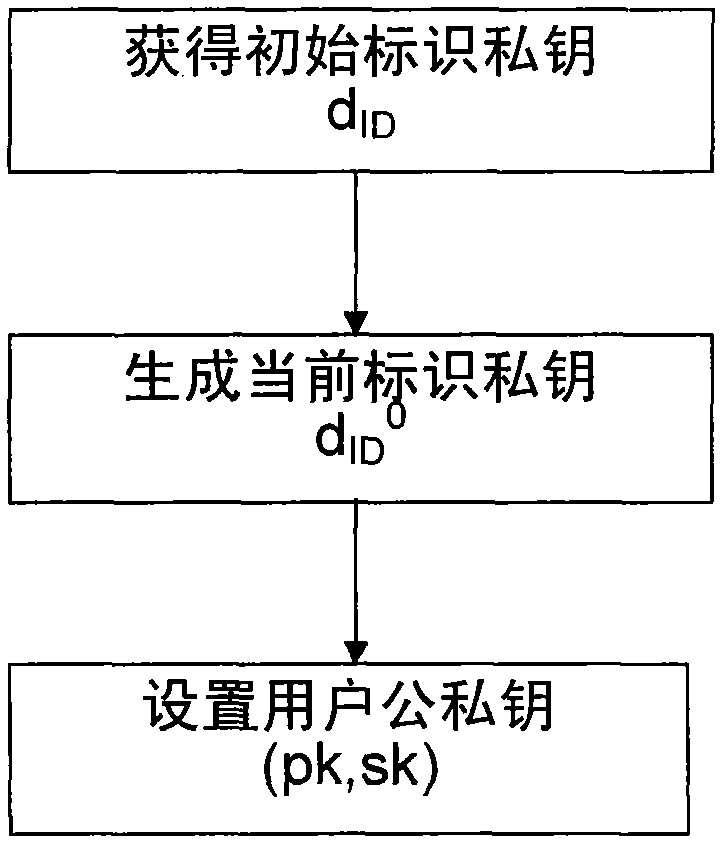
The invention discloses a method for constructing a certificateless public key cryptography, which aims to solve the problem of private key hosting of an identification cryptography. Compared with other similar methods, the method is universal, and signature and encryption schemes with relatively higher security can be easily obtained by the construction method. The method comprises a system establishment method, a key generation method, a signature and verification method and an encryption and decryption method. In the system establishment method, an unlinkable randomizable signature is utilized. The key generation method comprises an initial identification private key obtaining step, a current identification private key generation step, a user public and private key setting step and thelike. The signature and verification method comprises a temporary identification private key generation step, a signature generation step, a signature verification step and the like. The encryption and decryption method comprises a public key acquisition and encryption step, a step of performing decryption by utilizing a corresponding private key, and the like.
Owner:北京中兴通德科技创新有限公司
Distributed storage system and file sharing method thereof
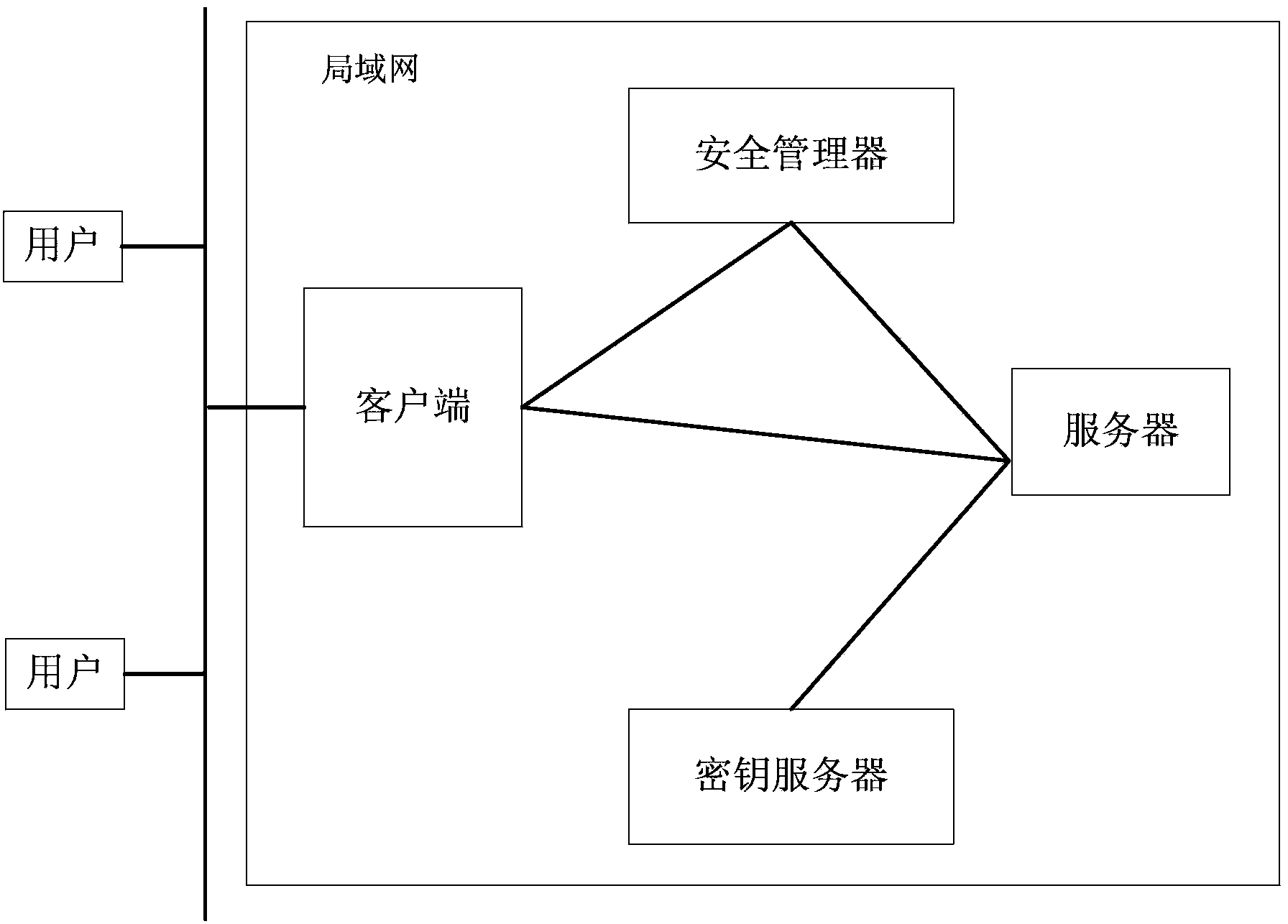
ActiveCN102821096AEliminate potential safety hazardsOvercoming the problem of excessive sharing overheadTransmissionClient-sidePOSIX
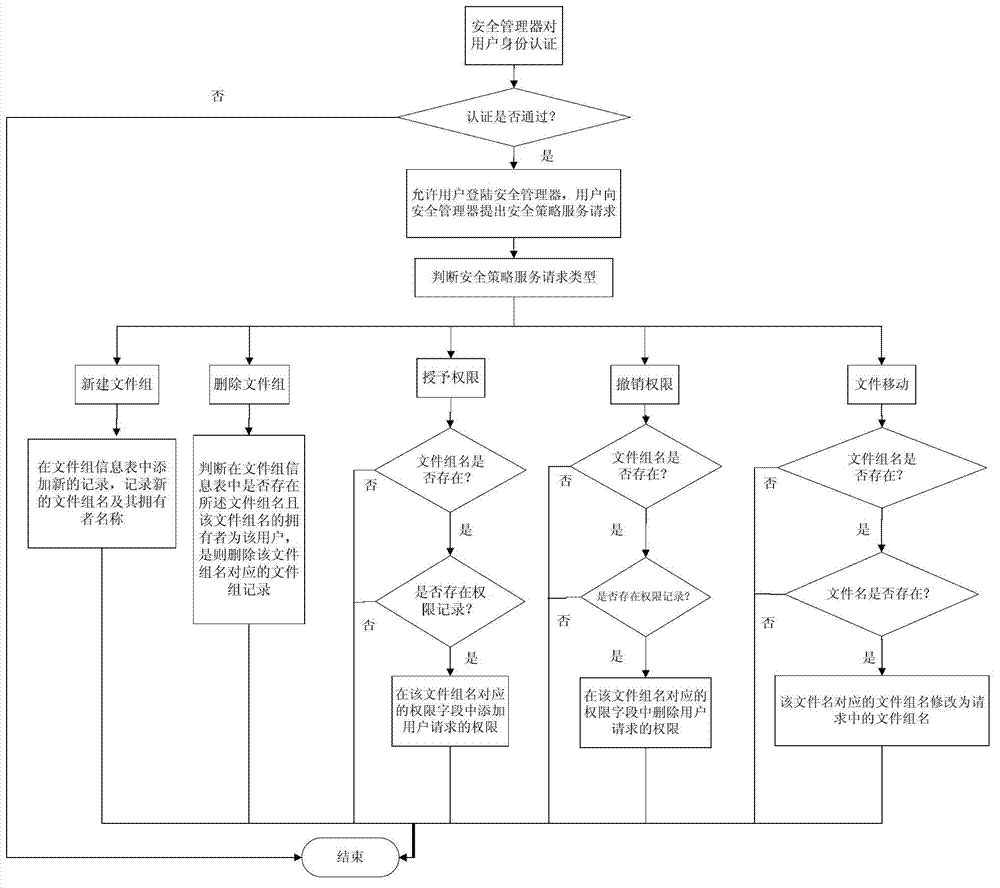
The invention discloses a distributed storage system and a file sharing method thereof, belonging to the technical field of computer memory and information security; the distributed storage system solves the problems that the existing secure storage system has complicated key management and the encrypt file has too large cost for sharing. The distributed storage system comprises a client, a server, a security manager and a key server and is established on the operation system for supporting the POSIX interface; the client is connected with the security manager and the key server respectively through the local area network. The distributed storage system sets the special key server management key, and the security manager only manages the file key number, so that the security defect and large file re-encryption cost caused by directly or indirectly exposing the file key to the share use are avoided, and the security and whole performance of the system are improved; the distributed storage system and the file sharing method effectively solve the problems that the key management is complicated, and the encrypt file has too large sharing load, and the distributed storage system is suitable for constructing the security storage system with large scale and high performance.
Owner:HUAZHONG UNIV OF SCI & TECH
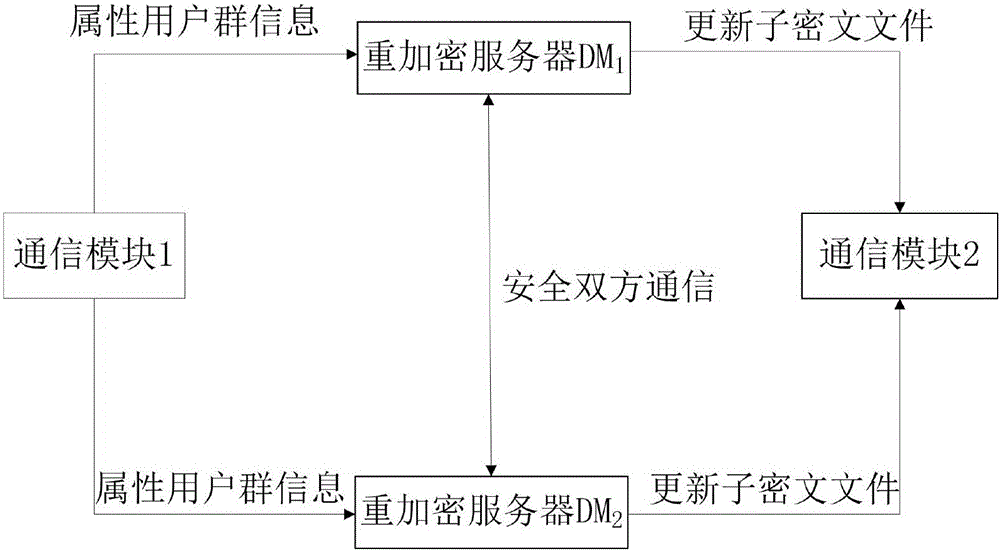
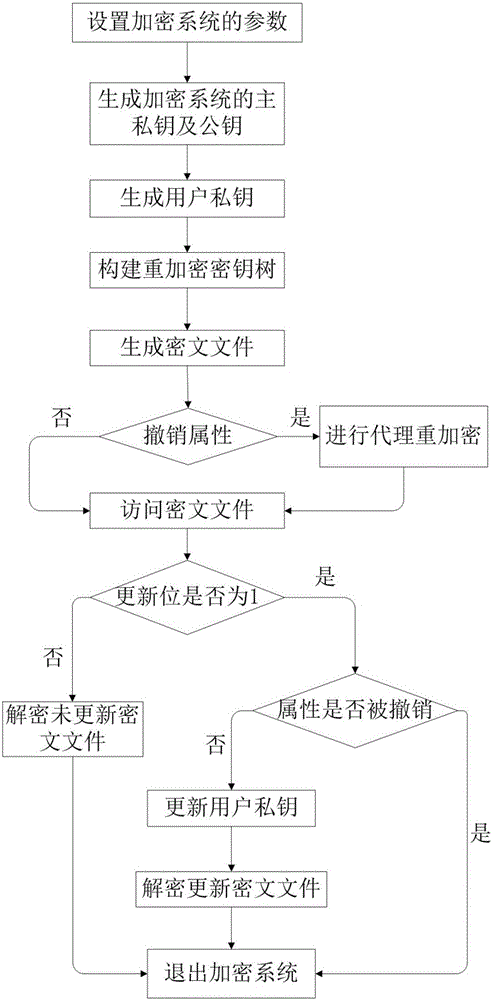
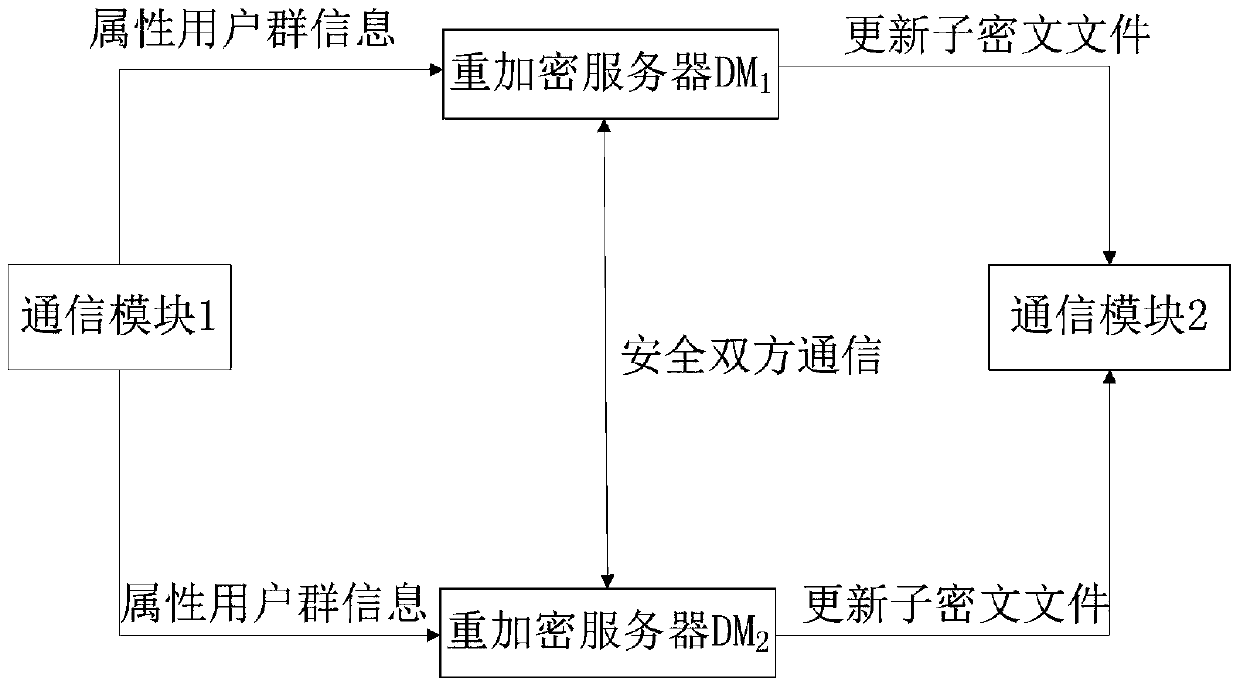
Encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes
ActiveCN106059768ALeak resistanceOvercoming property revocation flawsKey distribution for secure communicationPublic key for secure communicationCiphertextDisk encryption
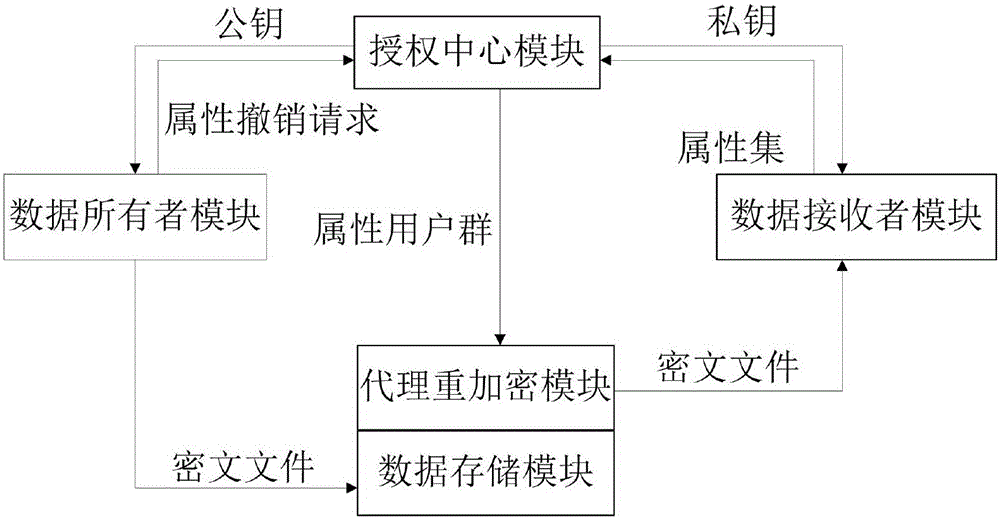
The present invention provides an encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes. The method comprises: 1, setting the parameters of an encryption system; 2, generating the main private key and the public key of the encryption system; 3, generating a user private key; 4, building a re-encryption key tree; 5, generating a cryptograph file; 6, cancelling attributes; 7, performing re-encryption agency; 8, accessing the cryptograph file; 9, determining whether the update position of the cryptograph file is 1 or not; 10, decrypting an un-updating cryptograph file; 11, updating the private key; 12, decrypting the update cryptograph file; and 13, quitting the encryption system. Through adoption of a dual-agency re-encryption server model, the encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes can resist the leakage of the re-encryption key. When the attributes are cancelled, an attribute user group is employed to construct the re-encryption key tree so as to effectively, timely and accurately cancel the indirect attributes. When the encryption is performed, the secret is dispersed to resist the conspiracy attack.
Owner:XIDIAN UNIV
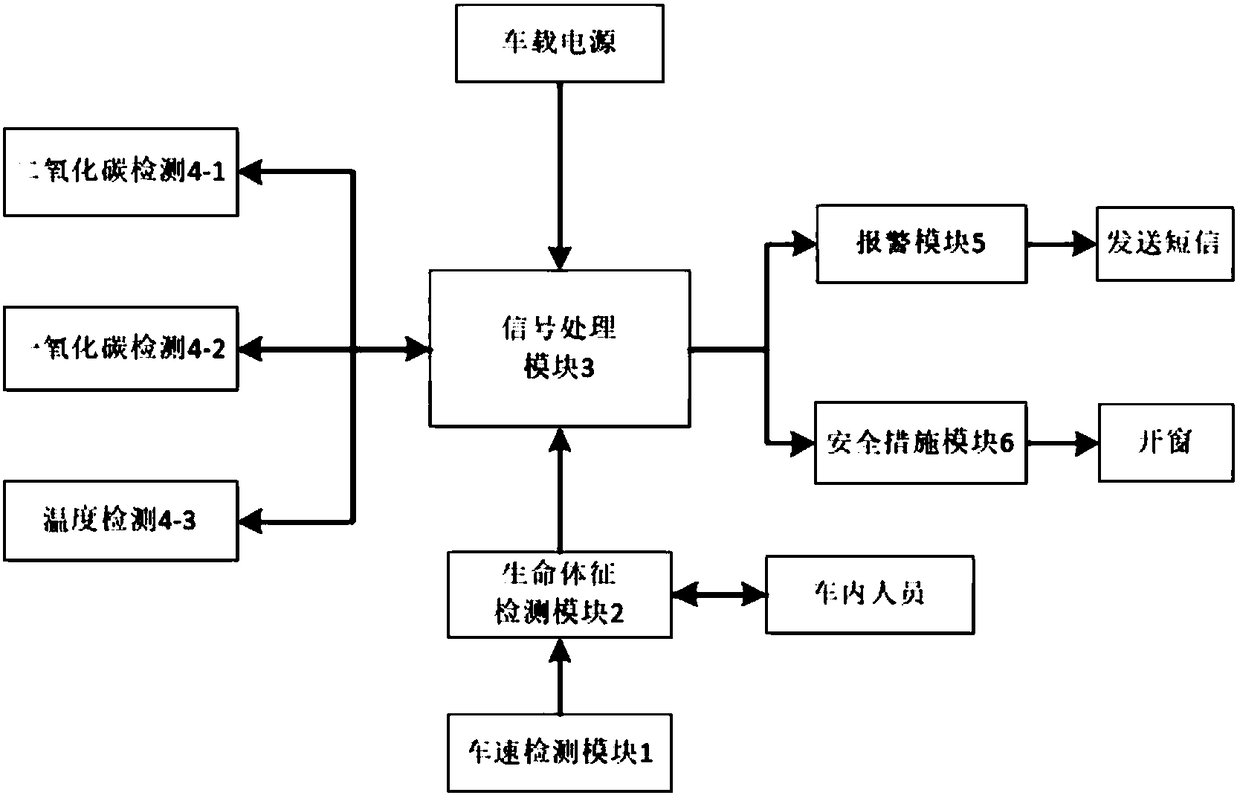
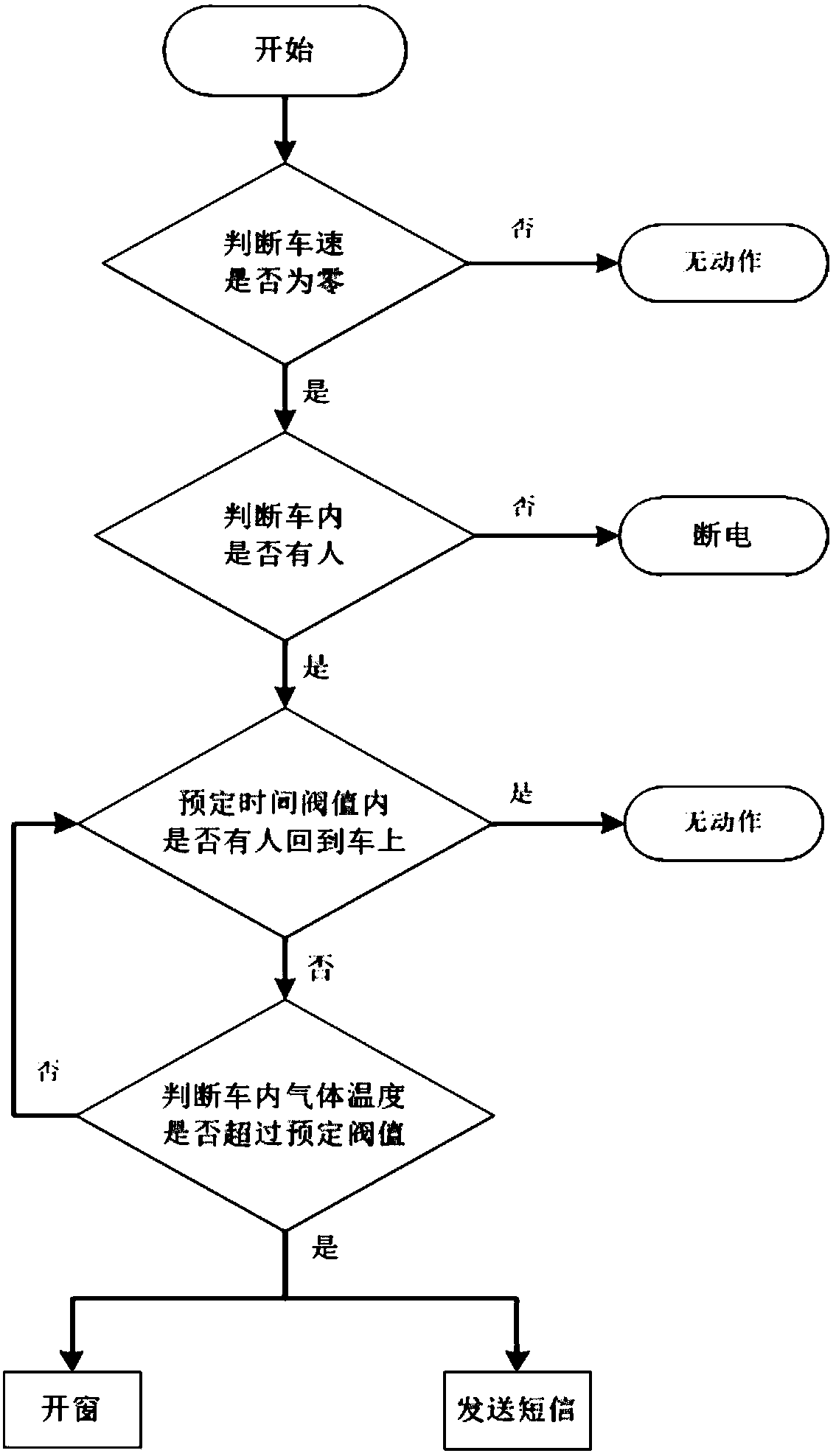
Asphyxia prevention intelligent control system for automobile
InactiveCN108549282AAddress security flawsAvoid choking incidentsProgramme controlMeasurement devicesAlarm messageVital sign detection
The invention discloses an asphyxia prevention intelligent control system for an automobile, and the system is an intelligent control device for preventing a child from being asphyxial when the childstays and sleeps in the automobile while an air conditioner of the automobile is turned on during parking. The control system includes a vehicle speed detecting module, a vital sign detecting module,an air temperature detecting module, a signal processing module, an alarm module, and a safety measure module. When the vehicle speed detecting module detects that a vehicle speed is zero, the vital sign detecting module starts to detect whether there is a person in the vehicle or not. When detecting a person in the vehicle, the gas temperature detecting module monitors the oxygen and carbon dioxide contents and temperature in the vehicle in real time if a vehicle owner does not come back within a preset time threshold. The signal processing module processes the information collected by the air temperature collecting module and judges whether the alarm module is activated to send an alarm message and the safety measure module opens a window or not. The system can effectively prevent the occurrence of asphyxia events.
Owner:ANHUI UNIV OF SCI & TECH
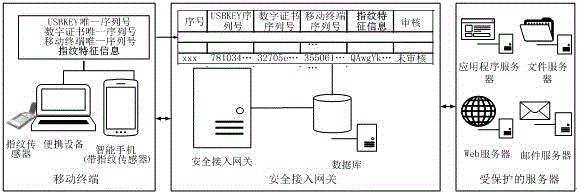
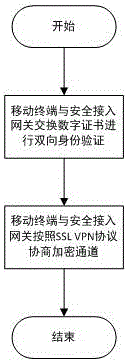
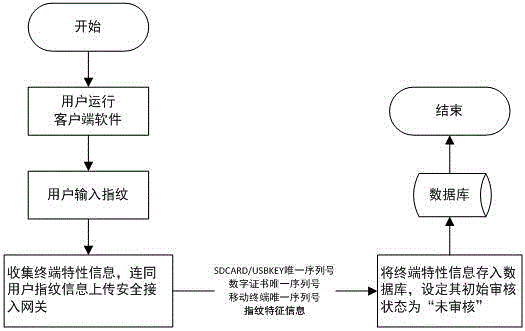
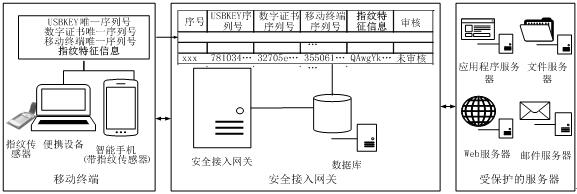
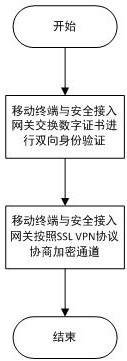
Mobile terminal safety access authentication method in combination with fingerprint
ActiveCN106488452APrevent unauthorized accessEnsure safetyDigital data authenticationSecurity arrangementIdentity recognitionInformation access
The invention provides a mobile terminal safety access authentication method in combination with fingerprint. The method comprises the four steps of establishing an encryption channel, user registering, user information checking and user business accessing. A client collects terminal feature information which comprises a USBKEY sequence number, a digital certificate sequence number, a mobile terminal sequence number and user fingerprint feature information, and the terminal feature information is uploaded to a safety access gateway through the encryption channel; the safety access gateway verifies the integrity and validity of the terminal information, and decides whether the terminal can access a protected server according to a verification result. The fingerprint recognition technology is combined with the traditional identity recognition mode, so that the medium for marking the identity is directly related to the natural person, the identity recognition and the recognized person are really corresponding to each other, the security level of the mobile terminal information access is effectively improved, and the convenient mobile technology can be facilitated to play effect in the information application.
Owner:JIANGSU ELECTRIC POWER CO +1
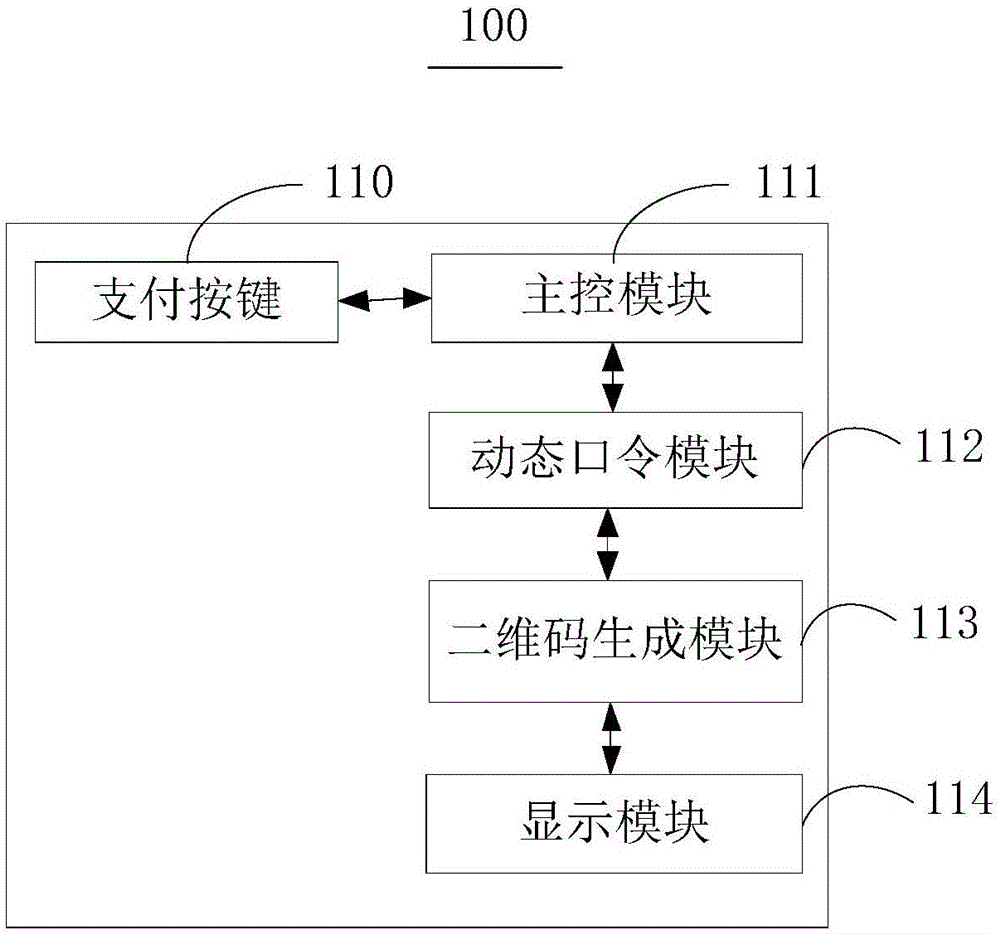
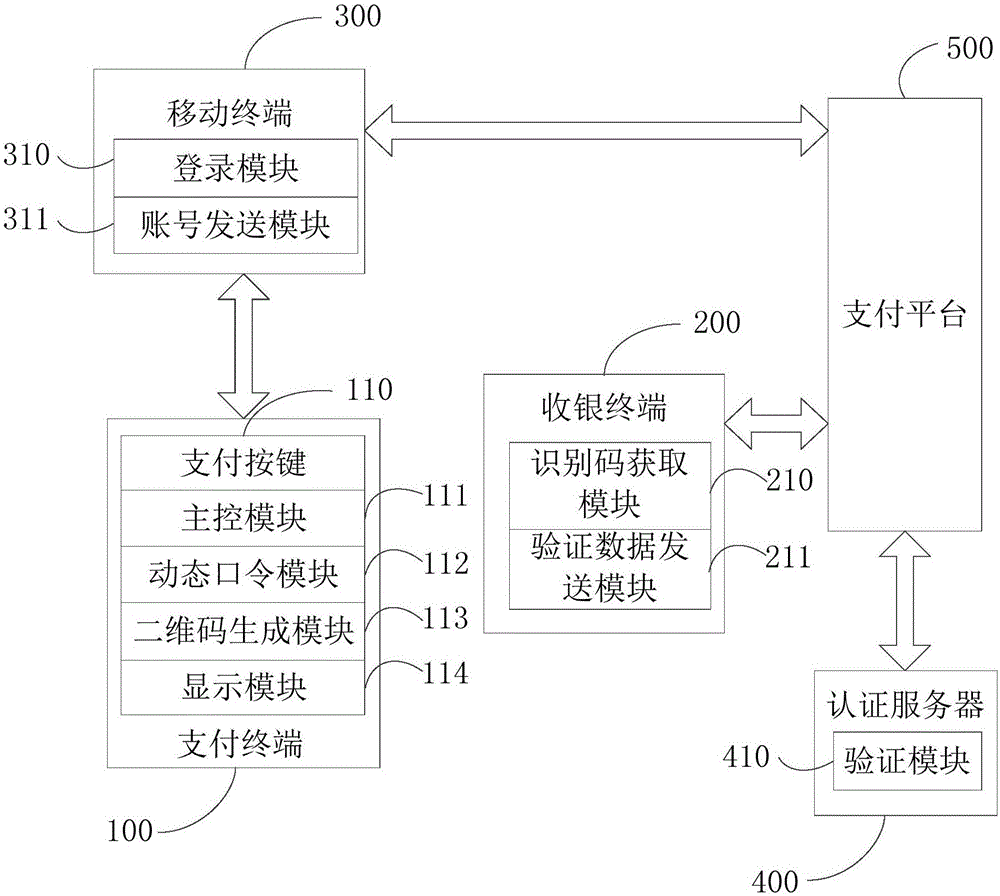
Payment terminal, system and method
InactiveCN106651378AAvoid dependenceImprove experienceProtocol authorisationPasswordComputer terminal
The embodiment of the invention provides a payment terminal, system and method. In one embodiment, the payment terminal comprises a dynamic password module and a two-dimensional code generation module. The dynamic password module is used for generating a dynamic authentication password when payment operations of a user are received. The two-dimensional code generation module is used for generating and displaying a payment identification code according to the dynamic authentication password and prestored payment account number information. When receiving the payment identification code, a cashier terminal analyzes the payment identification code, obtains verification data and sends the data to a payment platform, and the data is sent to an authentication server through the payment platform. The authentication server receives and verifies the verification data, and returns a verification result to the payment platform, so that the payment platform returns a corresponding payment result to the payment terminal according to the verification result. The security of payment of the terminal is improved.
Owner:BEIJING SUMAVISION PAYMENT TECH CO LTD
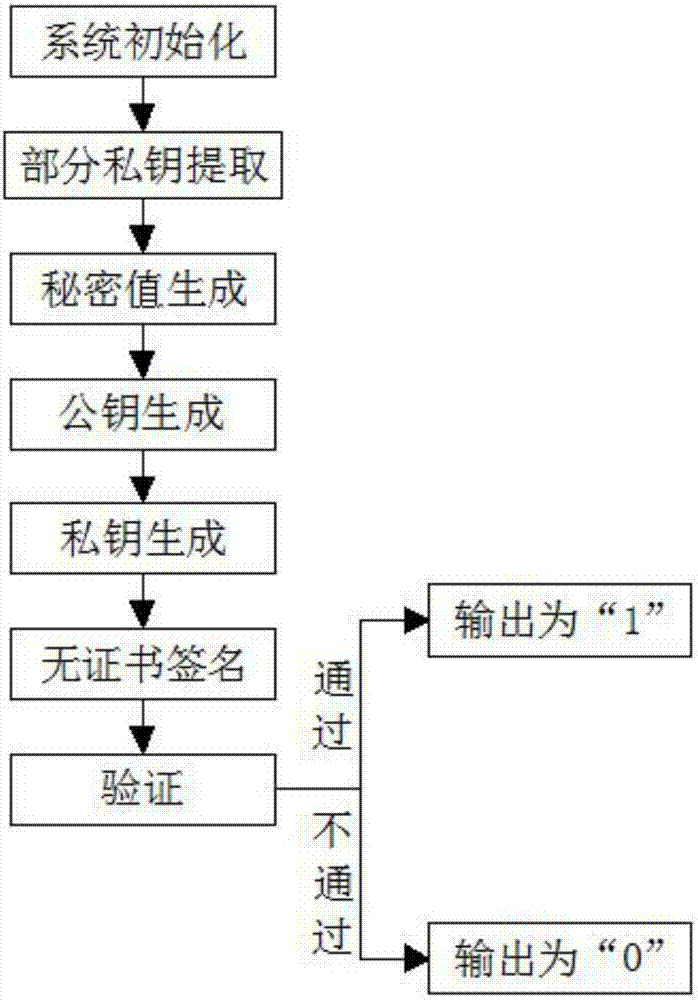
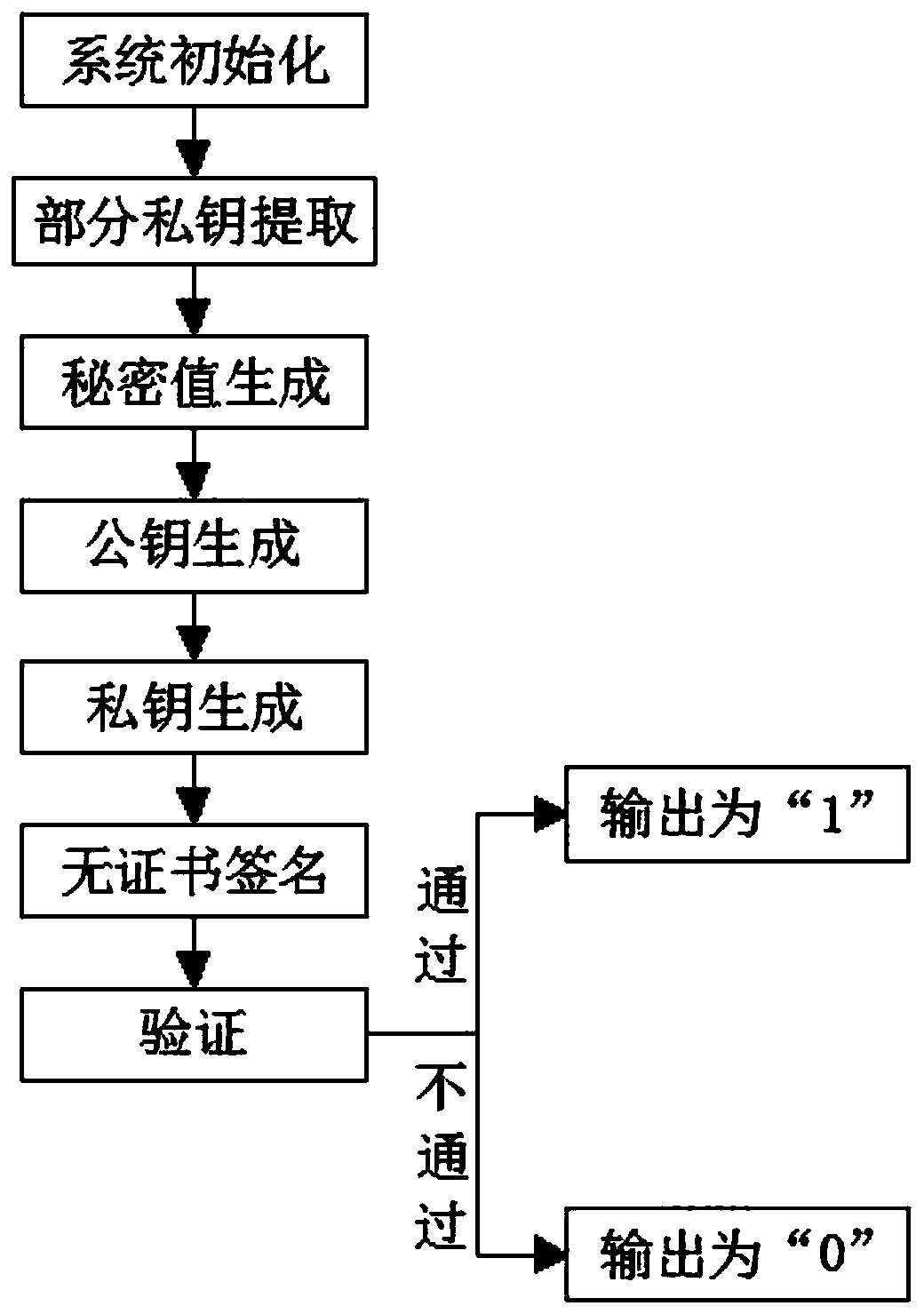
Construction method of certificateless public key cryptosystem
ActiveCN106936584AAddress security flawsImprove securityPublic key for secure communicationUser identity/authority verificationKey escrowInformation security
The invention discloses a construction method of a certificateless public key cryptosystem which belongs to the technical field of information security. The construction method of a certificateless public key cryptosystem comprises the following steps: S1, initializing a system; S2, picking up part of a private key; S3, generating a secret value; S4, generating a public key; S5, generating a private key; S6, performing certificateless signature; and S7, verifying. According to the invention, a certificateless signature system is adopted, when a signature verifier verifies a signature, the condition that the validity of a public key of a signer is needed to be verified in the traditional public key cryptosystem is avoided, so the method is free from a key escrow problem existing in a cryptosystem based on identity. Therefore, a security defect of the private key escrow of the identification cryptosystem can be solved and a better safety performance is realized.
Owner:PINGDINGSHAN UNIVERSITY
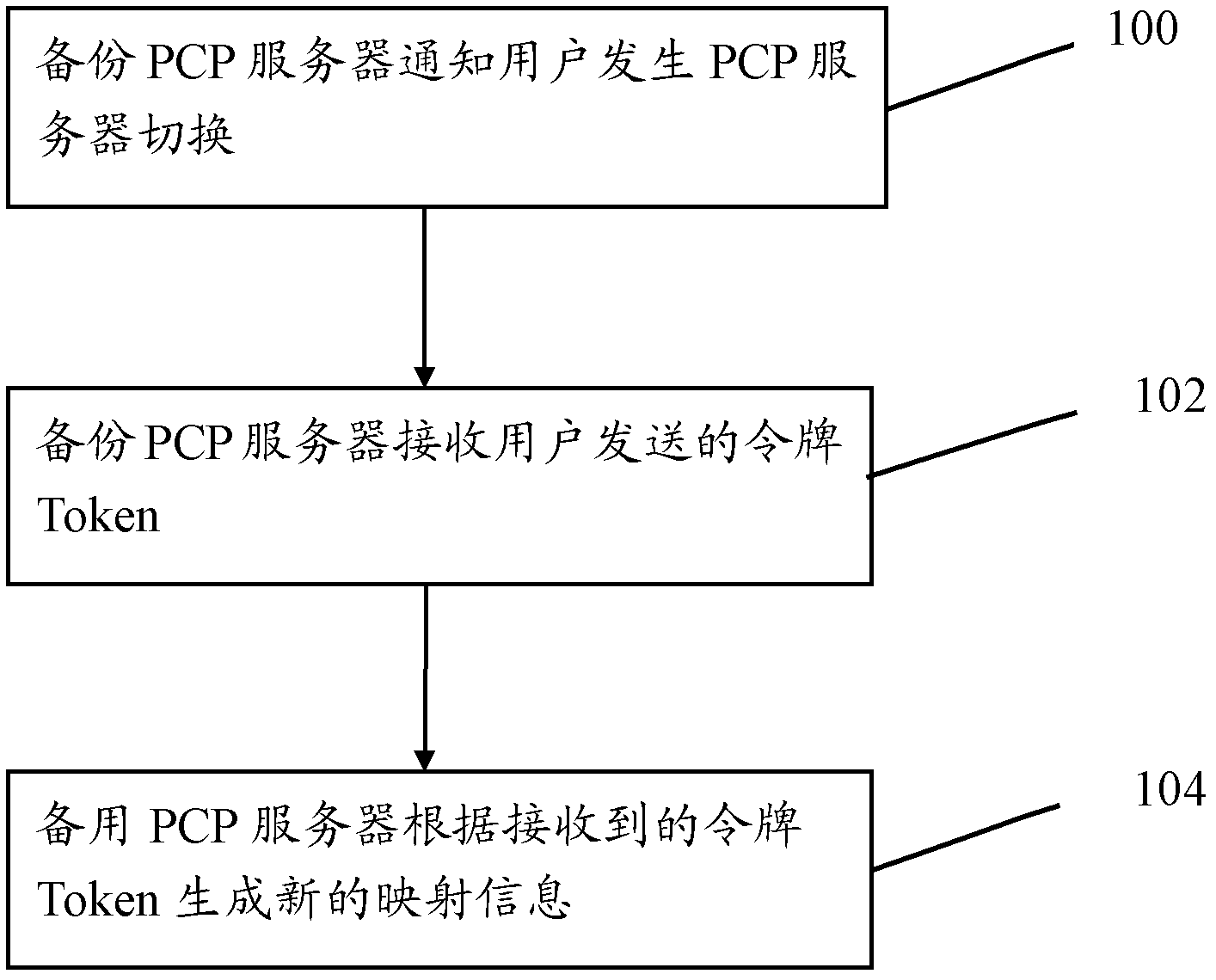
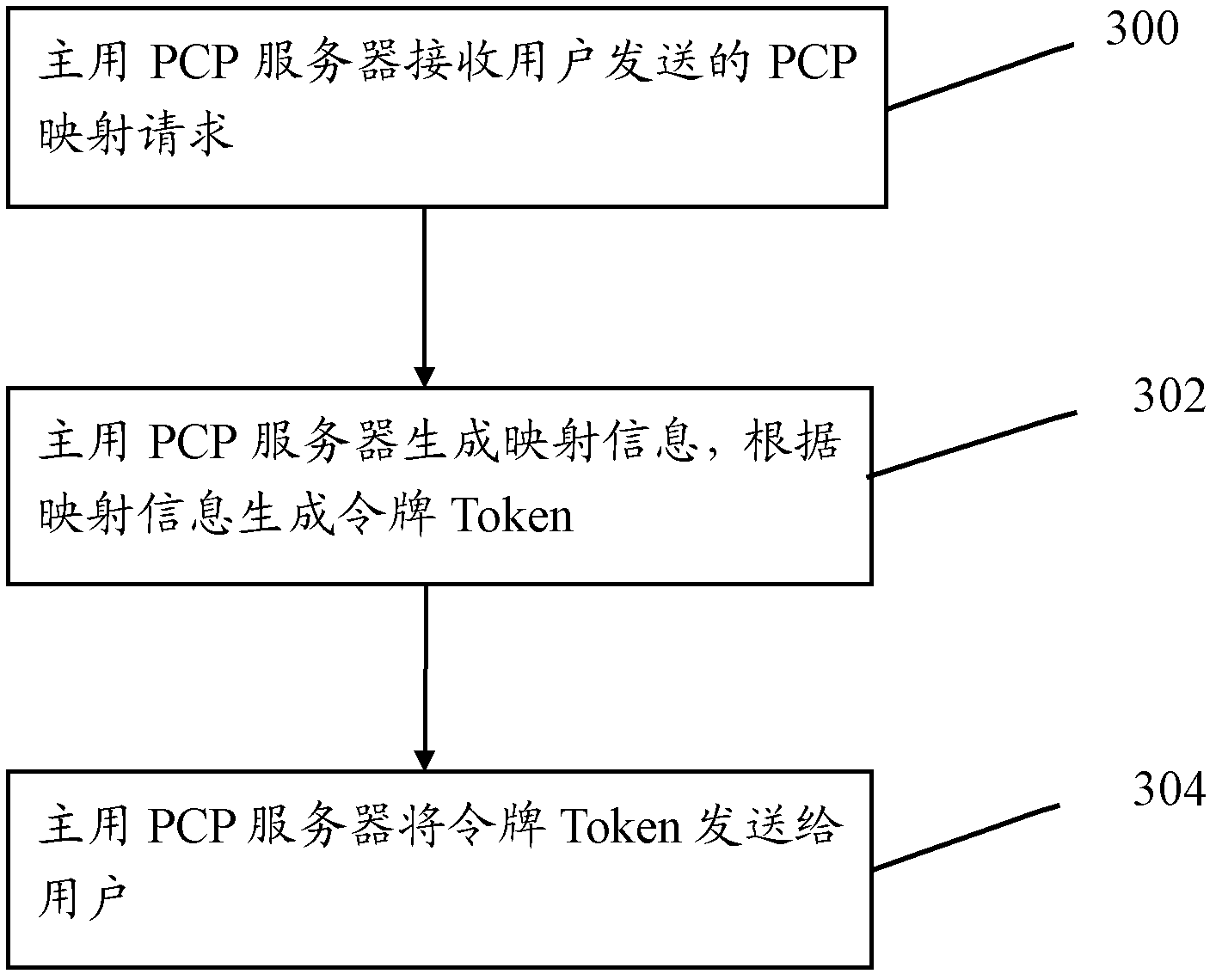
Method and device for rapidly recovering port control protocol
ActiveCN102611571AAddress security flawsKey distribution for secure communicationUser identity/authority verificationRTP Control ProtocolPort Control Protocol
The embodiment of the invention provides a method for rapidly recovering a port control protocol, which comprises the following steps that: a backup primary control program (PCP) server notifies a user to switch a PCP server; and the backup PCP server receives a Token sent by the user and generates new mapping information according to the received Token. According to the technical scheme provided by the embodiment of the invention, the Token is used to validate the identity validity of the user while the rapid PCP recovery is carried out, so that a main backup PCP server can complete the rapid switching safely and reliably; and the communication service of the user can be guaranteed to carry out normally.
Owner:泰州市海通资产管理有限公司
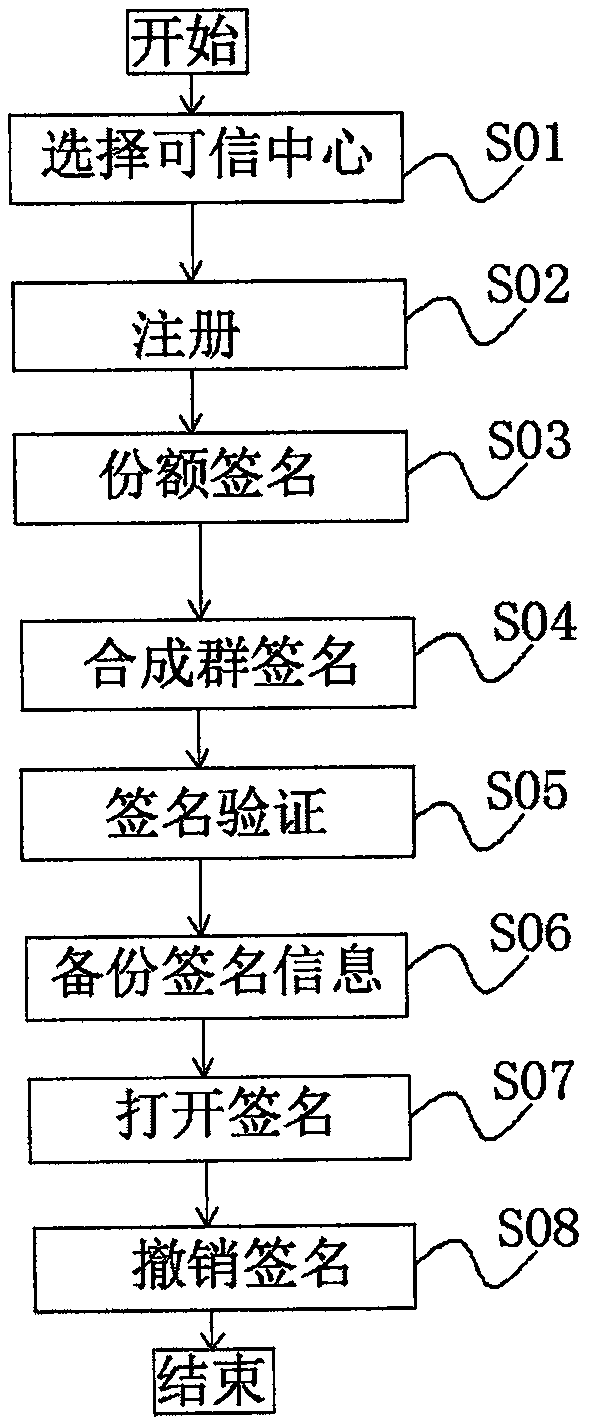
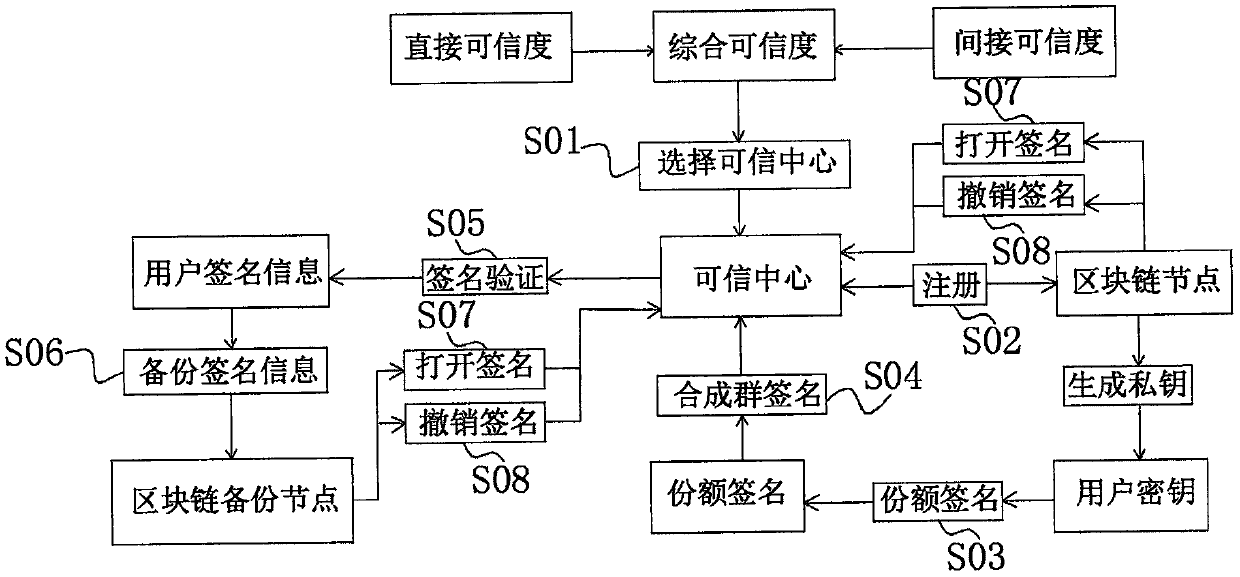
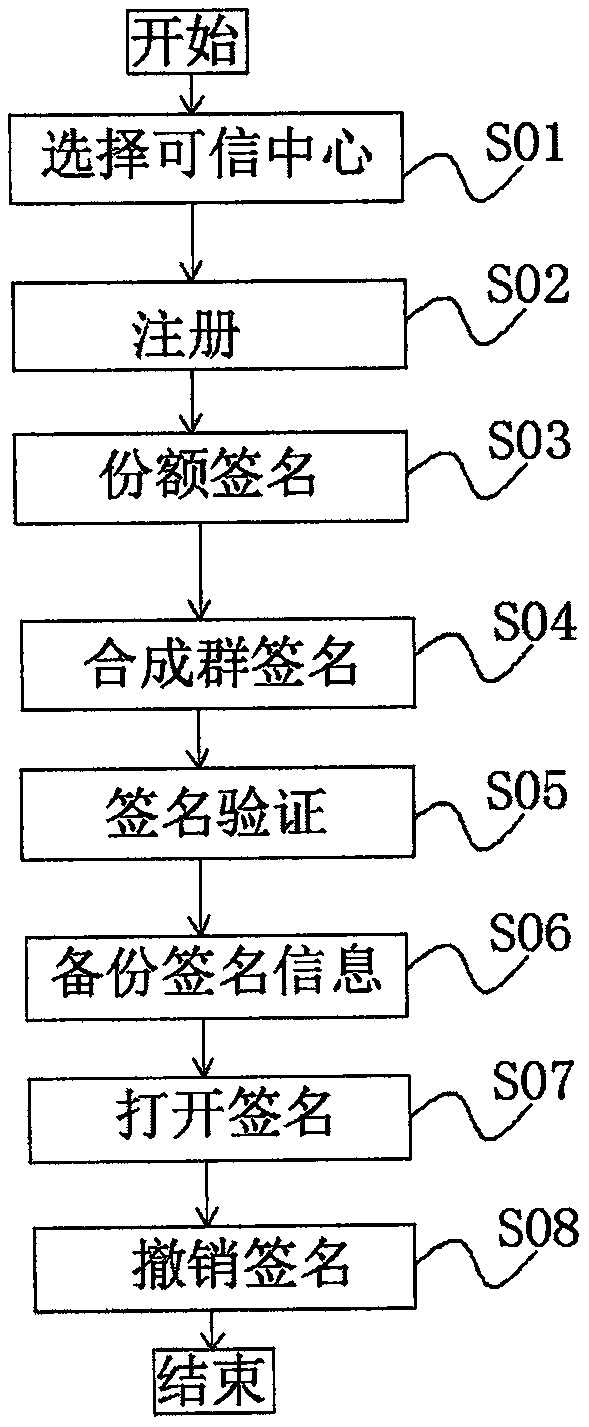
Voting method based on group signatures in block chain
PendingCN110009354ASmall amount of calculationResist impersonation attacksUser identity/authority verificationPayment protocolsBlockchainElliptic curve discrete logarithm
The invention discloses a voting method based on a group signature in a block chain, which can be applied to the fields of credit assessment, identity verification and the like. The method comprises the following steps: S01, selecting a trusted center; s02, carrying out registration; s03, carrying out share signature; s04, synthesizing a group signature; s05, performing signature verification; s06, backing up the signature information; s07, opening a signature; s08: canceling the signature. According to the invention, through cooperation of the user and the trusted center, the share signatureis generated and synthesized into the group signature. In order to protect the user identity information, blind processing is carried out on the user signature information. In order to solve the problem that a system is unavailable due to the fact that a trusted center is attacked, the user signature information of the trusted center is backed up; the credible center is allowed to be dynamically adjusted, the threshold group signature scheme makes up for anonymous vulnerabilities in the realization of the original block chain design, the difficulty is equivalent to the elliptic curve discretelogarithm, the false name attack can be effectively resisted, the calculation amount of the algorithm is lower, and the algorithm can be effectively adapted to the block chain application scene.
Owner:ZHENGZHOU NORMAL UNIV
Satellite test device and test method thereof
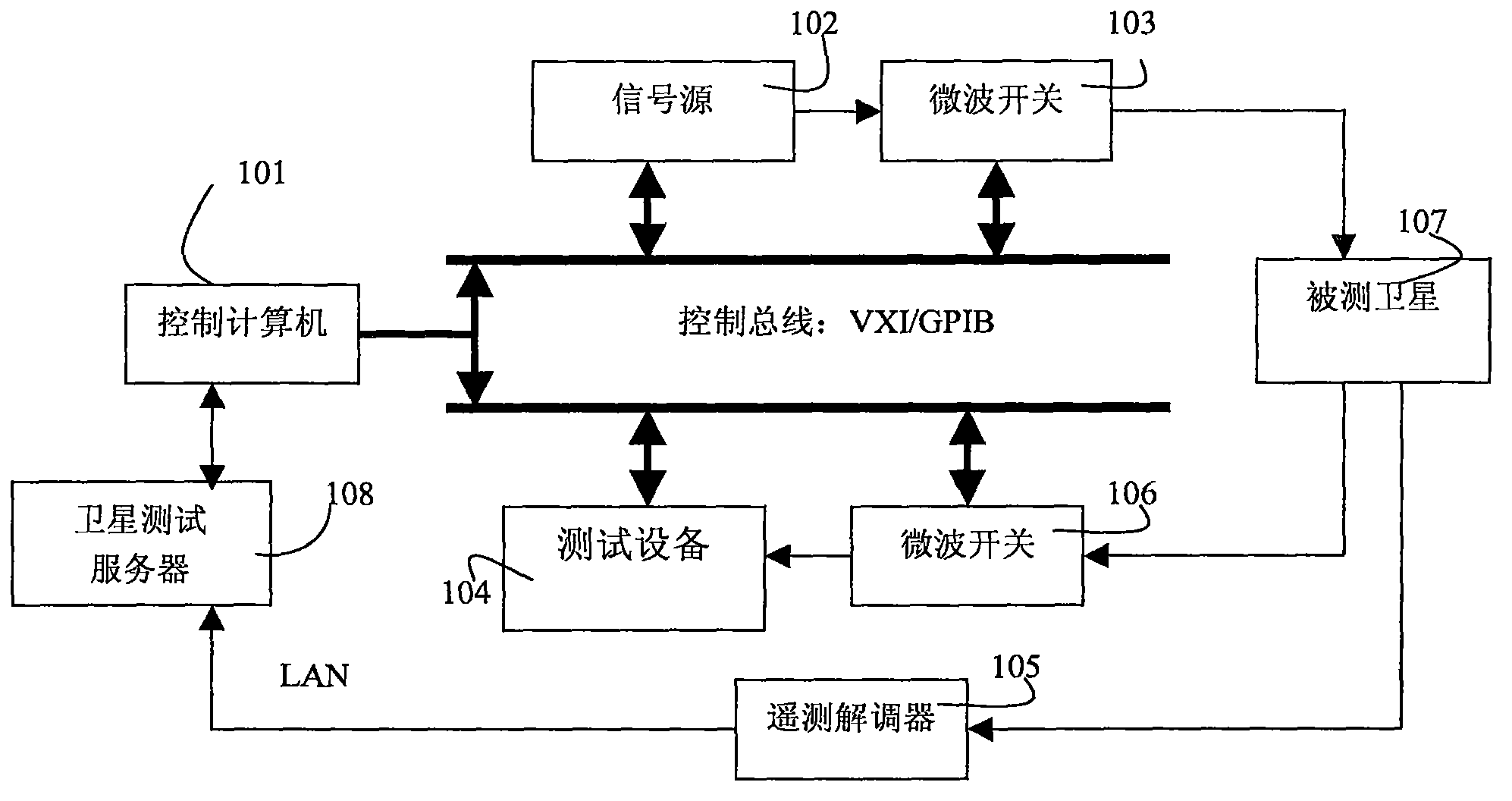
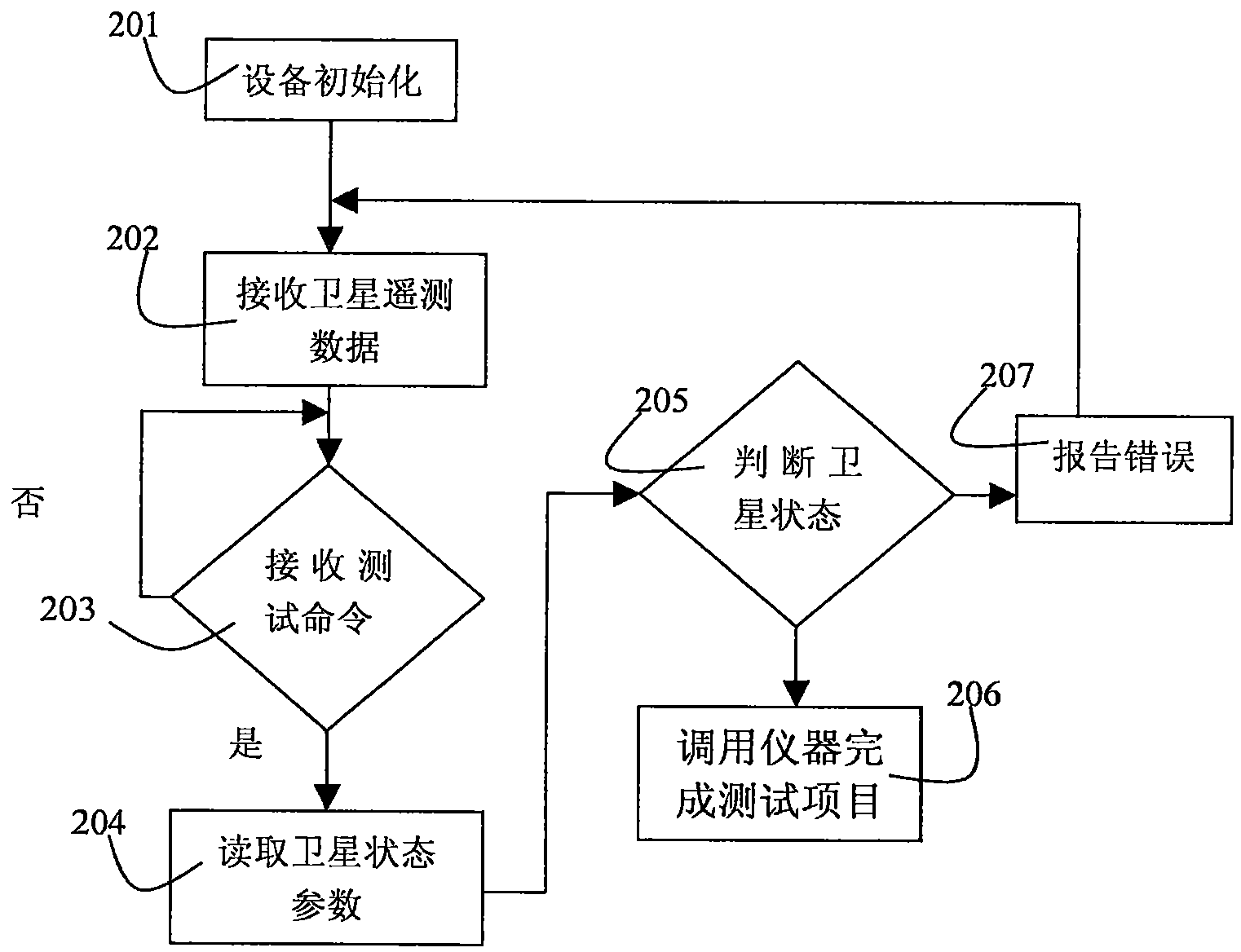
ActiveCN105122970BAddress security flawsAvoid destructionArtificial satellitesSoftware testing/debuggingOn boardEngineering
The invention discloses a satellite test device and a test method thereof, comprising: a downlink telemetry signal sent by a tested satellite, demodulated by a telemetry demodulator, sent to a satellite test server to complete satellite telemetry data processing, and sent to a control panel through a LAN network Computer: The control computer receives the satellite telemetry data in real time and waits for the test command: the test server sends the satellite test command to the control computer, and the control computer extracts the relevant satellite telemetry parameters of the test item, compares and judges with the preset parameters: if the status matches, call the relevant test The device conducts the indicator test of the project, and reports to the satellite test server after the test: if the status does not match, report that the satellite status is set incorrectly, and reset it. The invention solves the safety defect problem of the existing satellite automatic test system, achieves the beneficial effects of improving the test accuracy and avoiding damage to the equipment on the satellite.
Owner:SHANGHAI SATELLITE ENG INST
Virtual machine monitor dynamic integrity detection method based on security chip
ActiveCN106529342AImprove detection efficiencyImprove accuracyDigital data protectionPlatform integrity maintainanceHardware TrojanSecurity monitoring
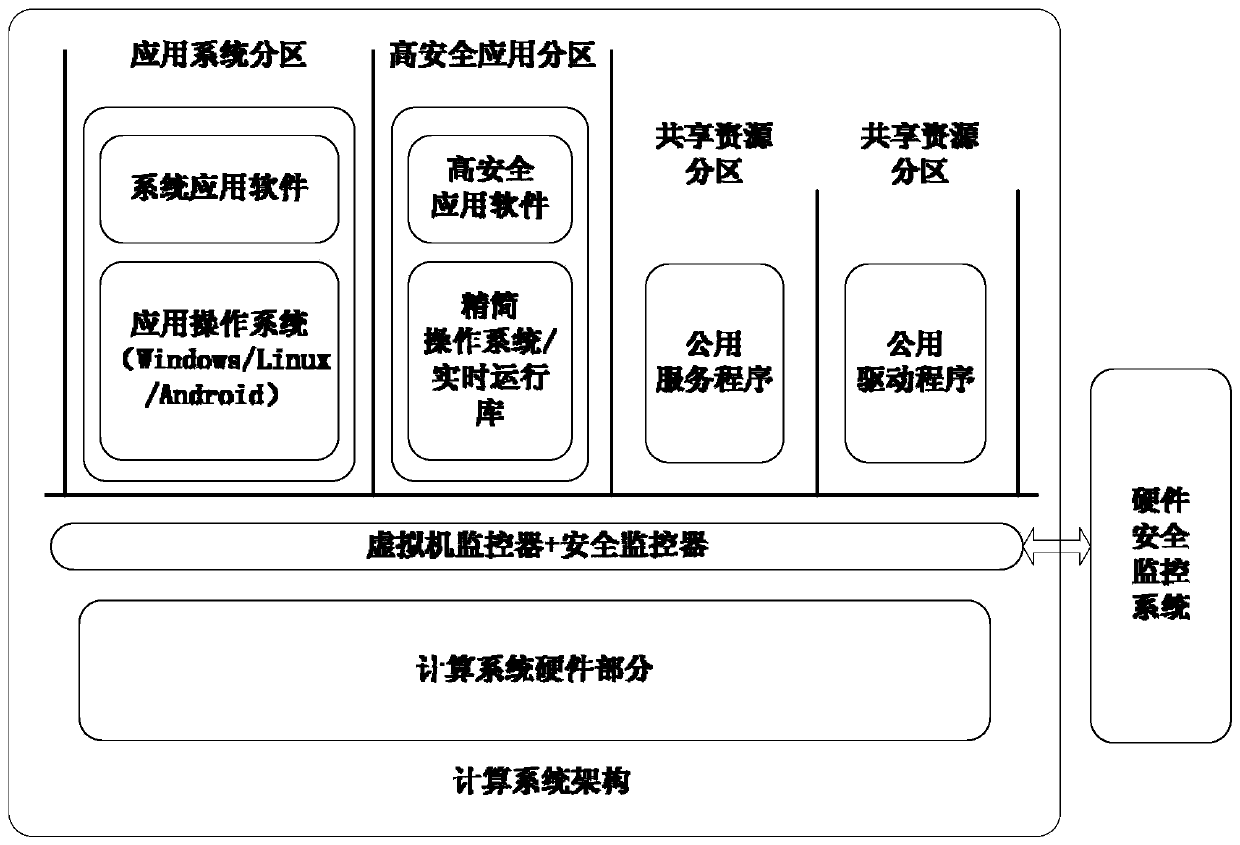
The invention provides a virtual machine monitor dynamic integrity detection method based on a security chip. The method comprises the following steps: a security monitor is arranged in a virtual machine monitor, and an independent hardware security monitoring system is arranged at the connecting part of the virtual machine monitor and a computing node; the virtual machine monitor communicates with the hardware security monitoring system, and the security detection on the virtual machine monitor is realized through the security monitor and the hardware security monitoring system. By use of the method provided by the invention, the problem of the lack of the deficiency of the dynamic integrity and security detection of the virtual machine monitor in the computing node is solved; the dynamic integrity of the virtual machine monitor is detected under the condition that the hardware Trojan possibly exists in the computing node hardware system, thereby achieving an aim of guaranteeing the security of the virtual machine monitor and the computing node.
Owner:SHENZHEN JULINGSHEN TECH CO LTD
Achievement method of custody, storage and intelligent management of important objects
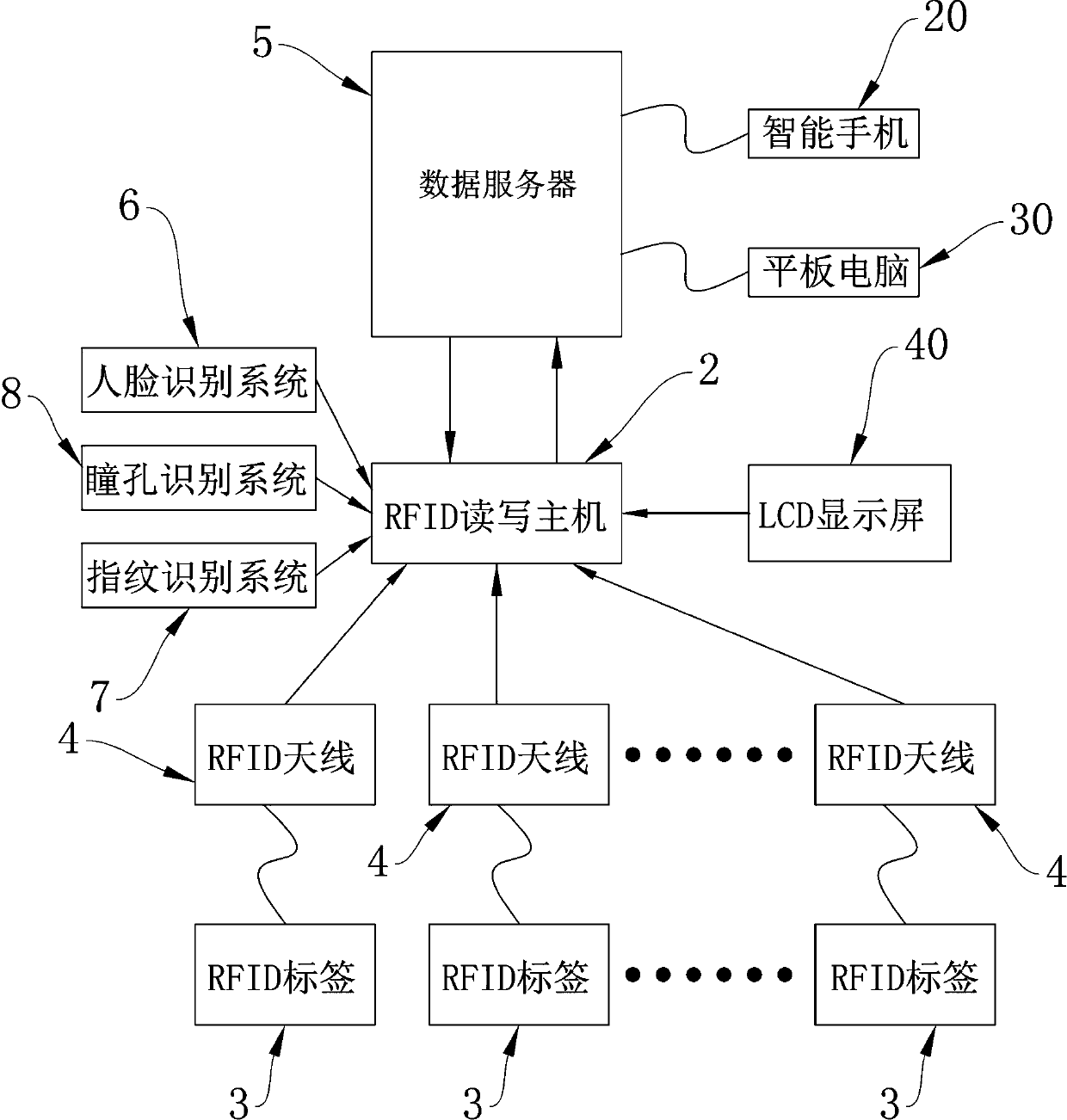
InactiveCN107481433AImprove securityAddress security flawsCo-operative working arrangementsApparatus for meter-controlled dispensingUltrahigh frequencyOperating system
The invention relates to an achievement method of custody, storage and intelligent management of important objects. According to the achievement method, by means of all-weather seamless real-time connection between ultrahigh-frequency RFID tags, RFID antennas, an RFID read-write mainframe and a data server, the objects in storage cabinets are monitored, the objects in each storage unit in the cabinets are under all-weather real-time monitoring, and monitoring signals of each storage unit are fed back to a computer system in time; meanwhile, when an abnormal situation happens, an alarm signal or prompt signal is sent out in time to inform the management staff; moreover, according to a storage cabinet system, object monitoring is not conducted through judging of whether or not a cabinet door is open, or times of open or close, so that a cabinet body scheme with or without the cabinet doors is implemented. By means of the storage cabinet system, the safety of custody and storage of the objects is greatly improved, and the problem of safety defects of existing storage cabinet systems is effectively solved.
Owner:广东亿锋物联网科技有限公司
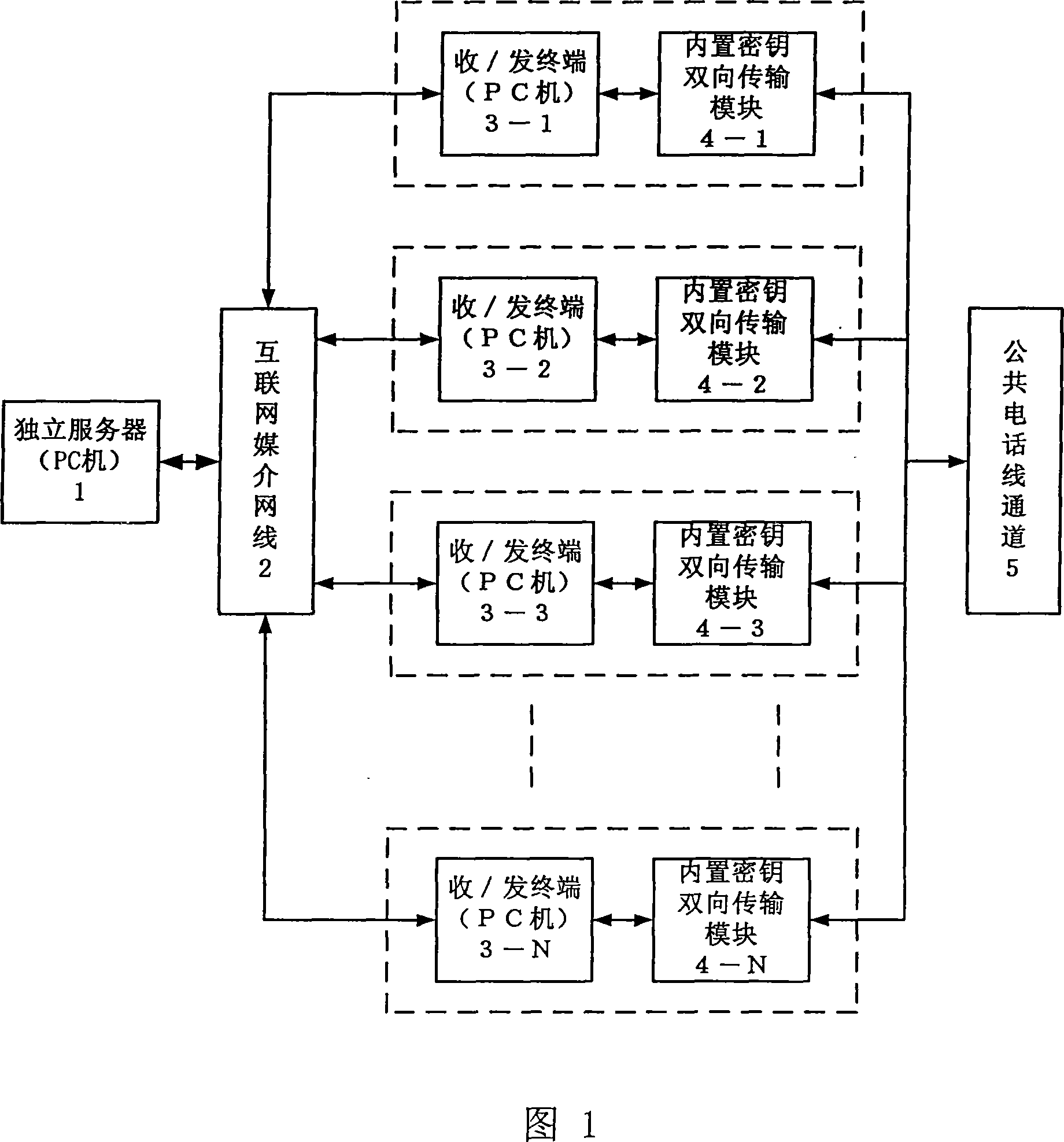
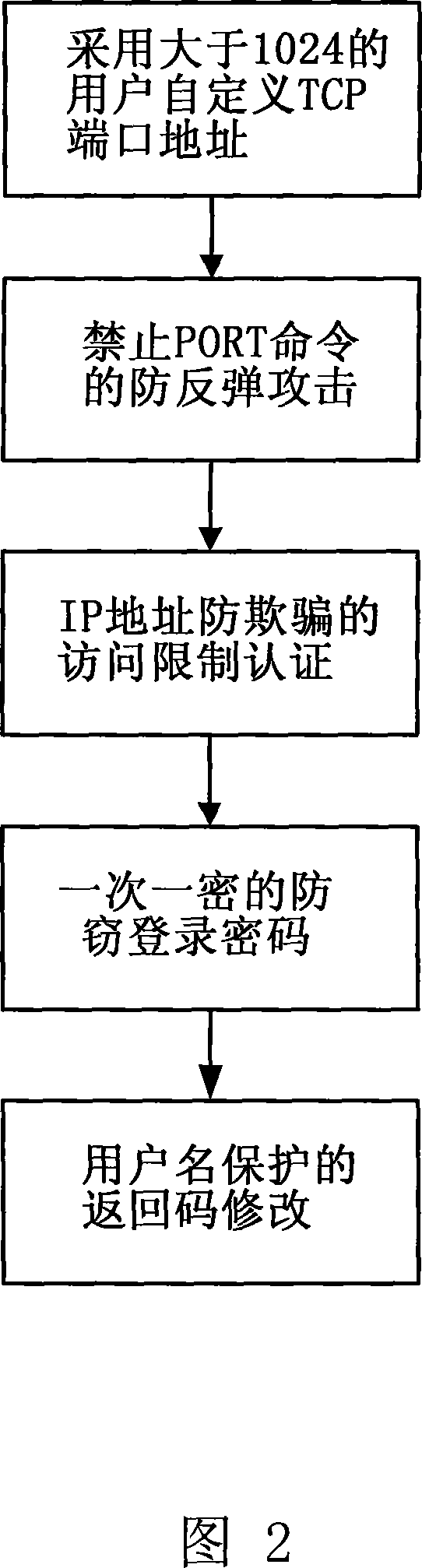
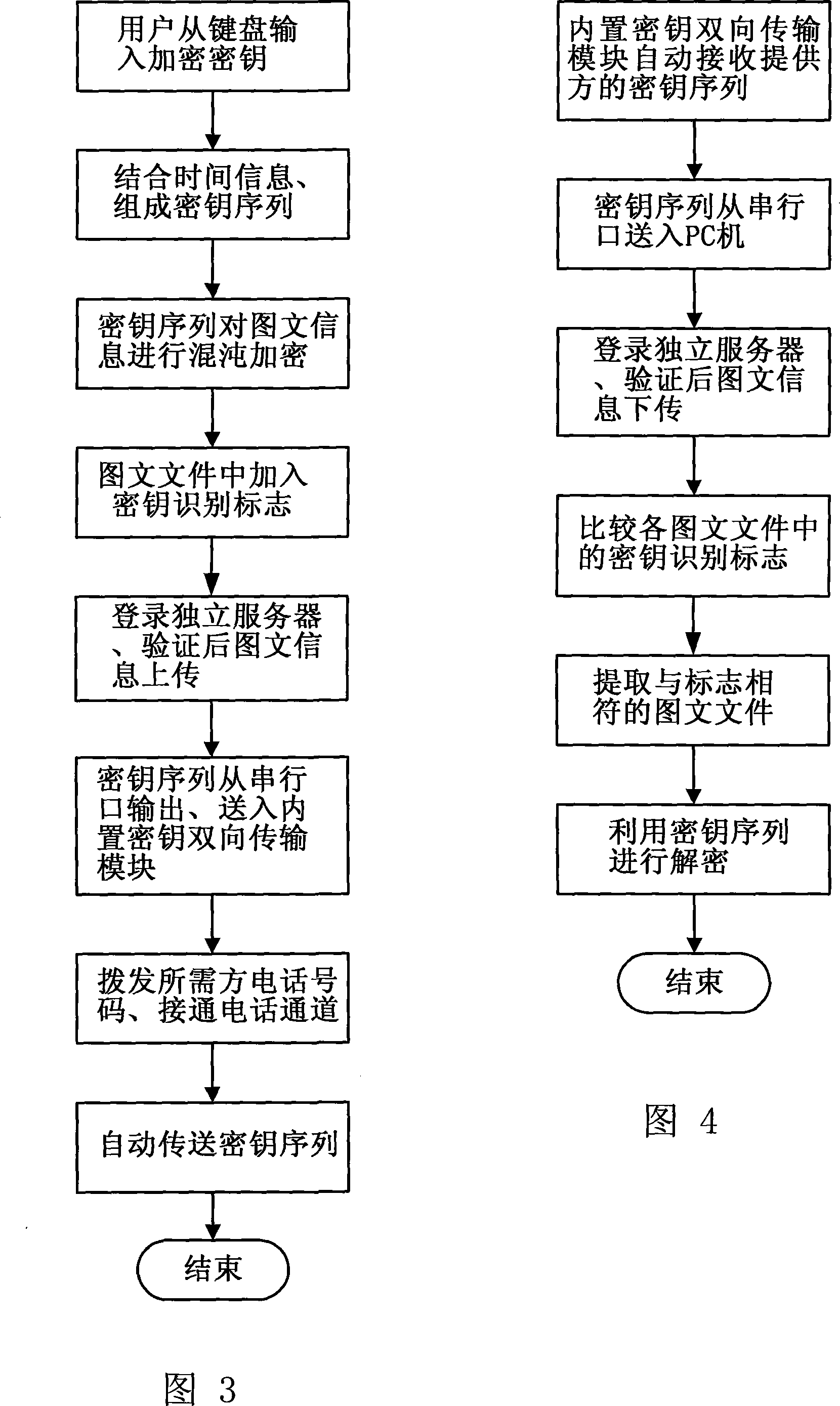
Communication system and communication method of chaos safety information internet transmission
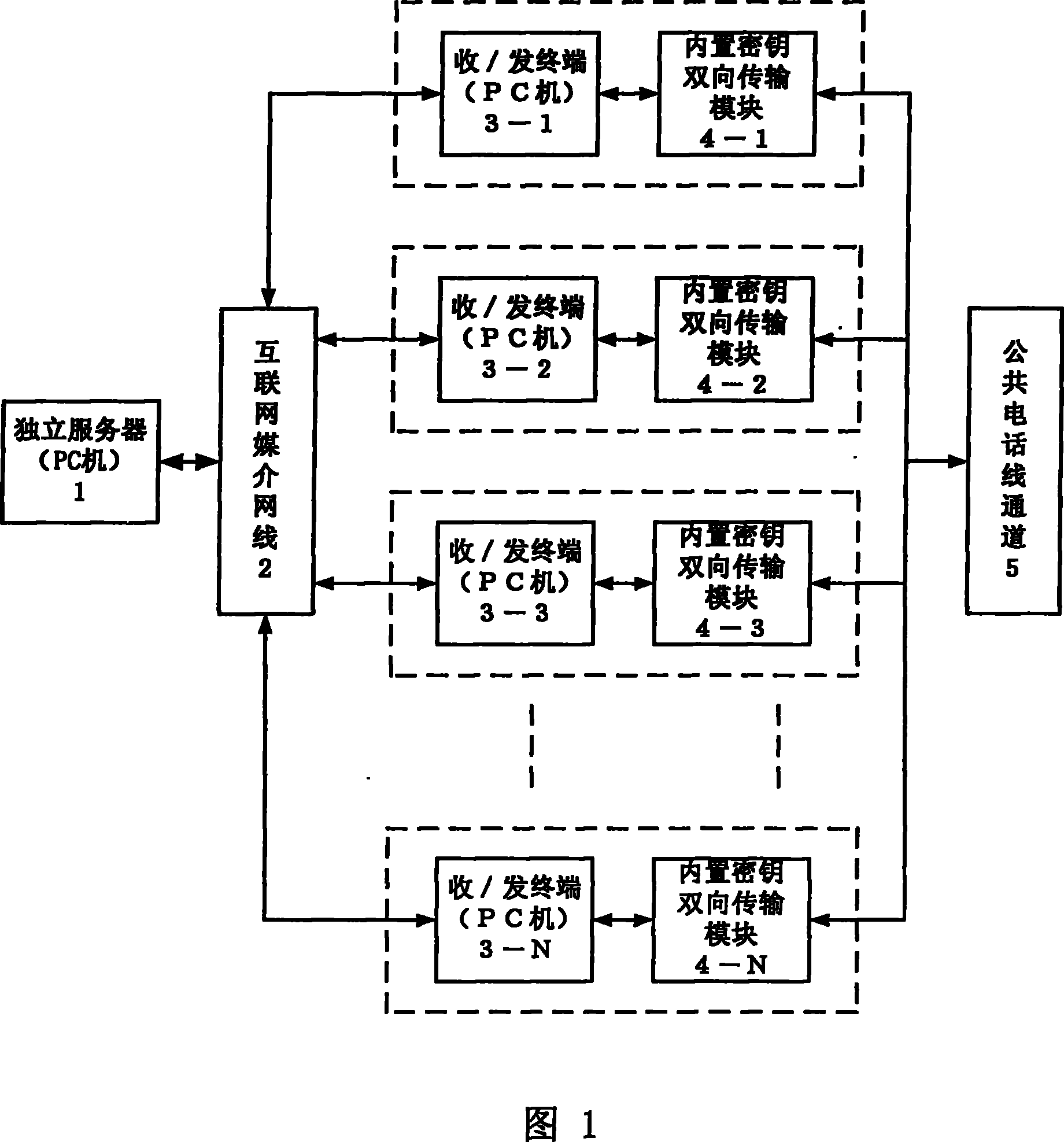
InactiveCN101162995AEnhanced Security IndependenceEnhance information theft prevention capabilitiesKey distribution for secure communicationUser identity/authority verificationTelephone lineInformation transfer
Owner:SOUTH CHINA UNIV OF TECH
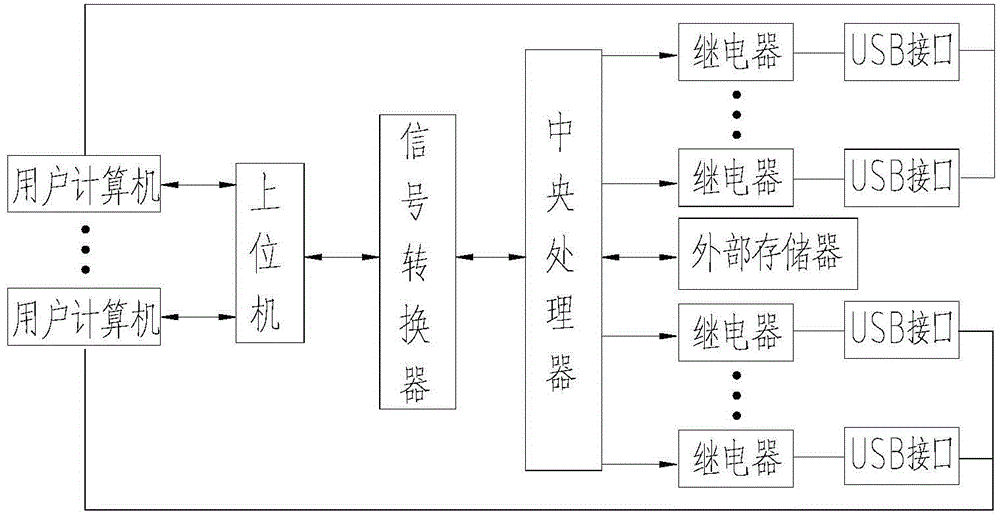
Physical isolation type USB port protection system and method
InactiveCN104915597AEnable secure accessPrevent internal leakageInternal/peripheral component protectionPlatform integrity maintainanceThree levelControllability
The invention discloses a physical isolation type USB port protection system and method. The protection system comprises a central processor, an upper computer connected with multiple user computers, an external memory used for storing user names and passwords and multiple relays used for controlling on-off of multiple USB ports in the user computers according to switching signals of the central processor. The upper computer is connected with the central processor through serial communication, and the control ends of the relays and the output end of the external memory are electrically connected with corresponding ports of the central processor. The protection method includes the steps that according to the user names, the central processor divides users into three levels, namely, common users, senior users and secret commissioners; the users input the user names and the passwords into the user computers, and the central processor controls login of the users according to the user names and the passwords; the central processor determines the levels of the users according to the user names and determines USB port use permission of the users. The protection method guarantees controllability of data in a computer.
Owner:王晓楠
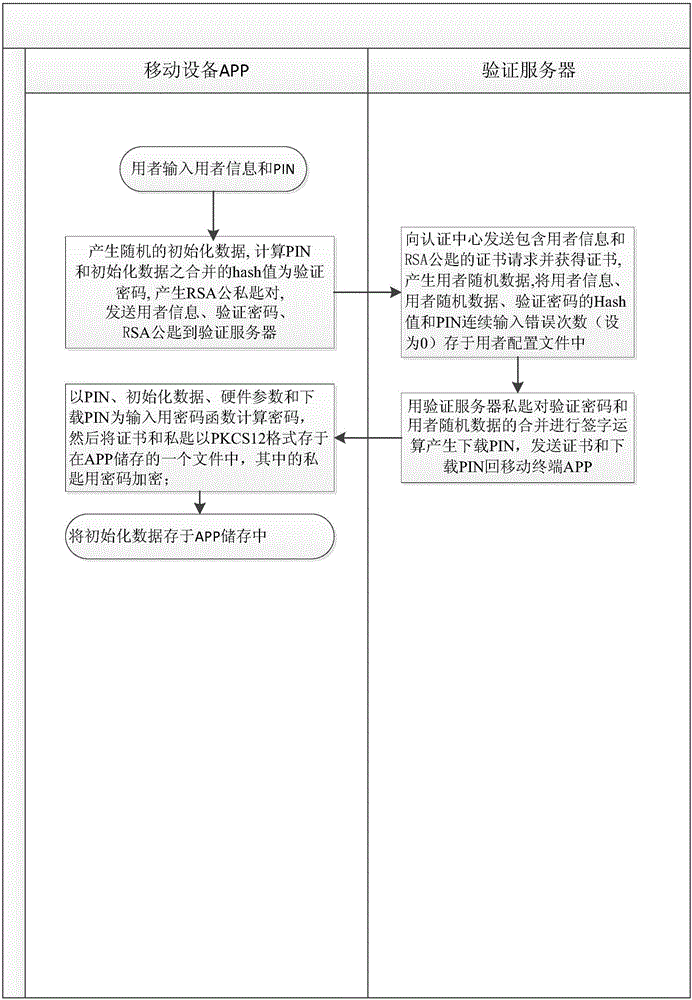
Network private key generating and applying method and system for mobile terminal
ActiveCN105873043AAddress security flawsImprove securitySecurity arrangementComputer terminalSoftware
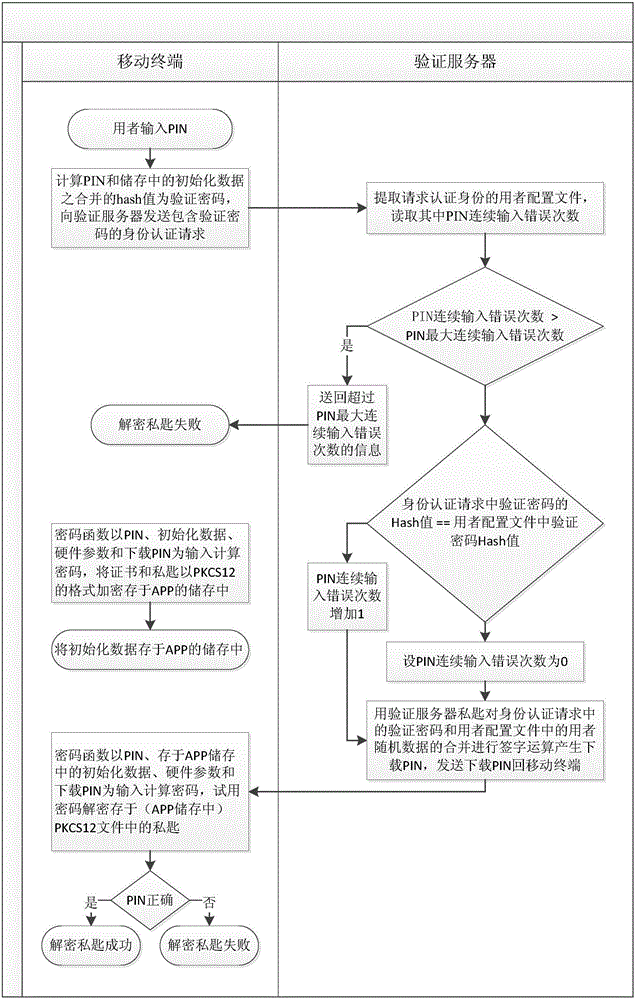
The invention provides a network private key generating and applying method and system for a mobile terminal. Compared with the conventional software private key, the method and the system are characterized in that data and operation for decrypting a private key are placed on the same terminal, and the difference is that a part of data and operation for decrypting the private key are moved to a verification server, and the verification server is provided with maximum continuous inputting error times of a PIN (Personal Identity Number) to prevent unlimited input of various different PINs. By adopting the method and the system, the safety defects that the software private key and the environment of the conventional mobile terminal can be duplicated, and hackers can input various different PINs in an unlimited way are overcome.
Owner:周波
Control method for enhancing using security of cryptographic machine by adopting dual-factor mandatory certification technology
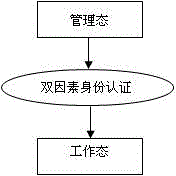
ActiveCN102737189AAvoid security risksImprove securityComputer security arrangementsPersonalizationSystems management
The invention discloses a control method for enhancing the using security of a cryptographic machine by adopting a dual-factor mandatory certification technology, and relates to the technical field of information security and cryptology. The control method comprises the following steps that: (1) a manager sets a running security strategy of the cryptographic machine; (2) the manager starts the cryptographic machine; (3) after being started, the cryptographic machine enters a function authority management state; (4) if the cryptographic machine is used at the first time, the cryptographic machine enters a personalized flow of the dual-factor mandatory certification technology; and (5) if the cryptographic machine is not used at the first time, the cryptographic machine enters a security service starting flow of the dual-factor mandatory certification technology. The method has the advantages that during actual application, the security risk caused by a reason that a non-authorized user operates the cryptographic machine is completely avoided, so that the overall application security of the cryptographic machine is improved; and furthermore, the authority of the manager is separated, so that problem that safety defect is brought to system management is avoided, and the management security of the cryptographic machine is improved.
Owner:中电科网络安全科技股份有限公司
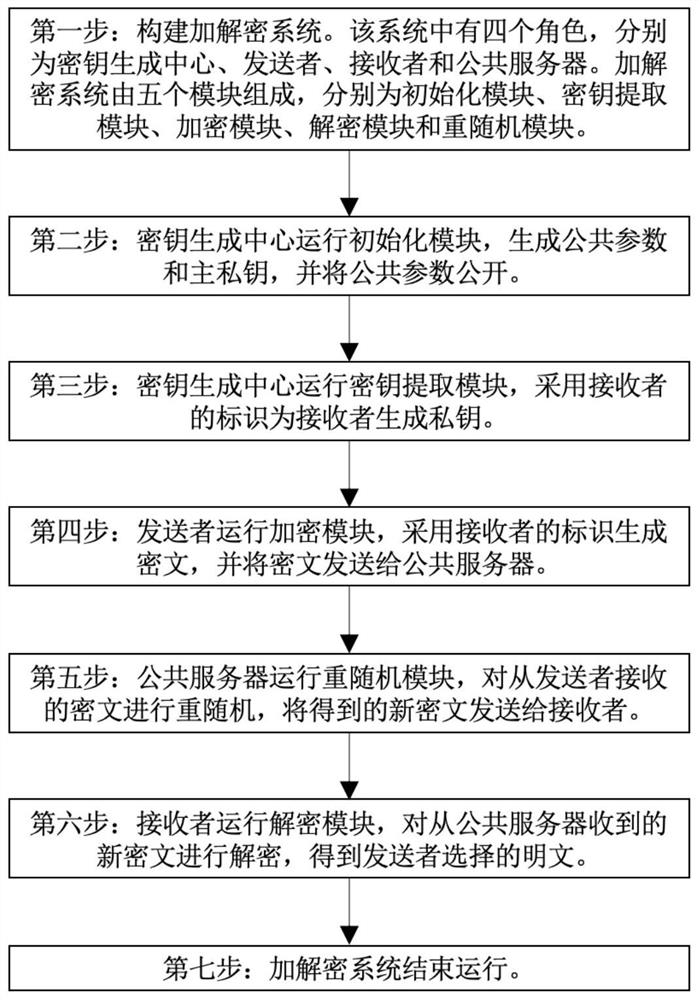
Rerandomizable identifier encryption and decryption method
ActiveCN111756539AAddress security flawsPublic key for secure communicationUser identity/authority verificationEngineeringChosen-ciphertext attack
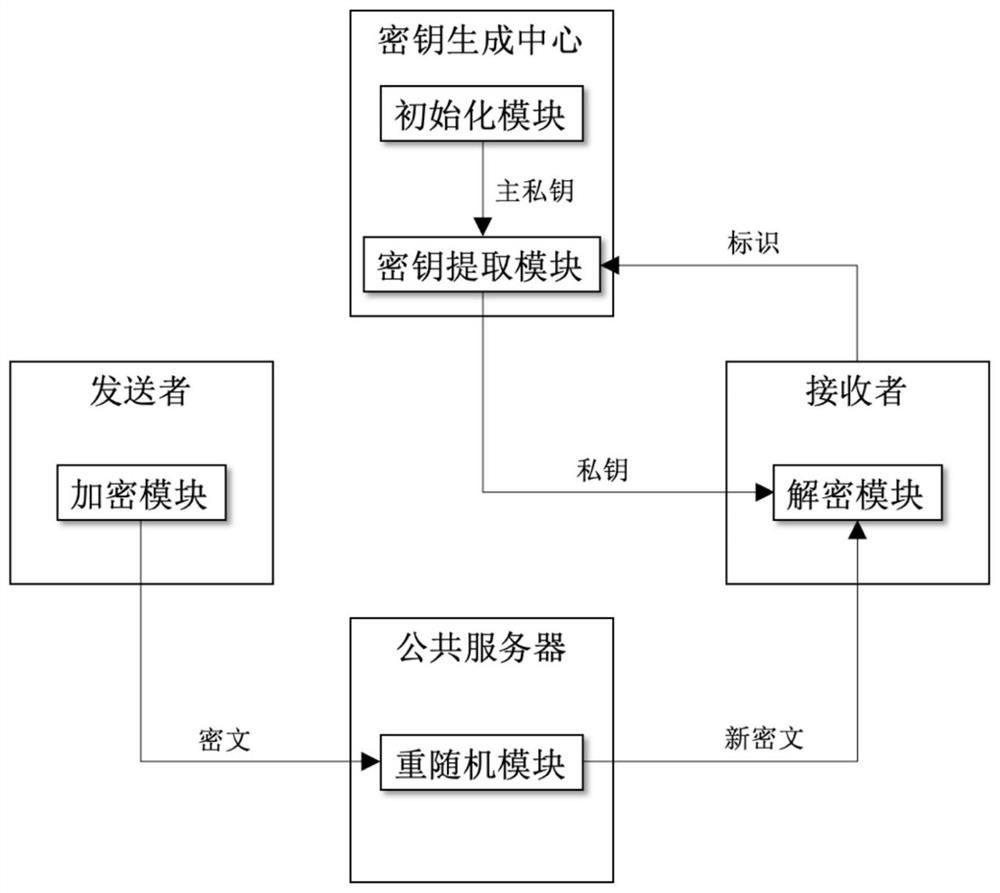
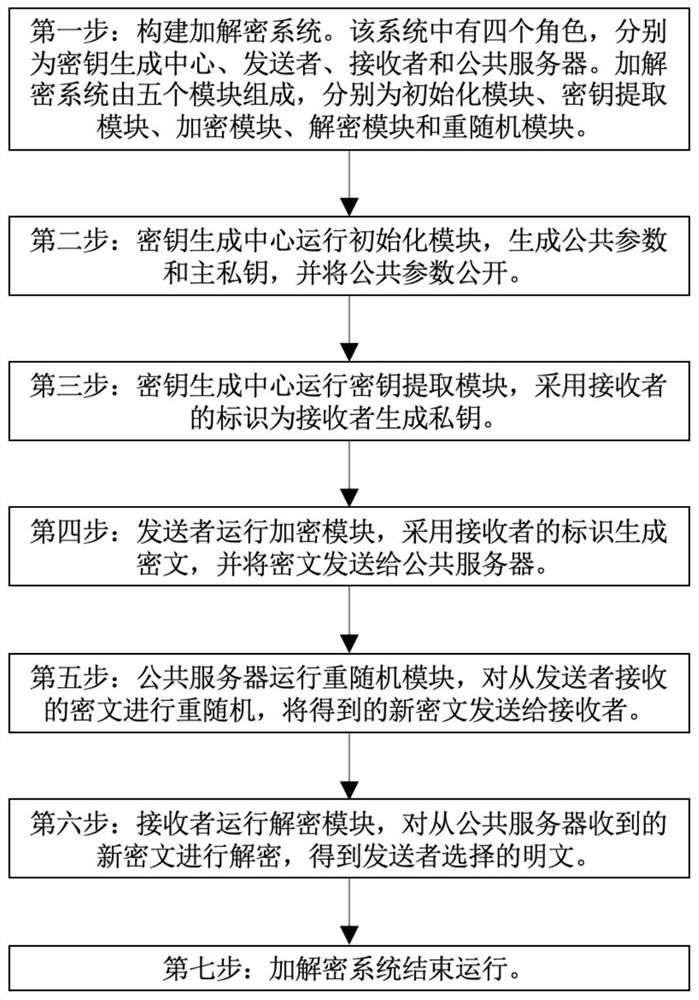
The invention discloses a rerandomizable identifier encryption and decryption method, and aims to solve the security defect of an existing rerandomizable identifier encryption and decryption method. According to the invention, the technical scheme is that the method comprises the steps: constructing an encryption and decryption system composed of an initialization module, a key extraction module,an encryption module, a decryption module and a re-random module; enabling the key generation center to operate the initialization module, generating a public parameter and a main private key, and disclosing the public parameter; enabling the key generation center to operate a key extraction module, and generating a private key for the receiver by adopting the identifier id of the receiver; enabling a sender to operate the encryption module, generating a ciphertext C by adopting the identifier id of the receiver, and sending the ciphertext C to the public server; enabling a public server to operate a re-randomization module to re-randomize the C, and sending the new ciphertext C' to a receiver; and enabling a receiver to operate the decryption module to decrypt the C'. According to the invention, the replayable selective ciphertext attack based on the identifier can be resisted, and the operation of the rerandom module does not need the identifier of a receiver, so the distribution ofthe identifier is avoided.
Owner:NAT UNIV OF DEFENSE TECH
Water discharge device of vehicle air cylinder
InactiveCN110979286AImprove drainage efficiencyEasy to operateAir treatment devicesPiping arrangementsWaste managementPiping
The invention discloses a water discharge device of a vehicle air cylinder. An air cylinder shell is of a cylindrical structure, an air inlet port and an air outlet port are formed at the two ends ofthe air cylinder shell correspondingly, a mixed liquid is arranged at the bottom in the air cylinder shell, a water drain valve is arranged at the right lower part of the air cylinder shell through awater drain valve installation base, the water drain valve is arranged below the water drain valve installation base, the water drain valve installation base is arranged below the air cylinder shell,a water drain pipe is arranged between the water drain valve and the water drain valve installation base and is in threaded connection with the water drain valve installation base, a three-way connector is arranged at the tail end of the water drain pipe, and the rear end of the three-way connector is connected with a water discharge valve and the water drain valve. The water drain valve and the water discharge valve are arranged below the air cylinder, the water drain efficiency is effectively improved through the connection relation of the water drain pipe, operation is easy, and use is convenient.
Owner:十堰安凯汽车零部件有限公司
A Construction Method of Certificateless Public Key Cryptosystem
ActiveCN106936584BAddress security flawsImprove securityPublic key for secure communicationUser identity/authority verificationKey escrowCryptogram
Owner:PINGDINGSHAN UNIVERSITY
A mobile terminal security access authentication method combined with fingerprint
ActiveCN106488452BEasy to appealAvoid accidental injuryDigital data authenticationSecurity arrangementInformation accessIdentity recognition
The invention provides a mobile terminal safety access authentication method combined with fingerprints, which includes four steps of establishing an encrypted channel, user registration, user information review and user service access. The client collects terminal characteristic information, including USBKEY serial number, digital certificate serial number, mobile terminal serial number and user fingerprint characteristic information, uploads it to the secure access gateway through an encrypted channel, and the secure access gateway verifies the integrity and validity of the terminal information , and determine whether the terminal can access the protected server according to the verification result. By combining fingerprint identification technology with traditional identification methods, the media for identifying identities is directly related to the natural person itself, realizing the real correspondence between identification and the identified person, and effectively improving the security level of mobile terminal information access , It is more conducive to the role of convenient mobile technology in information application.
Owner:JIANGSU ELECTRIC POWER CO +1
Security hardening method for virtual machine monitor based on security chip
ActiveCN106529284BImprove detection efficiencyImprove accuracyDigital data protectionPlatform integrity maintainanceEngineeringSecurity monitoring
The invention provides a security chip-based security reinforcement method for a virtual machine monitor. According to the method, a security monitor is arranged in the virtual machine monitor; an independent hardware security monitoring system is arranged at the joint of the virtual machine monitor and a computing node; the virtual machine monitor communicates with the hardware security monitoring system; and the virtual machine monitor is subjected to security reinforcement through the security monitor and the hardware security monitoring system. Through the security monitor, a key point in running of a virtual machine can be effectively selected for performing security detection, so that not only the detection efficiency but also the detection accuracy are improved.
Owner:SHENZHEN JULINGSHEN TECH CO LTD
Communication system and communication method of chaos safety information internet transmission
InactiveCN101162995BEnhanced Security IndependenceImprove anti-theft performanceKey distribution for secure communicationUser identity/authority verificationElectronic mailTransmitter
The invention discloses a communication system and a communication method for the Internet transmission of chaotic security information. An independent server, receiving and transmitting terminals and built-in bidirectional key transmission modules are mutually connected together to form the system. In the method, a transmitter encrypts image text information via chaotic security, which is then uploaded to the independent server, the encrypted key is independently sent to a receiver via a public telephone line channel, and the receiver downloads the chaotically encrypted image text information and utilizes the received encrypted key to decrypt the image text information. The image text information transmission between the receiving and transmitting terminals of the invention utilizes the point-to-multipoint communication method performed by Internet media, so the image text information transmission does not pass a third party normally using the Email transmission method, thus greatly enhancing the security and independence of information transmission on the Internet. The independent server applies multiple security measures aiming at the ftp protocol, thus enhancing the theft-proof capability of information. The transmission of chaotically encrypted keys in an independent telephone channel ensures the anti-attack capability of the image text information.
Owner:SOUTH CHINA UNIV OF TECH
Attribute reversible encryption system and method resistant to re-encryption key disclosure
ActiveCN106059768BLeak resistanceOvercoming property revocation flawsKey distribution for secure communicationPublic key for secure communicationCiphertextKey leakage
The present invention provides an encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes. The method comprises: 1, setting the parameters of an encryption system; 2, generating the main private key and the public key of the encryption system; 3, generating a user private key; 4, building a re-encryption key tree; 5, generating a cryptograph file; 6, cancelling attributes; 7, performing re-encryption agency; 8, accessing the cryptograph file; 9, determining whether the update position of the cryptograph file is 1 or not; 10, decrypting an un-updating cryptograph file; 11, updating the private key; 12, decrypting the update cryptograph file; and 13, quitting the encryption system. Through adoption of a dual-agency re-encryption server model, the encryption system and method for resisting re-encryption key leakage and capable of cancelling attributes can resist the leakage of the re-encryption key. When the attributes are cancelled, an attribute user group is employed to construct the re-encryption key tree so as to effectively, timely and accurately cancel the indirect attributes. When the encryption is performed, the secret is dispersed to resist the conspiracy attack.
Owner:XIDIAN UNIV
Dynamic Integrity Detection Method of Virtual Machine Monitor Based on Security Chip
ActiveCN106529342BImprove detection efficiencyImprove accuracyDigital data protectionPlatform integrity maintainanceHardware TrojanSecurity monitoring
Owner:SHENZHEN JULINGSHEN TECH CO LTD
Control method for enhancing using security of cryptographic machine by adopting dual-factor mandatory certification technology
ActiveCN102737189BAvoid security risksImprove securityDigital data authenticationPersonalizationSystems management
The invention discloses a control method for enhancing the using security of a cryptographic machine by adopting a dual-factor mandatory certification technology, and relates to the technical field of information security and cryptology. The control method comprises the following steps that: (1) a manager sets a running security strategy of the cryptographic machine; (2) the manager starts the cryptographic machine; (3) after being started, the cryptographic machine enters a function authority management state; (4) if the cryptographic machine is used at the first time, the cryptographic machine enters a personalized flow of the dual-factor mandatory certification technology; and (5) if the cryptographic machine is not used at the first time, the cryptographic machine enters a security service starting flow of the dual-factor mandatory certification technology. The method has the advantages that during actual application, the security risk caused by a reason that a non-authorized user operates the cryptographic machine is completely avoided, so that the overall application security of the cryptographic machine is improved; and furthermore, the authority of the manager is separated, so that problem that safety defect is brought to system management is avoided, and the management security of the cryptographic machine is improved.
Owner:中电科网络安全科技股份有限公司
A distributed storage system and its file sharing method
ActiveCN102821096BEliminate potential safety hazardsOvercoming the problem of excessive sharing overheadTransmissionOperational systemClient-side
The invention discloses a distributed storage system and a file sharing method thereof, belonging to the technical field of computer memory and information security; the distributed storage system solves the problems that the existing secure storage system has complicated key management and the encrypt file has too large cost for sharing. The distributed storage system comprises a client, a server, a security manager and a key server and is established on the operation system for supporting the POSIX interface; the client is connected with the security manager and the key server respectively through the local area network. The distributed storage system sets the special key server management key, and the security manager only manages the file key number, so that the security defect and large file re-encryption cost caused by directly or indirectly exposing the file key to the share use are avoided, and the security and whole performance of the system are improved; the distributed storage system and the file sharing method effectively solve the problems that the key management is complicated, and the encrypt file has too large sharing load, and the distributed storage system is suitable for constructing the security storage system with large scale and high performance.
Owner:HUAZHONG UNIV OF SCI & TECH
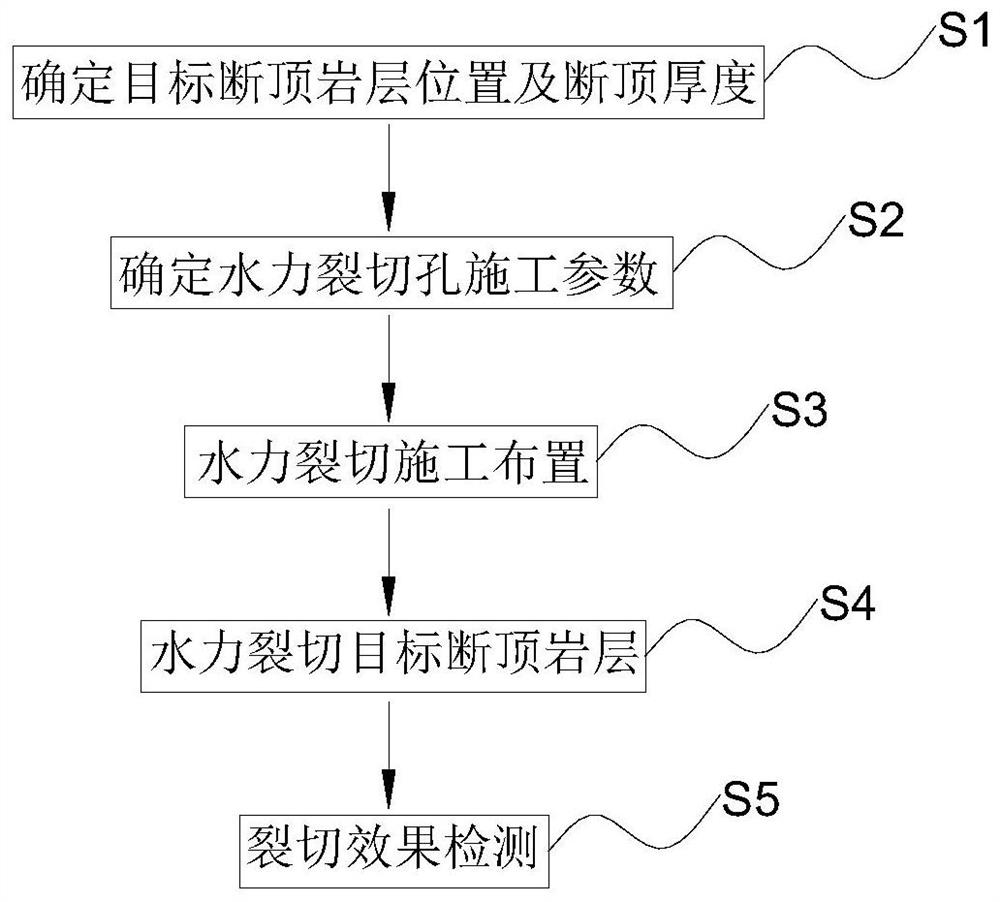
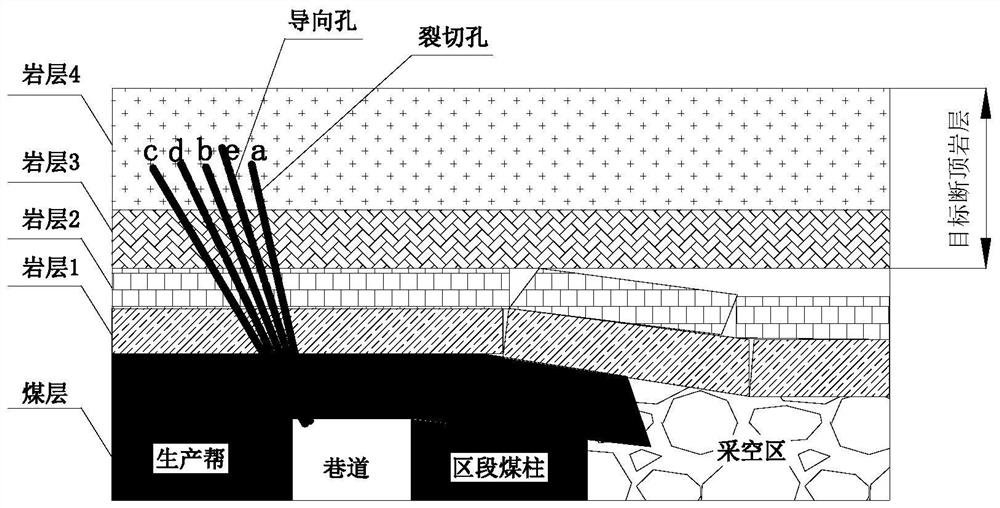
A pressure relief method for coal mine rock burst prevention and control of hydraulic cracking and cut-off roof
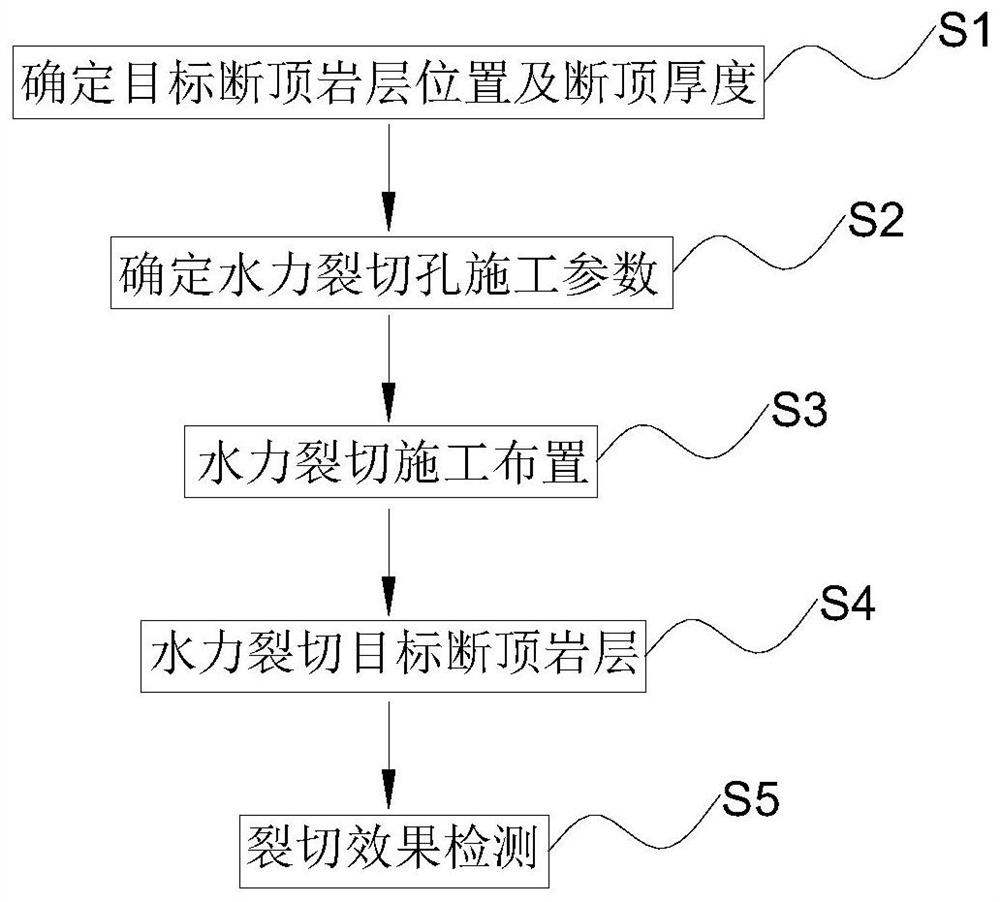
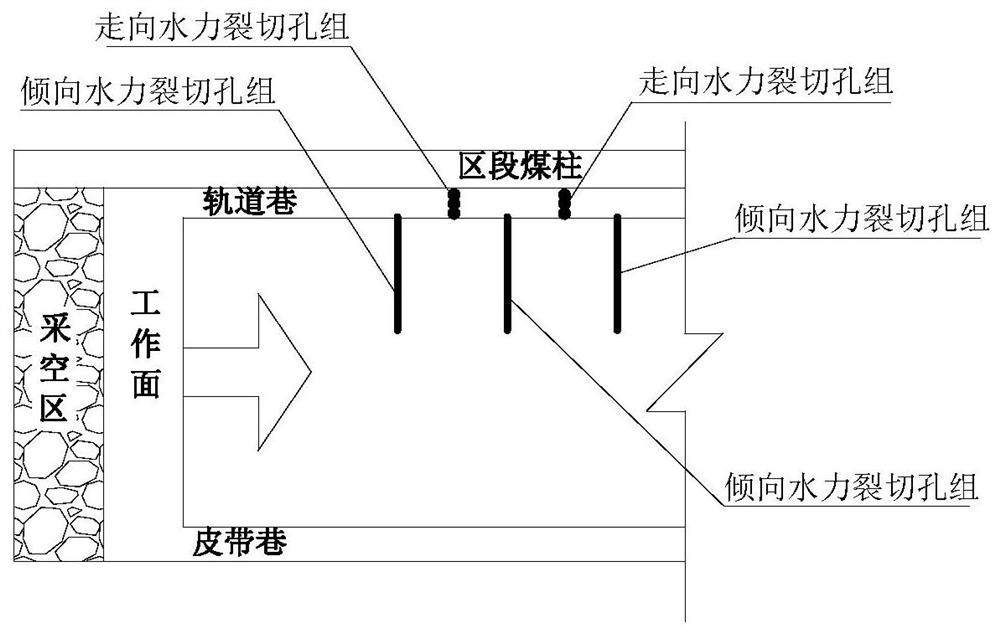
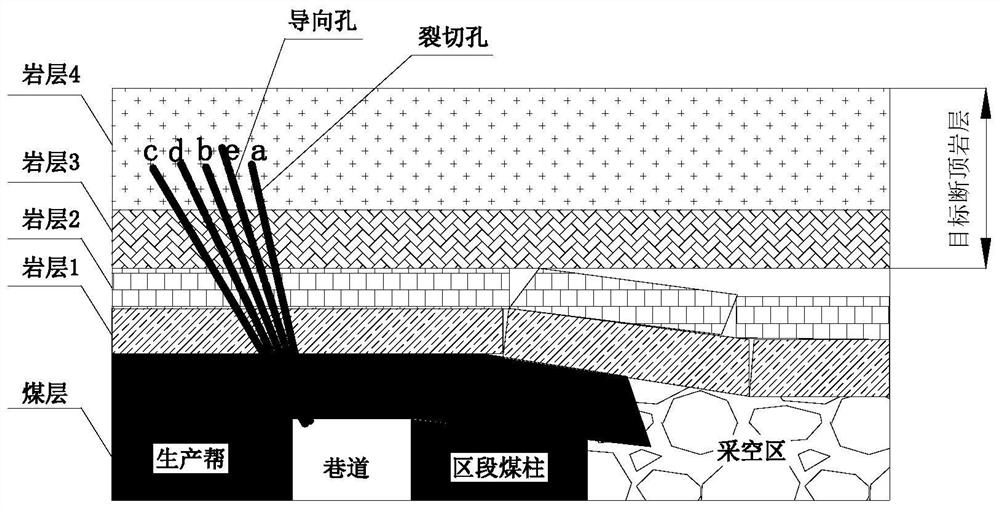
ActiveCN113669059BAddress security flawsAvoid construction disadvantagesDisloding machinesUnderground miningMining engineeringHydraulic fracturing
The invention provides a hydraulic cracking cut-off roof pressure relief method for prevention and control of rock burst in coal mines, and relates to the technical field of prevention and control of rock burst in coal mines. The method of the present invention comprises the following steps: step 1, determine the location of the target fault top rock layer and the thickness of the fault top; step 2, determine the construction parameters of the hydraulic splitting hole; step 3, the construction layout of the hydraulic splitting; step 4, the target fracture of the hydraulic splitting Top rock layer; step 5, cracking effect detection. The method for preventing and controlling hydraulic cracking in coal mine rock burst according to the present invention is applied to rock burst mines. The pressure relief of broken roof is safe and efficient, the construction operation is convenient, the expander can be used repeatedly, and the cost is greatly reduced; the goal of the roof is realized. Precise pre-cracking of the required fault top rock strata and fully connected caving under the action of overlying rock movement and mine pressure can reduce the damage of dynamic loads and avoid the safety defects and construction defects of explosive blasting top cutting. High application and promotion value.
Owner:CHINA UNIV OF MINING & TECH
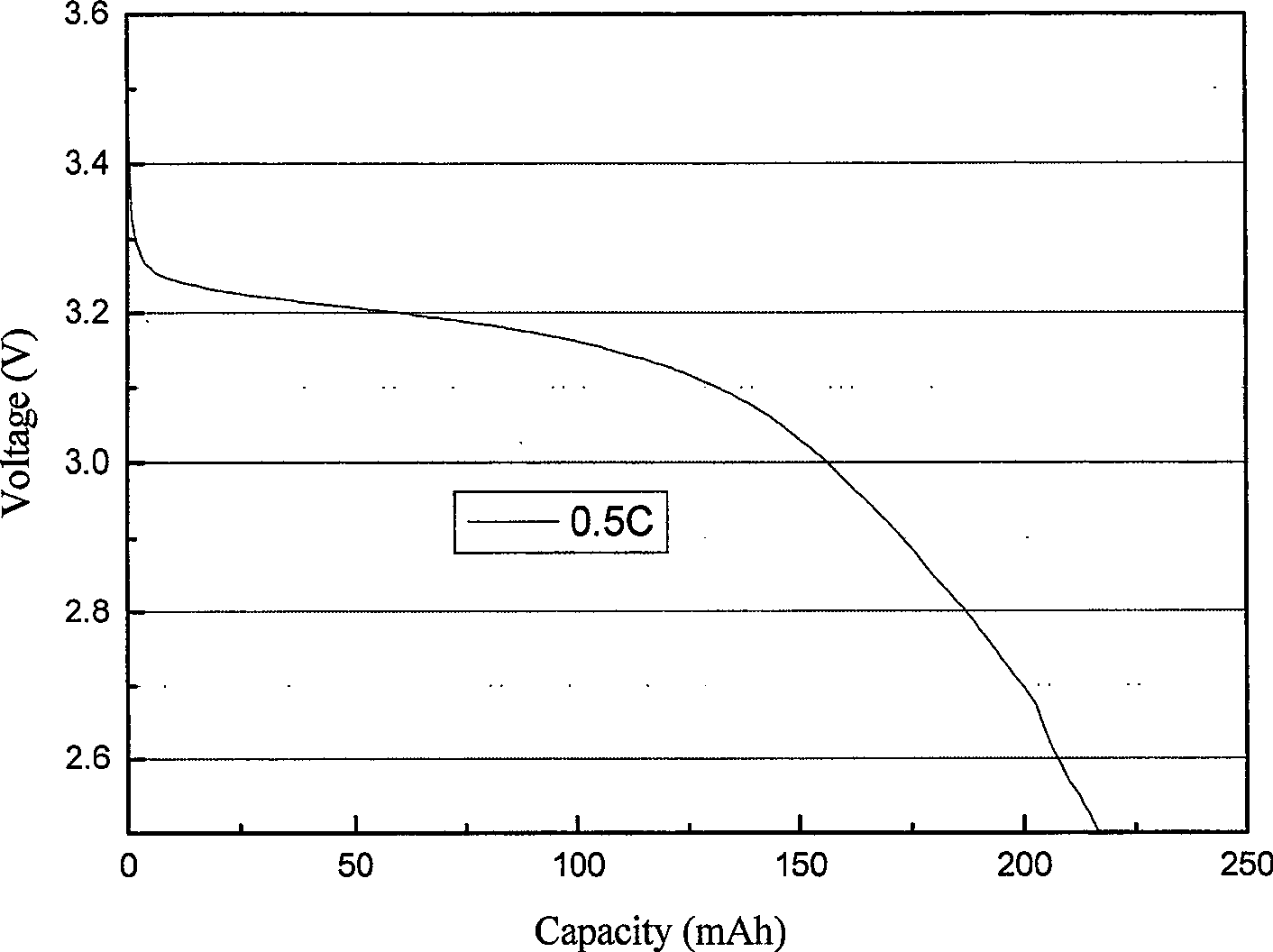
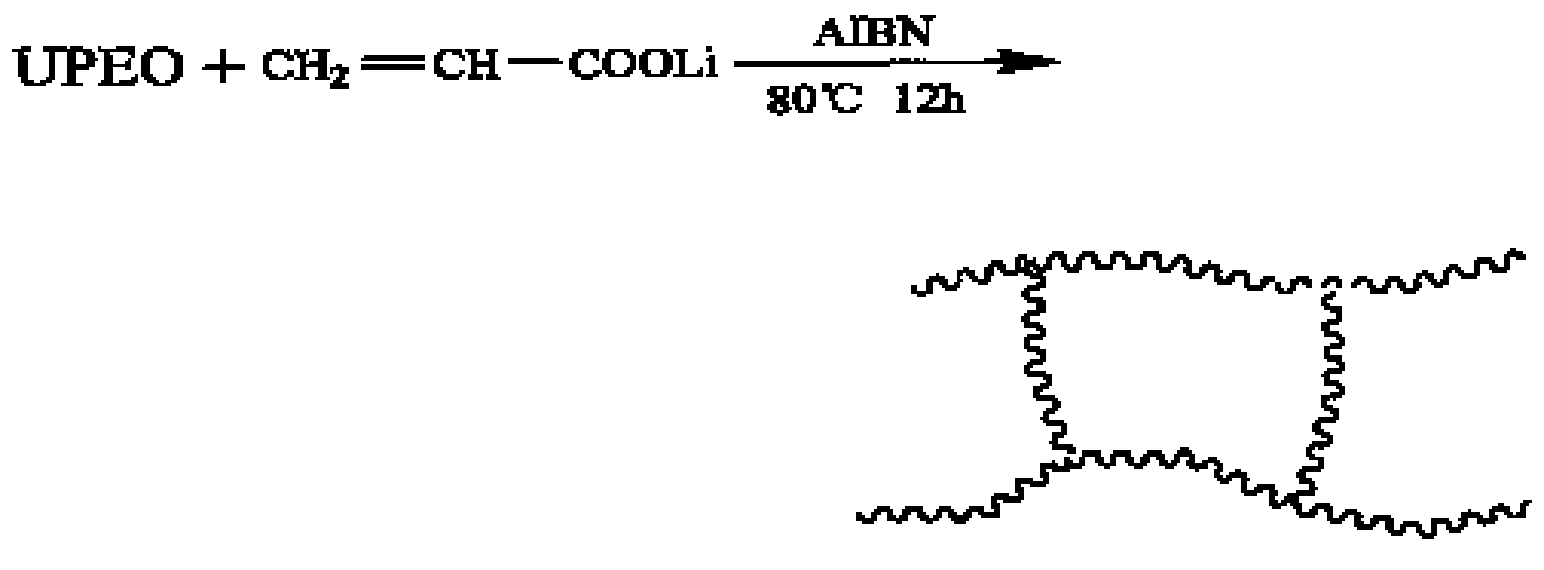
Lithium ion polymer electrolyte film and manufacturing method of lithium ion cell comprising the film
InactiveCN100544110CImprove mechanical propertiesStable chemical propertiesFinal product manufactureOrganic electrolyte cellsLithium-ion batteryMechanical property
The invention relates to a lithium ion polymer electrolyte membrane and a preparation method of a lithium ion battery containing the electrolyte membrane. In the present invention, a polymer matrix with high amorphous phase is prepared by free radical copolymerization with PEO macromonomer, ethylenic small monomer, and azobisisobutyronitrile, and the matrix is compounded with lithium salt and fast ion conductor nanopowder Finally, the lithium ion polymer electrolyte membrane is made by casting method, the electrolyte membrane has good mechanical properties, stable chemical properties, and high electrical conductivity; then lithium iron phosphate is used as the positive electrode material, and the electrolyte membrane is used as the separator to make the lithium ion polymer electrolyte membrane. Battery; the battery has good electrochemical performance, large capacity, long cycle life, safe and reliable charging and discharging process. The production process in the invention is simple, the yield is high, and the cost is low. The prepared positive and negative plates have uniform texture and uniform product performance, and are convenient to be combined into a battery pack to work.
Owner:ZHENGZHOU UNIV +1
A re-random identification encryption and decryption method
ActiveCN111756539BAddress security flawsPublic key for secure communicationUser identity/authority verificationComputer hardwareTheoretical computer science
The invention discloses a re-randomized identification encryption and decryption method, aiming to solve the security defect existing in the existing re-random identification encryption and decryption method. The technical solution is: build an encryption and decryption system consisting of an initialization module, a key extraction module, an encryption module, a decryption module and a rerandom module; the key generation center runs the initialization module, generates public parameters and master private keys, and makes the public parameters public ;The key generation center runs the key extraction module, uses the receiver's identification id to generate a private key for the receiver; the sender runs the encryption module, uses the receiver's identification id to generate ciphertext C, and sends C to the public server; the public server Run the re-random module to re-randomize C, and send the new ciphertext C' to the receiver; the receiver runs the decryption module to decrypt C'. The invention can resist the replayable selected ciphertext attack based on the logo, and the operation of the re-random module does not need the logo of the receiver, which avoids the distribution of the logo.
Owner:NAT UNIV OF DEFENSE TECH
Hydraulic fracturing roof-cutting pressure relief method for coal mine rock burst prevention and control
ActiveCN113669059AAddress security flawsAvoid construction disadvantagesDisloding machinesUnderground miningMining engineeringHydraulic fracturing
The invention provides a hydraulic fracturing roof-cutting pressure relief method for coal mine rock burst prevention and control, and relates to the technical field of coal mine rock burst prevention and control. The method comprises the following steps that 1, the position and the roof-cutting thickness of a target roof-cutting rock stratum are determined; 2, hydraulic fracturing hole construction parameters are determined; 3, hydraulic fracturing construction arrangement is conducted; 4, hydraulic fracturing is conducted on the target roof-cutting rock stratum; and 5, the fracturing effect is detected. The hydraulic fracturing roof-cutting pressure relief method for coal mine rock burst prevention and control is applied to a rock burst mine, roof-cutting pressure relief is safe and efficient, construction operation is convenient and fast, an expansion device and the like can be repeatedly used, and the cost is greatly reduced; and accurate pre-fracturing of the roof-cutting rock stratum needed by a roof target is achieved, full communication and caving are achieved under the action of overlying strata movement mine pressure, the dynamic load damage effect is reduced, the safety defects and the construction defects of explosive blasting roof cutting are avoided, and extremely high application and popularization value is achieved in coal mine rock burst prevention and control engineering practice.
Owner:CHINA UNIV OF MINING & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com