Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
162 results about "Hardware Trojan" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
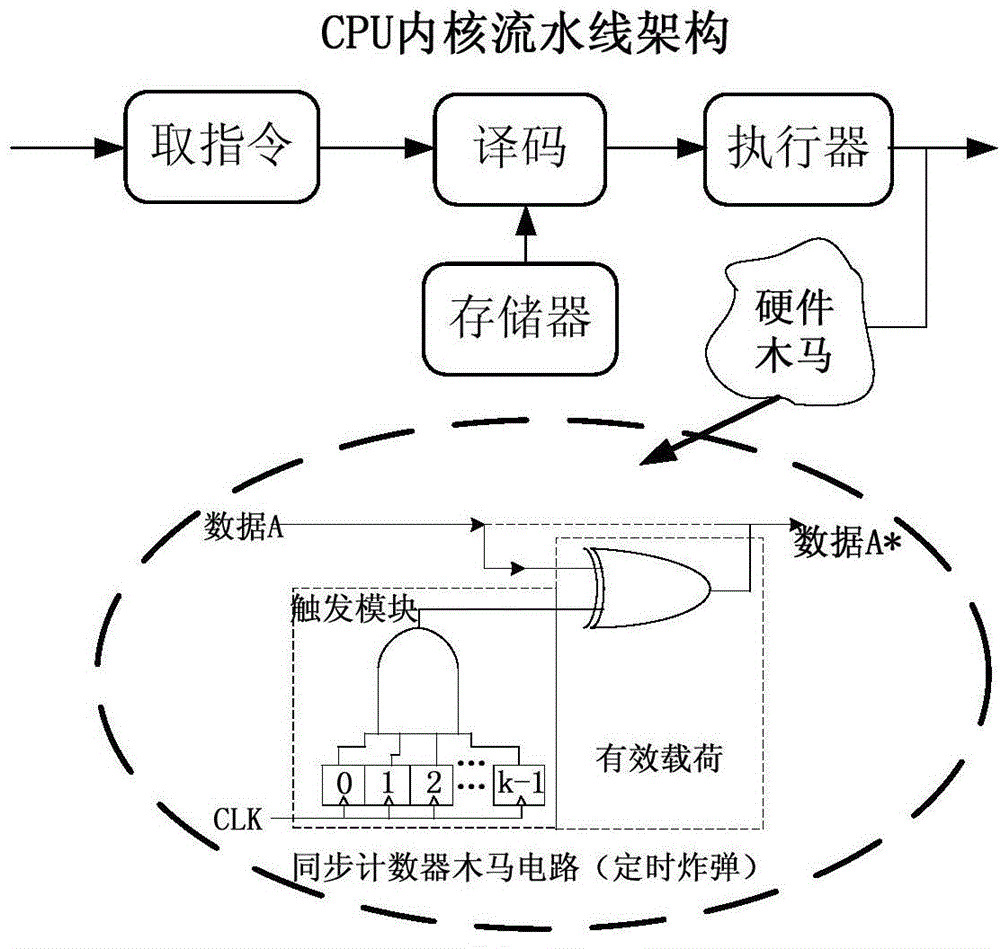
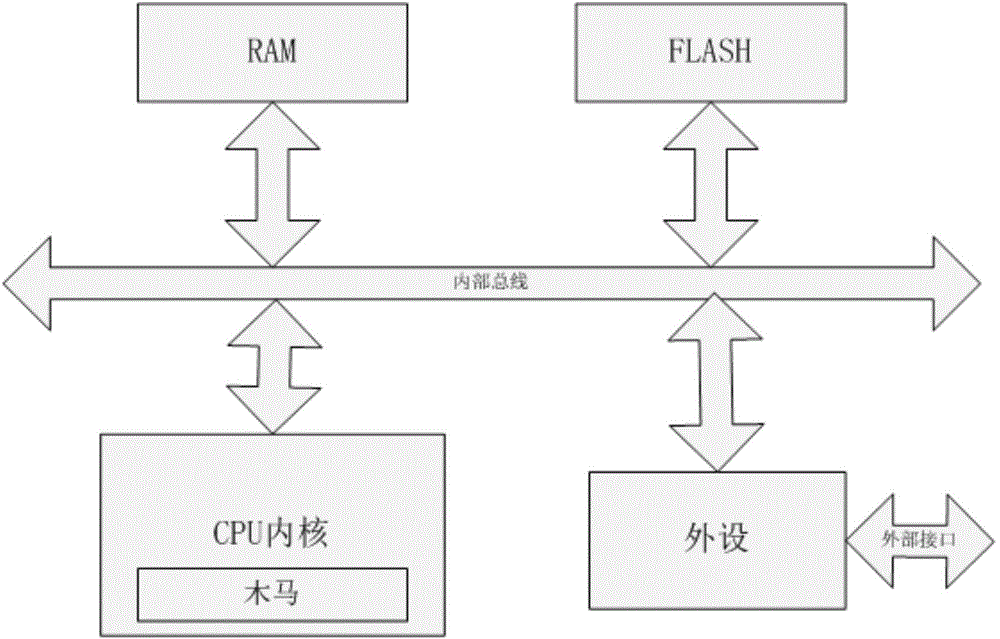
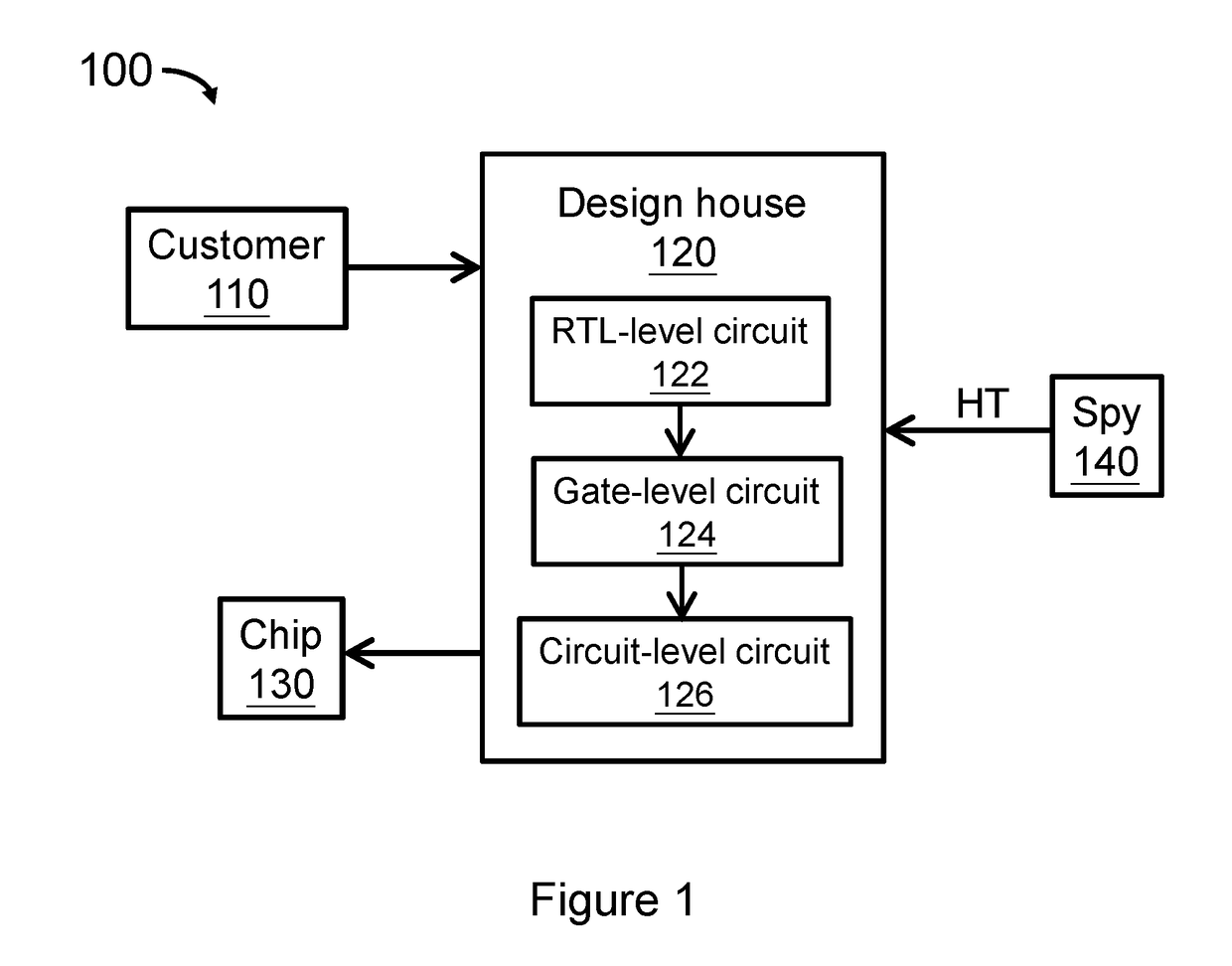
A Hardware Trojan (HT) is a malicious modification of the circuitry of an integrated circuit. A hardware Trojan is completely characterized by its physical representation and its behavior. The payload of an HT is the entire activity that the Trojan executes when it is triggered. In general, malicious Trojans try to bypass or disable the security fence of a system: It can leak confidential information by radio emission. HT's also could disable, derange or destroy the entire chip or components of it.
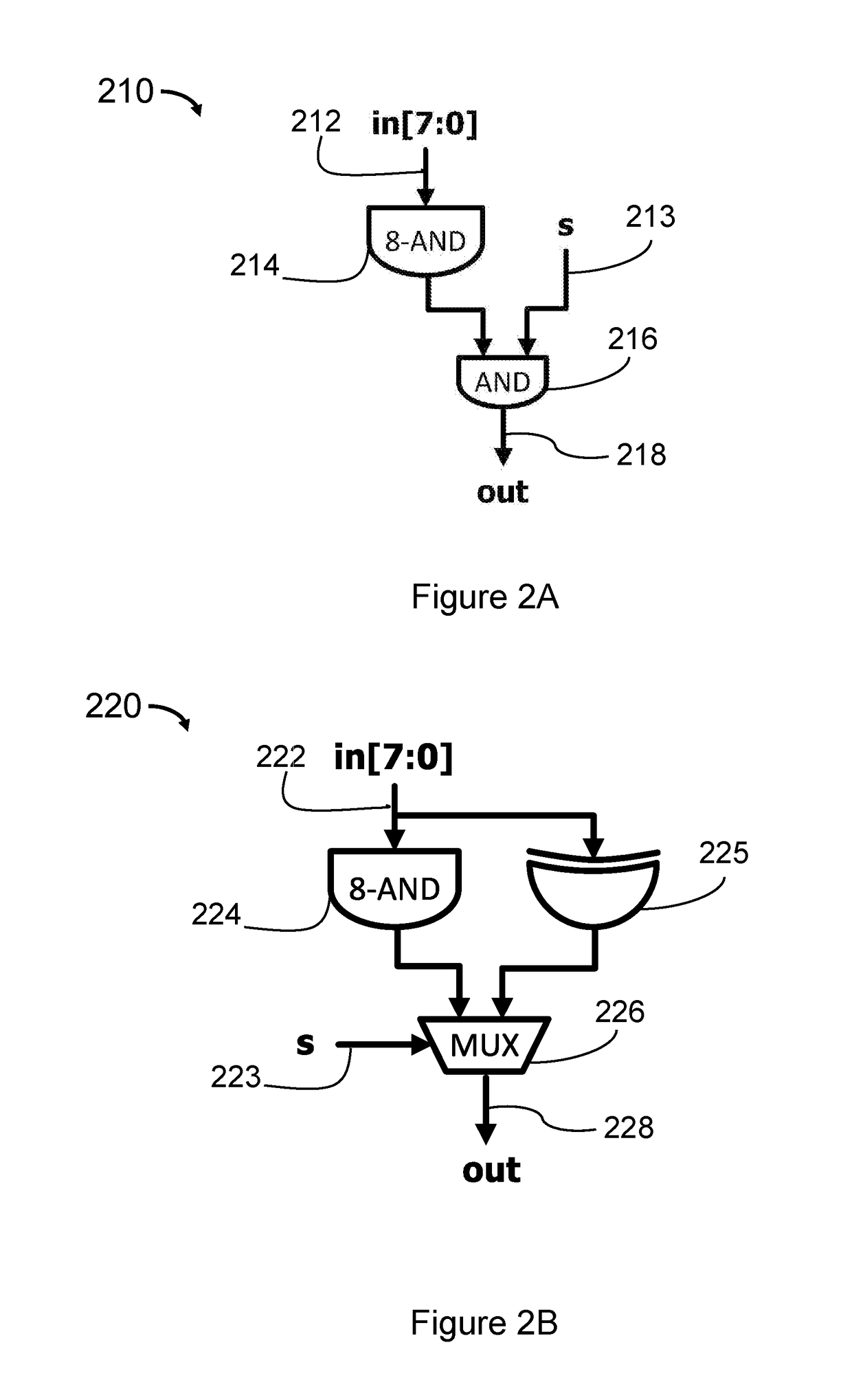
Design method of integrated circuit and hardware trojan detection method
ActiveCN104239616ALow costReduce overheadPlatform integrity maintainanceSpecial data processing applicationsHardware TrojanProcessor register
The invention relates to a design method of an integrated circuit and a hardware trojan detection method. The design method comprises the following steps of acquiring a code of a register transfer level of an initial integrated circuit design; confirming a node position embedded by a potential hardware Trojan in the initial integrated circuit design according to the code; simulating the initial integrated circuit design to obtain a simulating circuit; computing the logic value probability of an interconnection line of the node position in the simulating circuit, and carrying out insertion design of testability circuits on the interconnection line of the node position according to the logic value probability; sequentially connecting the testability circuits in the simulating circuit to form a scan chain, and acquiring a new integrated circuit design according to the simulating circuit with the scan chain, wherein the scan chain is used for detecting the position of the hardware trojan of the integrated circuit according to the input test signals and the output results. According to the integrated circuit designed by the scheme of the invention, the position of the hardware trojan can be found, and the cost is reduced.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
Activity measurement-based hardware trojan detection method
Disclosed in the invention is an activity measurement-based hardware trojan detection method, comprising three parts: bench file generation, circuit activity measurement and hardware tojan detection test vector set generation. More specifically, a circuit netlist is analyzed; activity values of internal nodes of the circuit are calculated; lists of circuit nodes with low 0 activity and low 1 activity are generated; and determination and grouping are carried out on the nodes to generate a hardware trojan detection test vector set. According to the invention, different activity threshold values can be arranged; there is no extra hardware cost for hardware trojan detection; and combined logical type hardware trojan can be effectively detected. Besides, the provided method can be applied for target node extraction in a hardware trojan detectable design method.
Owner:PEKING UNIV
Hardware Trojan horse detection method and hardware Trojan horse detection system based on test vectors
The invention discloses a hardware Trojan horse detection method and a hardware Trojan horse detection system based on test vectors. The method includes receiving reversal information and coverage information of each circuit node in an integrated circuit; selecting circuit nodes as candidate Trojan horse nodes, wherein the reversal information and the coverage information of the circuit nodes meet preset low reversal conditions and preset low coverage conditions respectively; selecting final test vectors from the test vectors according to the reversal information of each candidate Trojan horse node and combined reversal information of each group of candidate Trojan horse nodes; respectively applying the final test vectors to the input end of the integrated circuit, and performing Trojan horse detection on the integrated circuit. By the method and the system, whether or not the integrated circuit contains hardware Trojan horses can be quickly and accurately detected without damage to the integrated circuit.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
Method for shortening verification time of hardware Trojan in integrated circuit test
ActiveCN102854454AImprove detection efficiencyIncrease costElectronic circuit testingTest inputMultiway switching
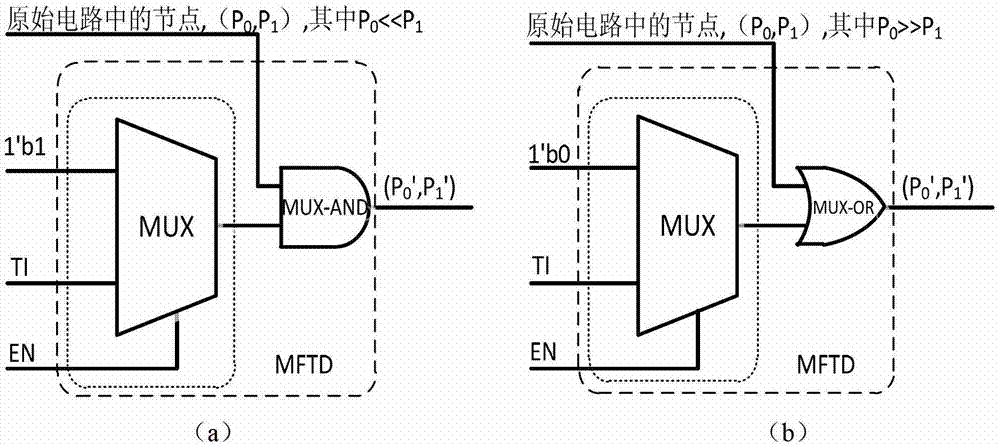
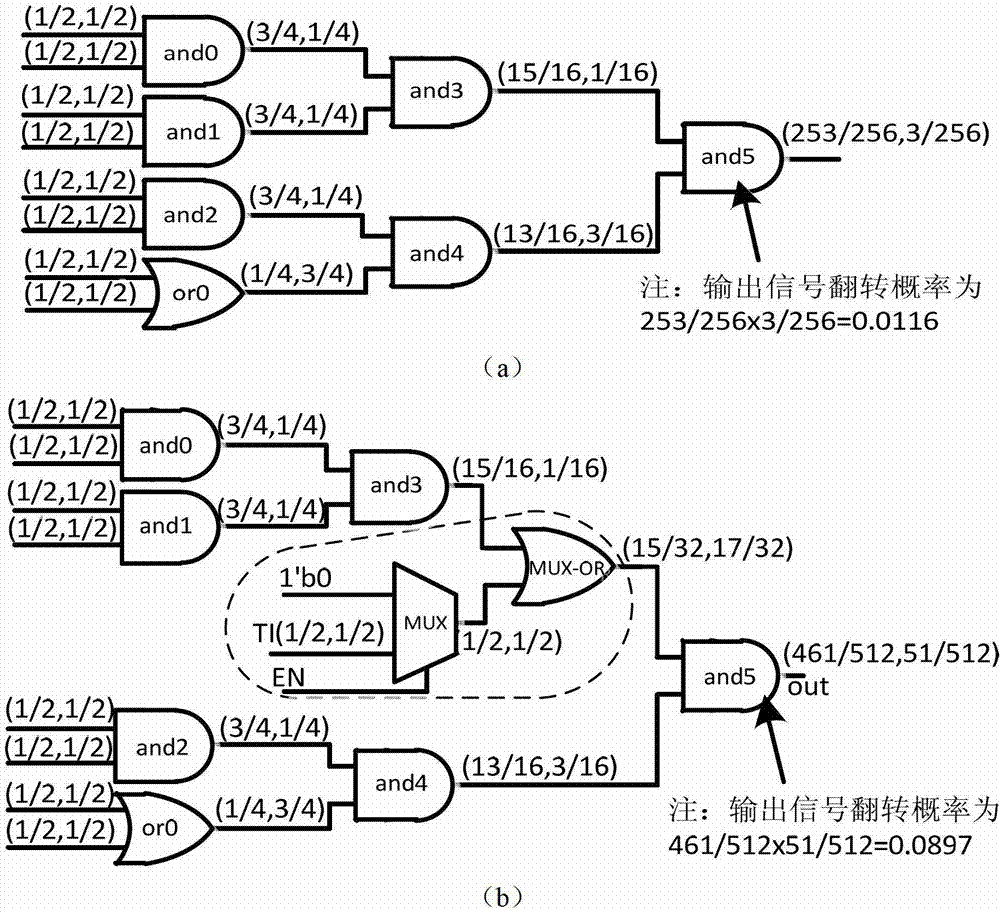
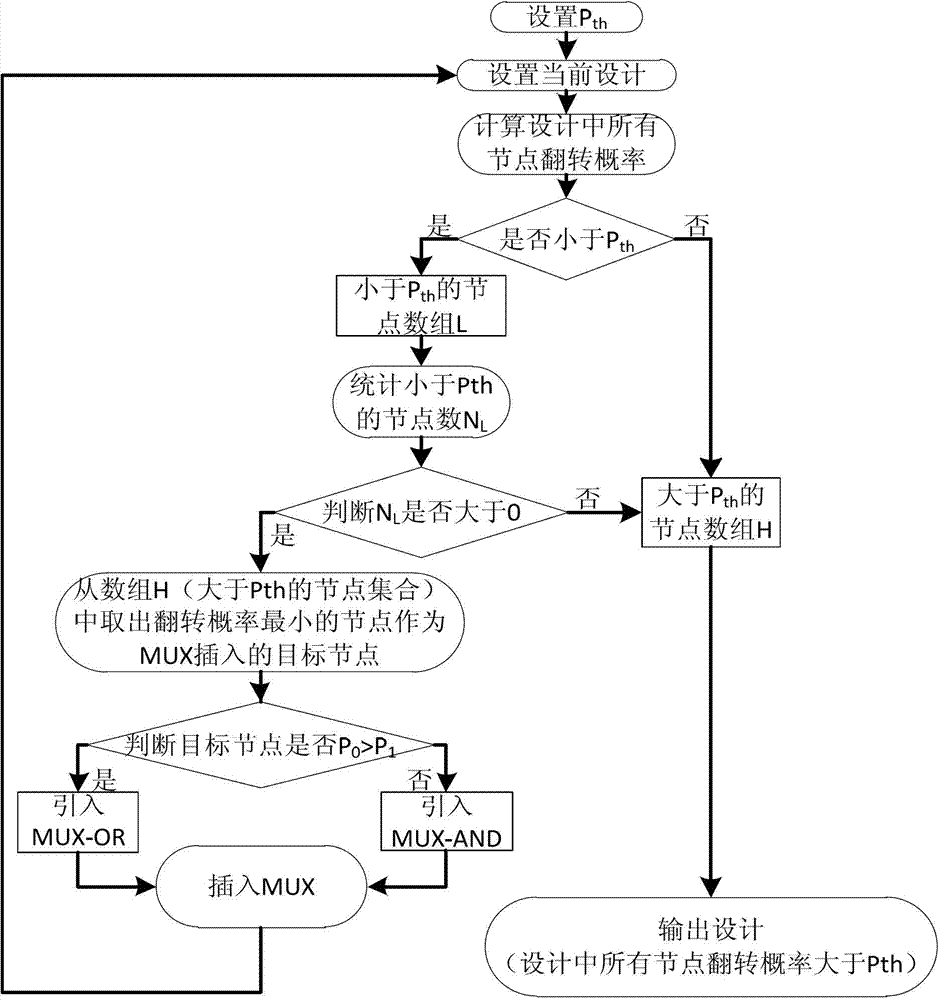
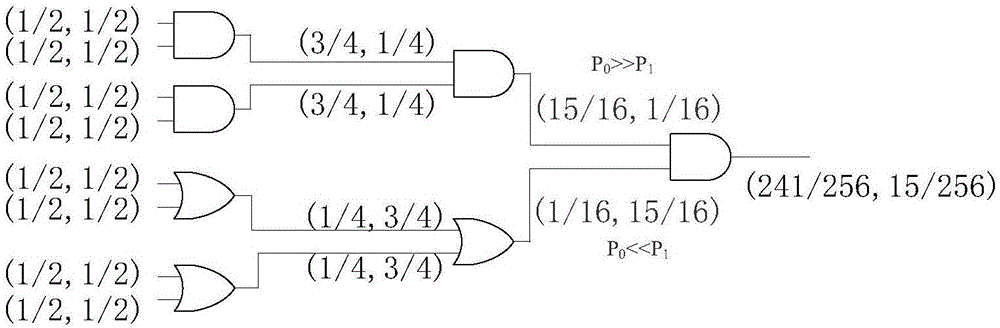
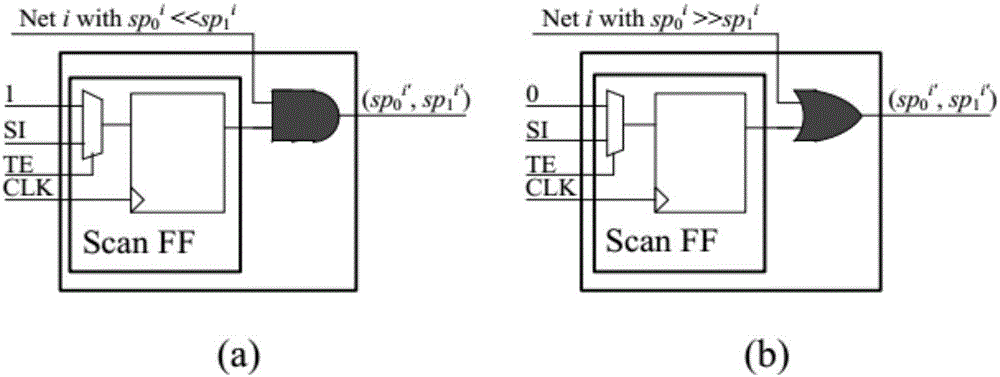
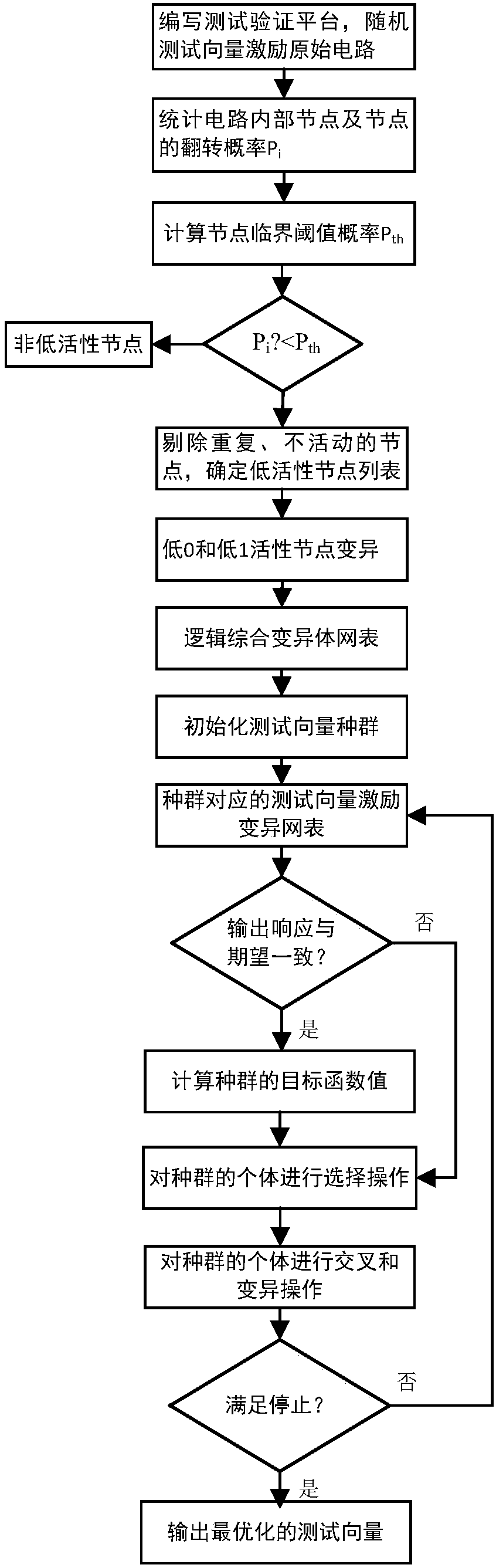
The invention discloses a method for shortening verification time of hardware Trojan in an integrated circuit test. A special structure comprises a gate cell and a multi-way switch, wherein the multi-way switch has a test input signal TI and a Trojan test mode enabling signal EN; the gate cell is used for performing logical adhesion with target nodes in the tested integrated circuit, and the type of the gate cell is decided by occurrence probability 0 and 1 of the nodes; the special structure MFTD is inserted by the following steps of: firstly, setting a probability threshold value Pth; classifying all nodes of the tested integrated circuit into the nodes of which the overturning probability is greater than the Pth and the nodes of which the overturning probability is less than the Pth; and then inserting the special structure MFTD by circularly selecting the target nodes until the overturning probability of all the nodes is greater than the Pth. According to the invention, the MFTD is inserted into the design stage of the integrated circuit, so that the activation degree of the hardware Trojan is effectively improved in the test, and the verification time of the hardware Trojan is shortened.
Owner:TIANJIN UNIV
Method for effectively improving hardware Trojan activation probability
InactiveCN106778263AHigh activation rateIncrease activationPlatform integrity maintainanceLow activityHardware Trojan
The invention relates to the technical field of integrated circuit trustworthiness detection, in order to effectively remove the low activity node in the circuit, to improve the activation of the circuit, to greatly shorten the activation time of the low active node and to reduce the random and the uncertainty of the activation time of the hardware Trojan horse in the process of the hardware Trojan horse detection to a great extent. In addition, in the combination of the bypass signal analysis method or the logic test method, the activation time of the hardware Trojan horse is greatly shortened and the detection rate of the hardware Trojan horse is effectively increased. The technical proposal of the method for effectively improving the hardware Trojan horse activation probability is an effective method for improving the activation probability of the hardware Trojan horse. The method comprises the following steps that1, generating a random test vector and an excitation circuit; 2, counting the transition information of each node of the circuit; 3, setting the critical probability threshold; 4, determining the location of the implanted node; 5, integrating the circuit and detecting. The integrated circuit trustworthiness detection is mainly applied to the case of the integrated circuit trustworthiness detection.
Owner:TIANJIN UNIV
Method and system for processing signals of hardware Trojan detection in integrated circuit
ActiveCN103698687AImprove securityImprove accuracyElectronic circuit testingFeature vectorTime domain
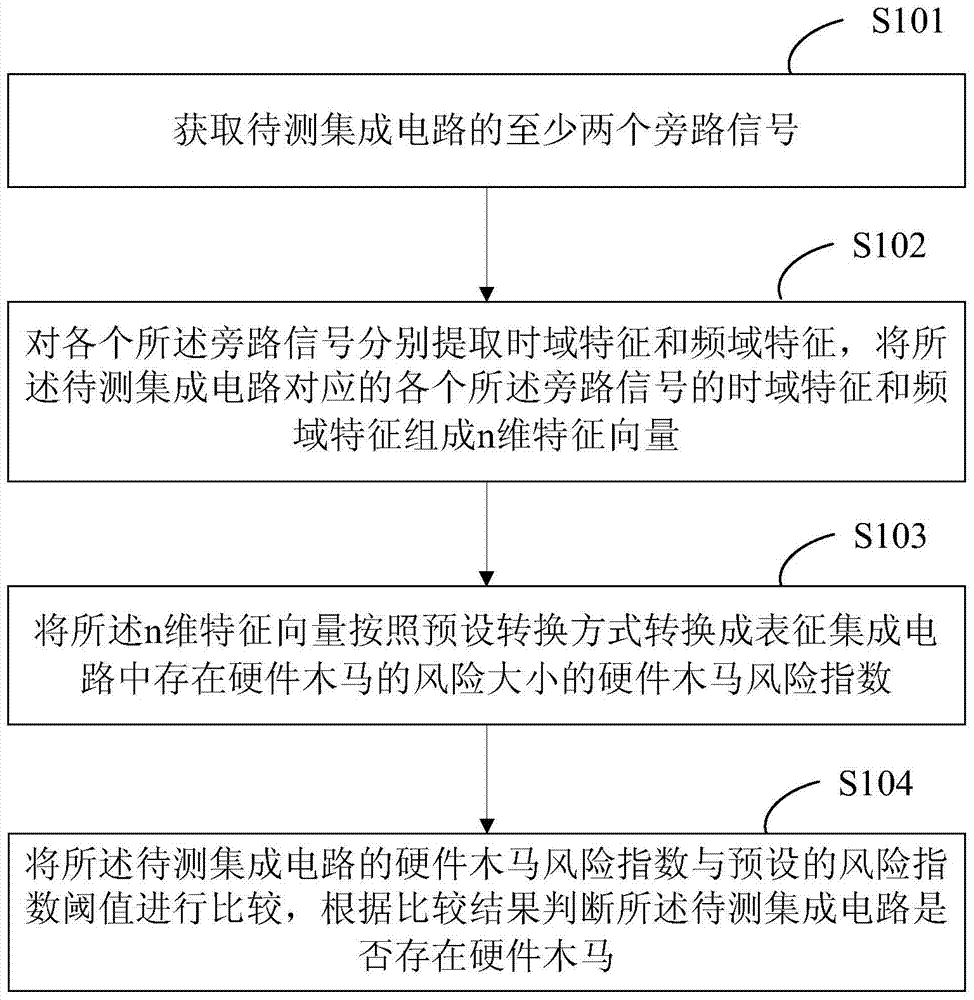
The invention provides a method and a system for processing signals of hardware Trojan detection in an integrated circuit. The method comprises the following steps of obtaining at least two bypass signals of the to-be-detected integrated circuit; respectively extracting a time domain feature and a frequency domain feature from each bypass signal, and enabling the time domain feature and the frequency domain feature of each bypass signal corresponding to the to-be-detected integrated circuit to form an n-dimension feature vector; converting the n-dimension feature vector into a hardware Trojan risk index by a preset conversion method, wherein the hardware Trojan risk index is used for featuring the degree of the risk of the hardware Trojan in the integrated circuit; comparing the hardware Trojan risk index of the to-be-detected integrated circuit with the preset risk index threshold value, and judging if the hardware Trojan exists in the to-be-detected integrated circuit according to the comparison result. The method and the system have the advantage that the hardware Trojan of the integrated circuit can be detected according to the bypass signals of a plurality of integrated circuits, so the safety of the integrated circuit is improved.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
Hardware Trojan side-channel detection method based on electromagnet and electric current
ActiveCN106841987AEfficient detectionImprove diff resolutionElectronic circuit testingHardware TrojanEngineering
The invention relates to the technical field of integrated circuit dependability testing, and provides a hardware Trojan side channel detection method based on the electromagnet and the electric current to achieve the detection of hardware Trojans. The hardware Trojan side channel detection method based on the electromagnet and the electric current comprises the steps that 1, the side channel tests of the to-be-measured chips are conducted; 2, pretreatments are performed on the side channel information of all the to-be-measured chips; 3, the proportion coefficient matrix R1xn of the electromagnetic differential information and the leaked electric current information of all the to-be-measured chips are determined; 4, the discrimination is conducted on the differences of the proportion coefficient matrix for part of the to-be-measured chips; 5, the discrimination is conducted on the hardware Trojan chips of the to-be-measured chips; 6, the online difference recognitions are conducted on the hardware Trojans. The hardware Trojan side channel detection method is mainly used in dependability detection tests of integrated circuits.
Owner:TIANJIN UNIV
Single-trigger hardware trojan horse detection method based on gate-level structure characteristics
InactiveCN107886012AReduce Detection ComplexityShorten detection timeInternal/peripheral component protectionDirected graphLevel structure
The invention discloses a single-trigger hardware trojan horse detection method based on gate-level structure characteristics. The single-trigger hardware trojan horse detection method comprises the following steps that 1, based on an existing hardware trojan horse reference circuit, the structure characteristics of single-trigger type hardware trojan horses are abstracted to form a hardware trojan horse structure library; 2, unknown circuits (3) to be detected are input to obtain corresponding netlist-form circuits; 4, the netlist-form circuits are abstracted into directed graphs; 5, fractionsequences of all logic gates in the circuits are obtained; 6, a preset abnormal value recognition algorithm is used for marking abnormal values in the fraction sequences, and the logic gates corresponding to abnormal fractions are added into a final trojan horse suspicious logic gate set. By adopting the method, trigger circuit characteristics of single-trigger type hardware trojan horses can bemore accurately abstracted, meanwhile a fraction accumulation algorithm is improved, namely the hardware trojan horse detecting time is effectively shortened while all the information of circuits is retained, and the hardware trojan horse detecting accuracy rate is improved.
Owner:TIANJIN UNIV
Hardware Trojan horse detection system based on puf
InactiveCN102799813AStable and efficient detectionComputer security arrangementsData analysisHardware Trojan
The invention relates to a hardware Trojan horse detection system based on puf. The system adds the puf into a plurality of modules of an integrated chip (IC) in an original IC design file, sends the IC design file with the puf to a factory for production, performs data acquisition on an IC sample produced by the factory according to the IC design file with the puf under a test mode, analyzes the acquired data through a data analysis module and outputs a judgment result; and a user judges whether the original IC design in an original data storage module is modified according to original data judged by a data judgment module and judges whether to put the original data into production. The hardware Trojan horse detection system has the advantages that the shortcomings that the conventional detection method is complicated, high in test cost and long in time period, and the original design or the original IC is needed are overcome; whether hardware Trojan horses are contained can be stably and effectively detected; naturally, the fact that the Trojan horses are very difficult to trigger is not considered; the Trojan horses are detected physically; and therefore, most hardware Trojan horses can be detected.
Owner:WUHAN UNIV
Hardware trojan detection method and system based on time delay
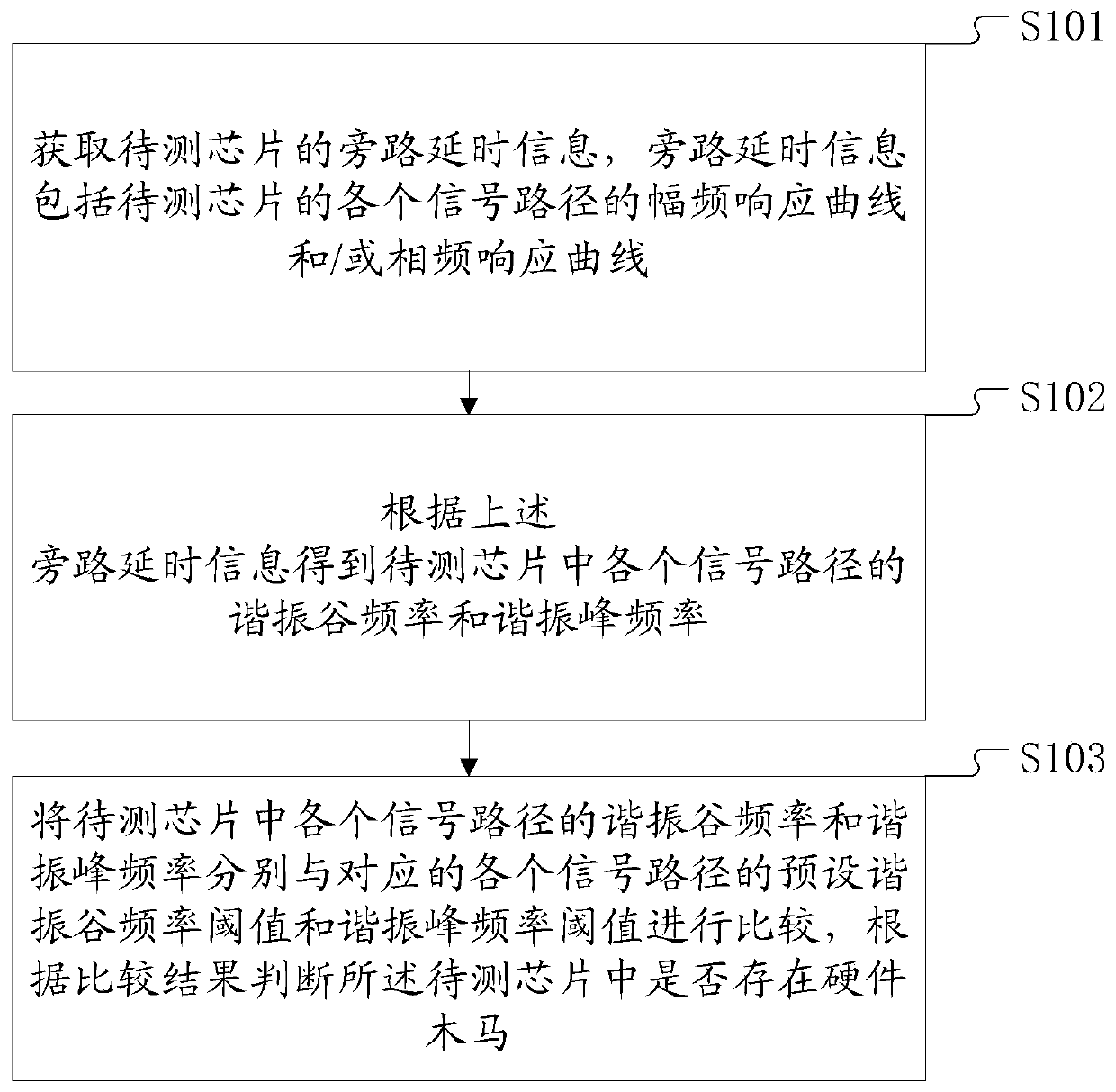
ActiveCN104950246AReduce workloadReduce testing costsElectronic circuit testingHardware TrojanTime delays
The invention discloses a hardware trojan detection method and system based on time delay. The method comprises the following steps of firstly obtaining bypass time delay information of a chip to be detected, wherein the bypass time delay information includes an amplitude frequency response curve and / or a phase frequency response curve of each signal path of the chip to be detected; obtaining the resonance valley frequency and the resonance peak frequency of each signal path in the chip to be detected according to the bypass time delay information; finally and respectively comparing the resonance valley frequency and the resonance peak frequency of each signal path in the chip to be detected with the corresponding preset resonance valley frequency threshold and the resonance peak frequency threshold of each signal path; judging whether hardware Trojan exists in the chip to be detected or not according to the comparison result. The addition of the additional chip area for test is not needed, the workload and the test cost are greatly reduced, and the work efficiency is improved.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
Hardware Trojan real-time detection system and design method thereof
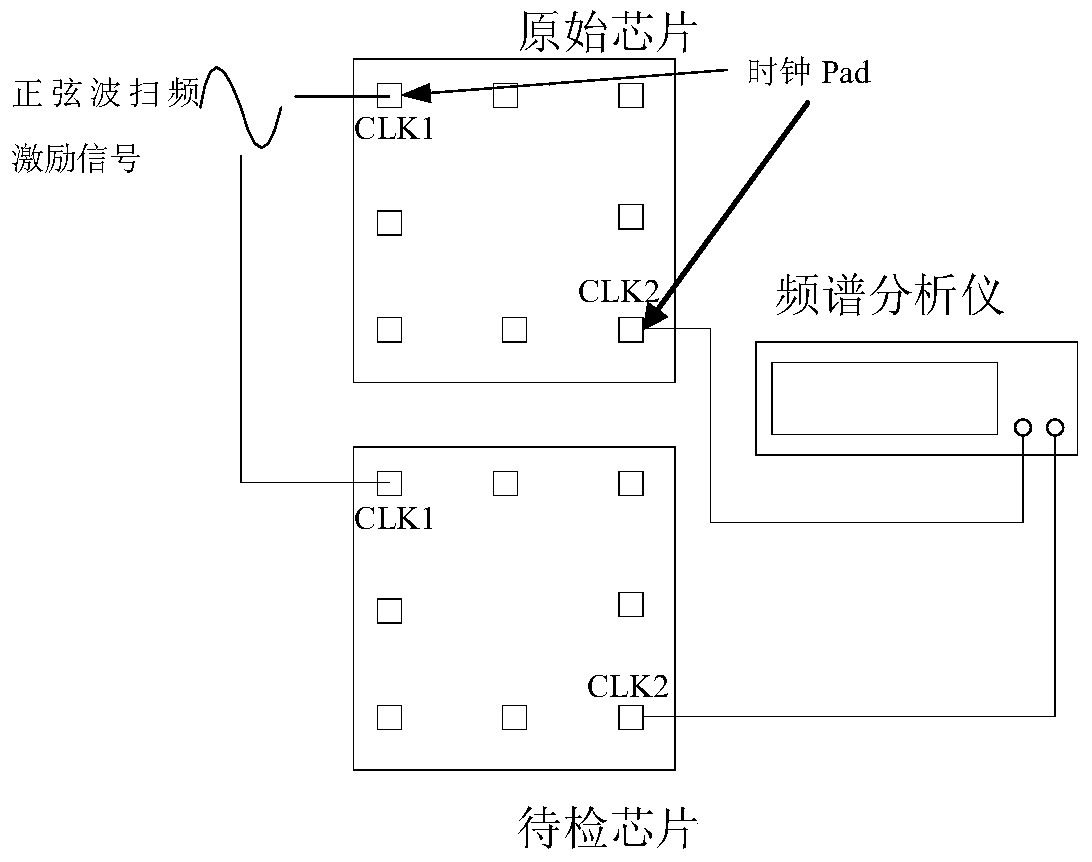
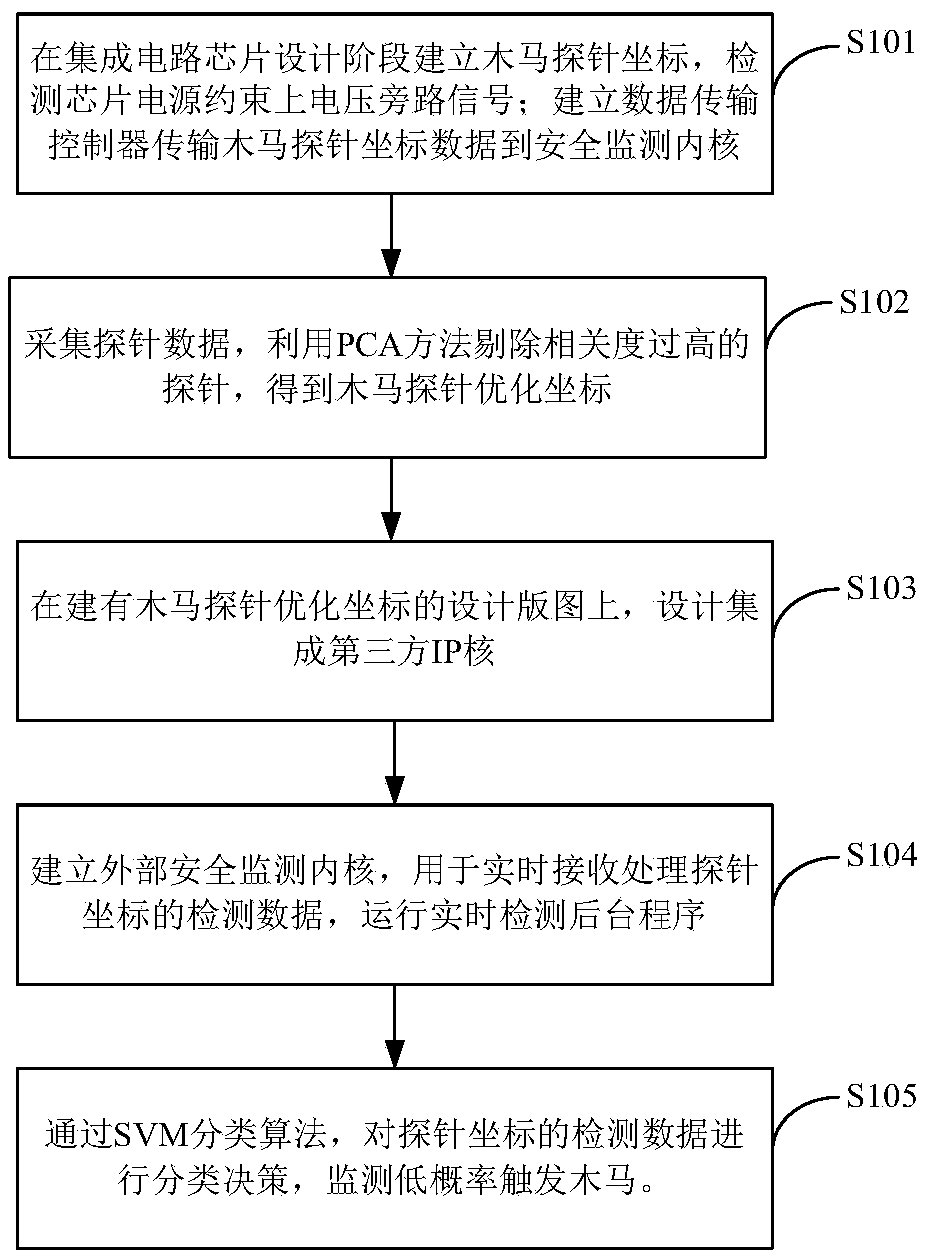
ActiveCN108846283ARealize detection and positioningRealize Trojan Horse BehaviorCharacter and pattern recognitionPlatform integrity maintainanceSignal onPrincipal component analysis
The invention provides a hardware Trojan horse real-time detection system and a design method thereof. The system comprises Trojan probes, a data transmission controller and a safety monitoring kernel. The Trojan probes acquire voltage bypass signals on power supply constraint lines inside an integrated circuit chip, and transmit the voltage bypass signals to the safety monitoring kernel for Trojan detection through the data transmission controller. The method comprises the following steps: the Trojan probes are implanted on the integrated circuit chip at the initial design stage to establishthe data transmission controller; a principal component analysis method is used to optimize the number of the Trojan probes and the optimal coordinates of the Trojan probes are obtained; a third-partyIP core is designed and integrated on the integrated circuit chip layout with the Trojan probe optimal coordinates; a security monitoring kernel is established to monitor the working state of IP corein real time; the abnormal behavior is identified by a support vector machine classification algorithm and the IP core with the Trojan is detected. The invention can detect and locate the IP core containing the Trojan in real time, and can find the Trojan behavior triggered under the low probability condition.
Owner:BEIHANG UNIV
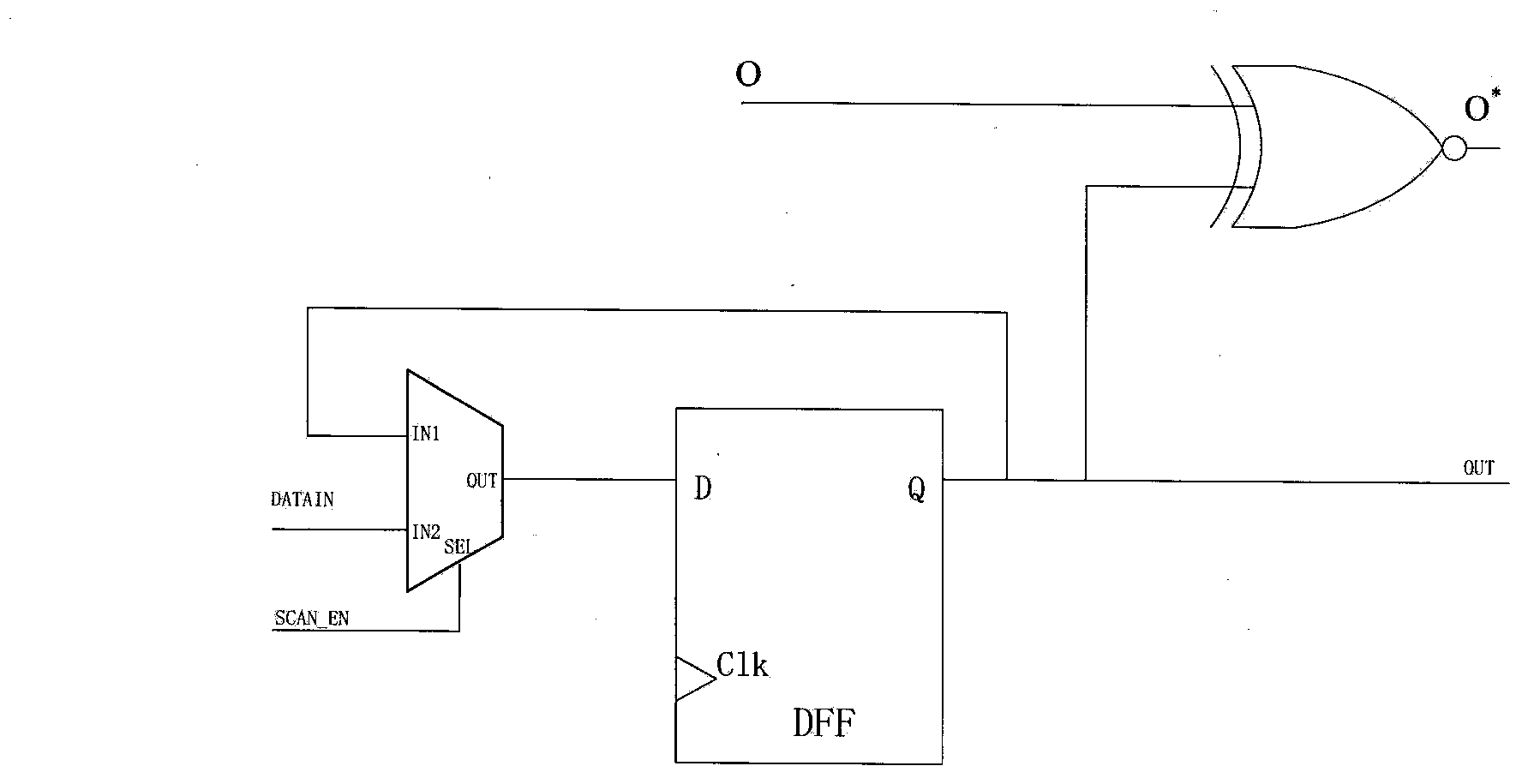
Hardware-Trojan-resisting circuit design method based on activation probability analysis
ActiveCN104101828AImprove the immunityIncreased protectionElectrical testingDesign for testingAlgorithm
The invention relates to the field of testability design of an integrated-circuit technology and discloses a hardware-Trojan-resisting circuit design method based on activation probability analysis. The method mainly includes two parts: a first part: circuit design of a probability fuzziness unit and a second part: an insertion algorithm of the probability fuzziness unit. Targeting at characteristics of high elusiveness and high perniciousness of hardware Trojans, through analysis of a circuit node activation probability, the method selects an appropriate node to insert the probability fuzziness unit circuit so that an attacker is incapable of correctly judging a signal jumping probability of nodes in the circuit and inserts hardware Trojans only based on the circuit which undergoes probability fuzziness. Compared with the prior art, the hardware-Trojan-resisting circuit design method based on activation probability analysis is capable of strengthening the hardware Trojan resisting capability of a design circuit so that implanted hardware Trojans are incapable of achieving a specific objective designed by an attacker and are easily detectable in a test period.
Owner:PEKING UNIV
Circuit security testable design method capable of detecting inactive hardware Trojan horse and detecting method of hardware Trojan horse
The invention relates to a circuit security testable design method capable of detecting an inactive hardware Trojan horse and a detecting method for the hardware Trojan horse. Firstly, the design and the verification on an original circuit are completed. Secondly, a security testing mode is added for the circuit, the clock frequency under the security testing mode is great less than the working frequency of the circuit, and work such as corresponding compositing, locating and wiring, timing sequence analyzing and designing is finished. In the chip testing process, the security testing mode is in use, and by means of a security testing clock with the using frequency which is great less than a functional clock, the dynamic power consumption during whole circuit running is lowered, so that the proportion of the static power consumption of the hardware Trojan horse in an idle state on the whole circuit power consumption is increased, and detecting on the hardware Trojan horse which is in a sleep mode is achieved.
Owner:58TH RES INST OF CETC
Method for detecting hardware Trojan based on active optical watermark
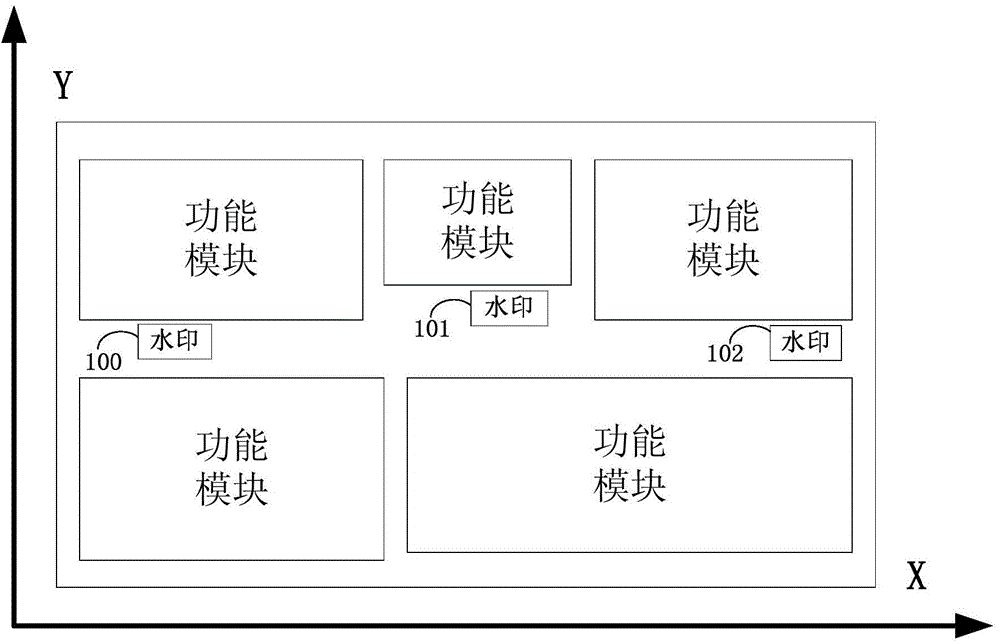
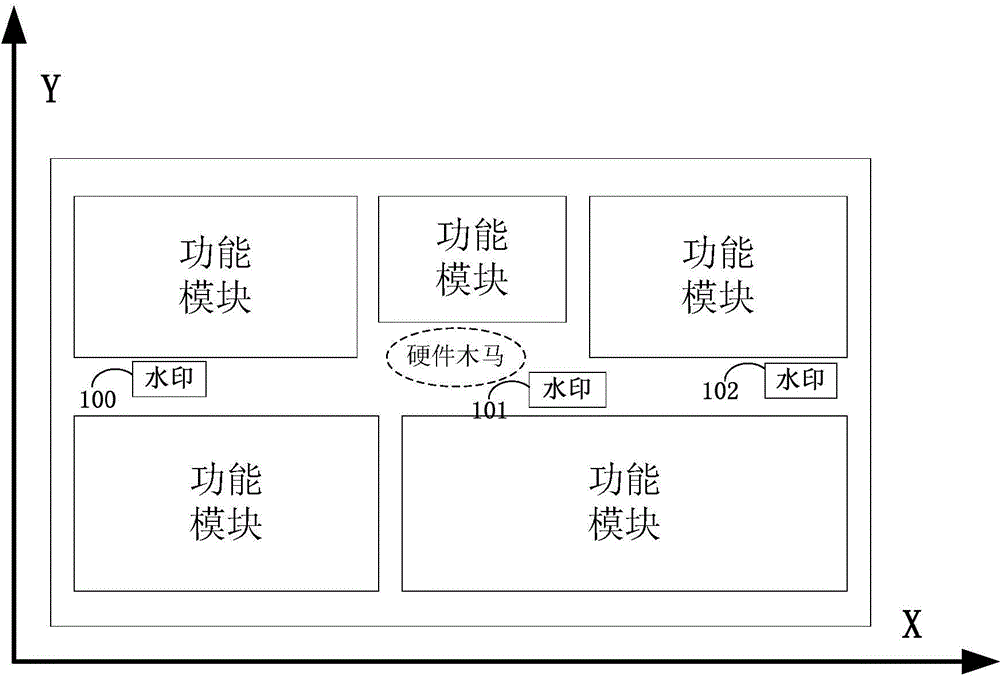
ActiveCN104614660AAccurate detectionEfficient detectionElectronic circuit testingProcess noiseHardware Trojan
The invention relates to a method for detecting hardware Trojan based on an active optical watermark. The method comprises the steps of inserting some special units which do not influence the circuit function and have the temperature superior to that of the surrounding adjacent units after being electrified into a circuit and distributing to the layout according to a certain rule, wherein such special units are the active optical watermarks of the circuit; simulating to obtain the heat distribution map of the whole circuit while electrifying; performing the same test to the circuit and photographing after the circuit is manufactured and before packaging; comparing the simulated watermarks with the actual watermarks; if the watermark position changes or disappears, determining that the hardware Trojan is in the circuit. With the adoption of the method, the circuit is avoided various complex tests; the influence of the process noise and measurement noise in the traditional method can be overcome; the detection complexity can be obviously reduced; the detection accuracy can be improved.
Owner:58TH RES INST OF CETC
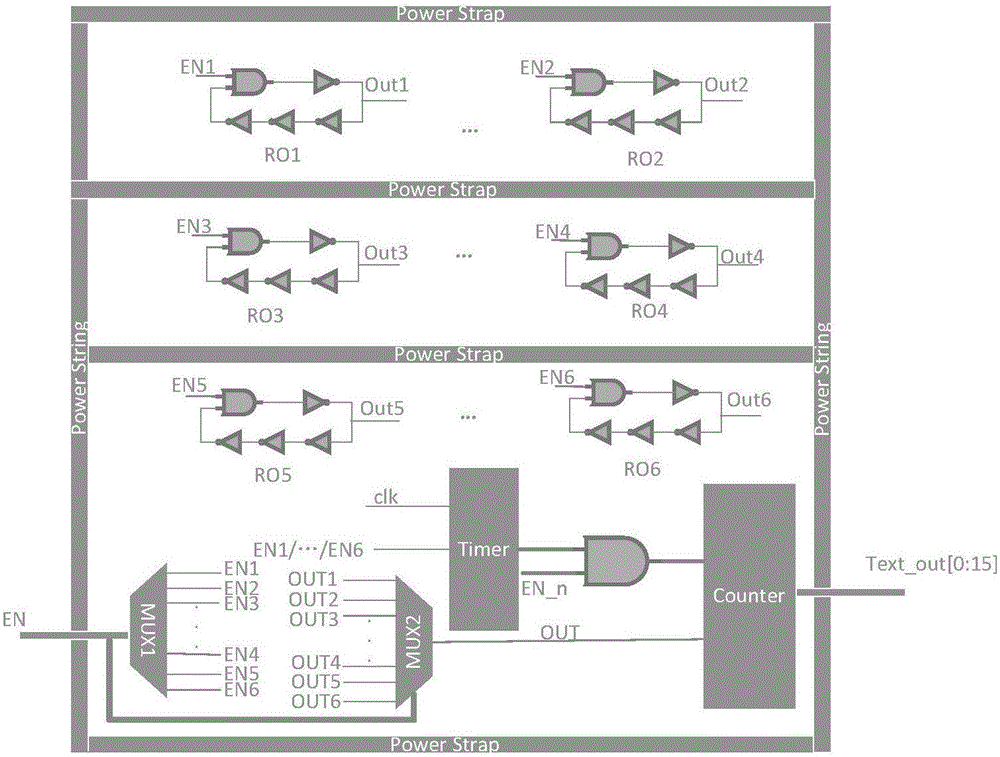
Local test vector generating and optimizing method based on annular oscillator network
InactiveCN106771960AIntuitive and effective screeningReduce complexityElectronic circuit testingTest efficiencySignal-to-noise ratio (imaging)
The invention relates to a local test vector generating and optimizing method based on an annular oscillator network, belongs to the technical field of trustiness detection of an integrated circuit, and aims at enhancing the circuit activity in the local area, further improving the resistance to hardware Trojans, improving the influencing signal to noise ratio of the hardware Trojans to certain extent under influence of technical noises, and improving the hardware Trojan testing efficiency greatly. According to the method, an original layout is not changed, active sensing units of a local area is inserted into a spare space in the layout, a test circuit is generated, and a local test vector is generated and optimized for the test circuit. The method comprises the following steps that 1) the test circuit is generated; 2) a local test vector generating and optimizing system is initialized; 3) a test vector set is generated randomly, and test vectors are applied; 4) data is collected; 5) determination is completed by test; and 5) the test vectors are optimized. The method is mainly applied to trustiness detection occasions of the integrated circuits.
Owner:TIANJIN UNIV
Circuit safety DFT (design for testability) method for accelerating hardware Trojan trigger and hardware Trojan detection method
The invention relates to a circuit safety DFT (design for testability) method for accelerating hardware Trojan trigger. The method comprises the following steps: firstly, function design and verification of a circuit are finished; secondly, clock frequency higher than that during normal operation is selected and taken as the clock frequency of a safe test mode; then work including corresponding synthesis, scan chain insertion, placing and routing, static timing analysis and the like is finished, and exactly correct functions and timing sequences for function test and scan chain test under the clock frequency of the safe test mode are guaranteed. Therefore, after the circuit is manufactured, the circuit is configured with the safety test mode with high clock frequency, and for hardware Trojans such as time bomb type hardware Trojans having a time-dependent trigger condition, the hardware Trojan trigger probability can be accelerated remarkably when the circuit designed with the method is used. The design method can further increase the hardware Trojan implantation difficulty.
Owner:58TH RES INST OF CETC
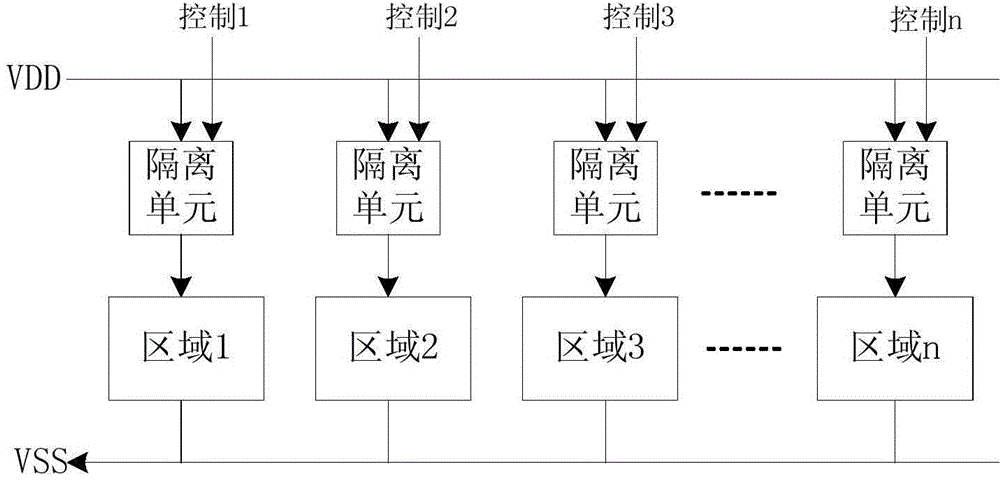
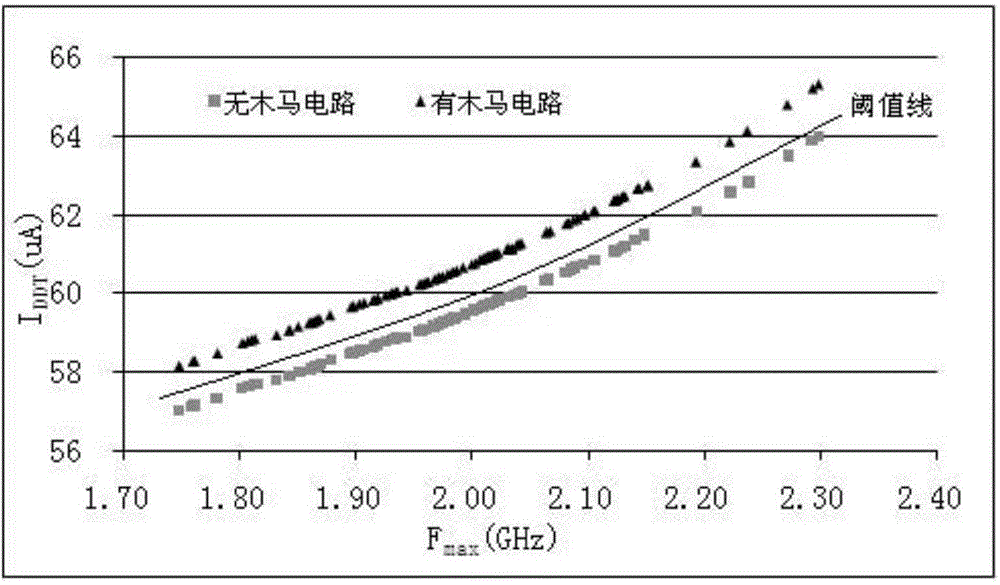
Circuit designing method for improving hardware Trojan detecting resolution based on power supply isolation and hardware Trojan detecting method
ActiveCN104615949ASmall scaleRaise the scale ratioInternal/peripheral component protectionChannel dataImage resolution
The invention provides a circuit designing method for improving hardware Trojan detecting resolution based on power supply isolation and a hardware Trojan detecting method. The circuit design method comprises the following steps: firstly, dividing a circuit into different areas according to a certain rule; secondly, designing an independent power supply network for each divided area, and controlling the on-off state of a power supply of each divided area by utilizing a power supply isolation unit; thirdly, producing a plurality of test vectors in the circuit by adding a self-testing module or utilizing the self-testing module which is in the circuit, wherein the vectors can serve as the input of each divided area in the circuit; finally, completely turning off the power supplies of other areas which are not required to be used during a chip testing process, and only testing side channel data when only one area works, so that the proportion of the side channel data produced by the hardware Trojan in the overall circuit side channel data is increased. The circuit which contains the hardware Trojan and the circuit which does not contain the hardware Trojan are distinguished better, so that the detecting resolution of the hardware Trojan is improved.
Owner:58TH RES INST OF CETC
Determining an aspect of behavior of an embedded device such as, for example, detecting unauthorized modifications of the code and/or behavior of an embedded device
The goal of detecting modifications, such as unauthorized modifications for example, of the code and / or behavior of an embedded device (e.g., unexpected / unauthorized remote reprogramming, re-flashing), changes to code at run-time (e.g., code injection, software parameter changes due to run-time reconfiguration commands), execution of unauthorized code, activation of hardware Trojans, and other attacks on the hardware and / or software of embedded devices (or more generally, for determining an aspect of behavior of an embedded device and / or an embedded system) is solved by (1) injecting at least one of (A) code and / or (B) inputs into the embedded system to cause the embedded system, when functioning as desired, to exhibit an identifiable baseline behavior determined from a sequence of patterns (also referred to as “fiduciary markers”) in observable side channel emissions of the embedded system; (2) measuring side channel emissions generated by the embedded system when the at least one of (A) code and / or (B) inputs is injected; (3) extracting features from the measured side channel emissions; and (4) determining the aspect of the behavior of the embedded system by analyzing the extracted features with respect to features of the baseline behavior.
Owner:NEW YORK UNIV
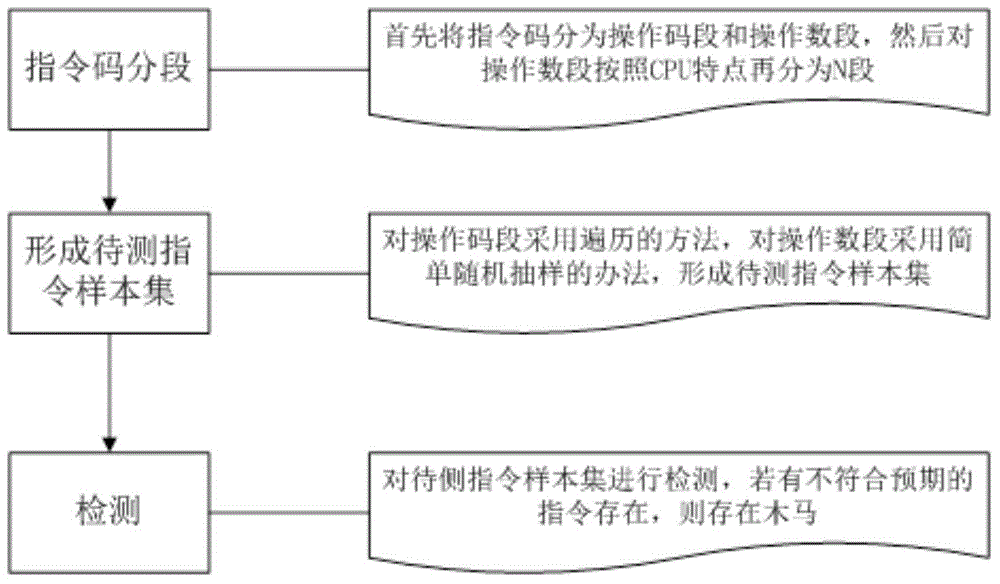
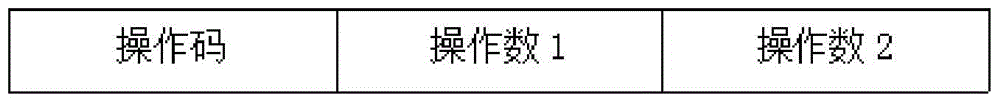
Detection method aiming at CPU internal hidden instruction type hardware trojan
ActiveCN104866766AImprove accuracyEfficient detectionPlatform integrity maintainanceHardware TrojanParallel computing
The invention provides a detection method aiming at a CPU internal hidden instruction type hardware trojan. The detection method comprises the following steps: firstly dividing a machine code of a CPU instruction into an operating code segment and an operating number segment, re-dividing the operation number segment into N segments according to characteristics of different CPU frameworks; secondly, for the N divided operation number segments, extracting one sample from each segment according to a certain rule to form a complete instruction with the operation codes; and then, traversing the operation code segment, simply and randomly sampling the operation number segment to form a to-be-tested instruction sample set; finally testing all instructions in the to-be-tested instruction sample set to judge whether the hidden instruction type hardware Trojan is existent in the CPU. Compared with the traditional full-traversing method, the testing time of the method provided by the invention is greatly reduced, and the hidden instruction type Trojan can be fast and effectively detected.
Owner:58TH RES INST OF CETC
Method for generating RTL hardware Trojan test vectors
The invention discloses a method for generating RTL hardware Trojan test vectors. The method mainly includes generation of a control flow chart, concurrent symbol execution, and satisfiability solving and generation of test vectors. The method provided by the invention adopts a method of statically analyzing Veri log codes, and adopts a multi-thread concurrency technology to realize concurrent symbol execution of the Veri log codes, thereby achieving the purpose of rapidly generating test vectors with a high path coverage rate.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Hardware trojan detection method independent of datum curve
The invention provides a hardware trojan detection method independent of a datum curve. The hardware trojan detection method comprises the following steps: firstly, testing all original test vectors, and judging whether hardware Trojan exists in a chip according to the output result; secondly, modifying each original test vector, so that the same test input in each test vector repeatedly appears for a plurality of times; the test input appears at an interval of a certain period of time in each time, so that partial test codes in each modified test vector repeatedly appear in different time windows for a plurality of times; applying all modified test vectors to a circuit test, and recording corresponding circuit transient current curves of all modified test vectors in the testing process; finally finding out a curve section corresponding to the same test code from each modified test vector in different time windows, and comparing the curve sections. If the fitted circuit transient current curves corresponding to different time windows do not exceed a threshold value, and are not crossed, then the hardware trojan is not contained.
Owner:58TH RES INST OF CETC
Apparatus, method and article of manufacture for partially resisting hardware trojan induced data leakage in sequential logics
ActiveUS20180137290A1Risk of problemDigital data protectionInternal/peripheral component protectionHardware TrojanSequential logic
Apparatus, method and article of manufacture providing a randomized encoding scheme for sequential logics, for resistance to data leakage. Invention employs dual-rail encoding to randomize the information in the chip, and employs three-dimensional integration technology to protect the critical information that is needed to decode the data anywhere on-chip. With the present invention, even when the entire design is completely known to the attacker who also has full access to the outsourced portion, it is still not always possible to identify the information in the chip using data leakage Trojans.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE
Hardware Trojan detection method based on bypass analysis
InactiveCN104764992AImprove efficiency during inspectionNon-destructiveElectronic circuit testingSingular value decompositionHardware Trojan
The invention discloses a hardware Trojan detection method based on bypass analysis. The hardware Trojan detection method has the advantages of being free of destructivity, small in implementing expenditure and the like, even in an environment with large measuring noise and technology noise, the detection method can be used for detecting the hardware Trojan with the area smaller than that of an original design circuit by two orders of magnitudes in chips, the signal processing technology which is more applicable than a singular value decomposition algorithm is discussed, the efficiency of detecting the hardware Trojan is improved, the influences of measuring noise can be eliminated by calculating the average value of L power consumption curves of each chip, the technology noise can be eliminated by calculating the average value of the average power consumption curve of N the hardware Trojan chips, P (t; C) is obtained, the calculated amount can be reduced, and time and labor are saved.
Owner:JIANGXI UNIV OF TECH
Methods and Apparatus for Automatic Detection and Elimination of Functional Hardware Trojans in IC Designs
ActiveUS20170213026A1Improve securitySimple methodInternal/peripheral component protectionPlatform integrity maintainanceHardware TrojanNetlist
A method detects, locates, and masks a hardware Trojan (HT) in an arithmetic circuit to improve circuit security. The method provides a first netlist and a second netlist of the arithmetic circuit, uses reverse engineering to extract 2-input XOR sub circuits, XOR trees, 1-bit adders, 1-bit adder graphs and arithmetic macros from the first netlist and the second netlist to obtain a first plurality of arithmetic macros and a second plurality of arithmetic macros, detects the HT by comparing the first plurality of arithmetic macros with the second plurality of arithmetic macros with functional ECO engine, locates the HT in the second netlist, and improves security of the arithmetic circuit by masking the HT with addition of a patch in the second netlist to obtain a patched netlist.
Owner:EASY LOGIC TECH LTD
Optimized test vector generation method based on genetic algorithm and variation analysis
InactiveCN107590313AEasy to identifyPurposefulGenetic modelsSpecial data processing applicationsHardware TrojanMutant
The invention relates to the technical field of trustworthiness of integrated circuits, and provides a hardware Trojan optimized test vector generation method. The method searches test vector spaces in parallel, is strong in purposiveness and more compactor in directionally-screened test vector, can activate hardware Trojan more effectively, and has higher test efficiency; the method can assist manifesting of the hardware Trojan and analysis of bypass signals to improve a hardware Trojan recognition level, and has certain actual meaning and reference value. The invention adopts a technical scheme as follows: the hardware Trojan optimized test vector generation method based on a genetic algorithm and variation analysis screens out low-activity nodes of a circuit through analyzing characteristics of a parent circuit meshwork list, performs mutation operation on the circuit structure of the low-activity node by using a mutation thought of a software test to generate a mutant, and at lastscreens out a test vector capable of killing mutant by combing with a method of a search thought of the genetic algorithm. The method provided by the invention is mainly applied to design and manufacture occasions of the integrated circuits.
Owner:TIANJIN UNIV
Hardware Trojan side channel detection method based on electromagnetism and delay
ActiveCN106872876AEfficient detectionImprove diff resolutionElectronic circuit testingHardware TrojanComputer science
The invention relates to a hardware Trojan detection technology based on electromagnetism and delay, and aims to realize hardware Trojan detection by use of electromagnetism information and delay information leaked by a chip in a working state. According to a hardware Trojan bypass detection method based on electromagnetism and delay of the invention, the corresponding proportional relationship between the current I(tot, m) consumed by a Trojan chip m and the maximum working frequency f(max, m) of a path is as follows: I(tot, m) / f(max, m) is approximately equal to n(tot, m)*k(g)*n(cri, m)*beta(g). A path has n(cri, m) switching tubes, there are n(tot, m) switching tubes working at the moment, and n(tot, m)>=n(tot, g). If a hardware Trojan is inserted onto a current path, n(cri, m)>=n(cri, g), or, n(cri, m)=n(cri, g). If a hardware Trojan is implanted onto the path, the maximum working frequency f(max, m) is proportional to the current I(tot, m) consumed, and identification can be carried out on the basis. The method is mainly applied to an occasion of delay design and manufacture of integrated circuits.
Owner:TIANJIN UNIV
An RTL hardware Trojan detection method based on the recursive descent algorithm
ActiveCN106407810APrecise positioningAccurately locate the location of the Trojan horsePlatform integrity maintainanceDescent algorithmHardware Trojan
The invention relates to an RTL hardware Trojan detection method based on the recursive descent algorithm. The detection method is characterized by designing RTL code rules according to a Trojan model, appointing word types including module declaration words, module end declaration words, signal declaration words, logic function block declaration words, middle words and closing words, and analyzing RTL files by using the recursive descent algorithm to find Trojan modules meeting the rules. The detection method is aimed at specific types of RTL code level hardware Trojans; compared with conventional method of detecting hardware Trojans on chips, the detection method shortens experiment time greatly, can detect RTL code level hardware Trojans effectively and rapidly and locate Trojans accurately, and increases working efficiency.
Owner:58TH RES INST OF CETC
Integrated circuit hardware Trojan detection method and system
ActiveCN104316861AImprove detection efficiencyLow costElectronic circuit testingHardware TrojanAnalysis working
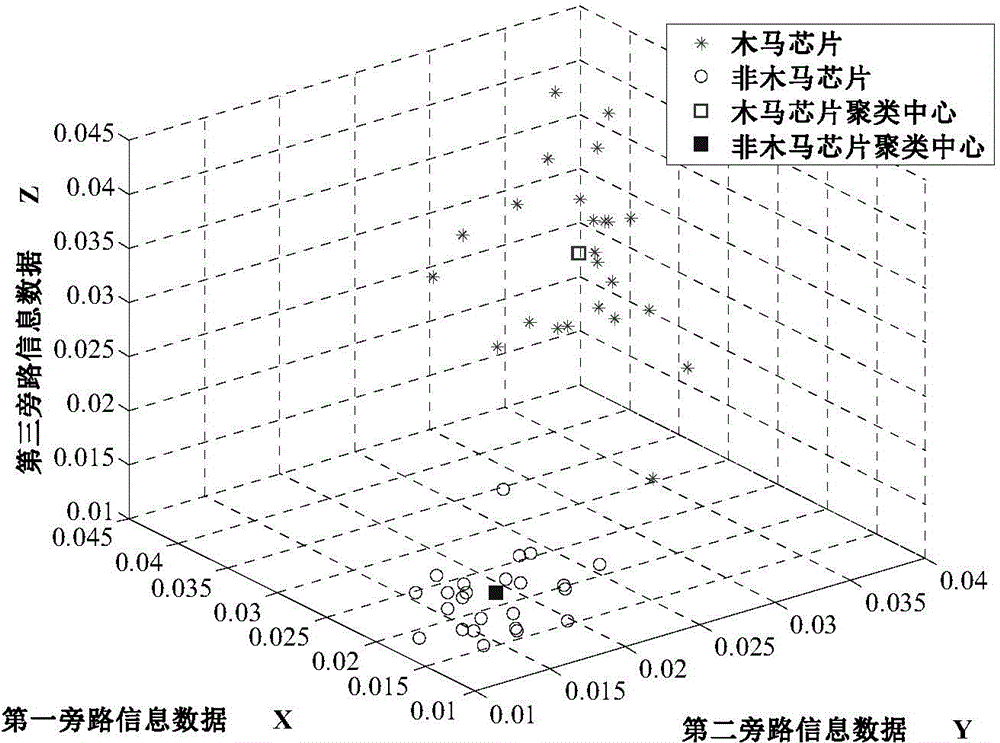
The invention provides an integrated circuit hardware Trojan detection method and system. The integrated circuit hardware Trojan detection method comprises obtaining the bypass information data of chips to be detected; extracting a plurality of sample chips from the chips to be detected to be clustered into two chip clusters and determining corresponding cluster centers; extracting several sample chips from the two clusters for reverse engineering hardware Trojan analysis and determining the types of the several sample chips; determining the types of the other chips to be detected according to the Euclidean distance between the other chips to be detected and the two cluster centers, wherein the other chips are except the cluster chips. According to the integrated circuit hardware Trojan detection method and system, the hardware Trojan detection work of the chips to be detected can be achieved without a large amount of integrated circuit hardware Trojan reverse engineering analysis work and accordingly the integrated circuit hardware Trojan detection efficiency is improved and the cost in the detection process is reduced.
Owner:FIFTH ELECTRONICS RES INST OF MINIST OF IND & INFORMATION TECH
Hardware Trojan detection and discrimination method based on support vector machine
InactiveCN108154051AImprove accuracySolve the problem of detecting whether there is a Trojan horse circuit in the hardware chipInternal/peripheral component protectionData setSmall sample
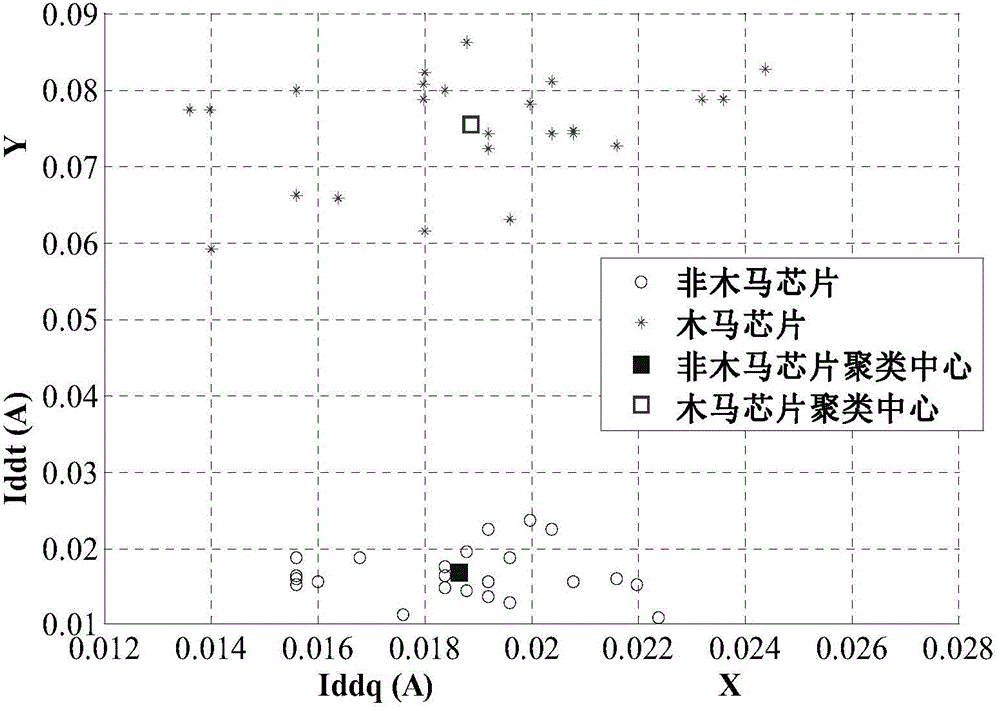
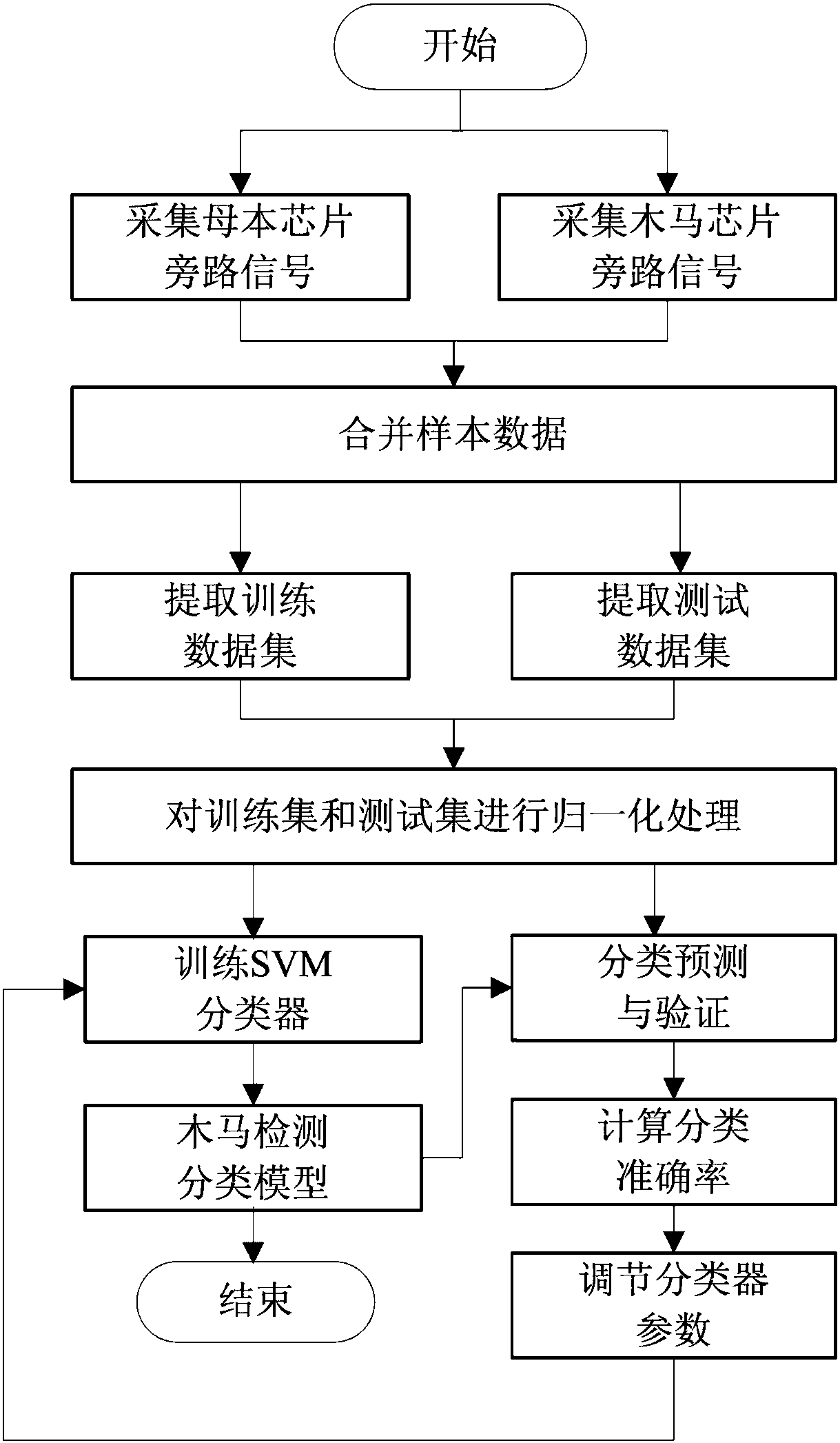
The invention relates to a hardware Trojan detection and discrimination method based on a support vector machine. The method is characterized by comprising the following steps that step 1, bypass signals of a bus chip and a Trojan chip are collected; step 2, normalization preprocessing is carried out on a training dataset and a testing dataset by using normalized mapping; step 3, the training dataset is used to train two classified support vector machine classifiers, and an initial hardware Trojan detection classification model is obtained; step 4, the classification effect of the initial model is verified; step 5, the initial Trojan detection classification model is optimized by using a cross validation method of K-CV; step 6, it is determined whether the to-be-detected chip has a Trojanor not. The method can better solve the practical problems of small sample, nonlinearity, high dimension and the like, the cost of a signal collection and detection platform and other hardware equipment is low, the efficiency and accuracy rate of an algorithm are high, and the detection of the hardware Trojan can be better realized.
Owner:TIANJIN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Hardware Trojan detecting and judging method based on distance measure distribution
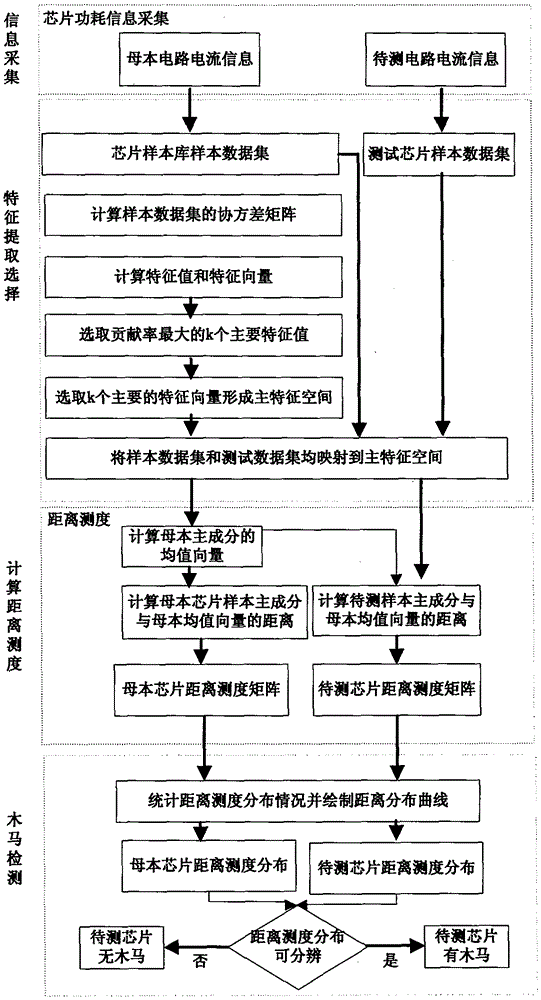
ActiveCN106815532ARapid detection and classificationSmall amount of calculationInternal/peripheral component protectionFeature extractionPower flow
The invention relates to a hardware Trojan detecting and judging method based on distance measure distribution, comprising: subjecting side channel current signal sample data of a female parent chip to characteristic extraction to arrive at compression and dimension reduction for high-dimensional data, calculating distance measure matrixes of centers for a chip sample to be detected and the female parent chip samples, and judging whether three is hardware Trojan circuity embedded or not according to their similarity in distance distribution modes. The method detects samples based on the characteristics of distance measure distribution of mode recognition, has low calculating quantity, high detection speed and high reliability, and allows hardware Trojans to be detected and classified quickly; hardware devices used herein, such as a signal acquisition and detection platform, are low in cost, the algorithm is simple and easily implantable, and the method can meet the actual needs of different occasions.
Owner:TIANJIN UNIVERSITY OF SCIENCE AND TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com