Detection method aiming at CPU internal hidden instruction type hardware trojan
A hardware Trojan and detection method technology, applied in the fields of instruments, electrical digital data processing, platform integrity maintenance, etc., can solve the problems of small change range, small scale, difficult to determine, etc., to achieve high accuracy, fast and effective detection and testing The effect of reducing the number of
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with specific drawings and embodiments.
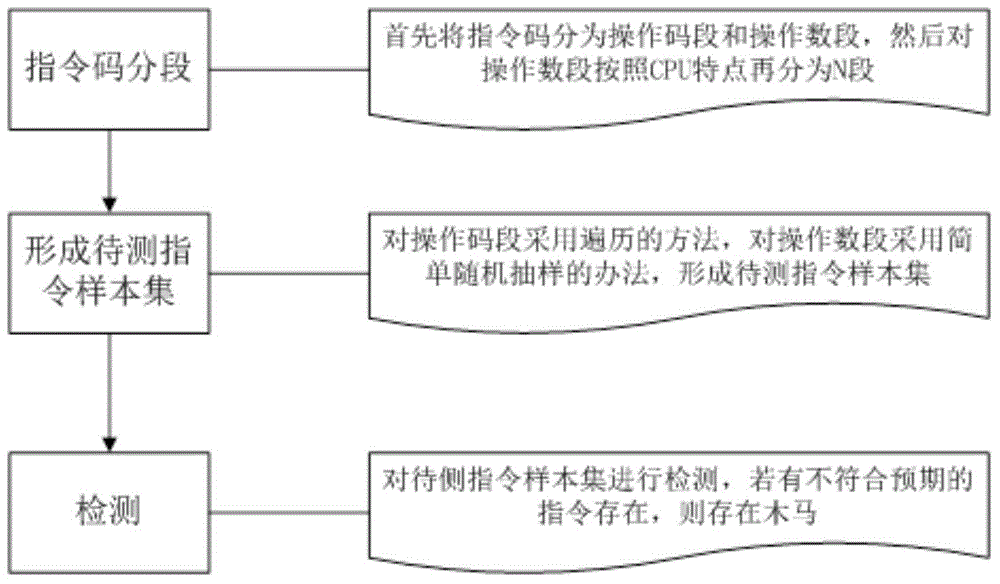
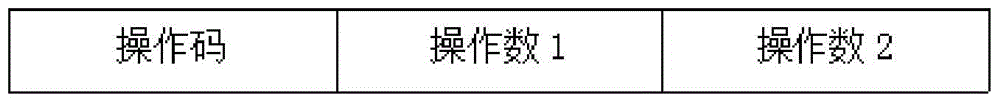
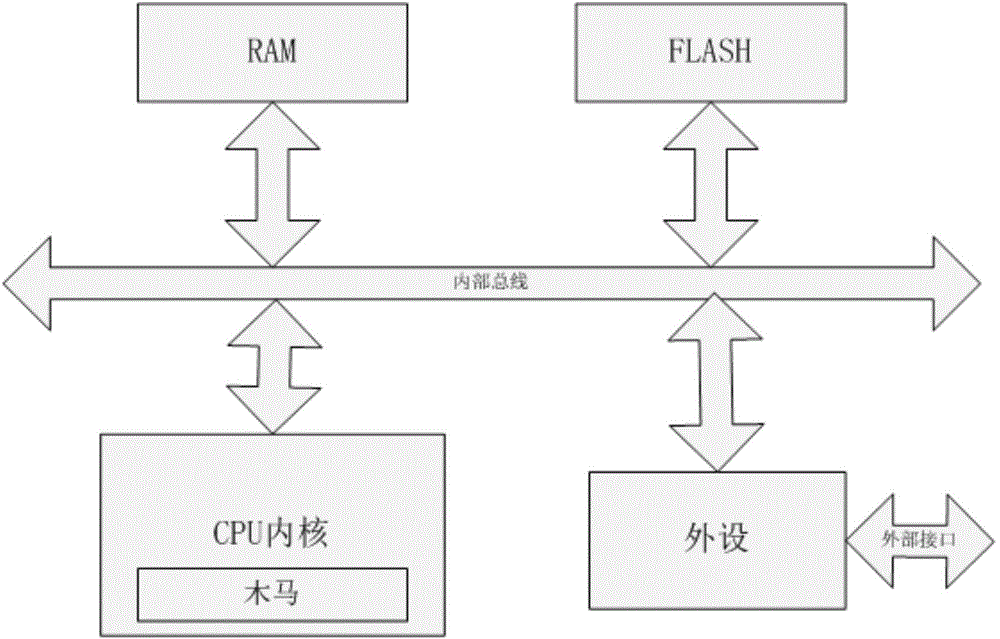
[0027] In the current CPU system, instructions are an important component, and various operations of the user on the CPU are completed through instructions. Since the most popular CPU architectures such as Intel X86, MIPS, ARM, etc., their instruction sets are developed by foreign companies, there is no way to know whether there are hidden instructions that are not in the instruction list, and they lack corresponding detection methods to identify their circuits. Or whether there is a backdoor function triggered by hidden commands in the IP. Once it has hidden instructions and is known to the attacker, the attacker can use these hidden instructions to gain control of the chip to complete the attack on the circuit or system.
[0028] Based on the above situation, the present invention provides a detection method specifically aimed at the hidden instructions that may ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com