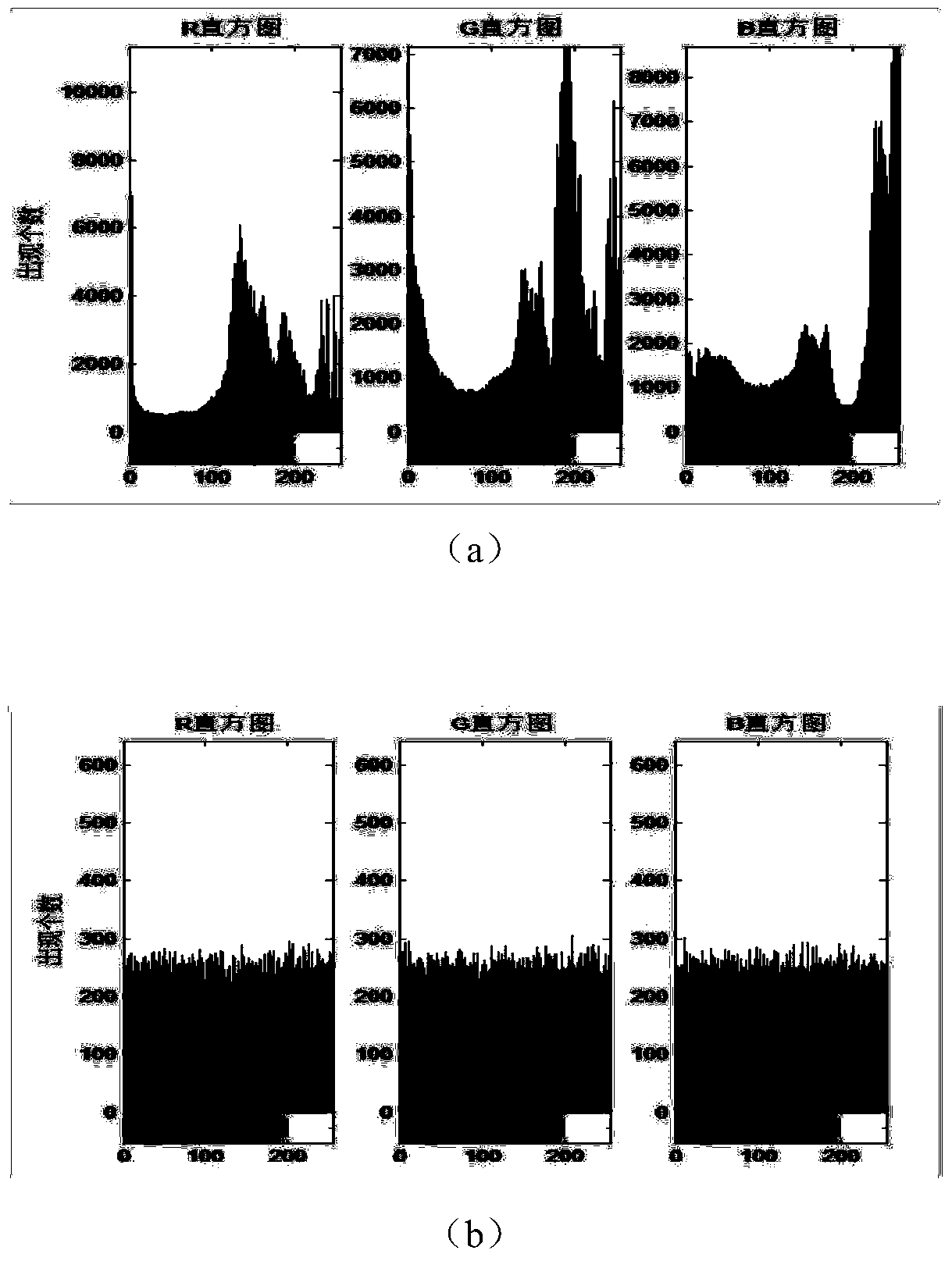
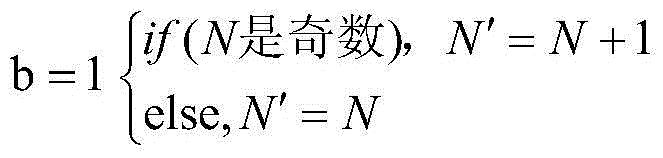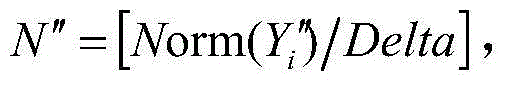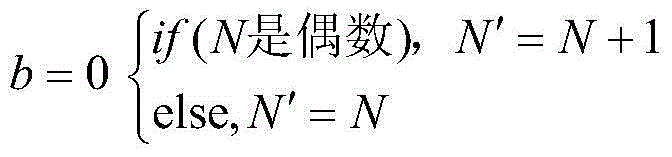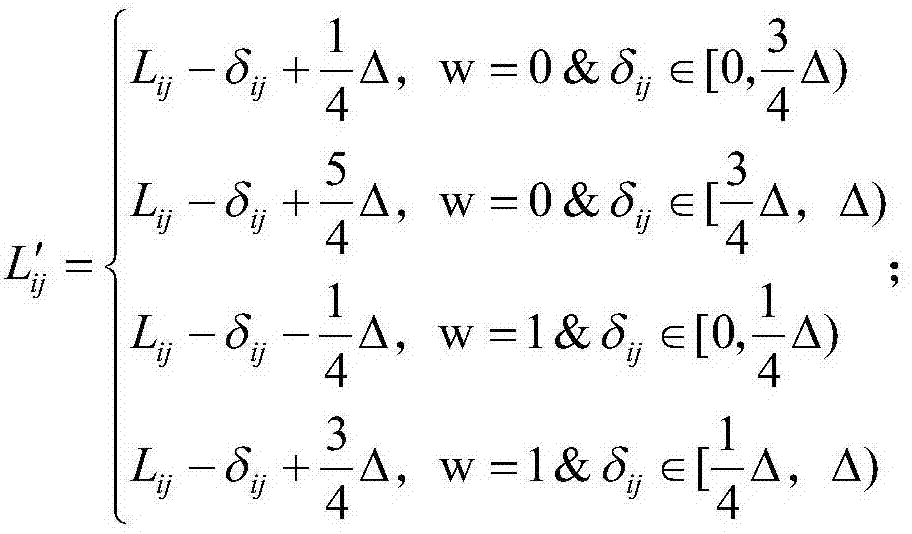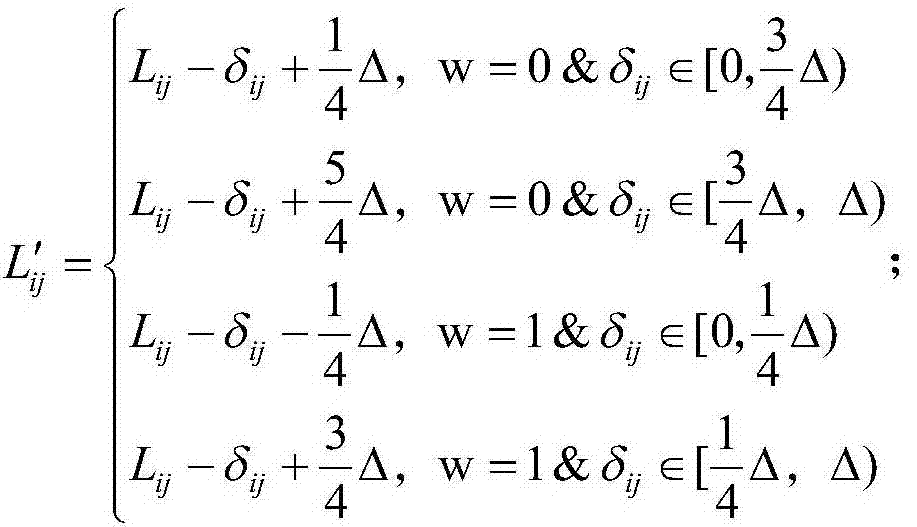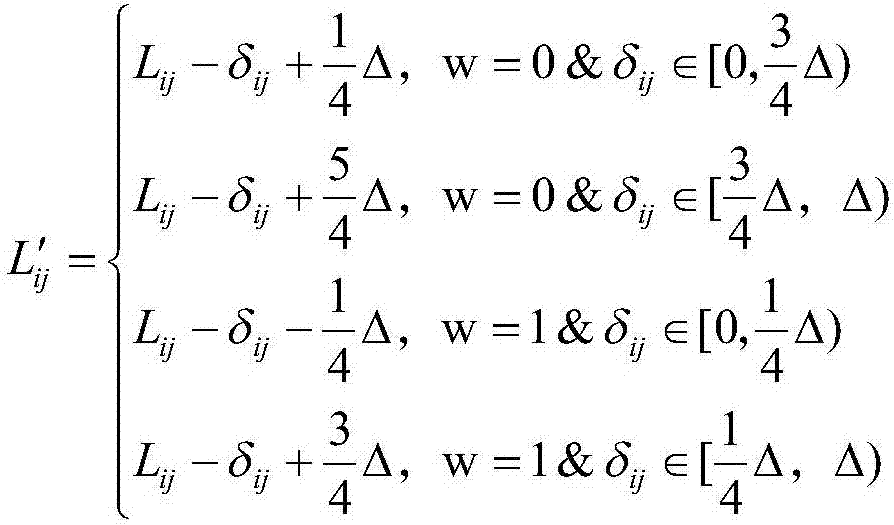Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
49results about How to "Good resistance to attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
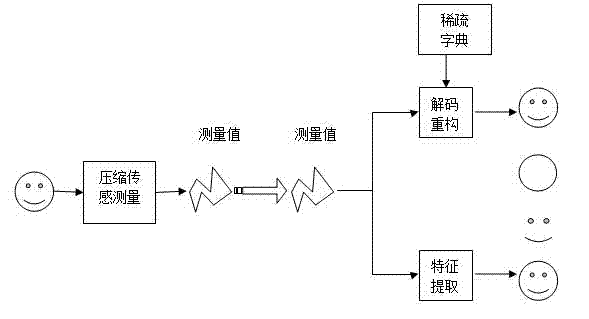
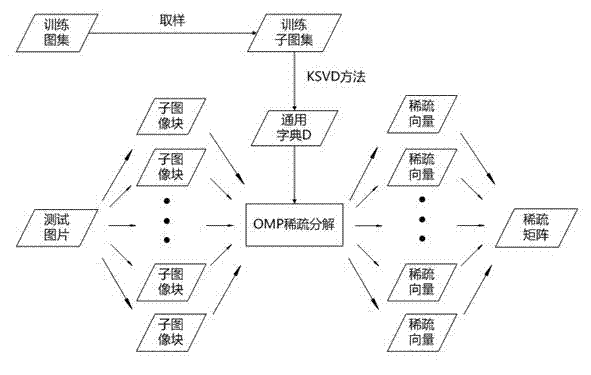
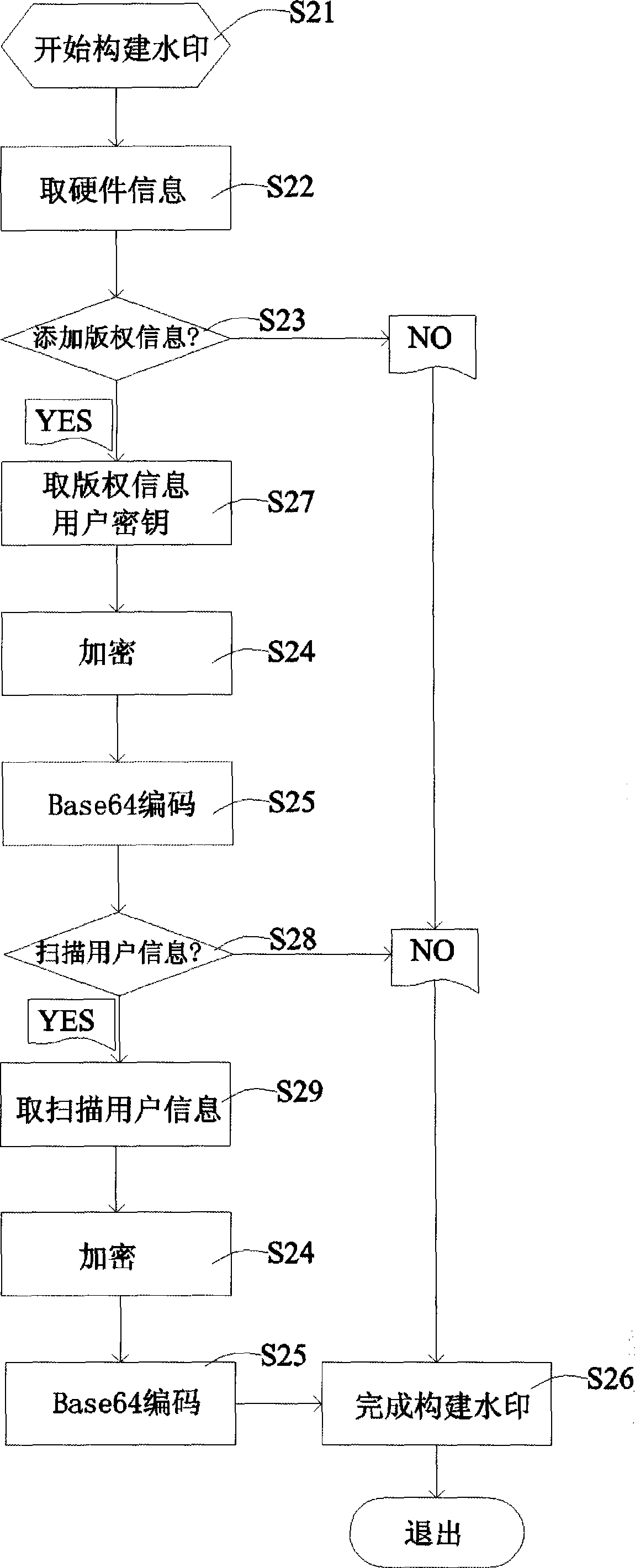
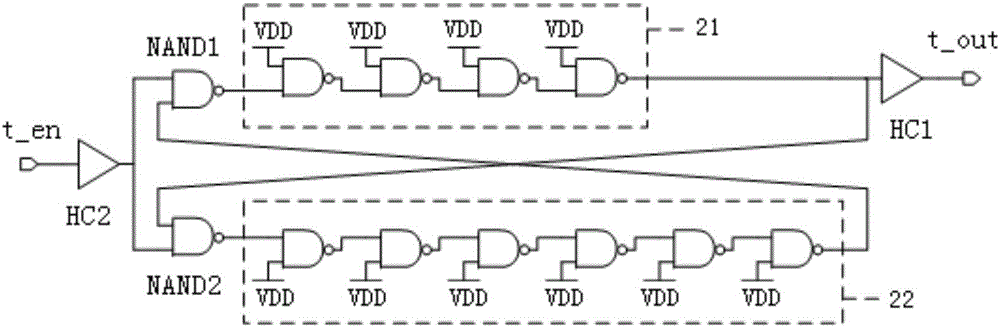
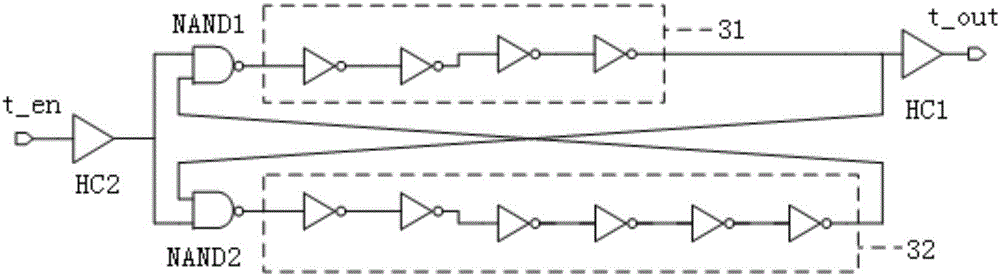
Combined image compression/encryption method based on compressed sensing
ActiveCN102891999AImproved attack resistance and robustnessImprove rate-distortion performanceTelevision systemsImage compressionImage storage
The invention discloses a combined image compression / encryption method based on compressed sensing, which comprises the following steps of: firstly, a dictionary is formed by combining sub dictionaries obtained by classifying and training by combining a K-SVD method; secondly, an improved orthogonal matching pursuit algorithm is adopted in sparse coding; and finally, encryption is embedded in a compression process so that an encryption / compression algorithm of an image is realized. According to the invention, encryption and compression are tightly linked, therefore, on the premise of no basic influence to rate distortion performance, the attack resistance property and the stability of a system are further improved, the rate distortion performance of static image compression is superior to that of international main trend algorithms such as JEFG2000 and SPIHT at present, the image encryption performance is increased, and common attacks such as cipher text-only attack, chosen-ciphertext attack, known-plaintext attack and chosen-plaintext attack can be resisted. The invention can be used in image storage and transmission in the information security transmission fields such as internet, mobile telephones and video conferences.
Owner:瑞金市工业投资发展有限公司
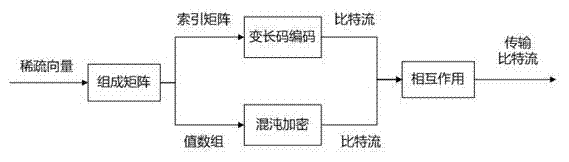
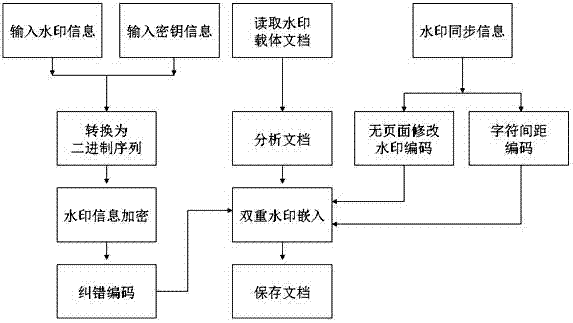
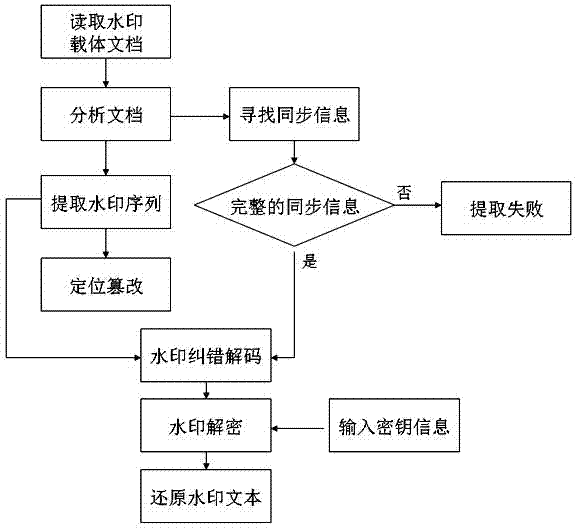
Character pitch encoding-based dual-watermark embedded text watermarking method
InactiveCN103049682AImprove robustnessRealize portabilityProgram/content distribution protectionSpecial data processing applicationsData integrityCovert communication
The invention relates to a character pitch encoding-based dual-watermark embedded text watermarking method, comprising the following steps of: converting watermark information M and a key D, which are required to be hidden, into a binary sequence, circularly executing modulus to get an encrypted binary sequence, adding error-correcting codes for the to-be-embedded watermark information, and finally embedding dual watermarks and synchronization information of the watermarks by encoding the attribute of a text object without page modification and encoding a character pitch. With the method, the text content cannot be changed, the watermark information is hidden well, and the method has the characteristics of high robustness and high capacity. By extracting the embedded watermark information, transmission and modification of a document can be controlled effectively, and whether the document is modified can be judged, and finally, the aims of digital copyright protection, data integrity authentication and safe covert communication for the text document are achieved.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
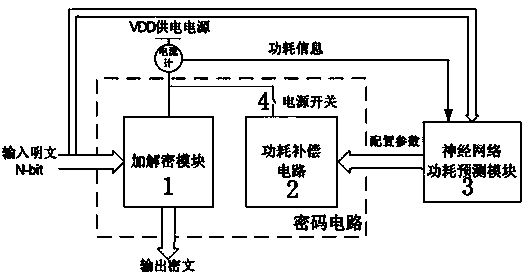
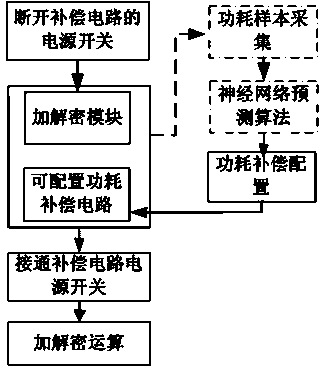
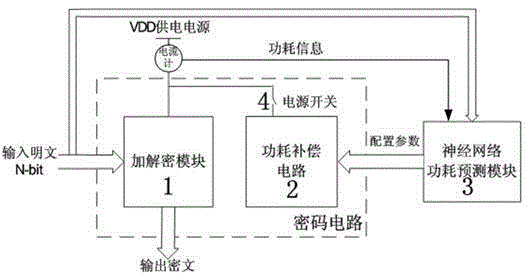
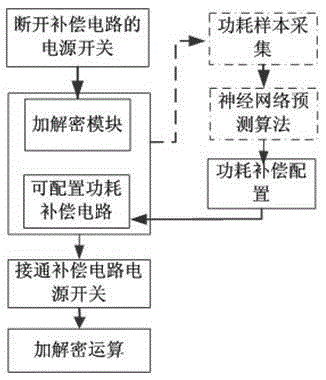
Power consumption compensation and attack resisting circuit based on neural network power consumption predication and control method
InactiveCN103646219AHigh anti-power consumption attack protection capabilityGood constant power performanceInternal/peripheral component protectionNeural learning methodsAdaptive learningNerve network
The invention discloses a power consumption compensation and attack resisting circuit based on neural network power consumption predication and a control method. The circuit is composed of an encryption and decryption module achieving an encryption and decryption algorithm function, a power consumption compensation circuit and a neural network prediction module, a neural network algorithm with adaptive learning capacity is adopted in the method to build a power consumption predication model, power consumption predication is carried out when a code circuit works, a configurable power consumption compensation circuit is built, the compensation circuit is controlled to carry out corresponding function configuration according to a power consumption predication result, the power consumption of the overall circuit tends to be a steady state value, the value is not changed along with the change of a secrete key and processed data, an intruder cannot acquire the dependency of the value and secrete key information, and therefore power consumption attack can be effectively resisted.
Owner:SOUTHEAST UNIV
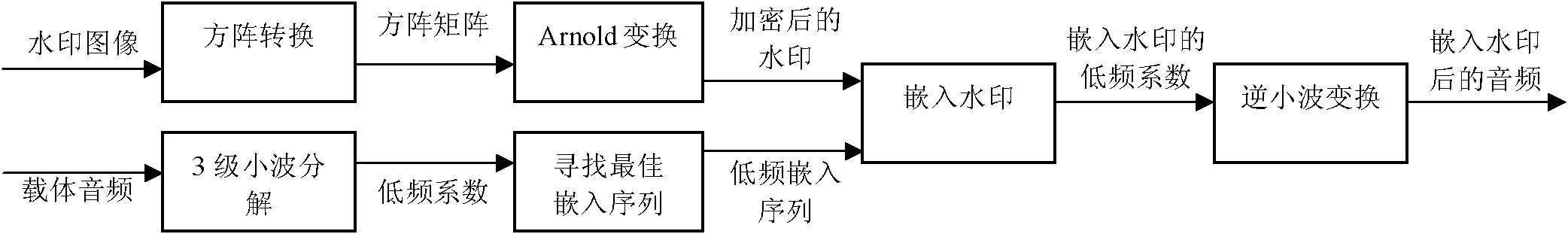
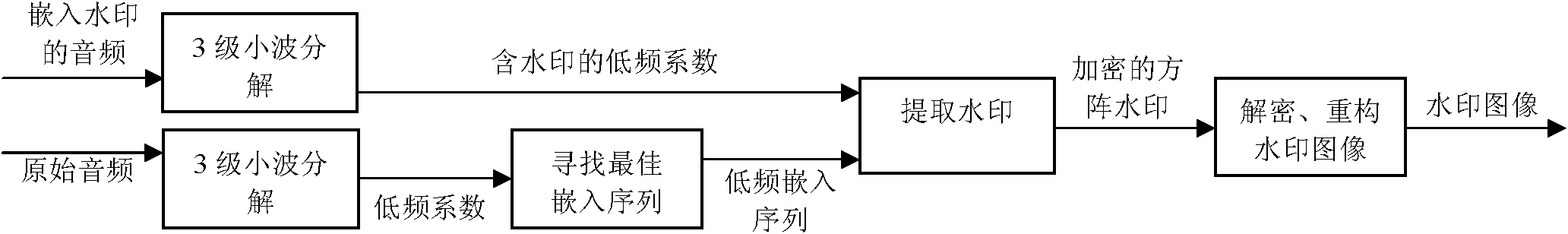
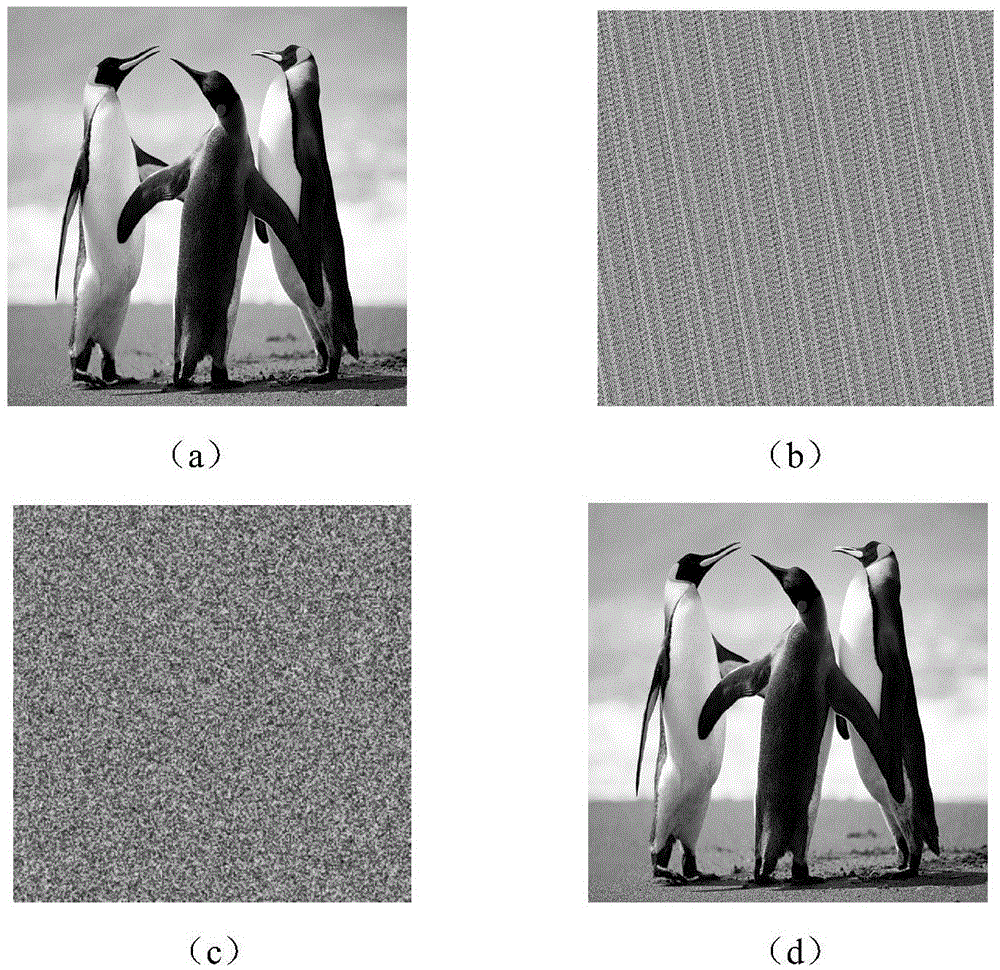
Wavelet transform and Arnold based adaptive gray-scale watermark embedded method
InactiveCN102142258ARobustEnhance confidentiality and securitySpeech analysisSelf adaptiveConvolution
The invention discloses a wavelet transform and Arnold based adaptive gray-scale watermark embedded method which comprises the following steps: carrying out square matrix conversion and scrambling processing on an original watermark image; carrying out wavelet transform (three times) on an original host audio to obtain wavelet low frequency coefficients as the embedded pre-selected position of a watermark; automatically searching an optimal embedded sequence from the low frequency coefficients, wherein the optimal embedded sequence is the optimal embedded position of the watermark; and carrying out convolution on a digital watermark image sequence and the optimal embedded sequence, namely, embedding the digital watermark image into the low frequency coefficients of audios. The method is characterized in that in the process of digital watermark extraction, the audios containing watermarks are detected according to the original audio, and a watermark image sequence is extracted from the audios; and in the process of digital watermark reduction, the length and width of the original image are taken as extraction keys, and the extracted watermarks are reduced through the utilization of reverse Arnold conversion and image reconstruction. The method disclosed by the invention is strong in function, quick in computing speed, easy and convenient to implement, and has certain practical values in the aspects of digital image copyright protection and information hiding.
Owner:SHANGHAI SECOND POLYTECHNIC UNIVERSITY
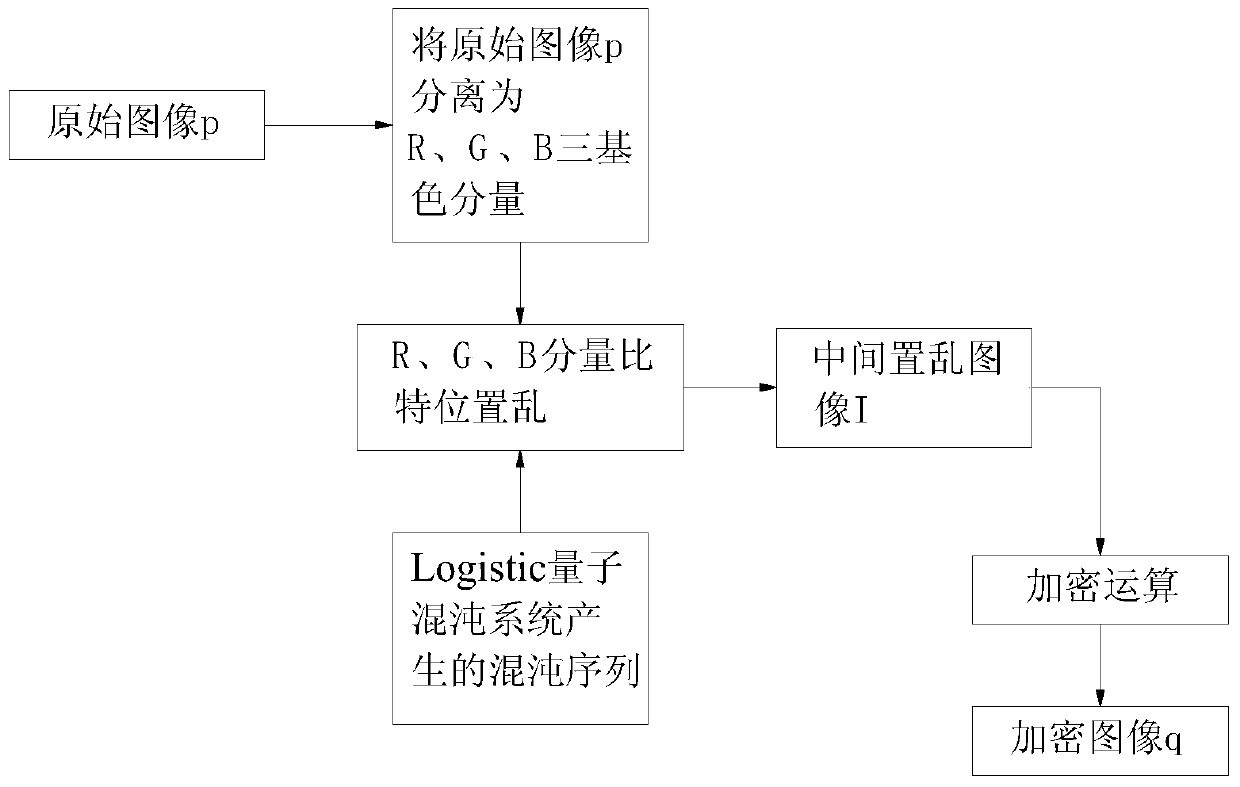
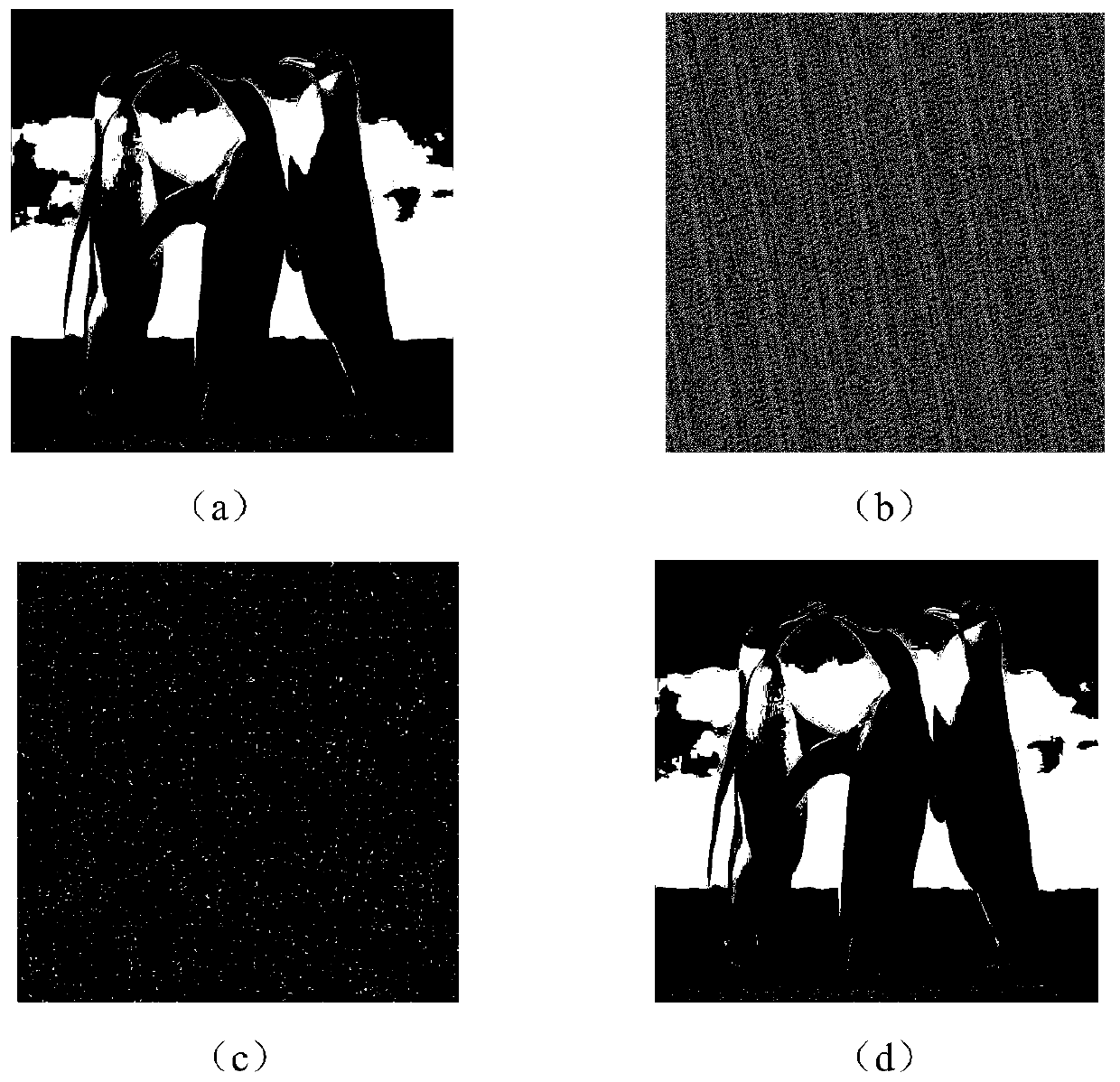
Quantum chaotic image encryption method based on bit scrambling
ActiveCN105631796ASimple physical structureResolve Loss of PrecisionImage data processing detailsComputer hardwareChaotic systems
The invention discloses a quantum chaotic image encryption method based on bit scrambling. The method comprises steps: a Logistic quantum chaotic system is used for generating a chaotic sequence, bit scrambling is carried out on R, G and B three-primary color component pixel values of an original image p, and a middle scrambling image I is obtained; and then, encryption operation is carried out on the middle scrambling image I, and a final encryption image q is obtained. The encryption method of the invention greatly increases the secret key space, the safety, the encryption effect and the secret key sensitivity are higher, the anti-attack ability is stronger, and the deciphering difficulty is greatly improved.
Owner:GUANGDONG UNIV OF TECH
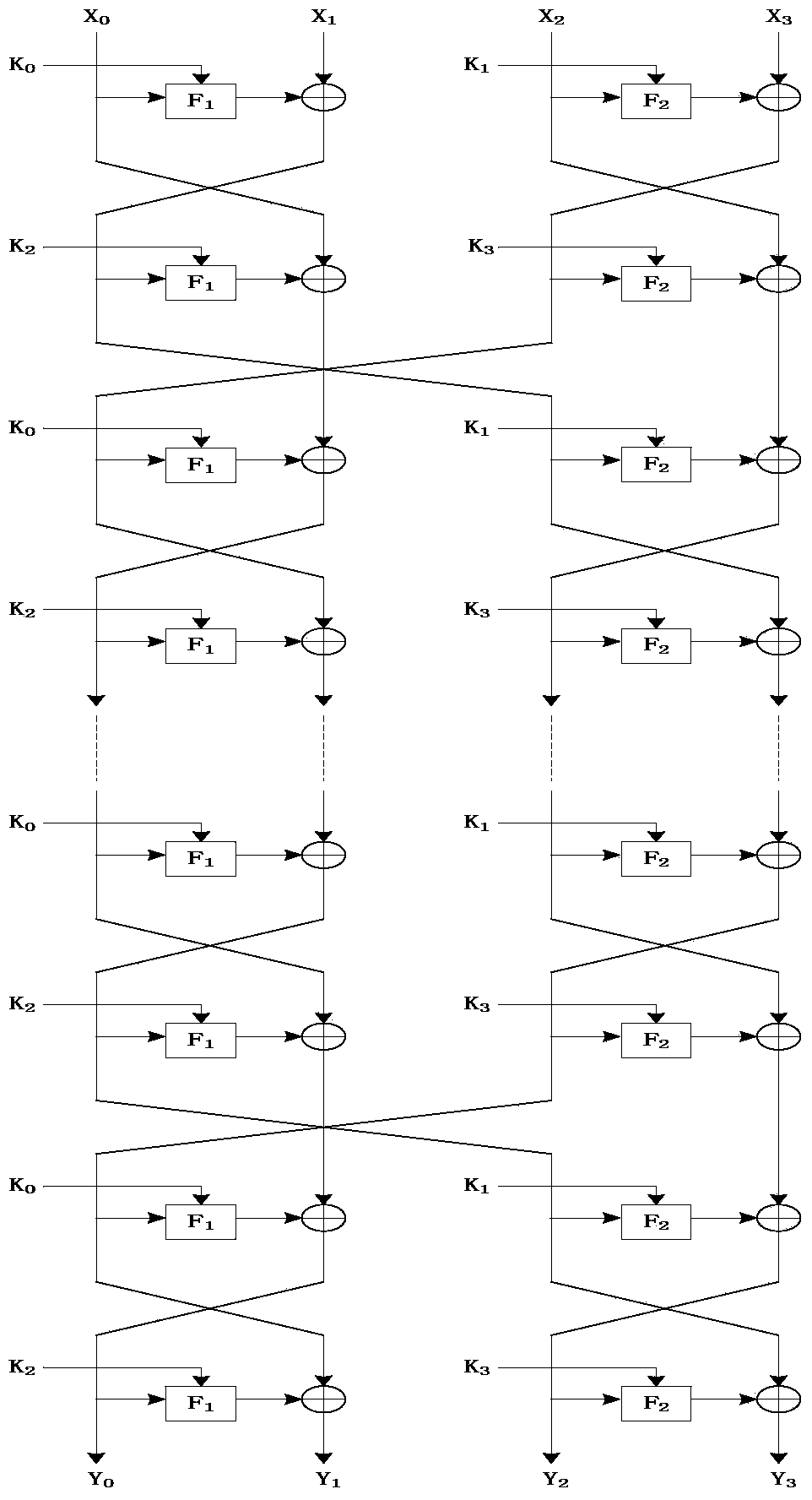
Novel ultra-lightweight QTL (Quasi-Transmission Line) block cipher implementation method
ActiveCN104333446AImprove diffusivitySimple and fast operationEncryption apparatus with shift registers/memoriesComputer hardwareS-box
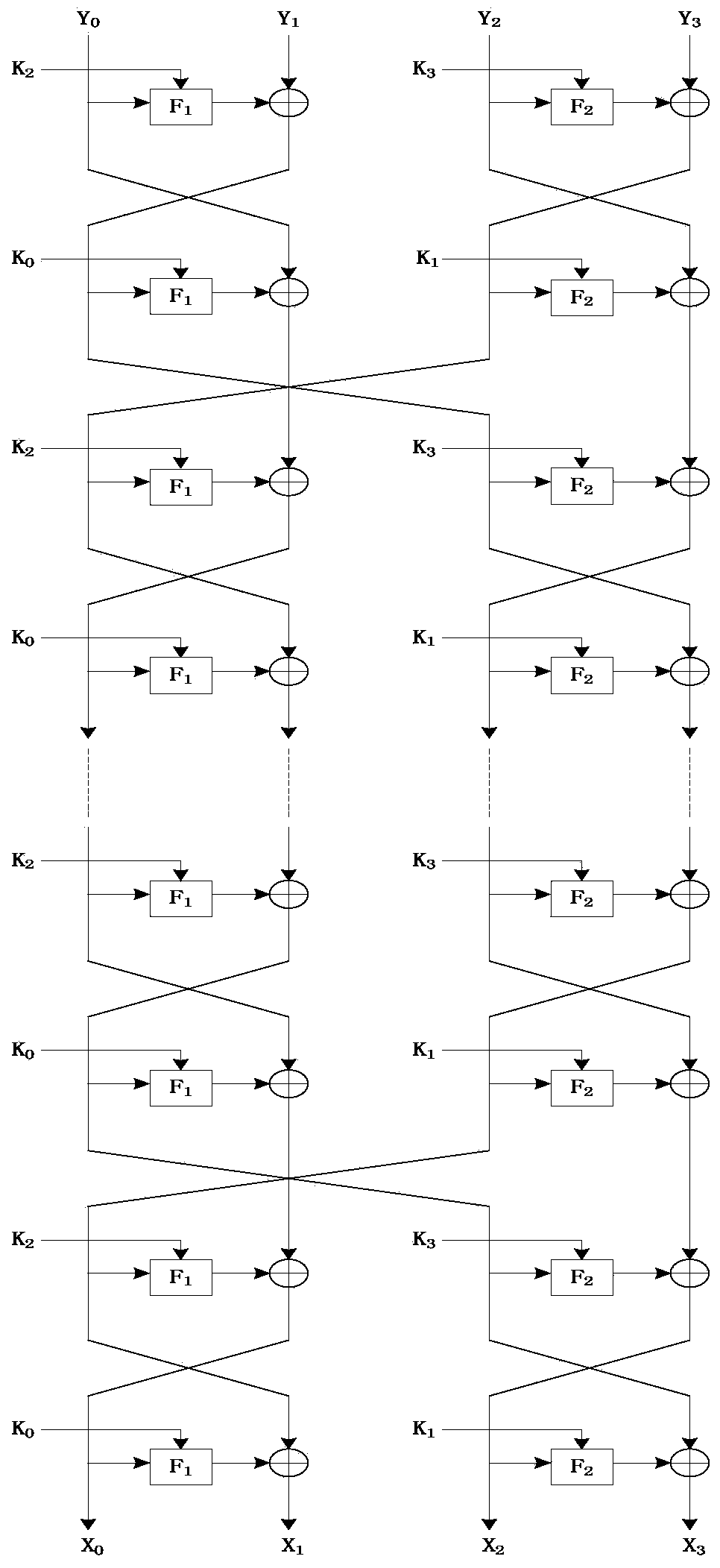
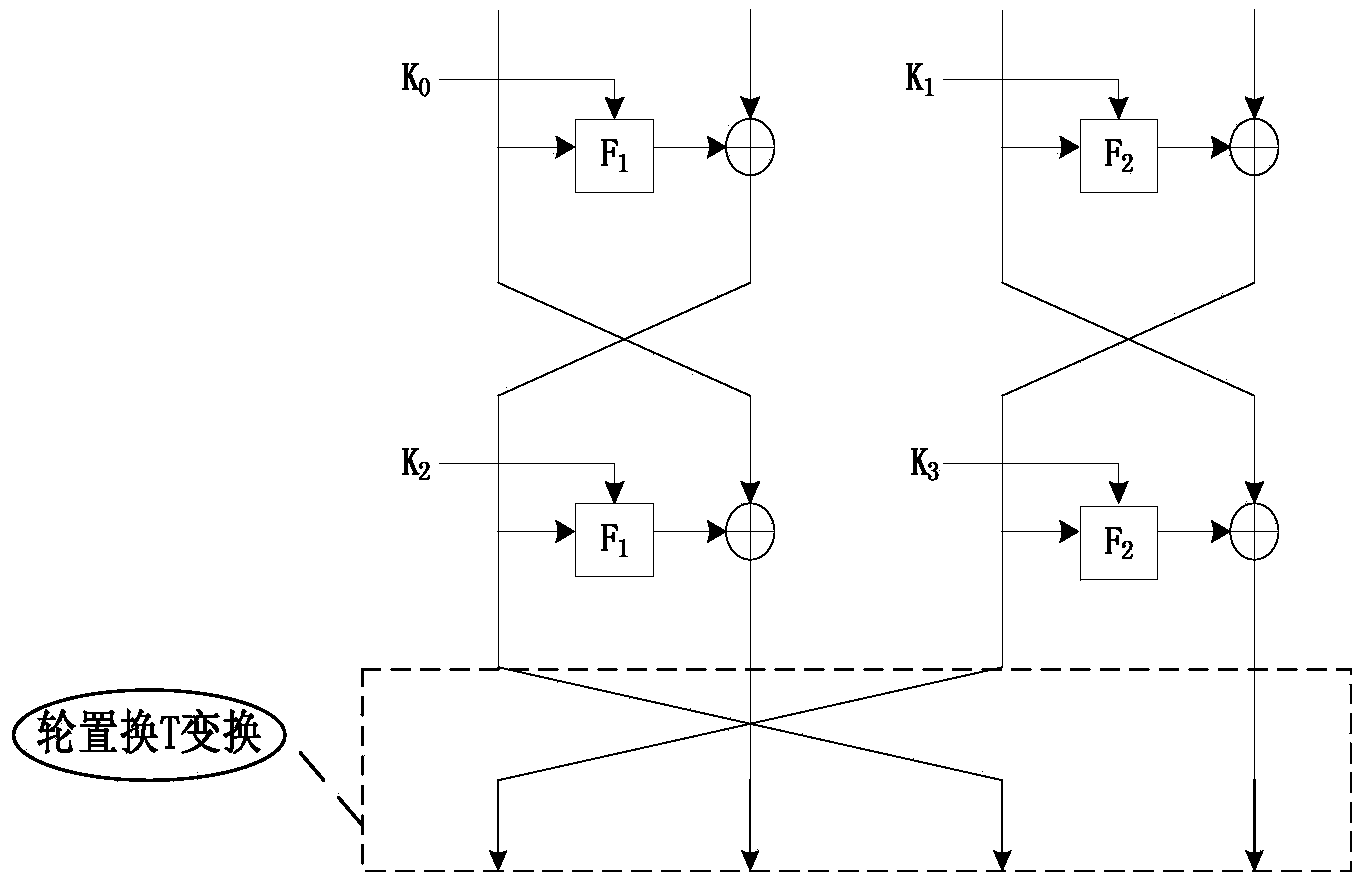
The invention discloses a novel ultra-lightweight QTL (Quasi-Transmission Line) block cipher implementation method. According to the method, a novel generalized Feistel network structure is designed; the structural algorithm overcomes the defect that only a half of grouped data is changed during one-round iterative operation of the conventional Feistel network structure, and realizes that all grouped data is changed by the one-round iterative operation. F functions in the round operation of the algorithm comprise an F1 function and an F2 function; S1 and S2 boxes are adopted respectively; the conversion process of the F functions comprises round key add, S box substitution, P replacement and S box substitution; different S box and P replacement only requires hardware connection; the F function of the light super S box is constructed. The algorithm structure is highly symmetric, an encryption module is decrypted and multiplexed by the algorithm, decryption can be performed by exchanging an encryption round key use sequence, the operation is easy and convenient, and extra resource is not required to be consumed by the decryption. Compared with the current lightweight password, the occupied resource is smaller, the encryption performance is high, and known attack can be resisted.
Owner:HENGYANG NORMAL UNIV
DWT-SVD geometric attack prevention blind watermark method based on SIFT
ActiveCN103955878AGood resistance to attackGood attackImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD geometric attack prevention blind watermark method based on SIFT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, and the watermarks are embedded into the maximum singular value of each small block through an optimal quantitative method, the SIFT feature points of a watermark image are stored as secret keys, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the utilization of the rotation, zoom and translation invariance of the SIFT feature points and the combination of the advantages of DWT and SVD in the digital watermark aspect, robustness on geometric attacks is remarkably improved.
Owner:HANGZHOU DIANZI UNIV
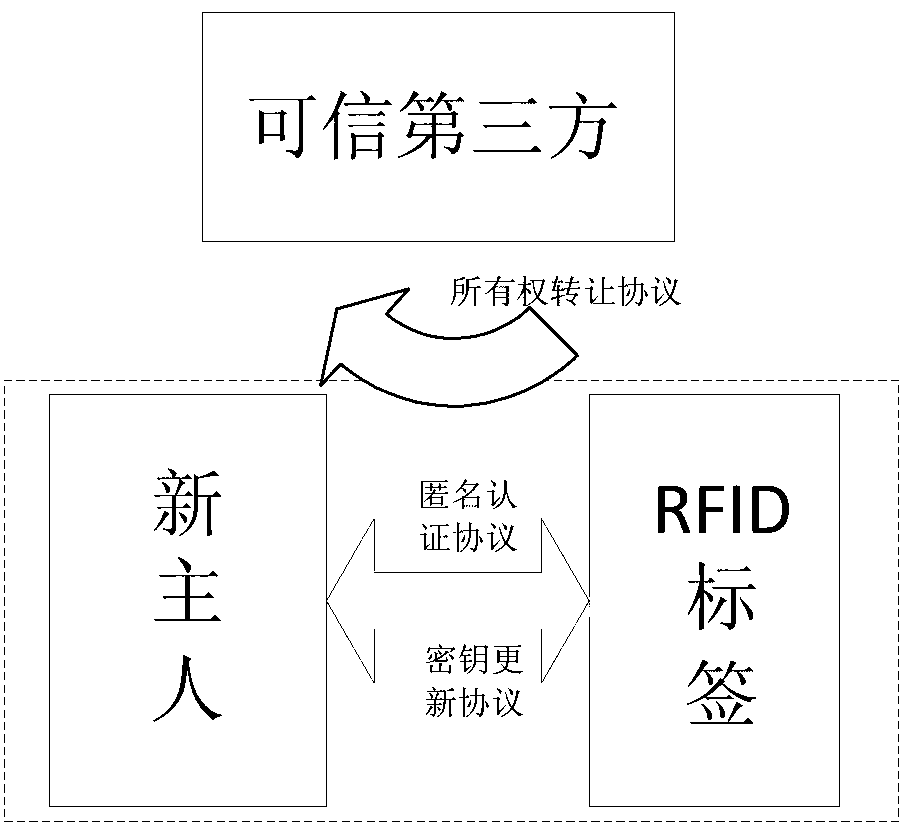
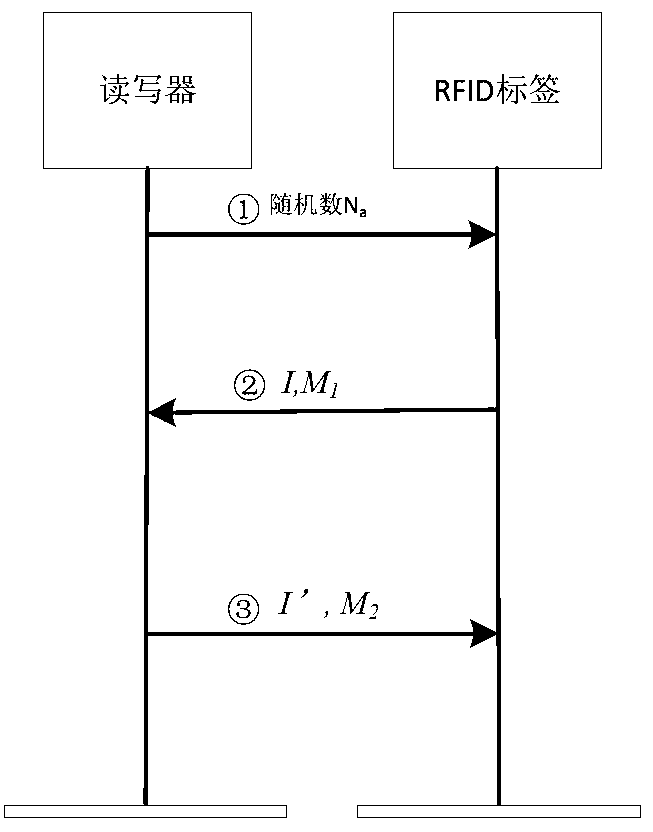
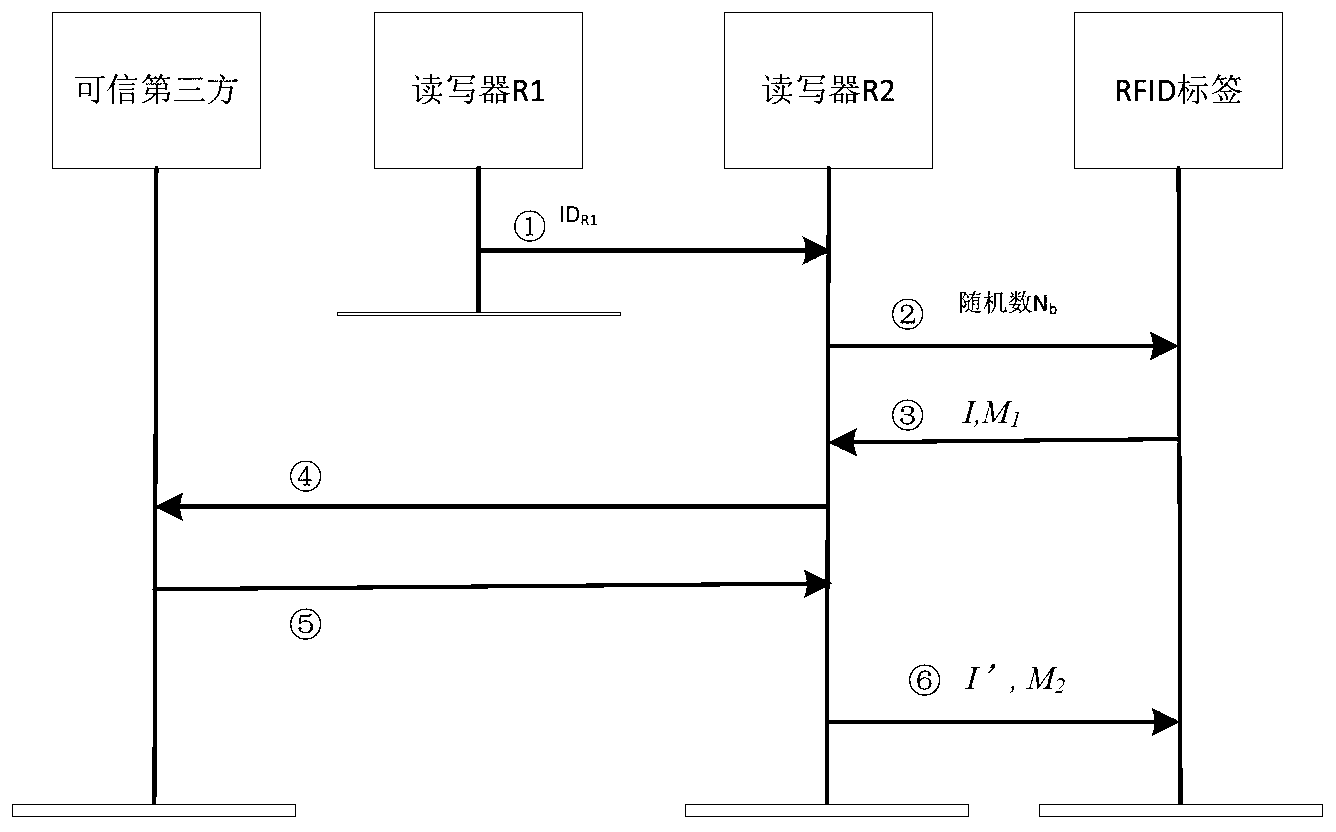
Safe and lightweight class RFID ownership transferring method based on bilinear pairings
InactiveCN103281194AEmphasis on privacy protectionImprove computing efficiencyUser identity/authority verificationThird partyPrivacy protection
A safe and lightweight class RFID ownership transferring method based on bilinear pairings is realized in a mode that a reliable third party, an FRID label, a manufacturer, an old owner, a new owner and a reader-writer execute two initializing sub-processes and three safe sub-protocols. The method has the advantages that through a safe and lightweight class RFID ownership transferring mechanism based on the bilinear pairings, good effects on improving safety of an RFID system, mainly emphasizing privacy protection to an RFID label owner, and resisting to aggressivity are achieved, operation efficiency is relatively high, and application value is obvious.
Owner:杨涛
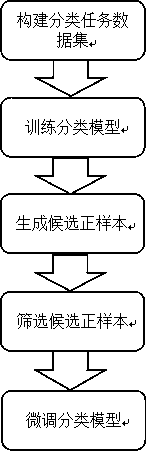
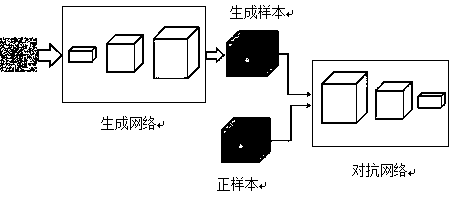
Method for optimizing medical image classification performance based on generative adversarial network
InactiveCN109635850AImprove robustnessImprove accuracyNeural architecturesNeural learning methodsPositive sampleData set
The invention provides a method for optimizing medical image classification performance based on a generative adversarial network. The method comprises the steps of constructing a classification taskdata set; training a classification algorithm model on the existing data; generating new positive sample candidate data by using the generative adversarial network; strictly screening the generated positive sample data by utilizing a voting mechanism; and fusing the generated data into the existing positive sample data fine tuning classification network according to a certain proportion. The medical image classification method has the technical advantages that the problems of poor algorithm generalization capability, easy overfitting, high manual data accumulation cost and the like caused by small positive sample data size in medical image classification are solved. In addition, the anti-attack capability of the algorithm can be improved to a certain extent while the performance of the medical image classification algorithm is improved.
Owner:杭州健培科技有限公司
Embedding method and extracting method for text watermark based on semantic role position mapping
ActiveCN105205355AAffects correct extractionImprove robustnessProgram/content distribution protectionCoded elementWatermark embedding
The invention relates to an embedding method and an extracting method for a text watermark based on semantic role position mapping. The embedding method comprises the following steps: 1) preprocessing the watermark information and converting a watermark character into code elements and forming an information string; 2) utilizing a natural language processing technique to search for the semantic role in the text, thereby acquiring the position information of the semantic role, and causing the semantic role category to be corresponding to the code elements one by one; 3) taking out the codes from the information string of the watermark one by one, mapping the codes to the position corresponding to the category of the semantic role, thereby finishing the embedding of the watermark. The extracting method comprises the following steps: searching for the semantic role on the position in the text according to the position information of the semantic role which is acquired during the process of watermark embedding; reversely mapping, thereby acquiring the information string of the watermark expressed by the code elements; lastly, converting the information string into the original watermark information. According to the method provided by the invention, the text format and content are free from any alteration, the hidden property and the robustness are excellent, and various conventional format conversions and attacks can be effectively resisted.
Owner:NANTONG UNIVERSITY
DWT-SVD robust blind watermark method based on Zernike moments
ActiveCN103955880AGood resistance to attackImprove robustnessImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD robust blind watermark method based on Zernike moments. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, the multiple Zernike moments of a watermark image are stored as secret keys by quantizing Euclidean norm embedded watermarks of a singular value matrix of each small block, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the combination of the advantages of DWT and SVD on the digital watermark respect and the utilization of the rotation and zoom invariance of the Zernike moments, conventional signal processing can be well resisted.
Owner:HANGZHOU DIANZI UNIV
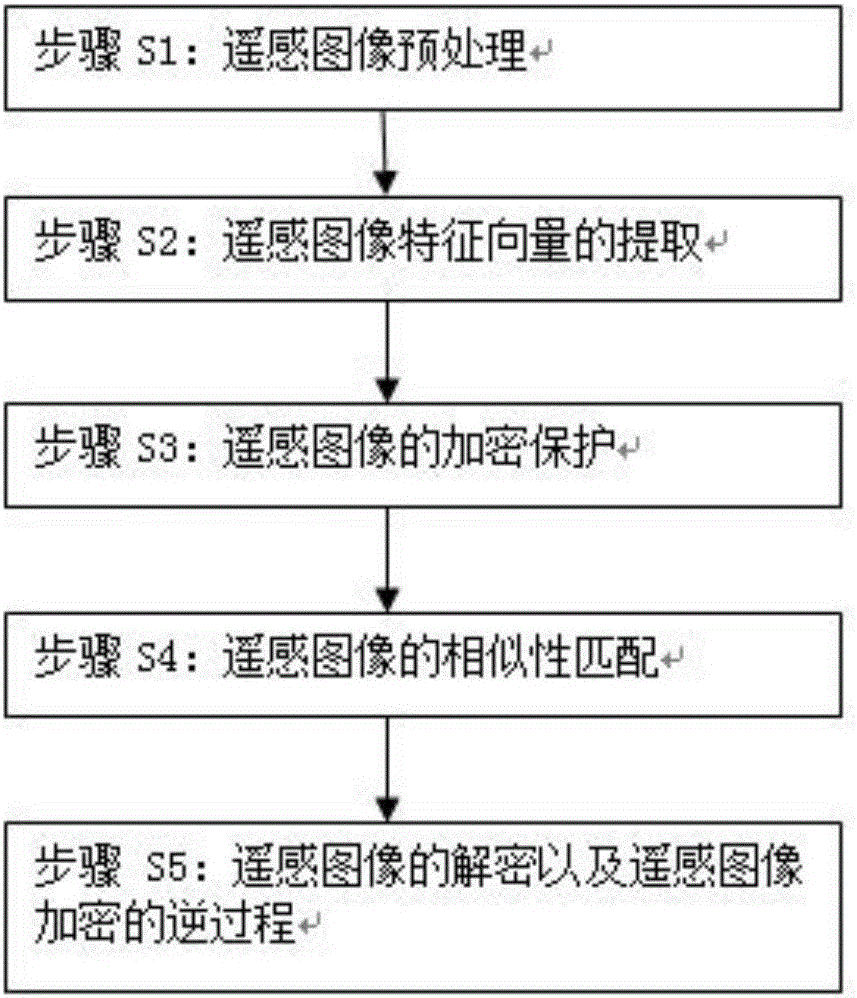
Remote sensing image encryption retrieval method based on Arnold chaotic mapping
ActiveCN106485742ASecure storageImprove securityImage enhancementImage analysisPlaintextFeature vector
The invention relates to a remote sensing image encryption retrieval method based on Arnold chaotic mapping. The method comprises the following steps: S1, a remote sensing image is pretreated; S2, a remote sensing image feature vector is extracted; S3, a remote sensing image is protected through encryption; S4, similarity matching on the remote sensing images is carried out; and S5, decryption of the remote sensing image and a remote sensing image encryption reverse process are carried out. The method of the invention has the advantages that the Arnold chaotic mapping-based encryption method is applied to the remote sensing image field, safe storage of the remote sensing image in a cloud environment is protected, and through building correlation characteristics between a plaintext and a ciphertext, a data user can directly carry out safety retrieval on the ciphertext remote sensing image through cloud computing.
Owner:SHANGHAI OCEAN UNIV
Scanner having digital copyright protection function and scanning method thereof
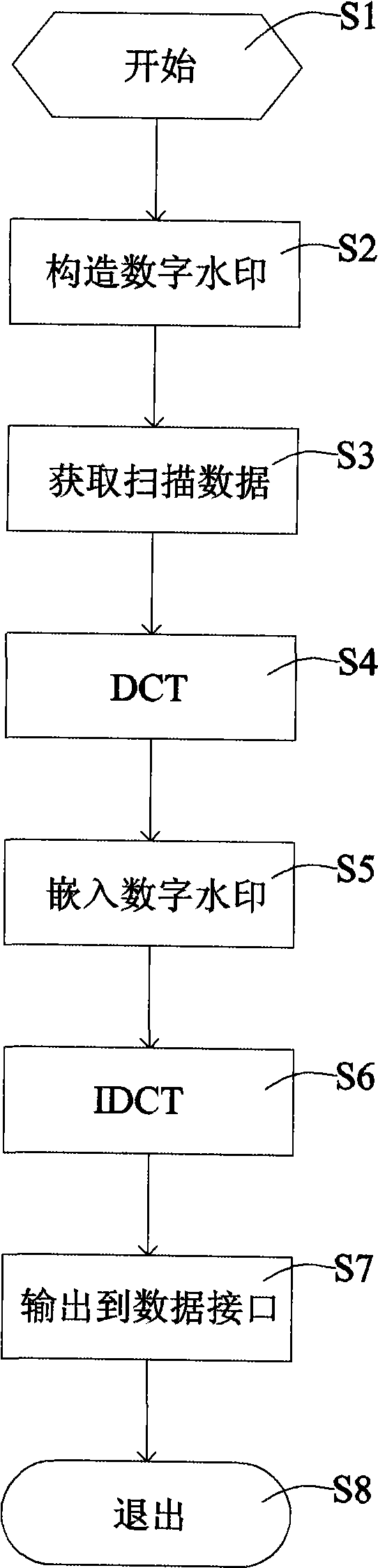
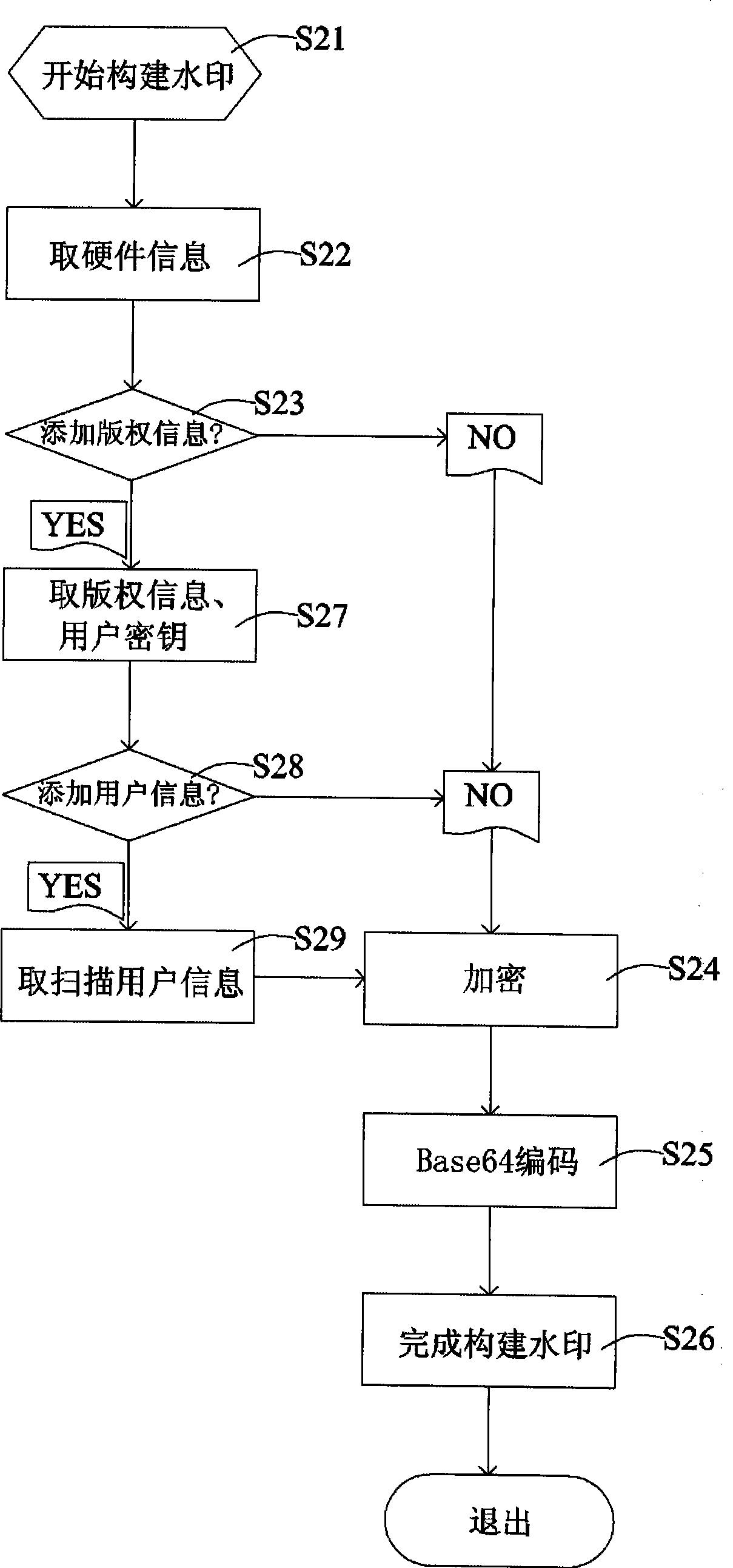
InactiveCN101489016AGood robustnessGood integrityImage data processing detailsPictoral communicationFrequency domainDiscrete cosine transform
The invention relates to a scanner having functions of digital copyright protection and scan source tracing, comprising: a digital watermark creating module for creating a digital watermark; a discrete cosine transform module for processing scan data to prepare for subsequent watermark embedding; a digital watermark embedding module for embedding the digital watermark into a scan data; and a discrete cosine inverse transform module for hiding the digital watermark. The scan method comprises the following steps of: creating a digital watermark based on the scan associated information as a resource mark; calling the scan data of the discrete cosine transform process, adding the digital watermark into a discrete cosine transform frequency domain space; embedding the digital watermark after the chaotic process into a scan data; and calling a discrete cosine inverse transform to hide the digital watermark.
Owner:LITE ON ELECTRONICS (GUANGZHOU) LTD +1
Neural network model encryption protection system and method involving domain transformation data encryption
ActiveCN108804931AImprove securityImprove concealmentBiological neural network modelsDigital data protectionNerve networkProtection mechanism
The invention belongs to the field of artificial neural network protection mechanisms, and relates to a neural network model encryption protection system and method involving domain transformation data encryption. The system comprises an encryption module; a frequency domain transformation module in the encryption module is used for transforming original input data into a two-dimensional structure, conducting domain transformation on the original input data obtained after structure transformation and transforming the original input data in the space domain into original frequency domain data in the frequency domain; a frequency domain data processing module in the encryption module is used for processing the original frequency domain data in a specific processing mode to generate encryptedfrequency domain data; and a frequency domain inverse transformation module in the encryption module is used for conducting inverse domain transformation corresponding to above-mentioned domain transformation on the encrypted frequency domain data and transforming the encrypted frequency domain data in the frequency domain into the encrypted input data in the space domain. According to the methodof achieving input data encryption through domain transformation, the concealment and the anti-attacking performance of password information are improved, and the security of a trained artificial neural network model can be improved.
Owner:CHENGDU PANOAI INTELLIGENT TECH CO LTD
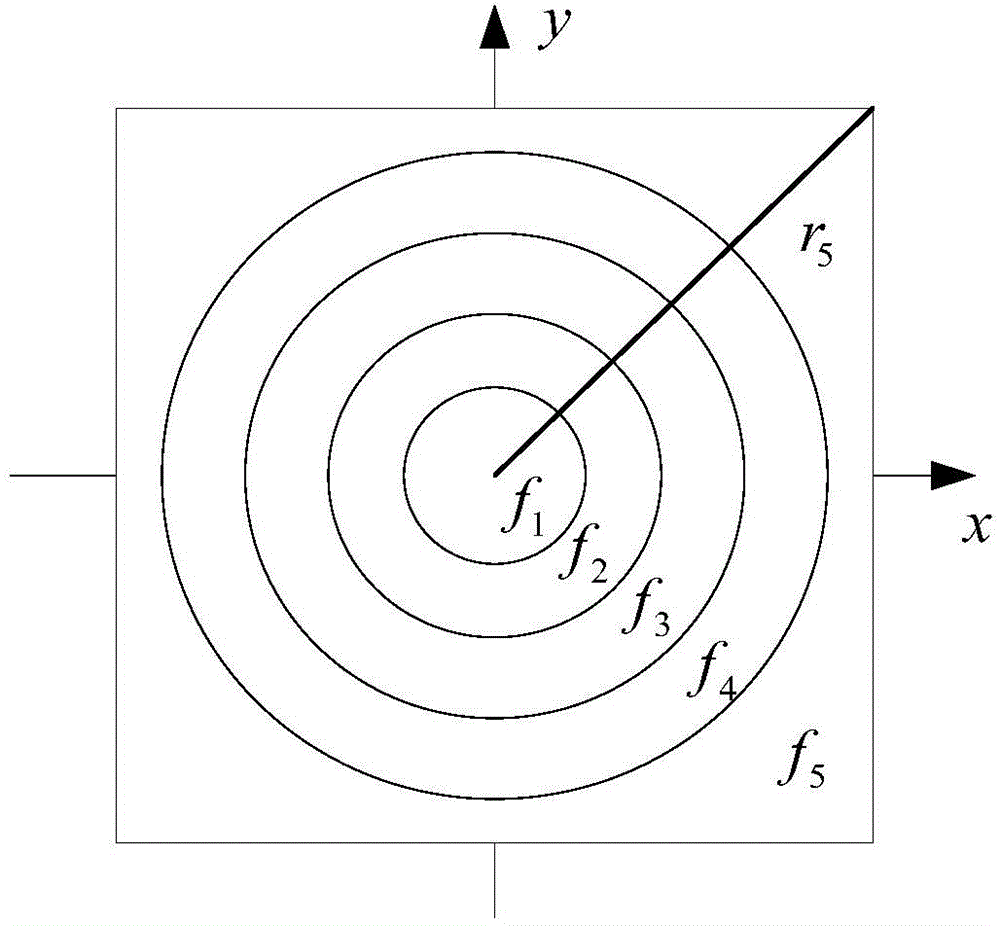
Multi-image encryption method based on fractional mellin transform
InactiveCN103593819AAchieve compressionImprove securityImage data processing detailsPictoral communicationFrequency spectrumMulti-image
The invention provides a multi-image encryption method based on fractional mellin transform. The method includes the steps of compressing multiple images according to a frequency spectrum cutting and splicing method, then, dividing an image obtained through compression into a plurality of sub-images according to an annular domain, conducting fractional mellin transform on all the sub-images, encrypting a fractional mellin transform outcome into a cryptograph image through magnitude and phase encoding, taking transform degrees of fractional mellin transform as secret keys, and taking a center coordinate for coordinate transform, an inner radius of the annular domain for implementation of transform and an outer radius of the annular domain for implementation of transform as secondary secret keys. According to the multi-image encryption method, the multiple images are compressed through the real-value characteristics of fractional cosine transform, and therefore overweight transmission loads are avoided, and the requirement for instantaneity of image data transmission is met. Fractional mellin transform is then conducted on the image obtained through compression, the fractional order characteristic, the nonlinear characteristic and the like of the fractional cosine transform are fully utilized, and the multi-image encryption method has quite high robustness in terms of clipping prevention and noise prevention. The nonlinear operation is introduced into an encryption system while multi-image encryption transmission can be ensured, and safety of the encryption system is enhanced.
Owner:NANCHANG UNIV
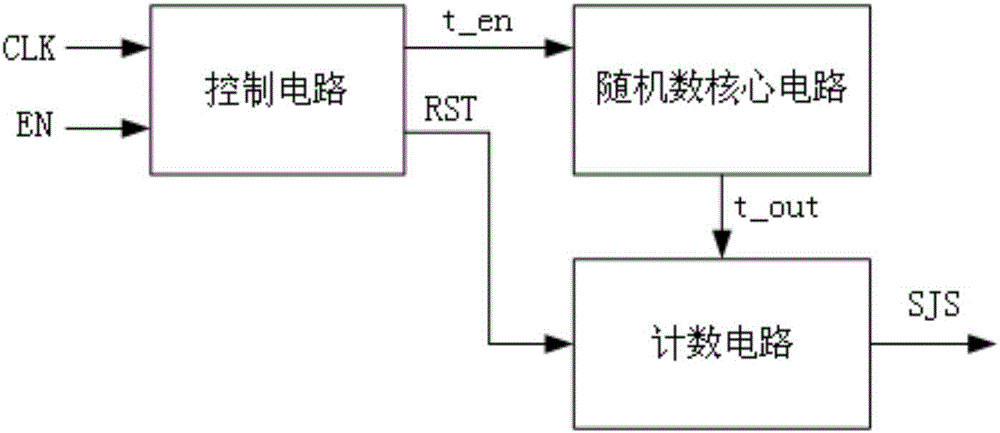
Random number generator based on transition effect ring oscillator
ActiveCN106484364AIncrease randomnessIncrease the oscillation frequencyRandom number generatorsHigh rateCryptosystem
The invention discloses a random number generator based on a transition effect ring oscillator. The random number generator consists of a random number core circuit which is used to generate an oscillation signal of unfixed time, and finally stabilizes at a fixed high level or low level; a control circuit which is used to generate resetting signals of the random number core circuit and a counter circuit; and a counter which enables the random number core circuit after the counter is reset, and is used for counting impulses generated by the random number core circuit. The invention has the advantages of a higher rate and a better anti-attack performance. The invention can be applied to all kinds of cryptosystems.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
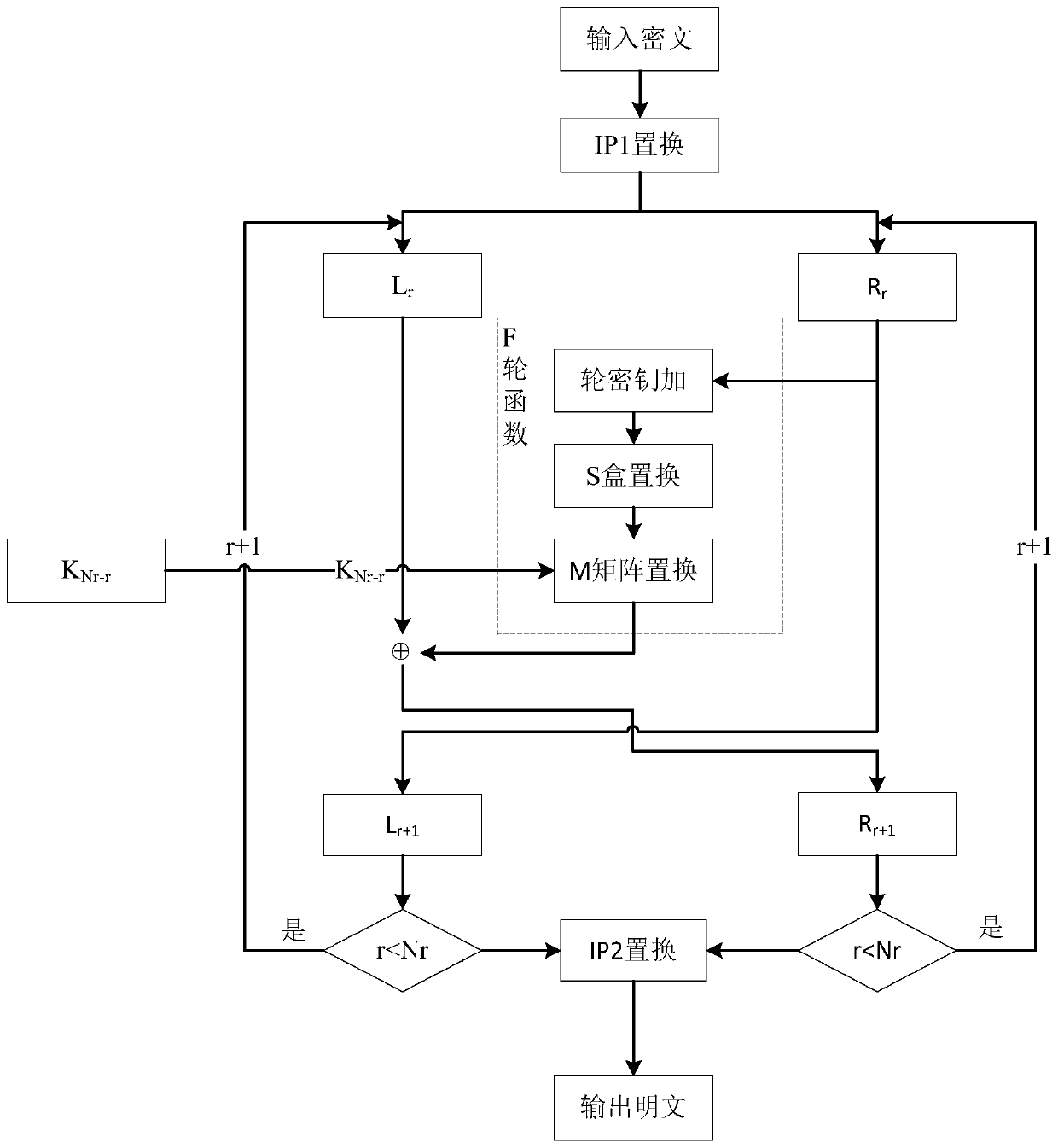
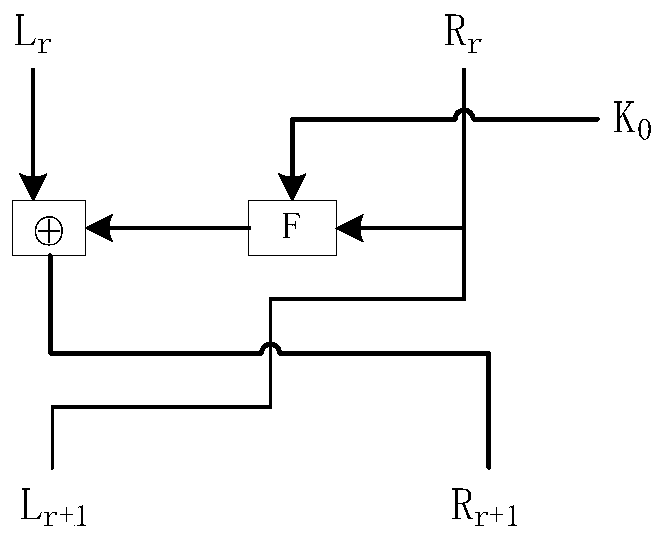
Lightweight cryptographic algorithm SCENERY implementation method and device and storage medium
ActiveCN110784307AImprove encryption efficiencyImprove securityEncryption apparatus with shift registers/memoriesPlaintextS-box
The invention discloses a lightweight cryptographic algorithm SCENERY implementation method, a lightweight cryptographic algorithm SCENERY implementation device and a storage medium. The method comprises the steps that a plaintext to be encrypted is acquired, IP1 initial replacement, a round function, key expansion and IP2 replacement are carried out in sequence, the round function comprises sequentially carrying out round key addition operation, S box replacement and M matrix replacement on data, and the key expansion comprises sequentially carrying out S box replacement, cyclic left shift, round constant addition operation and DP dynamic replacement on a key. An F function of an SPN structure is adopted as a round function, and a binary matrix M is constructed with the purpose of achieving high dependence when an F function linear layer is designed; a round constant and a key expansion intermediate result are selected as control signals for key expansion; DP dynamic replacement is carried out on a current round key expansion intermediate result to obtain a round key, which is a new key expansion mode, the relevance of single key iteration to front wheel input is reduced, the decoding difficulty is increased, the security is improved, and differential and linear attacks and algebraic attacks can be particularly and effectively resisted.
Owner:HENGYANG NORMAL UNIV
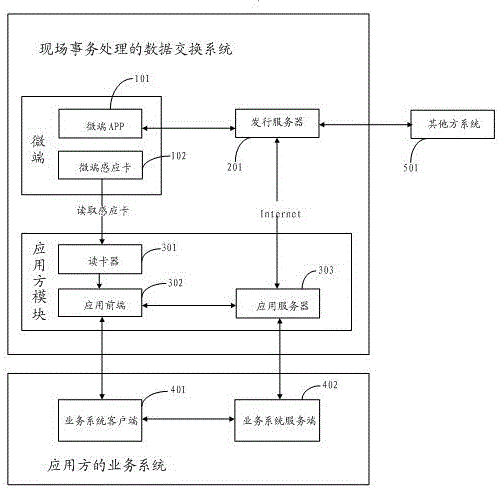
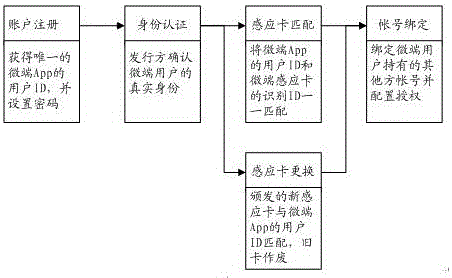
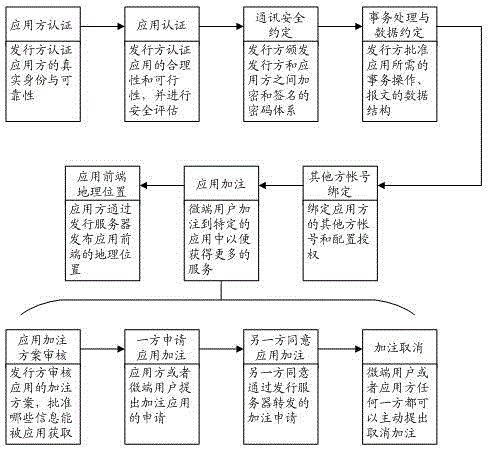
Data exchange system and method for onsite transaction processing
InactiveCN106327183AAvoid lostAvoid the inconvenience of replacement cardsCo-operative working arrangementsPayment protocolsPaymentApplication server
The invention discloses a data exchange system for onsite transaction processing, and the system comprises a micro-terminal induction card, a micro-terminal APP, a card reader, an application front end, an application server, and an issuing server. The micro-terminal induction card stores the identity recognition information, and the micro-terminal APP is a program which is installed on a mobile intelligent terminal and is used for identity authentication of a user and transaction processing. The issuing server is a program module which is used for the data exchange and the transaction processing. The card reader, the application front end and the application server form an application square block. The data exchange between the micro-terminal induction card and the micro-terminal APP is carried out through a circuit between the application front end and the application server and a circuit between the application front end and the issuing server. The invention also discloses a data exchange method for the onsite transaction processing, and the method comprises the steps: micro-terminal user registration and authentication, application access and marking, onsite transaction processing and abnormal transaction interception. The system can be used for replacing various types of payment cards, expense cards and identity verification cards, and is good in safety and resistance to attack.
Owner:常州真知信息技术有限公司
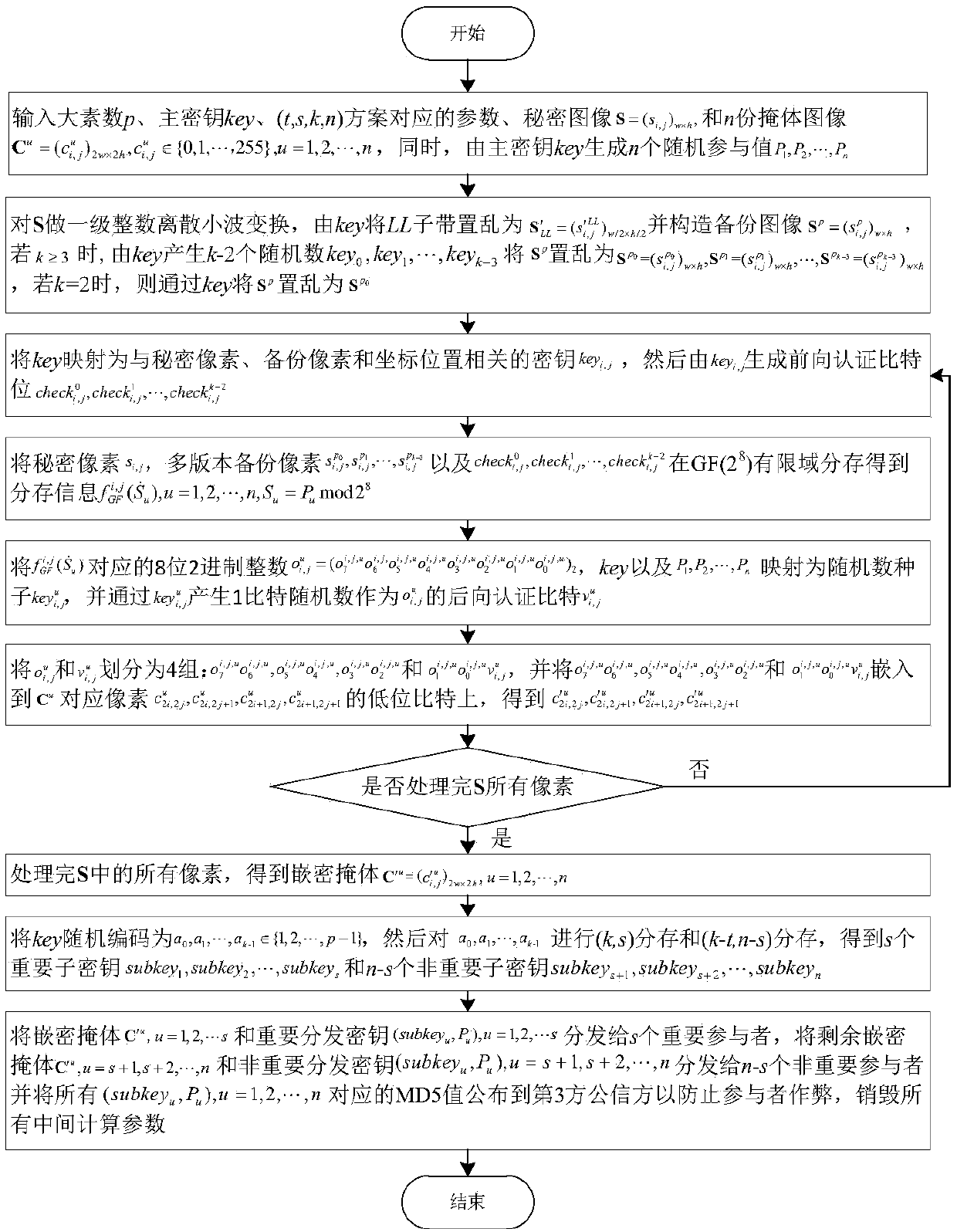
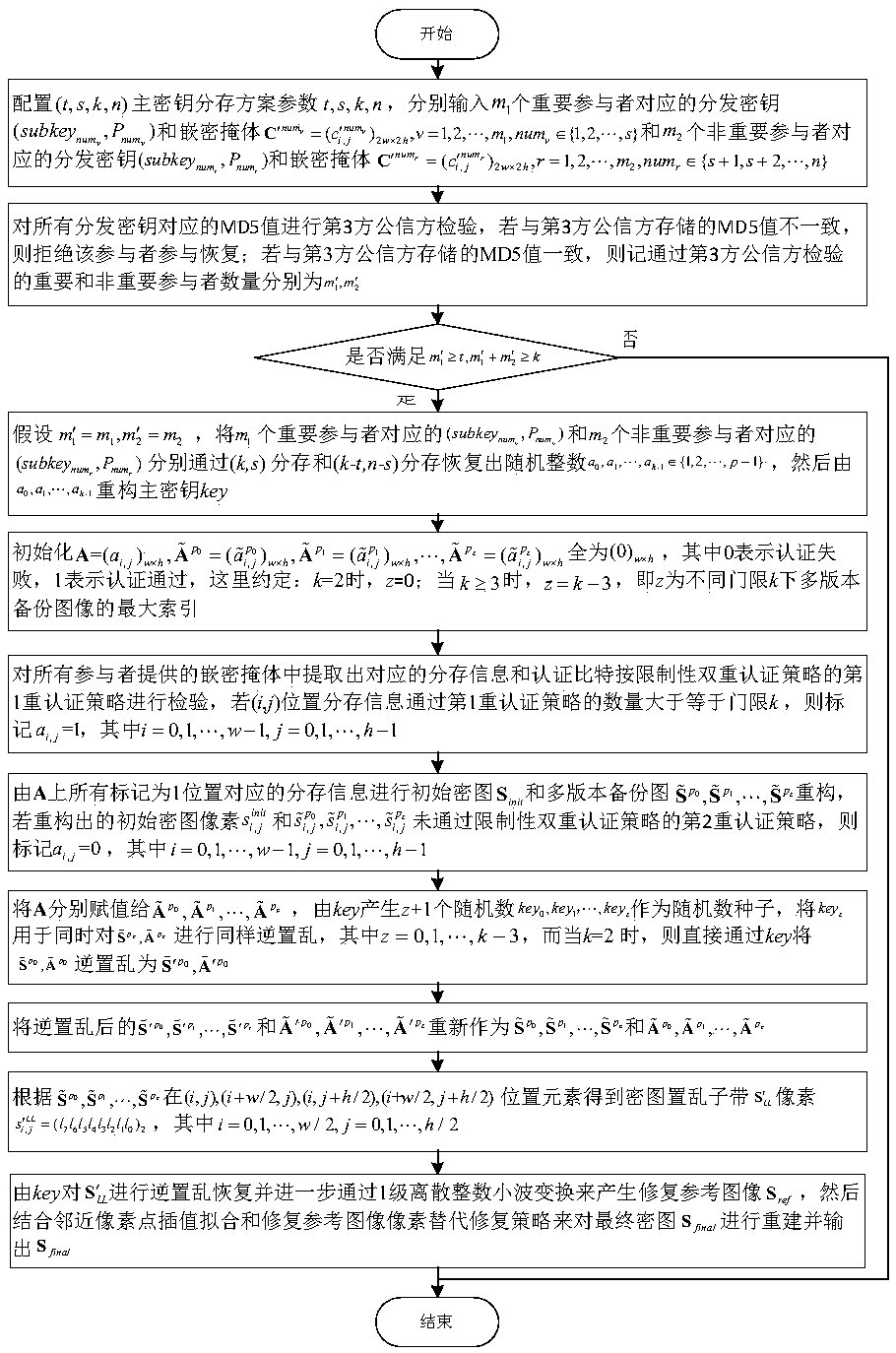
Image sharing method based on multi-version backup and restrictive dual-authentication master key (t, s, k, n)
ActiveCN108171665AAvoid number leakagePrevent malicious tamperingImage enhancementKey distribution for secure communicationComputer hardwareImage sharing
The invention provides an image sharing method based on multi-version backup and restrictive dual-authentication master key (t, s, k, n). On the basis of the constructed multi-version backup strategyand restrictive dual-authentication strategy, the high authentication accuracy is ensured and more embedding bits are used for backing up of backup images to form a plurality of versions of a backup image; and the pixels of the backup image are divided into salient, non-salient, and most salient bits further in each backup image version, wherein more salient bits are backed up and less non-salientbits are backed up. Therefore, the recovery capability of the single backup image is improved; and the recovery capability of the backup image is enhanced based on cooperative recovery of multiple versions of images. Meanwhile, according to the constructed multi-version backup strategy, high-confidence recovery of backup images is carried out by using the same bits stored at different positions;and the influence caused by the individual bits passing dual authentication luckily is eliminated by the statistic operation and the good anti-attack capability is realized.
Owner:SHAANXI NORMAL UNIV
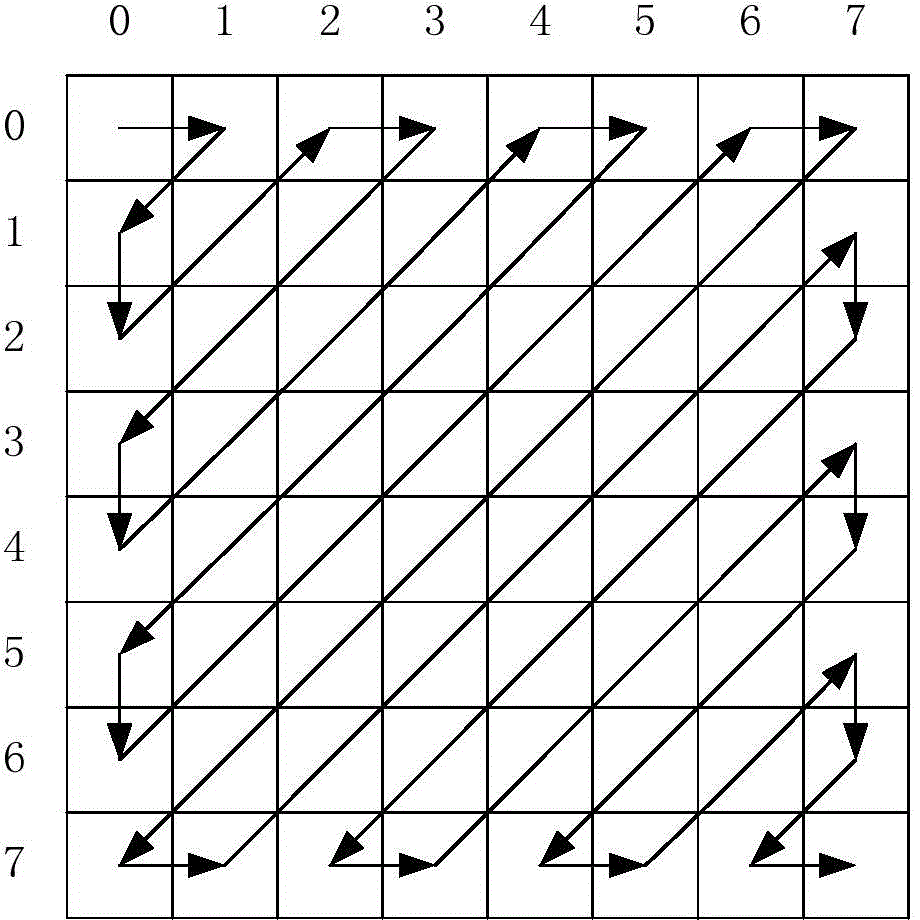
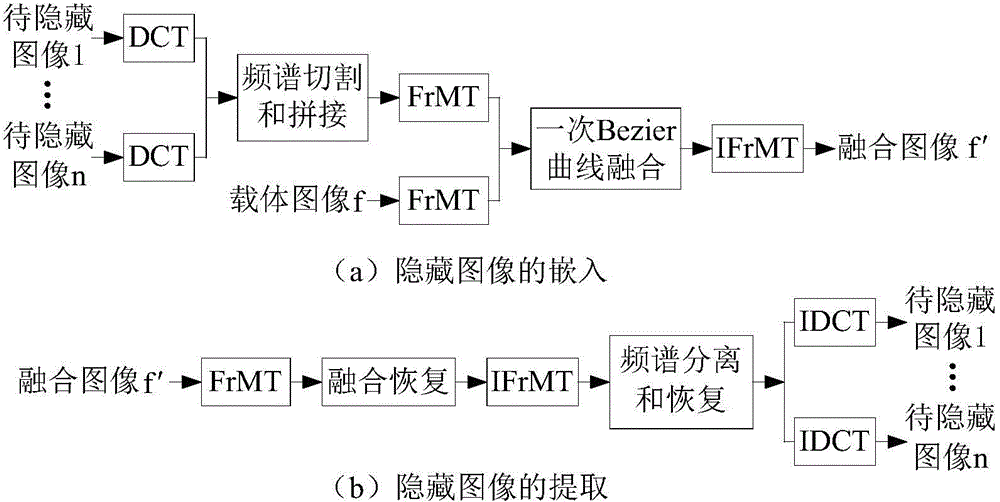
Multi-image hiding method based on fractional mellin transform
InactiveCN104408681AReduce redundancyAvoid affecting performanceImage data processing detailsFrequency spectrumMulti-image
The invention relates to a multi-image hiding method based on fractional mellin transform. According to the method, compression of multiple to-be-hidden images is carried out by utilizing a frequency spectrum cutting and splicing method, carrier images and compression images are respectively divided into multiple ring zone sub images, fractional mellin transform in different orders on each image is carried out, fusion of all results in a random combination mode is carried out by utilizing a primary Bezier curve, and fractional mellin transform is carried out by utilizing the same orders of carrier image transform to acquire fusion images containing to-be-hidden image information. The orders of fractional mellin transform and the fusion coefficients are taken as secret keys, and a center coordinate of coordinate transform and an inner radius and an outer radius for carrying out ring zone transform are taken as secondary secret keys. The method utilizes real property of discrete cosine transform to realize compression of the multiple images, increases hidden information amount in a frequency domain processing method, utilizes fractional mellin transform for encryption and improves anti-attacking capability and safety of systems.
Owner:NANCHANG UNIV
Novel brain-controlled intelligent rehabilitation method based on capsule network, and application thereof
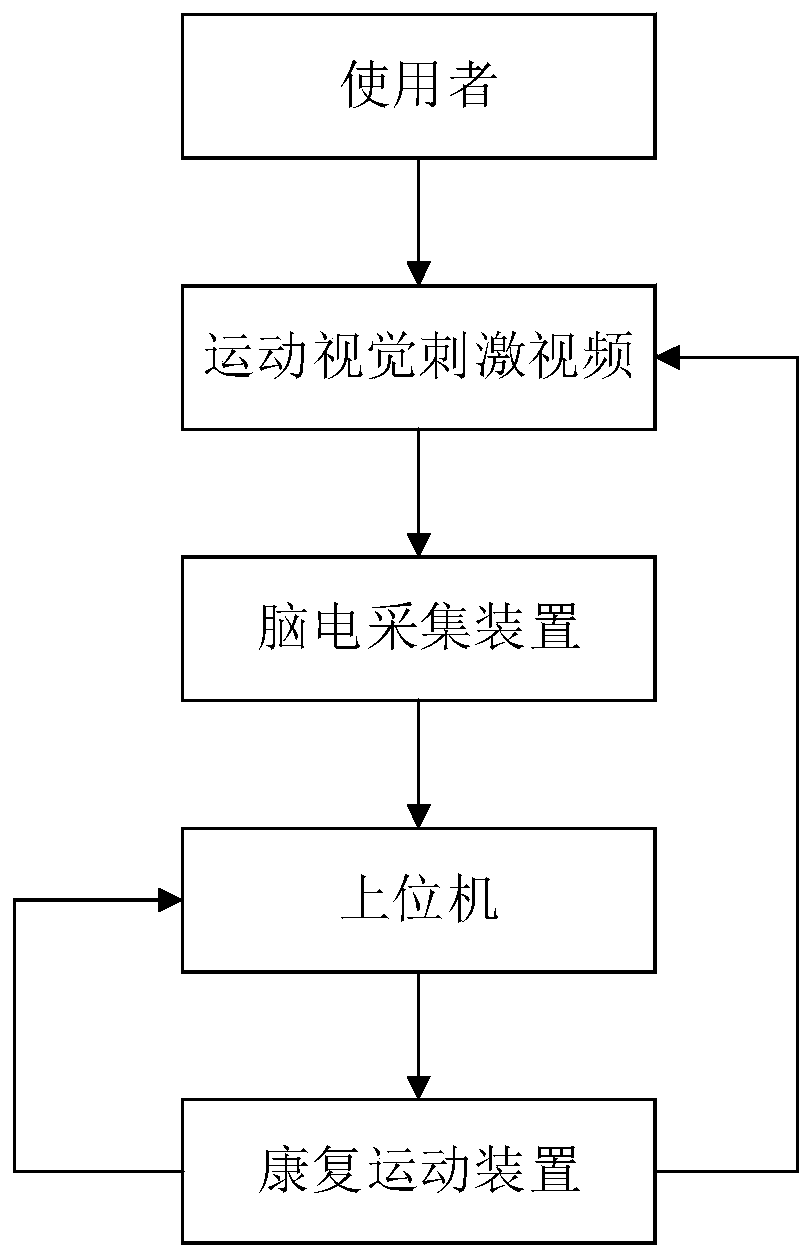
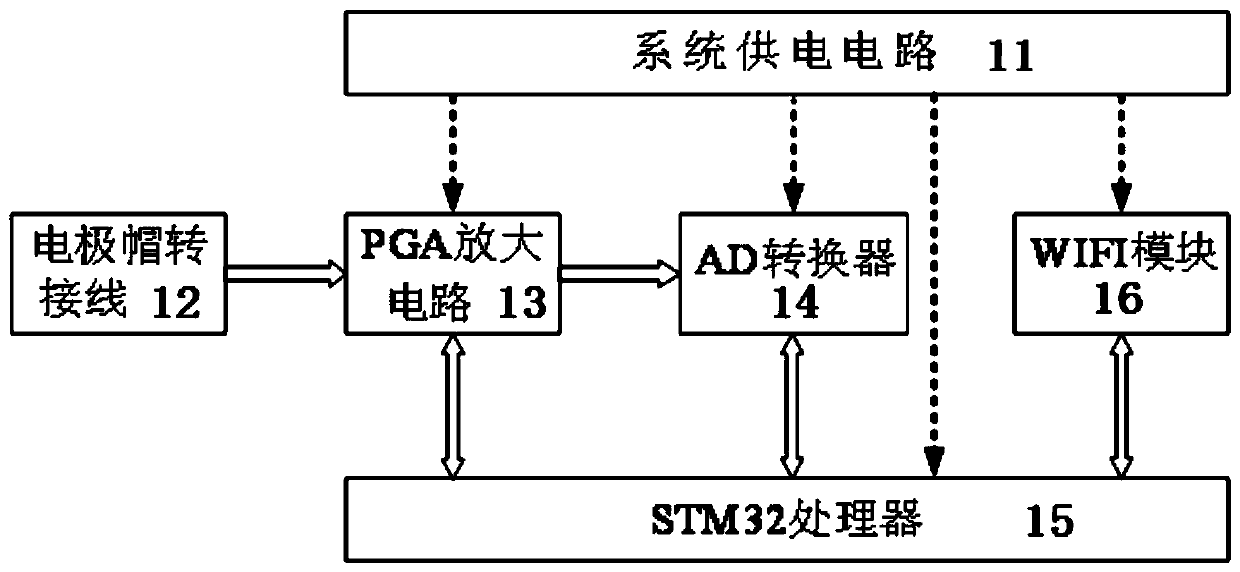
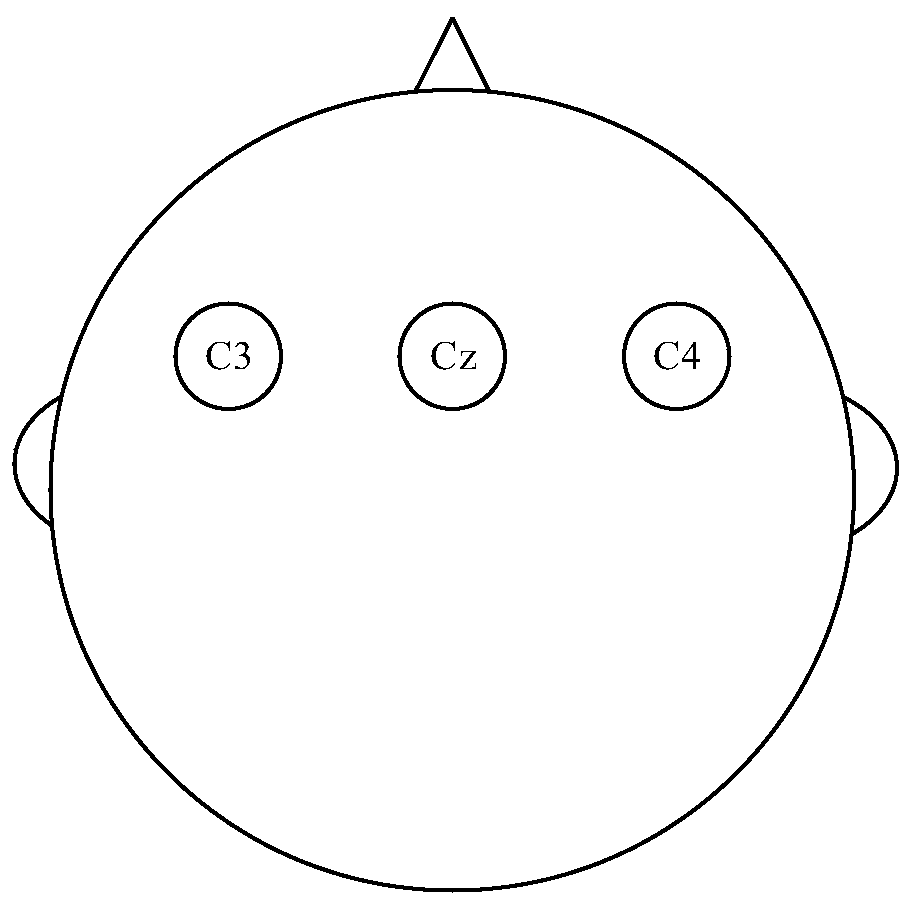
ActiveCN111584032AGuaranteed classification accuracyImprove work efficiencyPhysical therapies and activitiesCharacter and pattern recognitionMedicineControl signal
The invention discloses a novel brain-controlled intelligent rehabilitation method based on a capsule network, and application thereof. According to the method, an upper computer generates corresponding motion stimulation videos according to rehabilitation training items selected by a user, the motion stimulation videos are displayed to the user through a displayer, the user imagines correspondingactions, and synchronous motion imagination electroencephalogram signals of the user are collected through an electroencephalogram collecting device, subjected to amplifying and filtering preprocessing and transmitted to the upper computer in a wireless mode; after the upper computer receives the motion imagery electroencephalogram signals and processes the motion imagery electroencephalogram signals again, the features of the motion imagery electroencephalogram signals are extracted based on a capsule network algorithm, and are classified, the classification results are converted into corresponding rehabilitation training control signals, and the rehabilitation training control signals are transmitted to a rehabilitation exercise device; the rehabilitation exercise device drives the userto perform corresponding training actions and feeds back signal data of the training actions of the user to the upper computer; and the upper computer evaluates the signal data of the training actions of the user by adopting a Fugl-Meyer evaluation method. The safety of the brain-controlled rehabilitation system can be improved.
Owner:TIANJIN UNIV
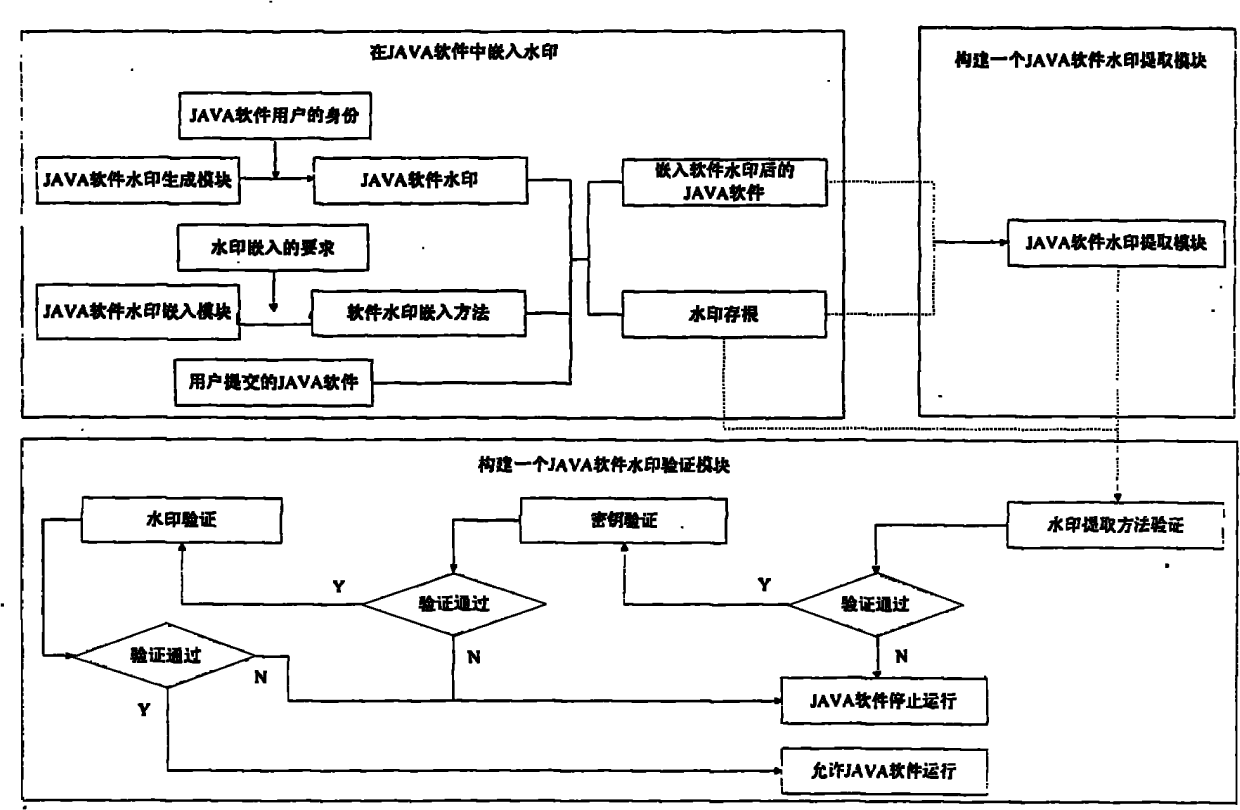
Method for restricting illegal JAVA software operation by using software watermarks
ActiveCN102122335BImprove privacyGood resistance to attackProgram/content distribution protectionUser needsConfidentiality
The invention relates to a method for restricting illegal JAVA software operation by using software watermarks, belonging to the technical field of software protection. The method comprises the following steps of: embedding a watermark in JAVA software submitted by a user; then, constructing a JAVA software extraction module and a JAVA software watermark verification module in a JAVA software operation system; extracting the watermark from the JAVA software submitted by the user with a watermark extraction method in the water extraction module; and verifying the extracted watermark to determine the validity of the JAVA software submitted by the user. The method in the invention has good confidentiality, high safety, and better attack resistance capacity for attacks of malicious software. In the method, the software watermark has short extraction time, and the software embedded with the watermark can still keep good operation performance. The method has good portability, a watermark method is selected according to user demands, and the JAVA software requirement on safety and operation efficiency can be better satisfied.
Owner:TSINGHUA UNIV
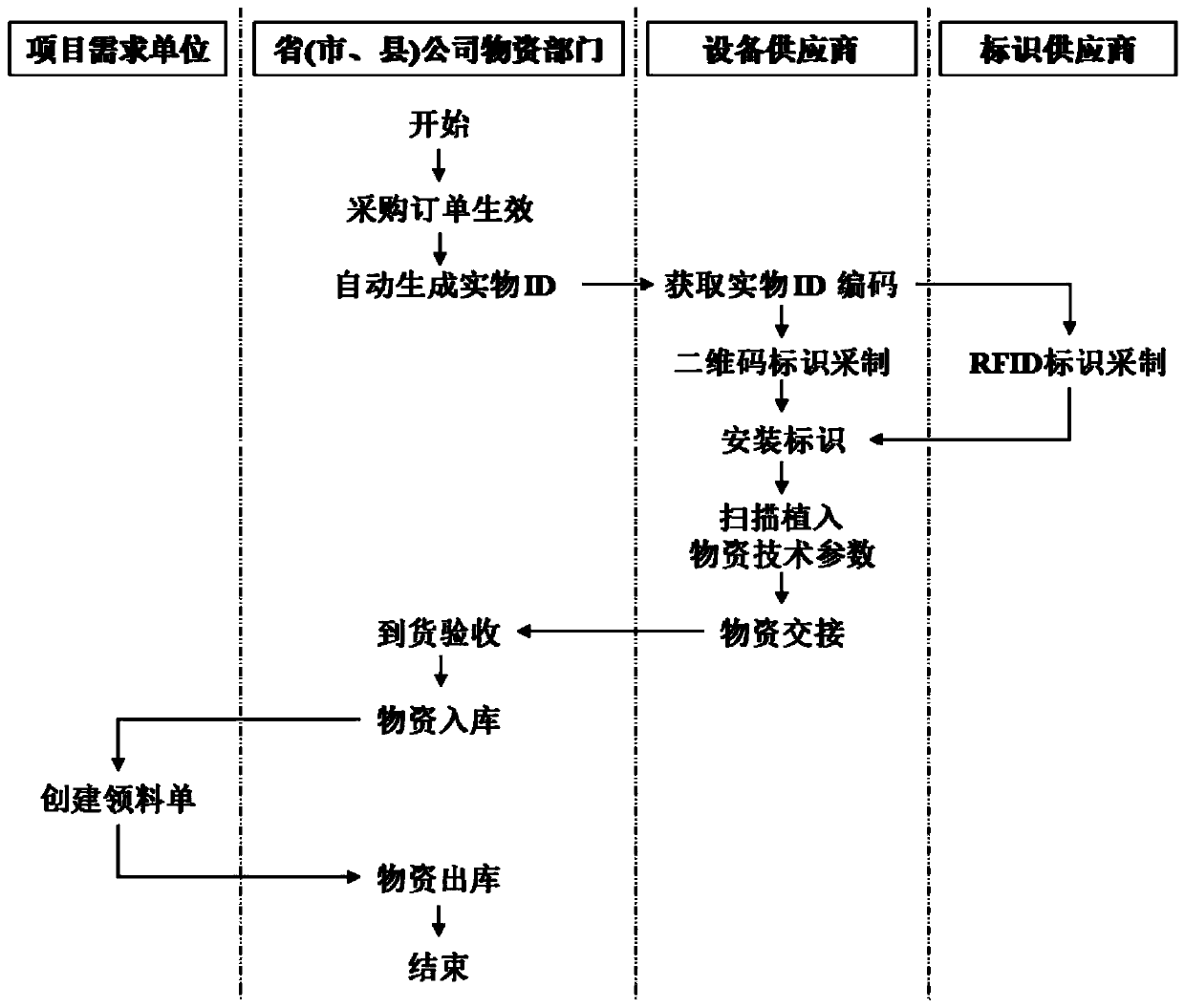
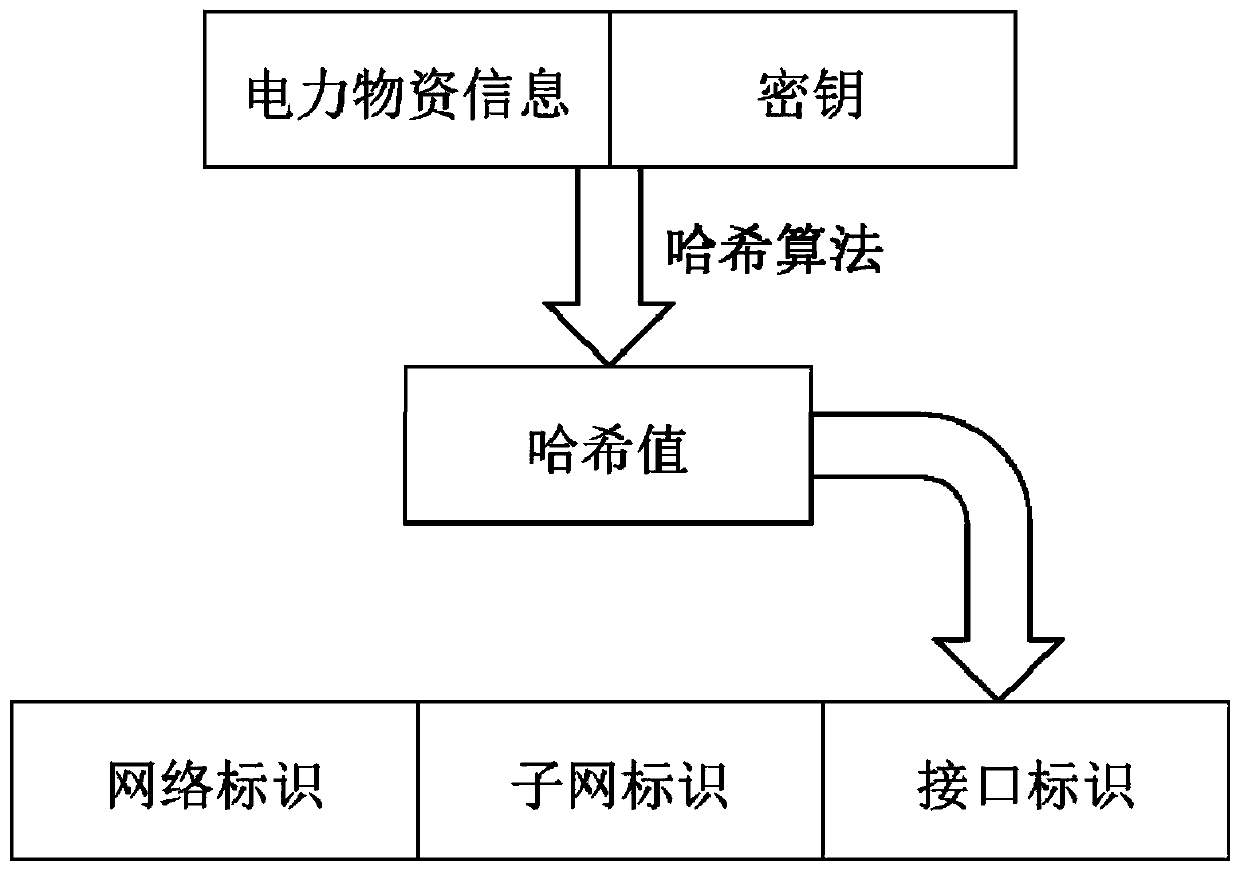
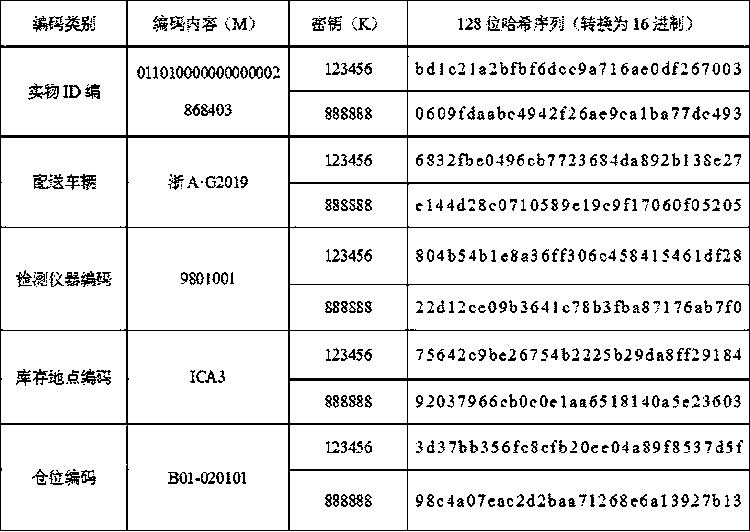
Electric power material coding optimization method based on hash algorithm
PendingCN110889595AImprove security strengthGood resistance to attackResourcesHash functionAlgorithm
The invention relates to an electric power material coding optimization method based on a hash algorithm. The method comprises steps of mixing the secret key with the message data by using an HMAC-MD5algorithm constructed on the basis of an MD5 message digest algorithm, performing hash calculation on a mixed result by using a hash function, mixing an obtained hash value with the secret key, and then applying the hash function again; and enabling the HMAC-MD5 to receive a secret key with any size and generate a hash sequence with the length of 128 bits. According to the invention, the hash algorithm is combined on the basis of the existing electric power material coding mode, and the electric power material coding security strength based on the HMAC-MD5 algorithm is high; codes based on anHMAC-MD5 algorithm and IPv6 are fused, codes generated based on a coding mode of the HMAC-MD5 algorithm are added with a secret key, an IPv6 address generated by a hash value with the secret key is fused, and the better anti-attack capacity is achieved.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER
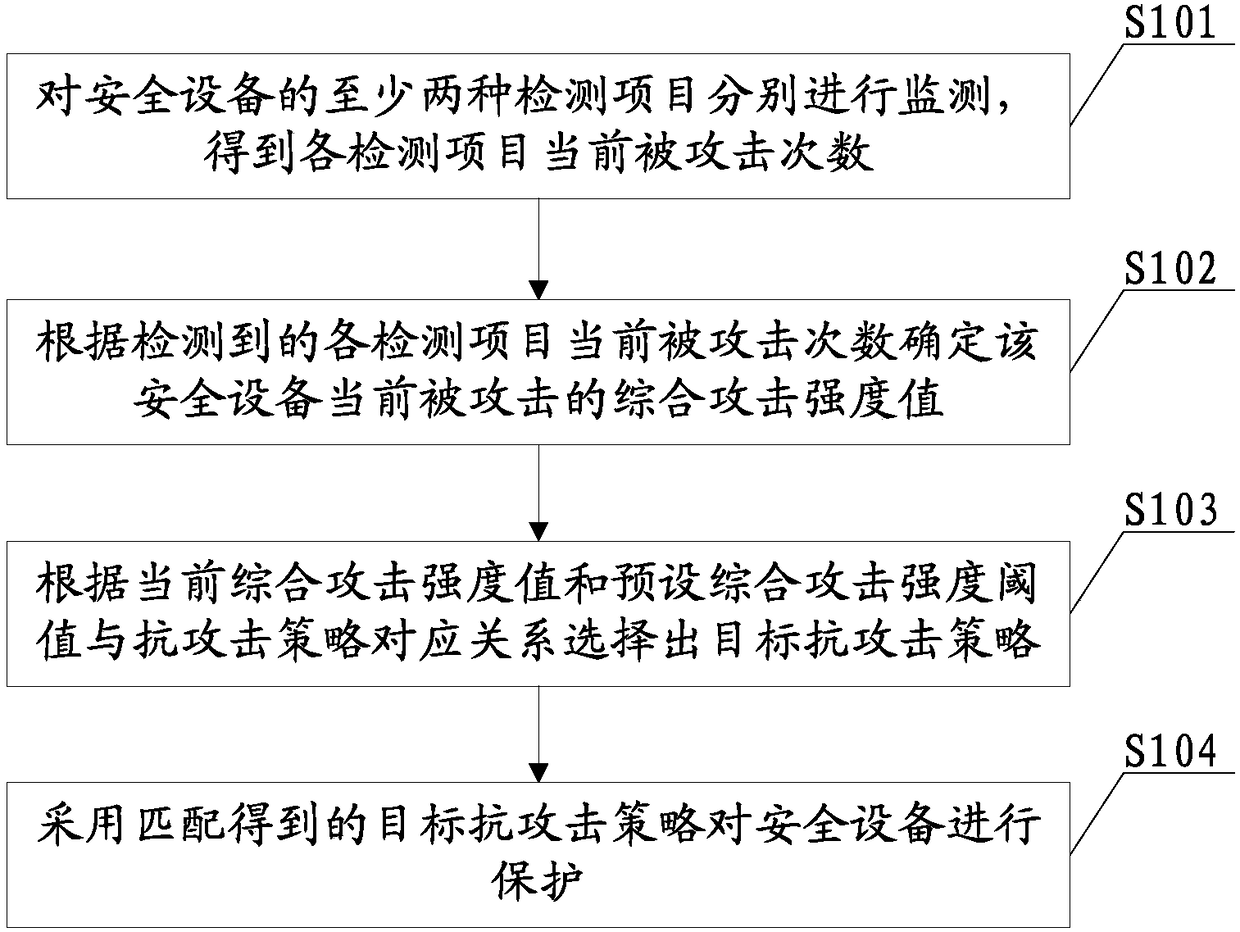
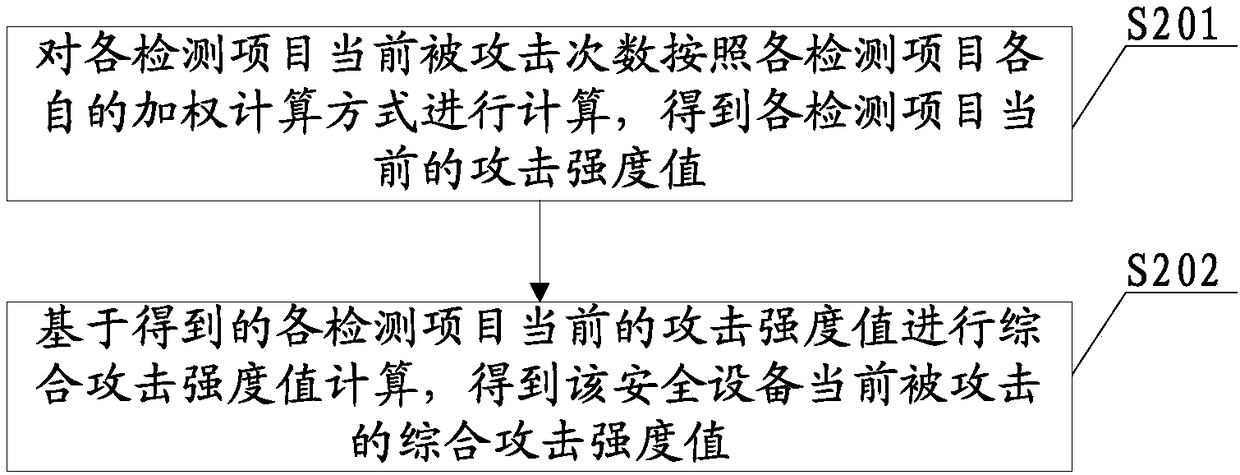
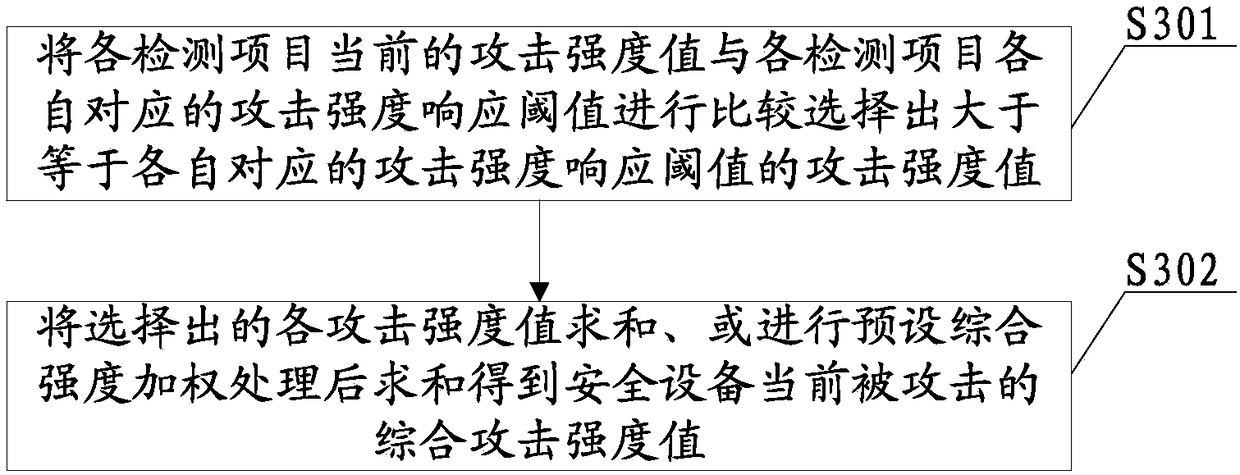
Safety device and anti-attack method thereof thereof
PendingCN109214173AImprove experienceGood resistance to attackPlatform integrity maintainanceAttack strategyUltimate tensile strength
The invention provides a safety device and an anti-attack method thereof. Firstly, a corresponding relationship between a comprehensive attack strength threshold and an anti-attack strategy is preset,and anti-attack strategies of different grades can be correspondingly set according to different comprehensive attack strength thresholds. Then at least two kinds of detection items of the safety equipment are monitored respectively to obtain the current attack times of each detection item. A comprehensive attack strength value of a security device currently attacked is determined according to the detected current attacked times of each detection item; Then, according to the relationship between the current comprehensive attack strength value and the preset comprehensive attack strength threshold and the anti-attack strategy, the anti-attack strategy matching the current comprehensive attack strength value is selected as the target anti-attack strategy, and the target anti-attack strategyis adopted to protect the security equipment. Thus, the invention can synthesize the attack strength of the current multiple attacks on the security device and call out the corresponding level anti-attack strategy to protect the security device, thereby better protecting the information security of the user.
Owner:NATIONZ TECH INC
Quantum chaos image encryption method based on bit scrambling
ActiveCN105631796BSimple physical structureResolve Loss of PrecisionImage data processing detailsComputer hardwareChaotic systems
The invention discloses a quantum chaotic image encryption method based on bit scrambling. The method comprises steps: a Logistic quantum chaotic system is used for generating a chaotic sequence, bit scrambling is carried out on R, G and B three-primary color component pixel values of an original image p, and a middle scrambling image I is obtained; and then, encryption operation is carried out on the middle scrambling image I, and a final encryption image q is obtained. The encryption method of the invention greatly increases the secret key space, the safety, the encryption effect and the secret key sensitivity are higher, the anti-attack ability is stronger, and the deciphering difficulty is greatly improved.
Owner:GUANGDONG UNIV OF TECH
SIFT-based blind watermarking method for dwt‑svd against geometric attacks
ActiveCN103955878BGood resistance to attackGood attackImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD geometric attack prevention blind watermark method based on SIFT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, and the watermarks are embedded into the maximum singular value of each small block through an optimal quantitative method, the SIFT feature points of a watermark image are stored as secret keys, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the utilization of the rotation, zoom and translation invariance of the SIFT feature points and the combination of the advantages of DWT and SVD in the digital watermark aspect, robustness on geometric attacks is remarkably improved.
Owner:HANGZHOU DIANZI UNIV
Power consumption compensation anti-attack circuit and control method based on neural network power consumption prediction
InactiveCN103646219BHigh anti-power consumption attack protection capabilityGood constant power performanceInternal/peripheral component protectionNeural learning methodsPower compensationAdaptive learning
Owner:SOUTHEAST UNIV
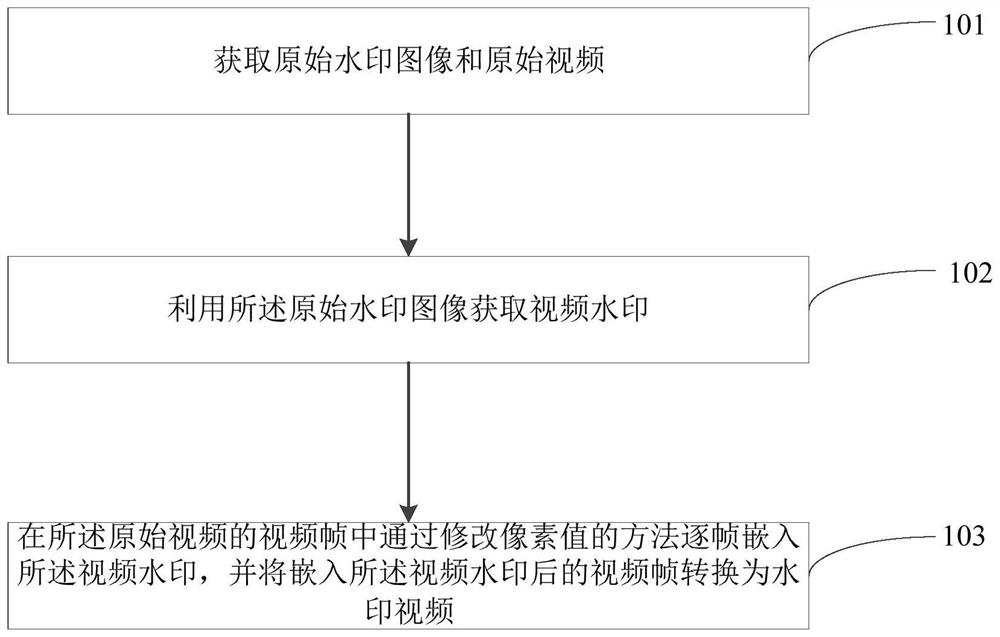
Watermark embedding method and device and watermark extracting method and device
ActiveCN113766242AGood resistance to attackDigital video signal modificationSelective content distributionPattern recognitionComputer graphics (images)
The invention provides a watermark embedding method and device and a watermark extracting method and device, and belongs to the technical field of digital image processing and information security. The watermark embedding method comprises the following steps: acquiring an original watermark image and an original video; acquiring a video watermark by using the original watermark image; and embedding the video watermark frame by frame in the video frame of the original video through a method of modifying a pixel value, and converting the video frame embedded with the video watermark into a watermark video. According to the technical scheme, video invisible watermark embedding can be realized.
Owner:CHINA MOBILE COMM LTD RES INST +1
A Text Watermark Embedding and Extraction Method Based on Semantic Role Position Mapping
ActiveCN105205355BAffects correct extractionImprove robustnessProgram/content distribution protectionPattern recognitionCoded element
The present invention relates to a text watermark embedding and extraction method based on semantic role position mapping. The embedding method includes the following steps: 1) preprocessing the watermark information, converting the watermark characters into an information string composed of code elements; 2) through natural language processing The technology finds out the semantic role in the text, obtains the position information of the semantic role, and corresponds the semantic role type with the code element representing the watermark information one by one; 3) Takes out the codewords in the watermark information string one by one, and compares the codeword with the corresponding A location of the semantic role of the type is mapped to complete the embedding of the watermark. The extraction method includes: according to the position information of the semantic role obtained when embedding the watermark, find the semantic role of the position in the text, and then reversely map to obtain the watermark information string represented by the code element, and finally convert it into the original watermark information. The above method does not make any changes to the text format and content, has good concealment and robustness, and can effectively resist various common format transformations and attacks.
Owner:NANTONG UNIVERSITY
Neural Network Model Encryption Protection System and Method Involving Specified Frequency Band Encryption
ActiveCN108900294BImprove securityImprove concealmentKey distribution for secure communicationEncryption apparatus with shift registers/memoriesAlgorithmTheoretical computer science
The invention belongs to the field of an artificial neural network protection mechanism, and relates to a neural network model encryption protection system and method involving specified frequency band encryption. The neural network model encryption protection system comprises a data input module, an encryption module, an encrypted data input module, an artificial neural network module and a dataoutput module, wherein the encryption module comprises a frequency domain transformation module, a frequency domain data processing module and a frequency domain inverse transformation module; and thefrequency domain data processing module comprises a frequency domain specifying module, a password generating module and a password embedding module. The neural network model encryption protection system can embed a protective password into an artificial neural network model trained based on input data through the encryption for the input data under the condition of not significantly increasing the calculation amount and mainlining the performance of the artificial neural network. In addition, a method for input data encryption is realized through domain transformation, the hiding and anti-attacking performance of password information are improved, and the safety of the trained artificial neural network model is enabled to be further improved.
Owner:CHENGDU PANOAI INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com