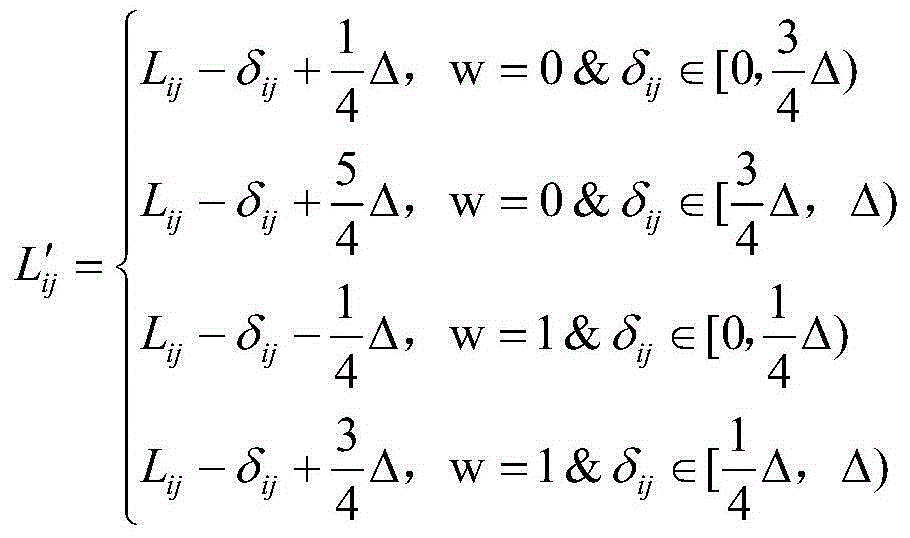Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
88results about How to "Good attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
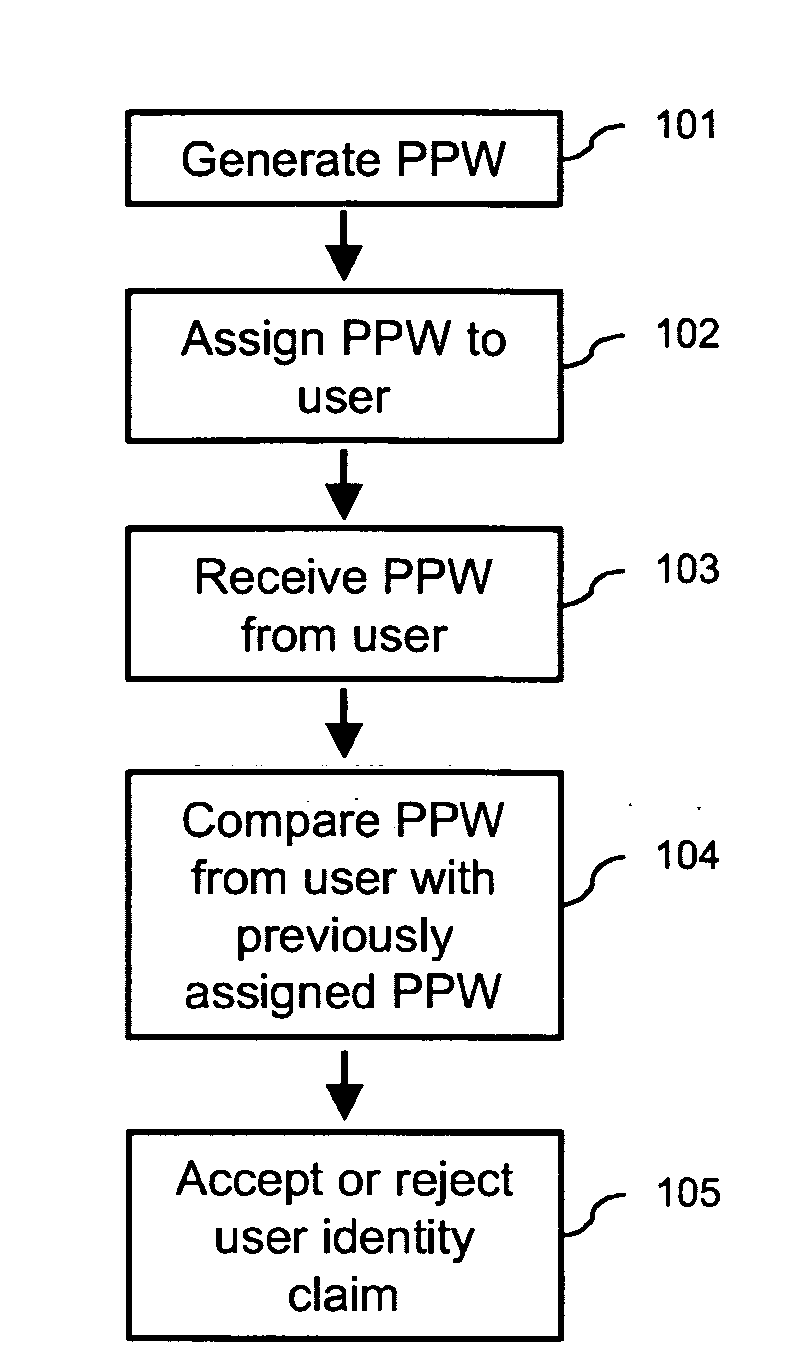
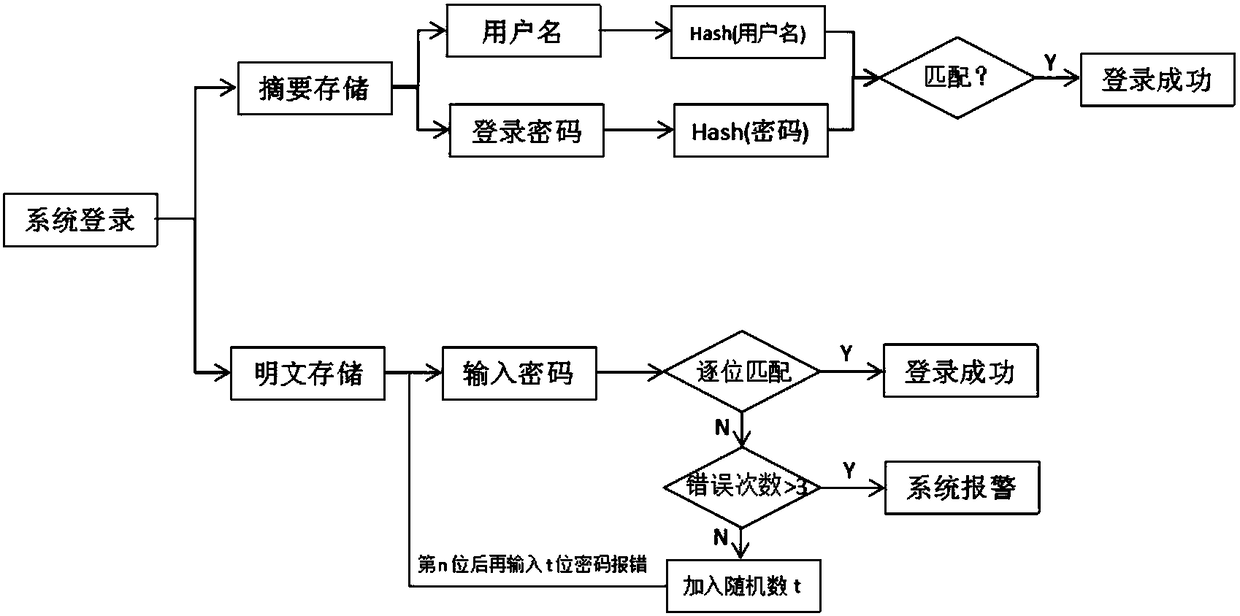
User authentication method and system and password management system
InactiveUS20090293119A1Good attackAcutation objectsDigital data processing detailsUser authenticationPassword management
In one embodiment of the present invention, a user authentication method including the steps of automatically generating a set of deviation parameters; deviating from a reference password object, within an object space defined by appearance parameters previously acquired from a training set of objects, in a direction and with an amount determined by the set of deviation parameters, to thereby synthesize a password object; assigning a perceptual password including the password object to a user, and receiving a user identity claim including a user-provided perceptual password. The method further includes the steps of comparing the user-provided perceptual password with the perceptual password assigned to the claimed user, and, based on the result of this comparison, accepting or rejecting the user identity claim.
Owner:CIPHERSTONE TECH
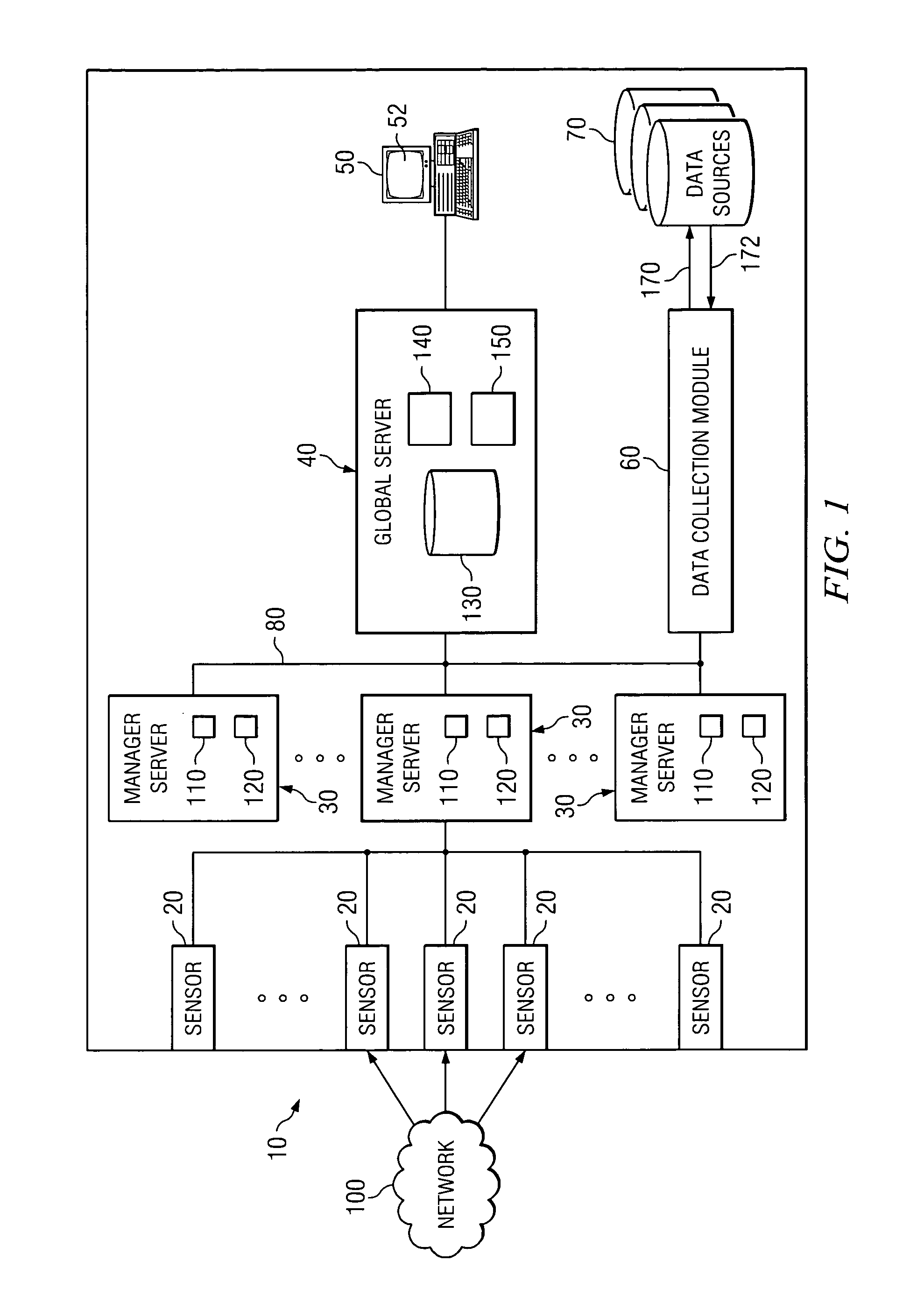
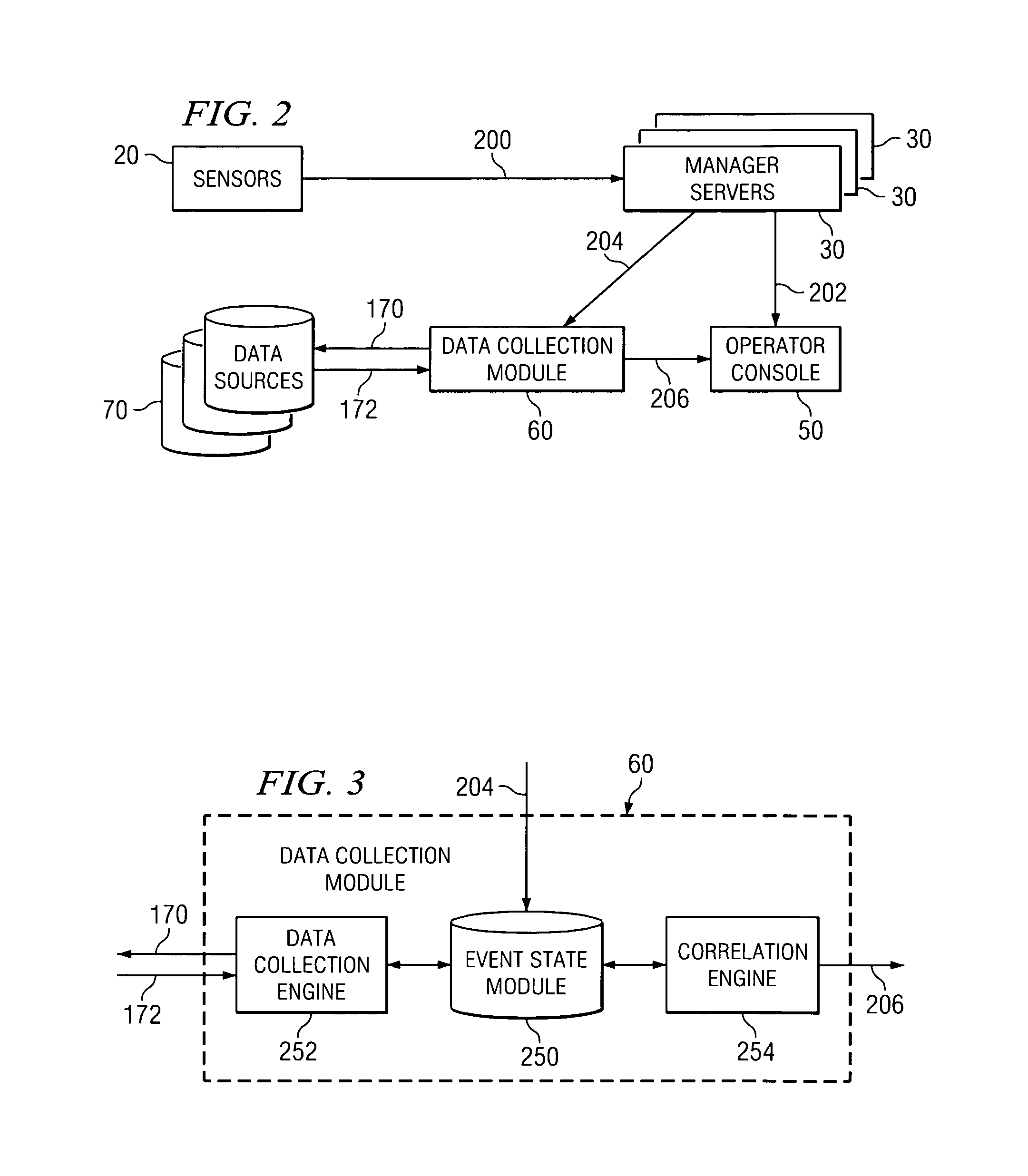
System and method for active data collection in a network security system
ActiveUS8572733B1Good correlationGood attackMemory loss protectionError detection/correctionInternet privacyData harvesting
A network security system comprises a plurality of sensors, a management server, and a data collection module. The plurality of sensors receive first data associated with potential attacks on the system. The manager server is coupled to at least one sensor and correlates at least a portion of the first data to detect potential attacks on the system. The data collection module is coupled to the manager server and generates at least one request for second data based upon at least one of the first data and the correlated data. The data collection module communicates the request to at least one source different from the plurality of sensors.
Owner:FORCEPOINT FEDERAL
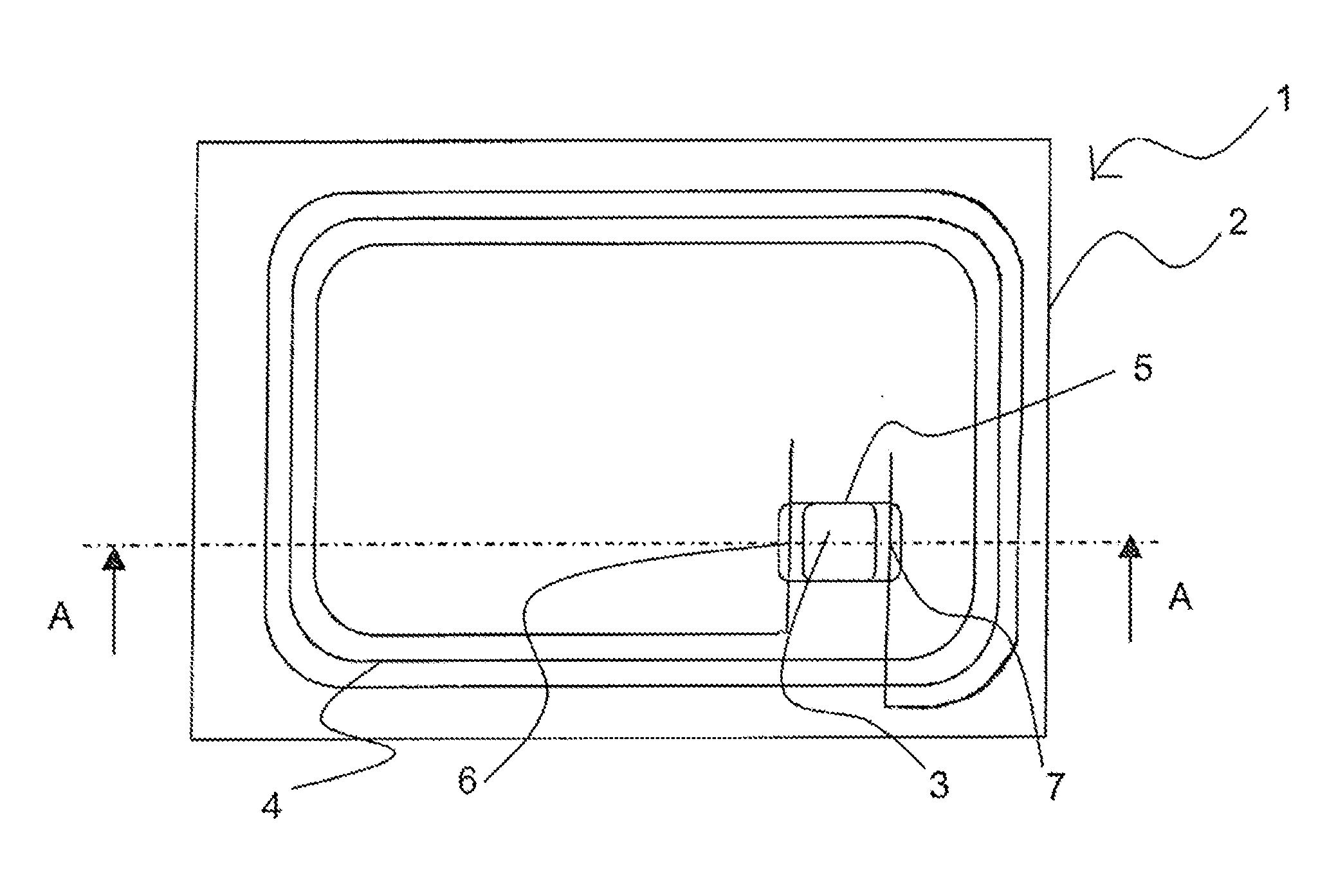
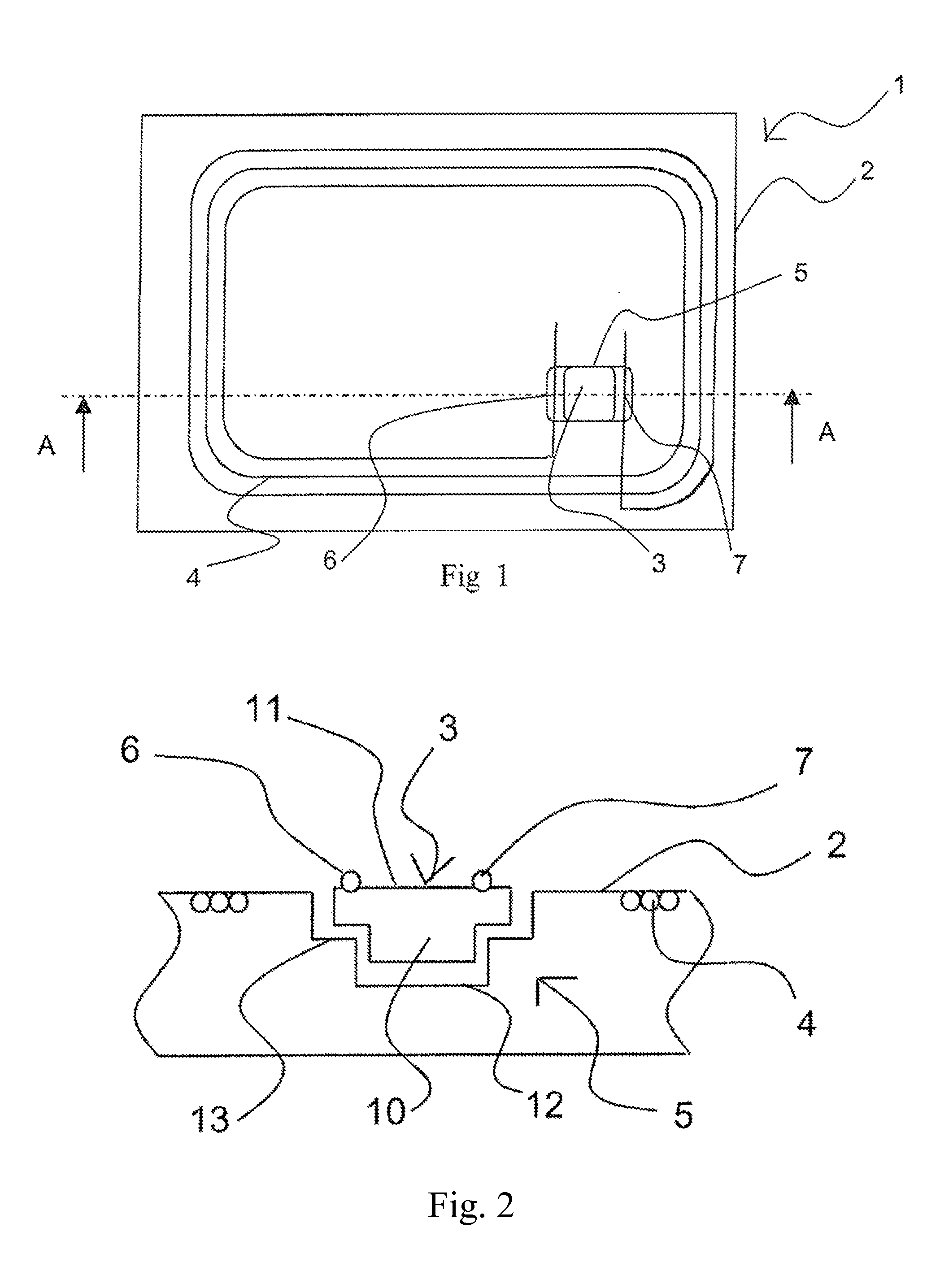
Fibrous insert consisting of a single layer and equipped with a contactless communication electronic device
InactiveUS20130062875A1Reduce thicknessSimple and inexpensive to fabricateOther printing matterWave amplification devicesFiberPaper document
The invention relates to a flat insert intended for being inserted in a security document, which includes a fibrous substrate (2) formed as a single layer having a cavity (5) and an electronic device (3) having contactless communication, housed in said cavity. Said cavity is in communication with a single surface of the fibrous substrate (2) and includes, in the cross-section thereof, a peripheral shoulder (13) for housing said electronic device in said cavity without generating a thickened portion of the insert, said fibrous substrate (2) including synthetic fibres.
Owner:ARJO WIGGINS SECURITY SAS
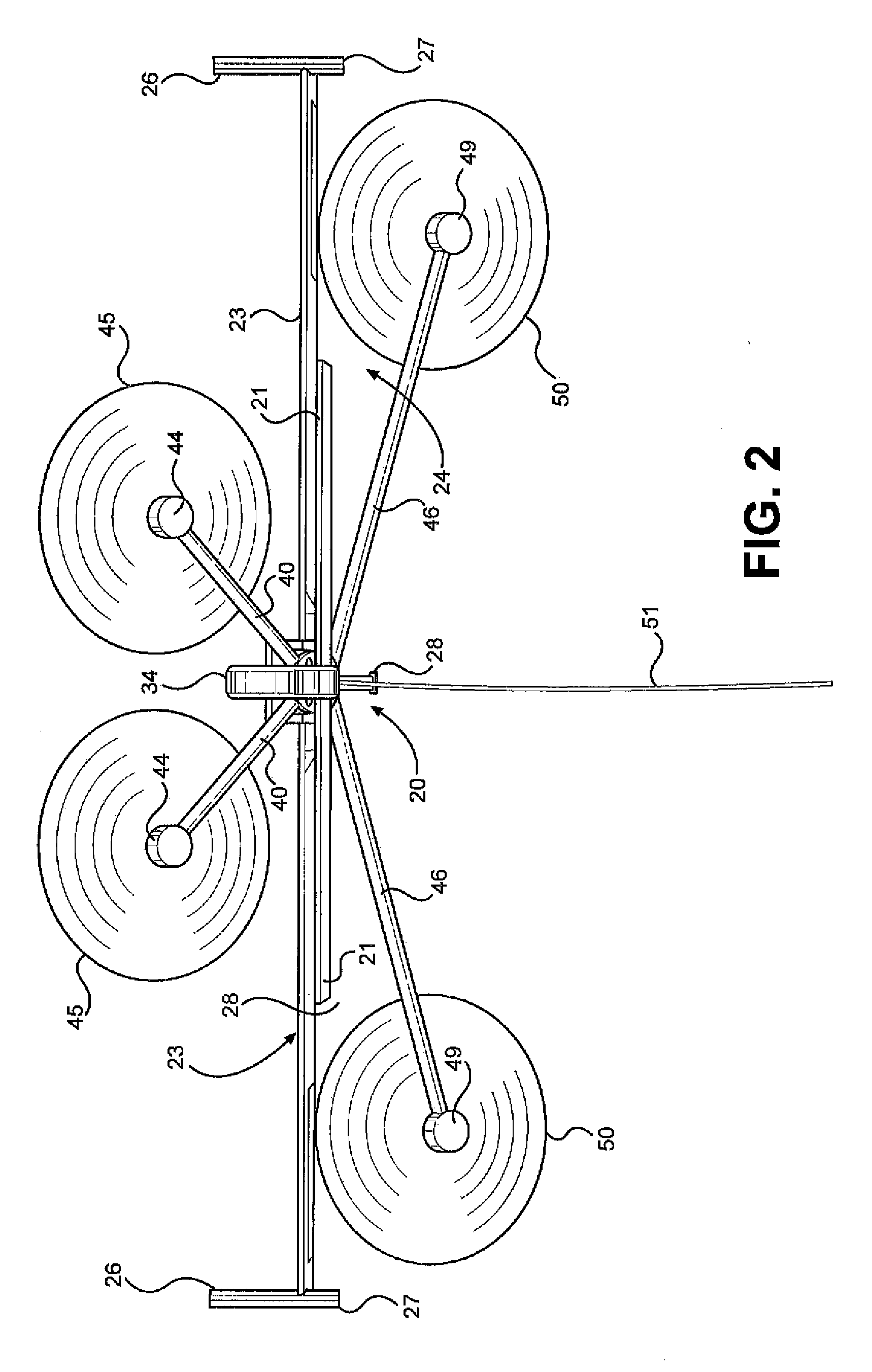
Auto-gyro rotor flying electric generator (FEG) with wing lift augmentation
InactiveUS20160010627A1High rotor angle of attackFull generating capacityUnmanned aerial vehiclesWind motor supports/mountsFuselageElectric generator
A flying electric generator for obtaining power from wind currents which includes a fuselage having fore and aft portions and an intermediate portion, a rotor assembly including at least two forward rotors mounted on a pair of forward extending support arms extending from the fuselage and at least two rear rotors mounted to a pair of rearward extending support arms extending from the fuselage and at least one first forward wing mounted to a forward portion of the fuselage and extending outwardly on opposite sides of the fuselage and at least one second rear wing mounted to a rear portion of the fuselage and extending outwardly on opposite side of the fuselage.
Owner:SKY WINDPOWER CORP
Machining of Ceramic Materials
ActiveUS20120219930A1Reduce processing timeMaintain strengthDental implantsWristbandsMetallurgyUltimate tensile strength
Owner:IVOCLAR VIVADENT AG
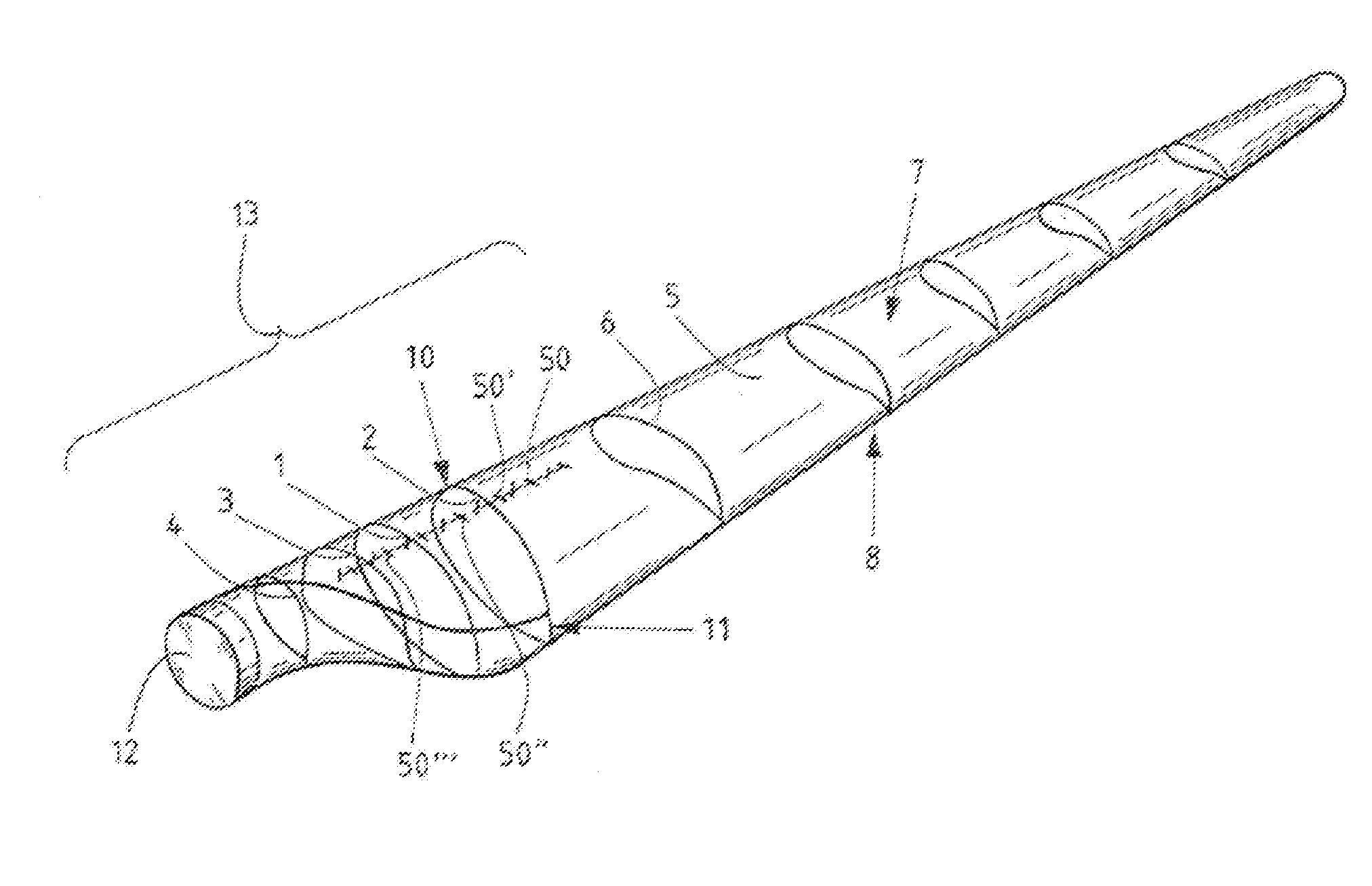
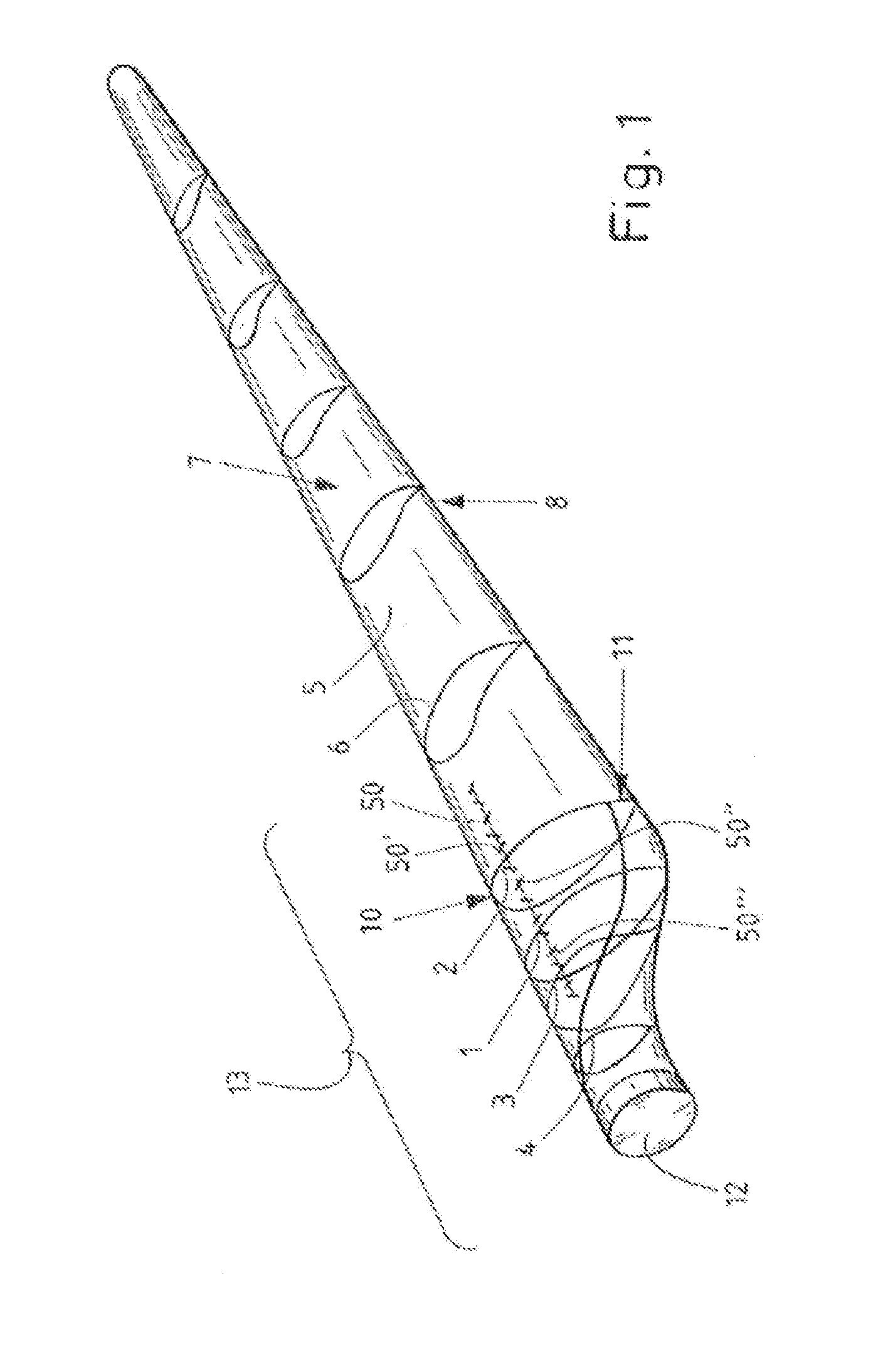
Rotor blade of a wind turbine
ActiveUS20150361952A1Increase lift coefficientReduce weightReaction enginesEngine componentsLeading edgeTrailing edge
A rotor blade (5) of a wind turbine, which has a profile (1-4) having an upper side (suction side) (7) and an underside (pressure side) (8). The profile (1-4) includes a camber line (21, 25) and a chord (18) between a leading edge (10) and a trailing edge (11) of the profile (1-4). The profile (1-4) has a relative profile thickness of more than 45%. At least one vortex generator (50, 50′, 50″, 50′″) is disposed, in the region of the profile (1-4), on the suction side (7) of the rotor blade (5). The profile (1-4) is provided with a blunt trailing edge. And, The thickness of the trailing edge is between 15% and 70% of the chord length.
Owner:SENVION DEUT GMBH
Outer door grip, in particular for vehicles
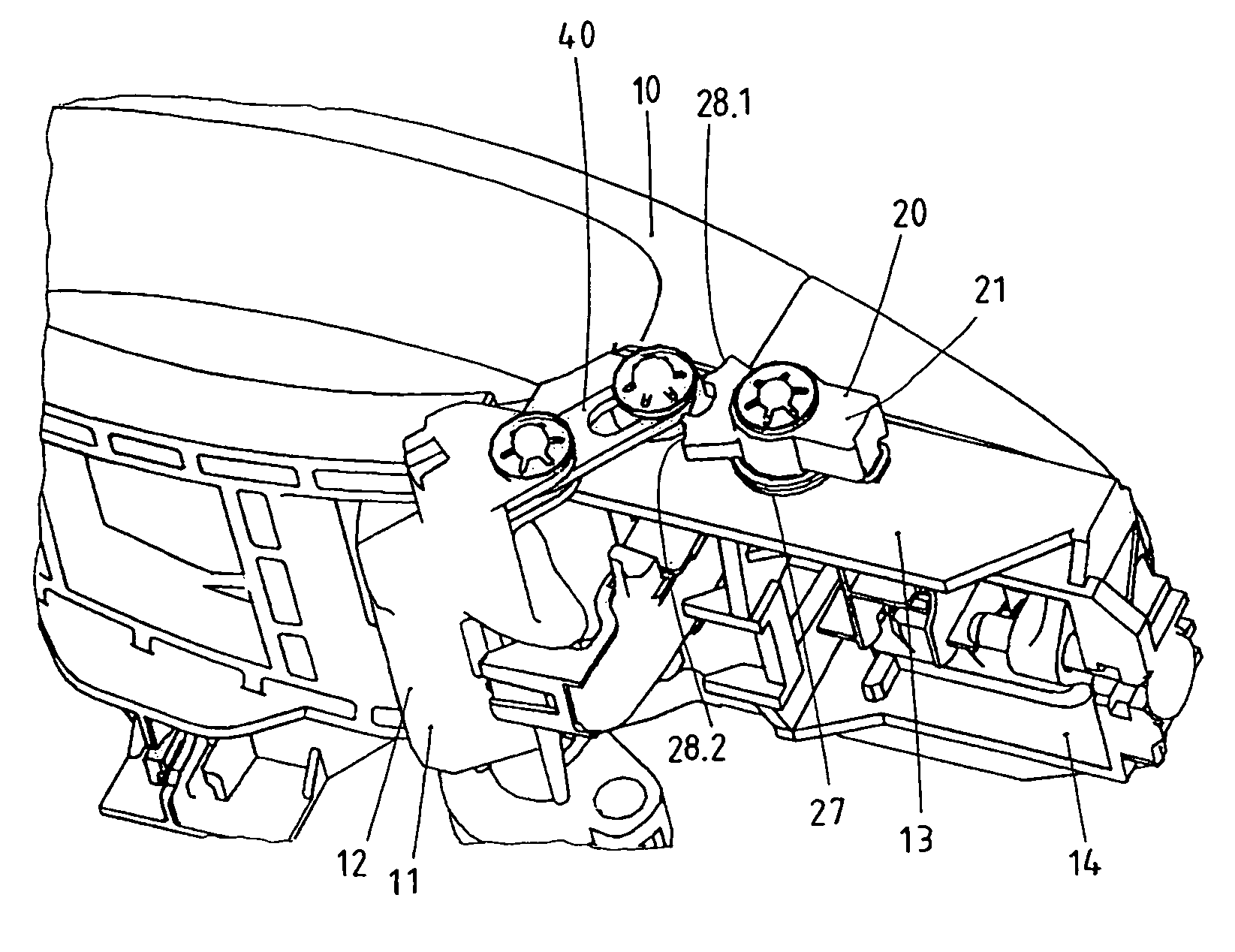
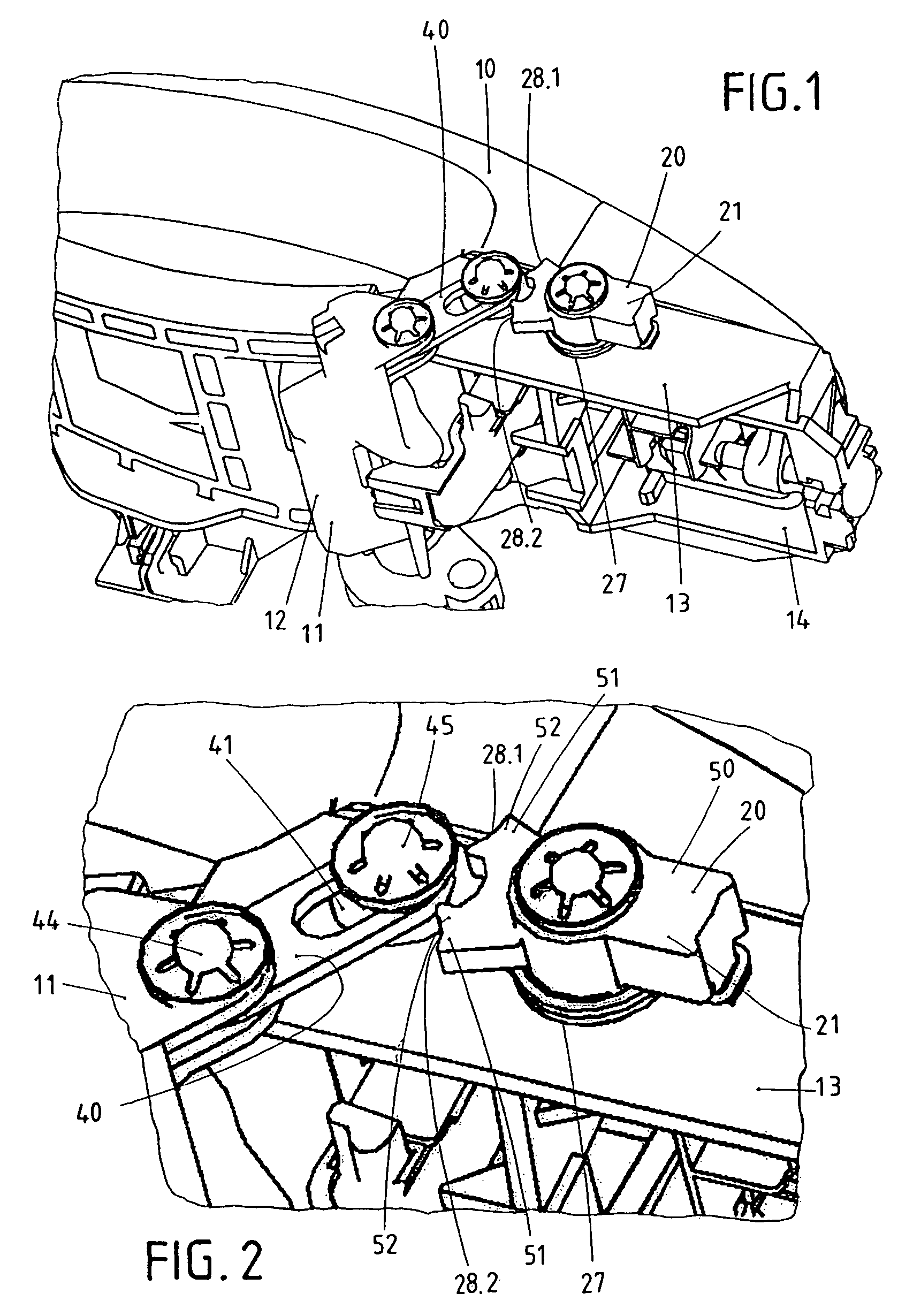
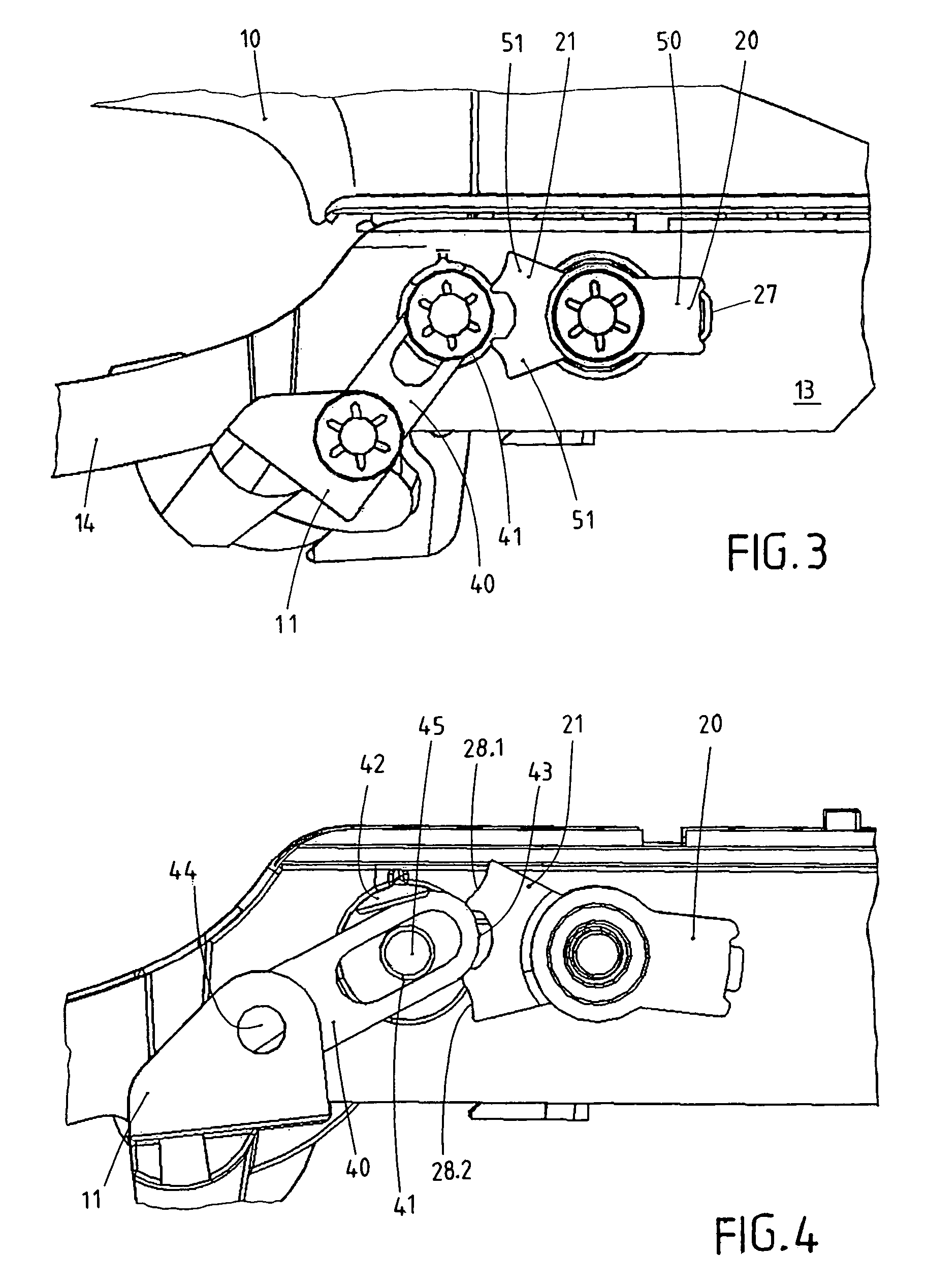
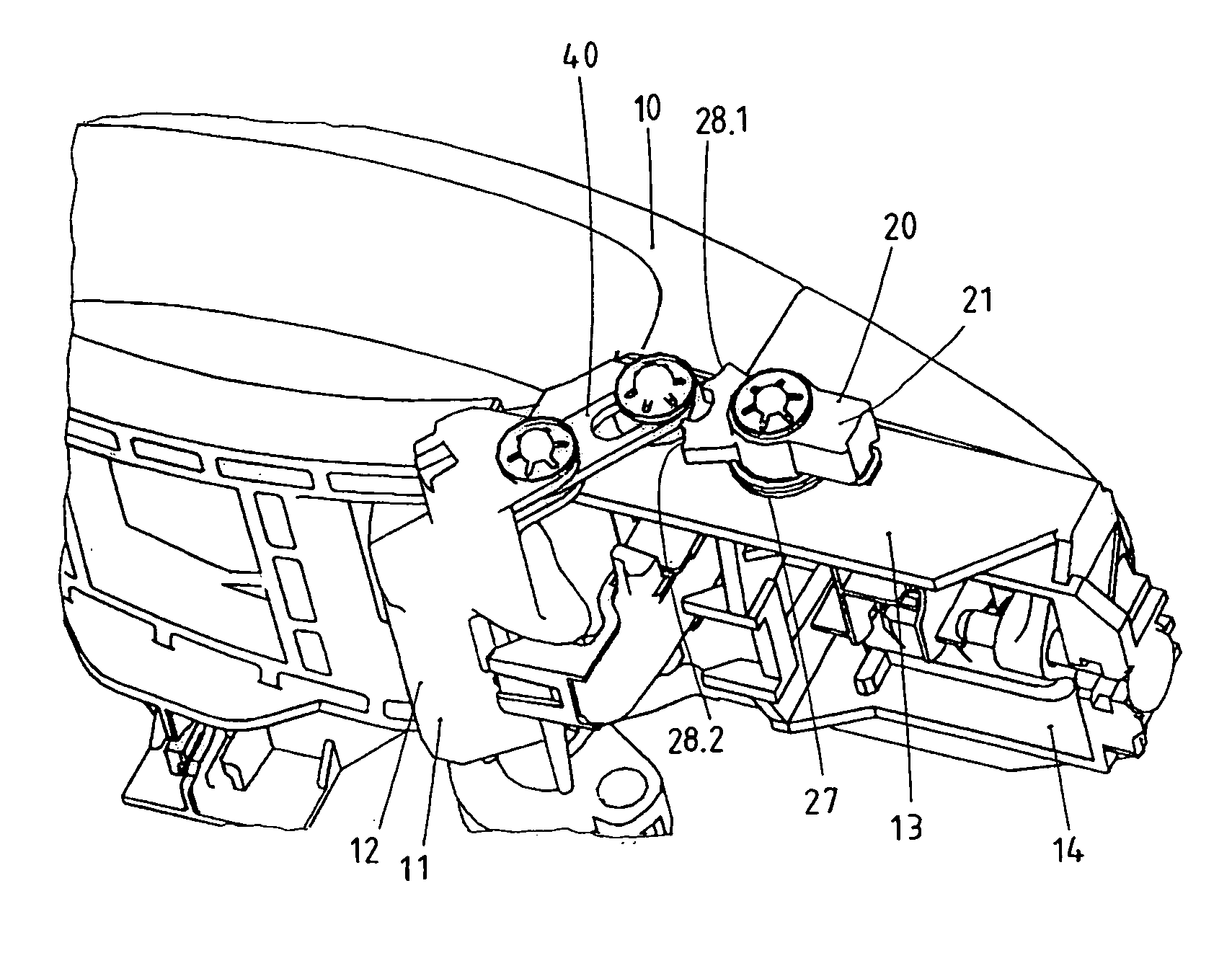
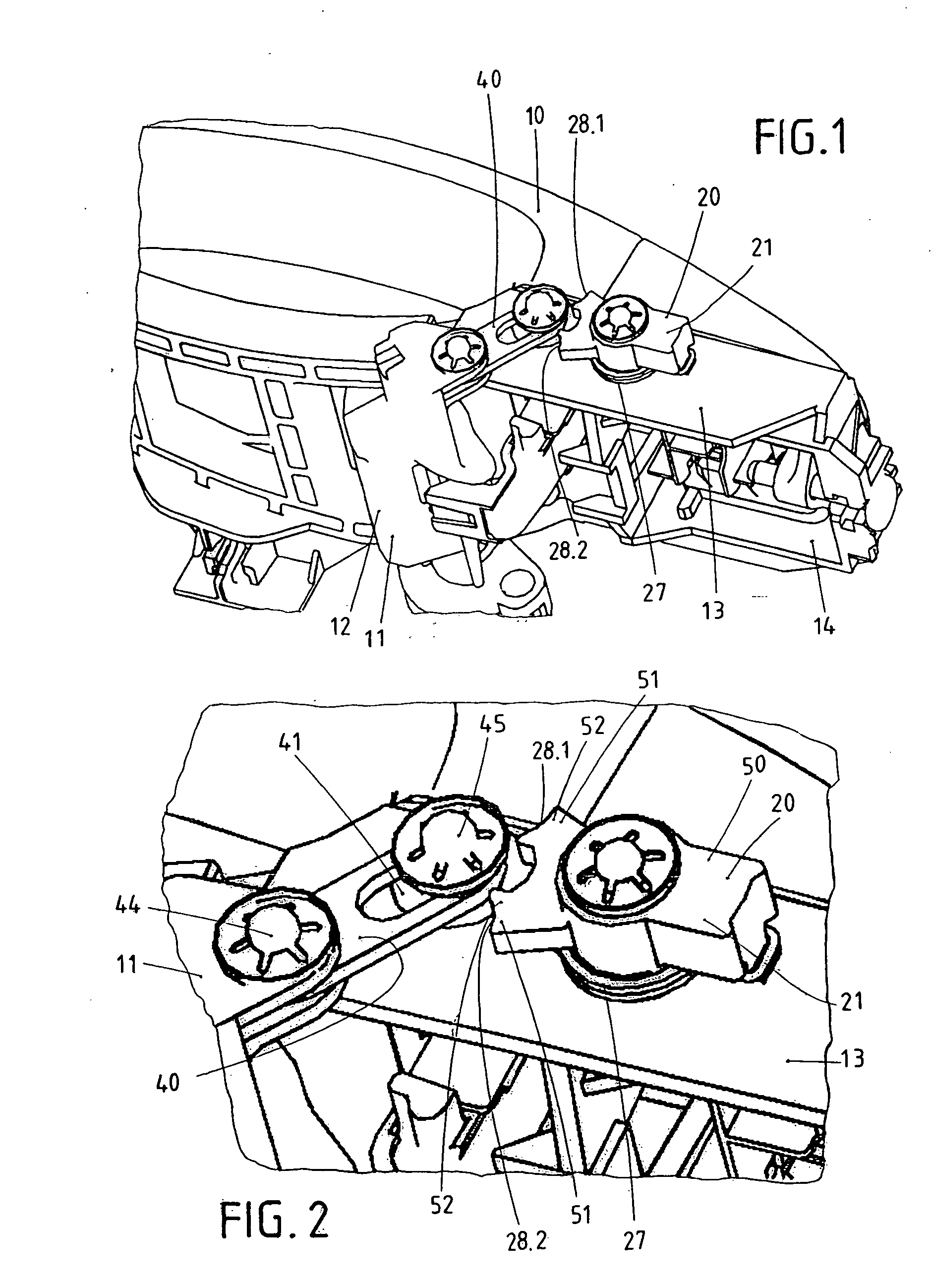
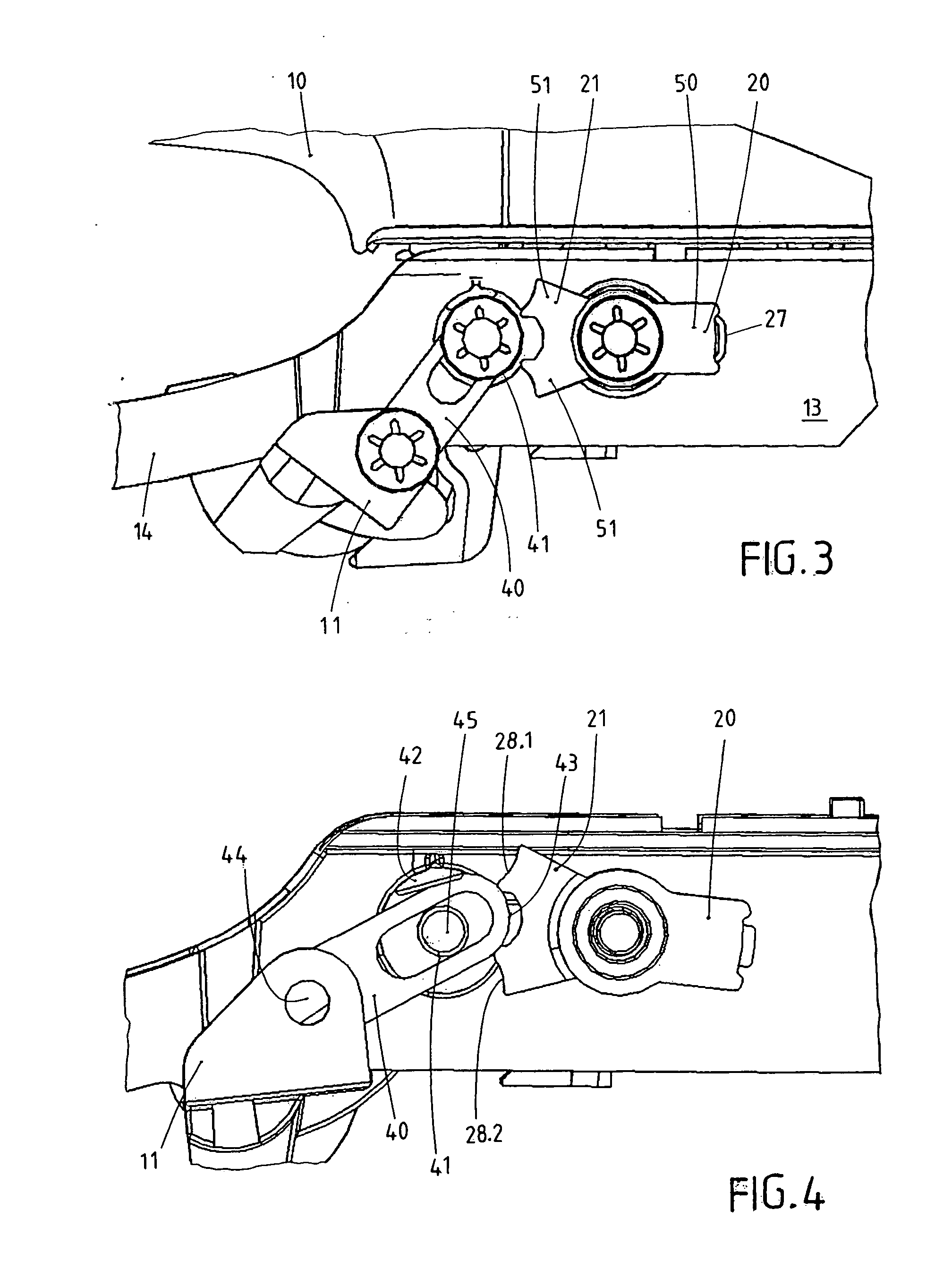
ActiveUS8424936B2Low costAvoid accidental activationAutomatic securing/unlockingConstruction fastening devicesElectrical and Electronics engineeringInertia
The invention concerns an outer door grip, in particular for vehicles. The outer door grip exhibits a handle (10), which can operate a lock disposed in the door upon actuation. The outer door grip exhibits a pivotal blocking member (20), which is normally placed in its ineffective release position (21) and therewith enables actuation of the handle (10). The blocking member (20) passes into an effective blocking position (22.1, 22.2) based on the inertia of the mass of the blocking member (20) in case of a crash, whereby the handle (10) becomes blocked. The blocking member (20) has available two blocking positions (22.1, 22.2), wherein the blocking member (20) moves into the first blocking position (22.1) upon a crash out of a first direction (30.1) and wherein the blocking member (20) moves into the second blocking position (22.2) upon a crash out of a second direction (30.2) located opposite to the first direction (30.1). A blocking lever (40) is furnished which is intermediately switched in the blocking position (22.1, 22.2) of the blocking member (20). The blocking lever (40) is thereby guided in a kind of connecting link guide (41).
Owner:HUF HULSBECK & FURST GMBH & CO KG
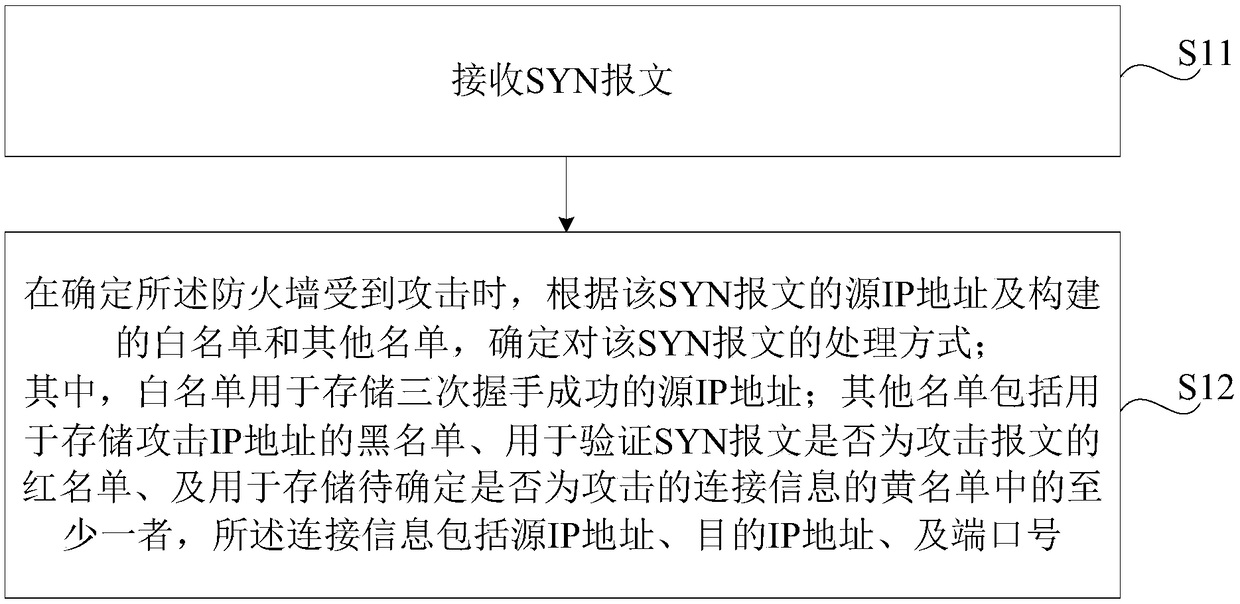
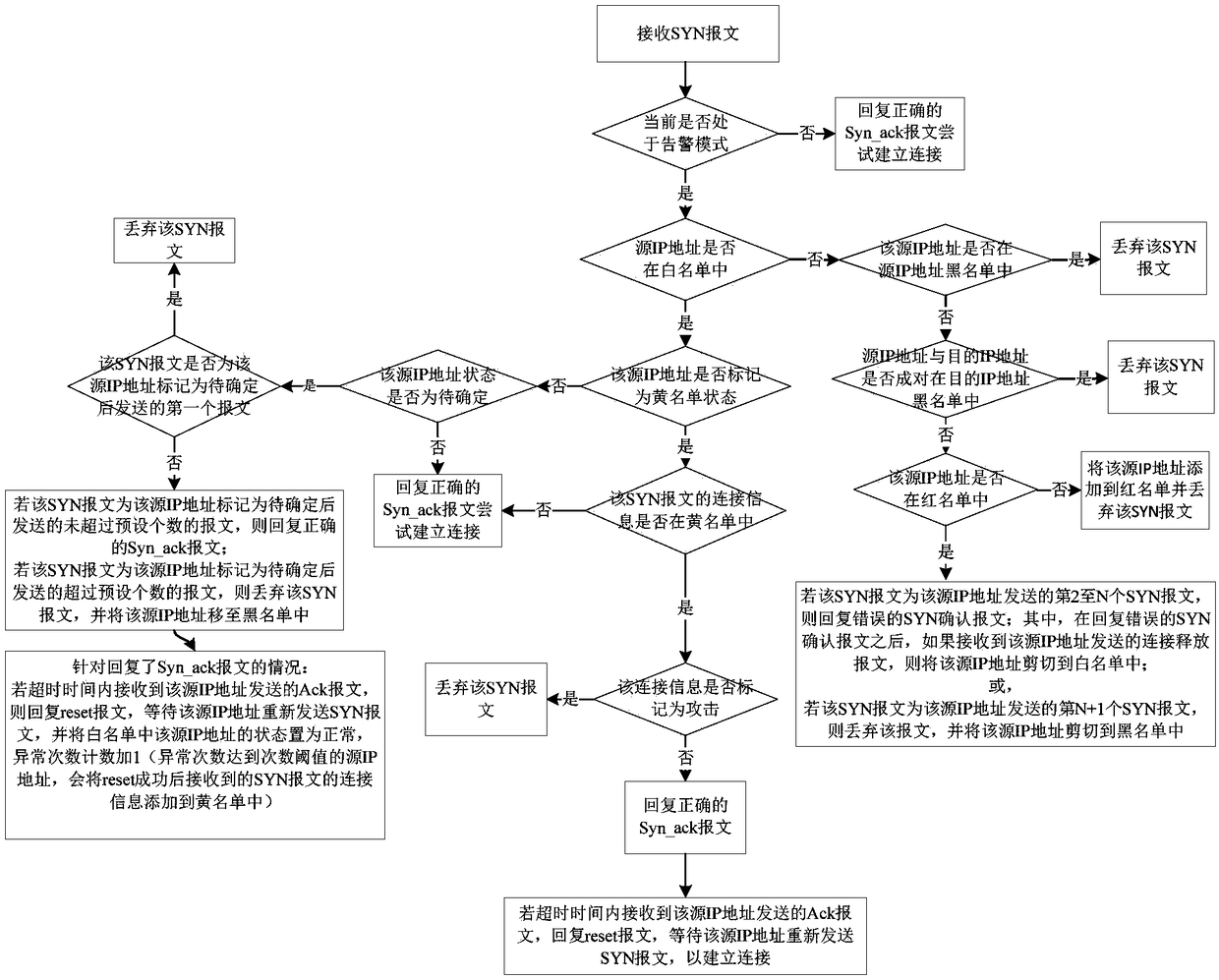
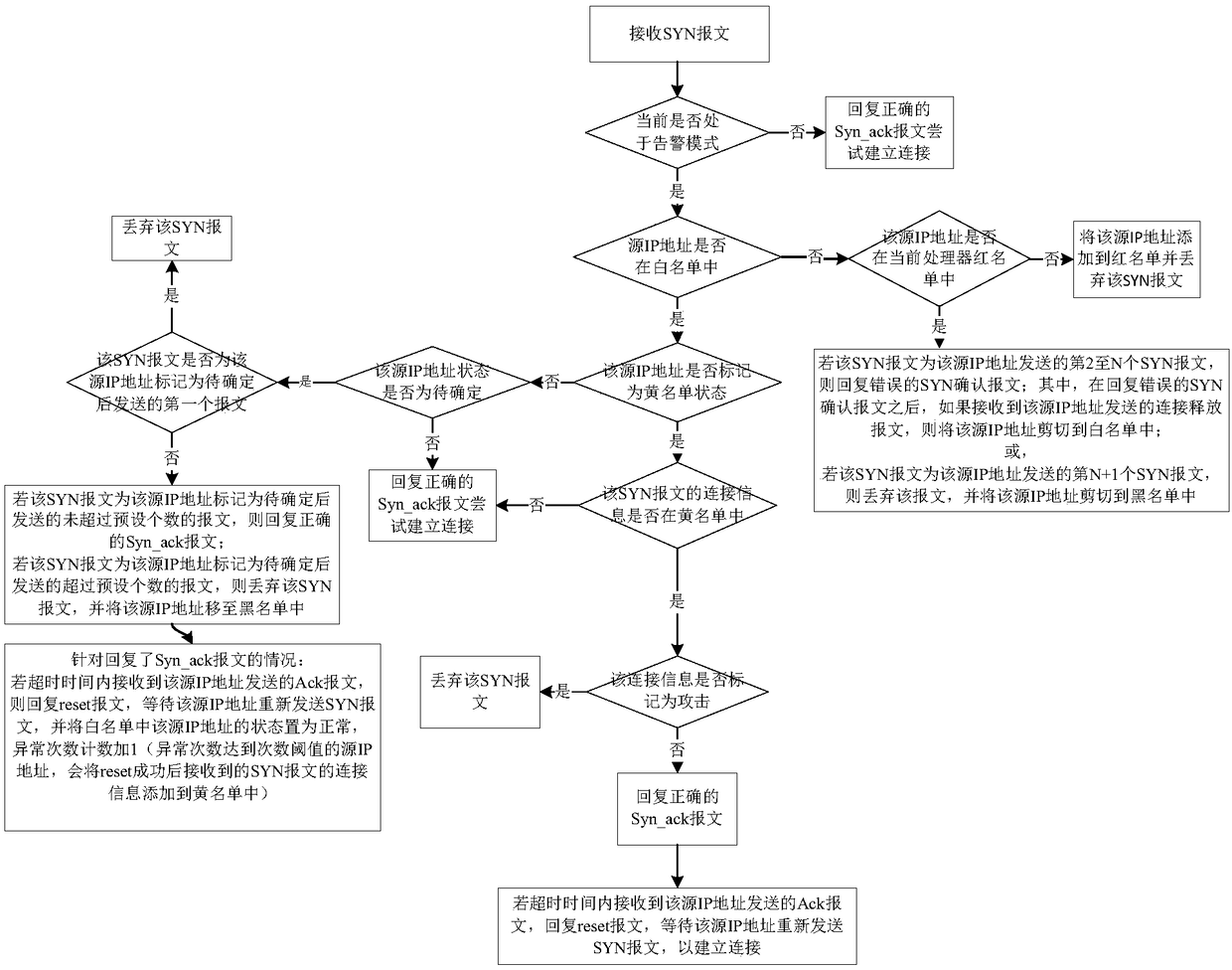
Anti-attack SYN message processing method, device, firewall and storage medium
The invention relates to an anti-attack SYN message processing method and device, firewall and a storage medium, and the performance of resisting the SYN Flood attack by the firewall is improved. Themethod comprises the following steps: receiving a SYN message; determining a processing way on the SYN message according to a source IP address of the SYN message and the constructed white list and other lists when determining the firewall is attacked, wherein the white list is used for storing source IP address of three-time successful handshaking, and the other lists comprises at least one of ablack list for storing the attack IP address, a red list for verifying whether the SYN message is the attack message, and a yellow list for storing the connection information to be determined whetheris the attack; and the connection information comprises the source IP address, the destination IP address and the port number.
Owner:NEUSOFT CORP
Machining of Ceramic Materials
ActiveUS20100058588A1Shorten the timeMinimises levelEdge grinding machinesImpression capsUltimate tensile strength
Owner:IVOCLAR VIVADENT AG
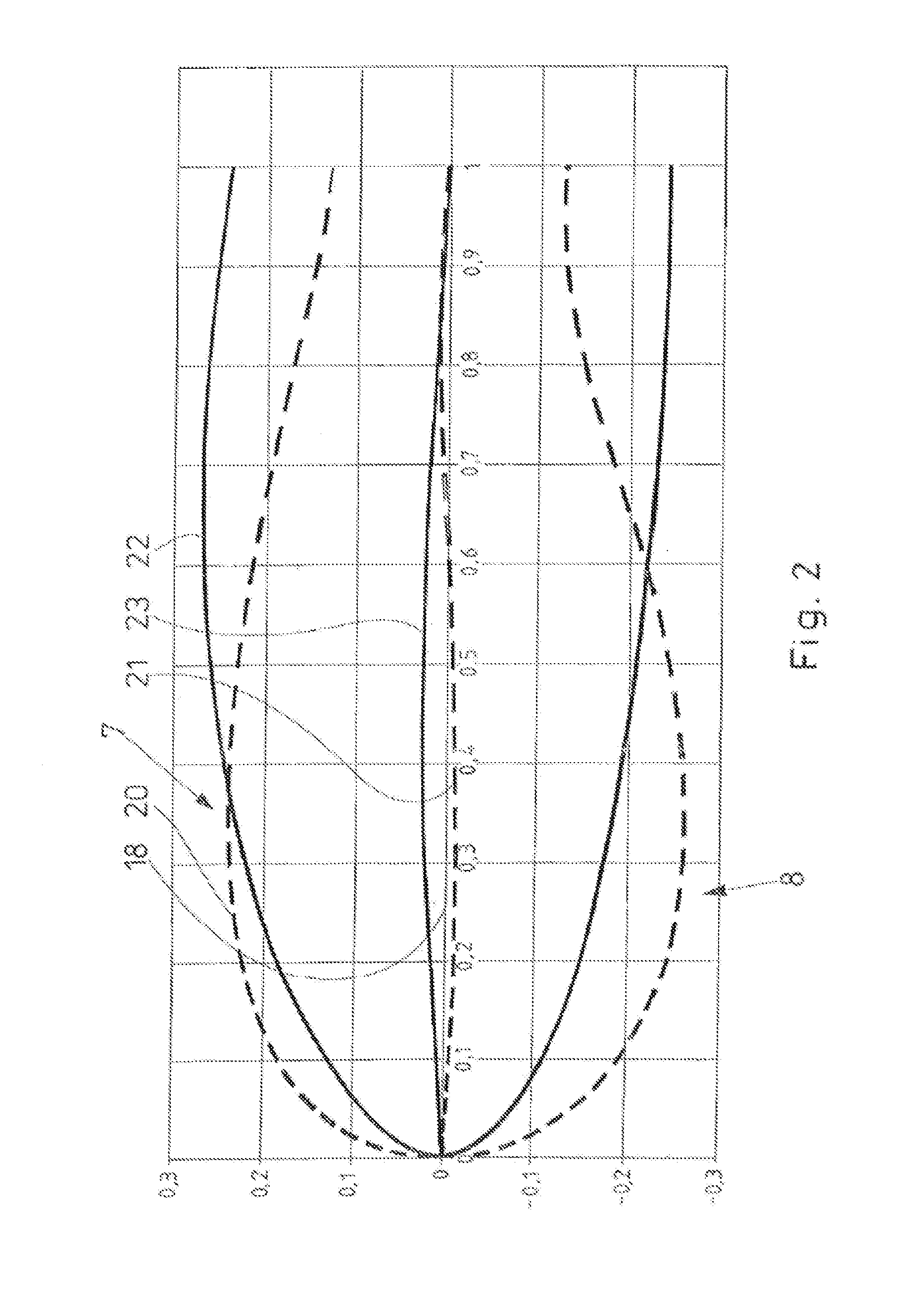
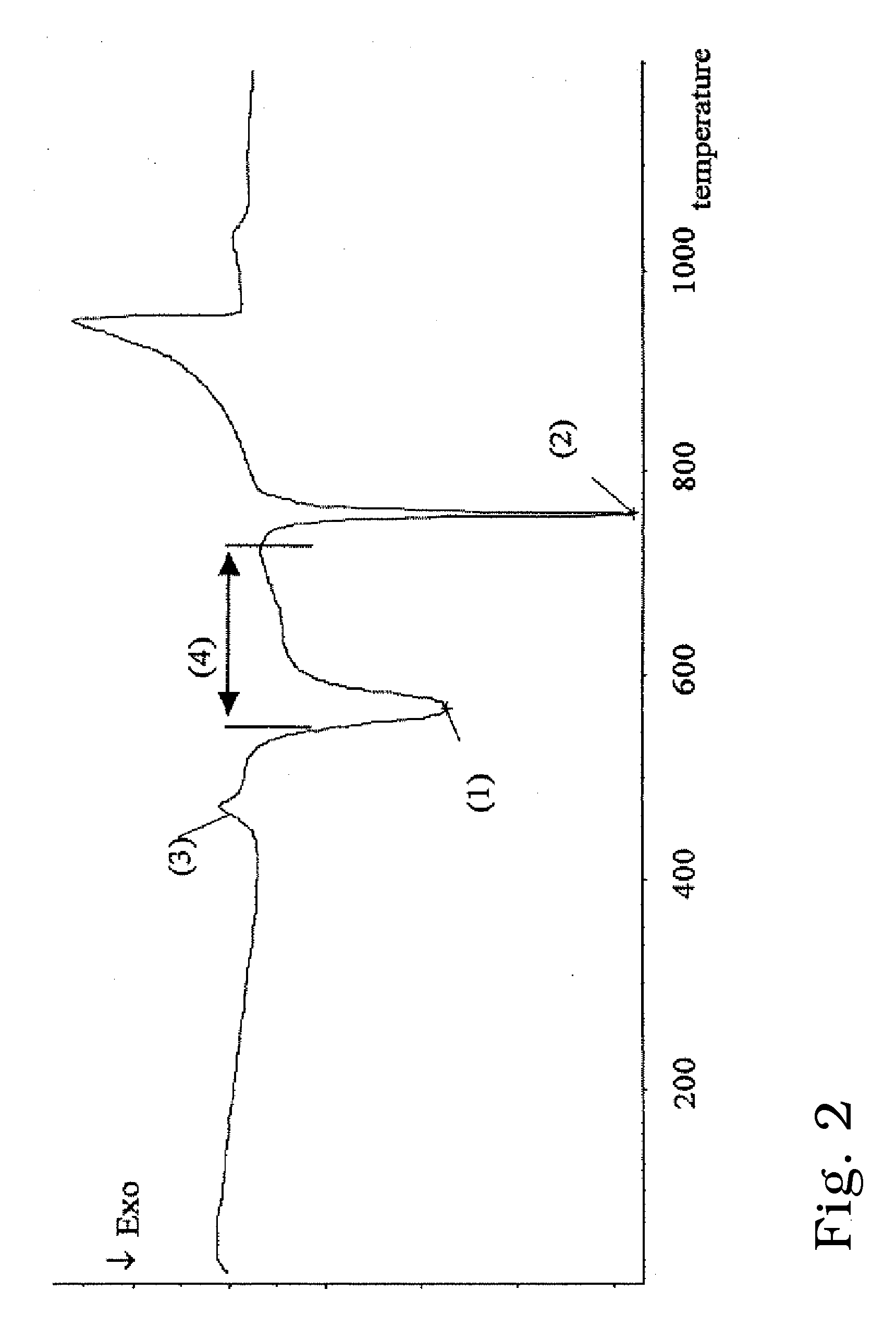
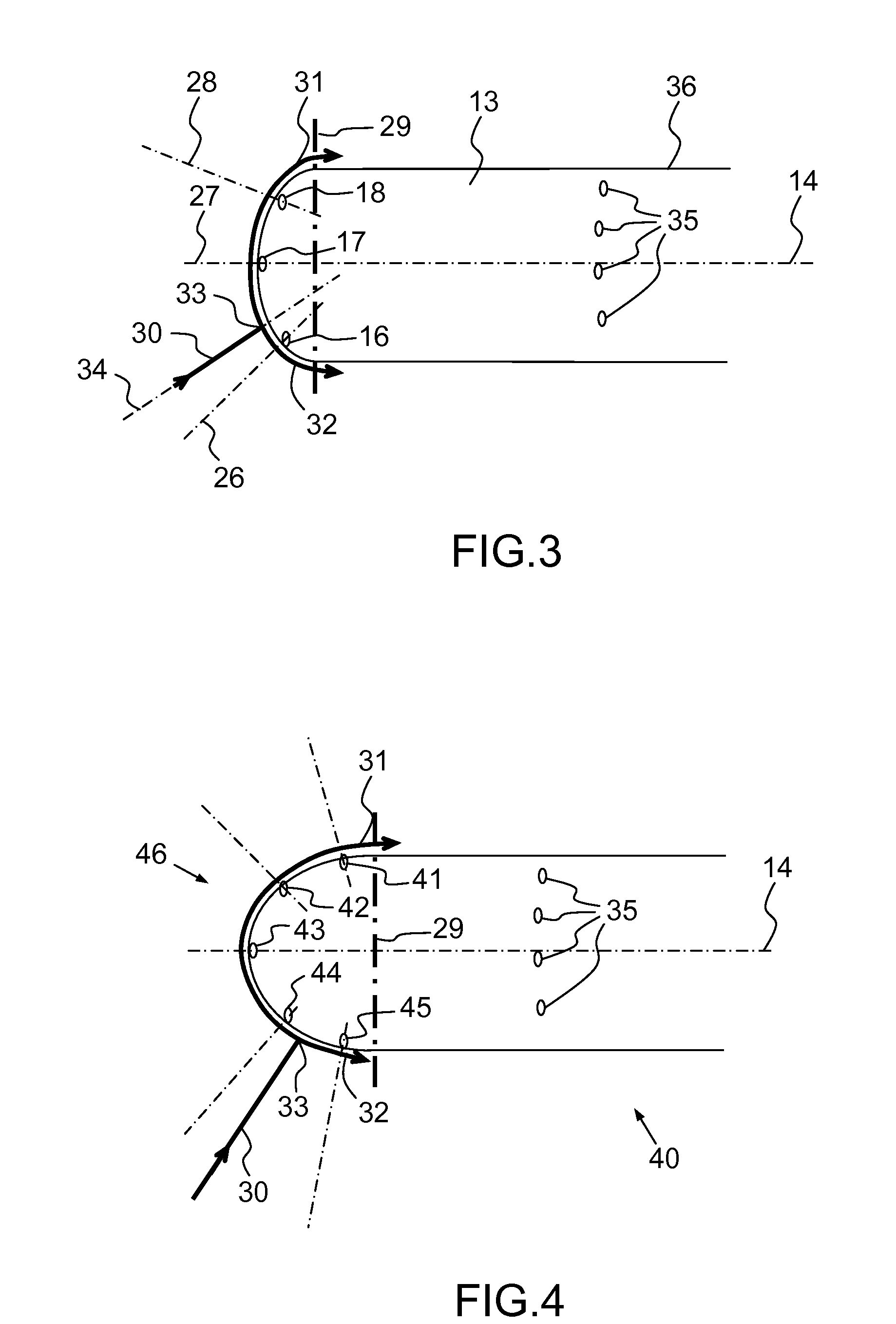
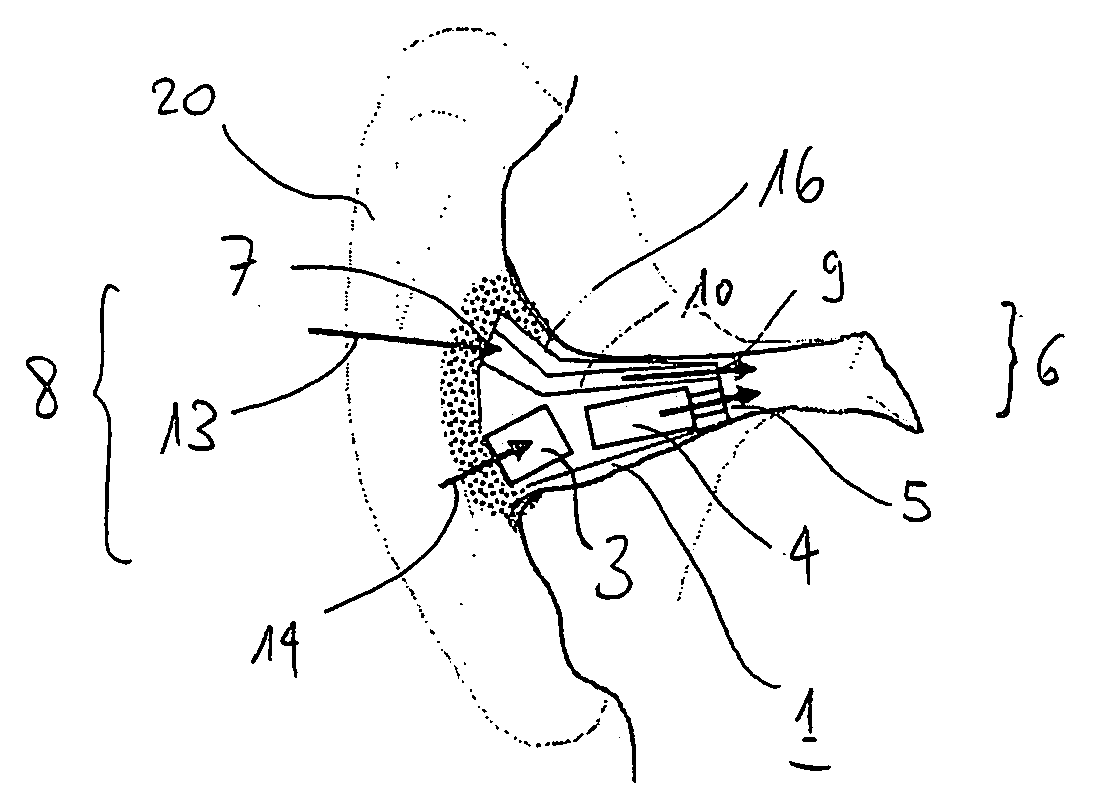
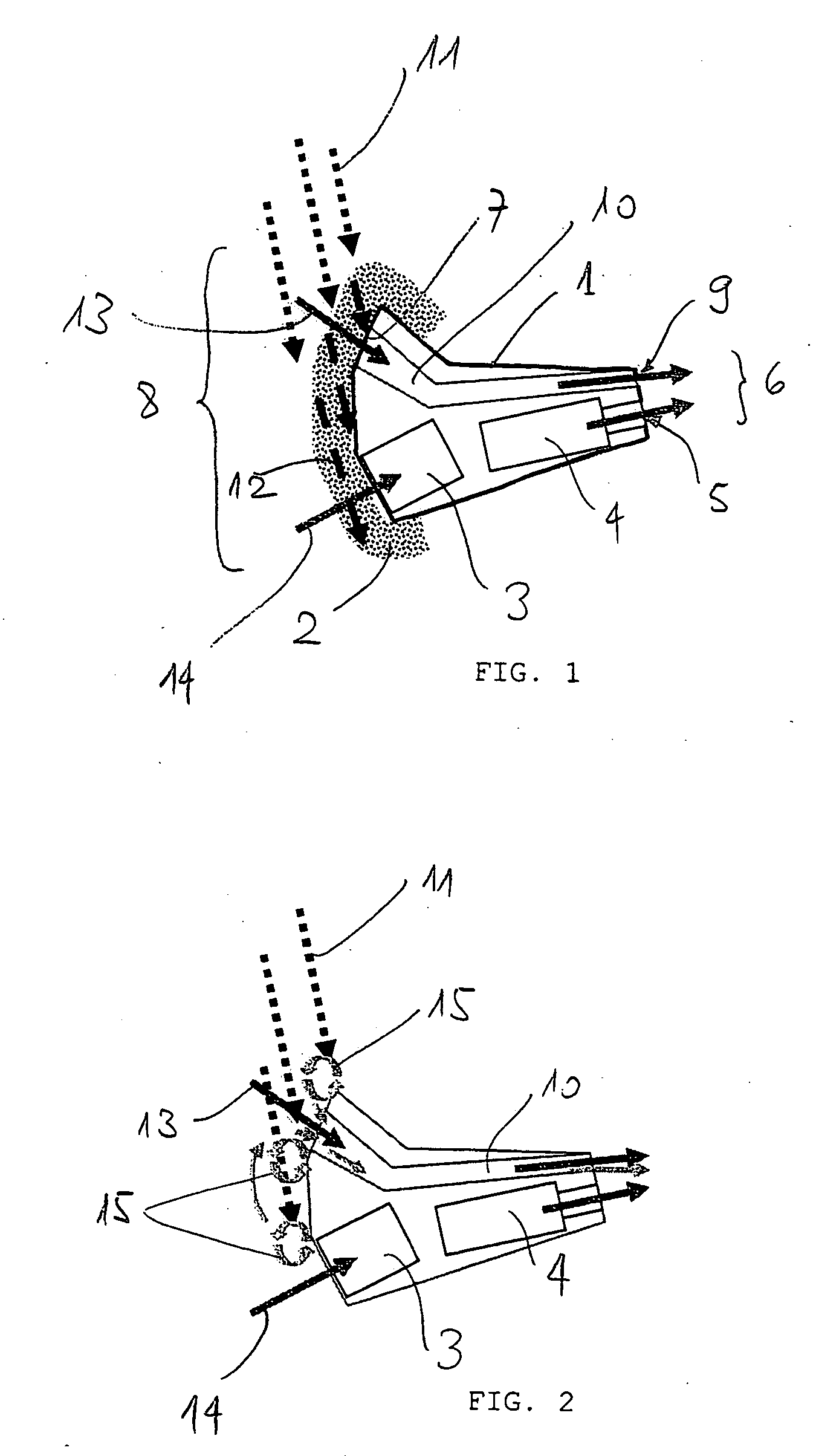
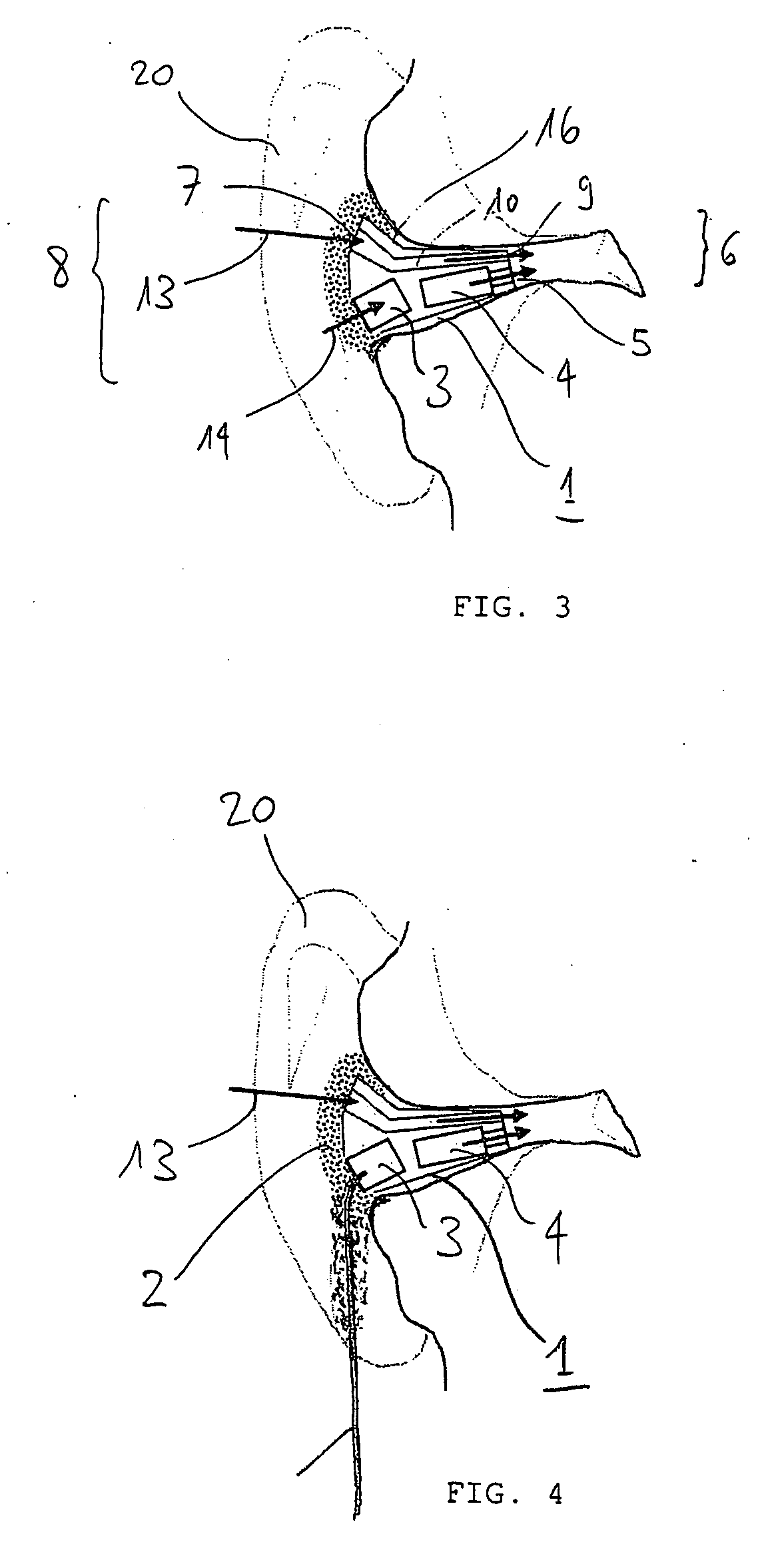
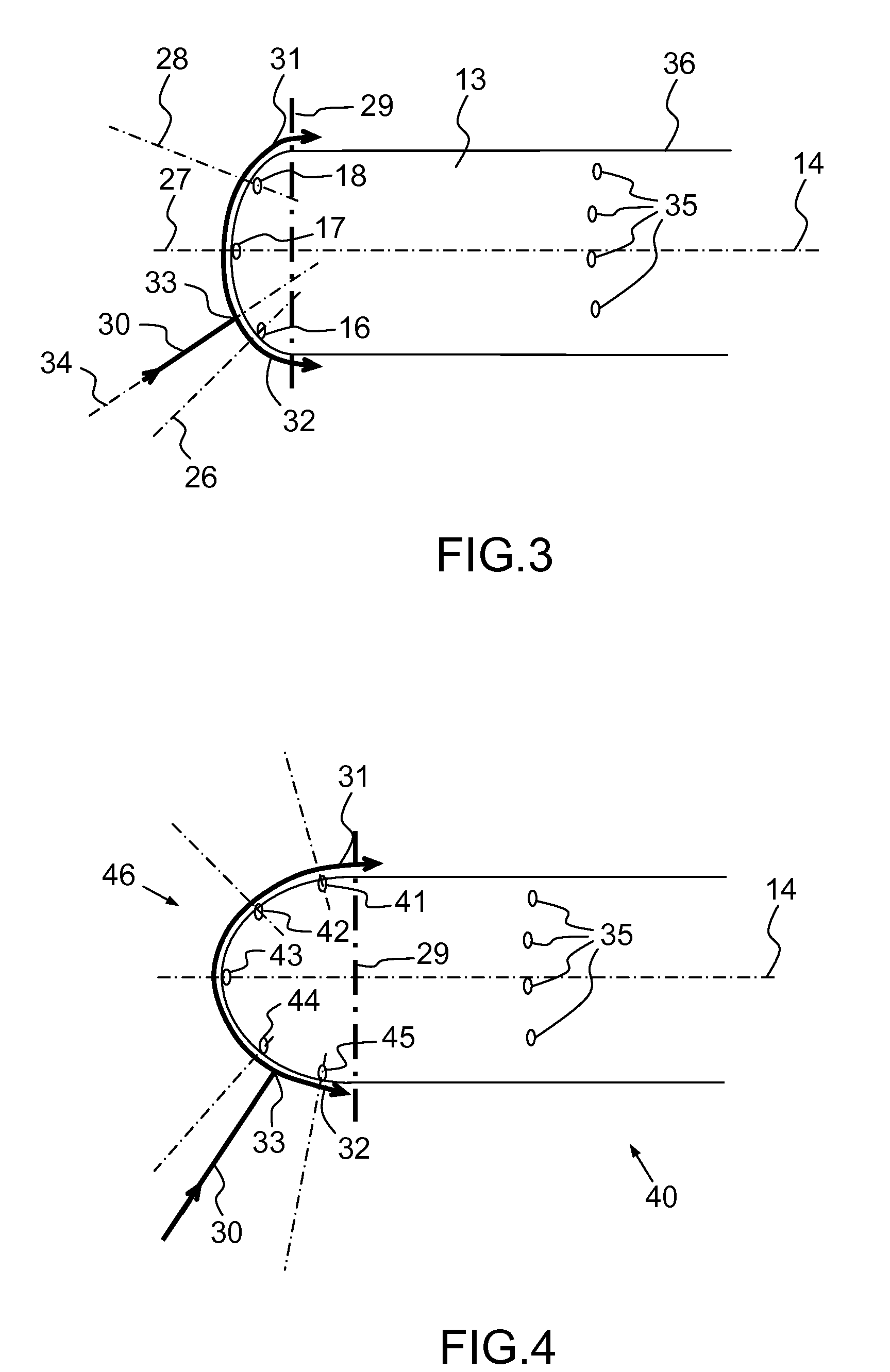
Probe for Measuring a Local Angle of Attack and Method Implementing Same
ActiveUS20130145836A1Accurate measurementGood attackAerodynamic testingFluid speed measurement using pressure differenceMeasurement deviceMeasurement precision
A probe for measuring a local angle of attack designed to be fixed to a wall and a method implementing the probe are provided. The probe comprises at least three pressure sampling ports disposed over a nose of the probe body, pressure measurement means associated with the pressure sampling ports and calculation means capable of determining an angle of attack of the flow with respect to the main direction of the probe body as a function of the pressures measured by the pressure measurement means. The calculation means are configured for choosing from amongst the pressure sampling ports those allowing the best measurement precision of the local angle of attack to be obtained and for calculating the local angle of attack with respect to the main direction using the pressure measurements carried out in the chosen pressure sampling ports.
Owner:THALES SA
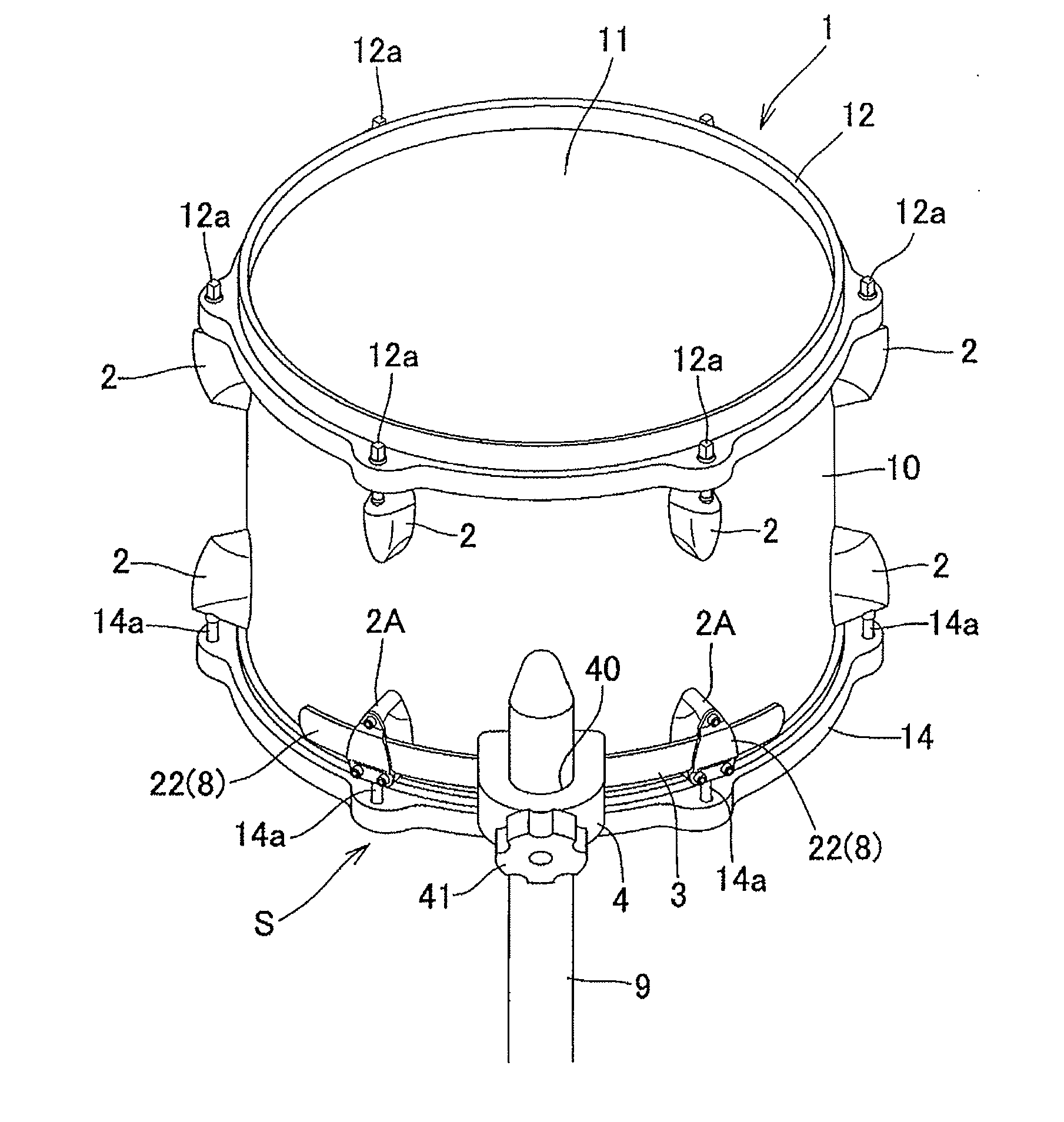
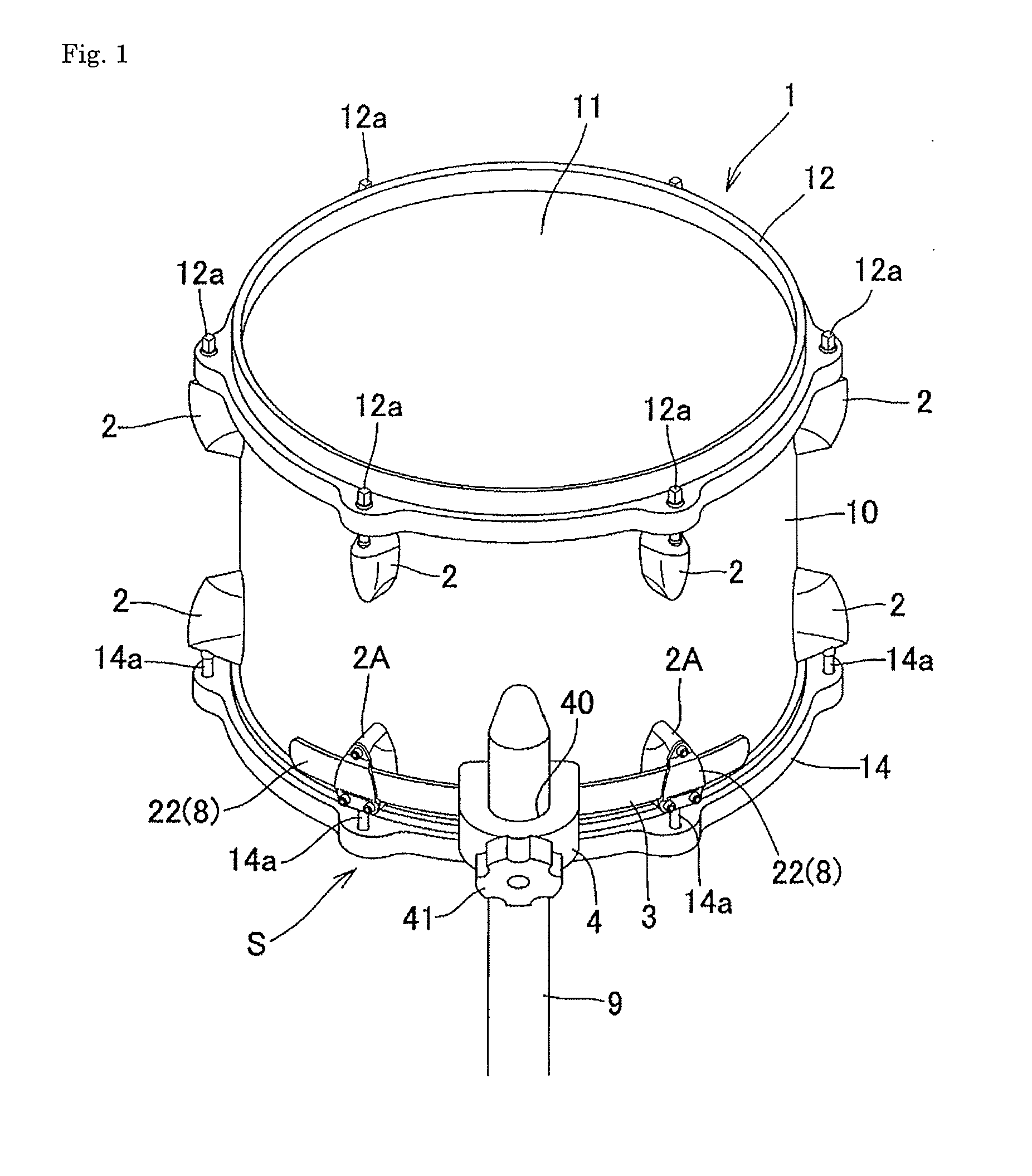
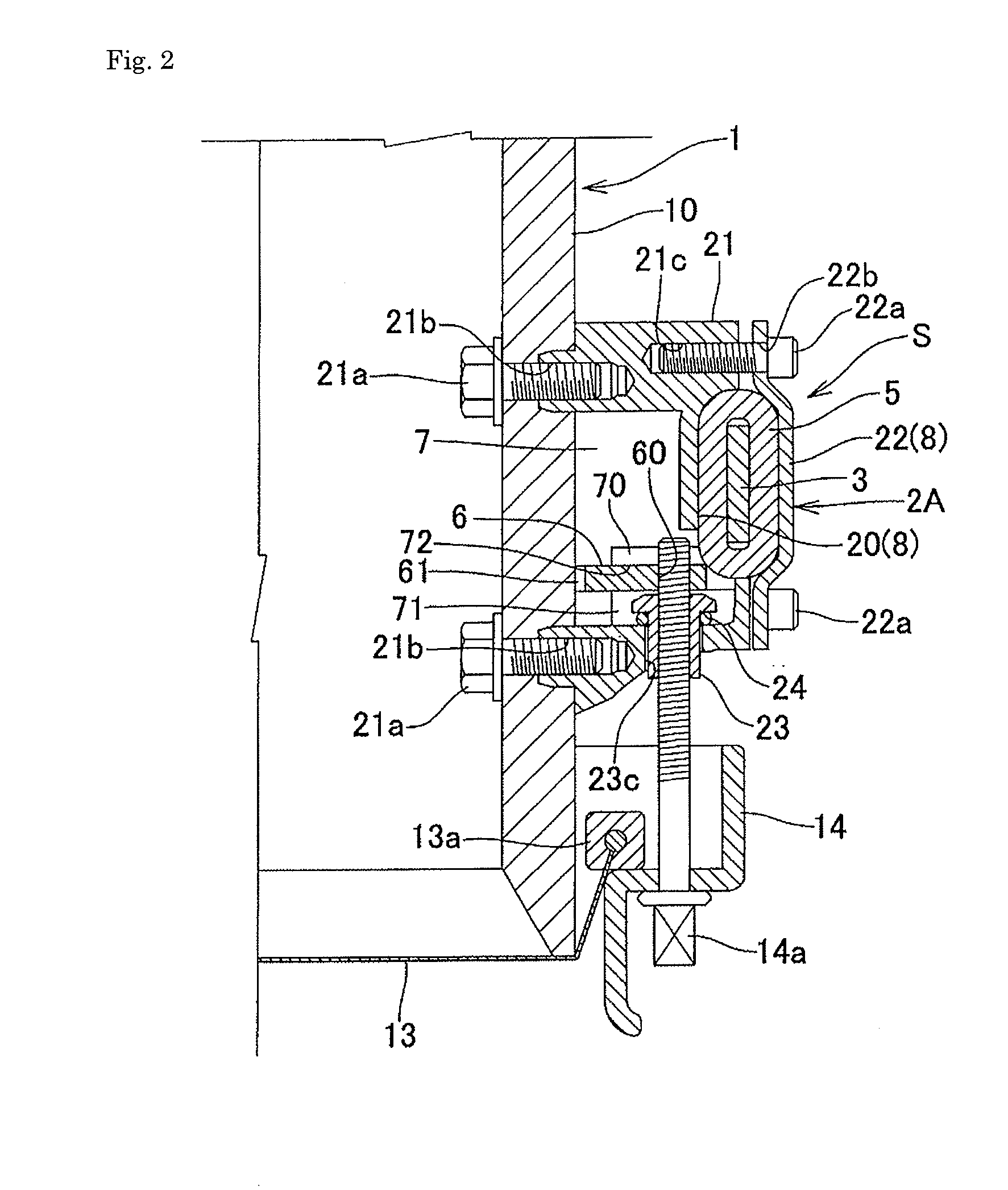
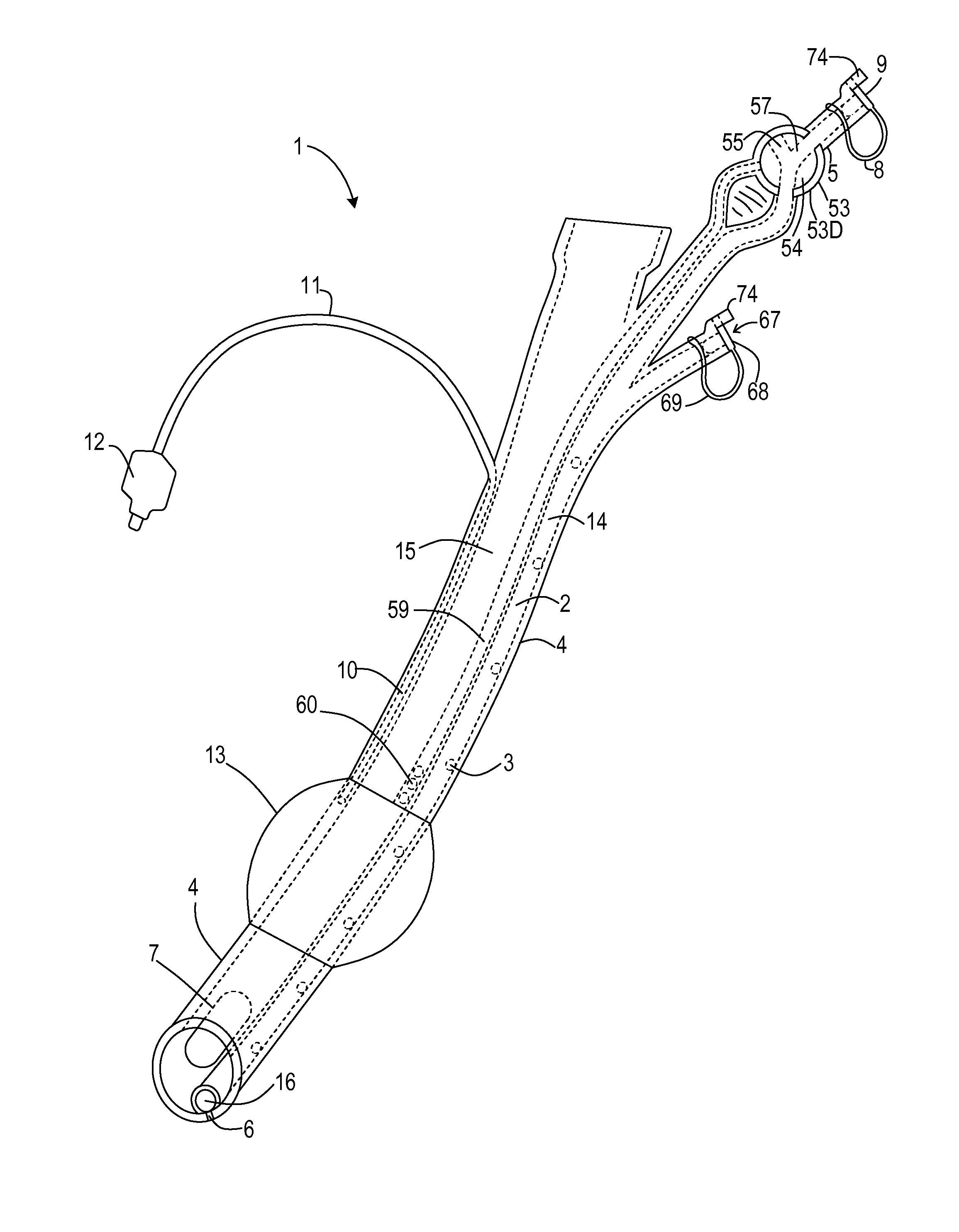
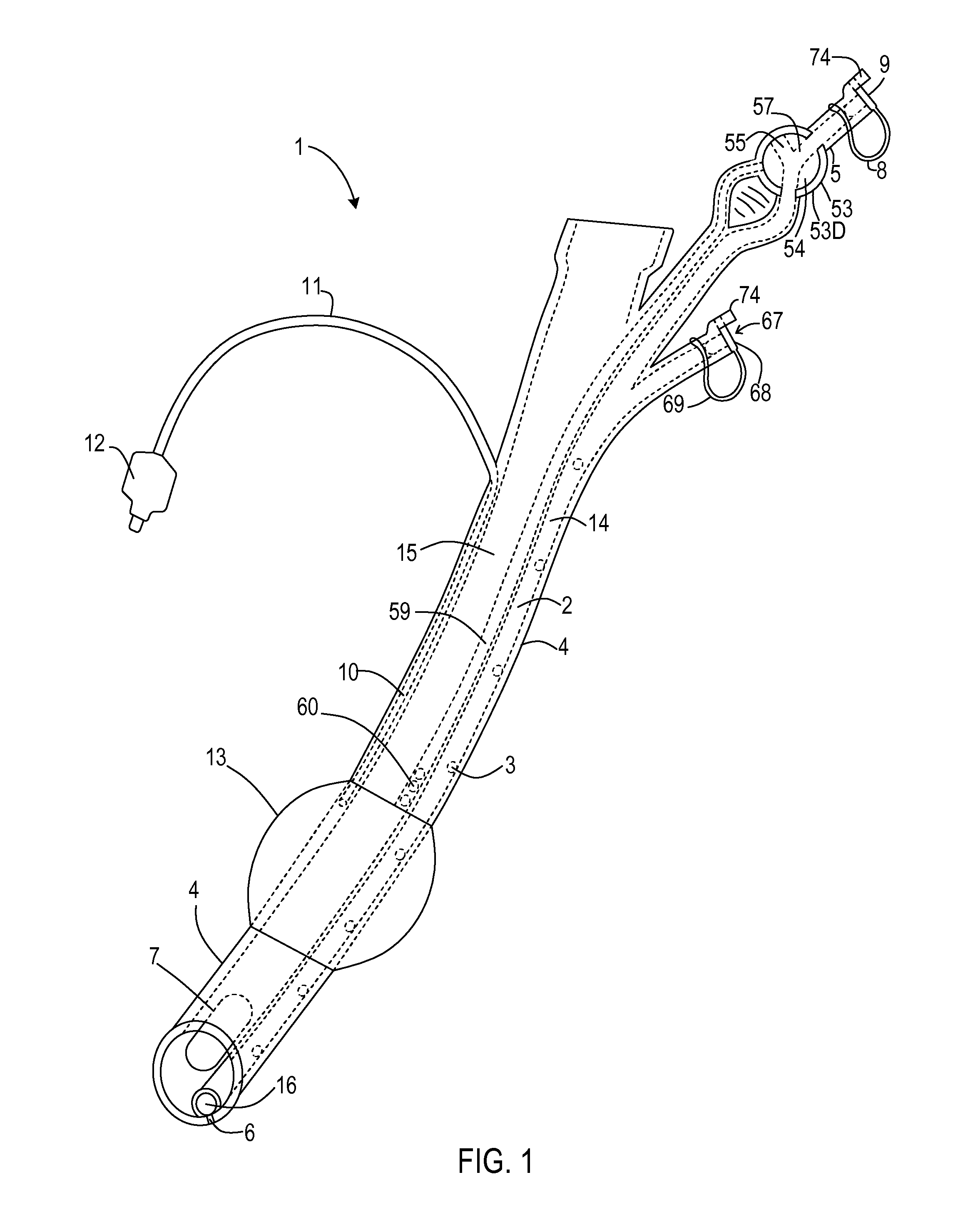
Drum holding structure and drum held by the holding structure
InactiveUS20110030531A1No adverse effect on tension conditionAvoid local concentrationPercussion musical instrumentsResonanceEngineering
To provide a drum holding structure that does not impair the resonance feature or the sound quality that the drum originally possesses, that is free of occurrence of strains or twists in the drum constituents despite a long term of use, and that is excellent in terms of workability, and a drum held by the holding structure.A holding structure for fixing a drum 1 to a drum holding rod 9, in which an elongated plate-like holder member 3 extending circumferentially is held by, out of a plurality of bottom-side lugs 2 and 2A arranged on the bottom side of the drum 1, at least two successive prescribed bottom-side lugs 2A arranged circumferentially. The holder member 3 is provided with a bracket member 4 for the drum holding rod 9 to thereby hold the drum 1.
Owner:SAKAE RHYTHM MUSICAL INSTR
Foreground and background separation-based image encryption and decryption methods
The invention relates to a foreground and background separation-based image encryption method and decryption method. According to the foreground and background separation-based image encryption method, an image to be encrypted is divided into arbitrarily-selected foreground areas and background areas; encryption with different intensities are performed on arbitrarily-selected critical areas and other areas in the image, and therefore, emphasized protection can be provided for the critical areas selected from the image, and sensitive areas in the image has little possibility of being exposed; and high-intensity encryption can be performed on any irregular sealed communicated areas selected by a user, and ordinary encryption is performed on other non-critical areas; and the encryption method is closely related to key parameters given by the user, and is closely related to the plaintext of the image to be encrypted and selected irregular sealed communicated foreground areas, and therefore, a whole encryption process is extremely sensitive to the initial keys and parameters of the user, the plaintext image of the image to be encrypted and the irregular foreground areas.
Owner:SHAANXI NORMAL UNIV
DWT-SVD geometric attack prevention blind watermark method based on SIFT
ActiveCN103955878AGood resistance to attackGood attackImage data processing detailsSingular value decompositionWatermark method
The invention relates to a DWT-SVD geometric attack prevention blind watermark method based on SIFT. The method comprises a watermark embedding method and a watermark extraction method. The watermark embedding method includes the steps that discrete waterlet transformation is conducted on an original image, a low-frequency sub-band of the original image is divided into small blocks, singular value decomposition is conducted on each small block, chaotic encryption is conducted on watermarks to be embedded, and the watermarks are embedded into the maximum singular value of each small block through an optimal quantitative method, the SIFT feature points of a watermark image are stored as secret keys, the types of geometric attacks are judged according to the secret keys, and correction is conducted. The watermark extraction method is the inverse process of the watermark embedding method and includes the steps of correction of attacked images, watermark extraction and watermark decryption and restoration. According to the method, by the utilization of the rotation, zoom and translation invariance of the SIFT feature points and the combination of the advantages of DWT and SVD in the digital watermark aspect, robustness on geometric attacks is remarkably improved.
Owner:HANGZHOU DIANZI UNIV
Method of using a feedstuff additive
InactiveUS7347997B1Increase concentrationPromote growthBiocideBacteriaBiotechnologyEnterococcus casseliflavus
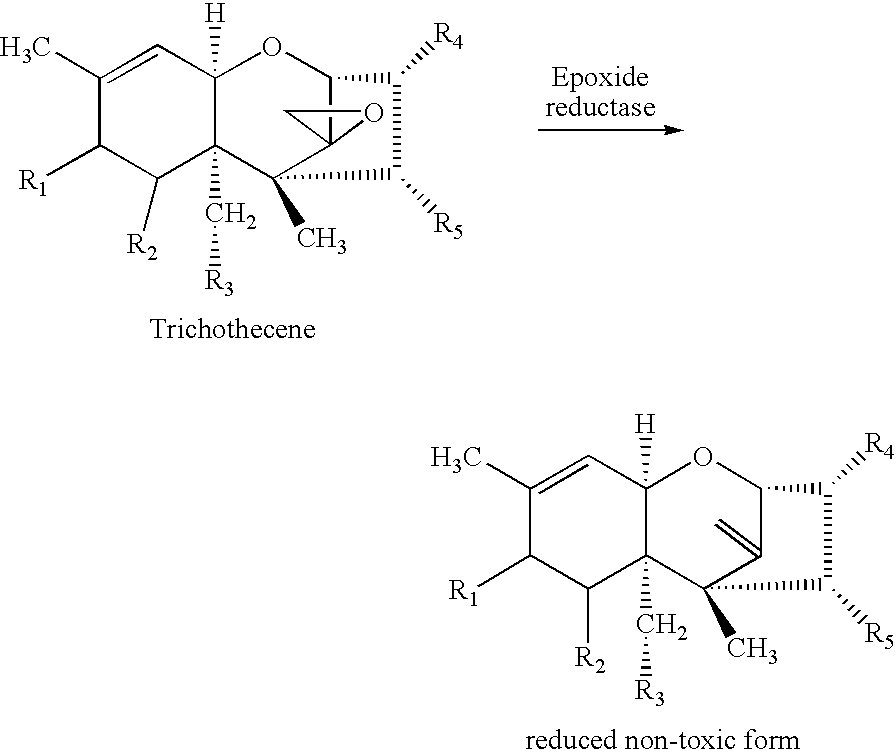
Microorganism of the genus Eubacterium, and its obtainment and use, which is suitable in pure culture, DSM 11798, and / or mixed culture with the strain Enterococcus casseliflavus, DSM 11799, or in mixed culture with other anaerobic microorganisms for the detoxification of trichothecenes.A feedstuff additive for the inactivation of trichothecenes in feedstuffs or in the digestive tract of animals contains a pure and / or mixed culture of the microorganism (DSM 11798 or DSM 11799) or a mixed culture with other anaerobic microorganisms in an amount from 0.2 to 3 kg, in particular 0.5 to 2.5 kg, per 1000 kg of feedstuff. The feedstuff additive containing DSM 11798 achieves probiotic effect on an animal and maintains or improves fertility performance of an animal subject to fusariotoxin-contaminated feed.
Owner:ERBER AG
In-ear device
InactiveUS7804975B2Increase physical strengthIncreasing the thicknessPiezoelectric/electrostrictive microphonesMicrophonesHearing apparatusEngineering
Owner:SONOVA AG
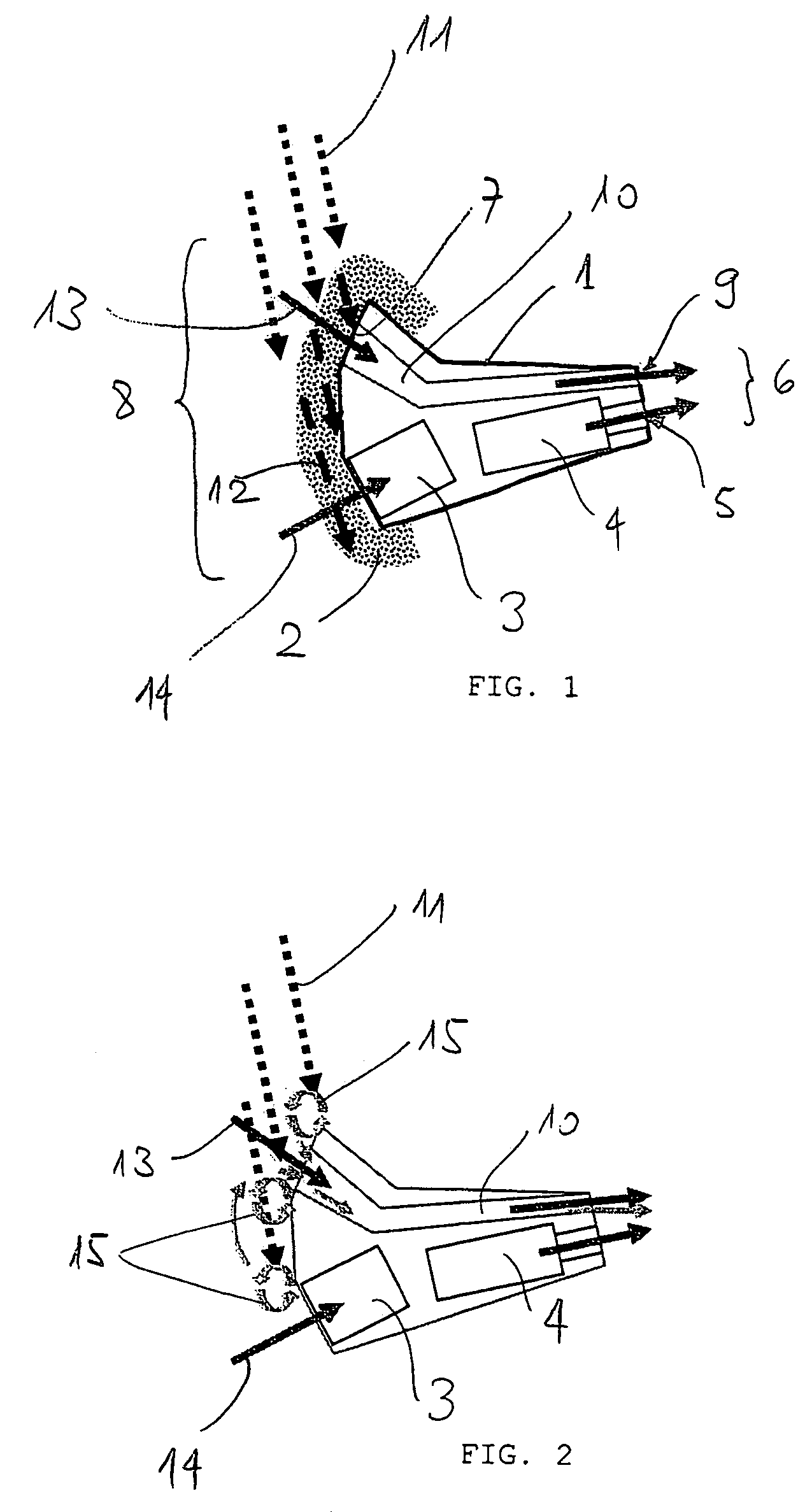
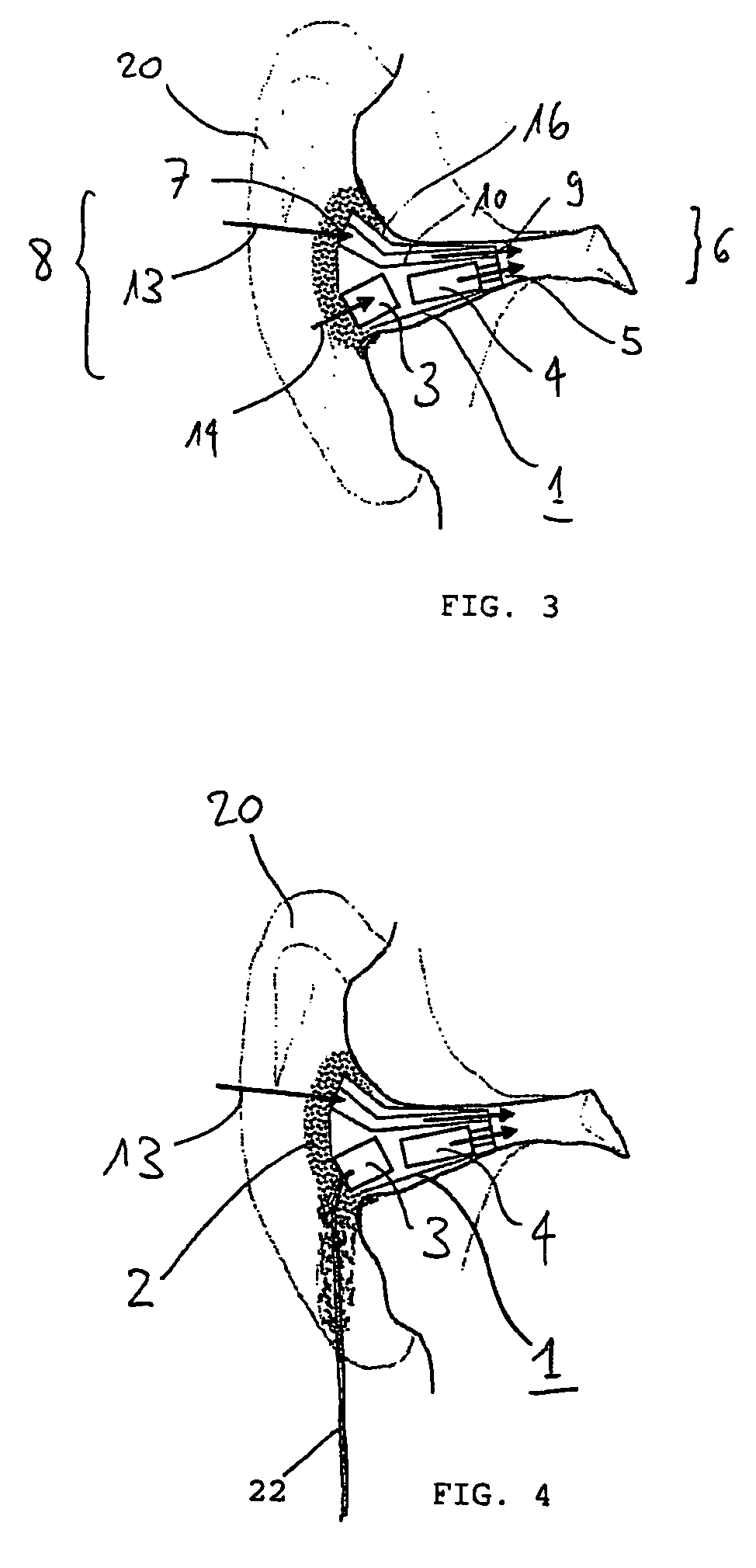
Endotracheal tube with intrinsic suction & endotracheal suction control valve
InactiveUS20110237896A1Easy to manageAccurate placementTracheal tubesBronchoscopesBronchial tubeIntratracheal intubation
An improved endotracheal tube providing a built in suction channel for the removal of excessive secretions from the lumen of said tube and the tracheobronchial system is disclosed. Control valves for regulating the suction feature are also disclosed. In at least one embodiment, the endotracheal tube includes an additional suction channel, an above-the-cuff suction channel adapted to remove secretions above the cuff outside the endotracheal tube and within the trachea. Additionally, in at least one embodiment, the endotracheal tube is configured for use with an endoscope for videolaryngoscopy, and the like. Furthermore, in at least one embodiment, an improved technology for the administration of medications within the tracheobronchial system is disclosed.
Owner:BLACK PAUL WILLIAM +1
Outer door grip, in particular for vehicles
ActiveUS20100225127A1Actuation is not avoidedLow costAutomatic securing/unlockingAccident situation locksEngineeringElectrical and Electronics engineering
The invention concerns an outer door grip, in particular for vehicles. The outer door grip exhibits a handle (10), which can operate a lock disposed in the door upon actuation. The outer door grip exhibits a pivotal blocking member (20), which is normally placed in its ineffective release position (21) and therewith enables actuation of the handle (10). The blocking member (20) passes into an effective blocking position (22.1, 22.2) based on the inertia of the mass of the blocking member (20) in case of a crash, whereby the handle (10) becomes blocked. The blocking member (20) has available two blocking positions (22.1, 22.2), wherein the blocking member (20) moves into the first blocking position (22.1) upon a crash out of a first direction (30.1) and wherein the blocking member (20) moves into the second blocking position (22.2) upon a crash out of a second direction (30.2) located opposite to the first direction (30.1). A blocking lever (40) is furnished which is intermediately switched in the blocking position (22.1, 22.2) of the blocking member (20). The blocking lever (40) is thereby guided in a kind of connecting link guide (41).
Owner:HUF HULSBECK & FURST GMBH & CO KG
In-ear device
InactiveUS20070003085A1Increase physical strengthIncreasing the thicknessPiezoelectric/electrostrictive microphonesMicrophonesEngineeringCommunication device
A housing inserted in to the ear of a user is disclosed, said housing comprising a lateral end defined by being a part of the housing which is directed towards surroundings if the housing is inserted into the ear, a medial end defined by being a part of the housing which is directed towards the inner ear of the user if the housing is inserted into the ear, said medial end comprising at least a medial opening, wherein at least the lateral end of the housing is covered by a cover element. The cover element is acoustically transparent and made of open porous foam. The inventive in-ear device can be used as hearing device to improve the hearing of a hearing impaired person or as a communication device for natural as well as for remote communication.
Owner:SONOVA AG
Cutting machine of fodder for giant salamanders
ActiveCN108789522AReduce swing frequencyIncrease the lengthFeeding-stuffMetal working apparatusGiant salamanderEngineering
The invention relates to a cutting machine of fodder for giant salamanders. The cutting machine comprises a machine frame, a first cutting mechanism and a driving mechanism. The machine frame is arranged close to an extrusion opening of a fodder hot-extrusion machine; the first cutting mechanism comprises a rotating shaft and a push rod, the rotating shaft is coaxially and fixedly connected with arotating disc, and the eccentric position of the rotating disc is fixedly connected with a supporting column; the lower portion of the push rod is rotatably connected to the machine frame, a slidinggroove is formed in the upper portion of the push rod in the length direction of the push rod, and the supporting column is slidably connected into the sliding groove; the bottom end of the push rod is fixedly connected with a sector gear, the sector gear is engaged with a rack, the rack is slidably connected to the machine frame, and cutting knife sets used for cutting the fodder are arranged atthe end of the rack; and the driving mechanism comprises a supporting plate rotatably connected to the machine frame, a swing rod is fixedly connected to the supporting plate, the two ends of the supporting plate are rotatably connected with a driving gear and a notched gear correspondingly, the rotating shaft is coaxially and fixedly connected with a rotating gear, and both the driving gear and the notched gear are engaged with the rotating gear intermittently. The cutting machine can cut the fodder in different lengths.
Owner:江苏拓诚农业发展有限公司
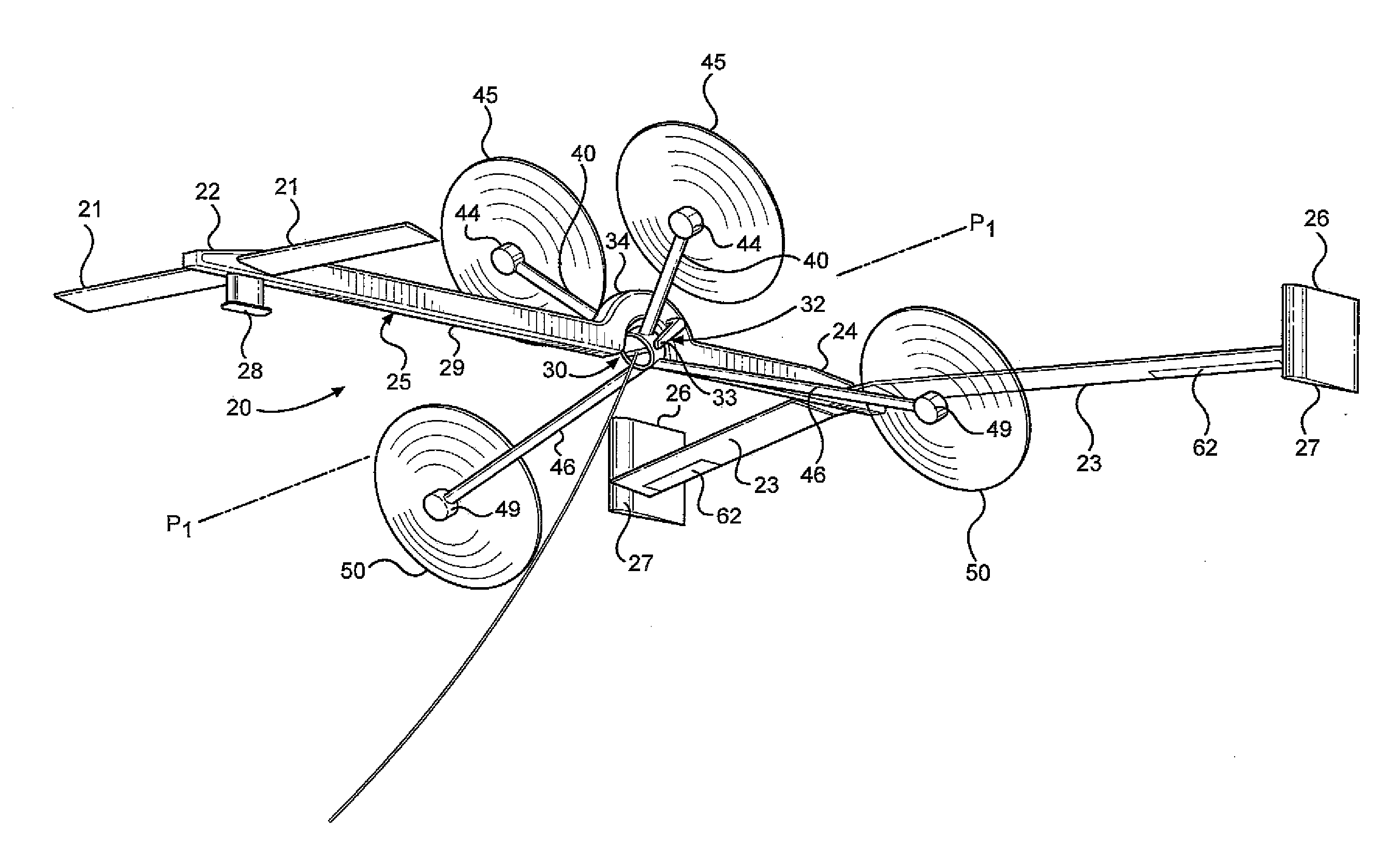
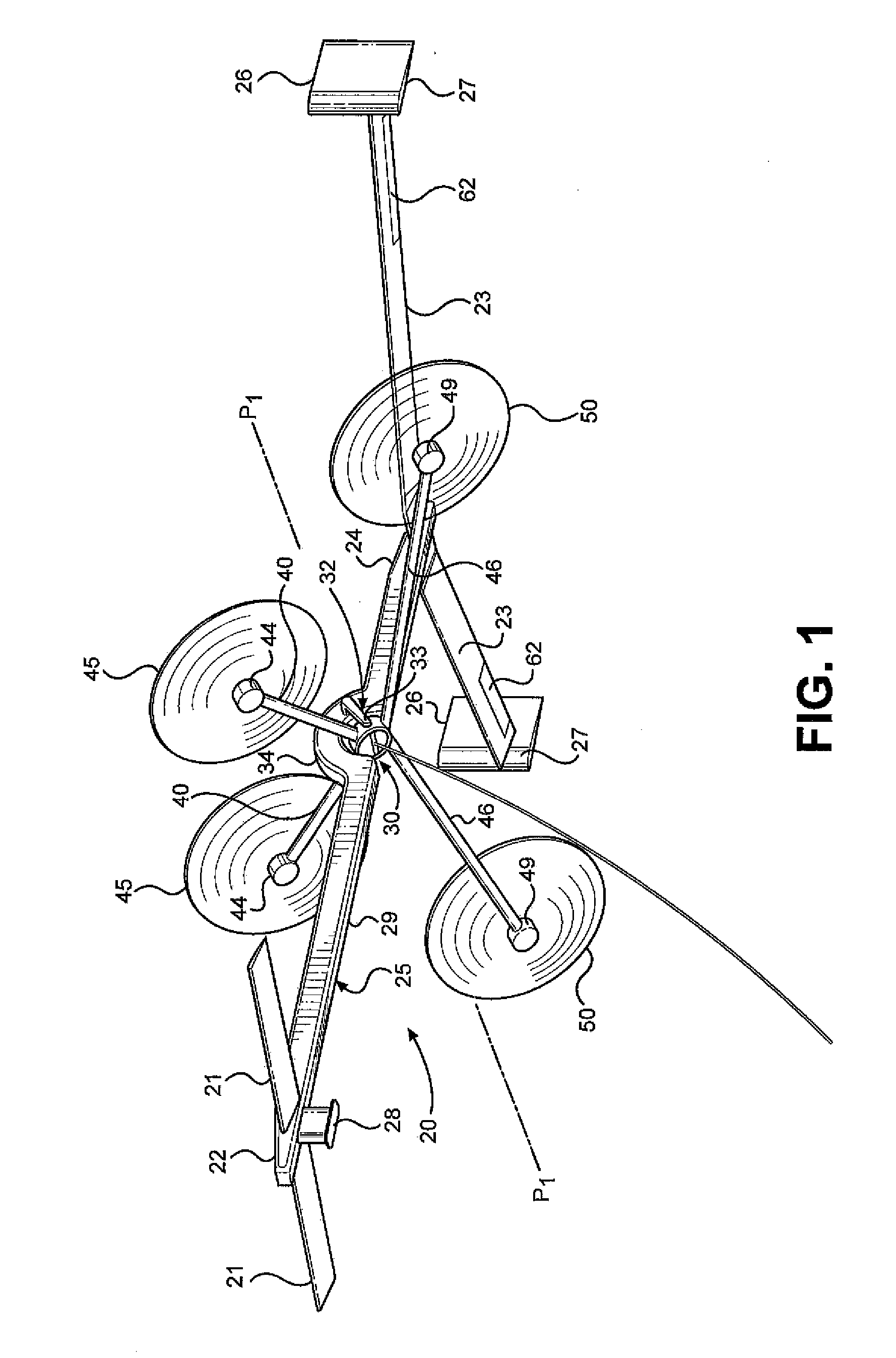
System and method for root loss reduction in wind turbine blades
InactiveUS20130156593A1Optimal angle of attackOptimal of lift generationPropellersPump componentsTrailing edgeWind force
A wind turbine blade includes a root region. A first extension (LEX) is attached to the leading edge side of the root region while a trailing edge strake (TES) is attached to the trailing edge side of the root region. The LEX and TES each include an outer profile that becomes more pronounced relative to their respective locations in the root region as the root region of the wind turbine blade morphs from a substantially cylindrical shape to a substantially airfoil shape. The LEX provides both optimal angle of attack and lift generation in the root region, while the TES mitigates airflow separation and enhances airfoil lift in the root region.
Owner:GENERAL ELECTRIC CO
Rotor blade of a wind turbine
ActiveUS9932960B2Good attackImprove compatibilityMachines/enginesEngine componentsLeading edgeTrailing edge
A rotor blade (5) of a wind turbine, which has a profile (1-4) having an upper side (suction side) (7) and an underside (pressure side) (8). The profile (1-4) includes a camber line (21, 25) and a chord (18) between a leading edge (10) and a trailing edge (11) of the profile (1-4). The profile (1-4) has a relative profile thickness of more than 45%. At least one vortex generator (50, 50′, 50″, 50′″) is disposed, in the region of the profile (1-4), on the suction side (7) of the rotor blade (5). The profile (1-4) is provided with a blunt trailing edge. And, The thickness of the trailing edge is between 15% and 70% of the chord length.
Owner:SIEMENS GAMESA RENEWABLE ENERGY SERVICE GMBH
Composition of multiple fungus possessing immunoloregulation function, preparation method and usage
InactiveCN1957953AGood market application prospectQuick fixBacteriaBacteria material medical ingredientsImmune systemBacteria
A multi-bacterium composition for regulating immunity by activating, repairing and reconfiguring immune system and preparing immunoregulator, anticancer medicine and health-care food is prepared from two or more lacticacid bacteria through culture. Its preparing process is also disclosed.
Owner:德阳创新生物工程有限公司
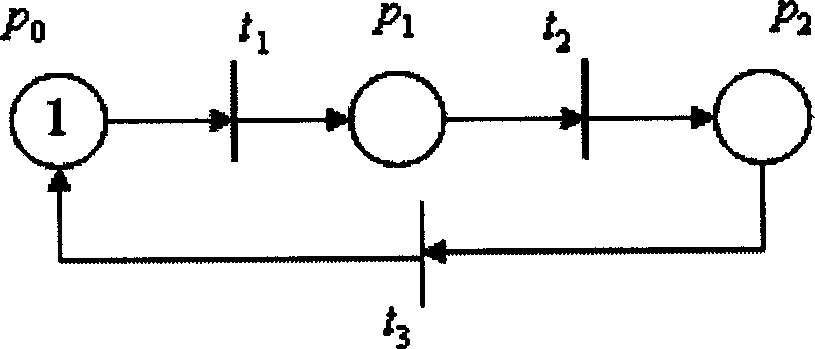
Probe for measuring a local angle of attack and method implementing same
ActiveUS8695412B2Accurate measurementGood attackAerodynamic testingFluid speed measurement using pressure differenceMeasurement precisionMeasurement design
A probe for measuring a local angle of attack designed to be fixed to a wall and a method implementing the probe are provided. The probe comprises at least three pressure sampling ports disposed over a nose of the probe body, pressure measurement means associated with the pressure sampling ports and calculation means capable of determining an angle of attack of the flow with respect to the main direction of the probe body as a function of the pressures measured by the pressure measurement means. The calculation means are configured for choosing from amongst the pressure sampling ports those allowing the best measurement precision of the local angle of attack to be obtained and for calculating the local angle of attack with respect to the main direction using the pressure measurements carried out in the chosen pressure sampling ports.
Owner:THALES SA
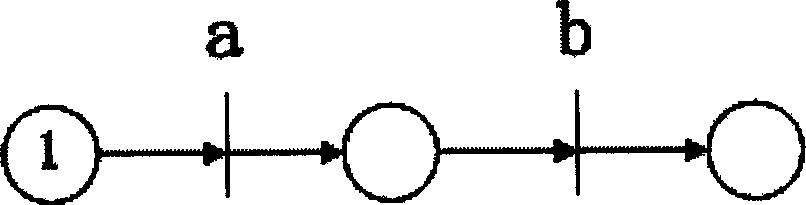
Formalized description method of network infection behaviour and normal behaviour
InactiveCN1477811AGood attackStrong concealmentUser identity/authority verificationTelegraphic message interchanged in timeNetwork behaviorEngineering
The present invention relates to a formalized description method of infection behaviour and normal behaviour in the network. It makes meticulous analysis for infection and aggressive behaviour in thenetwork, specially for distributed infection behaviour, on the basis, provides a formalized description method for infection behaviour and normal behaviour in the network. It uses ASSQ quadruple as theoretical basis, on the basis of existent Petri net model makes redefinition and modification, so that the method can be used for tracking and detecting infection behaviour and separating normal behaviour and infection behaviour.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Machining of Ceramic Materials
ActiveUS20110200966A1Shorten the timeMinimises levelEdge grinding machinesImpression capsUltimate tensile strength
Owner:IVOCLAR VIVADENT AG
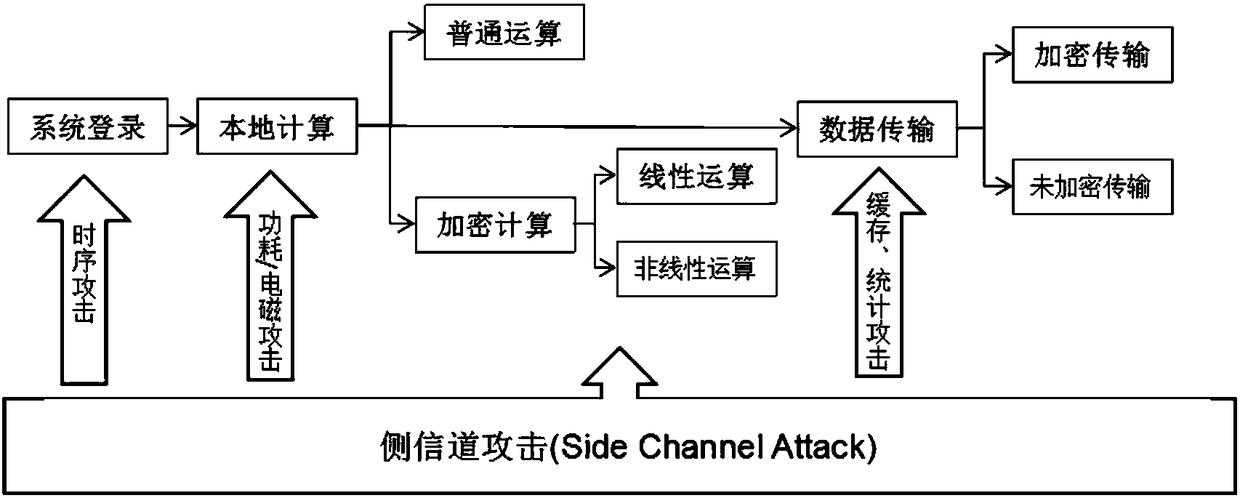
Side channel attack preventing algorithm applicable to full life cycle of system data
InactiveCN108521325AImprove controlGood attackCryptographic attack countermeasuresFull life cyclePassword
The invention relates to a side channel attack preventing algorithm applicable to the full life cycle of system data. The algorithm comprises the steps of S1, locally performing a timing sequence attack applied to password login authentication; S2, locally performing a common computation; S3, locally performing an encryption operation; and S4, executing a defense strategy when the information datais transmitting. The algorithm has the advantages that the full life cycle system running side channel attack defense frame is built for the side channel attack that may be suffered during the full running life cycle of the system data, so that the data and system security can be ensured during the whole running cycle of the system, the data is prevented from being leaked, and thus the information security is ensured.
Owner:林喆昊 +1
Composition, process for making using pressurized fluid, and uses thereof
InactiveUS20050170023A1Cosmetic propertyGood conditioning effectCosmetic preparationsBiocideHydrolysed proteinAmino acid
A process for preparing a composition by percolating a fluid containing steam, at a pressure of at least 3 bar, through at least one member selected from an amino acid, oligopeptide, peptide, optionally modified, optionally hydrolysed protein, and mixtures thereof, in solid or pasty form.
Owner:LOREAL SA
Auto-gyro rotor flying electric generator (FEG) with wing lift augmentation
InactiveUS9399982B2High rotor angle of attackFull generating capacityUnmanned aerial vehiclesWind motor supports/mountsFuselageElectric generator
A flying electric generator for obtaining power from wind currents which includes a fuselage having fore and aft portions and an intermediate portion, a rotor assembly including at least two forward rotors mounted on a pair of forward extending support arms extending from the fuselage and at least two rear rotors mounted to a pair of rearward extending support arms extending from the fuselage and at least one first forward wing mounted to a forward portion of the fuselage and extending outwardly on opposite sides of the fuselage and at least one second rear wing mounted to a rear portion of the fuselage and extending outwardly on opposite side of the fuselage.
Owner:SKY WINDPOWER CORP
Machining of ceramic materials
ActiveUS7955159B2Shorten the timeMinimises levelEdge grinding machinesImpression capsUltimate tensile strength
Owner:IVOCLAR VIVADENT AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com