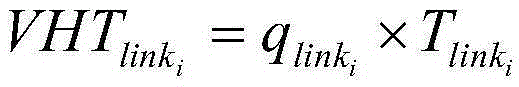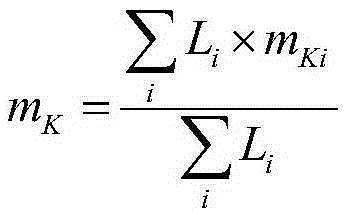Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
593results about How to "Strong concealment" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
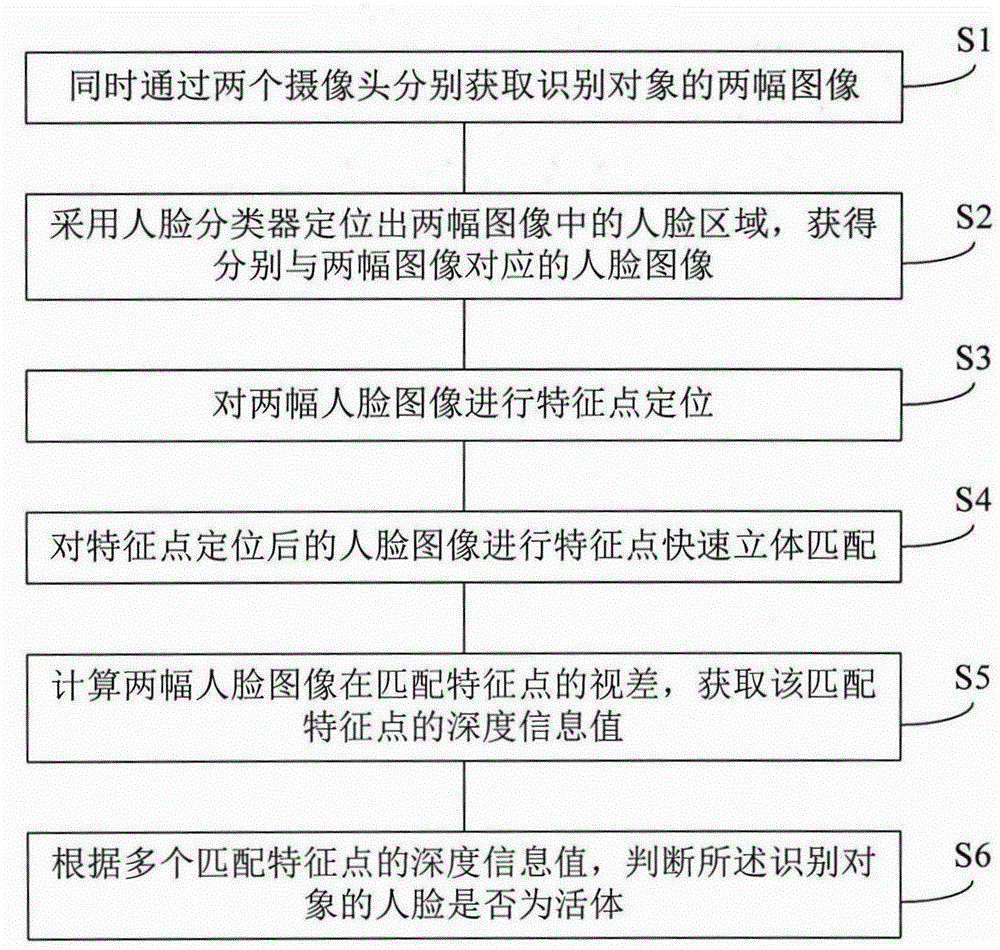
Face living body detection method and system
The present invention discloses a face in-vivo detection method and system. The face in-vivo detection method comprises the steps of: simultaneously and respectively acquiring two images of an identification object by two cameras; positioning face regions in the two images by adopting a face classifier so as to acquire face images which respectively correspond to the two images; carrying out feature point positioning on the two face images; carrying out feature point rapid stereo matching on the face images subjected to feature point positioning; calculating parallax errors of the two face image at match feature points and acquiring depth information values of the match feature points; and according to the depth information values of a plurality of match feature points, judging whether the face of the identification object is a living body. According to the present invention, excessive cooperation of a user is not required; safety is high; hidden performance is high; attitude adaptability is high; the application range is wide; a matching speed is high; and user experience is good.
Owner:INST OF SEMICONDUCTORS - CHINESE ACAD OF SCI +1
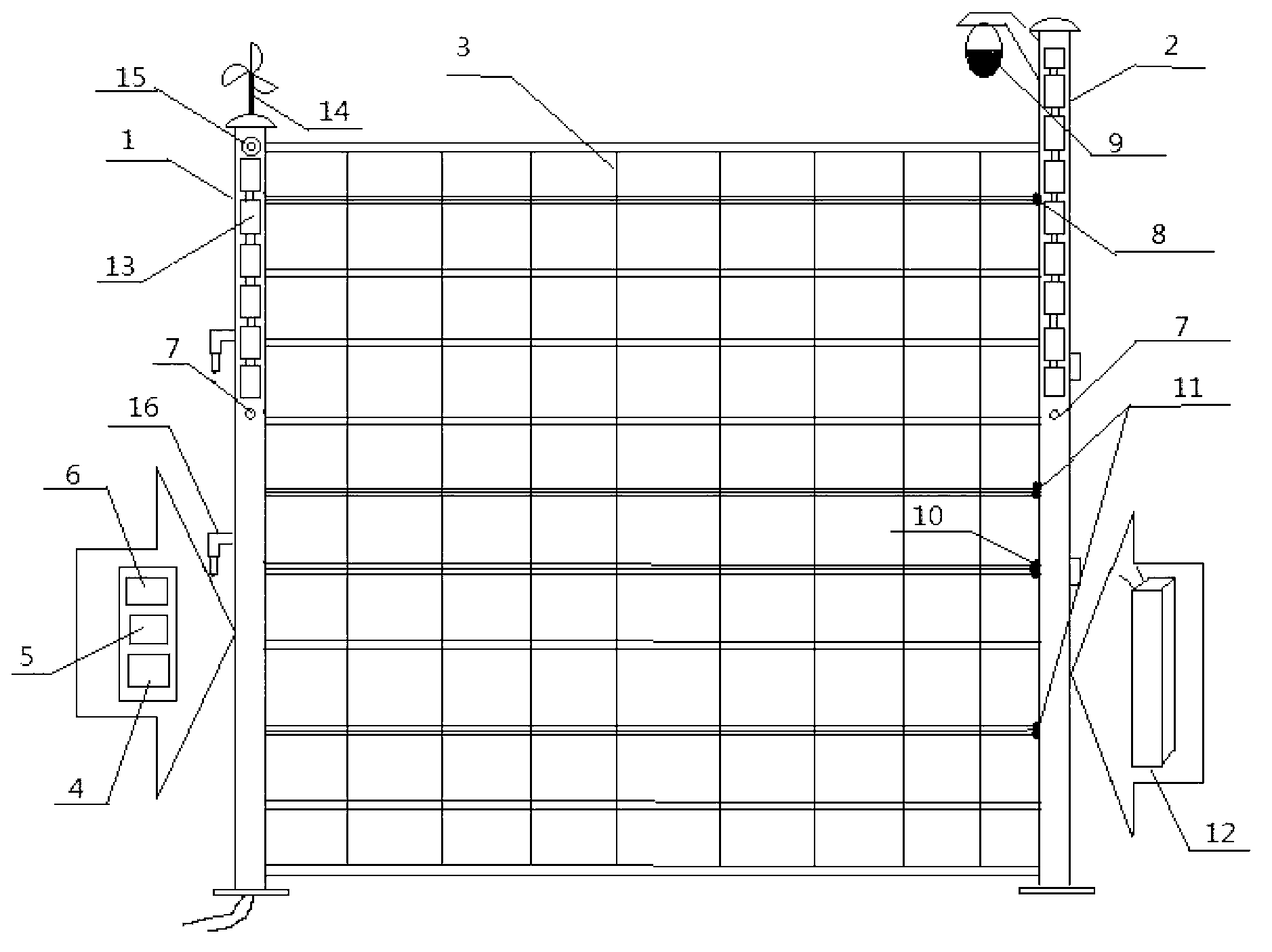
Smart safeguard fence
InactiveCN103075046AEfficient use ofGuaranteed validityEnergy efficient ICTFencingMicrocontrollerVideo monitoring
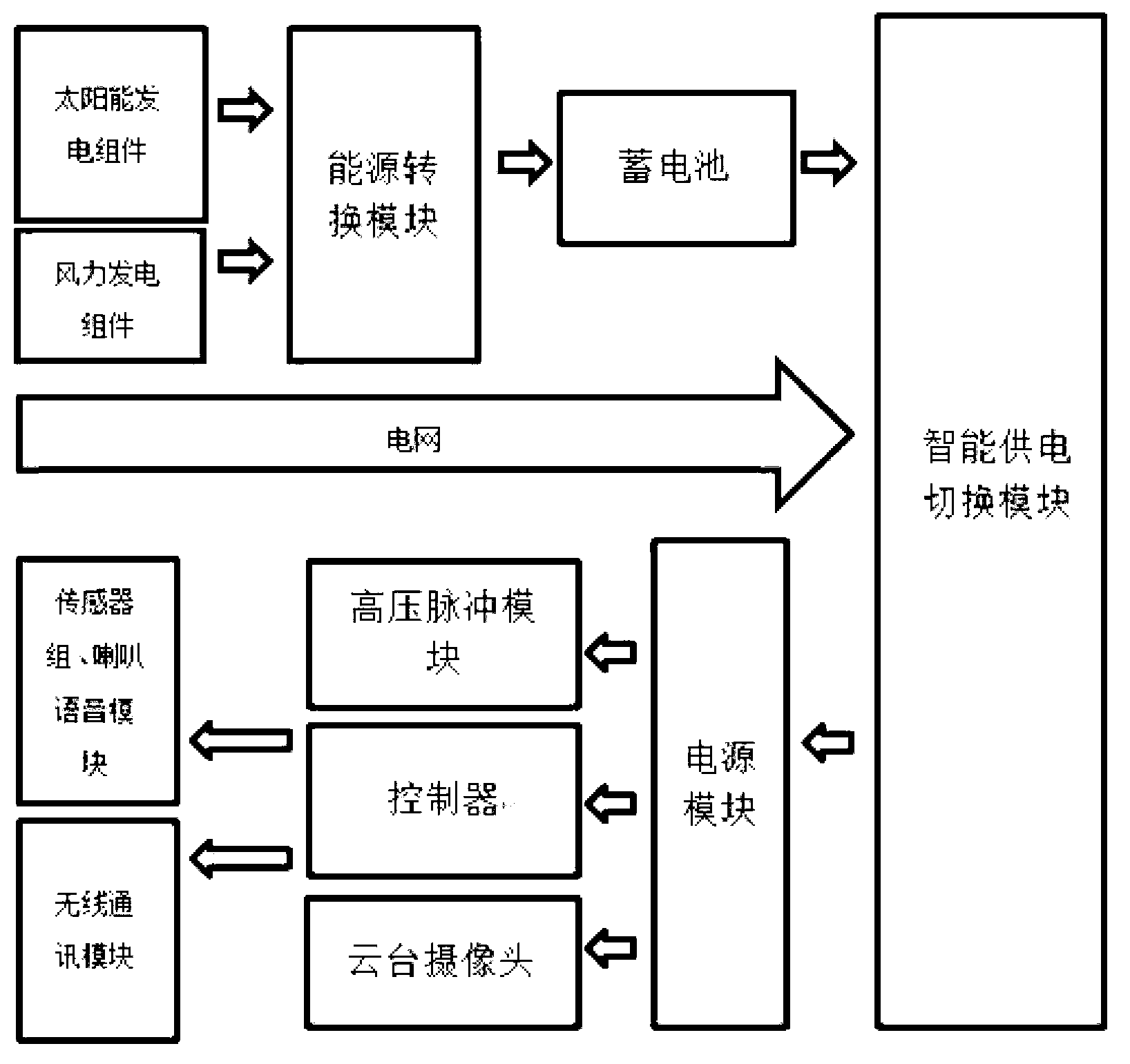
The invention discloses a smart safeguard fence, comprising a left upright post, a right upright post and a net fence between the left and right upright posts, wherein a vibration optical cable is arranged in the fence, two ends of the vibration optical cable are respectively connected with a tension sensor and a high voltage pulse module which are arranged in the upright posts, a passive infrared module, a wireless communication module, a microcontroller, a power source module and a storage cell are mounted further in the upright posts, the power source module comprises an energy conversion module, a smart power supplying switching module and a voltage varying and stabilizing module, cloud deck cameras are mounted at the tops of the upright posts, solar generating assemblies are paved at the outer faces of the upper parts of the upright posts, and the microcontroller is communicated with a monitoring center by the wireless communication module. Couplers are respectively arranged at the two upright posts, and a whole safeguard fence system is formed by connecting and inserting the couplers among multiple safeguard fences. The smart safeguard fence has the advantages of high alarming accuracy rate, strong video monitoring pertinence, good safe performance, energy and power saving, and the like.
Owner:JIANGNAN UNIV
Anti-UAV passive detection and direction finding positioning system
InactiveCN106932753ALong detection distanceThe detection distance is easy to realizePosition fixationWireless routerCountermeasure
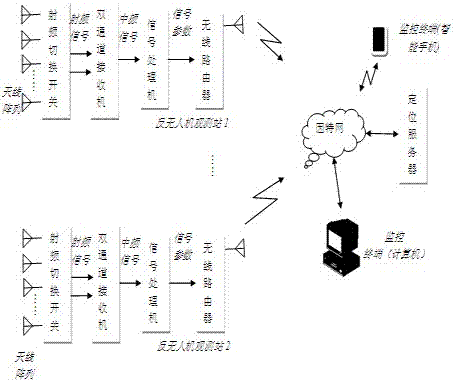
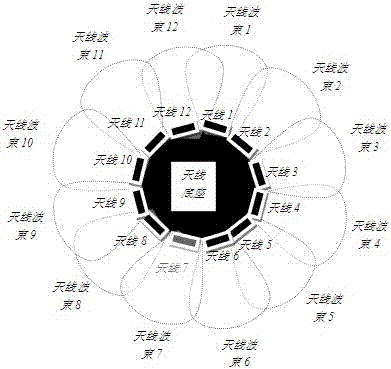
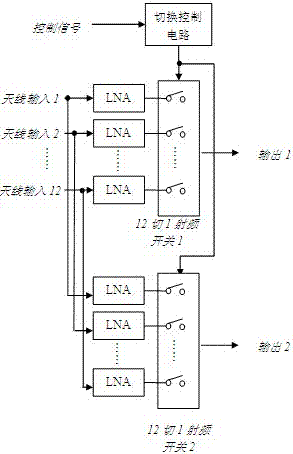
The invention relates to an anti-UAV (unmanned aerial vehicle) passive detection and direction finding positioning system which comprises an array antenna, a radio frequency switching switch, a double-channel receiver, a dual-channel signal processor, a wireless router, a positioning server, and a monitoring terminal. Through the antenna array, the measurement and control and image transmission radio frequency signals emitted by a UAV and an operator are passively intercepted and received, the double-channel receiver carries out frequency conversion of the intercepted and received signals into intermediate frequency signals, the signal detection and parameter estimation of the intermediate frequency signals are carried out, and the characteristic parameter of the UAV is obtained and is sent to the positioning server through the wireless router. After the positioning server receives the characteristic parameter of the UAV, the characteristic parameter of the UAV is subjected to direction finding cross positioning, and the detection, positioning and tracking of the UAV are realized. According to the system, the positioning and tracking of the UAV are realized so as to satisfy safety guarantee of an important key area and UAV countermeasure and interference requirements.
Owner:NAT UNIV OF DEFENSE TECH
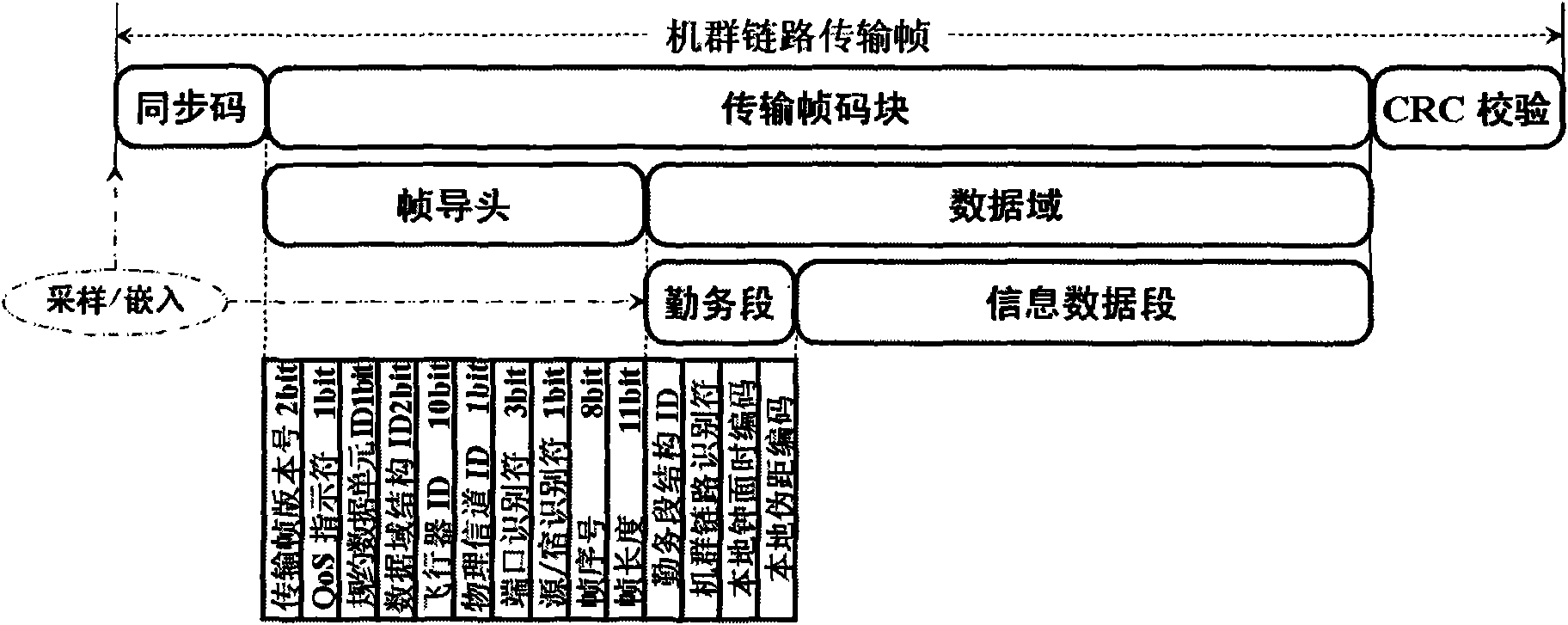
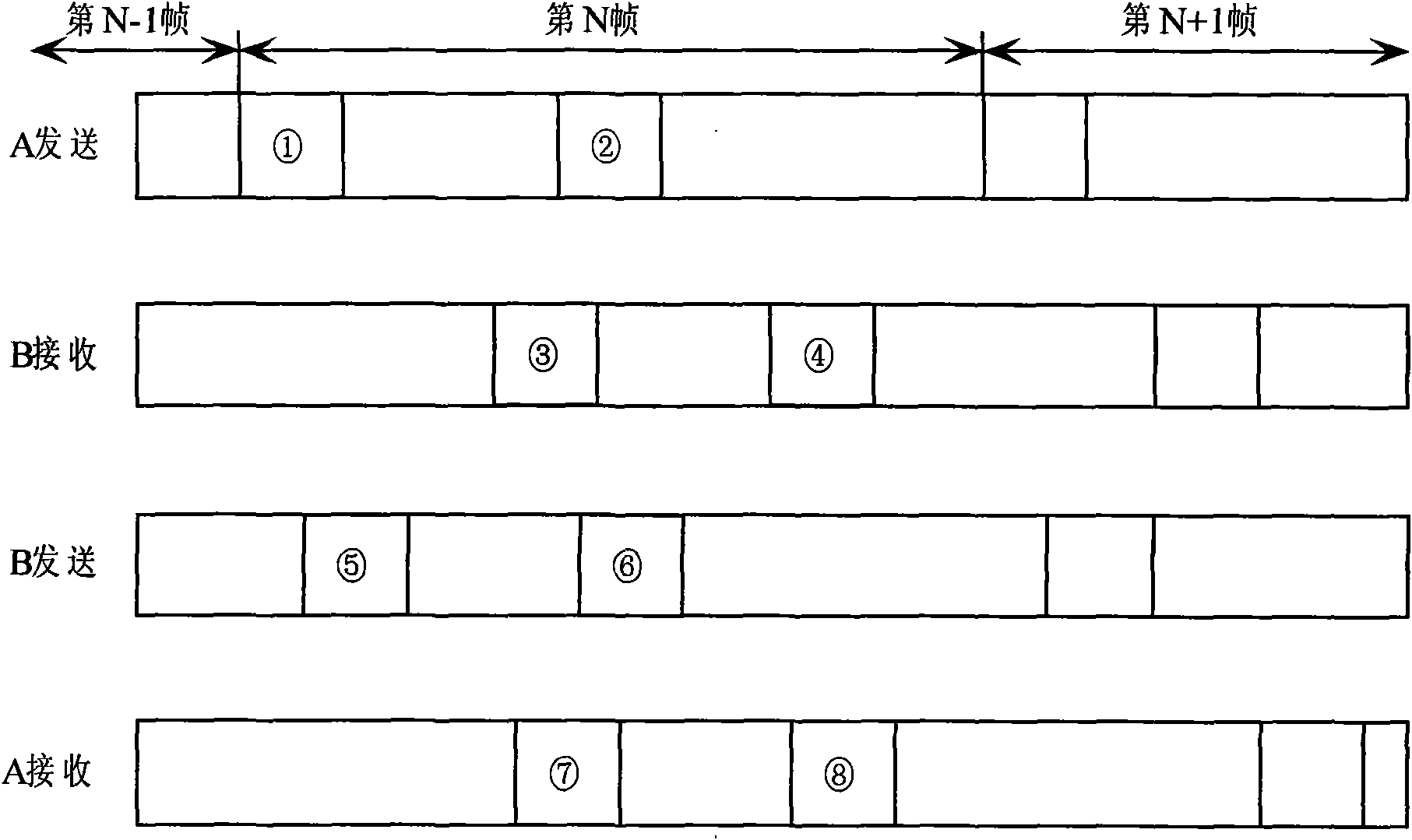
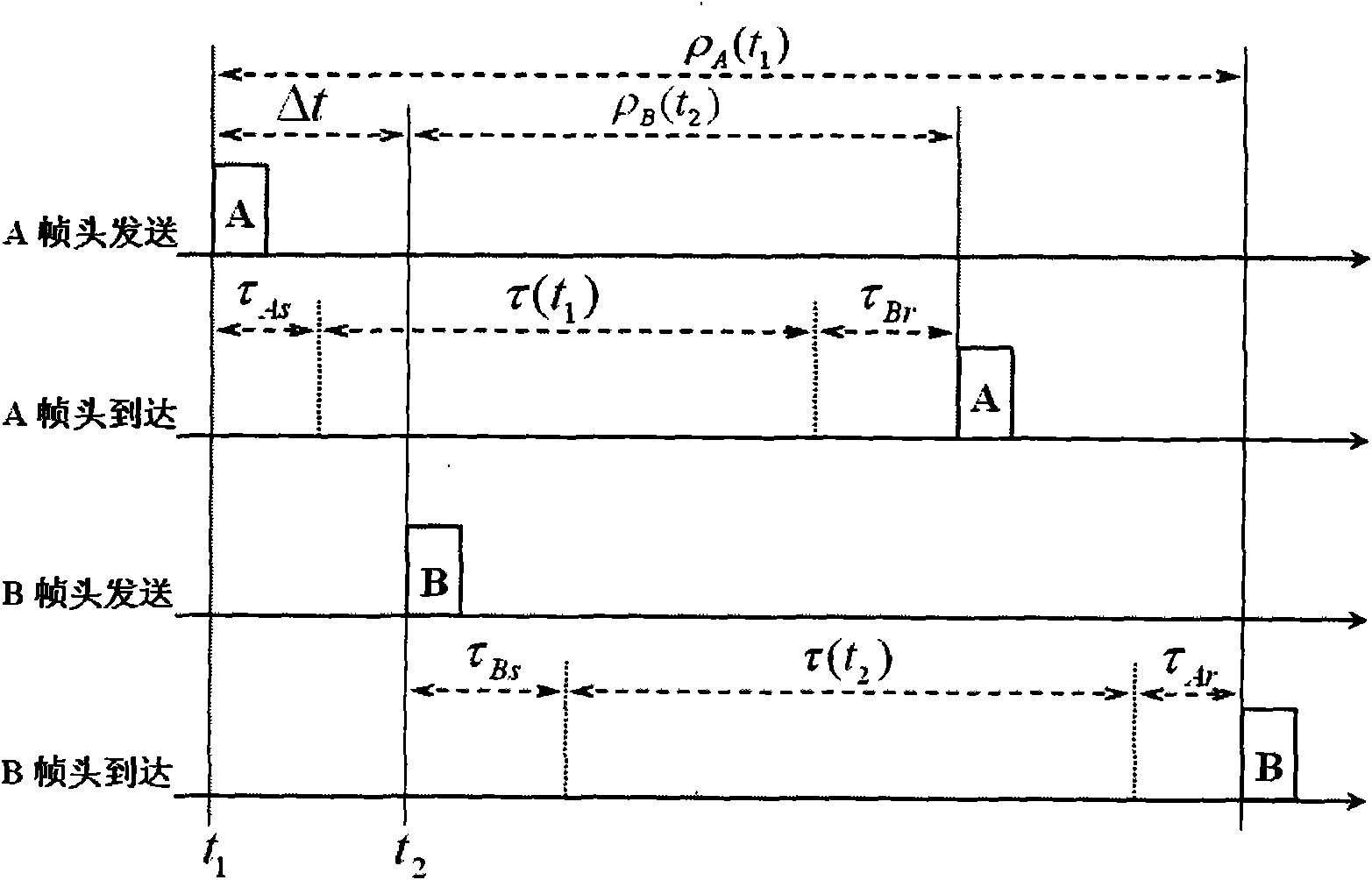
Noncoherent distance measurement/time synchronism system of cluster link two-way asynchronous communication channel
InactiveCN101789859AStrong autonomyStrong concealmentError preventionUsing reradiationFrame basedCompensation algorithm
The invention relates to a symmetrical noncoherent distance measurement / time synchronism system of a cluster link two-way asynchronous communication channel, belonging to the autonomous technical field of aviation data links, radio navigation and aircrafts. By the invention, a symmetrical noncoherent distance measurement / time synchronism method and a system framework can be realized on a DSP (Digital Signal Processor) of a circuit board and an FPGA (Field Programmable Gate Array). Based on the two-way asynchronous communication link between cluster link member nodes, the noncoherent distance measurement / time synchronism system provides a noncoherent spread spectrum distance measurement principle of a two-way asynchronous communication frame under a comprehensive channel system, constructs a noncoherent spread spectrum distance measurement algorithm structure of the air fleet link two-way asynchronous communication frame in a uniform form by adopting a communication frame based on CCSDS Proximity-1 version-3 and provides two algorithms of base line measurement and time synchronism measurement control: an interprocessor time synchronism recursive algorithm and a Doppler integral compensation algorithm. The invention overcomes the defects of the traditional coherent transferring distance measurement and the two-way synchronous noncoherent distance measurement and provides a distance measurement scheme, in which both parts of the two-way asynchronous communication distance measurement can equally acquire a measurement result.
Owner:NAT SPACE SCI CENT CAS
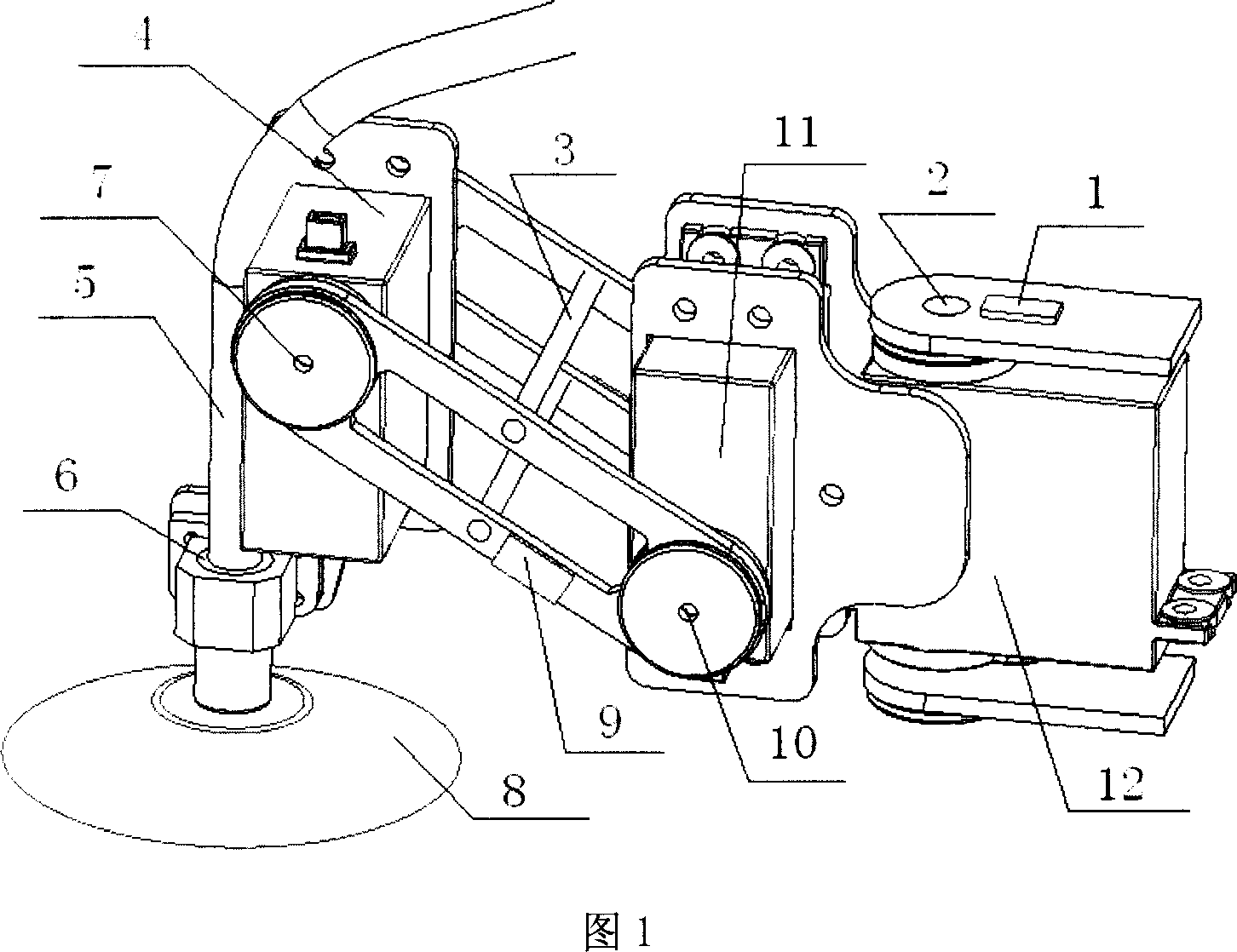
Wall gecko imitation mini-robot
InactiveCN1947959AImprove performanceReduce volumeProgramme-controlled manipulatorMicromanipulatorThighElectrical conductor
A miniature robot simulating gecko is composed of a circuit control unit and a mechanical structure unit which consists of 4 single leg structures comprising thigh, shank and suction cup, a body module comprising two waist-driving steering gears, two air pumps, two air releasing unit, two four-way jointers and 6 plastic guide tubes, and a negative-pressure sucking and releasing unit comprising steering gear, spring, steel cable, winder and fixed spring.
Owner:HARBIN ENG UNIV
Toilet seat overturning driving control method
InactiveCN105310590ADoes not affect appearanceStrong concealmentBathroom coversMechanical energy handlingControl theoryMechanical engineering
The invention discloses a toilet seat overturning driving control method. A fixing seat mounted on the surface of a toilet serves as a carrier, a swing component is mounted on the fixing seat through a rotating shaft, a transmission portion and a driving portion, which are used for driving the swing component to overturn upwards, are arranged, the driving portion forces the swing component to overturn upwards along the free rotating shaft through the transmission portion, and the swing component pushes a seat to overturn upwards while overturning upwards. The toilet seat overturns by 90 degrees by being driven by a pedal, the purposes that the toilet seat overturns when a user comes and pedals, and falls automatically when the user leaves are achieved, and accordingly the toilet seat is quite convenient to use; the user does not need to touch the toilet seat by hands, so that sanitation is achieved; wide popularization and low cost are achieved without modifications on existing toilets or toilet seats; normal use of the toilet cannot be affected, and good concealing performance is achieved; the toilet is most simplified and optimized in structure, easy to implement, simple to assemble and attractive and appropriate in appearance.
Owner:孙明英
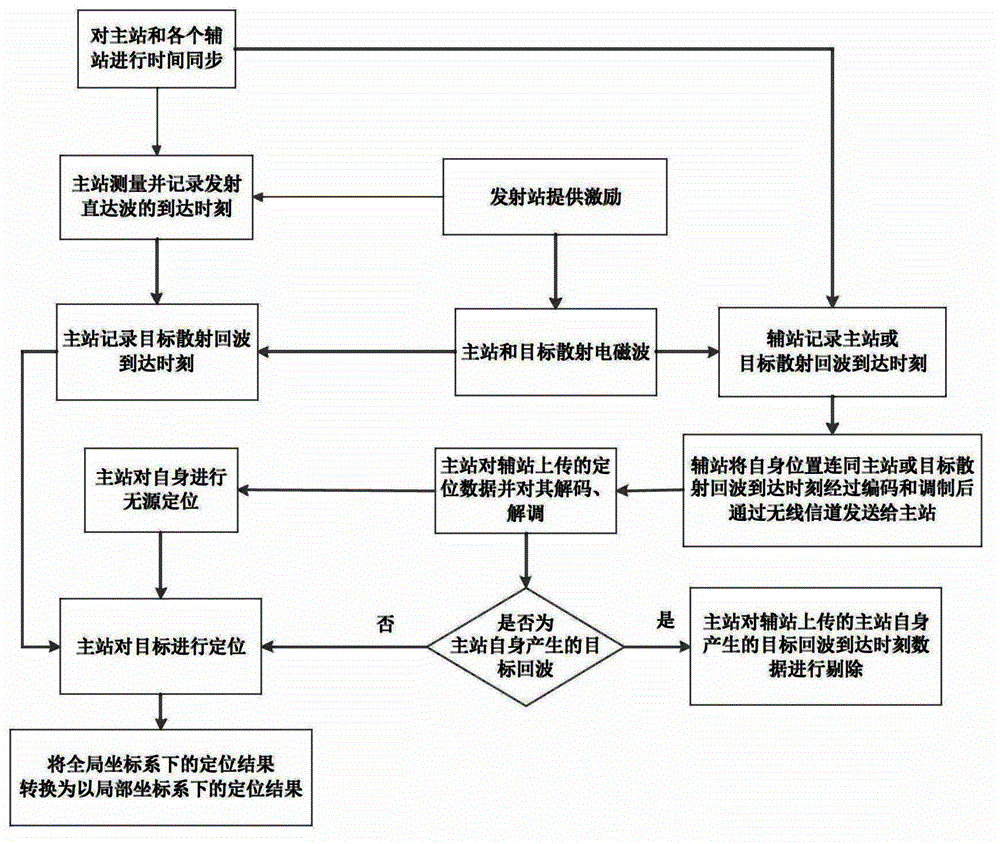
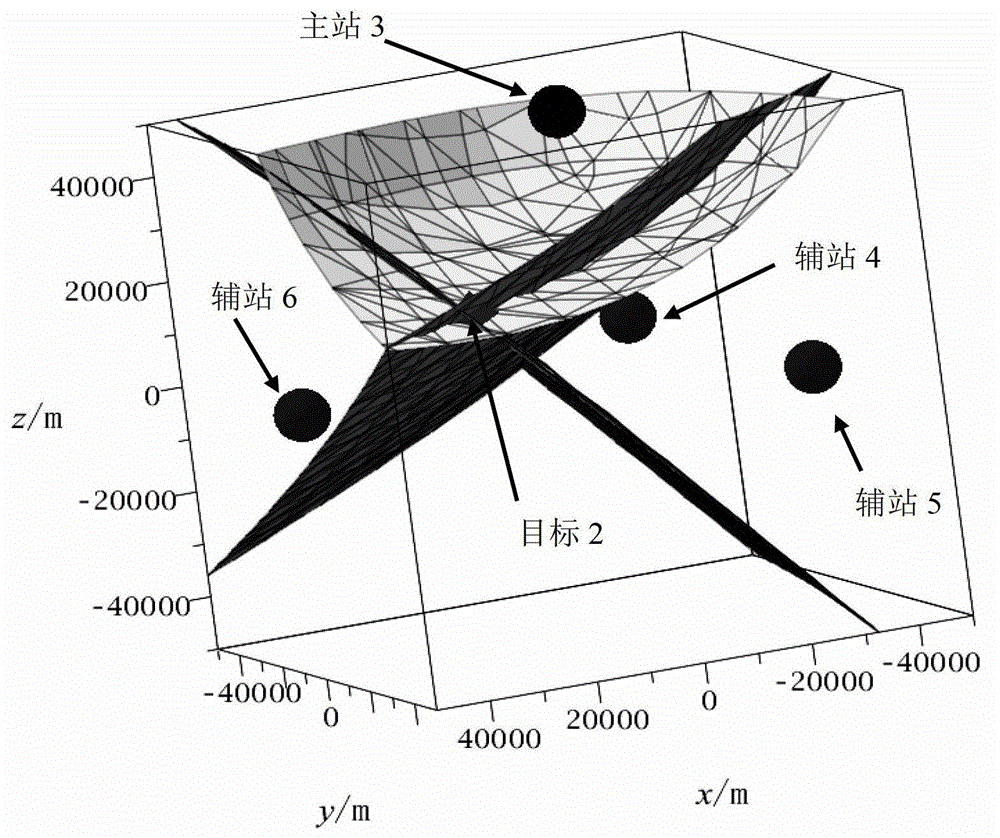
Method for three-dimensional passive positioning of targets by air moving platform
InactiveCN102981144ANot easily detectedStrong concealmentPosition fixationGlobal coordinate systemEngineering
The invention discloses a method for three-dimensional passive positioning of targets by an air moving platform. The method mainly solves the problem that air moving platforms in the prior art can not conduct passive positioning on air moving platforms and targets simultaneously. The method comprises that 1) time synchronization is conducted on a master station which receives target scattering echoes and all auxiliary stations; 2) a radar transmitting station radiates targets and detects required electromagnetic waves; 3) the master station records the arrival time of transmitted directed waves and records the arrival time of target scattering echoes, and all auxiliary stations record the arrival time of scattering echoes of the master station or the arrival time of scattering echoes of targets; 4) auxiliary stations transmit position information of auxiliary stations and the arrival time information of scattering echoes of the master station or the arrival time information of scattering echoes of targets to the master station; 5) the master station positions the master station and targets; and 6) positions of targets in a global coordinate system are converted into positions in a local coordinate system. The method has the advantages of being high in positioning precision and high in hiding performance and can be used for three-dimensional passive positioning of targets by the air moving platform.
Owner:XIDIAN UNIV
Mine roof and floor water inrush monitoring and prediction system and method
ActiveCN103529488AMonitoring water inrush problemsAvoid distractionsGeological measurementsPrediction systemPrediction methods
The invention discloses a mine roof and floor water inrush monitoring and prediction system and a mine roof and floor water inrush monitoring and prediction method. The system comprises a ground control room host terminal, an underground site host, a comprehensive cable assembly and a plurality of detection terminals, wherein the underground site host is connected with the ground control room host terminal; the comprehensive cable assembly is connected with the underground site host; the detection terminals are arranged on a roadway wall, a roadway floor or a roadway roof along the mine roadway direction; each detection terminal comprises a controller, a three-dimensional vibration sensor, an electrode and a memory connected with the controller; signal output ends of the three-dimensional vibration sensor and the electrode are connected with a signal input end of the controller; a data communication end of each controller is connected with the underground site host through the comprehensive cable assembly. According to the system and the method, the accuracy and the real-time property of a mine roof and floor water inrush monitoring result can be obviously improved.
Owner:WUHAN CONOURISH COALMINE SAFETY TECH
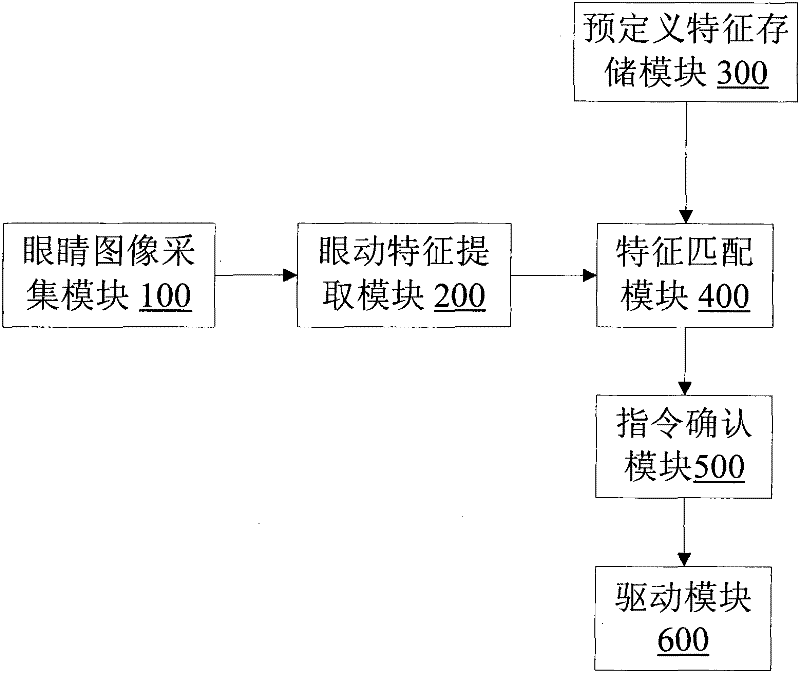
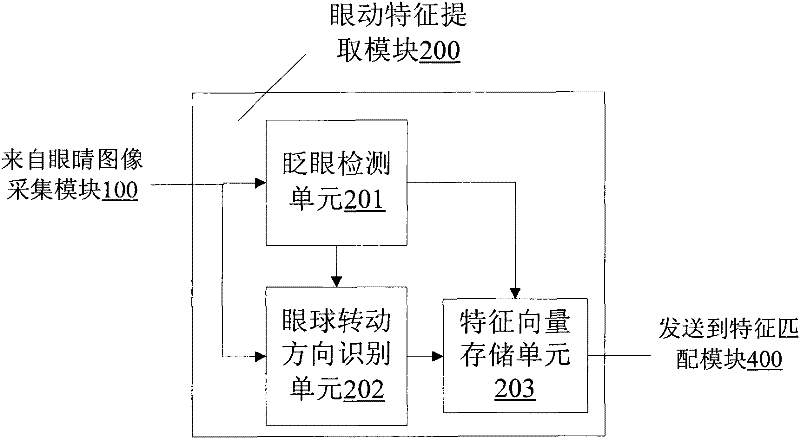
Control system and control method for controlling upper prosthesis to move by using eye movement signals
InactiveCN102309366AStrong concealmentEasy to controlCharacter and pattern recognitionProsthesisControl functionProsthesis
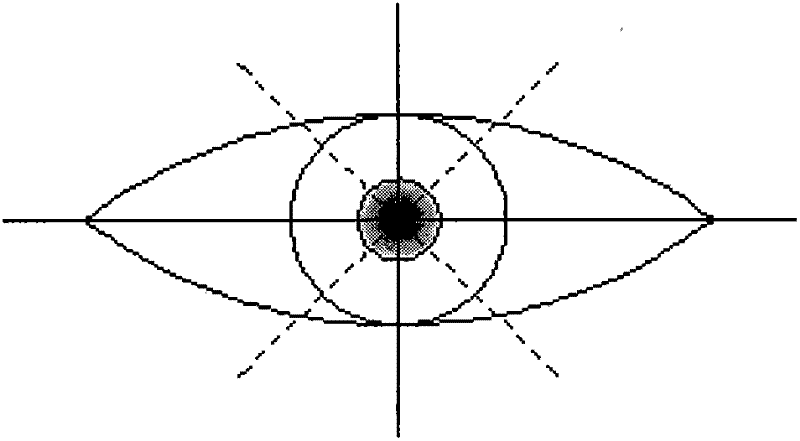
The invention discloses a control system and a control method for controlling the upper prosthesis to move by using eye movement signals. The control system comprises an eye image acquisition module, an eye movement characteristic extraction module, a predefined characteristic storage module, a characteristic matching module, an instruction confirming module and a driving module. By all the modules, the combination of the rotation event and the blinking event of the eyes is realized, and then various different characteristics are generated, so that more control functions are completed.
Owner:SHANDONG UNIV OF SCI & TECH
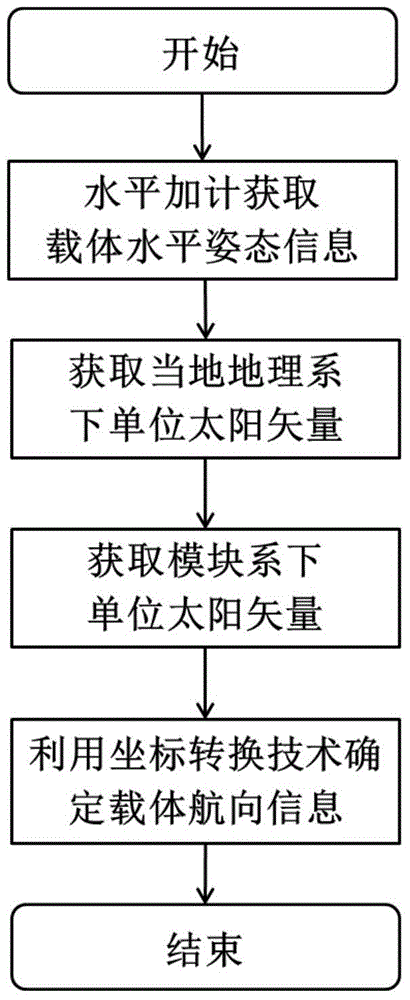
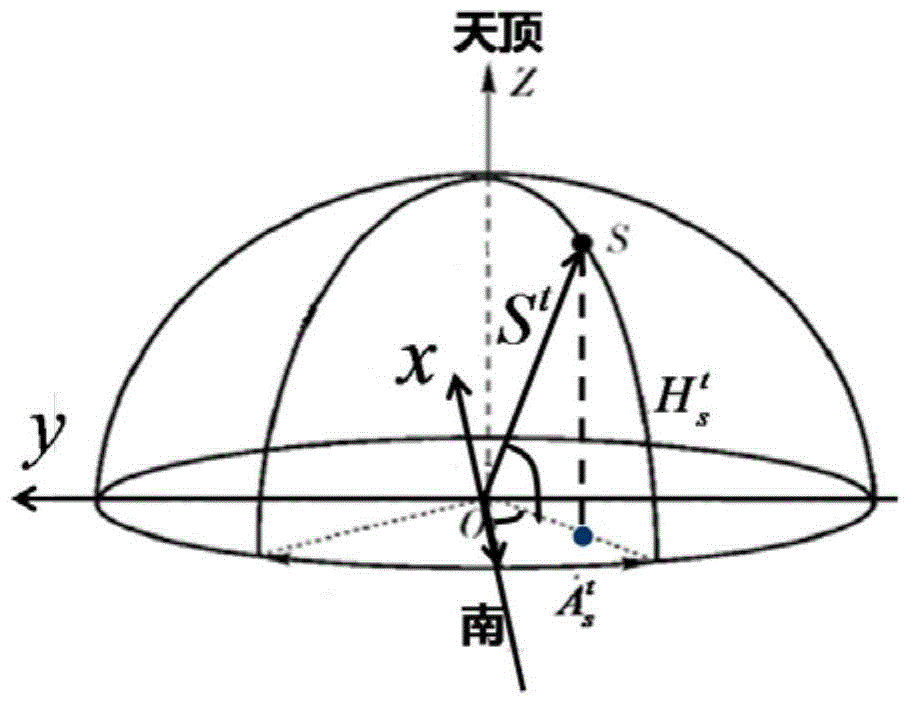
Carrier course angle calculation method based on polarization compass
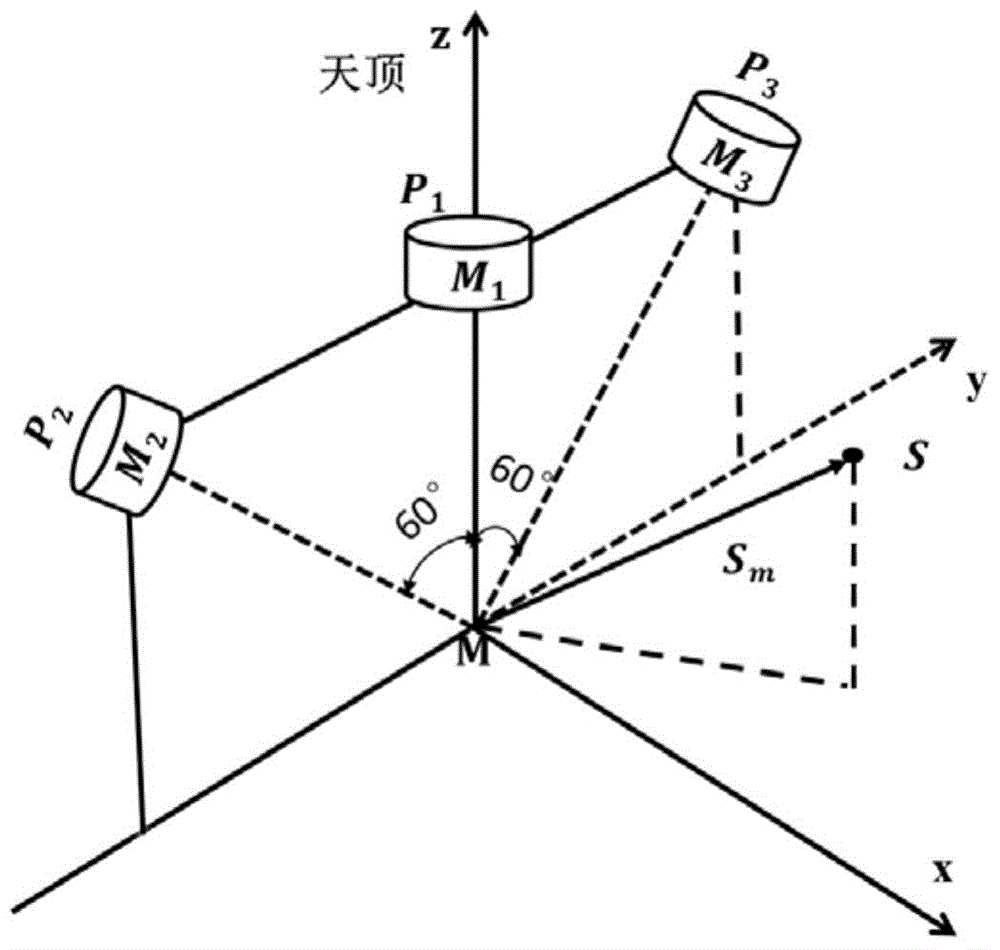
ActiveCN104880192ARealize solutionImplement fixesNavigational calculation instrumentsTime informationGeographic coordinate system
The invention relates to a carrier course angle calculation method based on a polarization compass. The polarization compass comprises two acceleration meters in the horizontal direction and three polarization sensors. The carrier course angle calculation method based on the polarization compass includes that firstly, using the acceleration meters in the horizontal direction to acquire the horizontal posture (pitch angle theta and roll angle gamma) of the carrier; secondly, using the geographical location information and time information of the carrier to calculate a unit sun vector St under a geographic coordinate system; thirdly, using the polarization sensors on the carrier to measure a polarization azimuth angle to calculate a unit sun vector Sm under a polarization sensor module coordinate system; finally, using the horizontal posture information and sun vector information to build the transformation relation of the unit sun vector between the geographic coordinate system and polarization sensor module coordinate system, and confirming the course information Psi of the carrier. The carrier course angle calculation method based on the polarization compass has advantages of high precision, less calculated amount, strong compatibility and the like.
Owner:青岛智融领航科技有限公司
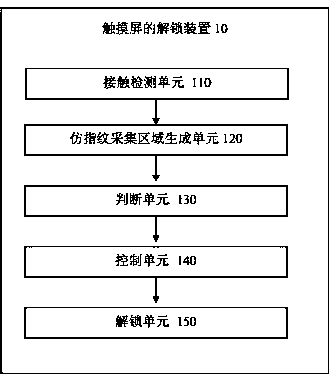
Unlocking method and device of touch screen terminal
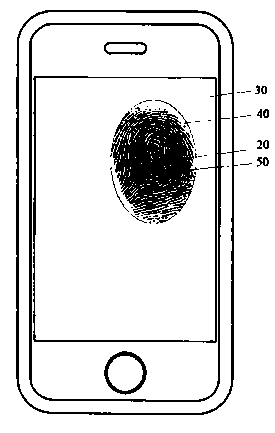
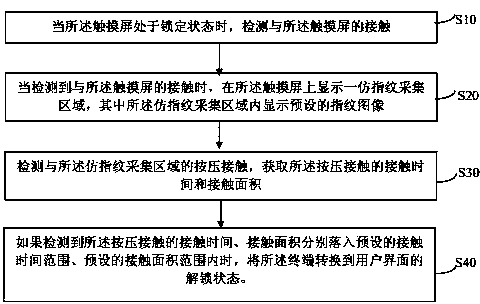
InactiveCN103984503AStrong concealmentSuppress attempts to unlock illegallyDigital data authenticationInput/output processes for data processingFingerprintTime range
The invention discloses an unlocking method of a touch screen terminal. The method comprises the steps that when contact with a touch screen is detected, a fingerprint-collection-simulation zone is displayed on the touch screen; pressing contact with the fingerprint-collection-simulation zone is detected, and the position and the contact time of a first contact point of the pressing contact are obtained; and if the fact that the first contact point is in a preset zone of the fingerprint-collection-simulation zone, and the contact time is in a preset time range is detected, the terminal is switched into an unlocking state of a user interface. According to the unlocking method and device of the touch screen terminal, touch screen fingerprint collection is simulated for unlocking, great stealthiness is achieved, unlocking safety and interestingness are improved, and user experience on touch screen unlocking operation is enriched.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
Unlocking method and device of touch screen
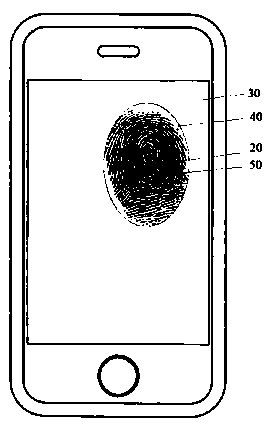
InactiveCN103984463ARich operating experienceStrong concealmentInput/output processes for data processingTime rangeTouchscreen
The invention discloses an unlocking method of a touch screen. The method comprises the steps that when touching with the touch screen is detected, a fingerprint-collection-simulation zone is displayed on the touch screen; the touching time and the touching area of pressing contact with the fingerprint-collection-simulation zone are detected; and if the fact that the touching time and the touching area of pressing contact are in the preset touching time range and the preset touching area range respectively is detected, a terminal is switched into an unlocking state of a user interface. According to the unlocking method and device of the touch screen, touch screen fingerprint collection is simulated for unlocking, great stealthiness is achieved, unlocking safety and interestingness are improved, and user experience on touch screen unlocking operation is enriched.
Owner:SHENZHEN ARATEK BIOMETRICS TECH CO LTD
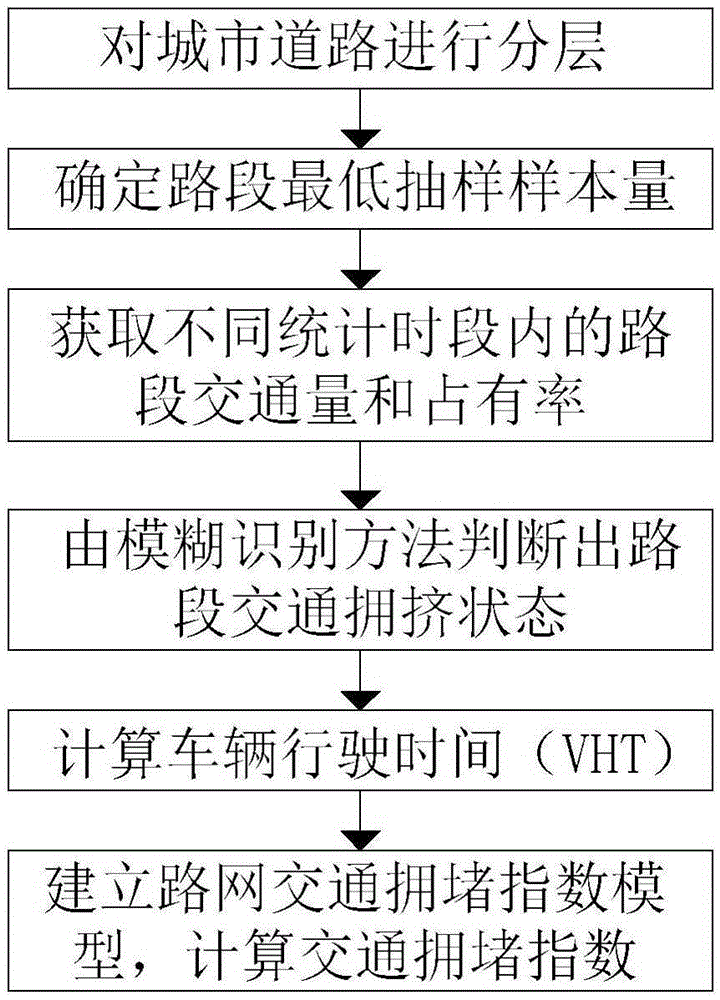
Hierarchical road network traffic jam evaluation method
InactiveCN105321347AStrong concealmentImprove rationalityDetection of traffic movementOccupancy rateRoad networks
The invention discloses a hierarchical road network traffic jam evaluation method, and the method solves the problem in the prior art that evaluation is mostly carried out on the operation state of a single road section. The method specifically comprises the following steps of: firstly, layering urban roads, utilizing a layered sampling method to calculate lowest road section sample sizes of different road sections; secondly, according to a traffic volume and an occupancy rate, utilizing a fuzzy identification method to judge the traffic jam state of each road section; and then, calculating the vehicle driving time, establishing a road network traffic jam evaluation module, and calculating a traffic jam index. Starting with road section traffic jam state analysis, the road network jam state is hierarchically evaluated from microscopic road sections to macroscopic road sections, so that the method is good in good in practicality, and reference bases are provided to traffic management departments for analyzing the jam phenomenon of an urban traffic system in the future.
Owner:XIDIAN UNIV
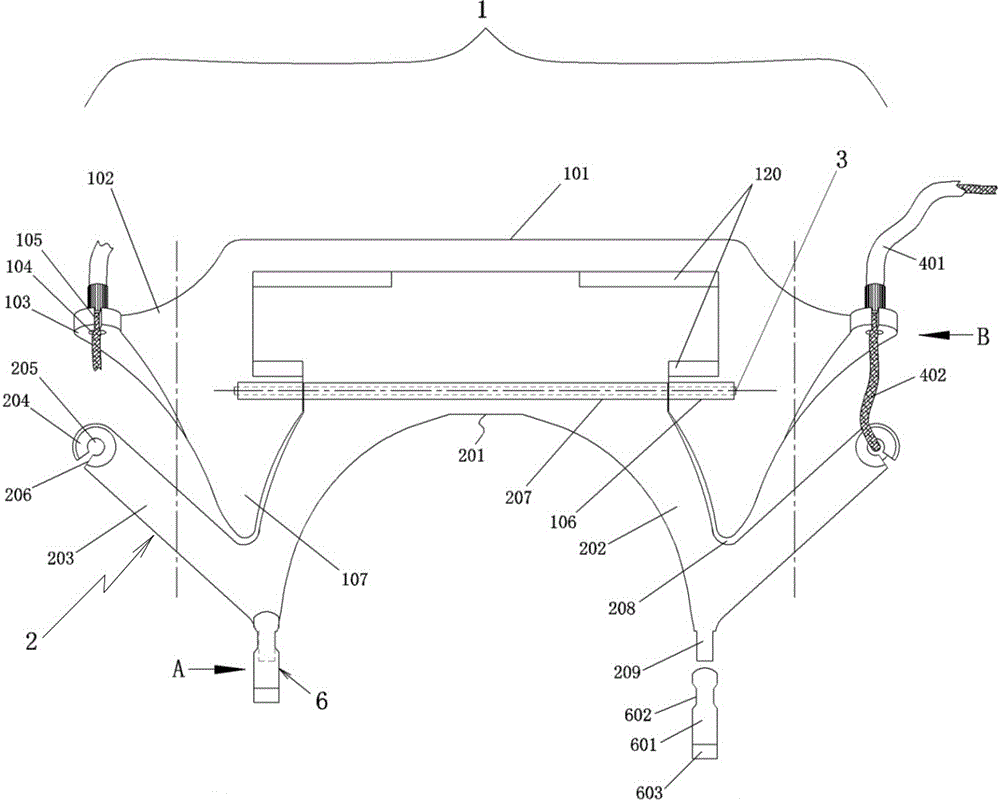
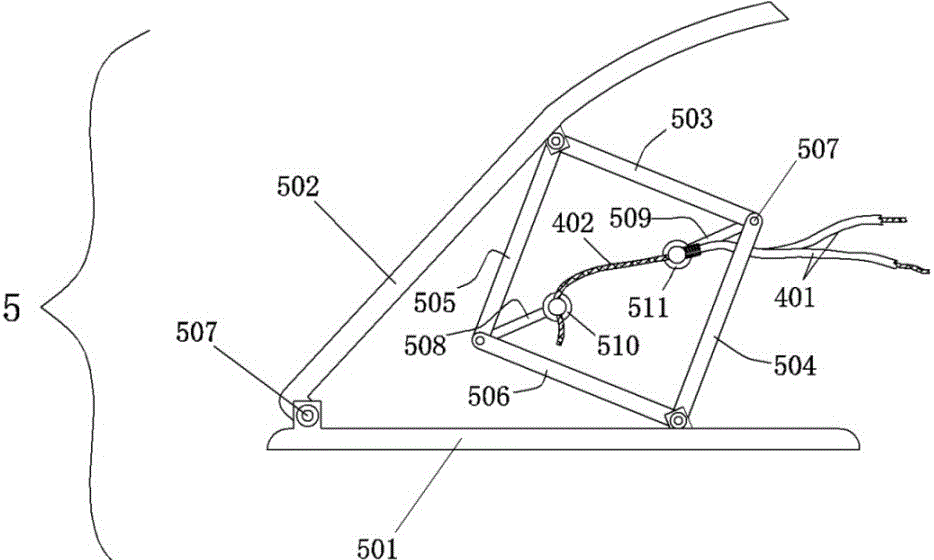
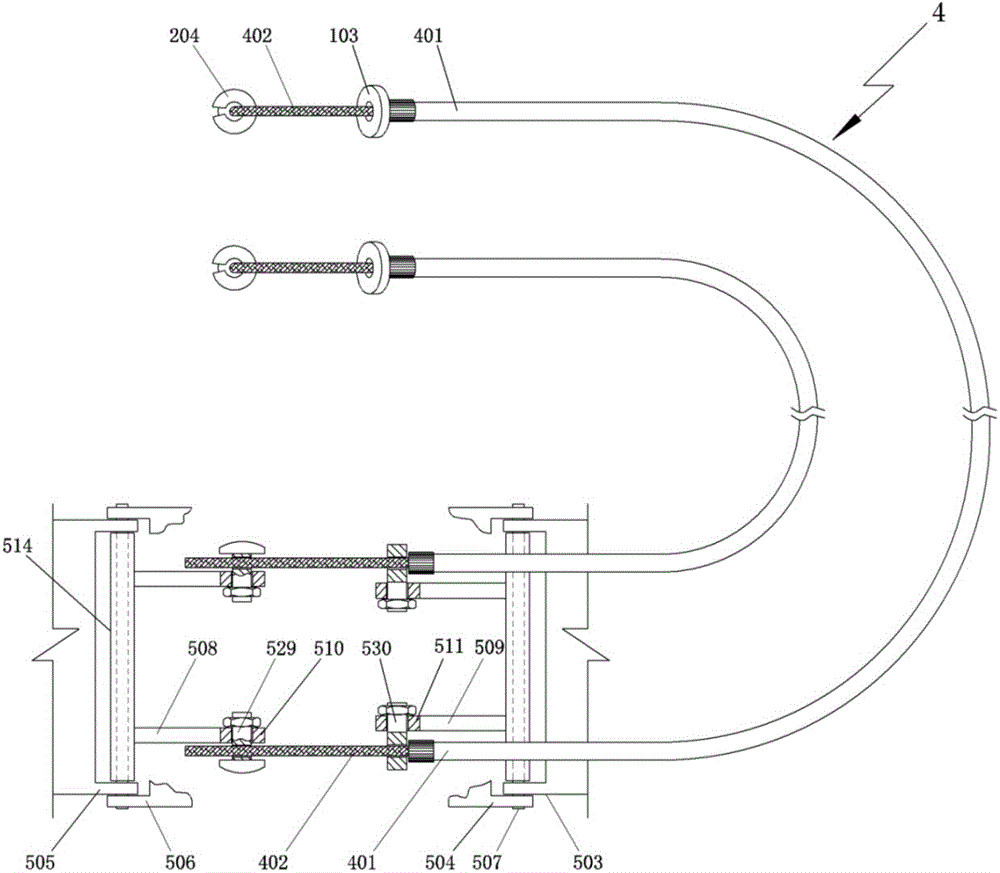
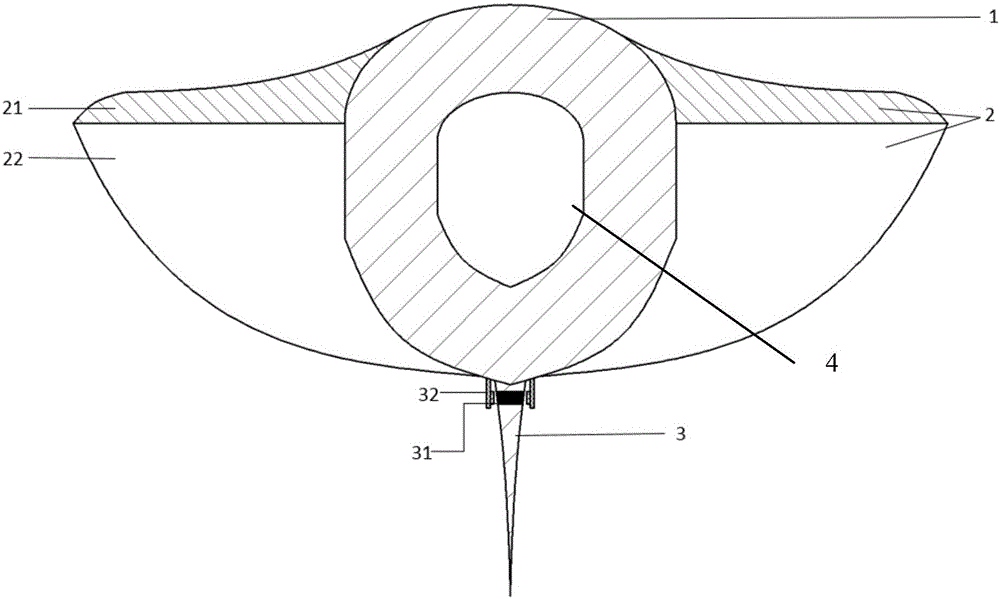
Rear-hanging pedestal pan cushion turning and driving device and fixing seat
The invention discloses a rear-hanging type pedestal pan cushion turning and driving device and a fixing seat. The rear-hanging type pedestal pan cushion turning and driving device comprises a turning portion, a transmission portion and a pedal portion; the turning portion comprises the fixing seat and a swinging part, the fixing seat is arranged on an outer frame located on the root of a cushion rotation seat in a sleeving or wrapping mode, the fixing seat is hinged to the swinging part, and the position of a movable support arranged on the fixed seat corresponds to that of a fixed support arranged on the swinging part; a first-end stop block of a brake cable of the transmission portion is fixed in the movable support in a clamping mode, the first end of a brake tube is jammed in the fixed support, and the tail end of the brake cable and the tail end of the brake tube are fixed on a front support and a rear support of the pedal portion in a clamping mode respectively. According to the rear-hanging type pedestal pan cushion turning and driving device and the fixing seat, a pedestal pan cushion is driven by a pedal to rotate ninety degrees, the purposes that the pedal is turned over when a person comes and automatically drops when the person leaves, use is very convenient, the hand does not need to touch the pedestal pan cushion, and cleanliness and sanitation are achieved; any modification does not need to be performed on an existing pedestal pan or cushion, and therefore the advantages of being wider in popularization and low in cost can be achieved; normal usage of the pedestal pan is not influenced, the invisibility is good, and the appearance is attractive and appropriate.
Owner:孙明英
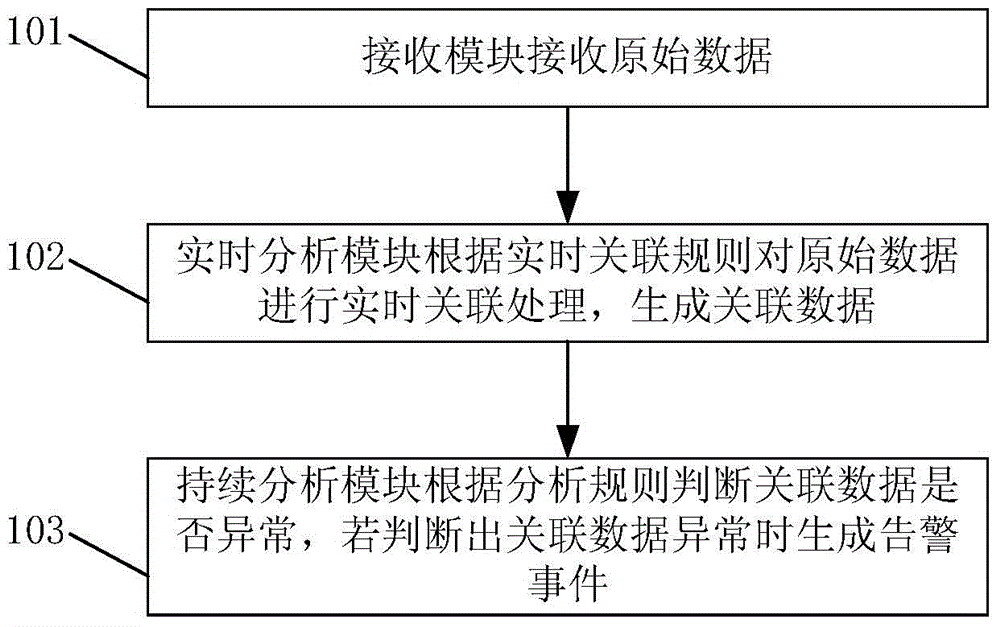
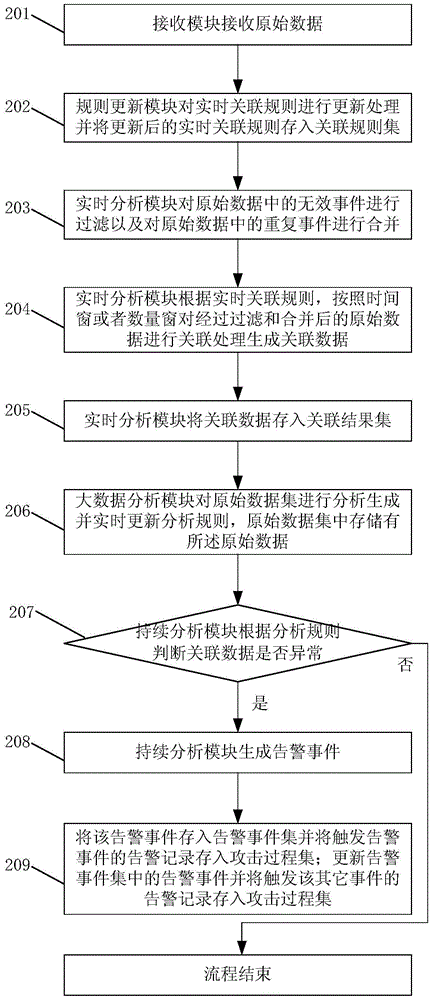
Association analysis method and association analysis system
InactiveCN105681286ALong cycleStrong concealmentData switching networksReal time analysisData mining
The invention discloses an association analysis method and an association analysis system. The method comprises the steps that: a receiving module receives original data; a real-time analysis module carries out real-time association processing on the original data according to a real-time association rule to generate association data; and a continuous analysis module judges whether the association data are abnormal according to an analysis rule and generates an alarm event when judging that the association data are abnormal. In the association analysis method in the technical scheme provided by the invention, the receiving module receives the original data, the real-time analysis module carries out the real-time association processing on the original data according to the real-time association rule to generate the association data, the continuous analysis module judges whether the association data are abnormal according to the analysis rule and generates the alarm event when judging that the association data are abnormal, and long-term association analysis is realized, so attack behaviors with long periods and strong concealment can be found.
Owner:CEC CYBERSPACE GREAT WALL
Concealed communication method
The invention discloses a concealed communication method. The method comprises the following steps that encryption is performed on first original data on a sending end and a receiving end so as to form concealed information and generate a binary sequence of the concealed information, and the binary sequence is recorded as a sending-end original cipher; the binary sequence of the concealed information is converted into a sending-end Chinese character sequence and is sent to the receiving end; the receiving end receives the concealed information and carries out decryption. Through the above mode, by using the concealed communication method provided in the invention, a Chinese character coding is used to embed the concealed communication into a Chinese character; through analyzing the concealed information which needs to be transmitted, the concealed information is converted into English letters in a split-up mode and then are converted into a Chinese character; then the Chinese character is transmitted to a target site through forms of a mail, a webpage and a picture so that a purpose of transmitting the concealed information is reached. A concealed channel established by using the method possesses advantages of a high capacity and high concealed performance. In the method, the concealed information is packed and transmitted in a data portion of an IP data packet.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
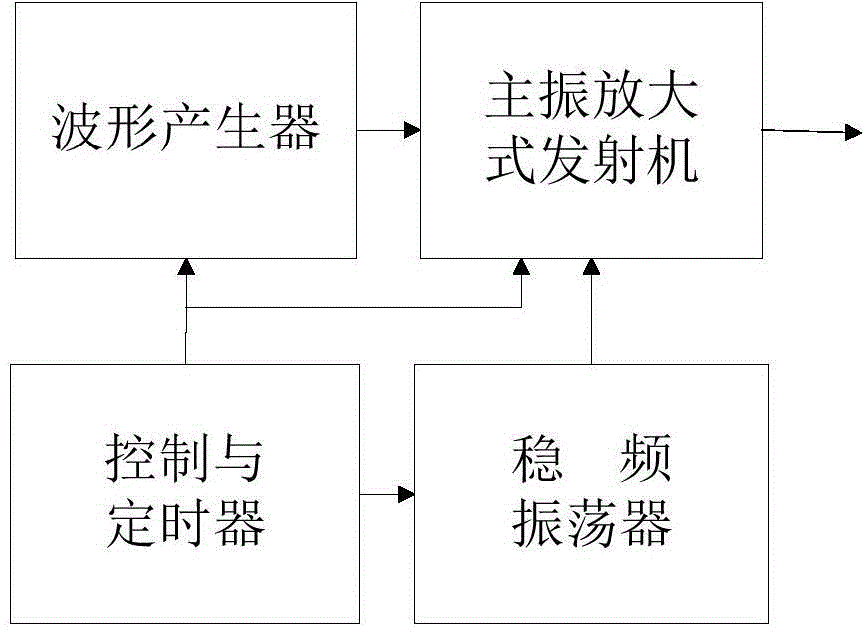
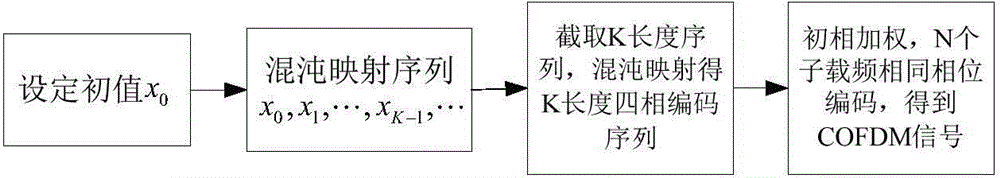
Radar pulse transmitter and generation method of orthogonal frequency division multiplexing (OFDM) pulse signal
InactiveCN104569927ALow intercept goodImprove securityWave based measurement systemsRadar systemsWave shape
The invention belongs to the field of pulse transmitters of radar systems and particularly relates to a generation method of an orthogonal frequency division multiplexing (OFDM) pulse signal and a radar transmitter generating radar signals through the method. The method aims to solve the technical problem of how to enable the radar transmitter to output an expected complicated radar signal waveform, wherein the waveform has a low intercept probability and a low envelope peak-to-average ratio, the number of sub-carrier frequencies is at will and the coding length is at will. The method is technically characterized by including the steps that a coding sequence at any length is constructed based on a Bernoulli chaos; the sub-carrier frequencies at any number are modulated; the envelope peak-to-average ratio is reduced through sub-carrier frequency initial phase weighting, and then the phase encoding OFDM signal is obtained.
Owner:NAT UNIV OF DEFENSE TECH
Underwater robot
InactiveCN105083510AImprove efficiencyReduce noisePropulsive elements of non-rotary typeRudderAdaptive capacity
The invention discloses an underwater robot. The underwater robot comprises a trunk. Boosting fins and a swinging rudder are installed on the trunk, the trunk is made of deformable materials, and a driving film for enabling the trunk to be deformed is pasted to the trunk. The underwater robot is simple in structure and easy to manufacture, a transmitting mechanism is avoided, and the using efficiency of driving force is high; the underwater robot does not need to be driven through a motor, and is small in noise and good in concealment; in addition, the underwater robot is of a flexible structure, the whole compression resistance and the whole impacting resistance are high, compressed deformation can be avoided, and the adaptive capacity to the environment is quite high.
Owner:ZHEJIANG UNIV
Concealed air bag system for boat
ActiveCN104986303AHigh degree of automationImproving the efficiency of emergency response to dangerous situationsVessel safetyPropellerEngineering
The invention provides a concealed air bag system for a boat. The concealed air bag system comprises an air bag, a guide rail plate, a hydraulic propeller, a locking device, an air inflation device, and an electric control system. If a boat crashes on the rocks, water enters into the board, and the boat inclines and sinks, the electric control system responds to the danger and early warns, then the an air bag guide cabin door is opened, the hydraulic propeller is started to push the guide rail plate out of the guide rail cabin; the support legs of the guide rail plate are unfolded to make horseshoes adhered on the pointed area of the inner wall of the cabin, the hydraulic propeller continues to pressure and push to make the horseshoes firmly adhered on the inner wall of the cabin, so the hydraulic propeller can be locked under the function of pressure; the horseshoes are locked by locking clamps so as to prevent the horseshoes from sliding; hooks on the guide rail plate can be used for locking a deck; after the guide rail plate is firmly locked, the air bag is inflated and unfolded; and the air inflation device is powered off after air inflation. The concealed air bag system can be reasonably arranged on the periphery of a boat in depend on the size, the tonnage, the shape and the use of the boat, and the concealed air bag system is high in concealment and degree of automation, firm and safe.
Owner:董志豪
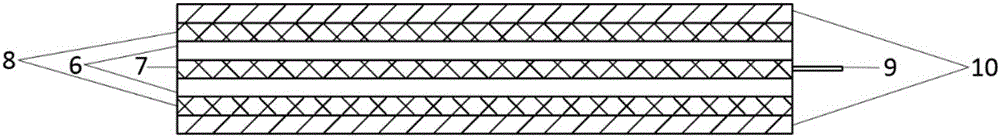
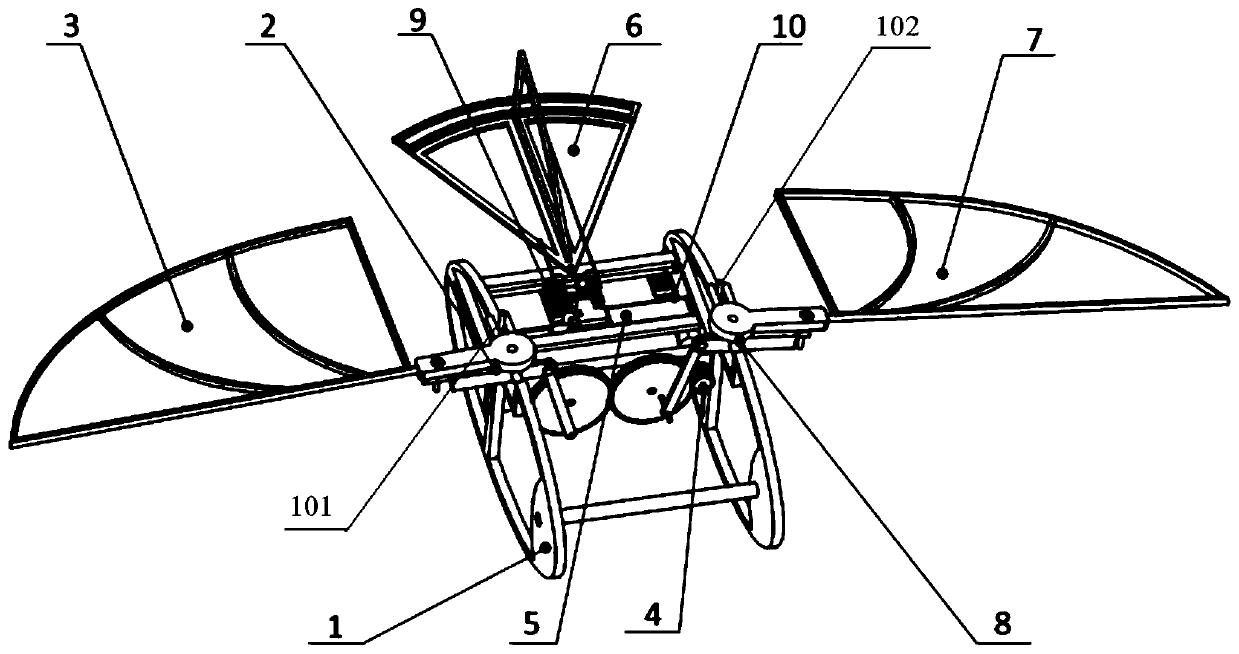
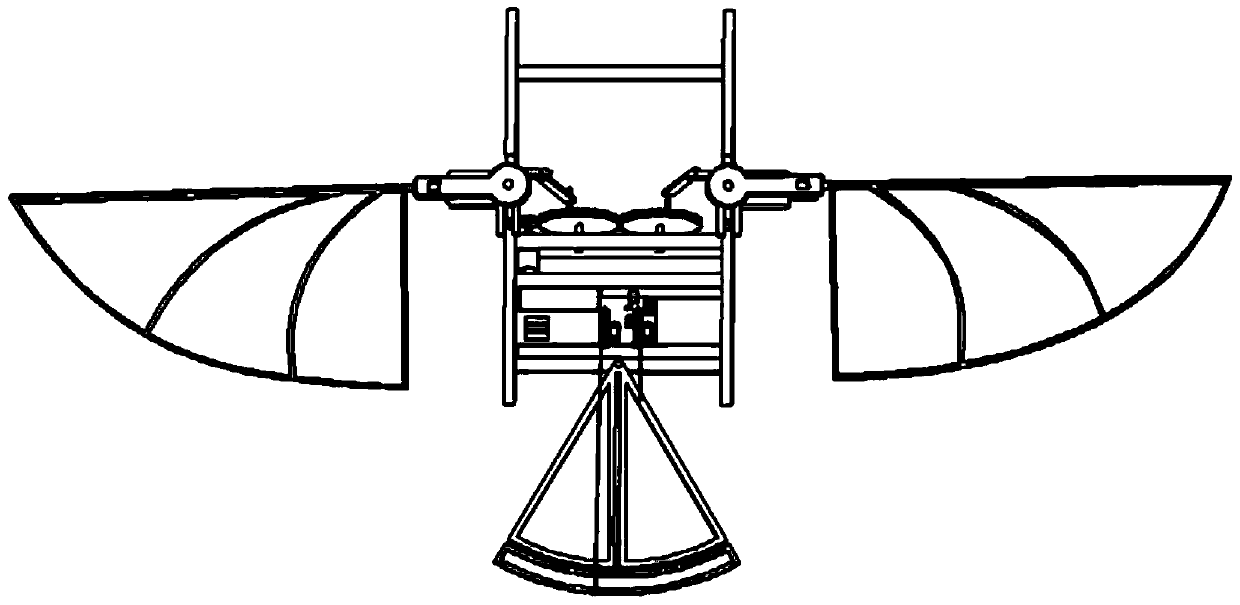
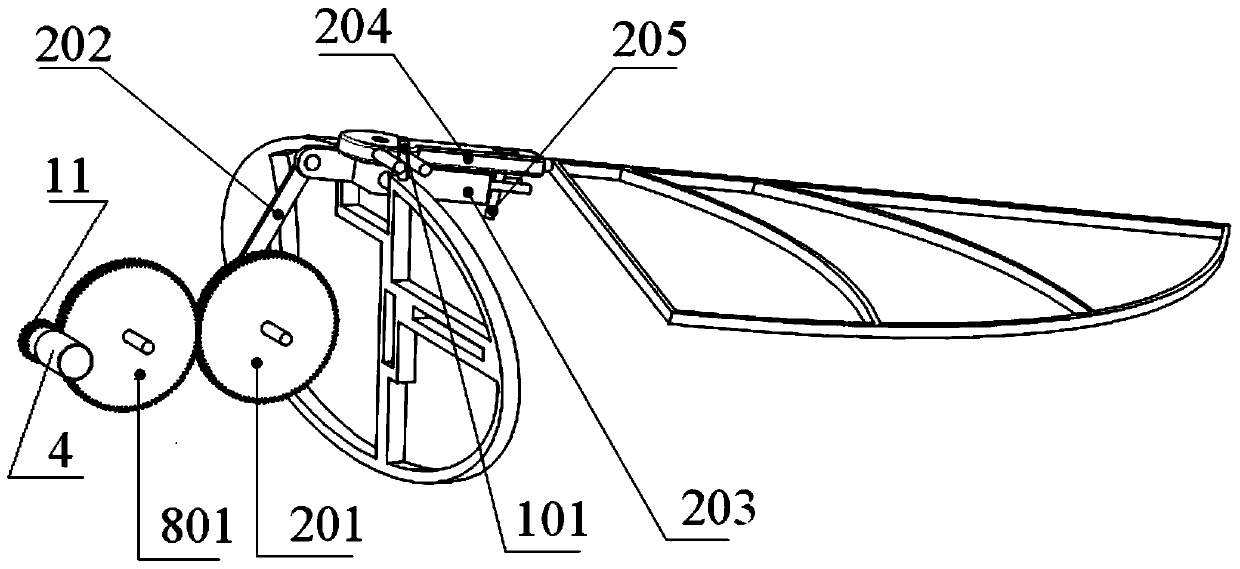
Passive-torsion sweeping-type three-degree-of-freedom micro flapping wing air vehicle
ActiveCN110171567AImprove aerodynamic performanceNovel structureOrnithoptersFlapping wingFlight vehicle
The invention relates to a passive-torsion sweeping-type three-degree-of-freedom micro flapping wing air vehicle, and belongs to a micro flapping wing air vehicle. A motor, a battery, a steering engine and a control circuit board are fixedly connected to the middle of a rack and connected through a wire, an empennage is fixedly connected to the tail of the rack and composed of a horizontal empennage and a vertical empennage, and the motor is connected with a speed reducing gear; the rack is of a rack structure which is symmetrical on the left side and the right side; a left flapping mechanismand a right flapping mechanism are the same in structure and parameter, are symmetrically arranged on the left side and the right side of the rack correspondingly, and are hinged to the rack; and a right flapping wing and a left flapping wing are the same in structure and parameter and are hinged to the right flapping mechanism and the left flapping mechanism correspondingly. The passive-torsion sweeping-type three-degree-of-freedom micro flapping wing air vehicle has the advantages that the structure is novel, the passive-torsion sweeping-type three-degree-of-freedom micro flapping wing air vehicle has the three degrees of freedom of flapping, sweeping and rotating, the movement trajectories of wingtips of the two wings are each in a spatial 8 shape and are similar to the movement modes of part of birds and flying insects in the natural world, the wings are subjected to passive sweeping and torsion, the aerodynamic performance of the air vehicle is improved, the bionic degree is high,and maneuverability is high.
Owner:JILIN UNIV
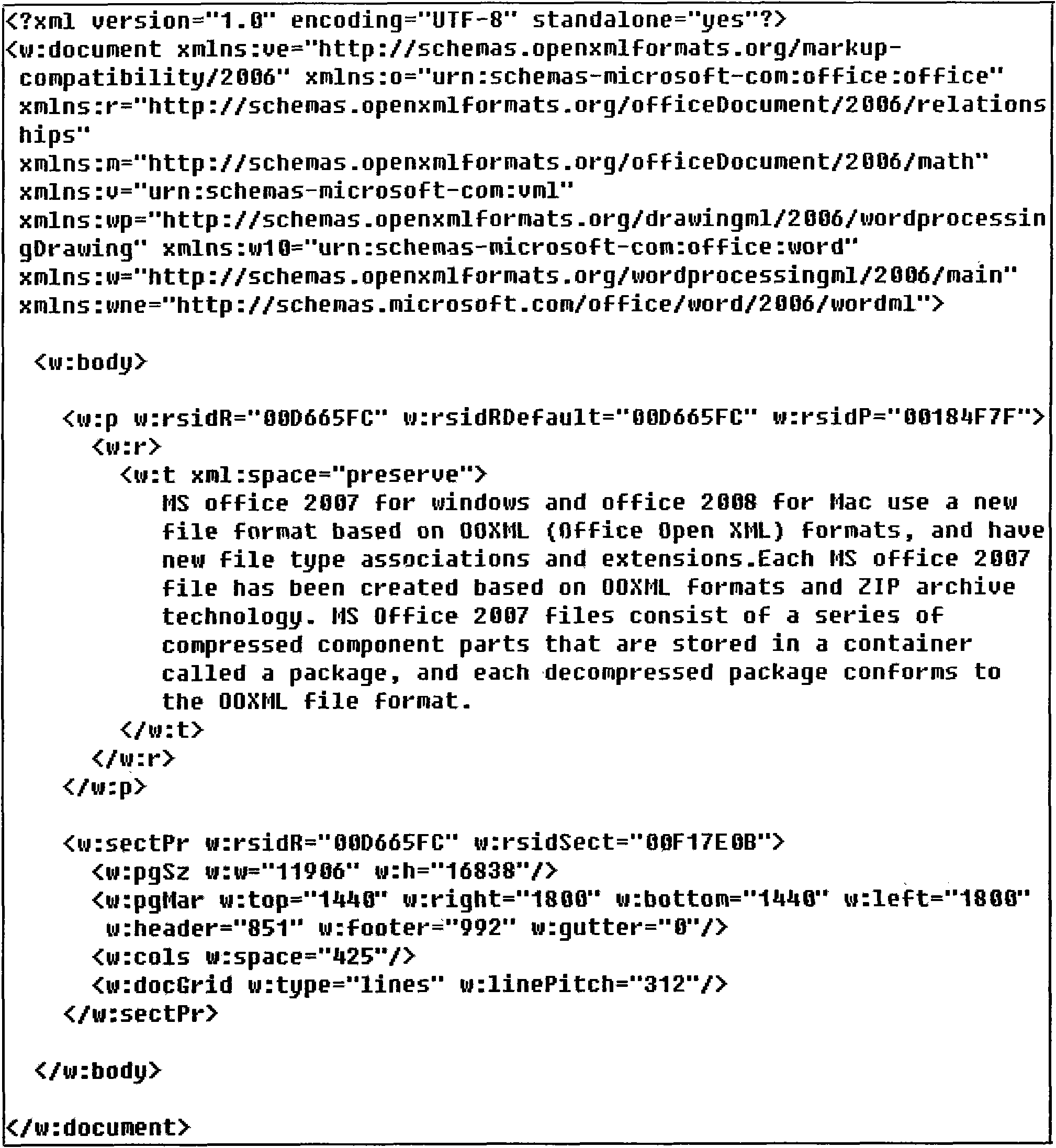
Method and device for hiding information based on word2007 text segmentation
InactiveCN102096787AWill not affect the displayStrong concealmentDigital data protectionSpecial data processing applicationsExtensible markupMicrosoft Office
The invention relates to a method and a device for hiding information based on word2007 text segmentation. An Office Open extensible markup language (XML) file format is a new file format which is adopted by Microsoft office 2007 and later versions thereof. In the method for hiding secret information, the secret information is converted into a numerical value so as to be embedded into run number of each paragraph according to the coding requirement of the secret information to be transmitted based on the paragraph serving as a unit by segmenting the number of run elements in each paragraph. Meanwhile, the robustness of the hiding method is improved by adding robust marks into the segmented run elements. The extraction process of the secret information is a reverse embedding process. In the method, any displayed content of an electronic document is not changed; the method has extremely strong concealment; the robustness of hidden information is enhanced by adding the robust marks; and the method can be applied to hidden transmission of confidential information such as national defense, politics, commerce and the like.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
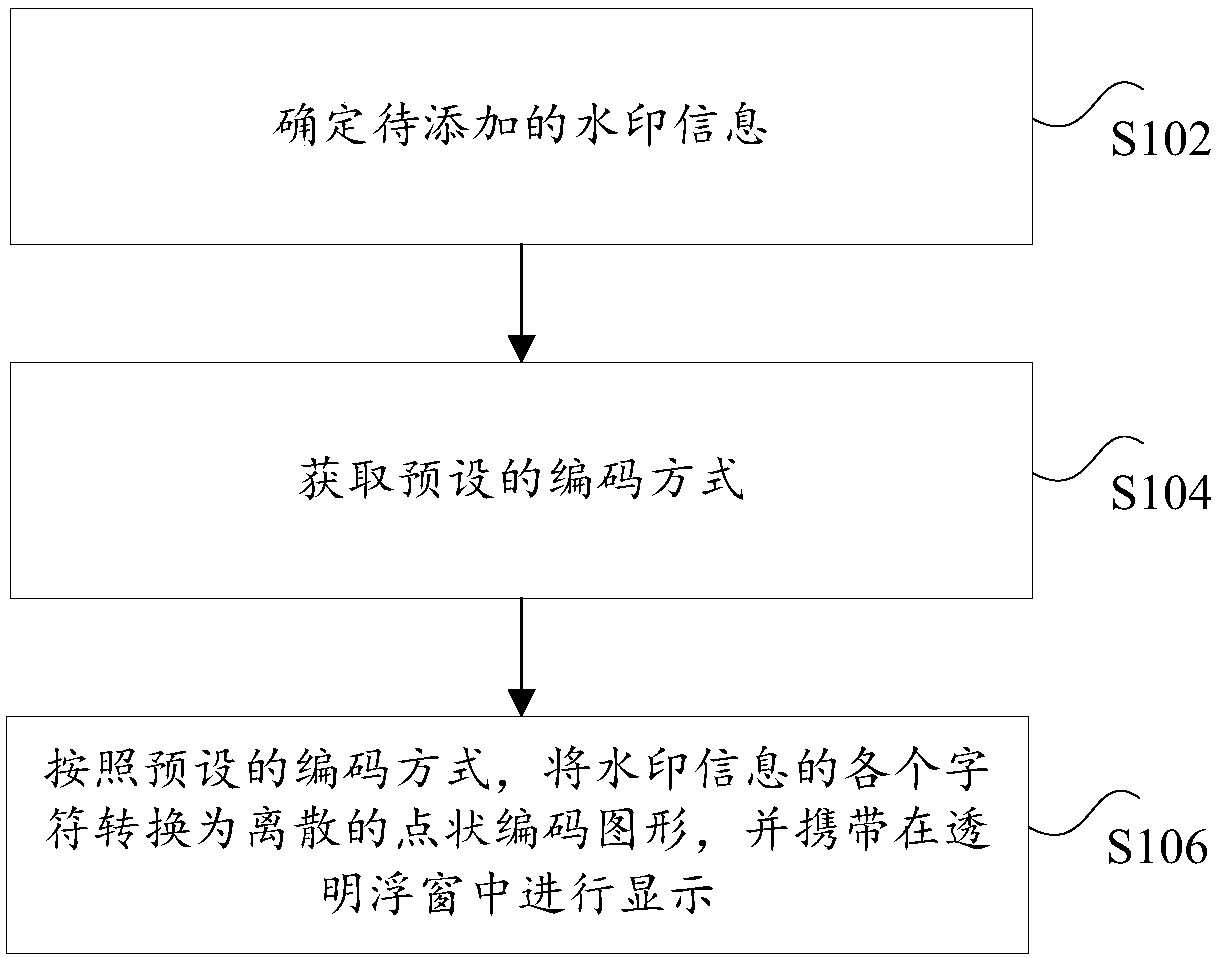
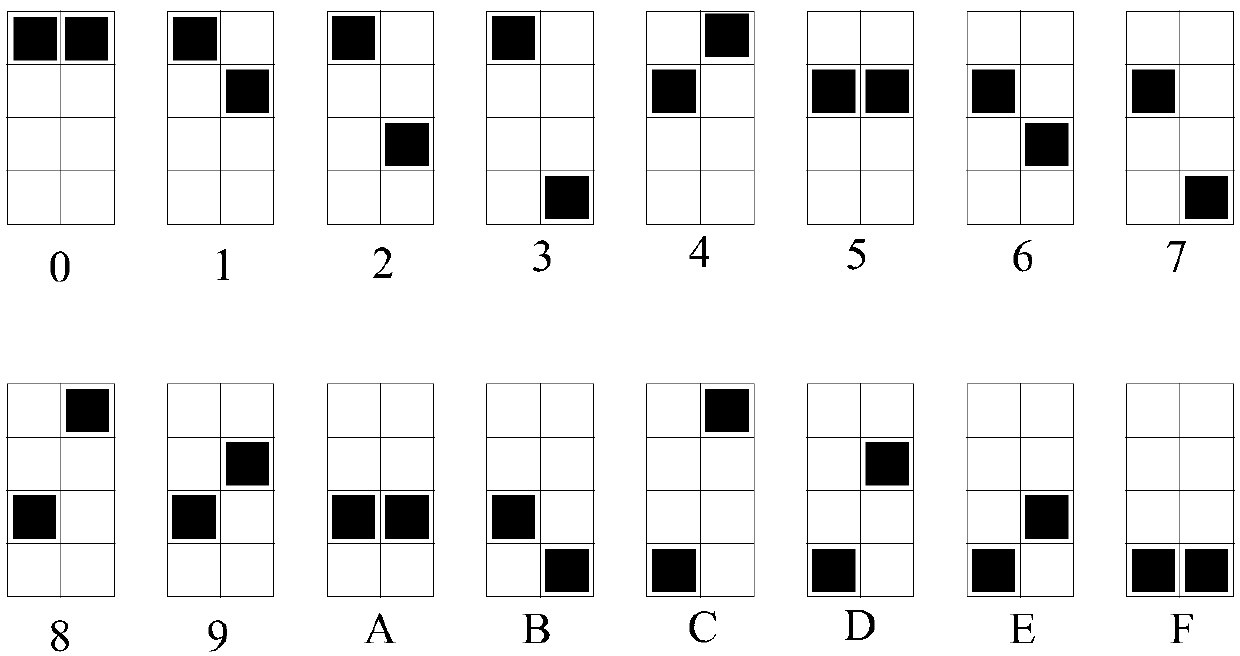
Watermark display method, device and system
ActiveCN107610038AAchieve the purpose of protectionMitigate less secure technical issuesImage codingImage data processing detailsGraphicsInvisibility
The invention provides a watermark display method, a device and a system and relates to the technical field of information media. The method comprises the following steps of determining the to-be-added watermark information; acquiring a preset coding mode, wherein the preset coding mode comprises the display conversion relation between different characters and dot-shaped coded graphs; according tothe preset coding mode, converting each character of the watermark information into a discrete point-shaped coded graph and displaying the discrete point-shaped coded graph in a transparent floatingwindow. The transparent floating window is a floating window which is arranged on a display screen in advance. The technical problem that the data safety is low due to poor invisibility of an existingwatermark technology is solved.
Owner:NEW H3C TECH CO LTD
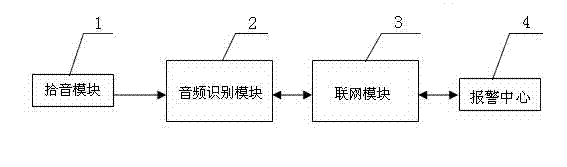
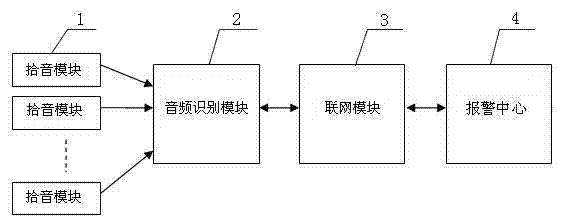
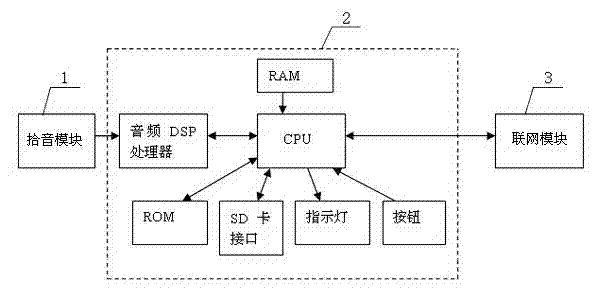
Networking alarm apparatus based on audio identification
The invention, which belongs to the alarm detection and networking alarm technology field, particularly relates to a networking alarm apparatus based on audio identification. The networking alarm apparatus is characterized in that: the apparatus comprises at least a pickup module, an audio identification module and a networking module; the pickup module and the audio identification module are successively connected with the networking module; the pickup module collects an audio signal; the audio identification module carries out analysis processing and identification on the audio signal collected by the pickup module as well as carries out comparison on the collected audio signal and an audio sample feature database stored in the audio identification module; and the networking module is connected with a telephone network or an internet and transmits alarm information to an alarm center. According to the invention, an audio identification technology is directly applied to alarm detection; a sound source of an alarm / dangerous scene is automatically collected and identified; information of an alarm property and an alarm site and the like is reported to a networking alarm center; and remote real-time monitoring or watching can be carried out on recording fragments before and after the alarm occurrence or video fragments of an associated camera.
Owner:杭州威威网络科技有限公司
Space object dimension acquisition method based on photoelectric observation
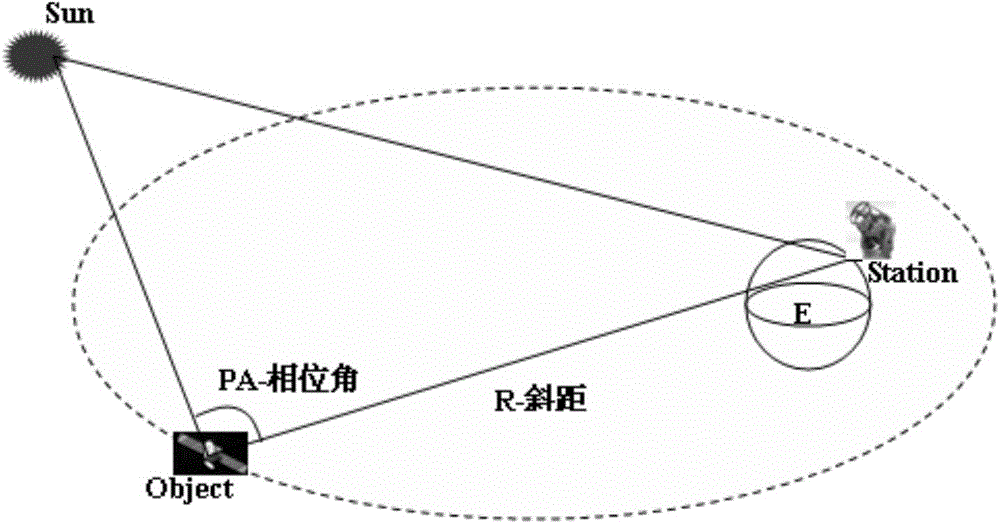
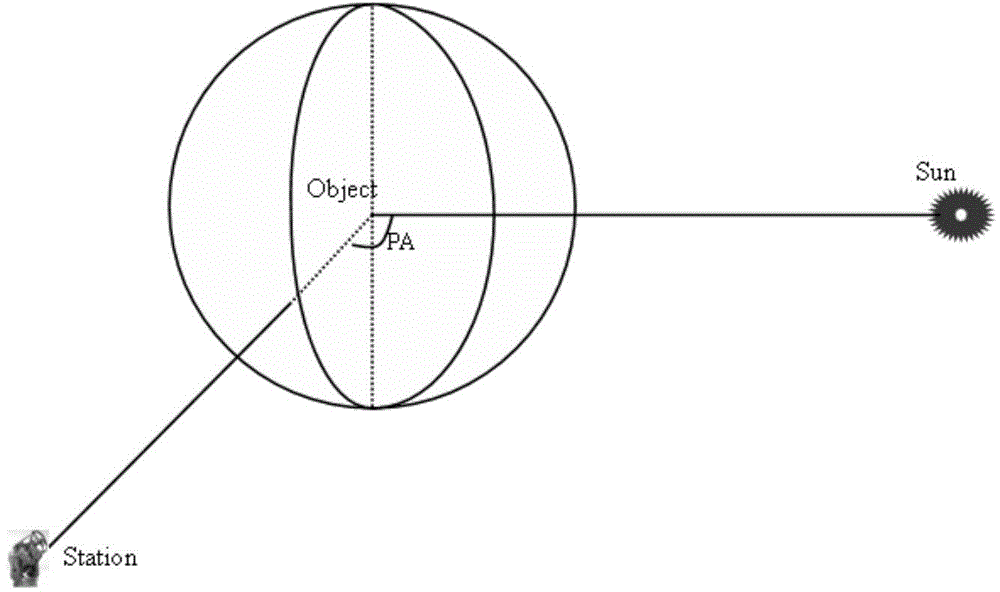
ActiveCN104101297AHas passive passive reception characteristicsProbing behavior is not easy to detectUsing optical meansElectricityScattering cross-section
The invention belongs to the field of foundation photoelectric observation and discloses a space object dimension acquisition method based on photoelectric observation. The method includes the steps of obtaining high-precision photometric information of a space object through observation; obtaining photometric calibration parameters through orbital calculation; performing photometric correction on the space object; calculating the dimension of the space object. The space object dimension acquisition method based on photoelectric observation overcomes the lack of observational capability on middle-orbit and high-orbit space objects in a radar method and is a method for acquiring the optical dimension of the middle-orbit and high-orbit space objects with an optical telescope system by obtaining the parameters of the optical scattering cross section indicating the dimension of the space object. Compared with a wireless method, the space object dimension acquisition method based on photoelectric observation can accurately obtain the dimension of the space object due to the fact that an optical band is longer than a radio band and not sensitive to edges and corners. The space object dimension acquisition method based on photoelectric observation can be rapidly popularized and applied to existing foundation photoelectric detection devices in China without hardware modification to form a certain capability of determining the dimension of the space object.
Owner:NAT ASTRONOMICAL OBSERVATORIES CHINESE ACAD OF SCI
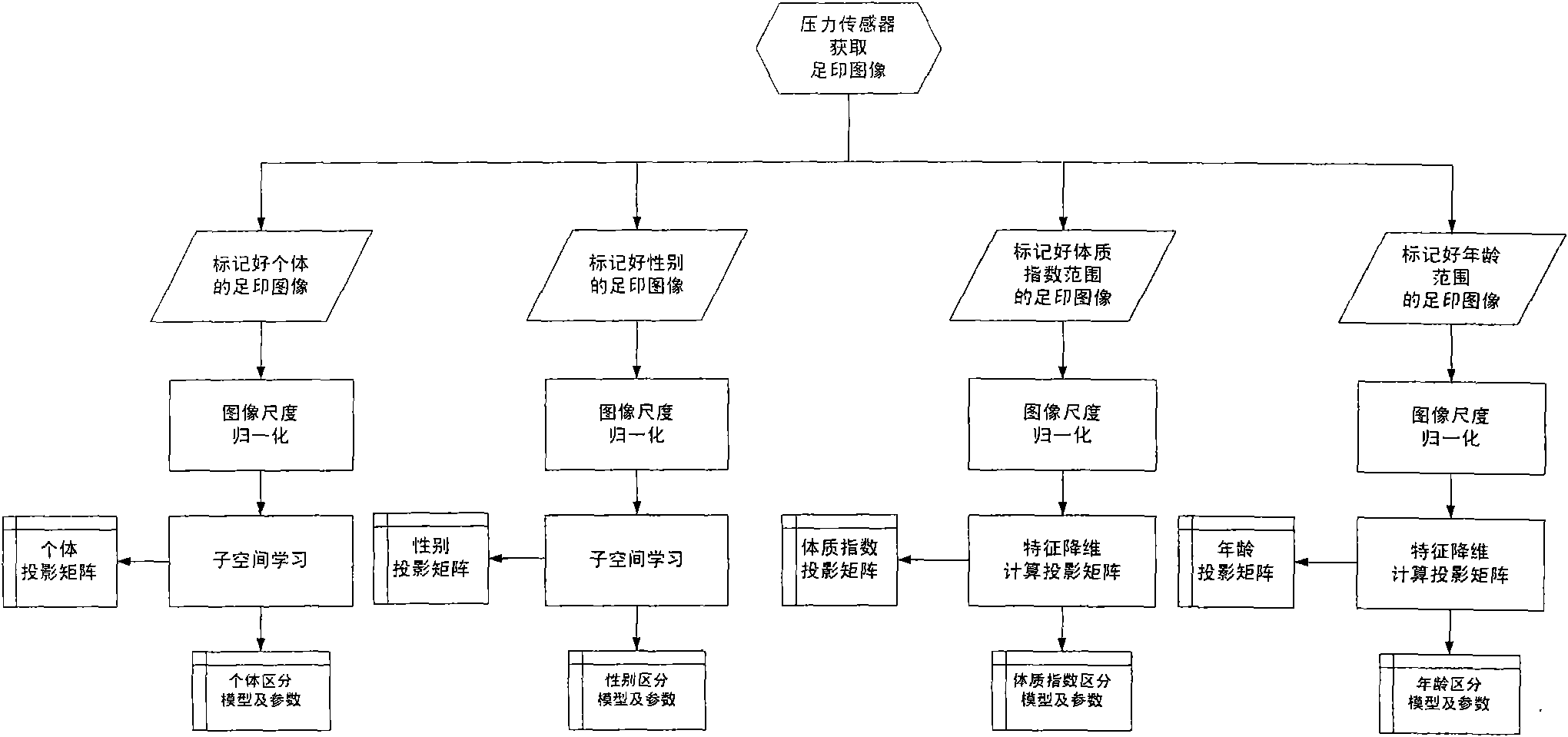
Method for biophysical analysis and identification of human body based on pressure accumulated footprint image
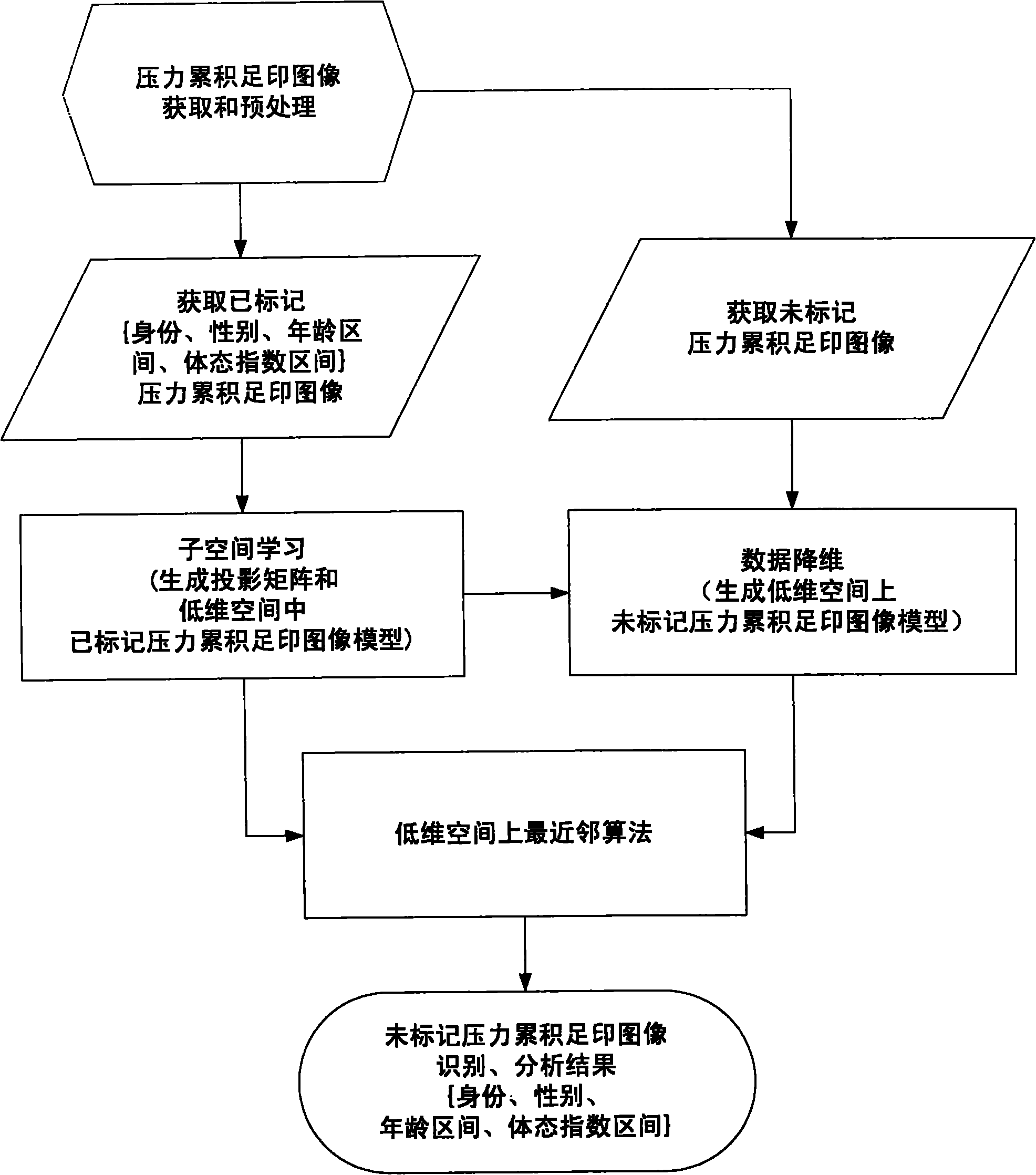
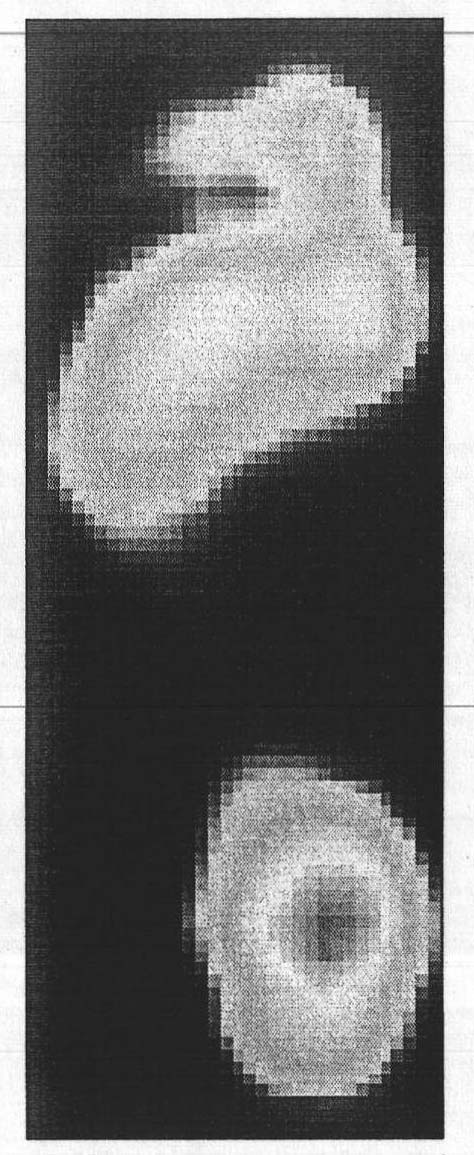
InactiveCN101874738AStrong concealmentImprove the accuracy of recognitionPerson identificationSensorsComputer visionNear neighbor
The invention discloses a method for biophysical analysis and identification of a human body based on a pressure accumulated footprint image, comprising the following steps of: acquiring a pressure accumulated footprint image and preprocessing the image; generating corresponding projection matrixes of physiologic information and identity information and a corresponding model vector of the pressure accumulated footprint image in a low-dimensional space aiming at groups of different people marked with different sexes, different intervals and a physical index interval and pressure accumulated footprint images by applying a subspace method; for the non-marked pressure accumulated footprint images, generating non-marked image vectors in the low-dimensional space through acquired projection matrixes of different physiologic information and identity information; and calculating and comparing the distance between the vectors of the non-marked pressure accumulated footprint images and the model vectors of the pressure accumulated footprint images of different physiologic information and identity information by using a nearest neighbor algorithm to obtain the discrimination of the non-marked pressure accumulated footprint images corresponding to the sexes, the age intervals, the physical index intervals and the identities of people.
Owner:INST OF AUTOMATION CHINESE ACAD OF SCI
Dolphin click simulating underwater acoustic communication method based on time-frequency spectrum translation
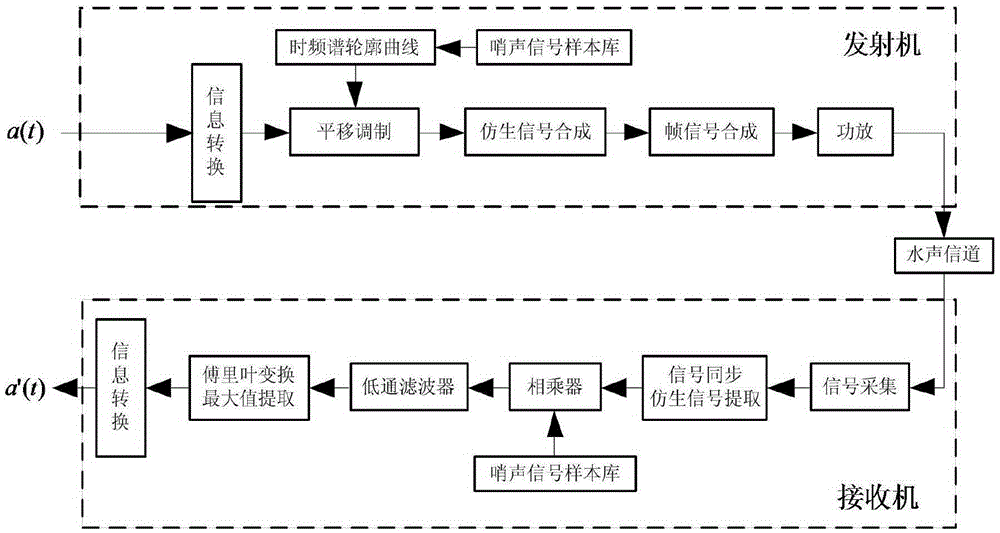
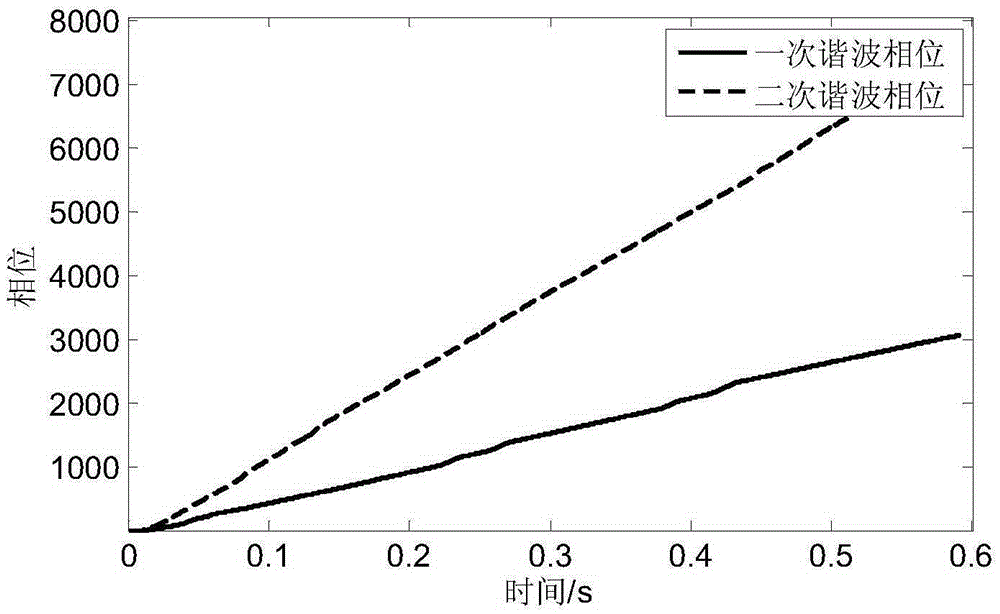
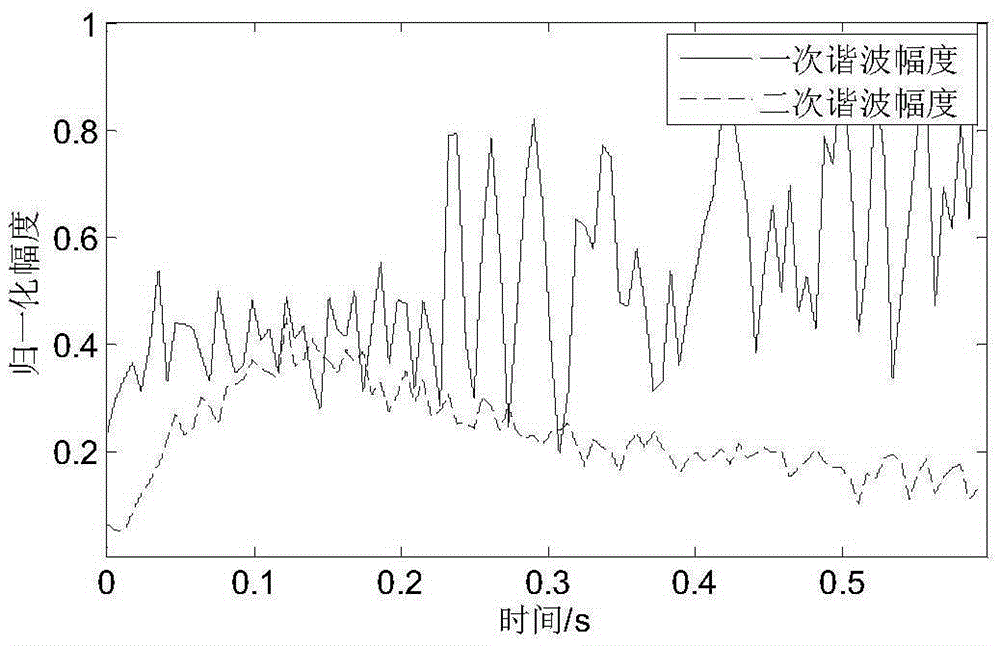
ActiveCN105391501ANovel and effective communication methodsNovel and effective modulation methodTransmissionFrequency spectrumTime frequency spectrum
The invention discloses a dolphin click simulating underwater acoustic communication method based on time-frequency spectrum translation. At a transmitting end, the time-frequency spectrum contour curve of a real dolphin whistle signal is translated in the vertical direction for loading digital information; signal combination is performed based on a modulated contour curve for obtaining a bionic communication signal; and an original whistle signal is added in front of the bionic communication signal as a synchronization signal, thereby forming a transmission signal frame. At the receiving end, the starting position of the bionic communication signal is determined through synchronization signal correlation; multiplication filtering and Fourier transform information demodulation or modulation are performed on the received bionic communication signal, thereby realizing information decoding. The bionic communication method has no specific requirement for characteristic and number of real dolphin whistle signal sample, and the combined coding signal accords with the characteristic of the dolphin whistle signal. Therefore the dolphin click simulating underwater acoustic communication method has high concealing performance.
Owner:HARBIN ENG UNIV
Loran-C passive radar TOA estimating method based on total variation and compressed sensing
InactiveCN104007421AUndetectableEffective targeting range is considerableBeacon systemsPassive radarCompressed sensing
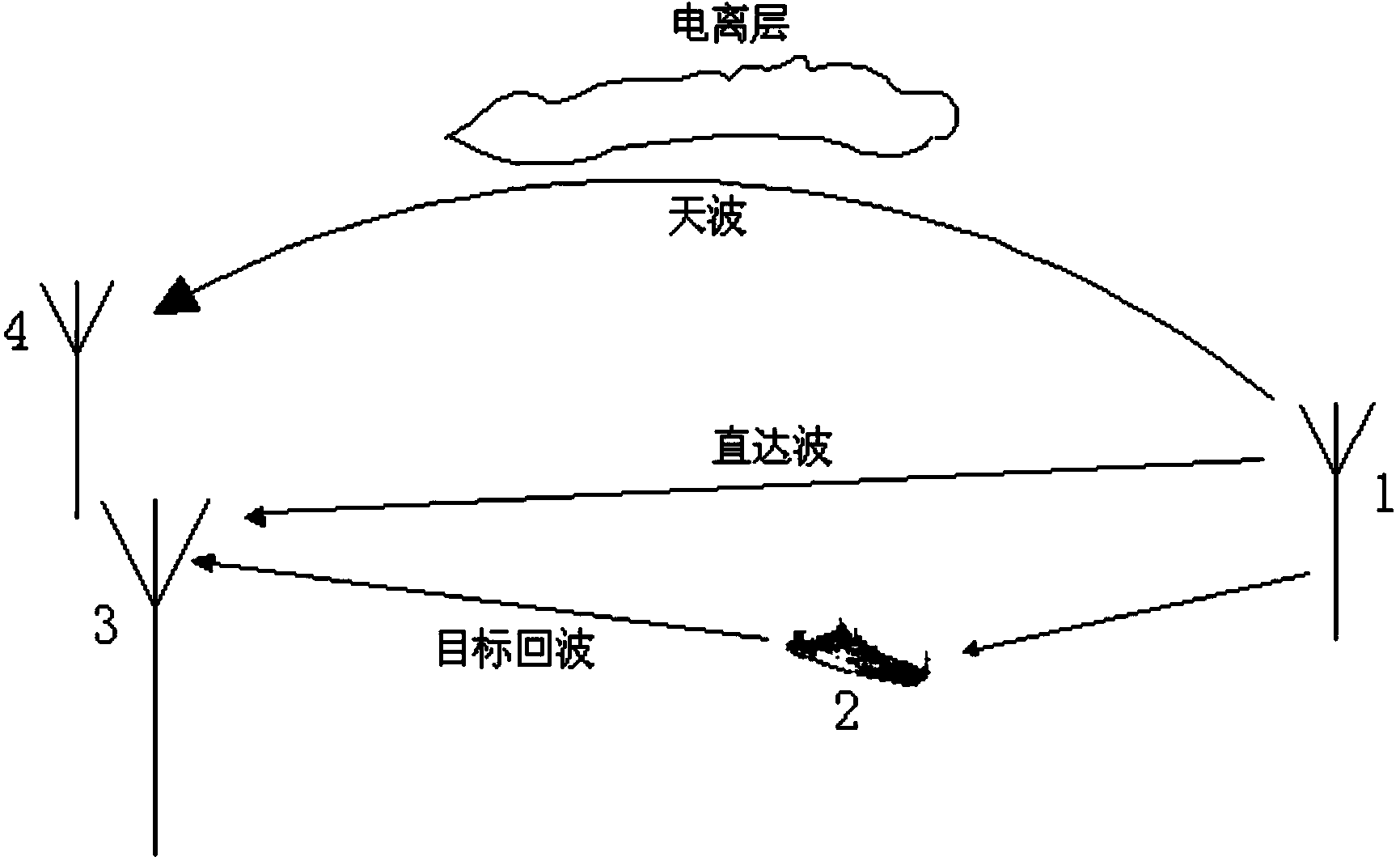
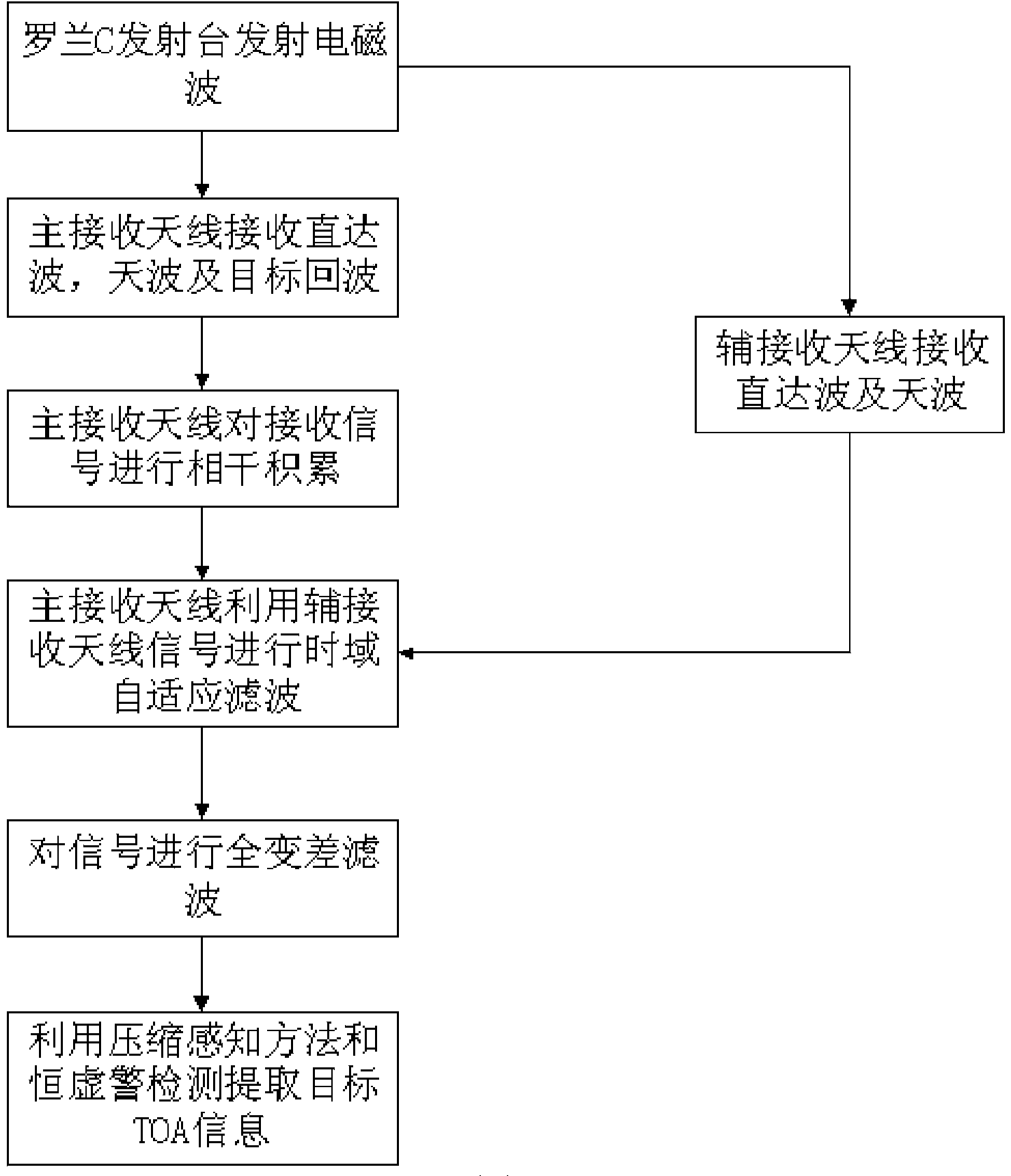
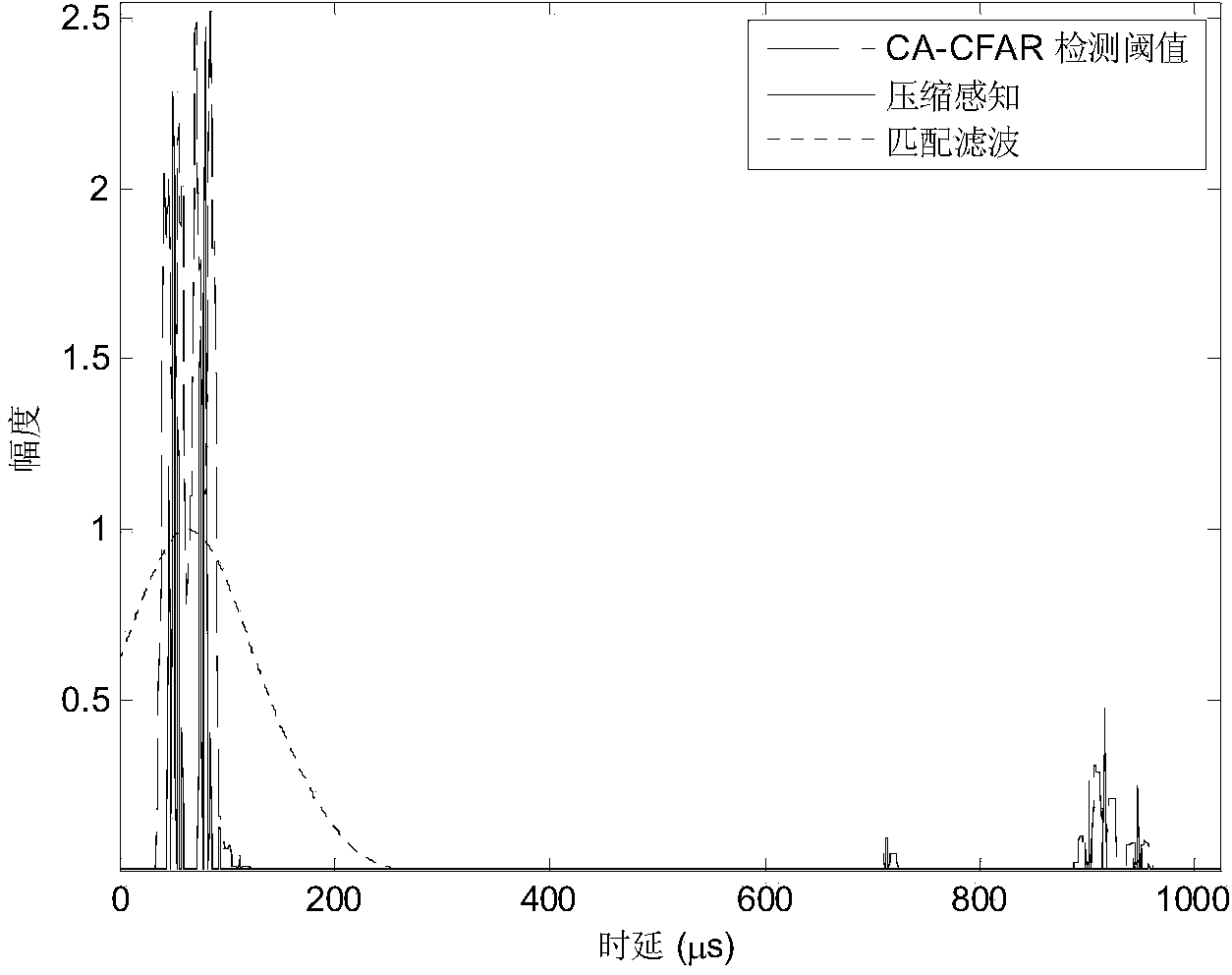
The invention belongs to the technical field of radar target passive positioning and particularly relates to a Loran-C passive radar TOA estimating method based on a total variation and compressed sensing. The Loran-C passive radar TOA estimating method based on the total variation and compressed sensing comprises the following steps that time domain self-adaptive filtering is carried out on Loran-C direct wave signals, Loran-C sky wave signals and Loran-C target echo signals to obtain signals after time domain self-adaptive filtering is carried out, wherein the Loran-C direct wave signals, the Loran-C sky wave signals and the Loran-C target echo signals are received by a passive radar; total variation filtering is carried out on the signals obtained after time domain self-adaptive filtering, and signals after total variation filtering is carried out are obtained; discrete Fourier transformation is carried out on the signals obtained after total variation filtering, and frequency domain signals after total variation filtering is carried out are obtained; according to the frequency domain signals obtained after total variation filtering, a compressed sensing method is adopted for reconstructing Loran-C target echo time domain sparse signals; according to the Loran-C target echo time domain sparse signals, the TOA of Loran-C target echoes is obtained.
Owner:XIDIAN UNIV
Digital image feedback encryption method based on image network
ActiveCN107220923AIncreased complexityStrong pseudo-randomnessImage data processing detailsPlaintextDiffusion
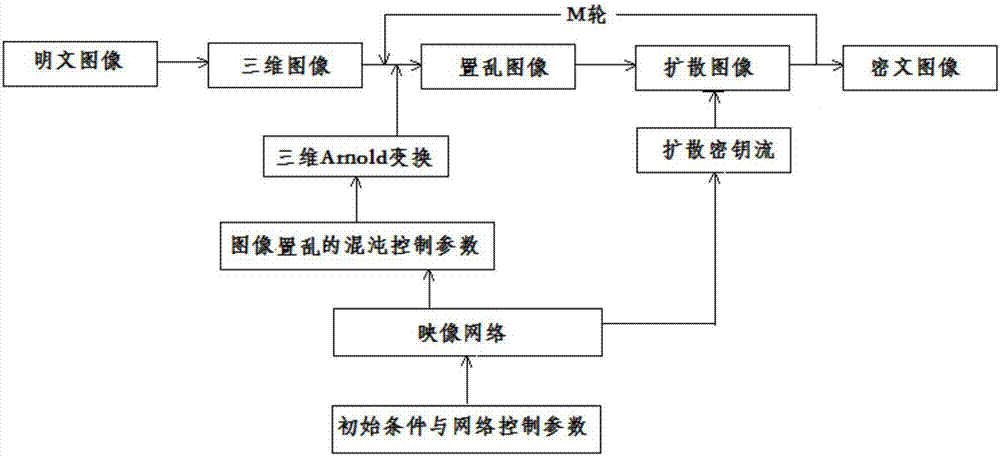
The invention discloses a digital image feedback encryption method based on an image network. The method comprises the following steps of processing a digital plaintext image; constructing the image network in which a node is a super-chaotic system and a non-neighbor connection mode is possessed; through three-dimensional Arnold, converting a scrambling image, wherein a scrambling matrix is driven by image-network space-time chaotic display and a current plaintext image; combining feedback information of the current plaintext image and a cryptograph image and carrying out image diffusion processing; alternatively operating scrambling and diffusion multiple times and acquiring the cryptograph image. In an encryption system, a scrambling-diffusion alternative-operated loop iteration structure is designed; during an encryption process, plaintext and cryptograph feedback mechanisms are introduced; and during each encryption, the used scrambling matrix and a secret key flow are dynamically changed and are different. An experiment result shows that the encryption method possesses high safety and high efficiency; and a capability of resisting various plaintext attacks, statistics attacks, violence attacks and difference attacks is high.
Owner:SHAANXI NORMAL UNIV
Intelligent equipment and unlock method thereof
InactiveCN104462938AEasy to rememberEasy inputDigital data authenticationMobile phoneIntelligent equipment
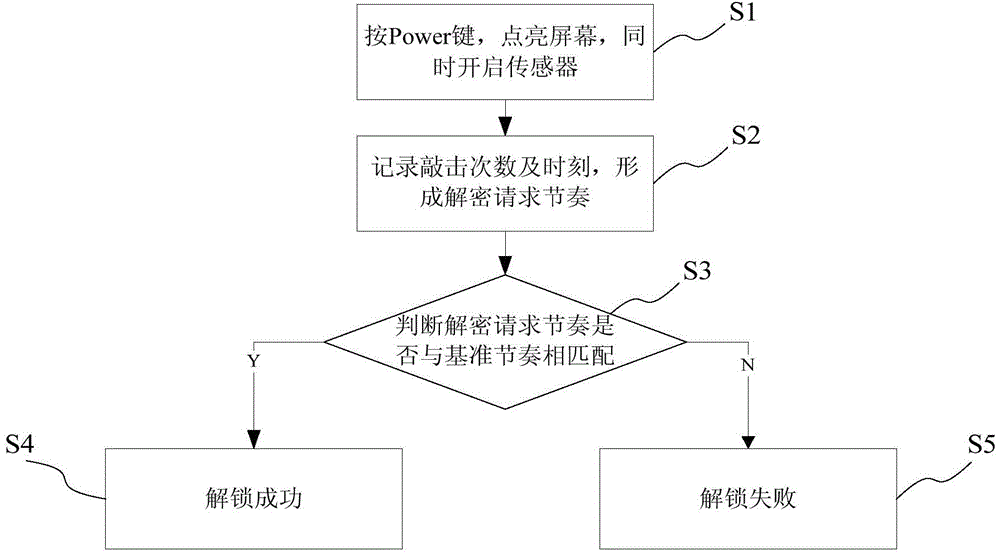
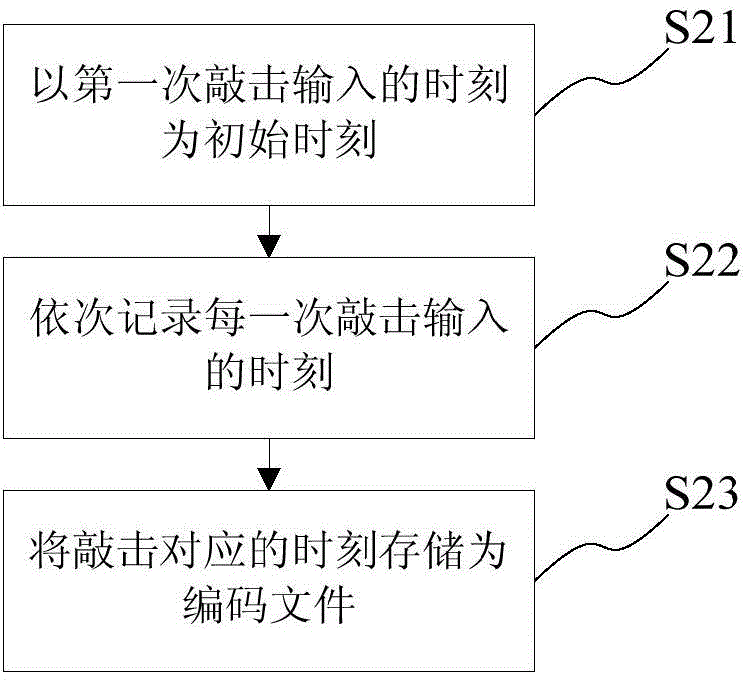
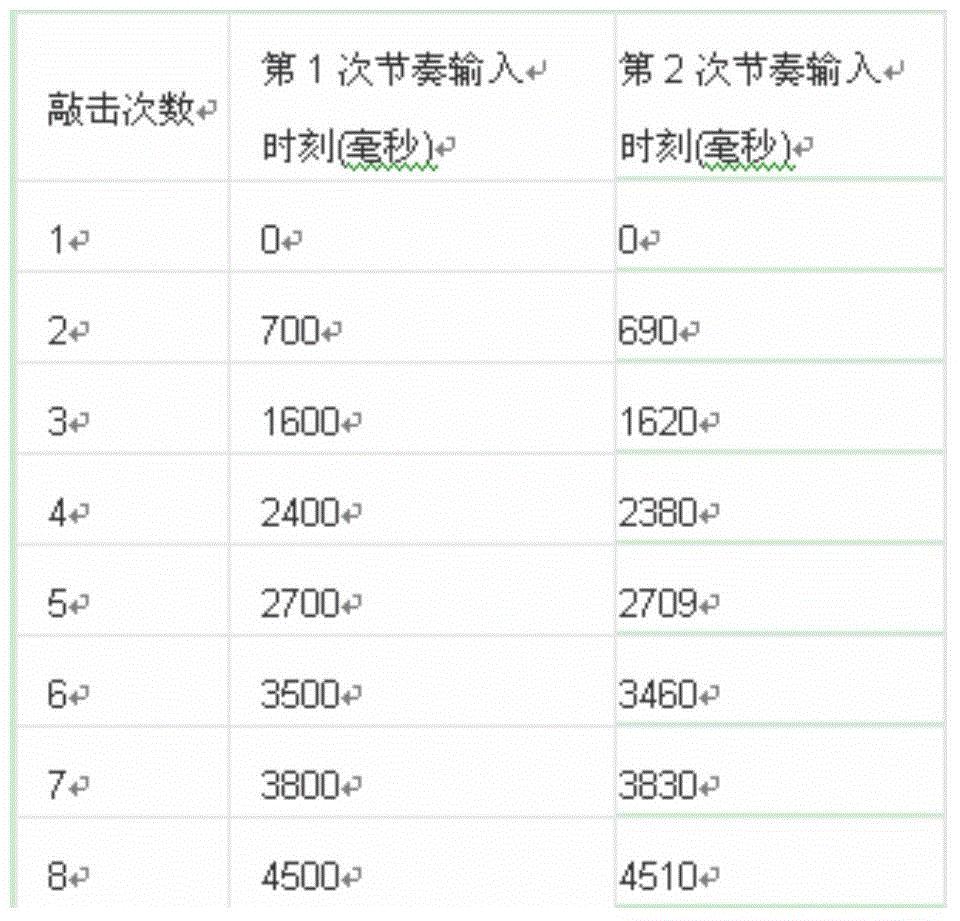
The invention provides intelligent equipment and an unlock method thereof. The unlock method includes when the intelligent equipment, such as an intelligent mobile phone or tablet, is in the interface locked situation, detecting the equipment clicking actions, recording the times and rhymes of the clicking actions, and judging whether the times and rhymes match with preset reference rhymes or not; if the input clicking times are consistent with those of the reference rhymes and the errors of the input clicking rhymes and reference rhymes are in a permitted range, determining the input is correct, unlocking the mobile phone successfully, and switching the interface into the unlocking state; or failing in unlocking, and maintaining the locking state of the user's interface.
Owner:PHICOMM (SHANGHAI) CO LTD
Image encryption method based on projection synchronization of hyperchaotic system
ActiveCN106997606AHas cryptographic propertiesIncreased complexityImage codingSecuring communication by chaotic signalsChosen-plaintext attackChaotic systems
The invention discloses an image encryption method based on the projection synchronization of a hyperchaotic system. The method comprises the steps of plaintext image quantifying and ciphertext image quantifying. The first step comprises generating of a hyperchaotic sequence of a hyperchaotic driving system, image row scrambling, image column scrambling, image diffusing, circulation image row scrambling, image column scrambling, multiple rounds of image diffusing, and a ciphertext image is acquired. The second step comprises ciphertext image quantifying, generating of a hyperchaotic sequence of a hyperchaotic response system, time acquiring, column scrambling index and line scrambling index valuing, image inverse diffusing, image inverse column scrambling, image inverse row scrambling, circulation image inverse diffusing, image inverse column scrambling, multiple rounds of image inverse row scrambling, and a decrypted image is acquired. According to the invention, a feedback mechanism with the current image is introduced; the row (column) scrambling address code and the key matrix are dynamically changed in each round of encryption; experiments show that the method has the advantages of good encryption effect, high security and large key space, can resist selected plaintext attacks, known plaintext attacks and various statistical attacks.
Owner:SHAANXI NORMAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com