Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
99results about "Telegraphic message interchanged in time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
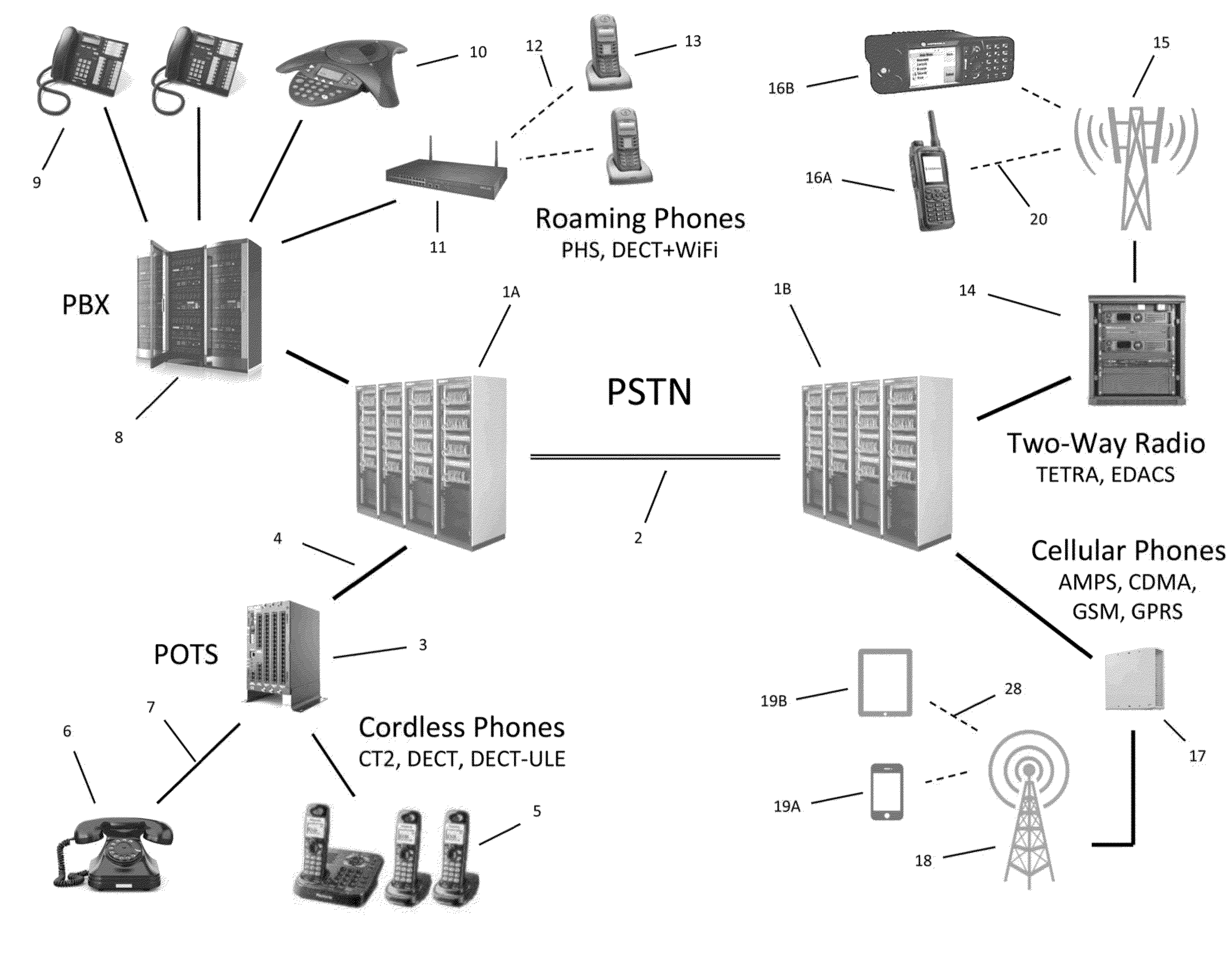
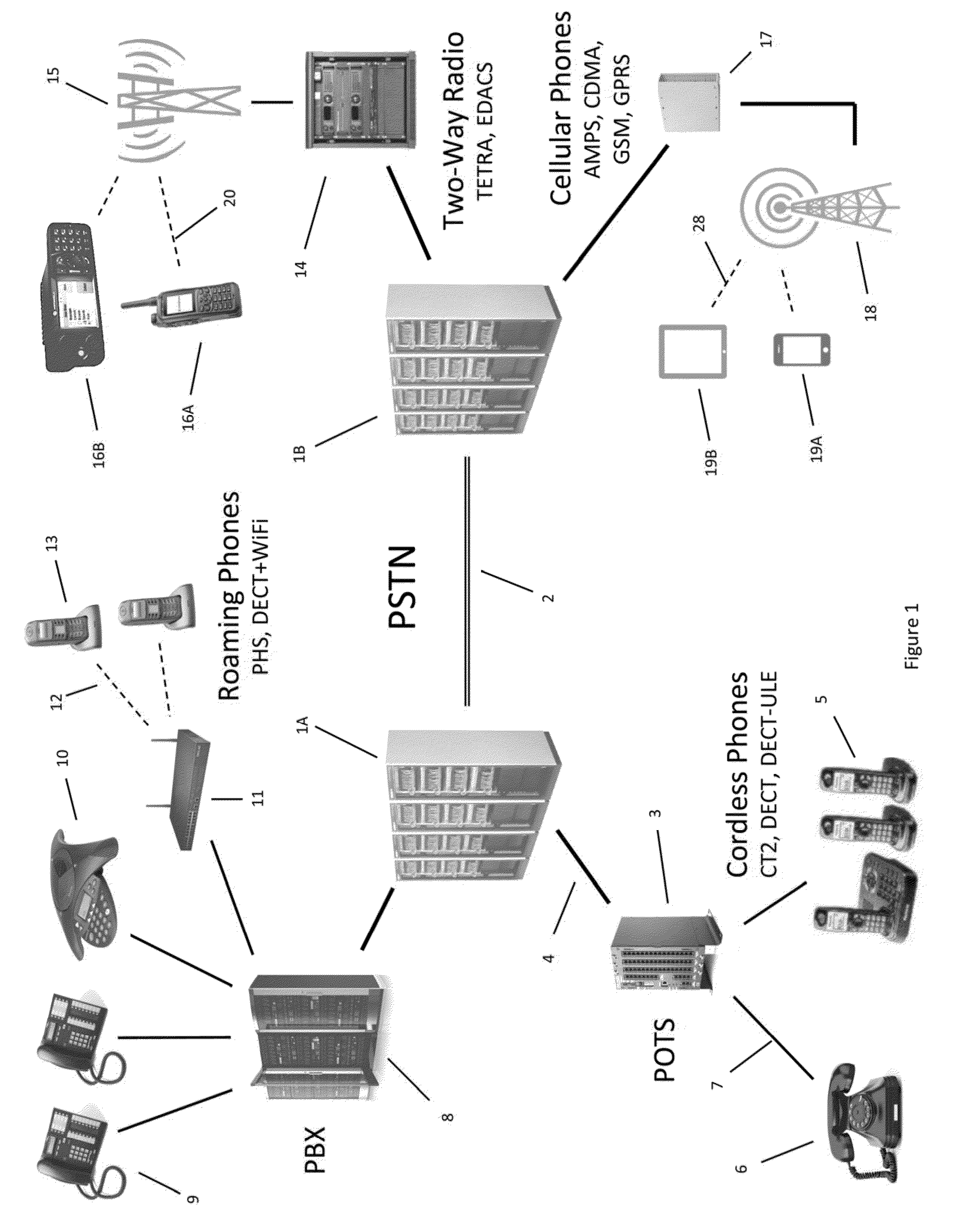
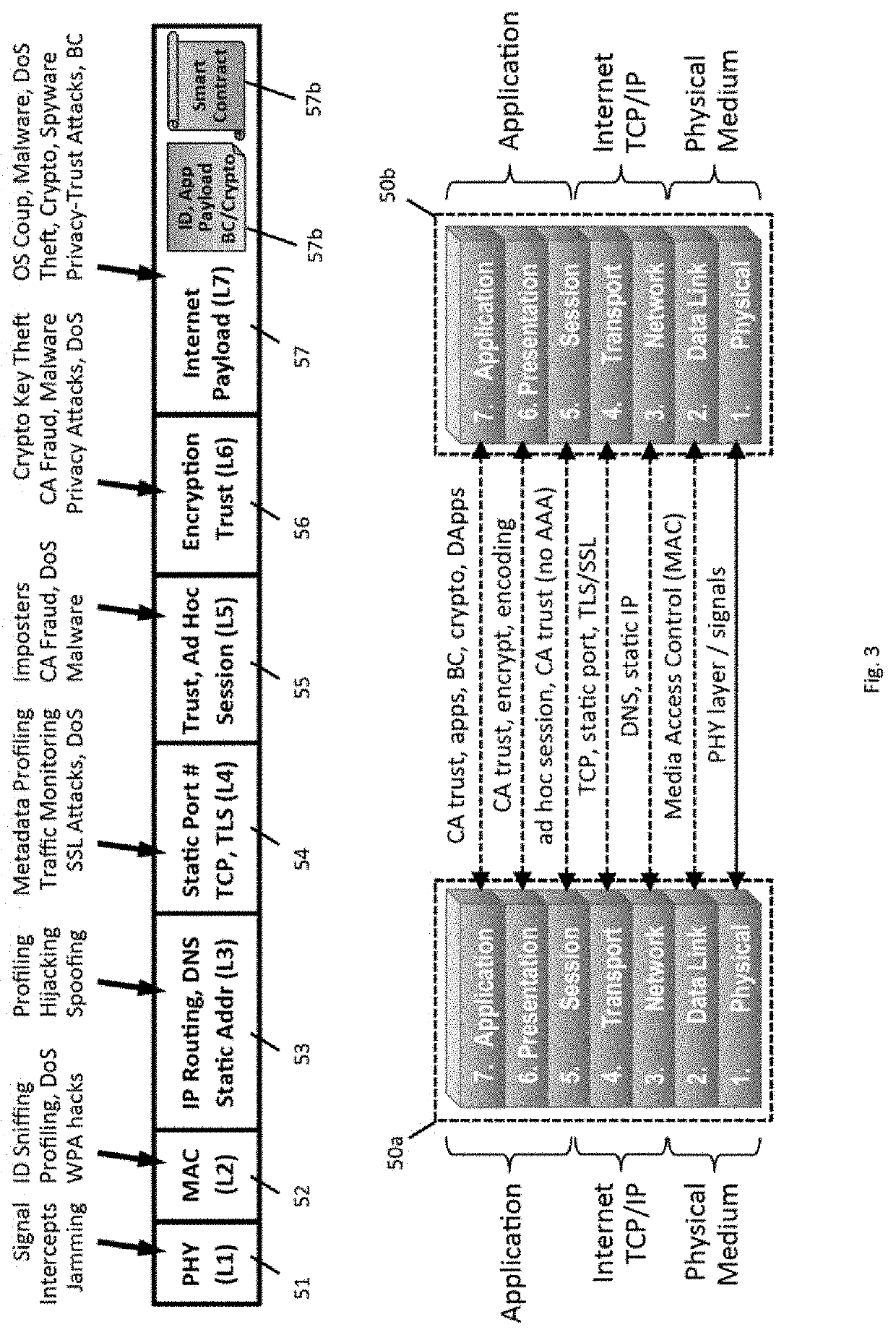
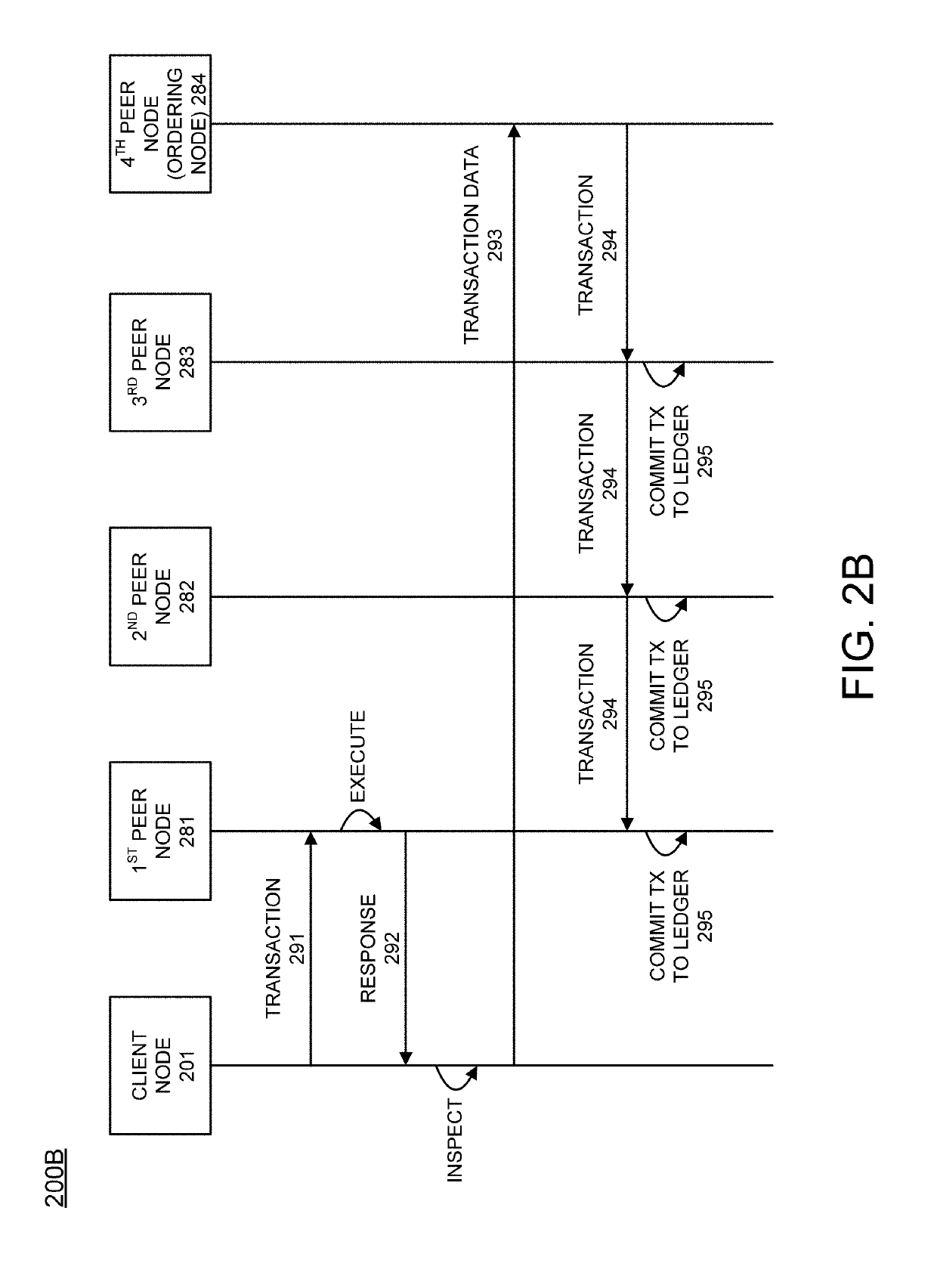
Secure Dynamic Communication Network And Protocol
ActiveUS20160219024A1Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageData taking preventionDigital dataData segment
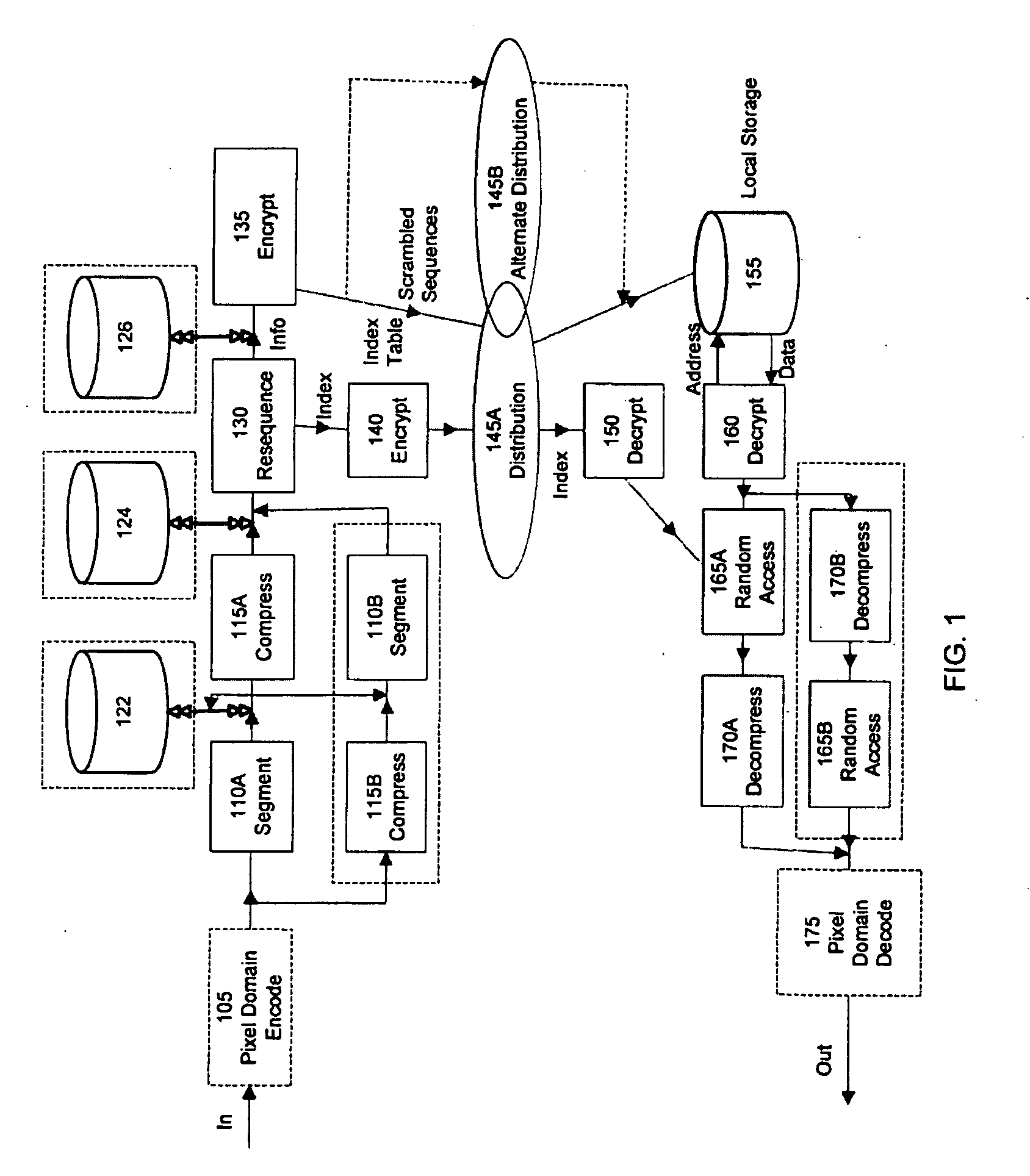
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
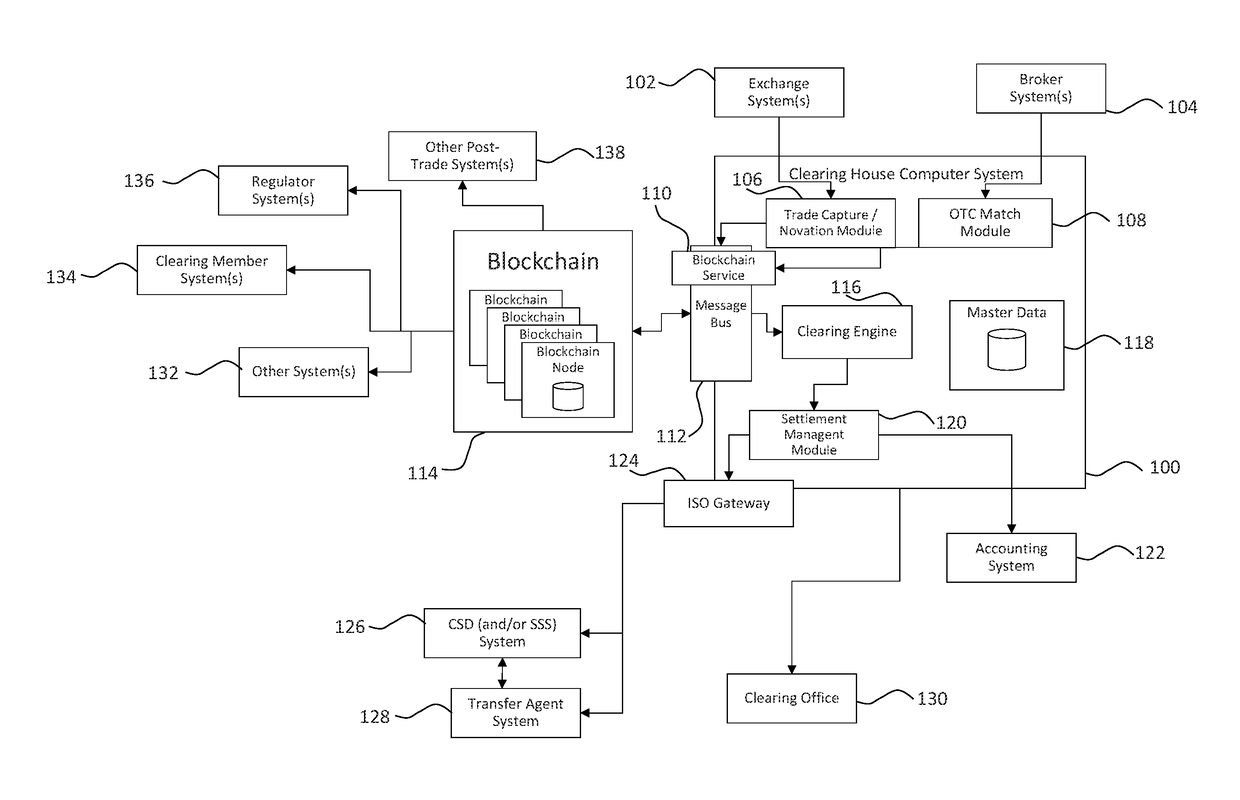
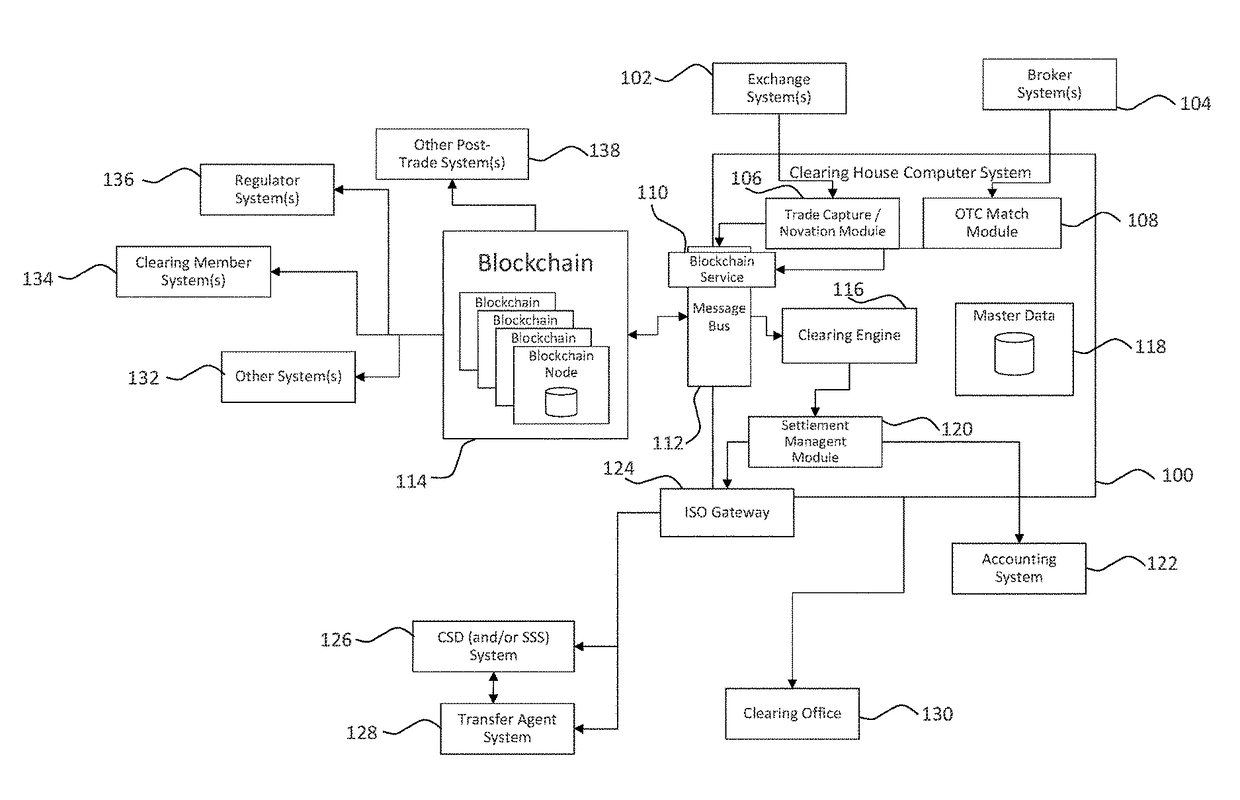
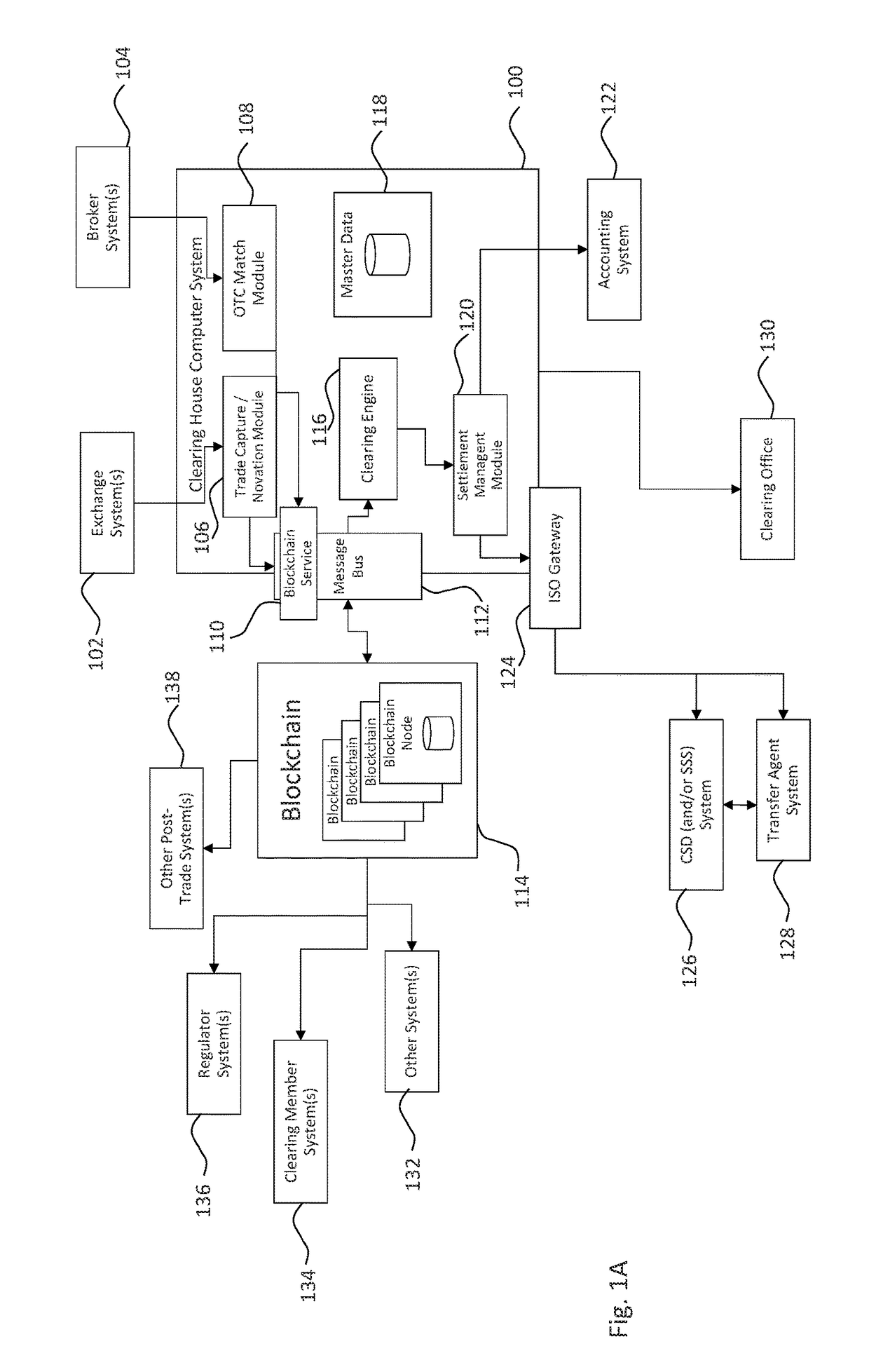
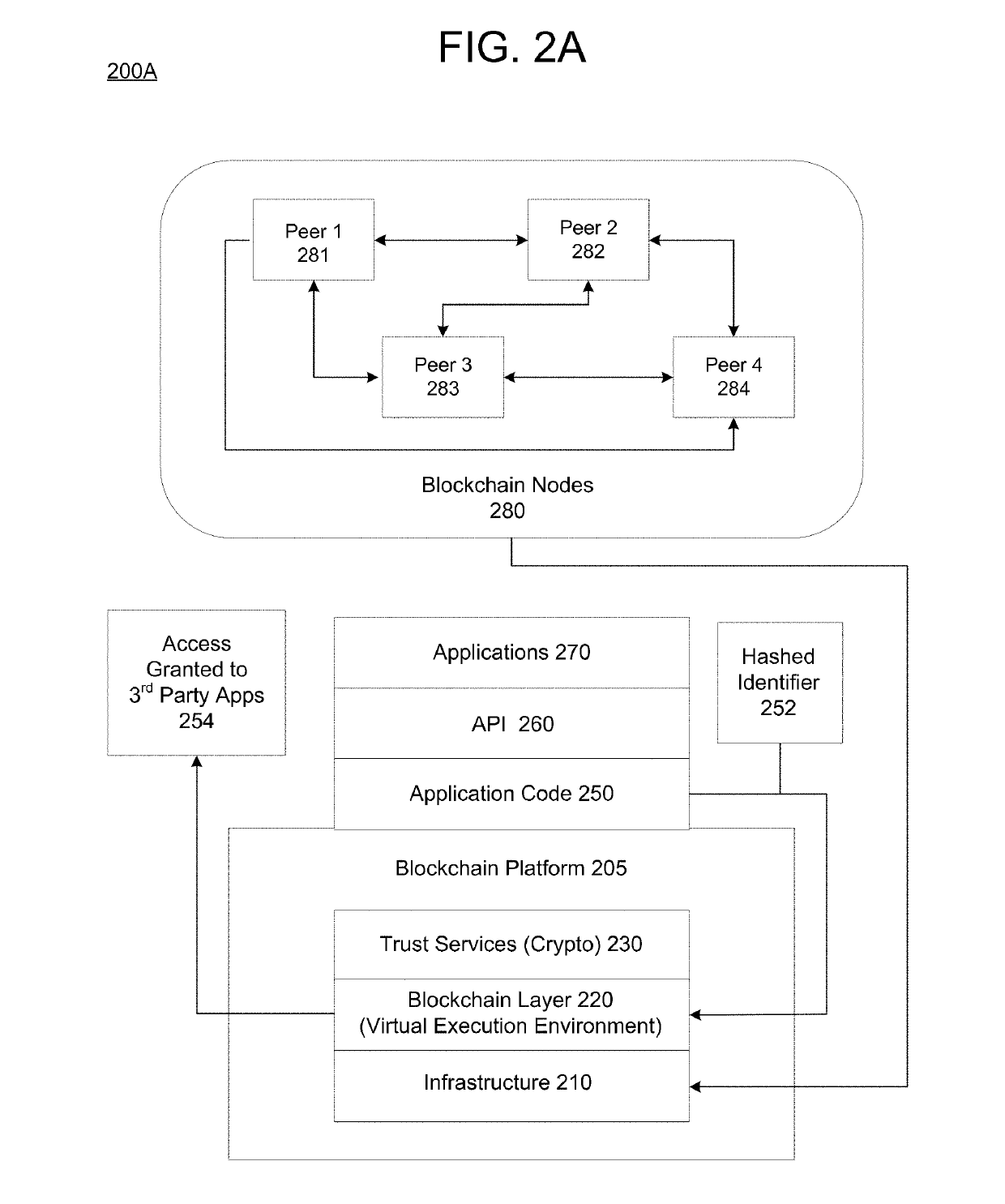
Systems and methods for storing and sharing transactional data using a distributed computing systems
ActiveUS20170230189A1FinanceEncryption apparatus with shift registers/memoriesComputerized systemComputing systems
A computer system that interfaces with a blockchain is provided. The computer system receives match data for a match between a first data transaction request that is associated with a first identifier and a second data transaction request that is associated with a second identifier. A first blockchain transaction is generated based on the match data and stored to a blockchain. At least one further blockchain transaction is generates that splits the match into two different transactions—one between the first identifier and an intermediary and the second between the intermediary. These are recorded to the blockchain via the further blockchain transactions.
Owner:NASDAQ TECHNOLOGY AB
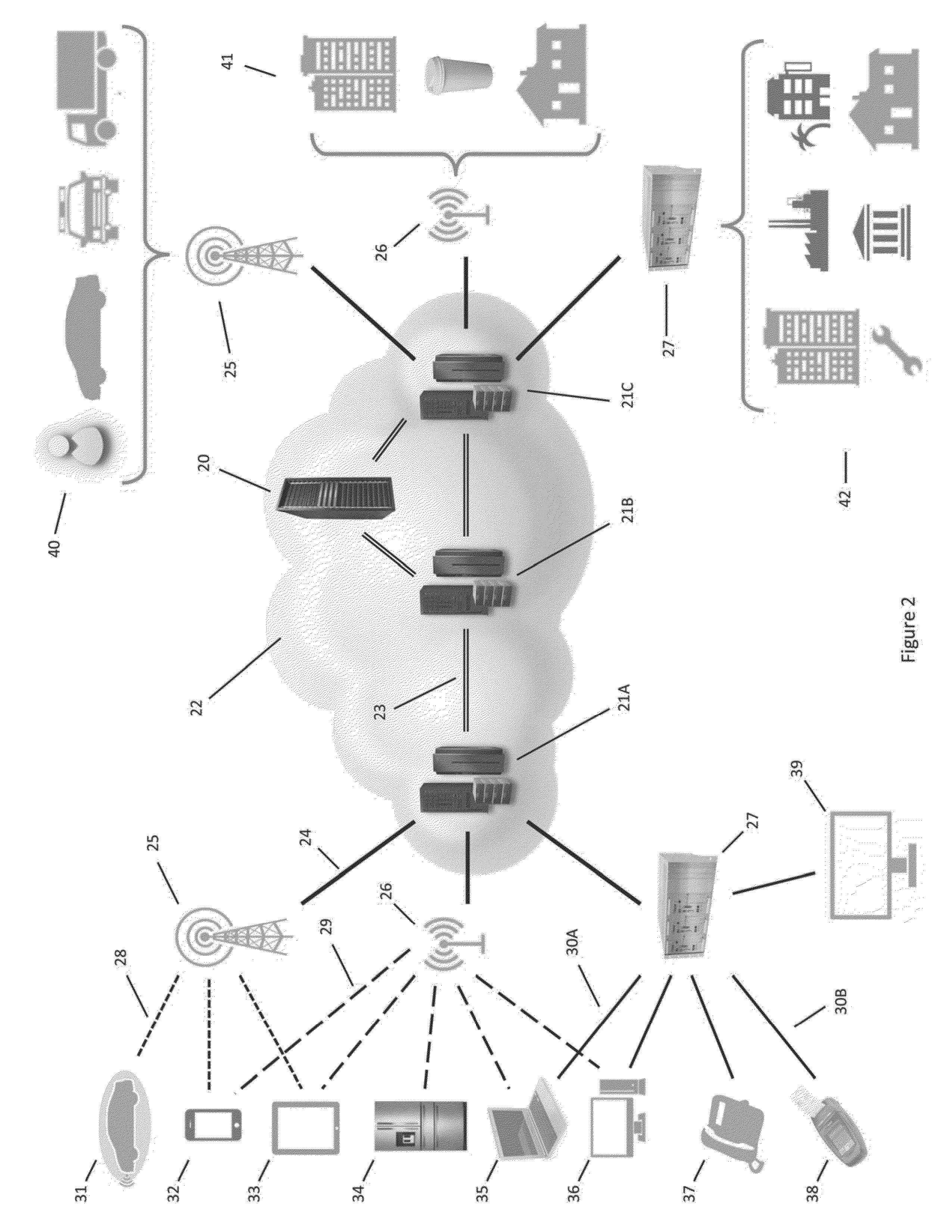
Decentralized Cybersecure Privacy Network For Cloud Communication, Computing And Global e-Commerce
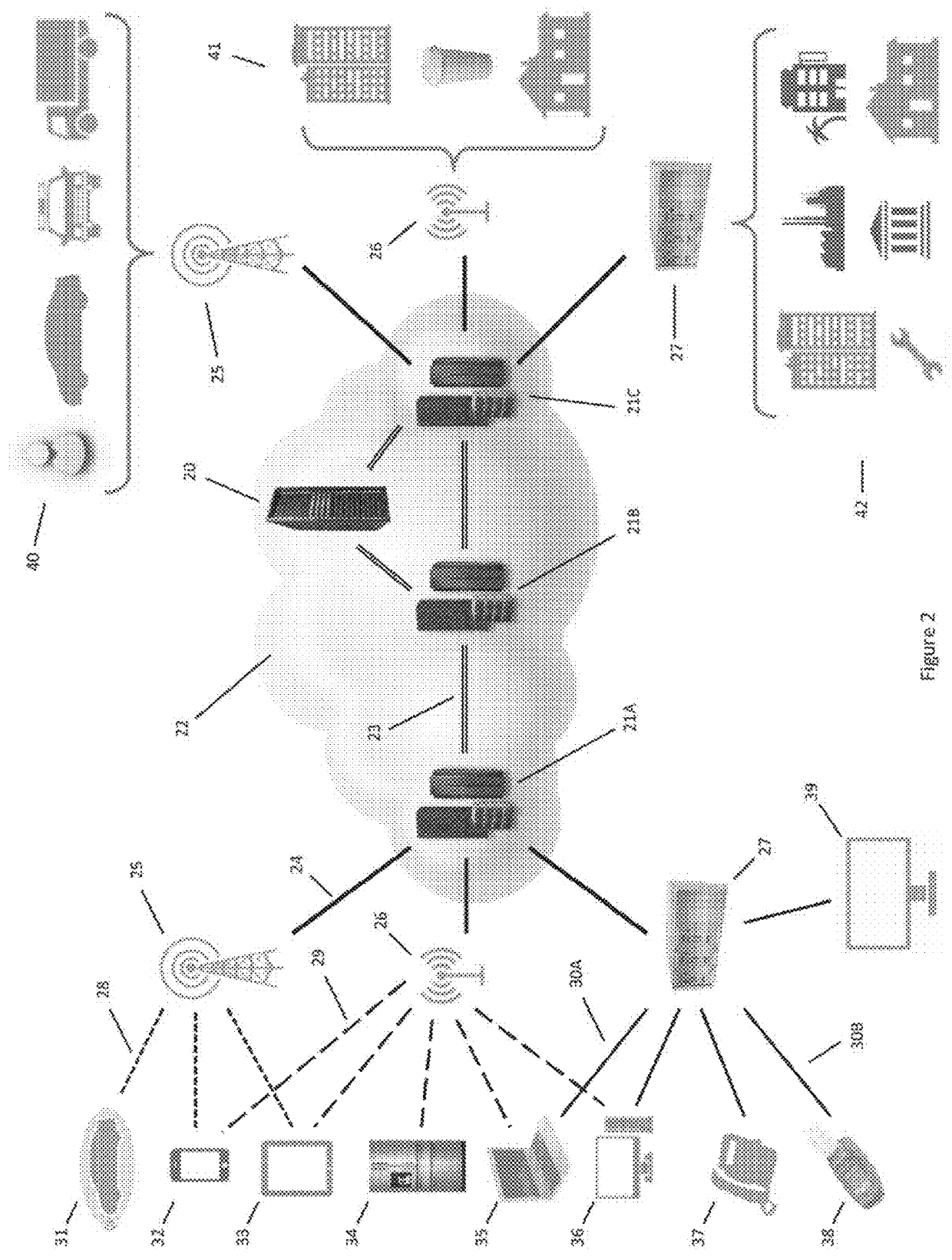
ActiveUS20190386969A1Encryption apparatus with shift registers/memoriesTelegraphic message interchanged in timeName serverNetwork packet
Software installed in the nodes in a communication network allows them to perform a “name server” function, which entails the management of a dynamic list of the client devices that are connected to the cloud, a “task” function, which entails the receipt and transmission of the packets, and an “authority” function, which entails the determination of the routes of the packets through the cloud. Each node is capable of performing only one function at a time. After completing a job, a node reverts to an undifferentiated, state awaiting its next performance request.
Owner:LISTAT LTD
Systems and methods for storing and sharing transactional data using distributed computing systems
ActiveUS9794074B2FinanceEncryption apparatus with shift registers/memoriesComputerized systemBlockchain
A computer system that interfaces with a blockchain is provided. The computer system receives match data for a match between a first data transaction request that is associated with a first identifier and a second data transaction request that is associated with a second identifier. A first blockchain transaction is generated based on the match data and stored to a blockchain. At least one further blockchain transaction is generates that splits the match into two different transactions—one between the first identifier and an intermediary and the second between the intermediary. These are recorded to the blockchain via the further blockchain transactions.
Owner:NASDAQ TECHNOLOGY AB
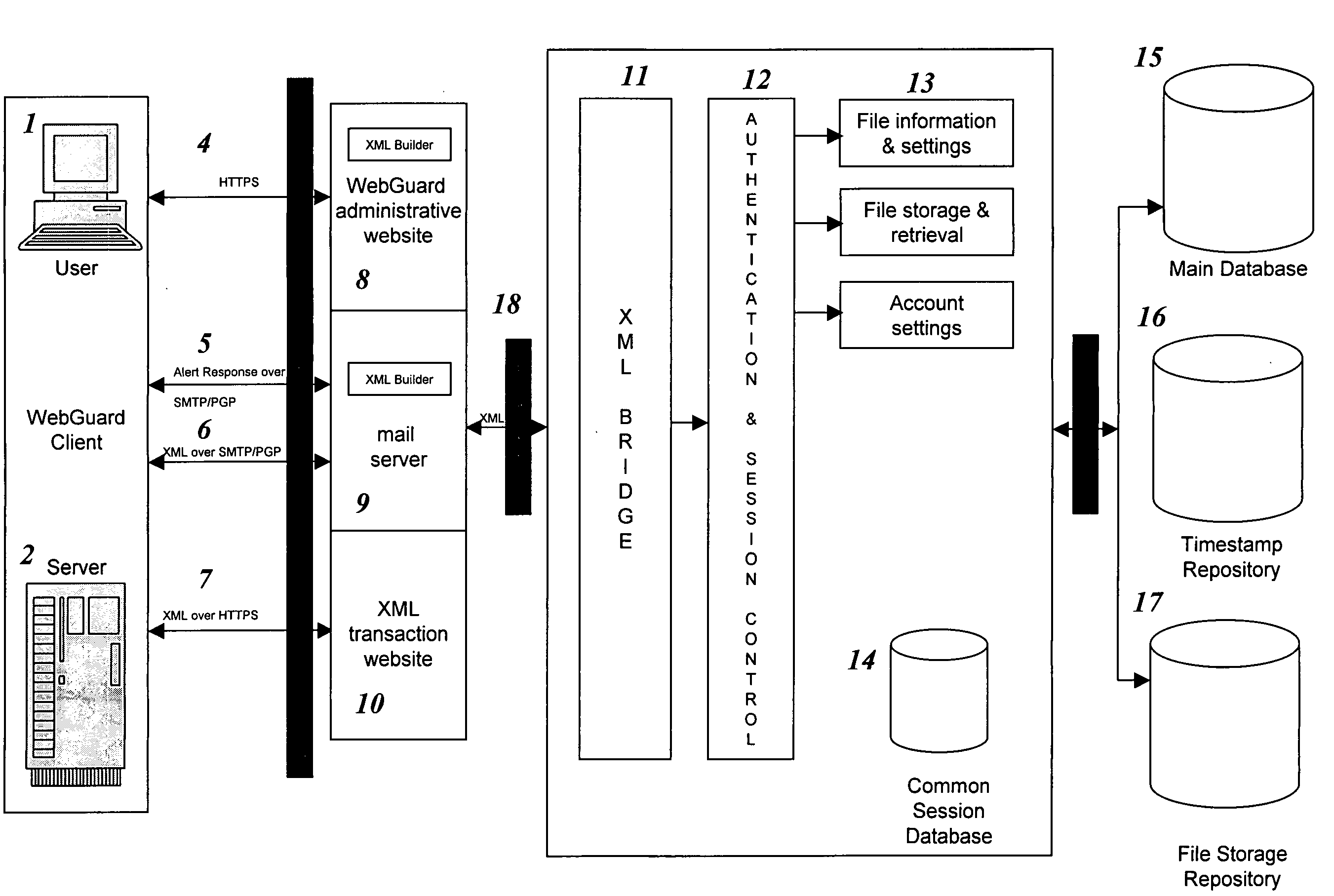
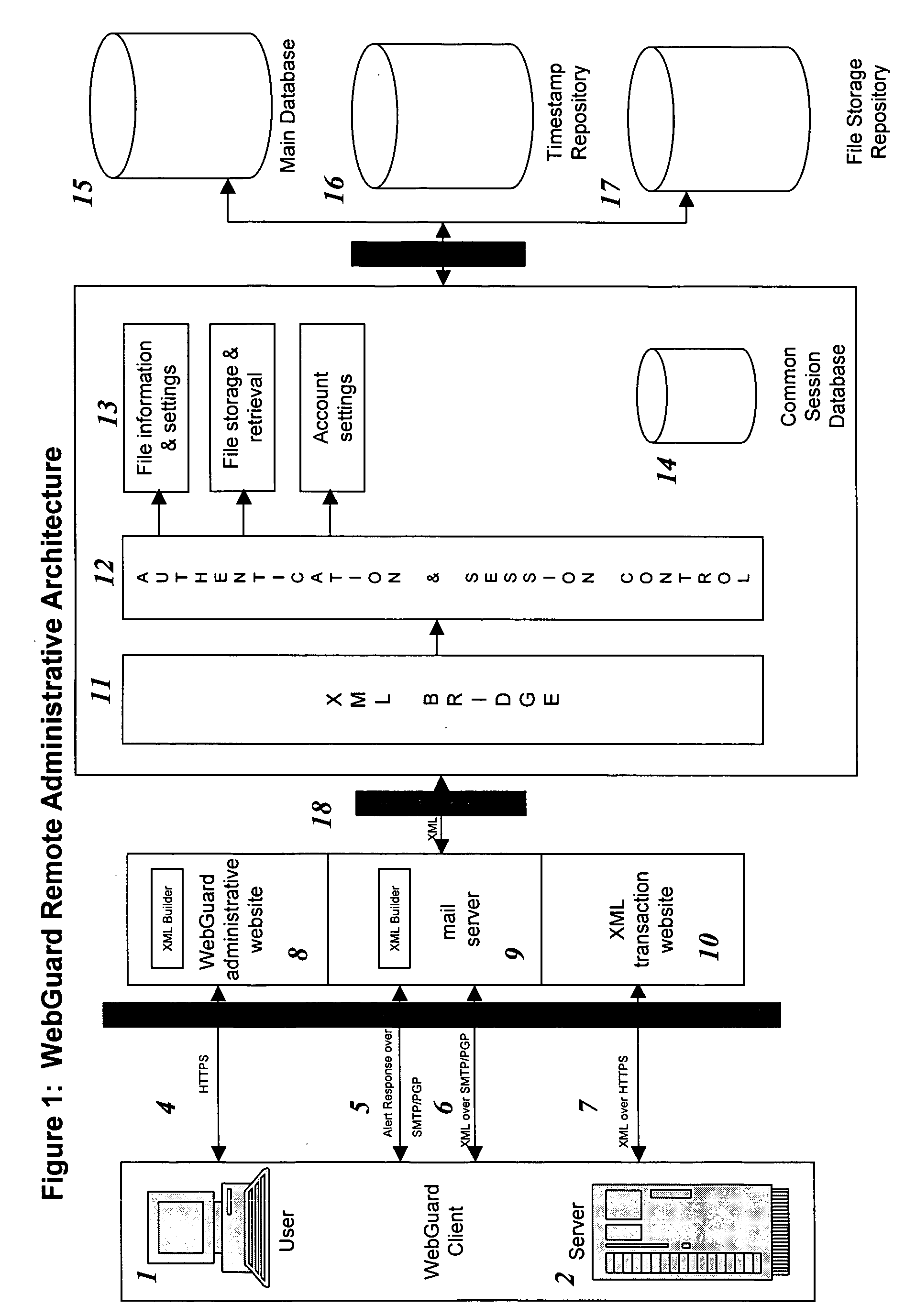
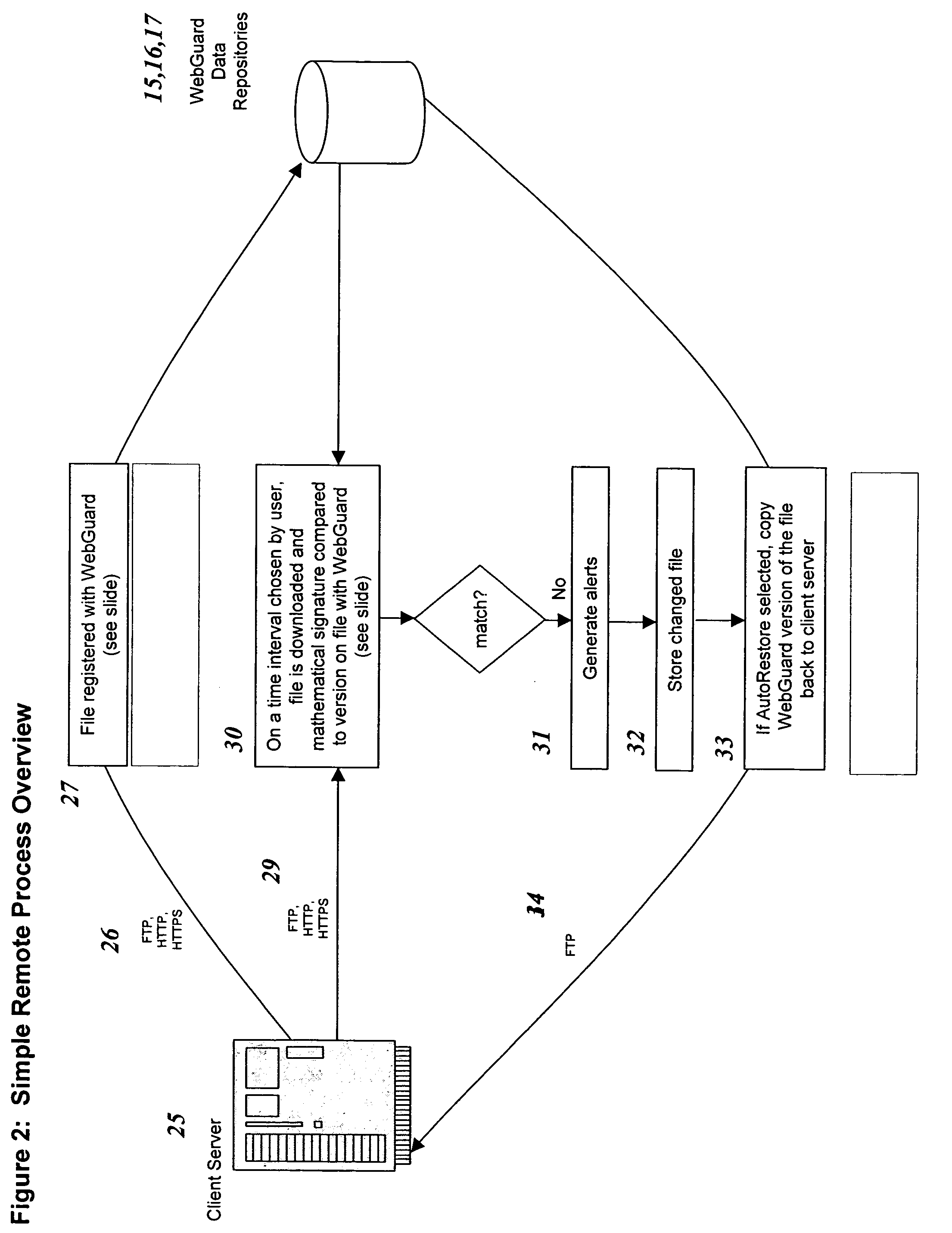
Remote web site security system
InactiveUS20050114658A1Digital data processing detailsUnauthorized memory use protectionWeb siteDatabase
The invention is a method for monitoring a file in a file security system, including providing a first file representation of a file in which the file is disposed at a first location and first processing the first file representation to provide first signals in accordance with the first file representation. The first signals are stored in a central repository disposed at a second location wherein the second location is remote from the first location. A second file representation of the file is provided wherein the file is disposed at a third location remote from the second location. Second processing of the second file representation is performed to provide second signals in accordance with the second file representation. The first signals are accessed from the central repository and the first signals are compared with the second signals. A status of the file is determined in accordance with the comparing.
Owner:SHORE VENTURE GROUP
Secure information distribution system utilizing information segment scrambling
InactiveUS7457415B2Data stream serial/continuous modificationMultiple keys/algorithms usageDistribution systemComputer security
Owner:AKIKAZE TECH
Method and system for encrypting and storing content to a user
Owner:ITECH GROUP
Secure encryption of data packets for transmission over unsecured networks
Pure random numbers from a sheet within a one-time pad are employed to encrypt the bytes of a source data packet and to order the encrypted bytes in a random order within the encrypted data packet. Pure random numbers fill remaining positions within the encrypted data packet. The resulting encrypted data packet is unconditionally secure (i.e., unbreakable). Sheets within the one-time pad are utilized only once, and the one-time pad is replaced when exhausted. For electronic checking applications, the one-time pad is distributed to the user stored in an electronic checkbook, with a copy retained by the bank. For cellular telephone applications, the one-time pad is stored in a replaceable memory chip within the mobile unit with a copy retained at a single, secured central computer. For client-server applications or applications involving sales over the Internet, the one-time pad may be provided to the user on a floppy disk or CD-ROM, with a copy retained by the vendor.
Owner:PAYPAL INC
System and method for interaction object reconciliation in a public ledger blockchain environment
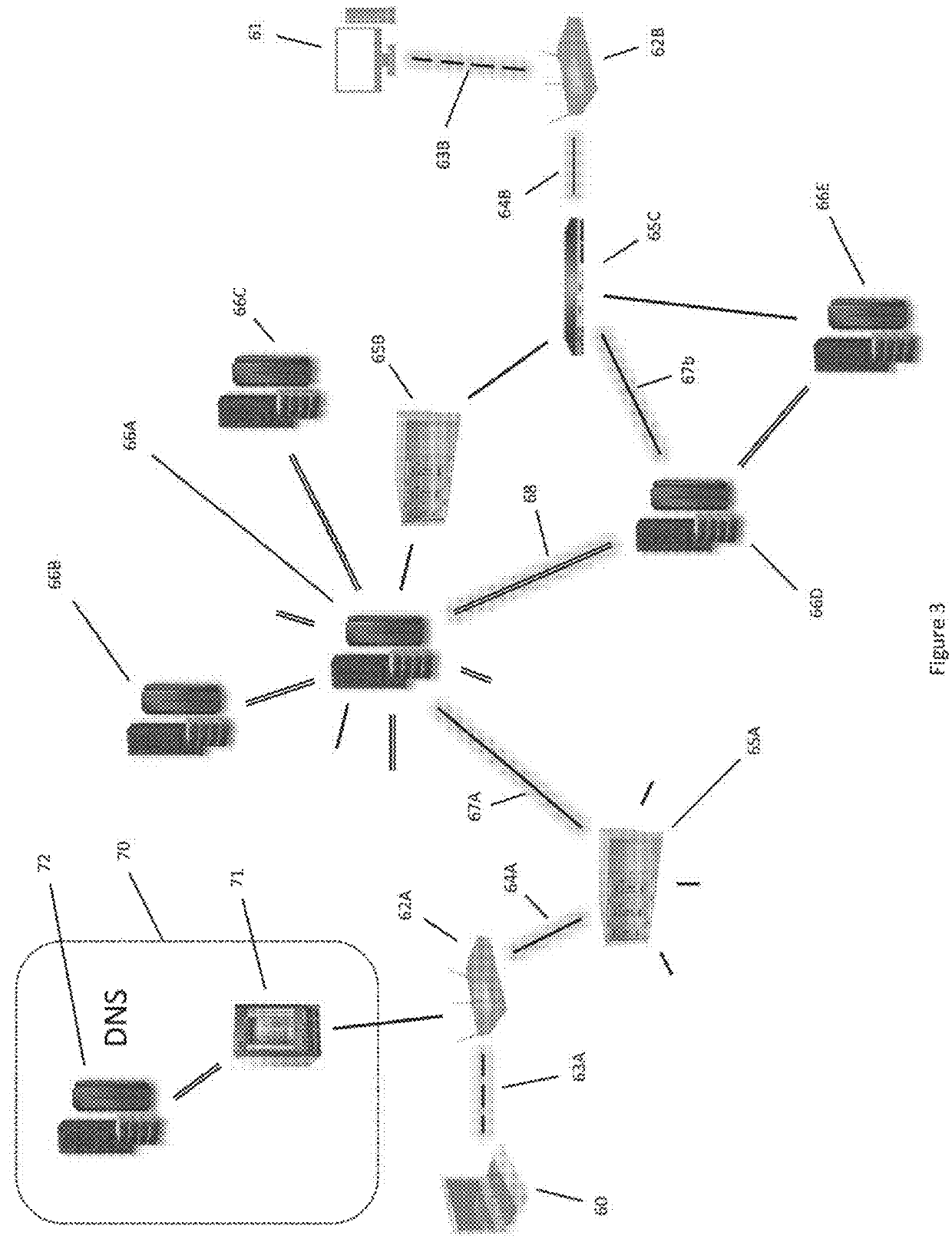
ActiveUS20180144156A1Secure data communicationEncryption apparatus with shift registers/memoriesTelegraphic message interchanged in timeObject basedNetwork connection
A system and method for block reconciliation of interactions comprising a network-connected block reconciliation computer connected to a plurality of connected devices and to one or more blockchains to enable an object compiler to receive a plurality of criteria from a requesting device. The compiler the receives a plurality of blocks from the public ledger blockchains based on the criteria. Each block corresponding to a preconfigured interaction object previously written by devices either during or after the completion of a transaction. The compiler analyzes the preconfigured interaction objects to determine if there is corresponding supplemental object. The compiler requests the supplemental blocks from the blockchains, and processes supplemental objects based on type, if no corresponding supplemental object it found, the associated interaction object is flagged.
Owner:COSTANZ MARIO A
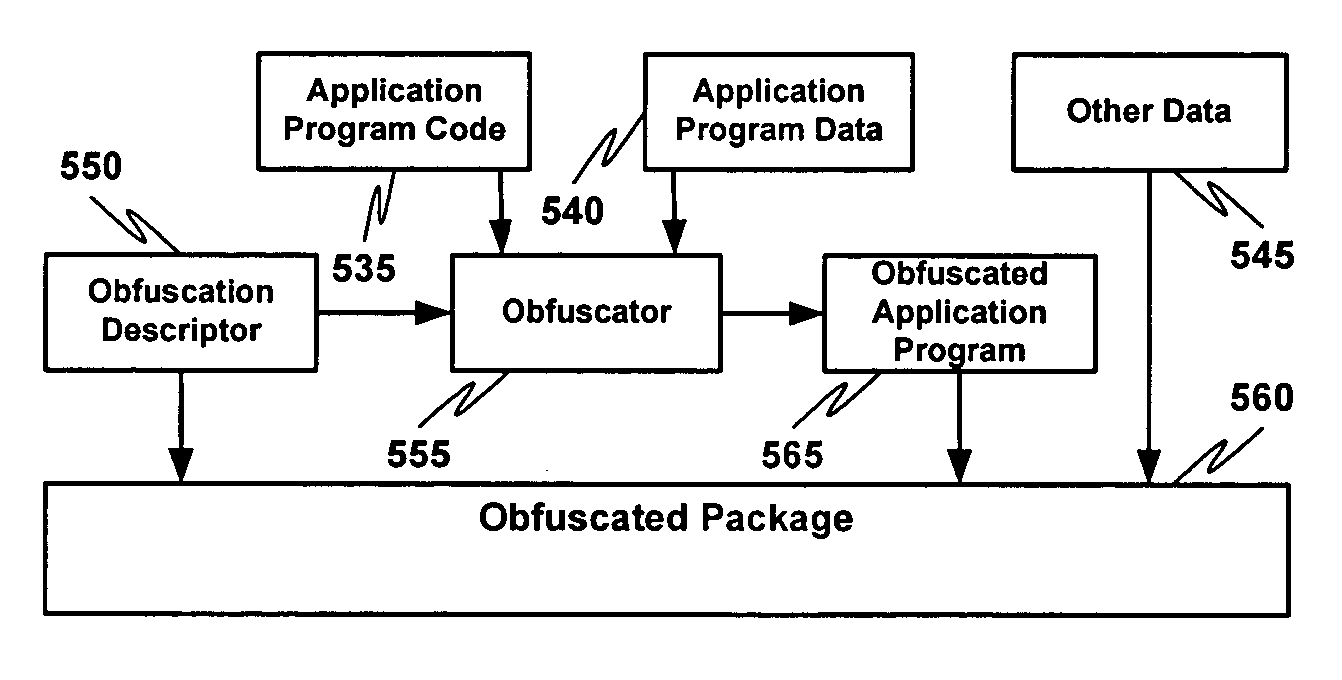
Non-linear execution of application program instructions for application program obfuscation
ActiveUS20050071653A1Key distribution for secure communicationUser identity/authority verificationProgram instructionParallel computing
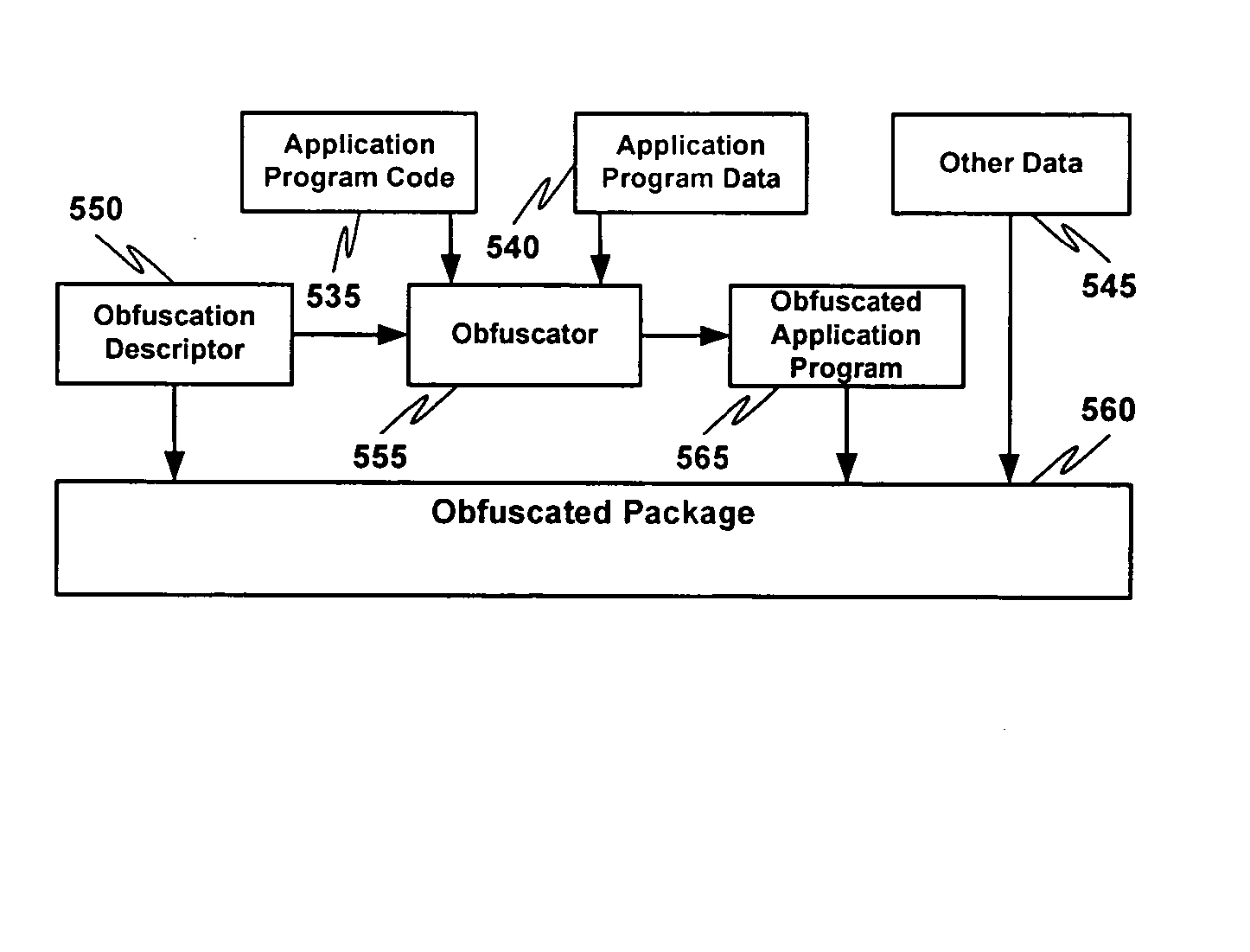
Obfuscating an application program comprises reading a first application program, determining an application program instruction location permutation that transforms the first application program into an obfuscated application program having at least one application program instruction stored at a memory location that is based at least in part on a permutation of the memory location where the corresponding application program instruction is stored in the first application program, applying the application program instruction location permutation to the first application program to create an obfuscated application program, and sending the obfuscated application program. Executing an obfuscated application program comprises receiving an application program, determining an application program instruction location permutation to apply to a current instruction counter value, receiving, applying the application program instruction location permutation to the current instruction counter value to obtain a reference to an application program instruction to execute, and executing the application program instruction to execute.
Owner:ORACLE INT CORP
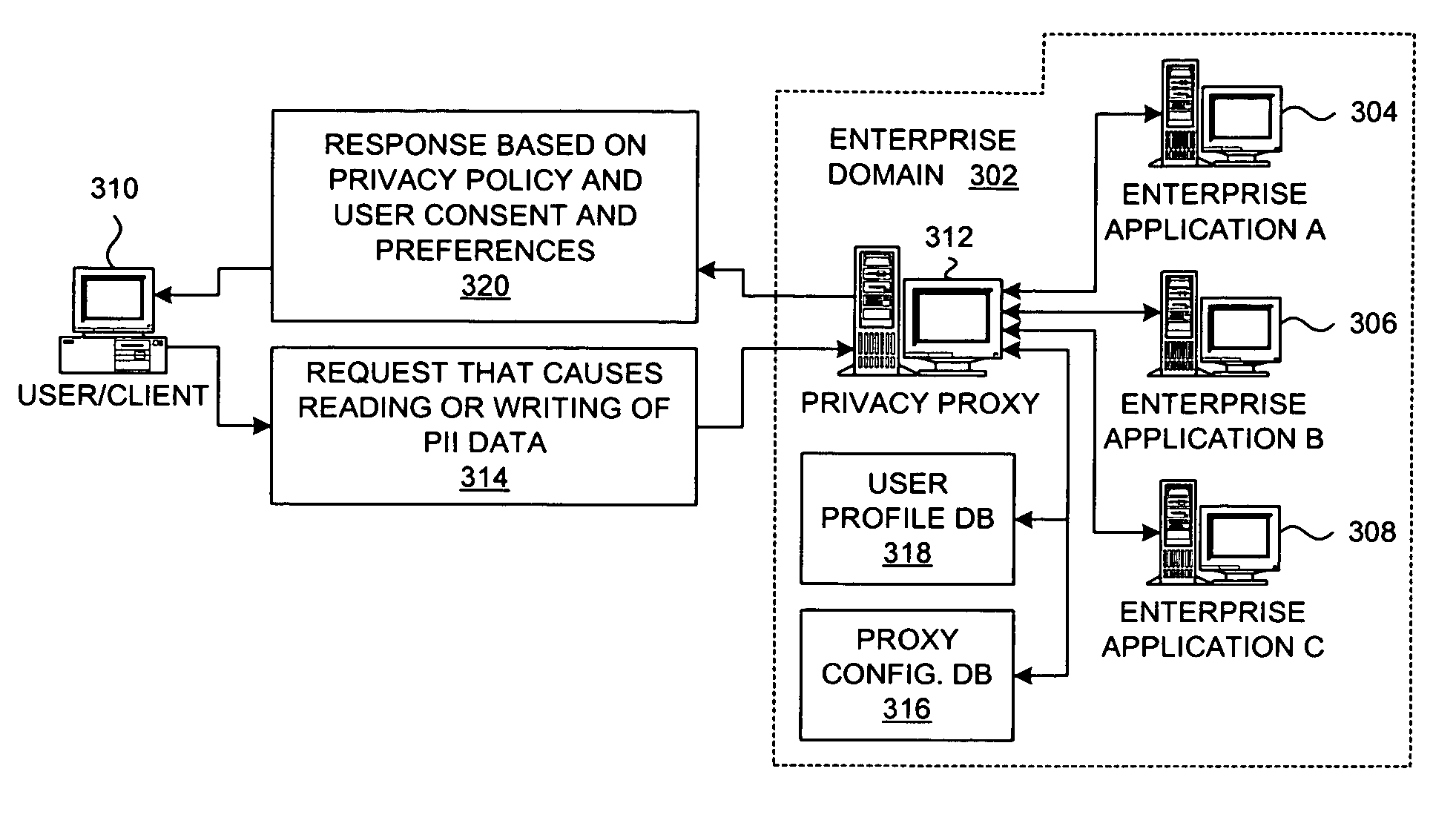
Method and system for implementing privacy policy enforcement with a privacy proxy
InactiveUS7797726B2Digital data processing detailsUser identity/authority verificationInternet privacyClient-side
Owner:LINKEDIN
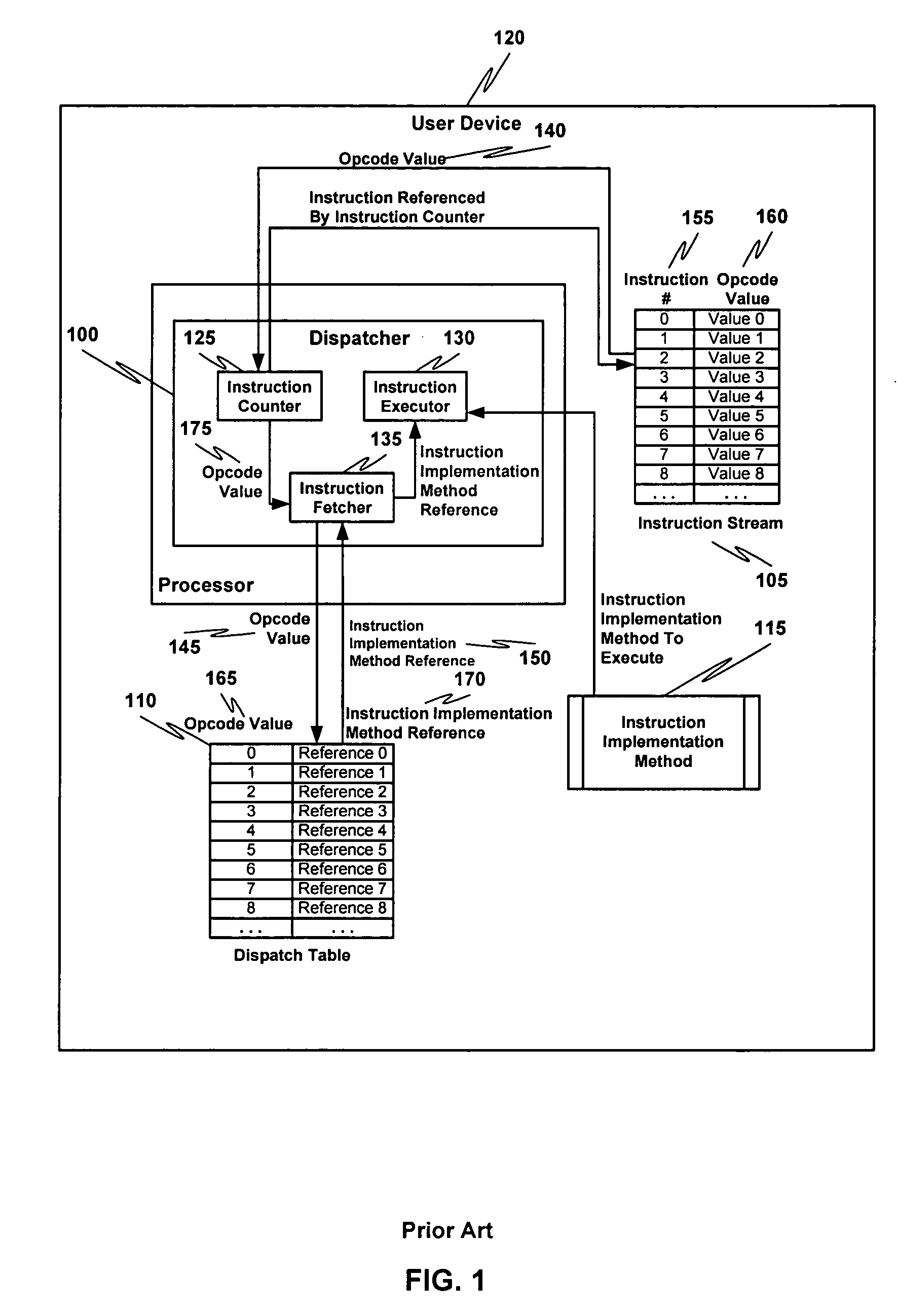
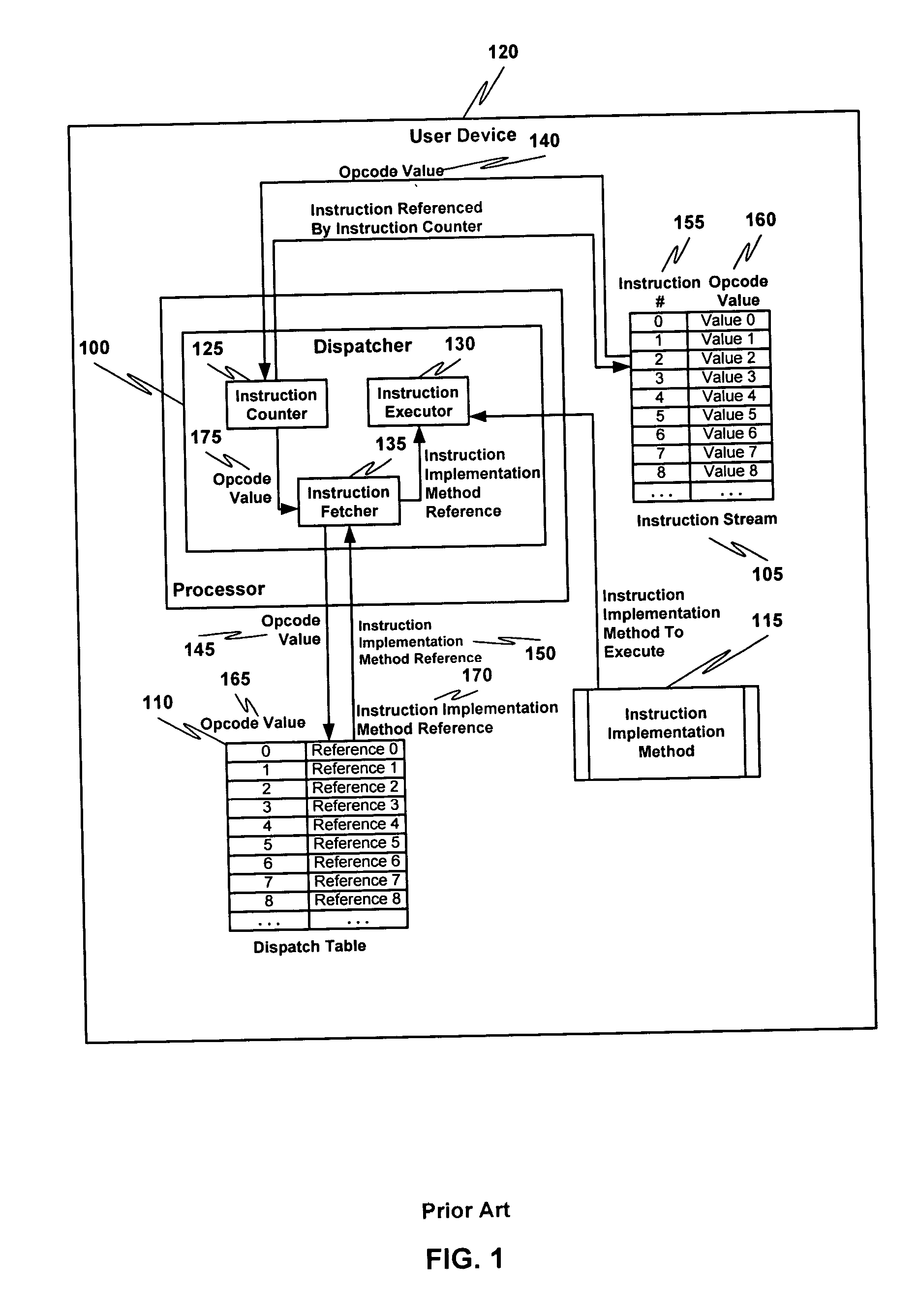
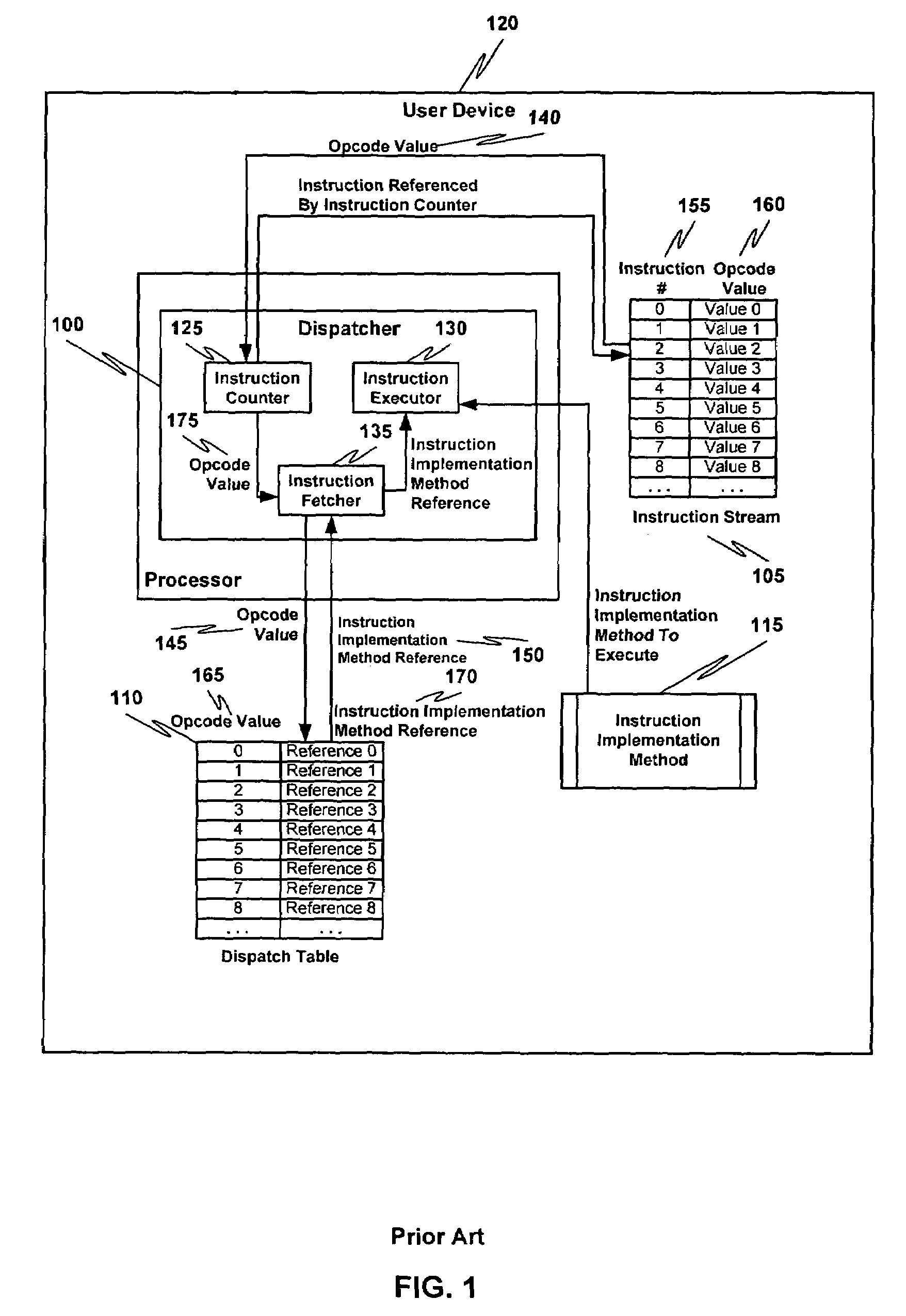
Multiple instruction dispatch tables for application program obfuscation
ActiveUS20050071652A1Key distribution for secure communicationDigital data processing detailsProgram instructionInstruction set
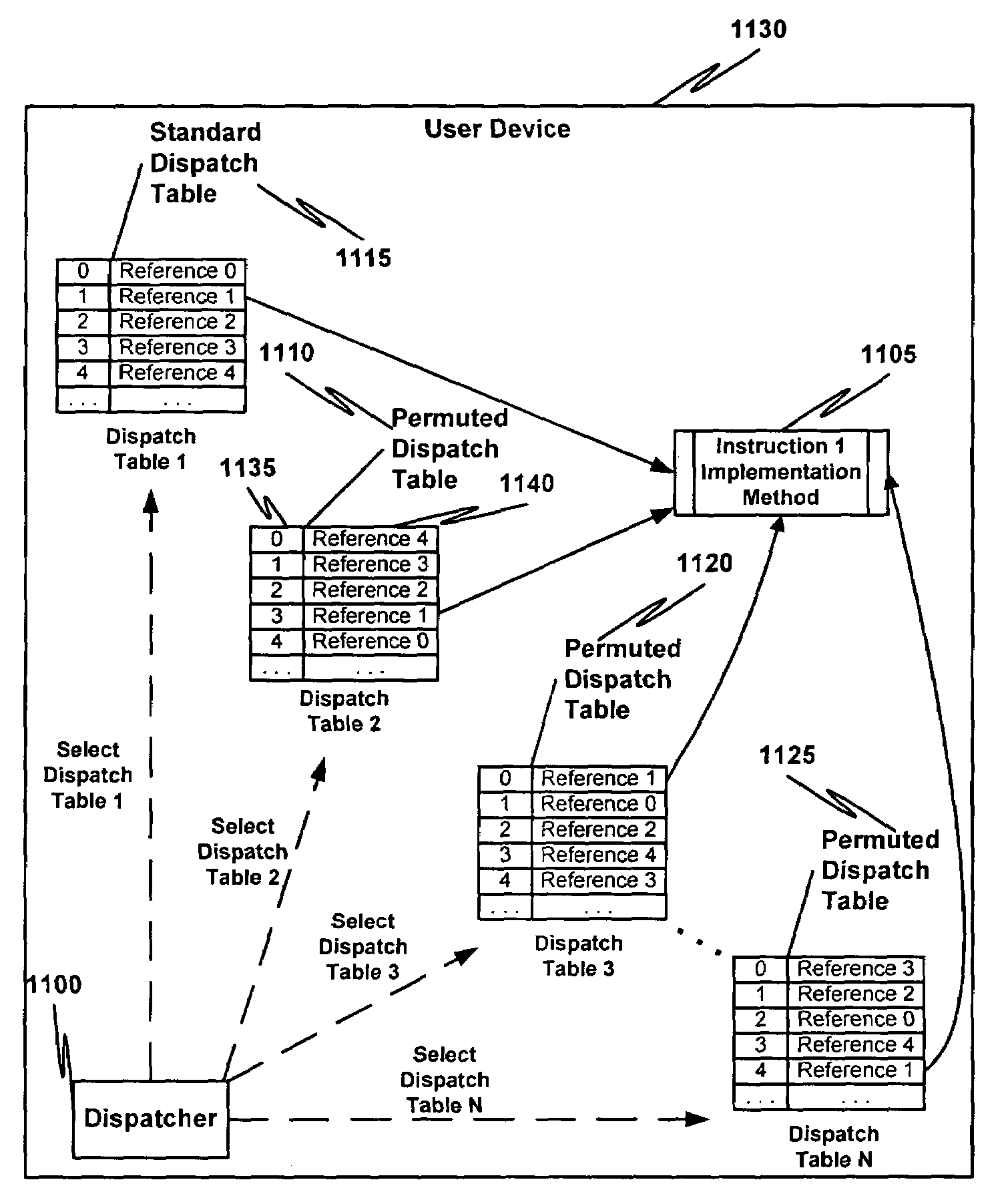
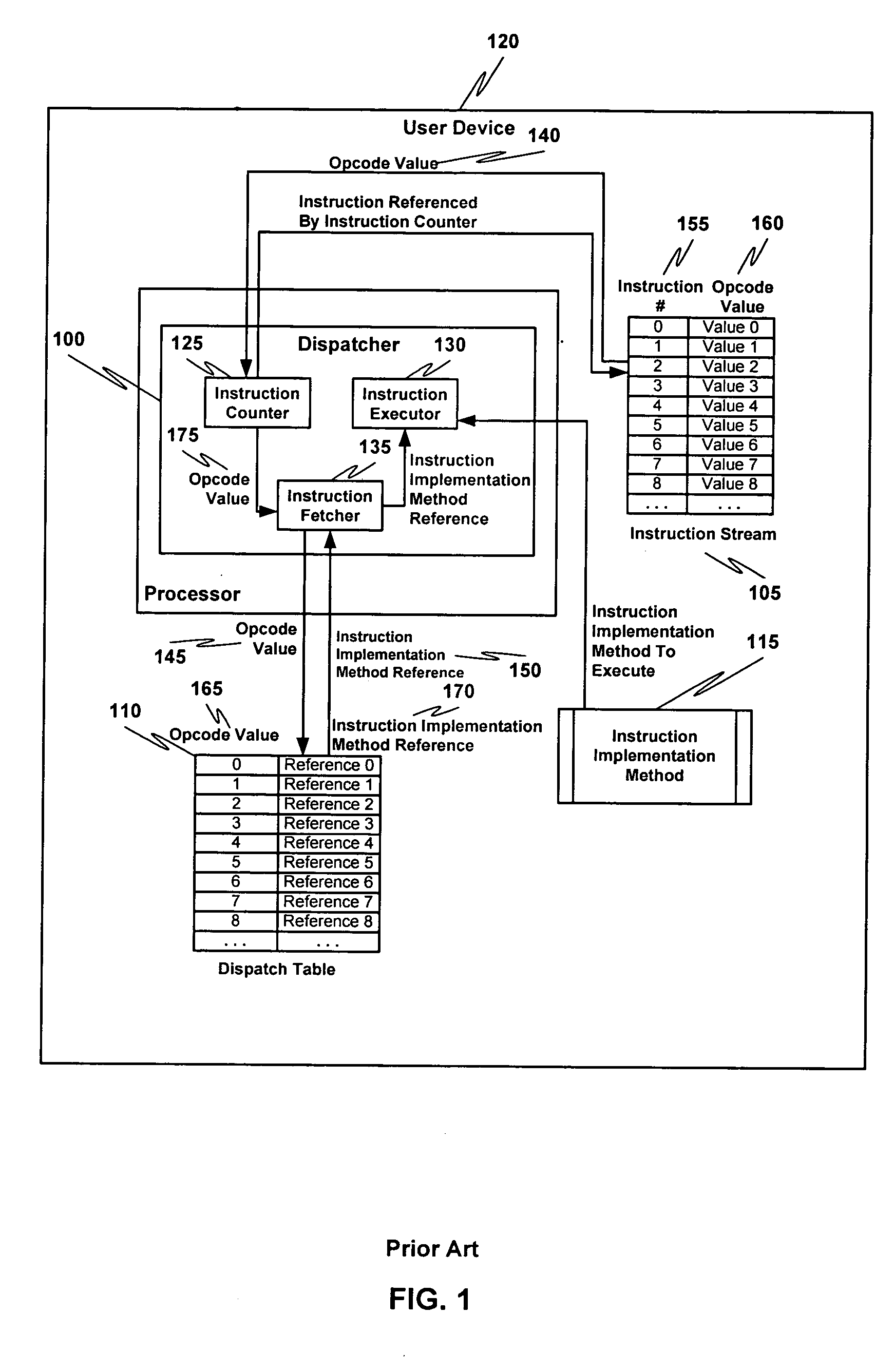
Obfuscating an application program comprises reading an application program comprising code, determining multiple dispatch tables associated with the application program, transforming the application program into application program code configured to utilize the dispatch tables during application program execution to determine the location of instruction implementation methods to be executed based at least in part on a current instruction counter value, and sending the application program code. Executing an obfuscated application program comprises receiving an obfuscated application program comprising at least one instruction opcode value encoded using one of multiple instruction set opcode value encoding schemes, receiving an application program instruction corresponding to a current instruction counter value, selecting an instruction dispatch table based at least in part on the current instruction counter value, and executing the application program instruction using the selected instruction dispatch table.
Owner:ORACLE INT CORP
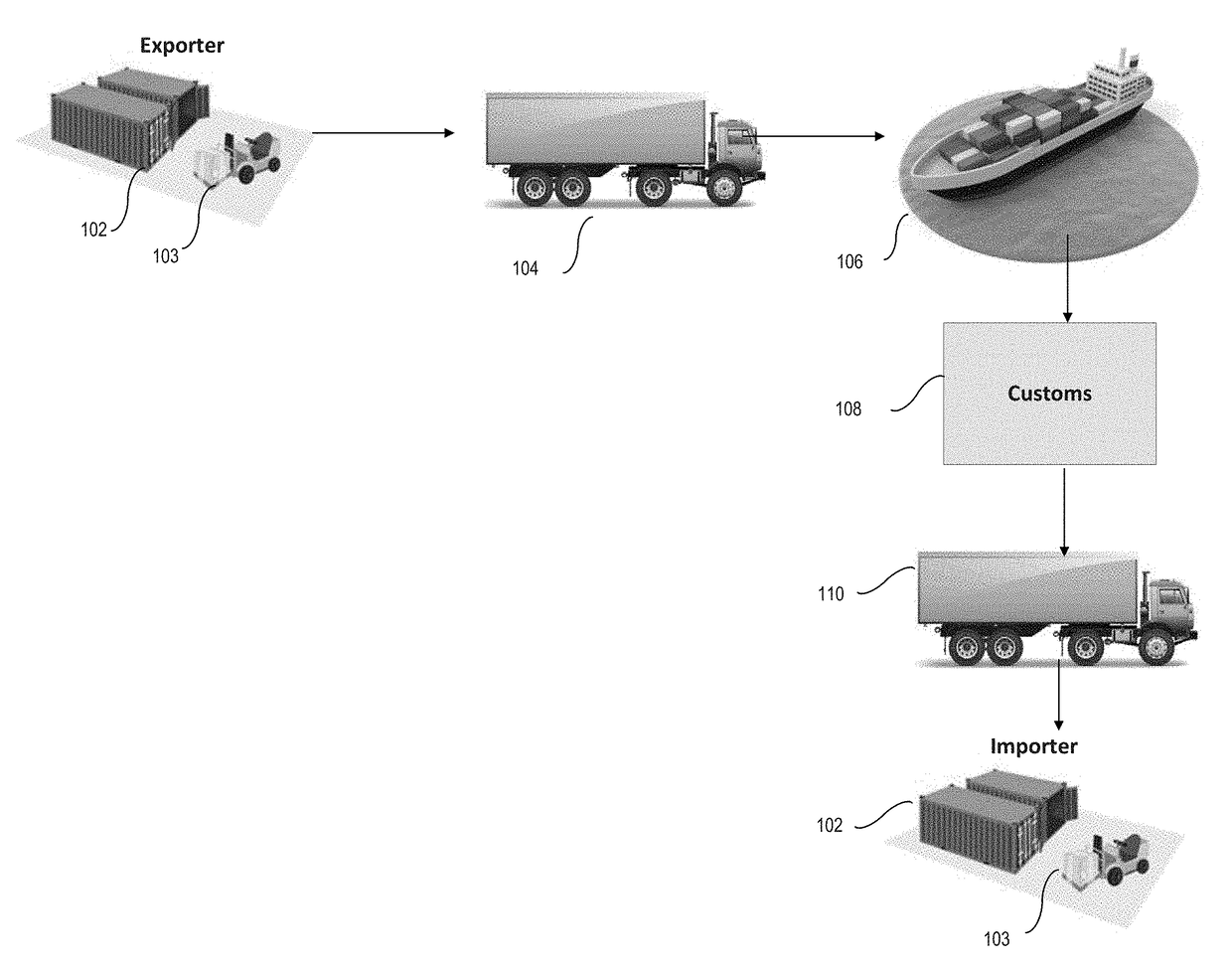
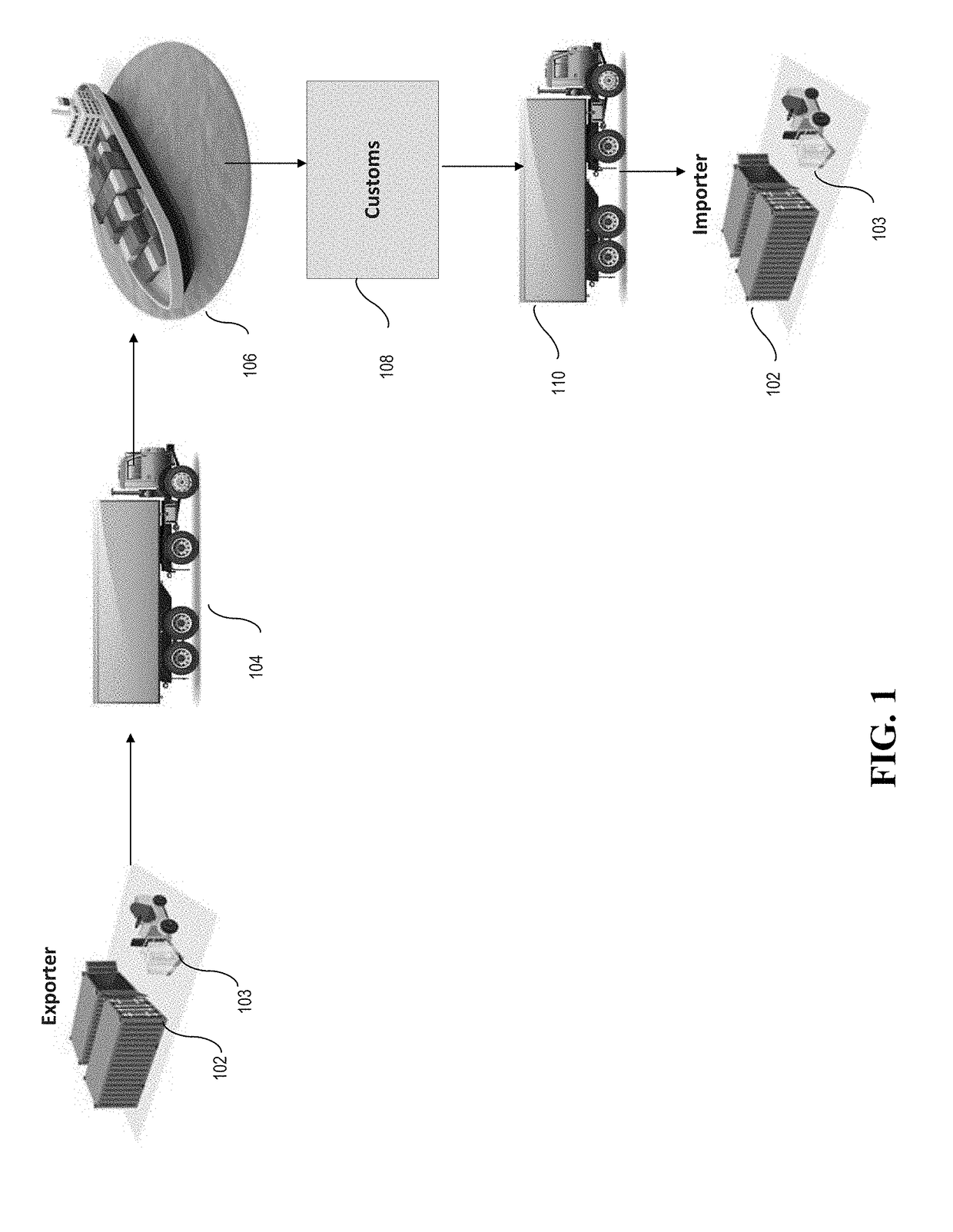
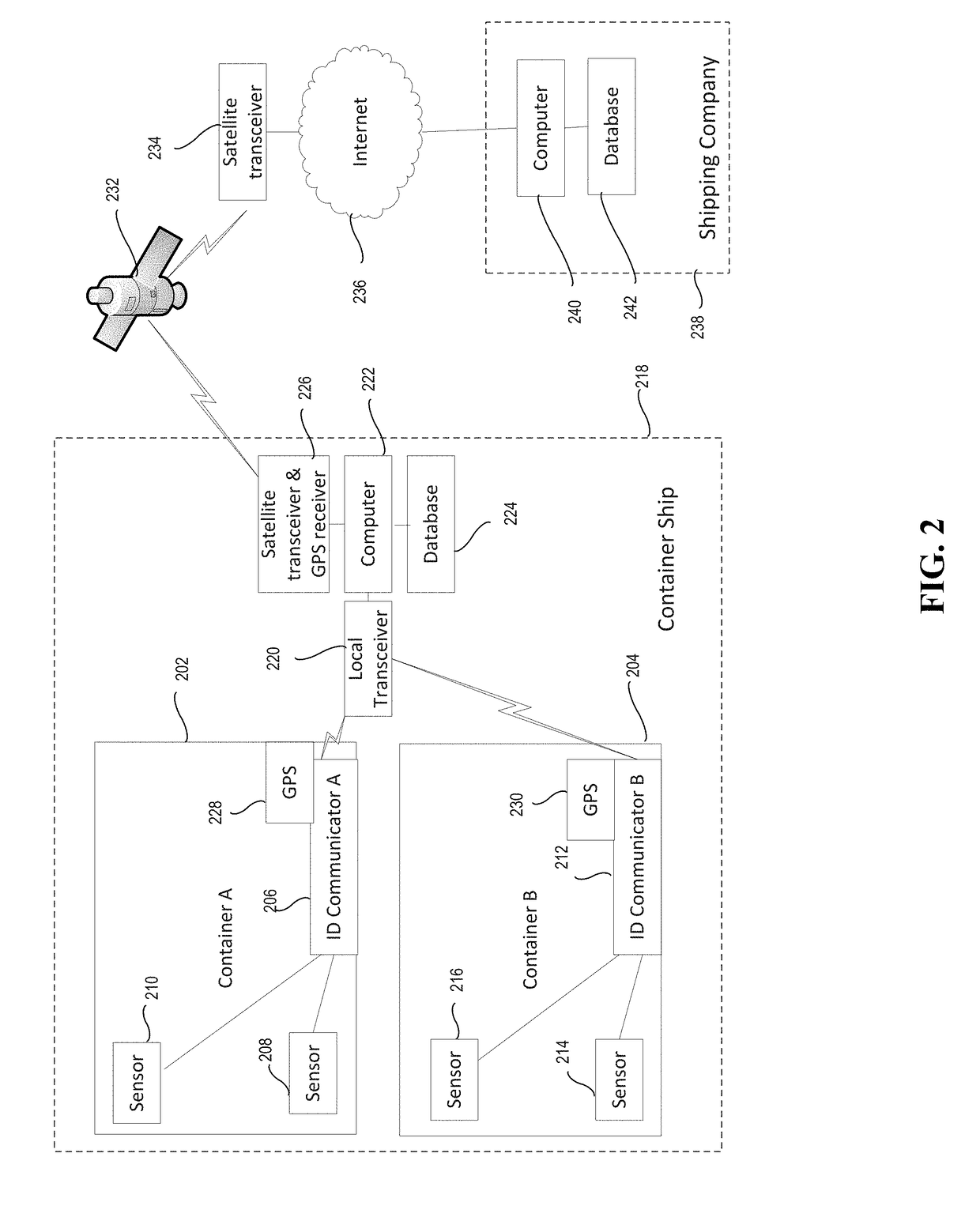
Tracking shipping using blockchain
In one embodiment, a secure tracking method and apparatus for cargo in a physical commodity (a container for physical goods) is provided. A wireless ID communicator is provided in each container. A receiver on a transporter (a ship, truck, airplane, or drone) receives periodic goods status updates from a plurality of wireless ID communicators in containers on the transporter. The status updates are transmitted to a central blockchain maintained in a central blockchain database remote from the transporter. The status updates are also added to a local sidechain of the blockchain maintained in a side chain database on the transporter.
Owner:CARNEROS BAY CAPITAL LLC
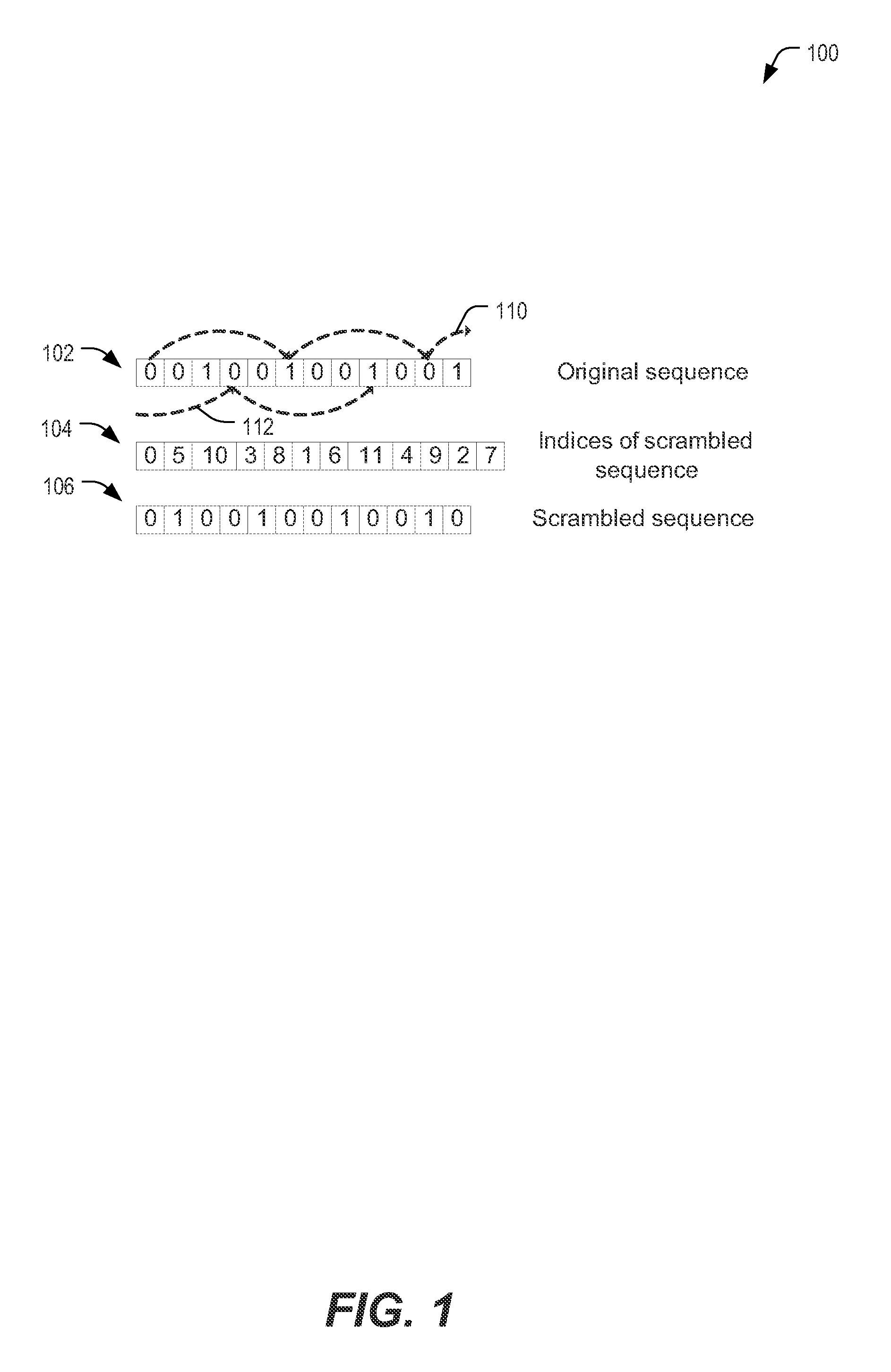
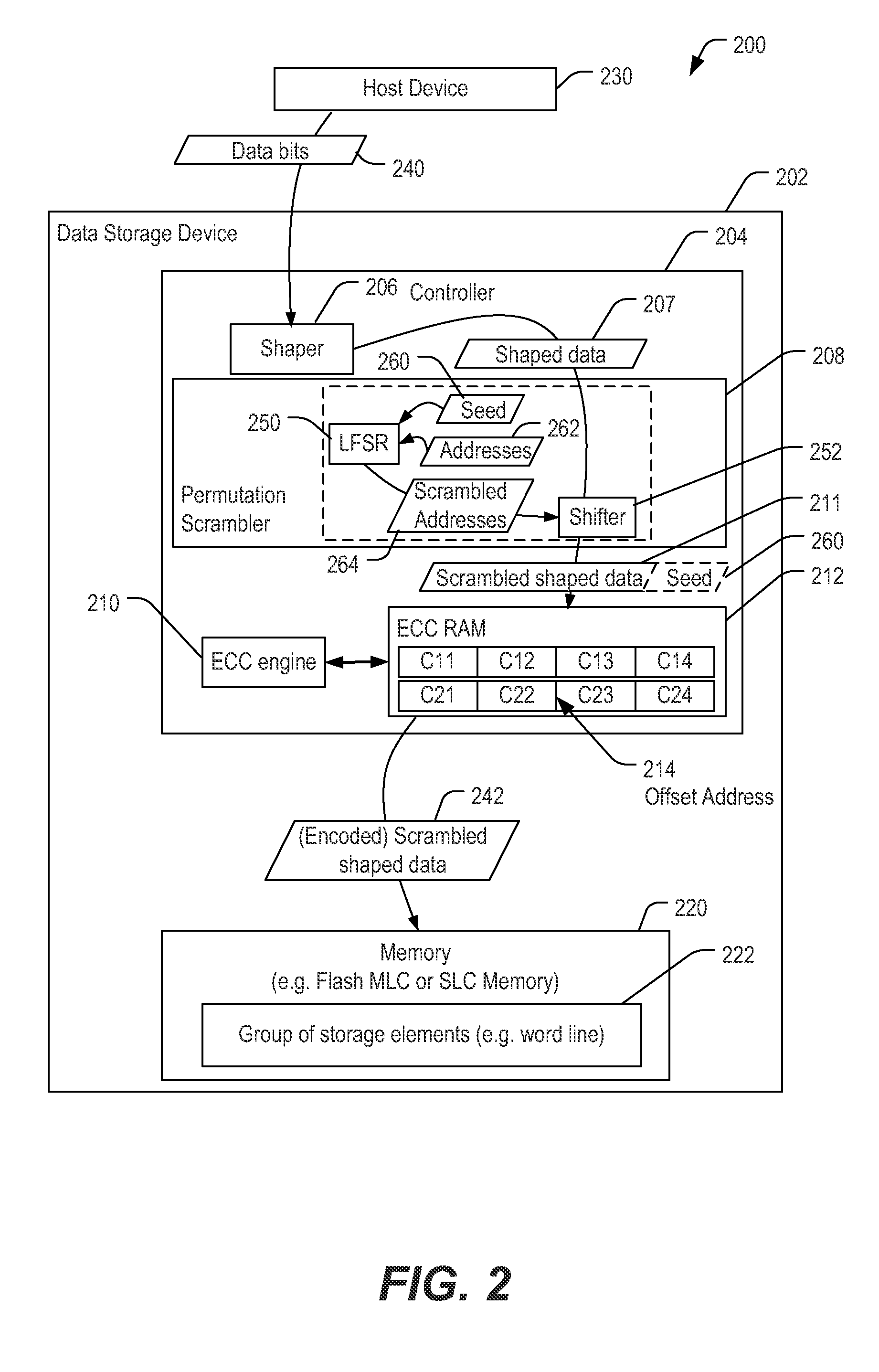
Method for scrambling shaped data
Owner:SANDISK TECH LLC
Multiple instruction dispatch tables for application program obfuscation
ActiveUS7353499B2Key distribution for secure communicationDigital data processing detailsProgram instructionScheduling instructions
Obfuscating an application program comprises reading an application program comprising code, determining multiple dispatch tables associated with the application program, transforming the application program into application program code configured to utilize the dispatch tables during application program execution to determine the location of instruction implementation methods to be executed based at least in part on a current instruction counter value, and sending the application program code. Executing an obfuscated application program comprises receiving an obfuscated application program comprising at least one instruction opcode value encoded using one of multiple instruction set opcode value encoding schemes, receiving an application program instruction corresponding to a current instruction counter value, selecting an instruction dispatch table based at least in part on the current instruction counter value, and executing the application program instruction using the selected instruction dispatch table.
Owner:ORACLE INT CORP
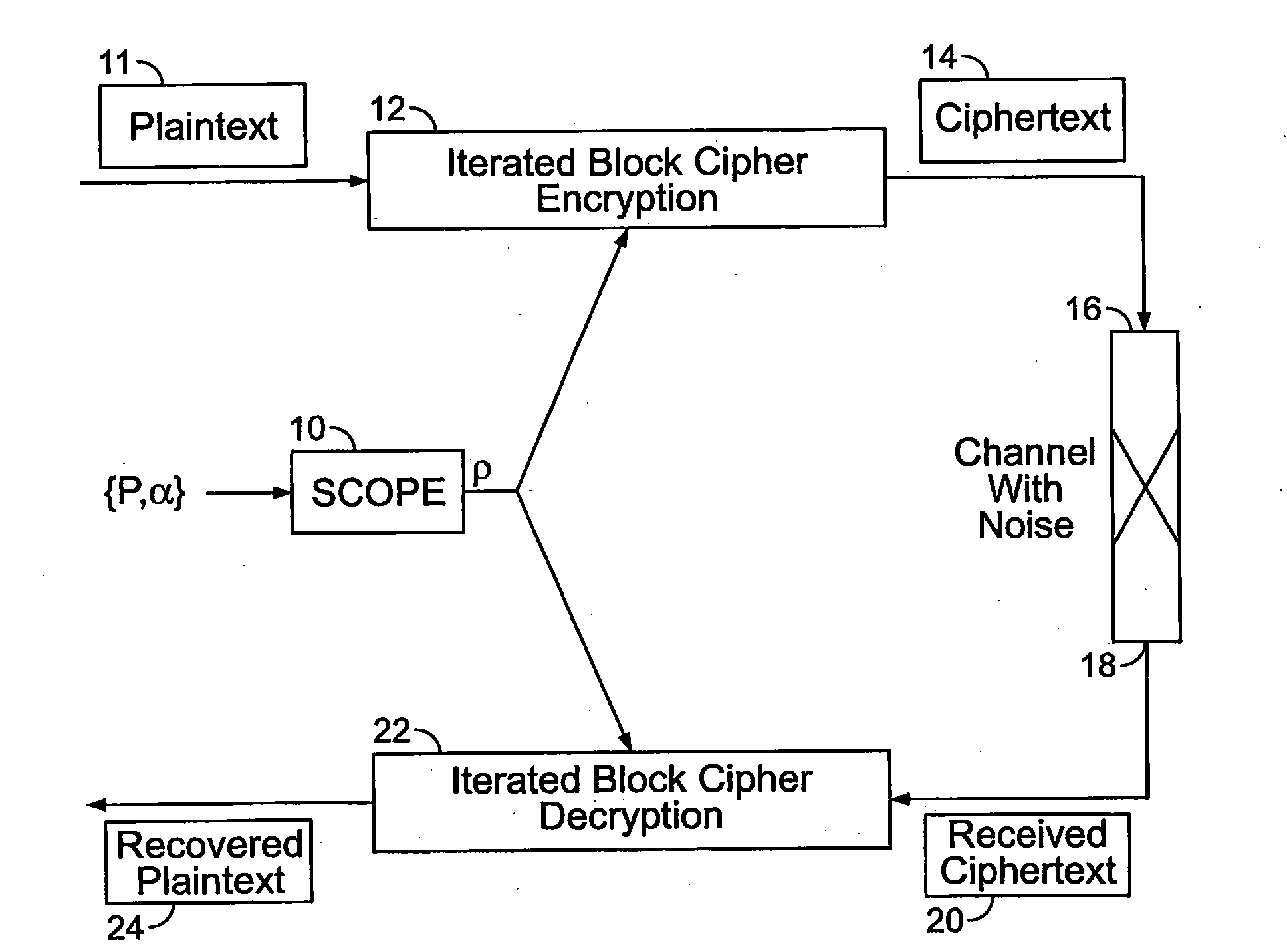
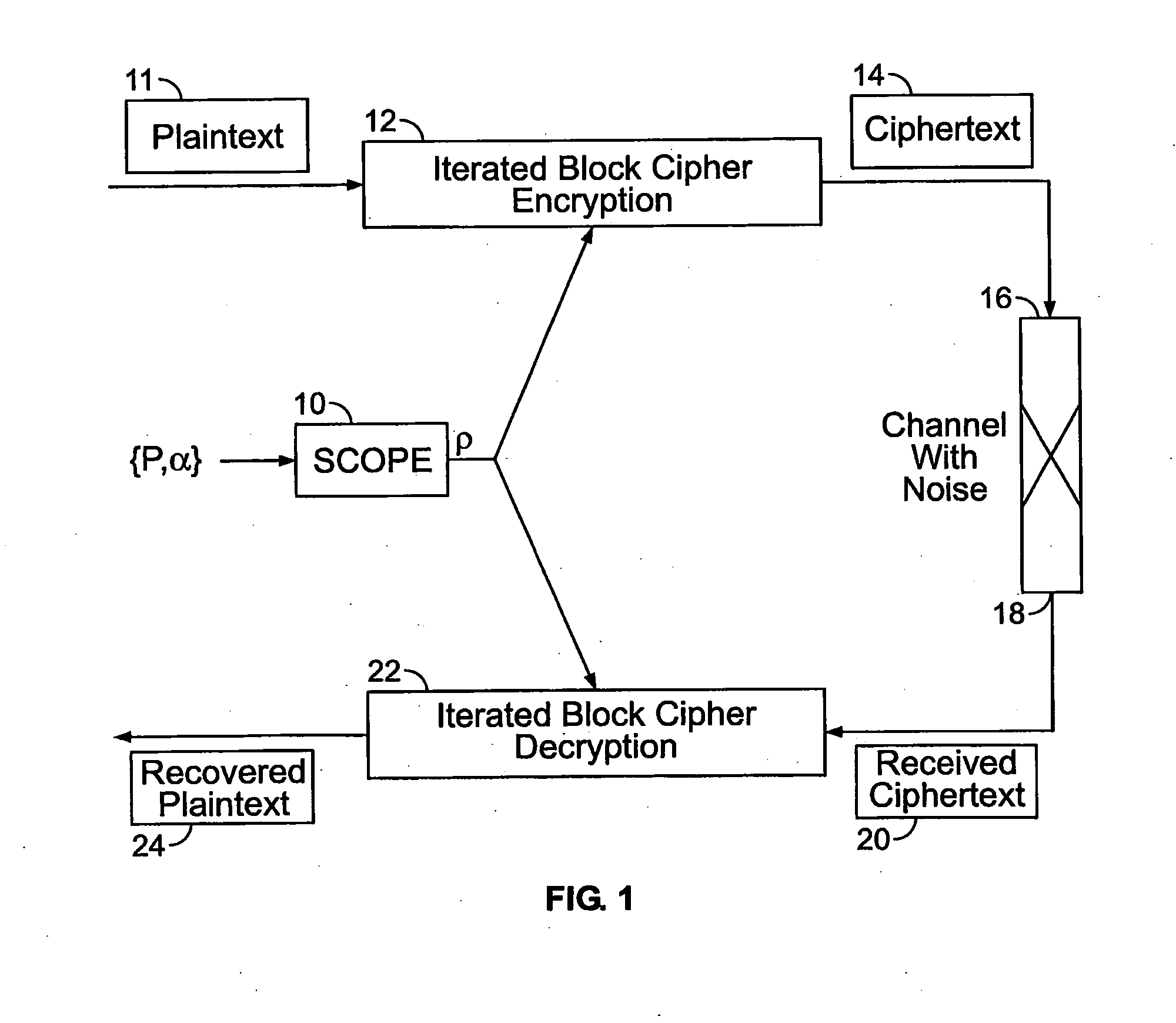
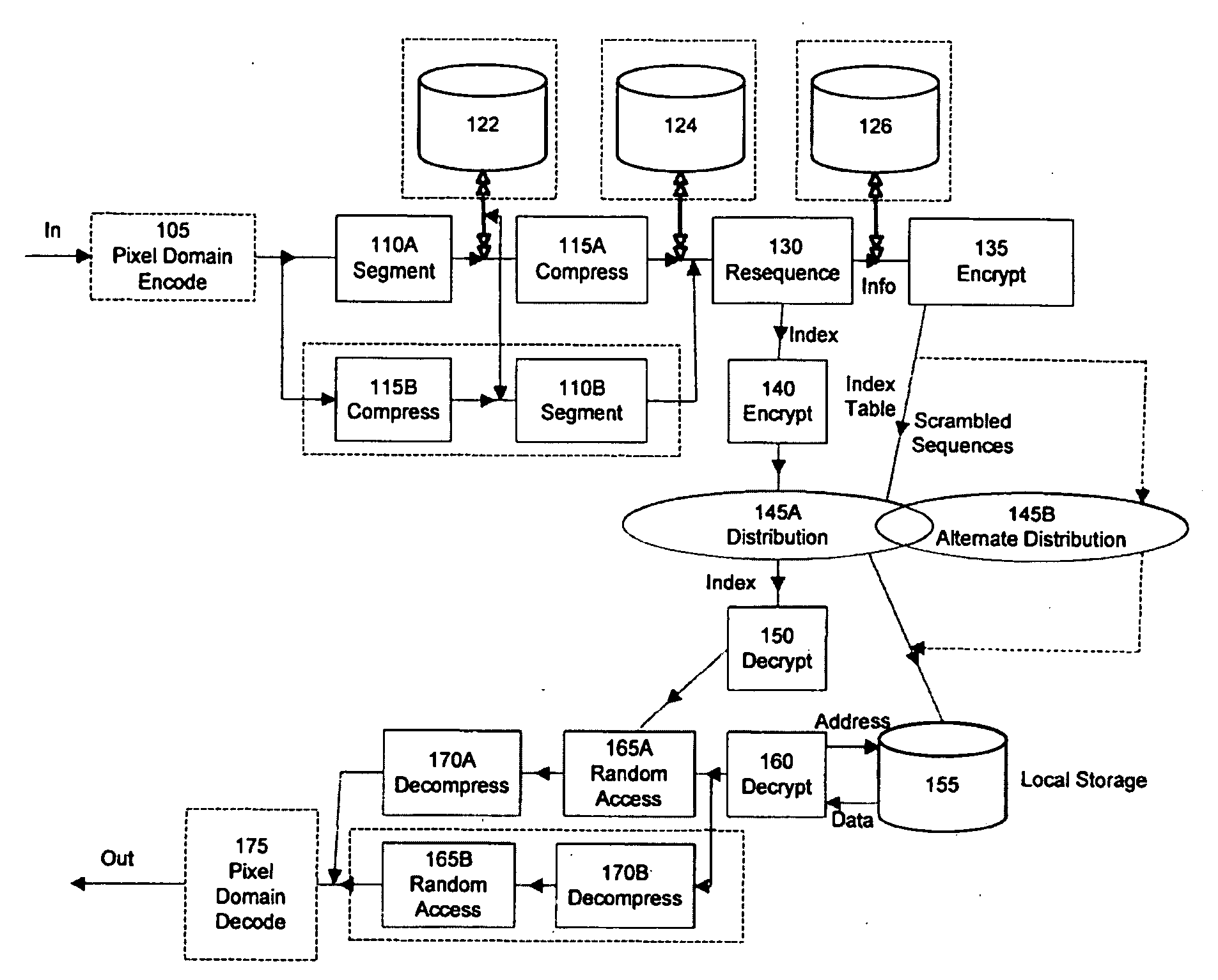
Method and apparatus for maintaining data integrity for block-encryption algorithms
InactiveUS20100067687A1Telegraphic message interchanged in timeSecret communicationPlaintextComputer hardware
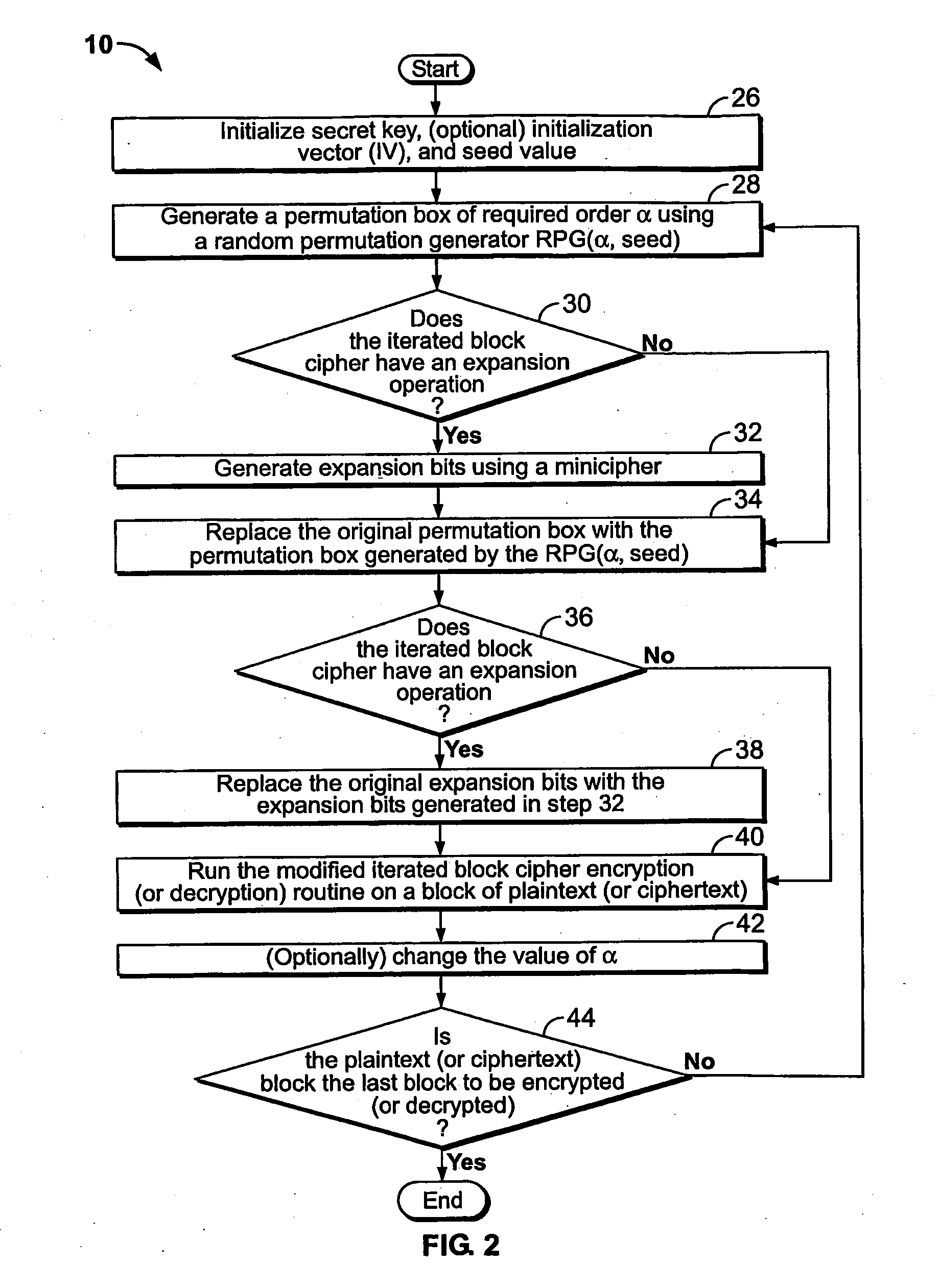
A method is disclosed for modifying an iterated block cipher by controlling the operations and transformations that cause diffusion. In one embodiment which is applicable to any iterated block cipher (12), a diffusion function (10), during encryption, is selected based on a parameter which measures the order of permutation of the diffusion function (10) and applies the diffusion function (10) to the encryption routine (12). The user chooses the required amount of diffusion for a given block of plaintext (11). The plaintext (11) is then encrypted using the modified diffusion function (10) to produce a ciphertext (14) which is then sent over a communications channel (16) which may be noisy. At the receiving end (18) of the communications channel (16), the received ciphertext (20), which now may be corrupted by bit errors, is passed through an iterated block cipher decryption routine (22) using the same diffusion function (10) selected earlier during encryption. In a second embodiment, the SCOPE method is applied to the DES encryption and decryption standard. The expansion bits (82) of DES are replaced with a minicipher (98a-98n), and the DES standard permutation box (88) is replaced with a permutation box (104a-104n) modified according to a user-specified order of permutation. In a third embodiment, the SCOPE method is applied to the AES encryption and decryption standard. In the SCOPE-enhanced version of AES, diffusion is controlled by altering the diffusion of the “MixColumn” or “InvMixColumn” transformation based on its branch number and by changing the number of shifts in the “ShiftRow” or “InvShfitRow” transformations.
Owner:STEVENS INSTITUTE OF TECHNOLOGY
Method for securing safety of electronic information
InactiveUS6957349B1Avoid interferenceImprove reliabilityData stream serial/continuous modificationDigital data processing detailsElectronic informationWorld Wide Web
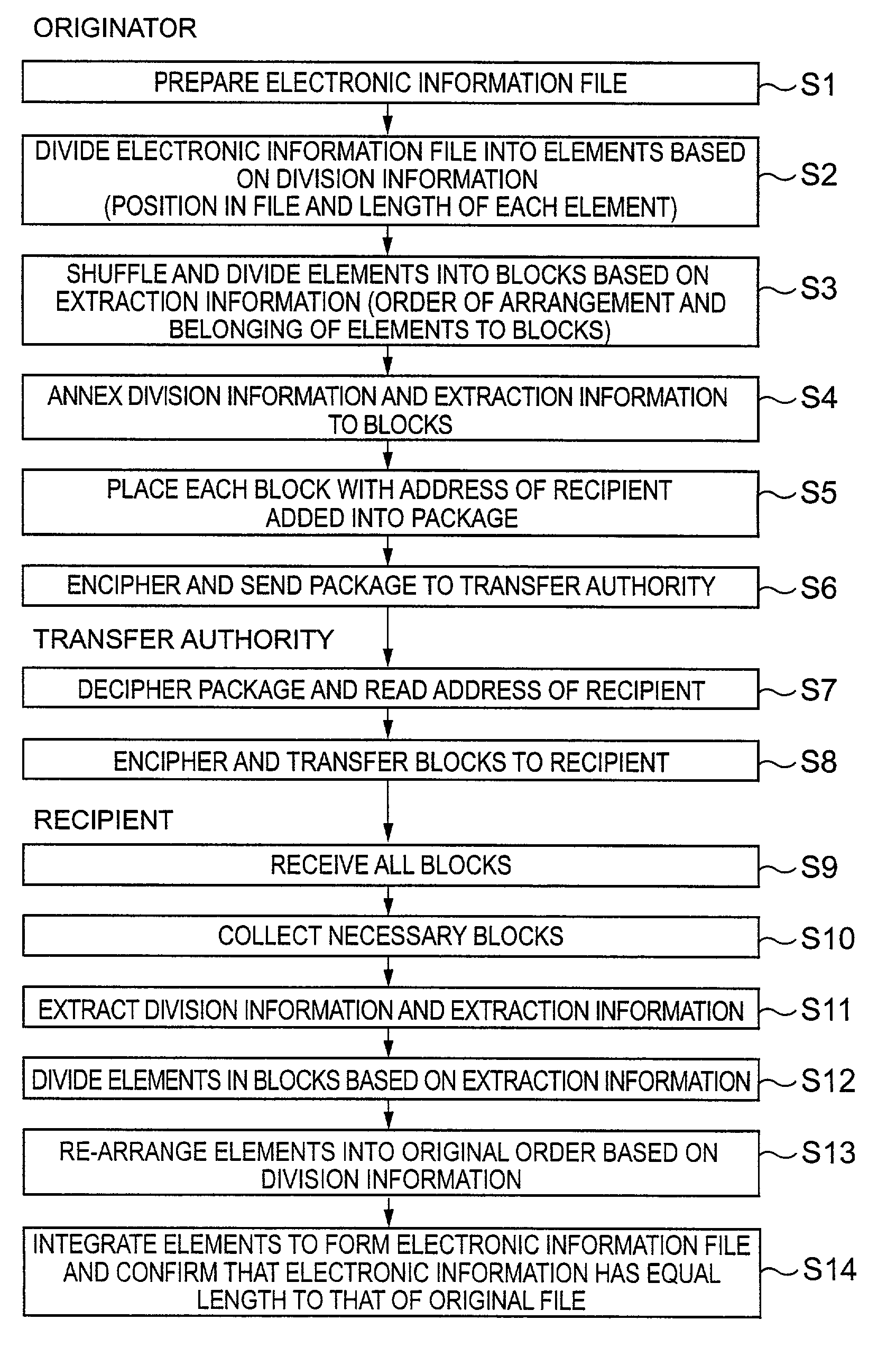
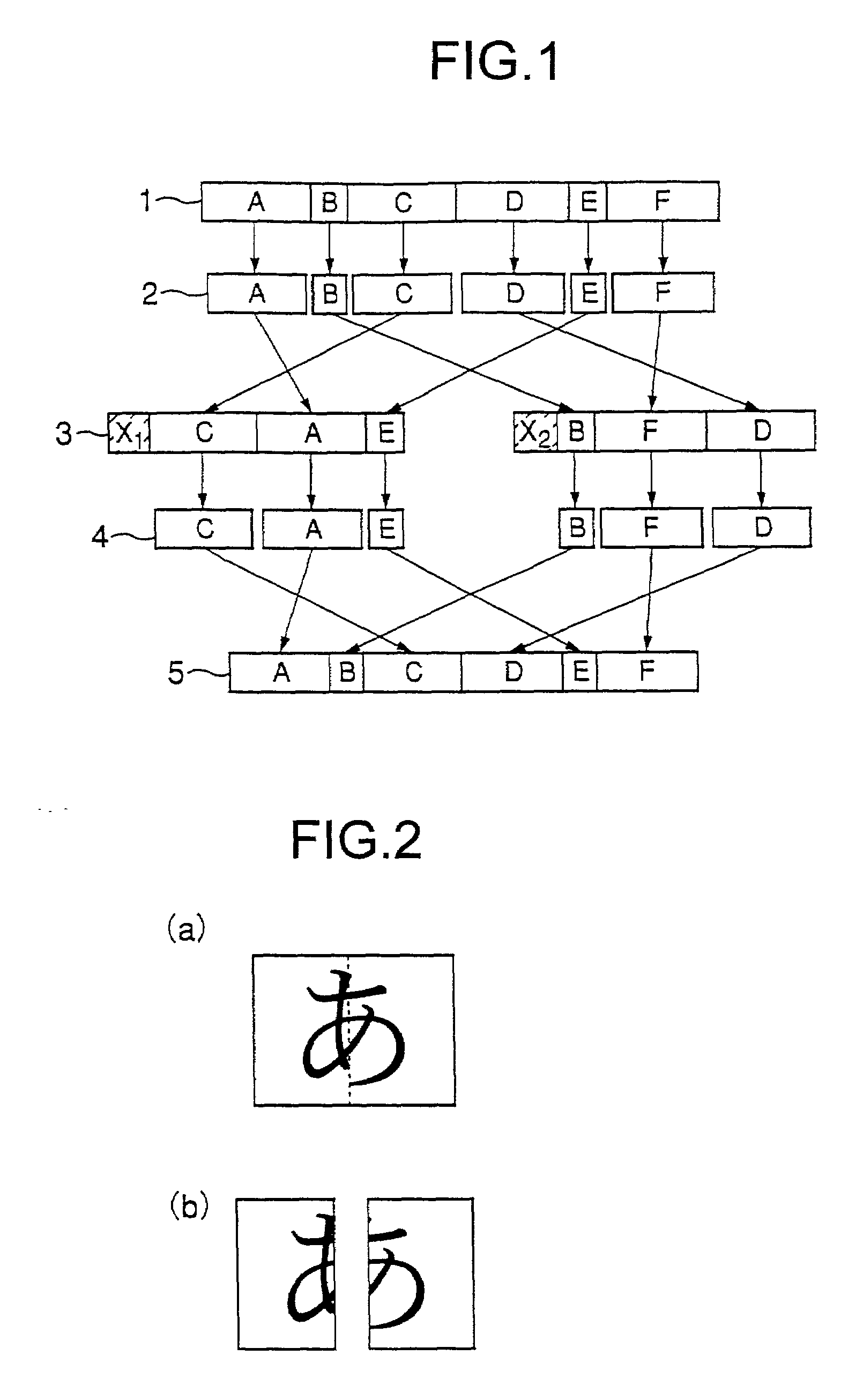
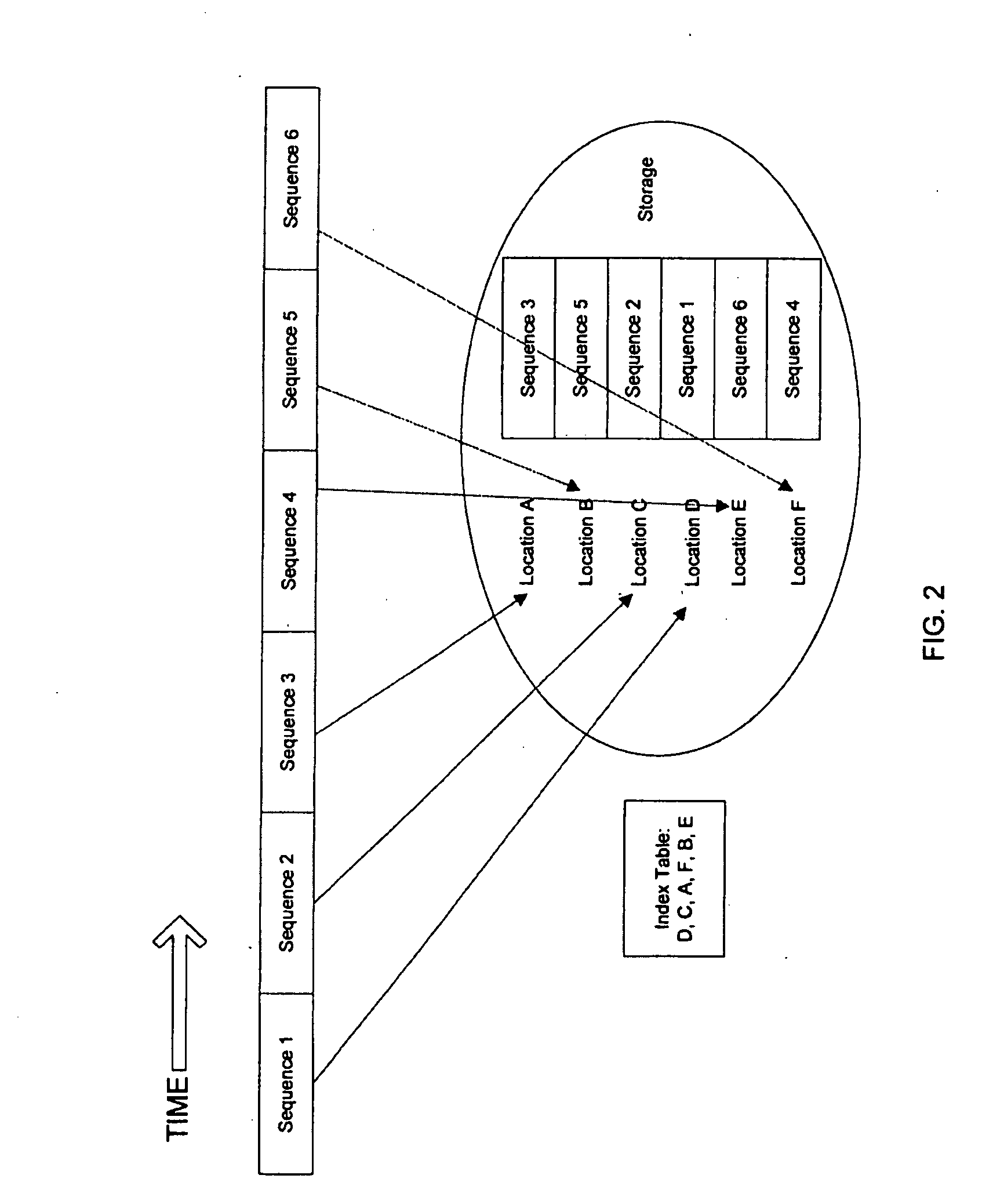
A security assurance technique for electronic information wherein an electronic information file 1 is divided into a plurality of information elements 2 and the divided information elements are selected and combined with their order changed to produce one or more information blocks 3, and division extraction data of the information elements is produced and the information blocks are formed and stored or transmitted, whereafter, when the electronic information is to be utilized, the information elements 4 included in the information blocks 3 are re-divided, re-arranged in the correct order and integrated based on the division extraction data to restore an original electronic information file 5, whereby, even if electronic information stored or being communicated is stolen, the value of the information is reduced to disable utilization of the information.
Owner:YASUKURA YUTAKA
Permutation of opcode values for application program obfuscation
ActiveUS7415618B2Key distribution for secure communicationData processing applicationsApplication softwareProgram obfuscation
Obfuscating an application program comprises reading an application program comprising code, transforming the application program code into transformed application program code that uses one of multiple opcode value encoding schemes of a dispatch table associated with the application program, and sending the transformed application program code. Executing an obfuscated application program comprises receiving an obfuscated application program comprising at least one instruction opcode value encoded using one of multiple instruction set opcode value encoding schemes, determining a dispatch table associated with the application program, and executing the application program using the associated dispatch table. The dispatch table corresponds to the one of multiple instruction set opcode value encoding schemes.
Owner:ORACLE INT CORP
Method and apparatus for performing network processing functions
ActiveUS7188250B1Effective serviceEasily configure networkEncryption apparatus with shift registers/memoriesUser identity/authority verificationNetwork processing unitNetwork architecture
A novel network architecture that integrates the functions of an internet protocol (IP) router into a network processing unit (NPU) that resides in a host computer's chipset such that the host computer's resources are perceived as separate network appliances. The NPU appears logically separate from the host computer even though, in one embodiment, it is sharing the same chip.
Owner:NVIDIA CORP
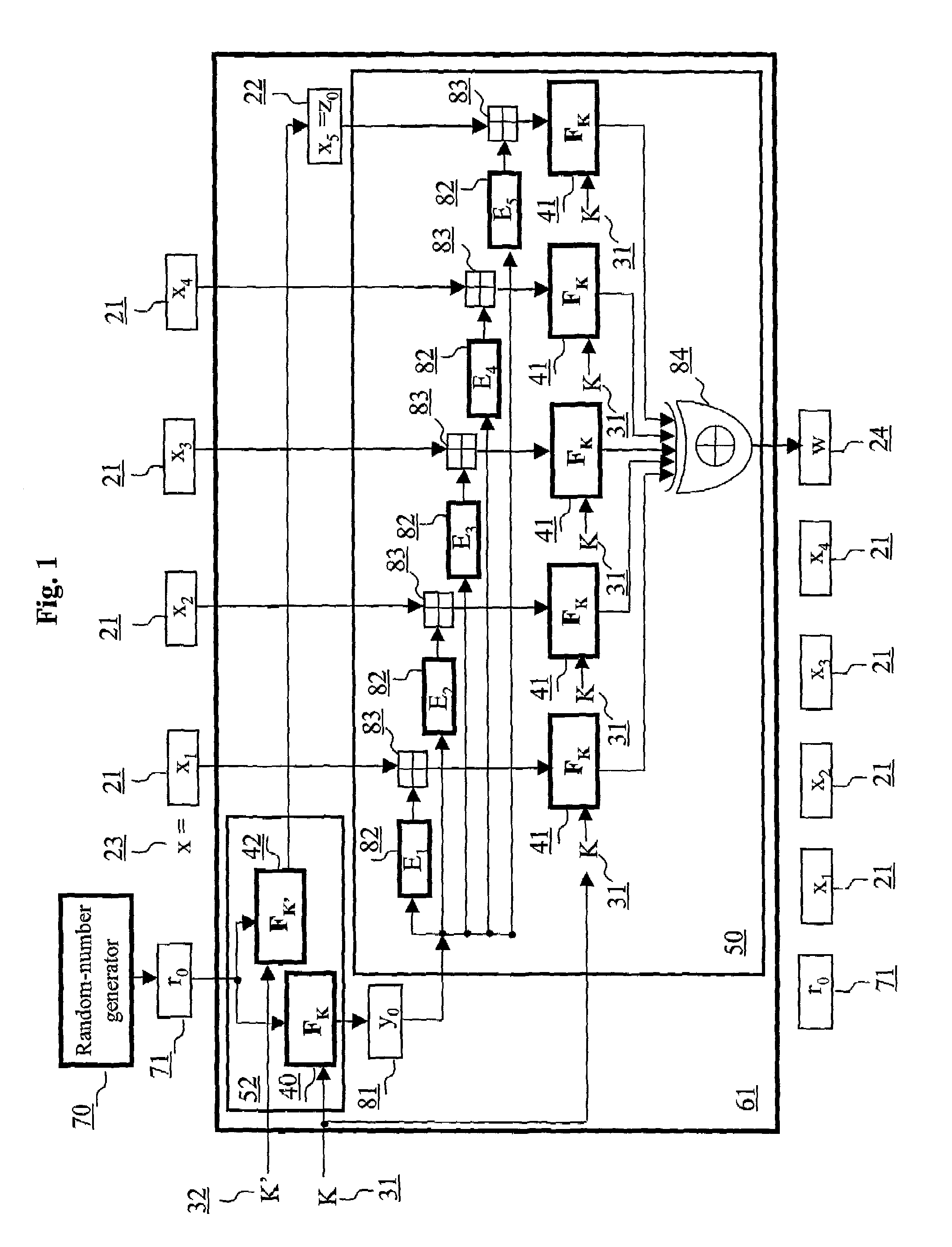
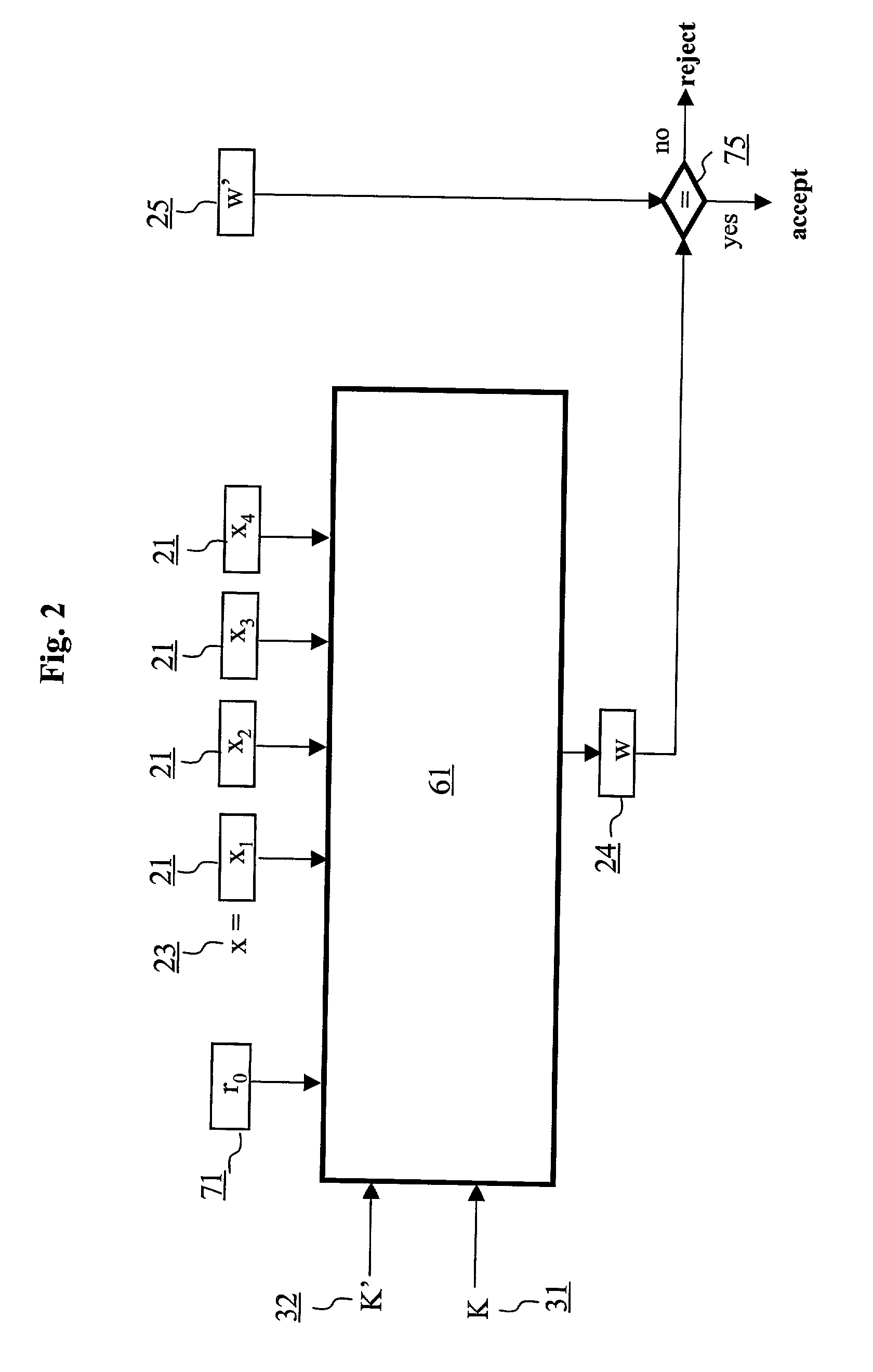
Authentication method and schemes for data integrity protection
ActiveUS7054445B2Public key for secure communicationUser identity/authority verificationComputer hardwareMessage length
An authentication method and schemes using a block cipher to protect data integrity (authenticity) during communication over insecure channels and during data storage on insecure media. The authentication method and schemes of this invention allow, in a further aspect, message and data signing and verification in parallel or pipelined manners, in addition to sequential operation, without requiring twice as many block enciphering operations as the number of input plaintext blocks. The present invention allows, in a yet further aspect, software and hardware implementations used in high-performance systems and networks where multiple processing units are available for block enciphering operations. In a yet further aspect, the authentication method and schemes of this invention allow incremental updates and out-of-order processing of authentication tags. In a yet further aspect, the authentication method and schemes of this invention are suitable for real-time applications where message length remains unknown until the entire message is received, and commencing message authentication cannot be deferred until the end of the message.
Owner:VDG
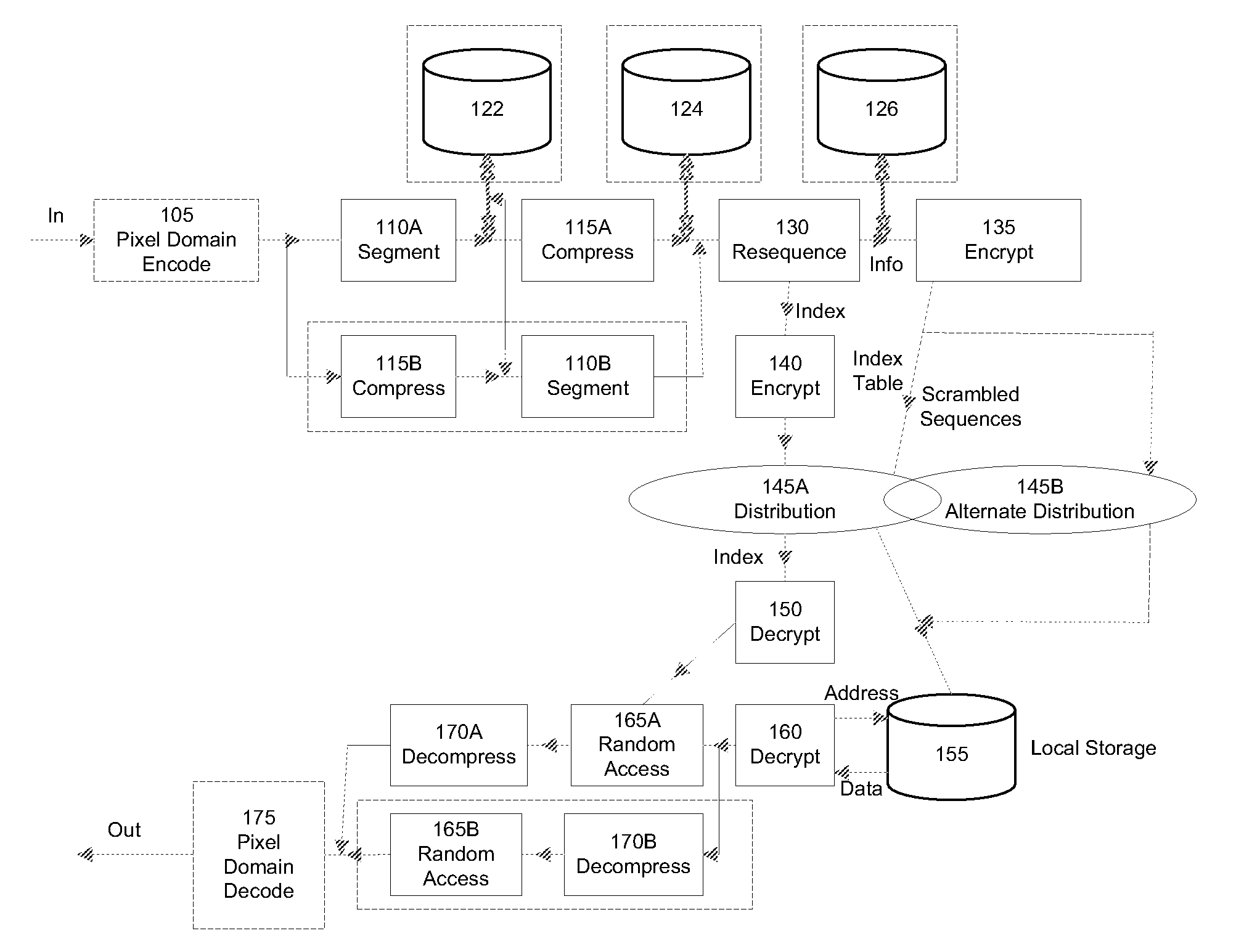
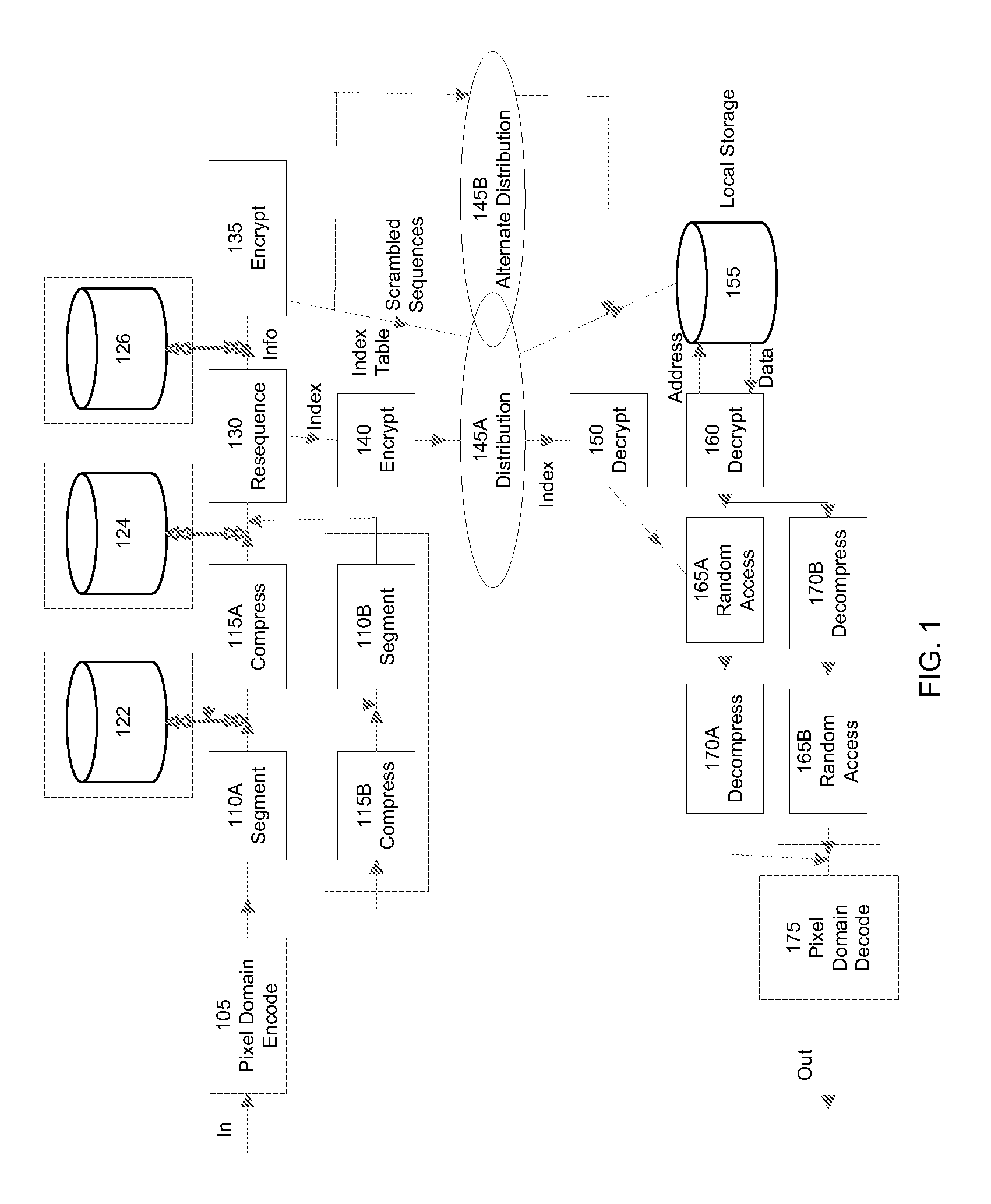
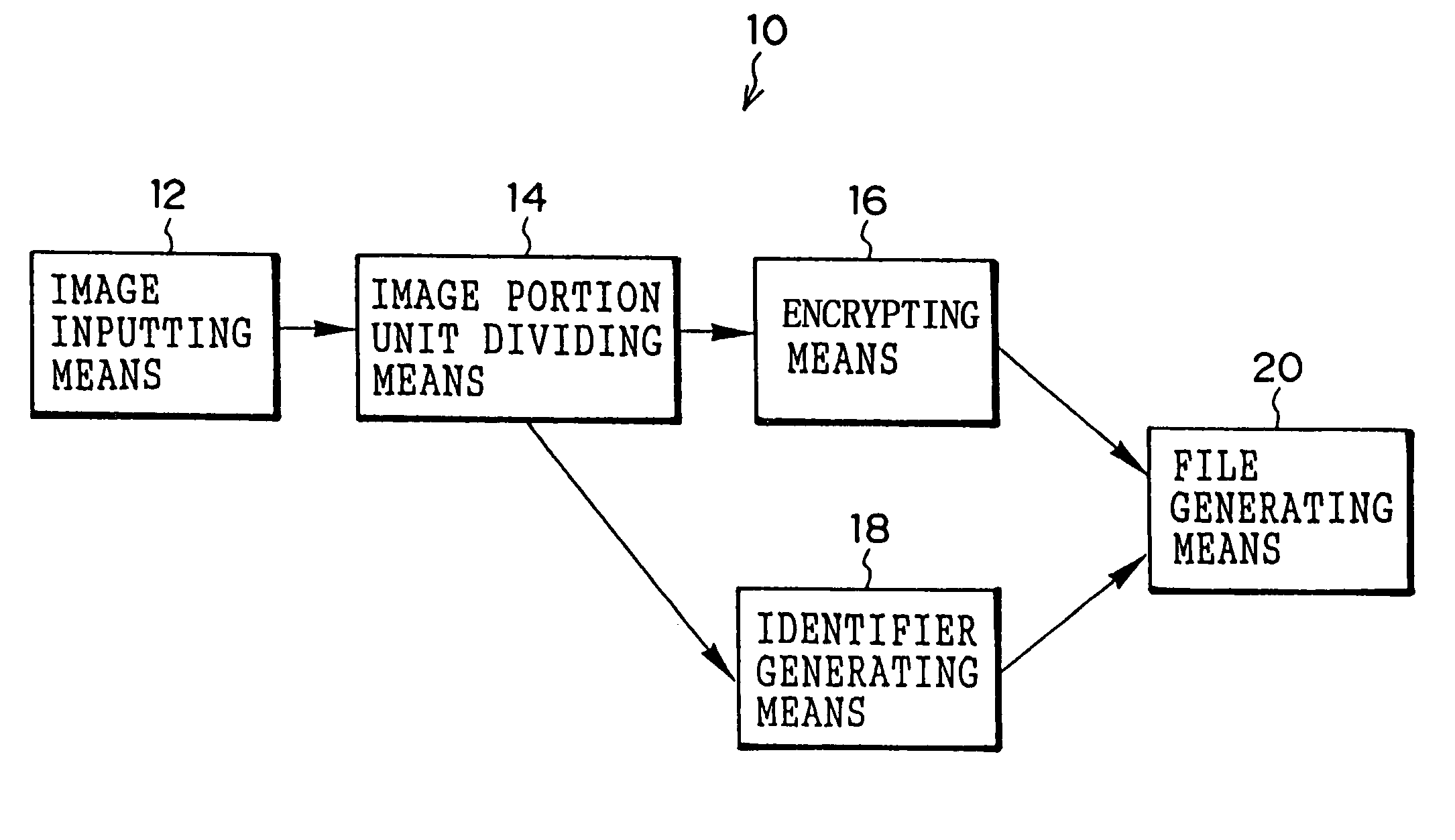
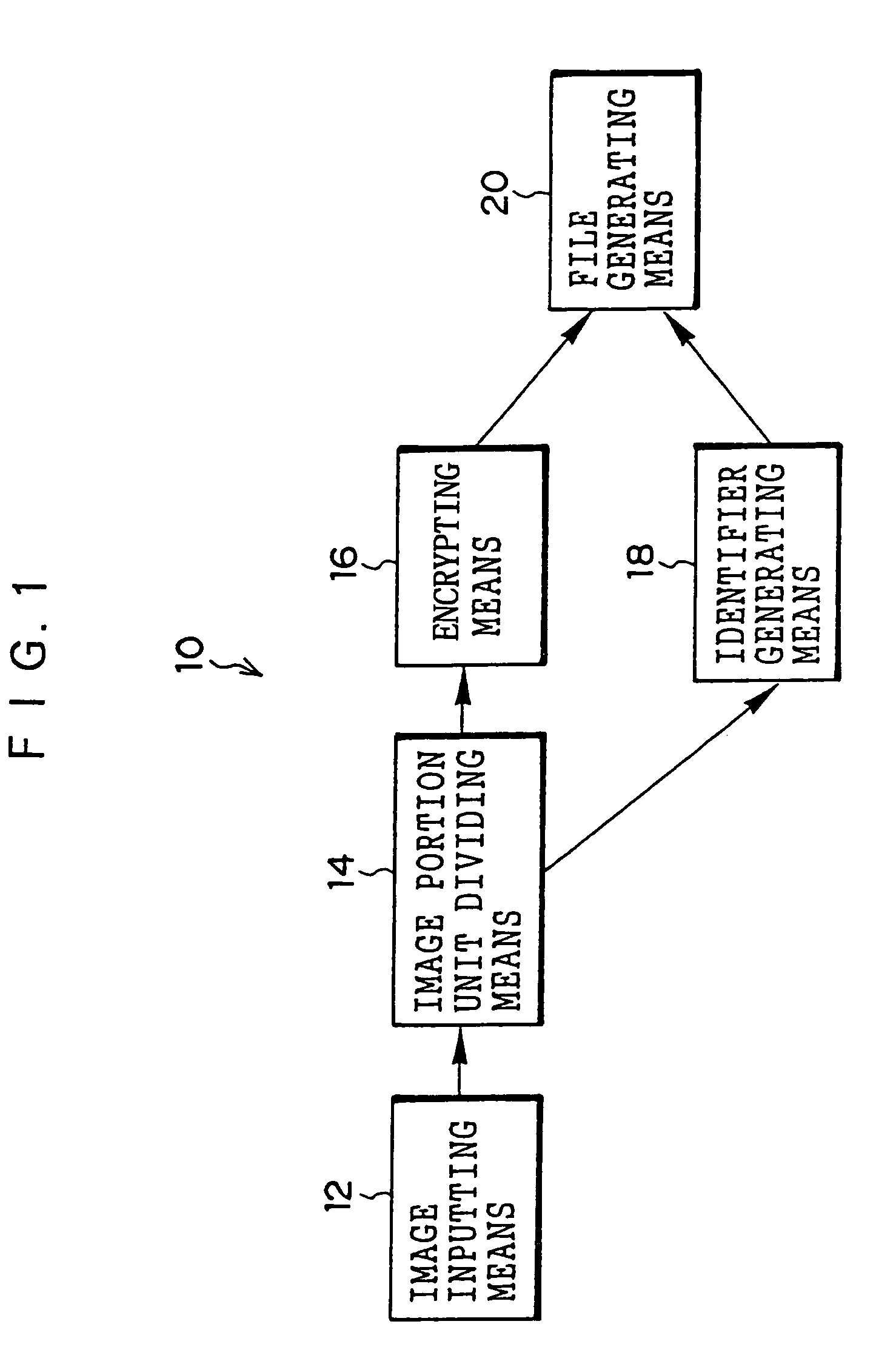
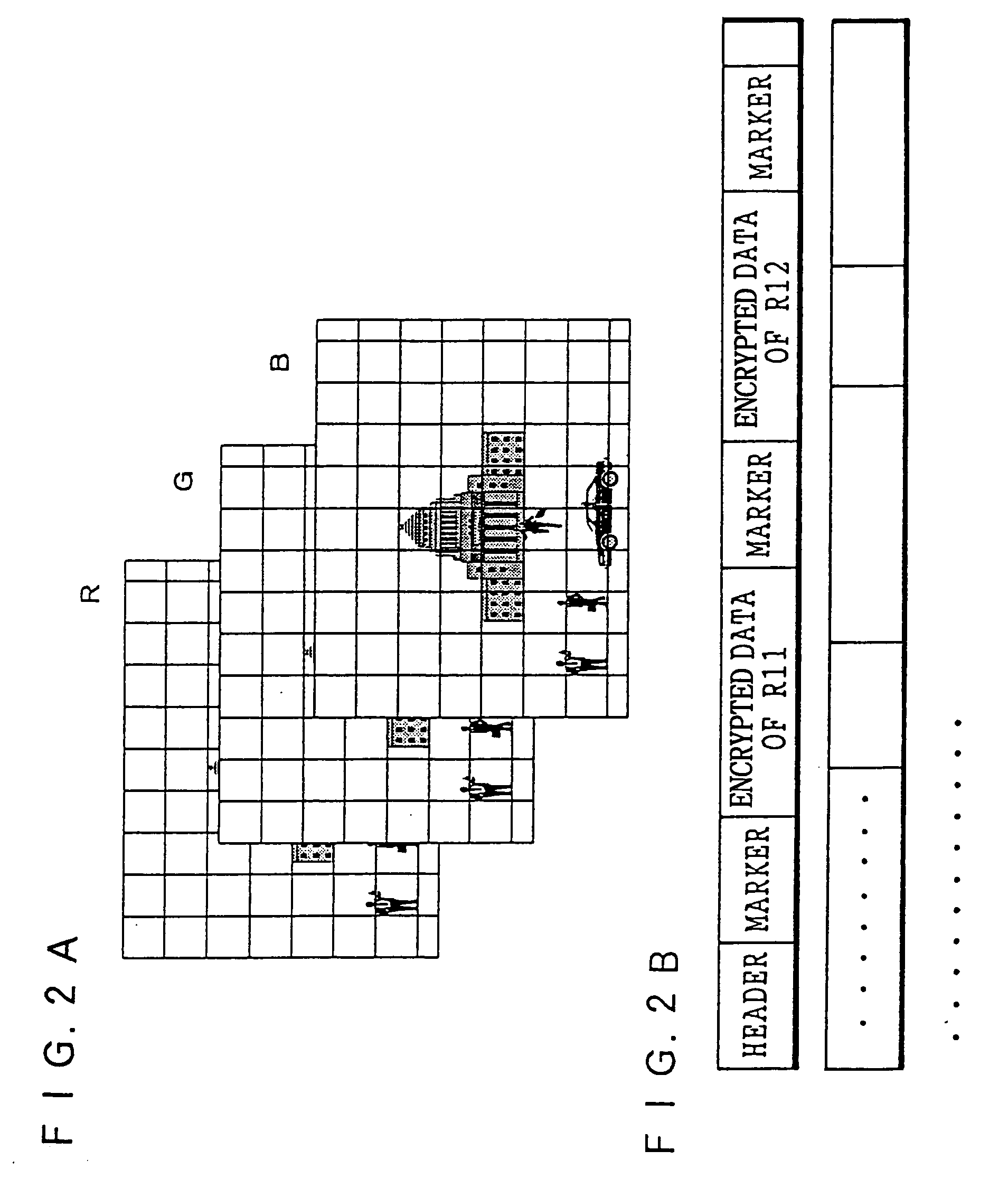
Image encrypting method, image encrypting device, recording medium on which image encrypting procedures are recorded, and recording medium on which encrypted image file is recorded
InactiveUS6938028B1Improve processing speedMeet demandStill image data retrievalData processing applicationsSingle imageImaging data
An image encrypting method, an image encrypting device, a recording medium on which image encrypting procedures are recorded, and a recording medium on which an encrypted image file is recorded are provided in order to be able to respond to a request for transmission of a portion of an image and improve a rate of processing image data, even when a device which stores the encrypted image file is not authorized to decrypt. An image inputting device reads an image file. An image portion unit dividing device divides a read image file into a portion image data of tile units. An encrypting device encrypts the portion image data. An identifier generating device generates information incidental to the portion image data. A file generating device generates a single image file from the incidental information and encrypted portion image data.
Owner:FUJIFILM CORP
Secure Information Distribution System Utilizing Information Segment Scrambling
InactiveUS20090041235A1Data stream serial/continuous modificationMultiple keys/algorithms usageDistribution systemComputer security
Owner:AKIKAZE TECH
Permutation of opcode values for application program obfuscation
ActiveUS20050071655A1Key distribution for secure communicationData processing applicationsApplication schedulingInstruction set
Obfuscating an application program comprises reading an application program comprising code, transforming the application program code into transformed application program code that uses one of multiple opcode value encoding schemes of a dispatch table associated with the application program, and sending the transformed application program code. Executing an obfuscated application program comprises receiving an obfuscated application program comprising at least one instruction opcode value encoded using one of multiple instruction set opcode value encoding schemes, determining a dispatch table associated with the application program, and executing the application program using the associated dispatch table. The dispatch table corresponds to the one of multiple instruction set opcode value encoding schemes.
Owner:ORACLE INT CORP
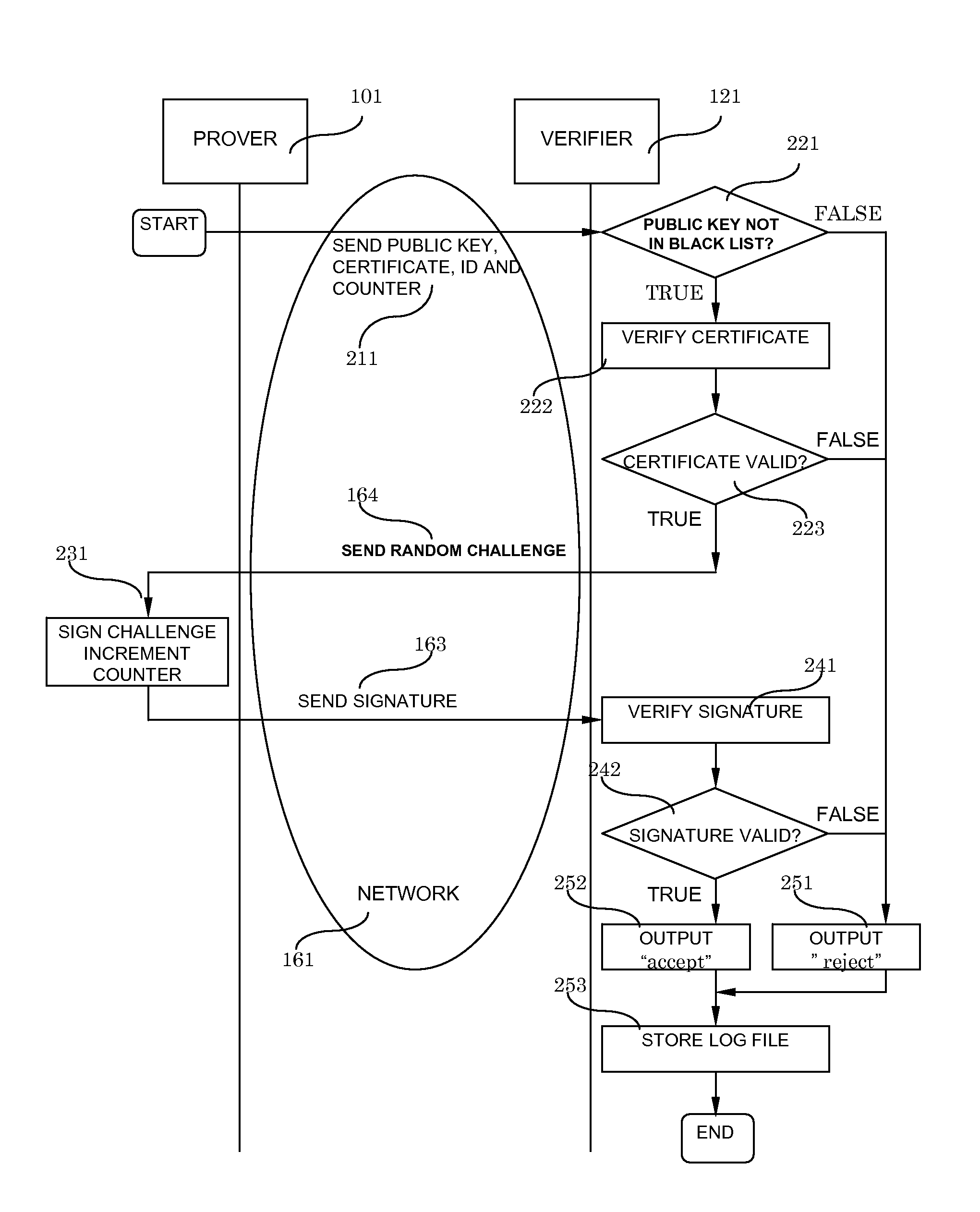
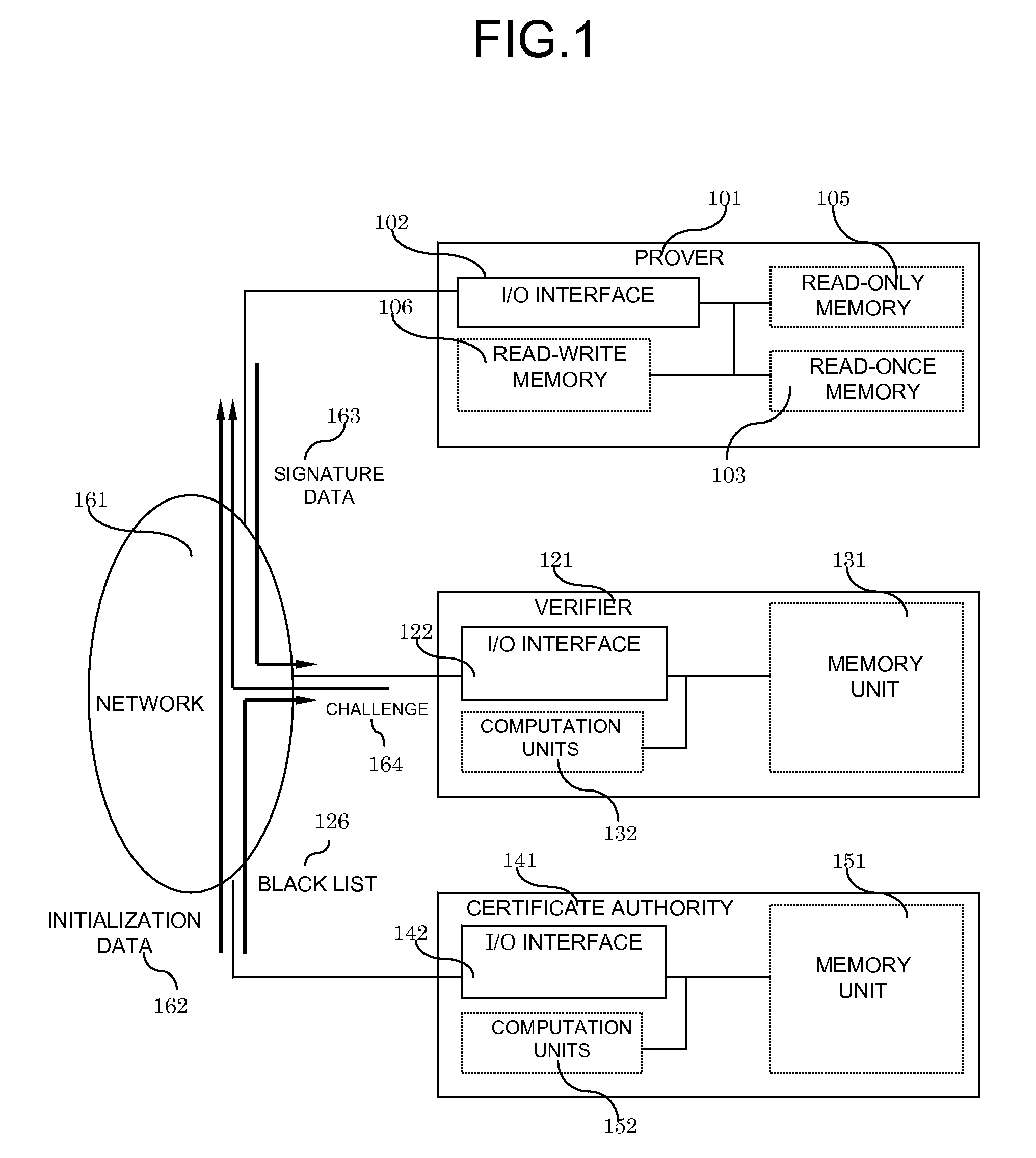
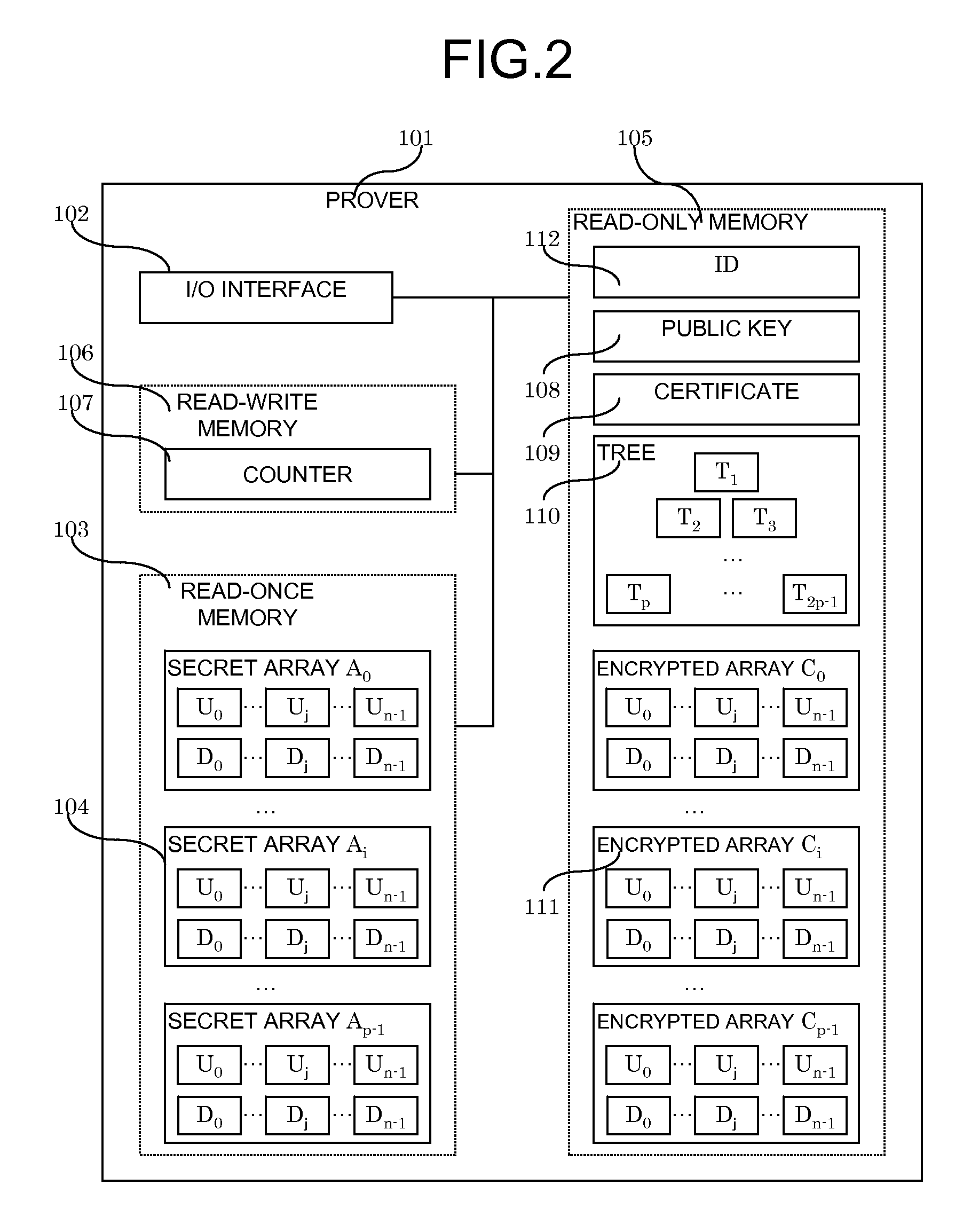
System and method for digital signatures and authentication
InactiveUS8291229B2Simple memory controllerPublic key for secure communicationUser identity/authority verificationDigital signatureKey issues
A system and method for authentication and digital signatures on memory-only supports, comprising a read-once memory unit storing secret arrays, whose contents are destroyed upon reading, a standard memory unit storing encrypted arrays, tree data authenticating the encrypted arrays to one single public key, and a certificate of the public key issued by a certificate authority. The memory support sends its public key and certificate to a verifier, receives a challenge which is signed by elements from secret arrays in the read-once memory. The verifier system checks the authenticity of the data revealed from the read-once memory by encrypting it and comparing the result to one of the encrypted arrays, and verifies that the encrypted array authenticates to the public key using tree data. Finally, the verifier checks the authenticity of the public key using the certificate.
Owner:HITACHI LTD
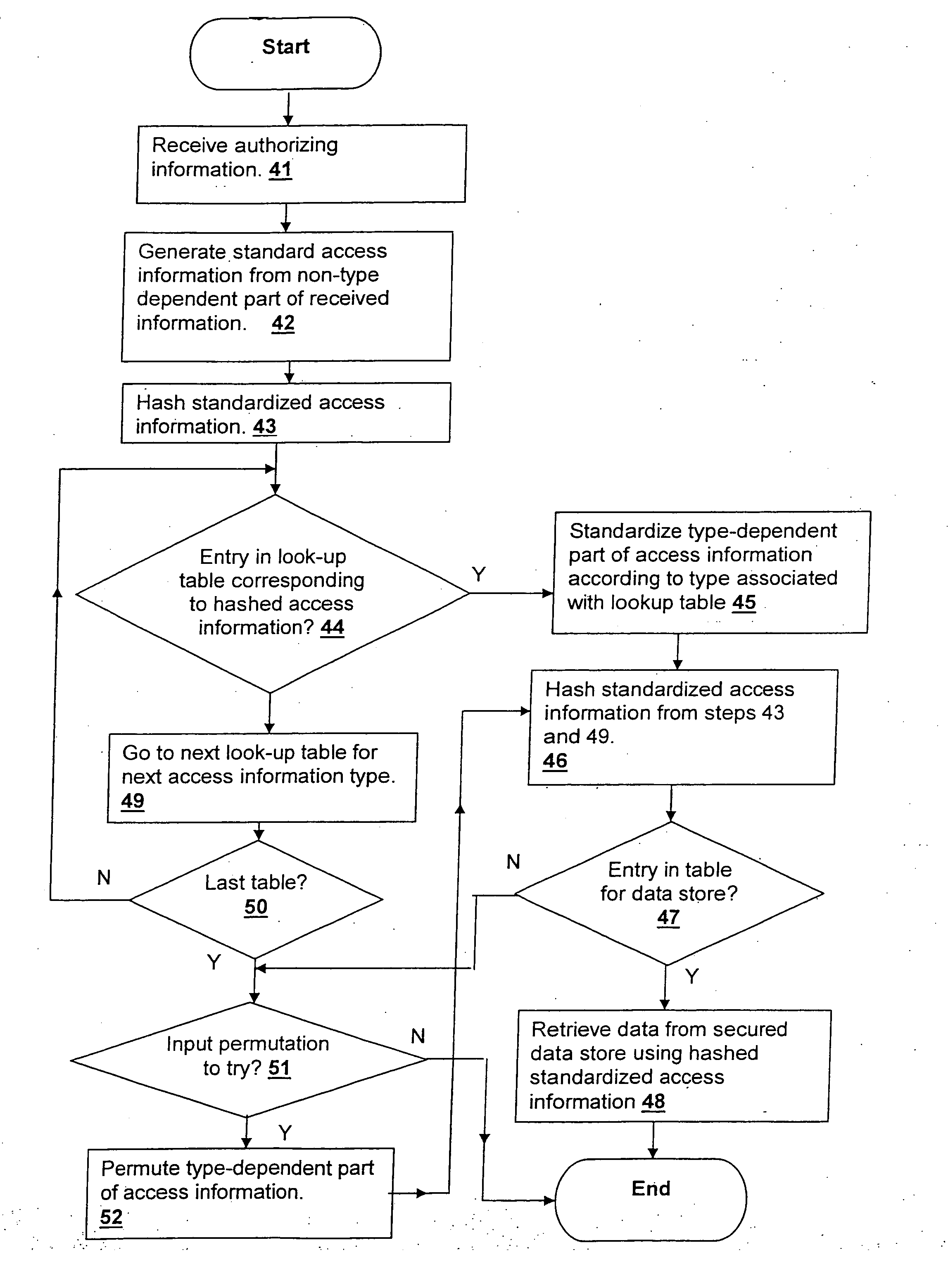
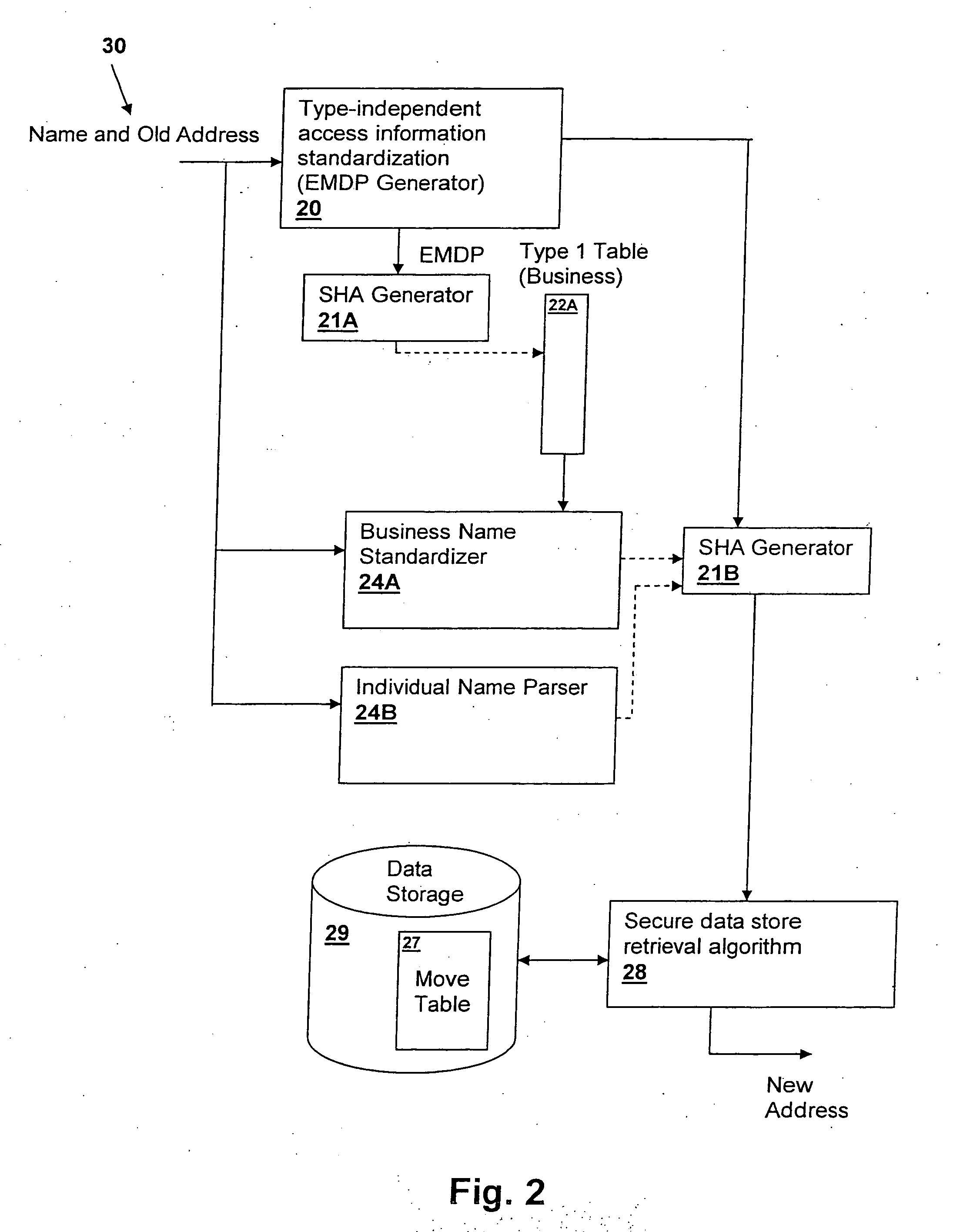
Method and system for efficientyly retrieving secured data by securely pre-processing provided access information
InactiveUS20060031213A1Data processing applicationsDigital data information retrievalInformation typeStorage security
A method and system for efficiently retrieving secured data by securely pre-processing provided access information, provides data store security based on only a single piece of access information, which is generally public, such as the proper name of a business or individual that is used to retrieve mailing address information. The access information is hashed for access to a secured data store and efficient access and low data storage for permutations of input access information are provided by verifying the presence of an entry for the hashed access information in a look-up table. If an entry is found, the data store is accessed using the hashed access information, but if an entry is not found, another look-up table corresponding to another information type may be tried or the input access information permuted and retried.
Owner:US POSTAL SERVICE
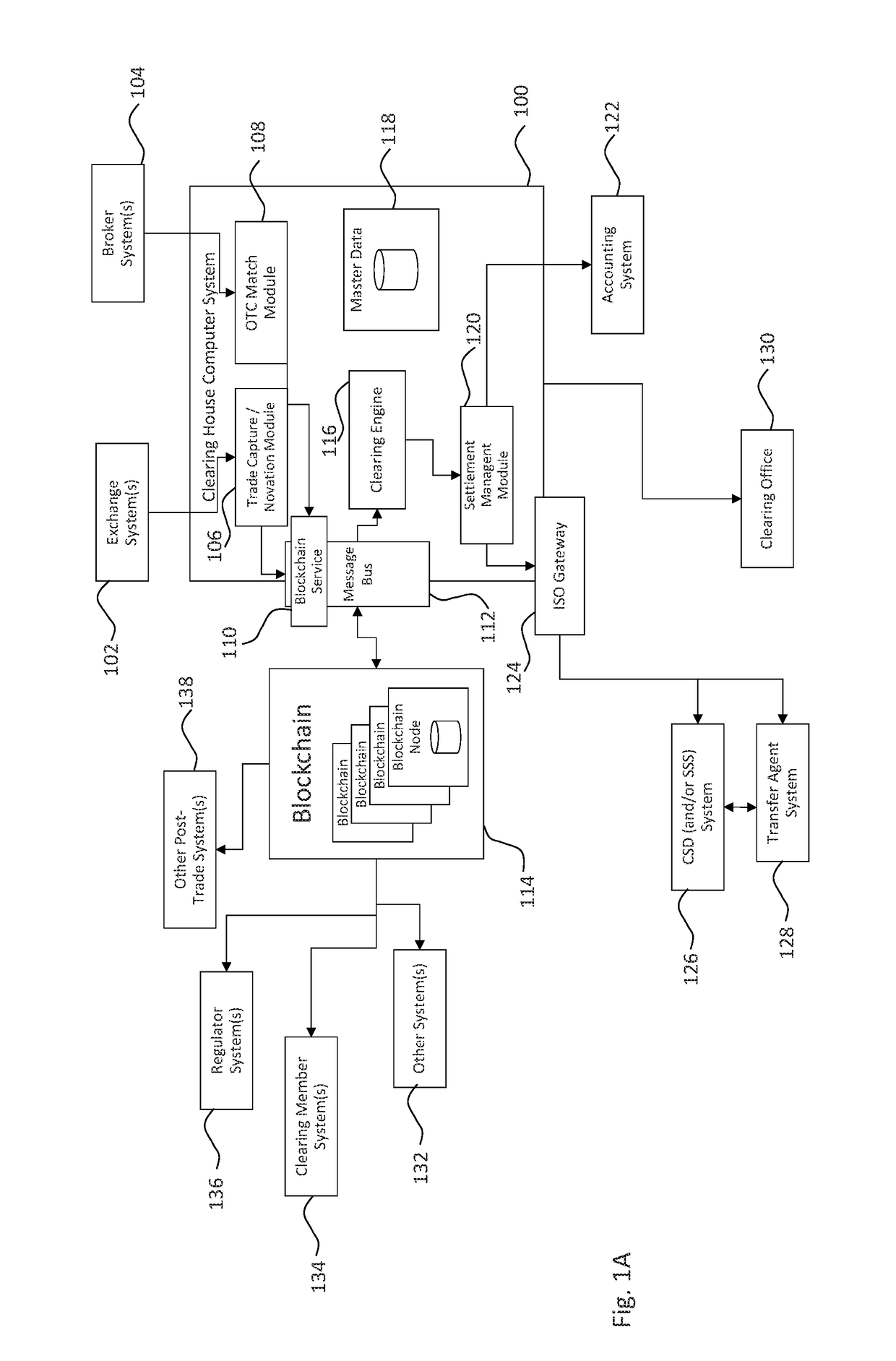
Secure dynamic communication network and protocol
ActiveUS9998434B2Increase the difficultyUsefulness of their knowledge would be short-livedMultiple keys/algorithms usageEncryption apparatus with shift registers/memoriesDigital dataData segment
In a secure cloud for transmitting packets of digital data, the packets may be repeatedly scrambled (i.e., their data segments reordered) and then unscrambled, split and then mixed, and / or encrypted and then decrypted as they pass through media nodes in the cloud. The methods used to scramble, split, mix and encrypt the packets may be varied in accordance with a state such as time, thereby making the task of a hacker virtually impossible inasmuch as he or she may be viewing only a fragment of a packet and the methods used to disguise the data are constantly changing.
Owner:LISTAT LTD
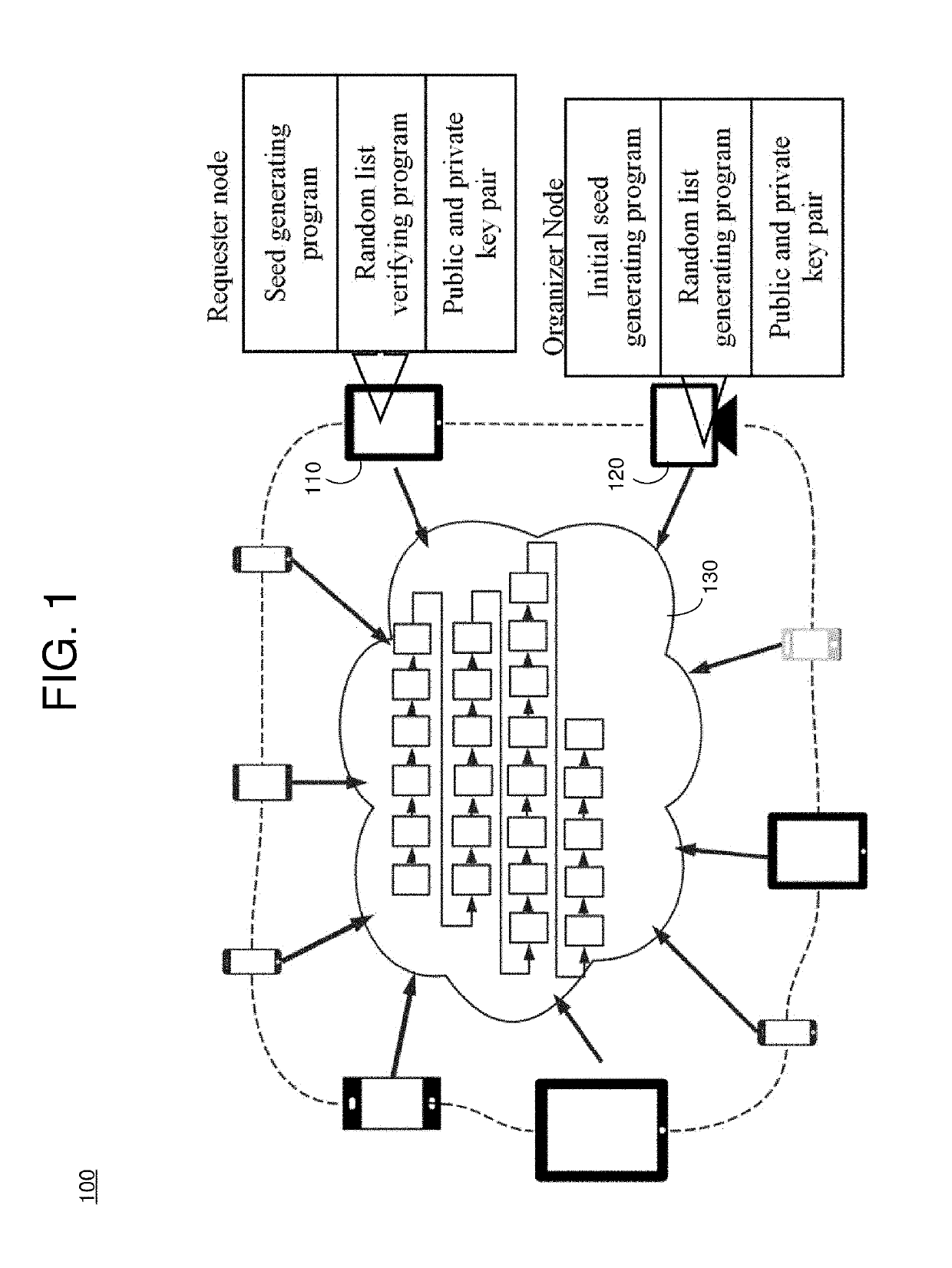
Distributed ledger for generating and verifying random sequence
ActiveUS20190273610A1Key distribution for secure communicationRandom number generatorsComputer hardwareDistributed ledger
An example operation may include one or more of generating an initial seed and allocating one or more authorized bits of the initial seed to a plurality of blocks in a distributed ledger, storing the initial seed and an identification of which authorized bits of the initial seed are allocated to each block of the distributed ledger, receiving a final seed value that is partially generated by each of a plurality of nodes configured to access the distributed ledger based on authorized bits of respective blocks updated by each respective node, and generating a random sequence value based on the final seed value and storing the random sequence value in a block of the distributed ledger.
Owner:IBM CORP
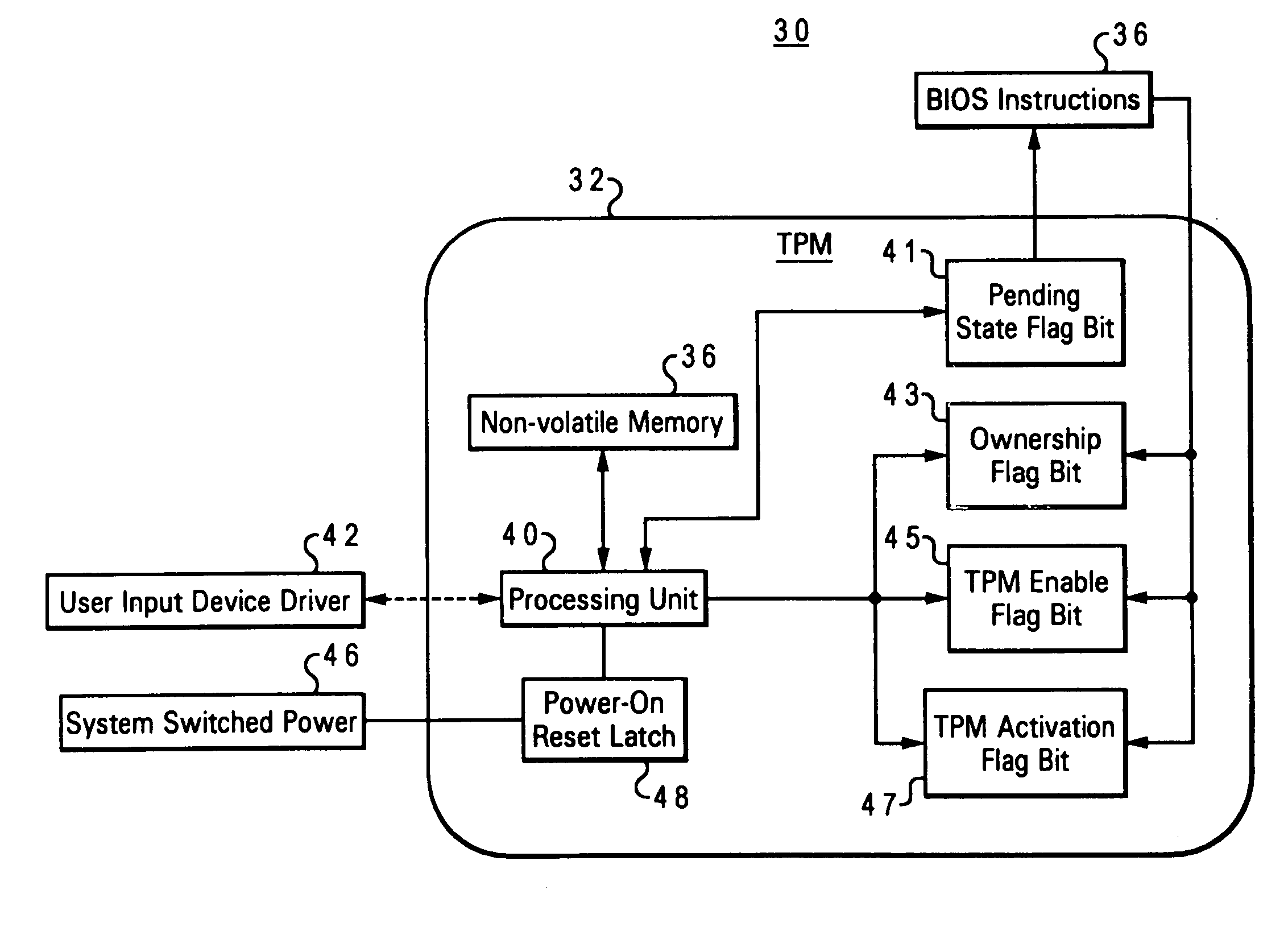
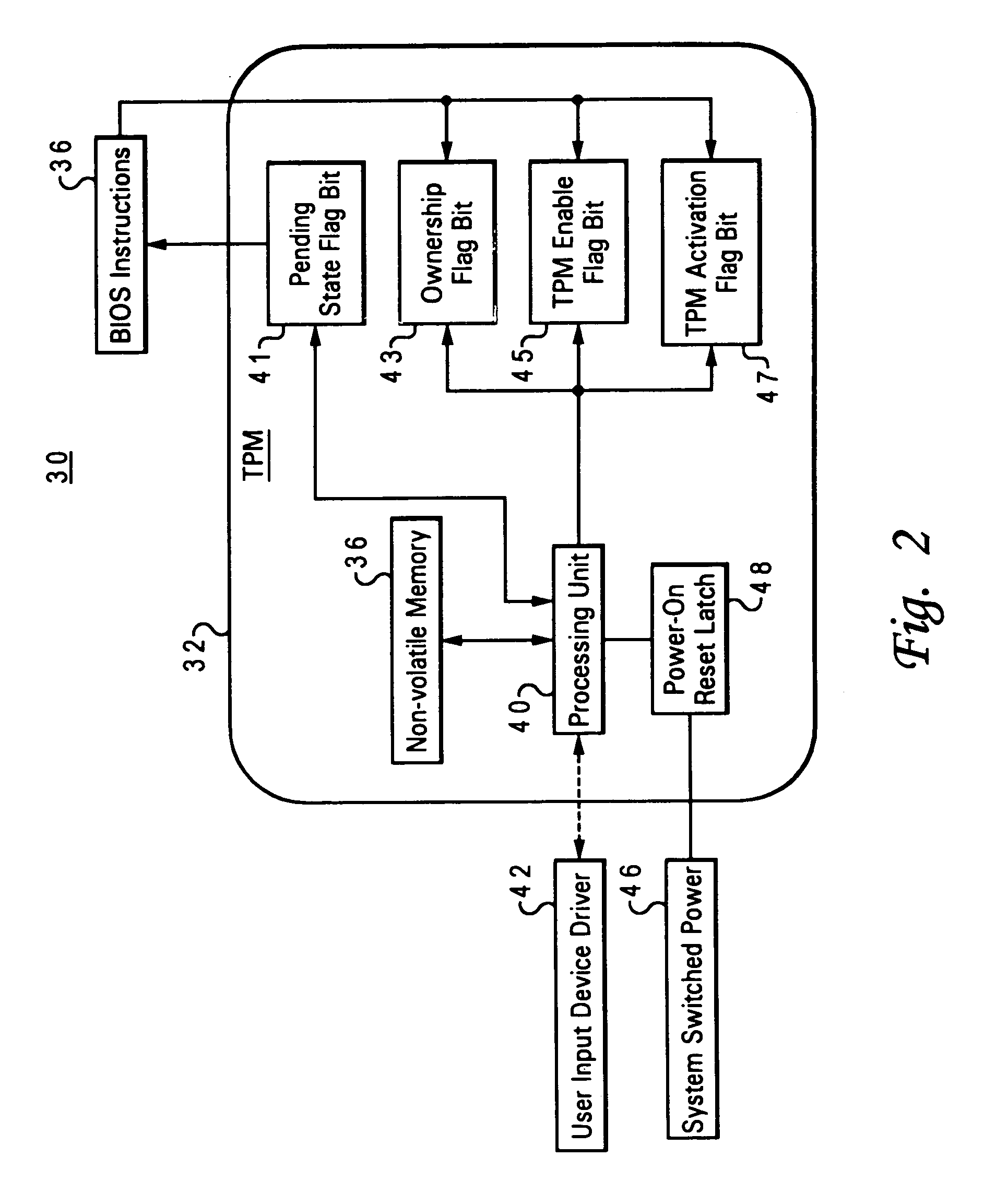
Method and system for securing enablement access to a data security device
ActiveUS7107460B2Digital data processing detailsUnauthorized memory use protectionData processing systemPower-on reset
An embedded security subsystem, and method for implementing the same, which provide secure controllability of a data security device within a data processing system. The embedded security subsystem of the present invention includes a persistent enable flag for providing control access to the data security device, wherein the persistent enable flag is accessible only in response to a power-on reset cycle of the data processing system. The persistent enable flag is read-only accessible to runtime program instructions. A pending state change flag that is write accessible by runtime program instructions is utilized for setting an intended next state of the persistent enable flag such that control access to the data security device is enabled only during a subsequent power-on reset of said data processing system.
Owner:MICROSOFT TECH LICENSING LLC
Non-autonomous dynamical orbit cryptography
ActiveUS20040228480A1Data stream serial/continuous modificationTelegraphic message interchanged in timeComputer hardwareOrbit
NADO is a process for encrypting and decrypting information in a variety of cryptographic devices. The underlying process is a fast stream-like cipher that can be implemented efficiently in analog or digital hardware or in software. The NADO process makes use of three novel methods in cryptography: 1) A sequence of permutations which scrambles and spreads out the encrypted information; (2) A state generator built with a non-autonomous dynamical system to generate an unpredictable sequence of states; (3) One or more perturbators which perturb both the non-autonomous dynamical system and the sequence of permutations in a non-periodic way.
Owner:FISKE SOTFWARE LLC
System and method for interaction object reconciliation in a blockchain environment
ActiveUS10192073B2Secure data communicationEncryption apparatus with shift registers/memoriesUser identity/authority verificationObject basedNetwork connection
Owner:ROCK INNOVATION LLC
Popular searches
Digital data protection Security arrangement Platform integrity maintainance Multiple digital computer combinations Special data processing applications Color television signals processing Television systems Digital video signal modification Coding/ciphering apparatus Program/content distribution protection
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com