Multi-image hiding method based on fractional mellin transform
A Merlin transformation and multi-image technology, applied in the field of information security, can solve the problem of limited amount of hidden information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the embodiments and drawings, but the protection scope of the present invention should not be limited thereby.
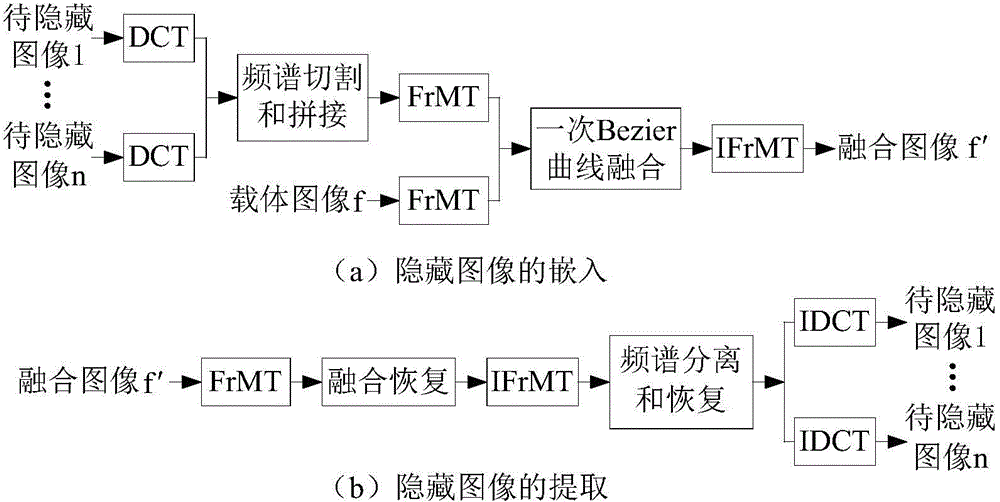
[0030] Step 1: Image compression.
[0031] (1) Discrete cosine transform (DCT) is performed on n=8 grayscale images with a size of 256×256 respectively to obtain 8 two-dimensional matrices.
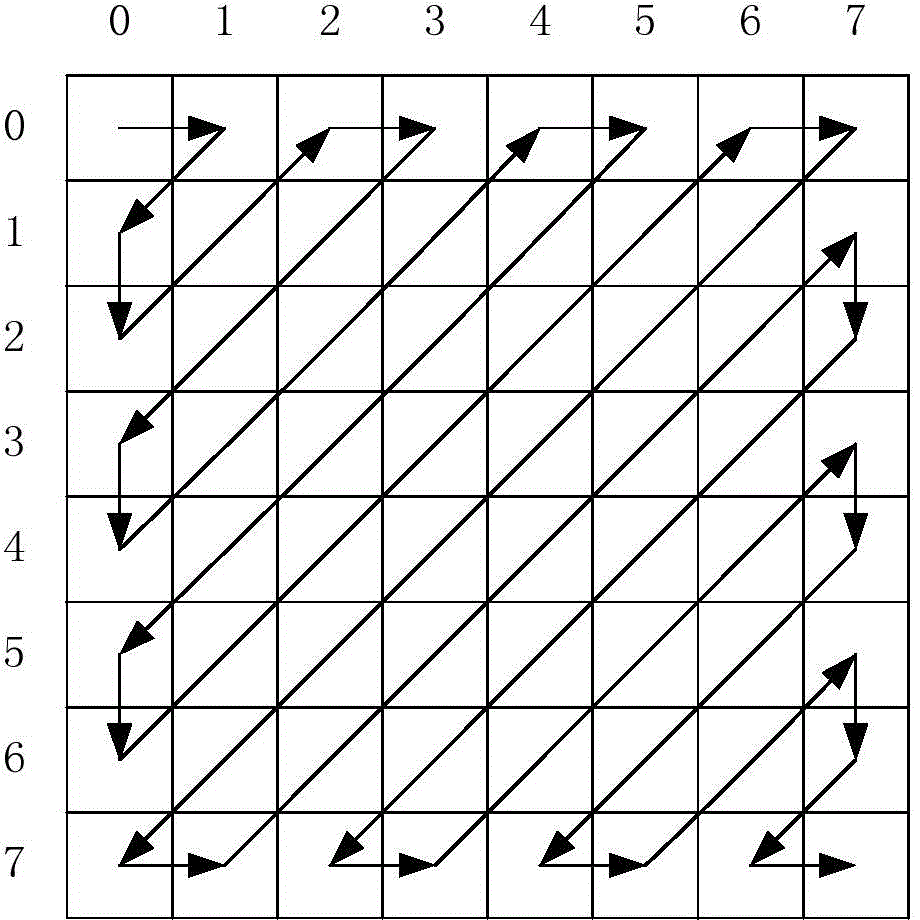
[0032] (2) Carry out Zigzag scanning on 8 two-dimensional matrices respectively to obtain 8 one-dimensional matrices.
[0033] (3) Starting from the first element respectively, 8 one-dimensional matrices are cut by the cutting coefficient M×N / n=8192, and the gained elements are formed into a one-dimensional matrix containing 256×256 elements, which are divided into rows ( or column) into a two-dimensional matrix with a size of 256×256 to obtain a compressed image W(x,y).
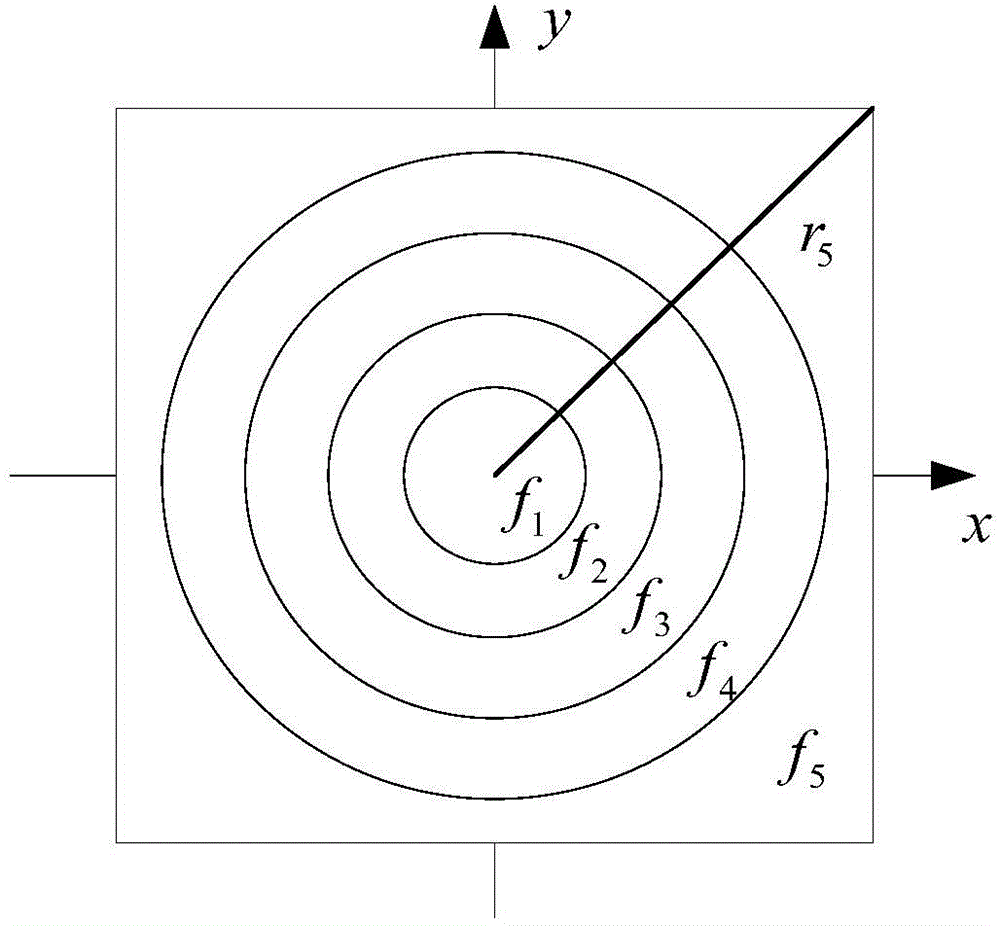
[0034] From step 3, when the number n of images to be compressed increases, the low-frequency part of each image will be kept...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com