Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
497results about How to "Prevent fraud" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
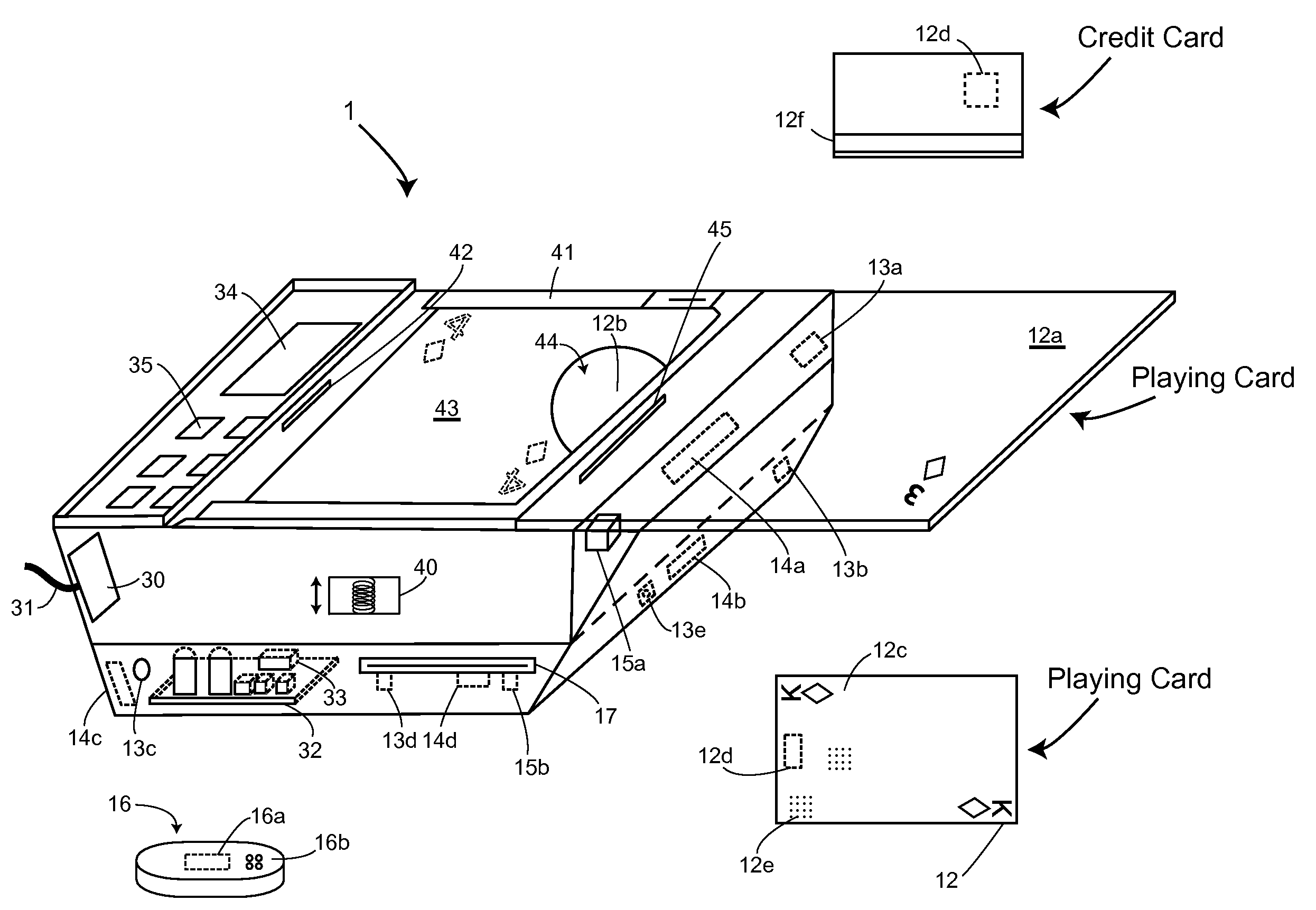
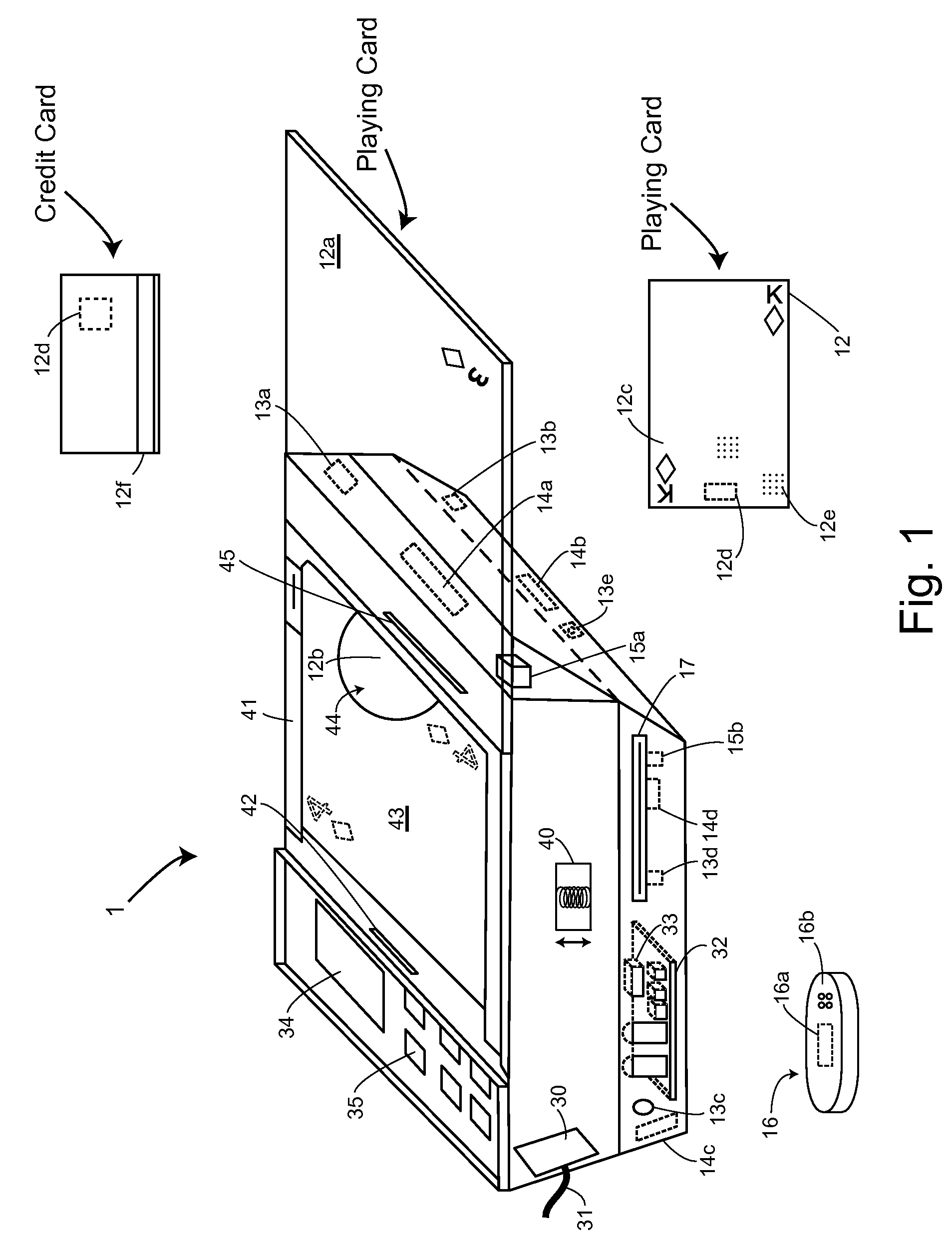
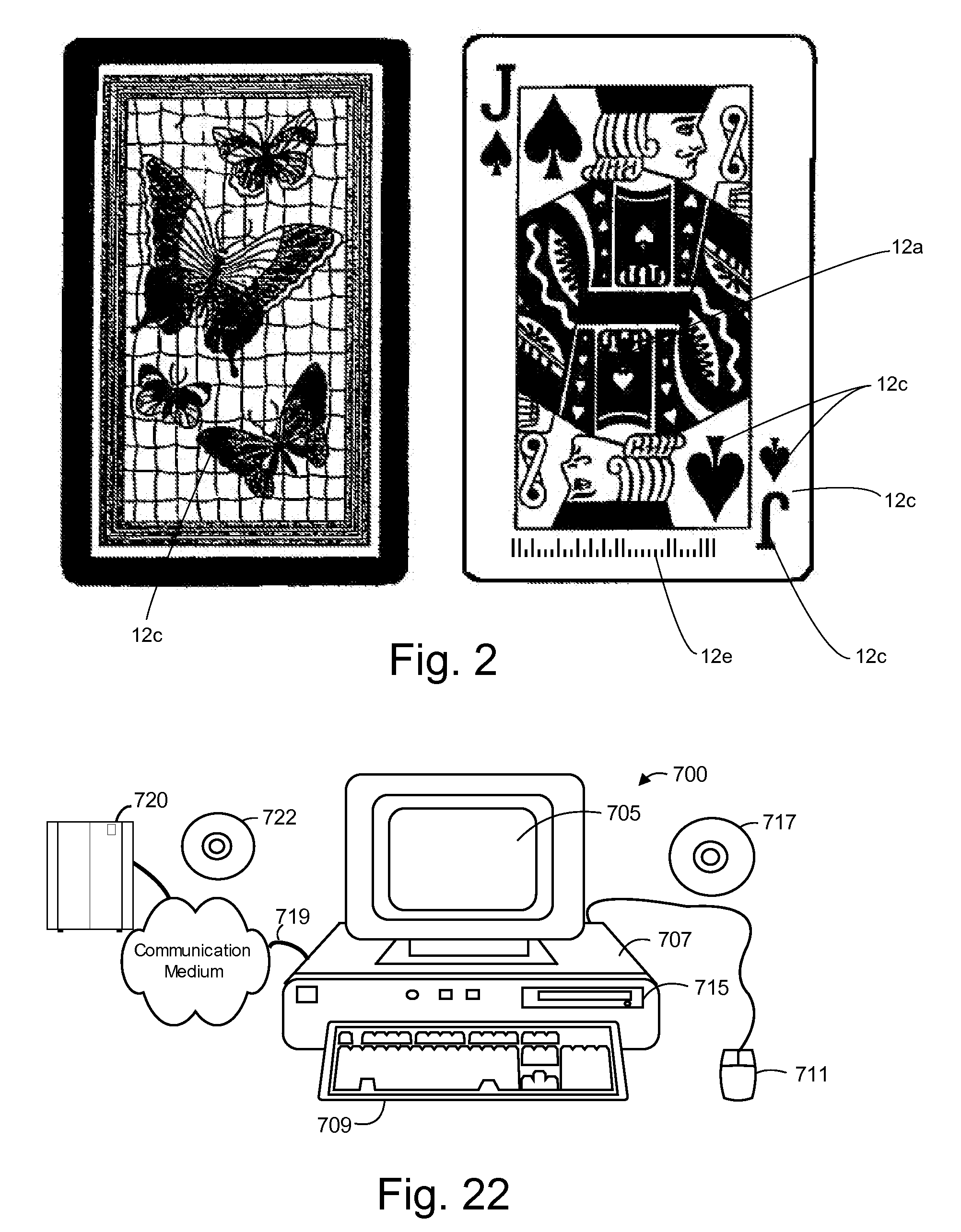
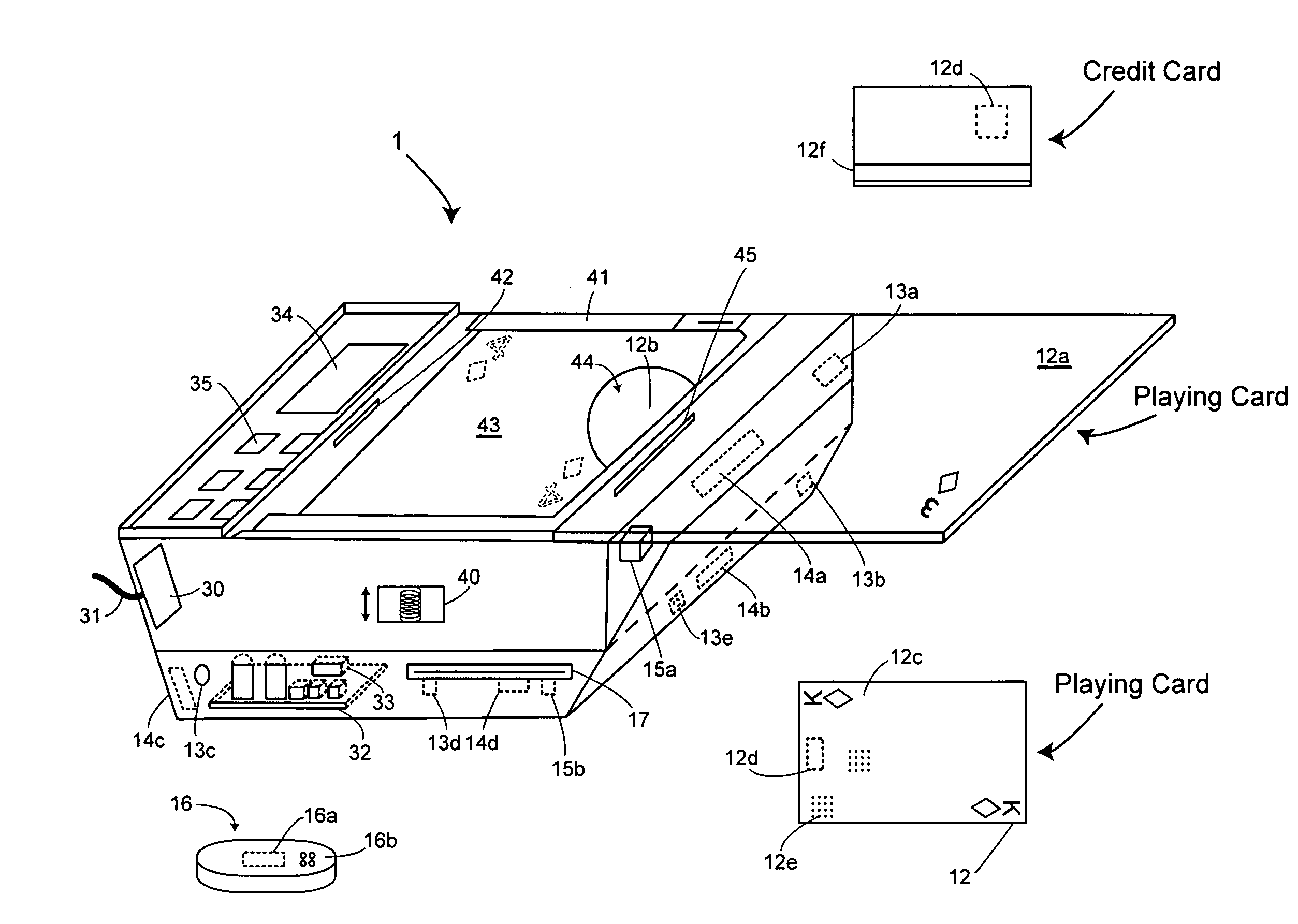
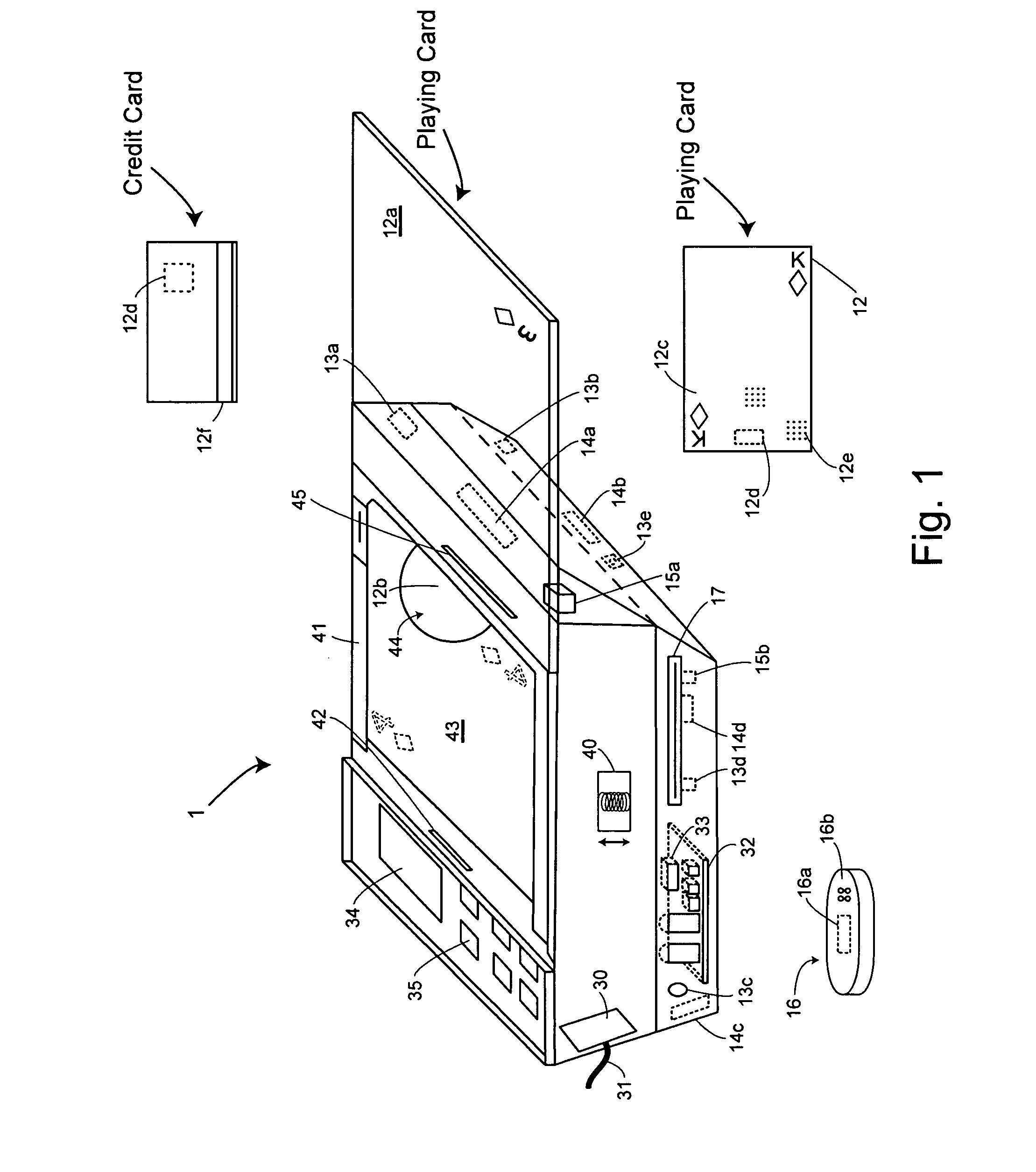
Table with sensors and smart card holder for automated gaming system and gaming cards
InactiveUS20090191933A1Low costMore secure and reliable gaming experienceCard gamesApparatus for meter-controlled dispensingHand heldSmart card
Methods and systems for intelligent tracking and / or play and / or management of card gaming use an intelligent card distribution or holding device with detectors for determining the value and unique identity of individual cards and for recording card play. Playing cards are equipped with a read / write data storage connected to a transponder and / or incorporated into electromagnetic writable particles or smart particles (smart dust). A system of the invention records various game play events on the playing cards themselves during game play and optionally also in a database on the system. In specific embodiments, the principal scanning and writing elements and electronic and optical interfaces are embodied into a hand-held card holder (HHCH). In specific embodiments, the system utilizes various types of sensors and / or indicators and / or and electronic circuits and software to scan, track, monitor, compute, and interface with electronic devices, to enable the automatic operation of Casino table games. The system can scan playing cards, scan gaming chips, indicate a players win / loss / draw, increase or decrease player betting positions, compute awards to players based on their playing activity, photograph individual players, and transmit player's images to casino security / surveillance departments and or other authorized casino personnel. The system may activate table displays that indicate each player's win / loss / draw of their bets, and / or dealers card count, indicate in the game of blackjack when a dealer has blackjack, or any other significant event that occurs such as indicating when a player has a winning / loss / draw on specific card combinations.
Owner:FRENCH JOHN B
Smart card holder for automated gaming system and gaming cards
InactiveUS20090048026A1Low costMore secure and reliable gaming experienceApparatus for meter-controlled dispensingVideo gamesPlaying cardSmart card
Methods and systems for intelligent tracking and / or play and / or management of card gaming use an intelligent card distribution or holding device with detectors for determine the value and unique identity of individual cards and for recording card play. In specific embodiments, the system utilizes various types of sensors and electronic circuits and software to scan, track, monitor, compute, and interface with electronic devices, to enable the automatic operation of Casino table games. The system can scan playing cards, scan gaming chips, indicate a players win / loss / draw, increase and or decrease player betting positions. Compute awards to players based on their playing activity, photograph individual players, and transmit player's images to casino security / surveillance departments and or other authorized casino personnel. The system may activate table displays that indicate each player's win / loss / draw of their bets, and or dealers card count, indicate in the game of blackjack when a dealer has blackjack, or any other significant event that occurs such as indicating when a player has a winning / loss / draw on specific card combinations.
Owner:FRENCH JOHN B
System, method, and apparatus for identifying and authenticating the presence of high value assets at remote locations
InactiveUS20040177032A1Avoid identificationPrevent fraudFinanceCo-operative working arrangementsOperating systemEngineering
A system, method, and apparatus for identifying and authenticating the presence of high value assets at remote location includes associating an identification tag with the asset. The identification tag includes identification information that can be electronically read and sent to a remote location for verifying the authenticity of the asset.
Owner:THE TB GROUP
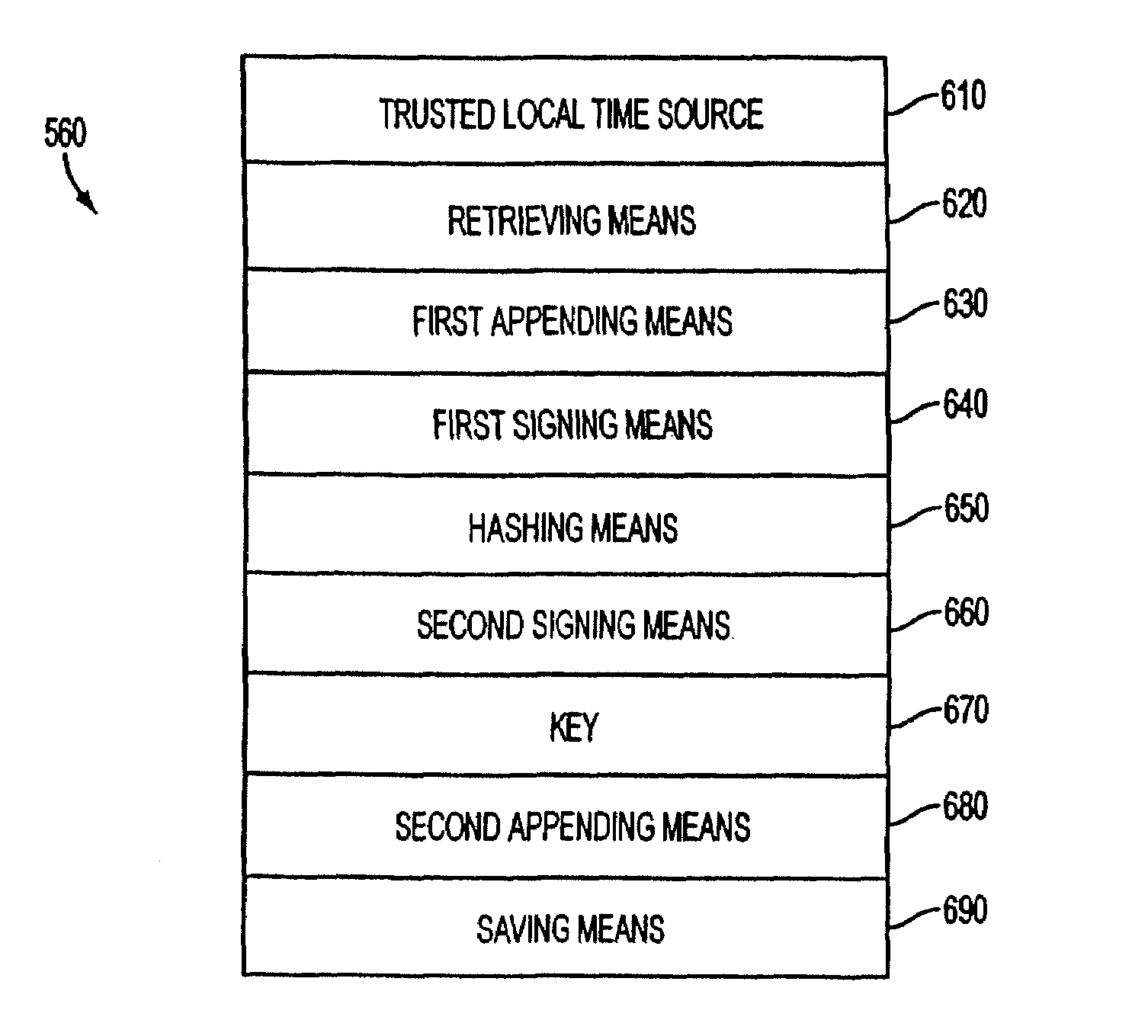
Personal computer system and methods for proving dates in digital data files
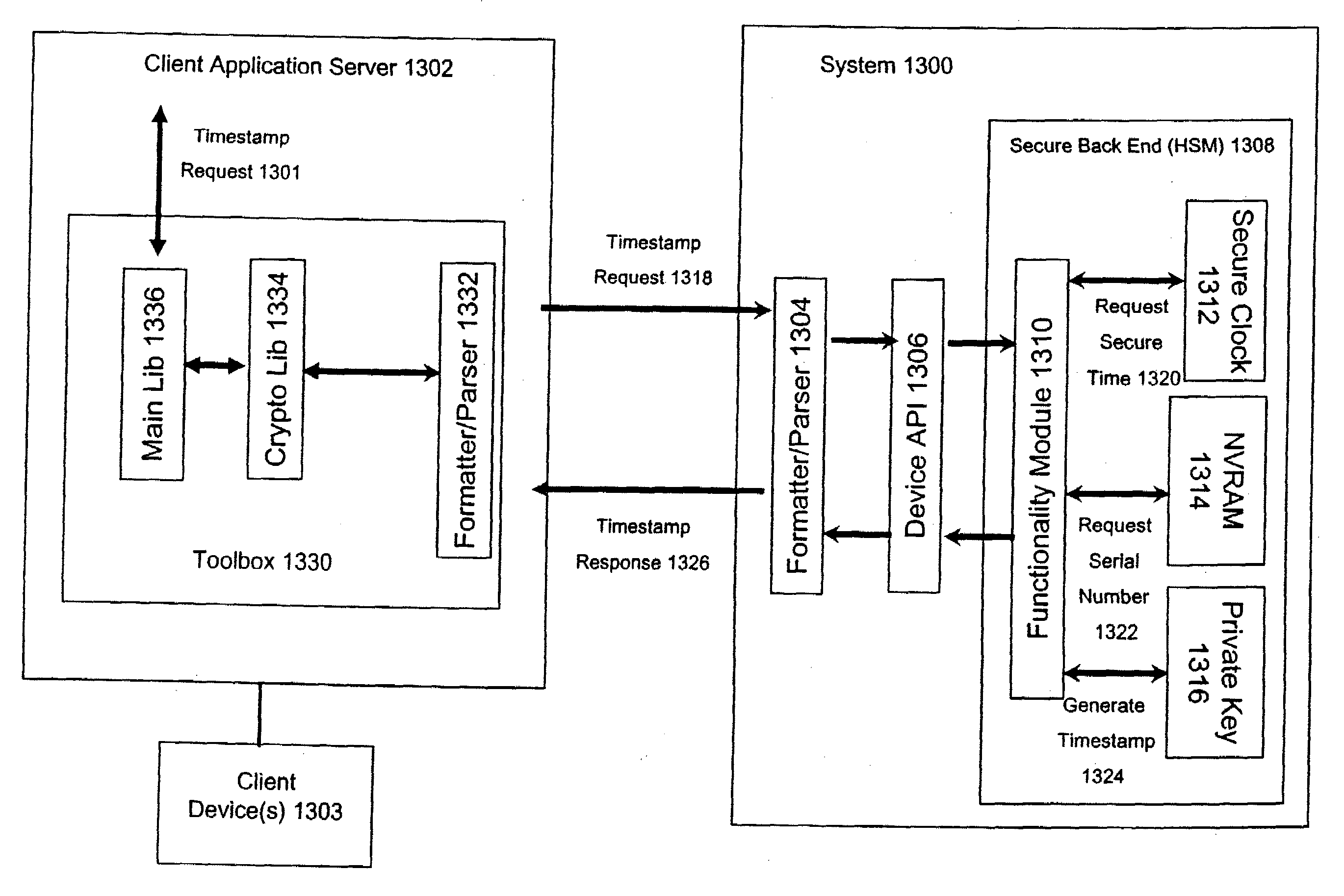
InactiveUS6898709B1Prevent fraudDigital data processing detailsUser identity/authority verificationDigital dataReal-time clock
A personal computer (PC) system and methods for proving dates of digital data files, which are accessed, created, modified, received, or transmitted by the PC includes a trusted time source in a tamperproof environment, a first subsystem for saving the file at a moment in time, a second subsystem for retrieving from the trusted time source a date and a time corresponding to the moment in time, a third subsystem for appending the date and the time retrieved from the trusted time source to the saved file, a fourth subsystem for signing the saved file with the date and the time retrieved from the trusted time source appended thereto, a fifth subsystem means for hashing the signed file to produce a digest, a sixth subsystem for signing the digest with a key to produce a certificate, a seventh subsystem for appending the certificate to the saved file, and an eighth subsystem for saving the file with the certificate appended thereto. The trusted time source is a real time clock, which is not resettable, is independent of any system clock of the PC, and is installed locally relative to the PC.
Owner:TIME CERTAIN
System and methods for distributing trusted time
InactiveUS20090083372A1Prevent fraudMultiple digital computer combinationsSecuring communicationDigital dataReal-time clock
Systems and methods for distributing trusted time, including trusted dates with digital data files, which are accessed, created, modified, received, or transmitted by devices that include a trusted time source in a tamperproof environment. The system includes one or more subsystems for providing trusted time for a moment in time. The trusted time source may be a real time clock, which is not resettable, is independent of any system clock of the devices, and where one or more devices may contribute to the distribution of trusted time among each other.
Owner:TEPPLER STEVEN W
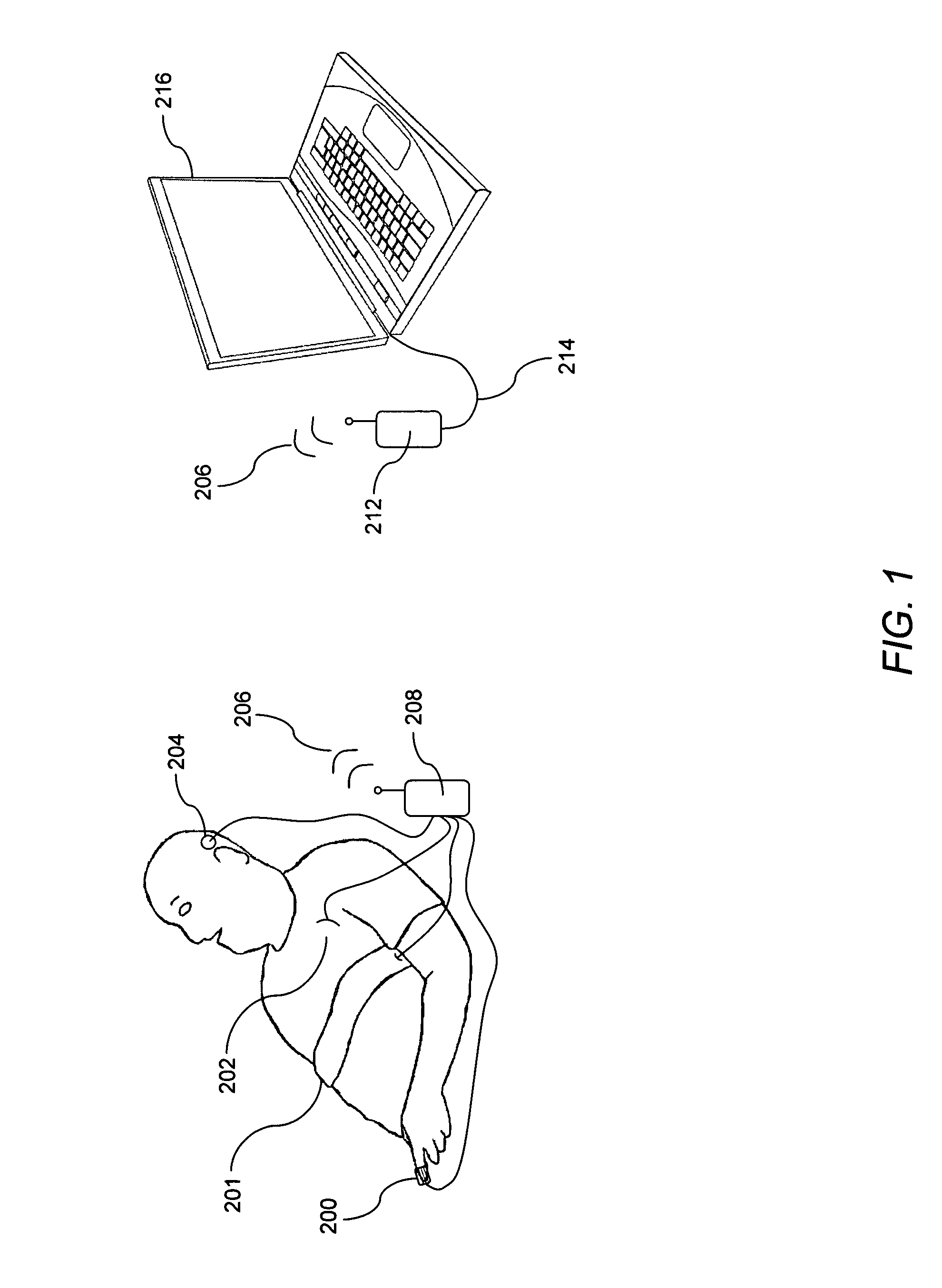
Medical device and method with improved biometric verification
ActiveUS8679012B1Prevents misuse and fraudPrevent fraudSensorsBiometric pattern recognitionComputer scienceMedical device
The present invention is both a device and a method for verifying a subject's identity while using a medical device or undergoing a medical diagnostic or therapeutic procedure, particularly at home or at a remote location. The method and device can be used for inpatient and remote sleep and signal analysis with biometric identification. The present invention is further related to the devices and sensors used in executing the method, and includes various embodiments of a method of inpatient and remote sleep analysis.
Owner:CLEVELAND MEDICAL DEVICES
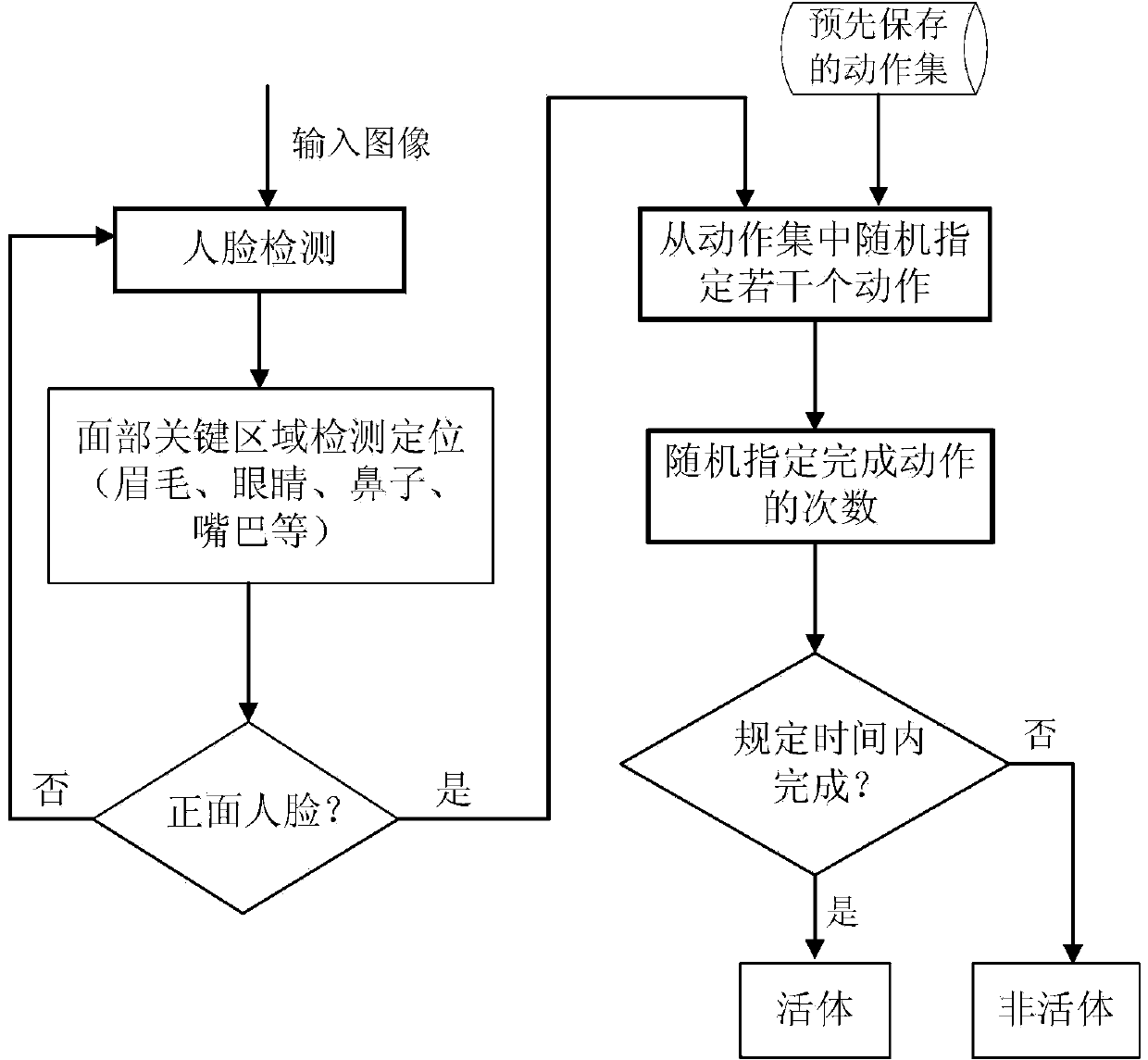
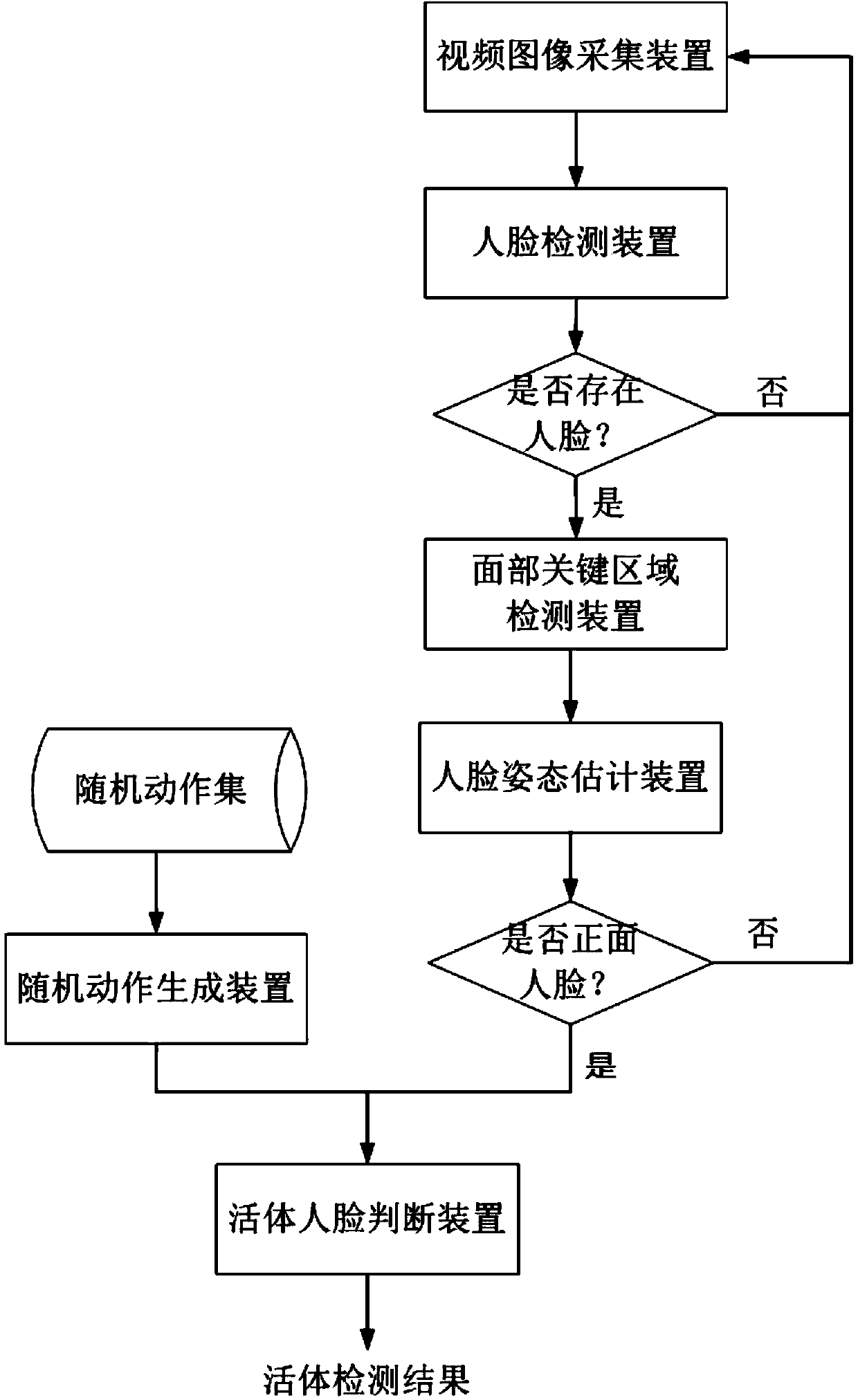
Method and system for detecting living body human face
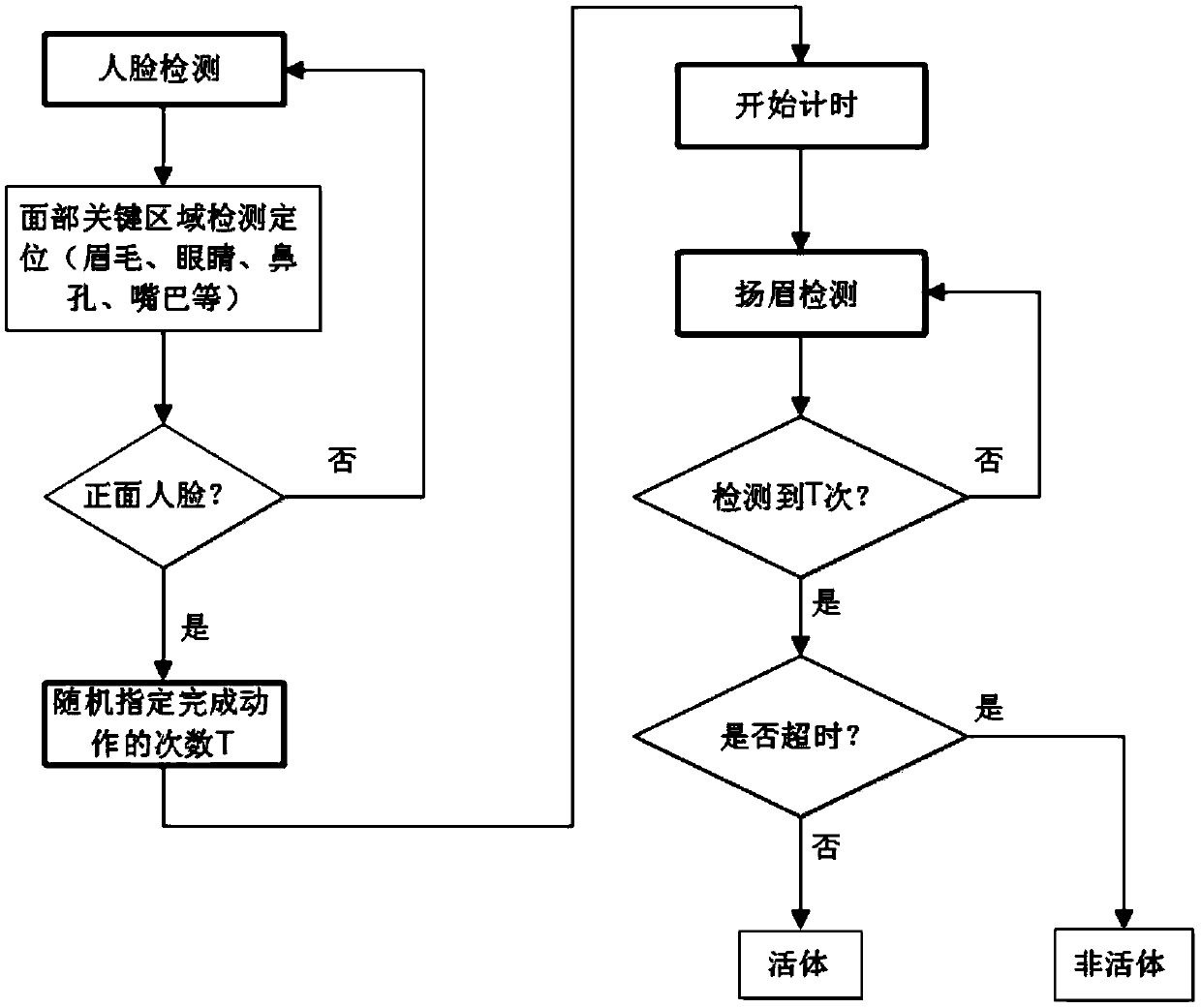
ActiveCN103440479APrevent fraudImprove reliabilityCharacter and pattern recognitionLiving bodyVideo sequence
The invention relates to a method and system for detecting a living body human face. The method comprises the steps of obtaining images from a shot video sequence, detecting a human face in the video images, carrying out location on facial critical areas, randomly selecting one or more kinds of movements in a movement collection through a critical area detection classifier, randomly selecting the completing times of the movements, prompting a user, and determining the user as a living body if the user completes the random selected movements for many times within an appointed time period, otherwise, determining the user as a non-living body. According to the method and system for detecting the living body human face, when living body detection is carried out, the system randomly selects certain movements and randomly appoints the completing times of the movements every time, and therefore the user cannot pass the living body detection by using photos for cheating. In addition, due to the fact that the detected items are selected randomly, the user cannot pass the living body detection through the mode of playing video clips. Therefore, the method and system for detecting the living body human face can better prevent cheating behaviors in the mode such as the photos and the video clips in the living body detection, and the reliability and the safety of the living body detection are made to be higher.
Owner:湖北微模式科技发展有限公司
Table with sensors and smart card holder for automated gaming system and gaming cards
InactiveUS8221244B2Low costMore secure and reliable gaming experienceCard gamesApparatus for meter-controlled dispensingPlaying cardHand held
Methods and systems are disclosed for intelligent tracking and / or play and / or management of card gaming use an intelligent card distribution or holding device with detectors for determining the value and unique identity of individual cards and for recording card play. Playing cards are equipped with a read / write data storage connected to a transponder and / or incorporated into electromagnetic writable particles or smart particles (smart dust). A system of the invention records various game play events on the playing cards themselves during game play and optionally also in a database on the system. In specific embodiments, the principal scanning and writing elements and electronic and optical interfaces are embodied into a hand-held card holder (HHCH). The system can scan playing cards, scan gaming chips, indicate a player's win / loss / draw, increase or decrease player betting positions, and compute awards to players based on their playing activity.
Owner:FRENCH JOHN B
Method for verifying user identity and age
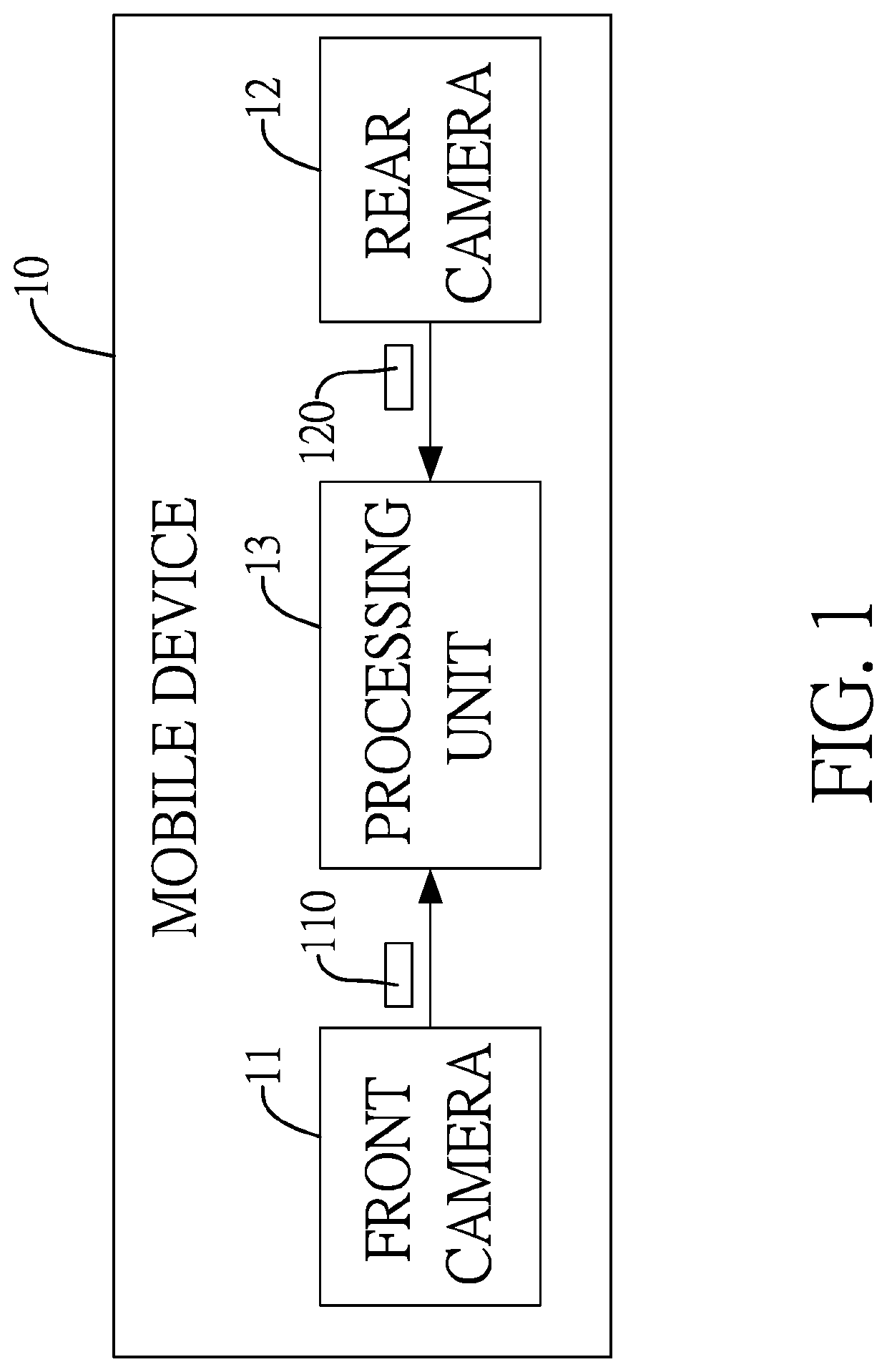
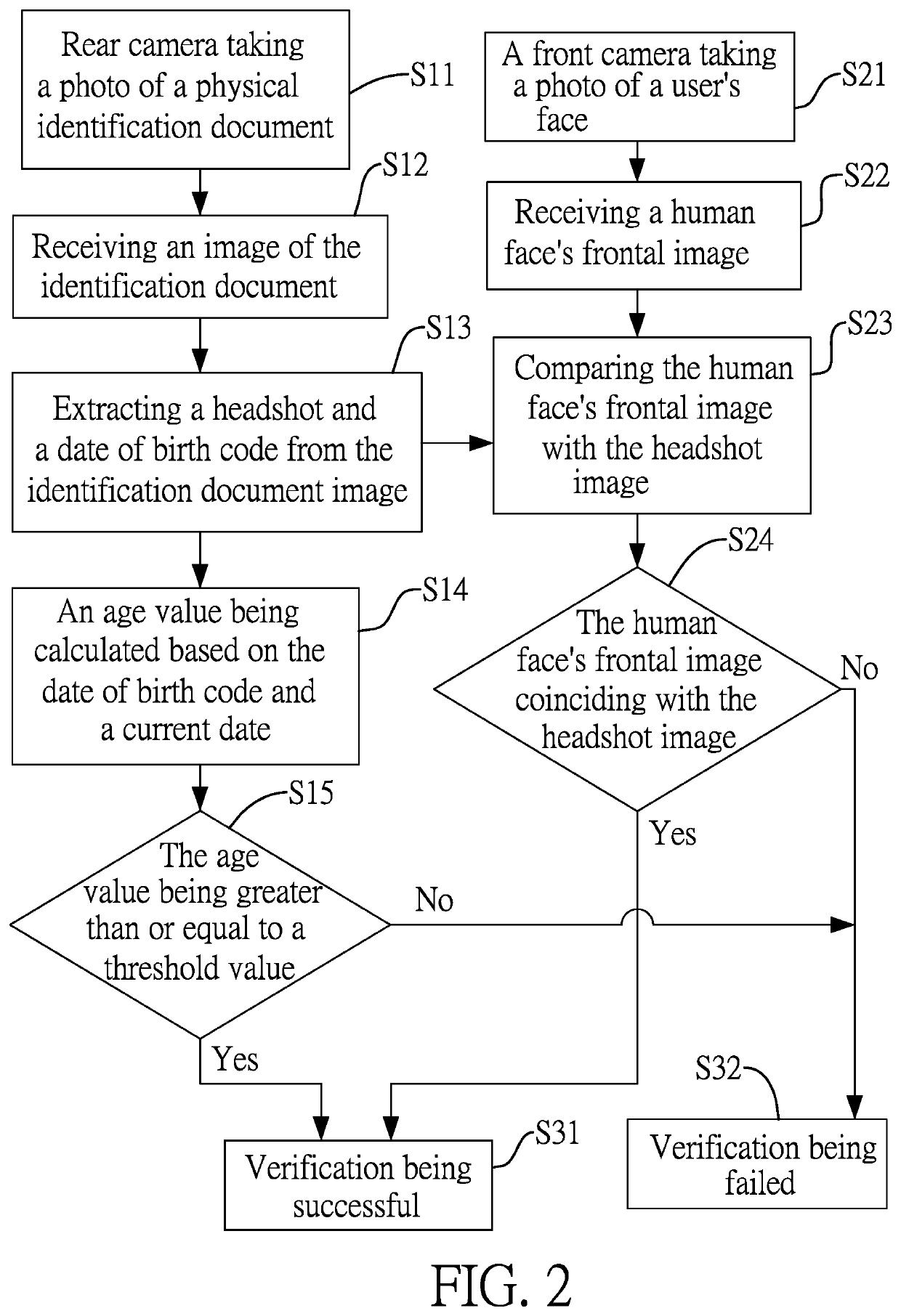
InactiveUS20190362169A1Prevent fraudAvoid identificationBuying/selling/leasing transactionsMultiple biometrics useComputer visionDate of birth
A method for verifying user identity and age includes: using a front camera to receive a frontal image of a human face; using a rear camera to receive an image of an identification document, from which a headshot and a date of birth code are extracted; determining whether there is a coincidence or not by comparing the face image and the headshot; determining whether an age value, calculated by comparing the date of birth code and a current date, is greater than or equal to a threshold value; when the face image coincides the headshot and the age value is larger than or equal to the threshold value, the verification is passed and an online transaction proceeds; when the face image is not consistent with the headshot or the age value is smaller than the threshold value, the verification fails and the online transaction is terminated.
Owner:GOOD COURAGE LTD
Block chain-based online taxi-hailing service system
InactiveCN107045650AReal-time time-consumingReduce uncertain attribute problemsReservationsTransmissionArtificial Intelligence SystemMobile client
The invention discloses a block chain-based online taxi-hailing service system. The system includes a traffic cloud database, a traffic cloud artificial intelligence system (TAI) and a mobile client. With the block chain-based online taxi-hailing service system adopted, a decentralized, trustless, collectively maintained, asymmetric cryptography reliable database basic infrastructure and underlying internet protocol can be provided for traffic cloud; and a mobile SaaS (Software-as-a-Service) application pattern, a distributed computing normal form and a group intelligence model which can establish high-degree connections for travelers based on time stamp, achieve travel resource allocation consensuses and provide services according to demands can be realized.
Owner:罗轶
Computer based methods and systems for establishing trust between two or more parties
InactiveUS20110167059A1Improve trustPrevent fraudDigital data processing detailsMultiple digital computer combinationsProfessional relationshipValue of information
Methods, devices and systems for moderating and policing voluntarily established transparency regarding past and present, and personal and professional relationships via online networking services. Identity of a person or commercial entity is verified before registration as a user. Each user is permitted a single profile. A profile includes a record of all relationships entered in the profile, some of which may be hidden by user. Each user is capable of linking his profile to profiles of other consenting users. Owner of a profile may flag inaccurate information on other linked profiles. The reliability or value of information in a profile is measured as a function of duration of existence of profile, transparency of the information in the profile, periods of inactivation, and number of times the profile is correctly flagged. A code is generated and used to allow gradual exposing of the profile of a user to his prospective contacts.
Owner:IDELAN
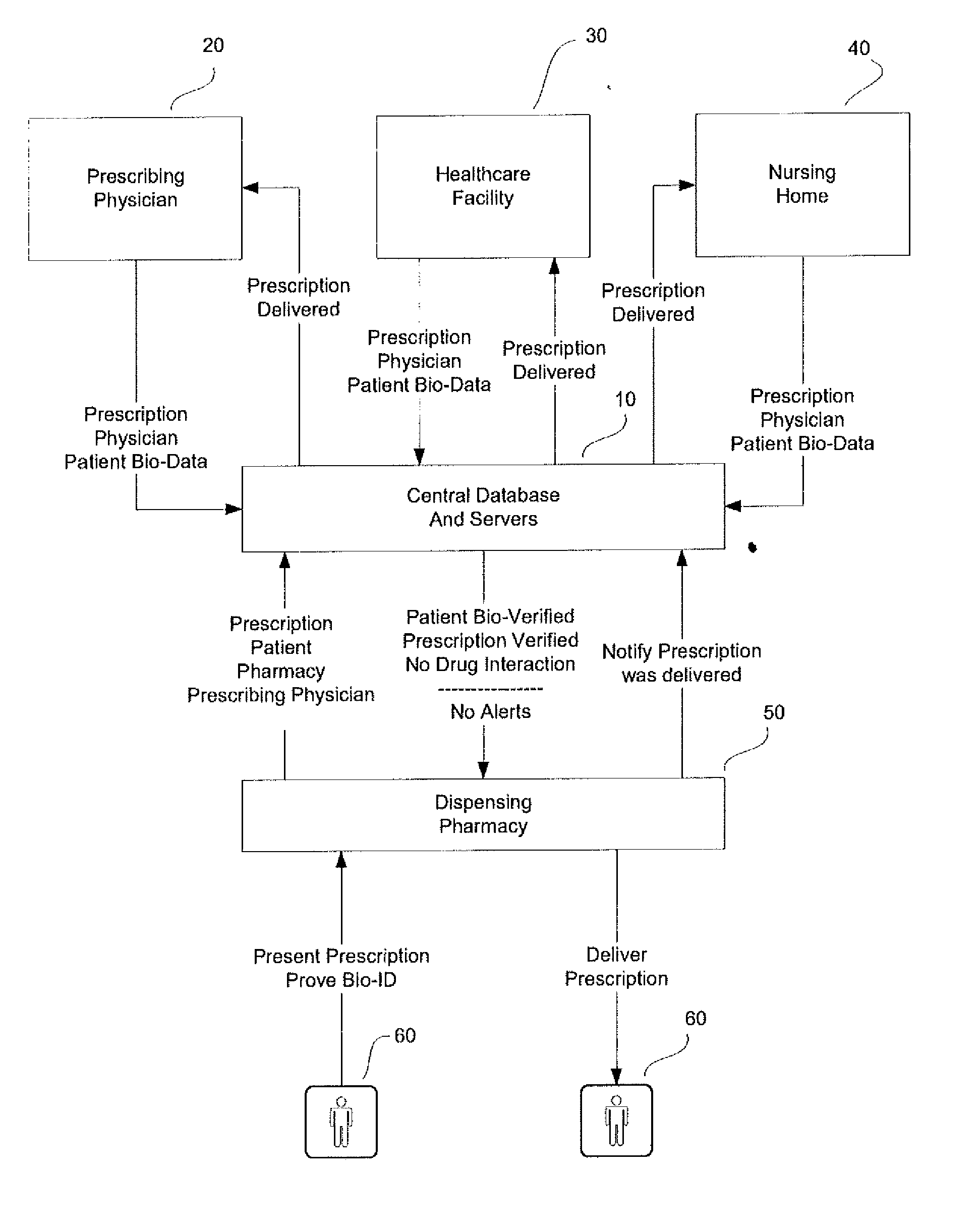
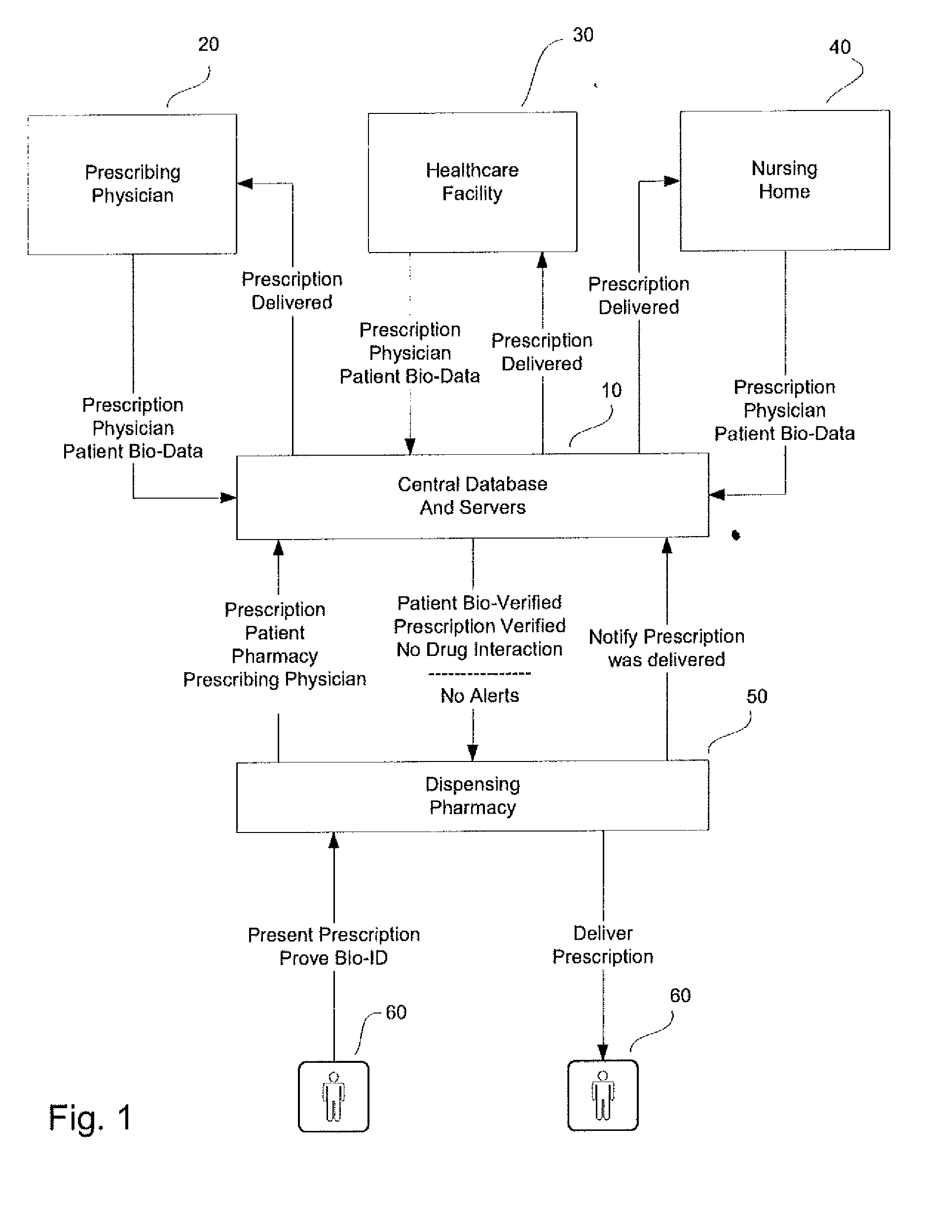
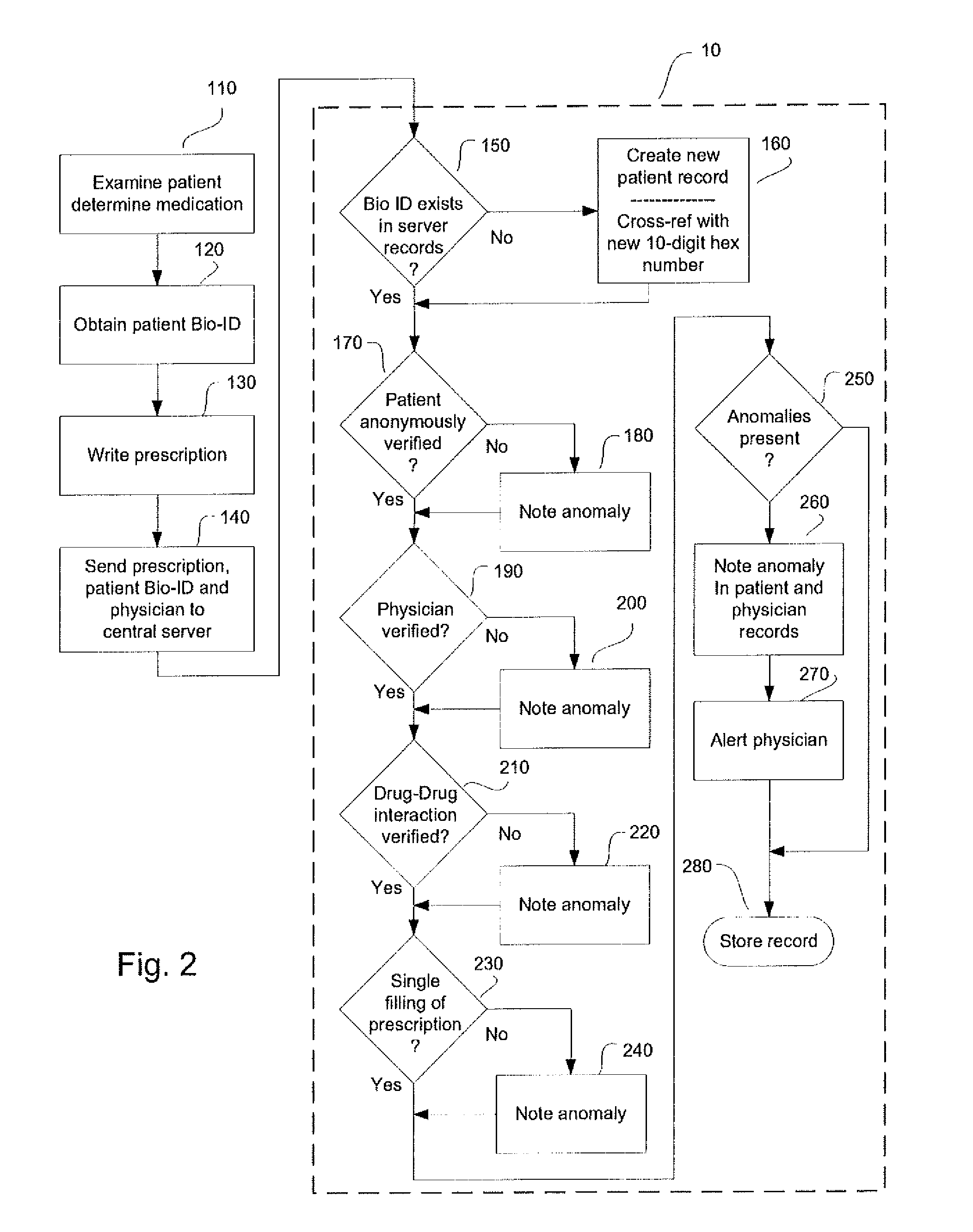
System and method for monitoring medication prescriptions using biometric identification and verification
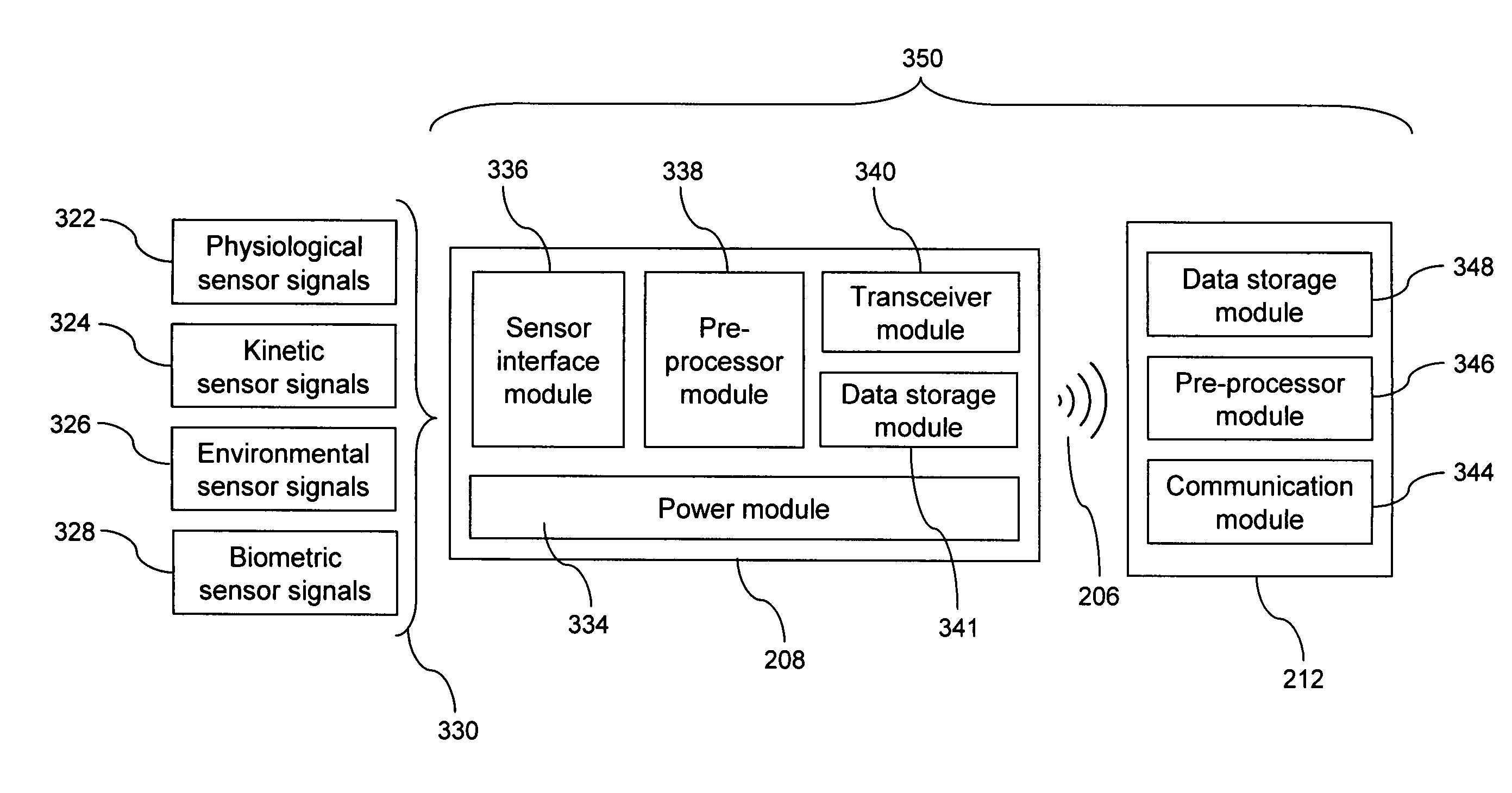
InactiveUS20100299158A1Quick measurementEasily verifiable biometricDrug and medicationsResourcesBiometric dataDrug interaction
This invention is a system and method for a matching system that cross-references patients anonymously with doctors and pharmacies. The invention uses patient-unique biometrics, such as fingerprinting, retinal scanning, or another such unique identifier, for patient identification and verification without revealing a patient's name or other personal information. The system tracks patient prescriptions and produces alerts to indicate potential problems, such as drug interactions or possible fraudulent behavior. The system utilizes the biometric data of the prescribing physician as authorization of the prescription. The system can produce a traceable paper trail, for investigation or prosecution, and protects the medical industry, patients, and the public from the consequences of doctor shopping.
Owner:BIO TECH MEDICAL SOFTWARE
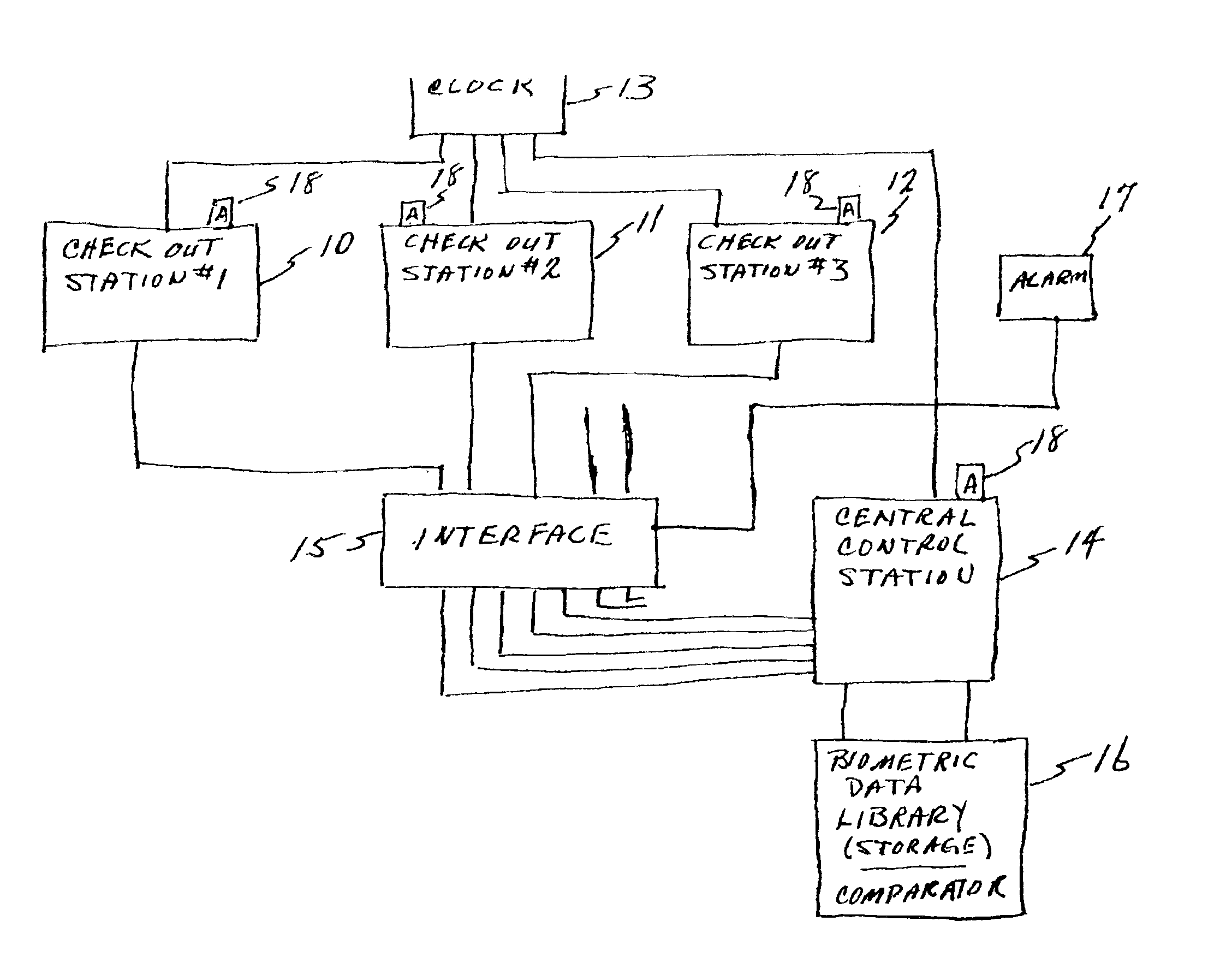
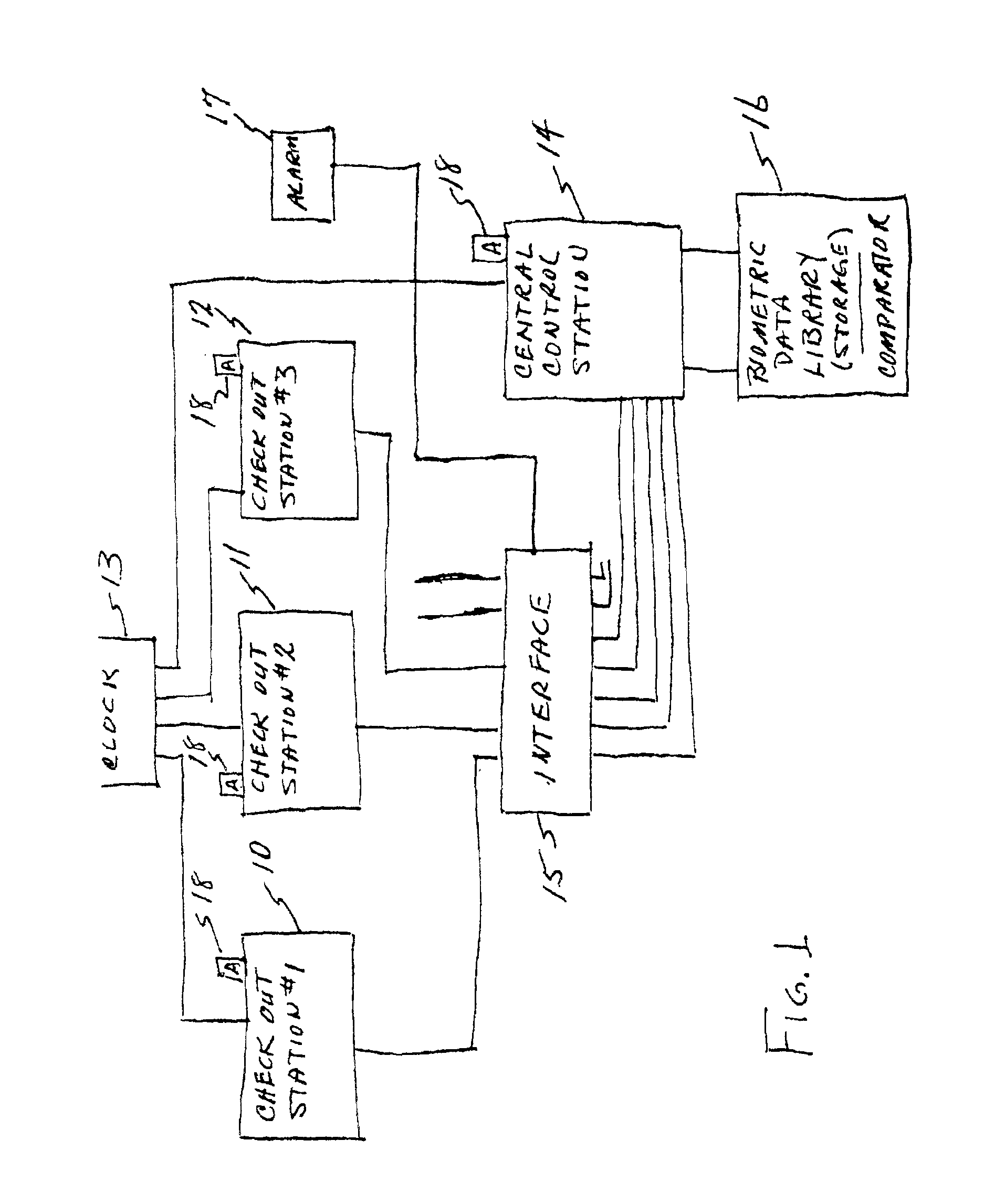
Biometric identification and security system associated with cash register
InactiveUS6883709B2Prevent theftReduce stepsCredit registering devices actuationCo-operative working arrangementsBiometric dataCheque
A wholesale and / or retail check out station system includes a biometric finger print reader and storage for reading and storing biometric data of employees having access to the cash registers of the check out stations in the system. Authorization to use a cash register in the system is programmed into the microprocessor in the system, limiting use of a cash register to authorized employees. Employees are identified by finger print using biometric technology. Limitations of use is extended to access to operate particular cash register(s); handling returned merchandise at a cash register; refunds on returned purchases require authorization of the manager and the cashier; cashing checks at a cash register, where the limitation includes only cashing of employer drawn payroll checks of employees; and, clearing errors made in tabulations at a cash register. Unauthorized persons attempting to gain access to cash registers to which they are not authorized serves to activate an alarm.
Owner:FAMOUS HORSE
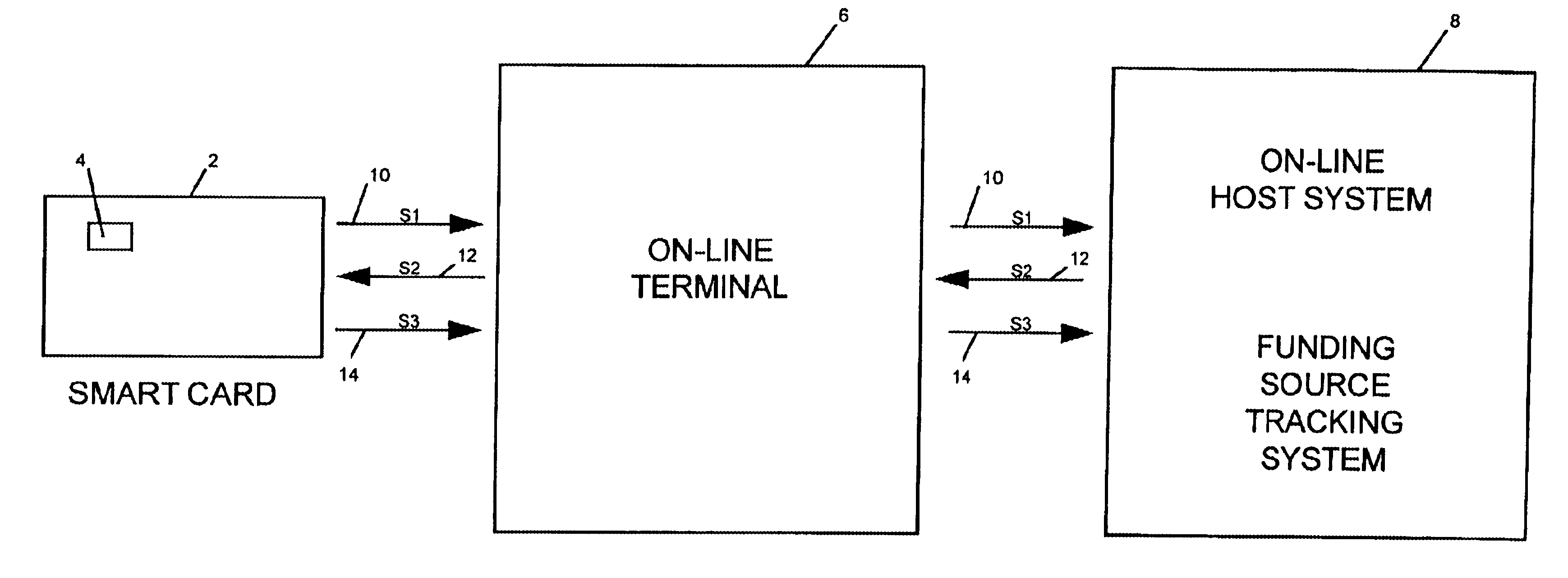
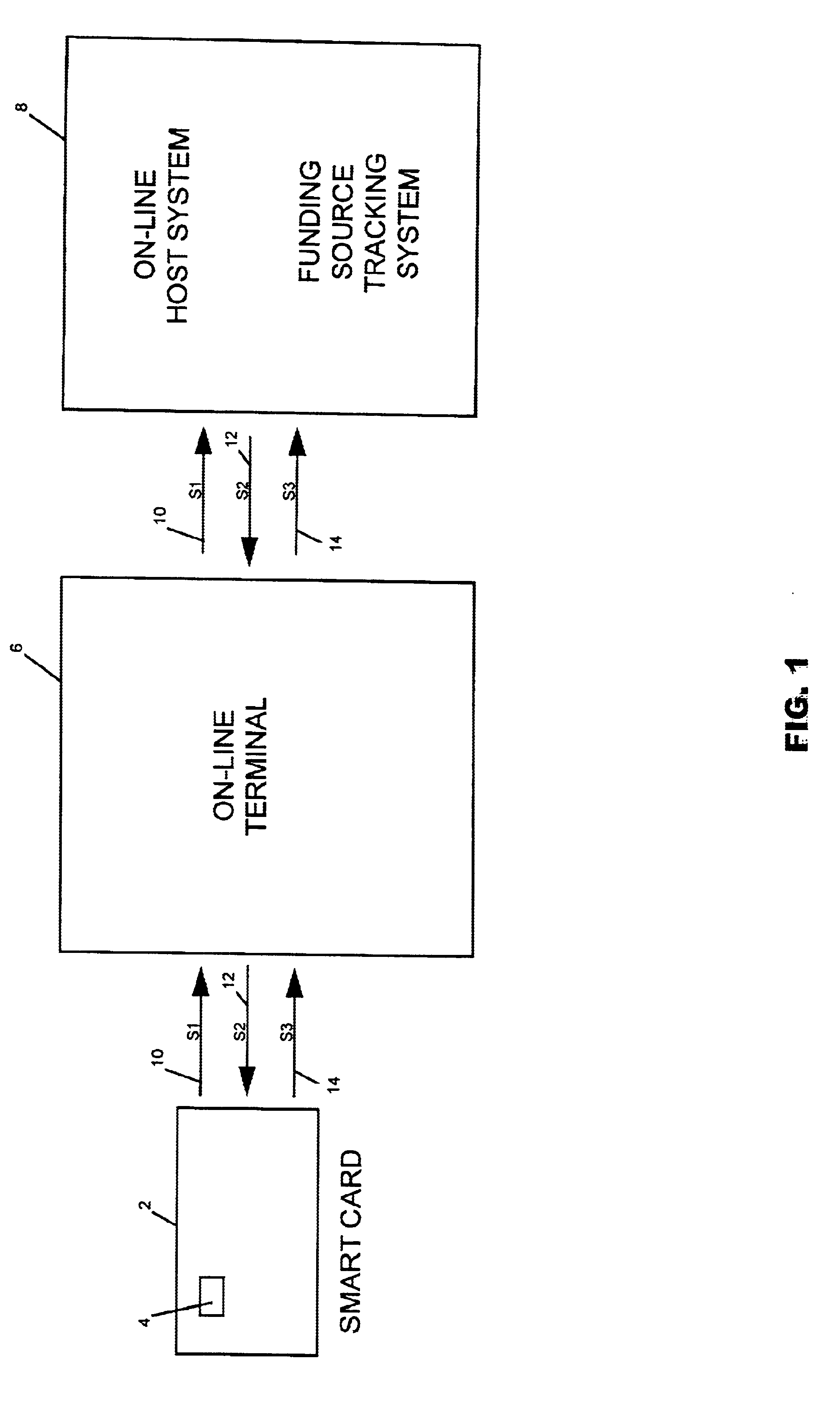
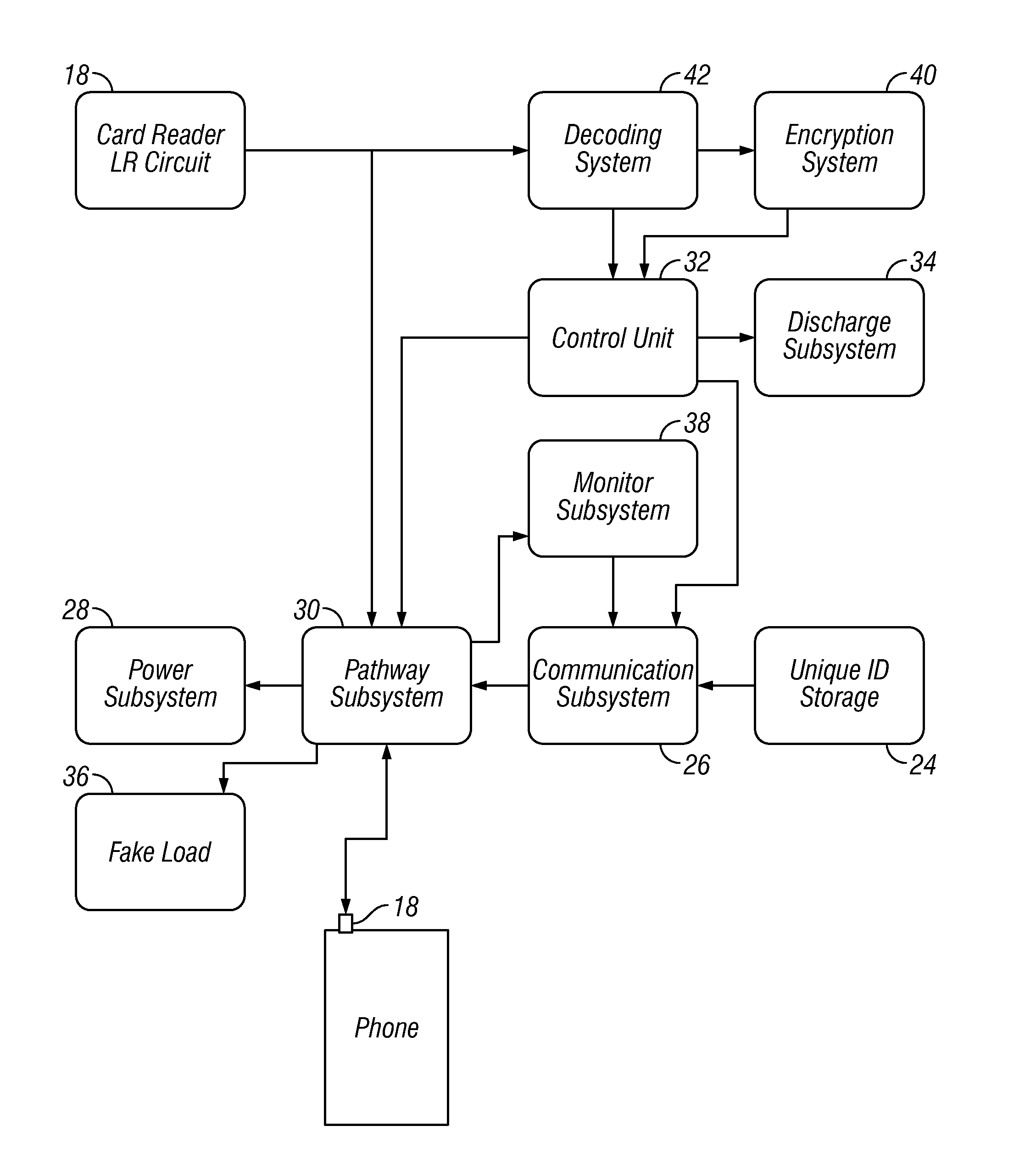
Method and system of tracking and providing an audit trail of smart card transactions
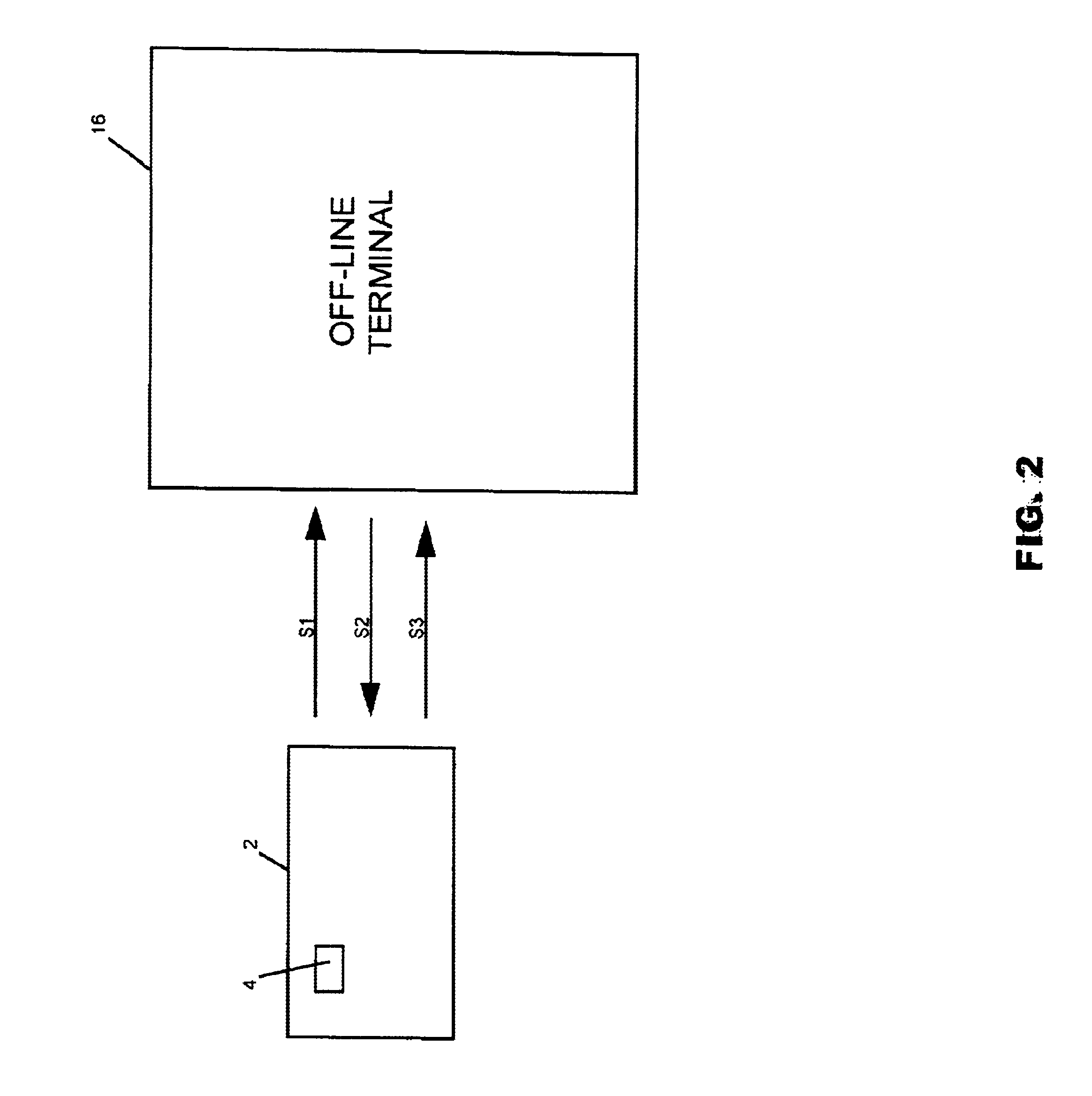
InactiveUS6913193B1Accelerated programPrevent fraudPayment architectureSpecial data processing applicationsSmart cardComputer terminal
A method and system for tracking and providing an audit trail for off-line smart card transactions includes storing information representing a monetary transaction in a permanent memo on an smart card microprocessor and holding the transaction amount in escrow until the stored information is transmitted from the smart card, for example, at an on-line terminal, to a host on-line system for logging to a tracking system. The monetary transaction includes a transaction with an off-line device, such as another smart card. The escrowed transaction amount represents, for example, a load transaction to one of the smart cards and an unload transaction to other smart card. Once the memo is deleted from the respective smart cards, the load values of the respective smart cards are incremented or decremented by the transaction amount. Alternatively, the smart cards may be provided with a card-to-card key, in which case, a permanent memo is stored only on the receiving smart card.
Owner:CITICORP CREDIT SERVICES INC (USA)
Secure Transaction Systems and Methods
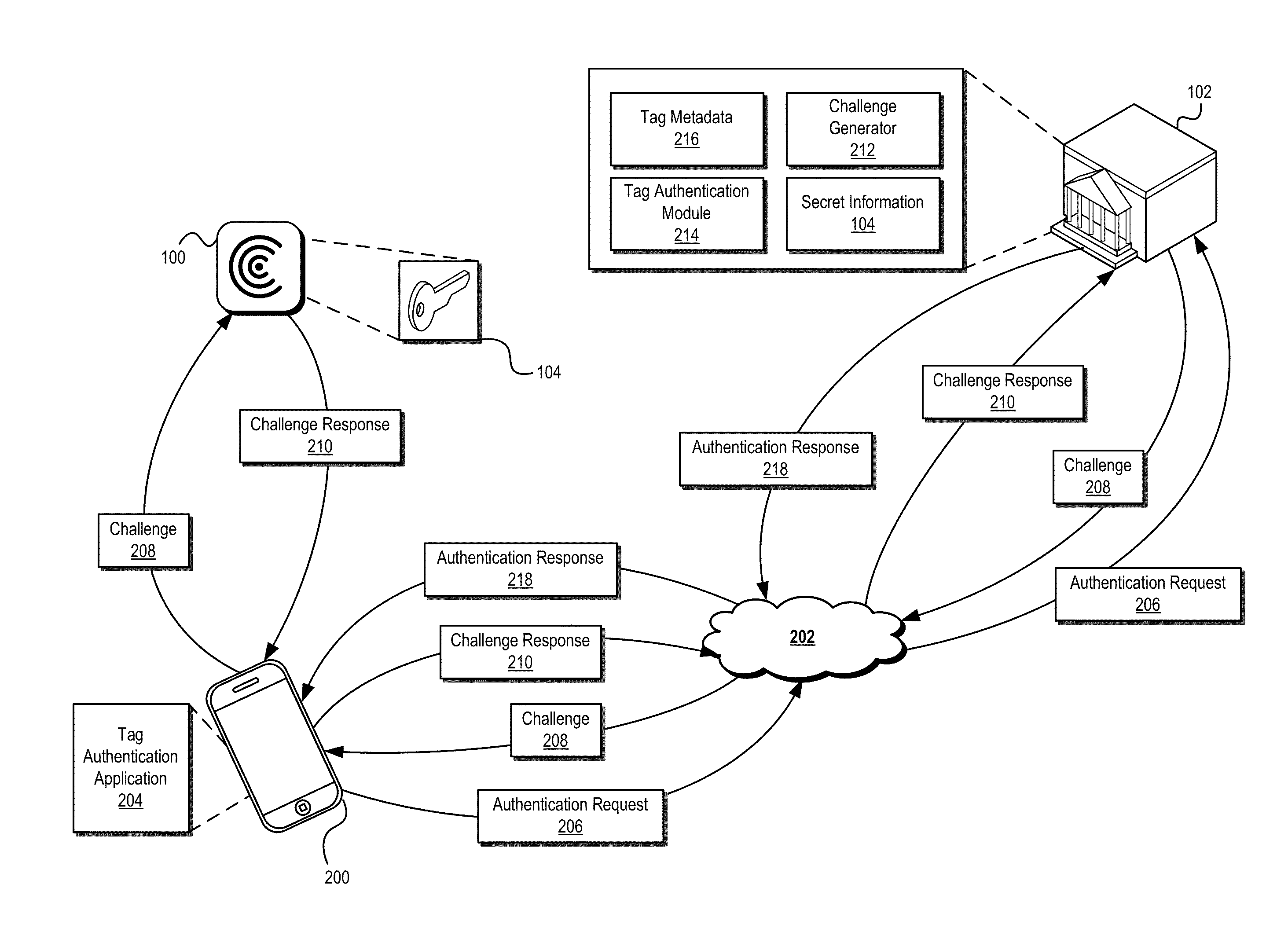
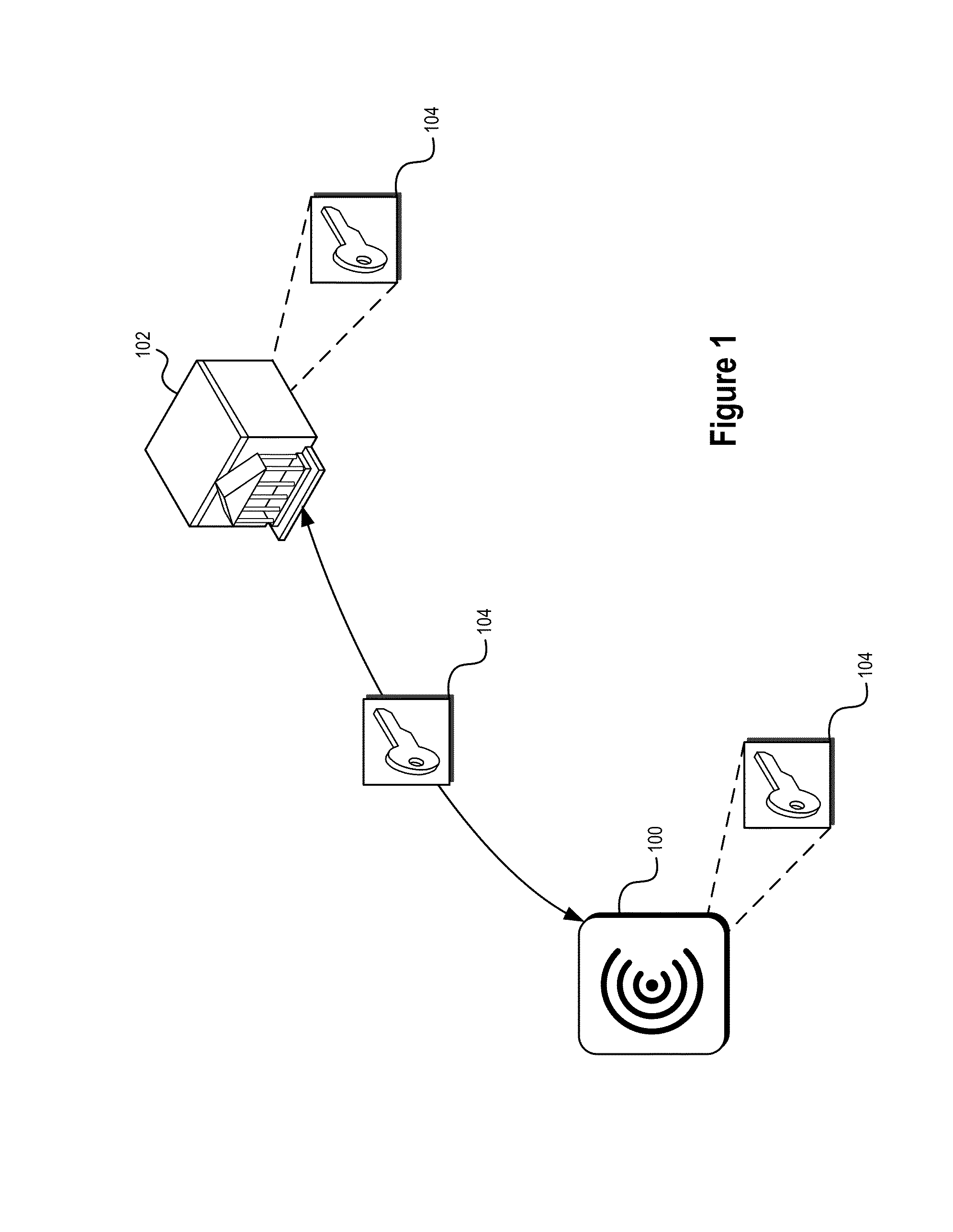
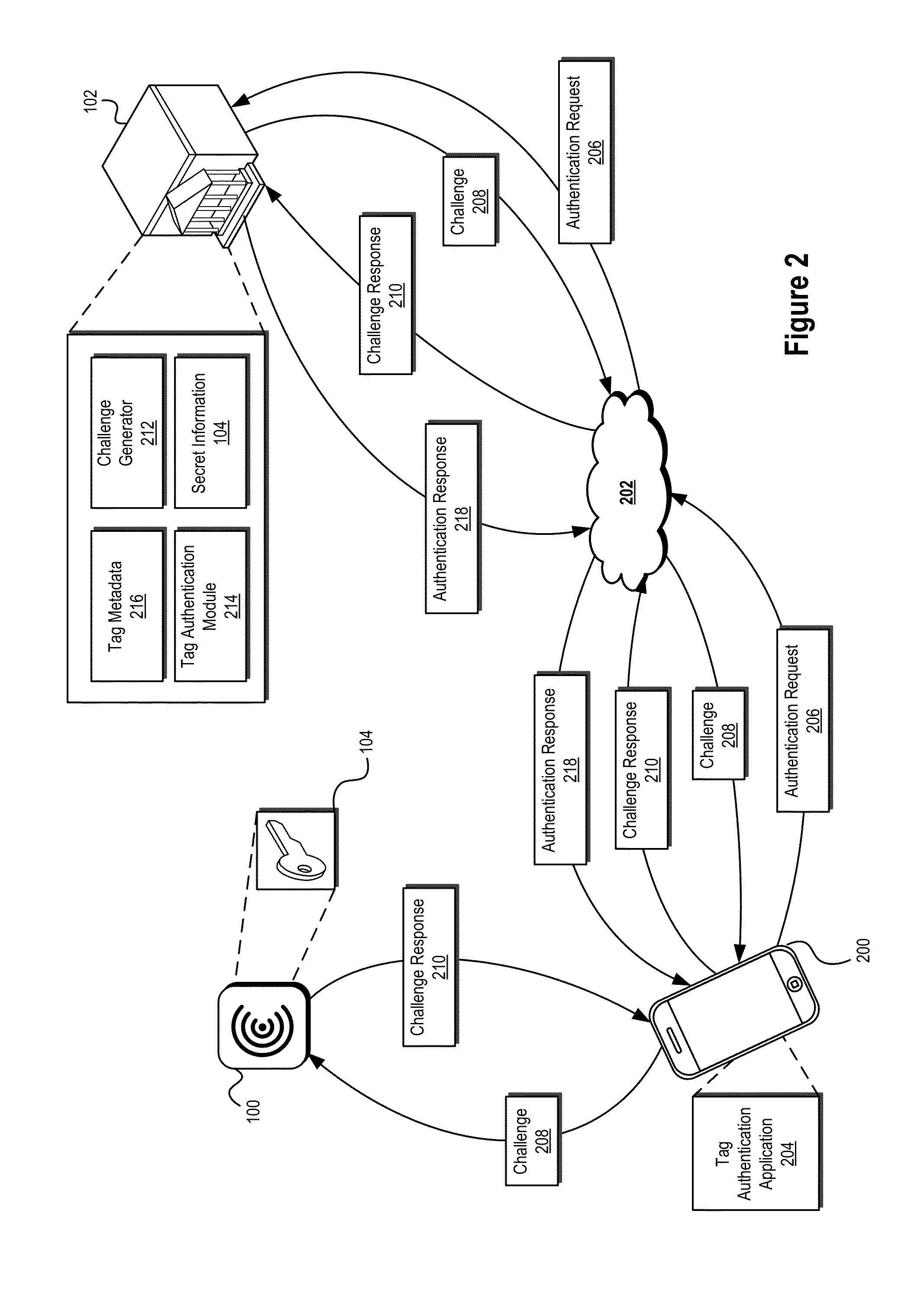
ActiveUS20140282974A1Prevent theftPrevent fraudDigital data processing detailsUser identity/authority verificationTrusted authorityInformation provision
Systems and methods are described that use tag authentication and presence verification techniques in connection with a variety of transactions. In certain embodiments, an authentication device may verify the authenticity of a secure tag by determining whether the secure tag stores secret information provisioned by a trusted authority. In some embodiments, such an authentication process may be performed without exposing the secret information to the authentication device, thereby maintaining integrity of the secure tag. In other embodiments, insecure tags and / or tags that do not include secret information are used.
Owner:INTERTRUST TECH CORP
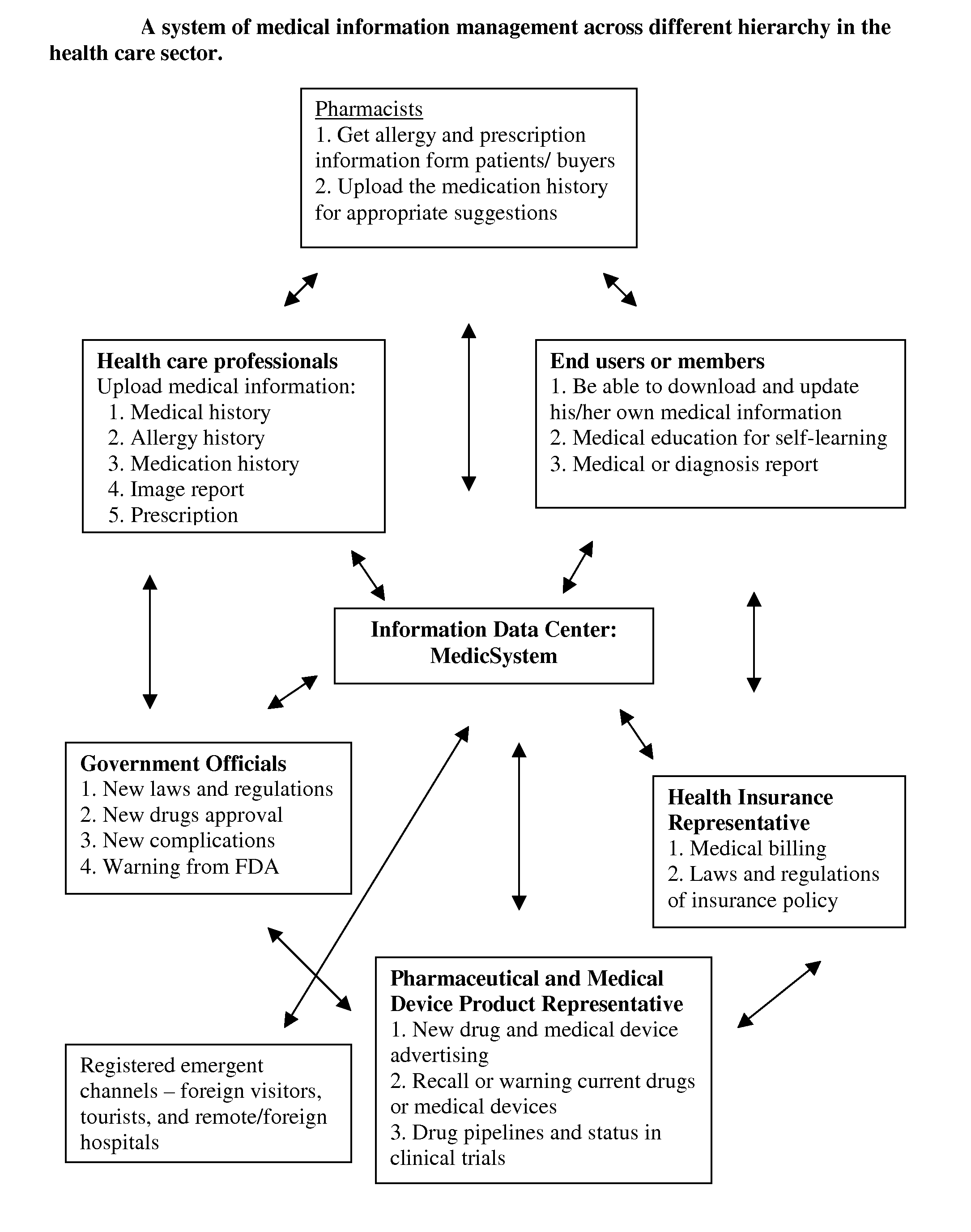
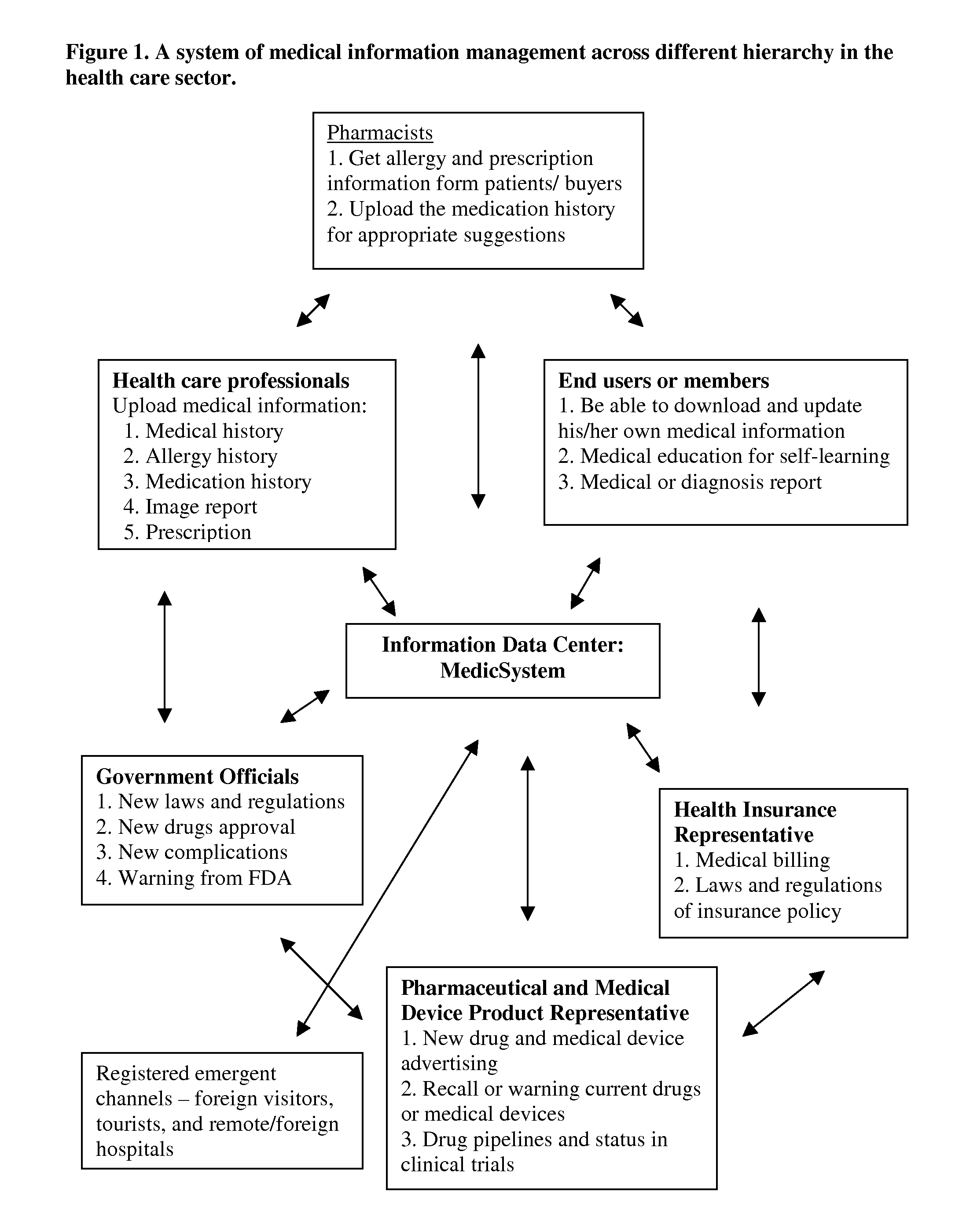
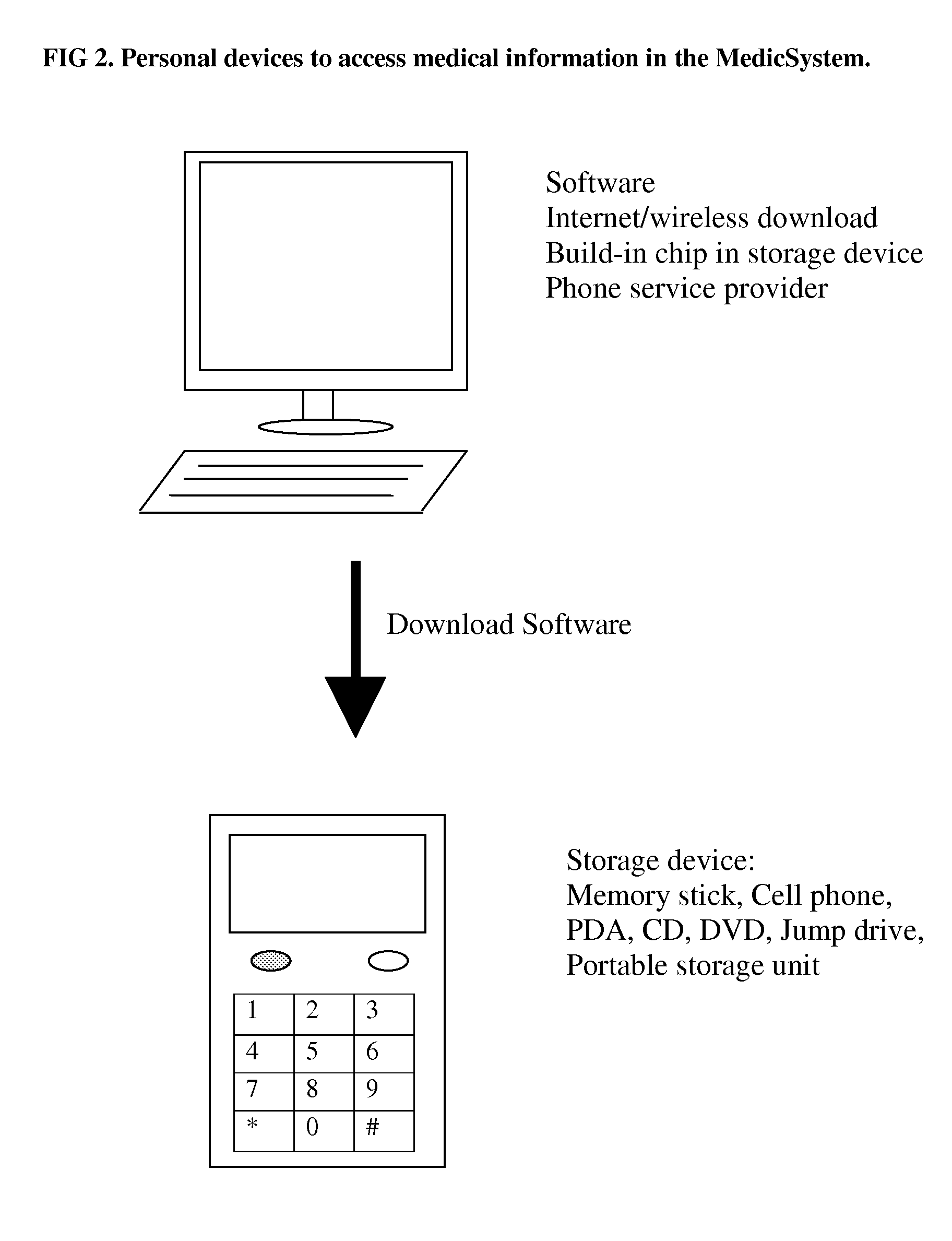
Medical information system for cost-effective management of health care
InactiveUS20100262436A1Rapid collection and analysisAccurately transmitOffice automationMedical imagesBilling systemQuality control
The invention is to solve the high cost problems in the current health care system and to increase efficiency and quality of medical care service by using an integrated medical information management system. The invention allows users or patients to manage their own medical information worldwide in a portable device to enhance medication adherence and self-management of personalized health care. A multi-functional medical information center is developed to manage medical information received from various resources to satisfy stakeholders by improving the efficacy, accuracy, and quality of health care information, but simultaneously operated at a cost-effective manner for stakeholders. In addition, the quality control of medical data management will be guarded by a side-by-side comparison technology to warn inconsistent information in medical billing history to prevent medical insurance fraudulent claims. The invention also makes the medical billing system more transparent and patients can find their desired medical doctors, preferred insurance policy, and price comparison of medical products at ease.
Owner:CHEN YING YU +1
Method and apparatus for providing specifically targeted advertising and preventing various forms of advertising fraud in electronic books
InactiveUS20070233562A1Preventing greatly reducing illegal unwanted disseminationPrevent fraudDiscounts/incentivesAdvertisementsTargeted advertisingAccess to information
A method and apparatus for providing specifically targeted advertisements and preventing various forms of advertising fraud in electronic books. In one embodiment, the method includes; receiving or having access to the contents of books; receiving or having access to subscriber target criteria; receiving, creating, or having access to advertisements; receiving or having access to information from subscribers ;receiving or having access to requests for electronic books; determining or having access to whether subscriber target criteria for the advertisements is satisfied by the information from the subscriber requesting the electronic books; selecting a set of advertisements for electronic books by choosing advertisements having associated subscriber target criteria that are satisfied by the information from the subscriber requesting the electronic books; inserting the selected advertisements for electronic books into the electronic books; and providing access to the electronic books to the subscribers who requested electronic books.
Owner:ROBB EVANS & ASSOC LLC POST JUDGMENT RECEIVER
Generating and managing decentralized identifiers
ActiveUS20190230092A1Prevent fraudPrevent misrepresentationMultiple keys/algorithms usagePublic key for secure communicationUser identifierAuthentication
The generation and management of decentralized identifiers of an entity. A decentralized identifier of a particular entity is recorded. Then, upon determining that the particular entity is granting a permission to another entity, the permission is signed based on the recorded decentralized identifier. As one example, the permission may be signed by a private key of the decentralized identifier. The permission may be verified upon request by authenticating the signed permission being associated with the recorded decentralized identifier; and authorizing the other entity to act upon the data depending on the authentication. As an example only, the authentication may occur using a public key associated with the recorded decentralized identifier.
Owner:MICROSOFT TECH LICENSING LLC
System and method for distributing trusted time
InactiveUS20060080536A1Prevent fraudSynchronising transmission/receiving encryption devicesUser identity/authority verificationDigital dataReal-time clock
Systems and methods for distributing trusted time, including trusted dates with digital data files, which are accessed, created, modified, received, or transmitted by devices that include a trusted time source in a tamperproof environment. The system includes one or more subsystems for providing trusted time for a moment in time. The trusted time source may be a real time clock, which is not resettable, is independent of any system clock of the devices, and where one or more devices may contribute to the distribution of trusted time among each other.
Owner:TIME CERTAIN
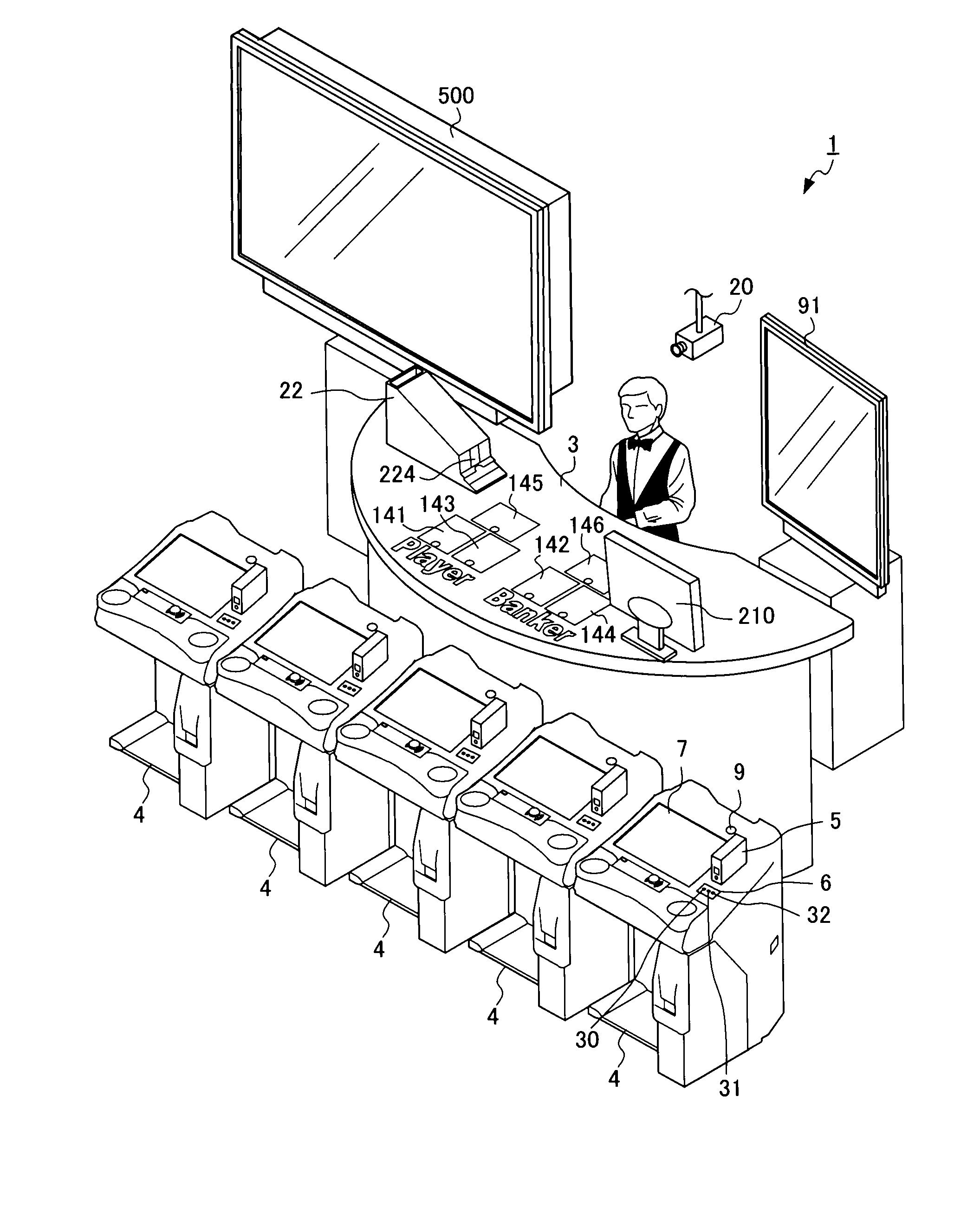
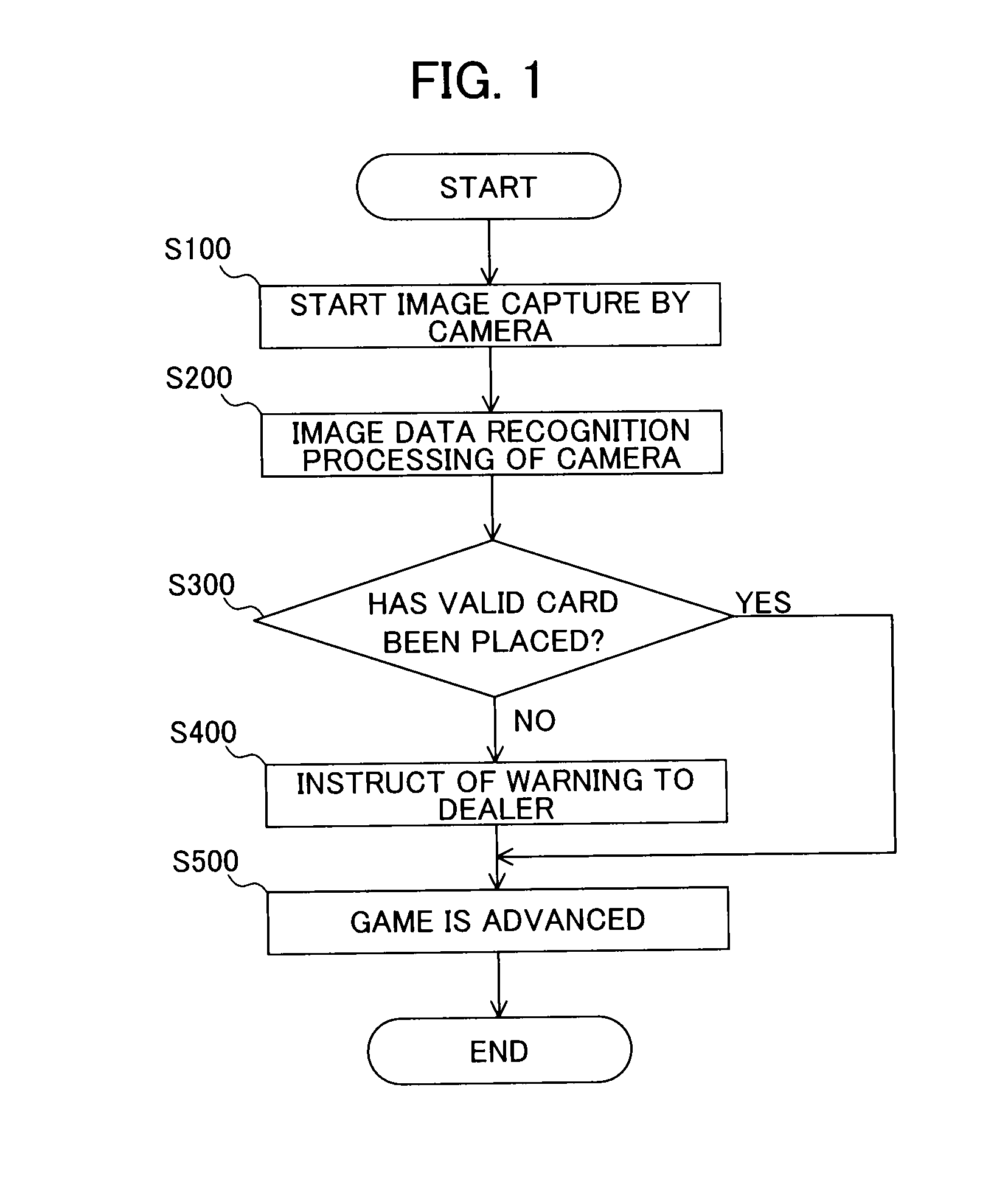
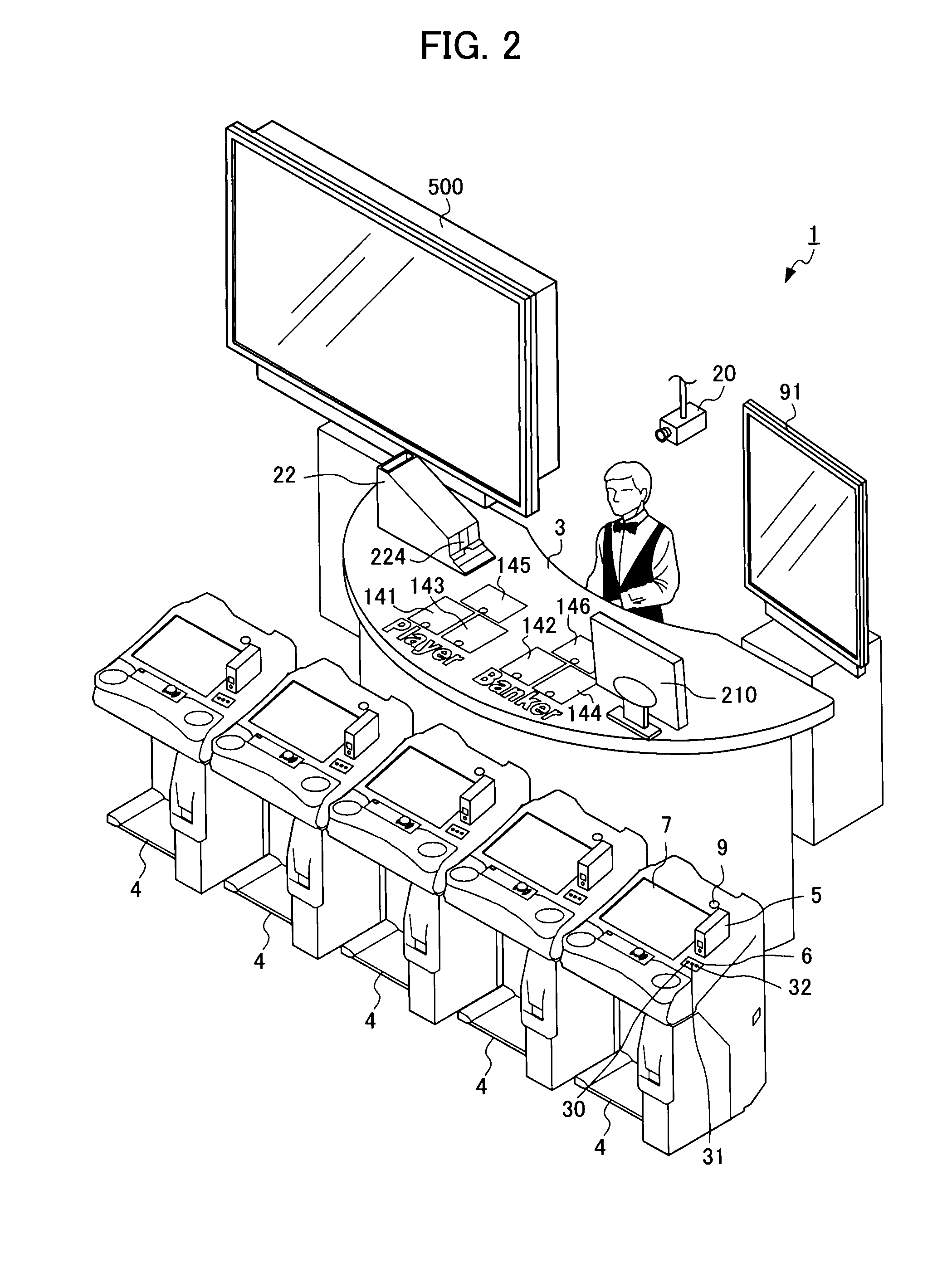
Gaming system that navigates dealer in game advancement and prevents fraud
ActiveUS20100331085A1Low costPrevent fraudApparatus for meter-controlled dispensingVideo gamesComputer graphics (images)Imaging data
The present invention provides a gaming system that can allow a game to be appropriately advanced even by an inexperienced dealer by way of navigating the dealer in game advancement, thereby allowing fraud to be avoided and cost to be reduced. An image input device, which captures images for displaying to players playing the game at a plurality of stations, captures an image of a side of a game portion on which the dealer is positioned to include card placement areas. Then, a controller performs image recognition processing of comparing image data of the card placement areas captured by the image input device with comparative image data stored in memory. Thereafter, in a case in which image recognition processing results in an image showing a card being included, the score of the card game is calculated based on recognition results of the images showing cards.
Owner:UNIVERSAL ENTERTAINMENT CORP +1
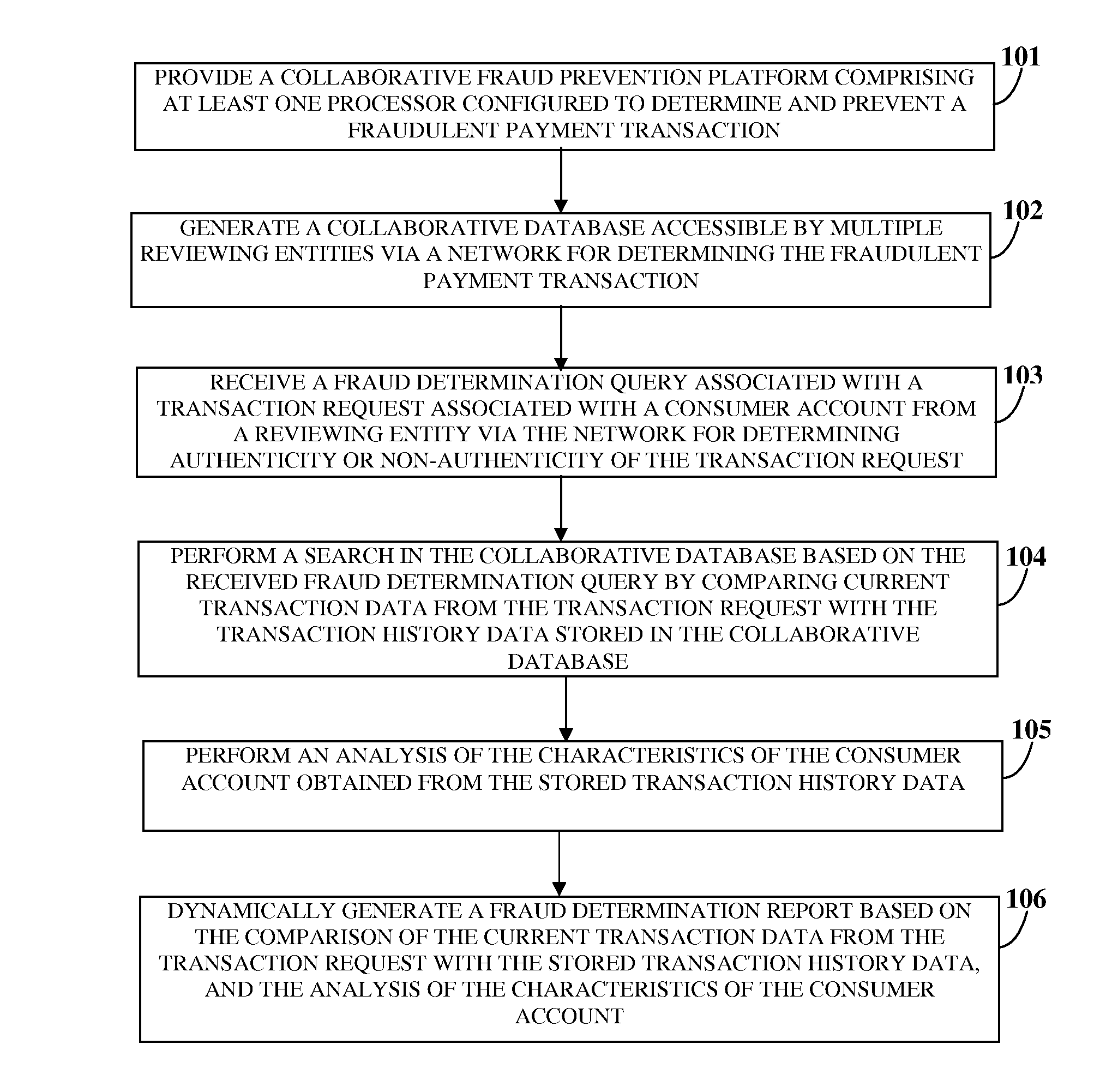
Collaborative Fraud Determination And Prevention
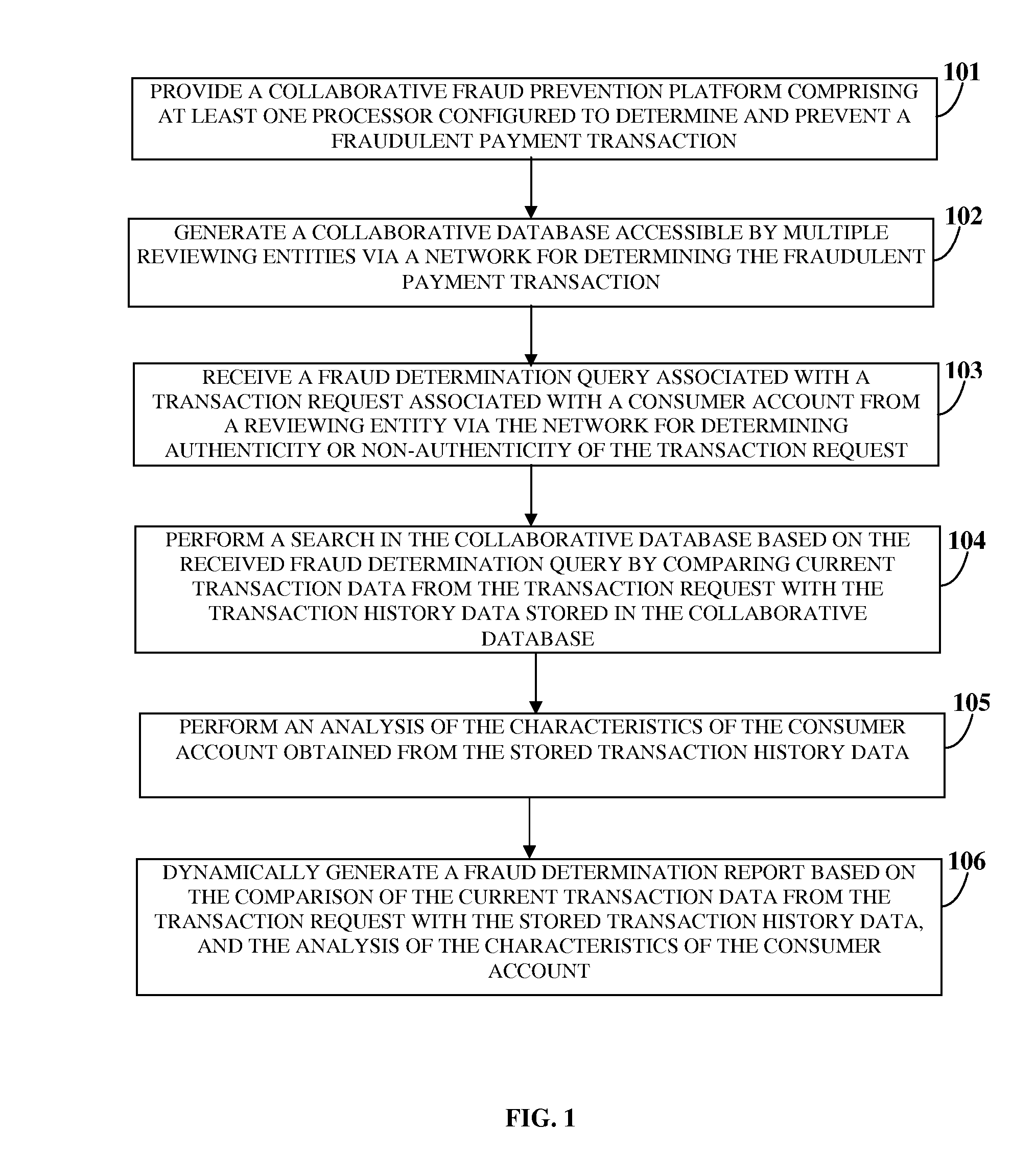
InactiveUS20140108251A1Prevent a substantial percentage of losses incurredFacilitate determinationFinanceProtocol authorisationPayment transactionTransaction data
A computer implemented method and system for determining a fraudulent payment transaction in a collaborative environment is provided. A collaborative database, accessible by multiple reviewing entities via a network, receives and stores transaction history data of payment transactions from the reviewing entities. A collaborative fraud prevention platform (CFPP) receives a fraud determination query associated with a transaction request associated with a consumer account. The CFPP performs a search in the collaborative database based on the fraud determination query by comparing current transaction data from the transaction request with the stored transaction history data, performs an analysis of characteristics of the consumer account, and generates a fraud determination report based on the comparison and analysis. The fraud determination report indicates authenticity or non-authenticity of the transaction request for configurable time periods to enable a reviewing entity to determine the fraudulent payment transaction and complete or discontinue processing of the transaction request.
Owner:ANDERSON ROBERT WHITNEY +1
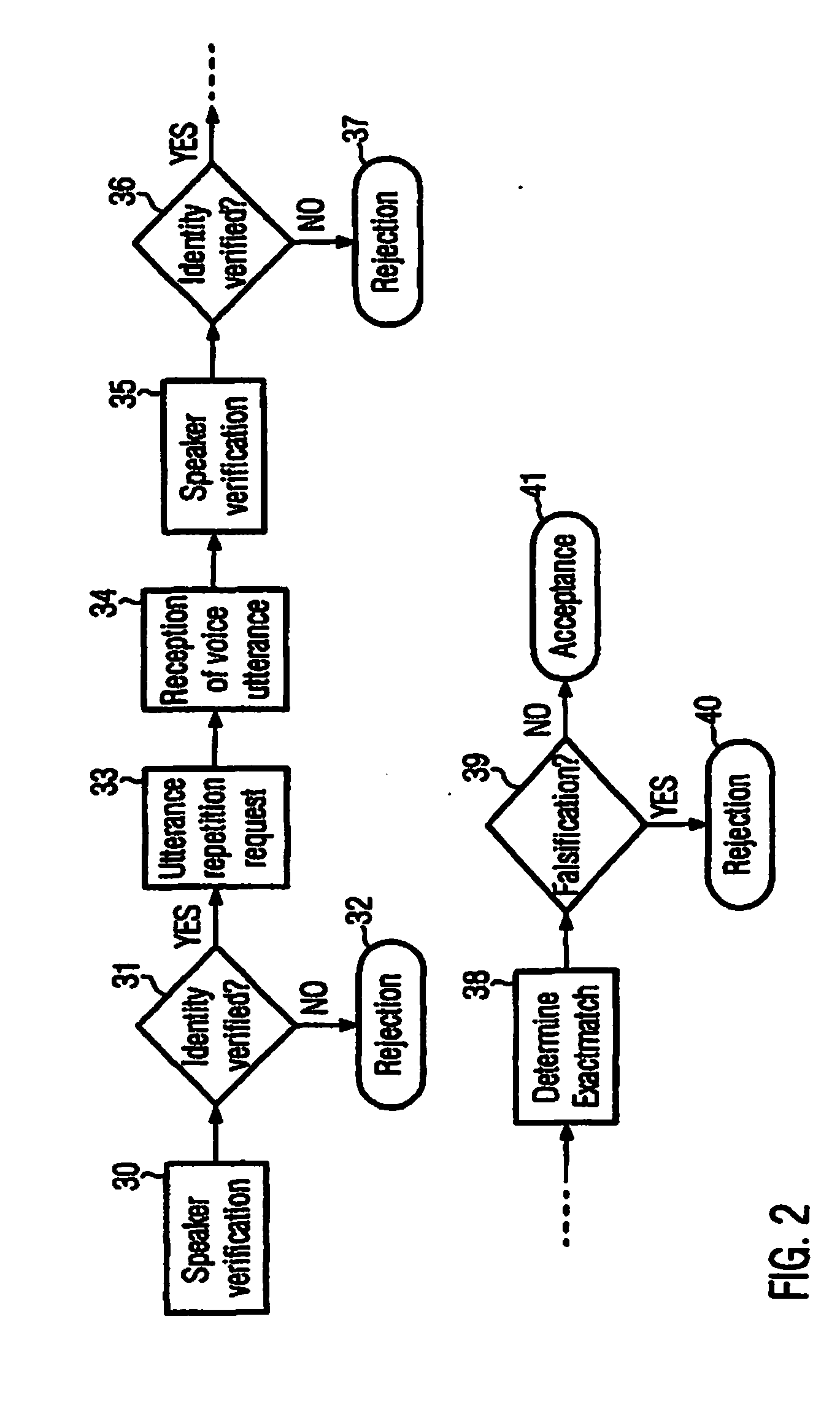
Method for verifying the identity of a speaker and related computer readable medium and computer
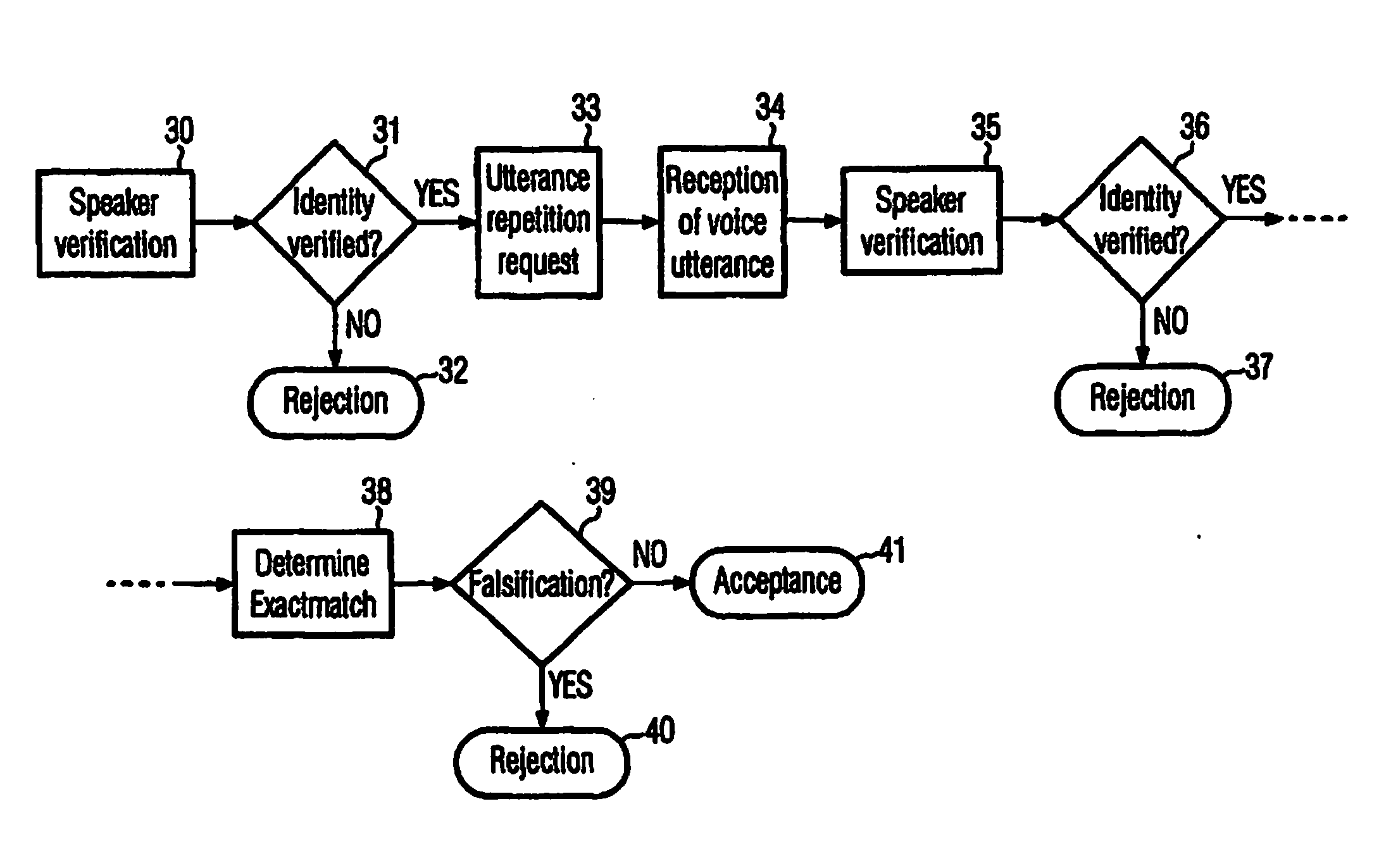
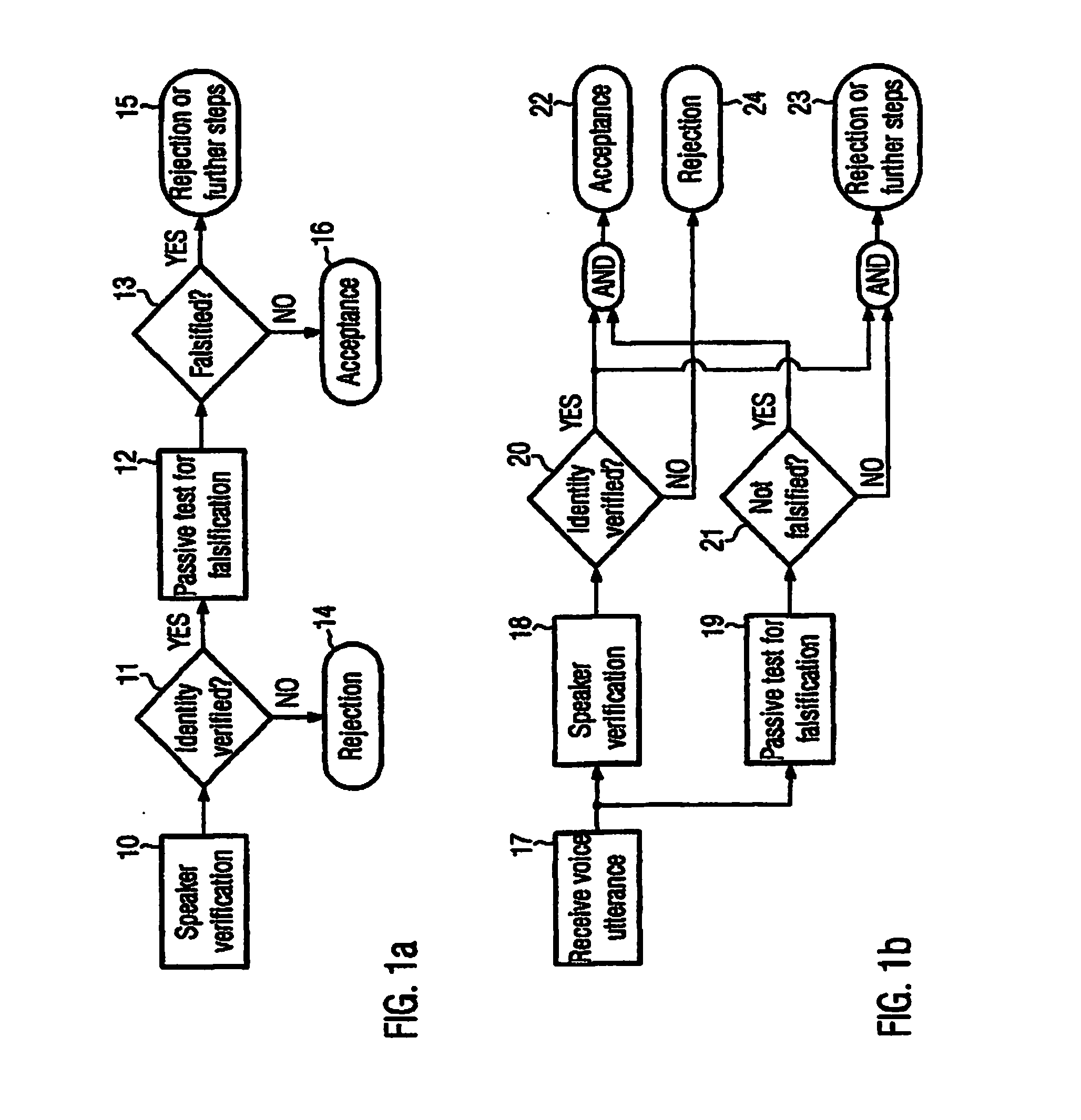
InactiveUS20150112682A1Improve securityPrevent fraudSpeech recognitionSpeech verificationSpeech sound
The present invention refers to a method for verifying the identity of a speaker based on the speaker's voice comprising the steps of: a) receiving a voice utterance; b) using biometric voice data to verify that the speakers voice corresponds to the speaker the identity of which is to be verified based on the received voice utterance; and c) verifying that the received voice utterance is not falsified, preferably after having verified the speakers voice; d) accepting the speaker's identity to be verified in case that both verification steps give a positive result and not accepting the speaker's identity to be verified if any of the verification steps give a negative result. The invention further refers to a corresponding computer readable medium and a computer.
Owner:AGNITIO
System and methods for distributing trusted time
Systems and methods for distributing trusted time, including trusted dates with digital data files, which are accessed, created, modified, received, or transmitted by devices that include a trusted time source in a tamperproof environment. The system includes one or more subsystems for providing trusted time for a moment in time. The trusted time source may be a real time clock, which is not resettable, is independent of any system clock of the devices, and where one or more devices may contribute to the distribution of trusted time among each other.
Owner:TEPPLER STEVEN W
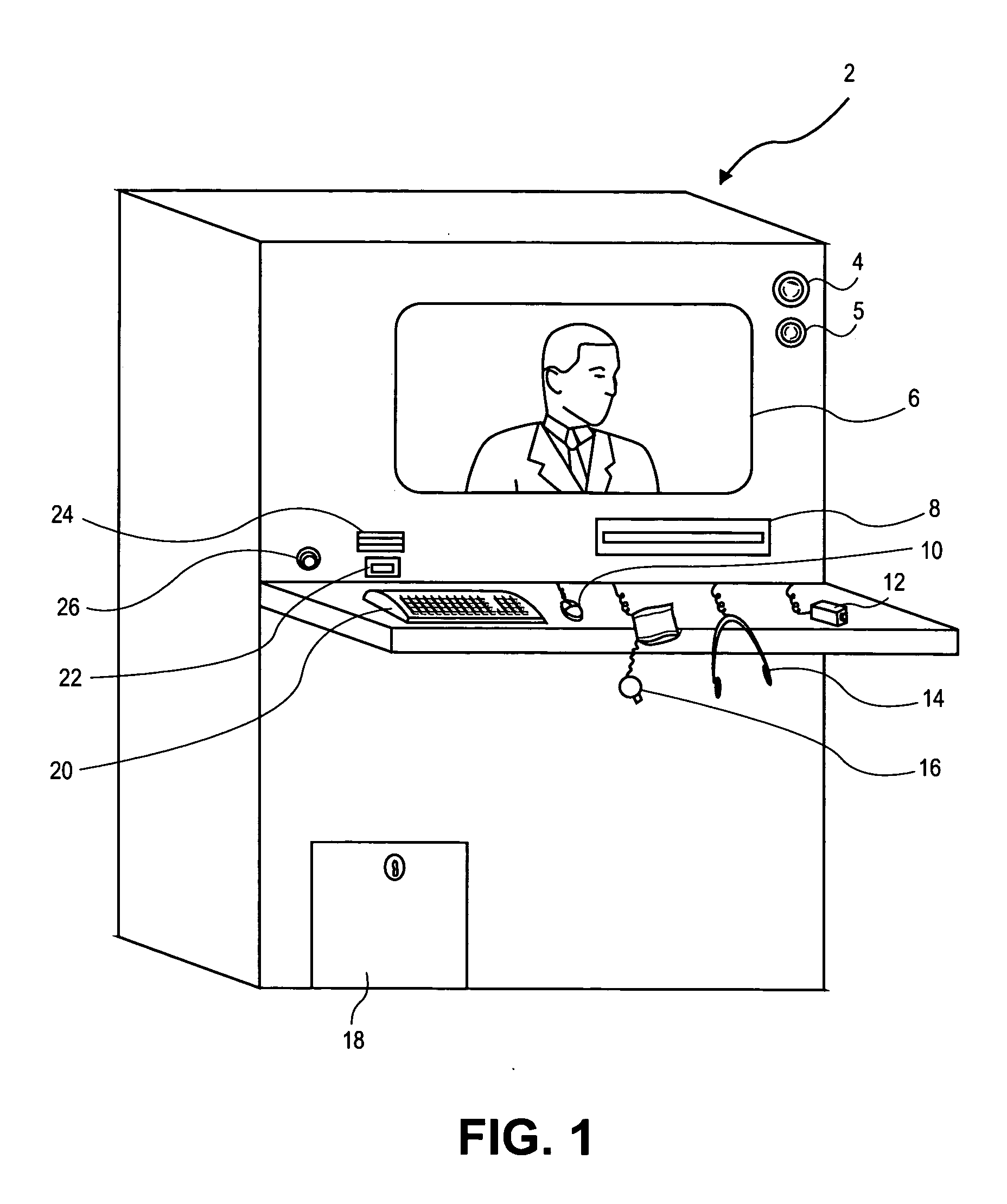
Emergency station kiosk and related methods
InactiveUS20050075907A1Prevent fraudPrevent mistreatmentDrug and medicationsStethoscopeDocumentationComputer science
Applications of the present invention are particularly useful in providing a system that allows the secure distribution of medical documents through a medical kiosk. The medical kiosk includes a customer interface and a camera that captures an image of the customer and attaches the image to a medical document. In order to receive a medical document through the kiosk, a customer requests a medical examination, enters information into the system by answering questions, and using medical instruments, and then requests the medical document. A picture of the customer is captured for attachment to the medical document. Another embodiment of the invention allows a customer to communicate directly with a medical professional during the examination process through a customer interface with the kiosk.
Owner:RAO JOHN
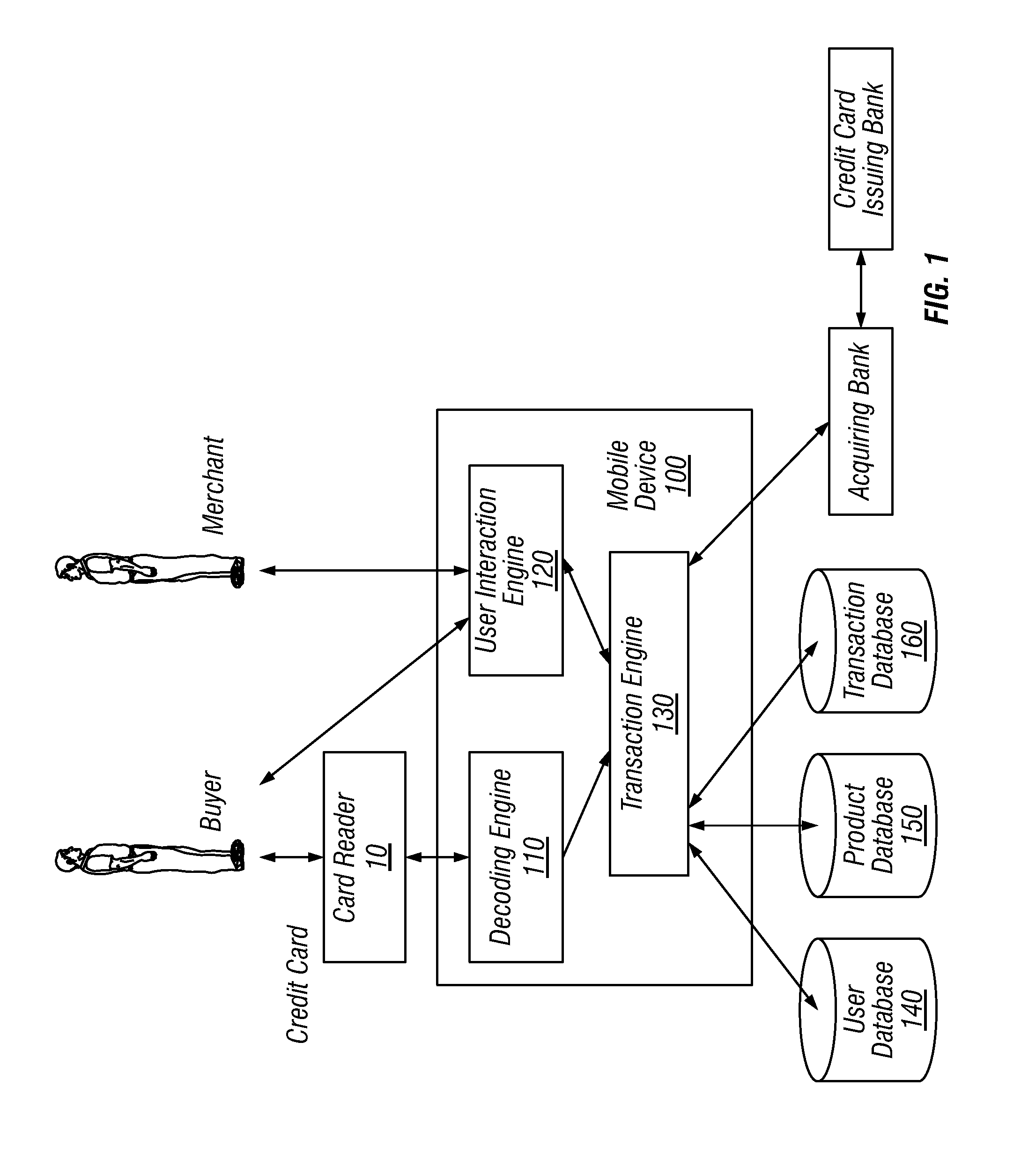
Systems and methods for financial transaction through miniaturized card reader with confirmation of payment sent to buyer
A system is provided that includes a transaction engine running on a mobile device. In response to a financial transaction between a buyer and a seller, the transaction uses the mobile device to accept information selected including but not limited to information from financial transaction or information pertaining to financial transaction card used by the buyer in the transaction. At least a portion of this information is communicated with a third party financial institution or payment network to authorize the transaction. The buyer receives confirmation of the payment.
Owner:BLOCK INC
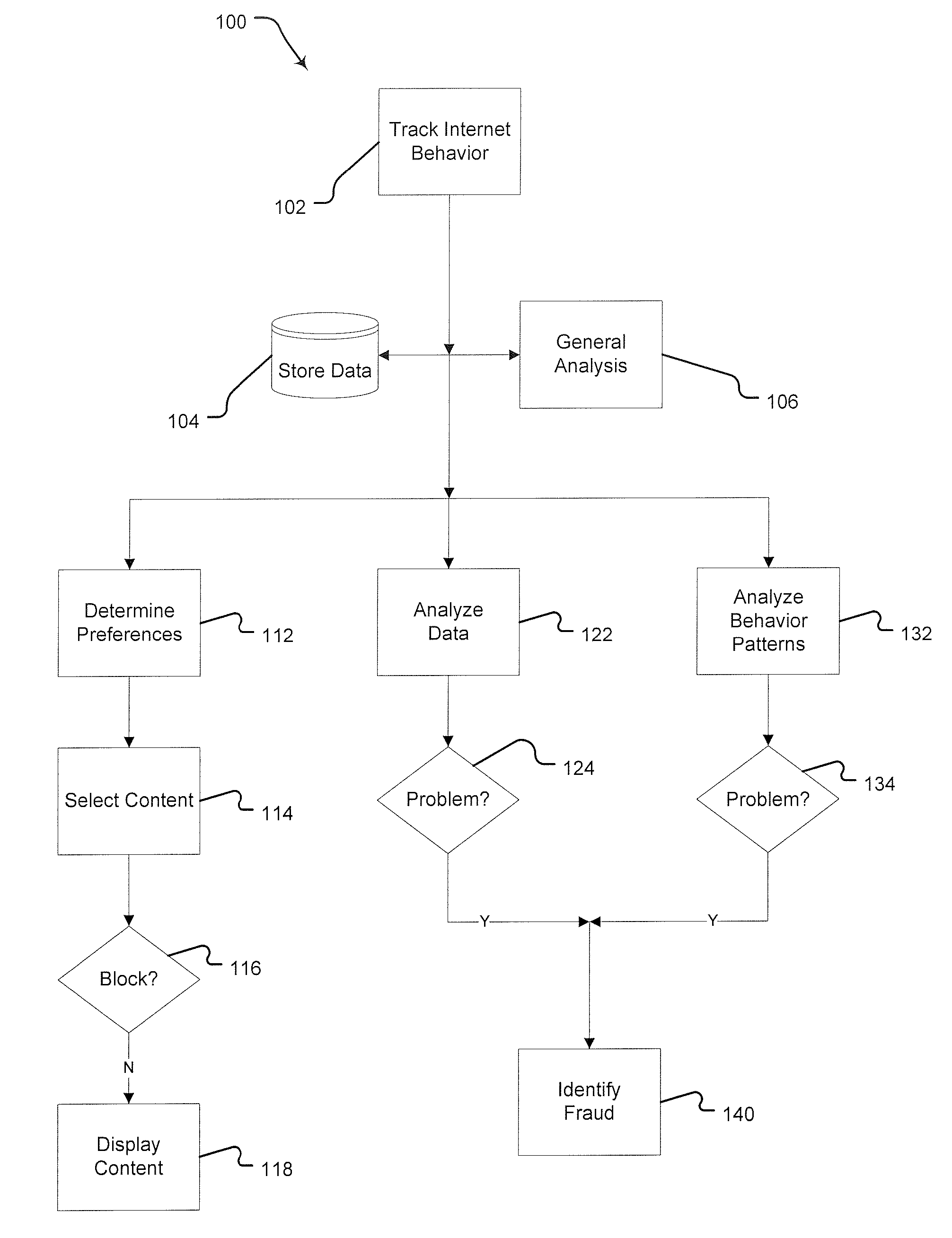
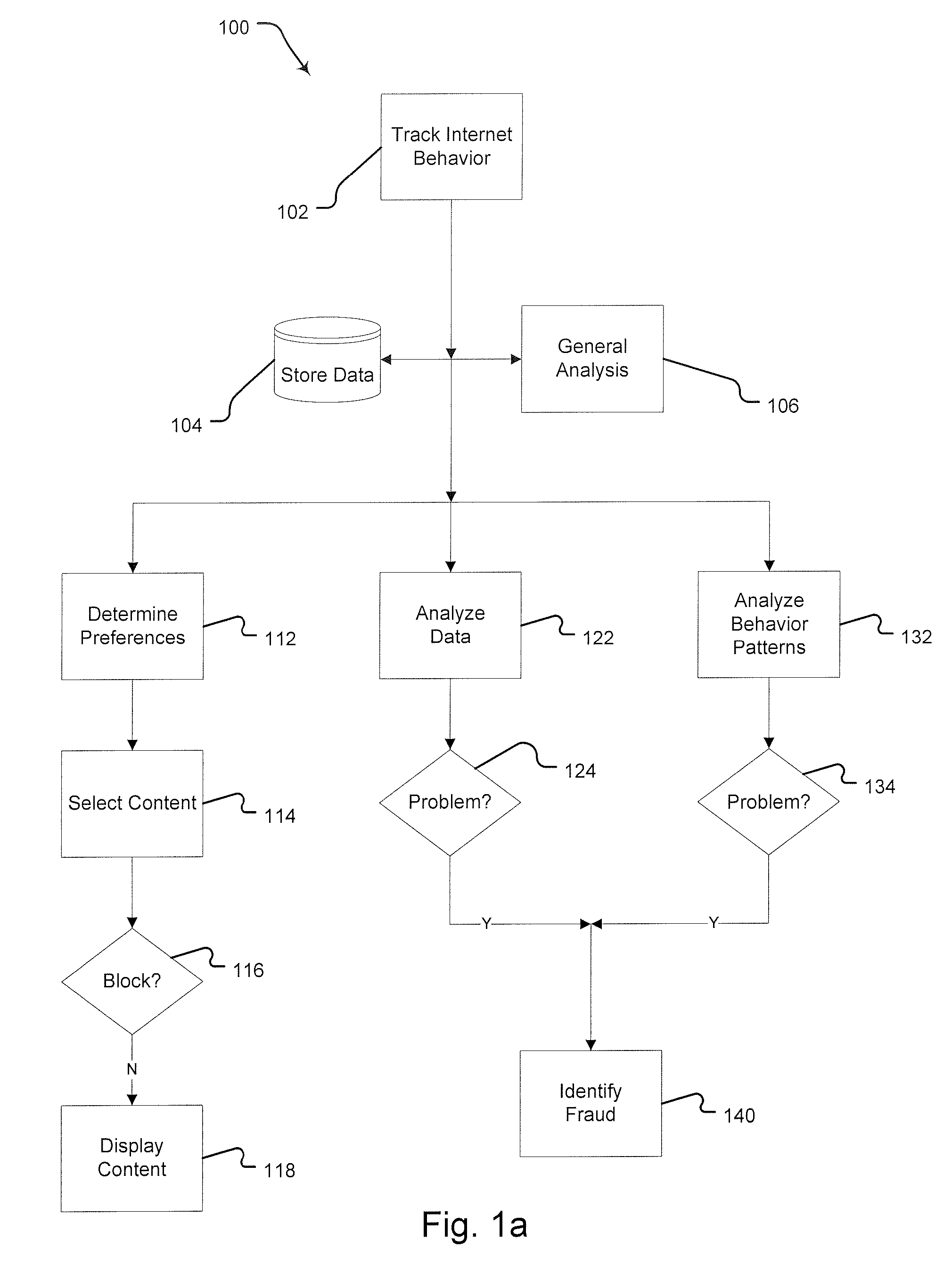
Method for Detecting and Preventing Fraudulent Internet Advertising Activity
InactiveUS20080288303A1Prevent fraudPlatform integrity maintainanceMarket data gatheringInternet privacyBehaviour pattern
A method for preventing fraud in Internet-based advertising. The first step of this method is providing behavior-tracking software on a user computer. That software tracks and analyzes the user's activity across multiple content providers. Next, the system displays content, including advertising, based on preferences inferred from previous activity. Finally, the system identifies behavior patterns consistent with fraudulent activity.
Owner:CARHAMM
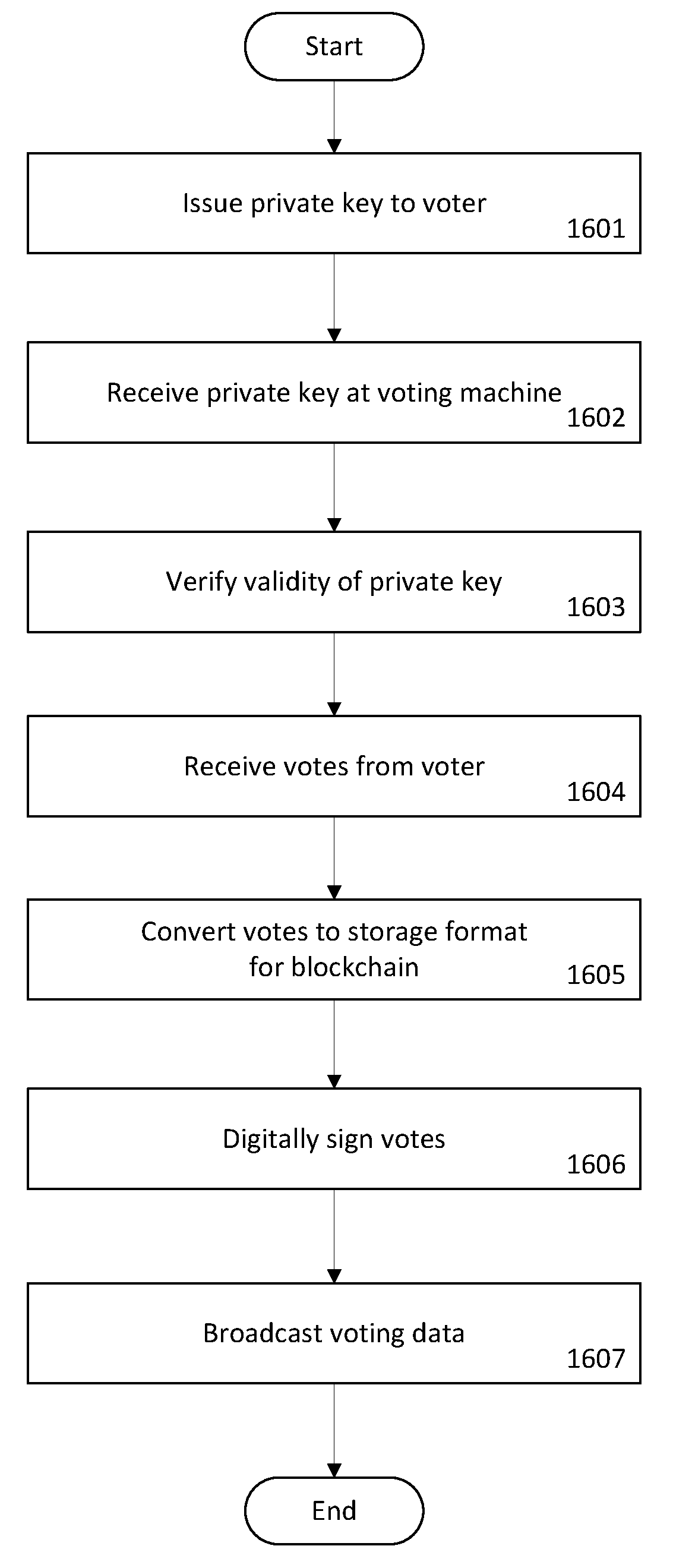
System and method for securely receiving and counting votes in an election
InactiveUS20170352219A1Improve securityPrevent fraudVoting arrangementVoting apparatusBarcodeComputerized system
The present invention generally relates to blockchain technology. Specifically, this invention relates to adapting blockchain technology for the storage of voting data in an electronic voting system. The system includes a distributed network of voting machines in communication with each other. Each voting machine has a barcode scanner, a network communications device and a computer system running a voting client. Votes are received through the barcode scanner or a voter interface system and stored securely on a blockchain. The tally for various candidates in the election is updated and stored as each vote is received and counted. This creates an auditable trail of votes and the tally which can be used to detect, correct, and prevent fraud and error in the vote counting process.
Owner:BLOCKCHAIN TECH
System and method for realizing electronic transaction risk control based on position scene identification
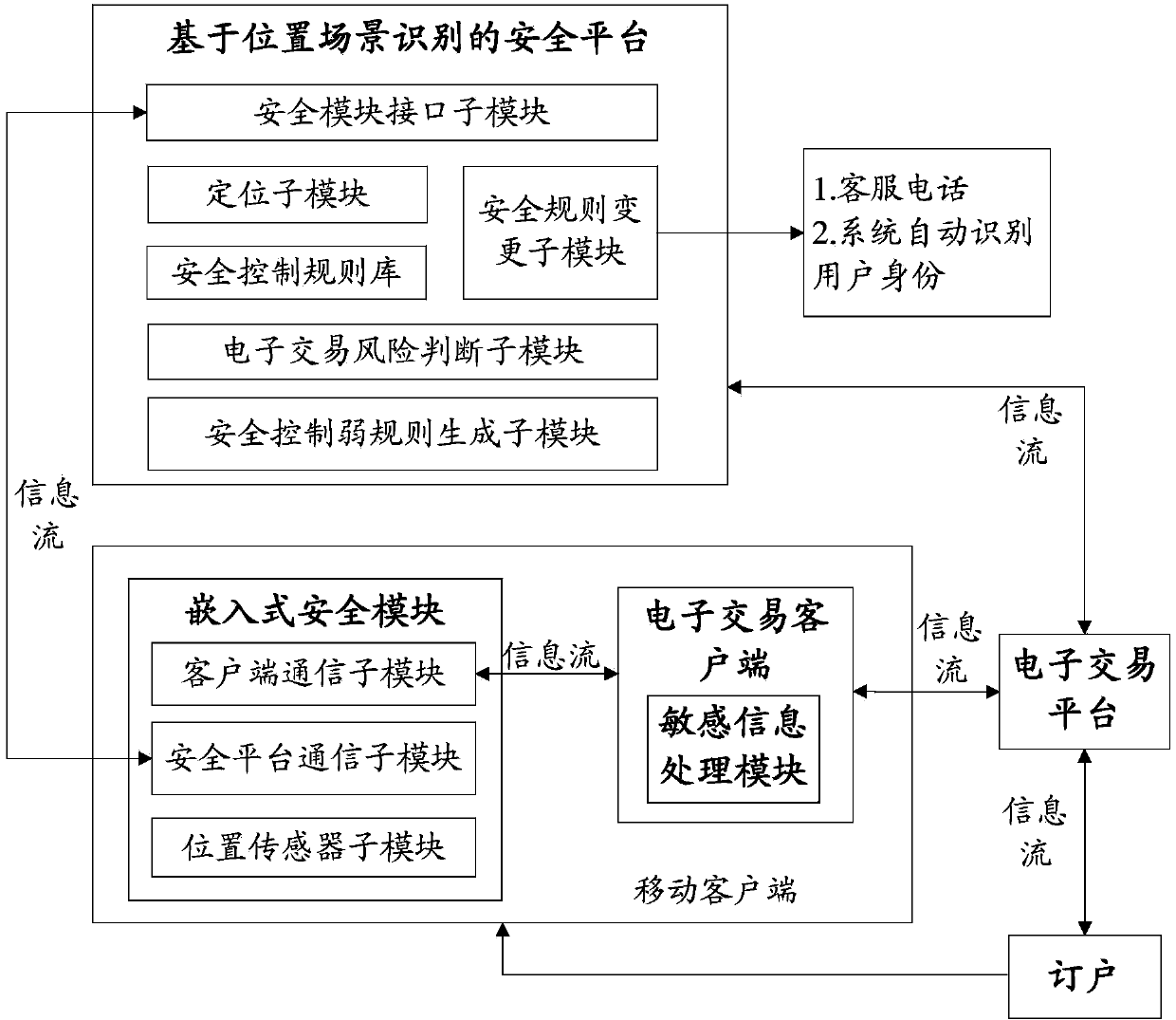
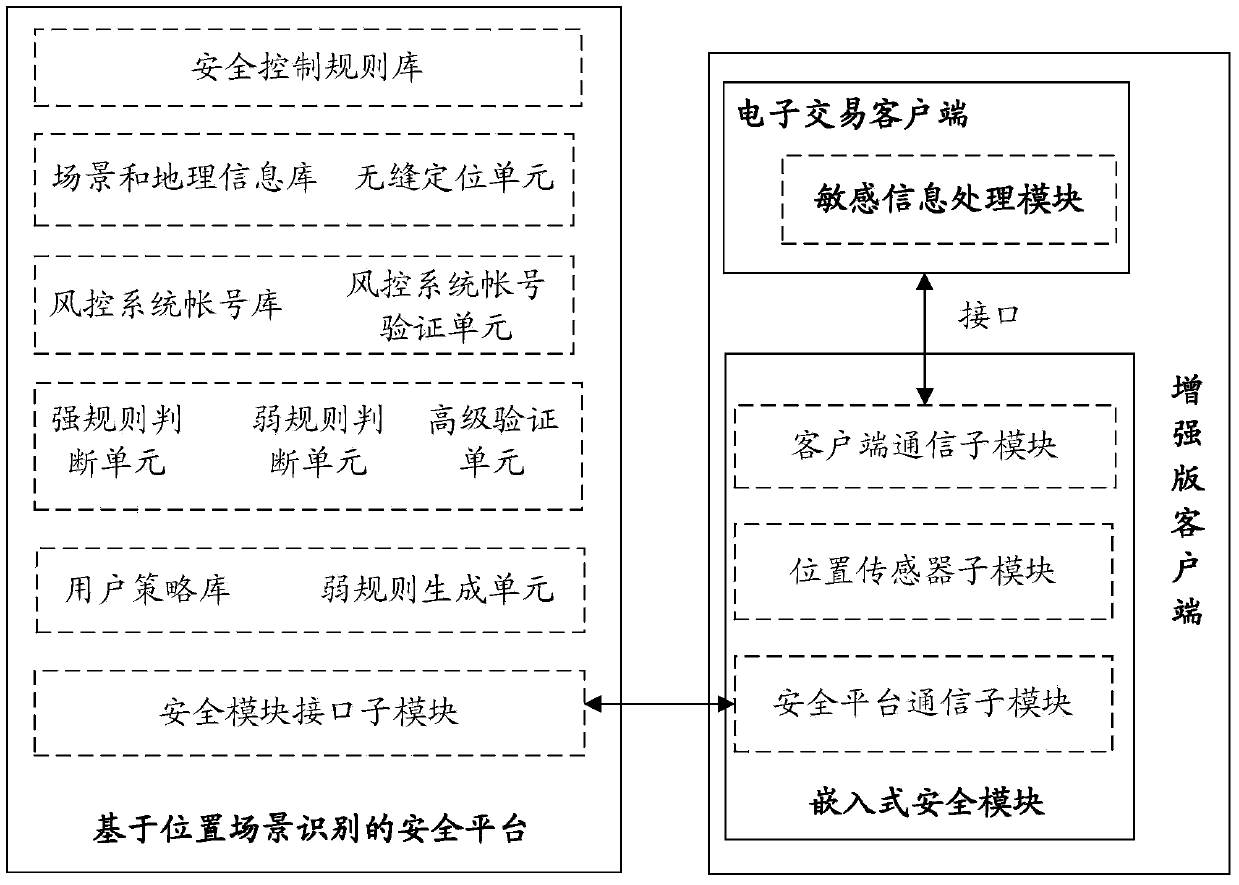
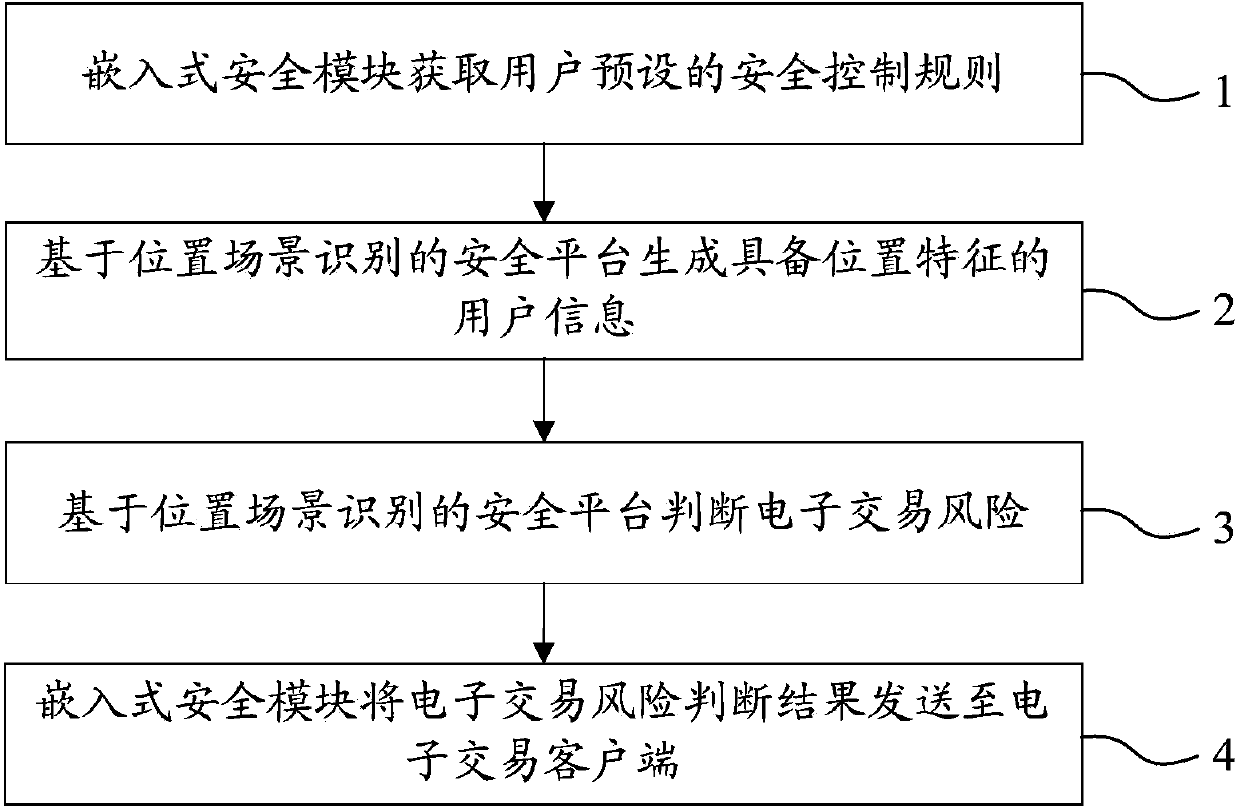
InactiveCN103745397APrevent fraudReduce personal property damageFinanceBuying/selling/leasing transactionsRisk ControlEmbedded security
The invention relates to a system for realizing electronic transaction risk control based on position scene identification. The system comprises a position scene identification-based security platform and an embedded security module, wherein the position scene identification-based security platform comprises a security interface sub-module, a positioning sub-module, a security control rule library, a security rule change sub-module, an electronic transaction risk judging sub-module and a security control weak rule generation sub-module, which are communicated with the embedded security module. The invention further relates to a method for realizing electronic transaction risk control based on position scene identification through the system. By adopting the system and the method for realizing electronic transaction risk control based on position scene identification, risk control over the electronic transactions of a user can be realized by providing positioning service and identifying a user position scene, so that the security of an electronic transaction process is enhanced, and losses caused by transaction security problems are reduced. The method is easy, convenient, and wider in application range.
Owner:YINLIAN FINANCIAL INFORMATION SERVICE BEIJING CO LTD
Apparatus and method for security tag detection
InactiveUS20070023521A1Improve securityPrevent fraudMaterial analysis by optical meansRecord carriers used with machinesAlcoholDrug product
The present invention relates, in general, to the field of securing, prevention of fraud, or theft of products such as pharmaceuticals, cigarettes, alcohol and other high value often counterfeited products. In particular the invention teaches an apparatus and method to encode packaging of the protected goods using a near infrared luminescing compound and detecting the compound through recognition of a characteristic spectral signature of its emission.
Owner:AUTHENTIX INC
Apparatus and method for securely monitoring the sales transactions of bulk vending machines
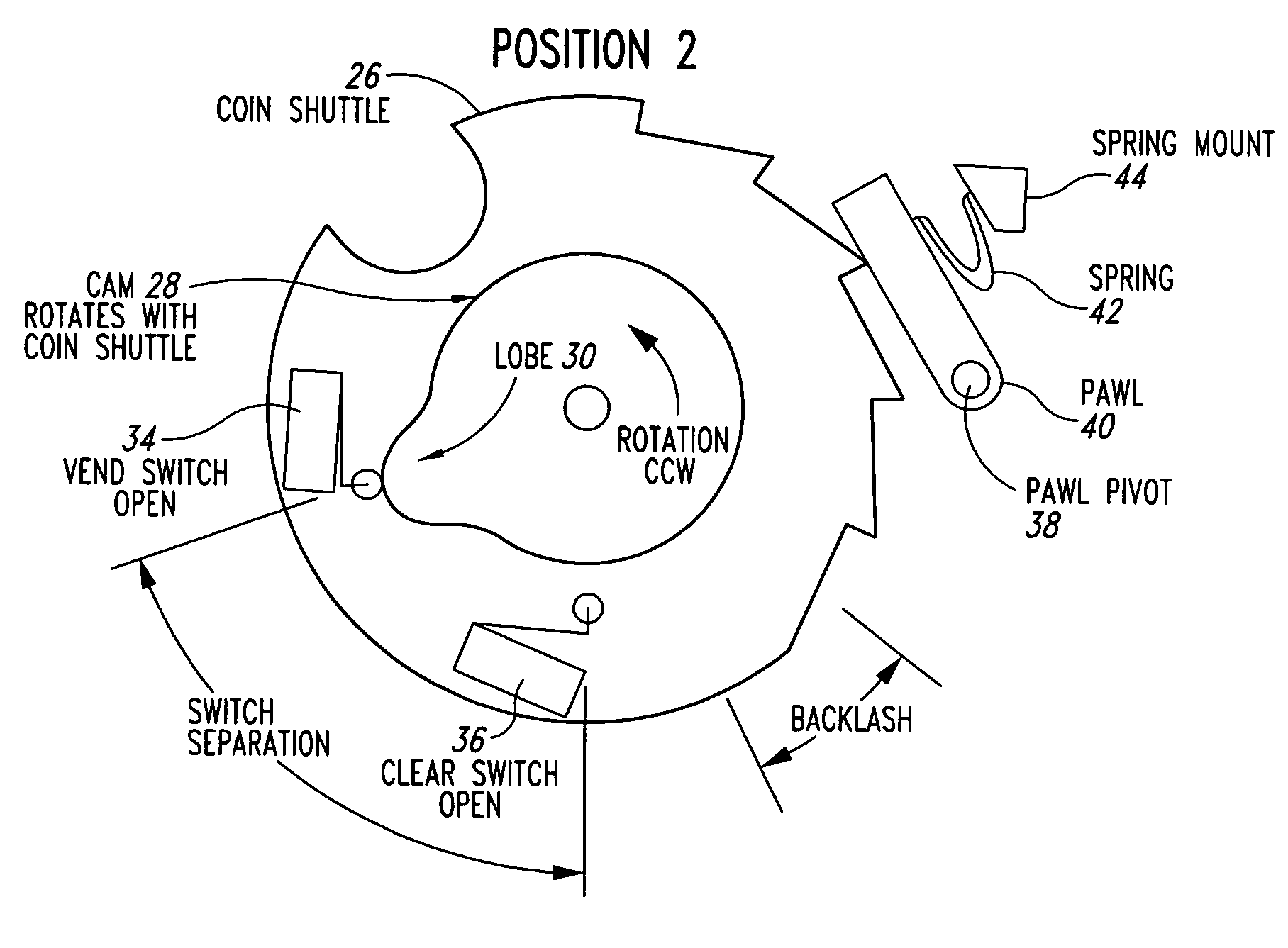
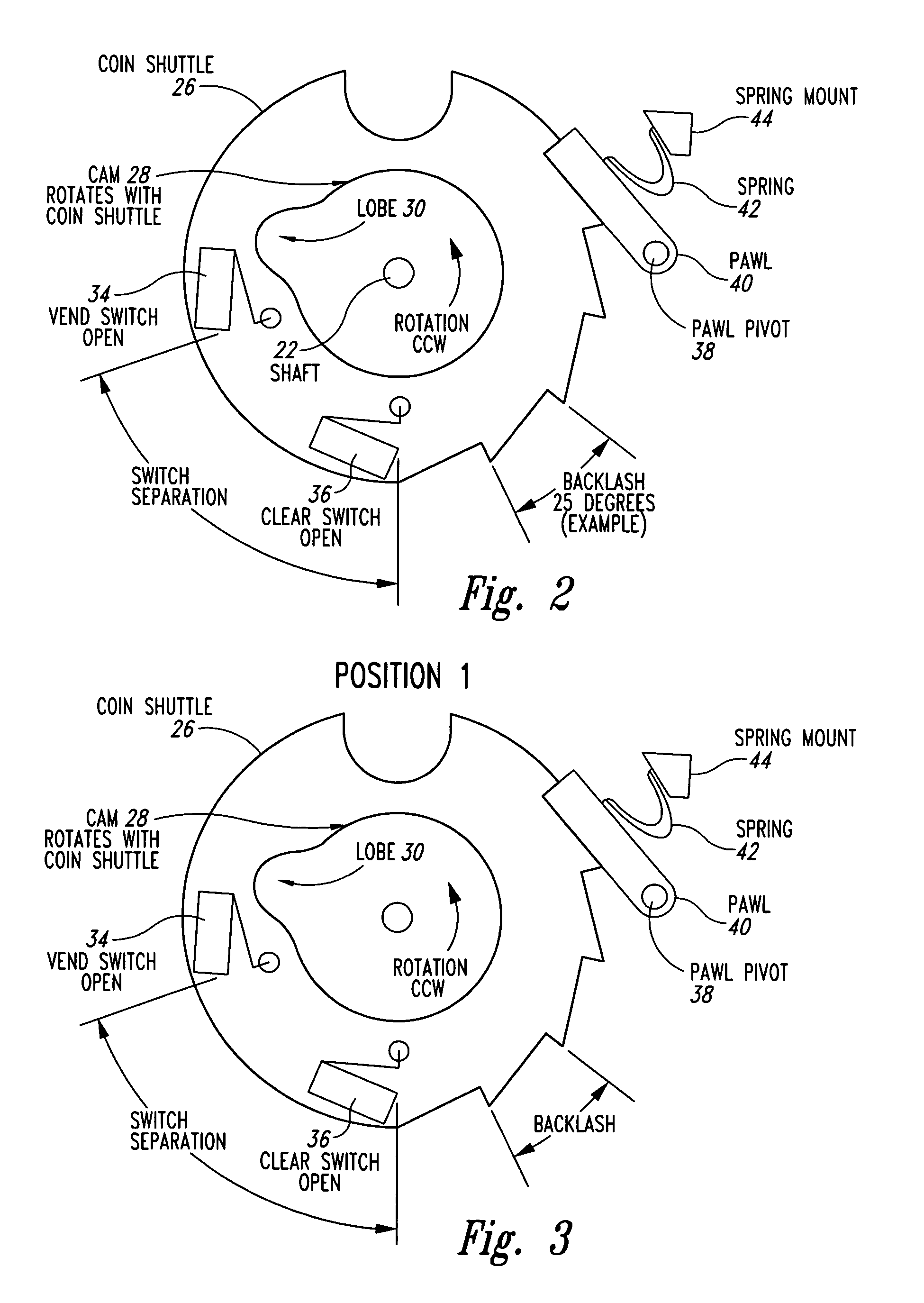
InactiveUS7083036B2Effectively and simultaneously guarantee precisionEffectively and simultaneously guarantee and accuracyRegistering coin as creditRecord information storageEngineeringCam
An apparatus for securely monitoring the sales transactions in bulk vending machines, said apparatus comprising at least one bulk vending machine having a coin mechanism. The coin mechanism includes a coin plate; a selectively rotatable shaft extending radially therefrom; a coin shuttle, a cam-bearing lobe and a coin mechanism adapter plate co-axially and collectively located around the selectively rotatable shaft; and a first switch and a second switch. The first and second switches are fixedly mounted and oriented on the coin mechanism adapter plate so that the maximum amount of backlash in the coin mechanism is less than the angular spread of the switches. The coin mechanism further includes a microprocessor having a sales counter; and means for communicatingly connecting the first and second switches to said microprocessor, whereby the microprocessor will advance the sales counter one numeric count and record a single vend only after the cam-borne lobe contacts and completely closes both first and second switches, when it is rotated as a result of a coin deposited in the coin mechanism.
Owner:NAT ENTERTAINMENT NETWORK LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com