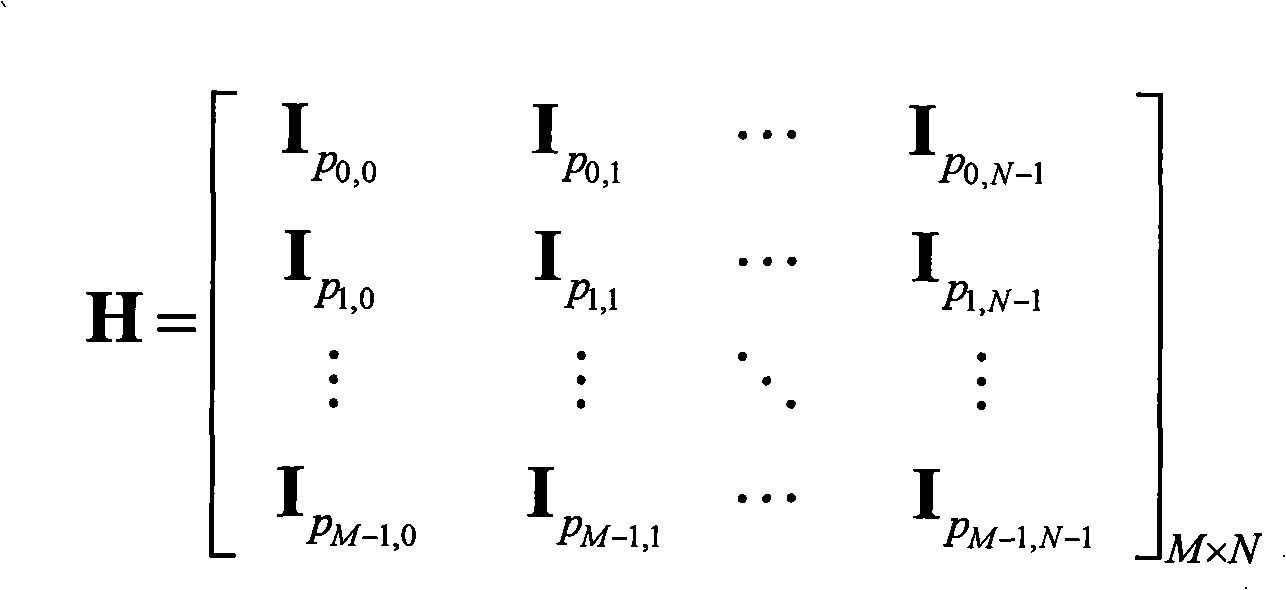Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
976 results about "Check digit" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
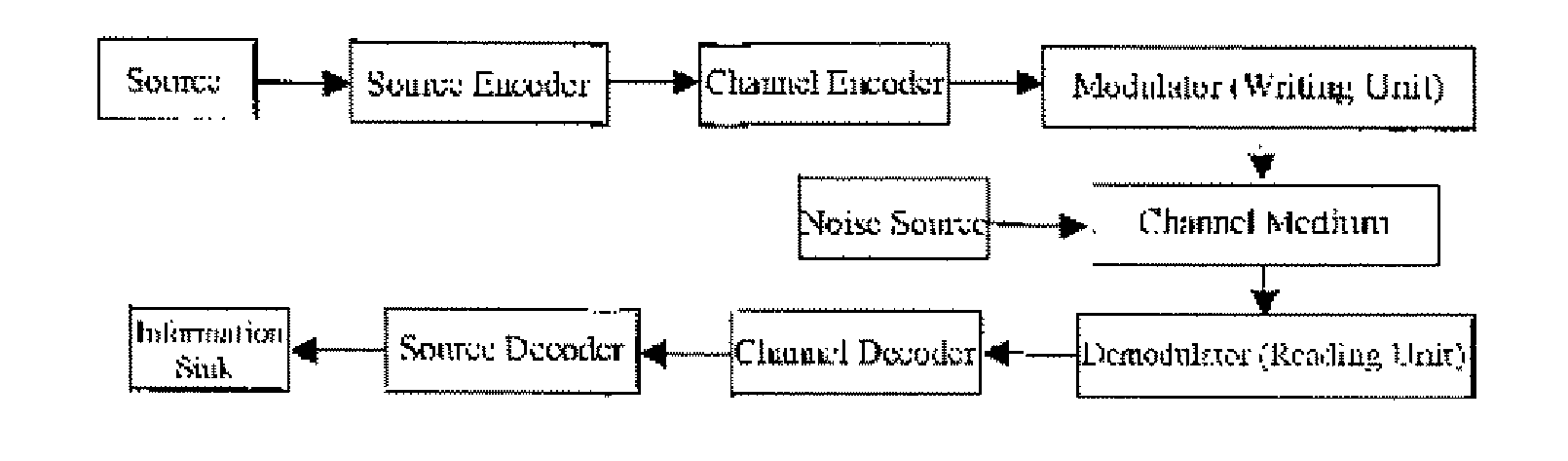
A check digit is a form of redundancy check used for error detection on identification numbers, such as bank account numbers, which are used in an application where they will at least sometimes be input manually. It is analogous to a binary parity bit used to check for errors in computer-generated data. It consists of one or more digits computed by an algorithm from the other digits (or letters) in the sequence input.
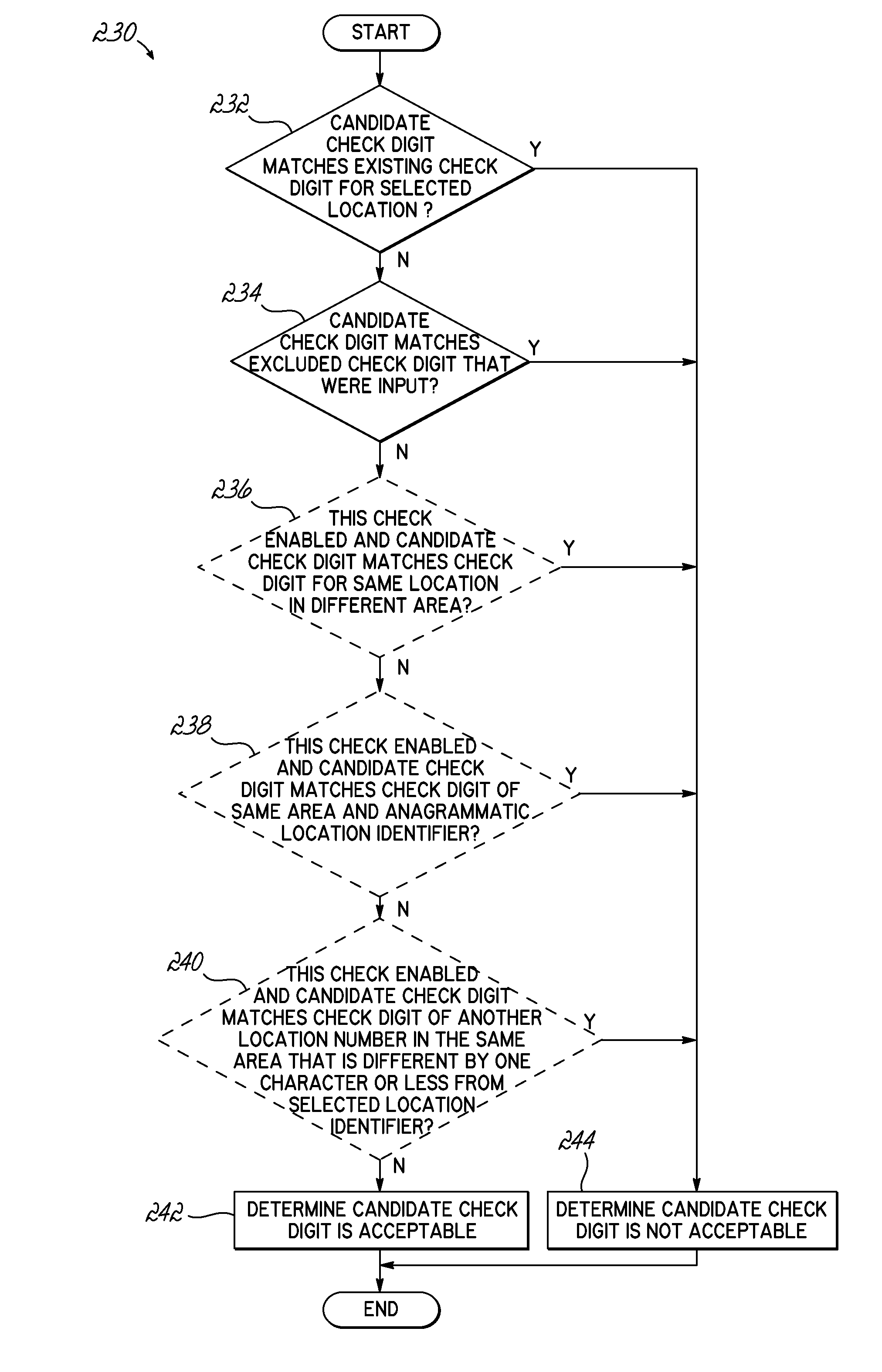
System and method for generating and updating location check digits
Method, apparatus and program product for generating check data for a location within an area of a workspace include receiving an identifier for a selected location that has check data associated therewith. Candidate check data for use with the selected location is generated. The candidate check data is evaluated for a match against at least one of existing check data for the selected location or check data associated with a related location. Based on the evaluation, a determination is made of whether the candidate check data is acceptable for use for the selected location.
Owner:VOCOLLECT
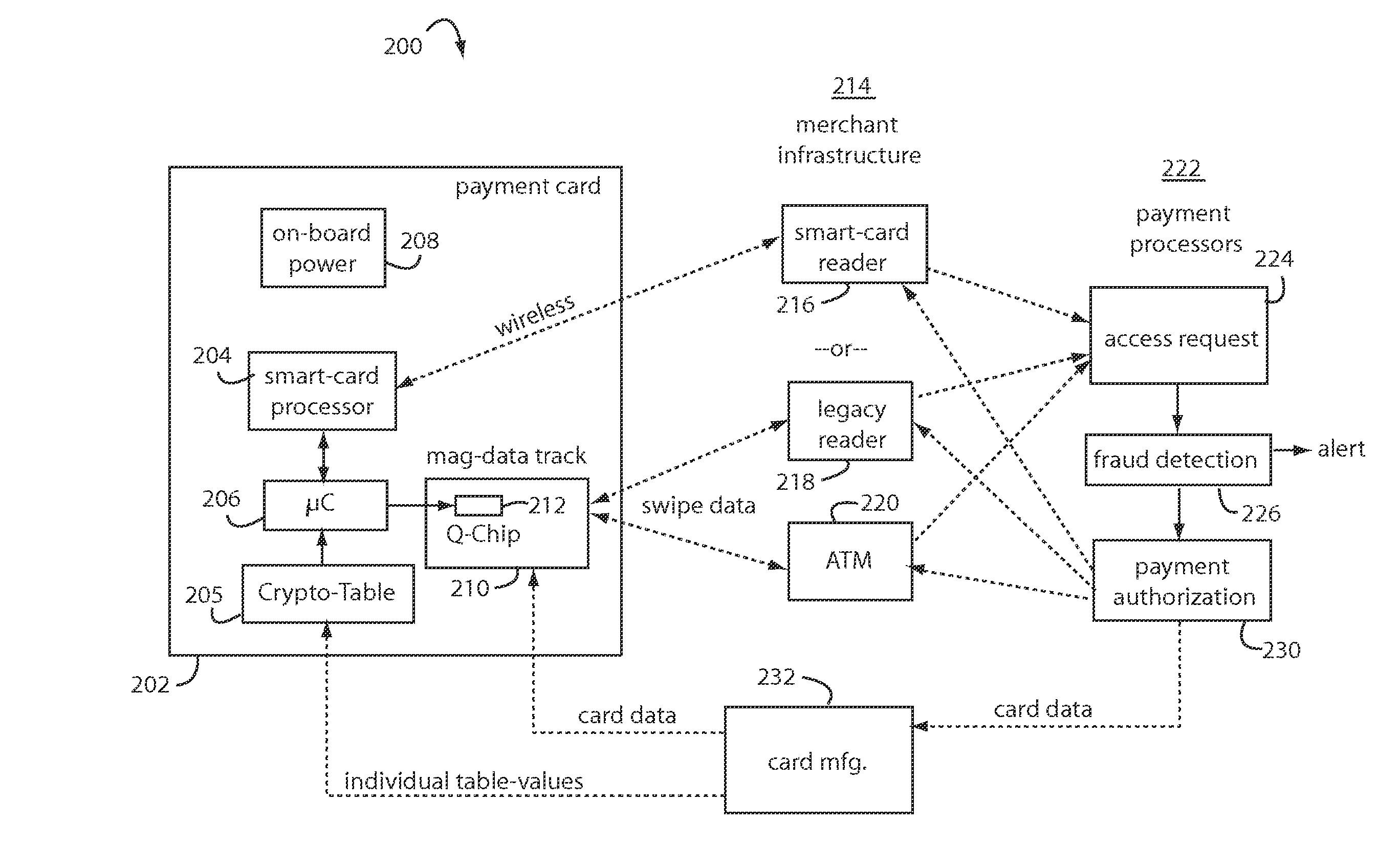
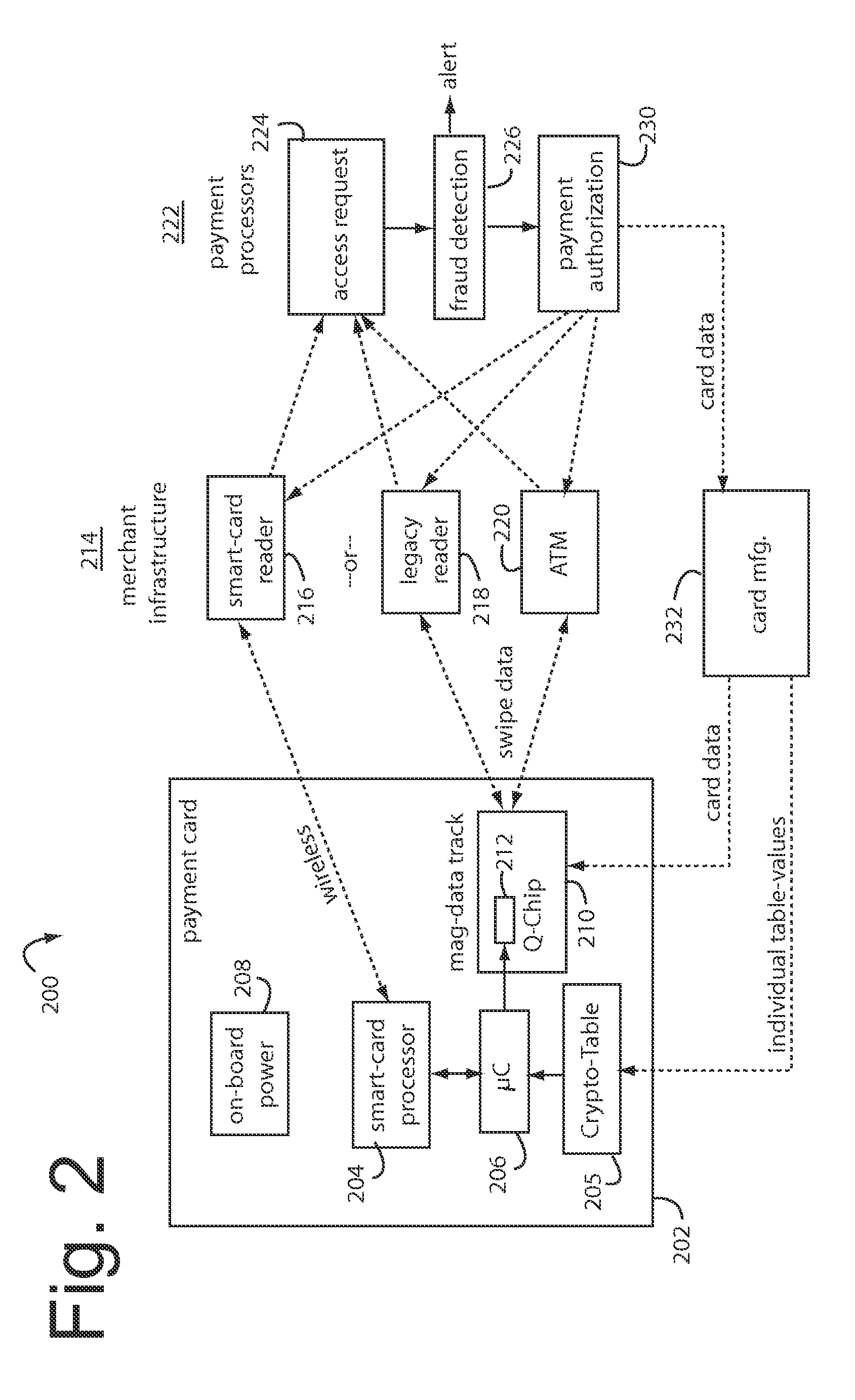
Financial transactions with dynamic personal account numbers
ActiveUS7580898B2Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
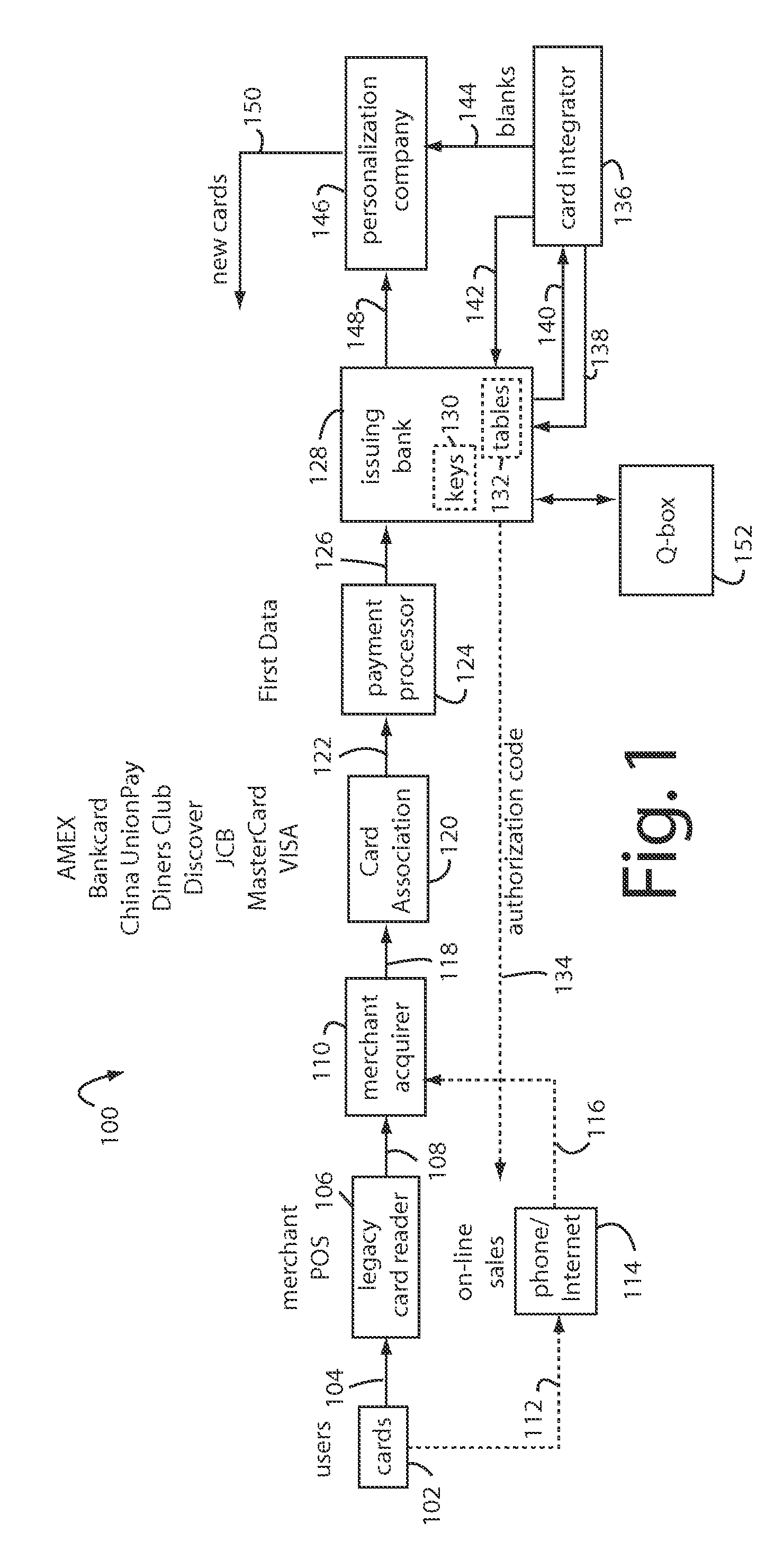
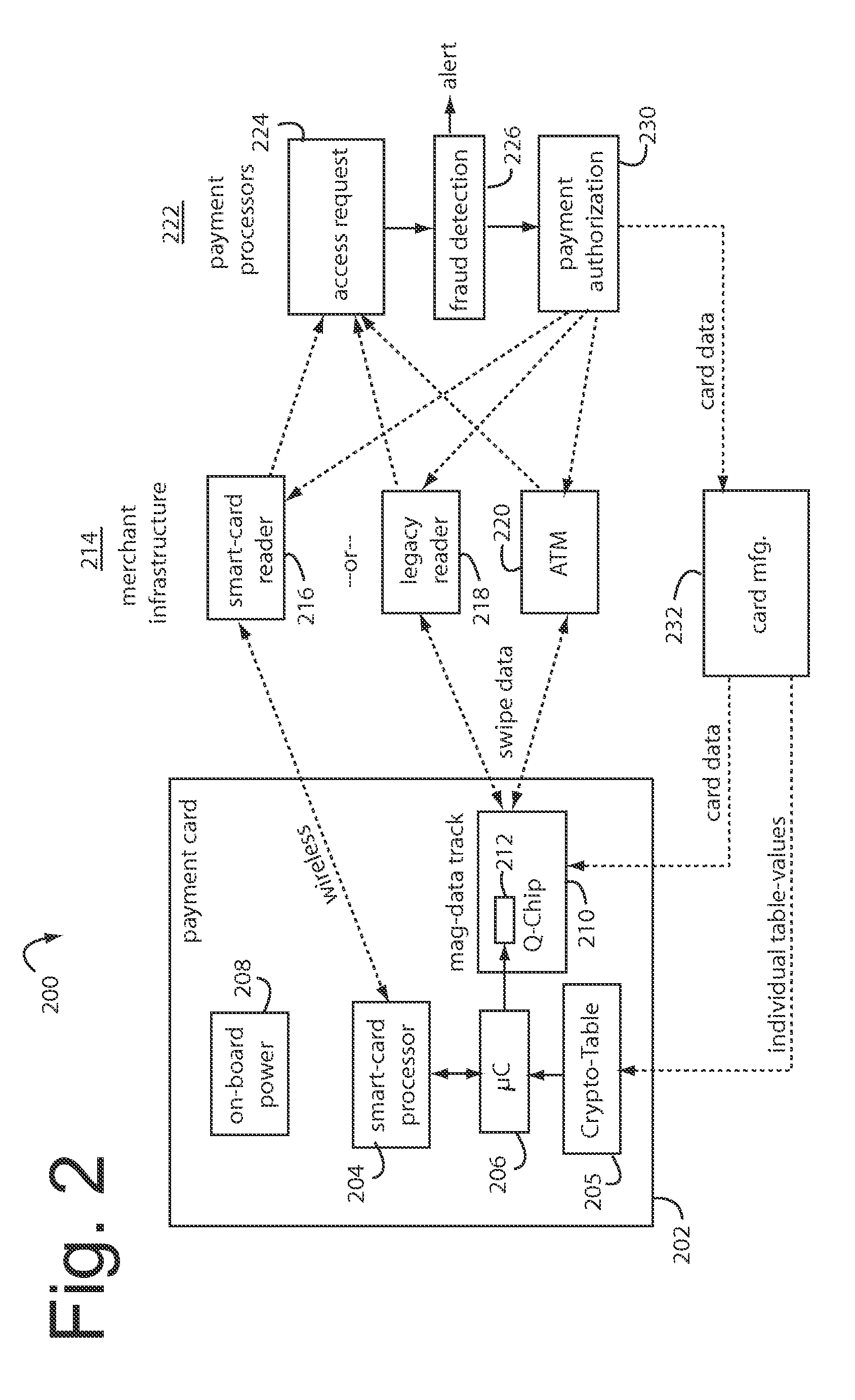
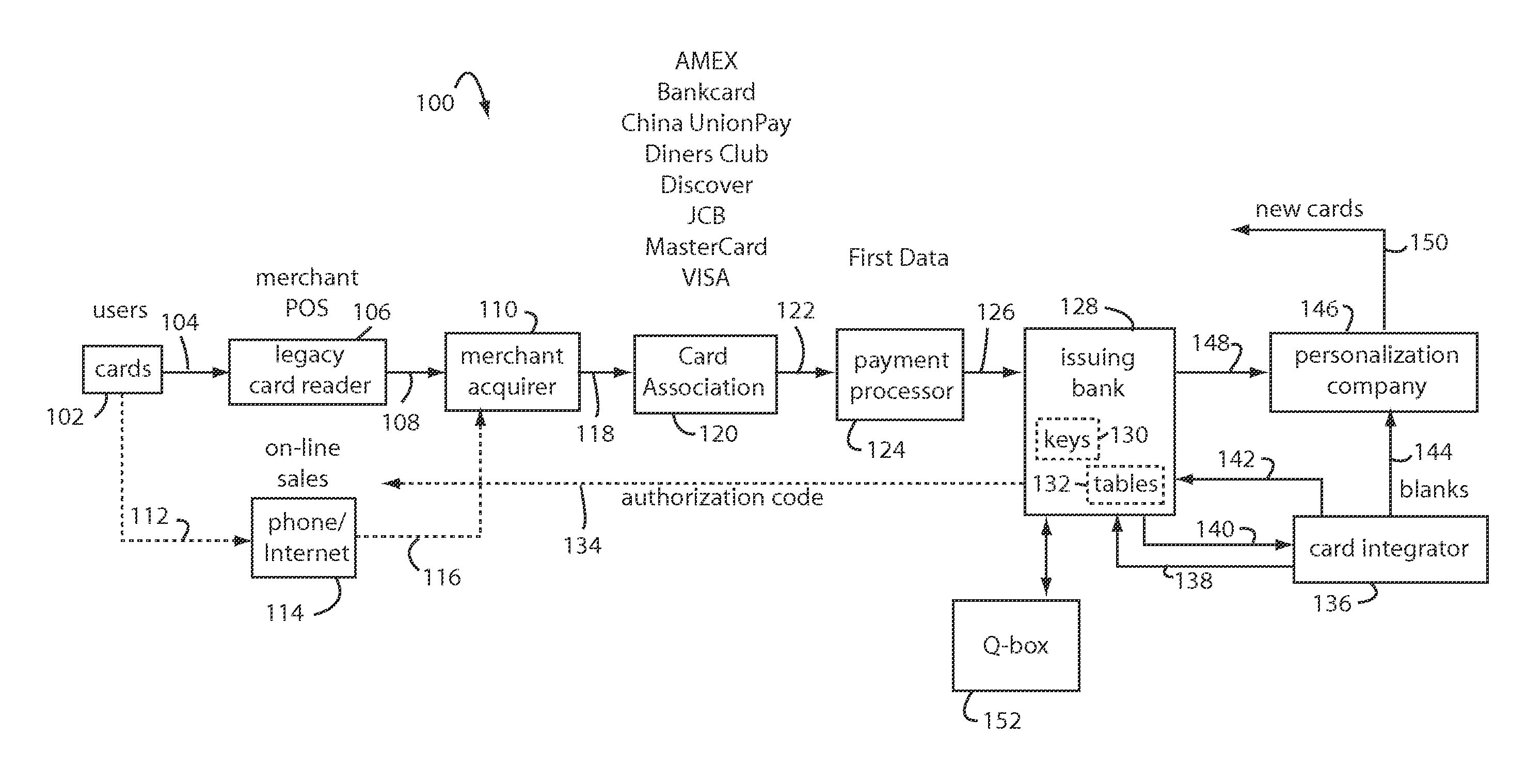
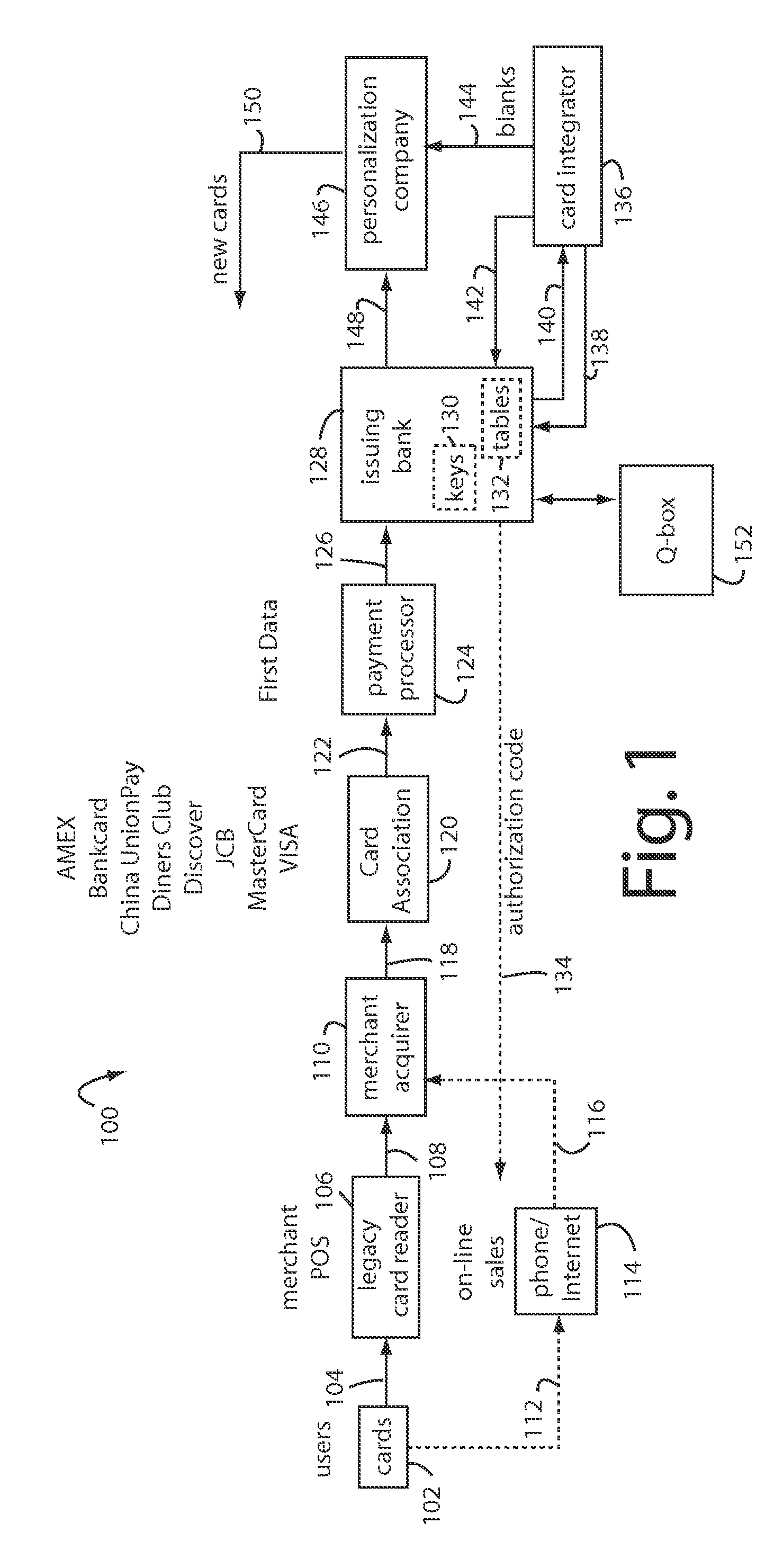
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
Financial transactions with dynamic personal account numbers
ActiveUS20070208671A1Sufficient dataComputer security arrangementsPayment architecturePersonalizationIssuing bank
A method for securing financial transactions involving payment cards includes associating a sixteen-digit personal account number (PAN) with a particular payment card and user, wherein are included fields for a system number, a bank / product number, a user account number, and a check digit. A four-digit expiration date (MMYY) associated with the PAN. A magnetic stripe on the payment card is encoded with the PAN for periodic reading by a magnetic card reader during a financial transaction. A table of cryptographic values associated with the PAN and the MMYY is stored on each user's payment card during personalization by an issuing bank. A next financial transaction being commenced with the payment card is sensed. A cryptographic value from the table of cryptographic values is selected for inclusion as a dynamic portion of the user account number with the PAN when a next financial transaction is sensed. Any cryptographic value from the table of cryptographic values will not be used again in another financial transaction after being used once. The issuing bank authorizes the next financial transaction only if the PAN includes a correct cryptographic value in the user account number field.
Owner:FITBIT INC
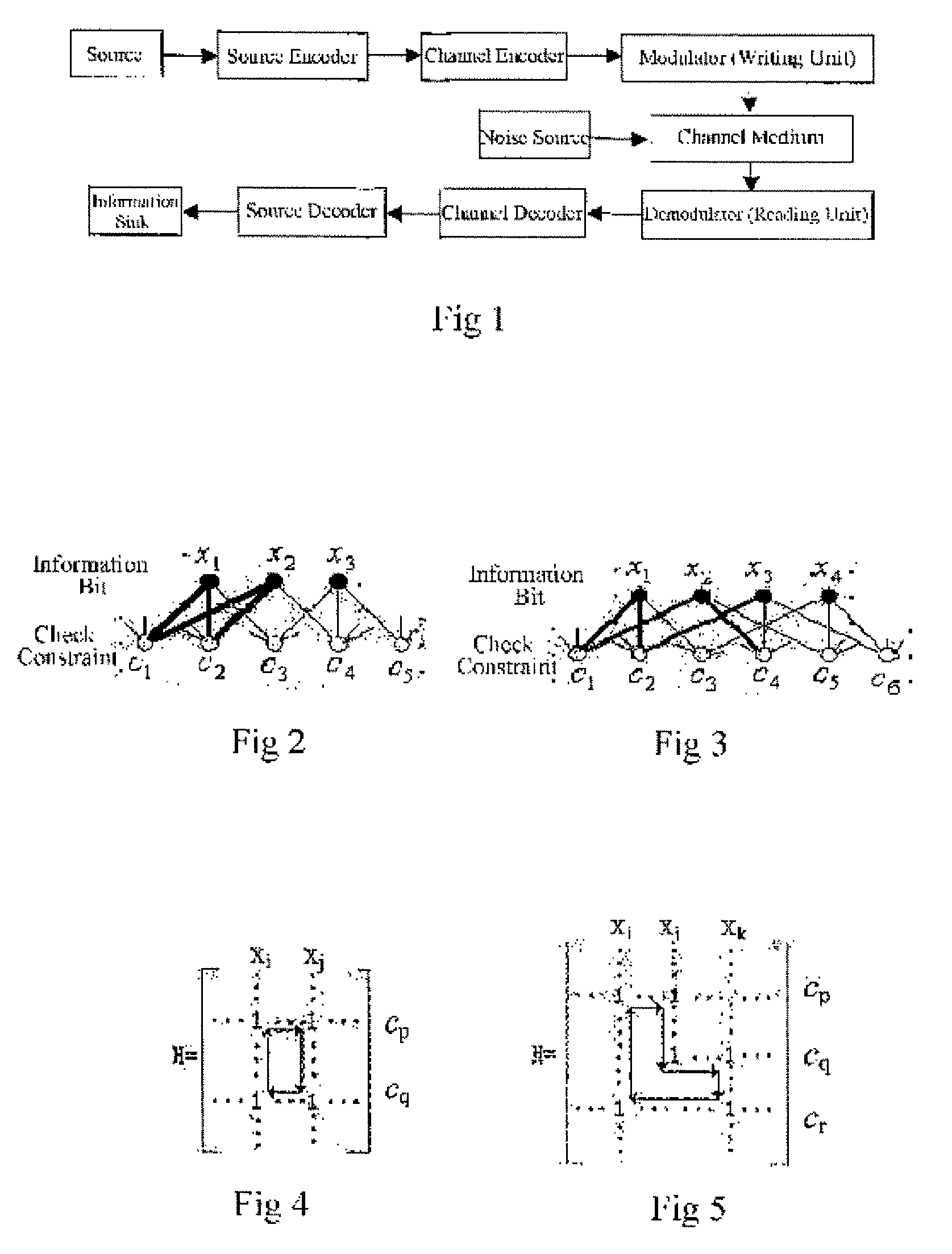
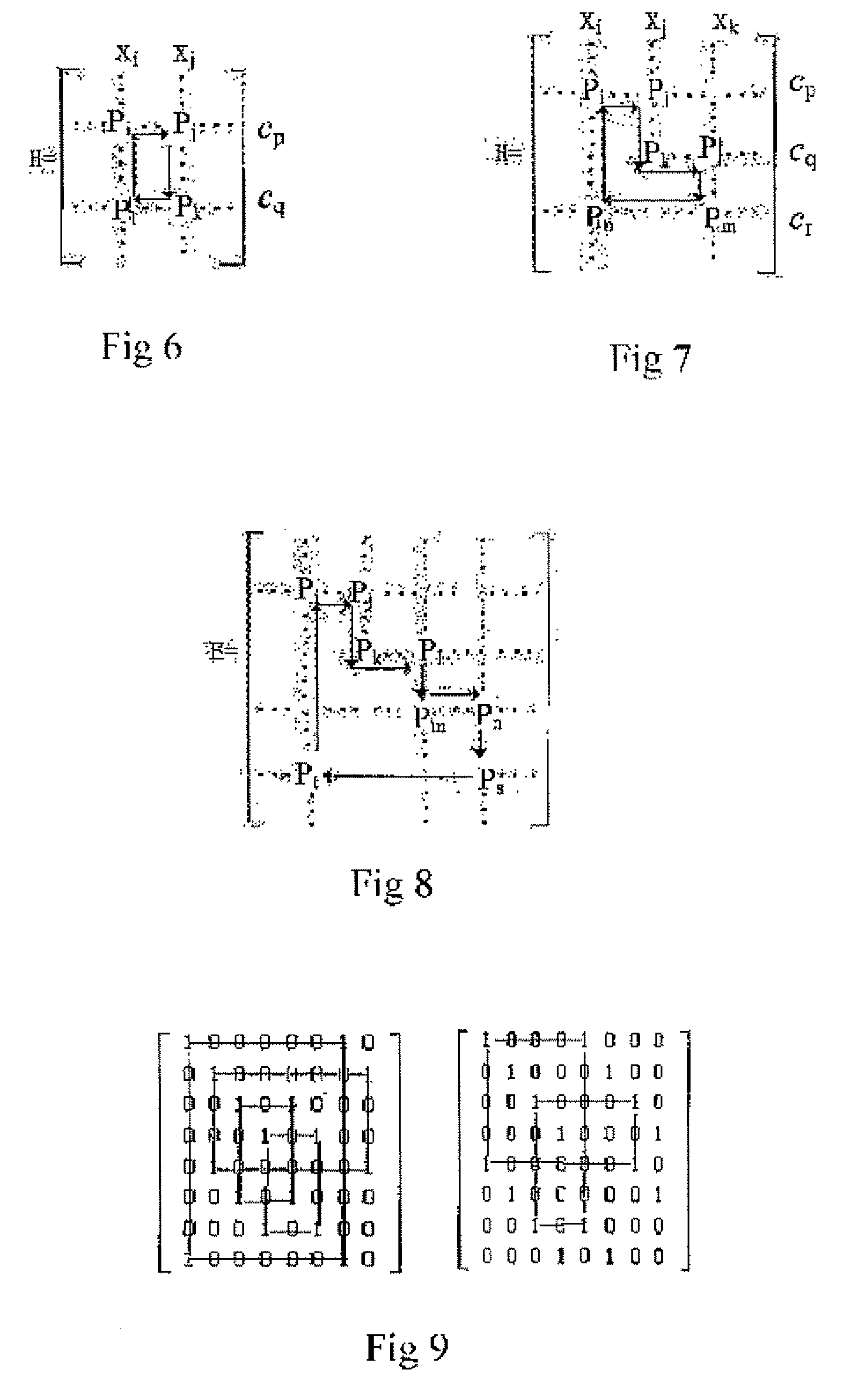
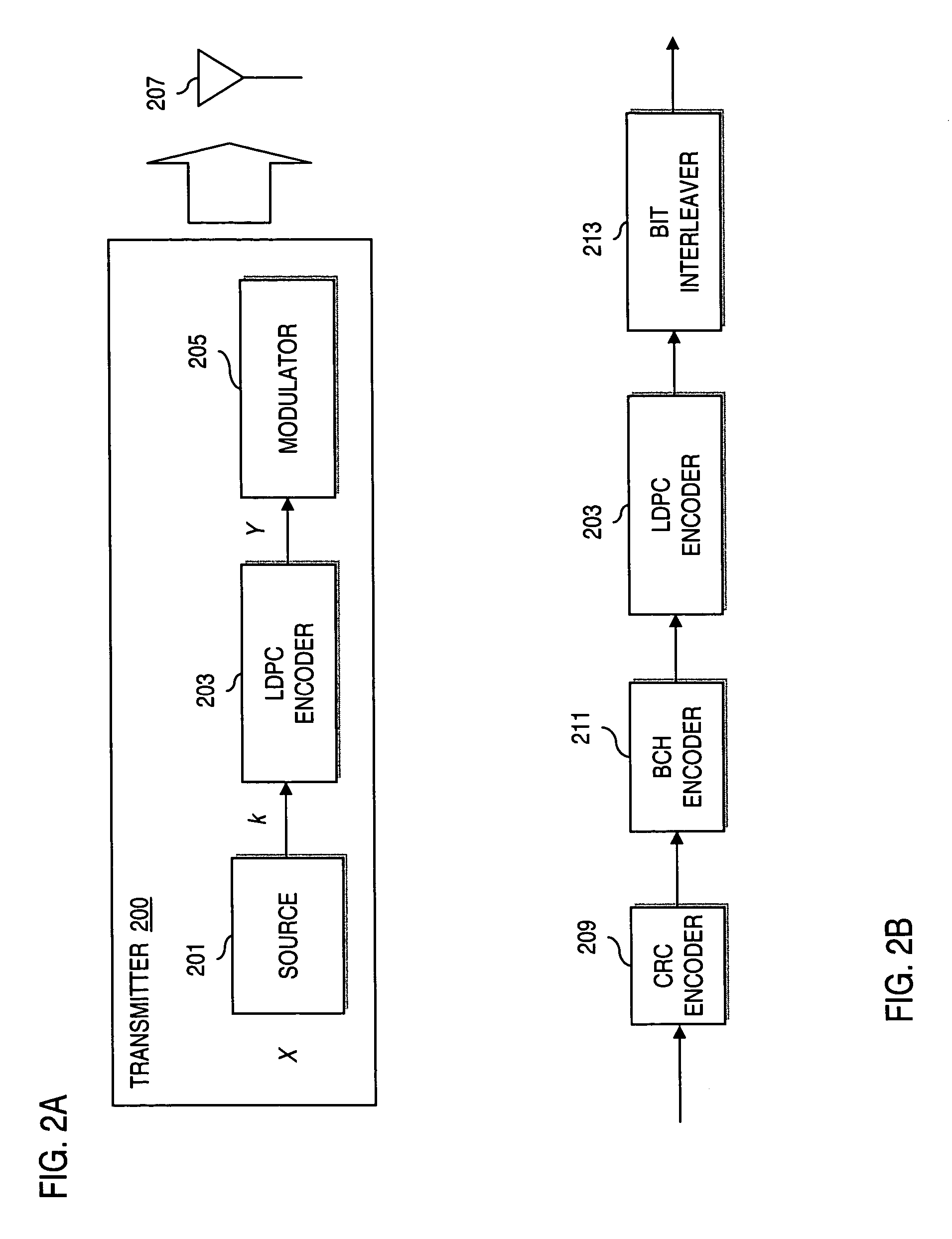
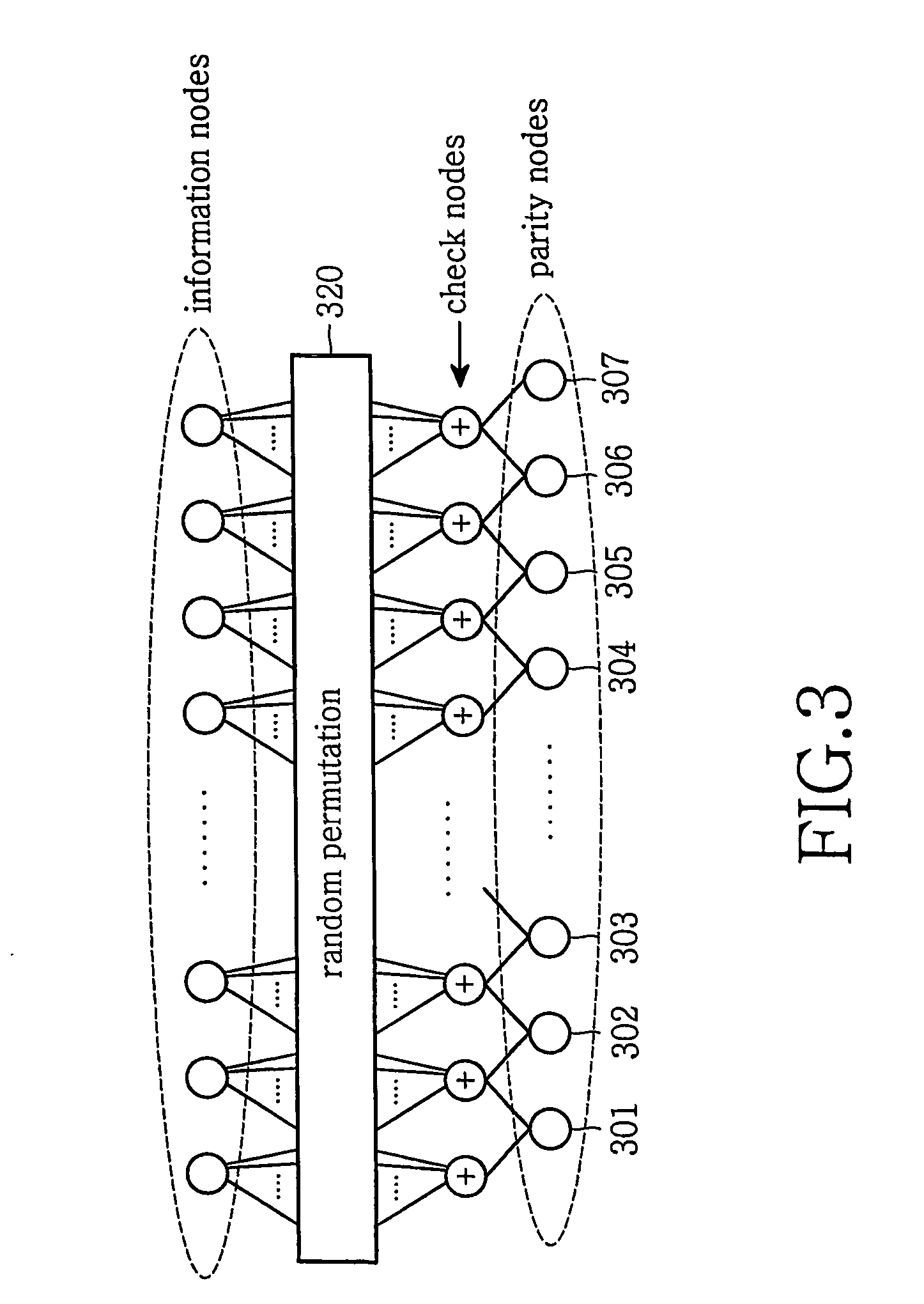
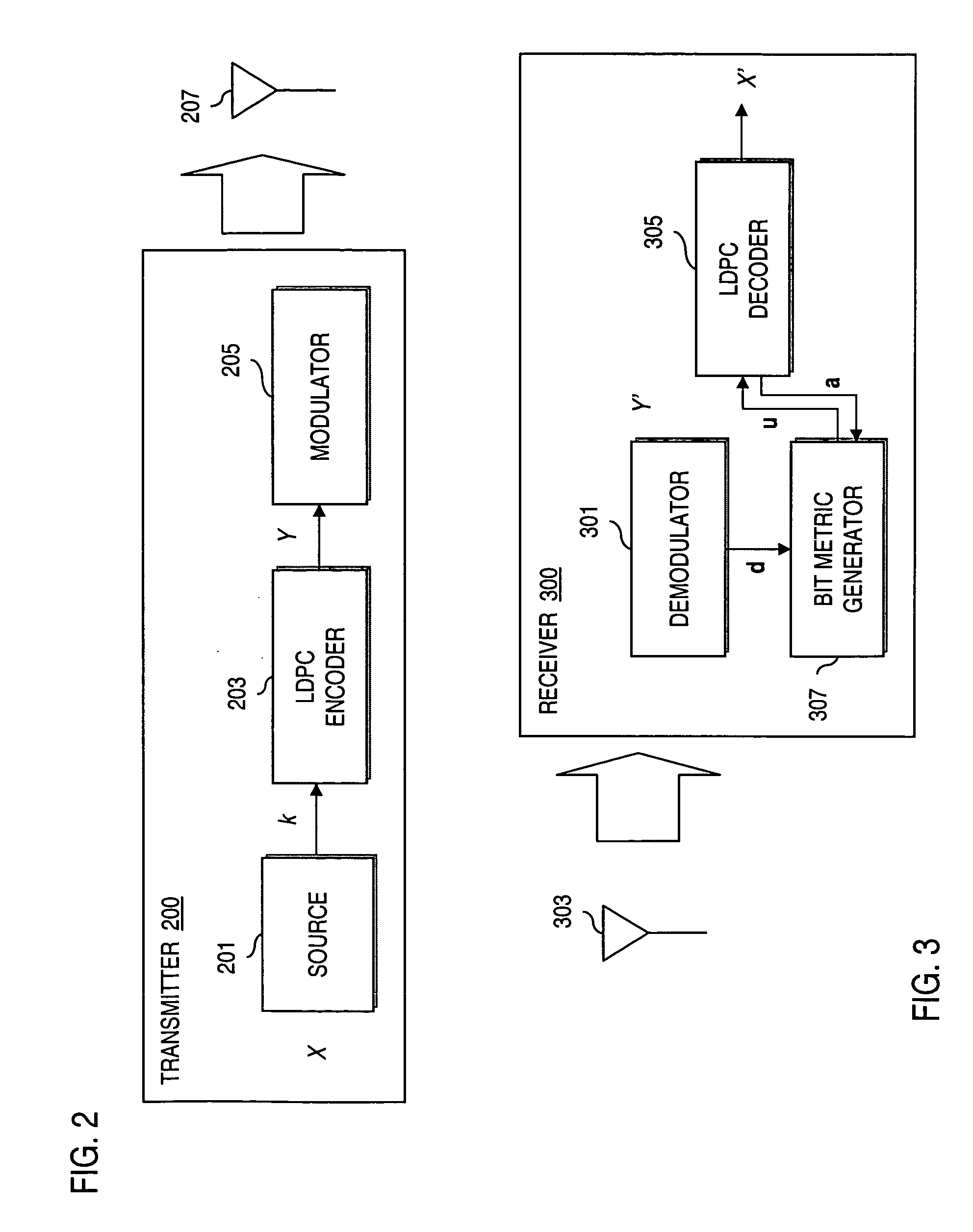
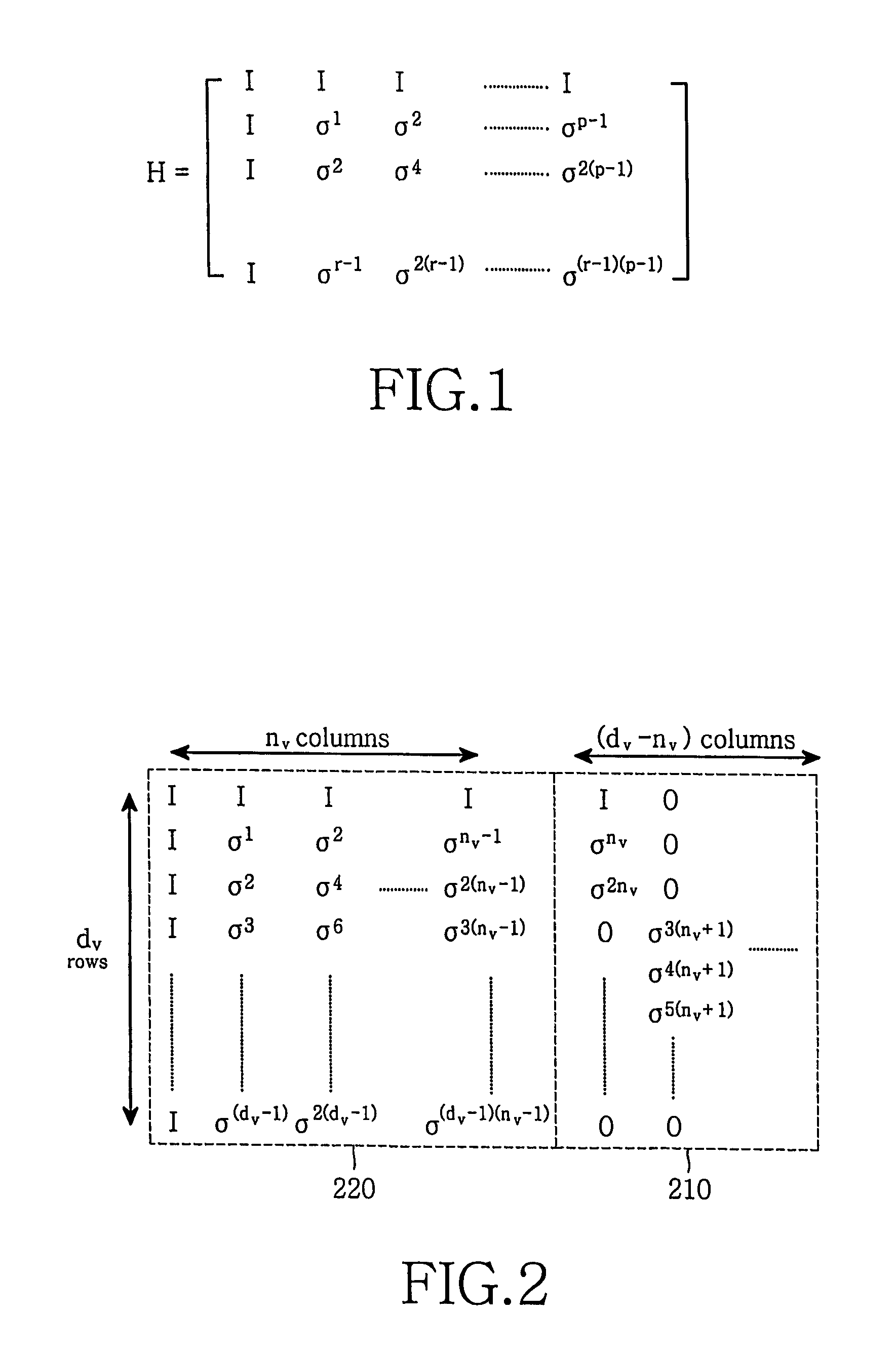
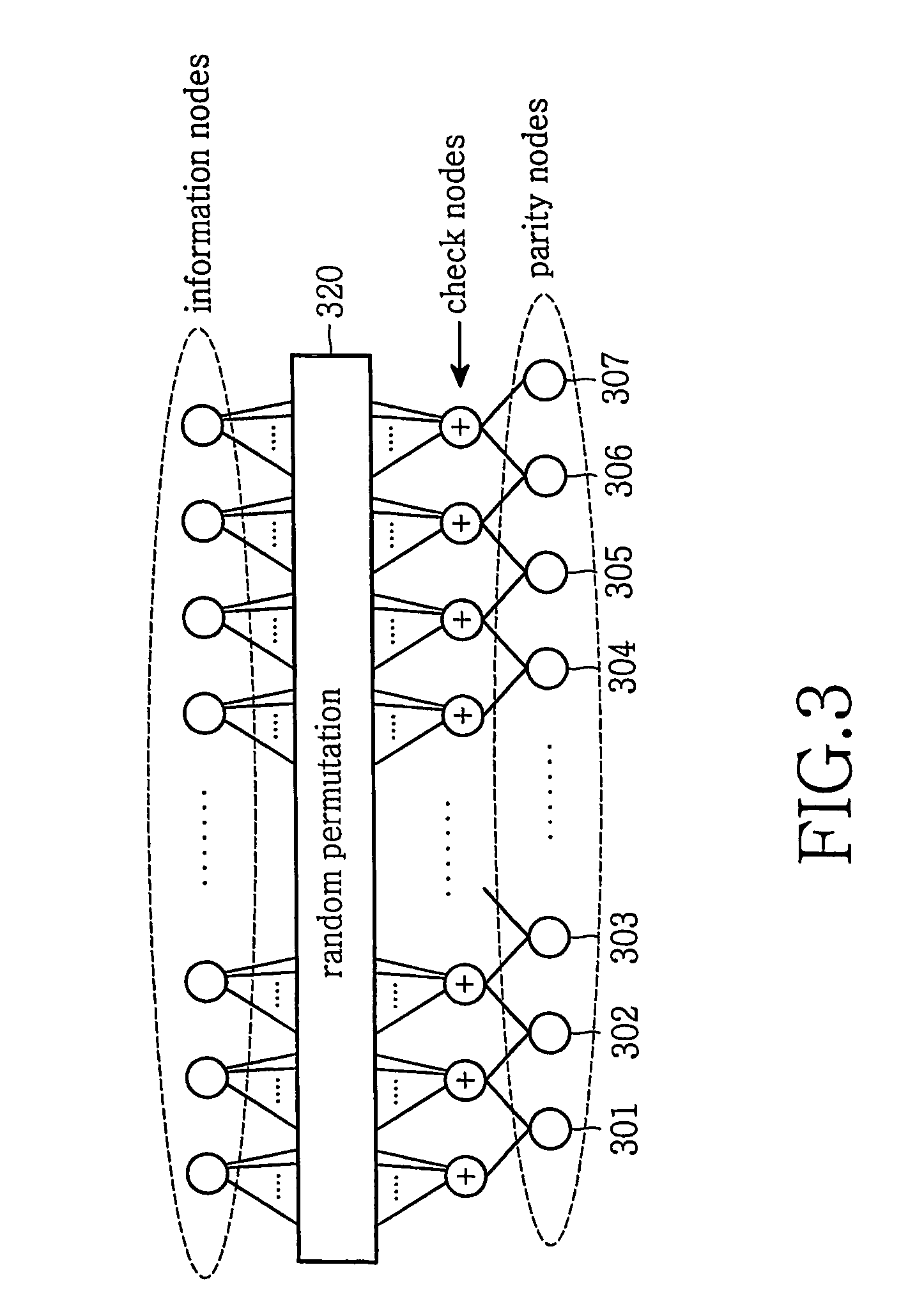
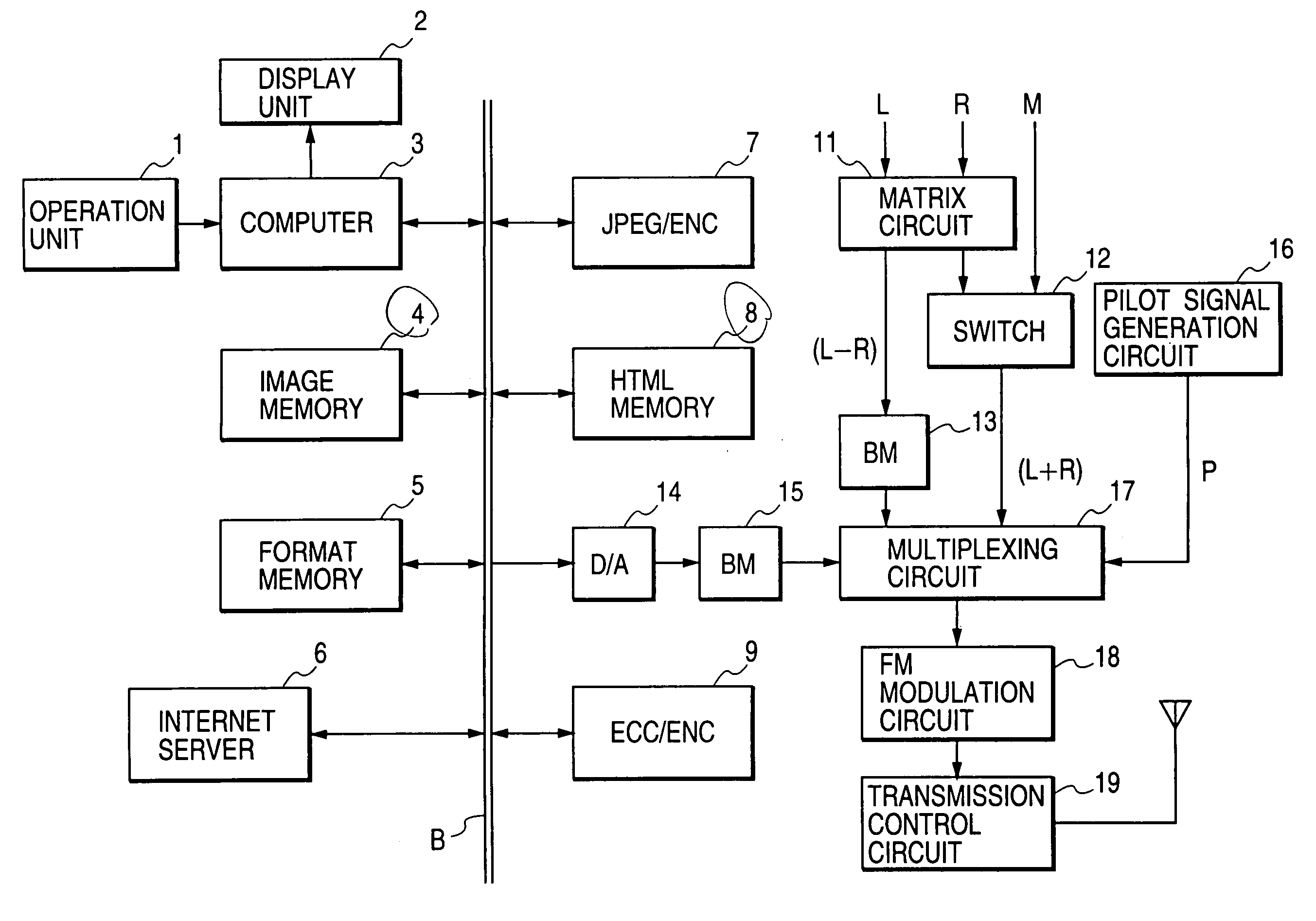
Method and system for providing low density parity check (LDPC) encoding
ActiveUS7191378B2Readily apparentInterconnection arrangementsError correction/detection using LDPC codesAlgorithmParity-check matrix
An approach is provided for a method of encoding structure Low Density Parity Check (LDPC) codes. Memory storing information representing a structured parity check matrix of Low Density Parity Check (LDPC) codes is accessed during the encoding process. The information is organized in tabular form, wherein each row represents occurrences of one values within a first column of a group of columns of the parity check matrix. The rows correspond to groups of columns of the parity check matrix, wherein subsequent columns within each of the groups are derived according to a predetermined operation. An LDPC coded signal is output based on the stored information representing the parity check matrix.
Owner:DTVG LICENSING INC
Adaptive error correction codes for data storage systems
ActiveUS20140115427A1Error detection/correctionUnequal/adaptive error protectionConcatenated error correction codeData encoding
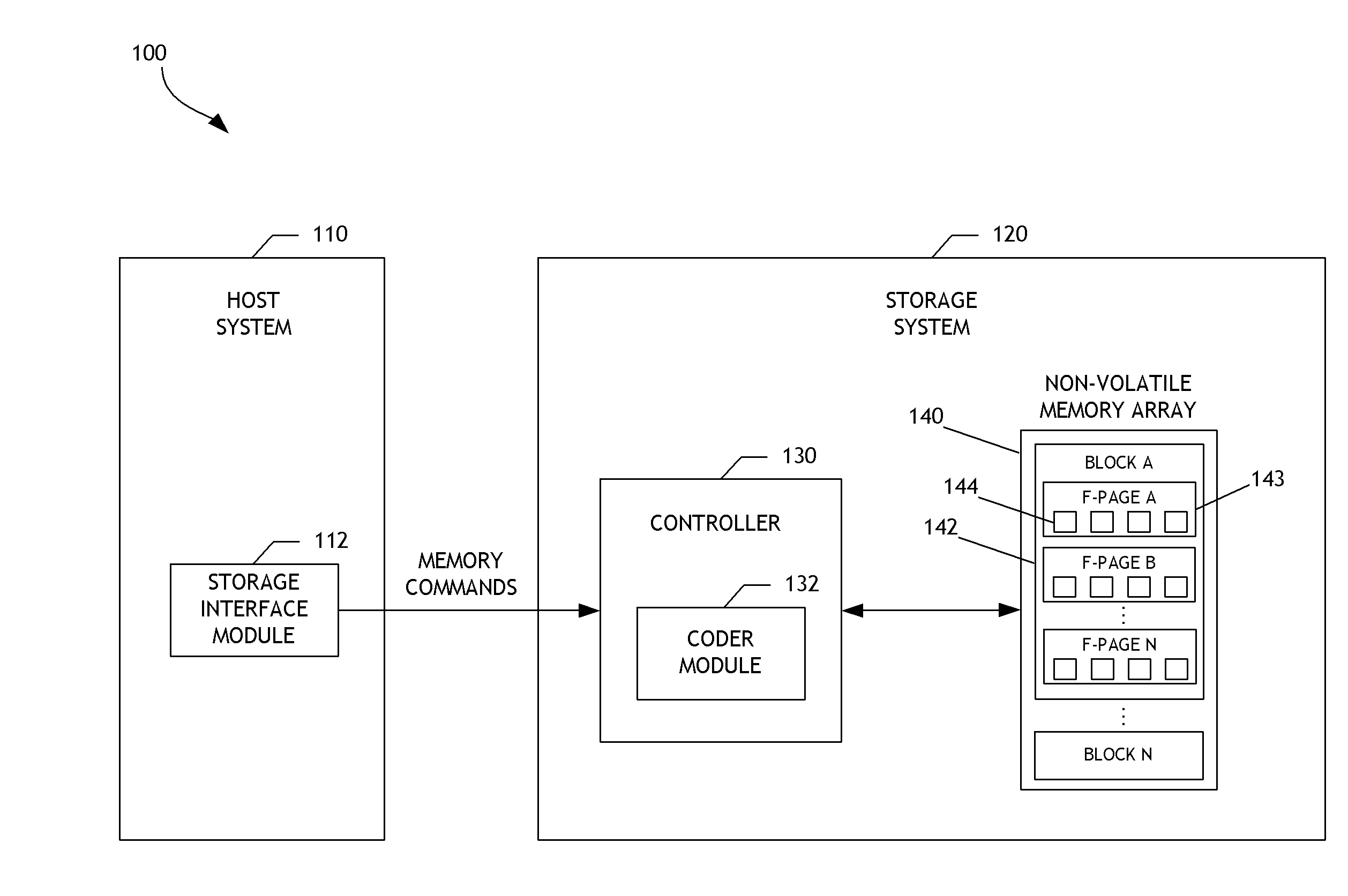
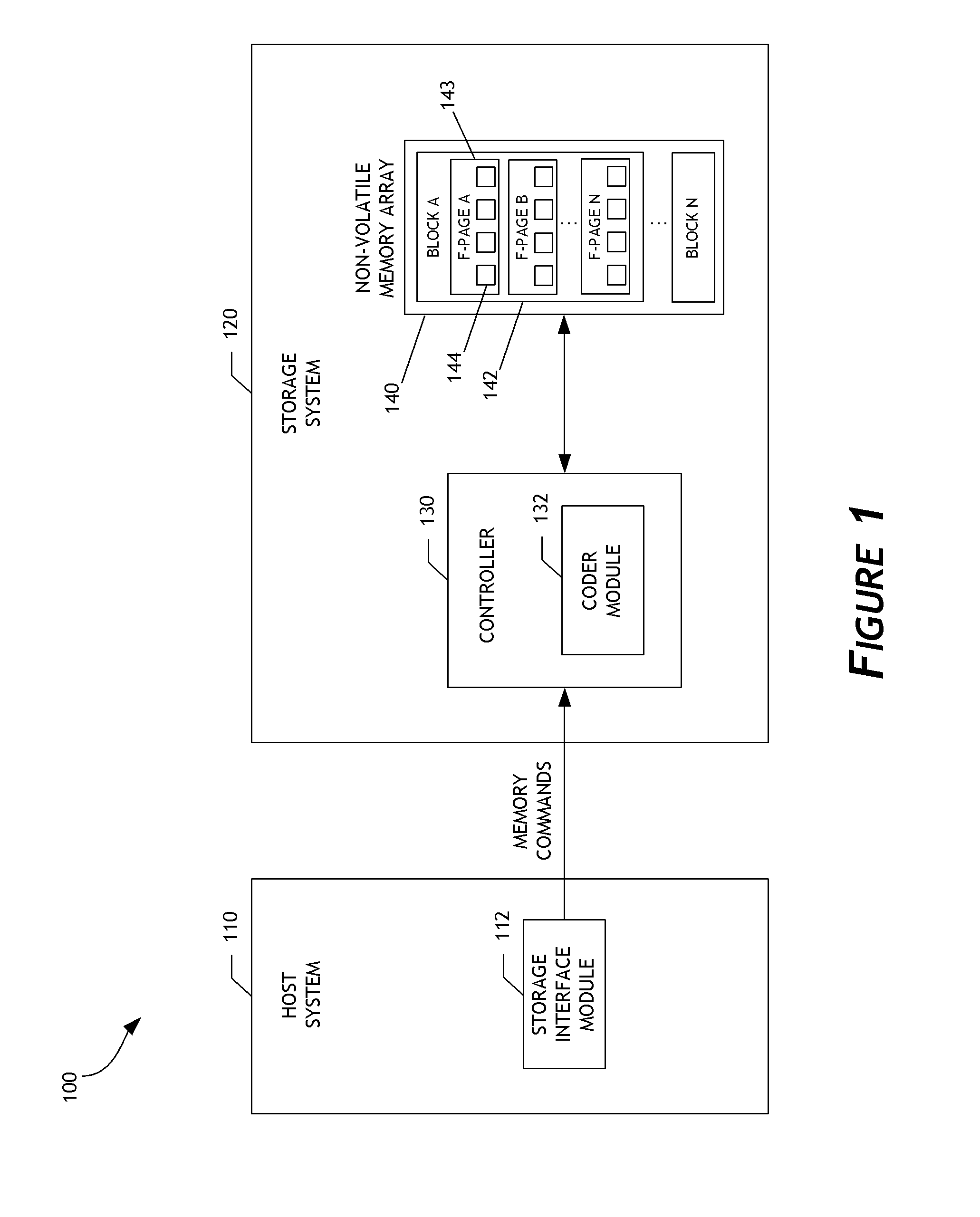
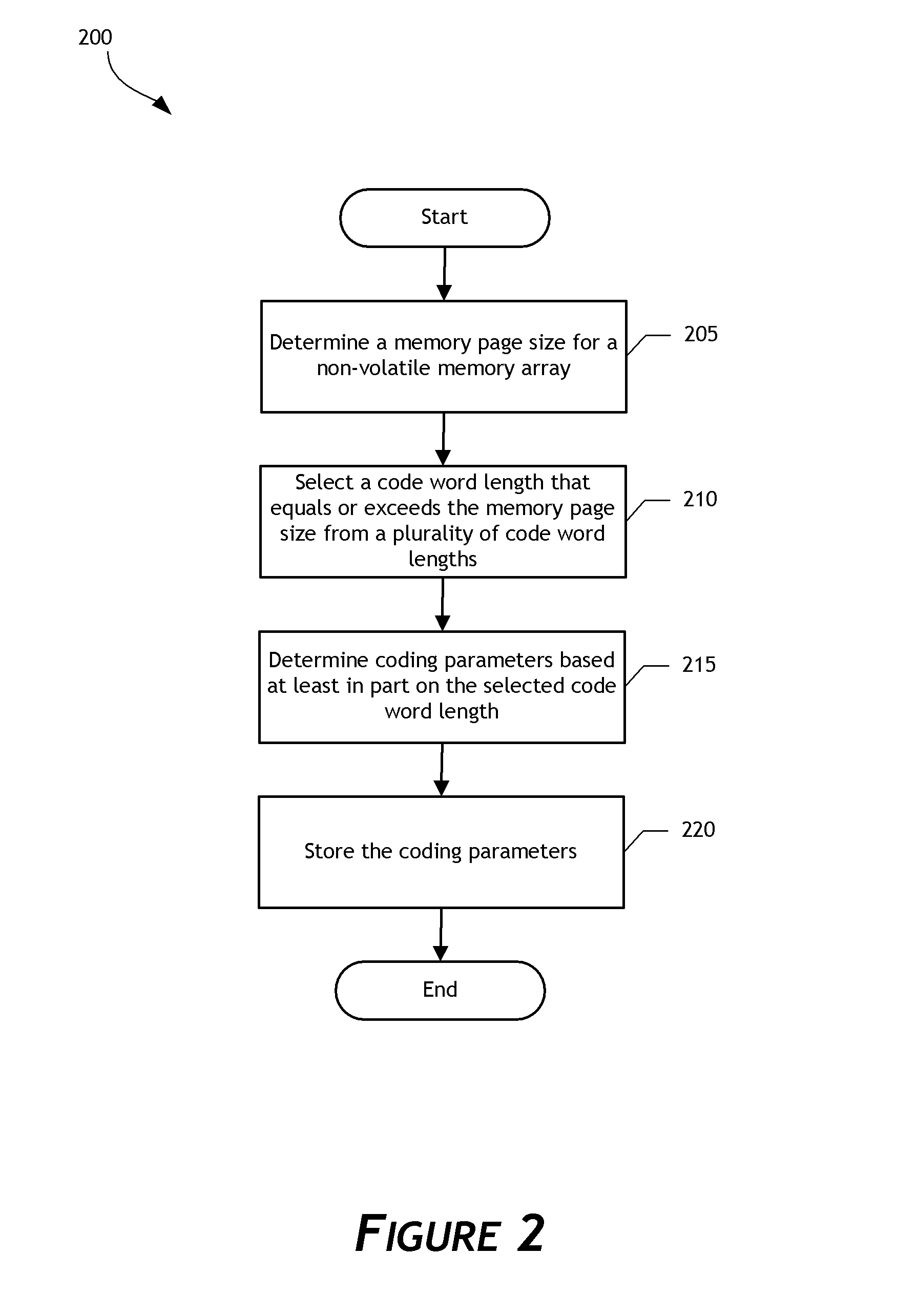
A data storage system configured to adaptively code data is disclosed. In one embodiment, a data storage system controller determines a common memory page size, such as an E-page size, for a non-volatile memory array. Based on the common memory page size, the controller selects a low-density parity-check (LDPC) code word length from a plurality of pre-defined LDPC code word lengths. The controller determines LDPC coding parameters for coding data written to or read from the memory array based on the selected LDPC code word length. By using the plurality of pre-defined LDPC code word lengths, the data storage system can support multiple non-volatile memory page formats, including memory page formats in which the common memory page size does not equal any LDPC code word length of the plurality of pre-defined LDPC code word lengths. Flexibility and efficiency of data coding can thereby be achieved.
Owner:WESTERN DIGITAL TECH INC
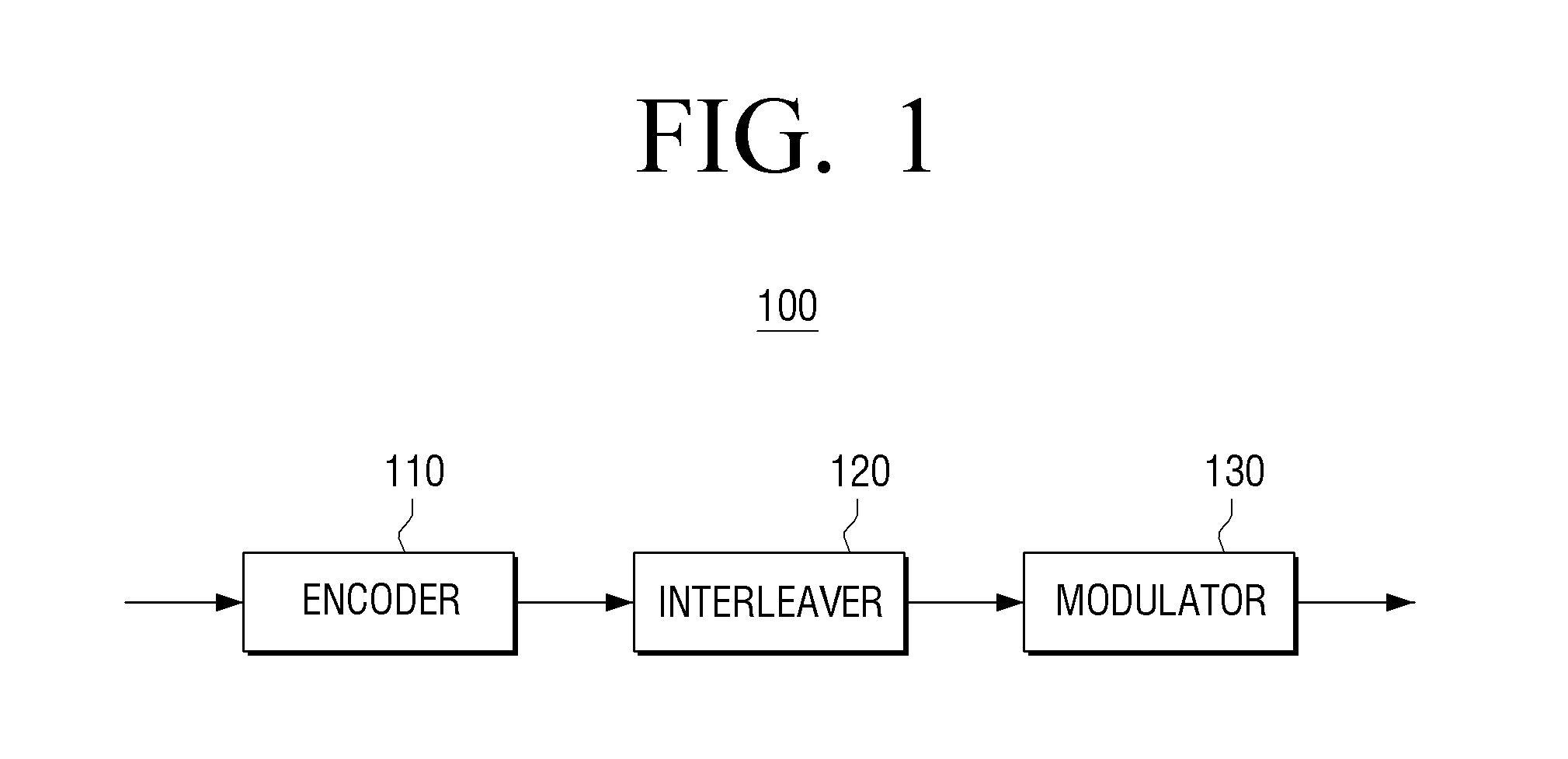
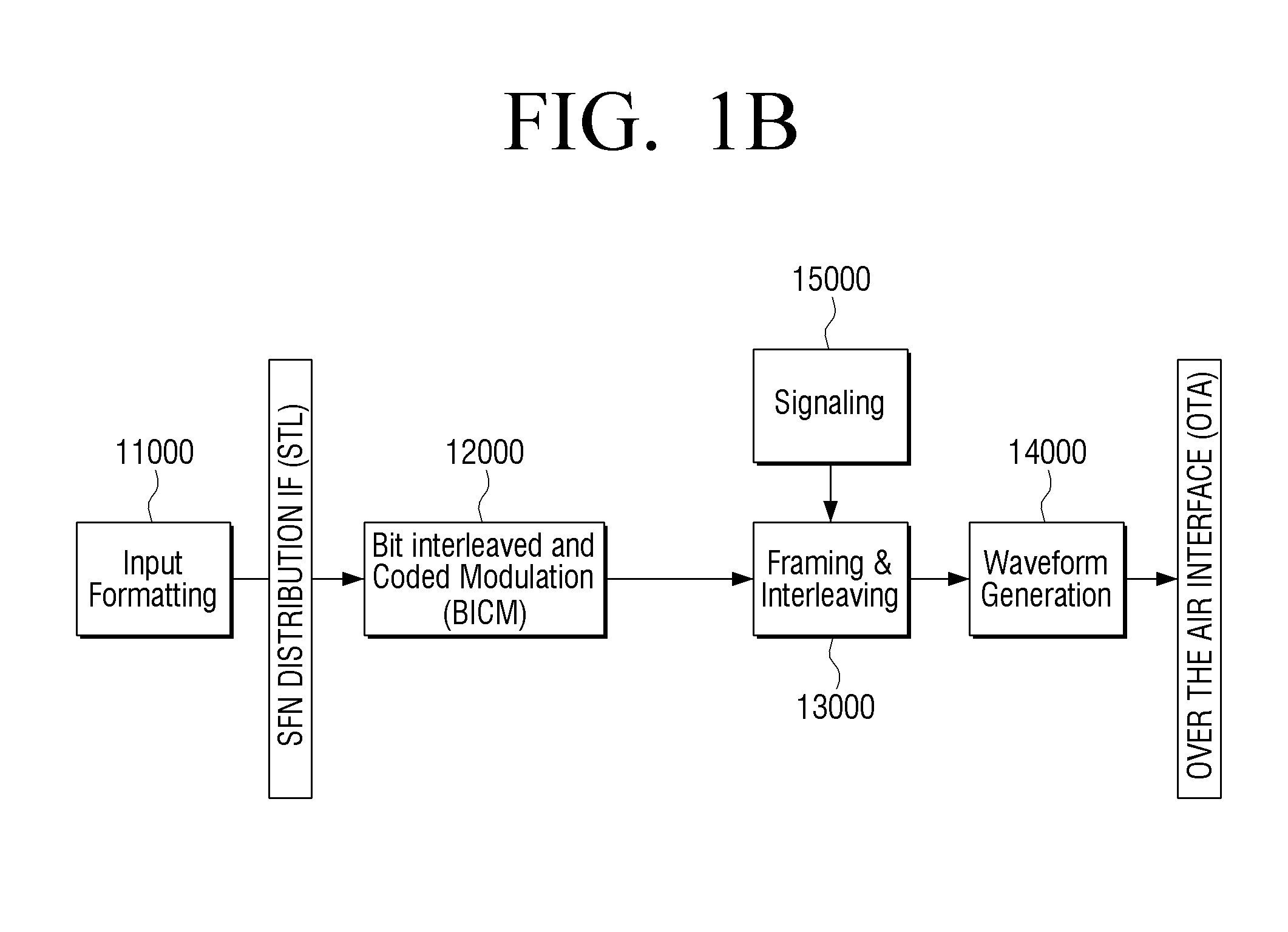
Transmitter apparatus and interleaving method thereof
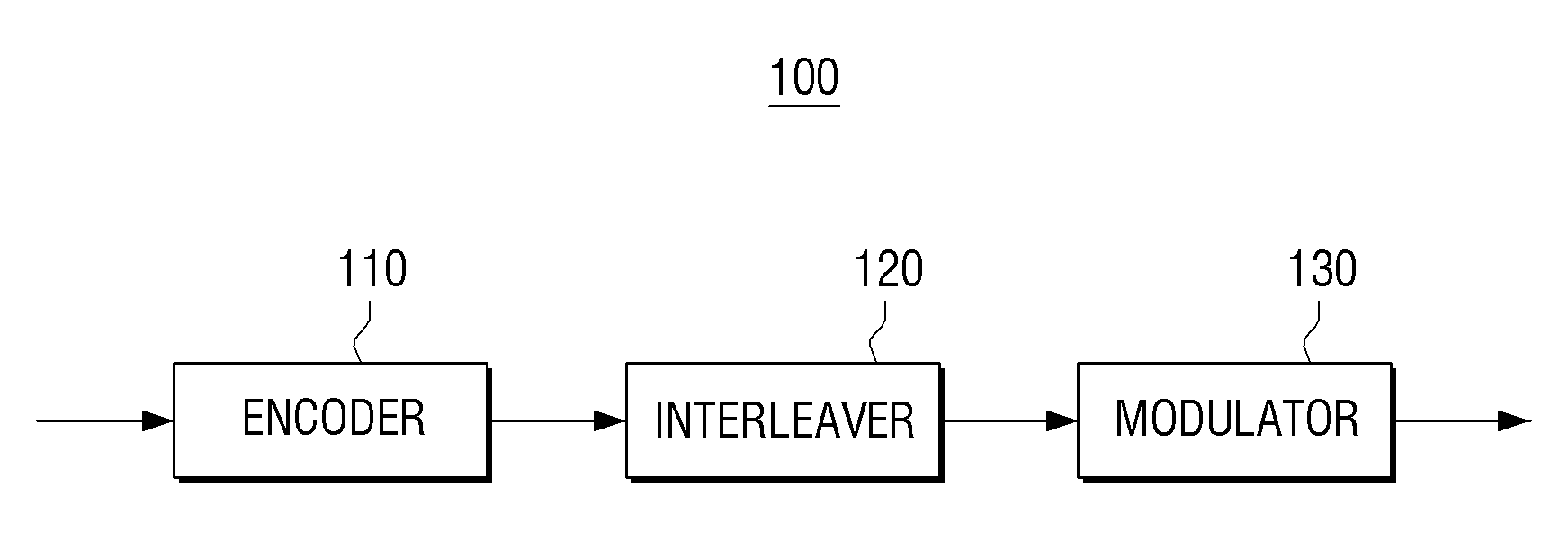
ActiveUS20150236816A1Improve decoding performanceImprove reception performanceModulated-carrier systemsError correction/detection using LDPC codesComputer hardwareParity-check matrix
A transmitting apparatus is provided. The transmitting apparatus includes: an encoder configured to generate a low-density parity check (LDPC) codeword by LDPC encoding based on a parity check matrix; an interleaver configured to interleave the LDPC codeword; and a modulator configured to map the interleaved LDPC codeword onto a modulation symbol, wherein the modulator is further configured to map a bit included in a predetermined bit group from among a plurality of bit groups constituting the LDPC codeword onto a predetermined bit of the modulation symbol.
Owner:SAMSUNG ELECTRONICS CO LTD
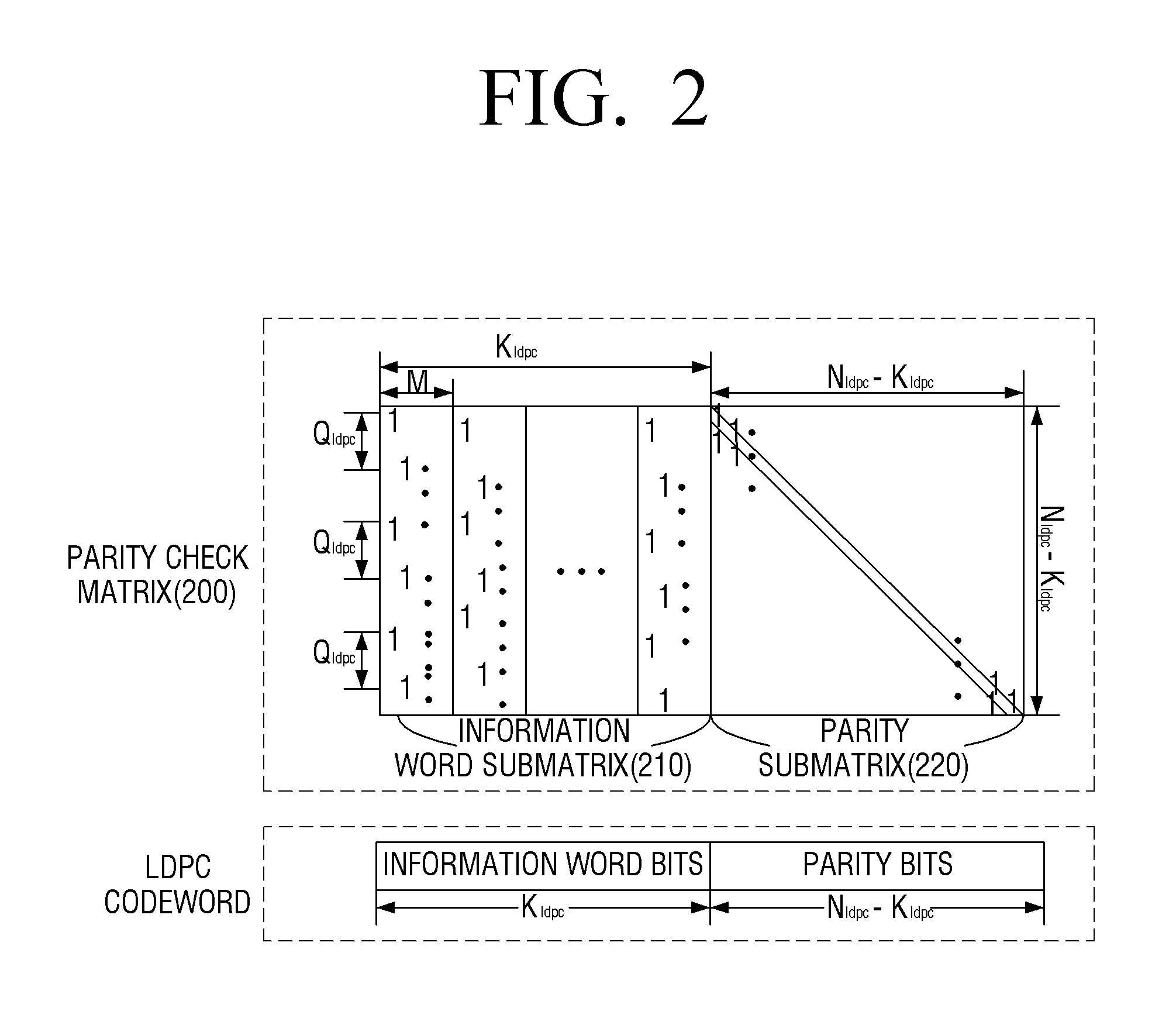
Transmitter apparatus and bit interleaving method thereof
ActiveUS20150341054A1Improve decoding performanceImprove reception performanceError correction/detection using concatenated codesError correction/detection using LDPC codesParity-check matrixCheck digit
A transmitting apparatus is provided. The transmitting apparatus includes: an encoder configured to generate a low-density parity check (LDPC) codeword by LDPC encoding of input bits based on a parity check matrix including information word bits and parity bits, the LDPC codeword including a plurality of bit groups each including a plurality of bits; an interleaver configured to interleave the LDPC codeword; and a modulator configured to map the interleaved LDPC codeword onto a modulation symbol, wherein the interleaver is further configured to interleave the LDPC codeword such that a bit included in a predetermined bit group from among the plurality of bit groups constituting the LDPC codeword onto a predetermined bit of the modulation symbol.
Owner:SAMSUNG ELECTRONICS CO LTD
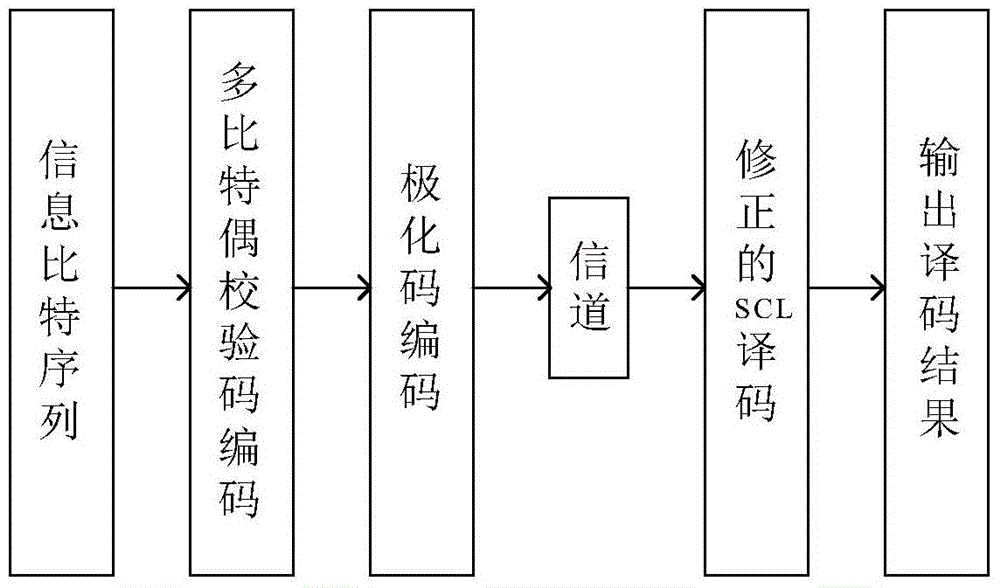
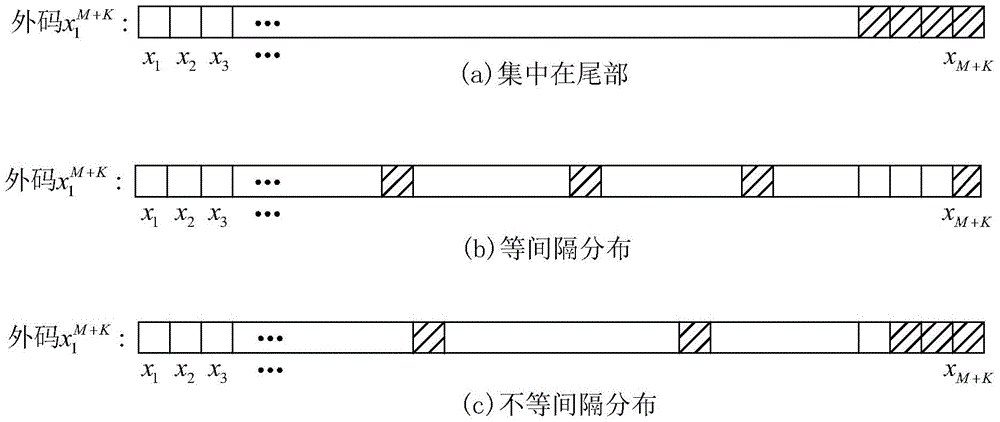
Polarization code and multi-bit even parity check code cascaded error correction coding method
ActiveCN105680883AImprove error correction performanceBreakthrough in error correction performanceCode conversionError correction/detection by combining multiple code structuresComputer hardwareError correction coding
The invention discloses a polarization code and multi-bit even parity check code cascaded error correction coding method. The method comprises the steps: a transmitting end encoder utilizes a multi-bit even parity check code as an outer code, and utilizes a polarization code as an inner code; a receiving end decoder decodes by utilizing a modified successive cancellation list (SCL) decoding algorithm. On the aspect of error correction performance, comparing with the prior art utilizing middle-short code length non-cascaded polarization codes of the SCL decoding algorithm, the polarization code and multi-bit even parity check code cascaded error correction coding method has the advantages that frame error rate performance of a system can be remarkably improved, and a maximum likelihood bound (ML Bound), which cannot be broken through by the SCL decoding algorithm, can be remarkably broken through. On the aspect of engineering realization, according to the polarization code and multi-bit even parity check code cascaded error correction coding method, the outer code utilizes the multi-bit even parity check code, which is simple to code; the modified SCL decoding algorithm is utilized to decode, bit decision and even parity check are combined to be carried out in a decoding process, and compared with the original SCL decoding algorithm, the method provided by the invention does not increase the decoding complexity, and facilitates the engineering realization.
Owner:HUAZHONG UNIV OF SCI & TECH
Transmitting apparatus and puncturing method thereof
InactiveUS20150082118A1Improve decoding performanceError correction/detection using multiple parity bitsCode conversionLow-density parity-check codeLow density
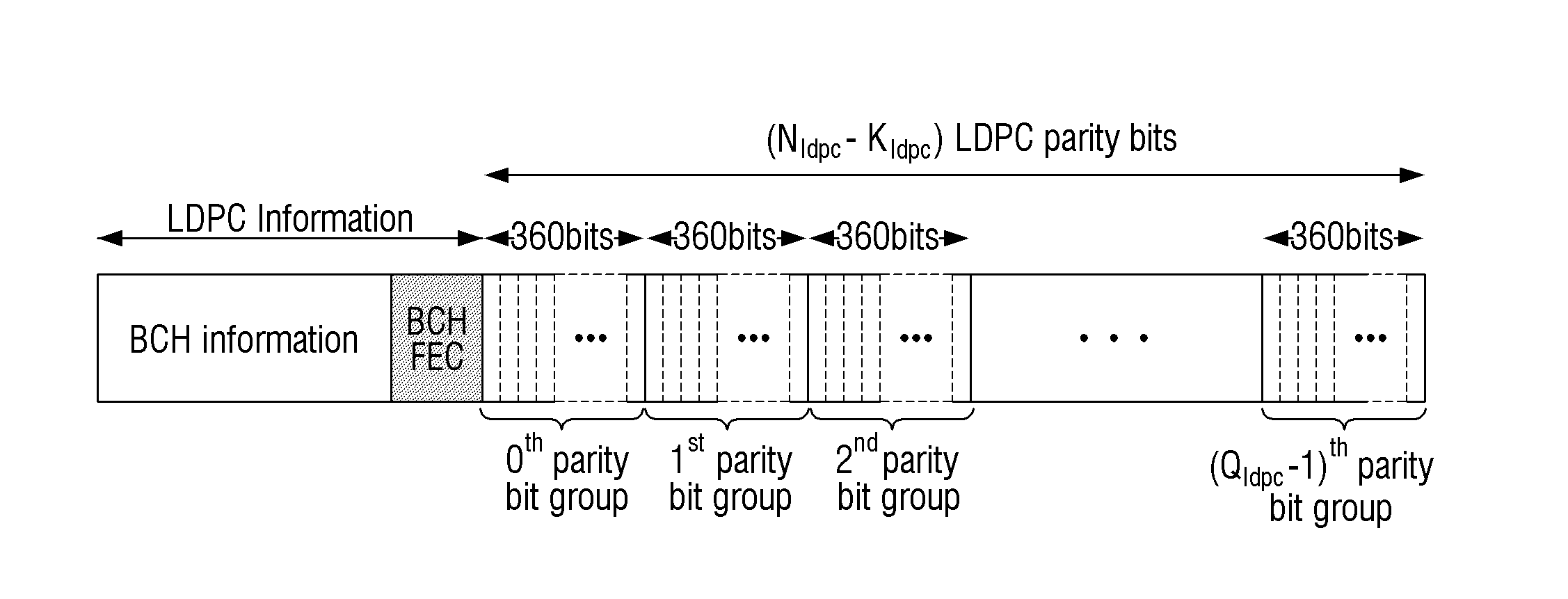
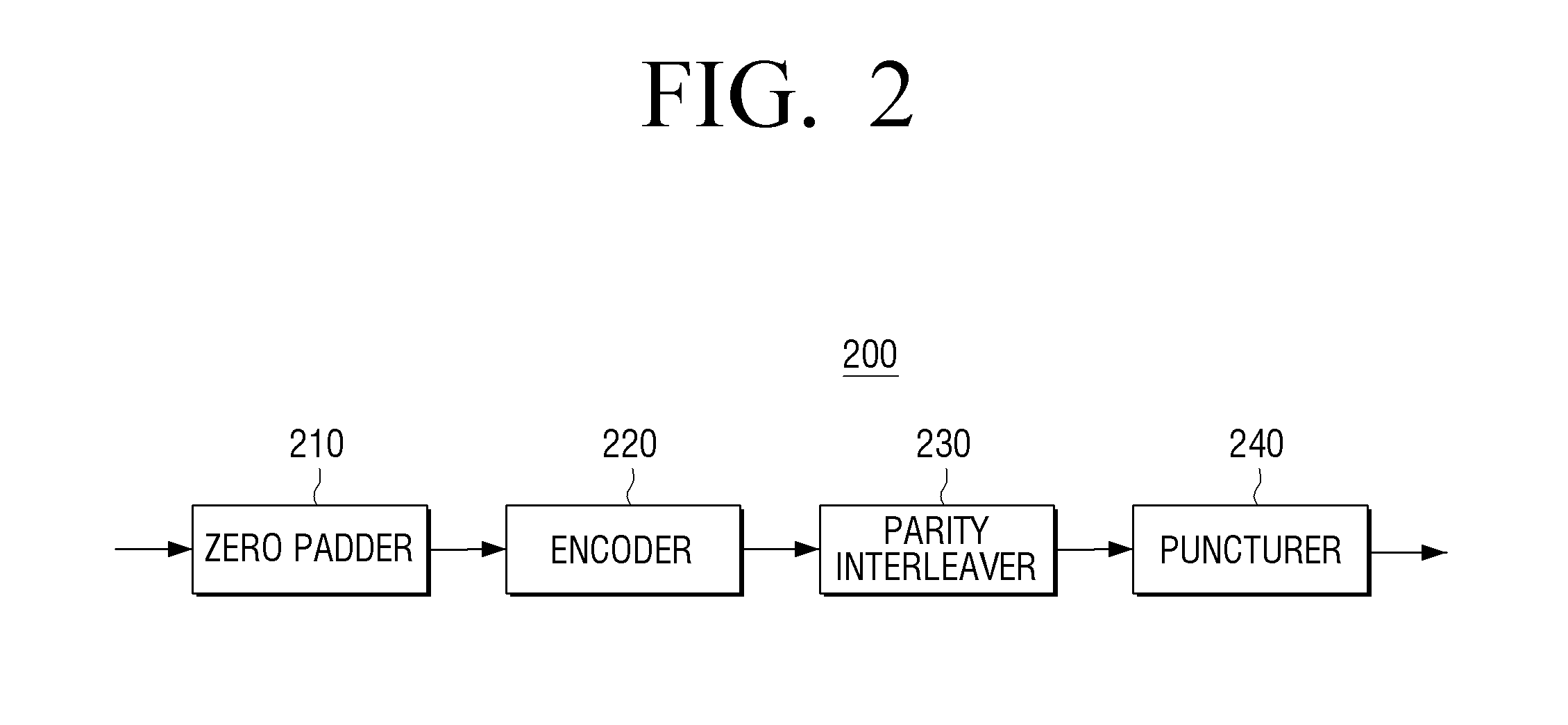
Provided are a transmitting apparatus, a receiving apparatus and methods of puncturing and depuncturing of parity bits. The transmitting apparatus includes: a zero padder configured to pad at least one zero bit to input bits; an encoder configured to generate a Low Density Parity Check (LDPC) codeword by performing LDPC encoding with respect to the bits to which the at least one zero bit is padded; a parity interleaver configured to interleave LDPC parity bits constituting the LDPC codeword; and a puncturer configured to puncture at least a part of the interleaved LDPC parity bits based on a pre-set puncturing pattern.
Owner:SAMSUNG ELECTRONICS CO LTD
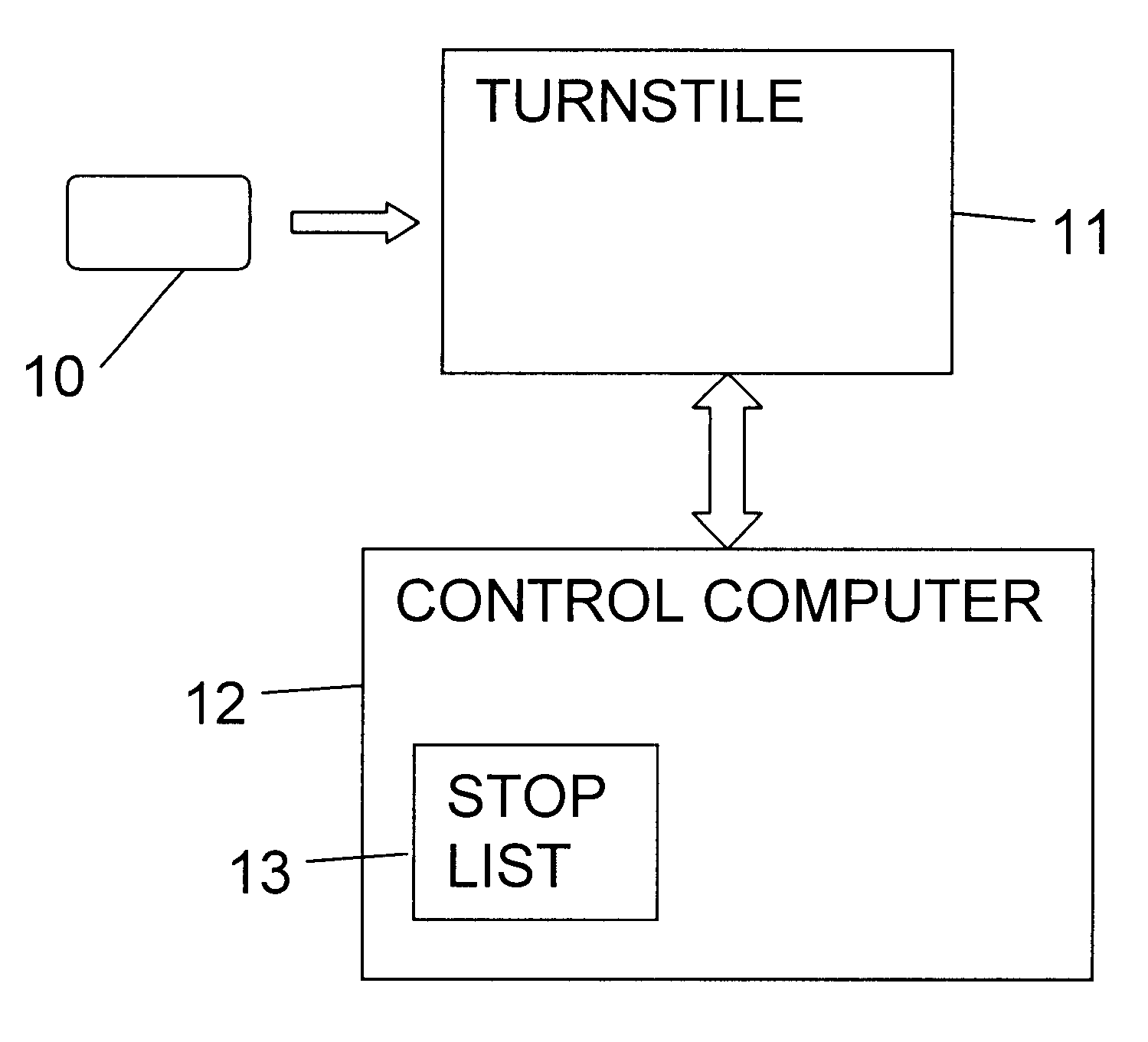
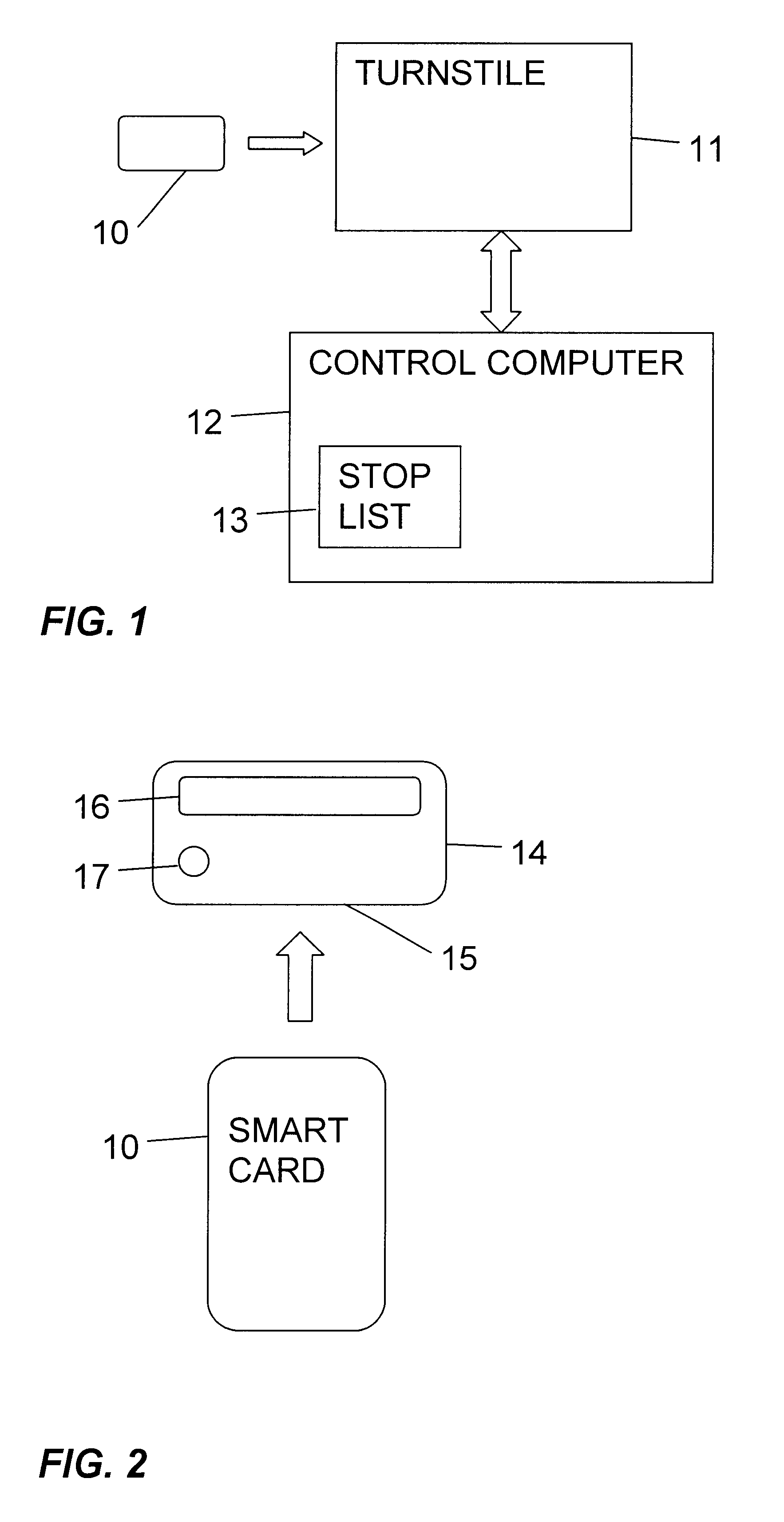
Cancellation method for an automatic ticket system
Subscribers are given access to a series of events by a smart card acting as an electronic ticket, which operates automatic turnstile. A subscriber can cancel the card in respect of a particular event by telephoning a cancellation office and verbally communicating the identifying number of the subscriber's card. This number is entered into a stop list for the event. The stop list automatically controls the automatic turnstile to prevent access to the event by use of any card on the stop list for this event. Each subscriber has a hand-held reader device, for displaying a sequence number and authentication code from the card. At the cancellation office, the card is authenticated by generating a check code from the sequence number and comparing it with the authentication code communicated by the subscriber.
Owner:INT COMP LTD
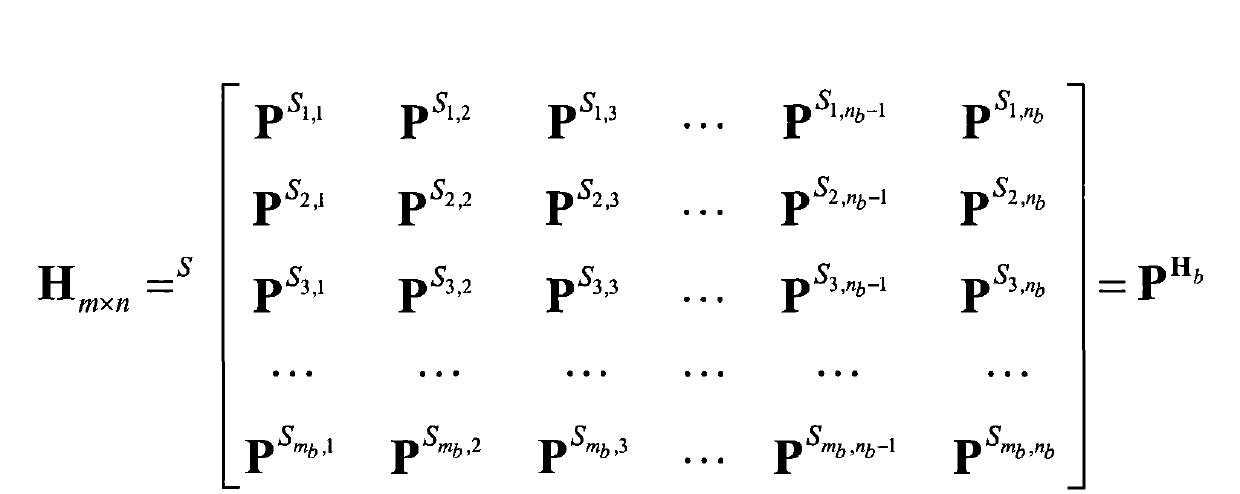
Basic Matrix, Coder/Encoder and Generation Method of the Low Density Parity Check Codes
ActiveUS20090106625A1Eliminate errorAccelerate decrease speedError correction/detection using multiple parity bitsCode conversionError ratioParity-check matrix
The invention relates to a base matrix, a encoder / decoder of Low Density Parity Check (LDPC) codes and a generation method thereof. The encoder / decoder is determined uniquely by the parity check matrix of the LDPC codes. With different code sizes, said parity check matrix can be obtained by expanding different base matrixes, and also can be obtained by expanding a unique base matrix after correction. Elements of said base matrix must meet an inequation in which the girth value is up to the standard, e.g. when girth ≧6, for any element i, j, k, l in the matrix which forms the short loop having a length of 4 in anticlockwise, there are always mod(i−j+k−l, z) unequal to 0. By this invention, the girth of the constructed base matrix is made as large as possible, the amount of the shortest loops is as few as possible when it is the same girth, thus the curve of bit error ratio (BER) is dropped quickly, the error floor of the LDPC codes is eliminated effectively, and the optimal performance of the LDPC codes is obtained.
Owner:ZTE CORP
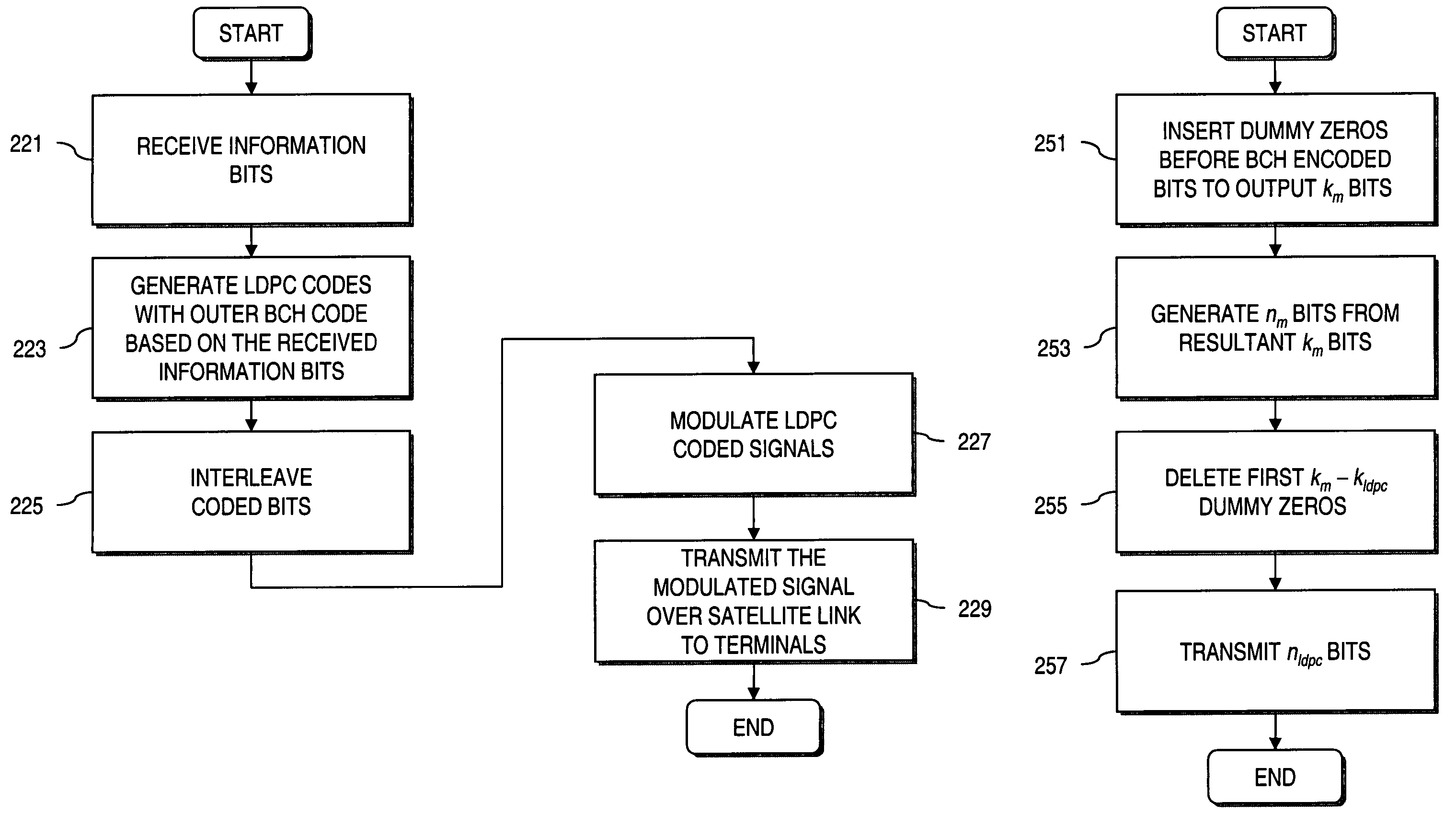
Method and system for providing short block length low density parity check (LDPC) codes
InactiveUS7334181B2Low ParityMinimize resourceTransmission systemsError correction/detection using LDPC codesDigital videoTheoretical computer science
An approach is provided for generating Low Density Parity Check (LDPC) codes. An LDPC encoder generates a short LDPC code by shortening longer mother codes. The short LDPC code has an outer Bose Chaudhuri Hocquenghem (BCH) code. According to another aspect, for an LDPC code with code rate of 3 / 5 utilizing 8-PSK (Phase Shift Keying) modulation, an interleaver provides for interleaving bits of the output LDPC code by serially writing data associated with the LDPC code column-wise into a table and reading the data row-wise from right to left. The above approach has particular application in digital video broadcast services over satellite.
Owner:DTVG LICENSING INC
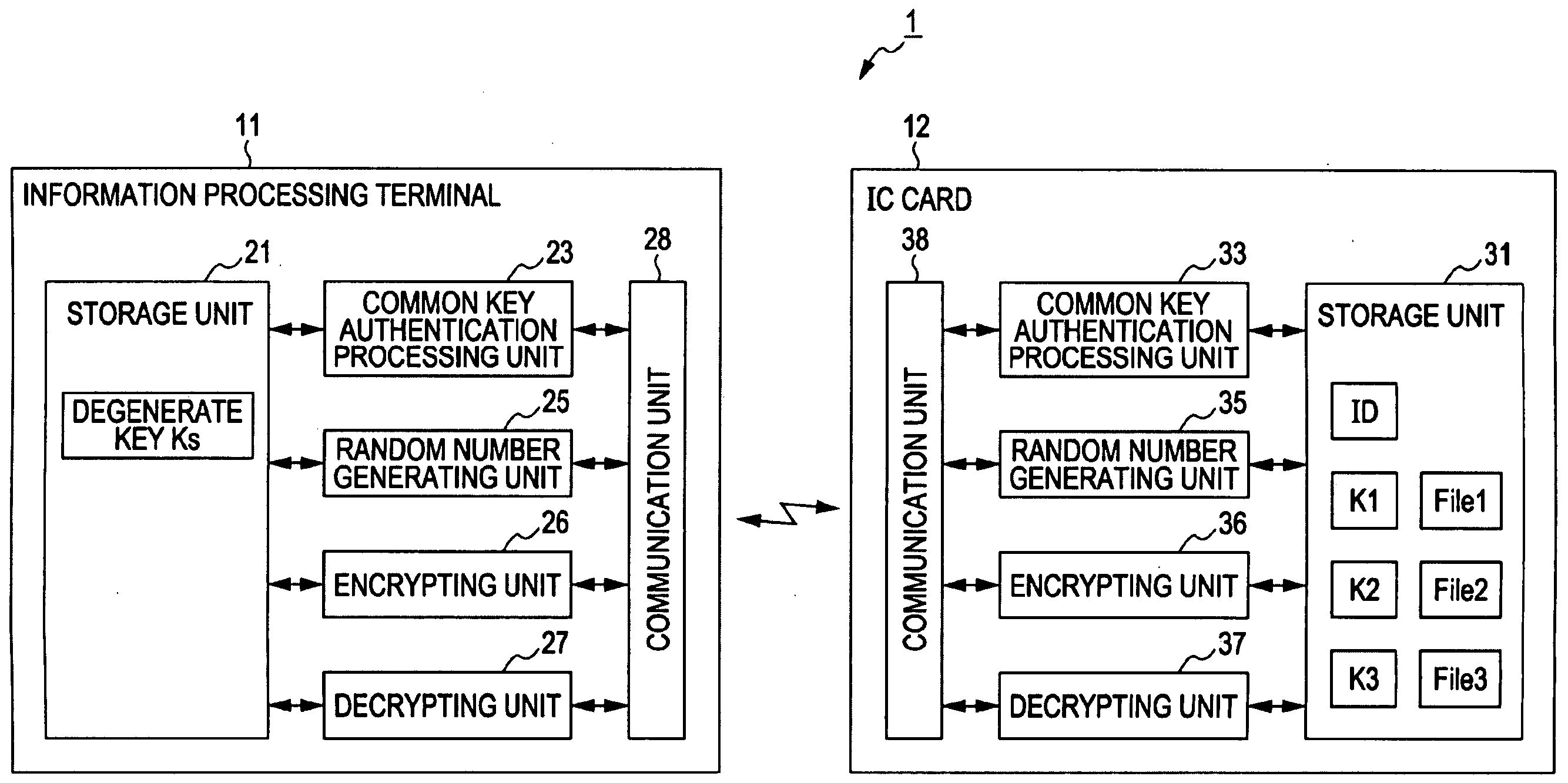
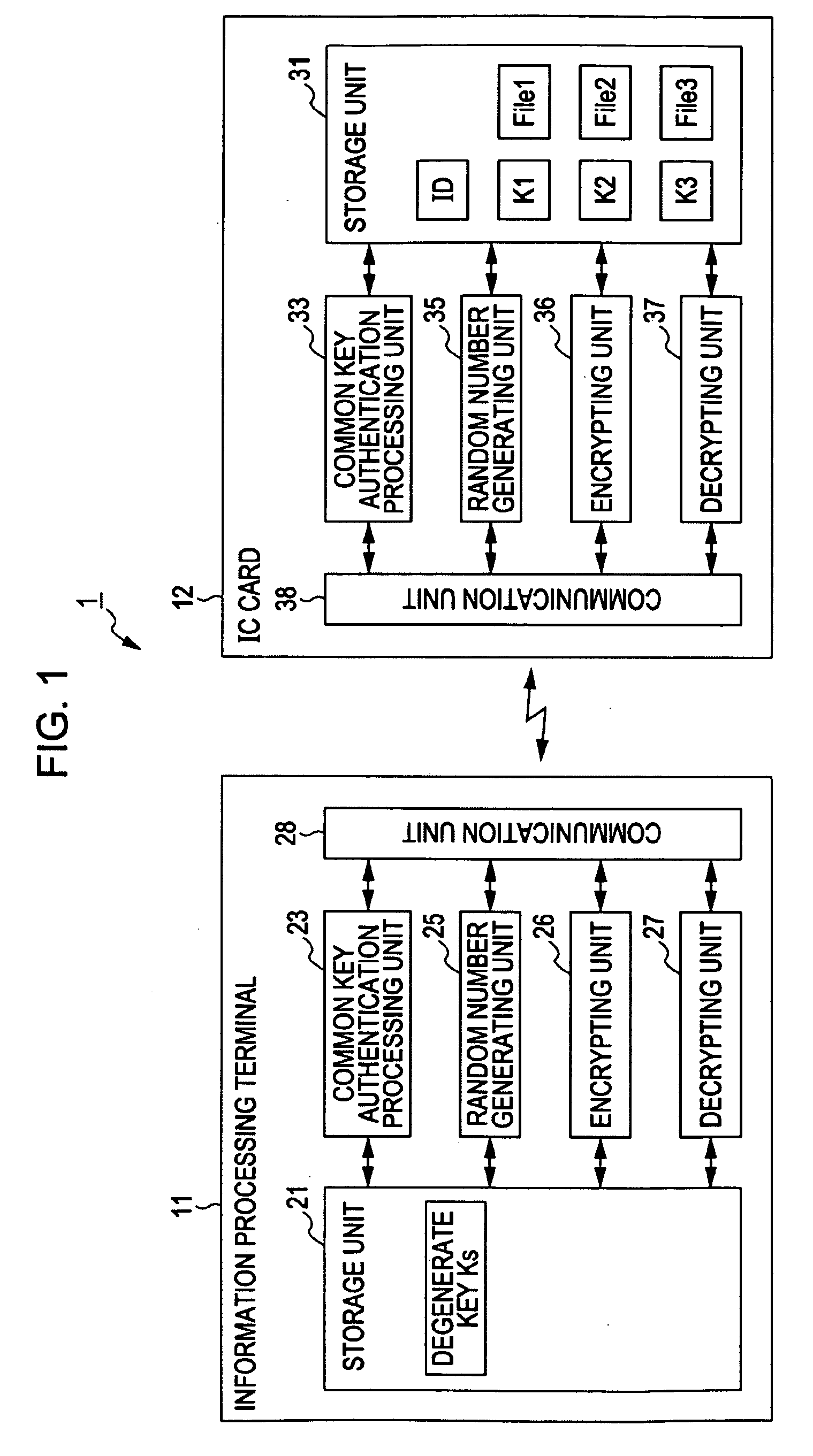
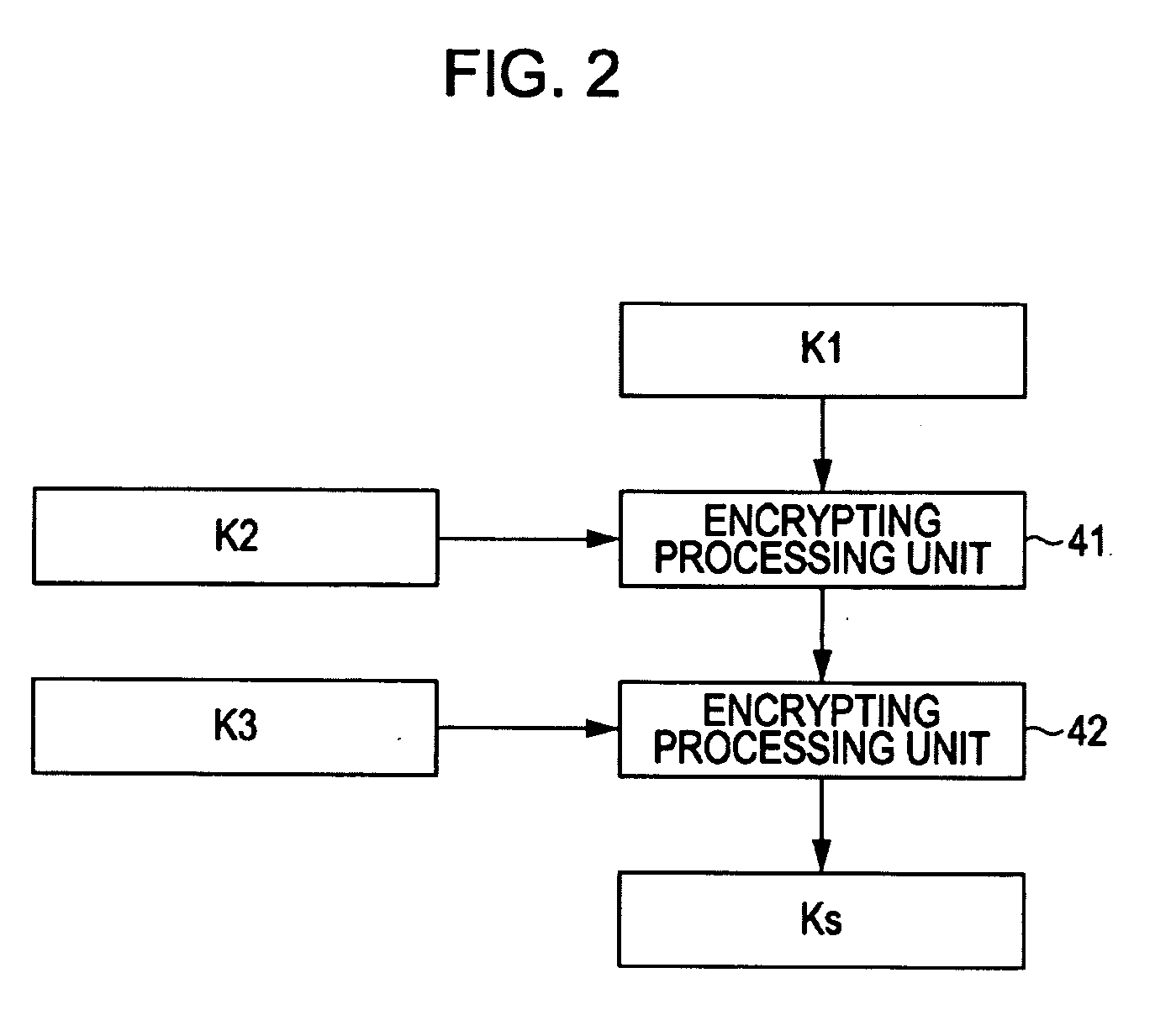
Information Processing Device and Method, Recording Medium, Program and Information Processing System
InactiveUS20090259850A1Quicker and saferKey distribution for secure communicationUser identity/authority verificationInformation processingCheck digit
An information processing device regarding which access to data held by the information processing device itself, in multiple regions, is requested from another information processing device, includes: an authenticating unit to perform authenticating processing of the other information processing device; a receiving unit to receive an access license ticket including an access code and a check digit; an access license ticket generating key generating unit to generate an access license ticket generating key, which is key information for computing a check digit using data held beforehand, a root key, an access control key, and other key information which is key information to manage data of a region other than the predetermined region, corresponding to an access code; check digit computing unit to compute a check digit corresponding to the access code described in the access license ticket; and access license ticket validating unit to validate the access license ticket.
Owner:SONY CORP
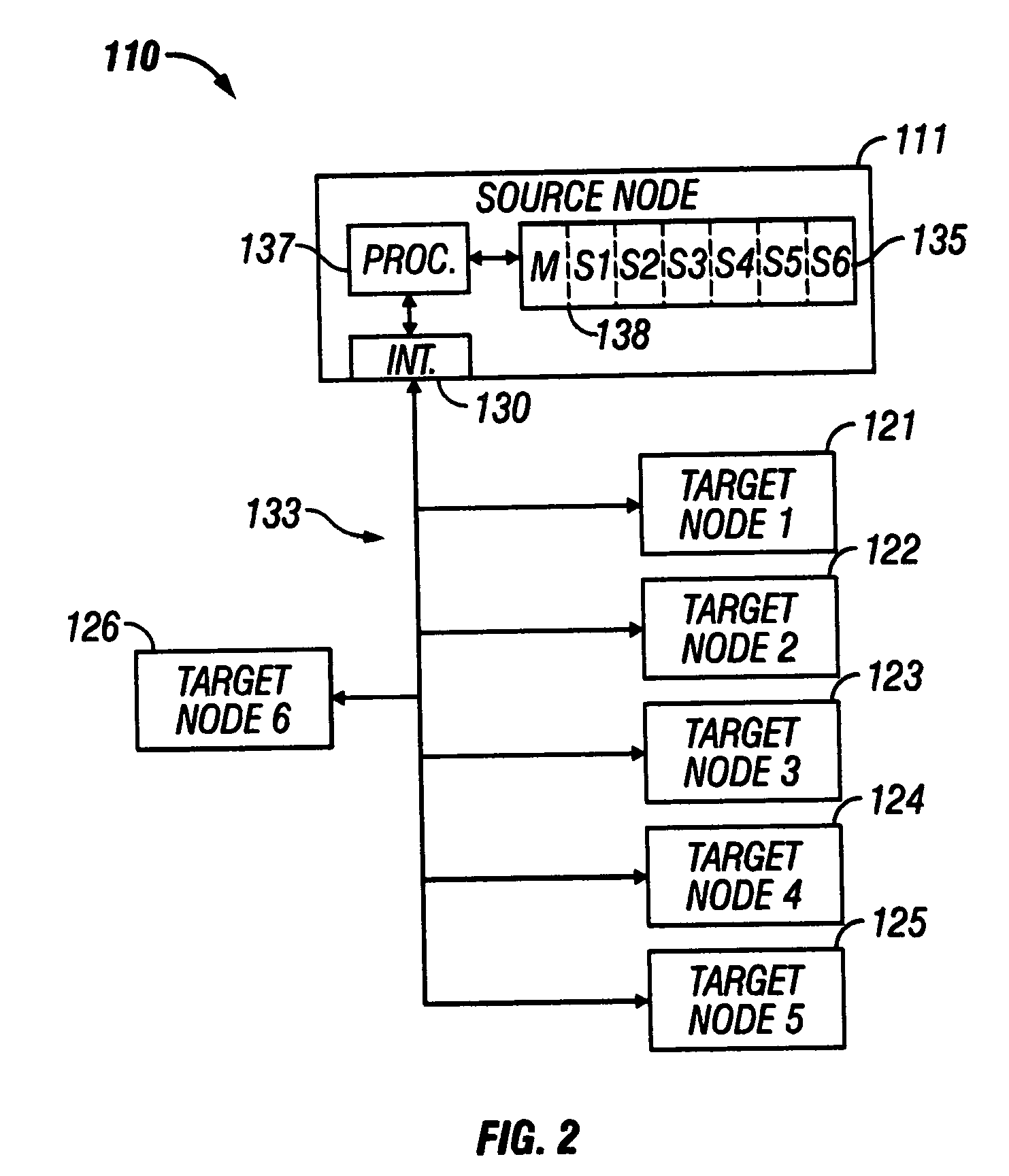
Updatable firmware having boot and/or communication redundancy
InactiveUS20050251673A1Preventing executionError detection/correctionDigital computer detailsObject codeProcessor node
A distributed nodal system with a source computer processor node storing program code for target node(s). A target node has an updatable firmware memory storing program code for operating a target processor. The target code comprises application code for controlling an embedded device, primary communication code for communicating with a network, backup communication code also having copy code for copying code between portions of the firmware memory, and primary boot code for booting the target processor and having check code. The check code determines whether the primary communication code is corrupted, and if it is corrupted, employs the copy code to overwrite the primary communication code with the backup code. If uncorrupted, the check code determines whether the application code is corrupted, and if corrupted, prevents execution of the code.
Owner:IBM CORP
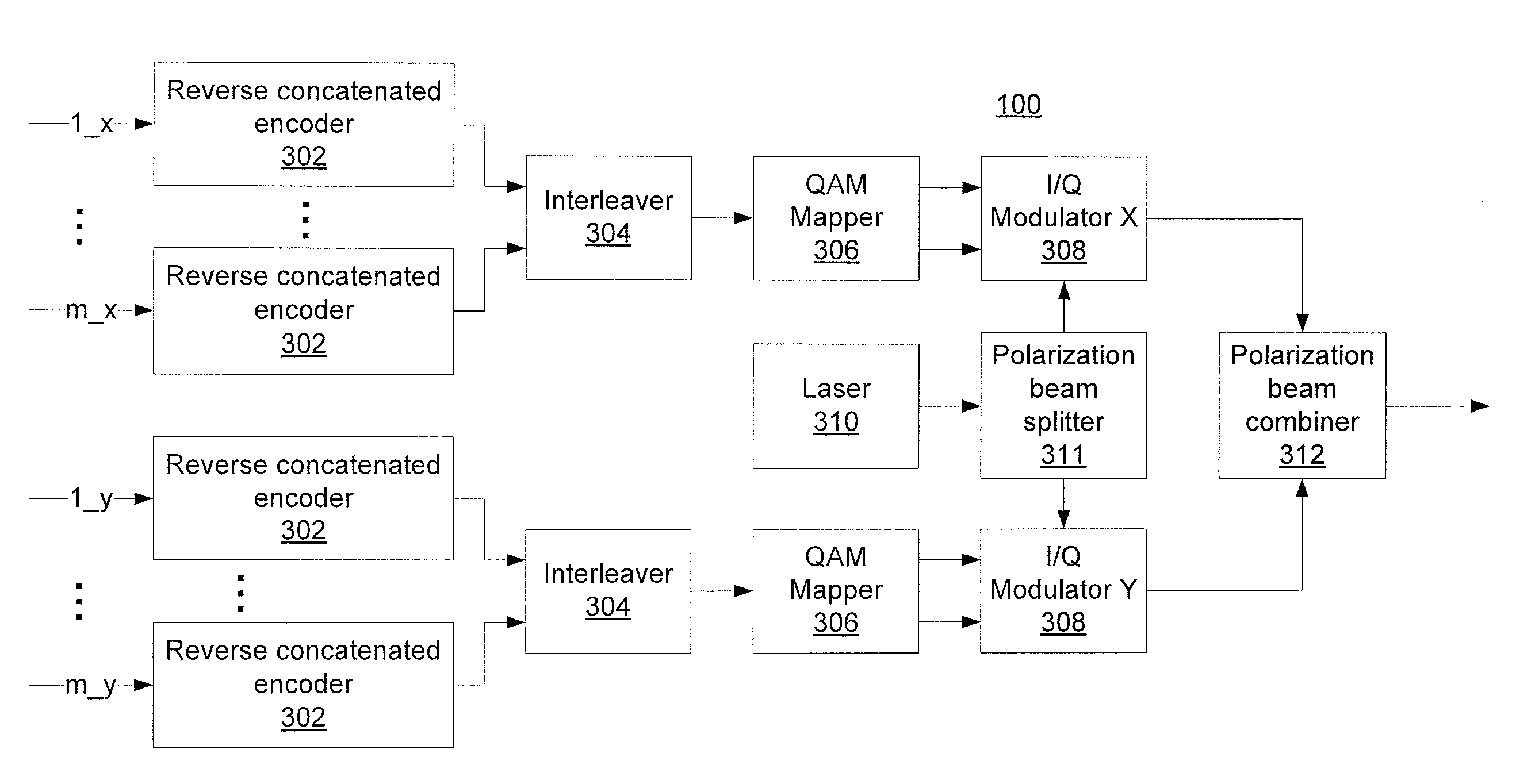
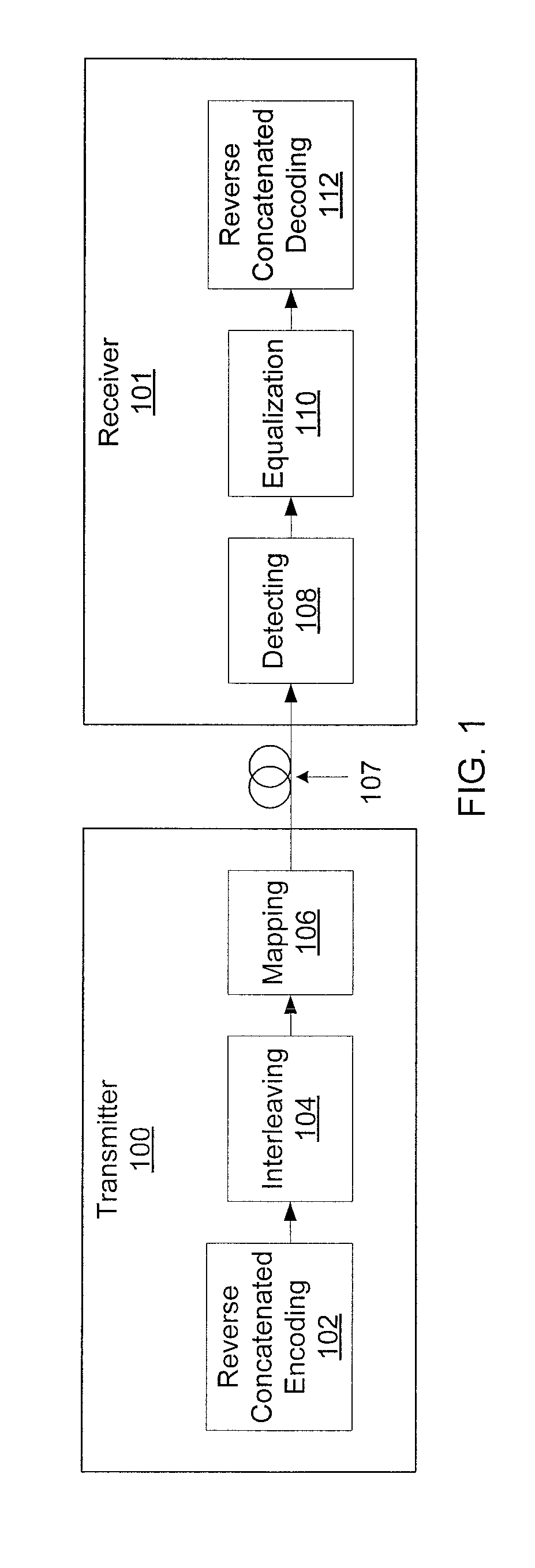
Reverse concatenated encoding and decoding
ActiveUS20120047415A1Improve decoding performanceReed-muller codesCode conversionComputer hardwareBlock code
Methods and systems for transmitting and receiving data include reverse concatenated encoding and decoding. Reverse concatenated decoding includes inner decoding the encoded stream with an inner decoder that uses a low-complexity linear-block code to produce an inner-decoder output stream, outer decoding the inner-decoder output stream with an outer decoder that uses a low-density parity-check code to produce an information stream, and iterating extrinsic bit reliabilities from the outer decoding for use in subsequent inner decoding to improve decoding performance.
Owner:NEC CORP
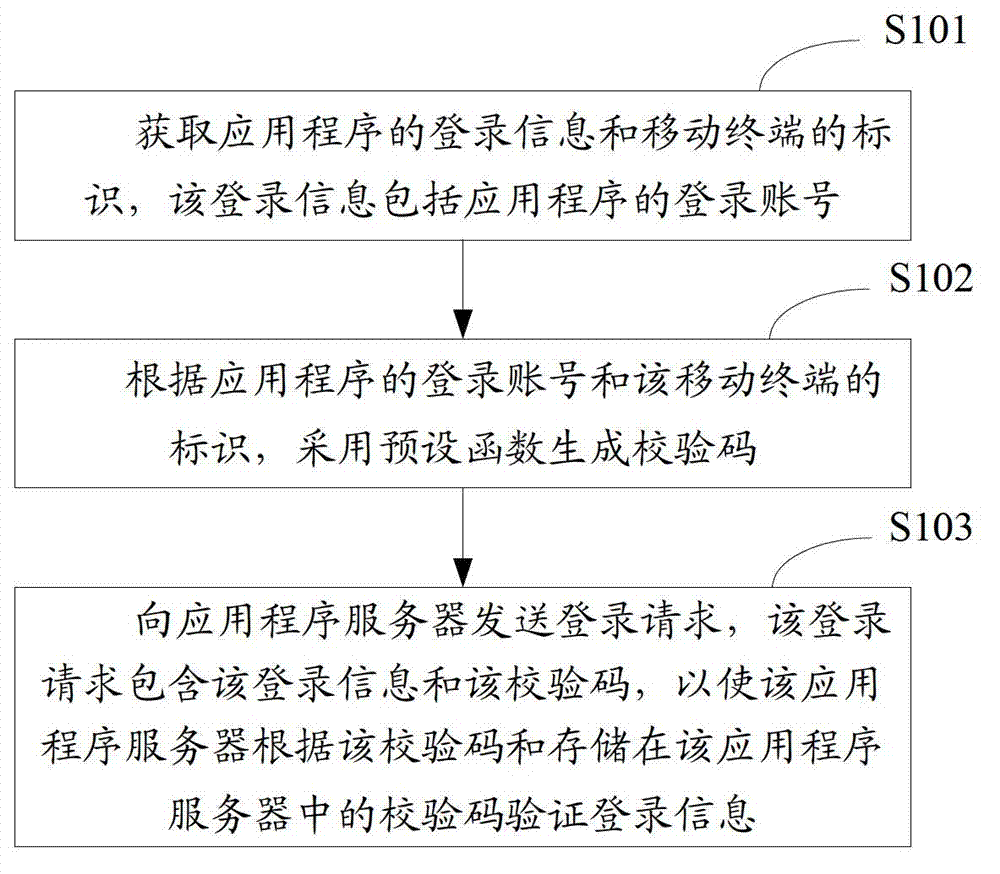
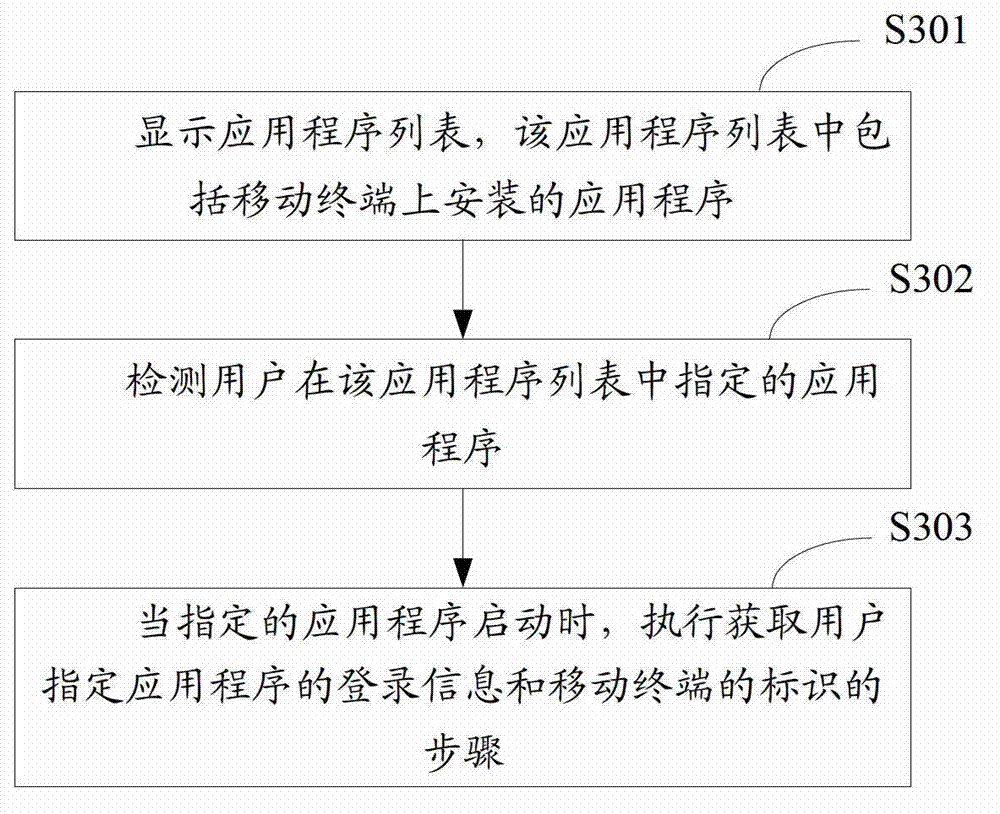
Login and verification method for application program
ActiveCN103095457APrevent illegal loginImprove securityUser identity/authority verificationSubstation equipmentApplication serverValidation methods
The invention belongs to the technical field of mobile terminals and provides a login and verification method for an application program. The login and verification method comprises the following steps: login information of the application program and identification of a mobile terminal are obtained, and the login information comprises a login account of the application program; according to the login account of the application program and the identification of the mobile terminal, a preset function is adopted to generate a check code; a login request is sent to an application program server, and the login request comprises the login information and the check code so that the application program server verifies the login information according to the check code and the check code stored in the application program server. In the login and verification method, when the generated check code and the check code stored in the application program server are different, the verification result of the login information proves to be illegal. Even when other people learn about the login account and the password, the people cannot succeed in login operation of the application program. Therefore, illegal login on a random mobile terminal is eliminated, and safety of multiple login accounts and the password is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
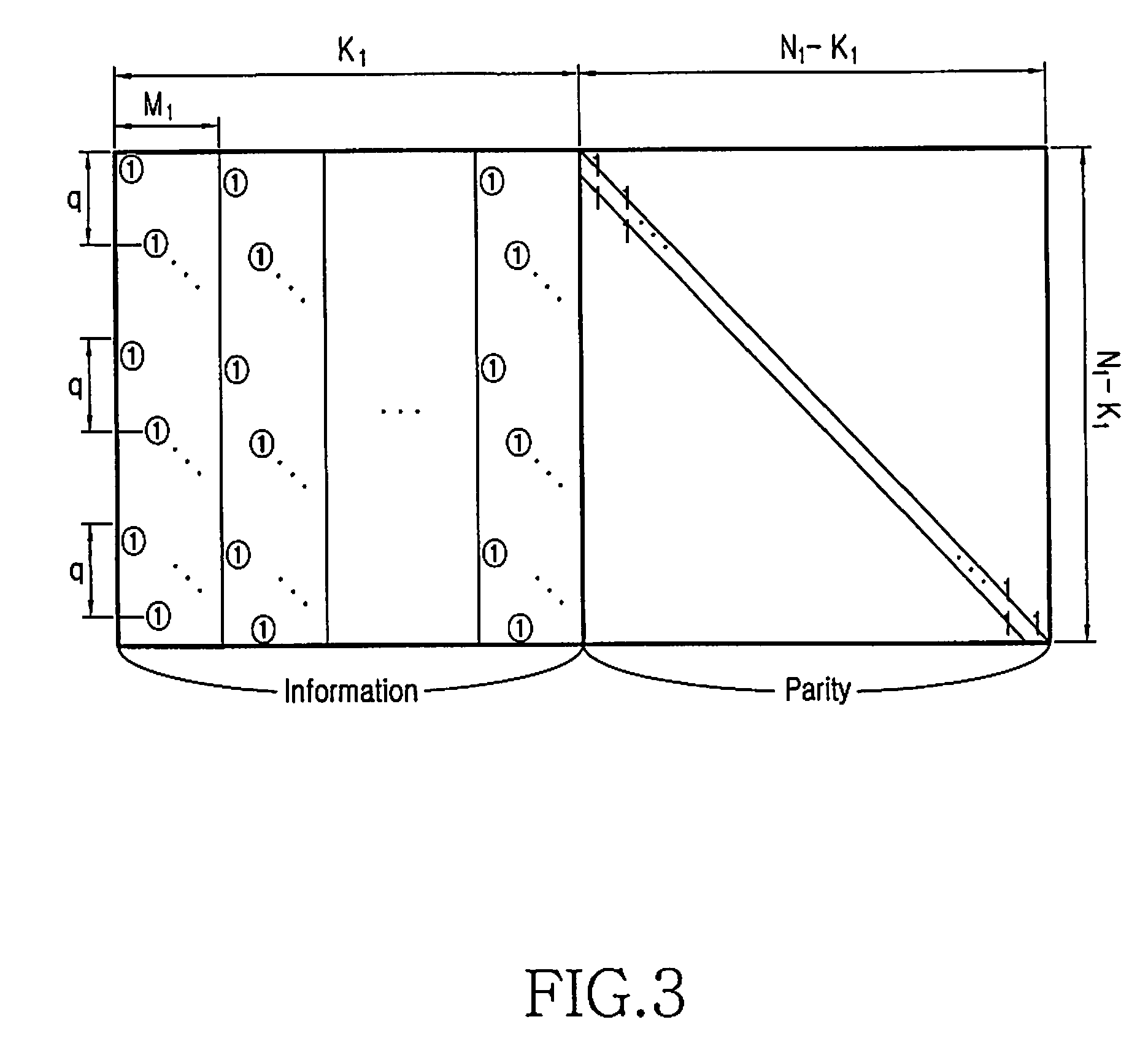
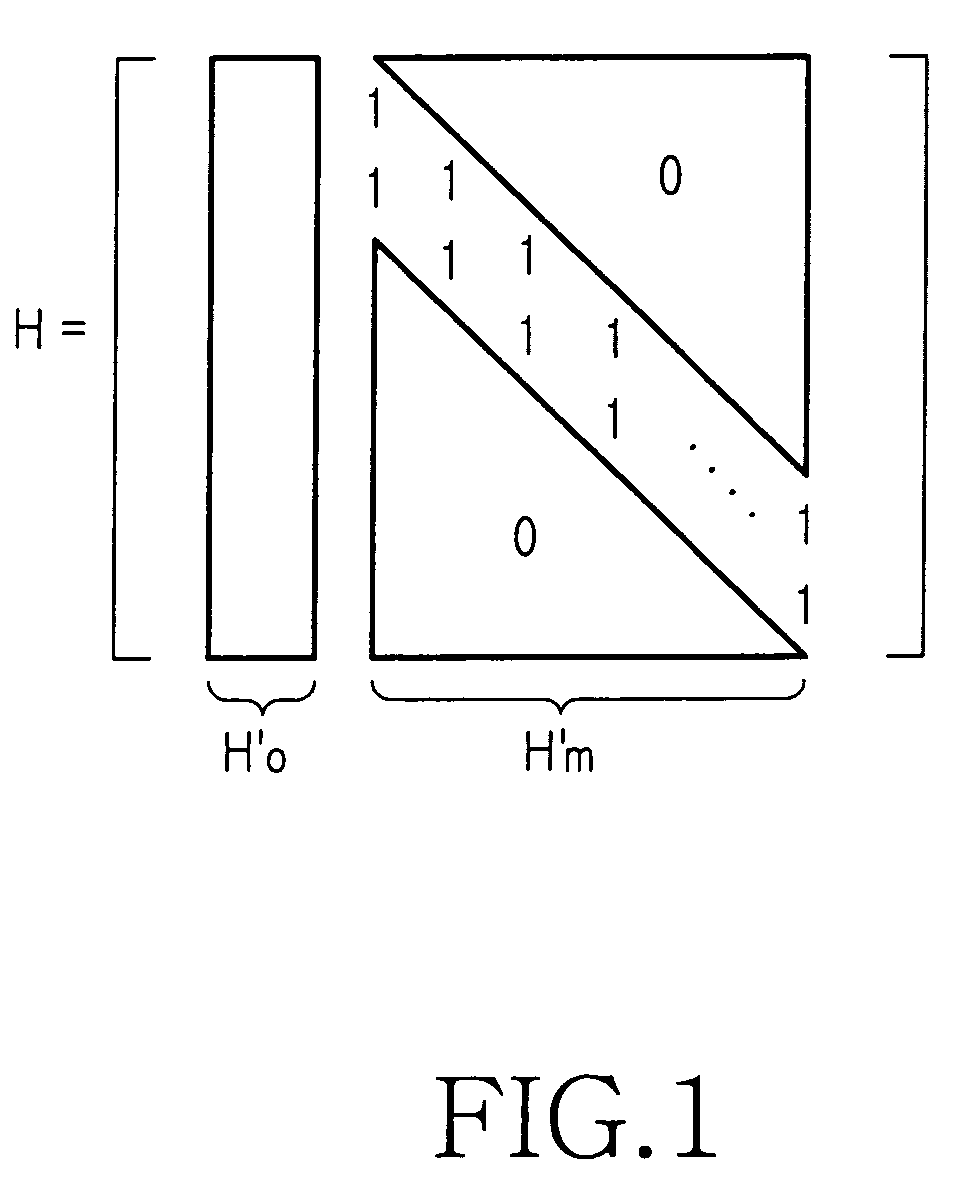
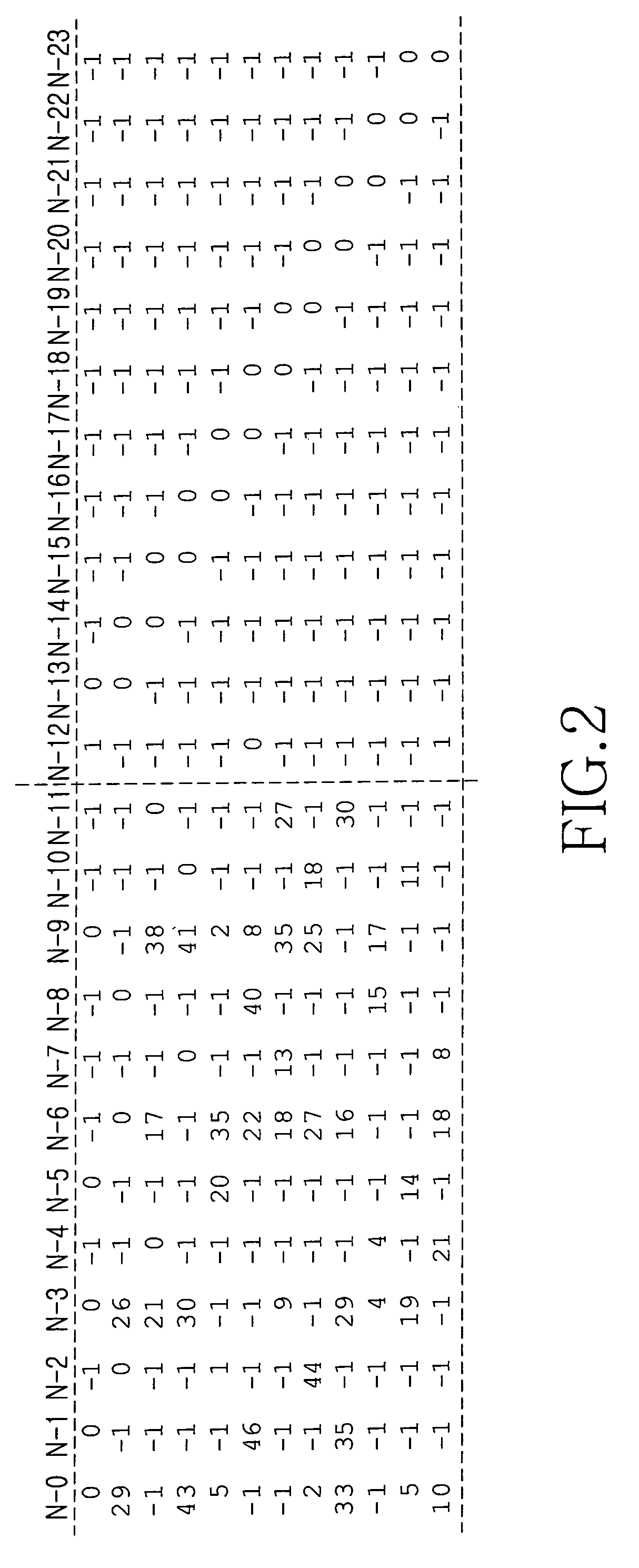
Method for encoding low-density parity check code
ActiveUS20070022354A1Simplify the coding processImprove performanceError detection/correctionError correction/detection using multiple parity bitsTheoretical computer scienceDiagonal matrix
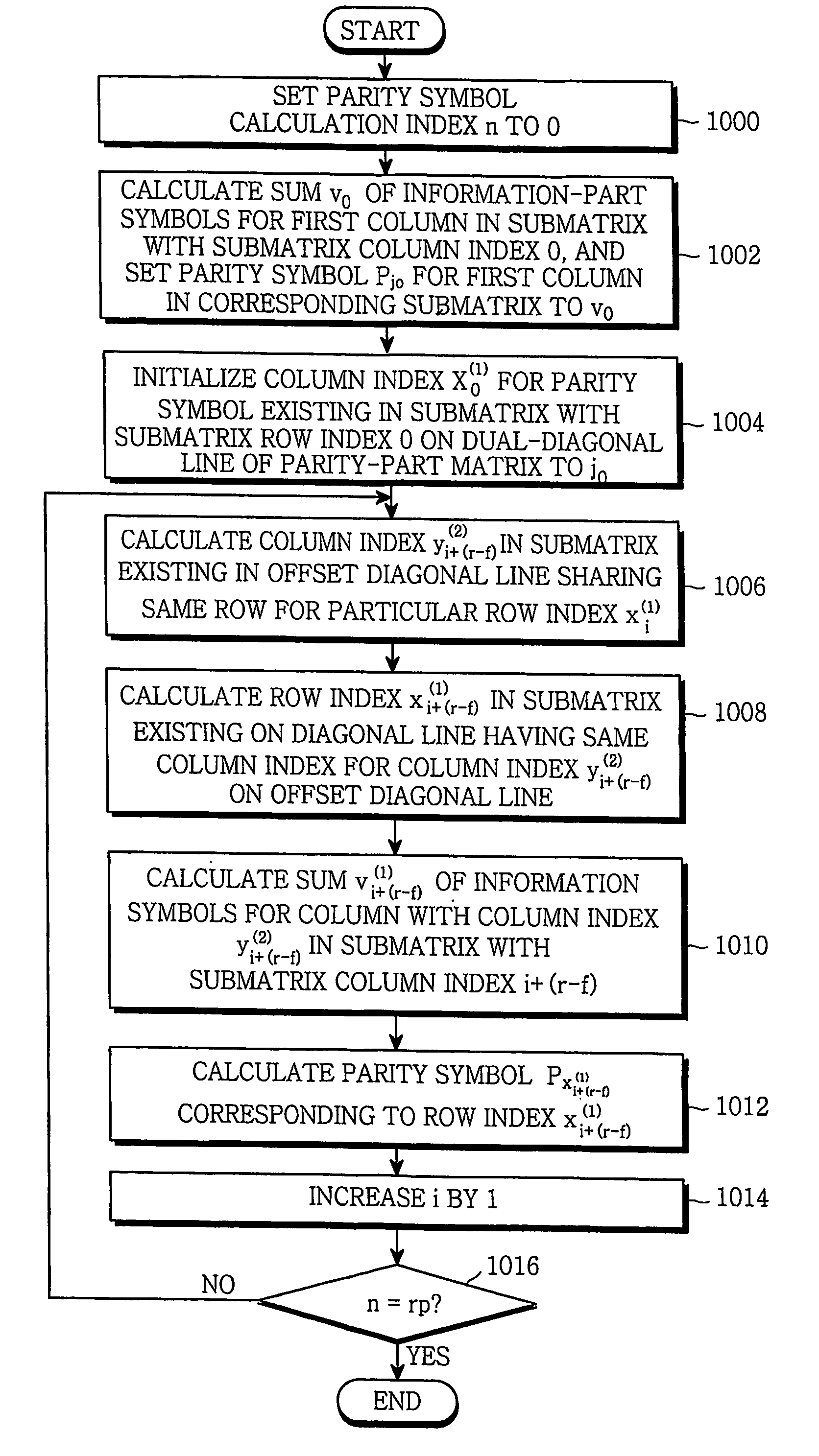
An apparatus and method for encoding low-density parity check (LDPC) codes. The method for generating a low-density parity check code formed of an information-part matrix and a parity-part matrix comprises the steps of converting the information-part matrix into an array code structure and assigning a degree sequence to each submatrix column; extending a dual-diagonal matrix corresponding to the parity-part matrix such that an offset value between diagonals has a random value; lifting the normalized dual-diagonal matrix; determining an offset value for cyclic column shift for each submatrix of the lifted normalized dual-diagonal matrix; and determining a parity symbol corresponding to a column of the parity-part matrix.
Owner:SAMSUNG ELECTRONICS CO LTD
Non-Concatenated FEC Codes for Ultra-High Speed Optical Transport Networks
ActiveUS20120221914A1Improves decoding processAvoid delayError preventionChecking code calculationsUltra high speedParallel computing
A decoder performs forward error correction based on quasi-cyclic regular column-partition low density parity check codes. A method for designing the parity check matrix reduces the number of short-cycles of the matrix to increase performance. An adaptive quantization post-processing technique further improves performance by eliminating error floors associated with the decoding. A parallel decoder architecture performs iterative decoding using a parallel pipelined architecture.
Owner:MARVELL ASIA PTE LTD
Method and device for generating and coding quasi-cyclic LDPC code
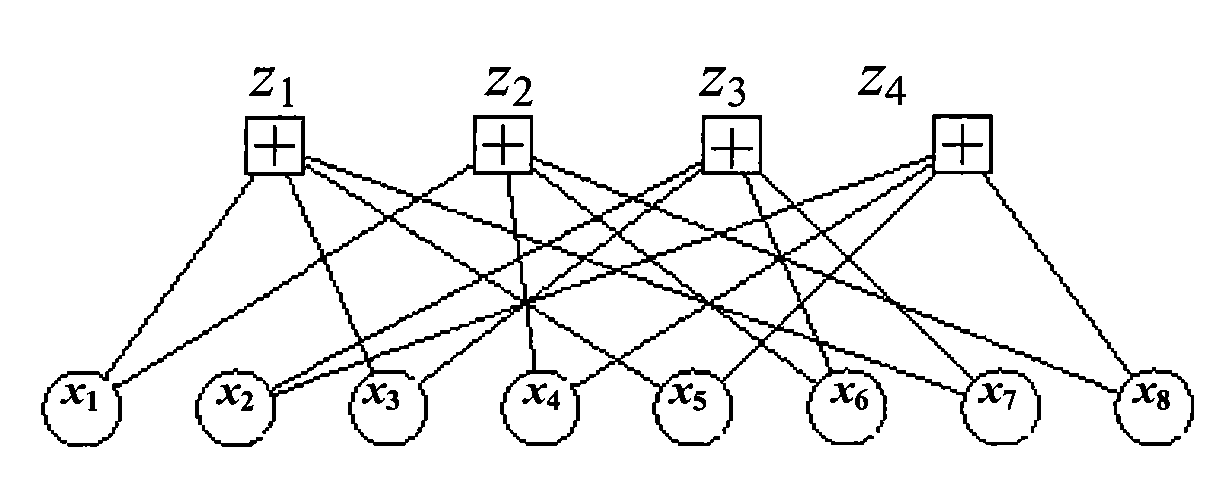
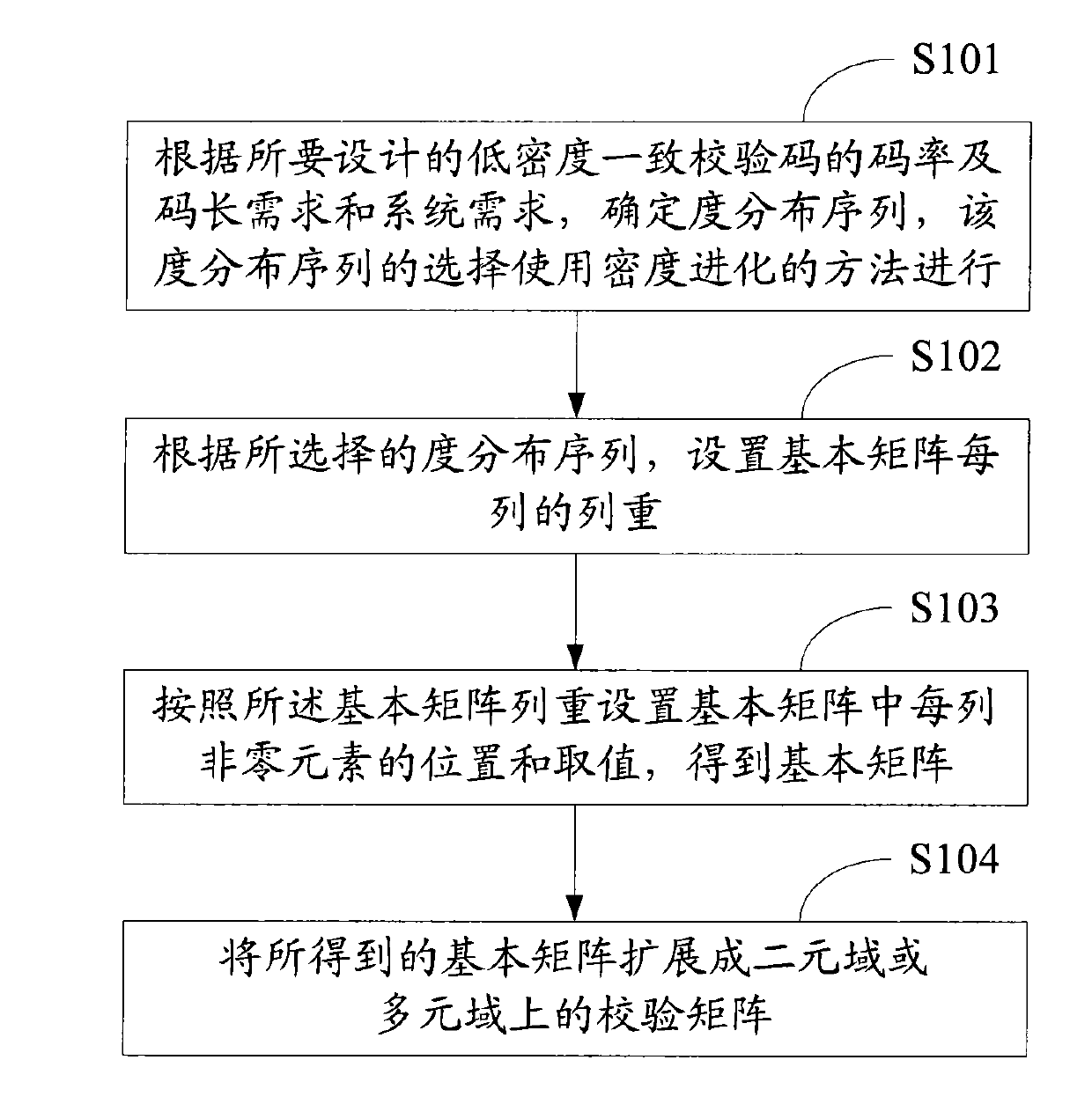
ActiveCN101662290AError correction/detection using multiple parity bitsCode conversionAlgorithmSystem requirements
The invention relates to the technical filed of the error correction and coding of communication and information systems and discloses a method for generating a quasi-cyclic low density parity check code. The method comprises the following steps: according to the requirements on code rate and code length of the low density parity check code to be designed and system requirements, determining a degree distribution sequence which is selected by adopting a density evolution method; setting the column weight of each column of a basic matrix according to the selected degree distribution sequence; setting the positions and values of non-zero elements in each column in the basic matrix according to the column weights of the basic matrix to obtain the basic matrix; and expanding the obtained basic matrix into a check matrix. At the same time, the invention also discloses a method for coding the quasi-cyclic low density parity check code and provides corresponding devices. The methods and the devices provided by the embodiment of the invention enable finally obtained code words to effectively reduce influences of cycle overlapping.
Owner:HONOR DEVICE CO LTD
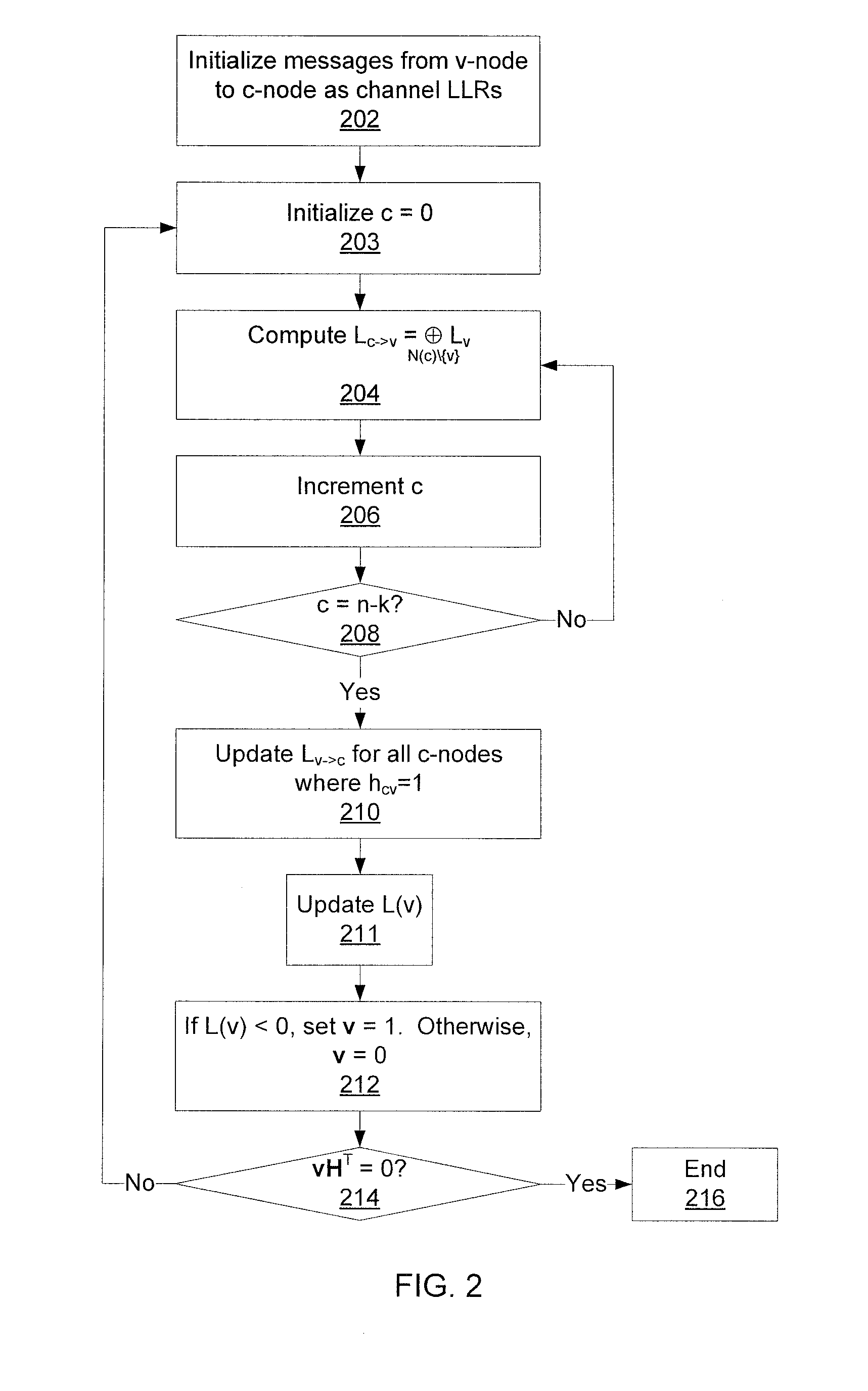
Apparatus and method for encoding and decoding channel in a communication system using low-density parity-check codes
ActiveUS20090210767A1Error correction/detection using multiple parity bitsCode conversionCommunications systemTheoretical computer science
An apparatus and method for generating a parity-check matrix of a Low-Density Parity-Check (LDPC) code are provided. Parameters for designing the LDPC code are determined, and a first parity-check matrix of a quasi-cyclic LDPC code is formed according to the determined parameters. A second parity-check matrix is created through the elimination of a predetermined portion of a parity part in the first parity-check matrix, and a third parity-check matrix is created by rearranging the second parity-check matrix.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Methods, circuits, architectures, software and systems for determining a data transmission error and/or checking or confirming such error determinations
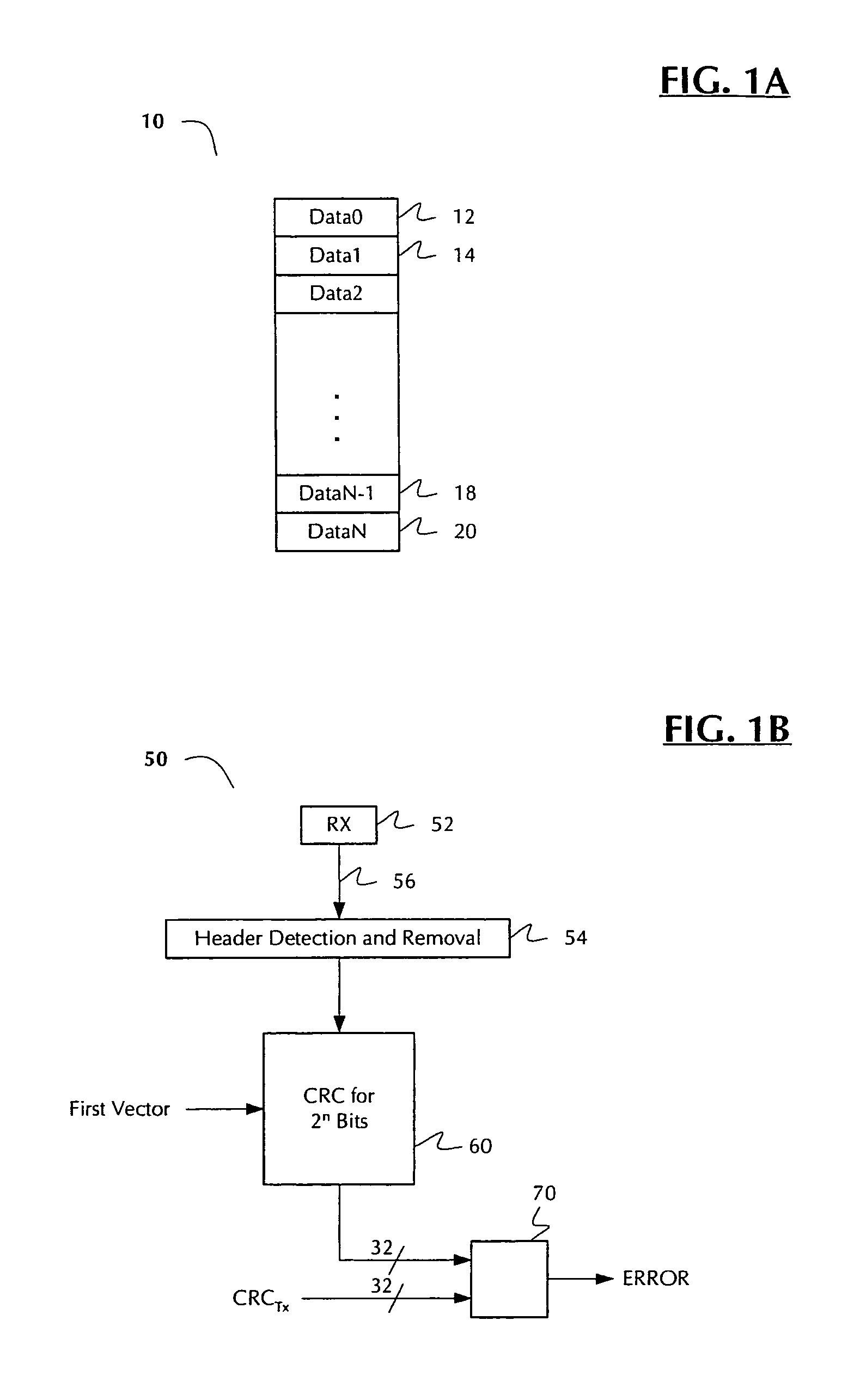
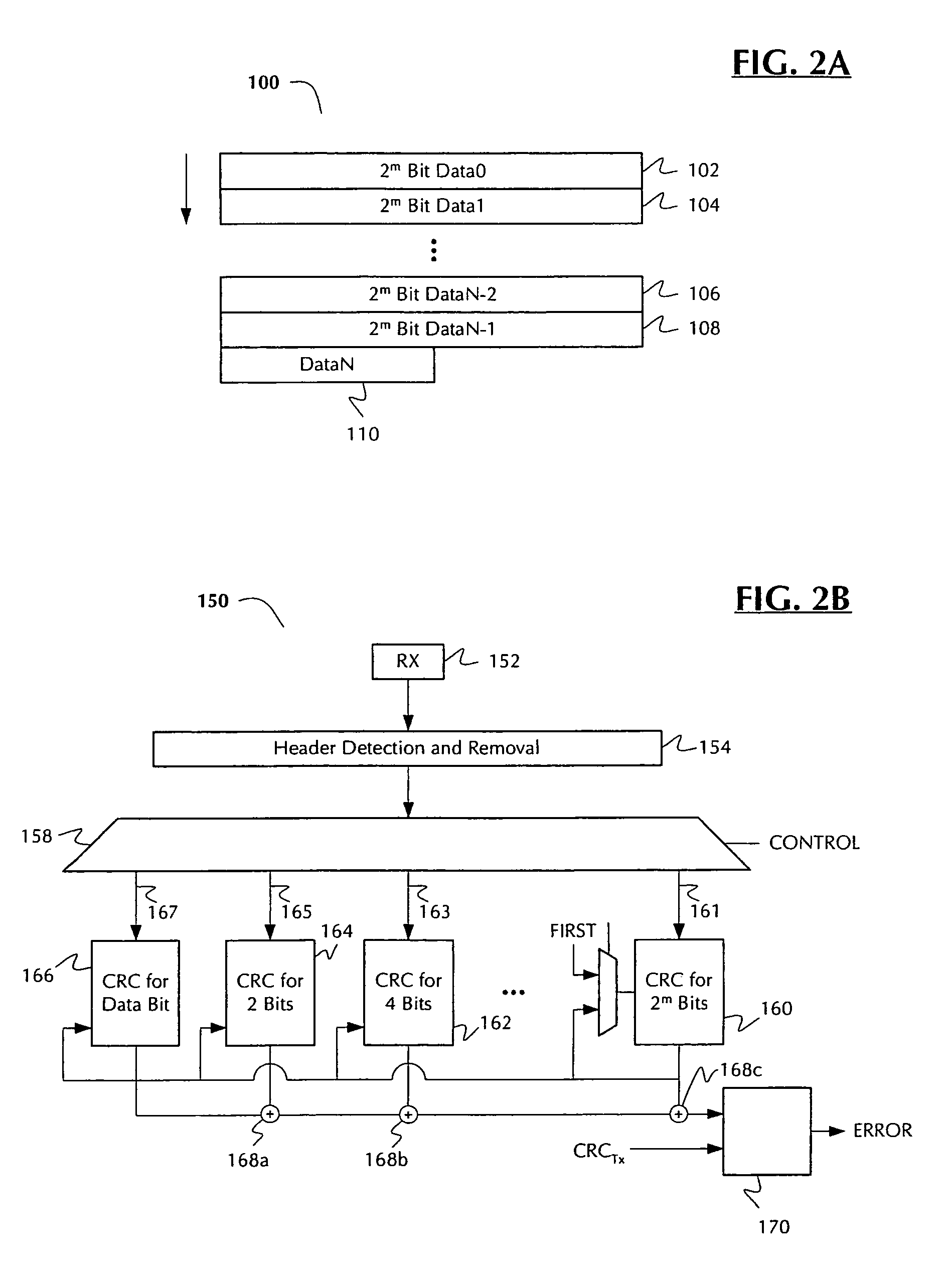
InactiveUS7434150B1Increase profitReduce power consumptionCode conversionError detection onlyError checkingPresent method
Methods, circuits, architectures, and systems for error detection in transmitted data. The method generally includes the steps of (a) performing an error checking calculation on the transmitted data and appended error checking code; (b) determining the calculated error checking code state; and (c) if it has a predetermined state, indicating that there is no error in the transmitted data. The circuitry generally comprises (1) an error checking code calculation circuit configured to calculate error checking code on the transmitted data and the appended error checking code; (2) a vector selector configured to select one of a plurality of error checking vectors; and (3) a logic circuit configured to determine the calculated error checking code state and, if it has a predetermined state, indicate that there is no error in the transmitted data. The software generally includes a set of instructions configured to implement or carry out the present method. The architectures and / or systems generally include those that embody one or more of the inventive concepts disclosed herein. In the present invention, an error checking calculation is performed on error checking code transmitted with the data. If the transmitted data and error checking code are error-free, the error checking calculation gives a result having a known and / or predetermined state. This technique enables one to confirm or determine that the data transmission was error-free without use of or need for a wide, complicated comparator, thereby reducing the chip area dedicated to error detection, increasing the utilization efficiency of the circuitry on the chip, and reducing power consumption.
Owner:MARVELL ISRAEL MISL
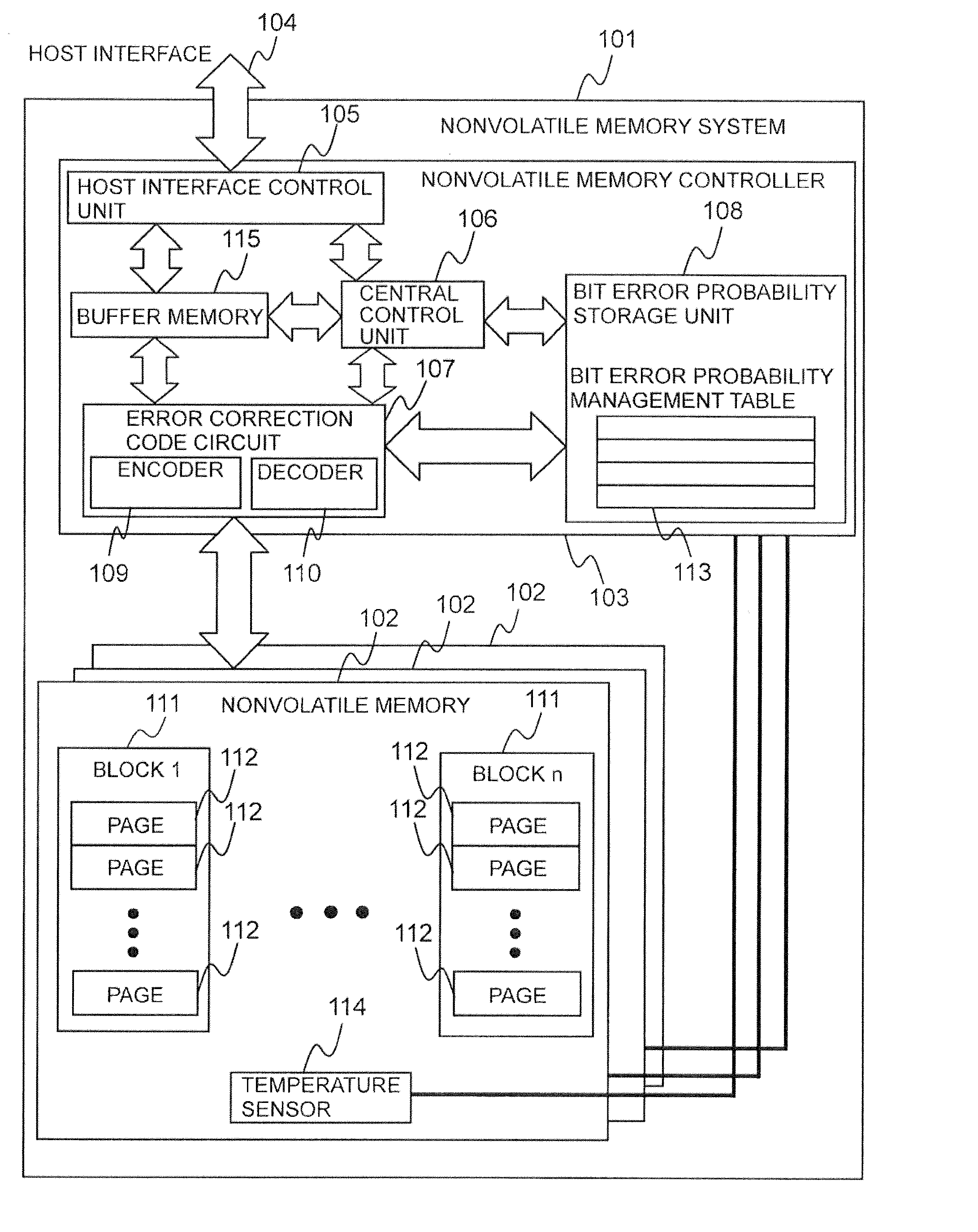
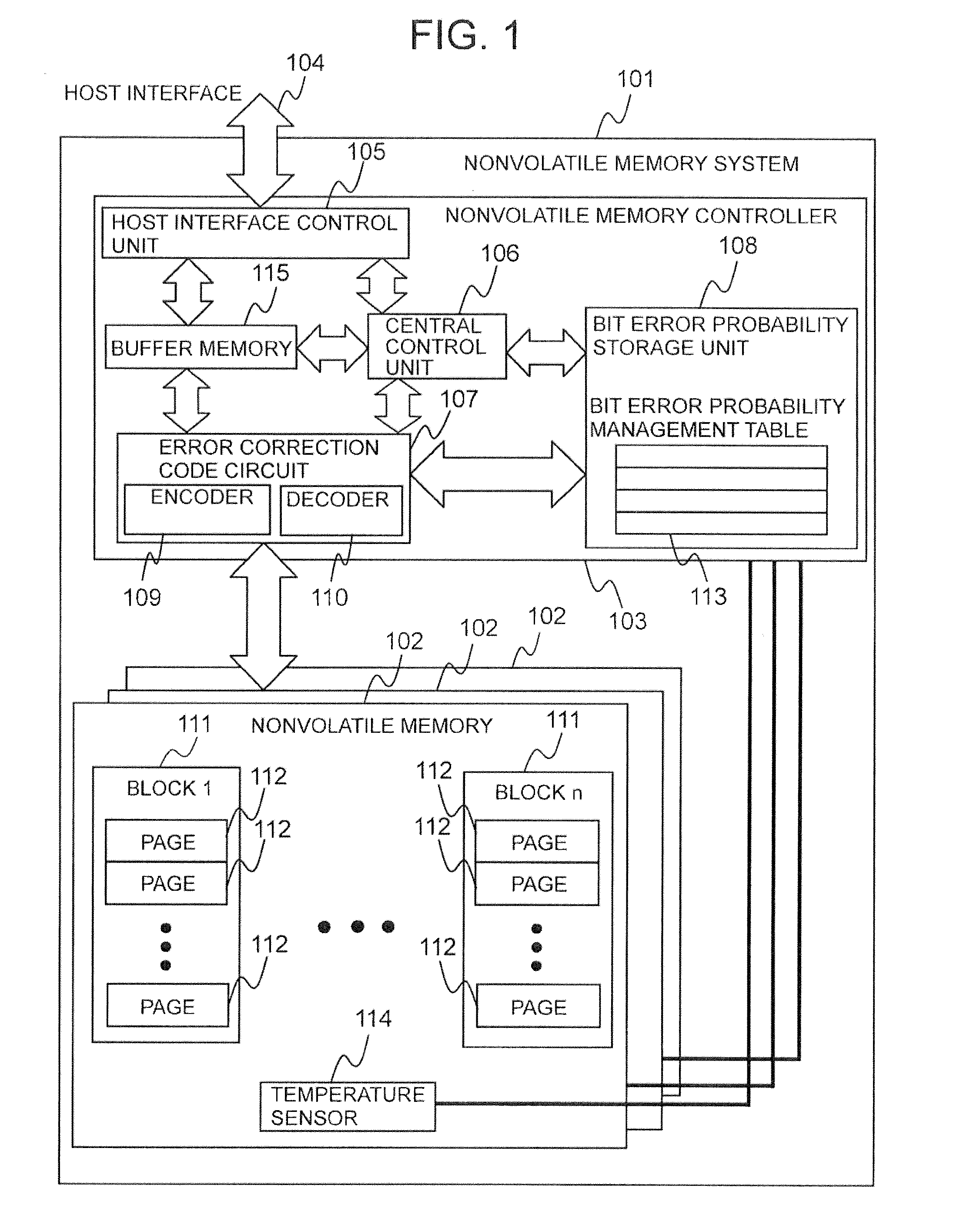
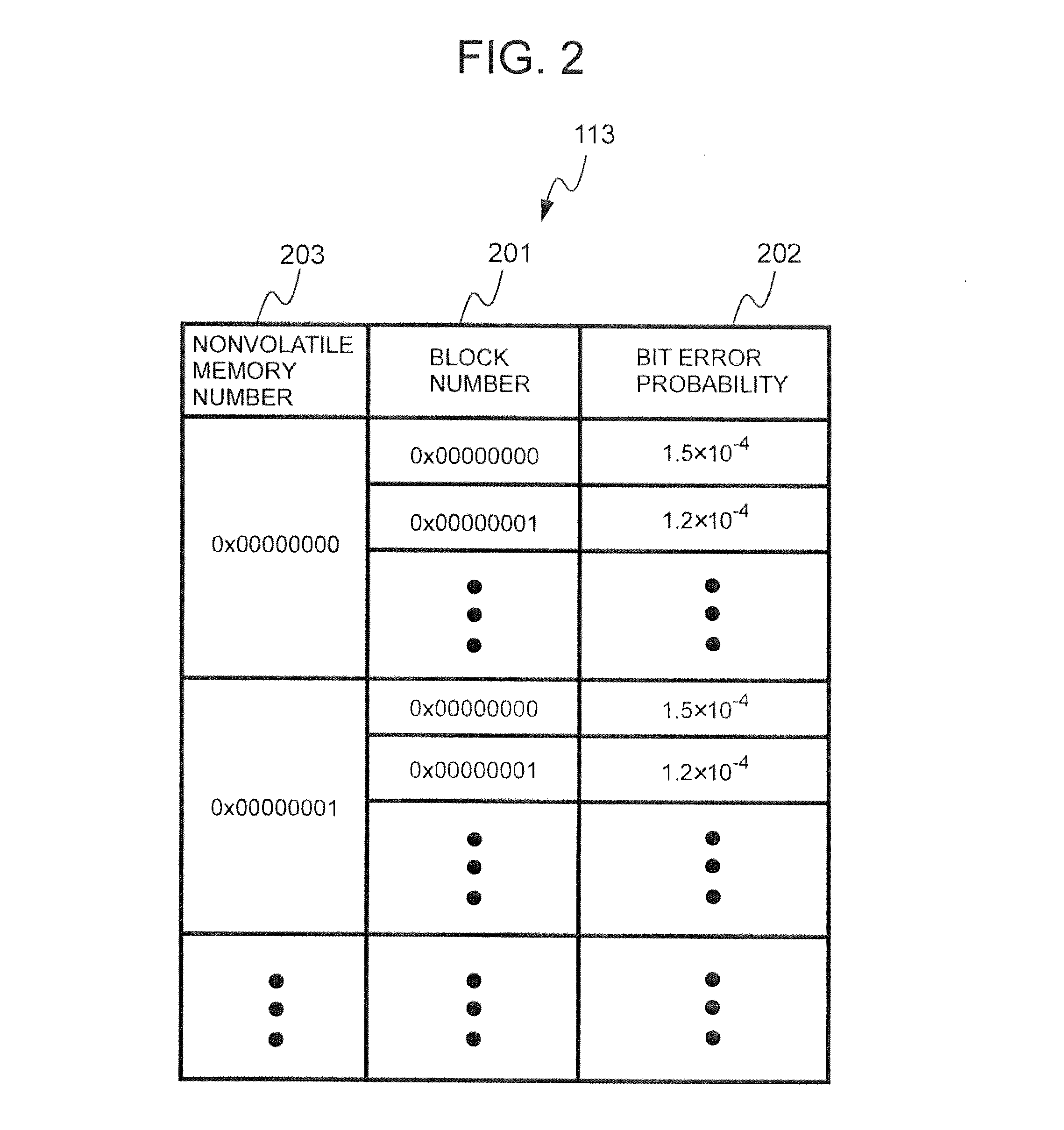
Non-volatile storage system compensating prior probability for low-density parity check codes
InactiveUS20130111299A1Without increasing size of circuitCode conversionCoding detailsLow-density parity-check codeStorage management
A nonvolatile storage system has multiple nonvolatile storage media and a controller coupled to the multiple nonvolatile storage media. The controller has a storage area for storing management information including probability management information denoting error probability information of a unit physical area in a nonvolatile storage medium, and an error correcting circuit for carrying out coding and decoding by a low density parity check code. An error probability is a probability that data within the unit physical area is incorrect, and is a prior probability, which is the probability of prior to this data having been read. The controller, in a data read process, identifies based on management information an error probability, which is the error probability of a unit physical area including the physical area of the read source and is better suited to the state of the read source in the current read process than the error probability identified for the same unit physical area in a past read process, and uses the identified error probability to correct the read data using the error correcting circuit.
Owner:HITACHI LTD
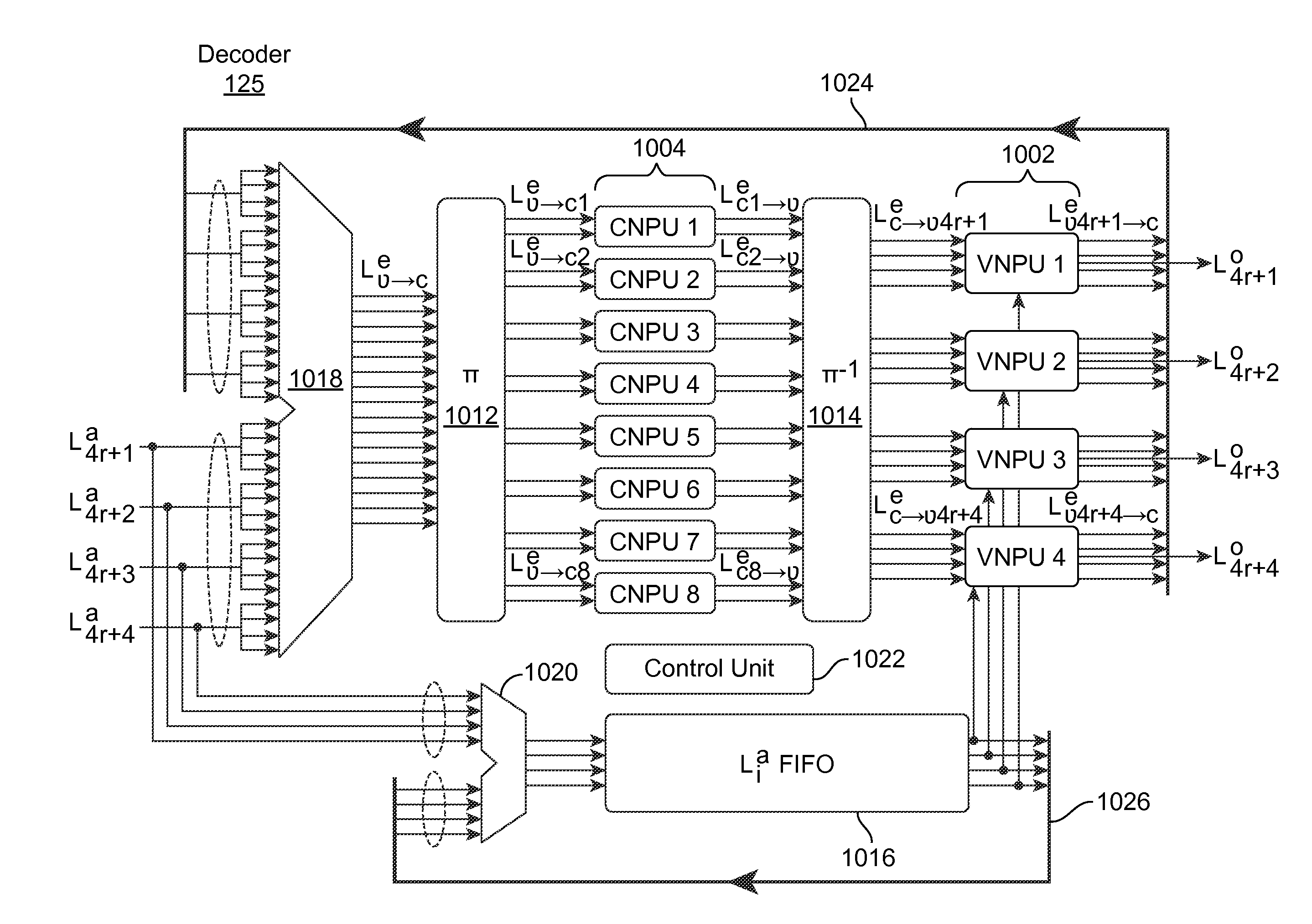
Method and system for generating parallel decodable low density parity check (LDPC) codes
ActiveUS20050005231A1Efficient memory architectureIncrease flexibilityError detection/prevention using signal quality detectorError correction/detection using multiple parity bitsLow-density parity-check codeLow density
An approach is provided for efficiently decoding low density parity check (LDPC) codes. An LDPC decoder includes a memory for storing a mapped matrix that satisfies a plurality of parallel decodable conditions for permitting a lumped memory structure. Additionally, the decoder includes a parallel processors accessing edge values from the stored mapped matrix decode the LDPC codes. The above approach has particular applicability to satellite broadcast systems.
Owner:DTVG LICENSING INC
Method for padding and puncturing low density parity check code
InactiveUS8006162B2Error correction/detection using multiple parity bitsCode conversionAlgorithmParity-check matrix
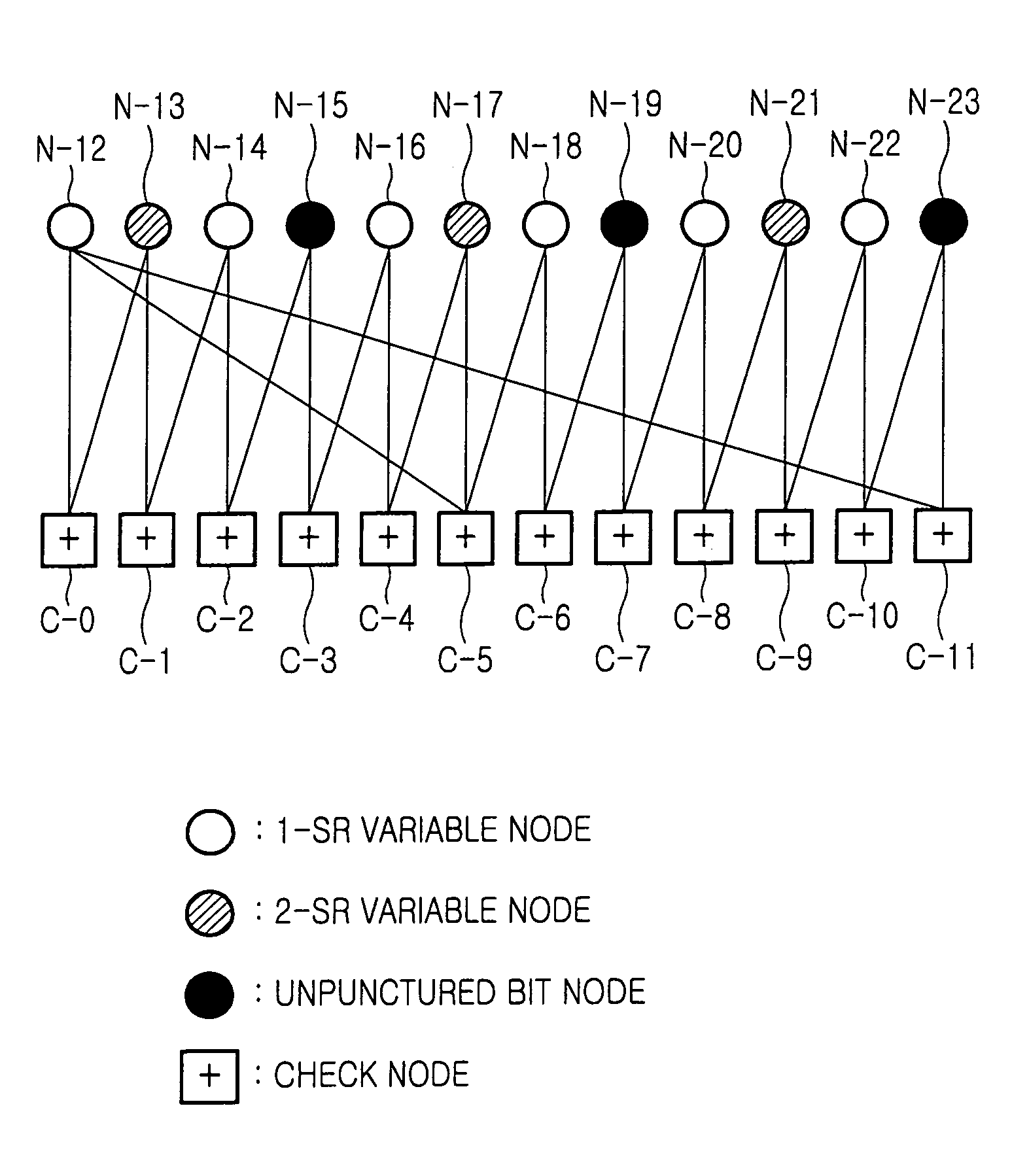
Disclosed is a method for puncturing a Low Density Parity Check (LDPC) code that is expressed by a factor graph having a check node and a variable node, connected to each other by an edge, and is decoded by a parity check matrix including a parity part having a single weight-3 column and a dual-diagonal matrix. The method includes selecting 1-step recoverable (1-SR) variable nodes with the highest quality including a variable node mapped to a weight-3 column, and setting a first puncturing priority group using the selected 1-SR variable nodes, selecting k-step recoverable (k-SR) variable nodes with the highest quality in the next step k taking into account the variable nodes selected in the current step, and setting a priority group for each individual step, puncturing an LDPC code mapped to a variable node belonging to a corresponding group according to priority of each group obtained in the preceding steps.
Owner:SAMSUNG ELECTRONICS CO LTD
A decoding method for block low-density check code and reconstruction of multi-mode decoder
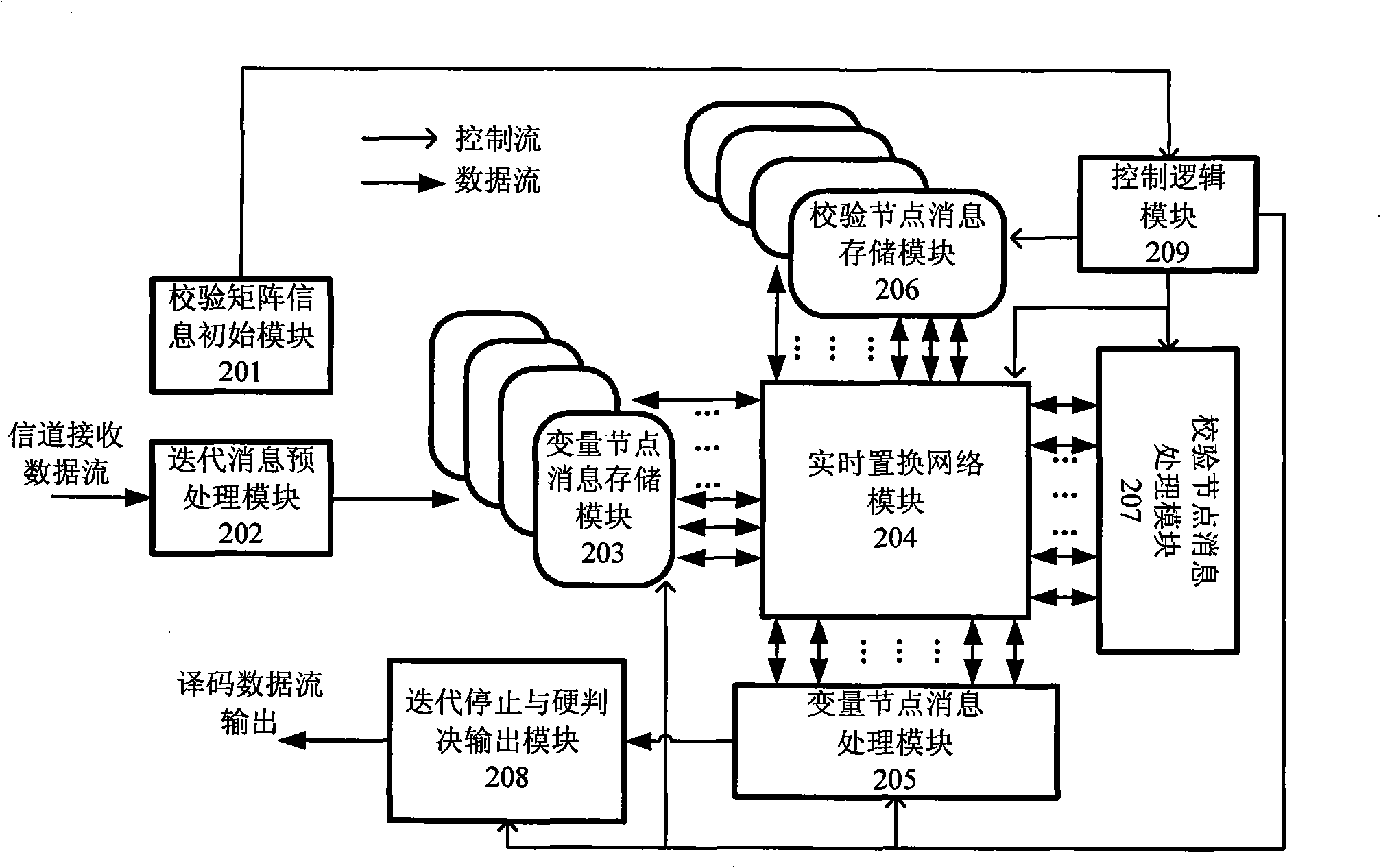
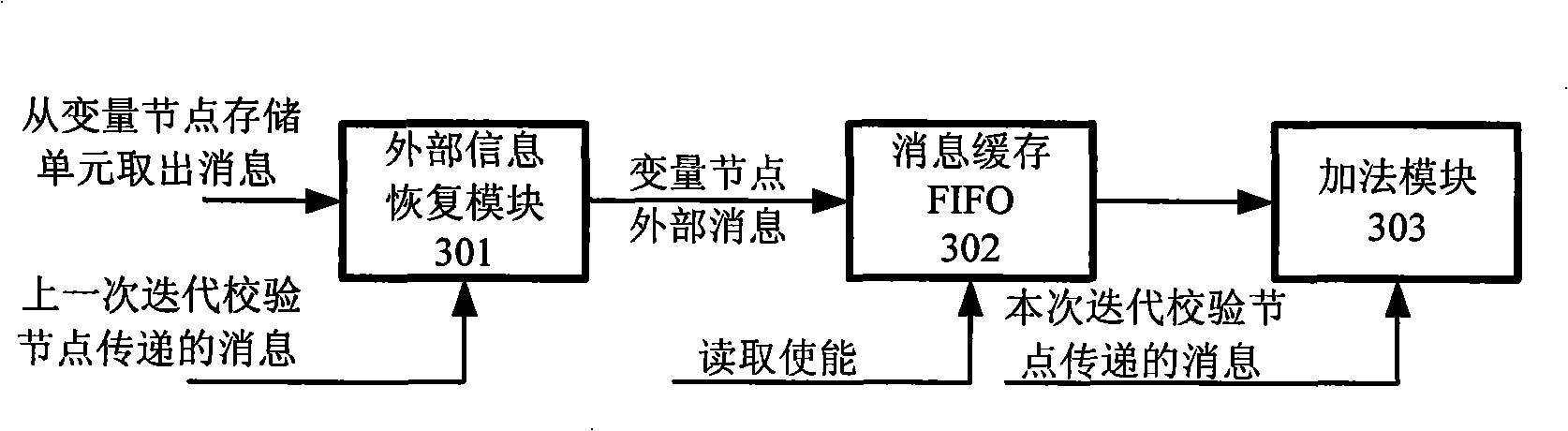
InactiveCN101262231AChange control outputSimple read and write access controlError preventionError correction/detection using multiple parity bitsResource utilizationLow complexity
The invention discloses a decoding method for a blocky check code with low density and a multi-mode reconfigurable decoder, and particularly relates to a decoding design based on the blocky check array of a unit cycle permutation array; the decoding method adopts partly collateral minimum and bias iterative compensation algorithm, and is characterized by low complexity and fast iterative convergence; the decoder has flexible configuration and high availability of resources, and the decoder is characterized in that: firstly, the decoder can support the blocky check array decoding with different code lengths under various code rates; secondly, the decoder can select and configure different messages to update concurrent factors according to the decoding delay and the throughput requirements; thirdly, node messages are stored in a distribution type, the write / read access control is easy, and the node messages are stored in a compression type, thereby effectively improving the utilitization of the stored resources; lastly, the iterative update adopts multi-level production line structure, thus fully improving the data throughput of the decoder. The method and the device of the invention have the advantages of stable performance, flexible configuration and good expansibility, etc.
Owner:ZHEJIANG UNIV
Method for encoding low-density parity check code
ActiveUS7458009B2Simplify the coding processImprove performanceError detection/correctionError correction/detection using multiple parity bitsAlgorithmDiagonal matrix
An apparatus and method for encoding low-density parity check (LDPC) codes. The method for generating a low-density parity check code formed of an information-part matrix and a parity-part matrix comprises the steps of converting the information-part matrix into an array code structure and assigning a degree sequence to each submatrix column; extending a dual-diagonal matrix corresponding to the parity-part matrix such that an offset value between diagonals has a random value; lifting the normalized dual-diagonal matrix; determining an offset value for cyclic column shift for each submatrix of the lifted normalized dual-diagonal matrix; and determining a parity symbol corresponding to a column of the parity-part matrix.
Owner:SAMSUNG ELECTRONICS CO LTD
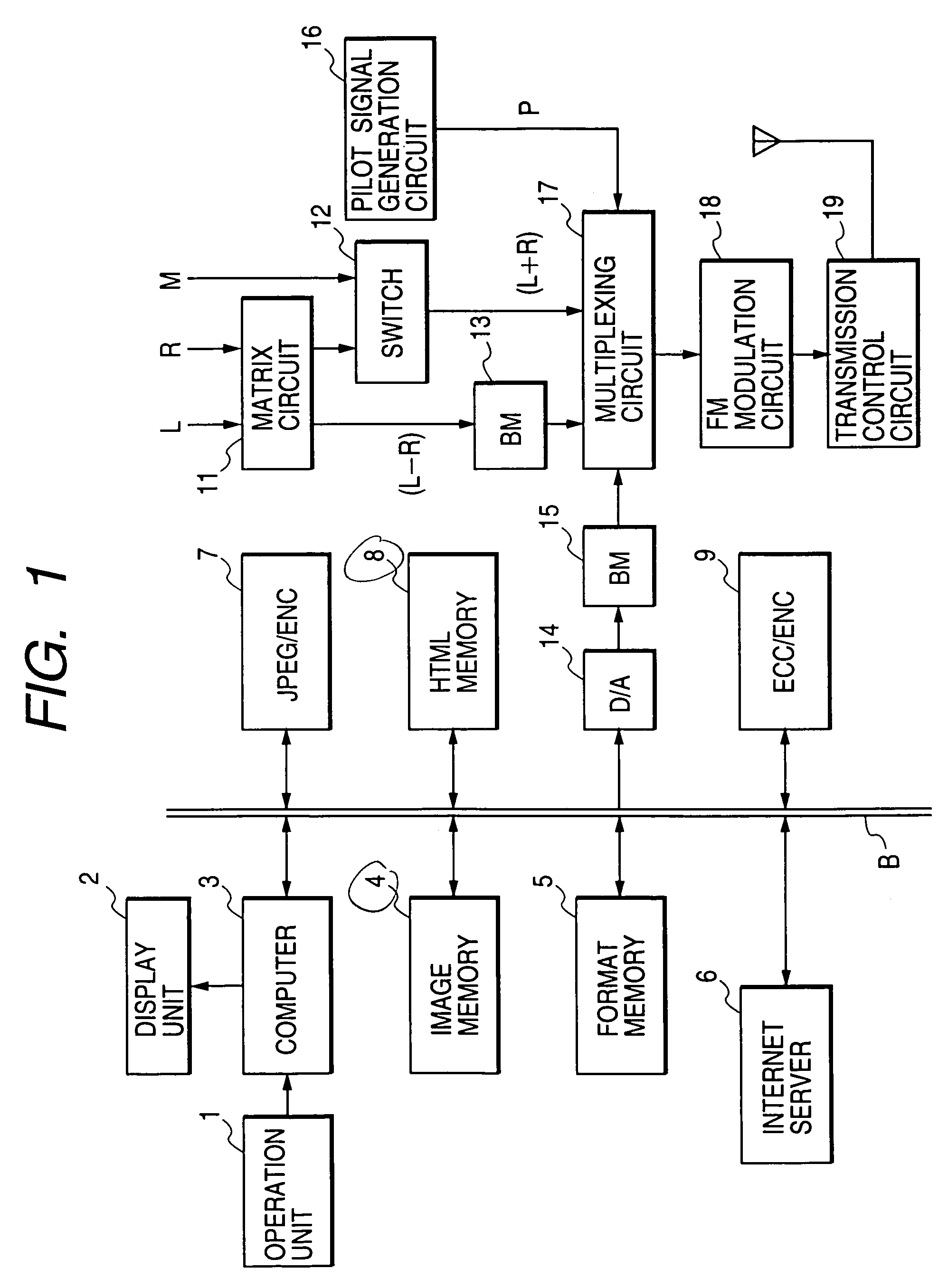
Information processing apparatus for and method of transmitting and/or receiving broadcast signal
InactiveUS6963589B1Improve reliabilityWithout requiring large-scale equipmentError preventionCode conversionInformation processingDescription format
An information processing apparatus / method employs error detection or correction to encode information to be distributed in a description format used in a multimedia network in which the error detection or correction encodes at least a portion in the header in the information to be distributed with higher redundancy than the entity in the information to be distributed. The encoded information to be distributed in a broadcast signal is multiplexed and transmitted. Alternatively, the information processing apparatus / method may involve: transmitting a portion of the header in the information to be distributed at least a plurality of number of times while the entity in the information to be distributed is transmitted; and / or transmitting a plurality of kinds of information as an entity in the information to be distributed, and using different error detection or correction ability in correspondence with the kind of information. The information processing apparatus / method may also involve inputting information data, and a check code for correcting an error of the information data, detecting the error state of the information data, setting an allowable error state of the information data, and controlling processing for the input information data in accordance with results in the setting step and the detection step.
Owner:CANON KK
Data transmission method and apparatus using multiple scrambling codes
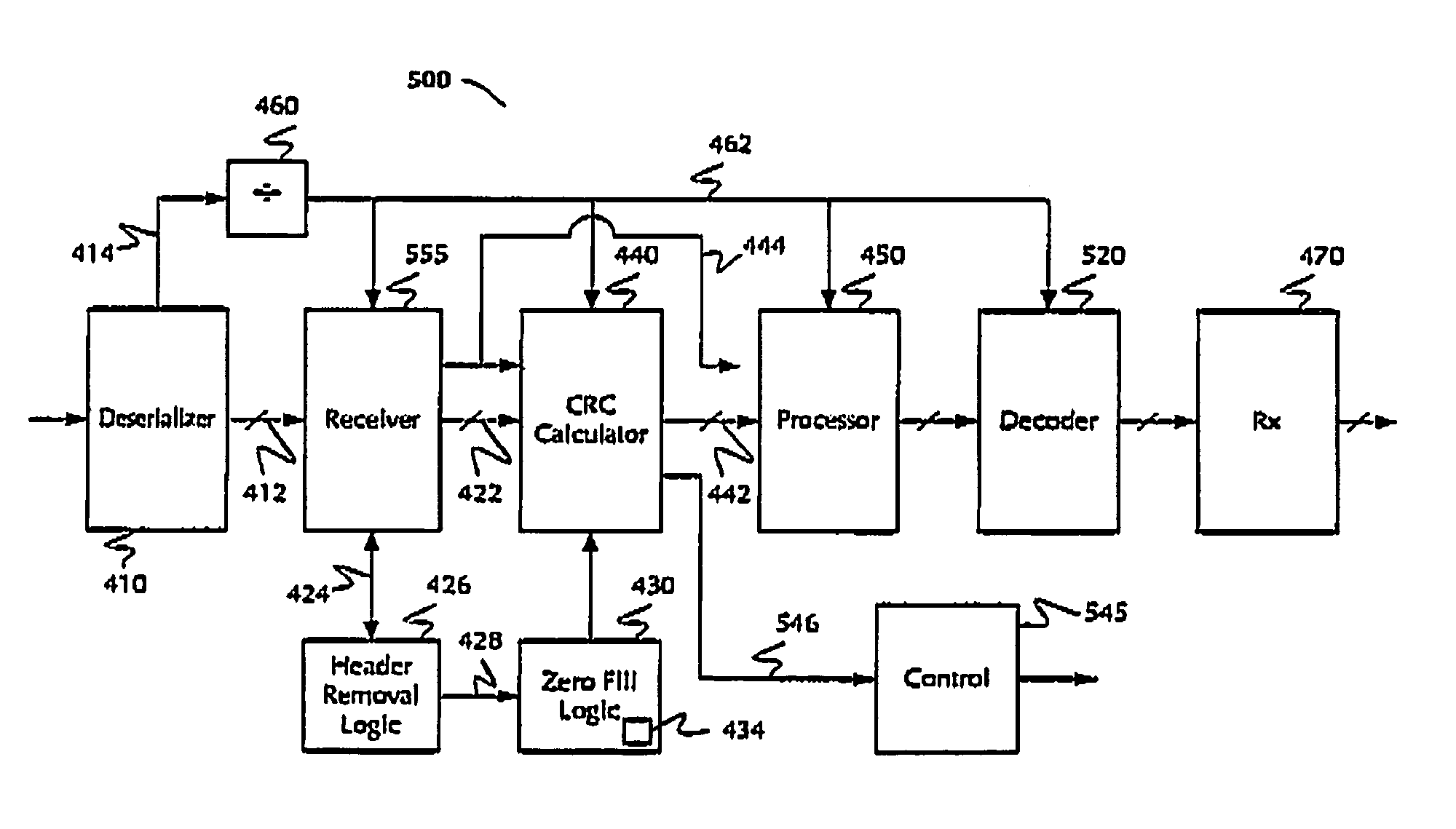
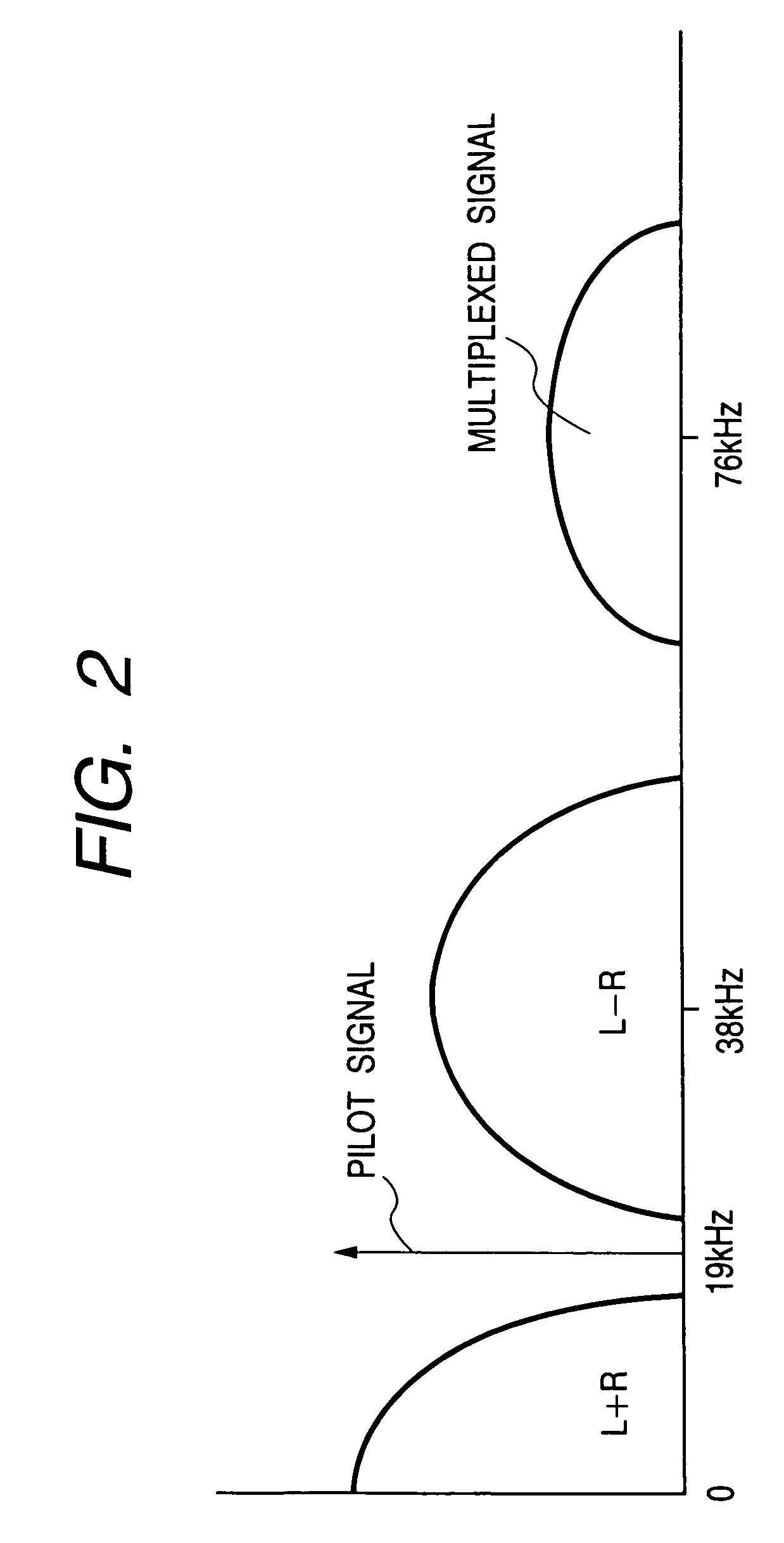
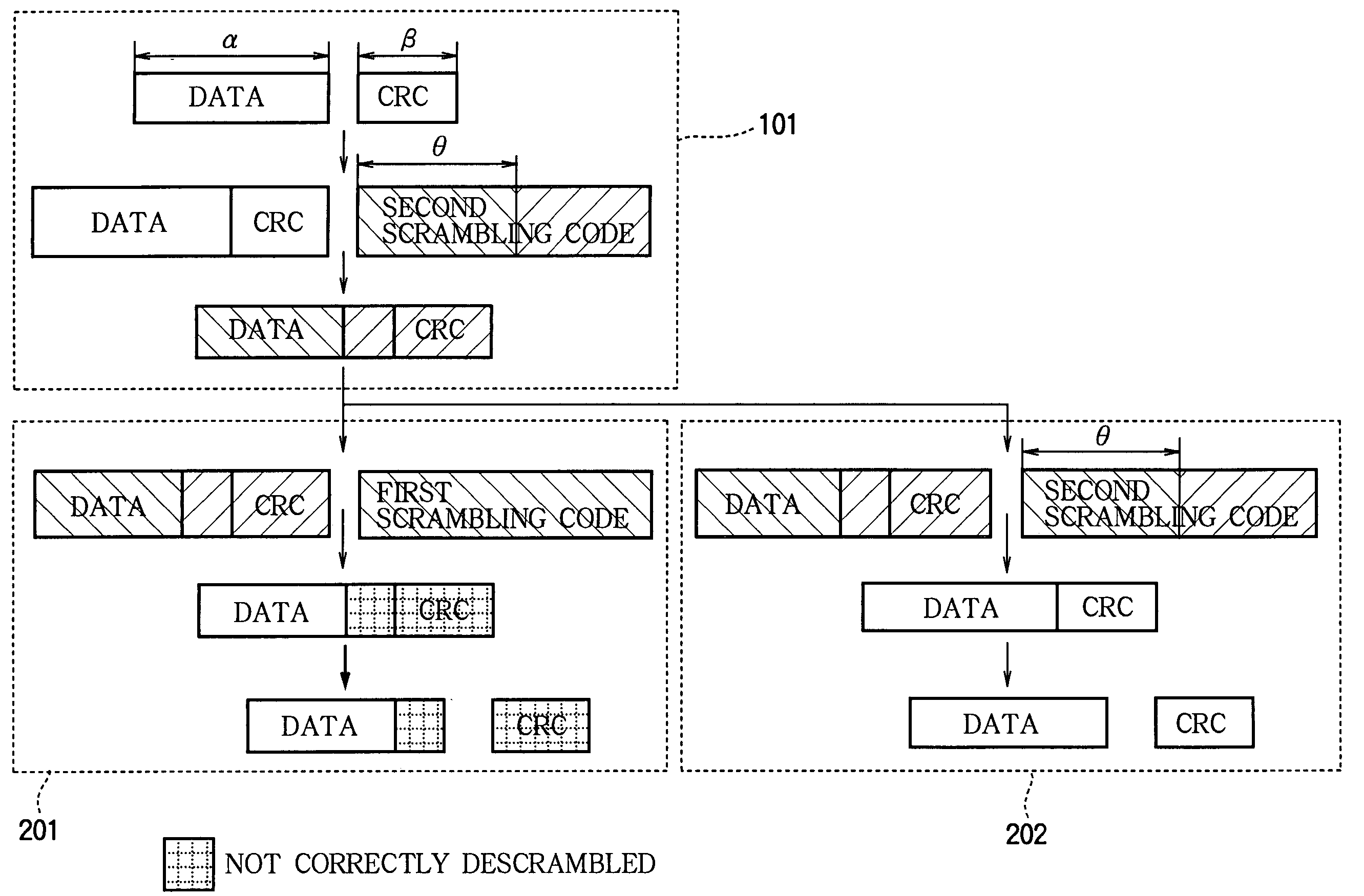
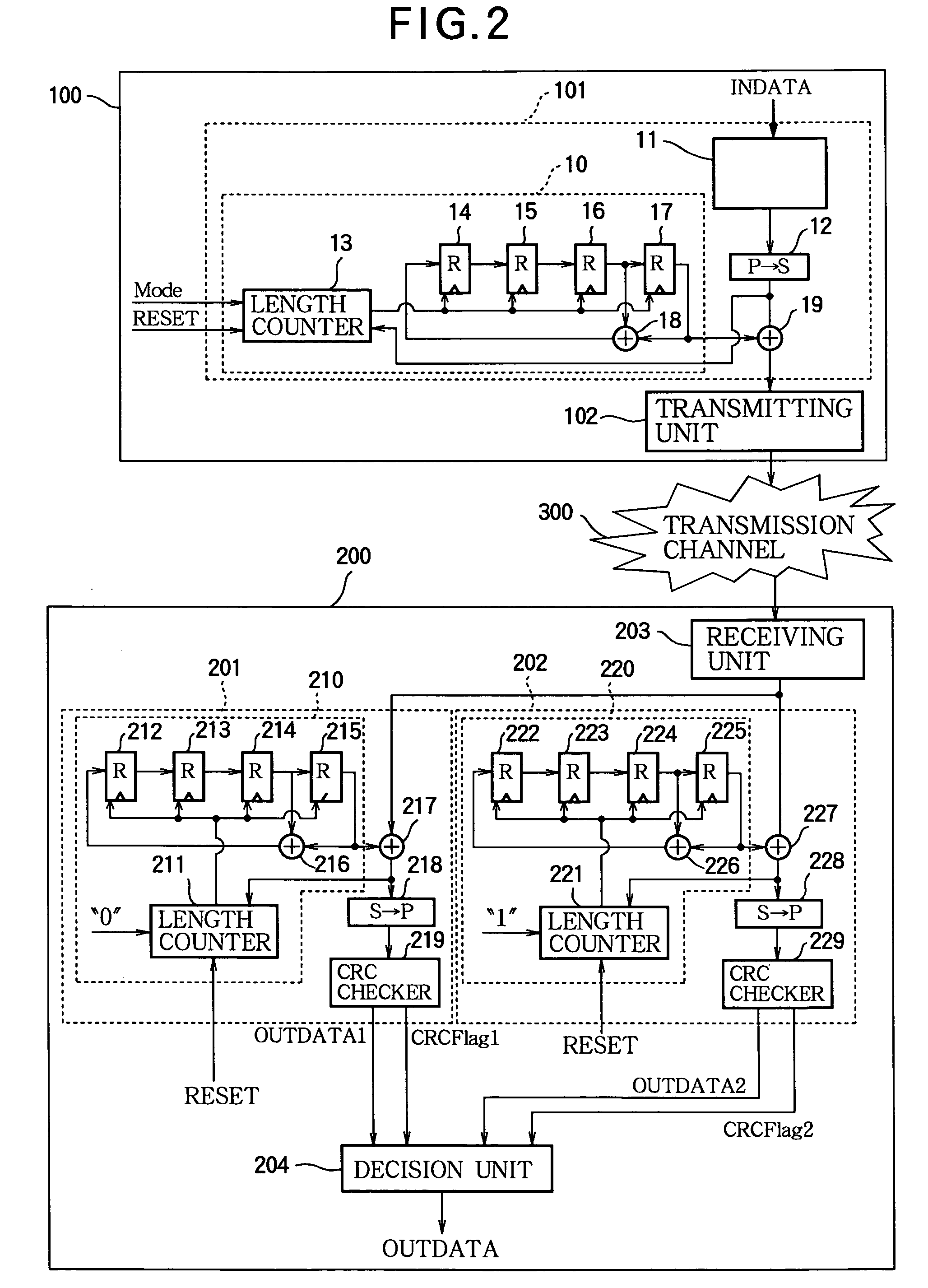
InactiveUS20060067531A1Easy to useIncrease overheadError preventionData stream serial/continuous modificationData packCheck digit
A packet including data and a cyclic redundancy check code is encoded by using a selectable one of N scrambling codes (N>1). The encoded packet is transmitted and received, then decoded N times by using the N scrambling codes. The cyclic redundancy check code is used to decide which one of the N scrambling codes enabled the encoded packet to be decoded correctly, and the correctly decoded data are used. Packets with different formats, in particular with headers of different lengths, can be distinguished by the use of different scrambling codes, so that different formats can be employed without the need to transmit extra data to indicate which format has been used.
Owner:LAPIS SEMICON CO LTD
Ultrahigh-speed and low-power-consumption QC-LDPC code decoder based on TDMP
InactiveCN101771421AReduce visitsAvoid access violationsError correction/detection using multiple parity bitsComputer architectureParallel computing
The invention belongs to the technical field of wireless communication and micro-electronics, in particular to an ultrahigh-speed low-power-consumption and low-density parity check code (QC-LDPC) decoder based on TDMP. Through symmetrizing six grades of production lines, interlacing row blocks and line blocks, re-sequencing nonzero sub matrixes, carrying out four-quadrant division on a sum value register pile and adopting the technology of reading and writing the bypass, the decoder carries out serial scanning in the row sequence, two nonzero sub matrixes are respectively processed in each clock period during horizontal updating and vertical updating. The horizontal updating and the vertical updating are fully overlapped. Particularly, the sum value register pile stores the sum values of variable nodes, and is also used as an FIFO for storing transient external information transferred between two phases. The structure of the decoder has strong configurability, can be easily transplanted into any other irregular or irregular QC-LDPC codes, and has the excellent decoding performance, the peak frequency can reach 214 MHz, the thuoughput can reach about 1 gigabit per second, and the chip power consumption is only 397 milliwatts.
Owner:FUDAN UNIV
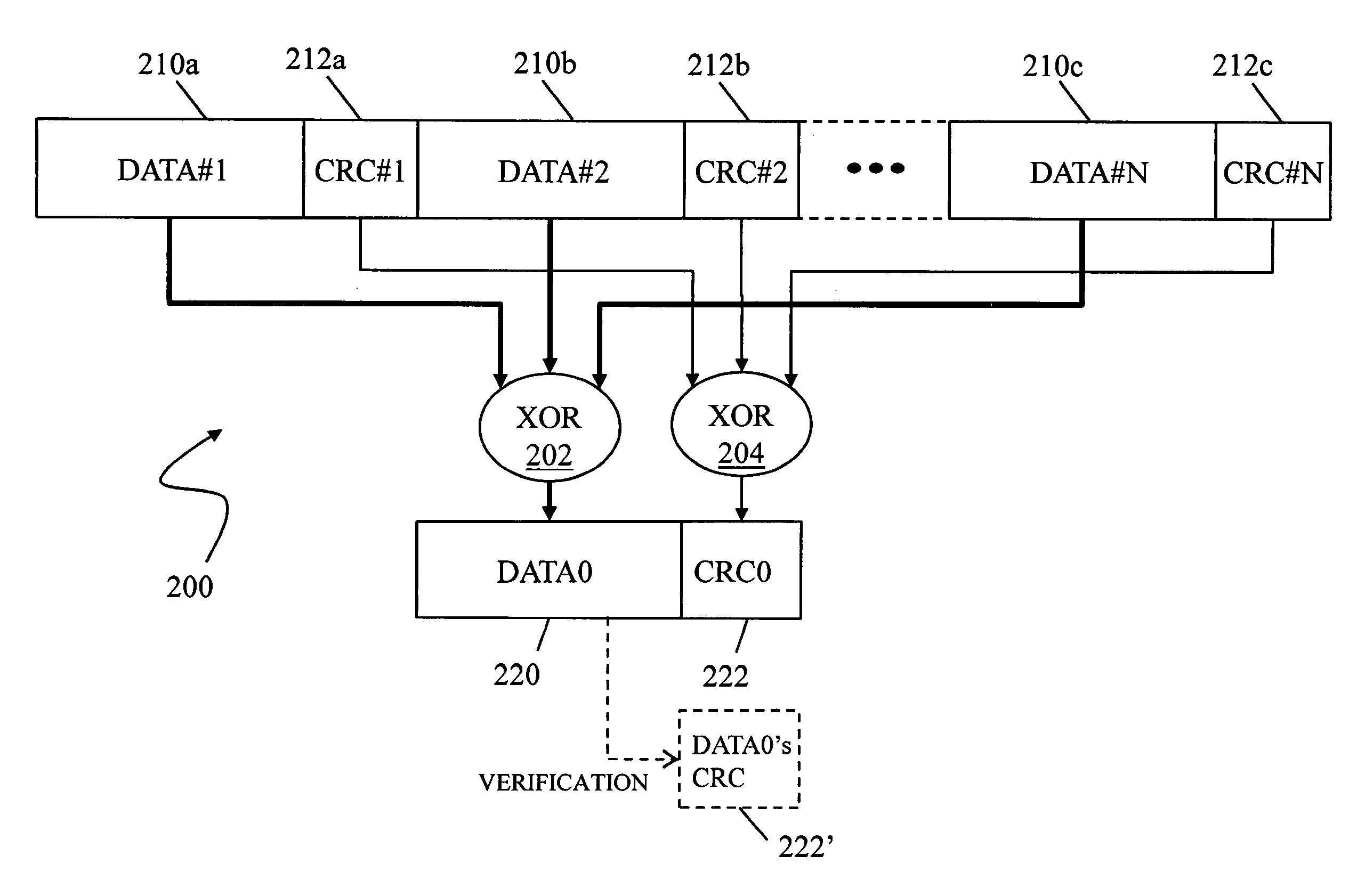
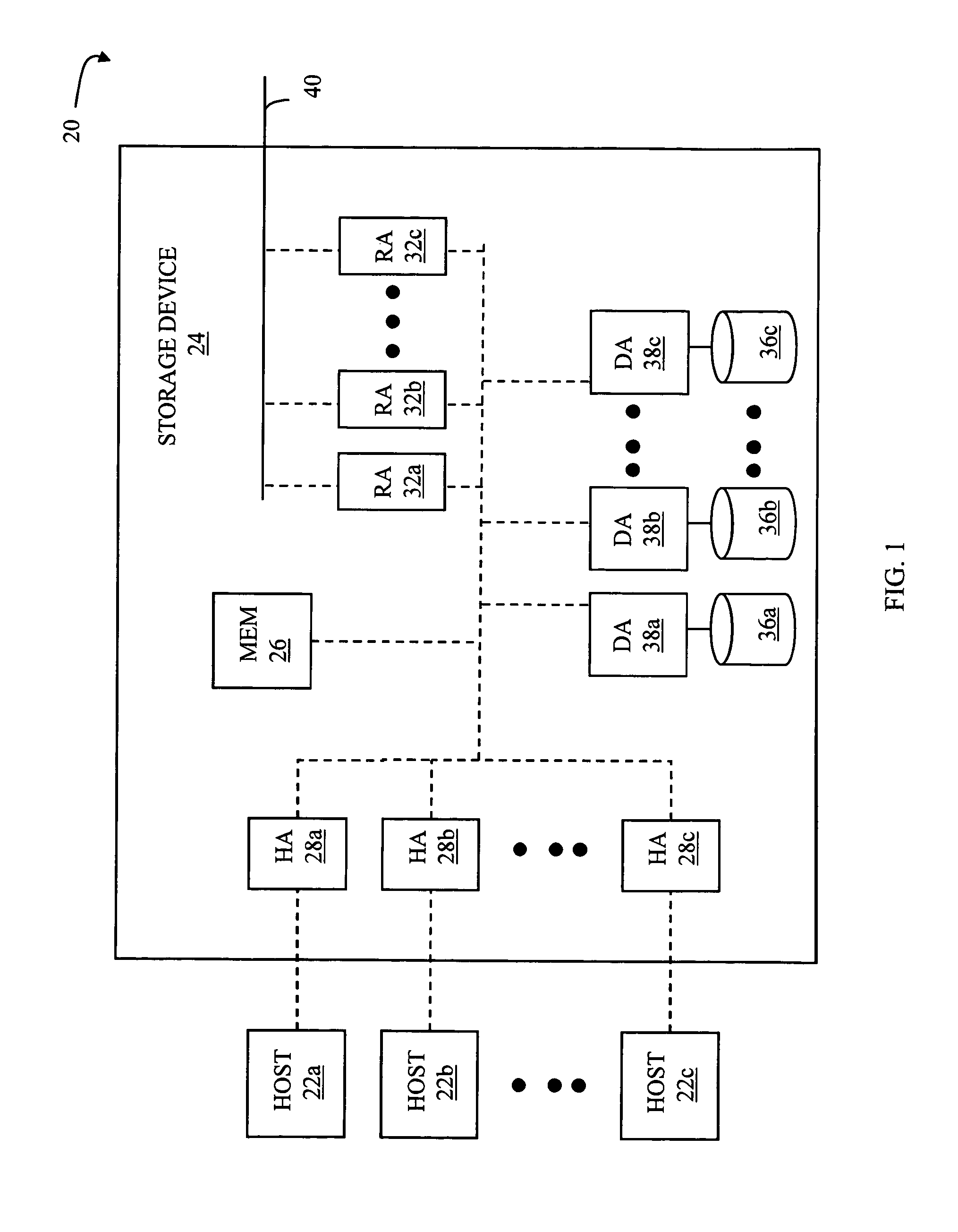
Fast verification of data block cycle redundancy checks
Detecting data errors in connection with a data transfer process includes performing an XOR operation on a plurality of data blocks to obtain a data block XOR result. An XOR operation may be performed on a plurality of cyclic redundancy check (CRC) codes associated with the plurality of data blocks to obtain a CRC XOR result. The data block XOR result and the CRC XOR result may be used to determine whether an error exists in the plurality of data blocks. The system may be used in connection with local IO transfers and in connection with local CPU XOR operations for a RAID system in which data may be mirrored, striped or otherwise distributed across multiple storage devices.
Owner:EMC IP HLDG CO LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com