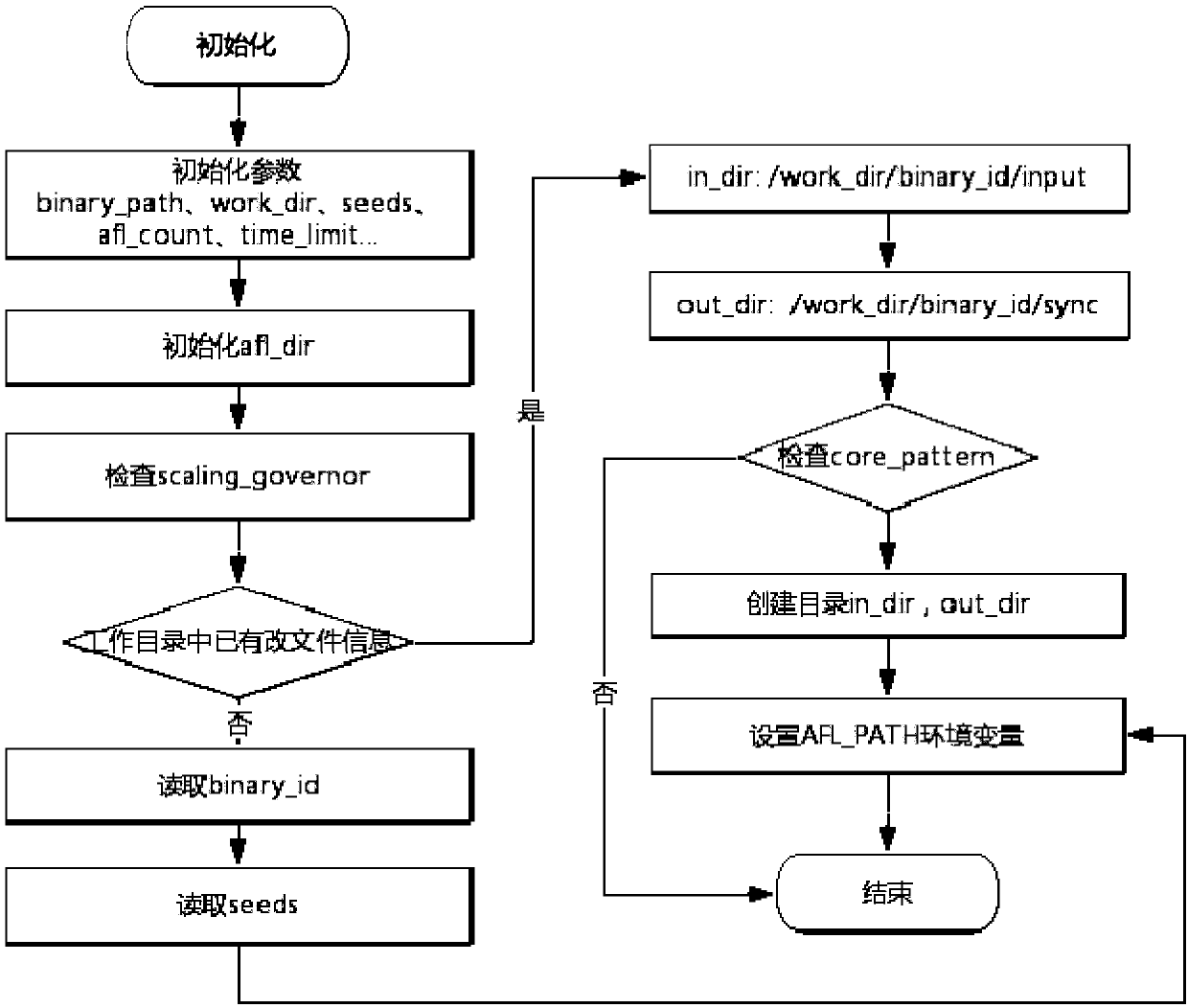
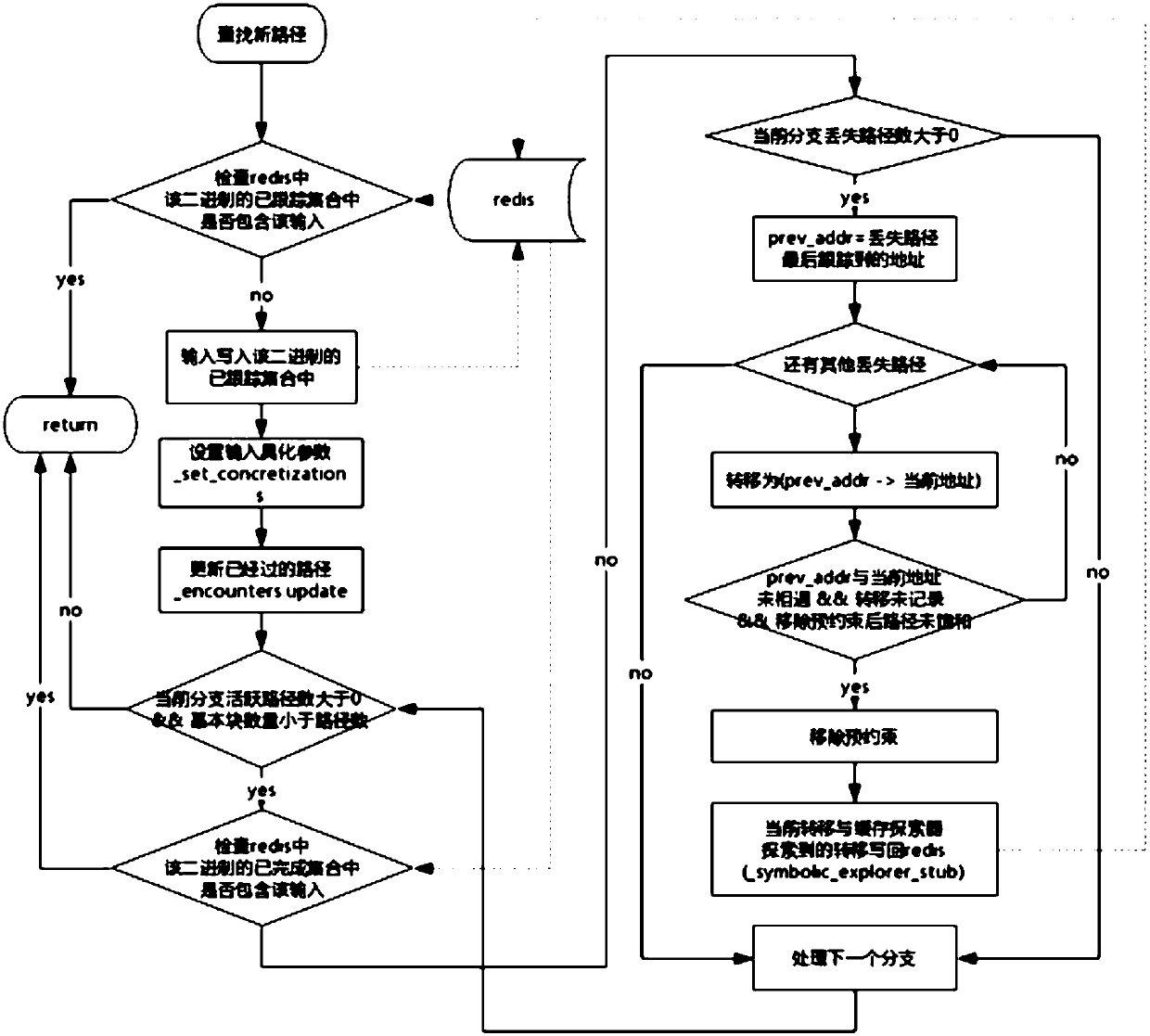
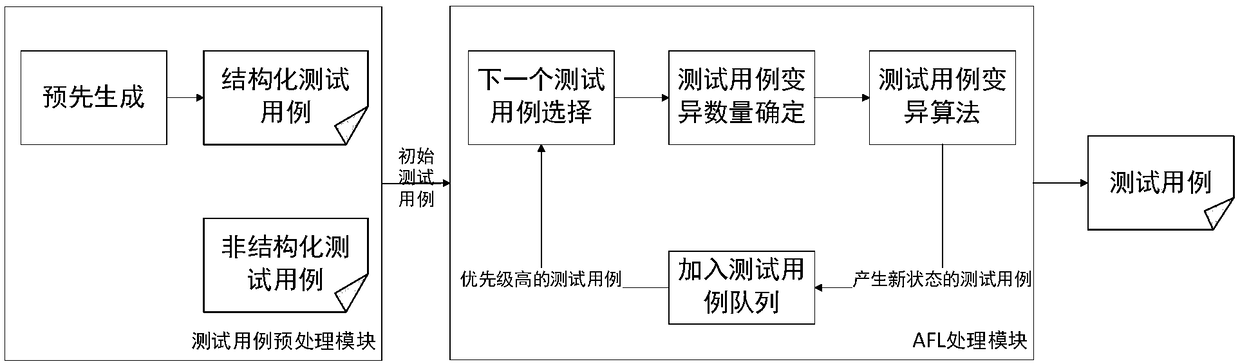
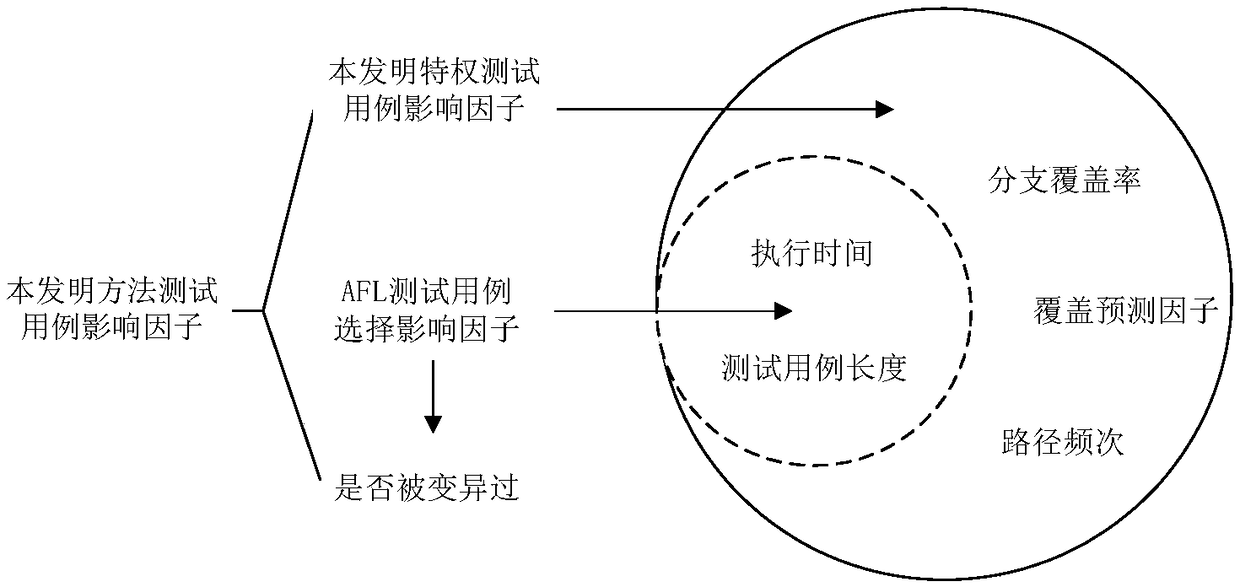
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
297 results about "Fuzz testing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
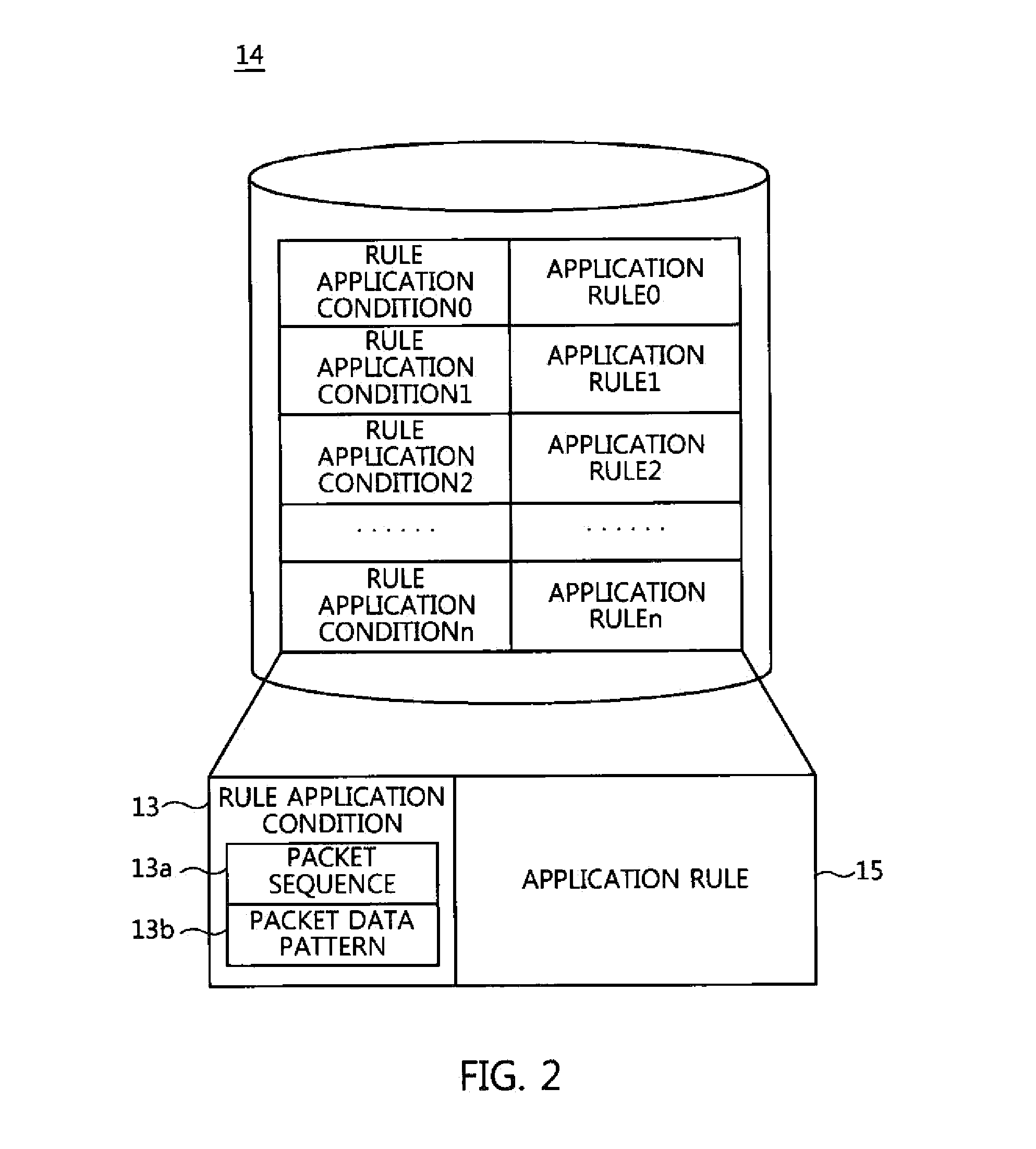
Patent Status
Application Year
Inventor
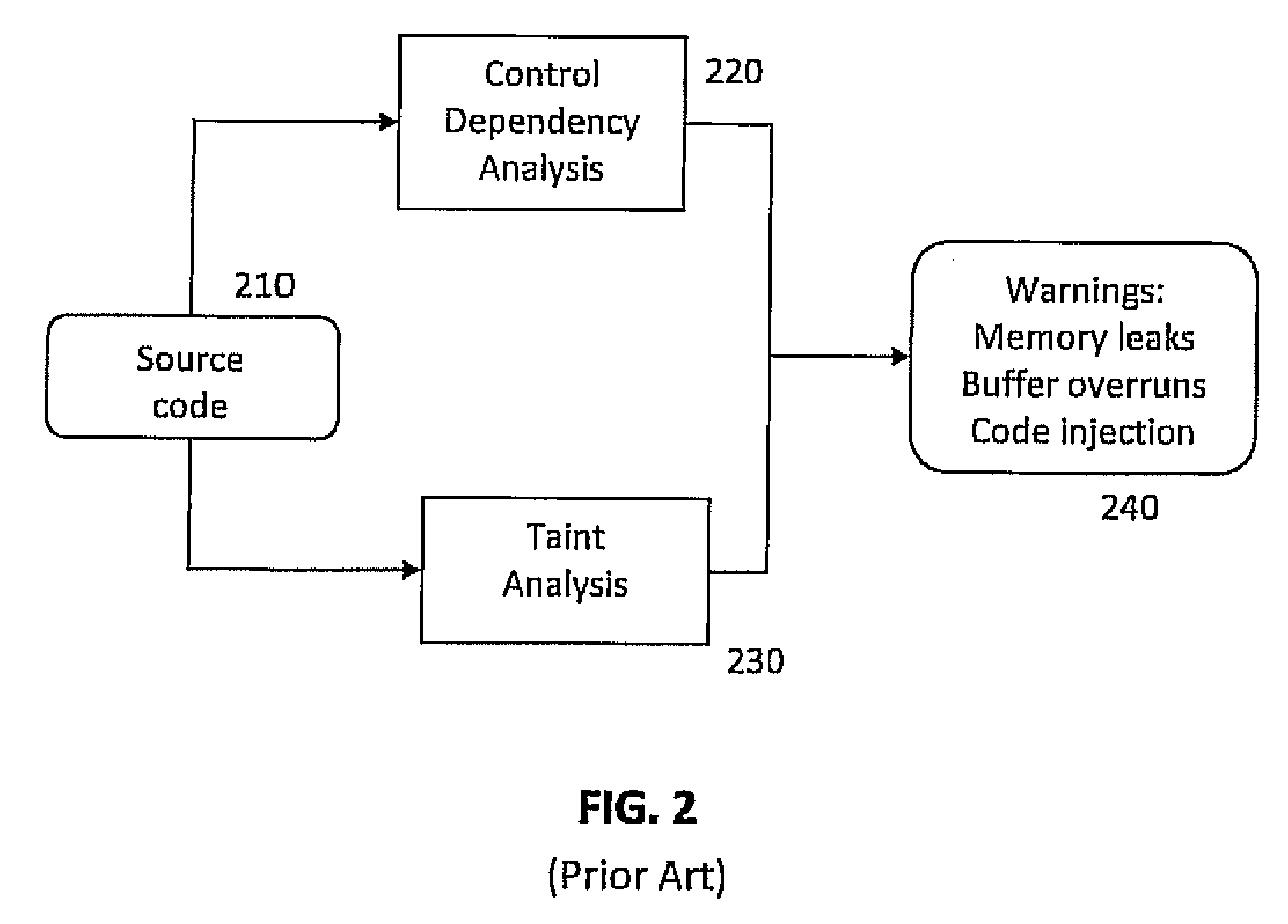
Fuzzing or fuzz testing is an automated software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer program. The program is then monitored for exceptions such as crashes, failing built-in code assertions, or potential memory leaks. Typically, fuzzers are used to test programs that take structured inputs. This structure is specified, e.g., in a file format or protocol and distinguishes valid from invalid input. An effective fuzzer generates semi-valid inputs that are "valid enough" in that they are not directly rejected by the parser, but do create unexpected behaviors deeper in the program and are "invalid enough" to expose corner cases that have not been properly dealt with.
Feedback-guided fuzz testing for learning inputs of coma
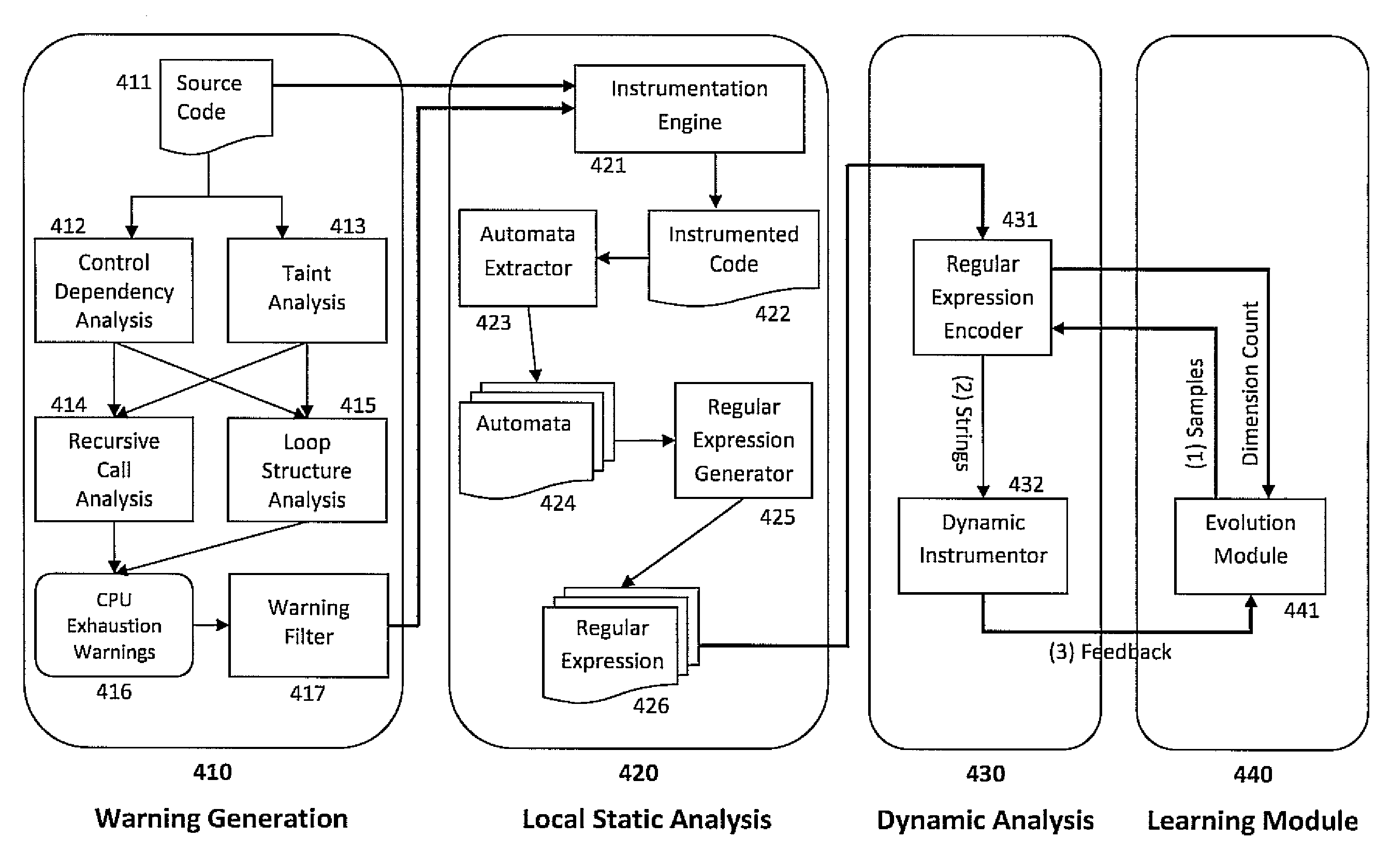
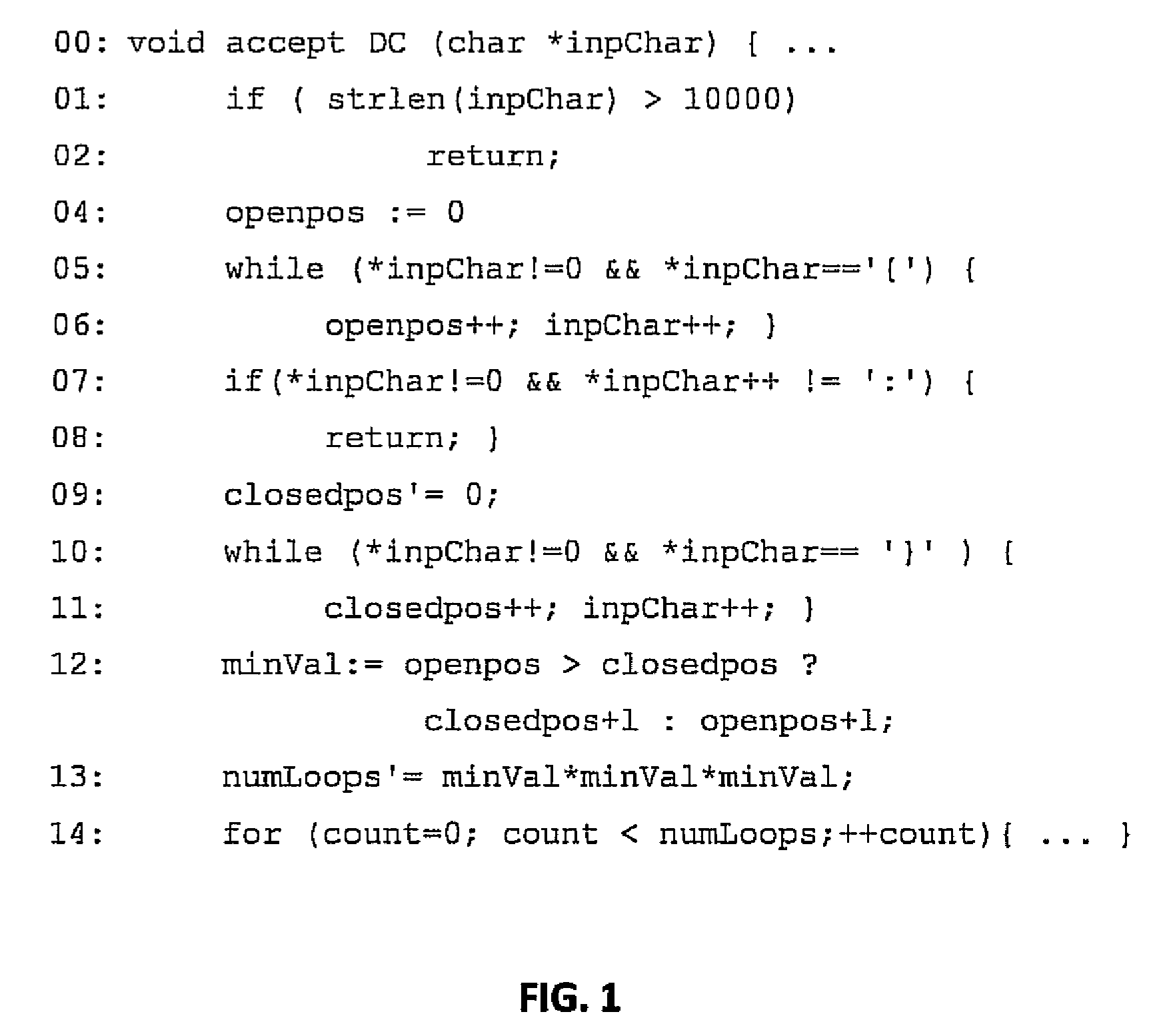
InactiveUS20100058475A1Maximize feedback scoreProcess safetyMemory loss protectionError detection/correctionUser inputCode segment
Embodiments of the present invention combine static analysis, source code instrumentation and feedback-guided fuzz testing to automatically detect resource exhaustion denial of service attacks in software and generate inputs of coma for vulnerable code segments. The static analysis of the code highlights portions that are potentially vulnerable, such as loops and recursions whose exit conditions are dependent on user input. The code segments are dynamically instrumented to provide a feedback value at the end of each execution. Evolutionary techniques are then employed to search among the possible inputs to find inputs that maximize the feedback score.
Owner:NEC LAB AMERICA
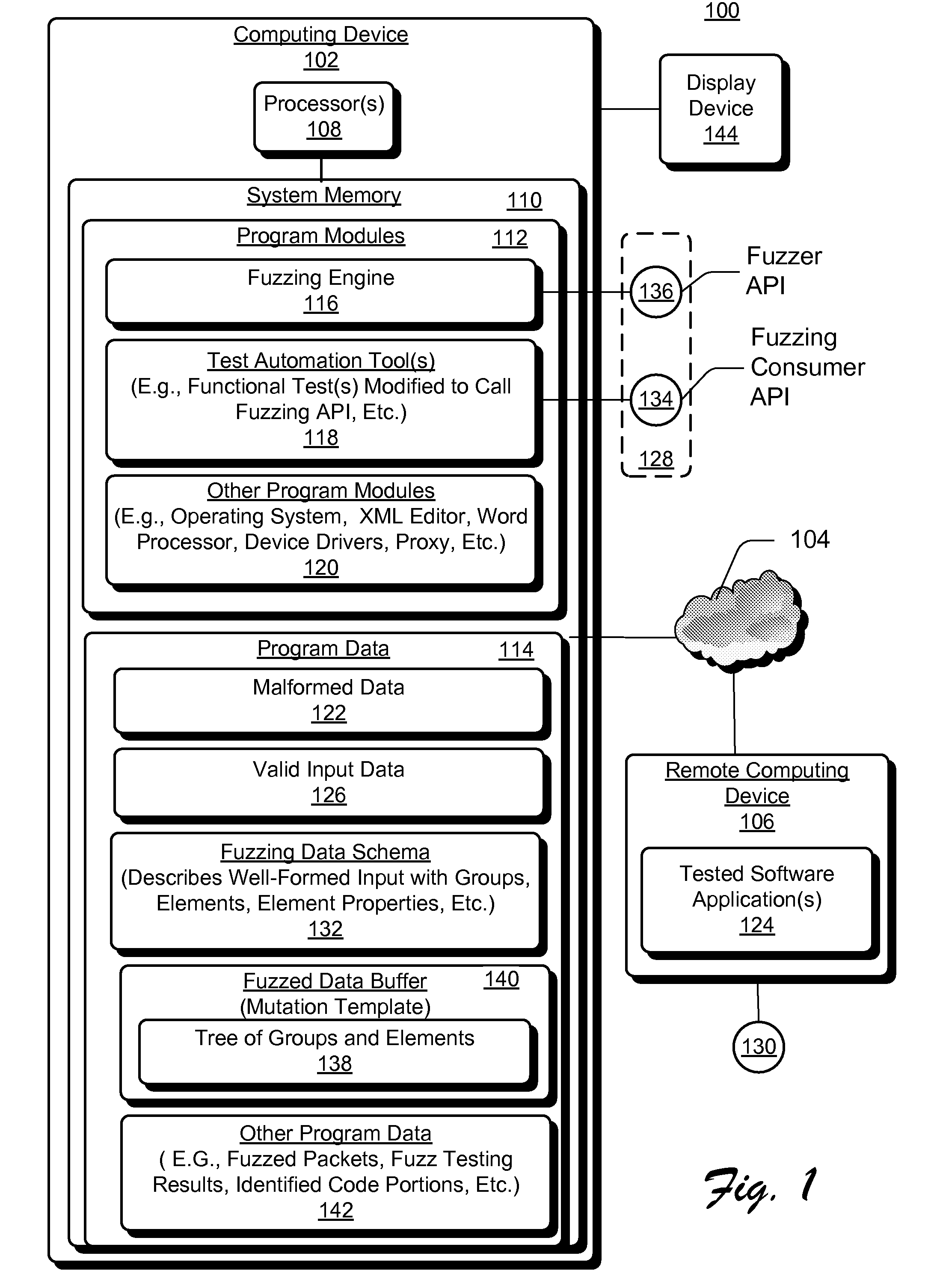
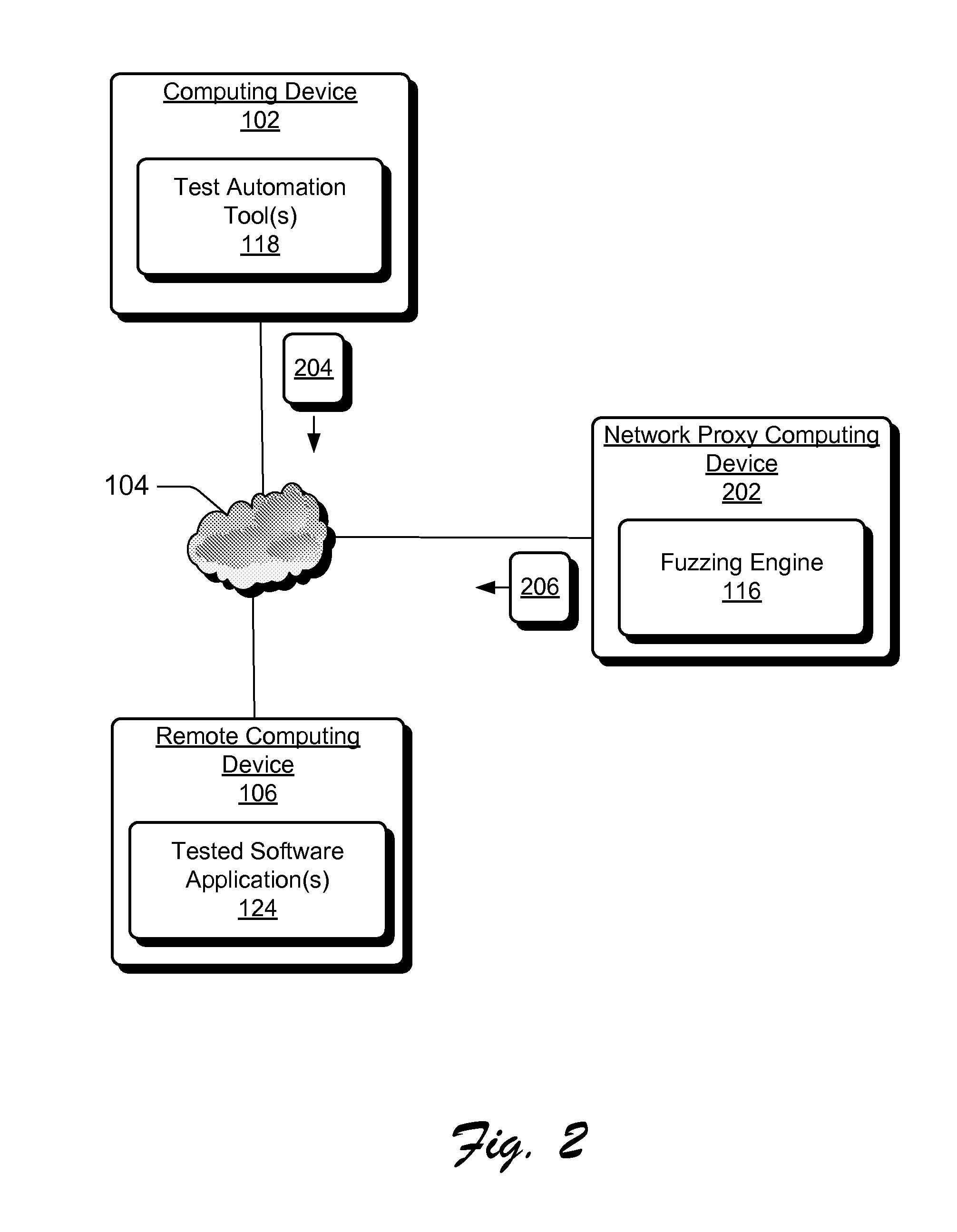
Delivering Malformed Data for Fuzz Testing to Software Applications
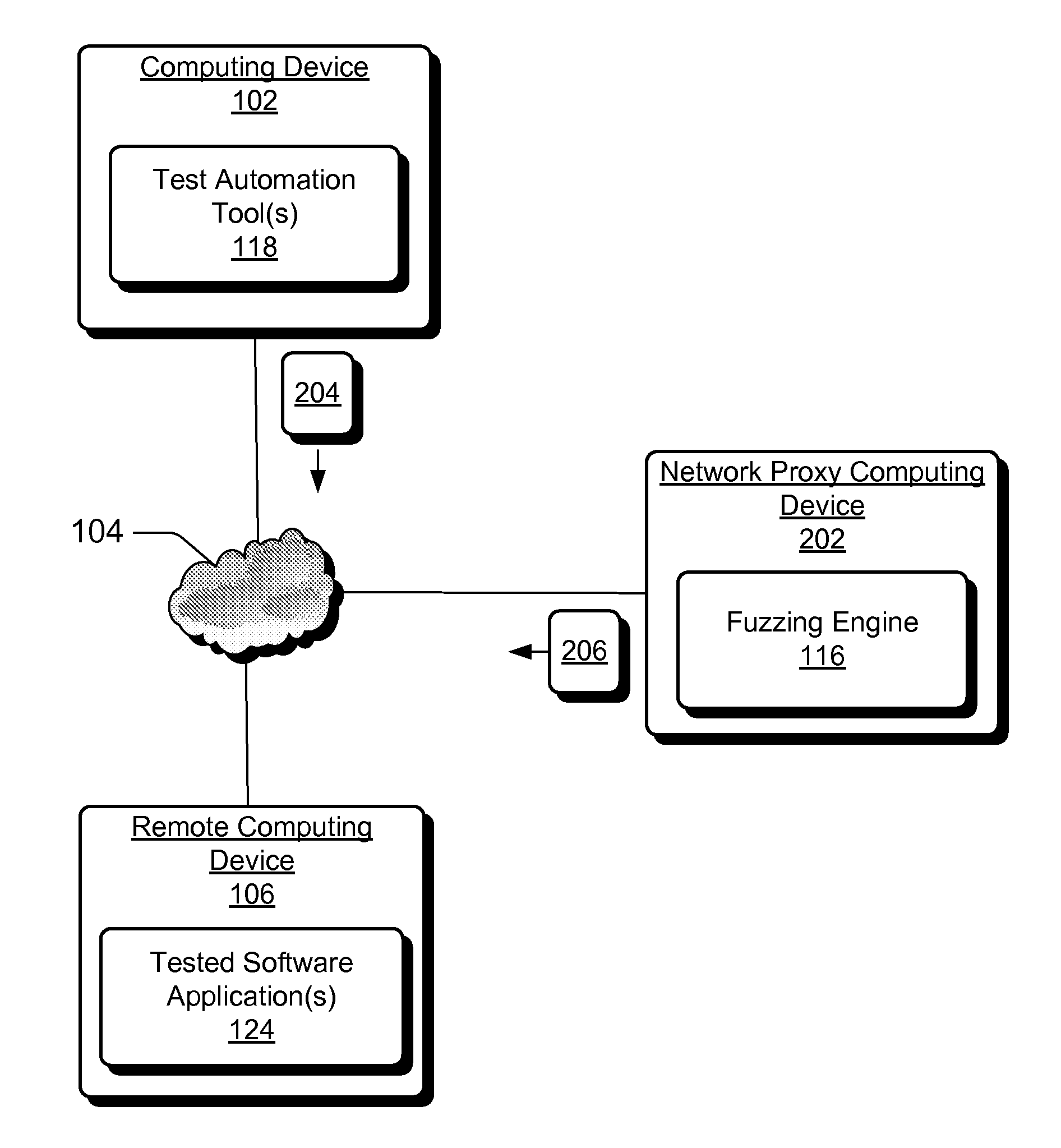
ActiveUS20080301647A1Well formedMemory loss protectionUnauthorized memory use protectionPathPingFunctional testing
Systems and methods to deliver malformed data for software application fuzzing are described. In one aspect, a fuzzing engine receives well-formed valid input data from a test automation tool. The received data is for input into a software application to implement a functional test. Responsive to receiving the well-formed valid input data, the fuzzing engine automatically generates corresponding malformed data based on characteristics of the well-formed valid input data. The application is then automatically fuzzed with the malformed data to notify an end-user of any security vulnerabilities in one or more code paths of the application used to process the malformed data.
Owner:MICROSOFT TECH LICENSING LLC
Fuzz testing method based on static detection
InactiveCN104573524AImprove efficiencyExclude false positivesPlatform integrity maintainanceSource codeFalse alarm
The invention belongs to the technical field of network security, and relates to a fuzz testing method based on static detection. The method comprises source code static analysis and executable code fuzz testing. According to the method, firstly, target software is subjected to static analysis through source code static analysis related software, and fuzz testing is carried out to obtain a static analysis result, then, code segments considered to have problems through the static analysis are subjected to pile inserting marking, and finally, testing cases are subjected to variation on the basis of the pile inserting marking, so that the testing cases can cover all code segments with problems. The fuzz testing method has the advantages that the advantages of the static detection and the fuzz testing are combined, the static detection is verified through the fuzz testing, and the false alarm condition of the static detection is excluded; on the other hand, the fuzz testing is guided by the static detection result, so that random testing cases used by the fuzz testing have a higher pertinence, and the fuzz testing efficiency is improved. The defects of high false alarm rate, low detection efficiency and the like of the traditional method adopting the random testing cases for testing are overcome.
Owner:706 INST SECOND RES INST OF CHINAAEROSPACE SCI & IND
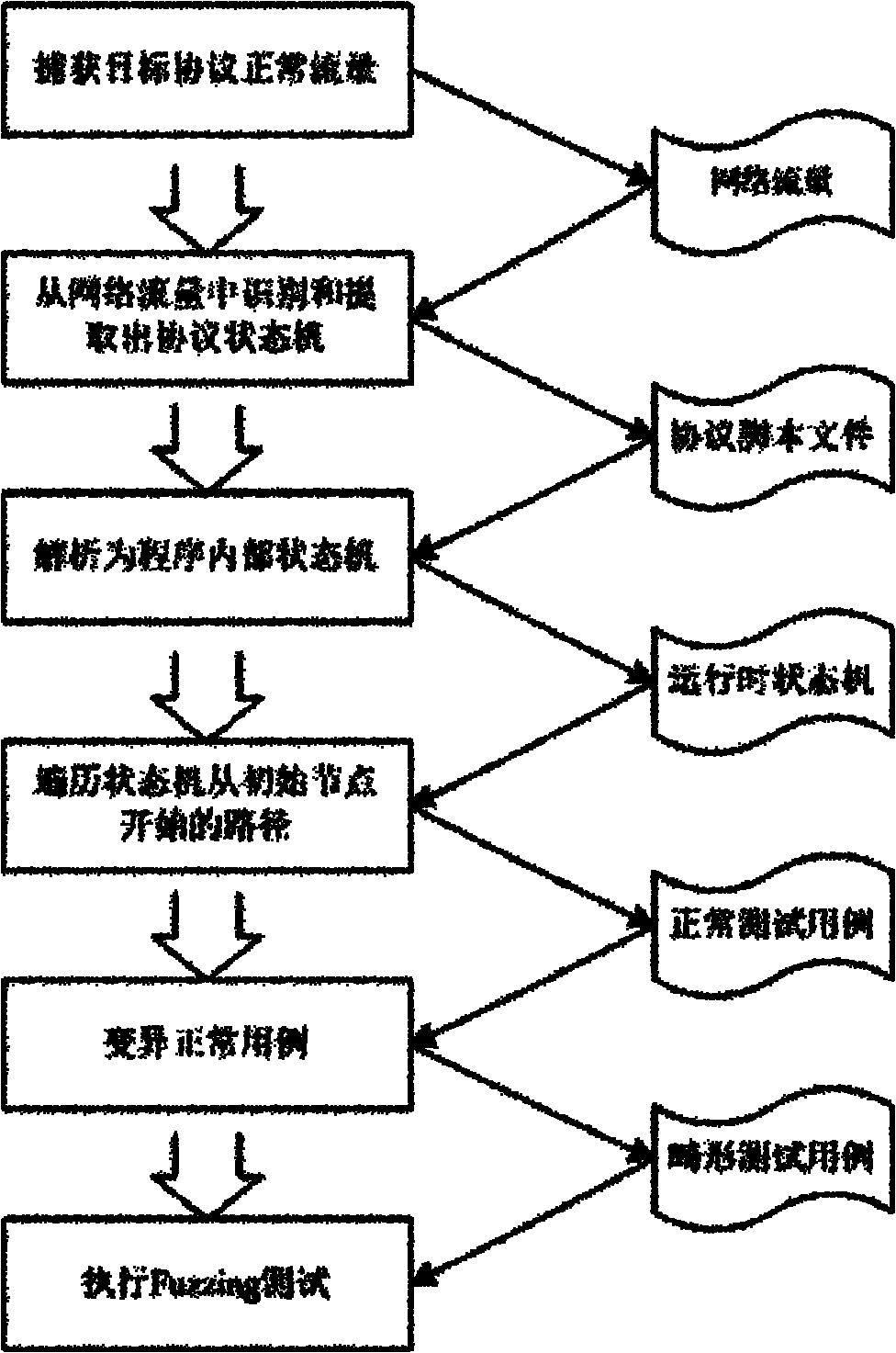
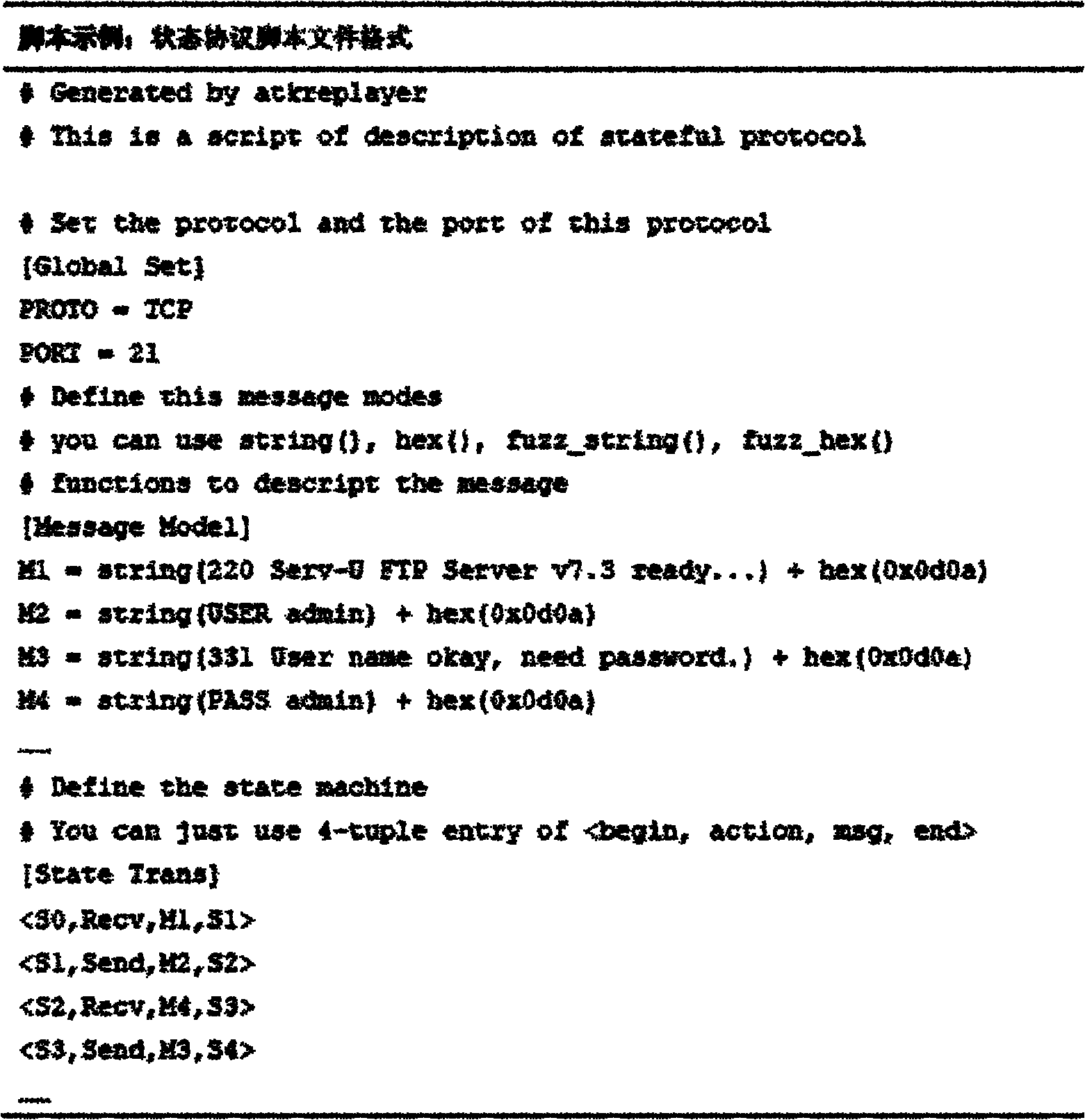
Method for realizing fuzzing of software on the basis of state protocol
InactiveCN102087631AAchieve technical effectImprove test coverageComputer security arrangementsSoftware testing/debuggingComputer hardwareTraffic capacity
The invention discloses a method for realizing fuzzing of software on the basis of a state protocol. The method comprises the following steps of: 1) acquiring a target state protocol to realize the normal interactive traffic of the software; 2) identifying and extracting a protocol interactive message and a message exchange process from the traffic to finally generate a protocol script file with a certain format; 3) traversing a target program protocol state machine to generate a normal test case ready for mutation; and 4) mutating the normal test case into an abnormal test case, and executing the fuzzing. The method can significantly improve the test coverage rate of the software on the basis of the state protocol by identifying the message and the interactive process of target program normal communication, establishing a state protocol state machine script, and traversing the protocol state machine to generate the test case.
Owner:NAT UNIV OF DEFENSE TECH
Method and device for producing test case
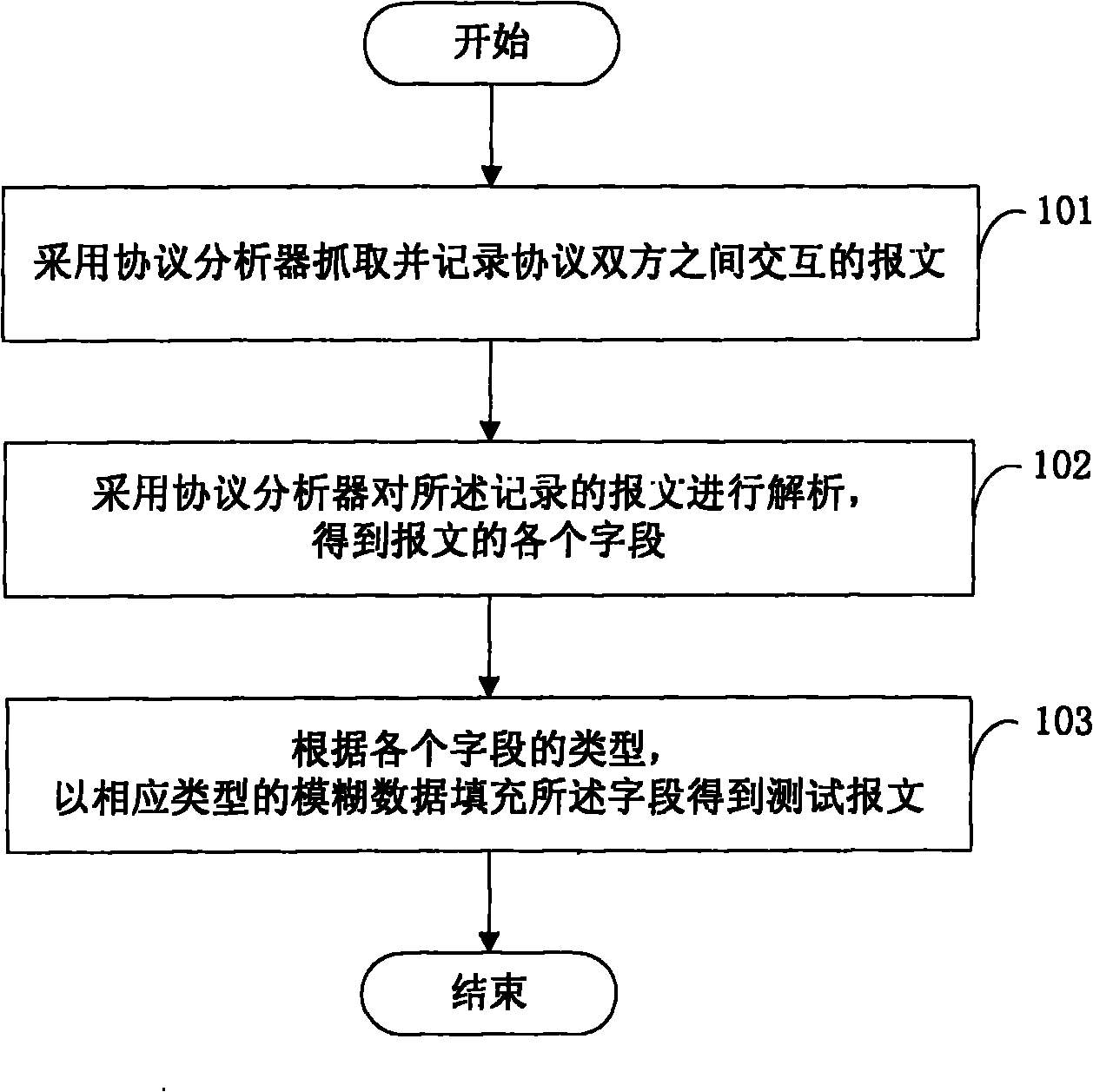
InactiveCN101902367AImprove effectivenessSave time and costData switching networksComputer hardwareComputer science
The invention discloses a method for producing a test case, which is used for performing fuzz testing on protocols and comprises the following steps: grabbing and recording interactive messages between both sides of a protocol by a protocol analyzer; analyzing the recorded messages by the protocol analyzer to obtain each field of the messages; and filling each field by fuzzy data with corresponding types to obtain test messages according to the type of each field. The invention also discloses a system for producing a test case. By the invention, a complete and effective test case can be produced in no need of understanding the relative knowledge of protocol specifications so as to completely and effectively evaluate the safety of a protocol product.
Owner:SIEMENS CHINA
Detection method for software vulnerability
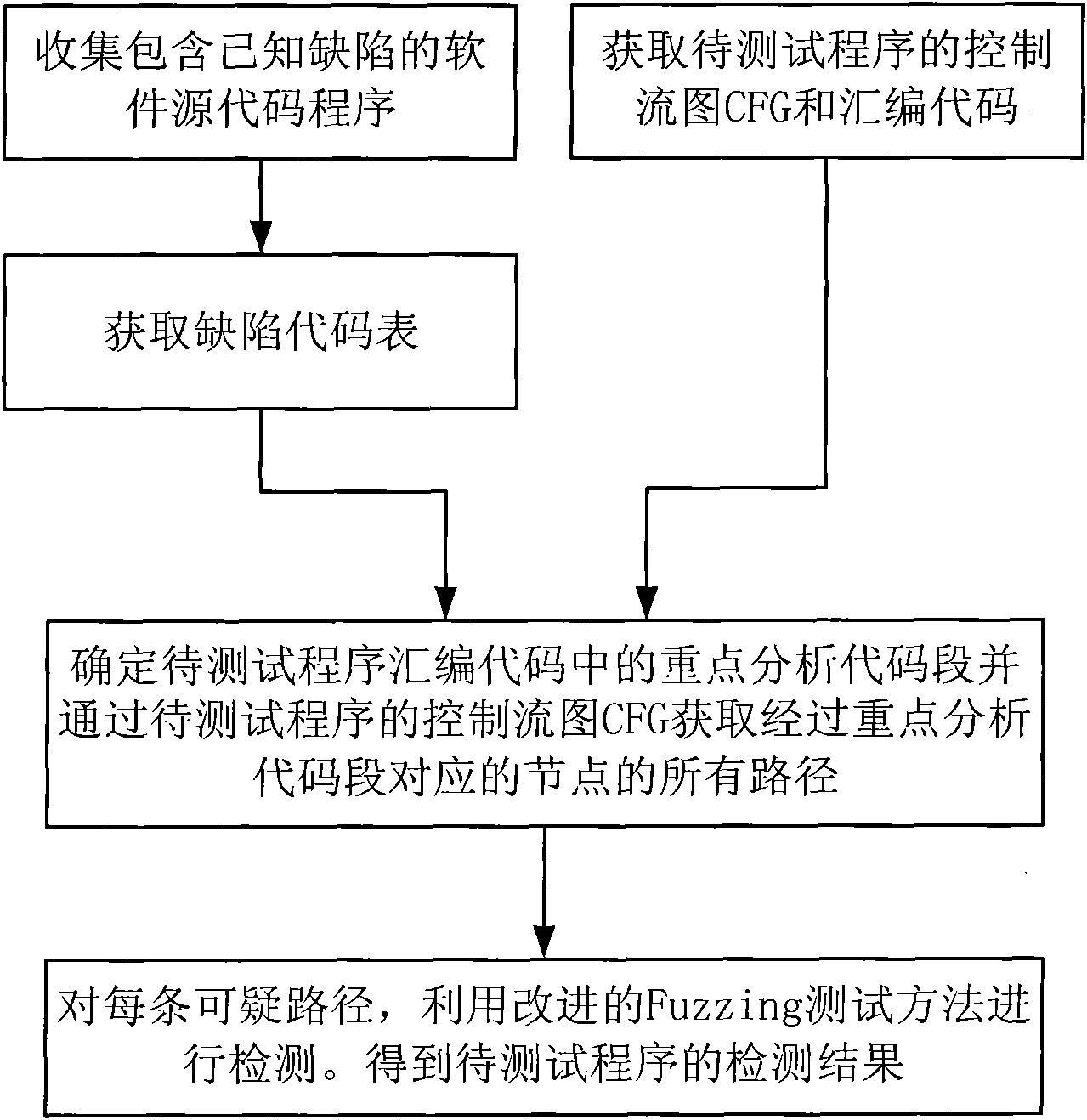
InactiveCN102385550AGuaranteed validityEfficient detectionSoftware testing/debuggingCode tableInformation security
The invention relates to a detection method for software vulnerability, and belongs to the technical field of information security. The detection method comprises the following specific steps of: (1) collecting a software source code program containing known vulnerability; (2) obtaining a vulnerability code table; (3) obtaining a control flow graph CFG and an assembly code of the program to be tested; (4) determining key analysis code segments in the assembly code of the program to be tested and obtaining all paths of passing through nodes corresponding to the key analysis code segments through the control flow graph CFG of the program to be tested; and (5) for each suspicious path, an improved Fuzzing test method is used for detection to obtain the test results of the program to be tested. In the invention, when a fitness function is determined, the dependence on the source code of the tested program is eliminated, and the availability of information is kept; and the redundant information in an abstract syntax tree is eliminated and the integrity of useful information is kept, therefore, the practicality is better, and the efficiency is higher.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method and system for fuzz testing
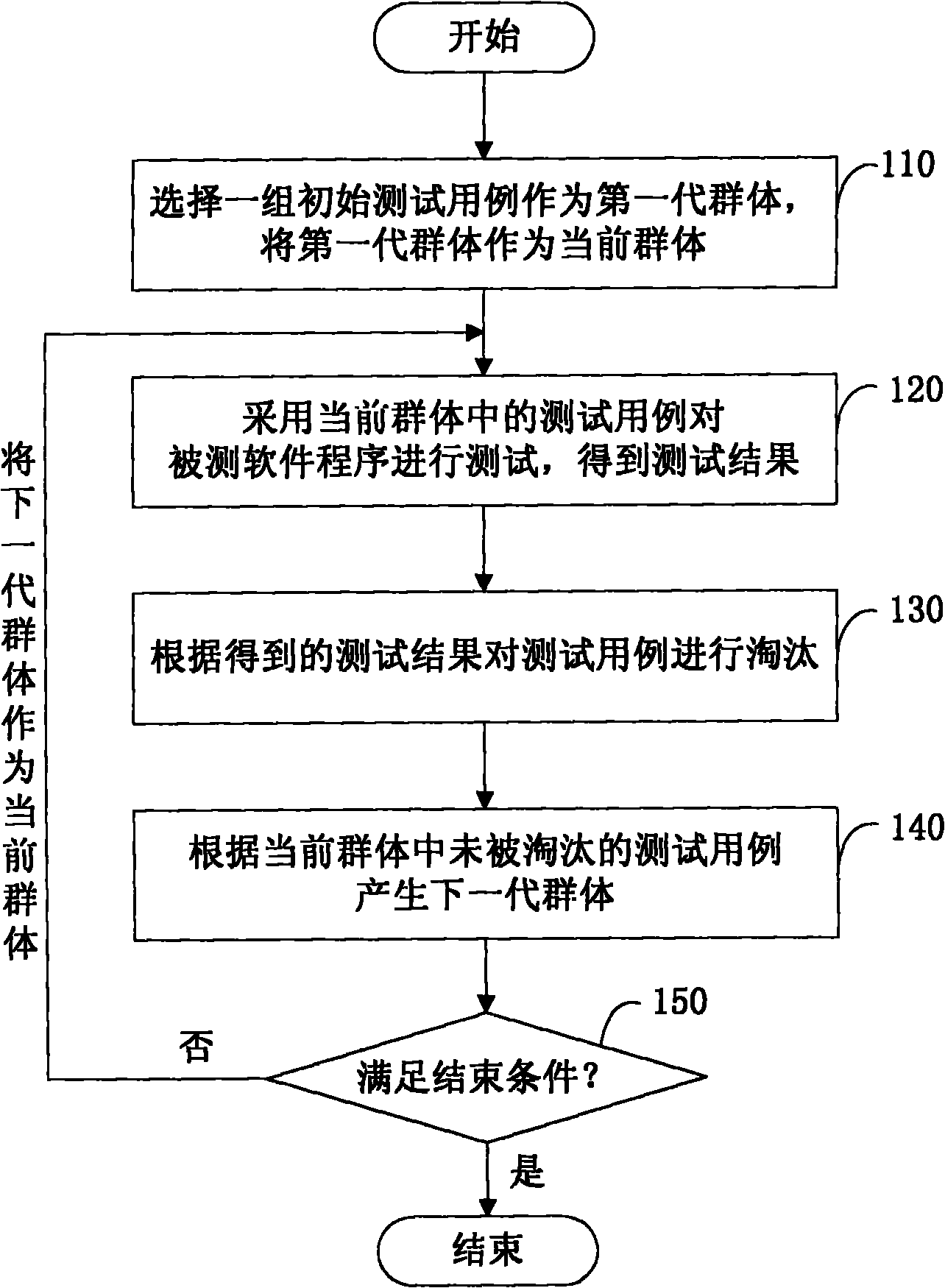
ActiveCN101859274AFind security flawsSecurity Defect ExclusionSoftware testing/debuggingFirst generationTest case
The invention discloses a method for fuzz testing, which comprises the following steps that: first, selecting a group of initial test cases as a first-generation group, and the first-generation group serves as a current group; then adopting the test cases in the current group to test a tested software program, eliminate the test cases according to the obtained test results, and generate a next-generation group according to the test cases which are not eliminated in the current group; at this time, if the end conditions are satisfied, ending the test; and if the end conditions are not satisfied, the obtained next-generation group serves as the current group to continue the test in a circulating way until the end conditions are satisfied. The invention also discloses a system for fuzz testing. The invention can improve the security of the tested software program.
Owner:SIEMENS CHINA
Position enquiring system based on free-running speech and position enquiring system based on key words
ActiveCN101136028AIncrease freedomFlexible offerRadio/inductive link selection arrangementsSpecial data processing applicationsFuzz testingLanguage model
The system comprises: a receiving unit used for receiving the nature language enquiry request; an access unit used for accessing the location body database and location enquiry language database; wherein, the location body database comprises the domain knowledge description in the location service; said location enquiry language database comprises a language model used for making the location service enquiry, a natural language enquiry process unit used for searching location body database and location enquiry language database; for the received natural language enquiry request, making fuzzing process for at least one of the request, and finding the corresponding location information from the location database; and a transmitting device used for transmitting the location information to the user end.
Owner:数据堂(北京)科技股份有限公司
Vulnerability detection system aiming at binary executable files and combining fuzz testing with symbolic execution
ActiveCN108052825ASpeed up explorationRun fastSoftware testing/debuggingPlatform integrity maintainanceData setParallel computing
The invention discloses a vulnerability detection system aiming at binary executable files and combining fuzz testing with symbolic execution, belongs to computer vulnerability detection software development technology and aims to increase detection depth and improve detection efficiency in binary file vulnerability detection scenes. The vulnerability detection system comprises a fuzzifier modulethrough optimization design, a symbolic execution module through optimization design and a fuzzifier skip symbol scheduling execution module, and a cache explorer and a task cooperation module are introduced. Advantages of fuzz testing and symbolic execution are combined for vulnerability detection of binary execution files. Evaluation experiments are conducted on the system, an application program provided by a qualification test of DARPA network challenge is adopted as a dataset, and contrast experiments are set on three objects including single fuzz testing, single symbolic execution and avulnerability mining system realized by the system. The system has remarkable effect, exploration of binary program compartment is accelerated, and running speed of the vulnerability mining system isincreased greatly.
Owner:HARBIN INST OF TECH
Distributed heterogeneous network vulnerability mining method based on Fuzzing algorithm
InactiveCN107046526AGood modelingValid data representationTransmissionNetworking protocolTest script
The invention relates to a distributed heterogeneous network vulnerability mining method based on the Fuzzing algorithm. The method comprises the following steps: performing automatic analysis on a network protocol of a test target, and determining protocol key information of the test target; performing comprehensive description on the protocol key information, combining the protocol key information into a specific data structure, and constructing a protocol test script; combining operation states of the protocol into a protocol vulnerability mining path map according to the protocol test script; sending a test script to the test target according to the protocol vulnerability mining path map and a control instruction, sending the control instruction to a target monitor, and receiving monitoring information from the target monitor; and storing the sent test script and the tested vulnerability information, and displaying the same in an information display interface. By adoption of the distributed heterogeneous network vulnerability mining method provided by the invention, the coverage and validity of protocol mining are improved, and the leakage probability of the vulnerability is reduced; and a friendly operation interface is provided to display corresponding information in real time, thereby facilitating the user check ad reducing the entry threshold of vulnerability mining.
Owner:BEIJING UNIV OF POSTS & TELECOMM +1
A fuzzy testing framework based on AFL
The invention discloses a fuzzy test framework based on AFL, which comprises a test case preprocessing module and an AFL processing module. In the AFL processing module, the test case selection sub-module sequentially selects the next test case to be mutated from the test case queue; before selection, according to the historical variation of test cases, those test cases with greater probability tofind new paths are identified as privileged test cases, and are selected as test cases to be mutated first. The test case mutation quantity determining sub-module adjusts the energy allocated to eachtest case according to the historical mutation of the test case, and then adjusts the mutation quantity of the test case to be mutated. The test case mutation sub-module determines the mutation byteaccording to the valid byte in the test case. The mutation is then performed according to the number of mutations and the mutation bytes. The invention solves the blindness problem of the current AFLtool in the test case generation strategy, and the insufficiency that the effective test case cannot be generated according to the highly structured data format.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Binary oriented hybrid fuzzing method
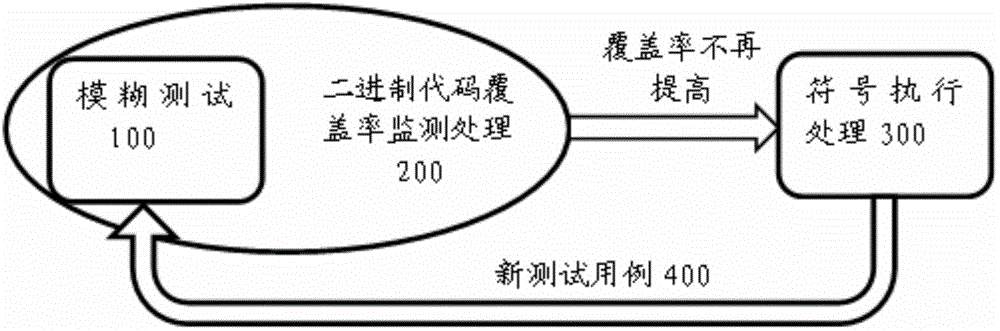
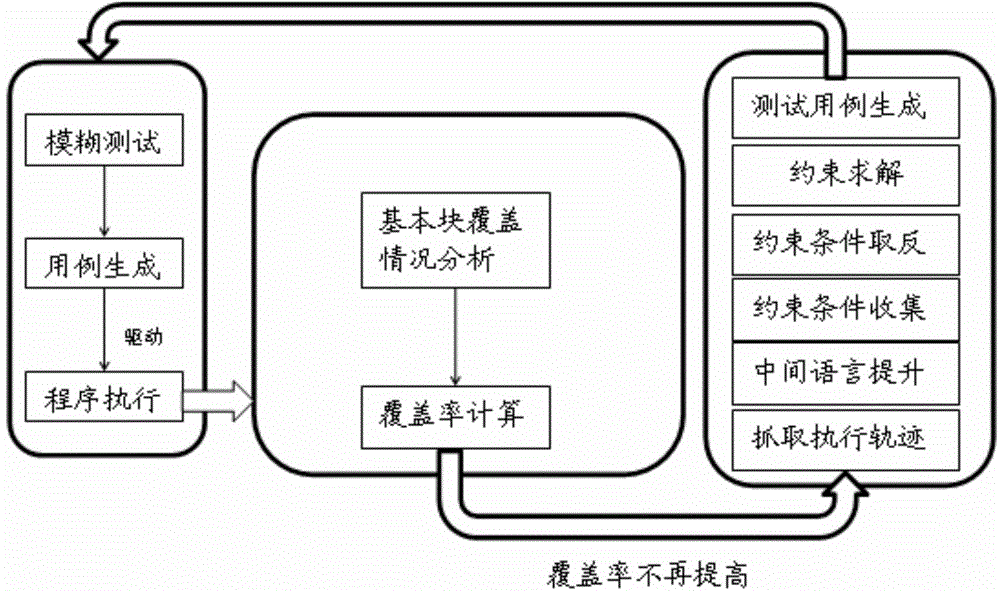
ActiveCN104375942AImprove usabilityEliminate blindnessSoftware testing/debuggingBasic blockTest case
The invention provides a binary oriented hybrid fuzzing method. The method includes: adopting fuzzing as front-end processing, and utilizing test cases to drive a tested program to be executed; adopting binary code coverage rate monitoring processing as intermediate layer processing, recording basic blocks covered by the tested program in the execution process of the tested program, and calculating coverage rate of fuzzing; when the calculated fuzzing coverage rate is no longer increased, executing symbolic execution processing serving as back-end processing, generating new test cases covering other paths different from the path of the current test case during symbolic execution processing, and then feeding back the new test cases to fuzzing to enable the new test cases to be used for driving the tested program to be executed by the fuzzing.
Owner:JIANGNAN INST OF COMPUTING TECH
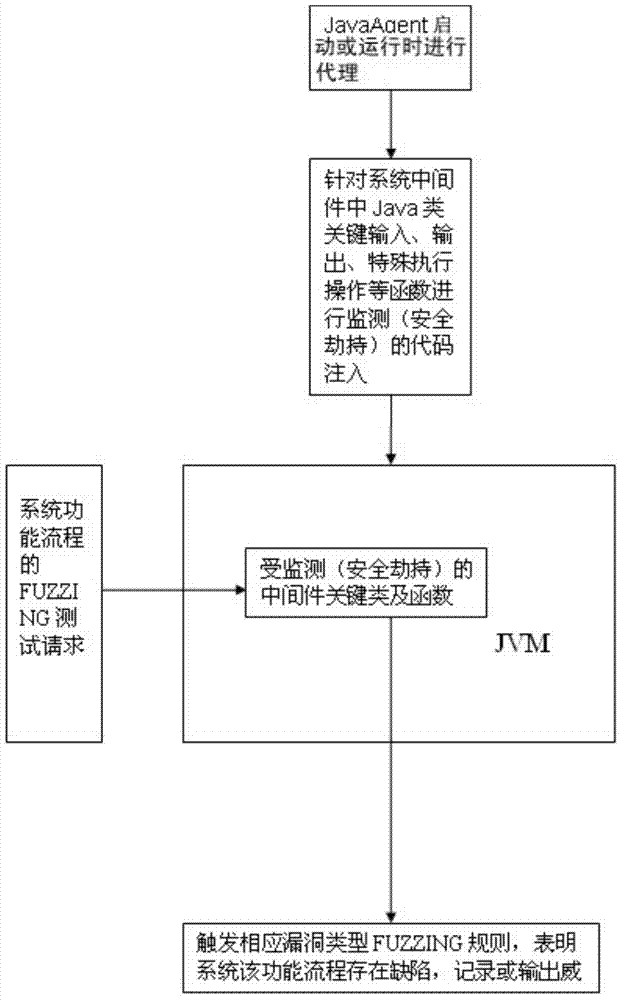
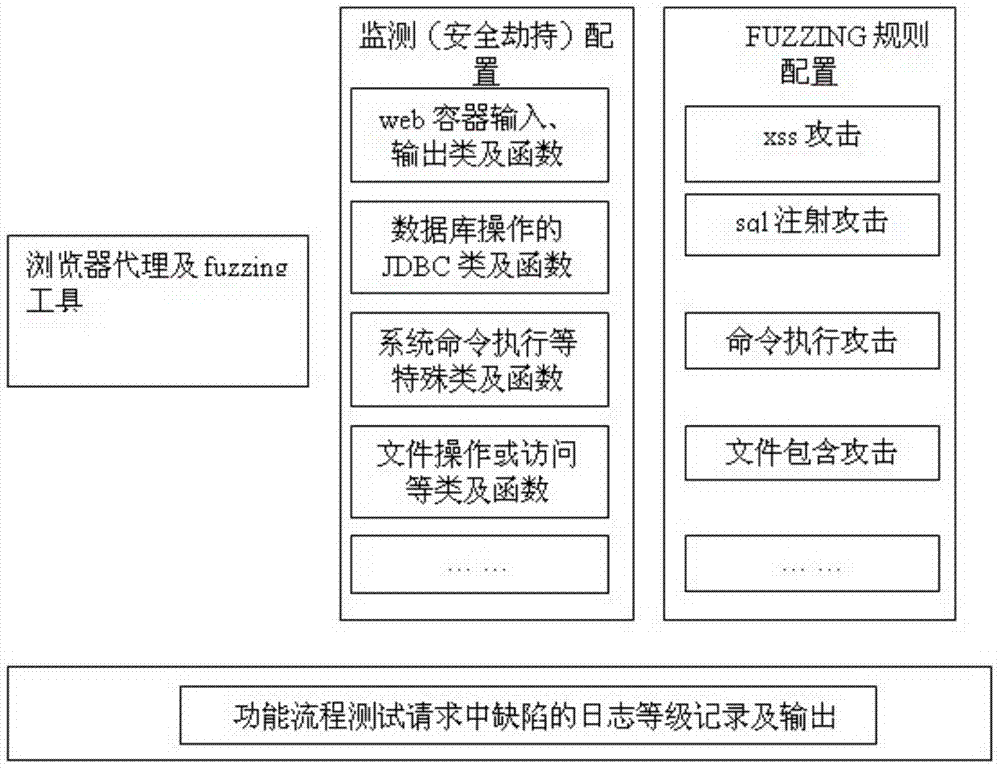
WEB dynamic security flaw detection method based on JAVA
The invention relates to a security test of WEB application, and aims to provide a WEB dynamic security flaw detection method based on JAVA. The WEB dynamic security flaw detection method based on JAVA is used for detecting the security flaws of a WEB application system, and comprises the following steps: modifying JAVA middleware; performing fuzzing test and dynamic flaw tracking. Due to the adoption of the WEB dynamic security flaw detection method, more WEB security flaw problems can be found rapidly, the security flaw range of black box test can be better covered, more deep WEB security problems can be found, the problem of high cost in white box test can be solved, the specific position of a flaw code can be determined more accurately, and lower missing report rate and error report rate in a detection process are ensured.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
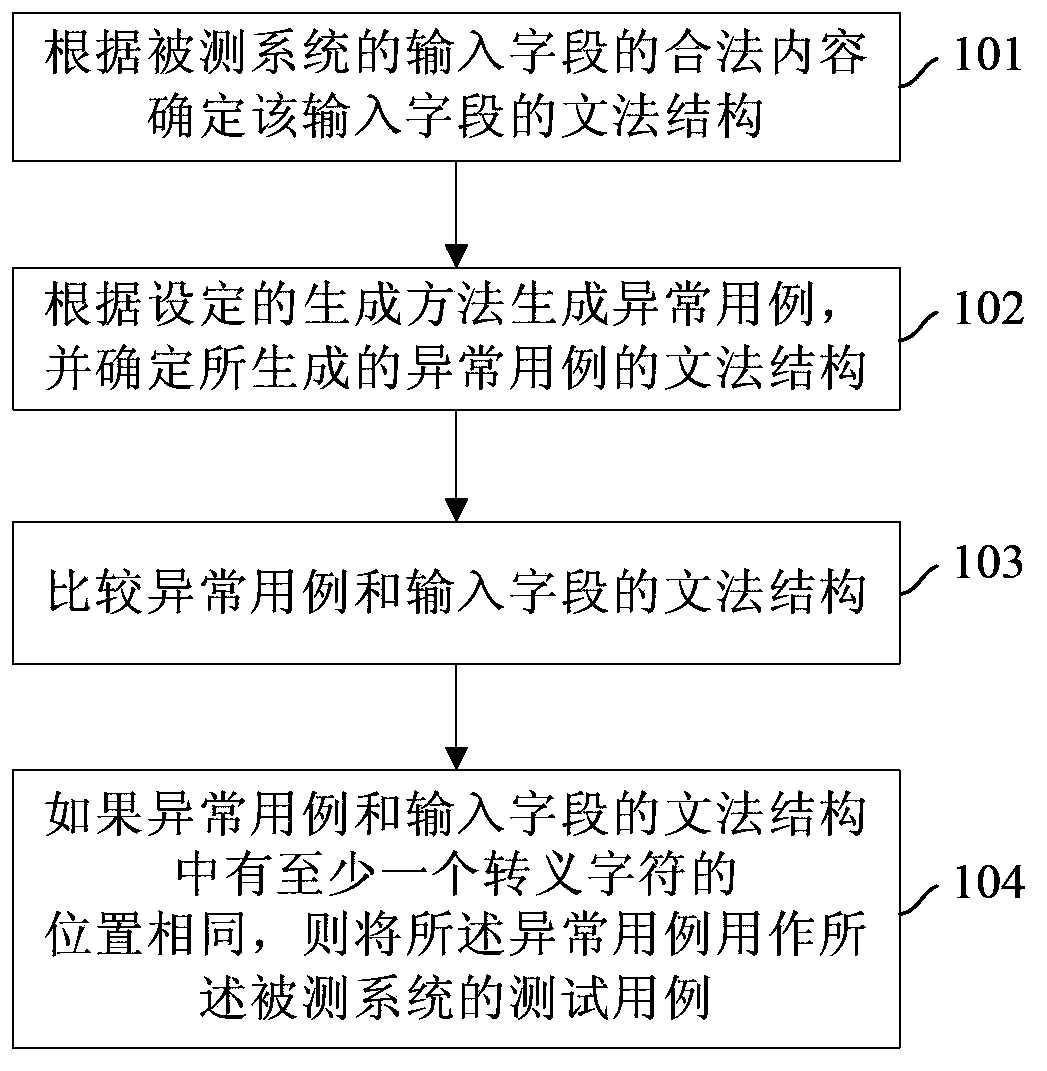
Test case generating method and device for fuzz testing
InactiveCN103853650AReduce rejectionImprove efficiencySoftware testing/debuggingProgramming languageAlgorithm
The invention provides a test case generating method and device for fuzz testing. The test case generating method comprises the steps of confirming grammatical structures of input fields according to legal contents of input fields of a tested system, wherein the grammatical structures of the input fields comprise special characters in the fields and positions of the special characters; generating abnormal use cases by adopting a set generating method and confirming grammatical structures of the abnormal use cases, wherein the grammatical structures of the abnormal use cases comprise special characters in the abnormal use cases and positions of the abnormal use cases; comparing the grammatical structures of the abnormal use cases with the grammatical structures of the input fields; if the grammatical structures of the abnormal use cases are identical to at least one special field in the grammatical structures of the input fields in position, the abnormal use cases are used as test cases of the tested system. By adopting the test case generating method and device for fuzz testing, the test cases for fuzz testing and input data of the tested system can have high similarity, and accordingly high-efficiency and comprehensive safe testing is achieved.
Owner:SIEMENS AG
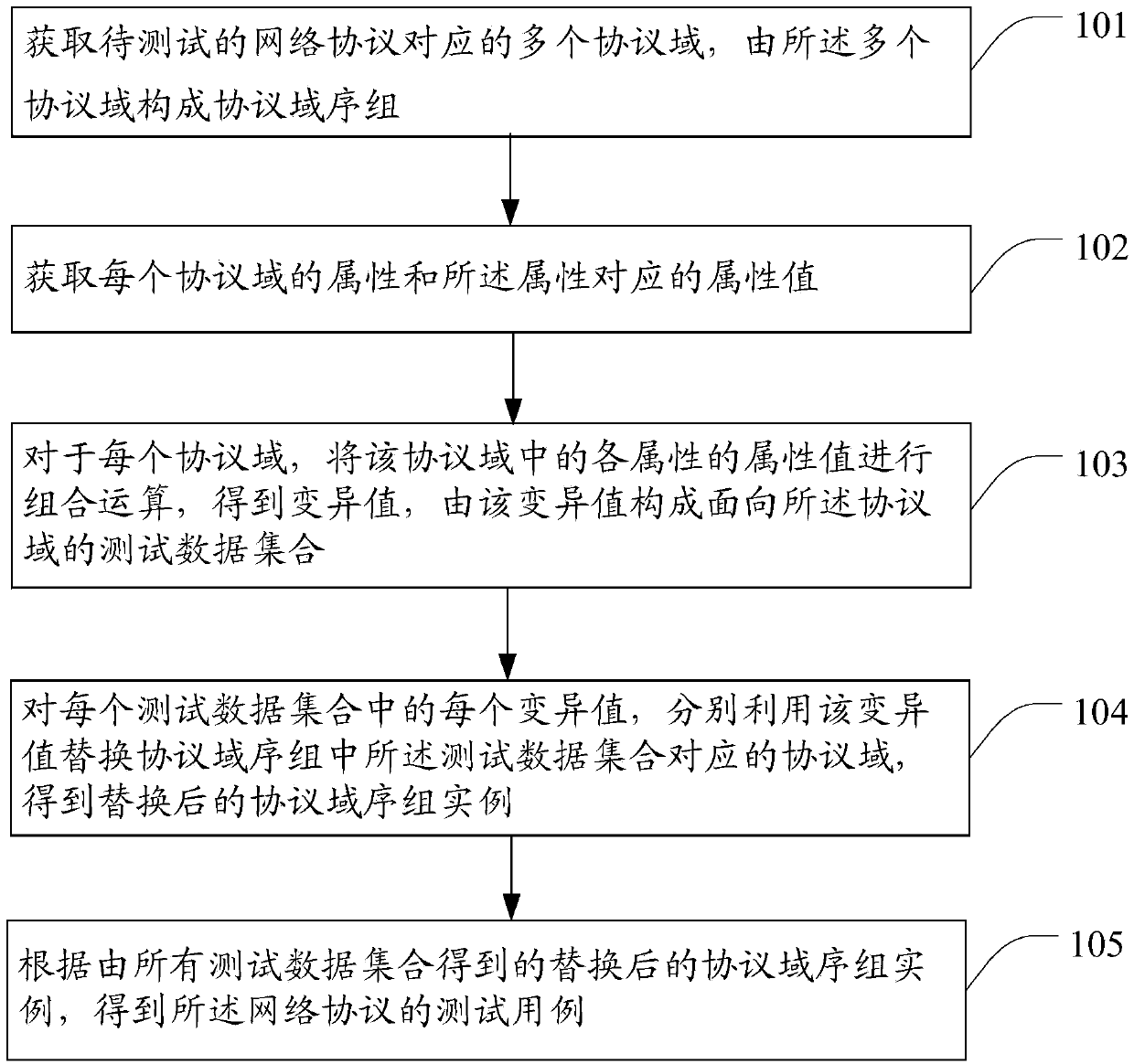
Network protocol fuzz testing method and device
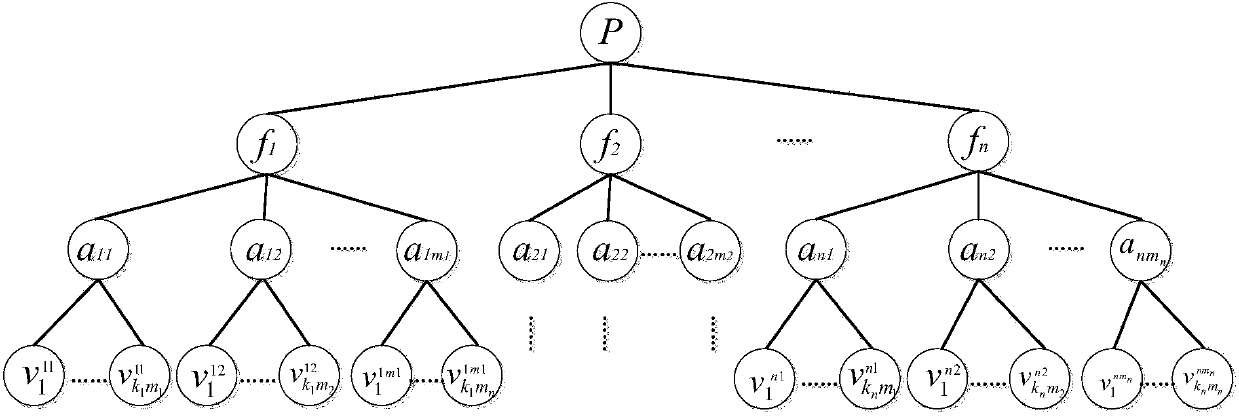
ActiveCN103812729AReduce build spaceGuaranteed efficiencyData switching networksComputer hardwareData set
The invention provides a network protocol fuzz testing method and device. The network protocol fuzz testing method and device can solves the defect that test case suites in existing network protocol fuzz testing modes are not intelligentized enough and can generate large amounts of redundant test cases. The method comprises the steps of, firstly, obtaining a plurality of protocol fields corresponding to a network protocol to be tested and composing a protocol field sequence group with the plurality of protocol fields; secondly, obtaining the attributes of every protocol field of the attribute values corresponding the attributes; thirdly, for every protocol field, performing combined operation on the attribute values of every attribute to obtain variance values, and composing a testing data set oriented to the protocol field with the variance values; fourthly, for every variance value in every testing data set, replacing the protocol field in the protocol field sequence group, which corresponds to the testing data set, with the variance value to obtain a replaced protocol field sequence group case; fifthly, according to the replaced protocol field sequence group cases of all the testing data sets, obtaining the testing cases of the network protocol.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Fabric fuzzing and pilling image segmentation method based on wavelet transformation and morphological algorithm
ActiveCN104021561ARobustImprove anti-interference abilityImage analysisImage segmentationVariance method
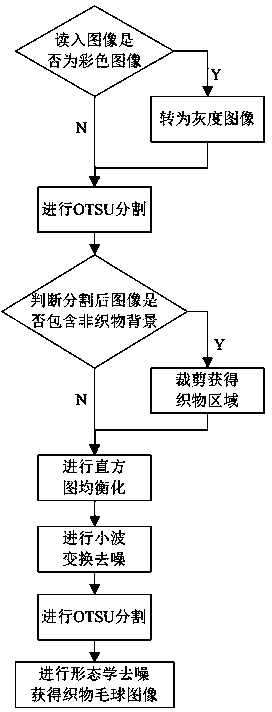
The invention discloses a fabric fuzzing and pilling image segmentation method based on wavelet transformation and the morphological algorithm. The method comprises the steps that firstly, histogram equalization is carried out on an acquired fabric fuzzing and pilling image, and eight-stage multi-resolution wavelet decomposition is carried out; secondly, after the coefficient of a first-stage wavelet decomposition layer, the coefficient of a second-stage wavelet decomposition layer and the coefficient of an approximate wavelet decomposition layer are set to be zero, the image is reconstructed, wherein the first-stage wavelet decomposition layer and the second-stage wavelet decomposition layer express the highest-frequency information, and the approximate wavelet decomposition layer expresses low-frequency information; thirdly, binaryzation is carried out on the constructed image according to the maximum between-cluster variance method, and erosion is carried out on the image through a horizontal linear structure element, a 45-degree linear structure element, a vertical linear structure element and a 135-degree linear structure element in sequence; fourthly, dilation is carried out on the eroded image through structure elements with the sequence opposite to that of the structure elements applied to erosion, namely, the 135-degree linear structure element, the vertical linear structure element, the 45-degree linear structure element and the horizontal linear structure element in sequence. By means of the method, the influence of the texture of fabric, illumination unevenness, the surface roughness of the fabric and the size difference and shape difference of fuzzy balls on fuzzing and pilling grade assessment on the fabric can be effectively avoided.
Owner:江苏世纪燎原针织有限公司
PLC firmware fuzz testing system and method based on stain analysis
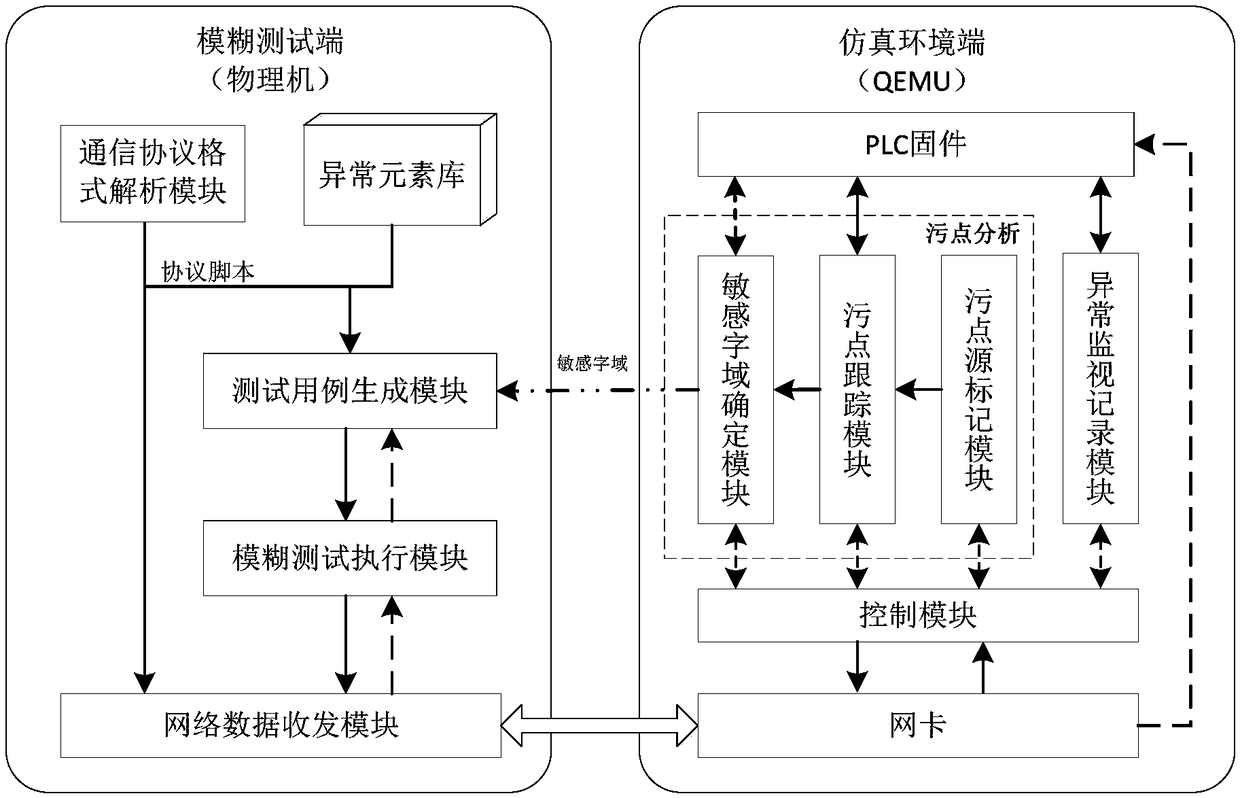
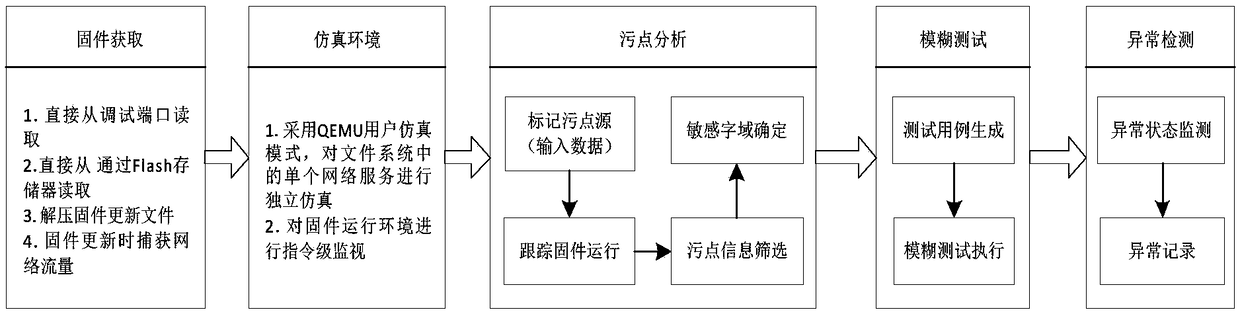
InactiveCN108255711AImprove targetingStrong penetrating powerSoftware testing/debuggingData switching networksFuzz testingResearch Object
The invention relates to the field of industrial control system safety, in particular to a PLC firmware fuzz testing system and method based on stain analysis. The testing system comprises a simulation environment end and a fuzz testing end, the fuzz testing end can be used for constructing a normal network data package and a fuzz testing case, and a communication link is established between the fuzz testing end and the simulation environment end; the simulation environment end comprises a simulation platform and a sub module; the sub module comprises a network card, a control module, a stainsource marking module, a stain tracking module, a sensitive word field determination module and an abnormity monitoring and recording module. According to the PLC firmware fuzz testing system and method, PLC firmware is used as a research object, by combining with a stain analysis and fuzz testing method, a network protocol data package which is input to a PLC is subjected to stain source markingand stain analysis under a simulation mode, and according to a data package sensitive word field which is marked in the stain analysis process, precise data variation is conducted, the fuzz testing case is constructed, and accordingly the pertinency and penetrability of fuzz testing for the PLC firmware are improved.
Owner:湖南优利泰克自动化系统有限公司 +1
Fuzz testing system for stateful network protocol
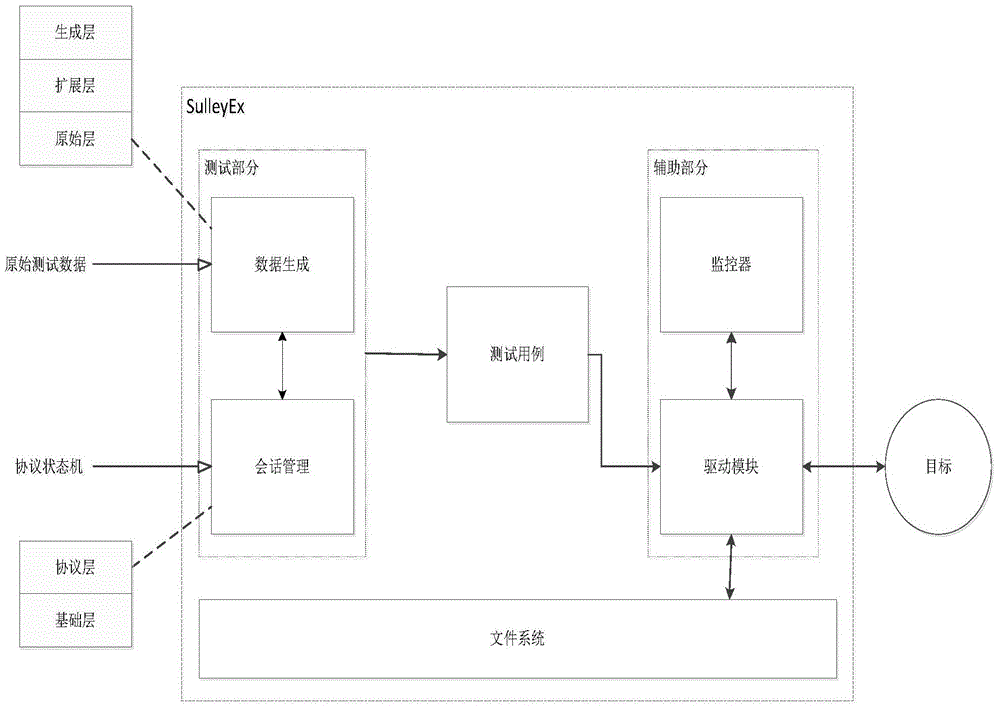
ActiveCN104796240ASolve the problem of inadequate testingEasy to operateCorrect operation testingSession managementNetworking protocol
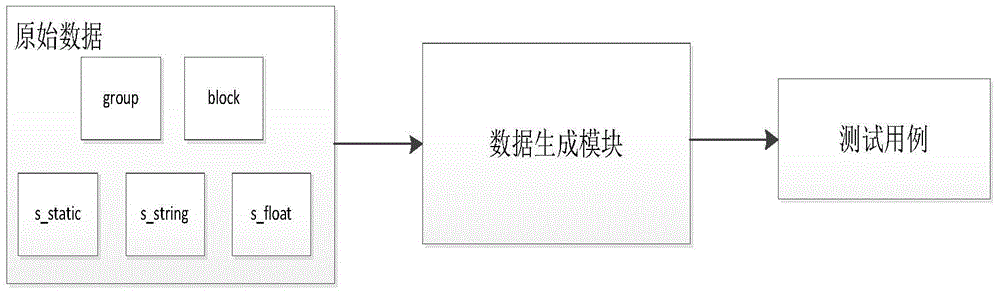
The invention provides a fuzz testing system for a stateful network protocol, and solves the problem the traditional network protocol fuzz test frame lacks support on complicated stateful protocols. The fuzz testing system comprises a data generation module, a session management module, a monitor and a driving module; the data generation module is used for storing raw data samples and fuzzing raw data based on a rule tree algorithm to generate fuzz testing cases; the session management module is used for connecting one or more requests defined in the fuzz testing cases into a directed acyclic graph, and then performing fuzz testing specific to each path; the monitor comprises a process monitor and a network monitor; the driving module is used for communicating with a to-be-tested target serve, sending test requests and receiving server response messages.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Modbus protocol-oriented fuzz testing method
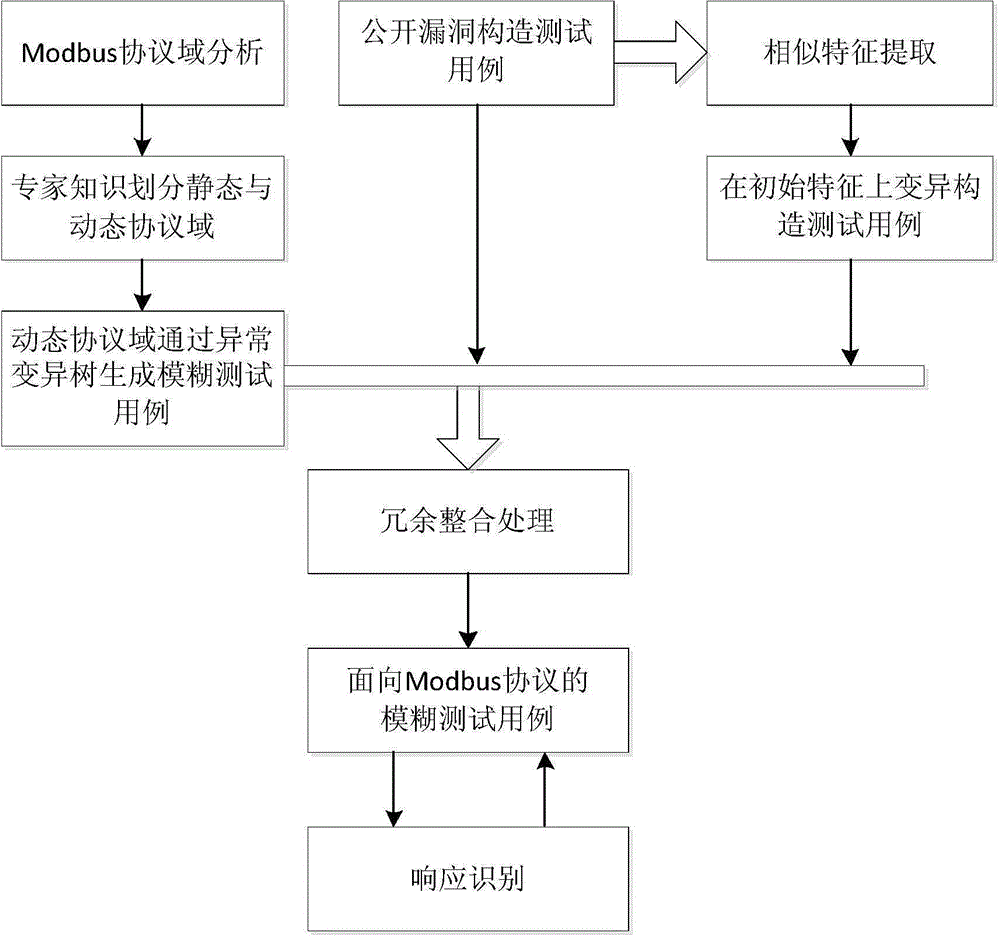
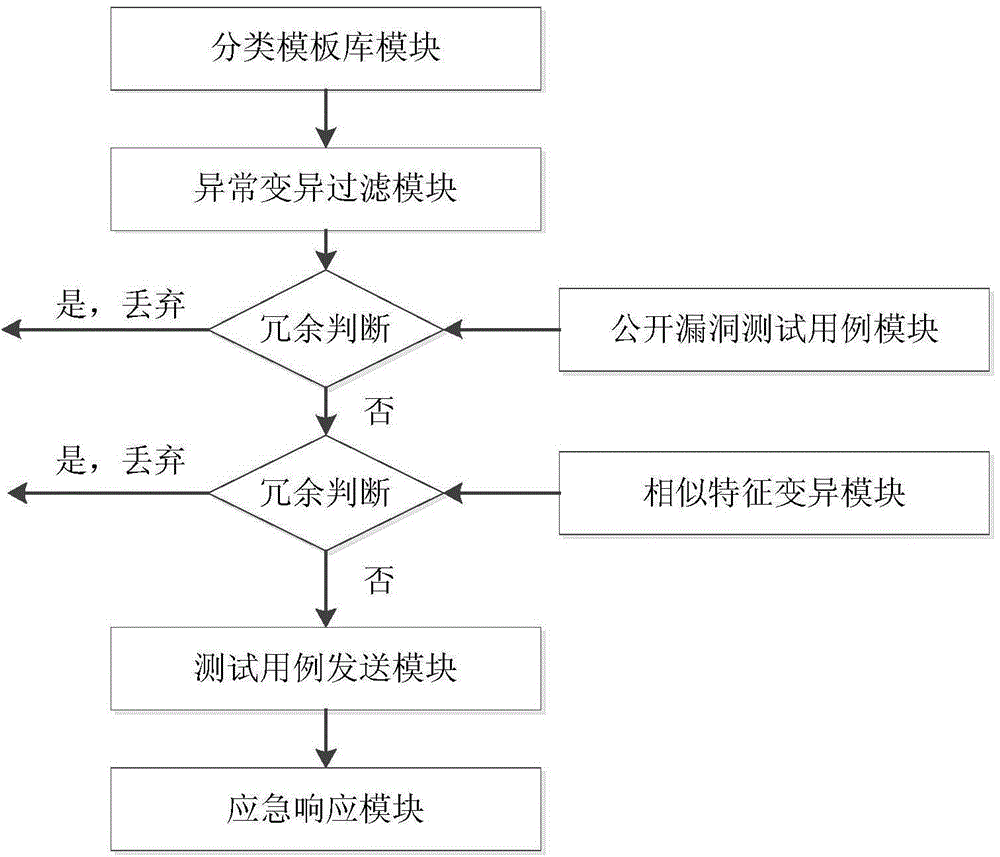
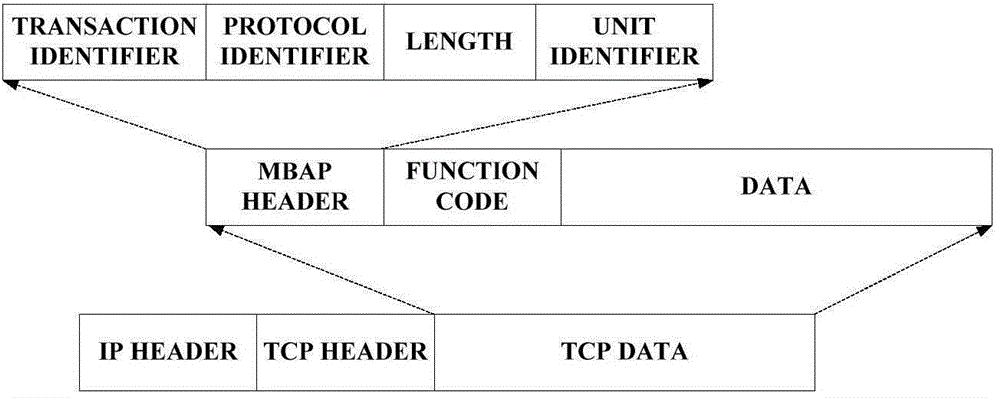
The invention provides a Modbus protocol-oriented fuzz testing method capable of discovering the processing defects of field equipment of an industry control system on Modbus protocol data. The method comprises the steps of dividing a Modbus protocol domain into a static portion and a dynamic portion via expert knowledge, constructing a test data set in the dynamic portion via an abnormal mutation tree method, and greatly filtering fuzz testing cases which do not easily cause faults; integrating the disclosed bug information to construct testing cases, and fusing the testing cases to the fuzz testing cases; mutating one or more testing cases via a genetic algorithm based on the similarity of the disclosed bug information, fusing the one or more testing cases to the fuzz testing cases, finally generating a Modbus protocol-oriented fuzz testing case, designing a response information recognition method of the fuzz testing case, and judging whether defects exist or not. A device for implementing the method works on a Modbus TCP / IP layer, and the processing defects of field equipment on Modbus protocol data can be effectively discovered only by simple point-to-point network configuration.
Owner:SHENYANG INST OF AUTOMATION - CHINESE ACAD OF SCI
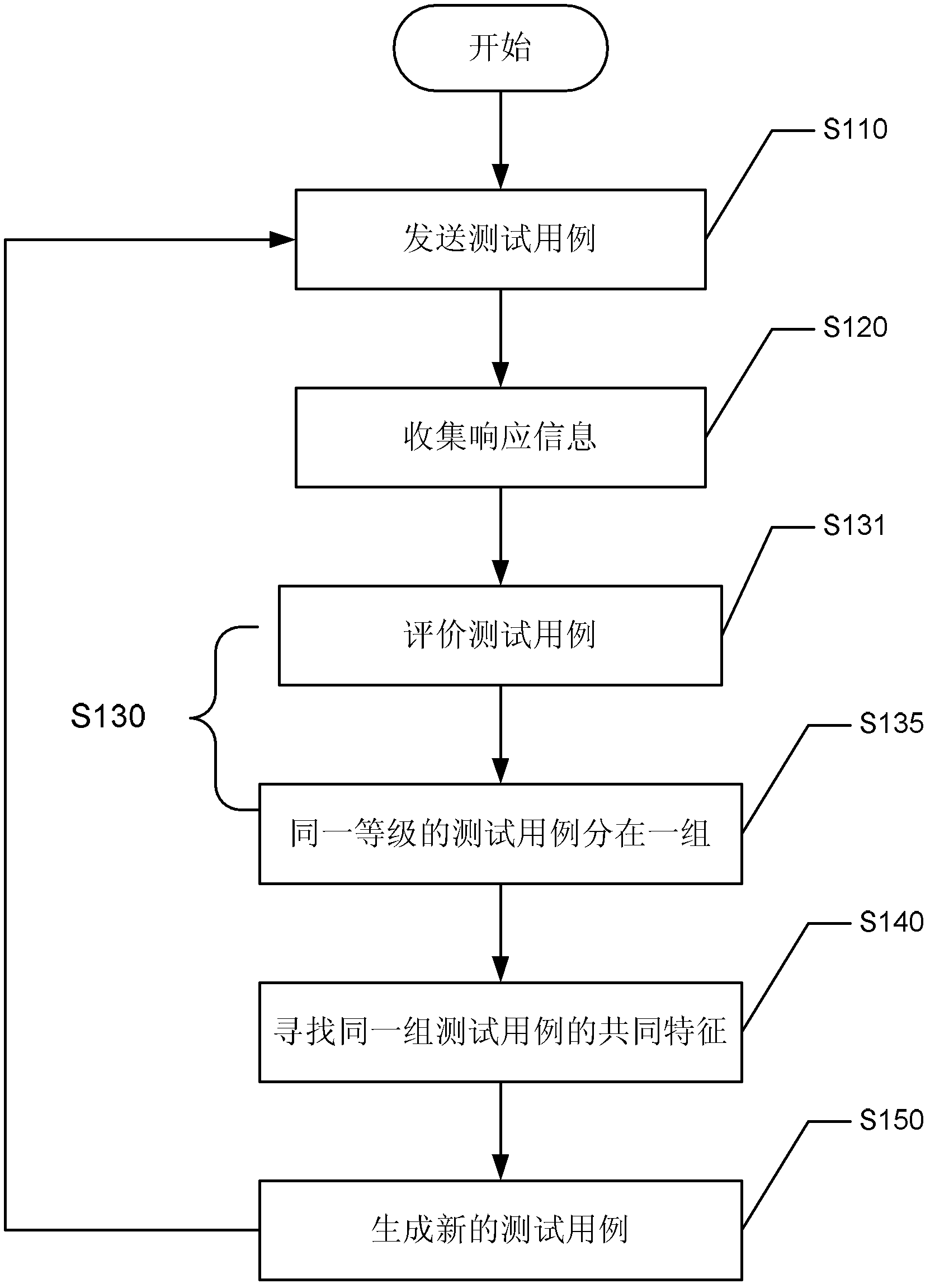
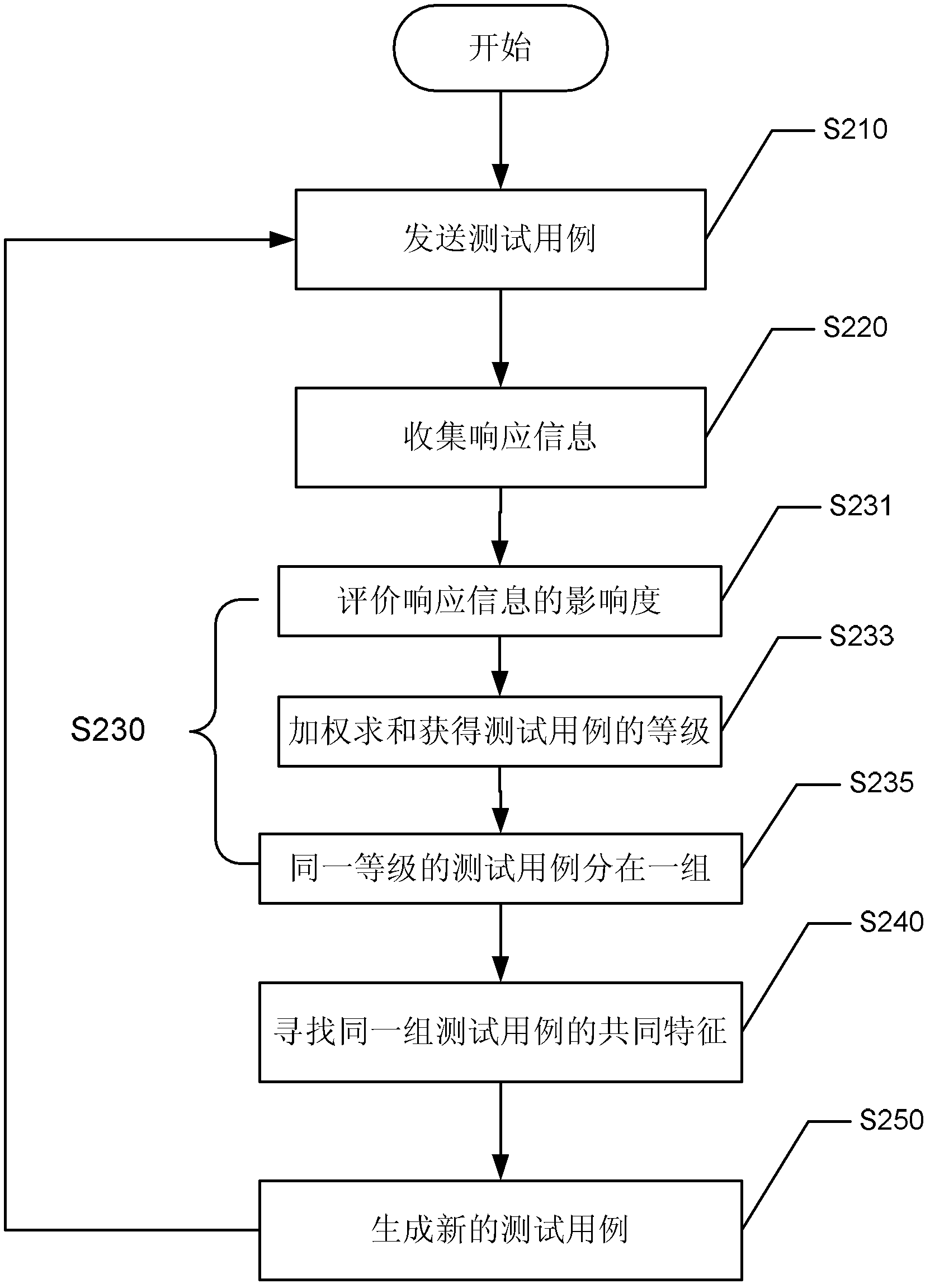
Method, device and system for fuzzing test
The invention provides a method and a device for a fuzzing test. The method comprises the following steps: inputting multiple test cases to a to-be-tested object; obtaining a response message which is relevant to the to-be-tested object for each test case; classifying the multiple test cases according to the obtained response message; analyzing common characteristics of one or multiple test cases in each classification; and generating one or multiple new test cases on the basis of the common characteristics, wherein one or multiple new test cases include the common characteristics. According to the method and the device for the fuzzing test, test cases which are enough to cause a failure can be effectively generated. In addition, preferably, by means of the method for the fuzzing test, informing of a file layout or a file protocol is not required.
Owner:SIEMENS AG
Security testing method and device for protocol implementation
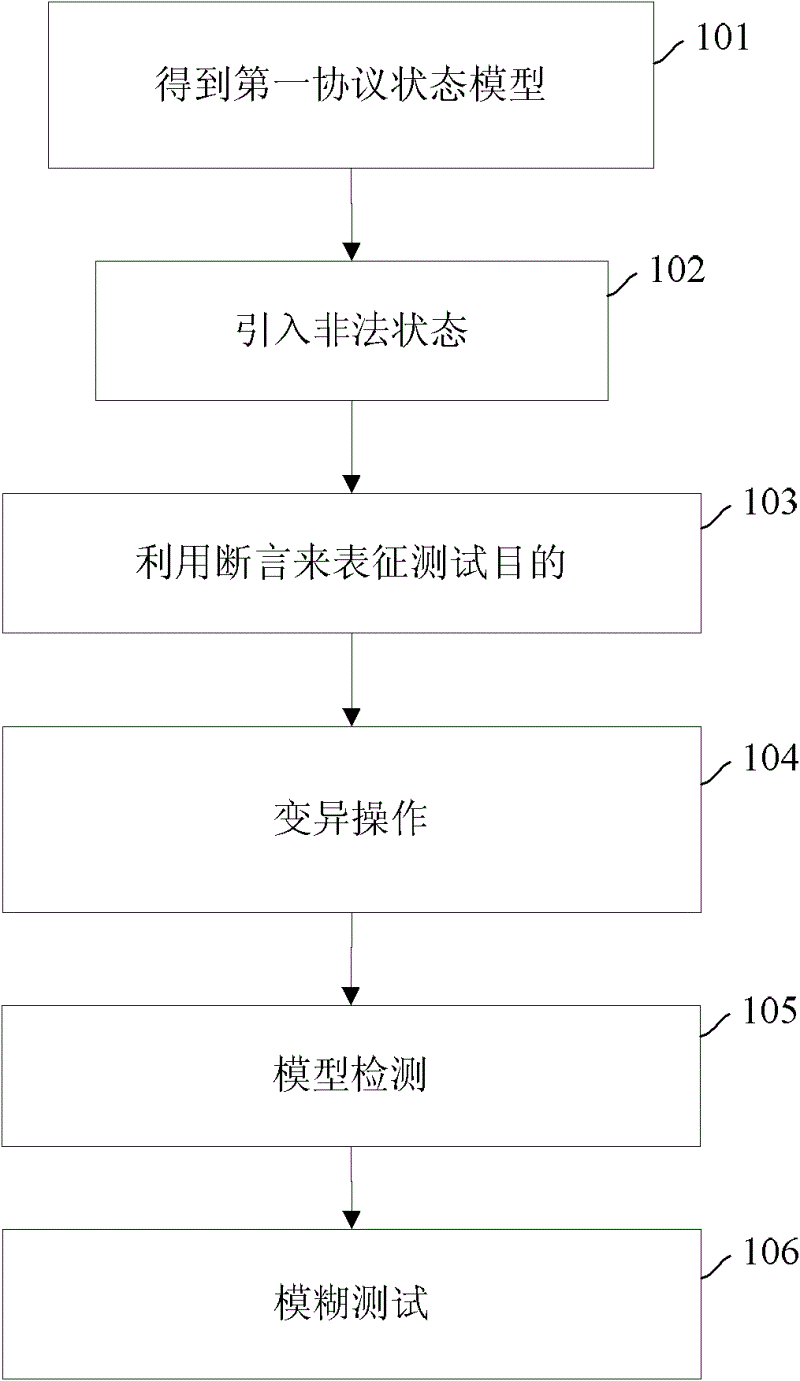
InactiveCN102624574AImprove execution efficiencyLow costData switching networksComputer hardwareState model
The embodiment of the invention provides a security testing method for protocol implementation, and comprises: mapping a protocol specification on which the protocol implementation is based to a first protocol state model; forming a second protocol state model by introducing an illegal state that corresponds to security failure into the first protocol state model; characterizing the testing purposes of the first protocol state model and the second protocol state model by utilizing an assertion; generating a mutated protocol state model by carrying out a mutative operation on the second protocol state model; performing a model test on the mutated protocol state model according to the assertion to generate a testing suite obtained from mapping a counter-example in the mutated protocol state model that violates the assertion; and carrying out a fuzzing test on the protocol implementation by a testing suite to test security holes in protocol implementation. The invented embodiment further provides a corresponding testing device. According to the invented embodiment, efficient and low-cost protocol security test is realized.
Owner:SIEMENS AG
Black box and white box combined parallel fuzz testing method for executing feedback driving
ActiveCN106155901AQuality improvementIncrease the number ofSoftware testing/debuggingSoftware engineeringQuantitative model
The invention relates to a black box and white box combined parallel fuzz testing method for executing feedback driving. The black box and white box combined parallel fuzz testing method comprises the following steps: (1) performing parallel fuzz testing on test software and an input seed document of the test software; (2) monitoring the executing process of the parallel fuzz testing and acquiring executing feedback information, wherein the executing feedback information comprises black box information and white box information; (3) establishing a quantitative model for the acquired black box information and white box information, and establishing a dispatching model according to quantified indexes; (4) performing dynamic dispatching executing on each time of the fuzz testing task by use of the dispatching module till the entire testing task is finished. The black box and white box combined parallel fuzz testing method utilizes the black box information and the white box information in combination for dynamic dispatching, and can excavate more bugs as much as possible while guaranteeing low expenditure, and the fuzz testing effect is improved.
Owner:INST OF INFORMATION ENG CAS
Xml-based fuzzy test language protocol test script and test engine
PendingCN110232012AImprove scalabilityGuaranteed flexibilitySoftware testing/debuggingData packTest script
The invention discloses an xml-based fuzzy test language protocol test script and a test engine. The protocol test script comprises a test script automatically generated based on a fuzzy test languageand a state machine according to industrial control and Internet of Things protocol message formats and a monitoring script generated based on the fuzzy test language and the state machine and aimingat the state of tested equipment. According to the xml-based fuzzy test language protocol test script and a test engine, the test script and the monitoring script are automatically generated based onthe language; and the test engine can automatically parse the script language to generate the test data packet and send the test data packet to the tested equipment to complete the test task, the efficient fuzzy test language enables the detection system to expand a new protocol very conveniently, and the test engine architecture also guarantees the flexibility and expansibility of a packet sending mechanism.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
Fuzz testing system on basis of multi-swarm collaboration evolution genetic algorithm
InactiveCN103914383AIncrease coverageImprove mining efficiencySoftware testing/debuggingTest sampleCode coverage
The invention discloses a fuzz testing system on the basis of a multi-swarm collaboration evolution genetic algorithm, and belongs to the field of software safety tests. The fuzz testing system comprises a fuzz testing end and a test sample generating end. The fuzz testing end is responsible for inputting test samples into systems to be tested and repeatedly testing and observing the systems to be tested; the test sample generating end is used for generating the test samples and transmitting the test samples to the fuzz testing ends via networks, computes individual adaptability values by the aid of collected information according to coverage frequencies of basic blocks and trigger conditions of unsafe functions, combines the individual adaptability values with the types of the unsafe functions and enables the test samples to evolve by the aid of a multi-swarm collaboration evolution genetic model, so that new samples can be generated. The fuzz testing system has the advantages that a code coverage rate can be increased when application programs of the networks are tested, and the vulnerability mining efficiency can be improved.
Owner:FUZHOU UNIV
Method for automatically detecting security vulnerability based on hybrid fuzzing, and apparatus thereof
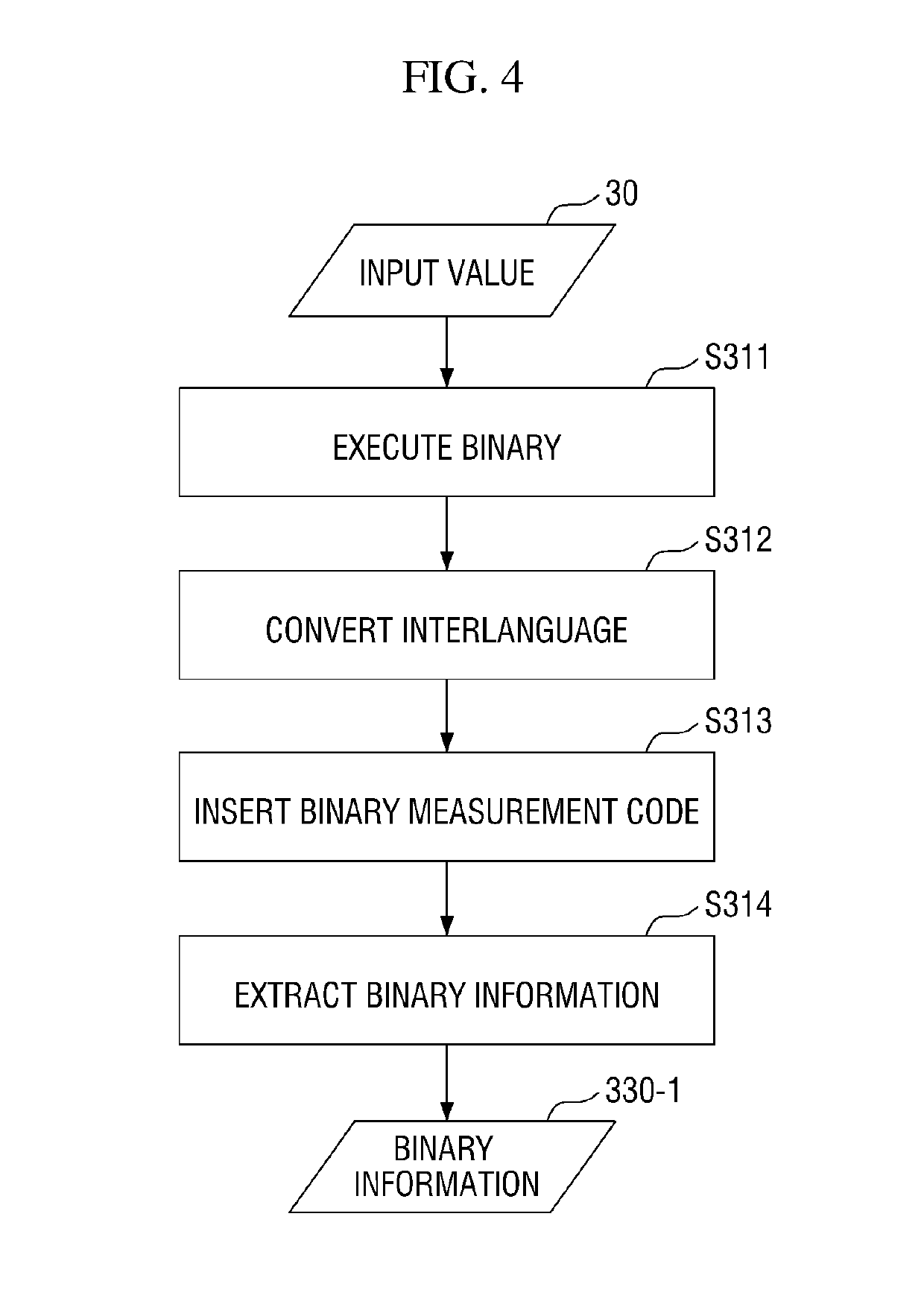
ActiveUS20190114436A1Efficient detectionSoftware testing/debuggingPlatform integrity maintainanceBinary informationVulnerability
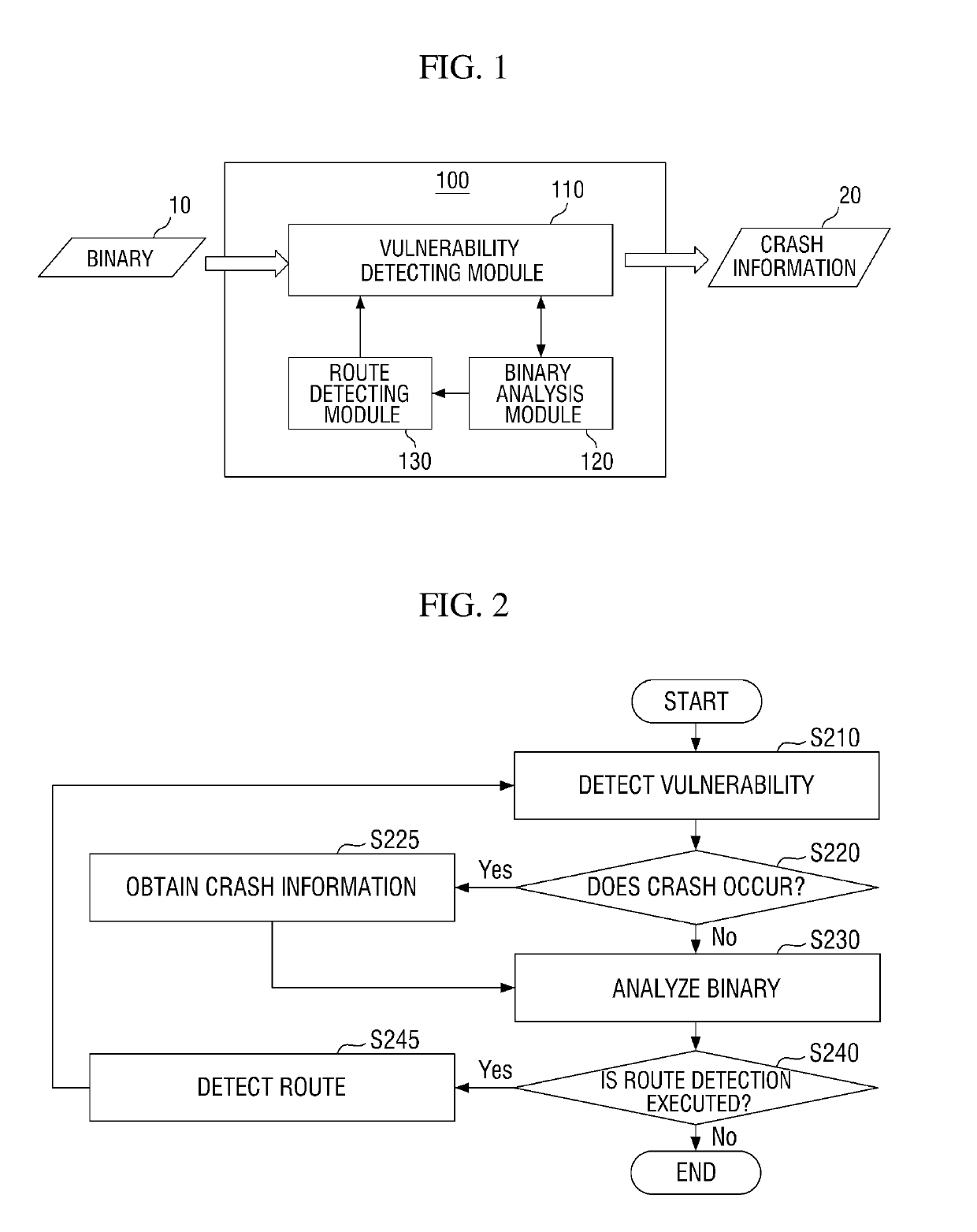
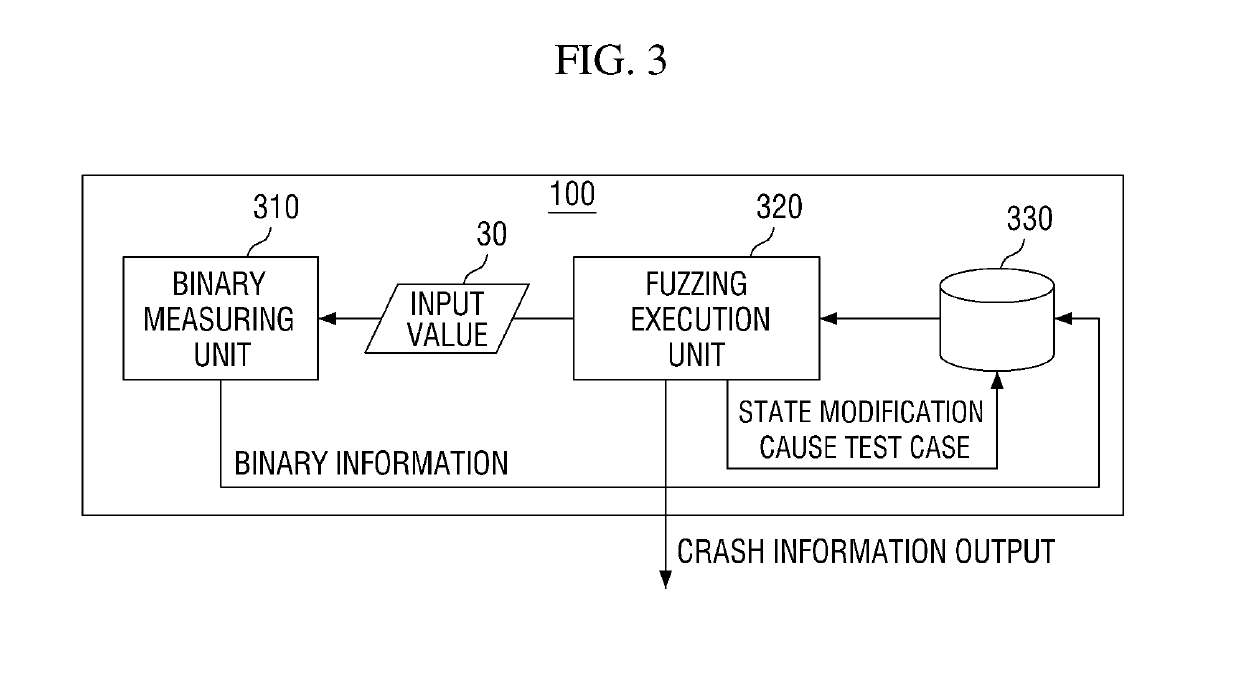
Provided are a method and a system capable of efficiently detecting security vulnerability of program. The system for detecting the security vulnerability according to an embodiment of the present invention includes a vulnerability detecting module that acquires crash information, a binary analysis module that determines priority of binary information and whether to execute the route detection, and a route detecting module that executes the route detection to generate a new test case.
Owner:KOREA INTERNET & SECURITY AGENCY
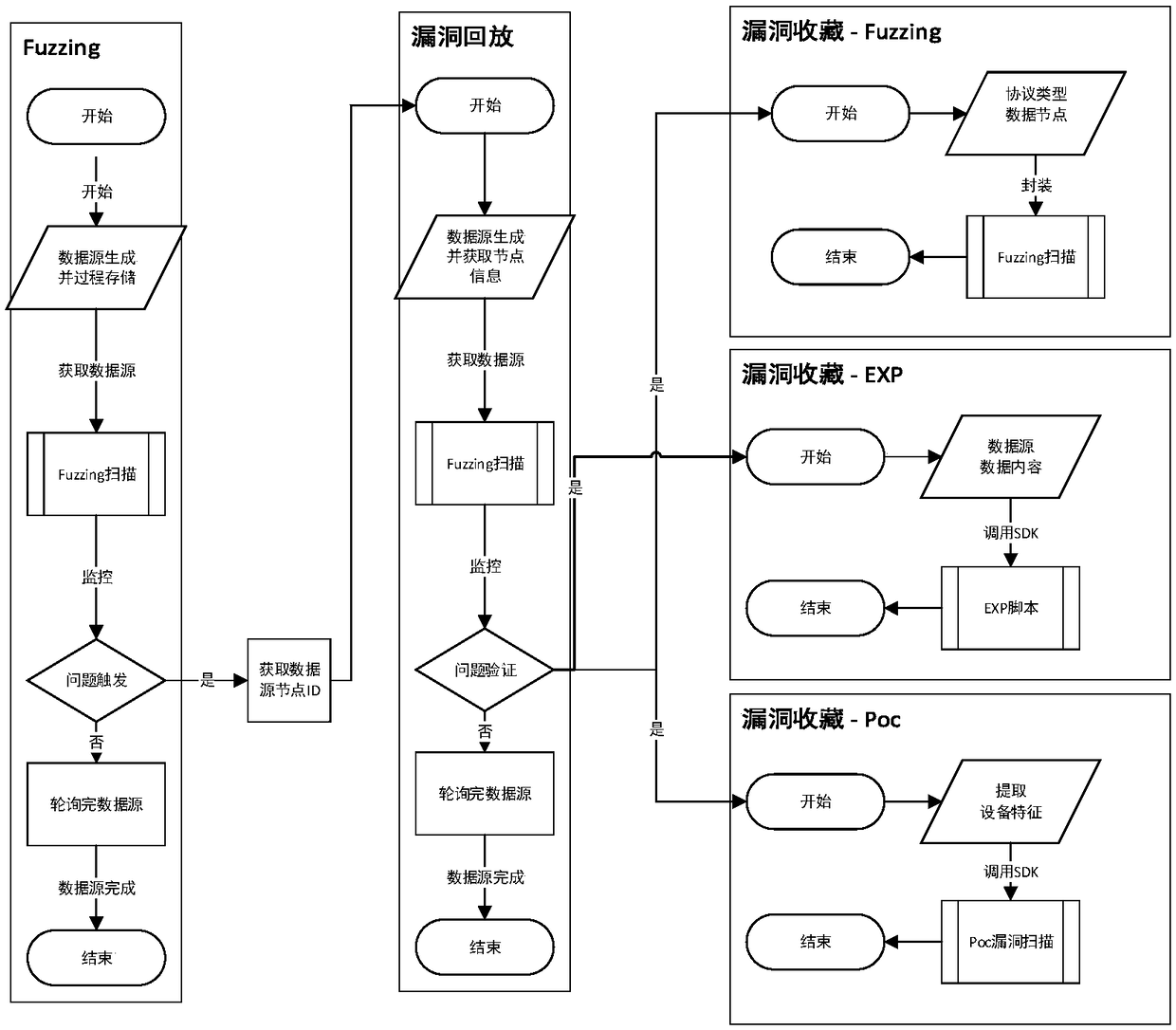
Automatic vulnerability detection plugin generation method and system for industrial control system
InactiveCN108920963AReduce digging timeImprove digging efficiencyPlatform integrity maintainanceData sourceData mining
The invention discloses an automatic vulnerability detection plugin generation method and system for an industrial control system. A current industrial control system vulnerability mining technology Fuzzing can find vulnerability but can not perform further processing on a vulnerability plugin. The method disclosed by the invention comprises a Fuzzing test link, a vulnerability playback link and avulnerability collecting link, the Fuzzing test link comprises the following sequential steps: constructing data sources and performing data storage; acquiring the data sources, starting to perform Fuzzing scanning, and mining vulnerability; monitoring a mining process; if all the data sources are completely polled and no problem is triggered, finishing the mining process; if a problem is triggered, acquiring node IDs of the data sources, and entering the vulnerability playback link; and the vulnerability playback link comprises the following sequential steps: generating the data sources andacquiring node information; acquiring the data sources, and starting to perform the Fuzzing scanning; and if no problem exists after verification, finishing, and if a problem exists, entering the vulnerability collecting link. The method disclosed by the invention can automatically generate a vulnerability detection plugin, converts unknown vulnerability into known vulnerability and improves vulnerability mining efficiency.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
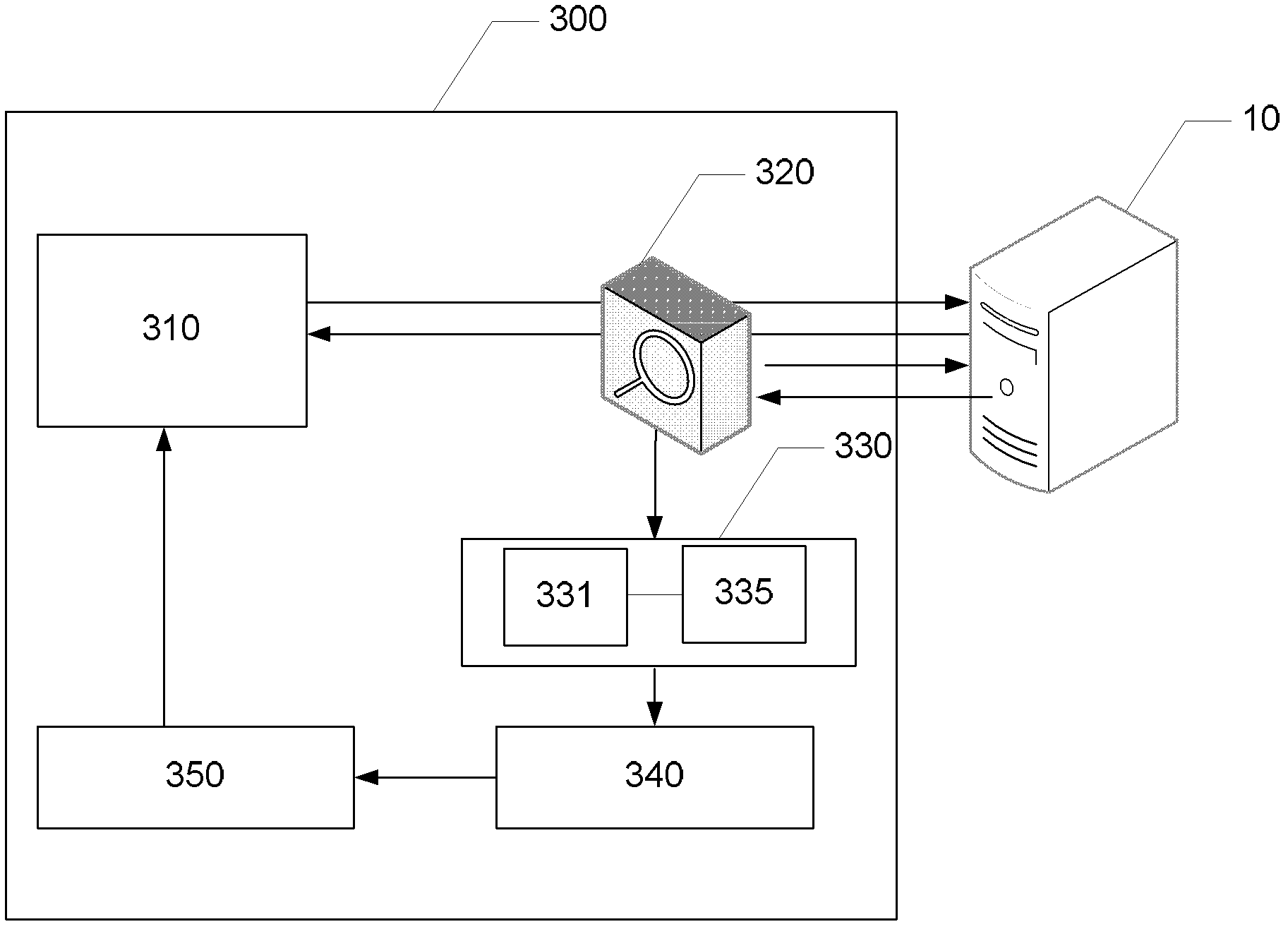
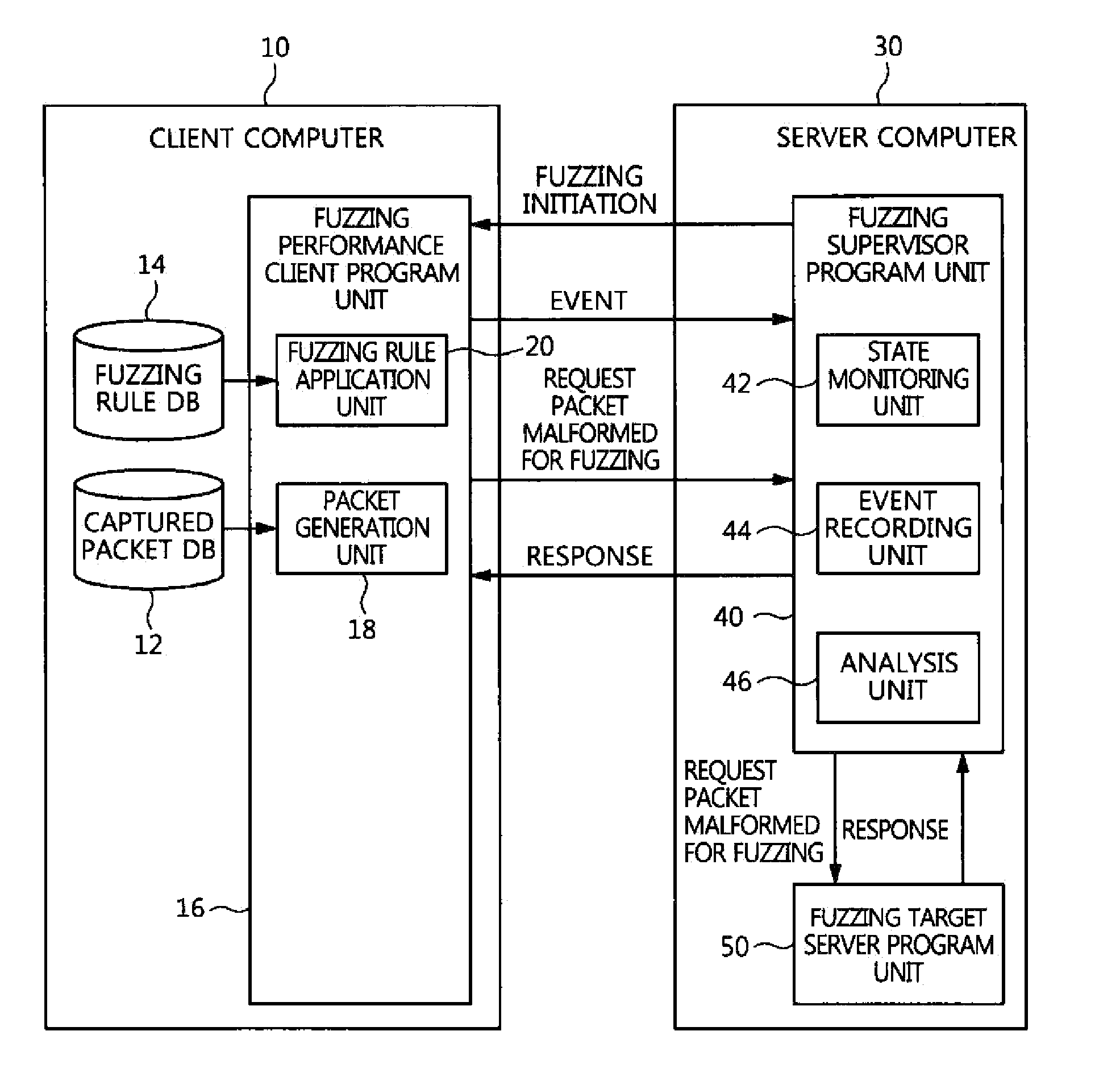
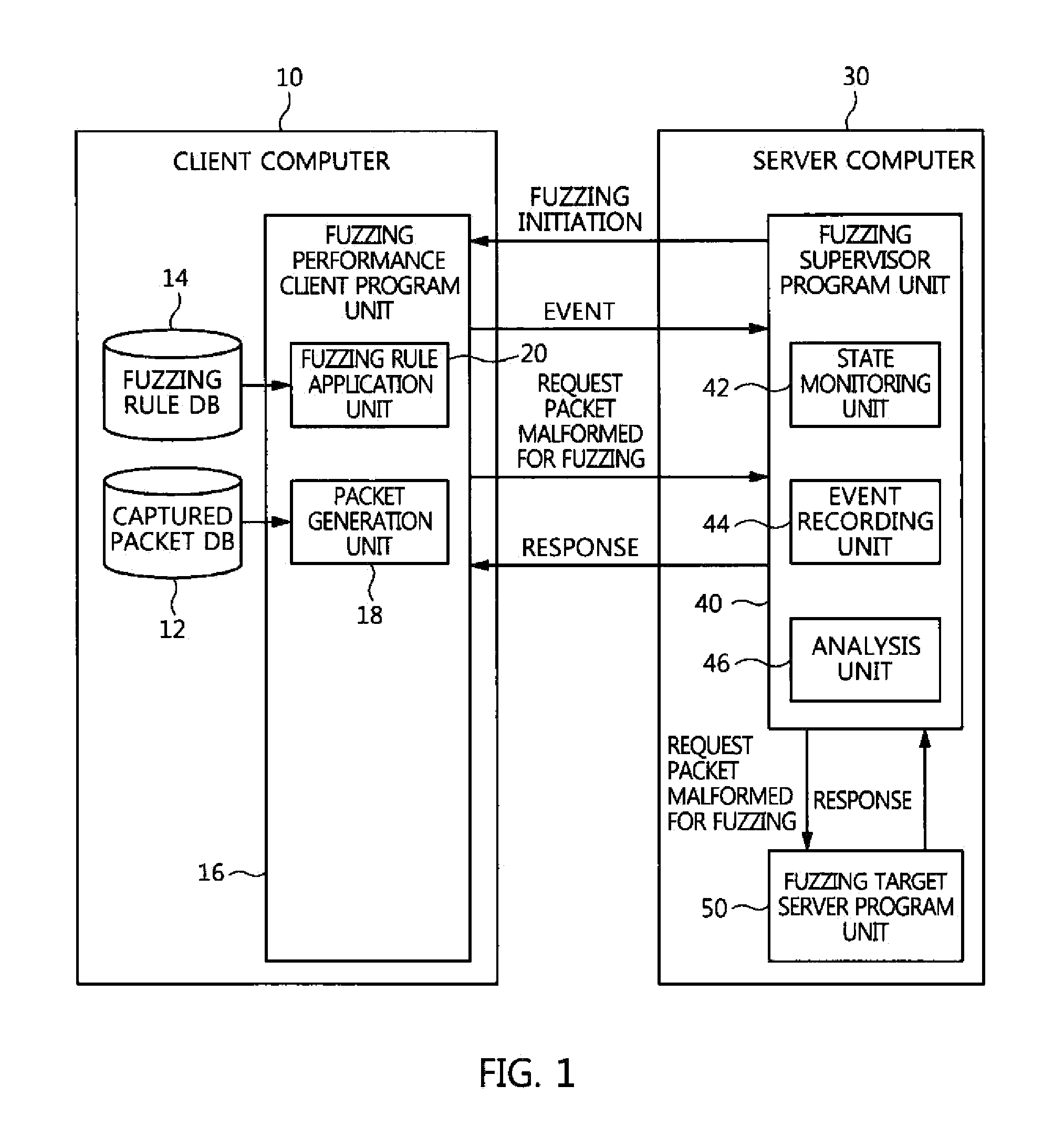
System and method for fuzzing network application program
A system and method for fuzzing a network application program, which use a captured packet upon fuzzing a network application program, and thus neither a protocol analysis procedure nor the production of a fuzzer program is required. The system for fuzzing a network application program includes a fuzzing performance client program unit for generating a packet to be transmitted from a captured packet, applying a fuzzing rule to the packet to be transmitted, and outputting a resulting packet. A fuzzing supervisor program unit provides the packet from the fuzzing performance client program unit to a target program to be fuzzed, monitors an event and abnormal termination of the target program to be fuzzed, and analyzes a situation of termination to verify security vulnerabilities if abnormal termination has occurred.
Owner:ELECTRONICS & TELECOMM RES INST
Reflective vulnerability detection method based on static and dynamic combination
ActiveCN109462583AAvoid security issuesArea clearPlatform integrity maintainanceTransmissionRandomized algorithmRandomization
The invention provides a reflective vulnerability detection method based on static and dynamic combination, which is a reflective XSS vulnerability detection method combining static stain propagationand dynamic Fuzzing test. Existing vulnerability detection is based on detection methods such as a single stain analysis or a genetic algorithm, and the stain analysis often uses a method combined with HTTP request packet interception analysis processing to track user's sensitive information and private data to prevent a malicious program code from being sent to a third party, which causes the leakage of user data. While the traditional genetic algorithm only contains the basic genetic operations of selection, crossover and mutation, only an approximate global optimal solution can be found dueto the inherent defects of the genetic algorithm in practice, but the global optimal solution cannot be guaranteed to be converged. The method simultaneously uses a randomization algorithm and a fuzzy test method to automatically detect the vulnerability while utilizing a static analysis source code and a stain propagation method to narrow the search range of the reflective XSS vulnerability, sothat the detection efficiency is high, and the method is highly feasible.
Owner:NANJING UNIV OF POSTS & TELECOMM
Sample format protection method and device for gray box fuzzy test
ActiveCN108171064AGuaranteed correctnessImprove fuzz testing efficiencySoftware testing/debuggingPlatform integrity maintainanceTest efficiencyTheoretical computer science
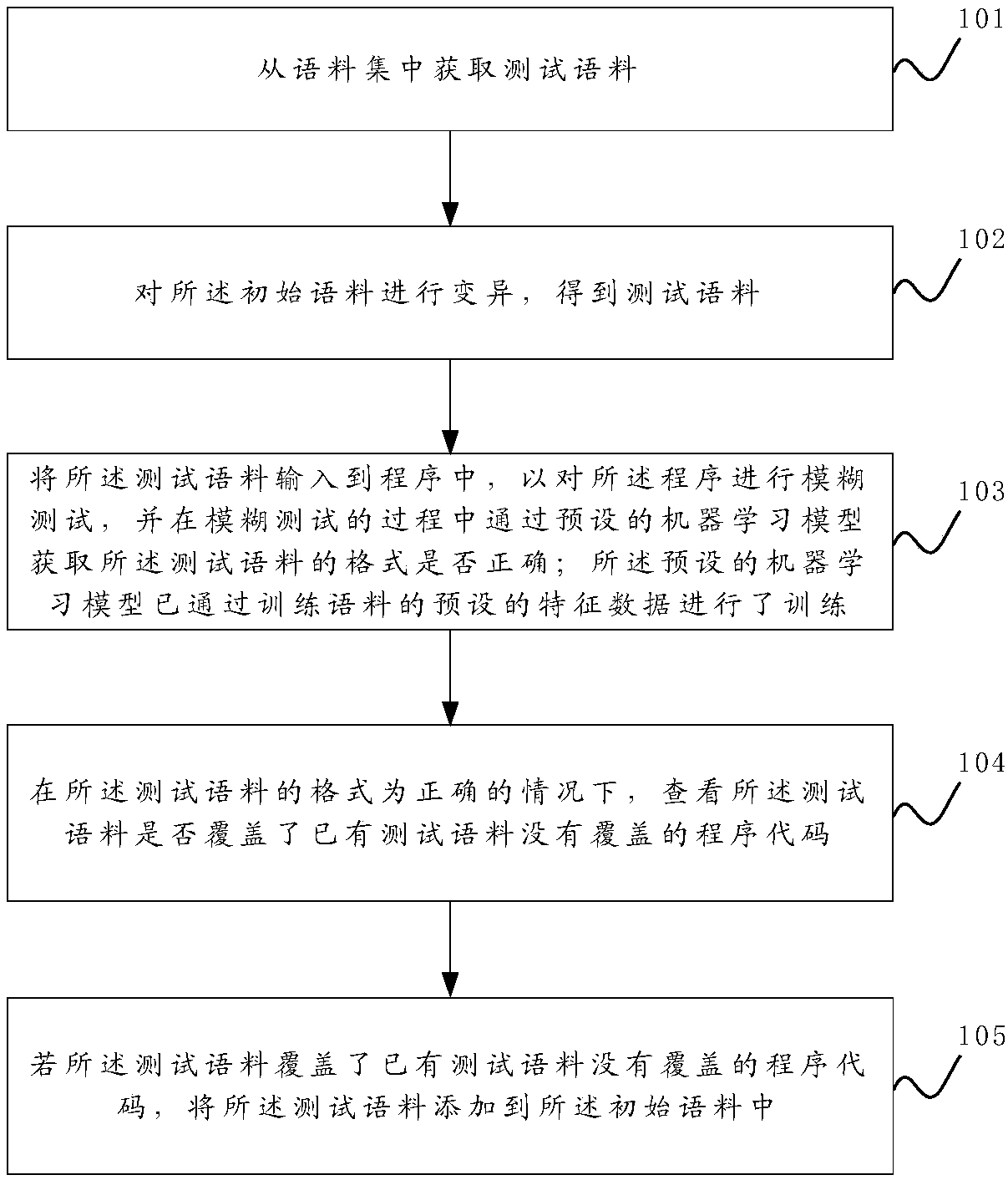
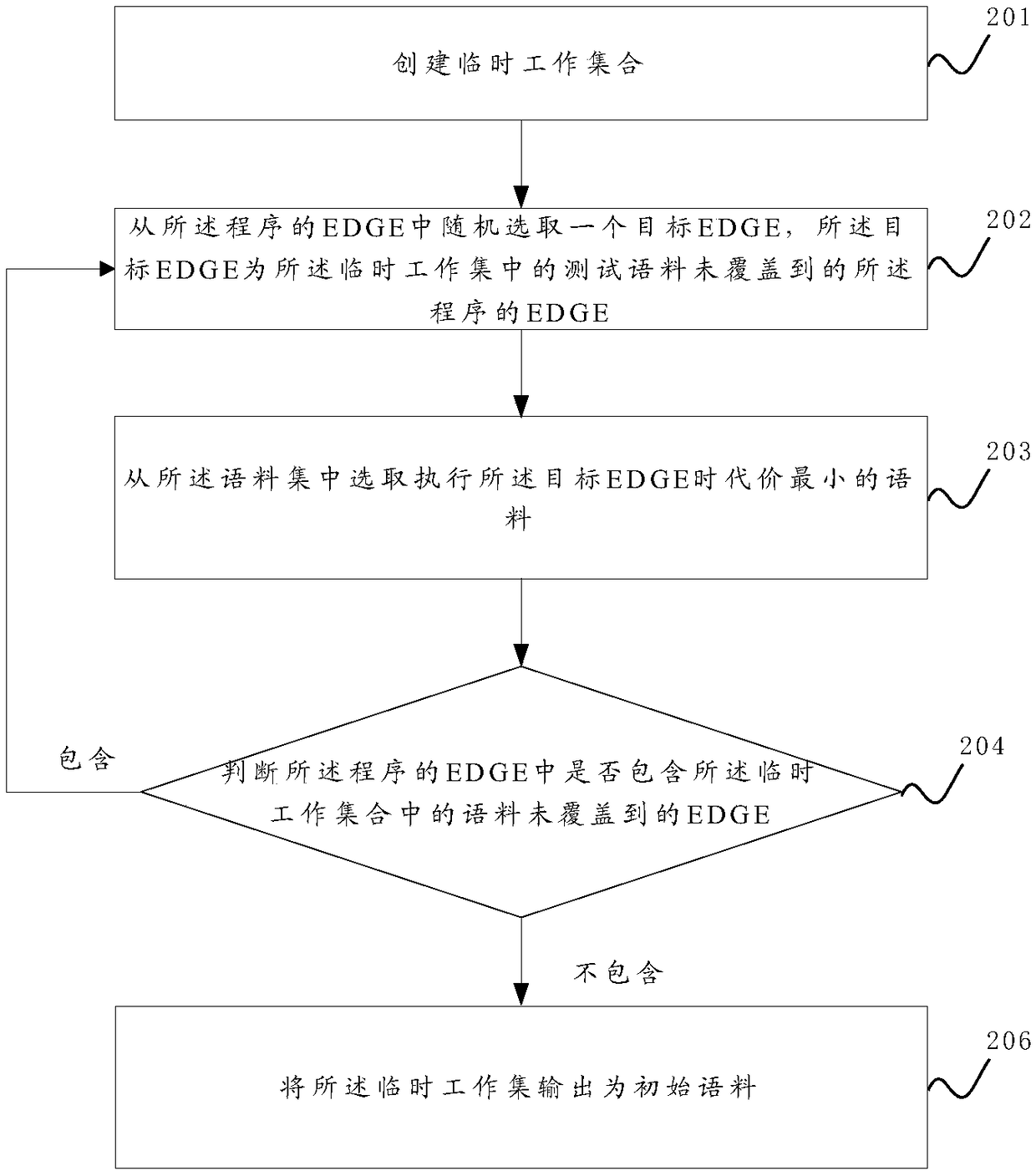
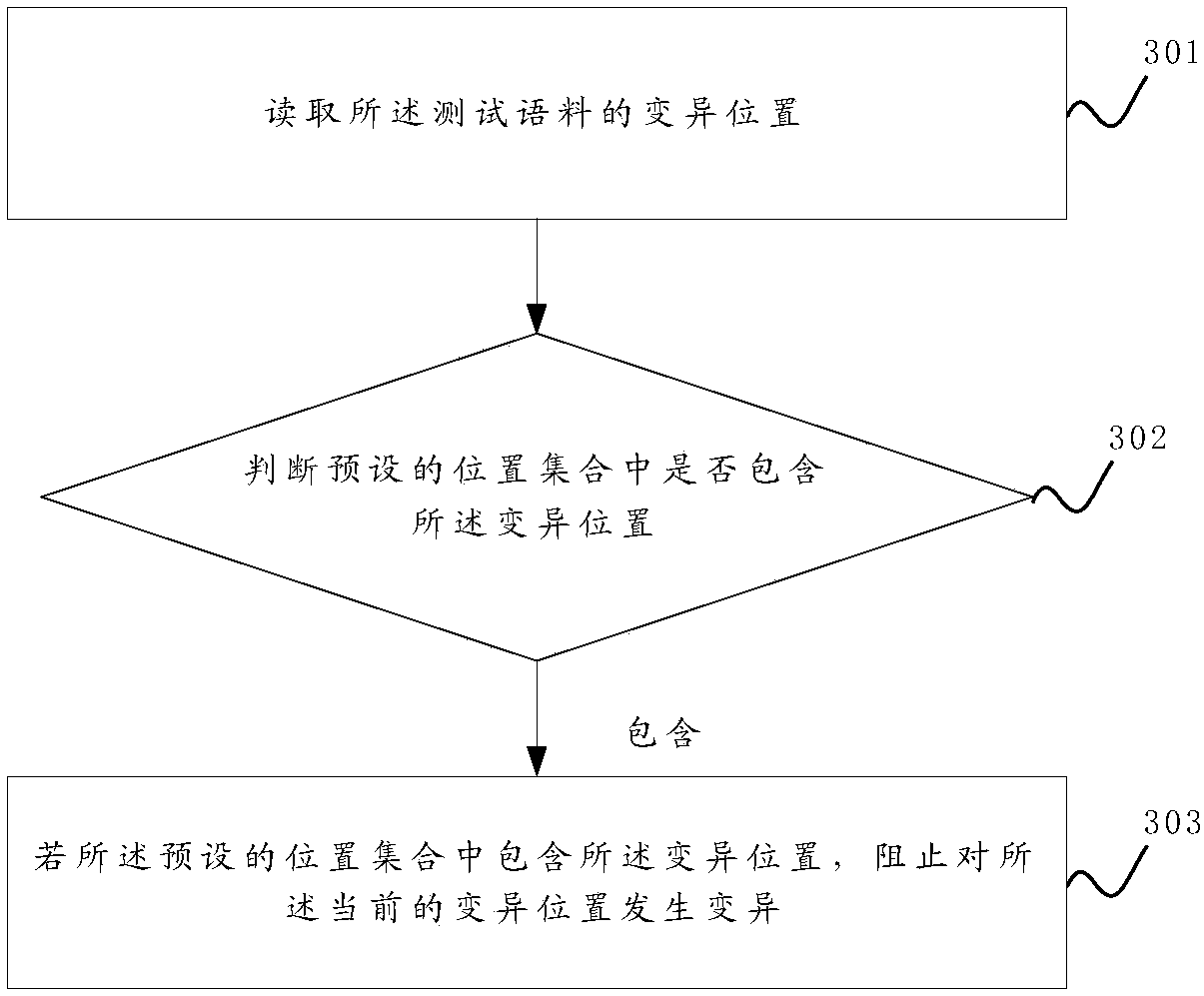
The invention discloses a sample format protection method and device for a gray box fuzzy test. The sample format protection method comprises the steps of training a machine learning model to enable the model to recognize the correctness of the format of a testing corpus; when the fuzzy test is conducted on a program, obtaining an initial corpus from a corpus set and mutating the initial corpus toobtain the testing corpus; using the testing corpus to conduct the fuzzy test on the program, and in the process of the fuzzy test, determining whether the format of the testing corpus is correct ornot through the model. When the format of the testing corpus is correct and the testing corpus covers a program code uncovered by an existing testing corpus, the testing corpus is added into the corpus set, and the process is repeated. In this way, the corpuses, with the correct format, determined in each fuzzy test is added into the corpus set, the correctness of the formats of the corpuses in the corpus set is guaranteed to the greatest extent, and the efficiency of the fuzzy test is improved. Moreover, through a position set, the mutation of the initial corpus is guided, an invalid mutationoperation is avoided, and the testing efficiency is further improved.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Warp knitting machine creel
InactiveCN103696117AImprove continuous working timeIncreased durabilityWarp knittingGlass fiberPolyether ether ketone
The invention relates to a warp knitting machine creel, comprising supports, wherein a plurality of groups of yarn guide plates are fixed between the supports; a plurality of yarn guide holes are formed in the yarn guide plates; cylindrical tension adjusting cross beams are arranged above cross beams; each group of yarn guide plates correspond to one tension adjusting cross beam; a tension adjuster is arranged on each tension adjusting cross beam in a sliding way and can rotate around the corresponding cross beam. According to the warp knitting machine creel, a whole glass fiber yarn drum is placed under the creel in a supporting way, the continuous working duration of a warp knitting machine is increased, the carry times of the yarn drum are greatly reduced, the labor intensity is greatly reduced, the yarn guide is stable, the production efficiency is improved, a wear-proof casing which is made of polyether-ether-ketone resin is adopted, the condition that the intensity of yarns is reduced due to the friction is prevented, the fuzzing of the yarns is effectively prevented, and the durability of the creel is improved.
Owner:JIANGSU CTC TECHN FABRICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com