Management-use separated computer encryption lock
A computer and encryption lock technology, applied in the field of electronic combination locks, can solve the problems of inconvenience, information leakage, and hardware being easily cloned and used, and achieve the effect of increasing security, high security, and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] In order to further illustrate the technical means adopted by the present invention and its effects, the following describes in detail in conjunction with preferred embodiments of the present invention and accompanying drawings.
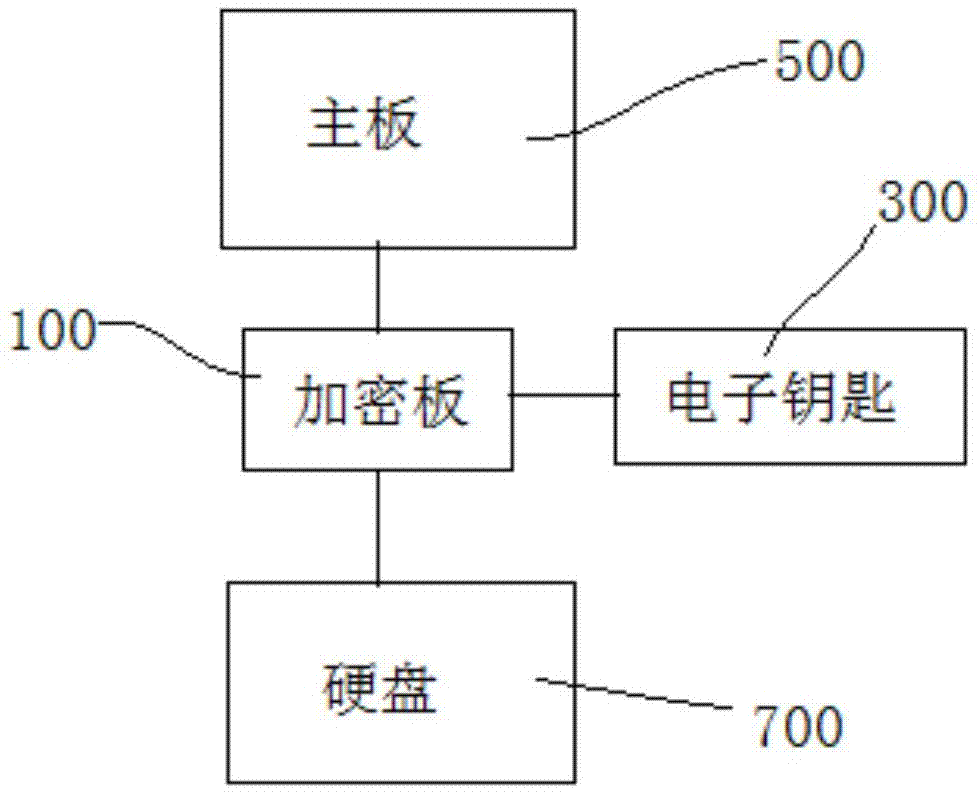
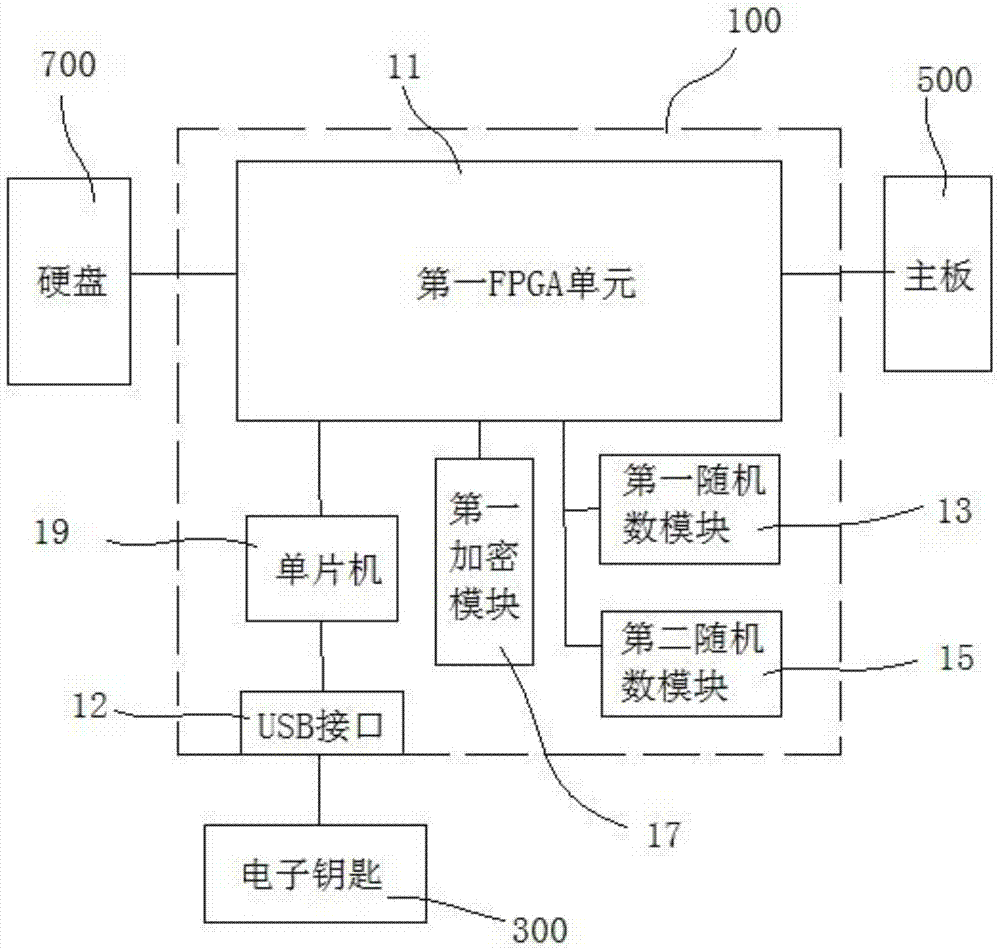
[0064] see figure 1 , The functional separate computer encryption lock provided by the present invention includes an encryption board 100 inserted between the main board of the computer and the hard disk 700, and an electronic key 300 plugged into the encryption board to perform identity authentication with the encryption board 100 .
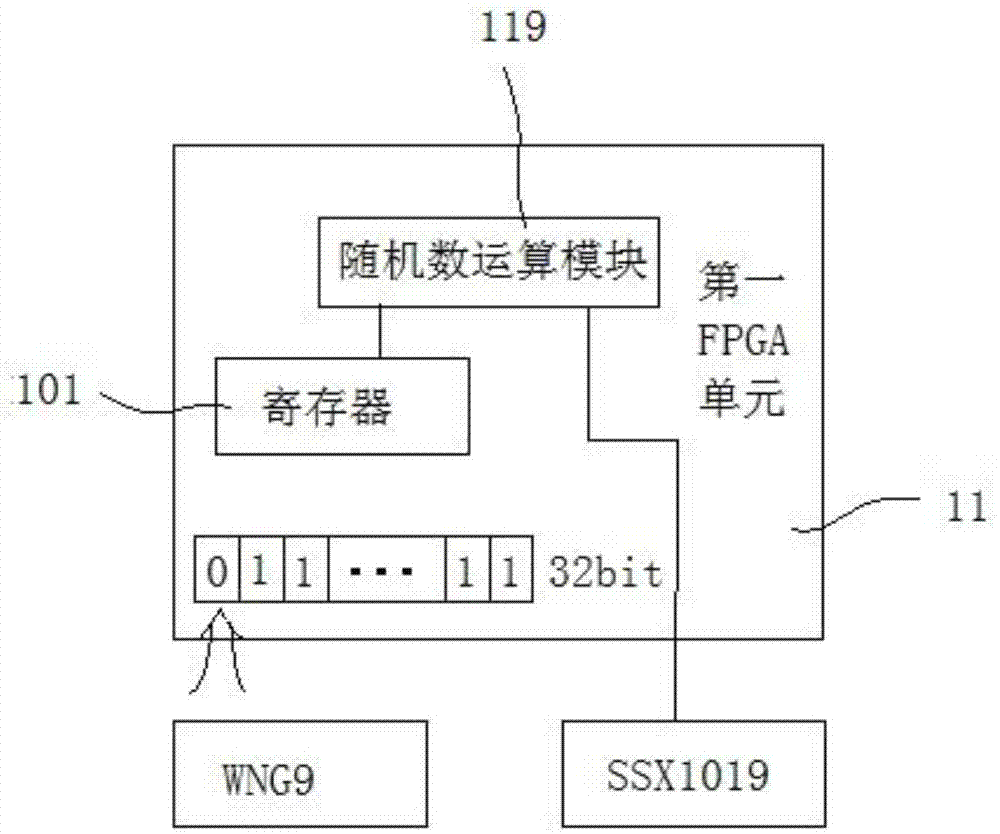
[0065] In the present invention, the encryption board 100 and the electronic key 300 respectively perform self-inspection on their own hardware after power-on, and after the self-inspection is completed, the electronic key 300 performs hardware pairing detection with the encryption board 100, and performs real-time identity authentication , after the identity authentication is passed, the encryption board 100 en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com