Network user identification verification method, server and client terminal
An identity verification method and identity verification technology, applied in the field of computer network security, can solve problems such as illegal use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
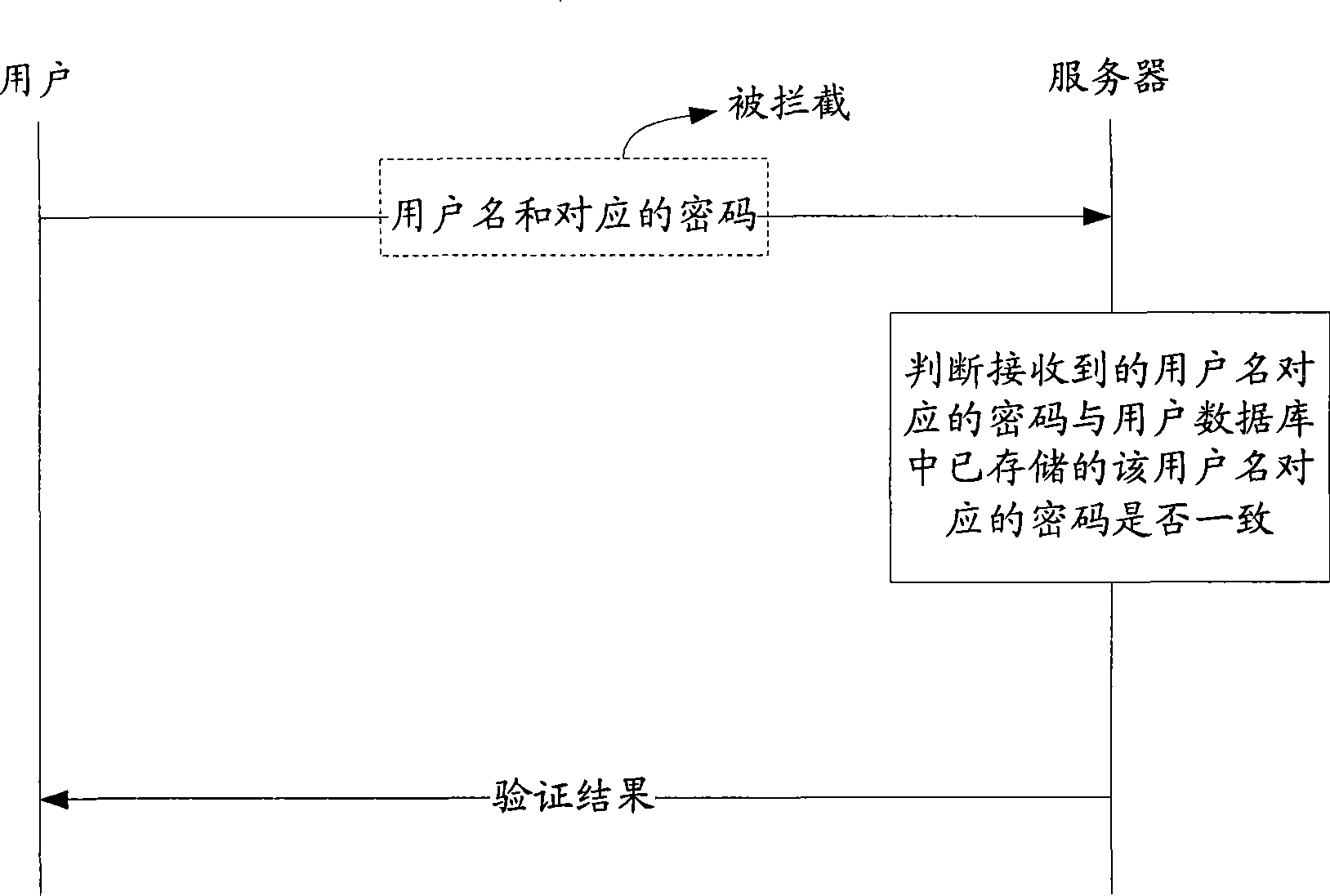
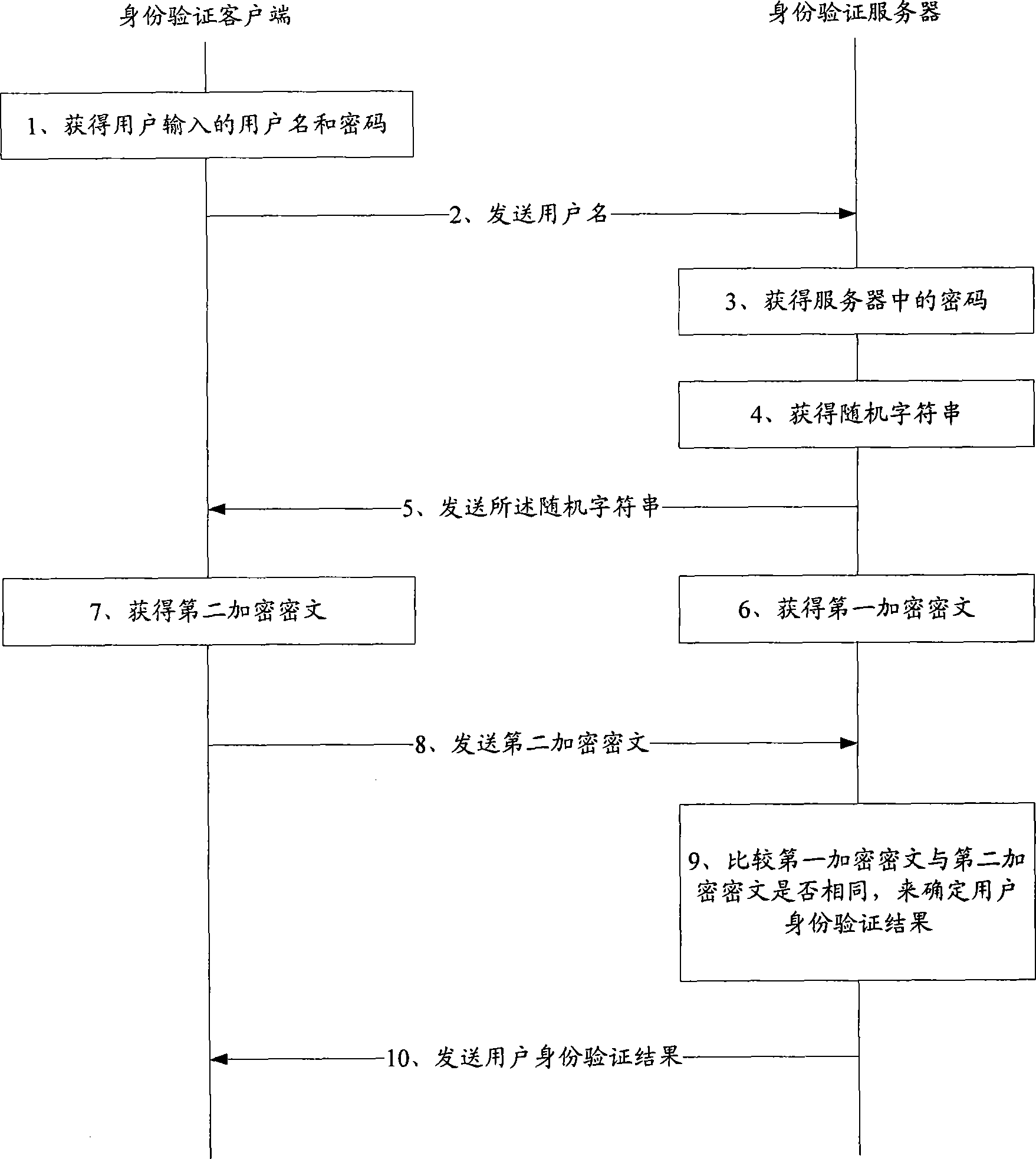
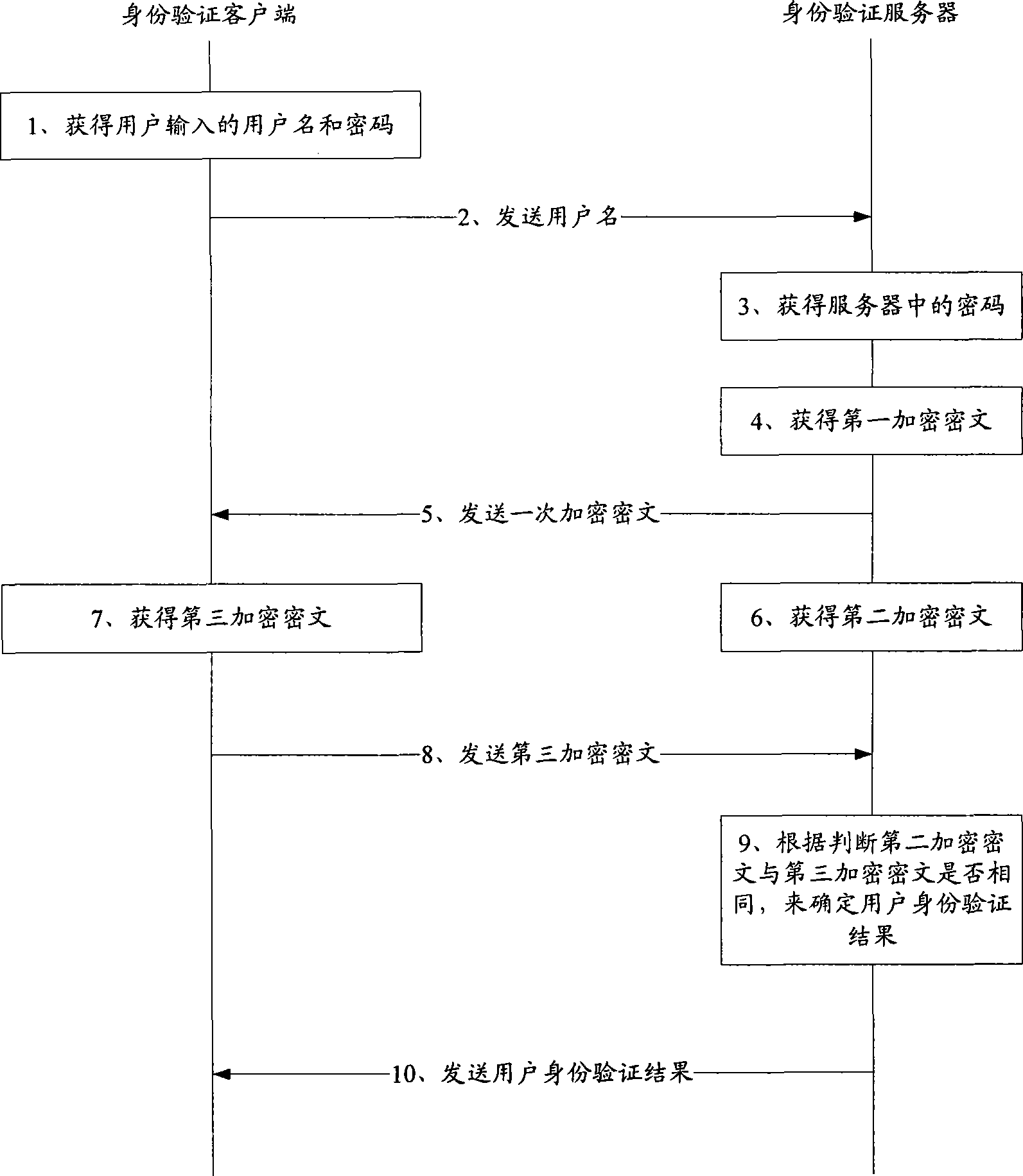
[0116]Due to the existing technology in the process of network user identity verification, the user needs to send the input user name and corresponding password information to the identity verification server in the network application system through the terminal, and the user name and corresponding password information may be transmitted during network transmission. intercepted and illegally used. To solve this problem, the technical solution proposed by the present invention only sends the user name to the identity verification server when the user logs in to the identity verification server, and then encrypts it by comparing the password sent by the client based on the user input. Whether the ciphertext is the same as the ciphertext encrypted based on the corresponding password of the user found in the user information database, to determine the identity verification result of the logged-in user. Adopting this solution preferably avoids the above-mentioned problems existing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com