Asymmetric encryption block chain identity information authentication method and device
An asymmetric encryption and identity information technology, applied in the field of asymmetric encrypted blockchain identity information verification, can solve the problems of single verification information and methods, unfavorable transaction information protection blockchain technology development, etc., to improve verification security, The effect of enhancing verification security and enhancing convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
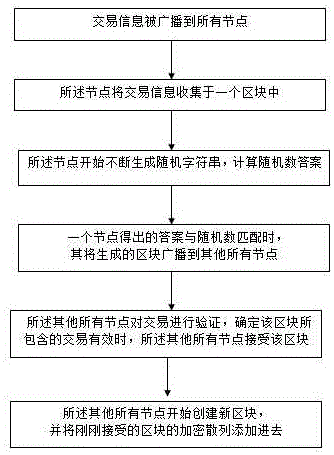
[0079] like figure 1 As shown, the transaction information is broadcast to all nodes;
[0080] the node collects transaction information in a block;
[0081] The node starts to generate random strings continuously, and calculates the random number answer;
[0082] When a node's answer matches a random number, it broadcasts the generated block to all other nodes;
[0083] All other nodes verify the transaction, and when it is determined that the transaction contained in the block is valid, all other nodes accept the block.
[0084] All the other nodes start creating new blocks and add the cryptographic hash of the block just accepted.
Embodiment 2
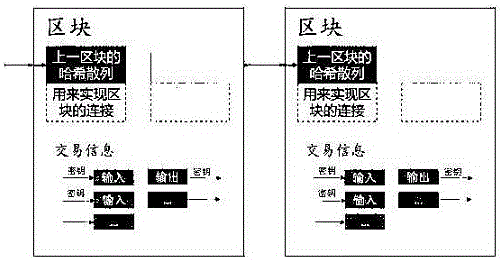
[0086] like figure 2 As shown, the blocks are randomly hashed and linked into a blockchain.
[0087] The cryptographic hash formed by the previous block is used to connect the blocks to realize the ordering of past transactions.
[0088] The blockchain must be linked to the previous block before the transaction can be further confirmed.
Embodiment 3
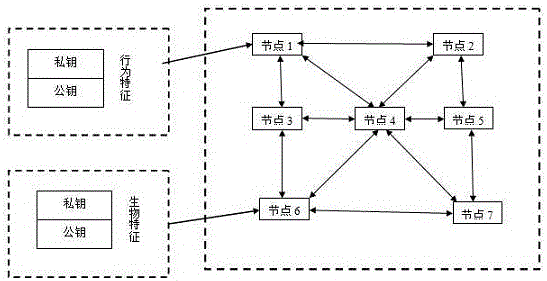
[0090] like image 3 shown, the verification includes a key pair;
[0091] The key pair includes a public key and a private key;
[0092] The public key has publicity and is used to encrypt a piece of information and prove the authenticity of the information;
[0093] The private key has privacy, and the private key is only mastered by the information owner to decrypt the information encrypted by the public key;
[0094] The information encrypted by the public key can only be decrypted by the person who has the corresponding private key;
[0095] The public key and the private key code have asymmetry, that is, the private key cannot be derived from the public key;
[0096] The private key signs the information, and the public key verifies the signature;
[0097] The information verified by the public key signature is confirmed to be issued by the private key holder;
[0098] The public key is issued by the previous block, and the private key is owned by the next block hol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com