Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3834results about How to "Increase authenticity" patented technology
Efficacy Topic
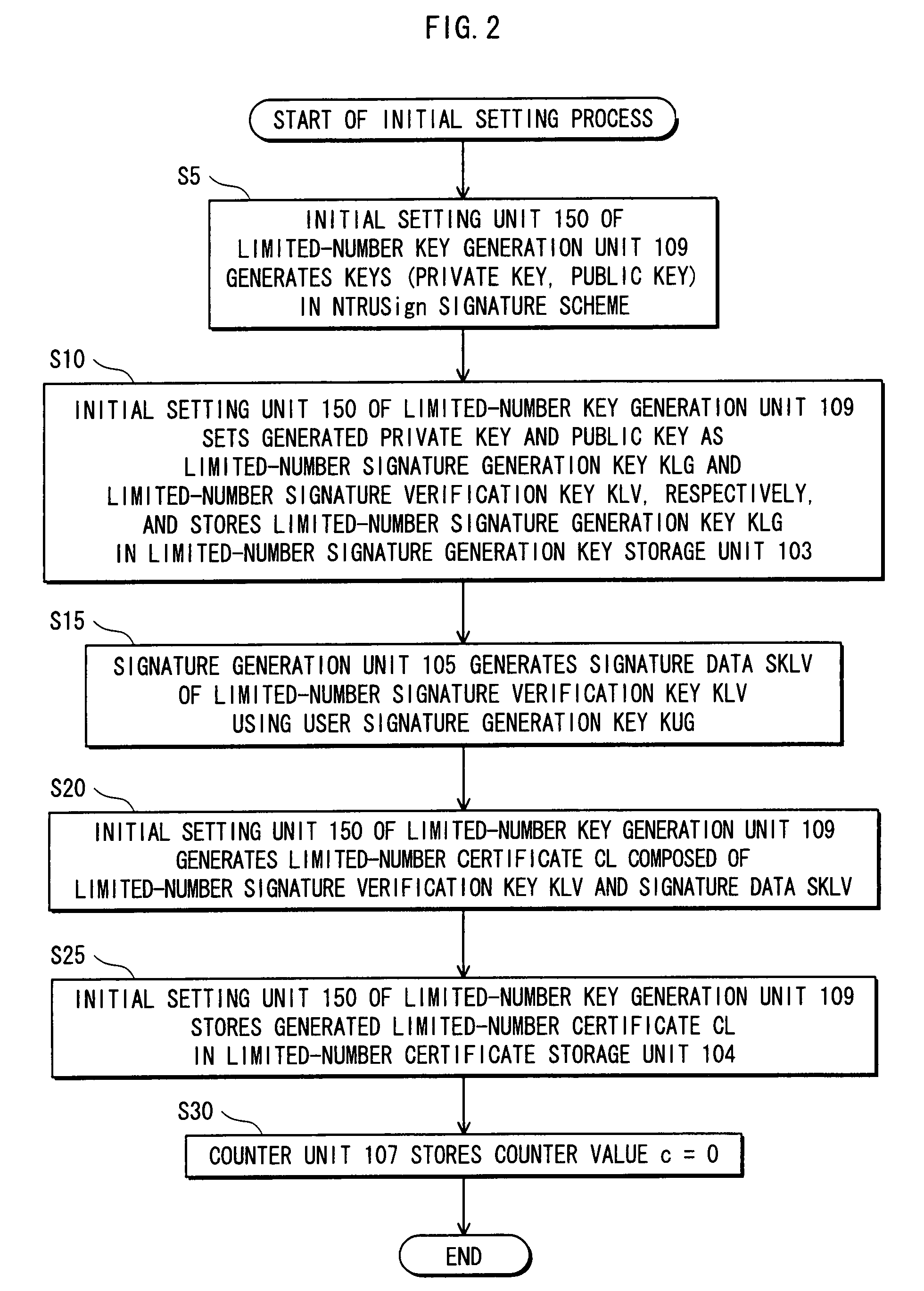
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
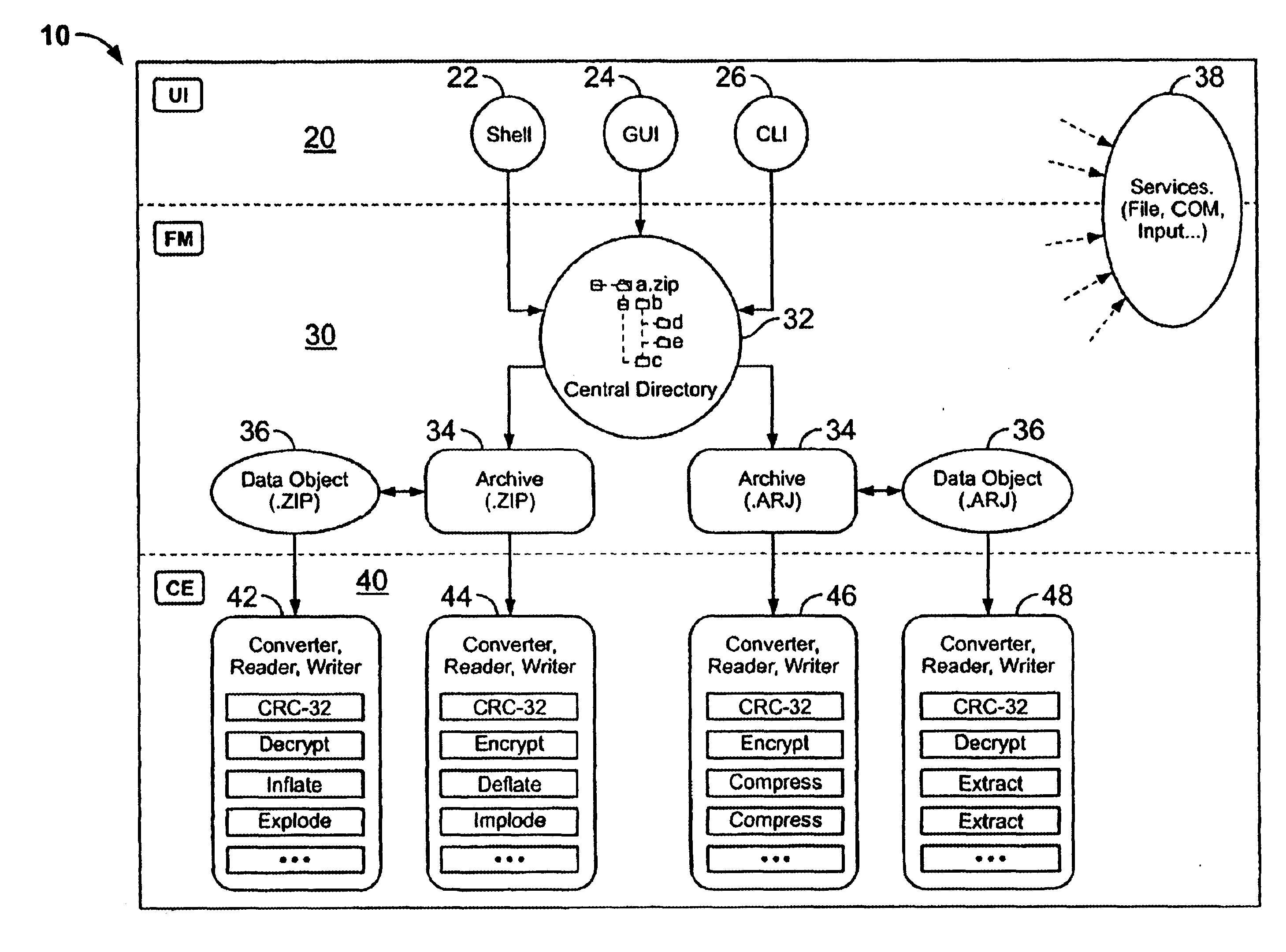
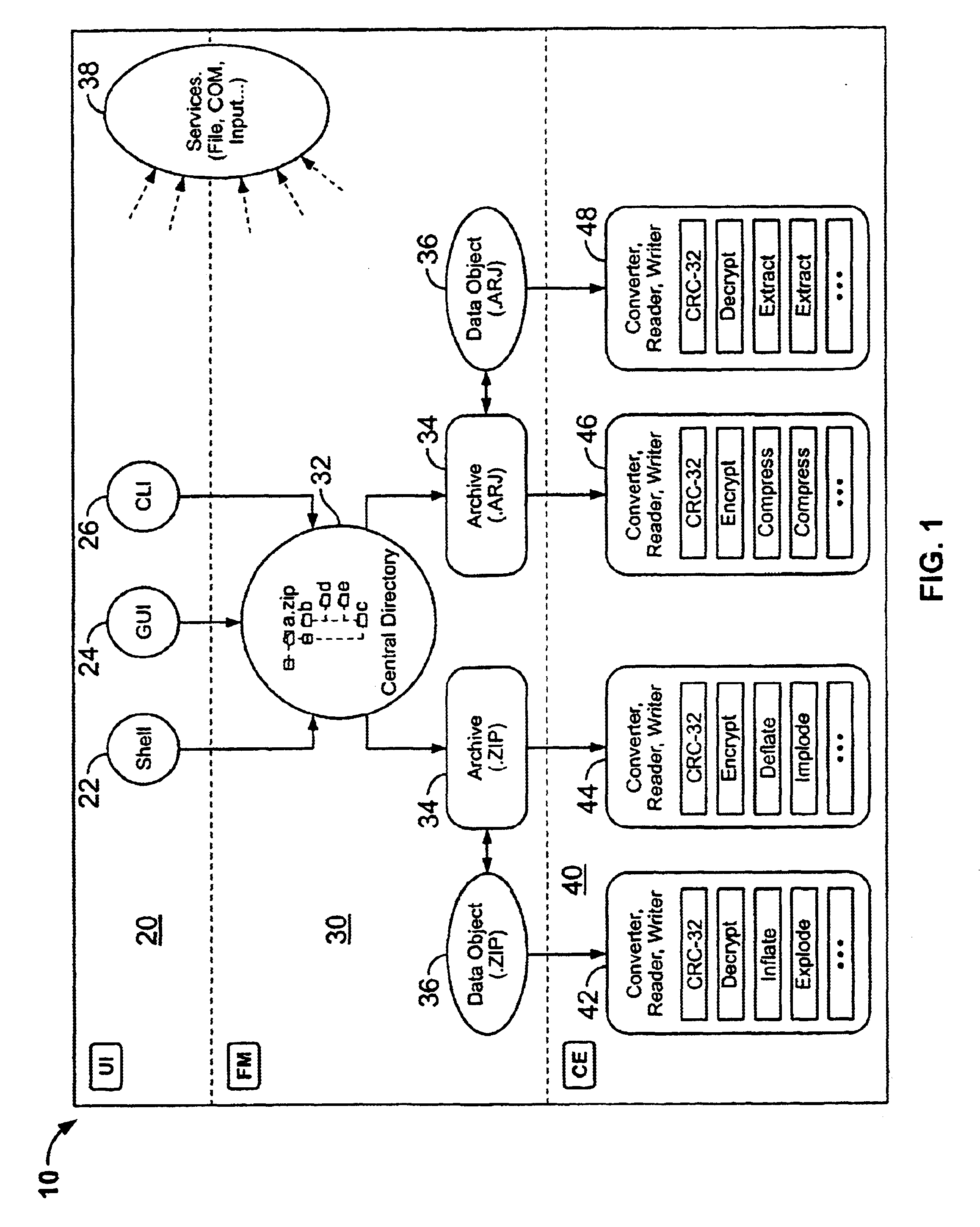
System and method for manipulating and managing computer archive files
InactiveUS6879988B2Easy to carryQuick and easy management and manipulationData processing applicationsDigital data information retrievalDrag and dropResource management
A computer program for managing and manipulating archive zip files of a computer. The program includes a system and method for opening, creating, modifying, and extracting zip archive files. The program is fully integrated into Microsoft Windows Explorer and is accessed via Explorer menus, toolbars, and / or drag and drop operations. An important feature of the program is the archive manager which may be used to open a zip file, create a new zip file, extract zip files, modify zip files, etc. The program is integrated into Microsoft Windows Explorer using the shell name space extension application program interface developed by Microsoft.
Owner:PKWARE
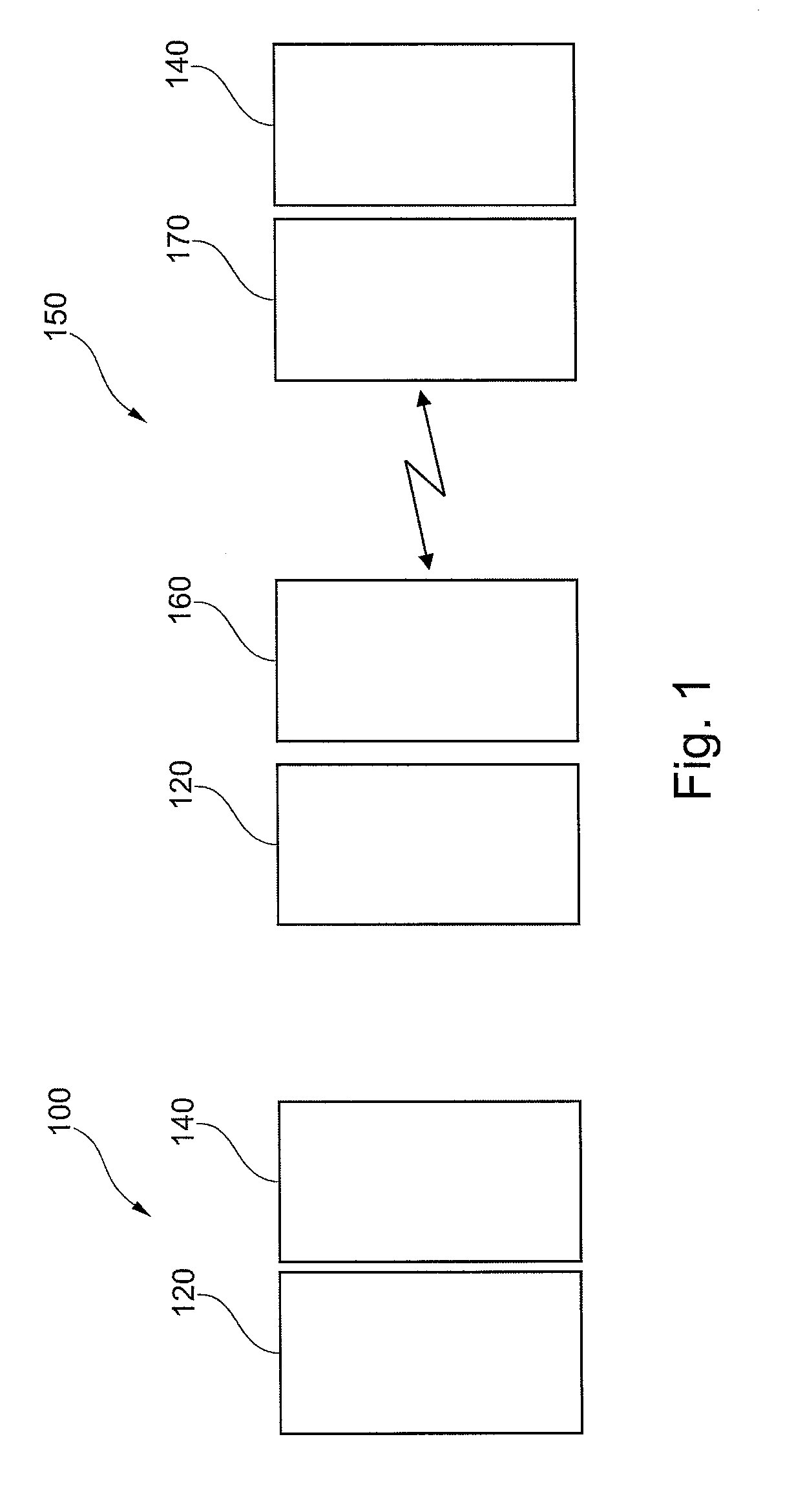
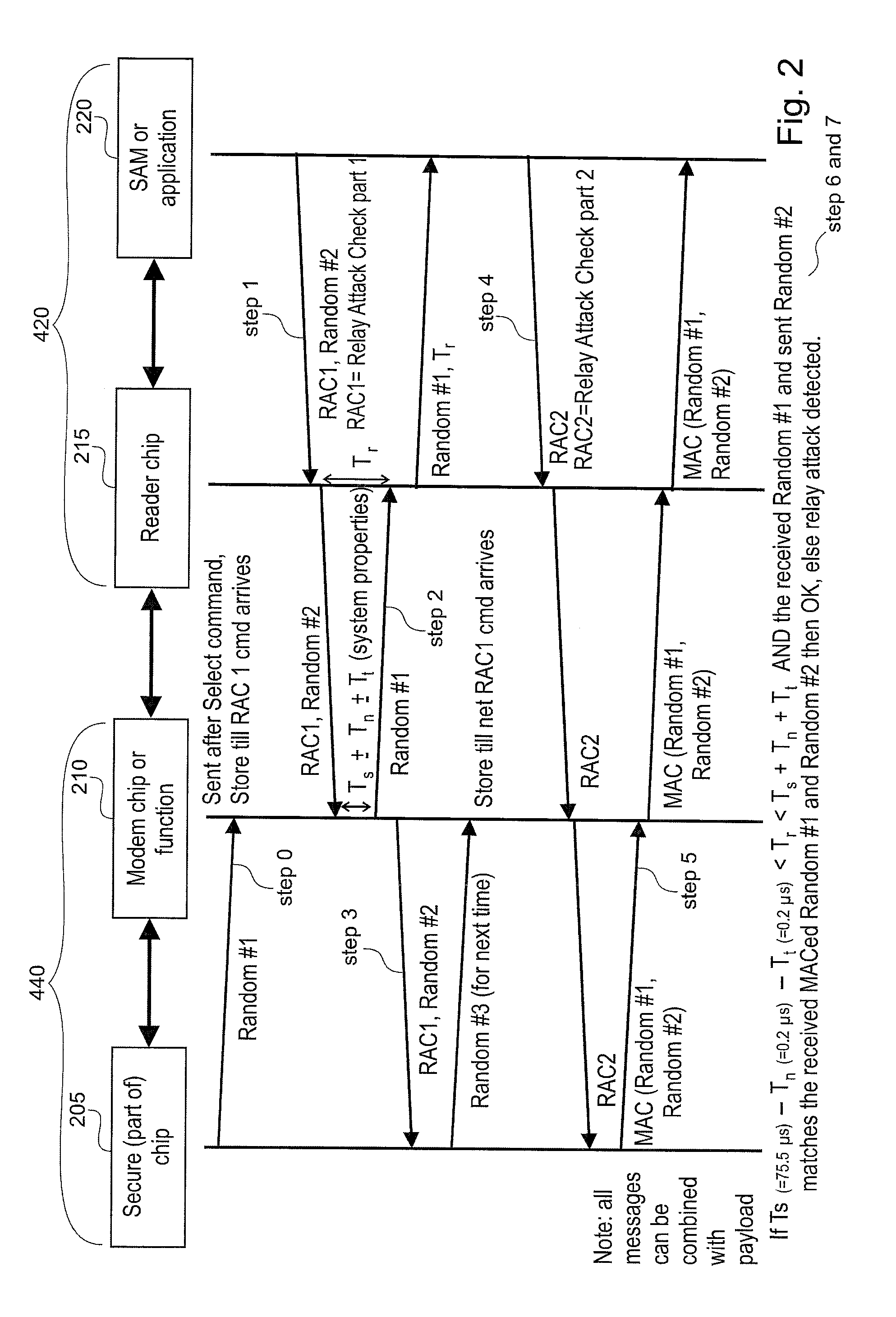
Decoupling of measuring the response time of a transponder and its authentication
ActiveUS20110078549A1Short response timeImprove reliabilityDigital data processing detailsUser identity/authority verificationEngineeringAuthentication
Reader (420) for determining the validity of a connection to a transponder (440), designed to measure a response time of a transponder (440) and to authenticate the transponder (440) in two separate steps. Transponder (440) for determining the validity of a connection to a reader (420), wherein the transponder (440) is designed to provide information for response time measurement to said reader (420) and to provide information for authentication to said reader (420) in two separate steps, wherein at least a part of data used for the authentication is included in a communication message transmitted between the reader (420) and the transponder (440) during the measuring of the response time.
Owner:NXP BV
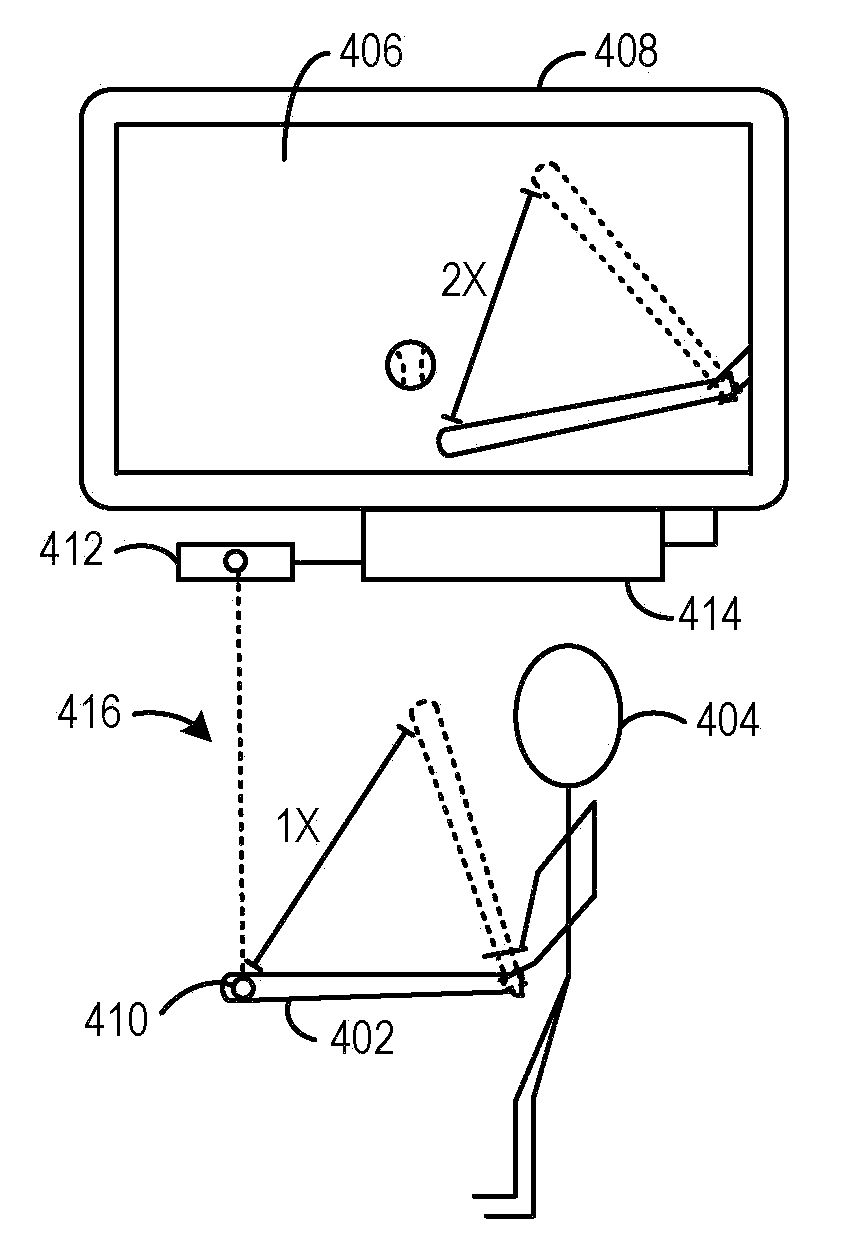
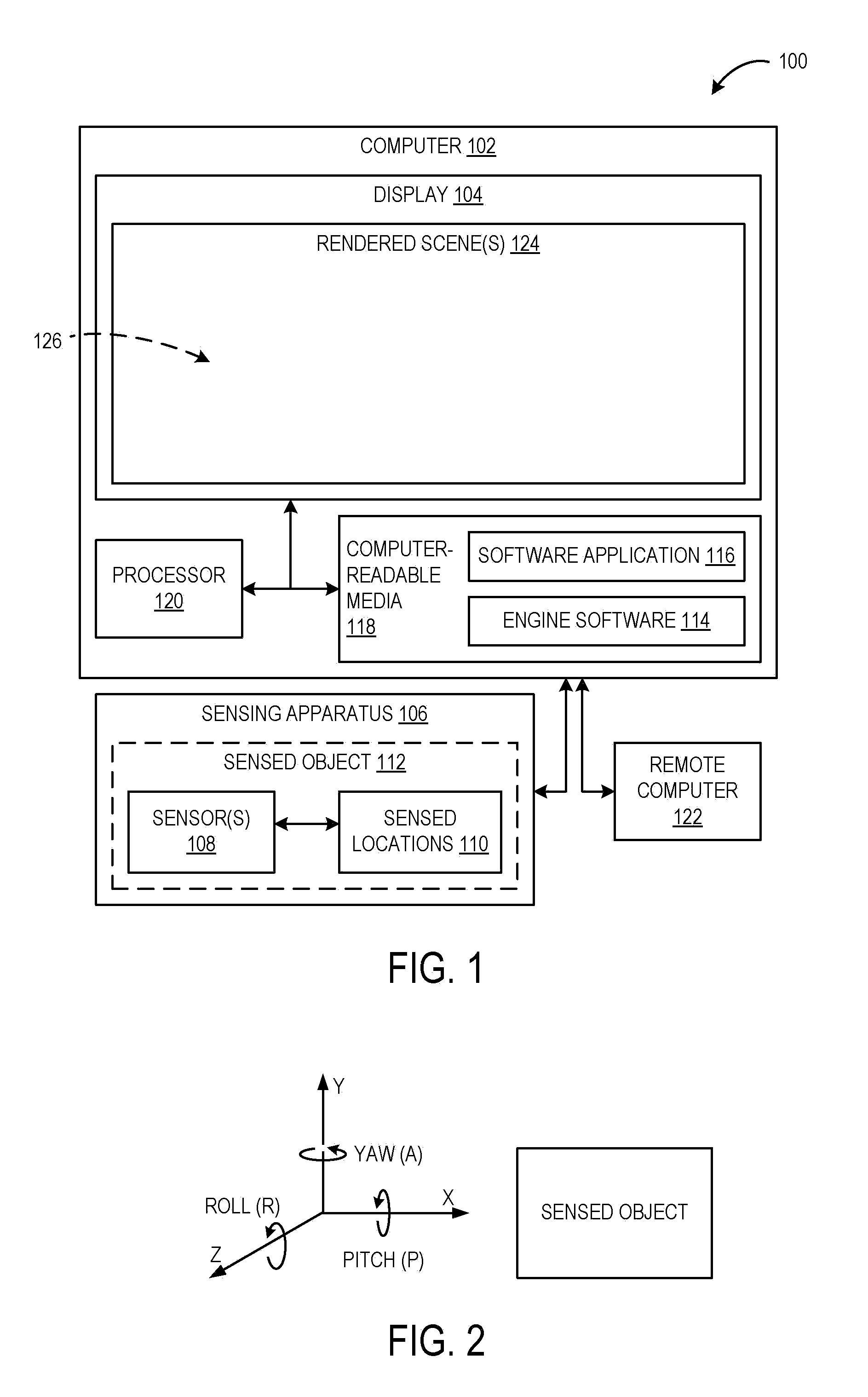
Approach for Merging Scaled Input of Movable Objects to Control Presentation of Aspects of a Shared Virtual Environment
InactiveUS20080211771A1Authenticity of be improveAccurately simulateCathode-ray tube indicatorsVideo gamesApplication softwareUser control
A system for controlling operation of a computer. The system includes, a sensing apparatus configured to obtain positional data of a sensed object controllable by a first user, such positional data varying in response to movement of the sensed object, and engine software operatively coupled with the sensing apparatus and configured to produce control commands based on the positional data, the control commands being operable to control, in a multi-user software application executable on the computer, presentation of a virtual representation of the sensed object in a virtual environment shared by the first user and a second user, the virtual representation of the sensed object being perceivable by the second user in a rendered scene of the virtual environment, where the engine software is configured so that the movement of the sensed object produces control commands which cause corresponding scaled movement of the virtual representation of the sensed object in the rendered scene that is perceivable by the second user.
Owner:NATURALPOINT
Three-dimension image processing method, device, storage medium and computer equipment
ActiveCN107564089AEasy to integrateIncrease authenticityImage enhancement3D-image renderingHat matrixImaging processing
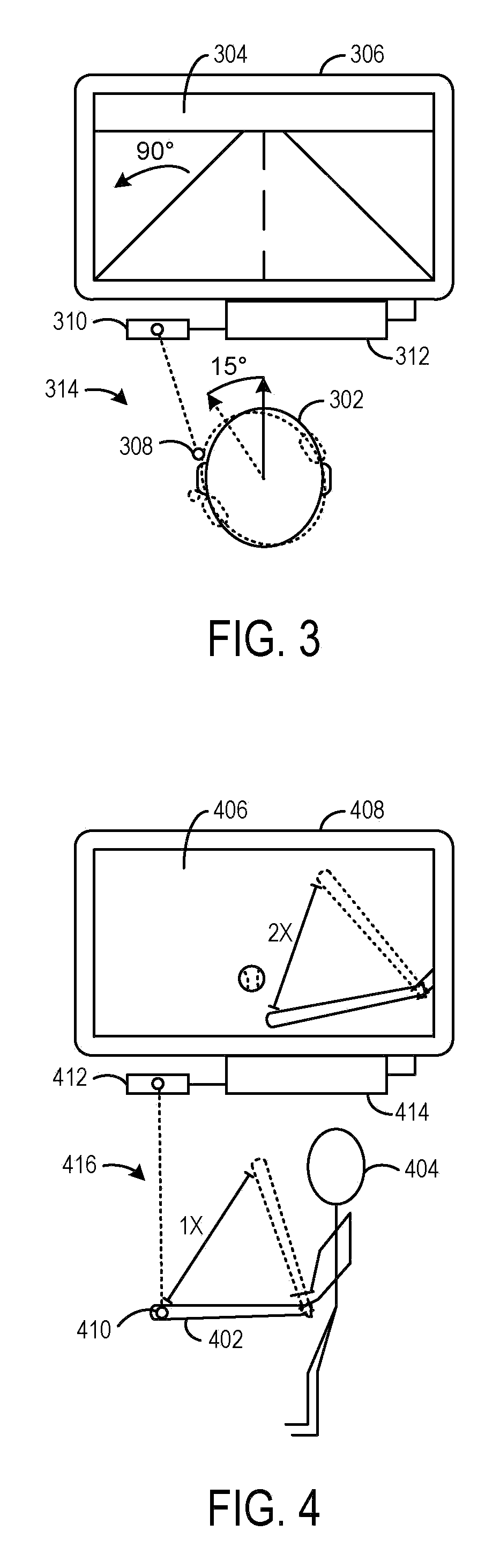
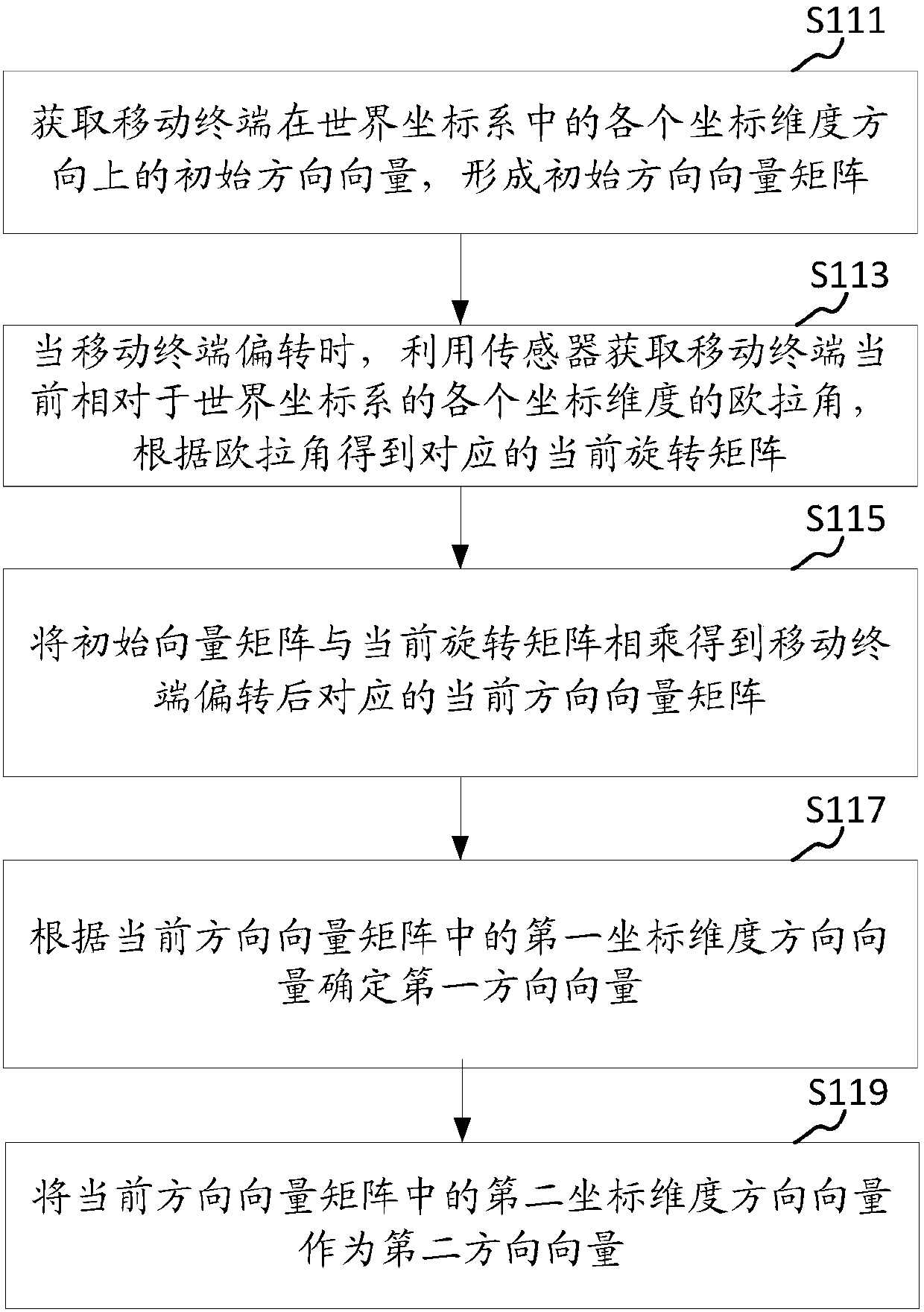
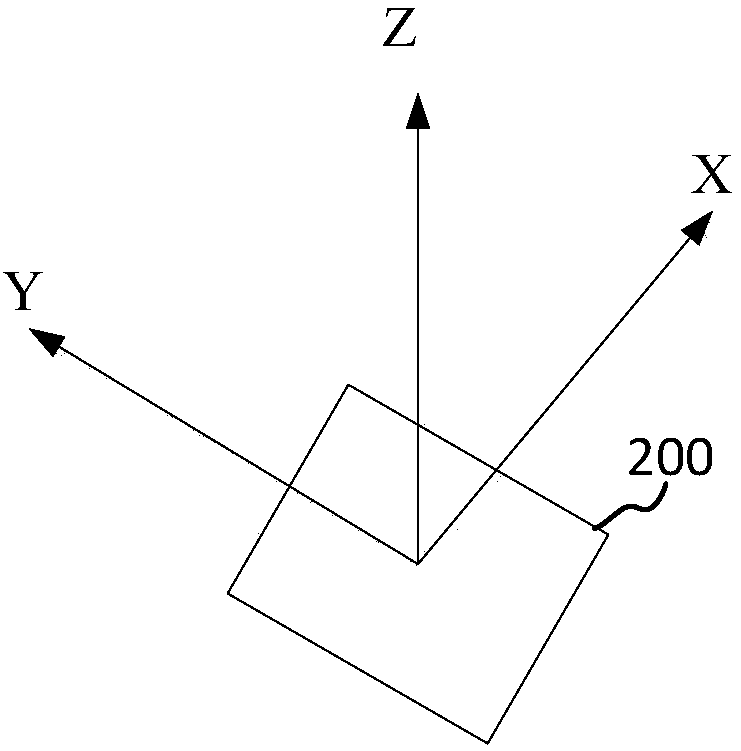
The invention provides a three-dimension image processing method comprising the following steps: obtaining current image acquisition device position coordinates from a world coordinate system, obtaining a first direction vector and a second direction vector, and using a view transformation algorithm to obtain a transparent matrix; obtaining preset near plane vertex coordinates a near plane distance and a far plane distance from an image acquisition device coordinate system, and using a projection transformation algorithm to obtain a projection matrix; multiplying the transparent matrix with the projection matrix so as to obtain a transformation matrix; multiplying the transformation matrix with texture initial vertex coordinates matched with added augmented reality elements so as to obtaintexture target vertex coordinates matched with the augmented reality elements; using the texture target vertex coordinates to render the augmented reality elements so as to form a three-dimension image. The mobile terminal can rotate to drive the image acquisition device to rotate, so the three-dimension image corresponding to the augmented reality elements can make corresponding rotations, thusincreasing the fusing level between the three-dimension image and a true background image, and improving the image authenticity; the invention also provides a three-dimension image processing device,a storage medium and computer equipment.
Owner:TENCENT TECH (SHENZHEN) CO LTD
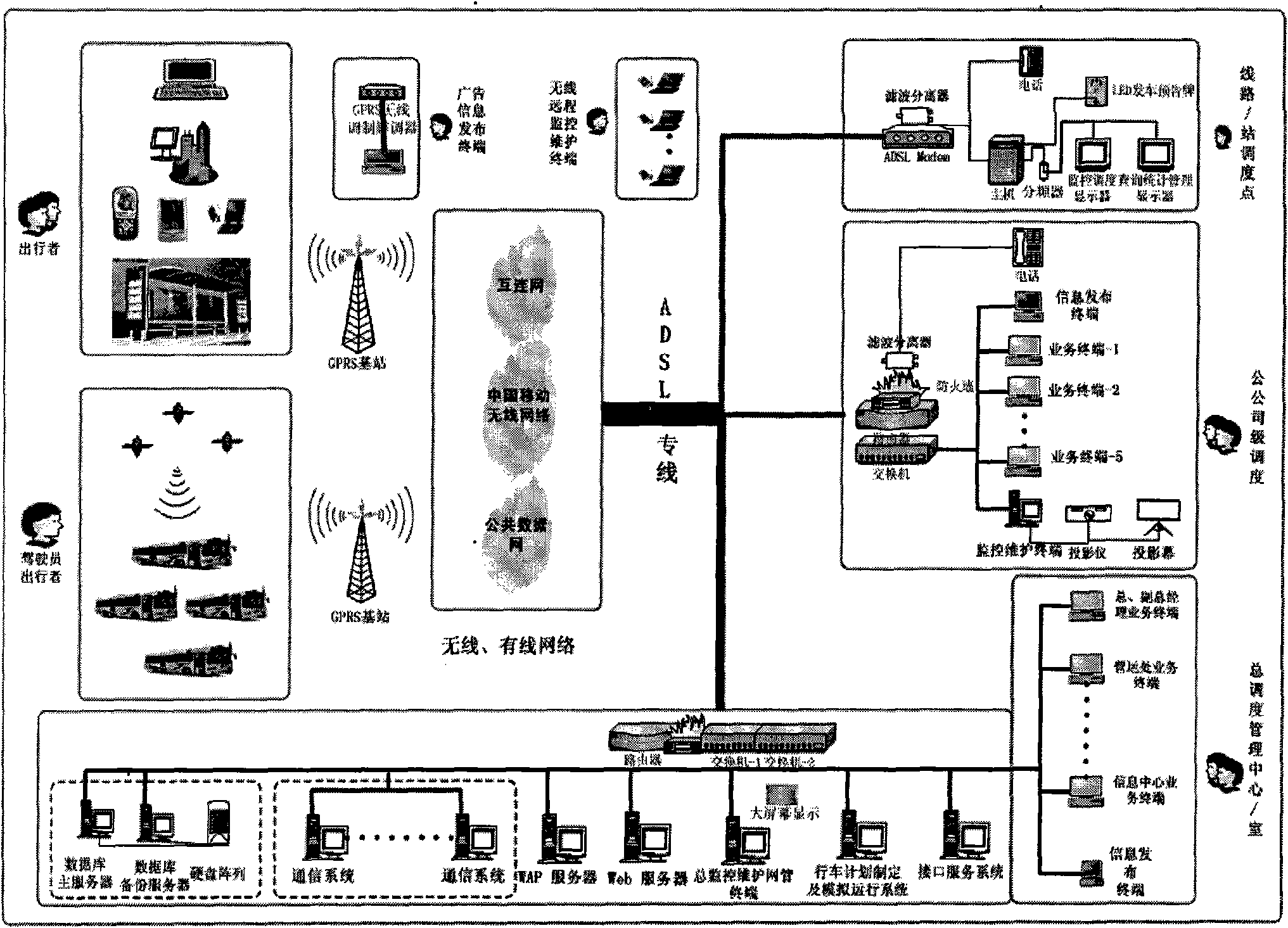
System and method for intelligently dispatching and managing urban public transports
ActiveCN101572011ARealize automatic collectionRealize transmissionArrangements for variable traffic instructionsPosition fixationExecution controlCentral database
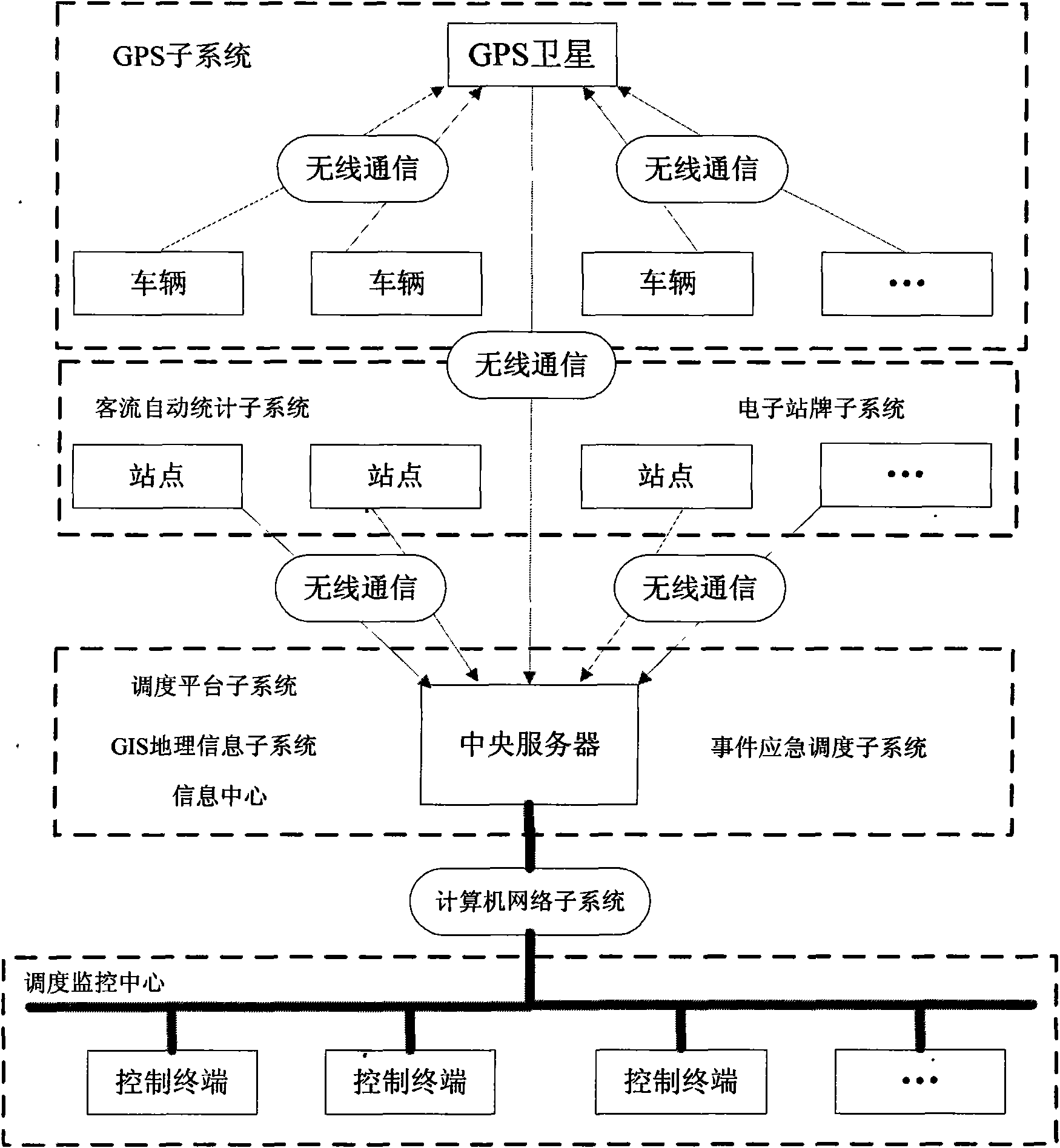
The invention relates to a system and a method for intelligently dispatching and managing urban public transports. A GPS subsystem acquires traffic data in real time, and the data is transmitted to a central server through a radio communication subsystem; the central server transmits a dispatching scheme to a control terminal through a computer network subsystem; vehicles execute the dispatching of the control terminal; and the control terminal displays the operation state of the vehicles on electronic maps based on a GIS geographic information subsystem, the automatic acquisition and transportation of operation information, passenger traffic volume and operation and production process information of the vehicles are realized through a computer network central database, the objectivity and the trueness of basic production information records of enterprises are improved, the checking requirements of different levels and different ranges are met, and the operation quality is detected. The system and the method can perform real-time optimum dispatching on operating vehicles and emergency repair vehicles under the assistance of a computer-based intelligent dispatching system, and strengthen the commanding capability and the response capability on the operation state.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
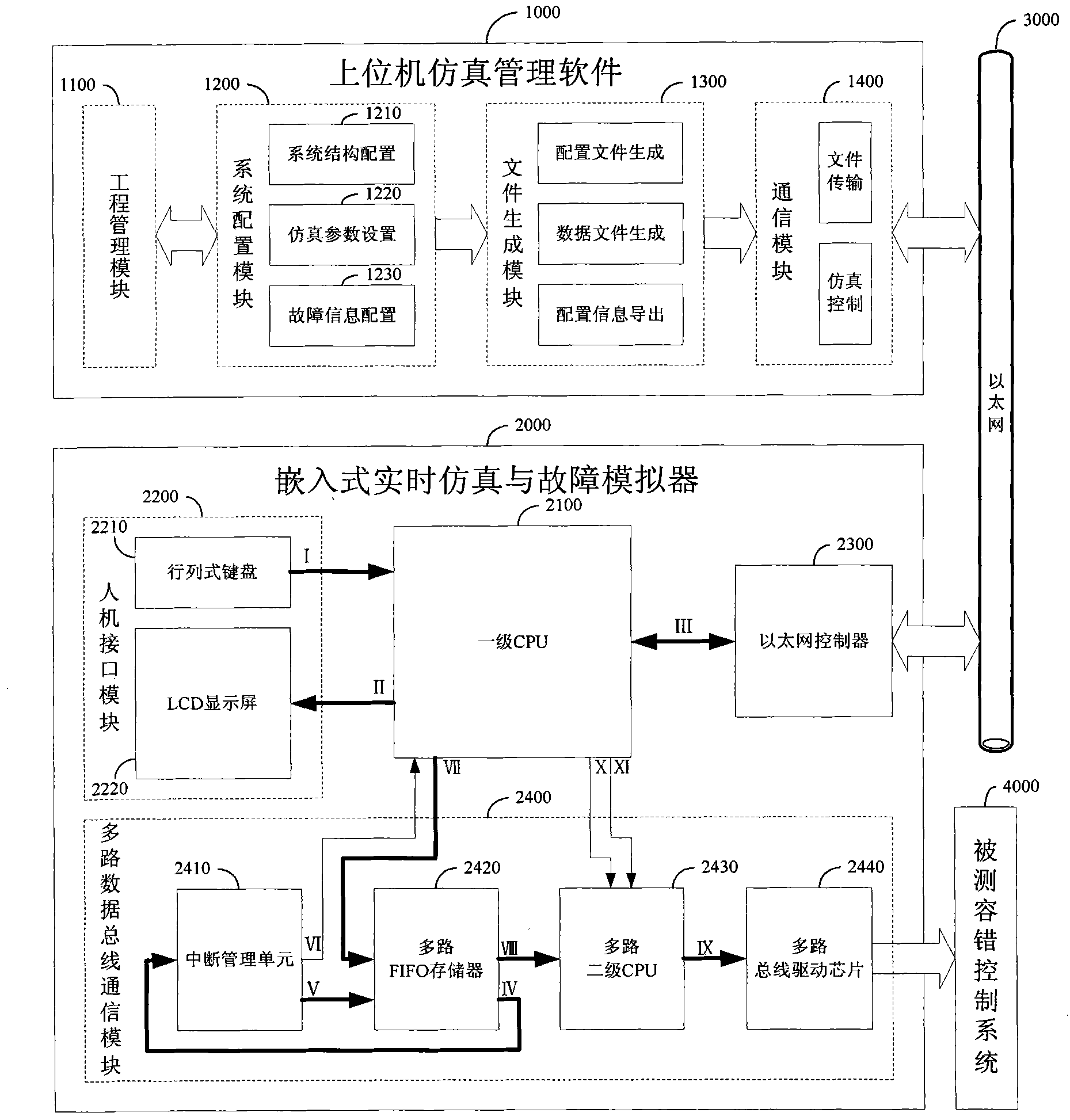
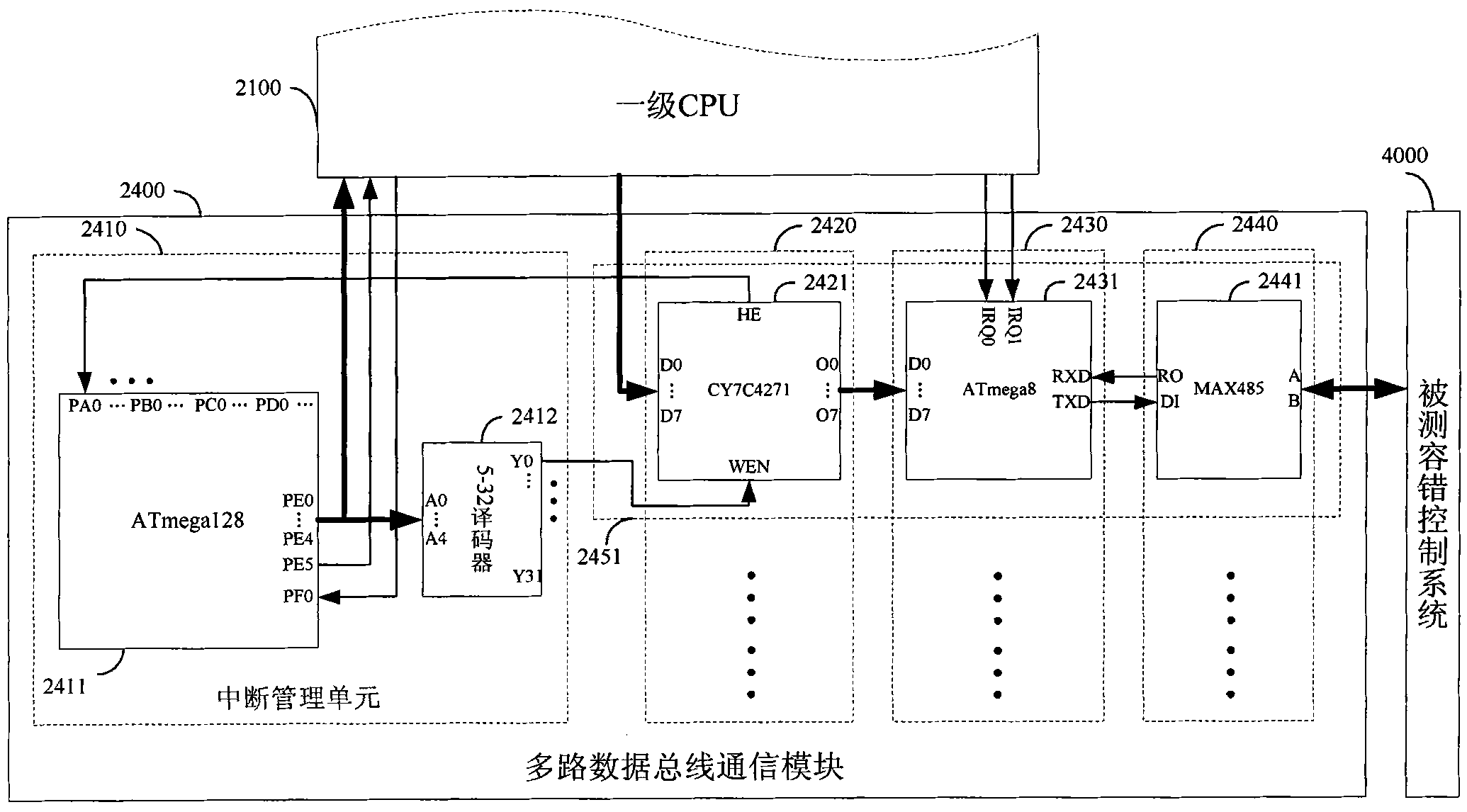
Embedded real-time emulation and fault simulation system based on multiple data buses
InactiveCN101937232AAvoid dependenceImprove versatilityElectric testing/monitoringData streamHuman–machine interface
The invention discloses an embedded real-time emulation and fault simulation system based on multiple data buses, comprising upper computer simulation management software and an embedded real-time emulation and fault simulation device. The upper computer simulation management software guides the user to perform emulation configuration and fault setting aiming at a fault-tolerant control system to be tested through a human-computer interface, and generates fault emulation data of multiple redundancy equipment. The embedded real-time emulation and fault simulation device outputs the fault emulation data in real-time and synchronously through the multiple data buses, simulates the fault of the multiple redundancy equipment and outputs the fault data stream. The upper computer and a lower computer communicate mutually through an Ethernet to achieve the downloading of the information configuration, the fault emulation data and the emulation control command of the upper computer, and the uploading of the working condition of the lower computer. The invention overcomes the defects of poor universality and lower synchronous precision of the traditional multiple equipment fault simulation device based on the emulation, and is suitable for the test and the verification of the different redundancy fault-tolerant designs of the complex spacecraft system with numerous equipment and frequent data exchange.
Owner:BEIHANG UNIV
Certifying device, verifying device, verifying system, computer program and integrated circuit
InactiveUS20090204806A1Increase authenticityVerify reliabilityError detection/correctionDigital data protectionSoftware engineeringIntegrated circuit layout
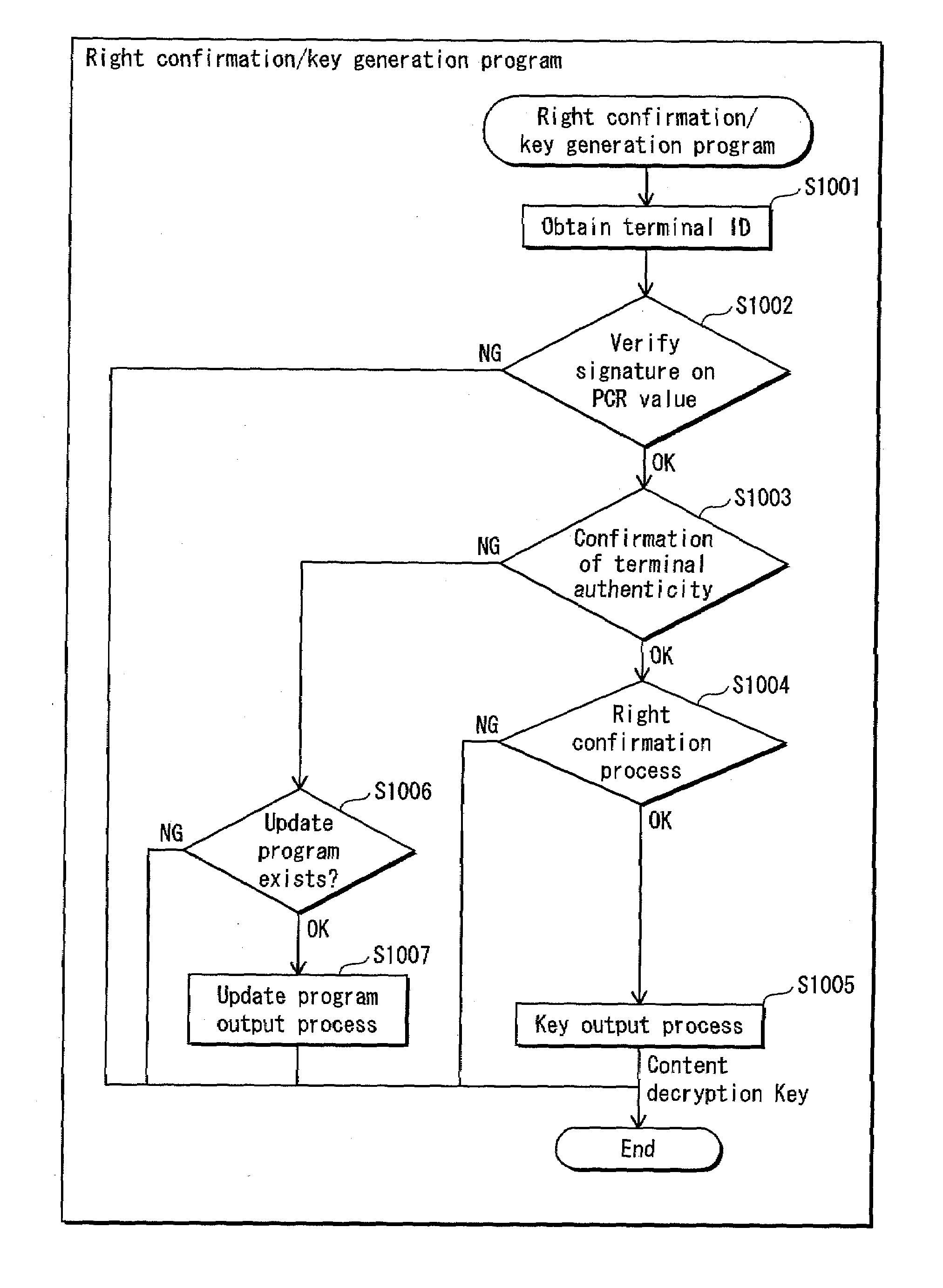
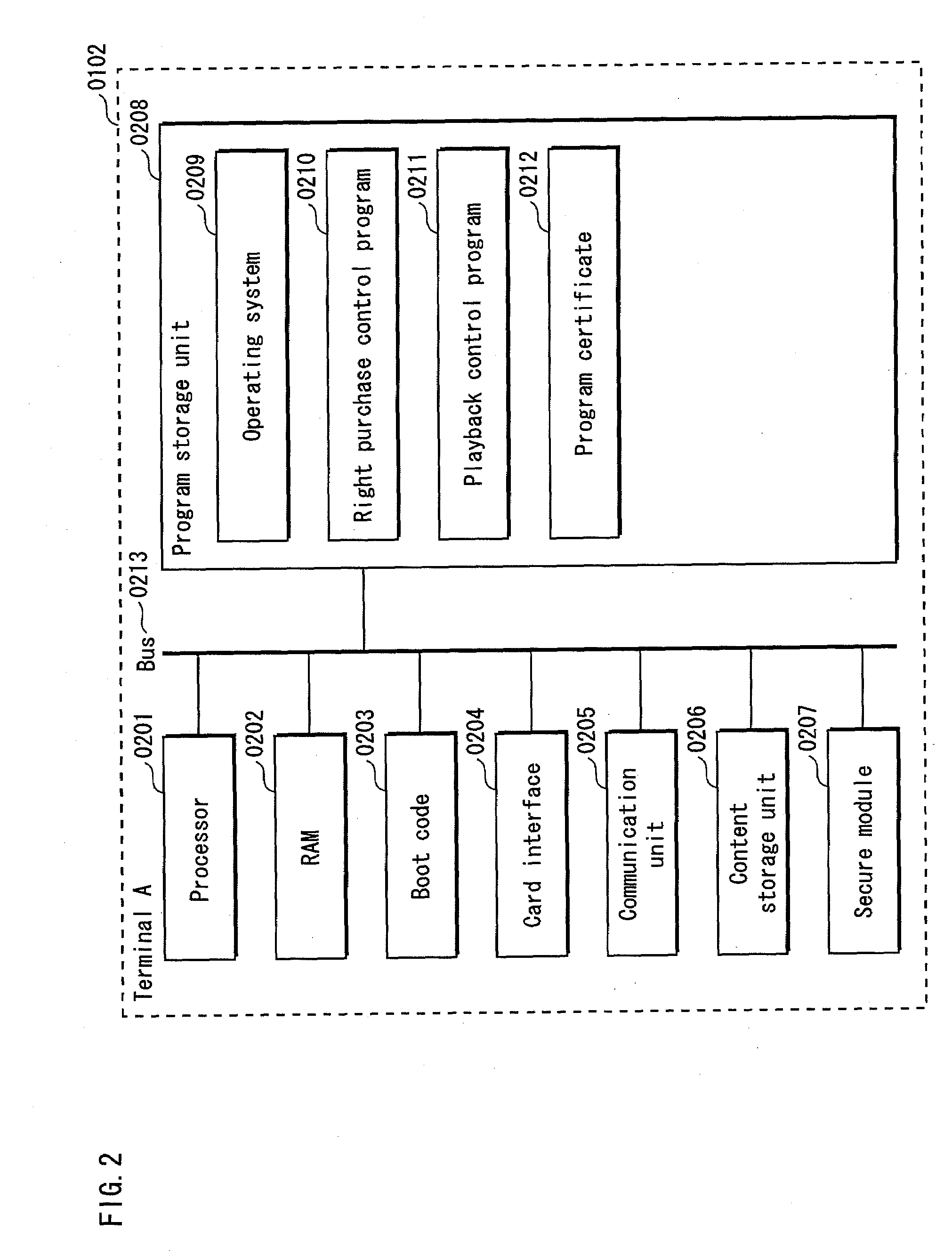
An authentication system that can show having an authentic computer program, can certify the authenticity of itself, and can verify the certification. The authentication system is composed of a terminal (requesting device) and a card (verifying device). The card stores secret information to be used by the terminal, and an update program for the terminal. The card verifies authenticity of the terminal using information obtained from the terminal. When it judges that the terminal is authentic, the card outputs the secret information to the terminal. When it judges that the terminal is not authentic, the card outputs the update program. With this structure, the terminal is forced to update the program when it attempts to use the secret information.
Owner:SOVEREIGN PEAK VENTURES LLC
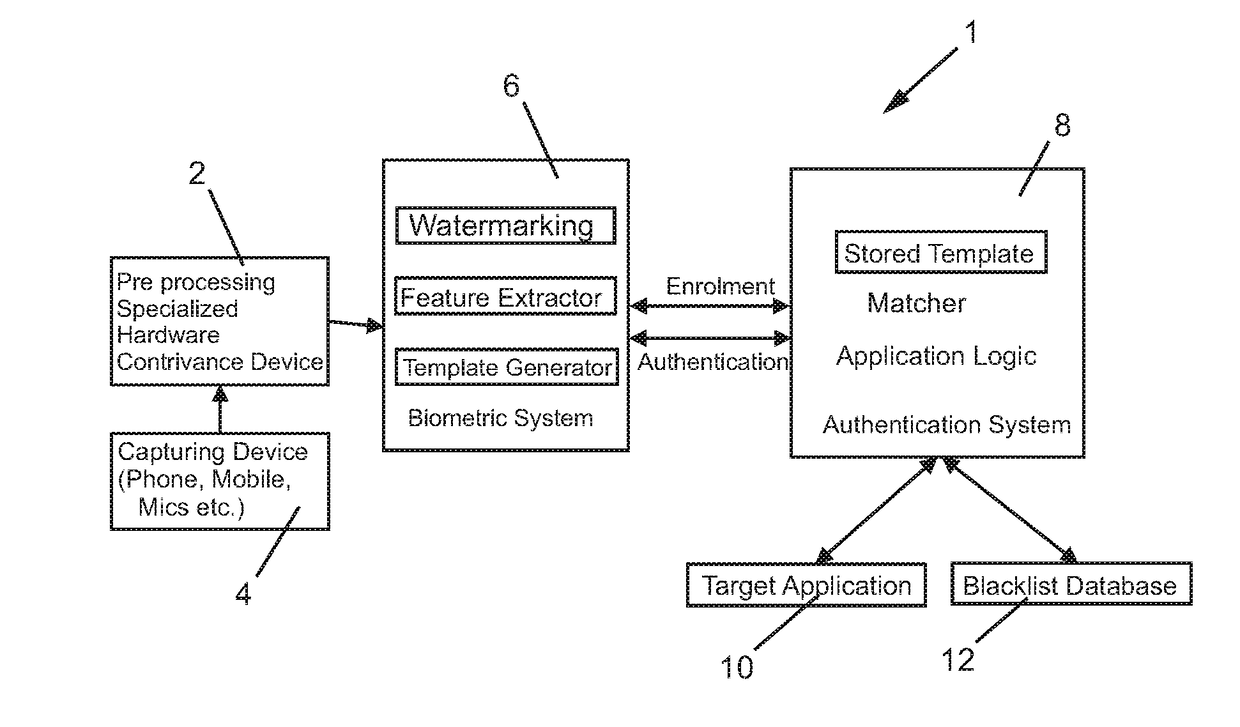
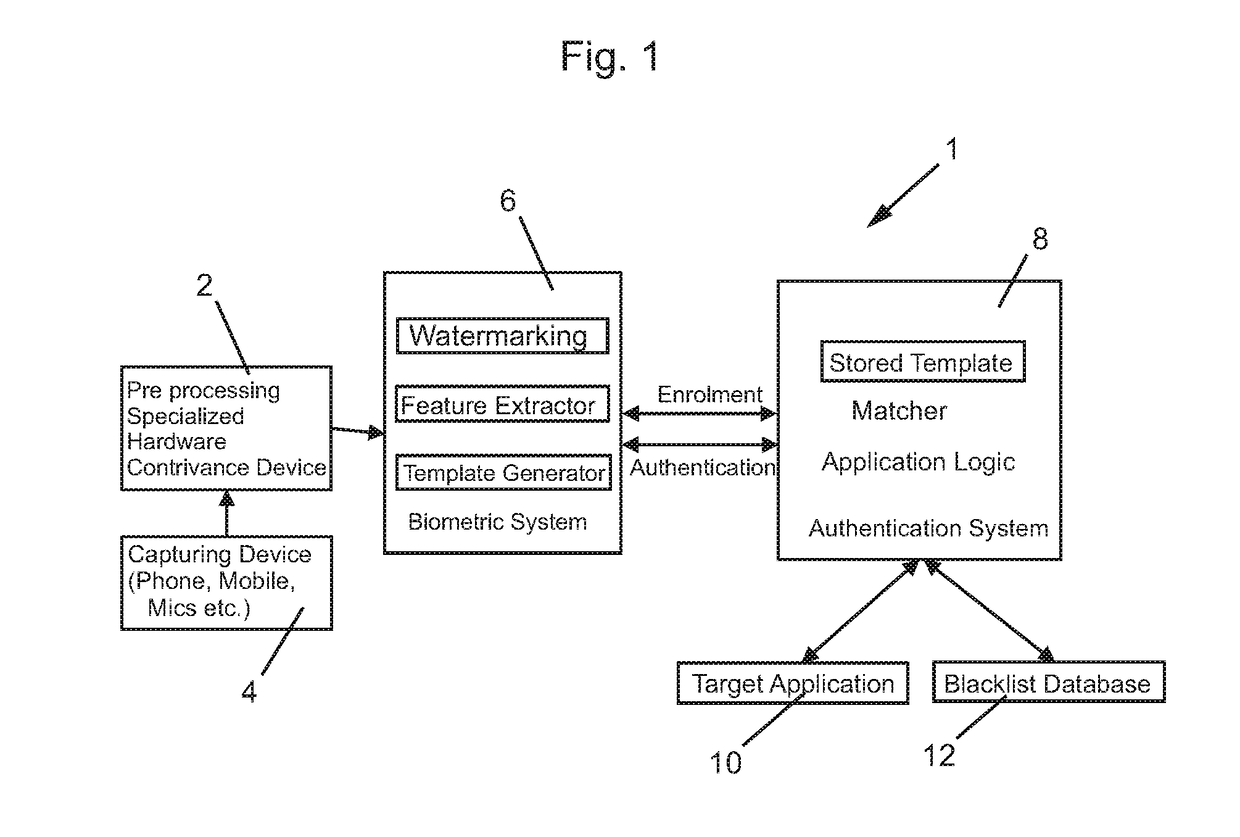
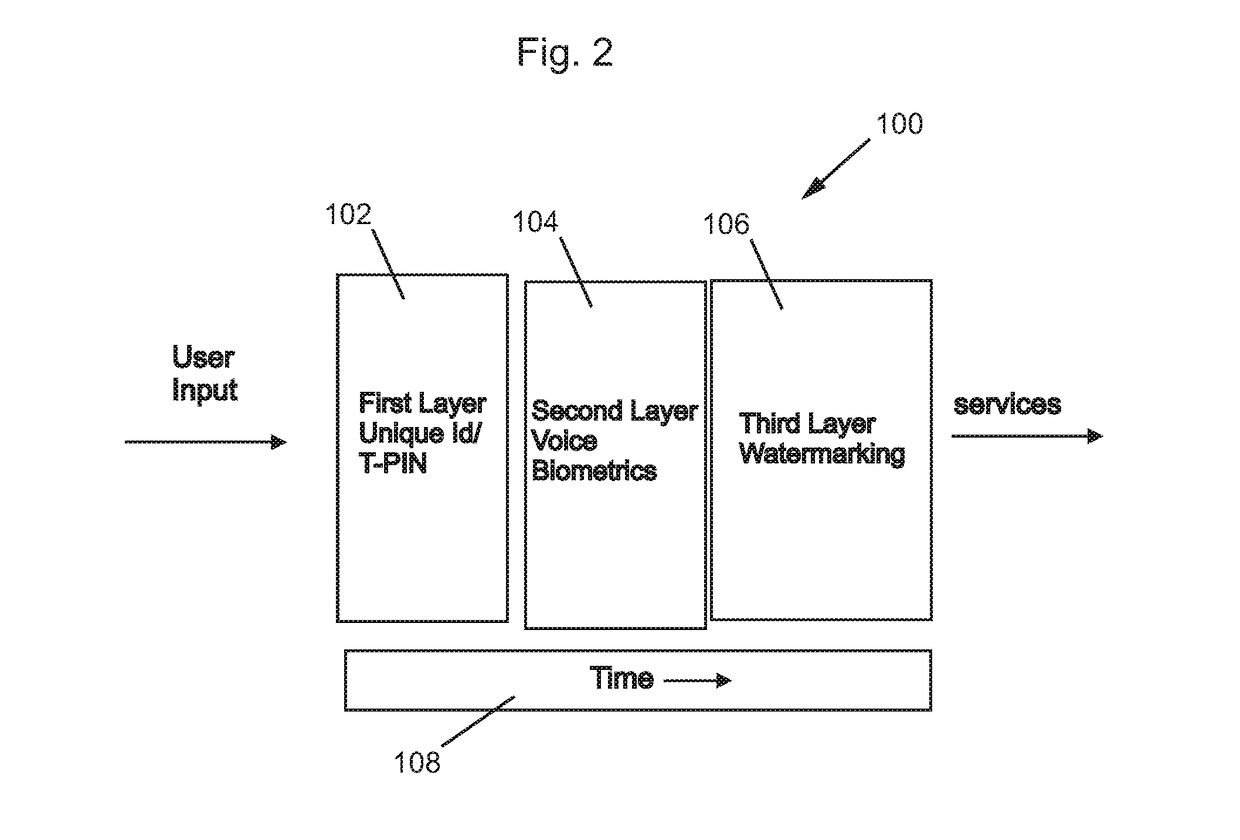
Method and apparatus for secured authentication using voice biometrics and watermarking
InactiveUS20180146370A1Increase authenticityImprove securityWeb data indexingSpeech analysisAudio watermarkComputer memory
Owner:KRISHNASWAMY ASHOK +1
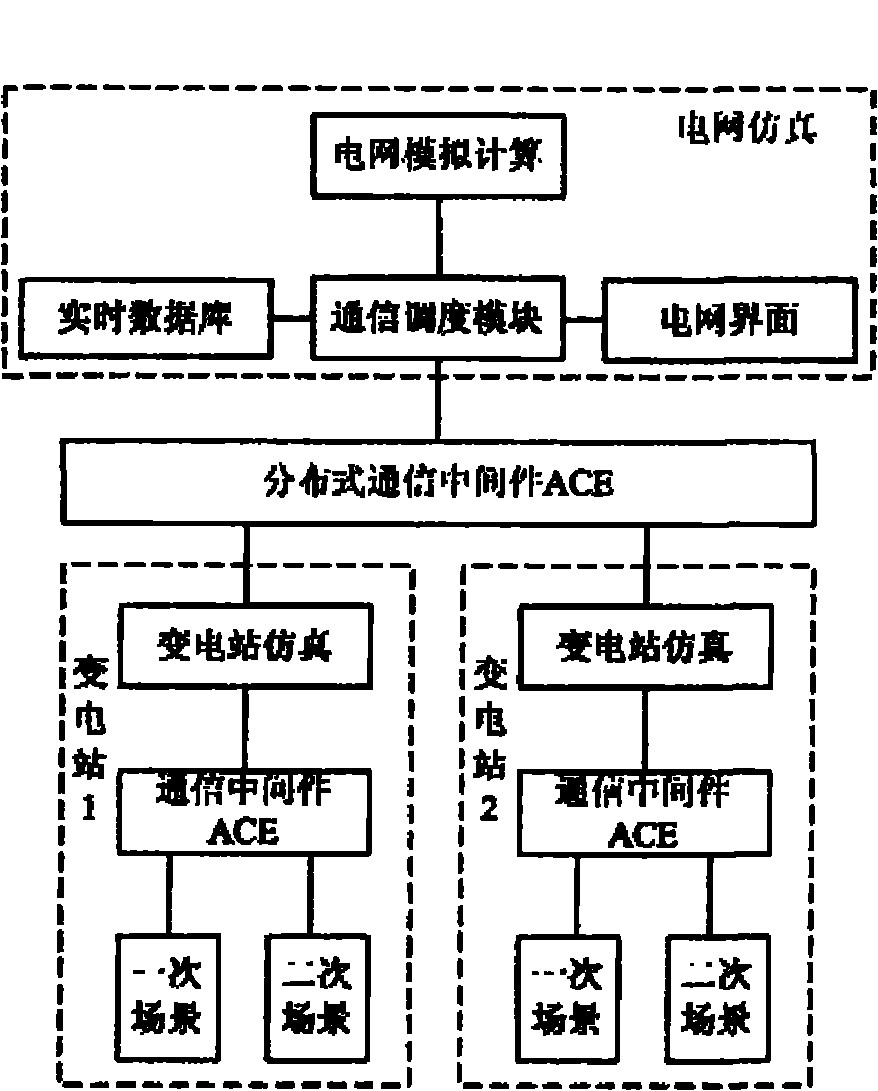
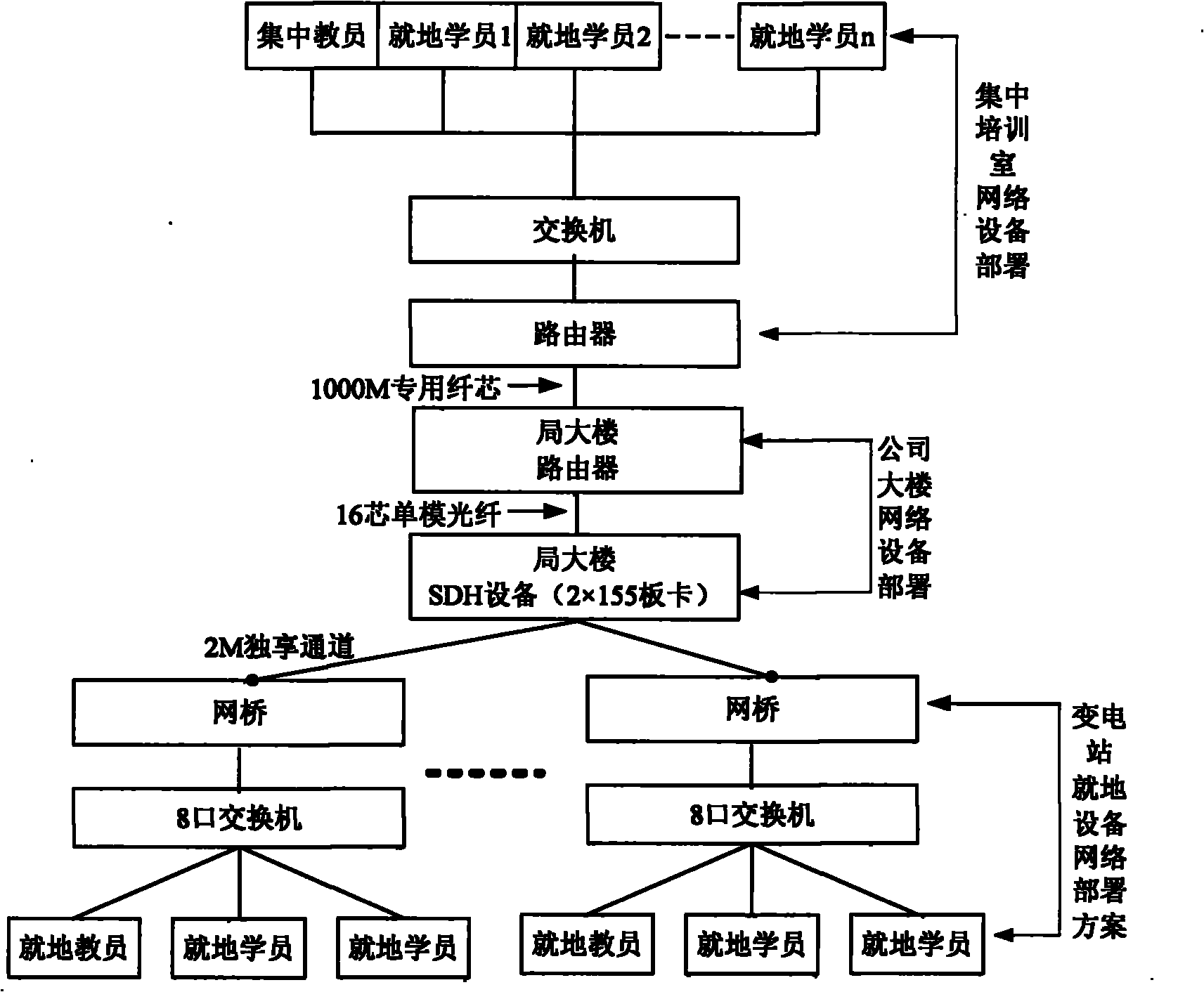
Distributed three-dimensional simulation training system for regional power system transformer station
ActiveCN101894488AReduce communication data trafficMeet actual training needsCosmonautic condition simulationsTransmissionThree dimensional simulationTransformer
The invention provides a distributed three-dimensional simulation training system for a regional power system transformer station and belongs to the field of data processing. The system comprises an integrated training classroom and a transformer station positioned at another place, wherein the integrated training classroom is provided with a first simulation training local area network; the transformer station is provided with a second simulation training local area network; the first simulation training local area network and the second simulation training local area network are connected with each other through public network resources such as an enterprise network / a wide area network and the like so as to form a network training system capable of performing remote joint simulation training as well as on-the-spot training; distributed simulation communication middleware is taken as the basis of distributed application and each simulation applying host computer is provided with the communication middleware; and the communication middleware provides universal communication and management services so as to realize a data interaction issuing / ordering mechanism and effectively reduce data traffic on the network. Simulation application distributed at different places is combined organically so as to form a distributed remote joint simulation training system. The system can be widely applied in the field of skill training of a power transformation and distribution system.
Owner:SHANGHAI MUNICIPAL ELECTRIC POWER CO +2
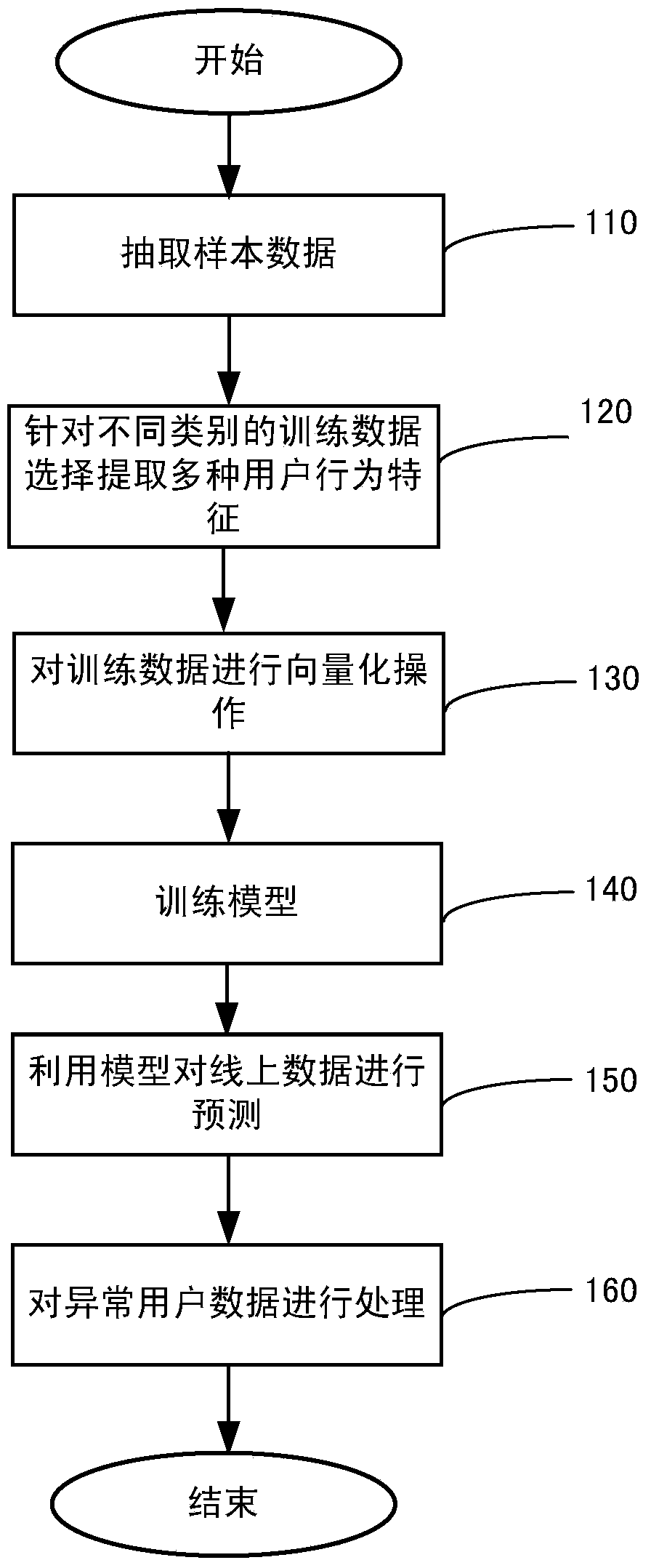
Fraudulent conduct identification system based on machine learning in classified information website
ActiveCN103793484AReduce the amount of falseIncrease authenticityDigital computer detailsWebsite content managementMachine learningMultiple dimension
The invention provides a method used for a fraudulent conduct identification system based on machine learning in a classified information website. The method includes the following steps that (a), sample data are extracted based on existing user behavior data and used for generating a model for the first time; (b), multiple user behavior characteristics are selected to be extracted according to training data of different service types; (c), based on the extracted user behavior characteristics, the sample training data are vectorized; (d), the vectorized sample training data are used for generating a prediction model; (e), on-line data are detected by using the generated model based on classification and cluster rules; (f), detected abnormal user data are processed. User behaviors can be identified in multiple dimensions through the method, and the false amount of trade information can be reduced efficiently. Moreover, the user behaviors of low quality can be identified well even if the training data contain noise data.
Owner:BEIJING 58 INFORMATION TECH
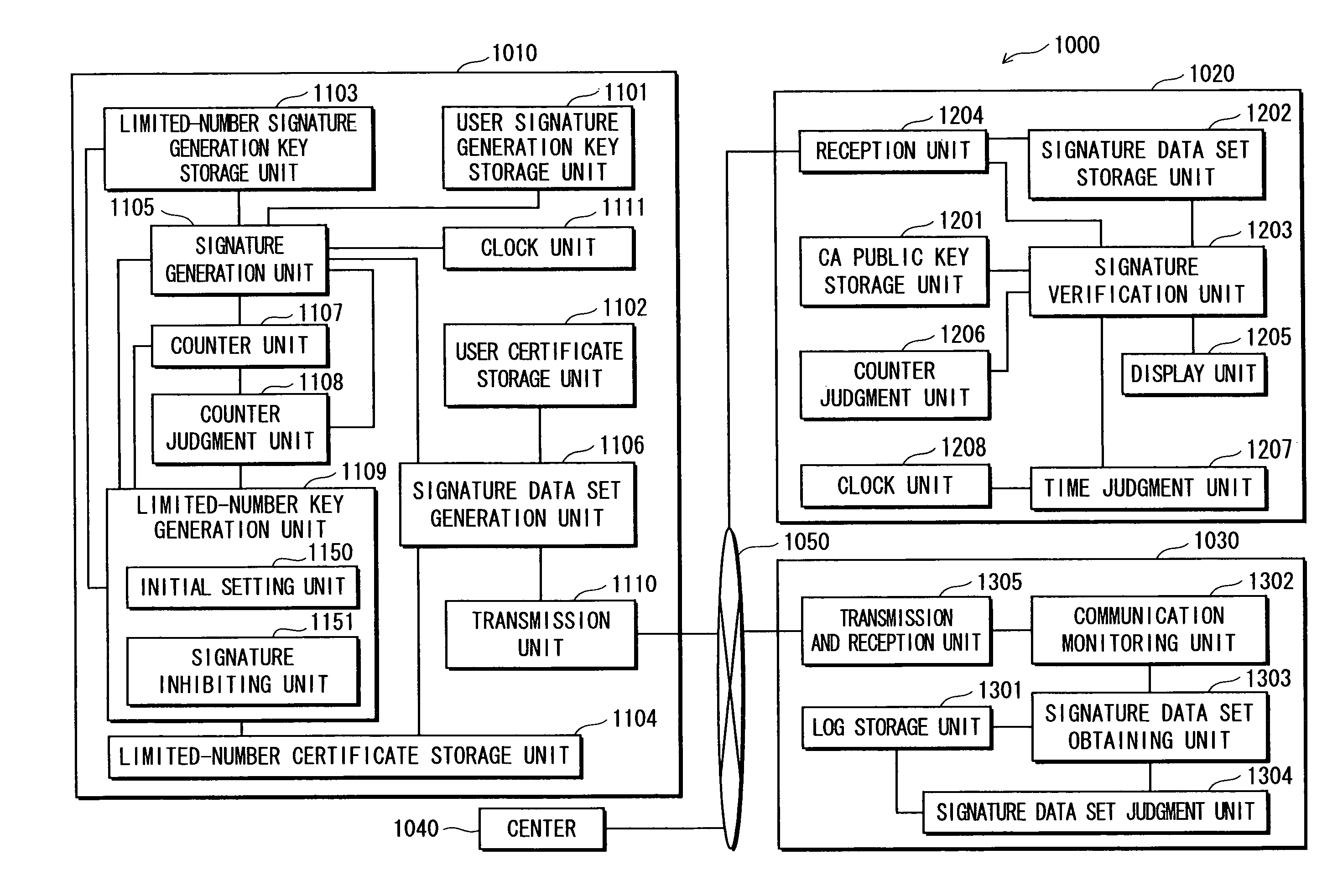
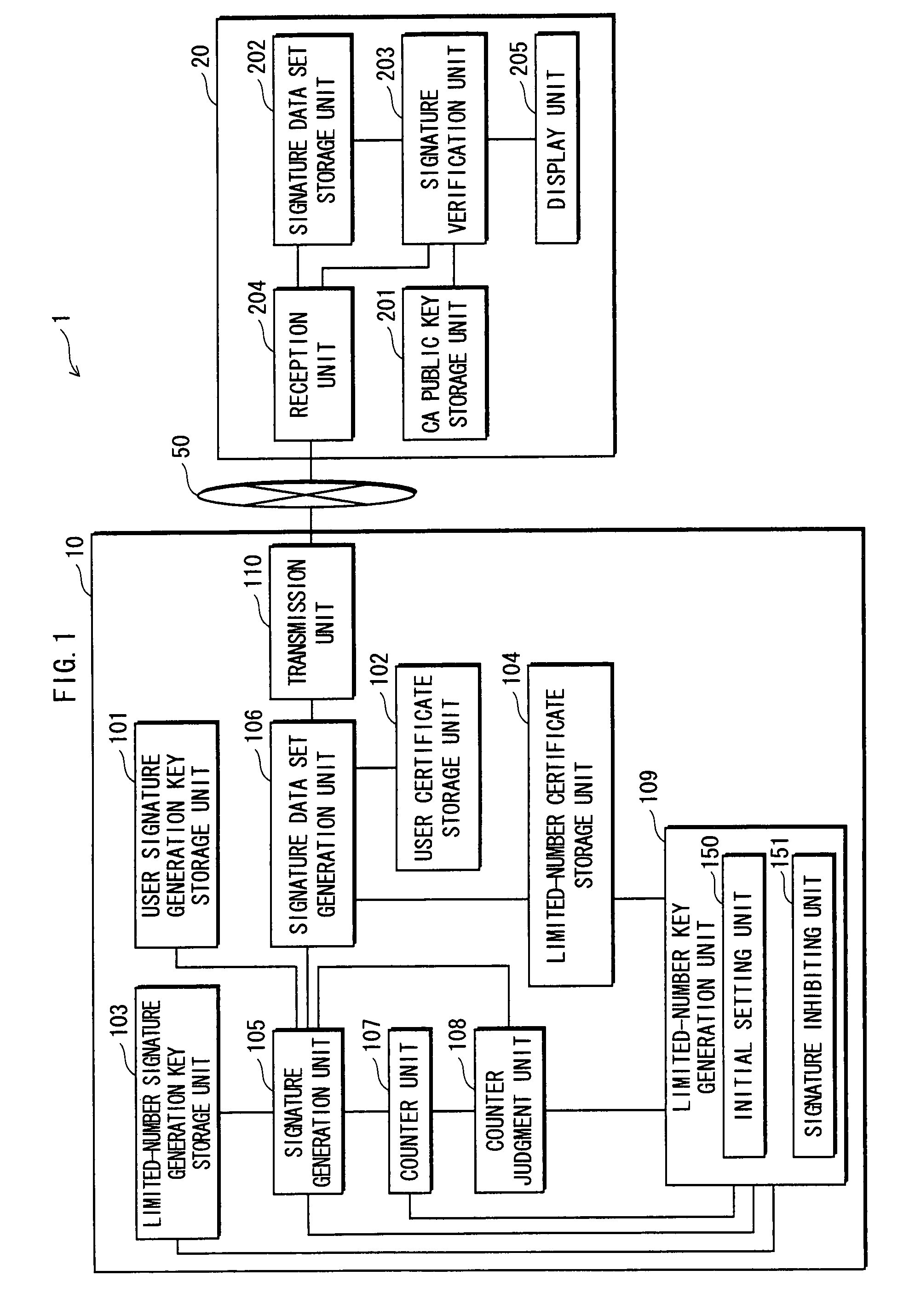
Signature generation device and signature verification device
ActiveUS7917764B2Avoid attackReduce usageKey distribution for secure communicationPublic key for secure communicationDigital signatureComputer security
A signature generation apparatus capable of preventing transcript attack on signature data is provided. The signature generation apparatus performing a digital signature operation with the use of a signature key: stores the signature key; performs the digital signature operation on signature target data with the use of the signature key to generate signature data; counts the cumulative count of digital signature operations having been performed by the signature generation unit with the use of the signature key; judges whether the cumulative count has reached a predetermined count; and inhibits the use of the signature key in the digital signature operation from then onward in a case where the judgment unit determines that the cumulative count has reached the predetermined count.
Owner:PANASONIC CORP
Fine-grained sentiment analysis system and method specific to product comment information
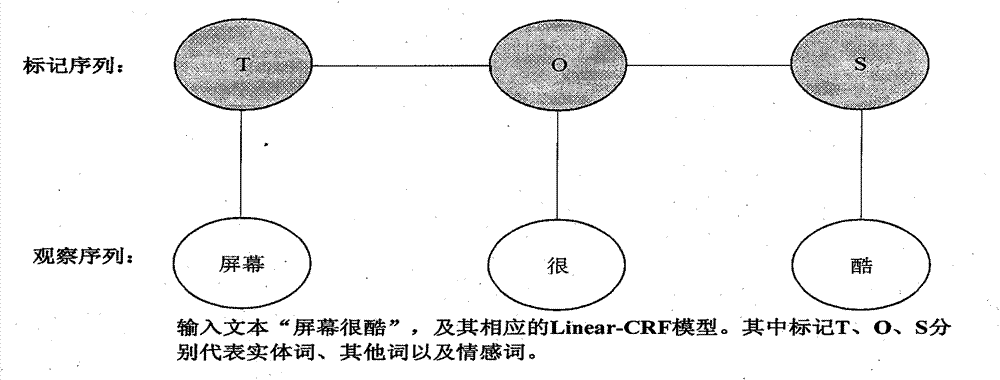
ActiveCN103207855ASmall granularityLarge amount of informationSpecial data processing applicationsMarketingSyntaxSentence segmentation
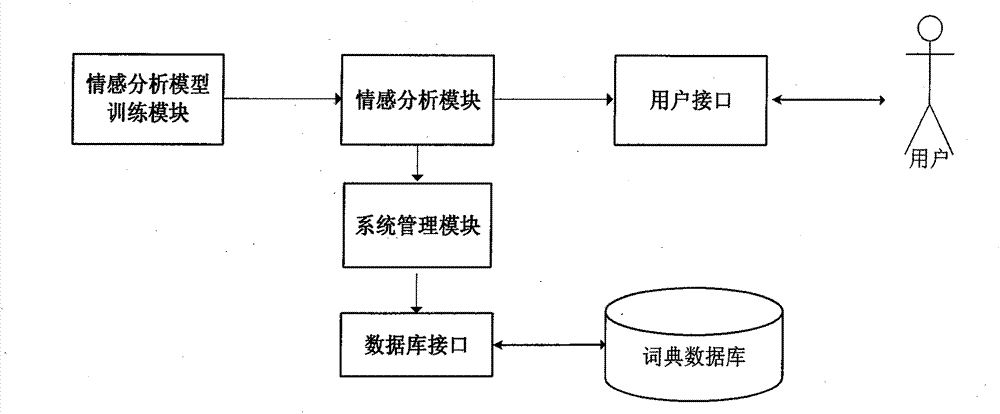
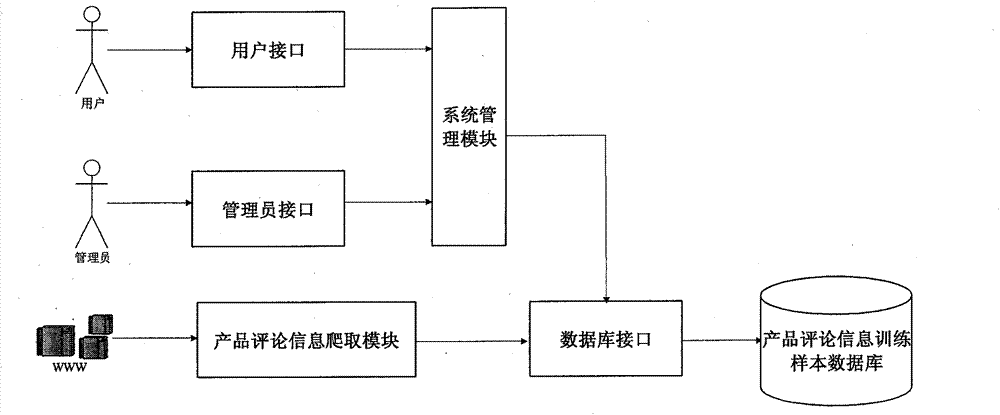
The invention discloses a fine-grained sentiment analysis system and method specific to product comment information. The system comprises a user interface, a product comment information training sample data base, a loading module of relevant dictionaries such as sentiment dictionaries, a text preprocessing module, a characteristic extraction module, a sentiment analysis model training module, a sentiment tendency judging module and a feedback module. A user can store and manage various tagged product comment information training samples and perform processes of sentence segmentation, word segmentation, part-of-speech tagging, syntactic analysis and the like by means of the system. The user can also add user-defined sentiment dictionaries to perform characteristic extraction and vectorization on well processed text information, train sentiment analysis models and use the sentiment analysis models to perform sentiment tendency judgment on vectorized text information. The system feeds sentiment analysis results back to the user to support the user to correct and store the analysis results.
Owner:GUANGDONG UNIV OF TECH
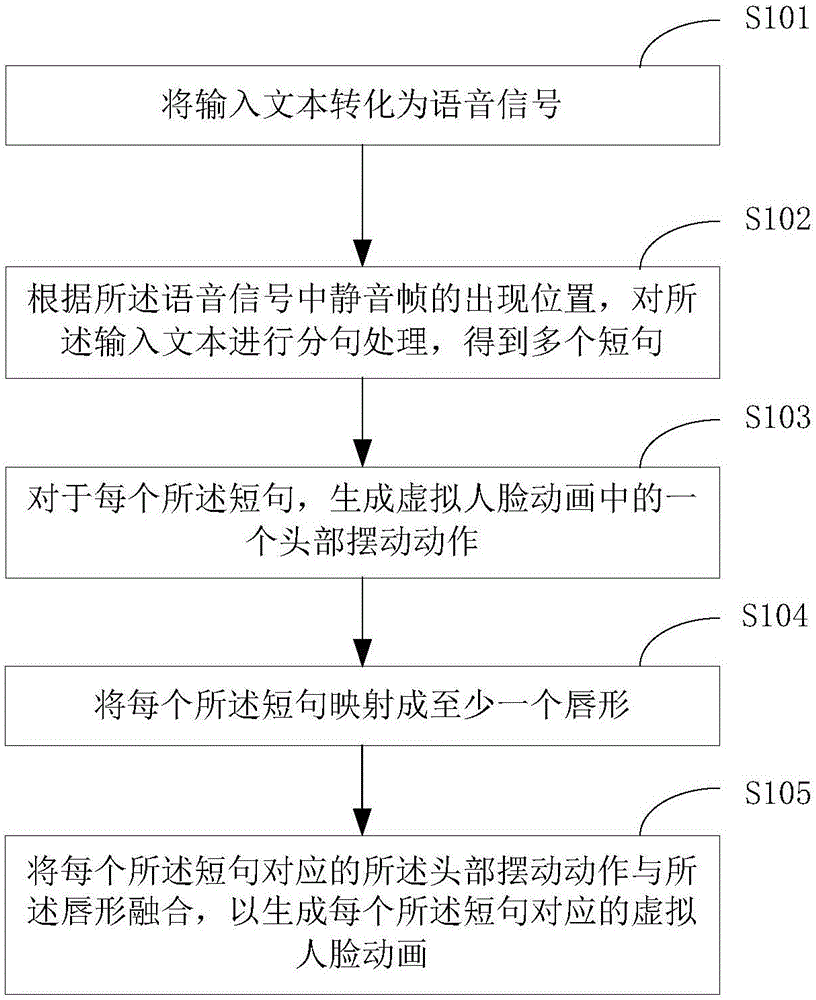
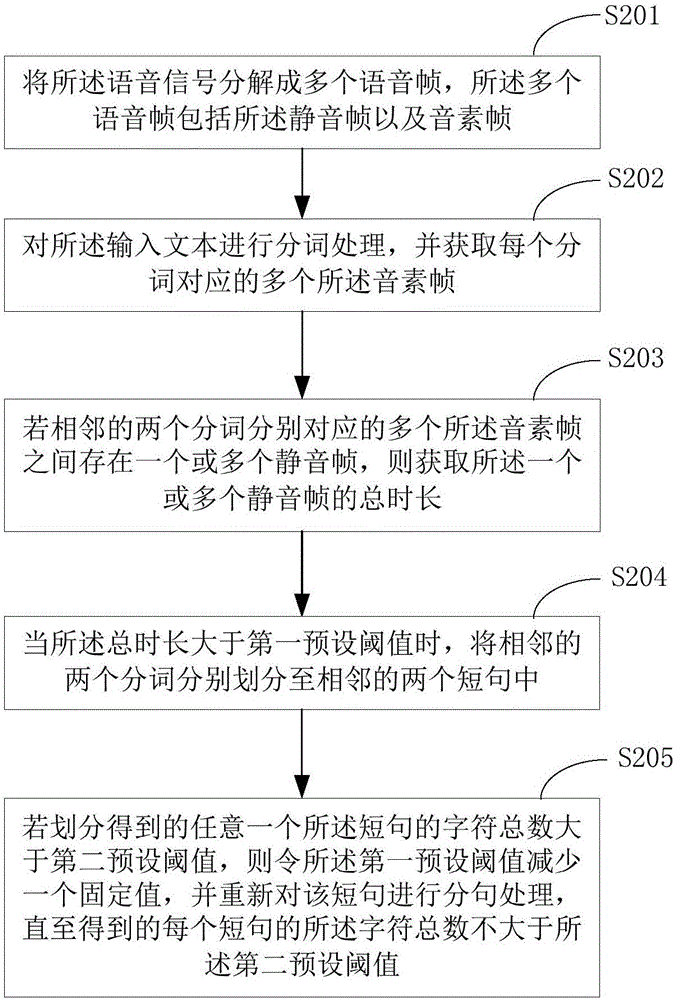
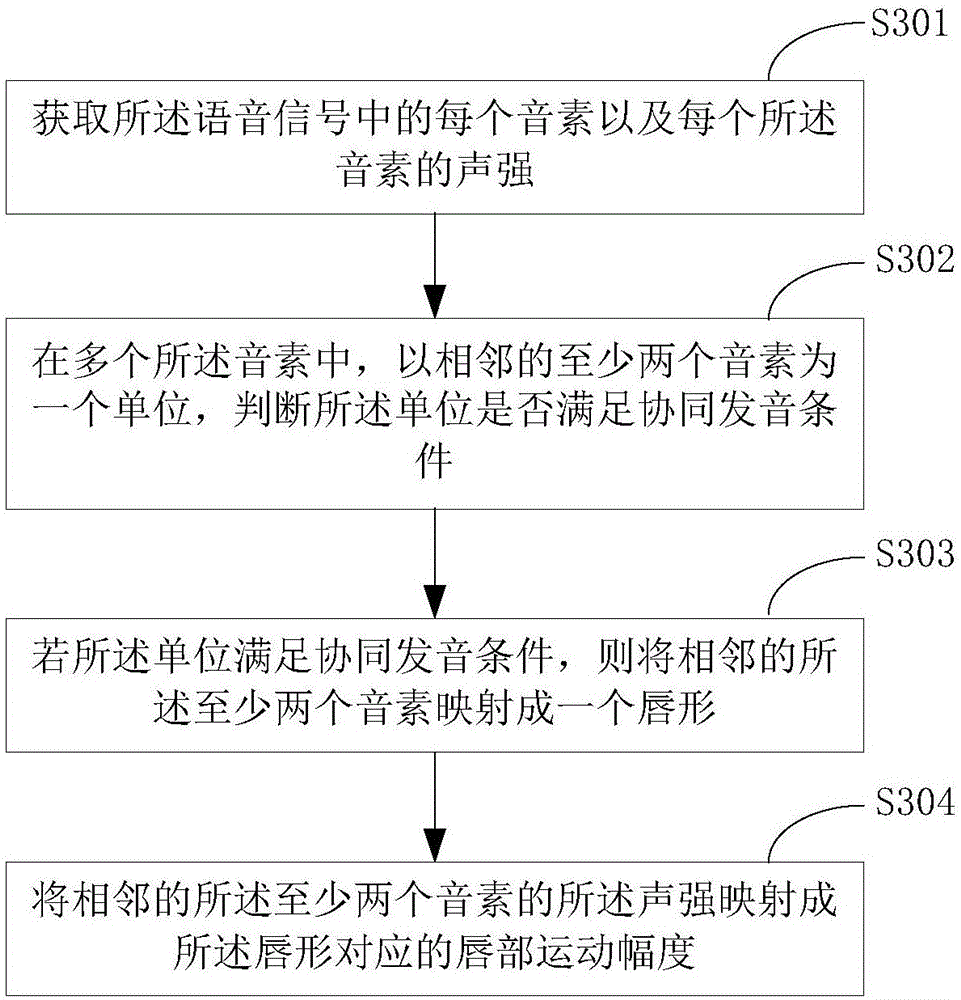
Virtual human face animation generation method and device
The invention is suitable for the technical field of artificial intelligence and provides a virtual human face animation generation method and device. The method comprises the following steps: an input text is converted into a voice signal; based on a position at which a silent frame occurs in the voice signal, the input text is subjected to phrasing operation, and a plurality of short sentences are obtained; for each short sentence, a head swinging movement in a virtual human face animation is generated, each short sentence is mapped to at least one lip shape, head swinging movements corresponding to all short sentences are combined with lip shapes, and therefore virtual human face animations corresponding to all the short sentences can be generated. According to the method and device disclosed in the invention, the virtual human face animations are generated based on combination of the text and voice, the head swinging movements and the lip shapes are generated and combined, visual sense close to reality is provided for users, a phenomenon that the obtained virtual human face animations only comprise lip shape information can be prevented, truthfulness of the virtual human face animations can be improved, dependence on expensive and complex equipment can be prevented, costs can be lowered, and an application scope of the virtual human face animations can be expanded.
Owner:TCL CORPORATION
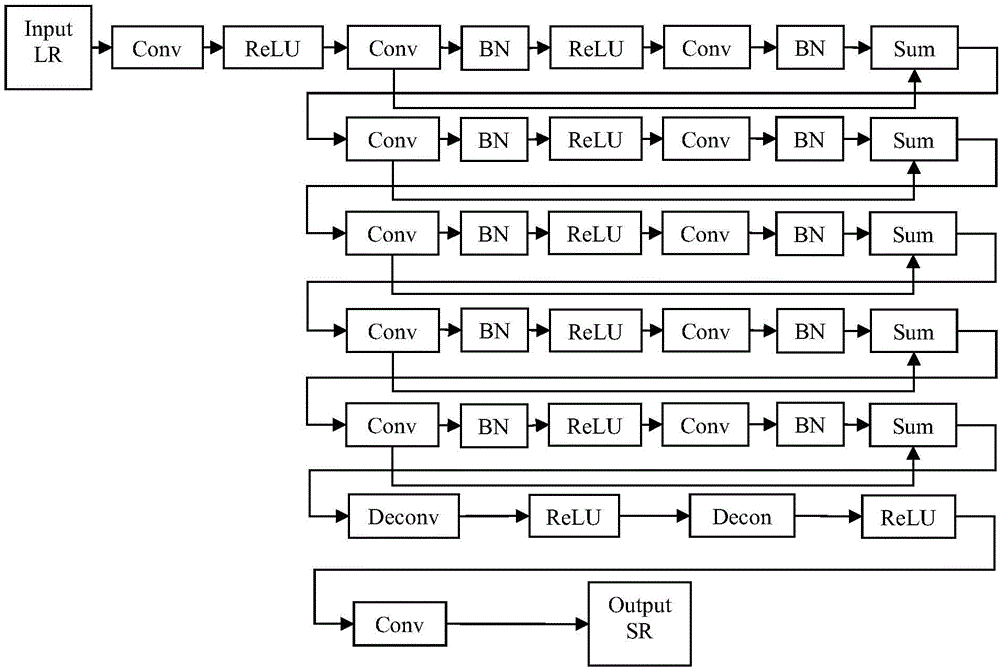
Image super-resolution method and image super-resolution equipment
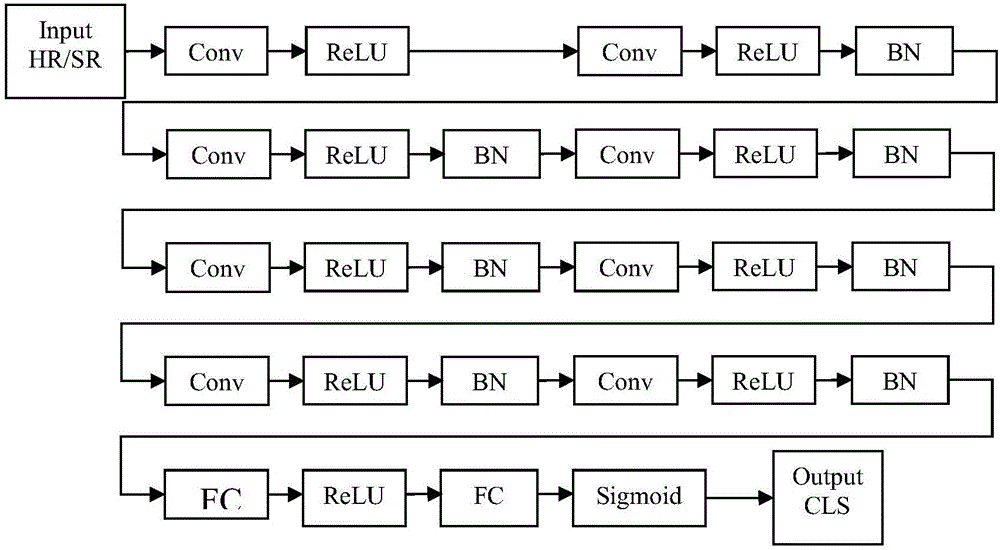
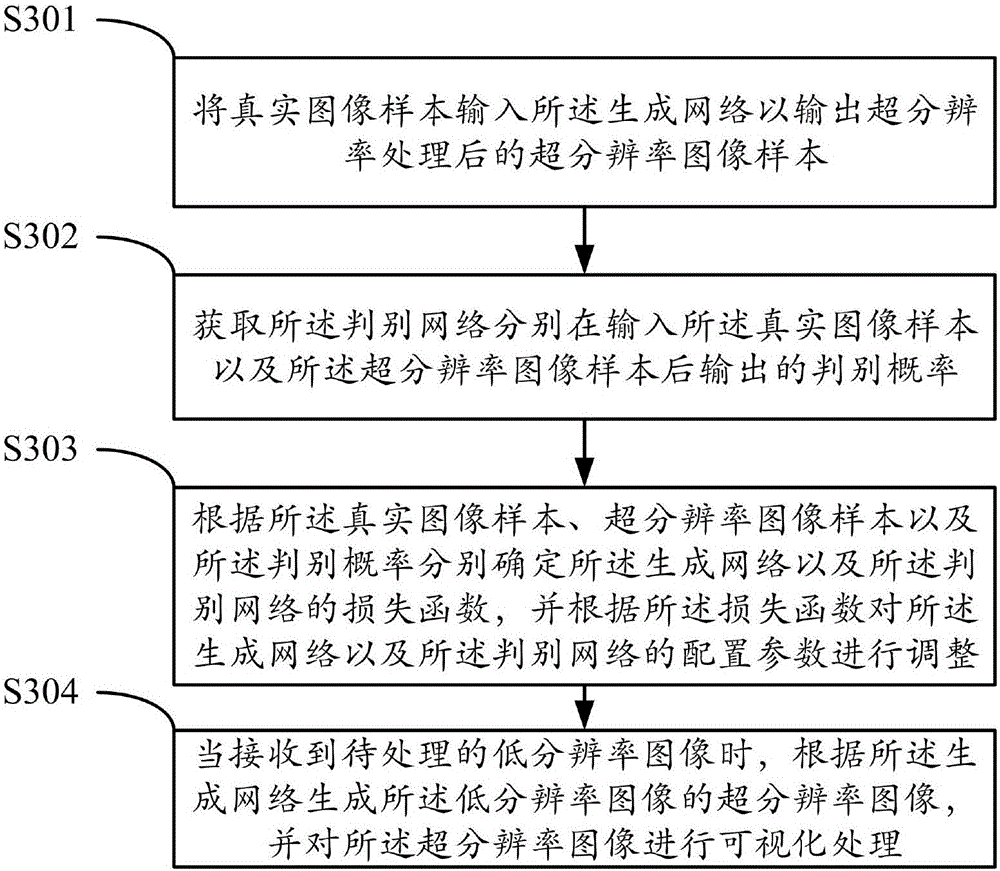
ActiveCN106683048AImprove the effect of super resolutionIncrease authenticityGeometric image transformationImage resolutionNetwork generation
The invention discloses a super-resolution image generation method. The super-resolution image generation method includes inputting a real image sample into a generation network so as to output a super-resolution image sample after the generation network and a distinguishing network are preset, acquiring distinguishing probabilities outputted by the distinguishing network after the real image sample and the super-resolution image sample are outputted, determining generation network loss functions and distinguishing network loss functions according to the real image sample, the super-resolution image sample and the distinguishing probabilities, and adjusting configuration parameters of the generation network and the distinguishing network according to the generation network loss functions and the distinguishing network loss functions; receiving a low-resolution image to be processed after adjustment is completed, generating a super-resolution image of the low-resolution image according to the generation network, and subjecting the super-resolution image to visualized processing. By the super-resolution image generation method, image super-resolution effect and realness of the super-resolution image are both improved remarkably.
Owner:XIAN UNIVIEW INFORMATION TECH CO LTD
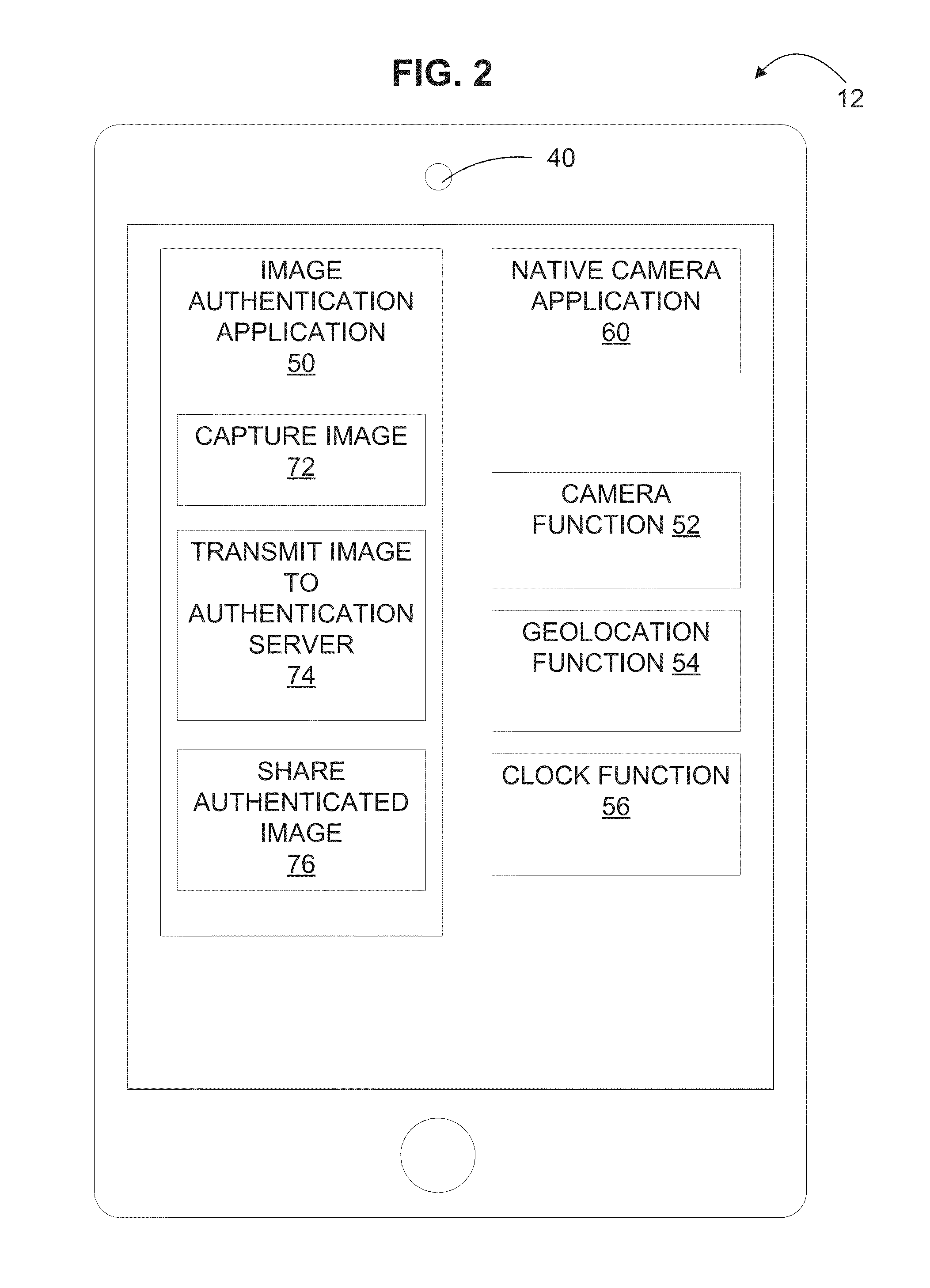
Systems and methods for authenticating photographic image data
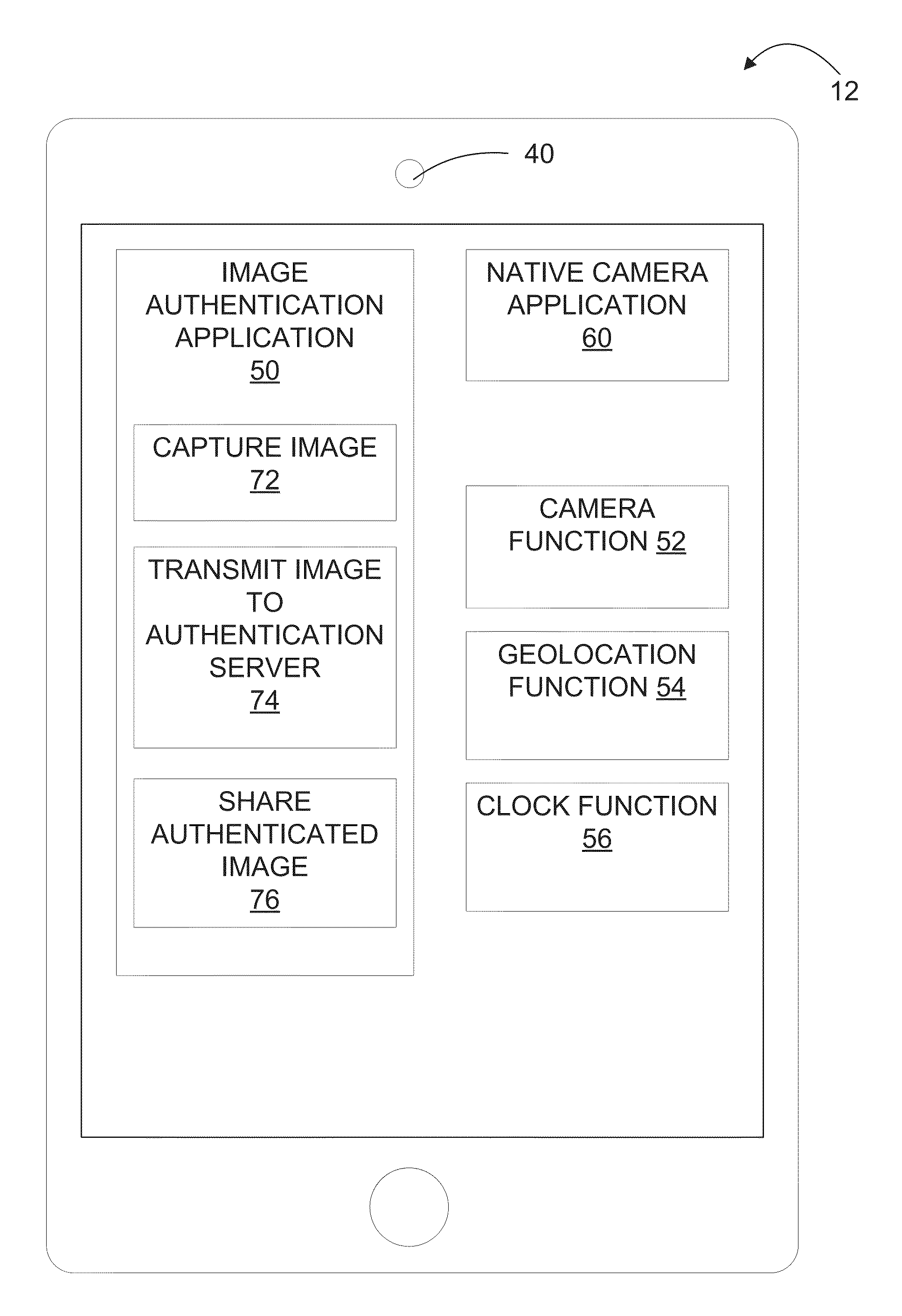
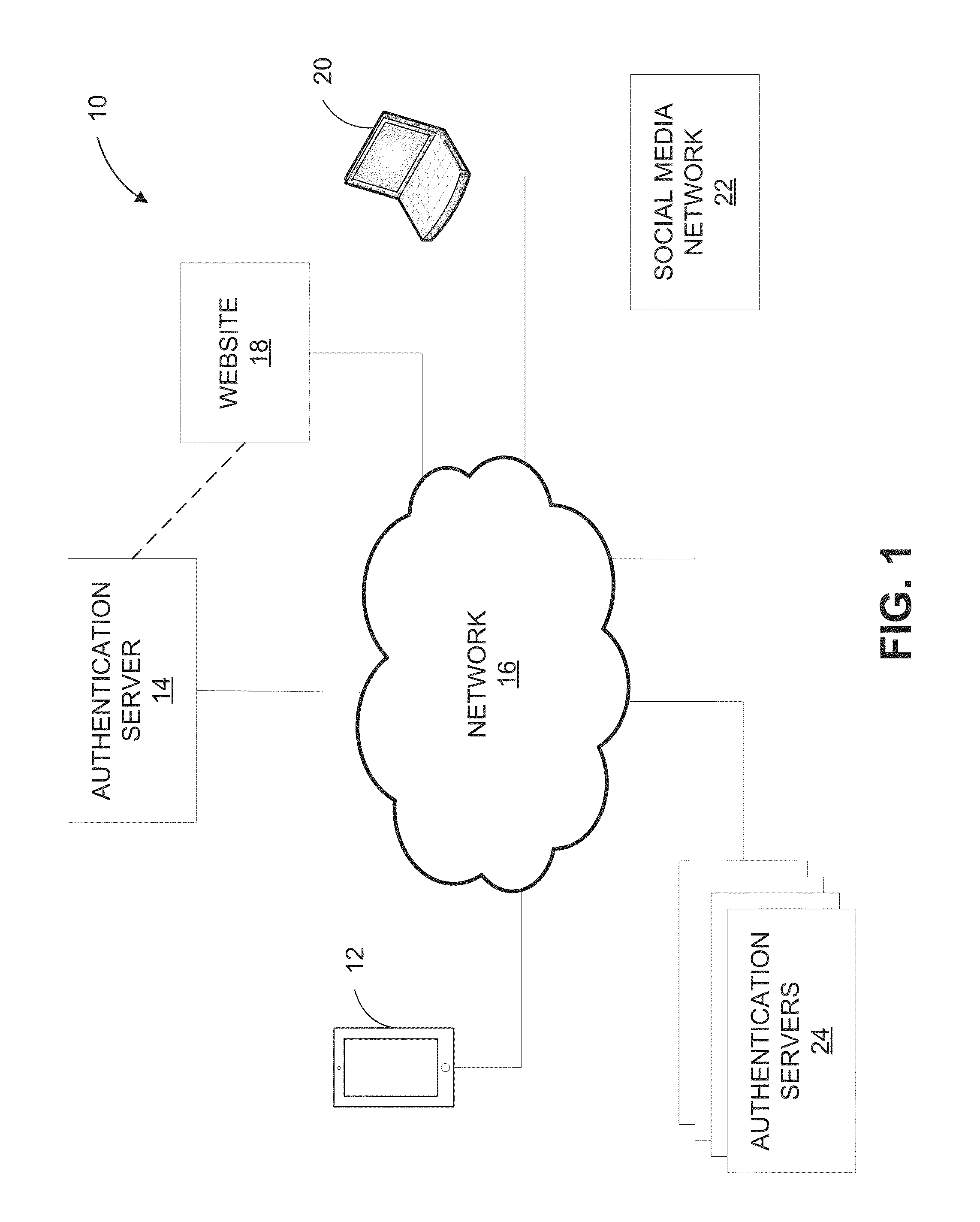
ActiveUS9300678B1Reduce the possibilityAlteration can be preventedDigital data protectionTransmissionTime informationData file
The present disclosure provides systems and methods for authenticating photographic data. In one embodiment, a method comprises providing an image authentication application for use on a client device, the application configured to control image capture and transmission; receiving an image data file from the application at the authentication server comprising a photographic image captured by the application and metadata associated therewith; applying a watermark to the photographic image to create a watermarked image; applying date and time information to the tagged image; applying location information to the tagged image; creating a web address associated with the image data file; uploading the photographic image, the tagged image, or both to the web address; and transmitting an authenticated image file to the client device, the authenticated image file comprising one or more of: the watermarked image, the photographic image, the date and time information, geographic information, and the web address.
Owner:TRUEPIC INC
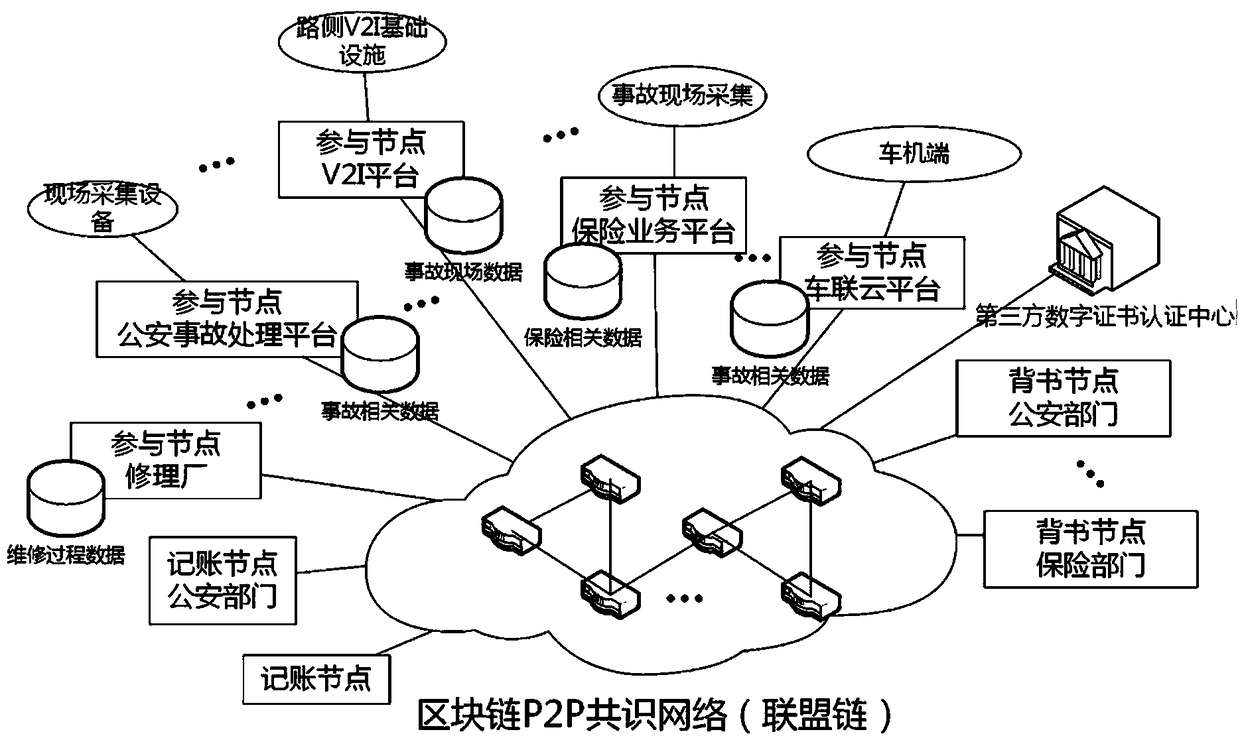
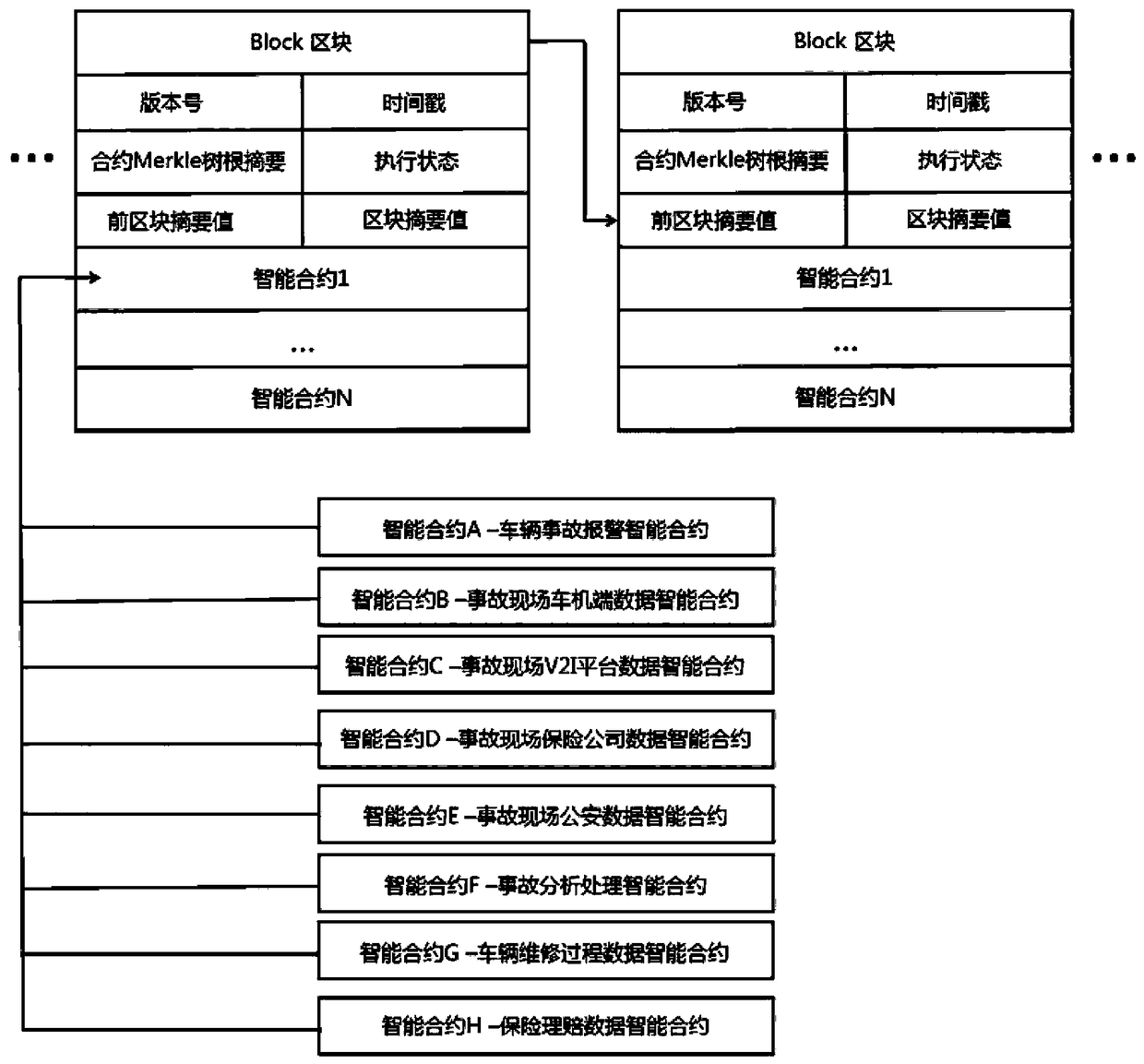
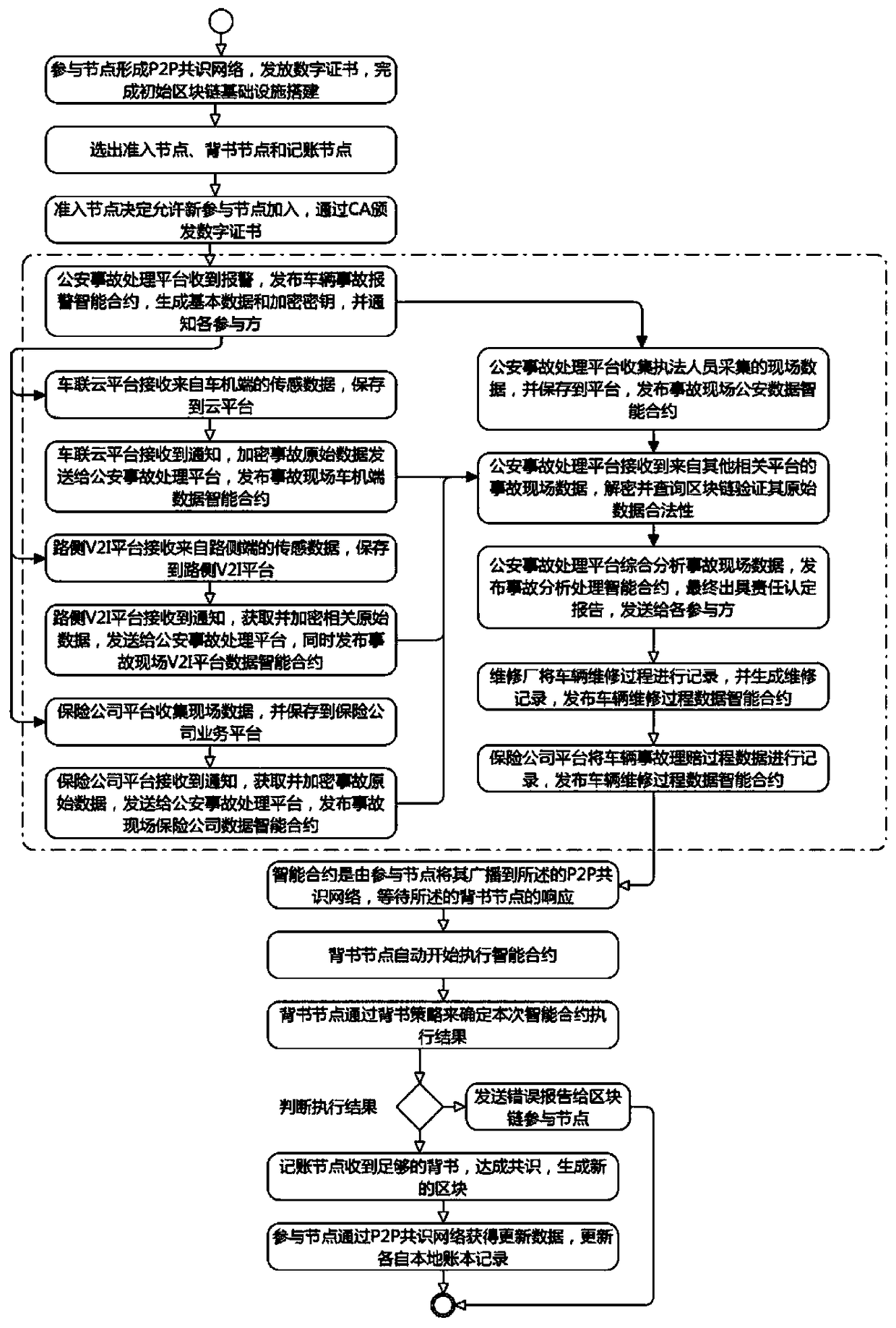
Network connected vehicle accurate accident handling method based on block chain
InactiveCN108446992AImprove accuracyImprove processing speedFinanceUser identity/authority verificationReal-time computingBlockchain
The invention discloses a network connected vehicle accurate accident handling method based on block chain. The implementation process of the method comprises: 1, firstly, through a block chain technology, connecting all participated joints which are associated with accident handling, based on a P2P consensus network, establishing an alliance chain, putting life cycle of accident handling in the block chain to record; through an intelligent terminal on a vehicle accident site, acquiring on-site data and uploading, the participated joints which are associated with accident handling completing accident handling. Compared with the prior art, the network connected vehicle accurate accident handling method based on block chain effectively solves a mutual trust problem of involve parties throughan unified and decentralized method, improves accident responsibility confirmation accuracy rate and handling speed, and provides an accident retroactive function, improves transparency of accident handling process, shortens accident handling time, and saves vehicle accident handling cost.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
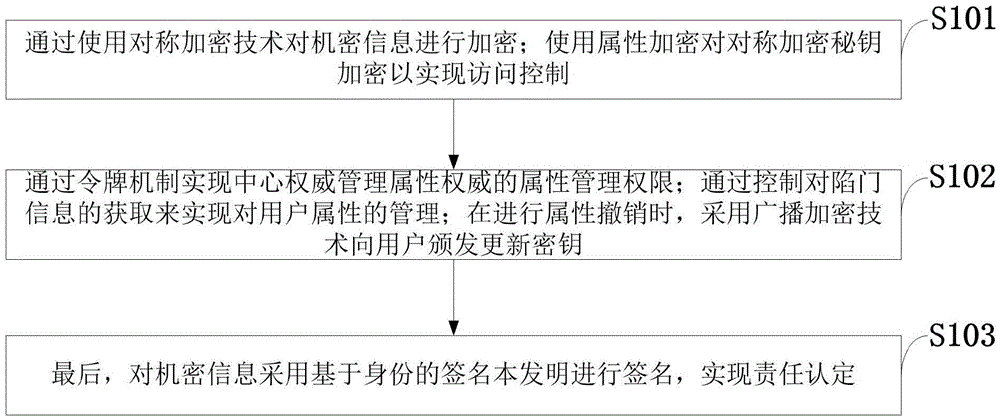
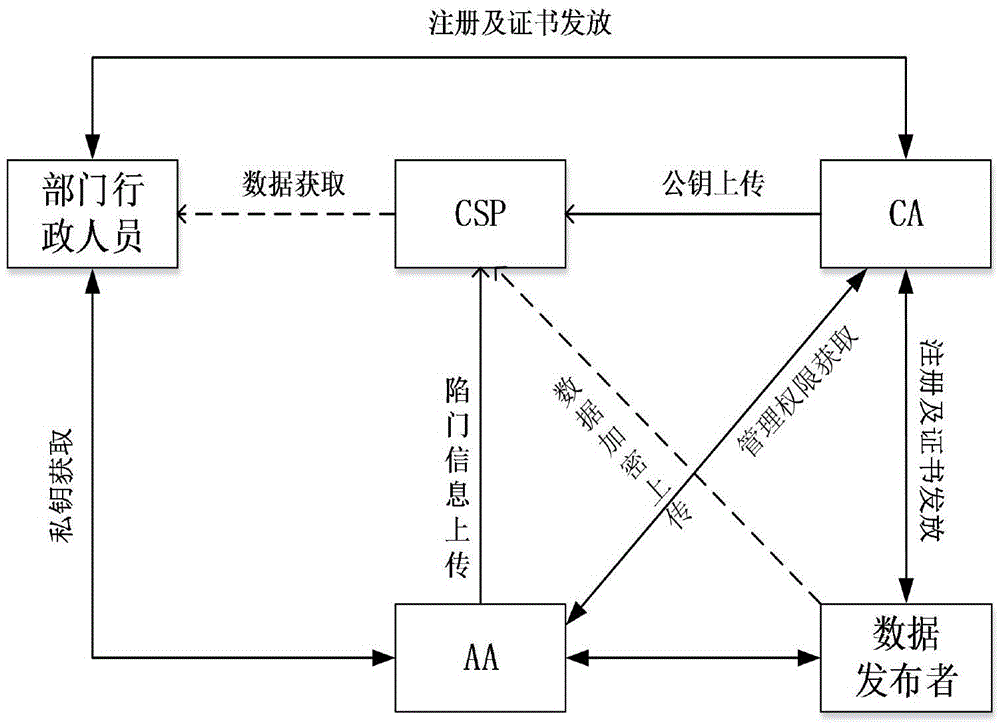
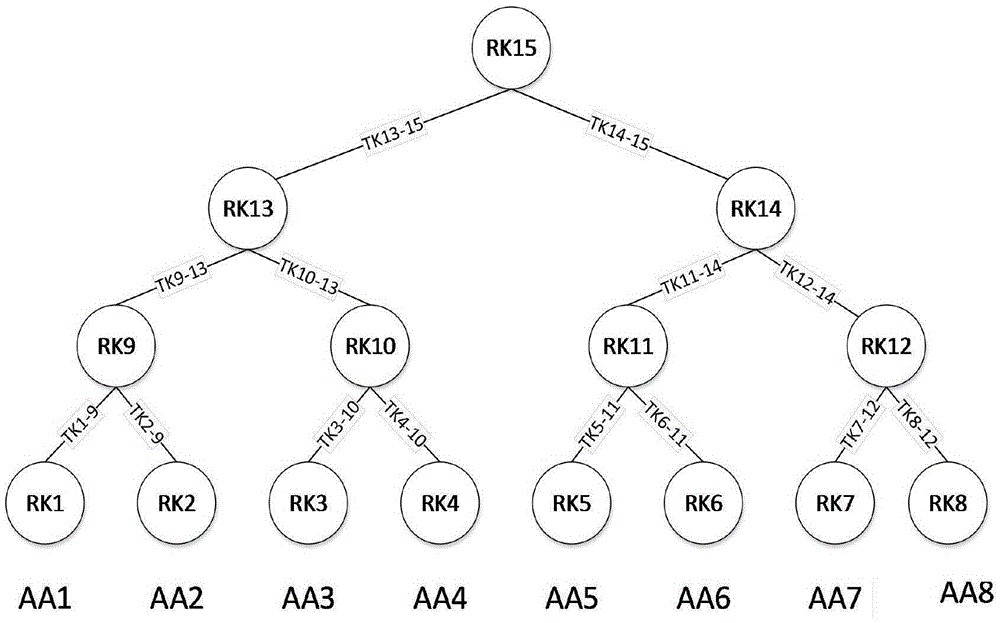
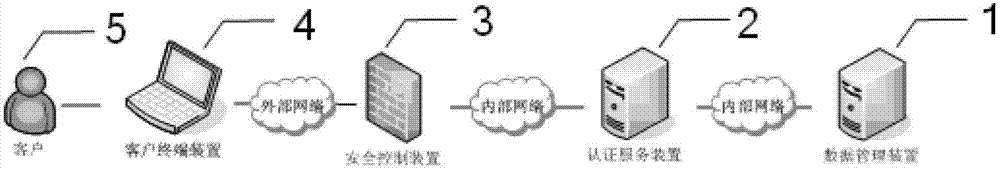
Government services cloud access control method based on attribute encryption
The invention discloses a government services cloud access control method based on attribute encryption. A central authority determines all attributes of a system, permits or revokes attribute authority management authority, and authenticates administrative staff; an attribute authority receives the login of administrative staff in the jurisdiction thereof and is simultaneously responsible for attribute revocation of the administrative staff; a cloud server stores data and carries out semi-decryption on an encrypted file when a user sends out a data request; a data uploader makes an access control strategy according to the security level of the file, and encrypts and uploads the file after name signing; and an access user sends out a data access request and finally decrypts the encrypted file. By adopting the attribute encryption scheme, the loads caused by user attribute revocation and encrypted file updating are reduced, the trap door information capturing of the user is controlled, and attribute revocation is carried out on the user under the condition that the encrypted file is not changed; in addition, by utilizing the name signing and attribute encryption scheme based on the identity, the safety authority of the user and fine-grained access control are realized.
Owner:XIDIAN UNIV
Bank identity identification method and system
InactiveCN102968612AHigh acceptanceImprove securityCharacter and pattern recognitionPayment architectureIdentification deviceComputer terminal
The invention discloses a bank identity identification method and a system. The system comprises a user login terminal with a camera, a network device, a face identification device, a gesture identification device and a bank service server, the user login terminal is used for acquiring face data and gesture data of a trader, the network device is connected with the user login terminal with the camera and used for transmitting the face data and gesture data, the face identification device is connected with the network device and used for receiving the face data and outputting face identification result data, the gesture identification device is connected with the network device and used for receiving the gesture data and outputting gesture identification result data, and the bank service server is respectively connected with the face identification device and the gesture identification device and used for receiving the face identification result data and the gesture identification result data. By means of the bank identity identification method and the system, the client identity can be identified through a counter video or a remote video.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Trade information processing method, device and system
ActiveCN106878396APrevent paralysis riskImprove trade experienceTransmissionInformation processingDependability
The invention discloses a trade information processing method, device and system. The method is applied to the supply node side of a trade object. The method comprises the steps that a supply node broadcasts trade information to be processed in the network where a block chain is located; after the broadcasted trade information acquires network consensus, the consensus trade information is stored in the block chain; the stored trade information is the maintained by one or more nodes in the network where the block chain is located; and the maintained trade information is stored in the block chain after network consensus is acquired. According to the embodiment of the invention, the reliability of dealing with the trade information is enhanced, and the trade experience of people is improved.
Owner:BUBI BEIJING NETWORK TECH CO LTD +1
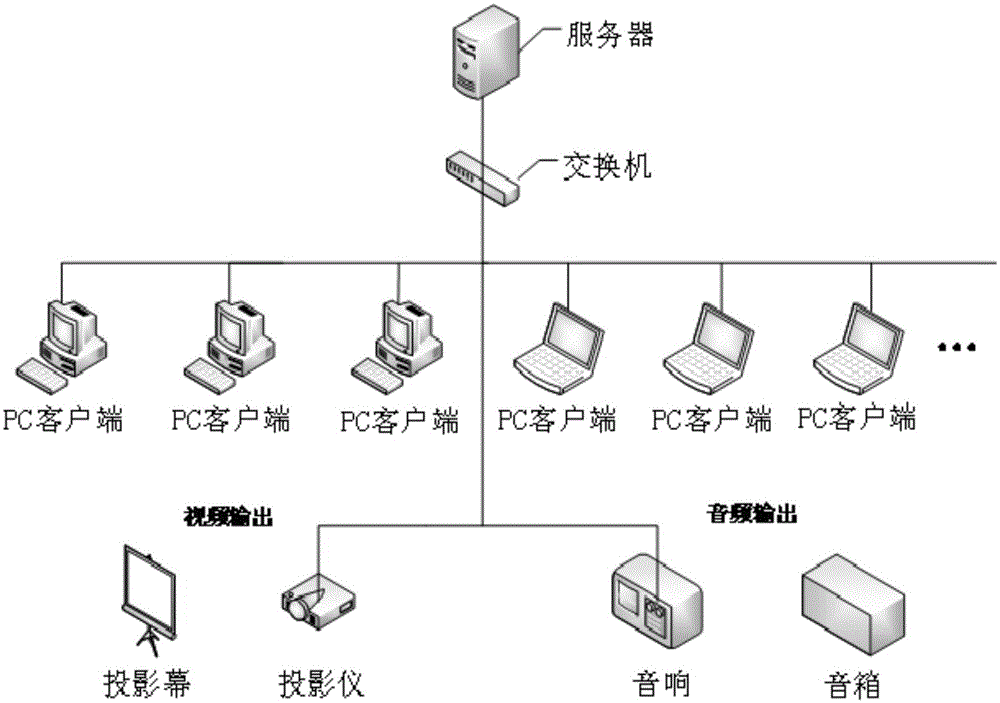
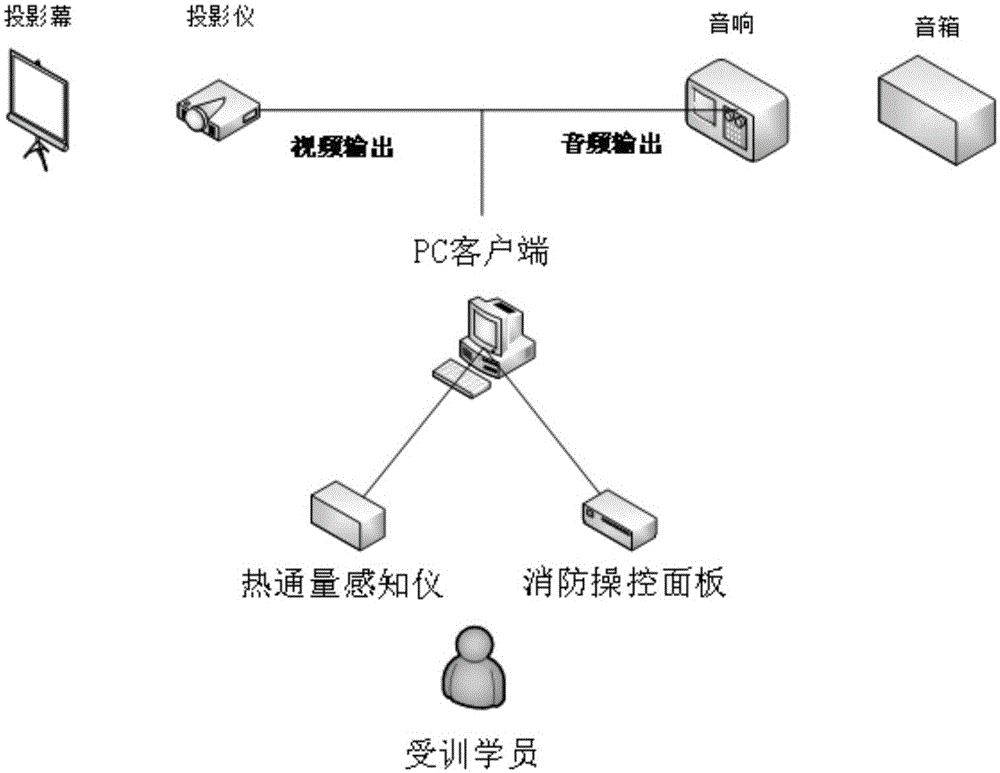
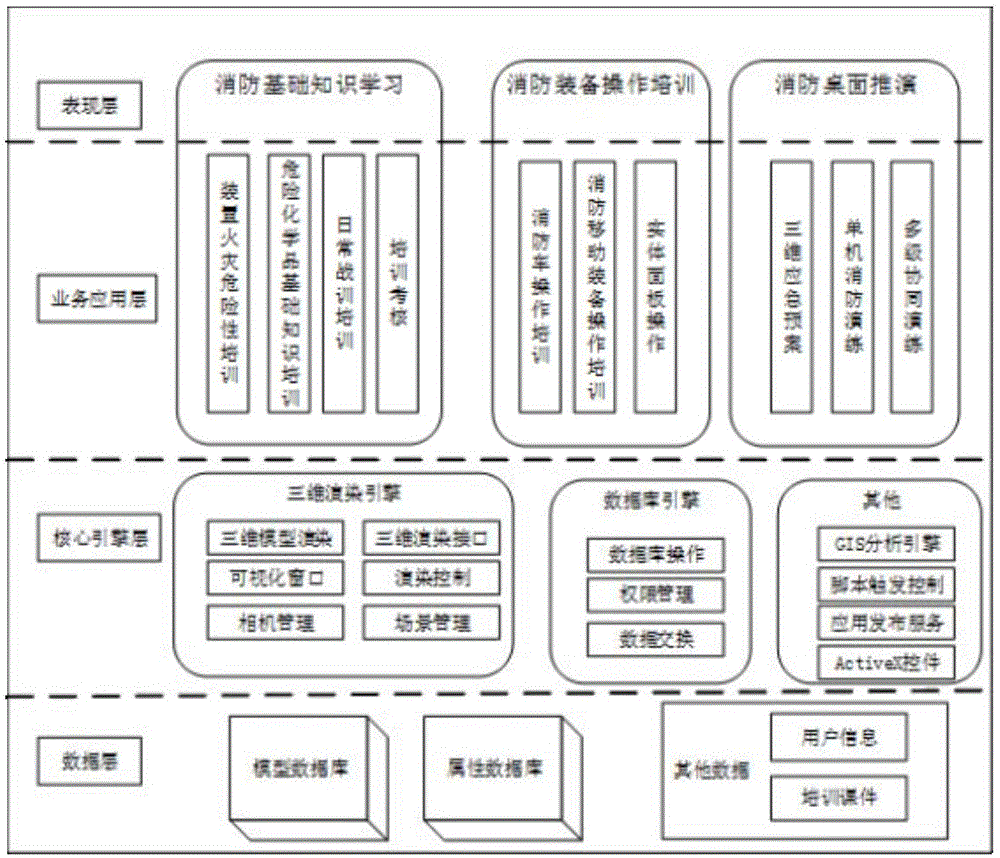
Multi-perception emergency training system for petrochemical fire scenario
ActiveCN105096685AConvenient maintenance and update workLow costCosmonautic condition simulationsSimulatorsBasic knowledgeSimulation
The invention relates to a multi-perception emergency training system for a petrochemical fire scenario, which mainly solves the problems of insufficient interaction and low scenario perceptibility in the prior art. The multi-perception emergency training system for the petrochemical fire scenario based on a B / S architecture comprises a 3D driving engine, a thermal flux sensor module, an equipment operation module, a basic knowledge database module, a scenario database module, a desktop deduction, examination and evaluation module, a server and a client computer. The system well solves the above problem, and can be used for multi-perception emergency training of petrochemical fire scenarios.
Owner:CHINA PETROLEUM & CHEM CORP +1
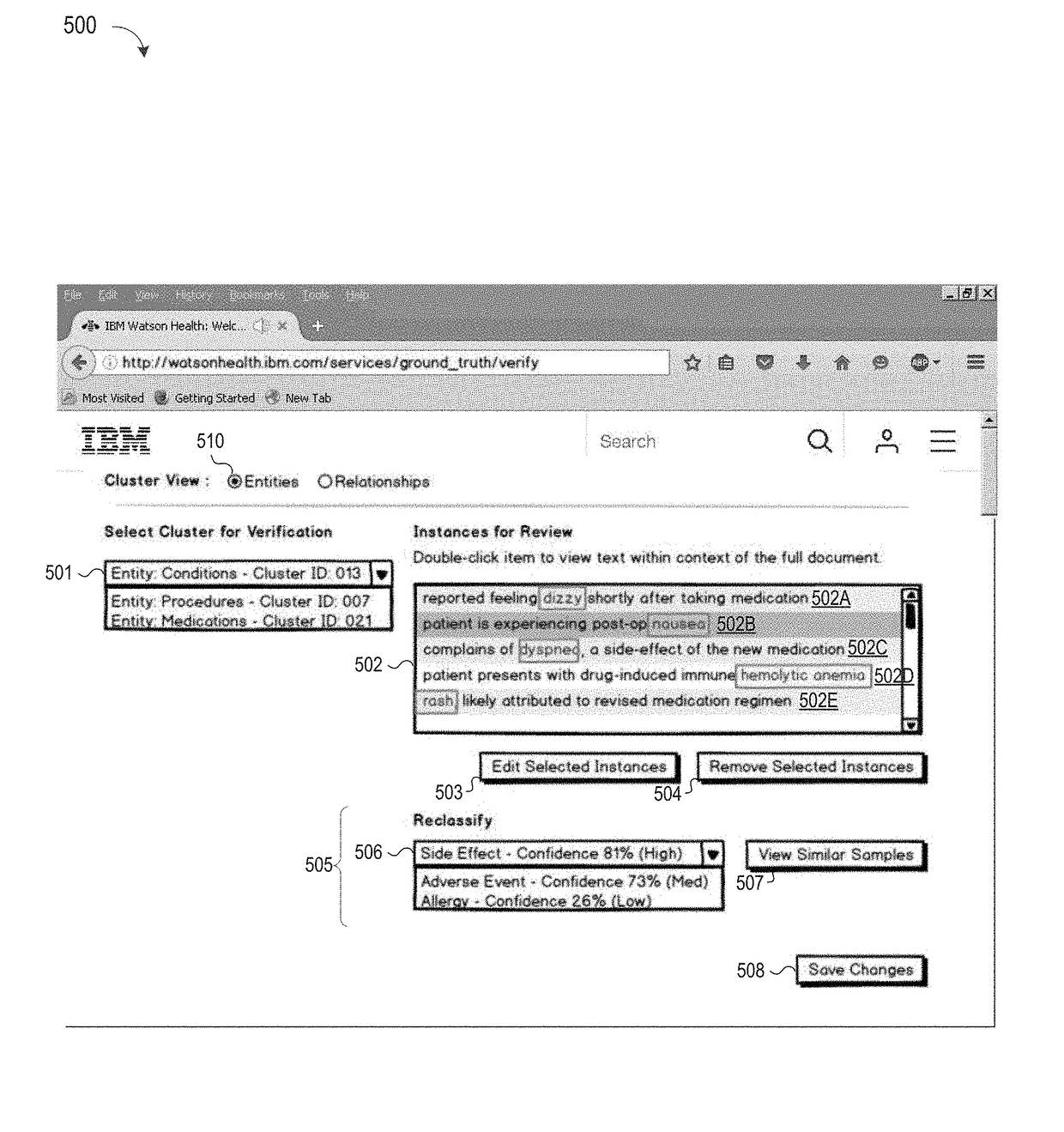
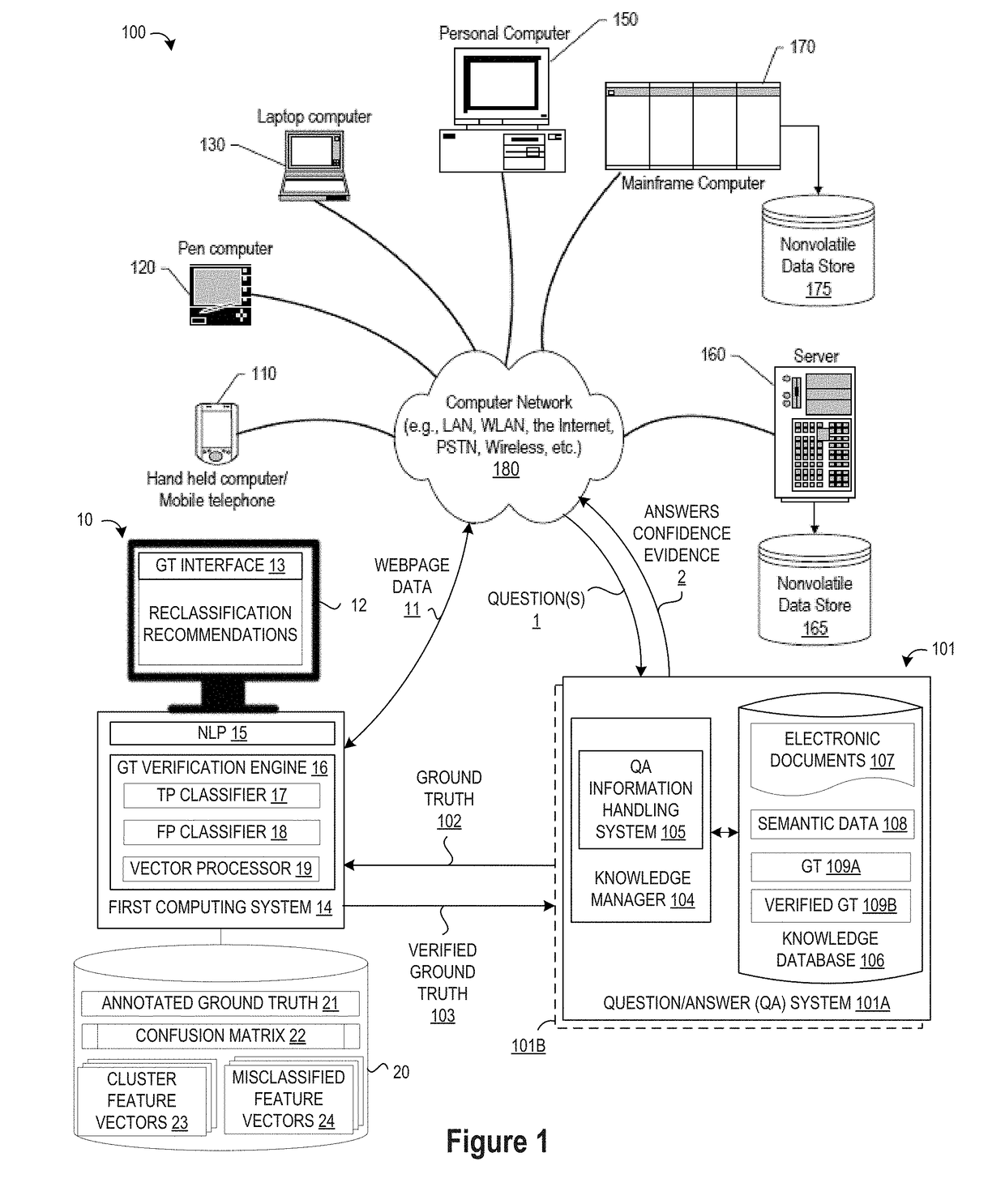
System and Method of Advising Human Verification of Often-Confused Class Predictions
InactiveUS20180075368A1Quickly and efficiently identifyIncrease authenticitySemantic analysisArtificial lifeGround truthSubject-matter expert
A method, system and a computer program product are provided for classifying elements in a ground truth training set by iteratively assigning machine-annotated training set elements to clusters which are analyzed to identify a prioritized cluster containing one or more elements which are frequently misclassified and display machine-annotated training set elements associated with the first prioritized cluster along with a warning that the first prioritized cluster contains one or more elements which are frequently misclassified to solicit verification or correction feedback from a human subject matter expert (SME) for inclusion in an accepted training set.
Owner:IBM CORP
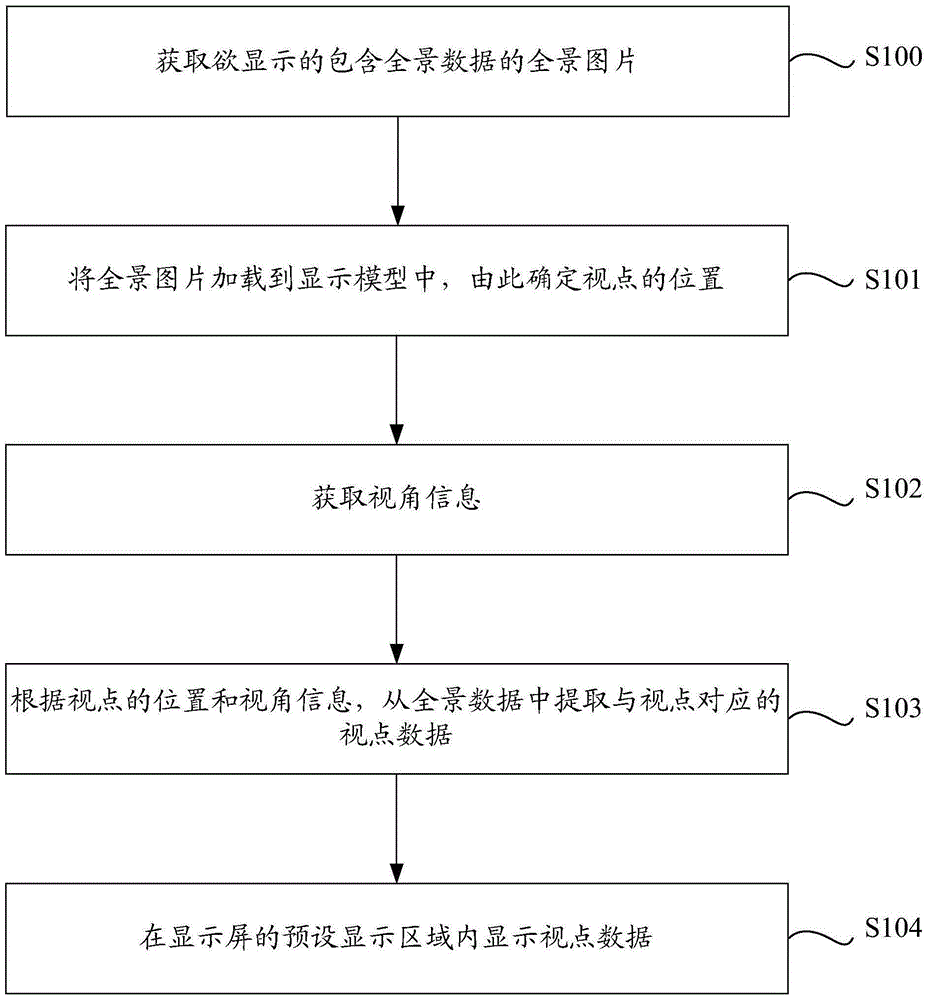
Method and device for displaying panoramic data
InactiveCN105208368AImprove the display effectIncrease authenticitySteroscopic systemsData displayViewpoints
The invention discloses a method and device for displaying panoramic data. The method comprises the steps that a to-be-displayed panoramic image containing the panoramic data is obtained; the panoramic image is loaded in a display model to determine the viewpoint position; visual angle information is obtained; viewpoint data corresponding to viewpoints are extracted from the panoramic data according to the viewpoint position and the visual angle information; the viewpoint data are displayed in a preset display area of a display screen. According to the method and device for displaying the panoramic data, the panoramic data can be displayed conveniently, good interactivity is achieved, the real effect of panoramic data display is improved, a user can have an experience feeling of being personally on the scene, the processed data volume is less, the response speed is high, and the display method of the panoramic data is optimized.
Owner:BEIJING QIHOO TECH CO LTD +1
Product Authenticator
InactiveUS20160027021A1Authenticity is easy to verifyIncrease authenticityCommerceTamper resistanceMessage authentication code
A product authenticator system and method for facilitating the verification of the authenticity of a product, by using a tamper-proof seal which either wholly or partially conceals an authentication code attached to a product. The said authentication code is unique and includes information which allows a user to verify the authenticity of the product. The authentication code can be scanned by a user using means such as a mobile phone, which can broadcast a notification of the consumption of the product via a computer network.
Owner:KERDEMELIDIS ANDREW
Weatherproof color shape bars in aluminium alloy, and manufacturing method
InactiveCN1760497AColorfulModerate costPattern printingSolid state diffusion coatingPolyesterSolid wood
The present invention relates to a superweathering color aluminum alloy section material and its production method. The composition of its base material is AlMg Si0.5-F22 alloy, according to Mg / Si=1.73, in which Mg (0.50-0.75%), Si (0.35-0.50%), Fe (less than 0.3%), Cu(less than 0.1%), Mn (less than 0.1%), Cr (less than 0.1%), Zn (less than 0.1%) and Ti (less than 0.1%); said base material is covered with chromized film whose thickness is 300-1000 mg / sq.m, and the chromized film also is covered with polyester powder coating layer which has imitation woodgrain pattern and whose thickness is 40-120 microns. Its production method includes the following steps: preparing aluminum alloy section base material, making pretreatment and chromizing process, spray-coating super weathering antistatic powder and heat transfer printing imitation woodgrain pattern.
Owner:SHANGHAI ZHENXING ALUMINUM IND
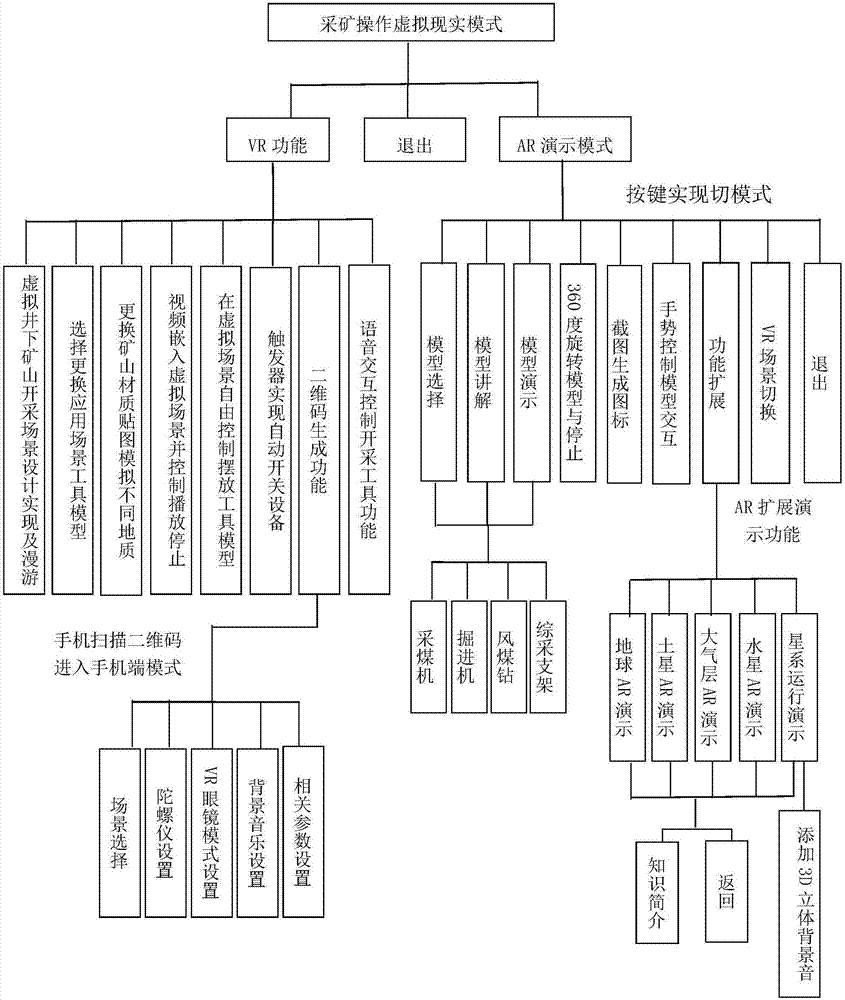
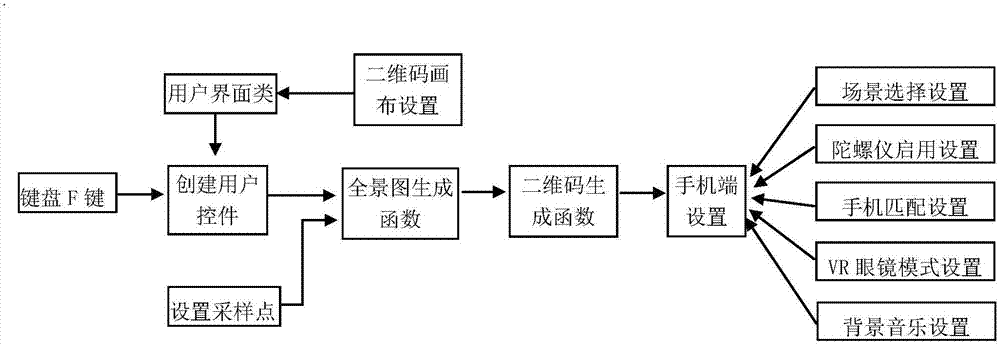
Mining operation multi-operation realization method based on virtual reality and augmented reality
ActiveCN107515674AReasonable designGood effectInput/output for user-computer interactionSpeech recognitionSkill setsComputer science
The invention discloses a mining operation multi-operation realization method based on virtual reality and augmented reality, and belongs to the technical field of the virtual reality and the augmented reality. The method comprises two patterns including the virtual reality and the augmented reality. Under a virtual reality scene, the selection and the replacement of a material and a material in the virtual reality scene can be realized, scene exploration is realized, the model can be moved and placed at will, a video is embedded, a two-dimensional code is generated, and a trigger realizes natural interaction, voice interaction and the like; under an augmented reality scene, the model can be selected, voice is played, the operation dynamics of the model can be demonstrated, and the rotation stopping, screen capture and function expansion of the model can be controlled; and under two patterns, various interaction ways of voice control, gesture control and keyboard mouse control can be realized. The method is applied to the virtual simulation application scene of the mining operation, can be used for training mine lot mining workers and students of the mining engineering specialty, reducing training capital and improving the skills of workers and provides an advanced and quick meaning for guiding production construction and science and technology studies.
Owner:SHANDONG UNIV OF SCI & TECH
Flame imitation manufacturing device of an electrical-heated fireplace
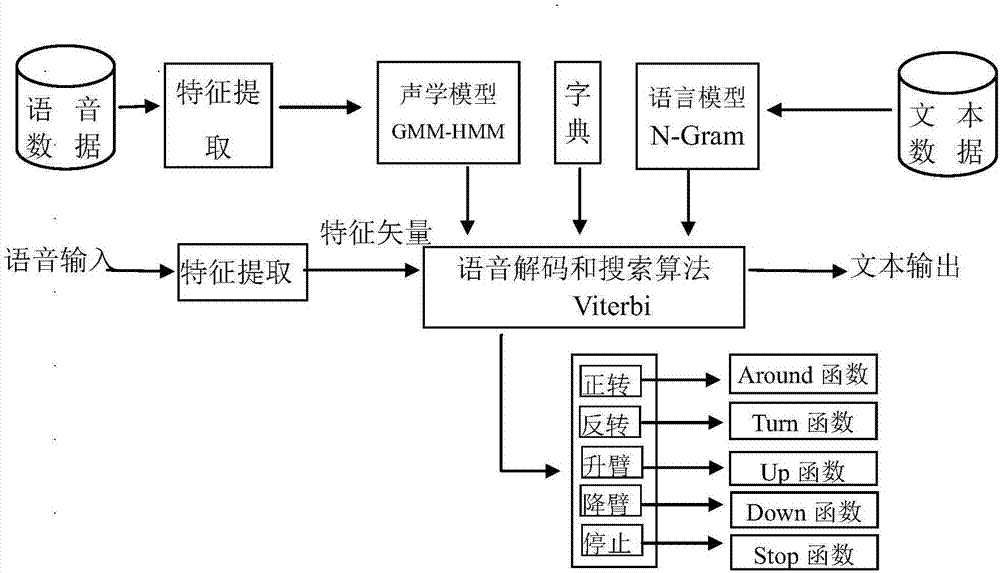
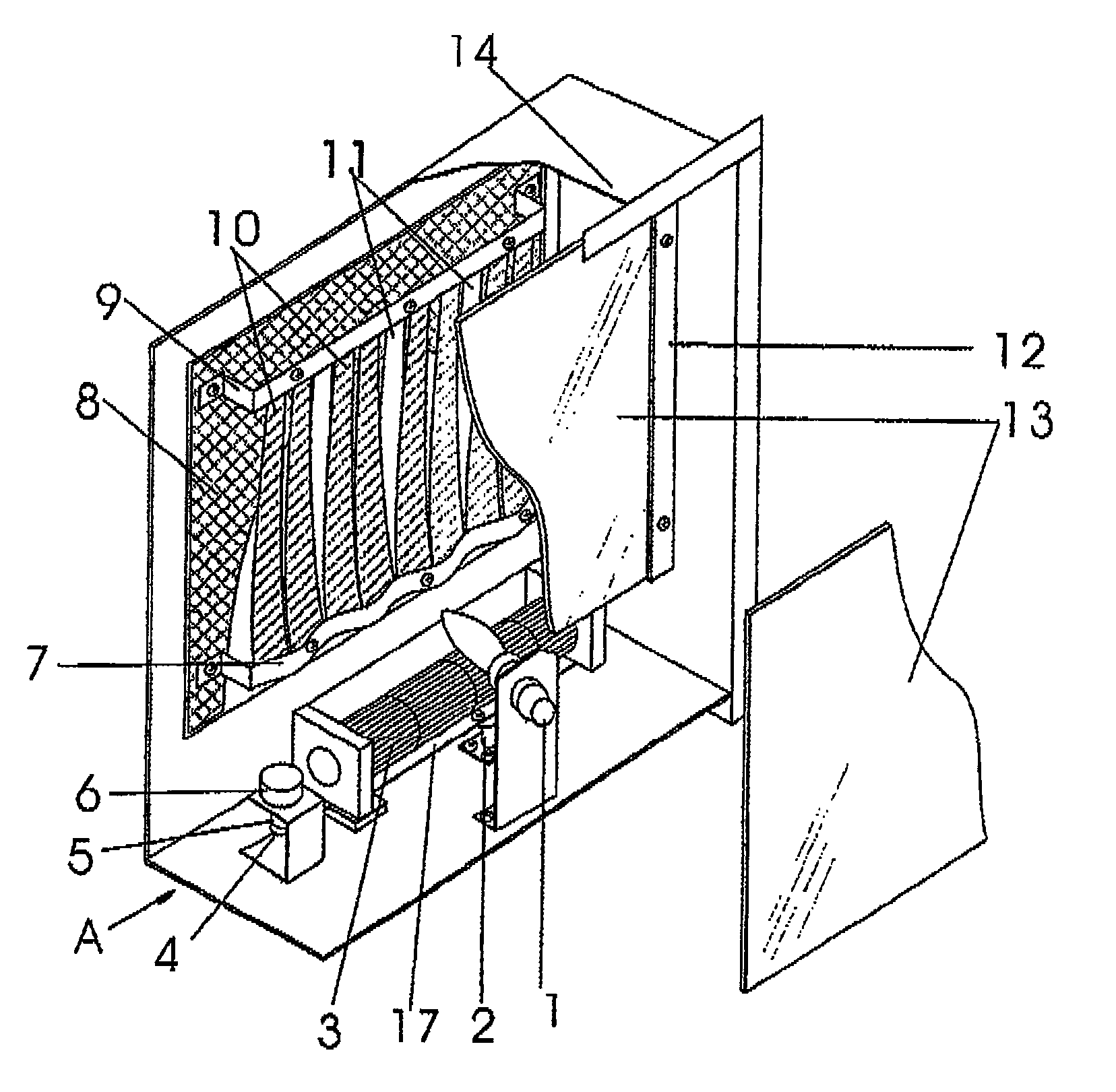
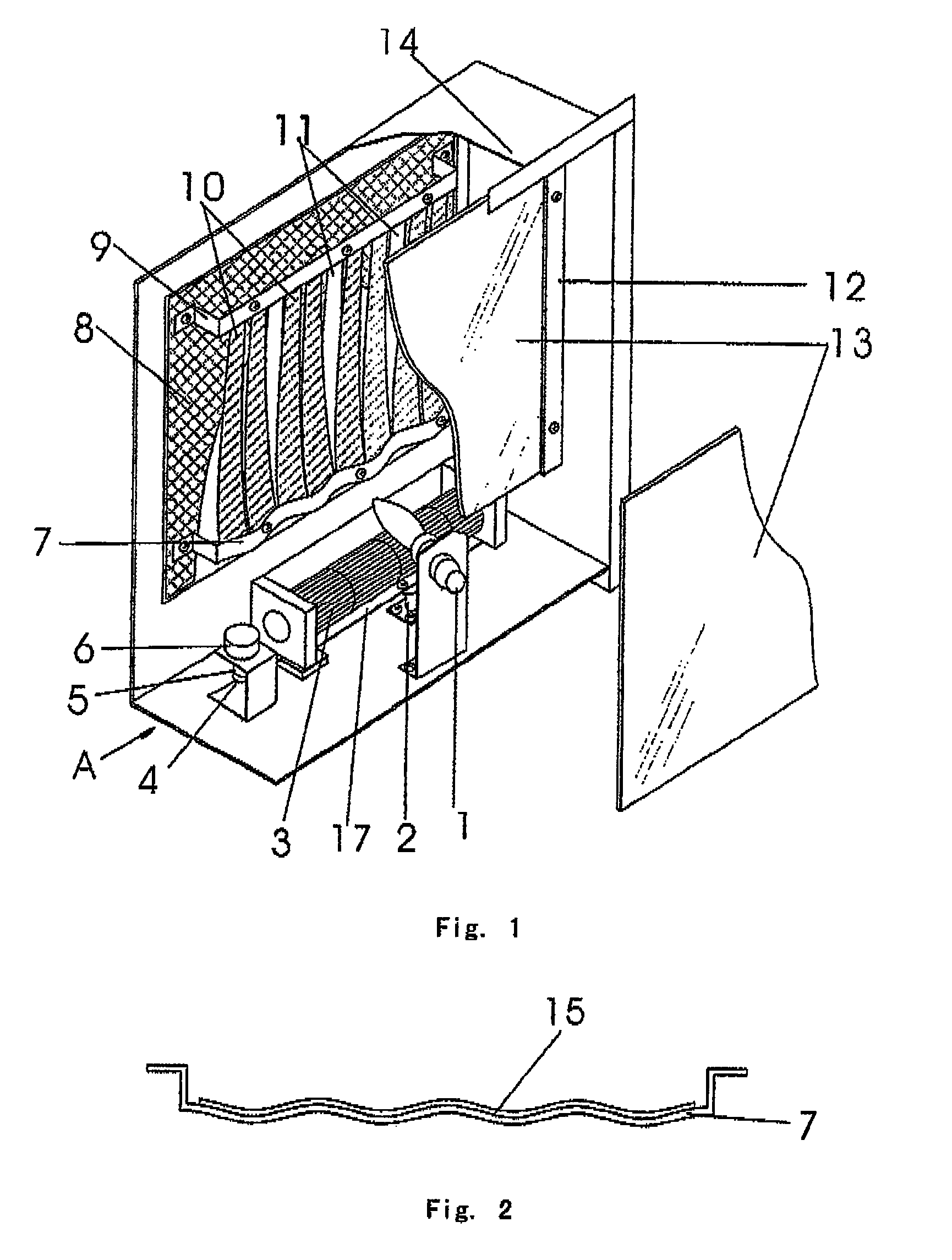
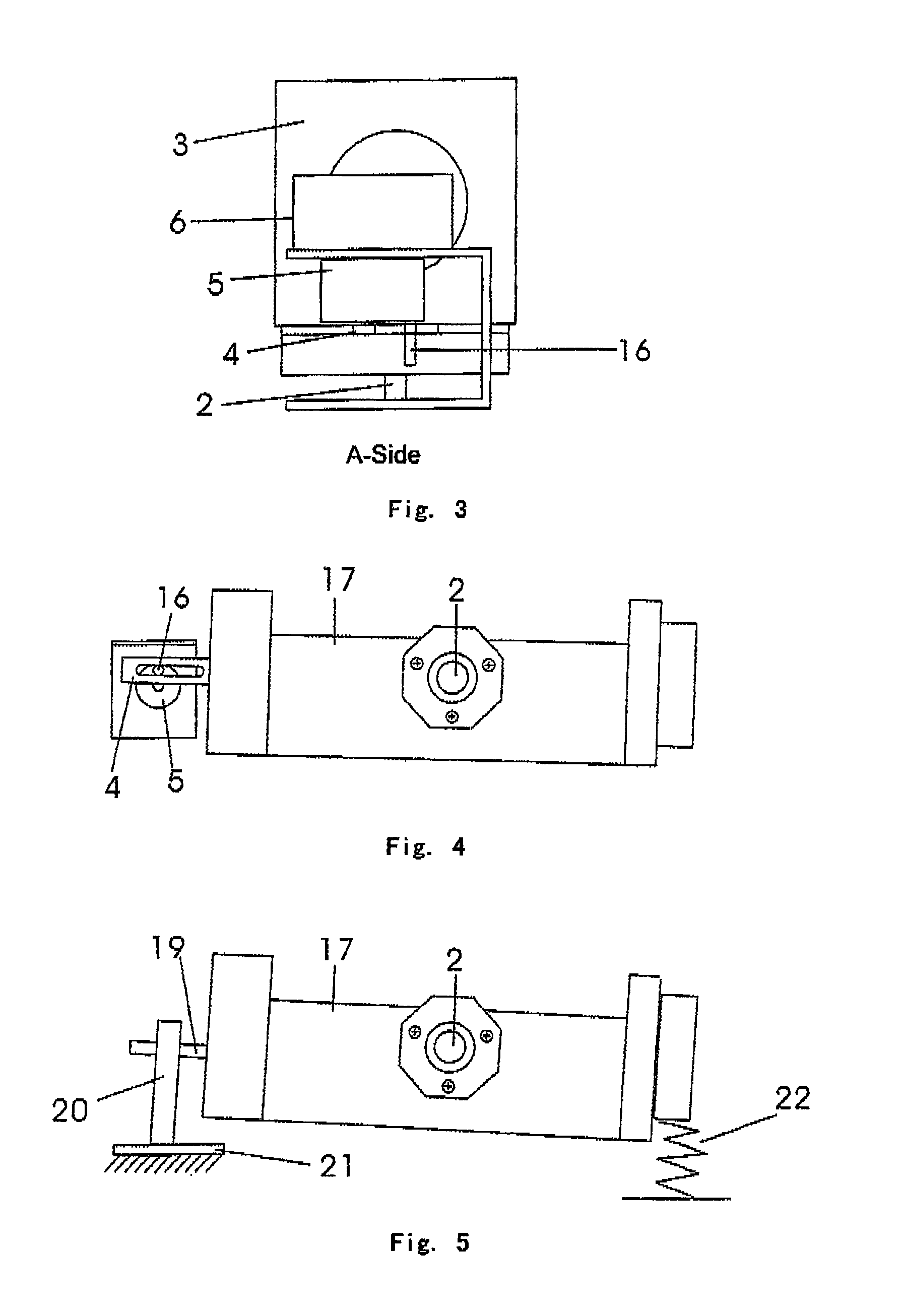
InactiveUS8081872B2Improve fidelityIncrease authenticityDomestic stoves or rangesHot-air central heatingEngineeringFireplace
A flame imitation manufacturing device of a fireplace relates to a flame imitation manufacturing device for simulating the burning state in a fireplace in the field of household appliances. Said device comprises a housing, a cross flow fan and a light source mounted on a base plate of the housing, a simulated fire chamber mounted on a back plate of the housing, ribbons mounted on the back plate of the housing by means of upper and lower strip bars and above the cross flow fan, and a light-transmitting glass plate mounted on the housing and in front of said ribbons. This invention, characterized in that said cross flow fan is a swinging one, is advantageous in that supplying wind non-directively by utilizing the swinging of said fan improves the flying state of ribbons so as to make the image state of burning flames more vivid, greatly enhances the authenticity of flames and lowers the cost thereof, and thus is adaptable to various flame imitation electrical-heated fireplaces and electrical appliances.
Owner:WANG ZHUHONG
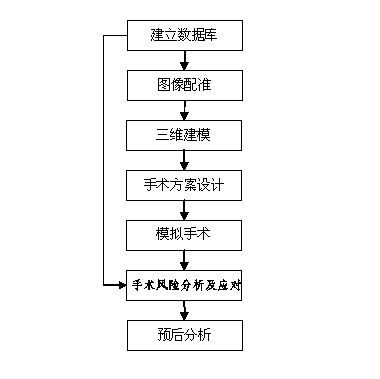
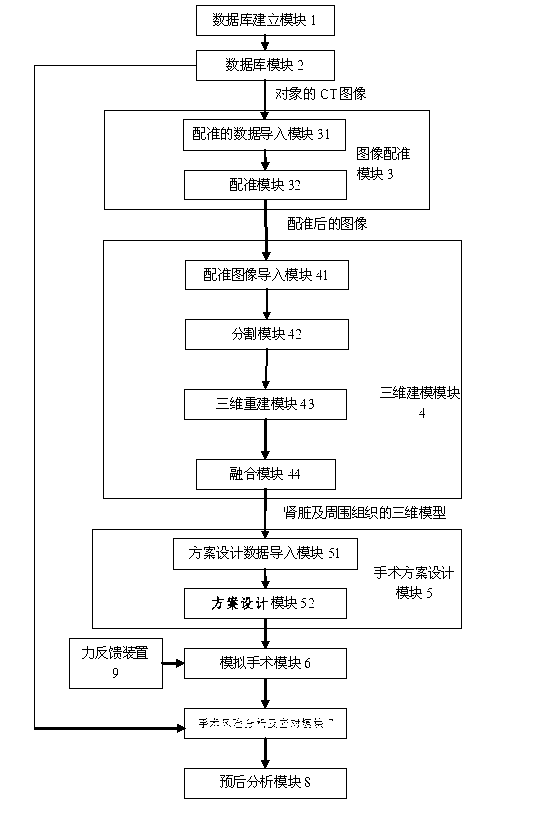
Three-dimensional kidney neoplasm surgery simulation method and platform based on computed tomography (CT) film
ActiveCN102982238AImprove surgical skillsImprove proficiencySpecial data processing applicationsSurgical riskGuideline
The invention discloses a three-dimensional kidney neoplasm surgery simulation method and a platform based on a computed tomography (CT) film. The method includes that firstly, a data base including object resources is built, multiple manners including CT film scanning are inputted into a CT faultage image, a sequence image is registered according to the sequence based on an outline gradient principle, a registered CT image is utilized to reconstruct segmentation tissue of an arterial phase, a venous phase and a lag phase by adopting of a three-dimensional reconstruction technology, and the segmentation tissue of the arterial phase, the venous phase and the lag phase are effectively fused in the same coordinate space. According to an imaging staging criteria and a treatment guideline of kidney neoplasm, and based on modeling results, various peration plan designing, operation stimulation, surgical risk analysis and response, and prognostic analysis are carried out, a personalized and benefit maximization treatment plan can be provided for an object, and skills and degree of proficiency of an operation can be improved, and the three-dimensional kidney neoplasm surgery simulation method can be used in medical teaching.
Owner:江苏瑞影医疗科技有限公司
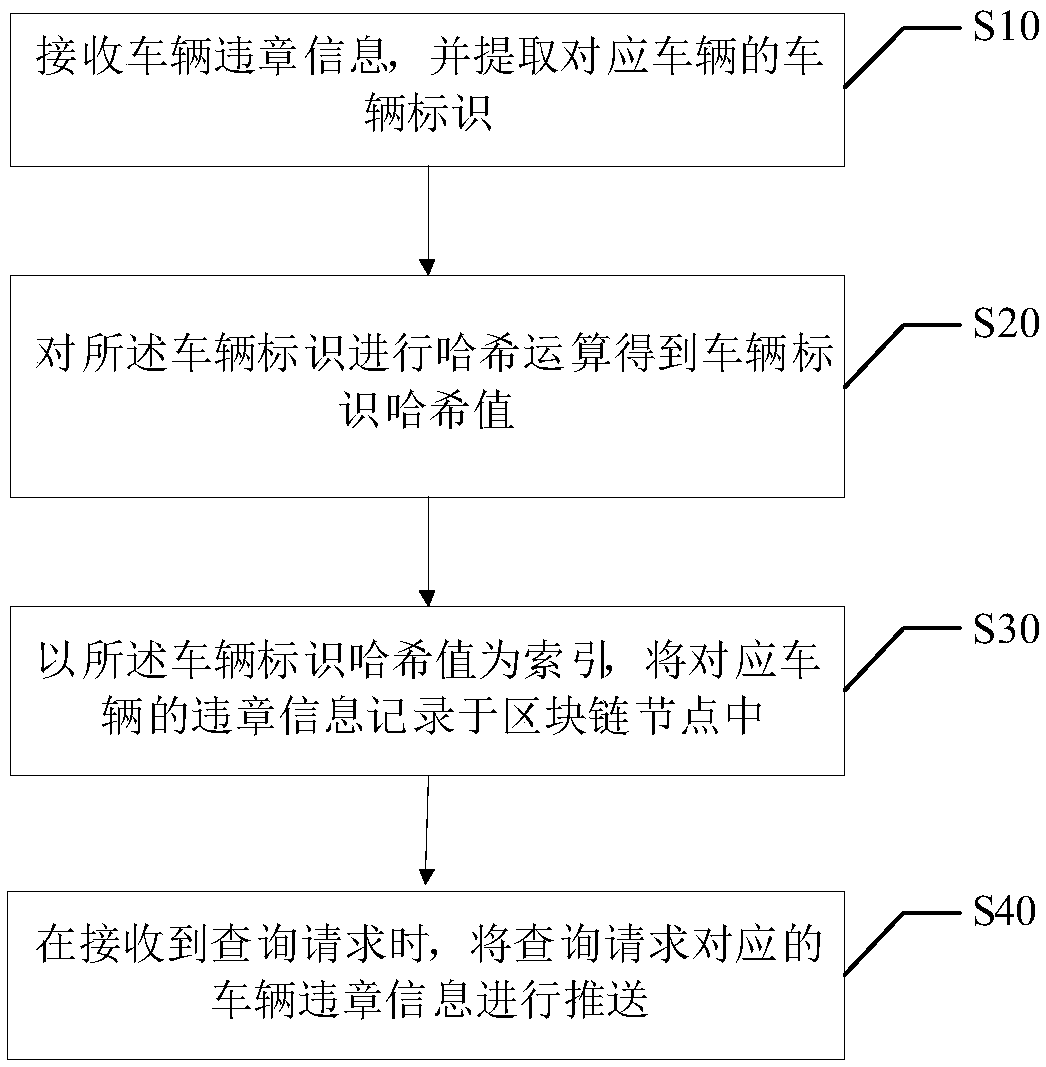
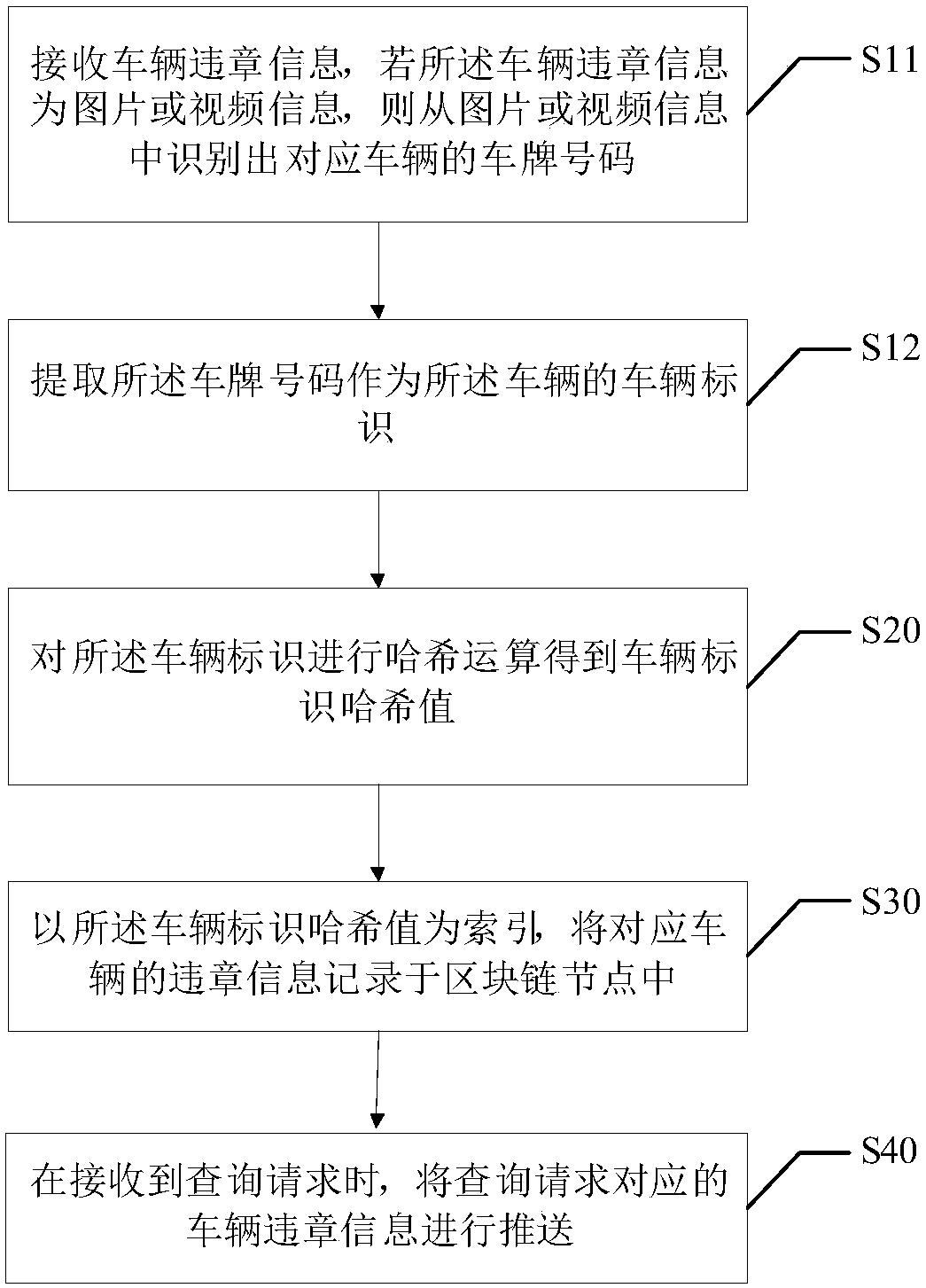
Block chain-based vehicle violation information management method, block chain and storage medium
InactiveCN107870983AIncrease authenticityIncrease opennessDatabase distribution/replicationDigital data protectionComputer scienceReal-time computing
The invention discloses a block chain-based vehicle violation information management method. The method comprises the following steps of: receiving vehicle violation information and extracting a vehicle identifier of a corresponding vehicle; carrying out hash operation on the vehicle identifier according to the vehicle violation information so as to obtain a vehicle identifier hash value; recording violation information of the corresponding vehicle in a block chain node by taking the vehicle identifier hash value as an index; and when a query request is received, pushing the vehicle violationinformation corresponding to the query request. The invention furthermore discloses a block chain and a storage medium. According to the block chain-based vehicle violation information management method, the block chain and the storage medium, the authenticity and openness of vehicle violation information can be enhanced.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
Amusement apparatus and method
InactiveUS20050014567A1Increase authenticityImprove illusionAmusementsStage arrangementsVertical planeRECREATIONAL EQUIPMENT
An amusement simulation apparatus and method is disclosed. The simulation apparatus includes screen, projector, rotating platform carrying passenger, rotating shaft and aligned passenger seats round the machine room positioned on the platform and hanging by the suspending structure. When the platform is in upright position, passengers seating in the passenger seats face the screen positioned in front and view the image (2D or 3D) projected on the screen. The passengers are almost in the same vertical plane but in up and down relation. The blocking plate divided the passengers in different rows. The platform and the passenger seats can both pivot upon their shaft. Passenger seats in the left and right columns can rotate round the longitudinal yawing shaft to achieve better viewing effect. Pivoting movement of the passenger seat, combining the special effect of wind blasting, simulates the flying experience vividly. The simulation apparatus is suitable for use in an amusement park or theme park, providing tourists with interesting and life like flying experience.
Owner:LI MING +3
Sign-in method based on two-dimensional code, mobile terminal and sign-in server
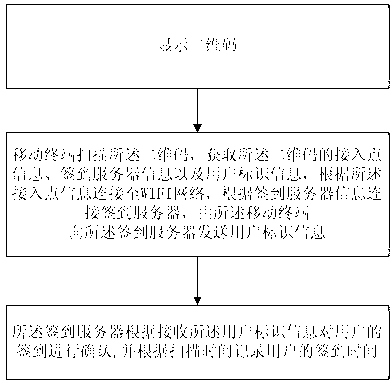
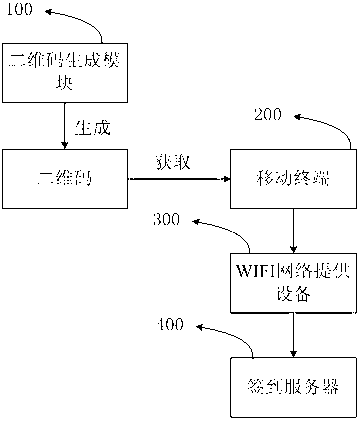
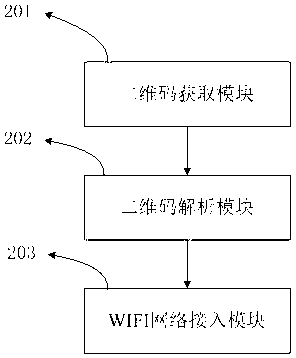
ActiveCN103346892AIncrease authenticityNo need to increase hardware costsRegistering/indicating time of eventsUser identity/authority verificationUser identifierReal-time computing
The invention discloses a sign-in method based on a two-dimensional code. The sign-in method based on the two-dimensional code is characterized by comprising the following steps of: displaying the two-dimensional code; scanning the two-dimensional code by a mobile terminal, analysing to obtain the access point information, sign-in server information and user identifier information of the two-dimensional code, connecting to a WIFI (wireless fidelity) network according to the access point information, connecting to a sign-in server according to the sign-in server information, and sending the user identifier information to the sign-in server by the mobile terminal; and confirming the sign-in of a user by the sign-in server according to the received user identifier information, and recording the sign-in time of the user according to a scanning time. With the adoption of the sign-in method based on the two-dimensional code disclosed by the invention, no-queuing sign-in can be realized, and the case of copying the two-dimensional code for allograph can be prevented. Simultaneously, the invention further discloses a mobile terminal and a sign-in server.
Owner:SHANGHAI LIANSHANG NETWORK TECHNOLOGY CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com